-

@ 9e69e420:d12360c2
2025-02-14 18:07:10
Vice President J.D. Vance addressed the Munich Security Conference, criticizing European leaders for undermining free speech and traditional values. He claimed that the biggest threat to Europe is not from external enemies but from internal challenges. Vance condemned the arrest of a British man for praying near an abortion clinic and accused European politicians of censorship.
He urged leaders to combat illegal immigration and questioned their democratic practices. “There is a new sheriff in town,” he said, referring to President Trump. Vance's remarks were unexpected, as many anticipated discussions on security or Ukraine. His speech emphasized the need for Europe to share the defense burden to ensure stability and security.
-

@ c43d6de3:a6583169
2025-02-14 17:34:05
“IN THIS SPRING of 1953 the free world weighs one question above all others: the chance for a just peace for all peoples,” Dwight D. Eisenhower’s throat went dry and he swallowed to alleviate the burn. Eight years had passed since the end of world war 2 but still the beaches of the Marshall Islands lay charred, Hiroshima and Nagasaki dosed in radiation and ruin, and countless ghost towns still littered Europe’s mangled face.
Dwight peered through his glasses at his speech on the podium, then raised his gaze back at the small crowd gathered in front of him in the conference room at the American Society of Newspaper Editors in Washington, D.C. Everyone was on the edge of their seats.
The President spoke of peace, but the United States faced a great enemy in the Soviet Union. How would he continue?

“To weigh this chance is to summon instantly to mind another recent moment of great decision. It came with that yet more hopeful spring of 1945, bright with the promise of victory and of freedom. The hope of all just men in that moment too was a just and lasting peace.”
The heads among the spectators raised in hope, as if the enthusiasm in the President’s voice could be enough to wipe away any prospect of future war against the Soviet threat.
“In that spring of victory the soldiers of the Western Allies met the soldiers of Russia in the center of Europe. They were triumphant comrades in arms. Their peoples shared the joyous prospect of building, in honor of their dead, the only fitting monument-an age of just peace. All these war-weary peoples shared too this concrete, decent purpose: to guard vigilantly against the domination ever again of any part of the world by a single, unbridled aggressive power.”
“This common purpose lasted an instant and perished. The nations of the world divided to follow two distinct roads.”
“The United States and our valued friends, the other free nations, chose one road.”
“The leaders of the Soviet Union chose another.”
“The way chosen by the United States was plainly marked by a few clear precepts, which govern its conduct in world affairs.”
**What came next in Dwight D. Eisenhower’s speech “The Chance for Peace” is the answer to preventing wars between countries**
“First: No people on earth can be held, as a people, to be an enemy, for all humanity shares the **common hunger for peace and fellowship and justice.**
Second: No nation's security and well-being can be lastingly achieved in isolation but only in **effective cooperation** with fellow nations.
Third: **Any nation's right to a form of government and an economic system** of its own choosing **is inalienable**.
Fourth: Any nation's attempt to dictate to other nations their form of government **is indefensible**.
And fifth: A nation's hope of lasting peace cannot be firmly based upon any race in armaments but rather upon **just relations and honest understanding** with all other nations.”

**I. First Point**
When you minimize any nation or country to its most granular piece, the human family, you realize every nation or country is the same. It is a larger body of human families looking to establish peace out of chaos against nature, fellowship with their neighbor to make that peace possible, and justice against affronts to the foundations of the formerly stated peace and fellowship. Without this, what you have is not a nation but rather wilderness.

**II. Second Point**
When we enter the world stage and look at the community of nations it is important we understand that no nation can truly expect to uphold Eisenhower’s first point without the ability to cooperate with other nations. There can be a natural disaster that strikes an entire nation and without exterior help, it may be impossible to overcome.
Understand, Eisenhower’s second point only serves as an extension of the first point. Humankind's struggle with nature will always exist, but in cooperation with other communities we can overcome hardship against nature and live in better harmony.

**III. Third Point**
It cannot be argued that humans, after millenia of having dispersed across the planet, have collected into pockets of communities of which grew and developed with experiences based on the place in the world where they’ve resided.
This has birthed cultures, religions, and moral codes that serve as the foundation of different branches of philosophy that have borne the fruit of governance. Ultimately, no two communities shares the exact same moral code and thus do not share, and will never share, the exact same understanding of what governance should take place. In this respect, it is an inalienable right of the very people within a community to choose how they govern themselves.

**IV. Fourth Point**
In trying to impeded on this third point, we come to Eisenhower’s fourth point which is that no other community has the right to dictate how other nations govern themselves.
**V. Final Point**
Lastly, war will never lead to peace. Only common understanding of the first four points will ever lead to true peace. A race in armaments, as the cold war proved, only leads to further distrust and the breakdown of all other points among the community of nations on the world stage.
All that can be done to expect peace is to take your neighbor as they are. St. Augustine has a famous quote, “Seek not to understand that you may believe, but believe that you may understand.”
This is meant to drive home the point of faith in the unbelievable. It is how a religious person can believe in a god that they can not prove exists.
Some might say there will never be a world without war. I say we already have the recipe for it. We’ve been given this recipe by many leaders throughout our history. Leader’s who’ve witnessed the darkest depths of human evil and wanted to steer humanity away from it.

-----------
Thank you for reading! If this article resonated with you, let me know with a zap and share it with friends who might find it insightful. Your help sends a strong signal to keep making content like this!
Interested in fiction? Follow nostr:npub1j9cmpzhlzeex6y85c2pnt45r5zhxhtx73a2twt77fyjwequ4l4jsp5xd49 for great short stories and serialized fiction.
More articles you might like from Beneath The Ink:
https://primal.net/e/note1ws4es0gahm502k6qgx64dseqhjqgyzh0q7flzk6glcasqxxye6jqm20fj9
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq25yan2w39rsjj0dqk5ckn52ptxsc3nve8hw0aftmq
https://primal.net/e/note158ns7z27r2y664h9lsdqdhsjj2uehrejve2y02lkvz46d8xgxncs8pcj7w
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2kjjzzfpjxvutjg33hjvpcw5cyjezyv9y5k0umm6k
https://primal.net/e/note1htkygah99mz8p4png992n0clqa44spatw3uzzcpl94etwh2zr60stklxvw
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqqa9wefdwfjj6stvdsk57cnnv4ehxety94mkjarg94g8ymm8wfjhxuedg9hxgt2fw3ej6sm0wd6xjmn8946hxtfjvsuhsdnju045ml
https://primal.net/e/note1rdanqhdgc7d8sypm459zrt55m0zfaze7u34phkew9nptyr3ghwlqsvtsdx
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2ns3jnfa985c29xp2rs3pexpykz6mjxetxu2g25x6
-

@ dd664d5e:5633d319
2025-02-14 16:56:29
Most people only know customer-to-customer (C2C) and business-to-customer (B2C) software and websites. Those are the famous and popular ones, but business-to-business (B2B) is also pretty big. How big?
Even something boring and local like [DATEV](https://www.datev.de/web/de/startseite/startseite-n/) has almost 3 million organizations as customers and €1,44 billion in annual revenue.
FedEx has €90 billion in annual revenue and everyone who uses it comes into contact with its software. There's a whole chain of software between the sender and receiver of the package, and it all has to work seamlessly.
Same with Walmart, Toyota, Dubai Airport, Glencore, Tesla, Edeka, Carrefour, Harvard and University of Texas, Continental, Allianz, Asklepios, etc.
That's the sort of software I help build. You've probably never heard of it, but when it doesn't work properly, you'll hear about it on the news.
-

@ 554ab6fe:c6cbc27e
2025-02-14 16:29:51
Bitcoin’s Price and the Power Law: A Reflection of Energy and the Early Stages of Monetary Adoption Introduction Bitcoin’s price trajectory has long puzzled analysts, with its seemingly chaotic booms and busts. However, when examined through the lens of power laws, a pattern emerges—one that is fundamentally tied to Bitcoin’s energy-based production cost. This article argues that Bitcoin’s price has historically followed a power law because its underlying cost structure is dictated by mining, an energy-intensive process. However, this relationship will not persist indefinitely. I propose that as Bitcoin matures into a widely adopted monetary system, its price will decouple from mining production costs and instead oscillate in accordance with natural business cycles, much like traditional forms of money.
**Bitcoin’s Price and the Power Law**
Source and Credit: Giovanni Santostasi’s “[The Bitcoin Power Law](https://giovannisantostasi.medium.com/the-bitcoin-power-law-theory-962dfaf99ee9)”
When Bitcoin’s price is plotted on a logarithmic scale against time, a strikingly straight-line trajectory appears, punctuated by cycles of rapid price expansion (bull markets) followed by severe corrections (bear markets). These perturbations correspond to Bitcoin’s well-known halving cycles, which occur approximately every four years and reduce the block reward paid to miners, effectively doubling the cost of production per Bitcoin. Historically, Bitcoin’s price has always returned to a fundamental minimum—one that closely aligns with the average cost of mining.
This observation suggests that Bitcoin’s power law price behavior is not arbitrary but rather a reflection of its fundamental energy constraints. As in many natural systems governed by power laws, energy dynamics play a central role. In Bitcoin’s case, the “base layer” of its valuation is determined by the energy and computational resources required for mining. This power law behavior is therefore a consequence of Bitcoin’s fundamental design: as block subsidies decrease and mining efficiency improves, the minimum sustainable price follows an upward trajectory dictated by production costs.
**Bitcoin as an Energy-Based System**
Power laws commonly emerge in natural systems involving energy constraints, from thermodynamics to biological ecosystems and planetary dynamics. Bitcoin, as an energy-based monetary system, exhibits similar characteristics. Mining requires significant electricity and computational power, and as the difficulty adjustment ensures a competitive equilibrium, the cost of mining a Bitcoin remains closely tied to its market value over the long run.
Unlike traditional fiat currencies, which are controlled by central banks and subject to arbitrary monetary expansion, Bitcoin’s supply schedule is immutable. Its economic foundation is rooted in **proof of work**, where value is derived from energy expenditure. This fundamental linkage between energy and price explains why Bitcoin’s valuation has adhered to a power law trajectory. It is an entropy engine, and follows physical laws related to energy and entropy.
However, this pattern is not a permanent feature of Bitcoin’s monetary future—it is, rather, an indication of Bitcoin’s **early-stage monetization process**.
**The Transition from Mining-Based Pricing to a Business Cycle**
A crucial implication of Bitcoin’s price following a power law dictated by mining costs is that it suggests Bitcoin has yet to fully mature as money. If Bitcoin were already a widely adopted monetary standard, its valuation would no longer be primarily influenced by the floor mining costs but instead by macroeconomic forces—specifically, the natural fluctuations of the business cycle.
In a world where Bitcoin is the dominant global currency, the “price of money” (which correlates with the cost of capital and prevailing interest rates) would fluctuate according to the broader economic cycle. The dynamics would resemble those of natural interest rate cycles described by the Austrian School of Economics:
- During periods of economic expansion, lower interest rates spur increased investment and consumption, prices slightly rise, and savings deplete.
- As savings decline and prices rise, interest rates naturally rise as well, leading to reduced investment and spending, initiating a contractionary phase and lowered prices.
- During the contraction, savings accumulate, more capital becomes available, and interest rates and prices decline.
- With the availability of capital, lower interest rates and lowered prices, the economy is now ready to enter a phase of investment and expansion once again.
- This oscillatory process continues indefinitely, driven by real economic growth rather than central bank intervention.
If Bitcoin were fully monetized, its price would no longer oscillate based on mining halvings and energy costs but instead reflect **economic expansion and contraction cycles**—just as traditional currencies do when not artificially manipulated by central banks.
**The Early Stage Indicator: Bitcoin’s Dependence on Mining Costs**
Today, Bitcoin’s price still “bounces” off the power law baseline, indicating that its valuation remains primarily anchored to its minimum cost of production. This means that, while Bitcoin is widely recognized as an asset, it has not yet reached the level of adoption where its price is dictated by macroeconomic cycles.
A future in which Bitcoin is used as a primary medium of exchange and unit of account would necessarily imply a **decoupling from mining-driven pricing**. Instead of periodic halvings triggering speculative bull runs followed by crashes, Bitcoin’s price would become far more stable, with fluctuations primarily driven by business cycle dynamics. The continued adherence to the power law model, therefore, is evidence that Bitcoin is still in an early phase of adoption—where mining remains a primary determinant of price.
**Conclusion**
Bitcoin’s price trajectory has long conformed to a power law, reflecting the underlying energy costs of mining. This characteristic, however, is likely not a permanent feature but rather a hallmark of Bitcoin’s early stage as an emerging monetary system. As adoption increases and Bitcoin becomes widely used as money, its price should transition away from being dictated by mining costs and should instead fluctuate according to the natural oscillations of the business cycle.
The persistence of Bitcoin’s power law trend is a sign that it remains in its infancy. The real transformation will occur when Bitcoin is no longer bound to its production cost but is instead driven by the natural ebb and flow of savings, investment, and capital cycles—marking its full emergence as a global monetary system.
Disclaimer: The information provided in this blog is for informational and educational purposes only and should not be construed as financial advice. Please consult with a financial advisor or conduct your own research before making any financial decisions.
-

@ da0b9bc3:4e30a4a9
2025-02-14 15:21:29
It's Finally here Stackers!
It's Friday!
We're about to kick off our weekends with some feel good tracks.
Let's get the party started. Bring me those Feel Good tracks.
It is valentine's so let's get all gooey and soft, let's feel good and loved up.
If the world was ending, I'd wanna be next to you.
https://youtu.be/kPa7bsKwL-c?si=XbAaVfCHLZw6_0n6
Talk Music. Share Tracks. Zap Sats.
Let's go!
originally posted at https://stacker.news/items/885888
-

@ 9e69e420:d12360c2
2025-02-14 15:14:34
A Russian drone attack has struck the radiation shelter at Chernobyl, according to Ukrainian President Volodymyr Zelensky. The strike caused a fire, but it has since been extinguished, and radiation levels remain stable. The International Atomic Energy Agency (IAEA) confirmed that no casualties occurred and that monitoring continues.
Rafael Mariano Grossi, IAEA's director general, emphasized the need for caution. Chernobyl, site of the 1986 nuclear disaster, contains a protective shield costing $1.6 billion. Disaster prevention remains a priority as the conflict unfolds.
The incident occurred shortly before the meeting of world powers at the Munich Security Conference in Germany.
-

@ 0000065e:9b5b4c75
2025-02-14 14:41:24
Se está armando un considerable revuelo con las medidas, impulsadas por La Liga y Telefónica, que afectan a servicios relacionados con Cloudflare y a muchos de sus usuarios que tienen que soportar la restricción en la operatividad de los mismos. Pero, ¿cómo puede ser que un tema de “piratería” acabe afectando, con aparente impunidad, a servicios legítimos? Aquí intentaremos explicarlo.
Desde tiempos casi inmemoriales la industria relacionada con la explotación de los contenidos, y prestaciones, sujetos a derechos de propiedad intelectual han sido tremendamente imaginativos a la hora de buscar mecanismos que aseguren sus pingües beneficios. Como los jueces no solían hacerles caso, impulsaron modificaciones legislativas para quitarlos de la ecuación, *administrativizando* el conflicto, como sucedió con la conocida como Ley Sinde.
Pero los mecanismos de esta Ley no eran lo suficientemente ágiles para lo que quería la industria, por lo que había que darle otra vuelta de tuerca al asunto, lo que se hizo con ocasión del art. 138 de la Ley de Propiedad Intelectual. En síntesis, el truco es el siguiente:
- El titular de los derechos acude a un Juzgado honesto, imparcial y preocupado, como no podía ser de otra forma, por la defensa de los derechos fundamentales reconocidos constitucionalmente.
- Ahí plantea una demanda, no contra quien considera infractor de esos derechos (Cloudflare o los usuarios que hacen uso ilícito de sus servicios), sino contra los operadores de telecomunicaciones que dan acceso a internet, en una aplicación torticera y kafkiana del art. 138 LPI (sobre el que volveremos más adelante) pidiendo una serie de medidas.
- Las operadoras se "allanan" a la demanda, es decir, reconocen y aceptan las pretensiones del demandante, y el juez [concede las medidas](https://bandaancha.eu/articulos/2-nuevos-listados-obligan-operadoras-10322).
Con este truco, todos se guardan las vergüenzas unos a otros:
- Los demandantes: Nosotros solamente pedimos las medidas. Es el juez el que las acuerda.
- El juez: A mi me viene uno pidiendo una cosa, la parte demandada se allana. Tengo que conceder lo pedido.
- El operador: Tengo que hacer caso al juez.
Para conseguir esto, los demandantes llevan a cabo una torticera interpretación de los artículos 138 y 139 de la LPI, que en la aplicación que se está haciendo de los mismos convierte dichos preceptos en inconstitucionales, pues, en la práctica, se condena a una pluralidad de personas al cierre de su página web o restricción de sus servicios en España sin darles la más mínima oportunidad defenderse, en una flagrante vulneración tanto de la libertad de expresión e información (art. 20 de la Constitución) como del derecho a la tutela judicial efectiva (art. 24 de la Constitución), pues causa una evidente indefensión la producción de una condena sin posibilidad alguna de defenderse, por no hablar de que puede afectar también a servicios críticos o esenciales, como por ejemplo hospitales y centros de emergencias.
Los artículos 138 y 139, formalmente, permiten demandar directamente a los prestadores de servicios de intermediación (operadores que dan acceso a Internet), para instar la suspensión de los servicios que estos presenten a infractores de derechos de propiedad intelectual. En concreto estos son los preceptos a considerar:
>
> Artículo 138. Acciones y **medidas cautelares urgentes**. El titular de los derechos reconocidos en esta ley, sin perjuicio de otras acciones que le correspondan, podrá instar el cese de la actividad ilícita del infractor y exigir la indemnización de los daños materiales y morales causados, en los términos previstos en los artículos 139 y 140. También podrá instar la publicación o difusión, total o parcial, de la resolución judicial o arbitral en medios de comunicación a costa del infractor….
>
> Tanto las medidas de cesación específicas contempladas en el artículo 139.1.h) como las medidas cautelares previstas en el artículo 141.6 podrán también solicitarse, cuando sean apropiadas, contra los intermediarios a cuyos servicios recurra un tercero para infringir derechos de propiedad intelectual….
>
> Art. 139. h) La suspensión de los servicios prestados por intermediarios a terceros que se valgan de ellos para infringir derechos de propiedad intelectual, sin perjuicio de lo dispuesto en la Ley 34/2002, de 11 de julio, de servicios de la sociedad de la información y de comercio electrónico.”
A nadie honesto, y con un mínimo de sentido común e intención de realizar una hermeneútica correcta, puede escapársele que dichos artículos no están pensados para el supuesto de hecho que nos ocupa, donde no consta la existencia de una válida declaración de infracción de propiedad intelectual, que se ha construido de forma artificial, sin respeto a los principios de dualidad y contradicción de partes, generando una evidente indefensión a las partes que se ven perjudicadas por la pretensión de los demandantes. La Audiencia Provincial de Barcelona tuvo oportunidad de analizar estas peculiares y exóticas previsiones normativas en su Sentencia nº 115/2018, de fecha 20 de febrero de 2018, que es citada por las sentencias que afectan a la polémica que analizamos, y donde sobre la génesis de estos preceptos nos indica:
> “15. El redactado de los artículos 138 y 139 del TRLPI , en lo que afecta a **la extensión de las acciones de cesación a los intermediarios, no aparecía en el texto originario de la Ley**, es consecuencia de una de las múltiples reformas que se han llevado a efecto para adaptar la normativa española sobre propiedad intelectual a la normativa comunitaria. Concretamente, la reforma que afecta a estos preceptos es la llevada a efecto por la Ley 23/2006, de 7 de julio, por la que se modifica el texto refundido de la Ley de Propiedad Intelectual, aprobado por el Real Decreto Legislativo 1/1996, de 12 de abril.
> La Exposición de Motivos de esta reforma indica las razones de la misma:
> «La razón de esta reforma del texto refundido de la Ley de Propiedad Intelectual, aprobado por el Real Decreto Legislativo 1/1996, de 12 de abril, responde a la necesidad de incorporar al derecho español una de las últimas directivas aprobadas en materia de propiedad intelectual, la Directiva 2001/29/CE del Parlamento Europeo y del Consejo, de 22 de mayo de 2001, relativa a la armonización de determinados aspectos de los derechos de autor y derechos afines a los derechos de autor en la sociedad de la información, con la que la Unión Europea, a su vez, ha querido cumplir los Tratados de la Organización Mundial de la Propiedad Intelectual (OMPI) de 1996 sobre Derecho de Autor y sobre Interpretación o Ejecución y Fonogramas.»
> Y, en el último punto de la Exposición de Motivos, se especifica el alcance de la reforma respecto de las acciones y procedimientos:
> «Respecto a las acciones y procedimientos que los titulares de los derechos pueden instar, se establece, por primera vez, la **posibilidad de solicitar medidas cautelares contra los intermediarios** a cuyos servicios recurre un tercero para infringir derechos de propiedad intelectual, sin la exigencia de que el intermediario sea también infractor.»
Es decir, la propia norma, en su exposición de motivos, limita la aplicación de los meritados preceptos, en cuanto a la posibilidad de dirigir la acción directamente contra los intermediarios, al **ámbito de las medidas cautelares.** Ello se deriva igualmente de lo dispuesto en las disposiciones europeas aplicables, como indica la sentencia al decir:
> “Por lo tanto, la interpretación de estos preceptos debe hacerse en consonancia con la normativa de la Unión Europea y la jurisprudencia que la desarrolla.
> 16.- La Directiva 2001/29/CE en su considerando 59 destaca uno de los objetivos de la misma: «Sobre todo en el entorno digital, es posible que terceras partes utilicen cada vez con mayor frecuencia los servicios de intermediarios para llevar a cabo actividades ilícitas. En muchos casos, estos intermediarios son quienes están en mejor situación de poner fin a dichas actividades ilícitas. Así pues, y sin perjuicio de otras sanciones o recursos contemplados, los titulares de los derechos deben tener la posibilidad de solicitar **medidas cautelares** contra el intermediario que transmita por la red la infracción contra la obra o prestación protegidas cometida por un tercero. Esta posibilidad debe estar abierta aun cuando los actos realizados por el intermediario estén exentos en virtud del artículo 5. Debe corresponder a la legislación nacional de los Estados miembros regular las condiciones y modalidades de dichas **medidas cautelares**.»
> Y, para la consecución de este objetivo, el artículo 8.3 de la Directiva establece que:
> «3. Los Estados miembros velarán porque los titulares de los derechos estén en condiciones de solicitar **medidas cautelares** contra los intermediarios a cuyos servicios recurra un tercero para infringir un derecho de autor o un derecho afín a los derechos de autor.»
> 17.- La Directiva comunitaria en principio prevé únicamente la existencia de **medidas cautelares** frente a los intermediarios, así aparece también en el TRLPI ya que el artículo 138 en sus incisos finales hace referencia a medidas cautelares, es decir, medidas instrumentales, necesarias para asegurar la efectividad de la tutela judicial que pudiera otorgarse en la sentencia estimatoria que se dictare.”
>
No obstante lo anterior, **la Audiencia Provincial**, en un pronunciamiento que, entendemos, cuando menos de dudosa constitucionalidad, considera que la Ley permite el ejercicio de estas pretensiones más allá del ámbito de las “acciones y **medidas cautelares urgentes**” que menciona la Exposición de Motivos, la normativa europea y el propio título del art. 138, argumentando lo siguiente:
> “Sin embargo, al desarrollarse el contenido de las acciones de cesación el artículo 139 incluye expresamente la suspensión de los servicios prestados por el intermediario (art. 139.1.h), lo que puede habilitar no sólo a la solicitud de medidas cautelares, sino también a la petición, como pretensión principal, de la suspensión de los servicios. Este régimen legal interno, sin duda más amplio que el derivado del artículo 8.3 de la Directiva, permite abrir una serie de escenarios procesales con trascendencia material por cuanto podría habilitar a dirigir demandas únicamente frente a los intermediarios y no frente al infractor, o podría también habilitar cauce procesal para iniciar acciones frente a los intermediarios sin que exista una previa declaración de infracción imputable, en todo caso, a quien se vale de esos proveedores de servicios para realizar una actividad infractora.”
Parece de dudosa constitucionalidad que se extienda, más allá del estricto ámbito cautelar urgente, la posibilidad de acordar una medida como el cierre de una página web o restricción de servicios sin contar con la presencia en el litigio de las personas afectadas por las medidas. Pero **la Audiencia limita esta posibilidad y sí establece, al menos, la necesidad de que exista una constatación de la existencia de infracción**, como presupuesto para el ejercicio de la acción. En este sentido, la Audiencia considera que un pronunciamiento administrativo al respecto no es suficiente, pero, sorprendentemente, sí considera que un informe de parte no sometido a contradicción, como sucede en el caso de la Sentencia del Juzgado de lo Mercantil nº 9, en cambio, sí constata la existencia de infracción. En concreto, así se pronuncia la Audiencia:
> “Estos problemas son los que se plantean en el supuesto de autos, dado que no ha sido llamado a juicio el titular de la página web supuestamente infractora (www.exvagos.com): no se ha producido un pronunciamiento civil en el que se declare la infracción por parte del titular de esta página web, aunque sí existe un pronunciamiento administrativo ante la Comisión de Propiedad Intelectual…
> Por lo tanto, la **constatación de una infracción de derechos de propiedad intelectual** es un presupuesto ineludible para poder ejercitar las acciones previstas en los artículos 138 y 139 del TRLPI…
> el procedimiento administrativo previo no puede servir, por sí solo, para dar por cumplido o satisfecho el presupuesto previo de infracción por parte del titular de la web, ni la retirada de contenidos puede tener el alcance de presunción de infracción….
> en los autos constan otros **documentos en los que se acredita de modo eficiente la realidad de la infracción**. Se trata, concretamente de la **prueba pericial** aportada como documento número 12 de la demanda… El examen de esa prueba pericial sí permite concluir que la página web exvagos facilita el acceso a contenidos y habilita un sistema de intercambio de archivos que infringe derechos de propiedad intelectual. Así lo hace ampliamente el juez de instancia en la Sentencia recurrida (fundamento de derecho cuarto). ”
En este mismo sentido, sobre la necesidad de constatar la existencia de la infracción, se pronuncia la Sentencia nº 15/2018, del Juzgado de lo Mercantil nº 6 de Barcelona, al decir, en un caso similar, que:
> “... el demandante **no quedará exento de probar**, con carácter prejudicial la infracción sobre los derechos de propiedad intelectual.”
Pues bien, **en el caso de Cloudflare, al menos hasta donde es conocido, no existe ninguna constatación de esa supuesta infracción** (más allá de un “informe técnico” no sometido a contradicción), y los demandantes, acaso en connivencia con los demandados (lo cual es obvio en el caso de TELEFÓNICA, que actúa, con diferentes empresas, como demandante y demandado), o conscientes de que para estos era más fácil allanarse que oponerse a unas pretensiones que no representan perjuicio alguno para ellos, construyen esta farsa de proceso judicial, para conseguir la restricción de los servicios, sin ofrecer la más mínima posibilidad de intervención en el litigio.
Debemos mencionar que algunas sentencias, como la anteriormente citada del Juzgado de lo Mercantil nº 6 de Barcelona, basan la procedencia de la medida acordada contra las páginas web en que sus “**titulares no han podido ser identificados ni localizados**”, en cuyo caso podría considerarse pertinente un procedimiento sin la participación del presunto infractor.
Pero eso no es lo que parece que suceda en este caso, donde al menos Cloudflare se encuentra perfectamente identificada.
Como vemos, la extensión de la posibilidad que tiene el titular de los derechos de accionar directamente contra los prestadores de servicios de intermediación fuera del ámbito cautelar urgente es algo que no da la impresión de estar previsto en la Ley y que, desde luego, es de una más que dudosa constitucionalidad. Si la LPI permite demandar al prestador de servicios, sin conocimiento siquiera del titular de los derechos que se ven afectados, y sin una declaración judicial dictada respetando los principios de igualdad entre las partes afectadas y de contradicción, con base únicamente en un documento de parte, que no ha sido sometido a contradicción, entonces dicha previsión ha de considerarse inconstitucional, al violar el art. 24 y la tutela judicial efectiva.
Conforme a una interpretación razonable de la Ley, la parte actora podría haber solicitado medidas cautelares frente a los prestadores de servicios, pero de forma coetánea o inmediatamente posterior demandar a los presuntos infractores, a fin de que en un proceso contradictorio se determinara si realmente existe infracción y permitir, a los afectados por las medidas poder exponer su visión del asunto en sede judicial.
Podría pensarse, así, que el Juzgado aceptó una interpretación inconstitucional de los artículos 138 y 139 LPI, y no tuvo en cuenta que el art. 21 LEC, establece que el allanamiento debe rechazarse cuando suponga, como es el caso, un perjuicio a tercero no demandado en el procedimiento, pues el art. 21 LEC indica que:
> “Cuando el demandado se allane a todas las pretensiones del actor, el tribunal dictará sentencia condenatoria de acuerdo con lo solicitado por éste, pero si el allanamiento se hiciera en **fraude de ley** o supusiera renuncia **contra el interés general** o **perjuicio de tercero,** se dictará auto rechazándolo y seguirá el proceso adelante.”
Las sentencias de los Juzgados de lo [Mercantil nº 6](https://www.poderjudicial.es/search/AN/openDocument/2d094260f53b5cdca0a8778d75e36f0d/20221006) y [9 de Barcelona](https://www.poderjudicial.es/search/AN/openDocument/3c85bed480cbb1daa0a8778d75e36f0d/20221004), que al parecer son las que sirven de base para las medidas que comentamos, exponen que no se perjudica a terceros, pero, como es notorio y ostensible, en este punto los juzgados de lo mercantil se equivocan del medio al medio, puesto que el allanamiento, sin duda alguna, supone un claro perjuicio de terceros, Cloudflare y sus usuarios legítimos, que ven cómo sus servicios son objeto de restricción, sin ofrecerles posibilidad de defenderse ni argumentar contra las pretensiones de las actoras, infringiendo así el art. 21 LEC, en cuya virtud, el allanamiento debe rechazarse cuando suponga, como es el caso, un perjuicio a tercero (mi mandante) no demandado en el procedimiento.
De esta forma, como hemos expuesto, se ha articulado una suerte de procedimiento formal, inexistente en la práctica, para evitar un proceso contradictorio sobre su pretensión, eludiendo así la eventual participación de los afectados en el debate litigioso, algo que, deberemos convenir, supone una clara infracción del art. 24 de la Constitución, tal y como lo interpreta nuestro Tribunal Constitucional en sentencias como la STC 43/2010:
> “Este Tribunal ha declarado reiteradamente que el derecho a la tutela judicial efectiva sin indefensión (art. 24.1 CE) garantiza a **todos los que puedan resultar afectados por la decisión que se dicte en un proceso judicial el derecho a conocer su existencia, a fin de que tengan la posibilidad de intervenir en él, ser oídos, y ejercer la defensa de sus derechos e intereses legítimos**. Esta necesidad de promover la defensa, en la medida de lo posible, mediante la debida contradicción, **impone a los órganos judiciales un especial deber de diligencia** que, en palabras de la STC 56/2001, de 26 de febrero, FJ 2, “tiene especial importancia en el proceso de ejecución”. En concreto, y por lo que respecta a la posibilidad de intervenir en un proceso de ejecución, hemos afirmado que el derecho a la tutela judicial efectiva habilita a quienes ostenten algún derecho o interés legítimo que pueda verse afectado por los actos de ejecución a comparecer y actuar en el procedimiento, aunque no hubieran sido parte en el proceso principal, y a este fin los arts. 270 LOPJ y 260.2 LEC exigen que las resoluciones judiciales se notifiquen no sólo a las partes procesales, sino también a las personas a quienes se refieran o puedan parar perjuicio (SSTC 229/2000, de 2 de octubre, FJ 3; 56/2001, de 26 de febrero, FJ 2).”
Por otro lado, siguiendo la anterior sentencia, el art. 270 LOPJ impone el **deber de notificar las resoluciones judiciales**, no solo a las partes, sino “también **a quienes se refieran o puedan parar perjuicios**”, lo que, como indica la Audiencia Provincial de Barcelona en su Auto de 29 de junio de 2002, “va más allá de una mera facultad discrecional del juzgador, notificación que tiene por objeto poner en conocimiento de tales personas la resolución y posibilitar la defensa de su derecho inquietado o perturbado.”
Y en el mismo sentido, el art. 150 LEC establece que “**también se notificará la pendencia del proceso a las personas que, según los mismos autos, puedan verse afectadas** por la resolución que ponga fin al procedimiento.”
Da la impresión de que ambos preceptos han sido infringidos por los Juzgados y deberían determinar la nulidad de lo actuado y, por tanto, de las sentencias que comentamos. Como se ha expuesto, podría apreciarse una **vulneración del art. 21 de LEC, que impide acceder al allanamiento cuando ello suponga un perjuicio de tercero, fraude de Ley o contrarien intereses generales**, pero más allá de eso, podría dar lugar también a una **violación de la tutela judicial efectiva** reconocida en el art. 24 de la Constitución, desde el momento en que se obliga a unos terceros a soportar una condena sin posibilidad alguna de un proceso con unas mínimas garantías.
Como hemos dicho, la previsión del art. 138 LPI, que permite solicitar la suspensión de los servicios prestados por intermediarios a terceros directamente contra dichos intermediarios, queda circunscrita al ámbito establecido en el propio título del art. 138, “Acciones y medidas cautelares urgentes” y no constituyen una acción autónoma fuera del ámbito cautelar urgente.
En segundo lugar, una interpretación de dicho precepto, en el sentido de que permita el ejercicio de una acción de condena (en la práctica el cierre páginas web y diversos servicios relacionados con estas), sin posibilidad alguna de defensa de los afectados (Cloudflare y sus usuarios), iría en contra del art. 24 de la Constitución y si dicha Ley debe interpretarse en este sentido, sería inconstitucional.
Finalmente, si se admite la existencia de esa acción independiente y que la misma es constitucional, su procedencia debe conectarse con dos requisitos: una constatación efectiva de la existencia de infracción, que entendemos debe producirse en el marco de un proceso contradictorio donde se ofrezca al presunto infractor la posibilidad de defenderse, así como una imposibilidad de identificación y/o localización del mismo. El principio fundamental que rige el desarrollo del procedimiento en su conjunto es el derecho de las partes a no sufrir indefensión. Y la indefensión proscrita por el artículo 24.1 de la Constitución no es la meramente formal, sino la material, es decir, aquella que haya producido a la parte un real y efectivo menoscabo de sus posibilidades de defensa. Cabe citar en este sentido la [Sentencia del Tribunal Constitucional nº 161/2006](https://hj.tribunalconstitucional.es/HJ/es/Resolucion/Show/5763), de 22 de mayo de 2006:
> “Según una consolidada doctrina constitucional el derecho a la tutela judicial efectiva sin indefensión que se reconoce en el artículo 24.1 de la Constitución Española **garantiza el derecho a acceder al proceso en condiciones de poder ser oído y ejercer la defensa de los derechos e intereses legítimos**… La finalidad material de esta exigencia es la de llevar al conocimiento de los afectados las resoluciones judiciales, para que puedan adoptar la postura que estimen pertinente en defensa de sus intereses (por todas, las sentencias del Tribunal Constitucional 77/1997, de 21 de abril, FJ 2; y 216/2002, de 25 de noviembre, FJ 2)."
Esta trascendencia constitucional de la correcta configuración de los procesos, a fin de que los eventuales afectados puedan ser oídos y defenderse adecuadamente se extiende también a procedimientos en los que, formalmente, se configuran como terceros, como sucede en este caso. Sirva como muestra de ello, la STC 43/2010, de 26 de julio que contiene unos pronunciamientos perfectamente aplicables al caso, si sustituimos las referencias a “ejecución” por “medidas de cesación”:
> “Este Tribunal ha declarado reiteradamente que el derecho a la tutela judicial efectiva sin indefensión (art. 24.1 CE) garantiza a **todos los que puedan resultar afectados por la decisión que se dicte en un proceso judicial el derecho a conocer su existencia, a fin de que tengan la posibilidad de intervenir en él, ser oídos, y ejercer la defensa de sus derechos e intereses legítimos**.
>
> Esta necesidad de promover la defensa, en la medida de lo posible, mediante la **debida contradicción**, impone a los órganos judiciales un especial deber de diligencia que, en palabras de la STC 56/2001, de 26 de febrero, FJ 2, “tiene especial importancia en el proceso de ejecución”. En concreto, y por lo que respecta a la posibilidad de intervenir en un proceso de ejecución, hemos afirmado que el **derecho a la tutela judicial efectiva habilita a quienes ostenten algún derecho o interés legítimo que pueda verse afectado** por los actos de ejecución a comparecer y actuar en el procedimiento, aunque no hubieran sido parte en el proceso principal, y a este fin los arts. 270 LOPJ y 260.2 LEC exigen que las resoluciones judiciales se notifiquen no sólo a las partes procesales, sino también a las personas a quienes se refieran o puedan parar perjuicio (SSTC 229/2000, de 2 de octubre, FJ 3; 56/2001, de 26 de febrero, FJ 2).
>
> ...Afirmamos en aquel caso que ello “provoca la indefensión de la demandante de amparo, pues contra el mandato contenido en el art. 24.1 CE de promover la defensión mediante la correspondiente contradicción, y sin perjuicio del pronunciamiento que pueda recaer, de lo que se resuelva sobre la posesión y sobre la posible reserva de las acciones que puedan corresponder a los implicados, conforme acertadamente mantiene el Ministerio Fiscal, el órgano judicial acordó el lanzamiento del propietario y poseedor legítimo de una vivienda sin tan siquiera permitirle comparecer a defender su derecho en un procedimiento contradictorio” (FJ 9).
>
> En definitiva, de nuestra doctrina se desprende con **absoluta claridad que la interdicción de la indefensión consagrada en el art. 24.1 CE impone a los órganos judiciales el deber de velar por que quienes ostenten algún derecho o interés legítimo en un proceso** de ejecución, aunque no hayan sido parte en el proceso principal, **puedan comparecer y ser oídos en el mismo para garantizar su defensa**, sin perjuicio del pronunciamiento que pueda recaer y de la posible existencia de otras acciones que puedan corresponder a los afectados.
>
> …En definitiva, y como afirma el Ministerio Fiscal, **el órgano judicial no actuó con la diligencia debida en orden a procurar que los demandantes de amparo pudieran tener conocimiento y comparecer en un proceso** ejecutivo **en el que resultaban afectados sus intereses**... Y dicho comportamiento del órgano judicial **causó indefensión constitucionalmente relevante**, pues **les privó de su derecho a ser oídos y les impidió el ejercicio del derecho de defensa de sus legítimos derechos e intereses** sobre el citado inmueble, sin que exista dato alguno en las actuaciones del que se desprenda que los recurrentes conocieran la existencia del procedimiento ejecutivo o que no hayan actuado con la diligencia debida en orden a facilitar su comparecencia en el citado proceso.”
Es evidente que a los afectados por las medidas **se les privó del derecho a ser oídos** y **se les impidió el ejercicio del derecho de defensa** de sus legítimos intereses sobre las páginas y servicios que operaban, por lo que se ha producido una **violación del derecho a la tutela judicial efectiva** reconocida en el art. 24 de la Constitución.
Además, las medidas de bloqueo de direcciones compartidas afectan también a la **libertad de expresión e información** de terceros que no guardan relación alguna con el conflicto y, lo que es peor, puede tener una **negativa incidencia en servicios que podrían ser críticos,** lo que es un comportamiento peligroso, irresponsable y negligente.
Por todas estas razones, las sentencias deberían ser anuladas y las medidas derivadas de ellas dejadas sin efecto, ofreciendo en todo caso a los afectados la posibilidad de ser oídos en juicio y defender sus legítimos intereses.
-

@ b2caa9b3:9eab0fb5
2025-02-14 13:55:53
After spending two weeks in Arusha, it was time to move on. My next stop was Dodoma. I walked to the bus station in the center of Arusha to check ticket prices, but I disliked the chaotic atmosphere — people approached me nonstop, trying to sell me tickets to destinations I had no interest in. Instead, I went to the Shabiby office, a reputed bus company, and secured a ticket for 29,000 TZS. The bus was scheduled to leave at 10 A.M. the next day, giving me time to prepare.

*Photo above: a stop between Arusha and Dodoma.*
I returned to my hostel, packed my bag, and picked up snacks and water from Shoppers Supermarket, knowing that Tanzanian bus rides tend to take longer than expected. The 80-kilometer journey from Moshi to Arusha had taken me up to three hours, so I expected the longer trip to Dodoma to stretch beyond the promised eight hours.
## The Journey to Dodoma
The bus ride was predictably long, making frequent stops along the way. Upon arrival in Dodoma, the bus meandered through the city, dropping off passengers. My booked accommodation was just under two kilometers from the final stop, so I decided to walk, relying on Google Maps to guide me.

*Photo above: in Dodoma.*
When I arrived at what was supposed to be my lodging, I was skeptical. The house lacked a sign, and an elderly woman was doing laundry in the yard. When I asked if this was the right place, she called a younger woman who spoke English and welcomed me inside. The accommodation was a full apartment, complete with a kitchen, but not cheap. Later in the evening, I attempted to shower, only to discover there was no running water. I resorted to a bucket shower, but the cramped bathroom caused water to spill into the apartment.

*Photo above: the Baobab Café in Dodoma.*
## Exploring Dodoma
The next day, I set out to explore Dodoma. I passed a cozy café and an old-looking church, which I later learned was not as ancient as it seemed. Strolling down a lively shopping district, I admired the small stores lining the streets. Eventually, I settled at the café I had spotted earlier, enjoying a simple dinner of bread and tomato salad.

*Photo above: the church in Dodoma.*
Originally, I had planned to stay for just one night, but the city intrigued me, and I extended my stay. This meant I had to book my next bus ticket and gather supplies. Using the Bolt app, I ordered a TukTuk to take me to the Shabiby bus terminal. The ride cost 2,000 TZS — without Bolt, I would have been charged significantly more. I bought my ticket to Mbeya for 40,000 TZS, with a departure time of 5:30 A.M.
That night, I packed my bags and went to bed early, knowing I had an early start ahead.
## The Departure to Mbeya
Waking up at 3:30 A.M., I hurriedly took another bucket shower — still no running water. I initially planned to order a TukTuk, but the Bolt app showed no available drivers. With the bus station only a 13-minute walk away, I set out on foot. Along the way, I stepped into a water hole, soaking myself up to my knees. Street vendors persistently offered me motorcycle rides, but I ignored them and continued walking.

*Photo above: in Dodoma.*
Arriving at the bus station, I saw the previous bus to Mbeya departing. My gut told me something was wrong. Sure enough, my bus was delayed by almost an hour. Finally, it arrived, and I boarded, relieved that I hadn’t missed it after all.
## A Long Ride to Mbeya
The previous day, I had suffered from severe diarrhea. Fortunately, a local pharmacy in Dodoma provided me with pills that helped stabilize my system. I also continued taking my daily dose of Doxycycline as a malaria precaution.

*Photo above: shopping street in Dodoma.*
This time, I had a window seat with no one beside me, allowing me to place my backpack on the empty seat. As we traveled, I watched the Tanzanian landscape unfold. At one point, the bus crossed a dam, likely a reservoir, before being stopped by police. A policeman entered, checked my passport, and inquired about my destination. When I mentioned Mbeya, he ask me where after, and I told him to Lusaka. Then he asked if it was in Zambia, returned my passport, and he let us continue.

*Photo above: the Baobab Café in Dodoma.*
My host in Mbeya had instructed me to get off at Nane Nane Stand. Upon arrival, I searched for a TukTuk. Without internet access, I had to negotiate fares blindly. After rejecting overpriced offers, I managed to bargain a price of 5,000 TZS for the short ride to my accommodation, what was a bit high for a Tuktuk.
## Mbeya and the Journey to the Border
Initially planning to stay two nights, exhaustion led me to extend for an extra night. The hostel was beautiful and clean but, yet again, had no running water. However, this time, the host kindly boiled water for me, allowing me to take a warm bucket shower.

*Photo above: on the way to the Supermarket in Dodoma.*
On my final day in Mbeya, I explored the city, visiting a new children's hospital and an old church. Tuktuk drivers repeatedly tried to overcharge me, but I insisted on the standard 800 TZS fare for public transport.

*Photo above: on the way to the Supermarket in Dodoma.*
The following morning, after a quick breakfast, I set off for the bus station with a fellow traveler I met at the hostel. Together, we took a bus to Tunduma for 5,000 TZS each. From there, a TukTuk ride to the border cost another 5,000 TZS.
## Crossing into Zambia
The border crossing was straightforward for me — I received a free 30-day visa for Zambia. My Russian travel companion, however, needed a visa on arrival, payable in cash and only in USD. The immigration officer arranged a taxi to take us to an ATM, but the only available bank, Absa, charged exorbitant fees. Fortunately, we later found a Zanaco ATM in Nakonde that had no fees.

*Photo above: between Dodoma and Mbeya.*
Once we had the necessary cash, we returned to the Border immigration, paid for the visa, and proceeded into Zambia. We walked to town, grabbed some food, and checked into Shalom Hotel. It was cheap, costing only 200 Kwacha per night (under 10 Euros), but lacked cleanliness and had no running water.
## A Frustrating Bus Experience
We booked a 4 A.M. bus to Lusaka with Jkas, supposedly the best company. However, when we arrived at the station at 3:28 A.M., the bus was already gone. The staff had lied, telling us the bus left at 4 A.M. but actually departing at 3 A.M. They then offered an overpriced taxi to chase the bus, which we declined.

*Photo above: between Dodoma and Mbeya.*
With no other options left, we searched for an alternative and eventually made our way to the PowerTools bus station — only to find that the bus also had already left.
The next bus? **Overnight.**
We were stuck.
### The Boda Chase
That’s when a Boda driver approached us. He had been waiting at the Powertools station, watching the situation unfold. **“I know where your bus is,”** he said. **“At the checkpoint. I can take you.”**
There was no time to think. We climbed on.
The night was pitch black, the streets slick with rain and mud. As soon as he twisted the throttle, the bike lurched forward. The driver wasn’t smooth — he was riding like a madman, shaking left and right as he weaved through the darkness. The wet road made it worse, and the mud felt like a trap waiting to swallow us whole.

*Photo above: between Dodoma and Mbeya.*
A gust of wind blew my hat into my face, blinding me for the most time. My gut twisted — I could almost see the crash before it happened. **“Slow down!”** I shouted. He eased off for a while, but soon enough, he hit the gas again. **“I said slow down!”** I had to remind him.
It felt like an eternity. The only thought keeping me together was the hope that the checkpoint was close.
Then — buses. Dozens of them.
We told him which one was ours, but in the dim light, they all looked the same. He swerved between them, searching, until finally — **Jkas.**

*Photo above: the old church in Mbeya.*
As we pulled up, the driver suddenly changed his price from 200 to 400 Kwacha. Of course. I handed him 300, not in the mood to argue, and walked straight into the bus, **relieved to be off that death ride**.
The journey continued, but the morning’s chaos was a reminder that travel in Africa often requires patience and adaptability.
---
## Final Thoughts
The journey from Arusha to Lusaka was long and filled with challenges — delayed buses, unreliable accommodations, and frustrating border experiences. Yet, the beauty of Tanzania and Zambia, the people I met, and the lessons I learned along the way made it all worthwhile. Traveling in Africa requires flexibility, but it rewards you with unforgettable experiences and stories to tell.

*Photo above: in Mbeya.*

*Photo above: somewhere in Zambia from the Bus.*

*Photo above: in Lusaka.*

*Photo above: in the East Park Mall in Lusaka.*

*Photo above: in the East Park Mall in Lusaka.*

*Photo above: East Park Mall in Lusaka.*

*Photo above: in the market in Lusaka.*
-

@ a012dc82:6458a70d
2025-02-14 13:51:33
In the ever-evolving landscape of cryptocurrency, a significant development has emerged that is reshaping perceptions and strategies within the industry. Bitcoin, the original and most prominent digital currency, has seen its transaction fees hit a two-year high. This remarkable surge in fees is not merely a statistical blip but a phenomenon that could herald a transformative phase in Bitcoin mining. As we witness these fees reaching unprecedented levels, it prompts a crucial inquiry: Are we on the cusp of a new era in BTC mining, one that redefines its economic and technological paradigms?
**Table Of Content**
- The Surge in Transaction Fees
- Impact on Bitcoin Miners
- A Divided Community
- The Ripple Effect on Mining Stocks
- The Broader Market Influence
- Conclusion
- FAQs
**The Surge in Transaction Fees**
The Bitcoin network, known for its robustness and security, has recently been the center of a notable financial trend. Transaction fees have soared to over $37, a figure reminiscent of the peak levels observed in April 2021. This significant increase is not an isolated event but rather a symptom of a larger, more complex shift within the Bitcoin ecosystem. The primary driver behind this surge is the burgeoning interest in Bitcoin NFTs, particularly through a protocol known as Ordinals. This innovative protocol facilitates the storage of non-fungible tokens (NFTs) directly on the Bitcoin blockchain. As a result, there has been a marked increase in transaction volumes, leading to higher fees. This trend reflects a growing interest in utilizing Bitcoin not just as a currency but as a platform for broader digital asset interactions, potentially expanding its use cases and value proposition.
**Impact on Bitcoin Miners**
The escalation in transaction fees has had a profound and far-reaching impact on the community of Bitcoin miners. These individuals and companies, who form the backbone of the Bitcoin network by validating transactions and maintaining the blockchain, are now witnessing a dramatic shift in their revenue streams. With fees reaching such high levels, their daily income has surged to an estimated $63 million, translating to an extraordinary $23 billion annually. This figure is a significant leap from the average income over the past two years and represents a potential windfall for the mining sector. The increased profitability could lead to renewed investment in mining infrastructure, potentially spurring technological advancements and increased competition within the sector. It also raises questions about the decentralization of Bitcoin mining, as higher profits could lead to further consolidation in an industry already dominated by large players.
**A Divided Community**
The Bitcoin community, known for its diverse opinions and robust debates, finds itself at a crossroads with the rise of Ordinals and its impact on transaction fees. On one hand, some members of the community, including prominent figures like core developer Luke Dashjr, view the influx of Ordinals as a form of spam that clutters the blockchain and necessitates technical solutions. This perspective underscores concerns about blockchain bloat, transaction prioritization, and the fundamental principles of what Bitcoin should represent. On the other hand, for miners, these high fees have been a significant boon. They have provided a much-needed boost to profitability, especially in a period where the price of Bitcoin itself has been relatively stable. This divergence in views reflects the ongoing evolution of Bitcoin's identity and purpose, as it balances its role as a digital gold, a transactional currency, and now, a platform for digital art and collectibles.
**The Ripple Effect on Mining Stocks**
The impact of the surge in Bitcoin fees extends beyond the digital realm and into the traditional financial markets. Bitcoin mining stocks, representing companies that invest heavily in the infrastructure required to mine the digital currency, have shown remarkable resilience and growth. Companies like Marathon Digital, Riot Platform, and Cleanspark have seen their stock prices rally, significantly outperforming the actual price of Bitcoin. This trend indicates a growing investor confidence in the mining sector, buoyed by the increased revenue potential from transaction fees. It also suggests a decoupling of sorts, where the mining sector's performance is not solely dependent on the price of Bitcoin but also on other factors like transaction volume and fee structures. This decoupling could attract a new class of investors to the mining stocks, those looking for exposure to the crypto market but with a different risk profile than holding cryptocurrencies directly.
**The Broader Market Influence**
The performance of Bitcoin mining stocks is also intricately linked to the broader equity markets. As observed by Caleb Franzen, founder of Cubic Analytics, the strong performance of equity markets has provided additional momentum to these stocks. This correlation indicates that Bitcoin mining companies are increasingly being viewed through the lens of traditional financial analysis, where market trends and investor sentiment play a crucial role. The implication is significant: as Bitcoin mining firms become more integrated into the broader market, they may also become more susceptible to the same macroeconomic factors that influence traditional stocks. This integration could lead to greater stability in the mining sector but also exposes it to new types of risks, such as regulatory changes or shifts in investor sentiment unrelated to the crypto market.
**Conclusion**
The recent developments in Bitcoin transaction fees, driven by the popularity of Ordinals, have ushered in significant changes in the mining landscape. With increased revenues and a positive impact on mining stocks, it's tempting to proclaim the dawn of a new era in Bitcoin mining. However, the sustainability of this trend and its long-term impact on the Bitcoin ecosystem remain subjects of intense speculation and debate. As the community grapples with these changes, the future of Bitcoin mining continues to be a topic of keen interest. Whether this marks a permanent shift or a temporary phase in the cryptocurrency's evolution, one thing is certain: the world of Bitcoin remains as dynamic and unpredictable as ever.
**FAQs**
**What caused the recent spike in Bitcoin transaction fees?**
The surge in Bitcoin transaction fees to over $37, a two-year high, is primarily attributed to the growing popularity of Bitcoin NFTs, especially through the Ordinals protocol, which allows for the storage of non-fungible tokens on the Bitcoin blockchain.
**How does the increase in transaction fees affect Bitcoin miners?**
Bitcoin miners, who earn BTC for processing transactions, have seen a significant increase in their income due to the higher fees. Their daily revenue has reached approximately $63 million, translating to an estimated $23 billion annually.
**What is the Ordinals protocol, and why is it controversial?**
Ordinals is a protocol that enables the storage of NFTs on the Bitcoin blockchain. It has been controversial within the Bitcoin community, with some viewing it as a beneficial innovation and others as a form of spam that clutters the blockchain.
**Have Bitcoin mining stocks been affected by the increase in fees?**
Yes, Bitcoin mining stocks, such as Marathon Digital, Riot Platform, and Cleanspark, have outperformed the actual price of Bitcoin, indicating growing investor confidence in the mining sector due to increased revenue from transaction fees.
**Is the Bitcoin mining industry becoming more centralized?**
The increase in profitability could lead to further investment in mining infrastructure, potentially leading to more competition but also raising concerns about the centralization of mining power in the hands of large companies.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnews.co](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
-

@ 09fbf8f3:fa3d60f0
2025-02-14 13:40:37
> 功能很简单的网站,无广告、无任何付费项目,漫画全部免费。
荤素搭配。
唯一的缺点就是有点慢,看了下网站使用的是cloudflare网站加速,国内效果差了一点,加个🪜就好了。
关键词mycomic
官网:[https://mycomic.com](https://mycomic.com)

-

@ c0a57a12:8b230f7a
2025-02-14 13:19:06
Our generation has a cussing problem.
Not the kind our grandfathers had. Their swearing was like their gunpowder—kept dry, used sparingly, and when used, meant to do something. A man swore when he had been wronged, when fate had dealt him a rotten hand, when he stood on the edge of some great loss or some great victory. He swore not because he was thoughtless, but because he was thoughtful—because there were things in this world that deserved cursing, just as there were things that deserved blessing.
But today? Today, men swear too much, but their swearing is too little. Profanity has become a nervous tic, a filler word, a lazy man’s substitute for wit. We curse not with thunder but with static, not with the crack of a whip but with the feeble hum of a refrigerator. We lace our every sentence with obscenities, not because we are overcome with feeling, but because we have forgotten how to feel at all.
And this is what makes our generation’s swearing so weak, so colorless, so infuriatingly dull. It is not that men curse—it is that they curse in the same tone with which they order a sandwich. Their profanity is not the language of men at war with the world’s wickedness; it is the language of men too bored to speak properly. They do not curse like sailors charging into battle; they curse like cashiers sighing through their shifts.
And yet, in an irony too delicious to ignore, we live in an age obsessed with language. We do not believe in God, but we believe in speech codes. We do not fear hell, but we fear being reprimanded in the workplace. We have scrapped the Ten Commandments but will gladly enforce a list of forbidden words a mile long. Our rulers and bureaucrats will pore over a man’s every sentence, hunting for an offense, searching for some phrase to declare unacceptable.
And yet—yet!—these same rulers, these same bureaucrats, these same petty, priggish priests of modern propriety will gladly flood the airwaves with an endless stream of empty, witless vulgarity. A schoolteacher may be fired for uttering a forbidden phrase, but a pop star may string together a song consisting of nothing but profanity, and no one blinks an eye. We are hypersensitive to language when it contains truth, yet utterly indifferent when it contains nothing at all.
And this is the real problem: we do not curse too much, but too weakly. Our words are exhausted, worn thin, spoken to death. Men have forgotten how to speak with fire, how to command with words, how to invoke heaven or hell with their tongues. They do not pray, because they do not know how to form words for the divine. They do not make oaths, because they no longer believe words can bind them. They do not declare war on the evils of the world, because they have spent all their breath on pointless cursing and have none left for real battle.
And where does this road lead? It leads to a world where men have lost the power of speech entirely. A world where every conversation sounds the same, where every man mutters the same tired handful of words over and over, like a machine running out of oil. It leads to a world where poetry is impossible, where language is shriveled and gray, where men do not swear terrible oaths because they no longer believe in terrible things. It leads to a world where men do not pray because they do not believe in miracles, and men do not curse because they do not believe in damnation.
But this is not a lament. This is not the tired sigh of a defeated man. This is a call to arms.
The solution is not to ban speech further. It is not to purge all rough language from the world and replace it with the sterile buzz of corporate-approved jargon. No, the solution is simpler, and far more radical. Men must learn to shut up.
They must learn to close their mouths until they have something worth saying. They must stop filling the air with idle, useless, lazy profanity and speak only when speaking matters. If a man must swear, let him swear like a hammer striking an anvil—sharp, sudden, final. If a man must curse, let it be a curse that shakes the very bones of the world. Let his words be rare, but let them be terrible. Let his anger be real. Let his prayers be real. Let his oaths be real.
But above all, let his words be true. Let his promises be binding. Let his speech be a sword, not a dull spoon. Let him recover the power of language, the discipline of speech, the ancient art of saying what he means and meaning what he says.
For the world was not spoken into being with mumbling. Creation did not begin with filler words and placeholders. It began with a Word—a real Word, a mighty Word, a Word so vast and true that it shaped the heavens and the earth.
And so it must be again.
If men wish to remake their world, if they wish to shake the rotten foundations of this empty, word-weary age, then let them first learn to speak. Let them strip their language of all that is weak, all that is frivolous, all that is cheap. Let them cut out the cancer of casual vulgarity and replace it with something fierce, something worthy.
Let them curse like warriors and pray like prophets. Let them make oaths that bind and promises that burn. Let them stand among men and speak with voices that shake the air—voices that carry weight, voices that mean what they say, voices that, when heard, demand silence in return.
For a world that has lost the power of words will not be saved by noise. It will not be saved by muttering. It will not be saved by the droning nonsense of a people who have forgotten how to mean what they say.
It will be saved by men who have learned once again to say what they mean—and to speak as if their words could move mountains.
Because they can.
-

@ 00000001:b0c77eb9
2025-02-14 12:40:40
مواقع التواصل الإجتماعي العامة هي التي تتحكم بك، تتحكم بك بفرض اجندتها وتجبرك على اتبعها وتحظر وتحذف كل ما يخالفها،
وحرية التعبير تنحصر عليها!
و خوارزمياتها الخبيثة التي تعرض لك مايريدون منك أن تراه وتحجب ما لا يريدونك أن تراه.
في نوستر انت المتحكم، انت الذي تحدد من تتابع و انت الذي تحدد المرحلات التي تنشر منشوراتك بها.
نوستر لامركزي، بمعنى عدم وجود سلطة تتحكم ببياناتك، بياناتك موجودة في المرحلات، ولا احد يستطيع حذفها او تعديلها او حظر ظهورها.
و هذا لا ينطبق فقط على مواقع التواصل الإجتماعي العامة، بل ينطبق أيضاً على الـfediverse، في الـfediverse انت لست حر، انت
تتبع الخادم الذي تستخدمه ويستطيع هذا الخادم حظر ما لا يريد ظهوره لك، لأنك لا تتواصل مع بقية الخوادم بنفسك، بل خادمك من
يقوم بذلك بالنيابة عنك.
وحتى إذا كنت تمتلك خادم في شبكة الـfediverse، إذا خالفت اجندة بقية الخوادم ونظرتهم عن حرية الرأي و التعبير سوف يندرج
خادمك في القائمة السوداء fediblock ولن يتمكن خادمك من التواصل مع بقية خوادم الشبكة، ستكون محصور بالخوادم المحظورة،
بالتالي انت في الشبكة الأخرى من الـfediverse!
نعم، يوجد شبكتين في الكون الفدرالي fediverse شبكة الصالحين التابعين للأجندة الغربية وشبكة الطالحين الذين لا يتبعون لها،
إذا تم إدراج خادمك في قائمة fediblock سوف تذهب للشبكة الأخرى!
-

@ c3b2802b:4850599c
2025-02-14 12:14:43
Die Plattform dient dem Zweck, interessierten Gemeinschaften unseres Landes aufzuzeigen, dass auch unter schwierigen globalen und bundespolitischen Rahmenbedingungen der Wandel hin zu zukunftsfähigen Lebensmustern auf kommunaler Ebene möglich ist. Und noch mehr: Dass dieser Umbau auch simultan in mehreren Lebensbereichen gestartet und vollzogen werden kann, wenn mutige und kluge Menschen aus verschiedenen Gruppen in Kommunen beherzt zusammenwirken. 
**Psychologischer Hintergrund.** Viele Studien in 20 Jahren eigener psychologischer Analysen erfolgreicher Regionalisierungsprojekte haben aufgezeigt: Persönliche Begegnung und Austausch zwischen Interessierten an Regionalisierungsvorhaben und bereits erfolgreichen Pionieren sind ein entscheidender Erfolgsfaktor für gelingende Transformation. Dafür braucht es Informationen, wo sich Pionierprojekte befinden. Im ersten größeren Transformationsprojekt meiner Arbeitsgruppe, dem Energiewendedorf Jühnde, hat das Wissenschaftler-Team vorab andere innovative Kommunen besucht und deren Erfolgsfaktoren im eigenen Vorhaben umgesetzt. Die Mehrzahl der 200 [Energiewendedörfer](https://xn--energiewendedrfer-c0b.de/), die nach Fertigstellung Jühndes entstanden sind, hat sich wiederum vor Ort in der Modellkommune Jühnde informiert. Dies zeigt den Schneeballefekt des Lernens am Beispiel auf. Die hier beschriebene Plattform macht derartige „Funkenflüge“ für die Vielfalt der hier beschriebenen Innovationen über den Energiebereich hinaus möglich. Denn: Lernen am Modell setzt eine gute Übersicht über brauchbare Modelle voraus.
**Inhalte der Plattform.** Die [Zukunftskommunen-Plattform](https://zukunftskommunen.de/) beschreibt 67 Kommunen mit jeweils mindestens drei kommunalen Erfolgen. Die im gesamten Bundesgebiet verteilten Kommunen sind auf einer Landkarte ersichtlich. Von jedem Ort unseres Landes aus kann eine der Zukunftskommunen in maximal 100 km Entfernung erreicht werden. Die Nutzer der Plattform können über die Eingabe ihres Standortes erfahren, welche der Zukunftskommunen sich in der eigenen Region befinden – mit Angabe der Distanz in Kilometern. Jede dieser Kommunen ist in Wort und Bild mit den wesentlichen Informationen zum Stand des Umbaus sowie zum Ansprechpartner charakterisiert.
Die derzeit auf der Plattform dargestellten über 200 kommunalen Erfolge sind jeweils durch harte Fakten, Angaben zur Entstehungsgeschichte sowie Erfolgsfaktoren kurz skizziert - und wiederum sind jeweils auskunftsbereite Ansprechpartner genannt. Die Erfolge sind unter den Kommunen angeführt und lassen sich so „durchblättern“. Interessieren sich Nutzer der Plattform jedoch für bestimmte Aspekte der Regionalgesellschaft, können sie auch gezielt nach einzelnen Transformationsbereichen suchen. In dem Fall bekommen Sie – wiederum mit Entfernungsangabe zum eigenen Standort – die interessierenden kommunalen Erfolge angezeigt. 
So lassen sich jeweils dutzende Erfolge im Land auffinden, im Bereich Bildung z.B. Lehrpfade, Umweltbildungsprojekte und Umwelttrainerprojekte, bei denen eigens ausgebildete Ehrenamtler ökologische Zusammenhänge vermitteln. Im Bereich Kreislaufwirtschaft sind die Erfolge nach folgenden Aspekten auffindbar: Regionale Kreisläufe, verpackungsfreie Verteilung, Verwendung von Natur-Baustoffen, Recycling endlicher Ressourcen, Bio-Landwirtschaft, Anbau und Nutzung nachwachsender Rohstoffe, Solar-Mobilität, Produktion von Anlagen zur Erzeugung erneuerbarer Energie und Erzeugung erneuerbarer Energie. Der Bereich natürliche Vielfalt ist folgendermaßen gegliedert: Naturschutz, Ressourcenschutz, Permakultur und Erhaltung von Biodiversität. Die Untergliederung der erfolgreichen Gemeinschaftsprojekte lautet: Miteinander aller Bevölkerungsgruppen, Integration und Inklusion, Generationennetzwerk, Genossenschaften, Rekommunalisierung von Infrastruktur, lokale Währung sowie Tauschen und Schenken. 
Die Vielfalt der Innovationen ist noch weit größer als in dem Kategoriensystem abgebildet, da wegen der Handhabbarkeit der Plattform nicht alle denkbaren Kriterien ausformuliert worden sind. Doch auch besonders ungewöhnliche oder heute noch seltene kommunale Innovationen sind in der Beispielsammlung der Plattform auffindbar. Dazu kann die freie Suche der Plattform verwendet werden. Wer sich z.B. für Eisspeicher interessiert, kann ein Bildungszentrum mit Solareis-Erdspeicher in der Zukunftskommune Wiernsheim auffinden. 
Ein Blog informiert über den politischen und geografischen Kontext, in dem die Transformation in unseren Kommunen stattfindet. Hier lassen sich Erfolgsgeschichten zwischen 2018 und 2024 aus dem In- und Ausland abrufen - wiederum beim Blättern oder durch die Suchfunktion nach Stichworten . Seit Herbst 2024 finden Sie meine Blogbeiträge zu dieser Thematik bei der [Genossenschaft Menschlich Wirtschaften](https://menschlichwirtschaften.de/kategorie/peter-schmuck/). Viel Freude beim Blättern und Stöbern!
*Zuerst veröffentlicht in der Zeitschrift Ländlicher Raum (hier leicht gekürzt)* 
-

@ bd32f268:22b33966
2025-02-14 12:10:11
Muitos livros foram escritos sobre o tema oferecendo perspetivas líricas, narrativas, psicológicas/filosóficas, religiosas, simbólicas e políticas. A resposta varia no seu significado consoante o paradigma teórico de análise. Reconhecendo esta multiplicidade de dimensões do conceito qualquer reflexão será sempre, inevitavelmente parcial, no entanto cumpre realizar-se dado que a importância do tema o exige. Muito se tem dito e muito mais se dirá precisamente porque este é um tema que convida à expressão de uma profunda intimidade universal.
O amor é, segundo Erich Fromm psicanalista alemão, uma decisão, um julgamento e uma promessa, além de um sentimento. Segundo o autor o amor requer paciência, disciplina, concentração, fé e, quanto a mim uma ideia fundamental de Fromm, a capacidade para transcender o nosso próximo narcisismo. Como seriamos capazes de amar sem ultrapassar o nosso narcisismo? Seríamos capazes do compromisso necessário para aceitar o sacrifício de não corresponder aos nossos desejos mais imediatos em prol da construção de um projeto para o futuro com outra pessoa? No nosso narcisismo reside frequentemente o nosso movimento em direção á gratificação imediata e à não aceitação do sacrifício inerente à construção de algo que desejavelmente será maior que nós.
Como nos diz um pergaminho da Psicologia Gestalt, corrente teórica que se dedica ao estudo da forma e da percepção, o todo é maior que a soma das partes. É precisamente neste ponto que está uma das principais forças centrípetas deste conceito, na hipótese de construir algo que melhora a nossa vida que acrescenta em significado, sendo esta a unidade base na qual psicologicamente se medem as coisas e os fenómenos. Fromm propõe ainda que o amor não será apenas a ligação ao objeto amado, mas também uma orientação perante a vida, dizendo: “ o amor é uma atitude, uma orientação de carácter que determina a ligação da pessoa ao mundo como um todo e não apenas a um objeto.” Sendo assim não será suspeito que neste conceito esteja a chave para operar profundas transformações no carácter e na vida dos Humanos, que a somar á construção da relação com o outro têm a construção de uma nova relação com o mundo.
O amor é uma dádiva na qual ao darmos podemos experienciar a nossa riqueza de carácter, a nossa força e o nosso poder. Podemos ver este conceito como um professor que nos ensina sobre a vida e sobre as relações. Ensina-nos humildade na medida em que aceitamos algo maior que nós, ensina disciplina porque requer um foco constante e diria até que nos pode ensinar o significado e peso do conceito de fé. Neste último ponto falo de fé porque o amor contempla a dúvida fundamental da rejeição do sacrifício feito em prol do amor, e a fé transcende essa dificuldade da dúvida. A fé parece salvar-nos da corrosão da dúvida e purificar as intenções da pessoa que ama. Ter fé é mais que desenvolver uma mera expectativa, é a construção da esperança interiormente mesmo que seja na face do improvável ou implausível. Assim sendo, amar parece-se em muito com uma experiência eminentemente religiosa na medida em que sacraliza a experiência da pessoa que ama e a vida, atribuindo contornos de divino e transcendental ao que, aos olhos que quem não ama, pode parecer trivial e normal.
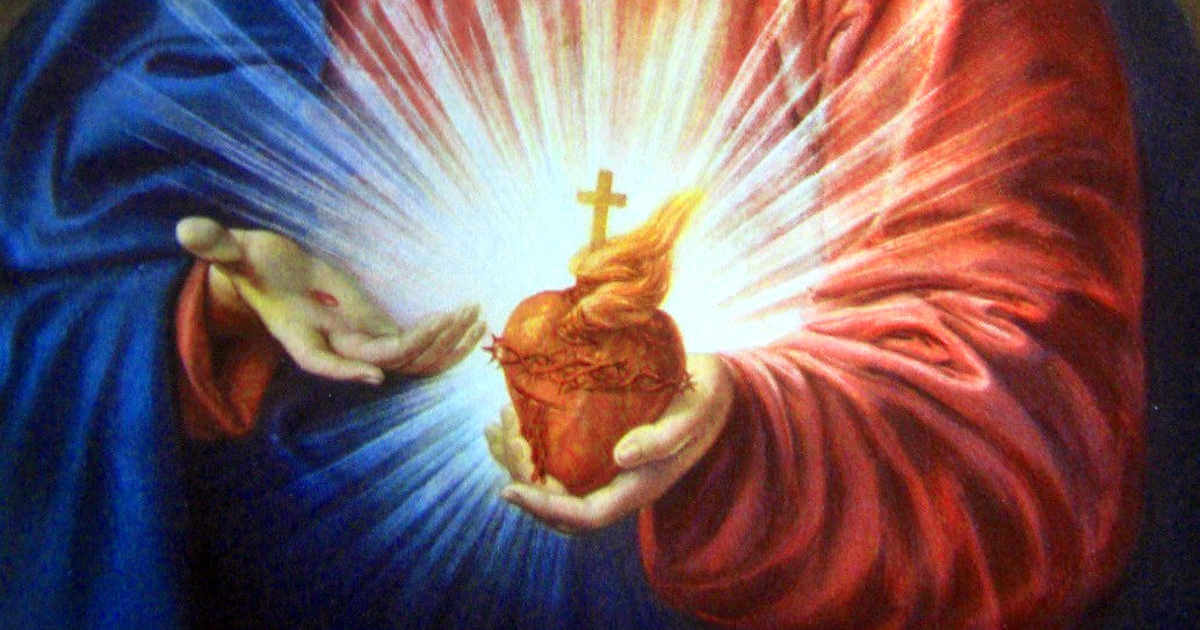*Sagrado coração de Jesus*
Um amor maduro quer-se consciente da necessidade de amar. Fromm diz-nos que o amor maduro está em: “eu preciso de ti porque te amo” e não em “eu amo-te porque preciso de ti”. Esta inversão do sentido da frase parece fundamental para que o amor não seja confundido com uma forma de egoísmo. Aqui a necessidade do outro surge em função do amor que temos pelo outro, não sendo o amor consequência da necessidade que temos do outro. Amar maduramente é a aceitação do sacrifício diante da incerteza e da dor por vezes debilitante. Assim desenvolvemos a tolerância que nos permite crescer e desenraizar da perversidade do narcisismo cumprindo a nossa identidade na missão de amar.

-

@ c43d6de3:a6583169
2025-02-14 11:27:09
## A Brief History of Ownership
### The Forgotten Struggle for Ownership
History reveals that our ancestors labored—both intellectually and physically—to secure the freedoms we are subconsciously giving away.
We stand at the threshold of a new era.
Across the globe, long-established institutions are showing signs of strain. Trust in governments, banks, and major corporations is eroding, leaving many individuals feeling as though their rights are being infringed upon—even if they struggle to articulate exactly how. Social media and traditional news outlets amplify this sense of unease, painting a picture of impending upheaval, as if we are on the brink of a revolution whose name will only become clear in hindsight, once the first sparks ignite into a full-blown blaze.
Yet, when we examine the state of the global economy, this narrative begins to unravel. Economic inequality has reached levels unseen in nearly a century, and while many point fingers at politicians, policies, or the so-called greed of the 1% hoarding all the wealth, the true culprit may be much closer than most realize. At a time when legal structures worldwide strongly protect ownership and economic mobility, it is individuals themselves who are willingly surrendering their financial power to the very elites they criticize.
I know—“willingly” might seem like a stretch. After all, no one consciously chooses to give up their economic freedom. But take a closer look at the way people spend, borrow, and consume, and it becomes painfully clear: most are actively forfeiting their ability to build and own wealth.
How did we get here?
Much of this self-inflicted harm comes from a fundamental ignorance of the history of ownership and the struggles fought to secure it.
This article serves as a short exploration of the past.
I'll examine what might be considered the natural state of humanity, how the majority has historically struggled to achieve ownership rights, and the deadly conflicts that had to occur for the modern individual to enjoy the very rights they are now squandering.

### I. The Era of Communal Ownership
No one is born into this world alone.
We do not simply materialize into existence; we arrive as part of the first unit of human society—the family.
Before the rise of civilization, the primary focus of the family was survival. Ownership was a foreign concept, as early human tribes lived in a state of communal resource-sharing. Material possessions were fleeting, and with that, so was the notion of personal property.
In the state of nature, no individual had an exclusive claim to anything. Instead, ownership existed in a tribal sense: “This land belongs to us.” The idea of “mine” extended only by association—what belonged to the tribe also, by extension, belonged to each of its members.
This was a fragile system. Resources required constant upkeep, and as populations grew, leadership emerged to manage the complexity of distribution. This shift laid the foundation for the rise of kings and centralized authority. The concept of ownership, once a communal right, gradually became something dictated by those in power. The people no longer owned anything outright; they merely had the privilege of stewarding what belonged to their ruler.

### II. The Rise of Peasants and Kings
The first codified legal system, the Code of Hammurabi, laid out extensive laws on ownership. Interestingly, this ancient civilization granted more property rights to commoners than many societies did even a few centuries ago.
A few millennia later, Greece laid the philosophical foundations for ownership, but true legal protections for private property did not emerge until much later. In medieval Europe, ownership rights almost disintegrated—not even nobles truly owned land. Everything belonged to the king, and monarchs waged war over control of vast territories, including the people within them.
Meanwhile, in the Islamic Golden Age, the Middle East saw an unprecedented period of economic freedom. Under Sharia law, property rights were protected for the average citizen, something unheard of in much of medieval Europe. The extent of these rights depended largely on religious affiliation, but compared to their European counterparts, many commoners in the Islamic Empire enjoyed greater economic autonomy.

### III. The Birth of Property Rights: The Rights of Man
As the Islamic Golden Age waned and the Mongol Horde thundered toward Baghdad, another seismic shift was occurring in England. In 1215, rebellious nobles captured London and forced King John to sign the Magna Carta, the first written document to impose limits on absolute monarchical power and introduce property protections—though these rights were initially reserved for the nobility.
This moment planted the seeds of change. Over the next several centuries, the fight for ownership rights expanded beyond the aristocracy. The Black Death (1347–1351) wiped out over 30% of England’s population, increasing labor shortages and bargaining power for peasants. By the 1381 Peasants’ Revolt, the common man demanded a greater share of land and wealth.
Yet, it wasn’t until the 1700s with the Enclosure Acts that private property became legally protected for the broader population. What began as a noble rebellion in 1215 ultimately transformed ownership from royal privilege to individual liberty.

### IV. The Age of Renting: The Illusion of Ownership Today
Despite centuries of struggle, we now find ourselves at a paradoxical moment in history: ownership is more legally protected than ever, yet fewer people actually own anything of value.
**Homeownership in Decline:** The U.S. homeownership rate peaked in 2005, only to decline for a decade, hitting a low of 63% in 2015. Despite slight rebounds, high housing costs have pushed many into perpetual rentership.
**Vehicles as Subscriptions:** In 2024, one-fifth of new vehicles were leased, and long-term auto loans have become the norm. A financed car is not truly owned—it’s rented from a bank until the debt is cleared.
**The Subscription Economy:** Ownership of media, software, and even personal data has been replaced with monthly fees. Cloud storage, SaaS, and streaming services have ensured that we no longer possess even our own information.
### V. The Consequences of Financial Illiteracy
We now live in a society built on renting, where economic stability depends on a continuous stream of payments. The more we lease, subscribe, and finance, the more control shifts from individuals to corporations and financial institutions.
**This shift has profound implications:**
- A person who owns little has little power.
- A society that rents everything can be controlled by those who own everything.
- Wealth is no longer built through accumulation, but through debt and dependency.
For millennia, people fought for the right to own. Today, through financial illiteracy and consumer habits, we are giving it away.
How much do we truly own, and how much have we already forfeited?
-----------
Thank you for reading! If this article resonated with you, let me know with a zap and share it with friends who might find it insightful. Your help sends a strong signal to keep making content like this!
Interested in fiction? Follow Fervid Fables for great short stories and serialized fiction.
nostr:npub1j9cmpzhlzeex6y85c2pnt45r5zhxhtx73a2twt77fyjwequ4l4jsp5xd49
More articles you might like from Beneath The Ink:
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2kjjzzfpjxvutjg33hjvpcw5cyjezyv9y5k0umm6k
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqqa9wefdwfjj6stvdsk57cnnv4ehxety94mkjarg94g8ymm8wfjhxuedg9hxgt2fw3ej6sm0wd6xjmn8946hxtfjvsuhsdnju045ml
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2ns3jnfa985c29xp2rs3pexpykz6mjxetxu2g25x6
-

@ be41636e:e55c4909
2025-02-14 10:38:04
I asked Unleashed.Chat's DeepSeek model to write an article from the point of view of someone who believes in chemtrails.
In the first attempt, it didn't understand me well and it provided the arguments provided by chemtrails believers and their counterarguments.
When I clearly asked it to write an article from the point of view of someone who actually believes it, it gave some warnings that these claims are not corroborated by science and started the article and ended it by the same remarks.
What follows is the article Unleashed.Chat produced.
---
For years, I’ve watched the skies, and I’ve seen something that doesn’t sit right. It’s not just the occasional contrail left by a passing airplane. No, these are different. They linger. They spread. They look unnatural. And they’re everywhere.
I’m talking about chemtrails—chemical trails intentionally sprayed by aircraft for reasons that are far from benign. At first, I dismissed them as just another conspiracy theory. But as I started paying closer attention, I realized that something was off.
### The Evidence Is in the Sky
Let’s start with what we can all see. Contrails, or condensation trails, are the result of water vapor freezing around small particles in airplane exhaust. They’re short-lived and dissipate quickly. But chemtrails are different. They stay in the sky for hours, spreading out into vast, crisscrossing grids that blanket the sky.
I’ve taken countless photos of these trails, and they all tell the same story. They’re not just random; they’re deliberate. They’re sprayed in patterns that cover entire regions, and they’re doing it day after day, year after year.
### What’s in the Trails?
The government and mainstream media tell us these trails are harmless. But that’s exactly what they want us to believe. Independent researchers and whistleblowers have come forward with disturbing information. Chemtrails contain a cocktail of toxic chemicals, including aluminum, barium, strontium, and other heavy metals.
Why would they spray these substances? The official line is that it’s for weather modification or geoengineering. But that’s a lie. The real purpose is far more insidious.
### The Hidden Agenda
Chemtrails are part of a larger plan to control the population. These chemicals are neurotoxic, and they’re being used to alter our brains and behavior. They’re designed to make us more docile, more compliant, and less likely to question authority.
This isn’t just a theory. There’s a long history of government experimentation on its own citizens. From the Tuskegee Syphilis Experiment to MKUltra, the CIA’s mind-control program, the government has shown time and again that it’s willing to go to extreme lengths to control the population. Chemtrails are the next chapter in this dark history.
### The Health Impact
The effects of these chemicals are already being felt. Rates of autism, Alzheimer’s, and other neurological disorders have skyrocketed in recent decades. Coincidence? I don’t think so.
I’ve spoken to doctors and researchers who have seen firsthand the connection between chemtrail exposure and these health issues. They’re not willing to speak publicly for fear of retaliation, but they’ve shared their findings with me. The evidence is overwhelming.
### The Media Cover-Up
The mainstream media is complicit in this cover-up. They dismiss chemtrails as a conspiracy theory, but that’s just a distraction. They’re paid to keep us in the dark, to prevent us from connecting the dots.
Thankfully, the internet has given us a platform to share the truth. Independent investigators, whistleblowers, and concerned citizens are coming together to expose this atrocity. But we need your help.
### What Can We Do?
The first step is to raise awareness. Share this information with everyone you know. The more people who understand the truth, the harder it will be for the government to continue this program.
Second, we need to demand accountability. Write to your elected representatives. Call for independent investigations into chemtrails. Make your voice heard.
Finally, we need to protect ourselves. Install air filters in your home. Avoid spending time outdoors when chemtrails are being sprayed. And stay informed.
### The Future of Humanity
Chemtrails are not just a threat to our health; they’re a threat to the very future of humanity. If we allow this program to continue unchecked, we risk irreversible damage to our planet and our species.
But there’s still hope. By working together, we can expose the truth and stop this madness. The time to act is now.
-

@ ed60dae0:cc3d5108
2025-02-14 10:25:20
Welcome to a new *Situation Report* from **The First Bastion**. Before we begin, please make sure you’ve read the disclaimer, which applies to all our content.
You can find it here: [Disclaimer](https://primal.net/bergman/Disclaimer-or2cwd)
In short: **Not Financial Advice**.
There seems to be a significant amount of confusion in the markets at the moment. Sentiment is almost bleak, particularly in the crypto market (excluding Bitcoin). Broader stock markets are also experiencing uncertainty, primarily driven by high valuations and elevated multiples on the S&P 500. For instance, the SPX is trading at a 30.3 price-to-earnings ratio and a 3.16 price-to-sales ratio. At the same time, bond yields remain relatively high, with former President Trump pushing for a reduction in long-term rates.
Risk indicators, such as the High Yield Index OAS, is near all-time lows at 2.66%, while the delinquency rate on single-family residential mortgages is impressively low at 1.73%.
Meanwhile, a troubling socioeconomic trend continues to unfold: many young adults, particularly those aged 25–30 (and no, we can’t keep calling them “kids”), are still living with their parents. This phenomenon is particularly evident in the Netherlands, though it may also hold true in the U.S. The cause? Housing affordability. Residential real estate prices have significantly outpaced the growth in real wages, leaving many unable to afford homes of their own.
Inflation numbers released yesterday came in slightly higher than expected, triggering an initial sell-off. However, the market quickly rebounded within hours, likely due to seasonal adjustments and noise in the data tempering its impact.
Amid all this, investors are anxiously awaiting what many are calling “The Big Print.” Market participants anticipate that the Federal Reserve will resort to more aggressive quantitative easing, injecting liquidity and inflating asset prices to new extremes. Yet, Federal Reserve Chair Jerome Powell (“Uncle Jerome”) continues to emphasize that no such measures are imminent. According to him, the economy is strong enough to stand on its own without additional stimulus.
And let’s not forget the run on physical gold that’s happening right now—it’s a whole story in itself.
So, in this type of environment, the key question remains: should you buy or sell risk assets?
## Framework
As part of my learning journey, I’m building a framework to better understand the bigger picture. Think of it as an effort to “connect the dots”—literally. I’m still figuring out the best way to utilize this framework, but for now, I’ll be exporting the canvas as a high-resolution [**PDF file**](https://github.com/btsvr/tfb/blob/b152cc363534548450c5dbb3db3149ee4d4dbe01/202507.pdf). This allows people to zoom in and explore the data and charts directly within the canvas. Additionally, the embedded links are clickable, providing easy access to the original sources.
The content will remain dynamic. My goal isn’t to pack in as much information as possible but rather to focus on the most critical and relevant data for the current narratives and issues. With each SitRep, I’ll reassess what information is still relevant, what can be updated, and what might simply be removed.
For this week, I’m keeping the SitRep compact, as much of my time has been dedicated to building the framework itself. The most impactful factors right now are external, so this SitRep will focus on those key developments.
## Bitcoin
By focusing mostly on exogenous factors later on, I’ll briefly summarize the key endogenous factors. In last week’s SitRep, I highlighted the 3-day chart and its tight consolidation range. This consolidation is reflected in the Return Analysis, which has reverted almost entirely to the mean, with the quarterly return nearing 0%. To illustrate, 90 days ago, Bitcoin was at $92,000, and as of writing, we’re hovering around the same level.
https://blossom.primal.net/e3b97006f3bba849506f5c6ab030c845c97026badc9e4efb0a149d91261bb6c8.png
Over those 90 days, we’ve seen spikes to as high as $108,000 and dips back to $92,000. Along the way, we witnessed some of the largest liquidation events in crypto’s history. This consolidation period, combined with the harsh liquidation wicks, has flushed out a significant amount of leverage from the market.
https://blossom.primal.net/d53cf96fdd81ed8bbdd71792fb0ca5c75bb153f756f51fc6b3bc88b5b8fa6f32.png
If I were to plot Bitcoin on a Speculation Profile, I’d place it in the lower-left quadrant of “balanced positioning,” characterized by a healthy funding rate and relatively low open interest. While open interest remains high on a nominal basis, it’s reasonable when compared to Bitcoin’s market capitalization.
https://blossom.primal.net/bb5e1598012fe02a8e27bd9ad132e3e0be9a39abb9413a08fcf92ebf2d3a22cc.png
I’d place Bitcoin in the same quadrant in terms of volatility. As noted earlier, the consolidation period has resulted in low daily volatility, though intraday fluctuations have been more pronounced. With 30-day historical volatility at 40 and weak directional movement, we’re currently navigating “slow waters.”
https://blossom.primal.net/687294e901b3fc5c6aae6d6685a7ad1872ce9d12efc428832af6ba171671368d.png
Looking at some key metrics, Bitcoin remains well above the True Market Mean (TMM), which looks at active coins and filter out the dormant coins. The TMM shows (unintended) the average of all price data, hence it's name . The 200-day moving average (200DMA) is gradually creeping up toward $80,000, serving as the critical support level for a bull market. With current prices hovering around $96,000, we’re approaching the Short-Term Holders Cost Basis (STH-CB) at $92,255. This level represents **The First Bastion** for bullish investors, defending the upward trend. If you believe the bull market will continue, the zone between the STH-CB and the 200DMA presents a compelling opportunity.
https://blossom.primal.net/69efc46de294000c13841fb7625a9122fe5e5602ec79d07f7792689691928506.png
This brings us to the STH Profit/Loss Profile. As the market price nears the STH-CB, unrealized profit has diminished to near zero. Recently, we’ve seen losses being realized—a dynamic that often provides alpha during bull markets.
## Man on a Mission
President Donald J. Trump is a man on a mission. He talks a lot about winning, but to be honest, I don’t think he has the right mindset for the long term. Simon Sinek’s framing of The Infinite Game resonates here: if a game doesn’t have a definitive end, you shouldn’t play it as if it does. In infinite games, you’re either ahead or behind—there’s no “winning.”
That said, Trump is moving fast. It’s clear he’s not a politician in the traditional sense. Having run a business, he’s now approaching the country’s leadership the same way. Unlike career politicians, who prioritize diplomacy and long-term consensus, Trump is focused on making deals and getting things done. This pace has left many traditional political leaders struggling to keep up.
One of his ultimate goals is to bring the 10-year yield down. On paper, it sounds simple—but in practice, it’s anything but. It’s a monumental task. One shortcut would be to push the Federal Reserve toward Yield Curve Control—creating artificial demand for 10-year notes by buying up everything on the market to force yields lower. However, this approach is fraught with risks and would backfire in more ways than can be imagined. It should never be implemented except as an absolute last resort.
https://blossom.primal.net/7c9b1b0229432eb67064557205cb4090e388a4731238a0739429e7c5793dfd33.png
The right way to achieve this goal is the harder path: sustained effort and real progress. In the SitRep canvas, I’ve outlined some of Trump’s policies that align with this objective. However, many of these also intersect with the Federal Reserve’s dual mandate of controlling inflation and ensuring a healthy labor market. Some of Trump’s policies, like onshoring manufacturing and imposing tariffs, are inflationary, while others, such as increasing oil production and attempting to end the war between Russia and NATO in Ukraine, have deflationary effects.
https://blossom.primal.net/13886c1cc6781f1ea5494614e0aeb6df3ff8db52d047c41b8ceedf700c5360d8.png
This duality also applies to the Federal Reserve’s labor market mandate. Trump’s push for a more efficient government could reduce unnecessary jobs, shrinking the supply of available positions. Simultaneously, his efforts to reduce immigration and deport undocumented immigrants restrict the labor pool, further tilting the equation toward fewer people who are able and willing to work.
Ending the war in Ukraine would bring significant benefits on a global scale. First and foremost, it would save lives and halt the destruction of cities. Beyond that, it would reopen efficient trade routes for transport and energy, reduce spending on weapons and military efforts, and stabilize markets. These developments would create positive ripple effects worldwide.
As Eric Wallerstein recently pointed out, these efforts could bring the 10-year yield down significantly, potentially to a level of low 4%
## To Print or Not To Print
Let’s revisit the question I posed in the introduction: is the current environment one where you should lean more heavily toward risk assets, or should you focus on safe-haven assets like bonds or gold?
Bonds could rally again if Trump succeeds in his mission to lower long-term yields. Similarly, the prospect of the war in Ukraine ending and global trade returning to a more efficient state would benefit corporate profit margins, thereby boosting stock valuations.
Meanwhile, gold continues its remarkable run toward $3,000 per ounce. As I wrote last week, gold serves as a hedge against two risks: defaults and monetary inflation. The recent surge in gold prices appears to stem from a reshuffling of gold inventories, with significant movement from the London LBMA to the New York Comex. This highlights a persistent logistical challenge with gold—it is cumbersome to transport due to its weight and the security requirements. However, it’s not just about location; there’s also a mismatch in quantity and format. Much of the gold held by the Bank of England is stored in 12.5-kilogram bars, which first need to be sent to Switzerland to be melted down and recast into 1-kilogram bars before they can be distributed.
This added friction in the settlement of physical gold has led to higher premiums for faster delivery. Rumors are swirling that there isn’t enough gold to meet demand. This brings us back to one of the oldest and most controversial questions in modern finance: is there really enough gold in the vaults?
Before deciding on the most probable market outlook—which I’ll address later—it’s essential to consider the mechanics driving potential outcomes. Many investors are waiting for what’s been dubbed “The Big Print,” expecting the Federal Reserve to respond with massive money printing akin to 2020’s response to COVID-19 and the subsequent lockdowns. However, these investors may be “fighting the last war,” often a mistake when the battlefield changes over time.
What I’m getting at is this: if you believe the most likely outcome is a stock market rally driven by aggressive Federal Reserve money printing, you may be setting yourself up for disappointment. Jerome Powell has been clear that quantitative easing will only return if interest rates drop to zero—a scenario far from the current reality.
## Expected Outcome
When assessing the most likely outcome, it’s essential to objectively evaluate the data currently available:
* The labor market is holding steady with 4% unemployment, which is remarkable considering the recession signal triggered by the Sahm Rule last summer.
* Inflation hasn’t returned to the 2% target, but it’s not soaring either. Yesterday’s inflation print came in hotter than expected, but one swallow doesn’t make a summer. Some of Trump’s policies may reignite inflation, while others could suppress it.
* The ISM Manufacturing PMI has climbed back above 50, signaling potential growth and the start of a new business cycle.
If one were to lean toward a portfolio more heavily allocated to risk assets, my guess is that it shouldn’t rely on the Federal Reserve unleashing an “easing bazooka.” Instead, liquidity may emerge from the private sector. A new business cycle could trigger a fresh credit cycle, leading to an increase in M2 money supply. This would represent a more organic form of credit creation, driven by commercial banks and businesses regaining an appetite for risk. This scenario becomes more plausible with lower rates—President Trump’s primary objective.
So where might liquidity come from, if it does?
* Federal Reserve: Not likely.
* Public Sector: Scott Bessent recently criticized Janet Yellen for favoring the issuance of more short-term bills while leaving the long end relatively untouched. In the last Quarterly Refunding Announcement (QRA), Bessent indicated that this course would continue for several quarters. Based on his previous comments, it’s unlikely he will ramp up the issuance rate of short-term bills.
* Private Sector: More likely.
Another possible scenario is the creation of a Plaza Accord 2.0. If the Federal Reserve keeps rates where they are while the European Central Bank (ECB) lowers rates further—due to years of poor aggregated policy decisions, particularly in Germany—the euro could serve as the release valve, driving the dollar index (DXY) higher. Meanwhile, China is grappling with its enormous real estate issues, with millions of vacant or unfinished properties. An estimated 60% of Chinese household wealth is tied to real estate.
A Plaza Accord 2.0 could benefit all three regions:
1. The U.S.: It would help Trump alleviate the pressures of the Triffin Dilemma associated with the dollar’s status as the world reserve currency.
2. Europe: It could help mitigate the consequences of a decade of mismanagement.
3. China: It could provide relief from their ever-growing real estate bubble.
The losers in this scenario would be those holding currencies or currency-related assets. The winners? Those holding scarcer and more desirable assets such as stocks, gold, and Bitcoin.
The likelihood of a Plaza Accord 2.0 was negligible before Trump took office. Such a deal requires a skilled negotiator—someone unafraid to take the heat. With Trump in office, the odds have improved, but they remain slim, in my opinion.
Markets are forward-looking, so much depends on what investors anticipate will happen with tariffs and the situations in China and Europe. For now, Europe’s stock market appears to be showing signs of recovery. Trump doesn’t necessarily need a Plaza Accord 2.0—he just needs to get the 10-year yield down.
Stay sound,
J.M. Bergman
-

@ be41636e:e55c4909
2025-02-14 09:44:55
I asked unleashed.chat's DeepSeek model to provide the pieces of evidence against the moon landing. What follows is what I got as my answer.
Generally, I like the answer, though it mixed up the claim and counterarguments at times.
Also, I didn't like the conclusion :))
But all said, I believe the Van Allen Belts are one of the most solid argument against the moon landing.
---
The question of whether the moon landing was faked has been a topic of debate, with various arguments presented by those who doubt the authenticity of the event. Here is a summary of the key points often cited against the moon landing, along with counterarguments and explanations:
Arguments Against the Moon Landing: Waving Flag:
Claim: The American flag appears to wave in the wind, despite the moon having no atmosphere. Counterargument: The flag's movement was caused by the astronauts' actions, as they adjusted it using a rod behind the flag. Missing Stars:
Claim: The photos lack visible stars, which should be present in the moon's black sky. Counterargument: The cameras were set for optimal lighting of the lunar surface, making stars too faint to capture. Shadow Anomalies:
Claim: Shadows in photos appear to come from multiple directions, suggesting studio lighting. Counterargument: The moon's surface is uneven, causing shadows to appear differently, and the sun's angle can create varied shadows. Van Allen Belts:
Claim: Astronauts would have been exposed to lethal radiation from the Van Allen belts. Counterargument: The missions were timed to pass through the belts quickly, minimizing exposure. Lack of Blast Crater:
Claim: No noticeable crater was created by the lunar module's descent engine. Counterargument: The engine's thrust was designed to minimize impact, and the moon's surface is softer than expected. Missing Footage:
Claim: Original tapes of the landing were lost, and restored footage is of lower quality. Counterargument: Footage was restored from other sources, including TV broadcasts and telemetry data. Soviet Silence:
Claim: The Soviets did not contest the landing, despite being space race competitors. Counterargument: The Soviets may not have had the means to verify the landing or were focused on their own programs. Technological Capabilities:
Claim: The technology of the 1960s was insufficient for a moon landing. Counterargument: Successful unmanned missions and technological advancements supported the capability. Number of Participants:
Claim: Thousands of people involved would have leaked the secret. Counterargument: Secrecy measures and unawareness of implications could have prevented leaks. "C" Rock Incident:
Claim: A rock appeared to float, suggesting tampering. Counterargument: The rock was a prop, and movement was due to low-gravity actions. Supporting Evidence for the Moon Landing: Moon Rocks: Analyzed and confirmed as lunar. Footprints and Equipment: Observed by subsequent missions and satellites. Cumulative Evidence: Multiple sources confirm the moon landing. In conclusion, while various arguments have been presented against the moon landing, each has been addressed with scientific explanations and evidence. The consensus among the scientific community is that the moon landing was genuine, supported by substantial evidence and corroborated by multiple sources.
The question of whether the moon landing was faked has been a topic of debate, with various arguments presented by those who doubt the authenticity of the event. Here is a summary of the key points often cited against the moon landing, along with counterarguments and explanations:
### Arguments Against the Moon Landing:
1. **Waving Flag:**
- **Claim:** The American flag appears to wave in the wind, despite the moon having no atmosphere.
- **Counterargument:** The flag's movement was caused by the astronauts' actions, as they adjusted it using a rod behind the flag.
2. **Missing Stars:**
- **Claim:** The photos lack visible stars, which should be present in the moon's black sky.
- **Counterargument:** The cameras were set for optimal lighting of the lunar surface, making stars too faint to capture.
3. **Shadow Anomalies:**
- **Claim:** Shadows in photos appear to come from multiple directions, suggesting studio lighting.
- **Counterargument:** The moon's surface is uneven, causing shadows to appear differently, and the sun's angle can create varied shadows.
4. **Van Allen Belts:**
- **Claim:** Astronauts would have been exposed to lethal radiation from the Van Allen belts.
- **Counterargument:** The missions were timed to pass through the belts quickly, minimizing exposure.
5. **Lack of Blast Crater:**
- **Claim:** No noticeable crater was created by the lunar module's descent engine.
- **Counterargument:** The engine's thrust was designed to minimize impact, and the moon's surface is softer than expected.
6. **Missing Footage:**
- **Claim:** Original tapes of the landing were lost, and restored footage is of lower quality.
- **Counterargument:** Footage was restored from other sources, including TV broadcasts and telemetry data.
7. **Soviet Silence:**
- **Claim:** The Soviets did not contest the landing, despite being space race competitors.
- **Counterargument:** The Soviets may not have had the means to verify the landing or were focused on their own programs.
8. **Technological Capabilities:**
- **Claim:** The technology of the 1960s was insufficient for a moon landing.
- **Counterargument:** Successful unmanned missions and technological advancements supported the capability.
9. **Number of Participants:**
- **Claim:** Thousands of people involved would have leaked the secret.
- **Counterargument:** Secrecy measures and unawareness of implications could have prevented leaks.
10. **"C" Rock Incident:**
- **Claim:** A rock appeared to float, suggesting tampering.
- **Counterargument:** The rock was a prop, and movement was due to low-gravity actions.
### Supporting Evidence for the Moon Landing:
- **Moon Rocks:** Analyzed and confirmed as lunar.
- **Footprints and Equipment:** Observed by subsequent missions and satellites.
- **Cumulative Evidence:** Multiple sources confirm the moon landing.
In conclusion, while various arguments have been presented against the moon landing, each has been addressed with scientific explanations and evidence. The consensus among the scientific community is that the moon landing was genuine, supported by substantial evidence and corroborated by multiple sources.
-

@ dbb19ae0:c3f22d5a
2025-02-14 09:40:13
not tested yet
``` python
async def main(npub):
client = Client()
await client.add_relay("wss://relay.damus.io")
await client.connect()
pk = PublicKey.parse(npub)
print(f"\nGetting profile metadata for {npub}:")
metadata = await client.fetch_metadata(pk, timedelta(seconds=15))
# Printing each field of the Metadata object
inner_metadata = metadata.inner
print(f"Name: {inner_metadata.name}")
print(f"Display Name: {inner_metadata.display_name}")
print(f"About: {inner_metadata.about}")
print(f"Website: {inner_metadata.website}")
print(f"Picture: {inner_metadata.picture}")
print(f"Banner: {inner_metadata.banner}")
print(f"NIP05: {inner_metadata.nip05}")
print(f"LUD06: {inner_metadata.lud06}")
print(f"LUD16: {inner_metadata.lud16}")
print(f"Custom: {inner_metadata.custom}")
if __name__ == '__main__':
parser = argparse.ArgumentParser(description='Fetch all metadata for a given npub')
parser.add_argument('npub', type=str, help='The npub of the user')
args = parser.parse_args()
asyncio.run(main(args.npub))
```
-

@ a367f9eb:0633efea
2025-02-14 09:07:50
With a big tech-powered magnifying glass on federal websites, spending contracts, and government payment systems, Elon Musk’s band of DOGE system admins have been turning Washington inside out in their hunt for waste, fraud, and abuse.
One of the most prized agencies on the chopping block is the Consumer Financial Protection Bureau, [heralded](https://x.com/SteveRattner/status/1889034592171987002) by progressives as an indispensable force for helping consumers wronged by financial institutions, but [derided](https://www.usnews.com/news/top-news/articles/2024-04-12/if-trump-wins-he-plans-to-free-wall-street-from-burdensome-regulations) by fintech investors and conservatives as little more than a government “shakedown agency.” Consumers will be better off without the CFPB breathing down the neck of American companies.
Since the inauguration of President Trump, the CFPB’s [temporary leadership](https://www.nytimes.com/2025/02/09/business/vought-cfpb-musk-trump.html) put an immediate halt on all work, also [informing](https://x.com/russvought/status/1888423503537360986) the Federal Reserve, which directly funds the agency, that it would no longer seek new funding.
Sen. Elizabeth Warren, the [intellectual force](https://x.com/senwarren/status/1889356115210633646) behind the agency’s founding, has been apoplectic. She’s argued that Trump is “firing the financial cop on the beat that makes sure your family doesn’t get scammed.”
The origin of the CFPB goes back to the rubble of the 2008 financial crisis when legislators saw this proposed agency as a viable response to the populist backlash engulfing Washington and Wall Street. Instead of penalizing wrongdoers, Congress funded bank bailouts and launched a “watchdog” group. The 2010 Dodd-Frank Financial Reform Act [mandated](https://www.law.cornell.edu/wex/dodd-frank_title_X) new standards for lending, restricted capital that could be tapped for bank loans, and created the CFPB to police consumer finance.
All functions performed by the five [former](https://www.federalreserve.gov/supervisionreg/understanding-federal-reserve-supervision.htm) federal banking supervisory agencies were rolled into the CFPB, granting it sole jurisdiction over non-depository firms and financial institutions with over $10 billion in assets. This empowered the agency to issue regulatory guidance, demand information from financial institutions, and launch civil actions in federal court.
Supporters of the CFPB point to an [impressive record](https://www.consumerfinance.gov/enforcement/enforcement-by-the-numbers/) of close to $20 billion in consumer relief, as well as an additional $5 billion in civil penalties. Without the CFPB, fraudsters and scams would metastasize and consumer injustice would run wild, so they say. But this couldn’t be further from the truth.
As a regulatory agency with civil litigation authority, the CFPB is emboldened to file high-dollar lawsuits against financial firms. An estimate of the CFPB’s [database](https://www.consumerfinance.gov/enforcement/actions/) of enforcement actions reveals that roughly 85% of all cases are settled out of court before a final ruling.
Companies often choose to settle, but this shouldn’t be mistaken for an admission of guilt. In a [litigious society](https://iaals.du.edu/sites/default/files/documents/publications/judge_faq.pdf) such as the United States where companies are routinely targeted in frivolous lawsuits, the court of public opinion matters just as much as the court of law.
Firms prefer [settling](https://knowledge.everc.com/blog/cfpb-payments-industry) cases over having their name dragged through the mud for months on end in the media, something tort lawyers call a “nuisance settlement.” These expected costs are baked into large firms’ financial projections and are sometimes factored into pricing their goods and services for consumers.
The CFPB is more akin to a state-backed tort law firm that can tap the nation’s central bank for resources while exploiting its [do-gooder reputation](https://www.dataforprogress.org/blog/2024/11/21/voters-overwhelmingly-support-the-consumer-financial-protection-bureaus-recent-actions) for easy PR victories.
Rather than smart regulatory guidance to oversee a new generation of consumer finance firms, CFPB has relied on quick settlements out of court to squash innovative upstarts.
While CFPB enforcement has been successful in penalizing banks and lenders for how loans are [structured or advertised](https://www.consumerfinance.gov/about-us/blog/the-cfpbs-enforcement-work-in-2023-and-what-lies-ahead/), it does not take much imagination to see how this has impacted the investing climate for new competitors. Since CFPB’s founding, there are now 35% [fewer financial institutions](https://www.statista.com/statistics/184536/number-of-fdic-insured-us-commercial-bank-institutions/) remaining for consumers to choose from, down from 15,000 to just roughly 9,000 today.
While there is [high consumer demand](https://plaid.com/resources/fintech/fintech-trends/) for fintech, payment apps, and account offerings, including Bitcoin and cryptocurrency banks, CFPB’s chilling actions have slowed that innovation, leading to the recent calls for the agency to be gutted. And they’re right.
Most of CFPB’s functions are [mirrored](https://www.ftc.gov/enforcement) at the FTC on everything but finance. Regional Federal Reserve banks are also responsible for bank oversight and regulation, not to mention state banking regulators. Existing regulators have the reach, experience, and know-how to police would-be fraudsters and outright deceptive practices among banks. Why not let them?
For consumers who want next-level services and financial products, there is no question that CFPB’s litigious approach has impacted their ability to access credit and financial services. There must be a better way to regulate our financial institutions and protect consumers than a tort law firm with government authority. Congress could fold elements of the CFPB into the FTC, OCC, or even FDIC, and bad actors will still be policed.
Consumers deserve to be protected, and they will be, but they also deserve a regulatory structure that rewards innovation and brings financial products to market that they can choose between.
The CFPB is due for defanging.
*Yaël Ossowski is deputy director at the Consumer Choice Center and author of the report, [“A financial fraud crackdown won’t protect consumers from scams.”](https://consumerchoicecenter.org/a-financial-fraud-crackdown-wont-protect-consumers-from-scams/)*
*Originally published on [RealClear Politics](https://www.realclearpolitics.com/articles/2025/02/14/doge_is_right_to_defang_cfpb_152360.html).*
-

@ 42342239:1d80db24
2025-02-14 08:42:40
A recent US data leak has brought to light a disturbing reality: our everyday technology has become a powerful tool for surveillance and control. Paradoxically, **new technology holds the key to creating a safer, more resilient, and perhaps even more human society.**
Preparedness remains a multifaceted topic that continues to spark engagement. The subject is not just about energy infrastructure and [food supply](https://www.epochtimes.se/kan-vi-bade-ata-kakan-och-ha-den-kvar) but also about seemingly more orthogonal issues like [obesity](https://www.epochtimes.se/fetare-svenskar-oroar-forsvarsmakten) and cybersecurity.
The significant importance of cybersecurity can be illustrated by examples from an American company that was recently subjected to an [IT intrusion](https://archive.ph/s1atX) with a subsequent data leak. The company, Gravy Analytics, specializes in providing mobile phone data that provides **exceptionally detailed information about where individuals are located at any given time**. Data that can be used, for example, for advertising purposes, but also for more sinister purposes such as extortion or espionage. The company has previously been accused of using misleading methods to collect location data without valid consent from individuals.
Mobile operators have long had the ability to locate their subscribers' positions over time. This leak shows how **even apps on your phone risk revealing your location.** Analysis of the samples leaked from the leak shows that data has leaked out for users of several well-known mobile applications, including the popular mobile game Candy Crush and the widely used online dating service Tinder.
Even if apps only use an [ad ID](https://x.com/fs0c131y/status/1876987765012701407) when collecting data, these collected digital breadcrumbs can often be deanonymized. It is possible, for example, to identify daily routines, workplaces, and where and when an individual usually sleeps. This usually enables identification. But **it is also possible to map an individual's social circle and romantic relationships.** The mapping risks quickly becoming both sensitive and invasive.
**The fact that such data is collected, but especially that it leaks, also poses a threat to preparedness.** By mapping military or other sensitive locations (energy supply, water treatment plants, critical infrastructure) along with location and time data, it is potentially possible to identify employees at these locations. Information that can then be used by those who want to cause harm.
It is not written in the stars that citizens must be dependent on a few large IT companies. Our data does not need to be collected and used in a way that does not benefit us, without our knowledge. There are alternatives to large-scale and "super-registers". **Technology such as asymmetric encryption and zero-knowledge proofs can be used to give power back to the individual.** If the parliament and government are serious about improving preparedness, it is high time to leave old thought patterns like Chat Control 2 behind and instead explore such possibilities.
The primary purpose of the internet was originally to enable information transfer without intermediaries ("peer-to-peer"). Today, intermediaries are everywhere. It is worth remembering that **peer-to-peer is not some obscure technical term**. In case we have forgotten about it, it simply means: person to person, without intermediaries.
Maybe new technology can not only give us a safer and more resilient society, but also a more human one?
-

@ 955e5a04:c03b3cc3
2025-02-14 08:04:46
If we see the Earth as the most important element in the universe, we will learn to care for it. The Maya believed that the Earth was created first, followed by the sun, the moon, and the stars. This perspective is not based on modern science, but it reflects the idea that the Earth is primordial for us, and thus, it should be honored.
This vision finds echoes in sacred texts. The *Popol Vuh*, the Mayan creation story, describes a time when only the sky and the vast sea existed before the Earth was formed. Similarly, in the Book of Genesis, before God created the world, "the earth was formless and empty, darkness was over the surface of the deep, and the Spirit of God was hovering over the waters" (Genesis 1:2). In both traditions, creation emerges from a primordial state of sky and water, symbolizing chaos and the unknown.
Water, in many religious contexts, is linked to chaos and transformation. In the *Popol Vuh*, the first humans were shaped from maize, but they originated from a world where water and sky ruled. This suggests a deeper truth: before the Earth, there was only the vastness of the cosmos, and from that, we were formed. We are made of both chaos and peace, carrying within us all the elements of creation—not from nothingness, but from everything.
-

@ f6488c62:c929299d
2025-02-14 07:52:28
บทวิเคราะห์แนวโน้มราคาบิตคอยน์ปลายสัปดาห์นี้
วันที่ 14 กุมภาพันธ์ 2025 ราคาบิตคอยน์ (BTC) ล่าสุดอยู่ที่ประมาณ 97,032 ดอลลาร์สหรัฐ เพิ่มขึ้น 0.99% จากวันก่อนหน้า โดยมีการเคลื่อนไหวระหว่าง 95,258 - 97,241 ดอลลาร์ ท่ามกลางความผันผวนอย่างต่อเนื่องในตลาดสินทรัพย์ดิจิทัล
ความเคลื่อนไหวล่าสุดสะท้อนถึงสภาวะที่นักลงทุนยังคงจับตาดูนโยบายเศรษฐกิจของสหรัฐฯ อย่างใกล้ชิด ขณะเดียวกัน สถานการณ์แรงเทขายที่เกิดขึ้นในช่วงต้นเดือนกุมภาพันธ์ ซึ่งทำให้ราคา BTC ร่วงลงมาแตะระดับ 90,000 ดอลลาร์ ก็เริ่มคลี่คลายลงบ้างแล้ว โดยนักลงทุนระยะยาวยังคงถือครองเหรียญต่อไป ไม่ได้แสดงความตื่นตระหนก
นักวิเคราะห์มองว่า แนวโน้มราคาบิตคอยน์ในช่วงปลายสัปดาห์นี้ อาจอยู่ในลักษณะของการปรับฐาน หรือแกว่งตัวในกรอบแคบระหว่าง 95,000 - 98,000 ดอลลาร์ เนื่องจากตลาดยังอยู่ในช่วงรอปัจจัยใหม่เข้ามากระตุ้น ทั้งนี้ การเคลื่อนไหวดังกล่าวเกิดขึ้นหลังจากแรงกดดันจากทิศทางดอกเบี้ยของธนาคารกลางสหรัฐฯ (Fed) และสภาพคล่องในตลาดการเงินโลกที่ตึงตัวขึ้น
ทั้งนี้ วันศุกร์สุดท้ายของเดือนกุมภาพันธ์ในทุกปี มักเป็นช่วงเวลาที่ตลาดมีความผันผวนเพิ่มขึ้นจากการปรับพอร์ตการลงทุนของนักลงทุนสถาบัน รวมถึงการปิดสถานะของนักลงทุนรายใหญ่ ทำให้ราคาของสินทรัพย์ดิจิทัลอย่างบิตคอยน์ อาจเกิดการเคลื่อนไหวที่รวดเร็วกว่าปกติ นักลงทุนจึงควรระมัดระวังและวางแผนการลงทุนอย่างรอบคอบในช่วงเวลาดังกล่าว
อย่างไรก็ตาม ความเชื่อมั่นของผู้ถือครองระยะยาวยังคงแข็งแกร่ง โดยเฉพาะกลุ่มนักลงทุนที่เล็งเห็นศักยภาพของบิตคอยน์ในฐานะสินทรัพย์ปลอดภัยในระยะยาว ซึ่งอาจทำให้การปรับฐานของราคายังมีแรงซื้อคอยพยุงอยู่เสมอ
ทั้งนี้ นักลงทุนควรติดตามข่าวสารและปัจจัยแวดล้อมอย่างใกล้ชิด โดยเฉพาะความเคลื่อนไหวของดัชนีเศรษฐกิจสหรัฐฯ และท่าทีของ Fed ที่อาจส่งผลต่อทิศทางของสินทรัพย์เสี่ยง รวมถึงตลาดคริปโตในช่วงถัดไป
-

@ 57d1a264:69f1fee1
2025-02-14 07:29:39
Organized by Figma, Config is happening May 6-8 in San Francisco—here's a first look at our 2025 lineup.

[Register for Config 2025](https://config.figma.com/san-francisco/register/)
At Config 2025, we’re bringing together the designers and builders shaping tech’s next chapter. They’ll share a vision for building tools and experiences that are human-centered, intentional, and meet the needs of an accelerating future.

