-

@ df173277:4ec96708
2025-01-28 17:49:54
> Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. Chats are synced automatically between devices so you can pick up where you left off.\
> [Start chatting for free.](https://trymaple.ai/)
We are excited to announce that [Maple AI](https://trymaple.ai/), our groundbreaking end-to-end encrypted AI chat app built on OpenSecret, is now publicly available. After months of beta testing, we are thrilled to bring this innovative technology to the world.
Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. It can boost your productivity on work tasks such as writing documentation, creating presentations, and drafting emails. You can also use it for personal items like brainstorming ideas, sorting out life's challenges, and tutoring you on difficult coursework. All your chats are synced automatically in a secure way, so you can start on one device and pick up where you left off on another.
#### Why Secure and Private AI?
In today's digital landscape, it is increasingly evident that security and privacy are essential for individuals and organizations alike. Unfortunately, the current state of AI tools falls short. A staggering 48% of organizations enter non-public company information into AI apps, according to a [recent report by Cisco](https://www.cisco.com/c/en/us/about/trust-center/data-privacy-benchmark-study.html#~key-findings). This practice poses significant risks to company security and intellectual property.
Another concern is for journalists, who often work with sensitive information in hostile environments. Journalists need verification that their information remains confidential and protected when researching topics and communicating with sources in various languages. They are left to use underpowered local AI or input their data into potentially compromised cloud services.
At OpenSecret, we believe it is possible to have both the benefits of AI and the assurance of security and privacy. That's why we created Maple, an app that combines AI productivity with the protection of end-to-end encryption. Our platform ensures that your conversations with AI remain confidential, even from us. The power of the cloud meets the privacy of local.
#### How Does It Work?
Our server code is [open source](https://github.com/OpenSecretCloud/opensecret), and we use confidential computing to provide cryptographic proof that the code running on our servers is the same as the open-source code available for review. This process allows you to verify that your conversations are handled securely and privately without relying on trust. We live by the principle of "Don't trust, verify," and we believe this approach is essential for building in the digital age. You can read a more in-depth write-up on our technology later this week on this site.
#### How Much Does It Cost?
We are committed to making Maple AI accessible to everyone, so we offer a range of pricing plans to suit different needs and budgets. [Our Free plan allows for 10 chats per week, while our Starter plan ($5.99/month) and Pro plan ($20/month)](https://trymaple.ai/pricing) offer more comprehensive solutions for individuals and organizations with heavier workloads. We accept credit cards and Bitcoin (10% discount), allowing you to choose your preferred payment method.
- Free: $0
- Starter: $5.99/month
- Pro: $20/month
Our goal with Maple AI is to create a product that is secure through transparency. By combining open-source code, cryptography, and confidential computing, we can create a new standard for AI conversations - one that prioritizes your security and privacy.
Maple has quickly become a daily tool of productivity for our own work and those of our beta testers. We believe it will bring value to you as well. [Sign up now and start chatting privately with AI for free.](https://trymaple.ai/) Your secrets are safe in the open.
#### Are You An App Developer?
You can build an app like Maple. [OpenSecret provides secure auth, private key management, encrypted data sync, private AI, and more.](https://blog.opensecret.cloud/introducing-opensecret/) Our straightforward API behaves like other backends but automatically adds security and privacy. Use it to secure existing apps or brand-new projects. Protect yourself and your users from the liability of hosting personal data by checking out [OpenSecret](https://opensecret.cloud/).
<img src="https://blossom.primal.net/feb746d5e164e89f0d015646286b88237dce4158f8985e3caaf7e427cebde608.png">
Enjoy private AI Chat 🤘
<img src="https://blossom.primal.net/0594ec56e249de2754ea7dfc225a7ebd46bc298b5af168279ce71f17c2afada0.jpg">
-

@ 9e69e420:d12360c2
2025-01-26 01:31:31
## Chef's notes
# arbitray
- test
- of
- chefs notes
## hedding 2
## Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 5
## Ingredients
- Test ingredient
- 2nd test ingredient
## Directions
1. Bake
2. Cool
-

@ 228dde34:b5d0345e
2025-01-25 01:59:57
##### By Jonathan Tan
##### Lead Editor
##### Hype Issue #60
##### JONATHAN TAN explores the recent rise in popularity of online gambling, and its consequences on the population’s most vulnerable.

The persistent rise in the gaming industry, fueled by the introduction of online gambling, seems to have no end. Experts are now worrying about the effects of this epidemic on public health and safety. “Many people might be really experiencing harms from gambling — we think that it’s probably around 72 million people globally,” said Louisa Degenhardt, a professor at the University of New South Wales in Sydney, in an[NBC article.](https://www.nbcnews.com/health/health-news/gambling-industry-growth-threat-public-health-report-rcna175356)
The online gambling craze has spread worldwide, and even Singapore, with its strict gambling regulations, is not immune to it. In a recent[survey](https://www.channelnewsasia.com/singapore/national-council-problem-gambling-rate-continues-fall-4761621)conducted by the National Council on Problem Gambling (NCPG), illegal online gambling rates have more than tripled since 2020, from 0.3% to 1.0% in the past 4 years.
This statistic alone highlights an already concerning trend. Even more troubling, however, is that the illegal nature of these websites means there are no regulatory laws or age restrictions. As a result, the proliferation of these online websites has allowed a brand new demographic to start gambling: the Singaporean youth.
### How to lose thousands before adulthood
“I started gambling when I was 13 years old, at a friend's house,” George (not his real name) shares. Now an 18-year-old student, George recalls how a simple game among friends slowly grew into an all-consuming gambling addiction.
 *In NCPG’s 2023 survey, 8% of respondents reported participating in social gambling activities: gambling which occurs within individuals’ homes, among family members. Photo from Shutterstock.*
Initially, George and his friends gambled with low stakes, like a dollar here and there. However, the games slowly escalated: from $1 to $10, then to $100, and eventually to $1000. Unsurprisingly, with such large sums at stake, George’s relationship with his friends began to strain.
“I realized that after a certain point, the more and more money we [bet], the more and more our relationship with each other [soured]; and so we decided to curb it at a maximum buy-in of $20 per game,” George says.
The new rule eased the tension between George and his friends, but it inadvertently created a new problem: George no longer felt the thrill of winning large sums. As a result, he began seeking other ways to gamble.
“The first time I gambled online was when I was 16 years old. A friend had introduced me to a gambling website,” he recalls. “And at first it was all right. I won a bit, I lost a bit, but no one got hurt.”
But it didn’t take long for him to get hooked; a single sports bet was what netted George his first big win. “On the first day, I went from $10 to $800 from a simple parlay bet,” George says. “I felt unstoppable. Adrenaline was pumping through my veins, and [I felt] I could never lose. [After] that day, I gambled like $100 almost every day for a straight month.”

*A parlay (a form of sports betting that has recently surged in popularity) is a single bet that combines two or more bets into one. While doing this drastically decreases the odds of winning, it also drastically increases the potential payout. Photo from Getty Images.*
Nothing could stop George’s gambling fervor. Even after losing nearly a thousand dollars on a single blackjack hand, all George did was place a bigger bet to try and win it back. “Every morning, when I [woke] up, all I could think about was gambling,” he shares.
And of course, George’s obsession with online gambling was only exacerbated by the accessibility of these websites.
First, the online nature of these websites allowed George to gamble anywhere, at any time. “For online gambling, you have it right at your fingertips. As soon as you wake up, you can just log on the computer and start betting huge amounts of money,” he mentions.
But more importantly, these illegal gambling websites enabled George to do something he was never old enough to do in the first place.
“I'm too young to gamble at a real casino or a physical casino. But online gambling makes it way more accessible because there's no verification of ID,” George says.
### Consequences, consequences
Therein lies the predatory nature of these illegal websites. While anyone can fall victim to a gambling addiction, certain factors may make the youth especially vulnerable.
“The adolescent brain is still developing, particularly the prefrontal cortex, which is responsible for decision-making, impulse control, and risk assessment. This makes young people more susceptible to impulsive behaviors,” says Jat Tan, the Communications and Events Executive at WE CARE Community Services.
 *The prefrontal cortex is primarily developed during adolescence, and is fully developed at the age of 25 years. Photo from iStock.*
Additionally, other factors such as peer pressure, social media, or limited life experience, could result in young Singaporeans being more open to gambling.
Lastly, one popular reason why the youth are drawn to gambling, is their limited financial freedom. “While youths are in school, they have a significantly lower earning power as opposed to adults. The demands from school usually means that they can only afford to work part-time jobs,” Mrs Tan shares.
Despite this, many young Singaporeans still want to live extravagant lifestyles. With the youth getting exposed to lavish, ostentatious lifestyles on social media, many begin to feel envious and yearn for the same luxuries. And now, with the introduction of illegal online sites, the lack of age restrictions allows these youths to gamble in an attempt to achieve this better life.
### What can be done?
The increase in the number of adolescent gamblers is a new challenge for the Singaporean government. Before the advent of online gambling, many safeguards were in place to protect Singaporeans from developing gambling addictions.
In particular, safeguards that limit Singaporeans’ access to legal gambling services seem to be working; the overall percentage of gambling Singaporeans has fallen from 44% to 40% from 2020 to 2023.
However, the unprecedented accessibility and convenience of online gambling sites have allowed Singapore’s tech-savvy youth to bypass these regulations; and now, the Singaporean government needs to update its laws to keep up with the growing gambling industry.
Of course, the Singaporean Government has been cracking down on illegal online gambling. As of September 2024, the Gambling Regulatory Authority (GRA) has blocked access to more than 1,900 remote gambling websites. But despite the GRA’s efforts, these online gambling providers continue to survive, like weeds in a garden.
“GRA recognises that the borderless nature of the Internet makes it easy for unlawful gambling operators to offer their products to users in Singapore any time and anywhere,” said a GRA spokesman in [a Straits Times article.](https://www.straitstimes.com/singapore/crackdown-on-illegal-online-gambling-but-addiction-can-be-hard-to-beat)
Currently, there are calls for the government to shift its focus. “While Singapore has done well putting in place responsible gaming and safety measures to mitigate the risks of casino gambling, it is timely to focus more attention to address the risk of illegal online gambling as well,” said Ms Tham, Clinical director of We Care Community Services, [in a Straits Times article.](https://www.straitstimes.com/singapore/fewer-singapore-residents-gambled-but-more-do-so-online-illegally)
Ultimately, as the gambling industry becomes more technologically advanced, it becomes harder for Singapore to regulate gambling the same way it used to. Thus, it may be time for the Singaporean government to consider a different solution.
“Better educating youths on the harms and consequences of gambling, as well as resources available should things go awry, would be the best option to nip the issue in the bud,” Ms Tan suggests. Instead of focusing on restrictive legislation, education could be a preventative measure used to curb adolescent gambling.
“A higher level of awareness would enable youths to face issues like gambling with their eyes wide open - they will have a rough idea of what they're getting themselves into, and will have a rough idea of what to do if things go wrong,” she shares.
-

@ bcea2b98:7ccef3c9
2025-01-24 23:21:05
originally posted at https://stacker.news/items/862840
-

@ 29af23a9:842ef0c1
2025-01-21 14:42:19
A Indústria Pornográfica se caracteriza pelo investimento pesado de grandes empresários americanos, desde 2014.
Na década de 90, filmes pornográficos eram feitos às coxas. Era basicamente duas pessoas fazendo sexo amador e sendo gravadas. Não tinha roteiro, nem produção, não tinha maquiagem, nada disso. A distribuição era rudimentar, os assinantes tinham que sair de suas casas, ir até a locadora, sofrer todo tipo de constrangimento para assistir a um filme pornô.
No começo dos anos 2000, o serviço de Pay Per View fez o número de vendas de filmes eróticos (filme erótico é bem mais leve) crescer mas nada se compara com os sites de filmes pornográficos por assinatura.
Com o advento dos serviços de Streaming, os sites que vendem filmes por assinatura se estabeleceram no mercado como nunca foi visto na história.
Hoje, os Produtores usam produtos para esticar os vasos sanguíneos do pênis dos atores e dopam as atrizes para que elas aguentem horas de gravação (a Série Black Mirror fez uma crítica a isso no episódio 1 milhão de méritos de forma sutil).
Além de toda a produção em volta das cenas. Que são gravadas em 4K, para focar bem as partes íntimas dos atores. Quadros fechados, iluminação, tudo isso faz essa Indústria ser "Artística" uma vez que tudo ali é falso. Um filme da Produtora Vixen, por exemplo, onde jovens mulheres transam em mansões com seus empresários estimula o esteriótipo da mina padrão que chama seu chefe rico de "daddy" e seduz ele até ele trair a esposa.
Sites como xvídeos, pornHub e outros nada mais são do que sites que salvam filmes dessas produtoras e hospedam as cenas com anúncios e pop-ups. Alguns sites hospedam o filme inteiro "de graça".
Esse tipo de filme estimula qualquer homem heterosexual com menos de 30 anos, que não tem o córtex frontal de seu cérebro totalmente desenvolvido (segundo estudos só é completamente desenvolvido quando o homem chega aos 31 anos).
A arte Pornográfica faz alguns fantasiarem ter relação sexual com uma gostosa americana branquinha, até escraviza-los. Muitos não conseguem sair do vício e preferem a Ficção à sua esposa real. Então pare de se enganar e admita.
A Pornografia faz mal para a saúde mental do homem.
Quem sonha em ter uma transa com Lana Rhodes, deve estar nesse estágio. Trata-se de uma atriz (pornstar) que ganhou muito dinheiro vendendo a ilusão da Arte Pornografica, como a Riley Reid que só gravava para grandes Produtoras. Ambas se arrependeram da carreira artística e agora tentam viver suas vidas como uma mulher comum.
As próprias atrizes se consideram artistas, como Mia Malkova, chegou a dizer que Pornografia é a vida dela, que é "Lindo e Sofisticado."
Mia Malkova inclusive faz questão de dizer que a industria não escravisa mulheres jovens. Trata-se de um negócio onde a mulher assina um contrato com uma produtora e recebe um cachê por isso. Diferente do discurso da Mia Khalifa em entrevista para a BBC, onde diz que as mulheres são exploradas por homens poderosos. Vai ela está confundindo o Conglomerado Vixen com a Rede Globo ou com a empresa do Harvey Weinstein.
Enfim, se você é um homem solteiro entre 18 e 40 anos que já consumiu ou que ainda consome pornografia, sabia que sofrerá consequências. Pois trata-se de "produções artísticas" da indústria audiovisual que altera os níveis de dopamina do seu cérebro, mudando a neuroplasticidade e diminuindo a massa cinzenta, deixando o homem com memória fraca, sem foco e com mente nebulosa.
Por que o Estado não proíbe/criminaliza a Pornografia se ela faz mal? E desde quando o Estado quer o nosso bem?
Existem grandes empresarios que financiam essa indústria ajudando governos a manterem o povo viciado e assim alienado. É um pão e circo, só que muito mais viciante e maléfico. Eu costume dizer aos meus amigos que existem grandes empresários jvdeus que são donos de grandes Produtoras de filmes pornográficos como o Conglomerado Vixen. Então se eles assistem vídeos pirateados de filmes dessas produtoras, eles estão no colo do Judeu.
-

@ cff1720e:15c7e2b2
2025-01-19 17:48:02
**Einleitung**\
\
Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\
Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie <roland@pareto.space> können sie sogar jederzeit umziehen, egal wohin. **Cool, das ist state of the art!** Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.

**Warum Nostr?**
Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz **"unserer Demokratie”** praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.

Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \
\
**Resümee:** keine Standards, keine Daten, keine Rechte = keine Zukunft!

\
**Wie funktioniert Nostr?**
Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum **“single point of failure”**, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\
\
Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. <roland@pareto.space> ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\
\
**Resümee:** ein offener Standard, alle Daten, alle Rechte = große Zukunft!

\
**Warum ist Nostr die Zukunft des Internet?**
“Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie **(Value4Value)**. OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.

\
**Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.**
<https://nostr.net/> \
<https://start.njump.me/>
**Hier das Interview zum Thema mit Radio Berliner Morgenröte**
<https://www.podbean.com/ew/pb-yxc36-17bb4be>
-

@ c631e267:c2b78d3e
2025-01-18 09:34:51
*Die grauenvollste Aussicht ist die der Technokratie –* *\
einer kontrollierenden Herrschaft,* *\
die durch verstümmelte und verstümmelnde Geister ausgeübt wird.* *\
Ernst Jünger*  
**«Davos ist nicht mehr sexy»,** das Weltwirtschaftsforum ([WEF](https://transition-news.org/wef-world-economic-forum)) mache Davos [kaputt](https://web.archive.org/web/20250116114956/https://www.handelszeitung.ch/wef-2025/wie-das-wef-davos-kaputt-macht-785098), diese Aussagen eines Einheimischen las ich kürzlich in der *Handelszeitung*. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
**Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen** dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den [vergangenen](https://transition-news.org/die-angst-der-eliten-vor-dem-pobel) vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
**Der deutsche WEF-Gründer hatte bei dieser Gelegenheit** immer höchst lobende Worte für seine Landsmännin: [2021](https://www.weforum.org/meetings/the-davos-agenda-2021/sessions/special-address-by-g20-head-of-state-government/) erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und [2022](https://www.weforum.org/meetings/the-davos-agenda-2022/sessions/special-address-by-ursula-von-der-leyen-president-of-the-european-commission-177737c164/) fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
**Von der Leyens Handeln während der sogenannten Corona-«Pandemie»** lobte Schwab damals bereits ebenso, wie es diese Woche das [Karlspreis](https://transition-news.org/von-der-leyen-erhalt-karlspreis-albert-bourla-erklart-pfizer-habe-wahrend-der)-Direktorium tat, als man der Beschuldigten im Fall [Pfizergate](https://transition-news.org/pfizergate-startet-ins-neue-jahr) die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
**Jene Herausforderungen durch «Krisen epochalen Ausmaßes»** werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im [Global Risks Report](https://www.zurich.com/knowledge/topics/global-risks/the-global-risks-report-2025) nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
**Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen** unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
**Ein** **[«Great Mental Reset»](https://transition-news.org/angriff-auf-unser-gehirn-michael-nehls-uber-den-great-mental-reset-teil-1)** **sei die Voraussetzung dafür,** dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
**Der aktuelle Zustand unserer Gesellschaften** ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die [Rechtsstaatlichkeit](https://transition-news.org/schweizer-rechtsstaat-in-der-krise-ein-anwalt-schlagt-alarm) stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/davos-europa-und-der-rest-der-welt)*** erschienen.
-