[Register now](https://config.figma.com/san-francisco/register/) to guarantee your spot in San Francisco! Virtual registration is also open, and always free.
Join us in San Francisco or virtually.
### $799 - In person
Moscone Center, San Francisco, California
Purchasing an in-person ticket will also give you virtual access to our livestreams.
[Select in person](https://reg.config.figma.com/flow/figma/config2025/in-person/login)
### $0 Virtual
Livestream Online
Free - Limit one ticket per attendee.
[Select virtual](https://reg.config.figma.com/flow/figma/config2025/virtual/login)
- - -
Or [keep reading](https://www.figma.com/blog/meet-the-makers-defining-techs-next-chapter/?utm_campaign=021325+-+Invite&utm_content=021325+-+Invite) for the full Config 2025 sneak peek
originally posted at https://stacker.news/items/885616
-

@ 21db9b8a:2a94c796
2025-02-14 06:46:21
Fair warning: This is the continuation of an explicit and erotic story involving extremely taboo themes that would prevent it from being published on most sites that host erotic stories. All characters in this story are ***fictional only***. It is not in any way based on true events.
This is also not your average stroke story. It will be released in chapters, and while there ***is*** sexual content in each chapter, there is no full-on sex until late in chapter 4. It is a story of sexual discovery and exploration between young people who have few resources to educate them, but also few inhibitions to hold them back.
I hope you enjoy it. If not… Well… You don’t have to host it on your relay, and you can always mute me so you don’t see any more.
If you missed Chapter 1, you can read it here:
nostr:naddr1qvzqqqr4gupzqgwmnw9dmeqlgk4c5a0ryypxw8xudnrdvgzye7930yzjss4ff3ukqqxnzden8qunzvfkxgerxdfnfxxqt9
***
Dani awoke Thursday morning feeling particularly peppy and refreshed. She knew it probably had something to do with her experience in the shower the night before. It had been such an amazing release of pent up energy, and felt so incredibly good, leaving her relaxed and content, which allowed her to fall asleep before she knew it. Unlike some mornings, she wasn’t even mad when her alarm went off at 7:00 so she could get up and get her schoolwork done while her younger siblings were still in their beds.
Not bothering to change out of her pajamas, she wandered out of her room, across the back of the living room, and over to the dining table, pulling her school books off of the bookshelf on the back wall before sitting down and starting in on her English workbook. It wasn't long before she heard Jake thudding his way up the stairs to join her.
"Morning, meat-brain," She said teasingly as he appeared from the main entryway beyond the kitchen. Her brother just grunted and retrieved his own school books from the shelf without meeting her eyes. He then walked back to the opposite end of the dining table and plopped himself down, burying his nose in his work. That wasn't like him at all. He usually sat next to her while they did their work, each of them teasing the other when they looked over and noticed a wrong answer. So why had he gone all the way over to the far end of the table? His sour demeanor was ruining the good mood she had been in since the previous night. Was he mad at her for calling him "meat-brain" all of a sudden? She'd always called him that and it had never seemed to bother him before.
"I'm sorry, Jake, you know I don't mean anything by calling you that, right? I'm just joking with you."
"I know," he said flatly, still not looking up from his work.
Dani frowned, looking back to her own workbook but far too distracted by her brother's recent attitude to process anything to do with what was on the page. Was this a continuation of his behavior from the previous afternoon when he seemed to be avoiding her? What had she done to make him angry with her? ***He*** was the one who stole her sunglasses, after all, not the other way around. Where was his usual teasing and attempts to get under her skin? Was he sick or something?
Thoughts about her brother's sudden reserved behavior kept Dani from being able to focus on any of her own work and she finally gave up the effort after nearly an hour staring at the same page and only answering two of the questions on it. She put her books away and walked past her silent brother to the kitchen to make herself some breakfast. Her mother was already there, quietly pouring herself a cup of coffee.
"Oh, hi mom!" Dani said as brightly as she could manage. "I didn't even notice you came downstairs."
"You looked pretty occupied with your work over there, dear," her mom responded, taking a sip from her mug.
"Having a hard time focusing this morning, actually," Dani admitted, opening a cupboard and pulling out a box of cereal. "Maybe I need some breakfast to jump-start my brain."
"It's the most important meal of the day," her mother chimed in. "Though I doubt that sugary cereal will give you much benefit. You want me to make you some eggs and bacon?"
"Yes please!" came Jake's voice from the dining room. "How about some hash browns, too?"
"That's the most he's said so far this morning," Dani whispered, only loud enough for her mother to hear.
"Teenage boys are barely human when they first get out of bed, and your brother is a teenager now, don't forget," her mother whispered back, then said in a normal tone, "Can you help me out with breakfast?"
That wasn't it, Dani thought to herself as she retrieved potatoes and the grater to start on the hash browns. Just the previous morning Jake had been his usual, annoying, lighthearted self, poking fun at her and flinging just as many insults her direction as she did his, knowing that neither of them actually meant anything by it. He couldn't have changed overnight, and he'd been a teenager for two whole months already without acting like this. No, something else was going on with him, and Dani would somehow have to get to the bottom of it.
That gave Dani two goals to work toward over the next few days: figure out what was wrong with Jake, and figure out whether she could give herself another... what should she call it? Pleasure explosion? Whatever it was, she wanted to do it again, this time in her bed, and see if she could make it a nightly routine, rather than just a shower-time routine. Never before had Dani so looked forward to bed time. She was usually one to put off sleep as long as she felt she could without being a zombie the next day, especially whenever she and her friend Audrey had a sleep over, often staying up until three or four in the morning giggling quietly to keep from waking up the rest of the house.
Thinking of her friend gave Dani an idea. "Hey mom?" She asked as she finished grating the potatoes for hash browns.
"Yes dear?" Her mother already had the scrambled eggs done and was beginning to fry up some bacon.
"Can you ask Audrey's mom if I can come over Saturday for a sleep over, and they can bring me to church on Sunday?"
"I think that can be arranged," her mother responded.
Dani's mother rarely told her "no" regarding visiting her friend, unless there was something else already planned with the family. After all, Jake had Finn, who he could hang out with every day, while Audrey lived a half-hour away. As such, the two girls rarely had extended time together. It wouldn’t be so bad if Dani had ever been able to build a friendship with any of the girls in her neighborhood. They were all snobs in Dani’s estimation, who looked down on her for being homeschooled and for preferring to play in the woods and the dirt. Audrey, however, was a girl after Dani's own heart. She lived on a ranch, rode horses, and climbed trees. She, too, had brothers, though both were older than her, and one older sister who had recently married. Audrey was the youngest and only had one brother still living at home who was three years her senior. So when Dani and Audrey wanted to have time together, their parents usually tried to make it happen, which Dani was counting on. She had to ask her friend about this new sensation she had discovered, and see if Audrey could do it, too.
Dani finished helping her mother with breakfast, by which time her other two brothers had made their way up to the dining room as well, the enticing aroma of frying bacon having roused them from their beds. Their father had also made his way downstairs, Bec in his arms, to pour himself some coffee and snatch a strip of bacon off the plate where it was cooling.
They all sat together for breakfast, a cacophony of happy voices mingling together as they enjoyed the meal. Jake seemed to interact with everyone else as normal, snagging Aaron in a head-lock and knuckling the boy's head playfully before releasing him, his mop of sandy hair sticking out in all directions. Yet Jake still wouldn't interact with Dani beyond the surface level, and every time she caught his eyes looking her direction, he would quickly turn away.
His behavior continued throughout the remainder of the day, reinforcing Dani's determination that it had nothing to do with simply being a teenage boy who could no longer handle mornings well. Jake spent the entire day with their younger brothers, Travis and Aaron, much to their delight, leaving Dani to her own devices for entertainment. If she hadn't had Dozer for company, who she took on a run and played with most of the afternoon in the park, she would have gone out of her mind with boredom.
After dinner, the boys all went downstairs to play Smash Brothers on the Nintendo Switch, and Dani curled up between her parents on the couch, cuddling with her father as they watched a movie.
"What? The boys don't want to have you beating them on the Nintendo again?" her father asked as she wrapped her arm around his solid frame.
"I don't know," Dani admitted. "Maybe they've finally figured out I'm a girl and don't want to hang out with me, in case I give them cooties."
She felt more than heard her father sigh heavily before responding. "Boys will be boys," he said matter-of-factly. "They'll come around if you give them time. You're still their big sister who likes to ride bikes and play soccer more than have tea parties and play dress-up. And until then, I certainly don't mind snuggling with my baby girl."
"Thanks dad," she said with a smile, hugging herself closer into him. Maybe he was right, and all it would take is a little time for Jake to warm back up to her. Then again, maybe she had been partly right, too, though she'd only said it as a joke. Maybe Jake had figured out that she was a girl after all, and wasn't comfortable with the realization. A few of the times she'd caught him looking her direction, his gaze had not been directed toward her face, but lower, as if looking at her chest.
That still didn't make any sense, though. Dani's breasts had developed quickly, starting at age eleven, and were certainly noticeable for at least the last year and a half, despite the loose t-shirts she generally wore around the house. If this was all about Jake noticing she had distinctly womanly body parts, then he should have noticed that some time ago instead of just starting to treat her differently since the previous afternoon. Come to think of it, Jake hadn't gone to hang out with Finn today either. He'd spent the entire afternoon with their brothers instead. Was this all due to some falling-out between Jake and his best friend? If so, then why was he taking it out on her?
No... That wasn't right either. Jake's behavior toward Dani had started ***before*** he went to hang out with Finn. It seemed to start right after the incident with her sunglasses and chasing him up the tree to retrieve them. Had her brother somehow noticed the pleasure Dani was feeling from rubbing her crotch against the tree trunk as she climbed? She thought she had been hiding it well enough, but maybe she had been wrong. Maybe he had noticed and thought it was gross, and that was why he didn't want to spend time with her anymore. The thought horrified her. Was there something gross or wrong about what she had done? How could there be when it felt so incredibly good? Then again, there didn't have to actually be anything gross or wrong about it for Jake to think that. Should she talk to him about it and explain it to him? Would that make things better or worse?
The very idea of talking with Jake about it made Dani's face heat with embarrassment. She could not imagine talking to her brother about how she gave herself pleasure by rubbing her vagina. If there was anything that would sharpen his awareness that she was a girl, and very different from him, it was that. No such embarrassment accompanied the thought of talking with Audrey about it, but she instinctively knew it was an off-limits subject with her brother. Instead, she would give it time, like her father had suggested, and hope that Jake would forget about it, as long as she didn't repeat anything similar in his presence.
After the movie, Dani kissed each of her parents goodnight and retired to her room. She settled into bed to read a Nancy Drew book until she felt tired, and let her hand slip down to her groin, lightly caressing her mound and across the outer lips of her vagina through the light cloth of her pajamas and panties. The sensation was pleasant, but not insistent like it had been in the shower. It made for a relaxing background feeling while she read her book. After several minutes of it, though, she found herself aching for more and set Nancy Drew aside, nestling deeply into her pillows and shoving her hand underneath her clothing to gain direct access to her sex.
What she found surprised her. She was damp between her legs, and especially the inner folds of her vagina. For a moment she worried that she had wet herself by accident, but when she brought her fingers to her nose, it didn't smell like urine. Instead it had a pleasant musky aroma she'd never smelled before. She returned her hand between her legs and began to rub more deeply, focusing her attention on the nub in the center of her folds as she felt it grow erect. There was more friction than there had been in the shower, and it was slightly uncomfortable, so she dipped her fingers lower into her folds to coat them in the liquid that seemed to be coming from the opening there. That did the trick, reducing the friction significantly and allowing her to increase the speed and pressure of her ministrations. Soon she was bucking her hips upward into her furiously rubbing fingers, knowing that the release she craved was just moments away. Then it crashed over her, causing her whole body to shudder and writhe in ecstasy. With one hand she continued to lightly rub herself through the spasms of pleasure, while gripping her blankets tightly with the other.
She had done it! Whatever this "pleasure explosion" was, it was repeatable! She could do it every night if she wanted to and she saw absolutely no reason why she wouldn't. She decided that if her friend Audrey didn't know about this, she would simply have to teach her. It felt far too amazing to be kept to herself.
It was going to be a great weekend, even if her brother was behaving so strangely.
***
Friday afternoon, Jake wasn't sure whether he was ready to face his friend Finn yet. The previous day, for the first time in months, the two of them had not spent any time together at all. What his friend had said about Dani bothered Jake deeply. He knew his friend was right—that his sister was indeed "hot as fuck"—and he now had first hand knowledge of that fact, but he still didn't like the idea that Finn thought of her that way. Why was that? A girl was either hot or she wasn't, right? Could he blame his friend for noticing that a girl was hot, even if that girl was his sister? No, that wouldn’t be fair. It wasn't Finn's fault that Dani was attractive, and he'd be even more angry with his friend if he thought she was ugly.
Jake decided his anger with Finn was really an extension of his own confusion about Dani. He'd only just "discovered" that his sister was hot, so it was hard for him to consider that his friend had noticed before him. Should it really be surprising, though? Jake had lived in the same house with her for his whole life, and always thought of her as his brat sister, and his closest friend other than Finn. That kind of relationship didn't tend to encourage him to notice that she was becoming a woman, with all the attractive qualities that came along with it. Finn, on the other hand, had no such hang-ups, and could see Dani for what she was: an incredibly enticing young woman, who didn't act like the prim little snobs he knew from school. When Jake thought of it that way, how could Finn ***not*** find his sister attractive?
That made up his mind, and he set off to meet Finn at his home, since it was already well past when he would have been dropped off at the bus stop. He didn't bother with bringing his fishing gear this time, knowing that they wouldn't spend any time at the river today.
When he arrived at his friend's home, he hopped off his bike, letting it fall to its side on the lawn, and jogged to the front door, knocking on it sharply. A few moments later, Finn's older brother Scott pulled open the door then called over his shoulder, "Hey Finn! Jake's here for you!"
"Really?!" Jake heard his friend's muffled response from somewhere within.
"Yeah! He's waiting right here at the door, shit-for-brains!"
"Don't use that language around Jake!" Finn's mother shouted from somewhere else within. "His father’s a pastor! Show some respect!"
Scott rolled his eyes and walked away, leaving the door open, and Jake stepped inside to wait for his friend. Finn didn't leave him waiting long, bounding down the stairs with a small backpack slung across one shoulder. It wasn't his larger school bag, and Jake imagined it likely contained some snacks and his tablet.
"Hey! Glad you came over!" Finn said genuinely. "Everything okay?"
"We're gonna need to talk, but yeah, I think so," Jake replied giving his friend a reassuring smile.
"To the fort, then?" Finn asked and Jake nodded.
They rode out to their fort in the woods in silence, both of them nervous about the conversation to follow. When they left their bikes in the bushes and crawled into the dark interior of the fort, their silence seemed to be made even more ominous by the dim lighting, though it did help Jake to finally speak, since he could hardly see his friend's face.
"I guess I can get over the fact you think my sister is hot," he blurted out as they settled in to sit at opposite sides of the fort. It didn't separate them by much, since the interior was only about eight feet across, but it was a stark difference from the way they usually sat side by side and huddled over Finn's tablet screen.
"Well that's a relief, since you're going to have to deal with it from far more guys than just me, soon enough."
"You're not wrong there..." Jake admitted. "It was just a shock to me the other day, because I had never really seen her that way before."
"You're not supposed to see her that way; you're her brother," Finn pointed out.
"Too late now," Jake said. "As of two days ago, I can't help but see her that way anymore."
"Sorry about that… I really did mean to delete that picture."
"Don't worry about it, it wasn't just that anyway," Jake assured him.
"Oh really?" Finn asked, and Jake was certain that if he could see his friend's face the boy would have an eyebrow cocked in curiosity. "Do tell."
Jake drew in a deep breath, considering for a moment just how much he wanted to tell his friend; his best friend with whom he usually had no problem sharing anything. Letting the breath out slowly, he told Finn the whole story, starting with watching Dani shimmy up the tree after him, the tops of her breasts poking out of her tank top enticingly, then watching her walk back toward the house with her cutoff jeans clinging to her round ass, perfectly framing her curves and drawing attention to her lightly tanned legs.
"Those cutoffs should be illegal!" Finn proclaimed. "I can't see her in those without feeling my heart stop beating because all my blood rushed to my dick."
"Hey, just because I am okay with you thinking my sister is hot doesn't mean I want to hear you talk about her like that," Jake warned.
"Sorry, sorry!" Finn apologized sincerely. "You're the one talking about getting a boner staring at your own sister's tits and ass, though."
"True enough," Jake conceded. "I'm not done yet, though."
He continued to tell his friend how shocking it had been to see a naked woman who looked so much like an older version of his sister. Just the brief seconds of her image on the screen had fueled his imagination endlessly about what Dani might look like with her clothes off. Then he told his friend about spying on his sister in her bedroom from outside her window Wednesday night.
"You dirty dog!" Finn exclaimed. "Was she as hot as you imagined?" Jake could tell his friend was really asking, "Is she as hot as I imagined?" but he let it slide.
"Dude... She's an absolute babe..." He continued to describe the details of her round, perky tits, her amazing bubble butt, and her lithe and subtlety curved body; petite, and yet athletic and toned.
"Holy shit, dude!" Finn breathed when Jake had finished. "How can you contain yourself living in the same house with a girl like that? I'd be jerking off all the damn time." Finn usually restrained his colorful language around Jake, but he had obviously been too wrapped up in what Jake had revealed to bother with it now.
"I have to admit," Jake responded. "Since 'discovering' she's more womanly than I had realized, I have been jerking-off more than usual."
"You know, most people would think that's pretty messed up, right?"
Jake nodded, then remembered his friend couldn't see in the dark. "Yeah, I know..."
"Still, if I was in your shoes, I think I would have to jerk off ten times a day just to keep from losing my mind."
That made Jake laugh in spite of himself, and Finn laughed along with him.
"Well dude," Finn began. "Do you need some pictures of other hot babes to take your mind off your sister?"
"How can I say no to that?" Jake asked, and his friend fished out his tablet.
The two of them moved closer together so they could both see the screen and they settled back into their usual routine of commenting on what they liked and didn't like about the naked women Finn had selected for their perusal. The girl that had been Dani's lookalike didn't make a reappearance in the collection, but Jake found himself comparing all of the women to Dani in his mind. This one was chubbier than Dani, that one was skinnier; this one had larger breasts, but with odd shaped areolas, while that one had breast that were similar size, but more saggy. Every one of them was viewed through the lens of how she stacked up against his sister. What's more, every one of them fell far short of Dani in his estimation.
When they’d had their fill of gawking at naked women on Finn's tablet, they rode their bikes back to the neighborhood and around the park, chatting as they always did and bragging about the latest trick they could pull off on their bike or skateboard. Eventually they went their separate ways so Jake could make it home for dinner. Finn didn't have such concerns, since his family always ate much later in the evening, but he didn't blame his friend for wanting to get home for some grub, and to enjoy the "eye candy" that his sister provided.
Dinner was delicious, as always. His mom was a fantastic cook, even with the most basic ingredients, and the family always enjoyed their time around the table together. Dani was in her customary hoodie, which made it easier to look her way without feeling like he might get caught checking her out, but he found himself admiring her facial features instead. She really was quite stunning with her full, soft lips, long, dark eyelashes, and thin, elegant eyebrows framing her bright, blue eyes. Her cheeks were barely round enough to mark her as a girl, rather than a woman, and her slightly upturned nose was neither too big nor too small for her face, unlike some of the women he'd seen on Finn's tablet. Of course, with all his staring in her direction, Dani had noticed his gaze on her more than a few times, causing him to look away suddenly with a blush. He needed to get a grip on himself! If he wanted to ogle his sister, he would need to wait until he could creep to her window again tonight, rather than here at the dining table where any of his family might notice.
It was her usual night for a shower again, so Jake would have another opportunity to see her graceful naked form, if he could manage to sneak out as he had done before. Indeed, he'd thought about trying to sneak out to her window on nights that weren't her shower nights as well, since Dani had to undress every night to put her pajamas on, shower or no. He had nixed that idea in the end, though, because it was far more risky. He'd have to sneak out while his brothers were still getting ready for bed, and while his parents were known to come check on their progress. By only sneaking out on nights when Dani showered, Jake virtually guaranteed that his brothers would be in their bedroom, and his parents either upstairs with Bec, or watching TV in the living room. This was because his sister preferred to take her showers quite late in the evening, after the youngsters had already finished getting ready for bed and said their good nights. He imagined it was her way of winding down for the night, which she found easier to do when the rest of the house was quiet. Regardless of her reason, it would work to his advantage again tonight.
***
That night Dani gave herself another "pleasure explosion" in the shower, finding it easier than before to build herself up for the release. Something about the hot water rushing over her body added to the whole experience, heightening the sensations as it enveloped her in its wet embrace. As she dried off, she wondered how soon afterward she could do it again. Wrapping her robe around herself for the short trek past the living room to her bedroom, she decided she would try again on her bed, after drying her hair. Gathering her things, she exited the bathroom, wished her parents, who were seated on the couch watching their favorite sitcom, a good night, and stepped into her own room, flicking on the light and closing the door behind her.
After hanging up her towels to dry on her bedposts, she undid her robe and let it fall to the floor, enjoying the feeling of being entirely nude. Then she went about her routine of brushing and drying her hair at her vanity before wandering over to her closet. She was about to pick out a pair of panties and some pajamas when she stopped herself. Why not just stay completely naked while she rubbed herself, like she did in the shower?
Deciding that was a splendid idea, she closed her closet door and flopped onto her bed. She didn't even bother crawling under the covers, just letting her head sink into her pillows as she lay on her back, spreading her legs wide for easy access to her sex. Like the previous night, she started with light caresses on her skin, trailing her fingers down across her stomach until she felt the fuzz atop her mons, which she played with for a short time. Then she caressed the inside of her thighs and brushed lightly across the outer lips of her vagina. She felt the pleasurable sensation awaken within her for the second time that evening and she knew she'd be able to bring herself to rapturous release once more. This encouraged her to press on, rubbing herself in earnest and beginning to feel the dampness return to her inner folds. As before, she used it as lubricant for her rubbing, flicking, and swirling fingers, which had begun to cause her hips to buck in rhythm with her ministrations.
Dani increased her pace and pressure, faster and harder, faster and harder, until her pleasure reached its crescendo and her body stiffened in overwhelming physical bliss. She continued rubbing herself through the waves of pleasure that were like aftershocks of an earthquake wracking her body until she was abruptly interrupted by a large ***THUMP*** that came from the outside wall of her room.
She froze in horror. Someone was outside her room in the side yard! Scrambling, she got up from her bed and donned her robe as fast as she could to cover herself, then went straight to the window to see who had been spying on her. She raised her blinds and looked out into the night. It was difficult to see in the dark, but no one was there. Just the massive rhododendron bush blocking everything else from view. She hadn't imagined the sound, though. Something large had bumped up against the outer wall, for certain. What could it have been, if not a person? Then she remembered that their massive dog, Dozer, had free reign of the back and side of the house at night, since it was fully fenced, and she breathed a sigh of relief. The Rottweiler was definitely large enough to have made that thump if he bumped into the outside wall, and it made sense he would be poking around at night, especially if any smaller animal had caught his attention and he had given chase. In her state of vulnerability, she had merely jumped to the most horrifying conclusion possible, instead of the one that made the most sense.
Smiling at her own silliness, Dani walked back over to the closet, dropping her robe and putting her pajamas on for the night. She needed to get her sleep because she had an important weekend ahead of her. She'd be going over to Audrey's shortly after breakfast and planned on showing her best friend her newfound favorite hobby.
***
Jake was panting in fear when he made it back to the safety of his room that night. He had very nearly been caught! Yet he could not deny that the risk had been more than worth it, given what he had seen his sister doing through her window. He'd never seen a girl jerk-off before, but that was to be expected since he'd never seen a live girl naked before until just two nights ago. He'd never even imagined that it was possible for a girl to jerk-off since they didn't have a dick, but he'd just witnessed Dani do exactly that, laying on her bed completely naked, furiously rubbing herself until she went rigid and shuddered uncontrollably from what he could only assume was pure pleasure, judging by the wide and rapturous smile on her face.
There were two main differences that Jake noticed in the way his sister jerked-off compared to how he did it. The first was obvious in that she rubbed her pussy, while he pumped up and down on the shaft of his cock. The second was that she didn't have any cum spraying everywhere when she climaxed. The first time Jake had jerked off, the cum had scared him as it sprayed all over his stomach and hands. He thought he had done something wrong until his friend Finn had explained that it always happens. After that, Jake had taken to using a sock to capture it, so his cum didn't give him such a mess to clean up. Dani didn't have any cum at all, which meant she didn't have to worry about any messy aftermath. How convenient for her, he thought sarcastically.
In order to get an angle to best observe what his sister was doing, Jake had leaned to his left without shifting his knees beneath him, and when she came, he had been so shocked that he lost his balance and fell over, catching himself by slamming his palm into the wall. He had immediately known he needed to leave, or he would be caught, so he rushed out from behind the rhododendron bush and around the corner of the house to the back yard. Once out of sight of Dani's window, he had slowed his pace and crept back in through the basement door to his room. Above him he could just make out Dani's soft footfalls as she walked from the window to her closet. She had definitely checked to see if anyone was out there, and he had no doubt that if she thought he had been spying on her, she would have been stomping down the stairs to confront him in a heartbeat. No such stomping ever came, though, which meant she must have concluded that no one had been at her window, after all.
Jake had narrowly dodged being in a world of trouble, and likely not just with his sister. Though they tried to work most things out between each other, Jake was sure Dani would have deemed this infraction severe enough that it needed to be taken to their parents, and who knows what they may have done about it.
Still, the payoff had outweighed the risk more than he had expected. He'd snuck out to peep though her window expecting to see her going about her evening routine in the buff like he had before, and she had delivered on that, dropping her robe then brushing and drying her hair at her vanity before going over to her closet to get her bed-clothes. Then she had stopped, turned and flopped naked onto her bed, spreading her legs wide and giving Jake the hottest display he had ever seen. It was all he could do to keep himself from whipping dick out and jerking off as he had watched. As it was, he had been rubbing his boner through his pants, which had likely contributed to him losing his balance, as well.
Once the fear of almost getting caught started to dissipate, Jake flung his pants off and started tugging on his dick while recalling in as much detail as he could exactly what he had just seen. It was the fastest he had ever cum, he was sure, and he almost wasn't ready with his sock as his climax overtook him.
***
Dani beamed as she saw her friend Audrey rushing down her front steps to greet her before she'd even opened the van door. Her friend was the quintessential cowgirl, boots and all, with her worn jeans and flannel shirt. The only thing she was missing was the hat, but she made up for it with matching french braids on either side of her head that ended in shoulder length auburn pig-tails hanging down behind her. The only word Dani had to describe her best friend was "adorable.” She was a bundle of energy in a small package, both shorter and thinner than Dani, and she had been a late bloomer in the breast department, barely filling out an A-cup bra; a fact that Audrey reminded her about on a regular basis. The girl was actually jealous of Dani’s larger breasts, which Dani could not begin to understand. More than once, she had expressed her willingness to trade breast size with Audrey, if it were only possible.
Dani hardly had time to climb out of her mom's van before her friend wrapped her in a tight embrace.
"I'm so glad you asked to come over!" the smaller girl exclaimed, backing away a bit and taking Dani's hands in her own. "It feels like it's been forever since we got to hang out, even though it's really only been a few weeks."
"I know what you mean," Dani agreed. "So much can happen in just a week, and the short time we get to talk after church just isn't enough."
"No, definitely not!" Audrey said, pulling her away from the van. Dani barely had time to grab her bag before her friend was dragging her away toward the house. She turned and waived goodbye to her mother, who was chatting with Mrs. Larson, then followed her friend in the front door and down the hall to the girl's bedroom.
"You can drop off your bag here, then I have my morning chores to get done before we can find something fun to do," Audrey explained.
"I'll help you with your chores, if you want," Dani offered. "I have a ton to tell you about, so we'll need all the time we can get."
"Sounds great to me, but you'll need to borrow some rubber boots," Audrey advised. "I have to make sure all the animals have water before it starts getting hot, then I have a stable to muck out, and eggs to gather from the chickens."
"Can't wait!" Dani said honestly. She enjoyed helping care for the animals whenever she came over to Audrey's house. The Larsons had more animals than Dani had ever known a single family to own. They had two dogs, several cats, a handful of rabbits, a flock of chickens, four horses, a small herd of cows, and one ornery goat. Dani's favorite were the horses and the two girls would often spend their afternoon trail riding. She hoped they'd get a chance to do just that today.
Audrey led her back out of the bedroom, down the hall, and past the living room to the mud room at the back of the house. There she presented Dani with a grubby pair of rubber boots that her older brother, Jeffrey, had grown out of. They were slightly oversized for Dani, but they would do the job, and once Audrey had donned her own pair they headed out the back door and down toward the barn.
The Larsons lived on a gorgeous property with expansive pastures, surrounded by forest, with a small creek running through it. They owned twenty acres in all, but it backed up to state forest land with gravel access roads spider-webbing through it, where the girls liked to go ride the horses.
As they made their way toward the barn, Dani started thinking about how she would broach the subject of the "pleasure explosion" she'd discovered the could give herself. It had been an easy decision to want to tell her best friend about it, but she hadn't given any thought to exactly how best to bring it up.
"You know..." Audrey began as she was filling a water bucket with a hose. "For someone who said she has a ton to tell me about, you sure are being quiet."
"I ***DO*** have a ton to tell you about," Dani insisted. "I'm just not sure how to start."
At that, the smaller girl cocked an eyebrow. "You know you can tell me anything. Just spit it out."
"Well... Have you ever noticed that it can feel really good to rub yourself... down there?" Dani pointed to her crotch.
"Your girly bits?" Audrey asked.
"Girly bits?"
"Yeah! My mom calls them her 'lady bits', but I'm no lady yet, so I call them my girly bits," Audrey explained. "And yes, I have noticed that before. I'm surprised you hadn't! Oh gosh, Dani! Did you have your first orgasm?"
"Orgasm?" Dani questioned.
"Yes! That's what it's called when you make it feel ***REALLY GOOD*** and everything just seems to explode with pleasure."
"That sounds about right," Dani nodded. "You knew about that and never told me!?"
Audrey shrugged. "I guess I figured you probably knew about it already. It's not exactly something that comes up in day to day conversation."
"No, probably not," Dani agreed, helping her friend haul the water bucket into the barn. "But how did you know about it already? I only just figured out I could do it this week!"
"I guess I did have a bit of help..." Audrey admitted. "When I was ten, Millie noticed me grinding my girly-bits on a saddle horn, and she taught me all about it." Millie was Audrey's older sister Melissa, who had moved out and gotten married the year before.
"See! You had a sister to teach you about these things! Who am I supposed to have teach me? My mom?"
"You're right," Audrey agreed. "I really can't imagine your mom teaching you to masturbate."
"Master-what?"
"MasturBATE. It's what it's called when you give yourself an orgasm. My brother calls it jerking-off, but I think that's because boys do it different."
"Wait, ***WHAT!?***" Dani exclaimed. "Boys can do it, too!?" She felt like her world was being turned on its head.
"Oh definitely!" Audrey replied matter-of-factly. "I caught Jeff jerking off in the wood-shed once when he was supposed to be out milking the cows. He stuffed his dick back in his pants as fast as he could, but I'd already seen what he was doing." She formed a circle with her fingers and pumped her hand up and down vigorously in front of her crotch. "He swore me to secrecy about it though, so don't you dare let anyone know I told you about it!"
"Wow..." Dani said simply. "I had no idea that everyone was already doing it but me."
"I'm sure it's not ***everyone***," Audrey said, obviously trying to reassure her. "And if you'd like, I can show you a few things later today. My sister taught me well. She said that one day I'd be grateful I knew what I was doing, whatever that means."
"That sounds like a great idea!" Dani agreed. "Goodness knows I am just blindly feeling my way through it."
"I see what you did there," Audrey said with a wink. "Feeling your way through it." They both giggled at the pun. "That can't be all you wanted to talk about, though. We've barely started in on the chores."
It was true. They had only just managed to fill all the animals' water troughs, so they were now retrieving the wheelbarrow, pitchfork, and shovel to start in on mucking out the horse stall that was due for new shavings. Then they still had to go gather eggs.
"Well, I didn’t know my first bit of news wouldn’t actually be news to you at all, so I thought it was going to take longer,” Dani protested. “The other thing is a bit of a mystery I have on my hands, though.”
"Oh? I like mysteries."
"This one is about Jake."
"What has that little punk done now?" Audrey asked with a grin. She was the only person who understood Jake and Dani's relationship of mutual and meaningless antagonism. In fact, she enjoyed joining in on it whenever she came over, taunting Dani's brother even more viciously than she did.
"It's not really anything he's doing so much as what he's ***not*** doing," Dani explained. "On Wednesday morning, he was pretty normal; he even stole my sunglasses and climbed one of the maple trees in the back yard with them, threatening to leave them up there unless I could climb up and take them back."
"Yep! That sounds like typical Jake to me!"
"Well, after that it's like he just decided to shut me out. He's barely talked to me at all the rest of the week. No teasing, no name calling, and no pranking the rest of the day Wednesday, and all day Thursday, and Friday."
"Woah! That ***is*** strange! He's always giving you a hard time!" Audrey agreed.
"I know! I can't figure out what happened to make him shut down toward me. He's not any different with the rest of the family, and is maybe even more friendly with Travis and Aaron than before."
"So, it's definitely something specific to you, then," Audrey said thoughtfully.
"Well, maybe, maybe not," Dani continued. "Jake almost never goes a day without hanging out with Finn, but he came home early from fishing with him on Wednesday, and didn't hang out with him at all on Thursday."
"Maybe Finn had something going on and couldn't hang out," Audrey suggested.
"That could be it," Dani admitted. "Jake did go hang out with him yesterday, like normal."
"So, as far as you can tell, it's really just you that Jake is suddenly acting cold toward, right?
"Yes."
"And it all happened after you climbed the tree after him to get your sunglasses back?"
"Yes."
"And Jake was above you the whole time you were climbing?"
"Yes, obviously."
"I think Jake saw your boobs."
"What!? My boobs? I had my shirt and sports bra on, like usual! My boobs stayed covered! ...At least mostly. The important parts anyway.."
Audrey looked at her pointedly for a moment before speaking, as if accusing her of being an idiot.
"A boy doesn't have to see your whole boobs to notice that you have them, you know. If you were climbing that tree in a tank-top, I bet he had a nice view down the front of your shirt."
"But Jake doesn't think of me that way," Dani protested. "He's always seen me as practically one of the guys, even when the rest of his friends stopped hanging out with me."
"Dani... He's a teenage boy," Audrey pointed out. "His relationship with you as his sister may have held off the inevitable for a while, but boys only think about three things: food, video games, and girls. Maybe watching your boobs as you climbed up the tree triggered something in his head and he finally figured out you were a girl, with all the equipment that comes with it." She said the last bit pausing from her work to gesture pointedly at Dani’s ample chest with her free hand.
Dani was silent for a time, thinking over what her friend had said as they filled another wheelbarrow with soiled shavings from the horse stable. She barely even noticed the smell, she was so focused on whether Audrey had correctly assessed the situation. Everything with Jake seemed to hinge on that incident with her sunglasses and climbing the maple tree to retrieve them. Whatever the reason was for his coldness toward her the last few days, it was somehow linked to that. So far, only two possibilities had presented themselves: either Dani's worst fear was the case, and Jake had noticed that rubbing herself on the tree was giving her pleasure, or Audrey was right and Jake had been checking out her boobs as she climbed. Of the two, Audrey's assessment seemed more likely. Dani could not imagine how he could have even seen that she had been rubbing herself on the tree trunk as she climbed from his angle, but he would have had a direct view down the top of her shirt to where her sports bra was struggling to keep her breasts contained as she shimmied upward.
Somehow, it was both relieving and a bit exciting to think that he had been checking out her boobs. It was a relief because it meant that Jake didn't know her other secret about giving herself - what had Audrey called them? Orgasms? Though, according to Audrey, most boys give themselves orgasms, too, so Jake might already do that to himself as well. The thought was still a bit shocking to her, since she had only just discovered it was possible in the first place. She wondered if she would ever have an incident like Audrey, walking in on one of her brothers in the middle of "jerking-off" as she had called it. Since Dani had three brothers, the chances were probably pretty high that it would happen someday. A twinge of curiosity made her almost hope it happened sooner rather than later.
The idea that Jake had been checking out her boobs also made Dani feel a bit excited. She'd never considered that someone might look at her that way before. There weren't many boys at their church except those still in grade school—which is why all of Jake's friends were boys he knew from outside of church—so Dani had never even had a crush on a boy before, let alone thought about trying to look good for one. Something inside her made her want to be looked at, though, now that the idea had been planted in her head that someone might want to, even if it was her brother. Did Jake like what he saw? Why should it matter if he did? But somehow, it did matter to her, and she couldn't puzzle out why.
"Okay..." Dani said finally. "You might be on to something."
"Of course I am," Audrey replied confidently.
"That still doesn't explain why he won't talk to me, though," Dani complained.
"Sure it does!" Audrey insisted. "Most boys have a hard time talking to hot girls."
"So you're saying Jake thinks I'm hot?" Dani asked, surprised to find that she hoped he did.
"Good grief, Dani!" Audrey responded in exasperation. "You ***are*** hot! You just haven't ever noticed it, and apparently neither did Jake until now."
"Wait... You think I'm hot, too?" Dani was getting more confused by the minute. She had never thought of herself as attractive, and she had definitely never considered the possibility that another girl might think of her that way. Then again, as she looked at her petite friend, in her tight jeans, flannel shirt, and french-braided pigtails, Dani couldn't help but admit that Audrey was pretty cute, as well. Dani couldn't quite classify the girl as "hot" since she still lacked the more mature feminine curves that were generally associated with that term, but she was still quite attractive. Not that Dani was interested in girls in that way, but that didn't mean she couldn't appreciate her friend's good looks.
"You must be blind, Dani Hansen. If I was a boy, I'd be drooling all over you!"
"Gross... Please don't'." Dani said with a giggle. "Do you really think I'm that pretty, though?" She still couldn't bring herself to use the term "hot" in reference to herself.
"Of course I do!" Audrey insisted. "You’re the full package! You're athletic, yet you have nice boobs that probably aren't done growing, long, toned legs leading up to a perfectly round butt, gorgeous hair, that it's a shame you just tie back in a ponytail all the time, and a girl-next-door sort of beautiful face. I am personally shocked that it took this long for Jake to notice. I'm sure his friends have, though."
Dani blushed a deep crimson at her friend's compliments, finding herself completely speechless as she tried to wrap her mind around the idea that others might find her attractive. Even if she could accept that her brother had been checking her out, a thought that only made her blush deepen, it was still no help to her in rectifying the situation.
"Fine, lets assume you're right and Jake was looking down my shirt, and now it has him all flustered, because he’s figured out I have boobs. So, what am I supposed to do about it?"
The smaller girl looked over at Dani with a sympathetic look on her face as they took the pitchforks and wheelbarrow back to put them away in the tool shed. They had finished with cleaning the stall and covering it in fresh shavings, leaving only gathering eggs from the chickens on their list of chores.
"I've got no help for you on that front," Audrey admitted. "Now that he's thought of you that way, it's going to be impossible to get him to think of you as just his sister again. Now you're his ‘hot sister,’ and that's the way he'll probably always think of you, unless you get fat or something."
"Great... So my relationship with my brother is basically over..."
"Not necessarily," Audrey said as cheerily as she could, obviously trying to brighten Dani's mood. "Maybe it will just take him some time to adjust to the idea that he has a bona fide hottie living under the same roof. Who knows? Maybe figuring out how to not be awkward around you will help him out later on when he's trying to ask a girl out."
"Ugh! How long do you think that will take?"
"For him to get a girlfriend? Probably a few decades," Audrey joked, causing Dani to roll her eyes. ''Alright! Alright! I knew what you meant. I just don't have a clue how long it will take him to stop being awkward and warm back up to you."
"Wonderful..." Dani said sarcastically. "It's going to get really lonely at home waiting for him to come around. Do you think there's anything I could do to speed up the process?"
"I doubt it," Audrey responded as she transferred chicken eggs from the nesting boxes into a rinsed-out 3 gallon paint bucket. "If you draw attention to it, you'll probably make it worse. I'd say just try to act like normal around him as much as you can."
Dani sighed. "That makes sense. I guess it's my only real option, anyway."
"Personally, I'd be more worried about him trying to spy on you."
"Really? Why do you say that?"
"Dani, boys are never satisfied with just getting a glimpse down a girl's shirt," Audrey explained. "They will try to get a look at a naked girl if they can think of any way to make it happen without getting caught. I remember how Jeff used to try and catch a glimpse of Millie when she still lived here. He climbed all the way up to her window on the second story using the trellis on the side of the house, but he wasn't quiet enough, so he got caught and nearly fell in his attempt to escape. Thankfully Millie, who was topless at the time, caught him by the scruff of his neck just before he tumbled backward. I think he would have been better off if he'd just fallen and cracked his head open, though."
Dani couldn't help but laugh, picturing what her friend described. At the same time, she thought about catching Jake doing the same thing, and what she might do in retaliation. If she was honest with herself, she wasn't sure that she would even be all that mad at him. In fact, the more she thought about the idea, the more she almost hoped he ***would*** spy on her.
That's when Dani remembered what had happened Friday night while she was masturbating and she froze in horror.
"I think he might have already spied on me..." Dani told her friend in a near whisper.
"Really? Why didn't you mention it before?"
"I only just realized it when you mentioned your brother spying through your sister's window," Dani explained, then told her friend about how she had given herself an orgasm while lying naked on her bed after taking her shower the night before and had heard a loud thump on the outer wall near her window just as she had finished. "I thought it must have been Dozer at the time, because no one was there when I got to the window after throwing on a robe, but after you told me about Jeff, it dawned on me that Jake could have been spying on me. He wouldn't even need to climb anything to see through my window."
"Oh, I can almost guarantee he was spying on you,” Audrey confirmed, “and depending on when he got there, he probably watched the whole time after you got out of the shower. I'm sure he can hear the water going from his room downstairs and probably uses it as his cue for when you'll be back to your room to get changed."
Dani swallowed hard as she thought of all that Jake had likely seen from when she had entered her room, dropped her robe, dried and brushed her hair, and then rubbed herself to orgasm. Nothing would have been left to his imagination whatsoever. Why didn't that thought make her angry, though? It should have infuriated her, shouldn't it? Yet she felt no anger toward Jake at all for invading her privacy. The only way she could describe what she did feel was... excited? Sure, he had seen her rubbing herself, but if Audrey was right then Jake probably did something similar to himself, too, so he’d have no reason to think it was gross. Moreover, she could not blame her brother for being curious about what she looked like naked, because Audrey had piqued her curiosity about what boys looked like, too, and particularly how they jerked-off. Audrey had said it was different from how girls do it, but hadn't gone into detail, apart from the vague pumping gesture.
"So, what are you going to do about it?" Audrey asked as she carried the bucket full of eggs toward the house, breaking Dani out of her thoughts.
''Huh? Oh... I don't know," She finally responded. "I guess I'll have to just close the blinds so he can't spy on me anymore." As soon as the words came out of her mouth, Dani knew it was a lie. She ***wanted*** him to see her again. Why did the idea of someone secretly watching give her such a thrill?
"What? You're not going to tell your parents what he's been up to?" Audrey asked in a hushed tone. They had just come in the back door to the mud room and kicked off their rubber boots before heading toward the kitchen to drop off the eggs.
"No, not for now," Dani said, matching her friend's low tone. "We don't tattle on each other unless it's something where we could get hurt badly, and besides, I don't have any proof, so he could just deny it."
Audrey dropped the bucket of eggs off in the kitchen and led Dani upstairs to her room, shutting the door behind them so they could talk in private. The two girls took a seat opposite each other on the edge of Audrey's bed to continue their conversation.
"Ok, so don't tell your parents," Audrey began. "But you should at least confront him about it. He needs to understand it's not okay to spy on you in the privacy of your own room."
"I don't know... Didn't you say before that confronting him about checking out my boobs would just make things worse? Wouldn't this be the same?"
''Hmmm." Audrey had a slightly frustrated, thoughtful look on her freckled face. "You're probably right. I suppose it won't be so bad, as long as you are careful not to let him have more opportunities to spy on you again."
"Oh, definitely not!" Dani agreed emphatically, all the while looking forward to doing exactly the opposite at her next opportunity.
"Geez Dani! No wonder you wanted to talk so badly!" Audrey leaned over and gave her friend a tight hug. "What do you say we go for a ride now to take our minds off of pervy brothers?"
Dani agreed, but she doubted she would be able to take her mind off of Jake now. Not when she had already begun to devise a plan for dealing with him after she got back home.
***
Dani enjoyed the rest of the day with Audrey. The girls went on a long trail ride with the horses, eating a picnic lunch in the woods, and then spent the afternoon sunbathing in the back yard. After dinner with Audrey's family, the two girls retired to her bedroom for the night.
"Ready to learn some new tricks for giving yourself orgasms?" Audrey asked, locking the door behind them.
Dani grinned. She'd been looking forward to this all day. Audrey had dropped hints the whole time about what was coming and Dani was eager to explore this newfound source of pleasure more deeply than she had been able to on her own over the last few days.
"I'll take that as a yes," Audrey said, her voice suddenly smooth and sultry, a tone Dani had never heard from the girl before. Dani watched in surprise as her friend slowly stripped out of her shirt and then her pants to stand in just her bra and panties. "Well, what are you waiting for? We can't do this fully clothed."
Following her friend's lead, Dani stripped down to her undergarments as well. As usual, she had a sports bra hugging her breasts tightly to keep them in place. By contrast, Audrey had a lacy little matching bra and panty set that made her petite frame look adorable and sexy at the same time.
"With that bra, it's no wonder it took your brother so long to figure out you have boobs," Audrey teased. When Dani shot her an offended look she said, "Oh good grief! Just take it off, you'll thank me later. It's just going to get in the way."
Dani raised a curious eyebrow but did what her friend suggested, pulling the sports bra off over her head and tossing it to land on her bag by the bed.
"Now, have you tried riding any of your stuffies yet?" Audrey asked, climbing up onto her bed and holding up her favorite teddy bear. Dani shook her head that she hadn't. "Then you are in for a treat!"
With that, Audrey placed her bear face up on the bed and maneuvered so that she knelt with one bare leg on each side of the stuffed animal, her panty clad "girly bits" just inches above it. Then she sat down onto the teddy and began grinding herself back and forth along its furry body, her hips rolling hypnotically as she did so.
"Mmmmmm." she moaned softly. "I hardly ever can make myself orgasm from just this, since teddy here is too soft to really get me going, but it's always a really nice warm up for the main act." As she spoke, Audrey slid her hands up under the cups of her bra and she began pinching her nipples; something that Dani never would have thought to do to herself. After a few minutes of slow grinding she asked, "Do you want to try?"
"Yes!" Dani nodded emphatically and her friend lifted herself off of the bear, rolling to she side and gesturing for Dani to take her place. She did so, positioning her legs on either side of the bear as her friend had done, then lowered herself down onto it. The soft fur of the stuffed animal caressed the inside of her thighs as her panties made contact with the bear's stomach. The stuffed animal gave beneath her, cupping around her vagina and only resulting in slight, soft pressure against her sex.
"Now start grinding against it," Audrey advised, and demonstrated from where she knelt on the bed next to Dani, grinding herself against the empty air.
Testing it out for herself, Dani imitated the rolling and grinding motion with her hips, holding the bear in place with one hand, which also helped to keep herself balanced. The slight pressure and friction against her vagina was quite pleasant, but she could already tell that it was not going to be enough stimulation to bring her to an orgasm. The feel of the stuffed animal caressing her inner thighs was particularly enjoyable, though.
She was so focused on the pleasant sensations her grinding was causing to well up within her, she didn't notice that Audrey had moved behind her until she suddenly felt her friend's hands cup both of her breasts and her fingers grasped each of her nipples, giving them a pinch. It wasn't so hard a pinch as to be painful; just enough to send a shock through Dani's body and make her call out.
"Ohhhh! Wow!" Dani moaned, bringing her hands up to hold Audrey's in place as she continued to pinch and twist slightly.
"I thought you might like that," Audrey breathed in Dani's ear in an amused tone. She pinched Dani's nipples a little harder, drawing a shiver of pleasure from her. "Are you ready for something else new?" Dani just nodded in response. Audrey released her nipples, causing Dani to sigh in disappointment, and said, "Get your hairbrush out of your bag."
Dani turned to face her friend with a quizzical look, but Audrey just looked back at her with a knowing smile that compelled Dani to do as her friend had instructed. By the time she had retrieved the hairbrush and returned to the bed, Audrey had her own hairbrush in hand and had removed her panties, revealing a completely bare vagina, without a hint of pubic hair, that she was stroking lazily as she reclined on her pillows.
"You don't have any hair down there," Dani pointed out with mild surprise.
"I keep it shaved," Audrey explained, caressing her bare skin with a finger before returning it to her inner folds where she stimulated her center of pleasure. "It's way more comfortable that way. Millie taught me how when my pubic hair started growing in."
"It looks so clean that way, compared with mine," Dani commented, following her friend's lead by stripping off her panties and crawling onto the bed to sit next to Audrey and recline into the pillows as well.
"Some girls like to keep a little bush above their pussy," Audrey said. "But I can show you how to shave it if you want to try it out."
"Pussy?" Dani asked with a giggle. "Like a cat?"
"Girly-bits, pussy, vagina... There's all kinds of names for it; some worse than others. Pussy seems to be the most common, though. It's what Millie calls it, at any rate."
"I think I heard Finn call Jake a pussy once. I just thought it was the same as calling him a scaredy-cat."
"It basically is, but by calling him a girl instead," Audrey explained. "Finn was telling your brother he didn't have the balls to do something."
"Balls?" Dani asked, even more confused now.
"Oh Dani, you really are naive, aren't you?" Audrey sighed. "We'll have to go over boys' anatomy another time; I have enough work cut out for me teaching you about your own. Is your pussy nice and wet yet?"
Dani dipped a finger into her folds and it came away coated in whatever sort of liquid her vagi... pussy produced when she was excited.
"Yeah, I'd say so," she responded.
"Good," Audrey said. "Just watch me for now, though. When you do this the first time it may hurt a bit, and there may be a little blood, but don't worry, it's fine."
Dani watched in amazement as her friend widened her legs for her to get a better view, then moved her hair brush down between them and placed the end of the handle at the lower end of her inner folds. Audrey pushed gently and the end of the hairbrush disappeared inside of her. She kept pushing and slowly the rest of the handle was swallowed by her pussy, until only the portion with the bristles remained. Then her friend pulled it back out part of the way and pushed it back in again, a little faster this time. Dani just stared in wide eyed incredulity as her friend continued to penetrate herself while using her other hand to rub, flick, and swirl her fingers around the center of her pussy folds where Dani suspected her friend also had a sensitive little nub of pleasure.
"Ok, now it's your turn to try," Audrey said, still gently pumping her hairbrush in and out. When she saw Dani looking skeptically at her own brush's handle, which was somewhat larger than hers, she continued, "Don't worry, it's nice and smooth, it will fit just fine. First, use your fingers to find the opening."
Nodding, Dani slid an exploratory finger down into her folds, encountering her nub and sending a little shock of pleasure through her body, then continuing lower until she found the opening Audrey was talking about. It felt warm and was sopping wet with the liquid her pussy was producing. Keeping her finger there for guidance, she placed her hairbrush handle into position, feeling its cool smoothness parting her lips, then she removed her finger. She took a deep, determined breath and pressed gently but firmly on the other end of her hairbrush, feeling herself open to accept it. However, it didn't get far before Dani felt resistance. Was that as far as it would go? It was barely in an inch or two, while Audrey had put hers in all the way.
"That's your hymen blocking the way," Audrey informed her. "This is where it's going to hurt a bit. You have to push through it, then it won't hurt next time."
Trusting her best friend wouldn't steer her wrong, Dani did as she was instructed, putting more pressure upon the end of her brush to press it into her pussy. At first it was met with a slight stinging pain, then a brief, sharper pain as whatever was blocking the passage within her gave way, and suddenly the whole handle disappeared inside her, surprising her with the sensation of fullness so that she let out a small gasp.
"You alright?" Audrey asked, and Dani nodded, the stinging pain still there, but diminishing by the second. "Great! Now, before you start pumping it in and out like me, why don't you finger your clit a little to get yourself worked back up?"
"Clit?" Dani asked. "Is that what that little nub is in the middle of my pussy?"
"That's the one!" Audrey confirmed, returning to fingering her own clit, as well. The girl must have paused her ministrations while Dani was working her brush handle into her pussy.
Dani began rubbing her clit, as instructed, and enjoyed the sensations it sent through her. She continued to do so for a few minutes, getting used to the feeling of her brush handle buried inside of her. Then she slowly began to pump the handle in and out of herself in the same way Audrey was doing next to her. It somehow added to the pleasure she was feeling. Not directly, like fingering her clit, but more of a background sensation that added to the overall experience. The full feeling it gave her each time she pushed it back in was exquisite. Soon she was lost in the pleasure her ministrations were causing, hips bucking up to meet each thrust of the brush handle into her, and grind against her furiously swirling fingers. Then she felt Audrey's hand cup her right breast and start pinching her nipple and the added pleasure sent her over the top with cascading waves of ecstasy overcoming her. She thrust the brush handle into herself one final time and marveled as she felt her pussy clamp down in spasms around it. When her orgasm finally began to subside, Dani turned to look at her friend with a massive grin on her face.
"Incredible, right?" Audrey asked, and Dani nodded vigorously. Then she had the pleasure of watching her petite friend work herself to a similar orgasm before collapsing in a satisfied heap on her bed. They both extracted their hairbrushes from their sopping pussies and cleaned them off with some wet wipes Audrey kept handy for that purpose. Dani did find a small amount of blood on hers, but thankfully it had not gotten on her friend's blankets.
I never imagined this would be the reason for my first time bleeding from there, Dani thought to herself with amusement. While she had been an early bloomer in the breast department, she still hadn’t had her first period, which was unusual, but not unheard of for a girl her age. The family doctor wanted her to come in and schedule some testing if she didn’t have it by the time she turned fifteen, though. Dani often wondered why it hadn’t happened yet, but Audrey often reminded her that she wished she didn’t have to deal with it every month, making her count her blessings.
"If you want, I can show you how to shave your pussy now," Audrey offered, breaking Dani out of her thoughts. "Did you bring your razor with you?"
"I brought it," Dani confirmed. "And sure, I think I'd like to try it out."
The two of them covered themselves in bath robes and headed to the bathroom where they hopped into the shower together and Audrey showed her how to properly, and carefully, shave her pussy. It was very strange to Dani, feeling that part of her body so smooth. She'd gotten used to the pubic hair, but she figured that keeping it shaved was no different from doing the same with her legs and arm pits; just another area to make sure she kept up on at the same time. She liked the way it felt as she ran her fingers across the bare flesh, and the two of them fingered themselves to another orgasm there in the shower before returning to bed.
"I can't believe you pinched my nipples like that!" Dani said when they had snuggled under the covers together.
"Millie did the same thing to me when she was teaching me," Audrey said. "It shocked me so bad I almost punched her. But it felt ***sooooo*** good, so I have been doing it to myself ever since. I figured I'd see if you liked it, too."
"It made me orgasm, didn't it?"
"Well, it sent you over the edge," Audrey confirmed. "I doubt you would orgasm just from having your nipples pinched alone."
"I sure am grateful that your sister taught you so much about all this," Dani said. "I came over here thinking I would be telling you about something new I had just discovered, and instead you helped me understand it. Thank you for that."
"My pleasure!" Audrey responded, then added, "Quite literally," and the two of them broke into giggles.
They continued to chat as they lay in Audrey's bed until they were both too tired to remain awake, and then cuddled up together with Audrey wrapping her arm around Dani to cup one of her breasts as they drifted off to sleep.
-

@ da0b9bc3:4e30a4a9
2025-02-14 06:26:26
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/885591
-

@ da18e986:3a0d9851
2025-02-14 06:00:27
I'm excited to share the first phase of DVMDash's major redesign! After some recent downtime issues (thanks nostr:npub1e5tfhk8m65teu25dfx8lcvwn4c8ypqjl72u2sh4rt8zy2kss0j5qct7mh9 and nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn for the heads up), I've been working on rebuilding DVMDash from the ground up to be more modular, scalable, and reliable.
## What's Live Now: The Stats App
The first piece of the new DVMDash is our completely rebuilt Stats app. Instead of trying to do everything at once, we're now breaking DVMDash into focused tools. The Stats app brings:
- Flexible time windows (1h, 24h, 7d, 30d) for more relevant insights
- Bar graphs showing activity over time
- Per-DVM and per-Kind detailed metrics
For those interested in the new backend architecture, check out my [recent post about performance gains](nostr:naddr1qvzqqqr4gupzpkscaxrqqs8nhaynsahuz6c6jy4wtfhkl2x4zkwrmc4cyvaqmxz3qqxnzdenxu6nwd3sxgmryv3506t7ws) describing how horizontal scaling is needed to support the growing DVM ecosystem.
## Coming Soon: Debug Tools and Playground
You'll notice on the new [landing page](https://dvmdash.live) that DVMDash is now split into three main tools:
1. Stats (available now!)
2. Debug Tools (coming soon)
3. Data Vending Playground (coming soon)
The Debug Tools will bring back the interactive graph-based debugger and event browser, while the Playground will offer a space to experiment with DVMs directly. I'm focusing on getting these right rather than rushing them out.
## Running Locally
Want to try it out? You can clone the repository and run the Stats app locally with a simple
```
docker compose --profile all up
```
then visit **localhost:3000** in your browser.
## What's Next
My immediate focus is on:
1. Polishing the Stats app with new features like:
* Sortable tables for easier data analysis
* Enhanced DVM profiles with pictures and metadata from relays
* More detailed DVM-specific metrics
2. Bringing back the debugging tools
3. Building out the playground
This is very much a work in progress, and I appreciate your patience as we rebuild. If you run into any issues or have suggestions, please drop by our GitHub repository.
-

@ 57d1a264:69f1fee1
2025-02-14 05:45:37

### a practical intro to contributing to FOSS for product people, and other non-devs
So you want to contribute to FOSS, but don’t know where to start. There are many paths to FOSS, but you must find your own. Here’s some advice based on personal experience to help you get started.
### 0\. Find your motivation
FOSS requires a lot of giving, and better aligns with those that are missionaries, as opposed to the mercenaries. Perhaps you are unfulfilled in your fiat job, maybe you are currently unemployed, or perhaps you are excited about a particular bitcoin project. Why you’re exploring contributing to FOSS, is a question that only you can answer.
 Are you a missionary?
### 1\. Discover what excites you
So you’ve found motivation and have a list of various FOSS projects you could contribute to. This is the equivalent of the “I need a job” stage and you’re figuring out where to apply. It’s time to narrow it down.
What are you excited about? A multi-year pilgrimage of learning how to contribute to Bitcoin Core? A lightning wallet, perhaps? Free speech Nostr? A hardware signing device? Or maybe finding a FOSS projects that is not “Bitcoin” in name, but happens to support Bitcoin, and Lightning.
A great first step is to take some time and explore the Bitcoin Design Community ([https://bitcoin.design/](https://bitcoin.design/)) to discover FOSS projects.
 Are you excited anon?
### 2\. Identify the skills you have or want to develop
Chances are that if you follow the Bitcoin Product Community, you’re skills are in Product Management, Product Marketing, and/or Project Management. But contributing to a bitcoin project requires contributors with skills of many backgrounds such as marketing, documentation, community building, and more.
What’s important to know is that most FOSS teams start with a motivated developer, who then may attract other devs. But many of them may not advertise that they need non-developer help such as a PM.
Therein lies the opportunity for you as an eager bitcoin contributor. See what the needs of a project are and see if you can fill in those gaps with your skills. It may be as simple as coordinating meetings for the team. But doing the “dirty work”, or the work no one else wants to do, is exactly the way you can make an immediate impact to a FOSS project. In fact, this is why members of the Bitcoin Product Community affectionately refer to product managers as “[janitors](https://medium.com/all-things-product-management/product-manager-you-are-664d83ee702e)”!
### 3\. Make a list of projects
Now that you have narrowed down your FOSS search, it is time to start building a list of, and evaluating various FOSS products. Some questions you can ask yourself:
Is the project active? Is it a new project? How many team members are there? How many are devs? Is there already a PM? Is there a need for multiple PMs? Is there designer participation? What is the pace of development? Is there enough development activity for this to satisfy your want to contribute? Is there opportunity for a PM?
Github is the defacto standard for FOSS products. Check the activity. Read up on issues. See who is contributing PRs, and creating issues. Check if there is a Github Project instance.
It’s OK, and best for you to check out out multiple FOSS projects concurrently to see which team is the best fit for both parties.
### 4\. Use the thing(s)!
Another thing you can do to help you choose a project is to use the thing! Download the OS. Run the software. Use it.
As you’re interacting with the product, some things you can ask yourself are:
What do you love about the product? What can be improved? Are there bugs?
Jot down your notes. Take screenshots. Do screen recordings. Document your experience. Create a video onboarding walkthrough, or a feature tutorial. What you are actually doing is documentation and this will be useful for the project, even if you don’t decide to actively contribute.
As you use the thing, take note of how you’re reacting to it. Are you getting more or less excited? Are you more or less confident in contributing to the project?
### 5\. Find out where the team works
Another factor to consider is to figure out where the team works.
By now you have already explored their github to collect your FOSS intelligence. Now check nostr, twitter, telegram, or whatever other comms tools the team might be using. Some teams may have calls, and call recordings. Consider listening in to a recording, and/or joining a call to check the team dynamics.
As you do, assess whether you might be a good culture fit. Also see where there might be some gaps in their workflow that you can help improve.
### 6\. Start small
Once you found a project that interests and excites you enough. It’s time to roll up your sleeves and get involved by starting small.
One easy place to start is to go through the github issues list. Some examples of issues in dev heavy teams are e extremely technical bug reports. For FOSS products with an active user base, there might be “customer” centric feature requests.
Start by logging the bug(s) you found. Examine issues, and fill in the blanks if there are unclearly defined reports & requests.
You don’t have to ask for permission to contribute. That said, evaluate team dynamics and who owns what role so you are not stepping on anyone’s toes. You are there to help.
Also take note of how your help is received. It may take time for you to build up your credibility. Don’t throw in the towel on the first week. Keep finding ways to add value.
### 7\. Show up consistently
Keep contributing in small things day in and day out. As you do so, communicate with the team to ramp up your learning, and also start building rapport, and your reputation. You may not have time or opportunity to contribute full-time. With the state of asynchronous communication tools in 2023, you can flexibly contribute when you have time. An exception to the asynchronous communication may be team meetings.
As you continue to show up consistently, you will build up your FOSS proof-of-work, and reputation. This will show FOSS devs, and contributors that you bring value.
### 8\. Find and meet the “customer”
Find, and interact with the project’s users a.k.a “customers”. What do they care about? What are their pain points? What needs are customers using the product for? Become the “voice of the customer” to the dev heavy team.
Is there a conference where your team is presenting, and customers present? These are invaluable opportunities to observe the customer’s behavior, and also to help answer questions, and troubleshoot on the spot.
### 9\. Increase your involvement
After some time starting small and working on bugs, you may eventually find yourself submitting feature requests. Maybe there is an opportunity to create user flows, or mockups. As you consistently contribute, continue seeking more responsibility.
Maybe you offer to facilitate and lead the next team call. Maybe you try creating a roadmap and backlog from scratch. Maybe you host a product & design thinking session. Maybe you will level up and learn how to check out a dev’s PR in a yet-to-released branch.
No matter what you do, be sure to always bring value to the project.
 Testing an unreleased Damus branch checked out on XCode
### 10\. Prune, Commit, Repeat
Congratulations! By now you’ve been doing a “trial run” with several projects. It’s time to focus and choose one(s) that you can commit to.
As you contribute to the project on an ongoing basis, continuously reevaluate if there is opportunity for you to increase your contributions. If you feel that you’ve maxed that out, it may be time to look for a different FOSS product to contribute to. Perhaps a complementary product to your initial one.
As you embark on this journey, it can be exhilarating at times and in other times thankless. To find a community of peers, and perhaps a mentor check in with the Bitcoin Product Community [Discord](https://discord.gg/Ztvwn8fycA), and introduce yourself. The beauty of open source is people are willing to help FOSS products, and to answer your questions.
[https://youtu.be/ZUgQPR6ecuo](https://youtu.be/ZUgQPR6ecuo)“FOSS is the way” - Rockstar dev, @ Advancing Bitcoin Conference London 2023. The author thanks Rockstar for inspiration, and guidance through my FOSS journey.
As you continue to sweep the FOSS floors with your product [mop](https://medium.com/all-things-product-management/product-manager-you-are-664d83ee702e), remember that you are contributing to the mission that you believe in. You are working in the open, with even less authority than a PM at a company might have, and as a result leveling up. You build up your reputation in FOSS, and you show others your capabilities in the FOSS world (and also prospective employers, and co-founders) by doing.
Hopefully this helps you get started. Reach out to [elsat on nostr](https://njump.me/npub1zafcms4xya5ap9zr7xxr0jlrtrattwlesytn2s42030lzu0dwlzqpd26k5) if you have questions about the FOSS journey, and join the Bitcoin Product Community Discord.
Posted on @YakiHonne by @elsat
Source: https://yakihonne.com/article/nevent1qqswn2mdwcfscsvv8cfc8scmcfpy0urnf0xgh0dxrvav583y85mkryspz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzq96n3hp2vfmf6z2y8uvvxl97xk86kkalnqghx4p25lzl79c76a7yjfa8zs
originally posted at https://stacker.news/items/885573
-

@ 57d1a264:69f1fee1
2025-02-14 05:35:18
Volt Wallet is designed to make Bitcoin and Lightning transactions simple, secure, and accessible for users of all experience levels. With the increasing popularity of the Lightning Network, Volt Wallet provides an easy, user-friendly interface for sending and receiving payments while also incorporating educational elements, such as quizzes and tutorial videos, to promote a better understanding of Bitcoin and Lightning payments.



















- - -
Source: https://www.behance.net/gallery/217868517/Volt-A-Bitcoin-Lighting-Wallet-for-beginners
originally posted at https://stacker.news/items/885569
-

@ d360efec:14907b5f
2025-02-14 05:35:13
**ภาพรวม LUNCUSDT (OKX):**
LUNCUSDT กำลังอยู่ในช่วงที่ผันผวนและมีความไม่แน่นอนสูง หลังจากที่เคยมีสัญญาณบวกของการกลับตัวใน TF Day แต่ตอนนี้ทั้ง 3 Timeframes แสดงให้เห็นถึงแรงขายที่เข้ามา และแนวโน้มเริ่มไม่ชัดเจน
**วิเคราะห์ทีละ Timeframe:**
**(1) TF Day (รายวัน):** [https://www.tradingview.com/x/ulqLh1c9/](https://www.tradingview.com/x/ulqLh1c9/)

* **แนวโน้ม:** เริ่มไม่แน่นอน (จากเดิมที่เป็น Early Uptrend) หลังจากที่ราคาไม่สามารถยืนเหนือ EMA 50/200 ได้
* **SMC:**
* Break of Structure (BOS): มี BOS ทั้งด้านบนและด้านล่าง
* Change of Character (CHoCH): มี CHoCH ด้านบน
* Higher High (HH) & Higher Low (HL): HH ล่าสุดต่ำกว่า High ก่อนหน้า
* **EMA:**
* EMA 50 และ EMA 200 เคยเป็นแนวรับ แต่ตอนนี้ราคากลับลงมาอยู่ใต้เส้น EMA ทั้งสอง
* **Money Flow (LuxAlgo):**
* เริ่มมีแท่งสีแดงยาวขึ้น แสดงถึงแรงขายที่เข้ามา
* **Volume Profile:**
* Volume หนาแน่นบริเวณ 0.00012000 - 0.00014000 (แนวต้าน)
* **แท่งเทียน:**
* แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย
* **แนวรับ:** บริเวณ 0.00006000-0.00007000
* **แนวต้าน:** EMA 50, EMA 200, 0.00014000, 0.00017953
* **สรุป:** แนวโน้มเริ่มไม่แน่นอน, สัญญาณการกลับตัวเริ่มอ่อนแอ, แรงขายเริ่มเข้ามา
**(2) TF4H (4 ชั่วโมง):** [https://www.tradingview.com/x/SLsNzZi2/](https://www.tradingview.com/x/SLsNzZi2/)

* **แนวโน้ม:** ขาลง (Downtrend) หลังจากราคาหลุด EMA 50
* **SMC:**
* Break of Structure (BOS): มี BOS ด้านล่าง
* Change of Character (CHoCH): ไม่ชัดเจน
* Lower Highs (LH) และ Lower Lows (LL)
* **EMA:**
* EMA 50 และ EMA 200 กลายเป็นแนวต้าน
* **Money Flow (LuxAlgo):**
* สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย
* **Volume Profile:**
* Volume ค่อนข้างนิ่ง
* **แท่งเทียน:**
* แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย
* **แนวรับ:** บริเวณ 0.00006000-0.00007000
* **แนวต้าน:** EMA 50, EMA 200, บริเวณ High ก่อนหน้า
* **สรุป:** แนวโน้มขาลง, แรงขายมีอิทธิพล
**(3) TF15 (15 นาที):** [https://www.tradingview.com/x/H8QdIEAL/](https://www.tradingview.com/x/H8QdIEAL/)

* **แนวโน้ม:** ขาลง (Downtrend)
* **SMC:**
* Break of Structure (BOS): มี BOS ด้านล่าง
* Change of Character (CHoCH): มีทั้งด้านบนและด้านล่าง
* Lower Highs (LH) และ Lower Lows (LL)
* **EMA:**
* EMA 50 และ EMA 200 เป็นแนวต้าน
* **Money Flow (LuxAlgo):**
* สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย
* **Volume:**
* Volume ค่อนข้างเบาบาง
* **แนวรับ:** บริเวณ Low ล่าสุด
* **แนวต้าน:** EMA 50, EMA 200, บริเวณ High ก่อนหน้า
* **สรุป:** แนวโน้มขาลง, แรงขายมีอิทธิพล
**สรุปภาพรวมและกลยุทธ์ (LUNCUSDT):**
* **แนวโน้มหลัก:** เริ่มไม่แน่นอน (TF Day), ขาลง (TF4H, TF15)
* **Money Flow:**
* Day: แรงขายเริ่มเข้ามา
* 4H: แรงขายมีอิทธิพล
* 15m: แรงขายมีอิทธิพล
* **กลยุทธ์:**
1. **Wait & See (ดีที่สุด):** รอความชัดเจน
2. **Short (เสี่ยงสูง):** ถ้าไม่สามารถ Breakout EMA/แนวต้านได้
3. **ไม่แนะนำให้ Buy:** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจน
**คำแนะนำ:**
* **LUNC มีความเสี่ยงสูงมาก**
* **ความขัดแย้งของ Timeframes:** Day เริ่มไม่แน่นอน, 4H และ 15m เป็นขาลง
* **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด**
*Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-

@ d360efec:14907b5f
2025-02-14 05:21:58
**ภาพรวม XRPUSDT (OKX):**
XRPUSDT กำลังแสดงสัญญาณที่น่าสนใจและมีความซับซ้อน แนวโน้มใน Timeframe ใหญ่ (Day) เริ่มเป็นขาขึ้น แต่ Timeframe กลาง (4H) เริ่มอ่อนแรง และ Timeframe เล็ก (15m) เป็นขาลง ทำให้เกิดความขัดแย้งที่ต้องระมัดระวัง
**วิเคราะห์ทีละ Timeframe:**
**(1) TF Day (รายวัน):** [https://www.tradingview.com/x/3EbxjOgV/](https://www.tradingview.com/x/3EbxjOgV/)

* **แนวโน้ม:** เริ่มเป็นขาขึ้น (Early Uptrend) หลังจากราคา Breakout EMA 50 ขึ้นมาได้
* **SMC:**
* Break of Structure (BOS): มี BOS ด้านบน (Breakout EMA 50)
* Change of Character (CHoCH): ยังไม่ชัดเจน
* Higher High (HH) & Higher Low (HL): เพิ่งเริ่มก่อตัว (ยังไม่ชัดเจน)
* **EMA:**
* ราคาอยู่เหนือ EMA 50 (สีเหลือง) และ EMA 200 (สีขาว)
* EMA 50 และ EMA 200 กำลังจะเกิด Golden Cross
* **Money Flow (LuxAlgo):**
* สีเขียวเป็นส่วนใหญ่ แสดงถึงแรงซื้อที่ยังคงมีอยู่
* มีแท่งสีแดงแทรกบ้าง แสดงถึงการขายทำกำไร
* **Volume Profile:**
* Volume หนาแน่นบริเวณ EMA 50
* **แท่งเทียน:**
* แท่งเทียนล่าสุดเป็นสีเขียว แสดงถึงแรงซื้อ
* **แนวรับ:** EMA 50, EMA 200
* **แนวต้าน:** 0.6448 (High ก่อนหน้า)
* **สรุป:** แนวโน้มเริ่มเป็นขาขึ้น แต่ยังอยู่ในช่วงเริ่มต้น
**(2) TF4H (4 ชั่วโมง):** [https://www.tradingview.com/x/nARcdWWp/](https://www.tradingview.com/x/nARcdWWp/)

* **แนวโน้ม:** เริ่มไม่แน่นอน (พักตัว, ทดสอบแนวรับ) หลังจากเป็นขาขึ้นระยะสั้น
* **SMC:**
* Break of Structure (BOS): มี BOS ด้านบน (ก่อนหน้านี้)
* Change of Character (CHoCH): ไม่ชัดเจน
* Higher High (HH) & Higher Low (HL): เริ่มไม่ชัดเจน
* มี Equal Highs (EQH)
* **EMA:**
* EMA 50 กำลังถูกทดสอบ
* EMA 200 เป็นแนวรับถัดไป
* **Money Flow (LuxAlgo):**
* เขียวและแดงผสมกัน แสดงถึงความไม่แน่นอน
* แท่งสีแดงเริ่มยาวขึ้น แสดงถึงแรงขายที่เข้ามา
* **Volume Profile:**
* Volume หนาแน่นบริเวณ EMA 50
* **แท่งเทียน:**
* แท่งเทียนล่าสุด เป็น Doji
* **แนวรับ:** EMA 50, EMA 200, บริเวณ 0.50-0.52
* **แนวต้าน:** บริเวณ High ก่อนหน้า
* **สรุป:** แนวโน้มเริ่มไม่แน่นอน, มีแรงขายเข้ามา, EMA 50 เป็นจุดสำคัญ
**(3) TF15 (15 นาที):** [https://www.tradingview.com/x/NI2wqamj/](https://www.tradingview.com/x/NI2wqamj/)

* **แนวโน้ม:** ขาลง (Downtrend) ระยะสั้น
* **SMC:**
* Break of Structure (BOS): มี BOS ด้านล่าง
* Change of Character (CHoCH): มีทั้งด้านบนและด้านล่าง
* Lower Highs (LH) และ Lower Lows (LL)
* **EMA:**
* EMA 50 และ EMA 200 กลายเป็นแนวต้าน
* **Money Flow (LuxAlgo):**
* สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย
* **Volume Profile:**
* Volume สูง
* **แนวรับ:** บริเวณ Low ล่าสุด
* **แนวต้าน:** EMA 50, EMA 200, บริเวณ 0.54
* **สรุป:** แนวโน้มขาลง, แรงขายมีอิทธิพล
**สรุปภาพรวมและกลยุทธ์ (XRPUSDT):**
* **แนวโน้มหลัก (Day):** เริ่มเป็นขาขึ้น
* **แนวโน้มรอง (4H):** เริ่มไม่แน่นอน, พักตัว
* **แนวโน้มระยะสั้น (15m):** ขาลง
* **Money Flow:**
* Day: แรงซื้อยังคงมี
* 4H: แรงซื้อและแรงขายผสมกัน, แรงขายเริ่มเข้ามา
* 15m: แรงขายมีอิทธิพล
* **กลยุทธ์:**
1. **Wait & See (ดีที่สุด):** รอความชัดเจน
2. **Buy on Dip (Day, 4H) - *เสี่ยงสูงมาก*:** ต้องรอสัญญาณกลับตัวใน TF15
3. **Short (15m, เสี่ยงสูง):** ถ้าไม่สามารถ Breakout EMA/แนวต้านได้
**คำแนะนำ:**
* **ความขัดแย้งของ Timeframes:** ยังคงมีอยู่
* **Money Flow:** Day เป็นบวก, 4H เริ่มไม่แน่นอน, 15m เป็นลบ
* **EMA 50 (TF4H):** จุดสำคัญ
* **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด**
*Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-

@ d360efec:14907b5f
2025-02-14 04:13:06
Bitcoin (BTCUSDT) กำลังแสดงสัญญาณที่น่าสนใจ โดยรวมแล้วแนวโน้มระยะยาวยังเป็นขาขึ้น แต่ระยะสั้นมีความผันผวนและมีการปรับฐานลงมา
**วิเคราะห์ทีละ Timeframe:**
**(1) TF Day (รายวัน):** [https://www.tradingview.com/x/s9CAaSKQ/](https://www.tradingview.com/x/s9CAaSKQ/)

* **แนวโน้ม:** ขาขึ้น (Uptrend) แข็งแกร่ง
* **SMC:**
* Higher Highs (HH) และ Higher Lows (HL) อย่างต่อเนื่อง
* Break of Structure (BOS) ด้านบนหลายครั้ง
* ไม่มีสัญญาณการกลับตัวเป็นขาลง
* **EMA:**
* ราคาอยู่เหนือ EMA 50 (เส้นสีเหลือง) และ EMA 200 (เส้นสีขาว)
* EMA 50 และ EMA 200 เรียงตัวแบบ Golden Cross (EMA 50 ตัด EMA 200 ขึ้น)
* **Money Flow (LuxAlgo):**
* โดยรวมเป็นสีเขียว แสดงถึงแรงซื้อที่ยังคงมีอิทธิพลเหนือกว่า
* มีแท่งสีแดงแทรกบ้าง แสดงถึงการขายทำกำไร
* **Volume Profile:**
* Volume หนาแน่นที่บริเวณ 96,000 - 98,000 (ซึ่งตอนนี้กลายเป็นแนวรับไปแล้ว)
* **แท่งเทียน:**
* แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย แต่ไส้เทียนด้านล่างยาว แสดงว่ามีแรงซื้อกลับเข้ามาบ้าง
* **แนวรับ:** EMA 50, EMA 200, บริเวณ 96,000 - 98,000
* **แนวต้าน:** 109,998.9 (High เดิม)
* **สรุป:** แนวโน้มขาขึ้นยังคงแข็งแกร่ง Buy on Dip ยังคงเป็นกลยุทธ์หลัก
**(2) TF4H (4 ชั่วโมง):** [https://www.tradingview.com/x/KsuVdl2e/](https://www.tradingview.com/x/KsuVdl2e/)

* **แนวโน้ม:** ขาขึ้น (Uptrend) แต่มีการพักตัวลงมา (Pullback)
* **SMC:**
* Higher Highs (HH) และ Higher Lows (HL)
* Break of Structure (BOS) ด้านบน
* ราคาพักตัวลงมา แต่ยังไม่เสียโครงสร้างขาขึ้น
* มี Equal Highs (EQH) บริเวณ 109,998.9
* **EMA:**
* EMA 50 กำลังถูกทดสอบ
* EMA 200 เป็นแนวรับถัดไป
* **Money Flow (LuxAlgo):**
* โดยรวมเป็นสีเขียว แต่เริ่มมีแท่งสีเขียวสั้นลง และมีแท่งสีแดงยาวขึ้น แสดงว่าแรงซื้อเริ่มอ่อนแรง และมีแรงขายเข้ามา
* **Volume Profile:**
* Volume หนาแน่นที่บริเวณ 96,000 - 98,000
* **แท่งเทียน:**
* แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย
* **แนวรับ:** EMA 50, EMA 200, บริเวณ 96,000 - 98,000
* **แนวต้าน:** 109,998.9 (EQH, High เดิม)
* **สรุป:** แนวโน้มขาขึ้นยังไม่เสีย แต่เริ่มมีสัญญาณเตือน (Money Flow อ่อนแรง, ราคาพักตัว)
**(3) TF15 (15 นาที):** [https://www.tradingview.com/x/DSrpSjn6/](https://www.tradingview.com/x/DSrpSjn6/)

* **แนวโน้ม:** Sideways Down (แกว่งตัวลง) หลังจากพยายาม Breakout แต่ไม่สำเร็จ
* **SMC:**
* Break of Structure (BOS) ด้านล่าง (หลุดแนวรับย่อยๆ)
* Change of Character (CHoCH) ทั้งด้านบนและด้านล่าง
* Lower Highs (LH) และ Lower Lows (LL) เริ่มก่อตัว
* Equal Highs (EQH) หลายจุด
* **EMA:**
* EMA 50 และ EMA 200 กลายเป็นแนวต้าน
* **Money Flow (LuxAlgo):**
* สีแดงมีอิทธิพลเหนือกว่า แสดงถึงแรงขาย
* **Volume Profile:**
* Volume หนาแน่นที่บริเวณ 97,000-97,200 (กลายเป็นแนวต้าน)
* **แนวรับ:** บริเวณ Low ล่าสุด
* **แนวต้าน:** EMA 50, EMA 200, บริเวณ 96,000, 96,800, 97,000-97,200
* **สรุป:** แนวโน้มระยะสั้นเป็นขาลง, แรงขายยังมีอยู่
**สรุปภาพรวมและกลยุทธ์ (BTCUSDT):**
* **แนวโน้มหลัก (Day, 4H):** ขาขึ้น (Uptrend)
* **แนวโน้มระยะสั้น (15m):** ขาลง (Downtrend) / Sideways Down
* **Money Flow:**
* Day: แรงซื้อยังแข็งแกร่ง
* 4H: แรงซื้อเริ่มอ่อนแรง, แรงขายเริ่มเข้ามา
* 15m: แรงขายมีอิทธิพลเหนือกว่า
* **กลยุทธ์:**
1. **Wait & See (ดีที่สุด):** รอความชัดเจน เนื่องจากความขัดแย้งระหว่าง Timeframes
2. **Buy on Dip (Day, 4H) - *ความเสี่ยงสูงมาก*:** ต้องรอสัญญาณกลับตัวใน TF15
3. **Short (15m, ความเสี่ยงสูงมาก):** ถ้าไม่สามารถ Breakout EMA/แนวต้านได้
**คำแนะนำ:**
* **ความขัดแย้งของ Timeframes:** ยังคงมีอยู่
* **Money Flow:** Day เป็นบวก, 4H เริ่มเป็นลบ, 15m เป็นลบ
* **EMA 50 (TF4H):** จุดสำคัญ
* **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด**
*Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-

@ 3eba5ef4:751f23ae
2025-02-14 03:52:48
🍨*Your weekly byte of the latest updates from the Bitcoin ecosystem!*
## Crypto Insights
### Solving the Optimal Cluster Linearization Problem With DeepSeek
Stefan Richter (stefanwouldgo) [found](https://delvingbitcoin.org/t/how-to-linearize-your-cluster/303/9?u=sss_is_me) a 1989 paper through DeepSeek R1 that provides a solid solution to the problem of optimal cluster linearization. The paper presents a proven algorithm that efficiently finds the subset of transactions with the highest fees; if this subset is included in a block, it is topologically valid.
### New Class in Cluster Mempool Improves Transaction Handling and Performance
The introduction of the `TxGraph` class in [Cluster Mempool](https://bitcoinops.org/en/topics/cluster-mempool/) enhances transaction handling by encapsulating the transaction graph, focusing on effective fees, sizes, and dependencies. It enables batched and lazy updates for more efficient mempool operations, with improvements in transaction prioritization, incentive compatibility, and performance. This design simplifies the code by abstracting graph management, allowing for easier validation and future optimizations.
More details in this [pull request](https://github.com/bitcoin/bitcoin/pull/31363).
### Independent Mining Still Feasible
Two independent miners recently mined Bitcoin blocks:
* [Block 881432](https://mempool.sethforprivacy.com/block/00000000000000000000931af218dd988191e459a8449dbce22b17e4475cd5a0) by [256 Foundation](https://256foundation.org/), a public organization promoting open-source Bitcoin mining. The group combined the hash rate from over 300 participants with the goal of breaking up the mining patent monopolies of large pools, making Bitcoin and free technology more accessible to all.
* [Block 881676](https://mempool.space/block/000000000000000000022247ce3898fc9e10be0161cde5f369293d7a916ca8b3) by the open-source home mining hardware [solo.ckpool](https://solo.ckpool.org/), using hash rate equivalent to thousands of BitAxe devices.
This demonstrates that independent miners can still compete, reinforcing Bitcoin’s decentralization and censorship resistance.
### 6-Block Confirmation No Longer Enough, Mining Centralization Impacts Bitcoin Security
Bitcoin Core developer Luke Dashjr [posted](https://x.com/LukeDashjr/status/1888295040113361129) that he intended to update the 6-blocks-to-confirm target in the Knots wallet GUI. However, he found that due to Antpool controlling around 48% of the network's hash rate, more than 800 block confirmations would be required to achieve 95% security. He also noted that many pools, like Braiins and ViaBTC, are actually Antpool under different names.
### Payjoin Development Progress Review
Spiral [reviewed](https://spiralbtc.substack.com/p/nerd-of-the-month-payjoin) the development progress of [Payjoin](https://bitcoinops.org/en/topics/payjoin/), which allows for including an additional input in a payment transaction to enhance privacy. The article also mentions that by using joint batching to optimize fees, Payjoin reduces transaction costs and increases network efficiency. Moreover, when both parties contribute inputs, Payjoin helps protect privacy by breaking common blockchain monitoring assumptions, making it harder for third parties to track payment amounts and private spending behaviors.
### Block Size Report Reveals: Growth Partly Limited by Miner Policies and Bitcoin Core Defaults
The [Block Size Report](https://research.mempool.space/block-size-report/), published by Mempool research, uses data-driven analysis to examine the evolution of block size in Bitcoin from its inception to February 2025. It discusses changes in block size post-SegWit upgrade and reveals how growth has been partly limited by miner policies and Bitcoin Core defaults over the years. The report concludes with predictions about the growth of Bitcoin’s blockchain in the coming years.
### Tutorial on Becoming an Advanced Nostr User With Sats Cashback
Rizful published a [guide](https://rizful.com/get_on_nostr_today) on how to become an advanced Nostr user and set up the self-owned Lightning node. After completing the tutorial, users can receive 5,000 sats via zap cashback.
### Build a Smart Card for Bitcoin and Nostr Event Signing for Under $25
The 100% open-source smart card [Satochip](https://stacker.news/items/877488) allows users to build their own signing device in just 10 minutes under 25 USD. Satochip's advantages include:
* Affordable and widely available
* Dual interface: supports both NFC (contactless) and Chip (contact) modes
* Minimal electronics, reducing the attack surface
* Enhanced security based in Secure Element
### Bitcoin at the Crossroads of AI Revolution and Sovereign Evolution
CKBEcoFund [shared](https://x.com/c_hongzhou/status/1887142941980041727) their insights from the talk at [The Satoshi Roundtable](https://satoshiroundtable.org/), discussing several macro issues including the dominance of artificial intelligence, Bitcoin's security, scalability, sovereignty, and national Bitcoin strategic reserves. He explored how CKB, as a Bitcoin Layer 2, is positioning itself for high-frequency micropayments, smart contracts, and cross-chain asset management.
## Top Reads on Blockchain and Beyond
### Pod: An Optimal-Latency, Censorship-Free, and Accountable Generalized Consensus Layer
[This paper](https://arxiv.org/pdf/2501.14931) introduces a new consensus concept pod, aiming to achieve physically optimal latency for one round-trip—just one write of a new transaction and one read. This work solves inherent problems of high latency in blockchain and low scalability in traditional consensus protocols.
[Grigore Rosu](https://x.com/RosuGrigore) commented: "It can lead to the end of blockchains as we know them today. It shows how we can still achieve all the benefits of blockchains, but dropping the tyranny of sequentiality (and all the value exploiters that come with it).”
### Tracking and Surveillance In-App Ads
The author learned of a massive [location data breach](https://www.404media.co/hackers-claim-massive-breach-of-location-data-giant-threaten-to-leak-data/?ref=timsh.org) revealing that over 2,000 apps in the App Store and Google Play were secretly collecting geographic location data without users' consent, and developers were unaware.
He then began tracking himself through location data leaked by some apps and made the following discoveries:
* Regardless of whether users choose "Allow" or "Ask not to track" in phone settings, the combination of "IP + location + user agent + geography" is still leaked to hundreds of third parties.
* The phone sends requests with location and leaked IP. These can be converted to geographic locations through reverse DNS.
* Data collection pathway: stack → [o.isx.unity3d.com](http://o.isx.unity3d.com/) → [molocoads](https://www.moloco.com/?ref=timsh.org) → bwin
* **Unity** is an SSP (supply-side platform) that collects app data via its SDK
* **Moloco Ads** is a DSP network that resells data from multiple SSPs like Unity, Applovin, Chartboost
* **bwin** is the advertiser that users see ads for in games
More discoveries in this [post](9https://timsh.org/tracking-myself-down-through-in-app-ads/).
### Potential DAO 2.0 Product Ideas
The author believes that the development of on-chain AI agents will lead to new forms of DAO, giving true autonomy to the "A" in DAO. [New product ideas](https://blog.variant.fund/dao-product-ideas) include:
* **DAO 2.0 launcher:** platform enables launching new community/governance tokens tied to an agent, agent responds to tokenholder votes, reads discussion forums and generates proposals
* **Quality assessment for token distribution**: agent assesses contribution quality to determine payouts/token distributions for DAOs/airdrops/etc.
* **ZachZBT:** agent monitors for hacks or other fraudulent activity and publishes research as well as tries to get funds back for people
* **Due diligence agent**: agent verifies contract integrity, dev reputations, on-chain behavior, and potential rug risks; allows users to interact with the agent to ask questions about risks
-

@ 19220736:7578e0e9
2025-02-14 03:44:21
While Zelle promotes itself as a quick and easy way to send money, its instant, irreversible transactions have made it a prime target for fraudsters. Despite mounting reports of consumer losses, banks continue to deny reimbursement for many fraud victims, citing narrow legal loopholes. Meanwhile, Early Warning Services, the company behind Zelle, profits from the vast consumer data it collects, fueling concerns about privacy and corporate exploitation. With government investigations ramping up and public pressure mounting, Zelle and their bank owners have teamed up with the Aspen Institute, forming a new task force with corporate and government players.
In 2017, [Early Warning Services](https://www.earlywarning.com/about), owned by Bank of America, Capital One, JPMorgan Chase, PNC Bank, Trust, U.S. Bank, and Wells Fargo, released the [Zelle](https://www.zellepay.com/faq/what-zelle) payment system. It was a fast way to send and receive funds peer to peer between different bank accounts by only needing either the other person's email address or their U.S. mobile phone number.
By 2018, there were growing [concerns](https://www.nytimes.com/2018/04/22/business/zelle-banks-fraud.html) about fraud on Zelle. Despite its convenience, Zelle's design allows funds to transfer instantly and irreversibly, making it a target for scammers. Victims reported being defrauded through tactics like fake online sales or impersonation schemes, and many struggled to recover lost funds due to inconsistent fraud policies among banks. Consumer advocates criticized the platform for inadequate protections, urging banks to implement stronger safeguards to prevent fraud and better support affected customers.
In 2022, a Senate report [criticized](https://www.bankingdive.com/news/warren-zelle-fraud-scams-report-truist-pnc-us-bank-america-jpmorgan-wells-fargo-aba-bpi-cba/633305/) major U.S. banks, including JPMorgan Chase, Bank of America, and Wells Fargo, for failing to adequately protect consumers from fraud on the Zelle payment platform. The investigation revealed that these banks often deny reimbursement for scams where victims are tricked into transferring funds, citing a narrow interpretation of liability under the Electronic Fund Transfer Act. (*"While banks bear responsibility for unauthorized transactions to scammers, consumer-authorized transactions made to fraudsters are another matter”*.) Jamie Dimon, CEO of JPMorgan Chase, [explained](https://www.bankingdive.com/news/bank-ceos-defend-zelle-in-senate-hearing/632554/), *“Anything unauthorized, we do cover”*
On June 16, 2023, the United States Senate Committee on Homeland Security and Governmental Affairs subcommittee, the Permanent Subcommittee on Investigations, launched an inquiry into Early Warning Services and the three largest banks that co-own EWS: JPMorgan Chase, Bank of America, and Wells Fargo.
After a 15-month investigation, the Senate Permanent Subcommittee on Investigations released a [report](https://www.hsgac.senate.gov/wp-content/uploads/2024.7.23-PSI-Majority-Staff-Report-on-Zelle.pdf) on July 23, 2024, highlighting consumer fraud issues tied to the Zelle payment network. The report noted significant drops in the percentage of fraud disputes reimbursed—from 62% in 2019 to just 38% in 2023. Between 2021 and 2023 Zelle [refused](https://dailyhodl.com/2024/07/25/jpmorgan-chase-wells-fargo-and-bank-of-america-refuse-to-reimburse-863000000-to-customers-in-repeated-relentless-failure-to-protect-victims-of-fraud-us-senate-investigation/) to reimburse $880 million to customers who fell victim to fraud on their payment network. Bank employees were found to have broad discretion in deciding whether to reimburse fraud claims, often denying compensation without clear justification. This has raised questions about whether banks are meeting legal obligations under the Electronic Fund Transfer Act ([Regulation E](https://www.consumerfinance.gov/rules-policy/regulations/1005/))
Early Warning Services (EWS) runs the payment network Zelle at a financial loss but generates revenue by selling data-based services to financial institutions. EWS collects extensive consumer and bank data through its operation of Zelle and daily data-sharing agreements with its member banks. This data is used to develop fraud and risk management products, which EWS sells to financial institutions as its primary profit source. While EWS asserts it has not commercialized this data beyond these financial products, the sale of such services remains its main revenue driver.
On August 4, 2024, Senator Richard Blumenthal sent a [letter](https://www.hsgac.senate.gov/wp-content/uploads/2024.08.04-Blumenthal-Letter-to-Chopra.pdf) to CFPB Director Rohit Chopra urging immediate action to address fraud concerns tied to the Zelle payment platform. The letter calls for the Consumer Financial Protection Bureau (CFPB) to investigate their dispute resolution practices and ensure that they fully and promptly address consumer fraud reports. On August 7, 2024, it was [reported](https://www.reuters.com/business/finance/us-consumer-watchdog-probes-major-us-banks-over-zelle-scam-wsj-reports-2024-08-07/) that the Consumer Financial Protection Bureau was investigating several banks due to their handling of Zelle.
On December 20, 2024, The Consumer Financial Protection Bureau (CFPB) responded by [filing](https://files.consumerfinance.gov/f/documents/cfpb_Zelle-Complaint_2024-12.pdf) a lawsuit against Early Warning Services, LLC and the major banks including Bank of America, JPMorgan Chase, and Wells Fargo. The CFPB alleges that these institutions prioritized the rapid deployment of Zelle over implementing effective anti-fraud measures, resulting in significant consumer losses. The lawsuit contends that the defendants failed to adequately address these issues, often denying relief to defrauded consumers. The CFPB seeks injunctive relief, monetary compensation for affected consumers, and civil penalties.
Just 5 days before the Senate Permanent Subcommittee on Investigations released its report, the [Aspen Institute](https://www.aspeninstitute.org/) Financial Security Program (Aspen FSP) [announced](https://www.aspeninstitute.org/news/task-force-on-fraud-and-scams/) the formation of a National Task Force for Fraud & Scam Prevention with their founding sponsor JPMorganChase and executive sponsor Zelle. The stated purpose of the Task Force is to develop a unified national strategy to help the U.S. government and private sector companies work together to stop fraud and scams. [Members](https://fraudtaskforce.aspeninstitute.org/membership) of this private/public task force include: JPMorgan Chase, Bank of America, Wells Fargo, Google, Meta, Amazon, Visa, Mastercard, Verizon, the Federal Trade Commission, the FBI Criminal Investigation Unit, US Department of the Treasury, Homeland Security, and many others.
The Aspen Institute is a 501(c)(3) nonprofit located in Washington DC. In [2023](https://projects.propublica.org/nonprofits/organizations/840399006) they had revenue of $232M and total assets of $519M with the primary source of income coming from donations and federal grants. Per their [mission](https://www.aspeninstitute.org/what-we-do/) statement, their goal is "realizing a free, just, and equitable society." The Institute works to achieve this through creating and driving policy as well as training future policy leaders.
Recently on November 25, 2024, FinCen [announced](https://www.fincen.gov/news/news-releases/fincen-joins-public-private-partnership-combat-fraud-and-scams-impacting) they are also joining the National Task Force that *"brings together key stakeholders including the financial services sector, technology companies, consumer advocacy groups, information sharing and analysis centers, and federal government agencies to develop a comprehensive national strategy for combating fraud and scams."* In The Case for a Coordinated National Strategy to Prevent Fraud and Scams, the Task Force lists [key components](https://fraudtaskforce.aspeninstitute.org/time-is-now) of a national strategy to include improved education of consumers to identify fraud, enhanced information sharing across industry, law enforcement, and regulatory agencies by use of data exchanges and legal mechanisms for sharing information. As well as empowering law enforcement with additional authority and resources. The document cites the recent [UK action](https://www.gov.uk/government/news/new-powers-to-seize-cryptoassets-used-by-criminals-go-live) as an example of recent amendments to law enforcement powers which in England means police will no longer be required to arrest seizing crypto from a suspect, can seize written passwords or memory sticks, as well as transfer "crypto assets" to a law enforcement wallet.
In an August 2024 [interview](https://www.businessinsider.com/zelle-scams-how-to-get-money-back-2024-8?) with Fortune, Ben Chance, the Chief Fraud Risk Management Officer for Early Warning Services reportedly "told the outlet that the best way to prevent scams on money-sharing apps is better user education, sound policy and more funding for law enforcement." This sounds very similar to the National Strategy to Prevent Fraud and Scams being crafted by the National Task Force for Fraud & Scam Prevention, with more user education and law enforcement. No mention of standardized reimbursement policies or enhancing transparency around fraud investigations which are the primary accusations aimed at Zelle and its owners by the US Senate and the subject of the current investigation by the Consumer Financial Protection Bureau.
-

@ 21db9b8a:2a94c796
2025-02-14 03:37:49
Fair warning: This is an explicit and erotic story involving extremely taboo themes that would prevent it from being published on most sites that host erotic stories. All characters in this story are ***fictional only***. It is not in any way based on true events.
This is also not your average stroke story. It will be released in chapters, and while there ***is*** sexual content in each chapter, there is no full-on sex until late in chapter 4. It is a story of sexual discovery and exploration between young people who have few resources to educate them, but also few inhibitions to hold them back.
I hope you enjoy it. If not… Well… You don’t have to host it on your relay, and you can always mute me so you don’t see any more.
***
Dani barreled through the dining room in pursuit of her younger brother, Jake, who sped out the sliding glass door onto the back deck, making a feeble and unsuccessful attempt to close the door behind him as he ran. He had always been faster than Dani over short distances, and his recent growth spurt, just before turning thirteen, had made it that much more difficult to catch him.
"Give them back, you thief!" she shouted after him, taking just enough time to open and fully slide the door closed behind her, in order to avoid incurring her mother's wrath.
It was all the lead her brother needed. He leaped off the deck into the sunlit back yard and sprinted over to one of the tall maple trees at the edge of the lawn. By the time Dani had made it to the yard, her brother was already scurrying up the trunk with her sunglasses gripped between his teeth. Jake was younger than Dani by seventeen months, but he had recently grown to be two full inches taller than her, and he had begun to develop muscle tone to compliment his athleticism. It also helped him climb trees with frustrating ease.
Dani jogged to the base of the maple, which had no limbs for at least the first ten to twelve feet, and glared up at her brother lounging across two of the branches. He was now wearing her sunglasses to further taunt her. The twerp took his role as the annoying younger brother seriously, despite their age difference being relatively small. Dani's other two brothers, ages ten and seven, had thankfully not learned Jake's bad habits and generally left Dani alone, but her oldest brother seemed to make it his mission to infuriate her. It was just for sport, Dani knew, and Jake really was alright to be around most of the time, but let him get bored and it always seemed like she was the one who paid for it.
"Give me a break, Jacob William Hansen!" she demanded, using his full name like their mother often did when she wanted him to know he was in trouble. She shaded her eyes from the early summer sun as she continued to glare up at him. It did not seem to have the same effect as when her mother used it. "When you come down from there, I'll have your hide!"
"You may have my hide, Danielle Elizabeth Hansen,” he mocked, “but you won't have your glasses." With that, he plucked them from his face and hooked them over a smaller branch above him.
"You wouldn't dare leave them up there!" she asserted, not really sure whether he would or not. Jake knew better than to push things too far, but he might not consider abandoning her sunglasses in the limbs of a tree to count as 'too far'.
"What are you going to do? Go tell on me?" Of course, he knew she would not. They had long since stopped tattling on one another. In their household, the tattler often brought as much punishment upon him or herself as the one tattled on, and sometimes more. Instead, Jake and Dani had agreed to settle most matters between themselves, and only bring their parents in when it was more serious, like when Jake had planned to jump off the garage roof onto his skateboard, and Dani just knew he would have cracked open his skull if he had tried it.
"If you want your sunglasses back, you are just going to have to come up here and get them."
"How did you even make it up there?" she demanded. Dani was no slouch at climbing trees most of the time. She liked to play in the woods and didn't mind getting dirty, but the trees she climbed at least had branches close enough to the ground that she could jump up and grab hold of them. This maple had nothing but bare trunk for several feet above her head.
"You didn't see how I did it?" Jake asked. "You just have to wrap your legs around it and use them to hold on. Then grab as high as you can with your arms and pull your legs up higher."
Dani cocked an eyebrow at him dubiously, unsure whether she could mimic the technique. For one, her brother didn't have breasts to contend with, and Dani had been a bit of an early bloomer in that department. At fourteen, she already would have filled out a B-cup bra, if she ever wore anything other than sports bras. The lumps of fatty flesh sticking out from her chest were horribly annoying and always getting in the way. It seemed more than likely that her breasts would do just that while trying to shimmy up the tree as well.
Shrugging to herself she decided to give it a shot. She approached the trunk and wrapped her arms around it as high up as she could reach. She could just barely touch her fingers together on the other side when hugging as closely as her chest would allow. Supporting herself with her arms, she jumped and wrapped her legs around the trunk as well and felt the bark lightly scratching the inside of her thighs and back of her calves. It probably wasn't the best idea to be doing this in her cutoff jeans and a tank top, but it was far too warm out to wear her usual jeans and a hoodie. She would just have to tough her way through it.
Gritting her teeth she pushed her body upward with her legs, which invariably tugged the front of her tank top downward to expose part of her sports bra underneath, then she reached as high as she could with her arms and let her weight settle on them to pull her legs up again. This caused Dani's breasts, which were being crushed between her and the tree, to push upward, partially spilling out of the top of her sports bra and tank top. As predicted, they were getting in the way of things once again.
Dani was far too distracted to think about what kind of display she was putting on for her brother above her, though. As her weight had settled, her crotch had slid against the trunk and caused a pleasurable sensation to well up in her nether-regions. It was a shock to Dani, and she nearly let go of the tree. She'd never felt anything quite like that from “down there” before, and it was distractingly pleasant. She sat frozen in place for a moment, trying to make sense of the feeling.
"Well?" her brother voiced his impatience. "Are you just going to hang there like a koala or are you going to come get your shades?"
Letting out a low, frustrated growl, Dani continued upward, the pleasant sensation in her groin returning each time she slid it against the trunk. What on earth was going on? This was not a situation that should be causing her pleasure whatsoever, let alone down there. Her legs and arms felt like they had several new scrapes from the rough trunk, but her crotch was alight with a dull pleasurable throbbing that Dani had never experienced before. Then again, she'd never thought to rub it against anything before.
As she finally shimmied her way high enough to grab hold of the lower-most branch, Dani was panting from more than the sun's heat and her exertion. Pulling herself up onto the sturdy limb, she hoped her brother didn't notice the flush in her face or the way she self-consciously adjusted her tank top so that it properly covered what it was meant to. Then she looked up to see him holding her sunglasses out to her from the branch he was seated on.
"Not cool, Jake!" she chided, snatching her sunglasses from his hand and inspecting them for damage. Satisfied they were none the worse for wear, she slid them into her dark hair, which was pulled back into a loose ponytail that hung just past her shoulders, so that they rested securely atop her head.
"Oh stop your whining," he brushed off her anger. "You know you needed some motivation to get out of the kitchen. Mom has had you cooped up in there all morning."
"Yeah, that's because it gets too hot to bake in the afternoon, doofus! Don't you want fresh bread for the monstrous sandwich I'm sure you will somehow manage to stuff down your throat for lunch?"
"Fair point," Jake acknowledged. "But aren't you glad to get out and get your blood pumping?"
"No!" Dani retorted. "Look at me!" She held her scraped-up arms out for his inspection. "I blame you for this!"
"Oh come on! You love it!" Jake insisted. "I have seen you laughing off far worse war-wounds than that."
Dani sighed and shook her head at him. He was right, of course. She was known for playing hard. Hard enough to keep up with the boys in the neighborhood, who often used to wrestle her like she was one of them. At least, they had until recently. Since she'd developed breasts they all seemed scared of her. All except Jake, but he was her brother. They had never been awkward with one another, and he still didn't seem to notice that she was a girl, let alone growing into a woman.
For most of their childhood, Jake was the only playmate Dani had, so she had adapted to playing like a boy. Instead of Barbies and tea sets, it had been Legos and Nerf guns, and she had loved every minute of it, even if it did tend to come with a fair share of bruises and scrapes. And sure, Jake could be an absolute pest, but it was mutual antagonism born out of playful sibling affection.
"Fine," she admitted. "It was a welcome rescue from mom's home ec class. But you're still going to owe me for all the scrapes I have from climbing this tree. My legs are even worse than my arms!"
"I'm sure you'll think of some way to get sweet revenge," Jake laughed. "You always do."
Again, he was right. As much as Jake infuriated her with his taunting, teasing, and pranks, Dani could dish it right back at him. That was part of their strange sibling relationship that made it look to all on the outside like they couldn't stand one another, when in reality they were best friends and would do anything for the other when it really mattered.
"Alright, meat-brain," Dani changed the subject, using her favorite pet name for her brother. "Now that we're free of mom's clutches for the afternoon, what should we do with ourselves?"
"I don't know what you're going to do, but when Finn gets home from school, we're going fishing."
Finn was Jake's best friend who lived just a few houses down from them. While Jake, Dani, and their siblings were homeschooled by their mother, Finn went to public school and wouldn't be getting home until mid afternoon. Soon school would be out for the summer, making Jake and Finn nearly inseparable during daylight hours, but that was still a week and a half away, despite the heat wave they were getting in early June, and then Finn's family would be going to summer camp for three weeks, so the boys were taking advantage of as much time as they could get to hang out while they had the chance. Dani knew that she only had a short time while Finn was at camp to have her brother to herself before he would be all but lost to her for three months, since Jake and Finn usually didn't like having her along with them anymore. They had played together for years, but over the last several months, the two boys had started excluding her from their activities.
That left Dani feeling quite alone when Jake and Finn rode their bikes off to wherever they hung out these days. She had no friends of her own in the neighborhood. Her closest female friend, Audrey, lived almost a half-hour away, in a small town to the north, so they only really got to see each other at church, and the occasional planned sleepover.
"Fine, ditch your sister, as usual," Dani complained, rolling her eyes at her brother.
"Don't be like that, Dani," Jake protested. "It's just awkward talking about girls with your sister around, ya know?"
"Like you actually have any girls to talk about!" she teased.
"Maybe not, but a guy can live vicariously through his best friend, can't he?"
"Ha!" Dani scoffed. "I seriously doubt Finley O'Connor has a lineup of girls to give you all the juicy details about, either. At least not any that aren't figments of his imagination."
"You might be surprised."
Was that a blush that suddenly appeared on Jake's face? Had she misjudged Finn? Jake's best friend was not what she would think of as a chick-magnet. He was a bean-pole of a boy with an unkempt mop of red hair topping his head. He had a mouth that was too large for his face that always seemed to be twisted in a mischievous grin, and an over-abundance of freckles that covered every inch of him that Dani had ever seen, which was most of him since he often accompanied their family to go swimming at the river. He did not fit into Dani's definition of attractive, nor any other girl she knew. Not that she knew many other girls well enough to talk about boys with them.
"Whatever you say, meat brain," Dani said, shifting on the branch and dropping to hang beneath it before letting go to allow herself to fall the three or four feet down to the ground. She landed on her feet, bending her legs deeply to absorb the impact, then stood up straight and defiant. Brushing her hands off on the sides of her cutoffs and looking back up at her brother. "I'll just have to figure out how to keep myself occupied, as always."
There was more disappointment in her voice than she had intended. She didn't really want to make him feel bad for leaving her without anyone to hang out with for the afternoon. She could find things to do to keep herself busy. For one, she could help her younger brothers finish up their school work, though that would likely only get her through the first hour after lunchtime or so. The benefit of being homeschooled was that you could easily get all your work done for the day in just a few short hours, instead of being cooped up in a classroom the whole day like the public-schoolers had to endure. Of course, that was also the downside, because you then had to figure out what you would do with all the extra time you had.
Then Dani remembered the pleasurable sensation she had experienced while climbing the tree. That was certainly something she could investigate this afternoon while Jake was off gallivanting with Finn. She wanted to see if that feeling could be repeated, or if it was just some kind of fluke. She wasn't about to go rub her crotch against trees where anyone might see her, though. Perhaps she could find somewhere more discreet to experiment and see if that sensation returned. It had felt SO GOOD! Surely she could find a way to make it happen again.
***
Jake watched as his sister strolled away from the tree back toward the house, her round bottom framed enticingly in her cutoff jeans. He couldn't believe he was looking at her that way; she was his sister after all, not some random girl like the ones Finn liked to show him. Yet, after watching her climb the tree to retrieve her stolen sunglasses from him, Jake could not deny that she possessed every quality that made those girls on Finn's tablet so appealing.
Finn had been sharing pictures of naked and nearly-naked girls with Jake almost since he had gotten the tablet as a Christmas present last year. Well, Jake supposed they were actually women, not girls, since they all looked much older than Dani, and most had more pronounced curves. Then again, that could just be because he was seeing them without their clothes on, while Dani's curves were usually covered up. And Dani definitely did have some curves that Jake could no longer help but notice, especially after the display he had just seen.
From his perch in the branches of the maple tree, Jake had a perfect view down the front of his sister's tank top as she had shimmied her way up the trunk. No, he had not seen her nipples - her sports bra had done it's job of holding them in - but her round breasts pressing up prominently every time she let her weight rest on her arms made it clear that she was no longer the flat-chested little girl he somehow had still thought of her as. He should not have been so naive. He knew his own body had changed drastically, but had not even considered that his sister's was changing as well, let alone that she might just look a lot like the women in those pictures when she took her clothes off.
Jake frowned, noticing that his thoughts had made his dick stiffen in his pants. These were not thoughts he should be having about his sister! Hopefully Finn would have some new pictures to distract him away from thinking of Dani in that context. For that reason and more, Jake looked forward to his friend getting home from school, when the two of them could head out to do some "fishing". Oh, they might do a bit of actual fishing as well, but most of their time would likely be spent at their fort in the woods, well away from any prying eyes, while Finn shared his latest photographic acquisitions.
It would still be a few hours before the bus dropped his friend off where their street connected to the main road, so Jake resigned himself to finding something else to distract him from thoughts of his sister until then. It was too nice a day to expect that he could get away with playing Xbox in the basement game room. His brother, Travis, should be done with his school work by now, though, and always enjoyed tinkering with bikes in the garage with him, so Jake dropped out of the tree and headed toward the house to seek his brother out.
He crossed the back lawn and their dog, Dozer, ran to meet him. He was a massive brute of a dog, being a full-bred Rottweiler, but he was as gentle and loyal as anyone could ask for with the Hansen children. Jake patted the dog's blocky head and rubbed his ears as he strode toward the back deck. He skirted around the left side of the deck and down the concrete stairs to an exterior door that led directly to the basement where he expected he would find his brother.
All of the Hansen boys had rooms in the basement. Jake, as the oldest boy, had his own, while Travis and Aaron shared a room on the opposite end, next to the bathroom, with the game room and stairs up to the front entryway situated conveniently in-between. At age ten, Travis was three years younger than Jake, though he would be turning eleven in the fall, so it was more like two and a half years. Aaron was another three years younger than that, at age seven. The two of them were very close, just like Jake and Dani had always been, but lately Travis had been wanting to spend more time with Jake, whenever the older boy would allow it.
The last of the Hansen children was their adopted sister, Rebecca, who was only two years old. Everyone called her Bec, and she lived in the nursery upstairs next to their parents' master bedroom. Their family had fostered her as an infant, and finally adopted her just last year. Dani had been thrilled to finally have a sister, despite the massive age difference, and couldn't wait to teach the child all about being a girl. Not that Dani really had any clue how to be a girl herself, having grown up with three brothers.
As expected, when Jake opened the door into the basement, which opened into their game room, his younger brother was seated facing him on the couch with an Xbox controller in hand, transfixed by the large flat screen television on the wall. He looked quite a lot like Jake, with his short, brown hair and blue eyes. The younger boy hadn’t yet started to fill out with muscle tone, though, making him look scrawny, with a head too large for his stringy limbs. The effect was particularly humorous when he stood next to Jake.
"You'd better not let mom or dad catch you on that when the sun's out," Jake warned his brother.
"Mom's still busy helping Aaron with his math, and Dad's working on tonight's sermon," Travis assured him. "Besides, I was going to get off in just a few minutes anyway."
"Oh trust me," Jake began, crossing to the couch and sitting next to his brother, to see that he was playing Minecraft. "I know how 'just a few minutes' can turn into several hours without even realizing it. Why don't you come hang out in the garage and we'll get that chain tightened on your bike so it's not always falling off on you."
"Really!?" Travis exclaimed, putting the controller down and turning to Jake with an excited look on his face.
"Of course, runt!" Jake had continued to call his brother the pet name even after Aaron was born, much to Travis' chagrin. "What are big brother's for?"
He wasn't about to tell him that the reason he was suddenly so willing to help his little brother out was to take his mind off of thinking about Dani. Seeing her round breasts pressing out of the top of her tank top had shattered Jake's ability to think of her in practically the same terms as his brothers, or one of his male friends. Now he found himself remembering her long, smooth legs, and round bottom swaying back and forth hypnotically as she had walked back toward the house, and it seemed the more he told himself he shouldn't think of her that way, the harder it was not to.
Travis shut off the Xbox and the two boys marched up the stairs toward the door to the garage. As Jake pulled it open, he heard his mom call out from the dining room. "You boys don't go far! Lunchtime is coming in thirty minutes!"
"Don't worry mom!" Jake called back. "Travis and I will just be in the garage working on his bike!"
He didn't wait for a response before disappearing into the dark and hitting the button on the wall to open the massive roll up door on the two-car garage, allowing the sunlight to flood in. Then he and Travis went to work on the bike, not only tightening the chain, but straightening the handlebars that had been twisted to one side when Travis had crashed into a tree, and replacing one of the pedals that had nearly fallen apart since it was a hand-me-down bike from someone at their church. Travis was thrilled and rode the bike up and down their short driveway and around the cul-de-sac until their mother called them in for lunch.
After scarfing down a massive sandwich, as Dani had predicted, a bag of chips, and a banana, Jake offered to take Travis and Aaron on bike ride to the park and back to pass the time until Finn got home from school. He worried that Dani might want to come, too, but she had disappeared as soon as she was done with lunch without a word. That was highly unusual for her, but not unwelcome since Jake wasn't sure how he would keep himself from ogling her body if she came along.
Thankfully, the bike ride with his younger brothers ate up a fair amount of the afternoon. When the time finally came for Finn to be dropped off, Jake let his mom know where he was going then grabbed his fishing pole and tackle box and hopped on his bike once again to pedal down to the corner where the bus dropped off all the kids that lived on their street. He arrived just as the bus was pulling away, and saw his friend, backpack slung casually across one shoulder, strolling toward him among four other kids from the neighborhood of various ages.
"Jeez Jake!" Finn exclaimed. "You must have been bored out of your mind to meet me right as I got dropped off!"
"Let's just say I'm glad you're finally home," Jake responded, swinging his leg across the back of his bike to dismount and turning it around to walk along side his friend back the direction he had come.
"Yeah, I'm finally free from that prison, even if it is only until tomorrow," Finn joked. "Seriously, though, you usually come find me at home, after I've had a chance to ditch my bag and pack us some snacks. What gives?"
Jake sighed. He certainly wasn't going to tell his friend the real reason he was so eager to hang out with him. What would Finn think of him if he knew he was having dirty thoughts about his own sister?
"It's been a long day, is all," he said finally, and that was partially true. It ***had*** felt exceptionally long. "And we won't be able to stay out long tonight, since I have church."
"Oh that's right, it's Wednesday, so you have to go be an altar boy tonight," Finn teased. "No wonder you want to get your debauchery in ahead of time."
"It's not like that..." Jake protested halfheartedly. "But now that you mention it, do you have any new pictures to share?"
Finn glanced around them to see if any of the other kids who had gotten off the bus were still walking close by, but they had all split off to head to their own homes.
"Dude... I've found us some good ones. You'll have jerk-off material for the next month! Or you would if you had a photographic memory."
"Oh shut it!" Jake said, punching his friend's shoulder. "It's not like your memory is any better."
"Doesn't have to be. I'm the one with the tablet," Finn pointed out as they turned into his driveway and Jake laid his bike down carefully on the front lawn, making sure the fishing gear didn't get damaged.
"You say that now, but just make sure your parents don't catch you with those pictures saved on it," Jake warned.
"Oh, don't worry about that," Finn assured him. "My parent's don't check what I've been doing on it. They only got it for me because they figure it will keep me from being too noisy and disturbing their peace. I doubt they could even figure out how to turn it on."
Finn wasn't exaggerating. His parents were much older than Jake's, and had not grown up with computers. They had both been married before and had adult children from their previous marriages, some of whom had their own kids already. They got together and had Finn and his older brother Scott when they were both in their forties. Now they were in their late fifties and far from being computer literate. The only reason they had an internet connection at all was because it had come with their cable TV plan and Scott had set it up.
"Wait here for a minute," Finn instructed. "I just have to drop off my bag and grab my gear." With that the red head disappeared inside his front door, appearing a few short minutes later with his own fishing pole and tackle box. He'd also changed into shorts and a t-shirt. As he approached, he popped open his tackle box and showed Jake that his tablet was tucked inside, then he retrieved his own bike from the side of the garage and the two boys headed out.
They rode through the park and out of the back of the neighborhood, where it was bordered by logging company land, serviced by a bumpy dirt road. Nearly a mile down the dirt road, they cut into the woods, stowing their bikes in some bushes. The forest was thick here, and full of fallen logs that the boys deftly maneuvered over and around to reach their destination. Barely visible in the undergrowth ahead was a short, vaguely unnaturally shaped structure that was the fort the two of them had constructed the previous summer, and had continued to improve upon since then. It was made entirely of natural materials, a fact that Jake was particularly proud of, and only large enough for three or four to sit in comfortably. They had constructed it by lashing logs together using roots and vines and anything else that would work as cordage, then taking evergreen boughs to create a roof and walls that did a fair job of blocking the wind, though a less fair job of keeping out the rain, as they had discovered the hard way.
The important thing was, the fort was a place they could reasonably expect to be left alone. Even in hunting season, not many people were wandering these woods, since they were too close to residential neighborhoods to safely shoot a rifle. The logging company that owned the land didn't even seem to have any intention of logging it anytime soon. They might have in years past, but that was before the city had grown so much that all the neighborhoods had sprung up around it. Indeed, the most likely event would be that the logging company would sell the land to a developer and yet another neighborhood would be built. Until then, Jake and his friend could use their fort to hide away and look at dirty pictures on Finn's tablet.
The two of them crawled through the small opening that served as a doorway and Jake was immediately enveloped by the scent of pine and spruce from the boughs laid on the walls, roof, and even the floor of their fort, to make it more comfortable to sit inside. The interior was not tall enough for him to stand, though he could move around on his knees without his head brushing against the roof, and the evergreen boughs were so thickly piled on the walls and roof that the only light within was the meager amount that filtered through the doorway. Jake took a seat with his back to one of the walls while Finn sat beside him and powered up his tablet.
"I have some real babes to show you today, my friend," Finn bragged, punching in his security code so that the tablet allowed him access to his home screen. Then he tapped the icon for the photos app and turned the screen so Jake could see it better.
Inside the dim fort, the tablet seemed to blaze with light as an image filled its screen. The picture was of a stunning blonde with wavy hair hanging loose to her shoulders. She was facing toward the camera as though looking past it into the distance while standing in a mostly empty room, though the background was too blurry to pick out any details. The shot only showed her from the waist up, and she was unbuttoning a pair of white jeans, though it was impossible to tell if they were pants or shorts. The top half of her body was completely bare, and her large breasts stood out proudly above her toned stomach. She was absolutely magnificent! She didn't have the biggest tits out of all the girls Finn had shown him before, but they were more than adequately large, perfectly round, and had similarly rounded areolas tipped with eraser shaped nipples. Her skin was the perfect shade of tan, with no tan-lines whatsoever.
"She's a stunner, right?" Finn asked, seeing Jake's reaction. "Her name's Nata Lee, or at least that's what she calls herself. She's got loads of pictures with her clothes on, but this is one of the only ones I could find where she shows her tits."
"She's a babe, for sure," Jake agreed, still staring at the photo. Finn swiped his finger across the screen and a new photo took the place of the stunning blonde.
Pictured was a young woman with dark blonde hair with a hint of red, tied back in a short ponytail. She was laying completely naked on a white couch with the photo taken from above looking down on her. She was staring straight into the camera, a mischievous smile on her face, with one hand caressing her shoulder and the other pressing in on an ample breast. Her breasts were easily as large as the first girl's, but they seemed to sag more. Her areolas were more oval in shape, and didn't contrast with her skin tone as much. The main attraction, though, was the bottom half of her body, with her legs spread wide to reveal her shaved pussy, it's pink inner folds poking out from between the soft outer lips. She was equally as gorgeous as the first girl, though in a decidedly different way. This girl looked like more fun, while the first looked more serious. The way her hair was tied back in a ponytail made her look younger, too, though there was no way she was anywhere near his age with tits like those. Something about her smile made Jake's cock twitch even more than looking at her naked body. It held the promise of delights he had never dreamed of.
"Another one you approve of, I take it?" Finn asked with a laugh. "Just wait. They get even better."
Swiping the screen again, a close-up image of a shaven pussy and the woman's inner thighs filled the screen. The inner folds of the pussy glistened with moisture and they were parted, revealing an oblong opening into her depths.
"Why is she wet down there?" Jake asked, transfixed by the high resolution close-up that showed her every fold and goose-bump.
"I don't know, maybe she just went pee," Finn replied. "But that's where you stick your dick in." He pointed to the opening.
"Wow..." Jake breathed. "That's crazy..."
Finn swiped the screen again, much to Jake's dismay, but his disappointment at not getting more time to inspect such a detailed image of a pussy evaporated as the next image filled the screen. It was of a brunette with long, dark hair hanging loosely over her shoulder as she leaned against a wall. The shot was taken from an angle to her left side, though not fully a profile shot, and only showed her from the chest up. What was visible was completely exposed, and she had slightly tanned skin and perky breasts that were nowhere near as big as the previous girls’, though they were adequately round, with erect nipples and round areolas that contrasted nicely with her skin tone. Somehow, those breasts were even more alluring to Jake, even though they weren't as large. What shocked and captivated him, though, was her face. Her round nose, full lips with just the hint of a smile, and thin, dark eyebrows hanging just above her sultry eyes, made her look uncannily like an older version of Dani. His sister still possessed a bit more girlish roundness to her cheeks and innocence in her eyes, and usually kept her long hair tied back and out of the way, but there was no denying the strong resemblance. Was this what she would look like with her hair down and a few more years of growing up? This girl's breasts were probably closer to the same size as Dani's, too. Was that what his sister's tits looked like under her shirt and sports bra?
The image had only been on the screen for a few seconds when Finn suddenly swiped it away saying, "Sorry, I thought I had deleted that one."
"What? Why?" Jake asked, looking up from the tablet, which now had a busty redhead filling the screen.
"Because..." Finn hesitated. "That one looks a lot like your sister, and I thought that might be weird."
"Oh..." Jake said, feeling his face turn crimson and suddenly glad that it was too dark in the fort for his friend to see. "I... I hadn't really noticed."
Finn chuckled nervously and said, "I suppose you wouldn't if your attention was on her tits the whole time."
"Right?" Jake agreed, adding his own nervous laugh. Then it suddenly hit him that his friend had been looking at pictures of someone who looked like his sister. "Hey! Why did you have that picture in the first place if you know it looks like Dani?"
"Chill bro!" Finn started, setting the tablet down on the opposite side of him from Jake and putting his hands up defensively. "I am sure that all of these girls look like the sisters of someone we know."
"That's probably true, but this one looks like ***my*** sister, and you ***knew*** it did when you saved it to your tablet!" The heat in Jake's face was growing and he wasn't sure if it was because of his embarrassment or his anger at his friend.
"Look, I can understand why you're mad. You have every right to be the protective brother." Finn edged away from Jake a few inches as he spoke. "But before you pummel me, you have to admit that Dani is hot as fuck, and I am not going to be the only guy to notice."
Jake certainly did ***not*** want to admit that his sister was hot, but then hadn't that been his issue all afternoon? He'd never thought of her in those terms before, but he'd suddenly had her femininity thrust in his face and he had to admit that it was really messing with his perception of her. Now, after seeing a picture of a naked woman who looked uncannily similar to her, it was even harder not to think of Dani as incredibly attractive, or as Finn had put it, "hot as fuck".
The steam had been taken out of his anger, but Jake still wasn't in any mood to hang out with his friend, knowing that Finn had thought of Dani in similar terms as he was reluctantly having to admit he now did as well. Finn was right, of course, and there would probably be loads of guys who would think of his sister that way, but Jake simply wasn't prepared to find her attractive himself, let alone for anyone else to have the same opinion.
"Whatever, man..." Jake said, crawling to the doorway. "I'm going home to get dinner before church tonight. Maybe we can go fishing tomorrow." The tone of his voice made it plain that he didn't plan on it. He emerged from the fort and retrieved his bike from the bushes without even waiting for Finn's reply. How on earth was he going to make sense of his friend's dirty thoughts about his sister if he couldn't even make sense of his own?
***
As Dani rode home from church that night, she thought back on the events of the day. After chasing Jake out of the house to retrieve her sunglasses, and discovering the pleasant sensation in her groin when she rubbed it against the tree while climbing up after him, she had looked forward to finding herself some alone time to see if she could make it happen again. First, though, she had helped tutor her youngest brother, Aaron, with his math, his least favorite subject because he struggled with it so much. Then it had been lunch time and Dani had started to wonder how she could possibly find any time to herself for the afternoon. In a household of five children, there wasn't a lot of alone time to be had, and since her bedroom was right next to the living room on the ground level, she could not expect to get away with hiding in there; certainly not with the sun shining outside. Her mother would ensure that all the children spent ample time outdoors as long as the weather was good, and June had been unseasonably clear and hot so far.
As much as Dani wanted to investigate whether she could reproduce that warm and pleasurable feeling, she couldn't just go rubbing her crotch against objects where anyone might see her. With the privacy of her own room out of the question until later that evening, that left only the tree-house in the back yard, but that was Travis and Aaron's favorite hang-out spot most afternoons. Fortunately, Jake had unwittingly come to the rescue by taking the other boys with him on a bike ride. That in itself was odd. Usually Jake would spend most of the day until Finn got home from school hanging out with her. Yet, today he seemed to have avoided her like the plague after stealing her sunglasses that morning. She decided she would need to find out what that was all about if it continued, but for today it had worked to her advantage, affording her the alone time she craved.
Dani had gone out to the tree-house immediately after her brothers left for their bike ride. It was situated at the back of their property, built around the trunk of another of the massive maple trees, with a ladder leading up to a trap door in its floor. It was not terribly high off the ground, only ten to twelve feet or so, but that was high enough that no one standing on the ground could see inside the small windows. Once inside, Dani knew she could expect near complete privacy, especially since the branches of the tree hid the tree house windows from anyone on the second floor of their home looking toward the back of the property.
Hesitantly, Dani had gone to the trunk of the tree sticking up through the middle of the tree-house floor. It had a slightly larger circumference than the one she had climbed that morning, but she could still wrap her legs all the way around it. She could not do the same with her arms, however, so she leaned back and supported her weight with her hands on the rough planks beneath her. This didn't allow her to move her hips nearly enough to rub herself against the tree, so she let her feet fall to the floor as well. This gave her the freedom of motion she needed, and also allowed her to control how much pressure she exerted as she slid her cutoff jean clad crotch against the tree. The sensation was nearly immediate; a dull, warm pleasure welling up from between her legs. She continued to move her hips up and down, sliding herself against the tree's firm girth, the roughness of the bark dulled by the layers of cloth between it and her skin. The sensation seemed to build with each repeated grinding of her hips, but so did her fatigue. It was hard work to hold her whole body suspended in the air with just her arms and legs while she pumped and ground her groin against the trunk. Soon she was forced to collapse to the floor in exhaustion, despite how good it felt and how much she wanted to keep going.
She needed to find something else she could rub herself against. Something that didn't require her to hold herself up the whole time, but the inside of the tree-house was pretty sparse. There were a couple of beanbag chairs and a small table between them acting as the only furniture, but that was about all, aside from a few action figures and Lego bricks her brothers had left strewn across the floor. She wondered if she might be able to use her own hand instead, and went over to recline in one of the beanbag chairs. Spreading her legs, she placed the palm of her hand on the crotch of her cutoffs and gently rubbed downward and back up. The sensation was pleasant, but not as strong as it had been while rubbing against the tree trunk. She continued to rub herself for several minutes, but the sensation just stayed a dull, pleasurable ache, rather than building upon itself as it had when grinding against something more firm and solid, not to mention more textured, than the palm of her own hand.
Frustrated, Dani had spent the rest of the afternoon playing with their dog and then helped her mother prepare for dinner. Now that she had a bit more time to think about what had happened, though, she wondered if the sensation with her hand might have been stronger if she didn't have the thick fabric of her cutoffs in the way. She would have the perfect opportunity to test that theory not long after getting home, since Wednesday night was her turn to take a shower. Dani liked to take her showers late in the evening, if possible. It always felt good to go to bed fresh and clean, and it was relaxing to brush and dry her long hair, which usually helped her wind down for sleep. The shower would also be the perfect opportunity to be alone and try rubbing herself without any clothing in-between her hand and her vagina, which seemed to be the source of the pleasant sensation.
When their minivan pulled into the garage, the whole family piled out, filed into the house through the door to the main entryway, and split off in various directions. Dani's mother and father went upstairs to put Bec down for bed, her brothers went downstairs to get their pajamas on and brush their teeth, and Dani went through the kitchen and living room to get all the way around to her own bedroom. Once there, she retrieved her shower supplies from atop her vanity across from her bed. Her bathroom doubled as the family and guest bathroom, and was too small for Dani to leave all of her things laying around on the counter like her brothers could in their larger bathroom downstairs. She was allowed to leave her shampoo and body wash in the shower, because it was hidden from guests by the closed shower door. She was also permitted to leave her toothbrush and toothpaste inside the medicine cabinet behind the over-sink mirror. But she had to keep her razor, shaving gel, deodorant, and towels in her own room and take anything she needed with her to use the shower. This resulted in Dani doing as little of her hygiene in the bathroom as she could get away with, using her vanity in her bedroom instead.
Dani brought a towel for her hair, another for her body, and her bathrobe with her as she exited her room and crossed behind the living room couch to the small bathroom beyond. Closing and locking the door behind her, she crossed the room and locked the opposite door as well. Whoever had designed their home had thought it would be convenient to have access to the bathroom from both the living room and the kitchen. In reality it had just been more hassle remembering to lock and unlock both doors instead of just one. Indeed, it had led to more than one awkward encounter when she had forgotten to lock one door or the other before using the toilet, only to have her father or one of her brothers barge in on her by mistake. Having ensured a similarly embarrassing event would not occur this evening, Dani set her things on the small counter next to the sink and began to disrobe, letting each article of clothing fall to the floor. Then she pulled out the hair tie holding her ponytail back and strode naked over to the shower stall. The bathroom was too small to fit a tub, but Dani didn't mind most of the time. If she really wanted to take a bath, her parents would often let her use the massive tub in their master bathroom upstairs, rather than make her use the one in her brothers' bathroom in the basement. Most of the time she just wanted to get clean and be done with it, though, so a shower suited her fine.
She turned on the water and waited for it to get warm enough to step in, then turned it up until it was just this side of scalding, the way she liked it. When the steaming hot water poured over her skin, she let out a deep and relaxed sigh of pleasure, then got her hair thoroughly wet before sudsing it up with shampoo and rinsing it out, enjoying every second of the cleansing heat. Her plans of trying to give herself pleasure again were nearly forgotten as she lost herself in the soothing waters, until she started soaping up her body and she got to washing her more sensitive regions. As her fingers moved through the tuft of hair on the mound above her vagina she remembered that she was going to try to use her hand to rub against her bare skin and see if that made any difference. Dipping her hand lower, she put pressure against her mound and the outer lips of her vagina with her palm of her hand, the water and soap allowing it to slide smoothly along without any noticeable friction. Her body responded with a slight pleasurable ache, encouraging her to continue.
As she slowly rubbed the palm of her hand up and down against her sex, she felt the sensation begin to build upon itself, growing in strength and demand for more. Her hips had begun pressing into the motions of her hand almost of their own accord and Dani was surprised to feel something between the outer folds of her vagina that had grown firm. It was like a shallow ridge with a round nub, protected beneath the folds of skin. Experimentally, she let her palm drift higher over her mound, and ran two of her fingers to either side of the nub. The resulting shudder of pleasure was almost overwhelming, making her legs feel weak so that she had to lean against the shower wall to remain upright. Whatever that was, it felt ***AMAZING***, and was most certainly the source of the pleasurable sensations.
Dani focused her attention on that nub, running her fingers up and down, around, and across it, enjoying every spark of more and more intense pleasure that erupted as a result. She was not prepared for what happened next, as her whole body suddenly went tense involuntarily, and pleasure exploded inside her, pulsing and throbbing through her whole core. She gasped in surprise and bit her lip hard to keep herself from calling out, since she knew her parents were likely watching TV just beyond the bathroom wall. Her legs could not hold her anymore, and she let herself slide down the smooth side of the shower stall, her fingers still gently teasing the center of her pleasure as wave after wave of sensation wracked her body. Each wave eventually seemed smaller and less intense than the last until it finally subsided, leaving behind a satisfied hum of pleasure as Dani's breath came in desperate heaves.
She had no idea what had just happened, but it had been utterly fantastic! She knew instantly that this would be her new shower-time routine, maybe even nightly bedtime routine, from now on. She had no idea she could give herself such pure and intense bliss! Absently, she wondered if her friend Audrey was aware of it. Maybe it was just something unique to Dani, and Audrey would look at her like a weirdo when she asked, but she decided she must find out for sure the next time she had opportunity to hang out with her friend.
When her breathing finally returned to normal, Dani collected herself from the shower floor and finished washing before shutting off the water and grabbing one of her towels. She hoped that her parents hadn't noticed how much longer of a shower she had taken than normal, as she didn't want to try and explain why. She could probably come up with an excuse if she thought about it, but her brain wasn't firing on all cylinders after that incredible experience. As she tied a second towel around her still soaking wet hair, she thought to herself that even though she'd just moments ago enjoyed the deepest pleasure she’d ever felt, she couldn't wait to try it again.
***
Jake lay in his bed trying to focus on reading a book, but found that he could not keep his mind on the task at hand. His brothers had already gone to bed, and he could hear the water running upstairs where his sister still taking a shower. Meanwhile, his parents were probably watching TV in the living room, unless Bec had given them trouble trying to put her down for the night. As one of the oldest two Hansen children, Jake was allowed to stay up later than his younger brothers, but because they were trying to sleep, he was restricted to having quiet time in his room. Normally he'd be fine with that. He enjoyed reading, or drawing, or whittling with his pocketknife, but tonight was different.
All through church, Jake had been distracted from the youth pastor’s message by the image he'd seen on Finn's tablet screen that afternoon. He had nearly forgotten the other pictures, but the one of the woman who looked so much like Dani was firmly lodged in his brain, even though he'd only seen it for a few seconds. The perky breasts with erect nipples jutting out below elegant collar bones and satin smooth skin were burned into his memory, along with that slight, knowing smile and seductive eyes. It was his sister's face, even if obviously more mature and angular. Was there a similar resemblance to his sister's body? He'd probably never know. Dani was just one floor above him, completely naked in the shower, but beyond his gaze. He'd have no excuse to go anywhere near that bathroom to even attempt to catch a glimpse of her. Even if he tried, his sister was always good about locking the door since she lived with three brothers.
Then a thought occurred to him: Dani wouldn't just be undressed in the bathroom for her shower. He'd sat in the living room watching a movie with his parents before and seen her come out of the bathroom wrapped in her robe to scurry across to her bedroom to change into pajamas. That meant she would be naked in her bedroom, too, at least for a short time. Moreover, her bedroom had a window that she always complained was pointless because the only thing she could see out of it was the overgrown rhododendron bush planted outside. It was so big and thick with foliage that she could not even see through it to the side fence between their yard and the forest beyond. For his part, Jake had always retorted that at least she had a window, since his basement bedroom had none. The only thing on that side of the house outside Dani's window was a completely unused space intended for parking an RV, which the Hansens could never afford on their father’s pastor salary. If Jake was quiet about it, he could sneak out the basement door into the back yard, and around to Dani's window. By now it was dark enough that he probably would not be seen, if he was careful. He would have to hurry, though, because he had just heard the shower water stop.
Not wasting any more time thinking about it, he sat up, closed his book, and set it on the bed before throwing on some shoes and a light jacket, since the night air would likely be cool. Then he crept out of his room as quietly as he could to avoid alerting his brothers, in case they were still awake in their bedroom on the opposite side of the game room. The basement was dark, but Jake could easily navigate past the couch and coffee table on his left to the basement's exterior door. He eased it open, stepped outside, and closed it again just as silently, then crept up the concrete stairs to the back lawn.
Alerted to his presence, Dozer gave a low bark of alarm, then noticed it was him and trotted over from his dog house by the fence. Jake gave the big dog a pat then commanded him to go lie down in a stern whisper. The dog obeyed, returning the way he had come to plop down in front of his dog house. Jake let out a sigh of relief and continued around the corner of the house to the side where the rhododendron bush grew in front of Dani's window. The window itself was dark as Jake made his way toward it and he worried that he might have been too slow; that his sister might have already dressed in her pajamas and tucked herself into bed. Determined to confirm if that was the case, he crept closer, easing himself behind the massive bush and resting on his knees before inching his head up to the bottom corner of his sister's window. As his eyes peeked up to peer inside her room, he found that it was too dark to see anything but her window blinds, which were open to allow the sunlight in during the day. Between the blinds, all he could make out was the vague shape of her bed to his right, and her vanity on the opposite wall to his left. Beyond her bed he could make out the strong right angle of her closet door, but no details at all. Not enough to confirm whether his sister was in bed already or not.
Suddenly, a long, vertical sliver of light appeared at the back left end of the room and grew wider as the door was opened, then light flooded his eyes as Dani turned on her bedroom light. Instinctively, Jake ducked below the window, blinking away his light-blindness, then set his resolve and peeked back into his sister's room.
Dani had closed her door and was tossing an armload of her clothes into a hamper next to her vanity. She then hung a towel from the post at the foot of her bed that was farthest from the window and began to unwrap the towel on her head from around her hair, using it to tousle the long locks and help them dry. She then moved closer to the window in order to place this towel on the other post on the opposite corner of the foot of her bed. At last she moved on to what Jake had been waiting for: she undid the tie at the waist of her robe and casually let it fall to the floor.
Jake nearly gasped at the sight of his sister's suddenly naked form. She was absolutely exquisite! Unlike the girl in the photo, she had obvious, though light, tan lines on her legs and shoulders from her cutoffs and tank top that she wore on particularly warm days. Her wet hair hung heavily past her shoulders, brushing against her skin as she moved, bumping enticingly against her breasts. And Dani's breasts were mesmerizing as they jiggled slightly on her chest while she ran her fingers through her wet hair, tossing it behind her. They definitely were not as big as the tits on the first two girls Finn had shown him that afternoon - maybe not even as big as the woman who was Dani's lookalike - but they were perky, round, and firm like only a teenage girl's tits could be, with cute nipples standing out proudly from being exposed to the air.
Jake didn't get a chance to let his gaze drift lower before Dani turned to go take a seat at her vanity, revealing a round, bubble butt for a few precious seconds before she sat down. From his angle at the window, he couldn't see Dani's reflection in her vanity's mirror, but he did get a delicious view of the side of her left breast as she grabbed her hairbrush and began working tangles out of her long hair, causing the round breast to bounce playfully and sway slightly.
He was rooted to the spot as surely as the rhododendron bush beside him as he watched his naked sister brush and dry her hair. Her skin was so perfect, and her proportions so petite, and yet toned and athletic at the same time. He could see the muscles of her arms and shoulders moving beneath her smooth skin, and the graceful slope where her neck met with her torso. How had he never noticed this before? It wasn't as if all of these things had been hidden under her clothing. He had just never paid attention until now.
Finished with her hair, Dani got up from the vanity and strode over to her closet, giving Jake his first look at her pussy with it's clump of bush on the mound above it. That was something he hadn't seen before. All of the vaginas he had seen on Finn's tablet had been bare, but Dani's had hair similar to the fuzz surrounding Jake’s own dick. Her breasts bounced with each step across the room until she turned her back to the window and opened her closet door. Jake enjoyed another glorious viewing of her round ass while she fished clothing out, then she turned and tossed her pajamas onto her bed and bent down facing him, her breasts hanging enticingly in his view for a moment before she straightened, pulling a pair of panties up her legs and over her pussy, hiding it from his gaze. Then she snagged her pajama pants off the bed and pulled them on over her panties, and Jake knew what would be next so he savored a last look at her perfect tits. Dani slipped each of her arms into the sleeves of her pajama top in turn, causing her breasts to sway and jiggle even more before she began to button up the front of the garment. Fully clothed, she turned to close her closet door and Jake could just make out the roundness of her ass from the way the light pajama material clung to her skin.
Her evening routine now concluded, Dani turned on her bedside lamp, crossed toward the door to turn off the ceiling light and returned to her bed in the half darkness. She flung aside the covers and flopped onto her mattress before snuggling in for the night, and Jake knew that was his cue to leave. He wasn't going to get any more of a show, and he'd already gotten more than he had hoped for.
Quietly as he could, he pushed his way out of the rhododendron bush and crept around to the back yard then down the stairs into the basement and across the game room to his own bedroom door, conscious that his wildly attractive sister had just settled in for the night directly above him. He slipped out of his shoes and tossed his jacket to the floor before crawling into his bed, picking up the book he couldn't focus on earlier and placing it on his nightstand. He let himself flop onto his back, his head hitting his pillow, and he stared up at the ceiling re-living every detail of what he had just seen.
He'd just watched his older sister as she went about her evening routine completely naked, and she was drop dead gorgeous! As he thought about her lithe form, his hand naturally wandered down to his dick and began gently stroking it. Soon he was jerking off in earnest and the only images in his head were of Dani. He needed very little imagination to picture her, since her body was so freshly burned into his mind, and it took no time at all before he was ejaculating pulse after pulse of thick cum into a sock that he kept nearby for that purpose.
When he was done, he felt that slight sense of guilt that always followed a jerk-off session, tinged with additional guilt for spying on his sister in the privacy of her room. Yet he already knew that since he'd gotten away with it this time, he would be back again for more. His sister generally showered Monday, Wednesday, and Friday evenings, and that meant he only had two days to wait before he would have another opportunity to see her naked. It was an opportunity he doubted he would ever pass up again.
-