@ f9cf4e94:96abc355
2025-01-18 06:09:50
Para esse exemplo iremos usar:
| Nome | Imagem | Descrição |
| --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ |
| Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** |
| Pen drive |  | **16Gb** |
Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.).
---
## Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
```bash
apt update
apt install tor
```
---
## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧
Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit
[Unit]
Description=Nostr Relay Server Service
After=network.target
[Service]
Type=simple
WorkingDirectory=/opt/nrs
ExecStart=/opt/nrs/nrs-arm64
Restart=on-failure
[Install]
WantedBy=multi-user.target
```
---
## Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases).
---
## Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
```bash
mkdir -p /opt/nrs /mnt/edriver
```
---
## Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
```bash
lsblk
```
---
## Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o:
```bash
mkfs.vfat /dev/sda
```
---
## Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta `/mnt/edriver`:
```bash
mount /dev/sda /mnt/edriver
```
---
## Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
```bash
blkid
```
---
## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝
Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:
```fstab
UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
```
---
## Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta `/opt/nrs`:
```bash
cp nrs-arm64 /opt/nrs
```
---
## Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`:
```yaml
app_env: production
info:
name: Nostr Relay Server
description: Nostr Relay Server
pub_key: ""
contact: ""
url: http://localhost:3334
icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png
base_path: /mnt/edriver
negentropy: true
```
---
## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`:
```bash
cp nrs.service /etc/systemd/system/
```
Recarregue os serviços e inicie o serviço `nrs`:
```bash
systemctl daemon-reload
systemctl enable --now nrs.service
```
---
## Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha:
```torrc
HiddenServiceDir /var/lib/tor/nostr_server/
HiddenServicePort 80 127.0.0.1:3334
```
---
## Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
```bash
systemctl enable --now tor.service
```
O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`.
---
## Observações ⚠️
- Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`.
---
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-

@ 378562cd:a6fc6773
2025-01-18 00:12:47
In the ever-changing world of decentralized networks, **Nostr** (Notes and Other Stuff Transmitted by Relays) is leading the charge. Its lightweight, open design has created an ecosystem that’s as adaptable as it is revolutionary. Whether you're chatting, publishing, or experimenting with new ways to connect, Nostr provides the foundation for a truly decentralized and censorship-resistant internet.
---
### **How Nostr Works: A Quick Overview**
At its heart, Nostr is built on simplicity and decentralization. Here’s a breakdown of its core components:
1. **Public and Private Keys**:\
Your public key acts as your identity, and private keys ensure your messages are securely signed.
2. **Relays**:\
Relays are decentralized servers that distribute messages. They don’t own your data but simply pass it along to those who request it.
3. **Clients**:\
Clients are the user-facing applications where you interact with Nostr, offering diverse features and designs.
---
### **Deep Dive: Events in Nostr**
Everything on Nostr revolves around **events**, which are cryptographically signed pieces of information containing various kinds of data. Here are the types of events currently supported and their use cases:
#### **1. Note Events (Type 1)**
- **What They Are**:\
These are the bread and butter of Nostr—text-based posts, much like tweets or status updates on traditional platforms.
- **Features**:
- Can include text, media links, and hashtags.
- Interact with others through likes, replies, and boosts (reposts).
- **Use Cases**:\
Perfect for microblogging, status updates, and general social interaction.
#### **2. Profile Metadata Events (Type 0)**
- **What They Are**:\
This event type stores and updates user profile information, such as your display name, bio, profile picture, and website.
- **Features**:
- Easily editable and updated across all Nostr clients.
- Keeps your identity consistent across platforms.
- **Use Cases**:\
Makes profile portability seamless—update once, and it reflects everywhere.
#### **3. Relay List Events (Type 2)**
- **What They Are**:\
These events store a list of relays that a user is connected to or prefers to use.
- **Features**:
- Share your relay preferences across devices or clients.
- Allows automatic relay connection in supported clients.
- **Use Cases**:\
Simplifies the onboarding process for users switching clients or devices.
#### **4. Direct Message Events (Type 4)**
- **What They Are**:\
End-to-end encrypted messages sent directly between two users.
- **Features**:
- Only readable by the intended recipient.
- Supports text and basic formatting.
- **Use Cases**:\
Secure communication for personal or professional purposes.
#### **5. Reaction Events (Type 7)**
- **What They Are**:\
Events that express reactions to other events, such as likes or emojis.
- **Features**:
- Provides social feedback (e.g., showing appreciation for a post).
- Lightweight and simple to implement.
- **Use Cases**:\
Enhances engagement and interaction within the network.
#### **6. Repost Events (Type 6)**
- **What They Are**:\
Events that allow users to reshare content, similar to retweets on Twitter.
- **Features**:
- Ensures the original poster retains credit.
- Enables broader content visibility.
- **Use Cases**:\
Amplifying content that resonates with users or is worth sharing.
#### **7. Custom Event Types (Beyond Type 7)**
- **What They Are**:\
Developers can create and define custom event types for specific applications.
- **Features**:
- Flexibility to introduce entirely new functionality.
- Supported based on client and relay compatibility.
- **Use Cases**:\
Enables innovation, from collaborative editing tools to advanced publishing workflows.
---
### **What Makes Events Special?**
1. **Portability**: Events follow your public key, not the client or relay, ensuring they’re available wherever you go.
2. **Interoperability**: All events are standardized, meaning any Nostr client can understand and process them.
3. **Extensibility**: Through custom event types, the protocol encourages experimentation and development.
---
### **Primal: A Favorite Client for Engaging Events**
Among the many clients, **Primal** stands out as a favorite for how it handles Nostr events. Its emphasis on **content discovery** and **rich user interaction** makes it an excellent choice for exploring everything the protocol offers. Whether it’s crafting note events, managing profile metadata, or diving into direct messaging, Primal delivers a polished experience that feels seamless.
---
### **The Future of Nostr Events**
As Nostr continues to evolve, so will the events it supports. Imagine event types for live streaming, collaborative workspaces, or even decentralized governance. The possibilities are limitless, driven by the creativity of the developers and the needs of the community.
**Have you explored the potential of Nostr events yet? What’s your favorite client or feature? Let’s discuss below!** ⚡️
#Nostr #Primal #Decentralization #NostrEvents #FutureOfWeb
-

@ e3ba5e1a:5e433365
2025-01-13 16:47:27
My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity.
A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur.
The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior.
And there are plenty of incentives beyond our direct control\! My son is *also* incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take.
## Why incentives matter
A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could **just** do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example:
* If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning.
* If people would just use the recycling bin, we wouldn’t have such a landfill problem.
* If people would just stop being lazy, our team would deliver our project on time.
In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally.
* The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do.
* No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle.
* If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.

My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want.
If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is.
## Running a company
Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions.
Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good.
What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off.
Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning.
When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.

Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks\! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money.
There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals.
Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature.
# Moral hazard
Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings.
What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.

But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I *don’t* turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all.
This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as:
1. We’re so habituated to turning off the water that we don’t even consider *not* turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off.
2. Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created.
3. We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?)
Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard.
A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard.
It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend?
And since we’re talking about the government already…
## Government moral hazards
As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a *huge* number of examples of moral hazards. I decided to cherry-pick a few for this post.
The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people?
The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet.
If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior\! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups.
You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”

And here’s the absolute best part of this: I can’t even truly blame either California *or* Wall Street. (I mean, I *do* blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits.
There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions.
# Non-monetary competition
At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home.
In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.)
Anyway, my professor’s wife had a friend. My professor described in *great* detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas.
This is a demonstration of *non-monetary compensation*. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules.
The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become *wealthier and whiter*, the exact opposite of their desired outcome. Why would that happen?
Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky.
She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls.
So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites.
You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences.
## Bureaucracy
These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences.
Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings.
Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could\! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate.
# Government incentivized behavior
This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples:
* Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to [malinvestment](https://en.wikipedia.org/wiki/Malinvestment) and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience.
* Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise.
* During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation.
* The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen.
* Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example).
* Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as [high living](https://www.youtube.com/watch?v=ZwNDd2_beTU).)
# Conclusion
The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives.
We can bemoan these realities all we want, but they *are* realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People *should* take advantage of the incentives around them. Because if they don’t, someone else will.
(If you want a literary example of that last comment, see the horse in Animal Farm.)
How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula:
* Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people.
* Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them.
* And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example.
And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining\!
-

@ e460cb14:01bb5ced
2025-01-13 13:30:13
## Brief intro
#glostr is a pet-project of mine to better understand how #nostr works. Since I'm an engineer, and somewhere between a game programmer and a graphics programmer, I'll do what I do best: write some graphics thing no one (but me) will use.
## Zappable Shadertoy
So, the idea is to create a small platform on top of #nostr where people can create, visualize, and share computer graphics programs (aka: shaders). Code shiny thing, see shiny, share shiny thing, and zap shiny thing. If you're familiar with [Shadertoy](https://shadertoy.com), #glostr is just that: **zappable shadertoy**.

## Milestone Zero
So, first step was to write a quick and dirty prototype client (remember, I specc'd into game dev, not into web dev, so I really mean _quick_ and I really mean _dirty_). I got an [ace editor](https://github.com/ajaxorg/ace) thing working, duct-taped it to a basic WebGL render, stole a couple shaders from shadertoy (jk, I gave credit), poured some CSS magic, glued some `nostr-rx`, and published it to GitHub pages.
After 2 or 3 days of iterating, and with some assistance from an LLM, you can see the result linked on my [notes](nostr:nevent1qqsf45hy66cw55e3s2ewt6upe3m073q875hmjjtyyre7qtaxw9hl5scpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qu3svk99639mcdfn43s2nawg4a2j4ejmgrq2n63l4t67wzqdmtnkss70qyf).
Yes. I used `kind 1` posts to spam GLSL code.
I AM SORRY. I KNOW BETTER NOW. I SWEAR.
So, right now #glostr is:
- Taking an npub on the url after the #
- Rendering all `kind 1` posts from that npub containing GLSL code between \`\`\`s
- Allowing the user to edit the code in real time

## Next Steps
What now? [Gorila](nostr:npub19tv378w29hx4ljy7wgydreg9nu96czrs6clu8wkzr3af8z86rr7sujx4xe) made me realize my _obvious_ `kind 1` spamming. After some brainstorming and skimming through NIPs and kinds, we arrived at the conclusion that [Long-form Notes (NIP-23)](https://github.com/nostr-protocol/nips/blob/master/23.md) are best suited for the content I want #glostr to display:
- Format is Markdown, which I like and which I was already somewhat expecting.
- It's editable content, so mistakes can be amended, which is more than usual in shader programming.
So, the next features I want to add are:
- Logging in
- Posting NIP-23 Notes
- Getting, parsing, and showing NIP-23 Notes
## When
I'll only work on this on the weekends for now, so I don't know. This is a pet project for fun right now.
## Wrapping Up
Repo: https://github.com/rowdaboat/glostr
Try it: https://rowdaboat.github.io/glostr/
As this is a Long-Form Note in itself, I'll finish it by sharing a shader based on [Inigo Quilez's awesome polygon shader](https://www.shadertoy.com/view/wdBXRW). This note should show as a shader on #glostr in the next iteration, but you can copy and paste the code in the editor for now:
```glsl
#version 300 es
precision mediump float;
uniform vec2 u_resolution;
uniform float u_time;
out vec4 fragColor;
const int N = 6;
vec3 yellow = vec3(0.45, 0.3, 0.15);
vec3 lightBlue = vec3(0.65, 0.85, 1.0);
float polygon(in vec2 p, in vec2[N] v)
{
const int num = v.length();
float d = dot(p - v[0], p - v[0]);
float s = 1.;
for(int i=0, j=num-1; i < num; j=i, i++ )
{
vec2 e = v[j] - v[i];
vec2 w = p - v[i];
vec2 b = w - e * clamp(dot(w, e) / dot(e, e), 0.0, 1.0);
d = min(d, dot(b,b));
bvec3 condition = bvec3(
p.y >= v[i].y,
p.y < v[j].y,
e.x * w.y > e.y * w.x
);
if (all(condition) || all(not(condition)))
s =- s;
}
return s * sqrt(d);
}
void main()
{
vec2 p = (2.0 * gl_FragCoord.xy - u_resolution.xy) / u_resolution.y;
float d = polygon(p, vec2[](
vec2( .2, .8), vec2(-.5, -.125), vec2( .0, -.125),
vec2(-.2, -.8), vec2( .5, .125), vec2( .0, .125)
));
vec3 color = d < 0.0 ? yellow : lightBlue;
color *= 1. - exp(-40. * abs(d));
color *= .8 + .2 * sin(10.0 * d - 10. * u_time) * sin(-1.25 * u_time);
color *= exp(1. - d * 2.25);
fragColor = vec4(color, 1.0);
}
```
-

@ a95c6243:d345522c
2025-01-13 10:09:57
*Ich begann, Social Media aufzubauen,* *\
um den Menschen eine Stimme zu geben.* *\
Mark Zuckerberg*
**Sind euch auch die Tränen gekommen, als ihr Mark Zuckerbergs** **[Wendehals-Deklaration](https://www.facebook.com/zuck/videos/1525382954801931)** bezüglich der Meinungsfreiheit auf seinen Portalen gehört habt? Rührend, oder? Während er früher die offensichtliche Zensur leugnete und später die Regierung Biden dafür verantwortlich machte, will er nun angeblich «die Zensur auf unseren Plattformen drastisch reduzieren».
**«Purer** **[Opportunismus](https://transition-news.org/facebook-grunder-zuckerberg-vom-trump-gegner-zum-trump-buddy-und-anti-zensor)» ob des anstehenden Regierungswechsels wäre als Klassifizierung** viel zu kurz gegriffen. Der jetzige Schachzug des Meta-Chefs ist genauso Teil einer kühl kalkulierten Business-Strategie, wie es die 180 Grad umgekehrte Praxis vorher war. Social Media sind ein höchst lukratives Geschäft. Hinzu kommt vielleicht noch ein bisschen verkorkstes Ego, weil derartig viel Einfluss und Geld sicher auch auf die Psyche schlagen. Verständlich.
> «Es ist an der Zeit, zu unseren Wurzeln der freien Meinungsäußerung auf Facebook und Instagram zurückzukehren. Ich begann, Social Media aufzubauen, um den Menschen eine Stimme zu geben», sagte Zuckerberg.
**Welche Wurzeln? Hat der Mann vergessen, dass er von der Überwachung,** dem Ausspionieren und dem Ausverkauf sämtlicher Daten und digitaler Spuren sowie der Manipulation seiner «Kunden» lebt? Das ist knallharter Kommerz, nichts anderes. Um freie Meinungsäußerung geht es bei diesem Geschäft ganz sicher nicht, und das war auch noch nie so. Die Wurzeln von Facebook liegen in einem Projekt des US-Militärs mit dem Namen [«LifeLog»](https://norberthaering.de/macht-kontrolle/lifelog/). Dessen Ziel war es, «ein digitales Protokoll vom Leben eines Menschen zu erstellen».
**Der Richtungswechsel kommt allerdings nicht überraschend.** Schon Anfang Dezember hatte Meta-Präsident Nick Clegg von «zu hoher Fehlerquote bei der Moderation» von Inhalten [gesprochen](https://www.theverge.com/2024/12/3/24311513/meta-content-moderation-mistakes-nick-clegg). Bei der Gelegenheit erwähnte er auch, dass Mark sehr daran interessiert sei, eine aktive Rolle in den Debatten über eine amerikanische Führungsrolle im technologischen Bereich zu spielen.
**Während Milliardärskollege und Big Tech-Konkurrent Elon Musk bereits seinen Posten** in der kommenden Trump-Regierung in Aussicht hat, möchte Zuckerberg also nicht nur seine Haut retten – Trump hatte ihn einmal einen «Feind des Volkes» genannt und ihm lebenslange Haft angedroht –, sondern am liebsten auch mitspielen. KI-Berater ist wohl die gewünschte Funktion, wie man nach einem Treffen Trump-Zuckerberg hörte. An seine [Verhaftung](https://transition-news.org/nicht-telegram-grunder-durow-sondern-zuckerberg-sollte-in-haft-sitzen-wegen-des) dachte vermutlich auch ein weiterer Multimilliardär mit eigener Social Media-Plattform, Pavel Durov, als er Zuckerberg jetzt [kritisierte](https://www.berliner-zeitung.de/news/ende-des-faktenchecks-bei-meta-telegram-gruender-kritisiert-zuckerberg-und-spricht-warnung-aus-li.2287988) und gleichzeitig warnte.
**Politik und Systemmedien drehen jedenfalls durch** – was zu viel ist, ist zu viel. Etwas weniger Zensur und mehr Meinungsfreiheit würden die Freiheit der Bürger schwächen und seien potenziell vernichtend für die Menschenrechte. Zuckerberg setze mit dem neuen Kurs die Demokratie aufs Spiel, das sei eine «Einladung zum nächsten [Völkermord](https://archive.is/PYeH0)», ernsthaft. Die Frage sei, ob sich die [EU gegen Musk und Zuckerberg](https://www.handelsblatt.com/politik/international/internet-regulierung-kann-sich-die-eu-gegen-musk-und-zuckerberg-behaupten/100099373.html) behaupten könne, Brüssel müsse jedenfalls hart durchgreifen.
**Auch um die** **[Faktenchecker](https://www.welt.de/kultur/medien/article255065352/Metas-Kurswechsel-Zuckerbergs-Entscheidung-und-die-Folgen-fuer-deutsche-Faktenchecker.html)** **macht man sich Sorgen.** Für die deutsche Nachrichtenagentur *dpa* und die «Experten» von *Correctiv*, die (noch) Partner für Fact-Checking-Aktivitäten von Facebook sind, sei das ein «lukratives Geschäftsmodell». Aber möglicherweise werden die Inhalte ohne diese vermeintlichen Korrektoren ja sogar besser. Anders als Meta wollen jedoch Scholz, Faeser und die *Tagesschau* keine Fehler zugeben und zum Beispiel *Correctiv*-[Falschaussagen](https://www.berliner-zeitung.de/politik-gesellschaft/correctiv-falschaussagen-exklusiv-scholz-faeser-und-tagesschau-wollen-sich-fuer-verbreitung-nicht-entschuldigen-li.2288126) einräumen.
**Bei derlei dramatischen Befürchtungen wundert es nicht,** dass der öffentliche Plausch auf X zwischen Elon Musk und AfD-Chefin Alice Weidel von 150 EU-Beamten überwacht wurde, falls es irgendwelche Rechtsverstöße geben sollte, die man ihnen ankreiden könnte. Auch der Deutsche Bundestag war wachsam. Gefunden haben dürften sie nichts. Das Ganze war eher eine Show, viel Wind wurde gemacht, aber letztlich gab es nichts als heiße Luft.
**Das** **[Anbiedern](https://transition-news.org/who-biedert-sich-bei-trump-an)** **bei Donald Trump ist indes gerade in Mode.** Die Weltgesundheitsorganisation (WHO) tut das auch, denn sie fürchtet um Spenden von über einer Milliarde Dollar. Eventuell könnte ja Elon Musk auch hier künftig aushelfen und der Organisation sowie deren größtem privaten Förderer, Bill Gates, etwas unter die Arme greifen. Nachdem Musks KI-Projekt xAI kürzlich von BlackRock & Co. [sechs Milliarden](https://x.ai/blog/series-c) eingestrichen hat, geht da vielleicht etwas.
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/milliardenschwere-wetterfahnchen-und-windmaschinen)*** erschienen.
-

@ 0d97beae:c5274a14
2025-01-11 16:52:08
This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs
## The reason why we have broken money
Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world.
In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes.
However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore.
Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too.
Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it.
## Bitcoin overcomes the "transfer of hard money" problem
Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design.
Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it.
Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive.
Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold.
## Bitcoin blurs the line between commodity and technology
Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules.
At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable.
Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases.
## The dangers of derivatives
A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold.
In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin.
Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense.
## Learn for yourself
If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody".
There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
-

@ 37fe9853:bcd1b039
2025-01-11 15:04:40
yoyoaa
-

@ 62033ff8:e4471203
2025-01-11 15:00:24
收录的内容中 kind=1的部分,实话说 质量不高。
所以我增加了kind=30023 长文的article,但是更新的太少,多个relays 的服务器也没有多少长文。
所有搜索nostr如果需要产生价值,需要有高质量的文章和新闻。
而且现在有很多机器人的文章充满着浪费空间的作用,其他作用都用不上。
https://www.duozhutuan.com 目前放的是给搜索引擎提供搜索的原材料。没有做UI给人类浏览。所以看上去是粗糙的。
我并没有打算去做一个发microblog的 web客户端,那类的客户端太多了。
我觉得nostr社区需要解决的还是应用。如果仅仅是microblog 感觉有点够呛
幸运的是npub.pro 建站这样的,我觉得有点意思。
yakihonne 智能widget 也有意思
我做的TaskQ5 我自己在用了。分布式的任务系统,也挺好的。
-

@ f3df9bc0:a95119eb
2025-01-10 02:58:08
# MPT Equations
### Geometric Mean
$$
\bar{x} = (\prod_{i=1}^{n} x_i)^{1 \over n }
$$
### Covariance
$$
COV(x,y) = {1\over{n-1}} \sum_{i=1}^{n}{(x_i - \bar{x})(y_i - \bar{y})}
$$
where $\bar{x}$ and $\bar{y}$ are the **geometric** mean.
### Variance
$$
VAR(x) = {1\over{n-1}} \sum_{i=1}^{n}{(x_i - \bar{x})^2}
$$
### Standard Deviation
$$
\sigma_x=\sqrt{VAR(x)}
$$
### Correlation Coefficient
$$
\rho_{xy} = {COV(x, y) \over \sigma_x\sigma_y}
$$
### Portfolio Variance
$$
VAR(P) = \sum_{ij}w_i w_j COV(i, j)
$$
Where $w_i$ and $w_j$ are the normalized weight of the asset in the portfolio.
Note that this summation should include when $i = j$. In this case $COV(i, j) = VAR(i) = VAR(j)$
### Expected Return
$$
E_P = \sum_{i}w_i E_i
$$
Where $w_i$ is the normalized weight of the asset, and $E_i$ is the expected return of the individual asset.
-

@ f33c8a96:5ec6f741
2025-01-09 18:38:50
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls>
<source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-5.mp4" type="video/mp4"/>
<source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-5.webm" type="video/webm"/>
</video></div>
# JavaScript: Building Your First Interactive Web App
## Introduction
In this lesson, we'll bring our web pages to life by adding dynamic functionality with JavaScript. We'll build a real-world application that displays and updates Bitcoin prices in real-time, teaching core JavaScript concepts along the way.
## Project Overview: Bitcoin Price Tracker
We'll build a web application that:
- Displays current Bitcoin price
- Updates automatically every 3 seconds
- Allows currency switching
- Includes interactive controls
- Shows current date/time
## Core JavaScript Concepts
### 1. Variables and Data Types
```javascript
// Variables can be declared with let or const
let currentCurrency = "USD"; // Can be changed
const interval = 3000; // Cannot be changed
// Basic data types
const price = 45000; // Number
const isVisible = true; // Boolean
const currency = "USD"; // String
```
### 2. DOM Manipulation
```javascript
// Getting elements
const priceElement = document.getElementById('price');
const button = document.getElementById('refresh-button');
// Modifying content
priceElement.textContent = `${price} ${currency}`;
// Changing styles
priceElement.style.display = 'none';
```
### 3. Event Listeners
```javascript
// Basic click handler
button.addEventListener('click', () => {
fetchBitcoinPrice();
});
// Change event for select elements
selector.addEventListener('change', (event) => {
handleCurrencyChange(event.value);
});
```
### 4. Async Operations & Fetch API
```javascript
async function fetchBitcoinPrice() {
try {
const response = await fetch(apiUrl);
const data = await response.json();
updatePrice(data.price);
} catch (error) {
console.error('Error:', error);
}
}
```
## Project Structure
### HTML Setup
```html
<!DOCTYPE html>
<html lang="en">
<head>
<title>Bitcoin Price Tracker</title>
<link rel="stylesheet" href="style.css">
<script src="index.js" defer></script>
</head>
<body>
<h1>Current Bitcoin Price</h1>
<p>The price is: <span id="price"></span></p>
<!-- Additional elements -->
</body>
</html>
```
### Core Functionality Implementation
1. **Setting Up the Timer**
```javascript
// Update price every 3 seconds
setInterval(fetchBitcoinPrice, 3000);
// Update date/time every second
setInterval(updateDateTime, 1000);
```
2. **Currency Selection**
```javascript
function handleCurrencyChange(newCurrency) {
currentCurrency = newCurrency;
fetchBitcoinPrice();
}
```
3. **Toggle Visibility**
```javascript
function togglePriceVisibility() {
const price = document.getElementById('price');
price.style.display = price.style.display === 'none'
? 'inline'
: 'none';
}
```
## Best Practices
### 1. Error Handling
- Always use try/catch with async operations
- Provide meaningful error messages
- Handle edge cases gracefully
### 2. Code Organization
- Keep functions focused and small
- Use meaningful variable names
- Group related functionality
- Add comments for clarity
### 3. Performance
- Avoid unnecessary DOM updates
- Use appropriate update intervals
- Clean up intervals when not needed
## Common Challenges & Solutions
### 1. API Issues
```javascript
// Handle API failures gracefully
catch (error) {
priceElement.textContent = 'Price unavailable';
console.error('API Error:', error);
}
```
### 2. Currency Formatting
```javascript
function formatPrice(price, currency) {
return new Intl.NumberFormat('en-US', {
style: 'currency',
currency: currency
}).format(price);
}
```
### 3. Time Zones
```javascript
function getLocalTime() {
return new Date().toLocaleString();
}
```
## Extending the Project
Consider adding these features for practice:
1. Price change indicators (up/down arrows)
2. Historical price chart
3. Multiple cryptocurrency support
4. Price alerts
5. Local storage for settings
## Debugging Tips
### Using Console
```javascript
console.log('Price fetched:', price);
console.error('Error occurred:', error);
console.table(priceHistory);
```
### Chrome DevTools
1. Network tab for API calls
2. Console for errors
3. Elements for DOM inspection
4. Sources for debugging
## Additional Resources
- MDN JavaScript Guide
- JavaScript.info
- CoinGecko API Documentation
- Chrome DevTools Documentation
## Next Steps
1. Add styling with CSS
2. Implement additional features
3. Learn about React for more complex applications
4. Explore other APIs and cryptocurrencies
Remember: The best way to learn is by doing. Don't be afraid to break things and experiment with the code. The developer console is your friend for debugging and understanding what's happening in your application.
Happy coding! 🚀
-

@ df173277:4ec96708
2025-01-09 17:12:08
> Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\
> [Join the waitlist to get early access.](https://trymaple.ai)
We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI.
Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations.
#### Building a Private Foundation
Maple is built on our flagship product, [OpenSecret](https://opensecret.cloud), a backend platform for app developers that turns private encryption on by default. [The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do.](nostr:naddr1qvzqqqr4gupzphchxfm3ste32hfhkvczzxapme9gz5qvqtget6tylyd7wa8vjecgqqe5jmn5wfhkgatrd9hxwt20wpjku5m9vdex2apdw35x2tt9de3hy7tsw3jkgttzv93kketwvskhgur5w9nx5h52tpj) We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win.
#### The Power of Encrypted AI Chat
AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short.
Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us.
#### Technical Overview
So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects:
- **Private Key:** Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data.
- **Secure Servers:** Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations.
- **Encrypted Sync:** One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised.
- **Attestation and Open Code:** We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public.
- **Open Source LLM:** Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased.
#### Personal and Work Use
Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe.
#### Local v Cloud
Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds.
#### Why the Maple name?
Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment.
#### Join the Waitlist
Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. [Join our waitlist today to be among the first to experience the power of private AI chat.](https://trymaple.ai)
[](https://trymaple.ai/waitlist)
-

@ df173277:4ec96708
2025-01-09 17:02:52
> OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. [Join our waitlist to get early access.](https://opensecret.cloud)
In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion.
Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online?
Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches?
> Cryptography at scale is hard.
#### The Cloud
The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers.
The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage.
> Private key encryption needs a UX upgrade.
## Enter OpenSecret
OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute.
Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.

### Private Key Management
Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone.
OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account.
The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.

### Encrypted Sync
With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go.
The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them.
### Private AI
Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything.
OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk.
**Check out Maple AI**\
Try private AI for yourself! We built an app built with this service called [Maple AI](https://trymaple.ai). It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. [Learn more about Maple AI - Private chat in the announcement post.](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/)

### Confidential Compute
Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave.
It's the new version of that lock on your web browser. When you see it, you know you're secure.

#### **But do we want our secrets to be open?**
OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable.
On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data.
> Don't trust, verify.
### **Join the Movement**
We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, [send us a message to get early access.](https://opensecret.cloud)
Users and companies deserve better encryption and privacy.\
Together, let's make that a reality.
[](https://opensecret.cloud)
-

@ f33c8a96:5ec6f741
2025-01-09 16:22:24
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls>
<source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-4.mp4" type="video/mp4"/>
<source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-4.webm" type="video/webm"/>
</video></div>
# CSS Fundamentals: Styling Your First Webpage
## Introduction
In our previous lesson, we created the structure of our webpage with HTML. Now, we'll learn how to style it using CSS (Cascading Style Sheets). While HTML provides the bones of our webpage, CSS adds the visual presentation - the colors, layouts, spacing, and overall aesthetics.
## What is CSS?
### Definition
CSS (Cascading Style Sheets) is a stylesheet language that controls the visual presentation of HTML documents. Think of it like the paint, decorations, and interior design of a house - it determines how everything looks and is arranged.
### Key Concepts
1. **Styling Capabilities**
- Fonts and typography
- Colors and backgrounds
- Margins and padding
- Element sizes
- Visual effects
- Layout and positioning
2. **Cascading Nature**
- Styles can be inherited from parent elements
- Multiple styles can apply to the same element
- Specificity determines which styles take precedence
- Styles "cascade" down through your document
## Basic CSS Syntax
```css
selector {
property: value;
}
```
### Example:
```css
h1 {
color: blue;
font-size: 24px;
margin-bottom: 20px;
}
```
## Connecting CSS to HTML
### Method 1: External Stylesheet (Recommended)
```html
<link rel="stylesheet" href="style.css">
```
### Method 2: Internal CSS
```html
<style>
h1 {
color: blue;
}
</style>
```
### Method 3: Inline CSS (Use Sparingly)
```html
<h1 style="color: blue;">Title</h1>
```
## The Box Model
Every HTML element is treated as a box in CSS, with:
```
┌──────────────────────┐
│ Margin │
│ ┌──────────────┐ │
│ │ Border │ │
│ │ ┌──────────┐ │ │
│ │ │ Padding │ │ │
│ │ │ ┌──────┐ │ │ │
│ │ │ │ │ │ │ │
│ │ │ │Content│ │ │ │
│ │ │ │ │ │ │ │
│ │ │ └──────┘ │ │ │
│ │ └──────────┘ │ │
│ └──────────────┘ │
└──────────────────────┘
```
- **Content**: The actual content of the element
- **Padding**: Space between content and border
- **Border**: The border around the padding
- **Margin**: Space outside the border
## CSS Units
### Absolute Units
- `px` - pixels
- `pt` - points
- `cm` - centimeters
- `mm` - millimeters
- `in` - inches
### Relative Units
- `%` - percentage relative to parent
- `em` - relative to font-size
- `rem` - relative to root font-size
- `vh` - viewport height
- `vw` - viewport width
## Practical Example: Styling Our Webpage
### 1. Basic Page Setup
```css
body {
min-height: 100vh;
margin: 0;
font-family: Arial, sans-serif;
background-color: #f0f0f0;
display: flex;
flex-direction: column;
}
```
### 2. Header Styling
```css
header {
background-color: #333;
color: white;
padding: 20px;
text-align: center;
}
```
### 3. Main Content Area
```css
main {
max-width: 800px;
margin: 0 auto;
padding: 20px;
flex: 1;
}
```
### 4. Footer Styling
```css
footer {
background-color: #333;
color: white;
padding: 10px;
text-align: center;
}
```
## Layout with Flexbox
### Basic Concept
Flexbox is a modern layout system that makes it easier to create flexible, responsive layouts.
### Key Properties
```css
.container {
display: flex;
flex-direction: row | column;
justify-content: center | space-between | space-around;
align-items: center | flex-start | flex-end;
}
```
### Common Use Cases
1. Centering content
2. Creating navigation bars
3. Building responsive layouts
4. Equal-height columns
5. Dynamic spacing
## Best Practices
### 1. Organization
- Use consistent naming conventions
- Group related styles together
- Comment your code for clarity
- Keep selectors simple and specific
### 2. Performance
- Avoid unnecessary specificity
- Use shorthand properties when possible
- Minimize redundant code
- Consider load time impact
### 3. Maintainability
- Use external stylesheets
- Follow a consistent formatting style
- Break large stylesheets into logical files
- Document important design decisions
## Debugging CSS
### Common Tools
1. Browser Developer Tools
- Element inspector
- Style inspector
- Box model viewer
### Common Issues
1. Specificity conflicts
2. Inheritance problems
3. Box model confusion
4. Flexbox alignment issues
## Exercises
### 1. Style Modifications
Try modifying these properties in your stylesheet:
```css
/* Change colors */
header {
background-color: #4a90e2;
}
/* Adjust spacing */
main {
padding: 40px;
}
/* Modify typography */
h1 {
font-size: 32px;
font-weight: bold;
}
```
### 2. Layout Challenge
Create a card layout using Flexbox:
```css
.card-container {
display: flex;
justify-content: space-between;
gap: 20px;
}
.card {
flex: 1;
padding: 20px;
background: white;
border-radius: 8px;
box-shadow: 0 2px 4px rgba(0,0,0,0.1);
}
```
## Additional Resources
### Learning Tools
1. [Flexbox Froggy](https://flexboxfroggy.com/) - Interactive Flexbox learning game
2. [CSS-Tricks](https://css-tricks.com) - Excellent CSS reference and tutorials
3. [MDN CSS Documentation](https://developer.mozilla.org/en-US/docs/Web/CSS)
### Practice Projects
1. Style your personal webpage
2. Create a responsive navigation menu
3. Build a flexible card layout
4. Design a custom button style
Remember: CSS is both an art and a science. Don't be afraid to experiment and break things - that's how you'll learn the most. The key is to start simple and gradually add complexity as you become more comfortable with the basics.
Next up, we'll dive into JavaScript to add interactivity to our webpage! 🚀
-

@ f33c8a96:5ec6f741
2025-01-09 16:20:27
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls>
<source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-3.mp4" type="video/mp4"/>
<source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-3.webm" type="video/webm"/>
</video></div>
## What is HTML?
HTML (HyperText Markup Language) is the foundation of all webpages. Think of it as the framing of a house - it provides the basic structure that everything else builds upon.
### Key Concepts
- HTML is a markup language, not a programming language
- It tells browsers how to structure web content
- Every HTML element is like a building block
- Browsers interpret HTML to display content
## The Building Analogy
When building a webpage, think of it like constructing a house:
- **HTML**: The framing and structure (walls, rooms, layout)
- **CSS**: The design elements (paint, decorations, styling)
- **JavaScript**: The functionality (plumbing, electrical, moving parts)
## Basic HTML Structure
### 1. HTML Boilerplate
Every webpage starts with a basic template:
```html
<!DOCTYPE html>
<html>
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Your Page Title</title>
</head>
<body>
<!-- Your content goes here -->
</body>
</html>
```
### 2. Understanding the Parts
- `<!DOCTYPE html>`: Tells browsers this is an HTML5 document
- `<html>`: The root element of the page
- `<head>`: Contains metadata about the document
- `<body>`: Contains the visible content
## Essential HTML Elements
### 1. Headings
HTML has six levels of headings:
```html
<h1>Main Title</h1>
<h2>Subtitle</h2>
<h3>Section Header</h3>
<!-- ... -->
<h6>Smallest Heading</h6>
```
### 2. Paragraphs
```html
<p>This is a paragraph of text. It can contain as much text as you need.</p>
```
### 3. Images
```html
<img src="path-to-image.jpg" alt="Description of image" width="300">
```
### 4. Links
```html
<a href="https://example.com">Click here</a>
```
## HTML Attributes
Attributes provide additional information or modify HTML elements:
```html
<tag attribute="value">Content</tag>
```
Common attributes:
- `src`: Source path for images
- `href`: Destination for links
- `alt`: Alternative text for images
- `class`: CSS class names
- `id`: Unique identifier
- `style`: Inline CSS styles
## Semantic HTML
### What is Semantic HTML?
Semantic HTML uses meaningful tags that describe their content's purpose. This improves:
- Accessibility
- SEO (Search Engine Optimization)
- Code readability
- Maintainability
### Common Semantic Elements
```html
<header>
<!-- Site header content -->
</header>
<nav>
<!-- Navigation menu -->
</nav>
<main>
<!-- Main content -->
<article>
<!-- Self-contained content -->
</article>
<section>
<!-- Grouped content -->
</section>
</main>
<footer>
<!-- Site footer content -->
</footer>
```
### Non-Semantic vs Semantic Example
Instead of:
```html
<div class="header">
<div class="navigation">
<div class="nav-item">Home</div>
</div>
</div>
```
Use:
```html
<header>
<nav>
<a href="/">Home</a>
</nav>
</header>
```
## Building Your First Webpage
### 1. Basic Structure
```html
<!DOCTYPE html>
<html>
<head>
<title>My First Webpage</title>
</head>
<body>
<header>
<h1>Welcome to My First Webpage!</h1>
</header>
<main>
<section>
<h2>About Me</h2>
<p>Hi, I'm learning web development with PlebDevs!</p>
</section>
<section>
<h2>My Interests</h2>
<p>I'm interested in Bitcoin, programming, and building cool stuff!</p>
</section>
</main>
<footer>
<p>Created by [Your Name] - 2024</p>
</footer>
</body>
</html>
```
## Best Practices
### 1. Structure
- Use proper indentation
- Keep code organized and readable
- Use semantic elements when possible
- Include all required elements (`DOCTYPE`, `html`, `head`, `body`)
### 2. Content
- Use appropriate heading levels (start with `h1`)
- Write descriptive `alt` text for images
- Keep content meaningful and organized
- Use comments to explain complex sections
### 3. Accessibility
- Use semantic HTML elements
- Provide alternative text for images
- Maintain a logical heading structure
- Ensure content makes sense when read linearly
## Common Issues and Solutions
### Problem: Images Not Loading
```html
<!-- Wrong -->
<img src="image.jpg">
<!-- Right -->
<img src="./images/image.jpg" alt="Description">
```
### Problem: Links Not Working
```html
<!-- Wrong -->
<a>Click here</a>
<!-- Right -->
<a href="https://example.com">Click here</a>
```
## Next Steps
1. **Practice Building**
- Create a personal webpage about yourself
- Include different types of content (text, images, links)
- Use semantic HTML elements
2. **Experiment with Structure**
- Try different layouts
- Use various HTML elements
- Pay attention to semantic meaning
3. **Prepare for CSS**
- Think about how you want your page to look
- Consider what styles you'll want to add
- Plan your layout structure
## Exercise: Create Your Profile Page
Try creating a simple profile page using what you've learned:
1. Use the HTML boilerplate
2. Add a header with your name
3. Include an "About Me" section
4. Add a photo (if you want)
5. List your interests or goals
6. Add a footer with contact information
Remember to:
- Use semantic HTML
- Include appropriate headings
- Add descriptive alt text for images
- Keep your code clean and well-organized
## Additional Resources
- [MDN HTML Guide](https://developer.mozilla.org/en-US/docs/Web/HTML)
- [HTML5 Doctor (Semantic Elements)](http://html5doctor.com/)
- [W3Schools HTML Tutorial](https://www.w3schools.com/html/)
Remember: HTML is the foundation of web development. Take time to understand these basics well, as they'll serve as the building blocks for everything else you'll learn. Happy coding! 🚀
-

@ f33c8a96:5ec6f741
2025-01-09 16:18:40
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls>
<source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-2.mp4" type="video/mp4"/>
<source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-2.webm" type="video/webm"/>
</video></div>
# Setting Up Git and GitHub: A Developer's Foundation
## Lesson Overview
In this lesson, we'll establish one of the most important foundations of your development journey: version control with Git and GitHub. This knowledge will enable you to track your code, back it up in the cloud, and start building your developer portfolio.
## Prerequisites
- Visual Studio Code installed
- Terminal/Command Line basics
- GitHub account (we'll create one in this lesson)
## Key Learning Objectives
- Understand what Git and GitHub are and why they're essential
- Set up Git locally and connect it to GitHub
- Learn basic Git commands and workflow
- Create your first repository and commit
- Establish good Git habits for your developer journey
## What is Git and GitHub?
### Git: Your Local Version Control
- A version control system that tracks code changes over time
- Prevents accidental overwrites of your work
- Enables multiple developers to work on the same project safely
- Runs locally on your machine
### GitHub: Your Code in the Cloud
- A web-based platform that extends Git
- Cloud storage for your code repositories
- Enables code sharing and collaboration
- Includes features like:
- Issue tracking
- Pull requests
- Project management tools
- Code review capabilities
## Why Use GitHub?
### 1. Portfolio Building
- Acts as your "proof of work" as a developer
- Shows your coding activity through contribution graphs
- Demonstrates your consistency and dedication
- Serves as a public showcase of your projects
### 2. Collaboration and Learning
- Access millions of open-source projects
- Learn from other developers' code
- Contribute to real-world projects
- Get feedback on your code
- Work effectively in teams
### 3. Code Safety and Access
- All your code is safely stored in the cloud
- Access your projects from anywhere
- Never lose your work due to computer issues
## Essential GitHub Terminology
| Term | Definition |
|------|------------|
| Repository (Repo) | A folder containing your project files and version history |
| Commit | A saved change or addition to your code |
| Staging | Marking changes to be included in your next commit |
| Push | Sending your local commits to GitHub |
| Branch | A separate version of your code for new features or experiments |
| Pull Request (PR) | A request to merge changes from one branch to another |
| Clone | Creating a local copy of a remote repository |
| Fork | Creating your own copy of someone else's repository |
## Hands-on Practice
### Setting Up Git
1. Install Git from https://git-scm.com/downloads
2. Configure your identity:
```bash
git config --global user.name "Your Name"
git config --global user.email "your.email@example.com"
```
### Your First Repository
1. Create a new repository on GitHub named "hello-world"
2. Initialize Git locally:
```bash
git init
git add .
git commit -m "My first commit"
git remote add origin <your-repository-url>
git push -u origin main
```
## Basic Git Workflow Quick Reference
### Pushing Code to GitHub
```bash
# 1. Stage your changes
git add .
# 2. Commit your changes with a message
git commit -m "Describe your changes here"
# 3. Push to GitHub
git push
```
### Getting Code from GitHub
```bash
# If you already have the repository locally:
git pull
# If you need to download a repository:
git clone https://github.com/username/repository.git
```
## Building Good Habits
### Daily Git Practice
- Make it a goal to push code every day
- Even small changes count
- Use your GitHub contribution graph as motivation
- Track your progress over time
### Best Practices
1. Commit often with clear messages
2. Pull before you start working
3. Push your changes when you finish
4. Keep each project in its own repository
5. Include README files to explain your projects
## Common Issues and Solutions
### "No upstream branch" Error
If you see this error when pushing:
```bash
git push --set-upstream origin main
```
### Changes Not Showing Up
1. Check if changes are staged:
```bash
git status
```
2. Make sure you've committed:
```bash
git commit -m "Your message"
```
3. Verify you've pushed:
```bash
git push
```
## Exercise: Start Your Journey
1. Create your GitHub account if you haven't already
2. Set up Git locally using the commands we covered
3. Create your first repository named "hello-world"
4. Make your first commit
5. Push your code to GitHub
6. Make a habit of pushing code daily
## Additional Resources
- [GitHub Documentation](https://docs.github.com)
- [Git Documentation](https://git-scm.com/doc)
- Practice with [GitHub Learning Lab](https://lab.github.com)
## Next Steps
- Start tracking all your code projects with Git
- Begin building your portfolio on GitHub
- Join the open-source community
- Collaborate with other developers
Remember: Every developer started where you are now. The key is consistency and persistence. Make pushing code to GitHub a daily habit, and you'll be amazed at your progress over time.
Happy coding! 🚀
-

@ f33c8a96:5ec6f741
2025-01-08 20:27:23
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls>
<source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-0.mp4" type="video/mp4"/>
<source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-0.webm" type="video/webm"/>
</video></div>
# Welcome to PlebDevs Starter Course
## Course Mission
Welcome to the PlebDevs starter course! I'm Austin, the founder of PlebDevs, and I'll be walking you through this short intro starter course that will get you up and running and interacting with the rest of the content on the platform. If you're here, I'm assuming you're new to coding or just starting out. If you already have experience and have your bearings down, there's lots more intermediate and advanced content on the platform. This course is designed for absolute beginners.
## Course Goals
### Overall PlebDevs Goals
1. Learn how to code
2. Build Bitcoin/Lightning/Nostr apps
3. Become a developer
This is a big journey with a lot of pieces and things to learn. The starter course is going to get you on that path as quickly as possible and make it a smooth journey.
### Starter Course Objectives
1. Give you an easy, high-level overview of the dev journey
2. Get you set up and comfortable in a development environment where you'll write and ship code
3. Give you basic experience in the languages covered in our courses and workshops
There's lots of material out there that will just tell you exactly what to do and not explain why but I want you to actually understand for yourself. I want you to have a good mental model of what this journey is going to be like, what it's going to be like actually writing and pushing code. And then we're going to start getting our hands dirty and gain real experience.
## What is a PlebDev?
### Origins and Philosophy
I started using the term "PlebDev" a few years ago to describe a unique approach to learning development in the Bitcoin space. It represents:
- **Inclusive Learning**: Anyone can become a developer, regardless of background
- **Growth Mindset**: Embracing the journey from beginner to professional
- **Practical Focus**: Emphasizing real-world application development
- **Community Support**: Learning and growing together
### Key Characteristics
- 🌱 **Growth-Focused**: PlebDevs are always learning and improving
- 🎯 **App-Centric**: Focus on building applications rather than protocol development
- 🆕 **Embrace Being New**: Being a new developer is infinitely better than being on the sidelines
- 🤝 **Community-Driven**: Bitcoin/Lightning/Nostr ecosystem needs more plebdevs like you!
## Our Learning Approach
### Core Principles
1. **Lower Barriers**
- Simplify complex concepts
- Focus on practical understanding
- Build confidence through action
2. **Project-Based Learning**
- Learn by doing
- Create real applications
- Build a portfolio as you learn
3. **MVP (Minimum Viable Product) Focus**
- Start with core functionality
- Get things working first
- Iterate and improve
4. **Actionable Knowledge**
- Focus on the 20% that delivers 80% of results
- Learn what you can use right away
- Build practical skills
### Teaching Methods
- Detailed concept breakdowns
- Line-by-line code explanations
- Interactive learning
- 1:1 support available
- Community-driven progress
## Course Structure
### The Learning Path
Instead of the traditional bottom-up approach, we use a project-focused method:
```
🏔️ Advanced Skills
🏔️ Projects & Practice
🏔️ Core Concepts
🏔️ Development Environment
🏔️ Getting Started
```
We'll create checkpoints through projects, allowing you to:
- Verify your understanding
- Build your portfolio
- See real progress
- Have reference points for review
## Student Expectations
### What We Expect From You
- **High Agency**: Take ownership of your learning journey
- **Active Participation**: Engage with the material and community
- **Persistence**: Push through challenges
- **Curiosity**: Ask questions and explore concepts
### What You Can Expect From Us
- Clear, practical instruction
- Comprehensive support
- Real-world applications
- Community backing
## Getting Started
### Next Steps
1. Ensure you're ready to commit to learning
2. Set up your development environment (next lesson)
3. Join our community
4. Start building!
## Resources and Support
### Where to Get Help
- plebdevs.com
### Tips for Success
1. Push code daily, even if it is small.
2. Focus on understanding rather than memorizing.
3. Build projects that interest you.
4. Engage with the community.
5. Don't be afraid to ask questions.
## Remember
You don't need to become a "10x developer" overnight. The goal is to start writing code, build useful things, and gradually improve. Every expert was once a beginner, and the journey of a thousand miles begins with a single line of code.
Ready to begin? Let's dive into the next lesson where we'll set up your development environment! 🚀
-

@ bcea2b98:7ccef3c9
2025-01-08 18:22:00
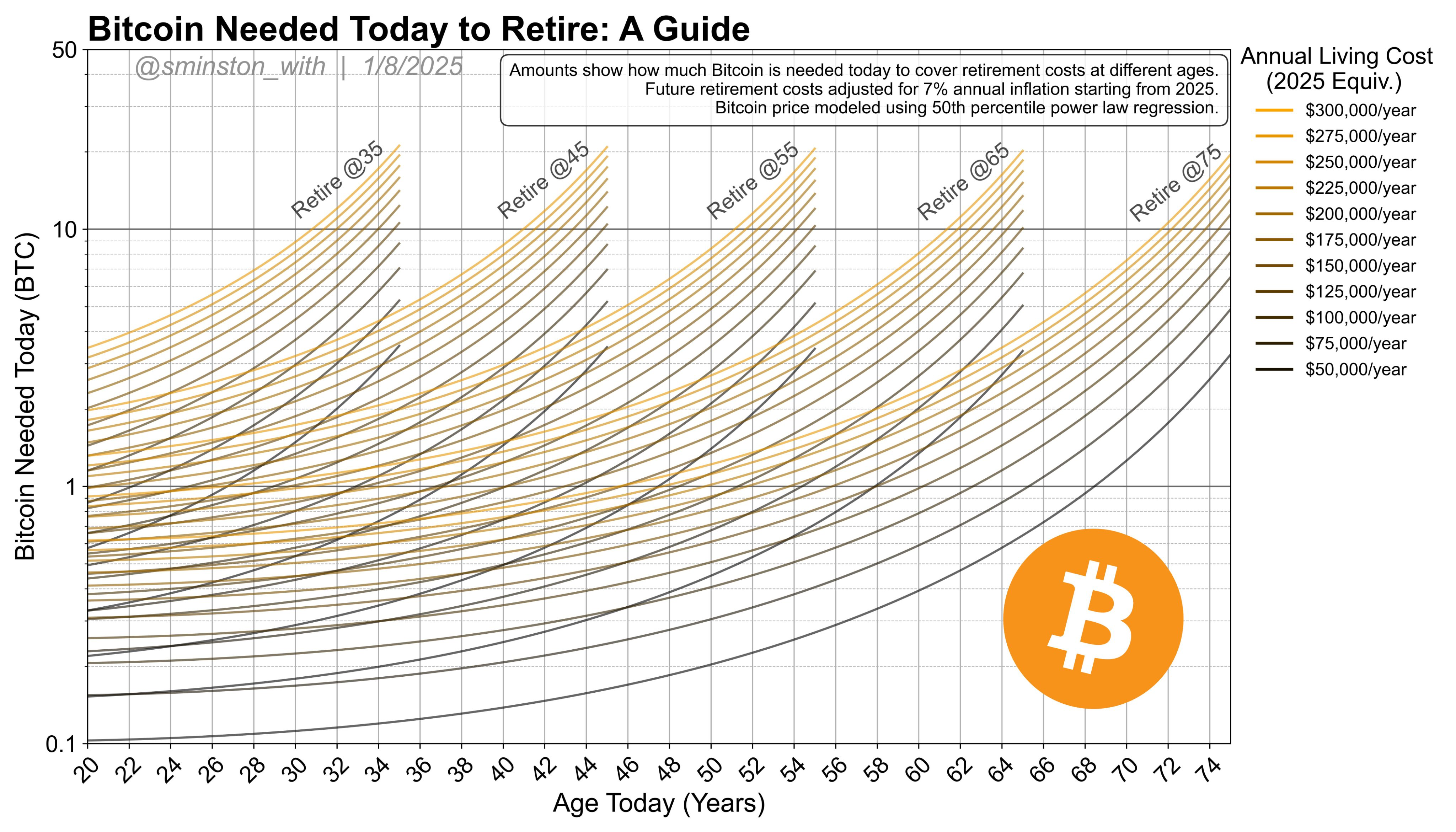
originally posted at https://stacker.news/items/842405
-

@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52
## **Necessário**
- Um Android que você não use mais (a câmera deve estar funcionando).
- Um cartão microSD (opcional, usado apenas uma vez).
- Um dispositivo para acompanhar seus fundos (provavelmente você já tem um).
## **Algumas coisas que você precisa saber**
- O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele.
- O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito.
- A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal.
---
## **O tutorial será dividido em dois módulos:**
- Módulo 1 - Criando uma carteira fria/assinador.
- Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
---
## **No final, teremos:**
- Uma carteira fria que também servirá como assinador.
- Um dispositivo para acompanhar os fundos da carteira.

---
## **Módulo 1 - Criando uma carteira fria/assinador**
1. Baixe o APK do Electrum na aba de **downloads** em <https://electrum.org/>. Fique à vontade para [verificar as assinaturas](https://electrum.readthedocs.io/en/latest/gpg-check.html) do software, garantindo sua autenticidade.
2. Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.

3. Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.

4. Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o **modo avião**.\
*(Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)*

5. Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.

6. No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. *(Aqui entra seu método pessoal de backup.)*

---
## **Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.**
1. Criar uma carteira **somente leitura** em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em <https://electrum.org/> ou da própria Play Store. *(ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)*
2. Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção **Usar uma chave mestra**.

3. Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em **Carteira > Detalhes da carteira > Compartilhar chave mestra pública**.

4. Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los.
5. Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: **Carteira > Addresses/Coins**.
6. Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.

7. No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.

8. No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede.
---
## **Conclusão**
**Pontos positivos do setup:**
- **Simplicidade:** Basta um dispositivo Android antigo.
- **Flexibilidade:** Funciona como uma ótima carteira fria, ideal para holders.
**Pontos negativos do setup:**
- **Padronização:** Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum.
- **Interface:** A aparência do Electrum pode parecer antiquada para alguns usuários.
Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: ***Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.***
Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível.
---
-

@ dd664d5e:5633d319
2025-01-07 19:57:14
## Hodling Bitcoin does not make you a capitalist
I've noticed that Bitcoin-mindedness seems to lead some people to communistic thinking because it's a hard-limited form of capital. Marx, like most Bitcoiners, heavily discounted the possibility of economic growth or transformation changing the economy enough to undermine some minority's control of some form of capital.
What few today understand, is that many of the Dirty Capitalists of Marx's era actually agreed with him; they were just disdainful of labor and worried that the workers finding out that Marxism is correct about the nature of capitalism would cause unrest. They were the original HFSP crowd.
This was the basic idea, that Marx had, and that many Bitcoiners would agree with:
> Capital is strictly limited and the people that control it can keep labor from attaining any, except when their labor is necessary.
And, as we know, automation will make human labor increasingly unnecessary.
## The math doesn't check out

That underlies all of the calculations of "Well, if I just grab this Bitcoin wallet and hodl for twenty years, then it will grow in value to equal half of everything in existence and then I can just buy up half the planet and rule over everyone like a god."
This is economic nonsense because it assumes that:
1) the value of all things remains static over time,
2) purchasing something with money gives you ownership of it,
3) people will always use that specific money (or any money, at all!) for all transactions,
4) there is no such thing as opportunity cost,
5) people will always value money more than any other thing, and therefore be willing to always trade it for anything else,
6) humans are passive, defenseless, and easy to rule over,
7) someone who is preoccupied with hodling an asset steadily and sharply rising in price would ever be emotionally ready to part with it.
## All monies can die.
People use money for everything because it is easy, fast and cheap. If money becomes too precious or scarce, they will simply switch to using other things (as we saw with gold). Humans replace tools that aren't working well, with those that work better, and money is just another tool. Bitcoin is more divisible than gold, but that won't matter, if enough of it is held by too few.
This is why there's a natural cap on the price of a money and why human productivity _in the here and now_ is not irrelevant or in vain.
-

@ 207ad2a0:e7cca7b0
2025-01-07 03:46:04
*Quick context: I wanted to check out Nostr's longform posts and this blog post seemed like a good one to try and mirror. It's originally from my [free to read/share attempt to write a novel](https://untitlednovel.dns7.top/contents/), but this post here is completely standalone - just describing how I used AI image generation to make a small piece of the work.*
Hold on, put your pitchforks down - outside of using Grammerly & Emacs for grammatical corrections - not a single character was generated or modified by computers; a non-insignificant portion of my first draft originating on pen & paper. No AI is ~~weird and crazy~~ imaginative enough to write like I do. The only successful AI contribution you'll find is a single image, the map, which I heavily edited. This post will go over how I generated and modified an image using AI, which I believe brought some value to the work, and cover a few quick thoughts about AI towards the end.
Let's be clear, I can't draw, but I wanted a map which I believed would improve the story I was working on. After getting abysmal results by prompting AI with text only I decided to use "Diffuse the Rest," a Stable Diffusion tool that allows you to provide a reference image + description to fine tune what you're looking for. I gave it this Microsoft Paint looking drawing:

and after a number of outputs, selected this one to work on:

The image is way better than the one I provided, but had I used it as is, I still feel it would have decreased the quality of my work instead of increasing it. After firing up Gimp I cropped out the top and bottom, expanded the ocean and separated the landmasses, then copied the top right corner of the large landmass to replace the bottom left that got cut off. Now we've got something that looks like concept art: not horrible, and gets the basic idea across, but it's still due for a lot more detail.

The next thing I did was add some texture to make it look more map like. I duplicated the layer in Gimp and applied the "Cartoon" filter to both for some texture. The top layer had a much lower effect strength to give it a more textured look, while the lower layer had a higher effect strength that looked a lot like mountains or other terrain features. Creating a layer mask allowed me to brush over spots to display the lower layer in certain areas, giving it some much needed features.

At this point I'd made it to where I felt it may improve the work instead of detracting from it - at least after labels and borders were added, but the colors seemed artificial and out of place. Luckily, however, this is when PhotoFunia could step in and apply a sketch effect to the image.

At this point I was pretty happy with how it was looking, it was close to what I envisioned and looked very visually appealing while still being a good way to portray information. All that was left was to make the white background transparent, add some minor details, and add the labels and borders. Below is the exact image I wound up using:

Overall, I'm very satisfied with how it turned out, and if you're working on a creative project, I'd recommend attempting something like this. It's not a central part of the work, but it improved the chapter a fair bit, and was doable despite lacking the talent and not intending to allocate a budget to my making of a free to read and share story.
#### The AI Generated Elephant in the Room
If you've read my non-fiction writing before, you'll know that I think AI will find its place around the skill floor as opposed to the skill ceiling. As you saw with my input, I have absolutely zero drawing talent, but with some elbow grease and an existing creative direction before and after generating an image I was able to get something well above what I could have otherwise accomplished. Outside of the lowest common denominators like stock photos for the sole purpose of a link preview being eye catching, however, I doubt AI will be wholesale replacing most creative works anytime soon. I can assure you that I tried numerous times to describe the map without providing a reference image, and if I used one of those outputs (or even just the unedited output after providing the reference image) it would have decreased the quality of my work instead of improving it.
I'm going to go out on a limb and expect that AI image, text, and video is all going to find its place in slop & generic content (such as AI generated slop replacing article spinners and stock photos respectively) and otherwise be used in a supporting role for various creative endeavors. For people working on projects like I'm working on (e.g. intended budget $0) it's helpful to have an AI capable of doing legwork - enabling projects to exist or be improved in ways they otherwise wouldn't have. I'm also guessing it'll find its way into more professional settings for grunt work - think a picture frame or fake TV show that would exist in the background of an animated project - likely a detail most people probably wouldn't notice, but that would save the creators time and money and/or allow them to focus more on the essential aspects of said work. Beyond that, as I've predicted before: I expect plenty of emails will be generated from a short list of bullet points, only to be summarized by the recipient's AI back into bullet points.
I will also make a prediction counter to what seems mainstream: AI is about to peak for a while. The start of AI image generation was with Google's DeepDream in 2015 - image recognition software that could be run in reverse to "recognize" patterns where there were none, effectively generating an image from digital noise or an unrelated image. While I'm not an expert by any means, I don't think we're too far off from that a decade later, just using very fine tuned tools that develop more coherent images. I guess that we're close to maxing out how efficiently we're able to generate images and video in that manner, and the hard caps on how much creative direction we can have when using AI - as well as the limits to how long we can keep it coherent (e.g. long videos or a chronologically consistent set of images) - will prevent AI from progressing too far beyond what it is currently unless/until another breakthrough occurs.
-

@ e6817453:b0ac3c39
2025-01-05 14:29:17
## The Rise of Graph RAGs and the Quest for Data Quality
As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence.
## Booming Interest in Graph RAGs
Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can:
* **Enhance LLM Outputs:** By grounding responses in structured knowledge, graphs significantly reduce hallucinations.
* **Support Complex Queries:** Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving.
Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs?
## Data Quality: The Foundation of Effective Graphs
A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why:
* **Richness of Entities:** Effective retrieval depends on graphs populated with rich, detailed entities.
* **Freedom from Hallucinations:** Poorly constructed graphs amplify inaccuracies rather than mitigating them.
Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs.
## Hybrid Graph RAGs and Variations
While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that:
* Handle diverse data sources with ease.
* Offer improved adaptability to complex queries.
Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing.
## Ontology: The Key to Graph Construction Quality
Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for:
* **Defining Relationships:** Clarifying how concepts connect within a domain.
* **Validating Graph Structures:** Ensuring constructed graphs are logically sound and align with domain-specific realities.
Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs?
## How to Build Ontology Expertise in a Startup Team
For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach:
1. **Assign a Knowledge Champion:** Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering.
2. **Provide Training:** Invest in courses, workshops, or certifications in knowledge graph and ontology creation.
3. **Leverage Partnerships:** Collaborate with academic institutions, domain experts, or consultants to build initial frameworks.
4. **Utilize Tools:** Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process.
5. **Iterate with Feedback:** Continuously refine ontologies through collaboration with domain experts and iterative testing.
So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts.
You could read about barefoot experts in my article :
Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise.
## How to Find or Create Ontologies
For teams venturing into Graph RAGs, several strategies can help address the ontology gap:
1. **Leverage Existing Ontologies:** Many industries and domains already have open ontologies. For instance:
* **Public Knowledge Graphs:** Resources like Wikipedia’s graph offer a wealth of structured knowledge.
* **Industry Standards:** Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields.
* **Business Framework Ontology (BFO):** A valuable resource for enterprises looking to define business processes and structures.
1. **Build In-House Expertise:** If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation.
2. **Utilize LLMs for Ontology Construction:** Interestingly, LLMs themselves can act as a starting point for ontology development:
* **Prompt-Based Extraction:** LLMs can generate draft ontologies by leveraging their extensive training on graph data.
* **Domain Expert Refinement:** Combine LLM-generated structures with insights from domain experts to create tailored ontologies.
## Parallel Ontology and Graph Extraction
An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as:
* **Detecting Hallucinations:** Differentiating between genuine insights and AI-generated inaccuracies.
* **Ensuring Completeness:** Ensuring no critical concepts are overlooked during extraction.
Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method.
## LLMs as Ontologists
While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to:
* **Generate Skeleton Ontologies:** Prompt LLMs with domain-specific information to draft initial ontology structures.
* **Validate and Refine Ontologies:** Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance.
However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes.
## Final Thoughts: Unlocking the Power of Graph RAGs
The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools.
As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding.
Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation!
-

@ bcea2b98:7ccef3c9
2025-01-03 22:31:38

originally posted at https://stacker.news/items/835751
-

@ f3df9bc0:a95119eb
2025-01-03 21:41:14
# MySql InnoDB Indexes for Developers
This article aims to be a high level reference for developers who just want to use Mysql InnoDB indexes effectively. Although you _can_ read this from top to bottom, I'd encourage you to save time by skipping to sections that interest you using the below table of contents.
# Contents
- [Quick Reference](#quick-reference) (Start here for guidelines you can use right away, without needing the _why_)
- [Index Structure](#index-structure)
- [Primary Index Structure & Paging](#primary-index--paging)
- [Secondary Indexes](#secondary-index-structure)
- [Composite Indexes](#composite-index-structure)
- [Index Navigation](#index-navigation)
- [ref-type Queries](#ref-type-queries)
- [range-type Queries](#range-type-queries)
- [Post-Index Computations](#post-index-computations)
- [Join Algorithms](#join-algorithms)
- [Nested Loop Join](#nested-loop-join)
- [Hash Join](#hash-join)
- [Compound Cursor Iteration](#compound-cursor-iteration)
<style type="text/css">
.box {
background: #cedce8;
padding: 1px 10px 5px 10px;
border-radius: 15px;
}
.box code {
background: #bfd7ec;
}
</style>
<div class="box" style="" markdown="1">
# Quick Reference
This is a quick list of the practical guidelines that you can use to make your applications more performant at the database layer. We'll dive into the _why_ each of these things are true, and give you mental models such that you can arrive at these guidelines yourself _without memorization_, at later sections of the article.
<button onclick="toggle_quickref();">Click To Expand ▼</button>
<script type="text/javascript">
function toggle_quickref() {
var x = document.getElementById("quick-reference-body");
if (x.style.display === "none") {
x.style.display = "block";
} else {
x.style.display = "none";
}
}
</script>
<div id="quick-reference-body" style="display:none" markdown="1">
**Structure**
- Every non-`PRIMARY` index is really a compound index with the `PRIMARY` index.
- `[foo]` is implicitly `[foo, id]`, likewise `[a, b]` is implicitly `[a, b, id]`
- Usually prefer high cardinality columns (those with many unique values) to come earlier in indexes.
- For example IDs have more unique values than boolean flags, so put the ID first in the index `[account_id, is_active]`
- *Note:* there are exceptions, especially when range queries are involved
- Only `SELECT`-ing columns contained in the index will significantly reduce memory paging.
- eg `SELECT foo, id` when the index `[foo]` is being used.
**Filtering**
- An index must be "used" from left to right. Given an index of `[a, b, c]`:
- 🟢 `WHERE b=2 AND a=1` will correctly use the `[a, b]` portion of the index
- 🟡 `WHERE a=1 AND c=4` will only use the `[a]` portion of the index
- 🔴 `WHERE b=5` will not be able to use this index at all
- A range filter prevents any columns to the "right" from being used. Given an index of `[a, b, c]`:
- 🟡 `WHERE a=1 AND b>4 AND c=10` will only use the `[a, b]` portion of the index
- 🔴 Implied by this is that queries containing ranges on two or more columns **cannot** be solved by indexes `WHERE a>5 AND b>2`
- Any filters that aren't solved as part of the index will require linear row scanning. The performance of this is correlated to the "hit ratio".
- Given an index of `[a]`, the performance of `WHERE a=1 AND c=4` will correlate to *what percentage of `a=1` rows also have `c=4`*. If this percentage is low, performance will be worse. Put another way: if there are a large number of rows where `a=1` but only a couple of those also have `c=4`, mysql will need to search through and discard many rows.
**Ordering**
- Indexes naturally return rows ordered by their structure.
- Selecting from index `[a, b]` will naturally give rows ordered by `[a, b, id]`
- Any unnatural ordering will require a O(nlogn) **filesort**, which can be very slow for large amounts of rows
- With an index of `[a]`, the query `WHERE a=1 ORDER BY b` will need to sort all rows that meet the filtering clause.
- Columns on the "left" of the index can be efficiently excluded from the `ORDER BY` clause, **if** they have been used in the `WHERE` clause as a **non-range** filter.
- Given an index of `[a, b]`, with a natural ordering of `[a, b, id]`:
- 🟢 `WHERE a=1 ORDER BY b,id` is also natural ordering
- 🔴 `WHERE a=1 ORDER BY id` is **not** natural ordering
- 🟢 `WHERE a=1 AND b>10 ORDER BY b,id` is natural ordering
- 🔴 `WHERE a=1 AND b>10 ORDER BY id` is **not** natural ordering
- 🟢 `WHERE a=1 AND b=2 ORDER BY id` is natural ordering
- 🟢 `WHERE a=1 AND b=2 AND id>5 ORDER BY id` is natural ordering
**Limit & Offset**
- Performance of `LIMIT` is correlated to the "hit density" when scanning rows. eg are the rows you're scanning for abundant? Or will mysql need to scan for a long time to find enough rows?
- `LIMIT` is applied **after** sorting, so will not improve the performance of a filesort
- Performance of `OFFSET n` is correclated to the value of `n`. Therefore it is not a good fit for pagination as the query will get slower as `n` increases.
</div>
</div>
-----
# Index Structure
Indexes are constructed from a B+tree structure. Understanding this structure is key to gaining an intuitive reasoning for how queries will perform using different indexes. Both the `PRIMARY` index and secondary indexes have a similar tree structure, differing only in what data is stored on the leaves of the tree.
## Primary Index Structure & Paging
Looking at the structure of a `PRIMARY` index first, we see that the full row is stored in each leaf of the tree, and each leaf is ordered sequentially on the disk:

<center><small style="color: #999">note: page size greatly reduced for illustration</small></center>
If possible, it is best to select the primary index for a table with data locality in mind, to reduce how many page loads need to take place to satisfy a query. For example, imagine a blogging application that almost always queries for posts on a specific blog: `SELECT * FROM posts WHERE blog_id=10`. Ideally we'd like for this table to have all the posts where `blog_id = 10` stored **sequentially** in the primary index. However, by using a standard primary index on `[id]` we see a structure where rows are stored in disk pages in the order they were **created**. The diagram below illistrates this (ID integer, colour coded by blog)

By insteading using a **composite primary key**, this table can be made much more efficient given its access pattern. In the below diagram I show the same data, but instead stored in a composite primary index of `[blog_id, id]`. This means rows are first sorted by `blog_id`, and then by `id` for each blog. When the data is stored in this manner, our query for `SELECT * FROM posts WHERE blog_id=10` is likely to load less pages from disk.

## Secondary Index Structure
Secondary indexes have a similar structure to that of primary indexes. However, instead of storing the _full row_ in the leaves of the tree, only the primary index value is stored:

This structure means that if additional columns are required (eg a `SELECT *`), then after traversing the secondary index, mysql must also traverse the primary index _for each selected row_ to actually load the required data. By only selecting columns available in the secondary index, mysql can skip this extra lookup step.
## Composite Index Structure
When multiple columns are specified in a compound index, we get a structure composed of **nested B+trees**. This is where the ordering of columns within an index definition becomes relevant. The root of the tree is defined by the _first_ column in the index definition, the second nested tree would be the _second_ column in the index definition, and so on.
The below diagram is the structure of a composite index `[blog_id, created_at]` (with the implied `id` column on the end):

# Index Navigation
We'll now look at how mysql navigates these indexes given various query structures, which should help give an intuitive understanding for why Mysql performance will vary.
## `ref`-type queries
With this tree-based model in place, we can see that to efficiently use an index like this we must navigate the tree _in the order that the index is defined_. If our query does not specify a value for all columns in an index, this is ok as long as the values we _do_ provide are at the top of the tree.
I've illustrated below two examples of the "happy path" for navigating a `[blog_id, user_id]` index. In the first, we have provided a filter on both `blog_id` and `user_id`, which allows for mysql to fully navigate the tree to the leaves. In the second, we only provide a filter on `blog_id`, but because this is the first column in the index mysql is still able to efficiently select all the rows that meet this criteria (it selects **all leaves from the sub tree**)

<div class="box" style="" markdown="1">
💡 Notice how the ordering of the rows appears to change depending on **how far mysql navigates the tree**. Rows in an index are always stored in the same ordering scheme as the index itself. That is to say that a `[blog_id, user_id]` index will naturally store rows in `blog_id, user_id, id` ordering. However, as we navigate further into the tree the ordering appears to "simplify". If we are selecting rows for a specific `blog=10 and user_id=50` then the rows appear to be ordered by `id`, because they all share the same values for both blog_id and user_id!
</div>
## `range`-type queries
The range-type lookup happens when a query selects _multiple values_ for an indexed column. There are many ways a query could end up in this scenario:
- `WHERE updated_at > X`
- `WHERE user_id != X`
- `WHERE blog_id IN (1, 5, 34, 200)`
- `WHERE user_id=10 OR user_id=50`
In such cases, mysql will need to navigate _multiple branches_ of the index. Consider the below query where we search for all recently created posts for a particular blog:

There are two things I'd like to point out about this pattern:
1. The ordering of the results is `created_at, id`. Sorting by `id` (for example) is not possible without a `filesort` operation.
2. There is no efficient way to navigate the deeper sections of the tree (ie the `id` portion of the index above) without iterating through all the selected branches of `created_at`. That is, if we were to add an additional filter on `id > 5` for example, then there is no single tree to navigate and provide these values. Mysql would instead need to iterate through every sub-tree (one per value of `created_at`) to complete this filtering operation (see diagram below)
A common application pattern that can suffer performance issues due to both these points is *ID-based pagination* (ie if your pagination system needs to filter on `WHERE id > x ORDER BY id`). See the section on [compound cursor iteration](#compound-cursor-iteration) for a potential solution.

# Post-Index Computations
Although Mysql will always start off by using an index if possible to reduce the amount of post-processing required, it goes without saying that not every query will be fully solved by an avilable index. There are a couple post-index computations that we should consider the relative performance of.
First, if the query is requesting an `ORDER` which differs from how the index sorts its rows, a filesort will be required. This is an expensive operation (`O(nlogn)`) if the number of rows to be sorted is large. In addition, sorting requires Mysql to temporarily buffer the entire dataset (eg you can't stream a sorting operation). See [ref-type queries](#ref-type-queries) for a reminder how indexes naturally sort rows.
If the `WHERE` clause of the query was not fully solved by the index, Mysql will also need to scan through the rows one after another to apply the remaining filtering. While this is faster than a filesort, it is also relatively slow for large data sets (`O(n)`). If the index reducing the dataset down to a reasonable size upfront, then this may not be a big deal.

There is one exception here: if the query also specifies a `LIMIT x`, Mysql need not scan the _entire_ dataset. Mysql will "short circuit" the row scan as soon as it has enough rows to satisfy the query condition. The performance of this kind of pattern is dependent on the "hit ratio" of rows. If there are relatively few rows that satisfy the filter condition compared to rows that must be dropped, then Mysql will need to scan for a longer time compared to if almost all the rows are valid. In addition, you may find that the "density" of interesting rows is not constant throughout the range being scanned! If your application is paginating through a large data set, you may find that different pages have different query times, depending on how many rows need to be filtered out on each page.

# Join Algorithms
## Nested-Loop Join
The primary algorithm used by Mysql to join tables is a couple variations on "nested-loop". This a very straightforward algorithm:
```
for each row in tableA:
for each matching row in tableB:
send to output steram
```
Because Mysql is often capable of streaming joins, when the join query includes a `LIMIT x` the full join may not have to be executed:
1. Mysql executes query in the outer table
2. For the first row in the range, look-up matching rows in the inner table
3. For each matching row, emit to output stream
4. Stop execution if enough rows found, otherwise move to next row and goto 2
Note that similar to un-indexed row scans, this does not apply to all conditions (for example, if sorting is required the full dataset is required in memory).
## Hash Join
The hash-join algorithm avoids the N+1 B-tree traversal by taking some time upfront (`O(n)`) to build an in-memory hash table. The reason this strategy can give a performance improvement over nested-loop in some cases is because a hash table lookup has an average profile of `O(1)` compared to B-tree traversal at `O(logn)`. Given we may have to do this lookup many times (`m` times), the overall performance profile of hash-join is `O(n + m)`, whereas nested-loop's profile is `O(nlogm)`.
The below plot shows the region (shaded blue) where the function `n+m` has a lower value than `n*logm`:

The tradeoff is of course that this (potentially large) hash table must fit into memory. For this reason one strategy to improve hash-join performance is to limit the size of this temporary table by `SELECT`-ing only those columns which you really need (to reduce width), and pre-filtering as many rows as possible (to reduce height).
The second thing to keep in mind for performance of hash-joins is that indexes on the join condition will not be used. Rather, the place to focus is on indexing any independent filters if possible. For example, consider the following query:
```sql
SELECT * FROM tableA t1 JOIN tableB t2
ON t1.shared_id = t2.shared_id
WHERE t1.colA = "foo"
AND t2.colB = "bar"
```
The best indexes for this query given a hash-join would be on `t1.colA` and a second index on `t2.colB`. Execution of this join would then look like:
1. Use the index on `colA` to find all rows in t1 where `colA = "foo"`.
2. For each row, build a hash table where the key is `t1.shared_id` and the value is the row.
3. Use the index on `colB` to find all rows in t2 where `colB = "bar"`.
4. For each row, look up the matching t1 rows from the hash table by `t2.shared_id`
# Compound Cursor Iteration
In the [range-type queries section](#range-type-queries) I briefly introduced the problem of using an ID based cursor to paginate through a dataset queried via a range-type query. One potential solution to this problem is to use a *compound cursor*. To work, this cursor must be constructed from the column being filtered with the range. For example, lets consider the query `SELECT * FROM blog_posts WHERE blog_id=10 AND created_at>"2023-01-01"`. The natural index to use for this range query would be `[blog_id, created_at]`.
Because the range query filter is performed on the `created_at` column, I will propose a compound cursor of `created_at, id`. Let's take a look at how the query structure changes. The first query of our iteration will look something like this:
```sql
SELECT * FROM blog_posts
WHERE blog_id = 10 AND created_at > "2023-01-01"
ORDER BY created_at, id ASC
LIMIT 100
```
This will get the first "page" of 100 results. Notice that we are ordering by `created_at, id`, which is the natural ordering of the index. This allows mysql to efficiently grab the first 100 rows it sees without scanning the full time range.

Now lets look at how we get the next "page" of results. The "cursor value" is defined as the `created_at` and `id` values from the last row in the batch of 100 previously selected. We'll call these values `x` and `y` for simplicity.
```ruby
x = batch.last.created_at,
y = batch.last.id
```
The structure of the query that loads the second page of results has this form:
```sql
SELECT * FROM blog_posts
WHERE blog_id = 10
AND (
created_at = x AND id > y
OR created_at > x
)
ORDER BY created_at, id ASC
LIMIT 100
```
Notice in this query that we have an `OR` clause, meaning mysql is going to navigate the index **two times**, once per "side" of the clause. Lets consider these as two seperate queries for the sake of a performance analysis.
```sql
-- Query A: the "left" side of the OR clause
SELECT * FROM blog_posts
WHERE blog_id = 10 AND created_at = x AND id > y
ORDER BY created_at, id ASC
LIMIT 100
-- Query B: the "right" side of the OR clause
SELECT * FROM blog_posts
WHERE blog_id = 10 AND created_at > x
ORDER BY created_at, id ASC
LIMIT 100
```
By analysing the OR clauses piece-wise like this, we can now see that each clause has only **one** range filter. Combining this with the fact that the `ORDER BY` is the natural ordering of these indexes, we have solved both of the original problems! No more filesort, no more unsolvable double-range filters.

🟡 A note of warning: this pattern may only work as you expect for columns that have **immutable** values. Like any data structure iteration, if a value changes during your iteration your process may either process a row twice or not at all! For example, consider if instead of iterating on `created_at, id` we were iterating on `updated_at, id`. If a row is updated (and therefore `updated_at` _increases_) while a process is already iterating through the dataset, we may see that updated row twice: once with its lower `updated_at` value, and again with the higher value.
-

@ a95c6243:d345522c
2025-01-03 20:26:47
*Was du bist hängt von drei Faktoren ab:* *\
Was du geerbt hast,* *\
was deine Umgebung aus dir machte* *\
und was du in freier Wahl* *\
aus deiner Umgebung und deinem Erbe gemacht hast.* *\
Aldous Huxley*
**Das brave Mitmachen und Mitlaufen in einem vorgegebenen, recht engen Rahmen** ist gewiss nicht neu, hat aber gerade wieder mal Konjunktur. Dies kann man deutlich beobachten, eigentlich egal, in welchem gesellschaftlichen Bereich man sich umschaut. Individualität ist nur soweit angesagt, wie sie in ein bestimmtes Schema von «Diversität» passt, und Freiheit verkommt zur Worthülse – nicht erst durch ein gewisses [Buch](https://www.nachdenkseiten.de/?p=126416) einer gewissen ehemaligen Regierungschefin.
**Erklärungsansätze für solche Entwicklungen sind bekannt,** und praktisch alle haben etwas mit Massenpsychologie zu tun. Der Herdentrieb, also der Trieb der Menschen, sich – zum Beispiel aus Unsicherheit oder Bequemlichkeit – lieber der Masse anzuschließen als selbstständig zu denken und zu handeln, ist einer der Erklärungsversuche. Andere drehen sich um Macht, Propaganda, Druck und Angst, also den gezielten Einsatz psychologischer [Herrschaftsinstrumente](https://transition-news.org/spip.php?recherche=nudging\&page=recherche_wall).
**Aber wollen die Menschen überhaupt Freiheit?** Durch Gespräche im privaten Umfeld bin ich diesbezüglich in der letzten Zeit etwas skeptisch geworden. Um die Jahreswende philosophiert man ja gerne ein wenig über das Erlebte und über die Erwartungen für die Zukunft. Dabei hatte ich hin und wieder den Eindruck, die totalitären Anwandlungen unserer «Repräsentanten» kämen manchen Leuten gerade recht.
**«Desinformation» ist so ein brisantes Thema.** Davor müsse man die Menschen doch schützen, hörte ich. Jemand müsse doch zum Beispiel diese ganzen merkwürdigen Inhalte in den Social Media filtern – zur [Ukraine](https://transition-news.org/spip.php?recherche=ukraine\&page=recherche_wall), zum [Klima](https://transition-news.org/spip.php?recherche=klima\&page=recherche_wall), zu [Gesundheitsthemen](https://transition-news.org/spip.php?recherche=impfung\&page=recherche_wall) oder zur [Migration](https://transition-news.org/spip.php?recherche=migration\&page=recherche_wall). Viele wüssten ja gar nicht einzuschätzen, was richtig und was falsch ist, sie bräuchten eine Führung.
**Freiheit bedingt Eigenverantwortung, ohne Zweifel.** Eventuell ist es einigen tatsächlich zu anspruchsvoll, die Verantwortung für das eigene Tun und Lassen zu übernehmen. Oder die persönliche Freiheit wird nicht als ausreichend wertvolles Gut angesehen, um sich dafür anzustrengen. In dem Fall wäre die mangelnde Selbstbestimmung wohl das kleinere Übel. Allerdings fehlt dann gemäß Aldous Huxley ein Teil der Persönlichkeit. Letztlich ist natürlich alles eine Frage der Abwägung.
**Sind viele Menschen möglicherweise schon so «eingenordet»,** dass freiheitliche Ambitionen gar nicht für eine ganze Gruppe, ein Kollektiv, verfolgt werden können? Solche Gedanken kamen mir auch, als ich mir kürzlich diverse Talks beim viertägigen [Hacker-Kongress](https://transition-news.org/der-38-kongress-des-chaos-computer-clubs-bot-mehr-enthullungen-als-nur-die) des Chaos Computer Clubs (38C3) anschaute. Ich war nicht nur überrascht, sondern reichlich erschreckt angesichts der in weiten Teilen mainstream-geformten Inhalte, mit denen ein dankbares Publikum beglückt wurde. Wo ich allgemein hellere Köpfe erwartet hatte, fand ich Konformismus und enthusiastisch untermauerte Narrative.
**Gibt es vielleicht so etwas wie eine Herdenimmunität gegen Indoktrination?** Ich denke, ja, zumindest eine gestärkte Widerstandsfähigkeit. Was wir brauchen, sind etwas gesunder Menschenverstand, offene Informationskanäle und der Mut, sich freier auch zwischen den Herden zu bewegen. Sie tun das bereits, aber sagen Sie es auch dieses Jahr ruhig weiter.
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/kann-es-sein-dass-die-menschen-gar-keine-freiheit-wollen)*** erschienen.
-

@ bd32f268:22b33966
2025-01-02 19:30:46
Texto publicado por *Foundation Father @FoundationDads* e traduzido para português.
Assumir responsabilidades numa época efeminada como a nossa é um superpoder.
Algumas pessoas não sabem o que significa "assumir responsabilidades", no entanto, porque nunca tiveram um pai ou outra pessoa que as ama-se o suficiente para lhes ensinar.
Então, aqui está como assumir responsabilidades.
## **Lembra-te que não és uma pessoa desamparada e incompetente.**
As coisas não te acontecem simplesmente enquanto olhas fixamente com a boca aberta, usando todo o teu poder cerebral para te lembrares de como respirar.
Tu tens poder de ação.
## Mantém estas perguntas em mente:
"Que papel desempenhei eu nesta situação ou como ajudei a formar o sistema em que estou inserido?"
"O que posso fazer agora mesmo para começar a corrigi-lo, por mais pequeno que seja?"
Aqui estão alguns exemplos de como aplicar estas perguntas.
*José Malhoa - Remédio*
## Saúde
Estás com excesso de peso e cansado o tempo todo? Deprimido?
Começa a caminhar 30 minutos por dia. De preferência ao ar livre.
Pára de comer snacks.
Marca uma consulta com um médico para fazer análises ao sangue.
Todas estas coisas estão ao teu alcance.
## Finanças
Estás a afogar-te em dívidas de cartão de crédito? Assumir responsabilidades significa reduzir drasticamente o teu consumo e iniciar um programa radical de pagamento do máximo de dívida que conseguires.
Obtém uma aplicação de orçamento e começa a planear.
Sentes-te preso no teu emprego sem futuro? Sentes que não ganhas o suficiente? Vai a entrevistas para vagas de emprego e descobre o teu verdadeiro valor no mercado.
Reserva 1 hora todas as noites para melhorares. A menos que já estejas a trabalhar em dois empregos, toda a gente tem pelo menos 1 hora todas as noites.
## Arredores imediatos
Se vês algo que precisa de ser feito, simplesmente faz. Não te queixes disso. Não resmungues baixinho. Não desejes que alguém tratasse disso. Simplesmente faz e não peças permissão.
Guarda o carrinho de compras. Lava a caneca de café no lava-loiça. Arranca as ervas daninhas. Repara a parede. Se o quintal do teu vizinho estiver cheio de ervas, vai lá e corta a relva tu mesmo. Limpa a água do lava-loiça. Arruma a bancada. Leva o lixo para fora. Leva bom café para o escritório.
## Os teus filhos
Muitos pais queixam-se do comportamento dos seus filhos como se não tivessem qualquer influência sobre o assunto. Mas os teus filhos farão o que tu os ensinaste a fazer.
"Fizemos o melhor que pudemos."
Não, não fizeram, e assumir responsabilidades significa admitir que foste permissivo e preguiçoso ou que querias sentir-te justo por não bater.
Que pequena coisa podes fazer agora mesmo para começar? Escolhe um único comportamento que queres que eles parem, senta-os e explica as consequências do comportamento. Pede desculpa por teres deixado andar durante tanto tempo.
Quando eles apresentarem o comportamento, aplica as consequências. Aconteça o que acontecer.
## Os teus relacionamentos
Não tens amigos ou o teu grupo de amigos atual é uma má influência? Podes fazer novos amigos. Assumir responsabilidades significa admitir que a tua solidão é em grande parte auto-infligida.
**O que podes fazer?**
Começa a jogar ténis ou futebol. Existem ligas em todo o lado. Encontra uma boa igreja local e encontra maneiras de te envolver. Existem encontros para todo o tipo de atividade. Participa num que se alinhe com as tuas preferências. Quando estiveres em público, sorri mais e puxa conversa.
Depois de conheceres algumas pessoas, estabelece uma cadência regular. Agenda almoços semanais ou mensais e alterna entre algumas pessoas. Ou talvez café de manhã.
Não acontecerá da noite para o dia, mas dando pequenos passos consistentemente durante alguns meses e vais perceber que tens uma vida social.
## Os teus erros
Se erraste, não te retires e escondas nem arranjes desculpas. Pede desculpa à pessoa que prejudicaste, diz-lhe porquê e oferece-te para compensar. Aceita as consequências com humildade.
Vais descobrir que nada te conquista mais respeito do que assumir os teus erros. Esta é a principal. Se aprenderes a fazer isto bem, cobrirá uma infinidade de pecados porque cria hábito. Mesmo que tenhas apenas 1% de culpa na situação, assumir a responsabilidade e pedir desculpa pelo teu 1% está a construir um certo grupo de músculos.
"Mas ele devia ter..." Pára com isso. Confiaste demasiado? Presumiste demasiado sem comunicar? Assume a responsabilidade por isso.
Estes exemplos podiam continuar para sempre, então vou parar e terminar com este princípio:
A tua resposta importa mais do que as tuas circunstâncias.
Existem vítimas reais, algumas de tragédias horríveis. Mas mesmo que não te tenhas atirado para areias movediças, ainda podes assumir a responsabilidade por como reages e pelo que escolhes fazer a seguir.
Às vezes, é agarrar numa corda de um transeunte e dizer: "Obrigado."
Não te afogues nas areias movediças até que alguém te dê uma palmadinha nas costas por quão difícil é para ti, e não continues a apontar para o teu tempo nas areias movediças para desculpares os teus fracassos.
Podes não ter escolhido uma batalha específica. Ainda podes assumir a responsabilidade por quão bem lutas a batalha. Num certo sentido, ninguém escolhe a principal batalha que enfrenta. Ninguém escolheu nascer. Ninguém escolheu a sua família. Ninguém escolheu as suas circunstâncias.
O mundo nunca será perfeito. Tens de assumir a responsabilidade pela tua parte dele de qualquer maneira. Pode ser difícil. Pode ser doloroso. Não te foi prometida uma vida fácil e sem dor.
Depois de começares a assumir responsabilidades, qual é o próximo passo?
Altura de assumir mais responsabilidades.
Por exemplo, se não tens problemas em fazer amigos e tens essa parte da tua vida resolvida, assume a responsabilidade por outra pessoa. Encontra um dos rapazes solitários na tua igreja que precisa de um amigo e adiciona-o à tua rotação de almoços.
A recompensa por assumir responsabilidades é subir de nível e, como consequência, as coisas devem tornar-se mais desafiantes.
Mas agora estás mais bem preparado para isso. Repete até morrer e, esperançosamente, a tua causa de morte será por viver e não por te queixares de não viver.
-

@ a4a6b584:1e05b95b
2025-01-02 18:13:31
## The Four-Layer Framework
### Layer 1: Zoom Out

Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what."
**Example**: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems.
- **Tip**: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage.
_Once you have the big picture in mind, it’s time to start breaking it down._
---
### Layer 2: Categorize and Connect

Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas.
**Example**: Studying biology? Group concepts into categories like cells, genetics, and ecosystems.
- **Tip**: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track.
_With your categories in place, you’re ready to dive into the details that bring them to life._
---
### Layer 3: Master the Details

Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable.
**Example**: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language.
- **Tip**: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding.
_Now that you’ve mastered the essentials, you can expand your knowledge to include extra material._
---
### Layer 4: Expand Your Horizons

Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams.
**Example**: Learn about rare programming quirks or historical trivia about a language’s development.
- **Tip**: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time.
---
## Pro Tips for Better Learning
### 1. Use Active Recall and Spaced Repetition
Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information.
### 2. Map It Out
Create visual aids like [diagrams or concept maps](https://excalidraw.com/) to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2.
### 3. Teach What You Learn
Explain the subject to someone else as if they’re hearing it for the first time. Teaching **exposes any gaps** in your understanding and **helps reinforce** the material.
### 4. Engage with LLMs and Discuss Concepts
Take advantage of tools like ChatGPT or similar large language models to **explore your topic** in greater depth. Use these tools to:
- Ask specific questions to clarify confusing points.
- Engage in discussions to simulate real-world applications of the subject.
- Generate examples or analogies that deepen your understanding.
**Tip**: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective.
---
## Get Started
Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
-

@ bcea2b98:7ccef3c9
2025-01-02 17:47:27
originally posted at https://stacker.news/items/833889
-

@ 5391098c:74403a0e
2025-01-02 16:50:29
Ensaio em Prosa sobre Fotografia Analógica
Tenho especial fascínio pela fotografia analógica. É que se trata dum processo artístico muito mais complexo que a fotografia digital, devemos entender todos os aspectos da fotografia para obter o resultado pretendido, desde aspectos mecânicos da câmera como abertura e tempo do obturador, foco, iluminação, até a sensibilidade do filme utilizado e o resultado, quando alcançado, é verdadeira obra de arte pintada, onde a tela é a película química.
Importante dizer que meu fascínio pela fotografia analógica não me impede de reconhecer a importância da fotografia digital, não fosse essa você não estaria vendo minhas obras de arte que foram digitalizadas…
Da mesma forma que meu fascínio pela máquina de escrever não me impede de ter essa e outras páginas na internet. Parte do meu livro FILOSOFIA FUNDAMENTAL foi escrito graças a inspiração da máquina de escrever, como ocorreu no capítulo sobre o que seria evolução, escrevi integralmente na minha Olivetti Studio 46, pois havia faltado luz: o que me fez refletir sobre se o computador realmente é a evolução da máquina de escrever.
Outro exemplo foi a inspiração que as lindas formas arredondas de minha máquina de escrever da marca Érika me proporcionou, acabou resultando numa bela performance a qual dei nome de Paixão Erótika.
Por isso, acredito que os equipamentos analógicos não ofuscam nossa criatividade e na fotografia não poderia deixar de ser diferente.
No conjunto de fotografias analógicas abaixo utilizei uma Canon T50, objetiva de 50mm e filme Kodak Pro Image 100, a qual se encontra auto-fotografada em espelho, vamos ver:
Na foto abaixo utilizei luz amarela indireta da direita superior para esquerda inferior, o desfoque ao redor foi proposital com o objetivo de parecer estar olhando o mundo através das lentes da câmera, nesse caso ela estava olhando para sí mesmo. Mesmo estando a parede e o espelho no mesmo plano, a profundidade de campo do espelho é diferente, por isso esse efeito foi possível. Destaque especial para o “olho” do diafragma, deve ter aberto até f5.6, pois a luz não era muito forte. Se a luz fosse mais forte o diafragma teria aberto o mínimo f16 o que aumentaria a profundidade de campo impedindo o desfoque pretendido. O resultado foi alcançado, ao mesmo tempo que a câmera aparece, essa fotografia transmite essa mensagem subliminar:
https://image.nostr.build/a7cbfbe68a4bb89ae731c360c373ac8eff7599a5a100d13035eb234b5d788626.jpg
PERFORMANCE
Performance é o nome dado à mescla de mais de uma linguagem artística (arte visual, música, teatro, etc.) clicando em https://davipinheiro.com/id/performance/ você pode ver todas minhas performances. Nos exemplos abaixo a mescla se deu pela mistura de artes visuais criadas por mim e captadas pela fotografia analógica, vamos ver:
A foto abaixo se trata dum terrário que criei num tronco de árvore, arte plástica. Para fotografar utilizei luz amarela superior, o desfoque foi para destacar o objeto, especial destaque para o reflexo da luz no vidro para dar noção tridimensional de algo transparente:
https://image.nostr.build/e8026f9e99fa16631959954f8bb925af6f1764911f0a315ab0125bb413e3e89b.jpg
Na foto abaixo o mesmo processo da foto anterior, também utilizando uma Canon T50 com filme Kodak Pro Image 100 e objetiva de 50mm, diferenciando o enquadramento e a luz direta frontal:
https://image.nostr.build/4c44a0baf2b5ddaf63f83420952ab1b2e84f7df292f8e413a65f8134a2e7db58.jpg
A foto abaixo retrata o processo de criação da obra. Ironicamente, nessa foto, meu galo Cara de Palhaço mesmo desfocado no fundo se destacou, parecendo estar em pé no tronco:
https://image.nostr.build/d0d5e73ecbcdefa79ffd858d0143f41915c9deab7864d271d5ee724b3927f9bc.jpg
A foto abaixo se trata do pisca-alerta original da minha super DT200R (viva os motores 2 tempos!) que caiu depois de uma trilha kkk. A Ideia nesta fotografia era fazer o sol parecer estar acendendo o alerta que deveria aparentar estar flutuando no céu. Infelizmente não fui bem sucedido, pois os fios que penduravam o objeto acabaram aparecendo. É impressionante a capacidade de cálculo da Canon T50 e a velocidade do seu obturador, a nitidez da objetiva e a resolução do filme Kodak Pro Image 100, cujo conjunto conseguiu captar até os pequenos fios de nylon transparentes. Eu imaginei que a foto ia estourar e os fios não apareceriam, ledo engano. Pelo menos o enquadramento ficou correto: objeto um pouco mais acima do centro para dar sensação de altitude e levemente de perfil para dar noção 3d. Quem sabe com uma câmera que seja possível ajustar a velocidade do obturador eu seja bem sucedido…
https://image.nostr.build/808243d34b6dbeade25d38189163f9d58f6a12da9d00df17c85651d501e1bed8.jpg
A foto abaixo se trata da minha performance favorita com a fotografia analógica, pois fotografei o primeiro quadro que pintei, o qual dei o nome de Elipsoíris sendo ele posteriormente capa do meu livro FILOSOFIA FUNDAMENTAL, então aí temos três linguagens artísticas profundas na mesma performance: O quadro que virou livro fotografado analogicamente. A ideia desta performance foi enquadrar o quadro desfocado, o qual somente pode ser desvendado com os olhos certos, por isso a lente. Utilizei luz natural e uma lente velha de óculos. Especial destaque para os dois pontos de luz que refletiram na lente parecendo dois olhos, isso não foi planejado e deu um toque especial para a fotografia, cabendo diversas interpretações, esse é o objeto da arte em geral. Fiquei muuuito contente com o resultado:
https://image.nostr.build/6bb5b802b3ad1bb7262b925225fcfb0b8b00654fa0fec240be57f648c32245af.jpg
Já na fotografia analógica abaixo considero uma performance porque não se trata duma fotografia comum de paisagem, flores, arquitetura, animais ou pessoas, visa passar uma mensagem. Utilizando apenas a luz natural, regulei o foco da Canon T50 para as lentes dos meus próprios óculos e escolhi um dia especialmente nublado e escuro para simbolizar as dificuldades pelas quais todos passamos no dia-a-dia, quando acreditamos por algum momento que as luzes estão apagadas para nós, até que com os óculos certos podemos enxergar com maior nitidez o horizonte, os óculos podem ser a palavra de Deus ou qualquer outra coisa que te ilumine e esclareça. Com certeza essa fotografia terá um bom uso em meus próximos escritos:
https://image.nostr.build/b44b573bb39cdf5f2eb446e818bbf59d5dab9d3815ac6e917440b2f6b1ff431c.jpg
DUPLA EXPOSIÇÃO
Eis aqui um recurso nato da fotografia analógica: a dupla exposição. Se trata de fotografar mais de uma vez em cima do mesmo filme de modo que as imagens se sobreponham. Como esse método podemos simular movimento numa única fotografia, fazer montagens de disco voador kkkk, enfim a imaginação é o limite, vamos ver:
Nessa fotografia analógica abaixo ocorreu uma quádrupla exposição, pois cliquei quatro enquadramentos diferentes sob o mesmo filme. Foi especialmente difícil fazer porque a Canon T50 não tem esse recurso, então tive que enganá-la pressionando o botão de rebobinar o filme ao mesmo tempo que disparava a câmera. Como eu estava usando o filme Kodak Pro Image que possui asa 100, também regulei a máquina como se estivesse usando um filme asa 25, então sabia que podia disparar quatro vezes sem queimar o filme. Pedi para a modelo (minha Mãe, kkk) ficar em três posições diferentes dando a impressão de movimento e não satisfeito no final ainda fotografei o sol. Adorei essa foto:
https://image.nostr.build/5f8e2962e2ee94259d4dd5d3b777976a4d20ba293a5a4e68e81e30a0e1975543.jpg
FOTOS EM MACRO OU CLOSE
Acredito ser possível obter uma fotografia analógica em macro mesmo sem lente especial, tudo depende da pecinha que fica atrás da câmera: você, kkkk. Devemos tentar, se não obtivermos uma fotografia em macro, ao menos um close teremos, vamos ver:
Na foto abaixo há um minúsculo cogumelo que cresceu num barranco qualquer, apareceu nitidamente no negativo, mesmo sem uso de lupa, por isso considero um macro, na verdade é apenas uma foto divertida:
https://image.nostr.build/02aa4bbdc0cf54519b694c75237693fc2a6569fe4f3167220b05c7498757b822.jpg
Já a foto abaixo é apenas um close, o ninho é especialmente profundo, por isso o leve desfoque nos ovos: para dar noção de profundidade. O foco dos quatro cantos da caixa está bem ajustada para dar noção tridimensional do objeto:
https://image.nostr.build/24e5dcdd0e5a3560b341fe4f0d0d93b7d562f2d58054ac308a8e312c2707100c.jpg
O PRIMEIRO QUADRO DO ROLO
Na fotografia analógica cada rolo de filme nos dá pelo menos um tipo de fotografia artística bem específica. Se trata do primeiro quadro do rolo, onde ocorre uma parcial sobre-exposição. Isso se deve a incidência da luz diretamente no filme quando estamos carregando a máquina com o filme. A maioria das máquinas analógicas somente começa a contar os fotogramas após alguns disparos para evitar isso. Cabe ao fotógrafo saber aproveitar os fotogramas existentes antes do número 1, enquadrando a cena normalmente e disparando antes do número 1. Os resultados são quase imprevisíveis e geralmente interessantes.
Abaixo uma fotografia analógica fantástica porque quase sempre a sobre-exposição do primeiro quadro do rolo ocorre nas extremidades da foto e nessa aí ocorreu no meio. Para conseguir esse efeito carreguei a máquina no escuro e acendi a luz no exato momento que estava fechando a tampa da câmera. Por uma fração de segundo o primeiro quadro do rolo foi exposto parcialmente a luz, sabia que iria ter uma fotografia diferente, jamais imaginei que a sobre-exposição iria sair no meio do fotograma, muito curioso:
https://image.nostr.build/a2e08aab686af64df949e83b4ff3b0a00952698a7a138412f7753ebc0dd63d1f.jpg
Na fotografia abaixo repeti o mesmo processo anterior. Como o tempo entre acender a luz e fechar da máquina foi diferente a sobre-exposição ficou bem visível na extremidade da foto. Especial destaque para sua incidência no lado direito, quando deveria incidir no lado esquerdo, pois na Canon T50 o filme roda da esquerda para direita. Essa aparente inversão de lados se deu porque fotografei com a máquina de cabeça para baixo:
https://image.nostr.build/270681be8de71b6c833507dda6bfe4b5233c9b871aa97ea8fc2ebdcdd46a682a.jpg
FOTOS DE AÇÃO
Registrar uma ação com fotografia analógica é especialmente difícil se a máquina não calcula a abertura e tempo de exposição automaticamente, porque tudo acontece muito rápido e você não tem tempo de ficar pensando. Felizmente a Canon T50 é muito boa para esse tipo de fotografia, tive que me preocupar apenas com o foco. O que essa máquina me fez suar para fazer as duplas exposições acima, tirou de letra esse memorável momento, vamos ver:
Na foto abaixo quando avistei esse grupo de corajosos saltando de paraglider corri pedir autorização para fotografá-los e rapidamente carreguei a máquina. Comecei a fotografar mesmo antes da máquina registrar o primeiro fotograma do rolo, tendo obtido esse lindo efeito de sobre-exposição de primeiro quadro do rolo:
https://image.nostr.build/8e32e22d3bf7c897d7111e85555146e38bb139985c50b2795fe809b31880c7d8.jpg
Já a foto abaixo foi a terceira do rolo. Tomei o cuidado de enquadrar tanto a alçada de vôo do paraglider quanto essa linda Veraneio, o que descreve em uma única foto o espírito aventureiro do pessoal. Reparem no sol refletindo sobre as nuvens, que lindo tudo:
https://image.nostr.build/5bf0444e4621406d858ab70725c1ee2f6a7e39b87663e23a18085a32b9a06f6a.jpg
Na foto abaixo tive que registrar mais uma dessa linda Veraneio, sou apaixonado por motores e mecânica, ela quase roubou a cena kkkk. Especial destaque para o detalhe do carro e da câmera que a fotografou serem da mesma época, sensível retorno ao passado. Verdadeira máquina do tempo essa foto. Se eu não dissesse que esta foto foi tirada no final do ano de 2020 daria para dizer que foi uma foto tirada de uma Veraneio Zero Km da época, segredinho nosso, kkk.
https://image.nostr.build/f5284ff30986ad84d22f137e0a330067f91564907da8acf04c9eb93a991cbcf2.jpg
Na foto abaixo voltando à cena, agora do Ângulo certo kkk. Esse foi a segunda foto, perceba ainda a presença do efeito de sobre-exposição do primeiro quadro. Aqui a máquina estava marcando o primeiro fotograma, tadinha kkk
https://image.nostr.build/5c1d73f7d802fd1f730427e29f921c82e410c5dce3112a3133d6fce294d310c6.jpg
Na foto abaixo a luz estava perfeita, o sol iluminava atrás de mim, incidindo frontalmente para o enquadramento da foto, linda essa:
https://image.nostr.build/156fc878dd18257ad1f59d1b5d3fd719c7e773937356fad6ea09b0ce1f151f12.jpg
Paraglider quase em posição de vôo, a foto ficou quase perfeita porque o momento em tela era a Hora de Ouro, momento do entardecer quando a posição do sol deixa o céu dourado, fenômeno muito querido pelos fotógrafos analógicos; até pelos digitais também. Mesmo assim eu não estava satisfeito, queria fotografar mais de perto. Dei zoom correndo para frente e o resultado você vê abaixo:
https://image.nostr.build/b1f610695bd57db8abe7408df318978b6e69e85fe620a589b12fb9bcaae66156.jpg
Abaixo a fotografia analógica simplesmente perfeita, sol na posição certa, hora de ouro, perfeito enquadramento e foco, tudo certo, universo conspirando à favor… ganhei o dia sem saber. Só descobri depois que revelei. O chão não foi cortado é que o piloto do paraglider já estava no desnível do chão pronto para saltar:
https://image.nostr.build/93a7e416d11c996b65a32b019667a43124d96985109d34fd1a9b239ef365bbfe.jpg
Abaixo O salto… tive que correr para o barranco para dar zoom, outra foto perfeita na hora de ouro:
https://image.nostr.build/f254c2e71863a233816b517564dd5fb7fe85ee0bd927b02687fba43bde53dcd6.jpg
FOTOGRAFIA ANALÓGICA DE ANIMAIS
É especialmente difícil fazer um animal posar para gente, temos que ter um pouco de comida pra negociar kkk. Não fosse a Canon T50 calcular a exposição sozinha seria ainda mais difícil porque os momentos são muito rápidos e você não tem tempo para regular a abertura e tempo de exposição, tive que regular apenas o foco. Mais um ponto para essa notável máquina que me fez apanhar na dupla exposição acima. A fotografia analógica de animais também é um tipo de fotografia de ação, temos que ser rápidos no gatilho, vamos ver os resultados:
Abaixo novamente dei zoom chegando bem perto, fotógrafo de verdade não tem medo, tudo pela arte!
https://image.nostr.build/5f0af116b1fd81edb3f21dfd5d7cce6c534751ac8660bd5fb58ce08c652d8aaf.jpg
Abaixo foco no segundo plano, acabei pegando os dois de perfil:
https://image.nostr.build/fbd78fcf71749569444d3438e0d5283d321fc3f3350cacc6e4a3e9a0cdc914f5.jpg
Abaixo foco no segundo plano. Aqui peguei os dois olhando para mim e dizendo xiiiis, kkk.
https://image.nostr.build/3a1f50ee1e3c6213b337654e69ee23819ab60100c8a1a049ee0b2b66fac0d8f8.jpg
Abaixo podemos comprovar que o fotômetro da Canon T50 é matricial e não pontual, porque o centro da foto tinha muito mais luz que os cantos:
https://image.nostr.build/11a8a5a7ff14a661755f04f743d70d3dd1a9d11e412791ce42f5cbf1da1c6be2.jpg
Abaixo linda foto: Cavalo da Montanha. Eu estava esperando a Hora de Ouro chegar, pena que quando chegou o modelo não quis mais ser fotografado kkk.
https://image.nostr.build/83429975966cb4b0e71e5e089651d4585513d823fea404014b0b78b21e859302.jpg
Abaixo lindo close de perfil com fundo totalmente desfocado. Preto absoluto, a fotometria esta certinha:
https://image.nostr.build/f36aed8fa89b6ba81dd77c7d3b32c24424483e626a9634cbadb16baf91427d66.jpg
Abaixo muita coisa acontecendo ao mesmo tempo: As galinhas comendo, o milho sendo jogado, a sombra do fotógrafo… Para obter essa foto joguei o milho para o alto e tive que ser tão rápido no gatilho quanto o Kid Morengueira. Você pode perceber na minha sombra que estou segurando apenas a câmera, o pote de milho já tinha voado longe kkk. Escolhi especialmente um dia ensolarado para que o fotômetro da Canon T50 usasse toda a velocidade possível no obturador, sendo possível congelar o milho no ar sem muito efeito borrão.
https://image.nostr.build/d566e46a8a3cba8855e80295910e5addb0a8aa7735093c9f93f129cac2379472.jpg
Abaixo galinha chocando numa roda de carro. Como amo animais e carros, para montar essa cena tive que forrar uma roda velha de carro para formar um ninho e esperar, esperar e esperar… No momento certo a Jurema se sentiu confiante para entrar na roda. Nem se incomodou com minha presença pois estava de papo cheio, pois é, também tive que negociar com a galinha, isso é a fotografia analógica de animais kkk. Percebam novamente que o fotômetro da Canon T50 é matricial, pois a maior parte da foto era com pouca luz e o raio de sol que entrava estourou a foto. Percebam ainda como eu estava perto da galinha, pois foquei em sua cabeça e o resto do corpo que estava um pouco mais distante saiu desfocado. Certamente a câmera estava com abertura máxima f1.8 e com uma velocidade bem lenta, o que explica a baixa profundidade de campo. Além disso se a Jurema tivesse mexido a cabeça na hora do disparo certamente teria saído um borrão por causa da baixa velocidade. Acabou saindo tudo certo e meus dias de espera por essa foto não foram em vão.
https://image.nostr.build/d7484609c8ff9be05ee6d518def402f66484a02109dc96ef5c734b11216385bf.jpg
FOTOGRAFIA ANALÓGICA DE ARQUITETURA
Na fotografia analógica de arquitetura devemos conhecer os conceitos básicos de iluminação e preenchimento, trabalhamos apenas com luz natural e deve ser bem usada para termos a noção tridimensional da construção. Conforme ensina Fernando Bagnola, a tridimensionalidade do objeto depende da incidência da luz em três pontos diferentes e com intensidades diferentes, algo difícil de se obter apenas com a luz do sol, vamos ver:
Abaixo se trata do Museu do Olho em Curitiba/PR. Como sua parte frontal é escura e o sol se posicionava atrás da construção tive de me posicional na sua lateral, assim consegui obter um resultado tridimensional, pois o sol iluminava a parte de cima, refletia na parte de baixo em menor intensidade e na parte frontal quase não havia luz. Se eu estivesse posicionando na frente da construção o efeito tridimensional seria impossível:
https://image.nostr.build/6f74c1c7e606f7950eaf45007868b92e9a0288722b3d5e580ecaa4930700e3ea.jpg
Abaixo para minha sorte, nesse exato momento um grupo de jovens contracultura (assim como eu) passavam pelo local, tornando a foto icônica pela presença de jovens modernos contracultura contrastando com arquitetura moderna da cultura tradicional. Minha posição em relação ao sol também favoreceu o sucesso desta fotografia, tendo iluminado corretamente todos os pontos de interesse:
https://image.nostr.build/7c374205d7df21985a6a71c6c17e4f67ab29baf452f0cd406b869df94d68296c.jpg
Abaixo esse aqui é um exemplo de fotografia analógica arquitetônica errada. O enquadramento foi frontal em razão do desejo de captar o reflexo dos edifícios nos vidros negros do “olho”:
https://image.nostr.build/f9a0869a165bc7e634944c01e59085203347ab6c353610bdcaace30ee3ed8d8a.jpg
Abaixo se trata do Panteon dos Heroes na Lapa/PR um monumento erguido para guardar os corpos dos soldados das forças republicanas que pereceram durante o chamado Cerco da Lapa, batalha da Revolução Federalista de 1894. Aqui o dia estava nublado, momento perfeito para fotografar uma arquitetura tão triste como essa. Não me importei com a questão tridimensional, pois era impossível, não havia sol. Quis retratar a tristeza na foto. O filme usado foi o mesmo (Kodak Pro Image 100). Aqui percebemos que a química desse filme é ajustada para a luz amarela do sol como branco absoluto, como o céu estava nublado, a luz natural estava com temperatura mais fria o que puxou o tom mais para o azul e o roxeado da foto devem ter sido os raios ultravioleta. Se eu estivesse usando um filtro ultravioleta provavelmente a foto sairia mais acinzentada. Me recordo que nesse dia estava tudo cinza. De qualquer forma adorei esse tom arroxeado da foto. Fica a dica: conseguimos o mesmo efeito de um filme Lomochrome Purple caríssimo com um filme baratinho, basta fotografar nessas condições:
https://image.nostr.build/24f91369c12e83861f7eec38ff99f1869f08ae1eec06c798ccbe08af62263a2e.jpg
Abaixo novamente o tom arrocheado com um filme barato. Para se ter uma ideia um Lomochrome Purple costuma custar seis vezes ou mais que um que o Kodak Pro Image 100 de R$ 30,00 à R$ 40,00 na data da publicação deste artigo em 09/04/21. Percebam que no momento desta foto as nuvens deram uma trégua e alguns raios de sol passaram dando uma leve noção tridimensional da arquitetura. O certo seria eu estar um pouco mais à esquerda para aproveitar bem a iluminação. Mesmo assim, me senti feliz com a triste foto kkk pois mesmo com a luz amarela do sol refletindo o efeito Lomo-Violeta ocorreu:
https://image.nostr.build/099a1a4d7857325e59f5b35805c0ebb5c3fa55af45de2096236f1dfbadca4d4a.jpg
Abaixo parece que a foto está mal enquadrada. E está mesmo. É que no lado direito havia um poste de energia elétrica muito feio, eu não queria que aparecesse. Me preocupei apenas com a iluminação e obtive sucesso com a noção de profundidade da arquitetura. A foto está puxando para o amarelo porque a Universidade Federal do Paraná em Curitiba é meio amarela mesmo.
https://image.nostr.build/48a4d517488fc1656e027568ad314688bc0fd9995e67289003f832eb904e5260.jpg
Abaixo para finalizar o conjunto de fotografias analógicas arquitetônicas nada melhor que um cemitério, afinal todos vamos morrer um dia, devemos sempre lembrar disso para fazer nossas vidas mundanas valerem a pena. Quando morremos não levamos nada a não ser nossas experiências evolucionais, nossas graças e pecados. Devemos deixar um legado, algo positivo para quem fica. Pois bem, foi nesse contexto a foto. Para mim a morte deve ser evitada. Quando ocorrer, se fizermos tudo certo vamos para luz, as trevas são aqui na terra mesmo. Portanto, ao contrário da maioria dos fotógrafos, escolhi um dia ensolarado para fotografar ali. Quis simbolizar a luz que nos aguarda após a morte. Então me posicionei dentro do cemitério para fotografar de dentro para fora. Esperei o sol se posicionar de forma que dos portões para fora houvesse pouca luz, tal como é o mundo, deixando toda a iluminação para dentro dos portões. Percebam como pequenos detalhes fazem toda a diferença numa fotografia analógica artística. Essa foto pode perfeitamente ser usada para ilustrar qualquer material que corrobore com esse pensamento. Se eu quisesse retratar que a vida é mil maravilhas e a morte um triste fim, deveria estar do lado de fora dos portões com tudo iluminado exceto o interior do cemitério. Interessante não…
https://image.nostr.build/051592db1d3612c719621547a69bc8dfd0319d6b89656451d5b60582ae864e8e.jpg
FOTOGRAFIA ANALÓGICA DE PESSOAS
Basicamente se divide em dois tipos, a cena e o retrato. Na cena a pessoa posa para a foto sem contudo revelar sua personalidade, é uma cena criada artificialmente. Já o retrato, no conceito artístico da fotografia, ocorre quando conseguimos captar o interior da pessoa. Por exemplo: se for uma pessoa triste ela aparecerá com semblante triste, se for uma pessoa alegre com semblante alegre, não necessariamente sorrido. Se for uma pessoa sofrida suas rugas, desasseios e receios ficarão visíveis. Se for uma pessoa engraçada sentiremos vontade de rir ao ver seu retrato. O retrato é algo verdadeiro e espontâneo da pessoa. Se uma pessoa triste aparece sorrido não é um retrato e sim uma cena, vamos ver:
Abaixo normalmente na fotografia analógica de pessoas o correto é deixar o segundo plano mais escuro e o primeiro plano mais claro. Ai quis fazer diferente. Pedi para o modelo (Meu Melhor Amigo) se posicionar de costas para o sol, pois já tinha avistado aquele arco-íris no fundo. Nesse caso foi um retrato pois meu amigo apareceu sorrindo sem eu pedir e sei que ele é uma pessoa feliz e engraçada, pois vive contando piadas e seu repertório é infinito. O interessante é que esse não é um retrato comum e sim um retrato artístico, pois inverti a iluminação dos planos e ainda captei uma arco-íris, foi uma cena construida para um retrato, ideia antagônica para fotografia analógica de pessoas. Como resultado obtive uma fotografia que parece uma montagem, onde a imagem do modelo ter-se-ia sido colada sobre a paisagem, tamanha foi a diferença de iluminação entre o primeiro e segundo plano. Contudo, um pequeno raio de sol que incidiu sobre o canteiro inferior esquerdo não me deixa mentir que a fotografia é autêntica. Além disso tendo os negativos que não mentem kkk. Essa foi minha fotografia preferida de pessoas, pela qualidade do resultado artístico e pela pessoa do modelo, um abração amigo! Vou chamar essa foto de “Meu Parça na Praça”:
https://image.nostr.build/51db1df7741227dc2d86529bc9e7a93cf27365f0f2d7b591a4e84a9a05855dfb.jpg
Abaixo sou eu. Se trata apenas de uma cena simples porque minha expressão não aparece e sequer minhas roupas traduziam minha personalidade. Regulei o foco da máquina para 5 metros, entreguei-a para meu amigo e contei alguns passos para trás. Não me preocupei muito em acertar minha posição em exatos 5 metros porque o dia estava bem ensolarado e sabia qua a Canon T50 iria abrir pouco o diafragma por causa disso, o que aumentou a profundidade de campo consideravelmente. Podemos perceber no fundo a Universidade Federal do Paraná sem qualquer desfoque por causa disso. O maldito poste que tentei evitar na foto arquitetônica da UFPR acima acabou aparecendo aqui, mesmo assim gostei da foto pelo tom de cores que só a fotografia analógica nos dá.
https://image.nostr.build/ce8af555274333fa8a26375247373ca92315e87d7414bcc9ad7b5a4840cb3a21.jpg
FOTOGRAFIA ANELÓGICA DE OBJETOS
A fotografia analógica de objetos, assim como a arquitetônica, deve se obedecer os conceitos básicos de iluminação para obter noção tridimensional do objeto. Além disso, a cena montada deve combinar com o objeto para entrar em sintonia com o conceito natural de beleza, vamos ver:
Abaixo queria fotografar um objeto qualquer, então peguei essa faca. Esse objeto combina muito bem com o ambiente rústico do campo, então a finquei-a num toco de árvore com vista para o campo, tomando cuidado para ela ficar levemente torcida e dar a noção tridimensional. Naturalmente a foto ornou porque o objeto esta em sintonia com a cena. Essa deve ser a combinação da fotografia analógica de objetos, por exemplo. A não ser que o fotógrafo busque justamente causar repudia invertendo a combinação do objeto com a cena. Por exemplo: para causar nojo pode-se fotografar barro em formato de cocô num prato. Merda e comida são coisas totalmente opostas e essa inversão naturalmente é perturbadora para qualquer ser humano. Existe uma lógica natural de combinação de objetos com a cena. Enfim, podemos inclusive combinar mais de um objeto secundário para criar uma cena ao objeto principal, como veremos mais abaixo com a xícara de café:
https://image.nostr.build/6474901ce85d34aef3421ce5f720e258208c50aeb57e9893c8a750c6dc8fc1df.jpg
Na foto abaixo o objeto principal é uma caneca de café. Para criar a cena utilizei outros três objetos. O palheiro que combina com café, a tampa da objetiva da minha Canon T50 que combina com o efeito da cafeína para pensar mais rápido sobre as cenas que irei montar, e o vazo de suculenta que remete a algo mais áspero e amargo como o café e o palheiro. Se o objeto principal fosse um copo de milkshake no lugar do palheiro haveriam balas coloridas, no lugar da tampa da máquina haveria um guardanapo e no lugar da suculenta haveria um flor fofa e cor de rosa. Falando em flor vou encerrar este ensaio com o tópico sobre fotografia analógica de flores para deixar todos felizes no final:
https://image.nostr.build/8e95c6bae536cfea47e3c5d44aa63725ab8fe20eacd1c6d5eeaae1720dd0a9e5.jpg
FOTOGRAFIA ANELÓGICA DE FLORES
É um tipo de fotografia livre da fotografia analógica, sem muitas preocupações para o fotógrafo analógico, devemos atentar apenas para a vivacidade das cores e para isso o dia deve estar especialmente ensolarado. Se for fotografia interna de preferência usar luz quente (amarela), o resto é só diversão, vamos ver:
https://image.nostr.build/fc8cf663300794761b0d8dc6f1a765e3a423c65a4ad4a85a7885b00716b46533.jpg
https://image.nostr.build/dc4fbe15a7b46817d66bdbeb3d0e11851999b2c1292c576fd457956436e75c77.jpg
https://image.nostr.build/73fa3b1b30a088954b342294e1b0aa555a693c3ad425dea9807d2238ec529747.jpg
Viva a fotografia analógica!
Se você deseja fazer um ensaio artístico com fotografia analógia comigo entre em contato e terei o prazer de agendar o serviço.
-

@ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08
### Tldr
- Nostr is an open and interoperable protocol
- You can integrate it with workflow automation tools to augment your experience
- n8n is a great low/no-code workflow automation tool which you can host yourself
- Nostrobots allows you to integrate Nostr into n8n
- In this blog I create some workflow automations for Nostr
- A simple form to delegate posting notes
- Push notifications for mentions on multiple accounts
- Push notifications for your favourite accounts when they post a note
- All workflows are provided as open source with MIT license for you to use
### Inter-op All The Things
Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In [Using NFC Cards with Nostr]() I explored the `nostr:` URI to launch Nostr clients from a card tap.
The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails.
My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted.
This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull.
So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications.
All we need are simple ways to plug things together.
### Nostr and Workflow Automation
Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective.
#### n8n for workflow automation
Many workflow automation tools exist. My favourite is [n8n](https://n8n.io/). n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to.
Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine.
#### Eating my own dogfood
It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do?
In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting.
I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up.
### Running n8n with Nostrobots
I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs my [HAVEN Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/) and [Albyhub Lightning Node](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/) in Docker containers,
- My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows.
#### Installing n8n
Self-hosting n8n could not be easier. I followed n8n's [Docker-Compose installation docs](https://docs.n8n.io/hosting/installation/server-setups/docker-compose/)–
- Install Docker and Docker-Compose if you haven't already,
- Create your ``docker-compose.yml`` and `.env` files from the docs,
- Create your data folder `sudo docker volume create n8n_data`,
- Start your container with `sudo docker compose up -d`,
- Your n8n instance should be online at port `5678`.
n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there.
#### Installing Nostrobots
To integrate n8n nicely with Nostr, I used the [Nostrobots](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) community node by [Ocknamo](nostr:npub1y6aja0kkc4fdvuxgqjcdv4fx0v7xv2epuqnddey2eyaxquznp9vq0tp75l).
In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in.
You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative).
To install a community node, [see n8n community node docs](https://docs.n8n.io/integrations/community-nodes/installation/gui-install/). From your workflow dashboard–
- Click the "..." in the bottom left corner beside your username, and click "settings",
- Cilck "community nodes" left sidebar,
- Click "Install",
- Enter the "npm Package Name" which is `n8n-nodes-nostrobots`,
- Accept the risks and click "Install",
- Nostrobots is now added to your n8n instance.
#### Using Nostrobots
Nostrobots gives you nodes to help you build Nostr-integrated workflows–
- **Nostr Write** – for posting Notes to the Nostr network,
- **Nostr Read** – for reading Notes from the Nostr network, and
- **Nostr Utils** – for performing certain conversions you may need (e.g. from bech32 to hex).
Nostrobots has [good documentation](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) on each node which focuses on simple use cases.
Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use.
What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible.
Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with [NIP-01](https://github.com/nostr-protocol/nips/blob/master/01.md)). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of.
#### Creating and adding workflows
With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation.
- Click "Add workflow" to go to the workflow builder screen,
- If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added,
- If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article).
### Nostr Workflow Automations
It's time to build some things!
#### A simple form to post a note to Nostr
I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily.
I needed a basic form with credentials that posted a Note.
For this I can use a very simple workflow–
- **A n8n Form node** – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted.
- **A Set node** – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain.
- **A Nostr Write node** (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays.
Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive".
It may also be the world's simplest Nostr client.
You can find the [Nostr Form to Post a Note workflow here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Form_to_Post_a_Note.json).
#### Push notifications on mentions and new notes
One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want–
- **To make sure I never miss a note addressed to any of my Npubs** – For this I want a push notification any time any Nostr user mentions any of my Npubs,
- **To make sure I always see all notes from key accounts** – For this I need a push notification any time any of my Npubs post any Notes to the network,
- **To get these notifications on all of my devices** – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day.
I needed to build a Nostr push notifications solution.
To build this workflow I had to string a few ideas together–
- **Triggering the node on a schedule** – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited,
- **Storing a list of Npubs in a Nostr list** – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists ([NIP-51, kind 30000](https://github.com/nostr-protocol/nips/blob/master/51.md)). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. [Listr.lol](https://listr.lol/npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft) or [Nostrudel.ninja](https://nostrudel.ninja/#/lists)). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions,
- **Using specific relays** – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata,
- **Querying Nostr events** (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do–
- I read the EventID of my Kind 30000 list, to return the desired pubkeys,
- For notifications on mentions, I read all Kind 1 notes that mention that pubkey,
- For notifications on new notes, I read all Kind 1 notes published by that pubkey,
- Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub,
- I transform the EventID into a Nevent to help clients find it.
- **Using the Nostr URI** – As I did with my NFC card article, I created a link with the `nostr:` URI prefix so that my phone's native client opens the link by default,
- **Push notifications solution** – I needed a push notifications solution. I found many with n8n integrations and chose to go with [Pushover](https://pushover.net/) which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license.
Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go.
You can find the [Nostr Push Notification If Mentioned here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json) and [If Posts a Note here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Post_a_Note.json).
In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible.
#### Use my workflows
I have open sourced all my workflows at my [Github](https://github.com/r0d8lsh0p/nostr-n8n) with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use.
To import any of my workflows–
- Click on the workflow of your choice, e.g. "[Nostr_Push_Notify_If_Mentioned.json](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json "Nostr_Push_Notify_If_Mentioned.json")",
- Click on the "raw" button to view the raw JSON, ex any Github page layout,
- Copy that URL,
- Enter that URL in the "import from URL" dialog [mentioned above](#creating-and-adding-workflows).
To configure them–
- Prerequisites, credentials, and variables are all stated,
- In general any variables required are entered into a Set Node that follows the trigger node,
- Pushover has some extra setup but is very straightforward and documented in the workflow.
### What next?
Over my first four blogs I explored creating a good Nostr setup with [Vanity Npub](https://rodbishop.npub.pro/post/mining-your-vanity-pubkey-4iupbf/), [Lightning Payments](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/), [Nostr Addresses at Your Domain](https://rodbishop.npub.pro/post/ee8a46bc/), and [Personal Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/).
Then in my latest two blogs I explored different types of interoperability [with NFC cards](https://rodbishop.npub.pro/post/edde8387/) and now n8n Workflow Automation.
Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this:
- Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds),
- Automated or scheduled posting (such as auto-liking everything [Lyn Alden](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) posts),
- Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming),
- All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr,
- All kinds of other automation (such as [BlackCoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) [controlling a coffee machine](https://primal.net/e/note16fzhh5yfc3u4kufx0mck63tsfperdrlpp96am2lmq066cnuqutds8retc3)),
- All kinds of AI Assistants and Agents,
In fact I have already released an open source workflow for an [AI Assistant](https://primal.net/p/npub1ahjpx53ewavp23g5zj9jgyfrpr8djmgjzg5mpe4xd0z69dqvq0kq2lf353), and will share more about that in my next blog.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-

@ a95c6243:d345522c
2025-01-01 17:39:51
**Heute möchte ich ein Gedicht mit euch teilen.** Es handelt sich um eine Ballade des österreichischen Lyrikers Johann Gabriel Seidl aus dem 19. Jahrhundert. Mir sind diese Worte fest in Erinnerung, da meine Mutter sie perfekt rezitieren konnte, auch als die Kräfte schon langsam schwanden.
**Dem originalen Titel «Die Uhr»** habe ich für mich immer das Wort «innere» hinzugefügt. Denn der Zeitmesser – hier vermutliche eine Taschenuhr – symbolisiert zwar in dem Kontext das damalige Zeitempfinden und die Umbrüche durch die industrielle Revolution, sozusagen den Zeitgeist und das moderne Leben. Aber der Autor setzt sich philosophisch mit der Zeit auseinander und gibt seinem Werk auch eine klar spirituelle Dimension.
**Das Ticken der Uhr und die Momente des Glücks und der Trauer** stehen sinnbildlich für das unaufhaltsame Fortschreiten und die Vergänglichkeit des Lebens. Insofern könnte man bei der Uhr auch an eine Sonnenuhr denken. Der Rhythmus der Ereignisse passt uns vielleicht nicht immer in den Kram.
**Was den Takt pocht, ist durchaus auch das Herz,** unser «inneres Uhrwerk». Wenn dieses Meisterwerk einmal stillsteht, ist es unweigerlich um uns geschehen. Hoffentlich können wir dann dankbar sagen: «Ich habe mein Bestes gegeben.»
*Ich trage, wo ich gehe, stets eine Uhr bei mir;* \
*Wieviel es geschlagen habe, genau seh ich an ihr.* \
*Es ist ein großer Meister, der künstlich ihr Werk gefügt,* \
*Wenngleich ihr Gang nicht immer dem törichten Wunsche genügt.*  
*Ich wollte, sie wäre rascher gegangen an manchem Tag;* *\
Ich wollte, sie hätte manchmal verzögert den raschen Schlag.* *\
In meinen Leiden und Freuden, in Sturm und in der Ruh,* *\
Was immer geschah im Leben, sie pochte den Takt dazu.*  
*Sie schlug am Sarge des Vaters, sie schlug an des Freundes Bahr,* *\
Sie schlug am Morgen der Liebe, sie schlug am Traualtar.* *\
Sie schlug an der Wiege des Kindes, sie schlägt, will's Gott, noch oft,* *\
Wenn bessere Tage kommen, wie meine Seele es hofft.*  
*Und ward sie auch einmal träger, und drohte zu stocken ihr Lauf,* *\
So zog der Meister immer großmütig sie wieder auf.* *\
Doch stände sie einmal stille, dann wär's um sie geschehn,* *\
Kein andrer, als der sie fügte, bringt die Zerstörte zum Gehn.*  
*Dann müßt ich zum Meister wandern, der wohnt am Ende wohl weit,* *\
Wohl draußen, jenseits der Erde, wohl dort in der Ewigkeit!* *\
Dann gäb ich sie ihm zurücke mit dankbar kindlichem Flehn:* *\
Sieh, Herr, ich hab nichts verdorben, sie blieb von selber stehn.*  
*Johann Gabriel Seidl (1804-1875)*
-

@ f9cf4e94:96abc355
2024-12-31 20:18:59
Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( [dominictarr]( https://github.com/dominictarr/scuttlebutt) ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt ([ssb]( https://github.com/ssbc/ssb-db)) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia.
Se você está se perguntando de onde diabos veio o nome Scuttlebutt:
> Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.

Marinheiros se reunindo em torno da rixa. ( [fonte]( https://twitter.com/IntEtymology/status/998879578851508224) )
Dominic descobriu o termo boato em um [artigo de pesquisa]( https://www.cs.cornell.edu/home/rvr/papers/flowgossip.pdf) que leu.
Em sistemas distribuídos, [fofocar]( https://en.wikipedia.org/wiki/Gossip_protocol) é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”.
**Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto.** **Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar.** Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário [de bordo]( https://en.wikipedia.org/wiki/Logbook) (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem.
Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. **Cada item adicionado a um log do usuário é chamado de mensagem.**
**Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações.** Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
**Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar.** Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. **Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.**
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de [Pubs públicos em que]( https://github.com/ssbc/ssb-server/wiki/Pub-Servers) todos podem participar **.** Explicaremos como ingressar em um posteriormente neste guia. **Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais.** Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.

Perspectivas dos participantes
## Scuttlebot
O software Pub é conhecido como servidor Scuttlebutt (servidor [ssb]( https://github.com/ssbc/ssb-server) ), mas também é conhecido como “Scuttlebot” e `sbot`na linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial.
**Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações.** Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
**Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar.** Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. **Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.**
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de [Pubs públicos em que]( https://github.com/ssbc/ssb-server/wiki/Pub-Servers) todos podem participar **.** Explicaremos como ingressar em um posteriormente neste guia. **Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais.** Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.


Perspectivas dos participantes
## Pubs - Hubs
### Pubs públicos
| Pub Name | Operator | Invite Code |
| ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ |
| `scuttle.us` | [@Ryan]( https://keybase.io/ryan_singer) | `scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=` |
| [pub1.upsocial.com]( https://upsocial.com/) | [@freedomrules]( https://github.com/freedomrules) | `pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=` |
| [Monero Pub]( https://xmr-pub.net/) | [@Denis]( https://github.com/Orville2112) | `xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=` |
| [FreeSocial]( https://freesocial.co/) | [@Jarland]( https://github.com/mxroute) | `pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=` |
| `ssb.vpn.net.br` | [@coffeverton]( https://about.me/coffeverton) | `ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=` |
| [gossip.noisebridge.info]( https://www.noisebridge.net/wiki/Pub) | [Noisebridge Hackerspace]( https://www.noisebridge.net/wiki/Unicorn) [@james.network]( https://james.network/) | `gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=` |
### Pubs privados
Você precisará entrar em contato com os proprietários desses bares para receber um convite.
| Pub Name | Operator | Contact |
| --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- |
| `many.butt.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) |
| `one.butt.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) |
| `ssb.mikey.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) |
| [ssb.celehner.com]( https://ssb.celehner.com/) | [@cel]( https://github.com/ssbc/ssb-server/wiki/@f/6sQ6d2CMxRUhLpspgGIulDxDCwYD7DzFzPNr7u5AU=.ed25519) | [cel@celehner.com](mailto:cel@celehner.com) |
### Pubs muito grandes
 *Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)* 
| Pub Name | Operator | Invite Code |
| --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ |
| `scuttlebutt.de` | [SolSoCoG]( https://solsocog.de/impressum) | `scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=` |
| `Lohn's Pub` | [@lohn]( https://github.com/lohn) | `p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=` |
| [Scuttle Space]( https://scuttle.space/) | [@guil-dot]( https://github.com/guil-dot) | Visit [scuttle.space]( https://scuttle.space/) |
| `SSB PeerNet US-East` | [timjrobinson]( https://github.com/timjrobinson) | `us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=` |
| Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= |
## GUI - Interface Gráfica do Utilizador(Usuário)
### Patchwork - Uma GUI SSB (Descontinuado)
[**Patchwork**]( https://github.com/ssbc/patchwork) **é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB** . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.

Fonte: [scuttlebutt.nz]( https://www.scuttlebutt.nz/getting-started)
**Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub.** Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs.
Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth.
### Patchbay - Uma GUI Alternativa
Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que [Patchwork]( https://github.com/ssbc/patchwork) e [Patchfoo]( https://github.com/ssbc/patchfoo) , então você pode facilmente dar uma volta com sua identidade existente.

### Planetary - GUI para IOS

[Planetary]( https://apps.apple.com/us/app/planetary-app/id1481617318) é um app com pubs pré-carregados para facilitar integração.
### Manyverse - GUI para Android

[Manyverse]( https://www.manyver.se/) é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone .
## Fontes
* https://scuttlebot.io/
* https://decentralized-id.com/decentralized-web/scuttlebot/#plugins
* https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd
* [**Secure Scuttlebutt**]( http://ssbc.github.io/secure-scuttlebutt/) **:** um protocolo de banco de dados global.
-

@ 3f770d65:7a745b24
2024-12-31 17:03:46
Here are my predictions for Nostr in 2025:
**Decentralization:** The outbox and inbox communication models, sometimes referred to as the Gossip model, will become the standard across the ecosystem. By the end of 2025, all major clients will support these models, providing seamless communication and enhanced decentralization. Clients that do not adopt outbox/inbox by then will be regarded as outdated or legacy systems.
**Privacy Standards:** Major clients such as Damus and Primal will move away from NIP-04 DMs, adopting more secure protocol possibilities like NIP-17 or NIP-104. These upgrades will ensure enhanced encryption and metadata protection. Additionally, NIP-104 MLS tools will drive the development of new clients and features, providing users with unprecedented control over the privacy of their communications.
**Interoperability:** Nostr's ecosystem will become even more interconnected. Platforms like the Olas image-sharing service will expand into prominent clients such as Primal, Damus, Coracle, and Snort, alongside existing integrations with Amethyst, Nostur, and Nostrudel. Similarly, audio and video tools like Nostr Nests and Zap.stream will gain seamless integration into major clients, enabling easy participation in live events across the ecosystem.
**Adoption and Migration:** Inspired by early pioneers like Fountain and Orange Pill App, more platforms will adopt Nostr for authentication, login, and social systems. In 2025, a significant migration from a high-profile application platform with hundreds of thousands of users will transpire, doubling Nostr’s daily activity and establishing it as a cornerstone of decentralized technologies.
-

@ e97aaffa:2ebd765d
2024-12-31 16:47:12
Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes.
Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais _mainstream_. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso.
# Código do Bitcoin
No final de 2025, possivelmente vamos ter um _fork_, as discussões sobre os _covenants_ já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos _covenants_, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido.
Depois dos _covenants,_ o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa.
Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos _bitcoiners_.
Espero que surjam avanços significativos no BitVM2 e BitVMX.
Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da _shitcoinagem_, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs.
Se querem ser levados a sério, têm que ser sérios.
> “À mulher de César não basta ser honesta, deve parecer honesta”
Se querem ter o apoio dos _bitcoiners_, sigam o _ethos_ do Bitcoin.
Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma _multisig_ ou com os _covenants_ na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos _covenants_ para melhorar a interoperabilidade e a soberania.
É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy:
> “Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país”
Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código.
# Reservas Estratégicas de Bitcoin
## Bancos centrais
Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito _mainstream_. Foi um _pivot_, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto.
A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário.
Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”.
Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar.
Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.

## Empresas
A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.

Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%.
Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de _shareholders_ com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft.
Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial.
# ETFs
Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os _inflows_ foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os _inflows_ foram brutais.
Também se beneficiou por ser um mercado novo, não existia _orderbook_ de vendas, não existia um mercado interno, praticamente era só _inflows_. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em _inflows_ ou _outflows_.
Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de _inflows_ em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar.
Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem.
Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes.
Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo.
# Preço
Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo.
# Stablecoins de dólar
Agora saindo um pouco do universo do Bitcoin, acho importante destacar as _stablecoins_.
No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas.
Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às _stablecoins_ de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas.
> “Casa onde não há pão, todos ralham e ninguém tem razão”
Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas.
Eu acredito que 2025, vai haver um forte crescimento na adoção das _stablecoins_ de dólares, esse forte crescimento vai agravar o problema sistémico que são as _stablecoins_. Vai ser o início do fim das _stablecoins_, pelo menos, como nós conhecemos hoje em dia.
## Problema sistémico
O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente.
Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas.
As _stablecoins_ são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema.
No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos.
A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário.
Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/_stablecoins_ para o resto do sistema financeiro, porque o _marketcap_ do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações.
Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do _carry trade_, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado.
Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações.
O mundo cripto é seu oposto, é _naife_ com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto.
Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025.
Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o _redeem_ dos dólares?
Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether?
Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente.
### Conta mestre
Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário.
O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com _full-reserves_. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com _full-reserves_, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos.
Eu concordo com o FED nesse ponto, que os bancos com _full-reserves_ são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos _full-reserves_, mas sim nos que têm reserva fracionária.
O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença.
Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de _compliance_, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o _compliance_ dos seus clientes.
A obrigação do KYC para ter _stablecoins_ iriam provocar um terramoto no mundo cripto.
Assim, é pouco provável que seja a solução para a Tether.
### FED
Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as _stablecoins_ de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as _stablecoins_ estão a colocar em causa a soberania monetária dos outros países. Atualmente as _stablecoins_ estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países.
Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo.
Será algo para acompanhar futuramente, mas só para 2026, talvez…
É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(_stablecoins_). A ironia do destino.
Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona.
# Europa
2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os _compliance_, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo.
O _Travel Route_ passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A _Travel Route_ é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos.
O MiCA também está a colocar problemas nas _stablecoins_ de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias.
O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade _stablecoins_ de euro, as restantes _stablecoins_ serão deslistadas.
Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado.
# Recessão
Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon.
Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro.
Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer.
Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar.
A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa.
Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal.
# Brasil
Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.

Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e _stablecoins_. No Brasil existe um forte adoção, será um bom _case study_, certamente irá repetir-se em outros países num futuro próximo.
Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin.
# Blockchain
Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em _blockchain_. Eu acredito que a BlackRock vai criar uma própria _blockchain_, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar.
-----------
Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião.
Isto é apenas a minha opinião, **Don’t Trust, Verify**!
-

@ 5188521b:008eb518
2024-12-31 16:46:45
<img src="https://blossom.primal.net/e4d7d32a4590123c901aef5d441a85be956c29eec8d321a1d8e5a17cb186862c.jpg">
My experience of [daily posting on LinkedIn](https://www.linkedin.com/in/totallyhumanwriter/) started around three years ago, when I became more serious about my coaching business. In that time, I amassed 25,000 followers and garnered around 3 million impressions on my writing.
It was a wild ride, but now it’s time to leave the theme park.
# Reasons I Quit Posting on LinkedIn
Here they are, in no particular order:
1. I went from coach to ghostwriter. 2024 threw up an unexpected career change. Since 2018, I've been a coach, moving from teaching English as a foreign language to working with groups of multilingual pro writers looking for better opportunities.
Coaching is a tough industry (maybe I'll write about that someday). My idea was to write more meaningful words and less copy to market my coaching business. Ultimately, writing to develop the Bitcoin ecosystem is what I find meaningful, and writing for hire doesn't require as much copywriting as being a coach.
With a solid portfolio, contacts, and profile, potential clients can see your results. You don't need to attract a ton of inbound leads by writing funny bits and wow-inducing educational posts on LinkedIn.
2. Time constraints Because of my own book marketing, new client work, and projects like [21 Futures](https://21futures.com/), I can't dedicate my creative efforts and several hours per week to writing on LinkedIn.
That time works better for me elsewhere.
3. Worsening distribution 'Creators' (a.k.a. active posters with many followers) often say changes to the algorithm don't matter. 'Get on with it. Adapt and move forward.'
I'd be lying if I said I'm happy seeing statistics for my posts plummet. In 2022 and 2023, a successful carousel might net 20,000 views with over 150 likes and 50+ comments. Now, an exceptional post for me attracts 5,000 views with 50 likes.
I won't bore you with charts and statistics, but this is an average, based on hundreds of posts. It seems LinkedIn is reducing the reach of big accounts in favour of tighter networks and distributing the work of those with <5k followers. That's fine. Perhaps that will make the platform less showy, and less boastful, finally ridding us of fake stories, surprising hacks, and ultimate guides.
Still, It makes creative types like me feel like failures. Does an 80% decrease in distribution seem fair for the three years of daily effort I've put in? Should I keep struggling for diminishing returns? No. Creative people must seek the best return on investment for their time.
The lesson? Distribution is more important than follower numbers.
I've also quit Medium, where I have 2,000 followers and regularly receive single-digit reads on my posts.
4. LinkedIn values machines over humans. Cost-cutting, extracting value, and planning for a robotic future. That's Microsoft's MO.
Despite being a social network with over 1 billion users, LinkedIn seemingly relies on automated support to make decisions on which content, people, and ideas are allowed on the platform.
Users' data is parsed without their express consent.\
LinkedIn seems desperate for us to use generative AI to express our 'insight'.\
We are constantly bombarded by LLM drivel and boring machine-made content. If you can't be bothered to write it, why should I bother to read it?
As somebody who brands himself a human-centric writer, why would I offer up personal takes and stories writing for free in an AI-filled swamp?
---
# What's next?
So I'm giving up posting on LinkedIn.
With that said, it can still produce a great benefit for its users, especially those in the bitcoin space.
Why? The ability to search for potential connections, present your profile, and share your expertise can make a huge difference to your work - investment, partnership, and customers.
If you have a smaller network and have the need to share personal takes, opinions, and expertise, posting on LinkedIn is worth it. So few are doing this in bitcoin, the opportunities in 2025 are mind-boggling.
Next year, thousands of new startups and ventures will be vying for our attention. Those who can build trust and stay true to their message will win. And if LinkedIn stops working, you can always take your followers elsewhere.
If you have read and enjoyed my words here on LinkedIn in the last three years, thank you.
It has been a much-needed creative outlet and has brought me opportunities, laughs, knowledge, new colleagues, and friends. I'll still be stalking your posts and writing sarcastic comments.
---
# Where can you find me:
Bitcoin writing - [X](https://x.com/21Futures), [StackerNews](https://stacker.news/21futures) [21futures.com](https://21futures.com/)\
NOSTR (npub12xy9yxej6s9hgzsn3rfyfc3xgtdr29wqlvulquzhz2fhqqywk5vqnyvqut),
[Totallyhumanwriter.com](https://totallyhumanwriter.com/) - website coming soon.
[Maximum Freedom, Minimum Bullshit](https://maximumfreedom.substack.com/) on Substack.
And you can reach me via email at philipcharterauthor@gmail.com
I'm interested to know your thoughts and plans for 2025. Where will you be writing and why?
-

@ f4d89779:2b522db9
2024-12-29 16:46:43
In the game of Ultimate Frisbee, there is a beloved phrase that captures one of the best aspects of playing. Ultimate is about decision making. It is played on a rectangular field with seven players on each side. Much like football, the object of the game is to score with a throw into the end zone.
To "HUCK", means to launch the disc down field in the hopes of scoring. You can probably guess what the "OR YOU'RE NOTHING" means but the spirit of it is that when the opportunity comes ...
PUT THE DISC IN THE AIR
<https://i.nostr.build/XyTpXdNOSpv5f8ZZ.jpg>
Sorry, I had to channel my inner ODELL there for a second. These are all caps kind of moments. Time feels like it stops, the disc floats in the air, the receiver and defender are sprinting all out, you can hear the collective breath of anticipation from the audience and then you score. If you're good that is.
You know what? You and I are civilized people, we use the NOSTR, so I won't limit myself to just words. Here are some of those moments:
<https://v.nostr.build/zav5o04BK97FiNAt.mp4>
During the course of play, teams get into a formation with a couple of the players doing the majority of the disc throwing. These players are called handlers. They handle the disc, they have the responsibility of moving the disc downfield, and handle most of the decision making.
A good handler develops a sort of instinct for each of their receivers, can guess the capabilities of each defender, and knows himself well enough to know if he has the throw. They know who is good and reliable at short cuts. They know who has the top end speed to throw a long floating pass into the end zone. With each play they are judging all of the moving objects on the field and deciding on real time risk of each throw and where things will lead.
Mistakes lead to turnovers and turnovers, like in many other sports, are death.
Hopefully, you start to see how ultimate relates to life and Bitcoin. Life is a field and you have defenders and you have receivers. It is your disc and the decisions you make have a huge impact on whether you win or lose.
Knowingly or not, you saw Bitcoin as a potential receiver and Governments, academics, shitcoiners, as defenders. In some ways those around you were also defenders. They whispered, or maybe still whisper the risk and probability of failure in your ear. Their fear weighed against what you know.
With the btc/usd exchange rate at $94k, and companies fighting over the best ways to get sats I think we can say that you did not get lucky. They called you crazy, they said that throw won't work, they said your receiver sucked but you knew better.
You saw that receiver leaving every defender in the dust and you HUCKED it and you are certainly not NOTHING.
-

@ ece127e2:745bab9c
2024-12-28 22:29:36
Un lugar ominoso ,un hoyo de conejo espiralado en el cual cada ser que aparece es más oscuro que el otro.
Un bosque de ramas secas que es mejor evitar ;si te tocan te secaran ,te extraerán luz hasta convertirte en uno de ellos . Árboles más altos tapan la luz que alimenta al suelo ,y éste se cubre de podredumbre.Esa miasma se te pega en los pies ,te atrapa ..te impide caminar y te hundes hasta no poder respirar.
-

@ f3df9bc0:a95119eb
2024-12-26 12:29:35
# Welcome! 🌱
Interesting places to start:
- Latest polished pieces: [[Latest Articles Index]]
- Index of all articles by discipline: [[Discipline Index]]
## About this site
This site is both a blog & wiki-style digital garden. Some ideas you’ll run into here may be of quality, others will be less interesting, not fully formed, or even just straight wrong. This is intentional. Content here is continuously cultivated and refined as I live my life and gain new experiences, and I welcome challenges to anything I’ve written.
The general idea behind this is that my unstructured thought is fast and divergent, but not coherent, and therefore difficult to use in any practical way. The process of writing is a forcing function for taking divergent thought and bringing it into a form that can be reasoned about, improved upon, or discarded as irrelevant. Stalling this process is counter-productive and can lead to a sort of comatose where the mind is stuck in the abstract, waiting for confidence on a particular strain of thought, but never making any progress.
Therefore there is no set topic for this garden, instead it’s purpose is to serve as an auxiliary brain for any and all topics that I find interesting and worth spending time refining.
## Contact
- nostr: [slipstream@htlc.io](https://nosta.me/slipstream@htlc.io)
- farcaster: [@htlc](http://warpcast.com/htlc)
-

@ bcea2b98:7ccef3c9
2024-12-25 03:11:27
It has been a fun year of learning and entertainment with you all. Merry Christmas!
originally posted at https://stacker.news/items/823433
-

@ dff95033:862fbf40
2024-12-23 20:52:00
Você sabia que o Bitcoin foi uma das melhores escolhas de investimento em 2024, superando até mesmo commodities tradicionais como ouro, soja e gás natural?
Chamado por alguns de **“Dinheiro Mágico da Internet”,** o Bitcoin provou ser mais do que isso, com um crescimento exponencial ao longo dos anos, destacando-se especialmente em 2024
## 📊 **Confira os números impressionantes:**
| **Commodity** | **Ganho(%)** |
| --- | --- |
| 🥇**Cacau** | **200%** |
| 🥈**Bitcoin** | **145%** |
| 🥉**Suco de Laranja** | **50%** |
| **Café Arábica** | **40%** |
| **Gás Natural** | **30%** |
| **Ouro** | **20%** |
| **Carne Suína** | **10%** |
| **Paládio** | **5%** |
| **Soja** | **0%** |
## Bitcoin deixou a concorrência para trás em 2024.
## 🔍 **O que impulsionou o Bitcoin em 2024?**
Se o cacau liderou com 200% graças a problemas de oferta global, o Bitcoin brilhou por outros motivos:
- **Demanda Crescente:** Cada vez mais pessoas buscaram o Bitcoin como reserva de valor.
- **Adoção Institucional:** Um aumento significativo de **30%** na adoção por grandes instituições, de acordo com dados da Glassnode.
- **Busca por Segurança:** O Bitcoin continuou sendo o principal ativo digital descentralizado, atraindo investidores de diferentes perfis.
- **Halving**: Em abril de 2024, ocorreu o "halving" do Bitcoin, um evento onde a recompensa que os mineradores recebem por adicionar transações ao blockchain é reduzida pela metade, de 6,25 para 3,125 Bitcoins por bloco. Isso diminui a oferta de novos Bitcoins, tornando-os mais raros e, por consequência, aumentando seu valor.
Esses fatores consolidaram o **Bitcoin** como o segundo ativo mais rentável do ano, com **145% de valorização**.
## 💡 **Por que investir em Bitcoin agora?**
1️⃣ **Potencial de Crescimento**: Historicamente, o Bitcoin mostra ciclos de valorização exponencial. Em 10 anos, um investimento inicial de $ 100 em Bitcoin poderia valer hoje $ 26.931,1, segundo dados do CoinMarketCap.\
2️⃣ **Diversificação**: O Bitcoin frequentemente se comporta de maneira independente em relação a ativos tradicionais, oferecendo uma oportunidade para diversificação de carteira, com correlações de preço às vezes negativas com ações e commodities.\
3️⃣ **Facilidade de Acesso**: Com a [**Stackfy**](https://t.me/stack_fy_bot?start=4C170C8E), você já pode ter os seus bitcoins com apenas **R$ 25**, de forma simples, rápida e segura!
---
> ⚠️ **Atenção:** Investir em criptomoedas envolve riscos devido à alta volatilidade do mercado. Sempre faça sua própria pesquisa e considere suas tolerâncias de risco antes de investir.
---
## 📈 **Não perca tempo!**
O Bitcoin está mostrando que o futuro dos investimentos está nas mãos de quem acredita em inovação. Prepare-se para 2025 e além! 🌟
➡️ **Ação:** Aproveite essa oportunidade única e faça parte da revolução financeira. Explore plataformas confiáveis como e comece sua jornada no Bitcoin hoje! 🚀
---
## **Referências:**
1. BLOOMBERG. [Cocoa caps 2024 as biggest commodity winner](https://www.bloomberg.com/news/articles/2024-12-21/cocoa-caps-2024-as-biggest-commodity-winner-it-s-not-over-yet). Acesso em: 21 dez. 2024.
2. MARKETWATCH. [Bitcoin valuation trends](https://www.marketwatch.com/story/cocoas-the-best-performing-commodity-in-2024-and-even-beat-bitcoin-whats-next-b8daf55d). Acesso em: 21 dez. 2024.
3. THE WALL STREET JOURNAL. [Cocoa surges past $12,000 on supply concerns](https://www.wsj.com/finance/commodities-futures/cocoa-surges-past-12-000-on-supply-concerns-912c91b4). Acesso em: 21 dez. 2024.
4. GLASSNODE. [Fasanara Digital + Glassnode Report: Institutional perspectives on digital assets](https://insights.glassnode.com/fasanara-digital-glassnode-report-institutional-perspectives-on-digital-assets/). Acesso em: 21 dez. 2024.
5. COINMARKETCAP. [Bitcoin (BTC) preço, gráfico, capitalização de mercado](https://coinmarketcap.com/pt-br/currencies/bitcoin/). Acesso em: 21 dez. 2024.
6. COINGECKO. [Bitcoin versus Traditional Assets: Price Returns.](https://www.coingecko.com/research/publications/bitcoin-versus-traditional-assets-price-returns) Acesso em: 21 dez. 2024.
-

@ 5af07946:98fca8c4
2024-12-22 14:05:19
On the surface, it appears the contest is between the `old guard` and the `new innovation`.
Old seeks to maintain a status quo to ensure a safe passage of their knowledge (wealth) to the new. And the new knows the old as a dependable trustee. The shift, however, must happen, and it needs a trigger - something unwarranted - a mishap to break the umbilical cord. Bigger the ensuing shift, bigger the mishap.
In a way, the mishap marks the beginning of the transition - start of a new time. It is a gun shot to initialize the race. The battle begins at this moment amongst many variants of "new". In fact, many new possibilities crop up to capitalize the opportunity. Having recognized the inevitable, they all stake their claim to being righteous and thus the earnest representation of truth. This happens over and over again as in "history repeats itself". There are many examples[^history] in our recent past though a keen observers may see them in their own backyard.
They occur for the consciousness must evolve to understand the nature of unity[^unit] - the smallest common factor. A mishap is thus a mere setback before the hitherto slow breeding innovations sling into top gear. Such triggers, driven by imperceptible evolution of consciousness are said to be caused by `Prarbdha`.
> `Prarbdha`, a `Sanskrit` word, means something that had already begun. It ties together the past, present and the future - the continuum `Bramh`. In that it also means "fate", because the fate had commenced before the material event physically occurred.
[^history]: Battles between old and new in recent history:
- IBM was the old. Microsoft and Apple battled for superiority in computing as contenders for new leadership title. For an observes in late 80s it appeared as if big blue is fighting Apple (and later Microsoft) but that was just a trigger. The real battle was between Apple and Microsoft.
- Laptop was old, the newcomers iOS and Android are battling for superiority in mobile computing. For quite some time it felt like mobile devices were the PC killers, but the truth is battle is never between the old and the new. It is always among many new contenders.
- It appears as big oil is at odds with the EVs or the hydrogen fuel cells. Though the truth is fossil fuel industry will be the biggest investors in sustainable future - because they know first hand about the shift. Sustainable energy is the opportunity for refiners because someone needs to do the work, and they are best positioned to take advantage of this massive opportunity. The real battle is among Solar, Wind , Nuclear and Hydrogen.
- Gold is old. It appears that bitcoin is trying to replace Gold. But that is not true. The real battle is with in Cryptos - BTC vs Ether vs Sol vs so many other possibilities. When the dust settles, we will see Gold has its own role to play just like laptop has its own role to play in the increasingly mobile world.
[^unit]: A unit is an immutable part of any measurement. Easy examples - a meter is an immutable unit of length. A kilo is an immutable unit of weight. A unit is part of every measurement - it lends meaning to what is being measured - it is implicit in what is being measured. It is a multiplication that outputs exactly what is being measured.
- Little harder example - Number “1” is the unit of multiplication itself. It is there inbuilt into every number (even zero) . It never changes the number when multiplied -> a unit when multiplied with what is being measured , must stay inert - never change the measurement ! But you can't measure anything without a unit … no number exists without "1"
- Hard question - What is the unit of consciousness ? By definition, it must be 1) immutable 2) part of every conscious being. 3) must stay inert.
- In `Vaidik` science , `Atma` is defined as the unit of consciousness. It is immutable, inert and essential. For humans, understanding `Atma` is as hard as understanding number 1 for say number 8.
-

@ 228dde34:b5d0345e
2024-12-20 09:25:14
##### BY Glenda Chong
##### Editorial Admin
##### Hype Issue #60
###### Join GLENDA CHONG as she steps into the electrifying energy of Singapore’s K-pop scene at *SCAPE’s K-POP ALL IN 2024 and finds out how events like these bring a community together.
*Dance crew 6IX giving their all on stage at K-POP ALL IN 2024. Photo by Glenda Chong.*
The *SCAPE Ground Theatre was still, save for the low murmur of voices as attendees shuffled in. But when the screen on stage flashed a bright orange and blue and the first beat of a K-pop track blasted through the speakers, the crowd's energy flipped “ON” like a switch.
This was K-POP ALL IN 2024, also known as KAI, an annual year-end party that brings K-pop enthusiasts together for a night of community and celebration. KAI’s theme this year, “TIME K-APSULE” invites both performers and attendees to honour iconic K-pop classics and artists that have shaped the genre’s past and spotlight the fresh energy of today’s favourites.
*Dance crew Onhit Dance covering K-pop girl group GFRIEND’s hit MAGO. Photo by Glenda Chong.*
As a K-pop fan myself, KAI wasn’t my first rodeo when it comes to *SCAPE’s K-pop-themed events. However, going to such an event alone was a first so I was just a touch anxious as to whether I would feel out of place.
Despite my nerves, I milled around the booths just behind the audience seating area before the show began. Aside from the performances, I was pleased to see that there were plenty of booths selling K-pop official and fan-made merchandise. From fan art to collectible photo cards and K-pop albums, it was a collector’s dream. The one booth that drew me in almost instantly, though, was by the NUS Korean Cultural Interest Group (KCIG) from the National University of Singapore (NUS).
As part of their efforts to raise funds for their annual K-pop dance production, the interest group had gotten a booth at KAI to sell not just unique merchandise such as shirts they designed, but even experiences like a “deco booth” and a photo-taking area. That extra effort really made their booth stand out from the other booths that were only selling ‘merch’.
The booth embodied connection through its “deco booth”, where K-pop fans could personalise photocard sleeves with decorative elements. Though typically a solo activity, many did it with friends, turning the booth into a vibrant hub of shared creativity and enthusiasm.
While you can say that the heart of Singapore’s K-pop scene lies in the music and the performances, this energy and sense of community extends beyond the stage. I got to chat with KCIG members, Abigail Tan and Wong Yan Rou, who were running KCIG’s booth, and I could feel how their interest group and booth are a microcosm of the wider K-pop community. The booth was more than just a fundraising opportunity, and their interest group isn’t just a place to explore Korean culture. Both allowed like-minded individuals to bond and be part of a bigger community.
*The writer decorated their own photocard sleeve to join in on the fun. Photo by Glenda Chong.*
And as for KCIG, its inclusivity is its hallmark. According to Yan Rou and Abigail, no auditions are required to join KCIG as “everyone” is welcome to “be part of the community,” which they believe makes KCIG highly welcoming. As such, in Yan Rou’s words, members “stay for a long time.” And just as KCIG brings people interested in Korean culture together, KAI does the same, which they can feel and see with their own eyes on a greater scale.
“Our efforts are ultimately school-level… but when we come out to events like this [KAI], we’ll be able to see the whole Singapore community,” Yan Rou said. “You’ll be able to see the people in this community, so I think it helps that you can build connections and make friends along the way.”
*Wong Yan Rou (left) and Abigail Tan (right) posing in KCIG’s photo-taking area. Photo by Glenda Chong.*
Just as we wrapped up our chat, the MCs’ voices cut through the music to announce the first few performers of the night. As I rushed to take my front row “seat” which was a spot on the ground I reserved with my belongings, the first act’s first performer, Justin Padayao took the stage.
When it comes to events like this, one might assume most audiences come to only support their performing friends. However, this assumption was quickly turned on its head when Justin experienced technical faults. Encouraging cheers rang from all four corners, giving him the much-needed boost to start again and hit all the right notes of “Into the New World”, the debut single of K-pop girl group Girls’ Generation. With its resolute lyrics, this timeless track is known for being a symbolic anthem of solidarity associated with South Korea’s protest culture.
*Justin Padayao performed a soulful ballad version of K-pop girl group Girls’ Generation’s Into the New World. Photo by Glenda Chong.*
That unity could be felt in the crowd, as we sang harmoniously to the song’s fully-Korean lines and used our phones’ flashlights to act as ‘lightsticks’, an essential part of showing support in K-pop culture. Throughout the rest of the first act’s performances, the energy never died down. When the first act ended and the following acts’ performers took over, it only continued to skyrocket. Other than solo acts, plenty of dance crews also performed, and one I had been keeping my eye on finally took the spotlight.
Named CODE:US, the all-female team danced with fierce precision to another Girls’ Generation classic, this time “The Boys”. Except, keeping in line with KAI 2024’s theme, the team danced to a cover of “The Boys” by K-pop group Kep1er who debuted years after Girls’ Generation did, which made for a perfect blend of the past and present.
*Dance crew CODE:US performing on stage. Photo by Glenda Chong.*
Having gotten to chat with CODE:US themselves, it seems that their choice to perform Kep1er’s version of “The Boys” was intentional, as it was the version they resonated with most despite multiple other covers being available. According to member Jing Yun, 19, she’s inspired by K-pop artists like ATEEZ’s San and aespa’s Karina as their powerful performances conveyed their emotions to their audiences.
“Whenever I perform, I do hope I can deliver the same type of feelings that the [K-pop artists] do, where they can just enjoy the stage with no regrets while also delivering something memorable to the audience and myself.” She said. And she and CODE:US definitely delivered, as the crowd and I could really feel their passion.
While I was impressed by every performance, what struck me the most was the diversity of performers. From fathers and working adults to youths as young as 14, KAI was not just a talent showcase; the performers and this year’s theme [TIME K-APSULE] were a testament to K-pop’s enduring ability to unite generations of fans and how the passion for it spans all walks of life.

*A member of a dance crew carrying his child who had been watching the team perform from behind the stage curtain after their performance. Photo by Glenda Chong.*
As the final performances wrapped up, the night was still young as the space transformed for KAI’s final staple event, K-pop Random Play Dance (KRPD). It was a fitting end to the night, as this was where you could truly witness the community’s unity. In true KRPD fashion, everyone, both performers and audience members alike, came together to dance to K-pop hits both old and new.
 *Team CODE:US posing for a photo before K-POP ALL IN 2024 began. Photo courtesy of CODE:US.*
“[We are] just glad that this community allows us all to be open and enjoy what we like together without being shamed or judged.” CODE:US mentioned. Reflecting on this, I couldn’t help but think of what a powerful reminder this was of what events like KAI represent: a chance to connect with and celebrate something larger than ourselves.
-

@ d61f3bc5:0da6ef4a
2024-12-18 16:52:18
January 2025 will mark two years since we started building Primal. Our goal was to create the best possible user experience for Nostr and make it accessible to everyone. We reached a big milestone towards realizing that vision with the recent Primal 2.0 release. It’s still early days, a lot more work lies ahead, but we thought the timing was right to introduce the Premium tier. Let’s explore what it is, why we built it, what’s included, and how it will evolve moving forward.
## What Primal Premium Is
The idea behind Primal Premium is simple: integrate all tools and services required for the best Nostr experience into a single package. For $7 per month, Premium users get a *Primal Name* and *Nostr Tools* built by Primal. We’ll cover those in more detail below, but first we should make a crucial point: by signing up for Premium, you are in no way locked in to Primal. Quite the contrary, you can pick and choose which Premium features you wish to enable and use within other Nostr products.
Openness is Nostr’s killer feature. Any product that wishes to truly empower the user needs to interoperate with Nostr’s budding ecosystem. The feed marketplace is a great example. External feeds are first-class citizens within all Primal apps. Primal feeds are available in other Nostr clients. We are working on Premium feeds, which our users will be able to enjoy within Primal or other Nostr apps. Media hosting is another example. Our upcoming support for the Blossom protocol will make Primal Premium media hosting interoperable with other Nostr apps and media hosting services. The common theme here is user choice. Nostr offers the highest level of user agency, and the compounding effect of interoperable products and services is bound to make Nostr immensely powerful.
## Why We Built Premium and Why Now
What is unfolding on Nostr right now is unique and special. The first truly self-sovereign network is being bootstrapped by this early cohort of users and builders. People are literally holding the keys to their online presence. Network infrastructure – relays, indexers, media hosting services, etc. – is being stood up organically and without any central planning or coordination. Hundreds of independent projects are adding new capabilities to Nostr without needing permission. The whole thing is truly a sight to behold.
In addition to fixing the fundamentals of the network, it is equally important that we fix the broken incentives that plague the legacy Web. The status quo of monetization via advertising, which turns users into products to be farmed, has overstayed its welcome. At Primal, we don’t monetize user data. Our users are our customers. We only make money when the user decides that we are providing a valuable service – and pays for it. That means that our users’ interests are aligned with ours. It allows us to wake up every morning and work all day to make the product better for our users.
Some might say that it is too early to try to monetize a Nostr product. We definitely need to be thoughtful about paywalling important features while the network is so young. For example, advanced search is a Primal Premium feature, but we enable it for all users up to 20 search results. That makes it quite usable for anyone on Nostr, but power users get the ability to save these searches and create powerful specialized feeds.
It is crucial to have commercially successful projects on Nostr that have their incentives aligned with those of their users. We are working on new features and monetization methods that follow this philosophy. The more we experiment on Nostr, the faster we will learn what works and unlock the full potential of this network. I have a feeling that a lot remains to be discovered, and Primal Premium is just the first step.
Now, let’s take a closer look at what is included in Premium: *Primal Name* and *Nostr Tools*.
## Primal Name
A Primal Name is a unique name on the primal.net domain that offers three features:
1. **Verified Nostr address (NIP-05)**. This signals to the Nostr network that your account (npub) has been verified by Primal. Note that we don’t perform identity verification; we are simply signaling that this is a Primal Premium user. Users can pay with sats, preserving their privacy while signaling to the network that this verified account is not a bot.
2. **Friendly Bitcoin Lightning address**. Primal’s built-in hosted wallet creates a randomly generated lightning address for every user. They look like this: bluedog25@primal.net. Premium users get to pick their name, so their lightning address is more personalized (e.g. preston@primal.net).
3. **VIP profile on primal.net**. This is simply a friendly URL to your profile on primal.net. We are working on adding profile customization features for Premium users; stay tuned!
In summary, a Primal Name makes you easier to find on Nostr. You are free to use any of these three Primal Name elements as you see fit. If you wish to use your Primal Nostr address and/or Lightning address, simply update your Nostr profile with those entries.
## Nostr Tools
Nostr Tools is a collection of features that we think would be useful to any Nostr power user. We are continuously working on expanding these capabilities, but the initial set of features includes:
- **Media management**. Primal Premium comes with 10GB of media storage (compared to 1GB for free accounts). We implemented a slick interface for managing all media you have on Primal.
- **Contact list backup**. Many Nostr users have experienced the loss of their contact list (i.e., their follow list) when using different clients. We store the history of the contact list for Primal Premium users and make it easy to recover.
- **Content backup**. Nostr users post their content to a collection of public relays. These relays typically don’t offer guarantees that they will store the content for any amount of time. We back up all content posted by Primal Premium users and make it easy to rebroadcast it to the specified relays at any time.
## Primal Legends
The idea for the Primal Legend tier was suggested to me by Gigi a couple of months prior to the launch of Primal 2.0. His argument was simple: “There are users on Nostr who really appreciate Primal and are willing to pay way more than $7 / month to support the project. You should *let them* pay and *recognize them* for doing so.”
I am really glad that Gigi convinced me to introduce the Legend tier. Nostr is truly a special place. The early users are extremely passionate and mission driven. They care about growing and improving Nostr as much as the builders do. At first, I thought of the term “Legend” as a bit tongue in cheek, but then I met and chatted with some of these people. Man, they are incredible. They just wish to support the network and the builders of open source software in any way they can. So now I think the term is appropriate.
We are humbled by the support we received. Our first Legend supporter was none other than Jack. He found this option in the product and paid for the Legend tier literally an hour after Primal 2.0 was released. Thank you, sir, and thank you to all the other Legends out there! 💜🫂
## What Comes Next?
We are delighted and encouraged by the market response to Primal Premium. It is already clear to us that we are on the right path. We will lean into it even harder from here. There will be MOAR Premium features, while at the same time we will make sure that the free product remains excellent. Since you, the user, are the customer, tell us what you would like to see added to Primal Premium.
Pura Vida 🤙
-

@ 266815e0:6cd408a5
2024-12-17 20:45:33
Finally another version of noStrudel. I keep telling myself I'm going to do more frequent releases but then time keeps getting away from me
This release comes with a bunch of news features and most importantly a lot of cleanup
## Features
### Olas media posts
You can now view a simple feed of media posts made on https://olas.app/ in the app and comment on them using NIP-22 comments
### Simple gif picker
This was mostly a test, but there is now a simple gif picker (and barely functional search) that is based on `k:1063` events
If you want a better search and to help populate the nostr gif library you can use https://gifbuddy.lol created by nostr:npub1hee433872q2gen90cqh2ypwcq9z7y5ugn23etrd2l2rrwpruss8qwmrsv6
### New support view
The *(tiny)* support button at the bottom of the side menu now hides a zap leader board that shows top supporters and any custom messages they leave
### Favorite DVM feeds
You can now favorite DVM feeds in the discover view
### Tools under notes
There is now a simpler tools menu under notes and threads
### Searching local cache relay
If your using [nostr-relay-tray](https://github.com/CodyTseng/nostr-relay-tray) the search view will now use it by default for searching. which should make it a little faster and more reliable
### Small features
- Add "Proactively authenticate to relays" option to privacy settings, defaults to off
- Add option for debug API
- Add option to hide noStrudel logo in nav bar
- Show unknown notifications in notification view
- Add templates to event publisher
## Bug fixes
- Show nostr mentions in markdown content
- Fix delete events not getting published to outbox
- Fix page changing from RTL when viewing some profiles
- Refresh relay info on relay page
- Fix bug with removing "about" in profile editor
- Fix automatically disconnecting from authenticated relays
## Applesauce
Over the past few months I've been doing tons of cleanup on the core of noStrudel *(677 changed files with 19,683 additions and 17,889 deletions)* and extracting it out into a friendly nostr SDK called [applesauce](https://hzrd149.github.io/applesauce/)
Its very much a work-in-progress but the idea with these libraries is to help myself (and maybe others) build the UI layer of nostr apps and eventually make noStrudel just another app that is built with applesauce
If your a developer and another nostr SDK sounds interesting to you. you can check out the [Getting Started](https://hzrd149.github.io/applesauce/introduction/getting-started.html) docs
-

@ 0f286a37:601a59e8
2024-12-17 19:56:41
#bitcoin #news I encourage every Bitcoiner to read The Blocksize War. Here are all of the links to all 21 chapters available on the BitMEX blog.
1. [Chapter 1 – First Strike](https://blog.bitmex.com/the-blocksize-war-chapter-1-first-strike/)
2. [Chapter 2 – March To War](https://blog.bitmex.com/the-blocksize-war-chapter-2-march-to-war/)
3. [Chapter 3 – Scaling I - Montreal](https://blog.bitmex.com/the-blocksize-war-chapter-3-scaling-i-montreal/)
4. [Chapter 4 – Scaling II - Hong Kong](https://blog.bitmex.com/the-blocksize-war-chapter-4-scaling-ii-hong-kong/)
5. [Chapter 5 – SegWit](https://blog.bitmex.com/the-blocksize-war-chapter-5-scaling-ii-segwit/)
6. [Chapter 6 – Lightning Network](https://blog.bitmex.com/the-blocksize-war-chapter-6-lightning-network/)
7. [Chapter 7 – Bitcoin Classic](https://blog.bitmex.com/the-blocksize-war-chapter-7-bitcoin-classic/)
8. [Chapter 8 – Hong Kong Roundtable](https://blog.bitmex.com/the-blocksize-war-chapter-8-hong-kong-roundtable/)
9. [Chapter 9 – Faketoshi](https://blog.bitmex.com/the-blocksize-war-chapter-9-faketoshi/)
10. [Chapter 10 – The DAO](https://blog.bitmex.com/the-blocksize-war-chapter-10-the-dao/)
11. [Chapter 11 – Scaling III – Milan](https://blog.bitmex.com/the-blocksize-war-chapter-11-scaling-iii-milan/)
12. [Chapter 12 – Bitcoin Unlimited](https://blog.bitmex.com/the-blocksize-war-chapter-12-bitcoin-unlimited/)
13. [Chapter 13 – Exchanges](https://blog.bitmex.com/the-blocksize-war-chapter-13-exchanges/)
14. [Chapter 14 – ASICBoost](https://blog.bitmex.com/the-blocksize-war-chapter-14-asicboost/)
15. [Chapter 15 – Dragons’ Den](https://blog.bitmex.com/the-blocksize-war-chapter-15-dragons-den/)
16. [Chapter 16 – Litecoin](https://blog.bitmex.com/the-blocksize-war-chapter-16-litecoin/)
17. [Chapter 17 – User-Activated Softfork](https://blog.bitmex.com/the-blocksize-war-chapter-17-user-activated-softfork/)
18. [Chapter 18 – New York Agreement](https://blog.bitmex.com/the-blocksize-war-chapter-18-new-york-agreement/)
19. [Chapter 19 - Bitcoin Cash](https://blog.bitmex.com/the-blocksize-war-chapter-19-bitcoin-cash/)
20. [Chapter 20 - SegWit2x](https://blog.bitmex.com/the-blocksize-war-chapter-20-segwit2x/)
21. [Chapter 21 - Victory] https://blog.bitmex.com/the-blocksize-war-chapter-21-victory/)
-

@ fe32298e:20516265
2024-12-16 20:59:13
Today I learned how to install [NVapi](https://github.com/sammcj/NVApi) to monitor my GPUs in Home Assistant.

**NVApi** is a lightweight API designed for monitoring NVIDIA GPU utilization and enabling automated power management. It provides real-time GPU metrics, supports integration with tools like Home Assistant, and offers flexible power management and PCIe link speed management based on workload and thermal conditions.
- **GPU Utilization Monitoring**: Utilization, memory usage, temperature, fan speed, and power consumption.
- **Automated Power Limiting**: Adjusts power limits dynamically based on temperature thresholds and total power caps, configurable per GPU or globally.
- **Cross-GPU Coordination**: Total power budget applies across multiple GPUs in the same system.
- **PCIe Link Speed Management**: Controls minimum and maximum PCIe link speeds with idle thresholds for power optimization.
- **Home Assistant Integration**: Uses the built-in RESTful platform and template sensors.
## Getting the Data
```
sudo apt install golang-go
git clone https://github.com/sammcj/NVApi.git
cd NVapi
go run main.go -port 9999 -rate 1
curl http://localhost:9999/gpu
```
Response for a single GPU:
```
[
{
"index": 0,
"name": "NVIDIA GeForce RTX 4090",
"gpu_utilisation": 0,
"memory_utilisation": 0,
"power_watts": 16,
"power_limit_watts": 450,
"memory_total_gb": 23.99,
"memory_used_gb": 0.46,
"memory_free_gb": 23.52,
"memory_usage_percent": 2,
"temperature": 38,
"processes": [],
"pcie_link_state": "not managed"
}
]
```
Response for multiple GPUs:
```
[
{
"index": 0,
"name": "NVIDIA GeForce RTX 3090",
"gpu_utilisation": 0,
"memory_utilisation": 0,
"power_watts": 14,
"power_limit_watts": 350,
"memory_total_gb": 24,
"memory_used_gb": 0.43,
"memory_free_gb": 23.57,
"memory_usage_percent": 2,
"temperature": 36,
"processes": [],
"pcie_link_state": "not managed"
},
{
"index": 1,
"name": "NVIDIA RTX A4000",
"gpu_utilisation": 0,
"memory_utilisation": 0,
"power_watts": 10,
"power_limit_watts": 140,
"memory_total_gb": 15.99,
"memory_used_gb": 0.56,
"memory_free_gb": 15.43,
"memory_usage_percent": 3,
"temperature": 41,
"processes": [],
"pcie_link_state": "not managed"
}
]
```
# Start at Boot
Create `/etc/systemd/system/nvapi.service`:
```
[Unit]
Description=Run NVapi
After=network.target
[Service]
Type=simple
Environment="GOPATH=/home/ansible/go"
WorkingDirectory=/home/ansible/NVapi
ExecStart=/usr/bin/go run main.go -port 9999 -rate 1
Restart=always
User=ansible
# Environment="GPU_TEMP_CHECK_INTERVAL=5"
# Environment="GPU_TOTAL_POWER_CAP=400"
# Environment="GPU_0_LOW_TEMP=40"
# Environment="GPU_0_MEDIUM_TEMP=70"
# Environment="GPU_0_LOW_TEMP_LIMIT=135"
# Environment="GPU_0_MEDIUM_TEMP_LIMIT=120"
# Environment="GPU_0_HIGH_TEMP_LIMIT=100"
# Environment="GPU_1_LOW_TEMP=45"
# Environment="GPU_1_MEDIUM_TEMP=75"
# Environment="GPU_1_LOW_TEMP_LIMIT=140"
# Environment="GPU_1_MEDIUM_TEMP_LIMIT=125"
# Environment="GPU_1_HIGH_TEMP_LIMIT=110"
[Install]
WantedBy=multi-user.target
```
## Home Assistant
Add to Home Assistant `configuration.yaml` and restart HA (completely).
For a single GPU, this works:
```
sensor:
- platform: rest
name: MYPC GPU Information
resource: http://mypc:9999
method: GET
headers:
Content-Type: application/json
value_template: "{{ value_json[0].index }}"
json_attributes:
- name
- gpu_utilisation
- memory_utilisation
- power_watts
- power_limit_watts
- memory_total_gb
- memory_used_gb
- memory_free_gb
- memory_usage_percent
- temperature
scan_interval: 1 # seconds
- platform: template
sensors:
mypc_gpu_0_gpu:
friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} GPU"
value_template: "{{ state_attr('sensor.mypc_gpu_information', 'gpu_utilisation') }}"
unit_of_measurement: "%"
mypc_gpu_0_memory:
friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Memory"
value_template: "{{ state_attr('sensor.mypc_gpu_information', 'memory_utilisation') }}"
unit_of_measurement: "%"
mypc_gpu_0_power:
friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power"
value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_watts') }}"
unit_of_measurement: "W"
mypc_gpu_0_power_limit:
friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power Limit"
value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_limit_watts') }}"
unit_of_measurement: "W"
mypc_gpu_0_temperature:
friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Temperature"
value_template: "{{ state_attr('sensor.mypc_gpu_information', 'temperature') }}"
unit_of_measurement: "°C"
```
For multiple GPUs:
```
rest:
scan_interval: 1
resource: http://mypc:9999
sensor:
- name: "MYPC GPU0 Information"
value_template: "{{ value_json[0].index }}"
json_attributes_path: "$.0"
json_attributes:
- name
- gpu_utilisation
- memory_utilisation
- power_watts
- power_limit_watts
- memory_total_gb
- memory_used_gb
- memory_free_gb
- memory_usage_percent
- temperature
- name: "MYPC GPU1 Information"
value_template: "{{ value_json[1].index }}"
json_attributes_path: "$.1"
json_attributes:
- name
- gpu_utilisation
- memory_utilisation
- power_watts
- power_limit_watts
- memory_total_gb
- memory_used_gb
- memory_free_gb
- memory_usage_percent
- temperature
- platform: template
sensors:
mypc_gpu_0_gpu:
friendly_name: "MYPC GPU0 GPU"
value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'gpu_utilisation') }}"
unit_of_measurement: "%"
mypc_gpu_0_memory:
friendly_name: "MYPC GPU0 Memory"
value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'memory_utilisation') }}"
unit_of_measurement: "%"
mypc_gpu_0_power:
friendly_name: "MYPC GPU0 Power"
value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_watts') }}"
unit_of_measurement: "W"
mypc_gpu_0_power_limit:
friendly_name: "MYPC GPU0 Power Limit"
value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_limit_watts') }}"
unit_of_measurement: "W"
mypc_gpu_0_temperature:
friendly_name: "MYPC GPU0 Temperature"
value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'temperature') }}"
unit_of_measurement: "C"
- platform: template
sensors:
mypc_gpu_1_gpu:
friendly_name: "MYPC GPU1 GPU"
value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'gpu_utilisation') }}"
unit_of_measurement: "%"
mypc_gpu_1_memory:
friendly_name: "MYPC GPU1 Memory"
value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'memory_utilisation') }}"
unit_of_measurement: "%"
mypc_gpu_1_power:
friendly_name: "MYPC GPU1 Power"
value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_watts') }}"
unit_of_measurement: "W"
mypc_gpu_1_power_limit:
friendly_name: "MYPC GPU1 Power Limit"
value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_limit_watts') }}"
unit_of_measurement: "W"
mypc_gpu_1_temperature:
friendly_name: "MYPC GPU1 Temperature"
value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'temperature') }}"
unit_of_measurement: "C"
```
Basic entity card:
```
type: entities
entities:
- entity: sensor.mypc_gpu_0_gpu
secondary_info: last-updated
- entity: sensor.mypc_gpu_0_memory
secondary_info: last-updated
- entity: sensor.mypc_gpu_0_power
secondary_info: last-updated
- entity: sensor.mypc_gpu_0_power_limit
secondary_info: last-updated
- entity: sensor.mypc_gpu_0_temperature
secondary_info: last-updated
```
# Ansible Role
```
---
- name: install go
become: true
package:
name: golang-go
state: present
- name: git clone
git:
repo: "https://github.com/sammcj/NVApi.git"
dest: "/home/ansible/NVapi"
update: yes
force: true
# go run main.go -port 9999 -rate 1
- name: install systemd service
become: true
copy:
src: nvapi.service
dest: /etc/systemd/system/nvapi.service
- name: Reload systemd daemons, enable, and restart nvapi
become: true
systemd:
name: nvapi
daemon_reload: yes
enabled: yes
state: restarted
```
-

@ ee11a5df:b76c4e49
2024-12-16 05:29:30
# Nostr 2?
## Breaking Changes in Nostr
Nostr was a huge leap forward. But it isn't perfect.
When developers notice a problem with nostr, they confer with each other to work out a solution to the problem. This is usually in the form of a NIP PR on the nips repo.
Some problems are easy. Just add something new and optional. No biggie. Zaps, git stuff, bunkers... just dream it up and add it.
Other problems can only be fixed by breaking changes. With a breaking change, the overall path forward is like this: Add the new way of doing it while preserving the old way. Push the major software to switch to the new way. Then deprecate the old way. This is a simplification, but it is the basic idea. It is how we solved markers/quotes/root and how we are upgrading encryption, among other things.
This process of pushing through a breaking change becomes more difficult as we have more and more existing nostr software out there that will break. Most of the time what happens is that the major software is driven to make the change (usually by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6), and the smaller software is left to fend for itself. A while back I introduced the BREAKING.md file to help people developing smaller lesser-known software keep up with these changes.
## Big Ideas
But some ideas just can't be applied to nostr. The idea is too big. The change is too breaking. It changes something fundamental. And nobody has come up with a smooth path to move from the old way to the new way.
And so we debate a bunch of things, and never settle on anything, and eventually nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 makes a post saying that we don't really want it anyways 😉.
As we encounter good ideas that are hard to apply to nostr, I've been filing them away in a repository I call "nostr-next", so we don't forget about them, in case we ever wanted to start over.
It seems to me that starting over every time we encountered such a thing would be unwise. However, once we collect enough changes that we couldn't reasonably phase into nostr, then a tipping point is crossed where it becomes worthwhile to start over. In terms of the "bang for the buck" metaphor, the bang becomes bigger and bigger but the buck (the pain and cost of starting over) doesn't grow as rapidly.
## WHAT? Start over?
IMHO starting over could be very bad if done in a cavalier way. The community could fracture. The new protocol could fail to take off due to lacking the network effect. The odds that a new protocol catches on are low, irrespective of how technically superior it could be.
So the big question is: can we preserve the nostr community and it's network effect while making a major step-change to the protocol and software?
I don't know the answer to that one, but I have an idea about it.
I think the new-protocol clients can be dual-stack, creating events in both systems and linking those events together via tags. The nostr key identity would still be used, and the new system identity too. This is better than things like the mostr bridge because each user would remain in custody of their own keys.
## The nitty gritty
Here are some of the things I think would make nostr better, but which nostr can't easily fix. A lot of these ideas have been mentioned before by multiple people and I didn't give credit to all of you (sorry) because my brain can't track it all. But I've been collecting these over time at https://github.com/mikedilger/nostr-next
* Events as CBOR or BEVE or MsgPack or a fixed-schema binary layout... anything but JSON text with its parsing, it's encoding ambiguity, it's requirement to copy fields before hashing them, its unlimited size constraints. (me, nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s)
* EdDSA ed25519 keys instead of secp256k1, to enable interoperability with a bunch of other stuff like ssh, pgp, TLS, Mainline DHT, and many more, plus just being better cryptography (me, Nuh, Orlovsky, except Orlovsky wanted Ristretto25519 for speed)
* Bootstrapping relay lists (and relay endpoints) from Mainline DHT (nostr:npub1jvxvaufrwtwj79s90n79fuxmm9pntk94rd8zwderdvqv4dcclnvs9s7yqz)
* Master keys and revocable subkeys / device keys (including having your nostr key as a subkey)
* Encryption to use different encryption-specific subkeys and ephemeral ones from the sender.
* Relay keypairs, TLS without certificates, relays known by keypair instead of URL
* Layered protocol (separate core from applications)
* Software remembering when they first saw an event, for 2 reasons, the main one being revocation (don't trust the date in the event, trust when you first saw it), the second being more precise time range queries.
* Upgrade/feature negotiation (HTTP headers prior to starting websockets)
* IDs starting with a timestamp so they are temporally adjacent (significantly better database performance) (Vitor's idea)
* Filters that allow boolean expressions on tag values, and also ID exclusions. Removing IDs from filters and moving to a GET command.
* Changing the transport (I'm against this but I know others want to)
## What would it look like?
Someone (Steve Farroll) has taken my nostr-next repo and turned it into a proposed protocol he calls [Mosaic](https://github.com/SteveFarroll/mosaic-spec). I think it is quite representative of that repo,
as it already includes most of those suggestions, so I've been contributing to it. Mosaic spec is rendered [here](https://stevefarroll.github.io/mosaic-spec/).
Of course, where Mosaic stands right now it is mostly my ideas (and Steve's), it doesn't have feedback or input from other nostr developers yet. That is what this blog post is about. I think it is time for other nostr devs to be made aware of this thing.
It is currently in the massive breaking changes phase. It might not look that way because of the detail and refinement of the documentation, but indeed everything is changing rapidly. It probably has some bad ideas and is probably missing some great ideas that you have.
Which is why this is a good time for other devs to start taking a look at it.
It is also the time to debate meta issues like "are you crazy Mike?" or "no we have to just break nostr but keep it nostr, we can't dual-stack" or whatever.
Personally I think mosaic-spec should develop and grow for quite a while before the "tipping point" happens. That is, I'm not sure we should jump in feet first yet, but rather we build up and refine this new protocol and spend a lot of time thinking about how to migrate smoothly, and break it a lot while nobody is using it.
So you can just reply to this, or DM me, or open issues or PRs at [Mosaic](https://github.com/SteveFarroll/mosaic-spec), or just whisper to each other while giving me the evil eye.
-

@ 6f6b50bb:a848e5a1
2024-12-15 15:09:52
Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
### Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
### Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
- **Scoperta.** Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
- **Efficienza.** La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
### Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
### Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
### Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
### Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
### Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
### Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!
Tradotto da:\
https://willwhitney.com/computing-inside-ai.htmlhttps://willwhitney.com/computing-inside-ai.html
-

@ 78c90fc4:4bff983c
2024-12-14 19:00:14
[Hier ist die Aufzeichnung des Vortrages von Cynthia Chung für die Aletheia Wissenschaftsgruppe vom 11.12.24](https://www.wissenschaftstehtauf.ch/Aletheia_Cynthia_Chung_Operation_Gladio_20241211.mp4)
 
Cynthia Chung ist Präsidentin und Mitbegründerin der [Rising Tide Foundation](https://risingtidefoundation.net/) (zusammen mit ihrem Ehemann Matthew Ehret, der am 4. September 2024 als Gastredner des Aletheia Science Forum über „Die britischen Wurzeln des Deep State verstehen“ sprach, aufgezeichnet hier: <https://www.wissenschaftstehtauf.ch/Matt_Ehret_20240904.mp4> ).\
\
Cynthia ist die Autorin der Bücher „[The Shaping of a World Religion](https://cynthiachung.substack.com/p/my-new-book-is-out-the-shaping-of)“ und „[The Empire on Which the Black Sun Never Set,](https://cynthiachung.substack.com/p/my-first-book-is-now-outthe-empire)“ sowie Mitautorin der Buchreihe „The Clash of the Two Americas“.\
\
Ihre Substack-Seite [„Through A Glass Darkly](https://cynthiachung.substack.com/) ([https://cynthiachung.substack.com](https://cynthiachung.substack.com/))“ hat über 11.000 Abonnenten. Sie schreibt über eine Vielzahl wichtiger Themen, die von geopolitischer Geschichte bis hin zu Kultur, Wissenschaft und Kunst reichen.\
\
In ihrem Vortrag konzenteriert sich Cynthia auf die Operation Gladio, das geheime „Stay-behind“-Netzwerk bewaffneter Widerstandsorganisationen, das während des Kalten Krieges in Westeuropa gegründet wurde.
Solche historischen Einblicke können uns in der heutigen Zeit helfen, uns durch die Stürme zu navigieren, die die Zivilisation erneut bedrohen.\
\
Einführung von Stefan Heeb <https://www.proethica.ch>
Weiterführende Analysen:
Daniele Ganser: NATO Geheimarmeen in Europa

[Die NATO und der rechtsextreme Staatsterror](https://x.com/RealWsiegrist/status/1867063935289139260)
[NATO/Gladio/Verdeckte Kriegsführung](https://waltisiegrist.locals.com/upost/1571799/manipulation-der-massen-durch-panik)
[NATO](https://waltisiegrist.locals.com/upost/1859885/die-geschichte-der-nato-ber-general-reinhard-gehlen-1902-1979-und-sein-netzwerk-in-der-wehrma)
-

@ ece127e2:745bab9c
2024-12-11 21:54:31
La palabra anarquía proviene del griego y significa sin gobierno; es decir la vida de un pueblo que se rige sin autoridad constituida, sin gobierno.La palabra *anarquía* proviene del griego y significa *sin gobierno*; es decir la vida de un pueblo que se rige sin autoridad constituida, sin gobierno.
Los anarquistas se sirven ordinariamente de la palabra Estado para expresar todo el conjunto de instituciones políticas, legislativas, judiciales, militares, financieras, etc., por medio de las cuales se sustrae al pueblo la gestión de sus propios asuntos, la dirección de su propia seguridad, para confiarlos a unos cuantos que usurpación o delegación se encuentran investidos de la facultad de hacer leyes sobre todo y para todos y de compeler al pueblo a ajustar a ellas su conducta, valiéndose, al efecto, de la fuerza de todos.
En este supuesto la palabra Estado significa por tanto como gobierno, o se quiere, la expresión impersonal, abstracta de este estado de cosas cuya personificación está representada por el gobierno: las expresiones abolir el Estado, sociedad sin Estado, etc., responden, pues, perfectamente a la idea que los anarquistas quieren expresar cuando hablan de la abolición de toda organización política fundada en la autoridad y de la constitución de una sociedad de hombres libres e iguales fundada en la armonía de los intereses y sobre el concurso voluntario de todos, a fin de satisfacer las necesidades sociales.
La palabra Estado tiene, empero, otras muchas significaciones, algunas de ellas susceptibles de inducir a error, sobre todo cuando se trata o discute con hombres que, a causa de su triste posición social, no han tenido ocasión de habituarse a las delicadas distinciones del lenguaje científico 0 cuando —y entonces peor— se trata con adversarios de mala fe, interesados en confundir los términos y en no querer comprender las cosas.Los anarquistas se sirven ordinariamente de la palabra *Estado* para expresar todo el conjunto de instituciones políticas, legislativas, judiciales, militares, financieras, etc., por medio de las cuales se sustrae al pueblo la gestión de sus propios asuntos, la dirección de su propia seguridad, para confiarlos a unos cuantos que usurpación o delegación se encuentran investidos de la facultad de hacer leyes sobre todo y para todos y de compeler al pueblo a ajustar a ellas su conducta, valiéndose, al efecto, de la fuerza de todos.
En este supuesto la palabra *Estado* significa por tanto como gobierno, o se quiere, la expresión impersonal, abstracta de este estado de cosas cuya personificación está representada por el gobierno: las expresiones *abolir el Estado, sociedad sin Estado*, etc., responden, pues, perfectamente a la idea que los anarquistas quieren expresar cuando hablan de la abolición de toda organización política fundada en la autoridad y de la constitución de una sociedad de hombres libres e iguales fundada en la armonía de los intereses y sobre el concurso voluntario de todos, a fin de satisfacer las necesidades sociales.
La palabra *Estado* tiene, empero, otras muchas significaciones, algunas de ellas susceptibles de inducir a error, sobre todo cuando se trata o discute con hombres que, a causa de su triste posición social, no han tenido ocasión de habituarse a las delicadas distinciones del lenguaje científico 0 cuando —y entonces peor— se trata con adversarios de mala fe, interesados en confundir los términos y en no querer comprender las cosas.
Hemos dicho anteriormente: «Anarquía es la sociedad sin gobierno». ¿es factible la supresión de los gobiernos?, ¿es deseable?, ¿puede preverse?
**¿Qué es el gobierno?**
La tendencia metafísica (que es una enfermedad del espíritu por causa de la cual el hombre, después de haber sufrido una especie de alucinación, se ve inducido a tomar lo abstracto por real), la tendencia metafísica, decimos, que, no obstante, y a pesar de los triunfos de la ciencia positiva tiene todavía tan profundas raíces en el espíritu de la mayoría de los contemporáneos, hace que muchos conciban el gobierno como una entidad moral, dotada de ciertos atributos de razón, de justicia, de equidad, independientes de las personas en que encarna.
Para ellos, el gobierno, o mas bien, el Estado, es el poder social abstracto; es el representante, abstracto siempre, de los intereses generales; es ya la expresión «derecho de todos», considerado como límite de los derechos de cada uno. Este modo de concebir el gobierno aparece apoyado por los interesados, a quienes importa salvar el principio de autoridad y hacerle prevalecer sobre las faltas y errores de los que se turnan en el ejercicio del poder.
Para nosotros el gobierno es la colectividad de gobernantes: reyes, presidentes, ministros, diputados, etc., son aquellos que aparecen adornados de la facultad de hacer las leyes para reglamentar las relaciones de los hombres entre sí, y hacer ejecutar estas leyes; debe decretar y recaudar los impuestos; debe forzar al servicio militar; debe juzgar y castigar las infracciones y contravenciones a las leyes; debe intervenir y sancionar los contratos privados; debe monopolizar ciertos ramos de la producción y ciertos servicios públicos, por no decir toda la producción y todos los servicios; debe favorecer o impedir el cambio de productos; debe declarar la guerra y ajustar la paz con los gobernantes de otros países; debe conceder o suprimir franquicias, etc. Los gobernantes, en una palabra, son los que tienen la facultad en grado más o menos elevado de servirse de las fuerzas sociales, o sea de la fuerza física, intelectual y económica de todos, para obligar a todo el mundo a hacer lo que entre en sus designios particulares. Esta facultad constituye, en nuestro sentir, el principio de gobierno, el principio de autoridad.Hemos dicho anteriormente, que la «*Anarquía* es la sociedad sin *gobierno*».
Ahora bien: ¿es factible la supresión de los gobiernos?, ¿es deseable?, ¿puede preverse? Veamos:
***¿Qué es el gobierno?***
La tendencia metafísica (que es una enfermedad del espíritu por causa de la cual el hombre, después de haber sufrido una especie de alucinación, se ve inducido a tomar lo abstracto por real), la tendencia metafísica, decimos, que, no obstante, y a pesar de los triunfos de la ciencia positiva tiene todavía tan profundas raíces en el espíritu de la mayoría de los contemporáneos, hace que muchos conciban el gobierno como una entidad moral, dotada de ciertos atributos de razón, de justicia, de equidad, independientes de las personas en que encarna.
Para ellos, el gobierno, o mas bien, el Estado, es el poder social abstracto; es el representante, abstracto siempre, de los intereses generales; es ya la expresión «derecho de todos», considerado como límite de los derechos de cada uno. Este modo de concebir el gobierno aparece apoyado por los interesados, a quienes importa salvar el principio de autoridad y hacerle prevalecer sobre las faltas y errores de los que se turnan en el ejercicio del poder.
Para nosotros el gobierno es la colectividad de gobernantes: reyes, presidentes, ministros, diputados, etc., son aquellos que aparecen adornados de la facultad de hacer las leyes para reglamentar las relaciones de los hombres entre sí, y hacer ejecutar estas leyes; debe decretar y recaudar los impuestos; debe forzar al servicio militar; debe juzgar y castigar las infracciones y contravenciones a las leyes; debe intervenir y sancionar los contratos privados; debe monopolizar ciertos ramos de la producción y ciertos servicios públicos, por no decir toda la producción y todos los servicios; debe favorecer o impedir el cambio de productos; debe declarar la guerra y ajustar la paz con los gobernantes de otros países; debe conceder o suprimir franquicias, etc. Los gobernantes, en una palabra, son los que tienen la facultad en grado más o menos elevado de servirse de las fuerzas sociales, o sea de la fuerza física, intelectual y económica de todos, para obligar a todo el mundo a hacer lo que entre en sus designios particulares. Esta facultad constituye, en nuestro sentir, el principio de gobierno, el principio de autoridad.
source : https://es.anarchistlibraries.net/library/errico-malatesta-la-anarquia
-

@ ece53feb:1edf277e
2024-12-11 21:19:19

-

@ ece53feb:1edf277e
2024-12-11 21:13:59
Had this been a real article, you would be less annoyed right now...
-

@ ece53feb:1edf277e
2024-12-11 18:25:15
Hi there, Nostr! I'm an engineer and maker who likes to talk a lot about a lot of things.
I'm made of opinions. Some of them are pretty good ones!
-

@ 468f729d:5ab4fd5e
2024-12-11 00:00:35
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/V_fvmyJ91m0?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 4ba8e86d:89d32de4
2024-12-09 23:12:11
A origem e o desenvolvimento do SearXNG começaram em meados de 2021, após o fork do conhecido mecanismo de metabusca Searx, inspirado pelo projeto Seeks. Ele garante privacidade básica ao misturar suas consultas com outras pesquisas, sem armazenar dados de busca. O SearXNG pode ser adicionado à barra de pesquisa do navegador e também configurado como mecanismo de busca padrão.
Embora o SearXNG não ofereça resultados tão personalizados quanto o Google, ele não gera um perfil sobre você. Controle Total sobre Seus Dados: com o SearXNG, você tem controle absoluto sobre suas informações de pesquisa. O histórico de busca é totalmente opcional e pode ser ativado ou desativado conforme sua preferência. Além disso, é possível excluir qualquer entrada a qualquer momento, garantindo sua privacidade. Resultados de Fontes Diversificadas: o SearXNG agrega informações de mais de 70 fontes diferentes, proporcionando uma pesquisa mais abrangente e relevante. Em vez de se limitar a uma única fonte, você obtém uma visão mais ampla e detalhada das informações disponíveis.
O SearXNG respeita sua privacidade, nunca compartilha dados com terceiros e não pode ser usado para comprometer sua segurança.
O SearXNG é um software livre com código 100% aberto, e qualquer pessoa é bem-vinda para contribuir com melhorias. Se você valoriza a privacidade, deseja ser um usuário consciente ou acredita na liberdade digital, faça do SearXNG seu mecanismo de busca padrão ou instale-o em seu próprio servidor.
O SearXNG reconhece sua preocupação com logs, por isso o código-fonte está disponível para que você possa executar sua própria instância:
https://github.com/searxng/searxng
Adicione sua instância à lista de instâncias públicas.
https://searx.space/
para ajudar outras pessoas a recuperar sua privacidade e tornar a internet mais livre. Quanto mais descentralizada for a internet, maior será a liberdade para todos!
Lista de Instâncias Públicas
https://searx.space/
Documentação de Instalação
https://docs.searxng.org/admin/installation.html#installation
SeaxrXNG : Instalação , configuração e publicação.
https://youtu.be/zcrFPje6Ug8?si=oOI6dqHfHij51rvd
https://youtu.be/8WHnO9gJTHk?si=-5SbXUsaVSoSGpps
-

@ dff95033:862fbf40
2024-12-09 22:42:32
<img src="https://blossom.primal.net/0ac86bb186d6ada9099d8c8aad442bd264ee51333e876c142858a3f4ba32d306.png">
## DADOS BIBLIOGRÁFICOS
- Autor: Daniel J. Levitin
- Título: A Mente Organizada: Como Pensar com Clareza na Era da Sobrecarga de Informação
- Título Original: The Organized Mind: Thinking Straight in the Age of Information Overload
- Tradutor: Regina Lyra
- Editora: Objetiva
- Ano de Publicação no Brasil: 2015
- Ano de Publicação Original: 2014
- ISBN (Edição Brasileira): 978-8539006465
- Páginas: 512
- Gênero: Psicologia, Ciência Cognitiva, Desenvolvimento Pessoal
## INTRODUÇÃO
> "Não se pode confiar na memória porque o sistema de arquivamento do cérebro destreinado é uma porcaria. Ele pega tudo que acontece com você e joga de qualquer jeito num grande armário escuro — quando você entra lá procurando algo, só consegue achar as coisas grandes e óbvias, como a morte de sua mãe, ou então coisas de que realmente não precisa. Coisas que você não está procurando, como a letra de ‘Copacabana’. Você não consegue encontrar o que precisa. Mas não entre em pânico, porque ainda está lá.” (The Mentalist, citado por Daniel Levitin em A Mente Organizada)
Quando me deparei com o livro “A Mente Organizada”, de Daniel Levitin, impulsivamente o adicionei à minha lista de leitura — apenas para deixá-lo esperando por meses. É irônico que um livro sobre organização estivesse preso no caos da minha própria lista, não estranhamente em uma era dopamínica — onde cada notificação e distração competem para roubar nossa atenção. No entanto, ao finalmente mergulhar em suas linhas, percebi que a obra é uma verdadeira ode à capacidade humana de organizar o conhecimento e a informação.
## ESTRUTURA E CONTEÚDO
Dividido em três partes, “A Mente Organizada” nos guia por um entendimento prático sobre a mente humana. A Parte Um apresenta o mecanismo de atenção do cérebro, explorando como ele lida com o fluxo incessante de informações e decisões. Levitin discute a importância da atenção e como ela é fundamental para processar a quantidade massiva de dados que enfrentamos diariamente. Ele argumenta que entender esses mecanismos é crucial para melhorar nossa capacidade de foco e eficiência.
A Parte Dois oferece estratégias que colaboram com esse mecanismo, ajudando a organizar nossos ambientes físico, profissional, social e temporal. Levitin sugere métodos práticos, como a categorização e a criação de listas, que podem facilitar a tomada de decisões e reduzir a sensação de sobrecarga informacional. A ênfase na organização do espaço físico e do tempo é particularmente relevante em uma era onde distrações são constantes. Com a estrutura bem definida, Levitin avança para aprofundar seu estilo e explorar a complexidade de transmitir conceitos desafiadores de maneira acessível.
Por fim, a Parte Três discute como preparar a próxima geração para enfrentar os desafios do mundo moderno, equilibrando organização e criatividade. Levitin enfatiza a importância da educação em habilidades organizacionais desde cedo, preparando os jovens para um futuro onde o gerenciamento eficaz da informação será ainda mais crítico. Essa abordagem não apenas prepara os jovens para um futuro de desafios, mas também nos faz refletir sobre o legado que estamos construindo hoje.
## ESTILO E APROFUNDAMENTO
A verbosidade de Levitin pode parecer desafiadora em alguns momentos, mas são nestes pontos que reside o valor do livro. Sua escrita flui como ondas: ora simples e objetiva, ora densa e desafiadora. Essa variação mantém o leitor engajado e instigado, permitindo uma compreensão mais profunda dos conceitos apresentados. Cada nuance tem seu propósito, oferecendo ao leitor as bases para compreender plenamente a obra ou para instigar novas inspirações e perspectivas.
Levitin se esforça para tornar pesquisas e estudos sobre o tema acessíveis a um público amplo, evitando tanto a superficialidade quanto a complexidade excessiva. Essa abordagem é especialmente valiosa em um contexto onde muitos textos acadêmicos podem se tornar herméticos.
## REFLEXÕES PESSOAIS
> Como frisei no decorrer deste livro, o princípio fundamental da organização, o mais crucial para evitar que percamos ou esqueçamos as coisas, é este: descarregue do cérebro para o mundo externo o ônus de organizar." (A Mente Organizada, Daniel Levitin).
Ler A Mente Organizada foi um desafio que me obrigou a encarar a zorra informacional do dia a dia de frente. Não foi apenas uma leitura, mas um embate com os meus próprios hábitos e uma pausa necessária para questionar: estou realmente lidando bem com os estímulos ao meu redor? À deriva em águas turbulentas, precisei aceitar, com humildade, as ferramentas oferecidas pelo livro para enfrentar os desafios atuais.
Senti-me provocado a observar com mais atenção tudo o que carrego, tanto física quanto mentalmente. Quantas ideias, compromissos e pensamentos acumulados passam despercebidos, sem nunca encontrar um lugar ou um significado real? Esse convite à introspecção foi um lembrete poderoso de que, mais do que organizar o que está fora, preciso organizar o que está dentro — e isso começa com um olhar honesto, e sim, doloroso, sobre o impacto que o excesso tem em minha vida.
Esse foi o verdadeiro desafio: perceber que minha forma de organização precisava de um novo olhar. Não basta apenas acumular ideias; é essencial dar-lhes estrutura, conectá-las e transformá-las em algo maior — ou descartá-las, quando necessário. Entender as miríades que moldam meu pensar e agir foi fundamental, e, neste ponto, o livro foi nada menos que revelador. A estética, o particionamento e o naturalismo solidificam as minhas bases, transformando a organização em algo mais do que uma sistemática: ela se torna uma expressão de qualidade de vida e saúde.
## CONCLUSÃO
A Mente Organizada é uma obra que, para alguns, será apenas um folhetim, enquanto para outros será um verdadeiro manancial de sabedoria. Mas, acima de tudo, o que Daniel Levitin nos oferece são possibilidades — um convite à lapidação dessa gema preciosa e instigante que é a busca por sermos melhores do que somos hoje. Se você chegou a este livro, consciente ou não, já deu o primeiro passo nessa jornada.
Assim, caro leitor, deixo em tuas mãos esta obra, singela em proposta, mas grandiosa em potencial. Que ela inspire sua apreciação e, acima de tudo, seu uso.
Fecho esta gaveta aqui e espero ter apreciado o que há dentro dela — ou não. Se trouxe alguma ordem à bagunça, compartilhe e, se puder, contribua com o café — porque até a organização precisa de combustível.
-

@ 8e56fde2:bb433b31
2024-12-09 21:04:00
So let us give a little bit on context first to get the WHOLE PICTURE.
We DoShitters are a trio of friends who one day decided we wanted to create some shit together.
We are artists from different fields, and at the time two of us were struggling from creative block, so we decided to create the ultimate tool to COMBAT CREATIVE BLOCK. It would be an Oracle about the creative process and it would be inspired on the Hero's Journey and on our own journeys as artists; and hence "DoShit!" was born.

Once we knew what we wanted to do, and it started to have a shape, we decided to go through the hardship of self-producing and selling the cards by ourselves directly on our website ( www.doshitters.com ), which allowed us to keep control of the product at all times during production, and to have a direct relationship with our audience and buyers. Besides from guaranteeing we weren't left with the tiniest percentage of the sales pie. (At least in Spain, when you get a big publisher involved, you can forget getting even 10% of sales, and you lose a lot of the creative control of your project).
We invested a lot of our own resources in making sure "DoShit!" was a quality product and we were lucky enough to get the help of a generous patreon who enabled us to create what is now the DoShit! deck. <3

We did local presentations of the product in both Barcelona and Madrid, and got the deck to be sold in cool local stores, where we offered to do live readings and got to talk with people of all kinds about the Shit they wanted to do.
Above all, DoShit! is an inspirational tool.
**And you must be asking yourself, "What does this have to do with Amazon?".
**
Well, one of the problems of self-producing and having local fulfilment of the product is that shipping costs just couldn't compete with what the average consumer has gotten used to because of Amazon's mass scale free shipping.
We were finding that, specially for our followers in the USA, it was impossible to assume shipping costs (which amounted to almost the same cost as the actual deck); but we didn't want to give up on the people who wanted to get inspired by DoShit! but lived on the other side of the world from us, so...
WE DECIDED TO MAKE A DEAL WITH THE DEVIL, aka Amazon.

We knew that selling our product on Amazon was going to result in less revenue from the sales for us, but for us it was mostly about GETTING DoShit! TO A WAREHOUSE IN THE USA to be able to offer the deck with Free Shipping. And that's what we did.
But we didn't know everything that would come as a result, (they don't really advertise the hidden costs and fees, or the speed at which they want you to expedite your sales) and we've been paying for that decision ever since.

In any case, they lured us in with a 3 months no cost promotion. You obviously assumed the cost of shipping it there, and they would take a cut from every sale that happened in their web, but we didn't have any way of knowing the cost that we would need to incur after those first three months.
Another thing that wasn't advertised is that IF YOU ACTUALLY WANT YOUR PRODUCT TO BE FEATURED ANYWHERE, you need to be eligible as an A+ content seller, which also comes at a cost, and you need to pay additionally for sponsored ads; otherwise, your product is basically shut down in a black hole of zero discoverability except for people using the direct link.

The three months went by fast and then the invoices started coming, and the automatic charges on our account started to empty our independent seller bank account.
As you can imagine, independent sellers like us sometimes require of TIME to be able to get the word out, to get people to buy your product... Besides, as artists with other projects on the pipeline, we couldn't really spend much time focusing on sales, nor did we want to. And in all honestly, we refused to give Amazon more money in sponsored ads and other programs to "gain visibility".
We knew we had no way of competing with the big sellers on the platform, but we just thought, "AT LEAST IT'S AVAILABLE FOR THOSE WHO WANT TO BUY IT".

But then, out of the blue, we noticed our link on Amazon wasn't working. A friend tipped us off that it wasn't allowing any sales, it was listed as "currently unavailable", without us having done anything to trigger that change.
Suddenly we received an email from the giant informing us that our account had been set to inactive due to "dormancy", and that we needed to re-verify our identity. Not only that, but since we were in Europe, and they didn't have an address in the US they could send the decks back to, if we didn't get everything solved in time, THEY WERE GOING TO DESTROY THE DECKS THEY HAD IN THEIR WAREHOUSE because of their "Automated removal" policy.
This caught us while we were on holidays, away from our desktops, seller logins and such and we did everything the seller support requested from us as rapidly as possible.
The nightmare of imagining our beautiful decks being destroyed really put us in a state of panic. We hoped everything would be solved after several support tickets stating our case, and pleading that they don't destroy the decks!

In the end, after several communications, they reactivated our listing which had apparently been set to inactive because of "stranded inventory" due to "excess inventory"; which is Amazon talk for: "YOU'RE NOT SELLING FAST ENOUGH".
After having gone through that experience we knew one thing for certain, WE WANTED TO BREAK FREE FROM AMAZON as soon as possible, but we still wanted to offer our DoShit! decks with Free Shipping for our customers; at least this Christmas...

So, best case scenario, all the DoShit! decks that are at Amazon get sold this Christmas campaign, with the jolly merry spirit, people and nostriches all around the world get excited about GIFTING INSPIRATION (and taking advantage of the Free Shipping) and help us to GET THE DECKS OUT OF AMAZON!

But we know this may be wishful thinking T.T ,
That is why we are also looking for independent shops in the USA that feel that DoShit! makes sense in their store, and would want to become the new home of the decks that remain in american soil after the Christmas campaign. So maybe somebody wants to become the "foster home" to these Oracles as they find their new home in 2025, so they decks can go from that abussive giant with high time preference, to a friendly purple shop with low time preference and no hidden tricks.
After all, many people kickstart the year with their minds set on their New Year Resolutions, they want to DO SHIT! So Who Knows?

In any case, to all the small sellers out there, BEWARE OF MAKING THAT PACT WITH THE DEVIL.
We knew we had never wanted to get our Shit on Amazon, we knew the system was rigged again us, but still, we wanted to make it more affordable for people to get their hands on the deck.
Artists struggle enough to have to additionally add exhorbitant shipping costs to acquire a creativity tool like "DoShit!".
And if you, like us, find yourself having to do that pact anyway, we hope our tale will at least help you navigate all the hidden traps that their system throws at you.

IF YOU WANT TO JOIN THE CREATIVE RESCUE MISSION TO FREE THE DECKS,
please, support us as best you can, share our story, recommend our deck, but best of all GIFT THE "DoShit!" DECK THIS CHRISTMAS! <3
You can find it at its captor's site at https://a.co/d/hrKXEBF , or if you'd rather NOT BUY SHIT ON AMAZON, you can always buy it at the Plebeian Market with your Sats, and we'll get one out of Amazon on your account.
(https://plebeian.market/p/f82c481a3ae2a284049631a50373f4b9262c0e0b80977a4de1a71fcc19c5635d/stall/c9744507a49cf647c5612204416b7e22bdab86fbaff85413cfbc41103a0d269a)

THANKS FOR CARING,
This 2025, we wish you all to DO THE SHIT THAT MATTERS TO YOU!
#DoShit! #JoinTheArtmy
-

@ ece53feb:1edf277e
2024-12-09 15:19:42
https://www.newyorkupstate.com/news/2024/12/upstate-ny-village-shuts-off-water-declares-state-of-emergency.html?utm_source=flipboard&utm_medium=activitypub
-

@ eac63075:b4988b48
2024-12-08 15:35:21
Imagine a large public square, illuminated by intense spotlights, where every individual who dares to approach the center is immediately recognized, photographed, and cataloged. In this square, every word spoken becomes indelibly tied to its speaker. Under such conditions, many would hesitate before speaking, fearing not only the disapproval of the audience but also the potential punishments that could follow the mere act of expressing an idea. Now, imagine a second square, where anyone can cover their face with a mask, allowing their voice to echo without revealing their identity. It is in this second square that true freedom of expression flourishes, and this metaphorical mask represents anonymity.
https://www.fountain.fm/episode/MweciiR21hySxjdsNa7u
In debates about freedom of expression—one of the fundamental pillars of democratic societies—anonymity often emerges as a controversial element. For some, it serves as a refuge for digital criminals or slanderers. For others, it is an indispensable tool, capable of protecting dissenting voices and inspiring authentic debates, with ideas judged on their merits rather than the messenger’s reputation. This article aims to explain, in a clear and instructive manner, why anonymity is essential to genuine freedom of expression, illustrating its value with metaphors, real-life examples, and historical references.
## **The Protective Mask: Avoiding Retaliation and Threats**
Just as a navigator uses guiding instruments to avoid jagged rocks at sea, anonymity functions like a shield, allowing bold voices to navigate oppressive reefs without foundering. There are countless examples of individuals who have risked their lives to expose crimes and injustices—from whistleblowers in authoritarian governments to investigative journalists uncovering the complex machinations of organized crime. Without the possibility of anonymity, many of these stories would never have come to light.
Organizations like the Electronic Frontier Foundation (EFF) and other digital rights advocacy groups emphasize that the ability to speak without revealing one’s identity is crucial when the cost of speaking out is dangerously high. In censorship-ridden regimes, criticizing the government can lead to imprisonment, torture, or even death. Human rights activists, LGBTQIA+ communities in hostile countries, and journalists investigating illicit dealings all rely on anonymity to continue their work without putting their own lives at immediate risk. In this context, anonymity is not a whim—it’s the chance to survive one’s own opinion.
## **The Voice of the Invisible: Empowering Marginalized Groups**
Think of anonymity as an invisible microphone placed at the disposal of those who, without it, would never dare to take the stage. Historically, marginalized groups have always faced additional barriers to making their voices heard. Women in patriarchal societies, ethnic minorities facing discrimination, or individuals persecuted for their sexual orientation find in anonymity a safe space to speak out, claim their rights, and share their experiences without fearing public humiliation or physical violence.
This “invisible microphone” not only gives voice to those who once remained silent but also transforms the arena of public debate into a more equitable space. By removing the link between idea and identity, it reduces the risk of immediate prejudice against the messenger. As a result, society can assess arguments more impartially. Here, ideas are judged on their content, not on the face that speaks them.
## **The Strength of History: The Precedent of the Federalist Papers**
History offers a famous example of the power of anonymous words: the Federalist Papers. Published between 1787 and 1788, these essays supported the ratification of the United States Constitution and were written under the pseudonym “Publius” by Alexander Hamilton, James Madison, and John Jay. The reason for concealing their identities was clear: to ensure that their ideas would be judged on their argumentative strength rather than the prestige or fame of the authors.
The precedent set by the Federalist Papers is emblematic. It shows that, in the building of one of the first modern democracies, anonymity was used as a legitimate tool to establish fundamental concepts. If the founders of the nation that prides itself on its First Amendment—the one that protects freedom of expression—resorted to anonymity, we should recognize that this resource is not only defensible but also an essential part of the framework of healthy public debate.
## **Faceless Messages: The Democracy of Pure Ideas**
In an ideal world, we would judge a message purely on its content. In reality, however, names, faces, social status, and economic position influence how we receive and interpret a person’s words. Anonymity removes these superficial layers, allowing the message to present itself bare, subject to rational evaluation without the veils of prejudice.
In this sense, anonymity acts as a “filter of equality”: by concealing the source, it prevents us from assigning credibility (or discredit) based on stereotypes, prejudices, or personal rivalries. Thus, ideas previously dismissed out of hand can now be heard with greater attention, opening paths to social innovation, political reflection, and challenges to the status quo. A contemporary example is online forums that allow anonymous posts. While we acknowledge that such spaces can be misused, we cannot ignore their potential to give voice to those who would never feel safe speaking under their own name in public.
## **Privacy, Intimacy, and the Freedom to Whisper**
Anonymity is not limited to the public or political sphere. In personal and professional relations, the ability to speak anonymously can allow someone to seek help or reveal extremely sensitive matters. Imagine a patient who needs to consult a doctor about a stigmatized health issue, or a person seeking legal advice in a delicate situation. The “mask” of anonymity offers a safe haven for sharing information without the anguish of being judged or exposed.
Thus, anonymity also safeguards our “right to whisper,” that is, the ability to exchange information, secrets, and confessions without the constant glare of a spotlight. Real or perceived surveillance can stifle communication and inhibit creativity, reporting, and the exchange of ideas. By shielding individuals from forced exposure, anonymity reinforces the very fabric of freedom of expression, preventing the fear of identification from silencing words before they are spoken.
## **Anonymity in the Digital Age: Between Encryption and Censorship**
In the digital age, the issue of anonymity becomes even more relevant. With the expansion of online surveillance and the growth of social networks, maintaining anonymity can be challenging. Social media platforms increasingly request personal data, and governments attempt to impose barriers against anonymity, often justifying them as measures of national security or crime prevention.
However, according to reports and documents from human rights organizations, such as the UN High Commissioner for Human Rights and the Association for Progressive Communications (APC), encryption and anonymity are key tools for freedom of expression in the digital environment. Without these resources, citizens and journalists, for instance, become more vulnerable to persecution. In various countries, the existence of anonymous and encrypted channels enables information to circulate, grievances to be reported, and societies to remain informed, even in the face of heavy censorship.
## **Legal Protection: Judicial Recognition of Anonymity**
The United States Supreme Court, as well as other constitutional courts around the world, recognizes anonymity as an integral part of the right to free expression. In the United States, the First Amendment has been applied in cases that defended the right to anonymous speech, viewing it as a bulwark against the tyranny of the majority. When minorities are protected by anonymity, personal reprisals against those who dare to question dogmas or denounce abuses are prevented.
This judicial understanding reinforces the legitimacy of anonymity and its direct association with the strengthening of democracy. After all, a robust democracy requires not only the absence of formal censorship but also the guarantee that minority or unpopular voices can speak out without fear.
## **Conclusion: The Cloak That Protects Freedom**
If freedom of expression is the heart of democracy, anonymity is the cloak that shields that heart from the poisoned darts of fear, persecution, and prejudice. It creates the right environment for ideas to flourish freely, for courageous voices to emerge from silence, and for society to debate its most complex issues in the light of reason rather than beneath the shadow of intimidation.
In a world where surveillance and political tensions are ever-present, anonymity preserves the essence of free speech: humanity’s ability to question, propose, denounce, criticize, and create without shackles. By recognizing the importance of this resource, we safeguard not only individual voices but also the very principle that makes democracy worthy of its name.
## **Selected References:**
- Electronic Frontier Foundation (EFF): <https://www.eff.org/issues/anonymity>
- Freedom Forum: <https://www.freedomforum.org/anonymous-speech/>
- Association for Progressive Communications (APC): <https://www.apc.org/>
- The First Amendment Encyclopedia: Anonymous Speech: <https://firstamendment.mtsu.edu/article/anonymous-speech/>
- The Federalist Papers: Historical context available at [Library of Congress](https://www.loc.gov/) and various printed and digital compilations.
---
Cover Photo by [Redd Francisco](https://unsplash.com/@reddfrancisco?utm_source=ghost&utm_medium=referral&utm_campaign=api-credit) / [Unsplash](https://unsplash.com/?utm_source=ghost&utm_medium=referral&utm_campaign=api-credit)
-

@ 65912a7a:5dc638bf
2024-12-08 05:33:02
## Chef's notes
This is my late partner's award winning Cajun rice & beans recipe. It's an updated take on the traditional Cajun comfort food.
Chef Darin was a classically trained chef who spent 30+ years in the kitchen perfecting his recipes, and delivering authentic Cajun and Creole food to his patrons. This is a 5-star dish that will earn the respect of the most discerning Cajun afficionado. You won't be disappointed.
I suggest making this recipe exactly as directed the first time, and then make whatever adjustments you want for future batches. Also, don't cheap out on the Andouille. No Johnsonville or Hillshire Farms. Chef Aidelle's is a good choice, as is Silva's from Whole Foods. They cost a few extra bucks, but it's absolutely worth it.
## Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 3 hours
- 🍽️ Servings: 12
## Ingredients
- 16oz small red beans, dry
- 2 cups long grain white rice
- 14-16oz andouille sausage, sliced
- 8oz ham, cubed
- 1 large yellow onion, chopped
- 1 green bell pepper, chopped
- 2-3 stalks celery, chopped
- 2 tbsp garlic (12 cloves), minced
- 7 cups water
- ¼ cup olive oil
- 2 large bay leaves
- 1 tbsp parsley, dried
- 1 tsp thyme, dried
- 1 tsp Cajun seasoning
- ½ tsp cayenne pepper, dried
- ¼ tsp sage, rubbed
- 1½ tsp salt (more or less to taste)
## Directions
1. Soak beans in a large pot of water overnight.
2. Heat oil in a large stockpot over medium heat. Cook onion, bell pepper, celery, garlic in olive oil for 3 to 4 minutes (until onion is translucent).
3. Add beans, bay leaves, parsley, thyme, salt, MSG, Cajun seasoning, cayenne pepper, Sage, and water. Stir, bring to a boil, and then reduce heat to medium-low (btwn 2-3). Cover and simmer for 2½ hours.
4. Remove bay leaves. Mash some of the beans. Stir Andouille and ham into beans, and simmer uncovered for an additional 30 minutes.
5. Meanwhile, prepare the rice. Bring water and rice to a boil in a saucepan. Reduce heat, cover, and simmer for 20 minutes.
6. Serve beans over steamed white rice.
-

@ e6817453:b0ac3c39
2024-12-07 15:06:43
I started a long series of articles about how to model different types of knowledge graphs in the relational model, which makes on-device memory models for AI agents possible.
We model-directed graphs
Also, graphs of entities
We even model hypergraphs
Last time, we discussed why classical triple and simple knowledge graphs are insufficient for AI agents and complex memory, especially in the domain of time-aware or multi-model knowledge.
So why do we need metagraphs, and what kind of challenge could they help us to solve?
- complex and nested event and temporal context and temporal relations as edges
- multi-mode and multilingual knowledge
- human-like memory for AI agents that has multiple contexts and relations between knowledge in neuron-like networks
## MetaGraphs
A meta graph is a concept that extends the idea of a graph by allowing edges to become graphs. Meta Edges connect a set of nodes, which could also be subgraphs. So, at some level, node and edge are pretty similar in properties but act in different roles in a different context.
Also, in some cases, edges could be referenced as nodes.
This approach enables the representation of more complex relationships and hierarchies than a traditional graph structure allows. Let’s break down each term to understand better metagraphs and how they differ from hypergraphs and graphs.
## Graph Basics
- A standard **graph** has a set of **nodes** (or vertices) and **edges** (connections between nodes).
- Edges are generally simple and typically represent a binary relationship between two nodes.
- For instance, an edge in a social network graph might indicate a “friend” relationship between two people (nodes).
## Hypergraph
- A **hypergraph** extends the concept of an edge by allowing it to connect any number of nodes, not just two.
- Each connection, called a **hyperedge**, can link multiple nodes.
- This feature allows hypergraphs to model more complex relationships involving multiple entities simultaneously. For example, a hyperedge in a hypergraph could represent a project team, connecting all team members in a single relation.
- Despite its flexibility, a hypergraph doesn’t capture hierarchical or nested structures; it only generalizes the number of connections in an edge.
## Metagraph
- A **metagraph** allows the edges to be graphs themselves. This means each edge can contain its own nodes and edges, creating nested, hierarchical structures.
- In a meta graph, an edge could represent a relationship defined by a graph. For instance, a meta graph could represent a network of organizations where each organization’s structure (departments and connections) is represented by its own internal graph and treated as an edge in the larger meta graph.
- This recursive structure allows metagraphs to model complex data with multiple layers of abstraction. They can capture multi-node relationships (as in hypergraphs) and detailed, structured information about each relationship.
## Named Graphs and Graph of Graphs
As you can notice, the structure of a metagraph is quite complex and could be complex to model in relational and classical RDF setups. It could create a challenge of luck of tools and software solutions for your problem.
If you need to model nested graphs, you could use a much simpler model of Named graphs, which could take you quite far.

The concept of the named graph came from the RDF community, which needed to group some sets of triples. In this way, you form subgraphs inside an existing graph. You could refer to the subgraph as a regular node. This setup simplifies complex graphs, introduces hierarchies, and even adds features and properties of hypergraphs while keeping a directed nature.
It looks complex, but it is not so hard to model it with a slight modification of a directed graph.
So, the node could host graphs inside. Let's reflect this fact with a location for a node. If a node belongs to a main graph, we could set the location to null or introduce a main node . it is up to you

Nodes could have edges to nodes in different subgraphs. This structure allows any kind of nesting graphs. Edges stay location-free
## Meta Graphs in Relational Model
Let’s try to make several attempts to model different meta-graphs with some constraints.
## Directed Metagraph where edges are not used as nodes and could not contain subgraphs

In this case, the edge always points to two sets of nodes. This introduces an overhead of creating a node set for a single node. In this model, we can model empty node sets that could require application-level constraints to prevent such cases.
## Directed Metagraph where edges are not used as nodes and could contain subgraphs

Adding a node set that could model a subgraph located in an edge is easy but could be separate from in-vertex or out-vert.
I also do not see a direct need to include subgraphs to a node, as we could just use a node set interchangeably, but it still could be a case.
## Directed Metagraph where edges are used as nodes and could contain subgraphs
As you can notice, we operate all the time with node sets. We could simply allow the extension node set to elements set that include node and edge IDs, but in this case, we need to use uuid or any other strategy to differentiate node IDs from edge IDs. In this case, we have a collision of ephemeral edges or ephemeral nodes when we want to change the role and purpose of the node as an edge or vice versa.

A full-scale metagraph model is way too complex for a relational database.
So we need a better model.
Now, we have more flexibility but loose structural constraints. We cannot show that the element should have one vertex, one vertex, or both. This type of constraint has been moved to the application level. Also, the crucial question is about query and retrieval needs.
Any meta-graph model should be more focused on domain and needs and should be used in raw form. We did it for a pure theoretical purpose.
-

@ e6817453:b0ac3c39
2024-12-07 15:03:06
Hey folks! Today, let’s dive into the intriguing world of neurosymbolic approaches, retrieval-augmented generation (RAG), and personal knowledge graphs (PKGs). Together, these concepts hold much potential for bringing true reasoning capabilities to large language models (LLMs). So, let’s break down how symbolic logic, knowledge graphs, and modern AI can come together to empower future AI systems to reason like humans.
## The Neurosymbolic Approach: What It Means ?
Neurosymbolic AI combines two historically separate streams of artificial intelligence: symbolic reasoning and neural networks. Symbolic AI uses formal logic to process knowledge, similar to how we might solve problems or deduce information. On the other hand, neural networks, like those underlying GPT-4, focus on learning patterns from vast amounts of data — they are probabilistic statistical models that excel in generating human-like language and recognizing patterns but often lack deep, explicit reasoning.
While GPT-4 can produce impressive text, it’s still not very effective at reasoning in a truly logical way. Its foundation, transformers, allows it to excel in pattern recognition, but the models struggle with reasoning because, at their core, they rely on statistical probabilities rather than true symbolic logic. This is where neurosymbolic methods and knowledge graphs come in.
## Symbolic Calculations and the Early Vision of AI
If we take a step back to the 1950s, the vision for artificial intelligence was very different. Early AI research was all about symbolic reasoning — where computers could perform logical calculations to derive new knowledge from a given set of rules and facts. Languages like **Lisp** emerged to support this vision, enabling programs to represent data and code as interchangeable symbols. Lisp was designed to be homoiconic, meaning it treated code as manipulatable data, making it capable of self-modification — a huge leap towards AI systems that could, in theory, understand and modify their own operations.
## Lisp: The Earlier AI-Language
**Lisp**, short for “LISt Processor,” was developed by John McCarthy in 1958, and it became the cornerstone of early AI research. Lisp’s power lay in its flexibility and its use of symbolic expressions, which allowed developers to create programs that could manipulate symbols in ways that were very close to human reasoning. One of the most groundbreaking features of Lisp was its ability to treat code as data, known as homoiconicity, which meant that Lisp programs could introspect and transform themselves dynamically. This ability to adapt and modify its own structure gave Lisp an edge in tasks that required a form of self-awareness, which was key in the early days of AI when researchers were exploring what it meant for machines to “think.”
Lisp was not just a programming language—it represented the vision for artificial intelligence, where machines could evolve their understanding and rewrite their own programming. This idea formed the conceptual basis for many of the self-modifying and adaptive algorithms that are still explored today in AI research. Despite its decline in mainstream programming, Lisp’s influence can still be seen in the concepts used in modern machine learning and symbolic AI approaches.
## Prolog: Formal Logic and Deductive Reasoning
In the 1970s, **Prolog** was developed—a language focused on formal logic and deductive reasoning. Unlike Lisp, based on lambda calculus, Prolog operates on formal logic rules, allowing it to perform deductive reasoning and solve logical puzzles. This made Prolog an ideal candidate for expert systems that needed to follow a sequence of logical steps, such as medical diagnostics or strategic planning.
Prolog, like Lisp, allowed symbols to be represented, understood, and used in calculations, creating another homoiconic language that allows reasoning. Prolog’s strength lies in its rule-based structure, which is well-suited for tasks that require logical inference and backtracking. These features made it a powerful tool for expert systems and AI research in the 1970s and 1980s.
The language is declarative in nature, meaning that you define the problem, and Prolog figures out **how** to solve it. By using formal logic and setting constraints, Prolog systems can derive conclusions from known facts, making it highly effective in fields requiring explicit logical frameworks, such as legal reasoning, diagnostics, and natural language understanding. These symbolic approaches were later overshadowed during the AI winter — but the ideas never really disappeared. They just evolved.
## Solvers and Their Role in Complementing LLMs
One of the most powerful features of **Prolog** and similar logic-based systems is their use of **solvers**. Solvers are mechanisms that can take a set of rules and constraints and automatically find solutions that satisfy these conditions. This capability is incredibly useful when combined with LLMs, which excel at generating human-like language but need help with logical consistency and structured reasoning.
For instance, imagine a scenario where an LLM needs to answer a question involving multiple logical steps or a complex query that requires deducing facts from various pieces of information. In this case, a **solver** can derive valid conclusions based on a given set of logical rules, providing structured answers that the LLM can then articulate in natural language. This allows the LLM to retrieve information and ensure the logical integrity of its responses, leading to much more robust answers.
Solvers are also ideal for handling **constraint satisfaction problems** — situations where multiple conditions must be met simultaneously. In practical applications, this could include scheduling tasks, generating optimal recommendations, or even diagnosing issues where a set of symptoms must match possible diagnoses. Prolog’s solver capabilities and LLM’s natural language processing power can make these systems highly effective at providing intelligent, rule-compliant responses that traditional LLMs would struggle to produce alone.
By integrating **neurosymbolic methods** that utilize solvers, we can provide LLMs with a form of deductive reasoning that is missing from pure deep-learning approaches. This combination has the potential to significantly improve the quality of outputs for use-cases that require explicit, structured problem-solving, from legal queries to scientific research and beyond. Solvers give LLMs the backbone they need to not just generate answers but to do so in a way that respects logical rigor and complex constraints.
## Graph of Rules for Enhanced Reasoning
Another powerful concept that complements LLMs is using a **graph of rules**. A graph of rules is essentially a structured collection of logical rules that interconnect in a network-like structure, defining how various entities and their relationships interact. This structured network allows for complex reasoning and information retrieval, as well as the ability to model intricate relationships between different pieces of knowledge.
In a **graph of rules**, each node represents a rule, and the edges define relationships between those rules — such as dependencies or causal links. This structure can be used to enhance LLM capabilities by providing them with a formal set of rules and relationships to follow, which improves logical consistency and reasoning depth. When an LLM encounters a problem or a question that requires multiple logical steps, it can traverse this graph of rules to generate an answer that is not only linguistically fluent but also logically robust.
For example, in a healthcare application, a graph of rules might include nodes for medical symptoms, possible diagnoses, and recommended treatments. When an LLM receives a query regarding a patient’s symptoms, it can use the graph to traverse from symptoms to potential diagnoses and then to treatment options, ensuring that the response is coherent and medically sound. The graph of rules guides reasoning, enabling LLMs to handle complex, multi-step questions that involve chains of reasoning, rather than merely generating surface-level responses.
Graphs of rules also enable **modular reasoning**, where different sets of rules can be activated based on the context or the type of question being asked. This modularity is crucial for creating adaptive AI systems that can apply specific sets of logical frameworks to distinct problem domains, thereby greatly enhancing their versatility. The combination of **neural fluency** with **rule-based structure** gives LLMs the ability to conduct more advanced reasoning, ultimately making them more reliable and effective in domains where accuracy and logical consistency are critical.
By implementing a graph of rules, LLMs are empowered to perform **deductive reasoning** alongside their generative capabilities, creating responses that are not only compelling but also logically aligned with the structured knowledge available in the system. This further enhances their potential applications in fields such as law, engineering, finance, and scientific research — domains where logical consistency is as important as linguistic coherence.
## Enhancing LLMs with Symbolic Reasoning
Now, with LLMs like GPT-4 being mainstream, there is an emerging need to add real reasoning capabilities to them. This is where **neurosymbolic approaches** shine. Instead of pitting neural networks against symbolic reasoning, these methods combine the best of both worlds. The neural aspect provides language fluency and recognition of complex patterns, while the symbolic side offers real reasoning power through formal logic and rule-based frameworks.
**Personal Knowledge Graphs (PKGs)** come into play here as well. Knowledge graphs are data structures that encode entities and their relationships — they’re essentially semantic networks that allow for structured information retrieval. When integrated with neurosymbolic approaches, LLMs can use these graphs to answer questions in a far more contextual and precise way. By retrieving relevant information from a knowledge graph, they can ground their responses in well-defined relationships, thus improving both the relevance and the logical consistency of their answers.
Imagine combining an LLM with a **graph of rules** that allow it to reason through the relationships encoded in a personal knowledge graph. This could involve using **deductive databases** to form a sophisticated way to represent and reason with symbolic data — essentially constructing a powerful hybrid system that uses LLM capabilities for language fluency and rule-based logic for structured problem-solving.
## My Research on Deductive Databases and Knowledge Graphs
I recently did some research on modeling **knowledge graphs using deductive databases**, such as DataLog — which can be thought of as a limited, data-oriented version of Prolog. What I’ve found is that it’s possible to use formal logic to model knowledge graphs, ontologies, and complex relationships elegantly as rules in a deductive system. Unlike classical RDF or traditional ontology-based models, which sometimes struggle with complex or evolving relationships, a deductive approach is more flexible and can easily support dynamic rules and reasoning.
**Prolog** and similar logic-driven frameworks can complement LLMs by handling the parts of reasoning where explicit rule-following is required. LLMs can benefit from these rule-based systems for tasks like entity recognition, logical inferences, and constructing or traversing knowledge graphs. We can even create a **graph of rules** that governs how relationships are formed or how logical deductions can be performed.
The future is really about creating an AI that is capable of both deep contextual understanding (using the powerful generative capacity of LLMs) and true reasoning (through symbolic systems and knowledge graphs). With the neurosymbolic approach, these AIs could be equipped not just to generate information but to explain their reasoning, form logical conclusions, and even improve their own understanding over time — getting us a step closer to true artificial general intelligence.
## Why It Matters for LLM Employment
Using **neurosymbolic RAG (retrieval-augmented generation)** in conjunction with personal knowledge graphs could revolutionize how LLMs work in real-world applications. Imagine an LLM that understands not just language but also the relationships between different concepts — one that can navigate, reason, and explain complex knowledge domains by actively engaging with a personalized set of facts and rules.
This could lead to practical applications in areas like healthcare, finance, legal reasoning, or even personal productivity — where LLMs can help users solve complex problems logically, providing relevant information and well-justified reasoning paths. The combination of **neural fluency** with **symbolic accuracy and deductive power** is precisely the bridge we need to move beyond purely predictive AI to truly intelligent systems.
Let's explore these ideas further if you’re as fascinated by this as I am. Feel free to reach out, follow my YouTube channel, or check out some articles I’ll link below. And if you’re working on anything in this field, I’d love to collaborate!
Until next time, folks. Stay curious, and keep pushing the boundaries of AI!
-

@ e6817453:b0ac3c39
2024-12-07 14:54:46
## Introduction: Personal Knowledge Graphs and Linked Data
We will explore the world of personal knowledge graphs and discuss how they can be used to model complex information structures. Personal knowledge graphs aren’t just abstract collections of nodes and edges—they encode meaningful relationships, contextualizing data in ways that enrich our understanding of it. While the core structure might be a directed graph, we layer semantic meaning on top, enabling nuanced connections between data points.
The origin of knowledge graphs is deeply tied to concepts from linked data and the semantic web, ideas that emerged to better link scattered pieces of information across the web. This approach created an infrastructure where data islands could connect — facilitating everything from more insightful AI to improved personal data management.
In this article, we will explore how these ideas have evolved into tools for modeling AI’s semantic memory and look at how knowledge graphs can serve as a flexible foundation for encoding rich data contexts. We’ll specifically discuss three major paradigms: RDF (Resource Description Framework), property graphs, and a third way of modeling entities as graphs of graphs. Let’s get started.
## Intro to RDF
The Resource Description Framework (RDF) has been one of the fundamental standards for linked data and knowledge graphs. RDF allows data to be modeled as triples: subject, predicate, and object. Essentially, you can think of it as a structured way to describe relationships: “X has a Y called Z.” For instance, “Berlin has a population of 3.5 million.” This modeling approach is quite flexible because RDF uses unique identifiers — usually URIs — to point to data entities, making linking straightforward and coherent.
RDFS, or RDF Schema, extends RDF to provide a basic vocabulary to structure the data even more. This lets us describe not only individual nodes but also relationships among types of data entities, like defining a class hierarchy or setting properties. For example, you could say that “Berlin” is an instance of a “City” and that cities are types of “Geographical Entities.” This kind of organization helps establish semantic meaning within the graph.
## RDF and Advanced Topics
## Lists and Sets in RDF
RDF also provides tools to model more complex data structures such as lists and sets, enabling the grouping of nodes. This extension makes it easier to model more natural, human-like knowledge, for example, describing attributes of an entity that may have multiple values. By adding RDF Schema and OWL (Web Ontology Language), you gain even more expressive power — being able to define logical rules or even derive new relationships from existing data.
## Graph of Graphs
A significant feature of RDF is the ability to form complex nested structures, often referred to as graphs of graphs. This allows you to create “named graphs,” essentially subgraphs that can be independently referenced. For example, you could create a named graph for a particular dataset describing Berlin and another for a different geographical area. Then, you could connect them, allowing for more modular and reusable knowledge modeling.
## Property Graphs
While RDF provides a robust framework, it’s not always the easiest to work with due to its heavy reliance on linking everything explicitly. This is where property graphs come into play. Property graphs are less focused on linking everything through triples and allow more expressive properties directly within nodes and edges.
For example, instead of using triples to represent each detail, a property graph might let you store all properties about an entity (e.g., “Berlin”) directly in a single node. This makes property graphs more intuitive for many developers and engineers because they more closely resemble object-oriented structures: you have entities (nodes) that possess attributes (properties) and are connected to other entities through relationships (edges).
The significant benefit here is a condensed representation, which speeds up traversal and queries in some scenarios. However, this also introduces a trade-off: while property graphs are more straightforward to query and maintain, they lack some complex relationship modeling features RDF offers, particularly when connecting properties to each other.
## Graph of Graphs and Subgraphs for Entity Modeling
A third approach — which takes elements from RDF and property graphs — involves modeling entities using subgraphs or nested graphs. In this model, each entity can be represented as a graph. This allows for a detailed and flexible description of attributes without exploding every detail into individual triples or lump them all together into properties.
For instance, consider a person entity with a complex employment history. Instead of representing every employment detail in one node (as in a property graph), or as several linked nodes (as in RDF), you can treat the employment history as a subgraph. This subgraph could then contain nodes for different jobs, each linked with specific properties and connections. This approach keeps the complexity where it belongs and provides better flexibility when new attributes or entities need to be added.
## Hypergraphs and Metagraphs
When discussing more advanced forms of graphs, we encounter hypergraphs and metagraphs. These take the idea of relationships to a new level. A hypergraph allows an edge to connect more than two nodes, which is extremely useful when modeling scenarios where relationships aren’t just pairwise. For example, a “Project” could connect multiple “People,” “Resources,” and “Outcomes,” all in a single edge. This way, hypergraphs help in reducing the complexity of modeling high-order relationships.
Metagraphs, on the other hand, enable nodes and edges to themselves be represented as graphs. This is an extremely powerful feature when we consider the needs of artificial intelligence, as it allows for the modeling of relationships between relationships, an essential aspect for any system that needs to capture not just facts, but their interdependencies and contexts.
## Balancing Structure and Properties
One of the recurring challenges when modeling knowledge is finding the balance between structure and properties. With RDF, you get high flexibility and standardization, but complexity can quickly escalate as you decompose everything into triples. Property graphs simplify the representation by using attributes but lose out on the depth of connection modeling. Meanwhile, the graph-of-graphs approach and hypergraphs offer advanced modeling capabilities at the cost of increased computational complexity.
So, how do you decide which model to use? It comes down to your use case. RDF and nested graphs are strong contenders if you need deep linkage and are working with highly variable data. For more straightforward, engineer-friendly modeling, property graphs shine. And when dealing with very complex multi-way relationships or meta-level knowledge, hypergraphs and metagraphs provide the necessary tools.
The key takeaway is that only some approaches are perfect. Instead, it’s all about the modeling goals: how do you want to query the graph, what relationships are meaningful, and how much complexity are you willing to manage?
## Conclusion
Modeling AI semantic memory using knowledge graphs is a challenging but rewarding process. The different approaches — RDF, property graphs, and advanced graph modeling techniques like nested graphs and hypergraphs — each offer unique strengths and weaknesses. Whether you are building a personal knowledge graph or scaling up to AI that integrates multiple streams of linked data, it’s essential to understand the trade-offs each approach brings.
In the end, the choice of representation comes down to the nature of your data and your specific needs for querying and maintaining semantic relationships. The world of knowledge graphs is vast, with many tools and frameworks to explore. Stay connected and keep experimenting to find the balance that works for your projects.
-

@ e6817453:b0ac3c39
2024-12-07 14:52:47
The temporal semantics and **temporal and time-aware knowledge graphs. We have different memory models for artificial intelligence agents. We all try to mimic somehow how the brain works, or at least how the declarative memory of the brain works. We have the split of episodic memory** and **semantic memory**. And we also have a lot of theories, right?
## Declarative Memory of the Human Brain
How is the semantic memory formed? We all know that our brain stores semantic memory quite close to the concept we have with the personal knowledge graphs, that it’s connected entities. They form a connection with each other and all those things. So far, so good. And actually, then we have a lot of concepts, how the episodic memory and our experiences gets transmitted to the semantic:
- hippocampus indexing and retrieval
- sanitization of episodic memories
- episodic-semantic shift theory
They all give a different perspective on how different parts of declarative memory cooperate.
We know that episodic memories get semanticized over time. You have semantic knowledge without the notion of time, and probably, your episodic memory is just decayed.
But, you know, it’s still an open question:
> do we want to mimic an AI agent’s memory as a human brain memory, or do we want to create something different?
It’s an open question to which we have no good answer. And if you go to the theory of neuroscience and check how episodic and semantic memory interfere, you will still find a lot of theories, yeah?
Some of them say that you have the hippocampus that keeps the indexes of the memory. Some others will say that you semantic the episodic memory. Some others say that you have some separate process that digests the episodic and experience to the semantics. But all of them agree on the plan that it’s operationally two separate areas of memories and even two separate regions of brain, and the semantic, it’s more, let’s say, protected.
So it’s harder to forget the semantical facts than the episodes and everything. And what I’m thinking about for a long time, it’s this, you know, the semantic memory.
## Temporal Semantics
It’s memory about the facts, but you somehow mix the time information with the semantics. I already described a lot of things, including how we could combine time with knowledge graphs and how people do it.
There are multiple ways we could persist such information, but we all hit the wall because the complexity of time and the semantics of time are highly complex concepts.
## Time in a Semantic context is not a timestamp.
What I mean is that when you have a fact, and you just mentioned that I was there at this particular moment, like, I don’t know, 15:40 on Monday, it’s already awake because we don’t know which Monday, right? So you need to give the exact date, but usually, you do not have experiences like that.
You do not record your memories like that, except you do the journaling and all of the things. So, usually, you have no direct time references. What I mean is that you could say that I was there and it was some event, blah, blah, blah.
Somehow, we form a chain of events that connect with each other and maybe will be connected to some period of time if we are lucky enough. This means that we could not easily represent temporal-aware information as just a timestamp or validity and all of the things.
For sure, the validity of the knowledge graphs (simple quintuple with start and end dates)is a big topic, and it could solve a lot of things. It could solve a lot of the time cases. It’s super simple because you give the end and start dates, and you are done, but it does not answer facts that have a relative time or time information in facts . It could solve many use cases but struggle with facts in an indirect temporal context. I like the simplicity of this idea. But the problem of this approach that in most cases, we simply don’t have these timestamps. We don’t have the timestamp where this information starts and ends. And it’s not modeling many events in our life, especially if you have the processes or ongoing activities or recurrent events.
I’m more about thinking about the time of semantics, where you have a time model as a **hybrid clock** or some **global clock** that does the partial ordering of the events. It’s mean that you have the chain of the experiences and you have the chain of the facts that have the different time contexts.
We could deduct the time from this chain of the events. But it’s a big, big topic for the research. But what I want to achieve, actually, it’s not separation on episodic and semantic memory. It’s having something in between.
## Blockchain of connected events and facts
I call it temporal-aware semantics or time-aware knowledge graphs, where we could encode the semantic fact together with the time component.I doubt that time should be the simple timestamp or the region of the two timestamps. For me, it is more a chain for facts that have a partial order and form a blockchain like a database or a partially ordered Acyclic graph of facts that are temporally connected. We could have some notion of time that is understandable to the agent and a model that allows us to order the events and focus on what the agent knows and how to order this time knowledge and create the chains of the events.
## Time anchors
We may have a particular time in the chain that allows us to arrange a more concrete time for the rest of the events. But it’s still an open topic for research. The temporal semantics gets split into a couple of domains. One domain is how to add time to the knowledge graphs. We already have many different solutions. I described them in my previous articles.
Another domain is the agent's memory and how the memory of the artificial intelligence treats the time. This one, it’s much more complex. Because here, we could not operate with the simple timestamps. We need to have the representation of time that are understandable by model and understandable by the agent that will work with this model. And this one, it’s way bigger topic for the research.”
-

@ 3b19f10a:4e1f94b4
2024-12-07 09:55:46
Sometimes perspective is everything...
#[artmodel]( https://bsky.app/hashtag/artmodel)
#[nude]( https://bsky.app/hashtag/nude)
#[nudemodel]( https://bsky.app/hashtag/nudemodel)
------



-

@ a95c6243:d345522c
2024-12-06 18:21:15
*Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\
dass wir Vorteile aus ihr ziehen;\
in jedem andern hegt man den Wunsch,\
dass der Unschuldige in Schutz genommen werde.\
Jean-Jacques Rousseau*
**Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen** – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden.
**Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen»** den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen [schadet der Psyche](https://transition-news.org/meisterwerk-von-studie-bestatigt-maskentragen-bei-kindern-sinnlos-und-schadlich) und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben [Menschen getötet](https://transition-news.org/lockdowns-und-zensur-haben-menschen-getotet)».
**Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft.** Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen [Erfahrungen als Kritikerin](https://transition-news.org/die-coronazeit-hat-mir-gezeigt-wie-die-menschen-manipuliert-werden-konnen) der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit *Transition News*. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften».
**Menschen, die aufrichtig andere schützen wollten,** werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter [Heinrich Habig](https://transition-news.org/arzte-mussten-ihr-vergehen-irgendwann-selbst-einsehen), [Bianca Witzschel](https://transition-news.org/anwalt-von-bianca-witzschel-das-ist-eindeutig-eine-politische-justiz) und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat *Transition News* mehrfach berichtet (z.B. [hier](https://transition-news.org/prozess-gegen-walter-weber-kai-kisielinski-fuhrt-mit-argumentationsfeuerwerk) und [hier](https://transition-news.org/prozess-gegen-walter-weber-tschentscher-und-schaade-doch-nicht-vor-gericht)). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie [Alexander Bittner](https://transition-news.org/verweigerung-der-covid-impfung-inhaftierter-bundeswehrsoldat-kundigt) erfahren mussten.
[**Die eigentlich Kriminellen**](https://transition-news.org/die-eigentlich-kriminellen-schutzen-sich-vor-der-verantwortung) **schützen sich derweil erfolgreich selber,** nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte [Verbrechen gegen die Menschheit](https://transition-news.org/das-grosste-verbrechen-gegen-die-menschheit)». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn [Hunter](https://transition-news.org/us-steuerbehorde-hat-prasidentschaftswahl-2020-fur-joe-biden-gestohlen) möglicherweise auch [Anthony Fauci begnadigen](https://transition-news.org/wird-biden-auch-fauci-begnadigen) wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte?
**Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten** und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken.
**Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers [Robert F. Kennedy Jr.](https://transition-news.org/usa-robert-f-kennedy-jr-als-gesundheitsminister-nominiert)** erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens [Călin Georgescu](https://transition-news.org/der-ausgang-der-rumanischen-prasidentschaftswahlen-konnte-mogliche), der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der [Panik im Wertewesten](https://www.euronews.com/2024/12/04/robert-f-kennedy-jr-denies-any-link-with-far-right-romanian-presidential-candidate).
**In Rumänien selber gab es gerade einen Paukenschlag:** Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das [Tabu gebrochen](https://tkp.at/2024/12/06/rumaenien-sagt-praesidenten-wahl-ab/), Wahlen zu verbieten, bevor sie etwas ändern können.
**Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen** und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: [Zensur](https://transition-news.org/fuhrende-politiker-der-welt-unterzeichnen-neue-zensurerklarung-bei-un)) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden.
---
Dieser Beitrag ist zuerst auf [*Transition News*](https://transition-news.org/schutz-wem-schutz-gebuhrt) erschienen.
-

@ 0d532801:197a0c30
2024-12-06 05:13:25
[Mr. Robot]( https://www.piktobet.net/2015/10/mr-robot.html)
Dünya tehlikeli bir yer. Kötülük yapanlar yüzünden değil, görüp de hiçbir şey yapmayanlar yüzünden.
İnsanları okumada çok iyiyimdir. İçlerindeki en kötü şeyi ararım.
Herkes çalar. Bu böyledir. İnsanlar tam anlamıyla hak ettiklerini mi kazanıyorlar? Hayır. Ya fazla ya da az alıyorlar ama zincirdeki biri her zaman kaymağını götürüyor.
Bir adama bir silah verirsen bir bankayı soyabilir ama bir adama bir banka verirsen dünyayı soyar.
İnsanlar her zaman umudumu boşa çıkarmanın bir yolunu buldu.
Bir holdingi kalbini hedef alarak çökertemezsin. Holdinglerin olayı budur, kalpleri olmaz. Onları parça parça çökertirsin. Ve çözülmeye başladıkları zaman kontrol yanılsamaları da çözülür.
Büyük bir fırsat ondan faydalanılmasını bekler.
Seçimlerimiz üzerinde kontrol sahibi olup olmadığımızı nasıl bileceğiz? Sadece önümüze gelen şeyin en iyisini yapmaya çalışıyoruz, olay bu. Sürekli iki seçenekten birini seçmeye çalışıyoruz. Tıpkı bekleme salonundaki iki tablo gibi. Ya da Coca-Cola ve Pepsi. Mcdonald's veya Burger King. Hyundai veya Honda. Hepsi aynı bulanıklığın parçası. Odak dışında kalan bulanıklık. Seçimin yanılsaması. Kendi istediğimiz kablolu yayın, doğalgaz ve elektrik şirketini bile seçemiyoruz. içtiğimiz su, sağlık sigortamız.. Seçebilseydik bile fark eder miydi ki? Eğer tek seçim şansımız kılıç ve kalkan arasında oluyorsa bu nasıl seçimdir amına koyayım? Aslında aynı değiller midir? Hayır, seçimlerimiz bizim için tayin edilmiş uzun zaman önce.
İnsanlar etrafta dolaşıp nefretin ne demek olduğunu biliyormuş gibi yapıyorlar. Hayır, kimse bilemez. Ta ki kendinden nefret edene kadar. Demek istediğim, gerçekten kendinden nefret etmek. Bu, güçtür.
İnsanlar iletişim kuramadıkları zaman öfkelenir.
İçinde yaşadığımız dünya bu. İnsanlar birbirlerinin hatalarına bel bağlıyor. Birbirlerini kandırmak için başkalarını kullanıyorlar. Hatta birbirleri ile ilişkili oluyorlar. Sıcak, dağınık bir insan çemberi.
Bu, kendimi korumanın tek yolu: onlara asla kaynak kodumu göstermemek. Kendimi kapatmak. Beni kimsenin bulamayacağı soğuk, kusursuz labirentimi yaratmak. Ama artık daha normal olacağım. Belki kız arkadaşım bile olabilir. Onunla birlikte aptal marvel filmlerine gideceğim. Spor salonuna yazılacağım. Instagram'da bir şeyleri beğeneceğim. Vanilyalı latteler içeceğim. Bu andan itibaren açıksız bir hayat süreceğim. Kusursuz labirentimi korumak için her şeyi yapacağım.
Bir maskeyi, artık maske olmayı bıraktığında nasıl çıkarırsın? Senin kadar senin bir parçan olduğunda.
-

@ a367f9eb:0633efea
2024-12-02 20:49:25
Though Bitcoin was born in the world of computers and code, it was destined to eventually face-off with the legacy banking system.
The first block ever mined on the blockchain, Satoshi’s Genesis block, contained a (then) recent headline from a British newspaper reacting to the 2008/9 financial crisis, inscribing “*The Times 03/Jan/2009 Chancellor on brink of second bailout for banks*”.
As Bitcoin adoption increased from 2009 to 2012, users began exchanging dollars and euros for the digital money, using peer-to-peer exchanges and ATMs and then eventually with business entities acting as full-scale brokerages.
Today, this space is dominated by what we call cryptocurrency exchanges, offering bitcoin and many of its crypto-offspring. On these exchanges, as well as in various custodial solutions, bitcoin is held, bought and sold for traditional currency, and sent to destination wallets.
As these volumes have increased, so has scrutiny from financial authorities and government agencies, defining how this new category of entities exchanging US dollars and bitcoin would be regulated.
###### **The beginning of Bitcoin’s regulatory dance**
In March 2013, the Financial Crimes Enforcement Network (FinCEN), a division of the Treasury Department, updated its [guidance](https://www.fincen.gov/news/news-releases/fincen-issues-guidance-virtual-currencies-and-regulatory-responsibilities) to inform firms that “make a business of exchanging, accepting, and transmitting” virtual currencies would be considered **Money Service Businesses** (MSBs) under the law.
MSBs are distinct from banks and other traditional institutions. This taxonomy usually applies to issuers of travelers checks, check cashing services, and remittance services like Western Union. FinCEN’s guidance, for the first time, applied this to virtual currency services that transmitted funds on behalf of users or offered a fiat on-off ramp.
As an MSB, the law prescribes certain obligations for transaction collection, maintenance, and reporting, as well as identification requirements kept on file, what we call Know Your Customer (KYC) regulations.
The obligations on MSBs [require](https://www.fincen.gov/money-services-business-msb-suspicious-activity-reporting) filing Suspicious Activity reports on all transactions over $2,000 that “do not serve business or apparent lawful purpose” or may otherwise appear to be illegal activity or “structured” so as to try to avoid the spirit of the law.
The specific law that forces these obligations on MSBs, as well as banks, is the **Bank Secrecy Act** of 1970. Though it’s been updated several times over the years, the principal goal of this bill is to partner with banks and financial institutions to try to thwart money laundering and other illicit activity.
###### **BSA and Bitcoin**
The consequences of the BSA and its imposed surveillance have reaped unintended havoc on millions of ordinary Americans. This is especially true for those who have undergone “debanking,” in which bank customers are [deemed](https://www.thomsonreuters.com/en-us/posts/investigation-fraud-and-risk/treasury-de-risking-strategy/) too “high risk” and have accounts closed on them, a function of regulatory pressure – or *jawboning* – faced by financial institutions.
Venture capitalist Marc Andreessen has [provided](https://www.realclearpolitics.com/video/2024/12/01/marc_andreessen_biden_admin_has_been_debanking_politically_exposed_persons_in_privatized_sanctions_regime.html) his own examples of debanking in Silicon Valley, with similar conclusions.
Many Bitcoin and cryptocurrency entrepreneurs have been debanked on the [sole grounds](https://www.axios.com/2024/12/01/debanked-crypto-andreessen-joe-rogan) of being involved in the virtual currency industry, while millions of others have been swept up in the dragnet of the BSA and financial regulators forcibly deputizing banks to cut off customers, often without explanation.
According to FinCEN guidance, financial institutions are [compelled](https://www.fincen.gov/resources/advisories/fincen-advisory-fin-2010-a014) to keep suspicious activity reports confidential, even from customers, or face criminal penalties. This just makes the problems worse.
The [excellent research](https://www.cato.org/policy-analysis/revising-bank-secrecy-act-protect-privacy-deter-criminals) by the team at the Cato Institute’s Center for Monetary and Financial Alternatives provides reams of data on these points. As put by Cato’s **Norbert Michael**, “People get wrapped up in BSA surveillance for simply spending their own money”.
When it comes to bitcoin, the most common understanding for years has been that self-custody options and noncustodial solutions would be exempt from MSB classification, not requiring developers or entrepreneurs to acquire Money Transmission Licenses at either the state or federal level.
FinCEN itself stated this in their guidance [released in 2019](https://www.fincen.gov/sites/default/files/2019-05/FinCEN%20Guidance%20CVC%20FINAL%20508.pdf), and builders developed code based on what the government itself said. In 2023, however, the US Attorneys in the Southern District of New York and the FBI took a different stance.
Beginning with the Ethereum smart contract platform **Tornado Cash**, and then the popular privacy service **Samourai Wallet**, the developers of these projects were [arrested](https://www.justice.gov/usao-sdny/pr/tornado-cash-founders-charged-money-laundering-and-sanctions-violations) and [charged](https://www.justice.gov/usao-sdny/pr/founders-and-ceo-cryptocurrency-mixing-service-arrested-and-charged-money-laundering) with a number of conspiracy and money laundering charges, as well as “conspiracy to operate an unlicensed money transmitting business”. It’s that latter charge that remains the most important to sovereign and noncustodial use of bitcoin going forward.
Though both of these projects are noncustodial by design, and never took control of anyone’s bitcoin or cryptocurrency private keys, the government has charged them with being money service businesses and failing to adhere to the law.
Neither of these trials have yet taken place, but considering the money transmission charges, it stands to reason that anyone advocating for noncustodial bitcoin tools should be worried.
*If you’re interested in donating to the legal defense teams in both of these cases, check out the [**P2P Rights Fund**](https://p2prights.org/).*
If these are the steps law enforcement is willing to take against noncustodial protocols and projects even legal experts determined were out of the scope of MSBs, what about bitcoin exchanges and brokerages?
While we know there is no carve out at the moment, there are some important reforms that could empower entrepreneurs and give more options to Bitcoin users.
###### **An update to BSA would be a powerful reform for Bitcoin**
While we would hope that the majority of people using Bitcoin will practice [self-custody](https://www.btcpolicy.org/articles/self-custody-is-nonnegotiable), which is one of the key advantages of using Satoshi’s innovation, we know that most will not.
Instead, custodial services and exchanges will provide a lot of functionality for users, meaning that more and more Bitcoin activity will fall under the auspices of the Bank Secrecy Act.
One bill that aims to peel back the layers of banking law to restore some measure of financial privacy is the [**Saving Privacy Act**](https://www.lee.senate.gov/2024/9/lee-introduces-the-saving-privacy-act-to-protect-americans-financial-data), introduced by Sens. Mike Lee (R-UT) and Rick Scott (R-FL).
The proposed law aims to maintain the record keeping of financial institutions and money service businesses, but would do away with the automatic reporting limits and requirements without judicial warrants among other important reforms.
It would also ban a Central Bank Digital Currency, [repeal](https://www.therage.co/corporate-transparency-act-privacy-at-risk/) the **Corporate Transparency Act**, scale back the audit powers of the SEC, require Congressional approval for any ID database of Americans, severely punish any government employee who abuses private financial information, and grant a private right of action to any citizen or firm harmed by illicit government activity on financial matters.
It is a beefy bill with aspirational goals to restore consumer financial privacy, and it would no doubt make it much easier for Bitcoin tools and exchanges to operate within the law.
With less of a reporting requirement for custodial bitcoin solutions classified as Money Service Businesses – while still maintaining record keeping – it would be a much more natural balance of innovation and regulatory certainty.
By scaling back the financial surveillance required of banks and all other financial institutions, it is clear that Bitcoin users would benefit.
If there is enough appetite for this bill among various Senators and in the House of Representatives, however, is anyone’s guess. But the issues of our current banking system and its relation to Bitcoin are clear and this is a worthy attempt.
While there are still many regulatory changes needed to fully unleash the sovereign money revolution promised by Bitcoin, we can have some hope that the right ideas are being discussed in the corridors of power. At least for now.
*Originally published on the [website](https://www.btcpolicy.org/articles/downgrading-the-bank-secrecy-act-is-a-powerful-reform-for-bitcoin) of the **Bitcoin Policy Institute**.*
-

@ b83e6f82:73c27758
2024-12-02 12:33:13
## Citrine 0.5.7
- Fix rotation resetting the app state when downloading your notes
- Fix timeout when downloading your notes when you have a lot of notes
Download it with [zap.store]( https://zap.store/download), [Obtainium]( https://github.com/ImranR98/Obtainium), [f-droid]( https://f-droid.org/packages/com.greenart7c3.citrine) or download it directly in the [releases page
]( https://github.com/greenart7c3/Citrine/releases/tag/v0.5.7)
If you like my work consider making a [donation]( https://greenart7c3.com)
## Verifying the release
In order to verify the release, you'll need to have `gpg` or `gpg2` installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:
``` bash
gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6D
```
Once you have his PGP key you can verify the release (assuming `manifest-v0.5.7.txt` and `manifest-v0.5.7.txt.sig` are in the current directory) with:
``` bash
gpg --verify manifest-v0.5.7.txt.sig manifest-v0.5.7.txt
```
You should see the following if the verification was successful:
``` bash
gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03
gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D
gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"
```
That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
``` bash
cat manifest-v0.5.7.txt
```
One can use the `shasum -a 256 <file name here>` tool in order to re-compute the `sha256` hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly.
-

@ 6d8e2a24:5faaca4c
2024-12-02 09:03:49
"if your boyfriend uses Tiktok, you have a girlfriend" worlds riches man. Elon Musk tells women.
What's your opinion, do you think Elon Musk is right by his statement?
-

@ eac63075:b4988b48
2024-12-02 02:40:18
Estonia is a small country with just 1.3 million inhabitants and an area similar to that of the state of Rio de Janeiro, but with a notable difference: while Rio has about 16 million residents, Estonia shines with its efficiency, innovation, and digitalization. It's no wonder it's known as the "digital nation." For many Brazilians, the country has become a strategic gateway to start a business and settle in Europe.
Listen the podcast
https://www.fountain.fm/episode/pizBLdhqqP5qQrKQILFb
## The Purpose of the Event and the Context
The meeting organized by Bloco and the Brazilian digital community aimed primarily to explore the opportunities that Estonia offers to those wishing to expand their businesses or start a new life in Europe. With pizza, networking, and straightforward presentations, the evening was dedicated to demystifying questions like "Why Estonia?" and "What makes this country a viable option for Brazilians?"
Additionally, the event highlighted the importance of E-Residency, a digital identity that allows you to open and manage a company in Estonia from anywhere in the world. But that's just the beginning. Let's explore what makes Estonia a standout point on the European scene.
## Where Is Estonia Located?
If you open a map of Europe and look for this small country, you're likely to have difficulty locating it. Situated to the north of what's called Eastern Europe, Estonia borders Russia and Latvia and is separated from Finland by the Baltic Sea. Although geographically positioned in the east, many Estonians prefer to identify with the north due to cultural and historical proximity to the Nordic countries.
There's something fascinating about Estonia's history. According to local legends, Vikings set out from their Estonian islands to conquer the world, later returning to reclaim their lands. This spirit of resilience and reinvention permeates the country's culture to this day.
## Digitalization: The Estonian Revolution
Thirty years ago, when Estonia gained its independence from the Soviet Union, the country decided to look to the future. The question was simple: how to ensure the sovereignty and survival of a small, vulnerable nation? The answer was bold: total digitalization.
In 2001, the X-Road was created—a decentralized infrastructure that connects all government institutions and allows citizens to access public services digitally. This system is so advanced that even the servers of the Estonian government are located outside the country, stored with backups at the European Commission in Brussels.
Through this infrastructure, Estonia eliminated information silos, decentralized data, and allowed its citizens to authorize the use of personal information with complete control. Today, 98% of the population has a digital identity, 95% file taxes online in less than three minutes, and 100% of public services are available digitally.
For those accustomed to Brazilian bureaucracy, it's impressive to know that opening a company in Estonia can be done in just 15 minutes, without the need for an accountant.
## E-Residency: A Digital Passport for Business
Launched in 2014, the E-Residency program made Estonia the first country in the world to offer a digital identity to non-residents. This digital ID card allows entrepreneurs to open a company in the European Union, sign documents, and manage businesses remotely without needing to visit the country.
Although it doesn't grant citizenship or physical residency, E-Residency is perfect for those who want to test the European market or operate a digital company. The program has already attracted over 118,000 e-residents from around the world, including 1,300 Brazilians who have opened 379 companies in the country.
## Advantages of Doing Business in Estonia
Starting a business in Estonia has many advantages. Let's discuss some of the main ones:
### **Simple and Clear Taxation:**
Estonia adopts a flat tax rate of 20% (which increased to 22% after the pandemic and will be 24% in 2025) on distributed profits. If you reinvest the profits in the company, the taxation is zero—a unique policy that encourages sustainable growth.
### **Low Cost to Start:**
Unlike Switzerland, which requires an initial deposit of 100,000 Swiss francs to open a company, in Estonia, only 2,500 euros are needed. And the best part: this amount only needs to be deposited when the company distributes profits for the first time.
### **Complete Digitalization:**
Digital signatures in Estonia eliminate the need for notaries and paper documents. Everything can be done online, from opening the company to filing taxes.
### **Support for Startups and Innovation:**
With the Startup Visa, entrepreneurs can move to Estonia with their entire family and receive support to expand their businesses. Additionally, the country has the highest number of unicorns (startups valued at over one billion dollars) per capita in the world, including companies like Skype, Bolt, and Wise.
### **Easy Access to Europe:**
Establishing your company in Estonia means access to the European market, with its unified regulations and a vibrant innovation ecosystem.
## The Startup Visa: An Invitation for Entrepreneurs
For those who want more than just operating remotely, the Startup Visa program offers the opportunity to physically move to Estonia. The initial visa is valid for one year and can be renewed for three consecutive years. After eight years, there's the possibility of applying for European citizenship, although Estonia doesn't allow dual nationality.
One of the unique features of the Startup Visa is that there's no limit to the number of partners or family members who can be included in the program. This means that the entire team of founders and their families can benefit from the residence permit.
Additionally, Estonia offers support through the International House and its Work in Estonia program, a center where newcomers can resolve everything from assistance with opening bank accounts to cultural and professional integration.
## Innovation and Access to Investments
Estonia is known for its culture of innovation. Events like Latitude 59, one of Europe's main startup gatherings, offer prizes of up to two million euros for winning startups. The country also facilitates direct connections with investment funds and venture capital, often without bureaucratic barriers.
For early-stage companies, the Estonian ecosystem is especially attractive. There are cases of entrepreneurs who managed to raise hundreds of thousands of euros with little more than a prototype or a good idea on paper.
## A Small Country with Global Ambitions
Although small in size, Estonia is big in ambition. Its model of digitalization and support for startups serves as an example to the world. With unique opportunities like E-Residency and the Startup Visa, the country positions itself as a viable and accessible gateway for Brazilians who wish to explore the European market.
For those seeking innovation, simplicity, and access to the global market, Estonia offers more than opportunities; it offers a vision of the future. Whether it's to open a business, operate remotely, or move with the family, the country proves that with the right strategies, even a small nation can make a giant impact.
-

@ 0d532801:197a0c30
2024-12-01 21:27:48

߹ İnsan, bilinçli olarak günah işlediğinde, aslında birçok içsel ve dışsal faktörün etkisi altındadır. Bu faktörlerin başında bireysel arzular, toplumsal baskılar, zayıflıklar, bilinçaltı dürtüler ve bazen de cehalet gelir. İnsan, sadece dürtülerine göre hareket etmeyi tercih edebilir ya da kısa vadeli tatmin için uzun vadeli sonuçları göz ardı edebilir. Peki, bir insan neden bilerek günah işler? Bu sorunun cevabı, sadece dini ya da etik perspektiflerle değil, psikolojik, toplumsal ve kültürel açılardan da ele alınmalıdır.
1. Bireysel Arzular ve Dürtüler
߹ İnsanın doğasında, zaman zaman nefsini tatmin etme isteği vardır. Bu istek, bazen mantık ve vicdanın önüne geçebilir. İnsan, kısa süreli hazları arzularken, bunun gelecekteki olumsuz sonuçlarını göz ardı edebilir. Örneğin, hırsızlık yapan bir kişi, anlık bir mal edinme arzusuyla hareket edebilir, ancak bu davranışın ona ve çevresine getireceği zararları düşünmektense, elde edeceği çıkarı daha önemli görür. Benzer şekilde, yalan söylemek ya da başkalarını manipüle etmek de kısa vadeli çıkarlar ve bireysel egolar tarafından beslenen bir davranış biçimidir.
2. Toplumsal Baskılar ve Çevresel Faktörler
߹ İnsan, toplumsal bir varlık olarak çevresinden büyük ölçüde etkilenir. Toplumun normları, kültürel değerleri, arkadaş gruplarının etkisi ve ailevi dinamikler, bireyin davranışlarını şekillendirir. Bazı durumlarda, kişi bilerek yanlış bir davranış sergileyebilir çünkü çevresindeki kişiler böyle yapmaktadır ve kendini dışlanmış hissetmemek için buna ayak uydurur. Örneğin, bir grup insanın başka birine kötü davranması ya da yalan söylemesi, bir bireyi de benzer şekilde davranmaya itebilir. Bu durum, bireyin vicdanı ve doğru-yanlış algısı ile çatışan bir durumdur.
3. Zayıflıklar ve İnsan Doğası
߹ Herkesin zayıf anları vardır. Zihinsel ve duygusal olarak zorlandığı anlarda insanlar bazen bilerek yanlış bir şey yapabilir. İnsan, öfke, stres, yalnızlık ya da korku gibi duygusal durumlar içinde daha kolay günah işleyebilir. Duygusal karmaşa, sağlıklı düşünme yeteneğini zayıflatabilir ve kişi, anlık bir rahatlama ya da kaçış için yanlış bir yolu seçebilir. Örneğin, öfkelenen bir kişi, karşısındaki kişiye hakaret etmek ya da ona zarar vermek isteyebilir. Bu tür eylemler, kişinin o anki duygusal durumunun bir sonucu olarak ortaya çıkar.
4. Cehalet ve Yanlış İnançlar
߹ Bazen insanlar, neyin doğru neyin yanlış olduğuna dair doğru bir bilgiye sahip olmayabilirler. Bilgi eksikliği ya da yanlış inanışlar, bireyin günah işlemesine neden olabilir. İnsan, kötü bir davranışın ne kadar zarar verebileceğini ya da o davranışın ahlaki ve dini boyutlarını tam anlamayabilir. Özellikle bazı insanlar, içinde bulundukları ortamın, alışkanlıkların ya da eğitim seviyelerinin etkisiyle, doğruyu ve yanlışı tam kavrayamayabilirler. Bu durum da, onların bilerek ve isteyerek günah işlemesine yol açabilir.
5. İçsel Çatışmalar ve Vicdanın Bastırılması
߹ İnsan, bazen kendi içsel çatışmalarına dayanamayabilir. Vicdanı, doğruyu yapması yönünde onu uyarırken, içindeki kötü duygular ya da arzular ona engel olamayacak kadar güçlü olabilir. İnsanın kendisini haklı çıkarma çabası da burada devreye girebilir. Bir insan, kendini iyi bir insan olarak görmek isterken, bazen içindeki kötü dürtüleri bastırmak yerine, bunları haklı göstermek için kendine çeşitli gerekçeler uydurur. Örneğin, bir kişi başkasının hakkını yemek için kendini “bunu herkes yapıyor” ya da “benim de buna ihtiyacım var” gibi bahanelerle kandırabilir.
6. Dini ve Ahlaki Değerlerin Zayıflaması
߹ Bir insanın dini inançları ya da ahlaki değerleri, doğru-yanlış algısını büyük ölçüde şekillendirir. Ancak zamanla, bireylerin inançları ya da değerleri zayıflayabilir. Toplumda sekülerleşmenin arttığı bir dönemde, dini ve ahlaki öğretiler zamanla insanların gözünde daha az değerli hâle gelebilir. Bu durumda, insanlar günah işleme konusunda daha az vicdan azabı duyarlar, çünkü dini ya da ahlaki sonuçları görmezden gelmeyi tercih edebilirler.
߹ _**Sonuç olarak, insanın bilerek günah işlemesi, karmaşık bir durumdur ve çok çeşitli faktörlere dayanır. İnsanlar bazen içsel isteklerine, bazen dışsal baskılara, bazen de bilinçli ya da bilinçsiz olarak zayıf noktalarına dayanarak yanlışlar yapabilirler. Önemli olan, insanın yaptığı hataları fark etmesi, bu hatalardan ders alması ve doğru yolu bulmaya çaba göstermesidir. Kişi, hatalarını kabul ederek ve daha bilinçli bir şekilde hareket ederek hem kendisine hem de çevresine faydalı bir yaşam sürebilir.**_
-

@ a95c6243:d345522c
2024-11-29 19:45:43
*Konsum ist Therapie.
Wolfgang Joop*
**Umweltbewusstes Verhalten und verantwortungsvoller Konsum** zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
**Heute ist also wieder mal «Black Friday»,** falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
**Warum fallen wir auf derartige Werbetricks herein** und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
**Gedankenlosigkeit und Maßlosigkeit können besonders bei der [Ernährung](https://transition-news.org/studie-208-millionen-us-amerikaner-sind-als-fettleibig-oder-ubergewichtig) zu ernsten Problemen führen.** Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
**Kritik am schwarzen Freitag und dem unnötigen Konsum** kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
**Die EU-Kommission lancierte 2015 den Begriff «Green Friday»** im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das [Pariser Abkommen](https://transition-news.org/cop29-wird-vom-geist-des-noch-kunftigen-us-prasidenten-heimgesucht) unterzeichnet werden sollte.
**Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt.** Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des [«Green New Deal»](https://transition-news.org/green-new-deal) verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um [Valencia](https://transition-news.org/flutkatastrophe-in-valencia-die-ungereimtheiten-haufen-sich) dazu sagen?
**Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020** eine «[grüne Erholung von Covid-19](https://news.un.org/en/story/2020/12/1079602), um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
**Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet** – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
**Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung** nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie [«verantwortungsvolle Risikobereitschaft»](https://transition-news.org/zuruck-zu-2008-grossbritannien-schlagt-lockere-regeln-fur-banker-boni-vor) unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
---
Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/auch-beim-freitag-ist-es-egal-ob-schwarz-oder-grun)* erschienen.
-

@ bc6ccd13:f53098e4
2024-11-28 15:35:54
Of all the common misconceptions about money, this is the deepest and most pervasive. It taps into the very psychology that makes money the most powerful tool in the world. Money works in large part because, for most practical purposes, you can assume that money and wealth are the same thing and be very successful in life.
The problem is, it's a completely false premise. And without purging that assumption from your mental framework, understanding money and economics at a fundamental level is impossible.
Luckily, money is such an effective tool that it can continue to "mostly" function even without anyone understanding it at a fundamental level. It's a lot like gravity in that regard. You don't need to understand general relativity to learn how to walk. But unlike gravity, money is a powerful tool that can easily be used to exploit the less knowledgeable. That's why the general acceptance of this particular false idea is such a tragedy; it enables theft and exploitation on a global scale, and leaves the victims unable to identify the perpetrators or understand their methods.
## Money as a Social Technology
So let's unpack this misconception. We can start with a simple example. You've been shipwrecked on a desert island with only the clothes on your back. After a day under the blistering sun, you're presented with two options: a billion dollars in cash, or a case of bottled water. Which one do you choose? If you chose the water, congratulations. You survived because you were able to differentiate money from real wealth.
Now run the same experiment, but place yourself in the water aisle at Costco. Suddenly you choose differently. This shows a few key requirements for money to be useful. One, you need the real wealth, the actual goods and services. If there is no bottled water on that island, all the money in the world won't do you a lick of good. Two, you need someone willing to exchange the real wealth for your money. If you're alone on that island and you find a bottle of water, you don't need money to drink it, you just help yourself. Both requirements are essential.
This shows us that money is a social technology. Understanding the purpose and function of this technology is critical to dispensing with misconceptions like "money=wealth".
## Money and Civilization
What's the difference between a subsistence hunter/gatherer lifestyle and the modern civilization we all enjoy today? Specialization of labor, and complex supply chains. And what enables those civilizational necessities? Money.
In a subsistence situation, everything you have is created start-to-finish by you or by your immediate family or tribe. Everyone has to be a sort of jack-of-all-trades, at least at a group level. If you want a shelter, you collect the natural materials and build it yourself. If you need clothes, you collect the fibers or skins, process them, and use the fabric to sew your own outfit.
Contrast that with the electronic device you're using to read these words right now. How many people does it take to build a smartphone? Millions. Can one person do it? Absolutely not. You could give anyone in the world an entire lifetime and there's no way they could mine, process, and assemble the raw materials into a functional smartphone. It's simply too complex, too many processes and too much specialized knowledge and machinery needed. Not to mention doing it at a cost that most people on the planet can afford. That miracle is only possible because millions of people specialize in one tiny specific task related to making one part of a complex item, over and over again. The efficiency of only doing one specific task instead of being a generalist is what makes civilization possible.
But there's a problem. The person who's doing one specific task to make part of one widget still needs to eat, have a place to live, clothes to wear, etc. But how do you get all that while working a full time job making widgets? You can't do it all yourself, you need to buy those things from someone else who, similarly, specializes in those necessities of life. You need money. Money is what makes the whole thing work.
## Money and Barter
So what exactly is money and how does it work? In a subsistence society, you can use barter to trade with strangers. You give them some fish, they give you some clothing, everyone is happy. But barter has major problems, and doesn't work at all in complex supply chains with specialized workers. Specialized jobs don't produce valuable finished goods that can be bartered. When you solder circuit boards all day, you can't go to your local farmer and trade ten "solder circuit board" for a dozen eggs.
Enter money. Money solves multiple problems that arise with barter. For one, it creates a way to compare extremely dissimilar things. How many fish is a pound of butter worth? How many eggs? With barter, every good or service has to be priced in relation to every other good or service it's exchanged for. This is impossibly cumbersome and inefficient. Having money as a unit of account is as essential to trade as having a uniform inch is to building a house. A single carpenter might be able to use the width of his hand to measure boards, but get two carpenters working together and that "handbreadth" no longer works.
Second, money solves the problem of not having the correct item to barter with. If your neighbor has butter and you have fish, but your neighbor hates fish and will only accept a chicken, barter won't work. But if you can just pay him with money, he can go buy whatever he prefers.
Third, money creates a way to value and reimburse specialized work. That's arguably the most important aspect.
## The Social Contract Underlying Money
So what makes money function? Why would someone accept a piece of paper with a picture of a dead president in exchange for a very real and very valuable good or service? Well, the obvious answer is that they can be certain they'll be able to exchange that piece of paper with someone else and get an equally valuable good or service in the future. This is circular logic though, and leads some economists to mistakenly attribute the value of money to a "collective delusion". But since every known advanced civilization has used some form of money, calling it a delusion is both inaccurate and boorishly pretentious.
To understand the real mechanism behind the phenomenon, we have to consider how money is acquired. As anyone who has ever earned an honest wage knows, getting a paycheck requires two things. One, producing a valuable good or service. And two, giving that good or service to someone else instead of immediately consuming it yourself.
The first point is self-explanatory. If what you produce isn't valuable, no one will buy it.
The second point needs a bit more explanation. Money is a social technology, it's only valuable in a purely monetary sense when there's someone else to trade with. When you make yourself a few eggs for breakfast, you don't pay yourself for frying the eggs. Obviously. But if you eat your eggs, then go to your job as a short-order cook at the local diner, you may spend the morning getting paid to do exactly what you did "for free" at home. The difference is in the deferred consumption.
When you do a favor for someone, morality and the spirit of fairness dictates that they would be willing to return the favor in the future when you need something from them. That's how it works in a family or small community. People "owe each other one," and favors are reciprocated regularly without any money changing hands in a kind of informal credit system. But if one person starts to take advantage of others' generosity and requests a lot of favors, but always fails to reciprocate when asked, people catch on quickly. The parasitic behavior will be met with increasing unwillingness to help from members of the family or community, and in extreme cases, even exile from the community itself.
This informal credit system is the simplest and most fundamental form of money, and we can learn the basic principle behind why money works by observing it. We can see that a person accumulates "credits" by contributing productive value to others without getting anything in return. The "credits" are informal mental ledger credits that represent "this person has done something productive and valuable for someone else, which means he deserves to receive something valuable in the future." If a person contributes generously enough to the community, he will build up so much "credit" with everyone that he can expect generous help in return from any member of the community.
The shortcomings of this informal credit system are that one, it doesn't provide a unit of measurement to compare different goods and services accurately. This can lead to misunderstanding and disputes when different people don't value services the same way. Someone can feel that they are contributing more to the community than they're getting back in return. And two, it relies heavily on trust, and only works between people who interact on a regular basis. It would be foolish to provide favors to a stranger of unknown reputation, or someone who's just traveling through the area, because in either case there's no expectation of establishing a reciprocal relationship with that individual.
Money is just a way to formalize and expand that local, informal mental ledger. It's a way to keep track, on a societal level, who has contributed their fair share to the community and is deserving of reciprocal treatment. When someone buys something from you, although you don't consciously think through what's happening, on a subconscious level you're participating in a societal dialogue that goes something like this: "This person has money, which means they're a capable, generous, reciprocal person who has contributed more to the community than they've taken. Fairness dictates that they deserve something of value as a reward for their pro-social behavior. By taking their money, and giving them something of value, I can perpetuate the cycle of rewarding people who generously and capably do work that benefits others, and that will be beneficial to me personally and also to society as a whole. By having the money they give me, I can then also signal to others that I'm the same type of generous, reciprocal, productive person, and I can expect to be rewarded for that in the future when I try to exchange this money for valuable goods and services."
So the money has value, not because of some inherent quality of the paper or gold or mental "credit," but because it represents past productive behavior, but without immediate consumption. The money itself is not wealth, it's just an abstract representation, a kind of scorecard or ledger entry, of the real wealth that the holder of the money has already produced.
## Money and Capital Formation
This dialogue or unwritten contract is the foundation of modern civilization. It's powerful, because deferred consumption is the mechanism of capital formation, and capital formation is the foundation of complex supply chains and technological progress.
You might be able to catch enough fish to feed your family with a crude rod and line. But building a modern fishing trawler (a valuable capital good) takes thousands of people working together for a long time. All that hard work doesn't result in any fish being caught throughout the process, and all those people could instead be out fishing and catching a lot of fish to eat. But by deferring that consumption and instead putting that effort into building a capital good, you end up with a huge fishing trawler. Once it's finished, a few of those thousands of people can catch more fish in a week than all the thousands of them combined could have caught over the whole time it took to build the trawler. That makes fishing much easier and more effective in the future, making food much more plentiful and increasing the standard of living for the whole society. And money is what makes all that possible on a global scale.
## Final Thoughts
Given how critical this system is to civilization, any attack on money and its function is an existential threat. Unfortunately, a failure to understand the true nature of money leads to reliance on less nuanced or completely false ideas like "money=wealth". And that gives psychological cover to parasitic anti-social behavior like creating money and giving it away to buy votes, and all sorts of other destructive and dishonest shenanigans. Understanding that money is not wealth exposes the folly of all these schemes that purport to make people wealthier simply by creating more money. Believing that money is wealth makes the MMT clowns and the Keynesian grifters sound at least marginally credible. But those are specific misconceptions that need their own detailed explanation.
For now, reprogramming your mental framework to draw a strong distinction between money and real wealth will give you a solid foundation to understand economics, and to critique the many incorrect theories presented by the parasitical elements who wish to muddy the waters and avoid scrutiny of their anti-civilizational exploitation.
-

@ 468f729d:5ab4fd5e
2024-11-25 21:46:31
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video src="http://localhost:3000/api/get-video-url?videoKey=starter-lesson-0.mp4" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls></video></div>
## Course Mission
Welcome to the PlebDevs starter course! I'm Austin, the founder of PlebDevs, and I'll be walking you through this short intro starter course that will get you up and running and interacting with the rest of the content on the platform. If you're here, I'm assuming you're new to coding or just starting out. If you already have experience and have your bearings down, there's lots more intermediate and advanced content on the platform. This course is designed for absolute beginners.
## Course Goals
### Overall PlebDevs Goals
1. Learn how to code
2. Build Bitcoin/Lightning/Nostr apps
3. Become a developer
This is a big journey with a lot of pieces and things to learn. The starter course is going to get you on that path as quickly as possible and make it a smooth journey.
### Starter Course Objectives
1. Give you an easy, high-level overview of the dev journey
2. Get you set up and comfortable in a development environment where you'll write and ship code
3. Give you basic experience in the languages covered in our courses and workshops
There's lots of material out there that will just tell you exactly what to do and not explain why but I want you to actually understand for yourself. I want you to have a good mental model of what this journey is going to be like, what it's going to be like actually writing and pushing code. And then we're going to start getting our hands dirty and gain real experience.
## What is a PlebDev?
### Origins and Philosophy
I started using the term "PlebDev" a few years ago to describe a unique approach to learning development in the Bitcoin space. It represents:
- **Inclusive Learning**: Anyone can become a developer, regardless of background
- **Growth Mindset**: Embracing the journey from beginner to professional
- **Practical Focus**: Emphasizing real-world application development
- **Community Support**: Learning and growing together
### Key Characteristics
- 🌱 **Growth-Focused**: PlebDevs are always learning and improving
- 🎯 **App-Centric**: Focus on building applications rather than protocol development
- 🆕 **Embrace Being New**: Being a new developer is infinitely better than being on the sidelines
- 🤝 **Community-Driven**: Bitcoin/Lightning/Nostr ecosystem needs more plebdevs like you!
## Our Learning Approach
### Core Principles
1. **Lower Barriers**
- Simplify complex concepts
- Focus on practical understanding
- Build confidence through action
2. **Project-Based Learning**
- Learn by doing
- Create real applications
- Build a portfolio as you learn
3. **MVP (Minimum Viable Product) Focus**
- Start with core functionality
- Get things working first
- Iterate and improve
4. **Actionable Knowledge**
- Focus on the 20% that delivers 80% of results
- Learn what you can use right away
- Build practical skills
### Teaching Methods
- Detailed concept breakdowns
- Line-by-line code explanations
- Interactive learning
- 1:1 support available
- Community-driven progress
## Course Structure
### The Learning Path
Instead of the traditional bottom-up approach, we use a project-focused method:
```
🏔️ Advanced Skills
🏔️ Projects & Practice
🏔️ Core Concepts
🏔️ Development Environment
🏔️ Getting Started
```
We'll create checkpoints through projects, allowing you to:
- Verify your understanding
- Build your portfolio
- See real progress
- Have reference points for review
## Student Expectations
### What We Expect From You
- **High Agency**: Take ownership of your learning journey
- **Active Participation**: Engage with the material and community
- **Persistence**: Push through challenges
- **Curiosity**: Ask questions and explore concepts
### What You Can Expect From Us
- Clear, practical instruction
- Comprehensive support
- Real-world applications
- Community backing
## Getting Started
### Next Steps
1. Ensure you're ready to commit to learning
2. Set up your development environment (next lesson)
3. Join our community
4. Start building!
## Resources and Support
### Where to Get Help
- plebdevs.com
### Tips for Success
1. Push code daily, even if it is small.
2. Focus on understanding rather than memorizing.
3. Build projects that interest you.
4. Engage with the community.
5. Don't be afraid to ask questions.
## Remember
You don't need to become a "10x developer" overnight. The goal is to start writing code, build useful things, and gradually improve. Every expert was once a beginner, and the journey of a thousand miles begins with a single line of code.
Ready to begin? Let's dive into the next lesson where we'll set up your development environment! 🚀
-

@ 228dde34:b5d0345e
2024-11-25 04:14:20
##### BY Cheryl Nya
##### Deputy Editor
##### Hype Issue #60
###### Join CHERYL NYA as she talks to competitive Darts player, Pay Yu Xuan, on her journey as a young athlete and her dreams to expand the Darts scene in Singapore.

*Pay Yu Xuan, 19, youngest Premier DARTSLIVE Ambassador and national Darts player. Photo by NJ Eshani.*
What does your bullseye look like? For some, it could come in the form of a scholarship or an academic achievement. Perhaps it’s a championship in your CCA and scoring long-lasting friendships. For Pay Yu Xuan, 19, her bullseye simply lies on a dartboard.
“I just thought it was different …, who would’ve thought to play Darts as a sport?” Yu Xuan, explains on how she picked up the sport. What began as a casual interest quickly turned into a remarkable journey that propelled her to the international stage at just 18 years of age. She is now the youngest Darts player representing Singapore.

*Yu Xuan (middle) beginning her competitive Darts journey representing Singapore Polytechnic. Photo courtesy of Pay Yu Xuan.*
Her Darts career started as a Co-Curricular Activity (CCA). “SP was the only Poly in Singapore that had Darts as a CCA and I thought that was really cool,” Yu Xuan recounts, “I started as a leisure player, but as I played, I saw myself getting closer to the target. Playing Darts [continuously] fuelled my sense of self-improvement and I just kept thinking that I could go further. That’s how I got hooked on it.”

*Yu Xuan wins the runner-up position in the Ladies Cricket Open category at the Hong Kong International Darts Festival. Photo courtesy of Pay Yu Xuan.*
Like every remarkable athlete, Yu Xuan’s pursuit of success has not been easy. “Darts is a mental game,” she says, “Especially during competitions. It’s so easy to start overthinking. When that happens, you might go into self-destruction mode and it’s hard to [focus on the target]. Sometimes when I’m in front of so many cameras and I see myself on the big screen, I really feel the nerves and start to be self-conscious. I cannot show any signs of nervousness.”
Not only has she had internal battles to fight, but her parents were also initially unsupportive of her dreams. With the game being tied closely to stereotypes such as drinking and smoking, Yu Xuan’s parents were afraid she might pick up unhealthy habits and had to think twice about allowing her to commit to the sport.

*Yu Xuan secures the champion position, in the selection for Singapore’s National Darts Team. Photo courtesy of Pay Yu Xuan.*
However, the turning point came in December last year, when Yu Xuan was chosen to represent Team Singapore in the Hong Kong International Darts Festival. Her hard work and dedication paid off when she emerged as champion in the selection process, successfully proving her capabilities and showing her parents how passionate she truly was for the sport.
After witnessing Yu Xuan’s potential, her parents eventually gave up their resistance.Seeing that she had a dream and she was about to conquer it, Yu Xuan instilled a deep confidence in them. From initially keeping away her passport to granting her permission and even giving her an allowance to compete overseas, her parents became her greatest support system.
The mental toll and pressure is unfortunately something that every athlete has to go through, no matter how much you enjoy your sport. “This is not a stable incline. You’re always going up and down, it’s not easy at all,” Yu Xuan replies when asked how she overcame her challenges. “Having a strong belief system is very important to me. I know that I’ve spent a lot of time training, so I [have] learned to believe in myself. I really can do it. And this self-confidence didn’t just appear out of nowhere. I’m constantly working on it and my friends and family are the support system who encourages me.”
Sharing her perspective on the beauty of Darts, Yu Xuan hits home: ”You can only hit your target if you believe you can. In this game, success is when you focus on mind over body.”

*Yu Xuan (left) with the players of Team Singapore in Hong Kong. Photo courtesy of Pay Yu Xuan.*
Although Yu Xuan is an exceptional Darts player with immense potential, a fact stubbornly remains: The ‘Darting’ scene in Singapore is extremely limited.
“Something that didn’t really sit well with me was that [Darts] is still too niche for the government to be supporting it, and the youths who are potentially national-level players don’t have [enough opportunities] to compete internationally,” she says.
Yu Xuan recalls the time she applied for a Leave Of Absence from her classes to compete in a tournament overseas. As Darts is not recognised as a sport under the National Sports Association, her appeal was unfortunately rejected. “It’s something I hope can change,” Yu Xuan shares sincerely.

*Yu Xuan (top row, second from the left) teaching the HYPE team how to play darts as a Premier DARTSLIVE ambassador. Photo courtesy of Pay Yu Xuan.*
In that effort, Yu Xuan has worked hard to prove her capabilities and has successfully qualified to be an Ambassador for DARTSLIVE, a company that provides the dartboards you see around in most SAFRA National Service Associations and bars. Not only is Yu Xuan the youngest Premier DARTSLIVE Ambassador, she is also the only female Ambassador. “Though females [tend to be] less dominant in the sport, I do hope to see more start to play Darts,” she shares.
Determined to grow the darts community and raise the sport's profile in Singapore, Yu Xuan has made a bold and generous move by launching her own workshop, offering free Darts lessons to new players. “Many people don’t have [access] to learning the basics, like your stance, [or] the way you hold your dart, for example. Even the current Darts players … I just wanted to help by giving them a foundation to keep playing. I like teaching and talking to people too. That’s why I opened my Darts clinic, even though I don’t earn [a salary] from it.”