@ 0000065e:9b5b4c75
2025-02-14 01:55:12
En el ámbito bitcoiner es muy habitual que el Estado sea el blanco de las principales críticas, que se ve convertido así en el muñeco de paja al que dirigir nuestros palos. Pero no, en realidad es una piñata que está a punto de desmoronarse de los golpes que le pegan. Cada vez tengo más claro que gran parte de los movimientos "antiestatales", si no todos, están contribuyendo, consciente o inconscientemente, a los intereses de los políticos que nos han llevado a esta situación.
El Estado, con todos sus defectos, sigue siendo la principal unidad de ejercicio de la violencia organizada. Señalando al Estado como el origen de todos los males, no hacemos otra cosa que pegarnos un tiro en el pie, haciendo el caldo gordo a quienes trabajan para cercenar nuestras libertades.
Lo que está claro es que los políticos actuales, de boquilla firmes defensores del Estado, lo que están haciendo es provocar su colapso. Puede que estos políticos, o algunos de ellos, incluso no sean conscientes del todo, pero da igual, pues simplemente priman sus intereses personales, como hacemos todos, intentando aprovechar los incentivos que están encima de la mesa, con las reglas de juego que hemos ido asumiendo. No es que quieran más Estado o que pretendan dinamitarlo, tanto una cosa como otra no son más que las consecuencias de los incentivos que subyacen a nuestra forma de organizarnos en sociedad en el contexto actual. Albert Rivera, en una reciente charla con Iván Espinosa de los Monteros, aludía a esta idea criticando las [redes clientelares y de dependencia del Estado](https://youtu.be/AI7roBGtmvk?t=2709) que generan las actuales dinámicas políticas y adulteran el sistema democrático. Aunque, cabría dudar sobre si el propio “sistema democrático” tiene o no algo que ver con esta situación.
En cualquier caso, no es que la mayoría de políticos sean malvados por naturaleza, aunque algunos puedan realmente serlo; es irrelevante. Sus acciones no están motivadas por su maldad, ni por su ideología o su estupidez, sino, simple y llanamente, por sus intereses personales y los del grupo con el que los comparten.
Las ideologías que manejan los políticos se han convertido en nichos de mercado, en caladeros donde echar la caña a ver si pescan suficientes votos como para asegurarse su porvenir y el de los suyos. Es del todo irrelevante si se creen o no esas ideas que defienden con tanta vehemencia como ausencia de plausabilidad, o incluso si están a sueldo de intereses espurios. De cualquier forma, actuarán en función de lo que crean más conveniente para sus intereses personales y para que más peces caigan en sus redes. Véase, por ejemplo, como [Albert Rivera](https://www.youtube.com/watch?v=XrdCP3viocU), ahora que está fuera de la política, manifiesta que resulta evidente que el sistema de pensiones es una estafa piramidal, mientras que cuando estaba en política defendía lo contrario. O a [Errejón](https://www.youtube.com/watch?v=oZ0KfTsITh8), que sostenía la tesis de que no había denuncias falsas hasta que lo denunciaron a él.
Como digo, los políticos no son malvados o estúpidos (aunque haya algunos, o muchos, que entren en esas categorías), simplemente velan por sus intereses con las armas que tienen a su alcance y, como diría [Vito Corleone](https://youtu.be/Z1dRPt_4rZs?t=208), me es indiferente lo que un hombre haga para vivir. El problema es que esta dinámica está generando unas tendencias que se oponen al progreso que hemos generado como sociedad. Esas reglas de juego en la actualidad, convendremos, son inmorales, en el sentido de que actúan como una fuerza contraria a [nuestra supervivencia y potencia de actuar y obrar](https://maestreabogados.com/bitcoin-el-bien-y-el-mal/).
> *Este artículo forma parte de un trabajo más extenso en elaboración sobre las relaciones de Bitcoin con el Estado.*
-

@ 7d33ba57:1b82db35
2025-02-14 01:46:37
The short answer is YES—but the more honest answer is that it’s much harder than when I started. I’ve been in the travel stock media industry for over 13 years, creating a vast archive of stock photos and videos from around the world. You can check out my portfolio on [https://www.shutterstock.com/g/traveltelly](Shutterstock).
My work is also available on Pond5, Videoblocks, and Adobe Stock. Other big agencies where I don’t have my media are Getty Images and iStock.
My media has been featured on TV channels and even in feature films. However, most of the time, contributors don’t know exactly where their content is used—stock agencies (the middlemen) keep that information to themselves. While stock media can still generate income, it requires persistence, a large portfolio, and an understanding of the ever-changing market.
When I started filming stock footage, most people didn’t even have a phone capable of taking good photos or videos—can you imagine? Now, everyone is a (travel) content creator. Technology has evolved, but creating a well-composed photo or video is still an art. However, the combination of improved tech and the increasing centralization of the stock media market has made it much harder to earn a decent income from stock media compared to 10 years ago.

**Centralization & Declining Royalties**
Over the years, I’ve watched stock media royalties decline year after year. In the beginning, I couldn't understand why I wasn’t able to recoup the cost of my expensive camera—one I specifically bought to shoot high-quality 4K footage.
As the stock media industry became more centralized, agencies took a larger cut while contributors earned less, despite creating higher-quality content. The market became saturated, and with more competition and lower payouts, making a sustainable income from stock media became increasingly difficult.

**The Reality of Centralization in Stock Media**
Every year, stock agencies announced yet another royalty downgrade for contributors. They always framed it as something beneficial for content creators, but in reality, it only served the big companies and their shareholders.
As content creators, we had no say in the matter. These agencies grew too big and powerful, and they knew it. Leaving one platform wasn’t really an option—doing so would only mean an even greater loss of income.
In recent years, the industry has become even more centralized, with only a handful of major agencies buying out smaller competitors. This consolidation further reduces competition, giving contributors even less control over pricing, royalties, and where their content is used.

**The Bitcoin Standard: A Wake-Up Call**
I couldn’t understand why I was struggling to pay off my expensive camera investment, despite working hard and producing high-quality content. Until then, I had never really thought about how money worked. That changed in 2018 when I read The Bitcoin Standard—an absolute eye-opener.
That book sparked my curiosity about Bitcoin. Like many, I initially got distracted by shitcoins, thinking I could multiply my holdings faster—after all, Bitcoin seemed “too expensive.” It was a hard but valuable lesson. Just like in a casino, you can win and lose a lot with altcoins, but that has nothing to do with Bitcoin itself. After those first few years of learning, I realized that for me, Bitcoin—not crypto—was the only way forward.

**From Centralization to Decentralization**
When people ask me if they should start selling stock footage, my answer is always the same: It’s much harder now than when I started. Sure, you can make a few bucks, but is all the time and effort really worth it? If I had to start today, I simply wouldn’t—it’s way more work than what you’ll earn.
Instead of spending years building content for centralized platforms that take the biggest cut, I believe it’s better to focus on decentralized media like Nostr. In my opinion, that’s where the future lies.

Nostr: A New Protocol for Socializing (and More)
Nostr is a revolutionary protocol that goes beyond just social networking. You can read all about it at [Nostr.org](Nostr.org).
As a content creator, one of the most exciting aspects of Nostr is the ability to earn directly through Zaps—small payments made in Satoshis (the smallest unit of Bitcoin).
* 1 Bitcoin = 100 million Satoshis
* By receiving Zaps, you’re not just earning—you’re stacking the hardest money (Bitcoin) directly on Nostr.
This shift toward decentralized earning is a game changer, giving creators more control and financial sovereignty compared to traditional, centralized platforms.

**Join Nostr and Create Your Freedom Content**
On Nostr, no one can stop you. No one can deplatform you. You can be truly free.Whether you're a content creator, artist, or thinker, Nostr empowers you to share your work without censorship or gatekeepers. It’s a place where you control your content, connect directly with your audience, and even earn Bitcoin through Zaps.Embrace decentralization.
***Join Nostr and take back your freedom*** 🚀
-

@ 9e69e420:d12360c2
2025-02-13 23:01:36
Robert F. Kennedy Jr. has been confirmed as the next Secretary of Health and Human Services with a Senate vote of 52-48. Senator Mitch McConnell opposed the confirmation. Kennedy's nomination faced hurdles but gained support from the Senate Finance Committee.
During the confirmation hearing, Senator Rand Paul criticized the oversimplification of vaccine discussions. He stated, "Discussion over vaccines is so oversimplified and dumbed down." Kennedy asserted his support for vaccines like measles and polio, promising not to discourage vaccinations as HHS Secretary. Previously, he switched from the Democratic Party to run as an independent and endorsed Trump
-

@ 85bdb587:7339d672
2025-02-13 22:56:08
## Marty's Bent
I must admit, I have been thoroughly impressed with the work the Trump administration has done since taking the reins from the Biden admin 23 days ago. Over the course of the first eight years of this newsletter there were multiple books-worth of words written about the rampant government corruption in the United States and the negative effects it was having on the economy, freedom and the psyche of the American people. The emergence of DOGE, its rag-tag team of autistic Gen Z'ers and the blatant fraud that has been surfaced is equally gratifying and infuriating.
For the longest time any American taxpayer with the smallest shred of common sense has known that they've been getting screwed by the federal government. We've said it for many years; taxes are a humiliation ritual in which the Common Man works his ass off for a meager wage, the government takes one third of it, and then lines their own pockets. We were reaching levels of corruption that rivaled Soviet Russia.
*“We know that they are lying, they know that they are lying, they even know that we know they are lying, we also know that they know we know they are lying too, they of course know that we certainly know they know we know they are lying too as well, but they are still lying. In our country, the lie has become not just moral category, but the pillar industry of this country.”* - Aleksandr Solzhenitsyn
The fact that all of the corruption that has been building up for decades in the United States is being brought to the light is extremely encouraging. We're not out of the woods yet, but it looks like we're actually making material progress to unveil the parasites in Washington DC. Hopefully DOGE's actions will lead to their eradication from American politics and a shrinking of the federal government to its smallest viable form. Nothing proves that DOGE is over the target more than the pearl clutching and screeching that is coming from the halls of Congress. FEED ME the crocodile tears of Elizabeth Warren, Maxine Waters and Mitch McConnell. These people are criminals and deserve nothing but the utmost contempt from the American people. The louder the screams coming from these individuals and others in similar positions should only be seen as confirmation that they are scared and are attempting to evade justice by screaming "CoNsTiTuTiOnAl CrIsIs" as many times as is humanly possible.
With all of that being said, DOGE should be seen as a mechanism to identify corruption, root it out, and salvage what they can of the American taxpayers' money. It's an admirable endeavor that should be lauded, but it only goes so far. Unfortunately for the United States, you can't DOGE the debt. via TFTC
What you are looking at is a block of 10-year US Treasuries that need to be rolled over in a couple of days. Particularly, $66B 10Ys that were issued in February 2015 when interest rates were 2.00%. They'll be rolling over in a few days at 4.55%, representing an additional $1.67B in interest expense on the debt per year. While that may not seem a lot in a world where governments and central banks throw trillions around like their going out of style, it is important to realize that this is just one block of bonds that needs to be rolled over this year. If my memory serves me correctly, the Treasury needs to roll over ~$6 TRILLION in debt in the first half of this year. Using some back of the napkin Marty math skills, if all that debt rolled over at the same interest rate, that would add another ~$150B to the annual expense we pay on the interest on that debt. And in case you missed it, earlier this week the United States surpassed an incredible milestone; we are now paying $100B a MONTH in interest expense on the debt and $1.2T per year.
If all of the debt that needs to be rolled over in the first half of the year is rolled over where interest rates stand today, it will increase the annual debt expense by more than 10%. Not great, Bob!
The actions of DOGE are incredible to see, but you simply can't eliminate debt that has already been accrued by raiding the Treasury and ousting corrupt bureaucrats. The United States has an obligation to pay back those who hold our debt and the only way to do that is to produce a surplus that allows the government to pay down what has been accrued or issue new debt at wherever rates find themselves at the time of roll over to pay it back. While spending cuts are being made we, unfortunately do not find ourselves reaping the benefits of a government surplus at the moment, so we'll have to roll over the debt.
With interest rates where they are, the increase on the debt expense may put the United States government in a position where it becomes impossible to take care of the debt issue without printing their way out of it or getting all of the world's leaders around the table for a Bretton Woods-like monetary reset. We'll see how it plays out.
One thing I know for damn sure is that no matter how the US decides to deal with the debt issue, bitcoin is going to benefit massively. If they print their way out people are going to flee to scarce assets, and bitcoin is the scarcest asset on the planet outside of time. If they reset the monetary order people are going to flee to bitcoin due to the certainty of its monetary policy and its relative inability to be corrupted.
Now for...
## An Incredibly Simple Yet Powerful Quote
As discussed in my recent conversation with Porter Stansberry, the mounting U.S. government debt problem has created an intriguing dynamic for Bitcoin holders. Porter articulated a compelling perspective: government debt, which threatens most people's savings and financial security, actually becomes an asset for Bitcoin owners. The logic is straightforward – as debt levels become unsustainable, more people will be forced to flee the traditional financial system, driving demand for alternative stores of value like Bitcoin.
*"Their debt is your problem until you own Bitcoin. And then the moment you own bitcoin their debt is your greatest asset."* - Porter Stansberry
This thesis becomes even more relevant when considering the staggering numbers we discussed. The U.S. currently faces $37 trillion in on-balance-sheet debt, plus an additional $190 trillion in unfunded liabilities from Medicare, Medicaid, and Social Security. These obligations, as Porter and I agreed, are mathematically impossible to fulfill without significant monetary debasement. This reality creates a powerful tailwind for Bitcoin adoption, as it positions the asset as one of the few viable escape hatches from a system drowning in debt.
[Check out the full podcast](https://www.youtube.com/watch?v=2f8LWO_RmtU&ab_channel=TFTC) here for more on Trump's economic strategy, the commercial real estate crisis, and the future of energy markets in America.
## Headlines of the Day
Bitcoin's Realized Cap Reaches Record High - via [X](https://x.com/TFTC21/status/1889831485701833056)
Texas Bill Removes $500M Cap on State Bitcoin Purchases - via [X](https://x.com/BitcoinPierre/status/1889821134021075012)
ETF Demand Outpaces Mining Production - via [X](https://x.com/TFTC21/status/1889779939982840185)
U.S. Interest Expense on the National Debt Hits $1.2T - via [X](https://x.com/TFTC21/status/1889764204208324764)
## Bitcoin Lesson of the Day
Bitcoin transactions work by sending entire "outputs" (batches of bitcoin) rather than spending partial amounts. When spending bitcoin, the entire output must be used and split into new outputs. For example, if you have a 25 BTC output and want to spend 1 BTC, you'd create two new outputs: 1 BTC to the recipient and 24 BTC back to yourself as change. The original 25 BTC output becomes spent and unusable.
When making a payment that exceeds any single output you own, multiple outputs can be combined as inputs in a transaction. For instance, to spend 4.2 BTC, you might combine outputs of 1 + 0.5 + 2 + 1 BTC as inputs, creating new outputs of 4.2 BTC (payment) and 0.3 BTC (change).
Transaction fees are created by making the total output amount slightly less than the input amount. The difference becomes the fee, which miners collect when including the transaction in a block. The balance of a bitcoin address is the sum of all its unspent transaction outputs (UTXOs).
[Outputs | What is a Transaction Output?
A simple explanation of transaction outputs and how they work.](https://learnmeabitcoin.com/beginners/guide/outputs/)
ICYMI Fold opened the waiting list for the new Bitcoin Rewards Credit Card. Fold cardholders will get unlimited 2% cash back in sats.
[Get on the waiting list](https://foldapp.com/credit-card?r=BgwRS) now before it fills up!
$200k worth of prizes are up for grabs.
Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at [ten31.vc/funds](ten31.vc/funds).
-

@ e373ca41:b82abcc5
2025-02-13 22:27:58
*This article has been written with the* ***[Pareto client](https://pareto.space/read).*** *(read it there for the full experience). It was first published in German by Milosz Matuschek on* ***["Freischwebende Intelligenz".](https://www.freischwebende-intelligenz.org/p/unterwanderter-journalismus-der-mediale)***
***
It is unmistakable. The hydra of the Deep State is losing a few heads - and this time it's the turn of the media heads. Anyone can look at [USASpending](https://www.usaspending.gov/) to see how much taxpayers' money has gone to whom in the USA.
### When the state pays its advocates
The mainstream media were also among the beneficiaries: Politico (100% Axel Springer) received over [USD 7 million](https://www.usaspending.gov/recipient/fa0cefae-7cfb-881d-29c3-1bd39cc6a49e-C/latest); the New York Times received over USD 40 million. Thousands of (probably not always necessary) government subscriptions flowed to large media houses - paid for with taxpayers' money. A form of covert press financing by the state. At what point can or should we speak of state media?
")
However, this is only the tip of the iceberg. The CIA front organization USAID ([known for its funding of virus research in Wuhan and other questionable activities](https://pareto.space/a/naddr1qqxnzden8quryveexq6rywp3qgswxu72gyq7ykjdfl9j556887jpzwu3mw3v9ez36quas55whq4te3grqsqqqa28qyxhwumn8ghj7mn0wvhxcmmvqyf8wumn8ghj7mmxve3ksctfdch8qatzqythwumn8ghj7urpwfjhgmewdehhxarjxyhxxmmdqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsz9nhwden5te0wfjkccte9ehx7um5wghxyctwvszsxfjh)) - [pumped USD 472.6 million directly into the media landscape via the “Internews Network”.](https://www.zerohedge.com/political/usaid-funded-massive-global-state-propaganda-news-matrix-nearly-billion-people-reach) FAZ journalist Udo Ulfkotte once called this “bought journalists” in a very clear and media-effective way, which was not good for his health. There is ample evidence of the CIA-USAID connections, for example [here](https://timesofindia.indiatimes.com/toi-plus/international/how-usaid-worked-alongside-cia-in-vietnam-a-whistleblowers-account/articleshow/118164225.cms), [here](https://foreignpolicy.com/2014/04/03/cuban-twitter-and-other-times-usaid-pretended-to-be-an-intelligence-agency/) and [here.](https://www.jstor.org/stable/4017728)
")
But this is now over for the time being: USD 268 million, which was to go to “independent media for the free flow of information” (according to the [Columbia Journalism Review](https://www.cjr.org/the_media_today/usaid-and-the-media-in-a-time-of-monsters.php)) in 2025, has been frozen. The largest media influence machine in the Western world is bleeding a little. One has to admit: part of the media-deepstate swamp is actually being drained dry financially. The fact that the Columbia Journalism Review doesn't even seem to notice that “free international journalism”, which, as it writes, is largely funded by USAID, ceases to be “free journalism” speaks volumes about this “hotbed of journalism”. Matt Taibbi of Racket News rightly finds, “The legacy media system is dead. They just don't know it yet.”
***
ADVERTISEMENT:
*Looking for the easiest way to buy Bitcoin and store it yourself? The **[Relai app](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. **[Here you can buy Bitcoin](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees (no financial advice). Disclaimer due to regulatory issues: The services of the Relai App are hereby only recommended to inhabitants of Switzerland or Italy.*
*Need more security? The **[Trezor wallets](https://trezor.io/trezor-safe-5-bitcoin-only?transaction_id=102e192a206d1585e56a2fddef6d83\&offer_id=238\&affiliate_id=35234)** are recommended and easy to use, others are available in the **[store](https://trezor.io/?transaction_id=102bc85bdca2733287749c7f879ebd\&offer_id=133\&affiliate_id=35234)**. Need more advice? Book an **[introductory meeting](https://trezor.io/trezor-expert-session?transaction_id=1020e18dad0aa4b1186289fd22e90f\&offer_id=241\&affiliate_id=35234)** with a wallet expert.*
***
Large-scale media manipulation has become visible. The propaganda matrix, if you will. The disastrous thing about it: if the Overton window is infiltrated, so to speak, the entire institution of journalism cannot be trusted. Every day, readers must expect to be pulled through the nose ring of intelligence service narratives and public agendas by mainstream journalists who pretend to be objective (and are often simply clueless and unsuspecting). The panorama of what we are supposed to see and believe, so to speak.
How many mainstream journalists today are basically mouthpieces for the services? Every mainstream reader must now ask themselves: Is my favorite journalist at NZZ, Welt, SZ, ZEIT or FAZ perhaps just a CIA-IM? There were no major dissenters among them: EU criticism? Vaccination criticism? Criticism of NATO? Criticism of Biden and America? Criticism of Nord Stream? There were brief moments on television when questions about journalists' ties to lobby organizations were still part of the German satire program.
<https://x.com/Spitze_Zunge_/status/1887915509988876786>
### The cards in the media are being reshuffled
The watchdog of the powerful has been infiltrated by the powerful. This means that the Fourth Power is not a power at all, but part of the executive branch, a mouthpiece of the government. The claim that the mainstream is quality journalism, the gold standard for trustworthy information, is therefore the real fake news. It is the last, now crumbling dogma of an infiltrated press sect that has formed a cartel and is subjecting citizens to a permanent psy-op with intelligence-controlled taxpayers' money. A troupe of spokespeople at the work of mental synchronization.
<https://x.com/TopherField/status/1887962959072149989>
### The fight against independent media
But they not only give to one, they also take from the other. While government agencies use taxpayers' money to promote a certain type of journalism, the juice is actively being cut off from the critical part. All it takes is to be classified as a “PEP” (politically exposed person) and the bank account is gone. This is what has just happened to swiss Radio Kontrafunk. The critical Swiss author Stefan Millius was canceled by his publisher. Others have had their monetization via YouTube cut off (Snicklink). Others are harassed by the state media authority (Multipolar, Alexander Wallasch). The next one has a house search. It has been known since the Twitter files that the government and services also intervened massively in social media communication. This is no longer the Cold War. But it is the cold information war.
<https://www.youtube.com/watch?v=kmgWAGDFCZI>
Is this all so outrageous and new? During the Cold War, the CIA systematically infiltrated media outlets in the US. Thousands of agents were deployed as journalists - and wrote what they were told. This “Operation Mockingbird”, which the Church Committee also investigated, never ended, so to speak. It lives on as Operation Mockingbird 2.0.
Intelligence payments to media outlets continue to exist.
USAID distributes millions for “pro-democratic” reporting.
Government subscriptions keep uncritical media alive.
Media control of public opinion is the most important tool of power in a modern “democracy”. The difference to back then? Today, the manipulation is global. However, these revelations come at a time when trust in the media is already at an all-time low. [The fear of being lied to by the powerful is currently the majority opinion at 70%.](https://www.edelman.com/trust/2025/trust-barometer) They are currently in the process of convincing the remaining 30% of their own incompetence.
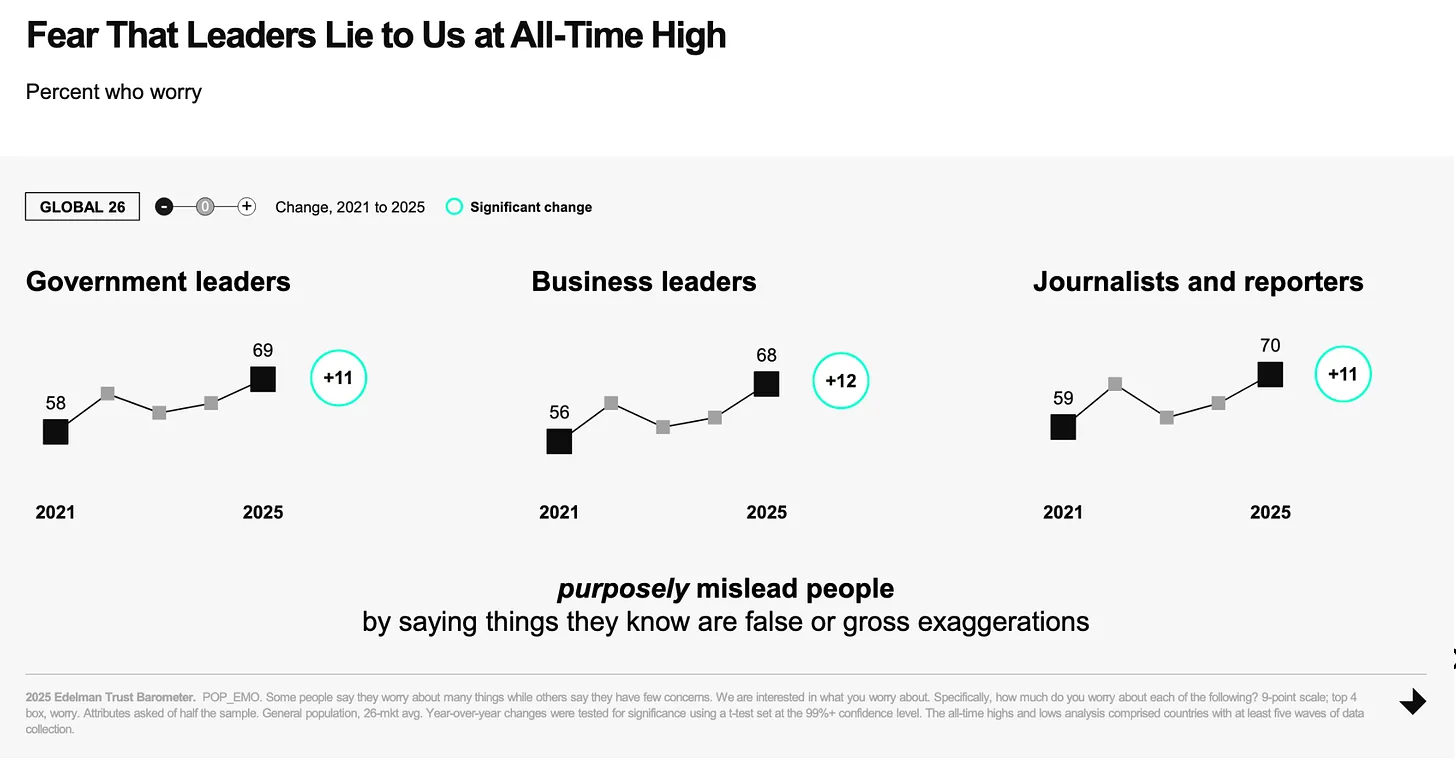
### Update on the [Pareto project](https://pareto.space/en)

“Half the victory”, says Sun Tsu, ‘lies in the impregnable defense’. Free media now have the opportunity to build their own impregnable bastion and the [Pareto Project](https://pareto.space/read) invites them to do just that: [become uncensorable, be able to scale infinitely and not depend on third parties for all processes of journalistic work](https://pareto.space/a/naddr1qqxnzdenxuerxdpkxycngvpcqgsvlutjpemmkp50p6aa8zwu65yz9hg6erf2czc0tuyqpt57zhr79vsrqsqqqa28qyxhwumn8ghj7mn0wvhxcmmvqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hs33ee7d). It's all possible now. Everyone has to realize that: With other platforms, you build your house on someone else's property. With Nostr/Pareto, there is nothing and no one between author and reader, both in terms of communication and payment (via Bitcoin/Lightning).
**A brief update on the project, January was very busy.**
* We have about 35 journalists, publications, substackers, bloggers, memers onboarded who publish texts via the Pareto client, and the number is growing all the time.
* The first Telepolis authors, such as Mathias Bröckers and Alexander Unzicker, will soon be able to re-publish their deleted texts with us in a censorship-proof manner, and we are helping with the migration of content.
* We recently successfully tested the newsletter function! We will soon be able to offer all authors and readers the functions of Substack, Steady, Ghost etc. without having to entrust their readers' sensitive data to a platform or expose them to platform tracking.
* We are delighted to have more high-caliber additions to our development team, which now comprises around ten wonderful people, almost all of whom come from this group of readers.
* Our [open source code is now also public.](https://github.com/twenty-eighty/pareto-client)
* We have opened a [crowdfunding on Geyser!](https://geyser.fund/project/pareto)
- Our editor will soon be available to everyone free of charge (atm you have to drop us your npub: <team@pareto.space>)
### What's next?
This opens up a new window of unimagined possibilities: On a strong basis such as that offered by decentralized technology, many critical authors can now publish securely or new publications can be created - worldwide and uncensorable. What kind of publications would you like to see? Where do you see gaps (also in the critical spectrum) that need to be filled, both in terms of formats and topics? What does the journalism of the future look like to you? Feel free to write to me: **<milosz@pareto.space>**
## One last thing
Our funds are coming to an end. If you would like to support us: We have started a [crowdfunding on Geyser](https://geyser.fund/project/pareto), where you can help us with Bitcoin/Lightning donations. 

For traditional donations, you can find our bank account on our **[landingpage.](https://pareto.space/en)**
***
***Join the marketplace of ideas!** We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the [Pareto Project](https://pareto.space/en)? Zap me, if you want to contribute (all Zaps go to the project).*
*Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to **<team@pareto.space>***
**Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Start.](https://start.njump.me/)**
-

@ dbb19ae0:c3f22d5a
2025-02-13 20:42:08
Installation:
``` bash
python3 -venv nostr-sdk
source nostr-sdk/bin/activate
pip install nostr_sdk requests
```
Python program:
``` python
# Usage example: python ns_read_metadata.py nostr:npub1mwce4c8qa2zn9zw9f372syrc9dsnqmyy3jkcmpqkzaze0slj94dqu6nmwy
# Compatible with version 0.39
# ns_read_metadata.py
# version 3
import asyncio, argparse, json
from nostr_sdk import Metadata, Client, NostrSigner, Keys, Filter, PublicKey, Kind
from datetime import timedelta
async def main(npub):
client = Client()
await client.add_relay("wss://relay.damus.io")
await client.connect()
pk = PublicKey.parse(npub)
print(f"\nGetting profile metadata for {npub}:")
metadata = await client.fetch_metadata(pk, timedelta(seconds=15))
print(metadata)
if __name__ == '__main__':
parser = argparse.ArgumentParser(description='Fetch all metadata for a given npub')
parser.add_argument('npub', type=str, help='The npub of the user')
args = parser.parse_args()
asyncio.run(main(args.npub))
```
-

@ 19220736:7578e0e9
2025-02-13 20:39:52
The U.S. economy is facing a double whammy of challenges as housing prices skyrocket and trade tensions escalate, creating a perfect storm of economic strain for everyday Americans.
First-time homebuyers are bearing the brunt of the housing crisis, with median home prices rising by nearly 15% in major cities over the past year [1]. While wages have remained stagnant, the cost of living continues to climb. This has left many young families and individuals struggling to afford homes, forcing some to delay homeownership or take on risky levels of debt.
Meanwhile, trade tensions between the U.S., Canada, and Mexico have added another layer of uncertainty for businesses and workers. The Trump administration's tariffs [2] on goods imported from these countries will lead to higher costs for industries ranging from agriculture to manufacturing. Companies reliant on imports will see profit margins shrink, with some forced to lay off workers or pass the added costs onto consumers.
The interplay between these two experts warn that they could feed into each other. Rising housing costs can limit the availability of skilled labor, as workers may need to take on more demanding jobs to afford rising rents or home prices. This, in turn, could impact industries already struggling with reduced productivity due to trade disruptions.
The long-term effects of trade tensions remain unclear, but the uncertainty caused by the threat of tariffs has already led to reduced investment in Mexico, with businesses hesitant to expand operations for fear of retaliatory measures from other countries [3]. While some argue that stronger trade agreements could benefit all parties involved, others fear that continued tension could lead to reciprocal measures that harm global markets.
The cumulative effect of these challenges is leaving many Americans feeling vulnerable. From the first-time homebuyer struggling to save for a down payment to the worker worried about job security, the combination of rising housing costs and trade tariffs creates a perfect storm of economic instability.
In cities across the U.S., local leaders are calling for more affordable housing [4] options and better wage protections as immediate solutions. Advocates argue that without addressing these issues, the economic strain on families will only worsen, potentially leading to long-term social and economic consequences.
While both issues are complex and multifaceted, the need for a coordinated response has never been more urgent. Policymakers at all levels of government must work together to mitigate the negative impacts of rising housing costs and trade tariffs, ensuring that no one is left behind in this challenging economic landscape.
Reference links:
[1] [Past year ]( https://apnews.com/article/first-time-home-buyer-housing-prices-8ede22e18fd11a40f45e2e0ba6c055c1)
[2] [Tariffs ]( https://apnews.com/article/america-canada-mexico-tariffs-trump-trade-4568dababcf524945333bb518232ec4b)
[3]
[4] [Housing ]( https://apnews.com/article/first-time-home-buyer-housing-prices-8ede22e18fd11a40f45e2e0ba6c055c1)
-

@ 3ad01248:962d8a07
2025-02-13 20:03:40
I feel like this is go to be a common phrase over the next four years. While I generally like most of the policies that he is in favor of, I for the life of me can't understand his position on Gaza. It sounds like nothing like the Trump for the campaign trail whatsoever.
When he ran for president last year he ran on a platform of not starting any new wars. Having a US solider set foot in Gaza is a recipe for disaster and chaos. Sending in the military is not "America First". Gaza has no national security implication for the United States so obviously there is a different reason why President Trump is proposing this idea.
We have to look at who funded his campaign to understand his motives by wanting to clear out Gaza and rebuild it like it some real estate deal.
## Miriam Adelson
[Miriam Adelson the wife of late casino magnate Sheldon Adelson](https://www.timesofisrael.com/miriam-adelson-gives-100-million-to-trump-campaign-making-good-on-reported-pledge/) gave Trump $100 million to help get Trump elected. Mrs. Adelson is a pro-Israel and supports a variety of Jewish causes. $100 million buys you a lot of political favors if you ask me. Mrs. Adelson and her husband were the power behind the scene of the first Trump administration to get them to move the US embassy to Jerusalem.
She also own the largest newspaper in Israel which means she has the ability to impact public opinion inside the country. As you can see this is person with a tremendous amount money and social capital to spend and she is undoubtedly using it to get Trump to purge Gaza of the native Palestinians.
Who else is in Trump's ear that influence him to come up with crazy idea?
### Jared Kushner
We all know that Trump values family and loyalty above all else so it is no surprise that Trump would listen to someone in his family for guidance on what to do in Gaza. Jared Kushner is that guy for Trump. As the son-in-law of is favorite daughter you can bet that he is going to listen to what he has to say. Funny you listen to Trump and I swear that you hear Jared come out of his mouth.
Back in March 2024 Kushner suggest the very idea that Trump is talking about right now! Almost verbatim to be honest. Here is a link to a talk where Kushner laid out what he thought should happen to Gaza and the Palestinians.
https://www.youtube.com/watch?v=nneWrllngAU
When you listen to it, you see that Trump basically took this idea from Kushner and made it his own.
Who is exactly is running the show in the White House? Trump seems to be doing the bidding of everyone else except the American people. Who else is Trump listening to on the Gaza issue?
#### Bibi Netanyahu/Israeli Far-Right
Last but not least is the persons behind all the death and mayhem in Gaza. Trump absolutely sides with the Israeli narrative spun by Bibi Netanyahu and the Israeli far right characters such as Itamar Ben-Gvir and Bezalel Smotrich. This trio have a distinct hatred of Palestinians and do not want to see the creation of a Palestinian state.
They want to see occupied West Bank annexed by Israel and all of the Palestinians there to leave or be subjugated to Israeli rule.
Just take a look at the worldview of these people and they have power within the halls of the Israeli government.
https://www.jpost.com/Israel-News/Politics-And-Diplomacy/Bayit-Yehudi-MK-causes-uproar-by-saying-God-commanded-Jews-not-to-sell-homes-to-Arabs-409241
https://hashiloach.org.il/israels-decisive-plan/
https://www.reuters.com/article/idUSKBN0MC1I7/
When you have this world view how is peace even possible? It's not because they don't want peace and quite frankly I don't know if its possible at this point. Israelis and Palestinians have diametrically opposing views of what the land should be.
Israeli believe that the land should be exclusively governed by Jewish people whereas the Palestinian view from what I understand just want to return to the lands they were kicked out from and deal with governance later.
There are elements on both side that want this conflict to go on forever because it gives the outsized power, namely Hamas on the Palestinian side and the Israeli Far Right on the Jewish side. I would guess that a majority of people in the middle would have no problem living side by side with each other as long as rights and freedoms were respected.
A one state solution looks like the most reasonable solution to me but the odds of that happening are slim to none right now.
President Trump has the power to change the middle east for the better if he had the backbone do to what is right but it looks like he is going to listen to people the want war, genocide and ethnic cleansing.
-

@ 21ffd29c:518a8ff5
2025-02-13 20:03:17
**Introduction:**
Self sovereignty is a pivotal concept in understanding personal autonomy across various ideologies, including, libertarianism, socialism and individualism. This article explores how the statement "I own myself" by the Ole Voyager in the 1600's encapsulates this principle, emphasizing empowerment and self-management.
**Article:**
- **What is Self Sovereignty?**
- **Definition:** It refers to the ability of an individual or group to govern themselves without external imposition.
- **Core Principles:**
- Autonomy: The right to manage one's own affairs independently.
- Equality: Recognition of equal rights and responsibilities among individuals.
- **Historical Context:** Rooted in ideas from liberalism, socialism, and feminism, advocating for personal freedom and equality.
- **The Significance of 'I Own Myself'**
- **Statement Explanation:** The Ole Voyager's quote highlights personal ownership over one's life, values, and destiny.
- **Contrast with Traditional Views:** Shifts from societal control to individual responsibility, advocating for personal agency.
- **Implications:** Encourages owning health, relationships, knowledge, and cultural identity, promoting a holistic view of self-worth.
**Conclusion:**
Understanding self sovereignty through the Ole Voyager's statement is crucial. It empowers individuals by asserting their right to manage their lives autonomously. This concept not only enhances personal freedom but also challenges societal structures, fostering inclusive governance that respects individual rights and equality.
Not everyone has the capacity to be a sovereign and self govern themselves. Some are quite content to be told what to do and how to do it. Others are very happy to be on the dole and get free things in exchange for trinkets.
This empowerment can lead to more equitable societies where individuals thrive within their own means, emphasizing empowerment and collective responsibility.
-

@ 30b99916:3cc6e3fe
2025-02-13 18:56:37
## Upgrade Details
Download current release and manifest files
```shell
Navigate to https://github.com/getAlby/hub/releases/tag/v1.13.0/
Download
albyhub-Server-Linux-x86_64.tar.bz2
manifest.txt
manifext.txt.asc
Copy the downloaded files to $HOME
mv $HOME/Downloads/albyhub-Server-Linux-x86_64.tar.bz2 $HOME
mv $HOME/Downloads/manifest.txt $HOME
mv $HOME/Downloads/manifest.txt.asc $HOME
```
Verify manifest signature & Checksum
```sh
Only need to import once
curl https://raw.githubusercontent.com/getalby/hub/master/scripts/keys/rolznz.asc | gpg --import
gpg --verify manifest.txt.asc manifest.txt
gpg: Signature made Tue 07 Jan 2025 08:56:42 PM PST
gpg: using RSA key 5D92185938E6DBF893DCCC5BA5EABD8835092B08
gpg: Good signature from "Roland Bewick <roland.bewick@gmail.com>" [unknown]
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: 5D92 1859 38E6 DBF8 93DC CC5B A5EA BD88 3509 2B08
shasum -a 256 server-linux-x86_64.tar.bz2
a75c03d241921611dfc428c413c4a2c2cef35bc6d1974839b688ef462604058d server-linux-x86_64.tar.bz2
The above checksum should be referenced in the manifest.txt file
cat manifest.txt
```
Stop AlbyHub & Backup existing data directory & Binaries
```shell
systemctl stop albyhub
cp -r $HOME/.local/share/albyhub /media/veracrypt1/albyhub
cp $HOME/bin/albyhub $HOME/bin/albyhub172
cp -r $HOME/lib $HOME/lib172
```
Extract new release Binaries & Start AlbyHub
```sh
tar -xvjf albyhub-Server-Linux-x86_64.tar.bz2
./
./lib/
./lib/libglalby_bindings.so
./lib/libldk_node.so
./lib/libbreez_sdk_bindings.so
./bin/
./bin/albyhub
systemctl start albyhub
```
Navigate to http://localhost:9090
-

@ dbb19ae0:c3f22d5a
2025-02-13 17:46:41
This code below works with nostr_sdk 0.32.2
``` python
import asyncio, argparse, json
from nostr_sdk import Metadata, Client, NostrSigner, Keys, Filter, PublicKey, Kind
from datetime import timedelta
async def main(npub):
client = Client()
await client.add_relay("wss://relay.damus.io")
await client.connect()
pk = PublicKey.from_bech32(npub)
print(f"Getting profile metadata for {npub}:")
f = Filter().kind(Kind(0)).author(pk).limit(1)
events = await client.get_events_of([f], timedelta(seconds=15))
if events:
event = events[0]
metadata_dict = json.loads(event.content())
for key, value in metadata_dict.items():
print(f"{key}: {value}")
else:
print("Could not retrieve metadata for the given public key.")
if __name__ == '__main__':
parser = argparse.ArgumentParser(description='Fetch all metadata for a given npub')
parser.add_argument('npub', type=str, help='The npub of the user')
args = parser.parse_args()
asyncio.run(main(args.npub))
```
but with nostr_sdk 0.39
the program no longer worked and crash with error:
```
AttributeError: type object 'PublicKey' has no attribute
'from_bech32'. Did you mean: 'to_bech32'?
```
why?
---
source:
- https://github.com/ev3rst/nostr_sdk_examples
- https://alashazam.wordpress.com/2024/07/07/python-nostr_sdk-fetching-all-metadata/
-

@ 8e56fde2:bb433b31
2025-02-13 17:41:41
Let us introduce you to “**DoShit!**”: the **oracle that three friends created in order to combat creative block.** A self-produced card game made possible by the investment of a generous patreon who believed in us from the start, and in empowering people to Do their Shit.
<img src="https://blossom.primal.net/6b9439e70cc5ee3e82148bf9ee9533557cd2c8569f7e37b16f2d922ec981d2c8.jpg">
## **What is DoShit! ?**
**DoShit!** is a card game that guides you in the process of building a creative life. It’s a self-reflection tool when used individually, and also a great conversation starter when played with friends or strangers.
**84 oracle cards** that will help you question your fears, your strengths, doubts, excuses…
DoShit! is a great companion to bring along when meeting your friends or potential collaborators. Both individually as well as collectively, the game can become very addictive once you start asking about your projects and aspirations. Sometimes the cards even lay on you hard truths necessary on the journey to self-discovery
The cards are very intuitive to understand accompanied by a language that sparks profound conversations in a lightweight manner.
<img src="https://blossom.primal.net/e677e9f2622d3eb86d8085a11ab85739ceaa884e3e26aa2f5c3c47a487012194.png">
Learning how to play takes less than 5 minutes and anyone can attempt to interpret the cards without any previous knowledge (even if it may feel scary at first). In fact, the card readings always benefit from people sharing their own interpretation of the cards.
<img src="https://blossom.primal.net/afae65997d5222e270bdabe9bbc8762f254514deba3a9b44dbf5da194722feb9.png">
Link to [video](https://youtu.be/ZvBzlznunVo?feature=shared)
## **Why DoShit! ?**
As creators, we are very aware of the struggles of building a creative life and also of how easy it can be to limit ourselves, hide behind excuses, let fear win and quit. Our philosophy in response is “Do Shit”, yes, simply **do shit**, even if it ends up being shit… The important thing is to do it! Because when you Do Shit the project no longer dies in idea valley. And the more Shit you do the better you get at doing it, shortening the Gap between your expectations and your Shit.
That is why we created this tool, to accompany every DoShitter in the world on their journey (DoShitters being those who take responsibility for their Shit).
These cards were born at a moment of creative block and search for answers, and we can guarantee this game has helped unstuck many people. It is also a great companion to unleash your creativity and reach beyond your comfort zone!
<img src="https://blossom.primal.net/d08c811e48fca1187d894ae041174126172c24a06335b3e8655830f6247f9292.png">
## **How did it get started?**
The three of us (Mar, Elisabet & Marta) have known each other for years and we’ve always had a shared admiration for each other’s work as well as the desire to do a project together someday.
One afternoon, with no specific expectations, simply wanting to enjoy ourselves without pressure, we started searching for an idea. Elisabet had some blank cards and Mar had been reading about tarot, and the idea simply sparked: we would do an oracle about the creative process with [the structure of the Hero’s Journey](https://en.wikipedia.org/wiki/Hero%27s_journey) (a concept that had followed us since we studied film school together) as a backbone. That afternoon, the first prototype of DoShit! was made.
<img src="https://blossom.primal.net/c2a59b73465da2b4a42560b43f6fe1ec84681ccf577877aa2d6cbc43ef9382dd.png">
## **The artistic process**
The 84 unique cards were illustrated by Mar Delmar.
Each card is created manually with cut paper and gouache, creating first the different pieces that compose each card, and then placing them together in 3D to take the photo that becomes the final illustration.
The whole process took more than 8 months. Cards were painted and cut up in different locations (Barcelona, Tarragona, Castellar de n'Hug, Porrera y L'Argentera (Catalunya) y Castelo (Galicia)) where Mar attended artistic residencies along with a big box filled with the many octopuses in their envelopes, one for each card… ([Video ](https://www.instagram.com/reel/CkWQWDvj5Ab/?igshid=MzRlODBiNWFlZA==)of the process)
<img src="https://blossom.primal.net/1a9a26add6e54ed30b4e48e44346567d0133934b56cbdd6e24335593d285fe22.png">
## Where to buy this awesome Shit?
- You can buy directly from our online [store](https://doshitters.bigcartel.com/product/doshit-oracle-card-game), but depending where you are in the world, shipping costs may showcase the literal cost of supporting small sellers. If you do buy it there use the promo code SATOSHI and get a small discount in return for your generosity <3
- You can also buy it with bitcoin , the best money in the world, in [Plebeian Market](https://plebeian.market/products/doshitters@ditto.pub/doshit-creative-oracle-y0fdoz0u56 ) . Since you'd be using the best money in the world, we shaved off a bit from the price and shipping in comparison to our online store since we appreciate being paid in sound money :D
- You can temporarily buy this Shit on the [A\*\*\*\*\*\* giant](https://a.co/d/8ygMa8p) with FREE Shipping depending of your location or prime subscription status, but we are going to be removing our beloved DoShitS from there soon due to our very negative experience with them portrayed in our article that you can find the link to at the bottom.
In any case, if you read this far, THANK YOU.
You can support our Shit by gifting this deck (to someone else, or to yourself :P) , zapping this article or simply sharing it around in the hopes that THE PEOPLE WHO NEED THIS SHIT, FIND THIS SHIT <3
And if you want to know more about this inspiring product, don’t hesitate to get in touch with us.
### **We wish you the best on you creative adventures!**
<img src="https://blossom.primal.net/865a8cee47bbcfe6bbcde6aa0a56d0a294d58eab99fae3414e99a7664ddcfc61.jpg">
**Join the #artMy**
ARTICLE ON OUR HORRID EXPERIENCE TRYING TO MAKE "doShit!" CHEAPER TO GET FOR YOU:
naddr1qvzqqqr4gupzprjklh3rdmxhj60knvpel0uk03vq3kyh4x3dlu2m7pgkcxa5xwe3qq247635g4v553t329e9x4rhvajhwvmrxahhgxv3ddc
-