“I would love to play Darts as a career in [the] future but [I will] probably have to do it overseas, in … Japan or Hong Kong, where [Darts has] a bigger community and their governments support it,” Yu Xuan shares, “I really hope Darts grows bigger in Singapore and maybe I could even work to become a coach here.”

*Hoping to encourage youths who also have a passion, she hopes that everyone can hit their own targets one day. Photo by NJ Eshani.*
To the young aspiring athletes looking to follow Yu Xuan’s footsteps and become national athletes, she has this to say: “Follow your passion, because passion is your energy, and it’s what drives you to keep doing what you love every day. In everything, we’re bound to meet setbacks, it’s about how you recover from it. That determines who will be the winners, who will stay ahead and who will fall back. I promise you, your hard work will pay off one day. Keep pushing and be confident! If you don’t believe in yourself then who will believe in you?”
-

@ d7c6d014:a6abb6b8
2024-11-23 18:40:47
こんにちは!kohei です。
久々のエントリ投下ですが、今回は先日弊 TL で話題になっていた、Android を P2P のローカルリレーサーバー化して Tor で公開する方法を紹介していこうと思います。
## 用意するもの
1. Android 端末
2. Orbot
3. Citrine
4. Amethyst
## 前提と下準備
今回は、Orbot の詳細設定は省いて、Power User Mode の設定が完了している前提でお話を進めます。
Android 端末を用意して、2~4 のアプリをインストールしておいてください。
## 設定方法
それでは早速設定していきましょう。
まず、Citrine を起動して、Settings のタブからローカルリレーの詳細を設定します。
設定が終了したら、ローカルリレーを起動します。
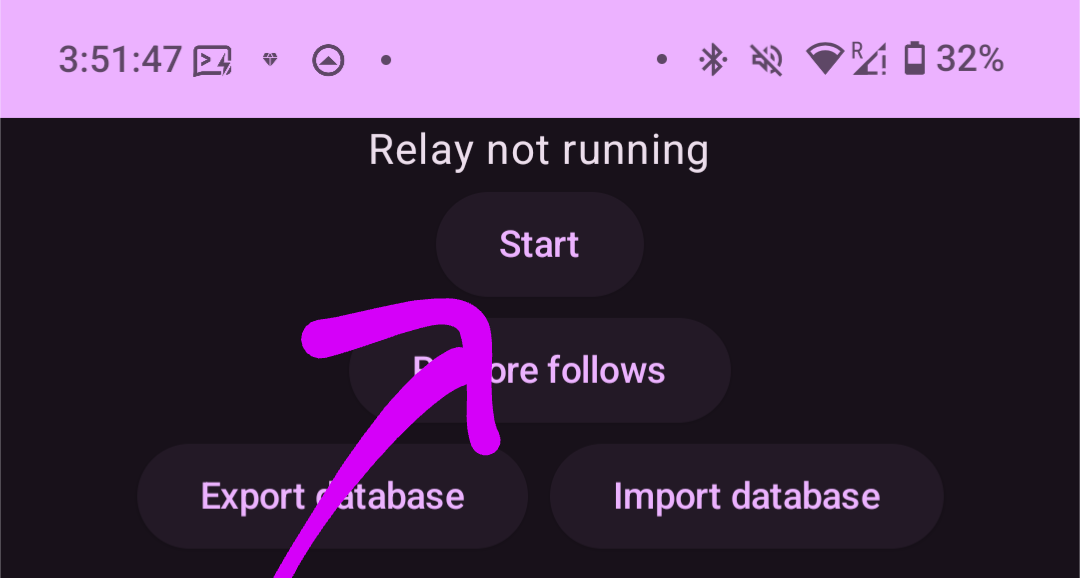
また、ここで表示されるポート番号をメモしてください。
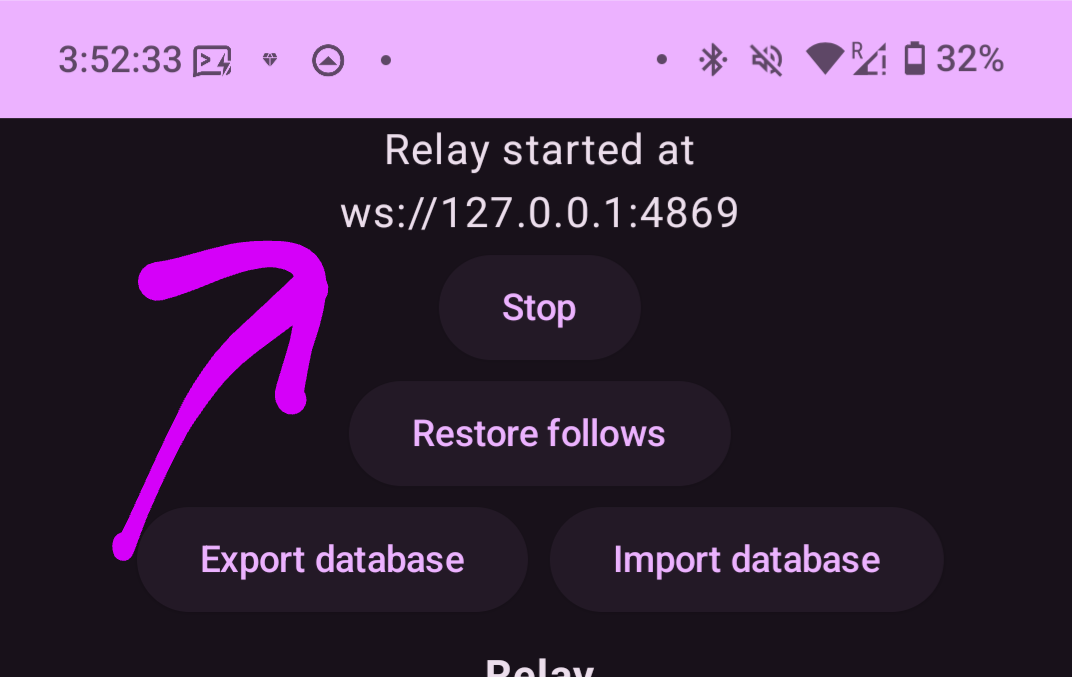
次に、More のタブに移り、Hosted Onion Services へアクセスし、Service Type の項目で User Services にチェックを入れて、右下の + マークをタップすると以下のポップアップが表示されます。(Orbot がスクショを許してくれないので一部画像割愛)
表示されたら、Name に任意の名前を、Local Port と Onion Port に先ほどメモした Citrine のポート番号を入力します。
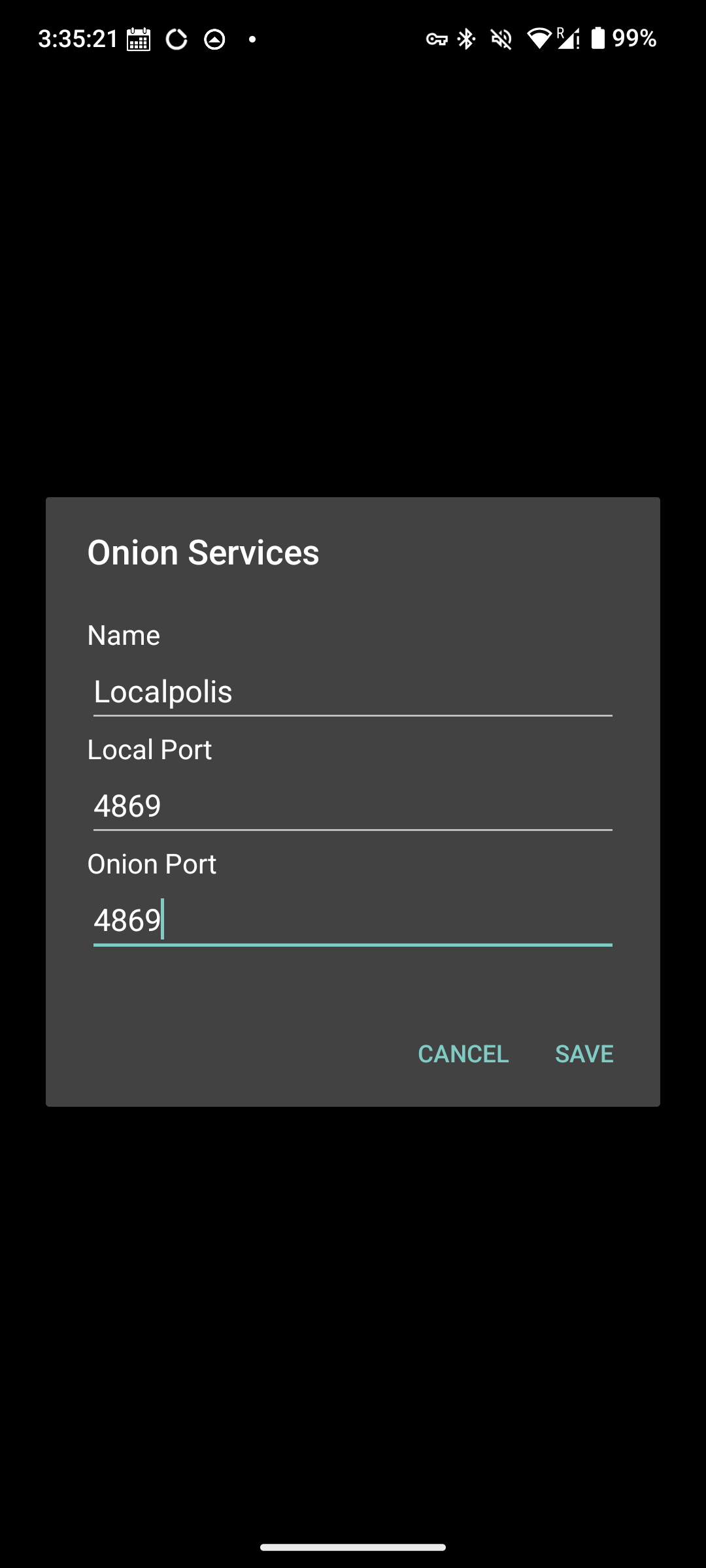
入力したら再起動を求められるので再起動してください。
再起動後に Hosted Onion Services の項目に .onion のアドレスが表示されたら成功です (何故か私の環境では、一回の再起動では設定が反映されなかったのですが、もし同じような現象が起きた場合は、再起動 -> Connect -> .onion アドレスが発行されてるかの確認、を数回試すと発行されるはずです)
発行されたら、.onion アドレスをタップしてクリップボードにコピーします。
次に、Amethyst を起動して、リレーの設定画面に入り、Outbox の設定にコピーした .onion アドレスを貼り付けて保存します。
後は、Amethyst 側で Orbot のポート番号を設定して Orbot に接続すれば BOOM! 設定完了です。
お疲れ様でした!
素敵な Nostr ライフを!
-

@ 228dde34:b5d0345e
2024-11-22 04:57:34
##### BY Glenda Chong
##### Editorial Admin
##### Hype Issue #60
###### Join GLENDA CHONG as she talks to founder of media and creative agency, DANAMIC, Danish Lukawski, on what it takes to learn to become an entrepreneur from the ground up.

*Danish Lukawski, founder of creative and media agency DANAMIC. Photo courtesy of Danish Lukawski.*
When you were ten years old, how did you get your pocket money? At that age, perhaps you begged your parents for money. Danish Lukawski did things differently; he started a business to earn his own.
What started as him wanting to put up photos of his pet hamsters online by learning the now-discontinued HTML editor tool Microsoft Frontpage, became a booming business when a friend’s father needed a site for his printer-selling business.
Looking back at his earliest venture, Danish had but two regrets: he should have taken the leap sooner, and he should have charged his family friend more than $20. While he can laugh at those early days now, those little lessons unknowingly set the stage for something bigger. I spoke to Danish Lukawski, founder of the creative and media agency DANAMIC on his unique journey and the lessons learnt to become the entrepreneur and associate lecturer he is today.
### How He Got Started
For most, school is a place with a clear-cut path where you take the courses that aid you in your journey to your future career. Danish took a diploma in Information Technology at Ngee Ann Polytechnic and explored his interest in media by augmenting his diploma with a few modules from the Mass Communication diploma.
However, the one other area he had equal passion for - entrepreneurship, wasn’t something the school offered at the time. So it seemed doubtful that, without the resources on offer, Danish could have hoped to become one. Despite this, he showed that the absence of a path doesn’t mean a lack of possibilities - sometimes, it’s an invitation to create your own.
Danish took it upon himself to explore the world of entrepreneurship by attending events linked to Ngee Ann Polytechnic. This was also where help from his Film & Media Studies teachers came in handy, with Mr. Jon Foo bringing him to film galas to meet directors and producers and Ms. Sharon Ismail helping him expand his professional network.
Outside of building connections with industry people, he also taught himself to build up his skills and qualifications to become an entrepreneur. Why self-taught, you might ask? Simply put, it boiled down to how entrepreneurial courses at the time felt “fluffy”. Instead he directed his energy into obtaining certifications, from companies like Meta, that give him credibility with clients.

*Danish (second from left) also took up a course directly from TikTok, allowing his company to be TikTok Ad certified. Photo courtesy of Danish Lukawski.*
### The Challenges He Faced Building DANAMIC
When asked about memorable mistakes, Danish mentioned how it took “19 to 29 different failures” before landing on his company’s first “Yes”. Rejection never gets easy, and he remembers it all too well.
“Back when we first got our first office, we tried to kind of knock on everyone’s door in the same building,” He said. Sadly, once his new building neighbours could pick up that they were attempting to sell something, doors were closed. Eventually, a clinic gave them a chance and tried his company’s media services for a few months.

*Danish’s company celebrating Christmas just after moving into their office. Photo courtesy of Danish Lukawski.*
Another big hurdle Danish had to overcome was hiring. Sometimes, some hires weren’t good fits and this is where he believes culture-fit is important. “If they didn’t fit in the culture then they either felt like the whole place is against them or they would always be working in a way that everyone else cannot figure out how to work with.” Ultimately, it’s better to be particular when hiring, rather than hiring incompatible employees that leave quickly and affect morale.
And just when you think that Danish has done it all, his story is far from over. Building his own business was not enough for him; he wanted to give back.
### Becoming an Associate Lecturer
You’d probably look at Danish as though he has two heads when he says this, but of the many reasons why he became an associate lecturer, one was that“it’s like taking a break”!
The one joke he shares whenever this gets brought up is that he traded his 9 to 5 to work 24/7. Becoming an associate lecturer meant he could “partition a day out” where he puts full focus into teaching classes at Ngee Ann Polytechnic’s School of Infocomm Technology whilst turning off from everything else.
The second reason was so he could “keep in touch with youth”. Danish admits that interacting with his students gives him plenty of direction in marketing when applied back to his main work, but ultimately keeping in touch with young people allows him “to keep on the ground”.
“It means a lot to me because I get to see what they care about, what they’re consuming and then I know where they’re at,” Danish said. In a nutshell, it helps to close the generation gap as he gets to understand the “psyche of where they are as a generation”.

*Aside from teaching at Ngee Ann Polytechnic and NUS, Danish also holds sharings across various schools, with this one being held at Greendale Secondary School. Photo courtesy of Danish Lukawski.*
Finally, the most important motivator for teaching at Ngee Ann Polytechnic was, of course, his desire to give back to the school. While he “could have gone to any other polytechnic”, Ngee Ann Polytechnic was one of the institutions that made him who he is today.
Aside from this, he also occasionally returns to his other alma mater, the National University of Singapore, as an industry specialist. This is where his journey comes full circle, as Danish becomes the teacher he didn’t have in his schooling years, imparting his knowledge in a course on entrepreneurship in the new age where students pitch their business ideas to him.

*Danish sharing on entrepreneurship at a cognitio event where founders of start-ups shared on their work, in NUS. Photo courtesy of Danish Lukawski.*
### Advice for Future Entrepreneurs
As Danish helps shape the minds of future innovators in the classroom, he also has additional insights to provide outside of it. When asked to advise anyone with a background similar to his wanting to be an entrepreneur, he has two messages to share.
Danish explains a mental model of thinking about “the land of prosperity” vs. “the land of scarcity”. “I believe in the land of prosperity because while everyone is fighting for that one strange plot of land, I’m going like ‘Guys, there are nine plots here. What are you all doing?’.”
Although there are chances that you might not be able to compete, “there’s always a chance to pivot” or if not, “there’s always a chance to disrupt”. And to him, just because something’s been done before, it doesn’t mean there aren’t better ways of going about it.
“Just gather all the opportunities you want,” Danish stated.
”There’s no harm in trying something and failing cause what do you have to lose? The most you lose is just the time or maybe a bit of money or whatever energy you’ve expended but the experience is invaluable than never trying at all.”
Another piece of advice Danish had: don't be afraid to share your ideas. Many partners he has worked with were unafraid to share because even if one stole an idea from the other, should the idea fail, they have helped the other “figure out that it was a stupid idea”.

*Danish (second from right) taking home an SME 500 Singapore Award awarded to DANAMIC at the SMESummit 2023. Photo courtesy of Danish Lukawski.*
Above all else, a willingness to share ideas opens many doors in business. When people come together and share, there will often be synergy, and that’s where enduring partnerships can form.
Or in Danish’s words, “I believe being open and true is better than being close-minded and scared.”
-

@ e373ca41:b82abcc5
2024-11-21 09:47:26

The last few years are unlikely to evoke positive associations for most people: corona madness, climate and trans ideology, a few wars in between and now the weather is also going crazy.
You feel more reminded of the biblical plagues and the apocalypse than motivated to make positive changes to the system. It seems as if the world is in the hands of fanatical do-gooders and globalist social engineers. But the world is always in the hands of everyone. There is no responsibility for the future in the hands of some kind of “elite”, unless the citizens voluntarily leave it to them. Apocalypse literally means “unveiling”. In times of crisis, the core of reality is peeled out and all illusions fall away.
**Golden times for system explorers**
In turbulent times like these, unbreakable forest dwellers and resisters, prognosticators, esotericists and also system busters cavort. This is also a constant in history: times of crisis were often times of new beginnings. In knowledge revolutions, new knowledge inevitably mixed with new technology and also a new spiritual orientation towards the world. Before the outside world is created, it must be conceived internally.
Around 500 years ago, the plague repeatedly cut new swathes through Europe, while at the same time Venice began its rise as a major trading power, the Medici banking system began to flourish and, a little later, so did art. This boom was preceded by something that at first glance seemed “boring”, such as the invention of double-entry bookkeeping by the monk Luca Pacioli at the end of the 15th century.
In the following century, the thinker Giordano Bruno moved from city to city in search of employment, and in the end, the system-breaker was burned as a heretic on the Campo de' Fiori in Rome. Meanwhile, astronomers, magicians, artists and alchemists bustled about at the court of the Habsburg Rudolf II in Prague. Some talked to angels, others tried their hand at producing gold. Those who ridicule alchemical experiments today as heresies should at least google how phosphorus and porcelain were discovered.
To be outmoded and unworldly means to be in search of something different.
Great visionaries from Rudolf Steiner to Albert Einstein, Nikola Tesla and Richard Buckminster-Fuller have always known that the best way to change the system is to go outside the system and create something new from there. You don't change the old by fighting it. The best way to replace it is to think in new forms that make the old forms obsolete, said Buckminster-Fuller.
**Brains moved the world more than the guillotine**
Working on the old is like dancing with zombies. Creating the new, on the other hand, inevitably brings the old into competition with the system. If the new is better, the old system is obsolete. “Video killed the Radio Star” sang the Buggles in 1979 (the first clip of the MTV era) and they were just as right as Steve Jobs, who threw several industries overboard with the iPhone. What you previously needed 20 devices for, from dictation machines to telephones and “Walkmans”, you now had in your pocket. Thinking outside the system, which you don't learn within the system, combined with technology, is the sharpest knife in history when it comes to change. Brains moved more than the guillotine.
In today's world, everyone is a potential system changer. There has never been a time when the tools of change have been available to as many people as they are today. At the same time, we live in a time in which fewer people than ever before determine the fate of everyone. How does this fit together? There is an infinite systematic potential for change, and this lies solely with the people who have not yet made use of the available tools. But this wave is irreversibly set in motion; it is rolling and no one knows when it will turn into a tsunami.
Free speech and critical journalism are under massive attack. With the [Pareto Project](https://www.freischwebende-intelligenz.org/p/pareto-projekt-beenden-wir-jetzt) we want to make censorship-resistant publishing the new standard. Today, we have the opportunity to consign the phenomenon of censorship to the landfill of history. Are you thinking along similar lines? What should the journalism of the future look like? Help us as a tester, migrate your content as a journalist or as a publication, support us as a developer or contribute your ideas: [Kontakt@idw-europe.org](mailto:kontakt@idw-europe.org)
**The great transformation**
We are living in the midst of a quiet revolution, with quiet revolutionaries. Pavel Durov from Telegram would certainly have got on well with Giordano Bruno. Bitcoin inventor Satoshi Nakamoto might have felt at home at the court of Rudolf II in the past.
The path to change follows similar patterns of transformation. In the past, the power of the individual was seen as being sand in the gears of the system. “Man of labor, wake up! And recognize your power! All wheels stand still when your strong arm wills it,” wrote Georg Herwegh. Today, anyone can create their own little system. With Bitcoin, uncensorable money is already in circulation. The next big battle is over the uncensorability of information and it is currently underway. The best way to share centralized power, whether it's media power or a central bank cartel, is to distribute power through decentralized systems. This is essentially a feudalistic redistribution: the old feudal system is being replaced by the reassertion of power for the individual.
What role will Switzerland, the country of countless inventions, play in this development? Hardly any other country is so innovative and therefore so well positioned for this system transformation. The most successful Bitcoin app in Europe already comes from Switzerland. The Relai app is an application for secure self-custody of Bitcoin, without the influence of others. Relai AG was recently voted the best crypto startup and second-best financial startup in the country, and is rushing from one growth success to the next. The company is currently preparing to conquer the European market even more effectively.
Gaining control for the individual means losing control for the old (money) system. This principle also applies in other sectors. For example, iVault AG from Thalwil is currently working on opening up the “sharing economy” market. Anyone who wants to easily rent out their e-bike, car or lawnmower to others, for example, can do so via the ivault.io app and benefit directly from their own sustainability. Here too, old centralized platforms are being disempowered and individuals are taking their fate into their own hands.
It's always the same pattern and principle: if you don't want to be managed by others, you have to manage yourself. This applies to money, information and even lawnmowers and e-bikes.
---
Want to learn more about the [Pareto Project](https://pareto.space)? We build a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Zap me, if you want to contribute (all Zaps go to the project).
-

@ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08
### Tldr
- Nostr is an open protocol which is interoperable with all kinds of other technologies
- You can use this interoperability to create custom solutions
- Nostr apps define a custom URI scheme handler "nostr:"
- In this blog I use this to integrate Nostr with NFC cards
- I create a Nostr NFC "login card" which allows me to log into Amethyst client
- I create a Nostr NFC "business card" which allows anyone to find my profile with a tap
### Inter-Op All The Things!
Nostr is a new open social protocol for the internet. This open nature is very exciting because it means Nostr can add new capabilities to all other internet-connected technologies, from browsers to web applications. In my view, it achieves this through three core capabilities.
- A lightweight decentralised identity (Nostr keys, "npubs" and "nsecs"),
- A lightweight data distribution network (Nostr relays),
- A set of data interoperability standards (The Nostr Improvement Protocols "NIPs"), including the "nostr:" URI which we'll use in this post.
The lightweight nature is its core strength. Very little is required to interoperate with Nostr, which means many existing technologies can be easily used with the network.
Over the next few blog posts, I'll explore different Nostr inter-op ideas, and also deliver my first small open source projects to the community. I'll cover–
- NFC cards integrated with Nostr (in this post),
- Workflow Automations integrated with Nostr,
- AI LLMs integrated with Nostr.
#### The "Nostr:" URI
One feature of Nostr is it defines a custom URI scheme handler "nostr:". What is that?
A URI is used to identify a resource in a system. A system will have a protocol handler registry used to store such URI's, and if a system has a URI registered, then it knows what to do when it sees it. You are probably already familiar with some URI schemes such as "http:" and "mailto:". For example, when you click an http link, the system knows that it describes an http resource and opens a web browser to fetch the content from the internet.
A nostr: link operates in the same way. The nostr: prefix indicates a custom URI scheme specifically designed for the Nostr protocol. If a system has a Nostr application installed, that application may have registered "nostr:" in the protocol handler registry. On that system when a "nostr:" URI is clicked, the system will know that it describes a nostr resource and open the Nostr client to fetch the content from the nostr relay network.
This inter-op with the protocol handler registry gives us the power to do nice and exciting things with other technologies.
### Nostr and NFC
Another technology that uses URIs is NFC cards. NFC (Near Field Communication) is a wireless technology that enables devices to exchange data over a few centimeters. It’s widely used in contactless payments, access control, and information sharing.
NFC tags are small chips embedded in cards or stickers which can store data like plain text, URLs, or custom URIs. They are very cheap (cents each) and widely available (Amazon with next day delivery).
When an NFC tag contains a URI, such as a http: (or nostr:) link, it acts as a trigger. Tapping the tag with an NFC-enabled device launches the associated application and processes the URI. For example, tapping a tag with "nostr:..." could open a Nostr client, directing it to a specific login page, public profile, or event.
This inter-op allows us to bridge the physical world to Nostr with just a tap.
#### Many useful ideas
There are many interesting ways to use this. Too many for me to explore. Perhaps some of these are interesting for your next side hustle?
- Nostr NFC "login cards" – tap to log into Amethyst on Android,
- Nostr NFC "business cards" – give to connections so they can tap to load your npub,
- Nostr NFC "payment cards" – integrating lightning network or ecash,
- Nostr NFC "doorbells", "punch cards", "drop boxes", or "dead drops" – put a tag in a specific place and tap to open a location-specific message or chat,
- Integrations with other access control systems,
- Integrations with other home automation systems,
- Many more ...
To start with I have built and use the "login card" and "business card" solutions. This blog post will show you how to do the same.
### Nostr Login Card
You can use an NFC card to log into your Nostr client.
Most Nostr clients accept a variety of login methods, from posting your nsec into the app (insecure) to using a remote signer (more secure). A less known but more secure method is to sign into a session with a tap of a specially-configured NFC card. Amethyst is a Nostr client on Android which supports this type of login.
- A secure method for logging in
- Optionally keeps no log in history on the device after logout
- Does not require users to know or understand how keys work
- Keys are kept secure on a physically-separated card to reduce risk of compromise
Nostr devs think that this is useful for anti-establishment actors–Fair enough. For me, I am interested in this login card pattern as it could be useful for rolling out identities within an organisation context with less training (office workers are already familiar with door access cards). This pattern potentially abstracts away key management to the IT or ops team who provision the cards.
I first discovered this when [Kohei](nostr:npub16lrdq99ng2q4hg5ufre5f8j0qpealp8544vq4ctn2wqyrf4tk6uqn8mfeq) demonstrated it in [his video](nostr:nevent1qqstx0jy5jvzgh7wr6entjuw7h58d7mapupfdpt9hkf7s4gze34a0vspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzp47x6q2txs5ptw3fcj8ngj0y7qrnm7z0ft2cptshx5uqgxn2hd4ckqyqd3).
Here's how you set it up at a high level–
1. Buy yourself some NFC cards
2. Get your Nostr key ready in an encrypted, password protected format called "nencryptsec"
3. Write the nencryptsec to the NFC card as a custom URI
4. Tap to load the login screen, and enter your password to login
Here it is in detail–
#### Buy yourself some NFC cards
I found no specific requirements. As usual with Nostr so far, I tried to the cheapest possible route and it worked. Generic brand NFC cards shipped from China, I believe it was 50X for $15 from Amazon. Your mileage may vary.
#### Get your Nostr key ready
Your key will be saved to the NFC card in an encrypted password-protected format called "nencryptsec". Several applications support this. As we'll be using this to login to Amethyst, we will use Amethyst to output the nencryptsec for us.
1. Login to Amethyst with your nsec,
2. Open the sidebar and click "Backup Keys",
3. Enter a password, and click "Encrypt and my secret key",
4. It will add the password-protected key to your clipboard in the format "ncryptsec1...",
5. Remember to backup your password.
#### Write the ncryptsec to the NFC card
1. Download the free [NFC Tools app](https://play.google.com/store/apps/details?id=com.wakdev.wdnfc) to your device, and open it,
2. Click "Write" and "Add a record", then click "Custom URL / URI",
3. Paste your nencryptsec with the nostr URI in front, i.e. "nostr:ncryptsec1..." and click OK,
4. Click "Write". NFC Tools will prompt you to "Approach an NFC tag",
5. Place your NFC card against your phone, and it will write to the card,
6. Your card is ready.
#### Tap to load the login screen
Tap the card against your phone again, and your phone should open the login screen of Amethyst and prompt you for your password.
Once you enter your password, Amethyst will decrypt your nsec and log you in.
Optionally, you can also set the app to forget you once you log out.
You have created a Nostr NFC "login card".
### Nostr Business Card
You can use another NFC card to give anyone you meet a link straight to your Nostr profile.
I attended [Peter McCormack](nostr:npub14mcddvsjsflnhgw7vxykz0ndfqj0rq04v7cjq5nnc95ftld0pv3shcfrlx)'s #CheatCode conference in Sydney and gave a few of these out following the Nostr panel, notably to [Preston Pysh](nostr:npub1s5yq6wadwrxde4lhfs56gn64hwzuhnfa6r9mj476r5s4hkunzgzqrs6q7z) where it [got some cut through](nostr:nevent1qqsdx0acma85u9knejnvfnfms9pfv27g97mfnnq9fnxslsa9vtrx73spremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzppggp5a66uxvmntlwnpf5384twu9e0xnm5xth9ta58fpt0dexysy26d4nm) and found me my first 100 followers. You can do the same.
To create your Nostr NFC "business card" is even easier than your NFC "login card".
1. Buy yourself some NFC cards,
2. Download the free [NFC Tools app](https://play.google.com/store/apps/details?id=com.wakdev.wdnfc) to your device, and open it,
2. Click "Write" and "Add a record", then click "Custom URL / URI",
3. Write your npub to the NFC card as a custom URI in the format "nostr:npub1..." (e.g. for me this is "nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft"),
4. Your card is ready.
Give the card to someone who is a Nostr user, and when they tap the card against their phone it will open their preferred Nostr client and go directly to your Nostr profile page.
You have created a Nostr NFC "business card".
### What I Did Wrong
I like to share what I did wrong so you don't have to make the same mistakes. This time, this was very easy, and little went wrong. In general
- When password-protecting your nsec, don't forget the password!
- When writing to the NFC card, make sure to use "Custom URI/URL" as this accepts your "nostr:" URI scheme. If you use generic "URI/URL" it won't work.
### What's Next
Over my first four blogs I have explored creating a good Nostr setup
- [Mined a Nostr pubkey and backed up the mnemonic](nostr:naddr1qqsy66twd9hxwtteda6hyt2kv9hxjare94g82cntv4uj6drfw4cxyeszyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c6e2ekw)
- [Set up Nostr payments with a Lightning wallet plus all the bells and whistles](nostr:naddr1qq34xet5w35kueedw4cz65rp09kk2mn5wvkk7m3dfehhxarj95mk7dnvwvmsygqmmflp7uukhk3drmueqv763lfdcd3gzpusm7d7vt6ezquth97ymypsgqqqw4rsuql6je)
- [Set up NIP-05 and Lighting Address at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqyghwumn8ghj7mn0wd68ytnhd9hx2tczyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c634nh0)
- [Set up a Personal Relay at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7q3qr0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvsxpqqqp65wmzpn9e)
Over the next few blogs I will be exploring different types of Nostr inter-op
- NFC cards integrated with Nostr (this post)
- Workflow Automations integrated with Nostr
- AI LLMs integrated with Nostr
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-

@ 87730827:746b7d35
2024-11-20 09:27:53
Original: https://techreport.com/crypto-news/brazil-central-bank-ban-monero-stablecoins/
Brazilian’s Central Bank Will Ban Monero and Algorithmic Stablecoins in the Country
===================================================================================
Brazil proposes crypto regulations banning Monero and algorithmic stablecoins and enforcing strict compliance for exchanges.
* * *
**KEY TAKEAWAYS**
* The Central Bank of Brazil has proposed **regulations prohibiting privacy-centric cryptocurrencies** like Monero.
* The regulations **categorize exchanges into intermediaries, custodians, and brokers**, each with specific capital requirements and compliance standards.
* While the proposed rules apply to cryptocurrencies, certain digital assets like non-fungible tokens **(NFTs) are still ‘deregulated’ in Brazil**.

In a Notice of Participation announcement, the Brazilian Central Bank (BCB) outlines **regulations for virtual asset service providers (VASPs)** operating in the country.
**_In the document, the Brazilian regulator specifies that privacy-focused coins, such as Monero, must be excluded from all digital asset companies that intend to operate in Brazil._**
Let’s unpack what effect these regulations will have.
Brazil’s Crackdown on Crypto Fraud
----------------------------------
If the BCB’s current rule is approved, **exchanges dealing with coins that provide anonymity must delist these currencies** or prevent Brazilians from accessing and operating these assets.
The Central Bank argues that currencies like Monero make it difficult and even prevent the identification of users, thus creating problems in complying with international AML obligations and policies to prevent the financing of terrorism.
According to the Central Bank of Brazil, the bans aim to **prevent criminals from using digital assets to launder money**. In Brazil, organized criminal syndicates such as the Primeiro Comando da Capital (PCC) and Comando Vermelho have been increasingly using digital assets for money laundering and foreign remittances.
> … restriction on the supply of virtual assets that contain characteristics of fragility, insecurity or risks that favor fraud or crime, such as virtual assets designed to favor money laundering and terrorist financing practices by facilitating anonymity or difficulty identification of the holder.
>
> – [Notice of Participation](https://www.gov.br/participamaisbrasil/edital-de-participacao-social-n-109-2024-proposta-de-regulamentacao-do-)
The Central Bank has identified that **removing algorithmic stablecoins is essential to guarantee the safety of users’ funds** and avoid events such as when Terraform Labs’ entire ecosystem collapsed, losing billions of investors’ dollars.
The Central Bank also wants to **control all digital assets traded by companies in Brazil**. According to the current proposal, the [national regulator](https://techreport.com/cryptocurrency/learning/crypto-regulations-global-view/) will have the **power to ask platforms to remove certain listed assets** if it considers that they do not meet local regulations.
However, the regulations will not include [NFTs](https://techreport.com/statistics/crypto/nft-awareness-adoption-statistics/), real-world asset (RWA) tokens, RWA tokens classified as securities, and tokenized movable or real estate assets. These assets are still ‘deregulated’ in Brazil.
Monero: What Is It and Why Is Brazil Banning It?
------------------------------------------------
Monero ($XMR) is a cryptocurrency that uses a protocol called CryptoNote. It launched in 2013 and ‘erases’ transaction data, preventing the sender and recipient addresses from being publicly known. The Monero network is based on a proof-of-work (PoW) consensus mechanism, which incentivizes miners to add blocks to the blockchain.
Like Brazil, **other nations are banning Monero** in search of regulatory compliance. Recently, Dubai’s new digital asset rules prohibited the issuance of activities related to anonymity-enhancing cryptocurrencies such as $XMR.
Furthermore, exchanges such as **Binance have already announced they will delist Monero** on their global platforms due to its anonymity features. Kraken did the same, removing Monero for their European-based users to comply with [MiCA regulations](https://techreport.com/crypto-news/eu-mica-rules-existential-threat-or-crypto-clarity/).
Data from Chainalysis shows that Brazil is the **seventh-largest Bitcoin market in the world**.

In Latin America, **Brazil is the largest market for digital assets**. Globally, it leads in the innovation of RWA tokens, with several companies already trading this type of asset.
In Closing
----------
Following other nations, Brazil’s regulatory proposals aim to combat illicit activities such as money laundering and terrorism financing.
Will the BCB’s move safeguard people’s digital assets while also stimulating growth and innovation in the crypto ecosystem? Only time will tell.
References
----------
Cassio Gusson is a journalist passionate about technology, cryptocurrencies, and the nuances of human nature. With a career spanning roles as Senior Crypto Journalist at CriptoFacil and Head of News at CoinTelegraph, he offers exclusive insights on South America’s crypto landscape. A graduate in Communication from Faccamp and a post-graduate in Globalization and Culture from FESPSP, Cassio explores the intersection of governance, decentralization, and the evolution of global systems.
[View all articles by Cassio Gusson](https://techreport.com/author/cassiog/)
-

@ 68c90cf3:99458f5c
2024-11-18 23:51:21
Three Bitaxe Supras mining a combined average of 2.7 TH/s.

_Left to right_
* From **Solo Satoshi** - stock heat sink, Noctua fan _(710 MHz/1.31V)_
* From **D-Central** - Argon THRML cooler, Noctua fan _(740 MHz/1.34V)_
* From **Altair** - stock heat sink, Noctua fan _(720 MHz/1.29V)_
All powered by a Meanwell LRS-200-5 PSU.
Connected to a local instance of Public Pool with Bitcoin Node on a Beelink EQ13 running umbrelOS.
#bitcoin #bitaxe #lotterymining 🤞🍀
-

@ f33c8a96:5ec6f741
2024-11-15 18:04:17
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/_G49vKrKbsU?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 468f729d:5ab4fd5e
2024-11-15 17:52:45
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/wV4I62NMiQ0?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ bcea2b98:7ccef3c9
2024-11-14 23:38:37
@chess a3
originally posted at https://stacker.news/items/768303
-

@ bcea2b98:7ccef3c9
2024-11-14 18:03:14
We all have that one movie or show we turn to when we need a little comfort. Whether it’s for the laughs, the nostalgia, or the familiar characters, these are the ones that never get old.
What’s a movie or series you can watch again and again? What makes it so comforting, and why do you keep coming back to it?
I enjoy The Office with Michael Scott and Dwight Schrute. We watched a lot of that in the past and then again during the pandemic during isolation.
originally posted at https://stacker.news/items/767870
-

@ bcea2b98:7ccef3c9
2024-11-14 00:42:08
Sometimes we come across values that resonate deeply only after going through certain experiences. These values may not have been obvious to us earlier, but now they play a meaningful role in how we approach life.
Is there a value you’ve discovered later in life that’s become important to you?
originally posted at https://stacker.news/items/766754
-

@ bcea2b98:7ccef3c9
2024-11-13 02:44:17
@chess a3
originally posted at https://stacker.news/items/765445
-

@ bcea2b98:7ccef3c9
2024-11-13 02:18:58
Sometimes our strongest values are the ones that people wouldn’t expect. These unique principles often reveal something special about who we are and what we believe in. Do you hold a value that might surprise others?
originally posted at https://stacker.news/items/765433
-

@ bcea2b98:7ccef3c9
2024-11-10 19:34:24
@chess a3
originally posted at https://stacker.news/items/762161
-

@ bcea2b98:7ccef3c9
2024-11-09 17:01:32
Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about?
For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully.
originally posted at https://stacker.news/items/760492
-

@ bcea2b98:7ccef3c9
2024-11-09 01:30:29
@chess h3
originally posted at https://stacker.news/items/759635
-

@ bcea2b98:7ccef3c9
2024-11-07 18:43:30
If you could accomplish one major goal, what would it be? Why does it matter to you, and how would it change your life or the lives of others?
My ultimate goal is to be part of a mission to Mars one day. I’ve always been fascinated by space exploration.
originally posted at https://stacker.news/items/757861
-

@ 3bf0c63f:aefa459d
2024-11-07 14:56:17
# The case against edits
Direct edits are a centralizing force on Nostr, a slippery slope that should not be accepted.
Edits are fine in other, more specialized event kinds, but the `kind:1` space shouldn't be compromised with such a push towards centralization, because [`kind:1` is the public square of Nostr, where all focus should be on decentralization and censorship-resistance](cd8ce2b7).
- _Why?_
Edits introduce too much complexity. If edits are widespread, all clients now have to download dozens of extra events at the same time while users are browsing a big feed of notes which are already coming from dozens of different relays using complicated outbox-model-based querying, then for each event they have to open yet another subscription to these relays -- or perform some other complicated batching of subscriptions which then requires more complexity on the event handling side and then when associating these edits with the original events. I can only imagine this will hurt apps performance, but it definitely raises the barrier to entry and thus necessarily decreases Nostr decentralization.
Some clients may be implemneted in way such that they download tons of events and then store them in a local databases, from which they then construct the feed that users see. Such clients may make edits potentially easier to deal with -- but this is hardly an answer to the point above, since such clients are already more complex to implement in the first place.
- _What do you have against complex clients?_
The point is not to say that all clients should be simple, but that it should be simple to write a client -- or at least as simple as physically possible.
You may not be thinking about it, but if you believe in the promise of Nostr then we should expect to see Nostr feeds in many other contexts other than on a big super app in a phone -- we should see Nostr notes being referenced from and injected in unrelated webpages, unrelated apps, hardware devices, comment sections and so on. All these micro-clients will have to implement some complicated edit-fetching logic now?
- _But aren't we already fetching likes and zaps and other things, why not fetch edits too?_
Likes, zaps and other similar things are optional. It's perfectly fine to use Nostr without seeing likes and/or zaps -- and, believe me, it does happen quite a lot. The point is basically that likes or zaps don't affect the content of the main post at all, while edits do.
- _But edits are optional!_
No, they are not optional. If edits become widespread they necessarily become mandatory. Any client that doesn't implement edits will be displaying false information to its users and their experience will be completely broken.
- _That's fine, as people will just move to clients that support edits!_
Exactly, that is what I expect to happen too, and this is why I am saying edits are a centralizing force that we should be fighting against, not embracing.
If you understand that edits are a centralizing force, then you must automatically agree that they aren't a desirable feature, given that if you are reading this now, with Nostr being so small, there is a 100% chance you care about decentralization and you're not just some kind of lazy influencer that is only doing this for money.
- _All other social networks support editing!_
This is not true at all. Bluesky has 10x more users than Nostr and doesn't support edits. Instagram doesn't support editing pictures after they're posted, and doesn't support editing comments. Tiktok doesn't support editing videos or comments after they're posted. YouTube doesn't support editing videos after they're posted. Most famously, email, the most widely used and widespread "social app" out there, does not support edits of any kind. Twitter didn't support edits for the first 15 years of its life, and, although some people complained, it didn't hurt the platform at all -- arguably it benefitted it.
If edits are such a straightforward feature to add that won't hurt performance, that won't introduce complexity, and also that is such an essential feature users could never live without them, then why don't these centralized platforms have edits on everything already? There must be something there.
- _Eventually someone will implement edits anyway, so why bother to oppose edits now?_
Once Nostr becomes big enough, maybe it will be already shielded from such centralizing forces by its sheer volume of users and quantity of clients, maybe not, we will see. All I'm saying is that we shouldn't just push for bad things now just because of a potential future in which they might come.
- _The market will decide what is better._
The market has decided for Facebook, Instagram, Twitter and TikTok. If we were to follow what the market had decided we wouldn't be here, and you wouldn't be reading this post.
- _OK, you have convinced me, edits are not good for the protocol. But what do we do about the users who just want to fix their typos?_
There are many ways. The annotations spec, for example, provides a simple way to append things to a note without being a full-blown edit, and they fall back gracefully to normal replies in clients that don't implement the full annotations spec.
Eventually we could have annotations that are expressed in form of simple (human-readable?) diffs that can be applied directly to the post, but fall back, again, to comments.
Besides these, a very simple idea that wasn't tried yet on Nostr yet is the idea that has been tried for emails and seems to work very well: delaying a post after the "submit" button is clicked and giving the user the opportunity to cancel and edit it again before it is actually posted.
Ultimately, if edits are so necessary, then maybe we could come up with a way to implement edits that is truly optional and falls back cleanly for clients that don't support them directly and don't hurt the protocol very much. Let's think about it and not rush towards defeat.
 @ df173277:4ec96708
2025-01-28 17:49:54> Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. Chats are synced automatically between devices so you can pick up where you left off.\ > [Start chatting for free.](https://trymaple.ai/) We are excited to announce that [Maple AI](https://trymaple.ai/), our groundbreaking end-to-end encrypted AI chat app built on OpenSecret, is now publicly available. After months of beta testing, we are thrilled to bring this innovative technology to the world. Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. It can boost your productivity on work tasks such as writing documentation, creating presentations, and drafting emails. You can also use it for personal items like brainstorming ideas, sorting out life's challenges, and tutoring you on difficult coursework. All your chats are synced automatically in a secure way, so you can start on one device and pick up where you left off on another. #### Why Secure and Private AI? In today's digital landscape, it is increasingly evident that security and privacy are essential for individuals and organizations alike. Unfortunately, the current state of AI tools falls short. A staggering 48% of organizations enter non-public company information into AI apps, according to a [recent report by Cisco](https://www.cisco.com/c/en/us/about/trust-center/data-privacy-benchmark-study.html#~key-findings). This practice poses significant risks to company security and intellectual property. Another concern is for journalists, who often work with sensitive information in hostile environments. Journalists need verification that their information remains confidential and protected when researching topics and communicating with sources in various languages. They are left to use underpowered local AI or input their data into potentially compromised cloud services. At OpenSecret, we believe it is possible to have both the benefits of AI and the assurance of security and privacy. That's why we created Maple, an app that combines AI productivity with the protection of end-to-end encryption. Our platform ensures that your conversations with AI remain confidential, even from us. The power of the cloud meets the privacy of local. #### How Does It Work? Our server code is [open source](https://github.com/OpenSecretCloud/opensecret), and we use confidential computing to provide cryptographic proof that the code running on our servers is the same as the open-source code available for review. This process allows you to verify that your conversations are handled securely and privately without relying on trust. We live by the principle of "Don't trust, verify," and we believe this approach is essential for building in the digital age. You can read a more in-depth write-up on our technology later this week on this site. #### How Much Does It Cost? We are committed to making Maple AI accessible to everyone, so we offer a range of pricing plans to suit different needs and budgets. [Our Free plan allows for 10 chats per week, while our Starter plan ($5.99/month) and Pro plan ($20/month)](https://trymaple.ai/pricing) offer more comprehensive solutions for individuals and organizations with heavier workloads. We accept credit cards and Bitcoin (10% discount), allowing you to choose your preferred payment method. - Free: $0 - Starter: $5.99/month - Pro: $20/month Our goal with Maple AI is to create a product that is secure through transparency. By combining open-source code, cryptography, and confidential computing, we can create a new standard for AI conversations - one that prioritizes your security and privacy. Maple has quickly become a daily tool of productivity for our own work and those of our beta testers. We believe it will bring value to you as well. [Sign up now and start chatting privately with AI for free.](https://trymaple.ai/) Your secrets are safe in the open. #### Are You An App Developer? You can build an app like Maple. [OpenSecret provides secure auth, private key management, encrypted data sync, private AI, and more.](https://blog.opensecret.cloud/introducing-opensecret/) Our straightforward API behaves like other backends but automatically adds security and privacy. Use it to secure existing apps or brand-new projects. Protect yourself and your users from the liability of hosting personal data by checking out [OpenSecret](https://opensecret.cloud/). <img src="https://blossom.primal.net/feb746d5e164e89f0d015646286b88237dce4158f8985e3caaf7e427cebde608.png"> Enjoy private AI Chat 🤘 <img src="https://blossom.primal.net/0594ec56e249de2754ea7dfc225a7ebd46bc298b5af168279ce71f17c2afada0.jpg">
@ df173277:4ec96708
2025-01-28 17:49:54> Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. Chats are synced automatically between devices so you can pick up where you left off.\ > [Start chatting for free.](https://trymaple.ai/) We are excited to announce that [Maple AI](https://trymaple.ai/), our groundbreaking end-to-end encrypted AI chat app built on OpenSecret, is now publicly available. After months of beta testing, we are thrilled to bring this innovative technology to the world. Maple is an AI chat tool that allows you to have private conversations with a general-purpose AI assistant. It can boost your productivity on work tasks such as writing documentation, creating presentations, and drafting emails. You can also use it for personal items like brainstorming ideas, sorting out life's challenges, and tutoring you on difficult coursework. All your chats are synced automatically in a secure way, so you can start on one device and pick up where you left off on another. #### Why Secure and Private AI? In today's digital landscape, it is increasingly evident that security and privacy are essential for individuals and organizations alike. Unfortunately, the current state of AI tools falls short. A staggering 48% of organizations enter non-public company information into AI apps, according to a [recent report by Cisco](https://www.cisco.com/c/en/us/about/trust-center/data-privacy-benchmark-study.html#~key-findings). This practice poses significant risks to company security and intellectual property. Another concern is for journalists, who often work with sensitive information in hostile environments. Journalists need verification that their information remains confidential and protected when researching topics and communicating with sources in various languages. They are left to use underpowered local AI or input their data into potentially compromised cloud services. At OpenSecret, we believe it is possible to have both the benefits of AI and the assurance of security and privacy. That's why we created Maple, an app that combines AI productivity with the protection of end-to-end encryption. Our platform ensures that your conversations with AI remain confidential, even from us. The power of the cloud meets the privacy of local. #### How Does It Work? Our server code is [open source](https://github.com/OpenSecretCloud/opensecret), and we use confidential computing to provide cryptographic proof that the code running on our servers is the same as the open-source code available for review. This process allows you to verify that your conversations are handled securely and privately without relying on trust. We live by the principle of "Don't trust, verify," and we believe this approach is essential for building in the digital age. You can read a more in-depth write-up on our technology later this week on this site. #### How Much Does It Cost? We are committed to making Maple AI accessible to everyone, so we offer a range of pricing plans to suit different needs and budgets. [Our Free plan allows for 10 chats per week, while our Starter plan ($5.99/month) and Pro plan ($20/month)](https://trymaple.ai/pricing) offer more comprehensive solutions for individuals and organizations with heavier workloads. We accept credit cards and Bitcoin (10% discount), allowing you to choose your preferred payment method. - Free: $0 - Starter: $5.99/month - Pro: $20/month Our goal with Maple AI is to create a product that is secure through transparency. By combining open-source code, cryptography, and confidential computing, we can create a new standard for AI conversations - one that prioritizes your security and privacy. Maple has quickly become a daily tool of productivity for our own work and those of our beta testers. We believe it will bring value to you as well. [Sign up now and start chatting privately with AI for free.](https://trymaple.ai/) Your secrets are safe in the open. #### Are You An App Developer? You can build an app like Maple. [OpenSecret provides secure auth, private key management, encrypted data sync, private AI, and more.](https://blog.opensecret.cloud/introducing-opensecret/) Our straightforward API behaves like other backends but automatically adds security and privacy. Use it to secure existing apps or brand-new projects. Protect yourself and your users from the liability of hosting personal data by checking out [OpenSecret](https://opensecret.cloud/). <img src="https://blossom.primal.net/feb746d5e164e89f0d015646286b88237dce4158f8985e3caaf7e427cebde608.png"> Enjoy private AI Chat 🤘 <img src="https://blossom.primal.net/0594ec56e249de2754ea7dfc225a7ebd46bc298b5af168279ce71f17c2afada0.jpg"> @ 9e69e420:d12360c2
2025-01-26 01:31:31## Chef's notes # arbitray - test - of - chefs notes ## hedding 2 ## Details - ⏲️ Prep time: 20 - 🍳 Cook time: 1 hour - 🍽️ Servings: 5 ## Ingredients - Test ingredient - 2nd test ingredient ## Directions 1. Bake 2. Cool
@ 9e69e420:d12360c2
2025-01-26 01:31:31## Chef's notes # arbitray - test - of - chefs notes ## hedding 2 ## Details - ⏲️ Prep time: 20 - 🍳 Cook time: 1 hour - 🍽️ Servings: 5 ## Ingredients - Test ingredient - 2nd test ingredient ## Directions 1. Bake 2. Cool @ 228dde34:b5d0345e
2025-01-25 01:59:57##### By Jonathan Tan ##### Lead Editor ##### Hype Issue #60 ##### JONATHAN TAN explores the recent rise in popularity of online gambling, and its consequences on the population’s most vulnerable.  The persistent rise in the gaming industry, fueled by the introduction of online gambling, seems to have no end. Experts are now worrying about the effects of this epidemic on public health and safety. “Many people might be really experiencing harms from gambling — we think that it’s probably around 72 million people globally,” said Louisa Degenhardt, a professor at the University of New South Wales in Sydney, in an[NBC article.](https://www.nbcnews.com/health/health-news/gambling-industry-growth-threat-public-health-report-rcna175356) The online gambling craze has spread worldwide, and even Singapore, with its strict gambling regulations, is not immune to it. In a recent[survey](https://www.channelnewsasia.com/singapore/national-council-problem-gambling-rate-continues-fall-4761621)conducted by the National Council on Problem Gambling (NCPG), illegal online gambling rates have more than tripled since 2020, from 0.3% to 1.0% in the past 4 years. This statistic alone highlights an already concerning trend. Even more troubling, however, is that the illegal nature of these websites means there are no regulatory laws or age restrictions. As a result, the proliferation of these online websites has allowed a brand new demographic to start gambling: the Singaporean youth. ### How to lose thousands before adulthood “I started gambling when I was 13 years old, at a friend's house,” George (not his real name) shares. Now an 18-year-old student, George recalls how a simple game among friends slowly grew into an all-consuming gambling addiction.  *In NCPG’s 2023 survey, 8% of respondents reported participating in social gambling activities: gambling which occurs within individuals’ homes, among family members. Photo from Shutterstock.* Initially, George and his friends gambled with low stakes, like a dollar here and there. However, the games slowly escalated: from $1 to $10, then to $100, and eventually to $1000. Unsurprisingly, with such large sums at stake, George’s relationship with his friends began to strain. “I realized that after a certain point, the more and more money we [bet], the more and more our relationship with each other [soured]; and so we decided to curb it at a maximum buy-in of $20 per game,” George says. The new rule eased the tension between George and his friends, but it inadvertently created a new problem: George no longer felt the thrill of winning large sums. As a result, he began seeking other ways to gamble. “The first time I gambled online was when I was 16 years old. A friend had introduced me to a gambling website,” he recalls. “And at first it was all right. I won a bit, I lost a bit, but no one got hurt.” But it didn’t take long for him to get hooked; a single sports bet was what netted George his first big win. “On the first day, I went from $10 to $800 from a simple parlay bet,” George says. “I felt unstoppable. Adrenaline was pumping through my veins, and [I felt] I could never lose. [After] that day, I gambled like $100 almost every day for a straight month.”  *A parlay (a form of sports betting that has recently surged in popularity) is a single bet that combines two or more bets into one. While doing this drastically decreases the odds of winning, it also drastically increases the potential payout. Photo from Getty Images.* Nothing could stop George’s gambling fervor. Even after losing nearly a thousand dollars on a single blackjack hand, all George did was place a bigger bet to try and win it back. “Every morning, when I [woke] up, all I could think about was gambling,” he shares. And of course, George’s obsession with online gambling was only exacerbated by the accessibility of these websites. First, the online nature of these websites allowed George to gamble anywhere, at any time. “For online gambling, you have it right at your fingertips. As soon as you wake up, you can just log on the computer and start betting huge amounts of money,” he mentions. But more importantly, these illegal gambling websites enabled George to do something he was never old enough to do in the first place. “I'm too young to gamble at a real casino or a physical casino. But online gambling makes it way more accessible because there's no verification of ID,” George says. ### Consequences, consequences Therein lies the predatory nature of these illegal websites. While anyone can fall victim to a gambling addiction, certain factors may make the youth especially vulnerable. “The adolescent brain is still developing, particularly the prefrontal cortex, which is responsible for decision-making, impulse control, and risk assessment. This makes young people more susceptible to impulsive behaviors,” says Jat Tan, the Communications and Events Executive at WE CARE Community Services.  *The prefrontal cortex is primarily developed during adolescence, and is fully developed at the age of 25 years. Photo from iStock.* Additionally, other factors such as peer pressure, social media, or limited life experience, could result in young Singaporeans being more open to gambling. Lastly, one popular reason why the youth are drawn to gambling, is their limited financial freedom. “While youths are in school, they have a significantly lower earning power as opposed to adults. The demands from school usually means that they can only afford to work part-time jobs,” Mrs Tan shares. Despite this, many young Singaporeans still want to live extravagant lifestyles. With the youth getting exposed to lavish, ostentatious lifestyles on social media, many begin to feel envious and yearn for the same luxuries. And now, with the introduction of illegal online sites, the lack of age restrictions allows these youths to gamble in an attempt to achieve this better life. ### What can be done? The increase in the number of adolescent gamblers is a new challenge for the Singaporean government. Before the advent of online gambling, many safeguards were in place to protect Singaporeans from developing gambling addictions. In particular, safeguards that limit Singaporeans’ access to legal gambling services seem to be working; the overall percentage of gambling Singaporeans has fallen from 44% to 40% from 2020 to 2023. However, the unprecedented accessibility and convenience of online gambling sites have allowed Singapore’s tech-savvy youth to bypass these regulations; and now, the Singaporean government needs to update its laws to keep up with the growing gambling industry. Of course, the Singaporean Government has been cracking down on illegal online gambling. As of September 2024, the Gambling Regulatory Authority (GRA) has blocked access to more than 1,900 remote gambling websites. But despite the GRA’s efforts, these online gambling providers continue to survive, like weeds in a garden. “GRA recognises that the borderless nature of the Internet makes it easy for unlawful gambling operators to offer their products to users in Singapore any time and anywhere,” said a GRA spokesman in [a Straits Times article.](https://www.straitstimes.com/singapore/crackdown-on-illegal-online-gambling-but-addiction-can-be-hard-to-beat) Currently, there are calls for the government to shift its focus. “While Singapore has done well putting in place responsible gaming and safety measures to mitigate the risks of casino gambling, it is timely to focus more attention to address the risk of illegal online gambling as well,” said Ms Tham, Clinical director of We Care Community Services, [in a Straits Times article.](https://www.straitstimes.com/singapore/fewer-singapore-residents-gambled-but-more-do-so-online-illegally) Ultimately, as the gambling industry becomes more technologically advanced, it becomes harder for Singapore to regulate gambling the same way it used to. Thus, it may be time for the Singaporean government to consider a different solution. “Better educating youths on the harms and consequences of gambling, as well as resources available should things go awry, would be the best option to nip the issue in the bud,” Ms Tan suggests. Instead of focusing on restrictive legislation, education could be a preventative measure used to curb adolescent gambling. “A higher level of awareness would enable youths to face issues like gambling with their eyes wide open - they will have a rough idea of what they're getting themselves into, and will have a rough idea of what to do if things go wrong,” she shares.
@ 228dde34:b5d0345e
2025-01-25 01:59:57##### By Jonathan Tan ##### Lead Editor ##### Hype Issue #60 ##### JONATHAN TAN explores the recent rise in popularity of online gambling, and its consequences on the population’s most vulnerable.  The persistent rise in the gaming industry, fueled by the introduction of online gambling, seems to have no end. Experts are now worrying about the effects of this epidemic on public health and safety. “Many people might be really experiencing harms from gambling — we think that it’s probably around 72 million people globally,” said Louisa Degenhardt, a professor at the University of New South Wales in Sydney, in an[NBC article.](https://www.nbcnews.com/health/health-news/gambling-industry-growth-threat-public-health-report-rcna175356) The online gambling craze has spread worldwide, and even Singapore, with its strict gambling regulations, is not immune to it. In a recent[survey](https://www.channelnewsasia.com/singapore/national-council-problem-gambling-rate-continues-fall-4761621)conducted by the National Council on Problem Gambling (NCPG), illegal online gambling rates have more than tripled since 2020, from 0.3% to 1.0% in the past 4 years. This statistic alone highlights an already concerning trend. Even more troubling, however, is that the illegal nature of these websites means there are no regulatory laws or age restrictions. As a result, the proliferation of these online websites has allowed a brand new demographic to start gambling: the Singaporean youth. ### How to lose thousands before adulthood “I started gambling when I was 13 years old, at a friend's house,” George (not his real name) shares. Now an 18-year-old student, George recalls how a simple game among friends slowly grew into an all-consuming gambling addiction.  *In NCPG’s 2023 survey, 8% of respondents reported participating in social gambling activities: gambling which occurs within individuals’ homes, among family members. Photo from Shutterstock.* Initially, George and his friends gambled with low stakes, like a dollar here and there. However, the games slowly escalated: from $1 to $10, then to $100, and eventually to $1000. Unsurprisingly, with such large sums at stake, George’s relationship with his friends began to strain. “I realized that after a certain point, the more and more money we [bet], the more and more our relationship with each other [soured]; and so we decided to curb it at a maximum buy-in of $20 per game,” George says. The new rule eased the tension between George and his friends, but it inadvertently created a new problem: George no longer felt the thrill of winning large sums. As a result, he began seeking other ways to gamble. “The first time I gambled online was when I was 16 years old. A friend had introduced me to a gambling website,” he recalls. “And at first it was all right. I won a bit, I lost a bit, but no one got hurt.” But it didn’t take long for him to get hooked; a single sports bet was what netted George his first big win. “On the first day, I went from $10 to $800 from a simple parlay bet,” George says. “I felt unstoppable. Adrenaline was pumping through my veins, and [I felt] I could never lose. [After] that day, I gambled like $100 almost every day for a straight month.”  *A parlay (a form of sports betting that has recently surged in popularity) is a single bet that combines two or more bets into one. While doing this drastically decreases the odds of winning, it also drastically increases the potential payout. Photo from Getty Images.* Nothing could stop George’s gambling fervor. Even after losing nearly a thousand dollars on a single blackjack hand, all George did was place a bigger bet to try and win it back. “Every morning, when I [woke] up, all I could think about was gambling,” he shares. And of course, George’s obsession with online gambling was only exacerbated by the accessibility of these websites. First, the online nature of these websites allowed George to gamble anywhere, at any time. “For online gambling, you have it right at your fingertips. As soon as you wake up, you can just log on the computer and start betting huge amounts of money,” he mentions. But more importantly, these illegal gambling websites enabled George to do something he was never old enough to do in the first place. “I'm too young to gamble at a real casino or a physical casino. But online gambling makes it way more accessible because there's no verification of ID,” George says. ### Consequences, consequences Therein lies the predatory nature of these illegal websites. While anyone can fall victim to a gambling addiction, certain factors may make the youth especially vulnerable. “The adolescent brain is still developing, particularly the prefrontal cortex, which is responsible for decision-making, impulse control, and risk assessment. This makes young people more susceptible to impulsive behaviors,” says Jat Tan, the Communications and Events Executive at WE CARE Community Services.  *The prefrontal cortex is primarily developed during adolescence, and is fully developed at the age of 25 years. Photo from iStock.* Additionally, other factors such as peer pressure, social media, or limited life experience, could result in young Singaporeans being more open to gambling. Lastly, one popular reason why the youth are drawn to gambling, is their limited financial freedom. “While youths are in school, they have a significantly lower earning power as opposed to adults. The demands from school usually means that they can only afford to work part-time jobs,” Mrs Tan shares. Despite this, many young Singaporeans still want to live extravagant lifestyles. With the youth getting exposed to lavish, ostentatious lifestyles on social media, many begin to feel envious and yearn for the same luxuries. And now, with the introduction of illegal online sites, the lack of age restrictions allows these youths to gamble in an attempt to achieve this better life. ### What can be done? The increase in the number of adolescent gamblers is a new challenge for the Singaporean government. Before the advent of online gambling, many safeguards were in place to protect Singaporeans from developing gambling addictions. In particular, safeguards that limit Singaporeans’ access to legal gambling services seem to be working; the overall percentage of gambling Singaporeans has fallen from 44% to 40% from 2020 to 2023. However, the unprecedented accessibility and convenience of online gambling sites have allowed Singapore’s tech-savvy youth to bypass these regulations; and now, the Singaporean government needs to update its laws to keep up with the growing gambling industry. Of course, the Singaporean Government has been cracking down on illegal online gambling. As of September 2024, the Gambling Regulatory Authority (GRA) has blocked access to more than 1,900 remote gambling websites. But despite the GRA’s efforts, these online gambling providers continue to survive, like weeds in a garden. “GRA recognises that the borderless nature of the Internet makes it easy for unlawful gambling operators to offer their products to users in Singapore any time and anywhere,” said a GRA spokesman in [a Straits Times article.](https://www.straitstimes.com/singapore/crackdown-on-illegal-online-gambling-but-addiction-can-be-hard-to-beat) Currently, there are calls for the government to shift its focus. “While Singapore has done well putting in place responsible gaming and safety measures to mitigate the risks of casino gambling, it is timely to focus more attention to address the risk of illegal online gambling as well,” said Ms Tham, Clinical director of We Care Community Services, [in a Straits Times article.](https://www.straitstimes.com/singapore/fewer-singapore-residents-gambled-but-more-do-so-online-illegally) Ultimately, as the gambling industry becomes more technologically advanced, it becomes harder for Singapore to regulate gambling the same way it used to. Thus, it may be time for the Singaporean government to consider a different solution. “Better educating youths on the harms and consequences of gambling, as well as resources available should things go awry, would be the best option to nip the issue in the bud,” Ms Tan suggests. Instead of focusing on restrictive legislation, education could be a preventative measure used to curb adolescent gambling. “A higher level of awareness would enable youths to face issues like gambling with their eyes wide open - they will have a rough idea of what they're getting themselves into, and will have a rough idea of what to do if things go wrong,” she shares. @ bcea2b98:7ccef3c9
2025-01-24 23:21:05originally posted at https://stacker.news/items/862840
@ bcea2b98:7ccef3c9
2025-01-24 23:21:05originally posted at https://stacker.news/items/862840 @ 29af23a9:842ef0c1
2025-01-21 14:42:19A Indústria Pornográfica se caracteriza pelo investimento pesado de grandes empresários americanos, desde 2014. Na década de 90, filmes pornográficos eram feitos às coxas. Era basicamente duas pessoas fazendo sexo amador e sendo gravadas. Não tinha roteiro, nem produção, não tinha maquiagem, nada disso. A distribuição era rudimentar, os assinantes tinham que sair de suas casas, ir até a locadora, sofrer todo tipo de constrangimento para assistir a um filme pornô. No começo dos anos 2000, o serviço de Pay Per View fez o número de vendas de filmes eróticos (filme erótico é bem mais leve) crescer mas nada se compara com os sites de filmes pornográficos por assinatura. Com o advento dos serviços de Streaming, os sites que vendem filmes por assinatura se estabeleceram no mercado como nunca foi visto na história. Hoje, os Produtores usam produtos para esticar os vasos sanguíneos do pênis dos atores e dopam as atrizes para que elas aguentem horas de gravação (a Série Black Mirror fez uma crítica a isso no episódio 1 milhão de méritos de forma sutil). Além de toda a produção em volta das cenas. Que são gravadas em 4K, para focar bem as partes íntimas dos atores. Quadros fechados, iluminação, tudo isso faz essa Indústria ser "Artística" uma vez que tudo ali é falso. Um filme da Produtora Vixen, por exemplo, onde jovens mulheres transam em mansões com seus empresários estimula o esteriótipo da mina padrão que chama seu chefe rico de "daddy" e seduz ele até ele trair a esposa. Sites como xvídeos, pornHub e outros nada mais são do que sites que salvam filmes dessas produtoras e hospedam as cenas com anúncios e pop-ups. Alguns sites hospedam o filme inteiro "de graça". Esse tipo de filme estimula qualquer homem heterosexual com menos de 30 anos, que não tem o córtex frontal de seu cérebro totalmente desenvolvido (segundo estudos só é completamente desenvolvido quando o homem chega aos 31 anos). A arte Pornográfica faz alguns fantasiarem ter relação sexual com uma gostosa americana branquinha, até escraviza-los. Muitos não conseguem sair do vício e preferem a Ficção à sua esposa real. Então pare de se enganar e admita. A Pornografia faz mal para a saúde mental do homem. Quem sonha em ter uma transa com Lana Rhodes, deve estar nesse estágio. Trata-se de uma atriz (pornstar) que ganhou muito dinheiro vendendo a ilusão da Arte Pornografica, como a Riley Reid que só gravava para grandes Produtoras. Ambas se arrependeram da carreira artística e agora tentam viver suas vidas como uma mulher comum. As próprias atrizes se consideram artistas, como Mia Malkova, chegou a dizer que Pornografia é a vida dela, que é "Lindo e Sofisticado." Mia Malkova inclusive faz questão de dizer que a industria não escravisa mulheres jovens. Trata-se de um negócio onde a mulher assina um contrato com uma produtora e recebe um cachê por isso. Diferente do discurso da Mia Khalifa em entrevista para a BBC, onde diz que as mulheres são exploradas por homens poderosos. Vai ela está confundindo o Conglomerado Vixen com a Rede Globo ou com a empresa do Harvey Weinstein. Enfim, se você é um homem solteiro entre 18 e 40 anos que já consumiu ou que ainda consome pornografia, sabia que sofrerá consequências. Pois trata-se de "produções artísticas" da indústria audiovisual que altera os níveis de dopamina do seu cérebro, mudando a neuroplasticidade e diminuindo a massa cinzenta, deixando o homem com memória fraca, sem foco e com mente nebulosa. Por que o Estado não proíbe/criminaliza a Pornografia se ela faz mal? E desde quando o Estado quer o nosso bem? Existem grandes empresarios que financiam essa indústria ajudando governos a manterem o povo viciado e assim alienado. É um pão e circo, só que muito mais viciante e maléfico. Eu costume dizer aos meus amigos que existem grandes empresários jvdeus que são donos de grandes Produtoras de filmes pornográficos como o Conglomerado Vixen. Então se eles assistem vídeos pirateados de filmes dessas produtoras, eles estão no colo do Judeu.
@ 29af23a9:842ef0c1
2025-01-21 14:42:19A Indústria Pornográfica se caracteriza pelo investimento pesado de grandes empresários americanos, desde 2014. Na década de 90, filmes pornográficos eram feitos às coxas. Era basicamente duas pessoas fazendo sexo amador e sendo gravadas. Não tinha roteiro, nem produção, não tinha maquiagem, nada disso. A distribuição era rudimentar, os assinantes tinham que sair de suas casas, ir até a locadora, sofrer todo tipo de constrangimento para assistir a um filme pornô. No começo dos anos 2000, o serviço de Pay Per View fez o número de vendas de filmes eróticos (filme erótico é bem mais leve) crescer mas nada se compara com os sites de filmes pornográficos por assinatura. Com o advento dos serviços de Streaming, os sites que vendem filmes por assinatura se estabeleceram no mercado como nunca foi visto na história. Hoje, os Produtores usam produtos para esticar os vasos sanguíneos do pênis dos atores e dopam as atrizes para que elas aguentem horas de gravação (a Série Black Mirror fez uma crítica a isso no episódio 1 milhão de méritos de forma sutil). Além de toda a produção em volta das cenas. Que são gravadas em 4K, para focar bem as partes íntimas dos atores. Quadros fechados, iluminação, tudo isso faz essa Indústria ser "Artística" uma vez que tudo ali é falso. Um filme da Produtora Vixen, por exemplo, onde jovens mulheres transam em mansões com seus empresários estimula o esteriótipo da mina padrão que chama seu chefe rico de "daddy" e seduz ele até ele trair a esposa. Sites como xvídeos, pornHub e outros nada mais são do que sites que salvam filmes dessas produtoras e hospedam as cenas com anúncios e pop-ups. Alguns sites hospedam o filme inteiro "de graça". Esse tipo de filme estimula qualquer homem heterosexual com menos de 30 anos, que não tem o córtex frontal de seu cérebro totalmente desenvolvido (segundo estudos só é completamente desenvolvido quando o homem chega aos 31 anos). A arte Pornográfica faz alguns fantasiarem ter relação sexual com uma gostosa americana branquinha, até escraviza-los. Muitos não conseguem sair do vício e preferem a Ficção à sua esposa real. Então pare de se enganar e admita. A Pornografia faz mal para a saúde mental do homem. Quem sonha em ter uma transa com Lana Rhodes, deve estar nesse estágio. Trata-se de uma atriz (pornstar) que ganhou muito dinheiro vendendo a ilusão da Arte Pornografica, como a Riley Reid que só gravava para grandes Produtoras. Ambas se arrependeram da carreira artística e agora tentam viver suas vidas como uma mulher comum. As próprias atrizes se consideram artistas, como Mia Malkova, chegou a dizer que Pornografia é a vida dela, que é "Lindo e Sofisticado." Mia Malkova inclusive faz questão de dizer que a industria não escravisa mulheres jovens. Trata-se de um negócio onde a mulher assina um contrato com uma produtora e recebe um cachê por isso. Diferente do discurso da Mia Khalifa em entrevista para a BBC, onde diz que as mulheres são exploradas por homens poderosos. Vai ela está confundindo o Conglomerado Vixen com a Rede Globo ou com a empresa do Harvey Weinstein. Enfim, se você é um homem solteiro entre 18 e 40 anos que já consumiu ou que ainda consome pornografia, sabia que sofrerá consequências. Pois trata-se de "produções artísticas" da indústria audiovisual que altera os níveis de dopamina do seu cérebro, mudando a neuroplasticidade e diminuindo a massa cinzenta, deixando o homem com memória fraca, sem foco e com mente nebulosa. Por que o Estado não proíbe/criminaliza a Pornografia se ela faz mal? E desde quando o Estado quer o nosso bem? Existem grandes empresarios que financiam essa indústria ajudando governos a manterem o povo viciado e assim alienado. É um pão e circo, só que muito mais viciante e maléfico. Eu costume dizer aos meus amigos que existem grandes empresários jvdeus que são donos de grandes Produtoras de filmes pornográficos como o Conglomerado Vixen. Então se eles assistem vídeos pirateados de filmes dessas produtoras, eles estão no colo do Judeu. @ cff1720e:15c7e2b2
2025-01-19 17:48:02**Einleitung**\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie <roland@pareto.space> können sie sogar jederzeit umziehen, egal wohin. **Cool, das ist state of the art!** Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.  **Warum Nostr?** Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz **"unserer Demokratie”** praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.  Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ **Resümee:** keine Standards, keine Daten, keine Rechte = keine Zukunft!  \ **Wie funktioniert Nostr?** Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum **“single point of failure”**, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. <roland@pareto.space> ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ **Resümee:** ein offener Standard, alle Daten, alle Rechte = große Zukunft!  \ **Warum ist Nostr die Zukunft des Internet?** “Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie **(Value4Value)**. OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.  \ **Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.** <https://nostr.net/> \ <https://start.njump.me/> **Hier das Interview zum Thema mit Radio Berliner Morgenröte** <https://www.podbean.com/ew/pb-yxc36-17bb4be>
@ cff1720e:15c7e2b2
2025-01-19 17:48:02**Einleitung**\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie <roland@pareto.space> können sie sogar jederzeit umziehen, egal wohin. **Cool, das ist state of the art!** Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.  **Warum Nostr?** Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz **"unserer Demokratie”** praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.  Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ **Resümee:** keine Standards, keine Daten, keine Rechte = keine Zukunft!  \ **Wie funktioniert Nostr?** Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum **“single point of failure”**, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. <roland@pareto.space> ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ **Resümee:** ein offener Standard, alle Daten, alle Rechte = große Zukunft!  \ **Warum ist Nostr die Zukunft des Internet?** “Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie **(Value4Value)**. OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.  \ **Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.** <https://nostr.net/> \ <https://start.njump.me/> **Hier das Interview zum Thema mit Radio Berliner Morgenröte** <https://www.podbean.com/ew/pb-yxc36-17bb4be> @ c631e267:c2b78d3e
2025-01-18 09:34:51*Die grauenvollste Aussicht ist die der Technokratie –* *\ einer kontrollierenden Herrschaft,* *\ die durch verstümmelte und verstümmelnde Geister ausgeübt wird.* *\ Ernst Jünger*   **«Davos ist nicht mehr sexy»,** das Weltwirtschaftsforum ([WEF](https://transition-news.org/wef-world-economic-forum)) mache Davos [kaputt](https://web.archive.org/web/20250116114956/https://www.handelszeitung.ch/wef-2025/wie-das-wef-davos-kaputt-macht-785098), diese Aussagen eines Einheimischen las ich kürzlich in der *Handelszeitung*. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher. **Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen** dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den [vergangenen](https://transition-news.org/die-angst-der-eliten-vor-dem-pobel) vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten. **Der deutsche WEF-Gründer hatte bei dieser Gelegenheit** immer höchst lobende Worte für seine Landsmännin: [2021](https://www.weforum.org/meetings/the-davos-agenda-2021/sessions/special-address-by-g20-head-of-state-government/) erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und [2022](https://www.weforum.org/meetings/the-davos-agenda-2022/sessions/special-address-by-ursula-von-der-leyen-president-of-the-european-commission-177737c164/) fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist». **Von der Leyens Handeln während der sogenannten Corona-«Pandemie»** lobte Schwab damals bereits ebenso, wie es diese Woche das [Karlspreis](https://transition-news.org/von-der-leyen-erhalt-karlspreis-albert-bourla-erklart-pfizer-habe-wahrend-der)-Direktorium tat, als man der Beschuldigten im Fall [Pfizergate](https://transition-news.org/pfizergate-startet-ins-neue-jahr) die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt. **Jene Herausforderungen durch «Krisen epochalen Ausmaßes»** werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im [Global Risks Report](https://www.zurich.com/knowledge/topics/global-risks/the-global-risks-report-2025) nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen. **Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen** unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz. **Ein** **[«Great Mental Reset»](https://transition-news.org/angriff-auf-unser-gehirn-michael-nehls-uber-den-great-mental-reset-teil-1)** **sei die Voraussetzung dafür,** dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden. **Der aktuelle Zustand unserer Gesellschaften** ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die [Rechtsstaatlichkeit](https://transition-news.org/schweizer-rechtsstaat-in-der-krise-ein-anwalt-schlagt-alarm) stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/davos-europa-und-der-rest-der-welt)*** erschienen.
@ c631e267:c2b78d3e
2025-01-18 09:34:51*Die grauenvollste Aussicht ist die der Technokratie –* *\ einer kontrollierenden Herrschaft,* *\ die durch verstümmelte und verstümmelnde Geister ausgeübt wird.* *\ Ernst Jünger*   **«Davos ist nicht mehr sexy»,** das Weltwirtschaftsforum ([WEF](https://transition-news.org/wef-world-economic-forum)) mache Davos [kaputt](https://web.archive.org/web/20250116114956/https://www.handelszeitung.ch/wef-2025/wie-das-wef-davos-kaputt-macht-785098), diese Aussagen eines Einheimischen las ich kürzlich in der *Handelszeitung*. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher. **Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen** dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den [vergangenen](https://transition-news.org/die-angst-der-eliten-vor-dem-pobel) vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten. **Der deutsche WEF-Gründer hatte bei dieser Gelegenheit** immer höchst lobende Worte für seine Landsmännin: [2021](https://www.weforum.org/meetings/the-davos-agenda-2021/sessions/special-address-by-g20-head-of-state-government/) erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und [2022](https://www.weforum.org/meetings/the-davos-agenda-2022/sessions/special-address-by-ursula-von-der-leyen-president-of-the-european-commission-177737c164/) fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist». **Von der Leyens Handeln während der sogenannten Corona-«Pandemie»** lobte Schwab damals bereits ebenso, wie es diese Woche das [Karlspreis](https://transition-news.org/von-der-leyen-erhalt-karlspreis-albert-bourla-erklart-pfizer-habe-wahrend-der)-Direktorium tat, als man der Beschuldigten im Fall [Pfizergate](https://transition-news.org/pfizergate-startet-ins-neue-jahr) die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt. **Jene Herausforderungen durch «Krisen epochalen Ausmaßes»** werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im [Global Risks Report](https://www.zurich.com/knowledge/topics/global-risks/the-global-risks-report-2025) nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen. **Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen** unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz. **Ein** **[«Great Mental Reset»](https://transition-news.org/angriff-auf-unser-gehirn-michael-nehls-uber-den-great-mental-reset-teil-1)** **sei die Voraussetzung dafür,** dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden. **Der aktuelle Zustand unserer Gesellschaften** ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die [Rechtsstaatlichkeit](https://transition-news.org/schweizer-rechtsstaat-in-der-krise-ein-anwalt-schlagt-alarm) stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/davos-europa-und-der-rest-der-welt)*** erschienen. @ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** | | Pen drive |  | **16Gb** | Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.). --- ## Passo 1: Atualizar o Sistema 🖥️ Primeiro, atualize seu sistema e instale o Tor: ```bash apt update apt install tor ``` --- ## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧 Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo: ```unit [Unit] Description=Nostr Relay Server Service After=network.target [Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure [Install] WantedBy=multi-user.target ``` --- ## Passo 3: Baixar o Binário do Nostr 🚀 Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases). --- ## Passo 4: Criar as Pastas Necessárias 📂 Agora, crie as pastas para o aplicativo e o pendrive: ```bash mkdir -p /opt/nrs /mnt/edriver ``` --- ## Passo 5: Listar os Dispositivos Conectados 🔌 Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados: ```bash lsblk ``` --- ## Passo 6: Formatando o Pendrive 💾 Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o: ```bash mkfs.vfat /dev/sda ``` --- ## Passo 7: Montar o Pendrive 💻 Monte o pendrive na pasta `/mnt/edriver`: ```bash mount /dev/sda /mnt/edriver ``` --- ## Passo 8: Verificar UUID dos Dispositivos 📋 Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados: ```bash blkid ``` --- ## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝 Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim: ```fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0 ``` --- ## Passo 10: Copiar o Binário para a Pasta Correta 📥 Agora, copie o binário baixado para a pasta `/opt/nrs`: ```bash cp nrs-arm64 /opt/nrs ``` --- ## Passo 11: Criar o Arquivo de Configuração 🛠️ Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`: ```yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true ``` --- ## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️ Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`: ```bash cp nrs.service /etc/systemd/system/ ``` Recarregue os serviços e inicie o serviço `nrs`: ```bash systemctl daemon-reload systemctl enable --now nrs.service ``` --- ## Passo 13: Configurar o Tor 🌐 Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha: ```torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334 ``` --- ## Passo 14: Habilitar e Iniciar o Tor 🧅 Agora, ative e inicie o serviço Tor: ```bash systemctl enable --now tor.service ``` O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`. --- ## Observações ⚠️ - Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi. - O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`. --- Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳 Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** | | Pen drive |  | **16Gb** | Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.). --- ## Passo 1: Atualizar o Sistema 🖥️ Primeiro, atualize seu sistema e instale o Tor: ```bash apt update apt install tor ``` --- ## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧 Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo: ```unit [Unit] Description=Nostr Relay Server Service After=network.target [Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure [Install] WantedBy=multi-user.target ``` --- ## Passo 3: Baixar o Binário do Nostr 🚀 Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases). --- ## Passo 4: Criar as Pastas Necessárias 📂 Agora, crie as pastas para o aplicativo e o pendrive: ```bash mkdir -p /opt/nrs /mnt/edriver ``` --- ## Passo 5: Listar os Dispositivos Conectados 🔌 Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados: ```bash lsblk ``` --- ## Passo 6: Formatando o Pendrive 💾 Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o: ```bash mkfs.vfat /dev/sda ``` --- ## Passo 7: Montar o Pendrive 💻 Monte o pendrive na pasta `/mnt/edriver`: ```bash mount /dev/sda /mnt/edriver ``` --- ## Passo 8: Verificar UUID dos Dispositivos 📋 Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados: ```bash blkid ``` --- ## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝 Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim: ```fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0 ``` --- ## Passo 10: Copiar o Binário para a Pasta Correta 📥 Agora, copie o binário baixado para a pasta `/opt/nrs`: ```bash cp nrs-arm64 /opt/nrs ``` --- ## Passo 11: Criar o Arquivo de Configuração 🛠️ Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`: ```yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true ``` --- ## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️ Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`: ```bash cp nrs.service /etc/systemd/system/ ``` Recarregue os serviços e inicie o serviço `nrs`: ```bash systemctl daemon-reload systemctl enable --now nrs.service ``` --- ## Passo 13: Configurar o Tor 🌐 Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha: ```torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334 ``` --- ## Passo 14: Habilitar e Iniciar o Tor 🧅 Agora, ative e inicie o serviço Tor: ```bash systemctl enable --now tor.service ``` O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`. --- ## Observações ⚠️ - Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi. - O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`. --- Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳 Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos. @ 378562cd:a6fc6773
2025-01-18 00:12:47In the ever-changing world of decentralized networks, **Nostr** (Notes and Other Stuff Transmitted by Relays) is leading the charge. Its lightweight, open design has created an ecosystem that’s as adaptable as it is revolutionary. Whether you're chatting, publishing, or experimenting with new ways to connect, Nostr provides the foundation for a truly decentralized and censorship-resistant internet. --- ### **How Nostr Works: A Quick Overview** At its heart, Nostr is built on simplicity and decentralization. Here’s a breakdown of its core components: 1. **Public and Private Keys**:\ Your public key acts as your identity, and private keys ensure your messages are securely signed. 2. **Relays**:\ Relays are decentralized servers that distribute messages. They don’t own your data but simply pass it along to those who request it. 3. **Clients**:\ Clients are the user-facing applications where you interact with Nostr, offering diverse features and designs. --- ### **Deep Dive: Events in Nostr** Everything on Nostr revolves around **events**, which are cryptographically signed pieces of information containing various kinds of data. Here are the types of events currently supported and their use cases: #### **1. Note Events (Type 1)** - **What They Are**:\ These are the bread and butter of Nostr—text-based posts, much like tweets or status updates on traditional platforms. - **Features**: - Can include text, media links, and hashtags. - Interact with others through likes, replies, and boosts (reposts). - **Use Cases**:\ Perfect for microblogging, status updates, and general social interaction. #### **2. Profile Metadata Events (Type 0)** - **What They Are**:\ This event type stores and updates user profile information, such as your display name, bio, profile picture, and website. - **Features**: - Easily editable and updated across all Nostr clients. - Keeps your identity consistent across platforms. - **Use Cases**:\ Makes profile portability seamless—update once, and it reflects everywhere. #### **3. Relay List Events (Type 2)** - **What They Are**:\ These events store a list of relays that a user is connected to or prefers to use. - **Features**: - Share your relay preferences across devices or clients. - Allows automatic relay connection in supported clients. - **Use Cases**:\ Simplifies the onboarding process for users switching clients or devices. #### **4. Direct Message Events (Type 4)** - **What They Are**:\ End-to-end encrypted messages sent directly between two users. - **Features**: - Only readable by the intended recipient. - Supports text and basic formatting. - **Use Cases**:\ Secure communication for personal or professional purposes. #### **5. Reaction Events (Type 7)** - **What They Are**:\ Events that express reactions to other events, such as likes or emojis. - **Features**: - Provides social feedback (e.g., showing appreciation for a post). - Lightweight and simple to implement. - **Use Cases**:\ Enhances engagement and interaction within the network. #### **6. Repost Events (Type 6)** - **What They Are**:\ Events that allow users to reshare content, similar to retweets on Twitter. - **Features**: - Ensures the original poster retains credit. - Enables broader content visibility. - **Use Cases**:\ Amplifying content that resonates with users or is worth sharing. #### **7. Custom Event Types (Beyond Type 7)** - **What They Are**:\ Developers can create and define custom event types for specific applications. - **Features**: - Flexibility to introduce entirely new functionality. - Supported based on client and relay compatibility. - **Use Cases**:\ Enables innovation, from collaborative editing tools to advanced publishing workflows. --- ### **What Makes Events Special?** 1. **Portability**: Events follow your public key, not the client or relay, ensuring they’re available wherever you go. 2. **Interoperability**: All events are standardized, meaning any Nostr client can understand and process them. 3. **Extensibility**: Through custom event types, the protocol encourages experimentation and development. --- ### **Primal: A Favorite Client for Engaging Events** Among the many clients, **Primal** stands out as a favorite for how it handles Nostr events. Its emphasis on **content discovery** and **rich user interaction** makes it an excellent choice for exploring everything the protocol offers. Whether it’s crafting note events, managing profile metadata, or diving into direct messaging, Primal delivers a polished experience that feels seamless. --- ### **The Future of Nostr Events** As Nostr continues to evolve, so will the events it supports. Imagine event types for live streaming, collaborative workspaces, or even decentralized governance. The possibilities are limitless, driven by the creativity of the developers and the needs of the community. **Have you explored the potential of Nostr events yet? What’s your favorite client or feature? Let’s discuss below!** ⚡️ #Nostr #Primal #Decentralization #NostrEvents #FutureOfWeb
@ 378562cd:a6fc6773
2025-01-18 00:12:47In the ever-changing world of decentralized networks, **Nostr** (Notes and Other Stuff Transmitted by Relays) is leading the charge. Its lightweight, open design has created an ecosystem that’s as adaptable as it is revolutionary. Whether you're chatting, publishing, or experimenting with new ways to connect, Nostr provides the foundation for a truly decentralized and censorship-resistant internet. --- ### **How Nostr Works: A Quick Overview** At its heart, Nostr is built on simplicity and decentralization. Here’s a breakdown of its core components: 1. **Public and Private Keys**:\ Your public key acts as your identity, and private keys ensure your messages are securely signed. 2. **Relays**:\ Relays are decentralized servers that distribute messages. They don’t own your data but simply pass it along to those who request it. 3. **Clients**:\ Clients are the user-facing applications where you interact with Nostr, offering diverse features and designs. --- ### **Deep Dive: Events in Nostr** Everything on Nostr revolves around **events**, which are cryptographically signed pieces of information containing various kinds of data. Here are the types of events currently supported and their use cases: #### **1. Note Events (Type 1)** - **What They Are**:\ These are the bread and butter of Nostr—text-based posts, much like tweets or status updates on traditional platforms. - **Features**: - Can include text, media links, and hashtags. - Interact with others through likes, replies, and boosts (reposts). - **Use Cases**:\ Perfect for microblogging, status updates, and general social interaction. #### **2. Profile Metadata Events (Type 0)** - **What They Are**:\ This event type stores and updates user profile information, such as your display name, bio, profile picture, and website. - **Features**: - Easily editable and updated across all Nostr clients. - Keeps your identity consistent across platforms. - **Use Cases**:\ Makes profile portability seamless—update once, and it reflects everywhere. #### **3. Relay List Events (Type 2)** - **What They Are**:\ These events store a list of relays that a user is connected to or prefers to use. - **Features**: - Share your relay preferences across devices or clients. - Allows automatic relay connection in supported clients. - **Use Cases**:\ Simplifies the onboarding process for users switching clients or devices. #### **4. Direct Message Events (Type 4)** - **What They Are**:\ End-to-end encrypted messages sent directly between two users. - **Features**: - Only readable by the intended recipient. - Supports text and basic formatting. - **Use Cases**:\ Secure communication for personal or professional purposes. #### **5. Reaction Events (Type 7)** - **What They Are**:\ Events that express reactions to other events, such as likes or emojis. - **Features**: - Provides social feedback (e.g., showing appreciation for a post). - Lightweight and simple to implement. - **Use Cases**:\ Enhances engagement and interaction within the network. #### **6. Repost Events (Type 6)** - **What They Are**:\ Events that allow users to reshare content, similar to retweets on Twitter. - **Features**: - Ensures the original poster retains credit. - Enables broader content visibility. - **Use Cases**:\ Amplifying content that resonates with users or is worth sharing. #### **7. Custom Event Types (Beyond Type 7)** - **What They Are**:\ Developers can create and define custom event types for specific applications. - **Features**: - Flexibility to introduce entirely new functionality. - Supported based on client and relay compatibility. - **Use Cases**:\ Enables innovation, from collaborative editing tools to advanced publishing workflows. --- ### **What Makes Events Special?** 1. **Portability**: Events follow your public key, not the client or relay, ensuring they’re available wherever you go. 2. **Interoperability**: All events are standardized, meaning any Nostr client can understand and process them. 3. **Extensibility**: Through custom event types, the protocol encourages experimentation and development. --- ### **Primal: A Favorite Client for Engaging Events** Among the many clients, **Primal** stands out as a favorite for how it handles Nostr events. Its emphasis on **content discovery** and **rich user interaction** makes it an excellent choice for exploring everything the protocol offers. Whether it’s crafting note events, managing profile metadata, or diving into direct messaging, Primal delivers a polished experience that feels seamless. --- ### **The Future of Nostr Events** As Nostr continues to evolve, so will the events it supports. Imagine event types for live streaming, collaborative workspaces, or even decentralized governance. The possibilities are limitless, driven by the creativity of the developers and the needs of the community. **Have you explored the potential of Nostr events yet? What’s your favorite client or feature? Let’s discuss below!** ⚡️ #Nostr #Primal #Decentralization #NostrEvents #FutureOfWeb @ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity. A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur. The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior. And there are plenty of incentives beyond our direct control\! My son is *also* incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take. ## Why incentives matter A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could **just** do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example: * If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning. * If people would just use the recycling bin, we wouldn’t have such a landfill problem. * If people would just stop being lazy, our team would deliver our project on time. In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally. * The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do. * No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle. * If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.  My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want. If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is. ## Running a company Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions. Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good. What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off. Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning. When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.  Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks\! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money. There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals. Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature. # Moral hazard Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings. What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.  But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I *don’t* turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all. This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as: 1. We’re so habituated to turning off the water that we don’t even consider *not* turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off. 2. Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created. 3. We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?) Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard. A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard. It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend? And since we’re talking about the government already… ## Government moral hazards As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a *huge* number of examples of moral hazards. I decided to cherry-pick a few for this post. The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people? The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet. If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior\! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups. You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”  And here’s the absolute best part of this: I can’t even truly blame either California *or* Wall Street. (I mean, I *do* blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits. There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions. # Non-monetary competition At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home. In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.) Anyway, my professor’s wife had a friend. My professor described in *great* detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas. This is a demonstration of *non-monetary compensation*. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules. The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become *wealthier and whiter*, the exact opposite of their desired outcome. Why would that happen? Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky. She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls. So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites. You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences. ## Bureaucracy These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences. Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings. Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could\! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate. # Government incentivized behavior This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples: * Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to [malinvestment](https://en.wikipedia.org/wiki/Malinvestment) and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience. * Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise. * During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation. * The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen. * Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example). * Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as [high living](https://www.youtube.com/watch?v=ZwNDd2_beTU).) # Conclusion The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives. We can bemoan these realities all we want, but they *are* realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People *should* take advantage of the incentives around them. Because if they don’t, someone else will. (If you want a literary example of that last comment, see the horse in Animal Farm.) How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula: * Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people. * Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them. * And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example. And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining\!
@ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity. A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur. The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior. And there are plenty of incentives beyond our direct control\! My son is *also* incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take. ## Why incentives matter A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could **just** do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example: * If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning. * If people would just use the recycling bin, we wouldn’t have such a landfill problem. * If people would just stop being lazy, our team would deliver our project on time. In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally. * The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do. * No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle. * If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.  My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want. If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is. ## Running a company Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions. Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good. What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off. Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning. When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.  Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks\! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money. There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals. Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature. # Moral hazard Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings. What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.  But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I *don’t* turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all. This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as: 1. We’re so habituated to turning off the water that we don’t even consider *not* turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off. 2. Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created. 3. We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?) Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard. A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard. It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend? And since we’re talking about the government already… ## Government moral hazards As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a *huge* number of examples of moral hazards. I decided to cherry-pick a few for this post. The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people? The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet. If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior\! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups. You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”  And here’s the absolute best part of this: I can’t even truly blame either California *or* Wall Street. (I mean, I *do* blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits. There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions. # Non-monetary competition At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home. In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.) Anyway, my professor’s wife had a friend. My professor described in *great* detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas. This is a demonstration of *non-monetary compensation*. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules. The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become *wealthier and whiter*, the exact opposite of their desired outcome. Why would that happen? Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky. She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls. So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites. You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences. ## Bureaucracy These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences. Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings. Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could\! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate. # Government incentivized behavior This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples: * Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to [malinvestment](https://en.wikipedia.org/wiki/Malinvestment) and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience. * Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise. * During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation. * The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen. * Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example). * Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as [high living](https://www.youtube.com/watch?v=ZwNDd2_beTU).) # Conclusion The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives. We can bemoan these realities all we want, but they *are* realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People *should* take advantage of the incentives around them. Because if they don’t, someone else will. (If you want a literary example of that last comment, see the horse in Animal Farm.) How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula: * Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people. * Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them. * And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example. And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining\! @ e460cb14:01bb5ced
2025-01-13 13:30:13## Brief intro #glostr is a pet-project of mine to better understand how #nostr works. Since I'm an engineer, and somewhere between a game programmer and a graphics programmer, I'll do what I do best: write some graphics thing no one (but me) will use. ## Zappable Shadertoy So, the idea is to create a small platform on top of #nostr where people can create, visualize, and share computer graphics programs (aka: shaders). Code shiny thing, see shiny, share shiny thing, and zap shiny thing. If you're familiar with [Shadertoy](https://shadertoy.com), #glostr is just that: **zappable shadertoy**.  ## Milestone Zero So, first step was to write a quick and dirty prototype client (remember, I specc'd into game dev, not into web dev, so I really mean _quick_ and I really mean _dirty_). I got an [ace editor](https://github.com/ajaxorg/ace) thing working, duct-taped it to a basic WebGL render, stole a couple shaders from shadertoy (jk, I gave credit), poured some CSS magic, glued some `nostr-rx`, and published it to GitHub pages. After 2 or 3 days of iterating, and with some assistance from an LLM, you can see the result linked on my [notes](nostr:nevent1qqsf45hy66cw55e3s2ewt6upe3m073q875hmjjtyyre7qtaxw9hl5scpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qu3svk99639mcdfn43s2nawg4a2j4ejmgrq2n63l4t67wzqdmtnkss70qyf). Yes. I used `kind 1` posts to spam GLSL code. I AM SORRY. I KNOW BETTER NOW. I SWEAR. So, right now #glostr is: - Taking an npub on the url after the # - Rendering all `kind 1` posts from that npub containing GLSL code between \`\`\`s - Allowing the user to edit the code in real time  ## Next Steps What now? [Gorila](nostr:npub19tv378w29hx4ljy7wgydreg9nu96czrs6clu8wkzr3af8z86rr7sujx4xe) made me realize my _obvious_ `kind 1` spamming. After some brainstorming and skimming through NIPs and kinds, we arrived at the conclusion that [Long-form Notes (NIP-23)](https://github.com/nostr-protocol/nips/blob/master/23.md) are best suited for the content I want #glostr to display: - Format is Markdown, which I like and which I was already somewhat expecting. - It's editable content, so mistakes can be amended, which is more than usual in shader programming. So, the next features I want to add are: - Logging in - Posting NIP-23 Notes - Getting, parsing, and showing NIP-23 Notes ## When I'll only work on this on the weekends for now, so I don't know. This is a pet project for fun right now. ## Wrapping Up Repo: https://github.com/rowdaboat/glostr Try it: https://rowdaboat.github.io/glostr/ As this is a Long-Form Note in itself, I'll finish it by sharing a shader based on [Inigo Quilez's awesome polygon shader](https://www.shadertoy.com/view/wdBXRW). This note should show as a shader on #glostr in the next iteration, but you can copy and paste the code in the editor for now: ```glsl #version 300 es precision mediump float; uniform vec2 u_resolution; uniform float u_time; out vec4 fragColor; const int N = 6; vec3 yellow = vec3(0.45, 0.3, 0.15); vec3 lightBlue = vec3(0.65, 0.85, 1.0); float polygon(in vec2 p, in vec2[N] v) { const int num = v.length(); float d = dot(p - v[0], p - v[0]); float s = 1.; for(int i=0, j=num-1; i < num; j=i, i++ ) { vec2 e = v[j] - v[i]; vec2 w = p - v[i]; vec2 b = w - e * clamp(dot(w, e) / dot(e, e), 0.0, 1.0); d = min(d, dot(b,b)); bvec3 condition = bvec3( p.y >= v[i].y, p.y < v[j].y, e.x * w.y > e.y * w.x ); if (all(condition) || all(not(condition))) s =- s; } return s * sqrt(d); } void main() { vec2 p = (2.0 * gl_FragCoord.xy - u_resolution.xy) / u_resolution.y; float d = polygon(p, vec2[]( vec2( .2, .8), vec2(-.5, -.125), vec2( .0, -.125), vec2(-.2, -.8), vec2( .5, .125), vec2( .0, .125) )); vec3 color = d < 0.0 ? yellow : lightBlue; color *= 1. - exp(-40. * abs(d)); color *= .8 + .2 * sin(10.0 * d - 10. * u_time) * sin(-1.25 * u_time); color *= exp(1. - d * 2.25); fragColor = vec4(color, 1.0); } ```
@ e460cb14:01bb5ced
2025-01-13 13:30:13## Brief intro #glostr is a pet-project of mine to better understand how #nostr works. Since I'm an engineer, and somewhere between a game programmer and a graphics programmer, I'll do what I do best: write some graphics thing no one (but me) will use. ## Zappable Shadertoy So, the idea is to create a small platform on top of #nostr where people can create, visualize, and share computer graphics programs (aka: shaders). Code shiny thing, see shiny, share shiny thing, and zap shiny thing. If you're familiar with [Shadertoy](https://shadertoy.com), #glostr is just that: **zappable shadertoy**.  ## Milestone Zero So, first step was to write a quick and dirty prototype client (remember, I specc'd into game dev, not into web dev, so I really mean _quick_ and I really mean _dirty_). I got an [ace editor](https://github.com/ajaxorg/ace) thing working, duct-taped it to a basic WebGL render, stole a couple shaders from shadertoy (jk, I gave credit), poured some CSS magic, glued some `nostr-rx`, and published it to GitHub pages. After 2 or 3 days of iterating, and with some assistance from an LLM, you can see the result linked on my [notes](nostr:nevent1qqsf45hy66cw55e3s2ewt6upe3m073q875hmjjtyyre7qtaxw9hl5scpp4mhxue69uhkummn9ekx7mqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qu3svk99639mcdfn43s2nawg4a2j4ejmgrq2n63l4t67wzqdmtnkss70qyf). Yes. I used `kind 1` posts to spam GLSL code. I AM SORRY. I KNOW BETTER NOW. I SWEAR. So, right now #glostr is: - Taking an npub on the url after the # - Rendering all `kind 1` posts from that npub containing GLSL code between \`\`\`s - Allowing the user to edit the code in real time  ## Next Steps What now? [Gorila](nostr:npub19tv378w29hx4ljy7wgydreg9nu96czrs6clu8wkzr3af8z86rr7sujx4xe) made me realize my _obvious_ `kind 1` spamming. After some brainstorming and skimming through NIPs and kinds, we arrived at the conclusion that [Long-form Notes (NIP-23)](https://github.com/nostr-protocol/nips/blob/master/23.md) are best suited for the content I want #glostr to display: - Format is Markdown, which I like and which I was already somewhat expecting. - It's editable content, so mistakes can be amended, which is more than usual in shader programming. So, the next features I want to add are: - Logging in - Posting NIP-23 Notes - Getting, parsing, and showing NIP-23 Notes ## When I'll only work on this on the weekends for now, so I don't know. This is a pet project for fun right now. ## Wrapping Up Repo: https://github.com/rowdaboat/glostr Try it: https://rowdaboat.github.io/glostr/ As this is a Long-Form Note in itself, I'll finish it by sharing a shader based on [Inigo Quilez's awesome polygon shader](https://www.shadertoy.com/view/wdBXRW). This note should show as a shader on #glostr in the next iteration, but you can copy and paste the code in the editor for now: ```glsl #version 300 es precision mediump float; uniform vec2 u_resolution; uniform float u_time; out vec4 fragColor; const int N = 6; vec3 yellow = vec3(0.45, 0.3, 0.15); vec3 lightBlue = vec3(0.65, 0.85, 1.0); float polygon(in vec2 p, in vec2[N] v) { const int num = v.length(); float d = dot(p - v[0], p - v[0]); float s = 1.; for(int i=0, j=num-1; i < num; j=i, i++ ) { vec2 e = v[j] - v[i]; vec2 w = p - v[i]; vec2 b = w - e * clamp(dot(w, e) / dot(e, e), 0.0, 1.0); d = min(d, dot(b,b)); bvec3 condition = bvec3( p.y >= v[i].y, p.y < v[j].y, e.x * w.y > e.y * w.x ); if (all(condition) || all(not(condition))) s =- s; } return s * sqrt(d); } void main() { vec2 p = (2.0 * gl_FragCoord.xy - u_resolution.xy) / u_resolution.y; float d = polygon(p, vec2[]( vec2( .2, .8), vec2(-.5, -.125), vec2( .0, -.125), vec2(-.2, -.8), vec2( .5, .125), vec2( .0, .125) )); vec3 color = d < 0.0 ? yellow : lightBlue; color *= 1. - exp(-40. * abs(d)); color *= .8 + .2 * sin(10.0 * d - 10. * u_time) * sin(-1.25 * u_time); color *= exp(1. - d * 2.25); fragColor = vec4(color, 1.0); } ``` @ a95c6243:d345522c
2025-01-13 10:09:57*Ich begann, Social Media aufzubauen,* *\ um den Menschen eine Stimme zu geben.* *\ Mark Zuckerberg* **Sind euch auch die Tränen gekommen, als ihr Mark Zuckerbergs** **[Wendehals-Deklaration](https://www.facebook.com/zuck/videos/1525382954801931)** bezüglich der Meinungsfreiheit auf seinen Portalen gehört habt? Rührend, oder? Während er früher die offensichtliche Zensur leugnete und später die Regierung Biden dafür verantwortlich machte, will er nun angeblich «die Zensur auf unseren Plattformen drastisch reduzieren». **«Purer** **[Opportunismus](https://transition-news.org/facebook-grunder-zuckerberg-vom-trump-gegner-zum-trump-buddy-und-anti-zensor)» ob des anstehenden Regierungswechsels wäre als Klassifizierung** viel zu kurz gegriffen. Der jetzige Schachzug des Meta-Chefs ist genauso Teil einer kühl kalkulierten Business-Strategie, wie es die 180 Grad umgekehrte Praxis vorher war. Social Media sind ein höchst lukratives Geschäft. Hinzu kommt vielleicht noch ein bisschen verkorkstes Ego, weil derartig viel Einfluss und Geld sicher auch auf die Psyche schlagen. Verständlich. > «Es ist an der Zeit, zu unseren Wurzeln der freien Meinungsäußerung auf Facebook und Instagram zurückzukehren. Ich begann, Social Media aufzubauen, um den Menschen eine Stimme zu geben», sagte Zuckerberg. **Welche Wurzeln? Hat der Mann vergessen, dass er von der Überwachung,** dem Ausspionieren und dem Ausverkauf sämtlicher Daten und digitaler Spuren sowie der Manipulation seiner «Kunden» lebt? Das ist knallharter Kommerz, nichts anderes. Um freie Meinungsäußerung geht es bei diesem Geschäft ganz sicher nicht, und das war auch noch nie so. Die Wurzeln von Facebook liegen in einem Projekt des US-Militärs mit dem Namen [«LifeLog»](https://norberthaering.de/macht-kontrolle/lifelog/). Dessen Ziel war es, «ein digitales Protokoll vom Leben eines Menschen zu erstellen». **Der Richtungswechsel kommt allerdings nicht überraschend.** Schon Anfang Dezember hatte Meta-Präsident Nick Clegg von «zu hoher Fehlerquote bei der Moderation» von Inhalten [gesprochen](https://www.theverge.com/2024/12/3/24311513/meta-content-moderation-mistakes-nick-clegg). Bei der Gelegenheit erwähnte er auch, dass Mark sehr daran interessiert sei, eine aktive Rolle in den Debatten über eine amerikanische Führungsrolle im technologischen Bereich zu spielen. **Während Milliardärskollege und Big Tech-Konkurrent Elon Musk bereits seinen Posten** in der kommenden Trump-Regierung in Aussicht hat, möchte Zuckerberg also nicht nur seine Haut retten – Trump hatte ihn einmal einen «Feind des Volkes» genannt und ihm lebenslange Haft angedroht –, sondern am liebsten auch mitspielen. KI-Berater ist wohl die gewünschte Funktion, wie man nach einem Treffen Trump-Zuckerberg hörte. An seine [Verhaftung](https://transition-news.org/nicht-telegram-grunder-durow-sondern-zuckerberg-sollte-in-haft-sitzen-wegen-des) dachte vermutlich auch ein weiterer Multimilliardär mit eigener Social Media-Plattform, Pavel Durov, als er Zuckerberg jetzt [kritisierte](https://www.berliner-zeitung.de/news/ende-des-faktenchecks-bei-meta-telegram-gruender-kritisiert-zuckerberg-und-spricht-warnung-aus-li.2287988) und gleichzeitig warnte. **Politik und Systemmedien drehen jedenfalls durch** – was zu viel ist, ist zu viel. Etwas weniger Zensur und mehr Meinungsfreiheit würden die Freiheit der Bürger schwächen und seien potenziell vernichtend für die Menschenrechte. Zuckerberg setze mit dem neuen Kurs die Demokratie aufs Spiel, das sei eine «Einladung zum nächsten [Völkermord](https://archive.is/PYeH0)», ernsthaft. Die Frage sei, ob sich die [EU gegen Musk und Zuckerberg](https://www.handelsblatt.com/politik/international/internet-regulierung-kann-sich-die-eu-gegen-musk-und-zuckerberg-behaupten/100099373.html) behaupten könne, Brüssel müsse jedenfalls hart durchgreifen. **Auch um die** **[Faktenchecker](https://www.welt.de/kultur/medien/article255065352/Metas-Kurswechsel-Zuckerbergs-Entscheidung-und-die-Folgen-fuer-deutsche-Faktenchecker.html)** **macht man sich Sorgen.** Für die deutsche Nachrichtenagentur *dpa* und die «Experten» von *Correctiv*, die (noch) Partner für Fact-Checking-Aktivitäten von Facebook sind, sei das ein «lukratives Geschäftsmodell». Aber möglicherweise werden die Inhalte ohne diese vermeintlichen Korrektoren ja sogar besser. Anders als Meta wollen jedoch Scholz, Faeser und die *Tagesschau* keine Fehler zugeben und zum Beispiel *Correctiv*-[Falschaussagen](https://www.berliner-zeitung.de/politik-gesellschaft/correctiv-falschaussagen-exklusiv-scholz-faeser-und-tagesschau-wollen-sich-fuer-verbreitung-nicht-entschuldigen-li.2288126) einräumen. **Bei derlei dramatischen Befürchtungen wundert es nicht,** dass der öffentliche Plausch auf X zwischen Elon Musk und AfD-Chefin Alice Weidel von 150 EU-Beamten überwacht wurde, falls es irgendwelche Rechtsverstöße geben sollte, die man ihnen ankreiden könnte. Auch der Deutsche Bundestag war wachsam. Gefunden haben dürften sie nichts. Das Ganze war eher eine Show, viel Wind wurde gemacht, aber letztlich gab es nichts als heiße Luft. **Das** **[Anbiedern](https://transition-news.org/who-biedert-sich-bei-trump-an)** **bei Donald Trump ist indes gerade in Mode.** Die Weltgesundheitsorganisation (WHO) tut das auch, denn sie fürchtet um Spenden von über einer Milliarde Dollar. Eventuell könnte ja Elon Musk auch hier künftig aushelfen und der Organisation sowie deren größtem privaten Förderer, Bill Gates, etwas unter die Arme greifen. Nachdem Musks KI-Projekt xAI kürzlich von BlackRock & Co. [sechs Milliarden](https://x.ai/blog/series-c) eingestrichen hat, geht da vielleicht etwas. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/milliardenschwere-wetterfahnchen-und-windmaschinen)*** erschienen.
@ a95c6243:d345522c
2025-01-13 10:09:57*Ich begann, Social Media aufzubauen,* *\ um den Menschen eine Stimme zu geben.* *\ Mark Zuckerberg* **Sind euch auch die Tränen gekommen, als ihr Mark Zuckerbergs** **[Wendehals-Deklaration](https://www.facebook.com/zuck/videos/1525382954801931)** bezüglich der Meinungsfreiheit auf seinen Portalen gehört habt? Rührend, oder? Während er früher die offensichtliche Zensur leugnete und später die Regierung Biden dafür verantwortlich machte, will er nun angeblich «die Zensur auf unseren Plattformen drastisch reduzieren». **«Purer** **[Opportunismus](https://transition-news.org/facebook-grunder-zuckerberg-vom-trump-gegner-zum-trump-buddy-und-anti-zensor)» ob des anstehenden Regierungswechsels wäre als Klassifizierung** viel zu kurz gegriffen. Der jetzige Schachzug des Meta-Chefs ist genauso Teil einer kühl kalkulierten Business-Strategie, wie es die 180 Grad umgekehrte Praxis vorher war. Social Media sind ein höchst lukratives Geschäft. Hinzu kommt vielleicht noch ein bisschen verkorkstes Ego, weil derartig viel Einfluss und Geld sicher auch auf die Psyche schlagen. Verständlich. > «Es ist an der Zeit, zu unseren Wurzeln der freien Meinungsäußerung auf Facebook und Instagram zurückzukehren. Ich begann, Social Media aufzubauen, um den Menschen eine Stimme zu geben», sagte Zuckerberg. **Welche Wurzeln? Hat der Mann vergessen, dass er von der Überwachung,** dem Ausspionieren und dem Ausverkauf sämtlicher Daten und digitaler Spuren sowie der Manipulation seiner «Kunden» lebt? Das ist knallharter Kommerz, nichts anderes. Um freie Meinungsäußerung geht es bei diesem Geschäft ganz sicher nicht, und das war auch noch nie so. Die Wurzeln von Facebook liegen in einem Projekt des US-Militärs mit dem Namen [«LifeLog»](https://norberthaering.de/macht-kontrolle/lifelog/). Dessen Ziel war es, «ein digitales Protokoll vom Leben eines Menschen zu erstellen». **Der Richtungswechsel kommt allerdings nicht überraschend.** Schon Anfang Dezember hatte Meta-Präsident Nick Clegg von «zu hoher Fehlerquote bei der Moderation» von Inhalten [gesprochen](https://www.theverge.com/2024/12/3/24311513/meta-content-moderation-mistakes-nick-clegg). Bei der Gelegenheit erwähnte er auch, dass Mark sehr daran interessiert sei, eine aktive Rolle in den Debatten über eine amerikanische Führungsrolle im technologischen Bereich zu spielen. **Während Milliardärskollege und Big Tech-Konkurrent Elon Musk bereits seinen Posten** in der kommenden Trump-Regierung in Aussicht hat, möchte Zuckerberg also nicht nur seine Haut retten – Trump hatte ihn einmal einen «Feind des Volkes» genannt und ihm lebenslange Haft angedroht –, sondern am liebsten auch mitspielen. KI-Berater ist wohl die gewünschte Funktion, wie man nach einem Treffen Trump-Zuckerberg hörte. An seine [Verhaftung](https://transition-news.org/nicht-telegram-grunder-durow-sondern-zuckerberg-sollte-in-haft-sitzen-wegen-des) dachte vermutlich auch ein weiterer Multimilliardär mit eigener Social Media-Plattform, Pavel Durov, als er Zuckerberg jetzt [kritisierte](https://www.berliner-zeitung.de/news/ende-des-faktenchecks-bei-meta-telegram-gruender-kritisiert-zuckerberg-und-spricht-warnung-aus-li.2287988) und gleichzeitig warnte. **Politik und Systemmedien drehen jedenfalls durch** – was zu viel ist, ist zu viel. Etwas weniger Zensur und mehr Meinungsfreiheit würden die Freiheit der Bürger schwächen und seien potenziell vernichtend für die Menschenrechte. Zuckerberg setze mit dem neuen Kurs die Demokratie aufs Spiel, das sei eine «Einladung zum nächsten [Völkermord](https://archive.is/PYeH0)», ernsthaft. Die Frage sei, ob sich die [EU gegen Musk und Zuckerberg](https://www.handelsblatt.com/politik/international/internet-regulierung-kann-sich-die-eu-gegen-musk-und-zuckerberg-behaupten/100099373.html) behaupten könne, Brüssel müsse jedenfalls hart durchgreifen. **Auch um die** **[Faktenchecker](https://www.welt.de/kultur/medien/article255065352/Metas-Kurswechsel-Zuckerbergs-Entscheidung-und-die-Folgen-fuer-deutsche-Faktenchecker.html)** **macht man sich Sorgen.** Für die deutsche Nachrichtenagentur *dpa* und die «Experten» von *Correctiv*, die (noch) Partner für Fact-Checking-Aktivitäten von Facebook sind, sei das ein «lukratives Geschäftsmodell». Aber möglicherweise werden die Inhalte ohne diese vermeintlichen Korrektoren ja sogar besser. Anders als Meta wollen jedoch Scholz, Faeser und die *Tagesschau* keine Fehler zugeben und zum Beispiel *Correctiv*-[Falschaussagen](https://www.berliner-zeitung.de/politik-gesellschaft/correctiv-falschaussagen-exklusiv-scholz-faeser-und-tagesschau-wollen-sich-fuer-verbreitung-nicht-entschuldigen-li.2288126) einräumen. **Bei derlei dramatischen Befürchtungen wundert es nicht,** dass der öffentliche Plausch auf X zwischen Elon Musk und AfD-Chefin Alice Weidel von 150 EU-Beamten überwacht wurde, falls es irgendwelche Rechtsverstöße geben sollte, die man ihnen ankreiden könnte. Auch der Deutsche Bundestag war wachsam. Gefunden haben dürften sie nichts. Das Ganze war eher eine Show, viel Wind wurde gemacht, aber letztlich gab es nichts als heiße Luft. **Das** **[Anbiedern](https://transition-news.org/who-biedert-sich-bei-trump-an)** **bei Donald Trump ist indes gerade in Mode.** Die Weltgesundheitsorganisation (WHO) tut das auch, denn sie fürchtet um Spenden von über einer Milliarde Dollar. Eventuell könnte ja Elon Musk auch hier künftig aushelfen und der Organisation sowie deren größtem privaten Förderer, Bill Gates, etwas unter die Arme greifen. Nachdem Musks KI-Projekt xAI kürzlich von BlackRock & Co. [sechs Milliarden](https://x.ai/blog/series-c) eingestrichen hat, geht da vielleicht etwas. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/milliardenschwere-wetterfahnchen-und-windmaschinen)*** erschienen. @ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs ## The reason why we have broken money Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world. In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes. However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore. Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too. Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it. ## Bitcoin overcomes the "transfer of hard money" problem Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design. Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it. Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive. Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold. ## Bitcoin blurs the line between commodity and technology Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules. At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable. Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases. ## The dangers of derivatives A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold. In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin. Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense. ## Learn for yourself If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody". There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
@ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs ## The reason why we have broken money Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world. In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes. However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore. Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too. Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it. ## Bitcoin overcomes the "transfer of hard money" problem Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design. Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it. Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive. Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold. ## Bitcoin blurs the line between commodity and technology Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules. At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable. Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases. ## The dangers of derivatives A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold. In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin. Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense. ## Learn for yourself If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody". There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance. @ 37fe9853:bcd1b039
2025-01-11 15:04:40yoyoaa
@ 37fe9853:bcd1b039
2025-01-11 15:04:40yoyoaa @ 62033ff8:e4471203
2025-01-11 15:00:24收录的内容中 kind=1的部分,实话说 质量不高。 所以我增加了kind=30023 长文的article,但是更新的太少,多个relays 的服务器也没有多少长文。 所有搜索nostr如果需要产生价值,需要有高质量的文章和新闻。 而且现在有很多机器人的文章充满着浪费空间的作用,其他作用都用不上。 https://www.duozhutuan.com 目前放的是给搜索引擎提供搜索的原材料。没有做UI给人类浏览。所以看上去是粗糙的。 我并没有打算去做一个发microblog的 web客户端,那类的客户端太多了。 我觉得nostr社区需要解决的还是应用。如果仅仅是microblog 感觉有点够呛 幸运的是npub.pro 建站这样的,我觉得有点意思。 yakihonne 智能widget 也有意思 我做的TaskQ5 我自己在用了。分布式的任务系统,也挺好的。
@ 62033ff8:e4471203
2025-01-11 15:00:24收录的内容中 kind=1的部分,实话说 质量不高。 所以我增加了kind=30023 长文的article,但是更新的太少,多个relays 的服务器也没有多少长文。 所有搜索nostr如果需要产生价值,需要有高质量的文章和新闻。 而且现在有很多机器人的文章充满着浪费空间的作用,其他作用都用不上。 https://www.duozhutuan.com 目前放的是给搜索引擎提供搜索的原材料。没有做UI给人类浏览。所以看上去是粗糙的。 我并没有打算去做一个发microblog的 web客户端,那类的客户端太多了。 我觉得nostr社区需要解决的还是应用。如果仅仅是microblog 感觉有点够呛 幸运的是npub.pro 建站这样的,我觉得有点意思。 yakihonne 智能widget 也有意思 我做的TaskQ5 我自己在用了。分布式的任务系统,也挺好的。 @ f3df9bc0:a95119eb
2025-01-10 02:58:08# MPT Equations ### Geometric Mean $$ \bar{x} = (\prod_{i=1}^{n} x_i)^{1 \over n } $$ ### Covariance $$ COV(x,y) = {1\over{n-1}} \sum_{i=1}^{n}{(x_i - \bar{x})(y_i - \bar{y})} $$ where $\bar{x}$ and $\bar{y}$ are the **geometric** mean. ### Variance $$ VAR(x) = {1\over{n-1}} \sum_{i=1}^{n}{(x_i - \bar{x})^2} $$ ### Standard Deviation $$ \sigma_x=\sqrt{VAR(x)} $$ ### Correlation Coefficient $$ \rho_{xy} = {COV(x, y) \over \sigma_x\sigma_y} $$ ### Portfolio Variance $$ VAR(P) = \sum_{ij}w_i w_j COV(i, j) $$ Where $w_i$ and $w_j$ are the normalized weight of the asset in the portfolio. Note that this summation should include when $i = j$. In this case $COV(i, j) = VAR(i) = VAR(j)$ ### Expected Return $$ E_P = \sum_{i}w_i E_i $$ Where $w_i$ is the normalized weight of the asset, and $E_i$ is the expected return of the individual asset.
@ f3df9bc0:a95119eb
2025-01-10 02:58:08# MPT Equations ### Geometric Mean $$ \bar{x} = (\prod_{i=1}^{n} x_i)^{1 \over n } $$ ### Covariance $$ COV(x,y) = {1\over{n-1}} \sum_{i=1}^{n}{(x_i - \bar{x})(y_i - \bar{y})} $$ where $\bar{x}$ and $\bar{y}$ are the **geometric** mean. ### Variance $$ VAR(x) = {1\over{n-1}} \sum_{i=1}^{n}{(x_i - \bar{x})^2} $$ ### Standard Deviation $$ \sigma_x=\sqrt{VAR(x)} $$ ### Correlation Coefficient $$ \rho_{xy} = {COV(x, y) \over \sigma_x\sigma_y} $$ ### Portfolio Variance $$ VAR(P) = \sum_{ij}w_i w_j COV(i, j) $$ Where $w_i$ and $w_j$ are the normalized weight of the asset in the portfolio. Note that this summation should include when $i = j$. In this case $COV(i, j) = VAR(i) = VAR(j)$ ### Expected Return $$ E_P = \sum_{i}w_i E_i $$ Where $w_i$ is the normalized weight of the asset, and $E_i$ is the expected return of the individual asset. @ f33c8a96:5ec6f741
2025-01-09 18:38:50<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-5.mp4" type="video/mp4"/> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-5.webm" type="video/webm"/> </video></div> # JavaScript: Building Your First Interactive Web App ## Introduction In this lesson, we'll bring our web pages to life by adding dynamic functionality with JavaScript. We'll build a real-world application that displays and updates Bitcoin prices in real-time, teaching core JavaScript concepts along the way. ## Project Overview: Bitcoin Price Tracker We'll build a web application that: - Displays current Bitcoin price - Updates automatically every 3 seconds - Allows currency switching - Includes interactive controls - Shows current date/time ## Core JavaScript Concepts ### 1. Variables and Data Types ```javascript // Variables can be declared with let or const let currentCurrency = "USD"; // Can be changed const interval = 3000; // Cannot be changed // Basic data types const price = 45000; // Number const isVisible = true; // Boolean const currency = "USD"; // String ``` ### 2. DOM Manipulation ```javascript // Getting elements const priceElement = document.getElementById('price'); const button = document.getElementById('refresh-button'); // Modifying content priceElement.textContent = `${price} ${currency}`; // Changing styles priceElement.style.display = 'none'; ``` ### 3. Event Listeners ```javascript // Basic click handler button.addEventListener('click', () => { fetchBitcoinPrice(); }); // Change event for select elements selector.addEventListener('change', (event) => { handleCurrencyChange(event.value); }); ``` ### 4. Async Operations & Fetch API ```javascript async function fetchBitcoinPrice() { try { const response = await fetch(apiUrl); const data = await response.json(); updatePrice(data.price); } catch (error) { console.error('Error:', error); } } ``` ## Project Structure ### HTML Setup ```html <!DOCTYPE html> <html lang="en"> <head> <title>Bitcoin Price Tracker</title> <link rel="stylesheet" href="style.css"> <script src="index.js" defer></script> </head> <body> <h1>Current Bitcoin Price</h1> <p>The price is: <span id="price"></span></p> <!-- Additional elements --> </body> </html> ``` ### Core Functionality Implementation 1. **Setting Up the Timer** ```javascript // Update price every 3 seconds setInterval(fetchBitcoinPrice, 3000); // Update date/time every second setInterval(updateDateTime, 1000); ``` 2. **Currency Selection** ```javascript function handleCurrencyChange(newCurrency) { currentCurrency = newCurrency; fetchBitcoinPrice(); } ``` 3. **Toggle Visibility** ```javascript function togglePriceVisibility() { const price = document.getElementById('price'); price.style.display = price.style.display === 'none' ? 'inline' : 'none'; } ``` ## Best Practices ### 1. Error Handling - Always use try/catch with async operations - Provide meaningful error messages - Handle edge cases gracefully ### 2. Code Organization - Keep functions focused and small - Use meaningful variable names - Group related functionality - Add comments for clarity ### 3. Performance - Avoid unnecessary DOM updates - Use appropriate update intervals - Clean up intervals when not needed ## Common Challenges & Solutions ### 1. API Issues ```javascript // Handle API failures gracefully catch (error) { priceElement.textContent = 'Price unavailable'; console.error('API Error:', error); } ``` ### 2. Currency Formatting ```javascript function formatPrice(price, currency) { return new Intl.NumberFormat('en-US', { style: 'currency', currency: currency }).format(price); } ``` ### 3. Time Zones ```javascript function getLocalTime() { return new Date().toLocaleString(); } ``` ## Extending the Project Consider adding these features for practice: 1. Price change indicators (up/down arrows) 2. Historical price chart 3. Multiple cryptocurrency support 4. Price alerts 5. Local storage for settings ## Debugging Tips ### Using Console ```javascript console.log('Price fetched:', price); console.error('Error occurred:', error); console.table(priceHistory); ``` ### Chrome DevTools 1. Network tab for API calls 2. Console for errors 3. Elements for DOM inspection 4. Sources for debugging ## Additional Resources - MDN JavaScript Guide - JavaScript.info - CoinGecko API Documentation - Chrome DevTools Documentation ## Next Steps 1. Add styling with CSS 2. Implement additional features 3. Learn about React for more complex applications 4. Explore other APIs and cryptocurrencies Remember: The best way to learn is by doing. Don't be afraid to break things and experiment with the code. The developer console is your friend for debugging and understanding what's happening in your application. Happy coding! 🚀
@ f33c8a96:5ec6f741
2025-01-09 18:38:50<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-5.mp4" type="video/mp4"/> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-5.webm" type="video/webm"/> </video></div> # JavaScript: Building Your First Interactive Web App ## Introduction In this lesson, we'll bring our web pages to life by adding dynamic functionality with JavaScript. We'll build a real-world application that displays and updates Bitcoin prices in real-time, teaching core JavaScript concepts along the way. ## Project Overview: Bitcoin Price Tracker We'll build a web application that: - Displays current Bitcoin price - Updates automatically every 3 seconds - Allows currency switching - Includes interactive controls - Shows current date/time ## Core JavaScript Concepts ### 1. Variables and Data Types ```javascript // Variables can be declared with let or const let currentCurrency = "USD"; // Can be changed const interval = 3000; // Cannot be changed // Basic data types const price = 45000; // Number const isVisible = true; // Boolean const currency = "USD"; // String ``` ### 2. DOM Manipulation ```javascript // Getting elements const priceElement = document.getElementById('price'); const button = document.getElementById('refresh-button'); // Modifying content priceElement.textContent = `${price} ${currency}`; // Changing styles priceElement.style.display = 'none'; ``` ### 3. Event Listeners ```javascript // Basic click handler button.addEventListener('click', () => { fetchBitcoinPrice(); }); // Change event for select elements selector.addEventListener('change', (event) => { handleCurrencyChange(event.value); }); ``` ### 4. Async Operations & Fetch API ```javascript async function fetchBitcoinPrice() { try { const response = await fetch(apiUrl); const data = await response.json(); updatePrice(data.price); } catch (error) { console.error('Error:', error); } } ``` ## Project Structure ### HTML Setup ```html <!DOCTYPE html> <html lang="en"> <head> <title>Bitcoin Price Tracker</title> <link rel="stylesheet" href="style.css"> <script src="index.js" defer></script> </head> <body> <h1>Current Bitcoin Price</h1> <p>The price is: <span id="price"></span></p> <!-- Additional elements --> </body> </html> ``` ### Core Functionality Implementation 1. **Setting Up the Timer** ```javascript // Update price every 3 seconds setInterval(fetchBitcoinPrice, 3000); // Update date/time every second setInterval(updateDateTime, 1000); ``` 2. **Currency Selection** ```javascript function handleCurrencyChange(newCurrency) { currentCurrency = newCurrency; fetchBitcoinPrice(); } ``` 3. **Toggle Visibility** ```javascript function togglePriceVisibility() { const price = document.getElementById('price'); price.style.display = price.style.display === 'none' ? 'inline' : 'none'; } ``` ## Best Practices ### 1. Error Handling - Always use try/catch with async operations - Provide meaningful error messages - Handle edge cases gracefully ### 2. Code Organization - Keep functions focused and small - Use meaningful variable names - Group related functionality - Add comments for clarity ### 3. Performance - Avoid unnecessary DOM updates - Use appropriate update intervals - Clean up intervals when not needed ## Common Challenges & Solutions ### 1. API Issues ```javascript // Handle API failures gracefully catch (error) { priceElement.textContent = 'Price unavailable'; console.error('API Error:', error); } ``` ### 2. Currency Formatting ```javascript function formatPrice(price, currency) { return new Intl.NumberFormat('en-US', { style: 'currency', currency: currency }).format(price); } ``` ### 3. Time Zones ```javascript function getLocalTime() { return new Date().toLocaleString(); } ``` ## Extending the Project Consider adding these features for practice: 1. Price change indicators (up/down arrows) 2. Historical price chart 3. Multiple cryptocurrency support 4. Price alerts 5. Local storage for settings ## Debugging Tips ### Using Console ```javascript console.log('Price fetched:', price); console.error('Error occurred:', error); console.table(priceHistory); ``` ### Chrome DevTools 1. Network tab for API calls 2. Console for errors 3. Elements for DOM inspection 4. Sources for debugging ## Additional Resources - MDN JavaScript Guide - JavaScript.info - CoinGecko API Documentation - Chrome DevTools Documentation ## Next Steps 1. Add styling with CSS 2. Implement additional features 3. Learn about React for more complex applications 4. Explore other APIs and cryptocurrencies Remember: The best way to learn is by doing. Don't be afraid to break things and experiment with the code. The developer console is your friend for debugging and understanding what's happening in your application. Happy coding! 🚀 @ df173277:4ec96708
2025-01-09 17:12:08> Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\ > [Join the waitlist to get early access.](https://trymaple.ai) We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI. Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations. #### Building a Private Foundation Maple is built on our flagship product, [OpenSecret](https://opensecret.cloud), a backend platform for app developers that turns private encryption on by default. [The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do.](nostr:naddr1qvzqqqr4gupzphchxfm3ste32hfhkvczzxapme9gz5qvqtget6tylyd7wa8vjecgqqe5jmn5wfhkgatrd9hxwt20wpjku5m9vdex2apdw35x2tt9de3hy7tsw3jkgttzv93kketwvskhgur5w9nx5h52tpj) We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win. #### The Power of Encrypted AI Chat AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short. Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us. #### Technical Overview So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects: - **Private Key:** Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data. - **Secure Servers:** Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations. - **Encrypted Sync:** One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised. - **Attestation and Open Code:** We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public. - **Open Source LLM:** Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased. #### Personal and Work Use Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe. #### Local v Cloud Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds. #### Why the Maple name? Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment. #### Join the Waitlist Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. [Join our waitlist today to be among the first to experience the power of private AI chat.](https://trymaple.ai) [](https://trymaple.ai/waitlist)
@ df173277:4ec96708
2025-01-09 17:12:08> Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\ > [Join the waitlist to get early access.](https://trymaple.ai) We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI. Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations. #### Building a Private Foundation Maple is built on our flagship product, [OpenSecret](https://opensecret.cloud), a backend platform for app developers that turns private encryption on by default. [The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do.](nostr:naddr1qvzqqqr4gupzphchxfm3ste32hfhkvczzxapme9gz5qvqtget6tylyd7wa8vjecgqqe5jmn5wfhkgatrd9hxwt20wpjku5m9vdex2apdw35x2tt9de3hy7tsw3jkgttzv93kketwvskhgur5w9nx5h52tpj) We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win. #### The Power of Encrypted AI Chat AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short. Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us. #### Technical Overview So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects: - **Private Key:** Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data. - **Secure Servers:** Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations. - **Encrypted Sync:** One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised. - **Attestation and Open Code:** We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public. - **Open Source LLM:** Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased. #### Personal and Work Use Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe. #### Local v Cloud Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds. #### Why the Maple name? Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment. #### Join the Waitlist Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. [Join our waitlist today to be among the first to experience the power of private AI chat.](https://trymaple.ai) [](https://trymaple.ai/waitlist) @ df173277:4ec96708
2025-01-09 17:02:52> OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. [Join our waitlist to get early access.](https://opensecret.cloud) In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion. Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online? Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches? > Cryptography at scale is hard. #### The Cloud The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers. The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage. > Private key encryption needs a UX upgrade. ## Enter OpenSecret OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute. Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.  ### Private Key Management Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone. OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account. The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.  ### Encrypted Sync With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go. The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them. ### Private AI Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything. OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk. **Check out Maple AI**\ Try private AI for yourself! We built an app built with this service called [Maple AI](https://trymaple.ai). It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. [Learn more about Maple AI - Private chat in the announcement post.](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/)  ### Confidential Compute Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave. It's the new version of that lock on your web browser. When you see it, you know you're secure.  #### **But do we want our secrets to be open?** OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable. On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data. > Don't trust, verify. ### **Join the Movement** We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, [send us a message to get early access.](https://opensecret.cloud) Users and companies deserve better encryption and privacy.\ Together, let's make that a reality. [](https://opensecret.cloud)
@ df173277:4ec96708
2025-01-09 17:02:52> OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. [Join our waitlist to get early access.](https://opensecret.cloud) In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion. Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online? Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches? > Cryptography at scale is hard. #### The Cloud The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers. The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage. > Private key encryption needs a UX upgrade. ## Enter OpenSecret OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute. Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.  ### Private Key Management Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone. OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account. The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.  ### Encrypted Sync With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go. The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them. ### Private AI Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything. OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk. **Check out Maple AI**\ Try private AI for yourself! We built an app built with this service called [Maple AI](https://trymaple.ai). It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. [Learn more about Maple AI - Private chat in the announcement post.](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/)  ### Confidential Compute Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave. It's the new version of that lock on your web browser. When you see it, you know you're secure.  #### **But do we want our secrets to be open?** OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable. On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data. > Don't trust, verify. ### **Join the Movement** We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, [send us a message to get early access.](https://opensecret.cloud) Users and companies deserve better encryption and privacy.\ Together, let's make that a reality. [](https://opensecret.cloud) @ f33c8a96:5ec6f741
2025-01-09 16:22:24<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-4.mp4" type="video/mp4"/> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-4.webm" type="video/webm"/> </video></div> # CSS Fundamentals: Styling Your First Webpage ## Introduction In our previous lesson, we created the structure of our webpage with HTML. Now, we'll learn how to style it using CSS (Cascading Style Sheets). While HTML provides the bones of our webpage, CSS adds the visual presentation - the colors, layouts, spacing, and overall aesthetics. ## What is CSS? ### Definition CSS (Cascading Style Sheets) is a stylesheet language that controls the visual presentation of HTML documents. Think of it like the paint, decorations, and interior design of a house - it determines how everything looks and is arranged. ### Key Concepts 1. **Styling Capabilities** - Fonts and typography - Colors and backgrounds - Margins and padding - Element sizes - Visual effects - Layout and positioning 2. **Cascading Nature** - Styles can be inherited from parent elements - Multiple styles can apply to the same element - Specificity determines which styles take precedence - Styles "cascade" down through your document ## Basic CSS Syntax ```css selector { property: value; } ``` ### Example: ```css h1 { color: blue; font-size: 24px; margin-bottom: 20px; } ``` ## Connecting CSS to HTML ### Method 1: External Stylesheet (Recommended) ```html <link rel="stylesheet" href="style.css"> ``` ### Method 2: Internal CSS ```html <style> h1 { color: blue; } </style> ``` ### Method 3: Inline CSS (Use Sparingly) ```html <h1 style="color: blue;">Title</h1> ``` ## The Box Model Every HTML element is treated as a box in CSS, with: ``` ┌──────────────────────┐ │ Margin │ │ ┌──────────────┐ │ │ │ Border │ │ │ │ ┌──────────┐ │ │ │ │ │ Padding │ │ │ │ │ │ ┌──────┐ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │Content│ │ │ │ │ │ │ │ │ │ │ │ │ │ │ └──────┘ │ │ │ │ │ └──────────┘ │ │ │ └──────────────┘ │ └──────────────────────┘ ``` - **Content**: The actual content of the element - **Padding**: Space between content and border - **Border**: The border around the padding - **Margin**: Space outside the border ## CSS Units ### Absolute Units - `px` - pixels - `pt` - points - `cm` - centimeters - `mm` - millimeters - `in` - inches ### Relative Units - `%` - percentage relative to parent - `em` - relative to font-size - `rem` - relative to root font-size - `vh` - viewport height - `vw` - viewport width ## Practical Example: Styling Our Webpage ### 1. Basic Page Setup ```css body { min-height: 100vh; margin: 0; font-family: Arial, sans-serif; background-color: #f0f0f0; display: flex; flex-direction: column; } ``` ### 2. Header Styling ```css header { background-color: #333; color: white; padding: 20px; text-align: center; } ``` ### 3. Main Content Area ```css main { max-width: 800px; margin: 0 auto; padding: 20px; flex: 1; } ``` ### 4. Footer Styling ```css footer { background-color: #333; color: white; padding: 10px; text-align: center; } ``` ## Layout with Flexbox ### Basic Concept Flexbox is a modern layout system that makes it easier to create flexible, responsive layouts. ### Key Properties ```css .container { display: flex; flex-direction: row | column; justify-content: center | space-between | space-around; align-items: center | flex-start | flex-end; } ``` ### Common Use Cases 1. Centering content 2. Creating navigation bars 3. Building responsive layouts 4. Equal-height columns 5. Dynamic spacing ## Best Practices ### 1. Organization - Use consistent naming conventions - Group related styles together - Comment your code for clarity - Keep selectors simple and specific ### 2. Performance - Avoid unnecessary specificity - Use shorthand properties when possible - Minimize redundant code - Consider load time impact ### 3. Maintainability - Use external stylesheets - Follow a consistent formatting style - Break large stylesheets into logical files - Document important design decisions ## Debugging CSS ### Common Tools 1. Browser Developer Tools - Element inspector - Style inspector - Box model viewer ### Common Issues 1. Specificity conflicts 2. Inheritance problems 3. Box model confusion 4. Flexbox alignment issues ## Exercises ### 1. Style Modifications Try modifying these properties in your stylesheet: ```css /* Change colors */ header { background-color: #4a90e2; } /* Adjust spacing */ main { padding: 40px; } /* Modify typography */ h1 { font-size: 32px; font-weight: bold; } ``` ### 2. Layout Challenge Create a card layout using Flexbox: ```css .card-container { display: flex; justify-content: space-between; gap: 20px; } .card { flex: 1; padding: 20px; background: white; border-radius: 8px; box-shadow: 0 2px 4px rgba(0,0,0,0.1); } ``` ## Additional Resources ### Learning Tools 1. [Flexbox Froggy](https://flexboxfroggy.com/) - Interactive Flexbox learning game 2. [CSS-Tricks](https://css-tricks.com) - Excellent CSS reference and tutorials 3. [MDN CSS Documentation](https://developer.mozilla.org/en-US/docs/Web/CSS) ### Practice Projects 1. Style your personal webpage 2. Create a responsive navigation menu 3. Build a flexible card layout 4. Design a custom button style Remember: CSS is both an art and a science. Don't be afraid to experiment and break things - that's how you'll learn the most. The key is to start simple and gradually add complexity as you become more comfortable with the basics. Next up, we'll dive into JavaScript to add interactivity to our webpage! 🚀
@ f33c8a96:5ec6f741
2025-01-09 16:22:24<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-4.mp4" type="video/mp4"/> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-4.webm" type="video/webm"/> </video></div> # CSS Fundamentals: Styling Your First Webpage ## Introduction In our previous lesson, we created the structure of our webpage with HTML. Now, we'll learn how to style it using CSS (Cascading Style Sheets). While HTML provides the bones of our webpage, CSS adds the visual presentation - the colors, layouts, spacing, and overall aesthetics. ## What is CSS? ### Definition CSS (Cascading Style Sheets) is a stylesheet language that controls the visual presentation of HTML documents. Think of it like the paint, decorations, and interior design of a house - it determines how everything looks and is arranged. ### Key Concepts 1. **Styling Capabilities** - Fonts and typography - Colors and backgrounds - Margins and padding - Element sizes - Visual effects - Layout and positioning 2. **Cascading Nature** - Styles can be inherited from parent elements - Multiple styles can apply to the same element - Specificity determines which styles take precedence - Styles "cascade" down through your document ## Basic CSS Syntax ```css selector { property: value; } ``` ### Example: ```css h1 { color: blue; font-size: 24px; margin-bottom: 20px; } ``` ## Connecting CSS to HTML ### Method 1: External Stylesheet (Recommended) ```html <link rel="stylesheet" href="style.css"> ``` ### Method 2: Internal CSS ```html <style> h1 { color: blue; } </style> ``` ### Method 3: Inline CSS (Use Sparingly) ```html <h1 style="color: blue;">Title</h1> ``` ## The Box Model Every HTML element is treated as a box in CSS, with: ``` ┌──────────────────────┐ │ Margin │ │ ┌──────────────┐ │ │ │ Border │ │ │ │ ┌──────────┐ │ │ │ │ │ Padding │ │ │ │ │ │ ┌──────┐ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │Content│ │ │ │ │ │ │ │ │ │ │ │ │ │ │ └──────┘ │ │ │ │ │ └──────────┘ │ │ │ └──────────────┘ │ └──────────────────────┘ ``` - **Content**: The actual content of the element - **Padding**: Space between content and border - **Border**: The border around the padding - **Margin**: Space outside the border ## CSS Units ### Absolute Units - `px` - pixels - `pt` - points - `cm` - centimeters - `mm` - millimeters - `in` - inches ### Relative Units - `%` - percentage relative to parent - `em` - relative to font-size - `rem` - relative to root font-size - `vh` - viewport height - `vw` - viewport width ## Practical Example: Styling Our Webpage ### 1. Basic Page Setup ```css body { min-height: 100vh; margin: 0; font-family: Arial, sans-serif; background-color: #f0f0f0; display: flex; flex-direction: column; } ``` ### 2. Header Styling ```css header { background-color: #333; color: white; padding: 20px; text-align: center; } ``` ### 3. Main Content Area ```css main { max-width: 800px; margin: 0 auto; padding: 20px; flex: 1; } ``` ### 4. Footer Styling ```css footer { background-color: #333; color: white; padding: 10px; text-align: center; } ``` ## Layout with Flexbox ### Basic Concept Flexbox is a modern layout system that makes it easier to create flexible, responsive layouts. ### Key Properties ```css .container { display: flex; flex-direction: row | column; justify-content: center | space-between | space-around; align-items: center | flex-start | flex-end; } ``` ### Common Use Cases 1. Centering content 2. Creating navigation bars 3. Building responsive layouts 4. Equal-height columns 5. Dynamic spacing ## Best Practices ### 1. Organization - Use consistent naming conventions - Group related styles together - Comment your code for clarity - Keep selectors simple and specific ### 2. Performance - Avoid unnecessary specificity - Use shorthand properties when possible - Minimize redundant code - Consider load time impact ### 3. Maintainability - Use external stylesheets - Follow a consistent formatting style - Break large stylesheets into logical files - Document important design decisions ## Debugging CSS ### Common Tools 1. Browser Developer Tools - Element inspector - Style inspector - Box model viewer ### Common Issues 1. Specificity conflicts 2. Inheritance problems 3. Box model confusion 4. Flexbox alignment issues ## Exercises ### 1. Style Modifications Try modifying these properties in your stylesheet: ```css /* Change colors */ header { background-color: #4a90e2; } /* Adjust spacing */ main { padding: 40px; } /* Modify typography */ h1 { font-size: 32px; font-weight: bold; } ``` ### 2. Layout Challenge Create a card layout using Flexbox: ```css .card-container { display: flex; justify-content: space-between; gap: 20px; } .card { flex: 1; padding: 20px; background: white; border-radius: 8px; box-shadow: 0 2px 4px rgba(0,0,0,0.1); } ``` ## Additional Resources ### Learning Tools 1. [Flexbox Froggy](https://flexboxfroggy.com/) - Interactive Flexbox learning game 2. [CSS-Tricks](https://css-tricks.com) - Excellent CSS reference and tutorials 3. [MDN CSS Documentation](https://developer.mozilla.org/en-US/docs/Web/CSS) ### Practice Projects 1. Style your personal webpage 2. Create a responsive navigation menu 3. Build a flexible card layout 4. Design a custom button style Remember: CSS is both an art and a science. Don't be afraid to experiment and break things - that's how you'll learn the most. The key is to start simple and gradually add complexity as you become more comfortable with the basics. Next up, we'll dive into JavaScript to add interactivity to our webpage! 🚀 @ f33c8a96:5ec6f741
2025-01-09 16:20:27<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-3.mp4" type="video/mp4"/> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-3.webm" type="video/webm"/> </video></div> ## What is HTML? HTML (HyperText Markup Language) is the foundation of all webpages. Think of it as the framing of a house - it provides the basic structure that everything else builds upon. ### Key Concepts - HTML is a markup language, not a programming language - It tells browsers how to structure web content - Every HTML element is like a building block - Browsers interpret HTML to display content ## The Building Analogy When building a webpage, think of it like constructing a house: - **HTML**: The framing and structure (walls, rooms, layout) - **CSS**: The design elements (paint, decorations, styling) - **JavaScript**: The functionality (plumbing, electrical, moving parts) ## Basic HTML Structure ### 1. HTML Boilerplate Every webpage starts with a basic template: ```html <!DOCTYPE html> <html> <head> <meta charset="UTF-8"> <meta name="viewport" content="width=device-width, initial-scale=1.0"> <title>Your Page Title</title> </head> <body> <!-- Your content goes here --> </body> </html> ``` ### 2. Understanding the Parts - `<!DOCTYPE html>`: Tells browsers this is an HTML5 document - `<html>`: The root element of the page - `<head>`: Contains metadata about the document - `<body>`: Contains the visible content ## Essential HTML Elements ### 1. Headings HTML has six levels of headings: ```html <h1>Main Title</h1> <h2>Subtitle</h2> <h3>Section Header</h3> <!-- ... --> <h6>Smallest Heading</h6> ``` ### 2. Paragraphs ```html <p>This is a paragraph of text. It can contain as much text as you need.</p> ``` ### 3. Images ```html <img src="path-to-image.jpg" alt="Description of image" width="300"> ``` ### 4. Links ```html <a href="https://example.com">Click here</a> ``` ## HTML Attributes Attributes provide additional information or modify HTML elements: ```html <tag attribute="value">Content</tag> ``` Common attributes: - `src`: Source path for images - `href`: Destination for links - `alt`: Alternative text for images - `class`: CSS class names - `id`: Unique identifier - `style`: Inline CSS styles ## Semantic HTML ### What is Semantic HTML? Semantic HTML uses meaningful tags that describe their content's purpose. This improves: - Accessibility - SEO (Search Engine Optimization) - Code readability - Maintainability ### Common Semantic Elements ```html <header> <!-- Site header content --> </header> <nav> <!-- Navigation menu --> </nav> <main> <!-- Main content --> <article> <!-- Self-contained content --> </article> <section> <!-- Grouped content --> </section> </main> <footer> <!-- Site footer content --> </footer> ``` ### Non-Semantic vs Semantic Example Instead of: ```html <div class="header"> <div class="navigation"> <div class="nav-item">Home</div> </div> </div> ``` Use: ```html <header> <nav> <a href="/">Home</a> </nav> </header> ``` ## Building Your First Webpage ### 1. Basic Structure ```html <!DOCTYPE html> <html> <head> <title>My First Webpage</title> </head> <body> <header> <h1>Welcome to My First Webpage!</h1> </header> <main> <section> <h2>About Me</h2> <p>Hi, I'm learning web development with PlebDevs!</p> </section> <section> <h2>My Interests</h2> <p>I'm interested in Bitcoin, programming, and building cool stuff!</p> </section> </main> <footer> <p>Created by [Your Name] - 2024</p> </footer> </body> </html> ``` ## Best Practices ### 1. Structure - Use proper indentation - Keep code organized and readable - Use semantic elements when possible - Include all required elements (`DOCTYPE`, `html`, `head`, `body`) ### 2. Content - Use appropriate heading levels (start with `h1`) - Write descriptive `alt` text for images - Keep content meaningful and organized - Use comments to explain complex sections ### 3. Accessibility - Use semantic HTML elements - Provide alternative text for images - Maintain a logical heading structure - Ensure content makes sense when read linearly ## Common Issues and Solutions ### Problem: Images Not Loading ```html <!-- Wrong --> <img src="image.jpg"> <!-- Right --> <img src="./images/image.jpg" alt="Description"> ``` ### Problem: Links Not Working ```html <!-- Wrong --> <a>Click here</a> <!-- Right --> <a href="https://example.com">Click here</a> ``` ## Next Steps 1. **Practice Building** - Create a personal webpage about yourself - Include different types of content (text, images, links) - Use semantic HTML elements 2. **Experiment with Structure** - Try different layouts - Use various HTML elements - Pay attention to semantic meaning 3. **Prepare for CSS** - Think about how you want your page to look - Consider what styles you'll want to add - Plan your layout structure ## Exercise: Create Your Profile Page Try creating a simple profile page using what you've learned: 1. Use the HTML boilerplate 2. Add a header with your name 3. Include an "About Me" section 4. Add a photo (if you want) 5. List your interests or goals 6. Add a footer with contact information Remember to: - Use semantic HTML - Include appropriate headings - Add descriptive alt text for images - Keep your code clean and well-organized ## Additional Resources - [MDN HTML Guide](https://developer.mozilla.org/en-US/docs/Web/HTML) - [HTML5 Doctor (Semantic Elements)](http://html5doctor.com/) - [W3Schools HTML Tutorial](https://www.w3schools.com/html/) Remember: HTML is the foundation of web development. Take time to understand these basics well, as they'll serve as the building blocks for everything else you'll learn. Happy coding! 🚀
@ f33c8a96:5ec6f741
2025-01-09 16:20:27<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-3.mp4" type="video/mp4"/> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-3.webm" type="video/webm"/> </video></div> ## What is HTML? HTML (HyperText Markup Language) is the foundation of all webpages. Think of it as the framing of a house - it provides the basic structure that everything else builds upon. ### Key Concepts - HTML is a markup language, not a programming language - It tells browsers how to structure web content - Every HTML element is like a building block - Browsers interpret HTML to display content ## The Building Analogy When building a webpage, think of it like constructing a house: - **HTML**: The framing and structure (walls, rooms, layout) - **CSS**: The design elements (paint, decorations, styling) - **JavaScript**: The functionality (plumbing, electrical, moving parts) ## Basic HTML Structure ### 1. HTML Boilerplate Every webpage starts with a basic template: ```html <!DOCTYPE html> <html> <head> <meta charset="UTF-8"> <meta name="viewport" content="width=device-width, initial-scale=1.0"> <title>Your Page Title</title> </head> <body> <!-- Your content goes here --> </body> </html> ``` ### 2. Understanding the Parts - `<!DOCTYPE html>`: Tells browsers this is an HTML5 document - `<html>`: The root element of the page - `<head>`: Contains metadata about the document - `<body>`: Contains the visible content ## Essential HTML Elements ### 1. Headings HTML has six levels of headings: ```html <h1>Main Title</h1> <h2>Subtitle</h2> <h3>Section Header</h3> <!-- ... --> <h6>Smallest Heading</h6> ``` ### 2. Paragraphs ```html <p>This is a paragraph of text. It can contain as much text as you need.</p> ``` ### 3. Images ```html <img src="path-to-image.jpg" alt="Description of image" width="300"> ``` ### 4. Links ```html <a href="https://example.com">Click here</a> ``` ## HTML Attributes Attributes provide additional information or modify HTML elements: ```html <tag attribute="value">Content</tag> ``` Common attributes: - `src`: Source path for images - `href`: Destination for links - `alt`: Alternative text for images - `class`: CSS class names - `id`: Unique identifier - `style`: Inline CSS styles ## Semantic HTML ### What is Semantic HTML? Semantic HTML uses meaningful tags that describe their content's purpose. This improves: - Accessibility - SEO (Search Engine Optimization) - Code readability - Maintainability ### Common Semantic Elements ```html <header> <!-- Site header content --> </header> <nav> <!-- Navigation menu --> </nav> <main> <!-- Main content --> <article> <!-- Self-contained content --> </article> <section> <!-- Grouped content --> </section> </main> <footer> <!-- Site footer content --> </footer> ``` ### Non-Semantic vs Semantic Example Instead of: ```html <div class="header"> <div class="navigation"> <div class="nav-item">Home</div> </div> </div> ``` Use: ```html <header> <nav> <a href="/">Home</a> </nav> </header> ``` ## Building Your First Webpage ### 1. Basic Structure ```html <!DOCTYPE html> <html> <head> <title>My First Webpage</title> </head> <body> <header> <h1>Welcome to My First Webpage!</h1> </header> <main> <section> <h2>About Me</h2> <p>Hi, I'm learning web development with PlebDevs!</p> </section> <section> <h2>My Interests</h2> <p>I'm interested in Bitcoin, programming, and building cool stuff!</p> </section> </main> <footer> <p>Created by [Your Name] - 2024</p> </footer> </body> </html> ``` ## Best Practices ### 1. Structure - Use proper indentation - Keep code organized and readable - Use semantic elements when possible - Include all required elements (`DOCTYPE`, `html`, `head`, `body`) ### 2. Content - Use appropriate heading levels (start with `h1`) - Write descriptive `alt` text for images - Keep content meaningful and organized - Use comments to explain complex sections ### 3. Accessibility - Use semantic HTML elements - Provide alternative text for images - Maintain a logical heading structure - Ensure content makes sense when read linearly ## Common Issues and Solutions ### Problem: Images Not Loading ```html <!-- Wrong --> <img src="image.jpg"> <!-- Right --> <img src="./images/image.jpg" alt="Description"> ``` ### Problem: Links Not Working ```html <!-- Wrong --> <a>Click here</a> <!-- Right --> <a href="https://example.com">Click here</a> ``` ## Next Steps 1. **Practice Building** - Create a personal webpage about yourself - Include different types of content (text, images, links) - Use semantic HTML elements 2. **Experiment with Structure** - Try different layouts - Use various HTML elements - Pay attention to semantic meaning 3. **Prepare for CSS** - Think about how you want your page to look - Consider what styles you'll want to add - Plan your layout structure ## Exercise: Create Your Profile Page Try creating a simple profile page using what you've learned: 1. Use the HTML boilerplate 2. Add a header with your name 3. Include an "About Me" section 4. Add a photo (if you want) 5. List your interests or goals 6. Add a footer with contact information Remember to: - Use semantic HTML - Include appropriate headings - Add descriptive alt text for images - Keep your code clean and well-organized ## Additional Resources - [MDN HTML Guide](https://developer.mozilla.org/en-US/docs/Web/HTML) - [HTML5 Doctor (Semantic Elements)](http://html5doctor.com/) - [W3Schools HTML Tutorial](https://www.w3schools.com/html/) Remember: HTML is the foundation of web development. Take time to understand these basics well, as they'll serve as the building blocks for everything else you'll learn. Happy coding! 🚀 @ f33c8a96:5ec6f741
2025-01-09 16:18:40<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-2.mp4" type="video/mp4"/> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-2.webm" type="video/webm"/> </video></div> # Setting Up Git and GitHub: A Developer's Foundation ## Lesson Overview In this lesson, we'll establish one of the most important foundations of your development journey: version control with Git and GitHub. This knowledge will enable you to track your code, back it up in the cloud, and start building your developer portfolio. ## Prerequisites - Visual Studio Code installed - Terminal/Command Line basics - GitHub account (we'll create one in this lesson) ## Key Learning Objectives - Understand what Git and GitHub are and why they're essential - Set up Git locally and connect it to GitHub - Learn basic Git commands and workflow - Create your first repository and commit - Establish good Git habits for your developer journey ## What is Git and GitHub? ### Git: Your Local Version Control - A version control system that tracks code changes over time - Prevents accidental overwrites of your work - Enables multiple developers to work on the same project safely - Runs locally on your machine ### GitHub: Your Code in the Cloud - A web-based platform that extends Git - Cloud storage for your code repositories - Enables code sharing and collaboration - Includes features like: - Issue tracking - Pull requests - Project management tools - Code review capabilities ## Why Use GitHub? ### 1. Portfolio Building - Acts as your "proof of work" as a developer - Shows your coding activity through contribution graphs - Demonstrates your consistency and dedication - Serves as a public showcase of your projects ### 2. Collaboration and Learning - Access millions of open-source projects - Learn from other developers' code - Contribute to real-world projects - Get feedback on your code - Work effectively in teams ### 3. Code Safety and Access - All your code is safely stored in the cloud - Access your projects from anywhere - Never lose your work due to computer issues ## Essential GitHub Terminology | Term | Definition | |------|------------| | Repository (Repo) | A folder containing your project files and version history | | Commit | A saved change or addition to your code | | Staging | Marking changes to be included in your next commit | | Push | Sending your local commits to GitHub | | Branch | A separate version of your code for new features or experiments | | Pull Request (PR) | A request to merge changes from one branch to another | | Clone | Creating a local copy of a remote repository | | Fork | Creating your own copy of someone else's repository | ## Hands-on Practice ### Setting Up Git 1. Install Git from https://git-scm.com/downloads 2. Configure your identity: ```bash git config --global user.name "Your Name" git config --global user.email "your.email@example.com" ``` ### Your First Repository 1. Create a new repository on GitHub named "hello-world" 2. Initialize Git locally: ```bash git init git add . git commit -m "My first commit" git remote add origin <your-repository-url> git push -u origin main ``` ## Basic Git Workflow Quick Reference ### Pushing Code to GitHub ```bash # 1. Stage your changes git add . # 2. Commit your changes with a message git commit -m "Describe your changes here" # 3. Push to GitHub git push ``` ### Getting Code from GitHub ```bash # If you already have the repository locally: git pull # If you need to download a repository: git clone https://github.com/username/repository.git ``` ## Building Good Habits ### Daily Git Practice - Make it a goal to push code every day - Even small changes count - Use your GitHub contribution graph as motivation - Track your progress over time ### Best Practices 1. Commit often with clear messages 2. Pull before you start working 3. Push your changes when you finish 4. Keep each project in its own repository 5. Include README files to explain your projects ## Common Issues and Solutions ### "No upstream branch" Error If you see this error when pushing: ```bash git push --set-upstream origin main ``` ### Changes Not Showing Up 1. Check if changes are staged: ```bash git status ``` 2. Make sure you've committed: ```bash git commit -m "Your message" ``` 3. Verify you've pushed: ```bash git push ``` ## Exercise: Start Your Journey 1. Create your GitHub account if you haven't already 2. Set up Git locally using the commands we covered 3. Create your first repository named "hello-world" 4. Make your first commit 5. Push your code to GitHub 6. Make a habit of pushing code daily ## Additional Resources - [GitHub Documentation](https://docs.github.com) - [Git Documentation](https://git-scm.com/doc) - Practice with [GitHub Learning Lab](https://lab.github.com) ## Next Steps - Start tracking all your code projects with Git - Begin building your portfolio on GitHub - Join the open-source community - Collaborate with other developers Remember: Every developer started where you are now. The key is consistency and persistence. Make pushing code to GitHub a daily habit, and you'll be amazed at your progress over time. Happy coding! 🚀
@ f33c8a96:5ec6f741
2025-01-09 16:18:40<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-2.mp4" type="video/mp4"/> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-2.webm" type="video/webm"/> </video></div> # Setting Up Git and GitHub: A Developer's Foundation ## Lesson Overview In this lesson, we'll establish one of the most important foundations of your development journey: version control with Git and GitHub. This knowledge will enable you to track your code, back it up in the cloud, and start building your developer portfolio. ## Prerequisites - Visual Studio Code installed - Terminal/Command Line basics - GitHub account (we'll create one in this lesson) ## Key Learning Objectives - Understand what Git and GitHub are and why they're essential - Set up Git locally and connect it to GitHub - Learn basic Git commands and workflow - Create your first repository and commit - Establish good Git habits for your developer journey ## What is Git and GitHub? ### Git: Your Local Version Control - A version control system that tracks code changes over time - Prevents accidental overwrites of your work - Enables multiple developers to work on the same project safely - Runs locally on your machine ### GitHub: Your Code in the Cloud - A web-based platform that extends Git - Cloud storage for your code repositories - Enables code sharing and collaboration - Includes features like: - Issue tracking - Pull requests - Project management tools - Code review capabilities ## Why Use GitHub? ### 1. Portfolio Building - Acts as your "proof of work" as a developer - Shows your coding activity through contribution graphs - Demonstrates your consistency and dedication - Serves as a public showcase of your projects ### 2. Collaboration and Learning - Access millions of open-source projects - Learn from other developers' code - Contribute to real-world projects - Get feedback on your code - Work effectively in teams ### 3. Code Safety and Access - All your code is safely stored in the cloud - Access your projects from anywhere - Never lose your work due to computer issues ## Essential GitHub Terminology | Term | Definition | |------|------------| | Repository (Repo) | A folder containing your project files and version history | | Commit | A saved change or addition to your code | | Staging | Marking changes to be included in your next commit | | Push | Sending your local commits to GitHub | | Branch | A separate version of your code for new features or experiments | | Pull Request (PR) | A request to merge changes from one branch to another | | Clone | Creating a local copy of a remote repository | | Fork | Creating your own copy of someone else's repository | ## Hands-on Practice ### Setting Up Git 1. Install Git from https://git-scm.com/downloads 2. Configure your identity: ```bash git config --global user.name "Your Name" git config --global user.email "your.email@example.com" ``` ### Your First Repository 1. Create a new repository on GitHub named "hello-world" 2. Initialize Git locally: ```bash git init git add . git commit -m "My first commit" git remote add origin <your-repository-url> git push -u origin main ``` ## Basic Git Workflow Quick Reference ### Pushing Code to GitHub ```bash # 1. Stage your changes git add . # 2. Commit your changes with a message git commit -m "Describe your changes here" # 3. Push to GitHub git push ``` ### Getting Code from GitHub ```bash # If you already have the repository locally: git pull # If you need to download a repository: git clone https://github.com/username/repository.git ``` ## Building Good Habits ### Daily Git Practice - Make it a goal to push code every day - Even small changes count - Use your GitHub contribution graph as motivation - Track your progress over time ### Best Practices 1. Commit often with clear messages 2. Pull before you start working 3. Push your changes when you finish 4. Keep each project in its own repository 5. Include README files to explain your projects ## Common Issues and Solutions ### "No upstream branch" Error If you see this error when pushing: ```bash git push --set-upstream origin main ``` ### Changes Not Showing Up 1. Check if changes are staged: ```bash git status ``` 2. Make sure you've committed: ```bash git commit -m "Your message" ``` 3. Verify you've pushed: ```bash git push ``` ## Exercise: Start Your Journey 1. Create your GitHub account if you haven't already 2. Set up Git locally using the commands we covered 3. Create your first repository named "hello-world" 4. Make your first commit 5. Push your code to GitHub 6. Make a habit of pushing code daily ## Additional Resources - [GitHub Documentation](https://docs.github.com) - [Git Documentation](https://git-scm.com/doc) - Practice with [GitHub Learning Lab](https://lab.github.com) ## Next Steps - Start tracking all your code projects with Git - Begin building your portfolio on GitHub - Join the open-source community - Collaborate with other developers Remember: Every developer started where you are now. The key is consistency and persistence. Make pushing code to GitHub a daily habit, and you'll be amazed at your progress over time. Happy coding! 🚀 @ f33c8a96:5ec6f741
2025-01-08 20:27:23<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-0.mp4" type="video/mp4"/> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-0.webm" type="video/webm"/> </video></div> # Welcome to PlebDevs Starter Course ## Course Mission Welcome to the PlebDevs starter course! I'm Austin, the founder of PlebDevs, and I'll be walking you through this short intro starter course that will get you up and running and interacting with the rest of the content on the platform. If you're here, I'm assuming you're new to coding or just starting out. If you already have experience and have your bearings down, there's lots more intermediate and advanced content on the platform. This course is designed for absolute beginners. ## Course Goals ### Overall PlebDevs Goals 1. Learn how to code 2. Build Bitcoin/Lightning/Nostr apps 3. Become a developer This is a big journey with a lot of pieces and things to learn. The starter course is going to get you on that path as quickly as possible and make it a smooth journey. ### Starter Course Objectives 1. Give you an easy, high-level overview of the dev journey 2. Get you set up and comfortable in a development environment where you'll write and ship code 3. Give you basic experience in the languages covered in our courses and workshops There's lots of material out there that will just tell you exactly what to do and not explain why but I want you to actually understand for yourself. I want you to have a good mental model of what this journey is going to be like, what it's going to be like actually writing and pushing code. And then we're going to start getting our hands dirty and gain real experience. ## What is a PlebDev? ### Origins and Philosophy I started using the term "PlebDev" a few years ago to describe a unique approach to learning development in the Bitcoin space. It represents: - **Inclusive Learning**: Anyone can become a developer, regardless of background - **Growth Mindset**: Embracing the journey from beginner to professional - **Practical Focus**: Emphasizing real-world application development - **Community Support**: Learning and growing together ### Key Characteristics - 🌱 **Growth-Focused**: PlebDevs are always learning and improving - 🎯 **App-Centric**: Focus on building applications rather than protocol development - 🆕 **Embrace Being New**: Being a new developer is infinitely better than being on the sidelines - 🤝 **Community-Driven**: Bitcoin/Lightning/Nostr ecosystem needs more plebdevs like you! ## Our Learning Approach ### Core Principles 1. **Lower Barriers** - Simplify complex concepts - Focus on practical understanding - Build confidence through action 2. **Project-Based Learning** - Learn by doing - Create real applications - Build a portfolio as you learn 3. **MVP (Minimum Viable Product) Focus** - Start with core functionality - Get things working first - Iterate and improve 4. **Actionable Knowledge** - Focus on the 20% that delivers 80% of results - Learn what you can use right away - Build practical skills ### Teaching Methods - Detailed concept breakdowns - Line-by-line code explanations - Interactive learning - 1:1 support available - Community-driven progress ## Course Structure ### The Learning Path Instead of the traditional bottom-up approach, we use a project-focused method: ``` 🏔️ Advanced Skills 🏔️ Projects & Practice 🏔️ Core Concepts 🏔️ Development Environment 🏔️ Getting Started ``` We'll create checkpoints through projects, allowing you to: - Verify your understanding - Build your portfolio - See real progress - Have reference points for review ## Student Expectations ### What We Expect From You - **High Agency**: Take ownership of your learning journey - **Active Participation**: Engage with the material and community - **Persistence**: Push through challenges - **Curiosity**: Ask questions and explore concepts ### What You Can Expect From Us - Clear, practical instruction - Comprehensive support - Real-world applications - Community backing ## Getting Started ### Next Steps 1. Ensure you're ready to commit to learning 2. Set up your development environment (next lesson) 3. Join our community 4. Start building! ## Resources and Support ### Where to Get Help - plebdevs.com ### Tips for Success 1. Push code daily, even if it is small. 2. Focus on understanding rather than memorizing. 3. Build projects that interest you. 4. Engage with the community. 5. Don't be afraid to ask questions. ## Remember You don't need to become a "10x developer" overnight. The goal is to start writing code, build useful things, and gradually improve. Every expert was once a beginner, and the journey of a thousand miles begins with a single line of code. Ready to begin? Let's dive into the next lesson where we'll set up your development environment! 🚀
@ f33c8a96:5ec6f741
2025-01-08 20:27:23<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-0.mp4" type="video/mp4"/> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-0.webm" type="video/webm"/> </video></div> # Welcome to PlebDevs Starter Course ## Course Mission Welcome to the PlebDevs starter course! I'm Austin, the founder of PlebDevs, and I'll be walking you through this short intro starter course that will get you up and running and interacting with the rest of the content on the platform. If you're here, I'm assuming you're new to coding or just starting out. If you already have experience and have your bearings down, there's lots more intermediate and advanced content on the platform. This course is designed for absolute beginners. ## Course Goals ### Overall PlebDevs Goals 1. Learn how to code 2. Build Bitcoin/Lightning/Nostr apps 3. Become a developer This is a big journey with a lot of pieces and things to learn. The starter course is going to get you on that path as quickly as possible and make it a smooth journey. ### Starter Course Objectives 1. Give you an easy, high-level overview of the dev journey 2. Get you set up and comfortable in a development environment where you'll write and ship code 3. Give you basic experience in the languages covered in our courses and workshops There's lots of material out there that will just tell you exactly what to do and not explain why but I want you to actually understand for yourself. I want you to have a good mental model of what this journey is going to be like, what it's going to be like actually writing and pushing code. And then we're going to start getting our hands dirty and gain real experience. ## What is a PlebDev? ### Origins and Philosophy I started using the term "PlebDev" a few years ago to describe a unique approach to learning development in the Bitcoin space. It represents: - **Inclusive Learning**: Anyone can become a developer, regardless of background - **Growth Mindset**: Embracing the journey from beginner to professional - **Practical Focus**: Emphasizing real-world application development - **Community Support**: Learning and growing together ### Key Characteristics - 🌱 **Growth-Focused**: PlebDevs are always learning and improving - 🎯 **App-Centric**: Focus on building applications rather than protocol development - 🆕 **Embrace Being New**: Being a new developer is infinitely better than being on the sidelines - 🤝 **Community-Driven**: Bitcoin/Lightning/Nostr ecosystem needs more plebdevs like you! ## Our Learning Approach ### Core Principles 1. **Lower Barriers** - Simplify complex concepts - Focus on practical understanding - Build confidence through action 2. **Project-Based Learning** - Learn by doing - Create real applications - Build a portfolio as you learn 3. **MVP (Minimum Viable Product) Focus** - Start with core functionality - Get things working first - Iterate and improve 4. **Actionable Knowledge** - Focus on the 20% that delivers 80% of results - Learn what you can use right away - Build practical skills ### Teaching Methods - Detailed concept breakdowns - Line-by-line code explanations - Interactive learning - 1:1 support available - Community-driven progress ## Course Structure ### The Learning Path Instead of the traditional bottom-up approach, we use a project-focused method: ``` 🏔️ Advanced Skills 🏔️ Projects & Practice 🏔️ Core Concepts 🏔️ Development Environment 🏔️ Getting Started ``` We'll create checkpoints through projects, allowing you to: - Verify your understanding - Build your portfolio - See real progress - Have reference points for review ## Student Expectations ### What We Expect From You - **High Agency**: Take ownership of your learning journey - **Active Participation**: Engage with the material and community - **Persistence**: Push through challenges - **Curiosity**: Ask questions and explore concepts ### What You Can Expect From Us - Clear, practical instruction - Comprehensive support - Real-world applications - Community backing ## Getting Started ### Next Steps 1. Ensure you're ready to commit to learning 2. Set up your development environment (next lesson) 3. Join our community 4. Start building! ## Resources and Support ### Where to Get Help - plebdevs.com ### Tips for Success 1. Push code daily, even if it is small. 2. Focus on understanding rather than memorizing. 3. Build projects that interest you. 4. Engage with the community. 5. Don't be afraid to ask questions. ## Remember You don't need to become a "10x developer" overnight. The goal is to start writing code, build useful things, and gradually improve. Every expert was once a beginner, and the journey of a thousand miles begins with a single line of code. Ready to begin? Let's dive into the next lesson where we'll set up your development environment! 🚀 @ bcea2b98:7ccef3c9
2025-01-08 18:22:00 originally posted at https://stacker.news/items/842405
@ bcea2b98:7ccef3c9
2025-01-08 18:22:00 originally posted at https://stacker.news/items/842405 @ 23b0e2f8:d8af76fc
2025-01-08 18:17:52## **Necessário** - Um Android que você não use mais (a câmera deve estar funcionando). - Um cartão microSD (opcional, usado apenas uma vez). - Um dispositivo para acompanhar seus fundos (provavelmente você já tem um). ## **Algumas coisas que você precisa saber** - O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele. - O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito. - A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal. --- ## **O tutorial será dividido em dois módulos:** - Módulo 1 - Criando uma carteira fria/assinador. - Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador. --- ## **No final, teremos:** - Uma carteira fria que também servirá como assinador. - Um dispositivo para acompanhar os fundos da carteira.  --- ## **Módulo 1 - Criando uma carteira fria/assinador** 1. Baixe o APK do Electrum na aba de **downloads** em <https://electrum.org/>. Fique à vontade para [verificar as assinaturas](https://electrum.readthedocs.io/en/latest/gpg-check.html) do software, garantindo sua autenticidade. 2. Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.  3. Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.  4. Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o **modo avião**.\ *(Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)*  5. Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.  6. No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. *(Aqui entra seu método pessoal de backup.)*  --- ## **Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.** 1. Criar uma carteira **somente leitura** em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em <https://electrum.org/> ou da própria Play Store. *(ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)* 2. Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção **Usar uma chave mestra**.  3. Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em **Carteira > Detalhes da carteira > Compartilhar chave mestra pública**.  4. Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los. 5. Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: **Carteira > Addresses/Coins**. 6. Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.  7. No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.  8. No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede. --- ## **Conclusão** **Pontos positivos do setup:** - **Simplicidade:** Basta um dispositivo Android antigo. - **Flexibilidade:** Funciona como uma ótima carteira fria, ideal para holders. **Pontos negativos do setup:** - **Padronização:** Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum. - **Interface:** A aparência do Electrum pode parecer antiquada para alguns usuários. Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: ***Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.*** Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível. ---
@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52## **Necessário** - Um Android que você não use mais (a câmera deve estar funcionando). - Um cartão microSD (opcional, usado apenas uma vez). - Um dispositivo para acompanhar seus fundos (provavelmente você já tem um). ## **Algumas coisas que você precisa saber** - O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele. - O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito. - A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal. --- ## **O tutorial será dividido em dois módulos:** - Módulo 1 - Criando uma carteira fria/assinador. - Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador. --- ## **No final, teremos:** - Uma carteira fria que também servirá como assinador. - Um dispositivo para acompanhar os fundos da carteira.  --- ## **Módulo 1 - Criando uma carteira fria/assinador** 1. Baixe o APK do Electrum na aba de **downloads** em <https://electrum.org/>. Fique à vontade para [verificar as assinaturas](https://electrum.readthedocs.io/en/latest/gpg-check.html) do software, garantindo sua autenticidade. 2. Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.  3. Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.  4. Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o **modo avião**.\ *(Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)*  5. Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.  6. No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. *(Aqui entra seu método pessoal de backup.)*  --- ## **Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.** 1. Criar uma carteira **somente leitura** em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em <https://electrum.org/> ou da própria Play Store. *(ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)* 2. Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção **Usar uma chave mestra**.  3. Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em **Carteira > Detalhes da carteira > Compartilhar chave mestra pública**.  4. Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los. 5. Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: **Carteira > Addresses/Coins**. 6. Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.  7. No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.  8. No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede. --- ## **Conclusão** **Pontos positivos do setup:** - **Simplicidade:** Basta um dispositivo Android antigo. - **Flexibilidade:** Funciona como uma ótima carteira fria, ideal para holders. **Pontos negativos do setup:** - **Padronização:** Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum. - **Interface:** A aparência do Electrum pode parecer antiquada para alguns usuários. Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: ***Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.*** Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível. --- @ dd664d5e:5633d319
2025-01-07 19:57:14## Hodling Bitcoin does not make you a capitalist I've noticed that Bitcoin-mindedness seems to lead some people to communistic thinking because it's a hard-limited form of capital. Marx, like most Bitcoiners, heavily discounted the possibility of economic growth or transformation changing the economy enough to undermine some minority's control of some form of capital. What few today understand, is that many of the Dirty Capitalists of Marx's era actually agreed with him; they were just disdainful of labor and worried that the workers finding out that Marxism is correct about the nature of capitalism would cause unrest. They were the original HFSP crowd. This was the basic idea, that Marx had, and that many Bitcoiners would agree with: > Capital is strictly limited and the people that control it can keep labor from attaining any, except when their labor is necessary. And, as we know, automation will make human labor increasingly unnecessary. ## The math doesn't check out  That underlies all of the calculations of "Well, if I just grab this Bitcoin wallet and hodl for twenty years, then it will grow in value to equal half of everything in existence and then I can just buy up half the planet and rule over everyone like a god." This is economic nonsense because it assumes that: 1) the value of all things remains static over time, 2) purchasing something with money gives you ownership of it, 3) people will always use that specific money (or any money, at all!) for all transactions, 4) there is no such thing as opportunity cost, 5) people will always value money more than any other thing, and therefore be willing to always trade it for anything else, 6) humans are passive, defenseless, and easy to rule over, 7) someone who is preoccupied with hodling an asset steadily and sharply rising in price would ever be emotionally ready to part with it. ## All monies can die. People use money for everything because it is easy, fast and cheap. If money becomes too precious or scarce, they will simply switch to using other things (as we saw with gold). Humans replace tools that aren't working well, with those that work better, and money is just another tool. Bitcoin is more divisible than gold, but that won't matter, if enough of it is held by too few. This is why there's a natural cap on the price of a money and why human productivity _in the here and now_ is not irrelevant or in vain.
@ dd664d5e:5633d319
2025-01-07 19:57:14## Hodling Bitcoin does not make you a capitalist I've noticed that Bitcoin-mindedness seems to lead some people to communistic thinking because it's a hard-limited form of capital. Marx, like most Bitcoiners, heavily discounted the possibility of economic growth or transformation changing the economy enough to undermine some minority's control of some form of capital. What few today understand, is that many of the Dirty Capitalists of Marx's era actually agreed with him; they were just disdainful of labor and worried that the workers finding out that Marxism is correct about the nature of capitalism would cause unrest. They were the original HFSP crowd. This was the basic idea, that Marx had, and that many Bitcoiners would agree with: > Capital is strictly limited and the people that control it can keep labor from attaining any, except when their labor is necessary. And, as we know, automation will make human labor increasingly unnecessary. ## The math doesn't check out  That underlies all of the calculations of "Well, if I just grab this Bitcoin wallet and hodl for twenty years, then it will grow in value to equal half of everything in existence and then I can just buy up half the planet and rule over everyone like a god." This is economic nonsense because it assumes that: 1) the value of all things remains static over time, 2) purchasing something with money gives you ownership of it, 3) people will always use that specific money (or any money, at all!) for all transactions, 4) there is no such thing as opportunity cost, 5) people will always value money more than any other thing, and therefore be willing to always trade it for anything else, 6) humans are passive, defenseless, and easy to rule over, 7) someone who is preoccupied with hodling an asset steadily and sharply rising in price would ever be emotionally ready to part with it. ## All monies can die. People use money for everything because it is easy, fast and cheap. If money becomes too precious or scarce, they will simply switch to using other things (as we saw with gold). Humans replace tools that aren't working well, with those that work better, and money is just another tool. Bitcoin is more divisible than gold, but that won't matter, if enough of it is held by too few. This is why there's a natural cap on the price of a money and why human productivity _in the here and now_ is not irrelevant or in vain. @ 207ad2a0:e7cca7b0
2025-01-07 03:46:04*Quick context: I wanted to check out Nostr's longform posts and this blog post seemed like a good one to try and mirror. It's originally from my [free to read/share attempt to write a novel](https://untitlednovel.dns7.top/contents/), but this post here is completely standalone - just describing how I used AI image generation to make a small piece of the work.* Hold on, put your pitchforks down - outside of using Grammerly & Emacs for grammatical corrections - not a single character was generated or modified by computers; a non-insignificant portion of my first draft originating on pen & paper. No AI is ~~weird and crazy~~ imaginative enough to write like I do. The only successful AI contribution you'll find is a single image, the map, which I heavily edited. This post will go over how I generated and modified an image using AI, which I believe brought some value to the work, and cover a few quick thoughts about AI towards the end. Let's be clear, I can't draw, but I wanted a map which I believed would improve the story I was working on. After getting abysmal results by prompting AI with text only I decided to use "Diffuse the Rest," a Stable Diffusion tool that allows you to provide a reference image + description to fine tune what you're looking for. I gave it this Microsoft Paint looking drawing:  and after a number of outputs, selected this one to work on:  The image is way better than the one I provided, but had I used it as is, I still feel it would have decreased the quality of my work instead of increasing it. After firing up Gimp I cropped out the top and bottom, expanded the ocean and separated the landmasses, then copied the top right corner of the large landmass to replace the bottom left that got cut off. Now we've got something that looks like concept art: not horrible, and gets the basic idea across, but it's still due for a lot more detail.  The next thing I did was add some texture to make it look more map like. I duplicated the layer in Gimp and applied the "Cartoon" filter to both for some texture. The top layer had a much lower effect strength to give it a more textured look, while the lower layer had a higher effect strength that looked a lot like mountains or other terrain features. Creating a layer mask allowed me to brush over spots to display the lower layer in certain areas, giving it some much needed features.  At this point I'd made it to where I felt it may improve the work instead of detracting from it - at least after labels and borders were added, but the colors seemed artificial and out of place. Luckily, however, this is when PhotoFunia could step in and apply a sketch effect to the image.  At this point I was pretty happy with how it was looking, it was close to what I envisioned and looked very visually appealing while still being a good way to portray information. All that was left was to make the white background transparent, add some minor details, and add the labels and borders. Below is the exact image I wound up using:  Overall, I'm very satisfied with how it turned out, and if you're working on a creative project, I'd recommend attempting something like this. It's not a central part of the work, but it improved the chapter a fair bit, and was doable despite lacking the talent and not intending to allocate a budget to my making of a free to read and share story. #### The AI Generated Elephant in the Room If you've read my non-fiction writing before, you'll know that I think AI will find its place around the skill floor as opposed to the skill ceiling. As you saw with my input, I have absolutely zero drawing talent, but with some elbow grease and an existing creative direction before and after generating an image I was able to get something well above what I could have otherwise accomplished. Outside of the lowest common denominators like stock photos for the sole purpose of a link preview being eye catching, however, I doubt AI will be wholesale replacing most creative works anytime soon. I can assure you that I tried numerous times to describe the map without providing a reference image, and if I used one of those outputs (or even just the unedited output after providing the reference image) it would have decreased the quality of my work instead of improving it. I'm going to go out on a limb and expect that AI image, text, and video is all going to find its place in slop & generic content (such as AI generated slop replacing article spinners and stock photos respectively) and otherwise be used in a supporting role for various creative endeavors. For people working on projects like I'm working on (e.g. intended budget $0) it's helpful to have an AI capable of doing legwork - enabling projects to exist or be improved in ways they otherwise wouldn't have. I'm also guessing it'll find its way into more professional settings for grunt work - think a picture frame or fake TV show that would exist in the background of an animated project - likely a detail most people probably wouldn't notice, but that would save the creators time and money and/or allow them to focus more on the essential aspects of said work. Beyond that, as I've predicted before: I expect plenty of emails will be generated from a short list of bullet points, only to be summarized by the recipient's AI back into bullet points. I will also make a prediction counter to what seems mainstream: AI is about to peak for a while. The start of AI image generation was with Google's DeepDream in 2015 - image recognition software that could be run in reverse to "recognize" patterns where there were none, effectively generating an image from digital noise or an unrelated image. While I'm not an expert by any means, I don't think we're too far off from that a decade later, just using very fine tuned tools that develop more coherent images. I guess that we're close to maxing out how efficiently we're able to generate images and video in that manner, and the hard caps on how much creative direction we can have when using AI - as well as the limits to how long we can keep it coherent (e.g. long videos or a chronologically consistent set of images) - will prevent AI from progressing too far beyond what it is currently unless/until another breakthrough occurs.
@ 207ad2a0:e7cca7b0
2025-01-07 03:46:04*Quick context: I wanted to check out Nostr's longform posts and this blog post seemed like a good one to try and mirror. It's originally from my [free to read/share attempt to write a novel](https://untitlednovel.dns7.top/contents/), but this post here is completely standalone - just describing how I used AI image generation to make a small piece of the work.* Hold on, put your pitchforks down - outside of using Grammerly & Emacs for grammatical corrections - not a single character was generated or modified by computers; a non-insignificant portion of my first draft originating on pen & paper. No AI is ~~weird and crazy~~ imaginative enough to write like I do. The only successful AI contribution you'll find is a single image, the map, which I heavily edited. This post will go over how I generated and modified an image using AI, which I believe brought some value to the work, and cover a few quick thoughts about AI towards the end. Let's be clear, I can't draw, but I wanted a map which I believed would improve the story I was working on. After getting abysmal results by prompting AI with text only I decided to use "Diffuse the Rest," a Stable Diffusion tool that allows you to provide a reference image + description to fine tune what you're looking for. I gave it this Microsoft Paint looking drawing:  and after a number of outputs, selected this one to work on:  The image is way better than the one I provided, but had I used it as is, I still feel it would have decreased the quality of my work instead of increasing it. After firing up Gimp I cropped out the top and bottom, expanded the ocean and separated the landmasses, then copied the top right corner of the large landmass to replace the bottom left that got cut off. Now we've got something that looks like concept art: not horrible, and gets the basic idea across, but it's still due for a lot more detail.  The next thing I did was add some texture to make it look more map like. I duplicated the layer in Gimp and applied the "Cartoon" filter to both for some texture. The top layer had a much lower effect strength to give it a more textured look, while the lower layer had a higher effect strength that looked a lot like mountains or other terrain features. Creating a layer mask allowed me to brush over spots to display the lower layer in certain areas, giving it some much needed features.  At this point I'd made it to where I felt it may improve the work instead of detracting from it - at least after labels and borders were added, but the colors seemed artificial and out of place. Luckily, however, this is when PhotoFunia could step in and apply a sketch effect to the image.  At this point I was pretty happy with how it was looking, it was close to what I envisioned and looked very visually appealing while still being a good way to portray information. All that was left was to make the white background transparent, add some minor details, and add the labels and borders. Below is the exact image I wound up using:  Overall, I'm very satisfied with how it turned out, and if you're working on a creative project, I'd recommend attempting something like this. It's not a central part of the work, but it improved the chapter a fair bit, and was doable despite lacking the talent and not intending to allocate a budget to my making of a free to read and share story. #### The AI Generated Elephant in the Room If you've read my non-fiction writing before, you'll know that I think AI will find its place around the skill floor as opposed to the skill ceiling. As you saw with my input, I have absolutely zero drawing talent, but with some elbow grease and an existing creative direction before and after generating an image I was able to get something well above what I could have otherwise accomplished. Outside of the lowest common denominators like stock photos for the sole purpose of a link preview being eye catching, however, I doubt AI will be wholesale replacing most creative works anytime soon. I can assure you that I tried numerous times to describe the map without providing a reference image, and if I used one of those outputs (or even just the unedited output after providing the reference image) it would have decreased the quality of my work instead of improving it. I'm going to go out on a limb and expect that AI image, text, and video is all going to find its place in slop & generic content (such as AI generated slop replacing article spinners and stock photos respectively) and otherwise be used in a supporting role for various creative endeavors. For people working on projects like I'm working on (e.g. intended budget $0) it's helpful to have an AI capable of doing legwork - enabling projects to exist or be improved in ways they otherwise wouldn't have. I'm also guessing it'll find its way into more professional settings for grunt work - think a picture frame or fake TV show that would exist in the background of an animated project - likely a detail most people probably wouldn't notice, but that would save the creators time and money and/or allow them to focus more on the essential aspects of said work. Beyond that, as I've predicted before: I expect plenty of emails will be generated from a short list of bullet points, only to be summarized by the recipient's AI back into bullet points. I will also make a prediction counter to what seems mainstream: AI is about to peak for a while. The start of AI image generation was with Google's DeepDream in 2015 - image recognition software that could be run in reverse to "recognize" patterns where there were none, effectively generating an image from digital noise or an unrelated image. While I'm not an expert by any means, I don't think we're too far off from that a decade later, just using very fine tuned tools that develop more coherent images. I guess that we're close to maxing out how efficiently we're able to generate images and video in that manner, and the hard caps on how much creative direction we can have when using AI - as well as the limits to how long we can keep it coherent (e.g. long videos or a chronologically consistent set of images) - will prevent AI from progressing too far beyond what it is currently unless/until another breakthrough occurs. @ e6817453:b0ac3c39
2025-01-05 14:29:17## The Rise of Graph RAGs and the Quest for Data Quality As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence. ## Booming Interest in Graph RAGs Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can: * **Enhance LLM Outputs:** By grounding responses in structured knowledge, graphs significantly reduce hallucinations. * **Support Complex Queries:** Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving. Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs? ## Data Quality: The Foundation of Effective Graphs A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why: * **Richness of Entities:** Effective retrieval depends on graphs populated with rich, detailed entities. * **Freedom from Hallucinations:** Poorly constructed graphs amplify inaccuracies rather than mitigating them. Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs. ## Hybrid Graph RAGs and Variations While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that: * Handle diverse data sources with ease. * Offer improved adaptability to complex queries. Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing. ## Ontology: The Key to Graph Construction Quality Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for: * **Defining Relationships:** Clarifying how concepts connect within a domain. * **Validating Graph Structures:** Ensuring constructed graphs are logically sound and align with domain-specific realities. Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs? ## How to Build Ontology Expertise in a Startup Team For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach: 1. **Assign a Knowledge Champion:** Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering. 2. **Provide Training:** Invest in courses, workshops, or certifications in knowledge graph and ontology creation. 3. **Leverage Partnerships:** Collaborate with academic institutions, domain experts, or consultants to build initial frameworks. 4. **Utilize Tools:** Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process. 5. **Iterate with Feedback:** Continuously refine ontologies through collaboration with domain experts and iterative testing. So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts. You could read about barefoot experts in my article : Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise. ## How to Find or Create Ontologies For teams venturing into Graph RAGs, several strategies can help address the ontology gap: 1. **Leverage Existing Ontologies:** Many industries and domains already have open ontologies. For instance: * **Public Knowledge Graphs:** Resources like Wikipedia’s graph offer a wealth of structured knowledge. * **Industry Standards:** Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields. * **Business Framework Ontology (BFO):** A valuable resource for enterprises looking to define business processes and structures. 1. **Build In-House Expertise:** If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation. 2. **Utilize LLMs for Ontology Construction:** Interestingly, LLMs themselves can act as a starting point for ontology development: * **Prompt-Based Extraction:** LLMs can generate draft ontologies by leveraging their extensive training on graph data. * **Domain Expert Refinement:** Combine LLM-generated structures with insights from domain experts to create tailored ontologies. ## Parallel Ontology and Graph Extraction An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as: * **Detecting Hallucinations:** Differentiating between genuine insights and AI-generated inaccuracies. * **Ensuring Completeness:** Ensuring no critical concepts are overlooked during extraction. Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method. ## LLMs as Ontologists While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to: * **Generate Skeleton Ontologies:** Prompt LLMs with domain-specific information to draft initial ontology structures. * **Validate and Refine Ontologies:** Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance. However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes. ## Final Thoughts: Unlocking the Power of Graph RAGs The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools. As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding. Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation!
@ e6817453:b0ac3c39
2025-01-05 14:29:17## The Rise of Graph RAGs and the Quest for Data Quality As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence. ## Booming Interest in Graph RAGs Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can: * **Enhance LLM Outputs:** By grounding responses in structured knowledge, graphs significantly reduce hallucinations. * **Support Complex Queries:** Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving. Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs? ## Data Quality: The Foundation of Effective Graphs A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why: * **Richness of Entities:** Effective retrieval depends on graphs populated with rich, detailed entities. * **Freedom from Hallucinations:** Poorly constructed graphs amplify inaccuracies rather than mitigating them. Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs. ## Hybrid Graph RAGs and Variations While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that: * Handle diverse data sources with ease. * Offer improved adaptability to complex queries. Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing. ## Ontology: The Key to Graph Construction Quality Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for: * **Defining Relationships:** Clarifying how concepts connect within a domain. * **Validating Graph Structures:** Ensuring constructed graphs are logically sound and align with domain-specific realities. Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs? ## How to Build Ontology Expertise in a Startup Team For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach: 1. **Assign a Knowledge Champion:** Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering. 2. **Provide Training:** Invest in courses, workshops, or certifications in knowledge graph and ontology creation. 3. **Leverage Partnerships:** Collaborate with academic institutions, domain experts, or consultants to build initial frameworks. 4. **Utilize Tools:** Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process. 5. **Iterate with Feedback:** Continuously refine ontologies through collaboration with domain experts and iterative testing. So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts. You could read about barefoot experts in my article : Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise. ## How to Find or Create Ontologies For teams venturing into Graph RAGs, several strategies can help address the ontology gap: 1. **Leverage Existing Ontologies:** Many industries and domains already have open ontologies. For instance: * **Public Knowledge Graphs:** Resources like Wikipedia’s graph offer a wealth of structured knowledge. * **Industry Standards:** Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields. * **Business Framework Ontology (BFO):** A valuable resource for enterprises looking to define business processes and structures. 1. **Build In-House Expertise:** If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation. 2. **Utilize LLMs for Ontology Construction:** Interestingly, LLMs themselves can act as a starting point for ontology development: * **Prompt-Based Extraction:** LLMs can generate draft ontologies by leveraging their extensive training on graph data. * **Domain Expert Refinement:** Combine LLM-generated structures with insights from domain experts to create tailored ontologies. ## Parallel Ontology and Graph Extraction An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as: * **Detecting Hallucinations:** Differentiating between genuine insights and AI-generated inaccuracies. * **Ensuring Completeness:** Ensuring no critical concepts are overlooked during extraction. Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method. ## LLMs as Ontologists While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to: * **Generate Skeleton Ontologies:** Prompt LLMs with domain-specific information to draft initial ontology structures. * **Validate and Refine Ontologies:** Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance. However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes. ## Final Thoughts: Unlocking the Power of Graph RAGs The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools. As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding. Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation! @ bcea2b98:7ccef3c9
2025-01-03 22:31:38 originally posted at https://stacker.news/items/835751
@ bcea2b98:7ccef3c9
2025-01-03 22:31:38 originally posted at https://stacker.news/items/835751 @ f3df9bc0:a95119eb
2025-01-03 21:41:14# MySql InnoDB Indexes for Developers This article aims to be a high level reference for developers who just want to use Mysql InnoDB indexes effectively. Although you _can_ read this from top to bottom, I'd encourage you to save time by skipping to sections that interest you using the below table of contents. # Contents - [Quick Reference](#quick-reference) (Start here for guidelines you can use right away, without needing the _why_) - [Index Structure](#index-structure) - [Primary Index Structure & Paging](#primary-index--paging) - [Secondary Indexes](#secondary-index-structure) - [Composite Indexes](#composite-index-structure) - [Index Navigation](#index-navigation) - [ref-type Queries](#ref-type-queries) - [range-type Queries](#range-type-queries) - [Post-Index Computations](#post-index-computations) - [Join Algorithms](#join-algorithms) - [Nested Loop Join](#nested-loop-join) - [Hash Join](#hash-join) - [Compound Cursor Iteration](#compound-cursor-iteration) <style type="text/css"> .box { background: #cedce8; padding: 1px 10px 5px 10px; border-radius: 15px; } .box code { background: #bfd7ec; } </style> <div class="box" style="" markdown="1"> # Quick Reference This is a quick list of the practical guidelines that you can use to make your applications more performant at the database layer. We'll dive into the _why_ each of these things are true, and give you mental models such that you can arrive at these guidelines yourself _without memorization_, at later sections of the article. <button onclick="toggle_quickref();">Click To Expand ▼</button> <script type="text/javascript"> function toggle_quickref() { var x = document.getElementById("quick-reference-body"); if (x.style.display === "none") { x.style.display = "block"; } else { x.style.display = "none"; } } </script> <div id="quick-reference-body" style="display:none" markdown="1"> **Structure** - Every non-`PRIMARY` index is really a compound index with the `PRIMARY` index. - `[foo]` is implicitly `[foo, id]`, likewise `[a, b]` is implicitly `[a, b, id]` - Usually prefer high cardinality columns (those with many unique values) to come earlier in indexes. - For example IDs have more unique values than boolean flags, so put the ID first in the index `[account_id, is_active]` - *Note:* there are exceptions, especially when range queries are involved - Only `SELECT`-ing columns contained in the index will significantly reduce memory paging. - eg `SELECT foo, id` when the index `[foo]` is being used. **Filtering** - An index must be "used" from left to right. Given an index of `[a, b, c]`: - 🟢 `WHERE b=2 AND a=1` will correctly use the `[a, b]` portion of the index - 🟡 `WHERE a=1 AND c=4` will only use the `[a]` portion of the index - 🔴 `WHERE b=5` will not be able to use this index at all - A range filter prevents any columns to the "right" from being used. Given an index of `[a, b, c]`: - 🟡 `WHERE a=1 AND b>4 AND c=10` will only use the `[a, b]` portion of the index - 🔴 Implied by this is that queries containing ranges on two or more columns **cannot** be solved by indexes `WHERE a>5 AND b>2` - Any filters that aren't solved as part of the index will require linear row scanning. The performance of this is correlated to the "hit ratio". - Given an index of `[a]`, the performance of `WHERE a=1 AND c=4` will correlate to *what percentage of `a=1` rows also have `c=4`*. If this percentage is low, performance will be worse. Put another way: if there are a large number of rows where `a=1` but only a couple of those also have `c=4`, mysql will need to search through and discard many rows. **Ordering** - Indexes naturally return rows ordered by their structure. - Selecting from index `[a, b]` will naturally give rows ordered by `[a, b, id]` - Any unnatural ordering will require a O(nlogn) **filesort**, which can be very slow for large amounts of rows - With an index of `[a]`, the query `WHERE a=1 ORDER BY b` will need to sort all rows that meet the filtering clause. - Columns on the "left" of the index can be efficiently excluded from the `ORDER BY` clause, **if** they have been used in the `WHERE` clause as a **non-range** filter. - Given an index of `[a, b]`, with a natural ordering of `[a, b, id]`: - 🟢 `WHERE a=1 ORDER BY b,id` is also natural ordering - 🔴 `WHERE a=1 ORDER BY id` is **not** natural ordering - 🟢 `WHERE a=1 AND b>10 ORDER BY b,id` is natural ordering - 🔴 `WHERE a=1 AND b>10 ORDER BY id` is **not** natural ordering - 🟢 `WHERE a=1 AND b=2 ORDER BY id` is natural ordering - 🟢 `WHERE a=1 AND b=2 AND id>5 ORDER BY id` is natural ordering **Limit & Offset** - Performance of `LIMIT` is correlated to the "hit density" when scanning rows. eg are the rows you're scanning for abundant? Or will mysql need to scan for a long time to find enough rows? - `LIMIT` is applied **after** sorting, so will not improve the performance of a filesort - Performance of `OFFSET n` is correclated to the value of `n`. Therefore it is not a good fit for pagination as the query will get slower as `n` increases. </div> </div> ----- # Index Structure Indexes are constructed from a B+tree structure. Understanding this structure is key to gaining an intuitive reasoning for how queries will perform using different indexes. Both the `PRIMARY` index and secondary indexes have a similar tree structure, differing only in what data is stored on the leaves of the tree. ## Primary Index Structure & Paging Looking at the structure of a `PRIMARY` index first, we see that the full row is stored in each leaf of the tree, and each leaf is ordered sequentially on the disk:  <center><small style="color: #999">note: page size greatly reduced for illustration</small></center> If possible, it is best to select the primary index for a table with data locality in mind, to reduce how many page loads need to take place to satisfy a query. For example, imagine a blogging application that almost always queries for posts on a specific blog: `SELECT * FROM posts WHERE blog_id=10`. Ideally we'd like for this table to have all the posts where `blog_id = 10` stored **sequentially** in the primary index. However, by using a standard primary index on `[id]` we see a structure where rows are stored in disk pages in the order they were **created**. The diagram below illistrates this (ID integer, colour coded by blog)  By insteading using a **composite primary key**, this table can be made much more efficient given its access pattern. In the below diagram I show the same data, but instead stored in a composite primary index of `[blog_id, id]`. This means rows are first sorted by `blog_id`, and then by `id` for each blog. When the data is stored in this manner, our query for `SELECT * FROM posts WHERE blog_id=10` is likely to load less pages from disk.  ## Secondary Index Structure Secondary indexes have a similar structure to that of primary indexes. However, instead of storing the _full row_ in the leaves of the tree, only the primary index value is stored:  This structure means that if additional columns are required (eg a `SELECT *`), then after traversing the secondary index, mysql must also traverse the primary index _for each selected row_ to actually load the required data. By only selecting columns available in the secondary index, mysql can skip this extra lookup step. ## Composite Index Structure When multiple columns are specified in a compound index, we get a structure composed of **nested B+trees**. This is where the ordering of columns within an index definition becomes relevant. The root of the tree is defined by the _first_ column in the index definition, the second nested tree would be the _second_ column in the index definition, and so on. The below diagram is the structure of a composite index `[blog_id, created_at]` (with the implied `id` column on the end):  # Index Navigation We'll now look at how mysql navigates these indexes given various query structures, which should help give an intuitive understanding for why Mysql performance will vary. ## `ref`-type queries With this tree-based model in place, we can see that to efficiently use an index like this we must navigate the tree _in the order that the index is defined_. If our query does not specify a value for all columns in an index, this is ok as long as the values we _do_ provide are at the top of the tree. I've illustrated below two examples of the "happy path" for navigating a `[blog_id, user_id]` index. In the first, we have provided a filter on both `blog_id` and `user_id`, which allows for mysql to fully navigate the tree to the leaves. In the second, we only provide a filter on `blog_id`, but because this is the first column in the index mysql is still able to efficiently select all the rows that meet this criteria (it selects **all leaves from the sub tree**)  <div class="box" style="" markdown="1"> 💡 Notice how the ordering of the rows appears to change depending on **how far mysql navigates the tree**. Rows in an index are always stored in the same ordering scheme as the index itself. That is to say that a `[blog_id, user_id]` index will naturally store rows in `blog_id, user_id, id` ordering. However, as we navigate further into the tree the ordering appears to "simplify". If we are selecting rows for a specific `blog=10 and user_id=50` then the rows appear to be ordered by `id`, because they all share the same values for both blog_id and user_id! </div> ## `range`-type queries The range-type lookup happens when a query selects _multiple values_ for an indexed column. There are many ways a query could end up in this scenario: - `WHERE updated_at > X` - `WHERE user_id != X` - `WHERE blog_id IN (1, 5, 34, 200)` - `WHERE user_id=10 OR user_id=50` In such cases, mysql will need to navigate _multiple branches_ of the index. Consider the below query where we search for all recently created posts for a particular blog:  There are two things I'd like to point out about this pattern: 1. The ordering of the results is `created_at, id`. Sorting by `id` (for example) is not possible without a `filesort` operation. 2. There is no efficient way to navigate the deeper sections of the tree (ie the `id` portion of the index above) without iterating through all the selected branches of `created_at`. That is, if we were to add an additional filter on `id > 5` for example, then there is no single tree to navigate and provide these values. Mysql would instead need to iterate through every sub-tree (one per value of `created_at`) to complete this filtering operation (see diagram below) A common application pattern that can suffer performance issues due to both these points is *ID-based pagination* (ie if your pagination system needs to filter on `WHERE id > x ORDER BY id`). See the section on [compound cursor iteration](#compound-cursor-iteration) for a potential solution.  # Post-Index Computations Although Mysql will always start off by using an index if possible to reduce the amount of post-processing required, it goes without saying that not every query will be fully solved by an avilable index. There are a couple post-index computations that we should consider the relative performance of. First, if the query is requesting an `ORDER` which differs from how the index sorts its rows, a filesort will be required. This is an expensive operation (`O(nlogn)`) if the number of rows to be sorted is large. In addition, sorting requires Mysql to temporarily buffer the entire dataset (eg you can't stream a sorting operation). See [ref-type queries](#ref-type-queries) for a reminder how indexes naturally sort rows. If the `WHERE` clause of the query was not fully solved by the index, Mysql will also need to scan through the rows one after another to apply the remaining filtering. While this is faster than a filesort, it is also relatively slow for large data sets (`O(n)`). If the index reducing the dataset down to a reasonable size upfront, then this may not be a big deal.  There is one exception here: if the query also specifies a `LIMIT x`, Mysql need not scan the _entire_ dataset. Mysql will "short circuit" the row scan as soon as it has enough rows to satisfy the query condition. The performance of this kind of pattern is dependent on the "hit ratio" of rows. If there are relatively few rows that satisfy the filter condition compared to rows that must be dropped, then Mysql will need to scan for a longer time compared to if almost all the rows are valid. In addition, you may find that the "density" of interesting rows is not constant throughout the range being scanned! If your application is paginating through a large data set, you may find that different pages have different query times, depending on how many rows need to be filtered out on each page.  # Join Algorithms ## Nested-Loop Join The primary algorithm used by Mysql to join tables is a couple variations on "nested-loop". This a very straightforward algorithm: ``` for each row in tableA: for each matching row in tableB: send to output steram ``` Because Mysql is often capable of streaming joins, when the join query includes a `LIMIT x` the full join may not have to be executed: 1. Mysql executes query in the outer table 2. For the first row in the range, look-up matching rows in the inner table 3. For each matching row, emit to output stream 4. Stop execution if enough rows found, otherwise move to next row and goto 2 Note that similar to un-indexed row scans, this does not apply to all conditions (for example, if sorting is required the full dataset is required in memory). ## Hash Join The hash-join algorithm avoids the N+1 B-tree traversal by taking some time upfront (`O(n)`) to build an in-memory hash table. The reason this strategy can give a performance improvement over nested-loop in some cases is because a hash table lookup has an average profile of `O(1)` compared to B-tree traversal at `O(logn)`. Given we may have to do this lookup many times (`m` times), the overall performance profile of hash-join is `O(n + m)`, whereas nested-loop's profile is `O(nlogm)`. The below plot shows the region (shaded blue) where the function `n+m` has a lower value than `n*logm`:  The tradeoff is of course that this (potentially large) hash table must fit into memory. For this reason one strategy to improve hash-join performance is to limit the size of this temporary table by `SELECT`-ing only those columns which you really need (to reduce width), and pre-filtering as many rows as possible (to reduce height). The second thing to keep in mind for performance of hash-joins is that indexes on the join condition will not be used. Rather, the place to focus is on indexing any independent filters if possible. For example, consider the following query: ```sql SELECT * FROM tableA t1 JOIN tableB t2 ON t1.shared_id = t2.shared_id WHERE t1.colA = "foo" AND t2.colB = "bar" ``` The best indexes for this query given a hash-join would be on `t1.colA` and a second index on `t2.colB`. Execution of this join would then look like: 1. Use the index on `colA` to find all rows in t1 where `colA = "foo"`. 2. For each row, build a hash table where the key is `t1.shared_id` and the value is the row. 3. Use the index on `colB` to find all rows in t2 where `colB = "bar"`. 4. For each row, look up the matching t1 rows from the hash table by `t2.shared_id` # Compound Cursor Iteration In the [range-type queries section](#range-type-queries) I briefly introduced the problem of using an ID based cursor to paginate through a dataset queried via a range-type query. One potential solution to this problem is to use a *compound cursor*. To work, this cursor must be constructed from the column being filtered with the range. For example, lets consider the query `SELECT * FROM blog_posts WHERE blog_id=10 AND created_at>"2023-01-01"`. The natural index to use for this range query would be `[blog_id, created_at]`. Because the range query filter is performed on the `created_at` column, I will propose a compound cursor of `created_at, id`. Let's take a look at how the query structure changes. The first query of our iteration will look something like this: ```sql SELECT * FROM blog_posts WHERE blog_id = 10 AND created_at > "2023-01-01" ORDER BY created_at, id ASC LIMIT 100 ``` This will get the first "page" of 100 results. Notice that we are ordering by `created_at, id`, which is the natural ordering of the index. This allows mysql to efficiently grab the first 100 rows it sees without scanning the full time range.  Now lets look at how we get the next "page" of results. The "cursor value" is defined as the `created_at` and `id` values from the last row in the batch of 100 previously selected. We'll call these values `x` and `y` for simplicity. ```ruby x = batch.last.created_at, y = batch.last.id ``` The structure of the query that loads the second page of results has this form: ```sql SELECT * FROM blog_posts WHERE blog_id = 10 AND ( created_at = x AND id > y OR created_at > x ) ORDER BY created_at, id ASC LIMIT 100 ``` Notice in this query that we have an `OR` clause, meaning mysql is going to navigate the index **two times**, once per "side" of the clause. Lets consider these as two seperate queries for the sake of a performance analysis. ```sql -- Query A: the "left" side of the OR clause SELECT * FROM blog_posts WHERE blog_id = 10 AND created_at = x AND id > y ORDER BY created_at, id ASC LIMIT 100 -- Query B: the "right" side of the OR clause SELECT * FROM blog_posts WHERE blog_id = 10 AND created_at > x ORDER BY created_at, id ASC LIMIT 100 ``` By analysing the OR clauses piece-wise like this, we can now see that each clause has only **one** range filter. Combining this with the fact that the `ORDER BY` is the natural ordering of these indexes, we have solved both of the original problems! No more filesort, no more unsolvable double-range filters.  🟡 A note of warning: this pattern may only work as you expect for columns that have **immutable** values. Like any data structure iteration, if a value changes during your iteration your process may either process a row twice or not at all! For example, consider if instead of iterating on `created_at, id` we were iterating on `updated_at, id`. If a row is updated (and therefore `updated_at` _increases_) while a process is already iterating through the dataset, we may see that updated row twice: once with its lower `updated_at` value, and again with the higher value.
@ f3df9bc0:a95119eb
2025-01-03 21:41:14# MySql InnoDB Indexes for Developers This article aims to be a high level reference for developers who just want to use Mysql InnoDB indexes effectively. Although you _can_ read this from top to bottom, I'd encourage you to save time by skipping to sections that interest you using the below table of contents. # Contents - [Quick Reference](#quick-reference) (Start here for guidelines you can use right away, without needing the _why_) - [Index Structure](#index-structure) - [Primary Index Structure & Paging](#primary-index--paging) - [Secondary Indexes](#secondary-index-structure) - [Composite Indexes](#composite-index-structure) - [Index Navigation](#index-navigation) - [ref-type Queries](#ref-type-queries) - [range-type Queries](#range-type-queries) - [Post-Index Computations](#post-index-computations) - [Join Algorithms](#join-algorithms) - [Nested Loop Join](#nested-loop-join) - [Hash Join](#hash-join) - [Compound Cursor Iteration](#compound-cursor-iteration) <style type="text/css"> .box { background: #cedce8; padding: 1px 10px 5px 10px; border-radius: 15px; } .box code { background: #bfd7ec; } </style> <div class="box" style="" markdown="1"> # Quick Reference This is a quick list of the practical guidelines that you can use to make your applications more performant at the database layer. We'll dive into the _why_ each of these things are true, and give you mental models such that you can arrive at these guidelines yourself _without memorization_, at later sections of the article. <button onclick="toggle_quickref();">Click To Expand ▼</button> <script type="text/javascript"> function toggle_quickref() { var x = document.getElementById("quick-reference-body"); if (x.style.display === "none") { x.style.display = "block"; } else { x.style.display = "none"; } } </script> <div id="quick-reference-body" style="display:none" markdown="1"> **Structure** - Every non-`PRIMARY` index is really a compound index with the `PRIMARY` index. - `[foo]` is implicitly `[foo, id]`, likewise `[a, b]` is implicitly `[a, b, id]` - Usually prefer high cardinality columns (those with many unique values) to come earlier in indexes. - For example IDs have more unique values than boolean flags, so put the ID first in the index `[account_id, is_active]` - *Note:* there are exceptions, especially when range queries are involved - Only `SELECT`-ing columns contained in the index will significantly reduce memory paging. - eg `SELECT foo, id` when the index `[foo]` is being used. **Filtering** - An index must be "used" from left to right. Given an index of `[a, b, c]`: - 🟢 `WHERE b=2 AND a=1` will correctly use the `[a, b]` portion of the index - 🟡 `WHERE a=1 AND c=4` will only use the `[a]` portion of the index - 🔴 `WHERE b=5` will not be able to use this index at all - A range filter prevents any columns to the "right" from being used. Given an index of `[a, b, c]`: - 🟡 `WHERE a=1 AND b>4 AND c=10` will only use the `[a, b]` portion of the index - 🔴 Implied by this is that queries containing ranges on two or more columns **cannot** be solved by indexes `WHERE a>5 AND b>2` - Any filters that aren't solved as part of the index will require linear row scanning. The performance of this is correlated to the "hit ratio". - Given an index of `[a]`, the performance of `WHERE a=1 AND c=4` will correlate to *what percentage of `a=1` rows also have `c=4`*. If this percentage is low, performance will be worse. Put another way: if there are a large number of rows where `a=1` but only a couple of those also have `c=4`, mysql will need to search through and discard many rows. **Ordering** - Indexes naturally return rows ordered by their structure. - Selecting from index `[a, b]` will naturally give rows ordered by `[a, b, id]` - Any unnatural ordering will require a O(nlogn) **filesort**, which can be very slow for large amounts of rows - With an index of `[a]`, the query `WHERE a=1 ORDER BY b` will need to sort all rows that meet the filtering clause. - Columns on the "left" of the index can be efficiently excluded from the `ORDER BY` clause, **if** they have been used in the `WHERE` clause as a **non-range** filter. - Given an index of `[a, b]`, with a natural ordering of `[a, b, id]`: - 🟢 `WHERE a=1 ORDER BY b,id` is also natural ordering - 🔴 `WHERE a=1 ORDER BY id` is **not** natural ordering - 🟢 `WHERE a=1 AND b>10 ORDER BY b,id` is natural ordering - 🔴 `WHERE a=1 AND b>10 ORDER BY id` is **not** natural ordering - 🟢 `WHERE a=1 AND b=2 ORDER BY id` is natural ordering - 🟢 `WHERE a=1 AND b=2 AND id>5 ORDER BY id` is natural ordering **Limit & Offset** - Performance of `LIMIT` is correlated to the "hit density" when scanning rows. eg are the rows you're scanning for abundant? Or will mysql need to scan for a long time to find enough rows? - `LIMIT` is applied **after** sorting, so will not improve the performance of a filesort - Performance of `OFFSET n` is correclated to the value of `n`. Therefore it is not a good fit for pagination as the query will get slower as `n` increases. </div> </div> ----- # Index Structure Indexes are constructed from a B+tree structure. Understanding this structure is key to gaining an intuitive reasoning for how queries will perform using different indexes. Both the `PRIMARY` index and secondary indexes have a similar tree structure, differing only in what data is stored on the leaves of the tree. ## Primary Index Structure & Paging Looking at the structure of a `PRIMARY` index first, we see that the full row is stored in each leaf of the tree, and each leaf is ordered sequentially on the disk:  <center><small style="color: #999">note: page size greatly reduced for illustration</small></center> If possible, it is best to select the primary index for a table with data locality in mind, to reduce how many page loads need to take place to satisfy a query. For example, imagine a blogging application that almost always queries for posts on a specific blog: `SELECT * FROM posts WHERE blog_id=10`. Ideally we'd like for this table to have all the posts where `blog_id = 10` stored **sequentially** in the primary index. However, by using a standard primary index on `[id]` we see a structure where rows are stored in disk pages in the order they were **created**. The diagram below illistrates this (ID integer, colour coded by blog)  By insteading using a **composite primary key**, this table can be made much more efficient given its access pattern. In the below diagram I show the same data, but instead stored in a composite primary index of `[blog_id, id]`. This means rows are first sorted by `blog_id`, and then by `id` for each blog. When the data is stored in this manner, our query for `SELECT * FROM posts WHERE blog_id=10` is likely to load less pages from disk.  ## Secondary Index Structure Secondary indexes have a similar structure to that of primary indexes. However, instead of storing the _full row_ in the leaves of the tree, only the primary index value is stored:  This structure means that if additional columns are required (eg a `SELECT *`), then after traversing the secondary index, mysql must also traverse the primary index _for each selected row_ to actually load the required data. By only selecting columns available in the secondary index, mysql can skip this extra lookup step. ## Composite Index Structure When multiple columns are specified in a compound index, we get a structure composed of **nested B+trees**. This is where the ordering of columns within an index definition becomes relevant. The root of the tree is defined by the _first_ column in the index definition, the second nested tree would be the _second_ column in the index definition, and so on. The below diagram is the structure of a composite index `[blog_id, created_at]` (with the implied `id` column on the end):  # Index Navigation We'll now look at how mysql navigates these indexes given various query structures, which should help give an intuitive understanding for why Mysql performance will vary. ## `ref`-type queries With this tree-based model in place, we can see that to efficiently use an index like this we must navigate the tree _in the order that the index is defined_. If our query does not specify a value for all columns in an index, this is ok as long as the values we _do_ provide are at the top of the tree. I've illustrated below two examples of the "happy path" for navigating a `[blog_id, user_id]` index. In the first, we have provided a filter on both `blog_id` and `user_id`, which allows for mysql to fully navigate the tree to the leaves. In the second, we only provide a filter on `blog_id`, but because this is the first column in the index mysql is still able to efficiently select all the rows that meet this criteria (it selects **all leaves from the sub tree**)  <div class="box" style="" markdown="1"> 💡 Notice how the ordering of the rows appears to change depending on **how far mysql navigates the tree**. Rows in an index are always stored in the same ordering scheme as the index itself. That is to say that a `[blog_id, user_id]` index will naturally store rows in `blog_id, user_id, id` ordering. However, as we navigate further into the tree the ordering appears to "simplify". If we are selecting rows for a specific `blog=10 and user_id=50` then the rows appear to be ordered by `id`, because they all share the same values for both blog_id and user_id! </div> ## `range`-type queries The range-type lookup happens when a query selects _multiple values_ for an indexed column. There are many ways a query could end up in this scenario: - `WHERE updated_at > X` - `WHERE user_id != X` - `WHERE blog_id IN (1, 5, 34, 200)` - `WHERE user_id=10 OR user_id=50` In such cases, mysql will need to navigate _multiple branches_ of the index. Consider the below query where we search for all recently created posts for a particular blog:  There are two things I'd like to point out about this pattern: 1. The ordering of the results is `created_at, id`. Sorting by `id` (for example) is not possible without a `filesort` operation. 2. There is no efficient way to navigate the deeper sections of the tree (ie the `id` portion of the index above) without iterating through all the selected branches of `created_at`. That is, if we were to add an additional filter on `id > 5` for example, then there is no single tree to navigate and provide these values. Mysql would instead need to iterate through every sub-tree (one per value of `created_at`) to complete this filtering operation (see diagram below) A common application pattern that can suffer performance issues due to both these points is *ID-based pagination* (ie if your pagination system needs to filter on `WHERE id > x ORDER BY id`). See the section on [compound cursor iteration](#compound-cursor-iteration) for a potential solution.  # Post-Index Computations Although Mysql will always start off by using an index if possible to reduce the amount of post-processing required, it goes without saying that not every query will be fully solved by an avilable index. There are a couple post-index computations that we should consider the relative performance of. First, if the query is requesting an `ORDER` which differs from how the index sorts its rows, a filesort will be required. This is an expensive operation (`O(nlogn)`) if the number of rows to be sorted is large. In addition, sorting requires Mysql to temporarily buffer the entire dataset (eg you can't stream a sorting operation). See [ref-type queries](#ref-type-queries) for a reminder how indexes naturally sort rows. If the `WHERE` clause of the query was not fully solved by the index, Mysql will also need to scan through the rows one after another to apply the remaining filtering. While this is faster than a filesort, it is also relatively slow for large data sets (`O(n)`). If the index reducing the dataset down to a reasonable size upfront, then this may not be a big deal.  There is one exception here: if the query also specifies a `LIMIT x`, Mysql need not scan the _entire_ dataset. Mysql will "short circuit" the row scan as soon as it has enough rows to satisfy the query condition. The performance of this kind of pattern is dependent on the "hit ratio" of rows. If there are relatively few rows that satisfy the filter condition compared to rows that must be dropped, then Mysql will need to scan for a longer time compared to if almost all the rows are valid. In addition, you may find that the "density" of interesting rows is not constant throughout the range being scanned! If your application is paginating through a large data set, you may find that different pages have different query times, depending on how many rows need to be filtered out on each page.  # Join Algorithms ## Nested-Loop Join The primary algorithm used by Mysql to join tables is a couple variations on "nested-loop". This a very straightforward algorithm: ``` for each row in tableA: for each matching row in tableB: send to output steram ``` Because Mysql is often capable of streaming joins, when the join query includes a `LIMIT x` the full join may not have to be executed: 1. Mysql executes query in the outer table 2. For the first row in the range, look-up matching rows in the inner table 3. For each matching row, emit to output stream 4. Stop execution if enough rows found, otherwise move to next row and goto 2 Note that similar to un-indexed row scans, this does not apply to all conditions (for example, if sorting is required the full dataset is required in memory). ## Hash Join The hash-join algorithm avoids the N+1 B-tree traversal by taking some time upfront (`O(n)`) to build an in-memory hash table. The reason this strategy can give a performance improvement over nested-loop in some cases is because a hash table lookup has an average profile of `O(1)` compared to B-tree traversal at `O(logn)`. Given we may have to do this lookup many times (`m` times), the overall performance profile of hash-join is `O(n + m)`, whereas nested-loop's profile is `O(nlogm)`. The below plot shows the region (shaded blue) where the function `n+m` has a lower value than `n*logm`:  The tradeoff is of course that this (potentially large) hash table must fit into memory. For this reason one strategy to improve hash-join performance is to limit the size of this temporary table by `SELECT`-ing only those columns which you really need (to reduce width), and pre-filtering as many rows as possible (to reduce height). The second thing to keep in mind for performance of hash-joins is that indexes on the join condition will not be used. Rather, the place to focus is on indexing any independent filters if possible. For example, consider the following query: ```sql SELECT * FROM tableA t1 JOIN tableB t2 ON t1.shared_id = t2.shared_id WHERE t1.colA = "foo" AND t2.colB = "bar" ``` The best indexes for this query given a hash-join would be on `t1.colA` and a second index on `t2.colB`. Execution of this join would then look like: 1. Use the index on `colA` to find all rows in t1 where `colA = "foo"`. 2. For each row, build a hash table where the key is `t1.shared_id` and the value is the row. 3. Use the index on `colB` to find all rows in t2 where `colB = "bar"`. 4. For each row, look up the matching t1 rows from the hash table by `t2.shared_id` # Compound Cursor Iteration In the [range-type queries section](#range-type-queries) I briefly introduced the problem of using an ID based cursor to paginate through a dataset queried via a range-type query. One potential solution to this problem is to use a *compound cursor*. To work, this cursor must be constructed from the column being filtered with the range. For example, lets consider the query `SELECT * FROM blog_posts WHERE blog_id=10 AND created_at>"2023-01-01"`. The natural index to use for this range query would be `[blog_id, created_at]`. Because the range query filter is performed on the `created_at` column, I will propose a compound cursor of `created_at, id`. Let's take a look at how the query structure changes. The first query of our iteration will look something like this: ```sql SELECT * FROM blog_posts WHERE blog_id = 10 AND created_at > "2023-01-01" ORDER BY created_at, id ASC LIMIT 100 ``` This will get the first "page" of 100 results. Notice that we are ordering by `created_at, id`, which is the natural ordering of the index. This allows mysql to efficiently grab the first 100 rows it sees without scanning the full time range.  Now lets look at how we get the next "page" of results. The "cursor value" is defined as the `created_at` and `id` values from the last row in the batch of 100 previously selected. We'll call these values `x` and `y` for simplicity. ```ruby x = batch.last.created_at, y = batch.last.id ``` The structure of the query that loads the second page of results has this form: ```sql SELECT * FROM blog_posts WHERE blog_id = 10 AND ( created_at = x AND id > y OR created_at > x ) ORDER BY created_at, id ASC LIMIT 100 ``` Notice in this query that we have an `OR` clause, meaning mysql is going to navigate the index **two times**, once per "side" of the clause. Lets consider these as two seperate queries for the sake of a performance analysis. ```sql -- Query A: the "left" side of the OR clause SELECT * FROM blog_posts WHERE blog_id = 10 AND created_at = x AND id > y ORDER BY created_at, id ASC LIMIT 100 -- Query B: the "right" side of the OR clause SELECT * FROM blog_posts WHERE blog_id = 10 AND created_at > x ORDER BY created_at, id ASC LIMIT 100 ``` By analysing the OR clauses piece-wise like this, we can now see that each clause has only **one** range filter. Combining this with the fact that the `ORDER BY` is the natural ordering of these indexes, we have solved both of the original problems! No more filesort, no more unsolvable double-range filters.  🟡 A note of warning: this pattern may only work as you expect for columns that have **immutable** values. Like any data structure iteration, if a value changes during your iteration your process may either process a row twice or not at all! For example, consider if instead of iterating on `created_at, id` we were iterating on `updated_at, id`. If a row is updated (and therefore `updated_at` _increases_) while a process is already iterating through the dataset, we may see that updated row twice: once with its lower `updated_at` value, and again with the higher value. @ a95c6243:d345522c
2025-01-03 20:26:47*Was du bist hängt von drei Faktoren ab:* *\ Was du geerbt hast,* *\ was deine Umgebung aus dir machte* *\ und was du in freier Wahl* *\ aus deiner Umgebung und deinem Erbe gemacht hast.* *\ Aldous Huxley* **Das brave Mitmachen und Mitlaufen in einem vorgegebenen, recht engen Rahmen** ist gewiss nicht neu, hat aber gerade wieder mal Konjunktur. Dies kann man deutlich beobachten, eigentlich egal, in welchem gesellschaftlichen Bereich man sich umschaut. Individualität ist nur soweit angesagt, wie sie in ein bestimmtes Schema von «Diversität» passt, und Freiheit verkommt zur Worthülse – nicht erst durch ein gewisses [Buch](https://www.nachdenkseiten.de/?p=126416) einer gewissen ehemaligen Regierungschefin. **Erklärungsansätze für solche Entwicklungen sind bekannt,** und praktisch alle haben etwas mit Massenpsychologie zu tun. Der Herdentrieb, also der Trieb der Menschen, sich – zum Beispiel aus Unsicherheit oder Bequemlichkeit – lieber der Masse anzuschließen als selbstständig zu denken und zu handeln, ist einer der Erklärungsversuche. Andere drehen sich um Macht, Propaganda, Druck und Angst, also den gezielten Einsatz psychologischer [Herrschaftsinstrumente](https://transition-news.org/spip.php?recherche=nudging\&page=recherche_wall). **Aber wollen die Menschen überhaupt Freiheit?** Durch Gespräche im privaten Umfeld bin ich diesbezüglich in der letzten Zeit etwas skeptisch geworden. Um die Jahreswende philosophiert man ja gerne ein wenig über das Erlebte und über die Erwartungen für die Zukunft. Dabei hatte ich hin und wieder den Eindruck, die totalitären Anwandlungen unserer «Repräsentanten» kämen manchen Leuten gerade recht. **«Desinformation» ist so ein brisantes Thema.** Davor müsse man die Menschen doch schützen, hörte ich. Jemand müsse doch zum Beispiel diese ganzen merkwürdigen Inhalte in den Social Media filtern – zur [Ukraine](https://transition-news.org/spip.php?recherche=ukraine\&page=recherche_wall), zum [Klima](https://transition-news.org/spip.php?recherche=klima\&page=recherche_wall), zu [Gesundheitsthemen](https://transition-news.org/spip.php?recherche=impfung\&page=recherche_wall) oder zur [Migration](https://transition-news.org/spip.php?recherche=migration\&page=recherche_wall). Viele wüssten ja gar nicht einzuschätzen, was richtig und was falsch ist, sie bräuchten eine Führung. **Freiheit bedingt Eigenverantwortung, ohne Zweifel.** Eventuell ist es einigen tatsächlich zu anspruchsvoll, die Verantwortung für das eigene Tun und Lassen zu übernehmen. Oder die persönliche Freiheit wird nicht als ausreichend wertvolles Gut angesehen, um sich dafür anzustrengen. In dem Fall wäre die mangelnde Selbstbestimmung wohl das kleinere Übel. Allerdings fehlt dann gemäß Aldous Huxley ein Teil der Persönlichkeit. Letztlich ist natürlich alles eine Frage der Abwägung. **Sind viele Menschen möglicherweise schon so «eingenordet»,** dass freiheitliche Ambitionen gar nicht für eine ganze Gruppe, ein Kollektiv, verfolgt werden können? Solche Gedanken kamen mir auch, als ich mir kürzlich diverse Talks beim viertägigen [Hacker-Kongress](https://transition-news.org/der-38-kongress-des-chaos-computer-clubs-bot-mehr-enthullungen-als-nur-die) des Chaos Computer Clubs (38C3) anschaute. Ich war nicht nur überrascht, sondern reichlich erschreckt angesichts der in weiten Teilen mainstream-geformten Inhalte, mit denen ein dankbares Publikum beglückt wurde. Wo ich allgemein hellere Köpfe erwartet hatte, fand ich Konformismus und enthusiastisch untermauerte Narrative. **Gibt es vielleicht so etwas wie eine Herdenimmunität gegen Indoktrination?** Ich denke, ja, zumindest eine gestärkte Widerstandsfähigkeit. Was wir brauchen, sind etwas gesunder Menschenverstand, offene Informationskanäle und der Mut, sich freier auch zwischen den Herden zu bewegen. Sie tun das bereits, aber sagen Sie es auch dieses Jahr ruhig weiter. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/kann-es-sein-dass-die-menschen-gar-keine-freiheit-wollen)*** erschienen.
@ a95c6243:d345522c
2025-01-03 20:26:47*Was du bist hängt von drei Faktoren ab:* *\ Was du geerbt hast,* *\ was deine Umgebung aus dir machte* *\ und was du in freier Wahl* *\ aus deiner Umgebung und deinem Erbe gemacht hast.* *\ Aldous Huxley* **Das brave Mitmachen und Mitlaufen in einem vorgegebenen, recht engen Rahmen** ist gewiss nicht neu, hat aber gerade wieder mal Konjunktur. Dies kann man deutlich beobachten, eigentlich egal, in welchem gesellschaftlichen Bereich man sich umschaut. Individualität ist nur soweit angesagt, wie sie in ein bestimmtes Schema von «Diversität» passt, und Freiheit verkommt zur Worthülse – nicht erst durch ein gewisses [Buch](https://www.nachdenkseiten.de/?p=126416) einer gewissen ehemaligen Regierungschefin. **Erklärungsansätze für solche Entwicklungen sind bekannt,** und praktisch alle haben etwas mit Massenpsychologie zu tun. Der Herdentrieb, also der Trieb der Menschen, sich – zum Beispiel aus Unsicherheit oder Bequemlichkeit – lieber der Masse anzuschließen als selbstständig zu denken und zu handeln, ist einer der Erklärungsversuche. Andere drehen sich um Macht, Propaganda, Druck und Angst, also den gezielten Einsatz psychologischer [Herrschaftsinstrumente](https://transition-news.org/spip.php?recherche=nudging\&page=recherche_wall). **Aber wollen die Menschen überhaupt Freiheit?** Durch Gespräche im privaten Umfeld bin ich diesbezüglich in der letzten Zeit etwas skeptisch geworden. Um die Jahreswende philosophiert man ja gerne ein wenig über das Erlebte und über die Erwartungen für die Zukunft. Dabei hatte ich hin und wieder den Eindruck, die totalitären Anwandlungen unserer «Repräsentanten» kämen manchen Leuten gerade recht. **«Desinformation» ist so ein brisantes Thema.** Davor müsse man die Menschen doch schützen, hörte ich. Jemand müsse doch zum Beispiel diese ganzen merkwürdigen Inhalte in den Social Media filtern – zur [Ukraine](https://transition-news.org/spip.php?recherche=ukraine\&page=recherche_wall), zum [Klima](https://transition-news.org/spip.php?recherche=klima\&page=recherche_wall), zu [Gesundheitsthemen](https://transition-news.org/spip.php?recherche=impfung\&page=recherche_wall) oder zur [Migration](https://transition-news.org/spip.php?recherche=migration\&page=recherche_wall). Viele wüssten ja gar nicht einzuschätzen, was richtig und was falsch ist, sie bräuchten eine Führung. **Freiheit bedingt Eigenverantwortung, ohne Zweifel.** Eventuell ist es einigen tatsächlich zu anspruchsvoll, die Verantwortung für das eigene Tun und Lassen zu übernehmen. Oder die persönliche Freiheit wird nicht als ausreichend wertvolles Gut angesehen, um sich dafür anzustrengen. In dem Fall wäre die mangelnde Selbstbestimmung wohl das kleinere Übel. Allerdings fehlt dann gemäß Aldous Huxley ein Teil der Persönlichkeit. Letztlich ist natürlich alles eine Frage der Abwägung. **Sind viele Menschen möglicherweise schon so «eingenordet»,** dass freiheitliche Ambitionen gar nicht für eine ganze Gruppe, ein Kollektiv, verfolgt werden können? Solche Gedanken kamen mir auch, als ich mir kürzlich diverse Talks beim viertägigen [Hacker-Kongress](https://transition-news.org/der-38-kongress-des-chaos-computer-clubs-bot-mehr-enthullungen-als-nur-die) des Chaos Computer Clubs (38C3) anschaute. Ich war nicht nur überrascht, sondern reichlich erschreckt angesichts der in weiten Teilen mainstream-geformten Inhalte, mit denen ein dankbares Publikum beglückt wurde. Wo ich allgemein hellere Köpfe erwartet hatte, fand ich Konformismus und enthusiastisch untermauerte Narrative. **Gibt es vielleicht so etwas wie eine Herdenimmunität gegen Indoktrination?** Ich denke, ja, zumindest eine gestärkte Widerstandsfähigkeit. Was wir brauchen, sind etwas gesunder Menschenverstand, offene Informationskanäle und der Mut, sich freier auch zwischen den Herden zu bewegen. Sie tun das bereits, aber sagen Sie es auch dieses Jahr ruhig weiter. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/kann-es-sein-dass-die-menschen-gar-keine-freiheit-wollen)*** erschienen. @ bd32f268:22b33966
2025-01-02 19:30:46Texto publicado por *Foundation Father @FoundationDads* e traduzido para português. Assumir responsabilidades numa época efeminada como a nossa é um superpoder. Algumas pessoas não sabem o que significa "assumir responsabilidades", no entanto, porque nunca tiveram um pai ou outra pessoa que as ama-se o suficiente para lhes ensinar. Então, aqui está como assumir responsabilidades. ## **Lembra-te que não és uma pessoa desamparada e incompetente.** As coisas não te acontecem simplesmente enquanto olhas fixamente com a boca aberta, usando todo o teu poder cerebral para te lembrares de como respirar. Tu tens poder de ação. ## Mantém estas perguntas em mente: "Que papel desempenhei eu nesta situação ou como ajudei a formar o sistema em que estou inserido?" "O que posso fazer agora mesmo para começar a corrigi-lo, por mais pequeno que seja?" Aqui estão alguns exemplos de como aplicar estas perguntas. *José Malhoa - Remédio* ## Saúde Estás com excesso de peso e cansado o tempo todo? Deprimido? Começa a caminhar 30 minutos por dia. De preferência ao ar livre. Pára de comer snacks. Marca uma consulta com um médico para fazer análises ao sangue. Todas estas coisas estão ao teu alcance. ## Finanças Estás a afogar-te em dívidas de cartão de crédito? Assumir responsabilidades significa reduzir drasticamente o teu consumo e iniciar um programa radical de pagamento do máximo de dívida que conseguires. Obtém uma aplicação de orçamento e começa a planear. Sentes-te preso no teu emprego sem futuro? Sentes que não ganhas o suficiente? Vai a entrevistas para vagas de emprego e descobre o teu verdadeiro valor no mercado. Reserva 1 hora todas as noites para melhorares. A menos que já estejas a trabalhar em dois empregos, toda a gente tem pelo menos 1 hora todas as noites. ## Arredores imediatos Se vês algo que precisa de ser feito, simplesmente faz. Não te queixes disso. Não resmungues baixinho. Não desejes que alguém tratasse disso. Simplesmente faz e não peças permissão. Guarda o carrinho de compras. Lava a caneca de café no lava-loiça. Arranca as ervas daninhas. Repara a parede. Se o quintal do teu vizinho estiver cheio de ervas, vai lá e corta a relva tu mesmo. Limpa a água do lava-loiça. Arruma a bancada. Leva o lixo para fora. Leva bom café para o escritório. ## Os teus filhos Muitos pais queixam-se do comportamento dos seus filhos como se não tivessem qualquer influência sobre o assunto. Mas os teus filhos farão o que tu os ensinaste a fazer. "Fizemos o melhor que pudemos." Não, não fizeram, e assumir responsabilidades significa admitir que foste permissivo e preguiçoso ou que querias sentir-te justo por não bater. Que pequena coisa podes fazer agora mesmo para começar? Escolhe um único comportamento que queres que eles parem, senta-os e explica as consequências do comportamento. Pede desculpa por teres deixado andar durante tanto tempo. Quando eles apresentarem o comportamento, aplica as consequências. Aconteça o que acontecer. ## Os teus relacionamentos Não tens amigos ou o teu grupo de amigos atual é uma má influência? Podes fazer novos amigos. Assumir responsabilidades significa admitir que a tua solidão é em grande parte auto-infligida. **O que podes fazer?** Começa a jogar ténis ou futebol. Existem ligas em todo o lado. Encontra uma boa igreja local e encontra maneiras de te envolver. Existem encontros para todo o tipo de atividade. Participa num que se alinhe com as tuas preferências. Quando estiveres em público, sorri mais e puxa conversa. Depois de conheceres algumas pessoas, estabelece uma cadência regular. Agenda almoços semanais ou mensais e alterna entre algumas pessoas. Ou talvez café de manhã. Não acontecerá da noite para o dia, mas dando pequenos passos consistentemente durante alguns meses e vais perceber que tens uma vida social. ## Os teus erros Se erraste, não te retires e escondas nem arranjes desculpas. Pede desculpa à pessoa que prejudicaste, diz-lhe porquê e oferece-te para compensar. Aceita as consequências com humildade. Vais descobrir que nada te conquista mais respeito do que assumir os teus erros. Esta é a principal. Se aprenderes a fazer isto bem, cobrirá uma infinidade de pecados porque cria hábito. Mesmo que tenhas apenas 1% de culpa na situação, assumir a responsabilidade e pedir desculpa pelo teu 1% está a construir um certo grupo de músculos. "Mas ele devia ter..." Pára com isso. Confiaste demasiado? Presumiste demasiado sem comunicar? Assume a responsabilidade por isso. Estes exemplos podiam continuar para sempre, então vou parar e terminar com este princípio: A tua resposta importa mais do que as tuas circunstâncias. Existem vítimas reais, algumas de tragédias horríveis. Mas mesmo que não te tenhas atirado para areias movediças, ainda podes assumir a responsabilidade por como reages e pelo que escolhes fazer a seguir. Às vezes, é agarrar numa corda de um transeunte e dizer: "Obrigado." Não te afogues nas areias movediças até que alguém te dê uma palmadinha nas costas por quão difícil é para ti, e não continues a apontar para o teu tempo nas areias movediças para desculpares os teus fracassos. Podes não ter escolhido uma batalha específica. Ainda podes assumir a responsabilidade por quão bem lutas a batalha. Num certo sentido, ninguém escolhe a principal batalha que enfrenta. Ninguém escolheu nascer. Ninguém escolheu a sua família. Ninguém escolheu as suas circunstâncias. O mundo nunca será perfeito. Tens de assumir a responsabilidade pela tua parte dele de qualquer maneira. Pode ser difícil. Pode ser doloroso. Não te foi prometida uma vida fácil e sem dor. Depois de começares a assumir responsabilidades, qual é o próximo passo? Altura de assumir mais responsabilidades. Por exemplo, se não tens problemas em fazer amigos e tens essa parte da tua vida resolvida, assume a responsabilidade por outra pessoa. Encontra um dos rapazes solitários na tua igreja que precisa de um amigo e adiciona-o à tua rotação de almoços. A recompensa por assumir responsabilidades é subir de nível e, como consequência, as coisas devem tornar-se mais desafiantes. Mas agora estás mais bem preparado para isso. Repete até morrer e, esperançosamente, a tua causa de morte será por viver e não por te queixares de não viver.
@ bd32f268:22b33966
2025-01-02 19:30:46Texto publicado por *Foundation Father @FoundationDads* e traduzido para português. Assumir responsabilidades numa época efeminada como a nossa é um superpoder. Algumas pessoas não sabem o que significa "assumir responsabilidades", no entanto, porque nunca tiveram um pai ou outra pessoa que as ama-se o suficiente para lhes ensinar. Então, aqui está como assumir responsabilidades. ## **Lembra-te que não és uma pessoa desamparada e incompetente.** As coisas não te acontecem simplesmente enquanto olhas fixamente com a boca aberta, usando todo o teu poder cerebral para te lembrares de como respirar. Tu tens poder de ação. ## Mantém estas perguntas em mente: "Que papel desempenhei eu nesta situação ou como ajudei a formar o sistema em que estou inserido?" "O que posso fazer agora mesmo para começar a corrigi-lo, por mais pequeno que seja?" Aqui estão alguns exemplos de como aplicar estas perguntas. *José Malhoa - Remédio* ## Saúde Estás com excesso de peso e cansado o tempo todo? Deprimido? Começa a caminhar 30 minutos por dia. De preferência ao ar livre. Pára de comer snacks. Marca uma consulta com um médico para fazer análises ao sangue. Todas estas coisas estão ao teu alcance. ## Finanças Estás a afogar-te em dívidas de cartão de crédito? Assumir responsabilidades significa reduzir drasticamente o teu consumo e iniciar um programa radical de pagamento do máximo de dívida que conseguires. Obtém uma aplicação de orçamento e começa a planear. Sentes-te preso no teu emprego sem futuro? Sentes que não ganhas o suficiente? Vai a entrevistas para vagas de emprego e descobre o teu verdadeiro valor no mercado. Reserva 1 hora todas as noites para melhorares. A menos que já estejas a trabalhar em dois empregos, toda a gente tem pelo menos 1 hora todas as noites. ## Arredores imediatos Se vês algo que precisa de ser feito, simplesmente faz. Não te queixes disso. Não resmungues baixinho. Não desejes que alguém tratasse disso. Simplesmente faz e não peças permissão. Guarda o carrinho de compras. Lava a caneca de café no lava-loiça. Arranca as ervas daninhas. Repara a parede. Se o quintal do teu vizinho estiver cheio de ervas, vai lá e corta a relva tu mesmo. Limpa a água do lava-loiça. Arruma a bancada. Leva o lixo para fora. Leva bom café para o escritório. ## Os teus filhos Muitos pais queixam-se do comportamento dos seus filhos como se não tivessem qualquer influência sobre o assunto. Mas os teus filhos farão o que tu os ensinaste a fazer. "Fizemos o melhor que pudemos." Não, não fizeram, e assumir responsabilidades significa admitir que foste permissivo e preguiçoso ou que querias sentir-te justo por não bater. Que pequena coisa podes fazer agora mesmo para começar? Escolhe um único comportamento que queres que eles parem, senta-os e explica as consequências do comportamento. Pede desculpa por teres deixado andar durante tanto tempo. Quando eles apresentarem o comportamento, aplica as consequências. Aconteça o que acontecer. ## Os teus relacionamentos Não tens amigos ou o teu grupo de amigos atual é uma má influência? Podes fazer novos amigos. Assumir responsabilidades significa admitir que a tua solidão é em grande parte auto-infligida. **O que podes fazer?** Começa a jogar ténis ou futebol. Existem ligas em todo o lado. Encontra uma boa igreja local e encontra maneiras de te envolver. Existem encontros para todo o tipo de atividade. Participa num que se alinhe com as tuas preferências. Quando estiveres em público, sorri mais e puxa conversa. Depois de conheceres algumas pessoas, estabelece uma cadência regular. Agenda almoços semanais ou mensais e alterna entre algumas pessoas. Ou talvez café de manhã. Não acontecerá da noite para o dia, mas dando pequenos passos consistentemente durante alguns meses e vais perceber que tens uma vida social. ## Os teus erros Se erraste, não te retires e escondas nem arranjes desculpas. Pede desculpa à pessoa que prejudicaste, diz-lhe porquê e oferece-te para compensar. Aceita as consequências com humildade. Vais descobrir que nada te conquista mais respeito do que assumir os teus erros. Esta é a principal. Se aprenderes a fazer isto bem, cobrirá uma infinidade de pecados porque cria hábito. Mesmo que tenhas apenas 1% de culpa na situação, assumir a responsabilidade e pedir desculpa pelo teu 1% está a construir um certo grupo de músculos. "Mas ele devia ter..." Pára com isso. Confiaste demasiado? Presumiste demasiado sem comunicar? Assume a responsabilidade por isso. Estes exemplos podiam continuar para sempre, então vou parar e terminar com este princípio: A tua resposta importa mais do que as tuas circunstâncias. Existem vítimas reais, algumas de tragédias horríveis. Mas mesmo que não te tenhas atirado para areias movediças, ainda podes assumir a responsabilidade por como reages e pelo que escolhes fazer a seguir. Às vezes, é agarrar numa corda de um transeunte e dizer: "Obrigado." Não te afogues nas areias movediças até que alguém te dê uma palmadinha nas costas por quão difícil é para ti, e não continues a apontar para o teu tempo nas areias movediças para desculpares os teus fracassos. Podes não ter escolhido uma batalha específica. Ainda podes assumir a responsabilidade por quão bem lutas a batalha. Num certo sentido, ninguém escolhe a principal batalha que enfrenta. Ninguém escolheu nascer. Ninguém escolheu a sua família. Ninguém escolheu as suas circunstâncias. O mundo nunca será perfeito. Tens de assumir a responsabilidade pela tua parte dele de qualquer maneira. Pode ser difícil. Pode ser doloroso. Não te foi prometida uma vida fácil e sem dor. Depois de começares a assumir responsabilidades, qual é o próximo passo? Altura de assumir mais responsabilidades. Por exemplo, se não tens problemas em fazer amigos e tens essa parte da tua vida resolvida, assume a responsabilidade por outra pessoa. Encontra um dos rapazes solitários na tua igreja que precisa de um amigo e adiciona-o à tua rotação de almoços. A recompensa por assumir responsabilidades é subir de nível e, como consequência, as coisas devem tornar-se mais desafiantes. Mas agora estás mais bem preparado para isso. Repete até morrer e, esperançosamente, a tua causa de morte será por viver e não por te queixares de não viver. @ a4a6b584:1e05b95b
2025-01-02 18:13:31## The Four-Layer Framework ### Layer 1: Zoom Out  Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what." **Example**: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems. - **Tip**: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage. _Once you have the big picture in mind, it’s time to start breaking it down._ --- ### Layer 2: Categorize and Connect  Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas. **Example**: Studying biology? Group concepts into categories like cells, genetics, and ecosystems. - **Tip**: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track. _With your categories in place, you’re ready to dive into the details that bring them to life._ --- ### Layer 3: Master the Details  Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable. **Example**: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language. - **Tip**: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding. _Now that you’ve mastered the essentials, you can expand your knowledge to include extra material._ --- ### Layer 4: Expand Your Horizons  Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams. **Example**: Learn about rare programming quirks or historical trivia about a language’s development. - **Tip**: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time. --- ## Pro Tips for Better Learning ### 1. Use Active Recall and Spaced Repetition Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information. ### 2. Map It Out Create visual aids like [diagrams or concept maps](https://excalidraw.com/) to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2. ### 3. Teach What You Learn Explain the subject to someone else as if they’re hearing it for the first time. Teaching **exposes any gaps** in your understanding and **helps reinforce** the material. ### 4. Engage with LLMs and Discuss Concepts Take advantage of tools like ChatGPT or similar large language models to **explore your topic** in greater depth. Use these tools to: - Ask specific questions to clarify confusing points. - Engage in discussions to simulate real-world applications of the subject. - Generate examples or analogies that deepen your understanding. **Tip**: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective. --- ## Get Started Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
@ a4a6b584:1e05b95b
2025-01-02 18:13:31## The Four-Layer Framework ### Layer 1: Zoom Out  Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what." **Example**: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems. - **Tip**: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage. _Once you have the big picture in mind, it’s time to start breaking it down._ --- ### Layer 2: Categorize and Connect  Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas. **Example**: Studying biology? Group concepts into categories like cells, genetics, and ecosystems. - **Tip**: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track. _With your categories in place, you’re ready to dive into the details that bring them to life._ --- ### Layer 3: Master the Details  Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable. **Example**: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language. - **Tip**: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding. _Now that you’ve mastered the essentials, you can expand your knowledge to include extra material._ --- ### Layer 4: Expand Your Horizons  Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams. **Example**: Learn about rare programming quirks or historical trivia about a language’s development. - **Tip**: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time. --- ## Pro Tips for Better Learning ### 1. Use Active Recall and Spaced Repetition Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information. ### 2. Map It Out Create visual aids like [diagrams or concept maps](https://excalidraw.com/) to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2. ### 3. Teach What You Learn Explain the subject to someone else as if they’re hearing it for the first time. Teaching **exposes any gaps** in your understanding and **helps reinforce** the material. ### 4. Engage with LLMs and Discuss Concepts Take advantage of tools like ChatGPT or similar large language models to **explore your topic** in greater depth. Use these tools to: - Ask specific questions to clarify confusing points. - Engage in discussions to simulate real-world applications of the subject. - Generate examples or analogies that deepen your understanding. **Tip**: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective. --- ## Get Started Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence. @ bcea2b98:7ccef3c9
2025-01-02 17:47:27originally posted at https://stacker.news/items/833889
@ bcea2b98:7ccef3c9
2025-01-02 17:47:27originally posted at https://stacker.news/items/833889 @ 5391098c:74403a0e
2025-01-02 16:50:29Ensaio em Prosa sobre Fotografia Analógica Tenho especial fascínio pela fotografia analógica. É que se trata dum processo artístico muito mais complexo que a fotografia digital, devemos entender todos os aspectos da fotografia para obter o resultado pretendido, desde aspectos mecânicos da câmera como abertura e tempo do obturador, foco, iluminação, até a sensibilidade do filme utilizado e o resultado, quando alcançado, é verdadeira obra de arte pintada, onde a tela é a película química. Importante dizer que meu fascínio pela fotografia analógica não me impede de reconhecer a importância da fotografia digital, não fosse essa você não estaria vendo minhas obras de arte que foram digitalizadas… Da mesma forma que meu fascínio pela máquina de escrever não me impede de ter essa e outras páginas na internet. Parte do meu livro FILOSOFIA FUNDAMENTAL foi escrito graças a inspiração da máquina de escrever, como ocorreu no capítulo sobre o que seria evolução, escrevi integralmente na minha Olivetti Studio 46, pois havia faltado luz: o que me fez refletir sobre se o computador realmente é a evolução da máquina de escrever. Outro exemplo foi a inspiração que as lindas formas arredondas de minha máquina de escrever da marca Érika me proporcionou, acabou resultando numa bela performance a qual dei nome de Paixão Erótika. Por isso, acredito que os equipamentos analógicos não ofuscam nossa criatividade e na fotografia não poderia deixar de ser diferente. No conjunto de fotografias analógicas abaixo utilizei uma Canon T50, objetiva de 50mm e filme Kodak Pro Image 100, a qual se encontra auto-fotografada em espelho, vamos ver: Na foto abaixo utilizei luz amarela indireta da direita superior para esquerda inferior, o desfoque ao redor foi proposital com o objetivo de parecer estar olhando o mundo através das lentes da câmera, nesse caso ela estava olhando para sí mesmo. Mesmo estando a parede e o espelho no mesmo plano, a profundidade de campo do espelho é diferente, por isso esse efeito foi possível. Destaque especial para o “olho” do diafragma, deve ter aberto até f5.6, pois a luz não era muito forte. Se a luz fosse mais forte o diafragma teria aberto o mínimo f16 o que aumentaria a profundidade de campo impedindo o desfoque pretendido. O resultado foi alcançado, ao mesmo tempo que a câmera aparece, essa fotografia transmite essa mensagem subliminar: https://image.nostr.build/a7cbfbe68a4bb89ae731c360c373ac8eff7599a5a100d13035eb234b5d788626.jpg PERFORMANCE Performance é o nome dado à mescla de mais de uma linguagem artística (arte visual, música, teatro, etc.) clicando em https://davipinheiro.com/id/performance/ você pode ver todas minhas performances. Nos exemplos abaixo a mescla se deu pela mistura de artes visuais criadas por mim e captadas pela fotografia analógica, vamos ver: A foto abaixo se trata dum terrário que criei num tronco de árvore, arte plástica. Para fotografar utilizei luz amarela superior, o desfoque foi para destacar o objeto, especial destaque para o reflexo da luz no vidro para dar noção tridimensional de algo transparente: https://image.nostr.build/e8026f9e99fa16631959954f8bb925af6f1764911f0a315ab0125bb413e3e89b.jpg Na foto abaixo o mesmo processo da foto anterior, também utilizando uma Canon T50 com filme Kodak Pro Image 100 e objetiva de 50mm, diferenciando o enquadramento e a luz direta frontal: https://image.nostr.build/4c44a0baf2b5ddaf63f83420952ab1b2e84f7df292f8e413a65f8134a2e7db58.jpg A foto abaixo retrata o processo de criação da obra. Ironicamente, nessa foto, meu galo Cara de Palhaço mesmo desfocado no fundo se destacou, parecendo estar em pé no tronco: https://image.nostr.build/d0d5e73ecbcdefa79ffd858d0143f41915c9deab7864d271d5ee724b3927f9bc.jpg A foto abaixo se trata do pisca-alerta original da minha super DT200R (viva os motores 2 tempos!) que caiu depois de uma trilha kkk. A Ideia nesta fotografia era fazer o sol parecer estar acendendo o alerta que deveria aparentar estar flutuando no céu. Infelizmente não fui bem sucedido, pois os fios que penduravam o objeto acabaram aparecendo. É impressionante a capacidade de cálculo da Canon T50 e a velocidade do seu obturador, a nitidez da objetiva e a resolução do filme Kodak Pro Image 100, cujo conjunto conseguiu captar até os pequenos fios de nylon transparentes. Eu imaginei que a foto ia estourar e os fios não apareceriam, ledo engano. Pelo menos o enquadramento ficou correto: objeto um pouco mais acima do centro para dar sensação de altitude e levemente de perfil para dar noção 3d. Quem sabe com uma câmera que seja possível ajustar a velocidade do obturador eu seja bem sucedido… https://image.nostr.build/808243d34b6dbeade25d38189163f9d58f6a12da9d00df17c85651d501e1bed8.jpg A foto abaixo se trata da minha performance favorita com a fotografia analógica, pois fotografei o primeiro quadro que pintei, o qual dei o nome de Elipsoíris sendo ele posteriormente capa do meu livro FILOSOFIA FUNDAMENTAL, então aí temos três linguagens artísticas profundas na mesma performance: O quadro que virou livro fotografado analogicamente. A ideia desta performance foi enquadrar o quadro desfocado, o qual somente pode ser desvendado com os olhos certos, por isso a lente. Utilizei luz natural e uma lente velha de óculos. Especial destaque para os dois pontos de luz que refletiram na lente parecendo dois olhos, isso não foi planejado e deu um toque especial para a fotografia, cabendo diversas interpretações, esse é o objeto da arte em geral. Fiquei muuuito contente com o resultado: https://image.nostr.build/6bb5b802b3ad1bb7262b925225fcfb0b8b00654fa0fec240be57f648c32245af.jpg Já na fotografia analógica abaixo considero uma performance porque não se trata duma fotografia comum de paisagem, flores, arquitetura, animais ou pessoas, visa passar uma mensagem. Utilizando apenas a luz natural, regulei o foco da Canon T50 para as lentes dos meus próprios óculos e escolhi um dia especialmente nublado e escuro para simbolizar as dificuldades pelas quais todos passamos no dia-a-dia, quando acreditamos por algum momento que as luzes estão apagadas para nós, até que com os óculos certos podemos enxergar com maior nitidez o horizonte, os óculos podem ser a palavra de Deus ou qualquer outra coisa que te ilumine e esclareça. Com certeza essa fotografia terá um bom uso em meus próximos escritos: https://image.nostr.build/b44b573bb39cdf5f2eb446e818bbf59d5dab9d3815ac6e917440b2f6b1ff431c.jpg DUPLA EXPOSIÇÃO Eis aqui um recurso nato da fotografia analógica: a dupla exposição. Se trata de fotografar mais de uma vez em cima do mesmo filme de modo que as imagens se sobreponham. Como esse método podemos simular movimento numa única fotografia, fazer montagens de disco voador kkkk, enfim a imaginação é o limite, vamos ver: Nessa fotografia analógica abaixo ocorreu uma quádrupla exposição, pois cliquei quatro enquadramentos diferentes sob o mesmo filme. Foi especialmente difícil fazer porque a Canon T50 não tem esse recurso, então tive que enganá-la pressionando o botão de rebobinar o filme ao mesmo tempo que disparava a câmera. Como eu estava usando o filme Kodak Pro Image que possui asa 100, também regulei a máquina como se estivesse usando um filme asa 25, então sabia que podia disparar quatro vezes sem queimar o filme. Pedi para a modelo (minha Mãe, kkk) ficar em três posições diferentes dando a impressão de movimento e não satisfeito no final ainda fotografei o sol. Adorei essa foto: https://image.nostr.build/5f8e2962e2ee94259d4dd5d3b777976a4d20ba293a5a4e68e81e30a0e1975543.jpg FOTOS EM MACRO OU CLOSE Acredito ser possível obter uma fotografia analógica em macro mesmo sem lente especial, tudo depende da pecinha que fica atrás da câmera: você, kkkk. Devemos tentar, se não obtivermos uma fotografia em macro, ao menos um close teremos, vamos ver: Na foto abaixo há um minúsculo cogumelo que cresceu num barranco qualquer, apareceu nitidamente no negativo, mesmo sem uso de lupa, por isso considero um macro, na verdade é apenas uma foto divertida: https://image.nostr.build/02aa4bbdc0cf54519b694c75237693fc2a6569fe4f3167220b05c7498757b822.jpg Já a foto abaixo é apenas um close, o ninho é especialmente profundo, por isso o leve desfoque nos ovos: para dar noção de profundidade. O foco dos quatro cantos da caixa está bem ajustada para dar noção tridimensional do objeto: https://image.nostr.build/24e5dcdd0e5a3560b341fe4f0d0d93b7d562f2d58054ac308a8e312c2707100c.jpg O PRIMEIRO QUADRO DO ROLO Na fotografia analógica cada rolo de filme nos dá pelo menos um tipo de fotografia artística bem específica. Se trata do primeiro quadro do rolo, onde ocorre uma parcial sobre-exposição. Isso se deve a incidência da luz diretamente no filme quando estamos carregando a máquina com o filme. A maioria das máquinas analógicas somente começa a contar os fotogramas após alguns disparos para evitar isso. Cabe ao fotógrafo saber aproveitar os fotogramas existentes antes do número 1, enquadrando a cena normalmente e disparando antes do número 1. Os resultados são quase imprevisíveis e geralmente interessantes. Abaixo uma fotografia analógica fantástica porque quase sempre a sobre-exposição do primeiro quadro do rolo ocorre nas extremidades da foto e nessa aí ocorreu no meio. Para conseguir esse efeito carreguei a máquina no escuro e acendi a luz no exato momento que estava fechando a tampa da câmera. Por uma fração de segundo o primeiro quadro do rolo foi exposto parcialmente a luz, sabia que iria ter uma fotografia diferente, jamais imaginei que a sobre-exposição iria sair no meio do fotograma, muito curioso: https://image.nostr.build/a2e08aab686af64df949e83b4ff3b0a00952698a7a138412f7753ebc0dd63d1f.jpg Na fotografia abaixo repeti o mesmo processo anterior. Como o tempo entre acender a luz e fechar da máquina foi diferente a sobre-exposição ficou bem visível na extremidade da foto. Especial destaque para sua incidência no lado direito, quando deveria incidir no lado esquerdo, pois na Canon T50 o filme roda da esquerda para direita. Essa aparente inversão de lados se deu porque fotografei com a máquina de cabeça para baixo: https://image.nostr.build/270681be8de71b6c833507dda6bfe4b5233c9b871aa97ea8fc2ebdcdd46a682a.jpg FOTOS DE AÇÃO Registrar uma ação com fotografia analógica é especialmente difícil se a máquina não calcula a abertura e tempo de exposição automaticamente, porque tudo acontece muito rápido e você não tem tempo de ficar pensando. Felizmente a Canon T50 é muito boa para esse tipo de fotografia, tive que me preocupar apenas com o foco. O que essa máquina me fez suar para fazer as duplas exposições acima, tirou de letra esse memorável momento, vamos ver: Na foto abaixo quando avistei esse grupo de corajosos saltando de paraglider corri pedir autorização para fotografá-los e rapidamente carreguei a máquina. Comecei a fotografar mesmo antes da máquina registrar o primeiro fotograma do rolo, tendo obtido esse lindo efeito de sobre-exposição de primeiro quadro do rolo: https://image.nostr.build/8e32e22d3bf7c897d7111e85555146e38bb139985c50b2795fe809b31880c7d8.jpg Já a foto abaixo foi a terceira do rolo. Tomei o cuidado de enquadrar tanto a alçada de vôo do paraglider quanto essa linda Veraneio, o que descreve em uma única foto o espírito aventureiro do pessoal. Reparem no sol refletindo sobre as nuvens, que lindo tudo: https://image.nostr.build/5bf0444e4621406d858ab70725c1ee2f6a7e39b87663e23a18085a32b9a06f6a.jpg Na foto abaixo tive que registrar mais uma dessa linda Veraneio, sou apaixonado por motores e mecânica, ela quase roubou a cena kkkk. Especial destaque para o detalhe do carro e da câmera que a fotografou serem da mesma época, sensível retorno ao passado. Verdadeira máquina do tempo essa foto. Se eu não dissesse que esta foto foi tirada no final do ano de 2020 daria para dizer que foi uma foto tirada de uma Veraneio Zero Km da época, segredinho nosso, kkk. https://image.nostr.build/f5284ff30986ad84d22f137e0a330067f91564907da8acf04c9eb93a991cbcf2.jpg Na foto abaixo voltando à cena, agora do Ângulo certo kkk. Esse foi a segunda foto, perceba ainda a presença do efeito de sobre-exposição do primeiro quadro. Aqui a máquina estava marcando o primeiro fotograma, tadinha kkk https://image.nostr.build/5c1d73f7d802fd1f730427e29f921c82e410c5dce3112a3133d6fce294d310c6.jpg Na foto abaixo a luz estava perfeita, o sol iluminava atrás de mim, incidindo frontalmente para o enquadramento da foto, linda essa: https://image.nostr.build/156fc878dd18257ad1f59d1b5d3fd719c7e773937356fad6ea09b0ce1f151f12.jpg Paraglider quase em posição de vôo, a foto ficou quase perfeita porque o momento em tela era a Hora de Ouro, momento do entardecer quando a posição do sol deixa o céu dourado, fenômeno muito querido pelos fotógrafos analógicos; até pelos digitais também. Mesmo assim eu não estava satisfeito, queria fotografar mais de perto. Dei zoom correndo para frente e o resultado você vê abaixo: https://image.nostr.build/b1f610695bd57db8abe7408df318978b6e69e85fe620a589b12fb9bcaae66156.jpg Abaixo a fotografia analógica simplesmente perfeita, sol na posição certa, hora de ouro, perfeito enquadramento e foco, tudo certo, universo conspirando à favor… ganhei o dia sem saber. Só descobri depois que revelei. O chão não foi cortado é que o piloto do paraglider já estava no desnível do chão pronto para saltar: https://image.nostr.build/93a7e416d11c996b65a32b019667a43124d96985109d34fd1a9b239ef365bbfe.jpg Abaixo O salto… tive que correr para o barranco para dar zoom, outra foto perfeita na hora de ouro: https://image.nostr.build/f254c2e71863a233816b517564dd5fb7fe85ee0bd927b02687fba43bde53dcd6.jpg FOTOGRAFIA ANALÓGICA DE ANIMAIS É especialmente difícil fazer um animal posar para gente, temos que ter um pouco de comida pra negociar kkk. Não fosse a Canon T50 calcular a exposição sozinha seria ainda mais difícil porque os momentos são muito rápidos e você não tem tempo para regular a abertura e tempo de exposição, tive que regular apenas o foco. Mais um ponto para essa notável máquina que me fez apanhar na dupla exposição acima. A fotografia analógica de animais também é um tipo de fotografia de ação, temos que ser rápidos no gatilho, vamos ver os resultados: Abaixo novamente dei zoom chegando bem perto, fotógrafo de verdade não tem medo, tudo pela arte! https://image.nostr.build/5f0af116b1fd81edb3f21dfd5d7cce6c534751ac8660bd5fb58ce08c652d8aaf.jpg Abaixo foco no segundo plano, acabei pegando os dois de perfil: https://image.nostr.build/fbd78fcf71749569444d3438e0d5283d321fc3f3350cacc6e4a3e9a0cdc914f5.jpg Abaixo foco no segundo plano. Aqui peguei os dois olhando para mim e dizendo xiiiis, kkk. https://image.nostr.build/3a1f50ee1e3c6213b337654e69ee23819ab60100c8a1a049ee0b2b66fac0d8f8.jpg Abaixo podemos comprovar que o fotômetro da Canon T50 é matricial e não pontual, porque o centro da foto tinha muito mais luz que os cantos: https://image.nostr.build/11a8a5a7ff14a661755f04f743d70d3dd1a9d11e412791ce42f5cbf1da1c6be2.jpg Abaixo linda foto: Cavalo da Montanha. Eu estava esperando a Hora de Ouro chegar, pena que quando chegou o modelo não quis mais ser fotografado kkk. https://image.nostr.build/83429975966cb4b0e71e5e089651d4585513d823fea404014b0b78b21e859302.jpg Abaixo lindo close de perfil com fundo totalmente desfocado. Preto absoluto, a fotometria esta certinha: https://image.nostr.build/f36aed8fa89b6ba81dd77c7d3b32c24424483e626a9634cbadb16baf91427d66.jpg Abaixo muita coisa acontecendo ao mesmo tempo: As galinhas comendo, o milho sendo jogado, a sombra do fotógrafo… Para obter essa foto joguei o milho para o alto e tive que ser tão rápido no gatilho quanto o Kid Morengueira. Você pode perceber na minha sombra que estou segurando apenas a câmera, o pote de milho já tinha voado longe kkk. Escolhi especialmente um dia ensolarado para que o fotômetro da Canon T50 usasse toda a velocidade possível no obturador, sendo possível congelar o milho no ar sem muito efeito borrão. https://image.nostr.build/d566e46a8a3cba8855e80295910e5addb0a8aa7735093c9f93f129cac2379472.jpg Abaixo galinha chocando numa roda de carro. Como amo animais e carros, para montar essa cena tive que forrar uma roda velha de carro para formar um ninho e esperar, esperar e esperar… No momento certo a Jurema se sentiu confiante para entrar na roda. Nem se incomodou com minha presença pois estava de papo cheio, pois é, também tive que negociar com a galinha, isso é a fotografia analógica de animais kkk. Percebam novamente que o fotômetro da Canon T50 é matricial, pois a maior parte da foto era com pouca luz e o raio de sol que entrava estourou a foto. Percebam ainda como eu estava perto da galinha, pois foquei em sua cabeça e o resto do corpo que estava um pouco mais distante saiu desfocado. Certamente a câmera estava com abertura máxima f1.8 e com uma velocidade bem lenta, o que explica a baixa profundidade de campo. Além disso se a Jurema tivesse mexido a cabeça na hora do disparo certamente teria saído um borrão por causa da baixa velocidade. Acabou saindo tudo certo e meus dias de espera por essa foto não foram em vão. https://image.nostr.build/d7484609c8ff9be05ee6d518def402f66484a02109dc96ef5c734b11216385bf.jpg FOTOGRAFIA ANALÓGICA DE ARQUITETURA Na fotografia analógica de arquitetura devemos conhecer os conceitos básicos de iluminação e preenchimento, trabalhamos apenas com luz natural e deve ser bem usada para termos a noção tridimensional da construção. Conforme ensina Fernando Bagnola, a tridimensionalidade do objeto depende da incidência da luz em três pontos diferentes e com intensidades diferentes, algo difícil de se obter apenas com a luz do sol, vamos ver: Abaixo se trata do Museu do Olho em Curitiba/PR. Como sua parte frontal é escura e o sol se posicionava atrás da construção tive de me posicional na sua lateral, assim consegui obter um resultado tridimensional, pois o sol iluminava a parte de cima, refletia na parte de baixo em menor intensidade e na parte frontal quase não havia luz. Se eu estivesse posicionando na frente da construção o efeito tridimensional seria impossível: https://image.nostr.build/6f74c1c7e606f7950eaf45007868b92e9a0288722b3d5e580ecaa4930700e3ea.jpg Abaixo para minha sorte, nesse exato momento um grupo de jovens contracultura (assim como eu) passavam pelo local, tornando a foto icônica pela presença de jovens modernos contracultura contrastando com arquitetura moderna da cultura tradicional. Minha posição em relação ao sol também favoreceu o sucesso desta fotografia, tendo iluminado corretamente todos os pontos de interesse: https://image.nostr.build/7c374205d7df21985a6a71c6c17e4f67ab29baf452f0cd406b869df94d68296c.jpg Abaixo esse aqui é um exemplo de fotografia analógica arquitetônica errada. O enquadramento foi frontal em razão do desejo de captar o reflexo dos edifícios nos vidros negros do “olho”: https://image.nostr.build/f9a0869a165bc7e634944c01e59085203347ab6c353610bdcaace30ee3ed8d8a.jpg Abaixo se trata do Panteon dos Heroes na Lapa/PR um monumento erguido para guardar os corpos dos soldados das forças republicanas que pereceram durante o chamado Cerco da Lapa, batalha da Revolução Federalista de 1894. Aqui o dia estava nublado, momento perfeito para fotografar uma arquitetura tão triste como essa. Não me importei com a questão tridimensional, pois era impossível, não havia sol. Quis retratar a tristeza na foto. O filme usado foi o mesmo (Kodak Pro Image 100). Aqui percebemos que a química desse filme é ajustada para a luz amarela do sol como branco absoluto, como o céu estava nublado, a luz natural estava com temperatura mais fria o que puxou o tom mais para o azul e o roxeado da foto devem ter sido os raios ultravioleta. Se eu estivesse usando um filtro ultravioleta provavelmente a foto sairia mais acinzentada. Me recordo que nesse dia estava tudo cinza. De qualquer forma adorei esse tom arroxeado da foto. Fica a dica: conseguimos o mesmo efeito de um filme Lomochrome Purple caríssimo com um filme baratinho, basta fotografar nessas condições: https://image.nostr.build/24f91369c12e83861f7eec38ff99f1869f08ae1eec06c798ccbe08af62263a2e.jpg Abaixo novamente o tom arrocheado com um filme barato. Para se ter uma ideia um Lomochrome Purple costuma custar seis vezes ou mais que um que o Kodak Pro Image 100 de R$ 30,00 à R$ 40,00 na data da publicação deste artigo em 09/04/21. Percebam que no momento desta foto as nuvens deram uma trégua e alguns raios de sol passaram dando uma leve noção tridimensional da arquitetura. O certo seria eu estar um pouco mais à esquerda para aproveitar bem a iluminação. Mesmo assim, me senti feliz com a triste foto kkk pois mesmo com a luz amarela do sol refletindo o efeito Lomo-Violeta ocorreu: https://image.nostr.build/099a1a4d7857325e59f5b35805c0ebb5c3fa55af45de2096236f1dfbadca4d4a.jpg Abaixo parece que a foto está mal enquadrada. E está mesmo. É que no lado direito havia um poste de energia elétrica muito feio, eu não queria que aparecesse. Me preocupei apenas com a iluminação e obtive sucesso com a noção de profundidade da arquitetura. A foto está puxando para o amarelo porque a Universidade Federal do Paraná em Curitiba é meio amarela mesmo. https://image.nostr.build/48a4d517488fc1656e027568ad314688bc0fd9995e67289003f832eb904e5260.jpg Abaixo para finalizar o conjunto de fotografias analógicas arquitetônicas nada melhor que um cemitério, afinal todos vamos morrer um dia, devemos sempre lembrar disso para fazer nossas vidas mundanas valerem a pena. Quando morremos não levamos nada a não ser nossas experiências evolucionais, nossas graças e pecados. Devemos deixar um legado, algo positivo para quem fica. Pois bem, foi nesse contexto a foto. Para mim a morte deve ser evitada. Quando ocorrer, se fizermos tudo certo vamos para luz, as trevas são aqui na terra mesmo. Portanto, ao contrário da maioria dos fotógrafos, escolhi um dia ensolarado para fotografar ali. Quis simbolizar a luz que nos aguarda após a morte. Então me posicionei dentro do cemitério para fotografar de dentro para fora. Esperei o sol se posicionar de forma que dos portões para fora houvesse pouca luz, tal como é o mundo, deixando toda a iluminação para dentro dos portões. Percebam como pequenos detalhes fazem toda a diferença numa fotografia analógica artística. Essa foto pode perfeitamente ser usada para ilustrar qualquer material que corrobore com esse pensamento. Se eu quisesse retratar que a vida é mil maravilhas e a morte um triste fim, deveria estar do lado de fora dos portões com tudo iluminado exceto o interior do cemitério. Interessante não… https://image.nostr.build/051592db1d3612c719621547a69bc8dfd0319d6b89656451d5b60582ae864e8e.jpg FOTOGRAFIA ANALÓGICA DE PESSOAS Basicamente se divide em dois tipos, a cena e o retrato. Na cena a pessoa posa para a foto sem contudo revelar sua personalidade, é uma cena criada artificialmente. Já o retrato, no conceito artístico da fotografia, ocorre quando conseguimos captar o interior da pessoa. Por exemplo: se for uma pessoa triste ela aparecerá com semblante triste, se for uma pessoa alegre com semblante alegre, não necessariamente sorrido. Se for uma pessoa sofrida suas rugas, desasseios e receios ficarão visíveis. Se for uma pessoa engraçada sentiremos vontade de rir ao ver seu retrato. O retrato é algo verdadeiro e espontâneo da pessoa. Se uma pessoa triste aparece sorrido não é um retrato e sim uma cena, vamos ver: Abaixo normalmente na fotografia analógica de pessoas o correto é deixar o segundo plano mais escuro e o primeiro plano mais claro. Ai quis fazer diferente. Pedi para o modelo (Meu Melhor Amigo) se posicionar de costas para o sol, pois já tinha avistado aquele arco-íris no fundo. Nesse caso foi um retrato pois meu amigo apareceu sorrindo sem eu pedir e sei que ele é uma pessoa feliz e engraçada, pois vive contando piadas e seu repertório é infinito. O interessante é que esse não é um retrato comum e sim um retrato artístico, pois inverti a iluminação dos planos e ainda captei uma arco-íris, foi uma cena construida para um retrato, ideia antagônica para fotografia analógica de pessoas. Como resultado obtive uma fotografia que parece uma montagem, onde a imagem do modelo ter-se-ia sido colada sobre a paisagem, tamanha foi a diferença de iluminação entre o primeiro e segundo plano. Contudo, um pequeno raio de sol que incidiu sobre o canteiro inferior esquerdo não me deixa mentir que a fotografia é autêntica. Além disso tendo os negativos que não mentem kkk. Essa foi minha fotografia preferida de pessoas, pela qualidade do resultado artístico e pela pessoa do modelo, um abração amigo! Vou chamar essa foto de “Meu Parça na Praça”: https://image.nostr.build/51db1df7741227dc2d86529bc9e7a93cf27365f0f2d7b591a4e84a9a05855dfb.jpg Abaixo sou eu. Se trata apenas de uma cena simples porque minha expressão não aparece e sequer minhas roupas traduziam minha personalidade. Regulei o foco da máquina para 5 metros, entreguei-a para meu amigo e contei alguns passos para trás. Não me preocupei muito em acertar minha posição em exatos 5 metros porque o dia estava bem ensolarado e sabia qua a Canon T50 iria abrir pouco o diafragma por causa disso, o que aumentou a profundidade de campo consideravelmente. Podemos perceber no fundo a Universidade Federal do Paraná sem qualquer desfoque por causa disso. O maldito poste que tentei evitar na foto arquitetônica da UFPR acima acabou aparecendo aqui, mesmo assim gostei da foto pelo tom de cores que só a fotografia analógica nos dá. https://image.nostr.build/ce8af555274333fa8a26375247373ca92315e87d7414bcc9ad7b5a4840cb3a21.jpg FOTOGRAFIA ANELÓGICA DE OBJETOS A fotografia analógica de objetos, assim como a arquitetônica, deve se obedecer os conceitos básicos de iluminação para obter noção tridimensional do objeto. Além disso, a cena montada deve combinar com o objeto para entrar em sintonia com o conceito natural de beleza, vamos ver: Abaixo queria fotografar um objeto qualquer, então peguei essa faca. Esse objeto combina muito bem com o ambiente rústico do campo, então a finquei-a num toco de árvore com vista para o campo, tomando cuidado para ela ficar levemente torcida e dar a noção tridimensional. Naturalmente a foto ornou porque o objeto esta em sintonia com a cena. Essa deve ser a combinação da fotografia analógica de objetos, por exemplo. A não ser que o fotógrafo busque justamente causar repudia invertendo a combinação do objeto com a cena. Por exemplo: para causar nojo pode-se fotografar barro em formato de cocô num prato. Merda e comida são coisas totalmente opostas e essa inversão naturalmente é perturbadora para qualquer ser humano. Existe uma lógica natural de combinação de objetos com a cena. Enfim, podemos inclusive combinar mais de um objeto secundário para criar uma cena ao objeto principal, como veremos mais abaixo com a xícara de café: https://image.nostr.build/6474901ce85d34aef3421ce5f720e258208c50aeb57e9893c8a750c6dc8fc1df.jpg Na foto abaixo o objeto principal é uma caneca de café. Para criar a cena utilizei outros três objetos. O palheiro que combina com café, a tampa da objetiva da minha Canon T50 que combina com o efeito da cafeína para pensar mais rápido sobre as cenas que irei montar, e o vazo de suculenta que remete a algo mais áspero e amargo como o café e o palheiro. Se o objeto principal fosse um copo de milkshake no lugar do palheiro haveriam balas coloridas, no lugar da tampa da máquina haveria um guardanapo e no lugar da suculenta haveria um flor fofa e cor de rosa. Falando em flor vou encerrar este ensaio com o tópico sobre fotografia analógica de flores para deixar todos felizes no final: https://image.nostr.build/8e95c6bae536cfea47e3c5d44aa63725ab8fe20eacd1c6d5eeaae1720dd0a9e5.jpg FOTOGRAFIA ANELÓGICA DE FLORES É um tipo de fotografia livre da fotografia analógica, sem muitas preocupações para o fotógrafo analógico, devemos atentar apenas para a vivacidade das cores e para isso o dia deve estar especialmente ensolarado. Se for fotografia interna de preferência usar luz quente (amarela), o resto é só diversão, vamos ver: https://image.nostr.build/fc8cf663300794761b0d8dc6f1a765e3a423c65a4ad4a85a7885b00716b46533.jpg https://image.nostr.build/dc4fbe15a7b46817d66bdbeb3d0e11851999b2c1292c576fd457956436e75c77.jpg https://image.nostr.build/73fa3b1b30a088954b342294e1b0aa555a693c3ad425dea9807d2238ec529747.jpg Viva a fotografia analógica! Se você deseja fazer um ensaio artístico com fotografia analógia comigo entre em contato e terei o prazer de agendar o serviço.
@ 5391098c:74403a0e
2025-01-02 16:50:29Ensaio em Prosa sobre Fotografia Analógica Tenho especial fascínio pela fotografia analógica. É que se trata dum processo artístico muito mais complexo que a fotografia digital, devemos entender todos os aspectos da fotografia para obter o resultado pretendido, desde aspectos mecânicos da câmera como abertura e tempo do obturador, foco, iluminação, até a sensibilidade do filme utilizado e o resultado, quando alcançado, é verdadeira obra de arte pintada, onde a tela é a película química. Importante dizer que meu fascínio pela fotografia analógica não me impede de reconhecer a importância da fotografia digital, não fosse essa você não estaria vendo minhas obras de arte que foram digitalizadas… Da mesma forma que meu fascínio pela máquina de escrever não me impede de ter essa e outras páginas na internet. Parte do meu livro FILOSOFIA FUNDAMENTAL foi escrito graças a inspiração da máquina de escrever, como ocorreu no capítulo sobre o que seria evolução, escrevi integralmente na minha Olivetti Studio 46, pois havia faltado luz: o que me fez refletir sobre se o computador realmente é a evolução da máquina de escrever. Outro exemplo foi a inspiração que as lindas formas arredondas de minha máquina de escrever da marca Érika me proporcionou, acabou resultando numa bela performance a qual dei nome de Paixão Erótika. Por isso, acredito que os equipamentos analógicos não ofuscam nossa criatividade e na fotografia não poderia deixar de ser diferente. No conjunto de fotografias analógicas abaixo utilizei uma Canon T50, objetiva de 50mm e filme Kodak Pro Image 100, a qual se encontra auto-fotografada em espelho, vamos ver: Na foto abaixo utilizei luz amarela indireta da direita superior para esquerda inferior, o desfoque ao redor foi proposital com o objetivo de parecer estar olhando o mundo através das lentes da câmera, nesse caso ela estava olhando para sí mesmo. Mesmo estando a parede e o espelho no mesmo plano, a profundidade de campo do espelho é diferente, por isso esse efeito foi possível. Destaque especial para o “olho” do diafragma, deve ter aberto até f5.6, pois a luz não era muito forte. Se a luz fosse mais forte o diafragma teria aberto o mínimo f16 o que aumentaria a profundidade de campo impedindo o desfoque pretendido. O resultado foi alcançado, ao mesmo tempo que a câmera aparece, essa fotografia transmite essa mensagem subliminar: https://image.nostr.build/a7cbfbe68a4bb89ae731c360c373ac8eff7599a5a100d13035eb234b5d788626.jpg PERFORMANCE Performance é o nome dado à mescla de mais de uma linguagem artística (arte visual, música, teatro, etc.) clicando em https://davipinheiro.com/id/performance/ você pode ver todas minhas performances. Nos exemplos abaixo a mescla se deu pela mistura de artes visuais criadas por mim e captadas pela fotografia analógica, vamos ver: A foto abaixo se trata dum terrário que criei num tronco de árvore, arte plástica. Para fotografar utilizei luz amarela superior, o desfoque foi para destacar o objeto, especial destaque para o reflexo da luz no vidro para dar noção tridimensional de algo transparente: https://image.nostr.build/e8026f9e99fa16631959954f8bb925af6f1764911f0a315ab0125bb413e3e89b.jpg Na foto abaixo o mesmo processo da foto anterior, também utilizando uma Canon T50 com filme Kodak Pro Image 100 e objetiva de 50mm, diferenciando o enquadramento e a luz direta frontal: https://image.nostr.build/4c44a0baf2b5ddaf63f83420952ab1b2e84f7df292f8e413a65f8134a2e7db58.jpg A foto abaixo retrata o processo de criação da obra. Ironicamente, nessa foto, meu galo Cara de Palhaço mesmo desfocado no fundo se destacou, parecendo estar em pé no tronco: https://image.nostr.build/d0d5e73ecbcdefa79ffd858d0143f41915c9deab7864d271d5ee724b3927f9bc.jpg A foto abaixo se trata do pisca-alerta original da minha super DT200R (viva os motores 2 tempos!) que caiu depois de uma trilha kkk. A Ideia nesta fotografia era fazer o sol parecer estar acendendo o alerta que deveria aparentar estar flutuando no céu. Infelizmente não fui bem sucedido, pois os fios que penduravam o objeto acabaram aparecendo. É impressionante a capacidade de cálculo da Canon T50 e a velocidade do seu obturador, a nitidez da objetiva e a resolução do filme Kodak Pro Image 100, cujo conjunto conseguiu captar até os pequenos fios de nylon transparentes. Eu imaginei que a foto ia estourar e os fios não apareceriam, ledo engano. Pelo menos o enquadramento ficou correto: objeto um pouco mais acima do centro para dar sensação de altitude e levemente de perfil para dar noção 3d. Quem sabe com uma câmera que seja possível ajustar a velocidade do obturador eu seja bem sucedido… https://image.nostr.build/808243d34b6dbeade25d38189163f9d58f6a12da9d00df17c85651d501e1bed8.jpg A foto abaixo se trata da minha performance favorita com a fotografia analógica, pois fotografei o primeiro quadro que pintei, o qual dei o nome de Elipsoíris sendo ele posteriormente capa do meu livro FILOSOFIA FUNDAMENTAL, então aí temos três linguagens artísticas profundas na mesma performance: O quadro que virou livro fotografado analogicamente. A ideia desta performance foi enquadrar o quadro desfocado, o qual somente pode ser desvendado com os olhos certos, por isso a lente. Utilizei luz natural e uma lente velha de óculos. Especial destaque para os dois pontos de luz que refletiram na lente parecendo dois olhos, isso não foi planejado e deu um toque especial para a fotografia, cabendo diversas interpretações, esse é o objeto da arte em geral. Fiquei muuuito contente com o resultado: https://image.nostr.build/6bb5b802b3ad1bb7262b925225fcfb0b8b00654fa0fec240be57f648c32245af.jpg Já na fotografia analógica abaixo considero uma performance porque não se trata duma fotografia comum de paisagem, flores, arquitetura, animais ou pessoas, visa passar uma mensagem. Utilizando apenas a luz natural, regulei o foco da Canon T50 para as lentes dos meus próprios óculos e escolhi um dia especialmente nublado e escuro para simbolizar as dificuldades pelas quais todos passamos no dia-a-dia, quando acreditamos por algum momento que as luzes estão apagadas para nós, até que com os óculos certos podemos enxergar com maior nitidez o horizonte, os óculos podem ser a palavra de Deus ou qualquer outra coisa que te ilumine e esclareça. Com certeza essa fotografia terá um bom uso em meus próximos escritos: https://image.nostr.build/b44b573bb39cdf5f2eb446e818bbf59d5dab9d3815ac6e917440b2f6b1ff431c.jpg DUPLA EXPOSIÇÃO Eis aqui um recurso nato da fotografia analógica: a dupla exposição. Se trata de fotografar mais de uma vez em cima do mesmo filme de modo que as imagens se sobreponham. Como esse método podemos simular movimento numa única fotografia, fazer montagens de disco voador kkkk, enfim a imaginação é o limite, vamos ver: Nessa fotografia analógica abaixo ocorreu uma quádrupla exposição, pois cliquei quatro enquadramentos diferentes sob o mesmo filme. Foi especialmente difícil fazer porque a Canon T50 não tem esse recurso, então tive que enganá-la pressionando o botão de rebobinar o filme ao mesmo tempo que disparava a câmera. Como eu estava usando o filme Kodak Pro Image que possui asa 100, também regulei a máquina como se estivesse usando um filme asa 25, então sabia que podia disparar quatro vezes sem queimar o filme. Pedi para a modelo (minha Mãe, kkk) ficar em três posições diferentes dando a impressão de movimento e não satisfeito no final ainda fotografei o sol. Adorei essa foto: https://image.nostr.build/5f8e2962e2ee94259d4dd5d3b777976a4d20ba293a5a4e68e81e30a0e1975543.jpg FOTOS EM MACRO OU CLOSE Acredito ser possível obter uma fotografia analógica em macro mesmo sem lente especial, tudo depende da pecinha que fica atrás da câmera: você, kkkk. Devemos tentar, se não obtivermos uma fotografia em macro, ao menos um close teremos, vamos ver: Na foto abaixo há um minúsculo cogumelo que cresceu num barranco qualquer, apareceu nitidamente no negativo, mesmo sem uso de lupa, por isso considero um macro, na verdade é apenas uma foto divertida: https://image.nostr.build/02aa4bbdc0cf54519b694c75237693fc2a6569fe4f3167220b05c7498757b822.jpg Já a foto abaixo é apenas um close, o ninho é especialmente profundo, por isso o leve desfoque nos ovos: para dar noção de profundidade. O foco dos quatro cantos da caixa está bem ajustada para dar noção tridimensional do objeto: https://image.nostr.build/24e5dcdd0e5a3560b341fe4f0d0d93b7d562f2d58054ac308a8e312c2707100c.jpg O PRIMEIRO QUADRO DO ROLO Na fotografia analógica cada rolo de filme nos dá pelo menos um tipo de fotografia artística bem específica. Se trata do primeiro quadro do rolo, onde ocorre uma parcial sobre-exposição. Isso se deve a incidência da luz diretamente no filme quando estamos carregando a máquina com o filme. A maioria das máquinas analógicas somente começa a contar os fotogramas após alguns disparos para evitar isso. Cabe ao fotógrafo saber aproveitar os fotogramas existentes antes do número 1, enquadrando a cena normalmente e disparando antes do número 1. Os resultados são quase imprevisíveis e geralmente interessantes. Abaixo uma fotografia analógica fantástica porque quase sempre a sobre-exposição do primeiro quadro do rolo ocorre nas extremidades da foto e nessa aí ocorreu no meio. Para conseguir esse efeito carreguei a máquina no escuro e acendi a luz no exato momento que estava fechando a tampa da câmera. Por uma fração de segundo o primeiro quadro do rolo foi exposto parcialmente a luz, sabia que iria ter uma fotografia diferente, jamais imaginei que a sobre-exposição iria sair no meio do fotograma, muito curioso: https://image.nostr.build/a2e08aab686af64df949e83b4ff3b0a00952698a7a138412f7753ebc0dd63d1f.jpg Na fotografia abaixo repeti o mesmo processo anterior. Como o tempo entre acender a luz e fechar da máquina foi diferente a sobre-exposição ficou bem visível na extremidade da foto. Especial destaque para sua incidência no lado direito, quando deveria incidir no lado esquerdo, pois na Canon T50 o filme roda da esquerda para direita. Essa aparente inversão de lados se deu porque fotografei com a máquina de cabeça para baixo: https://image.nostr.build/270681be8de71b6c833507dda6bfe4b5233c9b871aa97ea8fc2ebdcdd46a682a.jpg FOTOS DE AÇÃO Registrar uma ação com fotografia analógica é especialmente difícil se a máquina não calcula a abertura e tempo de exposição automaticamente, porque tudo acontece muito rápido e você não tem tempo de ficar pensando. Felizmente a Canon T50 é muito boa para esse tipo de fotografia, tive que me preocupar apenas com o foco. O que essa máquina me fez suar para fazer as duplas exposições acima, tirou de letra esse memorável momento, vamos ver: Na foto abaixo quando avistei esse grupo de corajosos saltando de paraglider corri pedir autorização para fotografá-los e rapidamente carreguei a máquina. Comecei a fotografar mesmo antes da máquina registrar o primeiro fotograma do rolo, tendo obtido esse lindo efeito de sobre-exposição de primeiro quadro do rolo: https://image.nostr.build/8e32e22d3bf7c897d7111e85555146e38bb139985c50b2795fe809b31880c7d8.jpg Já a foto abaixo foi a terceira do rolo. Tomei o cuidado de enquadrar tanto a alçada de vôo do paraglider quanto essa linda Veraneio, o que descreve em uma única foto o espírito aventureiro do pessoal. Reparem no sol refletindo sobre as nuvens, que lindo tudo: https://image.nostr.build/5bf0444e4621406d858ab70725c1ee2f6a7e39b87663e23a18085a32b9a06f6a.jpg Na foto abaixo tive que registrar mais uma dessa linda Veraneio, sou apaixonado por motores e mecânica, ela quase roubou a cena kkkk. Especial destaque para o detalhe do carro e da câmera que a fotografou serem da mesma época, sensível retorno ao passado. Verdadeira máquina do tempo essa foto. Se eu não dissesse que esta foto foi tirada no final do ano de 2020 daria para dizer que foi uma foto tirada de uma Veraneio Zero Km da época, segredinho nosso, kkk. https://image.nostr.build/f5284ff30986ad84d22f137e0a330067f91564907da8acf04c9eb93a991cbcf2.jpg Na foto abaixo voltando à cena, agora do Ângulo certo kkk. Esse foi a segunda foto, perceba ainda a presença do efeito de sobre-exposição do primeiro quadro. Aqui a máquina estava marcando o primeiro fotograma, tadinha kkk https://image.nostr.build/5c1d73f7d802fd1f730427e29f921c82e410c5dce3112a3133d6fce294d310c6.jpg Na foto abaixo a luz estava perfeita, o sol iluminava atrás de mim, incidindo frontalmente para o enquadramento da foto, linda essa: https://image.nostr.build/156fc878dd18257ad1f59d1b5d3fd719c7e773937356fad6ea09b0ce1f151f12.jpg Paraglider quase em posição de vôo, a foto ficou quase perfeita porque o momento em tela era a Hora de Ouro, momento do entardecer quando a posição do sol deixa o céu dourado, fenômeno muito querido pelos fotógrafos analógicos; até pelos digitais também. Mesmo assim eu não estava satisfeito, queria fotografar mais de perto. Dei zoom correndo para frente e o resultado você vê abaixo: https://image.nostr.build/b1f610695bd57db8abe7408df318978b6e69e85fe620a589b12fb9bcaae66156.jpg Abaixo a fotografia analógica simplesmente perfeita, sol na posição certa, hora de ouro, perfeito enquadramento e foco, tudo certo, universo conspirando à favor… ganhei o dia sem saber. Só descobri depois que revelei. O chão não foi cortado é que o piloto do paraglider já estava no desnível do chão pronto para saltar: https://image.nostr.build/93a7e416d11c996b65a32b019667a43124d96985109d34fd1a9b239ef365bbfe.jpg Abaixo O salto… tive que correr para o barranco para dar zoom, outra foto perfeita na hora de ouro: https://image.nostr.build/f254c2e71863a233816b517564dd5fb7fe85ee0bd927b02687fba43bde53dcd6.jpg FOTOGRAFIA ANALÓGICA DE ANIMAIS É especialmente difícil fazer um animal posar para gente, temos que ter um pouco de comida pra negociar kkk. Não fosse a Canon T50 calcular a exposição sozinha seria ainda mais difícil porque os momentos são muito rápidos e você não tem tempo para regular a abertura e tempo de exposição, tive que regular apenas o foco. Mais um ponto para essa notável máquina que me fez apanhar na dupla exposição acima. A fotografia analógica de animais também é um tipo de fotografia de ação, temos que ser rápidos no gatilho, vamos ver os resultados: Abaixo novamente dei zoom chegando bem perto, fotógrafo de verdade não tem medo, tudo pela arte! https://image.nostr.build/5f0af116b1fd81edb3f21dfd5d7cce6c534751ac8660bd5fb58ce08c652d8aaf.jpg Abaixo foco no segundo plano, acabei pegando os dois de perfil: https://image.nostr.build/fbd78fcf71749569444d3438e0d5283d321fc3f3350cacc6e4a3e9a0cdc914f5.jpg Abaixo foco no segundo plano. Aqui peguei os dois olhando para mim e dizendo xiiiis, kkk. https://image.nostr.build/3a1f50ee1e3c6213b337654e69ee23819ab60100c8a1a049ee0b2b66fac0d8f8.jpg Abaixo podemos comprovar que o fotômetro da Canon T50 é matricial e não pontual, porque o centro da foto tinha muito mais luz que os cantos: https://image.nostr.build/11a8a5a7ff14a661755f04f743d70d3dd1a9d11e412791ce42f5cbf1da1c6be2.jpg Abaixo linda foto: Cavalo da Montanha. Eu estava esperando a Hora de Ouro chegar, pena que quando chegou o modelo não quis mais ser fotografado kkk. https://image.nostr.build/83429975966cb4b0e71e5e089651d4585513d823fea404014b0b78b21e859302.jpg Abaixo lindo close de perfil com fundo totalmente desfocado. Preto absoluto, a fotometria esta certinha: https://image.nostr.build/f36aed8fa89b6ba81dd77c7d3b32c24424483e626a9634cbadb16baf91427d66.jpg Abaixo muita coisa acontecendo ao mesmo tempo: As galinhas comendo, o milho sendo jogado, a sombra do fotógrafo… Para obter essa foto joguei o milho para o alto e tive que ser tão rápido no gatilho quanto o Kid Morengueira. Você pode perceber na minha sombra que estou segurando apenas a câmera, o pote de milho já tinha voado longe kkk. Escolhi especialmente um dia ensolarado para que o fotômetro da Canon T50 usasse toda a velocidade possível no obturador, sendo possível congelar o milho no ar sem muito efeito borrão. https://image.nostr.build/d566e46a8a3cba8855e80295910e5addb0a8aa7735093c9f93f129cac2379472.jpg Abaixo galinha chocando numa roda de carro. Como amo animais e carros, para montar essa cena tive que forrar uma roda velha de carro para formar um ninho e esperar, esperar e esperar… No momento certo a Jurema se sentiu confiante para entrar na roda. Nem se incomodou com minha presença pois estava de papo cheio, pois é, também tive que negociar com a galinha, isso é a fotografia analógica de animais kkk. Percebam novamente que o fotômetro da Canon T50 é matricial, pois a maior parte da foto era com pouca luz e o raio de sol que entrava estourou a foto. Percebam ainda como eu estava perto da galinha, pois foquei em sua cabeça e o resto do corpo que estava um pouco mais distante saiu desfocado. Certamente a câmera estava com abertura máxima f1.8 e com uma velocidade bem lenta, o que explica a baixa profundidade de campo. Além disso se a Jurema tivesse mexido a cabeça na hora do disparo certamente teria saído um borrão por causa da baixa velocidade. Acabou saindo tudo certo e meus dias de espera por essa foto não foram em vão. https://image.nostr.build/d7484609c8ff9be05ee6d518def402f66484a02109dc96ef5c734b11216385bf.jpg FOTOGRAFIA ANALÓGICA DE ARQUITETURA Na fotografia analógica de arquitetura devemos conhecer os conceitos básicos de iluminação e preenchimento, trabalhamos apenas com luz natural e deve ser bem usada para termos a noção tridimensional da construção. Conforme ensina Fernando Bagnola, a tridimensionalidade do objeto depende da incidência da luz em três pontos diferentes e com intensidades diferentes, algo difícil de se obter apenas com a luz do sol, vamos ver: Abaixo se trata do Museu do Olho em Curitiba/PR. Como sua parte frontal é escura e o sol se posicionava atrás da construção tive de me posicional na sua lateral, assim consegui obter um resultado tridimensional, pois o sol iluminava a parte de cima, refletia na parte de baixo em menor intensidade e na parte frontal quase não havia luz. Se eu estivesse posicionando na frente da construção o efeito tridimensional seria impossível: https://image.nostr.build/6f74c1c7e606f7950eaf45007868b92e9a0288722b3d5e580ecaa4930700e3ea.jpg Abaixo para minha sorte, nesse exato momento um grupo de jovens contracultura (assim como eu) passavam pelo local, tornando a foto icônica pela presença de jovens modernos contracultura contrastando com arquitetura moderna da cultura tradicional. Minha posição em relação ao sol também favoreceu o sucesso desta fotografia, tendo iluminado corretamente todos os pontos de interesse: https://image.nostr.build/7c374205d7df21985a6a71c6c17e4f67ab29baf452f0cd406b869df94d68296c.jpg Abaixo esse aqui é um exemplo de fotografia analógica arquitetônica errada. O enquadramento foi frontal em razão do desejo de captar o reflexo dos edifícios nos vidros negros do “olho”: https://image.nostr.build/f9a0869a165bc7e634944c01e59085203347ab6c353610bdcaace30ee3ed8d8a.jpg Abaixo se trata do Panteon dos Heroes na Lapa/PR um monumento erguido para guardar os corpos dos soldados das forças republicanas que pereceram durante o chamado Cerco da Lapa, batalha da Revolução Federalista de 1894. Aqui o dia estava nublado, momento perfeito para fotografar uma arquitetura tão triste como essa. Não me importei com a questão tridimensional, pois era impossível, não havia sol. Quis retratar a tristeza na foto. O filme usado foi o mesmo (Kodak Pro Image 100). Aqui percebemos que a química desse filme é ajustada para a luz amarela do sol como branco absoluto, como o céu estava nublado, a luz natural estava com temperatura mais fria o que puxou o tom mais para o azul e o roxeado da foto devem ter sido os raios ultravioleta. Se eu estivesse usando um filtro ultravioleta provavelmente a foto sairia mais acinzentada. Me recordo que nesse dia estava tudo cinza. De qualquer forma adorei esse tom arroxeado da foto. Fica a dica: conseguimos o mesmo efeito de um filme Lomochrome Purple caríssimo com um filme baratinho, basta fotografar nessas condições: https://image.nostr.build/24f91369c12e83861f7eec38ff99f1869f08ae1eec06c798ccbe08af62263a2e.jpg Abaixo novamente o tom arrocheado com um filme barato. Para se ter uma ideia um Lomochrome Purple costuma custar seis vezes ou mais que um que o Kodak Pro Image 100 de R$ 30,00 à R$ 40,00 na data da publicação deste artigo em 09/04/21. Percebam que no momento desta foto as nuvens deram uma trégua e alguns raios de sol passaram dando uma leve noção tridimensional da arquitetura. O certo seria eu estar um pouco mais à esquerda para aproveitar bem a iluminação. Mesmo assim, me senti feliz com a triste foto kkk pois mesmo com a luz amarela do sol refletindo o efeito Lomo-Violeta ocorreu: https://image.nostr.build/099a1a4d7857325e59f5b35805c0ebb5c3fa55af45de2096236f1dfbadca4d4a.jpg Abaixo parece que a foto está mal enquadrada. E está mesmo. É que no lado direito havia um poste de energia elétrica muito feio, eu não queria que aparecesse. Me preocupei apenas com a iluminação e obtive sucesso com a noção de profundidade da arquitetura. A foto está puxando para o amarelo porque a Universidade Federal do Paraná em Curitiba é meio amarela mesmo. https://image.nostr.build/48a4d517488fc1656e027568ad314688bc0fd9995e67289003f832eb904e5260.jpg Abaixo para finalizar o conjunto de fotografias analógicas arquitetônicas nada melhor que um cemitério, afinal todos vamos morrer um dia, devemos sempre lembrar disso para fazer nossas vidas mundanas valerem a pena. Quando morremos não levamos nada a não ser nossas experiências evolucionais, nossas graças e pecados. Devemos deixar um legado, algo positivo para quem fica. Pois bem, foi nesse contexto a foto. Para mim a morte deve ser evitada. Quando ocorrer, se fizermos tudo certo vamos para luz, as trevas são aqui na terra mesmo. Portanto, ao contrário da maioria dos fotógrafos, escolhi um dia ensolarado para fotografar ali. Quis simbolizar a luz que nos aguarda após a morte. Então me posicionei dentro do cemitério para fotografar de dentro para fora. Esperei o sol se posicionar de forma que dos portões para fora houvesse pouca luz, tal como é o mundo, deixando toda a iluminação para dentro dos portões. Percebam como pequenos detalhes fazem toda a diferença numa fotografia analógica artística. Essa foto pode perfeitamente ser usada para ilustrar qualquer material que corrobore com esse pensamento. Se eu quisesse retratar que a vida é mil maravilhas e a morte um triste fim, deveria estar do lado de fora dos portões com tudo iluminado exceto o interior do cemitério. Interessante não… https://image.nostr.build/051592db1d3612c719621547a69bc8dfd0319d6b89656451d5b60582ae864e8e.jpg FOTOGRAFIA ANALÓGICA DE PESSOAS Basicamente se divide em dois tipos, a cena e o retrato. Na cena a pessoa posa para a foto sem contudo revelar sua personalidade, é uma cena criada artificialmente. Já o retrato, no conceito artístico da fotografia, ocorre quando conseguimos captar o interior da pessoa. Por exemplo: se for uma pessoa triste ela aparecerá com semblante triste, se for uma pessoa alegre com semblante alegre, não necessariamente sorrido. Se for uma pessoa sofrida suas rugas, desasseios e receios ficarão visíveis. Se for uma pessoa engraçada sentiremos vontade de rir ao ver seu retrato. O retrato é algo verdadeiro e espontâneo da pessoa. Se uma pessoa triste aparece sorrido não é um retrato e sim uma cena, vamos ver: Abaixo normalmente na fotografia analógica de pessoas o correto é deixar o segundo plano mais escuro e o primeiro plano mais claro. Ai quis fazer diferente. Pedi para o modelo (Meu Melhor Amigo) se posicionar de costas para o sol, pois já tinha avistado aquele arco-íris no fundo. Nesse caso foi um retrato pois meu amigo apareceu sorrindo sem eu pedir e sei que ele é uma pessoa feliz e engraçada, pois vive contando piadas e seu repertório é infinito. O interessante é que esse não é um retrato comum e sim um retrato artístico, pois inverti a iluminação dos planos e ainda captei uma arco-íris, foi uma cena construida para um retrato, ideia antagônica para fotografia analógica de pessoas. Como resultado obtive uma fotografia que parece uma montagem, onde a imagem do modelo ter-se-ia sido colada sobre a paisagem, tamanha foi a diferença de iluminação entre o primeiro e segundo plano. Contudo, um pequeno raio de sol que incidiu sobre o canteiro inferior esquerdo não me deixa mentir que a fotografia é autêntica. Além disso tendo os negativos que não mentem kkk. Essa foi minha fotografia preferida de pessoas, pela qualidade do resultado artístico e pela pessoa do modelo, um abração amigo! Vou chamar essa foto de “Meu Parça na Praça”: https://image.nostr.build/51db1df7741227dc2d86529bc9e7a93cf27365f0f2d7b591a4e84a9a05855dfb.jpg Abaixo sou eu. Se trata apenas de uma cena simples porque minha expressão não aparece e sequer minhas roupas traduziam minha personalidade. Regulei o foco da máquina para 5 metros, entreguei-a para meu amigo e contei alguns passos para trás. Não me preocupei muito em acertar minha posição em exatos 5 metros porque o dia estava bem ensolarado e sabia qua a Canon T50 iria abrir pouco o diafragma por causa disso, o que aumentou a profundidade de campo consideravelmente. Podemos perceber no fundo a Universidade Federal do Paraná sem qualquer desfoque por causa disso. O maldito poste que tentei evitar na foto arquitetônica da UFPR acima acabou aparecendo aqui, mesmo assim gostei da foto pelo tom de cores que só a fotografia analógica nos dá. https://image.nostr.build/ce8af555274333fa8a26375247373ca92315e87d7414bcc9ad7b5a4840cb3a21.jpg FOTOGRAFIA ANELÓGICA DE OBJETOS A fotografia analógica de objetos, assim como a arquitetônica, deve se obedecer os conceitos básicos de iluminação para obter noção tridimensional do objeto. Além disso, a cena montada deve combinar com o objeto para entrar em sintonia com o conceito natural de beleza, vamos ver: Abaixo queria fotografar um objeto qualquer, então peguei essa faca. Esse objeto combina muito bem com o ambiente rústico do campo, então a finquei-a num toco de árvore com vista para o campo, tomando cuidado para ela ficar levemente torcida e dar a noção tridimensional. Naturalmente a foto ornou porque o objeto esta em sintonia com a cena. Essa deve ser a combinação da fotografia analógica de objetos, por exemplo. A não ser que o fotógrafo busque justamente causar repudia invertendo a combinação do objeto com a cena. Por exemplo: para causar nojo pode-se fotografar barro em formato de cocô num prato. Merda e comida são coisas totalmente opostas e essa inversão naturalmente é perturbadora para qualquer ser humano. Existe uma lógica natural de combinação de objetos com a cena. Enfim, podemos inclusive combinar mais de um objeto secundário para criar uma cena ao objeto principal, como veremos mais abaixo com a xícara de café: https://image.nostr.build/6474901ce85d34aef3421ce5f720e258208c50aeb57e9893c8a750c6dc8fc1df.jpg Na foto abaixo o objeto principal é uma caneca de café. Para criar a cena utilizei outros três objetos. O palheiro que combina com café, a tampa da objetiva da minha Canon T50 que combina com o efeito da cafeína para pensar mais rápido sobre as cenas que irei montar, e o vazo de suculenta que remete a algo mais áspero e amargo como o café e o palheiro. Se o objeto principal fosse um copo de milkshake no lugar do palheiro haveriam balas coloridas, no lugar da tampa da máquina haveria um guardanapo e no lugar da suculenta haveria um flor fofa e cor de rosa. Falando em flor vou encerrar este ensaio com o tópico sobre fotografia analógica de flores para deixar todos felizes no final: https://image.nostr.build/8e95c6bae536cfea47e3c5d44aa63725ab8fe20eacd1c6d5eeaae1720dd0a9e5.jpg FOTOGRAFIA ANELÓGICA DE FLORES É um tipo de fotografia livre da fotografia analógica, sem muitas preocupações para o fotógrafo analógico, devemos atentar apenas para a vivacidade das cores e para isso o dia deve estar especialmente ensolarado. Se for fotografia interna de preferência usar luz quente (amarela), o resto é só diversão, vamos ver: https://image.nostr.build/fc8cf663300794761b0d8dc6f1a765e3a423c65a4ad4a85a7885b00716b46533.jpg https://image.nostr.build/dc4fbe15a7b46817d66bdbeb3d0e11851999b2c1292c576fd457956436e75c77.jpg https://image.nostr.build/73fa3b1b30a088954b342294e1b0aa555a693c3ad425dea9807d2238ec529747.jpg Viva a fotografia analógica! Se você deseja fazer um ensaio artístico com fotografia analógia comigo entre em contato e terei o prazer de agendar o serviço. @ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08### Tldr - Nostr is an open and interoperable protocol - You can integrate it with workflow automation tools to augment your experience - n8n is a great low/no-code workflow automation tool which you can host yourself - Nostrobots allows you to integrate Nostr into n8n - In this blog I create some workflow automations for Nostr - A simple form to delegate posting notes - Push notifications for mentions on multiple accounts - Push notifications for your favourite accounts when they post a note - All workflows are provided as open source with MIT license for you to use ### Inter-op All The Things Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In [Using NFC Cards with Nostr]() I explored the `nostr:` URI to launch Nostr clients from a card tap. The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails. My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted. This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull. So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications. All we need are simple ways to plug things together. ### Nostr and Workflow Automation Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective. #### n8n for workflow automation Many workflow automation tools exist. My favourite is [n8n](https://n8n.io/). n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to. Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine. #### Eating my own dogfood It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do? In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting. I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up. ### Running n8n with Nostrobots I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills. - I have a cheap VPS which currently runs my [HAVEN Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/) and [Albyhub Lightning Node](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/) in Docker containers, - My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows. #### Installing n8n Self-hosting n8n could not be easier. I followed n8n's [Docker-Compose installation docs](https://docs.n8n.io/hosting/installation/server-setups/docker-compose/)– - Install Docker and Docker-Compose if you haven't already, - Create your ``docker-compose.yml`` and `.env` files from the docs, - Create your data folder `sudo docker volume create n8n_data`, - Start your container with `sudo docker compose up -d`, - Your n8n instance should be online at port `5678`. n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there. #### Installing Nostrobots To integrate n8n nicely with Nostr, I used the [Nostrobots](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) community node by [Ocknamo](nostr:npub1y6aja0kkc4fdvuxgqjcdv4fx0v7xv2epuqnddey2eyaxquznp9vq0tp75l). In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in. You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative). To install a community node, [see n8n community node docs](https://docs.n8n.io/integrations/community-nodes/installation/gui-install/). From your workflow dashboard– - Click the "..." in the bottom left corner beside your username, and click "settings", - Cilck "community nodes" left sidebar, - Click "Install", - Enter the "npm Package Name" which is `n8n-nodes-nostrobots`, - Accept the risks and click "Install", - Nostrobots is now added to your n8n instance. #### Using Nostrobots Nostrobots gives you nodes to help you build Nostr-integrated workflows– - **Nostr Write** – for posting Notes to the Nostr network, - **Nostr Read** – for reading Notes from the Nostr network, and - **Nostr Utils** – for performing certain conversions you may need (e.g. from bech32 to hex). Nostrobots has [good documentation](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) on each node which focuses on simple use cases. Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use. What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible. Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with [NIP-01](https://github.com/nostr-protocol/nips/blob/master/01.md)). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of. #### Creating and adding workflows With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation. - Click "Add workflow" to go to the workflow builder screen, - If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added, - If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article). ### Nostr Workflow Automations It's time to build some things! #### A simple form to post a note to Nostr I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily. I needed a basic form with credentials that posted a Note. For this I can use a very simple workflow– - **A n8n Form node** – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted. - **A Set node** – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain. - **A Nostr Write node** (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays. Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive". It may also be the world's simplest Nostr client. You can find the [Nostr Form to Post a Note workflow here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Form_to_Post_a_Note.json). #### Push notifications on mentions and new notes One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want– - **To make sure I never miss a note addressed to any of my Npubs** – For this I want a push notification any time any Nostr user mentions any of my Npubs, - **To make sure I always see all notes from key accounts** – For this I need a push notification any time any of my Npubs post any Notes to the network, - **To get these notifications on all of my devices** – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day. I needed to build a Nostr push notifications solution. To build this workflow I had to string a few ideas together– - **Triggering the node on a schedule** – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited, - **Storing a list of Npubs in a Nostr list** – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists ([NIP-51, kind 30000](https://github.com/nostr-protocol/nips/blob/master/51.md)). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. [Listr.lol](https://listr.lol/npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft) or [Nostrudel.ninja](https://nostrudel.ninja/#/lists)). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions, - **Using specific relays** – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata, - **Querying Nostr events** (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do– - I read the EventID of my Kind 30000 list, to return the desired pubkeys, - For notifications on mentions, I read all Kind 1 notes that mention that pubkey, - For notifications on new notes, I read all Kind 1 notes published by that pubkey, - Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub, - I transform the EventID into a Nevent to help clients find it. - **Using the Nostr URI** – As I did with my NFC card article, I created a link with the `nostr:` URI prefix so that my phone's native client opens the link by default, - **Push notifications solution** – I needed a push notifications solution. I found many with n8n integrations and chose to go with [Pushover](https://pushover.net/) which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license. Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go. You can find the [Nostr Push Notification If Mentioned here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json) and [If Posts a Note here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Post_a_Note.json). In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible. #### Use my workflows I have open sourced all my workflows at my [Github](https://github.com/r0d8lsh0p/nostr-n8n) with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use. To import any of my workflows– - Click on the workflow of your choice, e.g. "[Nostr_Push_Notify_If_Mentioned.json](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json "Nostr_Push_Notify_If_Mentioned.json")", - Click on the "raw" button to view the raw JSON, ex any Github page layout, - Copy that URL, - Enter that URL in the "import from URL" dialog [mentioned above](#creating-and-adding-workflows). To configure them– - Prerequisites, credentials, and variables are all stated, - In general any variables required are entered into a Set Node that follows the trigger node, - Pushover has some extra setup but is very straightforward and documented in the workflow. ### What next? Over my first four blogs I explored creating a good Nostr setup with [Vanity Npub](https://rodbishop.npub.pro/post/mining-your-vanity-pubkey-4iupbf/), [Lightning Payments](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/), [Nostr Addresses at Your Domain](https://rodbishop.npub.pro/post/ee8a46bc/), and [Personal Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/). Then in my latest two blogs I explored different types of interoperability [with NFC cards](https://rodbishop.npub.pro/post/edde8387/) and now n8n Workflow Automation. Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this: - Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds), - Automated or scheduled posting (such as auto-liking everything [Lyn Alden](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) posts), - Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming), - All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr, - All kinds of other automation (such as [BlackCoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) [controlling a coffee machine](https://primal.net/e/note16fzhh5yfc3u4kufx0mck63tsfperdrlpp96am2lmq066cnuqutds8retc3)), - All kinds of AI Assistants and Agents, In fact I have already released an open source workflow for an [AI Assistant](https://primal.net/p/npub1ahjpx53ewavp23g5zj9jgyfrpr8djmgjzg5mpe4xd0z69dqvq0kq2lf353), and will share more about that in my next blog. Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle. GM Nostr.
@ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08### Tldr - Nostr is an open and interoperable protocol - You can integrate it with workflow automation tools to augment your experience - n8n is a great low/no-code workflow automation tool which you can host yourself - Nostrobots allows you to integrate Nostr into n8n - In this blog I create some workflow automations for Nostr - A simple form to delegate posting notes - Push notifications for mentions on multiple accounts - Push notifications for your favourite accounts when they post a note - All workflows are provided as open source with MIT license for you to use ### Inter-op All The Things Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In [Using NFC Cards with Nostr]() I explored the `nostr:` URI to launch Nostr clients from a card tap. The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails. My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted. This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull. So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications. All we need are simple ways to plug things together. ### Nostr and Workflow Automation Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective. #### n8n for workflow automation Many workflow automation tools exist. My favourite is [n8n](https://n8n.io/). n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to. Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine. #### Eating my own dogfood It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do? In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting. I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up. ### Running n8n with Nostrobots I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills. - I have a cheap VPS which currently runs my [HAVEN Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/) and [Albyhub Lightning Node](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/) in Docker containers, - My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows. #### Installing n8n Self-hosting n8n could not be easier. I followed n8n's [Docker-Compose installation docs](https://docs.n8n.io/hosting/installation/server-setups/docker-compose/)– - Install Docker and Docker-Compose if you haven't already, - Create your ``docker-compose.yml`` and `.env` files from the docs, - Create your data folder `sudo docker volume create n8n_data`, - Start your container with `sudo docker compose up -d`, - Your n8n instance should be online at port `5678`. n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there. #### Installing Nostrobots To integrate n8n nicely with Nostr, I used the [Nostrobots](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) community node by [Ocknamo](nostr:npub1y6aja0kkc4fdvuxgqjcdv4fx0v7xv2epuqnddey2eyaxquznp9vq0tp75l). In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in. You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative). To install a community node, [see n8n community node docs](https://docs.n8n.io/integrations/community-nodes/installation/gui-install/). From your workflow dashboard– - Click the "..." in the bottom left corner beside your username, and click "settings", - Cilck "community nodes" left sidebar, - Click "Install", - Enter the "npm Package Name" which is `n8n-nodes-nostrobots`, - Accept the risks and click "Install", - Nostrobots is now added to your n8n instance. #### Using Nostrobots Nostrobots gives you nodes to help you build Nostr-integrated workflows– - **Nostr Write** – for posting Notes to the Nostr network, - **Nostr Read** – for reading Notes from the Nostr network, and - **Nostr Utils** – for performing certain conversions you may need (e.g. from bech32 to hex). Nostrobots has [good documentation](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) on each node which focuses on simple use cases. Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use. What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible. Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with [NIP-01](https://github.com/nostr-protocol/nips/blob/master/01.md)). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of. #### Creating and adding workflows With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation. - Click "Add workflow" to go to the workflow builder screen, - If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added, - If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article). ### Nostr Workflow Automations It's time to build some things! #### A simple form to post a note to Nostr I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily. I needed a basic form with credentials that posted a Note. For this I can use a very simple workflow– - **A n8n Form node** – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted. - **A Set node** – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain. - **A Nostr Write node** (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays. Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive". It may also be the world's simplest Nostr client. You can find the [Nostr Form to Post a Note workflow here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Form_to_Post_a_Note.json). #### Push notifications on mentions and new notes One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want– - **To make sure I never miss a note addressed to any of my Npubs** – For this I want a push notification any time any Nostr user mentions any of my Npubs, - **To make sure I always see all notes from key accounts** – For this I need a push notification any time any of my Npubs post any Notes to the network, - **To get these notifications on all of my devices** – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day. I needed to build a Nostr push notifications solution. To build this workflow I had to string a few ideas together– - **Triggering the node on a schedule** – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited, - **Storing a list of Npubs in a Nostr list** – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists ([NIP-51, kind 30000](https://github.com/nostr-protocol/nips/blob/master/51.md)). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. [Listr.lol](https://listr.lol/npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft) or [Nostrudel.ninja](https://nostrudel.ninja/#/lists)). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions, - **Using specific relays** – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata, - **Querying Nostr events** (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do– - I read the EventID of my Kind 30000 list, to return the desired pubkeys, - For notifications on mentions, I read all Kind 1 notes that mention that pubkey, - For notifications on new notes, I read all Kind 1 notes published by that pubkey, - Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub, - I transform the EventID into a Nevent to help clients find it. - **Using the Nostr URI** – As I did with my NFC card article, I created a link with the `nostr:` URI prefix so that my phone's native client opens the link by default, - **Push notifications solution** – I needed a push notifications solution. I found many with n8n integrations and chose to go with [Pushover](https://pushover.net/) which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license. Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go. You can find the [Nostr Push Notification If Mentioned here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json) and [If Posts a Note here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Post_a_Note.json). In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible. #### Use my workflows I have open sourced all my workflows at my [Github](https://github.com/r0d8lsh0p/nostr-n8n) with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use. To import any of my workflows– - Click on the workflow of your choice, e.g. "[Nostr_Push_Notify_If_Mentioned.json](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json "Nostr_Push_Notify_If_Mentioned.json")", - Click on the "raw" button to view the raw JSON, ex any Github page layout, - Copy that URL, - Enter that URL in the "import from URL" dialog [mentioned above](#creating-and-adding-workflows). To configure them– - Prerequisites, credentials, and variables are all stated, - In general any variables required are entered into a Set Node that follows the trigger node, - Pushover has some extra setup but is very straightforward and documented in the workflow. ### What next? Over my first four blogs I explored creating a good Nostr setup with [Vanity Npub](https://rodbishop.npub.pro/post/mining-your-vanity-pubkey-4iupbf/), [Lightning Payments](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/), [Nostr Addresses at Your Domain](https://rodbishop.npub.pro/post/ee8a46bc/), and [Personal Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/). Then in my latest two blogs I explored different types of interoperability [with NFC cards](https://rodbishop.npub.pro/post/edde8387/) and now n8n Workflow Automation. Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this: - Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds), - Automated or scheduled posting (such as auto-liking everything [Lyn Alden](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) posts), - Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming), - All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr, - All kinds of other automation (such as [BlackCoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) [controlling a coffee machine](https://primal.net/e/note16fzhh5yfc3u4kufx0mck63tsfperdrlpp96am2lmq066cnuqutds8retc3)), - All kinds of AI Assistants and Agents, In fact I have already released an open source workflow for an [AI Assistant](https://primal.net/p/npub1ahjpx53ewavp23g5zj9jgyfrpr8djmgjzg5mpe4xd0z69dqvq0kq2lf353), and will share more about that in my next blog. Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle. GM Nostr. @ a95c6243:d345522c
2025-01-01 17:39:51**Heute möchte ich ein Gedicht mit euch teilen.** Es handelt sich um eine Ballade des österreichischen Lyrikers Johann Gabriel Seidl aus dem 19. Jahrhundert. Mir sind diese Worte fest in Erinnerung, da meine Mutter sie perfekt rezitieren konnte, auch als die Kräfte schon langsam schwanden. **Dem originalen Titel «Die Uhr»** habe ich für mich immer das Wort «innere» hinzugefügt. Denn der Zeitmesser – hier vermutliche eine Taschenuhr – symbolisiert zwar in dem Kontext das damalige Zeitempfinden und die Umbrüche durch die industrielle Revolution, sozusagen den Zeitgeist und das moderne Leben. Aber der Autor setzt sich philosophisch mit der Zeit auseinander und gibt seinem Werk auch eine klar spirituelle Dimension. **Das Ticken der Uhr und die Momente des Glücks und der Trauer** stehen sinnbildlich für das unaufhaltsame Fortschreiten und die Vergänglichkeit des Lebens. Insofern könnte man bei der Uhr auch an eine Sonnenuhr denken. Der Rhythmus der Ereignisse passt uns vielleicht nicht immer in den Kram. **Was den Takt pocht, ist durchaus auch das Herz,** unser «inneres Uhrwerk». Wenn dieses Meisterwerk einmal stillsteht, ist es unweigerlich um uns geschehen. Hoffentlich können wir dann dankbar sagen: «Ich habe mein Bestes gegeben.» *Ich trage, wo ich gehe, stets eine Uhr bei mir;* \ *Wieviel es geschlagen habe, genau seh ich an ihr.* \ *Es ist ein großer Meister, der künstlich ihr Werk gefügt,* \ *Wenngleich ihr Gang nicht immer dem törichten Wunsche genügt.*   *Ich wollte, sie wäre rascher gegangen an manchem Tag;* *\ Ich wollte, sie hätte manchmal verzögert den raschen Schlag.* *\ In meinen Leiden und Freuden, in Sturm und in der Ruh,* *\ Was immer geschah im Leben, sie pochte den Takt dazu.*   *Sie schlug am Sarge des Vaters, sie schlug an des Freundes Bahr,* *\ Sie schlug am Morgen der Liebe, sie schlug am Traualtar.* *\ Sie schlug an der Wiege des Kindes, sie schlägt, will's Gott, noch oft,* *\ Wenn bessere Tage kommen, wie meine Seele es hofft.*   *Und ward sie auch einmal träger, und drohte zu stocken ihr Lauf,* *\ So zog der Meister immer großmütig sie wieder auf.* *\ Doch stände sie einmal stille, dann wär's um sie geschehn,* *\ Kein andrer, als der sie fügte, bringt die Zerstörte zum Gehn.*   *Dann müßt ich zum Meister wandern, der wohnt am Ende wohl weit,* *\ Wohl draußen, jenseits der Erde, wohl dort in der Ewigkeit!* *\ Dann gäb ich sie ihm zurücke mit dankbar kindlichem Flehn:* *\ Sieh, Herr, ich hab nichts verdorben, sie blieb von selber stehn.*   *Johann Gabriel Seidl (1804-1875)*
@ a95c6243:d345522c
2025-01-01 17:39:51**Heute möchte ich ein Gedicht mit euch teilen.** Es handelt sich um eine Ballade des österreichischen Lyrikers Johann Gabriel Seidl aus dem 19. Jahrhundert. Mir sind diese Worte fest in Erinnerung, da meine Mutter sie perfekt rezitieren konnte, auch als die Kräfte schon langsam schwanden. **Dem originalen Titel «Die Uhr»** habe ich für mich immer das Wort «innere» hinzugefügt. Denn der Zeitmesser – hier vermutliche eine Taschenuhr – symbolisiert zwar in dem Kontext das damalige Zeitempfinden und die Umbrüche durch die industrielle Revolution, sozusagen den Zeitgeist und das moderne Leben. Aber der Autor setzt sich philosophisch mit der Zeit auseinander und gibt seinem Werk auch eine klar spirituelle Dimension. **Das Ticken der Uhr und die Momente des Glücks und der Trauer** stehen sinnbildlich für das unaufhaltsame Fortschreiten und die Vergänglichkeit des Lebens. Insofern könnte man bei der Uhr auch an eine Sonnenuhr denken. Der Rhythmus der Ereignisse passt uns vielleicht nicht immer in den Kram. **Was den Takt pocht, ist durchaus auch das Herz,** unser «inneres Uhrwerk». Wenn dieses Meisterwerk einmal stillsteht, ist es unweigerlich um uns geschehen. Hoffentlich können wir dann dankbar sagen: «Ich habe mein Bestes gegeben.» *Ich trage, wo ich gehe, stets eine Uhr bei mir;* \ *Wieviel es geschlagen habe, genau seh ich an ihr.* \ *Es ist ein großer Meister, der künstlich ihr Werk gefügt,* \ *Wenngleich ihr Gang nicht immer dem törichten Wunsche genügt.*   *Ich wollte, sie wäre rascher gegangen an manchem Tag;* *\ Ich wollte, sie hätte manchmal verzögert den raschen Schlag.* *\ In meinen Leiden und Freuden, in Sturm und in der Ruh,* *\ Was immer geschah im Leben, sie pochte den Takt dazu.*   *Sie schlug am Sarge des Vaters, sie schlug an des Freundes Bahr,* *\ Sie schlug am Morgen der Liebe, sie schlug am Traualtar.* *\ Sie schlug an der Wiege des Kindes, sie schlägt, will's Gott, noch oft,* *\ Wenn bessere Tage kommen, wie meine Seele es hofft.*   *Und ward sie auch einmal träger, und drohte zu stocken ihr Lauf,* *\ So zog der Meister immer großmütig sie wieder auf.* *\ Doch stände sie einmal stille, dann wär's um sie geschehn,* *\ Kein andrer, als der sie fügte, bringt die Zerstörte zum Gehn.*   *Dann müßt ich zum Meister wandern, der wohnt am Ende wohl weit,* *\ Wohl draußen, jenseits der Erde, wohl dort in der Ewigkeit!* *\ Dann gäb ich sie ihm zurücke mit dankbar kindlichem Flehn:* *\ Sieh, Herr, ich hab nichts verdorben, sie blieb von selber stehn.*   *Johann Gabriel Seidl (1804-1875)* @ f9cf4e94:96abc355
2024-12-31 20:18:59Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( [dominictarr]( https://github.com/dominictarr/scuttlebutt) ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt ([ssb]( https://github.com/ssbc/ssb-db)) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia. Se você está se perguntando de onde diabos veio o nome Scuttlebutt: > Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.  Marinheiros se reunindo em torno da rixa. ( [fonte]( https://twitter.com/IntEtymology/status/998879578851508224) ) Dominic descobriu o termo boato em um [artigo de pesquisa]( https://www.cs.cornell.edu/home/rvr/papers/flowgossip.pdf) que leu. Em sistemas distribuídos, [fofocar]( https://en.wikipedia.org/wiki/Gossip_protocol) é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”. **Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto.** **Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar.** Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário [de bordo]( https://en.wikipedia.org/wiki/Logbook) (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem. Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. **Cada item adicionado a um log do usuário é chamado de mensagem.** **Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações.** Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.  Estrutura de alto nível de um feed **Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar.** Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência. Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub. Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. **Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.** Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de [Pubs públicos em que]( https://github.com/ssbc/ssb-server/wiki/Pub-Servers) todos podem participar **.** Explicaremos como ingressar em um posteriormente neste guia. **Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais.** Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.  Perspectivas dos participantes ## Scuttlebot O software Pub é conhecido como servidor Scuttlebutt (servidor [ssb]( https://github.com/ssbc/ssb-server) ), mas também é conhecido como “Scuttlebot” e `sbot`na linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial. **Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações.** Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.  Estrutura de alto nível de um feed **Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar.** Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência. Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub. Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. **Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.** Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de [Pubs públicos em que]( https://github.com/ssbc/ssb-server/wiki/Pub-Servers) todos podem participar **.** Explicaremos como ingressar em um posteriormente neste guia. **Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais.** Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.   Perspectivas dos participantes ## Pubs - Hubs ### Pubs públicos | Pub Name | Operator | Invite Code | | ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ | | `scuttle.us` | [@Ryan]( https://keybase.io/ryan_singer) | `scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=` | | [pub1.upsocial.com]( https://upsocial.com/) | [@freedomrules]( https://github.com/freedomrules) | `pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=` | | [Monero Pub]( https://xmr-pub.net/) | [@Denis]( https://github.com/Orville2112) | `xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=` | | [FreeSocial]( https://freesocial.co/) | [@Jarland]( https://github.com/mxroute) | `pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=` | | `ssb.vpn.net.br` | [@coffeverton]( https://about.me/coffeverton) | `ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=` | | [gossip.noisebridge.info]( https://www.noisebridge.net/wiki/Pub) | [Noisebridge Hackerspace]( https://www.noisebridge.net/wiki/Unicorn) [@james.network]( https://james.network/) | `gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=` | ### Pubs privados Você precisará entrar em contato com os proprietários desses bares para receber um convite. | Pub Name | Operator | Contact | | --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- | | `many.butt.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) | | `one.butt.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) | | `ssb.mikey.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) | | [ssb.celehner.com]( https://ssb.celehner.com/) | [@cel]( https://github.com/ssbc/ssb-server/wiki/@f/6sQ6d2CMxRUhLpspgGIulDxDCwYD7DzFzPNr7u5AU=.ed25519) | [cel@celehner.com](mailto:cel@celehner.com) | ### Pubs muito grandes  *Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)*  | Pub Name | Operator | Invite Code | | --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ | | `scuttlebutt.de` | [SolSoCoG]( https://solsocog.de/impressum) | `scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=` | | `Lohn's Pub` | [@lohn]( https://github.com/lohn) | `p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=` | | [Scuttle Space]( https://scuttle.space/) | [@guil-dot]( https://github.com/guil-dot) | Visit [scuttle.space]( https://scuttle.space/) | | `SSB PeerNet US-East` | [timjrobinson]( https://github.com/timjrobinson) | `us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=` | | Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= | ## GUI - Interface Gráfica do Utilizador(Usuário) ### Patchwork - Uma GUI SSB (Descontinuado) [**Patchwork**]( https://github.com/ssbc/patchwork) **é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB** . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.  Fonte: [scuttlebutt.nz]( https://www.scuttlebutt.nz/getting-started) **Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub.** Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs. Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth. ### Patchbay - Uma GUI Alternativa Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que [Patchwork]( https://github.com/ssbc/patchwork) e [Patchfoo]( https://github.com/ssbc/patchfoo) , então você pode facilmente dar uma volta com sua identidade existente.  ### Planetary - GUI para IOS  [Planetary]( https://apps.apple.com/us/app/planetary-app/id1481617318) é um app com pubs pré-carregados para facilitar integração. ### Manyverse - GUI para Android  [Manyverse]( https://www.manyver.se/) é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone . ## Fontes * https://scuttlebot.io/ * https://decentralized-id.com/decentralized-web/scuttlebot/#plugins * https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd * [**Secure Scuttlebutt**]( http://ssbc.github.io/secure-scuttlebutt/) **:** um protocolo de banco de dados global.
@ f9cf4e94:96abc355
2024-12-31 20:18:59Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( [dominictarr]( https://github.com/dominictarr/scuttlebutt) ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt ([ssb]( https://github.com/ssbc/ssb-db)) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia. Se você está se perguntando de onde diabos veio o nome Scuttlebutt: > Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.  Marinheiros se reunindo em torno da rixa. ( [fonte]( https://twitter.com/IntEtymology/status/998879578851508224) ) Dominic descobriu o termo boato em um [artigo de pesquisa]( https://www.cs.cornell.edu/home/rvr/papers/flowgossip.pdf) que leu. Em sistemas distribuídos, [fofocar]( https://en.wikipedia.org/wiki/Gossip_protocol) é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”. **Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto.** **Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar.** Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário [de bordo]( https://en.wikipedia.org/wiki/Logbook) (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem. Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. **Cada item adicionado a um log do usuário é chamado de mensagem.** **Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações.** Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.  Estrutura de alto nível de um feed **Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar.** Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência. Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub. Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. **Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.** Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de [Pubs públicos em que]( https://github.com/ssbc/ssb-server/wiki/Pub-Servers) todos podem participar **.** Explicaremos como ingressar em um posteriormente neste guia. **Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais.** Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.  Perspectivas dos participantes ## Scuttlebot O software Pub é conhecido como servidor Scuttlebutt (servidor [ssb]( https://github.com/ssbc/ssb-server) ), mas também é conhecido como “Scuttlebot” e `sbot`na linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial. **Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações.** Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.  Estrutura de alto nível de um feed **Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar.** Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência. Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub. Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. **Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.** Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de [Pubs públicos em que]( https://github.com/ssbc/ssb-server/wiki/Pub-Servers) todos podem participar **.** Explicaremos como ingressar em um posteriormente neste guia. **Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais.** Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.   Perspectivas dos participantes ## Pubs - Hubs ### Pubs públicos | Pub Name | Operator | Invite Code | | ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ | | `scuttle.us` | [@Ryan]( https://keybase.io/ryan_singer) | `scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=` | | [pub1.upsocial.com]( https://upsocial.com/) | [@freedomrules]( https://github.com/freedomrules) | `pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=` | | [Monero Pub]( https://xmr-pub.net/) | [@Denis]( https://github.com/Orville2112) | `xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=` | | [FreeSocial]( https://freesocial.co/) | [@Jarland]( https://github.com/mxroute) | `pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=` | | `ssb.vpn.net.br` | [@coffeverton]( https://about.me/coffeverton) | `ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=` | | [gossip.noisebridge.info]( https://www.noisebridge.net/wiki/Pub) | [Noisebridge Hackerspace]( https://www.noisebridge.net/wiki/Unicorn) [@james.network]( https://james.network/) | `gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=` | ### Pubs privados Você precisará entrar em contato com os proprietários desses bares para receber um convite. | Pub Name | Operator | Contact | | --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- | | `many.butt.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) | | `one.butt.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) | | `ssb.mikey.nz` | [@dinosaur]( https://dinosaur.is/) | [mikey@enspiral.com](mailto:mikey@enspiral.com) | | [ssb.celehner.com]( https://ssb.celehner.com/) | [@cel]( https://github.com/ssbc/ssb-server/wiki/@f/6sQ6d2CMxRUhLpspgGIulDxDCwYD7DzFzPNr7u5AU=.ed25519) | [cel@celehner.com](mailto:cel@celehner.com) | ### Pubs muito grandes  *Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)*  | Pub Name | Operator | Invite Code | | --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ | | `scuttlebutt.de` | [SolSoCoG]( https://solsocog.de/impressum) | `scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=` | | `Lohn's Pub` | [@lohn]( https://github.com/lohn) | `p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=` | | [Scuttle Space]( https://scuttle.space/) | [@guil-dot]( https://github.com/guil-dot) | Visit [scuttle.space]( https://scuttle.space/) | | `SSB PeerNet US-East` | [timjrobinson]( https://github.com/timjrobinson) | `us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=` | | Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= | ## GUI - Interface Gráfica do Utilizador(Usuário) ### Patchwork - Uma GUI SSB (Descontinuado) [**Patchwork**]( https://github.com/ssbc/patchwork) **é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB** . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.  Fonte: [scuttlebutt.nz]( https://www.scuttlebutt.nz/getting-started) **Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub.** Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs. Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth. ### Patchbay - Uma GUI Alternativa Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que [Patchwork]( https://github.com/ssbc/patchwork) e [Patchfoo]( https://github.com/ssbc/patchfoo) , então você pode facilmente dar uma volta com sua identidade existente.  ### Planetary - GUI para IOS  [Planetary]( https://apps.apple.com/us/app/planetary-app/id1481617318) é um app com pubs pré-carregados para facilitar integração. ### Manyverse - GUI para Android  [Manyverse]( https://www.manyver.se/) é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone . ## Fontes * https://scuttlebot.io/ * https://decentralized-id.com/decentralized-web/scuttlebot/#plugins * https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd * [**Secure Scuttlebutt**]( http://ssbc.github.io/secure-scuttlebutt/) **:** um protocolo de banco de dados global. @ 3f770d65:7a745b24
2024-12-31 17:03:46Here are my predictions for Nostr in 2025: **Decentralization:** The outbox and inbox communication models, sometimes referred to as the Gossip model, will become the standard across the ecosystem. By the end of 2025, all major clients will support these models, providing seamless communication and enhanced decentralization. Clients that do not adopt outbox/inbox by then will be regarded as outdated or legacy systems. **Privacy Standards:** Major clients such as Damus and Primal will move away from NIP-04 DMs, adopting more secure protocol possibilities like NIP-17 or NIP-104. These upgrades will ensure enhanced encryption and metadata protection. Additionally, NIP-104 MLS tools will drive the development of new clients and features, providing users with unprecedented control over the privacy of their communications. **Interoperability:** Nostr's ecosystem will become even more interconnected. Platforms like the Olas image-sharing service will expand into prominent clients such as Primal, Damus, Coracle, and Snort, alongside existing integrations with Amethyst, Nostur, and Nostrudel. Similarly, audio and video tools like Nostr Nests and Zap.stream will gain seamless integration into major clients, enabling easy participation in live events across the ecosystem. **Adoption and Migration:** Inspired by early pioneers like Fountain and Orange Pill App, more platforms will adopt Nostr for authentication, login, and social systems. In 2025, a significant migration from a high-profile application platform with hundreds of thousands of users will transpire, doubling Nostr’s daily activity and establishing it as a cornerstone of decentralized technologies.
@ 3f770d65:7a745b24
2024-12-31 17:03:46Here are my predictions for Nostr in 2025: **Decentralization:** The outbox and inbox communication models, sometimes referred to as the Gossip model, will become the standard across the ecosystem. By the end of 2025, all major clients will support these models, providing seamless communication and enhanced decentralization. Clients that do not adopt outbox/inbox by then will be regarded as outdated or legacy systems. **Privacy Standards:** Major clients such as Damus and Primal will move away from NIP-04 DMs, adopting more secure protocol possibilities like NIP-17 or NIP-104. These upgrades will ensure enhanced encryption and metadata protection. Additionally, NIP-104 MLS tools will drive the development of new clients and features, providing users with unprecedented control over the privacy of their communications. **Interoperability:** Nostr's ecosystem will become even more interconnected. Platforms like the Olas image-sharing service will expand into prominent clients such as Primal, Damus, Coracle, and Snort, alongside existing integrations with Amethyst, Nostur, and Nostrudel. Similarly, audio and video tools like Nostr Nests and Zap.stream will gain seamless integration into major clients, enabling easy participation in live events across the ecosystem. **Adoption and Migration:** Inspired by early pioneers like Fountain and Orange Pill App, more platforms will adopt Nostr for authentication, login, and social systems. In 2025, a significant migration from a high-profile application platform with hundreds of thousands of users will transpire, doubling Nostr’s daily activity and establishing it as a cornerstone of decentralized technologies. @ e97aaffa:2ebd765d
2024-12-31 16:47:12Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes. Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais _mainstream_. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso. # Código do Bitcoin No final de 2025, possivelmente vamos ter um _fork_, as discussões sobre os _covenants_ já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos _covenants_, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido. Depois dos _covenants,_ o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa. Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos _bitcoiners_. Espero que surjam avanços significativos no BitVM2 e BitVMX. Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da _shitcoinagem_, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs. Se querem ser levados a sério, têm que ser sérios. > “À mulher de César não basta ser honesta, deve parecer honesta” Se querem ter o apoio dos _bitcoiners_, sigam o _ethos_ do Bitcoin. Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma _multisig_ ou com os _covenants_ na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos _covenants_ para melhorar a interoperabilidade e a soberania. É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy: > “Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país” Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código. # Reservas Estratégicas de Bitcoin ## Bancos centrais Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito _mainstream_. Foi um _pivot_, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto. A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário. Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”. Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar. Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.  ## Empresas A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.  Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%. Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de _shareholders_ com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft. Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial. # ETFs Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os _inflows_ foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os _inflows_ foram brutais. Também se beneficiou por ser um mercado novo, não existia _orderbook_ de vendas, não existia um mercado interno, praticamente era só _inflows_. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em _inflows_ ou _outflows_. Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de _inflows_ em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar. Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem. Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes. Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo. # Preço Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo. # Stablecoins de dólar Agora saindo um pouco do universo do Bitcoin, acho importante destacar as _stablecoins_. No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas. Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às _stablecoins_ de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas. > “Casa onde não há pão, todos ralham e ninguém tem razão” Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas. Eu acredito que 2025, vai haver um forte crescimento na adoção das _stablecoins_ de dólares, esse forte crescimento vai agravar o problema sistémico que são as _stablecoins_. Vai ser o início do fim das _stablecoins_, pelo menos, como nós conhecemos hoje em dia. ## Problema sistémico O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente. Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas. As _stablecoins_ são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema. No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos. A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário. Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/_stablecoins_ para o resto do sistema financeiro, porque o _marketcap_ do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações. Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do _carry trade_, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado. Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações. O mundo cripto é seu oposto, é _naife_ com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto. Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025. Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o _redeem_ dos dólares? Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether? Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente. ### Conta mestre Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário. O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com _full-reserves_. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com _full-reserves_, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos. Eu concordo com o FED nesse ponto, que os bancos com _full-reserves_ são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos _full-reserves_, mas sim nos que têm reserva fracionária. O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença. Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de _compliance_, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o _compliance_ dos seus clientes. A obrigação do KYC para ter _stablecoins_ iriam provocar um terramoto no mundo cripto. Assim, é pouco provável que seja a solução para a Tether. ### FED Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as _stablecoins_ de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as _stablecoins_ estão a colocar em causa a soberania monetária dos outros países. Atualmente as _stablecoins_ estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países. Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo. Será algo para acompanhar futuramente, mas só para 2026, talvez… É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(_stablecoins_). A ironia do destino. Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona. # Europa 2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os _compliance_, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo. O _Travel Route_ passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A _Travel Route_ é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos. O MiCA também está a colocar problemas nas _stablecoins_ de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias. O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade _stablecoins_ de euro, as restantes _stablecoins_ serão deslistadas. Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado. # Recessão Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon. Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro. Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer. Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar. A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa. Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal. # Brasil Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.  Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e _stablecoins_. No Brasil existe um forte adoção, será um bom _case study_, certamente irá repetir-se em outros países num futuro próximo. Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin. # Blockchain Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em _blockchain_. Eu acredito que a BlackRock vai criar uma própria _blockchain_, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar. ----------- Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião. Isto é apenas a minha opinião, **Don’t Trust, Verify**!
@ e97aaffa:2ebd765d
2024-12-31 16:47:12Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes. Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais _mainstream_. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso. # Código do Bitcoin No final de 2025, possivelmente vamos ter um _fork_, as discussões sobre os _covenants_ já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos _covenants_, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido. Depois dos _covenants,_ o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa. Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos _bitcoiners_. Espero que surjam avanços significativos no BitVM2 e BitVMX. Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da _shitcoinagem_, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs. Se querem ser levados a sério, têm que ser sérios. > “À mulher de César não basta ser honesta, deve parecer honesta” Se querem ter o apoio dos _bitcoiners_, sigam o _ethos_ do Bitcoin. Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma _multisig_ ou com os _covenants_ na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos _covenants_ para melhorar a interoperabilidade e a soberania. É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy: > “Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país” Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código. # Reservas Estratégicas de Bitcoin ## Bancos centrais Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito _mainstream_. Foi um _pivot_, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto. A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário. Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”. Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar. Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.  ## Empresas A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.  Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%. Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de _shareholders_ com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft. Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial. # ETFs Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os _inflows_ foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os _inflows_ foram brutais. Também se beneficiou por ser um mercado novo, não existia _orderbook_ de vendas, não existia um mercado interno, praticamente era só _inflows_. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em _inflows_ ou _outflows_. Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de _inflows_ em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar. Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem. Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes. Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo. # Preço Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo. # Stablecoins de dólar Agora saindo um pouco do universo do Bitcoin, acho importante destacar as _stablecoins_. No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas. Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às _stablecoins_ de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas. > “Casa onde não há pão, todos ralham e ninguém tem razão” Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas. Eu acredito que 2025, vai haver um forte crescimento na adoção das _stablecoins_ de dólares, esse forte crescimento vai agravar o problema sistémico que são as _stablecoins_. Vai ser o início do fim das _stablecoins_, pelo menos, como nós conhecemos hoje em dia. ## Problema sistémico O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente. Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas. As _stablecoins_ são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema. No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos. A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário. Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/_stablecoins_ para o resto do sistema financeiro, porque o _marketcap_ do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações. Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do _carry trade_, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado. Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações. O mundo cripto é seu oposto, é _naife_ com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto. Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025. Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o _redeem_ dos dólares? Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether? Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente. ### Conta mestre Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário. O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com _full-reserves_. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com _full-reserves_, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos. Eu concordo com o FED nesse ponto, que os bancos com _full-reserves_ são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos _full-reserves_, mas sim nos que têm reserva fracionária. O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença. Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de _compliance_, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o _compliance_ dos seus clientes. A obrigação do KYC para ter _stablecoins_ iriam provocar um terramoto no mundo cripto. Assim, é pouco provável que seja a solução para a Tether. ### FED Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as _stablecoins_ de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as _stablecoins_ estão a colocar em causa a soberania monetária dos outros países. Atualmente as _stablecoins_ estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países. Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo. Será algo para acompanhar futuramente, mas só para 2026, talvez… É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(_stablecoins_). A ironia do destino. Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona. # Europa 2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os _compliance_, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo. O _Travel Route_ passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A _Travel Route_ é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos. O MiCA também está a colocar problemas nas _stablecoins_ de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias. O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade _stablecoins_ de euro, as restantes _stablecoins_ serão deslistadas. Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado. # Recessão Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon. Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro. Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer. Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar. A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa. Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal. # Brasil Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.  Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e _stablecoins_. No Brasil existe um forte adoção, será um bom _case study_, certamente irá repetir-se em outros países num futuro próximo. Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin. # Blockchain Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em _blockchain_. Eu acredito que a BlackRock vai criar uma própria _blockchain_, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar. ----------- Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião. Isto é apenas a minha opinião, **Don’t Trust, Verify**! @ 5188521b:008eb518
2024-12-31 16:46:45<img src="https://blossom.primal.net/e4d7d32a4590123c901aef5d441a85be956c29eec8d321a1d8e5a17cb186862c.jpg"> My experience of [daily posting on LinkedIn](https://www.linkedin.com/in/totallyhumanwriter/) started around three years ago, when I became more serious about my coaching business. In that time, I amassed 25,000 followers and garnered around 3 million impressions on my writing. It was a wild ride, but now it’s time to leave the theme park. # Reasons I Quit Posting on LinkedIn Here they are, in no particular order: 1. I went from coach to ghostwriter. 2024 threw up an unexpected career change. Since 2018, I've been a coach, moving from teaching English as a foreign language to working with groups of multilingual pro writers looking for better opportunities. Coaching is a tough industry (maybe I'll write about that someday). My idea was to write more meaningful words and less copy to market my coaching business. Ultimately, writing to develop the Bitcoin ecosystem is what I find meaningful, and writing for hire doesn't require as much copywriting as being a coach. With a solid portfolio, contacts, and profile, potential clients can see your results. You don't need to attract a ton of inbound leads by writing funny bits and wow-inducing educational posts on LinkedIn. 2. Time constraints Because of my own book marketing, new client work, and projects like [21 Futures](https://21futures.com/), I can't dedicate my creative efforts and several hours per week to writing on LinkedIn. That time works better for me elsewhere. 3. Worsening distribution 'Creators' (a.k.a. active posters with many followers) often say changes to the algorithm don't matter. 'Get on with it. Adapt and move forward.' I'd be lying if I said I'm happy seeing statistics for my posts plummet. In 2022 and 2023, a successful carousel might net 20,000 views with over 150 likes and 50+ comments. Now, an exceptional post for me attracts 5,000 views with 50 likes. I won't bore you with charts and statistics, but this is an average, based on hundreds of posts. It seems LinkedIn is reducing the reach of big accounts in favour of tighter networks and distributing the work of those with <5k followers. That's fine. Perhaps that will make the platform less showy, and less boastful, finally ridding us of fake stories, surprising hacks, and ultimate guides. Still, It makes creative types like me feel like failures. Does an 80% decrease in distribution seem fair for the three years of daily effort I've put in? Should I keep struggling for diminishing returns? No. Creative people must seek the best return on investment for their time. The lesson? Distribution is more important than follower numbers. I've also quit Medium, where I have 2,000 followers and regularly receive single-digit reads on my posts. 4. LinkedIn values machines over humans. Cost-cutting, extracting value, and planning for a robotic future. That's Microsoft's MO. Despite being a social network with over 1 billion users, LinkedIn seemingly relies on automated support to make decisions on which content, people, and ideas are allowed on the platform. Users' data is parsed without their express consent.\ LinkedIn seems desperate for us to use generative AI to express our 'insight'.\ We are constantly bombarded by LLM drivel and boring machine-made content. If you can't be bothered to write it, why should I bother to read it? As somebody who brands himself a human-centric writer, why would I offer up personal takes and stories writing for free in an AI-filled swamp? --- # What's next? So I'm giving up posting on LinkedIn. With that said, it can still produce a great benefit for its users, especially those in the bitcoin space. Why? The ability to search for potential connections, present your profile, and share your expertise can make a huge difference to your work - investment, partnership, and customers. If you have a smaller network and have the need to share personal takes, opinions, and expertise, posting on LinkedIn is worth it. So few are doing this in bitcoin, the opportunities in 2025 are mind-boggling. Next year, thousands of new startups and ventures will be vying for our attention. Those who can build trust and stay true to their message will win. And if LinkedIn stops working, you can always take your followers elsewhere. If you have read and enjoyed my words here on LinkedIn in the last three years, thank you. It has been a much-needed creative outlet and has brought me opportunities, laughs, knowledge, new colleagues, and friends. I'll still be stalking your posts and writing sarcastic comments. --- # Where can you find me: Bitcoin writing - [X](https://x.com/21Futures), [StackerNews](https://stacker.news/21futures) [21futures.com](https://21futures.com/)\ NOSTR (npub12xy9yxej6s9hgzsn3rfyfc3xgtdr29wqlvulquzhz2fhqqywk5vqnyvqut), [Totallyhumanwriter.com](https://totallyhumanwriter.com/) - website coming soon. [Maximum Freedom, Minimum Bullshit](https://maximumfreedom.substack.com/) on Substack. And you can reach me via email at philipcharterauthor@gmail.com I'm interested to know your thoughts and plans for 2025. Where will you be writing and why?
@ 5188521b:008eb518
2024-12-31 16:46:45<img src="https://blossom.primal.net/e4d7d32a4590123c901aef5d441a85be956c29eec8d321a1d8e5a17cb186862c.jpg"> My experience of [daily posting on LinkedIn](https://www.linkedin.com/in/totallyhumanwriter/) started around three years ago, when I became more serious about my coaching business. In that time, I amassed 25,000 followers and garnered around 3 million impressions on my writing. It was a wild ride, but now it’s time to leave the theme park. # Reasons I Quit Posting on LinkedIn Here they are, in no particular order: 1. I went from coach to ghostwriter. 2024 threw up an unexpected career change. Since 2018, I've been a coach, moving from teaching English as a foreign language to working with groups of multilingual pro writers looking for better opportunities. Coaching is a tough industry (maybe I'll write about that someday). My idea was to write more meaningful words and less copy to market my coaching business. Ultimately, writing to develop the Bitcoin ecosystem is what I find meaningful, and writing for hire doesn't require as much copywriting as being a coach. With a solid portfolio, contacts, and profile, potential clients can see your results. You don't need to attract a ton of inbound leads by writing funny bits and wow-inducing educational posts on LinkedIn. 2. Time constraints Because of my own book marketing, new client work, and projects like [21 Futures](https://21futures.com/), I can't dedicate my creative efforts and several hours per week to writing on LinkedIn. That time works better for me elsewhere. 3. Worsening distribution 'Creators' (a.k.a. active posters with many followers) often say changes to the algorithm don't matter. 'Get on with it. Adapt and move forward.' I'd be lying if I said I'm happy seeing statistics for my posts plummet. In 2022 and 2023, a successful carousel might net 20,000 views with over 150 likes and 50+ comments. Now, an exceptional post for me attracts 5,000 views with 50 likes. I won't bore you with charts and statistics, but this is an average, based on hundreds of posts. It seems LinkedIn is reducing the reach of big accounts in favour of tighter networks and distributing the work of those with <5k followers. That's fine. Perhaps that will make the platform less showy, and less boastful, finally ridding us of fake stories, surprising hacks, and ultimate guides. Still, It makes creative types like me feel like failures. Does an 80% decrease in distribution seem fair for the three years of daily effort I've put in? Should I keep struggling for diminishing returns? No. Creative people must seek the best return on investment for their time. The lesson? Distribution is more important than follower numbers. I've also quit Medium, where I have 2,000 followers and regularly receive single-digit reads on my posts. 4. LinkedIn values machines over humans. Cost-cutting, extracting value, and planning for a robotic future. That's Microsoft's MO. Despite being a social network with over 1 billion users, LinkedIn seemingly relies on automated support to make decisions on which content, people, and ideas are allowed on the platform. Users' data is parsed without their express consent.\ LinkedIn seems desperate for us to use generative AI to express our 'insight'.\ We are constantly bombarded by LLM drivel and boring machine-made content. If you can't be bothered to write it, why should I bother to read it? As somebody who brands himself a human-centric writer, why would I offer up personal takes and stories writing for free in an AI-filled swamp? --- # What's next? So I'm giving up posting on LinkedIn. With that said, it can still produce a great benefit for its users, especially those in the bitcoin space. Why? The ability to search for potential connections, present your profile, and share your expertise can make a huge difference to your work - investment, partnership, and customers. If you have a smaller network and have the need to share personal takes, opinions, and expertise, posting on LinkedIn is worth it. So few are doing this in bitcoin, the opportunities in 2025 are mind-boggling. Next year, thousands of new startups and ventures will be vying for our attention. Those who can build trust and stay true to their message will win. And if LinkedIn stops working, you can always take your followers elsewhere. If you have read and enjoyed my words here on LinkedIn in the last three years, thank you. It has been a much-needed creative outlet and has brought me opportunities, laughs, knowledge, new colleagues, and friends. I'll still be stalking your posts and writing sarcastic comments. --- # Where can you find me: Bitcoin writing - [X](https://x.com/21Futures), [StackerNews](https://stacker.news/21futures) [21futures.com](https://21futures.com/)\ NOSTR (npub12xy9yxej6s9hgzsn3rfyfc3xgtdr29wqlvulquzhz2fhqqywk5vqnyvqut), [Totallyhumanwriter.com](https://totallyhumanwriter.com/) - website coming soon. [Maximum Freedom, Minimum Bullshit](https://maximumfreedom.substack.com/) on Substack. And you can reach me via email at philipcharterauthor@gmail.com I'm interested to know your thoughts and plans for 2025. Where will you be writing and why? @ f4d89779:2b522db9
2024-12-29 16:46:43In the game of Ultimate Frisbee, there is a beloved phrase that captures one of the best aspects of playing. Ultimate is about decision making. It is played on a rectangular field with seven players on each side. Much like football, the object of the game is to score with a throw into the end zone. To "HUCK", means to launch the disc down field in the hopes of scoring. You can probably guess what the "OR YOU'RE NOTHING" means but the spirit of it is that when the opportunity comes ... PUT THE DISC IN THE AIR <https://i.nostr.build/XyTpXdNOSpv5f8ZZ.jpg> Sorry, I had to channel my inner ODELL there for a second. These are all caps kind of moments. Time feels like it stops, the disc floats in the air, the receiver and defender are sprinting all out, you can hear the collective breath of anticipation from the audience and then you score. If you're good that is. You know what? You and I are civilized people, we use the NOSTR, so I won't limit myself to just words. Here are some of those moments: <https://v.nostr.build/zav5o04BK97FiNAt.mp4> During the course of play, teams get into a formation with a couple of the players doing the majority of the disc throwing. These players are called handlers. They handle the disc, they have the responsibility of moving the disc downfield, and handle most of the decision making. A good handler develops a sort of instinct for each of their receivers, can guess the capabilities of each defender, and knows himself well enough to know if he has the throw. They know who is good and reliable at short cuts. They know who has the top end speed to throw a long floating pass into the end zone. With each play they are judging all of the moving objects on the field and deciding on real time risk of each throw and where things will lead. Mistakes lead to turnovers and turnovers, like in many other sports, are death. Hopefully, you start to see how ultimate relates to life and Bitcoin. Life is a field and you have defenders and you have receivers. It is your disc and the decisions you make have a huge impact on whether you win or lose. Knowingly or not, you saw Bitcoin as a potential receiver and Governments, academics, shitcoiners, as defenders. In some ways those around you were also defenders. They whispered, or maybe still whisper the risk and probability of failure in your ear. Their fear weighed against what you know. With the btc/usd exchange rate at $94k, and companies fighting over the best ways to get sats I think we can say that you did not get lucky. They called you crazy, they said that throw won't work, they said your receiver sucked but you knew better. You saw that receiver leaving every defender in the dust and you HUCKED it and you are certainly not NOTHING.
@ f4d89779:2b522db9
2024-12-29 16:46:43In the game of Ultimate Frisbee, there is a beloved phrase that captures one of the best aspects of playing. Ultimate is about decision making. It is played on a rectangular field with seven players on each side. Much like football, the object of the game is to score with a throw into the end zone. To "HUCK", means to launch the disc down field in the hopes of scoring. You can probably guess what the "OR YOU'RE NOTHING" means but the spirit of it is that when the opportunity comes ... PUT THE DISC IN THE AIR <https://i.nostr.build/XyTpXdNOSpv5f8ZZ.jpg> Sorry, I had to channel my inner ODELL there for a second. These are all caps kind of moments. Time feels like it stops, the disc floats in the air, the receiver and defender are sprinting all out, you can hear the collective breath of anticipation from the audience and then you score. If you're good that is. You know what? You and I are civilized people, we use the NOSTR, so I won't limit myself to just words. Here are some of those moments: <https://v.nostr.build/zav5o04BK97FiNAt.mp4> During the course of play, teams get into a formation with a couple of the players doing the majority of the disc throwing. These players are called handlers. They handle the disc, they have the responsibility of moving the disc downfield, and handle most of the decision making. A good handler develops a sort of instinct for each of their receivers, can guess the capabilities of each defender, and knows himself well enough to know if he has the throw. They know who is good and reliable at short cuts. They know who has the top end speed to throw a long floating pass into the end zone. With each play they are judging all of the moving objects on the field and deciding on real time risk of each throw and where things will lead. Mistakes lead to turnovers and turnovers, like in many other sports, are death. Hopefully, you start to see how ultimate relates to life and Bitcoin. Life is a field and you have defenders and you have receivers. It is your disc and the decisions you make have a huge impact on whether you win or lose. Knowingly or not, you saw Bitcoin as a potential receiver and Governments, academics, shitcoiners, as defenders. In some ways those around you were also defenders. They whispered, or maybe still whisper the risk and probability of failure in your ear. Their fear weighed against what you know. With the btc/usd exchange rate at $94k, and companies fighting over the best ways to get sats I think we can say that you did not get lucky. They called you crazy, they said that throw won't work, they said your receiver sucked but you knew better. You saw that receiver leaving every defender in the dust and you HUCKED it and you are certainly not NOTHING. @ ece127e2:745bab9c
2024-12-28 22:29:36Un lugar ominoso ,un hoyo de conejo espiralado en el cual cada ser que aparece es más oscuro que el otro. Un bosque de ramas secas que es mejor evitar ;si te tocan te secaran ,te extraerán luz hasta convertirte en uno de ellos . Árboles más altos tapan la luz que alimenta al suelo ,y éste se cubre de podredumbre.Esa miasma se te pega en los pies ,te atrapa ..te impide caminar y te hundes hasta no poder respirar.
@ ece127e2:745bab9c
2024-12-28 22:29:36Un lugar ominoso ,un hoyo de conejo espiralado en el cual cada ser que aparece es más oscuro que el otro. Un bosque de ramas secas que es mejor evitar ;si te tocan te secaran ,te extraerán luz hasta convertirte en uno de ellos . Árboles más altos tapan la luz que alimenta al suelo ,y éste se cubre de podredumbre.Esa miasma se te pega en los pies ,te atrapa ..te impide caminar y te hundes hasta no poder respirar. @ f3df9bc0:a95119eb
2024-12-26 12:29:35# Welcome! 🌱 Interesting places to start: - Latest polished pieces: [[Latest Articles Index]] - Index of all articles by discipline: [[Discipline Index]] ## About this site This site is both a blog & wiki-style digital garden. Some ideas you’ll run into here may be of quality, others will be less interesting, not fully formed, or even just straight wrong. This is intentional. Content here is continuously cultivated and refined as I live my life and gain new experiences, and I welcome challenges to anything I’ve written. The general idea behind this is that my unstructured thought is fast and divergent, but not coherent, and therefore difficult to use in any practical way. The process of writing is a forcing function for taking divergent thought and bringing it into a form that can be reasoned about, improved upon, or discarded as irrelevant. Stalling this process is counter-productive and can lead to a sort of comatose where the mind is stuck in the abstract, waiting for confidence on a particular strain of thought, but never making any progress. Therefore there is no set topic for this garden, instead it’s purpose is to serve as an auxiliary brain for any and all topics that I find interesting and worth spending time refining. ## Contact - nostr: [slipstream@htlc.io](https://nosta.me/slipstream@htlc.io) - farcaster: [@htlc](http://warpcast.com/htlc)
@ f3df9bc0:a95119eb
2024-12-26 12:29:35# Welcome! 🌱 Interesting places to start: - Latest polished pieces: [[Latest Articles Index]] - Index of all articles by discipline: [[Discipline Index]] ## About this site This site is both a blog & wiki-style digital garden. Some ideas you’ll run into here may be of quality, others will be less interesting, not fully formed, or even just straight wrong. This is intentional. Content here is continuously cultivated and refined as I live my life and gain new experiences, and I welcome challenges to anything I’ve written. The general idea behind this is that my unstructured thought is fast and divergent, but not coherent, and therefore difficult to use in any practical way. The process of writing is a forcing function for taking divergent thought and bringing it into a form that can be reasoned about, improved upon, or discarded as irrelevant. Stalling this process is counter-productive and can lead to a sort of comatose where the mind is stuck in the abstract, waiting for confidence on a particular strain of thought, but never making any progress. Therefore there is no set topic for this garden, instead it’s purpose is to serve as an auxiliary brain for any and all topics that I find interesting and worth spending time refining. ## Contact - nostr: [slipstream@htlc.io](https://nosta.me/slipstream@htlc.io) - farcaster: [@htlc](http://warpcast.com/htlc) @ bcea2b98:7ccef3c9
2024-12-25 03:11:27It has been a fun year of learning and entertainment with you all. Merry Christmas! originally posted at https://stacker.news/items/823433
@ bcea2b98:7ccef3c9
2024-12-25 03:11:27It has been a fun year of learning and entertainment with you all. Merry Christmas! originally posted at https://stacker.news/items/823433 @ dff95033:862fbf40
2024-12-23 20:52:00Você sabia que o Bitcoin foi uma das melhores escolhas de investimento em 2024, superando até mesmo commodities tradicionais como ouro, soja e gás natural? Chamado por alguns de **“Dinheiro Mágico da Internet”,** o Bitcoin provou ser mais do que isso, com um crescimento exponencial ao longo dos anos, destacando-se especialmente em 2024 ## 📊 **Confira os números impressionantes:** | **Commodity** | **Ganho(%)** | | --- | --- | | 🥇**Cacau** | **200%** | | 🥈**Bitcoin** | **145%** | | 🥉**Suco de Laranja** | **50%** | | **Café Arábica** | **40%** | | **Gás Natural** | **30%** | | **Ouro** | **20%** | | **Carne Suína** | **10%** | | **Paládio** | **5%** | | **Soja** | **0%** | ## Bitcoin deixou a concorrência para trás em 2024. ## 🔍 **O que impulsionou o Bitcoin em 2024?** Se o cacau liderou com 200% graças a problemas de oferta global, o Bitcoin brilhou por outros motivos: - **Demanda Crescente:** Cada vez mais pessoas buscaram o Bitcoin como reserva de valor. - **Adoção Institucional:** Um aumento significativo de **30%** na adoção por grandes instituições, de acordo com dados da Glassnode. - **Busca por Segurança:** O Bitcoin continuou sendo o principal ativo digital descentralizado, atraindo investidores de diferentes perfis. - **Halving**: Em abril de 2024, ocorreu o "halving" do Bitcoin, um evento onde a recompensa que os mineradores recebem por adicionar transações ao blockchain é reduzida pela metade, de 6,25 para 3,125 Bitcoins por bloco. Isso diminui a oferta de novos Bitcoins, tornando-os mais raros e, por consequência, aumentando seu valor. Esses fatores consolidaram o **Bitcoin** como o segundo ativo mais rentável do ano, com **145% de valorização**. ## 💡 **Por que investir em Bitcoin agora?** 1️⃣ **Potencial de Crescimento**: Historicamente, o Bitcoin mostra ciclos de valorização exponencial. Em 10 anos, um investimento inicial de $ 100 em Bitcoin poderia valer hoje $ 26.931,1, segundo dados do CoinMarketCap.\ 2️⃣ **Diversificação**: O Bitcoin frequentemente se comporta de maneira independente em relação a ativos tradicionais, oferecendo uma oportunidade para diversificação de carteira, com correlações de preço às vezes negativas com ações e commodities.\ 3️⃣ **Facilidade de Acesso**: Com a [**Stackfy**](https://t.me/stack_fy_bot?start=4C170C8E), você já pode ter os seus bitcoins com apenas **R$ 25**, de forma simples, rápida e segura! --- > ⚠️ **Atenção:** Investir em criptomoedas envolve riscos devido à alta volatilidade do mercado. Sempre faça sua própria pesquisa e considere suas tolerâncias de risco antes de investir. --- ## 📈 **Não perca tempo!** O Bitcoin está mostrando que o futuro dos investimentos está nas mãos de quem acredita em inovação. Prepare-se para 2025 e além! 🌟 ➡️ **Ação:** Aproveite essa oportunidade única e faça parte da revolução financeira. Explore plataformas confiáveis como e comece sua jornada no Bitcoin hoje! 🚀 --- ## **Referências:** 1. BLOOMBERG. [Cocoa caps 2024 as biggest commodity winner](https://www.bloomberg.com/news/articles/2024-12-21/cocoa-caps-2024-as-biggest-commodity-winner-it-s-not-over-yet). Acesso em: 21 dez. 2024. 2. MARKETWATCH. [Bitcoin valuation trends](https://www.marketwatch.com/story/cocoas-the-best-performing-commodity-in-2024-and-even-beat-bitcoin-whats-next-b8daf55d). Acesso em: 21 dez. 2024. 3. THE WALL STREET JOURNAL. [Cocoa surges past $12,000 on supply concerns](https://www.wsj.com/finance/commodities-futures/cocoa-surges-past-12-000-on-supply-concerns-912c91b4). Acesso em: 21 dez. 2024. 4. GLASSNODE. [Fasanara Digital + Glassnode Report: Institutional perspectives on digital assets](https://insights.glassnode.com/fasanara-digital-glassnode-report-institutional-perspectives-on-digital-assets/). Acesso em: 21 dez. 2024. 5. COINMARKETCAP. [Bitcoin (BTC) preço, gráfico, capitalização de mercado](https://coinmarketcap.com/pt-br/currencies/bitcoin/). Acesso em: 21 dez. 2024. 6. COINGECKO. [Bitcoin versus Traditional Assets: Price Returns.](https://www.coingecko.com/research/publications/bitcoin-versus-traditional-assets-price-returns) Acesso em: 21 dez. 2024.
@ dff95033:862fbf40
2024-12-23 20:52:00Você sabia que o Bitcoin foi uma das melhores escolhas de investimento em 2024, superando até mesmo commodities tradicionais como ouro, soja e gás natural? Chamado por alguns de **“Dinheiro Mágico da Internet”,** o Bitcoin provou ser mais do que isso, com um crescimento exponencial ao longo dos anos, destacando-se especialmente em 2024 ## 📊 **Confira os números impressionantes:** | **Commodity** | **Ganho(%)** | | --- | --- | | 🥇**Cacau** | **200%** | | 🥈**Bitcoin** | **145%** | | 🥉**Suco de Laranja** | **50%** | | **Café Arábica** | **40%** | | **Gás Natural** | **30%** | | **Ouro** | **20%** | | **Carne Suína** | **10%** | | **Paládio** | **5%** | | **Soja** | **0%** | ## Bitcoin deixou a concorrência para trás em 2024. ## 🔍 **O que impulsionou o Bitcoin em 2024?** Se o cacau liderou com 200% graças a problemas de oferta global, o Bitcoin brilhou por outros motivos: - **Demanda Crescente:** Cada vez mais pessoas buscaram o Bitcoin como reserva de valor. - **Adoção Institucional:** Um aumento significativo de **30%** na adoção por grandes instituições, de acordo com dados da Glassnode. - **Busca por Segurança:** O Bitcoin continuou sendo o principal ativo digital descentralizado, atraindo investidores de diferentes perfis. - **Halving**: Em abril de 2024, ocorreu o "halving" do Bitcoin, um evento onde a recompensa que os mineradores recebem por adicionar transações ao blockchain é reduzida pela metade, de 6,25 para 3,125 Bitcoins por bloco. Isso diminui a oferta de novos Bitcoins, tornando-os mais raros e, por consequência, aumentando seu valor. Esses fatores consolidaram o **Bitcoin** como o segundo ativo mais rentável do ano, com **145% de valorização**. ## 💡 **Por que investir em Bitcoin agora?** 1️⃣ **Potencial de Crescimento**: Historicamente, o Bitcoin mostra ciclos de valorização exponencial. Em 10 anos, um investimento inicial de $ 100 em Bitcoin poderia valer hoje $ 26.931,1, segundo dados do CoinMarketCap.\ 2️⃣ **Diversificação**: O Bitcoin frequentemente se comporta de maneira independente em relação a ativos tradicionais, oferecendo uma oportunidade para diversificação de carteira, com correlações de preço às vezes negativas com ações e commodities.\ 3️⃣ **Facilidade de Acesso**: Com a [**Stackfy**](https://t.me/stack_fy_bot?start=4C170C8E), você já pode ter os seus bitcoins com apenas **R$ 25**, de forma simples, rápida e segura! --- > ⚠️ **Atenção:** Investir em criptomoedas envolve riscos devido à alta volatilidade do mercado. Sempre faça sua própria pesquisa e considere suas tolerâncias de risco antes de investir. --- ## 📈 **Não perca tempo!** O Bitcoin está mostrando que o futuro dos investimentos está nas mãos de quem acredita em inovação. Prepare-se para 2025 e além! 🌟 ➡️ **Ação:** Aproveite essa oportunidade única e faça parte da revolução financeira. Explore plataformas confiáveis como e comece sua jornada no Bitcoin hoje! 🚀 --- ## **Referências:** 1. BLOOMBERG. [Cocoa caps 2024 as biggest commodity winner](https://www.bloomberg.com/news/articles/2024-12-21/cocoa-caps-2024-as-biggest-commodity-winner-it-s-not-over-yet). Acesso em: 21 dez. 2024. 2. MARKETWATCH. [Bitcoin valuation trends](https://www.marketwatch.com/story/cocoas-the-best-performing-commodity-in-2024-and-even-beat-bitcoin-whats-next-b8daf55d). Acesso em: 21 dez. 2024. 3. THE WALL STREET JOURNAL. [Cocoa surges past $12,000 on supply concerns](https://www.wsj.com/finance/commodities-futures/cocoa-surges-past-12-000-on-supply-concerns-912c91b4). Acesso em: 21 dez. 2024. 4. GLASSNODE. [Fasanara Digital + Glassnode Report: Institutional perspectives on digital assets](https://insights.glassnode.com/fasanara-digital-glassnode-report-institutional-perspectives-on-digital-assets/). Acesso em: 21 dez. 2024. 5. COINMARKETCAP. [Bitcoin (BTC) preço, gráfico, capitalização de mercado](https://coinmarketcap.com/pt-br/currencies/bitcoin/). Acesso em: 21 dez. 2024. 6. COINGECKO. [Bitcoin versus Traditional Assets: Price Returns.](https://www.coingecko.com/research/publications/bitcoin-versus-traditional-assets-price-returns) Acesso em: 21 dez. 2024. @ 5af07946:98fca8c4
2024-12-22 14:05:19On the surface, it appears the contest is between the `old guard` and the `new innovation`. Old seeks to maintain a status quo to ensure a safe passage of their knowledge (wealth) to the new. And the new knows the old as a dependable trustee. The shift, however, must happen, and it needs a trigger - something unwarranted - a mishap to break the umbilical cord. Bigger the ensuing shift, bigger the mishap. In a way, the mishap marks the beginning of the transition - start of a new time. It is a gun shot to initialize the race. The battle begins at this moment amongst many variants of "new". In fact, many new possibilities crop up to capitalize the opportunity. Having recognized the inevitable, they all stake their claim to being righteous and thus the earnest representation of truth. This happens over and over again as in "history repeats itself". There are many examples[^history] in our recent past though a keen observers may see them in their own backyard. They occur for the consciousness must evolve to understand the nature of unity[^unit] - the smallest common factor. A mishap is thus a mere setback before the hitherto slow breeding innovations sling into top gear. Such triggers, driven by imperceptible evolution of consciousness are said to be caused by `Prarbdha`. > `Prarbdha`, a `Sanskrit` word, means something that had already begun. It ties together the past, present and the future - the continuum `Bramh`. In that it also means "fate", because the fate had commenced before the material event physically occurred. [^history]: Battles between old and new in recent history: - IBM was the old. Microsoft and Apple battled for superiority in computing as contenders for new leadership title. For an observes in late 80s it appeared as if big blue is fighting Apple (and later Microsoft) but that was just a trigger. The real battle was between Apple and Microsoft. - Laptop was old, the newcomers iOS and Android are battling for superiority in mobile computing. For quite some time it felt like mobile devices were the PC killers, but the truth is battle is never between the old and the new. It is always among many new contenders. - It appears as big oil is at odds with the EVs or the hydrogen fuel cells. Though the truth is fossil fuel industry will be the biggest investors in sustainable future - because they know first hand about the shift. Sustainable energy is the opportunity for refiners because someone needs to do the work, and they are best positioned to take advantage of this massive opportunity. The real battle is among Solar, Wind , Nuclear and Hydrogen. - Gold is old. It appears that bitcoin is trying to replace Gold. But that is not true. The real battle is with in Cryptos - BTC vs Ether vs Sol vs so many other possibilities. When the dust settles, we will see Gold has its own role to play just like laptop has its own role to play in the increasingly mobile world. [^unit]: A unit is an immutable part of any measurement. Easy examples - a meter is an immutable unit of length. A kilo is an immutable unit of weight. A unit is part of every measurement - it lends meaning to what is being measured - it is implicit in what is being measured. It is a multiplication that outputs exactly what is being measured. - Little harder example - Number “1” is the unit of multiplication itself. It is there inbuilt into every number (even zero) . It never changes the number when multiplied -> a unit when multiplied with what is being measured , must stay inert - never change the measurement ! But you can't measure anything without a unit … no number exists without "1" - Hard question - What is the unit of consciousness ? By definition, it must be 1) immutable 2) part of every conscious being. 3) must stay inert. - In `Vaidik` science , `Atma` is defined as the unit of consciousness. It is immutable, inert and essential. For humans, understanding `Atma` is as hard as understanding number 1 for say number 8.
@ 5af07946:98fca8c4
2024-12-22 14:05:19On the surface, it appears the contest is between the `old guard` and the `new innovation`. Old seeks to maintain a status quo to ensure a safe passage of their knowledge (wealth) to the new. And the new knows the old as a dependable trustee. The shift, however, must happen, and it needs a trigger - something unwarranted - a mishap to break the umbilical cord. Bigger the ensuing shift, bigger the mishap. In a way, the mishap marks the beginning of the transition - start of a new time. It is a gun shot to initialize the race. The battle begins at this moment amongst many variants of "new". In fact, many new possibilities crop up to capitalize the opportunity. Having recognized the inevitable, they all stake their claim to being righteous and thus the earnest representation of truth. This happens over and over again as in "history repeats itself". There are many examples[^history] in our recent past though a keen observers may see them in their own backyard. They occur for the consciousness must evolve to understand the nature of unity[^unit] - the smallest common factor. A mishap is thus a mere setback before the hitherto slow breeding innovations sling into top gear. Such triggers, driven by imperceptible evolution of consciousness are said to be caused by `Prarbdha`. > `Prarbdha`, a `Sanskrit` word, means something that had already begun. It ties together the past, present and the future - the continuum `Bramh`. In that it also means "fate", because the fate had commenced before the material event physically occurred. [^history]: Battles between old and new in recent history: - IBM was the old. Microsoft and Apple battled for superiority in computing as contenders for new leadership title. For an observes in late 80s it appeared as if big blue is fighting Apple (and later Microsoft) but that was just a trigger. The real battle was between Apple and Microsoft. - Laptop was old, the newcomers iOS and Android are battling for superiority in mobile computing. For quite some time it felt like mobile devices were the PC killers, but the truth is battle is never between the old and the new. It is always among many new contenders. - It appears as big oil is at odds with the EVs or the hydrogen fuel cells. Though the truth is fossil fuel industry will be the biggest investors in sustainable future - because they know first hand about the shift. Sustainable energy is the opportunity for refiners because someone needs to do the work, and they are best positioned to take advantage of this massive opportunity. The real battle is among Solar, Wind , Nuclear and Hydrogen. - Gold is old. It appears that bitcoin is trying to replace Gold. But that is not true. The real battle is with in Cryptos - BTC vs Ether vs Sol vs so many other possibilities. When the dust settles, we will see Gold has its own role to play just like laptop has its own role to play in the increasingly mobile world. [^unit]: A unit is an immutable part of any measurement. Easy examples - a meter is an immutable unit of length. A kilo is an immutable unit of weight. A unit is part of every measurement - it lends meaning to what is being measured - it is implicit in what is being measured. It is a multiplication that outputs exactly what is being measured. - Little harder example - Number “1” is the unit of multiplication itself. It is there inbuilt into every number (even zero) . It never changes the number when multiplied -> a unit when multiplied with what is being measured , must stay inert - never change the measurement ! But you can't measure anything without a unit … no number exists without "1" - Hard question - What is the unit of consciousness ? By definition, it must be 1) immutable 2) part of every conscious being. 3) must stay inert. - In `Vaidik` science , `Atma` is defined as the unit of consciousness. It is immutable, inert and essential. For humans, understanding `Atma` is as hard as understanding number 1 for say number 8. @ 228dde34:b5d0345e
2024-12-20 09:25:14##### BY Glenda Chong ##### Editorial Admin ##### Hype Issue #60 ###### Join GLENDA CHONG as she steps into the electrifying energy of Singapore’s K-pop scene at *SCAPE’s K-POP ALL IN 2024 and finds out how events like these bring a community together. *Dance crew 6IX giving their all on stage at K-POP ALL IN 2024. Photo by Glenda Chong.* The *SCAPE Ground Theatre was still, save for the low murmur of voices as attendees shuffled in. But when the screen on stage flashed a bright orange and blue and the first beat of a K-pop track blasted through the speakers, the crowd's energy flipped “ON” like a switch. This was K-POP ALL IN 2024, also known as KAI, an annual year-end party that brings K-pop enthusiasts together for a night of community and celebration. KAI’s theme this year, “TIME K-APSULE” invites both performers and attendees to honour iconic K-pop classics and artists that have shaped the genre’s past and spotlight the fresh energy of today’s favourites. *Dance crew Onhit Dance covering K-pop girl group GFRIEND’s hit MAGO. Photo by Glenda Chong.* As a K-pop fan myself, KAI wasn’t my first rodeo when it comes to *SCAPE’s K-pop-themed events. However, going to such an event alone was a first so I was just a touch anxious as to whether I would feel out of place. Despite my nerves, I milled around the booths just behind the audience seating area before the show began. Aside from the performances, I was pleased to see that there were plenty of booths selling K-pop official and fan-made merchandise. From fan art to collectible photo cards and K-pop albums, it was a collector’s dream. The one booth that drew me in almost instantly, though, was by the NUS Korean Cultural Interest Group (KCIG) from the National University of Singapore (NUS). As part of their efforts to raise funds for their annual K-pop dance production, the interest group had gotten a booth at KAI to sell not just unique merchandise such as shirts they designed, but even experiences like a “deco booth” and a photo-taking area. That extra effort really made their booth stand out from the other booths that were only selling ‘merch’. The booth embodied connection through its “deco booth”, where K-pop fans could personalise photocard sleeves with decorative elements. Though typically a solo activity, many did it with friends, turning the booth into a vibrant hub of shared creativity and enthusiasm. While you can say that the heart of Singapore’s K-pop scene lies in the music and the performances, this energy and sense of community extends beyond the stage. I got to chat with KCIG members, Abigail Tan and Wong Yan Rou, who were running KCIG’s booth, and I could feel how their interest group and booth are a microcosm of the wider K-pop community. The booth was more than just a fundraising opportunity, and their interest group isn’t just a place to explore Korean culture. Both allowed like-minded individuals to bond and be part of a bigger community. *The writer decorated their own photocard sleeve to join in on the fun. Photo by Glenda Chong.* And as for KCIG, its inclusivity is its hallmark. According to Yan Rou and Abigail, no auditions are required to join KCIG as “everyone” is welcome to “be part of the community,” which they believe makes KCIG highly welcoming. As such, in Yan Rou’s words, members “stay for a long time.” And just as KCIG brings people interested in Korean culture together, KAI does the same, which they can feel and see with their own eyes on a greater scale. “Our efforts are ultimately school-level… but when we come out to events like this [KAI], we’ll be able to see the whole Singapore community,” Yan Rou said. “You’ll be able to see the people in this community, so I think it helps that you can build connections and make friends along the way.” *Wong Yan Rou (left) and Abigail Tan (right) posing in KCIG’s photo-taking area. Photo by Glenda Chong.* Just as we wrapped up our chat, the MCs’ voices cut through the music to announce the first few performers of the night. As I rushed to take my front row “seat” which was a spot on the ground I reserved with my belongings, the first act’s first performer, Justin Padayao took the stage. When it comes to events like this, one might assume most audiences come to only support their performing friends. However, this assumption was quickly turned on its head when Justin experienced technical faults. Encouraging cheers rang from all four corners, giving him the much-needed boost to start again and hit all the right notes of “Into the New World”, the debut single of K-pop girl group Girls’ Generation. With its resolute lyrics, this timeless track is known for being a symbolic anthem of solidarity associated with South Korea’s protest culture. *Justin Padayao performed a soulful ballad version of K-pop girl group Girls’ Generation’s Into the New World. Photo by Glenda Chong.* That unity could be felt in the crowd, as we sang harmoniously to the song’s fully-Korean lines and used our phones’ flashlights to act as ‘lightsticks’, an essential part of showing support in K-pop culture. Throughout the rest of the first act’s performances, the energy never died down. When the first act ended and the following acts’ performers took over, it only continued to skyrocket. Other than solo acts, plenty of dance crews also performed, and one I had been keeping my eye on finally took the spotlight. Named CODE:US, the all-female team danced with fierce precision to another Girls’ Generation classic, this time “The Boys”. Except, keeping in line with KAI 2024’s theme, the team danced to a cover of “The Boys” by K-pop group Kep1er who debuted years after Girls’ Generation did, which made for a perfect blend of the past and present. *Dance crew CODE:US performing on stage. Photo by Glenda Chong.* Having gotten to chat with CODE:US themselves, it seems that their choice to perform Kep1er’s version of “The Boys” was intentional, as it was the version they resonated with most despite multiple other covers being available. According to member Jing Yun, 19, she’s inspired by K-pop artists like ATEEZ’s San and aespa’s Karina as their powerful performances conveyed their emotions to their audiences. “Whenever I perform, I do hope I can deliver the same type of feelings that the [K-pop artists] do, where they can just enjoy the stage with no regrets while also delivering something memorable to the audience and myself.” She said. And she and CODE:US definitely delivered, as the crowd and I could really feel their passion. While I was impressed by every performance, what struck me the most was the diversity of performers. From fathers and working adults to youths as young as 14, KAI was not just a talent showcase; the performers and this year’s theme [TIME K-APSULE] were a testament to K-pop’s enduring ability to unite generations of fans and how the passion for it spans all walks of life.  *A member of a dance crew carrying his child who had been watching the team perform from behind the stage curtain after their performance. Photo by Glenda Chong.* As the final performances wrapped up, the night was still young as the space transformed for KAI’s final staple event, K-pop Random Play Dance (KRPD). It was a fitting end to the night, as this was where you could truly witness the community’s unity. In true KRPD fashion, everyone, both performers and audience members alike, came together to dance to K-pop hits both old and new.  *Team CODE:US posing for a photo before K-POP ALL IN 2024 began. Photo courtesy of CODE:US.* “[We are] just glad that this community allows us all to be open and enjoy what we like together without being shamed or judged.” CODE:US mentioned. Reflecting on this, I couldn’t help but think of what a powerful reminder this was of what events like KAI represent: a chance to connect with and celebrate something larger than ourselves.
@ 228dde34:b5d0345e
2024-12-20 09:25:14##### BY Glenda Chong ##### Editorial Admin ##### Hype Issue #60 ###### Join GLENDA CHONG as she steps into the electrifying energy of Singapore’s K-pop scene at *SCAPE’s K-POP ALL IN 2024 and finds out how events like these bring a community together. *Dance crew 6IX giving their all on stage at K-POP ALL IN 2024. Photo by Glenda Chong.* The *SCAPE Ground Theatre was still, save for the low murmur of voices as attendees shuffled in. But when the screen on stage flashed a bright orange and blue and the first beat of a K-pop track blasted through the speakers, the crowd's energy flipped “ON” like a switch. This was K-POP ALL IN 2024, also known as KAI, an annual year-end party that brings K-pop enthusiasts together for a night of community and celebration. KAI’s theme this year, “TIME K-APSULE” invites both performers and attendees to honour iconic K-pop classics and artists that have shaped the genre’s past and spotlight the fresh energy of today’s favourites. *Dance crew Onhit Dance covering K-pop girl group GFRIEND’s hit MAGO. Photo by Glenda Chong.* As a K-pop fan myself, KAI wasn’t my first rodeo when it comes to *SCAPE’s K-pop-themed events. However, going to such an event alone was a first so I was just a touch anxious as to whether I would feel out of place. Despite my nerves, I milled around the booths just behind the audience seating area before the show began. Aside from the performances, I was pleased to see that there were plenty of booths selling K-pop official and fan-made merchandise. From fan art to collectible photo cards and K-pop albums, it was a collector’s dream. The one booth that drew me in almost instantly, though, was by the NUS Korean Cultural Interest Group (KCIG) from the National University of Singapore (NUS). As part of their efforts to raise funds for their annual K-pop dance production, the interest group had gotten a booth at KAI to sell not just unique merchandise such as shirts they designed, but even experiences like a “deco booth” and a photo-taking area. That extra effort really made their booth stand out from the other booths that were only selling ‘merch’. The booth embodied connection through its “deco booth”, where K-pop fans could personalise photocard sleeves with decorative elements. Though typically a solo activity, many did it with friends, turning the booth into a vibrant hub of shared creativity and enthusiasm. While you can say that the heart of Singapore’s K-pop scene lies in the music and the performances, this energy and sense of community extends beyond the stage. I got to chat with KCIG members, Abigail Tan and Wong Yan Rou, who were running KCIG’s booth, and I could feel how their interest group and booth are a microcosm of the wider K-pop community. The booth was more than just a fundraising opportunity, and their interest group isn’t just a place to explore Korean culture. Both allowed like-minded individuals to bond and be part of a bigger community. *The writer decorated their own photocard sleeve to join in on the fun. Photo by Glenda Chong.* And as for KCIG, its inclusivity is its hallmark. According to Yan Rou and Abigail, no auditions are required to join KCIG as “everyone” is welcome to “be part of the community,” which they believe makes KCIG highly welcoming. As such, in Yan Rou’s words, members “stay for a long time.” And just as KCIG brings people interested in Korean culture together, KAI does the same, which they can feel and see with their own eyes on a greater scale. “Our efforts are ultimately school-level… but when we come out to events like this [KAI], we’ll be able to see the whole Singapore community,” Yan Rou said. “You’ll be able to see the people in this community, so I think it helps that you can build connections and make friends along the way.” *Wong Yan Rou (left) and Abigail Tan (right) posing in KCIG’s photo-taking area. Photo by Glenda Chong.* Just as we wrapped up our chat, the MCs’ voices cut through the music to announce the first few performers of the night. As I rushed to take my front row “seat” which was a spot on the ground I reserved with my belongings, the first act’s first performer, Justin Padayao took the stage. When it comes to events like this, one might assume most audiences come to only support their performing friends. However, this assumption was quickly turned on its head when Justin experienced technical faults. Encouraging cheers rang from all four corners, giving him the much-needed boost to start again and hit all the right notes of “Into the New World”, the debut single of K-pop girl group Girls’ Generation. With its resolute lyrics, this timeless track is known for being a symbolic anthem of solidarity associated with South Korea’s protest culture. *Justin Padayao performed a soulful ballad version of K-pop girl group Girls’ Generation’s Into the New World. Photo by Glenda Chong.* That unity could be felt in the crowd, as we sang harmoniously to the song’s fully-Korean lines and used our phones’ flashlights to act as ‘lightsticks’, an essential part of showing support in K-pop culture. Throughout the rest of the first act’s performances, the energy never died down. When the first act ended and the following acts’ performers took over, it only continued to skyrocket. Other than solo acts, plenty of dance crews also performed, and one I had been keeping my eye on finally took the spotlight. Named CODE:US, the all-female team danced with fierce precision to another Girls’ Generation classic, this time “The Boys”. Except, keeping in line with KAI 2024’s theme, the team danced to a cover of “The Boys” by K-pop group Kep1er who debuted years after Girls’ Generation did, which made for a perfect blend of the past and present. *Dance crew CODE:US performing on stage. Photo by Glenda Chong.* Having gotten to chat with CODE:US themselves, it seems that their choice to perform Kep1er’s version of “The Boys” was intentional, as it was the version they resonated with most despite multiple other covers being available. According to member Jing Yun, 19, she’s inspired by K-pop artists like ATEEZ’s San and aespa’s Karina as their powerful performances conveyed their emotions to their audiences. “Whenever I perform, I do hope I can deliver the same type of feelings that the [K-pop artists] do, where they can just enjoy the stage with no regrets while also delivering something memorable to the audience and myself.” She said. And she and CODE:US definitely delivered, as the crowd and I could really feel their passion. While I was impressed by every performance, what struck me the most was the diversity of performers. From fathers and working adults to youths as young as 14, KAI was not just a talent showcase; the performers and this year’s theme [TIME K-APSULE] were a testament to K-pop’s enduring ability to unite generations of fans and how the passion for it spans all walks of life.  *A member of a dance crew carrying his child who had been watching the team perform from behind the stage curtain after their performance. Photo by Glenda Chong.* As the final performances wrapped up, the night was still young as the space transformed for KAI’s final staple event, K-pop Random Play Dance (KRPD). It was a fitting end to the night, as this was where you could truly witness the community’s unity. In true KRPD fashion, everyone, both performers and audience members alike, came together to dance to K-pop hits both old and new.  *Team CODE:US posing for a photo before K-POP ALL IN 2024 began. Photo courtesy of CODE:US.* “[We are] just glad that this community allows us all to be open and enjoy what we like together without being shamed or judged.” CODE:US mentioned. Reflecting on this, I couldn’t help but think of what a powerful reminder this was of what events like KAI represent: a chance to connect with and celebrate something larger than ourselves. @ d61f3bc5:0da6ef4a
2024-12-18 16:52:18January 2025 will mark two years since we started building Primal. Our goal was to create the best possible user experience for Nostr and make it accessible to everyone. We reached a big milestone towards realizing that vision with the recent Primal 2.0 release. It’s still early days, a lot more work lies ahead, but we thought the timing was right to introduce the Premium tier. Let’s explore what it is, why we built it, what’s included, and how it will evolve moving forward. ## What Primal Premium Is The idea behind Primal Premium is simple: integrate all tools and services required for the best Nostr experience into a single package. For $7 per month, Premium users get a *Primal Name* and *Nostr Tools* built by Primal. We’ll cover those in more detail below, but first we should make a crucial point: by signing up for Premium, you are in no way locked in to Primal. Quite the contrary, you can pick and choose which Premium features you wish to enable and use within other Nostr products. Openness is Nostr’s killer feature. Any product that wishes to truly empower the user needs to interoperate with Nostr’s budding ecosystem. The feed marketplace is a great example. External feeds are first-class citizens within all Primal apps. Primal feeds are available in other Nostr clients. We are working on Premium feeds, which our users will be able to enjoy within Primal or other Nostr apps. Media hosting is another example. Our upcoming support for the Blossom protocol will make Primal Premium media hosting interoperable with other Nostr apps and media hosting services. The common theme here is user choice. Nostr offers the highest level of user agency, and the compounding effect of interoperable products and services is bound to make Nostr immensely powerful. ## Why We Built Premium and Why Now What is unfolding on Nostr right now is unique and special. The first truly self-sovereign network is being bootstrapped by this early cohort of users and builders. People are literally holding the keys to their online presence. Network infrastructure – relays, indexers, media hosting services, etc. – is being stood up organically and without any central planning or coordination. Hundreds of independent projects are adding new capabilities to Nostr without needing permission. The whole thing is truly a sight to behold. In addition to fixing the fundamentals of the network, it is equally important that we fix the broken incentives that plague the legacy Web. The status quo of monetization via advertising, which turns users into products to be farmed, has overstayed its welcome. At Primal, we don’t monetize user data. Our users are our customers. We only make money when the user decides that we are providing a valuable service – and pays for it. That means that our users’ interests are aligned with ours. It allows us to wake up every morning and work all day to make the product better for our users. Some might say that it is too early to try to monetize a Nostr product. We definitely need to be thoughtful about paywalling important features while the network is so young. For example, advanced search is a Primal Premium feature, but we enable it for all users up to 20 search results. That makes it quite usable for anyone on Nostr, but power users get the ability to save these searches and create powerful specialized feeds. It is crucial to have commercially successful projects on Nostr that have their incentives aligned with those of their users. We are working on new features and monetization methods that follow this philosophy. The more we experiment on Nostr, the faster we will learn what works and unlock the full potential of this network. I have a feeling that a lot remains to be discovered, and Primal Premium is just the first step. Now, let’s take a closer look at what is included in Premium: *Primal Name* and *Nostr Tools*. ## Primal Name  A Primal Name is a unique name on the primal.net domain that offers three features: 1. **Verified Nostr address (NIP-05)**. This signals to the Nostr network that your account (npub) has been verified by Primal. Note that we don’t perform identity verification; we are simply signaling that this is a Primal Premium user. Users can pay with sats, preserving their privacy while signaling to the network that this verified account is not a bot. 2. **Friendly Bitcoin Lightning address**. Primal’s built-in hosted wallet creates a randomly generated lightning address for every user. They look like this: bluedog25@primal.net. Premium users get to pick their name, so their lightning address is more personalized (e.g. preston@primal.net). 3. **VIP profile on primal.net**. This is simply a friendly URL to your profile on primal.net. We are working on adding profile customization features for Premium users; stay tuned! In summary, a Primal Name makes you easier to find on Nostr. You are free to use any of these three Primal Name elements as you see fit. If you wish to use your Primal Nostr address and/or Lightning address, simply update your Nostr profile with those entries. ## Nostr Tools  Nostr Tools is a collection of features that we think would be useful to any Nostr power user. We are continuously working on expanding these capabilities, but the initial set of features includes: - **Media management**. Primal Premium comes with 10GB of media storage (compared to 1GB for free accounts). We implemented a slick interface for managing all media you have on Primal. - **Contact list backup**. Many Nostr users have experienced the loss of their contact list (i.e., their follow list) when using different clients. We store the history of the contact list for Primal Premium users and make it easy to recover. - **Content backup**. Nostr users post their content to a collection of public relays. These relays typically don’t offer guarantees that they will store the content for any amount of time. We back up all content posted by Primal Premium users and make it easy to rebroadcast it to the specified relays at any time. ## Primal Legends  The idea for the Primal Legend tier was suggested to me by Gigi a couple of months prior to the launch of Primal 2.0. His argument was simple: “There are users on Nostr who really appreciate Primal and are willing to pay way more than $7 / month to support the project. You should *let them* pay and *recognize them* for doing so.” I am really glad that Gigi convinced me to introduce the Legend tier. Nostr is truly a special place. The early users are extremely passionate and mission driven. They care about growing and improving Nostr as much as the builders do. At first, I thought of the term “Legend” as a bit tongue in cheek, but then I met and chatted with some of these people. Man, they are incredible. They just wish to support the network and the builders of open source software in any way they can. So now I think the term is appropriate. We are humbled by the support we received. Our first Legend supporter was none other than Jack. He found this option in the product and paid for the Legend tier literally an hour after Primal 2.0 was released. Thank you, sir, and thank you to all the other Legends out there! 💜🫂 ## What Comes Next? We are delighted and encouraged by the market response to Primal Premium. It is already clear to us that we are on the right path. We will lean into it even harder from here. There will be MOAR Premium features, while at the same time we will make sure that the free product remains excellent. Since you, the user, are the customer, tell us what you would like to see added to Primal Premium. Pura Vida 🤙
@ d61f3bc5:0da6ef4a
2024-12-18 16:52:18January 2025 will mark two years since we started building Primal. Our goal was to create the best possible user experience for Nostr and make it accessible to everyone. We reached a big milestone towards realizing that vision with the recent Primal 2.0 release. It’s still early days, a lot more work lies ahead, but we thought the timing was right to introduce the Premium tier. Let’s explore what it is, why we built it, what’s included, and how it will evolve moving forward. ## What Primal Premium Is The idea behind Primal Premium is simple: integrate all tools and services required for the best Nostr experience into a single package. For $7 per month, Premium users get a *Primal Name* and *Nostr Tools* built by Primal. We’ll cover those in more detail below, but first we should make a crucial point: by signing up for Premium, you are in no way locked in to Primal. Quite the contrary, you can pick and choose which Premium features you wish to enable and use within other Nostr products. Openness is Nostr’s killer feature. Any product that wishes to truly empower the user needs to interoperate with Nostr’s budding ecosystem. The feed marketplace is a great example. External feeds are first-class citizens within all Primal apps. Primal feeds are available in other Nostr clients. We are working on Premium feeds, which our users will be able to enjoy within Primal or other Nostr apps. Media hosting is another example. Our upcoming support for the Blossom protocol will make Primal Premium media hosting interoperable with other Nostr apps and media hosting services. The common theme here is user choice. Nostr offers the highest level of user agency, and the compounding effect of interoperable products and services is bound to make Nostr immensely powerful. ## Why We Built Premium and Why Now What is unfolding on Nostr right now is unique and special. The first truly self-sovereign network is being bootstrapped by this early cohort of users and builders. People are literally holding the keys to their online presence. Network infrastructure – relays, indexers, media hosting services, etc. – is being stood up organically and without any central planning or coordination. Hundreds of independent projects are adding new capabilities to Nostr without needing permission. The whole thing is truly a sight to behold. In addition to fixing the fundamentals of the network, it is equally important that we fix the broken incentives that plague the legacy Web. The status quo of monetization via advertising, which turns users into products to be farmed, has overstayed its welcome. At Primal, we don’t monetize user data. Our users are our customers. We only make money when the user decides that we are providing a valuable service – and pays for it. That means that our users’ interests are aligned with ours. It allows us to wake up every morning and work all day to make the product better for our users. Some might say that it is too early to try to monetize a Nostr product. We definitely need to be thoughtful about paywalling important features while the network is so young. For example, advanced search is a Primal Premium feature, but we enable it for all users up to 20 search results. That makes it quite usable for anyone on Nostr, but power users get the ability to save these searches and create powerful specialized feeds. It is crucial to have commercially successful projects on Nostr that have their incentives aligned with those of their users. We are working on new features and monetization methods that follow this philosophy. The more we experiment on Nostr, the faster we will learn what works and unlock the full potential of this network. I have a feeling that a lot remains to be discovered, and Primal Premium is just the first step. Now, let’s take a closer look at what is included in Premium: *Primal Name* and *Nostr Tools*. ## Primal Name  A Primal Name is a unique name on the primal.net domain that offers three features: 1. **Verified Nostr address (NIP-05)**. This signals to the Nostr network that your account (npub) has been verified by Primal. Note that we don’t perform identity verification; we are simply signaling that this is a Primal Premium user. Users can pay with sats, preserving their privacy while signaling to the network that this verified account is not a bot. 2. **Friendly Bitcoin Lightning address**. Primal’s built-in hosted wallet creates a randomly generated lightning address for every user. They look like this: bluedog25@primal.net. Premium users get to pick their name, so their lightning address is more personalized (e.g. preston@primal.net). 3. **VIP profile on primal.net**. This is simply a friendly URL to your profile on primal.net. We are working on adding profile customization features for Premium users; stay tuned! In summary, a Primal Name makes you easier to find on Nostr. You are free to use any of these three Primal Name elements as you see fit. If you wish to use your Primal Nostr address and/or Lightning address, simply update your Nostr profile with those entries. ## Nostr Tools  Nostr Tools is a collection of features that we think would be useful to any Nostr power user. We are continuously working on expanding these capabilities, but the initial set of features includes: - **Media management**. Primal Premium comes with 10GB of media storage (compared to 1GB for free accounts). We implemented a slick interface for managing all media you have on Primal. - **Contact list backup**. Many Nostr users have experienced the loss of their contact list (i.e., their follow list) when using different clients. We store the history of the contact list for Primal Premium users and make it easy to recover. - **Content backup**. Nostr users post their content to a collection of public relays. These relays typically don’t offer guarantees that they will store the content for any amount of time. We back up all content posted by Primal Premium users and make it easy to rebroadcast it to the specified relays at any time. ## Primal Legends  The idea for the Primal Legend tier was suggested to me by Gigi a couple of months prior to the launch of Primal 2.0. His argument was simple: “There are users on Nostr who really appreciate Primal and are willing to pay way more than $7 / month to support the project. You should *let them* pay and *recognize them* for doing so.” I am really glad that Gigi convinced me to introduce the Legend tier. Nostr is truly a special place. The early users are extremely passionate and mission driven. They care about growing and improving Nostr as much as the builders do. At first, I thought of the term “Legend” as a bit tongue in cheek, but then I met and chatted with some of these people. Man, they are incredible. They just wish to support the network and the builders of open source software in any way they can. So now I think the term is appropriate. We are humbled by the support we received. Our first Legend supporter was none other than Jack. He found this option in the product and paid for the Legend tier literally an hour after Primal 2.0 was released. Thank you, sir, and thank you to all the other Legends out there! 💜🫂 ## What Comes Next? We are delighted and encouraged by the market response to Primal Premium. It is already clear to us that we are on the right path. We will lean into it even harder from here. There will be MOAR Premium features, while at the same time we will make sure that the free product remains excellent. Since you, the user, are the customer, tell us what you would like to see added to Primal Premium. Pura Vida 🤙 @ 266815e0:6cd408a5
2024-12-17 20:45:33Finally another version of noStrudel. I keep telling myself I'm going to do more frequent releases but then time keeps getting away from me This release comes with a bunch of news features and most importantly a lot of cleanup ## Features ### Olas media posts You can now view a simple feed of media posts made on https://olas.app/ in the app and comment on them using NIP-22 comments  ### Simple gif picker This was mostly a test, but there is now a simple gif picker (and barely functional search) that is based on `k:1063` events If you want a better search and to help populate the nostr gif library you can use https://gifbuddy.lol created by nostr:npub1hee433872q2gen90cqh2ypwcq9z7y5ugn23etrd2l2rrwpruss8qwmrsv6  ### New support view The *(tiny)* support button at the bottom of the side menu now hides a zap leader board that shows top supporters and any custom messages they leave  ### Favorite DVM feeds You can now favorite DVM feeds in the discover view  ### Tools under notes There is now a simpler tools menu under notes and threads  ### Searching local cache relay If your using [nostr-relay-tray](https://github.com/CodyTseng/nostr-relay-tray) the search view will now use it by default for searching. which should make it a little faster and more reliable  ### Small features - Add "Proactively authenticate to relays" option to privacy settings, defaults to off - Add option for debug API - Add option to hide noStrudel logo in nav bar - Show unknown notifications in notification view - Add templates to event publisher ## Bug fixes - Show nostr mentions in markdown content - Fix delete events not getting published to outbox - Fix page changing from RTL when viewing some profiles - Refresh relay info on relay page - Fix bug with removing "about" in profile editor - Fix automatically disconnecting from authenticated relays ## Applesauce Over the past few months I've been doing tons of cleanup on the core of noStrudel *(677 changed files with 19,683 additions and 17,889 deletions)* and extracting it out into a friendly nostr SDK called [applesauce](https://hzrd149.github.io/applesauce/) Its very much a work-in-progress but the idea with these libraries is to help myself (and maybe others) build the UI layer of nostr apps and eventually make noStrudel just another app that is built with applesauce If your a developer and another nostr SDK sounds interesting to you. you can check out the [Getting Started](https://hzrd149.github.io/applesauce/introduction/getting-started.html) docs
@ 266815e0:6cd408a5
2024-12-17 20:45:33Finally another version of noStrudel. I keep telling myself I'm going to do more frequent releases but then time keeps getting away from me This release comes with a bunch of news features and most importantly a lot of cleanup ## Features ### Olas media posts You can now view a simple feed of media posts made on https://olas.app/ in the app and comment on them using NIP-22 comments  ### Simple gif picker This was mostly a test, but there is now a simple gif picker (and barely functional search) that is based on `k:1063` events If you want a better search and to help populate the nostr gif library you can use https://gifbuddy.lol created by nostr:npub1hee433872q2gen90cqh2ypwcq9z7y5ugn23etrd2l2rrwpruss8qwmrsv6  ### New support view The *(tiny)* support button at the bottom of the side menu now hides a zap leader board that shows top supporters and any custom messages they leave  ### Favorite DVM feeds You can now favorite DVM feeds in the discover view  ### Tools under notes There is now a simpler tools menu under notes and threads  ### Searching local cache relay If your using [nostr-relay-tray](https://github.com/CodyTseng/nostr-relay-tray) the search view will now use it by default for searching. which should make it a little faster and more reliable  ### Small features - Add "Proactively authenticate to relays" option to privacy settings, defaults to off - Add option for debug API - Add option to hide noStrudel logo in nav bar - Show unknown notifications in notification view - Add templates to event publisher ## Bug fixes - Show nostr mentions in markdown content - Fix delete events not getting published to outbox - Fix page changing from RTL when viewing some profiles - Refresh relay info on relay page - Fix bug with removing "about" in profile editor - Fix automatically disconnecting from authenticated relays ## Applesauce Over the past few months I've been doing tons of cleanup on the core of noStrudel *(677 changed files with 19,683 additions and 17,889 deletions)* and extracting it out into a friendly nostr SDK called [applesauce](https://hzrd149.github.io/applesauce/) Its very much a work-in-progress but the idea with these libraries is to help myself (and maybe others) build the UI layer of nostr apps and eventually make noStrudel just another app that is built with applesauce If your a developer and another nostr SDK sounds interesting to you. you can check out the [Getting Started](https://hzrd149.github.io/applesauce/introduction/getting-started.html) docs @ 0f286a37:601a59e8
2024-12-17 19:56:41#bitcoin #news I encourage every Bitcoiner to read The Blocksize War. Here are all of the links to all 21 chapters available on the BitMEX blog. 1. [Chapter 1 – First Strike](https://blog.bitmex.com/the-blocksize-war-chapter-1-first-strike/) 2. [Chapter 2 – March To War](https://blog.bitmex.com/the-blocksize-war-chapter-2-march-to-war/) 3. [Chapter 3 – Scaling I - Montreal](https://blog.bitmex.com/the-blocksize-war-chapter-3-scaling-i-montreal/) 4. [Chapter 4 – Scaling II - Hong Kong](https://blog.bitmex.com/the-blocksize-war-chapter-4-scaling-ii-hong-kong/) 5. [Chapter 5 – SegWit](https://blog.bitmex.com/the-blocksize-war-chapter-5-scaling-ii-segwit/) 6. [Chapter 6 – Lightning Network](https://blog.bitmex.com/the-blocksize-war-chapter-6-lightning-network/) 7. [Chapter 7 – Bitcoin Classic](https://blog.bitmex.com/the-blocksize-war-chapter-7-bitcoin-classic/) 8. [Chapter 8 – Hong Kong Roundtable](https://blog.bitmex.com/the-blocksize-war-chapter-8-hong-kong-roundtable/) 9. [Chapter 9 – Faketoshi](https://blog.bitmex.com/the-blocksize-war-chapter-9-faketoshi/) 10. [Chapter 10 – The DAO](https://blog.bitmex.com/the-blocksize-war-chapter-10-the-dao/) 11. [Chapter 11 – Scaling III – Milan](https://blog.bitmex.com/the-blocksize-war-chapter-11-scaling-iii-milan/) 12. [Chapter 12 – Bitcoin Unlimited](https://blog.bitmex.com/the-blocksize-war-chapter-12-bitcoin-unlimited/) 13. [Chapter 13 – Exchanges](https://blog.bitmex.com/the-blocksize-war-chapter-13-exchanges/) 14. [Chapter 14 – ASICBoost](https://blog.bitmex.com/the-blocksize-war-chapter-14-asicboost/) 15. [Chapter 15 – Dragons’ Den](https://blog.bitmex.com/the-blocksize-war-chapter-15-dragons-den/) 16. [Chapter 16 – Litecoin](https://blog.bitmex.com/the-blocksize-war-chapter-16-litecoin/) 17. [Chapter 17 – User-Activated Softfork](https://blog.bitmex.com/the-blocksize-war-chapter-17-user-activated-softfork/) 18. [Chapter 18 – New York Agreement](https://blog.bitmex.com/the-blocksize-war-chapter-18-new-york-agreement/) 19. [Chapter 19 - Bitcoin Cash](https://blog.bitmex.com/the-blocksize-war-chapter-19-bitcoin-cash/) 20. [Chapter 20 - SegWit2x](https://blog.bitmex.com/the-blocksize-war-chapter-20-segwit2x/) 21. [Chapter 21 - Victory] https://blog.bitmex.com/the-blocksize-war-chapter-21-victory/)
@ 0f286a37:601a59e8
2024-12-17 19:56:41#bitcoin #news I encourage every Bitcoiner to read The Blocksize War. Here are all of the links to all 21 chapters available on the BitMEX blog. 1. [Chapter 1 – First Strike](https://blog.bitmex.com/the-blocksize-war-chapter-1-first-strike/) 2. [Chapter 2 – March To War](https://blog.bitmex.com/the-blocksize-war-chapter-2-march-to-war/) 3. [Chapter 3 – Scaling I - Montreal](https://blog.bitmex.com/the-blocksize-war-chapter-3-scaling-i-montreal/) 4. [Chapter 4 – Scaling II - Hong Kong](https://blog.bitmex.com/the-blocksize-war-chapter-4-scaling-ii-hong-kong/) 5. [Chapter 5 – SegWit](https://blog.bitmex.com/the-blocksize-war-chapter-5-scaling-ii-segwit/) 6. [Chapter 6 – Lightning Network](https://blog.bitmex.com/the-blocksize-war-chapter-6-lightning-network/) 7. [Chapter 7 – Bitcoin Classic](https://blog.bitmex.com/the-blocksize-war-chapter-7-bitcoin-classic/) 8. [Chapter 8 – Hong Kong Roundtable](https://blog.bitmex.com/the-blocksize-war-chapter-8-hong-kong-roundtable/) 9. [Chapter 9 – Faketoshi](https://blog.bitmex.com/the-blocksize-war-chapter-9-faketoshi/) 10. [Chapter 10 – The DAO](https://blog.bitmex.com/the-blocksize-war-chapter-10-the-dao/) 11. [Chapter 11 – Scaling III – Milan](https://blog.bitmex.com/the-blocksize-war-chapter-11-scaling-iii-milan/) 12. [Chapter 12 – Bitcoin Unlimited](https://blog.bitmex.com/the-blocksize-war-chapter-12-bitcoin-unlimited/) 13. [Chapter 13 – Exchanges](https://blog.bitmex.com/the-blocksize-war-chapter-13-exchanges/) 14. [Chapter 14 – ASICBoost](https://blog.bitmex.com/the-blocksize-war-chapter-14-asicboost/) 15. [Chapter 15 – Dragons’ Den](https://blog.bitmex.com/the-blocksize-war-chapter-15-dragons-den/) 16. [Chapter 16 – Litecoin](https://blog.bitmex.com/the-blocksize-war-chapter-16-litecoin/) 17. [Chapter 17 – User-Activated Softfork](https://blog.bitmex.com/the-blocksize-war-chapter-17-user-activated-softfork/) 18. [Chapter 18 – New York Agreement](https://blog.bitmex.com/the-blocksize-war-chapter-18-new-york-agreement/) 19. [Chapter 19 - Bitcoin Cash](https://blog.bitmex.com/the-blocksize-war-chapter-19-bitcoin-cash/) 20. [Chapter 20 - SegWit2x](https://blog.bitmex.com/the-blocksize-war-chapter-20-segwit2x/) 21. [Chapter 21 - Victory] https://blog.bitmex.com/the-blocksize-war-chapter-21-victory/) @ fe32298e:20516265
2024-12-16 20:59:13Today I learned how to install [NVapi](https://github.com/sammcj/NVApi) to monitor my GPUs in Home Assistant.  **NVApi** is a lightweight API designed for monitoring NVIDIA GPU utilization and enabling automated power management. It provides real-time GPU metrics, supports integration with tools like Home Assistant, and offers flexible power management and PCIe link speed management based on workload and thermal conditions. - **GPU Utilization Monitoring**: Utilization, memory usage, temperature, fan speed, and power consumption. - **Automated Power Limiting**: Adjusts power limits dynamically based on temperature thresholds and total power caps, configurable per GPU or globally. - **Cross-GPU Coordination**: Total power budget applies across multiple GPUs in the same system. - **PCIe Link Speed Management**: Controls minimum and maximum PCIe link speeds with idle thresholds for power optimization. - **Home Assistant Integration**: Uses the built-in RESTful platform and template sensors. ## Getting the Data ``` sudo apt install golang-go git clone https://github.com/sammcj/NVApi.git cd NVapi go run main.go -port 9999 -rate 1 curl http://localhost:9999/gpu ``` Response for a single GPU: ``` [ { "index": 0, "name": "NVIDIA GeForce RTX 4090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 16, "power_limit_watts": 450, "memory_total_gb": 23.99, "memory_used_gb": 0.46, "memory_free_gb": 23.52, "memory_usage_percent": 2, "temperature": 38, "processes": [], "pcie_link_state": "not managed" } ] ``` Response for multiple GPUs: ``` [ { "index": 0, "name": "NVIDIA GeForce RTX 3090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 14, "power_limit_watts": 350, "memory_total_gb": 24, "memory_used_gb": 0.43, "memory_free_gb": 23.57, "memory_usage_percent": 2, "temperature": 36, "processes": [], "pcie_link_state": "not managed" }, { "index": 1, "name": "NVIDIA RTX A4000", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 10, "power_limit_watts": 140, "memory_total_gb": 15.99, "memory_used_gb": 0.56, "memory_free_gb": 15.43, "memory_usage_percent": 3, "temperature": 41, "processes": [], "pcie_link_state": "not managed" } ] ``` # Start at Boot Create `/etc/systemd/system/nvapi.service`: ``` [Unit] Description=Run NVapi After=network.target [Service] Type=simple Environment="GOPATH=/home/ansible/go" WorkingDirectory=/home/ansible/NVapi ExecStart=/usr/bin/go run main.go -port 9999 -rate 1 Restart=always User=ansible # Environment="GPU_TEMP_CHECK_INTERVAL=5" # Environment="GPU_TOTAL_POWER_CAP=400" # Environment="GPU_0_LOW_TEMP=40" # Environment="GPU_0_MEDIUM_TEMP=70" # Environment="GPU_0_LOW_TEMP_LIMIT=135" # Environment="GPU_0_MEDIUM_TEMP_LIMIT=120" # Environment="GPU_0_HIGH_TEMP_LIMIT=100" # Environment="GPU_1_LOW_TEMP=45" # Environment="GPU_1_MEDIUM_TEMP=75" # Environment="GPU_1_LOW_TEMP_LIMIT=140" # Environment="GPU_1_MEDIUM_TEMP_LIMIT=125" # Environment="GPU_1_HIGH_TEMP_LIMIT=110" [Install] WantedBy=multi-user.target ``` ## Home Assistant Add to Home Assistant `configuration.yaml` and restart HA (completely). For a single GPU, this works: ``` sensor: - platform: rest name: MYPC GPU Information resource: http://mypc:9999 method: GET headers: Content-Type: application/json value_template: "{{ value_json[0].index }}" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature scan_interval: 1 # seconds - platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} GPU" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Memory" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Temperature" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'temperature') }}" unit_of_measurement: "°C" ``` For multiple GPUs: ``` rest: scan_interval: 1 resource: http://mypc:9999 sensor: - name: "MYPC GPU0 Information" value_template: "{{ value_json[0].index }}" json_attributes_path: "$.0" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature - name: "MYPC GPU1 Information" value_template: "{{ value_json[1].index }}" json_attributes_path: "$.1" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature - platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC GPU0 GPU" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC GPU0 Memory" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC GPU0 Power" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC GPU0 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC GPU0 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'temperature') }}" unit_of_measurement: "C" - platform: template sensors: mypc_gpu_1_gpu: friendly_name: "MYPC GPU1 GPU" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_memory: friendly_name: "MYPC GPU1 Memory" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_power: friendly_name: "MYPC GPU1 Power" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_1_power_limit: friendly_name: "MYPC GPU1 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_1_temperature: friendly_name: "MYPC GPU1 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'temperature') }}" unit_of_measurement: "C" ``` Basic entity card: ``` type: entities entities: - entity: sensor.mypc_gpu_0_gpu secondary_info: last-updated - entity: sensor.mypc_gpu_0_memory secondary_info: last-updated - entity: sensor.mypc_gpu_0_power secondary_info: last-updated - entity: sensor.mypc_gpu_0_power_limit secondary_info: last-updated - entity: sensor.mypc_gpu_0_temperature secondary_info: last-updated ``` # Ansible Role ``` --- - name: install go become: true package: name: golang-go state: present - name: git clone git: repo: "https://github.com/sammcj/NVApi.git" dest: "/home/ansible/NVapi" update: yes force: true # go run main.go -port 9999 -rate 1 - name: install systemd service become: true copy: src: nvapi.service dest: /etc/systemd/system/nvapi.service - name: Reload systemd daemons, enable, and restart nvapi become: true systemd: name: nvapi daemon_reload: yes enabled: yes state: restarted ```
@ fe32298e:20516265
2024-12-16 20:59:13Today I learned how to install [NVapi](https://github.com/sammcj/NVApi) to monitor my GPUs in Home Assistant.  **NVApi** is a lightweight API designed for monitoring NVIDIA GPU utilization and enabling automated power management. It provides real-time GPU metrics, supports integration with tools like Home Assistant, and offers flexible power management and PCIe link speed management based on workload and thermal conditions. - **GPU Utilization Monitoring**: Utilization, memory usage, temperature, fan speed, and power consumption. - **Automated Power Limiting**: Adjusts power limits dynamically based on temperature thresholds and total power caps, configurable per GPU or globally. - **Cross-GPU Coordination**: Total power budget applies across multiple GPUs in the same system. - **PCIe Link Speed Management**: Controls minimum and maximum PCIe link speeds with idle thresholds for power optimization. - **Home Assistant Integration**: Uses the built-in RESTful platform and template sensors. ## Getting the Data ``` sudo apt install golang-go git clone https://github.com/sammcj/NVApi.git cd NVapi go run main.go -port 9999 -rate 1 curl http://localhost:9999/gpu ``` Response for a single GPU: ``` [ { "index": 0, "name": "NVIDIA GeForce RTX 4090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 16, "power_limit_watts": 450, "memory_total_gb": 23.99, "memory_used_gb": 0.46, "memory_free_gb": 23.52, "memory_usage_percent": 2, "temperature": 38, "processes": [], "pcie_link_state": "not managed" } ] ``` Response for multiple GPUs: ``` [ { "index": 0, "name": "NVIDIA GeForce RTX 3090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 14, "power_limit_watts": 350, "memory_total_gb": 24, "memory_used_gb": 0.43, "memory_free_gb": 23.57, "memory_usage_percent": 2, "temperature": 36, "processes": [], "pcie_link_state": "not managed" }, { "index": 1, "name": "NVIDIA RTX A4000", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 10, "power_limit_watts": 140, "memory_total_gb": 15.99, "memory_used_gb": 0.56, "memory_free_gb": 15.43, "memory_usage_percent": 3, "temperature": 41, "processes": [], "pcie_link_state": "not managed" } ] ``` # Start at Boot Create `/etc/systemd/system/nvapi.service`: ``` [Unit] Description=Run NVapi After=network.target [Service] Type=simple Environment="GOPATH=/home/ansible/go" WorkingDirectory=/home/ansible/NVapi ExecStart=/usr/bin/go run main.go -port 9999 -rate 1 Restart=always User=ansible # Environment="GPU_TEMP_CHECK_INTERVAL=5" # Environment="GPU_TOTAL_POWER_CAP=400" # Environment="GPU_0_LOW_TEMP=40" # Environment="GPU_0_MEDIUM_TEMP=70" # Environment="GPU_0_LOW_TEMP_LIMIT=135" # Environment="GPU_0_MEDIUM_TEMP_LIMIT=120" # Environment="GPU_0_HIGH_TEMP_LIMIT=100" # Environment="GPU_1_LOW_TEMP=45" # Environment="GPU_1_MEDIUM_TEMP=75" # Environment="GPU_1_LOW_TEMP_LIMIT=140" # Environment="GPU_1_MEDIUM_TEMP_LIMIT=125" # Environment="GPU_1_HIGH_TEMP_LIMIT=110" [Install] WantedBy=multi-user.target ``` ## Home Assistant Add to Home Assistant `configuration.yaml` and restart HA (completely). For a single GPU, this works: ``` sensor: - platform: rest name: MYPC GPU Information resource: http://mypc:9999 method: GET headers: Content-Type: application/json value_template: "{{ value_json[0].index }}" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature scan_interval: 1 # seconds - platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} GPU" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Memory" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Temperature" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'temperature') }}" unit_of_measurement: "°C" ``` For multiple GPUs: ``` rest: scan_interval: 1 resource: http://mypc:9999 sensor: - name: "MYPC GPU0 Information" value_template: "{{ value_json[0].index }}" json_attributes_path: "$.0" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature - name: "MYPC GPU1 Information" value_template: "{{ value_json[1].index }}" json_attributes_path: "$.1" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature - platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC GPU0 GPU" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC GPU0 Memory" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC GPU0 Power" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC GPU0 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC GPU0 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'temperature') }}" unit_of_measurement: "C" - platform: template sensors: mypc_gpu_1_gpu: friendly_name: "MYPC GPU1 GPU" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_memory: friendly_name: "MYPC GPU1 Memory" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_power: friendly_name: "MYPC GPU1 Power" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_1_power_limit: friendly_name: "MYPC GPU1 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_1_temperature: friendly_name: "MYPC GPU1 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'temperature') }}" unit_of_measurement: "C" ``` Basic entity card: ``` type: entities entities: - entity: sensor.mypc_gpu_0_gpu secondary_info: last-updated - entity: sensor.mypc_gpu_0_memory secondary_info: last-updated - entity: sensor.mypc_gpu_0_power secondary_info: last-updated - entity: sensor.mypc_gpu_0_power_limit secondary_info: last-updated - entity: sensor.mypc_gpu_0_temperature secondary_info: last-updated ``` # Ansible Role ``` --- - name: install go become: true package: name: golang-go state: present - name: git clone git: repo: "https://github.com/sammcj/NVApi.git" dest: "/home/ansible/NVapi" update: yes force: true # go run main.go -port 9999 -rate 1 - name: install systemd service become: true copy: src: nvapi.service dest: /etc/systemd/system/nvapi.service - name: Reload systemd daemons, enable, and restart nvapi become: true systemd: name: nvapi daemon_reload: yes enabled: yes state: restarted ``` @ ee11a5df:b76c4e49
2024-12-16 05:29:30# Nostr 2? ## Breaking Changes in Nostr Nostr was a huge leap forward. But it isn't perfect. When developers notice a problem with nostr, they confer with each other to work out a solution to the problem. This is usually in the form of a NIP PR on the nips repo. Some problems are easy. Just add something new and optional. No biggie. Zaps, git stuff, bunkers... just dream it up and add it. Other problems can only be fixed by breaking changes. With a breaking change, the overall path forward is like this: Add the new way of doing it while preserving the old way. Push the major software to switch to the new way. Then deprecate the old way. This is a simplification, but it is the basic idea. It is how we solved markers/quotes/root and how we are upgrading encryption, among other things. This process of pushing through a breaking change becomes more difficult as we have more and more existing nostr software out there that will break. Most of the time what happens is that the major software is driven to make the change (usually by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6), and the smaller software is left to fend for itself. A while back I introduced the BREAKING.md file to help people developing smaller lesser-known software keep up with these changes. ## Big Ideas But some ideas just can't be applied to nostr. The idea is too big. The change is too breaking. It changes something fundamental. And nobody has come up with a smooth path to move from the old way to the new way. And so we debate a bunch of things, and never settle on anything, and eventually nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 makes a post saying that we don't really want it anyways 😉. As we encounter good ideas that are hard to apply to nostr, I've been filing them away in a repository I call "nostr-next", so we don't forget about them, in case we ever wanted to start over. It seems to me that starting over every time we encountered such a thing would be unwise. However, once we collect enough changes that we couldn't reasonably phase into nostr, then a tipping point is crossed where it becomes worthwhile to start over. In terms of the "bang for the buck" metaphor, the bang becomes bigger and bigger but the buck (the pain and cost of starting over) doesn't grow as rapidly. ## WHAT? Start over? IMHO starting over could be very bad if done in a cavalier way. The community could fracture. The new protocol could fail to take off due to lacking the network effect. The odds that a new protocol catches on are low, irrespective of how technically superior it could be. So the big question is: can we preserve the nostr community and it's network effect while making a major step-change to the protocol and software? I don't know the answer to that one, but I have an idea about it. I think the new-protocol clients can be dual-stack, creating events in both systems and linking those events together via tags. The nostr key identity would still be used, and the new system identity too. This is better than things like the mostr bridge because each user would remain in custody of their own keys. ## The nitty gritty Here are some of the things I think would make nostr better, but which nostr can't easily fix. A lot of these ideas have been mentioned before by multiple people and I didn't give credit to all of you (sorry) because my brain can't track it all. But I've been collecting these over time at https://github.com/mikedilger/nostr-next * Events as CBOR or BEVE or MsgPack or a fixed-schema binary layout... anything but JSON text with its parsing, it's encoding ambiguity, it's requirement to copy fields before hashing them, its unlimited size constraints. (me, nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s) * EdDSA ed25519 keys instead of secp256k1, to enable interoperability with a bunch of other stuff like ssh, pgp, TLS, Mainline DHT, and many more, plus just being better cryptography (me, Nuh, Orlovsky, except Orlovsky wanted Ristretto25519 for speed) * Bootstrapping relay lists (and relay endpoints) from Mainline DHT (nostr:npub1jvxvaufrwtwj79s90n79fuxmm9pntk94rd8zwderdvqv4dcclnvs9s7yqz) * Master keys and revocable subkeys / device keys (including having your nostr key as a subkey) * Encryption to use different encryption-specific subkeys and ephemeral ones from the sender. * Relay keypairs, TLS without certificates, relays known by keypair instead of URL * Layered protocol (separate core from applications) * Software remembering when they first saw an event, for 2 reasons, the main one being revocation (don't trust the date in the event, trust when you first saw it), the second being more precise time range queries. * Upgrade/feature negotiation (HTTP headers prior to starting websockets) * IDs starting with a timestamp so they are temporally adjacent (significantly better database performance) (Vitor's idea) * Filters that allow boolean expressions on tag values, and also ID exclusions. Removing IDs from filters and moving to a GET command. * Changing the transport (I'm against this but I know others want to) ## What would it look like? Someone (Steve Farroll) has taken my nostr-next repo and turned it into a proposed protocol he calls [Mosaic](https://github.com/SteveFarroll/mosaic-spec). I think it is quite representative of that repo, as it already includes most of those suggestions, so I've been contributing to it. Mosaic spec is rendered [here](https://stevefarroll.github.io/mosaic-spec/). Of course, where Mosaic stands right now it is mostly my ideas (and Steve's), it doesn't have feedback or input from other nostr developers yet. That is what this blog post is about. I think it is time for other nostr devs to be made aware of this thing. It is currently in the massive breaking changes phase. It might not look that way because of the detail and refinement of the documentation, but indeed everything is changing rapidly. It probably has some bad ideas and is probably missing some great ideas that you have. Which is why this is a good time for other devs to start taking a look at it. It is also the time to debate meta issues like "are you crazy Mike?" or "no we have to just break nostr but keep it nostr, we can't dual-stack" or whatever. Personally I think mosaic-spec should develop and grow for quite a while before the "tipping point" happens. That is, I'm not sure we should jump in feet first yet, but rather we build up and refine this new protocol and spend a lot of time thinking about how to migrate smoothly, and break it a lot while nobody is using it. So you can just reply to this, or DM me, or open issues or PRs at [Mosaic](https://github.com/SteveFarroll/mosaic-spec), or just whisper to each other while giving me the evil eye.
@ ee11a5df:b76c4e49
2024-12-16 05:29:30# Nostr 2? ## Breaking Changes in Nostr Nostr was a huge leap forward. But it isn't perfect. When developers notice a problem with nostr, they confer with each other to work out a solution to the problem. This is usually in the form of a NIP PR on the nips repo. Some problems are easy. Just add something new and optional. No biggie. Zaps, git stuff, bunkers... just dream it up and add it. Other problems can only be fixed by breaking changes. With a breaking change, the overall path forward is like this: Add the new way of doing it while preserving the old way. Push the major software to switch to the new way. Then deprecate the old way. This is a simplification, but it is the basic idea. It is how we solved markers/quotes/root and how we are upgrading encryption, among other things. This process of pushing through a breaking change becomes more difficult as we have more and more existing nostr software out there that will break. Most of the time what happens is that the major software is driven to make the change (usually by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6), and the smaller software is left to fend for itself. A while back I introduced the BREAKING.md file to help people developing smaller lesser-known software keep up with these changes. ## Big Ideas But some ideas just can't be applied to nostr. The idea is too big. The change is too breaking. It changes something fundamental. And nobody has come up with a smooth path to move from the old way to the new way. And so we debate a bunch of things, and never settle on anything, and eventually nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 makes a post saying that we don't really want it anyways 😉. As we encounter good ideas that are hard to apply to nostr, I've been filing them away in a repository I call "nostr-next", so we don't forget about them, in case we ever wanted to start over. It seems to me that starting over every time we encountered such a thing would be unwise. However, once we collect enough changes that we couldn't reasonably phase into nostr, then a tipping point is crossed where it becomes worthwhile to start over. In terms of the "bang for the buck" metaphor, the bang becomes bigger and bigger but the buck (the pain and cost of starting over) doesn't grow as rapidly. ## WHAT? Start over? IMHO starting over could be very bad if done in a cavalier way. The community could fracture. The new protocol could fail to take off due to lacking the network effect. The odds that a new protocol catches on are low, irrespective of how technically superior it could be. So the big question is: can we preserve the nostr community and it's network effect while making a major step-change to the protocol and software? I don't know the answer to that one, but I have an idea about it. I think the new-protocol clients can be dual-stack, creating events in both systems and linking those events together via tags. The nostr key identity would still be used, and the new system identity too. This is better than things like the mostr bridge because each user would remain in custody of their own keys. ## The nitty gritty Here are some of the things I think would make nostr better, but which nostr can't easily fix. A lot of these ideas have been mentioned before by multiple people and I didn't give credit to all of you (sorry) because my brain can't track it all. But I've been collecting these over time at https://github.com/mikedilger/nostr-next * Events as CBOR or BEVE or MsgPack or a fixed-schema binary layout... anything but JSON text with its parsing, it's encoding ambiguity, it's requirement to copy fields before hashing them, its unlimited size constraints. (me, nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s) * EdDSA ed25519 keys instead of secp256k1, to enable interoperability with a bunch of other stuff like ssh, pgp, TLS, Mainline DHT, and many more, plus just being better cryptography (me, Nuh, Orlovsky, except Orlovsky wanted Ristretto25519 for speed) * Bootstrapping relay lists (and relay endpoints) from Mainline DHT (nostr:npub1jvxvaufrwtwj79s90n79fuxmm9pntk94rd8zwderdvqv4dcclnvs9s7yqz) * Master keys and revocable subkeys / device keys (including having your nostr key as a subkey) * Encryption to use different encryption-specific subkeys and ephemeral ones from the sender. * Relay keypairs, TLS without certificates, relays known by keypair instead of URL * Layered protocol (separate core from applications) * Software remembering when they first saw an event, for 2 reasons, the main one being revocation (don't trust the date in the event, trust when you first saw it), the second being more precise time range queries. * Upgrade/feature negotiation (HTTP headers prior to starting websockets) * IDs starting with a timestamp so they are temporally adjacent (significantly better database performance) (Vitor's idea) * Filters that allow boolean expressions on tag values, and also ID exclusions. Removing IDs from filters and moving to a GET command. * Changing the transport (I'm against this but I know others want to) ## What would it look like? Someone (Steve Farroll) has taken my nostr-next repo and turned it into a proposed protocol he calls [Mosaic](https://github.com/SteveFarroll/mosaic-spec). I think it is quite representative of that repo, as it already includes most of those suggestions, so I've been contributing to it. Mosaic spec is rendered [here](https://stevefarroll.github.io/mosaic-spec/). Of course, where Mosaic stands right now it is mostly my ideas (and Steve's), it doesn't have feedback or input from other nostr developers yet. That is what this blog post is about. I think it is time for other nostr devs to be made aware of this thing. It is currently in the massive breaking changes phase. It might not look that way because of the detail and refinement of the documentation, but indeed everything is changing rapidly. It probably has some bad ideas and is probably missing some great ideas that you have. Which is why this is a good time for other devs to start taking a look at it. It is also the time to debate meta issues like "are you crazy Mike?" or "no we have to just break nostr but keep it nostr, we can't dual-stack" or whatever. Personally I think mosaic-spec should develop and grow for quite a while before the "tipping point" happens. That is, I'm not sure we should jump in feet first yet, but rather we build up and refine this new protocol and spend a lot of time thinking about how to migrate smoothly, and break it a lot while nobody is using it. So you can just reply to this, or DM me, or open issues or PRs at [Mosaic](https://github.com/SteveFarroll/mosaic-spec), or just whisper to each other while giving me the evil eye. @ 6f6b50bb:a848e5a1
2024-12-15 15:09:52Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona? Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità. La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo? La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso? La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli? Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare. ### Metafore per l’interazione Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso. La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito. Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli. Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer. ### Usare un’IA come un computer Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer. Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona: - **Scoperta.** Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini. - **Efficienza.** La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente. A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio. ### Una bicicletta della mente proteiforme La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te. Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente. Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose. Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo. La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare. ### Un nuovo paradigma per l’informatica? I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità. All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale. Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle. Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi? Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona? Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità. La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo? La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso? La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli? Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare. ### Metafore per l’interazione Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso. La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito. Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli. Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer. ### Usare un’IA come un computer Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer. Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona: Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini. Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente. A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio. ### Una bicicletta della mente proteiforme La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te. Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente. Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose. Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo. La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare. ### Un nuovo paradigma per l’informatica? I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità. All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale. Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle. Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi? Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo! Tradotto da:\ https://willwhitney.com/computing-inside-ai.htmlhttps://willwhitney.com/computing-inside-ai.html
@ 6f6b50bb:a848e5a1
2024-12-15 15:09:52Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona? Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità. La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo? La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso? La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli? Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare. ### Metafore per l’interazione Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso. La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito. Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli. Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer. ### Usare un’IA come un computer Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer. Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona: - **Scoperta.** Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini. - **Efficienza.** La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente. A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio. ### Una bicicletta della mente proteiforme La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te. Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente. Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose. Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo. La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare. ### Un nuovo paradigma per l’informatica? I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità. All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale. Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle. Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi? Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona? Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità. La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo? La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso? La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli? Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare. ### Metafore per l’interazione Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso. La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito. Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli. Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer. ### Usare un’IA come un computer Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer. Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona: Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini. Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente. A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio. ### Una bicicletta della mente proteiforme La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te. Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente. Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose. Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo. La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare. ### Un nuovo paradigma per l’informatica? I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità. All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale. Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle. Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi? Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo! Tradotto da:\ https://willwhitney.com/computing-inside-ai.htmlhttps://willwhitney.com/computing-inside-ai.html @ 78c90fc4:4bff983c