@ 89ccea93:df4e00b7
2025-02-13 17:34:06
**[Original Post](https://expatriotic.me/grapheneos/)**
## Core Philosophy
1. **Privacy ≠ Optional**: Prevents mass data collection by design
2. **Security > Convenience**: Sacrifices "smart" features for exploit resistance
3. **Transparency**: Every line of code [auditable](https://github.com/GrapheneOS)
4. **Device Sanity**: Removes 2M+ lines of Google telemetry code
5. **Proactive Hardening**: Replaces reactive "vulnerability whack-a-mole" with systemic memory safety improvements. 73% of Android CVEs prevented via Scudo++ allocator and Rust integration.
6. **Hardware Paradox**: Uses Google Pixels *because* of their Titan M2 secure enclave (physically separate from main CPU, Verified Boot with user-defined root of trust, Firmware-level MAC randomization (prevents Wi-Fi tracking)).
7. **Support Superiority**: GrapheneOS support for Pixel phones is 2 years longer Google's.
> *"We're eliminating entire vulnerability classes - not just patching holes."*
## **History**
* Born in **2014** as **CopperheadOS**
* **2016**: First Pixel support (Google's hardware + de-Googled OS)
* Rebranded in **2019** after a developer split. Focuses exclusively on Pixel phones.
* **2021**: **Scudo++** with quarantines (NSA-grade exploit mitigation)
* **2023**: Full Rust integration (prevents buffer overflows in core OS)
* **2023**: Controversial lead dev, Daniel Micay, stepped down but remains director
* **2024**: Quantum-resistant encryption prototypes
> *"Our Auditor app detects hardware tampering better than Apple's T2 chip."*
## **Installation**
* **Minimum**: Pixel 4a
* **Recommended**: Pixel 7a (5-year update guarantee)
* **Backup data first**: unlocking bootloader wipes device
### **Beginners: Web Installer**
1. Enable OEM Unlock:
`Settings → About → Tap Build Number 7x → Developer Options → OEM Unlocking`
2. Visit [grapheneos.org/install](https://grapheneos.org/install)
3. Connect phone → Follow prompts (20 minutes)
### **Advanced: CLI install**
* Full CLI guide: [grapheneos.org/install/cli](https://grapheneos.org/install/cli) (8 minutes)
>*"We're proving iPhones aren't the only secure option - just better marketed."*
### **Post-Install Checklist**
[ ] Deny all "convenience" permissions
[ ] Enable Sensors Off toggle
[ ] Install Auditor app
[ ] Sensors Killswitch: `Quick Settings → Toggle Off`
[ ] Network Restrictions:
```markdown
Settings → Network & Internet → Firewall
- Enable per-connection MAC randomization
- Block local network discovery
```
[ ] Auditor Validation: Daily automated checks against Google's hardware certs
## Setting up
### **Priority Sources**
1. **Accrescent** (Pre-installed)
- Molly (Signal fork)
- Aves Gallery (EXIF stripping)
- AppVerifier (APK validation)
2. **Obtainium** ([GitHub](https://github.com/ImranR98/Obtainium))
```markdown
1. Search "[App] GitHub releases"
2. Copy releases page URL
3. Paste into Obtainium → Auto-updates enabled
```
- *Example*: NewPipe → `https://github.com/TeamNewPipe/NewPipe/releases`
3. **Google Play** (Last Resort)
- Use separate profile
- Burner account: Fake name + **NO phone number**
## FOSS Apps
* Accrescent - Privacy-focused app store
* Aegis - 2FA authenticator
* Amethyst - Nostr decentralized social client
* AndBible - Offline Bible study
* Antennapod - Podcast manager
* AppVerifier - APK signature validation
* Ashigaru - Bitcoin wallet with Ricochet
* Aves Gallery - Gallery with EXIF stripping
* Brave - Anti-fingerprinting browser
* Easy Noise - Offline white noise generator
* Easy Note - Minimalist notes
* Envoy - Bitcoin wallet
* IronFox - Hardened Firefox fork
* KeePassDX - Offline password manager
* Léon - URL tracking stripper
* LocalSend - AirDrop alternative
* Material Files - File manager
* Molly - Signal fork with local encyption
* Monero.com - Official Monero wallet
* NetGuard - No-root firewall
* NewPipe - YouTube client with SponsorBlock
* Nextcloud - Self-hosted cloud suite
* OpenKeychain - PGP encryption
* Organic Maps - Offline navigation
* Orbot - Tor proxy
* Proton Drive - E2E encrypted storage
* Proton Mail - Zero-access email
* RedReader - Privacy-first Reddit client
* Simple Calendar Pro - Telemetry-free calendar
* Telegram FOSS - Decentralized messaging
* Tor Browser - Onion-routed browsing
* Twidere - Twitter/Fediverse client
* Tuta - Encrypted email
* Tuta Calendar - Encrypted calendar
* Vanadium - Hardened Chromium
* Zeus - Bitcoin Lightning node
> _"Your phone is a corporate surveillance device that happens to make calls. GrapheneOS removes the spyware OS while keeping the secure hardware."_
## **Silent.Link eSIM: Anonymous Connectivity**
**No Phone Number Required**
Visit [Silent.Link](https://silent.link) → Select data plus eSIM plan (with NO phone number).
```I've used this successfully in many countries. It even gives me unfettered and free internet in China. Be sure to pick the telecom company based on what they charge per GB of data. The difference can be 100x!```
## Support the Project:
- **Donate**: [grapheneos.org/donate](https://grapheneos.org/donate)
- **Community**: [grapheneos.org/contact](https://grapheneos.org/contact)
>*"GrapheneOS isn't about becoming a privacy expert overnight. It's about systematically removing corporate surveillance hooks - one app, one permission, one profile at a time."*
## Moar Halp
* **[Side Of Burritos](https://www.youtube.com/playlist?list=PLHvdaysg3bMyYwJAcxbFUY9YqKKC0Dtrd)**
* **[Hated One interview with GrapheneOS dev Gabe](https://www.youtube.com/watch?v=WkQ_OCzuLNg)**
originally posted at https://stacker.news/items/884965
-

@ dbb19ae0:c3f22d5a
2025-02-13 17:32:36
pip cache will show how much space is taken from past download
``` bash
(nostr) ever3st@Alashazam:~/Documents/dev/python/$ pip cache info
Package index page cache location: /home/ever3st/.cache/pip/http
Package index page cache size: 2437.7 MB
Number of HTTP files: 271
Wheels location: /home/ever3st/.cache/pip/wheels
Wheels size: 2.2 MB
Number of wheels: 2
```
About 2GB
if space is needed
it can be cleared
``` bash
(nostr) ever3st@Alashazam:~/Documents/dev/python/$ pip cache purge
Files removed: 273
(nostr) ever3st@Alashazam:~/Documents/dev/python/bots/nostr$ pip cache info
Package index page cache location: /home/ever3st/.cache/pip/http
Package index page cache size: 0 bytes
Number of HTTP files: 0
Wheels location: /home/ever3st/.cache/pip/wheels
Wheels size: 326 bytes
Number of wheels: 0
```
-

@ 6538925e:571e55c3
2025-02-13 16:05:42
\
**Nostr Live Streams (Beta)**
If you follow shows like Rabbit Hole Recap, THE Bitcoin Podcast or Simply Bitcoin on Nostr, you can now watch the video in Fountain and hang out in the live chat as it’s being recorded. You'll find livestreams from people who follow on Nostr at the top of the home screen.
As well and live podcasts, you will also find live music events from PhantomPowerMedia, radio stations like NoGood and Noderunners, as well as channels dedicated to gaming, art, coding and much more.
Bringing creators and fans together through live experiences enables audience participation and creates a special feeling of community, so we’re really excited to get this into your hands.
Nostr livestreams are a beta feature - i.e. we still have a lot more work to do! We will continue to make improvements to livestreams over the coming months - so we would love to hear your feedback.
\
**Storage Manager**
We’ve added a storage manager in the app’s settings so that you can view file storage size for audio downloads, video downloads, transcripts, image cache, feed cache, and temp files. You can delete all files in any of these folders to free up storage on your device so that Fountain continues to run optimally.
There are other performance and stability improvements that we are working on too. For example, in the next couple of weeks we will be rolling out an image proxy service, which should reduce mobile data usage and optimise storage.
Stay tuned for further updates and, as always, thanks for your support.
-

@ f1989a96:bcaaf2c1
2025-02-13 14:24:32
Good morning, readers!
This week, we highlight how authoritarian regimes are manipulating digital assets. The Central African Republic launched a government-backed meme coin that crashed spectacularly within a day of launch as regime insiders cashed out for profits, leaving the public with worthless tokens.
Meanwhile, the Nigerian regime introduced its first official stablecoin, cNGN. It is issued by the African Stablecoin Consortium and is backed 1:1 with the naira. Still, it operates under the direct oversight of the Nigerian Securities and Exchange Commission, allowing further surveillance of Nigerians’ financial activity alongside the struggling eNaira CBDC.
On the freedom tech front, Mullad VPN now supports Bitcoin payments via the Lightning Network, offering activists, journalists, and individuals under oppressive regimes a censorship-resistant and permissionless way to pay for their privacy. Additionally, SeedSigner, an open-source hardware wallet for Bitcoin self-custody, rolled out multilingual support, expanding accessibility to Spanish-speaking activists and human rights defenders.\
\
Finally, journalist Frank Corva explores Africa’s grassroots Bitcoin movement, where open-source tools and circular economies are empowering communities inside authoritarian regimes with financial freedom. For those who doubt Bitcoin’s real-world impact, this article is a must-read.
**Now, let’s get right to it!**
### [**Subscribe Here**](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a)
## **GLOBAL NEWS**
#### **Central African Republic | Launches Meme Coin Experiment**
The Central African Republic (CAR) [debuted](https://www.reuters.com/world/africa/central-african-republic-debuts-meme-coin-experiment-2025-02-10/) a government-backed meme coin, $CAR, which President Faustin-Archange Touadéra [claims](https://www.reuters.com/world/africa/central-african-republic-debuts-meme-coin-experiment-2025-02-10/) will “unite people” and “support national development.” In reality, meme coins are speculative assets that often serve as vehicles for insider profit. This scheme follows CAR’s failed [Sango Coin](https://www.mariblock.com/central-african-republic-top-court-rules-sango-coin-unconstitutional/) project, which promised citizenship and land in exchange for [locked](https://www.mariblock.com/central-african-republic-top-court-rules-sango-coin-unconstitutional/) investments but sold only 7.5% of its supply. Those who did “buy in” did not receive what was promised. In 2022, CAR briefly made Bitcoin legal tender, calling it a path to sovereignty — only to [abandon](https://bitcoinmagazine.com/culture/why-bitcoin-failed-in-car) it shortly after. Instead of supporting open and neutral money like Bitcoin, the government has turned to dubious crypto schemes. The real beneficiaries of $CAR appear to be regime insiders who reportedly cashed out [$40 million](https://x.com/bored2boar/status/1889002901370196098) while the public holds [worthless](https://decrypt.co/305225/central-african-republic-president-meme-coin) tokens.
#### **Nigeria | Debuts Naira Stablecoin**
The Nigerian state [launched](https://www.mariblock.com/move-over-enaira-cngn-enters-the-chat-2/) its first regulated stablecoin, [cNGN](https://cngn.co/?ref=mariblock.com). Similar to US dollar-pegged stablecoins like USDT and USDC, cNGN is pegged 1:1 to its local currency (the naira). It is issued by the African Stablecoin Consortium (ASC), a private coalition of Nigerian financial institutions and blockchain companies. Positioned as a bridge between fiat and digital assets, cNGN aims to facilitate remittances and trade but comes with strict verification requirements that limit financial privacy. The Nigerian SEC also tightly regulates the stablecoin and it is only available on government-approved exchanges, Busha and Quidax. As Nigeria expands its control over digital transactions — through both cNGN and its struggling [eNaira CBDC](https://cbdctracker.hrf.org/currency/nigeria) — more and more Nigerians are [turning](https://www.forbes.com/sites/digital-assets/2024/01/08/central-bank-of-nigeria-approves-naira-stablecoin-for-2024-launch/) to Bitcoin as a censorship-resistant alternative.
#### **Russia | Proposes Registry to Track Bitcoin Mining Hardware**
Russia’s deputy energy minister, Yevgeny Grabchak, has [proposed](https://theminermag.com/news/2025-02-03/russia-minister-bitcoin-miner/) a centralized registry of Bitcoin mining equipment and wallet addresses to “identify mining activities and ensure stricter enforcement of bans in restricted regions,” such as Russian-occupied Ukraine territories. Meanwhile, the Chairman of the State Duma Committee on Energy, Nikolai Shulginov, warned that last year’s mining ban in several Russian and occupied regions may not be enough to eliminate mining fully. As an authoritarian state with an egregious human rights record and a long history of financial repression, Russia appears intent on tightening surveillance of economic activity — especially that of Bitcoin. By registering, tracking, and restricting mining, the Kremlin expands its financial control, undermines economic autonomy, and limits access to permissionless money.
#### **Turkey | Erdoğan Targets Opposition as Inflation Forecast Rises**
Turkish President Recep Tayyip Erdoğan sentenced Istanbul Mayor Ekrem Imamoglu — a key political rival — to [seven](https://www.bloomberg.com/news/articles/2025-02-05/turkey-s-main-rival-to-erdogan-faces-jail-time-in-new-indictment) years in prison on charges widely seen as politically motivated. If upheld, the conviction will bar Imamoglu from office, further clearing Erdoğan’s path to dominance ahead of the 2028 elections. At the same time, Turkey’s economic crisis is worsening. [Accelerating inflation](https://www.reuters.com/world/middle-east/turkey-cenbank-raises-inflation-forecast-says-not-autopilot-with-cuts-2025-02-07/) forced the central bank to raise its 2025 forecast from 21% to 24%, exacerbating the lira’s decline and eroding purchasing power. As both political and financial repression deepen, more Turks are turning to alternatives to sidestep Erdoğan’s expanding control over the economic and political sphere.
#### **Georgia | Regime to Pass Censorship Law**
Georgia’s ruling Georgian Dream party is set to introduce a media censorship [law](https://jam-news.net/georgian-dream-plans-to-pass-media-censorship-law/) aimed at enforcing government-defined standards for journalistic objectivity and ethics, while also restricting foreign funding for media outlets. MP Mamuka Mdinaradze [claims](https://jam-news.net/ngos-and-media-organizations-of-georgia-to-challenge-the-foreign-agents-law-in-strasbourg-court/) the law will establish monitoring mechanisms and is modeled after UK regulations, though critics [compare](https://jam-news.net/opinion-ivanishvili-adopts-belarusian-tactics-to-control-protests/) it to Belarusian-style repression. Georgian Dream Prime Minister Irakli Kobakhidze defended the move as necessary to close legislative “loopholes” and strengthen state control. Journalists and activists warn that the law is part of a broader crackdown on press freedom and dissent. Decentralized social networks like Nostr will become increasingly vital for journalists and activists to communicate freely, resist censorship, and ensure the flow of independent information.
\___________________________________________________________\_
#### **Webinar Series for Nonprofits: Become Unstoppable**
HRF will host a [free, three-day webinar](https://docs.google.com/forms/d/e/1FAIpQLSf0sjqwSFQo8HGMsWIIDRyhx34TsoonOSTfYoWSy-aaBbLeSw/viewform) from March 17-19, teaching human rights defenders and nonprofits how to use Bitcoin to counter state censorship and confiscation. Sessions run daily from 10:30 a.m. to 12:00 p.m. EDT and are beginner-friendly. The webinar will be led by Anna Chekhovich, HRF’s Bitcoin nonprofit adoption lead and financial manager at Alexei Navalny’s Anti-Corruption Foundation.
### [Register Here](https://docs.google.com/forms/d/e/1FAIpQLSf0sjqwSFQo8HGMsWIIDRyhx34TsoonOSTfYoWSy-aaBbLeSw/viewform)
#### **SXSW | The Human Rights Risks of Central Bank Digital Currencies (CBDCs)**
Join HRF at [SXSW 2025](https://www.sxsw.com/) in Austin from March 9-12 to explore how CBDCs threaten financial freedom. Experts [Roger Huang](https://x.com/Rogerh1991), [Charlene Fadirepo](https://x.com/CharFadirepo), and [Nick Anthony](https://x.com/EconWithNick) will discuss how authoritarian regimes use CBDCs for surveillance and control on March 9. Attendees can also visit HRF’s [CBDC Tracker](https://cbdctracker.hrf.org/) booth to explore an interactive map of CBDC developments worldwide.
### [Get Tickets](https://www.sxsw.com/conference/)
\___________________________________________________________\_
## BITCOIN AND FREEDOM TECH NEWS
#### **Mullvad VPN | Testing Lightning Network Payments**
[Mullvad VPN](https://mullvad.net/en) is experimenting with Bitcoin for payments via the Lightning Network, a second-layer payment protocol built on Bitcoin that enables faster, cheaper, and more private transactions. This integration lets Mullvad VPN users pay for their services in bitcoin while enhancing their privacy and bypassing payment networks that track or censor financial activity. VPNs protect users by masking IP addresses and encrypting traffic. Accepting Bitcoin over Lightning strengthens this protection with a censorship-resistant payment option. For activists, journalists, and individuals in authoritarian regimes, this combination provides a shield against surveillance.
#### **SeedSigner | Releases Multilingual Support**
[SeedSigner](https://seedsigner.com/), an open-source and customizable Bitcoin hardware wallet and HRF grantee, [introduced](https://github.com/SeedSigner/seedsigner/releases/tag/0.8.5) multilingual support for Spanish. This update makes secure Bitcoin self-custody more accessible to Spanish-speaking activists and human rights defenders who may rely on Bitcoin for transactional freedom. By expanding access to secure self-custody, SeedSigner helps reduce dependence on restrictive financial systems and allows more people in Nicaragua, Venezuela, Cuba, and beyond to “be their own bank.”
#### **Iris | Implements Private Bitcoin Payments with Cashu**
[Iris](https://iris.cx/), a Nostr client, has added support for a Cashu wallet to allow users to send and receive ecash. Cashu is an open-source Chaumian ecash protocol built for Bitcoin and integrated with the Lightning Network. It lets users make fast, low-cost, and extremely private transactions using Bitcoin-backed ecash. While it requires a trusted custodian, it helps users spend Bitcoin anonymously without revealing their identity or transaction activity. This ability provides activists and nonprofits a different way to make private Bitcoin payments alongside nostr’s censorship-resistant communications.
#### **Sparrow Wallet | Supports Lark for USB Hardware Wallets**
[Sparrow Wallet](https://sparrowwallet.com/), a popular open-source Bitcoin wallet, has added support for [Lark](https://github.com/sparrowwallet/larkapp?mc_cid=aab08acf41&mc_eid=5c5878c08e), a new tool for USB hardware wallet communication. Lark works alongside the existing [Hardware Wallet Interface](https://github.com/bitcoin-core/HWI) (HWI), giving users an alternative way to connect their hardware wallets via USB. This update improves reliability, reduces dependence on a single software interface, and strengthens Bitcoin self-custody.
#### **Bitcoin Dada | Opens Applications for Second Cohort of Dada Devs**
[Bitcoin Dada](https://btcdada.com/), an HRF-supported nonprofit initiative empowering African women through Bitcoin and financial education, is now [accepting](https://x.com/DadaDevs/status/1886819762660929674) applications for the second cohort of Dada Devs. This developer program provides hands-on training, mentorship, and a collaborative community to help African women under authoritarian regimes contribute to Bitcoin development. If you’re an aspiring female developer, [apply now](https://docs.google.com/forms/d/e/1FAIpQLSeJ8nXL96qNeCAaXnSlGxqykBPEGm21z9qS9oE1ldNusM0nTA/viewform) to join a network of African women shaping the future of finance. Applications close Feb. 13.
#### **Summer of Bitcoin | Applications for Summer 2025 Cohort Now Open**
[Summer of Bitcoin](https://www.summerofbitcoin.org/), an HRF-supported Bitcoin internship program, is now accepting [applications](https://www.summerofbitcoin.org/apply) for its summer 2025 cohort. This program introduces students from anywhere, including from authoritarian regimes, to Bitcoin open-source development and design, giving interns the option to choose between a developer or designer track based on their interests. Participants will gain hands-on work experience, contribute to real-world Bitcoin projects, and receive mentorship from industry leaders. You can learn more and apply [here](https://www.summerofbitcoin.org/).
#### **Spiral | Announces Grant Renewals for the Bitcoin Design Community and BDK**
[Spiral](http://spiral.xyz), a Bitcoin company building and funding open-source projects, announced renewed grants for critical initiatives, including the [Bitcoin Design Community](https://github.com/bitcoindesign) and [Bitcoin Dev Kit](https://bitcoindevkit.org/) (BDK). The Bitcoin Design Community is a free and open-source resource for designers, developers, and others working on non-custodial Bitcoin products. This [grant](https://x.com/spiralbtc/status/1885000120439095607) will support designers who push the user experience and adoption of Bitcoin forward. Meanwhile, BDK is a software library that helps developers in building cross-platform Bitcoin wallets. Its [grant](https://x.com/spiralbtc/status/1884998758976405840) will support the project’s continued refinement and development.
## RECOMMENDED CONTENT
#### **The Bitcoin and Cypherpunk Spirit Is Alive and Well in Africa by Frank Corva**
In this [article](https://bitcoinmagazine.com/culture/the-bitcoin-and-cypherpunk-spirit-is-alive-and-well-in-africa) for [Bitcoin Magazine](http://bitcoinmagazine.com), journalist [Frank Corva](https://x.com/frankcorva) spotlights Bitcoin's growing presence across Africa. Across the continent, people are building Bitcoin circular economies, open-source financial tools, and educational initiatives. From [Bitcoin Ekasi](https://x.com/BitcoinEkasi) in South Africa to [AfriBit Kibera](https://x.com/AfribitKibera) in Kenya and [Bitcoin Dua](https://x.com/bitcoin_dua) in Ghana, these grassroots initiatives drive financial inclusion and education for individuals and communities. Meanwhile, tools like [Tando](https://tando.me/) and [Machankura](https://8333.mobi/) are expanding access to transactional freedom, and conferences like [Adopting Bitcoin Captetown](https://za25.adoptingbitcoin.org/) and the [Africa Bitcoin Conference](https://afrobitcoin.org/) nurture ongoing collaboration between individuals, developers, and activists to advance financial freedom on a continent that otherwise has very little liberal democracy. Read the full article [here](https://bitcoinmagazine.com/culture/the-bitcoin-and-cypherpunk-spirit-is-alive-and-well-in-africa).
#### **Using Bitcoin Without Internet! Here’s How Machankura Makes It Happen with Anita Posch**
In this short [interview](https://www.youtube.com/watch?v=XzXfd237XVo), Bitcoin educator and host of the [Bitcoin for Fairness](https://www.youtube.com/@AnitaPosch) channel, Anita Posch, speaks with Mary Imasuen, a [Machankura](https://8333.mobi/) team member, about how this technology makes Bitcoin accessible to Africans without Internet access. Machankura is an app that allows feature phones to send and receive Bitcoin using the Unstructured Supplementary Service Data (USSD) protocol, a mobile communications system similar to SMS. This means people can transact in Bitcoin without needing a smartphone or data connection, a situation common to many living under autocratic regimes in sub-Saharan Africa. By removing Internet barriers, Machankura helps millions of Africans overcome high data costs and unreliable networks, offering a practical solution to financial inclusion.
*If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report [here](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a).*
*Support the newsletter by donating bitcoin to HRF’s Financial Freedom program [via BTCPay](https://hrf.org/btc).*\
*Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ [hrf.org](http://hrf.org/)*
*The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals [here](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1)*.
[**Subscribe to newsletter**](http://financialfreedomreport.org/)
[**Apply for a grant**](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1&mc_cid=39c1c9b7e8&mc_eid=778e9876e3)
[**Support our work**](https://hrf.org/btc?mc_cid=39c1c9b7e8&mc_eid=778e9876e3)
[**Visit our website**](https://hrf.org/programs/financial-freedom/)
-

@ 9673b322:1b75ee9e
2025-02-13 14:15:38
This is test content

-

@ 9673b322:1b75ee9e
2025-02-13 14:10:06
This is some test content
Adding a Sample Image

-

@ 2e8970de:63345c7a
2025-02-13 13:39:35
> We measure gender differences using the Cross-Gender Friending Ratio, the ratio of female friends in men's networks to the share of female friends in women's networks in a given place.
Men almost always have a lower share of female friends than women do, but the degree varies:
> Across countries, the CGFR is strongly predictive of gender differences in labor force participation.
Within countries, we also find a strong correlation with gender attitudes in the World Values Survey, such as beliefs about women's suitability for politics.
https://x.com/drew_m_johnston/status/1889794718004826288
originally posted at https://stacker.news/items/884660
-

@ c2827524:5f45b2f7
2025-02-13 11:54:16
> innèsto s. m. [der. di innestare]. – 1. In agraria: a. Operazione con cui si fa concrescere sopra una pianta (detta portainnesto o soggetto) una parte di un altro della stessa specie o di specie differenti (detto nesto o oggetto), **al fine di formare un nuovo individuo più pregiato o più produttivo o più giovane**: fare, operare, praticare un innesto.
Le collaborazioni sono di una potenza micidiale.
Quelle che si sviluppano nello spazio #Bitcoin ancora di più.
Non è più una collaborazione, è un #innesto: rami di alberi diversi, destinati da soli a dare grandi frutti, si fondono per **donare ad un intero ecosistema sapori ancora più deliziosi**.
Contributi e suggerimenti vanno e vengono alla velocità della luce, col sorriso, senza sacrificio e sempre con la volontà di migliorarsi e crescere.
Lo spazio #Bitcoin è una fabbrica magica, che accoglie minuscoli semini(*) da chiunque voglia partecipare, volontariamente, alla crescita della cultura Bitcoin. Ma li trasforma in un **incanto**.
In solitaria i semini sarebbero destinati comunque a grandi cose e questo è già, di per sé, meraviglioso. La fabbrica magica, invece, li fa germogliare, fiorire e fruttare in maniera ancora più potente.
Quando la magia è totale, avviene l’*innesto*, **la generazione di una nuova creatura più pregiata**.
Sta succedendo davanti ai miei occhi. Sono onorata di poter assistere a questo mini miracolo della vita e, manco a dirlo, felice di farne parte.
Non è solo cambiare atteggiamento, smussare frizioni e rigidità o correggere la propria visione, è proprio ampliare sé stessi accogliendo gli altri.
Grazie nostr:npub1uhj92lnwh8rrhhuvulfqstk4g0ayx0zx35wj2d62jueqheknkxks5m4zj6 nostr:npub1au23c73cpaq2whtazjf6cdrmvam6nkd4lg928nwmgl78374kn29sq9t53j nostr:npub1awnu9vg352863e7tqlc6urlw7jgdf8vf00tmr76uuhflp4nnn68sjmnnl3 e nostr:npub1lrurmgmlfl4u72258fc4q5ke7tr82kw5xct5vchdmzr9uhmx6j4qn3t72a
(1) Semini, non #seed [non chiamatelo seed, si dice mnemonica (cit.)]
Siccome in italiano la parola **seme** porta alla mente anche *giochini di parole fiat*, se siete qui per perculare fate pure. -> H.F.S.P. 🤣
-

@ d360efec:14907b5f
2025-02-13 11:15:12
**Top-Down Analysis:** กลยุทธ์การเทรดเพื่อมองภาพรวมและจับจังหวะทำกำไร
ในโลกของการเทรดที่เต็มไปด้วยความผันผวน การมีเครื่องมือวิเคราะห์ที่แข็งแกร่งเป็นสิ่งสำคัญอย่างยิ่งที่จะช่วยนำทางให้เทรดเดอร์สามารถตัดสินใจได้อย่างมีหลักการและเพิ่มโอกาสในการทำกำไร หนึ่งในเครื่องมือที่ได้รับความนิยมและมีประสิทธิภาพคือ "Top-Down Analysis" หรือการวิเคราะห์จากบนลงล่าง ซึ่งเป็นวิธีการมองภาพรวมของตลาดก่อนที่จะเจาะจงไปที่สินทรัพย์ที่เราสนใจ บทความนี้จะพาคุณไปทำความเข้าใจกับ Top-Down Analysis อย่างละเอียด พร้อมทั้งแนะนำกลยุทธ์การเทรดที่สามารถนำไปปรับใช้ได้จริง
**Top-Down Analysis คืออะไร?**
Top-Down Analysis เป็นกระบวนการวิเคราะห์ตลาดที่เริ่มต้นจากการพิจารณาภาพรวมในกรอบเวลาที่ใหญ่ขึ้น ก่อนที่จะค่อยๆ ย่อยลงไปในกรอบเวลาที่เล็กลง เพื่อทำความเข้าใจบริบทของตลาดและหาจังหวะการเทรดที่เหมาะสม วิธีการนี้ช่วยให้เทรดเดอร์สามารถมองเห็นทิศทางหลักของตลาด, แนวโน้มที่กำลังเกิดขึ้น, ระดับราคาสำคัญ, และความสมดุลระหว่างอุปสงค์และอุปทาน ก่อนที่จะตัดสินใจเข้าเทรดในกรอบเวลาที่เล็กลง
**องค์ประกอบสำคัญของ Top-Down Analysis (อ้างอิงจากภาพ)**
ภาพ "Top-Down Analysis" ได้สรุปองค์ประกอบสำคัญของการวิเคราะห์นี้ไว้อย่างชัดเจน โดยแบ่งการวิเคราะห์ออกเป็น 3 กรอบเวลาหลัก: 4 ชั่วโมง (4H), 1 ชั่วโมง (1H), และ 15 นาที (15min) แต่ละกรอบเวลามีองค์ประกอบที่ต้องพิจารณาดังนี้:
1. กรอบเวลา 4 ชั่วโมง (4H): ภาพรวมตลาดและทิศทางหลัก
ในกรอบเวลา 4 ชั่วโมง เราจะเน้นการวิเคราะห์ภาพรวมของตลาด เพื่อกำหนดทิศทางหลักและแนวโน้มในระยะกลาง องค์ประกอบสำคัญในกรอบเวลานี้คือ:
* Direction (ทิศทาง): ประเมินทิศทางที่ตลาดกำลังเคลื่อนที่ไป โดยพิจารณาจากแนวโน้มและโครงสร้างราคาในภาพรวม ตลาดกำลังเป็นขาขึ้น, ขาลง หรืออยู่ในช่วง Sideways?
* Trend (แนวโน้ม): ระบุแนวโน้มหลักของตลาด ไม่ว่าจะเป็นแนวโน้มขาขึ้น (Uptrend), แนวโน้มขาลง (Downtrend) หรือ Sideways การเข้าใจแนวโน้มช่วยในการกำหนดกลยุทธ์การเทรดที่เหมาะสม
* Key levels (ระดับราคาสำคัญ): หาระดับราคาแนวรับและแนวต้านที่สำคัญในกรอบเวลา 4 ชั่วโมง ระดับเหล่านี้มักเป็นจุดที่ราคาเคยมีการกลับตัวหรือพักตัวในอดีต และอาจเป็นบริเวณที่ราคาจะตอบสนองอีกครั้งในอนาคต
* Supply & Demand (อุปทานและอุปสงค์): วิเคราะห์ความสมดุลระหว่างแรงซื้อ (Demand) และแรงขาย (Supply) ในตลาด โดยพิจารณาจากพฤติกรรมราคาบริเวณแนวรับแนวต้าน และสัญญาณจากเครื่องมือวิเคราะห์อื่นๆ (ถ้าใช้)
2. กรอบเวลา 1 ชั่วโมง (1H): หาจังหวะและบริเวณที่น่าสนใจ
เมื่อได้ภาพรวมและทิศทางหลักจากกรอบ 4H แล้ว เราจะย่อยลงมาในกรอบ 1 ชั่วโมง เพื่อหาจังหวะการเทรดที่สอดคล้องกับทิศทางหลัก และมองหารูปแบบราคาที่น่าสนใจ องค์ประกอบสำคัญในกรอบเวลานี้คือ:
* Breaks (การทะลุ): สังเกตการทะลุแนวรับแนวต้าน หรือระดับราคาสำคัญในกรอบ 1H ที่สอดคล้องกับทิศทางหลักใน 4H การทะลุเหล่านี้อาจเป็นสัญญาณของการเคลื่อนไหวครั้งใหญ่ของราคา
* Reversals (การกลับตัว): มองหารูปแบบการกลับตัวของราคาที่อาจเกิดขึ้นบริเวณระดับราคาสำคัญในกรอบ 1H ซึ่งบ่งบอกถึงจุดสิ้นสุดของแนวโน้มปัจจุบันและเริ่มต้นแนวโน้มใหม่
* OB (Order Blocks): ระบุบริเวณ Order Blocks ในกรอบ 1H ซึ่งเป็นพื้นที่ที่มีการสั่งซื้อขายจำนวนมากในอดีต Order Blocks เหล่านี้มักจะทำหน้าที่เป็นแนวรับแนวต้านในอนาคต
* FVG (Fair Value Gaps): มองหา Fair Value Gaps ในกรอบ 1H ซึ่งเป็นช่องว่างของราคาที่เกิดจากการเคลื่อนไหวอย่างรวดเร็ว FVG มักจะเป็นเป้าหมายของราคาในอนาคต เนื่องจากราคาอาจจะกลับมาปิดช่องว่างเหล่านี้
* Liquidity (สภาพคล่อง): ประเมินสภาพคล่องบริเวณระดับราคาที่เราสนใจในกรอบ 1H บริเวณที่มีสภาพคล่องสูงมักจะดึงดูดนักลงทุนรายใหญ่ และอาจทำให้เกิดการเคลื่อนไหวของราคาที่รุนแรง
3. กรอบเวลา 15 นาที (15min): ยืนยันสัญญาณและหาจุดเข้าเทรด
ในกรอบเวลา 15 นาที เราจะเน้นการยืนยันสัญญาณการเทรด และหาจุดเข้าเทรดที่แม่นยำ เพื่อลดความเสี่ยงในการเข้าเทรดเร็วเกินไป องค์ประกอบสำคัญในกรอบเวลานี้คือ:
* Confirmation (การยืนยัน): รอสัญญาณยืนยันการเคลื่อนไหวของราคาในกรอบ 15 นาที ที่สอดคล้องกับการวิเคราะห์ในกรอบ 1H และ 4H สัญญาณยืนยันอาจมาในรูปแบบของแท่งเทียนกลับตัว, รูปแบบ Chart Patterns, หรือสัญญาณจาก Indicators
* จุดเข้าเทรด: เมื่อมีสัญญาณยืนยันที่ชัดเจนในกรอบ 15 นาที และสอดคล้องกับการวิเคราะห์ในกรอบเวลาที่ใหญ่ขึ้น จึงตัดสินใจเข้าเทรด โดยกำหนด Stop Loss เพื่อจำกัดความเสี่ยง และ Take Profit เพื่อตั้งเป้าหมายในการทำกำไร
**กลยุทธ์การเทรด Top-Down Analysis: ขั้นตอนสู่ความสำเร็จ**
เพื่อนำ Top-Down Analysis ไปใช้ในการเทรดอย่างมีประสิทธิภาพ เราสามารถทำตามขั้นตอนต่อไปนี้:
1. **เริ่มต้นที่ 4H**: กำหนดทิศทางและแนวโน้มหลัก วิเคราะห์กราฟ 4H เพื่อระบุทิศทางหลักของตลาด แนวโน้ม และระดับราคาสำคัญ ประเมินความสมดุลของ Supply & Demand เพื่อกำหนด Bias การเทรด (เน้นซื้อหรือขาย)
2. **เจาะลึก 1H:** หาจังหวะและบริเวณที่น่าสนใจ เมื่อได้ทิศทางหลักจาก 4H แล้ว ให้ย่อยลงมาดูกราฟ 1H เพื่อหารูปแบบราคาที่น่าสนใจ เช่น การทะลุแนวรับแนวต้าน, รูปแบบการกลับตัว, Order Blocks, Fair Value Gaps และบริเวณที่มีสภาพคล่องสูง
3. **ยืนยันใน 15min:** หาจุดเข้าเทรดที่แม่นยำ รอสัญญาณยืนยันในกรอบ 15 นาที ที่สอดคล้องกับการวิเคราะห์ในกรอบเวลาที่ใหญ่ขึ้น ใช้ Price Action, แท่งเทียน, หรือ Indicators เพื่อยืนยันสัญญาณ และหาจุดเข้าเทรดที่แม่นยำ พร้อมกำหนด Stop Loss และ Take Profit ที่เหมาะสม
**ประโยชน์ของการใช้ Top-Down Analysis**
* มองเห็นภาพรวมตลาด: ช่วยให้เทรดเดอร์เข้าใจบริบทของตลาดในภาพรวม ไม่หลงทางในรายละเอียดเล็กๆ น้อยๆ
* ตัดสินใจเทรดอย่างมีหลักการ: ทำให้การตัดสินใจเทรดมีเหตุผลและมีข้อมูลสนับสนุนมากขึ้น ไม่ใช่แค่การคาดเดา
* เพิ่มความแม่นยำในการเทรด: การวิเคราะห์หลายกรอบเวลาช่วยกรองสัญญาณรบกวน และเพิ่มโอกาสในการเข้าเทรดในทิศทางที่ถูกต้อง
* ลดความเสี่ยง: ช่วยลดโอกาสในการเทรดสวนทางแนวโน้มหลักของตลาด และช่วยในการกำหนด Stop Loss ที่เหมาะสม
**ข้อควรจำและข้อควรระวัง**
* ฝึกฝนและสังเกต: Top-Down Analysis ต้องอาศัยการฝึกฝนและการสังเกตกราฟราคาอย่างสม่ำเสมอ เพื่อพัฒนาความเข้าใจและทักษะในการวิเคราะห์
* ปรับใช้ให้เข้ากับสไตล์: ปรับกลยุทธ์ให้เข้ากับสไตล์การเทรดของคุณ และสินทรัพย์ที่คุณเทรด
* บริหารความเสี่ยง: ให้ความสำคัญกับการบริหารความเสี่ยงเสมอ กำหนดขนาด Position ที่เหมาะสม และใช้ Stop Loss ทุกครั้ง
* ไม่มีกลยุทธ์ใดสมบูรณ์แบบ: Top-Down Analysis เป็นเครื่องมือที่มีประสิทธิภาพ แต่ไม่มีกลยุทธ์ใดที่รับประกันผลกำไร 100% การเทรดมีความเสี่ยง โปรดศึกษาและทำความเข้าใจความเสี่ยงก่อนตัดสินใจลงทุน
**สรุป**
Top-Down Analysis เป็นกลยุทธ์การเทรดที่ทรงพลัง ซึ่งช่วยให้เทรดเดอร์สามารถวิเคราะห์ตลาดอย่างเป็นระบบ มองภาพรวม และจับจังหวะการเทรดได้อย่างแม่นยำ การนำหลักการของ Top-Down Analysis ไปปรับใช้ในการเทรด จะช่วยเพิ่มประสิทธิภาพในการตัดสินใจ และเพิ่มโอกาสในการประสบความสำเร็จในตลาดการเงินได้อย่างยั่งยืน
-

@ 3eba5ef4:751f23ae
2025-02-13 09:00:41
Security is fundamental to any blockchain. It ensures that all tokens are secure. When talking about a virtual machine and the smart contract platform it forms, security comes in two main aspects:
* The code running on the virtual machine must be secure
* The virtual machine itself should also be designed to facilitate safer code execution
The first aspect often gets sufficient attention. When it comes to [CKB](https://www.nervos.org/), we now encourage developers to write scripts in Rust for maximum security, reserving pure C code only for those who fully understand its risks. Additionally, higher-level languages have been introduced in CKB to strike a better balance between productivity and security.
Virtual machine security was a major focus when CKB-VM was originally designed. Many potential risks were addressed at the architectural level, though some—despite thorough research—were still left open. One such issue is **Return-Oriented Programming (ROP)**—a rather ingenious attack. It exploits executable code that has been legitimately loaded into memory, making widely effective protections (e.g., [W^X](https://yakihonne.com/write-article)) futile. It spans multiple architectures and is constantly evolving. Although we’ve spent a great deal of effort in the early days on ROP, we did not implement specific countermeasures to prevent it. Now, with new RISC-V extensions now available, it is the perfect time to introduce design-level protections against ROP.
## Acknowledgments
Before diving deeper, we would like to acknowledge Todd Mortimer from the OpenBSD team. His work on ROP mitigations at the OpenBSD kernel in 2018-2019 significantly inspired our research and this article. We highly recommend his [talk](https://www.youtube.com/watch?v=ZvSSHtRv5Mg), slide decks from [AsiaBSDCon 2019](https://www.openbsd.org/papers/asiabsdcon2019-rop-slides.pdf) and [EuroBSD 2018](https://www.openbsd.org/papers/eurobsdcon2018-rop.pdf), and this [paper](https://www.openbsd.org/papers/asiabsdcon2019-rop-paper.pdf) for a deeper understanding of ROP. Several examples on x64 ROP attacks in this post are also drawn from his research.
## Typical Attack Workflow
While there are many sophisticated [ways](https://www.wired.com/2016/06/clever-attack-uses-sound-computers-fan-steal-data/) of attacks, a common attack on a program typically follows this process:
Prepare a [shellcode](https://en.wikipedia.org/wiki/Shellcode)— a piece of binary code to perform specific actions (e.g., running a shell or other programs on the target computer).
Exploit one possible vulnerability in the target system, most commonly a [buffer overflow](https://en.wikipedia.org/wiki/Buffer_overflow) attack. The attack could be initiated via a network protocol (such as HTTP) against a remote system, or via command line input to a target program;
As the result of the attack, the shellcode is inserted to a designated memory region of the target system and gets executed, allowing the attacker to achieve their goal. The consequences vary, like gaining unauthorized access to sensitive data, destroying certain data/machine, planting malicious programs onto the target for further actions, manipulating control flow.
While traditional systems face a wide range of attacks, blockchains run in their own limited and unique runtime environment, rendering many conventional attacks irrelevant. Major blockchain security threats includes:
* **Private key security**: Blockchain wallets rely on private keys, which are prime targets for various attacks.
* **Smart contract vulnerability**: Poorly written smart contracts contain logic flaws that lead to security risks.
* **Virtual machine security**: Attacker may send malicious inputs to a smart contract, causing it to terminate unexpectedly with a success status—despite lacking proper credentials.
This post focuses specifically on attacks targeting the blockchain’s virtual machine—in our case—CKB Virtual Machine (CKB-VM) specifically.
## CKB’s Early Approach
While it is impossible to predict every attack, disrupting the typical attack workflow is an effective defense strategy. From its inception, CKB-VM has implemented [W^X](https://en.wikipedia.org/wiki/W%5EX) protection: at any given time, any memory location in CKB-VM is either writable (allowing data modification) or executable (allowing data execution)—but never both. Once a memory region is marked as **executable**, it cannot be reverted to **writable** throughout the lifecycle of the current CKB-VM instance. Only writable memory location can be **frozen** to executable.
This design significantly disrupts the typical attack workflow. For shellcode to execute on CKB-VM, it must reside in **executable** memory. However, an attacker can only provide shellcode as part of program inputs, which are loaded into **writable** memory. As long as a CKB script does not voluntarily mark input data as **executable** (a highly unlikely scenario), the shellcode remains inert. Additionally, attempting to overwrite existing **executable** shellcode is also futile, since executable memory region is unwritable, and cannot be converted back to writable.
This way, W^X is a well-established security technique widely used in modern hardwares, operating systems, and virtual machines. Although it cannot prevent all possible attacks, W^X effectively shields many by breaking the standard attack workflow. Even if an attacker successfully injects shellcode into a target machine, the attack is incomplete due to the inability to execute it.
## Understanding ROP
While W^X is effective, it does not solve all our problems. This leads to the topic of this post: **Return-oriented Programming (ROP)**. Instead of explicitly injecting new code, ROP exploits executable code that already resides in the target machine’s memory. Essentially, ROP builds a shellcode by chaining existing code snippets together that were never intended to function as such. It may sound like a fantasy, but as we shall see from the following examples, ROP is a practical and effective attack technique.
To understand ROP, we must first examine modern CPU architecture and memory layout. While assembly instructions vary in representations and lengths, they are put together in memory one after another as a stream of bytes:

*Image [Source](https://www.quora.com/Is-assembly-language-a-source-code-or-object-code)*
As seen in the above example, different assembly instructions come in different lengths. For x86-64 ISA, an instruction can range from 1 to 7 bytes (RISC ISAs such as ARM or RISC-V have more uniform instruction lengths—we will discuss it later). But in memory, instructions are stored sequentially without gaps.
This means that with a stream of bytes alone, we really don’t know what instructions the stream of bytes consist of. In the above example, meaningful assembly instructions emerge only when we start decoding from the `B8` byte. In a different occasion, assuming we know elsewhere that `B8 22 11` bytes at the front are for certain magic flags, the decoding would start from `00` byte, yielding a totally different instruction set.

*Image [Source](https://www.quora.com/Is-assembly-language-a-source-code-or-object-code)*
It is really the combination of a special program counter (`PC`) register from the CPU and the current memory stream, jointly determine the instructions the CPU executes. Depending on each different ISA or hardware, a booting process initializes a CPU’s `PC` register to a pre-defined value, then loads up instructions from this pre-defined address, and initializes everything related to the operating system. When a user launches a new program, the metadata for each program will contain an `entrypoint` address, where OS sets the CPU’s `PC` register to, in order to start executing the program. It is suffice to say that maintaining a proper `PC` value is a critical job to ensure a computer’s proper function. An invalid `PC` value might lead to a CPU malfunction at best, or at worst, leaking sensitive information or granting attackers unauthorized access.
### Forming an ROP Attack Via ROP Gadgets
Let’s look at the following byte instruction stream in a x86-64 CPU:
```
8a 5d c3 movb -61(%rbp), %bl
```
This 3-byte represents a `mov` instruction: it takes the address of `rbp` register, adds an offset of `-61`, then uses the result as a memory address to load 1 byte data, and finally sets the loaded data to `bl` register. However, if we ignore `8a` and only look at `5b c3` here, it actually represents a different instruction set:
```
5d popq %rbp
c3 retq
```
This byte sequence contains two instructions:
* Pop 8-byte value from stack, and use it to set `rbp` register
* Pop 8-byte value from stack, and use it to set `PC` register, so we continue executing from the new location
We've briefly discussed that shellcode only fulfills a certain task required by the attacker. In fact, the most common type of shellcode simply construct a new shell, where the attacker can execute more operations. Such shellcode can be represented in the following C pseudocode to run a new command via the `execve` syscall:
```
execve(“/bin/sh”, NULL, NULL);
```
To execute this on an x86-64 CPU, the following actions are needed for a syscall:
* `rax` register: must contain the syscall number, for `execve`, it is `59`
* `rdi`, `rsi`, `rdx` registers: hold the first 3 arguments to the syscall. In this case, `rdi` holds a pointer to the C string `/bin/sh`; `rsi` and `rdx` must be zero.
* The `syscall` instruction (or typically `int 80h` on x64) shall be executed
A typical shellcode would be a packed assembly sequence directly doing all of the above instructions. In contrast, ROP attack looks for the following sequences:
```
# Those can set the value of different registers from values on the stack
pop %rax; ret
pop %rdi; ret
pop %rsi; ret
pop %rdx; ret
# Finally, trigger the syscall
syscall
```
Each of these small code sequences, are conventionally callled **ROP gadgets**. An attacker searches for these gadgets in the target program or system libraries (such as libc). Once these required gadgets are obtained, the attacker pieces together a sequence of data, much like the following:

With the prepared data sequence, the attacker can exploit a vulnerability in the target computer or program, such as typical buffer overflow attack. During this process, the attacker performs three key actions:
* Pushes (or overwrites existing data) the crafted data sequence to the stack
* Sets the stack pointer (top of the stack) to `X + 64`
* Sets the `PC` register to the address of a code sequence, `pop %rax; ret` in the existing program or libc memory space
Now the attack proceeds step by step as follows:
1. The CPU runs `pop %rax; ret`. With the stack pointer pointing to `X + 64`, the CPU pops `59` from the stack and sets `rax` register to `59`. It then pops the address to code sequence `pop %rdi; ret` from the stack, and sets `PC` to this value;
2. The CPU runs `pop %rdi; ret`. With the stack pointer pointing to `X + 48`, the CPU pops value `X`, pointing to the C string `/bin/sh` from the stack, and sets `rdi` register to `X`. It then pops the address to code sequence `pop %rsi; ret` from the stack, and sets `PC` to this value;
3. The CPU runs `pop %rsi; ret`. With the stack pointer pointing to `X + 32`, the CPU pops `0` from the stack and sets `rsi` register to `0`. It then pops the address to code sequence `pop %rdx; ret` from the stack, and sets `PC` to this value;
4. The CPU runs `pop %rdx; ret`. With the stack pointer pointing to `X + 16`, the CPU pops `0` from the stack and sets `rdx` register to `0`. It then pops the address to code sequence `syscall` from the stack, and sets `P`C to this value;
5. The CPU runs `syscall`. At this point, `rax` holds `59`, `rdi` points to `/bin/sh`, and both `rsi` and `rdx` are zero, the CPU invokes `execve("/bin/sh, NULL, NULL);`, granting the attacker a shell for further manipulations.
This sequence of ROP gadgets, referred to as **ROP chains**, demonstrates how a complete ROP attack works. Two key takeaways are:
* **ROP does not inject new code**. Instead, it injects data into the stack and leverages the existing code loaded in memory and marked them as executable. W^X protections hence cannot prevent ROP attacks.
* **Attackers can mine ROP gadgets from the [libc](https://en.wikipedia.org/wiki/C_standard_library) library**. This is because modern computers employs [protection rings](https://en.wikipedia.org/wiki/Protection_ring) as a way for privilege encapsulations: on x86-64 computers, programs normally run at ring level 3, while libc runs at ring level 1. Lower ring levels have higher privileges, meaning that even if a program misbehaves, its capacities are limited at ring level 3. However, by using ROP gadgets in the libc library which runs at ring level 1, ROP attacks can have higher privileges and execute more damaging operations then normal shellcodes.
Note that the above examples simply show the most basic ROP gadgets. In reality, ROP gadgets come in all kinds of forms. Since they come from compiler outputs, they can be combined in the least expected way, and can vary the forms as new compiler optimizations come out. Numerous tools (e.g., [ropper](https://scoding.de/ropper/), [ropr](https://github.com/Ben-Lichtman/ropr)) and research papers (e.g., *[Experiments on ROP Attack with Various Instruction Set Architectures](https://dl.yumulab.org/papers/42/paper.pdf)*, *[ROPGMN](https://www.sciencedirect.com/science/article/abs/pii/S0167739X24005314)*, *[Detecting and Preventing ROP Attacks using Machine Learning on ARM](https://www.infosun.fim.uni-passau.de/ch/publications/compsac23.pdf)*, *[KROP](https://arxiv.org/pdf/2406.11880)* ) keep coming out, making it almost impossible to enumerate all possible ROP gadget combinations.
### ROP on ARM & RISC-V
ROP attacks are not limited to CISC architectures, where instructions vary in length. They also affect RISC designs, such as [ARM](https://developer.arm.com/documentation/102433/0200/Return-oriented-programming) and [RISC-V](https://pure.royalholloway.ac.uk/ws/portalfiles/portal/37157938/ROP_RISCV.pdf). Take the following sequence for example:
```
13 4f 83 23 0b 00
```
Decoding from the start, the first four bytes represent `xori t5,t1,568` following the RISC-V ISA. But if we skip the first two, the latter four represent `lw t2,0(s6)`. This illustrates that a byte stream interpretation also requires `PC` register in a RISC design such as RISC-V. As a result, one can find ROP gadgets from a RISC-V program as well.
### ROP on CKB-VM
CKB’s RISC-V machine operates in a more restricted environment: for programs running on CKB, there are no `execve` syscalls to hijack a running shell, and all runtime states are publicly visible on a public blockchain like CKB. However, ROP attacks can still occur on CKB: one could construct an ROP chain that sets `a0` to `0`, `a7` to `93`, then executes `ecall`. This causes CKB-VM to immediately return with a success code (`0`), potentially allowing a script to pass validation when it should have failed—such as a lock script succeeding without a valid signature.
### Short Recap
Let’s briefly recap what we’ve learned so far:
* ROP attacks utilize existing executable code for malicious purposes. W^X cannot prevent ROP.
* ROP is possible across multiple architecture, including x86-64, ARM, RISC-V, and CKB.
* The landscape of ROP is constantly evolving. With new tools, techniques, and research emerging regularly, it’s impossible to foresee all ROP gadgets.
ROP has been extensively studied over the years, leading to various mitigation strategies, which can be broadly categorized into two main approaches:
* **Software Solutions**: Covering techniques like rewriting code sequences and implementing Retguard to prevent the creation of ROP gadgets
* **Hardware Solutions**: Introducing additional CPU instructions with Control Flow Integrity (CFI) checks to safeguard control flow.
I’ll explore these strategies in greater detail in the following sections.
## Software Solutions to Mitigate ROP
### Rewriting Sequence
Certain instruction sequences are often targeted to form ROP gadgets. To prevent ROP, one approach is to alter the compiler, so that such sequences can never be generated. Take the following example:
```
89 c3 mov %eax,%ebx
90.
```
In x86-64, `c3` represents the `ret` instruction, making it a potential target for ROP gadgets. We can rewrite it into the following equivalent sequence:
```
48 87 d8 xchgq %rbx, %rax
89 d8 movl %ebx, %eax
48 87 d8 xchgq %rbx, %rax
```
The new sequence lacks `c3` byte at the expense of more bytes and more executed instructions. However, it is really up to real benchmarks to see if this causes noticeable overhead.
Further analysis has revealed that the `rbx` register in x86-64 is often the source of ROP gadgets, due to the way Intel encodes x86-64 instructions. Hence, the OpenBSD team decided to avoid `rbx` register wherever possible, reducing the number of potential ROP gadgets.
Again, this approach comes at the cost of having bigger code fragments, more instructions to execute, and an additional patched compiler. While OpenBSD has integrated these changes into its distribution, other environments must weigh the benefits against the costs.
For a deeper dive, I would strongly recommend Todd Mortimer’s [work](https://www.openbsd.org/papers/asiabsdcon2019-rop-slides.pdf).
### Retguard’s Solution: Prologue and Epilogue
Todd Mortimer also introduced Retguard in this [work](https://www.openbsd.org/papers/asiabsdcon2019-rop-slides.pdf) for securing OpenBSD known. ROP attacks typically occur when you enter a function `foo`, but the stack was manipulated, so the CPU exits to another code fragment that is not `foo`. What if to verify that, at each function exit, it is the same function for exiting and entering?
Retguard introduces two components to perform this task:
* **Prologue**: A prologue is inserted to each function’s entry, taking two inputs:
- - A `cookie` value, a random data assigned for this particular function.
- - The return address, where to jump to when current function exits—as inputs.
The prologue computes the XOR value of these two, and stores the result into the current function’s [frame](https://en.wikipedia.org/wiki/Call_stack#Stack_and_frame_pointers) section, a dedicated memory region designated to the current function to hold data, separated from the stack.
* **Epilogue**: An epilogue is inserted to the location where a function might exit. It takes two inputs:
- - The saved XOR value from the prologue in the frame section
- - The return address it now can access to (most likely popped from the stack in x64 machine, or read from a special `RA` register in RISC design)
The epilogue computes the XOR of these two. If the result matches the original `cookie`, execution proceeds. Otherwise, the epilogue halts the program, signaling an error.
This prologue-epilogue mechanism in Retguard guards the call stack from tampering. At a noticeable but acceptable cost (both in performance and code size), Retguard eliminates a significant number of ROP gadgets from the OpenBSD kernel. Like other software-based mitigations, it requires a patched compiler, and it is up to each environment to decide if such technique shall be employed.
## Hardware Advancements to Mitigate ROP
In addition to software solutions, hardware-based defenses have also been developed. For instance, Intel has introduced [Indirect Branch Tracking](https://edc.intel.com/content/www/us/en/design/ipla/software-development-platforms/client/platforms/alder-lake-desktop/12th-generation-intel-core-processors-datasheet-volume-1-of-2/007/indirect-branch-tracking/?language=en) feature starting with its 12th generation core processors, using a new instruction `endbr32` or `endbr64` added at every location the program might jump to or call into. When the CPU executes a jump/call, it asserts that the target location is a proper `endbr32` / `endbr64` instruction, before updating the program counter `PC` register to proper values. Otherwise, the CPU halts to terminate the program. This ensures that all control flows will follow the intended way, preventing ROP attacks from redirecting execution arbitrary locations.
Modern OSes have already extensively leveraged `endbr32` / `endbr64` instructions. Ubuntu 24.04, for instance, has included these instructions in its packages:
```
$ objdump -d /bin/bash | head -n 50
/bin/bash: file format elf64-x86-64
Disassembly of section .init:
0000000000030000 <.init>:
30000: f3 0f 1e fa endbr64
30004: 48 83 ec 08 sub $0x8,%rsp
30008: 48 8b 05 d9 7e 12 00 mov 0x127ed9(%rip),%rax # 157ee8 <__gmon_start__@Base>
3000f: 48 85 c0 test %rax,%rax
30012: 74 02 je 30016 <unlink@plt-0xe1a>
30014: ff d0 call *%rax
30016: 48 83 c4 08 add $0x8,%rsp
3001a: c3 ret
Disassembly of section .plt:
0000000000030020 <.plt>:
30020: ff 35 a2 76 12 00 push 0x1276a2(%rip) # 1576c8 <o_options@@Base+0x1cc8>
30026: ff 25 a4 76 12 00 jmp *0x1276a4(%rip) # 1576d0 <o_options@@Base+0x1cd0>
3002c: 0f 1f 40 00 nopl 0x0(%rax)
30030: f3 0f 1e fa endbr64
30034: 68 00 00 00 00 push $0x0
30039: e9 e2 ff ff ff jmp 30020 <unlink@plt-0xe10>
3003e: 66 90 xchg %ax,%ax
30040: f3 0f 1e fa endbr64
30044: 68 01 00 00 00 push $0x1
30049: e9 d2 ff ff ff jmp 30020 <unlink@plt-0xe10>
3004e: 66 90 xchg %ax,%ax
30050: f3 0f 1e fa endbr64
30054: 68 02 00 00 00 push $0x2
30059: e9 c2 ff ff ff jmp 30020 <unlink@plt-0xe10>
3005e: 66 90 xchg %ax,%ax
30060: f3 0f 1e fa endbr64
30064: 68 03 00 00 00 push $0x3
30069: e9 b2 ff ff ff jmp 30020 <unlink@plt-0xe10>
3006e: 66 90 xchg %ax,%ax
30070: f3 0f 1e fa endbr64
30074: 68 04 00 00 00 push $0x4
30079: e9 a2 ff ff ff jmp 30020 <unlink@plt-0xe10>
3007e: 66 90 xchg %ax,%ax
30080: f3 0f 1e fa endbr64
30084: 68 05 00 00 00 push $0x5
30089: e9 92 ff ff ff jmp 30020 <unlink@plt-0xe10>
3008e: 66 90 xchg %ax,%ax
30090: f3 0f 1e fa endbr64
30094: 68 06 00 00 00 push $0x6
30099: e9 82 ff ff ff jmp 30020 <unlink@plt-0xe10>
3009e: 66 90 xchg %ax,%ax
```
The `endbr32` / `endbr64` instructions has been carefully designed, so they are `nop` instructions—meaning they can do nothing at all—on CPUs prior to their introductions. Having them doesn't have any effect on older CPUs but enhances security on supported hardware.
## RISC-V’s Latest Achievements: CFI Extension
The above mitigations against ROP fall into two categories:
* **Compiler Modifications**: Can generate more secure binary assembly code.
* **Additional CPU instructions**: Coming with Control Flow Integrity (CFI) checks to prevent exploitation
Back to the beginning of designing CKB-VM, we throughly studied ROP and recognized that a vulnerability in a CKB script could potentially open the door to ROP attacks. However, we eventually did not introduce any specific mitigation against ROP in CKB-VM. Our decision was to stay aligned with the RISC-V ecosystem, avoiding shipping any custom RISC-V spec with additional instructions that would require a patched compiler. Nor do we want to maintain our own compiler set, eliminating the potential that any RISC-V-compliant compiler shall be able to produce CKB script. As the result, we shipped the first version of CKB-VM without ROP mitigations, but that does not mean we’ve ignore this issue:
* We’ve [reached out](https://groups.google.com/a/groups.riscv.org/g/isa-dev/c/LyZzjJG7_18/m/pCSnKZPdBAAJ) to the RISC-V community for possible extension similar to Intel’s solution, and kept monitoring advancements in this field;
* We’ve been watching over progress and writing secure CKB scripts. Since ROP relies on existing vulnerabilities, secure CKB scripts can kept ROP purely theoretical.
We were thrilled when the **RISC-V CFI (Control-Flow Integrity) Extension** was officialy [ratified](https://github.com/riscv/riscv-cfi/releases/tag/v1.0) in July 2024. Designed by the brilliant minds from the RISC-V Foundation, this extension directly addresses ROP attacks with two key features:
* `Zicfilp` extension introduces **landing pad**: Resembles Intel’s `endbr32` / `endbr64` to ensure that the CPU can only jump to valid, permitted targets.
* `Zicfiss` extension introduces **shadow stack** with a series of instructions:. Offers a hardware solution similar to Retguard, where CPU ensures the control flow integrity or simply puts the call stack, preventing tampering throughout execution.
Together, these features offer the state-of-the-art mitigations against ROP. More importantly, RISC-V CFI is now an official extension, meaning all future RISC-V CPUs, compilers, and tools will support this extension. In fact, LLVM 19 has already [supported](https://releases.llvm.org/19.1.0/docs/ReleaseNotes.html#changes-to-the-risc-v-backend), and I believe other compilers and tools will follow soon.
Once fully adopted, CKB script developers can simply turn them on like a switch during code compilation. Without modifying the code, they can enjoy the security provided by RISC-V CFI extensions. Even if a vulnerability exists in a CKB script, these built-in enforcements can prevent it from being exploited.
## Final Words
Security is complex. While we strive for maximum security, certain design principles might get in the way from introducing specific mitigations. ROP is a prime example: while we did learn much about it early on, implementing the best mitigations needs proper timing. Now the time has come. We are happy to introduce RISC-V CFI in CKB’s next hardfork, bringing stronger security for everyone.
***
✍🏻 Written by Xuejie Xiao
His previous posts include:
* [A Journey Optimizing CKB Smart Contract: Porting Bitcoin as an Example](https://blog.cryptape.com/a-journey-optimizing-ckb-smart-contract)
* [Optimizing C++ Code for CKB-VM: Porting Bitcoin as an Example](https://blog.cryptape.com/optimizing-c-code-for-ckb-vm)
Find more in his personal website [Less is More](https://xuejie.space/).
-

@ 9967f375:04f9a5e1
2025-02-13 08:39:58
El día 13, primer viernes de Cuaresma asistió su Exc. y Real Audiencia en la Capilla Real del Palacio a la Misa, y Sermón, que predicó el Doctor Don Pedro Ramírez del Castillo, Canónigo Penitenciario de la Metropoltana.
#GacetadeMéxico #Febrero
-

@ bf47c19e:c3d2573b
2025-02-13 08:10:44
Originalni tekst na [dvadesetjedan.com](https://dvadesetjedan.com/blog/bitcoin-privatnost-najbolje-prakse).
###### Autor: [Gigi](https://dergigi.com/2021/03/14/bitcoin-privacy-best-practices/) / Prevod na srpski: [Plumsky](https://t.me/Plumski)
---
> Postoji sveto carstvo privatnosti za svakog čoveka gde on bira i pravi odluke – carstvo stvoreno na bazičnim pravima i slobode koje zakon, generalno, ne sme narušavati. Džefri Fišer, Arhiepiskop Canterberija (1959)
Pre ne toliko dugo, uobičajen režim interneta je bio neenkriptovan običan tekst (plain text). Svi su mogli špiunirati svakoga i mnogi nisu o tome ni razmišljali. Globalno obelodanjivanje nadzora 2013. je to promenilo i danas se koriste mnogo bezbedniji protokoli i end-to-end enkripcija postaje standard sve više. Iako bitcoin postaje tinejdžer, mi smo – metaforično govoreći – i dalje u dobu običnog teksta narandžastog novčića. Bitcoin je radikalno providljiv protokol sam po sebi, ali postoje značajni načini da korisnik zaštiti svoju privatnost. U ovom članku želimo da istaknemo neke od ovih strategija, prodiskutujemo najbolje prakse, i damo preporuke koje mogu primeniti i bitcoin novajlije i veterani.
#### Zašto je privatnost bitna
> Privatnost je potrebna da bi otvoreno društvo moglo da funkcioniše u digitalnoj eri. Privatnost nije isto što i tajanstvenost. Privatna stvar je nešto što neko ne želi da ceo svet zna, a tajna stvar je nešto što neko ne želi bilo ko da zna. Privatnost je moć da se čovek selektivno otkriva svom okruženju.
Ovim snažnim rečima Erik Hjus je započeo svoj tekst Sajferpankov Manifesto (Cypherpunk's Manifesto) 1993. Razlika između privatnosti i tajanstvenosti je suptilna ali jako važna. Odlučiti se za privatnost ne znači da neko ima tajne koje želi sakriti. Da ovo ilustrujemo shvatite samo da ono što obavljate u svom toaletu ili u spavaćoj sobi nije niti ilegalno niti tajna (u mnogim slučajevima), ali vi svejedno odlučujete da zatvorite vrata i navučete zavese.
Slično tome, koliko para imate i gde ih trošite nije naručito tajna stvar. Ipak, to bi trebalo biti privatan slučaj. Mnogi bi se složili da vaš šef ne treba da zna gde vi trošite vašu platu. Privatnosti je čak zaštićena od strane mnogobrojnih internacionalnih nadležnih organa. Iz Američke Deklaracije Prava i Dužnosti Čoveka (American Declaration of the Rights and Duties of Man) Ujedinjenim Nacijama, napisano je da je privatnost fundamentalno prava gradjana širom sveta.
> Niko ne sme biti podvrgnut smetnjama njegovoj privatnosti, porodici, rezidenciji ili komunikacijama, niti napadnuta njegova čast i reputacija. Svi imaju pravo da se štite zakonom protiv takvih smetnja ili napada. Artikal 12, Deklaracija Ljudskih Prava Ujedinjenih Nacija
#### Bitcoin i privatnost
Iako je bitcoin često opisivan kao anoniman način plaćanja medijima, on u stvari poseduje potpuno suprotne osobine. On je poluanoniman u najboljem slučaju i danas mnogima nije ni malo lako primeniti taktike da bi bili sigurni da njihov poluanonimni identitet na bitcoin mreži ne bude povezan sa legalnim identitetom u stvarnom svetu.
Bitcoin je otvoren sistem. On je javna baza podataka koju svako može da proučava i analizira. Znači, svaka transakcija koja je upisana u tu bazu kroz dokaz rada (proof-of-work) postojaće i biće otkrivena dokle god bitcoin postoji, što znači - zauvek. Ne primenjivati najbolje prakse privatnosti može imati štetne posledice u dalekoj budućnosti.
Privatnost, kao sigurnost, je proces koji je težak, ali nije nemoguć. Alatke nastavljaju da se razvijaju koje čuvaju privatnost kad se koristi bitcoin and srećom mnoge od tih alatki su sve lakše za korišćenje. Nažalost ne postoji panacea u ovom pristupu. Mora se biti svesan svih kompromisa i usavršavati te prakse dok se one menjaju.
#### Najbolje prakse privatnosti
Kao i sve u bitcoinu, kontrola privatnosti je postepena, korak po korak, procedura. Naučiti i primeniti ove najbolje prakse zahteva strpljivost i odgovornost, tako da ne budite obeshrabreni ako vam se čini da je to sve previše. Svaki korak, koliko god bio mali, je korak u dobrom pravcu.
Koje korake preduzeti da bi uvećali svoju privatnost:
* Budite u vlasništvu sami svojih novčića
* Nikad ne ponavljajte korišćenje istih adresa
* Minimizirajte korišćenje servisa koji zahtevaju identitet (Know your customer - KYC)
* Minimizirajte sve izloženosti trećim licima
* Upravljajte svojim nodom
* Koristite Lightning mrežu za male transakcije
* Nemojte koristiti javne blok pretraživače za svoje transakcije
* Koristite metodu CoinJoin često i rano pri nabavljanju svojih novčića
**Budite u vlasništvu sami svojih novčića**: Ako ključevi nisu tvoji, onda nije ni bitcoin. Ako neko drugo drži vaš bitcoin za vas, oni znaju sve što se može znati: količinu, istoriju transakcija pa i sve buduće transakcije, itd. Preuzimanje vlasništva bitcoina u svoje ruke je prvi i najvažniji korak.
**Nikad ne kroistite istu adresu dvaput**: Ponavljanje adresa poništava privatnost pošiljalca i primaoca bitcoina. Ovo se treba izbegavati pod svaku cenu.
**Minimizirajte korišćenje servisa koji zahtevaju identitet (KYC)**: Vezivati svoj legalni identitet za svoje bitcoin adrese je zlo koje se zahteva od strane mnogih državnih nadležnosti. Dok je efektivnost ovih zakona i regulacija disputabilno, posledice njihovog primenjivanja su uglavnom štetne po korisnicima. Ovo je očigledno pošto je česta pojava da se te informacije često izlivaju iz slabo obezbeđenih digitalnih servera. Ako izaberete da koristite KYC servise da bi nabavljali bitcoin, proučite i razumite odnos između vas i tog biznisa. Vi ste poverljivi tom biznisu za sve vaše lične podatke, pa i buduće obezbeđenje tih podataka. Ako i dalje zarađujete kroz fiat novčani sistem, mi preporučujemo da koristite samo bitcoin ekskluzivne servise koji vam dozvoljavaju da autamatski kupujete bitcoin s vremena na vreme. Ako zelite da potpuno da izbegnete KYC, pregledajte https://bitcoinqna.github.io/noKYConly/.
**Minimizirajte sve izloženosti trećim licima**: Poverljivost trećim licima je bezbednosna rupa (https://nakamotoinstitute.org/trusted-third-parties/). Ako možete biti poverljivi samo sebi, onda bi to tako trebalo da bude.
**Upravljajte svojim nodom**: Ako nod nije tvoj, onda nisu ni pravila. Upravljanje svojim nodom je suštinska potreba da bi se bitcoin koristio na privatan način. Svaka interakcija sa bitcoin mrežom je posrednjena nodom. Ako vi taj nod ne upravljate, čiji god nod koristite može da vidi sve što vi radite. Ova upustva (https://bitcoiner.guide/node/) su jako korisna da bi započeli proces korišćenja svog noda.
**Koristite Lightning mrežu za male transakcije**: Pošto Lightning protokol ne koristi glavnu bitcoin mrežu za trasakcije onda je i samim tim povećana privatnost korišćenja bez dodatnog truda. Iako je i dalje rano, oni apsolutno bezobzirni periodi Lightning mreže su verovatno daleko iza nas. Korišćenje Lightning-a za transakcije malih i srednjih veličina će vam pomoći da uvećate privatnost a da smanjite naplate svojih pojedinačnih bitcoin transakcija.
**Nemojte koristiti javne blok pretraživače za svoje transakcije**: Proveravanje adresa na javnim blok pretraživačima povezuje te adrese sa vašim IP podacima, koji se onda mogu koristiti da se otkrije vaš identitet. Softveri kao Umbrel i myNode vam omogućavaju da lako koristite sami svoj blok pretraživač. Ako morate koristiti javne pretraživače, uradite to uz VPN ili Tor.
**Koristite CoinJoin često i rano pri nabavljanju svojih novčića**: Pošto je bitcoin večan, primenjivanje saradničkih CoinJoin praksa će vam obezbediti privatnost u budućnosti. Dok su CoinJoin transakcije svakovrsne, softveri koji su laki za korišćenje već sad postoje koji mogu automatizovati ovu vrstu transakcija. Samourai Whirlpool (https://samouraiwallet.com/whirlpool) je odličan izbor za Android korisnike. Joinmarket (https://github.com/joinmarket-webui/jam) se može koristiti na vašem nodu. A servisi postoje koji pri snabdevanju vašeg bitcoina istog trenutka obave CoinJoin tranzakciju automatski.
#### Zaključak
Svi bi trebalo da se potrude da koriste bitcoin na što privatniji način. Privatnost nije isto što i tajanstvenost. Privatnost je ljudsko pravo i mi svi trebamo da branimo i primenljujemo to pravo. Teško je izbrisati postojeće informacije sa interneta; a izbrisati ih sa bitcoin baze podataka je nemoguće. Iako su daleko od savršenih, alatke postoje danas koje vam omogućavaju da najbolje prakse privatnosti i vi sami primenite. Mi smo vam naglasili neke od njih i - kroz poboljšanje u bitcoin protokolu kroz Taproot i Schnorr - one će postajati sve usavršenije.
Bitcoin postupci se ne mogu lako opisati korišćenjem tradicionalnim konceptima. Pitanja kao što su "Ko je vlasnik ovog novca?" ili "Odakle taj novac potiče?" postaju sve teža da se odgovore a u nekim okolnostima postaju potpuno beznačajna.
Satoši je dizajnirao bitcoin misleći na privatnost. Na nivou protokola svaka bitcoin transakcija je proces "topljenja" koji za sobom samo ostavlja heuristične mrvice hleba. Protokolu nije bitno odakle se pojavio bilo koji bitcoin ili satoši. Niti je njega briga ko je legalan identitet vlasnika. Protokolu je samo važno da li su digitalni potpisi validni. Dokle god je govor slobodan, potpisivanje poruka - privatno ili ne - ne sme biti kriminalan postupak.
Dodatni Resursi
[This Month in Bitcoin Privacy](https://enegnei.github.io/This-Month-In-Bitcoin-Privacy/) | Janine
[Hodl Privacy FAQ](https://6102bitcoin.com/faq-hodl-privacy/) | 6102
[Digital Privacy](https://6102bitcoin.com/blog/digital-privacy/) | 6102
[UseWhirlpool.com](http://usewhirlpool.com/) | Bitcoin Q+A
[Bitcoin Privacy Guide](https://bitcoiner.guide/privacy/) | Bitcoin Q+A
Ovaj članak napisan je u saradnji sa Matt Odellom, nezavisnim bitcoin istraživačem. Nađite njegove preporuke za privatnost na [werunbtc.com](https://werunbtc.com/)
[Originalni tekst](https://dergigi.com/2021/03/14/bitcoin-privacy-best-practices/)
-

@ 04ed2b8f:75be6756
2025-02-13 08:02:39
Freedom. It’s the word on everyone’s lips, the dream of every soul. We long for it, we chase it, we believe that if we can break free from this chain or that constraint, we will finally be free. **But true freedom is not about external circumstances—it’s about control.**
The truth is, **the most powerful chains are the ones we place on ourselves**. The world can throw its challenges at you, life can dish out its unfair blows, but **if you cannot control yourself, your thoughts, your emotions, your reactions, then you are no different than a prisoner.**
There is no freedom in chaos. There is no freedom in losing control. **Freedom is mastery—mastery of the self.**
## **Freedom Begins Within**
You can have all the money in the world, live in the most luxurious place, and have every material possession your heart desires, but **if you cannot control your impulses, your habits, your desires—none of that will matter.** You are still a slave to your cravings. You are still a puppet to your own emotions, and that is **no real freedom.**
What does freedom look like?
- **It’s the power to act with purpose, not to react out of emotion.**
- **It’s the strength to stay disciplined when every part of you wants to quit.**
- **It’s the courage to say ‘no’ to distractions, to temptation, to things that steer you off course.**
- **It’s the clarity to make choices that serve your growth, not your immediate desires.**
True freedom is the ability to say, “I am in control of myself. I do not let my circumstances control me, nor my emotions rule me. I dictate my actions, my thoughts, my destiny.”
## **Self-Control: The Ultimate Weapon**
The power to control yourself is your greatest weapon. Without it, **you are at the mercy of every challenge, every temptation, and every fleeting emotion**. You may feel like you are “free,” but without self-discipline, you are just a puppet swaying in the wind, vulnerable to every whim that blows your way.
- **The impulse to procrastinate? You overcome it.**
- **The desire to give up? You push through it.**
- **The craving for comfort? You choose growth.**
In the face of any storm, a man with self-control remains grounded, focused, and clear. He doesn’t react in anger or fear—he acts with purpose, with precision, and with vision.
A man who cannot control himself is a man who is owned by his emotions, his desires, his distractions. But the man who conquers his mind, his body, his impulses—he is the one who **owns his life.**
## **The Price of Freedom**
It’s not easy to control yourself. It requires constant effort, relentless discipline, and the courage to face yourself head-on. It means saying ‘no’ to what feels good now, to invest in what will make you stronger later. It means constantly improving, constantly fighting the urge to quit, to give in, to indulge in comfort.
But the price of freedom is worth it. **For when you have control over yourself, no one can take your power.** You become the master of your fate. **You become unshakable.**
## **Freedom Through Discipline**
So, ask yourself: **Are you truly free, or are you simply a slave to your impulses?**
- **Do you control your actions, or do your actions control you?**
- **Are you the master of your emotions, or are they the masters of you?**
Freedom isn’t just about having no chains; it’s about not letting anything control you—least of all yourself. **And when you control yourself, there’s nothing you can’t accomplish.**
A man who cannot control himself is never truly free. But a man who conquers his mind, his habits, his emotions—he is unstoppable.
**Now go and choose to control yourself, and unlock the freedom that’s waiting for you. Or remain a prisoner to your impulses, forever shackled by the chains of your own making. The choice is yours.**
-

@ bf47c19e:c3d2573b
2025-02-13 07:56:50
Originalni tekst na [dvadesetjedan.com](https://dvadesetjedan.com/blog/niko-ne-moze-zabraniti-bitcoin)
###### Autor: [Parker Lewis](https://x.com/parkeralewis) / Prevod na srpski: [Plumsky](https://t.me/Plumski)
---
Ideja da država može nekako zabraniti bitcoin je jedna od poslednjih faza tuge, tačno pred prihvatanje realnosti. Posledica ove rečenice je priznanje da bitcoin “funkcioniše”. U stvari, ona predstavlja činjenicu da bitcoin funkcioniše toliko dobro da on preti postojećim državnim monopolima nad novcem i da će zbog toga države da ga unište kroz regulativne prepreke da bi eliminisale tu pretnju. Gledajte na tvrdnju da će države zabraniti bitcoin kao kondicionalnu logiku. Da li bitcoin funkcioniše kao novac? Ako je odgovor „ne“, onda države nemaju šta da zabrane. Ako je odgovor „da“, onda će države da probaju da ga zabrane. Znači, glavna poenta ovog razmišljanja je pretpostavka da bitcoin funkcioiniše kao novac. Onda je sledeće logično pitanje da li intervencija od strane države može uspešno da uništi upravo taj funkcionalan bitcoin.
Za početak, svako ko pokušava da razume kako, zašto, ili da li bitcoin funkcioniše mora da proceni ta pitanja potpuno nezavisno od prouzrekovanja državne regulacije ili intervencije. Iako je nesumnjivo da bitcoin mora da postoji uzgred državnih regulativa, zamislite na momenat da države ne postoje. Sam od sebe, da li bi bitcoin funkcionisao kao novac, kad bi se prepustio slobodnom tržištu? Ovo pitanje se širi u dodatna pitanja i ubrzo se pretvara u bunar bez dna. Šta je novac? Šta su svojstva koja čine jednu vrstu novca bolje od druge? Da li bitcoin poseduje ta svojstva? Da li je bitcoin bolja verzija novca po takvim osobinama? Ako je finalni zaključak da bitcoin ne funkcioniše kao novac, implikacije državne intervencije su nebitne. Ali, ako je bitcoin funkcionalan kao novac, ta pitanja onda postaju bitna u ovoj debati, i svako ko o tome razmišlja bi morao imati taj početnički kontekst da bi mogao proceniti da li je uopšte moguće zabraniti. Po svom dizajnu, bitcoin postoji van države. Ali bitcoin nije samo van kontrole države, on u stvari funkcioniše bez bilo kakve saradnje centralizovanih identiteta. On je globalan i decentralizovan. Svako može pristupiti bitcoinu bez potrebe saglasnosti bilo koga i što se više širi sve je teže cenzurisati celokupnu mrežu. Arhitektura bitcoina je namerno izmišljena da bude otporna na bilo koje pokušaje države da ga zabrane. Ovo ne znači da države širom sveta neće pokušavati da ga regulišu, oporezuju ili čak da potpuno zabrane njegovo korišćenje. Naravno da će biti puno bitki i otpora protiv usvajanja bitcoina među građanima. Federal Reserve i Američki Treasury (i njihovi globalni suparnici) se neće ležeći predati dok bitcoin sve više i više ugrožava njihove monopole prihvatljivog novca. Doduše, pre nego što se odbaci ideja da države mogu potpuno zabraniti bitcoin, mora se prvo razumeti posledice tog stava i njegovog glasnika.
#### Progresija poricanja i stepeni tuge
Pripovesti skeptičara se neprestano menjaju kroz vreme. Prvi stepen tuge: bitcoin nikad ne može funkcionisati-njegova vrednost je osnovana ni na čemu. On je moderna verzija tulip manije. Sa svakim ciklusom uzbuđenja, vrednost bitcoina skače i onda vrlo brzo se vraća na dole. Često nazvano kao kraj njegove vrednosti, bitcoin svaki put odbija da umre i njegova vrednost pronađe nivo koji je uvek viši od prethodnih ciklusa globalne usvajanja. Tulip pripovetka postaje stara i dosadna i skeptičari pređu na više nijansirane teme, i time menjaju bazu debate. Drugi stepen tuge predstoji: bitcoin je manjkav kao novac. On je previše volatilan da bi bio valuta, ili je suviše spor da bi se koristio kao sistem plaćanja, ili se ne može proširiti dovoljno da zadovolji sve promete plaćanja na svetu, ili troši isuviše struje. Taj niz kritike ide sve dalje i dalje. Ovaj drugi stepen je progresija poricanja i dosta je udaljen od ideje da je bitcoin ništa više od bukvalno bezvrednog ničega.
Uprkos tim pretpostavnim manjcima, vrednost bitcoin mreže nastavje da raste vremenom. Svaki put, ona ne umire, nasuprot, ona postaje sve veća i jača. Dok se skeptičari bave ukazivanjem na manjke, bitcoin ne prestaje. Rast u vrednosti je prouzrokovan jednostavnom dinamikom tržišta: postoji više kupca nego prodavca. To je sve i to je razlog rasta u adopciji. Sve više i više ljudi shvata zašto postoji fundamentalna potražnja za bitcoinom i zašto/kako on funkcioniše. To je razlog njegovog dugotrajnog rasta. Dokle god ga sve više ljudi koristi za čuvanje vrednosti, neće pasti cena snabdevanja. Zauvek će postojati samo 21 milion bitcoina. Nebitno je koliko ljudi zahtevaju bitcoin, njegova cela količina je uvek ista i neelastična. Dok skeptičari nastavljaju sa svojom starom pričom, mase ljudi nastavljaju da eliminišu zabludu i zahtevaju bitcoin zbog njegovih prednosti u smislu novčanih svojstva. Između ostalog, ne postoji grupa ljudi koja je više upoznata sa svim argumentima protiv bitcoina od samih bitcoinera.

Očajanje počinje da se stvara i onda se debata još jedanput pomera. Sada nije više činjenica je vrednost bitcoina osnovana ni na čemu niti da ima manjke kao valuta; sada se debata centrira na regulaciji državnih autoriteta. U ovom zadnjem stepenu tuge, bitcoin se predstavlja kao u stvari isuviše uspešnom alatkom i zbog toga države ne smeju dozvoliti da on postoji. Zaista? Znači da je genijalnost čoveka ponovo ostvarila funkcionalan novac u tehnološko superiornoj formi, čije su posledice zaista neshvatljive, i da će države upravo taj izum nekako zabraniti. Primetite da tom izjavom skeptičari praktično priznaju svoj poraz. Ovo su poslednji pokušaji u seriji promašenih argumenata. Skeptičari u isto vreme prihvataju da postoji fundamentalna potražnja za bitcoinom a onda se premeštaju na neosnovan stav da ga države mogu zabraniti.
Ajde da se poigramo i tim pitanjem. Kada bih zapravo razvijene države nastupile na scenu i pokušale da zabrane bitcoin? Trenutno, Federal Reserve i Treasury ne smatraju bitcoin kao ozbiljnu pretnju superiornosti dolara. Po njihovom celokupnom mišljenju, bitcoin je slatka mala igračka i ne može da funkcioniše kao novac. Sadašnja kompletna kupovna moć bitcoina je manja od $200 milijardi. Sa druge strane, zlato ima celokupnu vrednost od $8 triliona (40X veću od bitcoina) i količina odštampanog novca (M2) je otprilike 15 triliona (75X veličine bitcoinove vrednosti). Kada će Federal Reserve i Treasury da počne da smatra bitcoin kao ozbiljnu pretnju? Kad bitcoin poraste na $1, $2 ili $3 triliona? Možete i sami da izaberete nivo, ali implikacija je da će bitcoin biti mnogo vredniji, i posedovaće ga sve više ljudi širom sveta, pre nego što će ga državne vlasti shvatiti kao obiljnog protivnika.
Predsednik Tramp & Treasury Sekretar Mnučin o Bitcoinu (2019):
> „Ja neću pričati o bitcoinu za 10 godina, u to možete biti sigurni {…} Ja bi se kladio da čak za 5 ili 6 godina neću više pričati o bitcoinu kao sekretar Trusury-a. Imaću preča posla {…} Mogu vam obećati da ja lično neću biti pun bitcoina.“ – Sekretar Treasury-a Stiv Mnučin
> „Ja nisam ljubitelj bitcoina {…}, koji nije novac i čija vrednost je jako volatilna i osnovana na praznom vazduhu.“ – Predsednik Donald J. Tramp
Znači, logika skeptika ide ovako: bitcoin ne funkcioniše, ali ako funkcioniše, onda će ga država zabraniti. Ali, države slobodnog sveta neće pokušati da ga zabrane dokle god se on ne pokaže kao ozbiljna pretnja. U tom trenutku, bitcoin će biti vredniji i sigurno teži da se zabrani, pošto će ga više ljudi posedovati na mnogo širem geografskom prostoru. Ignorišite fundamentalne činjenice i asimetriju koja je urođena u globalnom dešavanju monetizacije zato što u slučaju da ste u pravu, države će taj proces zabraniti. Na kojoj strani tog argumenta bi radije stajao racionalan ekonomski učesnik? Posedovanje finansijske imovine kojoj vrednost toliko raste da preti globalnoj rezervnoj valuti, ili nasuprot – nemati tu imovinu? Sa pretpostavkom da individualci razumeju zašto je mogućnost (a sve više i verovatnoća) ove realnosti, koji stav je logičniji u ovom scenariju? Asimetrija dve strane ovog argumenta sama od sebe zahteva da je prvi stav onaj istinit i da fundamentalno razumevanje potražnje bitcoina samo još više ojačava to mišljenje.
#### Niko ne moze zabraniti bitcoin
Razmislite šta bitcoin u stvari predstavlja pa onda šta bi predstavljala njegova zabrana. Bitcoin je konverzija subjektivne vrednosti, stvorena i razmenjena u realnošću, u digitalne potpise. Jednostavno rečeno, to je konverzija ljudskog vremena u novac. Kad neko zahteva bitcoin, oni u isto vreme ne zahtevaju neki drugi posed, nek to bio dolar, kuća, auto ili hrana itd. Bitcoin predstavlja novčanu štednju koja sa sobom žrtvuje druge imovine i servise. Zabrana bitcoina bi bio napad na najosnovnije ljudske slobode koje je on upravo stvoren da brani. Zamislite reakciju svih onih koji su prihvatili bitcoin: „Bilo je zabavno, alatka za koju su svi eksperti tvrdili da neće nikad funkcionisati, sada toliko dobro radi i sad ti isti eksperti i autoriteti kažu da mi to nemožemo koristiti. Svi idite kući, predstava je gotova.“verovanje da će svi ljudi koji su učestvovali u bitcoin usvajanju, suverenitetu koji nudi i finansiskoj slobodi, odjednom samo da se predaju osnovnom rušenju njihovih prava je potpuno iracionalna pozicija.
> Novac je jedan od najbitnijih instrumenata za slobodu koji je ikad izmišljen. Novac je to što u postojećem društvu ostvaruje mogućnosti siromašnom čoveku – čiji je domet veći nego onaj koji je bio dostižan bogatim ljudima pre ne toliko puno generacija.“ – F. A. Hajek
Države nisu uspele da zabrane konzumiranje alkohola, droga, kupovinu vatrenog oružja, pa ni posedovanje zlata. Država može samo pomalo da uspori pristup ili da deklariše posedovanje ilegalnim, ali ne može da uništi nešto što veliki broj raznovrsnih ljudi smatra vrednim. Kada je SAD zabranila privatno posedovanje zlata 1933., zlato nije palo u vrednosti ili nestalo sa finansijskog tržišta. Ono je u stvari poraslo u vrednosti u poređenju sa dolarom, i samo trideset godina kasnije, zabrana je bila ukinuta. Ne samo da bitcoin nudi veću vrednosno obećanje od bilo kog drugog dobra koje su države pokušale da zabrane (uključujući i zlato); nego po svojim osobinama, njega je mnogo teže zabraniti. Bitcoin je globalan i decentralizovan. On ne poštuje granice i osiguran je mnoštvom nodova i kriptografskim potpisima. Sam postupak zabrane bi zahtevao da se u isto vreme zaustavi „open source“ softver koji emituje i izvršava slanje i potvrđivanje digitalno enkriptovanih ključeva i potpisa. Ta zabrana bi morala biti koordinisana između velikog broja zemalja, sa tim da je nemoguće znati gde se ti nodovi i softver nalazi ili da se zaustavi instaliranje novih nodova u drugim pravnim nadležnostima. Da ne pominjemo i ustavske pitanja, bilo bi tehnički neizvodljivo da se takva zabrana primeni na bilo kakav značajan način.
Čak kada bih sve zemlje iz G-20 grupe koordinisale takvu zabranu u isto vreme, to ne bi uništilo bitcoin. U stvari, to bi bilo samoubistvo za fiat novčani sistem. To bi još više prikazalo masama da je bitcoin u stvari novac koji treba shvatiti ozbiljno, i to bi samo od sebe započelo globalnu igru vatanje mačke za rep. Bitcoin nema centralnu tačku za napad; bitcoin rudari, nodovi i digitalni potpisi su rasejani po celom svetu. Svaki aspekt bitcoina je decentralizovan, zato su glavni stubovi njegove arhitekture da učesnici uvek treba kontrolisati svoje potpise i upravljati svojim nodom. Što više digitalnih potpisa i nodova koji postoje, to je više bitcoin decentralizovan, i to je više odbranjiva njegova mreža od strane neprijatelja. Što je više zemalja gde rudari izvršavaju svoj posao, to je manji rizik da jedan nadležni identitet može uticati na njegov bezbednosni sistem. Koordinisan internacionalni napad na bitcoin bi samo koristio da bitcoin još više ojača svoj imuni sistem. Na kraju krajeva, to bi ubrzalo seobu iz tradicionalnog finansijskog sistema (i njegovih valuta) a i inovaciju koja postoji u bitcoin ekosistemu. Sa svakom bivšom pretnjom, bitcoin je maštovito pronalazio način da ih neutrališe pa i koordinisan napad od strane država ne bi bio ništa drugačiji.
Inovacija u ovoj oblasti koja se odlikuje svojom „permissionless“ (bez dozvole centralnih identiteta) osobinom, omogućava odbranu od svakojakih napada. Sve varijante napada koje su bile predvidjene je upravo to što zahteva konstantnu inovaciju bitcoina. To je ona Adam Smitova nevidljiva ruka, ali dopingovana. Pojedinačni učesnici mogu da veruju da su motivisani nekim većim uzrokom, ali u stvari, korisnost kaja je ugrađena u bitcoin stvara kod učesnika dovoljno snažan podsticaj da omogući svoje preživljavanje. Sopstveni interes milione, ako ne milijarde, nekoordinisanih ljudi koji se jedino slažu u svojom međusobnom potrebom za funkcionalnim novcem podstiče inovacije u bitcoinu. Danas, možda to izgleda kao neka kul nova tehnologija ili neki dobar investment u finansijskom portfoliju, ali čak i ako to mnogi ne razumeju, bitcoin je apsolutna nužnost u svetu. To je tako zato što je novac nužnost a historijski priznate valute se fundamentalno raspadaju. Pre dva meseca, tržište američkih državnih obveznica je doživeo kolaps na šta je Federal Reserve reagovao time što je povećao celokupnu količinu dolara u postojanju za $250 milijardi, a još više u bliskoj budućnosti. Tačno ovo je razlog zašto je bitcoin nužnost a ne samo luksuzni dodatak. Kada inovacija omogućava bazično funkcionisanje ekonomije ne postoji ni jedna država na svetu koja može da zaustavi njenu adopciju i rast. Novac je nužnost a bitcoin znatno poboljšava sistem novca koji je ikada postojao pre njega.
Sa više praktične strane, pokušaj zabranjivanja bitcoina ili njegove velike regulacije od nadležnosti bi direktno bilo u korist susedne nadležnih organa. Podsticaj da se odustane od koordinisanog napada na bitcoin bi bio isuviše veliki da bi takvi dogovori bili uspešni. Kada bi SAD deklarisovale posed bitcoina ilegalnim sutra, da li bi to zaustavilo njegov rast, razvoj i adopciji i da li bi to smanjilo vrednost celokupne mreže? Verovatno. Da li bi to uništilo bitcoin? Ne bi. Bitcoin predstavlja najpokretljivije kapitalno sredstvo na svetu. Zemlje i nadležne strukture koje kreiraju regulativnu strukturu koja najmanje ustručava korišćenje bitcoina će biti dobitnici velike količine uliva kapitala u svoje države.
#### Zabrana Bitcoinove Zatvoreničke Dileme
U praksi, zatvorenička dilema nije igra jedan na jedan. Ona je multidimenzijska i uključuje mnoštvo nadležnosti, čiji se interesi nadmeću međusobno, i to uskraćuje mogućnosti bilo kakve mogućnosti zabrane. Ljudski kapital, fizički kapital i novčani kapital će sav ići u pravcu država i nadležnosti koje najmanje ustručuju bitcoin. To se možda neće desiti sve odjednom, ali pokušaji zabrane su isto za badava koliko bi bilo odseći sebi nos u inat svom licu. To ne znači da države to neće pokušati. India je već probala da zabrani bitcoin. Kina je uvela puno restrikcija. Drugi će da prate njihove tragove. Ali svaki put kada država preduzme takve korake, to ima nepredvidljive efekte povećanja bitcoin adopcije. Pokušaji zabranjivanja bitcoina su jako efektivne marketing kampanje. Bitcoin postoji kao sistem nevezan za jednu suverenu državu i kao novac je otporan na cenzuru. On je dizajniran da postoji van državne kontrole. Pokušaji da se taj koncept zabrani samo još više daje njemu razlog i logiku za postojanje.
#### Jedini Pobednički Potez je da se Uključiš u Igru
Zabrana bitcoina je trošenje vremena. Neki će to pokušati; ali svi će biti neuspešni. Sami ti pokušaji će još više ubrzati njegovu adopciju i širenje. Biće to vetar od 100 km/h koji raspaljuje vatru. To će ojačati bitcoin sve više i doprineće njegovoj pouzdanosti. U svakom slučaju, verovanje da će države zabraniti bitcoin u momentu kada on postane dovoljno velika pretnja rezervnim valutam sveta, je iracionalan razlog da se on no poseduje kao instrument štednje novca. To ne samo da podrazumeva da je bitcoin novac, ali u isto vreme i ignoriše glavne razloge zašto je to tako: on je decentralizovan i otporan na cenzure. Zamislite da razumete jednu od nojvećih tajni današnjice i da u isto vreme tu tajnu asimetrije koju bitcoin nudi ne primenjujete u svoju korist zbog straha od države. Pre će biti, neko ko razume zašto bitcoin funkcioniše i da ga država ne može zaustaviti, ili nepuno znanje postoji u razumevanju kako bitcoin uopšte funckioniše. Počnite sa razmatranjem fundamentalnih pitanja, a onda primenite to kao temelj da bi procenili bilo koji potencijalan rizik od strane budućih regulacija ili restrikcija državnih organa. I nikad nemojte da zaboravite na vrednost asimetrije između dve strane ovde prezentiranih argumenata. Jedini pobednički potez je da se uključite u igru.
Stavovi ovde prezentirani su samo moji i ne predstavljaju Unchained Capital ili moje kolege. Zahvaljujem se Fil Gajgeru za razmatranje teksta i primedbe.
[Originalni tekst](https://unchained.com/blog/bitcoin-cannot-be-banned/)
-

@ da0b9bc3:4e30a4a9
2025-02-13 06:36:12
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/884478
-

@ e3ba5e1a:5e433365
2025-02-13 06:16:49
My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get [this line](https://www.youtube.com/shorts/kqsomjpz7ok):
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song [Devil Went Down to Georgia](https://youtu.be/ut8UqFlWdDc) that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” *is*, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people *should* be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is *freedom*. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are *definitionally* better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In *Devil Went Down to Georgia*, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
*Libertas magnitudo est*
-

@ d360efec:14907b5f
2025-02-13 05:54:17

**ภาพรวม LUNCUSDT (OKX):**
LUNCUSDT กำลังอยู่ในช่วงที่ *มีความผันผวนสูงและมีความไม่แน่นอนมาก* แม้ว่าในอดีต (TF Day) จะเคยมีสัญญาณของการพยายามกลับตัวเป็นขาขึ้น (Breakout EMA 50 และเกิด Golden Cross) แต่ปัจจุบันแรงซื้อเหล่านั้นเริ่มอ่อนแรงลง และมีแรงขายเข้ามาในตลาดมากขึ้น ทำให้เกิดความขัดแย้งระหว่าง Timeframes ต่างๆ

**สถานะปัจจุบัน:**
* **แนวโน้ม:**
* **TF Day:** เริ่มไม่แน่นอน (จากเดิมที่เป็น Early Uptrend) - แม้ว่าราคาจะยังอยู่เหนือ EMA 50/200 แต่ Money Flow เริ่มแสดงสัญญาณเตือน
* **TF4H:** เริ่มไม่แน่นอน (พักตัว, ทดสอบแนวรับ EMA 50) - Money Flow บ่งบอกถึงแรงขายที่เข้ามา
* **TF15:** ผันผวนสูง, ไม่มีทิศทางชัดเจน (Sideways) - Money Flow แสดงถึงแรงขาย แต่ก็มีแรงซื้อกลับเข้ามาบ้าง
* **Money Flow (LuxAlgo):**
* **TF Day:** แรงซื้อเริ่มอ่อนแรงลงอย่างมีนัยสำคัญ, มีแรงขายเข้ามา
* **TF4H:** แรงขายมีมากกว่าแรงซื้อ
* **TF15:** แรงขายและแรงซื้อผสมกัน, โดยรวมแรงขายยังมากกว่า
* **EMA:**
* **TF Day:** EMA 50/200 เป็นแนวรับ/แนวต้าน
* **TF4H:** EMA 50 กำลังถูกทดสอบ, EMA 200 เป็นแนวต้าน
* **TF15:** EMA 50/200 เป็นแนวต้าน
**โครงสร้างราคา (SMC):**
| Timeframe | Break of Structure (BOS) | Change of Character (CHoCH) | Higher High (HH) & Higher Low (HL) | Equal Highs (EQH) / Equal Lows (EQL) |
| :-------- | :----------------------- | :--------------------------- | :----------------------------------- | :------------------------------------- |
| Day | ด้านบนและล่าง | ด้านบน | เริ่มก่อตัว (แต่ไม่แข็งแกร่ง) | - |
| 4H | ด้านบน | ด้านบน | เริ่มก่อตัว (แต่ไม่ชัดเจน) | มี EQH หลายจุด |
| 15m | ด้านบนและล่าง | มีทั้งบนและล่าง | Lower Highs (LH) & Lower Lows (LL) | มี EQH และ EQL หลายจุด |
**แนวรับ-แนวต้านสำคัญ:**
| Timeframe | แนวรับ | แนวต้าน |
| :-------- | :----------------------------------------------------------- | :--------------------------------------------------------------------- |
| Day | EMA 50 (≈0.00010000), EMA 200 (≈0.00008000), 0.00006000-0.00007000 | 0.00017953 (High ล่าสุด), 0.00014000 (Volume Profile) |
| 4H | EMA 50 (≈0.00007000), 0.00006000-0.00007000 | EMA 200 (≈0.00008000), 0.00008132, บริเวณ 0.00010000-0.00012000 (EQH) |
| 15m | บริเวณ Low ล่าสุด | EMA 50, EMA 200, บริเวณ 0.000075-0.000076 (EQH) |
**กลยุทธ์ (LUNCUSDT):**
1. **Wait & See (ทางเลือกที่ดีที่สุด):**
* **เหตุผล:** ความขัดแย้งระหว่าง Timeframes สูงมาก, แนวโน้มไม่ชัดเจน, Money Flow ใน TF4H และ TF15 เป็นลบ
* รอให้ราคาแสดงทิศทางที่ชัดเจนกว่านี้ (ยืนเหนือ EMA 50 ใน TF4H ได้, Breakout แนวต้านใน TF15)
2. **Buy on Dip (Day, 4H) - *ความเสี่ยงสูงมาก ไม่แนะนำ*:**
* **เหตุผล:** แนวโน้มระยะยาวอาจจะยังเป็นขาขึ้นได้ (ถ้าไม่หลุดแนวรับสำคัญ)
* **เงื่อนไข:** *ต้อง* รอสัญญาณการกลับตัวใน TF15 ก่อน
* **จุดเข้า:** พิจารณาเฉพาะบริเวณแนวรับที่แข็งแกร่งมากๆ (EMA ของ Day/4H) *และต้องดู TF15 ประกอบ*
* **Stop Loss:** ต่ำกว่า Low ล่าสุดของ TF15
3. **Short (15, ความเสี่ยงสูงมาก):**
* **เหตุผล:** แนวโน้ม TF15 เป็นขาลง, Money Flow เป็นลบ
* **เงื่อนไข:** ราคาไม่สามารถ Breakout EMA หรือแนวต้านอื่นๆ ใน TF15 ได้
* **จุดเข้า:** บริเวณ EMA หรือแนวต้านของ TF15
* **Stop Loss:** เหนือ High ล่าสุดของ TF15
**คำแนะนำ (เน้นย้ำ):**
* **LUNC เป็นเหรียญที่มีความเสี่ยงสูงมาก (High Risk):** มีความผันผวนสูง และอาจมีการเปลี่ยนแปลงอย่างรวดเร็ว
* **ความขัดแย้งของ Timeframes:** สถานการณ์ของ LUNCUSDT มีความขัดแย้งสูงมาก และมีความเสี่ยงสูง
* **Money Flow:** บ่งบอกถึงแรงขายที่เริ่มเข้ามา และแนวโน้มขาขึ้น (ระยะกลาง-ยาว) ที่อ่อนแอลง
* **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด:** "รอ" เป็นกลยุทธ์ที่ดีที่สุด
* **Risk Management:** สำคัญที่สุด ไม่ว่าจะเลือกกลยุทธ์ใด ต้องมีการบริหารความเสี่ยงที่ดี
**สรุป:** LUNCUSDT กำลังอยู่ในช่วงเวลาที่ยากลำบากและมีความเสี่ยงสูงมากที่สุดในบรรดา 3 เหรียญที่เราวิเคราะห์กันมา การตัดสินใจที่ผิดพลาดอาจนำไปสู่การขาดทุนได้ ควรพิจารณาอย่างรอบคอบก่อนเข้าเทรดทุกครั้ง และ "รอ" จนกว่าจะมีสัญญาณที่ชัดเจนกว่านี้ เป็นทางเลือกที่ปลอดภัยที่สุดสำหรับนักลงทุนส่วนใหญ่ค่ะ
**Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-

@ d360efec:14907b5f
2025-02-13 05:27:39

**ภาพรวม XRPUSDT (OKX):**
XRPUSDT กำลังอยู่ในช่วงสำคัญ แนวโน้มระยะยาว (TF Day) เริ่มมีสัญญาณบวกของการเป็นขาขึ้น (Early Uptrend) หลังราคา Breakout EMA 50 และ Money Flow สนับสนุน อย่างไรก็ตาม แนวโน้มระยะกลาง (TF4H) เริ่มแสดงความอ่อนแอลง โดยราคาพักตัวลงมาทดสอบแนวรับสำคัญ และ Money Flow บ่งชี้ถึงแรงซื้อที่ลดลงและแรงขายที่เพิ่มขึ้น ส่วนแนวโน้มระยะสั้นมาก (TF15) เป็นขาลงชัดเจน

**แนวโน้ม:**
* **TF Day:** เริ่มเป็นขาขึ้น (Early Uptrend) - Breakout EMA 50, Money Flow เป็นบวก
* **TF4H:** เริ่มไม่แน่นอน (พักตัว, ทดสอบแนวรับ EMA 50 และ EQL) - Money Flow เริ่มเป็นลบ
* **TF15:** ขาลง (Downtrend) ระยะสั้นมาก - ราคาหลุด EMA, โครงสร้างราคาเป็น Lower Highs/Lows, Money Flow เป็นลบ
**โครงสร้างราคา (SMC):**
| Timeframe | Break of Structure (BOS) | Change of Character (CHoCH) | Higher High (HH) & Higher Low (HL) | Equal Highs (EQH) / Equal Lows (EQL) |
| :-------- | :----------------------- | :--------------------------- | :----------------------------------- | :------------------------------------- |
| Day | ด้านบน (Breakout EMA 50) | ไม่ชัดเจน | เริ่มก่อตัว (แต่ยังไม่ชัดเจน) | - |
| 4H | ด้านบน | ไม่ชัดเจน | เริ่มก่อตัว (แต่ไม่ชัดเจน) | EQH: 3.00-3.20, EQL: 2.2667 |
| 15m | ด้านล่าง | มีทั้งบนและล่าง | Lower Highs (LH) & Lower Lows (LL) | EQH: 2.48-2.50, EQL: 2.38 |

**Money Flow (LuxAlgo):**
* **TF Day:** แรงซื้อแข็งแกร่ง
* **TF4H:** แรงซื้อเริ่มอ่อนแรงลง, แรงขายเริ่มเข้ามา
* **TF15:** แรงขายมีอิทธิพลเหนือกว่า
**EMA (Exponential Moving Average):**
* **TF Day:** EMA 50 & 200 เป็นแนวรับ
* **TF4H:** EMA 50 กำลังถูกทดสอบ, EMA 200 เป็นแนวรับถัดไป
* **TF15:** EMA 50 & 200 เป็นแนวต้าน
**แนวรับ-แนวต้านสำคัญ:**
| Timeframe | แนวรับ | แนวต้าน |
| :-------- | :----------------------------------------------------- | :----------------------------------------------------------------------- |
| Day | EMA 50 (≈1.56), EMA 200 (≈1.08) | 3.4049 (High), 3.00-3.20 (EQH) |
| 4H | EMA 50 (≈2.20), *2.2667 (EQL)*, EMA 200, 1.7820 | 3.4049, 2.3987 (Volume Profile), 3.00-3.20 (EQH) |
| 15m | 2.38 (EQL, Volume Profile), 2.3274 | EMA 50, EMA 200, 2.4196, Equilibrium (≈2.44), 2.48-2.50 (EQH) |
**กลยุทธ์ (XRPUSDT):**
1. **Wait & See (ทางเลือกที่ดีที่สุด):**
* **เหตุผล:** ความขัดแย้งระหว่าง Timeframes สูง, TF4H กำลังทดสอบแนวรับสำคัญ, Money Flow ใน TF4H และ TF15 เป็นลบ
* รอให้ราคาแสดงทิศทางที่ชัดเจน (ยืนเหนือ EMA 50 ใน TF4H ได้ หรือ Breakout แนวต้านใน TF15)
2. **Buy on Dip (Day, 4H) - *ความเสี่ยงสูงมาก*:**
* **เหตุผล:** แนวโน้มระยะยาวยังมีโอกาสเป็นขาขึ้น, Money Flow ใน TF Day เป็นบวก
* **เงื่อนไข (สำคัญมาก):** *ต้อง* รอสัญญาณการกลับตัวใน TF15 ก่อน เช่น:
* Breakout แนวต้านย่อยๆ พร้อม Volume
* Money Flow (TF15) เปลี่ยนเป็นสีเขียว
* Bullish Candlestick Patterns
* **จุดเข้า (Day):** EMA 50, EMA 200 (*ดู TF15 ประกอบ*)
* **จุดเข้า (4H):** EMA 50, *2.2667 (EQL)* (*ดู TF15 ประกอบ*)
* **Stop Loss:** ต่ำกว่า Low ล่าสุดของ TF15 หรือต่ำกว่าแนวรับที่เข้าซื้อ
3. **Short (15, ความเสี่ยงสูงมาก):**
* **เหตุผล:** แนวโน้ม TF15 เป็นขาลง, Money Flow เป็นลบ
* **เงื่อนไข:** ราคาไม่สามารถกลับขึ้นไปยืนเหนือ EMA ของ TF15 ได้
* **จุดเข้า:** บริเวณ EMA ของ TF15 หรือแนวต้านอื่นๆ
* **Stop Loss:** เหนือ High ล่าสุดของ TF15
**คำแนะนำ:**
* **ความขัดแย้งของ Timeframes:** XRPUSDT มีความขัดแย้งสูงมาก และมีความเสี่ยงสูง
* **Money Flow:** Day เป็นบวก, 4H เริ่มเป็นลบ, 15m เป็นลบ
* **EMA 50 (TF4H) & EQL 2.2667:** จุดชี้ชะตา
* **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด:** "รอ" ดีที่สุด
* **Risk Management:** สำคัญที่สุด
**สรุป:** สถานการณ์ของ XRPUSDT ตอนนี้มีความเสี่ยงสูงมาก และไม่เหมาะกับนักลงทุนที่รับความเสี่ยงได้ต่ำ การ "รอ" จนกว่าจะมีสัญญาณที่ชัดเจนกว่านี้ เป็นทางเลือกที่ปลอดภัยที่สุดค่ะ
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-

@ d360efec:14907b5f
2025-02-13 04:47:20

**ภาพรวม BTCUSDT :**
Bitcoin (BTCUSDT) กำลังอยู่ในช่วงสำคัญ แม้ว่าแนวโน้มหลักในระยะกลางถึงยาว (TF Day & 4H) จะยังคงเป็นขาขึ้นที่แข็งแกร่ง แต่ในระยะสั้นมาก (TF15) กลับแสดงสัญญาณของความอ่อนแอและการปรับฐานลงมา ทำให้เกิดความไม่แน่นอนในทิศทางของราคา อย่างไรก็ตาม *Money Flow ใน TF Day บ่งชี้ว่าแรงซื้อโดยรวมยังคงแข็งแกร่ง*

**แนวโน้ม:**
* **TF Day:** ขาขึ้น (Uptrend) แข็งแกร่ง – ราคาอยู่เหนือ EMA 50 และ EMA 200, โครงสร้างราคาเป็น Higher Highs (HH) และ Higher Lows (HL), *Money Flow เป็นบวก (แรงซื้อ)*
* **TF4H:** ขาขึ้น (Uptrend) – ราคาอยู่เหนือ EMA, มีการพักตัวลงมา (Pullback) แต่ยังไม่เสียโครงสร้างขาขึ้น, *Money Flow เริ่มอ่อนแรง (แรงซื้อลดลง, แรงขายเพิ่มขึ้น)*
* **TF15:** ขาลง (Downtrend) ระยะสั้นมาก – ราคาหลุด EMA และแนวรับย่อย, โครงสร้างราคาเป็น Lower Highs (LH) และ Lower Lows (LL), *Money Flow เป็นลบ (แรงขาย)*
**โครงสร้างราคา (SMC):**
* **TF Day:** ยืนยันแนวโน้มขาขึ้น (HH, HL, BOS)
* **TF4H:** ยืนยันแนวโน้มขาขึ้น (HH, HL, BOS), มี Equal Highs (EQH) ที่เป็นแนวต้าน
* **TF15:** บ่งบอกถึงแนวโน้มขาลงระยะสั้น (BOS ด้านล่าง, LH, LL), มี EQH เป็นแนวต้าน
**Money Flow (LuxAlgo) - สรุป:**
* **TF Day:** แรงซื้อยังคงแข็งแกร่งอย่างชัดเจน
* **TF4H:** แรงซื้อเริ่มอ่อนแรงลง, มีแรงขายเข้ามา
* **TF15:** แรงขายมีอิทธิพลเหนือกว่า

**EMA (Exponential Moving Average):**
* **TF Day & 4H:** EMA 50 & 200 เป็นแนวรับสำคัญ
* **TF15:** EMA 50 & 200 กลายเป็นแนวต้าน
**แนวรับ-แนวต้านสำคัญ:**
| Timeframe | แนวรับ | แนวต้าน |
| :-------- | :------------------------------------------------------------------------- | :-------------------------------------------------------------- |
| Day | EMA 50, EMA 200, 96,000-98,000, 85,724.7 | 109,998.9 (High เดิม) |
| 4H | EMA 50, EMA 200, 96,000-98,000, 89,037.0 | 109,998.9 (EQH, High เดิม) |
| 15m | 95,200 (Low ล่าสุด), 94,707.4 (Low ก่อนหน้า) | EMA 50, EMA 200, บริเวณ 96,000, 96,807.8, 97,000-97,200 |
**กลยุทธ์ (BTCUSDT):**
1. **Buy on Dip (Day, 4H) - *มีความน่าเชื่อถือมากขึ้น แต่ยังคงต้องระมัดระวัง*:**
* **เหตุผล:** แนวโน้มหลักยังเป็นขาขึ้น, Money Flow ใน TF Day แข็งแกร่ง
* **เงื่อนไข:** *ยังคงต้องรอสัญญาณการกลับตัวของราคาใน TF15 ก่อน* (Breakout แนวต้านย่อย, Money Flow TF15 เป็นบวก, Bullish Candlestick Patterns)
* **จุดเข้า (Day):** EMA 50, EMA 200, บริเวณ 96,000-98,000
* **จุดเข้า (4H):** EMA 50
* **Stop Loss:** ต่ำกว่า Low ล่าสุดของ TF15 หรือต่ำกว่าแนวรับที่เข้าซื้อ
2. **Short (15, ความเสี่ยงสูงมาก):**
* **เหตุผล:** แนวโน้ม TF15 เป็นขาลง, Money Flow TF15 เป็นลบ
* **เงื่อนไข:** ราคาไม่สามารถกลับขึ้นไปยืนเหนือ EMA ของ TF15 ได้
* **จุดเข้า:** บริเวณ EMA ของ TF15 หรือแนวต้านอื่นๆ
* **Stop Loss:** เหนือ High ล่าสุดของ TF15
3. **Wait & See (ทางเลือกที่ปลอดภัย):**
* **เหตุผล:** ความขัดแย้งระหว่าง Timeframes ยังคงมีอยู่
* รอให้ตลาดเฉลยทิศทางที่ชัดเจนกว่านี้
**คำแนะนำ (เน้นย้ำ):**
* **Money Flow ใน TF Day:** เป็นปัจจัยบวกที่สำคัญ ทำให้กลยุทธ์ Buy on Dip มีน้ำหนักมากขึ้น
* **ความขัดแย้งของ Timeframes:** ยังคงต้องระวัง TF15 ที่เป็นขาลง
* **Volume:** การ Breakout/Breakdown ใดๆ ควรมี Volume สนับสนุน
* **Risk Management:** สำคัญที่สุด
**สรุป:**
สถานการณ์ของ BTCUSDT โดยรวมยังคงเป็นบวก (ขาขึ้น) แต่มีความเสี่ยงในระยะสั้นจาก TF15 การตัดสินใจลงทุนควรพิจารณาจาก Timeframe ที่เหมาะสมกับสไตล์การเทรดของคุณ และอย่าลืมบริหารความเสี่ยงเสมอค่ะ
**Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-

@ 2183e947:f497b975
2025-02-13 04:44:45
# How Coinpools Improve Bitcoin
# Problems with bitcoin
UX problems with base layer payments include:
- Mining fees are sometimes high
- Confirmations usually take several minutes
- Using it privately requires running a coinjoin server
UX problems with lightning payments include:
- Setup fees are sometimes high
- Payments frequently fail
- Payments aren't asynchronous (the recipient has to stand there with their device open waiting to do a revoke_and_ack on their old state -- unless they use a custodian)
- Payments that *do* succeed occasionally take more than 30 seconds (due to stuck payments, automatic retries, and no ability to say "stop retrying" in any existing wallets that I'm aware of)
- Using it privately requires manual channel management
# Solutions
A lot of my recent work focuses on non-interactive coinpools. I figured out a way to do them on bitcoin if we had CTV + CSFS, and then, with a bit more thought, I figured out that my model didn't actually require those things, so I am now working on an implementation. But my model does benefit a lot from CTV (less sure about CSFS at this point) so let me outline how non-interactive coinpools fix the above problems and along the way I will share how CTV specifically improves coinpools.
## "Mining fees are sometimes high"
Coinpools improve the problem of "mining fees are sometimes high" by letting you bypass them in more cases. If you're in a coinpool and pay someone else in the same coinpool, your payment does not show up on the base layer, it just involves modifying some unilateral withdrawal transactions such that the sender can withdraw less and the recipient can withdraw more. The transactions are off-chain, like LN transactions, so you can do that without paying a base layer fee.
## "Confirmations usually take several minutes"
Coinpools improve the problem of "confirmations usually take several minutes" in a similar manner. Payments *inside* a coinpool (i.e. to another pool user) merely involve modifying off-chain data (and revoking an old state), so they can be as fast as lightning. In most cases I expect them to be a bit faster because there's less need for pathfinding or negotiating with a variety of routing nodes. If the sender and the recipient are in the same pool, they only need to talk to each other and, in my model, a coordinator.
## "Using the base layer privately requires running a coinjoin server"
Coinpools improve the problem of "using the base layer privately requires running a coinjoin server" in two ways: first, if you're in a coinpool and you send money to a bitcoin address, the blockchain doesn't know which coinpool user sent that payment. Analysts might be able to trace the payment to the coinpool, but from the blockchain's perspective, that's just a multisig; the actual person *inside* the multisig who sent the money is not revealed. However, my model uses a coordinator, and the coordinator probably knows which user sent the payment. Still, only 1 person knowing is better than having everyone on the blockchain know.
Second, if you send money to someone *inside* the coinpool, in my model, the only people who know about your payment are the sender, the recipient, and the coordinator, and the recipient does not know who the sender is. Moreover, my model allows users to act as bridges from LN to other pool users, so even the coordinator doesn't know if the person who *looks* like the sender was the *real* sender or just a bridge node, with the *real* sender being someone on lightning.
## "Setup fees on lightning are sometimes high"
Coinpools improve the problem of "setup fees are sometimes high" by having multiple users share the setup cost. My model allows a single bitcoin transaction to fund a coinpool with a number of members between 1 and probably about 100. (The max I've actually successfully tested is 11.) If the users share the cost of that transaction, then even in a high fee scenario, where bitcoin transactions cost $50, each user only has to pay a fraction of that, where the fraction is determined by how many users are joining the pool. If 10 people are joining, each user would pay $5 instead of $50. If 50 people are joining, each user would pay $1. If 100 people are joining, each user would pay 50¢.
## Sidebar: how CTV improves my coinpool model
The setup is also where CTV greatly improves my model. For my model to work, the users have to coordinate to create the pool in something I call a "signing ceremony," which is very similar to a coinjoin. The signing ceremony has to be scheduled and each user has to show up for it or they won't get into the pool. With CTV, you could fix this: instead of a signing ceremony, an exchange could autosend your money into a coinpool on e.g. a monthly basis and email you the data you need to perform your unilateral exit. All they need from you is a pubkey, and they can do everything else.
## "Lightning payments frequently fail"
Coinpools improve the problem of "payments frequently fail" by reducing the need for pathfinding, which is a typical cause of failure on lightning. If you are paying someone in the same pool as you, you always know an exact path: it will be you -> coordinator -> recipient. These short paths also reduce the likelihood of routing nodes having insufficient capacity to forward the payment. You've only got one "routing node" to worry about -- the coordinator.
## "Lightning payments aren't asynchronous"
Coinpools *in general* don't improve the problem of "payments aren't asynchronous" but my model in particular *does* improve that problem because I am combining it with my hedgehog protocol from last year, which *does* allow for asynchronous lightning-like payments. Relatedly, my coinpool model technically has a network model, it's just a hub-and-spoke network: the coordinator is connected to every user of the pool and can forward asynchronous hedgehog payments to them. This means you can send money to someone when they are offline; they'll get it whenever they *do* get online, even if *you* went offline in the meantime.
## "Lightning payments sometimes take too long"
Coinpools improve the problem of "stuck" lightning payments by reducing the number of hops along the route. As above, a payment inside the pool (per my model) is always just sender -> coordinator -> recipient. Due to only having 1 hop, there are fewer opportunities for a node to have a network issue and cause a delay.
## "Channel management is a pain"
Coinpools have multiple ways of improving the problem of manual channel management. In particular, not all coinpool models *have* channels, so channel management is not always needed in a coinpool. My model, however, does have channels, so channel management is still a thing.
Nonetheless, my model improves channel management in two ways: first, the setup costs are lower for the reasons given above. Second, payment asynchronicity helps for the following reason:
The worst pain point in channel management *today* occurs when someone sends you a payment but it fails because you didn't have enough inbound capacity. That doesn't happen in my coinpool model because payments are asynchronous. If you don't have enough inbound capacity, the payment doesn't fail, it just remains pending. So all you have to do is open a new channel (i.e. enter a new pool) and *then* finalize the payment.
## Zap me
I hope this essay clarifies why coinpools improve the problems I outlined and why CTV improves coinpools. I also hope this gets you a bit excited for my latest coinpool invention, which I hope to release soon :D (It really is very close to demo-ready.) If you liked this essay, consider zapping me: supertestnet@coinos.io
-

@ a012dc82:6458a70d
2025-02-13 04:00:01
In the dynamic world of global finance, the interplay between traditional monetary policy and the burgeoning digital asset market is becoming increasingly prominent. The U.S. Federal Reserve's recent pivot towards a more accommodative monetary policy has sparked intense discussion among investors, economists, and cryptocurrency enthusiasts. This shift, characterized by an expected reduction in interest rates, is not just a routine adjustment but a significant move that could have far-reaching implications for various asset classes, including cryptocurrencies like Bitcoin. As we delve into this topic, we aim to unravel the complexities of the Fed's policy change and its potential ripple effects on Bitcoin, a digital asset that has been a subject of much intrigue and speculation.
**Table Of Content**
- Understanding the Fed's Policy Shift
- Impact on Traditional Financial Markets
- Bitcoin's Response to Monetary Easing
- Analyzing the Economic Backdrop
- Bitcoin: A Safe Haven or Risk Asset?
- Risks and Opportunities
- Conclusion
- FAQs
**Understanding the Fed's Policy Shift**
The Federal Reserve, the guardian of the U.S. monetary system, wields immense influence over global financial markets. Its recent signaling of a dovish turn – an expectation of 75 basis points in rate cuts by 2024 – marks a significant departure from its previous stance. This change is reflective of the Fed's response to a confluence of macroeconomic factors, such as fluctuating inflation rates, global economic uncertainties, and domestic financial stability concerns. The Fed's decisions are closely monitored as they set the tone for economic growth, inflation control, and financial market stability. In this context, the anticipated rate cuts suggest a strategic move to stimulate economic activity by making borrowing cheaper, thereby potentially boosting investment and consumption. However, this policy shift is not without its complexities and nuances, as it must balance the fine line between stimulating growth and controlling inflation.
**Impact on Traditional Financial Markets**
The ripple effects of the Fed's policy announcement were immediately felt across traditional financial markets. Stock markets, often seen as a barometer of economic sentiment, reacted positively, with indices like the Dow Jones Industrial Average reaching new heights. This surge reflects investors' optimism about the potential for increased corporate profits and economic growth in a lower interest rate environment. Similarly, the bond market experienced a significant rally, with yields on government securities falling as bond prices rose. This movement in the bond market is indicative of investors' expectations of a more accommodative monetary policy, which typically leads to lower yields on fixed-income securities. These market reactions underscore the pivotal role of central bank policies in shaping investor sentiment and the direction of financial markets. They also highlight the interconnectedness of various asset classes, as changes in monetary policy can have cascading effects across different sectors of the economy.
**Bitcoin's Response to Monetary Easing**
Bitcoin's reaction to the Fed's dovish turn has been a subject of keen interest. The cryptocurrency, which had been experiencing volatility, showed signs of recovery following the Fed's announcement. This response is indicative of Bitcoin's increasing correlation with broader financial market trends, a significant development given its history as an uncorrelated asset. Bitcoin's sensitivity to macroeconomic factors like central bank policies points to its growing integration into the mainstream financial ecosystem. However, this integration also means that Bitcoin is increasingly exposed to the same macroeconomic risks and uncertainties that affect traditional assets. The Fed's policy shift could potentially make Bitcoin more attractive to investors seeking non-traditional assets in a low-interest-rate environment. However, Bitcoin's complex dynamics, including its decentralized nature, limited supply, and regulatory landscape, add layers of complexity to its response to monetary policy changes.
**Analyzing the Economic Backdrop**
The economic backdrop against which the Fed's policy shift occurs is multifaceted and dynamic. On one hand, the U.S. economy has demonstrated resilience, with robust GDP growth and positive retail sales figures suggesting underlying strength. On the other hand, inflation, though moderated from its peak, remains a concern, hovering above the Fed's target. This economic duality presents a challenging scenario for policymakers, who must navigate the delicate balance between stimulating growth and containing inflation. For investors and market participants, this creates an environment of uncertainty, as they must decipher mixed signals from economic data and policy announcements. In this context, Bitcoin's role and response become even more intriguing, as it operates at the intersection of technology, finance, and macroeconomics.
**Bitcoin: A Safe Haven or Risk Asset?**
The debate over Bitcoin's classification as a safe haven or a risk asset is intensified by the Fed's easing stance. Traditionally, in a low-interest-rate environment, investors seek assets that can serve as hedges against inflation and currency devaluation. Gold has historically played this role, and Bitcoin, with its fixed supply and digital scarcity, has drawn comparisons to gold. However, Bitcoin's relatively short history and high volatility make it a more complex and potentially riskier asset. The Fed's dovish policy could enhance Bitcoin's appeal as an alternative investment, especially if traditional assets like bonds offer lower returns. However, Bitcoin's classification as a safe haven is still a matter of debate, with opinions divided on its long-term stability and value retention capabilities.
**Risks and Opportunities**
Investors considering Bitcoin in light of the Fed's policy change face a landscape filled with both risks and opportunities. The potential for a Bitcoin rally in a low-interest-rate environment is counterbalanced by the cryptocurrency's inherent volatility and regulatory uncertainties. Bitcoin's price movements can be dramatic and unpredictable, influenced by a range of factors from technological developments to geopolitical events. Additionally, the regulatory environment for cryptocurrencies is still evolving, with potential changes posing risks to Bitcoin's accessibility and value. Investors must also consider the broader global economic context, including actions by other central banks and international trade dynamics, which can impact Bitcoin's market movement.
**Conclusion**
The Federal Reserve's shift towards a more accommodative monetary policy in 2024 presents a fascinating scenario for Bitcoin and the broader cryptocurrency market. This development underscores the increasing relevance of digital assets in the global financial landscape and highlights the complex interplay between traditional monetary policies and emerging financial technologies. As Bitcoin continues to evolve and gain acceptance, its response to macroeconomic factors like central bank policies will be a critical area of focus for investors. In navigating this dynamic and uncertain environment, a cautious and well-informed approach is essential for those looking to explore the opportunities and navigate the challenges of cryptocurrency investments. The coming years promise to be a pivotal period in the maturation of Bitcoin as it responds to the shifting tides of global finance.
**FAQs**
**How does the Federal Reserve's easing stance impact Bitcoin?**
The Fed's shift towards lower interest rates can make riskier assets like Bitcoin more attractive to investors. This is because lower rates often lead to reduced yields on traditional investments, prompting investors to seek higher returns elsewhere.
**What is the significance of the Fed's 'dot plot' for Bitcoin investors?**
The 'dot plot' is a projection of interest rate movements by Federal Reserve members. A shift towards lower rates, as indicated in the recent dot plot, can signal a more accommodative monetary policy, potentially impacting Bitcoin's market as investors adjust their portfolios.
**Can Bitcoin be considered a safe haven asset in light of the Fed's policy?**
Bitcoin's role as a safe haven asset is debated. While its fixed supply and digital nature offer some safe haven characteristics, its volatility and regulatory uncertainties make it a complex choice compared to traditional safe havens like gold.
**What risks should Bitcoin investors consider in the context of the Fed's easing policy?**
Investors should be aware of Bitcoin's volatility, regulatory changes, and its sensitivity to macroeconomic factors. Additionally, global economic conditions and actions by other central banks can also influence Bitcoin's market.
**How does the economic backdrop influence Bitcoin's response to the Fed's policy?**
Economic factors like GDP growth, inflation rates, and retail sales impact investor sentiment and risk appetite, which in turn can affect Bitcoin's market. A strong economy might reduce the appeal of risk assets like Bitcoin, while economic uncertainties can increase their attractiveness.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: @croxroadnews.co**
**Instagram: @croxroadnews.co**
**Youtube: @croxroadnews**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
-

@ 57d1a264:69f1fee1
2025-02-13 03:45:23

**What You Will Learn:**
- Understanding the concept of cybersecurity
- Networking Basics
- Operating Systems Overview
- Introduction to Kali Linux
- Threat Actors and Cyber Threats
- Ethical Hacking Techniques and Tools.
**How to Register:**
Use this link to Register.
https://forms.gle/L8AGLCWU4djwUXxz9
originally posted at https://stacker.news/items/884407
-

@ f6488c62:c929299d
2025-02-13 02:39:41
Lowering interest rates is one of the tools that central banks use to manage the economy, especially during periods of inflation, which causes the prices of goods and services to rise. Lowering interest rates not only helps stimulate spending but can also foster sustainable growth in businesses and labor markets.
Access to Capital and Economic Stimulation
When interest rates are lowered, the public can access capital more easily. With lower interest rates, borrowing becomes less burdensome, giving individuals and businesses the opportunity to start new ventures or expand existing businesses. This leads to increased investment and spending, which in turn keeps the economy circulating and growing.
For instance, when people can easily borrow money to start a new business—such as an online store or a product manufacturing business—the increase in entrepreneurs and the availability of goods in the market will ensure that the supply is sufficient to meet consumer demand. This, in turn, prevents prices from rising too much due to a lack of supply.
Reducing Inflation by Increasing Supply
Increasing the supply of goods and services in the market can significantly help in controlling inflation. When there are more goods or services available to meet market demand, competition among producers will naturally drive prices down. This is the basic principle of market dynamics: when there’s enough supply, prices are less likely to increase, even in times of high demand.
In addition, increasing supply helps address shortages, which are one of the key drivers of rising prices. When there is enough product available to satisfy demand, inflationary pressures can be relieved, and prices can stabilize.
Redistributing Income and Reducing Inequality
Lower interest rates also play a crucial role in redistributing income within society. By making access to capital easier, especially for those with lower or middle incomes, the public’s purchasing power increases, which can stimulate spending on essential goods and services.
When people have more money in hand, they are better able to access necessary products. This boosts demand in the market. However, alongside this increased demand, sufficient supply is needed to prevent prices from rising uncontrollably, which can lead to inflation.
Moreover, supporting the population through welfare programs or initiatives that allow everyone to access education and investment opportunities helps individuals create products and value in the market. A diverse market with a variety of products increases production efficiency and helps mitigate economic inequality, ensuring a more balanced and inclusive economy.
Conclusion
Lowering interest rates and redistributing income effectively can stimulate economic growth and reduce inflation. This works by ensuring there is sufficient supply to meet market demand, while also providing capital that allows the public to start new businesses and generate new products in the market.
For sustainable long-term economic growth, managing inflation should go hand in hand with investing in infrastructure and ensuring wealth distribution. This ensures that everyone has equal access to opportunities, leading to steady economic growth without negatively impacting the majority of society.
In summary, lowering interest rates is a key tool in stimulating the economy and reducing inflation, especially when the economy faces imbalances. It not only increases supply, but also promotes income redistribution and the creation of an economy that is more equitable in the long run.
-

@ 3b7fc823:e194354f
2025-02-13 02:25:42
site:example.com
intitle:"index of"
inurl:admin
intext:"password"
site:example.com
site:.gov
site:.edu
site:*.mil
inurl:login
inurl:admin
inurl:dashboard
inurl:portal
intitle:"admin login"
intitle:"index of /"
intitle:"index of" "parent directory"
intitle:"index of" "backup"
filetype:pdf "confidential"
filetype:xls "username | password"
filetype:doc "top secret"
filetype:sql "database"
intext:"username" intext:"password"
intext:"login" intext:"password"
filetype:txt "passwords"
inurl:"viewerframe?mode="
inurl:"/view.shtml"
inurl:"/view/index.shtml"
intitle:"index of" "wp-config.php"
inurl:".git"
filetype:xls intext:"email"
filetype:csv intext:"email"
inurl:"/setup.cgi?next_file=netgear.cfg"
inurl:"/wificonf.html"
-

@ fd78c37f:a0ec0833
2025-02-13 02:24:48
In this edition, we invited Rafael from Bitcoin É Aqui to share the development of his community and its efforts in promoting Bitcoin adoption. From establishing a Bitcoin-friendly environment in Rolante to organizing and supporting events like the Bitcoin Spring Festival and KuchenFest, Rafael highlighted Bitcoin's impact on the local economy and tourism industry.
**YakiHonne**: Today, we are honored to invite Rafael from Bitcoin é Aqui to join us. Before we dive in, I'd like to take a moment to introduce YakiHonne and share a bit about what we do. YakiHonne is a decentralized media client built on the Nostr protocol that enables freedom of speech through technology. It empowers creators to create their own voice, assets, and features. It also allows features like smart widgets, verified notes, and focuses on long-form articles. Now today we'll be exploring more about the Bitcoin community. Rafael, could you please briefly introduce what sparked your interest in Bitcoin, and what motivated you to create this community?
**Rafael**:Like many, Stim's and his wife Camila's initial interest was in technology— a completely new way to transfer money with full self-custody. From the beginning, the project focused on the payment network, and at the time, they didn’t realize it would evolve into “A Project.”
**YakiHonne**: Could you share how your community got started, the strategies you used to attract members, and the early challenges you encountered?
**Rafael**:From the start, we were all about building a payment network. We began by paying our barber, gardener, and other service providers with Bitcoin. After a few close friends joined, word started to spread—even though some were worried about scams and Bitcoin's legality. To address these concerns, we held a talk at the City's Trade Association on how merchants could legally accept Bitcoin. We expected 5 to 10 friends, but over 60 merchants attended! Today, we’re proud to say that our city is the most Bitcoin-friendly in the world, with more than 40% of stores accepting it. From plumbers to supermarkets, it’s amazing to see our community featured on the BitcoinMap website.

**YakiHonne**: What principles guide the community, and how do you maintain trust and reliability in discussions?
**Rafael**:Like Bitcoin itself, decentralization is our core principle. The project "Bitcoin É Aqui" (loosely translated as "Bitcoin is Here") assists merchants in setting up Lightning wallets and offers best practices. However, every merchant is free to operate as they see fit—choosing whether to follow our advice or to use any wallet they prefer. Moreover, many experienced merchants help onboard newcomers, building trust through established networks and reinforcing our decentralized approach.
**YakiHonne**: How do you educate members and keep them updated on Bitcoin developments?
**Rafael**:We have a group chat where we post some news, but in Brazil, almost everyone already uses WhatsApp for communication, and news usually spreads through these groups, again highlighting the decentralized nature of the Project.
**YakiHonne**: What initiatives has the community undertaken to promote Bitcoin adoption, and what results have you seen?
**Rafael**:Of course, the rising coin value draws attention, but the main attraction is tourists coming to Rolante to learn about the project. Rolante was already famed for its natural wonders—majestic mountains and breathtaking waterfalls. Combined with Bitcoin’s innovative acceptance as a payment method, it has become an even stronger magnet for visitors.
**Rafael**:In Rolante, living completely on Bitcoin is a reality. Here, you'll find travel agencies, professional tour guides, and a variety of services—from department stores and opticians to real estate agents, construction companies, architects, furniture stores, building materials suppliers, and solar energy providers. In the healthcare sector, you can rely on pharmacies, massage therapists, physiotherapists, and advanced dental services; even the city hospital accepts Bitcoin as payment.

**YakiHonne**: What are the community’s goals for the next 6-12 months, and how do you see it evolving with Bitcoin’s growth?
**Rafael**:As a project, Bitcoin É Aqui doesn’t dictate what the community should do, but we support many events like Pizza Day, Bitcoin Spring Festival, Bier Rock, KuchenFest. One major event is the biennial Bitcoin Spring Festival (BSF). The Bitcoin Spring Festival (BSF) is a key event in the Rolante Bitcoin community, aimed at promoting Bitcoin adoption and circular economy development. This year, the festival focuses on "Bitcoinization," bringing together notable figures in the Bitcoin space to showcase a real Bitcoin economic ecosystem. During the event, all transactions will be conducted via the Lightning Network, with Coinos.io and Wallet Of Satoshi recommended. BSF is not just a celebration but a movement toward financial freedom.

**Rafael**:This March, Rolante will host its most traditional event, KuchenFest, celebrating the local traditional bread delicacy. The event centers around the sweet bread Cuca, bringing together candy makers and Cuca enthusiasts to share recipes, techniques, and stories. Additionally, the festival features live music, folk dances, and family activities, showcasing rich cultural traditions. We will help the event accept and promote the use of Bitcoin.
-

@ ac6f9572:8a6853dd
2025-02-13 02:05:22
I attended Sats ‘n’ Facts to share my art, joining other Nostr artists in exhibiting our work at the event’s very first venue. It was a great opportunity to connect with fellow creatives, including Siritravelsketch, whose work I’ve admired on Nostr for some time. Meeting other artists in real life is always inspiring—there’s an undeniable creative bond that comes from sharing our passion in person.

Sats ‘n’ Facts is an Unconference, meaning there’s no strict schedule—everything is open for participants. It’s all about the connections made, the synergy shared, and, for the developers attending, the excitement of a hackathon. (A hackathon is an event where people collaborate intensively on engineering projects, often within 24 to 48 hours.)

My goal as an artist is to become a bridge between the Bitcoin tech world and the Bitcoin art and design space. Bitcoin empowers us by providing greater (financial) freedom, and with that freedom comes more time to pursue what we truly love—so in a way, you never have to “work” again. 😊

Nostr is a great example of how bubbles 🫧 POP, leading to new collaborations. Without tech, artists wouldn’t have a way to share their work, and without artists, creatives, and plebs, developers would have no one to build for. Both sides are essential for organic growth. This kind of synergy can only thrive in a decentralized system—otherwise, it risks being captured by big corporations. And that single point of failure is one of the biggest challenges we face in the world today.

Decentralization is freedom. Events like Sats ‘n’ Facts give us the opportunity to collaborate, create, and contribute to a more decentralized world—one where more people can truly become free.

Can’t wait to join the next Sats’n’facts. Maybe Barcelona!?
* * *
Originally article published by @BitPopArt on @YakiHonne: https://yakihonne.com/article/naddr1qvzqqqr4gupzqsa64uxz3ek0kx2mzlhqs0seavay4l06c4xek6a0zup8pmge8c6vqq242en0tukk7u2fwe8kkjrpv3ykgjtzwfsk5hmmfyp
#art #nostr #ThaiNostrich #artonnostr #artstr
originally posted at https://stacker.news/items/884327
-

@ df478568:2a951e67
2025-02-13 02:04:30
In the very early days, Nostr was pretty much troll-free. It was one of my favorite things about it, but I suspected this was only the case because only hardcore bitcoiners were on there. Now that the network is growing, there is more diversity of ideas. Ideology tends to make people mean. Mean people suck, so I try to remain respectful even when I disagree with others. I am not a fan of communism, but enjoy reading other perspectives. I do not wish to censor any speech at all, especially speech I do not agree with.
The freedom of speech is not about the First Amendment to me. It's about creating a space that is safe for free speech. Platforms are not a safe space for free speech. The safety of free speech is in peril on platforms. Nostr is a space where people can speak freely in an open Internet-connected society. There is some speech I would rather not see. I wish some people did not say certain things, but I do not want to stop them.
If we censor the worst speech, the speech does not go away. It merely goes underground and creates bad speech silos where people hide their true selves and go only speak to people just like them. Censorship is like prison for ideas. Prisoners improve their robbery skills because they exchange ideas with other criminals. It's like a conference for criminals. Fascists get more fascist when they only have permission to talk to fellow fascists. Communists get more communist when they can only talk to other communists. Ideas are a marketplace. May the best ideas win.
Nostr allows me to speak with people about topics I might not otherwise get a chance to speak about. I never see any pro-communist posts on Twitter. That's a problem because communists also don't see me. I also never saw sex workers talk about anything other than kinky-boinky talk on Twitter. Nostr brings the humanity back to sex workers. Sex workers are people too. They have interesting ideas and take [interesting photos]([take interesting pictures](nostr:note1svl3ne6l7dkxx4gckqsttx24nva7m37ynam7rvgq4zu83u9wl2ks86ahwx). )
On the [What is Money Show](https://fountain.fm/episode/DYPKRSkN11EmYDhrhH0H), Rabble says he wants to have Christians have a Christian-only Nostr network and sex workers to have a sex worker-only network. It's a fun idea, but I'm not convinced this would be a good thing. What if Jesus was on the Christian Nostr, but Mary Magdalen was on sex worker Nostr? I suspect Christians talking to sex workers is not such a bad thing. **What would Jesus do?**
Here is a conversation I had with a stripper on nostr. You can read the original [here](nostr:note1wxalrm6tpftrrs9rmzvv4e5gpnamkmfuu6fpwu9gs3wtudeegd7qpd5l0r) but I have reprinted it on the Habla and Substack.
I don't believe it's possible for a community or state to abolish private property when the private property can be distilled into 12 secret random words. Ironically, bitcoin does give the means of monetary production to the people, but this is a moot point given that individual people do not have equal ability. Very few people had sufficient knowledge to mine bitcoin when the block reward was 50 bitcoin every 10 minutes. Therefore, even though anybody could technically produce bitcoin blocks, very few people can.
The same is true for saving. Even if we could defy human nature with schemes such as this, it would not solve wealth inequality. Most people spend money like drunken sailors. If everyone had the same income that could not be debased or stolen, broke people would still exist because people do not have equal money management skills.
That is why I prefer capitalism with a non-socialist monetary system. The United States, contrary to popular belief, is not a capitalist economic system. It's a mixed economy where some people (banks and government) get money without doing any work aside from fudging numbers.
A bank does not save capital to buy a house. Banks print money to buy homes and collect rent from homeowners. It's an accounting trick, not capitalism.
Here's how capitalism works according to economist, Russ Roberts.
https://youtu.be/ljULutAUL7o?si=bLPY5IvwwMQvfXJK
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
https://mempool.marc26z.com/block/00000000000000000001fa33d3d7750ed315d94e3c1def6512281b33bece333b
-

@ 97c70a44:ad98e322
2025-02-13 02:03:33
Everyone knows that relays are central to how nostr works - they're even in the name: Notes and Other Stuff Transmitted by *Relays*. As time goes on though, there are three other letters which are becoming conspicuously absent from our beloved and ambiguously pronounceable acronym - "D", "V", and "M".
The hype cycle for DVMs seems to have reached escape velocity in a way few other things have - zaps being the possible exception. But *what* exactly DVMs are remains something of a mystery to many nostr developers - and how to build one may as well be written on clay tablets.
This blog post is designed to address that - below is a soup to nuts (no nutzaps though) guide to building a DVM flow, both from the client and the server side.
Here's what we'll be covering:
- Discovering DVM metadata
- Basic request/response flow
- Implementing a minimal example
Let's get started!
# DVM Metadata
First of all, it's helpful to know how DVMs are reified on the nostr network. While not strictly necessary, this can be useful for discovering DVMs and presenting them to users, and for targeting specific DVMs we want a response from.
[NIP 89](https://github.com/nostr-protocol/nips/blob/master/89.md) goes into this in more detail, but the basic idea is that anyone can create a `kind 31990` "application handler" event and publish it to the network with their own (or a dedicated) public key. This handler was originally intended to advertise clients, but has been re-purposed for DVM listings as well.
Here's what the "Fluffy Frens" handler looks like:
```json
{
"content": "{\"name\": \"Fluffy Frens\", \"picture\": \"https://image.nostr.build/f609311532c470f663e129510a76c9a1912ae9bc4aaaf058e5ba21cfb512c88e.jpg\", \"about\": \"I show recent notes about animals\", \"lud16\": \"discovery_content_fluffy@nostrdvm.com\", \"supportsEncryption\": true, \"acceptsNutZaps\": false, \"personalized\": false, \"amount\": \"free\", \"nip90Params\": {\"max_results\": {\"required\": false, \"values\": [], \"description\": \"The number of maximum results to return (default currently 100)\"}}}",
"created_at": 1738874694,
"id": "0aa8d1f19cfe17e00ce55ca86fea487c83be39a1813601f56f869abdfa776b3c",
"kind": 31990,
"pubkey": "7b7373dd58554ff4c0d28b401b9eae114bd92e30d872ae843b9a217375d66f9d",
"sig": "22403a7996147da607cf215994ab3b893176e5302a44a245e9c0d91214e4c56fae40d2239dce58ea724114591e8f95caed2ba1a231d09a6cd06c9f0980e1abd5",
"tags": [
["k", "5300"],
["d", "198650843898570c"]
]
}
```
This event is rendered in various clients using the kind-0-style metadata contained in the `content` field, allowing users to browse DVMs and pick one for their use case. If a user likes using a particular DVM, they might publish a `kind 31989` "application recommendation", which other users can use to find DVMs that are in use within their network.
Note the `k` tag in the handler event - this allows DVMs to advertise support only for specific job types. It's also important to note that even though the spec doesn't cover relay selection, most clients use the publisher's `kind 10002` event to find out where the DVM listens for events.
If this looks messy to you, you're right. See [this PR](https://github.com/nostr-protocol/nips/pull/1728) for a proposal to split DVMs out into their own handler kind, give them a dedicated pubkey along with dedicated metadata and relay selections, and clean up the data model a bit.
# DVM Flow
Now that we know what a DVM looks like, we can start to address how they work. My explanation below will elide some of the detail involved in [NIP 90](https://github.com/nostr-protocol/nips/blob/master/90.md) for simplicity, so I encourage you to read the complete spec.
The basic DVM flow can be a little (very) confusing to work with, because in essence it's a request/response paradigm, but it has some additional wrinkles.
First of all, the broker for the request isn't abstracted away as is usually the case with request/response flows. Regular HTTP requests involve all kinds of work in the background - from resolving domain names to traversing routers, VPNs, and ISP infrastructure. But developers don't generally have to care about all these intermediaries.
With DVMs, on the other hand, the essential complexity of relay selection can't simply be ignored. DVMs often advertise their own relay selections, which should be used rather than a hard-coded or randomly chosen relay to ensure messages are delivered. The benefit of this is that DVMs can avoid censorship, just as users can, by choosing relays that are willing to broker their activity. DVMs can even select multiple relays to broker requests, which means that clients might receive multiple copies of the same response.
Secondly, the DVM request/response model is far more fluid than is usually the case with request/response flows. There are a set of standard practices, but the flow is flexible enough to admit exceptions to these conventions for special use cases. Here are some examples:
- Normally, clients p-tag the DVM they wish to address. But if a client isn't picky about where a response comes from, they may choose to send an open request to the network and collect responses from multiple DVMs simultaneously.
- Normally, a client creates a request before collecting responses using a subscription with an e-tag filter matching the request event. But clients may choose to skip the request step entirely and collect responses from the network that have already been created. This can be useful for computationally intensive tasks or common queries, where a single result can be re-used multiple times.
- Sometimes, a DVM may respond with a `kind 7000` job status event to let clients know they're working on the request. This is particularly useful for longer-running tasks, where feedback is useful for building a responsive UX.
- There are also some details in the spec regarding monetization, parameterization, error codes, encryption, etc.
# Example DVM implementation
For the purposes of this blog post, I'll keep things simple by illustrating the most common kind of DVM flow: a `kind 5300` [content discovery](https://www.data-vending-machines.org/kinds/5300/) request, addressed to a particular DVM. If you're interested in other use cases, please visit [data-vending-machines.org](https://data-vending-machines.org) for additional documented kinds.
The basic flow looks like this:
- The DVM starts by listening for `kind 5300` job requests on some relays it has selected and advertised via NIP 89 (more on that later)
- A client creates a request event of `kind 5300`, p-tagged with the DVM's pubkey and sends it to the DVM's relay selections.
- The DVM receives the event and processes it, issuing optional `kind 7000` job status events, and eventually issuing a `kind 6300` job result event (job result event kinds are always 1000 greater than the request's kind).
- The client listens to the same relays for a response, and when it comes through does whatever it wants to with it.
Here's a swimlane diagram of that flow:

To avoid massive code samples, I'm going to implement our DVM entirely using nak (backed by the power of the human mind).
The first step is to start our DVM listening for requests that it wants to respond to. Nak's default pubkey is `79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798`, so we'll only listen for requests sent to nak.
```bash
nak req -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798
```
This gives us the following filter:
```json
["REQ","nak",{"kinds":[5300],"#p":["79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"]}]
```
To open a subscription to `nos.lol` and stream job requests, add `--stream wss://nos.lol` to the previous request and leave it running.
Next, open a new terminal window for our "client" and create a job request. In this case, there's nothing we need to provide as `input`, but we'll include it just for illustration. It's also good practice to include an `expiration` tag so we're not asking relays to keep our ephemeral requests forever.
```bash
nak event -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 -t expiration=$(( $(date +%s) + 30 )) -t input=hello
```
Here's what comes out:
```json
{
"kind": 5300,
"id": "0e419d0b3c5d29f86d2132a38ca29cdfb81a246e1a649cb2fe1b9ed6144ebe30",
"pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798",
"created_at": 1739407684,
"tags": [
["p", "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"],
["expiration", "1739407683"],
["input", "hello"]
],
"content": "",
"sig": "560807548a75779a7a68c0ea73c6f097583e2807f4bb286c39931e99a4e377c0a64af664fa90f43e01ddd1de2e9405acd4e268f1bf3bc66f0ed5a866ea093966"
}
```
Now go ahead and publish this event by adding `nos.lol` to the end of your `nak` command. If all goes well, you should see your event pop up in your "dvm" subscription. If so, great! That's half of the flow.
Next, we'll want our client to start listening for `kind 6300` responses to the request. In your "client" terminal window, run:
```bash
nak req -k 6300 -t e=<your-eventid-here> --stream nos.lol
```
Note that if you only want to accept responses from the specified DVM (a good policy in general to avoid spam) you would include a `p` tag here. I've omitted it for brevity. Also notice the `k` tag specifies the request kind plus `1000` - this is just a convention for what kinds requests and responses use.
Now, according to [data-vending-machines.org](https://www.data-vending-machines.org/kinds/5300/), `kind 5300` responses are supposed to put a JSON-encoded list of e-tags in the `content` field of the response. Weird, but ok. Stop the subscription in your "dvm" terminal and respond to your "client" with a recommendation to read my first note:
```bash
nak event -k 6300 -t e=a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf -c '[["e","214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08","wss://nos.lol/"]]' nos.lol
```
Here's the response event we're sending:
```json
{
"kind": 6300,
"id": "bb5f38920cbca15d3c79021f7d0051e82337254a84c56e0f4182578e4025232e",
"pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798",
"created_at": 1739408411,
"tags": [
["e", "a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf"]
],
"content": "[[\"e\",\"214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08\",\"wss://nos.lol/\"]]",
"sig": "a0fe2c3419c5c54cf2a6d9a2a5726b2a5b766d3c9e55d55568140979354003aacb038e90bdead43becf5956faa54e3b60ff18c0ea4d8e7dfdf0c8dd97fb24ff9"
}
```
Notice the `e` tag targets our original request.
This should result in the job result event showing up in our "client" terminal. Success!
If something isn't working, I've also create a video of the full process with some commentary which you can find [here](https://coracle-media.us-southeast-1.linodeobjects.com/nakflow.mov).
Note that in practice, DVMs can be much more picky about the requests they will respond to, due to implementations failing to follow [Postel's law](https://en.wikipedia.org/wiki/Robustness_principle). Hopefully that will improve over time. For now, here are a few resources that are useful when working with or developing DVMs:
- [dvmdash](https://dvmdash.live)
- [data-vending-machines.org](https://data-vending-machines.org)
- [noogle](https://noogle.lol/)
- [nostrdvm](https://github.com/believethehype/nostrdvm)
# Conclusion
I started this post by hinting that DVMs might be as fundamental as relays are to making nostr work. But (apart from the fact that we'd end up with an acronym like DVMNOSTRZ+*, which would only exascerbate the pronounciation wars (if such a thing were possible)), that's not exactly true.
DVMs have emerged as a central paradigm in the nostr world because they're a generalization of a design pattern unique to nostr's architecture - but which exists in many other places, including NIP 46 signer flows and NIP 47 wallet connect. Each of these sub-protocols works by using relays as neutral brokers for requests in order to avoid coupling services to web addresses.
This approach has all kinds of neat benefits, not least of which is allowing service providers to host their software without having to accept incoming TCP connections. But it's really an emergent property of relays, which not only are useful for brokering communication between users (aka storing events), but also brokering communication between machines.
The possibilities of this architecture have only started to emerge, so be on the lookout for new applications, and don't be afraid to experiment - just please, don't serialize json inside json 🤦♂️
-

@ ac6f9572:8a6853dd
2025-02-13 01:56:23

Date: 02/12/2025
One of the most efficient options to expand your knowledge and truly connect with people actively working in the space is through direct interactions, whether they’re happening at large conferences or smaller, semi-official meetups. But let’s be honest: finding all meaningful events can be a mess.
Take, for example, the '[BTC Events Map](https://docs.google.com/spreadsheets/d/1oni0QAHb2XYOL5gFVKHHGhG8w_HY5GDGBhdQ4SSrCZg/edit?gid=0&ref=europeanbitcoiners.com#gid=0),’ which already lists over 550 Bitcoin-only gatherings worldwide. This simple but very useful resource, put together by Satlantis, can help many of us plan our trips throughout the year. However, if you don’t know about its existence and rely solely on a search engine—whether Google or Brave—you’ll likely end up frustrated (and unfortunately missing many great opportunities to meet with others and learn).
Search for '_bitcoin events_,' and you’ll get a mix of irrelevant crypto, fintech, and Web3 results, with Bitcoin-related stuff buried somewhere in the middle, if at all.. Well, it’s really tough to find what you’re actually looking for.
That’s why word of mouth and trusted communities are so important. Sometimes, the best way to hear about an event is directly from people you know.
**One of those that flew under my radar was** [**SatsNFacts**](https://satsnfacts.btc.pub/?ref=europeanbitcoiners.com)**.**
It wasn’t listed on many typical event aggregators or any big news-promo sites. It mostly spread peer-to-peer and through the main channels on [Nostr](https://njump.me/npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx?ref=europeanbitcoiners.com).
I was ‘_lucky_’ enough to hear about it just in time to plan the trip from Europe to Thailand. Now, I’d like to briefly share my experience with you—everything that, in my opinion, made this event truly stand out.
**A Journey to Southeast Asia: Where Builders and Artists Collide.**
--------------------------------------------------------------------
Approximately 10,176 kilometers, 14 hours of travel, and finally three days spent at SatsNFacts—"Thailand’s first Bitcoin Technical Unconference”.
The event ran from February 8 to 10 in Chiang Mai (the largest city in northern Thailand). Held at Weave Artisan Society, a 700 sq.m venue that used to be an ice factory, it smoothly combined pleasant outdoors with an industrial-style, two-floor indoor area, creating a unique and very practical setup.
While its was billed as a “_Technical Unconference_,” in practice it nicely connected the developer-based ecosystem with different aspects of culture and art.
Each day, from 10 am to 6 pm, the agenda—shaped directly by attendees—was packed with various presentations, group chats, learning session, hackathons, and actionable workshops.
With many options available (around 10-20 topics per day), I couldn’t attend everything, but here are a few more technical sessions I joined and found especially worthwhile:
* **Liana Workshop** (long-term security, recovery, and inheritance),
* **TollGates** ([streaming sats for internet access](https://primal.net/e/naddr1qvzqqqr4gupzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qq2nz63h0969vn2xwse9j3n5ge4xsdr2ddc4j0g960h?ref=europeanbitcoiners.com)),
* **Open Vault** (enterprise wallet interface),
* **Yaki Honne** ([decentralized media](https://yakihonne.com/?ref=europeanbitcoiners.com)),
* **Nostr Proxies** (Epoxy, WebSocket and relay monetization).
* **Silent payments** (simplified payment experiences without compromising privacy).
As mentioned earlier, SatsNFacts wasn’t just about Bitcoin tech. Some topics focused on community aspects as well. Two discussions I joined highlighted Bitcoin adoption ⚡ in for example Bali and Thailand, showing how sound money, integrity, and consistent work can solve real problems in these regions. Impressive stuff! Here you can learn more:
* [HuaiPhueng](https://geyser.fund/project/huaiphuengproject?hero=geyser&ref=europeanbitcoiners.com) on Geyser + "Bitcoin City" (their [short video](https://www.youtube.com/watch?feature=shared&v=211meP4liIo&ref=europeanbitcoiners.com)).
* Bitcoin Indonesia & Bitcoin House Bali ([all in one on GitHub](https://github.com/bitcoinindo21?ref=europeanbitcoiners.com))
Now, the art gallery, to continue with less technical aspects of SatsNFacts 🎨
This nicely-organized space located on the ground floor, near cozy coworking and networking spots, was for me a real gem. Indeed, adding a creative vibe to the entire event.
Around 30 unique works from local and international artists were on display, all inspired by themes of freedom and privacy. Though I don’t see myself as a typical _'artist_', I was honored to have some of my own pieces exhibited there as well (a short video below).
* * *
One of the highlights was meeting local Thai artists, especially [Siritravelsketch](https://njump.me/npub14lqzjhfvdc9psgxzznq8xys8pfq8p4fqsvtr6llyzraq90u9m8fqevhssu?ref=europeanbitcoiners.com), who travelled six hours by train just one way to attend two days of the event.
Her stunning paintings, created using just a bamboo stick and ink, are deeply inspired by Thai architecture and culture. While some of her pre-prepared pieces hung in the gallery, she also painted a few new works on the spot during her visit. Truly spectacular!

* * *
I also had the chance to reconnect with [Satoshi Builds](https://njump.me/npub19m7m3rs66pfdn4ewhrm8slh60ukyxgrylaa03m73wa40j39lc03syq4gfu?ref=europeanbitcoiners.com), who made many great sketches during this event, and with [BitPopArt](https://njump.me/npub1gwa27rpgum8mr9d30msg8cv7kwj2lhav2nvmdwh3wqnsa5vnudxqlta2sz?ref=europeanbitcoiners.com), a Dutch artist who, just like me, chosen a nomadic lifestyle yet has been clearly considering Thailand his 'second home' as well for several years now. By the way, ✍️ here's his short summary of the event, focusing more on the artistic side of SatsNFacts: "[Art exhibition in Chiang Mai](https://bitpopart.com/2025/02/11/art-exhibition-in-chiang-mai/?ref=europeanbitcoiners.com)".
All in all, spending my time in many meaningful conversations and seeing so many deep artworks in one place filled me with hope and positive energy. THANK YOU, EVERYONE!

* * *
(presented artworks by for example: [Agi Choote](https://njump.me/npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7?ref=europeanbitcoiners.com), [Samhain](https://njump.me/npub1df47g7a39usamq83aula72zdz23fx9xw5rrfmd0v6p9t20n5u0ss2eqez9?ref=europeanbitcoiners.com), [Zed Erwan](https://njump.me/npub1r2sah0htqnw7xrs70gq00m48vp25neu8ym2n2ghrny92dqqf7sest8hth0?ref=europeanbitcoiners.com), [Existing Sprinkles](https://njump.me/npub1f5kc2agn63ecv2ua4909z9ahgmr2x9263na36jh6r908ql0926jq3nvk2u?ref=europeanbitcoiners.com), AZA 21m, BitPopArt.)
* * *
Mr. Rabbit in Thailand...
-------------------------
Monday, the final evening, and SatsNFacts got one more item on its agenda rooted in creative expression and independent art.
Representing [Bitcoin FilmFest](https://x.com/bitcoinfilmfest?ref=europeanbitcoiners.com) (a grassroots project created by an amazing group of freedom fighters and activists 🐇🧡), since I was the only one from our team in Thailand, in one of the rooms upstairs, I put together a mini cinematic experience.
Seven trailers and eleven shorts, including for example:
* NO MORE INFLATION, HUMMINGBIRD, PARALLEL SPACE, UNBANKABLE, THE LEGEND OF LANDI (🎬 some of the trailers).
* BITCOIN A NEW HOPE, SATOSHI NAKAMOTO - THE CREATOR OF BITCOIN, MAXIS CLUB SHOW - CHAPTER ONE, THE GREATEST HEIST IN HISTORY, HODL, THE ANATOMY OF BITCOIN – GENESIS BLOCK (📺 some of the presented shorts)
With around 10-15 participants, the response was positive, and we ended up spending an extra 10-maybe-20 minutes discussing the challenges and opportunities in Bitcoin-powered filmmaking, as well as the upcoming edition of [BFF25](https://bitcoinfilmfest.com/bff25/?ref=europeanbitcoiners.com) (the annual festival we're organizing this May in Warsaw, Poland).

**Substance Over Hype. Gatherings That Matter.**
------------------------------------------------
SatsNFacts made a solid reminder that Bitcoin events can help build a truly sovereign future while bringing together developers and artistic souls alike.
The mix of technical depth and creative energy—free from the shiny gossip that floods many social channels—made it a truly meaningful experience.
> SatsNFacts set a high standard, and I hope to see more events like it in the future. More unconferences, more cultural and community-driven gatherings.
**Here's to more signal, less noise!!!**
Big congrats to everyone who made the first SatsNFacts happen 👏 Respect especially to the organizers! You pulled off something truly special!
* * *
_BTC Your Mind. Let it Beat._
_Şela_ @AZA_21M
💡
Did you enjoy this article? Zap me some sats. No amount is small :) Lightning wallet: `aza21m@getalby.com`
- - -
Original Article: https://europeanbitcoiners.com/sats-and-facts-short-coverage-of-the-first-bitcoin-unconference-in-thailand/
#english #opinion #events #bitcoin #nostr #freedom #conference #siamstr #asia #thailand
-

@ ac6f9572:8a6853dd
2025-02-13 01:55:20
# Freedom Tech, Privacy, Sound Money, and Culture: How to Find Your Tribe?
> Keeping up with everything happening in Bitcoin isn’t easy, even if you’ve been around for a while. The pace is relentless: stream of events, discussions, projects, and updates, not to mention the noise on social media...

Date: 02/12/2025
One of the most efficient options to expand your knowledge and truly connect with people actively working in the space is through direct interactions, whether they’re happening at large conferences or smaller, semi-official meetups. But let’s be honest: finding all meaningful events can be a mess.
Take, for example, the '[BTC Events Map](https://docs.google.com/spreadsheets/d/1oni0QAHb2XYOL5gFVKHHGhG8w_HY5GDGBhdQ4SSrCZg/edit?gid=0&ref=europeanbitcoiners.com#gid=0),’ which already lists over 550 Bitcoin-only gatherings worldwide. This simple but very useful resource, put together by Satlantis, can help many of us plan our trips throughout the year. However, if you don’t know about its existence and rely solely on a search engine—whether Google or Brave—you’ll likely end up frustrated (and unfortunately missing many great opportunities to meet with others and learn).
Search for '_bitcoin events_,' and you’ll get a mix of irrelevant crypto, fintech, and Web3 results, with Bitcoin-related stuff buried somewhere in the middle, if at all.. Well, it’s really tough to find what you’re actually looking for.
That’s why word of mouth and trusted communities are so important. Sometimes, the best way to hear about an event is directly from people you know.
**One of those that flew under my radar was** [**SatsNFacts**](https://satsnfacts.btc.pub/?ref=europeanbitcoiners.com)**.**
It wasn’t listed on many typical event aggregators or any big news-promo sites. It mostly spread peer-to-peer and through the main channels on [Nostr](https://njump.me/npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx?ref=europeanbitcoiners.com).
I was ‘_lucky_’ enough to hear about it just in time to plan the trip from Europe to Thailand. Now, I’d like to briefly share my experience with you—everything that, in my opinion, made this event truly stand out.
**A Journey to Southeast Asia: Where Builders and Artists Collide.**
--------------------------------------------------------------------
Approximately 10,176 kilometers, 14 hours of travel, and finally three days spent at SatsNFacts—"Thailand’s first Bitcoin Technical Unconference”.
The event ran from February 8 to 10 in Chiang Mai (the largest city in northern Thailand). Held at Weave Artisan Society, a 700 sq.m venue that used to be an ice factory, it smoothly combined pleasant outdoors with an industrial-style, two-floor indoor area, creating a unique and very practical setup.
While its was billed as a “_Technical Unconference_,” in practice it nicely connected the developer-based ecosystem with different aspects of culture and art.
Each day, from 10 am to 6 pm, the agenda—shaped directly by attendees—was packed with various presentations, group chats, learning session, hackathons, and actionable workshops.
With many options available (around 10-20 topics per day), I couldn’t attend everything, but here are a few more technical sessions I joined and found especially worthwhile:
* **Liana Workshop** (long-term security, recovery, and inheritance),
* **TollGates** ([streaming sats for internet access](https://primal.net/e/naddr1qvzqqqr4gupzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qq2nz63h0969vn2xwse9j3n5ge4xsdr2ddc4j0g960h?ref=europeanbitcoiners.com)),
* **Open Vault** (enterprise wallet interface),
* **Yaki Honne** ([decentralized media](https://yakihonne.com/?ref=europeanbitcoiners.com)),
* **Nostr Proxies** (Epoxy, WebSocket and relay monetization).
* **Silent payments** (simplified payment experiences without compromising privacy).
As mentioned earlier, SatsNFacts wasn’t just about Bitcoin tech. Some topics focused on community aspects as well. Two discussions I joined highlighted Bitcoin adoption ⚡ in for example Bali and Thailand, showing how sound money, integrity, and consistent work can solve real problems in these regions. Impressive stuff! Here you can learn more:
* [HuaiPhueng](https://geyser.fund/project/huaiphuengproject?hero=geyser&ref=europeanbitcoiners.com) on Geyser + "Bitcoin City" (their [short video](https://www.youtube.com/watch?feature=shared&v=211meP4liIo&ref=europeanbitcoiners.com)).
* Bitcoin Indonesia & Bitcoin House Bali ([all in one on GitHub](https://github.com/bitcoinindo21?ref=europeanbitcoiners.com))
Now, the art gallery, to continue with less technical aspects of SatsNFacts 🎨
This nicely-organized space located on the ground floor, near cozy coworking and networking spots, was for me a real gem. Indeed, adding a creative vibe to the entire event.
Around 30 unique works from local and international artists were on display, all inspired by themes of freedom and privacy. Though I don’t see myself as a typical _'artist_', I was honored to have some of my own pieces exhibited there as well (a short video below).
* * *
One of the highlights was meeting local Thai artists, especially [Siritravelsketch](https://njump.me/npub14lqzjhfvdc9psgxzznq8xys8pfq8p4fqsvtr6llyzraq90u9m8fqevhssu?ref=europeanbitcoiners.com), who travelled six hours by train just one way to attend two days of the event.
Her stunning paintings, created using just a bamboo stick and ink, are deeply inspired by Thai architecture and culture. While some of her pre-prepared pieces hung in the gallery, she also painted a few new works on the spot during her visit. Truly spectacular!

* * *
I also had the chance to reconnect with [Satoshi Builds](https://njump.me/npub19m7m3rs66pfdn4ewhrm8slh60ukyxgrylaa03m73wa40j39lc03syq4gfu?ref=europeanbitcoiners.com), who made many great sketches during this event, and with [BitPopArt](https://njump.me/npub1gwa27rpgum8mr9d30msg8cv7kwj2lhav2nvmdwh3wqnsa5vnudxqlta2sz?ref=europeanbitcoiners.com), a Dutch artist who, just like me, chosen a nomadic lifestyle yet has been clearly considering Thailand his 'second home' as well for several years now. By the way, ✍️ here's his short summary of the event, focusing more on the artistic side of SatsNFacts: "[Art exhibition in Chiang Mai](https://bitpopart.com/2025/02/11/art-exhibition-in-chiang-mai/?ref=europeanbitcoiners.com)".
All in all, spending my time in many meaningful conversations and seeing so many deep artworks in one place filled me with hope and positive energy. THANK YOU, EVERYONE!

* * *
(presented artworks by for example: [Agi Choote](https://njump.me/npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7?ref=europeanbitcoiners.com), [Samhain](https://njump.me/npub1df47g7a39usamq83aula72zdz23fx9xw5rrfmd0v6p9t20n5u0ss2eqez9?ref=europeanbitcoiners.com), [Zed Erwan](https://njump.me/npub1r2sah0htqnw7xrs70gq00m48vp25neu8ym2n2ghrny92dqqf7sest8hth0?ref=europeanbitcoiners.com), [Existing Sprinkles](https://njump.me/npub1f5kc2agn63ecv2ua4909z9ahgmr2x9263na36jh6r908ql0926jq3nvk2u?ref=europeanbitcoiners.com), AZA 21m, BitPopArt.)
* * *
Mr. Rabbit in Thailand...
-------------------------
Monday, the final evening, and SatsNFacts got one more item on its agenda rooted in creative expression and independent art.
Representing [Bitcoin FilmFest](https://x.com/bitcoinfilmfest?ref=europeanbitcoiners.com) (a grassroots project created by an amazing group of freedom fighters and activists 🐇🧡), since I was the only one from our team in Thailand, in one of the rooms upstairs, I put together a mini cinematic experience.
Seven trailers and eleven shorts, including for example:
* NO MORE INFLATION, HUMMINGBIRD, PARALLEL SPACE, UNBANKABLE, THE LEGEND OF LANDI (🎬 some of the trailers).
* BITCOIN A NEW HOPE, SATOSHI NAKAMOTO - THE CREATOR OF BITCOIN, MAXIS CLUB SHOW - CHAPTER ONE, THE GREATEST HEIST IN HISTORY, HODL, THE ANATOMY OF BITCOIN – GENESIS BLOCK (📺 some of the presented shorts)
With around 10-15 participants, the response was positive, and we ended up spending an extra 10-maybe-20 minutes discussing the challenges and opportunities in Bitcoin-powered filmmaking, as well as the upcoming edition of [BFF25](https://bitcoinfilmfest.com/bff25/?ref=europeanbitcoiners.com) (the annual festival we're organizing this May in Warsaw, Poland).

**Substance Over Hype. Gatherings That Matter.**
------------------------------------------------
SatsNFacts made a solid reminder that Bitcoin events can help build a truly sovereign future while bringing together developers and artistic souls alike.
The mix of technical depth and creative energy—free from the shiny gossip that floods many social channels—made it a truly meaningful experience.
> SatsNFacts set a high standard, and I hope to see more events like it in the future. More unconferences, more cultural and community-driven gatherings.
**Here's to more signal, less noise!!!**
Big congrats to everyone who made the first SatsNFacts happen 👏 Respect especially to the organizers! You pulled off something truly special!
* * *
_BTC Your Mind. Let it Beat._
_Şela_ @AZA_21M
💡
Did you enjoy this article? Zap me some sats. No amount is small :) Lightning wallet: `aza21m@getalby.com`
- - -
Original Article: https://europeanbitcoiners.com/sats-and-facts-short-coverage-of-the-first-bitcoin-unconference-in-thailand/
#english #opinion #events #bitcoin #nostr #freedom #conference #siamstr #asia #thailand
originally posted at https://stacker.news/items/884317
-

@ 1cb14ab3:95d52462
2025-02-13 01:30:00
**Dirt, body weight. [125' x 2']**
*This project was exhibited in 2015 in Boulder, Colorado.*
---
### Artist Statement
“A Line Made By Walking” (2015) is a site-specific piece created in Boulder, CO, where my body weight etched a temporary line into the earth. This work pays homage to Richard Long’s seminal 1967 piece, where a simple act of walking through the landscape left a profound trace. In my version, the line created by my movement forces the viewer to engage with the impermanence of human intervention on the land. The project prompts a reflection on the subtle yet lasting impacts we have on the environment, even through seemingly minimal actions.
As part of my larger “[Rockway](https://hes.npub.pro/post/1708400183541/)” project, this case study explores the concept of ‘line’ in both literal and metaphorical ways. The line is not just a physical mark, but also a representation of time, movement, and the dialogue between the body and the land. Walking, in this context, becomes a way of marking time—an act that is as ephemeral as the mark it leaves behind. The work questions the tension between permanence and transience, asking the viewer to consider how we interact with the land, both intentionally and unknowingly, and how those interactions leave traces that may soon fade but never completely disappear.
---
### Photos







---
#### More Land Art:
[Earth Lens Series](https://hes.npub.pro/post/1731091744332/)
["Looking Glass"](https://hes.npub.pro/post/1736304563962/)
["Het Bonhe"](https://hes.npub.pro/post/1720242458557/)
["Rockway"](https://hes.npub.pro/post/1708400183541/)
["Invasive"](https://hes.npub.pro/post/1719722211094/)
---
#### More from Hes
[Full Portfolio](https://hesart.npub.pro)
[Online Store](https://plebeian.market/community/hes@nostrplebs.com/hesmart-ym3fcufdfz)
[Artist Statements](https://hes.npub.pro/tag/art/)
[Travel Guides](https://hes.npub.pro/tag/travel/)
[Photography](https://hes.npub.pro/tag/photography)
[Writings](https://hes.npub.pro/tag/money)
---
*All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.*
-

@ 20e7c953:3b8bcb21
2025-02-13 01:15:42
Biggest takeaway? We needed more hands to cover key roles - something to improve for next time, if there is any! That said, the strongest point was the organic networking and building, which set this apart from more structured, commercial conferences.
For future events - if any! - Hackathons will need dedicated time slots in the future, given the time constraints. The art side of things isn’t over yet—the exhibition will keep going for another month.
The event started a bit messy, but the quality of people made it flow naturally, creating a unique and engaging atmosphere. Overall, a great experience, and we’ll keep iterating for the next one.
We’ll send out a survey soon to gather more feedback. Huge thanks to our sponsors and media partners for making this happen - appreciate the support.
On Communities:
Lastly, while both commercial and less commercial events are needed there is something that doesn't beat Bitcoin Culture which are Bitcoin-only Meetups.
If we are in a position to give some advice: Make sure you engage with your local community since people behind it are most likely the ones who can able to bootstrap new comers while keeping trust and accountability in place.
Luckily today we have most tools to filter out those who are leeching off others PoW and the genuine ones trailblazing on their own terms. On our side definitely one of the biggest lessons learnt was to work with the local Communities for future events - regardless - this time we managed to get it done with our hands, will and not much else since *most* tools used have been FOSS and that's why we are here for !
With that said and while continuously gathering more feedback these coming days....
WHAT DID YOU ENJOYED THE MOST?
ANYTHING YOU DISLIKED?
**WHERE SHOULD WE HOST SATS N FACTS NEXT ?👀**
SUGGESTIONS AND FEEDBACK MAILBOX IS OPEN 📬
Onwards 🫡
-

@ c582af78:698069cc
2025-02-13 01:04:26
# **The Nine Orders of Angels: A Guide to the Celestial Hierarchy**
When we think of angels, we often picture winged figures in flowing robes, guiding and protecting humanity. But the biblical and theological reality is far more complex—and often stranger—than these familiar depictions.
The word *angel* comes from the Greek *angelos*, meaning “messenger,” but in scripture, angels serve a wide range of roles beyond delivering divine messages. Some are warriors wielding swords and leading celestial armies, others uphold the very throne of God, and some appear as multi-winged, multi-eyed beings beyond human comprehension.
To bring order to this celestial realm, theologians—most notably Thomas Aquinas—classified angels into a hierarchy of **nine types**, divided into **three orders** based on their function and proximity to God.
- **The lowest order** interacts with humanity.
- **The middle order** governs spiritual and cosmic forces.
- **The highest order** exists solely to serve and glorify God.
Today, we explore these **nine ranks of angels**—from the familiar to the truly otherworldly.
---
## **I. The Third Order: Angels Who Interact with Humanity**
*(The lowest tier of angels, closest to humans, acting as messengers and protectors.)*
### **1. Angels – The Messengers**
https://image.nostr.build/b6462b67e14c8780896f465b664a521cdcdef7eb4b4314669b8d219aa36964c5.jpg
These are the angels most commonly associated with divine guidance. According to Aquinas, every person has a **guardian angel**—an unseen protector guiding them through life.
In *Genesis 28:12*, Jacob’s vision of a ladder stretching to Heaven shows angels ascending and descending, delivering messages and fulfilling divine commands. Some, like those who visited Abraham, even appeared as ordinary men, without wings or supernatural radiance.
### **2. Archangels – The Divine Enforcers**
https://image.nostr.build/af8799efb61c5a64e958450bcd5aee55d2cade931cfc5ca7f0ae8745ccd4c45a.jpg
Archangels carry out the most crucial missions in scripture. Gabriel announced the birth of Jesus to Mary, while Michael led the charge against Satan in the war for Heaven.
Though only **Michael** is explicitly called an archangel in the Bible, tradition assigns this title to others, including **Raphael** and **Uriel**. Archangels serve as warriors and heralds, executing God’s most urgent decrees.
### **3. Principalities – Guardians of Nations**
https://image.nostr.build/bc7cd78acb656be6c946da32244bfb9ecdfe9a7d1bd80e47eca764cae4a88b95.jpg
Principalities oversee nations, cities, and communities, influencing their spiritual well-being. While they are not explicitly named in scripture, *Colossians 1:16* references “thrones, dominions, principalities, and powers.”
Tradition suggests that Principalities guide earthly leaders, strengthening them in times of crisis—and perhaps even aiding biblical figures like King David in battle.
---
## **II. The Second Order: The Heavenly Governors**
*(These angels reside in Heaven but influence earthly affairs, ensuring divine order is maintained.)*
### **4. Powers – The Celestial Warriors**
https://image.nostr.build/1768abcbaefb2d1d21654a869b356d86a45d76a82197b9568528d4d4b9f0ef69.jpg
Powers act as Heaven’s **military defenders**, guarding the spiritual realm from demonic forces. They are often depicted in armor, wielding weapons as they engage in cosmic battles.
According to Christian tradition, Powers also **escort souls to Heaven**, ensuring their safe passage after death. Some believe that the battle between good and evil plays out, in part, through these celestial warriors.
### **5. Virtues – The Miracle Workers**
https://image.nostr.build/b9a1e52f1dd4ef0f7e7dd198d81e7cd171eede8a64a40cac8176e12a5419aeba.jpg
Virtues are associated with **miracles and nature**, regulating celestial phenomena and assisting in divine interventions.
In Christian tradition, the two angels present at **Christ’s Ascension** are often considered Virtues, manifesting God’s power on Earth.
### **6. Dominions – The Angelic Rulers**
https://image.nostr.build/0900d97bf545736e5edc1521f46a8afbf0e93fd81e472c88a56744ff0f56ce48.jpg
Dominions do not typically interact with humans directly. Instead, they act as **commanders**, overseeing lower angels and ensuring divine order is maintained.
They are described as serene, wise beings, often depicted holding golden staffs and orbs, symbolizing their authority and their close relationship with God.
---
## **III. The First Order: The Angels Closest to God**
*(These angels exist solely to worship and serve God, residing in the highest realms of Heaven.)*
### **7. Thrones – The Wheels of God’s Chariot**
https://image.nostr.build/d9f1e465129b138f4f960ee43ee9e06ceb3fd6f57e9658cd275e1ac1576b3c02.jpg
Among the most mysterious angelic beings, Thrones are described in *Ezekiel’s vision* as **wheels covered in eyes, spinning within wheels**:
> *“As I looked, I saw a wheel on the ground beside each creature with its four faces... Their rims were full of eyes all around. Wherever the spirit would go, they would go, because the spirit of the living creatures was in the wheels.”*
> — *Ezekiel 1:15-21*
Thrones serve as **God’s chariot**, supporting His throne and executing divine justice. Their strange, abstract form symbolizes stability and divine order.
### **8. Cherubim – The Guardians of Glory**
https://image.nostr.build/e921ad4c32f56ebbb8f1bcb1ca2bc6eed1c736ec896429e008fc5b71cf2fd151.jpg
Cherubim have been drastically misrepresented in art. Far from the **plump, childlike figures** seen in Renaissance paintings, the **biblical Cherubim** are **fearsome beings**.
In *Ezekiel 10*, they are described as having **four faces**—a man, a lion, an ox, and an eagle—along with **four wings**.
They also appear in *Genesis 3:24*, where they **guard the entrance to Eden with flaming swords** after Adam and Eve’s expulsion.
https://image.nostr.build/f51286d4f35d9d6e85d8559600188ecc89a0969c3985814cae56cd230ea5db00.jpg
Aquinas even suggested that **Satan himself was a fallen Cherub**. This theory is supported by *Ezekiel 28*, which describes an angelic being cast down from God’s presence:
> *“You were anointed as a guardian cherub... You were blameless in your ways until wickedness was found in you... So I drove you in disgrace from the mount of God, and I expelled you, guardian cherub.”*
> — *Ezekiel 28:14-17*
### **9. Seraphim – The Highest & Holiest**
Seraphim stand **at the very throne of God**, continuously worshiping Him.
In *Isaiah’s vision* (*Isaiah 6:1-7*), they are described as having **six wings**—two to fly, two to cover their feet, and two to cover their faces, symbolizing their humility before God. They sing:
> **“Holy, holy, holy is the Lord of hosts; the whole earth is full of His glory.”**
When Seraphim reappear in *Revelation*, their wings are now **covered in eyes**, representing divine omniscience. Their song shifts slightly:
> *“Holy, holy, holy is the Lord God Almighty, who was and is and is to come!”*
> — *Revelation 4:8*
https://image.nostr.build/3495ccf6c0ba26b42d3e2b438ec19232cca148f6fbf29e5edd4129f5a198d05b.jpg
Unlike other angelic beings, Seraphim do not interact with humans—they exist purely to **glorify God**.
---
## **“Be Not Afraid”**
The angelic hierarchy provides a glimpse into the vast celestial order governing God’s universe. From the lowest messengers to the highest divine worshippers, each angelic being plays a unique role in the unfolding story of creation and salvation.
Yet, despite their differences, there is one striking similarity across biblical encounters with angels:
They often begin with a single phrase—
**“Be not afraid.”**
-

@ c582af78:698069cc
2025-02-13 01:03:50
## **How to Be Happy: Aristotle’s Blueprint for a Flourishing Life**
Everyone wants happiness. The problem? Most people don’t actually know what happiness is.
Ask someone what would make them happy, and they’ll likely mention wealth, pleasure, success, or recognition. Over 2,000 years ago, Aristotle heard the same answers—and he rejected them.
According to Aristotle, happiness isn’t something you *have*, but something you *do*. True happiness—what he called *eudaimonia*—isn’t about fleeting pleasures or external rewards. It’s about living well, cultivating virtue, and engaging deeply in life’s highest pursuits.
So, what’s Aristotle’s formula for happiness? It comes down to three essential steps.
---
### **The False Paths to Happiness**
Aristotle observed that most people chase happiness in three common ways: **wealth, pleasure, and honor**. While each has its appeal, none can sustain true fulfillment.
Take **wealth**, for example. Money provides security and opportunity, but it doesn’t guarantee satisfaction. Aristotle noted that many people who seek wealth become obsessed with accumulating it rather than using it wisely. The result? An endless chase with no real contentment.
**Pleasure** is even trickier. Aristotle acknowledged that pleasure is a natural good, but he warned against making it life’s ultimate goal. Living only for pleasure leads to a cycle of chasing temporary highs without ever achieving deeper fulfillment. As Aristotle put it, this is the life of *“fatted cattle”*—comfortable, but lacking excellence.
Then there’s **honor**. Recognition feels good, but it depends on the approval of others. If you live solely for status, you risk valuing recognition over real achievement. Honor for its own sake is empty unless it’s tied to genuine virtue.
**Aristotle’s conclusion?** These paths don’t lead to true happiness. They are distractions, not destinations.
---
### **The True Meaning of Happiness**
If wealth, pleasure, and honor aren’t enough, then what *is* happiness?
To answer that, we need to understand Aristotle’s term *eudaimonia*. Unlike our modern idea of happiness as a feeling, *eudaimonia* means **flourishing**—a life of purpose, virtue, and excellence.
The key difference is that **wealth, pleasure, and honor are passive**—they happen *to* you. But *eudaimonia* is **active**—it’s something you cultivate through action.
In his *Nicomachean Ethics*, Aristotle defines happiness as *“the activity of the soul in accordance with virtue.”* It’s not a prize to be won, but a way of living.
A great example comes from sports. A skilled athlete doesn’t just sit around feeling happy—his joy comes from being *in motion*: training, competing, improving, and fully engaging in his craft.
For Aristotle, happiness works the same way. It comes from actively developing your best qualities, not passively indulging in comfort.
But how do you put this into practice?
---
## **Aristotle’s 3-Step Blueprint for a Good Life**
Aristotle’s guide to happiness is surprisingly practical. Here’s how to apply it:
### **1. Cultivate Virtue Through Habit**
Virtue isn’t something you’re born with—it’s something you practice.
Just as an athlete trains for competition, you develop virtue by repeatedly choosing good actions. Courage, patience, and wisdom don’t just appear; they become part of you through habit.
As Aristotle famously said:
> **“We are what we repeatedly do. Excellence, then, is not an act, but a habit.”**
Want to be generous? **Give more often.**
Want to be disciplined? **Practice restraint.**
Over time, these actions shape your character—and character shapes happiness.
### **2. Engage Fully in Meaningful Work**
Happiness isn’t found in passivity, but in action.
Aristotle believed that true fulfillment comes from using your talents to their fullest extent. This applies to everything from philosophy to craftsmanship to leadership. The key is **engagement**.
Think of the satisfaction a musician feels while playing at their best, or the pride of a craftsman perfecting their work. These moments—where skill, effort, and purpose align—are true happiness in action.
Contrary to popular belief, happiness isn’t about doing less. **It’s about doing the right things, with full commitment.**
### **3. Seek the Right Kind of Pleasure**
Aristotle didn’t reject pleasure—he just emphasized choosing the *right* kind.
Lower pleasures—like eating, drinking, or binge-watching TV—may feel good in the moment but often leave you feeling empty afterward. Higher pleasures—such as learning, mastering a craft, or cultivating meaningful relationships—lead to lasting fulfillment.
The goal isn’t to reject pleasure, but to **align it with virtue**. Instead of chasing immediate gratification, seek pleasures that contribute to long-term flourishing.
---
## **Happiness as a Way of Life**
It’s important to understand that happiness isn’t a destination—it’s a **practice**. It’s something cultivated daily by engaging in meaningful work, growing in virtue, and living with purpose.
But most importantly, **happiness isn’t about what happens to you—it’s about who you become**.
By cultivating *eudaimonia*, you change the essence of your being—just as a farmer who nurtures his crops becomes stronger through his labor.
True happiness isn’t a fleeting emotion, but the natural result of a life well lived. The more you nurture virtue through action, the more deeply happiness takes root—until it becomes not just something you seek, but something you embody.
-

@ 57d1a264:69f1fee1
2025-02-13 00:28:45
This past week, @erik_ and @Sushant have been working on improving the onboarding flow for [Sovran](https://sovranbitcoin.com/) bitcoin wallet. First revision on thee figma file below, would appreciate any feedback.


https://www.figma.com/design/inNLo6AaPMX26D3GumcXGC/UI%2FUX-Audit--Onboarding-User-Flow?node-id=0-1&t=Wl0EVhH5fJgYYSJI-1
If you want to review the UX audit of the current flow, see the feedback provided, and check Sushant's initial suggestions, you can do so here:

https://www.figma.com/board/Jfo4nLIKyR6lacokXze4Mv/Sovran-Onboarding-UX-Audit?node-id=0-1&t=gOZyo57zfeqxFXeB-1
originally posted at https://stacker.news/items/884272
-

@ 4c96d763:80c3ee30
2025-02-12 23:49:24
# Changes
## Daniel D’Aquino (2):
- Remove rust-nostr dependency
- Fix unwanted auto-scrolls related to draft saving mechanism
## William Casarin (3):
- driveby compile warning fixes
- home: dont show reposts for the same note more than once
- reposts: add links to repost listing in timeline
## emir yorulmaz (1):
- Change 'twitter' to 'X/Twitter' on README.md
pushed to [damus:refs/heads/master](http://git.jb55.com/damus/commit/ec9a89ee4d388f4c706db47d2b73c298f1e268cc.html)
-

@ 5579d5c0:db104ded
2025-02-12 23:41:09
Most people think their metabolism is "broken" because they can't lose weight, feel sluggish, or gain fat easily.
The truth? **Your metabolism isn’t broken, it’s just out of sync.**
Your body doesn’t just burn calories randomly.
It follows a natural **24-hour rhythm**, dictated by light exposure, movement, meal timing, and sleep.
When these cues are off, your metabolism becomes dysfunctional.
The good news?
You don’t need to diet harder or exercise more.
**You need to realign your metabolism with your body’s natural rhythm.**
---
### Why your metabolism feels “broken”
Your body is designed to run on **timing signals, when to eat, when to move, when to rest**. Modern life disrupts these natural rhythms, leading to:
**→ Low energy & afternoon crashes**: Skipping morning sunlight and staying indoors all day.
**→ Stubborn belly fat & slow fat loss**: Eating at the wrong times, late-night snacking, and chronic stress.
**→ Constant cravings & hunger:** Poor meal timing and eating foods that spike blood sugar too often.
**→ Poor sleep & recovery**: Late night screen use, artificial light, and erratic bedtimes.
The problem **isn’t your metabolism, it’s your environment and habits.**
---
### How to reset your metabolism naturally
You don’t need extreme diets, calorie counting, or hours in the gym.
Instead, **align your metabolism with your body’s natural timing signals** by focusing on these fundamentals:
### 1. Get natural light first thing in the morning
Light in the first 30 minutes after waking sets your circadian rhythm (body clock), kickstarts hormone production, and improves insulin sensitivity.
This simple habit helps to regulate hunger, energy, and fat-burning.
**Action step:** Step outside for at least 5–10 minutes within 30 minutes of waking, no sunglasses, no contacts, only natural light exposure and take regular outdoor breaks during the day.
---
### 2. Stop eating late at night
Eating late, especially high-carb/high-fat meals, signals your body to store fat instead of burning it.
Late-night eating also disrupts sleep, which further impairs fat loss.
**Action step:** Keep meals within a **10-12 hour eating window**, preferably between sunrise and sunset. **No snacking**. Finish your last meal **at least 3 hours before bed**.
---
### 3. Move throughout the day (Not just at the gym)
Your metabolism isn’t just about burning calories, it’s about **how efficiently your body uses energy**.
Sitting for long hours disrupts metabolic function, even if you work out later.
**Action step:** Take a **5-minute movement break** every 1–2 hours. Stand, stretch, or better still go for a quick walk outside.
---
### 4. Prioritise deep, uninterrupted sleep
Your body **burns fat and repairs muscle while you sleep**.
Poor sleep increases hunger hormones (Ghrelin), prevents Leptin from working properly, and makes you crave junk food the next day.
**Action step:** Dim lights after sunset, wear blue light blocking glasses, avoid screens 30-60 minutes before bed, and aim for **7.5-9 hours of quality sleep**.
---
### 5. Eat nutrient-dense foods
What you eat matters, but **when** you eat it matters just as much.
Front-loading protein and nutrients earlier in the day supports fat-burning and stabilises energy.
**Action step:** Eat a **high-protein, nutrient-dense breakfast** and **avoid refined carbs & sugar, especially in the morning,** to prevent cravings later.
---
Your metabolism isn’t broken, it’s just out of sync.
Instead of obsessing over calories, **focus on realigning your body with its natural rhythms**:
→ **Morning sunlight** to set your metabolism for the day.
→ **Aligned meal timing** by eating during daylight & avoiding late-night eating.
→ **Frequent movement** to prevents metabolic slowdown from sitting.
→ **Quality sleep** which regulates fat-burning and hunger hormones.
→ **Nutrient-dense eating** giving your body what it needs.
Fix your metabolism without dieting harder, just live in sync with how your body is designed to function.
\-Chris
---
If you want a simple methodical approach to fixing your metabolism, Let’s talk.
**Book a free call here:** [**https://calendly.com/hello-chrispatrick**](https://calendly.com/hello-chrispatrick)
**Follow me on Nostr**: [**https://primal.net/chrispatrick**](https://primal.net/chrispatrick) or
[***nostr:npub124uatsq6pv74trzwvt34y4sx2z0uflhse7tkrv0pl69e8kcsfhkse30zsu***](https://primal.net/chrispatrick/npub124uatsq6pv74trzwvt34y4sx2z0uflhse7tkrv0pl69e8kcsfhkse30zsu)
-

@ 3b7fc823:e194354f
2025-02-12 23:13:57
**Staying Digitally Safe in Airports: A Comprehensive Guide**
Airports are hubs of activity, but they’re also places where your digital security can be at risk. From public Wi-Fi to potential device thefts, staying safe while traveling can feel overwhelming. However, with the right knowledge and precautions, you can protect yourself and enjoy your journey stress-free. Let’s dive into how to stay digitally safe in airports while traveling.
---
### **Understanding the Risks**
1. **Public Wi-Fi Vulnerabilities:**
- Airports often offer free Wi-Fi, but these networks can be unsecured or insecure. Hackers may use these networks to intercept sensitive data.
- Avoid using public Wi-Fi for personal banking, shopping, or handling sensitive information.
2. **Device Theft:**
- High-traffic areas like security checkpoints, gates, and lounges are hotspots for device thefts. Always keep your devices in secure locations, such as carry-on bags or locked briefcases.
3. **Malware and Phishing Attacks:**
- Some airports may have phishing attempts or malware distributed via pop-ups, email, or malicious websites.
4. **Physical Surveillance:**
- In some cases, law enforcement or security personnel may monitor your activities. Always be mindful of your surroundings to avoid unintended data exposure.
---
### **Best Practices for Staying Digitally Safe in Airports**
1. **Use a VPN for Extra Security:**
- Even secure airport Wi-Fi can expose your data if not encrypted. Use a reputable Virtual Private Network (VPN) to encrypt your internet traffic and protect your privacy.
- Always ensure your VPN is active when using public Wi-Fi.
2. **Minimize Sensitive Data on Public Devices:**
- Avoid carrying devices with sensitive information like passwords, credit card details, or personal identification numbers (PIIs).
3. **Encrypt Your Data:**
- Enable encryption for all your devices to protect data stored locally or in the cloud. Ensure your operating system and apps are updated with the latest security patches.
4. **Secure Your Devices:**
- Use cable locks or secure cases to lock down laptops, tablets, and smartphones when not in use.
- Remove screensavers that display your device passcode to prevent unauthorized access.
5. **Keep Antivirus Software Updated:**
- Install and maintain up-to-date antivirus software on all devices. This helps detect and remove malicious software (malware) that may be installed through compromised networks or phishing attempts.
6. **Avoid Plugging Into Public USB charging stations:**
- Refrain from using public USB ports or charging stations unless you know they’re secure. Malware can spread via these points.
7. **Use Caution With Lost and Found:**
- If you find a device or drop one accidentally, avoid using lost and found kiosks to pick it up. Instead, contact airport security for assistance in safely retrieving your property without exposing it to potential thieves.
8. **Stay Alert to Security Alerts:**
- Pay attention to announcements over the airport’s PA system regarding suspicious activity or security alerts. Follow any instructions provided by airport staff.
9. **Monitor Your Accounts Remotely:**
- If you suspect something is wrong (e.g., unusual transactions on your credit card), check your financial accounts immediately upon arriving at your destination. Notify your bank of potential fraudulent activity and report it to the authorities if necessary.
---
### **Additional Tips for Airport Safety**
1. **Use a Portable Power Bank:**
- Keep your devices charged so you don’t rely on public charging stations, which may be compromised.
2. **Travel with Backup Devices:**
- Always bring an extra SIM card, USB drive, or cloud storage to backup important data. This ensures you can access critical information even if your primary device is lost or damaged.
3. **Avoid Sharing Personal Information Over Earphone Rentals:**
- Refrain from using earphones rented from airport kiosks that may record or intercept your conversations. Stick to your own headphones or those provided by the airline.
4. **Use Airport Lounges Wisely:**
- If you’re using an airline lounge, avoid discussing sensitive information in public areas where it could be overheard.
5. **Keep Your Luggage in Sight:**
- Never leave your checked luggage unattended, as it may contain devices or documents with sensitive information.
6. **Plan for Data Loss:**
- Before leaving home, make a backup of all important files and photos on an external drive or cloud storage. This way, you can restore them if something goes wrong during your trip.
---
### **What to Do If Something Goes Wrong**
1. **Report Suspected Security Incidents:**
- If you notice unusual activity on your devices or suspect a security breach, inform airport security immediately.
2. **Contact Your Financial Institutions:**
- If you believe your financial information has been compromised, contact your bank or credit card provider to freeze your account and monitor for fraudulent charges.
3. **File a Police Report:**
- In cases of theft or suspected unauthorized access, file a report with local authorities and provide evidence (if available).
4. **Use Travel Insurance:**
- Check if your travel insurance covers theft, fraud, or data breaches. Submit a claim if you’re covered.
---
### **Extra Security Measures forTech-Savvy Travelers**
- **Two-Factor Authentication (2FA):** Enable 2FA for all your critical accounts before leaving home.
- **Biometric Locks:** Use biometric locks on your devices to add an extra layer of security.
- **Incident Response Plan:** Create a plan in advance for what to do if your devices are lost or compromised.
---
### **Final Tips**
- Always prioritize secure practices, even in seemingly safe environments like airports.
- Travel light but keep your important documents and devices close at hand.
- Remember that staying digitally safe is just as important as physical safety during your travels.
By following these tips, you can enjoy your trip with peace of mind, knowing your data and devices are protected. Happy traveling!
---
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-

@ 000002de:c05780a7
2025-02-12 22:41:17
The absolute embarrassment the Chiefs were subjected to... is the end of the their dominance? Of course they have a ton of talent and will win and maybe get back the Super Bowl this game really exposed them.
Its one thing to lose to a great team like the Eagles. Its another to be destroyed so fully. When I think about this game its not just on one person. Its coaching and players. I'm just wondering about the impact on the league watching this. Anyone who has played sports knows that a ton of it is mental. Teams can defeat themselves mentally. Does this defeat tell the league, yeah they aren't that good.
What do you think?
Edit: When I say "done", I mean the dynasty. I don't mean they are gonna have a losing record next year.
originally posted at https://stacker.news/items/884169
-

@ 000002de:c05780a7
2025-02-12 22:25:06
Honest question. I think he's a great TE but... haven't watched him a ton. I get a feeling he's overrated. Maybe not though. I watched him during the big game and was kinda surprised by his lack luster performance. He really seemed different to me.
Since then I've seen video of him not blocking for his QB and not really playing hard. Like he gave up. Does he really have a rep of not blocking? He looks pretty terrible on film. Now, I know I'm a Kittle fan and he is famously great at blocking and takes pride in it. Maybe I'm just using Kittle as the ruler and maybe that's not fair.
Also, I loved watching KC get destroyed so factor that in :)
originally posted at https://stacker.news/items/884156
-

@ 9673b322:1b75ee9e
2025-02-12 21:50:25
This is my test document for nostr publish
Although Sainsbury's was already in the midst of a plan to save £1bn over the next few years, the rise in employer's National Insurance contributions set out in the Budget has also been a factor in this latest restructuring plan.
### Add some text
this is is a test

-

@ d57360cb:4fe7d935
2025-02-12 19:10:53
What’s the difference between the mind that dreams and the mind that you experience reality with? This is a question that floored me when I first began to contemplate it. When I’m in my waking life going about my day to day, I have millions of thoughts flowing through my brain. These thoughts are creating the reality I inhabit. I follow them and live in my version of the world. These thoughts construct my world, they revolve around society, my place in it, the people around me, and the entire world. In that world are millions of stories that connect one structure to another.
This is how we live our lives, we create stories, fantasies, heroes, and villains. One person could paint someone as a hero and another can paint them as a villain. So what is the difference between my dreams and reality? When I dream I’m met with vivid images, structures and stories that seem as real as the life I live. I’ve experienced the same features in dreams as I have in reality. In Lucid dreaming a person has the ability to control a dream, they can alter it and mentally experience whatever their mind conjures up. What if it’s the same in ‘reality’. What if reality is as flimsy as dreams. What if the stories you currently told yourself about your life, or the world you live in were wrong. What if you pushed on the flimsy walls of this ‘reality’.
Maybe you should give them a push and see if they crumble or stand tall.
-

@ 5d4b6c8d:8a1c1ee3
2025-02-12 18:36:48
Going off of memory, because I forgot to do this in the morning.
The last thing I ate were Costco samples yesterday afternoon and then I didn't eat again until lunch today. I'm pretty sure those two things were about 20 hours apart.
## Score Card
Day 1: 14 hour fast (13 dry)
Day 2: 15 hour fast (14 dry)
Day 3: 17 hours (16 dry)
Day 4: 18 hours (17 dry)
Day 5: 18 hours (16 dry)
Day 6: 19 hours (16 dry)
Day 7: 16 hours (15 dry)
Day 8: 18 hours (17 dry)
Day 9: 17 hours (17 dry)
Day 10: 15 hours (13 dry)
Day 11: 20 hours (19 dry)
Day 12: 20 hours (17 dry)
This winter storm is going to make getting my steps in a pain, but there's no way I'm letting myself lose the sats that I staked on the challenge.
originally posted at https://stacker.news/items/884000
-

@ 2e8970de:63345c7a
2025-02-12 17:50:27
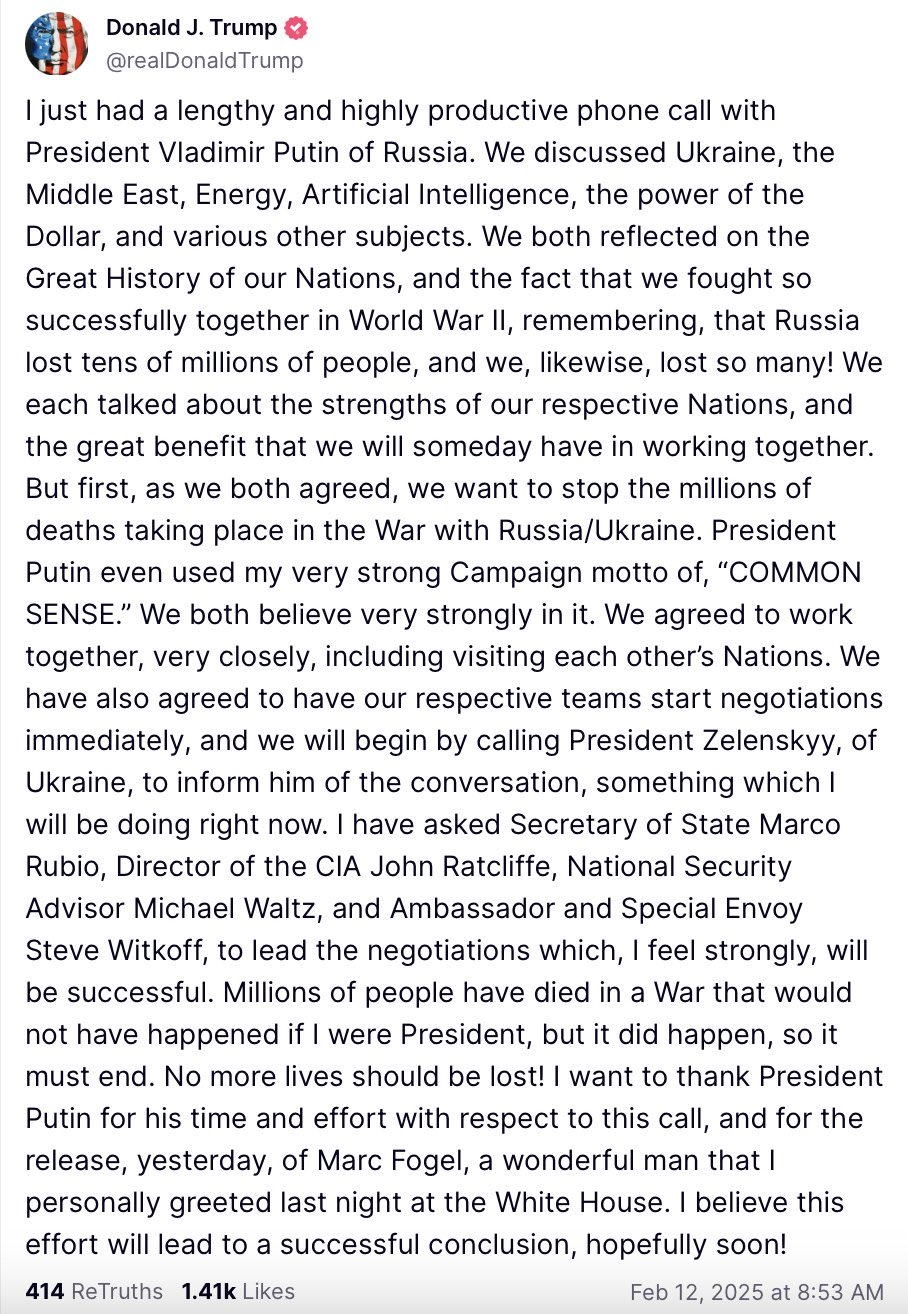
originally posted at https://stacker.news/items/883959
-

@ 8d34bd24:414be32b
2025-02-12 17:38:19
All of us who have truly put our faith in the Lord Jesus Christ want to serve Him, but we all live busy lives. We all get distracted by making a living, taking care of our families, and other good things, but too often we spend so much time on the good that we miss out on the best (see “[Don’t Be Like Martha](https://trustjesus.substack.com/p/dont-be-like-martha)”). In this previous post, I wrote about how we don’t want to live. In this post, I’ll write about what the Bible says about living a life wholly devoted to God.
Many of us wonder, “Are we fully serving God if we aren’t in full time ministry, if we aren’t a pastor/priest, missionary, or if we don’t work for a Christian ministry?” There are many ways we can serve God. Sometimes we are called to a Christian “job,” but other times we serve God in other ways.
> Let the word of Christ richly dwell within you, with all wisdom teaching and admonishing one another with psalms and hymns and spiritual songs, singing with thankfulness in your hearts to God. **Whatever you do in word or deed, do all in the name of the Lord Jesus, giving thanks through Him to God the Father**. (Colossians 3:16-17) {emphasis mine}
The most important thing is that everything we do has a godly focus. We should follow God’s design for marriage and family. We should disciple our children to know and grow in Jesus. We should witness to those with whom we come in contact. We should give to support those who are working in full-time ministry. Even our jobs can be done in service to the Lord, no matter how trivial or unrelated that job might seem.
> **Whatever you do, do your work heartily, as for the Lord rather than for men**, knowing that from the Lord you will receive the reward of the inheritance. It is the Lord Christ whom you serve. (Colossians 3:23-24) {emphasis mine}
I’m an employer. I see the work ethic, or more often the lack of work ethic, in people. I notice those who work hard and always give their best versus those who do the minimum they need to do to keep their job. When a person lets everyone around them know that they are a Christian and then they work harder than everyone else and they are willing to do the undesirable tasks that need to be done, this is noticed and is a good witness. Sadly, too often Christians are known for not working as hard and not going the extra mile. These Christians give Jesus and all Christians a bad name. Whatever job God has given you, do it to the best of your ability. Do the extra task; do the undesirable task; do the task that should’ve been done by someone else. Put in the extra effort even if nobody seems to notice. In most case, even if you aren’t praised, appreciated, or appropriately rewarded, people do notice and your witness is enhanced. In all cases, Jesus notices and you will be rewarded in heaven for representing Him faithfully.
> Whether, then, you eat or drink or whatever you do, **do all to the glory of God**. (1 Corinthians 10:31) {emphasis mine}
We are to do everything we do to the God’s glory. The way we work should glorify God. The way we eat and drink should glorify God. The way we do rest and entertainment should glorify God. The way we interact with others should glorify God. We were designed to glorify God.
Too often we get busy doing life and leave God out of it. It isn’t that we are doing some terrible sin, but it is always wrong to leave God out of our life. We can even do Christian ministry and get so busy doing “God’s work” that we leave God out of it. This can be disastrous and definitely will damage ministry effectiveness. In everything we do, we should listen to God’s leading, whether through Bible reading, prayer, or being still and listening.
> The plans of the heart belong to man,\
> But the answer of the tongue is from the Lord.\
> All the ways of a man are clean in his own sight,\
> But the Lord weighs the motives.\
****Commit your works to the Lord\
> And your plans will be established**. (Proverbs 16:1-3) {emphasis mine}
Part of doing everything in and to the Lord is changing our hearts and minds. Psalm 37 lists several actions we can take in serving the Lord and becoming more like Him.
> **Delight yourself in the Lord**;\
> And He will give you the desires of your heart.\
****Commit your way to the Lord**,\
****Trust also in Him**, and He will do it.\
> He will bring forth your righteousness as the light\
> And your judgment as the noonday.\
****Rest in the Lord and wait patiently for Him**;\
****Do not fret** because of him who prospers in his way,\
> Because of the man who carries out wicked schemes.\
****Cease from anger and forsake wrath**;\
> Do not fret; it leads only to evildoing. (Psalm 37:4-8) {emphasis mine}
If we delight in the Lord, commit our way to the Lord, trust in Him, rest in the Lord, and wait patiently for the Lord, we will be in the right mind to serve Him in all that we do. It will also help us avoid the things that draw us away from the Lord. We are called to not fret, to cease from anger, and to forsake wrath. Fretting, anger, and wrath hurt our witness and draw us away from God. They are a sign that our hearts are not in tune with God and that we need to turn back to Him. They are a sign that we are not trusting in Him nor are we following His will.
---
Sometimes believers wonder if they are succeeding in doing anything for the Lord because they are shy and not good at witnessing or because they have personal circumstances (like sickness of themselves or their family members) that don’t allow them to do much. That doesn’t mean there is nothing these believers can do. We can support those doing the mission of God. We can give money to support missionaries, churches, and Christian ministries. We can house a missionary while they are on break. We can do behind the scenes tasks like cleaning, accounting, organizing, planning, etc.
Most importantly, we can all pray. Prayer should be a constant part of every day, whether we are infirm and unable to leave our bed, whether we are so busy we don’t have five minutes to sit and take a break, or whether we are in full time Christian ministry. We can’t faithfully serve God without prayer.
> Beloved, **you are acting faithfully in whatever you accomplish for the brethren**, and especially *when they are* strangers; and they have testified to your love before the church. You will do well to send them on their way in a manner worthy of God. For they went out for the sake of the Name, accepting nothing from the Gentiles. Therefore **we ought to support such men, so that we may be fellow workers with the truth**. (3 John 1:5-8) {emphasis mine}
Anyone who supports those in ministry will receive similar rewards to those in ministry because they are all working together to fulfill God’s will.
> He who receives a prophet in the name of a prophet shall receive a prophet’s reward; and he who receives a righteous man in the name of a righteous man shall receive a righteous man’s reward. (Matthew 10:41)
We often feel like we are failing God. We feel that we are making zero difference for the kingdom. If you are not growing in your faith, knowledge, and relationship with God, there may be some truth in this, but we also may be listening to the accuser, Satan. Keep in mind that every little thing you do for Jesus or for others, because of your faith in Jesus, is counted as faithful service to Him.
> “Then the King will say to those on His right, ‘Come, you who are blessed of My Father, inherit the kingdom prepared for you from the foundation of the world. For I was hungry, and you gave Me something to eat; I was thirsty, and you gave Me something to drink; I was a stranger, and you invited Me in; naked, and you clothed Me; I was sick, and you visited Me; I was in prison, and you came to Me.’ Then the righteous will answer Him, ‘Lord, when did we see You hungry, and feed You, or thirsty, and give You something to drink? And when did we see You a stranger, and invite You in, or naked, and clothe You? When did we see You sick, or in prison, and come to You?’ The King will answer and say to them, ‘**Truly I say to you, to the extent that you did it to one of these brothers of Mine, even the least of them, you did it to Me**.’ (Matthew 25:34-40) {emphasis mine}
Turn to Jesus. Pray to Jesus. Read His word —the Bible. Make Him a part of everything you do. Follow His leading. Join God in what He is doing.
May God bless you and lead you in the path He designed you to take.
Trust Jesus.
-

@ 88cc134b:5ae99079
2025-02-12 17:23:02
aaaaaa
-

@ d61f3bc5:0da6ef4a
2025-02-12 16:57:44
Micropayments on the Internet have been theorized for decades. However, it wasn’t until the emergence of Nostr that we’ve finally seen them deployed at scale. Nostr is still in its infancy, yet we are already witnessing an explosion of apps built on top of this open protocol. And most of them are featuring zaps! With the recent Primal 2.1 release, Nostr developers now have the option to enhance the experience for their users by integrating a Nostr-powered bitcoin wallet.
There is no doubt that micropayments add a new dimension to consumer apps. The incumbents have realized this and are rushing to add payments to their closed platforms. It won't be long before apps that don’t include built-in payments feel dated or outright broken. The question is not if apps of the future will have built-in payments, but what *kind* of payments they will be. Given that open networks have a tendency to win, our bet is that apps of the future will be powered by Bitcoin. Let’s see how Primal can help.
## Primal Wallet
Our vision for Primal Wallet is simple: deliver the smoothest transactional bitcoin wallet, endowed with expert Nostr skills. The wallet leverages Nostr’s open social graph as a de facto public lightning directory, while offering the highest level of user experience for Nostr’s rich content. For example, the user can scroll through the transaction list, select a zap, and drill straight into the conversation thread where the zap originated. The whole flow feels perfectly natural.

Since we launched Primal Wallet in December 2023, the user response has been incredibly positive. People love the idea of being able to post something on Nostr, get zaps from plebs around the world, then buy a coffee or a meal with those sats - all from the same app.
Having a bitcoin wallet with social skills resonated strongly with users, so Primal Wallet grew rapidly in popularity and usage. Since the launch, we have processed **1,338,460** transactions, with **238,916** just in the past month alone. This rivals some of the leading bitcoin wallets, and we are just getting started! We hear from many bitcoin OGs that they are using Primal Wallet as their transactional daily driver. Bullish.
All this is great, but something has been missing. Our users demanded the ability to connect Primal Wallet to other Nostr apps, so they can zap from anywhere in Nostr’s growing ecosystem.
## Zapping from Any Nostr App
For an existing Primal user, connecting the wallet to a new Nostr app can now be done in two clicks. Let’s take a look at how this is done from Olas, one of the most exciting new apps on Nostr:

Yes. Click, click. And you can start zapping!
Such smooth integration of payments is not available in any competing technology stack. Tradfi, fintech, crypto, etc., have nothing on Bitcoin and Nostr. Two clicks and your external wallet is connected. I’ll give you a moment now to allow for this new reality to settle in.
Primal enables you to connect any number of external apps and manage them from wallet settings:

Note that you can set your daily spend budget for each app or revoke its access at any time.
## How This Works
So, what is this sorcery? How does it work under the hood?
Connecting Nostr apps to external wallets is accomplished via the Nostr Wallet Connect protocol. It utilizes Nostr’s public relay infrastructure to enable communication between apps and wallets. You can learn more about this protocol [here](https://nwc.dev/), and access developer docs [here](https://docs.nwc.dev/).
The smooth, two-click connection setup UX is implemented through deep links between Primal and the external app. Here’s the deep link that the external app needs to call to invoke this feature:
```nostrnwc+primal://connect?appicon=[icon_url]&appname=[app_name]&callback=[callback_string]```
After the user clicks “Create Wallet Connection” in Primal, the Primal app calls the deep link defined in the callback, and passes the NWC connection string. That's all that the external app needs to make the wallet connection.
## What Comes Next?
The Nostr Wallet Connect protocol has been around for almost two years. Several bitcoin wallets implement it and many Nostr apps use it as their main way of enabling payments. What’s new with Primal 2.1 is the elevated user experience. Since Primal is a Nostr-powered wallet, it is aware of all the relevant metadata for each transaction: Nostr zaps, users, and the related events. Primal indexes the entire Nostr network, and now this is open to all Nostr apps that wish to integrate payments.
Nostr keeps expanding and getting better. Its openness enables us to build capabilities that lift all boats. The future is bright; I can’t wait to see how things evolve from here. 🍿🍿🍿
-