2024-12-14 19:00:14[Hier ist die Aufzeichnung des Vortrages von Cynthia Chung für die Aletheia Wissenschaftsgruppe vom 11.12.24](https://www.wissenschaftstehtauf.ch/Aletheia_Cynthia_Chung_Operation_Gladio_20241211.mp4)   Cynthia Chung ist Präsidentin und Mitbegründerin der [Rising Tide Foundation](https://risingtidefoundation.net/) (zusammen mit ihrem Ehemann Matthew Ehret, der am 4. September 2024 als Gastredner des Aletheia Science Forum über „Die britischen Wurzeln des Deep State verstehen“ sprach, aufgezeichnet hier: <https://www.wissenschaftstehtauf.ch/Matt_Ehret_20240904.mp4> ).\ \ Cynthia ist die Autorin der Bücher „[The Shaping of a World Religion](https://cynthiachung.substack.com/p/my-new-book-is-out-the-shaping-of)“ und „[The Empire on Which the Black Sun Never Set,](https://cynthiachung.substack.com/p/my-first-book-is-now-outthe-empire)“ sowie Mitautorin der Buchreihe „The Clash of the Two Americas“.\ \ Ihre Substack-Seite [„Through A Glass Darkly](https://cynthiachung.substack.com/) ([https://cynthiachung.substack.com](https://cynthiachung.substack.com/))“ hat über 11.000 Abonnenten. Sie schreibt über eine Vielzahl wichtiger Themen, die von geopolitischer Geschichte bis hin zu Kultur, Wissenschaft und Kunst reichen.\ \ In ihrem Vortrag konzenteriert sich Cynthia auf die Operation Gladio, das geheime „Stay-behind“-Netzwerk bewaffneter Widerstandsorganisationen, das während des Kalten Krieges in Westeuropa gegründet wurde. Solche historischen Einblicke können uns in der heutigen Zeit helfen, uns durch die Stürme zu navigieren, die die Zivilisation erneut bedrohen.\ \ Einführung von Stefan Heeb <https://www.proethica.ch> Weiterführende Analysen: Daniele Ganser: NATO Geheimarmeen in Europa  [Die NATO und der rechtsextreme Staatsterror](https://x.com/RealWsiegrist/status/1867063935289139260) [NATO/Gladio/Verdeckte Kriegsführung](https://waltisiegrist.locals.com/upost/1571799/manipulation-der-massen-durch-panik) [NATO](https://waltisiegrist.locals.com/upost/1859885/die-geschichte-der-nato-ber-general-reinhard-gehlen-1902-1979-und-sein-netzwerk-in-der-wehrma)
@ 78c90fc4:4bff983c
2024-12-14 19:00:14[Hier ist die Aufzeichnung des Vortrages von Cynthia Chung für die Aletheia Wissenschaftsgruppe vom 11.12.24](https://www.wissenschaftstehtauf.ch/Aletheia_Cynthia_Chung_Operation_Gladio_20241211.mp4)   Cynthia Chung ist Präsidentin und Mitbegründerin der [Rising Tide Foundation](https://risingtidefoundation.net/) (zusammen mit ihrem Ehemann Matthew Ehret, der am 4. September 2024 als Gastredner des Aletheia Science Forum über „Die britischen Wurzeln des Deep State verstehen“ sprach, aufgezeichnet hier: <https://www.wissenschaftstehtauf.ch/Matt_Ehret_20240904.mp4> ).\ \ Cynthia ist die Autorin der Bücher „[The Shaping of a World Religion](https://cynthiachung.substack.com/p/my-new-book-is-out-the-shaping-of)“ und „[The Empire on Which the Black Sun Never Set,](https://cynthiachung.substack.com/p/my-first-book-is-now-outthe-empire)“ sowie Mitautorin der Buchreihe „The Clash of the Two Americas“.\ \ Ihre Substack-Seite [„Through A Glass Darkly](https://cynthiachung.substack.com/) ([https://cynthiachung.substack.com](https://cynthiachung.substack.com/))“ hat über 11.000 Abonnenten. Sie schreibt über eine Vielzahl wichtiger Themen, die von geopolitischer Geschichte bis hin zu Kultur, Wissenschaft und Kunst reichen.\ \ In ihrem Vortrag konzenteriert sich Cynthia auf die Operation Gladio, das geheime „Stay-behind“-Netzwerk bewaffneter Widerstandsorganisationen, das während des Kalten Krieges in Westeuropa gegründet wurde. Solche historischen Einblicke können uns in der heutigen Zeit helfen, uns durch die Stürme zu navigieren, die die Zivilisation erneut bedrohen.\ \ Einführung von Stefan Heeb <https://www.proethica.ch> Weiterführende Analysen: Daniele Ganser: NATO Geheimarmeen in Europa  [Die NATO und der rechtsextreme Staatsterror](https://x.com/RealWsiegrist/status/1867063935289139260) [NATO/Gladio/Verdeckte Kriegsführung](https://waltisiegrist.locals.com/upost/1571799/manipulation-der-massen-durch-panik) [NATO](https://waltisiegrist.locals.com/upost/1859885/die-geschichte-der-nato-ber-general-reinhard-gehlen-1902-1979-und-sein-netzwerk-in-der-wehrma) @ ece127e2:745bab9c
2024-12-11 21:54:31La palabra anarquía proviene del griego y significa sin gobierno; es decir la vida de un pueblo que se rige sin autoridad constituida, sin gobierno.La palabra *anarquía* proviene del griego y significa *sin gobierno*; es decir la vida de un pueblo que se rige sin autoridad constituida, sin gobierno. Los anarquistas se sirven ordinariamente de la palabra Estado para expresar todo el conjunto de instituciones políticas, legislativas, judiciales, militares, financieras, etc., por medio de las cuales se sustrae al pueblo la gestión de sus propios asuntos, la dirección de su propia seguridad, para confiarlos a unos cuantos que usurpación o delegación se encuentran investidos de la facultad de hacer leyes sobre todo y para todos y de compeler al pueblo a ajustar a ellas su conducta, valiéndose, al efecto, de la fuerza de todos. En este supuesto la palabra Estado significa por tanto como gobierno, o se quiere, la expresión impersonal, abstracta de este estado de cosas cuya personificación está representada por el gobierno: las expresiones abolir el Estado, sociedad sin Estado, etc., responden, pues, perfectamente a la idea que los anarquistas quieren expresar cuando hablan de la abolición de toda organización política fundada en la autoridad y de la constitución de una sociedad de hombres libres e iguales fundada en la armonía de los intereses y sobre el concurso voluntario de todos, a fin de satisfacer las necesidades sociales. La palabra Estado tiene, empero, otras muchas significaciones, algunas de ellas susceptibles de inducir a error, sobre todo cuando se trata o discute con hombres que, a causa de su triste posición social, no han tenido ocasión de habituarse a las delicadas distinciones del lenguaje científico 0 cuando —y entonces peor— se trata con adversarios de mala fe, interesados en confundir los términos y en no querer comprender las cosas.Los anarquistas se sirven ordinariamente de la palabra *Estado* para expresar todo el conjunto de instituciones políticas, legislativas, judiciales, militares, financieras, etc., por medio de las cuales se sustrae al pueblo la gestión de sus propios asuntos, la dirección de su propia seguridad, para confiarlos a unos cuantos que usurpación o delegación se encuentran investidos de la facultad de hacer leyes sobre todo y para todos y de compeler al pueblo a ajustar a ellas su conducta, valiéndose, al efecto, de la fuerza de todos. En este supuesto la palabra *Estado* significa por tanto como gobierno, o se quiere, la expresión impersonal, abstracta de este estado de cosas cuya personificación está representada por el gobierno: las expresiones *abolir el Estado, sociedad sin Estado*, etc., responden, pues, perfectamente a la idea que los anarquistas quieren expresar cuando hablan de la abolición de toda organización política fundada en la autoridad y de la constitución de una sociedad de hombres libres e iguales fundada en la armonía de los intereses y sobre el concurso voluntario de todos, a fin de satisfacer las necesidades sociales. La palabra *Estado* tiene, empero, otras muchas significaciones, algunas de ellas susceptibles de inducir a error, sobre todo cuando se trata o discute con hombres que, a causa de su triste posición social, no han tenido ocasión de habituarse a las delicadas distinciones del lenguaje científico 0 cuando —y entonces peor— se trata con adversarios de mala fe, interesados en confundir los términos y en no querer comprender las cosas. Hemos dicho anteriormente: «Anarquía es la sociedad sin gobierno». ¿es factible la supresión de los gobiernos?, ¿es deseable?, ¿puede preverse? **¿Qué es el gobierno?** La tendencia metafísica (que es una enfermedad del espíritu por causa de la cual el hombre, después de haber sufrido una especie de alucinación, se ve inducido a tomar lo abstracto por real), la tendencia metafísica, decimos, que, no obstante, y a pesar de los triunfos de la ciencia positiva tiene todavía tan profundas raíces en el espíritu de la mayoría de los contemporáneos, hace que muchos conciban el gobierno como una entidad moral, dotada de ciertos atributos de razón, de justicia, de equidad, independientes de las personas en que encarna. Para ellos, el gobierno, o mas bien, el Estado, es el poder social abstracto; es el representante, abstracto siempre, de los intereses generales; es ya la expresión «derecho de todos», considerado como límite de los derechos de cada uno. Este modo de concebir el gobierno aparece apoyado por los interesados, a quienes importa salvar el principio de autoridad y hacerle prevalecer sobre las faltas y errores de los que se turnan en el ejercicio del poder. Para nosotros el gobierno es la colectividad de gobernantes: reyes, presidentes, ministros, diputados, etc., son aquellos que aparecen adornados de la facultad de hacer las leyes para reglamentar las relaciones de los hombres entre sí, y hacer ejecutar estas leyes; debe decretar y recaudar los impuestos; debe forzar al servicio militar; debe juzgar y castigar las infracciones y contravenciones a las leyes; debe intervenir y sancionar los contratos privados; debe monopolizar ciertos ramos de la producción y ciertos servicios públicos, por no decir toda la producción y todos los servicios; debe favorecer o impedir el cambio de productos; debe declarar la guerra y ajustar la paz con los gobernantes de otros países; debe conceder o suprimir franquicias, etc. Los gobernantes, en una palabra, son los que tienen la facultad en grado más o menos elevado de servirse de las fuerzas sociales, o sea de la fuerza física, intelectual y económica de todos, para obligar a todo el mundo a hacer lo que entre en sus designios particulares. Esta facultad constituye, en nuestro sentir, el principio de gobierno, el principio de autoridad.Hemos dicho anteriormente, que la «*Anarquía* es la sociedad sin *gobierno*». Ahora bien: ¿es factible la supresión de los gobiernos?, ¿es deseable?, ¿puede preverse? Veamos: ***¿Qué es el gobierno?*** La tendencia metafísica (que es una enfermedad del espíritu por causa de la cual el hombre, después de haber sufrido una especie de alucinación, se ve inducido a tomar lo abstracto por real), la tendencia metafísica, decimos, que, no obstante, y a pesar de los triunfos de la ciencia positiva tiene todavía tan profundas raíces en el espíritu de la mayoría de los contemporáneos, hace que muchos conciban el gobierno como una entidad moral, dotada de ciertos atributos de razón, de justicia, de equidad, independientes de las personas en que encarna. Para ellos, el gobierno, o mas bien, el Estado, es el poder social abstracto; es el representante, abstracto siempre, de los intereses generales; es ya la expresión «derecho de todos», considerado como límite de los derechos de cada uno. Este modo de concebir el gobierno aparece apoyado por los interesados, a quienes importa salvar el principio de autoridad y hacerle prevalecer sobre las faltas y errores de los que se turnan en el ejercicio del poder. Para nosotros el gobierno es la colectividad de gobernantes: reyes, presidentes, ministros, diputados, etc., son aquellos que aparecen adornados de la facultad de hacer las leyes para reglamentar las relaciones de los hombres entre sí, y hacer ejecutar estas leyes; debe decretar y recaudar los impuestos; debe forzar al servicio militar; debe juzgar y castigar las infracciones y contravenciones a las leyes; debe intervenir y sancionar los contratos privados; debe monopolizar ciertos ramos de la producción y ciertos servicios públicos, por no decir toda la producción y todos los servicios; debe favorecer o impedir el cambio de productos; debe declarar la guerra y ajustar la paz con los gobernantes de otros países; debe conceder o suprimir franquicias, etc. Los gobernantes, en una palabra, son los que tienen la facultad en grado más o menos elevado de servirse de las fuerzas sociales, o sea de la fuerza física, intelectual y económica de todos, para obligar a todo el mundo a hacer lo que entre en sus designios particulares. Esta facultad constituye, en nuestro sentir, el principio de gobierno, el principio de autoridad. source : https://es.anarchistlibraries.net/library/errico-malatesta-la-anarquia
@ ece127e2:745bab9c
2024-12-11 21:54:31La palabra anarquía proviene del griego y significa sin gobierno; es decir la vida de un pueblo que se rige sin autoridad constituida, sin gobierno.La palabra *anarquía* proviene del griego y significa *sin gobierno*; es decir la vida de un pueblo que se rige sin autoridad constituida, sin gobierno. Los anarquistas se sirven ordinariamente de la palabra Estado para expresar todo el conjunto de instituciones políticas, legislativas, judiciales, militares, financieras, etc., por medio de las cuales se sustrae al pueblo la gestión de sus propios asuntos, la dirección de su propia seguridad, para confiarlos a unos cuantos que usurpación o delegación se encuentran investidos de la facultad de hacer leyes sobre todo y para todos y de compeler al pueblo a ajustar a ellas su conducta, valiéndose, al efecto, de la fuerza de todos. En este supuesto la palabra Estado significa por tanto como gobierno, o se quiere, la expresión impersonal, abstracta de este estado de cosas cuya personificación está representada por el gobierno: las expresiones abolir el Estado, sociedad sin Estado, etc., responden, pues, perfectamente a la idea que los anarquistas quieren expresar cuando hablan de la abolición de toda organización política fundada en la autoridad y de la constitución de una sociedad de hombres libres e iguales fundada en la armonía de los intereses y sobre el concurso voluntario de todos, a fin de satisfacer las necesidades sociales. La palabra Estado tiene, empero, otras muchas significaciones, algunas de ellas susceptibles de inducir a error, sobre todo cuando se trata o discute con hombres que, a causa de su triste posición social, no han tenido ocasión de habituarse a las delicadas distinciones del lenguaje científico 0 cuando —y entonces peor— se trata con adversarios de mala fe, interesados en confundir los términos y en no querer comprender las cosas.Los anarquistas se sirven ordinariamente de la palabra *Estado* para expresar todo el conjunto de instituciones políticas, legislativas, judiciales, militares, financieras, etc., por medio de las cuales se sustrae al pueblo la gestión de sus propios asuntos, la dirección de su propia seguridad, para confiarlos a unos cuantos que usurpación o delegación se encuentran investidos de la facultad de hacer leyes sobre todo y para todos y de compeler al pueblo a ajustar a ellas su conducta, valiéndose, al efecto, de la fuerza de todos. En este supuesto la palabra *Estado* significa por tanto como gobierno, o se quiere, la expresión impersonal, abstracta de este estado de cosas cuya personificación está representada por el gobierno: las expresiones *abolir el Estado, sociedad sin Estado*, etc., responden, pues, perfectamente a la idea que los anarquistas quieren expresar cuando hablan de la abolición de toda organización política fundada en la autoridad y de la constitución de una sociedad de hombres libres e iguales fundada en la armonía de los intereses y sobre el concurso voluntario de todos, a fin de satisfacer las necesidades sociales. La palabra *Estado* tiene, empero, otras muchas significaciones, algunas de ellas susceptibles de inducir a error, sobre todo cuando se trata o discute con hombres que, a causa de su triste posición social, no han tenido ocasión de habituarse a las delicadas distinciones del lenguaje científico 0 cuando —y entonces peor— se trata con adversarios de mala fe, interesados en confundir los términos y en no querer comprender las cosas. Hemos dicho anteriormente: «Anarquía es la sociedad sin gobierno». ¿es factible la supresión de los gobiernos?, ¿es deseable?, ¿puede preverse? **¿Qué es el gobierno?** La tendencia metafísica (que es una enfermedad del espíritu por causa de la cual el hombre, después de haber sufrido una especie de alucinación, se ve inducido a tomar lo abstracto por real), la tendencia metafísica, decimos, que, no obstante, y a pesar de los triunfos de la ciencia positiva tiene todavía tan profundas raíces en el espíritu de la mayoría de los contemporáneos, hace que muchos conciban el gobierno como una entidad moral, dotada de ciertos atributos de razón, de justicia, de equidad, independientes de las personas en que encarna. Para ellos, el gobierno, o mas bien, el Estado, es el poder social abstracto; es el representante, abstracto siempre, de los intereses generales; es ya la expresión «derecho de todos», considerado como límite de los derechos de cada uno. Este modo de concebir el gobierno aparece apoyado por los interesados, a quienes importa salvar el principio de autoridad y hacerle prevalecer sobre las faltas y errores de los que se turnan en el ejercicio del poder. Para nosotros el gobierno es la colectividad de gobernantes: reyes, presidentes, ministros, diputados, etc., son aquellos que aparecen adornados de la facultad de hacer las leyes para reglamentar las relaciones de los hombres entre sí, y hacer ejecutar estas leyes; debe decretar y recaudar los impuestos; debe forzar al servicio militar; debe juzgar y castigar las infracciones y contravenciones a las leyes; debe intervenir y sancionar los contratos privados; debe monopolizar ciertos ramos de la producción y ciertos servicios públicos, por no decir toda la producción y todos los servicios; debe favorecer o impedir el cambio de productos; debe declarar la guerra y ajustar la paz con los gobernantes de otros países; debe conceder o suprimir franquicias, etc. Los gobernantes, en una palabra, son los que tienen la facultad en grado más o menos elevado de servirse de las fuerzas sociales, o sea de la fuerza física, intelectual y económica de todos, para obligar a todo el mundo a hacer lo que entre en sus designios particulares. Esta facultad constituye, en nuestro sentir, el principio de gobierno, el principio de autoridad.Hemos dicho anteriormente, que la «*Anarquía* es la sociedad sin *gobierno*». Ahora bien: ¿es factible la supresión de los gobiernos?, ¿es deseable?, ¿puede preverse? Veamos: ***¿Qué es el gobierno?*** La tendencia metafísica (que es una enfermedad del espíritu por causa de la cual el hombre, después de haber sufrido una especie de alucinación, se ve inducido a tomar lo abstracto por real), la tendencia metafísica, decimos, que, no obstante, y a pesar de los triunfos de la ciencia positiva tiene todavía tan profundas raíces en el espíritu de la mayoría de los contemporáneos, hace que muchos conciban el gobierno como una entidad moral, dotada de ciertos atributos de razón, de justicia, de equidad, independientes de las personas en que encarna. Para ellos, el gobierno, o mas bien, el Estado, es el poder social abstracto; es el representante, abstracto siempre, de los intereses generales; es ya la expresión «derecho de todos», considerado como límite de los derechos de cada uno. Este modo de concebir el gobierno aparece apoyado por los interesados, a quienes importa salvar el principio de autoridad y hacerle prevalecer sobre las faltas y errores de los que se turnan en el ejercicio del poder. Para nosotros el gobierno es la colectividad de gobernantes: reyes, presidentes, ministros, diputados, etc., son aquellos que aparecen adornados de la facultad de hacer las leyes para reglamentar las relaciones de los hombres entre sí, y hacer ejecutar estas leyes; debe decretar y recaudar los impuestos; debe forzar al servicio militar; debe juzgar y castigar las infracciones y contravenciones a las leyes; debe intervenir y sancionar los contratos privados; debe monopolizar ciertos ramos de la producción y ciertos servicios públicos, por no decir toda la producción y todos los servicios; debe favorecer o impedir el cambio de productos; debe declarar la guerra y ajustar la paz con los gobernantes de otros países; debe conceder o suprimir franquicias, etc. Los gobernantes, en una palabra, son los que tienen la facultad en grado más o menos elevado de servirse de las fuerzas sociales, o sea de la fuerza física, intelectual y económica de todos, para obligar a todo el mundo a hacer lo que entre en sus designios particulares. Esta facultad constituye, en nuestro sentir, el principio de gobierno, el principio de autoridad. source : https://es.anarchistlibraries.net/library/errico-malatesta-la-anarquia @ ece53feb:1edf277e
2024-12-11 21:19:19
@ ece53feb:1edf277e
2024-12-11 21:19:19 @ ece53feb:1edf277e
2024-12-11 21:13:59Had this been a real article, you would be less annoyed right now...
@ ece53feb:1edf277e
2024-12-11 21:13:59Had this been a real article, you would be less annoyed right now... @ ece53feb:1edf277e
2024-12-11 18:25:15Hi there, Nostr! I'm an engineer and maker who likes to talk a lot about a lot of things. I'm made of opinions. Some of them are pretty good ones!
@ ece53feb:1edf277e
2024-12-11 18:25:15Hi there, Nostr! I'm an engineer and maker who likes to talk a lot about a lot of things. I'm made of opinions. Some of them are pretty good ones! @ 468f729d:5ab4fd5e
2024-12-11 00:00:35<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/V_fvmyJ91m0?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 468f729d:5ab4fd5e
2024-12-11 00:00:35<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/V_fvmyJ91m0?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 4ba8e86d:89d32de4
2024-12-09 23:12:11A origem e o desenvolvimento do SearXNG começaram em meados de 2021, após o fork do conhecido mecanismo de metabusca Searx, inspirado pelo projeto Seeks. Ele garante privacidade básica ao misturar suas consultas com outras pesquisas, sem armazenar dados de busca. O SearXNG pode ser adicionado à barra de pesquisa do navegador e também configurado como mecanismo de busca padrão. Embora o SearXNG não ofereça resultados tão personalizados quanto o Google, ele não gera um perfil sobre você. Controle Total sobre Seus Dados: com o SearXNG, você tem controle absoluto sobre suas informações de pesquisa. O histórico de busca é totalmente opcional e pode ser ativado ou desativado conforme sua preferência. Além disso, é possível excluir qualquer entrada a qualquer momento, garantindo sua privacidade. Resultados de Fontes Diversificadas: o SearXNG agrega informações de mais de 70 fontes diferentes, proporcionando uma pesquisa mais abrangente e relevante. Em vez de se limitar a uma única fonte, você obtém uma visão mais ampla e detalhada das informações disponíveis. O SearXNG respeita sua privacidade, nunca compartilha dados com terceiros e não pode ser usado para comprometer sua segurança. O SearXNG é um software livre com código 100% aberto, e qualquer pessoa é bem-vinda para contribuir com melhorias. Se você valoriza a privacidade, deseja ser um usuário consciente ou acredita na liberdade digital, faça do SearXNG seu mecanismo de busca padrão ou instale-o em seu próprio servidor. O SearXNG reconhece sua preocupação com logs, por isso o código-fonte está disponível para que você possa executar sua própria instância: https://github.com/searxng/searxng Adicione sua instância à lista de instâncias públicas. https://searx.space/ para ajudar outras pessoas a recuperar sua privacidade e tornar a internet mais livre. Quanto mais descentralizada for a internet, maior será a liberdade para todos! Lista de Instâncias Públicas https://searx.space/ Documentação de Instalação https://docs.searxng.org/admin/installation.html#installation SeaxrXNG : Instalação , configuração e publicação. https://youtu.be/zcrFPje6Ug8?si=oOI6dqHfHij51rvd https://youtu.be/8WHnO9gJTHk?si=-5SbXUsaVSoSGpps
@ 4ba8e86d:89d32de4
2024-12-09 23:12:11A origem e o desenvolvimento do SearXNG começaram em meados de 2021, após o fork do conhecido mecanismo de metabusca Searx, inspirado pelo projeto Seeks. Ele garante privacidade básica ao misturar suas consultas com outras pesquisas, sem armazenar dados de busca. O SearXNG pode ser adicionado à barra de pesquisa do navegador e também configurado como mecanismo de busca padrão. Embora o SearXNG não ofereça resultados tão personalizados quanto o Google, ele não gera um perfil sobre você. Controle Total sobre Seus Dados: com o SearXNG, você tem controle absoluto sobre suas informações de pesquisa. O histórico de busca é totalmente opcional e pode ser ativado ou desativado conforme sua preferência. Além disso, é possível excluir qualquer entrada a qualquer momento, garantindo sua privacidade. Resultados de Fontes Diversificadas: o SearXNG agrega informações de mais de 70 fontes diferentes, proporcionando uma pesquisa mais abrangente e relevante. Em vez de se limitar a uma única fonte, você obtém uma visão mais ampla e detalhada das informações disponíveis. O SearXNG respeita sua privacidade, nunca compartilha dados com terceiros e não pode ser usado para comprometer sua segurança. O SearXNG é um software livre com código 100% aberto, e qualquer pessoa é bem-vinda para contribuir com melhorias. Se você valoriza a privacidade, deseja ser um usuário consciente ou acredita na liberdade digital, faça do SearXNG seu mecanismo de busca padrão ou instale-o em seu próprio servidor. O SearXNG reconhece sua preocupação com logs, por isso o código-fonte está disponível para que você possa executar sua própria instância: https://github.com/searxng/searxng Adicione sua instância à lista de instâncias públicas. https://searx.space/ para ajudar outras pessoas a recuperar sua privacidade e tornar a internet mais livre. Quanto mais descentralizada for a internet, maior será a liberdade para todos! Lista de Instâncias Públicas https://searx.space/ Documentação de Instalação https://docs.searxng.org/admin/installation.html#installation SeaxrXNG : Instalação , configuração e publicação. https://youtu.be/zcrFPje6Ug8?si=oOI6dqHfHij51rvd https://youtu.be/8WHnO9gJTHk?si=-5SbXUsaVSoSGpps @ dff95033:862fbf40
2024-12-09 22:42:32<img src="https://blossom.primal.net/0ac86bb186d6ada9099d8c8aad442bd264ee51333e876c142858a3f4ba32d306.png"> ## DADOS BIBLIOGRÁFICOS - Autor: Daniel J. Levitin - Título: A Mente Organizada: Como Pensar com Clareza na Era da Sobrecarga de Informação - Título Original: The Organized Mind: Thinking Straight in the Age of Information Overload - Tradutor: Regina Lyra - Editora: Objetiva - Ano de Publicação no Brasil: 2015 - Ano de Publicação Original: 2014 - ISBN (Edição Brasileira): 978-8539006465 - Páginas: 512 - Gênero: Psicologia, Ciência Cognitiva, Desenvolvimento Pessoal ## INTRODUÇÃO > "Não se pode confiar na memória porque o sistema de arquivamento do cérebro destreinado é uma porcaria. Ele pega tudo que acontece com você e joga de qualquer jeito num grande armário escuro — quando você entra lá procurando algo, só consegue achar as coisas grandes e óbvias, como a morte de sua mãe, ou então coisas de que realmente não precisa. Coisas que você não está procurando, como a letra de ‘Copacabana’. Você não consegue encontrar o que precisa. Mas não entre em pânico, porque ainda está lá.” (The Mentalist, citado por Daniel Levitin em A Mente Organizada) Quando me deparei com o livro “A Mente Organizada”, de Daniel Levitin, impulsivamente o adicionei à minha lista de leitura — apenas para deixá-lo esperando por meses. É irônico que um livro sobre organização estivesse preso no caos da minha própria lista, não estranhamente em uma era dopamínica — onde cada notificação e distração competem para roubar nossa atenção. No entanto, ao finalmente mergulhar em suas linhas, percebi que a obra é uma verdadeira ode à capacidade humana de organizar o conhecimento e a informação. ## ESTRUTURA E CONTEÚDO Dividido em três partes, “A Mente Organizada” nos guia por um entendimento prático sobre a mente humana. A Parte Um apresenta o mecanismo de atenção do cérebro, explorando como ele lida com o fluxo incessante de informações e decisões. Levitin discute a importância da atenção e como ela é fundamental para processar a quantidade massiva de dados que enfrentamos diariamente. Ele argumenta que entender esses mecanismos é crucial para melhorar nossa capacidade de foco e eficiência. A Parte Dois oferece estratégias que colaboram com esse mecanismo, ajudando a organizar nossos ambientes físico, profissional, social e temporal. Levitin sugere métodos práticos, como a categorização e a criação de listas, que podem facilitar a tomada de decisões e reduzir a sensação de sobrecarga informacional. A ênfase na organização do espaço físico e do tempo é particularmente relevante em uma era onde distrações são constantes. Com a estrutura bem definida, Levitin avança para aprofundar seu estilo e explorar a complexidade de transmitir conceitos desafiadores de maneira acessível. Por fim, a Parte Três discute como preparar a próxima geração para enfrentar os desafios do mundo moderno, equilibrando organização e criatividade. Levitin enfatiza a importância da educação em habilidades organizacionais desde cedo, preparando os jovens para um futuro onde o gerenciamento eficaz da informação será ainda mais crítico. Essa abordagem não apenas prepara os jovens para um futuro de desafios, mas também nos faz refletir sobre o legado que estamos construindo hoje. ## ESTILO E APROFUNDAMENTO A verbosidade de Levitin pode parecer desafiadora em alguns momentos, mas são nestes pontos que reside o valor do livro. Sua escrita flui como ondas: ora simples e objetiva, ora densa e desafiadora. Essa variação mantém o leitor engajado e instigado, permitindo uma compreensão mais profunda dos conceitos apresentados. Cada nuance tem seu propósito, oferecendo ao leitor as bases para compreender plenamente a obra ou para instigar novas inspirações e perspectivas. Levitin se esforça para tornar pesquisas e estudos sobre o tema acessíveis a um público amplo, evitando tanto a superficialidade quanto a complexidade excessiva. Essa abordagem é especialmente valiosa em um contexto onde muitos textos acadêmicos podem se tornar herméticos. ## REFLEXÕES PESSOAIS > Como frisei no decorrer deste livro, o princípio fundamental da organização, o mais crucial para evitar que percamos ou esqueçamos as coisas, é este: descarregue do cérebro para o mundo externo o ônus de organizar." (A Mente Organizada, Daniel Levitin). Ler A Mente Organizada foi um desafio que me obrigou a encarar a zorra informacional do dia a dia de frente. Não foi apenas uma leitura, mas um embate com os meus próprios hábitos e uma pausa necessária para questionar: estou realmente lidando bem com os estímulos ao meu redor? À deriva em águas turbulentas, precisei aceitar, com humildade, as ferramentas oferecidas pelo livro para enfrentar os desafios atuais. Senti-me provocado a observar com mais atenção tudo o que carrego, tanto física quanto mentalmente. Quantas ideias, compromissos e pensamentos acumulados passam despercebidos, sem nunca encontrar um lugar ou um significado real? Esse convite à introspecção foi um lembrete poderoso de que, mais do que organizar o que está fora, preciso organizar o que está dentro — e isso começa com um olhar honesto, e sim, doloroso, sobre o impacto que o excesso tem em minha vida. Esse foi o verdadeiro desafio: perceber que minha forma de organização precisava de um novo olhar. Não basta apenas acumular ideias; é essencial dar-lhes estrutura, conectá-las e transformá-las em algo maior — ou descartá-las, quando necessário. Entender as miríades que moldam meu pensar e agir foi fundamental, e, neste ponto, o livro foi nada menos que revelador. A estética, o particionamento e o naturalismo solidificam as minhas bases, transformando a organização em algo mais do que uma sistemática: ela se torna uma expressão de qualidade de vida e saúde. ## CONCLUSÃO A Mente Organizada é uma obra que, para alguns, será apenas um folhetim, enquanto para outros será um verdadeiro manancial de sabedoria. Mas, acima de tudo, o que Daniel Levitin nos oferece são possibilidades — um convite à lapidação dessa gema preciosa e instigante que é a busca por sermos melhores do que somos hoje. Se você chegou a este livro, consciente ou não, já deu o primeiro passo nessa jornada. Assim, caro leitor, deixo em tuas mãos esta obra, singela em proposta, mas grandiosa em potencial. Que ela inspire sua apreciação e, acima de tudo, seu uso. Fecho esta gaveta aqui e espero ter apreciado o que há dentro dela — ou não. Se trouxe alguma ordem à bagunça, compartilhe e, se puder, contribua com o café — porque até a organização precisa de combustível.
@ dff95033:862fbf40
2024-12-09 22:42:32<img src="https://blossom.primal.net/0ac86bb186d6ada9099d8c8aad442bd264ee51333e876c142858a3f4ba32d306.png"> ## DADOS BIBLIOGRÁFICOS - Autor: Daniel J. Levitin - Título: A Mente Organizada: Como Pensar com Clareza na Era da Sobrecarga de Informação - Título Original: The Organized Mind: Thinking Straight in the Age of Information Overload - Tradutor: Regina Lyra - Editora: Objetiva - Ano de Publicação no Brasil: 2015 - Ano de Publicação Original: 2014 - ISBN (Edição Brasileira): 978-8539006465 - Páginas: 512 - Gênero: Psicologia, Ciência Cognitiva, Desenvolvimento Pessoal ## INTRODUÇÃO > "Não se pode confiar na memória porque o sistema de arquivamento do cérebro destreinado é uma porcaria. Ele pega tudo que acontece com você e joga de qualquer jeito num grande armário escuro — quando você entra lá procurando algo, só consegue achar as coisas grandes e óbvias, como a morte de sua mãe, ou então coisas de que realmente não precisa. Coisas que você não está procurando, como a letra de ‘Copacabana’. Você não consegue encontrar o que precisa. Mas não entre em pânico, porque ainda está lá.” (The Mentalist, citado por Daniel Levitin em A Mente Organizada) Quando me deparei com o livro “A Mente Organizada”, de Daniel Levitin, impulsivamente o adicionei à minha lista de leitura — apenas para deixá-lo esperando por meses. É irônico que um livro sobre organização estivesse preso no caos da minha própria lista, não estranhamente em uma era dopamínica — onde cada notificação e distração competem para roubar nossa atenção. No entanto, ao finalmente mergulhar em suas linhas, percebi que a obra é uma verdadeira ode à capacidade humana de organizar o conhecimento e a informação. ## ESTRUTURA E CONTEÚDO Dividido em três partes, “A Mente Organizada” nos guia por um entendimento prático sobre a mente humana. A Parte Um apresenta o mecanismo de atenção do cérebro, explorando como ele lida com o fluxo incessante de informações e decisões. Levitin discute a importância da atenção e como ela é fundamental para processar a quantidade massiva de dados que enfrentamos diariamente. Ele argumenta que entender esses mecanismos é crucial para melhorar nossa capacidade de foco e eficiência. A Parte Dois oferece estratégias que colaboram com esse mecanismo, ajudando a organizar nossos ambientes físico, profissional, social e temporal. Levitin sugere métodos práticos, como a categorização e a criação de listas, que podem facilitar a tomada de decisões e reduzir a sensação de sobrecarga informacional. A ênfase na organização do espaço físico e do tempo é particularmente relevante em uma era onde distrações são constantes. Com a estrutura bem definida, Levitin avança para aprofundar seu estilo e explorar a complexidade de transmitir conceitos desafiadores de maneira acessível. Por fim, a Parte Três discute como preparar a próxima geração para enfrentar os desafios do mundo moderno, equilibrando organização e criatividade. Levitin enfatiza a importância da educação em habilidades organizacionais desde cedo, preparando os jovens para um futuro onde o gerenciamento eficaz da informação será ainda mais crítico. Essa abordagem não apenas prepara os jovens para um futuro de desafios, mas também nos faz refletir sobre o legado que estamos construindo hoje. ## ESTILO E APROFUNDAMENTO A verbosidade de Levitin pode parecer desafiadora em alguns momentos, mas são nestes pontos que reside o valor do livro. Sua escrita flui como ondas: ora simples e objetiva, ora densa e desafiadora. Essa variação mantém o leitor engajado e instigado, permitindo uma compreensão mais profunda dos conceitos apresentados. Cada nuance tem seu propósito, oferecendo ao leitor as bases para compreender plenamente a obra ou para instigar novas inspirações e perspectivas. Levitin se esforça para tornar pesquisas e estudos sobre o tema acessíveis a um público amplo, evitando tanto a superficialidade quanto a complexidade excessiva. Essa abordagem é especialmente valiosa em um contexto onde muitos textos acadêmicos podem se tornar herméticos. ## REFLEXÕES PESSOAIS > Como frisei no decorrer deste livro, o princípio fundamental da organização, o mais crucial para evitar que percamos ou esqueçamos as coisas, é este: descarregue do cérebro para o mundo externo o ônus de organizar." (A Mente Organizada, Daniel Levitin). Ler A Mente Organizada foi um desafio que me obrigou a encarar a zorra informacional do dia a dia de frente. Não foi apenas uma leitura, mas um embate com os meus próprios hábitos e uma pausa necessária para questionar: estou realmente lidando bem com os estímulos ao meu redor? À deriva em águas turbulentas, precisei aceitar, com humildade, as ferramentas oferecidas pelo livro para enfrentar os desafios atuais. Senti-me provocado a observar com mais atenção tudo o que carrego, tanto física quanto mentalmente. Quantas ideias, compromissos e pensamentos acumulados passam despercebidos, sem nunca encontrar um lugar ou um significado real? Esse convite à introspecção foi um lembrete poderoso de que, mais do que organizar o que está fora, preciso organizar o que está dentro — e isso começa com um olhar honesto, e sim, doloroso, sobre o impacto que o excesso tem em minha vida. Esse foi o verdadeiro desafio: perceber que minha forma de organização precisava de um novo olhar. Não basta apenas acumular ideias; é essencial dar-lhes estrutura, conectá-las e transformá-las em algo maior — ou descartá-las, quando necessário. Entender as miríades que moldam meu pensar e agir foi fundamental, e, neste ponto, o livro foi nada menos que revelador. A estética, o particionamento e o naturalismo solidificam as minhas bases, transformando a organização em algo mais do que uma sistemática: ela se torna uma expressão de qualidade de vida e saúde. ## CONCLUSÃO A Mente Organizada é uma obra que, para alguns, será apenas um folhetim, enquanto para outros será um verdadeiro manancial de sabedoria. Mas, acima de tudo, o que Daniel Levitin nos oferece são possibilidades — um convite à lapidação dessa gema preciosa e instigante que é a busca por sermos melhores do que somos hoje. Se você chegou a este livro, consciente ou não, já deu o primeiro passo nessa jornada. Assim, caro leitor, deixo em tuas mãos esta obra, singela em proposta, mas grandiosa em potencial. Que ela inspire sua apreciação e, acima de tudo, seu uso. Fecho esta gaveta aqui e espero ter apreciado o que há dentro dela — ou não. Se trouxe alguma ordem à bagunça, compartilhe e, se puder, contribua com o café — porque até a organização precisa de combustível. @ 8e56fde2:bb433b31
2024-12-09 21:04:00So let us give a little bit on context first to get the WHOLE PICTURE. We DoShitters are a trio of friends who one day decided we wanted to create some shit together. We are artists from different fields, and at the time two of us were struggling from creative block, so we decided to create the ultimate tool to COMBAT CREATIVE BLOCK. It would be an Oracle about the creative process and it would be inspired on the Hero's Journey and on our own journeys as artists; and hence "DoShit!" was born.  Once we knew what we wanted to do, and it started to have a shape, we decided to go through the hardship of self-producing and selling the cards by ourselves directly on our website ( www.doshitters.com ), which allowed us to keep control of the product at all times during production, and to have a direct relationship with our audience and buyers. Besides from guaranteeing we weren't left with the tiniest percentage of the sales pie. (At least in Spain, when you get a big publisher involved, you can forget getting even 10% of sales, and you lose a lot of the creative control of your project). We invested a lot of our own resources in making sure "DoShit!" was a quality product and we were lucky enough to get the help of a generous patreon who enabled us to create what is now the DoShit! deck. <3  We did local presentations of the product in both Barcelona and Madrid, and got the deck to be sold in cool local stores, where we offered to do live readings and got to talk with people of all kinds about the Shit they wanted to do. Above all, DoShit! is an inspirational tool. **And you must be asking yourself, "What does this have to do with Amazon?". ** Well, one of the problems of self-producing and having local fulfilment of the product is that shipping costs just couldn't compete with what the average consumer has gotten used to because of Amazon's mass scale free shipping. We were finding that, specially for our followers in the USA, it was impossible to assume shipping costs (which amounted to almost the same cost as the actual deck); but we didn't want to give up on the people who wanted to get inspired by DoShit! but lived on the other side of the world from us, so... WE DECIDED TO MAKE A DEAL WITH THE DEVIL, aka Amazon.  We knew that selling our product on Amazon was going to result in less revenue from the sales for us, but for us it was mostly about GETTING DoShit! TO A WAREHOUSE IN THE USA to be able to offer the deck with Free Shipping. And that's what we did. But we didn't know everything that would come as a result, (they don't really advertise the hidden costs and fees, or the speed at which they want you to expedite your sales) and we've been paying for that decision ever since.  In any case, they lured us in with a 3 months no cost promotion. You obviously assumed the cost of shipping it there, and they would take a cut from every sale that happened in their web, but we didn't have any way of knowing the cost that we would need to incur after those first three months. Another thing that wasn't advertised is that IF YOU ACTUALLY WANT YOUR PRODUCT TO BE FEATURED ANYWHERE, you need to be eligible as an A+ content seller, which also comes at a cost, and you need to pay additionally for sponsored ads; otherwise, your product is basically shut down in a black hole of zero discoverability except for people using the direct link.  The three months went by fast and then the invoices started coming, and the automatic charges on our account started to empty our independent seller bank account. As you can imagine, independent sellers like us sometimes require of TIME to be able to get the word out, to get people to buy your product... Besides, as artists with other projects on the pipeline, we couldn't really spend much time focusing on sales, nor did we want to. And in all honestly, we refused to give Amazon more money in sponsored ads and other programs to "gain visibility". We knew we had no way of competing with the big sellers on the platform, but we just thought, "AT LEAST IT'S AVAILABLE FOR THOSE WHO WANT TO BUY IT".  But then, out of the blue, we noticed our link on Amazon wasn't working. A friend tipped us off that it wasn't allowing any sales, it was listed as "currently unavailable", without us having done anything to trigger that change. Suddenly we received an email from the giant informing us that our account had been set to inactive due to "dormancy", and that we needed to re-verify our identity. Not only that, but since we were in Europe, and they didn't have an address in the US they could send the decks back to, if we didn't get everything solved in time, THEY WERE GOING TO DESTROY THE DECKS THEY HAD IN THEIR WAREHOUSE because of their "Automated removal" policy. This caught us while we were on holidays, away from our desktops, seller logins and such and we did everything the seller support requested from us as rapidly as possible. The nightmare of imagining our beautiful decks being destroyed really put us in a state of panic. We hoped everything would be solved after several support tickets stating our case, and pleading that they don't destroy the decks!  In the end, after several communications, they reactivated our listing which had apparently been set to inactive because of "stranded inventory" due to "excess inventory"; which is Amazon talk for: "YOU'RE NOT SELLING FAST ENOUGH". After having gone through that experience we knew one thing for certain, WE WANTED TO BREAK FREE FROM AMAZON as soon as possible, but we still wanted to offer our DoShit! decks with Free Shipping for our customers; at least this Christmas...  So, best case scenario, all the DoShit! decks that are at Amazon get sold this Christmas campaign, with the jolly merry spirit, people and nostriches all around the world get excited about GIFTING INSPIRATION (and taking advantage of the Free Shipping) and help us to GET THE DECKS OUT OF AMAZON!  But we know this may be wishful thinking T.T , That is why we are also looking for independent shops in the USA that feel that DoShit! makes sense in their store, and would want to become the new home of the decks that remain in american soil after the Christmas campaign. So maybe somebody wants to become the "foster home" to these Oracles as they find their new home in 2025, so they decks can go from that abussive giant with high time preference, to a friendly purple shop with low time preference and no hidden tricks. After all, many people kickstart the year with their minds set on their New Year Resolutions, they want to DO SHIT! So Who Knows?  In any case, to all the small sellers out there, BEWARE OF MAKING THAT PACT WITH THE DEVIL. We knew we had never wanted to get our Shit on Amazon, we knew the system was rigged again us, but still, we wanted to make it more affordable for people to get their hands on the deck. Artists struggle enough to have to additionally add exhorbitant shipping costs to acquire a creativity tool like "DoShit!". And if you, like us, find yourself having to do that pact anyway, we hope our tale will at least help you navigate all the hidden traps that their system throws at you.  IF YOU WANT TO JOIN THE CREATIVE RESCUE MISSION TO FREE THE DECKS, please, support us as best you can, share our story, recommend our deck, but best of all GIFT THE "DoShit!" DECK THIS CHRISTMAS! <3 You can find it at its captor's site at https://a.co/d/hrKXEBF , or if you'd rather NOT BUY SHIT ON AMAZON, you can always buy it at the Plebeian Market with your Sats, and we'll get one out of Amazon on your account. (https://plebeian.market/p/f82c481a3ae2a284049631a50373f4b9262c0e0b80977a4de1a71fcc19c5635d/stall/c9744507a49cf647c5612204416b7e22bdab86fbaff85413cfbc41103a0d269a)  THANKS FOR CARING, This 2025, we wish you all to DO THE SHIT THAT MATTERS TO YOU! #DoShit! #JoinTheArtmy
@ 8e56fde2:bb433b31
2024-12-09 21:04:00So let us give a little bit on context first to get the WHOLE PICTURE. We DoShitters are a trio of friends who one day decided we wanted to create some shit together. We are artists from different fields, and at the time two of us were struggling from creative block, so we decided to create the ultimate tool to COMBAT CREATIVE BLOCK. It would be an Oracle about the creative process and it would be inspired on the Hero's Journey and on our own journeys as artists; and hence "DoShit!" was born.  Once we knew what we wanted to do, and it started to have a shape, we decided to go through the hardship of self-producing and selling the cards by ourselves directly on our website ( www.doshitters.com ), which allowed us to keep control of the product at all times during production, and to have a direct relationship with our audience and buyers. Besides from guaranteeing we weren't left with the tiniest percentage of the sales pie. (At least in Spain, when you get a big publisher involved, you can forget getting even 10% of sales, and you lose a lot of the creative control of your project). We invested a lot of our own resources in making sure "DoShit!" was a quality product and we were lucky enough to get the help of a generous patreon who enabled us to create what is now the DoShit! deck. <3  We did local presentations of the product in both Barcelona and Madrid, and got the deck to be sold in cool local stores, where we offered to do live readings and got to talk with people of all kinds about the Shit they wanted to do. Above all, DoShit! is an inspirational tool. **And you must be asking yourself, "What does this have to do with Amazon?". ** Well, one of the problems of self-producing and having local fulfilment of the product is that shipping costs just couldn't compete with what the average consumer has gotten used to because of Amazon's mass scale free shipping. We were finding that, specially for our followers in the USA, it was impossible to assume shipping costs (which amounted to almost the same cost as the actual deck); but we didn't want to give up on the people who wanted to get inspired by DoShit! but lived on the other side of the world from us, so... WE DECIDED TO MAKE A DEAL WITH THE DEVIL, aka Amazon.  We knew that selling our product on Amazon was going to result in less revenue from the sales for us, but for us it was mostly about GETTING DoShit! TO A WAREHOUSE IN THE USA to be able to offer the deck with Free Shipping. And that's what we did. But we didn't know everything that would come as a result, (they don't really advertise the hidden costs and fees, or the speed at which they want you to expedite your sales) and we've been paying for that decision ever since.  In any case, they lured us in with a 3 months no cost promotion. You obviously assumed the cost of shipping it there, and they would take a cut from every sale that happened in their web, but we didn't have any way of knowing the cost that we would need to incur after those first three months. Another thing that wasn't advertised is that IF YOU ACTUALLY WANT YOUR PRODUCT TO BE FEATURED ANYWHERE, you need to be eligible as an A+ content seller, which also comes at a cost, and you need to pay additionally for sponsored ads; otherwise, your product is basically shut down in a black hole of zero discoverability except for people using the direct link.  The three months went by fast and then the invoices started coming, and the automatic charges on our account started to empty our independent seller bank account. As you can imagine, independent sellers like us sometimes require of TIME to be able to get the word out, to get people to buy your product... Besides, as artists with other projects on the pipeline, we couldn't really spend much time focusing on sales, nor did we want to. And in all honestly, we refused to give Amazon more money in sponsored ads and other programs to "gain visibility". We knew we had no way of competing with the big sellers on the platform, but we just thought, "AT LEAST IT'S AVAILABLE FOR THOSE WHO WANT TO BUY IT".  But then, out of the blue, we noticed our link on Amazon wasn't working. A friend tipped us off that it wasn't allowing any sales, it was listed as "currently unavailable", without us having done anything to trigger that change. Suddenly we received an email from the giant informing us that our account had been set to inactive due to "dormancy", and that we needed to re-verify our identity. Not only that, but since we were in Europe, and they didn't have an address in the US they could send the decks back to, if we didn't get everything solved in time, THEY WERE GOING TO DESTROY THE DECKS THEY HAD IN THEIR WAREHOUSE because of their "Automated removal" policy. This caught us while we were on holidays, away from our desktops, seller logins and such and we did everything the seller support requested from us as rapidly as possible. The nightmare of imagining our beautiful decks being destroyed really put us in a state of panic. We hoped everything would be solved after several support tickets stating our case, and pleading that they don't destroy the decks!  In the end, after several communications, they reactivated our listing which had apparently been set to inactive because of "stranded inventory" due to "excess inventory"; which is Amazon talk for: "YOU'RE NOT SELLING FAST ENOUGH". After having gone through that experience we knew one thing for certain, WE WANTED TO BREAK FREE FROM AMAZON as soon as possible, but we still wanted to offer our DoShit! decks with Free Shipping for our customers; at least this Christmas...  So, best case scenario, all the DoShit! decks that are at Amazon get sold this Christmas campaign, with the jolly merry spirit, people and nostriches all around the world get excited about GIFTING INSPIRATION (and taking advantage of the Free Shipping) and help us to GET THE DECKS OUT OF AMAZON!  But we know this may be wishful thinking T.T , That is why we are also looking for independent shops in the USA that feel that DoShit! makes sense in their store, and would want to become the new home of the decks that remain in american soil after the Christmas campaign. So maybe somebody wants to become the "foster home" to these Oracles as they find their new home in 2025, so they decks can go from that abussive giant with high time preference, to a friendly purple shop with low time preference and no hidden tricks. After all, many people kickstart the year with their minds set on their New Year Resolutions, they want to DO SHIT! So Who Knows?  In any case, to all the small sellers out there, BEWARE OF MAKING THAT PACT WITH THE DEVIL. We knew we had never wanted to get our Shit on Amazon, we knew the system was rigged again us, but still, we wanted to make it more affordable for people to get their hands on the deck. Artists struggle enough to have to additionally add exhorbitant shipping costs to acquire a creativity tool like "DoShit!". And if you, like us, find yourself having to do that pact anyway, we hope our tale will at least help you navigate all the hidden traps that their system throws at you.  IF YOU WANT TO JOIN THE CREATIVE RESCUE MISSION TO FREE THE DECKS, please, support us as best you can, share our story, recommend our deck, but best of all GIFT THE "DoShit!" DECK THIS CHRISTMAS! <3 You can find it at its captor's site at https://a.co/d/hrKXEBF , or if you'd rather NOT BUY SHIT ON AMAZON, you can always buy it at the Plebeian Market with your Sats, and we'll get one out of Amazon on your account. (https://plebeian.market/p/f82c481a3ae2a284049631a50373f4b9262c0e0b80977a4de1a71fcc19c5635d/stall/c9744507a49cf647c5612204416b7e22bdab86fbaff85413cfbc41103a0d269a)  THANKS FOR CARING, This 2025, we wish you all to DO THE SHIT THAT MATTERS TO YOU! #DoShit! #JoinTheArtmy @ ece53feb:1edf277e
2024-12-09 15:19:42https://www.newyorkupstate.com/news/2024/12/upstate-ny-village-shuts-off-water-declares-state-of-emergency.html?utm_source=flipboard&utm_medium=activitypub
@ ece53feb:1edf277e
2024-12-09 15:19:42https://www.newyorkupstate.com/news/2024/12/upstate-ny-village-shuts-off-water-declares-state-of-emergency.html?utm_source=flipboard&utm_medium=activitypub @ eac63075:b4988b48
2024-12-08 15:35:21Imagine a large public square, illuminated by intense spotlights, where every individual who dares to approach the center is immediately recognized, photographed, and cataloged. In this square, every word spoken becomes indelibly tied to its speaker. Under such conditions, many would hesitate before speaking, fearing not only the disapproval of the audience but also the potential punishments that could follow the mere act of expressing an idea. Now, imagine a second square, where anyone can cover their face with a mask, allowing their voice to echo without revealing their identity. It is in this second square that true freedom of expression flourishes, and this metaphorical mask represents anonymity. https://www.fountain.fm/episode/MweciiR21hySxjdsNa7u In debates about freedom of expression—one of the fundamental pillars of democratic societies—anonymity often emerges as a controversial element. For some, it serves as a refuge for digital criminals or slanderers. For others, it is an indispensable tool, capable of protecting dissenting voices and inspiring authentic debates, with ideas judged on their merits rather than the messenger’s reputation. This article aims to explain, in a clear and instructive manner, why anonymity is essential to genuine freedom of expression, illustrating its value with metaphors, real-life examples, and historical references. ## **The Protective Mask: Avoiding Retaliation and Threats** Just as a navigator uses guiding instruments to avoid jagged rocks at sea, anonymity functions like a shield, allowing bold voices to navigate oppressive reefs without foundering. There are countless examples of individuals who have risked their lives to expose crimes and injustices—from whistleblowers in authoritarian governments to investigative journalists uncovering the complex machinations of organized crime. Without the possibility of anonymity, many of these stories would never have come to light. Organizations like the Electronic Frontier Foundation (EFF) and other digital rights advocacy groups emphasize that the ability to speak without revealing one’s identity is crucial when the cost of speaking out is dangerously high. In censorship-ridden regimes, criticizing the government can lead to imprisonment, torture, or even death. Human rights activists, LGBTQIA+ communities in hostile countries, and journalists investigating illicit dealings all rely on anonymity to continue their work without putting their own lives at immediate risk. In this context, anonymity is not a whim—it’s the chance to survive one’s own opinion. ## **The Voice of the Invisible: Empowering Marginalized Groups** Think of anonymity as an invisible microphone placed at the disposal of those who, without it, would never dare to take the stage. Historically, marginalized groups have always faced additional barriers to making their voices heard. Women in patriarchal societies, ethnic minorities facing discrimination, or individuals persecuted for their sexual orientation find in anonymity a safe space to speak out, claim their rights, and share their experiences without fearing public humiliation or physical violence. This “invisible microphone” not only gives voice to those who once remained silent but also transforms the arena of public debate into a more equitable space. By removing the link between idea and identity, it reduces the risk of immediate prejudice against the messenger. As a result, society can assess arguments more impartially. Here, ideas are judged on their content, not on the face that speaks them. ## **The Strength of History: The Precedent of the Federalist Papers** History offers a famous example of the power of anonymous words: the Federalist Papers. Published between 1787 and 1788, these essays supported the ratification of the United States Constitution and were written under the pseudonym “Publius” by Alexander Hamilton, James Madison, and John Jay. The reason for concealing their identities was clear: to ensure that their ideas would be judged on their argumentative strength rather than the prestige or fame of the authors. The precedent set by the Federalist Papers is emblematic. It shows that, in the building of one of the first modern democracies, anonymity was used as a legitimate tool to establish fundamental concepts. If the founders of the nation that prides itself on its First Amendment—the one that protects freedom of expression—resorted to anonymity, we should recognize that this resource is not only defensible but also an essential part of the framework of healthy public debate. ## **Faceless Messages: The Democracy of Pure Ideas** In an ideal world, we would judge a message purely on its content. In reality, however, names, faces, social status, and economic position influence how we receive and interpret a person’s words. Anonymity removes these superficial layers, allowing the message to present itself bare, subject to rational evaluation without the veils of prejudice. In this sense, anonymity acts as a “filter of equality”: by concealing the source, it prevents us from assigning credibility (or discredit) based on stereotypes, prejudices, or personal rivalries. Thus, ideas previously dismissed out of hand can now be heard with greater attention, opening paths to social innovation, political reflection, and challenges to the status quo. A contemporary example is online forums that allow anonymous posts. While we acknowledge that such spaces can be misused, we cannot ignore their potential to give voice to those who would never feel safe speaking under their own name in public. ## **Privacy, Intimacy, and the Freedom to Whisper** Anonymity is not limited to the public or political sphere. In personal and professional relations, the ability to speak anonymously can allow someone to seek help or reveal extremely sensitive matters. Imagine a patient who needs to consult a doctor about a stigmatized health issue, or a person seeking legal advice in a delicate situation. The “mask” of anonymity offers a safe haven for sharing information without the anguish of being judged or exposed. Thus, anonymity also safeguards our “right to whisper,” that is, the ability to exchange information, secrets, and confessions without the constant glare of a spotlight. Real or perceived surveillance can stifle communication and inhibit creativity, reporting, and the exchange of ideas. By shielding individuals from forced exposure, anonymity reinforces the very fabric of freedom of expression, preventing the fear of identification from silencing words before they are spoken. ## **Anonymity in the Digital Age: Between Encryption and Censorship** In the digital age, the issue of anonymity becomes even more relevant. With the expansion of online surveillance and the growth of social networks, maintaining anonymity can be challenging. Social media platforms increasingly request personal data, and governments attempt to impose barriers against anonymity, often justifying them as measures of national security or crime prevention. However, according to reports and documents from human rights organizations, such as the UN High Commissioner for Human Rights and the Association for Progressive Communications (APC), encryption and anonymity are key tools for freedom of expression in the digital environment. Without these resources, citizens and journalists, for instance, become more vulnerable to persecution. In various countries, the existence of anonymous and encrypted channels enables information to circulate, grievances to be reported, and societies to remain informed, even in the face of heavy censorship. ## **Legal Protection: Judicial Recognition of Anonymity** The United States Supreme Court, as well as other constitutional courts around the world, recognizes anonymity as an integral part of the right to free expression. In the United States, the First Amendment has been applied in cases that defended the right to anonymous speech, viewing it as a bulwark against the tyranny of the majority. When minorities are protected by anonymity, personal reprisals against those who dare to question dogmas or denounce abuses are prevented. This judicial understanding reinforces the legitimacy of anonymity and its direct association with the strengthening of democracy. After all, a robust democracy requires not only the absence of formal censorship but also the guarantee that minority or unpopular voices can speak out without fear. ## **Conclusion: The Cloak That Protects Freedom** If freedom of expression is the heart of democracy, anonymity is the cloak that shields that heart from the poisoned darts of fear, persecution, and prejudice. It creates the right environment for ideas to flourish freely, for courageous voices to emerge from silence, and for society to debate its most complex issues in the light of reason rather than beneath the shadow of intimidation. In a world where surveillance and political tensions are ever-present, anonymity preserves the essence of free speech: humanity’s ability to question, propose, denounce, criticize, and create without shackles. By recognizing the importance of this resource, we safeguard not only individual voices but also the very principle that makes democracy worthy of its name. ## **Selected References:** - Electronic Frontier Foundation (EFF): <https://www.eff.org/issues/anonymity> - Freedom Forum: <https://www.freedomforum.org/anonymous-speech/> - Association for Progressive Communications (APC): <https://www.apc.org/> - The First Amendment Encyclopedia: Anonymous Speech: <https://firstamendment.mtsu.edu/article/anonymous-speech/> - The Federalist Papers: Historical context available at [Library of Congress](https://www.loc.gov/) and various printed and digital compilations. --- Cover Photo by [Redd Francisco](https://unsplash.com/@reddfrancisco?utm_source=ghost&utm_medium=referral&utm_campaign=api-credit) / [Unsplash](https://unsplash.com/?utm_source=ghost&utm_medium=referral&utm_campaign=api-credit)
@ eac63075:b4988b48
2024-12-08 15:35:21Imagine a large public square, illuminated by intense spotlights, where every individual who dares to approach the center is immediately recognized, photographed, and cataloged. In this square, every word spoken becomes indelibly tied to its speaker. Under such conditions, many would hesitate before speaking, fearing not only the disapproval of the audience but also the potential punishments that could follow the mere act of expressing an idea. Now, imagine a second square, where anyone can cover their face with a mask, allowing their voice to echo without revealing their identity. It is in this second square that true freedom of expression flourishes, and this metaphorical mask represents anonymity. https://www.fountain.fm/episode/MweciiR21hySxjdsNa7u In debates about freedom of expression—one of the fundamental pillars of democratic societies—anonymity often emerges as a controversial element. For some, it serves as a refuge for digital criminals or slanderers. For others, it is an indispensable tool, capable of protecting dissenting voices and inspiring authentic debates, with ideas judged on their merits rather than the messenger’s reputation. This article aims to explain, in a clear and instructive manner, why anonymity is essential to genuine freedom of expression, illustrating its value with metaphors, real-life examples, and historical references. ## **The Protective Mask: Avoiding Retaliation and Threats** Just as a navigator uses guiding instruments to avoid jagged rocks at sea, anonymity functions like a shield, allowing bold voices to navigate oppressive reefs without foundering. There are countless examples of individuals who have risked their lives to expose crimes and injustices—from whistleblowers in authoritarian governments to investigative journalists uncovering the complex machinations of organized crime. Without the possibility of anonymity, many of these stories would never have come to light. Organizations like the Electronic Frontier Foundation (EFF) and other digital rights advocacy groups emphasize that the ability to speak without revealing one’s identity is crucial when the cost of speaking out is dangerously high. In censorship-ridden regimes, criticizing the government can lead to imprisonment, torture, or even death. Human rights activists, LGBTQIA+ communities in hostile countries, and journalists investigating illicit dealings all rely on anonymity to continue their work without putting their own lives at immediate risk. In this context, anonymity is not a whim—it’s the chance to survive one’s own opinion. ## **The Voice of the Invisible: Empowering Marginalized Groups** Think of anonymity as an invisible microphone placed at the disposal of those who, without it, would never dare to take the stage. Historically, marginalized groups have always faced additional barriers to making their voices heard. Women in patriarchal societies, ethnic minorities facing discrimination, or individuals persecuted for their sexual orientation find in anonymity a safe space to speak out, claim their rights, and share their experiences without fearing public humiliation or physical violence. This “invisible microphone” not only gives voice to those who once remained silent but also transforms the arena of public debate into a more equitable space. By removing the link between idea and identity, it reduces the risk of immediate prejudice against the messenger. As a result, society can assess arguments more impartially. Here, ideas are judged on their content, not on the face that speaks them. ## **The Strength of History: The Precedent of the Federalist Papers** History offers a famous example of the power of anonymous words: the Federalist Papers. Published between 1787 and 1788, these essays supported the ratification of the United States Constitution and were written under the pseudonym “Publius” by Alexander Hamilton, James Madison, and John Jay. The reason for concealing their identities was clear: to ensure that their ideas would be judged on their argumentative strength rather than the prestige or fame of the authors. The precedent set by the Federalist Papers is emblematic. It shows that, in the building of one of the first modern democracies, anonymity was used as a legitimate tool to establish fundamental concepts. If the founders of the nation that prides itself on its First Amendment—the one that protects freedom of expression—resorted to anonymity, we should recognize that this resource is not only defensible but also an essential part of the framework of healthy public debate. ## **Faceless Messages: The Democracy of Pure Ideas** In an ideal world, we would judge a message purely on its content. In reality, however, names, faces, social status, and economic position influence how we receive and interpret a person’s words. Anonymity removes these superficial layers, allowing the message to present itself bare, subject to rational evaluation without the veils of prejudice. In this sense, anonymity acts as a “filter of equality”: by concealing the source, it prevents us from assigning credibility (or discredit) based on stereotypes, prejudices, or personal rivalries. Thus, ideas previously dismissed out of hand can now be heard with greater attention, opening paths to social innovation, political reflection, and challenges to the status quo. A contemporary example is online forums that allow anonymous posts. While we acknowledge that such spaces can be misused, we cannot ignore their potential to give voice to those who would never feel safe speaking under their own name in public. ## **Privacy, Intimacy, and the Freedom to Whisper** Anonymity is not limited to the public or political sphere. In personal and professional relations, the ability to speak anonymously can allow someone to seek help or reveal extremely sensitive matters. Imagine a patient who needs to consult a doctor about a stigmatized health issue, or a person seeking legal advice in a delicate situation. The “mask” of anonymity offers a safe haven for sharing information without the anguish of being judged or exposed. Thus, anonymity also safeguards our “right to whisper,” that is, the ability to exchange information, secrets, and confessions without the constant glare of a spotlight. Real or perceived surveillance can stifle communication and inhibit creativity, reporting, and the exchange of ideas. By shielding individuals from forced exposure, anonymity reinforces the very fabric of freedom of expression, preventing the fear of identification from silencing words before they are spoken. ## **Anonymity in the Digital Age: Between Encryption and Censorship** In the digital age, the issue of anonymity becomes even more relevant. With the expansion of online surveillance and the growth of social networks, maintaining anonymity can be challenging. Social media platforms increasingly request personal data, and governments attempt to impose barriers against anonymity, often justifying them as measures of national security or crime prevention. However, according to reports and documents from human rights organizations, such as the UN High Commissioner for Human Rights and the Association for Progressive Communications (APC), encryption and anonymity are key tools for freedom of expression in the digital environment. Without these resources, citizens and journalists, for instance, become more vulnerable to persecution. In various countries, the existence of anonymous and encrypted channels enables information to circulate, grievances to be reported, and societies to remain informed, even in the face of heavy censorship. ## **Legal Protection: Judicial Recognition of Anonymity** The United States Supreme Court, as well as other constitutional courts around the world, recognizes anonymity as an integral part of the right to free expression. In the United States, the First Amendment has been applied in cases that defended the right to anonymous speech, viewing it as a bulwark against the tyranny of the majority. When minorities are protected by anonymity, personal reprisals against those who dare to question dogmas or denounce abuses are prevented. This judicial understanding reinforces the legitimacy of anonymity and its direct association with the strengthening of democracy. After all, a robust democracy requires not only the absence of formal censorship but also the guarantee that minority or unpopular voices can speak out without fear. ## **Conclusion: The Cloak That Protects Freedom** If freedom of expression is the heart of democracy, anonymity is the cloak that shields that heart from the poisoned darts of fear, persecution, and prejudice. It creates the right environment for ideas to flourish freely, for courageous voices to emerge from silence, and for society to debate its most complex issues in the light of reason rather than beneath the shadow of intimidation. In a world where surveillance and political tensions are ever-present, anonymity preserves the essence of free speech: humanity’s ability to question, propose, denounce, criticize, and create without shackles. By recognizing the importance of this resource, we safeguard not only individual voices but also the very principle that makes democracy worthy of its name. ## **Selected References:** - Electronic Frontier Foundation (EFF): <https://www.eff.org/issues/anonymity> - Freedom Forum: <https://www.freedomforum.org/anonymous-speech/> - Association for Progressive Communications (APC): <https://www.apc.org/> - The First Amendment Encyclopedia: Anonymous Speech: <https://firstamendment.mtsu.edu/article/anonymous-speech/> - The Federalist Papers: Historical context available at [Library of Congress](https://www.loc.gov/) and various printed and digital compilations. --- Cover Photo by [Redd Francisco](https://unsplash.com/@reddfrancisco?utm_source=ghost&utm_medium=referral&utm_campaign=api-credit) / [Unsplash](https://unsplash.com/?utm_source=ghost&utm_medium=referral&utm_campaign=api-credit) @ 65912a7a:5dc638bf
2024-12-08 05:33:02## Chef's notes This is my late partner's award winning Cajun rice & beans recipe. It's an updated take on the traditional Cajun comfort food. Chef Darin was a classically trained chef who spent 30+ years in the kitchen perfecting his recipes, and delivering authentic Cajun and Creole food to his patrons. This is a 5-star dish that will earn the respect of the most discerning Cajun afficionado. You won't be disappointed. I suggest making this recipe exactly as directed the first time, and then make whatever adjustments you want for future batches. Also, don't cheap out on the Andouille. No Johnsonville or Hillshire Farms. Chef Aidelle's is a good choice, as is Silva's from Whole Foods. They cost a few extra bucks, but it's absolutely worth it. ## Details - ⏲️ Prep time: 30 min - 🍳 Cook time: 3 hours - 🍽️ Servings: 12 ## Ingredients - 16oz small red beans, dry - 2 cups long grain white rice - 14-16oz andouille sausage, sliced - 8oz ham, cubed - 1 large yellow onion, chopped - 1 green bell pepper, chopped - 2-3 stalks celery, chopped - 2 tbsp garlic (12 cloves), minced - 7 cups water - ¼ cup olive oil - 2 large bay leaves - 1 tbsp parsley, dried - 1 tsp thyme, dried - 1 tsp Cajun seasoning - ½ tsp cayenne pepper, dried - ¼ tsp sage, rubbed - 1½ tsp salt (more or less to taste) ## Directions 1. Soak beans in a large pot of water overnight. 2. Heat oil in a large stockpot over medium heat. Cook onion, bell pepper, celery, garlic in olive oil for 3 to 4 minutes (until onion is translucent). 3. Add beans, bay leaves, parsley, thyme, salt, MSG, Cajun seasoning, cayenne pepper, Sage, and water. Stir, bring to a boil, and then reduce heat to medium-low (btwn 2-3). Cover and simmer for 2½ hours. 4. Remove bay leaves. Mash some of the beans. Stir Andouille and ham into beans, and simmer uncovered for an additional 30 minutes. 5. Meanwhile, prepare the rice. Bring water and rice to a boil in a saucepan. Reduce heat, cover, and simmer for 20 minutes. 6. Serve beans over steamed white rice.
@ 65912a7a:5dc638bf
2024-12-08 05:33:02## Chef's notes This is my late partner's award winning Cajun rice & beans recipe. It's an updated take on the traditional Cajun comfort food. Chef Darin was a classically trained chef who spent 30+ years in the kitchen perfecting his recipes, and delivering authentic Cajun and Creole food to his patrons. This is a 5-star dish that will earn the respect of the most discerning Cajun afficionado. You won't be disappointed. I suggest making this recipe exactly as directed the first time, and then make whatever adjustments you want for future batches. Also, don't cheap out on the Andouille. No Johnsonville or Hillshire Farms. Chef Aidelle's is a good choice, as is Silva's from Whole Foods. They cost a few extra bucks, but it's absolutely worth it. ## Details - ⏲️ Prep time: 30 min - 🍳 Cook time: 3 hours - 🍽️ Servings: 12 ## Ingredients - 16oz small red beans, dry - 2 cups long grain white rice - 14-16oz andouille sausage, sliced - 8oz ham, cubed - 1 large yellow onion, chopped - 1 green bell pepper, chopped - 2-3 stalks celery, chopped - 2 tbsp garlic (12 cloves), minced - 7 cups water - ¼ cup olive oil - 2 large bay leaves - 1 tbsp parsley, dried - 1 tsp thyme, dried - 1 tsp Cajun seasoning - ½ tsp cayenne pepper, dried - ¼ tsp sage, rubbed - 1½ tsp salt (more or less to taste) ## Directions 1. Soak beans in a large pot of water overnight. 2. Heat oil in a large stockpot over medium heat. Cook onion, bell pepper, celery, garlic in olive oil for 3 to 4 minutes (until onion is translucent). 3. Add beans, bay leaves, parsley, thyme, salt, MSG, Cajun seasoning, cayenne pepper, Sage, and water. Stir, bring to a boil, and then reduce heat to medium-low (btwn 2-3). Cover and simmer for 2½ hours. 4. Remove bay leaves. Mash some of the beans. Stir Andouille and ham into beans, and simmer uncovered for an additional 30 minutes. 5. Meanwhile, prepare the rice. Bring water and rice to a boil in a saucepan. Reduce heat, cover, and simmer for 20 minutes. 6. Serve beans over steamed white rice. @ e6817453:b0ac3c39
2024-12-07 15:06:43I started a long series of articles about how to model different types of knowledge graphs in the relational model, which makes on-device memory models for AI agents possible. We model-directed graphs Also, graphs of entities We even model hypergraphs Last time, we discussed why classical triple and simple knowledge graphs are insufficient for AI agents and complex memory, especially in the domain of time-aware or multi-model knowledge. So why do we need metagraphs, and what kind of challenge could they help us to solve? - complex and nested event and temporal context and temporal relations as edges - multi-mode and multilingual knowledge - human-like memory for AI agents that has multiple contexts and relations between knowledge in neuron-like networks ## MetaGraphs A meta graph is a concept that extends the idea of a graph by allowing edges to become graphs. Meta Edges connect a set of nodes, which could also be subgraphs. So, at some level, node and edge are pretty similar in properties but act in different roles in a different context. Also, in some cases, edges could be referenced as nodes. This approach enables the representation of more complex relationships and hierarchies than a traditional graph structure allows. Let’s break down each term to understand better metagraphs and how they differ from hypergraphs and graphs. ## Graph Basics - A standard **graph** has a set of **nodes** (or vertices) and **edges** (connections between nodes). - Edges are generally simple and typically represent a binary relationship between two nodes. - For instance, an edge in a social network graph might indicate a “friend” relationship between two people (nodes). ## Hypergraph - A **hypergraph** extends the concept of an edge by allowing it to connect any number of nodes, not just two. - Each connection, called a **hyperedge**, can link multiple nodes. - This feature allows hypergraphs to model more complex relationships involving multiple entities simultaneously. For example, a hyperedge in a hypergraph could represent a project team, connecting all team members in a single relation. - Despite its flexibility, a hypergraph doesn’t capture hierarchical or nested structures; it only generalizes the number of connections in an edge. ## Metagraph - A **metagraph** allows the edges to be graphs themselves. This means each edge can contain its own nodes and edges, creating nested, hierarchical structures. - In a meta graph, an edge could represent a relationship defined by a graph. For instance, a meta graph could represent a network of organizations where each organization’s structure (departments and connections) is represented by its own internal graph and treated as an edge in the larger meta graph. - This recursive structure allows metagraphs to model complex data with multiple layers of abstraction. They can capture multi-node relationships (as in hypergraphs) and detailed, structured information about each relationship. ## Named Graphs and Graph of Graphs As you can notice, the structure of a metagraph is quite complex and could be complex to model in relational and classical RDF setups. It could create a challenge of luck of tools and software solutions for your problem. If you need to model nested graphs, you could use a much simpler model of Named graphs, which could take you quite far.  The concept of the named graph came from the RDF community, which needed to group some sets of triples. In this way, you form subgraphs inside an existing graph. You could refer to the subgraph as a regular node. This setup simplifies complex graphs, introduces hierarchies, and even adds features and properties of hypergraphs while keeping a directed nature. It looks complex, but it is not so hard to model it with a slight modification of a directed graph. So, the node could host graphs inside. Let's reflect this fact with a location for a node. If a node belongs to a main graph, we could set the location to null or introduce a main node . it is up to you  Nodes could have edges to nodes in different subgraphs. This structure allows any kind of nesting graphs. Edges stay location-free ## Meta Graphs in Relational Model Let’s try to make several attempts to model different meta-graphs with some constraints. ## Directed Metagraph where edges are not used as nodes and could not contain subgraphs  In this case, the edge always points to two sets of nodes. This introduces an overhead of creating a node set for a single node. In this model, we can model empty node sets that could require application-level constraints to prevent such cases. ## Directed Metagraph where edges are not used as nodes and could contain subgraphs  Adding a node set that could model a subgraph located in an edge is easy but could be separate from in-vertex or out-vert. I also do not see a direct need to include subgraphs to a node, as we could just use a node set interchangeably, but it still could be a case. ## Directed Metagraph where edges are used as nodes and could contain subgraphs As you can notice, we operate all the time with node sets. We could simply allow the extension node set to elements set that include node and edge IDs, but in this case, we need to use uuid or any other strategy to differentiate node IDs from edge IDs. In this case, we have a collision of ephemeral edges or ephemeral nodes when we want to change the role and purpose of the node as an edge or vice versa.  A full-scale metagraph model is way too complex for a relational database. So we need a better model. Now, we have more flexibility but loose structural constraints. We cannot show that the element should have one vertex, one vertex, or both. This type of constraint has been moved to the application level. Also, the crucial question is about query and retrieval needs. Any meta-graph model should be more focused on domain and needs and should be used in raw form. We did it for a pure theoretical purpose.
@ e6817453:b0ac3c39
2024-12-07 15:06:43I started a long series of articles about how to model different types of knowledge graphs in the relational model, which makes on-device memory models for AI agents possible. We model-directed graphs Also, graphs of entities We even model hypergraphs Last time, we discussed why classical triple and simple knowledge graphs are insufficient for AI agents and complex memory, especially in the domain of time-aware or multi-model knowledge. So why do we need metagraphs, and what kind of challenge could they help us to solve? - complex and nested event and temporal context and temporal relations as edges - multi-mode and multilingual knowledge - human-like memory for AI agents that has multiple contexts and relations between knowledge in neuron-like networks ## MetaGraphs A meta graph is a concept that extends the idea of a graph by allowing edges to become graphs. Meta Edges connect a set of nodes, which could also be subgraphs. So, at some level, node and edge are pretty similar in properties but act in different roles in a different context. Also, in some cases, edges could be referenced as nodes. This approach enables the representation of more complex relationships and hierarchies than a traditional graph structure allows. Let’s break down each term to understand better metagraphs and how they differ from hypergraphs and graphs. ## Graph Basics - A standard **graph** has a set of **nodes** (or vertices) and **edges** (connections between nodes). - Edges are generally simple and typically represent a binary relationship between two nodes. - For instance, an edge in a social network graph might indicate a “friend” relationship between two people (nodes). ## Hypergraph - A **hypergraph** extends the concept of an edge by allowing it to connect any number of nodes, not just two. - Each connection, called a **hyperedge**, can link multiple nodes. - This feature allows hypergraphs to model more complex relationships involving multiple entities simultaneously. For example, a hyperedge in a hypergraph could represent a project team, connecting all team members in a single relation. - Despite its flexibility, a hypergraph doesn’t capture hierarchical or nested structures; it only generalizes the number of connections in an edge. ## Metagraph - A **metagraph** allows the edges to be graphs themselves. This means each edge can contain its own nodes and edges, creating nested, hierarchical structures. - In a meta graph, an edge could represent a relationship defined by a graph. For instance, a meta graph could represent a network of organizations where each organization’s structure (departments and connections) is represented by its own internal graph and treated as an edge in the larger meta graph. - This recursive structure allows metagraphs to model complex data with multiple layers of abstraction. They can capture multi-node relationships (as in hypergraphs) and detailed, structured information about each relationship. ## Named Graphs and Graph of Graphs As you can notice, the structure of a metagraph is quite complex and could be complex to model in relational and classical RDF setups. It could create a challenge of luck of tools and software solutions for your problem. If you need to model nested graphs, you could use a much simpler model of Named graphs, which could take you quite far.  The concept of the named graph came from the RDF community, which needed to group some sets of triples. In this way, you form subgraphs inside an existing graph. You could refer to the subgraph as a regular node. This setup simplifies complex graphs, introduces hierarchies, and even adds features and properties of hypergraphs while keeping a directed nature. It looks complex, but it is not so hard to model it with a slight modification of a directed graph. So, the node could host graphs inside. Let's reflect this fact with a location for a node. If a node belongs to a main graph, we could set the location to null or introduce a main node . it is up to you  Nodes could have edges to nodes in different subgraphs. This structure allows any kind of nesting graphs. Edges stay location-free ## Meta Graphs in Relational Model Let’s try to make several attempts to model different meta-graphs with some constraints. ## Directed Metagraph where edges are not used as nodes and could not contain subgraphs  In this case, the edge always points to two sets of nodes. This introduces an overhead of creating a node set for a single node. In this model, we can model empty node sets that could require application-level constraints to prevent such cases. ## Directed Metagraph where edges are not used as nodes and could contain subgraphs  Adding a node set that could model a subgraph located in an edge is easy but could be separate from in-vertex or out-vert. I also do not see a direct need to include subgraphs to a node, as we could just use a node set interchangeably, but it still could be a case. ## Directed Metagraph where edges are used as nodes and could contain subgraphs As you can notice, we operate all the time with node sets. We could simply allow the extension node set to elements set that include node and edge IDs, but in this case, we need to use uuid or any other strategy to differentiate node IDs from edge IDs. In this case, we have a collision of ephemeral edges or ephemeral nodes when we want to change the role and purpose of the node as an edge or vice versa.  A full-scale metagraph model is way too complex for a relational database. So we need a better model. Now, we have more flexibility but loose structural constraints. We cannot show that the element should have one vertex, one vertex, or both. This type of constraint has been moved to the application level. Also, the crucial question is about query and retrieval needs. Any meta-graph model should be more focused on domain and needs and should be used in raw form. We did it for a pure theoretical purpose. @ e6817453:b0ac3c39
2024-12-07 15:03:06Hey folks! Today, let’s dive into the intriguing world of neurosymbolic approaches, retrieval-augmented generation (RAG), and personal knowledge graphs (PKGs). Together, these concepts hold much potential for bringing true reasoning capabilities to large language models (LLMs). So, let’s break down how symbolic logic, knowledge graphs, and modern AI can come together to empower future AI systems to reason like humans. ## The Neurosymbolic Approach: What It Means ? Neurosymbolic AI combines two historically separate streams of artificial intelligence: symbolic reasoning and neural networks. Symbolic AI uses formal logic to process knowledge, similar to how we might solve problems or deduce information. On the other hand, neural networks, like those underlying GPT-4, focus on learning patterns from vast amounts of data — they are probabilistic statistical models that excel in generating human-like language and recognizing patterns but often lack deep, explicit reasoning. While GPT-4 can produce impressive text, it’s still not very effective at reasoning in a truly logical way. Its foundation, transformers, allows it to excel in pattern recognition, but the models struggle with reasoning because, at their core, they rely on statistical probabilities rather than true symbolic logic. This is where neurosymbolic methods and knowledge graphs come in. ## Symbolic Calculations and the Early Vision of AI If we take a step back to the 1950s, the vision for artificial intelligence was very different. Early AI research was all about symbolic reasoning — where computers could perform logical calculations to derive new knowledge from a given set of rules and facts. Languages like **Lisp** emerged to support this vision, enabling programs to represent data and code as interchangeable symbols. Lisp was designed to be homoiconic, meaning it treated code as manipulatable data, making it capable of self-modification — a huge leap towards AI systems that could, in theory, understand and modify their own operations. ## Lisp: The Earlier AI-Language **Lisp**, short for “LISt Processor,” was developed by John McCarthy in 1958, and it became the cornerstone of early AI research. Lisp’s power lay in its flexibility and its use of symbolic expressions, which allowed developers to create programs that could manipulate symbols in ways that were very close to human reasoning. One of the most groundbreaking features of Lisp was its ability to treat code as data, known as homoiconicity, which meant that Lisp programs could introspect and transform themselves dynamically. This ability to adapt and modify its own structure gave Lisp an edge in tasks that required a form of self-awareness, which was key in the early days of AI when researchers were exploring what it meant for machines to “think.” Lisp was not just a programming language—it represented the vision for artificial intelligence, where machines could evolve their understanding and rewrite their own programming. This idea formed the conceptual basis for many of the self-modifying and adaptive algorithms that are still explored today in AI research. Despite its decline in mainstream programming, Lisp’s influence can still be seen in the concepts used in modern machine learning and symbolic AI approaches. ## Prolog: Formal Logic and Deductive Reasoning In the 1970s, **Prolog** was developed—a language focused on formal logic and deductive reasoning. Unlike Lisp, based on lambda calculus, Prolog operates on formal logic rules, allowing it to perform deductive reasoning and solve logical puzzles. This made Prolog an ideal candidate for expert systems that needed to follow a sequence of logical steps, such as medical diagnostics or strategic planning. Prolog, like Lisp, allowed symbols to be represented, understood, and used in calculations, creating another homoiconic language that allows reasoning. Prolog’s strength lies in its rule-based structure, which is well-suited for tasks that require logical inference and backtracking. These features made it a powerful tool for expert systems and AI research in the 1970s and 1980s. The language is declarative in nature, meaning that you define the problem, and Prolog figures out **how** to solve it. By using formal logic and setting constraints, Prolog systems can derive conclusions from known facts, making it highly effective in fields requiring explicit logical frameworks, such as legal reasoning, diagnostics, and natural language understanding. These symbolic approaches were later overshadowed during the AI winter — but the ideas never really disappeared. They just evolved. ## Solvers and Their Role in Complementing LLMs One of the most powerful features of **Prolog** and similar logic-based systems is their use of **solvers**. Solvers are mechanisms that can take a set of rules and constraints and automatically find solutions that satisfy these conditions. This capability is incredibly useful when combined with LLMs, which excel at generating human-like language but need help with logical consistency and structured reasoning. For instance, imagine a scenario where an LLM needs to answer a question involving multiple logical steps or a complex query that requires deducing facts from various pieces of information. In this case, a **solver** can derive valid conclusions based on a given set of logical rules, providing structured answers that the LLM can then articulate in natural language. This allows the LLM to retrieve information and ensure the logical integrity of its responses, leading to much more robust answers. Solvers are also ideal for handling **constraint satisfaction problems** — situations where multiple conditions must be met simultaneously. In practical applications, this could include scheduling tasks, generating optimal recommendations, or even diagnosing issues where a set of symptoms must match possible diagnoses. Prolog’s solver capabilities and LLM’s natural language processing power can make these systems highly effective at providing intelligent, rule-compliant responses that traditional LLMs would struggle to produce alone. By integrating **neurosymbolic methods** that utilize solvers, we can provide LLMs with a form of deductive reasoning that is missing from pure deep-learning approaches. This combination has the potential to significantly improve the quality of outputs for use-cases that require explicit, structured problem-solving, from legal queries to scientific research and beyond. Solvers give LLMs the backbone they need to not just generate answers but to do so in a way that respects logical rigor and complex constraints. ## Graph of Rules for Enhanced Reasoning Another powerful concept that complements LLMs is using a **graph of rules**. A graph of rules is essentially a structured collection of logical rules that interconnect in a network-like structure, defining how various entities and their relationships interact. This structured network allows for complex reasoning and information retrieval, as well as the ability to model intricate relationships between different pieces of knowledge. In a **graph of rules**, each node represents a rule, and the edges define relationships between those rules — such as dependencies or causal links. This structure can be used to enhance LLM capabilities by providing them with a formal set of rules and relationships to follow, which improves logical consistency and reasoning depth. When an LLM encounters a problem or a question that requires multiple logical steps, it can traverse this graph of rules to generate an answer that is not only linguistically fluent but also logically robust. For example, in a healthcare application, a graph of rules might include nodes for medical symptoms, possible diagnoses, and recommended treatments. When an LLM receives a query regarding a patient’s symptoms, it can use the graph to traverse from symptoms to potential diagnoses and then to treatment options, ensuring that the response is coherent and medically sound. The graph of rules guides reasoning, enabling LLMs to handle complex, multi-step questions that involve chains of reasoning, rather than merely generating surface-level responses. Graphs of rules also enable **modular reasoning**, where different sets of rules can be activated based on the context or the type of question being asked. This modularity is crucial for creating adaptive AI systems that can apply specific sets of logical frameworks to distinct problem domains, thereby greatly enhancing their versatility. The combination of **neural fluency** with **rule-based structure** gives LLMs the ability to conduct more advanced reasoning, ultimately making them more reliable and effective in domains where accuracy and logical consistency are critical. By implementing a graph of rules, LLMs are empowered to perform **deductive reasoning** alongside their generative capabilities, creating responses that are not only compelling but also logically aligned with the structured knowledge available in the system. This further enhances their potential applications in fields such as law, engineering, finance, and scientific research — domains where logical consistency is as important as linguistic coherence. ## Enhancing LLMs with Symbolic Reasoning Now, with LLMs like GPT-4 being mainstream, there is an emerging need to add real reasoning capabilities to them. This is where **neurosymbolic approaches** shine. Instead of pitting neural networks against symbolic reasoning, these methods combine the best of both worlds. The neural aspect provides language fluency and recognition of complex patterns, while the symbolic side offers real reasoning power through formal logic and rule-based frameworks. **Personal Knowledge Graphs (PKGs)** come into play here as well. Knowledge graphs are data structures that encode entities and their relationships — they’re essentially semantic networks that allow for structured information retrieval. When integrated with neurosymbolic approaches, LLMs can use these graphs to answer questions in a far more contextual and precise way. By retrieving relevant information from a knowledge graph, they can ground their responses in well-defined relationships, thus improving both the relevance and the logical consistency of their answers. Imagine combining an LLM with a **graph of rules** that allow it to reason through the relationships encoded in a personal knowledge graph. This could involve using **deductive databases** to form a sophisticated way to represent and reason with symbolic data — essentially constructing a powerful hybrid system that uses LLM capabilities for language fluency and rule-based logic for structured problem-solving. ## My Research on Deductive Databases and Knowledge Graphs I recently did some research on modeling **knowledge graphs using deductive databases**, such as DataLog — which can be thought of as a limited, data-oriented version of Prolog. What I’ve found is that it’s possible to use formal logic to model knowledge graphs, ontologies, and complex relationships elegantly as rules in a deductive system. Unlike classical RDF or traditional ontology-based models, which sometimes struggle with complex or evolving relationships, a deductive approach is more flexible and can easily support dynamic rules and reasoning. **Prolog** and similar logic-driven frameworks can complement LLMs by handling the parts of reasoning where explicit rule-following is required. LLMs can benefit from these rule-based systems for tasks like entity recognition, logical inferences, and constructing or traversing knowledge graphs. We can even create a **graph of rules** that governs how relationships are formed or how logical deductions can be performed. The future is really about creating an AI that is capable of both deep contextual understanding (using the powerful generative capacity of LLMs) and true reasoning (through symbolic systems and knowledge graphs). With the neurosymbolic approach, these AIs could be equipped not just to generate information but to explain their reasoning, form logical conclusions, and even improve their own understanding over time — getting us a step closer to true artificial general intelligence. ## Why It Matters for LLM Employment Using **neurosymbolic RAG (retrieval-augmented generation)** in conjunction with personal knowledge graphs could revolutionize how LLMs work in real-world applications. Imagine an LLM that understands not just language but also the relationships between different concepts — one that can navigate, reason, and explain complex knowledge domains by actively engaging with a personalized set of facts and rules. This could lead to practical applications in areas like healthcare, finance, legal reasoning, or even personal productivity — where LLMs can help users solve complex problems logically, providing relevant information and well-justified reasoning paths. The combination of **neural fluency** with **symbolic accuracy and deductive power** is precisely the bridge we need to move beyond purely predictive AI to truly intelligent systems. Let's explore these ideas further if you’re as fascinated by this as I am. Feel free to reach out, follow my YouTube channel, or check out some articles I’ll link below. And if you’re working on anything in this field, I’d love to collaborate! Until next time, folks. Stay curious, and keep pushing the boundaries of AI!
@ e6817453:b0ac3c39
2024-12-07 15:03:06Hey folks! Today, let’s dive into the intriguing world of neurosymbolic approaches, retrieval-augmented generation (RAG), and personal knowledge graphs (PKGs). Together, these concepts hold much potential for bringing true reasoning capabilities to large language models (LLMs). So, let’s break down how symbolic logic, knowledge graphs, and modern AI can come together to empower future AI systems to reason like humans. ## The Neurosymbolic Approach: What It Means ? Neurosymbolic AI combines two historically separate streams of artificial intelligence: symbolic reasoning and neural networks. Symbolic AI uses formal logic to process knowledge, similar to how we might solve problems or deduce information. On the other hand, neural networks, like those underlying GPT-4, focus on learning patterns from vast amounts of data — they are probabilistic statistical models that excel in generating human-like language and recognizing patterns but often lack deep, explicit reasoning. While GPT-4 can produce impressive text, it’s still not very effective at reasoning in a truly logical way. Its foundation, transformers, allows it to excel in pattern recognition, but the models struggle with reasoning because, at their core, they rely on statistical probabilities rather than true symbolic logic. This is where neurosymbolic methods and knowledge graphs come in. ## Symbolic Calculations and the Early Vision of AI If we take a step back to the 1950s, the vision for artificial intelligence was very different. Early AI research was all about symbolic reasoning — where computers could perform logical calculations to derive new knowledge from a given set of rules and facts. Languages like **Lisp** emerged to support this vision, enabling programs to represent data and code as interchangeable symbols. Lisp was designed to be homoiconic, meaning it treated code as manipulatable data, making it capable of self-modification — a huge leap towards AI systems that could, in theory, understand and modify their own operations. ## Lisp: The Earlier AI-Language **Lisp**, short for “LISt Processor,” was developed by John McCarthy in 1958, and it became the cornerstone of early AI research. Lisp’s power lay in its flexibility and its use of symbolic expressions, which allowed developers to create programs that could manipulate symbols in ways that were very close to human reasoning. One of the most groundbreaking features of Lisp was its ability to treat code as data, known as homoiconicity, which meant that Lisp programs could introspect and transform themselves dynamically. This ability to adapt and modify its own structure gave Lisp an edge in tasks that required a form of self-awareness, which was key in the early days of AI when researchers were exploring what it meant for machines to “think.” Lisp was not just a programming language—it represented the vision for artificial intelligence, where machines could evolve their understanding and rewrite their own programming. This idea formed the conceptual basis for many of the self-modifying and adaptive algorithms that are still explored today in AI research. Despite its decline in mainstream programming, Lisp’s influence can still be seen in the concepts used in modern machine learning and symbolic AI approaches. ## Prolog: Formal Logic and Deductive Reasoning In the 1970s, **Prolog** was developed—a language focused on formal logic and deductive reasoning. Unlike Lisp, based on lambda calculus, Prolog operates on formal logic rules, allowing it to perform deductive reasoning and solve logical puzzles. This made Prolog an ideal candidate for expert systems that needed to follow a sequence of logical steps, such as medical diagnostics or strategic planning. Prolog, like Lisp, allowed symbols to be represented, understood, and used in calculations, creating another homoiconic language that allows reasoning. Prolog’s strength lies in its rule-based structure, which is well-suited for tasks that require logical inference and backtracking. These features made it a powerful tool for expert systems and AI research in the 1970s and 1980s. The language is declarative in nature, meaning that you define the problem, and Prolog figures out **how** to solve it. By using formal logic and setting constraints, Prolog systems can derive conclusions from known facts, making it highly effective in fields requiring explicit logical frameworks, such as legal reasoning, diagnostics, and natural language understanding. These symbolic approaches were later overshadowed during the AI winter — but the ideas never really disappeared. They just evolved. ## Solvers and Their Role in Complementing LLMs One of the most powerful features of **Prolog** and similar logic-based systems is their use of **solvers**. Solvers are mechanisms that can take a set of rules and constraints and automatically find solutions that satisfy these conditions. This capability is incredibly useful when combined with LLMs, which excel at generating human-like language but need help with logical consistency and structured reasoning. For instance, imagine a scenario where an LLM needs to answer a question involving multiple logical steps or a complex query that requires deducing facts from various pieces of information. In this case, a **solver** can derive valid conclusions based on a given set of logical rules, providing structured answers that the LLM can then articulate in natural language. This allows the LLM to retrieve information and ensure the logical integrity of its responses, leading to much more robust answers. Solvers are also ideal for handling **constraint satisfaction problems** — situations where multiple conditions must be met simultaneously. In practical applications, this could include scheduling tasks, generating optimal recommendations, or even diagnosing issues where a set of symptoms must match possible diagnoses. Prolog’s solver capabilities and LLM’s natural language processing power can make these systems highly effective at providing intelligent, rule-compliant responses that traditional LLMs would struggle to produce alone. By integrating **neurosymbolic methods** that utilize solvers, we can provide LLMs with a form of deductive reasoning that is missing from pure deep-learning approaches. This combination has the potential to significantly improve the quality of outputs for use-cases that require explicit, structured problem-solving, from legal queries to scientific research and beyond. Solvers give LLMs the backbone they need to not just generate answers but to do so in a way that respects logical rigor and complex constraints. ## Graph of Rules for Enhanced Reasoning Another powerful concept that complements LLMs is using a **graph of rules**. A graph of rules is essentially a structured collection of logical rules that interconnect in a network-like structure, defining how various entities and their relationships interact. This structured network allows for complex reasoning and information retrieval, as well as the ability to model intricate relationships between different pieces of knowledge. In a **graph of rules**, each node represents a rule, and the edges define relationships between those rules — such as dependencies or causal links. This structure can be used to enhance LLM capabilities by providing them with a formal set of rules and relationships to follow, which improves logical consistency and reasoning depth. When an LLM encounters a problem or a question that requires multiple logical steps, it can traverse this graph of rules to generate an answer that is not only linguistically fluent but also logically robust. For example, in a healthcare application, a graph of rules might include nodes for medical symptoms, possible diagnoses, and recommended treatments. When an LLM receives a query regarding a patient’s symptoms, it can use the graph to traverse from symptoms to potential diagnoses and then to treatment options, ensuring that the response is coherent and medically sound. The graph of rules guides reasoning, enabling LLMs to handle complex, multi-step questions that involve chains of reasoning, rather than merely generating surface-level responses. Graphs of rules also enable **modular reasoning**, where different sets of rules can be activated based on the context or the type of question being asked. This modularity is crucial for creating adaptive AI systems that can apply specific sets of logical frameworks to distinct problem domains, thereby greatly enhancing their versatility. The combination of **neural fluency** with **rule-based structure** gives LLMs the ability to conduct more advanced reasoning, ultimately making them more reliable and effective in domains where accuracy and logical consistency are critical. By implementing a graph of rules, LLMs are empowered to perform **deductive reasoning** alongside their generative capabilities, creating responses that are not only compelling but also logically aligned with the structured knowledge available in the system. This further enhances their potential applications in fields such as law, engineering, finance, and scientific research — domains where logical consistency is as important as linguistic coherence. ## Enhancing LLMs with Symbolic Reasoning Now, with LLMs like GPT-4 being mainstream, there is an emerging need to add real reasoning capabilities to them. This is where **neurosymbolic approaches** shine. Instead of pitting neural networks against symbolic reasoning, these methods combine the best of both worlds. The neural aspect provides language fluency and recognition of complex patterns, while the symbolic side offers real reasoning power through formal logic and rule-based frameworks. **Personal Knowledge Graphs (PKGs)** come into play here as well. Knowledge graphs are data structures that encode entities and their relationships — they’re essentially semantic networks that allow for structured information retrieval. When integrated with neurosymbolic approaches, LLMs can use these graphs to answer questions in a far more contextual and precise way. By retrieving relevant information from a knowledge graph, they can ground their responses in well-defined relationships, thus improving both the relevance and the logical consistency of their answers. Imagine combining an LLM with a **graph of rules** that allow it to reason through the relationships encoded in a personal knowledge graph. This could involve using **deductive databases** to form a sophisticated way to represent and reason with symbolic data — essentially constructing a powerful hybrid system that uses LLM capabilities for language fluency and rule-based logic for structured problem-solving. ## My Research on Deductive Databases and Knowledge Graphs I recently did some research on modeling **knowledge graphs using deductive databases**, such as DataLog — which can be thought of as a limited, data-oriented version of Prolog. What I’ve found is that it’s possible to use formal logic to model knowledge graphs, ontologies, and complex relationships elegantly as rules in a deductive system. Unlike classical RDF or traditional ontology-based models, which sometimes struggle with complex or evolving relationships, a deductive approach is more flexible and can easily support dynamic rules and reasoning. **Prolog** and similar logic-driven frameworks can complement LLMs by handling the parts of reasoning where explicit rule-following is required. LLMs can benefit from these rule-based systems for tasks like entity recognition, logical inferences, and constructing or traversing knowledge graphs. We can even create a **graph of rules** that governs how relationships are formed or how logical deductions can be performed. The future is really about creating an AI that is capable of both deep contextual understanding (using the powerful generative capacity of LLMs) and true reasoning (through symbolic systems and knowledge graphs). With the neurosymbolic approach, these AIs could be equipped not just to generate information but to explain their reasoning, form logical conclusions, and even improve their own understanding over time — getting us a step closer to true artificial general intelligence. ## Why It Matters for LLM Employment Using **neurosymbolic RAG (retrieval-augmented generation)** in conjunction with personal knowledge graphs could revolutionize how LLMs work in real-world applications. Imagine an LLM that understands not just language but also the relationships between different concepts — one that can navigate, reason, and explain complex knowledge domains by actively engaging with a personalized set of facts and rules. This could lead to practical applications in areas like healthcare, finance, legal reasoning, or even personal productivity — where LLMs can help users solve complex problems logically, providing relevant information and well-justified reasoning paths. The combination of **neural fluency** with **symbolic accuracy and deductive power** is precisely the bridge we need to move beyond purely predictive AI to truly intelligent systems. Let's explore these ideas further if you’re as fascinated by this as I am. Feel free to reach out, follow my YouTube channel, or check out some articles I’ll link below. And if you’re working on anything in this field, I’d love to collaborate! Until next time, folks. Stay curious, and keep pushing the boundaries of AI! @ e6817453:b0ac3c39
2024-12-07 14:54:46## Introduction: Personal Knowledge Graphs and Linked Data We will explore the world of personal knowledge graphs and discuss how they can be used to model complex information structures. Personal knowledge graphs aren’t just abstract collections of nodes and edges—they encode meaningful relationships, contextualizing data in ways that enrich our understanding of it. While the core structure might be a directed graph, we layer semantic meaning on top, enabling nuanced connections between data points. The origin of knowledge graphs is deeply tied to concepts from linked data and the semantic web, ideas that emerged to better link scattered pieces of information across the web. This approach created an infrastructure where data islands could connect — facilitating everything from more insightful AI to improved personal data management. In this article, we will explore how these ideas have evolved into tools for modeling AI’s semantic memory and look at how knowledge graphs can serve as a flexible foundation for encoding rich data contexts. We’ll specifically discuss three major paradigms: RDF (Resource Description Framework), property graphs, and a third way of modeling entities as graphs of graphs. Let’s get started. ## Intro to RDF The Resource Description Framework (RDF) has been one of the fundamental standards for linked data and knowledge graphs. RDF allows data to be modeled as triples: subject, predicate, and object. Essentially, you can think of it as a structured way to describe relationships: “X has a Y called Z.” For instance, “Berlin has a population of 3.5 million.” This modeling approach is quite flexible because RDF uses unique identifiers — usually URIs — to point to data entities, making linking straightforward and coherent. RDFS, or RDF Schema, extends RDF to provide a basic vocabulary to structure the data even more. This lets us describe not only individual nodes but also relationships among types of data entities, like defining a class hierarchy or setting properties. For example, you could say that “Berlin” is an instance of a “City” and that cities are types of “Geographical Entities.” This kind of organization helps establish semantic meaning within the graph. ## RDF and Advanced Topics ## Lists and Sets in RDF RDF also provides tools to model more complex data structures such as lists and sets, enabling the grouping of nodes. This extension makes it easier to model more natural, human-like knowledge, for example, describing attributes of an entity that may have multiple values. By adding RDF Schema and OWL (Web Ontology Language), you gain even more expressive power — being able to define logical rules or even derive new relationships from existing data. ## Graph of Graphs A significant feature of RDF is the ability to form complex nested structures, often referred to as graphs of graphs. This allows you to create “named graphs,” essentially subgraphs that can be independently referenced. For example, you could create a named graph for a particular dataset describing Berlin and another for a different geographical area. Then, you could connect them, allowing for more modular and reusable knowledge modeling. ## Property Graphs While RDF provides a robust framework, it’s not always the easiest to work with due to its heavy reliance on linking everything explicitly. This is where property graphs come into play. Property graphs are less focused on linking everything through triples and allow more expressive properties directly within nodes and edges. For example, instead of using triples to represent each detail, a property graph might let you store all properties about an entity (e.g., “Berlin”) directly in a single node. This makes property graphs more intuitive for many developers and engineers because they more closely resemble object-oriented structures: you have entities (nodes) that possess attributes (properties) and are connected to other entities through relationships (edges). The significant benefit here is a condensed representation, which speeds up traversal and queries in some scenarios. However, this also introduces a trade-off: while property graphs are more straightforward to query and maintain, they lack some complex relationship modeling features RDF offers, particularly when connecting properties to each other. ## Graph of Graphs and Subgraphs for Entity Modeling A third approach — which takes elements from RDF and property graphs — involves modeling entities using subgraphs or nested graphs. In this model, each entity can be represented as a graph. This allows for a detailed and flexible description of attributes without exploding every detail into individual triples or lump them all together into properties. For instance, consider a person entity with a complex employment history. Instead of representing every employment detail in one node (as in a property graph), or as several linked nodes (as in RDF), you can treat the employment history as a subgraph. This subgraph could then contain nodes for different jobs, each linked with specific properties and connections. This approach keeps the complexity where it belongs and provides better flexibility when new attributes or entities need to be added. ## Hypergraphs and Metagraphs When discussing more advanced forms of graphs, we encounter hypergraphs and metagraphs. These take the idea of relationships to a new level. A hypergraph allows an edge to connect more than two nodes, which is extremely useful when modeling scenarios where relationships aren’t just pairwise. For example, a “Project” could connect multiple “People,” “Resources,” and “Outcomes,” all in a single edge. This way, hypergraphs help in reducing the complexity of modeling high-order relationships. Metagraphs, on the other hand, enable nodes and edges to themselves be represented as graphs. This is an extremely powerful feature when we consider the needs of artificial intelligence, as it allows for the modeling of relationships between relationships, an essential aspect for any system that needs to capture not just facts, but their interdependencies and contexts. ## Balancing Structure and Properties One of the recurring challenges when modeling knowledge is finding the balance between structure and properties. With RDF, you get high flexibility and standardization, but complexity can quickly escalate as you decompose everything into triples. Property graphs simplify the representation by using attributes but lose out on the depth of connection modeling. Meanwhile, the graph-of-graphs approach and hypergraphs offer advanced modeling capabilities at the cost of increased computational complexity. So, how do you decide which model to use? It comes down to your use case. RDF and nested graphs are strong contenders if you need deep linkage and are working with highly variable data. For more straightforward, engineer-friendly modeling, property graphs shine. And when dealing with very complex multi-way relationships or meta-level knowledge, hypergraphs and metagraphs provide the necessary tools. The key takeaway is that only some approaches are perfect. Instead, it’s all about the modeling goals: how do you want to query the graph, what relationships are meaningful, and how much complexity are you willing to manage? ## Conclusion Modeling AI semantic memory using knowledge graphs is a challenging but rewarding process. The different approaches — RDF, property graphs, and advanced graph modeling techniques like nested graphs and hypergraphs — each offer unique strengths and weaknesses. Whether you are building a personal knowledge graph or scaling up to AI that integrates multiple streams of linked data, it’s essential to understand the trade-offs each approach brings. In the end, the choice of representation comes down to the nature of your data and your specific needs for querying and maintaining semantic relationships. The world of knowledge graphs is vast, with many tools and frameworks to explore. Stay connected and keep experimenting to find the balance that works for your projects.
@ e6817453:b0ac3c39
2024-12-07 14:54:46## Introduction: Personal Knowledge Graphs and Linked Data We will explore the world of personal knowledge graphs and discuss how they can be used to model complex information structures. Personal knowledge graphs aren’t just abstract collections of nodes and edges—they encode meaningful relationships, contextualizing data in ways that enrich our understanding of it. While the core structure might be a directed graph, we layer semantic meaning on top, enabling nuanced connections between data points. The origin of knowledge graphs is deeply tied to concepts from linked data and the semantic web, ideas that emerged to better link scattered pieces of information across the web. This approach created an infrastructure where data islands could connect — facilitating everything from more insightful AI to improved personal data management. In this article, we will explore how these ideas have evolved into tools for modeling AI’s semantic memory and look at how knowledge graphs can serve as a flexible foundation for encoding rich data contexts. We’ll specifically discuss three major paradigms: RDF (Resource Description Framework), property graphs, and a third way of modeling entities as graphs of graphs. Let’s get started. ## Intro to RDF The Resource Description Framework (RDF) has been one of the fundamental standards for linked data and knowledge graphs. RDF allows data to be modeled as triples: subject, predicate, and object. Essentially, you can think of it as a structured way to describe relationships: “X has a Y called Z.” For instance, “Berlin has a population of 3.5 million.” This modeling approach is quite flexible because RDF uses unique identifiers — usually URIs — to point to data entities, making linking straightforward and coherent. RDFS, or RDF Schema, extends RDF to provide a basic vocabulary to structure the data even more. This lets us describe not only individual nodes but also relationships among types of data entities, like defining a class hierarchy or setting properties. For example, you could say that “Berlin” is an instance of a “City” and that cities are types of “Geographical Entities.” This kind of organization helps establish semantic meaning within the graph. ## RDF and Advanced Topics ## Lists and Sets in RDF RDF also provides tools to model more complex data structures such as lists and sets, enabling the grouping of nodes. This extension makes it easier to model more natural, human-like knowledge, for example, describing attributes of an entity that may have multiple values. By adding RDF Schema and OWL (Web Ontology Language), you gain even more expressive power — being able to define logical rules or even derive new relationships from existing data. ## Graph of Graphs A significant feature of RDF is the ability to form complex nested structures, often referred to as graphs of graphs. This allows you to create “named graphs,” essentially subgraphs that can be independently referenced. For example, you could create a named graph for a particular dataset describing Berlin and another for a different geographical area. Then, you could connect them, allowing for more modular and reusable knowledge modeling. ## Property Graphs While RDF provides a robust framework, it’s not always the easiest to work with due to its heavy reliance on linking everything explicitly. This is where property graphs come into play. Property graphs are less focused on linking everything through triples and allow more expressive properties directly within nodes and edges. For example, instead of using triples to represent each detail, a property graph might let you store all properties about an entity (e.g., “Berlin”) directly in a single node. This makes property graphs more intuitive for many developers and engineers because they more closely resemble object-oriented structures: you have entities (nodes) that possess attributes (properties) and are connected to other entities through relationships (edges). The significant benefit here is a condensed representation, which speeds up traversal and queries in some scenarios. However, this also introduces a trade-off: while property graphs are more straightforward to query and maintain, they lack some complex relationship modeling features RDF offers, particularly when connecting properties to each other. ## Graph of Graphs and Subgraphs for Entity Modeling A third approach — which takes elements from RDF and property graphs — involves modeling entities using subgraphs or nested graphs. In this model, each entity can be represented as a graph. This allows for a detailed and flexible description of attributes without exploding every detail into individual triples or lump them all together into properties. For instance, consider a person entity with a complex employment history. Instead of representing every employment detail in one node (as in a property graph), or as several linked nodes (as in RDF), you can treat the employment history as a subgraph. This subgraph could then contain nodes for different jobs, each linked with specific properties and connections. This approach keeps the complexity where it belongs and provides better flexibility when new attributes or entities need to be added. ## Hypergraphs and Metagraphs When discussing more advanced forms of graphs, we encounter hypergraphs and metagraphs. These take the idea of relationships to a new level. A hypergraph allows an edge to connect more than two nodes, which is extremely useful when modeling scenarios where relationships aren’t just pairwise. For example, a “Project” could connect multiple “People,” “Resources,” and “Outcomes,” all in a single edge. This way, hypergraphs help in reducing the complexity of modeling high-order relationships. Metagraphs, on the other hand, enable nodes and edges to themselves be represented as graphs. This is an extremely powerful feature when we consider the needs of artificial intelligence, as it allows for the modeling of relationships between relationships, an essential aspect for any system that needs to capture not just facts, but their interdependencies and contexts. ## Balancing Structure and Properties One of the recurring challenges when modeling knowledge is finding the balance between structure and properties. With RDF, you get high flexibility and standardization, but complexity can quickly escalate as you decompose everything into triples. Property graphs simplify the representation by using attributes but lose out on the depth of connection modeling. Meanwhile, the graph-of-graphs approach and hypergraphs offer advanced modeling capabilities at the cost of increased computational complexity. So, how do you decide which model to use? It comes down to your use case. RDF and nested graphs are strong contenders if you need deep linkage and are working with highly variable data. For more straightforward, engineer-friendly modeling, property graphs shine. And when dealing with very complex multi-way relationships or meta-level knowledge, hypergraphs and metagraphs provide the necessary tools. The key takeaway is that only some approaches are perfect. Instead, it’s all about the modeling goals: how do you want to query the graph, what relationships are meaningful, and how much complexity are you willing to manage? ## Conclusion Modeling AI semantic memory using knowledge graphs is a challenging but rewarding process. The different approaches — RDF, property graphs, and advanced graph modeling techniques like nested graphs and hypergraphs — each offer unique strengths and weaknesses. Whether you are building a personal knowledge graph or scaling up to AI that integrates multiple streams of linked data, it’s essential to understand the trade-offs each approach brings. In the end, the choice of representation comes down to the nature of your data and your specific needs for querying and maintaining semantic relationships. The world of knowledge graphs is vast, with many tools and frameworks to explore. Stay connected and keep experimenting to find the balance that works for your projects. @ e6817453:b0ac3c39
2024-12-07 14:52:47The temporal semantics and **temporal and time-aware knowledge graphs. We have different memory models for artificial intelligence agents. We all try to mimic somehow how the brain works, or at least how the declarative memory of the brain works. We have the split of episodic memory** and **semantic memory**. And we also have a lot of theories, right? ## Declarative Memory of the Human Brain How is the semantic memory formed? We all know that our brain stores semantic memory quite close to the concept we have with the personal knowledge graphs, that it’s connected entities. They form a connection with each other and all those things. So far, so good. And actually, then we have a lot of concepts, how the episodic memory and our experiences gets transmitted to the semantic: - hippocampus indexing and retrieval - sanitization of episodic memories - episodic-semantic shift theory They all give a different perspective on how different parts of declarative memory cooperate. We know that episodic memories get semanticized over time. You have semantic knowledge without the notion of time, and probably, your episodic memory is just decayed. But, you know, it’s still an open question: > do we want to mimic an AI agent’s memory as a human brain memory, or do we want to create something different? It’s an open question to which we have no good answer. And if you go to the theory of neuroscience and check how episodic and semantic memory interfere, you will still find a lot of theories, yeah? Some of them say that you have the hippocampus that keeps the indexes of the memory. Some others will say that you semantic the episodic memory. Some others say that you have some separate process that digests the episodic and experience to the semantics. But all of them agree on the plan that it’s operationally two separate areas of memories and even two separate regions of brain, and the semantic, it’s more, let’s say, protected. So it’s harder to forget the semantical facts than the episodes and everything. And what I’m thinking about for a long time, it’s this, you know, the semantic memory. ## Temporal Semantics It’s memory about the facts, but you somehow mix the time information with the semantics. I already described a lot of things, including how we could combine time with knowledge graphs and how people do it. There are multiple ways we could persist such information, but we all hit the wall because the complexity of time and the semantics of time are highly complex concepts. ## Time in a Semantic context is not a timestamp. What I mean is that when you have a fact, and you just mentioned that I was there at this particular moment, like, I don’t know, 15:40 on Monday, it’s already awake because we don’t know which Monday, right? So you need to give the exact date, but usually, you do not have experiences like that. You do not record your memories like that, except you do the journaling and all of the things. So, usually, you have no direct time references. What I mean is that you could say that I was there and it was some event, blah, blah, blah. Somehow, we form a chain of events that connect with each other and maybe will be connected to some period of time if we are lucky enough. This means that we could not easily represent temporal-aware information as just a timestamp or validity and all of the things. For sure, the validity of the knowledge graphs (simple quintuple with start and end dates)is a big topic, and it could solve a lot of things. It could solve a lot of the time cases. It’s super simple because you give the end and start dates, and you are done, but it does not answer facts that have a relative time or time information in facts . It could solve many use cases but struggle with facts in an indirect temporal context. I like the simplicity of this idea. But the problem of this approach that in most cases, we simply don’t have these timestamps. We don’t have the timestamp where this information starts and ends. And it’s not modeling many events in our life, especially if you have the processes or ongoing activities or recurrent events. I’m more about thinking about the time of semantics, where you have a time model as a **hybrid clock** or some **global clock** that does the partial ordering of the events. It’s mean that you have the chain of the experiences and you have the chain of the facts that have the different time contexts. We could deduct the time from this chain of the events. But it’s a big, big topic for the research. But what I want to achieve, actually, it’s not separation on episodic and semantic memory. It’s having something in between. ## Blockchain of connected events and facts I call it temporal-aware semantics or time-aware knowledge graphs, where we could encode the semantic fact together with the time component.I doubt that time should be the simple timestamp or the region of the two timestamps. For me, it is more a chain for facts that have a partial order and form a blockchain like a database or a partially ordered Acyclic graph of facts that are temporally connected. We could have some notion of time that is understandable to the agent and a model that allows us to order the events and focus on what the agent knows and how to order this time knowledge and create the chains of the events. ## Time anchors We may have a particular time in the chain that allows us to arrange a more concrete time for the rest of the events. But it’s still an open topic for research. The temporal semantics gets split into a couple of domains. One domain is how to add time to the knowledge graphs. We already have many different solutions. I described them in my previous articles. Another domain is the agent's memory and how the memory of the artificial intelligence treats the time. This one, it’s much more complex. Because here, we could not operate with the simple timestamps. We need to have the representation of time that are understandable by model and understandable by the agent that will work with this model. And this one, it’s way bigger topic for the research.”
@ e6817453:b0ac3c39
2024-12-07 14:52:47The temporal semantics and **temporal and time-aware knowledge graphs. We have different memory models for artificial intelligence agents. We all try to mimic somehow how the brain works, or at least how the declarative memory of the brain works. We have the split of episodic memory** and **semantic memory**. And we also have a lot of theories, right? ## Declarative Memory of the Human Brain How is the semantic memory formed? We all know that our brain stores semantic memory quite close to the concept we have with the personal knowledge graphs, that it’s connected entities. They form a connection with each other and all those things. So far, so good. And actually, then we have a lot of concepts, how the episodic memory and our experiences gets transmitted to the semantic: - hippocampus indexing and retrieval - sanitization of episodic memories - episodic-semantic shift theory They all give a different perspective on how different parts of declarative memory cooperate. We know that episodic memories get semanticized over time. You have semantic knowledge without the notion of time, and probably, your episodic memory is just decayed. But, you know, it’s still an open question: > do we want to mimic an AI agent’s memory as a human brain memory, or do we want to create something different? It’s an open question to which we have no good answer. And if you go to the theory of neuroscience and check how episodic and semantic memory interfere, you will still find a lot of theories, yeah? Some of them say that you have the hippocampus that keeps the indexes of the memory. Some others will say that you semantic the episodic memory. Some others say that you have some separate process that digests the episodic and experience to the semantics. But all of them agree on the plan that it’s operationally two separate areas of memories and even two separate regions of brain, and the semantic, it’s more, let’s say, protected. So it’s harder to forget the semantical facts than the episodes and everything. And what I’m thinking about for a long time, it’s this, you know, the semantic memory. ## Temporal Semantics It’s memory about the facts, but you somehow mix the time information with the semantics. I already described a lot of things, including how we could combine time with knowledge graphs and how people do it. There are multiple ways we could persist such information, but we all hit the wall because the complexity of time and the semantics of time are highly complex concepts. ## Time in a Semantic context is not a timestamp. What I mean is that when you have a fact, and you just mentioned that I was there at this particular moment, like, I don’t know, 15:40 on Monday, it’s already awake because we don’t know which Monday, right? So you need to give the exact date, but usually, you do not have experiences like that. You do not record your memories like that, except you do the journaling and all of the things. So, usually, you have no direct time references. What I mean is that you could say that I was there and it was some event, blah, blah, blah. Somehow, we form a chain of events that connect with each other and maybe will be connected to some period of time if we are lucky enough. This means that we could not easily represent temporal-aware information as just a timestamp or validity and all of the things. For sure, the validity of the knowledge graphs (simple quintuple with start and end dates)is a big topic, and it could solve a lot of things. It could solve a lot of the time cases. It’s super simple because you give the end and start dates, and you are done, but it does not answer facts that have a relative time or time information in facts . It could solve many use cases but struggle with facts in an indirect temporal context. I like the simplicity of this idea. But the problem of this approach that in most cases, we simply don’t have these timestamps. We don’t have the timestamp where this information starts and ends. And it’s not modeling many events in our life, especially if you have the processes or ongoing activities or recurrent events. I’m more about thinking about the time of semantics, where you have a time model as a **hybrid clock** or some **global clock** that does the partial ordering of the events. It’s mean that you have the chain of the experiences and you have the chain of the facts that have the different time contexts. We could deduct the time from this chain of the events. But it’s a big, big topic for the research. But what I want to achieve, actually, it’s not separation on episodic and semantic memory. It’s having something in between. ## Blockchain of connected events and facts I call it temporal-aware semantics or time-aware knowledge graphs, where we could encode the semantic fact together with the time component.I doubt that time should be the simple timestamp or the region of the two timestamps. For me, it is more a chain for facts that have a partial order and form a blockchain like a database or a partially ordered Acyclic graph of facts that are temporally connected. We could have some notion of time that is understandable to the agent and a model that allows us to order the events and focus on what the agent knows and how to order this time knowledge and create the chains of the events. ## Time anchors We may have a particular time in the chain that allows us to arrange a more concrete time for the rest of the events. But it’s still an open topic for research. The temporal semantics gets split into a couple of domains. One domain is how to add time to the knowledge graphs. We already have many different solutions. I described them in my previous articles. Another domain is the agent's memory and how the memory of the artificial intelligence treats the time. This one, it’s much more complex. Because here, we could not operate with the simple timestamps. We need to have the representation of time that are understandable by model and understandable by the agent that will work with this model. And this one, it’s way bigger topic for the research.” @ 3b19f10a:4e1f94b4
2024-12-07 09:55:46Sometimes perspective is everything... #[artmodel]( https://bsky.app/hashtag/artmodel) #[nude]( https://bsky.app/hashtag/nude) #[nudemodel]( https://bsky.app/hashtag/nudemodel) ------   
@ 3b19f10a:4e1f94b4
2024-12-07 09:55:46Sometimes perspective is everything... #[artmodel]( https://bsky.app/hashtag/artmodel) #[nude]( https://bsky.app/hashtag/nude) #[nudemodel]( https://bsky.app/hashtag/nudemodel) ------    @ a95c6243:d345522c
2024-12-06 18:21:15*Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\ dass wir Vorteile aus ihr ziehen;\ in jedem andern hegt man den Wunsch,\ dass der Unschuldige in Schutz genommen werde.\ Jean-Jacques Rousseau* **Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen** – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden. **Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen»** den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen [schadet der Psyche](https://transition-news.org/meisterwerk-von-studie-bestatigt-maskentragen-bei-kindern-sinnlos-und-schadlich) und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben [Menschen getötet](https://transition-news.org/lockdowns-und-zensur-haben-menschen-getotet)». **Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft.** Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen [Erfahrungen als Kritikerin](https://transition-news.org/die-coronazeit-hat-mir-gezeigt-wie-die-menschen-manipuliert-werden-konnen) der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit *Transition News*. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften». **Menschen, die aufrichtig andere schützen wollten,** werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter [Heinrich Habig](https://transition-news.org/arzte-mussten-ihr-vergehen-irgendwann-selbst-einsehen), [Bianca Witzschel](https://transition-news.org/anwalt-von-bianca-witzschel-das-ist-eindeutig-eine-politische-justiz) und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat *Transition News* mehrfach berichtet (z.B. [hier](https://transition-news.org/prozess-gegen-walter-weber-kai-kisielinski-fuhrt-mit-argumentationsfeuerwerk) und [hier](https://transition-news.org/prozess-gegen-walter-weber-tschentscher-und-schaade-doch-nicht-vor-gericht)). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie [Alexander Bittner](https://transition-news.org/verweigerung-der-covid-impfung-inhaftierter-bundeswehrsoldat-kundigt) erfahren mussten. [**Die eigentlich Kriminellen**](https://transition-news.org/die-eigentlich-kriminellen-schutzen-sich-vor-der-verantwortung) **schützen sich derweil erfolgreich selber,** nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte [Verbrechen gegen die Menschheit](https://transition-news.org/das-grosste-verbrechen-gegen-die-menschheit)». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn [Hunter](https://transition-news.org/us-steuerbehorde-hat-prasidentschaftswahl-2020-fur-joe-biden-gestohlen) möglicherweise auch [Anthony Fauci begnadigen](https://transition-news.org/wird-biden-auch-fauci-begnadigen) wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte? **Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten** und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken. **Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers [Robert F. Kennedy Jr.](https://transition-news.org/usa-robert-f-kennedy-jr-als-gesundheitsminister-nominiert)** erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens [Călin Georgescu](https://transition-news.org/der-ausgang-der-rumanischen-prasidentschaftswahlen-konnte-mogliche), der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der [Panik im Wertewesten](https://www.euronews.com/2024/12/04/robert-f-kennedy-jr-denies-any-link-with-far-right-romanian-presidential-candidate). **In Rumänien selber gab es gerade einen Paukenschlag:** Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das [Tabu gebrochen](https://tkp.at/2024/12/06/rumaenien-sagt-praesidenten-wahl-ab/), Wahlen zu verbieten, bevor sie etwas ändern können. **Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen** und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: [Zensur](https://transition-news.org/fuhrende-politiker-der-welt-unterzeichnen-neue-zensurerklarung-bei-un)) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden. --- Dieser Beitrag ist zuerst auf [*Transition News*](https://transition-news.org/schutz-wem-schutz-gebuhrt) erschienen.
@ a95c6243:d345522c
2024-12-06 18:21:15*Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\ dass wir Vorteile aus ihr ziehen;\ in jedem andern hegt man den Wunsch,\ dass der Unschuldige in Schutz genommen werde.\ Jean-Jacques Rousseau* **Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen** – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden. **Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen»** den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen [schadet der Psyche](https://transition-news.org/meisterwerk-von-studie-bestatigt-maskentragen-bei-kindern-sinnlos-und-schadlich) und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben [Menschen getötet](https://transition-news.org/lockdowns-und-zensur-haben-menschen-getotet)». **Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft.** Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen [Erfahrungen als Kritikerin](https://transition-news.org/die-coronazeit-hat-mir-gezeigt-wie-die-menschen-manipuliert-werden-konnen) der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit *Transition News*. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften». **Menschen, die aufrichtig andere schützen wollten,** werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter [Heinrich Habig](https://transition-news.org/arzte-mussten-ihr-vergehen-irgendwann-selbst-einsehen), [Bianca Witzschel](https://transition-news.org/anwalt-von-bianca-witzschel-das-ist-eindeutig-eine-politische-justiz) und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat *Transition News* mehrfach berichtet (z.B. [hier](https://transition-news.org/prozess-gegen-walter-weber-kai-kisielinski-fuhrt-mit-argumentationsfeuerwerk) und [hier](https://transition-news.org/prozess-gegen-walter-weber-tschentscher-und-schaade-doch-nicht-vor-gericht)). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie [Alexander Bittner](https://transition-news.org/verweigerung-der-covid-impfung-inhaftierter-bundeswehrsoldat-kundigt) erfahren mussten. [**Die eigentlich Kriminellen**](https://transition-news.org/die-eigentlich-kriminellen-schutzen-sich-vor-der-verantwortung) **schützen sich derweil erfolgreich selber,** nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte [Verbrechen gegen die Menschheit](https://transition-news.org/das-grosste-verbrechen-gegen-die-menschheit)». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn [Hunter](https://transition-news.org/us-steuerbehorde-hat-prasidentschaftswahl-2020-fur-joe-biden-gestohlen) möglicherweise auch [Anthony Fauci begnadigen](https://transition-news.org/wird-biden-auch-fauci-begnadigen) wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte? **Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten** und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken. **Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers [Robert F. Kennedy Jr.](https://transition-news.org/usa-robert-f-kennedy-jr-als-gesundheitsminister-nominiert)** erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens [Călin Georgescu](https://transition-news.org/der-ausgang-der-rumanischen-prasidentschaftswahlen-konnte-mogliche), der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der [Panik im Wertewesten](https://www.euronews.com/2024/12/04/robert-f-kennedy-jr-denies-any-link-with-far-right-romanian-presidential-candidate). **In Rumänien selber gab es gerade einen Paukenschlag:** Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das [Tabu gebrochen](https://tkp.at/2024/12/06/rumaenien-sagt-praesidenten-wahl-ab/), Wahlen zu verbieten, bevor sie etwas ändern können. **Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen** und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: [Zensur](https://transition-news.org/fuhrende-politiker-der-welt-unterzeichnen-neue-zensurerklarung-bei-un)) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden. --- Dieser Beitrag ist zuerst auf [*Transition News*](https://transition-news.org/schutz-wem-schutz-gebuhrt) erschienen. @ 0d532801:197a0c30
2024-12-06 05:13:25[Mr. Robot]( https://www.piktobet.net/2015/10/mr-robot.html) Dünya tehlikeli bir yer. Kötülük yapanlar yüzünden değil, görüp de hiçbir şey yapmayanlar yüzünden. İnsanları okumada çok iyiyimdir. İçlerindeki en kötü şeyi ararım. Herkes çalar. Bu böyledir. İnsanlar tam anlamıyla hak ettiklerini mi kazanıyorlar? Hayır. Ya fazla ya da az alıyorlar ama zincirdeki biri her zaman kaymağını götürüyor. Bir adama bir silah verirsen bir bankayı soyabilir ama bir adama bir banka verirsen dünyayı soyar. İnsanlar her zaman umudumu boşa çıkarmanın bir yolunu buldu. Bir holdingi kalbini hedef alarak çökertemezsin. Holdinglerin olayı budur, kalpleri olmaz. Onları parça parça çökertirsin. Ve çözülmeye başladıkları zaman kontrol yanılsamaları da çözülür. Büyük bir fırsat ondan faydalanılmasını bekler. Seçimlerimiz üzerinde kontrol sahibi olup olmadığımızı nasıl bileceğiz? Sadece önümüze gelen şeyin en iyisini yapmaya çalışıyoruz, olay bu. Sürekli iki seçenekten birini seçmeye çalışıyoruz. Tıpkı bekleme salonundaki iki tablo gibi. Ya da Coca-Cola ve Pepsi. Mcdonald's veya Burger King. Hyundai veya Honda. Hepsi aynı bulanıklığın parçası. Odak dışında kalan bulanıklık. Seçimin yanılsaması. Kendi istediğimiz kablolu yayın, doğalgaz ve elektrik şirketini bile seçemiyoruz. içtiğimiz su, sağlık sigortamız.. Seçebilseydik bile fark eder miydi ki? Eğer tek seçim şansımız kılıç ve kalkan arasında oluyorsa bu nasıl seçimdir amına koyayım? Aslında aynı değiller midir? Hayır, seçimlerimiz bizim için tayin edilmiş uzun zaman önce. İnsanlar etrafta dolaşıp nefretin ne demek olduğunu biliyormuş gibi yapıyorlar. Hayır, kimse bilemez. Ta ki kendinden nefret edene kadar. Demek istediğim, gerçekten kendinden nefret etmek. Bu, güçtür. İnsanlar iletişim kuramadıkları zaman öfkelenir. İçinde yaşadığımız dünya bu. İnsanlar birbirlerinin hatalarına bel bağlıyor. Birbirlerini kandırmak için başkalarını kullanıyorlar. Hatta birbirleri ile ilişkili oluyorlar. Sıcak, dağınık bir insan çemberi. Bu, kendimi korumanın tek yolu: onlara asla kaynak kodumu göstermemek. Kendimi kapatmak. Beni kimsenin bulamayacağı soğuk, kusursuz labirentimi yaratmak. Ama artık daha normal olacağım. Belki kız arkadaşım bile olabilir. Onunla birlikte aptal marvel filmlerine gideceğim. Spor salonuna yazılacağım. Instagram'da bir şeyleri beğeneceğim. Vanilyalı latteler içeceğim. Bu andan itibaren açıksız bir hayat süreceğim. Kusursuz labirentimi korumak için her şeyi yapacağım. Bir maskeyi, artık maske olmayı bıraktığında nasıl çıkarırsın? Senin kadar senin bir parçan olduğunda.
@ 0d532801:197a0c30
2024-12-06 05:13:25[Mr. Robot]( https://www.piktobet.net/2015/10/mr-robot.html) Dünya tehlikeli bir yer. Kötülük yapanlar yüzünden değil, görüp de hiçbir şey yapmayanlar yüzünden. İnsanları okumada çok iyiyimdir. İçlerindeki en kötü şeyi ararım. Herkes çalar. Bu böyledir. İnsanlar tam anlamıyla hak ettiklerini mi kazanıyorlar? Hayır. Ya fazla ya da az alıyorlar ama zincirdeki biri her zaman kaymağını götürüyor. Bir adama bir silah verirsen bir bankayı soyabilir ama bir adama bir banka verirsen dünyayı soyar. İnsanlar her zaman umudumu boşa çıkarmanın bir yolunu buldu. Bir holdingi kalbini hedef alarak çökertemezsin. Holdinglerin olayı budur, kalpleri olmaz. Onları parça parça çökertirsin. Ve çözülmeye başladıkları zaman kontrol yanılsamaları da çözülür. Büyük bir fırsat ondan faydalanılmasını bekler. Seçimlerimiz üzerinde kontrol sahibi olup olmadığımızı nasıl bileceğiz? Sadece önümüze gelen şeyin en iyisini yapmaya çalışıyoruz, olay bu. Sürekli iki seçenekten birini seçmeye çalışıyoruz. Tıpkı bekleme salonundaki iki tablo gibi. Ya da Coca-Cola ve Pepsi. Mcdonald's veya Burger King. Hyundai veya Honda. Hepsi aynı bulanıklığın parçası. Odak dışında kalan bulanıklık. Seçimin yanılsaması. Kendi istediğimiz kablolu yayın, doğalgaz ve elektrik şirketini bile seçemiyoruz. içtiğimiz su, sağlık sigortamız.. Seçebilseydik bile fark eder miydi ki? Eğer tek seçim şansımız kılıç ve kalkan arasında oluyorsa bu nasıl seçimdir amına koyayım? Aslında aynı değiller midir? Hayır, seçimlerimiz bizim için tayin edilmiş uzun zaman önce. İnsanlar etrafta dolaşıp nefretin ne demek olduğunu biliyormuş gibi yapıyorlar. Hayır, kimse bilemez. Ta ki kendinden nefret edene kadar. Demek istediğim, gerçekten kendinden nefret etmek. Bu, güçtür. İnsanlar iletişim kuramadıkları zaman öfkelenir. İçinde yaşadığımız dünya bu. İnsanlar birbirlerinin hatalarına bel bağlıyor. Birbirlerini kandırmak için başkalarını kullanıyorlar. Hatta birbirleri ile ilişkili oluyorlar. Sıcak, dağınık bir insan çemberi. Bu, kendimi korumanın tek yolu: onlara asla kaynak kodumu göstermemek. Kendimi kapatmak. Beni kimsenin bulamayacağı soğuk, kusursuz labirentimi yaratmak. Ama artık daha normal olacağım. Belki kız arkadaşım bile olabilir. Onunla birlikte aptal marvel filmlerine gideceğim. Spor salonuna yazılacağım. Instagram'da bir şeyleri beğeneceğim. Vanilyalı latteler içeceğim. Bu andan itibaren açıksız bir hayat süreceğim. Kusursuz labirentimi korumak için her şeyi yapacağım. Bir maskeyi, artık maske olmayı bıraktığında nasıl çıkarırsın? Senin kadar senin bir parçan olduğunda. @ a367f9eb:0633efea
2024-12-02 20:49:25Though Bitcoin was born in the world of computers and code, it was destined to eventually face-off with the legacy banking system. The first block ever mined on the blockchain, Satoshi’s Genesis block, contained a (then) recent headline from a British newspaper reacting to the 2008/9 financial crisis, inscribing “*The Times 03/Jan/2009 Chancellor on brink of second bailout for banks*”. As Bitcoin adoption increased from 2009 to 2012, users began exchanging dollars and euros for the digital money, using peer-to-peer exchanges and ATMs and then eventually with business entities acting as full-scale brokerages. Today, this space is dominated by what we call cryptocurrency exchanges, offering bitcoin and many of its crypto-offspring. On these exchanges, as well as in various custodial solutions, bitcoin is held, bought and sold for traditional currency, and sent to destination wallets. As these volumes have increased, so has scrutiny from financial authorities and government agencies, defining how this new category of entities exchanging US dollars and bitcoin would be regulated. ###### **The beginning of Bitcoin’s regulatory dance** In March 2013, the Financial Crimes Enforcement Network (FinCEN), a division of the Treasury Department, updated its [guidance](https://www.fincen.gov/news/news-releases/fincen-issues-guidance-virtual-currencies-and-regulatory-responsibilities) to inform firms that “make a business of exchanging, accepting, and transmitting” virtual currencies would be considered **Money Service Businesses** (MSBs) under the law. MSBs are distinct from banks and other traditional institutions. This taxonomy usually applies to issuers of travelers checks, check cashing services, and remittance services like Western Union. FinCEN’s guidance, for the first time, applied this to virtual currency services that transmitted funds on behalf of users or offered a fiat on-off ramp. As an MSB, the law prescribes certain obligations for transaction collection, maintenance, and reporting, as well as identification requirements kept on file, what we call Know Your Customer (KYC) regulations. The obligations on MSBs [require](https://www.fincen.gov/money-services-business-msb-suspicious-activity-reporting) filing Suspicious Activity reports on all transactions over $2,000 that “do not serve business or apparent lawful purpose” or may otherwise appear to be illegal activity or “structured” so as to try to avoid the spirit of the law. The specific law that forces these obligations on MSBs, as well as banks, is the **Bank Secrecy Act** of 1970. Though it’s been updated several times over the years, the principal goal of this bill is to partner with banks and financial institutions to try to thwart money laundering and other illicit activity. ###### **BSA and Bitcoin** The consequences of the BSA and its imposed surveillance have reaped unintended havoc on millions of ordinary Americans. This is especially true for those who have undergone “debanking,” in which bank customers are [deemed](https://www.thomsonreuters.com/en-us/posts/investigation-fraud-and-risk/treasury-de-risking-strategy/) too “high risk” and have accounts closed on them, a function of regulatory pressure – or *jawboning* – faced by financial institutions. Venture capitalist Marc Andreessen has [provided](https://www.realclearpolitics.com/video/2024/12/01/marc_andreessen_biden_admin_has_been_debanking_politically_exposed_persons_in_privatized_sanctions_regime.html) his own examples of debanking in Silicon Valley, with similar conclusions. Many Bitcoin and cryptocurrency entrepreneurs have been debanked on the [sole grounds](https://www.axios.com/2024/12/01/debanked-crypto-andreessen-joe-rogan) of being involved in the virtual currency industry, while millions of others have been swept up in the dragnet of the BSA and financial regulators forcibly deputizing banks to cut off customers, often without explanation. According to FinCEN guidance, financial institutions are [compelled](https://www.fincen.gov/resources/advisories/fincen-advisory-fin-2010-a014) to keep suspicious activity reports confidential, even from customers, or face criminal penalties. This just makes the problems worse. The [excellent research](https://www.cato.org/policy-analysis/revising-bank-secrecy-act-protect-privacy-deter-criminals) by the team at the Cato Institute’s Center for Monetary and Financial Alternatives provides reams of data on these points. As put by Cato’s **Norbert Michael**, “People get wrapped up in BSA surveillance for simply spending their own money”. When it comes to bitcoin, the most common understanding for years has been that self-custody options and noncustodial solutions would be exempt from MSB classification, not requiring developers or entrepreneurs to acquire Money Transmission Licenses at either the state or federal level. FinCEN itself stated this in their guidance [released in 2019](https://www.fincen.gov/sites/default/files/2019-05/FinCEN%20Guidance%20CVC%20FINAL%20508.pdf), and builders developed code based on what the government itself said. In 2023, however, the US Attorneys in the Southern District of New York and the FBI took a different stance. Beginning with the Ethereum smart contract platform **Tornado Cash**, and then the popular privacy service **Samourai Wallet**, the developers of these projects were [arrested](https://www.justice.gov/usao-sdny/pr/tornado-cash-founders-charged-money-laundering-and-sanctions-violations) and [charged](https://www.justice.gov/usao-sdny/pr/founders-and-ceo-cryptocurrency-mixing-service-arrested-and-charged-money-laundering) with a number of conspiracy and money laundering charges, as well as “conspiracy to operate an unlicensed money transmitting business”. It’s that latter charge that remains the most important to sovereign and noncustodial use of bitcoin going forward. Though both of these projects are noncustodial by design, and never took control of anyone’s bitcoin or cryptocurrency private keys, the government has charged them with being money service businesses and failing to adhere to the law. Neither of these trials have yet taken place, but considering the money transmission charges, it stands to reason that anyone advocating for noncustodial bitcoin tools should be worried. *If you’re interested in donating to the legal defense teams in both of these cases, check out the [**P2P Rights Fund**](https://p2prights.org/).* If these are the steps law enforcement is willing to take against noncustodial protocols and projects even legal experts determined were out of the scope of MSBs, what about bitcoin exchanges and brokerages? While we know there is no carve out at the moment, there are some important reforms that could empower entrepreneurs and give more options to Bitcoin users. ###### **An update to BSA would be a powerful reform for Bitcoin** While we would hope that the majority of people using Bitcoin will practice [self-custody](https://www.btcpolicy.org/articles/self-custody-is-nonnegotiable), which is one of the key advantages of using Satoshi’s innovation, we know that most will not. Instead, custodial services and exchanges will provide a lot of functionality for users, meaning that more and more Bitcoin activity will fall under the auspices of the Bank Secrecy Act. One bill that aims to peel back the layers of banking law to restore some measure of financial privacy is the [**Saving Privacy Act**](https://www.lee.senate.gov/2024/9/lee-introduces-the-saving-privacy-act-to-protect-americans-financial-data), introduced by Sens. Mike Lee (R-UT) and Rick Scott (R-FL). The proposed law aims to maintain the record keeping of financial institutions and money service businesses, but would do away with the automatic reporting limits and requirements without judicial warrants among other important reforms. It would also ban a Central Bank Digital Currency, [repeal](https://www.therage.co/corporate-transparency-act-privacy-at-risk/) the **Corporate Transparency Act**, scale back the audit powers of the SEC, require Congressional approval for any ID database of Americans, severely punish any government employee who abuses private financial information, and grant a private right of action to any citizen or firm harmed by illicit government activity on financial matters. It is a beefy bill with aspirational goals to restore consumer financial privacy, and it would no doubt make it much easier for Bitcoin tools and exchanges to operate within the law. With less of a reporting requirement for custodial bitcoin solutions classified as Money Service Businesses – while still maintaining record keeping – it would be a much more natural balance of innovation and regulatory certainty. By scaling back the financial surveillance required of banks and all other financial institutions, it is clear that Bitcoin users would benefit. If there is enough appetite for this bill among various Senators and in the House of Representatives, however, is anyone’s guess. But the issues of our current banking system and its relation to Bitcoin are clear and this is a worthy attempt. While there are still many regulatory changes needed to fully unleash the sovereign money revolution promised by Bitcoin, we can have some hope that the right ideas are being discussed in the corridors of power. At least for now. *Originally published on the [website](https://www.btcpolicy.org/articles/downgrading-the-bank-secrecy-act-is-a-powerful-reform-for-bitcoin) of the **Bitcoin Policy Institute**.*
@ a367f9eb:0633efea