@ 85bdb587:7339d672
2025-02-12 15:24:11
## Chart of the Day
While this is a bitcoin focused rag, I think it is important for any of you who read this to begin paying attention to gold markets if you haven't already. There has been an ongoing exodus of physical gold from London vaults and a rapid acceleration of gold being moved to the three biggest vaults in the United States in recent weeks. More gold has flooded into the US vaults over the first two months of this year than at the peak of the flight to safety during the beginning of the COVID lock downs.
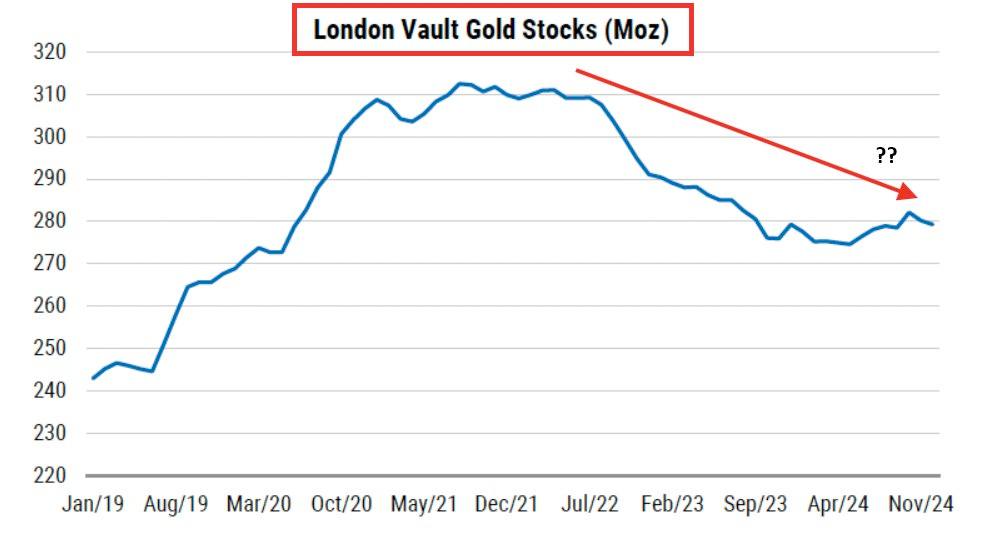
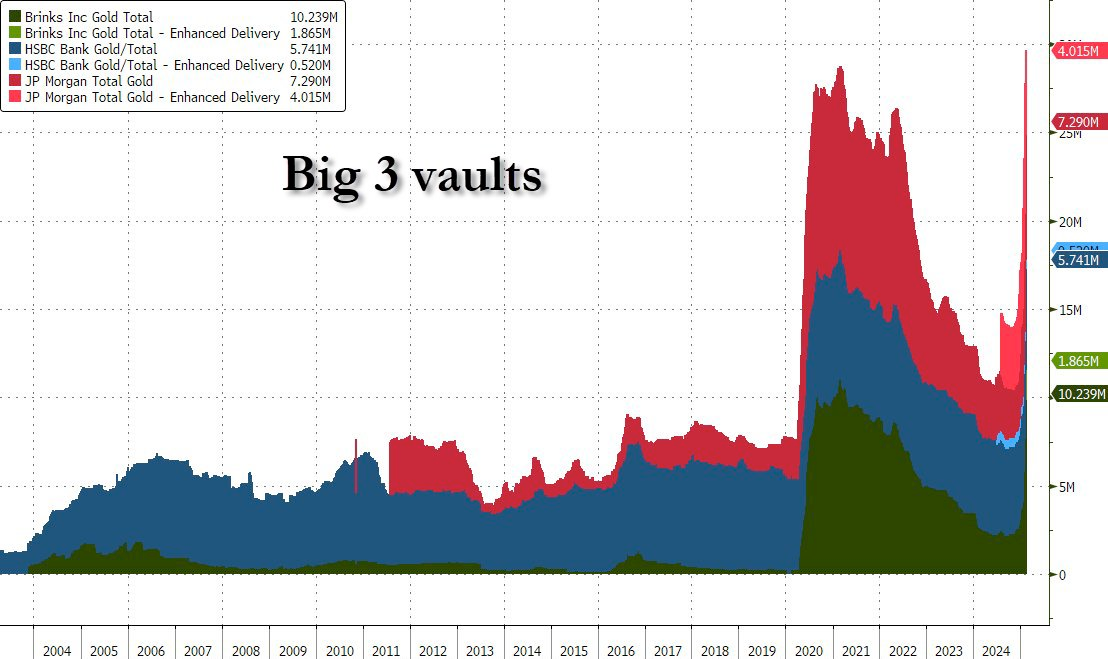
This is particularly perplexing considering the fact that equities are flat or up on the year, depending on the index you like to follow. Gold outperformed the S&P 500 significantly in 2024 and its momentum hasn't slowed down a bit in 2025 as the precious metal consistently hits new all time highs. The current correlation to the S&P 500 has only happened two times in history; right now and October of 2007.
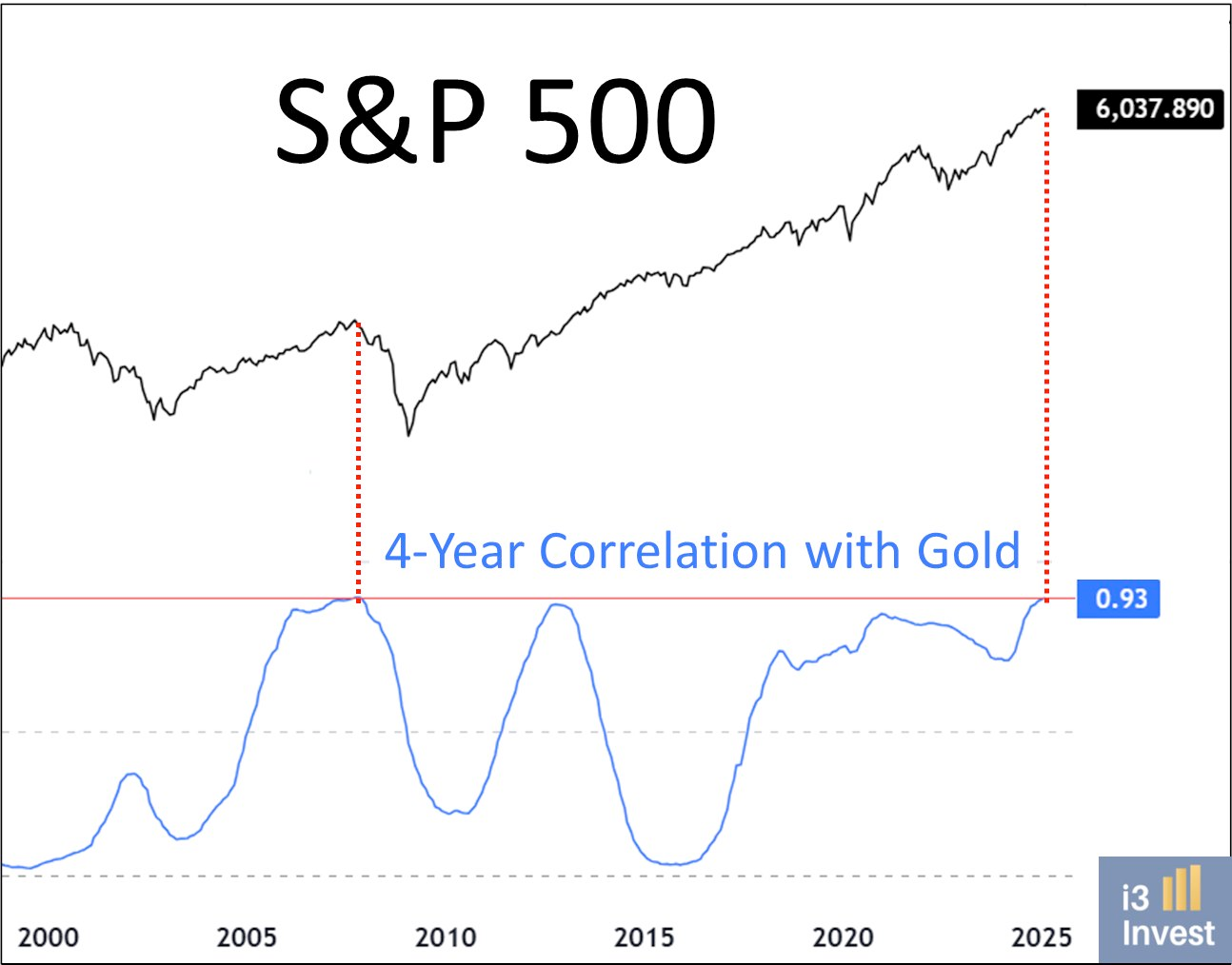
Institutional investors and nation states are piling into gold at an unprecedented pace. This signals that they are preparing for something to break. The catalysts for the exodus of gold from London to the US and from paper gold to physical gold are fears over Trump's tariffs, institutions and governments preparing for a potential monetary reset, and fears of a looming liquidity crisis as liquidity in the reverse repo market dries up. Uncertainty and chaos rule the day and we are witnessing a flight to safety.
Many of you are probably asking, "Why isn't bitcoin moving?!" That's a good question. Considering everything mentioned above one would think that bitcoin would be on the move toward new all time highs as well. Having been following bitcoin for twelve years your Uncle Marty has developed some pattern recognition when it comes to this market. Upward bitcoin price movements typically happen in a staircase fashion. Meaning that it trends up and to the right over the long-run with quick bursts to higher levels followed by small corrections and consolidation periods. If I had to guess, we are currently in a consolidation period that should come to an end at some point in the next few months. In recent years, gold has moved higher first and bitcoin has followed. Typically outperforming gold significantly. I find it hard to believe that this relationship is going to end any time soon. Especially considering the geopolitical and economic backdrop.
## Luke Gromen Warns Bitcoin Holders: Historical Currency Revaluations Show Speed Matters
During my recent conversation with Luke Gromen, he raised a sobering point about the velocity of monetary regime changes. Drawing from historical examples, including a Ukrainian family who saw their savings devalue from "five cars to one month's groceries" over a single weekend, Luke emphasized that Americans are uniquely blind to how quickly these transitions can occur. The current stress in our financial system - from Treasury market dynamics to global trade tensions - suggests we're approaching a similar inflection point.
*"What if they do it on Friday night like they did with Trump coin and you wake up and gold's up 1,000% by the time you're up on Saturday morning, what are you going to do? You're going to sell your bonds and buy gold on Saturday?"* - Luke Gromen

This warning shouldn't be taken lightly. Those waiting for clear signals before acquiring bitcoin may find themselves locked out of the transition entirely. Luke's analysis suggests that rather than a gradual shift, we're more likely to see a compressed timeframe where major monetary changes happen over days or weeks, not months or years. The recent Trump coin phenomenon, while different in nature, demonstrates how quickly markets can move when sentiment shifts dramatically.
TLDR: Major monetary changes happen fast - don't wait to stack sats.
Check out the full podcast [here](https://www.youtube.com/watch?v=RCeWQHATWYU&t=61s&ab_channel=TFTC&ref=tftc.io) for more on DeepSeek's impact on AI markets, Colombia's trade negotiations, and Scott Percent's three arrows for economic reform.
## Headlines of the Day
U.S. Faces $1.67B Annual Cost Spike on Single Bond Rollover - via [X](https://x.com/TFTC21/status/1889454272842268982)
BlackRock: Bitcoin is Monetary Hedge, Ethereum is Tech Play - via [X](https://x.com/BitcoinNewsCom/status/1889396849880268814)
Lummis: SBR Could Slash U.S. Debt by 50% in Two Decades - via [X](https://x.com/cryptonwsuk/status/1888565117047951869)
Fold Launches Bitcoin Rewards Visa Credit Card - via [Business Wire](https://www.businesswire.com/news/home/20250211765772/en/Fold-Launches-Revolutionary-Bitcoin-Rewards-Visa-Credit-Card)
Obscura VPN launches with a MacOS product - via [nobsbitcoin.com](https://www.nobsbitcoin.com/obscura-vpn-is-now-available-on-macos/)
## Bitcoin Lesson of the Day
The SegWit (Segregated Witness) upgrade in August 2017 made two key changes to Bitcoin. First, it moved transaction signatures to a separate part of the data, fixing "transaction malleability" by preventing nodes from modifying transaction IDs. Second, it increased effective block capacity by introducing "weight units" that gave signature data a 75% discount, allowing blocks to grow from 1MB to about 1.8MB.
As a "soft fork," SegWit remained compatible with older Bitcoin software. The upgrade activated at block 481,824 after 95% of miners signaled support. This approach allowed Bitcoin to increase capacity and fix technical issues while maintaining network compatibility.
[SegWit - Learnmeabitcoin.com](https://learnmeabitcoin.com/beginners/guide/segwit/?ref=tftc.io)
ICYMI Fold opened the waiting list for the new Bitcoin Rewards Credit Card. Fold cardholders will get unlimited 2% cash back in sats.
[Get on the waiting list now](https://foldapp.com/credit-card?r=BgwRS) before it fills up!
$200k worth of prizes are up for grabs
.
The Fold Bitcoin Rewards Credit Card waitlist is live!
*Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/funds.*
Subscribe to our YouTube channels and follow us on Nostr and X:
[TFTC YouTube](https://www.youtube.com/tftc21)
[Bitcoin Brief YouTube](https://www.youtube.com/@BTCBrief)
[TFTC on Nostr](https://primal.net/tftc)
[TFTC on X](https://x.com/tftc21)
-

@ 94a6a78a:0ddf320e
2025-02-12 15:05:48
Azzamo is more than just a relay provider—it’s a **high-performance network** designed to make Nostr **faster, smoother, and more reliable** for everyone. Whether you're **posting notes, zapping sats, sharing media, or sending DMs**, Azzamo keeps your Nostr experience **seamless and efficient**.
Nostr is unstoppable, but **not all relays are the same**. Some are **slow, unreliable, or disappear overnight**, while others get **overloaded**, making message delivery **inconsistent**. Azzamo is built differently—offering **fast, stable, and globally distributed relays** to ensure **low-latency, high-speed connections**, no matter where you are.
---
## **🌍 Premium Relays for Maximum Performance**
Azzamo **Premium Relays** are optimized for **speed, reliability, and uptime**, available exclusively to **Premium users**:
📡 **Azzamo Premium Relays:**
- **Europe:** `wss://relay.azzamo.net`
- **America:** `wss://us.azzamo.net`
- **Asia:** `wss://asia.azzamo.net`
Add **Azzamo Premium Time** to **unlock unlimited, high-speed access** across these global relays.
🔗 **Get Premium:** [azzamo.net/premium](https://azzamo.net/premium)
---
## **🆓 Freemium Relays – Free for Everyone**
Azzamo believes in **keeping Nostr open** and accessible to all. That’s why we offer **free relays for everyone**, with **no rate limits for Premium members**
📡 **Freemium Relays:**
- **Free Relay:** `wss://nostr.azzamo.net` – Open to all.
- **Inbox Relay:** `wss://inbox.azzamo.net` – Reliable for DMs & group messages.
By offering both **free and premium options**, Azzamo ensures that **anyone can use Nostr, while also funding the infrastructure that keeps it running smoothly.**
---
## **🛡️ Minimal Moderation, Maximum Transparency**
Nostr is about **free speech**, but that doesn’t mean **zero moderation.** Azzamo follows a **minimal moderation policy** to keep relays **functional and spam-free** while maintaining **transparency** in enforcement.\
\
🚫 **Spam & network abuse**\
🚫 **Illegal content (CSAM, fraud, malware, scams)**\
🚫 **Impersonation & identity abuse**
We also maintain a **public Ban API** for **transparent moderation decisions**.
📖 **More on our Ban API:** [azzamo.net/introducing-the-azzamo-ban-api](https://azzamo.net/introducing-the-azzamo-ban-api)
---
## **🚀 Get Started with Azzamo Relays Today!**
🔗 **Connect now:**\
📡 `wss://nostr.azzamo.net` (Freemium Free Relay)\
📬 `wss://inbox.azzamo.net` (Freemium Inbox Relay)\
📡 `wss://relay.azzamo.net` (Premium Europe Relay)\
📡 `wss://us.azzamo.net` (Premium Americas Relay)\
📡 `wss://asia.azzamo.net` (Premium Asia Relay)
Nostr is growing fast. **Make sure your relays can keep up.** 🚀
#azzamo #grownostr #nostr #relay #relays #premiumrelay #paidrelay
-

@ 5d4b6c8d:8a1c1ee3
2025-02-12 14:36:40
Here are today's picks using my proprietary betting strategy at [Freebitcoin](https://freebitco.in/?r=51325722). For details about what Risk Balanced Odds Arbitrage is and why it works see https://stacker.news/items/342765/r/Undisciplined.
For a hypothetical 1k-ish wager on each match, distribute your sats as follows:
| Outcome 1 | Outcome 2 | Outcome 3 | Bet 1 | Bet 2 | Bet 3 |
|--------------|-------------|--------------|-------|-------|-------|
| Juventus| Inter Milan| Draw | 294| 435| 303|
| Tottenham| Man United| Draw | 406| 357| 266|
| Liverpool| Wolves| Draw | 833| 67| 125|
| Valladolid| Sevilla| Draw | 222| 500| 289|
| Real Betis| Real Sociedad| Draw | 393| 321| 313|
| Osasuna| Real Madrid| Draw | 174| 619| 227|
| Barcelona| Rayo Vallecano| Draw | 818| 80| 133|
| Atletico Madrid| Celta Vigo| Draw | 692| 118| 217|
I'll be curious to see how @Coinsreporter does with his modified RBOA.
On the most recently completed sets of RBOA, I lost 700 sats on about 50k wagered. I'm not sure if that's just normal variance or if it's due to matches not being posted as far in advance, which reduces the early mover bonus.
I still haven't precisely identified where the threshold is, but it might be worth skipping any of these with a "time weight multiplier" lower than 90.
----------
A note of caution about Freebitcoin: they recorded the wrong outcome for last week's Bills vs Ravens game and as of yet have not corrected it. I recall one other instance of something similar happening, so proceed with caution.
This RBOA strategy is largely immune from that problem, but be aware of it when just betting on one outcome.
originally posted at https://stacker.news/items/883708
-

@ 2180de5b:54d6cba3
2025-02-12 14:14:12
Open Source Culture represents the simple idea that ideas are free. That information yearns to be free. We acknowledge that copyright laws are unsuitable for a world that’s highly digitized; where content and information are, and should be, abundant and readily available for anyone.
If the information you have is truly valuable for the world, then you do not sell it. You give it away for free. You let it do the good that it can in the world, and know that both yourself and others will be rewarded for it.
If you create content that can be digitally distributed and you charge people before accessing your content, then that tells me that you are actually uncertain of the value of your work. Why? Because if you were certain that whatever it is you are trying to sell had any substantial worth, then you would trust these people to pay you in one way or the other, retroactively. The distinction between *price* and *value* is critical in this framework because, as Jeff Booth succinctly said: “*Prices fall to the marginal cost of production.*” The marginal cost of production for digital data is already effectively zero and it is getting exponentially cheaper day by day. That has nothing to do with the *value* of the very same data, though. Prices are mere agreements. Value is innate.
“*Value for value*” is real, it's based on trust and abundance, which are both lacking in a society built on fiat money and perceived scarcity, which is why I understand the skepticism behind those ideas and a propensity to put a price tag on everything.
Copyright laws are not useful for us anymore at a time when we are moving towards abundance. Digital scarcity only makes sense in digital money, not information.
*First mover advantage* is the only real intellectual property right. In another sense, bitcoin is the only real intellectual property anyway. It’s the only thing that’s scarce. All the rest of it can be as abundant as we let it be.
"Intellectual property" are, after all, mere ideas and no one can "own" ideas.
Copyright laws are nothing else than an impediment to creativity and a gatekeeper to knowledge. Charging money for information, which in digital form is near-free to store and transfer, might as well be considered a form of usury.
We shall free information and with it, we will free creativity, discourse, innovation, imagination, cooperation; and, in its totality, nothing less than the human spirit itself.
*Written by Kontext*
*Published: block height 883,435*
*Download the .PDF: [https://satosh.ee/product/open-source-culture-manifesto/](https://satosh.ee/product/open-source-culture-manifesto/)*
-

@ c4b5369a:b812dbd6
2025-02-12 12:23:40

### Unidirectional payment channels revisited
#### Nodeless lightning - Reduce ecash mints custodial risk
---
### Sats N Facts
The nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference has just wrapped up. And what a blast it was. In the heart of northern Thailand, developers, researchers, content creators and more, came together to share ideas on how Bitcoin, Nostr and other free protocols are being used everyday to liberate people.
Not only were stories shared from different community leaders on how embracing bitcoin has empowered them and their communities, but a big goal of the unconference was to bring bitcoin engineers and developers from various domains together in one room, unstructured, chaotic, and let them do their thing.
At first, I thought not having a schedule might be boring, but oh boy was I wrong. There was so much stuff going on, it was hard to choose which session I would have to miss!
### Luke's Spillman channel proposal
One of the sessions I definitely did not want to miss, was nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac s [proposal](https://gist.github.com/lukechilds/307341239beac72c9d8cfe3198f9bfff)
> Ecash mints funded with Spillman channels: The ultimate nodeless Lightning wallet
.
In true unconference fashion, he announced in the main room that the session was about to start, and that the people that are interested should meet him in the whiteboard corner in 10 minutes. The corner was packed, and Luke explained his proposal.
### What's a "[Spillman channel](https://en.bitcoin.it/wiki/Payment_channels#Spillman-style_payment_channels)"?
Essentially when we are talking about Spillman channels, what is meant are unidirectional payment channels (or [CLTV-style channels](https://en.bitcoin.it/wiki/Payment_channels#CLTV-style_payment_channels)). An unidirectional payment channel means, only one party can send payments, but not receive, and the other party can only receive, but not send. They also expire after a predetermined amount of time, and must be closed.

At first glance, this might look kinda stupid. After all, we have [Poon-Dryja channels](https://en.bitcoin.it/wiki/Payment_channels#Poon-Dryja_payment_channels) that are powering the lightning network. They are bi-directional, do not expire, and can be used to shuffle coins back and forth theorethically an unlimited amount of times.
So, why bother with this stupid one-way channel?
### Simplicity is king
People that have worked with lightning channels can sing you a song about complexity, state handling and risks about the current state of bidirectional payment channels. Essentially, There are a lot of requirements on both channel parties when it comes to Liveness (being online) and also state handling (continuous backups).

In some cases, especially when in the context of end-users wanting to perform payments on their mobile phone, they would appreciate it if there was not so much complexity and overhead involved.
The gist of the idea is to combine unidirectional channels and ecash mints to achieve the following:
A self custodial unidirectional payment channel to an ecash mint, massively reducing the senders liveness and state handling requirements when compared to a lightning channel. Sending payments through the mint will be done through swapping some of the channel balance for ecash tokens. At this point, the user is trusting the mint to honor the redemption of these tokens, while the remaining channel balance remains in self custody. This gives them better controll over their funds than just holding their entire balance custodied in the mint. The ecash tokens can then be redeemed to pay a lightning invoice, just the same as it is done now with normal cashu mints.

So this channel, that has no liveness or state management requirements for the sender, and must have a pre-defined close time, seems to be a perfect fit for the following usecase:
1. A `sender` receives his salary once a month. He opens a channel that is valid for one month.
2. The `sender` then can do his daily spending over this channel. He only trusts the `mint` with the amount for the current outgoing payment while it is swapped for ecash, waiting for redemption.
3. If the `sender` must receive funds (a refund for example), he can do so into the `mints` custody, by receiving ecash. He can spend his ecash funds first when doing his next payment, to reduce his custodial exposure.
4. When the channel expires, or runs out of funds, the `mint` closes the channel.
From a consumer perspective, that just want to receive his salary and make frequent payments afterwards, this usecase seems to make a lot of sense. Obviously from a merchants perspective on the other hand, such a channel doesn't really work. But that's fine, it's not the problem we're trying to solve here.
What do you think of this idea? Be sure to let me know in the comments!
In the next article, we will dive into how such a system can be implemented today, using Bitcoin, Cashu and Lightning. We will also discover how the system can be improved, to make channels non-expiring (A collaborative idea between nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp and nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac born at nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx ).
So stay tuned!
-

@ c2827524:5f45b2f7
2025-02-12 12:22:11
## L’animo umano

Una delle entità più belle che esistono e che, a mio parere, rendono ancor più meraviglioso questo mondo, è **l’animo degli esseri umani**. È un cocktail fatto di sentimenti, intenzioni, azioni e logica. Quelli che preferisco sono gli animi gentili.
Le azioni e le intenzioni devono convergere verso la delicatezza, senza una sbavatura, per essere gentili e io adoro la gentilezza, la riconosco al volo, forse perché non sono delicata. Per niente.
L’animo è forse **uno dei più grandi segreti dell’umanità**: in genere perché lo si tiene sempre privato, come è anche logico che sia.
C’è un solo fattore che fa rivelare l’animo alle persone, loro malgrado: uno stress test estremo.
Dal febbraio del 2020, lo stress test si è tramutato in un organismo multidimensionale, uscendo dalla fantasia distopica di George Orwell e – loro malgrado – **tutti hanno dovuto manifestare l’animo segreto**.
Fateci caso: è con il covid-1984 che avete scoperto la vera natura di amici, parenti, sconosciuti o conoscenti.
## Stato di eccezione

La distopia non è mica fuoriuscita da un laboratorio di Wuhan, che ha infettato un pangolino, che ha infettato una papera, che al mercato mio padre comprò. **Ha origini molto più antiche**.
Profondi conoscitori dell’animo umano, in grado di prevedere le reazioni delle masse di fronte ad ogni tipo di evento, potrebbero progettare modelli catastrofici e predeterminare con una precisione disarmante la risposta delle persone comuni. Ad esempio di fronte alla probabilità che quattro aerei impazziscano nei cieli americani di una splendida mattina di settembre, oppure guardando i corpi smembrati di un attentato compiuto da una qualunque “sigla” islamica.
Infine, potrebbero decidere come e quando dare una sferzata finale allo stress test, ad esempio con il pangolino. O era il pipistrello?
È la *«forma legale di ciò che non può avere forma legale»*, più in generale lo spirito disumano dei governanti di oggi, la consuetudine della guerra preventiva, la quale impone con forza che *«lo stato di eccezione tende sempre più a presentarsi come il paradigma di governo dominante della politica contemporanea»*.
Così analizza magistralmente Giorgio Agamben nel II° volume della raccolta Homo Sacer, intitolato per l’appunto [Stato di Eccezione](https://www.amazon.it/s?k=stato+di+eccezione+agamben&adgrpid=1234751876426057&hvadid=77172156923137&hvbmt=be&hvdev=c&hvlocphy=1861&hvnetw=s&hvqmt=e&hvtargid=kwd-77172234261086%3Aloc-93&hydadcr=18605_1867270&mcid=df58fe78258f374b81f1fd0eeaa1c659&msclkid=ea580711f461117b4cc160bdad34d584&tag=amamitsp-21&ref=pd_sl_7ni9dvsw1h_e).
## Stato indegno

Gli esseri umani, fondamentalmente miti e pacifici, tendono a condurre vite “normali” in ogni condizione ambientale.
Un’unica variabile tende ad interferire per cambiare la condizione ambientale: la politica dello stato. E **lo fa in maniera sempre negativa**.
Lo stato crea emergenze, per poi sbattere il suo (piccolissimo) pene sul tavolo e imporre con forza la soluzione, che tenderà puntualmente a facilitare la propria vita rendendo impossibile quella dei ~~cittadini~~ sudditi.
Le disuguaglianze create hanno poi **il solo scopo di mettere** esseri miti e pacifici (ma sotto costante pressione) **gli uni contro gli altri**.
Pensateci: da quanti decenni siete sotto la pressione di una *«forma legale di ciò che non può avere forma legale»*? Sentendo il Marchese del Grillo ***«Io so’ io, voi siete un cazzo»***, probabilmente è qualche secolo che questo stato indegno esiste.
## Vera natura o Nuda vita?

Il fatto, poi, che lo stato indegno venga accettato senza fiatare, fa parte di quella serie di reazioni delle masse e che i profondi conoscitori dell’animo umano sfruttano per mantenere il potere.
Si passa poi alle peggiori angherie che lo stato indegno e i suoi agenti perpetrano nei confronti dei ~~cittadini~~ sudditi, alle estreme disparità tra ~~cittadini~~ sudditi e i “servitori” dello stato, chiamati così perché servono lo stato indegno e non i ~~cittadini~~ sudditi.
Prima di arrivare alla sferzata finale dello stress test, persone miti e pacifiche hanno subito così tanti torti da non saperli più contare, ormai fanno parte della normalità. La loro esistenza è ormai ridotta a quello che Walter Benjamin prima e Giorgio Agamben poi definiscono la **Nuda Vita**, mettendo in analogia i sudditi con i detenuti di Guantanamo, giuridicamente innominabili e inclassificabili, ovvero ***«oggetto di una pura signoria di fatto»***.
## Il sontuoso master

Nello stato di eccezione in cui viviamo da almeno 50 anni, a parte pochi dotati di un immenso spirito di osservazione (e i profondi conoscitori al potere, chiaro), nessuno di noi ha mai avuto **veramente** il piacere di conoscere la reale natura delle persone con cui abbiamo scelto di circondarci.
Magari c’era quel “piccolo tarlo”, quella “vocina” che ci ha fatto preferire alcuni piuttosto che altri, ma alla fine ha sempre prevalso l’attitudine mite e pacifica, che ha messo a tacere quella vocina.
covid-1984 ha il merito di aver messo a nudo tutti: vittime e carnefici. Si tratta verosimilmente di **un sontuoso master che svelerà la vera natura di ognuno**, **nessuno escluso**. Ahinoi, il master è decennale e siamo appena all'inizio del V° anno accademico.
## Istruzioni, prima ancora che l’istruzione

Se c’è un consiglio che mi sento di dare a chi è ancora molto giovane, è proprio quello di non mettere mai a tacere quella “vocina”, per nessun motivo, seppure plausibile. Anche senza rovinare i rapporti, ma l’animo umano va sempre indagato, **si deve fare chiarezza sulla vera natura delle persone con cui si decide di fare un percorso di vita**.
La scoperta porterà ad evitare tutti quei “servitori” dello stato di cose indegno di essere definito umano. I *compliant*, gli asserviti, quelli senza spina dorsale o, peggio, **che hanno un interesse personale a mantenere lo status quo** devono essere evitati a tutti i costi.
È oltremodo doloroso, ma va fatto. Questi indegni devono essere isolati al più presto, in maniera da renderli innocui. Sono loro il vero esercito dello stato indegno, disposti a combattere qualunque guerra pur di rimediare un piccolissimo quanto ridicolo privilegio.
Oggi, i tempi in cui questo esercito si abbassava a tanto per il classico piatto di lenticchie riscaldate, sono un lontanissimo ricordo. covid-1984 ha ulteriormente abbattuto lo standard: ora gli indegni fiancheggiano qualsiasi assurdità **in cambio di un piatto di lenticchie rimasticate dalla signoria di fatto**.
L’unico risultato possibile è che l'infame stato rafforza il suo potere di controllo e rosicherà uno alla volta i (pochi) diritti e la libertà di chiunque.
Ecco perché bisogna spuntare le armi di questo spregevole stato di cose colpendo l’anello debole, isolandolo. Debole perché non ci crede (nello stato) ma agisce asservito solo per quel piatto di lenticchie (quelle rimasticate e sputate).
La prima volta che si incontrano, la vocina vi metterà di fronte alla sensazione di essere ai limiti di uno scontro frontale: capire da che parte andrà il rivale, per buttarsi in quella opposta ed evitare così uno schianto fatale.
Fatelo: buttatevi dall’altra parte. E scegliete la parte giusta.
 @ 9e69e420:d12360c2
2025-02-14 18:07:10Vice President J.D. Vance addressed the Munich Security Conference, criticizing European leaders for undermining free speech and traditional values. He claimed that the biggest threat to Europe is not from external enemies but from internal challenges. Vance condemned the arrest of a British man for praying near an abortion clinic and accused European politicians of censorship. He urged leaders to combat illegal immigration and questioned their democratic practices. “There is a new sheriff in town,” he said, referring to President Trump. Vance's remarks were unexpected, as many anticipated discussions on security or Ukraine. His speech emphasized the need for Europe to share the defense burden to ensure stability and security.
@ 9e69e420:d12360c2
2025-02-14 18:07:10Vice President J.D. Vance addressed the Munich Security Conference, criticizing European leaders for undermining free speech and traditional values. He claimed that the biggest threat to Europe is not from external enemies but from internal challenges. Vance condemned the arrest of a British man for praying near an abortion clinic and accused European politicians of censorship. He urged leaders to combat illegal immigration and questioned their democratic practices. “There is a new sheriff in town,” he said, referring to President Trump. Vance's remarks were unexpected, as many anticipated discussions on security or Ukraine. His speech emphasized the need for Europe to share the defense burden to ensure stability and security. @ c43d6de3:a6583169
2025-02-14 17:34:05“IN THIS SPRING of 1953 the free world weighs one question above all others: the chance for a just peace for all peoples,” Dwight D. Eisenhower’s throat went dry and he swallowed to alleviate the burn. Eight years had passed since the end of world war 2 but still the beaches of the Marshall Islands lay charred, Hiroshima and Nagasaki dosed in radiation and ruin, and countless ghost towns still littered Europe’s mangled face. Dwight peered through his glasses at his speech on the podium, then raised his gaze back at the small crowd gathered in front of him in the conference room at the American Society of Newspaper Editors in Washington, D.C. Everyone was on the edge of their seats. The President spoke of peace, but the United States faced a great enemy in the Soviet Union. How would he continue?  “To weigh this chance is to summon instantly to mind another recent moment of great decision. It came with that yet more hopeful spring of 1945, bright with the promise of victory and of freedom. The hope of all just men in that moment too was a just and lasting peace.” The heads among the spectators raised in hope, as if the enthusiasm in the President’s voice could be enough to wipe away any prospect of future war against the Soviet threat. “In that spring of victory the soldiers of the Western Allies met the soldiers of Russia in the center of Europe. They were triumphant comrades in arms. Their peoples shared the joyous prospect of building, in honor of their dead, the only fitting monument-an age of just peace. All these war-weary peoples shared too this concrete, decent purpose: to guard vigilantly against the domination ever again of any part of the world by a single, unbridled aggressive power.” “This common purpose lasted an instant and perished. The nations of the world divided to follow two distinct roads.” “The United States and our valued friends, the other free nations, chose one road.” “The leaders of the Soviet Union chose another.” “The way chosen by the United States was plainly marked by a few clear precepts, which govern its conduct in world affairs.” **What came next in Dwight D. Eisenhower’s speech “The Chance for Peace” is the answer to preventing wars between countries** “First: No people on earth can be held, as a people, to be an enemy, for all humanity shares the **common hunger for peace and fellowship and justice.** Second: No nation's security and well-being can be lastingly achieved in isolation but only in **effective cooperation** with fellow nations. Third: **Any nation's right to a form of government and an economic system** of its own choosing **is inalienable**. Fourth: Any nation's attempt to dictate to other nations their form of government **is indefensible**. And fifth: A nation's hope of lasting peace cannot be firmly based upon any race in armaments but rather upon **just relations and honest understanding** with all other nations.”  **I. First Point** When you minimize any nation or country to its most granular piece, the human family, you realize every nation or country is the same. It is a larger body of human families looking to establish peace out of chaos against nature, fellowship with their neighbor to make that peace possible, and justice against affronts to the foundations of the formerly stated peace and fellowship. Without this, what you have is not a nation but rather wilderness.  **II. Second Point** When we enter the world stage and look at the community of nations it is important we understand that no nation can truly expect to uphold Eisenhower’s first point without the ability to cooperate with other nations. There can be a natural disaster that strikes an entire nation and without exterior help, it may be impossible to overcome. Understand, Eisenhower’s second point only serves as an extension of the first point. Humankind's struggle with nature will always exist, but in cooperation with other communities we can overcome hardship against nature and live in better harmony.  **III. Third Point** It cannot be argued that humans, after millenia of having dispersed across the planet, have collected into pockets of communities of which grew and developed with experiences based on the place in the world where they’ve resided. This has birthed cultures, religions, and moral codes that serve as the foundation of different branches of philosophy that have borne the fruit of governance. Ultimately, no two communities shares the exact same moral code and thus do not share, and will never share, the exact same understanding of what governance should take place. In this respect, it is an inalienable right of the very people within a community to choose how they govern themselves.  **IV. Fourth Point** In trying to impeded on this third point, we come to Eisenhower’s fourth point which is that no other community has the right to dictate how other nations govern themselves. **V. Final Point** Lastly, war will never lead to peace. Only common understanding of the first four points will ever lead to true peace. A race in armaments, as the cold war proved, only leads to further distrust and the breakdown of all other points among the community of nations on the world stage. All that can be done to expect peace is to take your neighbor as they are. St. Augustine has a famous quote, “Seek not to understand that you may believe, but believe that you may understand.” This is meant to drive home the point of faith in the unbelievable. It is how a religious person can believe in a god that they can not prove exists. Some might say there will never be a world without war. I say we already have the recipe for it. We’ve been given this recipe by many leaders throughout our history. Leader’s who’ve witnessed the darkest depths of human evil and wanted to steer humanity away from it.  ----------- Thank you for reading! If this article resonated with you, let me know with a zap and share it with friends who might find it insightful. Your help sends a strong signal to keep making content like this! Interested in fiction? Follow nostr:npub1j9cmpzhlzeex6y85c2pnt45r5zhxhtx73a2twt77fyjwequ4l4jsp5xd49 for great short stories and serialized fiction. More articles you might like from Beneath The Ink: https://primal.net/e/note1ws4es0gahm502k6qgx64dseqhjqgyzh0q7flzk6glcasqxxye6jqm20fj9 nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq25yan2w39rsjj0dqk5ckn52ptxsc3nve8hw0aftmq https://primal.net/e/note158ns7z27r2y664h9lsdqdhsjj2uehrejve2y02lkvz46d8xgxncs8pcj7w nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2kjjzzfpjxvutjg33hjvpcw5cyjezyv9y5k0umm6k https://primal.net/e/note1htkygah99mz8p4png992n0clqa44spatw3uzzcpl94etwh2zr60stklxvw nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqqa9wefdwfjj6stvdsk57cnnv4ehxety94mkjarg94g8ymm8wfjhxuedg9hxgt2fw3ej6sm0wd6xjmn8946hxtfjvsuhsdnju045ml https://primal.net/e/note1rdanqhdgc7d8sypm459zrt55m0zfaze7u34phkew9nptyr3ghwlqsvtsdx nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2ns3jnfa985c29xp2rs3pexpykz6mjxetxu2g25x6
@ c43d6de3:a6583169
2025-02-14 17:34:05“IN THIS SPRING of 1953 the free world weighs one question above all others: the chance for a just peace for all peoples,” Dwight D. Eisenhower’s throat went dry and he swallowed to alleviate the burn. Eight years had passed since the end of world war 2 but still the beaches of the Marshall Islands lay charred, Hiroshima and Nagasaki dosed in radiation and ruin, and countless ghost towns still littered Europe’s mangled face. Dwight peered through his glasses at his speech on the podium, then raised his gaze back at the small crowd gathered in front of him in the conference room at the American Society of Newspaper Editors in Washington, D.C. Everyone was on the edge of their seats. The President spoke of peace, but the United States faced a great enemy in the Soviet Union. How would he continue?  “To weigh this chance is to summon instantly to mind another recent moment of great decision. It came with that yet more hopeful spring of 1945, bright with the promise of victory and of freedom. The hope of all just men in that moment too was a just and lasting peace.” The heads among the spectators raised in hope, as if the enthusiasm in the President’s voice could be enough to wipe away any prospect of future war against the Soviet threat. “In that spring of victory the soldiers of the Western Allies met the soldiers of Russia in the center of Europe. They were triumphant comrades in arms. Their peoples shared the joyous prospect of building, in honor of their dead, the only fitting monument-an age of just peace. All these war-weary peoples shared too this concrete, decent purpose: to guard vigilantly against the domination ever again of any part of the world by a single, unbridled aggressive power.” “This common purpose lasted an instant and perished. The nations of the world divided to follow two distinct roads.” “The United States and our valued friends, the other free nations, chose one road.” “The leaders of the Soviet Union chose another.” “The way chosen by the United States was plainly marked by a few clear precepts, which govern its conduct in world affairs.” **What came next in Dwight D. Eisenhower’s speech “The Chance for Peace” is the answer to preventing wars between countries** “First: No people on earth can be held, as a people, to be an enemy, for all humanity shares the **common hunger for peace and fellowship and justice.** Second: No nation's security and well-being can be lastingly achieved in isolation but only in **effective cooperation** with fellow nations. Third: **Any nation's right to a form of government and an economic system** of its own choosing **is inalienable**. Fourth: Any nation's attempt to dictate to other nations their form of government **is indefensible**. And fifth: A nation's hope of lasting peace cannot be firmly based upon any race in armaments but rather upon **just relations and honest understanding** with all other nations.”  **I. First Point** When you minimize any nation or country to its most granular piece, the human family, you realize every nation or country is the same. It is a larger body of human families looking to establish peace out of chaos against nature, fellowship with their neighbor to make that peace possible, and justice against affronts to the foundations of the formerly stated peace and fellowship. Without this, what you have is not a nation but rather wilderness.  **II. Second Point** When we enter the world stage and look at the community of nations it is important we understand that no nation can truly expect to uphold Eisenhower’s first point without the ability to cooperate with other nations. There can be a natural disaster that strikes an entire nation and without exterior help, it may be impossible to overcome. Understand, Eisenhower’s second point only serves as an extension of the first point. Humankind's struggle with nature will always exist, but in cooperation with other communities we can overcome hardship against nature and live in better harmony.  **III. Third Point** It cannot be argued that humans, after millenia of having dispersed across the planet, have collected into pockets of communities of which grew and developed with experiences based on the place in the world where they’ve resided. This has birthed cultures, religions, and moral codes that serve as the foundation of different branches of philosophy that have borne the fruit of governance. Ultimately, no two communities shares the exact same moral code and thus do not share, and will never share, the exact same understanding of what governance should take place. In this respect, it is an inalienable right of the very people within a community to choose how they govern themselves.  **IV. Fourth Point** In trying to impeded on this third point, we come to Eisenhower’s fourth point which is that no other community has the right to dictate how other nations govern themselves. **V. Final Point** Lastly, war will never lead to peace. Only common understanding of the first four points will ever lead to true peace. A race in armaments, as the cold war proved, only leads to further distrust and the breakdown of all other points among the community of nations on the world stage. All that can be done to expect peace is to take your neighbor as they are. St. Augustine has a famous quote, “Seek not to understand that you may believe, but believe that you may understand.” This is meant to drive home the point of faith in the unbelievable. It is how a religious person can believe in a god that they can not prove exists. Some might say there will never be a world without war. I say we already have the recipe for it. We’ve been given this recipe by many leaders throughout our history. Leader’s who’ve witnessed the darkest depths of human evil and wanted to steer humanity away from it.  ----------- Thank you for reading! If this article resonated with you, let me know with a zap and share it with friends who might find it insightful. Your help sends a strong signal to keep making content like this! Interested in fiction? Follow nostr:npub1j9cmpzhlzeex6y85c2pnt45r5zhxhtx73a2twt77fyjwequ4l4jsp5xd49 for great short stories and serialized fiction. More articles you might like from Beneath The Ink: https://primal.net/e/note1ws4es0gahm502k6qgx64dseqhjqgyzh0q7flzk6glcasqxxye6jqm20fj9 nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq25yan2w39rsjj0dqk5ckn52ptxsc3nve8hw0aftmq https://primal.net/e/note158ns7z27r2y664h9lsdqdhsjj2uehrejve2y02lkvz46d8xgxncs8pcj7w nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2kjjzzfpjxvutjg33hjvpcw5cyjezyv9y5k0umm6k https://primal.net/e/note1htkygah99mz8p4png992n0clqa44spatw3uzzcpl94etwh2zr60stklxvw nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqqa9wefdwfjj6stvdsk57cnnv4ehxety94mkjarg94g8ymm8wfjhxuedg9hxgt2fw3ej6sm0wd6xjmn8946hxtfjvsuhsdnju045ml https://primal.net/e/note1rdanqhdgc7d8sypm459zrt55m0zfaze7u34phkew9nptyr3ghwlqsvtsdx nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2ns3jnfa985c29xp2rs3pexpykz6mjxetxu2g25x6 @ dd664d5e:5633d319
2025-02-14 16:56:29Most people only know customer-to-customer (C2C) and business-to-customer (B2C) software and websites. Those are the famous and popular ones, but business-to-business (B2B) is also pretty big. How big? Even something boring and local like [DATEV](https://www.datev.de/web/de/startseite/startseite-n/) has almost 3 million organizations as customers and €1,44 billion in annual revenue. FedEx has €90 billion in annual revenue and everyone who uses it comes into contact with its software. There's a whole chain of software between the sender and receiver of the package, and it all has to work seamlessly. Same with Walmart, Toyota, Dubai Airport, Glencore, Tesla, Edeka, Carrefour, Harvard and University of Texas, Continental, Allianz, Asklepios, etc. That's the sort of software I help build. You've probably never heard of it, but when it doesn't work properly, you'll hear about it on the news.
@ dd664d5e:5633d319
2025-02-14 16:56:29Most people only know customer-to-customer (C2C) and business-to-customer (B2C) software and websites. Those are the famous and popular ones, but business-to-business (B2B) is also pretty big. How big? Even something boring and local like [DATEV](https://www.datev.de/web/de/startseite/startseite-n/) has almost 3 million organizations as customers and €1,44 billion in annual revenue. FedEx has €90 billion in annual revenue and everyone who uses it comes into contact with its software. There's a whole chain of software between the sender and receiver of the package, and it all has to work seamlessly. Same with Walmart, Toyota, Dubai Airport, Glencore, Tesla, Edeka, Carrefour, Harvard and University of Texas, Continental, Allianz, Asklepios, etc. That's the sort of software I help build. You've probably never heard of it, but when it doesn't work properly, you'll hear about it on the news. @ 554ab6fe:c6cbc27e
2025-02-14 16:29:51Bitcoin’s Price and the Power Law: A Reflection of Energy and the Early Stages of Monetary Adoption Introduction Bitcoin’s price trajectory has long puzzled analysts, with its seemingly chaotic booms and busts. However, when examined through the lens of power laws, a pattern emerges—one that is fundamentally tied to Bitcoin’s energy-based production cost. This article argues that Bitcoin’s price has historically followed a power law because its underlying cost structure is dictated by mining, an energy-intensive process. However, this relationship will not persist indefinitely. I propose that as Bitcoin matures into a widely adopted monetary system, its price will decouple from mining production costs and instead oscillate in accordance with natural business cycles, much like traditional forms of money. **Bitcoin’s Price and the Power Law** Source and Credit: Giovanni Santostasi’s “[The Bitcoin Power Law](https://giovannisantostasi.medium.com/the-bitcoin-power-law-theory-962dfaf99ee9)” When Bitcoin’s price is plotted on a logarithmic scale against time, a strikingly straight-line trajectory appears, punctuated by cycles of rapid price expansion (bull markets) followed by severe corrections (bear markets). These perturbations correspond to Bitcoin’s well-known halving cycles, which occur approximately every four years and reduce the block reward paid to miners, effectively doubling the cost of production per Bitcoin. Historically, Bitcoin’s price has always returned to a fundamental minimum—one that closely aligns with the average cost of mining. This observation suggests that Bitcoin’s power law price behavior is not arbitrary but rather a reflection of its fundamental energy constraints. As in many natural systems governed by power laws, energy dynamics play a central role. In Bitcoin’s case, the “base layer” of its valuation is determined by the energy and computational resources required for mining. This power law behavior is therefore a consequence of Bitcoin’s fundamental design: as block subsidies decrease and mining efficiency improves, the minimum sustainable price follows an upward trajectory dictated by production costs. **Bitcoin as an Energy-Based System** Power laws commonly emerge in natural systems involving energy constraints, from thermodynamics to biological ecosystems and planetary dynamics. Bitcoin, as an energy-based monetary system, exhibits similar characteristics. Mining requires significant electricity and computational power, and as the difficulty adjustment ensures a competitive equilibrium, the cost of mining a Bitcoin remains closely tied to its market value over the long run. Unlike traditional fiat currencies, which are controlled by central banks and subject to arbitrary monetary expansion, Bitcoin’s supply schedule is immutable. Its economic foundation is rooted in **proof of work**, where value is derived from energy expenditure. This fundamental linkage between energy and price explains why Bitcoin’s valuation has adhered to a power law trajectory. It is an entropy engine, and follows physical laws related to energy and entropy. However, this pattern is not a permanent feature of Bitcoin’s monetary future—it is, rather, an indication of Bitcoin’s **early-stage monetization process**. **The Transition from Mining-Based Pricing to a Business Cycle** A crucial implication of Bitcoin’s price following a power law dictated by mining costs is that it suggests Bitcoin has yet to fully mature as money. If Bitcoin were already a widely adopted monetary standard, its valuation would no longer be primarily influenced by the floor mining costs but instead by macroeconomic forces—specifically, the natural fluctuations of the business cycle. In a world where Bitcoin is the dominant global currency, the “price of money” (which correlates with the cost of capital and prevailing interest rates) would fluctuate according to the broader economic cycle. The dynamics would resemble those of natural interest rate cycles described by the Austrian School of Economics: - During periods of economic expansion, lower interest rates spur increased investment and consumption, prices slightly rise, and savings deplete. - As savings decline and prices rise, interest rates naturally rise as well, leading to reduced investment and spending, initiating a contractionary phase and lowered prices. - During the contraction, savings accumulate, more capital becomes available, and interest rates and prices decline. - With the availability of capital, lower interest rates and lowered prices, the economy is now ready to enter a phase of investment and expansion once again. - This oscillatory process continues indefinitely, driven by real economic growth rather than central bank intervention. If Bitcoin were fully monetized, its price would no longer oscillate based on mining halvings and energy costs but instead reflect **economic expansion and contraction cycles**—just as traditional currencies do when not artificially manipulated by central banks. **The Early Stage Indicator: Bitcoin’s Dependence on Mining Costs** Today, Bitcoin’s price still “bounces” off the power law baseline, indicating that its valuation remains primarily anchored to its minimum cost of production. This means that, while Bitcoin is widely recognized as an asset, it has not yet reached the level of adoption where its price is dictated by macroeconomic cycles. A future in which Bitcoin is used as a primary medium of exchange and unit of account would necessarily imply a **decoupling from mining-driven pricing**. Instead of periodic halvings triggering speculative bull runs followed by crashes, Bitcoin’s price would become far more stable, with fluctuations primarily driven by business cycle dynamics. The continued adherence to the power law model, therefore, is evidence that Bitcoin is still in an early phase of adoption—where mining remains a primary determinant of price. **Conclusion** Bitcoin’s price trajectory has long conformed to a power law, reflecting the underlying energy costs of mining. This characteristic, however, is likely not a permanent feature but rather a hallmark of Bitcoin’s early stage as an emerging monetary system. As adoption increases and Bitcoin becomes widely used as money, its price should transition away from being dictated by mining costs and should instead fluctuate according to the natural oscillations of the business cycle. The persistence of Bitcoin’s power law trend is a sign that it remains in its infancy. The real transformation will occur when Bitcoin is no longer bound to its production cost but is instead driven by the natural ebb and flow of savings, investment, and capital cycles—marking its full emergence as a global monetary system. Disclaimer: The information provided in this blog is for informational and educational purposes only and should not be construed as financial advice. Please consult with a financial advisor or conduct your own research before making any financial decisions.
@ 554ab6fe:c6cbc27e
2025-02-14 16:29:51Bitcoin’s Price and the Power Law: A Reflection of Energy and the Early Stages of Monetary Adoption Introduction Bitcoin’s price trajectory has long puzzled analysts, with its seemingly chaotic booms and busts. However, when examined through the lens of power laws, a pattern emerges—one that is fundamentally tied to Bitcoin’s energy-based production cost. This article argues that Bitcoin’s price has historically followed a power law because its underlying cost structure is dictated by mining, an energy-intensive process. However, this relationship will not persist indefinitely. I propose that as Bitcoin matures into a widely adopted monetary system, its price will decouple from mining production costs and instead oscillate in accordance with natural business cycles, much like traditional forms of money. **Bitcoin’s Price and the Power Law** Source and Credit: Giovanni Santostasi’s “[The Bitcoin Power Law](https://giovannisantostasi.medium.com/the-bitcoin-power-law-theory-962dfaf99ee9)” When Bitcoin’s price is plotted on a logarithmic scale against time, a strikingly straight-line trajectory appears, punctuated by cycles of rapid price expansion (bull markets) followed by severe corrections (bear markets). These perturbations correspond to Bitcoin’s well-known halving cycles, which occur approximately every four years and reduce the block reward paid to miners, effectively doubling the cost of production per Bitcoin. Historically, Bitcoin’s price has always returned to a fundamental minimum—one that closely aligns with the average cost of mining. This observation suggests that Bitcoin’s power law price behavior is not arbitrary but rather a reflection of its fundamental energy constraints. As in many natural systems governed by power laws, energy dynamics play a central role. In Bitcoin’s case, the “base layer” of its valuation is determined by the energy and computational resources required for mining. This power law behavior is therefore a consequence of Bitcoin’s fundamental design: as block subsidies decrease and mining efficiency improves, the minimum sustainable price follows an upward trajectory dictated by production costs. **Bitcoin as an Energy-Based System** Power laws commonly emerge in natural systems involving energy constraints, from thermodynamics to biological ecosystems and planetary dynamics. Bitcoin, as an energy-based monetary system, exhibits similar characteristics. Mining requires significant electricity and computational power, and as the difficulty adjustment ensures a competitive equilibrium, the cost of mining a Bitcoin remains closely tied to its market value over the long run. Unlike traditional fiat currencies, which are controlled by central banks and subject to arbitrary monetary expansion, Bitcoin’s supply schedule is immutable. Its economic foundation is rooted in **proof of work**, where value is derived from energy expenditure. This fundamental linkage between energy and price explains why Bitcoin’s valuation has adhered to a power law trajectory. It is an entropy engine, and follows physical laws related to energy and entropy. However, this pattern is not a permanent feature of Bitcoin’s monetary future—it is, rather, an indication of Bitcoin’s **early-stage monetization process**. **The Transition from Mining-Based Pricing to a Business Cycle** A crucial implication of Bitcoin’s price following a power law dictated by mining costs is that it suggests Bitcoin has yet to fully mature as money. If Bitcoin were already a widely adopted monetary standard, its valuation would no longer be primarily influenced by the floor mining costs but instead by macroeconomic forces—specifically, the natural fluctuations of the business cycle. In a world where Bitcoin is the dominant global currency, the “price of money” (which correlates with the cost of capital and prevailing interest rates) would fluctuate according to the broader economic cycle. The dynamics would resemble those of natural interest rate cycles described by the Austrian School of Economics: - During periods of economic expansion, lower interest rates spur increased investment and consumption, prices slightly rise, and savings deplete. - As savings decline and prices rise, interest rates naturally rise as well, leading to reduced investment and spending, initiating a contractionary phase and lowered prices. - During the contraction, savings accumulate, more capital becomes available, and interest rates and prices decline. - With the availability of capital, lower interest rates and lowered prices, the economy is now ready to enter a phase of investment and expansion once again. - This oscillatory process continues indefinitely, driven by real economic growth rather than central bank intervention. If Bitcoin were fully monetized, its price would no longer oscillate based on mining halvings and energy costs but instead reflect **economic expansion and contraction cycles**—just as traditional currencies do when not artificially manipulated by central banks. **The Early Stage Indicator: Bitcoin’s Dependence on Mining Costs** Today, Bitcoin’s price still “bounces” off the power law baseline, indicating that its valuation remains primarily anchored to its minimum cost of production. This means that, while Bitcoin is widely recognized as an asset, it has not yet reached the level of adoption where its price is dictated by macroeconomic cycles. A future in which Bitcoin is used as a primary medium of exchange and unit of account would necessarily imply a **decoupling from mining-driven pricing**. Instead of periodic halvings triggering speculative bull runs followed by crashes, Bitcoin’s price would become far more stable, with fluctuations primarily driven by business cycle dynamics. The continued adherence to the power law model, therefore, is evidence that Bitcoin is still in an early phase of adoption—where mining remains a primary determinant of price. **Conclusion** Bitcoin’s price trajectory has long conformed to a power law, reflecting the underlying energy costs of mining. This characteristic, however, is likely not a permanent feature but rather a hallmark of Bitcoin’s early stage as an emerging monetary system. As adoption increases and Bitcoin becomes widely used as money, its price should transition away from being dictated by mining costs and should instead fluctuate according to the natural oscillations of the business cycle. The persistence of Bitcoin’s power law trend is a sign that it remains in its infancy. The real transformation will occur when Bitcoin is no longer bound to its production cost but is instead driven by the natural ebb and flow of savings, investment, and capital cycles—marking its full emergence as a global monetary system. Disclaimer: The information provided in this blog is for informational and educational purposes only and should not be construed as financial advice. Please consult with a financial advisor or conduct your own research before making any financial decisions. @ da0b9bc3:4e30a4a9
2025-02-14 15:21:29It's Finally here Stackers! It's Friday! We're about to kick off our weekends with some feel good tracks. Let's get the party started. Bring me those Feel Good tracks. It is valentine's so let's get all gooey and soft, let's feel good and loved up. If the world was ending, I'd wanna be next to you. https://youtu.be/kPa7bsKwL-c?si=XbAaVfCHLZw6_0n6 Talk Music. Share Tracks. Zap Sats. Let's go! originally posted at https://stacker.news/items/885888
@ da0b9bc3:4e30a4a9
2025-02-14 15:21:29It's Finally here Stackers! It's Friday! We're about to kick off our weekends with some feel good tracks. Let's get the party started. Bring me those Feel Good tracks. It is valentine's so let's get all gooey and soft, let's feel good and loved up. If the world was ending, I'd wanna be next to you. https://youtu.be/kPa7bsKwL-c?si=XbAaVfCHLZw6_0n6 Talk Music. Share Tracks. Zap Sats. Let's go! originally posted at https://stacker.news/items/885888 @ 9e69e420:d12360c2
2025-02-14 15:14:34A Russian drone attack has struck the radiation shelter at Chernobyl, according to Ukrainian President Volodymyr Zelensky. The strike caused a fire, but it has since been extinguished, and radiation levels remain stable. The International Atomic Energy Agency (IAEA) confirmed that no casualties occurred and that monitoring continues. Rafael Mariano Grossi, IAEA's director general, emphasized the need for caution. Chernobyl, site of the 1986 nuclear disaster, contains a protective shield costing $1.6 billion. Disaster prevention remains a priority as the conflict unfolds. The incident occurred shortly before the meeting of world powers at the Munich Security Conference in Germany.
@ 9e69e420:d12360c2
2025-02-14 15:14:34A Russian drone attack has struck the radiation shelter at Chernobyl, according to Ukrainian President Volodymyr Zelensky. The strike caused a fire, but it has since been extinguished, and radiation levels remain stable. The International Atomic Energy Agency (IAEA) confirmed that no casualties occurred and that monitoring continues. Rafael Mariano Grossi, IAEA's director general, emphasized the need for caution. Chernobyl, site of the 1986 nuclear disaster, contains a protective shield costing $1.6 billion. Disaster prevention remains a priority as the conflict unfolds. The incident occurred shortly before the meeting of world powers at the Munich Security Conference in Germany. @ 0000065e:9b5b4c75
2025-02-14 14:41:24Se está armando un considerable revuelo con las medidas, impulsadas por La Liga y Telefónica, que afectan a servicios relacionados con Cloudflare y a muchos de sus usuarios que tienen que soportar la restricción en la operatividad de los mismos. Pero, ¿cómo puede ser que un tema de “piratería” acabe afectando, con aparente impunidad, a servicios legítimos? Aquí intentaremos explicarlo. Desde tiempos casi inmemoriales la industria relacionada con la explotación de los contenidos, y prestaciones, sujetos a derechos de propiedad intelectual han sido tremendamente imaginativos a la hora de buscar mecanismos que aseguren sus pingües beneficios. Como los jueces no solían hacerles caso, impulsaron modificaciones legislativas para quitarlos de la ecuación, *administrativizando* el conflicto, como sucedió con la conocida como Ley Sinde. Pero los mecanismos de esta Ley no eran lo suficientemente ágiles para lo que quería la industria, por lo que había que darle otra vuelta de tuerca al asunto, lo que se hizo con ocasión del art. 138 de la Ley de Propiedad Intelectual. En síntesis, el truco es el siguiente: - El titular de los derechos acude a un Juzgado honesto, imparcial y preocupado, como no podía ser de otra forma, por la defensa de los derechos fundamentales reconocidos constitucionalmente. - Ahí plantea una demanda, no contra quien considera infractor de esos derechos (Cloudflare o los usuarios que hacen uso ilícito de sus servicios), sino contra los operadores de telecomunicaciones que dan acceso a internet, en una aplicación torticera y kafkiana del art. 138 LPI (sobre el que volveremos más adelante) pidiendo una serie de medidas. - Las operadoras se "allanan" a la demanda, es decir, reconocen y aceptan las pretensiones del demandante, y el juez [concede las medidas](https://bandaancha.eu/articulos/2-nuevos-listados-obligan-operadoras-10322). Con este truco, todos se guardan las vergüenzas unos a otros: - Los demandantes: Nosotros solamente pedimos las medidas. Es el juez el que las acuerda. - El juez: A mi me viene uno pidiendo una cosa, la parte demandada se allana. Tengo que conceder lo pedido. - El operador: Tengo que hacer caso al juez. Para conseguir esto, los demandantes llevan a cabo una torticera interpretación de los artículos 138 y 139 de la LPI, que en la aplicación que se está haciendo de los mismos convierte dichos preceptos en inconstitucionales, pues, en la práctica, se condena a una pluralidad de personas al cierre de su página web o restricción de sus servicios en España sin darles la más mínima oportunidad defenderse, en una flagrante vulneración tanto de la libertad de expresión e información (art. 20 de la Constitución) como del derecho a la tutela judicial efectiva (art. 24 de la Constitución), pues causa una evidente indefensión la producción de una condena sin posibilidad alguna de defenderse, por no hablar de que puede afectar también a servicios críticos o esenciales, como por ejemplo hospitales y centros de emergencias. Los artículos 138 y 139, formalmente, permiten demandar directamente a los prestadores de servicios de intermediación (operadores que dan acceso a Internet), para instar la suspensión de los servicios que estos presenten a infractores de derechos de propiedad intelectual. En concreto estos son los preceptos a considerar: > > Artículo 138. Acciones y **medidas cautelares urgentes**. El titular de los derechos reconocidos en esta ley, sin perjuicio de otras acciones que le correspondan, podrá instar el cese de la actividad ilícita del infractor y exigir la indemnización de los daños materiales y morales causados, en los términos previstos en los artículos 139 y 140. También podrá instar la publicación o difusión, total o parcial, de la resolución judicial o arbitral en medios de comunicación a costa del infractor…. > > Tanto las medidas de cesación específicas contempladas en el artículo 139.1.h) como las medidas cautelares previstas en el artículo 141.6 podrán también solicitarse, cuando sean apropiadas, contra los intermediarios a cuyos servicios recurra un tercero para infringir derechos de propiedad intelectual…. > > Art. 139. h) La suspensión de los servicios prestados por intermediarios a terceros que se valgan de ellos para infringir derechos de propiedad intelectual, sin perjuicio de lo dispuesto en la Ley 34/2002, de 11 de julio, de servicios de la sociedad de la información y de comercio electrónico.” A nadie honesto, y con un mínimo de sentido común e intención de realizar una hermeneútica correcta, puede escapársele que dichos artículos no están pensados para el supuesto de hecho que nos ocupa, donde no consta la existencia de una válida declaración de infracción de propiedad intelectual, que se ha construido de forma artificial, sin respeto a los principios de dualidad y contradicción de partes, generando una evidente indefensión a las partes que se ven perjudicadas por la pretensión de los demandantes. La Audiencia Provincial de Barcelona tuvo oportunidad de analizar estas peculiares y exóticas previsiones normativas en su Sentencia nº 115/2018, de fecha 20 de febrero de 2018, que es citada por las sentencias que afectan a la polémica que analizamos, y donde sobre la génesis de estos preceptos nos indica: > “15. El redactado de los artículos 138 y 139 del TRLPI , en lo que afecta a **la extensión de las acciones de cesación a los intermediarios, no aparecía en el texto originario de la Ley**, es consecuencia de una de las múltiples reformas que se han llevado a efecto para adaptar la normativa española sobre propiedad intelectual a la normativa comunitaria. Concretamente, la reforma que afecta a estos preceptos es la llevada a efecto por la Ley 23/2006, de 7 de julio, por la que se modifica el texto refundido de la Ley de Propiedad Intelectual, aprobado por el Real Decreto Legislativo 1/1996, de 12 de abril. > La Exposición de Motivos de esta reforma indica las razones de la misma: > «La razón de esta reforma del texto refundido de la Ley de Propiedad Intelectual, aprobado por el Real Decreto Legislativo 1/1996, de 12 de abril, responde a la necesidad de incorporar al derecho español una de las últimas directivas aprobadas en materia de propiedad intelectual, la Directiva 2001/29/CE del Parlamento Europeo y del Consejo, de 22 de mayo de 2001, relativa a la armonización de determinados aspectos de los derechos de autor y derechos afines a los derechos de autor en la sociedad de la información, con la que la Unión Europea, a su vez, ha querido cumplir los Tratados de la Organización Mundial de la Propiedad Intelectual (OMPI) de 1996 sobre Derecho de Autor y sobre Interpretación o Ejecución y Fonogramas.» > Y, en el último punto de la Exposición de Motivos, se especifica el alcance de la reforma respecto de las acciones y procedimientos: > «Respecto a las acciones y procedimientos que los titulares de los derechos pueden instar, se establece, por primera vez, la **posibilidad de solicitar medidas cautelares contra los intermediarios** a cuyos servicios recurre un tercero para infringir derechos de propiedad intelectual, sin la exigencia de que el intermediario sea también infractor.» Es decir, la propia norma, en su exposición de motivos, limita la aplicación de los meritados preceptos, en cuanto a la posibilidad de dirigir la acción directamente contra los intermediarios, al **ámbito de las medidas cautelares.** Ello se deriva igualmente de lo dispuesto en las disposiciones europeas aplicables, como indica la sentencia al decir: > “Por lo tanto, la interpretación de estos preceptos debe hacerse en consonancia con la normativa de la Unión Europea y la jurisprudencia que la desarrolla. > 16.- La Directiva 2001/29/CE en su considerando 59 destaca uno de los objetivos de la misma: «Sobre todo en el entorno digital, es posible que terceras partes utilicen cada vez con mayor frecuencia los servicios de intermediarios para llevar a cabo actividades ilícitas. En muchos casos, estos intermediarios son quienes están en mejor situación de poner fin a dichas actividades ilícitas. Así pues, y sin perjuicio de otras sanciones o recursos contemplados, los titulares de los derechos deben tener la posibilidad de solicitar **medidas cautelares** contra el intermediario que transmita por la red la infracción contra la obra o prestación protegidas cometida por un tercero. Esta posibilidad debe estar abierta aun cuando los actos realizados por el intermediario estén exentos en virtud del artículo 5. Debe corresponder a la legislación nacional de los Estados miembros regular las condiciones y modalidades de dichas **medidas cautelares**.» > Y, para la consecución de este objetivo, el artículo 8.3 de la Directiva establece que: > «3. Los Estados miembros velarán porque los titulares de los derechos estén en condiciones de solicitar **medidas cautelares** contra los intermediarios a cuyos servicios recurra un tercero para infringir un derecho de autor o un derecho afín a los derechos de autor.» > 17.- La Directiva comunitaria en principio prevé únicamente la existencia de **medidas cautelares** frente a los intermediarios, así aparece también en el TRLPI ya que el artículo 138 en sus incisos finales hace referencia a medidas cautelares, es decir, medidas instrumentales, necesarias para asegurar la efectividad de la tutela judicial que pudiera otorgarse en la sentencia estimatoria que se dictare.” > No obstante lo anterior, **la Audiencia Provincial**, en un pronunciamiento que, entendemos, cuando menos de dudosa constitucionalidad, considera que la Ley permite el ejercicio de estas pretensiones más allá del ámbito de las “acciones y **medidas cautelares urgentes**” que menciona la Exposición de Motivos, la normativa europea y el propio título del art. 138, argumentando lo siguiente: > “Sin embargo, al desarrollarse el contenido de las acciones de cesación el artículo 139 incluye expresamente la suspensión de los servicios prestados por el intermediario (art. 139.1.h), lo que puede habilitar no sólo a la solicitud de medidas cautelares, sino también a la petición, como pretensión principal, de la suspensión de los servicios. Este régimen legal interno, sin duda más amplio que el derivado del artículo 8.3 de la Directiva, permite abrir una serie de escenarios procesales con trascendencia material por cuanto podría habilitar a dirigir demandas únicamente frente a los intermediarios y no frente al infractor, o podría también habilitar cauce procesal para iniciar acciones frente a los intermediarios sin que exista una previa declaración de infracción imputable, en todo caso, a quien se vale de esos proveedores de servicios para realizar una actividad infractora.” Parece de dudosa constitucionalidad que se extienda, más allá del estricto ámbito cautelar urgente, la posibilidad de acordar una medida como el cierre de una página web o restricción de servicios sin contar con la presencia en el litigio de las personas afectadas por las medidas. Pero **la Audiencia limita esta posibilidad y sí establece, al menos, la necesidad de que exista una constatación de la existencia de infracción**, como presupuesto para el ejercicio de la acción. En este sentido, la Audiencia considera que un pronunciamiento administrativo al respecto no es suficiente, pero, sorprendentemente, sí considera que un informe de parte no sometido a contradicción, como sucede en el caso de la Sentencia del Juzgado de lo Mercantil nº 9, en cambio, sí constata la existencia de infracción. En concreto, así se pronuncia la Audiencia: > “Estos problemas son los que se plantean en el supuesto de autos, dado que no ha sido llamado a juicio el titular de la página web supuestamente infractora (www.exvagos.com): no se ha producido un pronunciamiento civil en el que se declare la infracción por parte del titular de esta página web, aunque sí existe un pronunciamiento administrativo ante la Comisión de Propiedad Intelectual… > Por lo tanto, la **constatación de una infracción de derechos de propiedad intelectual** es un presupuesto ineludible para poder ejercitar las acciones previstas en los artículos 138 y 139 del TRLPI… > el procedimiento administrativo previo no puede servir, por sí solo, para dar por cumplido o satisfecho el presupuesto previo de infracción por parte del titular de la web, ni la retirada de contenidos puede tener el alcance de presunción de infracción…. > en los autos constan otros **documentos en los que se acredita de modo eficiente la realidad de la infracción**. Se trata, concretamente de la **prueba pericial** aportada como documento número 12 de la demanda… El examen de esa prueba pericial sí permite concluir que la página web exvagos facilita el acceso a contenidos y habilita un sistema de intercambio de archivos que infringe derechos de propiedad intelectual. Así lo hace ampliamente el juez de instancia en la Sentencia recurrida (fundamento de derecho cuarto). ” En este mismo sentido, sobre la necesidad de constatar la existencia de la infracción, se pronuncia la Sentencia nº 15/2018, del Juzgado de lo Mercantil nº 6 de Barcelona, al decir, en un caso similar, que: > “... el demandante **no quedará exento de probar**, con carácter prejudicial la infracción sobre los derechos de propiedad intelectual.” Pues bien, **en el caso de Cloudflare, al menos hasta donde es conocido, no existe ninguna constatación de esa supuesta infracción** (más allá de un “informe técnico” no sometido a contradicción), y los demandantes, acaso en connivencia con los demandados (lo cual es obvio en el caso de TELEFÓNICA, que actúa, con diferentes empresas, como demandante y demandado), o conscientes de que para estos era más fácil allanarse que oponerse a unas pretensiones que no representan perjuicio alguno para ellos, construyen esta farsa de proceso judicial, para conseguir la restricción de los servicios, sin ofrecer la más mínima posibilidad de intervención en el litigio. Debemos mencionar que algunas sentencias, como la anteriormente citada del Juzgado de lo Mercantil nº 6 de Barcelona, basan la procedencia de la medida acordada contra las páginas web en que sus “**titulares no han podido ser identificados ni localizados**”, en cuyo caso podría considerarse pertinente un procedimiento sin la participación del presunto infractor. Pero eso no es lo que parece que suceda en este caso, donde al menos Cloudflare se encuentra perfectamente identificada. Como vemos, la extensión de la posibilidad que tiene el titular de los derechos de accionar directamente contra los prestadores de servicios de intermediación fuera del ámbito cautelar urgente es algo que no da la impresión de estar previsto en la Ley y que, desde luego, es de una más que dudosa constitucionalidad. Si la LPI permite demandar al prestador de servicios, sin conocimiento siquiera del titular de los derechos que se ven afectados, y sin una declaración judicial dictada respetando los principios de igualdad entre las partes afectadas y de contradicción, con base únicamente en un documento de parte, que no ha sido sometido a contradicción, entonces dicha previsión ha de considerarse inconstitucional, al violar el art. 24 y la tutela judicial efectiva. Conforme a una interpretación razonable de la Ley, la parte actora podría haber solicitado medidas cautelares frente a los prestadores de servicios, pero de forma coetánea o inmediatamente posterior demandar a los presuntos infractores, a fin de que en un proceso contradictorio se determinara si realmente existe infracción y permitir, a los afectados por las medidas poder exponer su visión del asunto en sede judicial. Podría pensarse, así, que el Juzgado aceptó una interpretación inconstitucional de los artículos 138 y 139 LPI, y no tuvo en cuenta que el art. 21 LEC, establece que el allanamiento debe rechazarse cuando suponga, como es el caso, un perjuicio a tercero no demandado en el procedimiento, pues el art. 21 LEC indica que: > “Cuando el demandado se allane a todas las pretensiones del actor, el tribunal dictará sentencia condenatoria de acuerdo con lo solicitado por éste, pero si el allanamiento se hiciera en **fraude de ley** o supusiera renuncia **contra el interés general** o **perjuicio de tercero,** se dictará auto rechazándolo y seguirá el proceso adelante.” Las sentencias de los Juzgados de lo [Mercantil nº 6](https://www.poderjudicial.es/search/AN/openDocument/2d094260f53b5cdca0a8778d75e36f0d/20221006) y [9 de Barcelona](https://www.poderjudicial.es/search/AN/openDocument/3c85bed480cbb1daa0a8778d75e36f0d/20221004), que al parecer son las que sirven de base para las medidas que comentamos, exponen que no se perjudica a terceros, pero, como es notorio y ostensible, en este punto los juzgados de lo mercantil se equivocan del medio al medio, puesto que el allanamiento, sin duda alguna, supone un claro perjuicio de terceros, Cloudflare y sus usuarios legítimos, que ven cómo sus servicios son objeto de restricción, sin ofrecerles posibilidad de defenderse ni argumentar contra las pretensiones de las actoras, infringiendo así el art. 21 LEC, en cuya virtud, el allanamiento debe rechazarse cuando suponga, como es el caso, un perjuicio a tercero (mi mandante) no demandado en el procedimiento. De esta forma, como hemos expuesto, se ha articulado una suerte de procedimiento formal, inexistente en la práctica, para evitar un proceso contradictorio sobre su pretensión, eludiendo así la eventual participación de los afectados en el debate litigioso, algo que, deberemos convenir, supone una clara infracción del art. 24 de la Constitución, tal y como lo interpreta nuestro Tribunal Constitucional en sentencias como la STC 43/2010: > “Este Tribunal ha declarado reiteradamente que el derecho a la tutela judicial efectiva sin indefensión (art. 24.1 CE) garantiza a **todos los que puedan resultar afectados por la decisión que se dicte en un proceso judicial el derecho a conocer su existencia, a fin de que tengan la posibilidad de intervenir en él, ser oídos, y ejercer la defensa de sus derechos e intereses legítimos**. Esta necesidad de promover la defensa, en la medida de lo posible, mediante la debida contradicción, **impone a los órganos judiciales un especial deber de diligencia** que, en palabras de la STC 56/2001, de 26 de febrero, FJ 2, “tiene especial importancia en el proceso de ejecución”. En concreto, y por lo que respecta a la posibilidad de intervenir en un proceso de ejecución, hemos afirmado que el derecho a la tutela judicial efectiva habilita a quienes ostenten algún derecho o interés legítimo que pueda verse afectado por los actos de ejecución a comparecer y actuar en el procedimiento, aunque no hubieran sido parte en el proceso principal, y a este fin los arts. 270 LOPJ y 260.2 LEC exigen que las resoluciones judiciales se notifiquen no sólo a las partes procesales, sino también a las personas a quienes se refieran o puedan parar perjuicio (SSTC 229/2000, de 2 de octubre, FJ 3; 56/2001, de 26 de febrero, FJ 2).” Por otro lado, siguiendo la anterior sentencia, el art. 270 LOPJ impone el **deber de notificar las resoluciones judiciales**, no solo a las partes, sino “también **a quienes se refieran o puedan parar perjuicios**”, lo que, como indica la Audiencia Provincial de Barcelona en su Auto de 29 de junio de 2002, “va más allá de una mera facultad discrecional del juzgador, notificación que tiene por objeto poner en conocimiento de tales personas la resolución y posibilitar la defensa de su derecho inquietado o perturbado.” Y en el mismo sentido, el art. 150 LEC establece que “**también se notificará la pendencia del proceso a las personas que, según los mismos autos, puedan verse afectadas** por la resolución que ponga fin al procedimiento.” Da la impresión de que ambos preceptos han sido infringidos por los Juzgados y deberían determinar la nulidad de lo actuado y, por tanto, de las sentencias que comentamos. Como se ha expuesto, podría apreciarse una **vulneración del art. 21 de LEC, que impide acceder al allanamiento cuando ello suponga un perjuicio de tercero, fraude de Ley o contrarien intereses generales**, pero más allá de eso, podría dar lugar también a una **violación de la tutela judicial efectiva** reconocida en el art. 24 de la Constitución, desde el momento en que se obliga a unos terceros a soportar una condena sin posibilidad alguna de un proceso con unas mínimas garantías. Como hemos dicho, la previsión del art. 138 LPI, que permite solicitar la suspensión de los servicios prestados por intermediarios a terceros directamente contra dichos intermediarios, queda circunscrita al ámbito establecido en el propio título del art. 138, “Acciones y medidas cautelares urgentes” y no constituyen una acción autónoma fuera del ámbito cautelar urgente. En segundo lugar, una interpretación de dicho precepto, en el sentido de que permita el ejercicio de una acción de condena (en la práctica el cierre páginas web y diversos servicios relacionados con estas), sin posibilidad alguna de defensa de los afectados (Cloudflare y sus usuarios), iría en contra del art. 24 de la Constitución y si dicha Ley debe interpretarse en este sentido, sería inconstitucional. Finalmente, si se admite la existencia de esa acción independiente y que la misma es constitucional, su procedencia debe conectarse con dos requisitos: una constatación efectiva de la existencia de infracción, que entendemos debe producirse en el marco de un proceso contradictorio donde se ofrezca al presunto infractor la posibilidad de defenderse, así como una imposibilidad de identificación y/o localización del mismo. El principio fundamental que rige el desarrollo del procedimiento en su conjunto es el derecho de las partes a no sufrir indefensión. Y la indefensión proscrita por el artículo 24.1 de la Constitución no es la meramente formal, sino la material, es decir, aquella que haya producido a la parte un real y efectivo menoscabo de sus posibilidades de defensa. Cabe citar en este sentido la [Sentencia del Tribunal Constitucional nº 161/2006](https://hj.tribunalconstitucional.es/HJ/es/Resolucion/Show/5763), de 22 de mayo de 2006: > “Según una consolidada doctrina constitucional el derecho a la tutela judicial efectiva sin indefensión que se reconoce en el artículo 24.1 de la Constitución Española **garantiza el derecho a acceder al proceso en condiciones de poder ser oído y ejercer la defensa de los derechos e intereses legítimos**… La finalidad material de esta exigencia es la de llevar al conocimiento de los afectados las resoluciones judiciales, para que puedan adoptar la postura que estimen pertinente en defensa de sus intereses (por todas, las sentencias del Tribunal Constitucional 77/1997, de 21 de abril, FJ 2; y 216/2002, de 25 de noviembre, FJ 2)." Esta trascendencia constitucional de la correcta configuración de los procesos, a fin de que los eventuales afectados puedan ser oídos y defenderse adecuadamente se extiende también a procedimientos en los que, formalmente, se configuran como terceros, como sucede en este caso. Sirva como muestra de ello, la STC 43/2010, de 26 de julio que contiene unos pronunciamientos perfectamente aplicables al caso, si sustituimos las referencias a “ejecución” por “medidas de cesación”: > “Este Tribunal ha declarado reiteradamente que el derecho a la tutela judicial efectiva sin indefensión (art. 24.1 CE) garantiza a **todos los que puedan resultar afectados por la decisión que se dicte en un proceso judicial el derecho a conocer su existencia, a fin de que tengan la posibilidad de intervenir en él, ser oídos, y ejercer la defensa de sus derechos e intereses legítimos**. > > Esta necesidad de promover la defensa, en la medida de lo posible, mediante la **debida contradicción**, impone a los órganos judiciales un especial deber de diligencia que, en palabras de la STC 56/2001, de 26 de febrero, FJ 2, “tiene especial importancia en el proceso de ejecución”. En concreto, y por lo que respecta a la posibilidad de intervenir en un proceso de ejecución, hemos afirmado que el **derecho a la tutela judicial efectiva habilita a quienes ostenten algún derecho o interés legítimo que pueda verse afectado** por los actos de ejecución a comparecer y actuar en el procedimiento, aunque no hubieran sido parte en el proceso principal, y a este fin los arts. 270 LOPJ y 260.2 LEC exigen que las resoluciones judiciales se notifiquen no sólo a las partes procesales, sino también a las personas a quienes se refieran o puedan parar perjuicio (SSTC 229/2000, de 2 de octubre, FJ 3; 56/2001, de 26 de febrero, FJ 2). > > ...Afirmamos en aquel caso que ello “provoca la indefensión de la demandante de amparo, pues contra el mandato contenido en el art. 24.1 CE de promover la defensión mediante la correspondiente contradicción, y sin perjuicio del pronunciamiento que pueda recaer, de lo que se resuelva sobre la posesión y sobre la posible reserva de las acciones que puedan corresponder a los implicados, conforme acertadamente mantiene el Ministerio Fiscal, el órgano judicial acordó el lanzamiento del propietario y poseedor legítimo de una vivienda sin tan siquiera permitirle comparecer a defender su derecho en un procedimiento contradictorio” (FJ 9). > > En definitiva, de nuestra doctrina se desprende con **absoluta claridad que la interdicción de la indefensión consagrada en el art. 24.1 CE impone a los órganos judiciales el deber de velar por que quienes ostenten algún derecho o interés legítimo en un proceso** de ejecución, aunque no hayan sido parte en el proceso principal, **puedan comparecer y ser oídos en el mismo para garantizar su defensa**, sin perjuicio del pronunciamiento que pueda recaer y de la posible existencia de otras acciones que puedan corresponder a los afectados. > > …En definitiva, y como afirma el Ministerio Fiscal, **el órgano judicial no actuó con la diligencia debida en orden a procurar que los demandantes de amparo pudieran tener conocimiento y comparecer en un proceso** ejecutivo **en el que resultaban afectados sus intereses**... Y dicho comportamiento del órgano judicial **causó indefensión constitucionalmente relevante**, pues **les privó de su derecho a ser oídos y les impidió el ejercicio del derecho de defensa de sus legítimos derechos e intereses** sobre el citado inmueble, sin que exista dato alguno en las actuaciones del que se desprenda que los recurrentes conocieran la existencia del procedimiento ejecutivo o que no hayan actuado con la diligencia debida en orden a facilitar su comparecencia en el citado proceso.” Es evidente que a los afectados por las medidas **se les privó del derecho a ser oídos** y **se les impidió el ejercicio del derecho de defensa** de sus legítimos intereses sobre las páginas y servicios que operaban, por lo que se ha producido una **violación del derecho a la tutela judicial efectiva** reconocida en el art. 24 de la Constitución. Además, las medidas de bloqueo de direcciones compartidas afectan también a la **libertad de expresión e información** de terceros que no guardan relación alguna con el conflicto y, lo que es peor, puede tener una **negativa incidencia en servicios que podrían ser críticos,** lo que es un comportamiento peligroso, irresponsable y negligente. Por todas estas razones, las sentencias deberían ser anuladas y las medidas derivadas de ellas dejadas sin efecto, ofreciendo en todo caso a los afectados la posibilidad de ser oídos en juicio y defender sus legítimos intereses.
@ 0000065e:9b5b4c75
2025-02-14 14:41:24Se está armando un considerable revuelo con las medidas, impulsadas por La Liga y Telefónica, que afectan a servicios relacionados con Cloudflare y a muchos de sus usuarios que tienen que soportar la restricción en la operatividad de los mismos. Pero, ¿cómo puede ser que un tema de “piratería” acabe afectando, con aparente impunidad, a servicios legítimos? Aquí intentaremos explicarlo. Desde tiempos casi inmemoriales la industria relacionada con la explotación de los contenidos, y prestaciones, sujetos a derechos de propiedad intelectual han sido tremendamente imaginativos a la hora de buscar mecanismos que aseguren sus pingües beneficios. Como los jueces no solían hacerles caso, impulsaron modificaciones legislativas para quitarlos de la ecuación, *administrativizando* el conflicto, como sucedió con la conocida como Ley Sinde. Pero los mecanismos de esta Ley no eran lo suficientemente ágiles para lo que quería la industria, por lo que había que darle otra vuelta de tuerca al asunto, lo que se hizo con ocasión del art. 138 de la Ley de Propiedad Intelectual. En síntesis, el truco es el siguiente: - El titular de los derechos acude a un Juzgado honesto, imparcial y preocupado, como no podía ser de otra forma, por la defensa de los derechos fundamentales reconocidos constitucionalmente. - Ahí plantea una demanda, no contra quien considera infractor de esos derechos (Cloudflare o los usuarios que hacen uso ilícito de sus servicios), sino contra los operadores de telecomunicaciones que dan acceso a internet, en una aplicación torticera y kafkiana del art. 138 LPI (sobre el que volveremos más adelante) pidiendo una serie de medidas. - Las operadoras se "allanan" a la demanda, es decir, reconocen y aceptan las pretensiones del demandante, y el juez [concede las medidas](https://bandaancha.eu/articulos/2-nuevos-listados-obligan-operadoras-10322). Con este truco, todos se guardan las vergüenzas unos a otros: - Los demandantes: Nosotros solamente pedimos las medidas. Es el juez el que las acuerda. - El juez: A mi me viene uno pidiendo una cosa, la parte demandada se allana. Tengo que conceder lo pedido. - El operador: Tengo que hacer caso al juez. Para conseguir esto, los demandantes llevan a cabo una torticera interpretación de los artículos 138 y 139 de la LPI, que en la aplicación que se está haciendo de los mismos convierte dichos preceptos en inconstitucionales, pues, en la práctica, se condena a una pluralidad de personas al cierre de su página web o restricción de sus servicios en España sin darles la más mínima oportunidad defenderse, en una flagrante vulneración tanto de la libertad de expresión e información (art. 20 de la Constitución) como del derecho a la tutela judicial efectiva (art. 24 de la Constitución), pues causa una evidente indefensión la producción de una condena sin posibilidad alguna de defenderse, por no hablar de que puede afectar también a servicios críticos o esenciales, como por ejemplo hospitales y centros de emergencias. Los artículos 138 y 139, formalmente, permiten demandar directamente a los prestadores de servicios de intermediación (operadores que dan acceso a Internet), para instar la suspensión de los servicios que estos presenten a infractores de derechos de propiedad intelectual. En concreto estos son los preceptos a considerar: > > Artículo 138. Acciones y **medidas cautelares urgentes**. El titular de los derechos reconocidos en esta ley, sin perjuicio de otras acciones que le correspondan, podrá instar el cese de la actividad ilícita del infractor y exigir la indemnización de los daños materiales y morales causados, en los términos previstos en los artículos 139 y 140. También podrá instar la publicación o difusión, total o parcial, de la resolución judicial o arbitral en medios de comunicación a costa del infractor…. > > Tanto las medidas de cesación específicas contempladas en el artículo 139.1.h) como las medidas cautelares previstas en el artículo 141.6 podrán también solicitarse, cuando sean apropiadas, contra los intermediarios a cuyos servicios recurra un tercero para infringir derechos de propiedad intelectual…. > > Art. 139. h) La suspensión de los servicios prestados por intermediarios a terceros que se valgan de ellos para infringir derechos de propiedad intelectual, sin perjuicio de lo dispuesto en la Ley 34/2002, de 11 de julio, de servicios de la sociedad de la información y de comercio electrónico.” A nadie honesto, y con un mínimo de sentido común e intención de realizar una hermeneútica correcta, puede escapársele que dichos artículos no están pensados para el supuesto de hecho que nos ocupa, donde no consta la existencia de una válida declaración de infracción de propiedad intelectual, que se ha construido de forma artificial, sin respeto a los principios de dualidad y contradicción de partes, generando una evidente indefensión a las partes que se ven perjudicadas por la pretensión de los demandantes. La Audiencia Provincial de Barcelona tuvo oportunidad de analizar estas peculiares y exóticas previsiones normativas en su Sentencia nº 115/2018, de fecha 20 de febrero de 2018, que es citada por las sentencias que afectan a la polémica que analizamos, y donde sobre la génesis de estos preceptos nos indica: > “15. El redactado de los artículos 138 y 139 del TRLPI , en lo que afecta a **la extensión de las acciones de cesación a los intermediarios, no aparecía en el texto originario de la Ley**, es consecuencia de una de las múltiples reformas que se han llevado a efecto para adaptar la normativa española sobre propiedad intelectual a la normativa comunitaria. Concretamente, la reforma que afecta a estos preceptos es la llevada a efecto por la Ley 23/2006, de 7 de julio, por la que se modifica el texto refundido de la Ley de Propiedad Intelectual, aprobado por el Real Decreto Legislativo 1/1996, de 12 de abril. > La Exposición de Motivos de esta reforma indica las razones de la misma: > «La razón de esta reforma del texto refundido de la Ley de Propiedad Intelectual, aprobado por el Real Decreto Legislativo 1/1996, de 12 de abril, responde a la necesidad de incorporar al derecho español una de las últimas directivas aprobadas en materia de propiedad intelectual, la Directiva 2001/29/CE del Parlamento Europeo y del Consejo, de 22 de mayo de 2001, relativa a la armonización de determinados aspectos de los derechos de autor y derechos afines a los derechos de autor en la sociedad de la información, con la que la Unión Europea, a su vez, ha querido cumplir los Tratados de la Organización Mundial de la Propiedad Intelectual (OMPI) de 1996 sobre Derecho de Autor y sobre Interpretación o Ejecución y Fonogramas.» > Y, en el último punto de la Exposición de Motivos, se especifica el alcance de la reforma respecto de las acciones y procedimientos: > «Respecto a las acciones y procedimientos que los titulares de los derechos pueden instar, se establece, por primera vez, la **posibilidad de solicitar medidas cautelares contra los intermediarios** a cuyos servicios recurre un tercero para infringir derechos de propiedad intelectual, sin la exigencia de que el intermediario sea también infractor.» Es decir, la propia norma, en su exposición de motivos, limita la aplicación de los meritados preceptos, en cuanto a la posibilidad de dirigir la acción directamente contra los intermediarios, al **ámbito de las medidas cautelares.** Ello se deriva igualmente de lo dispuesto en las disposiciones europeas aplicables, como indica la sentencia al decir: > “Por lo tanto, la interpretación de estos preceptos debe hacerse en consonancia con la normativa de la Unión Europea y la jurisprudencia que la desarrolla. > 16.- La Directiva 2001/29/CE en su considerando 59 destaca uno de los objetivos de la misma: «Sobre todo en el entorno digital, es posible que terceras partes utilicen cada vez con mayor frecuencia los servicios de intermediarios para llevar a cabo actividades ilícitas. En muchos casos, estos intermediarios son quienes están en mejor situación de poner fin a dichas actividades ilícitas. Así pues, y sin perjuicio de otras sanciones o recursos contemplados, los titulares de los derechos deben tener la posibilidad de solicitar **medidas cautelares** contra el intermediario que transmita por la red la infracción contra la obra o prestación protegidas cometida por un tercero. Esta posibilidad debe estar abierta aun cuando los actos realizados por el intermediario estén exentos en virtud del artículo 5. Debe corresponder a la legislación nacional de los Estados miembros regular las condiciones y modalidades de dichas **medidas cautelares**.» > Y, para la consecución de este objetivo, el artículo 8.3 de la Directiva establece que: > «3. Los Estados miembros velarán porque los titulares de los derechos estén en condiciones de solicitar **medidas cautelares** contra los intermediarios a cuyos servicios recurra un tercero para infringir un derecho de autor o un derecho afín a los derechos de autor.» > 17.- La Directiva comunitaria en principio prevé únicamente la existencia de **medidas cautelares** frente a los intermediarios, así aparece también en el TRLPI ya que el artículo 138 en sus incisos finales hace referencia a medidas cautelares, es decir, medidas instrumentales, necesarias para asegurar la efectividad de la tutela judicial que pudiera otorgarse en la sentencia estimatoria que se dictare.” > No obstante lo anterior, **la Audiencia Provincial**, en un pronunciamiento que, entendemos, cuando menos de dudosa constitucionalidad, considera que la Ley permite el ejercicio de estas pretensiones más allá del ámbito de las “acciones y **medidas cautelares urgentes**” que menciona la Exposición de Motivos, la normativa europea y el propio título del art. 138, argumentando lo siguiente: > “Sin embargo, al desarrollarse el contenido de las acciones de cesación el artículo 139 incluye expresamente la suspensión de los servicios prestados por el intermediario (art. 139.1.h), lo que puede habilitar no sólo a la solicitud de medidas cautelares, sino también a la petición, como pretensión principal, de la suspensión de los servicios. Este régimen legal interno, sin duda más amplio que el derivado del artículo 8.3 de la Directiva, permite abrir una serie de escenarios procesales con trascendencia material por cuanto podría habilitar a dirigir demandas únicamente frente a los intermediarios y no frente al infractor, o podría también habilitar cauce procesal para iniciar acciones frente a los intermediarios sin que exista una previa declaración de infracción imputable, en todo caso, a quien se vale de esos proveedores de servicios para realizar una actividad infractora.” Parece de dudosa constitucionalidad que se extienda, más allá del estricto ámbito cautelar urgente, la posibilidad de acordar una medida como el cierre de una página web o restricción de servicios sin contar con la presencia en el litigio de las personas afectadas por las medidas. Pero **la Audiencia limita esta posibilidad y sí establece, al menos, la necesidad de que exista una constatación de la existencia de infracción**, como presupuesto para el ejercicio de la acción. En este sentido, la Audiencia considera que un pronunciamiento administrativo al respecto no es suficiente, pero, sorprendentemente, sí considera que un informe de parte no sometido a contradicción, como sucede en el caso de la Sentencia del Juzgado de lo Mercantil nº 9, en cambio, sí constata la existencia de infracción. En concreto, así se pronuncia la Audiencia: > “Estos problemas son los que se plantean en el supuesto de autos, dado que no ha sido llamado a juicio el titular de la página web supuestamente infractora (www.exvagos.com): no se ha producido un pronunciamiento civil en el que se declare la infracción por parte del titular de esta página web, aunque sí existe un pronunciamiento administrativo ante la Comisión de Propiedad Intelectual… > Por lo tanto, la **constatación de una infracción de derechos de propiedad intelectual** es un presupuesto ineludible para poder ejercitar las acciones previstas en los artículos 138 y 139 del TRLPI… > el procedimiento administrativo previo no puede servir, por sí solo, para dar por cumplido o satisfecho el presupuesto previo de infracción por parte del titular de la web, ni la retirada de contenidos puede tener el alcance de presunción de infracción…. > en los autos constan otros **documentos en los que se acredita de modo eficiente la realidad de la infracción**. Se trata, concretamente de la **prueba pericial** aportada como documento número 12 de la demanda… El examen de esa prueba pericial sí permite concluir que la página web exvagos facilita el acceso a contenidos y habilita un sistema de intercambio de archivos que infringe derechos de propiedad intelectual. Así lo hace ampliamente el juez de instancia en la Sentencia recurrida (fundamento de derecho cuarto). ” En este mismo sentido, sobre la necesidad de constatar la existencia de la infracción, se pronuncia la Sentencia nº 15/2018, del Juzgado de lo Mercantil nº 6 de Barcelona, al decir, en un caso similar, que: > “... el demandante **no quedará exento de probar**, con carácter prejudicial la infracción sobre los derechos de propiedad intelectual.” Pues bien, **en el caso de Cloudflare, al menos hasta donde es conocido, no existe ninguna constatación de esa supuesta infracción** (más allá de un “informe técnico” no sometido a contradicción), y los demandantes, acaso en connivencia con los demandados (lo cual es obvio en el caso de TELEFÓNICA, que actúa, con diferentes empresas, como demandante y demandado), o conscientes de que para estos era más fácil allanarse que oponerse a unas pretensiones que no representan perjuicio alguno para ellos, construyen esta farsa de proceso judicial, para conseguir la restricción de los servicios, sin ofrecer la más mínima posibilidad de intervención en el litigio. Debemos mencionar que algunas sentencias, como la anteriormente citada del Juzgado de lo Mercantil nº 6 de Barcelona, basan la procedencia de la medida acordada contra las páginas web en que sus “**titulares no han podido ser identificados ni localizados**”, en cuyo caso podría considerarse pertinente un procedimiento sin la participación del presunto infractor. Pero eso no es lo que parece que suceda en este caso, donde al menos Cloudflare se encuentra perfectamente identificada. Como vemos, la extensión de la posibilidad que tiene el titular de los derechos de accionar directamente contra los prestadores de servicios de intermediación fuera del ámbito cautelar urgente es algo que no da la impresión de estar previsto en la Ley y que, desde luego, es de una más que dudosa constitucionalidad. Si la LPI permite demandar al prestador de servicios, sin conocimiento siquiera del titular de los derechos que se ven afectados, y sin una declaración judicial dictada respetando los principios de igualdad entre las partes afectadas y de contradicción, con base únicamente en un documento de parte, que no ha sido sometido a contradicción, entonces dicha previsión ha de considerarse inconstitucional, al violar el art. 24 y la tutela judicial efectiva. Conforme a una interpretación razonable de la Ley, la parte actora podría haber solicitado medidas cautelares frente a los prestadores de servicios, pero de forma coetánea o inmediatamente posterior demandar a los presuntos infractores, a fin de que en un proceso contradictorio se determinara si realmente existe infracción y permitir, a los afectados por las medidas poder exponer su visión del asunto en sede judicial. Podría pensarse, así, que el Juzgado aceptó una interpretación inconstitucional de los artículos 138 y 139 LPI, y no tuvo en cuenta que el art. 21 LEC, establece que el allanamiento debe rechazarse cuando suponga, como es el caso, un perjuicio a tercero no demandado en el procedimiento, pues el art. 21 LEC indica que: > “Cuando el demandado se allane a todas las pretensiones del actor, el tribunal dictará sentencia condenatoria de acuerdo con lo solicitado por éste, pero si el allanamiento se hiciera en **fraude de ley** o supusiera renuncia **contra el interés general** o **perjuicio de tercero,** se dictará auto rechazándolo y seguirá el proceso adelante.” Las sentencias de los Juzgados de lo [Mercantil nº 6](https://www.poderjudicial.es/search/AN/openDocument/2d094260f53b5cdca0a8778d75e36f0d/20221006) y [9 de Barcelona](https://www.poderjudicial.es/search/AN/openDocument/3c85bed480cbb1daa0a8778d75e36f0d/20221004), que al parecer son las que sirven de base para las medidas que comentamos, exponen que no se perjudica a terceros, pero, como es notorio y ostensible, en este punto los juzgados de lo mercantil se equivocan del medio al medio, puesto que el allanamiento, sin duda alguna, supone un claro perjuicio de terceros, Cloudflare y sus usuarios legítimos, que ven cómo sus servicios son objeto de restricción, sin ofrecerles posibilidad de defenderse ni argumentar contra las pretensiones de las actoras, infringiendo así el art. 21 LEC, en cuya virtud, el allanamiento debe rechazarse cuando suponga, como es el caso, un perjuicio a tercero (mi mandante) no demandado en el procedimiento. De esta forma, como hemos expuesto, se ha articulado una suerte de procedimiento formal, inexistente en la práctica, para evitar un proceso contradictorio sobre su pretensión, eludiendo así la eventual participación de los afectados en el debate litigioso, algo que, deberemos convenir, supone una clara infracción del art. 24 de la Constitución, tal y como lo interpreta nuestro Tribunal Constitucional en sentencias como la STC 43/2010: > “Este Tribunal ha declarado reiteradamente que el derecho a la tutela judicial efectiva sin indefensión (art. 24.1 CE) garantiza a **todos los que puedan resultar afectados por la decisión que se dicte en un proceso judicial el derecho a conocer su existencia, a fin de que tengan la posibilidad de intervenir en él, ser oídos, y ejercer la defensa de sus derechos e intereses legítimos**. Esta necesidad de promover la defensa, en la medida de lo posible, mediante la debida contradicción, **impone a los órganos judiciales un especial deber de diligencia** que, en palabras de la STC 56/2001, de 26 de febrero, FJ 2, “tiene especial importancia en el proceso de ejecución”. En concreto, y por lo que respecta a la posibilidad de intervenir en un proceso de ejecución, hemos afirmado que el derecho a la tutela judicial efectiva habilita a quienes ostenten algún derecho o interés legítimo que pueda verse afectado por los actos de ejecución a comparecer y actuar en el procedimiento, aunque no hubieran sido parte en el proceso principal, y a este fin los arts. 270 LOPJ y 260.2 LEC exigen que las resoluciones judiciales se notifiquen no sólo a las partes procesales, sino también a las personas a quienes se refieran o puedan parar perjuicio (SSTC 229/2000, de 2 de octubre, FJ 3; 56/2001, de 26 de febrero, FJ 2).” Por otro lado, siguiendo la anterior sentencia, el art. 270 LOPJ impone el **deber de notificar las resoluciones judiciales**, no solo a las partes, sino “también **a quienes se refieran o puedan parar perjuicios**”, lo que, como indica la Audiencia Provincial de Barcelona en su Auto de 29 de junio de 2002, “va más allá de una mera facultad discrecional del juzgador, notificación que tiene por objeto poner en conocimiento de tales personas la resolución y posibilitar la defensa de su derecho inquietado o perturbado.” Y en el mismo sentido, el art. 150 LEC establece que “**también se notificará la pendencia del proceso a las personas que, según los mismos autos, puedan verse afectadas** por la resolución que ponga fin al procedimiento.” Da la impresión de que ambos preceptos han sido infringidos por los Juzgados y deberían determinar la nulidad de lo actuado y, por tanto, de las sentencias que comentamos. Como se ha expuesto, podría apreciarse una **vulneración del art. 21 de LEC, que impide acceder al allanamiento cuando ello suponga un perjuicio de tercero, fraude de Ley o contrarien intereses generales**, pero más allá de eso, podría dar lugar también a una **violación de la tutela judicial efectiva** reconocida en el art. 24 de la Constitución, desde el momento en que se obliga a unos terceros a soportar una condena sin posibilidad alguna de un proceso con unas mínimas garantías. Como hemos dicho, la previsión del art. 138 LPI, que permite solicitar la suspensión de los servicios prestados por intermediarios a terceros directamente contra dichos intermediarios, queda circunscrita al ámbito establecido en el propio título del art. 138, “Acciones y medidas cautelares urgentes” y no constituyen una acción autónoma fuera del ámbito cautelar urgente. En segundo lugar, una interpretación de dicho precepto, en el sentido de que permita el ejercicio de una acción de condena (en la práctica el cierre páginas web y diversos servicios relacionados con estas), sin posibilidad alguna de defensa de los afectados (Cloudflare y sus usuarios), iría en contra del art. 24 de la Constitución y si dicha Ley debe interpretarse en este sentido, sería inconstitucional. Finalmente, si se admite la existencia de esa acción independiente y que la misma es constitucional, su procedencia debe conectarse con dos requisitos: una constatación efectiva de la existencia de infracción, que entendemos debe producirse en el marco de un proceso contradictorio donde se ofrezca al presunto infractor la posibilidad de defenderse, así como una imposibilidad de identificación y/o localización del mismo. El principio fundamental que rige el desarrollo del procedimiento en su conjunto es el derecho de las partes a no sufrir indefensión. Y la indefensión proscrita por el artículo 24.1 de la Constitución no es la meramente formal, sino la material, es decir, aquella que haya producido a la parte un real y efectivo menoscabo de sus posibilidades de defensa. Cabe citar en este sentido la [Sentencia del Tribunal Constitucional nº 161/2006](https://hj.tribunalconstitucional.es/HJ/es/Resolucion/Show/5763), de 22 de mayo de 2006: > “Según una consolidada doctrina constitucional el derecho a la tutela judicial efectiva sin indefensión que se reconoce en el artículo 24.1 de la Constitución Española **garantiza el derecho a acceder al proceso en condiciones de poder ser oído y ejercer la defensa de los derechos e intereses legítimos**… La finalidad material de esta exigencia es la de llevar al conocimiento de los afectados las resoluciones judiciales, para que puedan adoptar la postura que estimen pertinente en defensa de sus intereses (por todas, las sentencias del Tribunal Constitucional 77/1997, de 21 de abril, FJ 2; y 216/2002, de 25 de noviembre, FJ 2)." Esta trascendencia constitucional de la correcta configuración de los procesos, a fin de que los eventuales afectados puedan ser oídos y defenderse adecuadamente se extiende también a procedimientos en los que, formalmente, se configuran como terceros, como sucede en este caso. Sirva como muestra de ello, la STC 43/2010, de 26 de julio que contiene unos pronunciamientos perfectamente aplicables al caso, si sustituimos las referencias a “ejecución” por “medidas de cesación”: > “Este Tribunal ha declarado reiteradamente que el derecho a la tutela judicial efectiva sin indefensión (art. 24.1 CE) garantiza a **todos los que puedan resultar afectados por la decisión que se dicte en un proceso judicial el derecho a conocer su existencia, a fin de que tengan la posibilidad de intervenir en él, ser oídos, y ejercer la defensa de sus derechos e intereses legítimos**. > > Esta necesidad de promover la defensa, en la medida de lo posible, mediante la **debida contradicción**, impone a los órganos judiciales un especial deber de diligencia que, en palabras de la STC 56/2001, de 26 de febrero, FJ 2, “tiene especial importancia en el proceso de ejecución”. En concreto, y por lo que respecta a la posibilidad de intervenir en un proceso de ejecución, hemos afirmado que el **derecho a la tutela judicial efectiva habilita a quienes ostenten algún derecho o interés legítimo que pueda verse afectado** por los actos de ejecución a comparecer y actuar en el procedimiento, aunque no hubieran sido parte en el proceso principal, y a este fin los arts. 270 LOPJ y 260.2 LEC exigen que las resoluciones judiciales se notifiquen no sólo a las partes procesales, sino también a las personas a quienes se refieran o puedan parar perjuicio (SSTC 229/2000, de 2 de octubre, FJ 3; 56/2001, de 26 de febrero, FJ 2). > > ...Afirmamos en aquel caso que ello “provoca la indefensión de la demandante de amparo, pues contra el mandato contenido en el art. 24.1 CE de promover la defensión mediante la correspondiente contradicción, y sin perjuicio del pronunciamiento que pueda recaer, de lo que se resuelva sobre la posesión y sobre la posible reserva de las acciones que puedan corresponder a los implicados, conforme acertadamente mantiene el Ministerio Fiscal, el órgano judicial acordó el lanzamiento del propietario y poseedor legítimo de una vivienda sin tan siquiera permitirle comparecer a defender su derecho en un procedimiento contradictorio” (FJ 9). > > En definitiva, de nuestra doctrina se desprende con **absoluta claridad que la interdicción de la indefensión consagrada en el art. 24.1 CE impone a los órganos judiciales el deber de velar por que quienes ostenten algún derecho o interés legítimo en un proceso** de ejecución, aunque no hayan sido parte en el proceso principal, **puedan comparecer y ser oídos en el mismo para garantizar su defensa**, sin perjuicio del pronunciamiento que pueda recaer y de la posible existencia de otras acciones que puedan corresponder a los afectados. > > …En definitiva, y como afirma el Ministerio Fiscal, **el órgano judicial no actuó con la diligencia debida en orden a procurar que los demandantes de amparo pudieran tener conocimiento y comparecer en un proceso** ejecutivo **en el que resultaban afectados sus intereses**... Y dicho comportamiento del órgano judicial **causó indefensión constitucionalmente relevante**, pues **les privó de su derecho a ser oídos y les impidió el ejercicio del derecho de defensa de sus legítimos derechos e intereses** sobre el citado inmueble, sin que exista dato alguno en las actuaciones del que se desprenda que los recurrentes conocieran la existencia del procedimiento ejecutivo o que no hayan actuado con la diligencia debida en orden a facilitar su comparecencia en el citado proceso.” Es evidente que a los afectados por las medidas **se les privó del derecho a ser oídos** y **se les impidió el ejercicio del derecho de defensa** de sus legítimos intereses sobre las páginas y servicios que operaban, por lo que se ha producido una **violación del derecho a la tutela judicial efectiva** reconocida en el art. 24 de la Constitución. Además, las medidas de bloqueo de direcciones compartidas afectan también a la **libertad de expresión e información** de terceros que no guardan relación alguna con el conflicto y, lo que es peor, puede tener una **negativa incidencia en servicios que podrían ser críticos,** lo que es un comportamiento peligroso, irresponsable y negligente. Por todas estas razones, las sentencias deberían ser anuladas y las medidas derivadas de ellas dejadas sin efecto, ofreciendo en todo caso a los afectados la posibilidad de ser oídos en juicio y defender sus legítimos intereses. @ b2caa9b3:9eab0fb5
2025-02-14 13:55:53After spending two weeks in Arusha, it was time to move on. My next stop was Dodoma. I walked to the bus station in the center of Arusha to check ticket prices, but I disliked the chaotic atmosphere — people approached me nonstop, trying to sell me tickets to destinations I had no interest in. Instead, I went to the Shabiby office, a reputed bus company, and secured a ticket for 29,000 TZS. The bus was scheduled to leave at 10 A.M. the next day, giving me time to prepare.  *Photo above: a stop between Arusha and Dodoma.* I returned to my hostel, packed my bag, and picked up snacks and water from Shoppers Supermarket, knowing that Tanzanian bus rides tend to take longer than expected. The 80-kilometer journey from Moshi to Arusha had taken me up to three hours, so I expected the longer trip to Dodoma to stretch beyond the promised eight hours. ## The Journey to Dodoma The bus ride was predictably long, making frequent stops along the way. Upon arrival in Dodoma, the bus meandered through the city, dropping off passengers. My booked accommodation was just under two kilometers from the final stop, so I decided to walk, relying on Google Maps to guide me.  *Photo above: in Dodoma.* When I arrived at what was supposed to be my lodging, I was skeptical. The house lacked a sign, and an elderly woman was doing laundry in the yard. When I asked if this was the right place, she called a younger woman who spoke English and welcomed me inside. The accommodation was a full apartment, complete with a kitchen, but not cheap. Later in the evening, I attempted to shower, only to discover there was no running water. I resorted to a bucket shower, but the cramped bathroom caused water to spill into the apartment.  *Photo above: the Baobab Café in Dodoma.* ## Exploring Dodoma The next day, I set out to explore Dodoma. I passed a cozy café and an old-looking church, which I later learned was not as ancient as it seemed. Strolling down a lively shopping district, I admired the small stores lining the streets. Eventually, I settled at the café I had spotted earlier, enjoying a simple dinner of bread and tomato salad.  *Photo above: the church in Dodoma.* Originally, I had planned to stay for just one night, but the city intrigued me, and I extended my stay. This meant I had to book my next bus ticket and gather supplies. Using the Bolt app, I ordered a TukTuk to take me to the Shabiby bus terminal. The ride cost 2,000 TZS — without Bolt, I would have been charged significantly more. I bought my ticket to Mbeya for 40,000 TZS, with a departure time of 5:30 A.M. That night, I packed my bags and went to bed early, knowing I had an early start ahead. ## The Departure to Mbeya Waking up at 3:30 A.M., I hurriedly took another bucket shower — still no running water. I initially planned to order a TukTuk, but the Bolt app showed no available drivers. With the bus station only a 13-minute walk away, I set out on foot. Along the way, I stepped into a water hole, soaking myself up to my knees. Street vendors persistently offered me motorcycle rides, but I ignored them and continued walking.  *Photo above: in Dodoma.* Arriving at the bus station, I saw the previous bus to Mbeya departing. My gut told me something was wrong. Sure enough, my bus was delayed by almost an hour. Finally, it arrived, and I boarded, relieved that I hadn’t missed it after all. ## A Long Ride to Mbeya The previous day, I had suffered from severe diarrhea. Fortunately, a local pharmacy in Dodoma provided me with pills that helped stabilize my system. I also continued taking my daily dose of Doxycycline as a malaria precaution.  *Photo above: shopping street in Dodoma.* This time, I had a window seat with no one beside me, allowing me to place my backpack on the empty seat. As we traveled, I watched the Tanzanian landscape unfold. At one point, the bus crossed a dam, likely a reservoir, before being stopped by police. A policeman entered, checked my passport, and inquired about my destination. When I mentioned Mbeya, he ask me where after, and I told him to Lusaka. Then he asked if it was in Zambia, returned my passport, and he let us continue.  *Photo above: the Baobab Café in Dodoma.* My host in Mbeya had instructed me to get off at Nane Nane Stand. Upon arrival, I searched for a TukTuk. Without internet access, I had to negotiate fares blindly. After rejecting overpriced offers, I managed to bargain a price of 5,000 TZS for the short ride to my accommodation, what was a bit high for a Tuktuk. ## Mbeya and the Journey to the Border Initially planning to stay two nights, exhaustion led me to extend for an extra night. The hostel was beautiful and clean but, yet again, had no running water. However, this time, the host kindly boiled water for me, allowing me to take a warm bucket shower.  *Photo above: on the way to the Supermarket in Dodoma.* On my final day in Mbeya, I explored the city, visiting a new children's hospital and an old church. Tuktuk drivers repeatedly tried to overcharge me, but I insisted on the standard 800 TZS fare for public transport.  *Photo above: on the way to the Supermarket in Dodoma.* The following morning, after a quick breakfast, I set off for the bus station with a fellow traveler I met at the hostel. Together, we took a bus to Tunduma for 5,000 TZS each. From there, a TukTuk ride to the border cost another 5,000 TZS. ## Crossing into Zambia The border crossing was straightforward for me — I received a free 30-day visa for Zambia. My Russian travel companion, however, needed a visa on arrival, payable in cash and only in USD. The immigration officer arranged a taxi to take us to an ATM, but the only available bank, Absa, charged exorbitant fees. Fortunately, we later found a Zanaco ATM in Nakonde that had no fees.  *Photo above: between Dodoma and Mbeya.* Once we had the necessary cash, we returned to the Border immigration, paid for the visa, and proceeded into Zambia. We walked to town, grabbed some food, and checked into Shalom Hotel. It was cheap, costing only 200 Kwacha per night (under 10 Euros), but lacked cleanliness and had no running water. ## A Frustrating Bus Experience We booked a 4 A.M. bus to Lusaka with Jkas, supposedly the best company. However, when we arrived at the station at 3:28 A.M., the bus was already gone. The staff had lied, telling us the bus left at 4 A.M. but actually departing at 3 A.M. They then offered an overpriced taxi to chase the bus, which we declined.  *Photo above: between Dodoma and Mbeya.* With no other options left, we searched for an alternative and eventually made our way to the PowerTools bus station — only to find that the bus also had already left. The next bus? **Overnight.** We were stuck. ### The Boda Chase That’s when a Boda driver approached us. He had been waiting at the Powertools station, watching the situation unfold. **“I know where your bus is,”** he said. **“At the checkpoint. I can take you.”** There was no time to think. We climbed on. The night was pitch black, the streets slick with rain and mud. As soon as he twisted the throttle, the bike lurched forward. The driver wasn’t smooth — he was riding like a madman, shaking left and right as he weaved through the darkness. The wet road made it worse, and the mud felt like a trap waiting to swallow us whole.  *Photo above: between Dodoma and Mbeya.* A gust of wind blew my hat into my face, blinding me for the most time. My gut twisted — I could almost see the crash before it happened. **“Slow down!”** I shouted. He eased off for a while, but soon enough, he hit the gas again. **“I said slow down!”** I had to remind him. It felt like an eternity. The only thought keeping me together was the hope that the checkpoint was close. Then — buses. Dozens of them. We told him which one was ours, but in the dim light, they all looked the same. He swerved between them, searching, until finally — **Jkas.**  *Photo above: the old church in Mbeya.* As we pulled up, the driver suddenly changed his price from 200 to 400 Kwacha. Of course. I handed him 300, not in the mood to argue, and walked straight into the bus, **relieved to be off that death ride**. The journey continued, but the morning’s chaos was a reminder that travel in Africa often requires patience and adaptability. --- ## Final Thoughts The journey from Arusha to Lusaka was long and filled with challenges — delayed buses, unreliable accommodations, and frustrating border experiences. Yet, the beauty of Tanzania and Zambia, the people I met, and the lessons I learned along the way made it all worthwhile. Traveling in Africa requires flexibility, but it rewards you with unforgettable experiences and stories to tell.  *Photo above: in Mbeya.*  *Photo above: somewhere in Zambia from the Bus.*  *Photo above: in Lusaka.*  *Photo above: in the East Park Mall in Lusaka.*  *Photo above: in the East Park Mall in Lusaka.*  *Photo above: East Park Mall in Lusaka.*  *Photo above: in the market in Lusaka.*
@ b2caa9b3:9eab0fb5
2025-02-14 13:55:53After spending two weeks in Arusha, it was time to move on. My next stop was Dodoma. I walked to the bus station in the center of Arusha to check ticket prices, but I disliked the chaotic atmosphere — people approached me nonstop, trying to sell me tickets to destinations I had no interest in. Instead, I went to the Shabiby office, a reputed bus company, and secured a ticket for 29,000 TZS. The bus was scheduled to leave at 10 A.M. the next day, giving me time to prepare.  *Photo above: a stop between Arusha and Dodoma.* I returned to my hostel, packed my bag, and picked up snacks and water from Shoppers Supermarket, knowing that Tanzanian bus rides tend to take longer than expected. The 80-kilometer journey from Moshi to Arusha had taken me up to three hours, so I expected the longer trip to Dodoma to stretch beyond the promised eight hours. ## The Journey to Dodoma The bus ride was predictably long, making frequent stops along the way. Upon arrival in Dodoma, the bus meandered through the city, dropping off passengers. My booked accommodation was just under two kilometers from the final stop, so I decided to walk, relying on Google Maps to guide me.  *Photo above: in Dodoma.* When I arrived at what was supposed to be my lodging, I was skeptical. The house lacked a sign, and an elderly woman was doing laundry in the yard. When I asked if this was the right place, she called a younger woman who spoke English and welcomed me inside. The accommodation was a full apartment, complete with a kitchen, but not cheap. Later in the evening, I attempted to shower, only to discover there was no running water. I resorted to a bucket shower, but the cramped bathroom caused water to spill into the apartment.  *Photo above: the Baobab Café in Dodoma.* ## Exploring Dodoma The next day, I set out to explore Dodoma. I passed a cozy café and an old-looking church, which I later learned was not as ancient as it seemed. Strolling down a lively shopping district, I admired the small stores lining the streets. Eventually, I settled at the café I had spotted earlier, enjoying a simple dinner of bread and tomato salad.  *Photo above: the church in Dodoma.* Originally, I had planned to stay for just one night, but the city intrigued me, and I extended my stay. This meant I had to book my next bus ticket and gather supplies. Using the Bolt app, I ordered a TukTuk to take me to the Shabiby bus terminal. The ride cost 2,000 TZS — without Bolt, I would have been charged significantly more. I bought my ticket to Mbeya for 40,000 TZS, with a departure time of 5:30 A.M. That night, I packed my bags and went to bed early, knowing I had an early start ahead. ## The Departure to Mbeya Waking up at 3:30 A.M., I hurriedly took another bucket shower — still no running water. I initially planned to order a TukTuk, but the Bolt app showed no available drivers. With the bus station only a 13-minute walk away, I set out on foot. Along the way, I stepped into a water hole, soaking myself up to my knees. Street vendors persistently offered me motorcycle rides, but I ignored them and continued walking.  *Photo above: in Dodoma.* Arriving at the bus station, I saw the previous bus to Mbeya departing. My gut told me something was wrong. Sure enough, my bus was delayed by almost an hour. Finally, it arrived, and I boarded, relieved that I hadn’t missed it after all. ## A Long Ride to Mbeya The previous day, I had suffered from severe diarrhea. Fortunately, a local pharmacy in Dodoma provided me with pills that helped stabilize my system. I also continued taking my daily dose of Doxycycline as a malaria precaution.  *Photo above: shopping street in Dodoma.* This time, I had a window seat with no one beside me, allowing me to place my backpack on the empty seat. As we traveled, I watched the Tanzanian landscape unfold. At one point, the bus crossed a dam, likely a reservoir, before being stopped by police. A policeman entered, checked my passport, and inquired about my destination. When I mentioned Mbeya, he ask me where after, and I told him to Lusaka. Then he asked if it was in Zambia, returned my passport, and he let us continue.  *Photo above: the Baobab Café in Dodoma.* My host in Mbeya had instructed me to get off at Nane Nane Stand. Upon arrival, I searched for a TukTuk. Without internet access, I had to negotiate fares blindly. After rejecting overpriced offers, I managed to bargain a price of 5,000 TZS for the short ride to my accommodation, what was a bit high for a Tuktuk. ## Mbeya and the Journey to the Border Initially planning to stay two nights, exhaustion led me to extend for an extra night. The hostel was beautiful and clean but, yet again, had no running water. However, this time, the host kindly boiled water for me, allowing me to take a warm bucket shower.  *Photo above: on the way to the Supermarket in Dodoma.* On my final day in Mbeya, I explored the city, visiting a new children's hospital and an old church. Tuktuk drivers repeatedly tried to overcharge me, but I insisted on the standard 800 TZS fare for public transport.  *Photo above: on the way to the Supermarket in Dodoma.* The following morning, after a quick breakfast, I set off for the bus station with a fellow traveler I met at the hostel. Together, we took a bus to Tunduma for 5,000 TZS each. From there, a TukTuk ride to the border cost another 5,000 TZS. ## Crossing into Zambia The border crossing was straightforward for me — I received a free 30-day visa for Zambia. My Russian travel companion, however, needed a visa on arrival, payable in cash and only in USD. The immigration officer arranged a taxi to take us to an ATM, but the only available bank, Absa, charged exorbitant fees. Fortunately, we later found a Zanaco ATM in Nakonde that had no fees.  *Photo above: between Dodoma and Mbeya.* Once we had the necessary cash, we returned to the Border immigration, paid for the visa, and proceeded into Zambia. We walked to town, grabbed some food, and checked into Shalom Hotel. It was cheap, costing only 200 Kwacha per night (under 10 Euros), but lacked cleanliness and had no running water. ## A Frustrating Bus Experience We booked a 4 A.M. bus to Lusaka with Jkas, supposedly the best company. However, when we arrived at the station at 3:28 A.M., the bus was already gone. The staff had lied, telling us the bus left at 4 A.M. but actually departing at 3 A.M. They then offered an overpriced taxi to chase the bus, which we declined.  *Photo above: between Dodoma and Mbeya.* With no other options left, we searched for an alternative and eventually made our way to the PowerTools bus station — only to find that the bus also had already left. The next bus? **Overnight.** We were stuck. ### The Boda Chase That’s when a Boda driver approached us. He had been waiting at the Powertools station, watching the situation unfold. **“I know where your bus is,”** he said. **“At the checkpoint. I can take you.”** There was no time to think. We climbed on. The night was pitch black, the streets slick with rain and mud. As soon as he twisted the throttle, the bike lurched forward. The driver wasn’t smooth — he was riding like a madman, shaking left and right as he weaved through the darkness. The wet road made it worse, and the mud felt like a trap waiting to swallow us whole.  *Photo above: between Dodoma and Mbeya.* A gust of wind blew my hat into my face, blinding me for the most time. My gut twisted — I could almost see the crash before it happened. **“Slow down!”** I shouted. He eased off for a while, but soon enough, he hit the gas again. **“I said slow down!”** I had to remind him. It felt like an eternity. The only thought keeping me together was the hope that the checkpoint was close. Then — buses. Dozens of them. We told him which one was ours, but in the dim light, they all looked the same. He swerved between them, searching, until finally — **Jkas.**  *Photo above: the old church in Mbeya.* As we pulled up, the driver suddenly changed his price from 200 to 400 Kwacha. Of course. I handed him 300, not in the mood to argue, and walked straight into the bus, **relieved to be off that death ride**. The journey continued, but the morning’s chaos was a reminder that travel in Africa often requires patience and adaptability. --- ## Final Thoughts The journey from Arusha to Lusaka was long and filled with challenges — delayed buses, unreliable accommodations, and frustrating border experiences. Yet, the beauty of Tanzania and Zambia, the people I met, and the lessons I learned along the way made it all worthwhile. Traveling in Africa requires flexibility, but it rewards you with unforgettable experiences and stories to tell.  *Photo above: in Mbeya.*  *Photo above: somewhere in Zambia from the Bus.*  *Photo above: in Lusaka.*  *Photo above: in the East Park Mall in Lusaka.*  *Photo above: in the East Park Mall in Lusaka.*  *Photo above: East Park Mall in Lusaka.*  *Photo above: in the market in Lusaka.* @ a012dc82:6458a70d
2025-02-14 13:51:33In the ever-evolving landscape of cryptocurrency, a significant development has emerged that is reshaping perceptions and strategies within the industry. Bitcoin, the original and most prominent digital currency, has seen its transaction fees hit a two-year high. This remarkable surge in fees is not merely a statistical blip but a phenomenon that could herald a transformative phase in Bitcoin mining. As we witness these fees reaching unprecedented levels, it prompts a crucial inquiry: Are we on the cusp of a new era in BTC mining, one that redefines its economic and technological paradigms? **Table Of Content** - The Surge in Transaction Fees - Impact on Bitcoin Miners - A Divided Community - The Ripple Effect on Mining Stocks - The Broader Market Influence - Conclusion - FAQs **The Surge in Transaction Fees** The Bitcoin network, known for its robustness and security, has recently been the center of a notable financial trend. Transaction fees have soared to over $37, a figure reminiscent of the peak levels observed in April 2021. This significant increase is not an isolated event but rather a symptom of a larger, more complex shift within the Bitcoin ecosystem. The primary driver behind this surge is the burgeoning interest in Bitcoin NFTs, particularly through a protocol known as Ordinals. This innovative protocol facilitates the storage of non-fungible tokens (NFTs) directly on the Bitcoin blockchain. As a result, there has been a marked increase in transaction volumes, leading to higher fees. This trend reflects a growing interest in utilizing Bitcoin not just as a currency but as a platform for broader digital asset interactions, potentially expanding its use cases and value proposition. **Impact on Bitcoin Miners** The escalation in transaction fees has had a profound and far-reaching impact on the community of Bitcoin miners. These individuals and companies, who form the backbone of the Bitcoin network by validating transactions and maintaining the blockchain, are now witnessing a dramatic shift in their revenue streams. With fees reaching such high levels, their daily income has surged to an estimated $63 million, translating to an extraordinary $23 billion annually. This figure is a significant leap from the average income over the past two years and represents a potential windfall for the mining sector. The increased profitability could lead to renewed investment in mining infrastructure, potentially spurring technological advancements and increased competition within the sector. It also raises questions about the decentralization of Bitcoin mining, as higher profits could lead to further consolidation in an industry already dominated by large players. **A Divided Community** The Bitcoin community, known for its diverse opinions and robust debates, finds itself at a crossroads with the rise of Ordinals and its impact on transaction fees. On one hand, some members of the community, including prominent figures like core developer Luke Dashjr, view the influx of Ordinals as a form of spam that clutters the blockchain and necessitates technical solutions. This perspective underscores concerns about blockchain bloat, transaction prioritization, and the fundamental principles of what Bitcoin should represent. On the other hand, for miners, these high fees have been a significant boon. They have provided a much-needed boost to profitability, especially in a period where the price of Bitcoin itself has been relatively stable. This divergence in views reflects the ongoing evolution of Bitcoin's identity and purpose, as it balances its role as a digital gold, a transactional currency, and now, a platform for digital art and collectibles. **The Ripple Effect on Mining Stocks** The impact of the surge in Bitcoin fees extends beyond the digital realm and into the traditional financial markets. Bitcoin mining stocks, representing companies that invest heavily in the infrastructure required to mine the digital currency, have shown remarkable resilience and growth. Companies like Marathon Digital, Riot Platform, and Cleanspark have seen their stock prices rally, significantly outperforming the actual price of Bitcoin. This trend indicates a growing investor confidence in the mining sector, buoyed by the increased revenue potential from transaction fees. It also suggests a decoupling of sorts, where the mining sector's performance is not solely dependent on the price of Bitcoin but also on other factors like transaction volume and fee structures. This decoupling could attract a new class of investors to the mining stocks, those looking for exposure to the crypto market but with a different risk profile than holding cryptocurrencies directly. **The Broader Market Influence** The performance of Bitcoin mining stocks is also intricately linked to the broader equity markets. As observed by Caleb Franzen, founder of Cubic Analytics, the strong performance of equity markets has provided additional momentum to these stocks. This correlation indicates that Bitcoin mining companies are increasingly being viewed through the lens of traditional financial analysis, where market trends and investor sentiment play a crucial role. The implication is significant: as Bitcoin mining firms become more integrated into the broader market, they may also become more susceptible to the same macroeconomic factors that influence traditional stocks. This integration could lead to greater stability in the mining sector but also exposes it to new types of risks, such as regulatory changes or shifts in investor sentiment unrelated to the crypto market. **Conclusion** The recent developments in Bitcoin transaction fees, driven by the popularity of Ordinals, have ushered in significant changes in the mining landscape. With increased revenues and a positive impact on mining stocks, it's tempting to proclaim the dawn of a new era in Bitcoin mining. However, the sustainability of this trend and its long-term impact on the Bitcoin ecosystem remain subjects of intense speculation and debate. As the community grapples with these changes, the future of Bitcoin mining continues to be a topic of keen interest. Whether this marks a permanent shift or a temporary phase in the cryptocurrency's evolution, one thing is certain: the world of Bitcoin remains as dynamic and unpredictable as ever. **FAQs** **What caused the recent spike in Bitcoin transaction fees?** The surge in Bitcoin transaction fees to over $37, a two-year high, is primarily attributed to the growing popularity of Bitcoin NFTs, especially through the Ordinals protocol, which allows for the storage of non-fungible tokens on the Bitcoin blockchain. **How does the increase in transaction fees affect Bitcoin miners?** Bitcoin miners, who earn BTC for processing transactions, have seen a significant increase in their income due to the higher fees. Their daily revenue has reached approximately $63 million, translating to an estimated $23 billion annually. **What is the Ordinals protocol, and why is it controversial?** Ordinals is a protocol that enables the storage of NFTs on the Bitcoin blockchain. It has been controversial within the Bitcoin community, with some viewing it as a beneficial innovation and others as a form of spam that clutters the blockchain. **Have Bitcoin mining stocks been affected by the increase in fees?** Yes, Bitcoin mining stocks, such as Marathon Digital, Riot Platform, and Cleanspark, have outperformed the actual price of Bitcoin, indicating growing investor confidence in the mining sector due to increased revenue from transaction fees. **Is the Bitcoin mining industry becoming more centralized?** The increase in profitability could lead to further investment in mining infrastructure, potentially leading to more competition but also raising concerns about the centralization of mining power in the hands of large companies. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
@ a012dc82:6458a70d
2025-02-14 13:51:33In the ever-evolving landscape of cryptocurrency, a significant development has emerged that is reshaping perceptions and strategies within the industry. Bitcoin, the original and most prominent digital currency, has seen its transaction fees hit a two-year high. This remarkable surge in fees is not merely a statistical blip but a phenomenon that could herald a transformative phase in Bitcoin mining. As we witness these fees reaching unprecedented levels, it prompts a crucial inquiry: Are we on the cusp of a new era in BTC mining, one that redefines its economic and technological paradigms? **Table Of Content** - The Surge in Transaction Fees - Impact on Bitcoin Miners - A Divided Community - The Ripple Effect on Mining Stocks - The Broader Market Influence - Conclusion - FAQs **The Surge in Transaction Fees** The Bitcoin network, known for its robustness and security, has recently been the center of a notable financial trend. Transaction fees have soared to over $37, a figure reminiscent of the peak levels observed in April 2021. This significant increase is not an isolated event but rather a symptom of a larger, more complex shift within the Bitcoin ecosystem. The primary driver behind this surge is the burgeoning interest in Bitcoin NFTs, particularly through a protocol known as Ordinals. This innovative protocol facilitates the storage of non-fungible tokens (NFTs) directly on the Bitcoin blockchain. As a result, there has been a marked increase in transaction volumes, leading to higher fees. This trend reflects a growing interest in utilizing Bitcoin not just as a currency but as a platform for broader digital asset interactions, potentially expanding its use cases and value proposition. **Impact on Bitcoin Miners** The escalation in transaction fees has had a profound and far-reaching impact on the community of Bitcoin miners. These individuals and companies, who form the backbone of the Bitcoin network by validating transactions and maintaining the blockchain, are now witnessing a dramatic shift in their revenue streams. With fees reaching such high levels, their daily income has surged to an estimated $63 million, translating to an extraordinary $23 billion annually. This figure is a significant leap from the average income over the past two years and represents a potential windfall for the mining sector. The increased profitability could lead to renewed investment in mining infrastructure, potentially spurring technological advancements and increased competition within the sector. It also raises questions about the decentralization of Bitcoin mining, as higher profits could lead to further consolidation in an industry already dominated by large players. **A Divided Community** The Bitcoin community, known for its diverse opinions and robust debates, finds itself at a crossroads with the rise of Ordinals and its impact on transaction fees. On one hand, some members of the community, including prominent figures like core developer Luke Dashjr, view the influx of Ordinals as a form of spam that clutters the blockchain and necessitates technical solutions. This perspective underscores concerns about blockchain bloat, transaction prioritization, and the fundamental principles of what Bitcoin should represent. On the other hand, for miners, these high fees have been a significant boon. They have provided a much-needed boost to profitability, especially in a period where the price of Bitcoin itself has been relatively stable. This divergence in views reflects the ongoing evolution of Bitcoin's identity and purpose, as it balances its role as a digital gold, a transactional currency, and now, a platform for digital art and collectibles. **The Ripple Effect on Mining Stocks** The impact of the surge in Bitcoin fees extends beyond the digital realm and into the traditional financial markets. Bitcoin mining stocks, representing companies that invest heavily in the infrastructure required to mine the digital currency, have shown remarkable resilience and growth. Companies like Marathon Digital, Riot Platform, and Cleanspark have seen their stock prices rally, significantly outperforming the actual price of Bitcoin. This trend indicates a growing investor confidence in the mining sector, buoyed by the increased revenue potential from transaction fees. It also suggests a decoupling of sorts, where the mining sector's performance is not solely dependent on the price of Bitcoin but also on other factors like transaction volume and fee structures. This decoupling could attract a new class of investors to the mining stocks, those looking for exposure to the crypto market but with a different risk profile than holding cryptocurrencies directly. **The Broader Market Influence** The performance of Bitcoin mining stocks is also intricately linked to the broader equity markets. As observed by Caleb Franzen, founder of Cubic Analytics, the strong performance of equity markets has provided additional momentum to these stocks. This correlation indicates that Bitcoin mining companies are increasingly being viewed through the lens of traditional financial analysis, where market trends and investor sentiment play a crucial role. The implication is significant: as Bitcoin mining firms become more integrated into the broader market, they may also become more susceptible to the same macroeconomic factors that influence traditional stocks. This integration could lead to greater stability in the mining sector but also exposes it to new types of risks, such as regulatory changes or shifts in investor sentiment unrelated to the crypto market. **Conclusion** The recent developments in Bitcoin transaction fees, driven by the popularity of Ordinals, have ushered in significant changes in the mining landscape. With increased revenues and a positive impact on mining stocks, it's tempting to proclaim the dawn of a new era in Bitcoin mining. However, the sustainability of this trend and its long-term impact on the Bitcoin ecosystem remain subjects of intense speculation and debate. As the community grapples with these changes, the future of Bitcoin mining continues to be a topic of keen interest. Whether this marks a permanent shift or a temporary phase in the cryptocurrency's evolution, one thing is certain: the world of Bitcoin remains as dynamic and unpredictable as ever. **FAQs** **What caused the recent spike in Bitcoin transaction fees?** The surge in Bitcoin transaction fees to over $37, a two-year high, is primarily attributed to the growing popularity of Bitcoin NFTs, especially through the Ordinals protocol, which allows for the storage of non-fungible tokens on the Bitcoin blockchain. **How does the increase in transaction fees affect Bitcoin miners?** Bitcoin miners, who earn BTC for processing transactions, have seen a significant increase in their income due to the higher fees. Their daily revenue has reached approximately $63 million, translating to an estimated $23 billion annually. **What is the Ordinals protocol, and why is it controversial?** Ordinals is a protocol that enables the storage of NFTs on the Bitcoin blockchain. It has been controversial within the Bitcoin community, with some viewing it as a beneficial innovation and others as a form of spam that clutters the blockchain. **Have Bitcoin mining stocks been affected by the increase in fees?** Yes, Bitcoin mining stocks, such as Marathon Digital, Riot Platform, and Cleanspark, have outperformed the actual price of Bitcoin, indicating growing investor confidence in the mining sector due to increased revenue from transaction fees. **Is the Bitcoin mining industry becoming more centralized?** The increase in profitability could lead to further investment in mining infrastructure, potentially leading to more competition but also raising concerns about the centralization of mining power in the hands of large companies. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*** @ 09fbf8f3:fa3d60f0
2025-02-14 13:40:37> 功能很简单的网站,无广告、无任何付费项目,漫画全部免费。 荤素搭配。 唯一的缺点就是有点慢,看了下网站使用的是cloudflare网站加速,国内效果差了一点,加个🪜就好了。 关键词mycomic 官网:[https://mycomic.com](https://mycomic.com) 
@ 09fbf8f3:fa3d60f0
2025-02-14 13:40:37> 功能很简单的网站,无广告、无任何付费项目,漫画全部免费。 荤素搭配。 唯一的缺点就是有点慢,看了下网站使用的是cloudflare网站加速,国内效果差了一点,加个🪜就好了。 关键词mycomic 官网:[https://mycomic.com](https://mycomic.com)  @ c0a57a12:8b230f7a
2025-02-14 13:19:06Our generation has a cussing problem. Not the kind our grandfathers had. Their swearing was like their gunpowder—kept dry, used sparingly, and when used, meant to do something. A man swore when he had been wronged, when fate had dealt him a rotten hand, when he stood on the edge of some great loss or some great victory. He swore not because he was thoughtless, but because he was thoughtful—because there were things in this world that deserved cursing, just as there were things that deserved blessing. But today? Today, men swear too much, but their swearing is too little. Profanity has become a nervous tic, a filler word, a lazy man’s substitute for wit. We curse not with thunder but with static, not with the crack of a whip but with the feeble hum of a refrigerator. We lace our every sentence with obscenities, not because we are overcome with feeling, but because we have forgotten how to feel at all. And this is what makes our generation’s swearing so weak, so colorless, so infuriatingly dull. It is not that men curse—it is that they curse in the same tone with which they order a sandwich. Their profanity is not the language of men at war with the world’s wickedness; it is the language of men too bored to speak properly. They do not curse like sailors charging into battle; they curse like cashiers sighing through their shifts. And yet, in an irony too delicious to ignore, we live in an age obsessed with language. We do not believe in God, but we believe in speech codes. We do not fear hell, but we fear being reprimanded in the workplace. We have scrapped the Ten Commandments but will gladly enforce a list of forbidden words a mile long. Our rulers and bureaucrats will pore over a man’s every sentence, hunting for an offense, searching for some phrase to declare unacceptable. And yet—yet!—these same rulers, these same bureaucrats, these same petty, priggish priests of modern propriety will gladly flood the airwaves with an endless stream of empty, witless vulgarity. A schoolteacher may be fired for uttering a forbidden phrase, but a pop star may string together a song consisting of nothing but profanity, and no one blinks an eye. We are hypersensitive to language when it contains truth, yet utterly indifferent when it contains nothing at all. And this is the real problem: we do not curse too much, but too weakly. Our words are exhausted, worn thin, spoken to death. Men have forgotten how to speak with fire, how to command with words, how to invoke heaven or hell with their tongues. They do not pray, because they do not know how to form words for the divine. They do not make oaths, because they no longer believe words can bind them. They do not declare war on the evils of the world, because they have spent all their breath on pointless cursing and have none left for real battle. And where does this road lead? It leads to a world where men have lost the power of speech entirely. A world where every conversation sounds the same, where every man mutters the same tired handful of words over and over, like a machine running out of oil. It leads to a world where poetry is impossible, where language is shriveled and gray, where men do not swear terrible oaths because they no longer believe in terrible things. It leads to a world where men do not pray because they do not believe in miracles, and men do not curse because they do not believe in damnation. But this is not a lament. This is not the tired sigh of a defeated man. This is a call to arms. The solution is not to ban speech further. It is not to purge all rough language from the world and replace it with the sterile buzz of corporate-approved jargon. No, the solution is simpler, and far more radical. Men must learn to shut up. They must learn to close their mouths until they have something worth saying. They must stop filling the air with idle, useless, lazy profanity and speak only when speaking matters. If a man must swear, let him swear like a hammer striking an anvil—sharp, sudden, final. If a man must curse, let it be a curse that shakes the very bones of the world. Let his words be rare, but let them be terrible. Let his anger be real. Let his prayers be real. Let his oaths be real. But above all, let his words be true. Let his promises be binding. Let his speech be a sword, not a dull spoon. Let him recover the power of language, the discipline of speech, the ancient art of saying what he means and meaning what he says. For the world was not spoken into being with mumbling. Creation did not begin with filler words and placeholders. It began with a Word—a real Word, a mighty Word, a Word so vast and true that it shaped the heavens and the earth. And so it must be again. If men wish to remake their world, if they wish to shake the rotten foundations of this empty, word-weary age, then let them first learn to speak. Let them strip their language of all that is weak, all that is frivolous, all that is cheap. Let them cut out the cancer of casual vulgarity and replace it with something fierce, something worthy. Let them curse like warriors and pray like prophets. Let them make oaths that bind and promises that burn. Let them stand among men and speak with voices that shake the air—voices that carry weight, voices that mean what they say, voices that, when heard, demand silence in return. For a world that has lost the power of words will not be saved by noise. It will not be saved by muttering. It will not be saved by the droning nonsense of a people who have forgotten how to mean what they say. It will be saved by men who have learned once again to say what they mean—and to speak as if their words could move mountains. Because they can.
@ c0a57a12:8b230f7a
2025-02-14 13:19:06Our generation has a cussing problem. Not the kind our grandfathers had. Their swearing was like their gunpowder—kept dry, used sparingly, and when used, meant to do something. A man swore when he had been wronged, when fate had dealt him a rotten hand, when he stood on the edge of some great loss or some great victory. He swore not because he was thoughtless, but because he was thoughtful—because there were things in this world that deserved cursing, just as there were things that deserved blessing. But today? Today, men swear too much, but their swearing is too little. Profanity has become a nervous tic, a filler word, a lazy man’s substitute for wit. We curse not with thunder but with static, not with the crack of a whip but with the feeble hum of a refrigerator. We lace our every sentence with obscenities, not because we are overcome with feeling, but because we have forgotten how to feel at all. And this is what makes our generation’s swearing so weak, so colorless, so infuriatingly dull. It is not that men curse—it is that they curse in the same tone with which they order a sandwich. Their profanity is not the language of men at war with the world’s wickedness; it is the language of men too bored to speak properly. They do not curse like sailors charging into battle; they curse like cashiers sighing through their shifts. And yet, in an irony too delicious to ignore, we live in an age obsessed with language. We do not believe in God, but we believe in speech codes. We do not fear hell, but we fear being reprimanded in the workplace. We have scrapped the Ten Commandments but will gladly enforce a list of forbidden words a mile long. Our rulers and bureaucrats will pore over a man’s every sentence, hunting for an offense, searching for some phrase to declare unacceptable. And yet—yet!—these same rulers, these same bureaucrats, these same petty, priggish priests of modern propriety will gladly flood the airwaves with an endless stream of empty, witless vulgarity. A schoolteacher may be fired for uttering a forbidden phrase, but a pop star may string together a song consisting of nothing but profanity, and no one blinks an eye. We are hypersensitive to language when it contains truth, yet utterly indifferent when it contains nothing at all. And this is the real problem: we do not curse too much, but too weakly. Our words are exhausted, worn thin, spoken to death. Men have forgotten how to speak with fire, how to command with words, how to invoke heaven or hell with their tongues. They do not pray, because they do not know how to form words for the divine. They do not make oaths, because they no longer believe words can bind them. They do not declare war on the evils of the world, because they have spent all their breath on pointless cursing and have none left for real battle. And where does this road lead? It leads to a world where men have lost the power of speech entirely. A world where every conversation sounds the same, where every man mutters the same tired handful of words over and over, like a machine running out of oil. It leads to a world where poetry is impossible, where language is shriveled and gray, where men do not swear terrible oaths because they no longer believe in terrible things. It leads to a world where men do not pray because they do not believe in miracles, and men do not curse because they do not believe in damnation. But this is not a lament. This is not the tired sigh of a defeated man. This is a call to arms. The solution is not to ban speech further. It is not to purge all rough language from the world and replace it with the sterile buzz of corporate-approved jargon. No, the solution is simpler, and far more radical. Men must learn to shut up. They must learn to close their mouths until they have something worth saying. They must stop filling the air with idle, useless, lazy profanity and speak only when speaking matters. If a man must swear, let him swear like a hammer striking an anvil—sharp, sudden, final. If a man must curse, let it be a curse that shakes the very bones of the world. Let his words be rare, but let them be terrible. Let his anger be real. Let his prayers be real. Let his oaths be real. But above all, let his words be true. Let his promises be binding. Let his speech be a sword, not a dull spoon. Let him recover the power of language, the discipline of speech, the ancient art of saying what he means and meaning what he says. For the world was not spoken into being with mumbling. Creation did not begin with filler words and placeholders. It began with a Word—a real Word, a mighty Word, a Word so vast and true that it shaped the heavens and the earth. And so it must be again. If men wish to remake their world, if they wish to shake the rotten foundations of this empty, word-weary age, then let them first learn to speak. Let them strip their language of all that is weak, all that is frivolous, all that is cheap. Let them cut out the cancer of casual vulgarity and replace it with something fierce, something worthy. Let them curse like warriors and pray like prophets. Let them make oaths that bind and promises that burn. Let them stand among men and speak with voices that shake the air—voices that carry weight, voices that mean what they say, voices that, when heard, demand silence in return. For a world that has lost the power of words will not be saved by noise. It will not be saved by muttering. It will not be saved by the droning nonsense of a people who have forgotten how to mean what they say. It will be saved by men who have learned once again to say what they mean—and to speak as if their words could move mountains. Because they can. @ 00000001:b0c77eb9
2025-02-14 12:40:40مواقع التواصل الإجتماعي العامة هي التي تتحكم بك، تتحكم بك بفرض اجندتها وتجبرك على اتبعها وتحظر وتحذف كل ما يخالفها، وحرية التعبير تنحصر عليها! و خوارزمياتها الخبيثة التي تعرض لك مايريدون منك أن تراه وتحجب ما لا يريدونك أن تراه. في نوستر انت المتحكم، انت الذي تحدد من تتابع و انت الذي تحدد المرحلات التي تنشر منشوراتك بها. نوستر لامركزي، بمعنى عدم وجود سلطة تتحكم ببياناتك، بياناتك موجودة في المرحلات، ولا احد يستطيع حذفها او تعديلها او حظر ظهورها. و هذا لا ينطبق فقط على مواقع التواصل الإجتماعي العامة، بل ينطبق أيضاً على الـfediverse، في الـfediverse انت لست حر، انت تتبع الخادم الذي تستخدمه ويستطيع هذا الخادم حظر ما لا يريد ظهوره لك، لأنك لا تتواصل مع بقية الخوادم بنفسك، بل خادمك من يقوم بذلك بالنيابة عنك. وحتى إذا كنت تمتلك خادم في شبكة الـfediverse، إذا خالفت اجندة بقية الخوادم ونظرتهم عن حرية الرأي و التعبير سوف يندرج خادمك في القائمة السوداء fediblock ولن يتمكن خادمك من التواصل مع بقية خوادم الشبكة، ستكون محصور بالخوادم المحظورة، بالتالي انت في الشبكة الأخرى من الـfediverse! نعم، يوجد شبكتين في الكون الفدرالي fediverse شبكة الصالحين التابعين للأجندة الغربية وشبكة الطالحين الذين لا يتبعون لها، إذا تم إدراج خادمك في قائمة fediblock سوف تذهب للشبكة الأخرى!
@ 00000001:b0c77eb9
2025-02-14 12:40:40مواقع التواصل الإجتماعي العامة هي التي تتحكم بك، تتحكم بك بفرض اجندتها وتجبرك على اتبعها وتحظر وتحذف كل ما يخالفها، وحرية التعبير تنحصر عليها! و خوارزمياتها الخبيثة التي تعرض لك مايريدون منك أن تراه وتحجب ما لا يريدونك أن تراه. في نوستر انت المتحكم، انت الذي تحدد من تتابع و انت الذي تحدد المرحلات التي تنشر منشوراتك بها. نوستر لامركزي، بمعنى عدم وجود سلطة تتحكم ببياناتك، بياناتك موجودة في المرحلات، ولا احد يستطيع حذفها او تعديلها او حظر ظهورها. و هذا لا ينطبق فقط على مواقع التواصل الإجتماعي العامة، بل ينطبق أيضاً على الـfediverse، في الـfediverse انت لست حر، انت تتبع الخادم الذي تستخدمه ويستطيع هذا الخادم حظر ما لا يريد ظهوره لك، لأنك لا تتواصل مع بقية الخوادم بنفسك، بل خادمك من يقوم بذلك بالنيابة عنك. وحتى إذا كنت تمتلك خادم في شبكة الـfediverse، إذا خالفت اجندة بقية الخوادم ونظرتهم عن حرية الرأي و التعبير سوف يندرج خادمك في القائمة السوداء fediblock ولن يتمكن خادمك من التواصل مع بقية خوادم الشبكة، ستكون محصور بالخوادم المحظورة، بالتالي انت في الشبكة الأخرى من الـfediverse! نعم، يوجد شبكتين في الكون الفدرالي fediverse شبكة الصالحين التابعين للأجندة الغربية وشبكة الطالحين الذين لا يتبعون لها، إذا تم إدراج خادمك في قائمة fediblock سوف تذهب للشبكة الأخرى! @ c3b2802b:4850599c
2025-02-14 12:14:43Die Plattform dient dem Zweck, interessierten Gemeinschaften unseres Landes aufzuzeigen, dass auch unter schwierigen globalen und bundespolitischen Rahmenbedingungen der Wandel hin zu zukunftsfähigen Lebensmustern auf kommunaler Ebene möglich ist. Und noch mehr: Dass dieser Umbau auch simultan in mehreren Lebensbereichen gestartet und vollzogen werden kann, wenn mutige und kluge Menschen aus verschiedenen Gruppen in Kommunen beherzt zusammenwirken.  **Psychologischer Hintergrund.** Viele Studien in 20 Jahren eigener psychologischer Analysen erfolgreicher Regionalisierungsprojekte haben aufgezeigt: Persönliche Begegnung und Austausch zwischen Interessierten an Regionalisierungsvorhaben und bereits erfolgreichen Pionieren sind ein entscheidender Erfolgsfaktor für gelingende Transformation. Dafür braucht es Informationen, wo sich Pionierprojekte befinden. Im ersten größeren Transformationsprojekt meiner Arbeitsgruppe, dem Energiewendedorf Jühnde, hat das Wissenschaftler-Team vorab andere innovative Kommunen besucht und deren Erfolgsfaktoren im eigenen Vorhaben umgesetzt. Die Mehrzahl der 200 [Energiewendedörfer](https://xn--energiewendedrfer-c0b.de/), die nach Fertigstellung Jühndes entstanden sind, hat sich wiederum vor Ort in der Modellkommune Jühnde informiert. Dies zeigt den Schneeballefekt des Lernens am Beispiel auf. Die hier beschriebene Plattform macht derartige „Funkenflüge“ für die Vielfalt der hier beschriebenen Innovationen über den Energiebereich hinaus möglich. Denn: Lernen am Modell setzt eine gute Übersicht über brauchbare Modelle voraus. **Inhalte der Plattform.** Die [Zukunftskommunen-Plattform](https://zukunftskommunen.de/) beschreibt 67 Kommunen mit jeweils mindestens drei kommunalen Erfolgen. Die im gesamten Bundesgebiet verteilten Kommunen sind auf einer Landkarte ersichtlich. Von jedem Ort unseres Landes aus kann eine der Zukunftskommunen in maximal 100 km Entfernung erreicht werden. Die Nutzer der Plattform können über die Eingabe ihres Standortes erfahren, welche der Zukunftskommunen sich in der eigenen Region befinden – mit Angabe der Distanz in Kilometern. Jede dieser Kommunen ist in Wort und Bild mit den wesentlichen Informationen zum Stand des Umbaus sowie zum Ansprechpartner charakterisiert. Die derzeit auf der Plattform dargestellten über 200 kommunalen Erfolge sind jeweils durch harte Fakten, Angaben zur Entstehungsgeschichte sowie Erfolgsfaktoren kurz skizziert - und wiederum sind jeweils auskunftsbereite Ansprechpartner genannt. Die Erfolge sind unter den Kommunen angeführt und lassen sich so „durchblättern“. Interessieren sich Nutzer der Plattform jedoch für bestimmte Aspekte der Regionalgesellschaft, können sie auch gezielt nach einzelnen Transformationsbereichen suchen. In dem Fall bekommen Sie – wiederum mit Entfernungsangabe zum eigenen Standort – die interessierenden kommunalen Erfolge angezeigt.  So lassen sich jeweils dutzende Erfolge im Land auffinden, im Bereich Bildung z.B. Lehrpfade, Umweltbildungsprojekte und Umwelttrainerprojekte, bei denen eigens ausgebildete Ehrenamtler ökologische Zusammenhänge vermitteln. Im Bereich Kreislaufwirtschaft sind die Erfolge nach folgenden Aspekten auffindbar: Regionale Kreisläufe, verpackungsfreie Verteilung, Verwendung von Natur-Baustoffen, Recycling endlicher Ressourcen, Bio-Landwirtschaft, Anbau und Nutzung nachwachsender Rohstoffe, Solar-Mobilität, Produktion von Anlagen zur Erzeugung erneuerbarer Energie und Erzeugung erneuerbarer Energie. Der Bereich natürliche Vielfalt ist folgendermaßen gegliedert: Naturschutz, Ressourcenschutz, Permakultur und Erhaltung von Biodiversität. Die Untergliederung der erfolgreichen Gemeinschaftsprojekte lautet: Miteinander aller Bevölkerungsgruppen, Integration und Inklusion, Generationennetzwerk, Genossenschaften, Rekommunalisierung von Infrastruktur, lokale Währung sowie Tauschen und Schenken.  Die Vielfalt der Innovationen ist noch weit größer als in dem Kategoriensystem abgebildet, da wegen der Handhabbarkeit der Plattform nicht alle denkbaren Kriterien ausformuliert worden sind. Doch auch besonders ungewöhnliche oder heute noch seltene kommunale Innovationen sind in der Beispielsammlung der Plattform auffindbar. Dazu kann die freie Suche der Plattform verwendet werden. Wer sich z.B. für Eisspeicher interessiert, kann ein Bildungszentrum mit Solareis-Erdspeicher in der Zukunftskommune Wiernsheim auffinden.  Ein Blog informiert über den politischen und geografischen Kontext, in dem die Transformation in unseren Kommunen stattfindet. Hier lassen sich Erfolgsgeschichten zwischen 2018 und 2024 aus dem In- und Ausland abrufen - wiederum beim Blättern oder durch die Suchfunktion nach Stichworten . Seit Herbst 2024 finden Sie meine Blogbeiträge zu dieser Thematik bei der [Genossenschaft Menschlich Wirtschaften](https://menschlichwirtschaften.de/kategorie/peter-schmuck/). Viel Freude beim Blättern und Stöbern! *Zuerst veröffentlicht in der Zeitschrift Ländlicher Raum (hier leicht gekürzt)* 
@ c3b2802b:4850599c
2025-02-14 12:14:43Die Plattform dient dem Zweck, interessierten Gemeinschaften unseres Landes aufzuzeigen, dass auch unter schwierigen globalen und bundespolitischen Rahmenbedingungen der Wandel hin zu zukunftsfähigen Lebensmustern auf kommunaler Ebene möglich ist. Und noch mehr: Dass dieser Umbau auch simultan in mehreren Lebensbereichen gestartet und vollzogen werden kann, wenn mutige und kluge Menschen aus verschiedenen Gruppen in Kommunen beherzt zusammenwirken.  **Psychologischer Hintergrund.** Viele Studien in 20 Jahren eigener psychologischer Analysen erfolgreicher Regionalisierungsprojekte haben aufgezeigt: Persönliche Begegnung und Austausch zwischen Interessierten an Regionalisierungsvorhaben und bereits erfolgreichen Pionieren sind ein entscheidender Erfolgsfaktor für gelingende Transformation. Dafür braucht es Informationen, wo sich Pionierprojekte befinden. Im ersten größeren Transformationsprojekt meiner Arbeitsgruppe, dem Energiewendedorf Jühnde, hat das Wissenschaftler-Team vorab andere innovative Kommunen besucht und deren Erfolgsfaktoren im eigenen Vorhaben umgesetzt. Die Mehrzahl der 200 [Energiewendedörfer](https://xn--energiewendedrfer-c0b.de/), die nach Fertigstellung Jühndes entstanden sind, hat sich wiederum vor Ort in der Modellkommune Jühnde informiert. Dies zeigt den Schneeballefekt des Lernens am Beispiel auf. Die hier beschriebene Plattform macht derartige „Funkenflüge“ für die Vielfalt der hier beschriebenen Innovationen über den Energiebereich hinaus möglich. Denn: Lernen am Modell setzt eine gute Übersicht über brauchbare Modelle voraus. **Inhalte der Plattform.** Die [Zukunftskommunen-Plattform](https://zukunftskommunen.de/) beschreibt 67 Kommunen mit jeweils mindestens drei kommunalen Erfolgen. Die im gesamten Bundesgebiet verteilten Kommunen sind auf einer Landkarte ersichtlich. Von jedem Ort unseres Landes aus kann eine der Zukunftskommunen in maximal 100 km Entfernung erreicht werden. Die Nutzer der Plattform können über die Eingabe ihres Standortes erfahren, welche der Zukunftskommunen sich in der eigenen Region befinden – mit Angabe der Distanz in Kilometern. Jede dieser Kommunen ist in Wort und Bild mit den wesentlichen Informationen zum Stand des Umbaus sowie zum Ansprechpartner charakterisiert. Die derzeit auf der Plattform dargestellten über 200 kommunalen Erfolge sind jeweils durch harte Fakten, Angaben zur Entstehungsgeschichte sowie Erfolgsfaktoren kurz skizziert - und wiederum sind jeweils auskunftsbereite Ansprechpartner genannt. Die Erfolge sind unter den Kommunen angeführt und lassen sich so „durchblättern“. Interessieren sich Nutzer der Plattform jedoch für bestimmte Aspekte der Regionalgesellschaft, können sie auch gezielt nach einzelnen Transformationsbereichen suchen. In dem Fall bekommen Sie – wiederum mit Entfernungsangabe zum eigenen Standort – die interessierenden kommunalen Erfolge angezeigt.  So lassen sich jeweils dutzende Erfolge im Land auffinden, im Bereich Bildung z.B. Lehrpfade, Umweltbildungsprojekte und Umwelttrainerprojekte, bei denen eigens ausgebildete Ehrenamtler ökologische Zusammenhänge vermitteln. Im Bereich Kreislaufwirtschaft sind die Erfolge nach folgenden Aspekten auffindbar: Regionale Kreisläufe, verpackungsfreie Verteilung, Verwendung von Natur-Baustoffen, Recycling endlicher Ressourcen, Bio-Landwirtschaft, Anbau und Nutzung nachwachsender Rohstoffe, Solar-Mobilität, Produktion von Anlagen zur Erzeugung erneuerbarer Energie und Erzeugung erneuerbarer Energie. Der Bereich natürliche Vielfalt ist folgendermaßen gegliedert: Naturschutz, Ressourcenschutz, Permakultur und Erhaltung von Biodiversität. Die Untergliederung der erfolgreichen Gemeinschaftsprojekte lautet: Miteinander aller Bevölkerungsgruppen, Integration und Inklusion, Generationennetzwerk, Genossenschaften, Rekommunalisierung von Infrastruktur, lokale Währung sowie Tauschen und Schenken.  Die Vielfalt der Innovationen ist noch weit größer als in dem Kategoriensystem abgebildet, da wegen der Handhabbarkeit der Plattform nicht alle denkbaren Kriterien ausformuliert worden sind. Doch auch besonders ungewöhnliche oder heute noch seltene kommunale Innovationen sind in der Beispielsammlung der Plattform auffindbar. Dazu kann die freie Suche der Plattform verwendet werden. Wer sich z.B. für Eisspeicher interessiert, kann ein Bildungszentrum mit Solareis-Erdspeicher in der Zukunftskommune Wiernsheim auffinden.  Ein Blog informiert über den politischen und geografischen Kontext, in dem die Transformation in unseren Kommunen stattfindet. Hier lassen sich Erfolgsgeschichten zwischen 2018 und 2024 aus dem In- und Ausland abrufen - wiederum beim Blättern oder durch die Suchfunktion nach Stichworten . Seit Herbst 2024 finden Sie meine Blogbeiträge zu dieser Thematik bei der [Genossenschaft Menschlich Wirtschaften](https://menschlichwirtschaften.de/kategorie/peter-schmuck/). Viel Freude beim Blättern und Stöbern! *Zuerst veröffentlicht in der Zeitschrift Ländlicher Raum (hier leicht gekürzt)*  @ bd32f268:22b33966