2024-12-02 20:49:25Though Bitcoin was born in the world of computers and code, it was destined to eventually face-off with the legacy banking system. The first block ever mined on the blockchain, Satoshi’s Genesis block, contained a (then) recent headline from a British newspaper reacting to the 2008/9 financial crisis, inscribing “*The Times 03/Jan/2009 Chancellor on brink of second bailout for banks*”. As Bitcoin adoption increased from 2009 to 2012, users began exchanging dollars and euros for the digital money, using peer-to-peer exchanges and ATMs and then eventually with business entities acting as full-scale brokerages. Today, this space is dominated by what we call cryptocurrency exchanges, offering bitcoin and many of its crypto-offspring. On these exchanges, as well as in various custodial solutions, bitcoin is held, bought and sold for traditional currency, and sent to destination wallets. As these volumes have increased, so has scrutiny from financial authorities and government agencies, defining how this new category of entities exchanging US dollars and bitcoin would be regulated. ###### **The beginning of Bitcoin’s regulatory dance** In March 2013, the Financial Crimes Enforcement Network (FinCEN), a division of the Treasury Department, updated its [guidance](https://www.fincen.gov/news/news-releases/fincen-issues-guidance-virtual-currencies-and-regulatory-responsibilities) to inform firms that “make a business of exchanging, accepting, and transmitting” virtual currencies would be considered **Money Service Businesses** (MSBs) under the law. MSBs are distinct from banks and other traditional institutions. This taxonomy usually applies to issuers of travelers checks, check cashing services, and remittance services like Western Union. FinCEN’s guidance, for the first time, applied this to virtual currency services that transmitted funds on behalf of users or offered a fiat on-off ramp. As an MSB, the law prescribes certain obligations for transaction collection, maintenance, and reporting, as well as identification requirements kept on file, what we call Know Your Customer (KYC) regulations. The obligations on MSBs [require](https://www.fincen.gov/money-services-business-msb-suspicious-activity-reporting) filing Suspicious Activity reports on all transactions over $2,000 that “do not serve business or apparent lawful purpose” or may otherwise appear to be illegal activity or “structured” so as to try to avoid the spirit of the law. The specific law that forces these obligations on MSBs, as well as banks, is the **Bank Secrecy Act** of 1970. Though it’s been updated several times over the years, the principal goal of this bill is to partner with banks and financial institutions to try to thwart money laundering and other illicit activity. ###### **BSA and Bitcoin** The consequences of the BSA and its imposed surveillance have reaped unintended havoc on millions of ordinary Americans. This is especially true for those who have undergone “debanking,” in which bank customers are [deemed](https://www.thomsonreuters.com/en-us/posts/investigation-fraud-and-risk/treasury-de-risking-strategy/) too “high risk” and have accounts closed on them, a function of regulatory pressure – or *jawboning* – faced by financial institutions. Venture capitalist Marc Andreessen has [provided](https://www.realclearpolitics.com/video/2024/12/01/marc_andreessen_biden_admin_has_been_debanking_politically_exposed_persons_in_privatized_sanctions_regime.html) his own examples of debanking in Silicon Valley, with similar conclusions. Many Bitcoin and cryptocurrency entrepreneurs have been debanked on the [sole grounds](https://www.axios.com/2024/12/01/debanked-crypto-andreessen-joe-rogan) of being involved in the virtual currency industry, while millions of others have been swept up in the dragnet of the BSA and financial regulators forcibly deputizing banks to cut off customers, often without explanation. According to FinCEN guidance, financial institutions are [compelled](https://www.fincen.gov/resources/advisories/fincen-advisory-fin-2010-a014) to keep suspicious activity reports confidential, even from customers, or face criminal penalties. This just makes the problems worse. The [excellent research](https://www.cato.org/policy-analysis/revising-bank-secrecy-act-protect-privacy-deter-criminals) by the team at the Cato Institute’s Center for Monetary and Financial Alternatives provides reams of data on these points. As put by Cato’s **Norbert Michael**, “People get wrapped up in BSA surveillance for simply spending their own money”. When it comes to bitcoin, the most common understanding for years has been that self-custody options and noncustodial solutions would be exempt from MSB classification, not requiring developers or entrepreneurs to acquire Money Transmission Licenses at either the state or federal level. FinCEN itself stated this in their guidance [released in 2019](https://www.fincen.gov/sites/default/files/2019-05/FinCEN%20Guidance%20CVC%20FINAL%20508.pdf), and builders developed code based on what the government itself said. In 2023, however, the US Attorneys in the Southern District of New York and the FBI took a different stance. Beginning with the Ethereum smart contract platform **Tornado Cash**, and then the popular privacy service **Samourai Wallet**, the developers of these projects were [arrested](https://www.justice.gov/usao-sdny/pr/tornado-cash-founders-charged-money-laundering-and-sanctions-violations) and [charged](https://www.justice.gov/usao-sdny/pr/founders-and-ceo-cryptocurrency-mixing-service-arrested-and-charged-money-laundering) with a number of conspiracy and money laundering charges, as well as “conspiracy to operate an unlicensed money transmitting business”. It’s that latter charge that remains the most important to sovereign and noncustodial use of bitcoin going forward. Though both of these projects are noncustodial by design, and never took control of anyone’s bitcoin or cryptocurrency private keys, the government has charged them with being money service businesses and failing to adhere to the law. Neither of these trials have yet taken place, but considering the money transmission charges, it stands to reason that anyone advocating for noncustodial bitcoin tools should be worried. *If you’re interested in donating to the legal defense teams in both of these cases, check out the [**P2P Rights Fund**](https://p2prights.org/).* If these are the steps law enforcement is willing to take against noncustodial protocols and projects even legal experts determined were out of the scope of MSBs, what about bitcoin exchanges and brokerages? While we know there is no carve out at the moment, there are some important reforms that could empower entrepreneurs and give more options to Bitcoin users. ###### **An update to BSA would be a powerful reform for Bitcoin** While we would hope that the majority of people using Bitcoin will practice [self-custody](https://www.btcpolicy.org/articles/self-custody-is-nonnegotiable), which is one of the key advantages of using Satoshi’s innovation, we know that most will not. Instead, custodial services and exchanges will provide a lot of functionality for users, meaning that more and more Bitcoin activity will fall under the auspices of the Bank Secrecy Act. One bill that aims to peel back the layers of banking law to restore some measure of financial privacy is the [**Saving Privacy Act**](https://www.lee.senate.gov/2024/9/lee-introduces-the-saving-privacy-act-to-protect-americans-financial-data), introduced by Sens. Mike Lee (R-UT) and Rick Scott (R-FL). The proposed law aims to maintain the record keeping of financial institutions and money service businesses, but would do away with the automatic reporting limits and requirements without judicial warrants among other important reforms. It would also ban a Central Bank Digital Currency, [repeal](https://www.therage.co/corporate-transparency-act-privacy-at-risk/) the **Corporate Transparency Act**, scale back the audit powers of the SEC, require Congressional approval for any ID database of Americans, severely punish any government employee who abuses private financial information, and grant a private right of action to any citizen or firm harmed by illicit government activity on financial matters. It is a beefy bill with aspirational goals to restore consumer financial privacy, and it would no doubt make it much easier for Bitcoin tools and exchanges to operate within the law. With less of a reporting requirement for custodial bitcoin solutions classified as Money Service Businesses – while still maintaining record keeping – it would be a much more natural balance of innovation and regulatory certainty. By scaling back the financial surveillance required of banks and all other financial institutions, it is clear that Bitcoin users would benefit. If there is enough appetite for this bill among various Senators and in the House of Representatives, however, is anyone’s guess. But the issues of our current banking system and its relation to Bitcoin are clear and this is a worthy attempt. While there are still many regulatory changes needed to fully unleash the sovereign money revolution promised by Bitcoin, we can have some hope that the right ideas are being discussed in the corridors of power. At least for now. *Originally published on the [website](https://www.btcpolicy.org/articles/downgrading-the-bank-secrecy-act-is-a-powerful-reform-for-bitcoin) of the **Bitcoin Policy Institute**.* @ b83e6f82:73c27758
2024-12-02 12:33:13## Citrine 0.5.7 - Fix rotation resetting the app state when downloading your notes - Fix timeout when downloading your notes when you have a lot of notes Download it with [zap.store]( https://zap.store/download), [Obtainium]( https://github.com/ImranR98/Obtainium), [f-droid]( https://f-droid.org/packages/com.greenart7c3.citrine) or download it directly in the [releases page ]( https://github.com/greenart7c3/Citrine/releases/tag/v0.5.7) If you like my work consider making a [donation]( https://greenart7c3.com) ## Verifying the release In order to verify the release, you'll need to have `gpg` or `gpg2` installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already: ``` bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6D ``` Once you have his PGP key you can verify the release (assuming `manifest-v0.5.7.txt` and `manifest-v0.5.7.txt.sig` are in the current directory) with: ``` bash gpg --verify manifest-v0.5.7.txt.sig manifest-v0.5.7.txt ``` You should see the following if the verification was successful: ``` bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>" ``` That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes: ``` bash cat manifest-v0.5.7.txt ``` One can use the `shasum -a 256 <file name here>` tool in order to re-compute the `sha256` hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly.
@ b83e6f82:73c27758
2024-12-02 12:33:13## Citrine 0.5.7 - Fix rotation resetting the app state when downloading your notes - Fix timeout when downloading your notes when you have a lot of notes Download it with [zap.store]( https://zap.store/download), [Obtainium]( https://github.com/ImranR98/Obtainium), [f-droid]( https://f-droid.org/packages/com.greenart7c3.citrine) or download it directly in the [releases page ]( https://github.com/greenart7c3/Citrine/releases/tag/v0.5.7) If you like my work consider making a [donation]( https://greenart7c3.com) ## Verifying the release In order to verify the release, you'll need to have `gpg` or `gpg2` installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already: ``` bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6D ``` Once you have his PGP key you can verify the release (assuming `manifest-v0.5.7.txt` and `manifest-v0.5.7.txt.sig` are in the current directory) with: ``` bash gpg --verify manifest-v0.5.7.txt.sig manifest-v0.5.7.txt ``` You should see the following if the verification was successful: ``` bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>" ``` That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes: ``` bash cat manifest-v0.5.7.txt ``` One can use the `shasum -a 256 <file name here>` tool in order to re-compute the `sha256` hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly. @ 6d8e2a24:5faaca4c
2024-12-02 09:03:49"if your boyfriend uses Tiktok, you have a girlfriend" worlds riches man. Elon Musk tells women.  What's your opinion, do you think Elon Musk is right by his statement?
@ 6d8e2a24:5faaca4c
2024-12-02 09:03:49"if your boyfriend uses Tiktok, you have a girlfriend" worlds riches man. Elon Musk tells women.  What's your opinion, do you think Elon Musk is right by his statement? @ eac63075:b4988b48
2024-12-02 02:40:18Estonia is a small country with just 1.3 million inhabitants and an area similar to that of the state of Rio de Janeiro, but with a notable difference: while Rio has about 16 million residents, Estonia shines with its efficiency, innovation, and digitalization. It's no wonder it's known as the "digital nation." For many Brazilians, the country has become a strategic gateway to start a business and settle in Europe. Listen the podcast https://www.fountain.fm/episode/pizBLdhqqP5qQrKQILFb ## The Purpose of the Event and the Context The meeting organized by Bloco and the Brazilian digital community aimed primarily to explore the opportunities that Estonia offers to those wishing to expand their businesses or start a new life in Europe. With pizza, networking, and straightforward presentations, the evening was dedicated to demystifying questions like "Why Estonia?" and "What makes this country a viable option for Brazilians?" Additionally, the event highlighted the importance of E-Residency, a digital identity that allows you to open and manage a company in Estonia from anywhere in the world. But that's just the beginning. Let's explore what makes Estonia a standout point on the European scene. ## Where Is Estonia Located? If you open a map of Europe and look for this small country, you're likely to have difficulty locating it. Situated to the north of what's called Eastern Europe, Estonia borders Russia and Latvia and is separated from Finland by the Baltic Sea. Although geographically positioned in the east, many Estonians prefer to identify with the north due to cultural and historical proximity to the Nordic countries. There's something fascinating about Estonia's history. According to local legends, Vikings set out from their Estonian islands to conquer the world, later returning to reclaim their lands. This spirit of resilience and reinvention permeates the country's culture to this day. ## Digitalization: The Estonian Revolution Thirty years ago, when Estonia gained its independence from the Soviet Union, the country decided to look to the future. The question was simple: how to ensure the sovereignty and survival of a small, vulnerable nation? The answer was bold: total digitalization. In 2001, the X-Road was created—a decentralized infrastructure that connects all government institutions and allows citizens to access public services digitally. This system is so advanced that even the servers of the Estonian government are located outside the country, stored with backups at the European Commission in Brussels. Through this infrastructure, Estonia eliminated information silos, decentralized data, and allowed its citizens to authorize the use of personal information with complete control. Today, 98% of the population has a digital identity, 95% file taxes online in less than three minutes, and 100% of public services are available digitally. For those accustomed to Brazilian bureaucracy, it's impressive to know that opening a company in Estonia can be done in just 15 minutes, without the need for an accountant. ## E-Residency: A Digital Passport for Business Launched in 2014, the E-Residency program made Estonia the first country in the world to offer a digital identity to non-residents. This digital ID card allows entrepreneurs to open a company in the European Union, sign documents, and manage businesses remotely without needing to visit the country. Although it doesn't grant citizenship or physical residency, E-Residency is perfect for those who want to test the European market or operate a digital company. The program has already attracted over 118,000 e-residents from around the world, including 1,300 Brazilians who have opened 379 companies in the country. ## Advantages of Doing Business in Estonia Starting a business in Estonia has many advantages. Let's discuss some of the main ones: ### **Simple and Clear Taxation:** Estonia adopts a flat tax rate of 20% (which increased to 22% after the pandemic and will be 24% in 2025) on distributed profits. If you reinvest the profits in the company, the taxation is zero—a unique policy that encourages sustainable growth. ### **Low Cost to Start:** Unlike Switzerland, which requires an initial deposit of 100,000 Swiss francs to open a company, in Estonia, only 2,500 euros are needed. And the best part: this amount only needs to be deposited when the company distributes profits for the first time. ### **Complete Digitalization:** Digital signatures in Estonia eliminate the need for notaries and paper documents. Everything can be done online, from opening the company to filing taxes. ### **Support for Startups and Innovation:** With the Startup Visa, entrepreneurs can move to Estonia with their entire family and receive support to expand their businesses. Additionally, the country has the highest number of unicorns (startups valued at over one billion dollars) per capita in the world, including companies like Skype, Bolt, and Wise. ### **Easy Access to Europe:** Establishing your company in Estonia means access to the European market, with its unified regulations and a vibrant innovation ecosystem. ## The Startup Visa: An Invitation for Entrepreneurs For those who want more than just operating remotely, the Startup Visa program offers the opportunity to physically move to Estonia. The initial visa is valid for one year and can be renewed for three consecutive years. After eight years, there's the possibility of applying for European citizenship, although Estonia doesn't allow dual nationality. One of the unique features of the Startup Visa is that there's no limit to the number of partners or family members who can be included in the program. This means that the entire team of founders and their families can benefit from the residence permit. Additionally, Estonia offers support through the International House and its Work in Estonia program, a center where newcomers can resolve everything from assistance with opening bank accounts to cultural and professional integration. ## Innovation and Access to Investments Estonia is known for its culture of innovation. Events like Latitude 59, one of Europe's main startup gatherings, offer prizes of up to two million euros for winning startups. The country also facilitates direct connections with investment funds and venture capital, often without bureaucratic barriers. For early-stage companies, the Estonian ecosystem is especially attractive. There are cases of entrepreneurs who managed to raise hundreds of thousands of euros with little more than a prototype or a good idea on paper. ## A Small Country with Global Ambitions Although small in size, Estonia is big in ambition. Its model of digitalization and support for startups serves as an example to the world. With unique opportunities like E-Residency and the Startup Visa, the country positions itself as a viable and accessible gateway for Brazilians who wish to explore the European market. For those seeking innovation, simplicity, and access to the global market, Estonia offers more than opportunities; it offers a vision of the future. Whether it's to open a business, operate remotely, or move with the family, the country proves that with the right strategies, even a small nation can make a giant impact.
@ eac63075:b4988b48
2024-12-02 02:40:18Estonia is a small country with just 1.3 million inhabitants and an area similar to that of the state of Rio de Janeiro, but with a notable difference: while Rio has about 16 million residents, Estonia shines with its efficiency, innovation, and digitalization. It's no wonder it's known as the "digital nation." For many Brazilians, the country has become a strategic gateway to start a business and settle in Europe. Listen the podcast https://www.fountain.fm/episode/pizBLdhqqP5qQrKQILFb ## The Purpose of the Event and the Context The meeting organized by Bloco and the Brazilian digital community aimed primarily to explore the opportunities that Estonia offers to those wishing to expand their businesses or start a new life in Europe. With pizza, networking, and straightforward presentations, the evening was dedicated to demystifying questions like "Why Estonia?" and "What makes this country a viable option for Brazilians?" Additionally, the event highlighted the importance of E-Residency, a digital identity that allows you to open and manage a company in Estonia from anywhere in the world. But that's just the beginning. Let's explore what makes Estonia a standout point on the European scene. ## Where Is Estonia Located? If you open a map of Europe and look for this small country, you're likely to have difficulty locating it. Situated to the north of what's called Eastern Europe, Estonia borders Russia and Latvia and is separated from Finland by the Baltic Sea. Although geographically positioned in the east, many Estonians prefer to identify with the north due to cultural and historical proximity to the Nordic countries. There's something fascinating about Estonia's history. According to local legends, Vikings set out from their Estonian islands to conquer the world, later returning to reclaim their lands. This spirit of resilience and reinvention permeates the country's culture to this day. ## Digitalization: The Estonian Revolution Thirty years ago, when Estonia gained its independence from the Soviet Union, the country decided to look to the future. The question was simple: how to ensure the sovereignty and survival of a small, vulnerable nation? The answer was bold: total digitalization. In 2001, the X-Road was created—a decentralized infrastructure that connects all government institutions and allows citizens to access public services digitally. This system is so advanced that even the servers of the Estonian government are located outside the country, stored with backups at the European Commission in Brussels. Through this infrastructure, Estonia eliminated information silos, decentralized data, and allowed its citizens to authorize the use of personal information with complete control. Today, 98% of the population has a digital identity, 95% file taxes online in less than three minutes, and 100% of public services are available digitally. For those accustomed to Brazilian bureaucracy, it's impressive to know that opening a company in Estonia can be done in just 15 minutes, without the need for an accountant. ## E-Residency: A Digital Passport for Business Launched in 2014, the E-Residency program made Estonia the first country in the world to offer a digital identity to non-residents. This digital ID card allows entrepreneurs to open a company in the European Union, sign documents, and manage businesses remotely without needing to visit the country. Although it doesn't grant citizenship or physical residency, E-Residency is perfect for those who want to test the European market or operate a digital company. The program has already attracted over 118,000 e-residents from around the world, including 1,300 Brazilians who have opened 379 companies in the country. ## Advantages of Doing Business in Estonia Starting a business in Estonia has many advantages. Let's discuss some of the main ones: ### **Simple and Clear Taxation:** Estonia adopts a flat tax rate of 20% (which increased to 22% after the pandemic and will be 24% in 2025) on distributed profits. If you reinvest the profits in the company, the taxation is zero—a unique policy that encourages sustainable growth. ### **Low Cost to Start:** Unlike Switzerland, which requires an initial deposit of 100,000 Swiss francs to open a company, in Estonia, only 2,500 euros are needed. And the best part: this amount only needs to be deposited when the company distributes profits for the first time. ### **Complete Digitalization:** Digital signatures in Estonia eliminate the need for notaries and paper documents. Everything can be done online, from opening the company to filing taxes. ### **Support for Startups and Innovation:** With the Startup Visa, entrepreneurs can move to Estonia with their entire family and receive support to expand their businesses. Additionally, the country has the highest number of unicorns (startups valued at over one billion dollars) per capita in the world, including companies like Skype, Bolt, and Wise. ### **Easy Access to Europe:** Establishing your company in Estonia means access to the European market, with its unified regulations and a vibrant innovation ecosystem. ## The Startup Visa: An Invitation for Entrepreneurs For those who want more than just operating remotely, the Startup Visa program offers the opportunity to physically move to Estonia. The initial visa is valid for one year and can be renewed for three consecutive years. After eight years, there's the possibility of applying for European citizenship, although Estonia doesn't allow dual nationality. One of the unique features of the Startup Visa is that there's no limit to the number of partners or family members who can be included in the program. This means that the entire team of founders and their families can benefit from the residence permit. Additionally, Estonia offers support through the International House and its Work in Estonia program, a center where newcomers can resolve everything from assistance with opening bank accounts to cultural and professional integration. ## Innovation and Access to Investments Estonia is known for its culture of innovation. Events like Latitude 59, one of Europe's main startup gatherings, offer prizes of up to two million euros for winning startups. The country also facilitates direct connections with investment funds and venture capital, often without bureaucratic barriers. For early-stage companies, the Estonian ecosystem is especially attractive. There are cases of entrepreneurs who managed to raise hundreds of thousands of euros with little more than a prototype or a good idea on paper. ## A Small Country with Global Ambitions Although small in size, Estonia is big in ambition. Its model of digitalization and support for startups serves as an example to the world. With unique opportunities like E-Residency and the Startup Visa, the country positions itself as a viable and accessible gateway for Brazilians who wish to explore the European market. For those seeking innovation, simplicity, and access to the global market, Estonia offers more than opportunities; it offers a vision of the future. Whether it's to open a business, operate remotely, or move with the family, the country proves that with the right strategies, even a small nation can make a giant impact. @ 0d532801:197a0c30
2024-12-01 21:27:48 ߹ İnsan, bilinçli olarak günah işlediğinde, aslında birçok içsel ve dışsal faktörün etkisi altındadır. Bu faktörlerin başında bireysel arzular, toplumsal baskılar, zayıflıklar, bilinçaltı dürtüler ve bazen de cehalet gelir. İnsan, sadece dürtülerine göre hareket etmeyi tercih edebilir ya da kısa vadeli tatmin için uzun vadeli sonuçları göz ardı edebilir. Peki, bir insan neden bilerek günah işler? Bu sorunun cevabı, sadece dini ya da etik perspektiflerle değil, psikolojik, toplumsal ve kültürel açılardan da ele alınmalıdır. 1. Bireysel Arzular ve Dürtüler ߹ İnsanın doğasında, zaman zaman nefsini tatmin etme isteği vardır. Bu istek, bazen mantık ve vicdanın önüne geçebilir. İnsan, kısa süreli hazları arzularken, bunun gelecekteki olumsuz sonuçlarını göz ardı edebilir. Örneğin, hırsızlık yapan bir kişi, anlık bir mal edinme arzusuyla hareket edebilir, ancak bu davranışın ona ve çevresine getireceği zararları düşünmektense, elde edeceği çıkarı daha önemli görür. Benzer şekilde, yalan söylemek ya da başkalarını manipüle etmek de kısa vadeli çıkarlar ve bireysel egolar tarafından beslenen bir davranış biçimidir. 2. Toplumsal Baskılar ve Çevresel Faktörler ߹ İnsan, toplumsal bir varlık olarak çevresinden büyük ölçüde etkilenir. Toplumun normları, kültürel değerleri, arkadaş gruplarının etkisi ve ailevi dinamikler, bireyin davranışlarını şekillendirir. Bazı durumlarda, kişi bilerek yanlış bir davranış sergileyebilir çünkü çevresindeki kişiler böyle yapmaktadır ve kendini dışlanmış hissetmemek için buna ayak uydurur. Örneğin, bir grup insanın başka birine kötü davranması ya da yalan söylemesi, bir bireyi de benzer şekilde davranmaya itebilir. Bu durum, bireyin vicdanı ve doğru-yanlış algısı ile çatışan bir durumdur. 3. Zayıflıklar ve İnsan Doğası ߹ Herkesin zayıf anları vardır. Zihinsel ve duygusal olarak zorlandığı anlarda insanlar bazen bilerek yanlış bir şey yapabilir. İnsan, öfke, stres, yalnızlık ya da korku gibi duygusal durumlar içinde daha kolay günah işleyebilir. Duygusal karmaşa, sağlıklı düşünme yeteneğini zayıflatabilir ve kişi, anlık bir rahatlama ya da kaçış için yanlış bir yolu seçebilir. Örneğin, öfkelenen bir kişi, karşısındaki kişiye hakaret etmek ya da ona zarar vermek isteyebilir. Bu tür eylemler, kişinin o anki duygusal durumunun bir sonucu olarak ortaya çıkar. 4. Cehalet ve Yanlış İnançlar ߹ Bazen insanlar, neyin doğru neyin yanlış olduğuna dair doğru bir bilgiye sahip olmayabilirler. Bilgi eksikliği ya da yanlış inanışlar, bireyin günah işlemesine neden olabilir. İnsan, kötü bir davranışın ne kadar zarar verebileceğini ya da o davranışın ahlaki ve dini boyutlarını tam anlamayabilir. Özellikle bazı insanlar, içinde bulundukları ortamın, alışkanlıkların ya da eğitim seviyelerinin etkisiyle, doğruyu ve yanlışı tam kavrayamayabilirler. Bu durum da, onların bilerek ve isteyerek günah işlemesine yol açabilir. 5. İçsel Çatışmalar ve Vicdanın Bastırılması ߹ İnsan, bazen kendi içsel çatışmalarına dayanamayabilir. Vicdanı, doğruyu yapması yönünde onu uyarırken, içindeki kötü duygular ya da arzular ona engel olamayacak kadar güçlü olabilir. İnsanın kendisini haklı çıkarma çabası da burada devreye girebilir. Bir insan, kendini iyi bir insan olarak görmek isterken, bazen içindeki kötü dürtüleri bastırmak yerine, bunları haklı göstermek için kendine çeşitli gerekçeler uydurur. Örneğin, bir kişi başkasının hakkını yemek için kendini “bunu herkes yapıyor” ya da “benim de buna ihtiyacım var” gibi bahanelerle kandırabilir. 6. Dini ve Ahlaki Değerlerin Zayıflaması ߹ Bir insanın dini inançları ya da ahlaki değerleri, doğru-yanlış algısını büyük ölçüde şekillendirir. Ancak zamanla, bireylerin inançları ya da değerleri zayıflayabilir. Toplumda sekülerleşmenin arttığı bir dönemde, dini ve ahlaki öğretiler zamanla insanların gözünde daha az değerli hâle gelebilir. Bu durumda, insanlar günah işleme konusunda daha az vicdan azabı duyarlar, çünkü dini ya da ahlaki sonuçları görmezden gelmeyi tercih edebilirler. ߹ _**Sonuç olarak, insanın bilerek günah işlemesi, karmaşık bir durumdur ve çok çeşitli faktörlere dayanır. İnsanlar bazen içsel isteklerine, bazen dışsal baskılara, bazen de bilinçli ya da bilinçsiz olarak zayıf noktalarına dayanarak yanlışlar yapabilirler. Önemli olan, insanın yaptığı hataları fark etmesi, bu hatalardan ders alması ve doğru yolu bulmaya çaba göstermesidir. Kişi, hatalarını kabul ederek ve daha bilinçli bir şekilde hareket ederek hem kendisine hem de çevresine faydalı bir yaşam sürebilir.**_
@ 0d532801:197a0c30
2024-12-01 21:27:48 ߹ İnsan, bilinçli olarak günah işlediğinde, aslında birçok içsel ve dışsal faktörün etkisi altındadır. Bu faktörlerin başında bireysel arzular, toplumsal baskılar, zayıflıklar, bilinçaltı dürtüler ve bazen de cehalet gelir. İnsan, sadece dürtülerine göre hareket etmeyi tercih edebilir ya da kısa vadeli tatmin için uzun vadeli sonuçları göz ardı edebilir. Peki, bir insan neden bilerek günah işler? Bu sorunun cevabı, sadece dini ya da etik perspektiflerle değil, psikolojik, toplumsal ve kültürel açılardan da ele alınmalıdır. 1. Bireysel Arzular ve Dürtüler ߹ İnsanın doğasında, zaman zaman nefsini tatmin etme isteği vardır. Bu istek, bazen mantık ve vicdanın önüne geçebilir. İnsan, kısa süreli hazları arzularken, bunun gelecekteki olumsuz sonuçlarını göz ardı edebilir. Örneğin, hırsızlık yapan bir kişi, anlık bir mal edinme arzusuyla hareket edebilir, ancak bu davranışın ona ve çevresine getireceği zararları düşünmektense, elde edeceği çıkarı daha önemli görür. Benzer şekilde, yalan söylemek ya da başkalarını manipüle etmek de kısa vadeli çıkarlar ve bireysel egolar tarafından beslenen bir davranış biçimidir. 2. Toplumsal Baskılar ve Çevresel Faktörler ߹ İnsan, toplumsal bir varlık olarak çevresinden büyük ölçüde etkilenir. Toplumun normları, kültürel değerleri, arkadaş gruplarının etkisi ve ailevi dinamikler, bireyin davranışlarını şekillendirir. Bazı durumlarda, kişi bilerek yanlış bir davranış sergileyebilir çünkü çevresindeki kişiler böyle yapmaktadır ve kendini dışlanmış hissetmemek için buna ayak uydurur. Örneğin, bir grup insanın başka birine kötü davranması ya da yalan söylemesi, bir bireyi de benzer şekilde davranmaya itebilir. Bu durum, bireyin vicdanı ve doğru-yanlış algısı ile çatışan bir durumdur. 3. Zayıflıklar ve İnsan Doğası ߹ Herkesin zayıf anları vardır. Zihinsel ve duygusal olarak zorlandığı anlarda insanlar bazen bilerek yanlış bir şey yapabilir. İnsan, öfke, stres, yalnızlık ya da korku gibi duygusal durumlar içinde daha kolay günah işleyebilir. Duygusal karmaşa, sağlıklı düşünme yeteneğini zayıflatabilir ve kişi, anlık bir rahatlama ya da kaçış için yanlış bir yolu seçebilir. Örneğin, öfkelenen bir kişi, karşısındaki kişiye hakaret etmek ya da ona zarar vermek isteyebilir. Bu tür eylemler, kişinin o anki duygusal durumunun bir sonucu olarak ortaya çıkar. 4. Cehalet ve Yanlış İnançlar ߹ Bazen insanlar, neyin doğru neyin yanlış olduğuna dair doğru bir bilgiye sahip olmayabilirler. Bilgi eksikliği ya da yanlış inanışlar, bireyin günah işlemesine neden olabilir. İnsan, kötü bir davranışın ne kadar zarar verebileceğini ya da o davranışın ahlaki ve dini boyutlarını tam anlamayabilir. Özellikle bazı insanlar, içinde bulundukları ortamın, alışkanlıkların ya da eğitim seviyelerinin etkisiyle, doğruyu ve yanlışı tam kavrayamayabilirler. Bu durum da, onların bilerek ve isteyerek günah işlemesine yol açabilir. 5. İçsel Çatışmalar ve Vicdanın Bastırılması ߹ İnsan, bazen kendi içsel çatışmalarına dayanamayabilir. Vicdanı, doğruyu yapması yönünde onu uyarırken, içindeki kötü duygular ya da arzular ona engel olamayacak kadar güçlü olabilir. İnsanın kendisini haklı çıkarma çabası da burada devreye girebilir. Bir insan, kendini iyi bir insan olarak görmek isterken, bazen içindeki kötü dürtüleri bastırmak yerine, bunları haklı göstermek için kendine çeşitli gerekçeler uydurur. Örneğin, bir kişi başkasının hakkını yemek için kendini “bunu herkes yapıyor” ya da “benim de buna ihtiyacım var” gibi bahanelerle kandırabilir. 6. Dini ve Ahlaki Değerlerin Zayıflaması ߹ Bir insanın dini inançları ya da ahlaki değerleri, doğru-yanlış algısını büyük ölçüde şekillendirir. Ancak zamanla, bireylerin inançları ya da değerleri zayıflayabilir. Toplumda sekülerleşmenin arttığı bir dönemde, dini ve ahlaki öğretiler zamanla insanların gözünde daha az değerli hâle gelebilir. Bu durumda, insanlar günah işleme konusunda daha az vicdan azabı duyarlar, çünkü dini ya da ahlaki sonuçları görmezden gelmeyi tercih edebilirler. ߹ _**Sonuç olarak, insanın bilerek günah işlemesi, karmaşık bir durumdur ve çok çeşitli faktörlere dayanır. İnsanlar bazen içsel isteklerine, bazen dışsal baskılara, bazen de bilinçli ya da bilinçsiz olarak zayıf noktalarına dayanarak yanlışlar yapabilirler. Önemli olan, insanın yaptığı hataları fark etmesi, bu hatalardan ders alması ve doğru yolu bulmaya çaba göstermesidir. Kişi, hatalarını kabul ederek ve daha bilinçli bir şekilde hareket ederek hem kendisine hem de çevresine faydalı bir yaşam sürebilir.**_ @ a95c6243:d345522c
2024-11-29 19:45:43*Konsum ist Therapie. Wolfgang Joop* **Umweltbewusstes Verhalten und verantwortungsvoller Konsum** zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch. **Heute ist also wieder mal «Black Friday»,** falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich. **Warum fallen wir auf derartige Werbetricks herein** und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf. **Gedankenlosigkeit und Maßlosigkeit können besonders bei der [Ernährung](https://transition-news.org/studie-208-millionen-us-amerikaner-sind-als-fettleibig-oder-ubergewichtig) zu ernsten Problemen führen.** Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen. **Kritik am schwarzen Freitag und dem unnötigen Konsum** kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch. **Die EU-Kommission lancierte 2015 den Begriff «Green Friday»** im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das [Pariser Abkommen](https://transition-news.org/cop29-wird-vom-geist-des-noch-kunftigen-us-prasidenten-heimgesucht) unterzeichnet werden sollte. **Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt.** Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des [«Green New Deal»](https://transition-news.org/green-new-deal) verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um [Valencia](https://transition-news.org/flutkatastrophe-in-valencia-die-ungereimtheiten-haufen-sich) dazu sagen? **Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020** eine «[grüne Erholung von Covid-19](https://news.un.org/en/story/2020/12/1079602), um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort. **Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet** – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben. **Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung** nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie [«verantwortungsvolle Risikobereitschaft»](https://transition-news.org/zuruck-zu-2008-grossbritannien-schlagt-lockere-regeln-fur-banker-boni-vor) unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde. --- Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/auch-beim-freitag-ist-es-egal-ob-schwarz-oder-grun)* erschienen.
@ a95c6243:d345522c
2024-11-29 19:45:43*Konsum ist Therapie. Wolfgang Joop* **Umweltbewusstes Verhalten und verantwortungsvoller Konsum** zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch. **Heute ist also wieder mal «Black Friday»,** falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich. **Warum fallen wir auf derartige Werbetricks herein** und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf. **Gedankenlosigkeit und Maßlosigkeit können besonders bei der [Ernährung](https://transition-news.org/studie-208-millionen-us-amerikaner-sind-als-fettleibig-oder-ubergewichtig) zu ernsten Problemen führen.** Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen. **Kritik am schwarzen Freitag und dem unnötigen Konsum** kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch. **Die EU-Kommission lancierte 2015 den Begriff «Green Friday»** im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das [Pariser Abkommen](https://transition-news.org/cop29-wird-vom-geist-des-noch-kunftigen-us-prasidenten-heimgesucht) unterzeichnet werden sollte. **Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt.** Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des [«Green New Deal»](https://transition-news.org/green-new-deal) verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um [Valencia](https://transition-news.org/flutkatastrophe-in-valencia-die-ungereimtheiten-haufen-sich) dazu sagen? **Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020** eine «[grüne Erholung von Covid-19](https://news.un.org/en/story/2020/12/1079602), um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort. **Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet** – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben. **Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung** nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie [«verantwortungsvolle Risikobereitschaft»](https://transition-news.org/zuruck-zu-2008-grossbritannien-schlagt-lockere-regeln-fur-banker-boni-vor) unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde. --- Dieser Beitrag ist zuerst auf *[Transition News](https://transition-news.org/auch-beim-freitag-ist-es-egal-ob-schwarz-oder-grun)* erschienen. @ bc6ccd13:f53098e4
2024-11-28 15:35:54Of all the common misconceptions about money, this is the deepest and most pervasive. It taps into the very psychology that makes money the most powerful tool in the world. Money works in large part because, for most practical purposes, you can assume that money and wealth are the same thing and be very successful in life. The problem is, it's a completely false premise. And without purging that assumption from your mental framework, understanding money and economics at a fundamental level is impossible. Luckily, money is such an effective tool that it can continue to "mostly" function even without anyone understanding it at a fundamental level. It's a lot like gravity in that regard. You don't need to understand general relativity to learn how to walk. But unlike gravity, money is a powerful tool that can easily be used to exploit the less knowledgeable. That's why the general acceptance of this particular false idea is such a tragedy; it enables theft and exploitation on a global scale, and leaves the victims unable to identify the perpetrators or understand their methods. ## Money as a Social Technology So let's unpack this misconception. We can start with a simple example. You've been shipwrecked on a desert island with only the clothes on your back. After a day under the blistering sun, you're presented with two options: a billion dollars in cash, or a case of bottled water. Which one do you choose? If you chose the water, congratulations. You survived because you were able to differentiate money from real wealth. Now run the same experiment, but place yourself in the water aisle at Costco. Suddenly you choose differently. This shows a few key requirements for money to be useful. One, you need the real wealth, the actual goods and services. If there is no bottled water on that island, all the money in the world won't do you a lick of good. Two, you need someone willing to exchange the real wealth for your money. If you're alone on that island and you find a bottle of water, you don't need money to drink it, you just help yourself. Both requirements are essential. This shows us that money is a social technology. Understanding the purpose and function of this technology is critical to dispensing with misconceptions like "money=wealth". ## Money and Civilization What's the difference between a subsistence hunter/gatherer lifestyle and the modern civilization we all enjoy today? Specialization of labor, and complex supply chains. And what enables those civilizational necessities? Money. In a subsistence situation, everything you have is created start-to-finish by you or by your immediate family or tribe. Everyone has to be a sort of jack-of-all-trades, at least at a group level. If you want a shelter, you collect the natural materials and build it yourself. If you need clothes, you collect the fibers or skins, process them, and use the fabric to sew your own outfit. Contrast that with the electronic device you're using to read these words right now. How many people does it take to build a smartphone? Millions. Can one person do it? Absolutely not. You could give anyone in the world an entire lifetime and there's no way they could mine, process, and assemble the raw materials into a functional smartphone. It's simply too complex, too many processes and too much specialized knowledge and machinery needed. Not to mention doing it at a cost that most people on the planet can afford. That miracle is only possible because millions of people specialize in one tiny specific task related to making one part of a complex item, over and over again. The efficiency of only doing one specific task instead of being a generalist is what makes civilization possible. But there's a problem. The person who's doing one specific task to make part of one widget still needs to eat, have a place to live, clothes to wear, etc. But how do you get all that while working a full time job making widgets? You can't do it all yourself, you need to buy those things from someone else who, similarly, specializes in those necessities of life. You need money. Money is what makes the whole thing work. ## Money and Barter So what exactly is money and how does it work? In a subsistence society, you can use barter to trade with strangers. You give them some fish, they give you some clothing, everyone is happy. But barter has major problems, and doesn't work at all in complex supply chains with specialized workers. Specialized jobs don't produce valuable finished goods that can be bartered. When you solder circuit boards all day, you can't go to your local farmer and trade ten "solder circuit board" for a dozen eggs. Enter money. Money solves multiple problems that arise with barter. For one, it creates a way to compare extremely dissimilar things. How many fish is a pound of butter worth? How many eggs? With barter, every good or service has to be priced in relation to every other good or service it's exchanged for. This is impossibly cumbersome and inefficient. Having money as a unit of account is as essential to trade as having a uniform inch is to building a house. A single carpenter might be able to use the width of his hand to measure boards, but get two carpenters working together and that "handbreadth" no longer works. Second, money solves the problem of not having the correct item to barter with. If your neighbor has butter and you have fish, but your neighbor hates fish and will only accept a chicken, barter won't work. But if you can just pay him with money, he can go buy whatever he prefers. Third, money creates a way to value and reimburse specialized work. That's arguably the most important aspect. ## The Social Contract Underlying Money So what makes money function? Why would someone accept a piece of paper with a picture of a dead president in exchange for a very real and very valuable good or service? Well, the obvious answer is that they can be certain they'll be able to exchange that piece of paper with someone else and get an equally valuable good or service in the future. This is circular logic though, and leads some economists to mistakenly attribute the value of money to a "collective delusion". But since every known advanced civilization has used some form of money, calling it a delusion is both inaccurate and boorishly pretentious. To understand the real mechanism behind the phenomenon, we have to consider how money is acquired. As anyone who has ever earned an honest wage knows, getting a paycheck requires two things. One, producing a valuable good or service. And two, giving that good or service to someone else instead of immediately consuming it yourself. The first point is self-explanatory. If what you produce isn't valuable, no one will buy it. The second point needs a bit more explanation. Money is a social technology, it's only valuable in a purely monetary sense when there's someone else to trade with. When you make yourself a few eggs for breakfast, you don't pay yourself for frying the eggs. Obviously. But if you eat your eggs, then go to your job as a short-order cook at the local diner, you may spend the morning getting paid to do exactly what you did "for free" at home. The difference is in the deferred consumption. When you do a favor for someone, morality and the spirit of fairness dictates that they would be willing to return the favor in the future when you need something from them. That's how it works in a family or small community. People "owe each other one," and favors are reciprocated regularly without any money changing hands in a kind of informal credit system. But if one person starts to take advantage of others' generosity and requests a lot of favors, but always fails to reciprocate when asked, people catch on quickly. The parasitic behavior will be met with increasing unwillingness to help from members of the family or community, and in extreme cases, even exile from the community itself. This informal credit system is the simplest and most fundamental form of money, and we can learn the basic principle behind why money works by observing it. We can see that a person accumulates "credits" by contributing productive value to others without getting anything in return. The "credits" are informal mental ledger credits that represent "this person has done something productive and valuable for someone else, which means he deserves to receive something valuable in the future." If a person contributes generously enough to the community, he will build up so much "credit" with everyone that he can expect generous help in return from any member of the community. The shortcomings of this informal credit system are that one, it doesn't provide a unit of measurement to compare different goods and services accurately. This can lead to misunderstanding and disputes when different people don't value services the same way. Someone can feel that they are contributing more to the community than they're getting back in return. And two, it relies heavily on trust, and only works between people who interact on a regular basis. It would be foolish to provide favors to a stranger of unknown reputation, or someone who's just traveling through the area, because in either case there's no expectation of establishing a reciprocal relationship with that individual. Money is just a way to formalize and expand that local, informal mental ledger. It's a way to keep track, on a societal level, who has contributed their fair share to the community and is deserving of reciprocal treatment. When someone buys something from you, although you don't consciously think through what's happening, on a subconscious level you're participating in a societal dialogue that goes something like this: "This person has money, which means they're a capable, generous, reciprocal person who has contributed more to the community than they've taken. Fairness dictates that they deserve something of value as a reward for their pro-social behavior. By taking their money, and giving them something of value, I can perpetuate the cycle of rewarding people who generously and capably do work that benefits others, and that will be beneficial to me personally and also to society as a whole. By having the money they give me, I can then also signal to others that I'm the same type of generous, reciprocal, productive person, and I can expect to be rewarded for that in the future when I try to exchange this money for valuable goods and services." So the money has value, not because of some inherent quality of the paper or gold or mental "credit," but because it represents past productive behavior, but without immediate consumption. The money itself is not wealth, it's just an abstract representation, a kind of scorecard or ledger entry, of the real wealth that the holder of the money has already produced. ## Money and Capital Formation This dialogue or unwritten contract is the foundation of modern civilization. It's powerful, because deferred consumption is the mechanism of capital formation, and capital formation is the foundation of complex supply chains and technological progress. You might be able to catch enough fish to feed your family with a crude rod and line. But building a modern fishing trawler (a valuable capital good) takes thousands of people working together for a long time. All that hard work doesn't result in any fish being caught throughout the process, and all those people could instead be out fishing and catching a lot of fish to eat. But by deferring that consumption and instead putting that effort into building a capital good, you end up with a huge fishing trawler. Once it's finished, a few of those thousands of people can catch more fish in a week than all the thousands of them combined could have caught over the whole time it took to build the trawler. That makes fishing much easier and more effective in the future, making food much more plentiful and increasing the standard of living for the whole society. And money is what makes all that possible on a global scale. ## Final Thoughts Given how critical this system is to civilization, any attack on money and its function is an existential threat. Unfortunately, a failure to understand the true nature of money leads to reliance on less nuanced or completely false ideas like "money=wealth". And that gives psychological cover to parasitic anti-social behavior like creating money and giving it away to buy votes, and all sorts of other destructive and dishonest shenanigans. Understanding that money is not wealth exposes the folly of all these schemes that purport to make people wealthier simply by creating more money. Believing that money is wealth makes the MMT clowns and the Keynesian grifters sound at least marginally credible. But those are specific misconceptions that need their own detailed explanation. For now, reprogramming your mental framework to draw a strong distinction between money and real wealth will give you a solid foundation to understand economics, and to critique the many incorrect theories presented by the parasitical elements who wish to muddy the waters and avoid scrutiny of their anti-civilizational exploitation.
@ bc6ccd13:f53098e4
2024-11-28 15:35:54Of all the common misconceptions about money, this is the deepest and most pervasive. It taps into the very psychology that makes money the most powerful tool in the world. Money works in large part because, for most practical purposes, you can assume that money and wealth are the same thing and be very successful in life. The problem is, it's a completely false premise. And without purging that assumption from your mental framework, understanding money and economics at a fundamental level is impossible. Luckily, money is such an effective tool that it can continue to "mostly" function even without anyone understanding it at a fundamental level. It's a lot like gravity in that regard. You don't need to understand general relativity to learn how to walk. But unlike gravity, money is a powerful tool that can easily be used to exploit the less knowledgeable. That's why the general acceptance of this particular false idea is such a tragedy; it enables theft and exploitation on a global scale, and leaves the victims unable to identify the perpetrators or understand their methods. ## Money as a Social Technology So let's unpack this misconception. We can start with a simple example. You've been shipwrecked on a desert island with only the clothes on your back. After a day under the blistering sun, you're presented with two options: a billion dollars in cash, or a case of bottled water. Which one do you choose? If you chose the water, congratulations. You survived because you were able to differentiate money from real wealth. Now run the same experiment, but place yourself in the water aisle at Costco. Suddenly you choose differently. This shows a few key requirements for money to be useful. One, you need the real wealth, the actual goods and services. If there is no bottled water on that island, all the money in the world won't do you a lick of good. Two, you need someone willing to exchange the real wealth for your money. If you're alone on that island and you find a bottle of water, you don't need money to drink it, you just help yourself. Both requirements are essential. This shows us that money is a social technology. Understanding the purpose and function of this technology is critical to dispensing with misconceptions like "money=wealth". ## Money and Civilization What's the difference between a subsistence hunter/gatherer lifestyle and the modern civilization we all enjoy today? Specialization of labor, and complex supply chains. And what enables those civilizational necessities? Money. In a subsistence situation, everything you have is created start-to-finish by you or by your immediate family or tribe. Everyone has to be a sort of jack-of-all-trades, at least at a group level. If you want a shelter, you collect the natural materials and build it yourself. If you need clothes, you collect the fibers or skins, process them, and use the fabric to sew your own outfit. Contrast that with the electronic device you're using to read these words right now. How many people does it take to build a smartphone? Millions. Can one person do it? Absolutely not. You could give anyone in the world an entire lifetime and there's no way they could mine, process, and assemble the raw materials into a functional smartphone. It's simply too complex, too many processes and too much specialized knowledge and machinery needed. Not to mention doing it at a cost that most people on the planet can afford. That miracle is only possible because millions of people specialize in one tiny specific task related to making one part of a complex item, over and over again. The efficiency of only doing one specific task instead of being a generalist is what makes civilization possible. But there's a problem. The person who's doing one specific task to make part of one widget still needs to eat, have a place to live, clothes to wear, etc. But how do you get all that while working a full time job making widgets? You can't do it all yourself, you need to buy those things from someone else who, similarly, specializes in those necessities of life. You need money. Money is what makes the whole thing work. ## Money and Barter So what exactly is money and how does it work? In a subsistence society, you can use barter to trade with strangers. You give them some fish, they give you some clothing, everyone is happy. But barter has major problems, and doesn't work at all in complex supply chains with specialized workers. Specialized jobs don't produce valuable finished goods that can be bartered. When you solder circuit boards all day, you can't go to your local farmer and trade ten "solder circuit board" for a dozen eggs. Enter money. Money solves multiple problems that arise with barter. For one, it creates a way to compare extremely dissimilar things. How many fish is a pound of butter worth? How many eggs? With barter, every good or service has to be priced in relation to every other good or service it's exchanged for. This is impossibly cumbersome and inefficient. Having money as a unit of account is as essential to trade as having a uniform inch is to building a house. A single carpenter might be able to use the width of his hand to measure boards, but get two carpenters working together and that "handbreadth" no longer works. Second, money solves the problem of not having the correct item to barter with. If your neighbor has butter and you have fish, but your neighbor hates fish and will only accept a chicken, barter won't work. But if you can just pay him with money, he can go buy whatever he prefers. Third, money creates a way to value and reimburse specialized work. That's arguably the most important aspect. ## The Social Contract Underlying Money So what makes money function? Why would someone accept a piece of paper with a picture of a dead president in exchange for a very real and very valuable good or service? Well, the obvious answer is that they can be certain they'll be able to exchange that piece of paper with someone else and get an equally valuable good or service in the future. This is circular logic though, and leads some economists to mistakenly attribute the value of money to a "collective delusion". But since every known advanced civilization has used some form of money, calling it a delusion is both inaccurate and boorishly pretentious. To understand the real mechanism behind the phenomenon, we have to consider how money is acquired. As anyone who has ever earned an honest wage knows, getting a paycheck requires two things. One, producing a valuable good or service. And two, giving that good or service to someone else instead of immediately consuming it yourself. The first point is self-explanatory. If what you produce isn't valuable, no one will buy it. The second point needs a bit more explanation. Money is a social technology, it's only valuable in a purely monetary sense when there's someone else to trade with. When you make yourself a few eggs for breakfast, you don't pay yourself for frying the eggs. Obviously. But if you eat your eggs, then go to your job as a short-order cook at the local diner, you may spend the morning getting paid to do exactly what you did "for free" at home. The difference is in the deferred consumption. When you do a favor for someone, morality and the spirit of fairness dictates that they would be willing to return the favor in the future when you need something from them. That's how it works in a family or small community. People "owe each other one," and favors are reciprocated regularly without any money changing hands in a kind of informal credit system. But if one person starts to take advantage of others' generosity and requests a lot of favors, but always fails to reciprocate when asked, people catch on quickly. The parasitic behavior will be met with increasing unwillingness to help from members of the family or community, and in extreme cases, even exile from the community itself. This informal credit system is the simplest and most fundamental form of money, and we can learn the basic principle behind why money works by observing it. We can see that a person accumulates "credits" by contributing productive value to others without getting anything in return. The "credits" are informal mental ledger credits that represent "this person has done something productive and valuable for someone else, which means he deserves to receive something valuable in the future." If a person contributes generously enough to the community, he will build up so much "credit" with everyone that he can expect generous help in return from any member of the community. The shortcomings of this informal credit system are that one, it doesn't provide a unit of measurement to compare different goods and services accurately. This can lead to misunderstanding and disputes when different people don't value services the same way. Someone can feel that they are contributing more to the community than they're getting back in return. And two, it relies heavily on trust, and only works between people who interact on a regular basis. It would be foolish to provide favors to a stranger of unknown reputation, or someone who's just traveling through the area, because in either case there's no expectation of establishing a reciprocal relationship with that individual. Money is just a way to formalize and expand that local, informal mental ledger. It's a way to keep track, on a societal level, who has contributed their fair share to the community and is deserving of reciprocal treatment. When someone buys something from you, although you don't consciously think through what's happening, on a subconscious level you're participating in a societal dialogue that goes something like this: "This person has money, which means they're a capable, generous, reciprocal person who has contributed more to the community than they've taken. Fairness dictates that they deserve something of value as a reward for their pro-social behavior. By taking their money, and giving them something of value, I can perpetuate the cycle of rewarding people who generously and capably do work that benefits others, and that will be beneficial to me personally and also to society as a whole. By having the money they give me, I can then also signal to others that I'm the same type of generous, reciprocal, productive person, and I can expect to be rewarded for that in the future when I try to exchange this money for valuable goods and services." So the money has value, not because of some inherent quality of the paper or gold or mental "credit," but because it represents past productive behavior, but without immediate consumption. The money itself is not wealth, it's just an abstract representation, a kind of scorecard or ledger entry, of the real wealth that the holder of the money has already produced. ## Money and Capital Formation This dialogue or unwritten contract is the foundation of modern civilization. It's powerful, because deferred consumption is the mechanism of capital formation, and capital formation is the foundation of complex supply chains and technological progress. You might be able to catch enough fish to feed your family with a crude rod and line. But building a modern fishing trawler (a valuable capital good) takes thousands of people working together for a long time. All that hard work doesn't result in any fish being caught throughout the process, and all those people could instead be out fishing and catching a lot of fish to eat. But by deferring that consumption and instead putting that effort into building a capital good, you end up with a huge fishing trawler. Once it's finished, a few of those thousands of people can catch more fish in a week than all the thousands of them combined could have caught over the whole time it took to build the trawler. That makes fishing much easier and more effective in the future, making food much more plentiful and increasing the standard of living for the whole society. And money is what makes all that possible on a global scale. ## Final Thoughts Given how critical this system is to civilization, any attack on money and its function is an existential threat. Unfortunately, a failure to understand the true nature of money leads to reliance on less nuanced or completely false ideas like "money=wealth". And that gives psychological cover to parasitic anti-social behavior like creating money and giving it away to buy votes, and all sorts of other destructive and dishonest shenanigans. Understanding that money is not wealth exposes the folly of all these schemes that purport to make people wealthier simply by creating more money. Believing that money is wealth makes the MMT clowns and the Keynesian grifters sound at least marginally credible. But those are specific misconceptions that need their own detailed explanation. For now, reprogramming your mental framework to draw a strong distinction between money and real wealth will give you a solid foundation to understand economics, and to critique the many incorrect theories presented by the parasitical elements who wish to muddy the waters and avoid scrutiny of their anti-civilizational exploitation. @ 468f729d:5ab4fd5e
2024-11-25 21:46:31<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video src="http://localhost:3000/api/get-video-url?videoKey=starter-lesson-0.mp4" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls></video></div> ## Course Mission Welcome to the PlebDevs starter course! I'm Austin, the founder of PlebDevs, and I'll be walking you through this short intro starter course that will get you up and running and interacting with the rest of the content on the platform. If you're here, I'm assuming you're new to coding or just starting out. If you already have experience and have your bearings down, there's lots more intermediate and advanced content on the platform. This course is designed for absolute beginners. ## Course Goals ### Overall PlebDevs Goals 1. Learn how to code 2. Build Bitcoin/Lightning/Nostr apps 3. Become a developer This is a big journey with a lot of pieces and things to learn. The starter course is going to get you on that path as quickly as possible and make it a smooth journey. ### Starter Course Objectives 1. Give you an easy, high-level overview of the dev journey 2. Get you set up and comfortable in a development environment where you'll write and ship code 3. Give you basic experience in the languages covered in our courses and workshops There's lots of material out there that will just tell you exactly what to do and not explain why but I want you to actually understand for yourself. I want you to have a good mental model of what this journey is going to be like, what it's going to be like actually writing and pushing code. And then we're going to start getting our hands dirty and gain real experience. ## What is a PlebDev? ### Origins and Philosophy I started using the term "PlebDev" a few years ago to describe a unique approach to learning development in the Bitcoin space. It represents: - **Inclusive Learning**: Anyone can become a developer, regardless of background - **Growth Mindset**: Embracing the journey from beginner to professional - **Practical Focus**: Emphasizing real-world application development - **Community Support**: Learning and growing together ### Key Characteristics - 🌱 **Growth-Focused**: PlebDevs are always learning and improving - 🎯 **App-Centric**: Focus on building applications rather than protocol development - 🆕 **Embrace Being New**: Being a new developer is infinitely better than being on the sidelines - 🤝 **Community-Driven**: Bitcoin/Lightning/Nostr ecosystem needs more plebdevs like you! ## Our Learning Approach ### Core Principles 1. **Lower Barriers** - Simplify complex concepts - Focus on practical understanding - Build confidence through action 2. **Project-Based Learning** - Learn by doing - Create real applications - Build a portfolio as you learn 3. **MVP (Minimum Viable Product) Focus** - Start with core functionality - Get things working first - Iterate and improve 4. **Actionable Knowledge** - Focus on the 20% that delivers 80% of results - Learn what you can use right away - Build practical skills ### Teaching Methods - Detailed concept breakdowns - Line-by-line code explanations - Interactive learning - 1:1 support available - Community-driven progress ## Course Structure ### The Learning Path Instead of the traditional bottom-up approach, we use a project-focused method: ``` 🏔️ Advanced Skills 🏔️ Projects & Practice 🏔️ Core Concepts 🏔️ Development Environment 🏔️ Getting Started ``` We'll create checkpoints through projects, allowing you to: - Verify your understanding - Build your portfolio - See real progress - Have reference points for review ## Student Expectations ### What We Expect From You - **High Agency**: Take ownership of your learning journey - **Active Participation**: Engage with the material and community - **Persistence**: Push through challenges - **Curiosity**: Ask questions and explore concepts ### What You Can Expect From Us - Clear, practical instruction - Comprehensive support - Real-world applications - Community backing ## Getting Started ### Next Steps 1. Ensure you're ready to commit to learning 2. Set up your development environment (next lesson) 3. Join our community 4. Start building! ## Resources and Support ### Where to Get Help - plebdevs.com ### Tips for Success 1. Push code daily, even if it is small. 2. Focus on understanding rather than memorizing. 3. Build projects that interest you. 4. Engage with the community. 5. Don't be afraid to ask questions. ## Remember You don't need to become a "10x developer" overnight. The goal is to start writing code, build useful things, and gradually improve. Every expert was once a beginner, and the journey of a thousand miles begins with a single line of code. Ready to begin? Let's dive into the next lesson where we'll set up your development environment! 🚀
@ 468f729d:5ab4fd5e
2024-11-25 21:46:31<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video src="http://localhost:3000/api/get-video-url?videoKey=starter-lesson-0.mp4" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls></video></div> ## Course Mission Welcome to the PlebDevs starter course! I'm Austin, the founder of PlebDevs, and I'll be walking you through this short intro starter course that will get you up and running and interacting with the rest of the content on the platform. If you're here, I'm assuming you're new to coding or just starting out. If you already have experience and have your bearings down, there's lots more intermediate and advanced content on the platform. This course is designed for absolute beginners. ## Course Goals ### Overall PlebDevs Goals 1. Learn how to code 2. Build Bitcoin/Lightning/Nostr apps 3. Become a developer This is a big journey with a lot of pieces and things to learn. The starter course is going to get you on that path as quickly as possible and make it a smooth journey. ### Starter Course Objectives 1. Give you an easy, high-level overview of the dev journey 2. Get you set up and comfortable in a development environment where you'll write and ship code 3. Give you basic experience in the languages covered in our courses and workshops There's lots of material out there that will just tell you exactly what to do and not explain why but I want you to actually understand for yourself. I want you to have a good mental model of what this journey is going to be like, what it's going to be like actually writing and pushing code. And then we're going to start getting our hands dirty and gain real experience. ## What is a PlebDev? ### Origins and Philosophy I started using the term "PlebDev" a few years ago to describe a unique approach to learning development in the Bitcoin space. It represents: - **Inclusive Learning**: Anyone can become a developer, regardless of background - **Growth Mindset**: Embracing the journey from beginner to professional - **Practical Focus**: Emphasizing real-world application development - **Community Support**: Learning and growing together ### Key Characteristics - 🌱 **Growth-Focused**: PlebDevs are always learning and improving - 🎯 **App-Centric**: Focus on building applications rather than protocol development - 🆕 **Embrace Being New**: Being a new developer is infinitely better than being on the sidelines - 🤝 **Community-Driven**: Bitcoin/Lightning/Nostr ecosystem needs more plebdevs like you! ## Our Learning Approach ### Core Principles 1. **Lower Barriers** - Simplify complex concepts - Focus on practical understanding - Build confidence through action 2. **Project-Based Learning** - Learn by doing - Create real applications - Build a portfolio as you learn 3. **MVP (Minimum Viable Product) Focus** - Start with core functionality - Get things working first - Iterate and improve 4. **Actionable Knowledge** - Focus on the 20% that delivers 80% of results - Learn what you can use right away - Build practical skills ### Teaching Methods - Detailed concept breakdowns - Line-by-line code explanations - Interactive learning - 1:1 support available - Community-driven progress ## Course Structure ### The Learning Path Instead of the traditional bottom-up approach, we use a project-focused method: ``` 🏔️ Advanced Skills 🏔️ Projects & Practice 🏔️ Core Concepts 🏔️ Development Environment 🏔️ Getting Started ``` We'll create checkpoints through projects, allowing you to: - Verify your understanding - Build your portfolio - See real progress - Have reference points for review ## Student Expectations ### What We Expect From You - **High Agency**: Take ownership of your learning journey - **Active Participation**: Engage with the material and community - **Persistence**: Push through challenges - **Curiosity**: Ask questions and explore concepts ### What You Can Expect From Us - Clear, practical instruction - Comprehensive support - Real-world applications - Community backing ## Getting Started ### Next Steps 1. Ensure you're ready to commit to learning 2. Set up your development environment (next lesson) 3. Join our community 4. Start building! ## Resources and Support ### Where to Get Help - plebdevs.com ### Tips for Success 1. Push code daily, even if it is small. 2. Focus on understanding rather than memorizing. 3. Build projects that interest you. 4. Engage with the community. 5. Don't be afraid to ask questions. ## Remember You don't need to become a "10x developer" overnight. The goal is to start writing code, build useful things, and gradually improve. Every expert was once a beginner, and the journey of a thousand miles begins with a single line of code. Ready to begin? Let's dive into the next lesson where we'll set up your development environment! 🚀 @ 228dde34:b5d0345e
2024-11-25 04:14:20##### BY Cheryl Nya ##### Deputy Editor ##### Hype Issue #60 ###### Join CHERYL NYA as she talks to competitive Darts player, Pay Yu Xuan, on her journey as a young athlete and her dreams to expand the Darts scene in Singapore.  *Pay Yu Xuan, 19, youngest Premier DARTSLIVE Ambassador and national Darts player. Photo by NJ Eshani.* What does your bullseye look like? For some, it could come in the form of a scholarship or an academic achievement. Perhaps it’s a championship in your CCA and scoring long-lasting friendships. For Pay Yu Xuan, 19, her bullseye simply lies on a dartboard. “I just thought it was different …, who would’ve thought to play Darts as a sport?” Yu Xuan, explains on how she picked up the sport. What began as a casual interest quickly turned into a remarkable journey that propelled her to the international stage at just 18 years of age. She is now the youngest Darts player representing Singapore.  *Yu Xuan (middle) beginning her competitive Darts journey representing Singapore Polytechnic. Photo courtesy of Pay Yu Xuan.* Her Darts career started as a Co-Curricular Activity (CCA). “SP was the only Poly in Singapore that had Darts as a CCA and I thought that was really cool,” Yu Xuan recounts, “I started as a leisure player, but as I played, I saw myself getting closer to the target. Playing Darts [continuously] fuelled my sense of self-improvement and I just kept thinking that I could go further. That’s how I got hooked on it.”  *Yu Xuan wins the runner-up position in the Ladies Cricket Open category at the Hong Kong International Darts Festival. Photo courtesy of Pay Yu Xuan.* Like every remarkable athlete, Yu Xuan’s pursuit of success has not been easy. “Darts is a mental game,” she says, “Especially during competitions. It’s so easy to start overthinking. When that happens, you might go into self-destruction mode and it’s hard to [focus on the target]. Sometimes when I’m in front of so many cameras and I see myself on the big screen, I really feel the nerves and start to be self-conscious. I cannot show any signs of nervousness.” Not only has she had internal battles to fight, but her parents were also initially unsupportive of her dreams. With the game being tied closely to stereotypes such as drinking and smoking, Yu Xuan’s parents were afraid she might pick up unhealthy habits and had to think twice about allowing her to commit to the sport.  *Yu Xuan secures the champion position, in the selection for Singapore’s National Darts Team. Photo courtesy of Pay Yu Xuan.* However, the turning point came in December last year, when Yu Xuan was chosen to represent Team Singapore in the Hong Kong International Darts Festival. Her hard work and dedication paid off when she emerged as champion in the selection process, successfully proving her capabilities and showing her parents how passionate she truly was for the sport. After witnessing Yu Xuan’s potential, her parents eventually gave up their resistance.Seeing that she had a dream and she was about to conquer it, Yu Xuan instilled a deep confidence in them. From initially keeping away her passport to granting her permission and even giving her an allowance to compete overseas, her parents became her greatest support system. The mental toll and pressure is unfortunately something that every athlete has to go through, no matter how much you enjoy your sport. “This is not a stable incline. You’re always going up and down, it’s not easy at all,” Yu Xuan replies when asked how she overcame her challenges. “Having a strong belief system is very important to me. I know that I’ve spent a lot of time training, so I [have] learned to believe in myself. I really can do it. And this self-confidence didn’t just appear out of nowhere. I’m constantly working on it and my friends and family are the support system who encourages me.” Sharing her perspective on the beauty of Darts, Yu Xuan hits home: ”You can only hit your target if you believe you can. In this game, success is when you focus on mind over body.”  *Yu Xuan (left) with the players of Team Singapore in Hong Kong. Photo courtesy of Pay Yu Xuan.* Although Yu Xuan is an exceptional Darts player with immense potential, a fact stubbornly remains: The ‘Darting’ scene in Singapore is extremely limited. “Something that didn’t really sit well with me was that [Darts] is still too niche for the government to be supporting it, and the youths who are potentially national-level players don’t have [enough opportunities] to compete internationally,” she says. Yu Xuan recalls the time she applied for a Leave Of Absence from her classes to compete in a tournament overseas. As Darts is not recognised as a sport under the National Sports Association, her appeal was unfortunately rejected. “It’s something I hope can change,” Yu Xuan shares sincerely.  *Yu Xuan (top row, second from the left) teaching the HYPE team how to play darts as a Premier DARTSLIVE ambassador. Photo courtesy of Pay Yu Xuan.* In that effort, Yu Xuan has worked hard to prove her capabilities and has successfully qualified to be an Ambassador for DARTSLIVE, a company that provides the dartboards you see around in most SAFRA National Service Associations and bars. Not only is Yu Xuan the youngest Premier DARTSLIVE Ambassador, she is also the only female Ambassador. “Though females [tend to be] less dominant in the sport, I do hope to see more start to play Darts,” she shares. Determined to grow the darts community and raise the sport's profile in Singapore, Yu Xuan has made a bold and generous move by launching her own workshop, offering free Darts lessons to new players. “Many people don’t have [access] to learning the basics, like your stance, [or] the way you hold your dart, for example. Even the current Darts players … I just wanted to help by giving them a foundation to keep playing. I like teaching and talking to people too. That’s why I opened my Darts clinic, even though I don’t earn [a salary] from it.” “I would love to play Darts as a career in [the] future but [I will] probably have to do it overseas, in … Japan or Hong Kong, where [Darts has] a bigger community and their governments support it,” Yu Xuan shares, “I really hope Darts grows bigger in Singapore and maybe I could even work to become a coach here.”  *Hoping to encourage youths who also have a passion, she hopes that everyone can hit their own targets one day. Photo by NJ Eshani.* To the young aspiring athletes looking to follow Yu Xuan’s footsteps and become national athletes, she has this to say: “Follow your passion, because passion is your energy, and it’s what drives you to keep doing what you love every day. In everything, we’re bound to meet setbacks, it’s about how you recover from it. That determines who will be the winners, who will stay ahead and who will fall back. I promise you, your hard work will pay off one day. Keep pushing and be confident! If you don’t believe in yourself then who will believe in you?”
@ 228dde34:b5d0345e
2024-11-25 04:14:20##### BY Cheryl Nya ##### Deputy Editor ##### Hype Issue #60 ###### Join CHERYL NYA as she talks to competitive Darts player, Pay Yu Xuan, on her journey as a young athlete and her dreams to expand the Darts scene in Singapore.  *Pay Yu Xuan, 19, youngest Premier DARTSLIVE Ambassador and national Darts player. Photo by NJ Eshani.* What does your bullseye look like? For some, it could come in the form of a scholarship or an academic achievement. Perhaps it’s a championship in your CCA and scoring long-lasting friendships. For Pay Yu Xuan, 19, her bullseye simply lies on a dartboard. “I just thought it was different …, who would’ve thought to play Darts as a sport?” Yu Xuan, explains on how she picked up the sport. What began as a casual interest quickly turned into a remarkable journey that propelled her to the international stage at just 18 years of age. She is now the youngest Darts player representing Singapore.  *Yu Xuan (middle) beginning her competitive Darts journey representing Singapore Polytechnic. Photo courtesy of Pay Yu Xuan.* Her Darts career started as a Co-Curricular Activity (CCA). “SP was the only Poly in Singapore that had Darts as a CCA and I thought that was really cool,” Yu Xuan recounts, “I started as a leisure player, but as I played, I saw myself getting closer to the target. Playing Darts [continuously] fuelled my sense of self-improvement and I just kept thinking that I could go further. That’s how I got hooked on it.”  *Yu Xuan wins the runner-up position in the Ladies Cricket Open category at the Hong Kong International Darts Festival. Photo courtesy of Pay Yu Xuan.* Like every remarkable athlete, Yu Xuan’s pursuit of success has not been easy. “Darts is a mental game,” she says, “Especially during competitions. It’s so easy to start overthinking. When that happens, you might go into self-destruction mode and it’s hard to [focus on the target]. Sometimes when I’m in front of so many cameras and I see myself on the big screen, I really feel the nerves and start to be self-conscious. I cannot show any signs of nervousness.” Not only has she had internal battles to fight, but her parents were also initially unsupportive of her dreams. With the game being tied closely to stereotypes such as drinking and smoking, Yu Xuan’s parents were afraid she might pick up unhealthy habits and had to think twice about allowing her to commit to the sport.  *Yu Xuan secures the champion position, in the selection for Singapore’s National Darts Team. Photo courtesy of Pay Yu Xuan.* However, the turning point came in December last year, when Yu Xuan was chosen to represent Team Singapore in the Hong Kong International Darts Festival. Her hard work and dedication paid off when she emerged as champion in the selection process, successfully proving her capabilities and showing her parents how passionate she truly was for the sport. After witnessing Yu Xuan’s potential, her parents eventually gave up their resistance.Seeing that she had a dream and she was about to conquer it, Yu Xuan instilled a deep confidence in them. From initially keeping away her passport to granting her permission and even giving her an allowance to compete overseas, her parents became her greatest support system. The mental toll and pressure is unfortunately something that every athlete has to go through, no matter how much you enjoy your sport. “This is not a stable incline. You’re always going up and down, it’s not easy at all,” Yu Xuan replies when asked how she overcame her challenges. “Having a strong belief system is very important to me. I know that I’ve spent a lot of time training, so I [have] learned to believe in myself. I really can do it. And this self-confidence didn’t just appear out of nowhere. I’m constantly working on it and my friends and family are the support system who encourages me.” Sharing her perspective on the beauty of Darts, Yu Xuan hits home: ”You can only hit your target if you believe you can. In this game, success is when you focus on mind over body.”  *Yu Xuan (left) with the players of Team Singapore in Hong Kong. Photo courtesy of Pay Yu Xuan.* Although Yu Xuan is an exceptional Darts player with immense potential, a fact stubbornly remains: The ‘Darting’ scene in Singapore is extremely limited. “Something that didn’t really sit well with me was that [Darts] is still too niche for the government to be supporting it, and the youths who are potentially national-level players don’t have [enough opportunities] to compete internationally,” she says. Yu Xuan recalls the time she applied for a Leave Of Absence from her classes to compete in a tournament overseas. As Darts is not recognised as a sport under the National Sports Association, her appeal was unfortunately rejected. “It’s something I hope can change,” Yu Xuan shares sincerely.  *Yu Xuan (top row, second from the left) teaching the HYPE team how to play darts as a Premier DARTSLIVE ambassador. Photo courtesy of Pay Yu Xuan.* In that effort, Yu Xuan has worked hard to prove her capabilities and has successfully qualified to be an Ambassador for DARTSLIVE, a company that provides the dartboards you see around in most SAFRA National Service Associations and bars. Not only is Yu Xuan the youngest Premier DARTSLIVE Ambassador, she is also the only female Ambassador. “Though females [tend to be] less dominant in the sport, I do hope to see more start to play Darts,” she shares. Determined to grow the darts community and raise the sport's profile in Singapore, Yu Xuan has made a bold and generous move by launching her own workshop, offering free Darts lessons to new players. “Many people don’t have [access] to learning the basics, like your stance, [or] the way you hold your dart, for example. Even the current Darts players … I just wanted to help by giving them a foundation to keep playing. I like teaching and talking to people too. That’s why I opened my Darts clinic, even though I don’t earn [a salary] from it.” “I would love to play Darts as a career in [the] future but [I will] probably have to do it overseas, in … Japan or Hong Kong, where [Darts has] a bigger community and their governments support it,” Yu Xuan shares, “I really hope Darts grows bigger in Singapore and maybe I could even work to become a coach here.”  *Hoping to encourage youths who also have a passion, she hopes that everyone can hit their own targets one day. Photo by NJ Eshani.* To the young aspiring athletes looking to follow Yu Xuan’s footsteps and become national athletes, she has this to say: “Follow your passion, because passion is your energy, and it’s what drives you to keep doing what you love every day. In everything, we’re bound to meet setbacks, it’s about how you recover from it. That determines who will be the winners, who will stay ahead and who will fall back. I promise you, your hard work will pay off one day. Keep pushing and be confident! If you don’t believe in yourself then who will believe in you?” @ d7c6d014:a6abb6b8
2024-11-23 18:40:47こんにちは!kohei です。 久々のエントリ投下ですが、今回は先日弊 TL で話題になっていた、Android を P2P のローカルリレーサーバー化して Tor で公開する方法を紹介していこうと思います。 ## 用意するもの 1. Android 端末 2. Orbot 3. Citrine 4. Amethyst ## 前提と下準備 今回は、Orbot の詳細設定は省いて、Power User Mode の設定が完了している前提でお話を進めます。 Android 端末を用意して、2~4 のアプリをインストールしておいてください。 ## 設定方法 それでは早速設定していきましょう。 まず、Citrine を起動して、Settings のタブからローカルリレーの詳細を設定します。  設定が終了したら、ローカルリレーを起動します。  また、ここで表示されるポート番号をメモしてください。  次に、More のタブに移り、Hosted Onion Services へアクセスし、Service Type の項目で User Services にチェックを入れて、右下の + マークをタップすると以下のポップアップが表示されます。(Orbot がスクショを許してくれないので一部画像割愛) 表示されたら、Name に任意の名前を、Local Port と Onion Port に先ほどメモした Citrine のポート番号を入力します。  入力したら再起動を求められるので再起動してください。 再起動後に Hosted Onion Services の項目に .onion のアドレスが表示されたら成功です (何故か私の環境では、一回の再起動では設定が反映されなかったのですが、もし同じような現象が起きた場合は、再起動 -> Connect -> .onion アドレスが発行されてるかの確認、を数回試すと発行されるはずです) 発行されたら、.onion アドレスをタップしてクリップボードにコピーします。 次に、Amethyst を起動して、リレーの設定画面に入り、Outbox の設定にコピーした .onion アドレスを貼り付けて保存します。  後は、Amethyst 側で Orbot のポート番号を設定して Orbot に接続すれば BOOM! 設定完了です。  お疲れ様でした! 素敵な Nostr ライフを!
@ d7c6d014:a6abb6b8
2024-11-23 18:40:47こんにちは!kohei です。 久々のエントリ投下ですが、今回は先日弊 TL で話題になっていた、Android を P2P のローカルリレーサーバー化して Tor で公開する方法を紹介していこうと思います。 ## 用意するもの 1. Android 端末 2. Orbot 3. Citrine 4. Amethyst ## 前提と下準備 今回は、Orbot の詳細設定は省いて、Power User Mode の設定が完了している前提でお話を進めます。 Android 端末を用意して、2~4 のアプリをインストールしておいてください。 ## 設定方法 それでは早速設定していきましょう。 まず、Citrine を起動して、Settings のタブからローカルリレーの詳細を設定します。  設定が終了したら、ローカルリレーを起動します。  また、ここで表示されるポート番号をメモしてください。  次に、More のタブに移り、Hosted Onion Services へアクセスし、Service Type の項目で User Services にチェックを入れて、右下の + マークをタップすると以下のポップアップが表示されます。(Orbot がスクショを許してくれないので一部画像割愛) 表示されたら、Name に任意の名前を、Local Port と Onion Port に先ほどメモした Citrine のポート番号を入力します。  入力したら再起動を求められるので再起動してください。 再起動後に Hosted Onion Services の項目に .onion のアドレスが表示されたら成功です (何故か私の環境では、一回の再起動では設定が反映されなかったのですが、もし同じような現象が起きた場合は、再起動 -> Connect -> .onion アドレスが発行されてるかの確認、を数回試すと発行されるはずです) 発行されたら、.onion アドレスをタップしてクリップボードにコピーします。 次に、Amethyst を起動して、リレーの設定画面に入り、Outbox の設定にコピーした .onion アドレスを貼り付けて保存します。  後は、Amethyst 側で Orbot のポート番号を設定して Orbot に接続すれば BOOM! 設定完了です。  お疲れ様でした! 素敵な Nostr ライフを! @ 228dde34:b5d0345e
2024-11-22 04:57:34##### BY Glenda Chong ##### Editorial Admin ##### Hype Issue #60 ###### Join GLENDA CHONG as she talks to founder of media and creative agency, DANAMIC, Danish Lukawski, on what it takes to learn to become an entrepreneur from the ground up.  *Danish Lukawski, founder of creative and media agency DANAMIC. Photo courtesy of Danish Lukawski.* When you were ten years old, how did you get your pocket money? At that age, perhaps you begged your parents for money. Danish Lukawski did things differently; he started a business to earn his own. What started as him wanting to put up photos of his pet hamsters online by learning the now-discontinued HTML editor tool Microsoft Frontpage, became a booming business when a friend’s father needed a site for his printer-selling business. Looking back at his earliest venture, Danish had but two regrets: he should have taken the leap sooner, and he should have charged his family friend more than $20. While he can laugh at those early days now, those little lessons unknowingly set the stage for something bigger. I spoke to Danish Lukawski, founder of the creative and media agency DANAMIC on his unique journey and the lessons learnt to become the entrepreneur and associate lecturer he is today. ### How He Got Started For most, school is a place with a clear-cut path where you take the courses that aid you in your journey to your future career. Danish took a diploma in Information Technology at Ngee Ann Polytechnic and explored his interest in media by augmenting his diploma with a few modules from the Mass Communication diploma. However, the one other area he had equal passion for - entrepreneurship, wasn’t something the school offered at the time. So it seemed doubtful that, without the resources on offer, Danish could have hoped to become one. Despite this, he showed that the absence of a path doesn’t mean a lack of possibilities - sometimes, it’s an invitation to create your own. Danish took it upon himself to explore the world of entrepreneurship by attending events linked to Ngee Ann Polytechnic. This was also where help from his Film & Media Studies teachers came in handy, with Mr. Jon Foo bringing him to film galas to meet directors and producers and Ms. Sharon Ismail helping him expand his professional network. Outside of building connections with industry people, he also taught himself to build up his skills and qualifications to become an entrepreneur. Why self-taught, you might ask? Simply put, it boiled down to how entrepreneurial courses at the time felt “fluffy”. Instead he directed his energy into obtaining certifications, from companies like Meta, that give him credibility with clients.  *Danish (second from left) also took up a course directly from TikTok, allowing his company to be TikTok Ad certified. Photo courtesy of Danish Lukawski.* ### The Challenges He Faced Building DANAMIC When asked about memorable mistakes, Danish mentioned how it took “19 to 29 different failures” before landing on his company’s first “Yes”. Rejection never gets easy, and he remembers it all too well. “Back when we first got our first office, we tried to kind of knock on everyone’s door in the same building,” He said. Sadly, once his new building neighbours could pick up that they were attempting to sell something, doors were closed. Eventually, a clinic gave them a chance and tried his company’s media services for a few months.  *Danish’s company celebrating Christmas just after moving into their office. Photo courtesy of Danish Lukawski.* Another big hurdle Danish had to overcome was hiring. Sometimes, some hires weren’t good fits and this is where he believes culture-fit is important. “If they didn’t fit in the culture then they either felt like the whole place is against them or they would always be working in a way that everyone else cannot figure out how to work with.” Ultimately, it’s better to be particular when hiring, rather than hiring incompatible employees that leave quickly and affect morale. And just when you think that Danish has done it all, his story is far from over. Building his own business was not enough for him; he wanted to give back. ### Becoming an Associate Lecturer You’d probably look at Danish as though he has two heads when he says this, but of the many reasons why he became an associate lecturer, one was that“it’s like taking a break”! The one joke he shares whenever this gets brought up is that he traded his 9 to 5 to work 24/7. Becoming an associate lecturer meant he could “partition a day out” where he puts full focus into teaching classes at Ngee Ann Polytechnic’s School of Infocomm Technology whilst turning off from everything else. The second reason was so he could “keep in touch with youth”. Danish admits that interacting with his students gives him plenty of direction in marketing when applied back to his main work, but ultimately keeping in touch with young people allows him “to keep on the ground”. “It means a lot to me because I get to see what they care about, what they’re consuming and then I know where they’re at,” Danish said. In a nutshell, it helps to close the generation gap as he gets to understand the “psyche of where they are as a generation”.  *Aside from teaching at Ngee Ann Polytechnic and NUS, Danish also holds sharings across various schools, with this one being held at Greendale Secondary School. Photo courtesy of Danish Lukawski.* Finally, the most important motivator for teaching at Ngee Ann Polytechnic was, of course, his desire to give back to the school. While he “could have gone to any other polytechnic”, Ngee Ann Polytechnic was one of the institutions that made him who he is today. Aside from this, he also occasionally returns to his other alma mater, the National University of Singapore, as an industry specialist. This is where his journey comes full circle, as Danish becomes the teacher he didn’t have in his schooling years, imparting his knowledge in a course on entrepreneurship in the new age where students pitch their business ideas to him.  *Danish sharing on entrepreneurship at a cognitio event where founders of start-ups shared on their work, in NUS. Photo courtesy of Danish Lukawski.* ### Advice for Future Entrepreneurs As Danish helps shape the minds of future innovators in the classroom, he also has additional insights to provide outside of it. When asked to advise anyone with a background similar to his wanting to be an entrepreneur, he has two messages to share. Danish explains a mental model of thinking about “the land of prosperity” vs. “the land of scarcity”. “I believe in the land of prosperity because while everyone is fighting for that one strange plot of land, I’m going like ‘Guys, there are nine plots here. What are you all doing?’.” Although there are chances that you might not be able to compete, “there’s always a chance to pivot” or if not, “there’s always a chance to disrupt”. And to him, just because something’s been done before, it doesn’t mean there aren’t better ways of going about it. “Just gather all the opportunities you want,” Danish stated. ”There’s no harm in trying something and failing cause what do you have to lose? The most you lose is just the time or maybe a bit of money or whatever energy you’ve expended but the experience is invaluable than never trying at all.” Another piece of advice Danish had: don't be afraid to share your ideas. Many partners he has worked with were unafraid to share because even if one stole an idea from the other, should the idea fail, they have helped the other “figure out that it was a stupid idea”.  *Danish (second from right) taking home an SME 500 Singapore Award awarded to DANAMIC at the SMESummit 2023. Photo courtesy of Danish Lukawski.* Above all else, a willingness to share ideas opens many doors in business. When people come together and share, there will often be synergy, and that’s where enduring partnerships can form. Or in Danish’s words, “I believe being open and true is better than being close-minded and scared.”
@ 228dde34:b5d0345e
2024-11-22 04:57:34##### BY Glenda Chong ##### Editorial Admin ##### Hype Issue #60 ###### Join GLENDA CHONG as she talks to founder of media and creative agency, DANAMIC, Danish Lukawski, on what it takes to learn to become an entrepreneur from the ground up.  *Danish Lukawski, founder of creative and media agency DANAMIC. Photo courtesy of Danish Lukawski.* When you were ten years old, how did you get your pocket money? At that age, perhaps you begged your parents for money. Danish Lukawski did things differently; he started a business to earn his own. What started as him wanting to put up photos of his pet hamsters online by learning the now-discontinued HTML editor tool Microsoft Frontpage, became a booming business when a friend’s father needed a site for his printer-selling business. Looking back at his earliest venture, Danish had but two regrets: he should have taken the leap sooner, and he should have charged his family friend more than $20. While he can laugh at those early days now, those little lessons unknowingly set the stage for something bigger. I spoke to Danish Lukawski, founder of the creative and media agency DANAMIC on his unique journey and the lessons learnt to become the entrepreneur and associate lecturer he is today. ### How He Got Started For most, school is a place with a clear-cut path where you take the courses that aid you in your journey to your future career. Danish took a diploma in Information Technology at Ngee Ann Polytechnic and explored his interest in media by augmenting his diploma with a few modules from the Mass Communication diploma. However, the one other area he had equal passion for - entrepreneurship, wasn’t something the school offered at the time. So it seemed doubtful that, without the resources on offer, Danish could have hoped to become one. Despite this, he showed that the absence of a path doesn’t mean a lack of possibilities - sometimes, it’s an invitation to create your own. Danish took it upon himself to explore the world of entrepreneurship by attending events linked to Ngee Ann Polytechnic. This was also where help from his Film & Media Studies teachers came in handy, with Mr. Jon Foo bringing him to film galas to meet directors and producers and Ms. Sharon Ismail helping him expand his professional network. Outside of building connections with industry people, he also taught himself to build up his skills and qualifications to become an entrepreneur. Why self-taught, you might ask? Simply put, it boiled down to how entrepreneurial courses at the time felt “fluffy”. Instead he directed his energy into obtaining certifications, from companies like Meta, that give him credibility with clients.  *Danish (second from left) also took up a course directly from TikTok, allowing his company to be TikTok Ad certified. Photo courtesy of Danish Lukawski.* ### The Challenges He Faced Building DANAMIC When asked about memorable mistakes, Danish mentioned how it took “19 to 29 different failures” before landing on his company’s first “Yes”. Rejection never gets easy, and he remembers it all too well. “Back when we first got our first office, we tried to kind of knock on everyone’s door in the same building,” He said. Sadly, once his new building neighbours could pick up that they were attempting to sell something, doors were closed. Eventually, a clinic gave them a chance and tried his company’s media services for a few months.  *Danish’s company celebrating Christmas just after moving into their office. Photo courtesy of Danish Lukawski.* Another big hurdle Danish had to overcome was hiring. Sometimes, some hires weren’t good fits and this is where he believes culture-fit is important. “If they didn’t fit in the culture then they either felt like the whole place is against them or they would always be working in a way that everyone else cannot figure out how to work with.” Ultimately, it’s better to be particular when hiring, rather than hiring incompatible employees that leave quickly and affect morale. And just when you think that Danish has done it all, his story is far from over. Building his own business was not enough for him; he wanted to give back. ### Becoming an Associate Lecturer You’d probably look at Danish as though he has two heads when he says this, but of the many reasons why he became an associate lecturer, one was that“it’s like taking a break”! The one joke he shares whenever this gets brought up is that he traded his 9 to 5 to work 24/7. Becoming an associate lecturer meant he could “partition a day out” where he puts full focus into teaching classes at Ngee Ann Polytechnic’s School of Infocomm Technology whilst turning off from everything else. The second reason was so he could “keep in touch with youth”. Danish admits that interacting with his students gives him plenty of direction in marketing when applied back to his main work, but ultimately keeping in touch with young people allows him “to keep on the ground”. “It means a lot to me because I get to see what they care about, what they’re consuming and then I know where they’re at,” Danish said. In a nutshell, it helps to close the generation gap as he gets to understand the “psyche of where they are as a generation”.  *Aside from teaching at Ngee Ann Polytechnic and NUS, Danish also holds sharings across various schools, with this one being held at Greendale Secondary School. Photo courtesy of Danish Lukawski.* Finally, the most important motivator for teaching at Ngee Ann Polytechnic was, of course, his desire to give back to the school. While he “could have gone to any other polytechnic”, Ngee Ann Polytechnic was one of the institutions that made him who he is today. Aside from this, he also occasionally returns to his other alma mater, the National University of Singapore, as an industry specialist. This is where his journey comes full circle, as Danish becomes the teacher he didn’t have in his schooling years, imparting his knowledge in a course on entrepreneurship in the new age where students pitch their business ideas to him.  *Danish sharing on entrepreneurship at a cognitio event where founders of start-ups shared on their work, in NUS. Photo courtesy of Danish Lukawski.* ### Advice for Future Entrepreneurs As Danish helps shape the minds of future innovators in the classroom, he also has additional insights to provide outside of it. When asked to advise anyone with a background similar to his wanting to be an entrepreneur, he has two messages to share. Danish explains a mental model of thinking about “the land of prosperity” vs. “the land of scarcity”. “I believe in the land of prosperity because while everyone is fighting for that one strange plot of land, I’m going like ‘Guys, there are nine plots here. What are you all doing?’.” Although there are chances that you might not be able to compete, “there’s always a chance to pivot” or if not, “there’s always a chance to disrupt”. And to him, just because something’s been done before, it doesn’t mean there aren’t better ways of going about it. “Just gather all the opportunities you want,” Danish stated. ”There’s no harm in trying something and failing cause what do you have to lose? The most you lose is just the time or maybe a bit of money or whatever energy you’ve expended but the experience is invaluable than never trying at all.” Another piece of advice Danish had: don't be afraid to share your ideas. Many partners he has worked with were unafraid to share because even if one stole an idea from the other, should the idea fail, they have helped the other “figure out that it was a stupid idea”.  *Danish (second from right) taking home an SME 500 Singapore Award awarded to DANAMIC at the SMESummit 2023. Photo courtesy of Danish Lukawski.* Above all else, a willingness to share ideas opens many doors in business. When people come together and share, there will often be synergy, and that’s where enduring partnerships can form. Or in Danish’s words, “I believe being open and true is better than being close-minded and scared.” @ e373ca41:b82abcc5
2024-11-21 09:47:26 The last few years are unlikely to evoke positive associations for most people: corona madness, climate and trans ideology, a few wars in between and now the weather is also going crazy. You feel more reminded of the biblical plagues and the apocalypse than motivated to make positive changes to the system. It seems as if the world is in the hands of fanatical do-gooders and globalist social engineers. But the world is always in the hands of everyone. There is no responsibility for the future in the hands of some kind of “elite”, unless the citizens voluntarily leave it to them. Apocalypse literally means “unveiling”. In times of crisis, the core of reality is peeled out and all illusions fall away. **Golden times for system explorers** In turbulent times like these, unbreakable forest dwellers and resisters, prognosticators, esotericists and also system busters cavort. This is also a constant in history: times of crisis were often times of new beginnings. In knowledge revolutions, new knowledge inevitably mixed with new technology and also a new spiritual orientation towards the world. Before the outside world is created, it must be conceived internally. Around 500 years ago, the plague repeatedly cut new swathes through Europe, while at the same time Venice began its rise as a major trading power, the Medici banking system began to flourish and, a little later, so did art. This boom was preceded by something that at first glance seemed “boring”, such as the invention of double-entry bookkeeping by the monk Luca Pacioli at the end of the 15th century. In the following century, the thinker Giordano Bruno moved from city to city in search of employment, and in the end, the system-breaker was burned as a heretic on the Campo de' Fiori in Rome. Meanwhile, astronomers, magicians, artists and alchemists bustled about at the court of the Habsburg Rudolf II in Prague. Some talked to angels, others tried their hand at producing gold. Those who ridicule alchemical experiments today as heresies should at least google how phosphorus and porcelain were discovered. To be outmoded and unworldly means to be in search of something different. Great visionaries from Rudolf Steiner to Albert Einstein, Nikola Tesla and Richard Buckminster-Fuller have always known that the best way to change the system is to go outside the system and create something new from there. You don't change the old by fighting it. The best way to replace it is to think in new forms that make the old forms obsolete, said Buckminster-Fuller. **Brains moved the world more than the guillotine** Working on the old is like dancing with zombies. Creating the new, on the other hand, inevitably brings the old into competition with the system. If the new is better, the old system is obsolete. “Video killed the Radio Star” sang the Buggles in 1979 (the first clip of the MTV era) and they were just as right as Steve Jobs, who threw several industries overboard with the iPhone. What you previously needed 20 devices for, from dictation machines to telephones and “Walkmans”, you now had in your pocket. Thinking outside the system, which you don't learn within the system, combined with technology, is the sharpest knife in history when it comes to change. Brains moved more than the guillotine. In today's world, everyone is a potential system changer. There has never been a time when the tools of change have been available to as many people as they are today. At the same time, we live in a time in which fewer people than ever before determine the fate of everyone. How does this fit together? There is an infinite systematic potential for change, and this lies solely with the people who have not yet made use of the available tools. But this wave is irreversibly set in motion; it is rolling and no one knows when it will turn into a tsunami. Free speech and critical journalism are under massive attack. With the [Pareto Project](https://www.freischwebende-intelligenz.org/p/pareto-projekt-beenden-wir-jetzt) we want to make censorship-resistant publishing the new standard. Today, we have the opportunity to consign the phenomenon of censorship to the landfill of history. Are you thinking along similar lines? What should the journalism of the future look like? Help us as a tester, migrate your content as a journalist or as a publication, support us as a developer or contribute your ideas: [Kontakt@idw-europe.org](mailto:kontakt@idw-europe.org) **The great transformation** We are living in the midst of a quiet revolution, with quiet revolutionaries. Pavel Durov from Telegram would certainly have got on well with Giordano Bruno. Bitcoin inventor Satoshi Nakamoto might have felt at home at the court of Rudolf II in the past. The path to change follows similar patterns of transformation. In the past, the power of the individual was seen as being sand in the gears of the system. “Man of labor, wake up! And recognize your power! All wheels stand still when your strong arm wills it,” wrote Georg Herwegh. Today, anyone can create their own little system. With Bitcoin, uncensorable money is already in circulation. The next big battle is over the uncensorability of information and it is currently underway. The best way to share centralized power, whether it's media power or a central bank cartel, is to distribute power through decentralized systems. This is essentially a feudalistic redistribution: the old feudal system is being replaced by the reassertion of power for the individual. What role will Switzerland, the country of countless inventions, play in this development? Hardly any other country is so innovative and therefore so well positioned for this system transformation. The most successful Bitcoin app in Europe already comes from Switzerland. The Relai app is an application for secure self-custody of Bitcoin, without the influence of others. Relai AG was recently voted the best crypto startup and second-best financial startup in the country, and is rushing from one growth success to the next. The company is currently preparing to conquer the European market even more effectively. Gaining control for the individual means losing control for the old (money) system. This principle also applies in other sectors. For example, iVault AG from Thalwil is currently working on opening up the “sharing economy” market. Anyone who wants to easily rent out their e-bike, car or lawnmower to others, for example, can do so via the ivault.io app and benefit directly from their own sustainability. Here too, old centralized platforms are being disempowered and individuals are taking their fate into their own hands. It's always the same pattern and principle: if you don't want to be managed by others, you have to manage yourself. This applies to money, information and even lawnmowers and e-bikes. --- Want to learn more about the [Pareto Project](https://pareto.space)? We build a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Zap me, if you want to contribute (all Zaps go to the project).
@ e373ca41:b82abcc5
2024-11-21 09:47:26 The last few years are unlikely to evoke positive associations for most people: corona madness, climate and trans ideology, a few wars in between and now the weather is also going crazy. You feel more reminded of the biblical plagues and the apocalypse than motivated to make positive changes to the system. It seems as if the world is in the hands of fanatical do-gooders and globalist social engineers. But the world is always in the hands of everyone. There is no responsibility for the future in the hands of some kind of “elite”, unless the citizens voluntarily leave it to them. Apocalypse literally means “unveiling”. In times of crisis, the core of reality is peeled out and all illusions fall away. **Golden times for system explorers** In turbulent times like these, unbreakable forest dwellers and resisters, prognosticators, esotericists and also system busters cavort. This is also a constant in history: times of crisis were often times of new beginnings. In knowledge revolutions, new knowledge inevitably mixed with new technology and also a new spiritual orientation towards the world. Before the outside world is created, it must be conceived internally. Around 500 years ago, the plague repeatedly cut new swathes through Europe, while at the same time Venice began its rise as a major trading power, the Medici banking system began to flourish and, a little later, so did art. This boom was preceded by something that at first glance seemed “boring”, such as the invention of double-entry bookkeeping by the monk Luca Pacioli at the end of the 15th century. In the following century, the thinker Giordano Bruno moved from city to city in search of employment, and in the end, the system-breaker was burned as a heretic on the Campo de' Fiori in Rome. Meanwhile, astronomers, magicians, artists and alchemists bustled about at the court of the Habsburg Rudolf II in Prague. Some talked to angels, others tried their hand at producing gold. Those who ridicule alchemical experiments today as heresies should at least google how phosphorus and porcelain were discovered. To be outmoded and unworldly means to be in search of something different. Great visionaries from Rudolf Steiner to Albert Einstein, Nikola Tesla and Richard Buckminster-Fuller have always known that the best way to change the system is to go outside the system and create something new from there. You don't change the old by fighting it. The best way to replace it is to think in new forms that make the old forms obsolete, said Buckminster-Fuller. **Brains moved the world more than the guillotine** Working on the old is like dancing with zombies. Creating the new, on the other hand, inevitably brings the old into competition with the system. If the new is better, the old system is obsolete. “Video killed the Radio Star” sang the Buggles in 1979 (the first clip of the MTV era) and they were just as right as Steve Jobs, who threw several industries overboard with the iPhone. What you previously needed 20 devices for, from dictation machines to telephones and “Walkmans”, you now had in your pocket. Thinking outside the system, which you don't learn within the system, combined with technology, is the sharpest knife in history when it comes to change. Brains moved more than the guillotine. In today's world, everyone is a potential system changer. There has never been a time when the tools of change have been available to as many people as they are today. At the same time, we live in a time in which fewer people than ever before determine the fate of everyone. How does this fit together? There is an infinite systematic potential for change, and this lies solely with the people who have not yet made use of the available tools. But this wave is irreversibly set in motion; it is rolling and no one knows when it will turn into a tsunami. Free speech and critical journalism are under massive attack. With the [Pareto Project](https://www.freischwebende-intelligenz.org/p/pareto-projekt-beenden-wir-jetzt) we want to make censorship-resistant publishing the new standard. Today, we have the opportunity to consign the phenomenon of censorship to the landfill of history. Are you thinking along similar lines? What should the journalism of the future look like? Help us as a tester, migrate your content as a journalist or as a publication, support us as a developer or contribute your ideas: [Kontakt@idw-europe.org](mailto:kontakt@idw-europe.org) **The great transformation** We are living in the midst of a quiet revolution, with quiet revolutionaries. Pavel Durov from Telegram would certainly have got on well with Giordano Bruno. Bitcoin inventor Satoshi Nakamoto might have felt at home at the court of Rudolf II in the past. The path to change follows similar patterns of transformation. In the past, the power of the individual was seen as being sand in the gears of the system. “Man of labor, wake up! And recognize your power! All wheels stand still when your strong arm wills it,” wrote Georg Herwegh. Today, anyone can create their own little system. With Bitcoin, uncensorable money is already in circulation. The next big battle is over the uncensorability of information and it is currently underway. The best way to share centralized power, whether it's media power or a central bank cartel, is to distribute power through decentralized systems. This is essentially a feudalistic redistribution: the old feudal system is being replaced by the reassertion of power for the individual. What role will Switzerland, the country of countless inventions, play in this development? Hardly any other country is so innovative and therefore so well positioned for this system transformation. The most successful Bitcoin app in Europe already comes from Switzerland. The Relai app is an application for secure self-custody of Bitcoin, without the influence of others. Relai AG was recently voted the best crypto startup and second-best financial startup in the country, and is rushing from one growth success to the next. The company is currently preparing to conquer the European market even more effectively. Gaining control for the individual means losing control for the old (money) system. This principle also applies in other sectors. For example, iVault AG from Thalwil is currently working on opening up the “sharing economy” market. Anyone who wants to easily rent out their e-bike, car or lawnmower to others, for example, can do so via the ivault.io app and benefit directly from their own sustainability. Here too, old centralized platforms are being disempowered and individuals are taking their fate into their own hands. It's always the same pattern and principle: if you don't want to be managed by others, you have to manage yourself. This applies to money, information and even lawnmowers and e-bikes. --- Want to learn more about the [Pareto Project](https://pareto.space)? We build a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Zap me, if you want to contribute (all Zaps go to the project). @ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08### Tldr - Nostr is an open protocol which is interoperable with all kinds of other technologies - You can use this interoperability to create custom solutions - Nostr apps define a custom URI scheme handler "nostr:" - In this blog I use this to integrate Nostr with NFC cards - I create a Nostr NFC "login card" which allows me to log into Amethyst client - I create a Nostr NFC "business card" which allows anyone to find my profile with a tap ### Inter-Op All The Things! Nostr is a new open social protocol for the internet. This open nature is very exciting because it means Nostr can add new capabilities to all other internet-connected technologies, from browsers to web applications. In my view, it achieves this through three core capabilities. - A lightweight decentralised identity (Nostr keys, "npubs" and "nsecs"), - A lightweight data distribution network (Nostr relays), - A set of data interoperability standards (The Nostr Improvement Protocols "NIPs"), including the "nostr:" URI which we'll use in this post. The lightweight nature is its core strength. Very little is required to interoperate with Nostr, which means many existing technologies can be easily used with the network. Over the next few blog posts, I'll explore different Nostr inter-op ideas, and also deliver my first small open source projects to the community. I'll cover– - NFC cards integrated with Nostr (in this post), - Workflow Automations integrated with Nostr, - AI LLMs integrated with Nostr. #### The "Nostr:" URI One feature of Nostr is it defines a custom URI scheme handler "nostr:". What is that? A URI is used to identify a resource in a system. A system will have a protocol handler registry used to store such URI's, and if a system has a URI registered, then it knows what to do when it sees it. You are probably already familiar with some URI schemes such as "http:" and "mailto:". For example, when you click an http link, the system knows that it describes an http resource and opens a web browser to fetch the content from the internet. A nostr: link operates in the same way. The nostr: prefix indicates a custom URI scheme specifically designed for the Nostr protocol. If a system has a Nostr application installed, that application may have registered "nostr:" in the protocol handler registry. On that system when a "nostr:" URI is clicked, the system will know that it describes a nostr resource and open the Nostr client to fetch the content from the nostr relay network. This inter-op with the protocol handler registry gives us the power to do nice and exciting things with other technologies. ### Nostr and NFC Another technology that uses URIs is NFC cards. NFC (Near Field Communication) is a wireless technology that enables devices to exchange data over a few centimeters. It’s widely used in contactless payments, access control, and information sharing. NFC tags are small chips embedded in cards or stickers which can store data like plain text, URLs, or custom URIs. They are very cheap (cents each) and widely available (Amazon with next day delivery). When an NFC tag contains a URI, such as a http: (or nostr:) link, it acts as a trigger. Tapping the tag with an NFC-enabled device launches the associated application and processes the URI. For example, tapping a tag with "nostr:..." could open a Nostr client, directing it to a specific login page, public profile, or event. This inter-op allows us to bridge the physical world to Nostr with just a tap. #### Many useful ideas There are many interesting ways to use this. Too many for me to explore. Perhaps some of these are interesting for your next side hustle? - Nostr NFC "login cards" – tap to log into Amethyst on Android, - Nostr NFC "business cards" – give to connections so they can tap to load your npub, - Nostr NFC "payment cards" – integrating lightning network or ecash, - Nostr NFC "doorbells", "punch cards", "drop boxes", or "dead drops" – put a tag in a specific place and tap to open a location-specific message or chat, - Integrations with other access control systems, - Integrations with other home automation systems, - Many more ... To start with I have built and use the "login card" and "business card" solutions. This blog post will show you how to do the same. ### Nostr Login Card You can use an NFC card to log into your Nostr client. Most Nostr clients accept a variety of login methods, from posting your nsec into the app (insecure) to using a remote signer (more secure). A less known but more secure method is to sign into a session with a tap of a specially-configured NFC card. Amethyst is a Nostr client on Android which supports this type of login. - A secure method for logging in - Optionally keeps no log in history on the device after logout - Does not require users to know or understand how keys work - Keys are kept secure on a physically-separated card to reduce risk of compromise Nostr devs think that this is useful for anti-establishment actors–Fair enough. For me, I am interested in this login card pattern as it could be useful for rolling out identities within an organisation context with less training (office workers are already familiar with door access cards). This pattern potentially abstracts away key management to the IT or ops team who provision the cards. I first discovered this when [Kohei](nostr:npub16lrdq99ng2q4hg5ufre5f8j0qpealp8544vq4ctn2wqyrf4tk6uqn8mfeq) demonstrated it in [his video](nostr:nevent1qqstx0jy5jvzgh7wr6entjuw7h58d7mapupfdpt9hkf7s4gze34a0vspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzp47x6q2txs5ptw3fcj8ngj0y7qrnm7z0ft2cptshx5uqgxn2hd4ckqyqd3). Here's how you set it up at a high level– 1. Buy yourself some NFC cards 2. Get your Nostr key ready in an encrypted, password protected format called "nencryptsec" 3. Write the nencryptsec to the NFC card as a custom URI 4. Tap to load the login screen, and enter your password to login Here it is in detail– #### Buy yourself some NFC cards I found no specific requirements. As usual with Nostr so far, I tried to the cheapest possible route and it worked. Generic brand NFC cards shipped from China, I believe it was 50X for $15 from Amazon. Your mileage may vary. #### Get your Nostr key ready Your key will be saved to the NFC card in an encrypted password-protected format called "nencryptsec". Several applications support this. As we'll be using this to login to Amethyst, we will use Amethyst to output the nencryptsec for us. 1. Login to Amethyst with your nsec, 2. Open the sidebar and click "Backup Keys", 3. Enter a password, and click "Encrypt and my secret key", 4. It will add the password-protected key to your clipboard in the format "ncryptsec1...", 5. Remember to backup your password. #### Write the ncryptsec to the NFC card 1. Download the free [NFC Tools app](https://play.google.com/store/apps/details?id=com.wakdev.wdnfc) to your device, and open it, 2. Click "Write" and "Add a record", then click "Custom URL / URI", 3. Paste your nencryptsec with the nostr URI in front, i.e. "nostr:ncryptsec1..." and click OK, 4. Click "Write". NFC Tools will prompt you to "Approach an NFC tag", 5. Place your NFC card against your phone, and it will write to the card, 6. Your card is ready. #### Tap to load the login screen Tap the card against your phone again, and your phone should open the login screen of Amethyst and prompt you for your password. Once you enter your password, Amethyst will decrypt your nsec and log you in. Optionally, you can also set the app to forget you once you log out. You have created a Nostr NFC "login card". ### Nostr Business Card You can use another NFC card to give anyone you meet a link straight to your Nostr profile. I attended [Peter McCormack](nostr:npub14mcddvsjsflnhgw7vxykz0ndfqj0rq04v7cjq5nnc95ftld0pv3shcfrlx)'s #CheatCode conference in Sydney and gave a few of these out following the Nostr panel, notably to [Preston Pysh](nostr:npub1s5yq6wadwrxde4lhfs56gn64hwzuhnfa6r9mj476r5s4hkunzgzqrs6q7z) where it [got some cut through](nostr:nevent1qqsdx0acma85u9knejnvfnfms9pfv27g97mfnnq9fnxslsa9vtrx73spremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzppggp5a66uxvmntlwnpf5384twu9e0xnm5xth9ta58fpt0dexysy26d4nm) and found me my first 100 followers. You can do the same. To create your Nostr NFC "business card" is even easier than your NFC "login card". 1. Buy yourself some NFC cards, 2. Download the free [NFC Tools app](https://play.google.com/store/apps/details?id=com.wakdev.wdnfc) to your device, and open it, 2. Click "Write" and "Add a record", then click "Custom URL / URI", 3. Write your npub to the NFC card as a custom URI in the format "nostr:npub1..." (e.g. for me this is "nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft"), 4. Your card is ready. Give the card to someone who is a Nostr user, and when they tap the card against their phone it will open their preferred Nostr client and go directly to your Nostr profile page. You have created a Nostr NFC "business card". ### What I Did Wrong I like to share what I did wrong so you don't have to make the same mistakes. This time, this was very easy, and little went wrong. In general - When password-protecting your nsec, don't forget the password! - When writing to the NFC card, make sure to use "Custom URI/URL" as this accepts your "nostr:" URI scheme. If you use generic "URI/URL" it won't work. ### What's Next Over my first four blogs I have explored creating a good Nostr setup - [Mined a Nostr pubkey and backed up the mnemonic](nostr:naddr1qqsy66twd9hxwtteda6hyt2kv9hxjare94g82cntv4uj6drfw4cxyeszyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c6e2ekw) - [Set up Nostr payments with a Lightning wallet plus all the bells and whistles](nostr:naddr1qq34xet5w35kueedw4cz65rp09kk2mn5wvkk7m3dfehhxarj95mk7dnvwvmsygqmmflp7uukhk3drmueqv763lfdcd3gzpusm7d7vt6ezquth97ymypsgqqqw4rsuql6je) - [Set up NIP-05 and Lighting Address at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqyghwumn8ghj7mn0wd68ytnhd9hx2tczyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c634nh0) - [Set up a Personal Relay at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7q3qr0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvsxpqqqp65wmzpn9e) Over the next few blogs I will be exploring different types of Nostr inter-op - NFC cards integrated with Nostr (this post) - Workflow Automations integrated with Nostr - AI LLMs integrated with Nostr Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle. GM Nostr.
@ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08### Tldr - Nostr is an open protocol which is interoperable with all kinds of other technologies - You can use this interoperability to create custom solutions - Nostr apps define a custom URI scheme handler "nostr:" - In this blog I use this to integrate Nostr with NFC cards - I create a Nostr NFC "login card" which allows me to log into Amethyst client - I create a Nostr NFC "business card" which allows anyone to find my profile with a tap ### Inter-Op All The Things! Nostr is a new open social protocol for the internet. This open nature is very exciting because it means Nostr can add new capabilities to all other internet-connected technologies, from browsers to web applications. In my view, it achieves this through three core capabilities. - A lightweight decentralised identity (Nostr keys, "npubs" and "nsecs"), - A lightweight data distribution network (Nostr relays), - A set of data interoperability standards (The Nostr Improvement Protocols "NIPs"), including the "nostr:" URI which we'll use in this post. The lightweight nature is its core strength. Very little is required to interoperate with Nostr, which means many existing technologies can be easily used with the network. Over the next few blog posts, I'll explore different Nostr inter-op ideas, and also deliver my first small open source projects to the community. I'll cover– - NFC cards integrated with Nostr (in this post), - Workflow Automations integrated with Nostr, - AI LLMs integrated with Nostr. #### The "Nostr:" URI One feature of Nostr is it defines a custom URI scheme handler "nostr:". What is that? A URI is used to identify a resource in a system. A system will have a protocol handler registry used to store such URI's, and if a system has a URI registered, then it knows what to do when it sees it. You are probably already familiar with some URI schemes such as "http:" and "mailto:". For example, when you click an http link, the system knows that it describes an http resource and opens a web browser to fetch the content from the internet. A nostr: link operates in the same way. The nostr: prefix indicates a custom URI scheme specifically designed for the Nostr protocol. If a system has a Nostr application installed, that application may have registered "nostr:" in the protocol handler registry. On that system when a "nostr:" URI is clicked, the system will know that it describes a nostr resource and open the Nostr client to fetch the content from the nostr relay network. This inter-op with the protocol handler registry gives us the power to do nice and exciting things with other technologies. ### Nostr and NFC Another technology that uses URIs is NFC cards. NFC (Near Field Communication) is a wireless technology that enables devices to exchange data over a few centimeters. It’s widely used in contactless payments, access control, and information sharing. NFC tags are small chips embedded in cards or stickers which can store data like plain text, URLs, or custom URIs. They are very cheap (cents each) and widely available (Amazon with next day delivery). When an NFC tag contains a URI, such as a http: (or nostr:) link, it acts as a trigger. Tapping the tag with an NFC-enabled device launches the associated application and processes the URI. For example, tapping a tag with "nostr:..." could open a Nostr client, directing it to a specific login page, public profile, or event. This inter-op allows us to bridge the physical world to Nostr with just a tap. #### Many useful ideas There are many interesting ways to use this. Too many for me to explore. Perhaps some of these are interesting for your next side hustle? - Nostr NFC "login cards" – tap to log into Amethyst on Android, - Nostr NFC "business cards" – give to connections so they can tap to load your npub, - Nostr NFC "payment cards" – integrating lightning network or ecash, - Nostr NFC "doorbells", "punch cards", "drop boxes", or "dead drops" – put a tag in a specific place and tap to open a location-specific message or chat, - Integrations with other access control systems, - Integrations with other home automation systems, - Many more ... To start with I have built and use the "login card" and "business card" solutions. This blog post will show you how to do the same. ### Nostr Login Card You can use an NFC card to log into your Nostr client. Most Nostr clients accept a variety of login methods, from posting your nsec into the app (insecure) to using a remote signer (more secure). A less known but more secure method is to sign into a session with a tap of a specially-configured NFC card. Amethyst is a Nostr client on Android which supports this type of login. - A secure method for logging in - Optionally keeps no log in history on the device after logout - Does not require users to know or understand how keys work - Keys are kept secure on a physically-separated card to reduce risk of compromise Nostr devs think that this is useful for anti-establishment actors–Fair enough. For me, I am interested in this login card pattern as it could be useful for rolling out identities within an organisation context with less training (office workers are already familiar with door access cards). This pattern potentially abstracts away key management to the IT or ops team who provision the cards. I first discovered this when [Kohei](nostr:npub16lrdq99ng2q4hg5ufre5f8j0qpealp8544vq4ctn2wqyrf4tk6uqn8mfeq) demonstrated it in [his video](nostr:nevent1qqstx0jy5jvzgh7wr6entjuw7h58d7mapupfdpt9hkf7s4gze34a0vspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzp47x6q2txs5ptw3fcj8ngj0y7qrnm7z0ft2cptshx5uqgxn2hd4ckqyqd3). Here's how you set it up at a high level– 1. Buy yourself some NFC cards 2. Get your Nostr key ready in an encrypted, password protected format called "nencryptsec" 3. Write the nencryptsec to the NFC card as a custom URI 4. Tap to load the login screen, and enter your password to login Here it is in detail– #### Buy yourself some NFC cards I found no specific requirements. As usual with Nostr so far, I tried to the cheapest possible route and it worked. Generic brand NFC cards shipped from China, I believe it was 50X for $15 from Amazon. Your mileage may vary. #### Get your Nostr key ready Your key will be saved to the NFC card in an encrypted password-protected format called "nencryptsec". Several applications support this. As we'll be using this to login to Amethyst, we will use Amethyst to output the nencryptsec for us. 1. Login to Amethyst with your nsec, 2. Open the sidebar and click "Backup Keys", 3. Enter a password, and click "Encrypt and my secret key", 4. It will add the password-protected key to your clipboard in the format "ncryptsec1...", 5. Remember to backup your password. #### Write the ncryptsec to the NFC card 1. Download the free [NFC Tools app](https://play.google.com/store/apps/details?id=com.wakdev.wdnfc) to your device, and open it, 2. Click "Write" and "Add a record", then click "Custom URL / URI", 3. Paste your nencryptsec with the nostr URI in front, i.e. "nostr:ncryptsec1..." and click OK, 4. Click "Write". NFC Tools will prompt you to "Approach an NFC tag", 5. Place your NFC card against your phone, and it will write to the card, 6. Your card is ready. #### Tap to load the login screen Tap the card against your phone again, and your phone should open the login screen of Amethyst and prompt you for your password. Once you enter your password, Amethyst will decrypt your nsec and log you in. Optionally, you can also set the app to forget you once you log out. You have created a Nostr NFC "login card". ### Nostr Business Card You can use another NFC card to give anyone you meet a link straight to your Nostr profile. I attended [Peter McCormack](nostr:npub14mcddvsjsflnhgw7vxykz0ndfqj0rq04v7cjq5nnc95ftld0pv3shcfrlx)'s #CheatCode conference in Sydney and gave a few of these out following the Nostr panel, notably to [Preston Pysh](nostr:npub1s5yq6wadwrxde4lhfs56gn64hwzuhnfa6r9mj476r5s4hkunzgzqrs6q7z) where it [got some cut through](nostr:nevent1qqsdx0acma85u9knejnvfnfms9pfv27g97mfnnq9fnxslsa9vtrx73spremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzppggp5a66uxvmntlwnpf5384twu9e0xnm5xth9ta58fpt0dexysy26d4nm) and found me my first 100 followers. You can do the same. To create your Nostr NFC "business card" is even easier than your NFC "login card". 1. Buy yourself some NFC cards, 2. Download the free [NFC Tools app](https://play.google.com/store/apps/details?id=com.wakdev.wdnfc) to your device, and open it, 2. Click "Write" and "Add a record", then click "Custom URL / URI", 3. Write your npub to the NFC card as a custom URI in the format "nostr:npub1..." (e.g. for me this is "nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft"), 4. Your card is ready. Give the card to someone who is a Nostr user, and when they tap the card against their phone it will open their preferred Nostr client and go directly to your Nostr profile page. You have created a Nostr NFC "business card". ### What I Did Wrong I like to share what I did wrong so you don't have to make the same mistakes. This time, this was very easy, and little went wrong. In general - When password-protecting your nsec, don't forget the password! - When writing to the NFC card, make sure to use "Custom URI/URL" as this accepts your "nostr:" URI scheme. If you use generic "URI/URL" it won't work. ### What's Next Over my first four blogs I have explored creating a good Nostr setup - [Mined a Nostr pubkey and backed up the mnemonic](nostr:naddr1qqsy66twd9hxwtteda6hyt2kv9hxjare94g82cntv4uj6drfw4cxyeszyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c6e2ekw) - [Set up Nostr payments with a Lightning wallet plus all the bells and whistles](nostr:naddr1qq34xet5w35kueedw4cz65rp09kk2mn5wvkk7m3dfehhxarj95mk7dnvwvmsygqmmflp7uukhk3drmueqv763lfdcd3gzpusm7d7vt6ezquth97ymypsgqqqw4rsuql6je) - [Set up NIP-05 and Lighting Address at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqyghwumn8ghj7mn0wd68ytnhd9hx2tczyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c634nh0) - [Set up a Personal Relay at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7q3qr0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvsxpqqqp65wmzpn9e) Over the next few blogs I will be exploring different types of Nostr inter-op - NFC cards integrated with Nostr (this post) - Workflow Automations integrated with Nostr - AI LLMs integrated with Nostr Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle. GM Nostr. @ 87730827:746b7d35
2024-11-20 09:27:53Original: https://techreport.com/crypto-news/brazil-central-bank-ban-monero-stablecoins/ Brazilian’s Central Bank Will Ban Monero and Algorithmic Stablecoins in the Country =================================================================================== Brazil proposes crypto regulations banning Monero and algorithmic stablecoins and enforcing strict compliance for exchanges. * * * **KEY TAKEAWAYS** * The Central Bank of Brazil has proposed **regulations prohibiting privacy-centric cryptocurrencies** like Monero. * The regulations **categorize exchanges into intermediaries, custodians, and brokers**, each with specific capital requirements and compliance standards. * While the proposed rules apply to cryptocurrencies, certain digital assets like non-fungible tokens **(NFTs) are still ‘deregulated’ in Brazil**.  In a Notice of Participation announcement, the Brazilian Central Bank (BCB) outlines **regulations for virtual asset service providers (VASPs)** operating in the country. **_In the document, the Brazilian regulator specifies that privacy-focused coins, such as Monero, must be excluded from all digital asset companies that intend to operate in Brazil._** Let’s unpack what effect these regulations will have. Brazil’s Crackdown on Crypto Fraud ---------------------------------- If the BCB’s current rule is approved, **exchanges dealing with coins that provide anonymity must delist these currencies** or prevent Brazilians from accessing and operating these assets. The Central Bank argues that currencies like Monero make it difficult and even prevent the identification of users, thus creating problems in complying with international AML obligations and policies to prevent the financing of terrorism. According to the Central Bank of Brazil, the bans aim to **prevent criminals from using digital assets to launder money**. In Brazil, organized criminal syndicates such as the Primeiro Comando da Capital (PCC) and Comando Vermelho have been increasingly using digital assets for money laundering and foreign remittances. > … restriction on the supply of virtual assets that contain characteristics of fragility, insecurity or risks that favor fraud or crime, such as virtual assets designed to favor money laundering and terrorist financing practices by facilitating anonymity or difficulty identification of the holder. > > – [Notice of Participation](https://www.gov.br/participamaisbrasil/edital-de-participacao-social-n-109-2024-proposta-de-regulamentacao-do-) The Central Bank has identified that **removing algorithmic stablecoins is essential to guarantee the safety of users’ funds** and avoid events such as when Terraform Labs’ entire ecosystem collapsed, losing billions of investors’ dollars. The Central Bank also wants to **control all digital assets traded by companies in Brazil**. According to the current proposal, the [national regulator](https://techreport.com/cryptocurrency/learning/crypto-regulations-global-view/) will have the **power to ask platforms to remove certain listed assets** if it considers that they do not meet local regulations. However, the regulations will not include [NFTs](https://techreport.com/statistics/crypto/nft-awareness-adoption-statistics/), real-world asset (RWA) tokens, RWA tokens classified as securities, and tokenized movable or real estate assets. These assets are still ‘deregulated’ in Brazil. Monero: What Is It and Why Is Brazil Banning It? ------------------------------------------------ Monero ($XMR) is a cryptocurrency that uses a protocol called CryptoNote. It launched in 2013 and ‘erases’ transaction data, preventing the sender and recipient addresses from being publicly known. The Monero network is based on a proof-of-work (PoW) consensus mechanism, which incentivizes miners to add blocks to the blockchain. Like Brazil, **other nations are banning Monero** in search of regulatory compliance. Recently, Dubai’s new digital asset rules prohibited the issuance of activities related to anonymity-enhancing cryptocurrencies such as $XMR. Furthermore, exchanges such as **Binance have already announced they will delist Monero** on their global platforms due to its anonymity features. Kraken did the same, removing Monero for their European-based users to comply with [MiCA regulations](https://techreport.com/crypto-news/eu-mica-rules-existential-threat-or-crypto-clarity/). Data from Chainalysis shows that Brazil is the **seventh-largest Bitcoin market in the world**.  In Latin America, **Brazil is the largest market for digital assets**. Globally, it leads in the innovation of RWA tokens, with several companies already trading this type of asset. In Closing ---------- Following other nations, Brazil’s regulatory proposals aim to combat illicit activities such as money laundering and terrorism financing. Will the BCB’s move safeguard people’s digital assets while also stimulating growth and innovation in the crypto ecosystem? Only time will tell. References ---------- Cassio Gusson is a journalist passionate about technology, cryptocurrencies, and the nuances of human nature. With a career spanning roles as Senior Crypto Journalist at CriptoFacil and Head of News at CoinTelegraph, he offers exclusive insights on South America’s crypto landscape. A graduate in Communication from Faccamp and a post-graduate in Globalization and Culture from FESPSP, Cassio explores the intersection of governance, decentralization, and the evolution of global systems. [View all articles by Cassio Gusson](https://techreport.com/author/cassiog/)
@ 87730827:746b7d35
2024-11-20 09:27:53Original: https://techreport.com/crypto-news/brazil-central-bank-ban-monero-stablecoins/ Brazilian’s Central Bank Will Ban Monero and Algorithmic Stablecoins in the Country =================================================================================== Brazil proposes crypto regulations banning Monero and algorithmic stablecoins and enforcing strict compliance for exchanges. * * * **KEY TAKEAWAYS** * The Central Bank of Brazil has proposed **regulations prohibiting privacy-centric cryptocurrencies** like Monero. * The regulations **categorize exchanges into intermediaries, custodians, and brokers**, each with specific capital requirements and compliance standards. * While the proposed rules apply to cryptocurrencies, certain digital assets like non-fungible tokens **(NFTs) are still ‘deregulated’ in Brazil**.  In a Notice of Participation announcement, the Brazilian Central Bank (BCB) outlines **regulations for virtual asset service providers (VASPs)** operating in the country. **_In the document, the Brazilian regulator specifies that privacy-focused coins, such as Monero, must be excluded from all digital asset companies that intend to operate in Brazil._** Let’s unpack what effect these regulations will have. Brazil’s Crackdown on Crypto Fraud ---------------------------------- If the BCB’s current rule is approved, **exchanges dealing with coins that provide anonymity must delist these currencies** or prevent Brazilians from accessing and operating these assets. The Central Bank argues that currencies like Monero make it difficult and even prevent the identification of users, thus creating problems in complying with international AML obligations and policies to prevent the financing of terrorism. According to the Central Bank of Brazil, the bans aim to **prevent criminals from using digital assets to launder money**. In Brazil, organized criminal syndicates such as the Primeiro Comando da Capital (PCC) and Comando Vermelho have been increasingly using digital assets for money laundering and foreign remittances. > … restriction on the supply of virtual assets that contain characteristics of fragility, insecurity or risks that favor fraud or crime, such as virtual assets designed to favor money laundering and terrorist financing practices by facilitating anonymity or difficulty identification of the holder. > > – [Notice of Participation](https://www.gov.br/participamaisbrasil/edital-de-participacao-social-n-109-2024-proposta-de-regulamentacao-do-) The Central Bank has identified that **removing algorithmic stablecoins is essential to guarantee the safety of users’ funds** and avoid events such as when Terraform Labs’ entire ecosystem collapsed, losing billions of investors’ dollars. The Central Bank also wants to **control all digital assets traded by companies in Brazil**. According to the current proposal, the [national regulator](https://techreport.com/cryptocurrency/learning/crypto-regulations-global-view/) will have the **power to ask platforms to remove certain listed assets** if it considers that they do not meet local regulations. However, the regulations will not include [NFTs](https://techreport.com/statistics/crypto/nft-awareness-adoption-statistics/), real-world asset (RWA) tokens, RWA tokens classified as securities, and tokenized movable or real estate assets. These assets are still ‘deregulated’ in Brazil. Monero: What Is It and Why Is Brazil Banning It? ------------------------------------------------ Monero ($XMR) is a cryptocurrency that uses a protocol called CryptoNote. It launched in 2013 and ‘erases’ transaction data, preventing the sender and recipient addresses from being publicly known. The Monero network is based on a proof-of-work (PoW) consensus mechanism, which incentivizes miners to add blocks to the blockchain. Like Brazil, **other nations are banning Monero** in search of regulatory compliance. Recently, Dubai’s new digital asset rules prohibited the issuance of activities related to anonymity-enhancing cryptocurrencies such as $XMR. Furthermore, exchanges such as **Binance have already announced they will delist Monero** on their global platforms due to its anonymity features. Kraken did the same, removing Monero for their European-based users to comply with [MiCA regulations](https://techreport.com/crypto-news/eu-mica-rules-existential-threat-or-crypto-clarity/). Data from Chainalysis shows that Brazil is the **seventh-largest Bitcoin market in the world**.  In Latin America, **Brazil is the largest market for digital assets**. Globally, it leads in the innovation of RWA tokens, with several companies already trading this type of asset. In Closing ---------- Following other nations, Brazil’s regulatory proposals aim to combat illicit activities such as money laundering and terrorism financing. Will the BCB’s move safeguard people’s digital assets while also stimulating growth and innovation in the crypto ecosystem? Only time will tell. References ---------- Cassio Gusson is a journalist passionate about technology, cryptocurrencies, and the nuances of human nature. With a career spanning roles as Senior Crypto Journalist at CriptoFacil and Head of News at CoinTelegraph, he offers exclusive insights on South America’s crypto landscape. A graduate in Communication from Faccamp and a post-graduate in Globalization and Culture from FESPSP, Cassio explores the intersection of governance, decentralization, and the evolution of global systems. [View all articles by Cassio Gusson](https://techreport.com/author/cassiog/) @ 68c90cf3:99458f5c
2024-11-18 23:51:21Three Bitaxe Supras mining a combined average of 2.7 TH/s.  _Left to right_ * From **Solo Satoshi** - stock heat sink, Noctua fan _(710 MHz/1.31V)_ * From **D-Central** - Argon THRML cooler, Noctua fan _(740 MHz/1.34V)_ * From **Altair** - stock heat sink, Noctua fan _(720 MHz/1.29V)_  All powered by a Meanwell LRS-200-5 PSU. Connected to a local instance of Public Pool with Bitcoin Node on a Beelink EQ13 running umbrelOS. #bitcoin #bitaxe #lotterymining 🤞🍀
@ 68c90cf3:99458f5c
2024-11-18 23:51:21Three Bitaxe Supras mining a combined average of 2.7 TH/s.  _Left to right_ * From **Solo Satoshi** - stock heat sink, Noctua fan _(710 MHz/1.31V)_ * From **D-Central** - Argon THRML cooler, Noctua fan _(740 MHz/1.34V)_ * From **Altair** - stock heat sink, Noctua fan _(720 MHz/1.29V)_  All powered by a Meanwell LRS-200-5 PSU. Connected to a local instance of Public Pool with Bitcoin Node on a Beelink EQ13 running umbrelOS. #bitcoin #bitaxe #lotterymining 🤞🍀 @ f33c8a96:5ec6f741
2024-11-15 18:04:17<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/_G49vKrKbsU?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ f33c8a96:5ec6f741
2024-11-15 18:04:17<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/_G49vKrKbsU?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 468f729d:5ab4fd5e
2024-11-15 17:52:45<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/wV4I62NMiQ0?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 468f729d:5ab4fd5e
2024-11-15 17:52:45<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/wV4I62NMiQ0?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ bcea2b98:7ccef3c9
2024-11-14 23:38:37@chess a3 originally posted at https://stacker.news/items/768303
@ bcea2b98:7ccef3c9
2024-11-14 23:38:37@chess a3 originally posted at https://stacker.news/items/768303 @ bcea2b98:7ccef3c9
2024-11-14 18:03:14We all have that one movie or show we turn to when we need a little comfort. Whether it’s for the laughs, the nostalgia, or the familiar characters, these are the ones that never get old. What’s a movie or series you can watch again and again? What makes it so comforting, and why do you keep coming back to it? I enjoy The Office with Michael Scott and Dwight Schrute. We watched a lot of that in the past and then again during the pandemic during isolation. originally posted at https://stacker.news/items/767870
@ bcea2b98:7ccef3c9
2024-11-14 18:03:14We all have that one movie or show we turn to when we need a little comfort. Whether it’s for the laughs, the nostalgia, or the familiar characters, these are the ones that never get old. What’s a movie or series you can watch again and again? What makes it so comforting, and why do you keep coming back to it? I enjoy The Office with Michael Scott and Dwight Schrute. We watched a lot of that in the past and then again during the pandemic during isolation. originally posted at https://stacker.news/items/767870 @ bcea2b98:7ccef3c9
2024-11-14 00:42:08Sometimes we come across values that resonate deeply only after going through certain experiences. These values may not have been obvious to us earlier, but now they play a meaningful role in how we approach life. Is there a value you’ve discovered later in life that’s become important to you? originally posted at https://stacker.news/items/766754
@ bcea2b98:7ccef3c9
2024-11-14 00:42:08Sometimes we come across values that resonate deeply only after going through certain experiences. These values may not have been obvious to us earlier, but now they play a meaningful role in how we approach life. Is there a value you’ve discovered later in life that’s become important to you? originally posted at https://stacker.news/items/766754 @ bcea2b98:7ccef3c9
2024-11-13 02:44:17@chess a3 originally posted at https://stacker.news/items/765445
@ bcea2b98:7ccef3c9
2024-11-13 02:44:17@chess a3 originally posted at https://stacker.news/items/765445 @ bcea2b98:7ccef3c9
2024-11-13 02:18:58Sometimes our strongest values are the ones that people wouldn’t expect. These unique principles often reveal something special about who we are and what we believe in. Do you hold a value that might surprise others? originally posted at https://stacker.news/items/765433
@ bcea2b98:7ccef3c9
2024-11-13 02:18:58Sometimes our strongest values are the ones that people wouldn’t expect. These unique principles often reveal something special about who we are and what we believe in. Do you hold a value that might surprise others? originally posted at https://stacker.news/items/765433 @ bcea2b98:7ccef3c9
2024-11-10 19:34:24@chess a3 originally posted at https://stacker.news/items/762161
@ bcea2b98:7ccef3c9
2024-11-10 19:34:24@chess a3 originally posted at https://stacker.news/items/762161 @ bcea2b98:7ccef3c9
2024-11-09 17:01:32Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about? For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully. originally posted at https://stacker.news/items/760492
@ bcea2b98:7ccef3c9
2024-11-09 17:01:32Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about? For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully. originally posted at https://stacker.news/items/760492 @ bcea2b98:7ccef3c9
2024-11-09 01:30:29@chess h3 originally posted at https://stacker.news/items/759635
@ bcea2b98:7ccef3c9
2024-11-09 01:30:29@chess h3 originally posted at https://stacker.news/items/759635 @ bcea2b98:7ccef3c9
2024-11-07 18:43:30If you could accomplish one major goal, what would it be? Why does it matter to you, and how would it change your life or the lives of others? My ultimate goal is to be part of a mission to Mars one day. I’ve always been fascinated by space exploration. originally posted at https://stacker.news/items/757861
@ bcea2b98:7ccef3c9
2024-11-07 18:43:30If you could accomplish one major goal, what would it be? Why does it matter to you, and how would it change your life or the lives of others? My ultimate goal is to be part of a mission to Mars one day. I’ve always been fascinated by space exploration. originally posted at https://stacker.news/items/757861 @ 3bf0c63f:aefa459d
2024-11-07 14:56:17# The case against edits Direct edits are a centralizing force on Nostr, a slippery slope that should not be accepted. Edits are fine in other, more specialized event kinds, but the `kind:1` space shouldn't be compromised with such a push towards centralization, because [`kind:1` is the public square of Nostr, where all focus should be on decentralization and censorship-resistance](cd8ce2b7). - _Why?_ Edits introduce too much complexity. If edits are widespread, all clients now have to download dozens of extra events at the same time while users are browsing a big feed of notes which are already coming from dozens of different relays using complicated outbox-model-based querying, then for each event they have to open yet another subscription to these relays -- or perform some other complicated batching of subscriptions which then requires more complexity on the event handling side and then when associating these edits with the original events. I can only imagine this will hurt apps performance, but it definitely raises the barrier to entry and thus necessarily decreases Nostr decentralization. Some clients may be implemneted in way such that they download tons of events and then store them in a local databases, from which they then construct the feed that users see. Such clients may make edits potentially easier to deal with -- but this is hardly an answer to the point above, since such clients are already more complex to implement in the first place. - _What do you have against complex clients?_ The point is not to say that all clients should be simple, but that it should be simple to write a client -- or at least as simple as physically possible. You may not be thinking about it, but if you believe in the promise of Nostr then we should expect to see Nostr feeds in many other contexts other than on a big super app in a phone -- we should see Nostr notes being referenced from and injected in unrelated webpages, unrelated apps, hardware devices, comment sections and so on. All these micro-clients will have to implement some complicated edit-fetching logic now? - _But aren't we already fetching likes and zaps and other things, why not fetch edits too?_ Likes, zaps and other similar things are optional. It's perfectly fine to use Nostr without seeing likes and/or zaps -- and, believe me, it does happen quite a lot. The point is basically that likes or zaps don't affect the content of the main post at all, while edits do. - _But edits are optional!_ No, they are not optional. If edits become widespread they necessarily become mandatory. Any client that doesn't implement edits will be displaying false information to its users and their experience will be completely broken. - _That's fine, as people will just move to clients that support edits!_ Exactly, that is what I expect to happen too, and this is why I am saying edits are a centralizing force that we should be fighting against, not embracing. If you understand that edits are a centralizing force, then you must automatically agree that they aren't a desirable feature, given that if you are reading this now, with Nostr being so small, there is a 100% chance you care about decentralization and you're not just some kind of lazy influencer that is only doing this for money. - _All other social networks support editing!_ This is not true at all. Bluesky has 10x more users than Nostr and doesn't support edits. Instagram doesn't support editing pictures after they're posted, and doesn't support editing comments. Tiktok doesn't support editing videos or comments after they're posted. YouTube doesn't support editing videos after they're posted. Most famously, email, the most widely used and widespread "social app" out there, does not support edits of any kind. Twitter didn't support edits for the first 15 years of its life, and, although some people complained, it didn't hurt the platform at all -- arguably it benefitted it. If edits are such a straightforward feature to add that won't hurt performance, that won't introduce complexity, and also that is such an essential feature users could never live without them, then why don't these centralized platforms have edits on everything already? There must be something there. - _Eventually someone will implement edits anyway, so why bother to oppose edits now?_ Once Nostr becomes big enough, maybe it will be already shielded from such centralizing forces by its sheer volume of users and quantity of clients, maybe not, we will see. All I'm saying is that we shouldn't just push for bad things now just because of a potential future in which they might come. - _The market will decide what is better._ The market has decided for Facebook, Instagram, Twitter and TikTok. If we were to follow what the market had decided we wouldn't be here, and you wouldn't be reading this post. - _OK, you have convinced me, edits are not good for the protocol. But what do we do about the users who just want to fix their typos?_ There are many ways. The annotations spec, for example, provides a simple way to append things to a note without being a full-blown edit, and they fall back gracefully to normal replies in clients that don't implement the full annotations spec. Eventually we could have annotations that are expressed in form of simple (human-readable?) diffs that can be applied directly to the post, but fall back, again, to comments. Besides these, a very simple idea that wasn't tried yet on Nostr yet is the idea that has been tried for emails and seems to work very well: delaying a post after the "submit" button is clicked and giving the user the opportunity to cancel and edit it again before it is actually posted. Ultimately, if edits are so necessary, then maybe we could come up with a way to implement edits that is truly optional and falls back cleanly for clients that don't support them directly and don't hurt the protocol very much. Let's think about it and not rush towards defeat.
@ 3bf0c63f:aefa459d
2024-11-07 14:56:17# The case against edits Direct edits are a centralizing force on Nostr, a slippery slope that should not be accepted. Edits are fine in other, more specialized event kinds, but the `kind:1` space shouldn't be compromised with such a push towards centralization, because [`kind:1` is the public square of Nostr, where all focus should be on decentralization and censorship-resistance](cd8ce2b7). - _Why?_ Edits introduce too much complexity. If edits are widespread, all clients now have to download dozens of extra events at the same time while users are browsing a big feed of notes which are already coming from dozens of different relays using complicated outbox-model-based querying, then for each event they have to open yet another subscription to these relays -- or perform some other complicated batching of subscriptions which then requires more complexity on the event handling side and then when associating these edits with the original events. I can only imagine this will hurt apps performance, but it definitely raises the barrier to entry and thus necessarily decreases Nostr decentralization. Some clients may be implemneted in way such that they download tons of events and then store them in a local databases, from which they then construct the feed that users see. Such clients may make edits potentially easier to deal with -- but this is hardly an answer to the point above, since such clients are already more complex to implement in the first place. - _What do you have against complex clients?_ The point is not to say that all clients should be simple, but that it should be simple to write a client -- or at least as simple as physically possible. You may not be thinking about it, but if you believe in the promise of Nostr then we should expect to see Nostr feeds in many other contexts other than on a big super app in a phone -- we should see Nostr notes being referenced from and injected in unrelated webpages, unrelated apps, hardware devices, comment sections and so on. All these micro-clients will have to implement some complicated edit-fetching logic now? - _But aren't we already fetching likes and zaps and other things, why not fetch edits too?_ Likes, zaps and other similar things are optional. It's perfectly fine to use Nostr without seeing likes and/or zaps -- and, believe me, it does happen quite a lot. The point is basically that likes or zaps don't affect the content of the main post at all, while edits do. - _But edits are optional!_ No, they are not optional. If edits become widespread they necessarily become mandatory. Any client that doesn't implement edits will be displaying false information to its users and their experience will be completely broken. - _That's fine, as people will just move to clients that support edits!_ Exactly, that is what I expect to happen too, and this is why I am saying edits are a centralizing force that we should be fighting against, not embracing. If you understand that edits are a centralizing force, then you must automatically agree that they aren't a desirable feature, given that if you are reading this now, with Nostr being so small, there is a 100% chance you care about decentralization and you're not just some kind of lazy influencer that is only doing this for money. - _All other social networks support editing!_ This is not true at all. Bluesky has 10x more users than Nostr and doesn't support edits. Instagram doesn't support editing pictures after they're posted, and doesn't support editing comments. Tiktok doesn't support editing videos or comments after they're posted. YouTube doesn't support editing videos after they're posted. Most famously, email, the most widely used and widespread "social app" out there, does not support edits of any kind. Twitter didn't support edits for the first 15 years of its life, and, although some people complained, it didn't hurt the platform at all -- arguably it benefitted it. If edits are such a straightforward feature to add that won't hurt performance, that won't introduce complexity, and also that is such an essential feature users could never live without them, then why don't these centralized platforms have edits on everything already? There must be something there. - _Eventually someone will implement edits anyway, so why bother to oppose edits now?_ Once Nostr becomes big enough, maybe it will be already shielded from such centralizing forces by its sheer volume of users and quantity of clients, maybe not, we will see. All I'm saying is that we shouldn't just push for bad things now just because of a potential future in which they might come. - _The market will decide what is better._ The market has decided for Facebook, Instagram, Twitter and TikTok. If we were to follow what the market had decided we wouldn't be here, and you wouldn't be reading this post. - _OK, you have convinced me, edits are not good for the protocol. But what do we do about the users who just want to fix their typos?_ There are many ways. The annotations spec, for example, provides a simple way to append things to a note without being a full-blown edit, and they fall back gracefully to normal replies in clients that don't implement the full annotations spec. Eventually we could have annotations that are expressed in form of simple (human-readable?) diffs that can be applied directly to the post, but fall back, again, to comments. Besides these, a very simple idea that wasn't tried yet on Nostr yet is the idea that has been tried for emails and seems to work very well: delaying a post after the "submit" button is clicked and giving the user the opportunity to cancel and edit it again before it is actually posted. Ultimately, if edits are so necessary, then maybe we could come up with a way to implement edits that is truly optional and falls back cleanly for clients that don't support them directly and don't hurt the protocol very much. Let's think about it and not rush towards defeat.