2025-02-14 12:10:11Muitos livros foram escritos sobre o tema oferecendo perspetivas líricas, narrativas, psicológicas/filosóficas, religiosas, simbólicas e políticas. A resposta varia no seu significado consoante o paradigma teórico de análise. Reconhecendo esta multiplicidade de dimensões do conceito qualquer reflexão será sempre, inevitavelmente parcial, no entanto cumpre realizar-se dado que a importância do tema o exige. Muito se tem dito e muito mais se dirá precisamente porque este é um tema que convida à expressão de uma profunda intimidade universal. O amor é, segundo Erich Fromm psicanalista alemão, uma decisão, um julgamento e uma promessa, além de um sentimento. Segundo o autor o amor requer paciência, disciplina, concentração, fé e, quanto a mim uma ideia fundamental de Fromm, a capacidade para transcender o nosso próximo narcisismo. Como seriamos capazes de amar sem ultrapassar o nosso narcisismo? Seríamos capazes do compromisso necessário para aceitar o sacrifício de não corresponder aos nossos desejos mais imediatos em prol da construção de um projeto para o futuro com outra pessoa? No nosso narcisismo reside frequentemente o nosso movimento em direção á gratificação imediata e à não aceitação do sacrifício inerente à construção de algo que desejavelmente será maior que nós. Como nos diz um pergaminho da Psicologia Gestalt, corrente teórica que se dedica ao estudo da forma e da percepção, o todo é maior que a soma das partes. É precisamente neste ponto que está uma das principais forças centrípetas deste conceito, na hipótese de construir algo que melhora a nossa vida que acrescenta em significado, sendo esta a unidade base na qual psicologicamente se medem as coisas e os fenómenos. Fromm propõe ainda que o amor não será apenas a ligação ao objeto amado, mas também uma orientação perante a vida, dizendo: “ o amor é uma atitude, uma orientação de carácter que determina a ligação da pessoa ao mundo como um todo e não apenas a um objeto.” Sendo assim não será suspeito que neste conceito esteja a chave para operar profundas transformações no carácter e na vida dos Humanos, que a somar á construção da relação com o outro têm a construção de uma nova relação com o mundo. O amor é uma dádiva na qual ao darmos podemos experienciar a nossa riqueza de carácter, a nossa força e o nosso poder. Podemos ver este conceito como um professor que nos ensina sobre a vida e sobre as relações. Ensina-nos humildade na medida em que aceitamos algo maior que nós, ensina disciplina porque requer um foco constante e diria até que nos pode ensinar o significado e peso do conceito de fé. Neste último ponto falo de fé porque o amor contempla a dúvida fundamental da rejeição do sacrifício feito em prol do amor, e a fé transcende essa dificuldade da dúvida. A fé parece salvar-nos da corrosão da dúvida e purificar as intenções da pessoa que ama. Ter fé é mais que desenvolver uma mera expectativa, é a construção da esperança interiormente mesmo que seja na face do improvável ou implausível. Assim sendo, amar parece-se em muito com uma experiência eminentemente religiosa na medida em que sacraliza a experiência da pessoa que ama e a vida, atribuindo contornos de divino e transcendental ao que, aos olhos que quem não ama, pode parecer trivial e normal. *Sagrado coração de Jesus* Um amor maduro quer-se consciente da necessidade de amar. Fromm diz-nos que o amor maduro está em: “eu preciso de ti porque te amo” e não em “eu amo-te porque preciso de ti”. Esta inversão do sentido da frase parece fundamental para que o amor não seja confundido com uma forma de egoísmo. Aqui a necessidade do outro surge em função do amor que temos pelo outro, não sendo o amor consequência da necessidade que temos do outro. Amar maduramente é a aceitação do sacrifício diante da incerteza e da dor por vezes debilitante. Assim desenvolvemos a tolerância que nos permite crescer e desenraizar da perversidade do narcisismo cumprindo a nossa identidade na missão de amar. 
@ bd32f268:22b33966
2025-02-14 12:10:11Muitos livros foram escritos sobre o tema oferecendo perspetivas líricas, narrativas, psicológicas/filosóficas, religiosas, simbólicas e políticas. A resposta varia no seu significado consoante o paradigma teórico de análise. Reconhecendo esta multiplicidade de dimensões do conceito qualquer reflexão será sempre, inevitavelmente parcial, no entanto cumpre realizar-se dado que a importância do tema o exige. Muito se tem dito e muito mais se dirá precisamente porque este é um tema que convida à expressão de uma profunda intimidade universal. O amor é, segundo Erich Fromm psicanalista alemão, uma decisão, um julgamento e uma promessa, além de um sentimento. Segundo o autor o amor requer paciência, disciplina, concentração, fé e, quanto a mim uma ideia fundamental de Fromm, a capacidade para transcender o nosso próximo narcisismo. Como seriamos capazes de amar sem ultrapassar o nosso narcisismo? Seríamos capazes do compromisso necessário para aceitar o sacrifício de não corresponder aos nossos desejos mais imediatos em prol da construção de um projeto para o futuro com outra pessoa? No nosso narcisismo reside frequentemente o nosso movimento em direção á gratificação imediata e à não aceitação do sacrifício inerente à construção de algo que desejavelmente será maior que nós. Como nos diz um pergaminho da Psicologia Gestalt, corrente teórica que se dedica ao estudo da forma e da percepção, o todo é maior que a soma das partes. É precisamente neste ponto que está uma das principais forças centrípetas deste conceito, na hipótese de construir algo que melhora a nossa vida que acrescenta em significado, sendo esta a unidade base na qual psicologicamente se medem as coisas e os fenómenos. Fromm propõe ainda que o amor não será apenas a ligação ao objeto amado, mas também uma orientação perante a vida, dizendo: “ o amor é uma atitude, uma orientação de carácter que determina a ligação da pessoa ao mundo como um todo e não apenas a um objeto.” Sendo assim não será suspeito que neste conceito esteja a chave para operar profundas transformações no carácter e na vida dos Humanos, que a somar á construção da relação com o outro têm a construção de uma nova relação com o mundo. O amor é uma dádiva na qual ao darmos podemos experienciar a nossa riqueza de carácter, a nossa força e o nosso poder. Podemos ver este conceito como um professor que nos ensina sobre a vida e sobre as relações. Ensina-nos humildade na medida em que aceitamos algo maior que nós, ensina disciplina porque requer um foco constante e diria até que nos pode ensinar o significado e peso do conceito de fé. Neste último ponto falo de fé porque o amor contempla a dúvida fundamental da rejeição do sacrifício feito em prol do amor, e a fé transcende essa dificuldade da dúvida. A fé parece salvar-nos da corrosão da dúvida e purificar as intenções da pessoa que ama. Ter fé é mais que desenvolver uma mera expectativa, é a construção da esperança interiormente mesmo que seja na face do improvável ou implausível. Assim sendo, amar parece-se em muito com uma experiência eminentemente religiosa na medida em que sacraliza a experiência da pessoa que ama e a vida, atribuindo contornos de divino e transcendental ao que, aos olhos que quem não ama, pode parecer trivial e normal. *Sagrado coração de Jesus* Um amor maduro quer-se consciente da necessidade de amar. Fromm diz-nos que o amor maduro está em: “eu preciso de ti porque te amo” e não em “eu amo-te porque preciso de ti”. Esta inversão do sentido da frase parece fundamental para que o amor não seja confundido com uma forma de egoísmo. Aqui a necessidade do outro surge em função do amor que temos pelo outro, não sendo o amor consequência da necessidade que temos do outro. Amar maduramente é a aceitação do sacrifício diante da incerteza e da dor por vezes debilitante. Assim desenvolvemos a tolerância que nos permite crescer e desenraizar da perversidade do narcisismo cumprindo a nossa identidade na missão de amar.  @ c43d6de3:a6583169
2025-02-14 11:27:09## A Brief History of Ownership ### The Forgotten Struggle for Ownership History reveals that our ancestors labored—both intellectually and physically—to secure the freedoms we are subconsciously giving away. We stand at the threshold of a new era. Across the globe, long-established institutions are showing signs of strain. Trust in governments, banks, and major corporations is eroding, leaving many individuals feeling as though their rights are being infringed upon—even if they struggle to articulate exactly how. Social media and traditional news outlets amplify this sense of unease, painting a picture of impending upheaval, as if we are on the brink of a revolution whose name will only become clear in hindsight, once the first sparks ignite into a full-blown blaze. Yet, when we examine the state of the global economy, this narrative begins to unravel. Economic inequality has reached levels unseen in nearly a century, and while many point fingers at politicians, policies, or the so-called greed of the 1% hoarding all the wealth, the true culprit may be much closer than most realize. At a time when legal structures worldwide strongly protect ownership and economic mobility, it is individuals themselves who are willingly surrendering their financial power to the very elites they criticize. I know—“willingly” might seem like a stretch. After all, no one consciously chooses to give up their economic freedom. But take a closer look at the way people spend, borrow, and consume, and it becomes painfully clear: most are actively forfeiting their ability to build and own wealth. How did we get here? Much of this self-inflicted harm comes from a fundamental ignorance of the history of ownership and the struggles fought to secure it. This article serves as a short exploration of the past. I'll examine what might be considered the natural state of humanity, how the majority has historically struggled to achieve ownership rights, and the deadly conflicts that had to occur for the modern individual to enjoy the very rights they are now squandering.  ### I. The Era of Communal Ownership No one is born into this world alone. We do not simply materialize into existence; we arrive as part of the first unit of human society—the family. Before the rise of civilization, the primary focus of the family was survival. Ownership was a foreign concept, as early human tribes lived in a state of communal resource-sharing. Material possessions were fleeting, and with that, so was the notion of personal property. In the state of nature, no individual had an exclusive claim to anything. Instead, ownership existed in a tribal sense: “This land belongs to us.” The idea of “mine” extended only by association—what belonged to the tribe also, by extension, belonged to each of its members. This was a fragile system. Resources required constant upkeep, and as populations grew, leadership emerged to manage the complexity of distribution. This shift laid the foundation for the rise of kings and centralized authority. The concept of ownership, once a communal right, gradually became something dictated by those in power. The people no longer owned anything outright; they merely had the privilege of stewarding what belonged to their ruler.  ### II. The Rise of Peasants and Kings The first codified legal system, the Code of Hammurabi, laid out extensive laws on ownership. Interestingly, this ancient civilization granted more property rights to commoners than many societies did even a few centuries ago. A few millennia later, Greece laid the philosophical foundations for ownership, but true legal protections for private property did not emerge until much later. In medieval Europe, ownership rights almost disintegrated—not even nobles truly owned land. Everything belonged to the king, and monarchs waged war over control of vast territories, including the people within them. Meanwhile, in the Islamic Golden Age, the Middle East saw an unprecedented period of economic freedom. Under Sharia law, property rights were protected for the average citizen, something unheard of in much of medieval Europe. The extent of these rights depended largely on religious affiliation, but compared to their European counterparts, many commoners in the Islamic Empire enjoyed greater economic autonomy.  ### III. The Birth of Property Rights: The Rights of Man As the Islamic Golden Age waned and the Mongol Horde thundered toward Baghdad, another seismic shift was occurring in England. In 1215, rebellious nobles captured London and forced King John to sign the Magna Carta, the first written document to impose limits on absolute monarchical power and introduce property protections—though these rights were initially reserved for the nobility. This moment planted the seeds of change. Over the next several centuries, the fight for ownership rights expanded beyond the aristocracy. The Black Death (1347–1351) wiped out over 30% of England’s population, increasing labor shortages and bargaining power for peasants. By the 1381 Peasants’ Revolt, the common man demanded a greater share of land and wealth. Yet, it wasn’t until the 1700s with the Enclosure Acts that private property became legally protected for the broader population. What began as a noble rebellion in 1215 ultimately transformed ownership from royal privilege to individual liberty.  ### IV. The Age of Renting: The Illusion of Ownership Today Despite centuries of struggle, we now find ourselves at a paradoxical moment in history: ownership is more legally protected than ever, yet fewer people actually own anything of value. **Homeownership in Decline:** The U.S. homeownership rate peaked in 2005, only to decline for a decade, hitting a low of 63% in 2015. Despite slight rebounds, high housing costs have pushed many into perpetual rentership. **Vehicles as Subscriptions:** In 2024, one-fifth of new vehicles were leased, and long-term auto loans have become the norm. A financed car is not truly owned—it’s rented from a bank until the debt is cleared. **The Subscription Economy:** Ownership of media, software, and even personal data has been replaced with monthly fees. Cloud storage, SaaS, and streaming services have ensured that we no longer possess even our own information. ### V. The Consequences of Financial Illiteracy We now live in a society built on renting, where economic stability depends on a continuous stream of payments. The more we lease, subscribe, and finance, the more control shifts from individuals to corporations and financial institutions. **This shift has profound implications:** - A person who owns little has little power. - A society that rents everything can be controlled by those who own everything. - Wealth is no longer built through accumulation, but through debt and dependency. For millennia, people fought for the right to own. Today, through financial illiteracy and consumer habits, we are giving it away. How much do we truly own, and how much have we already forfeited? ----------- Thank you for reading! If this article resonated with you, let me know with a zap and share it with friends who might find it insightful. Your help sends a strong signal to keep making content like this! Interested in fiction? Follow Fervid Fables for great short stories and serialized fiction. nostr:npub1j9cmpzhlzeex6y85c2pnt45r5zhxhtx73a2twt77fyjwequ4l4jsp5xd49 More articles you might like from Beneath The Ink: nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2kjjzzfpjxvutjg33hjvpcw5cyjezyv9y5k0umm6k nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqqa9wefdwfjj6stvdsk57cnnv4ehxety94mkjarg94g8ymm8wfjhxuedg9hxgt2fw3ej6sm0wd6xjmn8946hxtfjvsuhsdnju045ml nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2ns3jnfa985c29xp2rs3pexpykz6mjxetxu2g25x6
@ c43d6de3:a6583169
2025-02-14 11:27:09## A Brief History of Ownership ### The Forgotten Struggle for Ownership History reveals that our ancestors labored—both intellectually and physically—to secure the freedoms we are subconsciously giving away. We stand at the threshold of a new era. Across the globe, long-established institutions are showing signs of strain. Trust in governments, banks, and major corporations is eroding, leaving many individuals feeling as though their rights are being infringed upon—even if they struggle to articulate exactly how. Social media and traditional news outlets amplify this sense of unease, painting a picture of impending upheaval, as if we are on the brink of a revolution whose name will only become clear in hindsight, once the first sparks ignite into a full-blown blaze. Yet, when we examine the state of the global economy, this narrative begins to unravel. Economic inequality has reached levels unseen in nearly a century, and while many point fingers at politicians, policies, or the so-called greed of the 1% hoarding all the wealth, the true culprit may be much closer than most realize. At a time when legal structures worldwide strongly protect ownership and economic mobility, it is individuals themselves who are willingly surrendering their financial power to the very elites they criticize. I know—“willingly” might seem like a stretch. After all, no one consciously chooses to give up their economic freedom. But take a closer look at the way people spend, borrow, and consume, and it becomes painfully clear: most are actively forfeiting their ability to build and own wealth. How did we get here? Much of this self-inflicted harm comes from a fundamental ignorance of the history of ownership and the struggles fought to secure it. This article serves as a short exploration of the past. I'll examine what might be considered the natural state of humanity, how the majority has historically struggled to achieve ownership rights, and the deadly conflicts that had to occur for the modern individual to enjoy the very rights they are now squandering.  ### I. The Era of Communal Ownership No one is born into this world alone. We do not simply materialize into existence; we arrive as part of the first unit of human society—the family. Before the rise of civilization, the primary focus of the family was survival. Ownership was a foreign concept, as early human tribes lived in a state of communal resource-sharing. Material possessions were fleeting, and with that, so was the notion of personal property. In the state of nature, no individual had an exclusive claim to anything. Instead, ownership existed in a tribal sense: “This land belongs to us.” The idea of “mine” extended only by association—what belonged to the tribe also, by extension, belonged to each of its members. This was a fragile system. Resources required constant upkeep, and as populations grew, leadership emerged to manage the complexity of distribution. This shift laid the foundation for the rise of kings and centralized authority. The concept of ownership, once a communal right, gradually became something dictated by those in power. The people no longer owned anything outright; they merely had the privilege of stewarding what belonged to their ruler.  ### II. The Rise of Peasants and Kings The first codified legal system, the Code of Hammurabi, laid out extensive laws on ownership. Interestingly, this ancient civilization granted more property rights to commoners than many societies did even a few centuries ago. A few millennia later, Greece laid the philosophical foundations for ownership, but true legal protections for private property did not emerge until much later. In medieval Europe, ownership rights almost disintegrated—not even nobles truly owned land. Everything belonged to the king, and monarchs waged war over control of vast territories, including the people within them. Meanwhile, in the Islamic Golden Age, the Middle East saw an unprecedented period of economic freedom. Under Sharia law, property rights were protected for the average citizen, something unheard of in much of medieval Europe. The extent of these rights depended largely on religious affiliation, but compared to their European counterparts, many commoners in the Islamic Empire enjoyed greater economic autonomy.  ### III. The Birth of Property Rights: The Rights of Man As the Islamic Golden Age waned and the Mongol Horde thundered toward Baghdad, another seismic shift was occurring in England. In 1215, rebellious nobles captured London and forced King John to sign the Magna Carta, the first written document to impose limits on absolute monarchical power and introduce property protections—though these rights were initially reserved for the nobility. This moment planted the seeds of change. Over the next several centuries, the fight for ownership rights expanded beyond the aristocracy. The Black Death (1347–1351) wiped out over 30% of England’s population, increasing labor shortages and bargaining power for peasants. By the 1381 Peasants’ Revolt, the common man demanded a greater share of land and wealth. Yet, it wasn’t until the 1700s with the Enclosure Acts that private property became legally protected for the broader population. What began as a noble rebellion in 1215 ultimately transformed ownership from royal privilege to individual liberty.  ### IV. The Age of Renting: The Illusion of Ownership Today Despite centuries of struggle, we now find ourselves at a paradoxical moment in history: ownership is more legally protected than ever, yet fewer people actually own anything of value. **Homeownership in Decline:** The U.S. homeownership rate peaked in 2005, only to decline for a decade, hitting a low of 63% in 2015. Despite slight rebounds, high housing costs have pushed many into perpetual rentership. **Vehicles as Subscriptions:** In 2024, one-fifth of new vehicles were leased, and long-term auto loans have become the norm. A financed car is not truly owned—it’s rented from a bank until the debt is cleared. **The Subscription Economy:** Ownership of media, software, and even personal data has been replaced with monthly fees. Cloud storage, SaaS, and streaming services have ensured that we no longer possess even our own information. ### V. The Consequences of Financial Illiteracy We now live in a society built on renting, where economic stability depends on a continuous stream of payments. The more we lease, subscribe, and finance, the more control shifts from individuals to corporations and financial institutions. **This shift has profound implications:** - A person who owns little has little power. - A society that rents everything can be controlled by those who own everything. - Wealth is no longer built through accumulation, but through debt and dependency. For millennia, people fought for the right to own. Today, through financial illiteracy and consumer habits, we are giving it away. How much do we truly own, and how much have we already forfeited? ----------- Thank you for reading! If this article resonated with you, let me know with a zap and share it with friends who might find it insightful. Your help sends a strong signal to keep making content like this! Interested in fiction? Follow Fervid Fables for great short stories and serialized fiction. nostr:npub1j9cmpzhlzeex6y85c2pnt45r5zhxhtx73a2twt77fyjwequ4l4jsp5xd49 More articles you might like from Beneath The Ink: nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2kjjzzfpjxvutjg33hjvpcw5cyjezyv9y5k0umm6k nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqqa9wefdwfjj6stvdsk57cnnv4ehxety94mkjarg94g8ymm8wfjhxuedg9hxgt2fw3ej6sm0wd6xjmn8946hxtfjvsuhsdnju045ml nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2ns3jnfa985c29xp2rs3pexpykz6mjxetxu2g25x6 @ be41636e:e55c4909
2025-02-14 10:38:04I asked Unleashed.Chat's DeepSeek model to write an article from the point of view of someone who believes in chemtrails. In the first attempt, it didn't understand me well and it provided the arguments provided by chemtrails believers and their counterarguments. When I clearly asked it to write an article from the point of view of someone who actually believes it, it gave some warnings that these claims are not corroborated by science and started the article and ended it by the same remarks. What follows is the article Unleashed.Chat produced. --- For years, I’ve watched the skies, and I’ve seen something that doesn’t sit right. It’s not just the occasional contrail left by a passing airplane. No, these are different. They linger. They spread. They look unnatural. And they’re everywhere. I’m talking about chemtrails—chemical trails intentionally sprayed by aircraft for reasons that are far from benign. At first, I dismissed them as just another conspiracy theory. But as I started paying closer attention, I realized that something was off. ### The Evidence Is in the Sky Let’s start with what we can all see. Contrails, or condensation trails, are the result of water vapor freezing around small particles in airplane exhaust. They’re short-lived and dissipate quickly. But chemtrails are different. They stay in the sky for hours, spreading out into vast, crisscrossing grids that blanket the sky. I’ve taken countless photos of these trails, and they all tell the same story. They’re not just random; they’re deliberate. They’re sprayed in patterns that cover entire regions, and they’re doing it day after day, year after year. ### What’s in the Trails? The government and mainstream media tell us these trails are harmless. But that’s exactly what they want us to believe. Independent researchers and whistleblowers have come forward with disturbing information. Chemtrails contain a cocktail of toxic chemicals, including aluminum, barium, strontium, and other heavy metals. Why would they spray these substances? The official line is that it’s for weather modification or geoengineering. But that’s a lie. The real purpose is far more insidious. ### The Hidden Agenda Chemtrails are part of a larger plan to control the population. These chemicals are neurotoxic, and they’re being used to alter our brains and behavior. They’re designed to make us more docile, more compliant, and less likely to question authority. This isn’t just a theory. There’s a long history of government experimentation on its own citizens. From the Tuskegee Syphilis Experiment to MKUltra, the CIA’s mind-control program, the government has shown time and again that it’s willing to go to extreme lengths to control the population. Chemtrails are the next chapter in this dark history. ### The Health Impact The effects of these chemicals are already being felt. Rates of autism, Alzheimer’s, and other neurological disorders have skyrocketed in recent decades. Coincidence? I don’t think so. I’ve spoken to doctors and researchers who have seen firsthand the connection between chemtrail exposure and these health issues. They’re not willing to speak publicly for fear of retaliation, but they’ve shared their findings with me. The evidence is overwhelming. ### The Media Cover-Up The mainstream media is complicit in this cover-up. They dismiss chemtrails as a conspiracy theory, but that’s just a distraction. They’re paid to keep us in the dark, to prevent us from connecting the dots. Thankfully, the internet has given us a platform to share the truth. Independent investigators, whistleblowers, and concerned citizens are coming together to expose this atrocity. But we need your help. ### What Can We Do? The first step is to raise awareness. Share this information with everyone you know. The more people who understand the truth, the harder it will be for the government to continue this program. Second, we need to demand accountability. Write to your elected representatives. Call for independent investigations into chemtrails. Make your voice heard. Finally, we need to protect ourselves. Install air filters in your home. Avoid spending time outdoors when chemtrails are being sprayed. And stay informed. ### The Future of Humanity Chemtrails are not just a threat to our health; they’re a threat to the very future of humanity. If we allow this program to continue unchecked, we risk irreversible damage to our planet and our species. But there’s still hope. By working together, we can expose the truth and stop this madness. The time to act is now.
@ be41636e:e55c4909
2025-02-14 10:38:04I asked Unleashed.Chat's DeepSeek model to write an article from the point of view of someone who believes in chemtrails. In the first attempt, it didn't understand me well and it provided the arguments provided by chemtrails believers and their counterarguments. When I clearly asked it to write an article from the point of view of someone who actually believes it, it gave some warnings that these claims are not corroborated by science and started the article and ended it by the same remarks. What follows is the article Unleashed.Chat produced. --- For years, I’ve watched the skies, and I’ve seen something that doesn’t sit right. It’s not just the occasional contrail left by a passing airplane. No, these are different. They linger. They spread. They look unnatural. And they’re everywhere. I’m talking about chemtrails—chemical trails intentionally sprayed by aircraft for reasons that are far from benign. At first, I dismissed them as just another conspiracy theory. But as I started paying closer attention, I realized that something was off. ### The Evidence Is in the Sky Let’s start with what we can all see. Contrails, or condensation trails, are the result of water vapor freezing around small particles in airplane exhaust. They’re short-lived and dissipate quickly. But chemtrails are different. They stay in the sky for hours, spreading out into vast, crisscrossing grids that blanket the sky. I’ve taken countless photos of these trails, and they all tell the same story. They’re not just random; they’re deliberate. They’re sprayed in patterns that cover entire regions, and they’re doing it day after day, year after year. ### What’s in the Trails? The government and mainstream media tell us these trails are harmless. But that’s exactly what they want us to believe. Independent researchers and whistleblowers have come forward with disturbing information. Chemtrails contain a cocktail of toxic chemicals, including aluminum, barium, strontium, and other heavy metals. Why would they spray these substances? The official line is that it’s for weather modification or geoengineering. But that’s a lie. The real purpose is far more insidious. ### The Hidden Agenda Chemtrails are part of a larger plan to control the population. These chemicals are neurotoxic, and they’re being used to alter our brains and behavior. They’re designed to make us more docile, more compliant, and less likely to question authority. This isn’t just a theory. There’s a long history of government experimentation on its own citizens. From the Tuskegee Syphilis Experiment to MKUltra, the CIA’s mind-control program, the government has shown time and again that it’s willing to go to extreme lengths to control the population. Chemtrails are the next chapter in this dark history. ### The Health Impact The effects of these chemicals are already being felt. Rates of autism, Alzheimer’s, and other neurological disorders have skyrocketed in recent decades. Coincidence? I don’t think so. I’ve spoken to doctors and researchers who have seen firsthand the connection between chemtrail exposure and these health issues. They’re not willing to speak publicly for fear of retaliation, but they’ve shared their findings with me. The evidence is overwhelming. ### The Media Cover-Up The mainstream media is complicit in this cover-up. They dismiss chemtrails as a conspiracy theory, but that’s just a distraction. They’re paid to keep us in the dark, to prevent us from connecting the dots. Thankfully, the internet has given us a platform to share the truth. Independent investigators, whistleblowers, and concerned citizens are coming together to expose this atrocity. But we need your help. ### What Can We Do? The first step is to raise awareness. Share this information with everyone you know. The more people who understand the truth, the harder it will be for the government to continue this program. Second, we need to demand accountability. Write to your elected representatives. Call for independent investigations into chemtrails. Make your voice heard. Finally, we need to protect ourselves. Install air filters in your home. Avoid spending time outdoors when chemtrails are being sprayed. And stay informed. ### The Future of Humanity Chemtrails are not just a threat to our health; they’re a threat to the very future of humanity. If we allow this program to continue unchecked, we risk irreversible damage to our planet and our species. But there’s still hope. By working together, we can expose the truth and stop this madness. The time to act is now. @ ed60dae0:cc3d5108
2025-02-14 10:25:20Welcome to a new *Situation Report* from **The First Bastion**. Before we begin, please make sure you’ve read the disclaimer, which applies to all our content. You can find it here: [Disclaimer](https://primal.net/bergman/Disclaimer-or2cwd) In short: **Not Financial Advice**. There seems to be a significant amount of confusion in the markets at the moment. Sentiment is almost bleak, particularly in the crypto market (excluding Bitcoin). Broader stock markets are also experiencing uncertainty, primarily driven by high valuations and elevated multiples on the S&P 500. For instance, the SPX is trading at a 30.3 price-to-earnings ratio and a 3.16 price-to-sales ratio. At the same time, bond yields remain relatively high, with former President Trump pushing for a reduction in long-term rates. Risk indicators, such as the High Yield Index OAS, is near all-time lows at 2.66%, while the delinquency rate on single-family residential mortgages is impressively low at 1.73%. Meanwhile, a troubling socioeconomic trend continues to unfold: many young adults, particularly those aged 25–30 (and no, we can’t keep calling them “kids”), are still living with their parents. This phenomenon is particularly evident in the Netherlands, though it may also hold true in the U.S. The cause? Housing affordability. Residential real estate prices have significantly outpaced the growth in real wages, leaving many unable to afford homes of their own. Inflation numbers released yesterday came in slightly higher than expected, triggering an initial sell-off. However, the market quickly rebounded within hours, likely due to seasonal adjustments and noise in the data tempering its impact. Amid all this, investors are anxiously awaiting what many are calling “The Big Print.” Market participants anticipate that the Federal Reserve will resort to more aggressive quantitative easing, injecting liquidity and inflating asset prices to new extremes. Yet, Federal Reserve Chair Jerome Powell (“Uncle Jerome”) continues to emphasize that no such measures are imminent. According to him, the economy is strong enough to stand on its own without additional stimulus. And let’s not forget the run on physical gold that’s happening right now—it’s a whole story in itself. So, in this type of environment, the key question remains: should you buy or sell risk assets? ## Framework As part of my learning journey, I’m building a framework to better understand the bigger picture. Think of it as an effort to “connect the dots”—literally. I’m still figuring out the best way to utilize this framework, but for now, I’ll be exporting the canvas as a high-resolution [**PDF file**](https://github.com/btsvr/tfb/blob/b152cc363534548450c5dbb3db3149ee4d4dbe01/202507.pdf). This allows people to zoom in and explore the data and charts directly within the canvas. Additionally, the embedded links are clickable, providing easy access to the original sources. The content will remain dynamic. My goal isn’t to pack in as much information as possible but rather to focus on the most critical and relevant data for the current narratives and issues. With each SitRep, I’ll reassess what information is still relevant, what can be updated, and what might simply be removed. For this week, I’m keeping the SitRep compact, as much of my time has been dedicated to building the framework itself. The most impactful factors right now are external, so this SitRep will focus on those key developments. ## Bitcoin By focusing mostly on exogenous factors later on, I’ll briefly summarize the key endogenous factors. In last week’s SitRep, I highlighted the 3-day chart and its tight consolidation range. This consolidation is reflected in the Return Analysis, which has reverted almost entirely to the mean, with the quarterly return nearing 0%. To illustrate, 90 days ago, Bitcoin was at $92,000, and as of writing, we’re hovering around the same level. https://blossom.primal.net/e3b97006f3bba849506f5c6ab030c845c97026badc9e4efb0a149d91261bb6c8.png Over those 90 days, we’ve seen spikes to as high as $108,000 and dips back to $92,000. Along the way, we witnessed some of the largest liquidation events in crypto’s history. This consolidation period, combined with the harsh liquidation wicks, has flushed out a significant amount of leverage from the market. https://blossom.primal.net/d53cf96fdd81ed8bbdd71792fb0ca5c75bb153f756f51fc6b3bc88b5b8fa6f32.png If I were to plot Bitcoin on a Speculation Profile, I’d place it in the lower-left quadrant of “balanced positioning,” characterized by a healthy funding rate and relatively low open interest. While open interest remains high on a nominal basis, it’s reasonable when compared to Bitcoin’s market capitalization. https://blossom.primal.net/bb5e1598012fe02a8e27bd9ad132e3e0be9a39abb9413a08fcf92ebf2d3a22cc.png I’d place Bitcoin in the same quadrant in terms of volatility. As noted earlier, the consolidation period has resulted in low daily volatility, though intraday fluctuations have been more pronounced. With 30-day historical volatility at 40 and weak directional movement, we’re currently navigating “slow waters.” https://blossom.primal.net/687294e901b3fc5c6aae6d6685a7ad1872ce9d12efc428832af6ba171671368d.png Looking at some key metrics, Bitcoin remains well above the True Market Mean (TMM), which looks at active coins and filter out the dormant coins. The TMM shows (unintended) the average of all price data, hence it's name . The 200-day moving average (200DMA) is gradually creeping up toward $80,000, serving as the critical support level for a bull market. With current prices hovering around $96,000, we’re approaching the Short-Term Holders Cost Basis (STH-CB) at $92,255. This level represents **The First Bastion** for bullish investors, defending the upward trend. If you believe the bull market will continue, the zone between the STH-CB and the 200DMA presents a compelling opportunity. https://blossom.primal.net/69efc46de294000c13841fb7625a9122fe5e5602ec79d07f7792689691928506.png This brings us to the STH Profit/Loss Profile. As the market price nears the STH-CB, unrealized profit has diminished to near zero. Recently, we’ve seen losses being realized—a dynamic that often provides alpha during bull markets. ## Man on a Mission President Donald J. Trump is a man on a mission. He talks a lot about winning, but to be honest, I don’t think he has the right mindset for the long term. Simon Sinek’s framing of The Infinite Game resonates here: if a game doesn’t have a definitive end, you shouldn’t play it as if it does. In infinite games, you’re either ahead or behind—there’s no “winning.” That said, Trump is moving fast. It’s clear he’s not a politician in the traditional sense. Having run a business, he’s now approaching the country’s leadership the same way. Unlike career politicians, who prioritize diplomacy and long-term consensus, Trump is focused on making deals and getting things done. This pace has left many traditional political leaders struggling to keep up. One of his ultimate goals is to bring the 10-year yield down. On paper, it sounds simple—but in practice, it’s anything but. It’s a monumental task. One shortcut would be to push the Federal Reserve toward Yield Curve Control—creating artificial demand for 10-year notes by buying up everything on the market to force yields lower. However, this approach is fraught with risks and would backfire in more ways than can be imagined. It should never be implemented except as an absolute last resort. https://blossom.primal.net/7c9b1b0229432eb67064557205cb4090e388a4731238a0739429e7c5793dfd33.png The right way to achieve this goal is the harder path: sustained effort and real progress. In the SitRep canvas, I’ve outlined some of Trump’s policies that align with this objective. However, many of these also intersect with the Federal Reserve’s dual mandate of controlling inflation and ensuring a healthy labor market. Some of Trump’s policies, like onshoring manufacturing and imposing tariffs, are inflationary, while others, such as increasing oil production and attempting to end the war between Russia and NATO in Ukraine, have deflationary effects. https://blossom.primal.net/13886c1cc6781f1ea5494614e0aeb6df3ff8db52d047c41b8ceedf700c5360d8.png This duality also applies to the Federal Reserve’s labor market mandate. Trump’s push for a more efficient government could reduce unnecessary jobs, shrinking the supply of available positions. Simultaneously, his efforts to reduce immigration and deport undocumented immigrants restrict the labor pool, further tilting the equation toward fewer people who are able and willing to work. Ending the war in Ukraine would bring significant benefits on a global scale. First and foremost, it would save lives and halt the destruction of cities. Beyond that, it would reopen efficient trade routes for transport and energy, reduce spending on weapons and military efforts, and stabilize markets. These developments would create positive ripple effects worldwide. As Eric Wallerstein recently pointed out, these efforts could bring the 10-year yield down significantly, potentially to a level of low 4% ## To Print or Not To Print Let’s revisit the question I posed in the introduction: is the current environment one where you should lean more heavily toward risk assets, or should you focus on safe-haven assets like bonds or gold? Bonds could rally again if Trump succeeds in his mission to lower long-term yields. Similarly, the prospect of the war in Ukraine ending and global trade returning to a more efficient state would benefit corporate profit margins, thereby boosting stock valuations. Meanwhile, gold continues its remarkable run toward $3,000 per ounce. As I wrote last week, gold serves as a hedge against two risks: defaults and monetary inflation. The recent surge in gold prices appears to stem from a reshuffling of gold inventories, with significant movement from the London LBMA to the New York Comex. This highlights a persistent logistical challenge with gold—it is cumbersome to transport due to its weight and the security requirements. However, it’s not just about location; there’s also a mismatch in quantity and format. Much of the gold held by the Bank of England is stored in 12.5-kilogram bars, which first need to be sent to Switzerland to be melted down and recast into 1-kilogram bars before they can be distributed. This added friction in the settlement of physical gold has led to higher premiums for faster delivery. Rumors are swirling that there isn’t enough gold to meet demand. This brings us back to one of the oldest and most controversial questions in modern finance: is there really enough gold in the vaults? Before deciding on the most probable market outlook—which I’ll address later—it’s essential to consider the mechanics driving potential outcomes. Many investors are waiting for what’s been dubbed “The Big Print,” expecting the Federal Reserve to respond with massive money printing akin to 2020’s response to COVID-19 and the subsequent lockdowns. However, these investors may be “fighting the last war,” often a mistake when the battlefield changes over time. What I’m getting at is this: if you believe the most likely outcome is a stock market rally driven by aggressive Federal Reserve money printing, you may be setting yourself up for disappointment. Jerome Powell has been clear that quantitative easing will only return if interest rates drop to zero—a scenario far from the current reality. ## Expected Outcome When assessing the most likely outcome, it’s essential to objectively evaluate the data currently available: * The labor market is holding steady with 4% unemployment, which is remarkable considering the recession signal triggered by the Sahm Rule last summer. * Inflation hasn’t returned to the 2% target, but it’s not soaring either. Yesterday’s inflation print came in hotter than expected, but one swallow doesn’t make a summer. Some of Trump’s policies may reignite inflation, while others could suppress it. * The ISM Manufacturing PMI has climbed back above 50, signaling potential growth and the start of a new business cycle. If one were to lean toward a portfolio more heavily allocated to risk assets, my guess is that it shouldn’t rely on the Federal Reserve unleashing an “easing bazooka.” Instead, liquidity may emerge from the private sector. A new business cycle could trigger a fresh credit cycle, leading to an increase in M2 money supply. This would represent a more organic form of credit creation, driven by commercial banks and businesses regaining an appetite for risk. This scenario becomes more plausible with lower rates—President Trump’s primary objective. So where might liquidity come from, if it does? * Federal Reserve: Not likely. * Public Sector: Scott Bessent recently criticized Janet Yellen for favoring the issuance of more short-term bills while leaving the long end relatively untouched. In the last Quarterly Refunding Announcement (QRA), Bessent indicated that this course would continue for several quarters. Based on his previous comments, it’s unlikely he will ramp up the issuance rate of short-term bills. * Private Sector: More likely. Another possible scenario is the creation of a Plaza Accord 2.0. If the Federal Reserve keeps rates where they are while the European Central Bank (ECB) lowers rates further—due to years of poor aggregated policy decisions, particularly in Germany—the euro could serve as the release valve, driving the dollar index (DXY) higher. Meanwhile, China is grappling with its enormous real estate issues, with millions of vacant or unfinished properties. An estimated 60% of Chinese household wealth is tied to real estate. A Plaza Accord 2.0 could benefit all three regions: 1. The U.S.: It would help Trump alleviate the pressures of the Triffin Dilemma associated with the dollar’s status as the world reserve currency. 2. Europe: It could help mitigate the consequences of a decade of mismanagement. 3. China: It could provide relief from their ever-growing real estate bubble. The losers in this scenario would be those holding currencies or currency-related assets. The winners? Those holding scarcer and more desirable assets such as stocks, gold, and Bitcoin. The likelihood of a Plaza Accord 2.0 was negligible before Trump took office. Such a deal requires a skilled negotiator—someone unafraid to take the heat. With Trump in office, the odds have improved, but they remain slim, in my opinion. Markets are forward-looking, so much depends on what investors anticipate will happen with tariffs and the situations in China and Europe. For now, Europe’s stock market appears to be showing signs of recovery. Trump doesn’t necessarily need a Plaza Accord 2.0—he just needs to get the 10-year yield down. Stay sound, J.M. Bergman
@ ed60dae0:cc3d5108
2025-02-14 10:25:20Welcome to a new *Situation Report* from **The First Bastion**. Before we begin, please make sure you’ve read the disclaimer, which applies to all our content. You can find it here: [Disclaimer](https://primal.net/bergman/Disclaimer-or2cwd) In short: **Not Financial Advice**. There seems to be a significant amount of confusion in the markets at the moment. Sentiment is almost bleak, particularly in the crypto market (excluding Bitcoin). Broader stock markets are also experiencing uncertainty, primarily driven by high valuations and elevated multiples on the S&P 500. For instance, the SPX is trading at a 30.3 price-to-earnings ratio and a 3.16 price-to-sales ratio. At the same time, bond yields remain relatively high, with former President Trump pushing for a reduction in long-term rates. Risk indicators, such as the High Yield Index OAS, is near all-time lows at 2.66%, while the delinquency rate on single-family residential mortgages is impressively low at 1.73%. Meanwhile, a troubling socioeconomic trend continues to unfold: many young adults, particularly those aged 25–30 (and no, we can’t keep calling them “kids”), are still living with their parents. This phenomenon is particularly evident in the Netherlands, though it may also hold true in the U.S. The cause? Housing affordability. Residential real estate prices have significantly outpaced the growth in real wages, leaving many unable to afford homes of their own. Inflation numbers released yesterday came in slightly higher than expected, triggering an initial sell-off. However, the market quickly rebounded within hours, likely due to seasonal adjustments and noise in the data tempering its impact. Amid all this, investors are anxiously awaiting what many are calling “The Big Print.” Market participants anticipate that the Federal Reserve will resort to more aggressive quantitative easing, injecting liquidity and inflating asset prices to new extremes. Yet, Federal Reserve Chair Jerome Powell (“Uncle Jerome”) continues to emphasize that no such measures are imminent. According to him, the economy is strong enough to stand on its own without additional stimulus. And let’s not forget the run on physical gold that’s happening right now—it’s a whole story in itself. So, in this type of environment, the key question remains: should you buy or sell risk assets? ## Framework As part of my learning journey, I’m building a framework to better understand the bigger picture. Think of it as an effort to “connect the dots”—literally. I’m still figuring out the best way to utilize this framework, but for now, I’ll be exporting the canvas as a high-resolution [**PDF file**](https://github.com/btsvr/tfb/blob/b152cc363534548450c5dbb3db3149ee4d4dbe01/202507.pdf). This allows people to zoom in and explore the data and charts directly within the canvas. Additionally, the embedded links are clickable, providing easy access to the original sources. The content will remain dynamic. My goal isn’t to pack in as much information as possible but rather to focus on the most critical and relevant data for the current narratives and issues. With each SitRep, I’ll reassess what information is still relevant, what can be updated, and what might simply be removed. For this week, I’m keeping the SitRep compact, as much of my time has been dedicated to building the framework itself. The most impactful factors right now are external, so this SitRep will focus on those key developments. ## Bitcoin By focusing mostly on exogenous factors later on, I’ll briefly summarize the key endogenous factors. In last week’s SitRep, I highlighted the 3-day chart and its tight consolidation range. This consolidation is reflected in the Return Analysis, which has reverted almost entirely to the mean, with the quarterly return nearing 0%. To illustrate, 90 days ago, Bitcoin was at $92,000, and as of writing, we’re hovering around the same level. https://blossom.primal.net/e3b97006f3bba849506f5c6ab030c845c97026badc9e4efb0a149d91261bb6c8.png Over those 90 days, we’ve seen spikes to as high as $108,000 and dips back to $92,000. Along the way, we witnessed some of the largest liquidation events in crypto’s history. This consolidation period, combined with the harsh liquidation wicks, has flushed out a significant amount of leverage from the market. https://blossom.primal.net/d53cf96fdd81ed8bbdd71792fb0ca5c75bb153f756f51fc6b3bc88b5b8fa6f32.png If I were to plot Bitcoin on a Speculation Profile, I’d place it in the lower-left quadrant of “balanced positioning,” characterized by a healthy funding rate and relatively low open interest. While open interest remains high on a nominal basis, it’s reasonable when compared to Bitcoin’s market capitalization. https://blossom.primal.net/bb5e1598012fe02a8e27bd9ad132e3e0be9a39abb9413a08fcf92ebf2d3a22cc.png I’d place Bitcoin in the same quadrant in terms of volatility. As noted earlier, the consolidation period has resulted in low daily volatility, though intraday fluctuations have been more pronounced. With 30-day historical volatility at 40 and weak directional movement, we’re currently navigating “slow waters.” https://blossom.primal.net/687294e901b3fc5c6aae6d6685a7ad1872ce9d12efc428832af6ba171671368d.png Looking at some key metrics, Bitcoin remains well above the True Market Mean (TMM), which looks at active coins and filter out the dormant coins. The TMM shows (unintended) the average of all price data, hence it's name . The 200-day moving average (200DMA) is gradually creeping up toward $80,000, serving as the critical support level for a bull market. With current prices hovering around $96,000, we’re approaching the Short-Term Holders Cost Basis (STH-CB) at $92,255. This level represents **The First Bastion** for bullish investors, defending the upward trend. If you believe the bull market will continue, the zone between the STH-CB and the 200DMA presents a compelling opportunity. https://blossom.primal.net/69efc46de294000c13841fb7625a9122fe5e5602ec79d07f7792689691928506.png This brings us to the STH Profit/Loss Profile. As the market price nears the STH-CB, unrealized profit has diminished to near zero. Recently, we’ve seen losses being realized—a dynamic that often provides alpha during bull markets. ## Man on a Mission President Donald J. Trump is a man on a mission. He talks a lot about winning, but to be honest, I don’t think he has the right mindset for the long term. Simon Sinek’s framing of The Infinite Game resonates here: if a game doesn’t have a definitive end, you shouldn’t play it as if it does. In infinite games, you’re either ahead or behind—there’s no “winning.” That said, Trump is moving fast. It’s clear he’s not a politician in the traditional sense. Having run a business, he’s now approaching the country’s leadership the same way. Unlike career politicians, who prioritize diplomacy and long-term consensus, Trump is focused on making deals and getting things done. This pace has left many traditional political leaders struggling to keep up. One of his ultimate goals is to bring the 10-year yield down. On paper, it sounds simple—but in practice, it’s anything but. It’s a monumental task. One shortcut would be to push the Federal Reserve toward Yield Curve Control—creating artificial demand for 10-year notes by buying up everything on the market to force yields lower. However, this approach is fraught with risks and would backfire in more ways than can be imagined. It should never be implemented except as an absolute last resort. https://blossom.primal.net/7c9b1b0229432eb67064557205cb4090e388a4731238a0739429e7c5793dfd33.png The right way to achieve this goal is the harder path: sustained effort and real progress. In the SitRep canvas, I’ve outlined some of Trump’s policies that align with this objective. However, many of these also intersect with the Federal Reserve’s dual mandate of controlling inflation and ensuring a healthy labor market. Some of Trump’s policies, like onshoring manufacturing and imposing tariffs, are inflationary, while others, such as increasing oil production and attempting to end the war between Russia and NATO in Ukraine, have deflationary effects. https://blossom.primal.net/13886c1cc6781f1ea5494614e0aeb6df3ff8db52d047c41b8ceedf700c5360d8.png This duality also applies to the Federal Reserve’s labor market mandate. Trump’s push for a more efficient government could reduce unnecessary jobs, shrinking the supply of available positions. Simultaneously, his efforts to reduce immigration and deport undocumented immigrants restrict the labor pool, further tilting the equation toward fewer people who are able and willing to work. Ending the war in Ukraine would bring significant benefits on a global scale. First and foremost, it would save lives and halt the destruction of cities. Beyond that, it would reopen efficient trade routes for transport and energy, reduce spending on weapons and military efforts, and stabilize markets. These developments would create positive ripple effects worldwide. As Eric Wallerstein recently pointed out, these efforts could bring the 10-year yield down significantly, potentially to a level of low 4% ## To Print or Not To Print Let’s revisit the question I posed in the introduction: is the current environment one where you should lean more heavily toward risk assets, or should you focus on safe-haven assets like bonds or gold? Bonds could rally again if Trump succeeds in his mission to lower long-term yields. Similarly, the prospect of the war in Ukraine ending and global trade returning to a more efficient state would benefit corporate profit margins, thereby boosting stock valuations. Meanwhile, gold continues its remarkable run toward $3,000 per ounce. As I wrote last week, gold serves as a hedge against two risks: defaults and monetary inflation. The recent surge in gold prices appears to stem from a reshuffling of gold inventories, with significant movement from the London LBMA to the New York Comex. This highlights a persistent logistical challenge with gold—it is cumbersome to transport due to its weight and the security requirements. However, it’s not just about location; there’s also a mismatch in quantity and format. Much of the gold held by the Bank of England is stored in 12.5-kilogram bars, which first need to be sent to Switzerland to be melted down and recast into 1-kilogram bars before they can be distributed. This added friction in the settlement of physical gold has led to higher premiums for faster delivery. Rumors are swirling that there isn’t enough gold to meet demand. This brings us back to one of the oldest and most controversial questions in modern finance: is there really enough gold in the vaults? Before deciding on the most probable market outlook—which I’ll address later—it’s essential to consider the mechanics driving potential outcomes. Many investors are waiting for what’s been dubbed “The Big Print,” expecting the Federal Reserve to respond with massive money printing akin to 2020’s response to COVID-19 and the subsequent lockdowns. However, these investors may be “fighting the last war,” often a mistake when the battlefield changes over time. What I’m getting at is this: if you believe the most likely outcome is a stock market rally driven by aggressive Federal Reserve money printing, you may be setting yourself up for disappointment. Jerome Powell has been clear that quantitative easing will only return if interest rates drop to zero—a scenario far from the current reality. ## Expected Outcome When assessing the most likely outcome, it’s essential to objectively evaluate the data currently available: * The labor market is holding steady with 4% unemployment, which is remarkable considering the recession signal triggered by the Sahm Rule last summer. * Inflation hasn’t returned to the 2% target, but it’s not soaring either. Yesterday’s inflation print came in hotter than expected, but one swallow doesn’t make a summer. Some of Trump’s policies may reignite inflation, while others could suppress it. * The ISM Manufacturing PMI has climbed back above 50, signaling potential growth and the start of a new business cycle. If one were to lean toward a portfolio more heavily allocated to risk assets, my guess is that it shouldn’t rely on the Federal Reserve unleashing an “easing bazooka.” Instead, liquidity may emerge from the private sector. A new business cycle could trigger a fresh credit cycle, leading to an increase in M2 money supply. This would represent a more organic form of credit creation, driven by commercial banks and businesses regaining an appetite for risk. This scenario becomes more plausible with lower rates—President Trump’s primary objective. So where might liquidity come from, if it does? * Federal Reserve: Not likely. * Public Sector: Scott Bessent recently criticized Janet Yellen for favoring the issuance of more short-term bills while leaving the long end relatively untouched. In the last Quarterly Refunding Announcement (QRA), Bessent indicated that this course would continue for several quarters. Based on his previous comments, it’s unlikely he will ramp up the issuance rate of short-term bills. * Private Sector: More likely. Another possible scenario is the creation of a Plaza Accord 2.0. If the Federal Reserve keeps rates where they are while the European Central Bank (ECB) lowers rates further—due to years of poor aggregated policy decisions, particularly in Germany—the euro could serve as the release valve, driving the dollar index (DXY) higher. Meanwhile, China is grappling with its enormous real estate issues, with millions of vacant or unfinished properties. An estimated 60% of Chinese household wealth is tied to real estate. A Plaza Accord 2.0 could benefit all three regions: 1. The U.S.: It would help Trump alleviate the pressures of the Triffin Dilemma associated with the dollar’s status as the world reserve currency. 2. Europe: It could help mitigate the consequences of a decade of mismanagement. 3. China: It could provide relief from their ever-growing real estate bubble. The losers in this scenario would be those holding currencies or currency-related assets. The winners? Those holding scarcer and more desirable assets such as stocks, gold, and Bitcoin. The likelihood of a Plaza Accord 2.0 was negligible before Trump took office. Such a deal requires a skilled negotiator—someone unafraid to take the heat. With Trump in office, the odds have improved, but they remain slim, in my opinion. Markets are forward-looking, so much depends on what investors anticipate will happen with tariffs and the situations in China and Europe. For now, Europe’s stock market appears to be showing signs of recovery. Trump doesn’t necessarily need a Plaza Accord 2.0—he just needs to get the 10-year yield down. Stay sound, J.M. Bergman @ be41636e:e55c4909
2025-02-14 09:44:55I asked unleashed.chat's DeepSeek model to provide the pieces of evidence against the moon landing. What follows is what I got as my answer. Generally, I like the answer, though it mixed up the claim and counterarguments at times. Also, I didn't like the conclusion :)) But all said, I believe the Van Allen Belts are one of the most solid argument against the moon landing. --- The question of whether the moon landing was faked has been a topic of debate, with various arguments presented by those who doubt the authenticity of the event. Here is a summary of the key points often cited against the moon landing, along with counterarguments and explanations: Arguments Against the Moon Landing: Waving Flag: Claim: The American flag appears to wave in the wind, despite the moon having no atmosphere. Counterargument: The flag's movement was caused by the astronauts' actions, as they adjusted it using a rod behind the flag. Missing Stars: Claim: The photos lack visible stars, which should be present in the moon's black sky. Counterargument: The cameras were set for optimal lighting of the lunar surface, making stars too faint to capture. Shadow Anomalies: Claim: Shadows in photos appear to come from multiple directions, suggesting studio lighting. Counterargument: The moon's surface is uneven, causing shadows to appear differently, and the sun's angle can create varied shadows. Van Allen Belts: Claim: Astronauts would have been exposed to lethal radiation from the Van Allen belts. Counterargument: The missions were timed to pass through the belts quickly, minimizing exposure. Lack of Blast Crater: Claim: No noticeable crater was created by the lunar module's descent engine. Counterargument: The engine's thrust was designed to minimize impact, and the moon's surface is softer than expected. Missing Footage: Claim: Original tapes of the landing were lost, and restored footage is of lower quality. Counterargument: Footage was restored from other sources, including TV broadcasts and telemetry data. Soviet Silence: Claim: The Soviets did not contest the landing, despite being space race competitors. Counterargument: The Soviets may not have had the means to verify the landing or were focused on their own programs. Technological Capabilities: Claim: The technology of the 1960s was insufficient for a moon landing. Counterargument: Successful unmanned missions and technological advancements supported the capability. Number of Participants: Claim: Thousands of people involved would have leaked the secret. Counterargument: Secrecy measures and unawareness of implications could have prevented leaks. "C" Rock Incident: Claim: A rock appeared to float, suggesting tampering. Counterargument: The rock was a prop, and movement was due to low-gravity actions. Supporting Evidence for the Moon Landing: Moon Rocks: Analyzed and confirmed as lunar. Footprints and Equipment: Observed by subsequent missions and satellites. Cumulative Evidence: Multiple sources confirm the moon landing. In conclusion, while various arguments have been presented against the moon landing, each has been addressed with scientific explanations and evidence. The consensus among the scientific community is that the moon landing was genuine, supported by substantial evidence and corroborated by multiple sources. The question of whether the moon landing was faked has been a topic of debate, with various arguments presented by those who doubt the authenticity of the event. Here is a summary of the key points often cited against the moon landing, along with counterarguments and explanations: ### Arguments Against the Moon Landing: 1. **Waving Flag:** - **Claim:** The American flag appears to wave in the wind, despite the moon having no atmosphere. - **Counterargument:** The flag's movement was caused by the astronauts' actions, as they adjusted it using a rod behind the flag. 2. **Missing Stars:** - **Claim:** The photos lack visible stars, which should be present in the moon's black sky. - **Counterargument:** The cameras were set for optimal lighting of the lunar surface, making stars too faint to capture. 3. **Shadow Anomalies:** - **Claim:** Shadows in photos appear to come from multiple directions, suggesting studio lighting. - **Counterargument:** The moon's surface is uneven, causing shadows to appear differently, and the sun's angle can create varied shadows. 4. **Van Allen Belts:** - **Claim:** Astronauts would have been exposed to lethal radiation from the Van Allen belts. - **Counterargument:** The missions were timed to pass through the belts quickly, minimizing exposure. 5. **Lack of Blast Crater:** - **Claim:** No noticeable crater was created by the lunar module's descent engine. - **Counterargument:** The engine's thrust was designed to minimize impact, and the moon's surface is softer than expected. 6. **Missing Footage:** - **Claim:** Original tapes of the landing were lost, and restored footage is of lower quality. - **Counterargument:** Footage was restored from other sources, including TV broadcasts and telemetry data. 7. **Soviet Silence:** - **Claim:** The Soviets did not contest the landing, despite being space race competitors. - **Counterargument:** The Soviets may not have had the means to verify the landing or were focused on their own programs. 8. **Technological Capabilities:** - **Claim:** The technology of the 1960s was insufficient for a moon landing. - **Counterargument:** Successful unmanned missions and technological advancements supported the capability. 9. **Number of Participants:** - **Claim:** Thousands of people involved would have leaked the secret. - **Counterargument:** Secrecy measures and unawareness of implications could have prevented leaks. 10. **"C" Rock Incident:** - **Claim:** A rock appeared to float, suggesting tampering. - **Counterargument:** The rock was a prop, and movement was due to low-gravity actions. ### Supporting Evidence for the Moon Landing: - **Moon Rocks:** Analyzed and confirmed as lunar. - **Footprints and Equipment:** Observed by subsequent missions and satellites. - **Cumulative Evidence:** Multiple sources confirm the moon landing. In conclusion, while various arguments have been presented against the moon landing, each has been addressed with scientific explanations and evidence. The consensus among the scientific community is that the moon landing was genuine, supported by substantial evidence and corroborated by multiple sources.
@ be41636e:e55c4909
2025-02-14 09:44:55I asked unleashed.chat's DeepSeek model to provide the pieces of evidence against the moon landing. What follows is what I got as my answer. Generally, I like the answer, though it mixed up the claim and counterarguments at times. Also, I didn't like the conclusion :)) But all said, I believe the Van Allen Belts are one of the most solid argument against the moon landing. --- The question of whether the moon landing was faked has been a topic of debate, with various arguments presented by those who doubt the authenticity of the event. Here is a summary of the key points often cited against the moon landing, along with counterarguments and explanations: Arguments Against the Moon Landing: Waving Flag: Claim: The American flag appears to wave in the wind, despite the moon having no atmosphere. Counterargument: The flag's movement was caused by the astronauts' actions, as they adjusted it using a rod behind the flag. Missing Stars: Claim: The photos lack visible stars, which should be present in the moon's black sky. Counterargument: The cameras were set for optimal lighting of the lunar surface, making stars too faint to capture. Shadow Anomalies: Claim: Shadows in photos appear to come from multiple directions, suggesting studio lighting. Counterargument: The moon's surface is uneven, causing shadows to appear differently, and the sun's angle can create varied shadows. Van Allen Belts: Claim: Astronauts would have been exposed to lethal radiation from the Van Allen belts. Counterargument: The missions were timed to pass through the belts quickly, minimizing exposure. Lack of Blast Crater: Claim: No noticeable crater was created by the lunar module's descent engine. Counterargument: The engine's thrust was designed to minimize impact, and the moon's surface is softer than expected. Missing Footage: Claim: Original tapes of the landing were lost, and restored footage is of lower quality. Counterargument: Footage was restored from other sources, including TV broadcasts and telemetry data. Soviet Silence: Claim: The Soviets did not contest the landing, despite being space race competitors. Counterargument: The Soviets may not have had the means to verify the landing or were focused on their own programs. Technological Capabilities: Claim: The technology of the 1960s was insufficient for a moon landing. Counterargument: Successful unmanned missions and technological advancements supported the capability. Number of Participants: Claim: Thousands of people involved would have leaked the secret. Counterargument: Secrecy measures and unawareness of implications could have prevented leaks. "C" Rock Incident: Claim: A rock appeared to float, suggesting tampering. Counterargument: The rock was a prop, and movement was due to low-gravity actions. Supporting Evidence for the Moon Landing: Moon Rocks: Analyzed and confirmed as lunar. Footprints and Equipment: Observed by subsequent missions and satellites. Cumulative Evidence: Multiple sources confirm the moon landing. In conclusion, while various arguments have been presented against the moon landing, each has been addressed with scientific explanations and evidence. The consensus among the scientific community is that the moon landing was genuine, supported by substantial evidence and corroborated by multiple sources. The question of whether the moon landing was faked has been a topic of debate, with various arguments presented by those who doubt the authenticity of the event. Here is a summary of the key points often cited against the moon landing, along with counterarguments and explanations: ### Arguments Against the Moon Landing: 1. **Waving Flag:** - **Claim:** The American flag appears to wave in the wind, despite the moon having no atmosphere. - **Counterargument:** The flag's movement was caused by the astronauts' actions, as they adjusted it using a rod behind the flag. 2. **Missing Stars:** - **Claim:** The photos lack visible stars, which should be present in the moon's black sky. - **Counterargument:** The cameras were set for optimal lighting of the lunar surface, making stars too faint to capture. 3. **Shadow Anomalies:** - **Claim:** Shadows in photos appear to come from multiple directions, suggesting studio lighting. - **Counterargument:** The moon's surface is uneven, causing shadows to appear differently, and the sun's angle can create varied shadows. 4. **Van Allen Belts:** - **Claim:** Astronauts would have been exposed to lethal radiation from the Van Allen belts. - **Counterargument:** The missions were timed to pass through the belts quickly, minimizing exposure. 5. **Lack of Blast Crater:** - **Claim:** No noticeable crater was created by the lunar module's descent engine. - **Counterargument:** The engine's thrust was designed to minimize impact, and the moon's surface is softer than expected. 6. **Missing Footage:** - **Claim:** Original tapes of the landing were lost, and restored footage is of lower quality. - **Counterargument:** Footage was restored from other sources, including TV broadcasts and telemetry data. 7. **Soviet Silence:** - **Claim:** The Soviets did not contest the landing, despite being space race competitors. - **Counterargument:** The Soviets may not have had the means to verify the landing or were focused on their own programs. 8. **Technological Capabilities:** - **Claim:** The technology of the 1960s was insufficient for a moon landing. - **Counterargument:** Successful unmanned missions and technological advancements supported the capability. 9. **Number of Participants:** - **Claim:** Thousands of people involved would have leaked the secret. - **Counterargument:** Secrecy measures and unawareness of implications could have prevented leaks. 10. **"C" Rock Incident:** - **Claim:** A rock appeared to float, suggesting tampering. - **Counterargument:** The rock was a prop, and movement was due to low-gravity actions. ### Supporting Evidence for the Moon Landing: - **Moon Rocks:** Analyzed and confirmed as lunar. - **Footprints and Equipment:** Observed by subsequent missions and satellites. - **Cumulative Evidence:** Multiple sources confirm the moon landing. In conclusion, while various arguments have been presented against the moon landing, each has been addressed with scientific explanations and evidence. The consensus among the scientific community is that the moon landing was genuine, supported by substantial evidence and corroborated by multiple sources. @ dbb19ae0:c3f22d5a
2025-02-14 09:40:13not tested yet ``` python async def main(npub): client = Client() await client.add_relay("wss://relay.damus.io") await client.connect() pk = PublicKey.parse(npub) print(f"\nGetting profile metadata for {npub}:") metadata = await client.fetch_metadata(pk, timedelta(seconds=15)) # Printing each field of the Metadata object inner_metadata = metadata.inner print(f"Name: {inner_metadata.name}") print(f"Display Name: {inner_metadata.display_name}") print(f"About: {inner_metadata.about}") print(f"Website: {inner_metadata.website}") print(f"Picture: {inner_metadata.picture}") print(f"Banner: {inner_metadata.banner}") print(f"NIP05: {inner_metadata.nip05}") print(f"LUD06: {inner_metadata.lud06}") print(f"LUD16: {inner_metadata.lud16}") print(f"Custom: {inner_metadata.custom}") if __name__ == '__main__': parser = argparse.ArgumentParser(description='Fetch all metadata for a given npub') parser.add_argument('npub', type=str, help='The npub of the user') args = parser.parse_args() asyncio.run(main(args.npub)) ```
@ dbb19ae0:c3f22d5a
2025-02-14 09:40:13not tested yet ``` python async def main(npub): client = Client() await client.add_relay("wss://relay.damus.io") await client.connect() pk = PublicKey.parse(npub) print(f"\nGetting profile metadata for {npub}:") metadata = await client.fetch_metadata(pk, timedelta(seconds=15)) # Printing each field of the Metadata object inner_metadata = metadata.inner print(f"Name: {inner_metadata.name}") print(f"Display Name: {inner_metadata.display_name}") print(f"About: {inner_metadata.about}") print(f"Website: {inner_metadata.website}") print(f"Picture: {inner_metadata.picture}") print(f"Banner: {inner_metadata.banner}") print(f"NIP05: {inner_metadata.nip05}") print(f"LUD06: {inner_metadata.lud06}") print(f"LUD16: {inner_metadata.lud16}") print(f"Custom: {inner_metadata.custom}") if __name__ == '__main__': parser = argparse.ArgumentParser(description='Fetch all metadata for a given npub') parser.add_argument('npub', type=str, help='The npub of the user') args = parser.parse_args() asyncio.run(main(args.npub)) ``` @ a367f9eb:0633efea
2025-02-14 09:07:50With a big tech-powered magnifying glass on federal websites, spending contracts, and government payment systems, Elon Musk’s band of DOGE system admins have been turning Washington inside out in their hunt for waste, fraud, and abuse. One of the most prized agencies on the chopping block is the Consumer Financial Protection Bureau, [heralded](https://x.com/SteveRattner/status/1889034592171987002) by progressives as an indispensable force for helping consumers wronged by financial institutions, but [derided](https://www.usnews.com/news/top-news/articles/2024-04-12/if-trump-wins-he-plans-to-free-wall-street-from-burdensome-regulations) by fintech investors and conservatives as little more than a government “shakedown agency.” Consumers will be better off without the CFPB breathing down the neck of American companies. Since the inauguration of President Trump, the CFPB’s [temporary leadership](https://www.nytimes.com/2025/02/09/business/vought-cfpb-musk-trump.html) put an immediate halt on all work, also [informing](https://x.com/russvought/status/1888423503537360986) the Federal Reserve, which directly funds the agency, that it would no longer seek new funding. Sen. Elizabeth Warren, the [intellectual force](https://x.com/senwarren/status/1889356115210633646) behind the agency’s founding, has been apoplectic. She’s argued that Trump is “firing the financial cop on the beat that makes sure your family doesn’t get scammed.” The origin of the CFPB goes back to the rubble of the 2008 financial crisis when legislators saw this proposed agency as a viable response to the populist backlash engulfing Washington and Wall Street. Instead of penalizing wrongdoers, Congress funded bank bailouts and launched a “watchdog” group. The 2010 Dodd-Frank Financial Reform Act [mandated](https://www.law.cornell.edu/wex/dodd-frank_title_X) new standards for lending, restricted capital that could be tapped for bank loans, and created the CFPB to police consumer finance. All functions performed by the five [former](https://www.federalreserve.gov/supervisionreg/understanding-federal-reserve-supervision.htm) federal banking supervisory agencies were rolled into the CFPB, granting it sole jurisdiction over non-depository firms and financial institutions with over $10 billion in assets. This empowered the agency to issue regulatory guidance, demand information from financial institutions, and launch civil actions in federal court. Supporters of the CFPB point to an [impressive record](https://www.consumerfinance.gov/enforcement/enforcement-by-the-numbers/) of close to $20 billion in consumer relief, as well as an additional $5 billion in civil penalties. Without the CFPB, fraudsters and scams would metastasize and consumer injustice would run wild, so they say. But this couldn’t be further from the truth. As a regulatory agency with civil litigation authority, the CFPB is emboldened to file high-dollar lawsuits against financial firms. An estimate of the CFPB’s [database](https://www.consumerfinance.gov/enforcement/actions/) of enforcement actions reveals that roughly 85% of all cases are settled out of court before a final ruling. Companies often choose to settle, but this shouldn’t be mistaken for an admission of guilt. In a [litigious society](https://iaals.du.edu/sites/default/files/documents/publications/judge_faq.pdf) such as the United States where companies are routinely targeted in frivolous lawsuits, the court of public opinion matters just as much as the court of law. Firms prefer [settling](https://knowledge.everc.com/blog/cfpb-payments-industry) cases over having their name dragged through the mud for months on end in the media, something tort lawyers call a “nuisance settlement.” These expected costs are baked into large firms’ financial projections and are sometimes factored into pricing their goods and services for consumers. The CFPB is more akin to a state-backed tort law firm that can tap the nation’s central bank for resources while exploiting its [do-gooder reputation](https://www.dataforprogress.org/blog/2024/11/21/voters-overwhelmingly-support-the-consumer-financial-protection-bureaus-recent-actions) for easy PR victories. Rather than smart regulatory guidance to oversee a new generation of consumer finance firms, CFPB has relied on quick settlements out of court to squash innovative upstarts. While CFPB enforcement has been successful in penalizing banks and lenders for how loans are [structured or advertised](https://www.consumerfinance.gov/about-us/blog/the-cfpbs-enforcement-work-in-2023-and-what-lies-ahead/), it does not take much imagination to see how this has impacted the investing climate for new competitors. Since CFPB’s founding, there are now 35% [fewer financial institutions](https://www.statista.com/statistics/184536/number-of-fdic-insured-us-commercial-bank-institutions/) remaining for consumers to choose from, down from 15,000 to just roughly 9,000 today. While there is [high consumer demand](https://plaid.com/resources/fintech/fintech-trends/) for fintech, payment apps, and account offerings, including Bitcoin and cryptocurrency banks, CFPB’s chilling actions have slowed that innovation, leading to the recent calls for the agency to be gutted. And they’re right. Most of CFPB’s functions are [mirrored](https://www.ftc.gov/enforcement) at the FTC on everything but finance. Regional Federal Reserve banks are also responsible for bank oversight and regulation, not to mention state banking regulators. Existing regulators have the reach, experience, and know-how to police would-be fraudsters and outright deceptive practices among banks. Why not let them? For consumers who want next-level services and financial products, there is no question that CFPB’s litigious approach has impacted their ability to access credit and financial services. There must be a better way to regulate our financial institutions and protect consumers than a tort law firm with government authority. Congress could fold elements of the CFPB into the FTC, OCC, or even FDIC, and bad actors will still be policed. Consumers deserve to be protected, and they will be, but they also deserve a regulatory structure that rewards innovation and brings financial products to market that they can choose between. The CFPB is due for defanging. *Yaël Ossowski is deputy director at the Consumer Choice Center and author of the report, [“A financial fraud crackdown won’t protect consumers from scams.”](https://consumerchoicecenter.org/a-financial-fraud-crackdown-wont-protect-consumers-from-scams/)* *Originally published on [RealClear Politics](https://www.realclearpolitics.com/articles/2025/02/14/doge_is_right_to_defang_cfpb_152360.html).*
@ a367f9eb:0633efea
2025-02-14 09:07:50With a big tech-powered magnifying glass on federal websites, spending contracts, and government payment systems, Elon Musk’s band of DOGE system admins have been turning Washington inside out in their hunt for waste, fraud, and abuse. One of the most prized agencies on the chopping block is the Consumer Financial Protection Bureau, [heralded](https://x.com/SteveRattner/status/1889034592171987002) by progressives as an indispensable force for helping consumers wronged by financial institutions, but [derided](https://www.usnews.com/news/top-news/articles/2024-04-12/if-trump-wins-he-plans-to-free-wall-street-from-burdensome-regulations) by fintech investors and conservatives as little more than a government “shakedown agency.” Consumers will be better off without the CFPB breathing down the neck of American companies. Since the inauguration of President Trump, the CFPB’s [temporary leadership](https://www.nytimes.com/2025/02/09/business/vought-cfpb-musk-trump.html) put an immediate halt on all work, also [informing](https://x.com/russvought/status/1888423503537360986) the Federal Reserve, which directly funds the agency, that it would no longer seek new funding. Sen. Elizabeth Warren, the [intellectual force](https://x.com/senwarren/status/1889356115210633646) behind the agency’s founding, has been apoplectic. She’s argued that Trump is “firing the financial cop on the beat that makes sure your family doesn’t get scammed.” The origin of the CFPB goes back to the rubble of the 2008 financial crisis when legislators saw this proposed agency as a viable response to the populist backlash engulfing Washington and Wall Street. Instead of penalizing wrongdoers, Congress funded bank bailouts and launched a “watchdog” group. The 2010 Dodd-Frank Financial Reform Act [mandated](https://www.law.cornell.edu/wex/dodd-frank_title_X) new standards for lending, restricted capital that could be tapped for bank loans, and created the CFPB to police consumer finance. All functions performed by the five [former](https://www.federalreserve.gov/supervisionreg/understanding-federal-reserve-supervision.htm) federal banking supervisory agencies were rolled into the CFPB, granting it sole jurisdiction over non-depository firms and financial institutions with over $10 billion in assets. This empowered the agency to issue regulatory guidance, demand information from financial institutions, and launch civil actions in federal court. Supporters of the CFPB point to an [impressive record](https://www.consumerfinance.gov/enforcement/enforcement-by-the-numbers/) of close to $20 billion in consumer relief, as well as an additional $5 billion in civil penalties. Without the CFPB, fraudsters and scams would metastasize and consumer injustice would run wild, so they say. But this couldn’t be further from the truth. As a regulatory agency with civil litigation authority, the CFPB is emboldened to file high-dollar lawsuits against financial firms. An estimate of the CFPB’s [database](https://www.consumerfinance.gov/enforcement/actions/) of enforcement actions reveals that roughly 85% of all cases are settled out of court before a final ruling. Companies often choose to settle, but this shouldn’t be mistaken for an admission of guilt. In a [litigious society](https://iaals.du.edu/sites/default/files/documents/publications/judge_faq.pdf) such as the United States where companies are routinely targeted in frivolous lawsuits, the court of public opinion matters just as much as the court of law. Firms prefer [settling](https://knowledge.everc.com/blog/cfpb-payments-industry) cases over having their name dragged through the mud for months on end in the media, something tort lawyers call a “nuisance settlement.” These expected costs are baked into large firms’ financial projections and are sometimes factored into pricing their goods and services for consumers. The CFPB is more akin to a state-backed tort law firm that can tap the nation’s central bank for resources while exploiting its [do-gooder reputation](https://www.dataforprogress.org/blog/2024/11/21/voters-overwhelmingly-support-the-consumer-financial-protection-bureaus-recent-actions) for easy PR victories. Rather than smart regulatory guidance to oversee a new generation of consumer finance firms, CFPB has relied on quick settlements out of court to squash innovative upstarts. While CFPB enforcement has been successful in penalizing banks and lenders for how loans are [structured or advertised](https://www.consumerfinance.gov/about-us/blog/the-cfpbs-enforcement-work-in-2023-and-what-lies-ahead/), it does not take much imagination to see how this has impacted the investing climate for new competitors. Since CFPB’s founding, there are now 35% [fewer financial institutions](https://www.statista.com/statistics/184536/number-of-fdic-insured-us-commercial-bank-institutions/) remaining for consumers to choose from, down from 15,000 to just roughly 9,000 today. While there is [high consumer demand](https://plaid.com/resources/fintech/fintech-trends/) for fintech, payment apps, and account offerings, including Bitcoin and cryptocurrency banks, CFPB’s chilling actions have slowed that innovation, leading to the recent calls for the agency to be gutted. And they’re right. Most of CFPB’s functions are [mirrored](https://www.ftc.gov/enforcement) at the FTC on everything but finance. Regional Federal Reserve banks are also responsible for bank oversight and regulation, not to mention state banking regulators. Existing regulators have the reach, experience, and know-how to police would-be fraudsters and outright deceptive practices among banks. Why not let them? For consumers who want next-level services and financial products, there is no question that CFPB’s litigious approach has impacted their ability to access credit and financial services. There must be a better way to regulate our financial institutions and protect consumers than a tort law firm with government authority. Congress could fold elements of the CFPB into the FTC, OCC, or even FDIC, and bad actors will still be policed. Consumers deserve to be protected, and they will be, but they also deserve a regulatory structure that rewards innovation and brings financial products to market that they can choose between. The CFPB is due for defanging. *Yaël Ossowski is deputy director at the Consumer Choice Center and author of the report, [“A financial fraud crackdown won’t protect consumers from scams.”](https://consumerchoicecenter.org/a-financial-fraud-crackdown-wont-protect-consumers-from-scams/)* *Originally published on [RealClear Politics](https://www.realclearpolitics.com/articles/2025/02/14/doge_is_right_to_defang_cfpb_152360.html).* @ 42342239:1d80db24
2025-02-14 08:42:40A recent US data leak has brought to light a disturbing reality: our everyday technology has become a powerful tool for surveillance and control. Paradoxically, **new technology holds the key to creating a safer, more resilient, and perhaps even more human society.** Preparedness remains a multifaceted topic that continues to spark engagement. The subject is not just about energy infrastructure and [food supply](https://www.epochtimes.se/kan-vi-bade-ata-kakan-och-ha-den-kvar) but also about seemingly more orthogonal issues like [obesity](https://www.epochtimes.se/fetare-svenskar-oroar-forsvarsmakten) and cybersecurity. The significant importance of cybersecurity can be illustrated by examples from an American company that was recently subjected to an [IT intrusion](https://archive.ph/s1atX) with a subsequent data leak. The company, Gravy Analytics, specializes in providing mobile phone data that provides **exceptionally detailed information about where individuals are located at any given time**. Data that can be used, for example, for advertising purposes, but also for more sinister purposes such as extortion or espionage. The company has previously been accused of using misleading methods to collect location data without valid consent from individuals. Mobile operators have long had the ability to locate their subscribers' positions over time. This leak shows how **even apps on your phone risk revealing your location.** Analysis of the samples leaked from the leak shows that data has leaked out for users of several well-known mobile applications, including the popular mobile game Candy Crush and the widely used online dating service Tinder. Even if apps only use an [ad ID](https://x.com/fs0c131y/status/1876987765012701407) when collecting data, these collected digital breadcrumbs can often be deanonymized. It is possible, for example, to identify daily routines, workplaces, and where and when an individual usually sleeps. This usually enables identification. But **it is also possible to map an individual's social circle and romantic relationships.** The mapping risks quickly becoming both sensitive and invasive. **The fact that such data is collected, but especially that it leaks, also poses a threat to preparedness.** By mapping military or other sensitive locations (energy supply, water treatment plants, critical infrastructure) along with location and time data, it is potentially possible to identify employees at these locations. Information that can then be used by those who want to cause harm. It is not written in the stars that citizens must be dependent on a few large IT companies. Our data does not need to be collected and used in a way that does not benefit us, without our knowledge. There are alternatives to large-scale and "super-registers". **Technology such as asymmetric encryption and zero-knowledge proofs can be used to give power back to the individual.** If the parliament and government are serious about improving preparedness, it is high time to leave old thought patterns like Chat Control 2 behind and instead explore such possibilities. The primary purpose of the internet was originally to enable information transfer without intermediaries ("peer-to-peer"). Today, intermediaries are everywhere. It is worth remembering that **peer-to-peer is not some obscure technical term**. In case we have forgotten about it, it simply means: person to person, without intermediaries. Maybe new technology can not only give us a safer and more resilient society, but also a more human one?
@ 42342239:1d80db24
2025-02-14 08:42:40A recent US data leak has brought to light a disturbing reality: our everyday technology has become a powerful tool for surveillance and control. Paradoxically, **new technology holds the key to creating a safer, more resilient, and perhaps even more human society.** Preparedness remains a multifaceted topic that continues to spark engagement. The subject is not just about energy infrastructure and [food supply](https://www.epochtimes.se/kan-vi-bade-ata-kakan-och-ha-den-kvar) but also about seemingly more orthogonal issues like [obesity](https://www.epochtimes.se/fetare-svenskar-oroar-forsvarsmakten) and cybersecurity. The significant importance of cybersecurity can be illustrated by examples from an American company that was recently subjected to an [IT intrusion](https://archive.ph/s1atX) with a subsequent data leak. The company, Gravy Analytics, specializes in providing mobile phone data that provides **exceptionally detailed information about where individuals are located at any given time**. Data that can be used, for example, for advertising purposes, but also for more sinister purposes such as extortion or espionage. The company has previously been accused of using misleading methods to collect location data without valid consent from individuals. Mobile operators have long had the ability to locate their subscribers' positions over time. This leak shows how **even apps on your phone risk revealing your location.** Analysis of the samples leaked from the leak shows that data has leaked out for users of several well-known mobile applications, including the popular mobile game Candy Crush and the widely used online dating service Tinder. Even if apps only use an [ad ID](https://x.com/fs0c131y/status/1876987765012701407) when collecting data, these collected digital breadcrumbs can often be deanonymized. It is possible, for example, to identify daily routines, workplaces, and where and when an individual usually sleeps. This usually enables identification. But **it is also possible to map an individual's social circle and romantic relationships.** The mapping risks quickly becoming both sensitive and invasive. **The fact that such data is collected, but especially that it leaks, also poses a threat to preparedness.** By mapping military or other sensitive locations (energy supply, water treatment plants, critical infrastructure) along with location and time data, it is potentially possible to identify employees at these locations. Information that can then be used by those who want to cause harm. It is not written in the stars that citizens must be dependent on a few large IT companies. Our data does not need to be collected and used in a way that does not benefit us, without our knowledge. There are alternatives to large-scale and "super-registers". **Technology such as asymmetric encryption and zero-knowledge proofs can be used to give power back to the individual.** If the parliament and government are serious about improving preparedness, it is high time to leave old thought patterns like Chat Control 2 behind and instead explore such possibilities. The primary purpose of the internet was originally to enable information transfer without intermediaries ("peer-to-peer"). Today, intermediaries are everywhere. It is worth remembering that **peer-to-peer is not some obscure technical term**. In case we have forgotten about it, it simply means: person to person, without intermediaries. Maybe new technology can not only give us a safer and more resilient society, but also a more human one? @ 955e5a04:c03b3cc3
2025-02-14 08:04:46If we see the Earth as the most important element in the universe, we will learn to care for it. The Maya believed that the Earth was created first, followed by the sun, the moon, and the stars. This perspective is not based on modern science, but it reflects the idea that the Earth is primordial for us, and thus, it should be honored. This vision finds echoes in sacred texts. The *Popol Vuh*, the Mayan creation story, describes a time when only the sky and the vast sea existed before the Earth was formed. Similarly, in the Book of Genesis, before God created the world, "the earth was formless and empty, darkness was over the surface of the deep, and the Spirit of God was hovering over the waters" (Genesis 1:2). In both traditions, creation emerges from a primordial state of sky and water, symbolizing chaos and the unknown. Water, in many religious contexts, is linked to chaos and transformation. In the *Popol Vuh*, the first humans were shaped from maize, but they originated from a world where water and sky ruled. This suggests a deeper truth: before the Earth, there was only the vastness of the cosmos, and from that, we were formed. We are made of both chaos and peace, carrying within us all the elements of creation—not from nothingness, but from everything.
@ 955e5a04:c03b3cc3
2025-02-14 08:04:46If we see the Earth as the most important element in the universe, we will learn to care for it. The Maya believed that the Earth was created first, followed by the sun, the moon, and the stars. This perspective is not based on modern science, but it reflects the idea that the Earth is primordial for us, and thus, it should be honored. This vision finds echoes in sacred texts. The *Popol Vuh*, the Mayan creation story, describes a time when only the sky and the vast sea existed before the Earth was formed. Similarly, in the Book of Genesis, before God created the world, "the earth was formless and empty, darkness was over the surface of the deep, and the Spirit of God was hovering over the waters" (Genesis 1:2). In both traditions, creation emerges from a primordial state of sky and water, symbolizing chaos and the unknown. Water, in many religious contexts, is linked to chaos and transformation. In the *Popol Vuh*, the first humans were shaped from maize, but they originated from a world where water and sky ruled. This suggests a deeper truth: before the Earth, there was only the vastness of the cosmos, and from that, we were formed. We are made of both chaos and peace, carrying within us all the elements of creation—not from nothingness, but from everything. @ f6488c62:c929299d
2025-02-14 07:52:28บทวิเคราะห์แนวโน้มราคาบิตคอยน์ปลายสัปดาห์นี้ วันที่ 14 กุมภาพันธ์ 2025 ราคาบิตคอยน์ (BTC) ล่าสุดอยู่ที่ประมาณ 97,032 ดอลลาร์สหรัฐ เพิ่มขึ้น 0.99% จากวันก่อนหน้า โดยมีการเคลื่อนไหวระหว่าง 95,258 - 97,241 ดอลลาร์ ท่ามกลางความผันผวนอย่างต่อเนื่องในตลาดสินทรัพย์ดิจิทัล ความเคลื่อนไหวล่าสุดสะท้อนถึงสภาวะที่นักลงทุนยังคงจับตาดูนโยบายเศรษฐกิจของสหรัฐฯ อย่างใกล้ชิด ขณะเดียวกัน สถานการณ์แรงเทขายที่เกิดขึ้นในช่วงต้นเดือนกุมภาพันธ์ ซึ่งทำให้ราคา BTC ร่วงลงมาแตะระดับ 90,000 ดอลลาร์ ก็เริ่มคลี่คลายลงบ้างแล้ว โดยนักลงทุนระยะยาวยังคงถือครองเหรียญต่อไป ไม่ได้แสดงความตื่นตระหนก นักวิเคราะห์มองว่า แนวโน้มราคาบิตคอยน์ในช่วงปลายสัปดาห์นี้ อาจอยู่ในลักษณะของการปรับฐาน หรือแกว่งตัวในกรอบแคบระหว่าง 95,000 - 98,000 ดอลลาร์ เนื่องจากตลาดยังอยู่ในช่วงรอปัจจัยใหม่เข้ามากระตุ้น ทั้งนี้ การเคลื่อนไหวดังกล่าวเกิดขึ้นหลังจากแรงกดดันจากทิศทางดอกเบี้ยของธนาคารกลางสหรัฐฯ (Fed) และสภาพคล่องในตลาดการเงินโลกที่ตึงตัวขึ้น ทั้งนี้ วันศุกร์สุดท้ายของเดือนกุมภาพันธ์ในทุกปี มักเป็นช่วงเวลาที่ตลาดมีความผันผวนเพิ่มขึ้นจากการปรับพอร์ตการลงทุนของนักลงทุนสถาบัน รวมถึงการปิดสถานะของนักลงทุนรายใหญ่ ทำให้ราคาของสินทรัพย์ดิจิทัลอย่างบิตคอยน์ อาจเกิดการเคลื่อนไหวที่รวดเร็วกว่าปกติ นักลงทุนจึงควรระมัดระวังและวางแผนการลงทุนอย่างรอบคอบในช่วงเวลาดังกล่าว อย่างไรก็ตาม ความเชื่อมั่นของผู้ถือครองระยะยาวยังคงแข็งแกร่ง โดยเฉพาะกลุ่มนักลงทุนที่เล็งเห็นศักยภาพของบิตคอยน์ในฐานะสินทรัพย์ปลอดภัยในระยะยาว ซึ่งอาจทำให้การปรับฐานของราคายังมีแรงซื้อคอยพยุงอยู่เสมอ ทั้งนี้ นักลงทุนควรติดตามข่าวสารและปัจจัยแวดล้อมอย่างใกล้ชิด โดยเฉพาะความเคลื่อนไหวของดัชนีเศรษฐกิจสหรัฐฯ และท่าทีของ Fed ที่อาจส่งผลต่อทิศทางของสินทรัพย์เสี่ยง รวมถึงตลาดคริปโตในช่วงถัดไป
@ f6488c62:c929299d
2025-02-14 07:52:28บทวิเคราะห์แนวโน้มราคาบิตคอยน์ปลายสัปดาห์นี้ วันที่ 14 กุมภาพันธ์ 2025 ราคาบิตคอยน์ (BTC) ล่าสุดอยู่ที่ประมาณ 97,032 ดอลลาร์สหรัฐ เพิ่มขึ้น 0.99% จากวันก่อนหน้า โดยมีการเคลื่อนไหวระหว่าง 95,258 - 97,241 ดอลลาร์ ท่ามกลางความผันผวนอย่างต่อเนื่องในตลาดสินทรัพย์ดิจิทัล ความเคลื่อนไหวล่าสุดสะท้อนถึงสภาวะที่นักลงทุนยังคงจับตาดูนโยบายเศรษฐกิจของสหรัฐฯ อย่างใกล้ชิด ขณะเดียวกัน สถานการณ์แรงเทขายที่เกิดขึ้นในช่วงต้นเดือนกุมภาพันธ์ ซึ่งทำให้ราคา BTC ร่วงลงมาแตะระดับ 90,000 ดอลลาร์ ก็เริ่มคลี่คลายลงบ้างแล้ว โดยนักลงทุนระยะยาวยังคงถือครองเหรียญต่อไป ไม่ได้แสดงความตื่นตระหนก นักวิเคราะห์มองว่า แนวโน้มราคาบิตคอยน์ในช่วงปลายสัปดาห์นี้ อาจอยู่ในลักษณะของการปรับฐาน หรือแกว่งตัวในกรอบแคบระหว่าง 95,000 - 98,000 ดอลลาร์ เนื่องจากตลาดยังอยู่ในช่วงรอปัจจัยใหม่เข้ามากระตุ้น ทั้งนี้ การเคลื่อนไหวดังกล่าวเกิดขึ้นหลังจากแรงกดดันจากทิศทางดอกเบี้ยของธนาคารกลางสหรัฐฯ (Fed) และสภาพคล่องในตลาดการเงินโลกที่ตึงตัวขึ้น ทั้งนี้ วันศุกร์สุดท้ายของเดือนกุมภาพันธ์ในทุกปี มักเป็นช่วงเวลาที่ตลาดมีความผันผวนเพิ่มขึ้นจากการปรับพอร์ตการลงทุนของนักลงทุนสถาบัน รวมถึงการปิดสถานะของนักลงทุนรายใหญ่ ทำให้ราคาของสินทรัพย์ดิจิทัลอย่างบิตคอยน์ อาจเกิดการเคลื่อนไหวที่รวดเร็วกว่าปกติ นักลงทุนจึงควรระมัดระวังและวางแผนการลงทุนอย่างรอบคอบในช่วงเวลาดังกล่าว อย่างไรก็ตาม ความเชื่อมั่นของผู้ถือครองระยะยาวยังคงแข็งแกร่ง โดยเฉพาะกลุ่มนักลงทุนที่เล็งเห็นศักยภาพของบิตคอยน์ในฐานะสินทรัพย์ปลอดภัยในระยะยาว ซึ่งอาจทำให้การปรับฐานของราคายังมีแรงซื้อคอยพยุงอยู่เสมอ ทั้งนี้ นักลงทุนควรติดตามข่าวสารและปัจจัยแวดล้อมอย่างใกล้ชิด โดยเฉพาะความเคลื่อนไหวของดัชนีเศรษฐกิจสหรัฐฯ และท่าทีของ Fed ที่อาจส่งผลต่อทิศทางของสินทรัพย์เสี่ยง รวมถึงตลาดคริปโตในช่วงถัดไป @ 57d1a264:69f1fee1
2025-02-14 07:29:39Organized by Figma, Config is happening May 6-8 in San Francisco—here's a first look at our 2025 lineup.  [Register for Config 2025](https://config.figma.com/san-francisco/register/) At Config 2025, we’re bringing together the designers and builders shaping tech’s next chapter. They’ll share a vision for building tools and experiences that are human-centered, intentional, and meet the needs of an accelerating future.  [Register now](https://config.figma.com/san-francisco/register/) to guarantee your spot in San Francisco! Virtual registration is also open, and always free. Join us in San Francisco or virtually. ### $799 - In person Moscone Center, San Francisco, California Purchasing an in-person ticket will also give you virtual access to our livestreams. [Select in person](https://reg.config.figma.com/flow/figma/config2025/in-person/login) ### $0 Virtual Livestream Online Free - Limit one ticket per attendee. [Select virtual](https://reg.config.figma.com/flow/figma/config2025/virtual/login) - - - Or [keep reading](https://www.figma.com/blog/meet-the-makers-defining-techs-next-chapter/?utm_campaign=021325+-+Invite&utm_content=021325+-+Invite) for the full Config 2025 sneak peek originally posted at https://stacker.news/items/885616
@ 57d1a264:69f1fee1
2025-02-14 07:29:39Organized by Figma, Config is happening May 6-8 in San Francisco—here's a first look at our 2025 lineup.  [Register for Config 2025](https://config.figma.com/san-francisco/register/) At Config 2025, we’re bringing together the designers and builders shaping tech’s next chapter. They’ll share a vision for building tools and experiences that are human-centered, intentional, and meet the needs of an accelerating future.  [Register now](https://config.figma.com/san-francisco/register/) to guarantee your spot in San Francisco! Virtual registration is also open, and always free. Join us in San Francisco or virtually. ### $799 - In person Moscone Center, San Francisco, California Purchasing an in-person ticket will also give you virtual access to our livestreams. [Select in person](https://reg.config.figma.com/flow/figma/config2025/in-person/login) ### $0 Virtual Livestream Online Free - Limit one ticket per attendee. [Select virtual](https://reg.config.figma.com/flow/figma/config2025/virtual/login) - - - Or [keep reading](https://www.figma.com/blog/meet-the-makers-defining-techs-next-chapter/?utm_campaign=021325+-+Invite&utm_content=021325+-+Invite) for the full Config 2025 sneak peek originally posted at https://stacker.news/items/885616 @ 21db9b8a:2a94c796
2025-02-14 06:46:21Fair warning: This is the continuation of an explicit and erotic story involving extremely taboo themes that would prevent it from being published on most sites that host erotic stories. All characters in this story are ***fictional only***. It is not in any way based on true events. This is also not your average stroke story. It will be released in chapters, and while there ***is*** sexual content in each chapter, there is no full-on sex until late in chapter 4. It is a story of sexual discovery and exploration between young people who have few resources to educate them, but also few inhibitions to hold them back. I hope you enjoy it. If not… Well… You don’t have to host it on your relay, and you can always mute me so you don’t see any more. If you missed Chapter 1, you can read it here: nostr:naddr1qvzqqqr4gupzqgwmnw9dmeqlgk4c5a0ryypxw8xudnrdvgzye7930yzjss4ff3ukqqxnzden8qunzvfkxgerxdfnfxxqt9 *** Dani awoke Thursday morning feeling particularly peppy and refreshed. She knew it probably had something to do with her experience in the shower the night before. It had been such an amazing release of pent up energy, and felt so incredibly good, leaving her relaxed and content, which allowed her to fall asleep before she knew it. Unlike some mornings, she wasn’t even mad when her alarm went off at 7:00 so she could get up and get her schoolwork done while her younger siblings were still in their beds. Not bothering to change out of her pajamas, she wandered out of her room, across the back of the living room, and over to the dining table, pulling her school books off of the bookshelf on the back wall before sitting down and starting in on her English workbook. It wasn't long before she heard Jake thudding his way up the stairs to join her. "Morning, meat-brain," She said teasingly as he appeared from the main entryway beyond the kitchen. Her brother just grunted and retrieved his own school books from the shelf without meeting her eyes. He then walked back to the opposite end of the dining table and plopped himself down, burying his nose in his work. That wasn't like him at all. He usually sat next to her while they did their work, each of them teasing the other when they looked over and noticed a wrong answer. So why had he gone all the way over to the far end of the table? His sour demeanor was ruining the good mood she had been in since the previous night. Was he mad at her for calling him "meat-brain" all of a sudden? She'd always called him that and it had never seemed to bother him before. "I'm sorry, Jake, you know I don't mean anything by calling you that, right? I'm just joking with you." "I know," he said flatly, still not looking up from his work. Dani frowned, looking back to her own workbook but far too distracted by her brother's recent attitude to process anything to do with what was on the page. Was this a continuation of his behavior from the previous afternoon when he seemed to be avoiding her? What had she done to make him angry with her? ***He*** was the one who stole her sunglasses, after all, not the other way around. Where was his usual teasing and attempts to get under her skin? Was he sick or something? Thoughts about her brother's sudden reserved behavior kept Dani from being able to focus on any of her own work and she finally gave up the effort after nearly an hour staring at the same page and only answering two of the questions on it. She put her books away and walked past her silent brother to the kitchen to make herself some breakfast. Her mother was already there, quietly pouring herself a cup of coffee. "Oh, hi mom!" Dani said as brightly as she could manage. "I didn't even notice you came downstairs." "You looked pretty occupied with your work over there, dear," her mom responded, taking a sip from her mug. "Having a hard time focusing this morning, actually," Dani admitted, opening a cupboard and pulling out a box of cereal. "Maybe I need some breakfast to jump-start my brain." "It's the most important meal of the day," her mother chimed in. "Though I doubt that sugary cereal will give you much benefit. You want me to make you some eggs and bacon?" "Yes please!" came Jake's voice from the dining room. "How about some hash browns, too?" "That's the most he's said so far this morning," Dani whispered, only loud enough for her mother to hear. "Teenage boys are barely human when they first get out of bed, and your brother is a teenager now, don't forget," her mother whispered back, then said in a normal tone, "Can you help me out with breakfast?" That wasn't it, Dani thought to herself as she retrieved potatoes and the grater to start on the hash browns. Just the previous morning Jake had been his usual, annoying, lighthearted self, poking fun at her and flinging just as many insults her direction as she did his, knowing that neither of them actually meant anything by it. He couldn't have changed overnight, and he'd been a teenager for two whole months already without acting like this. No, something else was going on with him, and Dani would somehow have to get to the bottom of it. That gave Dani two goals to work toward over the next few days: figure out what was wrong with Jake, and figure out whether she could give herself another... what should she call it? Pleasure explosion? Whatever it was, she wanted to do it again, this time in her bed, and see if she could make it a nightly routine, rather than just a shower-time routine. Never before had Dani so looked forward to bed time. She was usually one to put off sleep as long as she felt she could without being a zombie the next day, especially whenever she and her friend Audrey had a sleep over, often staying up until three or four in the morning giggling quietly to keep from waking up the rest of the house. Thinking of her friend gave Dani an idea. "Hey mom?" She asked as she finished grating the potatoes for hash browns. "Yes dear?" Her mother already had the scrambled eggs done and was beginning to fry up some bacon. "Can you ask Audrey's mom if I can come over Saturday for a sleep over, and they can bring me to church on Sunday?" "I think that can be arranged," her mother responded. Dani's mother rarely told her "no" regarding visiting her friend, unless there was something else already planned with the family. After all, Jake had Finn, who he could hang out with every day, while Audrey lived a half-hour away. As such, the two girls rarely had extended time together. It wouldn’t be so bad if Dani had ever been able to build a friendship with any of the girls in her neighborhood. They were all snobs in Dani’s estimation, who looked down on her for being homeschooled and for preferring to play in the woods and the dirt. Audrey, however, was a girl after Dani's own heart. She lived on a ranch, rode horses, and climbed trees. She, too, had brothers, though both were older than her, and one older sister who had recently married. Audrey was the youngest and only had one brother still living at home who was three years her senior. So when Dani and Audrey wanted to have time together, their parents usually tried to make it happen, which Dani was counting on. She had to ask her friend about this new sensation she had discovered, and see if Audrey could do it, too. Dani finished helping her mother with breakfast, by which time her other two brothers had made their way up to the dining room as well, the enticing aroma of frying bacon having roused them from their beds. Their father had also made his way downstairs, Bec in his arms, to pour himself some coffee and snatch a strip of bacon off the plate where it was cooling. They all sat together for breakfast, a cacophony of happy voices mingling together as they enjoyed the meal. Jake seemed to interact with everyone else as normal, snagging Aaron in a head-lock and knuckling the boy's head playfully before releasing him, his mop of sandy hair sticking out in all directions. Yet Jake still wouldn't interact with Dani beyond the surface level, and every time she caught his eyes looking her direction, he would quickly turn away. His behavior continued throughout the remainder of the day, reinforcing Dani's determination that it had nothing to do with simply being a teenage boy who could no longer handle mornings well. Jake spent the entire day with their younger brothers, Travis and Aaron, much to their delight, leaving Dani to her own devices for entertainment. If she hadn't had Dozer for company, who she took on a run and played with most of the afternoon in the park, she would have gone out of her mind with boredom. After dinner, the boys all went downstairs to play Smash Brothers on the Nintendo Switch, and Dani curled up between her parents on the couch, cuddling with her father as they watched a movie. "What? The boys don't want to have you beating them on the Nintendo again?" her father asked as she wrapped her arm around his solid frame. "I don't know," Dani admitted. "Maybe they've finally figured out I'm a girl and don't want to hang out with me, in case I give them cooties." She felt more than heard her father sigh heavily before responding. "Boys will be boys," he said matter-of-factly. "They'll come around if you give them time. You're still their big sister who likes to ride bikes and play soccer more than have tea parties and play dress-up. And until then, I certainly don't mind snuggling with my baby girl." "Thanks dad," she said with a smile, hugging herself closer into him. Maybe he was right, and all it would take is a little time for Jake to warm back up to her. Then again, maybe she had been partly right, too, though she'd only said it as a joke. Maybe Jake had figured out that she was a girl after all, and wasn't comfortable with the realization. A few of the times she'd caught him looking her direction, his gaze had not been directed toward her face, but lower, as if looking at her chest. That still didn't make any sense, though. Dani's breasts had developed quickly, starting at age eleven, and were certainly noticeable for at least the last year and a half, despite the loose t-shirts she generally wore around the house. If this was all about Jake noticing she had distinctly womanly body parts, then he should have noticed that some time ago instead of just starting to treat her differently since the previous afternoon. Come to think of it, Jake hadn't gone to hang out with Finn today either. He'd spent the entire afternoon with their brothers instead. Was this all due to some falling-out between Jake and his best friend? If so, then why was he taking it out on her? No... That wasn't right either. Jake's behavior toward Dani had started ***before*** he went to hang out with Finn. It seemed to start right after the incident with her sunglasses and chasing him up the tree to retrieve them. Had her brother somehow noticed the pleasure Dani was feeling from rubbing her crotch against the tree trunk as she climbed? She thought she had been hiding it well enough, but maybe she had been wrong. Maybe he had noticed and thought it was gross, and that was why he didn't want to spend time with her anymore. The thought horrified her. Was there something gross or wrong about what she had done? How could there be when it felt so incredibly good? Then again, there didn't have to actually be anything gross or wrong about it for Jake to think that. Should she talk to him about it and explain it to him? Would that make things better or worse? The very idea of talking with Jake about it made Dani's face heat with embarrassment. She could not imagine talking to her brother about how she gave herself pleasure by rubbing her vagina. If there was anything that would sharpen his awareness that she was a girl, and very different from him, it was that. No such embarrassment accompanied the thought of talking with Audrey about it, but she instinctively knew it was an off-limits subject with her brother. Instead, she would give it time, like her father had suggested, and hope that Jake would forget about it, as long as she didn't repeat anything similar in his presence. After the movie, Dani kissed each of her parents goodnight and retired to her room. She settled into bed to read a Nancy Drew book until she felt tired, and let her hand slip down to her groin, lightly caressing her mound and across the outer lips of her vagina through the light cloth of her pajamas and panties. The sensation was pleasant, but not insistent like it had been in the shower. It made for a relaxing background feeling while she read her book. After several minutes of it, though, she found herself aching for more and set Nancy Drew aside, nestling deeply into her pillows and shoving her hand underneath her clothing to gain direct access to her sex. What she found surprised her. She was damp between her legs, and especially the inner folds of her vagina. For a moment she worried that she had wet herself by accident, but when she brought her fingers to her nose, it didn't smell like urine. Instead it had a pleasant musky aroma she'd never smelled before. She returned her hand between her legs and began to rub more deeply, focusing her attention on the nub in the center of her folds as she felt it grow erect. There was more friction than there had been in the shower, and it was slightly uncomfortable, so she dipped her fingers lower into her folds to coat them in the liquid that seemed to be coming from the opening there. That did the trick, reducing the friction significantly and allowing her to increase the speed and pressure of her ministrations. Soon she was bucking her hips upward into her furiously rubbing fingers, knowing that the release she craved was just moments away. Then it crashed over her, causing her whole body to shudder and writhe in ecstasy. With one hand she continued to lightly rub herself through the spasms of pleasure, while gripping her blankets tightly with the other. She had done it! Whatever this "pleasure explosion" was, it was repeatable! She could do it every night if she wanted to and she saw absolutely no reason why she wouldn't. She decided that if her friend Audrey didn't know about this, she would simply have to teach her. It felt far too amazing to be kept to herself. It was going to be a great weekend, even if her brother was behaving so strangely. *** Friday afternoon, Jake wasn't sure whether he was ready to face his friend Finn yet. The previous day, for the first time in months, the two of them had not spent any time together at all. What his friend had said about Dani bothered Jake deeply. He knew his friend was right—that his sister was indeed "hot as fuck"—and he now had first hand knowledge of that fact, but he still didn't like the idea that Finn thought of her that way. Why was that? A girl was either hot or she wasn't, right? Could he blame his friend for noticing that a girl was hot, even if that girl was his sister? No, that wouldn’t be fair. It wasn't Finn's fault that Dani was attractive, and he'd be even more angry with his friend if he thought she was ugly. Jake decided his anger with Finn was really an extension of his own confusion about Dani. He'd only just "discovered" that his sister was hot, so it was hard for him to consider that his friend had noticed before him. Should it really be surprising, though? Jake had lived in the same house with her for his whole life, and always thought of her as his brat sister, and his closest friend other than Finn. That kind of relationship didn't tend to encourage him to notice that she was becoming a woman, with all the attractive qualities that came along with it. Finn, on the other hand, had no such hang-ups, and could see Dani for what she was: an incredibly enticing young woman, who didn't act like the prim little snobs he knew from school. When Jake thought of it that way, how could Finn ***not*** find his sister attractive? That made up his mind, and he set off to meet Finn at his home, since it was already well past when he would have been dropped off at the bus stop. He didn't bother with bringing his fishing gear this time, knowing that they wouldn't spend any time at the river today. When he arrived at his friend's home, he hopped off his bike, letting it fall to its side on the lawn, and jogged to the front door, knocking on it sharply. A few moments later, Finn's older brother Scott pulled open the door then called over his shoulder, "Hey Finn! Jake's here for you!" "Really?!" Jake heard his friend's muffled response from somewhere within. "Yeah! He's waiting right here at the door, shit-for-brains!" "Don't use that language around Jake!" Finn's mother shouted from somewhere else within. "His father’s a pastor! Show some respect!" Scott rolled his eyes and walked away, leaving the door open, and Jake stepped inside to wait for his friend. Finn didn't leave him waiting long, bounding down the stairs with a small backpack slung across one shoulder. It wasn't his larger school bag, and Jake imagined it likely contained some snacks and his tablet. "Hey! Glad you came over!" Finn said genuinely. "Everything okay?" "We're gonna need to talk, but yeah, I think so," Jake replied giving his friend a reassuring smile. "To the fort, then?" Finn asked and Jake nodded. They rode out to their fort in the woods in silence, both of them nervous about the conversation to follow. When they left their bikes in the bushes and crawled into the dark interior of the fort, their silence seemed to be made even more ominous by the dim lighting, though it did help Jake to finally speak, since he could hardly see his friend's face. "I guess I can get over the fact you think my sister is hot," he blurted out as they settled in to sit at opposite sides of the fort. It didn't separate them by much, since the interior was only about eight feet across, but it was a stark difference from the way they usually sat side by side and huddled over Finn's tablet screen. "Well that's a relief, since you're going to have to deal with it from far more guys than just me, soon enough." "You're not wrong there..." Jake admitted. "It was just a shock to me the other day, because I had never really seen her that way before." "You're not supposed to see her that way; you're her brother," Finn pointed out. "Too late now," Jake said. "As of two days ago, I can't help but see her that way anymore." "Sorry about that… I really did mean to delete that picture." "Don't worry about it, it wasn't just that anyway," Jake assured him. "Oh really?" Finn asked, and Jake was certain that if he could see his friend's face the boy would have an eyebrow cocked in curiosity. "Do tell." Jake drew in a deep breath, considering for a moment just how much he wanted to tell his friend; his best friend with whom he usually had no problem sharing anything. Letting the breath out slowly, he told Finn the whole story, starting with watching Dani shimmy up the tree after him, the tops of her breasts poking out of her tank top enticingly, then watching her walk back toward the house with her cutoff jeans clinging to her round ass, perfectly framing her curves and drawing attention to her lightly tanned legs. "Those cutoffs should be illegal!" Finn proclaimed. "I can't see her in those without feeling my heart stop beating because all my blood rushed to my dick." "Hey, just because I am okay with you thinking my sister is hot doesn't mean I want to hear you talk about her like that," Jake warned. "Sorry, sorry!" Finn apologized sincerely. "You're the one talking about getting a boner staring at your own sister's tits and ass, though." "True enough," Jake conceded. "I'm not done yet, though." He continued to tell his friend how shocking it had been to see a naked woman who looked so much like an older version of his sister. Just the brief seconds of her image on the screen had fueled his imagination endlessly about what Dani might look like with her clothes off. Then he told his friend about spying on his sister in her bedroom from outside her window Wednesday night. "You dirty dog!" Finn exclaimed. "Was she as hot as you imagined?" Jake could tell his friend was really asking, "Is she as hot as I imagined?" but he let it slide. "Dude... She's an absolute babe..." He continued to describe the details of her round, perky tits, her amazing bubble butt, and her lithe and subtlety curved body; petite, and yet athletic and toned. "Holy shit, dude!" Finn breathed when Jake had finished. "How can you contain yourself living in the same house with a girl like that? I'd be jerking off all the damn time." Finn usually restrained his colorful language around Jake, but he had obviously been too wrapped up in what Jake had revealed to bother with it now. "I have to admit," Jake responded. "Since 'discovering' she's more womanly than I had realized, I have been jerking-off more than usual." "You know, most people would think that's pretty messed up, right?" Jake nodded, then remembered his friend couldn't see in the dark. "Yeah, I know..." "Still, if I was in your shoes, I think I would have to jerk off ten times a day just to keep from losing my mind." That made Jake laugh in spite of himself, and Finn laughed along with him. "Well dude," Finn began. "Do you need some pictures of other hot babes to take your mind off your sister?" "How can I say no to that?" Jake asked, and his friend fished out his tablet. The two of them moved closer together so they could both see the screen and they settled back into their usual routine of commenting on what they liked and didn't like about the naked women Finn had selected for their perusal. The girl that had been Dani's lookalike didn't make a reappearance in the collection, but Jake found himself comparing all of the women to Dani in his mind. This one was chubbier than Dani, that one was skinnier; this one had larger breasts, but with odd shaped areolas, while that one had breast that were similar size, but more saggy. Every one of them was viewed through the lens of how she stacked up against his sister. What's more, every one of them fell far short of Dani in his estimation. When they’d had their fill of gawking at naked women on Finn's tablet, they rode their bikes back to the neighborhood and around the park, chatting as they always did and bragging about the latest trick they could pull off on their bike or skateboard. Eventually they went their separate ways so Jake could make it home for dinner. Finn didn't have such concerns, since his family always ate much later in the evening, but he didn't blame his friend for wanting to get home for some grub, and to enjoy the "eye candy" that his sister provided. Dinner was delicious, as always. His mom was a fantastic cook, even with the most basic ingredients, and the family always enjoyed their time around the table together. Dani was in her customary hoodie, which made it easier to look her way without feeling like he might get caught checking her out, but he found himself admiring her facial features instead. She really was quite stunning with her full, soft lips, long, dark eyelashes, and thin, elegant eyebrows framing her bright, blue eyes. Her cheeks were barely round enough to mark her as a girl, rather than a woman, and her slightly upturned nose was neither too big nor too small for her face, unlike some of the women he'd seen on Finn's tablet. Of course, with all his staring in her direction, Dani had noticed his gaze on her more than a few times, causing him to look away suddenly with a blush. He needed to get a grip on himself! If he wanted to ogle his sister, he would need to wait until he could creep to her window again tonight, rather than here at the dining table where any of his family might notice. It was her usual night for a shower again, so Jake would have another opportunity to see her graceful naked form, if he could manage to sneak out as he had done before. Indeed, he'd thought about trying to sneak out to her window on nights that weren't her shower nights as well, since Dani had to undress every night to put her pajamas on, shower or no. He had nixed that idea in the end, though, because it was far more risky. He'd have to sneak out while his brothers were still getting ready for bed, and while his parents were known to come check on their progress. By only sneaking out on nights when Dani showered, Jake virtually guaranteed that his brothers would be in their bedroom, and his parents either upstairs with Bec, or watching TV in the living room. This was because his sister preferred to take her showers quite late in the evening, after the youngsters had already finished getting ready for bed and said their good nights. He imagined it was her way of winding down for the night, which she found easier to do when the rest of the house was quiet. Regardless of her reason, it would work to his advantage again tonight. *** That night Dani gave herself another "pleasure explosion" in the shower, finding it easier than before to build herself up for the release. Something about the hot water rushing over her body added to the whole experience, heightening the sensations as it enveloped her in its wet embrace. As she dried off, she wondered how soon afterward she could do it again. Wrapping her robe around herself for the short trek past the living room to her bedroom, she decided she would try again on her bed, after drying her hair. Gathering her things, she exited the bathroom, wished her parents, who were seated on the couch watching their favorite sitcom, a good night, and stepped into her own room, flicking on the light and closing the door behind her. After hanging up her towels to dry on her bedposts, she undid her robe and let it fall to the floor, enjoying the feeling of being entirely nude. Then she went about her routine of brushing and drying her hair at her vanity before wandering over to her closet. She was about to pick out a pair of panties and some pajamas when she stopped herself. Why not just stay completely naked while she rubbed herself, like she did in the shower? Deciding that was a splendid idea, she closed her closet door and flopped onto her bed. She didn't even bother crawling under the covers, just letting her head sink into her pillows as she lay on her back, spreading her legs wide for easy access to her sex. Like the previous night, she started with light caresses on her skin, trailing her fingers down across her stomach until she felt the fuzz atop her mons, which she played with for a short time. Then she caressed the inside of her thighs and brushed lightly across the outer lips of her vagina. She felt the pleasurable sensation awaken within her for the second time that evening and she knew she'd be able to bring herself to rapturous release once more. This encouraged her to press on, rubbing herself in earnest and beginning to feel the dampness return to her inner folds. As before, she used it as lubricant for her rubbing, flicking, and swirling fingers, which had begun to cause her hips to buck in rhythm with her ministrations. Dani increased her pace and pressure, faster and harder, faster and harder, until her pleasure reached its crescendo and her body stiffened in overwhelming physical bliss. She continued rubbing herself through the waves of pleasure that were like aftershocks of an earthquake wracking her body until she was abruptly interrupted by a large ***THUMP*** that came from the outside wall of her room. She froze in horror. Someone was outside her room in the side yard! Scrambling, she got up from her bed and donned her robe as fast as she could to cover herself, then went straight to the window to see who had been spying on her. She raised her blinds and looked out into the night. It was difficult to see in the dark, but no one was there. Just the massive rhododendron bush blocking everything else from view. She hadn't imagined the sound, though. Something large had bumped up against the outer wall, for certain. What could it have been, if not a person? Then she remembered that their massive dog, Dozer, had free reign of the back and side of the house at night, since it was fully fenced, and she breathed a sigh of relief. The Rottweiler was definitely large enough to have made that thump if he bumped into the outside wall, and it made sense he would be poking around at night, especially if any smaller animal had caught his attention and he had given chase. In her state of vulnerability, she had merely jumped to the most horrifying conclusion possible, instead of the one that made the most sense. Smiling at her own silliness, Dani walked back over to the closet, dropping her robe and putting her pajamas on for the night. She needed to get her sleep because she had an important weekend ahead of her. She'd be going over to Audrey's shortly after breakfast and planned on showing her best friend her newfound favorite hobby. *** Jake was panting in fear when he made it back to the safety of his room that night. He had very nearly been caught! Yet he could not deny that the risk had been more than worth it, given what he had seen his sister doing through her window. He'd never seen a girl jerk-off before, but that was to be expected since he'd never seen a live girl naked before until just two nights ago. He'd never even imagined that it was possible for a girl to jerk-off since they didn't have a dick, but he'd just witnessed Dani do exactly that, laying on her bed completely naked, furiously rubbing herself until she went rigid and shuddered uncontrollably from what he could only assume was pure pleasure, judging by the wide and rapturous smile on her face. There were two main differences that Jake noticed in the way his sister jerked-off compared to how he did it. The first was obvious in that she rubbed her pussy, while he pumped up and down on the shaft of his cock. The second was that she didn't have any cum spraying everywhere when she climaxed. The first time Jake had jerked off, the cum had scared him as it sprayed all over his stomach and hands. He thought he had done something wrong until his friend Finn had explained that it always happens. After that, Jake had taken to using a sock to capture it, so his cum didn't give him such a mess to clean up. Dani didn't have any cum at all, which meant she didn't have to worry about any messy aftermath. How convenient for her, he thought sarcastically. In order to get an angle to best observe what his sister was doing, Jake had leaned to his left without shifting his knees beneath him, and when she came, he had been so shocked that he lost his balance and fell over, catching himself by slamming his palm into the wall. He had immediately known he needed to leave, or he would be caught, so he rushed out from behind the rhododendron bush and around the corner of the house to the back yard. Once out of sight of Dani's window, he had slowed his pace and crept back in through the basement door to his room. Above him he could just make out Dani's soft footfalls as she walked from the window to her closet. She had definitely checked to see if anyone was out there, and he had no doubt that if she thought he had been spying on her, she would have been stomping down the stairs to confront him in a heartbeat. No such stomping ever came, though, which meant she must have concluded that no one had been at her window, after all. Jake had narrowly dodged being in a world of trouble, and likely not just with his sister. Though they tried to work most things out between each other, Jake was sure Dani would have deemed this infraction severe enough that it needed to be taken to their parents, and who knows what they may have done about it. Still, the payoff had outweighed the risk more than he had expected. He'd snuck out to peep though her window expecting to see her going about her evening routine in the buff like he had before, and she had delivered on that, dropping her robe then brushing and drying her hair at her vanity before going over to her closet to get her bed-clothes. Then she had stopped, turned and flopped naked onto her bed, spreading her legs wide and giving Jake the hottest display he had ever seen. It was all he could do to keep himself from whipping dick out and jerking off as he had watched. As it was, he had been rubbing his boner through his pants, which had likely contributed to him losing his balance, as well. Once the fear of almost getting caught started to dissipate, Jake flung his pants off and started tugging on his dick while recalling in as much detail as he could exactly what he had just seen. It was the fastest he had ever cum, he was sure, and he almost wasn't ready with his sock as his climax overtook him. *** Dani beamed as she saw her friend Audrey rushing down her front steps to greet her before she'd even opened the van door. Her friend was the quintessential cowgirl, boots and all, with her worn jeans and flannel shirt. The only thing she was missing was the hat, but she made up for it with matching french braids on either side of her head that ended in shoulder length auburn pig-tails hanging down behind her. The only word Dani had to describe her best friend was "adorable.” She was a bundle of energy in a small package, both shorter and thinner than Dani, and she had been a late bloomer in the breast department, barely filling out an A-cup bra; a fact that Audrey reminded her about on a regular basis. The girl was actually jealous of Dani’s larger breasts, which Dani could not begin to understand. More than once, she had expressed her willingness to trade breast size with Audrey, if it were only possible. Dani hardly had time to climb out of her mom's van before her friend wrapped her in a tight embrace. "I'm so glad you asked to come over!" the smaller girl exclaimed, backing away a bit and taking Dani's hands in her own. "It feels like it's been forever since we got to hang out, even though it's really only been a few weeks." "I know what you mean," Dani agreed. "So much can happen in just a week, and the short time we get to talk after church just isn't enough." "No, definitely not!" Audrey said, pulling her away from the van. Dani barely had time to grab her bag before her friend was dragging her away toward the house. She turned and waived goodbye to her mother, who was chatting with Mrs. Larson, then followed her friend in the front door and down the hall to the girl's bedroom. "You can drop off your bag here, then I have my morning chores to get done before we can find something fun to do," Audrey explained. "I'll help you with your chores, if you want," Dani offered. "I have a ton to tell you about, so we'll need all the time we can get." "Sounds great to me, but you'll need to borrow some rubber boots," Audrey advised. "I have to make sure all the animals have water before it starts getting hot, then I have a stable to muck out, and eggs to gather from the chickens." "Can't wait!" Dani said honestly. She enjoyed helping care for the animals whenever she came over to Audrey's house. The Larsons had more animals than Dani had ever known a single family to own. They had two dogs, several cats, a handful of rabbits, a flock of chickens, four horses, a small herd of cows, and one ornery goat. Dani's favorite were the horses and the two girls would often spend their afternoon trail riding. She hoped they'd get a chance to do just that today. Audrey led her back out of the bedroom, down the hall, and past the living room to the mud room at the back of the house. There she presented Dani with a grubby pair of rubber boots that her older brother, Jeffrey, had grown out of. They were slightly oversized for Dani, but they would do the job, and once Audrey had donned her own pair they headed out the back door and down toward the barn. The Larsons lived on a gorgeous property with expansive pastures, surrounded by forest, with a small creek running through it. They owned twenty acres in all, but it backed up to state forest land with gravel access roads spider-webbing through it, where the girls liked to go ride the horses. As they made their way toward the barn, Dani started thinking about how she would broach the subject of the "pleasure explosion" she'd discovered the could give herself. It had been an easy decision to want to tell her best friend about it, but she hadn't given any thought to exactly how best to bring it up. "You know..." Audrey began as she was filling a water bucket with a hose. "For someone who said she has a ton to tell me about, you sure are being quiet." "I ***DO*** have a ton to tell you about," Dani insisted. "I'm just not sure how to start." At that, the smaller girl cocked an eyebrow. "You know you can tell me anything. Just spit it out." "Well... Have you ever noticed that it can feel really good to rub yourself... down there?" Dani pointed to her crotch. "Your girly bits?" Audrey asked. "Girly bits?" "Yeah! My mom calls them her 'lady bits', but I'm no lady yet, so I call them my girly bits," Audrey explained. "And yes, I have noticed that before. I'm surprised you hadn't! Oh gosh, Dani! Did you have your first orgasm?" "Orgasm?" Dani questioned. "Yes! That's what it's called when you make it feel ***REALLY GOOD*** and everything just seems to explode with pleasure." "That sounds about right," Dani nodded. "You knew about that and never told me!?" Audrey shrugged. "I guess I figured you probably knew about it already. It's not exactly something that comes up in day to day conversation." "No, probably not," Dani agreed, helping her friend haul the water bucket into the barn. "But how did you know about it already? I only just figured out I could do it this week!" "I guess I did have a bit of help..." Audrey admitted. "When I was ten, Millie noticed me grinding my girly-bits on a saddle horn, and she taught me all about it." Millie was Audrey's older sister Melissa, who had moved out and gotten married the year before. "See! You had a sister to teach you about these things! Who am I supposed to have teach me? My mom?" "You're right," Audrey agreed. "I really can't imagine your mom teaching you to masturbate." "Master-what?" "MasturBATE. It's what it's called when you give yourself an orgasm. My brother calls it jerking-off, but I think that's because boys do it different." "Wait, ***WHAT!?***" Dani exclaimed. "Boys can do it, too!?" She felt like her world was being turned on its head. "Oh definitely!" Audrey replied matter-of-factly. "I caught Jeff jerking off in the wood-shed once when he was supposed to be out milking the cows. He stuffed his dick back in his pants as fast as he could, but I'd already seen what he was doing." She formed a circle with her fingers and pumped her hand up and down vigorously in front of her crotch. "He swore me to secrecy about it though, so don't you dare let anyone know I told you about it!" "Wow..." Dani said simply. "I had no idea that everyone was already doing it but me." "I'm sure it's not ***everyone***," Audrey said, obviously trying to reassure her. "And if you'd like, I can show you a few things later today. My sister taught me well. She said that one day I'd be grateful I knew what I was doing, whatever that means." "That sounds like a great idea!" Dani agreed. "Goodness knows I am just blindly feeling my way through it." "I see what you did there," Audrey said with a wink. "Feeling your way through it." They both giggled at the pun. "That can't be all you wanted to talk about, though. We've barely started in on the chores." It was true. They had only just managed to fill all the animals' water troughs, so they were now retrieving the wheelbarrow, pitchfork, and shovel to start in on mucking out the horse stall that was due for new shavings. Then they still had to go gather eggs. "Well, I didn’t know my first bit of news wouldn’t actually be news to you at all, so I thought it was going to take longer,” Dani protested. “The other thing is a bit of a mystery I have on my hands, though.” "Oh? I like mysteries." "This one is about Jake." "What has that little punk done now?" Audrey asked with a grin. She was the only person who understood Jake and Dani's relationship of mutual and meaningless antagonism. In fact, she enjoyed joining in on it whenever she came over, taunting Dani's brother even more viciously than she did. "It's not really anything he's doing so much as what he's ***not*** doing," Dani explained. "On Wednesday morning, he was pretty normal; he even stole my sunglasses and climbed one of the maple trees in the back yard with them, threatening to leave them up there unless I could climb up and take them back." "Yep! That sounds like typical Jake to me!" "Well, after that it's like he just decided to shut me out. He's barely talked to me at all the rest of the week. No teasing, no name calling, and no pranking the rest of the day Wednesday, and all day Thursday, and Friday." "Woah! That ***is*** strange! He's always giving you a hard time!" Audrey agreed. "I know! I can't figure out what happened to make him shut down toward me. He's not any different with the rest of the family, and is maybe even more friendly with Travis and Aaron than before." "So, it's definitely something specific to you, then," Audrey said thoughtfully. "Well, maybe, maybe not," Dani continued. "Jake almost never goes a day without hanging out with Finn, but he came home early from fishing with him on Wednesday, and didn't hang out with him at all on Thursday." "Maybe Finn had something going on and couldn't hang out," Audrey suggested. "That could be it," Dani admitted. "Jake did go hang out with him yesterday, like normal." "So, as far as you can tell, it's really just you that Jake is suddenly acting cold toward, right? "Yes." "And it all happened after you climbed the tree after him to get your sunglasses back?" "Yes." "And Jake was above you the whole time you were climbing?" "Yes, obviously." "I think Jake saw your boobs." "What!? My boobs? I had my shirt and sports bra on, like usual! My boobs stayed covered! ...At least mostly. The important parts anyway.." Audrey looked at her pointedly for a moment before speaking, as if accusing her of being an idiot. "A boy doesn't have to see your whole boobs to notice that you have them, you know. If you were climbing that tree in a tank-top, I bet he had a nice view down the front of your shirt." "But Jake doesn't think of me that way," Dani protested. "He's always seen me as practically one of the guys, even when the rest of his friends stopped hanging out with me." "Dani... He's a teenage boy," Audrey pointed out. "His relationship with you as his sister may have held off the inevitable for a while, but boys only think about three things: food, video games, and girls. Maybe watching your boobs as you climbed up the tree triggered something in his head and he finally figured out you were a girl, with all the equipment that comes with it." She said the last bit pausing from her work to gesture pointedly at Dani’s ample chest with her free hand. Dani was silent for a time, thinking over what her friend had said as they filled another wheelbarrow with soiled shavings from the horse stable. She barely even noticed the smell, she was so focused on whether Audrey had correctly assessed the situation. Everything with Jake seemed to hinge on that incident with her sunglasses and climbing the maple tree to retrieve them. Whatever the reason was for his coldness toward her the last few days, it was somehow linked to that. So far, only two possibilities had presented themselves: either Dani's worst fear was the case, and Jake had noticed that rubbing herself on the tree was giving her pleasure, or Audrey was right and Jake had been checking out her boobs as she climbed. Of the two, Audrey's assessment seemed more likely. Dani could not imagine how he could have even seen that she had been rubbing herself on the tree trunk as she climbed from his angle, but he would have had a direct view down the top of her shirt to where her sports bra was struggling to keep her breasts contained as she shimmied upward. Somehow, it was both relieving and a bit exciting to think that he had been checking out her boobs. It was a relief because it meant that Jake didn't know her other secret about giving herself - what had Audrey called them? Orgasms? Though, according to Audrey, most boys give themselves orgasms, too, so Jake might already do that to himself as well. The thought was still a bit shocking to her, since she had only just discovered it was possible in the first place. She wondered if she would ever have an incident like Audrey, walking in on one of her brothers in the middle of "jerking-off" as she had called it. Since Dani had three brothers, the chances were probably pretty high that it would happen someday. A twinge of curiosity made her almost hope it happened sooner rather than later. The idea that Jake had been checking out her boobs also made Dani feel a bit excited. She'd never considered that someone might look at her that way before. There weren't many boys at their church except those still in grade school—which is why all of Jake's friends were boys he knew from outside of church—so Dani had never even had a crush on a boy before, let alone thought about trying to look good for one. Something inside her made her want to be looked at, though, now that the idea had been planted in her head that someone might want to, even if it was her brother. Did Jake like what he saw? Why should it matter if he did? But somehow, it did matter to her, and she couldn't puzzle out why. "Okay..." Dani said finally. "You might be on to something." "Of course I am," Audrey replied confidently. "That still doesn't explain why he won't talk to me, though," Dani complained. "Sure it does!" Audrey insisted. "Most boys have a hard time talking to hot girls." "So you're saying Jake thinks I'm hot?" Dani asked, surprised to find that she hoped he did. "Good grief, Dani!" Audrey responded in exasperation. "You ***are*** hot! You just haven't ever noticed it, and apparently neither did Jake until now." "Wait... You think I'm hot, too?" Dani was getting more confused by the minute. She had never thought of herself as attractive, and she had definitely never considered the possibility that another girl might think of her that way. Then again, as she looked at her petite friend, in her tight jeans, flannel shirt, and french-braided pigtails, Dani couldn't help but admit that Audrey was pretty cute, as well. Dani couldn't quite classify the girl as "hot" since she still lacked the more mature feminine curves that were generally associated with that term, but she was still quite attractive. Not that Dani was interested in girls in that way, but that didn't mean she couldn't appreciate her friend's good looks. "You must be blind, Dani Hansen. If I was a boy, I'd be drooling all over you!" "Gross... Please don't'." Dani said with a giggle. "Do you really think I'm that pretty, though?" She still couldn't bring herself to use the term "hot" in reference to herself. "Of course I do!" Audrey insisted. "You’re the full package! You're athletic, yet you have nice boobs that probably aren't done growing, long, toned legs leading up to a perfectly round butt, gorgeous hair, that it's a shame you just tie back in a ponytail all the time, and a girl-next-door sort of beautiful face. I am personally shocked that it took this long for Jake to notice. I'm sure his friends have, though." Dani blushed a deep crimson at her friend's compliments, finding herself completely speechless as she tried to wrap her mind around the idea that others might find her attractive. Even if she could accept that her brother had been checking her out, a thought that only made her blush deepen, it was still no help to her in rectifying the situation. "Fine, lets assume you're right and Jake was looking down my shirt, and now it has him all flustered, because he’s figured out I have boobs. So, what am I supposed to do about it?" The smaller girl looked over at Dani with a sympathetic look on her face as they took the pitchforks and wheelbarrow back to put them away in the tool shed. They had finished with cleaning the stall and covering it in fresh shavings, leaving only gathering eggs from the chickens on their list of chores. "I've got no help for you on that front," Audrey admitted. "Now that he's thought of you that way, it's going to be impossible to get him to think of you as just his sister again. Now you're his ‘hot sister,’ and that's the way he'll probably always think of you, unless you get fat or something." "Great... So my relationship with my brother is basically over..." "Not necessarily," Audrey said as cheerily as she could, obviously trying to brighten Dani's mood. "Maybe it will just take him some time to adjust to the idea that he has a bona fide hottie living under the same roof. Who knows? Maybe figuring out how to not be awkward around you will help him out later on when he's trying to ask a girl out." "Ugh! How long do you think that will take?" "For him to get a girlfriend? Probably a few decades," Audrey joked, causing Dani to roll her eyes. ''Alright! Alright! I knew what you meant. I just don't have a clue how long it will take him to stop being awkward and warm back up to you." "Wonderful..." Dani said sarcastically. "It's going to get really lonely at home waiting for him to come around. Do you think there's anything I could do to speed up the process?" "I doubt it," Audrey responded as she transferred chicken eggs from the nesting boxes into a rinsed-out 3 gallon paint bucket. "If you draw attention to it, you'll probably make it worse. I'd say just try to act like normal around him as much as you can." Dani sighed. "That makes sense. I guess it's my only real option, anyway." "Personally, I'd be more worried about him trying to spy on you." "Really? Why do you say that?" "Dani, boys are never satisfied with just getting a glimpse down a girl's shirt," Audrey explained. "They will try to get a look at a naked girl if they can think of any way to make it happen without getting caught. I remember how Jeff used to try and catch a glimpse of Millie when she still lived here. He climbed all the way up to her window on the second story using the trellis on the side of the house, but he wasn't quiet enough, so he got caught and nearly fell in his attempt to escape. Thankfully Millie, who was topless at the time, caught him by the scruff of his neck just before he tumbled backward. I think he would have been better off if he'd just fallen and cracked his head open, though." Dani couldn't help but laugh, picturing what her friend described. At the same time, she thought about catching Jake doing the same thing, and what she might do in retaliation. If she was honest with herself, she wasn't sure that she would even be all that mad at him. In fact, the more she thought about the idea, the more she almost hoped he ***would*** spy on her. That's when Dani remembered what had happened Friday night while she was masturbating and she froze in horror. "I think he might have already spied on me..." Dani told her friend in a near whisper. "Really? Why didn't you mention it before?" "I only just realized it when you mentioned your brother spying through your sister's window," Dani explained, then told her friend about how she had given herself an orgasm while lying naked on her bed after taking her shower the night before and had heard a loud thump on the outer wall near her window just as she had finished. "I thought it must have been Dozer at the time, because no one was there when I got to the window after throwing on a robe, but after you told me about Jeff, it dawned on me that Jake could have been spying on me. He wouldn't even need to climb anything to see through my window." "Oh, I can almost guarantee he was spying on you,” Audrey confirmed, “and depending on when he got there, he probably watched the whole time after you got out of the shower. I'm sure he can hear the water going from his room downstairs and probably uses it as his cue for when you'll be back to your room to get changed." Dani swallowed hard as she thought of all that Jake had likely seen from when she had entered her room, dropped her robe, dried and brushed her hair, and then rubbed herself to orgasm. Nothing would have been left to his imagination whatsoever. Why didn't that thought make her angry, though? It should have infuriated her, shouldn't it? Yet she felt no anger toward Jake at all for invading her privacy. The only way she could describe what she did feel was... excited? Sure, he had seen her rubbing herself, but if Audrey was right then Jake probably did something similar to himself, too, so he’d have no reason to think it was gross. Moreover, she could not blame her brother for being curious about what she looked like naked, because Audrey had piqued her curiosity about what boys looked like, too, and particularly how they jerked-off. Audrey had said it was different from how girls do it, but hadn't gone into detail, apart from the vague pumping gesture. "So, what are you going to do about it?" Audrey asked as she carried the bucket full of eggs toward the house, breaking Dani out of her thoughts. ''Huh? Oh... I don't know," She finally responded. "I guess I'll have to just close the blinds so he can't spy on me anymore." As soon as the words came out of her mouth, Dani knew it was a lie. She ***wanted*** him to see her again. Why did the idea of someone secretly watching give her such a thrill? "What? You're not going to tell your parents what he's been up to?" Audrey asked in a hushed tone. They had just come in the back door to the mud room and kicked off their rubber boots before heading toward the kitchen to drop off the eggs. "No, not for now," Dani said, matching her friend's low tone. "We don't tattle on each other unless it's something where we could get hurt badly, and besides, I don't have any proof, so he could just deny it." Audrey dropped the bucket of eggs off in the kitchen and led Dani upstairs to her room, shutting the door behind them so they could talk in private. The two girls took a seat opposite each other on the edge of Audrey's bed to continue their conversation. "Ok, so don't tell your parents," Audrey began. "But you should at least confront him about it. He needs to understand it's not okay to spy on you in the privacy of your own room." "I don't know... Didn't you say before that confronting him about checking out my boobs would just make things worse? Wouldn't this be the same?" ''Hmmm." Audrey had a slightly frustrated, thoughtful look on her freckled face. "You're probably right. I suppose it won't be so bad, as long as you are careful not to let him have more opportunities to spy on you again." "Oh, definitely not!" Dani agreed emphatically, all the while looking forward to doing exactly the opposite at her next opportunity. "Geez Dani! No wonder you wanted to talk so badly!" Audrey leaned over and gave her friend a tight hug. "What do you say we go for a ride now to take our minds off of pervy brothers?" Dani agreed, but she doubted she would be able to take her mind off of Jake now. Not when she had already begun to devise a plan for dealing with him after she got back home. *** Dani enjoyed the rest of the day with Audrey. The girls went on a long trail ride with the horses, eating a picnic lunch in the woods, and then spent the afternoon sunbathing in the back yard. After dinner with Audrey's family, the two girls retired to her bedroom for the night. "Ready to learn some new tricks for giving yourself orgasms?" Audrey asked, locking the door behind them. Dani grinned. She'd been looking forward to this all day. Audrey had dropped hints the whole time about what was coming and Dani was eager to explore this newfound source of pleasure more deeply than she had been able to on her own over the last few days. "I'll take that as a yes," Audrey said, her voice suddenly smooth and sultry, a tone Dani had never heard from the girl before. Dani watched in surprise as her friend slowly stripped out of her shirt and then her pants to stand in just her bra and panties. "Well, what are you waiting for? We can't do this fully clothed." Following her friend's lead, Dani stripped down to her undergarments as well. As usual, she had a sports bra hugging her breasts tightly to keep them in place. By contrast, Audrey had a lacy little matching bra and panty set that made her petite frame look adorable and sexy at the same time. "With that bra, it's no wonder it took your brother so long to figure out you have boobs," Audrey teased. When Dani shot her an offended look she said, "Oh good grief! Just take it off, you'll thank me later. It's just going to get in the way." Dani raised a curious eyebrow but did what her friend suggested, pulling the sports bra off over her head and tossing it to land on her bag by the bed. "Now, have you tried riding any of your stuffies yet?" Audrey asked, climbing up onto her bed and holding up her favorite teddy bear. Dani shook her head that she hadn't. "Then you are in for a treat!" With that, Audrey placed her bear face up on the bed and maneuvered so that she knelt with one bare leg on each side of the stuffed animal, her panty clad "girly bits" just inches above it. Then she sat down onto the teddy and began grinding herself back and forth along its furry body, her hips rolling hypnotically as she did so. "Mmmmmm." she moaned softly. "I hardly ever can make myself orgasm from just this, since teddy here is too soft to really get me going, but it's always a really nice warm up for the main act." As she spoke, Audrey slid her hands up under the cups of her bra and she began pinching her nipples; something that Dani never would have thought to do to herself. After a few minutes of slow grinding she asked, "Do you want to try?" "Yes!" Dani nodded emphatically and her friend lifted herself off of the bear, rolling to she side and gesturing for Dani to take her place. She did so, positioning her legs on either side of the bear as her friend had done, then lowered herself down onto it. The soft fur of the stuffed animal caressed the inside of her thighs as her panties made contact with the bear's stomach. The stuffed animal gave beneath her, cupping around her vagina and only resulting in slight, soft pressure against her sex. "Now start grinding against it," Audrey advised, and demonstrated from where she knelt on the bed next to Dani, grinding herself against the empty air. Testing it out for herself, Dani imitated the rolling and grinding motion with her hips, holding the bear in place with one hand, which also helped to keep herself balanced. The slight pressure and friction against her vagina was quite pleasant, but she could already tell that it was not going to be enough stimulation to bring her to an orgasm. The feel of the stuffed animal caressing her inner thighs was particularly enjoyable, though. She was so focused on the pleasant sensations her grinding was causing to well up within her, she didn't notice that Audrey had moved behind her until she suddenly felt her friend's hands cup both of her breasts and her fingers grasped each of her nipples, giving them a pinch. It wasn't so hard a pinch as to be painful; just enough to send a shock through Dani's body and make her call out. "Ohhhh! Wow!" Dani moaned, bringing her hands up to hold Audrey's in place as she continued to pinch and twist slightly. "I thought you might like that," Audrey breathed in Dani's ear in an amused tone. She pinched Dani's nipples a little harder, drawing a shiver of pleasure from her. "Are you ready for something else new?" Dani just nodded in response. Audrey released her nipples, causing Dani to sigh in disappointment, and said, "Get your hairbrush out of your bag." Dani turned to face her friend with a quizzical look, but Audrey just looked back at her with a knowing smile that compelled Dani to do as her friend had instructed. By the time she had retrieved the hairbrush and returned to the bed, Audrey had her own hairbrush in hand and had removed her panties, revealing a completely bare vagina, without a hint of pubic hair, that she was stroking lazily as she reclined on her pillows. "You don't have any hair down there," Dani pointed out with mild surprise. "I keep it shaved," Audrey explained, caressing her bare skin with a finger before returning it to her inner folds where she stimulated her center of pleasure. "It's way more comfortable that way. Millie taught me how when my pubic hair started growing in." "It looks so clean that way, compared with mine," Dani commented, following her friend's lead by stripping off her panties and crawling onto the bed to sit next to Audrey and recline into the pillows as well. "Some girls like to keep a little bush above their pussy," Audrey said. "But I can show you how to shave it if you want to try it out." "Pussy?" Dani asked with a giggle. "Like a cat?" "Girly-bits, pussy, vagina... There's all kinds of names for it; some worse than others. Pussy seems to be the most common, though. It's what Millie calls it, at any rate." "I think I heard Finn call Jake a pussy once. I just thought it was the same as calling him a scaredy-cat." "It basically is, but by calling him a girl instead," Audrey explained. "Finn was telling your brother he didn't have the balls to do something." "Balls?" Dani asked, even more confused now. "Oh Dani, you really are naive, aren't you?" Audrey sighed. "We'll have to go over boys' anatomy another time; I have enough work cut out for me teaching you about your own. Is your pussy nice and wet yet?" Dani dipped a finger into her folds and it came away coated in whatever sort of liquid her vagi... pussy produced when she was excited. "Yeah, I'd say so," she responded. "Good," Audrey said. "Just watch me for now, though. When you do this the first time it may hurt a bit, and there may be a little blood, but don't worry, it's fine." Dani watched in amazement as her friend widened her legs for her to get a better view, then moved her hair brush down between them and placed the end of the handle at the lower end of her inner folds. Audrey pushed gently and the end of the hairbrush disappeared inside of her. She kept pushing and slowly the rest of the handle was swallowed by her pussy, until only the portion with the bristles remained. Then her friend pulled it back out part of the way and pushed it back in again, a little faster this time. Dani just stared in wide eyed incredulity as her friend continued to penetrate herself while using her other hand to rub, flick, and swirl her fingers around the center of her pussy folds where Dani suspected her friend also had a sensitive little nub of pleasure. "Ok, now it's your turn to try," Audrey said, still gently pumping her hairbrush in and out. When she saw Dani looking skeptically at her own brush's handle, which was somewhat larger than hers, she continued, "Don't worry, it's nice and smooth, it will fit just fine. First, use your fingers to find the opening." Nodding, Dani slid an exploratory finger down into her folds, encountering her nub and sending a little shock of pleasure through her body, then continuing lower until she found the opening Audrey was talking about. It felt warm and was sopping wet with the liquid her pussy was producing. Keeping her finger there for guidance, she placed her hairbrush handle into position, feeling its cool smoothness parting her lips, then she removed her finger. She took a deep, determined breath and pressed gently but firmly on the other end of her hairbrush, feeling herself open to accept it. However, it didn't get far before Dani felt resistance. Was that as far as it would go? It was barely in an inch or two, while Audrey had put hers in all the way. "That's your hymen blocking the way," Audrey informed her. "This is where it's going to hurt a bit. You have to push through it, then it won't hurt next time." Trusting her best friend wouldn't steer her wrong, Dani did as she was instructed, putting more pressure upon the end of her brush to press it into her pussy. At first it was met with a slight stinging pain, then a brief, sharper pain as whatever was blocking the passage within her gave way, and suddenly the whole handle disappeared inside her, surprising her with the sensation of fullness so that she let out a small gasp. "You alright?" Audrey asked, and Dani nodded, the stinging pain still there, but diminishing by the second. "Great! Now, before you start pumping it in and out like me, why don't you finger your clit a little to get yourself worked back up?" "Clit?" Dani asked. "Is that what that little nub is in the middle of my pussy?" "That's the one!" Audrey confirmed, returning to fingering her own clit, as well. The girl must have paused her ministrations while Dani was working her brush handle into her pussy. Dani began rubbing her clit, as instructed, and enjoyed the sensations it sent through her. She continued to do so for a few minutes, getting used to the feeling of her brush handle buried inside of her. Then she slowly began to pump the handle in and out of herself in the same way Audrey was doing next to her. It somehow added to the pleasure she was feeling. Not directly, like fingering her clit, but more of a background sensation that added to the overall experience. The full feeling it gave her each time she pushed it back in was exquisite. Soon she was lost in the pleasure her ministrations were causing, hips bucking up to meet each thrust of the brush handle into her, and grind against her furiously swirling fingers. Then she felt Audrey's hand cup her right breast and start pinching her nipple and the added pleasure sent her over the top with cascading waves of ecstasy overcoming her. She thrust the brush handle into herself one final time and marveled as she felt her pussy clamp down in spasms around it. When her orgasm finally began to subside, Dani turned to look at her friend with a massive grin on her face. "Incredible, right?" Audrey asked, and Dani nodded vigorously. Then she had the pleasure of watching her petite friend work herself to a similar orgasm before collapsing in a satisfied heap on her bed. They both extracted their hairbrushes from their sopping pussies and cleaned them off with some wet wipes Audrey kept handy for that purpose. Dani did find a small amount of blood on hers, but thankfully it had not gotten on her friend's blankets. I never imagined this would be the reason for my first time bleeding from there, Dani thought to herself with amusement. While she had been an early bloomer in the breast department, she still hadn’t had her first period, which was unusual, but not unheard of for a girl her age. The family doctor wanted her to come in and schedule some testing if she didn’t have it by the time she turned fifteen, though. Dani often wondered why it hadn’t happened yet, but Audrey often reminded her that she wished she didn’t have to deal with it every month, making her count her blessings. "If you want, I can show you how to shave your pussy now," Audrey offered, breaking Dani out of her thoughts. "Did you bring your razor with you?" "I brought it," Dani confirmed. "And sure, I think I'd like to try it out." The two of them covered themselves in bath robes and headed to the bathroom where they hopped into the shower together and Audrey showed her how to properly, and carefully, shave her pussy. It was very strange to Dani, feeling that part of her body so smooth. She'd gotten used to the pubic hair, but she figured that keeping it shaved was no different from doing the same with her legs and arm pits; just another area to make sure she kept up on at the same time. She liked the way it felt as she ran her fingers across the bare flesh, and the two of them fingered themselves to another orgasm there in the shower before returning to bed. "I can't believe you pinched my nipples like that!" Dani said when they had snuggled under the covers together. "Millie did the same thing to me when she was teaching me," Audrey said. "It shocked me so bad I almost punched her. But it felt ***sooooo*** good, so I have been doing it to myself ever since. I figured I'd see if you liked it, too." "It made me orgasm, didn't it?" "Well, it sent you over the edge," Audrey confirmed. "I doubt you would orgasm just from having your nipples pinched alone." "I sure am grateful that your sister taught you so much about all this," Dani said. "I came over here thinking I would be telling you about something new I had just discovered, and instead you helped me understand it. Thank you for that." "My pleasure!" Audrey responded, then added, "Quite literally," and the two of them broke into giggles. They continued to chat as they lay in Audrey's bed until they were both too tired to remain awake, and then cuddled up together with Audrey wrapping her arm around Dani to cup one of her breasts as they drifted off to sleep.
@ 21db9b8a:2a94c796
2025-02-14 06:46:21Fair warning: This is the continuation of an explicit and erotic story involving extremely taboo themes that would prevent it from being published on most sites that host erotic stories. All characters in this story are ***fictional only***. It is not in any way based on true events. This is also not your average stroke story. It will be released in chapters, and while there ***is*** sexual content in each chapter, there is no full-on sex until late in chapter 4. It is a story of sexual discovery and exploration between young people who have few resources to educate them, but also few inhibitions to hold them back. I hope you enjoy it. If not… Well… You don’t have to host it on your relay, and you can always mute me so you don’t see any more. If you missed Chapter 1, you can read it here: nostr:naddr1qvzqqqr4gupzqgwmnw9dmeqlgk4c5a0ryypxw8xudnrdvgzye7930yzjss4ff3ukqqxnzden8qunzvfkxgerxdfnfxxqt9 *** Dani awoke Thursday morning feeling particularly peppy and refreshed. She knew it probably had something to do with her experience in the shower the night before. It had been such an amazing release of pent up energy, and felt so incredibly good, leaving her relaxed and content, which allowed her to fall asleep before she knew it. Unlike some mornings, she wasn’t even mad when her alarm went off at 7:00 so she could get up and get her schoolwork done while her younger siblings were still in their beds. Not bothering to change out of her pajamas, she wandered out of her room, across the back of the living room, and over to the dining table, pulling her school books off of the bookshelf on the back wall before sitting down and starting in on her English workbook. It wasn't long before she heard Jake thudding his way up the stairs to join her. "Morning, meat-brain," She said teasingly as he appeared from the main entryway beyond the kitchen. Her brother just grunted and retrieved his own school books from the shelf without meeting her eyes. He then walked back to the opposite end of the dining table and plopped himself down, burying his nose in his work. That wasn't like him at all. He usually sat next to her while they did their work, each of them teasing the other when they looked over and noticed a wrong answer. So why had he gone all the way over to the far end of the table? His sour demeanor was ruining the good mood she had been in since the previous night. Was he mad at her for calling him "meat-brain" all of a sudden? She'd always called him that and it had never seemed to bother him before. "I'm sorry, Jake, you know I don't mean anything by calling you that, right? I'm just joking with you." "I know," he said flatly, still not looking up from his work. Dani frowned, looking back to her own workbook but far too distracted by her brother's recent attitude to process anything to do with what was on the page. Was this a continuation of his behavior from the previous afternoon when he seemed to be avoiding her? What had she done to make him angry with her? ***He*** was the one who stole her sunglasses, after all, not the other way around. Where was his usual teasing and attempts to get under her skin? Was he sick or something? Thoughts about her brother's sudden reserved behavior kept Dani from being able to focus on any of her own work and she finally gave up the effort after nearly an hour staring at the same page and only answering two of the questions on it. She put her books away and walked past her silent brother to the kitchen to make herself some breakfast. Her mother was already there, quietly pouring herself a cup of coffee. "Oh, hi mom!" Dani said as brightly as she could manage. "I didn't even notice you came downstairs." "You looked pretty occupied with your work over there, dear," her mom responded, taking a sip from her mug. "Having a hard time focusing this morning, actually," Dani admitted, opening a cupboard and pulling out a box of cereal. "Maybe I need some breakfast to jump-start my brain." "It's the most important meal of the day," her mother chimed in. "Though I doubt that sugary cereal will give you much benefit. You want me to make you some eggs and bacon?" "Yes please!" came Jake's voice from the dining room. "How about some hash browns, too?" "That's the most he's said so far this morning," Dani whispered, only loud enough for her mother to hear. "Teenage boys are barely human when they first get out of bed, and your brother is a teenager now, don't forget," her mother whispered back, then said in a normal tone, "Can you help me out with breakfast?" That wasn't it, Dani thought to herself as she retrieved potatoes and the grater to start on the hash browns. Just the previous morning Jake had been his usual, annoying, lighthearted self, poking fun at her and flinging just as many insults her direction as she did his, knowing that neither of them actually meant anything by it. He couldn't have changed overnight, and he'd been a teenager for two whole months already without acting like this. No, something else was going on with him, and Dani would somehow have to get to the bottom of it. That gave Dani two goals to work toward over the next few days: figure out what was wrong with Jake, and figure out whether she could give herself another... what should she call it? Pleasure explosion? Whatever it was, she wanted to do it again, this time in her bed, and see if she could make it a nightly routine, rather than just a shower-time routine. Never before had Dani so looked forward to bed time. She was usually one to put off sleep as long as she felt she could without being a zombie the next day, especially whenever she and her friend Audrey had a sleep over, often staying up until three or four in the morning giggling quietly to keep from waking up the rest of the house. Thinking of her friend gave Dani an idea. "Hey mom?" She asked as she finished grating the potatoes for hash browns. "Yes dear?" Her mother already had the scrambled eggs done and was beginning to fry up some bacon. "Can you ask Audrey's mom if I can come over Saturday for a sleep over, and they can bring me to church on Sunday?" "I think that can be arranged," her mother responded. Dani's mother rarely told her "no" regarding visiting her friend, unless there was something else already planned with the family. After all, Jake had Finn, who he could hang out with every day, while Audrey lived a half-hour away. As such, the two girls rarely had extended time together. It wouldn’t be so bad if Dani had ever been able to build a friendship with any of the girls in her neighborhood. They were all snobs in Dani’s estimation, who looked down on her for being homeschooled and for preferring to play in the woods and the dirt. Audrey, however, was a girl after Dani's own heart. She lived on a ranch, rode horses, and climbed trees. She, too, had brothers, though both were older than her, and one older sister who had recently married. Audrey was the youngest and only had one brother still living at home who was three years her senior. So when Dani and Audrey wanted to have time together, their parents usually tried to make it happen, which Dani was counting on. She had to ask her friend about this new sensation she had discovered, and see if Audrey could do it, too. Dani finished helping her mother with breakfast, by which time her other two brothers had made their way up to the dining room as well, the enticing aroma of frying bacon having roused them from their beds. Their father had also made his way downstairs, Bec in his arms, to pour himself some coffee and snatch a strip of bacon off the plate where it was cooling. They all sat together for breakfast, a cacophony of happy voices mingling together as they enjoyed the meal. Jake seemed to interact with everyone else as normal, snagging Aaron in a head-lock and knuckling the boy's head playfully before releasing him, his mop of sandy hair sticking out in all directions. Yet Jake still wouldn't interact with Dani beyond the surface level, and every time she caught his eyes looking her direction, he would quickly turn away. His behavior continued throughout the remainder of the day, reinforcing Dani's determination that it had nothing to do with simply being a teenage boy who could no longer handle mornings well. Jake spent the entire day with their younger brothers, Travis and Aaron, much to their delight, leaving Dani to her own devices for entertainment. If she hadn't had Dozer for company, who she took on a run and played with most of the afternoon in the park, she would have gone out of her mind with boredom. After dinner, the boys all went downstairs to play Smash Brothers on the Nintendo Switch, and Dani curled up between her parents on the couch, cuddling with her father as they watched a movie. "What? The boys don't want to have you beating them on the Nintendo again?" her father asked as she wrapped her arm around his solid frame. "I don't know," Dani admitted. "Maybe they've finally figured out I'm a girl and don't want to hang out with me, in case I give them cooties." She felt more than heard her father sigh heavily before responding. "Boys will be boys," he said matter-of-factly. "They'll come around if you give them time. You're still their big sister who likes to ride bikes and play soccer more than have tea parties and play dress-up. And until then, I certainly don't mind snuggling with my baby girl." "Thanks dad," she said with a smile, hugging herself closer into him. Maybe he was right, and all it would take is a little time for Jake to warm back up to her. Then again, maybe she had been partly right, too, though she'd only said it as a joke. Maybe Jake had figured out that she was a girl after all, and wasn't comfortable with the realization. A few of the times she'd caught him looking her direction, his gaze had not been directed toward her face, but lower, as if looking at her chest. That still didn't make any sense, though. Dani's breasts had developed quickly, starting at age eleven, and were certainly noticeable for at least the last year and a half, despite the loose t-shirts she generally wore around the house. If this was all about Jake noticing she had distinctly womanly body parts, then he should have noticed that some time ago instead of just starting to treat her differently since the previous afternoon. Come to think of it, Jake hadn't gone to hang out with Finn today either. He'd spent the entire afternoon with their brothers instead. Was this all due to some falling-out between Jake and his best friend? If so, then why was he taking it out on her? No... That wasn't right either. Jake's behavior toward Dani had started ***before*** he went to hang out with Finn. It seemed to start right after the incident with her sunglasses and chasing him up the tree to retrieve them. Had her brother somehow noticed the pleasure Dani was feeling from rubbing her crotch against the tree trunk as she climbed? She thought she had been hiding it well enough, but maybe she had been wrong. Maybe he had noticed and thought it was gross, and that was why he didn't want to spend time with her anymore. The thought horrified her. Was there something gross or wrong about what she had done? How could there be when it felt so incredibly good? Then again, there didn't have to actually be anything gross or wrong about it for Jake to think that. Should she talk to him about it and explain it to him? Would that make things better or worse? The very idea of talking with Jake about it made Dani's face heat with embarrassment. She could not imagine talking to her brother about how she gave herself pleasure by rubbing her vagina. If there was anything that would sharpen his awareness that she was a girl, and very different from him, it was that. No such embarrassment accompanied the thought of talking with Audrey about it, but she instinctively knew it was an off-limits subject with her brother. Instead, she would give it time, like her father had suggested, and hope that Jake would forget about it, as long as she didn't repeat anything similar in his presence. After the movie, Dani kissed each of her parents goodnight and retired to her room. She settled into bed to read a Nancy Drew book until she felt tired, and let her hand slip down to her groin, lightly caressing her mound and across the outer lips of her vagina through the light cloth of her pajamas and panties. The sensation was pleasant, but not insistent like it had been in the shower. It made for a relaxing background feeling while she read her book. After several minutes of it, though, she found herself aching for more and set Nancy Drew aside, nestling deeply into her pillows and shoving her hand underneath her clothing to gain direct access to her sex. What she found surprised her. She was damp between her legs, and especially the inner folds of her vagina. For a moment she worried that she had wet herself by accident, but when she brought her fingers to her nose, it didn't smell like urine. Instead it had a pleasant musky aroma she'd never smelled before. She returned her hand between her legs and began to rub more deeply, focusing her attention on the nub in the center of her folds as she felt it grow erect. There was more friction than there had been in the shower, and it was slightly uncomfortable, so she dipped her fingers lower into her folds to coat them in the liquid that seemed to be coming from the opening there. That did the trick, reducing the friction significantly and allowing her to increase the speed and pressure of her ministrations. Soon she was bucking her hips upward into her furiously rubbing fingers, knowing that the release she craved was just moments away. Then it crashed over her, causing her whole body to shudder and writhe in ecstasy. With one hand she continued to lightly rub herself through the spasms of pleasure, while gripping her blankets tightly with the other. She had done it! Whatever this "pleasure explosion" was, it was repeatable! She could do it every night if she wanted to and she saw absolutely no reason why she wouldn't. She decided that if her friend Audrey didn't know about this, she would simply have to teach her. It felt far too amazing to be kept to herself. It was going to be a great weekend, even if her brother was behaving so strangely. *** Friday afternoon, Jake wasn't sure whether he was ready to face his friend Finn yet. The previous day, for the first time in months, the two of them had not spent any time together at all. What his friend had said about Dani bothered Jake deeply. He knew his friend was right—that his sister was indeed "hot as fuck"—and he now had first hand knowledge of that fact, but he still didn't like the idea that Finn thought of her that way. Why was that? A girl was either hot or she wasn't, right? Could he blame his friend for noticing that a girl was hot, even if that girl was his sister? No, that wouldn’t be fair. It wasn't Finn's fault that Dani was attractive, and he'd be even more angry with his friend if he thought she was ugly. Jake decided his anger with Finn was really an extension of his own confusion about Dani. He'd only just "discovered" that his sister was hot, so it was hard for him to consider that his friend had noticed before him. Should it really be surprising, though? Jake had lived in the same house with her for his whole life, and always thought of her as his brat sister, and his closest friend other than Finn. That kind of relationship didn't tend to encourage him to notice that she was becoming a woman, with all the attractive qualities that came along with it. Finn, on the other hand, had no such hang-ups, and could see Dani for what she was: an incredibly enticing young woman, who didn't act like the prim little snobs he knew from school. When Jake thought of it that way, how could Finn ***not*** find his sister attractive? That made up his mind, and he set off to meet Finn at his home, since it was already well past when he would have been dropped off at the bus stop. He didn't bother with bringing his fishing gear this time, knowing that they wouldn't spend any time at the river today. When he arrived at his friend's home, he hopped off his bike, letting it fall to its side on the lawn, and jogged to the front door, knocking on it sharply. A few moments later, Finn's older brother Scott pulled open the door then called over his shoulder, "Hey Finn! Jake's here for you!" "Really?!" Jake heard his friend's muffled response from somewhere within. "Yeah! He's waiting right here at the door, shit-for-brains!" "Don't use that language around Jake!" Finn's mother shouted from somewhere else within. "His father’s a pastor! Show some respect!" Scott rolled his eyes and walked away, leaving the door open, and Jake stepped inside to wait for his friend. Finn didn't leave him waiting long, bounding down the stairs with a small backpack slung across one shoulder. It wasn't his larger school bag, and Jake imagined it likely contained some snacks and his tablet. "Hey! Glad you came over!" Finn said genuinely. "Everything okay?" "We're gonna need to talk, but yeah, I think so," Jake replied giving his friend a reassuring smile. "To the fort, then?" Finn asked and Jake nodded. They rode out to their fort in the woods in silence, both of them nervous about the conversation to follow. When they left their bikes in the bushes and crawled into the dark interior of the fort, their silence seemed to be made even more ominous by the dim lighting, though it did help Jake to finally speak, since he could hardly see his friend's face. "I guess I can get over the fact you think my sister is hot," he blurted out as they settled in to sit at opposite sides of the fort. It didn't separate them by much, since the interior was only about eight feet across, but it was a stark difference from the way they usually sat side by side and huddled over Finn's tablet screen. "Well that's a relief, since you're going to have to deal with it from far more guys than just me, soon enough." "You're not wrong there..." Jake admitted. "It was just a shock to me the other day, because I had never really seen her that way before." "You're not supposed to see her that way; you're her brother," Finn pointed out. "Too late now," Jake said. "As of two days ago, I can't help but see her that way anymore." "Sorry about that… I really did mean to delete that picture." "Don't worry about it, it wasn't just that anyway," Jake assured him. "Oh really?" Finn asked, and Jake was certain that if he could see his friend's face the boy would have an eyebrow cocked in curiosity. "Do tell." Jake drew in a deep breath, considering for a moment just how much he wanted to tell his friend; his best friend with whom he usually had no problem sharing anything. Letting the breath out slowly, he told Finn the whole story, starting with watching Dani shimmy up the tree after him, the tops of her breasts poking out of her tank top enticingly, then watching her walk back toward the house with her cutoff jeans clinging to her round ass, perfectly framing her curves and drawing attention to her lightly tanned legs. "Those cutoffs should be illegal!" Finn proclaimed. "I can't see her in those without feeling my heart stop beating because all my blood rushed to my dick." "Hey, just because I am okay with you thinking my sister is hot doesn't mean I want to hear you talk about her like that," Jake warned. "Sorry, sorry!" Finn apologized sincerely. "You're the one talking about getting a boner staring at your own sister's tits and ass, though." "True enough," Jake conceded. "I'm not done yet, though." He continued to tell his friend how shocking it had been to see a naked woman who looked so much like an older version of his sister. Just the brief seconds of her image on the screen had fueled his imagination endlessly about what Dani might look like with her clothes off. Then he told his friend about spying on his sister in her bedroom from outside her window Wednesday night. "You dirty dog!" Finn exclaimed. "Was she as hot as you imagined?" Jake could tell his friend was really asking, "Is she as hot as I imagined?" but he let it slide. "Dude... She's an absolute babe..." He continued to describe the details of her round, perky tits, her amazing bubble butt, and her lithe and subtlety curved body; petite, and yet athletic and toned. "Holy shit, dude!" Finn breathed when Jake had finished. "How can you contain yourself living in the same house with a girl like that? I'd be jerking off all the damn time." Finn usually restrained his colorful language around Jake, but he had obviously been too wrapped up in what Jake had revealed to bother with it now. "I have to admit," Jake responded. "Since 'discovering' she's more womanly than I had realized, I have been jerking-off more than usual." "You know, most people would think that's pretty messed up, right?" Jake nodded, then remembered his friend couldn't see in the dark. "Yeah, I know..." "Still, if I was in your shoes, I think I would have to jerk off ten times a day just to keep from losing my mind." That made Jake laugh in spite of himself, and Finn laughed along with him. "Well dude," Finn began. "Do you need some pictures of other hot babes to take your mind off your sister?" "How can I say no to that?" Jake asked, and his friend fished out his tablet. The two of them moved closer together so they could both see the screen and they settled back into their usual routine of commenting on what they liked and didn't like about the naked women Finn had selected for their perusal. The girl that had been Dani's lookalike didn't make a reappearance in the collection, but Jake found himself comparing all of the women to Dani in his mind. This one was chubbier than Dani, that one was skinnier; this one had larger breasts, but with odd shaped areolas, while that one had breast that were similar size, but more saggy. Every one of them was viewed through the lens of how she stacked up against his sister. What's more, every one of them fell far short of Dani in his estimation. When they’d had their fill of gawking at naked women on Finn's tablet, they rode their bikes back to the neighborhood and around the park, chatting as they always did and bragging about the latest trick they could pull off on their bike or skateboard. Eventually they went their separate ways so Jake could make it home for dinner. Finn didn't have such concerns, since his family always ate much later in the evening, but he didn't blame his friend for wanting to get home for some grub, and to enjoy the "eye candy" that his sister provided. Dinner was delicious, as always. His mom was a fantastic cook, even with the most basic ingredients, and the family always enjoyed their time around the table together. Dani was in her customary hoodie, which made it easier to look her way without feeling like he might get caught checking her out, but he found himself admiring her facial features instead. She really was quite stunning with her full, soft lips, long, dark eyelashes, and thin, elegant eyebrows framing her bright, blue eyes. Her cheeks were barely round enough to mark her as a girl, rather than a woman, and her slightly upturned nose was neither too big nor too small for her face, unlike some of the women he'd seen on Finn's tablet. Of course, with all his staring in her direction, Dani had noticed his gaze on her more than a few times, causing him to look away suddenly with a blush. He needed to get a grip on himself! If he wanted to ogle his sister, he would need to wait until he could creep to her window again tonight, rather than here at the dining table where any of his family might notice. It was her usual night for a shower again, so Jake would have another opportunity to see her graceful naked form, if he could manage to sneak out as he had done before. Indeed, he'd thought about trying to sneak out to her window on nights that weren't her shower nights as well, since Dani had to undress every night to put her pajamas on, shower or no. He had nixed that idea in the end, though, because it was far more risky. He'd have to sneak out while his brothers were still getting ready for bed, and while his parents were known to come check on their progress. By only sneaking out on nights when Dani showered, Jake virtually guaranteed that his brothers would be in their bedroom, and his parents either upstairs with Bec, or watching TV in the living room. This was because his sister preferred to take her showers quite late in the evening, after the youngsters had already finished getting ready for bed and said their good nights. He imagined it was her way of winding down for the night, which she found easier to do when the rest of the house was quiet. Regardless of her reason, it would work to his advantage again tonight. *** That night Dani gave herself another "pleasure explosion" in the shower, finding it easier than before to build herself up for the release. Something about the hot water rushing over her body added to the whole experience, heightening the sensations as it enveloped her in its wet embrace. As she dried off, she wondered how soon afterward she could do it again. Wrapping her robe around herself for the short trek past the living room to her bedroom, she decided she would try again on her bed, after drying her hair. Gathering her things, she exited the bathroom, wished her parents, who were seated on the couch watching their favorite sitcom, a good night, and stepped into her own room, flicking on the light and closing the door behind her. After hanging up her towels to dry on her bedposts, she undid her robe and let it fall to the floor, enjoying the feeling of being entirely nude. Then she went about her routine of brushing and drying her hair at her vanity before wandering over to her closet. She was about to pick out a pair of panties and some pajamas when she stopped herself. Why not just stay completely naked while she rubbed herself, like she did in the shower? Deciding that was a splendid idea, she closed her closet door and flopped onto her bed. She didn't even bother crawling under the covers, just letting her head sink into her pillows as she lay on her back, spreading her legs wide for easy access to her sex. Like the previous night, she started with light caresses on her skin, trailing her fingers down across her stomach until she felt the fuzz atop her mons, which she played with for a short time. Then she caressed the inside of her thighs and brushed lightly across the outer lips of her vagina. She felt the pleasurable sensation awaken within her for the second time that evening and she knew she'd be able to bring herself to rapturous release once more. This encouraged her to press on, rubbing herself in earnest and beginning to feel the dampness return to her inner folds. As before, she used it as lubricant for her rubbing, flicking, and swirling fingers, which had begun to cause her hips to buck in rhythm with her ministrations. Dani increased her pace and pressure, faster and harder, faster and harder, until her pleasure reached its crescendo and her body stiffened in overwhelming physical bliss. She continued rubbing herself through the waves of pleasure that were like aftershocks of an earthquake wracking her body until she was abruptly interrupted by a large ***THUMP*** that came from the outside wall of her room. She froze in horror. Someone was outside her room in the side yard! Scrambling, she got up from her bed and donned her robe as fast as she could to cover herself, then went straight to the window to see who had been spying on her. She raised her blinds and looked out into the night. It was difficult to see in the dark, but no one was there. Just the massive rhododendron bush blocking everything else from view. She hadn't imagined the sound, though. Something large had bumped up against the outer wall, for certain. What could it have been, if not a person? Then she remembered that their massive dog, Dozer, had free reign of the back and side of the house at night, since it was fully fenced, and she breathed a sigh of relief. The Rottweiler was definitely large enough to have made that thump if he bumped into the outside wall, and it made sense he would be poking around at night, especially if any smaller animal had caught his attention and he had given chase. In her state of vulnerability, she had merely jumped to the most horrifying conclusion possible, instead of the one that made the most sense. Smiling at her own silliness, Dani walked back over to the closet, dropping her robe and putting her pajamas on for the night. She needed to get her sleep because she had an important weekend ahead of her. She'd be going over to Audrey's shortly after breakfast and planned on showing her best friend her newfound favorite hobby. *** Jake was panting in fear when he made it back to the safety of his room that night. He had very nearly been caught! Yet he could not deny that the risk had been more than worth it, given what he had seen his sister doing through her window. He'd never seen a girl jerk-off before, but that was to be expected since he'd never seen a live girl naked before until just two nights ago. He'd never even imagined that it was possible for a girl to jerk-off since they didn't have a dick, but he'd just witnessed Dani do exactly that, laying on her bed completely naked, furiously rubbing herself until she went rigid and shuddered uncontrollably from what he could only assume was pure pleasure, judging by the wide and rapturous smile on her face. There were two main differences that Jake noticed in the way his sister jerked-off compared to how he did it. The first was obvious in that she rubbed her pussy, while he pumped up and down on the shaft of his cock. The second was that she didn't have any cum spraying everywhere when she climaxed. The first time Jake had jerked off, the cum had scared him as it sprayed all over his stomach and hands. He thought he had done something wrong until his friend Finn had explained that it always happens. After that, Jake had taken to using a sock to capture it, so his cum didn't give him such a mess to clean up. Dani didn't have any cum at all, which meant she didn't have to worry about any messy aftermath. How convenient for her, he thought sarcastically. In order to get an angle to best observe what his sister was doing, Jake had leaned to his left without shifting his knees beneath him, and when she came, he had been so shocked that he lost his balance and fell over, catching himself by slamming his palm into the wall. He had immediately known he needed to leave, or he would be caught, so he rushed out from behind the rhododendron bush and around the corner of the house to the back yard. Once out of sight of Dani's window, he had slowed his pace and crept back in through the basement door to his room. Above him he could just make out Dani's soft footfalls as she walked from the window to her closet. She had definitely checked to see if anyone was out there, and he had no doubt that if she thought he had been spying on her, she would have been stomping down the stairs to confront him in a heartbeat. No such stomping ever came, though, which meant she must have concluded that no one had been at her window, after all. Jake had narrowly dodged being in a world of trouble, and likely not just with his sister. Though they tried to work most things out between each other, Jake was sure Dani would have deemed this infraction severe enough that it needed to be taken to their parents, and who knows what they may have done about it. Still, the payoff had outweighed the risk more than he had expected. He'd snuck out to peep though her window expecting to see her going about her evening routine in the buff like he had before, and she had delivered on that, dropping her robe then brushing and drying her hair at her vanity before going over to her closet to get her bed-clothes. Then she had stopped, turned and flopped naked onto her bed, spreading her legs wide and giving Jake the hottest display he had ever seen. It was all he could do to keep himself from whipping dick out and jerking off as he had watched. As it was, he had been rubbing his boner through his pants, which had likely contributed to him losing his balance, as well. Once the fear of almost getting caught started to dissipate, Jake flung his pants off and started tugging on his dick while recalling in as much detail as he could exactly what he had just seen. It was the fastest he had ever cum, he was sure, and he almost wasn't ready with his sock as his climax overtook him. *** Dani beamed as she saw her friend Audrey rushing down her front steps to greet her before she'd even opened the van door. Her friend was the quintessential cowgirl, boots and all, with her worn jeans and flannel shirt. The only thing she was missing was the hat, but she made up for it with matching french braids on either side of her head that ended in shoulder length auburn pig-tails hanging down behind her. The only word Dani had to describe her best friend was "adorable.” She was a bundle of energy in a small package, both shorter and thinner than Dani, and she had been a late bloomer in the breast department, barely filling out an A-cup bra; a fact that Audrey reminded her about on a regular basis. The girl was actually jealous of Dani’s larger breasts, which Dani could not begin to understand. More than once, she had expressed her willingness to trade breast size with Audrey, if it were only possible. Dani hardly had time to climb out of her mom's van before her friend wrapped her in a tight embrace. "I'm so glad you asked to come over!" the smaller girl exclaimed, backing away a bit and taking Dani's hands in her own. "It feels like it's been forever since we got to hang out, even though it's really only been a few weeks." "I know what you mean," Dani agreed. "So much can happen in just a week, and the short time we get to talk after church just isn't enough." "No, definitely not!" Audrey said, pulling her away from the van. Dani barely had time to grab her bag before her friend was dragging her away toward the house. She turned and waived goodbye to her mother, who was chatting with Mrs. Larson, then followed her friend in the front door and down the hall to the girl's bedroom. "You can drop off your bag here, then I have my morning chores to get done before we can find something fun to do," Audrey explained. "I'll help you with your chores, if you want," Dani offered. "I have a ton to tell you about, so we'll need all the time we can get." "Sounds great to me, but you'll need to borrow some rubber boots," Audrey advised. "I have to make sure all the animals have water before it starts getting hot, then I have a stable to muck out, and eggs to gather from the chickens." "Can't wait!" Dani said honestly. She enjoyed helping care for the animals whenever she came over to Audrey's house. The Larsons had more animals than Dani had ever known a single family to own. They had two dogs, several cats, a handful of rabbits, a flock of chickens, four horses, a small herd of cows, and one ornery goat. Dani's favorite were the horses and the two girls would often spend their afternoon trail riding. She hoped they'd get a chance to do just that today. Audrey led her back out of the bedroom, down the hall, and past the living room to the mud room at the back of the house. There she presented Dani with a grubby pair of rubber boots that her older brother, Jeffrey, had grown out of. They were slightly oversized for Dani, but they would do the job, and once Audrey had donned her own pair they headed out the back door and down toward the barn. The Larsons lived on a gorgeous property with expansive pastures, surrounded by forest, with a small creek running through it. They owned twenty acres in all, but it backed up to state forest land with gravel access roads spider-webbing through it, where the girls liked to go ride the horses. As they made their way toward the barn, Dani started thinking about how she would broach the subject of the "pleasure explosion" she'd discovered the could give herself. It had been an easy decision to want to tell her best friend about it, but she hadn't given any thought to exactly how best to bring it up. "You know..." Audrey began as she was filling a water bucket with a hose. "For someone who said she has a ton to tell me about, you sure are being quiet." "I ***DO*** have a ton to tell you about," Dani insisted. "I'm just not sure how to start." At that, the smaller girl cocked an eyebrow. "You know you can tell me anything. Just spit it out." "Well... Have you ever noticed that it can feel really good to rub yourself... down there?" Dani pointed to her crotch. "Your girly bits?" Audrey asked. "Girly bits?" "Yeah! My mom calls them her 'lady bits', but I'm no lady yet, so I call them my girly bits," Audrey explained. "And yes, I have noticed that before. I'm surprised you hadn't! Oh gosh, Dani! Did you have your first orgasm?" "Orgasm?" Dani questioned. "Yes! That's what it's called when you make it feel ***REALLY GOOD*** and everything just seems to explode with pleasure." "That sounds about right," Dani nodded. "You knew about that and never told me!?" Audrey shrugged. "I guess I figured you probably knew about it already. It's not exactly something that comes up in day to day conversation." "No, probably not," Dani agreed, helping her friend haul the water bucket into the barn. "But how did you know about it already? I only just figured out I could do it this week!" "I guess I did have a bit of help..." Audrey admitted. "When I was ten, Millie noticed me grinding my girly-bits on a saddle horn, and she taught me all about it." Millie was Audrey's older sister Melissa, who had moved out and gotten married the year before. "See! You had a sister to teach you about these things! Who am I supposed to have teach me? My mom?" "You're right," Audrey agreed. "I really can't imagine your mom teaching you to masturbate." "Master-what?" "MasturBATE. It's what it's called when you give yourself an orgasm. My brother calls it jerking-off, but I think that's because boys do it different." "Wait, ***WHAT!?***" Dani exclaimed. "Boys can do it, too!?" She felt like her world was being turned on its head. "Oh definitely!" Audrey replied matter-of-factly. "I caught Jeff jerking off in the wood-shed once when he was supposed to be out milking the cows. He stuffed his dick back in his pants as fast as he could, but I'd already seen what he was doing." She formed a circle with her fingers and pumped her hand up and down vigorously in front of her crotch. "He swore me to secrecy about it though, so don't you dare let anyone know I told you about it!" "Wow..." Dani said simply. "I had no idea that everyone was already doing it but me." "I'm sure it's not ***everyone***," Audrey said, obviously trying to reassure her. "And if you'd like, I can show you a few things later today. My sister taught me well. She said that one day I'd be grateful I knew what I was doing, whatever that means." "That sounds like a great idea!" Dani agreed. "Goodness knows I am just blindly feeling my way through it." "I see what you did there," Audrey said with a wink. "Feeling your way through it." They both giggled at the pun. "That can't be all you wanted to talk about, though. We've barely started in on the chores." It was true. They had only just managed to fill all the animals' water troughs, so they were now retrieving the wheelbarrow, pitchfork, and shovel to start in on mucking out the horse stall that was due for new shavings. Then they still had to go gather eggs. "Well, I didn’t know my first bit of news wouldn’t actually be news to you at all, so I thought it was going to take longer,” Dani protested. “The other thing is a bit of a mystery I have on my hands, though.” "Oh? I like mysteries." "This one is about Jake." "What has that little punk done now?" Audrey asked with a grin. She was the only person who understood Jake and Dani's relationship of mutual and meaningless antagonism. In fact, she enjoyed joining in on it whenever she came over, taunting Dani's brother even more viciously than she did. "It's not really anything he's doing so much as what he's ***not*** doing," Dani explained. "On Wednesday morning, he was pretty normal; he even stole my sunglasses and climbed one of the maple trees in the back yard with them, threatening to leave them up there unless I could climb up and take them back." "Yep! That sounds like typical Jake to me!" "Well, after that it's like he just decided to shut me out. He's barely talked to me at all the rest of the week. No teasing, no name calling, and no pranking the rest of the day Wednesday, and all day Thursday, and Friday." "Woah! That ***is*** strange! He's always giving you a hard time!" Audrey agreed. "I know! I can't figure out what happened to make him shut down toward me. He's not any different with the rest of the family, and is maybe even more friendly with Travis and Aaron than before." "So, it's definitely something specific to you, then," Audrey said thoughtfully. "Well, maybe, maybe not," Dani continued. "Jake almost never goes a day without hanging out with Finn, but he came home early from fishing with him on Wednesday, and didn't hang out with him at all on Thursday." "Maybe Finn had something going on and couldn't hang out," Audrey suggested. "That could be it," Dani admitted. "Jake did go hang out with him yesterday, like normal." "So, as far as you can tell, it's really just you that Jake is suddenly acting cold toward, right? "Yes." "And it all happened after you climbed the tree after him to get your sunglasses back?" "Yes." "And Jake was above you the whole time you were climbing?" "Yes, obviously." "I think Jake saw your boobs." "What!? My boobs? I had my shirt and sports bra on, like usual! My boobs stayed covered! ...At least mostly. The important parts anyway.." Audrey looked at her pointedly for a moment before speaking, as if accusing her of being an idiot. "A boy doesn't have to see your whole boobs to notice that you have them, you know. If you were climbing that tree in a tank-top, I bet he had a nice view down the front of your shirt." "But Jake doesn't think of me that way," Dani protested. "He's always seen me as practically one of the guys, even when the rest of his friends stopped hanging out with me." "Dani... He's a teenage boy," Audrey pointed out. "His relationship with you as his sister may have held off the inevitable for a while, but boys only think about three things: food, video games, and girls. Maybe watching your boobs as you climbed up the tree triggered something in his head and he finally figured out you were a girl, with all the equipment that comes with it." She said the last bit pausing from her work to gesture pointedly at Dani’s ample chest with her free hand. Dani was silent for a time, thinking over what her friend had said as they filled another wheelbarrow with soiled shavings from the horse stable. She barely even noticed the smell, she was so focused on whether Audrey had correctly assessed the situation. Everything with Jake seemed to hinge on that incident with her sunglasses and climbing the maple tree to retrieve them. Whatever the reason was for his coldness toward her the last few days, it was somehow linked to that. So far, only two possibilities had presented themselves: either Dani's worst fear was the case, and Jake had noticed that rubbing herself on the tree was giving her pleasure, or Audrey was right and Jake had been checking out her boobs as she climbed. Of the two, Audrey's assessment seemed more likely. Dani could not imagine how he could have even seen that she had been rubbing herself on the tree trunk as she climbed from his angle, but he would have had a direct view down the top of her shirt to where her sports bra was struggling to keep her breasts contained as she shimmied upward. Somehow, it was both relieving and a bit exciting to think that he had been checking out her boobs. It was a relief because it meant that Jake didn't know her other secret about giving herself - what had Audrey called them? Orgasms? Though, according to Audrey, most boys give themselves orgasms, too, so Jake might already do that to himself as well. The thought was still a bit shocking to her, since she had only just discovered it was possible in the first place. She wondered if she would ever have an incident like Audrey, walking in on one of her brothers in the middle of "jerking-off" as she had called it. Since Dani had three brothers, the chances were probably pretty high that it would happen someday. A twinge of curiosity made her almost hope it happened sooner rather than later. The idea that Jake had been checking out her boobs also made Dani feel a bit excited. She'd never considered that someone might look at her that way before. There weren't many boys at their church except those still in grade school—which is why all of Jake's friends were boys he knew from outside of church—so Dani had never even had a crush on a boy before, let alone thought about trying to look good for one. Something inside her made her want to be looked at, though, now that the idea had been planted in her head that someone might want to, even if it was her brother. Did Jake like what he saw? Why should it matter if he did? But somehow, it did matter to her, and she couldn't puzzle out why. "Okay..." Dani said finally. "You might be on to something." "Of course I am," Audrey replied confidently. "That still doesn't explain why he won't talk to me, though," Dani complained. "Sure it does!" Audrey insisted. "Most boys have a hard time talking to hot girls." "So you're saying Jake thinks I'm hot?" Dani asked, surprised to find that she hoped he did. "Good grief, Dani!" Audrey responded in exasperation. "You ***are*** hot! You just haven't ever noticed it, and apparently neither did Jake until now." "Wait... You think I'm hot, too?" Dani was getting more confused by the minute. She had never thought of herself as attractive, and she had definitely never considered the possibility that another girl might think of her that way. Then again, as she looked at her petite friend, in her tight jeans, flannel shirt, and french-braided pigtails, Dani couldn't help but admit that Audrey was pretty cute, as well. Dani couldn't quite classify the girl as "hot" since she still lacked the more mature feminine curves that were generally associated with that term, but she was still quite attractive. Not that Dani was interested in girls in that way, but that didn't mean she couldn't appreciate her friend's good looks. "You must be blind, Dani Hansen. If I was a boy, I'd be drooling all over you!" "Gross... Please don't'." Dani said with a giggle. "Do you really think I'm that pretty, though?" She still couldn't bring herself to use the term "hot" in reference to herself. "Of course I do!" Audrey insisted. "You’re the full package! You're athletic, yet you have nice boobs that probably aren't done growing, long, toned legs leading up to a perfectly round butt, gorgeous hair, that it's a shame you just tie back in a ponytail all the time, and a girl-next-door sort of beautiful face. I am personally shocked that it took this long for Jake to notice. I'm sure his friends have, though." Dani blushed a deep crimson at her friend's compliments, finding herself completely speechless as she tried to wrap her mind around the idea that others might find her attractive. Even if she could accept that her brother had been checking her out, a thought that only made her blush deepen, it was still no help to her in rectifying the situation. "Fine, lets assume you're right and Jake was looking down my shirt, and now it has him all flustered, because he’s figured out I have boobs. So, what am I supposed to do about it?" The smaller girl looked over at Dani with a sympathetic look on her face as they took the pitchforks and wheelbarrow back to put them away in the tool shed. They had finished with cleaning the stall and covering it in fresh shavings, leaving only gathering eggs from the chickens on their list of chores. "I've got no help for you on that front," Audrey admitted. "Now that he's thought of you that way, it's going to be impossible to get him to think of you as just his sister again. Now you're his ‘hot sister,’ and that's the way he'll probably always think of you, unless you get fat or something." "Great... So my relationship with my brother is basically over..." "Not necessarily," Audrey said as cheerily as she could, obviously trying to brighten Dani's mood. "Maybe it will just take him some time to adjust to the idea that he has a bona fide hottie living under the same roof. Who knows? Maybe figuring out how to not be awkward around you will help him out later on when he's trying to ask a girl out." "Ugh! How long do you think that will take?" "For him to get a girlfriend? Probably a few decades," Audrey joked, causing Dani to roll her eyes. ''Alright! Alright! I knew what you meant. I just don't have a clue how long it will take him to stop being awkward and warm back up to you." "Wonderful..." Dani said sarcastically. "It's going to get really lonely at home waiting for him to come around. Do you think there's anything I could do to speed up the process?" "I doubt it," Audrey responded as she transferred chicken eggs from the nesting boxes into a rinsed-out 3 gallon paint bucket. "If you draw attention to it, you'll probably make it worse. I'd say just try to act like normal around him as much as you can." Dani sighed. "That makes sense. I guess it's my only real option, anyway." "Personally, I'd be more worried about him trying to spy on you." "Really? Why do you say that?" "Dani, boys are never satisfied with just getting a glimpse down a girl's shirt," Audrey explained. "They will try to get a look at a naked girl if they can think of any way to make it happen without getting caught. I remember how Jeff used to try and catch a glimpse of Millie when she still lived here. He climbed all the way up to her window on the second story using the trellis on the side of the house, but he wasn't quiet enough, so he got caught and nearly fell in his attempt to escape. Thankfully Millie, who was topless at the time, caught him by the scruff of his neck just before he tumbled backward. I think he would have been better off if he'd just fallen and cracked his head open, though." Dani couldn't help but laugh, picturing what her friend described. At the same time, she thought about catching Jake doing the same thing, and what she might do in retaliation. If she was honest with herself, she wasn't sure that she would even be all that mad at him. In fact, the more she thought about the idea, the more she almost hoped he ***would*** spy on her. That's when Dani remembered what had happened Friday night while she was masturbating and she froze in horror. "I think he might have already spied on me..." Dani told her friend in a near whisper. "Really? Why didn't you mention it before?" "I only just realized it when you mentioned your brother spying through your sister's window," Dani explained, then told her friend about how she had given herself an orgasm while lying naked on her bed after taking her shower the night before and had heard a loud thump on the outer wall near her window just as she had finished. "I thought it must have been Dozer at the time, because no one was there when I got to the window after throwing on a robe, but after you told me about Jeff, it dawned on me that Jake could have been spying on me. He wouldn't even need to climb anything to see through my window." "Oh, I can almost guarantee he was spying on you,” Audrey confirmed, “and depending on when he got there, he probably watched the whole time after you got out of the shower. I'm sure he can hear the water going from his room downstairs and probably uses it as his cue for when you'll be back to your room to get changed." Dani swallowed hard as she thought of all that Jake had likely seen from when she had entered her room, dropped her robe, dried and brushed her hair, and then rubbed herself to orgasm. Nothing would have been left to his imagination whatsoever. Why didn't that thought make her angry, though? It should have infuriated her, shouldn't it? Yet she felt no anger toward Jake at all for invading her privacy. The only way she could describe what she did feel was... excited? Sure, he had seen her rubbing herself, but if Audrey was right then Jake probably did something similar to himself, too, so he’d have no reason to think it was gross. Moreover, she could not blame her brother for being curious about what she looked like naked, because Audrey had piqued her curiosity about what boys looked like, too, and particularly how they jerked-off. Audrey had said it was different from how girls do it, but hadn't gone into detail, apart from the vague pumping gesture. "So, what are you going to do about it?" Audrey asked as she carried the bucket full of eggs toward the house, breaking Dani out of her thoughts. ''Huh? Oh... I don't know," She finally responded. "I guess I'll have to just close the blinds so he can't spy on me anymore." As soon as the words came out of her mouth, Dani knew it was a lie. She ***wanted*** him to see her again. Why did the idea of someone secretly watching give her such a thrill? "What? You're not going to tell your parents what he's been up to?" Audrey asked in a hushed tone. They had just come in the back door to the mud room and kicked off their rubber boots before heading toward the kitchen to drop off the eggs. "No, not for now," Dani said, matching her friend's low tone. "We don't tattle on each other unless it's something where we could get hurt badly, and besides, I don't have any proof, so he could just deny it." Audrey dropped the bucket of eggs off in the kitchen and led Dani upstairs to her room, shutting the door behind them so they could talk in private. The two girls took a seat opposite each other on the edge of Audrey's bed to continue their conversation. "Ok, so don't tell your parents," Audrey began. "But you should at least confront him about it. He needs to understand it's not okay to spy on you in the privacy of your own room." "I don't know... Didn't you say before that confronting him about checking out my boobs would just make things worse? Wouldn't this be the same?" ''Hmmm." Audrey had a slightly frustrated, thoughtful look on her freckled face. "You're probably right. I suppose it won't be so bad, as long as you are careful not to let him have more opportunities to spy on you again." "Oh, definitely not!" Dani agreed emphatically, all the while looking forward to doing exactly the opposite at her next opportunity. "Geez Dani! No wonder you wanted to talk so badly!" Audrey leaned over and gave her friend a tight hug. "What do you say we go for a ride now to take our minds off of pervy brothers?" Dani agreed, but she doubted she would be able to take her mind off of Jake now. Not when she had already begun to devise a plan for dealing with him after she got back home. *** Dani enjoyed the rest of the day with Audrey. The girls went on a long trail ride with the horses, eating a picnic lunch in the woods, and then spent the afternoon sunbathing in the back yard. After dinner with Audrey's family, the two girls retired to her bedroom for the night. "Ready to learn some new tricks for giving yourself orgasms?" Audrey asked, locking the door behind them. Dani grinned. She'd been looking forward to this all day. Audrey had dropped hints the whole time about what was coming and Dani was eager to explore this newfound source of pleasure more deeply than she had been able to on her own over the last few days. "I'll take that as a yes," Audrey said, her voice suddenly smooth and sultry, a tone Dani had never heard from the girl before. Dani watched in surprise as her friend slowly stripped out of her shirt and then her pants to stand in just her bra and panties. "Well, what are you waiting for? We can't do this fully clothed." Following her friend's lead, Dani stripped down to her undergarments as well. As usual, she had a sports bra hugging her breasts tightly to keep them in place. By contrast, Audrey had a lacy little matching bra and panty set that made her petite frame look adorable and sexy at the same time. "With that bra, it's no wonder it took your brother so long to figure out you have boobs," Audrey teased. When Dani shot her an offended look she said, "Oh good grief! Just take it off, you'll thank me later. It's just going to get in the way." Dani raised a curious eyebrow but did what her friend suggested, pulling the sports bra off over her head and tossing it to land on her bag by the bed. "Now, have you tried riding any of your stuffies yet?" Audrey asked, climbing up onto her bed and holding up her favorite teddy bear. Dani shook her head that she hadn't. "Then you are in for a treat!" With that, Audrey placed her bear face up on the bed and maneuvered so that she knelt with one bare leg on each side of the stuffed animal, her panty clad "girly bits" just inches above it. Then she sat down onto the teddy and began grinding herself back and forth along its furry body, her hips rolling hypnotically as she did so. "Mmmmmm." she moaned softly. "I hardly ever can make myself orgasm from just this, since teddy here is too soft to really get me going, but it's always a really nice warm up for the main act." As she spoke, Audrey slid her hands up under the cups of her bra and she began pinching her nipples; something that Dani never would have thought to do to herself. After a few minutes of slow grinding she asked, "Do you want to try?" "Yes!" Dani nodded emphatically and her friend lifted herself off of the bear, rolling to she side and gesturing for Dani to take her place. She did so, positioning her legs on either side of the bear as her friend had done, then lowered herself down onto it. The soft fur of the stuffed animal caressed the inside of her thighs as her panties made contact with the bear's stomach. The stuffed animal gave beneath her, cupping around her vagina and only resulting in slight, soft pressure against her sex. "Now start grinding against it," Audrey advised, and demonstrated from where she knelt on the bed next to Dani, grinding herself against the empty air. Testing it out for herself, Dani imitated the rolling and grinding motion with her hips, holding the bear in place with one hand, which also helped to keep herself balanced. The slight pressure and friction against her vagina was quite pleasant, but she could already tell that it was not going to be enough stimulation to bring her to an orgasm. The feel of the stuffed animal caressing her inner thighs was particularly enjoyable, though. She was so focused on the pleasant sensations her grinding was causing to well up within her, she didn't notice that Audrey had moved behind her until she suddenly felt her friend's hands cup both of her breasts and her fingers grasped each of her nipples, giving them a pinch. It wasn't so hard a pinch as to be painful; just enough to send a shock through Dani's body and make her call out. "Ohhhh! Wow!" Dani moaned, bringing her hands up to hold Audrey's in place as she continued to pinch and twist slightly. "I thought you might like that," Audrey breathed in Dani's ear in an amused tone. She pinched Dani's nipples a little harder, drawing a shiver of pleasure from her. "Are you ready for something else new?" Dani just nodded in response. Audrey released her nipples, causing Dani to sigh in disappointment, and said, "Get your hairbrush out of your bag." Dani turned to face her friend with a quizzical look, but Audrey just looked back at her with a knowing smile that compelled Dani to do as her friend had instructed. By the time she had retrieved the hairbrush and returned to the bed, Audrey had her own hairbrush in hand and had removed her panties, revealing a completely bare vagina, without a hint of pubic hair, that she was stroking lazily as she reclined on her pillows. "You don't have any hair down there," Dani pointed out with mild surprise. "I keep it shaved," Audrey explained, caressing her bare skin with a finger before returning it to her inner folds where she stimulated her center of pleasure. "It's way more comfortable that way. Millie taught me how when my pubic hair started growing in." "It looks so clean that way, compared with mine," Dani commented, following her friend's lead by stripping off her panties and crawling onto the bed to sit next to Audrey and recline into the pillows as well. "Some girls like to keep a little bush above their pussy," Audrey said. "But I can show you how to shave it if you want to try it out." "Pussy?" Dani asked with a giggle. "Like a cat?" "Girly-bits, pussy, vagina... There's all kinds of names for it; some worse than others. Pussy seems to be the most common, though. It's what Millie calls it, at any rate." "I think I heard Finn call Jake a pussy once. I just thought it was the same as calling him a scaredy-cat." "It basically is, but by calling him a girl instead," Audrey explained. "Finn was telling your brother he didn't have the balls to do something." "Balls?" Dani asked, even more confused now. "Oh Dani, you really are naive, aren't you?" Audrey sighed. "We'll have to go over boys' anatomy another time; I have enough work cut out for me teaching you about your own. Is your pussy nice and wet yet?" Dani dipped a finger into her folds and it came away coated in whatever sort of liquid her vagi... pussy produced when she was excited. "Yeah, I'd say so," she responded. "Good," Audrey said. "Just watch me for now, though. When you do this the first time it may hurt a bit, and there may be a little blood, but don't worry, it's fine." Dani watched in amazement as her friend widened her legs for her to get a better view, then moved her hair brush down between them and placed the end of the handle at the lower end of her inner folds. Audrey pushed gently and the end of the hairbrush disappeared inside of her. She kept pushing and slowly the rest of the handle was swallowed by her pussy, until only the portion with the bristles remained. Then her friend pulled it back out part of the way and pushed it back in again, a little faster this time. Dani just stared in wide eyed incredulity as her friend continued to penetrate herself while using her other hand to rub, flick, and swirl her fingers around the center of her pussy folds where Dani suspected her friend also had a sensitive little nub of pleasure. "Ok, now it's your turn to try," Audrey said, still gently pumping her hairbrush in and out. When she saw Dani looking skeptically at her own brush's handle, which was somewhat larger than hers, she continued, "Don't worry, it's nice and smooth, it will fit just fine. First, use your fingers to find the opening." Nodding, Dani slid an exploratory finger down into her folds, encountering her nub and sending a little shock of pleasure through her body, then continuing lower until she found the opening Audrey was talking about. It felt warm and was sopping wet with the liquid her pussy was producing. Keeping her finger there for guidance, she placed her hairbrush handle into position, feeling its cool smoothness parting her lips, then she removed her finger. She took a deep, determined breath and pressed gently but firmly on the other end of her hairbrush, feeling herself open to accept it. However, it didn't get far before Dani felt resistance. Was that as far as it would go? It was barely in an inch or two, while Audrey had put hers in all the way. "That's your hymen blocking the way," Audrey informed her. "This is where it's going to hurt a bit. You have to push through it, then it won't hurt next time." Trusting her best friend wouldn't steer her wrong, Dani did as she was instructed, putting more pressure upon the end of her brush to press it into her pussy. At first it was met with a slight stinging pain, then a brief, sharper pain as whatever was blocking the passage within her gave way, and suddenly the whole handle disappeared inside her, surprising her with the sensation of fullness so that she let out a small gasp. "You alright?" Audrey asked, and Dani nodded, the stinging pain still there, but diminishing by the second. "Great! Now, before you start pumping it in and out like me, why don't you finger your clit a little to get yourself worked back up?" "Clit?" Dani asked. "Is that what that little nub is in the middle of my pussy?" "That's the one!" Audrey confirmed, returning to fingering her own clit, as well. The girl must have paused her ministrations while Dani was working her brush handle into her pussy. Dani began rubbing her clit, as instructed, and enjoyed the sensations it sent through her. She continued to do so for a few minutes, getting used to the feeling of her brush handle buried inside of her. Then she slowly began to pump the handle in and out of herself in the same way Audrey was doing next to her. It somehow added to the pleasure she was feeling. Not directly, like fingering her clit, but more of a background sensation that added to the overall experience. The full feeling it gave her each time she pushed it back in was exquisite. Soon she was lost in the pleasure her ministrations were causing, hips bucking up to meet each thrust of the brush handle into her, and grind against her furiously swirling fingers. Then she felt Audrey's hand cup her right breast and start pinching her nipple and the added pleasure sent her over the top with cascading waves of ecstasy overcoming her. She thrust the brush handle into herself one final time and marveled as she felt her pussy clamp down in spasms around it. When her orgasm finally began to subside, Dani turned to look at her friend with a massive grin on her face. "Incredible, right?" Audrey asked, and Dani nodded vigorously. Then she had the pleasure of watching her petite friend work herself to a similar orgasm before collapsing in a satisfied heap on her bed. They both extracted their hairbrushes from their sopping pussies and cleaned them off with some wet wipes Audrey kept handy for that purpose. Dani did find a small amount of blood on hers, but thankfully it had not gotten on her friend's blankets. I never imagined this would be the reason for my first time bleeding from there, Dani thought to herself with amusement. While she had been an early bloomer in the breast department, she still hadn’t had her first period, which was unusual, but not unheard of for a girl her age. The family doctor wanted her to come in and schedule some testing if she didn’t have it by the time she turned fifteen, though. Dani often wondered why it hadn’t happened yet, but Audrey often reminded her that she wished she didn’t have to deal with it every month, making her count her blessings. "If you want, I can show you how to shave your pussy now," Audrey offered, breaking Dani out of her thoughts. "Did you bring your razor with you?" "I brought it," Dani confirmed. "And sure, I think I'd like to try it out." The two of them covered themselves in bath robes and headed to the bathroom where they hopped into the shower together and Audrey showed her how to properly, and carefully, shave her pussy. It was very strange to Dani, feeling that part of her body so smooth. She'd gotten used to the pubic hair, but she figured that keeping it shaved was no different from doing the same with her legs and arm pits; just another area to make sure she kept up on at the same time. She liked the way it felt as she ran her fingers across the bare flesh, and the two of them fingered themselves to another orgasm there in the shower before returning to bed. "I can't believe you pinched my nipples like that!" Dani said when they had snuggled under the covers together. "Millie did the same thing to me when she was teaching me," Audrey said. "It shocked me so bad I almost punched her. But it felt ***sooooo*** good, so I have been doing it to myself ever since. I figured I'd see if you liked it, too." "It made me orgasm, didn't it?" "Well, it sent you over the edge," Audrey confirmed. "I doubt you would orgasm just from having your nipples pinched alone." "I sure am grateful that your sister taught you so much about all this," Dani said. "I came over here thinking I would be telling you about something new I had just discovered, and instead you helped me understand it. Thank you for that." "My pleasure!" Audrey responded, then added, "Quite literally," and the two of them broke into giggles. They continued to chat as they lay in Audrey's bed until they were both too tired to remain awake, and then cuddled up together with Audrey wrapping her arm around Dani to cup one of her breasts as they drifted off to sleep. @ da0b9bc3:4e30a4a9
2025-02-14 06:26:26Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/885591
@ da0b9bc3:4e30a4a9
2025-02-14 06:26:26Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/885591 @ da18e986:3a0d9851
2025-02-14 06:00:27I'm excited to share the first phase of DVMDash's major redesign! After some recent downtime issues (thanks nostr:npub1e5tfhk8m65teu25dfx8lcvwn4c8ypqjl72u2sh4rt8zy2kss0j5qct7mh9 and nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn for the heads up), I've been working on rebuilding DVMDash from the ground up to be more modular, scalable, and reliable. ## What's Live Now: The Stats App The first piece of the new DVMDash is our completely rebuilt Stats app. Instead of trying to do everything at once, we're now breaking DVMDash into focused tools. The Stats app brings: - Flexible time windows (1h, 24h, 7d, 30d) for more relevant insights - Bar graphs showing activity over time - Per-DVM and per-Kind detailed metrics For those interested in the new backend architecture, check out my [recent post about performance gains](nostr:naddr1qvzqqqr4gupzpkscaxrqqs8nhaynsahuz6c6jy4wtfhkl2x4zkwrmc4cyvaqmxz3qqxnzdenxu6nwd3sxgmryv3506t7ws) describing how horizontal scaling is needed to support the growing DVM ecosystem. ## Coming Soon: Debug Tools and Playground You'll notice on the new [landing page](https://dvmdash.live) that DVMDash is now split into three main tools: 1. Stats (available now!) 2. Debug Tools (coming soon) 3. Data Vending Playground (coming soon) The Debug Tools will bring back the interactive graph-based debugger and event browser, while the Playground will offer a space to experiment with DVMs directly. I'm focusing on getting these right rather than rushing them out. ## Running Locally Want to try it out? You can clone the repository and run the Stats app locally with a simple ``` docker compose --profile all up ``` then visit **localhost:3000** in your browser. ## What's Next My immediate focus is on: 1. Polishing the Stats app with new features like: * Sortable tables for easier data analysis * Enhanced DVM profiles with pictures and metadata from relays * More detailed DVM-specific metrics 2. Bringing back the debugging tools 3. Building out the playground This is very much a work in progress, and I appreciate your patience as we rebuild. If you run into any issues or have suggestions, please drop by our GitHub repository.
@ da18e986:3a0d9851
2025-02-14 06:00:27I'm excited to share the first phase of DVMDash's major redesign! After some recent downtime issues (thanks nostr:npub1e5tfhk8m65teu25dfx8lcvwn4c8ypqjl72u2sh4rt8zy2kss0j5qct7mh9 and nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn for the heads up), I've been working on rebuilding DVMDash from the ground up to be more modular, scalable, and reliable. ## What's Live Now: The Stats App The first piece of the new DVMDash is our completely rebuilt Stats app. Instead of trying to do everything at once, we're now breaking DVMDash into focused tools. The Stats app brings: - Flexible time windows (1h, 24h, 7d, 30d) for more relevant insights - Bar graphs showing activity over time - Per-DVM and per-Kind detailed metrics For those interested in the new backend architecture, check out my [recent post about performance gains](nostr:naddr1qvzqqqr4gupzpkscaxrqqs8nhaynsahuz6c6jy4wtfhkl2x4zkwrmc4cyvaqmxz3qqxnzdenxu6nwd3sxgmryv3506t7ws) describing how horizontal scaling is needed to support the growing DVM ecosystem. ## Coming Soon: Debug Tools and Playground You'll notice on the new [landing page](https://dvmdash.live) that DVMDash is now split into three main tools: 1. Stats (available now!) 2. Debug Tools (coming soon) 3. Data Vending Playground (coming soon) The Debug Tools will bring back the interactive graph-based debugger and event browser, while the Playground will offer a space to experiment with DVMs directly. I'm focusing on getting these right rather than rushing them out. ## Running Locally Want to try it out? You can clone the repository and run the Stats app locally with a simple ``` docker compose --profile all up ``` then visit **localhost:3000** in your browser. ## What's Next My immediate focus is on: 1. Polishing the Stats app with new features like: * Sortable tables for easier data analysis * Enhanced DVM profiles with pictures and metadata from relays * More detailed DVM-specific metrics 2. Bringing back the debugging tools 3. Building out the playground This is very much a work in progress, and I appreciate your patience as we rebuild. If you run into any issues or have suggestions, please drop by our GitHub repository. @ 57d1a264:69f1fee1
2025-02-14 05:45:37 ### a practical intro to contributing to FOSS for product people, and other non-devs So you want to contribute to FOSS, but don’t know where to start. There are many paths to FOSS, but you must find your own. Here’s some advice based on personal experience to help you get started. ### 0\. Find your motivation FOSS requires a lot of giving, and better aligns with those that are missionaries, as opposed to the mercenaries. Perhaps you are unfulfilled in your fiat job, maybe you are currently unemployed, or perhaps you are excited about a particular bitcoin project. Why you’re exploring contributing to FOSS, is a question that only you can answer.  Are you a missionary? ### 1\. Discover what excites you So you’ve found motivation and have a list of various FOSS projects you could contribute to. This is the equivalent of the “I need a job” stage and you’re figuring out where to apply. It’s time to narrow it down. What are you excited about? A multi-year pilgrimage of learning how to contribute to Bitcoin Core? A lightning wallet, perhaps? Free speech Nostr? A hardware signing device? Or maybe finding a FOSS projects that is not “Bitcoin” in name, but happens to support Bitcoin, and Lightning. A great first step is to take some time and explore the Bitcoin Design Community ([https://bitcoin.design/](https://bitcoin.design/)) to discover FOSS projects.  Are you excited anon? ### 2\. Identify the skills you have or want to develop Chances are that if you follow the Bitcoin Product Community, you’re skills are in Product Management, Product Marketing, and/or Project Management. But contributing to a bitcoin project requires contributors with skills of many backgrounds such as marketing, documentation, community building, and more. What’s important to know is that most FOSS teams start with a motivated developer, who then may attract other devs. But many of them may not advertise that they need non-developer help such as a PM. Therein lies the opportunity for you as an eager bitcoin contributor. See what the needs of a project are and see if you can fill in those gaps with your skills. It may be as simple as coordinating meetings for the team. But doing the “dirty work”, or the work no one else wants to do, is exactly the way you can make an immediate impact to a FOSS project. In fact, this is why members of the Bitcoin Product Community affectionately refer to product managers as “[janitors](https://medium.com/all-things-product-management/product-manager-you-are-664d83ee702e)”! ### 3\. Make a list of projects Now that you have narrowed down your FOSS search, it is time to start building a list of, and evaluating various FOSS products. Some questions you can ask yourself: Is the project active? Is it a new project? How many team members are there? How many are devs? Is there already a PM? Is there a need for multiple PMs? Is there designer participation? What is the pace of development? Is there enough development activity for this to satisfy your want to contribute? Is there opportunity for a PM? Github is the defacto standard for FOSS products. Check the activity. Read up on issues. See who is contributing PRs, and creating issues. Check if there is a Github Project instance. It’s OK, and best for you to check out out multiple FOSS projects concurrently to see which team is the best fit for both parties. ### 4\. Use the thing(s)! Another thing you can do to help you choose a project is to use the thing! Download the OS. Run the software. Use it. As you’re interacting with the product, some things you can ask yourself are: What do you love about the product? What can be improved? Are there bugs? Jot down your notes. Take screenshots. Do screen recordings. Document your experience. Create a video onboarding walkthrough, or a feature tutorial. What you are actually doing is documentation and this will be useful for the project, even if you don’t decide to actively contribute. As you use the thing, take note of how you’re reacting to it. Are you getting more or less excited? Are you more or less confident in contributing to the project? ### 5\. Find out where the team works Another factor to consider is to figure out where the team works. By now you have already explored their github to collect your FOSS intelligence. Now check nostr, twitter, telegram, or whatever other comms tools the team might be using. Some teams may have calls, and call recordings. Consider listening in to a recording, and/or joining a call to check the team dynamics. As you do, assess whether you might be a good culture fit. Also see where there might be some gaps in their workflow that you can help improve. ### 6\. Start small Once you found a project that interests and excites you enough. It’s time to roll up your sleeves and get involved by starting small. One easy place to start is to go through the github issues list. Some examples of issues in dev heavy teams are e extremely technical bug reports. For FOSS products with an active user base, there might be “customer” centric feature requests. Start by logging the bug(s) you found. Examine issues, and fill in the blanks if there are unclearly defined reports & requests. You don’t have to ask for permission to contribute. That said, evaluate team dynamics and who owns what role so you are not stepping on anyone’s toes. You are there to help. Also take note of how your help is received. It may take time for you to build up your credibility. Don’t throw in the towel on the first week. Keep finding ways to add value. ### 7\. Show up consistently Keep contributing in small things day in and day out. As you do so, communicate with the team to ramp up your learning, and also start building rapport, and your reputation. You may not have time or opportunity to contribute full-time. With the state of asynchronous communication tools in 2023, you can flexibly contribute when you have time. An exception to the asynchronous communication may be team meetings. As you continue to show up consistently, you will build up your FOSS proof-of-work, and reputation. This will show FOSS devs, and contributors that you bring value. ### 8\. Find and meet the “customer” Find, and interact with the project’s users a.k.a “customers”. What do they care about? What are their pain points? What needs are customers using the product for? Become the “voice of the customer” to the dev heavy team. Is there a conference where your team is presenting, and customers present? These are invaluable opportunities to observe the customer’s behavior, and also to help answer questions, and troubleshoot on the spot. ### 9\. Increase your involvement After some time starting small and working on bugs, you may eventually find yourself submitting feature requests. Maybe there is an opportunity to create user flows, or mockups. As you consistently contribute, continue seeking more responsibility. Maybe you offer to facilitate and lead the next team call. Maybe you try creating a roadmap and backlog from scratch. Maybe you host a product & design thinking session. Maybe you will level up and learn how to check out a dev’s PR in a yet-to-released branch. No matter what you do, be sure to always bring value to the project.  Testing an unreleased Damus branch checked out on XCode ### 10\. Prune, Commit, Repeat Congratulations! By now you’ve been doing a “trial run” with several projects. It’s time to focus and choose one(s) that you can commit to. As you contribute to the project on an ongoing basis, continuously reevaluate if there is opportunity for you to increase your contributions. If you feel that you’ve maxed that out, it may be time to look for a different FOSS product to contribute to. Perhaps a complementary product to your initial one. As you embark on this journey, it can be exhilarating at times and in other times thankless. To find a community of peers, and perhaps a mentor check in with the Bitcoin Product Community [Discord](https://discord.gg/Ztvwn8fycA), and introduce yourself. The beauty of open source is people are willing to help FOSS products, and to answer your questions. [https://youtu.be/ZUgQPR6ecuo](https://youtu.be/ZUgQPR6ecuo)“FOSS is the way” - Rockstar dev, @ Advancing Bitcoin Conference London 2023. The author thanks Rockstar for inspiration, and guidance through my FOSS journey. As you continue to sweep the FOSS floors with your product [mop](https://medium.com/all-things-product-management/product-manager-you-are-664d83ee702e), remember that you are contributing to the mission that you believe in. You are working in the open, with even less authority than a PM at a company might have, and as a result leveling up. You build up your reputation in FOSS, and you show others your capabilities in the FOSS world (and also prospective employers, and co-founders) by doing. Hopefully this helps you get started. Reach out to [elsat on nostr](https://njump.me/npub1zafcms4xya5ap9zr7xxr0jlrtrattwlesytn2s42030lzu0dwlzqpd26k5) if you have questions about the FOSS journey, and join the Bitcoin Product Community Discord. Posted on @YakiHonne by @elsat Source: https://yakihonne.com/article/nevent1qqswn2mdwcfscsvv8cfc8scmcfpy0urnf0xgh0dxrvav583y85mkryspz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzq96n3hp2vfmf6z2y8uvvxl97xk86kkalnqghx4p25lzl79c76a7yjfa8zs originally posted at https://stacker.news/items/885573
@ 57d1a264:69f1fee1
2025-02-14 05:45:37 ### a practical intro to contributing to FOSS for product people, and other non-devs So you want to contribute to FOSS, but don’t know where to start. There are many paths to FOSS, but you must find your own. Here’s some advice based on personal experience to help you get started. ### 0\. Find your motivation FOSS requires a lot of giving, and better aligns with those that are missionaries, as opposed to the mercenaries. Perhaps you are unfulfilled in your fiat job, maybe you are currently unemployed, or perhaps you are excited about a particular bitcoin project. Why you’re exploring contributing to FOSS, is a question that only you can answer.  Are you a missionary? ### 1\. Discover what excites you So you’ve found motivation and have a list of various FOSS projects you could contribute to. This is the equivalent of the “I need a job” stage and you’re figuring out where to apply. It’s time to narrow it down. What are you excited about? A multi-year pilgrimage of learning how to contribute to Bitcoin Core? A lightning wallet, perhaps? Free speech Nostr? A hardware signing device? Or maybe finding a FOSS projects that is not “Bitcoin” in name, but happens to support Bitcoin, and Lightning. A great first step is to take some time and explore the Bitcoin Design Community ([https://bitcoin.design/](https://bitcoin.design/)) to discover FOSS projects.  Are you excited anon? ### 2\. Identify the skills you have or want to develop Chances are that if you follow the Bitcoin Product Community, you’re skills are in Product Management, Product Marketing, and/or Project Management. But contributing to a bitcoin project requires contributors with skills of many backgrounds such as marketing, documentation, community building, and more. What’s important to know is that most FOSS teams start with a motivated developer, who then may attract other devs. But many of them may not advertise that they need non-developer help such as a PM. Therein lies the opportunity for you as an eager bitcoin contributor. See what the needs of a project are and see if you can fill in those gaps with your skills. It may be as simple as coordinating meetings for the team. But doing the “dirty work”, or the work no one else wants to do, is exactly the way you can make an immediate impact to a FOSS project. In fact, this is why members of the Bitcoin Product Community affectionately refer to product managers as “[janitors](https://medium.com/all-things-product-management/product-manager-you-are-664d83ee702e)”! ### 3\. Make a list of projects Now that you have narrowed down your FOSS search, it is time to start building a list of, and evaluating various FOSS products. Some questions you can ask yourself: Is the project active? Is it a new project? How many team members are there? How many are devs? Is there already a PM? Is there a need for multiple PMs? Is there designer participation? What is the pace of development? Is there enough development activity for this to satisfy your want to contribute? Is there opportunity for a PM? Github is the defacto standard for FOSS products. Check the activity. Read up on issues. See who is contributing PRs, and creating issues. Check if there is a Github Project instance. It’s OK, and best for you to check out out multiple FOSS projects concurrently to see which team is the best fit for both parties. ### 4\. Use the thing(s)! Another thing you can do to help you choose a project is to use the thing! Download the OS. Run the software. Use it. As you’re interacting with the product, some things you can ask yourself are: What do you love about the product? What can be improved? Are there bugs? Jot down your notes. Take screenshots. Do screen recordings. Document your experience. Create a video onboarding walkthrough, or a feature tutorial. What you are actually doing is documentation and this will be useful for the project, even if you don’t decide to actively contribute. As you use the thing, take note of how you’re reacting to it. Are you getting more or less excited? Are you more or less confident in contributing to the project? ### 5\. Find out where the team works Another factor to consider is to figure out where the team works. By now you have already explored their github to collect your FOSS intelligence. Now check nostr, twitter, telegram, or whatever other comms tools the team might be using. Some teams may have calls, and call recordings. Consider listening in to a recording, and/or joining a call to check the team dynamics. As you do, assess whether you might be a good culture fit. Also see where there might be some gaps in their workflow that you can help improve. ### 6\. Start small Once you found a project that interests and excites you enough. It’s time to roll up your sleeves and get involved by starting small. One easy place to start is to go through the github issues list. Some examples of issues in dev heavy teams are e extremely technical bug reports. For FOSS products with an active user base, there might be “customer” centric feature requests. Start by logging the bug(s) you found. Examine issues, and fill in the blanks if there are unclearly defined reports & requests. You don’t have to ask for permission to contribute. That said, evaluate team dynamics and who owns what role so you are not stepping on anyone’s toes. You are there to help. Also take note of how your help is received. It may take time for you to build up your credibility. Don’t throw in the towel on the first week. Keep finding ways to add value. ### 7\. Show up consistently Keep contributing in small things day in and day out. As you do so, communicate with the team to ramp up your learning, and also start building rapport, and your reputation. You may not have time or opportunity to contribute full-time. With the state of asynchronous communication tools in 2023, you can flexibly contribute when you have time. An exception to the asynchronous communication may be team meetings. As you continue to show up consistently, you will build up your FOSS proof-of-work, and reputation. This will show FOSS devs, and contributors that you bring value. ### 8\. Find and meet the “customer” Find, and interact with the project’s users a.k.a “customers”. What do they care about? What are their pain points? What needs are customers using the product for? Become the “voice of the customer” to the dev heavy team. Is there a conference where your team is presenting, and customers present? These are invaluable opportunities to observe the customer’s behavior, and also to help answer questions, and troubleshoot on the spot. ### 9\. Increase your involvement After some time starting small and working on bugs, you may eventually find yourself submitting feature requests. Maybe there is an opportunity to create user flows, or mockups. As you consistently contribute, continue seeking more responsibility. Maybe you offer to facilitate and lead the next team call. Maybe you try creating a roadmap and backlog from scratch. Maybe you host a product & design thinking session. Maybe you will level up and learn how to check out a dev’s PR in a yet-to-released branch. No matter what you do, be sure to always bring value to the project.  Testing an unreleased Damus branch checked out on XCode ### 10\. Prune, Commit, Repeat Congratulations! By now you’ve been doing a “trial run” with several projects. It’s time to focus and choose one(s) that you can commit to. As you contribute to the project on an ongoing basis, continuously reevaluate if there is opportunity for you to increase your contributions. If you feel that you’ve maxed that out, it may be time to look for a different FOSS product to contribute to. Perhaps a complementary product to your initial one. As you embark on this journey, it can be exhilarating at times and in other times thankless. To find a community of peers, and perhaps a mentor check in with the Bitcoin Product Community [Discord](https://discord.gg/Ztvwn8fycA), and introduce yourself. The beauty of open source is people are willing to help FOSS products, and to answer your questions. [https://youtu.be/ZUgQPR6ecuo](https://youtu.be/ZUgQPR6ecuo)“FOSS is the way” - Rockstar dev, @ Advancing Bitcoin Conference London 2023. The author thanks Rockstar for inspiration, and guidance through my FOSS journey. As you continue to sweep the FOSS floors with your product [mop](https://medium.com/all-things-product-management/product-manager-you-are-664d83ee702e), remember that you are contributing to the mission that you believe in. You are working in the open, with even less authority than a PM at a company might have, and as a result leveling up. You build up your reputation in FOSS, and you show others your capabilities in the FOSS world (and also prospective employers, and co-founders) by doing. Hopefully this helps you get started. Reach out to [elsat on nostr](https://njump.me/npub1zafcms4xya5ap9zr7xxr0jlrtrattwlesytn2s42030lzu0dwlzqpd26k5) if you have questions about the FOSS journey, and join the Bitcoin Product Community Discord. Posted on @YakiHonne by @elsat Source: https://yakihonne.com/article/nevent1qqswn2mdwcfscsvv8cfc8scmcfpy0urnf0xgh0dxrvav583y85mkryspz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzq96n3hp2vfmf6z2y8uvvxl97xk86kkalnqghx4p25lzl79c76a7yjfa8zs originally posted at https://stacker.news/items/885573 @ 57d1a264:69f1fee1
2025-02-14 05:35:18Volt Wallet is designed to make Bitcoin and Lightning transactions simple, secure, and accessible for users of all experience levels. With the increasing popularity of the Lightning Network, Volt Wallet provides an easy, user-friendly interface for sending and receiving payments while also incorporating educational elements, such as quizzes and tutorial videos, to promote a better understanding of Bitcoin and Lightning payments.                    - - - Source: https://www.behance.net/gallery/217868517/Volt-A-Bitcoin-Lighting-Wallet-for-beginners originally posted at https://stacker.news/items/885569
@ 57d1a264:69f1fee1
2025-02-14 05:35:18Volt Wallet is designed to make Bitcoin and Lightning transactions simple, secure, and accessible for users of all experience levels. With the increasing popularity of the Lightning Network, Volt Wallet provides an easy, user-friendly interface for sending and receiving payments while also incorporating educational elements, such as quizzes and tutorial videos, to promote a better understanding of Bitcoin and Lightning payments.                    - - - Source: https://www.behance.net/gallery/217868517/Volt-A-Bitcoin-Lighting-Wallet-for-beginners originally posted at https://stacker.news/items/885569 @ d360efec:14907b5f
2025-02-14 05:35:13**ภาพรวม LUNCUSDT (OKX):** LUNCUSDT กำลังอยู่ในช่วงที่ผันผวนและมีความไม่แน่นอนสูง หลังจากที่เคยมีสัญญาณบวกของการกลับตัวใน TF Day แต่ตอนนี้ทั้ง 3 Timeframes แสดงให้เห็นถึงแรงขายที่เข้ามา และแนวโน้มเริ่มไม่ชัดเจน **วิเคราะห์ทีละ Timeframe:** **(1) TF Day (รายวัน):** [https://www.tradingview.com/x/ulqLh1c9/](https://www.tradingview.com/x/ulqLh1c9/)  * **แนวโน้ม:** เริ่มไม่แน่นอน (จากเดิมที่เป็น Early Uptrend) หลังจากที่ราคาไม่สามารถยืนเหนือ EMA 50/200 ได้ * **SMC:** * Break of Structure (BOS): มี BOS ทั้งด้านบนและด้านล่าง * Change of Character (CHoCH): มี CHoCH ด้านบน * Higher High (HH) & Higher Low (HL): HH ล่าสุดต่ำกว่า High ก่อนหน้า * **EMA:** * EMA 50 และ EMA 200 เคยเป็นแนวรับ แต่ตอนนี้ราคากลับลงมาอยู่ใต้เส้น EMA ทั้งสอง * **Money Flow (LuxAlgo):** * เริ่มมีแท่งสีแดงยาวขึ้น แสดงถึงแรงขายที่เข้ามา * **Volume Profile:** * Volume หนาแน่นบริเวณ 0.00012000 - 0.00014000 (แนวต้าน) * **แท่งเทียน:** * แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย * **แนวรับ:** บริเวณ 0.00006000-0.00007000 * **แนวต้าน:** EMA 50, EMA 200, 0.00014000, 0.00017953 * **สรุป:** แนวโน้มเริ่มไม่แน่นอน, สัญญาณการกลับตัวเริ่มอ่อนแอ, แรงขายเริ่มเข้ามา **(2) TF4H (4 ชั่วโมง):** [https://www.tradingview.com/x/SLsNzZi2/](https://www.tradingview.com/x/SLsNzZi2/)  * **แนวโน้ม:** ขาลง (Downtrend) หลังจากราคาหลุด EMA 50 * **SMC:** * Break of Structure (BOS): มี BOS ด้านล่าง * Change of Character (CHoCH): ไม่ชัดเจน * Lower Highs (LH) และ Lower Lows (LL) * **EMA:** * EMA 50 และ EMA 200 กลายเป็นแนวต้าน * **Money Flow (LuxAlgo):** * สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย * **Volume Profile:** * Volume ค่อนข้างนิ่ง * **แท่งเทียน:** * แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย * **แนวรับ:** บริเวณ 0.00006000-0.00007000 * **แนวต้าน:** EMA 50, EMA 200, บริเวณ High ก่อนหน้า * **สรุป:** แนวโน้มขาลง, แรงขายมีอิทธิพล **(3) TF15 (15 นาที):** [https://www.tradingview.com/x/H8QdIEAL/](https://www.tradingview.com/x/H8QdIEAL/)  * **แนวโน้ม:** ขาลง (Downtrend) * **SMC:** * Break of Structure (BOS): มี BOS ด้านล่าง * Change of Character (CHoCH): มีทั้งด้านบนและด้านล่าง * Lower Highs (LH) และ Lower Lows (LL) * **EMA:** * EMA 50 และ EMA 200 เป็นแนวต้าน * **Money Flow (LuxAlgo):** * สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย * **Volume:** * Volume ค่อนข้างเบาบาง * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA 50, EMA 200, บริเวณ High ก่อนหน้า * **สรุป:** แนวโน้มขาลง, แรงขายมีอิทธิพล **สรุปภาพรวมและกลยุทธ์ (LUNCUSDT):** * **แนวโน้มหลัก:** เริ่มไม่แน่นอน (TF Day), ขาลง (TF4H, TF15) * **Money Flow:** * Day: แรงขายเริ่มเข้ามา * 4H: แรงขายมีอิทธิพล * 15m: แรงขายมีอิทธิพล * **กลยุทธ์:** 1. **Wait & See (ดีที่สุด):** รอความชัดเจน 2. **Short (เสี่ยงสูง):** ถ้าไม่สามารถ Breakout EMA/แนวต้านได้ 3. **ไม่แนะนำให้ Buy:** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจน **คำแนะนำ:** * **LUNC มีความเสี่ยงสูงมาก** * **ความขัดแย้งของ Timeframes:** Day เริ่มไม่แน่นอน, 4H และ 15m เป็นขาลง * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด** *Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
@ d360efec:14907b5f
2025-02-14 05:35:13**ภาพรวม LUNCUSDT (OKX):** LUNCUSDT กำลังอยู่ในช่วงที่ผันผวนและมีความไม่แน่นอนสูง หลังจากที่เคยมีสัญญาณบวกของการกลับตัวใน TF Day แต่ตอนนี้ทั้ง 3 Timeframes แสดงให้เห็นถึงแรงขายที่เข้ามา และแนวโน้มเริ่มไม่ชัดเจน **วิเคราะห์ทีละ Timeframe:** **(1) TF Day (รายวัน):** [https://www.tradingview.com/x/ulqLh1c9/](https://www.tradingview.com/x/ulqLh1c9/)  * **แนวโน้ม:** เริ่มไม่แน่นอน (จากเดิมที่เป็น Early Uptrend) หลังจากที่ราคาไม่สามารถยืนเหนือ EMA 50/200 ได้ * **SMC:** * Break of Structure (BOS): มี BOS ทั้งด้านบนและด้านล่าง * Change of Character (CHoCH): มี CHoCH ด้านบน * Higher High (HH) & Higher Low (HL): HH ล่าสุดต่ำกว่า High ก่อนหน้า * **EMA:** * EMA 50 และ EMA 200 เคยเป็นแนวรับ แต่ตอนนี้ราคากลับลงมาอยู่ใต้เส้น EMA ทั้งสอง * **Money Flow (LuxAlgo):** * เริ่มมีแท่งสีแดงยาวขึ้น แสดงถึงแรงขายที่เข้ามา * **Volume Profile:** * Volume หนาแน่นบริเวณ 0.00012000 - 0.00014000 (แนวต้าน) * **แท่งเทียน:** * แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย * **แนวรับ:** บริเวณ 0.00006000-0.00007000 * **แนวต้าน:** EMA 50, EMA 200, 0.00014000, 0.00017953 * **สรุป:** แนวโน้มเริ่มไม่แน่นอน, สัญญาณการกลับตัวเริ่มอ่อนแอ, แรงขายเริ่มเข้ามา **(2) TF4H (4 ชั่วโมง):** [https://www.tradingview.com/x/SLsNzZi2/](https://www.tradingview.com/x/SLsNzZi2/)  * **แนวโน้ม:** ขาลง (Downtrend) หลังจากราคาหลุด EMA 50 * **SMC:** * Break of Structure (BOS): มี BOS ด้านล่าง * Change of Character (CHoCH): ไม่ชัดเจน * Lower Highs (LH) และ Lower Lows (LL) * **EMA:** * EMA 50 และ EMA 200 กลายเป็นแนวต้าน * **Money Flow (LuxAlgo):** * สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย * **Volume Profile:** * Volume ค่อนข้างนิ่ง * **แท่งเทียน:** * แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย * **แนวรับ:** บริเวณ 0.00006000-0.00007000 * **แนวต้าน:** EMA 50, EMA 200, บริเวณ High ก่อนหน้า * **สรุป:** แนวโน้มขาลง, แรงขายมีอิทธิพล **(3) TF15 (15 นาที):** [https://www.tradingview.com/x/H8QdIEAL/](https://www.tradingview.com/x/H8QdIEAL/)  * **แนวโน้ม:** ขาลง (Downtrend) * **SMC:** * Break of Structure (BOS): มี BOS ด้านล่าง * Change of Character (CHoCH): มีทั้งด้านบนและด้านล่าง * Lower Highs (LH) และ Lower Lows (LL) * **EMA:** * EMA 50 และ EMA 200 เป็นแนวต้าน * **Money Flow (LuxAlgo):** * สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย * **Volume:** * Volume ค่อนข้างเบาบาง * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA 50, EMA 200, บริเวณ High ก่อนหน้า * **สรุป:** แนวโน้มขาลง, แรงขายมีอิทธิพล **สรุปภาพรวมและกลยุทธ์ (LUNCUSDT):** * **แนวโน้มหลัก:** เริ่มไม่แน่นอน (TF Day), ขาลง (TF4H, TF15) * **Money Flow:** * Day: แรงขายเริ่มเข้ามา * 4H: แรงขายมีอิทธิพล * 15m: แรงขายมีอิทธิพล * **กลยุทธ์:** 1. **Wait & See (ดีที่สุด):** รอความชัดเจน 2. **Short (เสี่ยงสูง):** ถ้าไม่สามารถ Breakout EMA/แนวต้านได้ 3. **ไม่แนะนำให้ Buy:** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจน **คำแนะนำ:** * **LUNC มีความเสี่ยงสูงมาก** * **ความขัดแย้งของ Timeframes:** Day เริ่มไม่แน่นอน, 4H และ 15m เป็นขาลง * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด** *Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ @ d360efec:14907b5f
2025-02-14 05:21:58**ภาพรวม XRPUSDT (OKX):** XRPUSDT กำลังแสดงสัญญาณที่น่าสนใจและมีความซับซ้อน แนวโน้มใน Timeframe ใหญ่ (Day) เริ่มเป็นขาขึ้น แต่ Timeframe กลาง (4H) เริ่มอ่อนแรง และ Timeframe เล็ก (15m) เป็นขาลง ทำให้เกิดความขัดแย้งที่ต้องระมัดระวัง **วิเคราะห์ทีละ Timeframe:** **(1) TF Day (รายวัน):** [https://www.tradingview.com/x/3EbxjOgV/](https://www.tradingview.com/x/3EbxjOgV/)  * **แนวโน้ม:** เริ่มเป็นขาขึ้น (Early Uptrend) หลังจากราคา Breakout EMA 50 ขึ้นมาได้ * **SMC:** * Break of Structure (BOS): มี BOS ด้านบน (Breakout EMA 50) * Change of Character (CHoCH): ยังไม่ชัดเจน * Higher High (HH) & Higher Low (HL): เพิ่งเริ่มก่อตัว (ยังไม่ชัดเจน) * **EMA:** * ราคาอยู่เหนือ EMA 50 (สีเหลือง) และ EMA 200 (สีขาว) * EMA 50 และ EMA 200 กำลังจะเกิด Golden Cross * **Money Flow (LuxAlgo):** * สีเขียวเป็นส่วนใหญ่ แสดงถึงแรงซื้อที่ยังคงมีอยู่ * มีแท่งสีแดงแทรกบ้าง แสดงถึงการขายทำกำไร * **Volume Profile:** * Volume หนาแน่นบริเวณ EMA 50 * **แท่งเทียน:** * แท่งเทียนล่าสุดเป็นสีเขียว แสดงถึงแรงซื้อ * **แนวรับ:** EMA 50, EMA 200 * **แนวต้าน:** 0.6448 (High ก่อนหน้า) * **สรุป:** แนวโน้มเริ่มเป็นขาขึ้น แต่ยังอยู่ในช่วงเริ่มต้น **(2) TF4H (4 ชั่วโมง):** [https://www.tradingview.com/x/nARcdWWp/](https://www.tradingview.com/x/nARcdWWp/)  * **แนวโน้ม:** เริ่มไม่แน่นอน (พักตัว, ทดสอบแนวรับ) หลังจากเป็นขาขึ้นระยะสั้น * **SMC:** * Break of Structure (BOS): มี BOS ด้านบน (ก่อนหน้านี้) * Change of Character (CHoCH): ไม่ชัดเจน * Higher High (HH) & Higher Low (HL): เริ่มไม่ชัดเจน * มี Equal Highs (EQH) * **EMA:** * EMA 50 กำลังถูกทดสอบ * EMA 200 เป็นแนวรับถัดไป * **Money Flow (LuxAlgo):** * เขียวและแดงผสมกัน แสดงถึงความไม่แน่นอน * แท่งสีแดงเริ่มยาวขึ้น แสดงถึงแรงขายที่เข้ามา * **Volume Profile:** * Volume หนาแน่นบริเวณ EMA 50 * **แท่งเทียน:** * แท่งเทียนล่าสุด เป็น Doji * **แนวรับ:** EMA 50, EMA 200, บริเวณ 0.50-0.52 * **แนวต้าน:** บริเวณ High ก่อนหน้า * **สรุป:** แนวโน้มเริ่มไม่แน่นอน, มีแรงขายเข้ามา, EMA 50 เป็นจุดสำคัญ **(3) TF15 (15 นาที):** [https://www.tradingview.com/x/NI2wqamj/](https://www.tradingview.com/x/NI2wqamj/)  * **แนวโน้ม:** ขาลง (Downtrend) ระยะสั้น * **SMC:** * Break of Structure (BOS): มี BOS ด้านล่าง * Change of Character (CHoCH): มีทั้งด้านบนและด้านล่าง * Lower Highs (LH) และ Lower Lows (LL) * **EMA:** * EMA 50 และ EMA 200 กลายเป็นแนวต้าน * **Money Flow (LuxAlgo):** * สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย * **Volume Profile:** * Volume สูง * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA 50, EMA 200, บริเวณ 0.54 * **สรุป:** แนวโน้มขาลง, แรงขายมีอิทธิพล **สรุปภาพรวมและกลยุทธ์ (XRPUSDT):** * **แนวโน้มหลัก (Day):** เริ่มเป็นขาขึ้น * **แนวโน้มรอง (4H):** เริ่มไม่แน่นอน, พักตัว * **แนวโน้มระยะสั้น (15m):** ขาลง * **Money Flow:** * Day: แรงซื้อยังคงมี * 4H: แรงซื้อและแรงขายผสมกัน, แรงขายเริ่มเข้ามา * 15m: แรงขายมีอิทธิพล * **กลยุทธ์:** 1. **Wait & See (ดีที่สุด):** รอความชัดเจน 2. **Buy on Dip (Day, 4H) - *เสี่ยงสูงมาก*:** ต้องรอสัญญาณกลับตัวใน TF15 3. **Short (15m, เสี่ยงสูง):** ถ้าไม่สามารถ Breakout EMA/แนวต้านได้ **คำแนะนำ:** * **ความขัดแย้งของ Timeframes:** ยังคงมีอยู่ * **Money Flow:** Day เป็นบวก, 4H เริ่มไม่แน่นอน, 15m เป็นลบ * **EMA 50 (TF4H):** จุดสำคัญ * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด** *Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
@ d360efec:14907b5f
2025-02-14 05:21:58**ภาพรวม XRPUSDT (OKX):** XRPUSDT กำลังแสดงสัญญาณที่น่าสนใจและมีความซับซ้อน แนวโน้มใน Timeframe ใหญ่ (Day) เริ่มเป็นขาขึ้น แต่ Timeframe กลาง (4H) เริ่มอ่อนแรง และ Timeframe เล็ก (15m) เป็นขาลง ทำให้เกิดความขัดแย้งที่ต้องระมัดระวัง **วิเคราะห์ทีละ Timeframe:** **(1) TF Day (รายวัน):** [https://www.tradingview.com/x/3EbxjOgV/](https://www.tradingview.com/x/3EbxjOgV/)  * **แนวโน้ม:** เริ่มเป็นขาขึ้น (Early Uptrend) หลังจากราคา Breakout EMA 50 ขึ้นมาได้ * **SMC:** * Break of Structure (BOS): มี BOS ด้านบน (Breakout EMA 50) * Change of Character (CHoCH): ยังไม่ชัดเจน * Higher High (HH) & Higher Low (HL): เพิ่งเริ่มก่อตัว (ยังไม่ชัดเจน) * **EMA:** * ราคาอยู่เหนือ EMA 50 (สีเหลือง) และ EMA 200 (สีขาว) * EMA 50 และ EMA 200 กำลังจะเกิด Golden Cross * **Money Flow (LuxAlgo):** * สีเขียวเป็นส่วนใหญ่ แสดงถึงแรงซื้อที่ยังคงมีอยู่ * มีแท่งสีแดงแทรกบ้าง แสดงถึงการขายทำกำไร * **Volume Profile:** * Volume หนาแน่นบริเวณ EMA 50 * **แท่งเทียน:** * แท่งเทียนล่าสุดเป็นสีเขียว แสดงถึงแรงซื้อ * **แนวรับ:** EMA 50, EMA 200 * **แนวต้าน:** 0.6448 (High ก่อนหน้า) * **สรุป:** แนวโน้มเริ่มเป็นขาขึ้น แต่ยังอยู่ในช่วงเริ่มต้น **(2) TF4H (4 ชั่วโมง):** [https://www.tradingview.com/x/nARcdWWp/](https://www.tradingview.com/x/nARcdWWp/)  * **แนวโน้ม:** เริ่มไม่แน่นอน (พักตัว, ทดสอบแนวรับ) หลังจากเป็นขาขึ้นระยะสั้น * **SMC:** * Break of Structure (BOS): มี BOS ด้านบน (ก่อนหน้านี้) * Change of Character (CHoCH): ไม่ชัดเจน * Higher High (HH) & Higher Low (HL): เริ่มไม่ชัดเจน * มี Equal Highs (EQH) * **EMA:** * EMA 50 กำลังถูกทดสอบ * EMA 200 เป็นแนวรับถัดไป * **Money Flow (LuxAlgo):** * เขียวและแดงผสมกัน แสดงถึงความไม่แน่นอน * แท่งสีแดงเริ่มยาวขึ้น แสดงถึงแรงขายที่เข้ามา * **Volume Profile:** * Volume หนาแน่นบริเวณ EMA 50 * **แท่งเทียน:** * แท่งเทียนล่าสุด เป็น Doji * **แนวรับ:** EMA 50, EMA 200, บริเวณ 0.50-0.52 * **แนวต้าน:** บริเวณ High ก่อนหน้า * **สรุป:** แนวโน้มเริ่มไม่แน่นอน, มีแรงขายเข้ามา, EMA 50 เป็นจุดสำคัญ **(3) TF15 (15 นาที):** [https://www.tradingview.com/x/NI2wqamj/](https://www.tradingview.com/x/NI2wqamj/)  * **แนวโน้ม:** ขาลง (Downtrend) ระยะสั้น * **SMC:** * Break of Structure (BOS): มี BOS ด้านล่าง * Change of Character (CHoCH): มีทั้งด้านบนและด้านล่าง * Lower Highs (LH) และ Lower Lows (LL) * **EMA:** * EMA 50 และ EMA 200 กลายเป็นแนวต้าน * **Money Flow (LuxAlgo):** * สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย * **Volume Profile:** * Volume สูง * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA 50, EMA 200, บริเวณ 0.54 * **สรุป:** แนวโน้มขาลง, แรงขายมีอิทธิพล **สรุปภาพรวมและกลยุทธ์ (XRPUSDT):** * **แนวโน้มหลัก (Day):** เริ่มเป็นขาขึ้น * **แนวโน้มรอง (4H):** เริ่มไม่แน่นอน, พักตัว * **แนวโน้มระยะสั้น (15m):** ขาลง * **Money Flow:** * Day: แรงซื้อยังคงมี * 4H: แรงซื้อและแรงขายผสมกัน, แรงขายเริ่มเข้ามา * 15m: แรงขายมีอิทธิพล * **กลยุทธ์:** 1. **Wait & See (ดีที่สุด):** รอความชัดเจน 2. **Buy on Dip (Day, 4H) - *เสี่ยงสูงมาก*:** ต้องรอสัญญาณกลับตัวใน TF15 3. **Short (15m, เสี่ยงสูง):** ถ้าไม่สามารถ Breakout EMA/แนวต้านได้ **คำแนะนำ:** * **ความขัดแย้งของ Timeframes:** ยังคงมีอยู่ * **Money Flow:** Day เป็นบวก, 4H เริ่มไม่แน่นอน, 15m เป็นลบ * **EMA 50 (TF4H):** จุดสำคัญ * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด** *Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ @ d360efec:14907b5f
2025-02-14 04:13:06Bitcoin (BTCUSDT) กำลังแสดงสัญญาณที่น่าสนใจ โดยรวมแล้วแนวโน้มระยะยาวยังเป็นขาขึ้น แต่ระยะสั้นมีความผันผวนและมีการปรับฐานลงมา **วิเคราะห์ทีละ Timeframe:** **(1) TF Day (รายวัน):** [https://www.tradingview.com/x/s9CAaSKQ/](https://www.tradingview.com/x/s9CAaSKQ/)  * **แนวโน้ม:** ขาขึ้น (Uptrend) แข็งแกร่ง * **SMC:** * Higher Highs (HH) และ Higher Lows (HL) อย่างต่อเนื่อง * Break of Structure (BOS) ด้านบนหลายครั้ง * ไม่มีสัญญาณการกลับตัวเป็นขาลง * **EMA:** * ราคาอยู่เหนือ EMA 50 (เส้นสีเหลือง) และ EMA 200 (เส้นสีขาว) * EMA 50 และ EMA 200 เรียงตัวแบบ Golden Cross (EMA 50 ตัด EMA 200 ขึ้น) * **Money Flow (LuxAlgo):** * โดยรวมเป็นสีเขียว แสดงถึงแรงซื้อที่ยังคงมีอิทธิพลเหนือกว่า * มีแท่งสีแดงแทรกบ้าง แสดงถึงการขายทำกำไร * **Volume Profile:** * Volume หนาแน่นที่บริเวณ 96,000 - 98,000 (ซึ่งตอนนี้กลายเป็นแนวรับไปแล้ว) * **แท่งเทียน:** * แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย แต่ไส้เทียนด้านล่างยาว แสดงว่ามีแรงซื้อกลับเข้ามาบ้าง * **แนวรับ:** EMA 50, EMA 200, บริเวณ 96,000 - 98,000 * **แนวต้าน:** 109,998.9 (High เดิม) * **สรุป:** แนวโน้มขาขึ้นยังคงแข็งแกร่ง Buy on Dip ยังคงเป็นกลยุทธ์หลัก **(2) TF4H (4 ชั่วโมง):** [https://www.tradingview.com/x/KsuVdl2e/](https://www.tradingview.com/x/KsuVdl2e/)  * **แนวโน้ม:** ขาขึ้น (Uptrend) แต่มีการพักตัวลงมา (Pullback) * **SMC:** * Higher Highs (HH) และ Higher Lows (HL) * Break of Structure (BOS) ด้านบน * ราคาพักตัวลงมา แต่ยังไม่เสียโครงสร้างขาขึ้น * มี Equal Highs (EQH) บริเวณ 109,998.9 * **EMA:** * EMA 50 กำลังถูกทดสอบ * EMA 200 เป็นแนวรับถัดไป * **Money Flow (LuxAlgo):** * โดยรวมเป็นสีเขียว แต่เริ่มมีแท่งสีเขียวสั้นลง และมีแท่งสีแดงยาวขึ้น แสดงว่าแรงซื้อเริ่มอ่อนแรง และมีแรงขายเข้ามา * **Volume Profile:** * Volume หนาแน่นที่บริเวณ 96,000 - 98,000 * **แท่งเทียน:** * แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย * **แนวรับ:** EMA 50, EMA 200, บริเวณ 96,000 - 98,000 * **แนวต้าน:** 109,998.9 (EQH, High เดิม) * **สรุป:** แนวโน้มขาขึ้นยังไม่เสีย แต่เริ่มมีสัญญาณเตือน (Money Flow อ่อนแรง, ราคาพักตัว) **(3) TF15 (15 นาที):** [https://www.tradingview.com/x/DSrpSjn6/](https://www.tradingview.com/x/DSrpSjn6/)  * **แนวโน้ม:** Sideways Down (แกว่งตัวลง) หลังจากพยายาม Breakout แต่ไม่สำเร็จ * **SMC:** * Break of Structure (BOS) ด้านล่าง (หลุดแนวรับย่อยๆ) * Change of Character (CHoCH) ทั้งด้านบนและด้านล่าง * Lower Highs (LH) และ Lower Lows (LL) เริ่มก่อตัว * Equal Highs (EQH) หลายจุด * **EMA:** * EMA 50 และ EMA 200 กลายเป็นแนวต้าน * **Money Flow (LuxAlgo):** * สีแดงมีอิทธิพลเหนือกว่า แสดงถึงแรงขาย * **Volume Profile:** * Volume หนาแน่นที่บริเวณ 97,000-97,200 (กลายเป็นแนวต้าน) * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA 50, EMA 200, บริเวณ 96,000, 96,800, 97,000-97,200 * **สรุป:** แนวโน้มระยะสั้นเป็นขาลง, แรงขายยังมีอยู่ **สรุปภาพรวมและกลยุทธ์ (BTCUSDT):** * **แนวโน้มหลัก (Day, 4H):** ขาขึ้น (Uptrend) * **แนวโน้มระยะสั้น (15m):** ขาลง (Downtrend) / Sideways Down * **Money Flow:** * Day: แรงซื้อยังแข็งแกร่ง * 4H: แรงซื้อเริ่มอ่อนแรง, แรงขายเริ่มเข้ามา * 15m: แรงขายมีอิทธิพลเหนือกว่า * **กลยุทธ์:** 1. **Wait & See (ดีที่สุด):** รอความชัดเจน เนื่องจากความขัดแย้งระหว่าง Timeframes 2. **Buy on Dip (Day, 4H) - *ความเสี่ยงสูงมาก*:** ต้องรอสัญญาณกลับตัวใน TF15 3. **Short (15m, ความเสี่ยงสูงมาก):** ถ้าไม่สามารถ Breakout EMA/แนวต้านได้ **คำแนะนำ:** * **ความขัดแย้งของ Timeframes:** ยังคงมีอยู่ * **Money Flow:** Day เป็นบวก, 4H เริ่มเป็นลบ, 15m เป็นลบ * **EMA 50 (TF4H):** จุดสำคัญ * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด** *Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
@ d360efec:14907b5f
2025-02-14 04:13:06Bitcoin (BTCUSDT) กำลังแสดงสัญญาณที่น่าสนใจ โดยรวมแล้วแนวโน้มระยะยาวยังเป็นขาขึ้น แต่ระยะสั้นมีความผันผวนและมีการปรับฐานลงมา **วิเคราะห์ทีละ Timeframe:** **(1) TF Day (รายวัน):** [https://www.tradingview.com/x/s9CAaSKQ/](https://www.tradingview.com/x/s9CAaSKQ/)  * **แนวโน้ม:** ขาขึ้น (Uptrend) แข็งแกร่ง * **SMC:** * Higher Highs (HH) และ Higher Lows (HL) อย่างต่อเนื่อง * Break of Structure (BOS) ด้านบนหลายครั้ง * ไม่มีสัญญาณการกลับตัวเป็นขาลง * **EMA:** * ราคาอยู่เหนือ EMA 50 (เส้นสีเหลือง) และ EMA 200 (เส้นสีขาว) * EMA 50 และ EMA 200 เรียงตัวแบบ Golden Cross (EMA 50 ตัด EMA 200 ขึ้น) * **Money Flow (LuxAlgo):** * โดยรวมเป็นสีเขียว แสดงถึงแรงซื้อที่ยังคงมีอิทธิพลเหนือกว่า * มีแท่งสีแดงแทรกบ้าง แสดงถึงการขายทำกำไร * **Volume Profile:** * Volume หนาแน่นที่บริเวณ 96,000 - 98,000 (ซึ่งตอนนี้กลายเป็นแนวรับไปแล้ว) * **แท่งเทียน:** * แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย แต่ไส้เทียนด้านล่างยาว แสดงว่ามีแรงซื้อกลับเข้ามาบ้าง * **แนวรับ:** EMA 50, EMA 200, บริเวณ 96,000 - 98,000 * **แนวต้าน:** 109,998.9 (High เดิม) * **สรุป:** แนวโน้มขาขึ้นยังคงแข็งแกร่ง Buy on Dip ยังคงเป็นกลยุทธ์หลัก **(2) TF4H (4 ชั่วโมง):** [https://www.tradingview.com/x/KsuVdl2e/](https://www.tradingview.com/x/KsuVdl2e/)  * **แนวโน้ม:** ขาขึ้น (Uptrend) แต่มีการพักตัวลงมา (Pullback) * **SMC:** * Higher Highs (HH) และ Higher Lows (HL) * Break of Structure (BOS) ด้านบน * ราคาพักตัวลงมา แต่ยังไม่เสียโครงสร้างขาขึ้น * มี Equal Highs (EQH) บริเวณ 109,998.9 * **EMA:** * EMA 50 กำลังถูกทดสอบ * EMA 200 เป็นแนวรับถัดไป * **Money Flow (LuxAlgo):** * โดยรวมเป็นสีเขียว แต่เริ่มมีแท่งสีเขียวสั้นลง และมีแท่งสีแดงยาวขึ้น แสดงว่าแรงซื้อเริ่มอ่อนแรง และมีแรงขายเข้ามา * **Volume Profile:** * Volume หนาแน่นที่บริเวณ 96,000 - 98,000 * **แท่งเทียน:** * แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย * **แนวรับ:** EMA 50, EMA 200, บริเวณ 96,000 - 98,000 * **แนวต้าน:** 109,998.9 (EQH, High เดิม) * **สรุป:** แนวโน้มขาขึ้นยังไม่เสีย แต่เริ่มมีสัญญาณเตือน (Money Flow อ่อนแรง, ราคาพักตัว) **(3) TF15 (15 นาที):** [https://www.tradingview.com/x/DSrpSjn6/](https://www.tradingview.com/x/DSrpSjn6/)  * **แนวโน้ม:** Sideways Down (แกว่งตัวลง) หลังจากพยายาม Breakout แต่ไม่สำเร็จ * **SMC:** * Break of Structure (BOS) ด้านล่าง (หลุดแนวรับย่อยๆ) * Change of Character (CHoCH) ทั้งด้านบนและด้านล่าง * Lower Highs (LH) และ Lower Lows (LL) เริ่มก่อตัว * Equal Highs (EQH) หลายจุด * **EMA:** * EMA 50 และ EMA 200 กลายเป็นแนวต้าน * **Money Flow (LuxAlgo):** * สีแดงมีอิทธิพลเหนือกว่า แสดงถึงแรงขาย * **Volume Profile:** * Volume หนาแน่นที่บริเวณ 97,000-97,200 (กลายเป็นแนวต้าน) * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA 50, EMA 200, บริเวณ 96,000, 96,800, 97,000-97,200 * **สรุป:** แนวโน้มระยะสั้นเป็นขาลง, แรงขายยังมีอยู่ **สรุปภาพรวมและกลยุทธ์ (BTCUSDT):** * **แนวโน้มหลัก (Day, 4H):** ขาขึ้น (Uptrend) * **แนวโน้มระยะสั้น (15m):** ขาลง (Downtrend) / Sideways Down * **Money Flow:** * Day: แรงซื้อยังแข็งแกร่ง * 4H: แรงซื้อเริ่มอ่อนแรง, แรงขายเริ่มเข้ามา * 15m: แรงขายมีอิทธิพลเหนือกว่า * **กลยุทธ์:** 1. **Wait & See (ดีที่สุด):** รอความชัดเจน เนื่องจากความขัดแย้งระหว่าง Timeframes 2. **Buy on Dip (Day, 4H) - *ความเสี่ยงสูงมาก*:** ต้องรอสัญญาณกลับตัวใน TF15 3. **Short (15m, ความเสี่ยงสูงมาก):** ถ้าไม่สามารถ Breakout EMA/แนวต้านได้ **คำแนะนำ:** * **ความขัดแย้งของ Timeframes:** ยังคงมีอยู่ * **Money Flow:** Day เป็นบวก, 4H เริ่มเป็นลบ, 15m เป็นลบ * **EMA 50 (TF4H):** จุดสำคัญ * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด** *Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ @ 3eba5ef4:751f23ae
2025-02-14 03:52:48🍨*Your weekly byte of the latest updates from the Bitcoin ecosystem!* ## Crypto Insights ### Solving the Optimal Cluster Linearization Problem With DeepSeek Stefan Richter (stefanwouldgo) [found](https://delvingbitcoin.org/t/how-to-linearize-your-cluster/303/9?u=sss_is_me) a 1989 paper through DeepSeek R1 that provides a solid solution to the problem of optimal cluster linearization. The paper presents a proven algorithm that efficiently finds the subset of transactions with the highest fees; if this subset is included in a block, it is topologically valid. ### New Class in Cluster Mempool Improves Transaction Handling and Performance The introduction of the `TxGraph` class in [Cluster Mempool](https://bitcoinops.org/en/topics/cluster-mempool/) enhances transaction handling by encapsulating the transaction graph, focusing on effective fees, sizes, and dependencies. It enables batched and lazy updates for more efficient mempool operations, with improvements in transaction prioritization, incentive compatibility, and performance. This design simplifies the code by abstracting graph management, allowing for easier validation and future optimizations. More details in this [pull request](https://github.com/bitcoin/bitcoin/pull/31363). ### Independent Mining Still Feasible Two independent miners recently mined Bitcoin blocks: * [Block 881432](https://mempool.sethforprivacy.com/block/00000000000000000000931af218dd988191e459a8449dbce22b17e4475cd5a0) by [256 Foundation](https://256foundation.org/), a public organization promoting open-source Bitcoin mining. The group combined the hash rate from over 300 participants with the goal of breaking up the mining patent monopolies of large pools, making Bitcoin and free technology more accessible to all. * [Block 881676](https://mempool.space/block/000000000000000000022247ce3898fc9e10be0161cde5f369293d7a916ca8b3) by the open-source home mining hardware [solo.ckpool](https://solo.ckpool.org/), using hash rate equivalent to thousands of BitAxe devices. This demonstrates that independent miners can still compete, reinforcing Bitcoin’s decentralization and censorship resistance. ### 6-Block Confirmation No Longer Enough, Mining Centralization Impacts Bitcoin Security Bitcoin Core developer Luke Dashjr [posted](https://x.com/LukeDashjr/status/1888295040113361129) that he intended to update the 6-blocks-to-confirm target in the Knots wallet GUI. However, he found that due to Antpool controlling around 48% of the network's hash rate, more than 800 block confirmations would be required to achieve 95% security. He also noted that many pools, like Braiins and ViaBTC, are actually Antpool under different names. ### Payjoin Development Progress Review Spiral [reviewed](https://spiralbtc.substack.com/p/nerd-of-the-month-payjoin) the development progress of [Payjoin](https://bitcoinops.org/en/topics/payjoin/), which allows for including an additional input in a payment transaction to enhance privacy. The article also mentions that by using joint batching to optimize fees, Payjoin reduces transaction costs and increases network efficiency. Moreover, when both parties contribute inputs, Payjoin helps protect privacy by breaking common blockchain monitoring assumptions, making it harder for third parties to track payment amounts and private spending behaviors. ### Block Size Report Reveals: Growth Partly Limited by Miner Policies and Bitcoin Core Defaults The [Block Size Report](https://research.mempool.space/block-size-report/), published by Mempool research, uses data-driven analysis to examine the evolution of block size in Bitcoin from its inception to February 2025. It discusses changes in block size post-SegWit upgrade and reveals how growth has been partly limited by miner policies and Bitcoin Core defaults over the years. The report concludes with predictions about the growth of Bitcoin’s blockchain in the coming years. ### Tutorial on Becoming an Advanced Nostr User With Sats Cashback Rizful published a [guide](https://rizful.com/get_on_nostr_today) on how to become an advanced Nostr user and set up the self-owned Lightning node. After completing the tutorial, users can receive 5,000 sats via zap cashback. ### Build a Smart Card for Bitcoin and Nostr Event Signing for Under $25 The 100% open-source smart card [Satochip](https://stacker.news/items/877488) allows users to build their own signing device in just 10 minutes under 25 USD. Satochip's advantages include: * Affordable and widely available * Dual interface: supports both NFC (contactless) and Chip (contact) modes * Minimal electronics, reducing the attack surface * Enhanced security based in Secure Element ### Bitcoin at the Crossroads of AI Revolution and Sovereign Evolution CKBEcoFund [shared](https://x.com/c_hongzhou/status/1887142941980041727) their insights from the talk at [The Satoshi Roundtable](https://satoshiroundtable.org/), discussing several macro issues including the dominance of artificial intelligence, Bitcoin's security, scalability, sovereignty, and national Bitcoin strategic reserves. He explored how CKB, as a Bitcoin Layer 2, is positioning itself for high-frequency micropayments, smart contracts, and cross-chain asset management. ## Top Reads on Blockchain and Beyond ### Pod: An Optimal-Latency, Censorship-Free, and Accountable Generalized Consensus Layer [This paper](https://arxiv.org/pdf/2501.14931) introduces a new consensus concept pod, aiming to achieve physically optimal latency for one round-trip—just one write of a new transaction and one read. This work solves inherent problems of high latency in blockchain and low scalability in traditional consensus protocols. [Grigore Rosu](https://x.com/RosuGrigore) commented: "It can lead to the end of blockchains as we know them today. It shows how we can still achieve all the benefits of blockchains, but dropping the tyranny of sequentiality (and all the value exploiters that come with it).” ### Tracking and Surveillance In-App Ads The author learned of a massive [location data breach](https://www.404media.co/hackers-claim-massive-breach-of-location-data-giant-threaten-to-leak-data/?ref=timsh.org) revealing that over 2,000 apps in the App Store and Google Play were secretly collecting geographic location data without users' consent, and developers were unaware. He then began tracking himself through location data leaked by some apps and made the following discoveries: * Regardless of whether users choose "Allow" or "Ask not to track" in phone settings, the combination of "IP + location + user agent + geography" is still leaked to hundreds of third parties. * The phone sends requests with location and leaked IP. These can be converted to geographic locations through reverse DNS. * Data collection pathway: stack → [o.isx.unity3d.com](http://o.isx.unity3d.com/) → [molocoads](https://www.moloco.com/?ref=timsh.org) → bwin * **Unity** is an SSP (supply-side platform) that collects app data via its SDK * **Moloco Ads** is a DSP network that resells data from multiple SSPs like Unity, Applovin, Chartboost * **bwin** is the advertiser that users see ads for in games More discoveries in this [post](9https://timsh.org/tracking-myself-down-through-in-app-ads/). ### Potential DAO 2.0 Product Ideas The author believes that the development of on-chain AI agents will lead to new forms of DAO, giving true autonomy to the "A" in DAO. [New product ideas](https://blog.variant.fund/dao-product-ideas) include: * **DAO 2.0 launcher:** platform enables launching new community/governance tokens tied to an agent, agent responds to tokenholder votes, reads discussion forums and generates proposals * **Quality assessment for token distribution**: agent assesses contribution quality to determine payouts/token distributions for DAOs/airdrops/etc. * **ZachZBT:** agent monitors for hacks or other fraudulent activity and publishes research as well as tries to get funds back for people * **Due diligence agent**: agent verifies contract integrity, dev reputations, on-chain behavior, and potential rug risks; allows users to interact with the agent to ask questions about risks
@ 3eba5ef4:751f23ae
2025-02-14 03:52:48🍨*Your weekly byte of the latest updates from the Bitcoin ecosystem!* ## Crypto Insights ### Solving the Optimal Cluster Linearization Problem With DeepSeek Stefan Richter (stefanwouldgo) [found](https://delvingbitcoin.org/t/how-to-linearize-your-cluster/303/9?u=sss_is_me) a 1989 paper through DeepSeek R1 that provides a solid solution to the problem of optimal cluster linearization. The paper presents a proven algorithm that efficiently finds the subset of transactions with the highest fees; if this subset is included in a block, it is topologically valid. ### New Class in Cluster Mempool Improves Transaction Handling and Performance The introduction of the `TxGraph` class in [Cluster Mempool](https://bitcoinops.org/en/topics/cluster-mempool/) enhances transaction handling by encapsulating the transaction graph, focusing on effective fees, sizes, and dependencies. It enables batched and lazy updates for more efficient mempool operations, with improvements in transaction prioritization, incentive compatibility, and performance. This design simplifies the code by abstracting graph management, allowing for easier validation and future optimizations. More details in this [pull request](https://github.com/bitcoin/bitcoin/pull/31363). ### Independent Mining Still Feasible Two independent miners recently mined Bitcoin blocks: * [Block 881432](https://mempool.sethforprivacy.com/block/00000000000000000000931af218dd988191e459a8449dbce22b17e4475cd5a0) by [256 Foundation](https://256foundation.org/), a public organization promoting open-source Bitcoin mining. The group combined the hash rate from over 300 participants with the goal of breaking up the mining patent monopolies of large pools, making Bitcoin and free technology more accessible to all. * [Block 881676](https://mempool.space/block/000000000000000000022247ce3898fc9e10be0161cde5f369293d7a916ca8b3) by the open-source home mining hardware [solo.ckpool](https://solo.ckpool.org/), using hash rate equivalent to thousands of BitAxe devices. This demonstrates that independent miners can still compete, reinforcing Bitcoin’s decentralization and censorship resistance. ### 6-Block Confirmation No Longer Enough, Mining Centralization Impacts Bitcoin Security Bitcoin Core developer Luke Dashjr [posted](https://x.com/LukeDashjr/status/1888295040113361129) that he intended to update the 6-blocks-to-confirm target in the Knots wallet GUI. However, he found that due to Antpool controlling around 48% of the network's hash rate, more than 800 block confirmations would be required to achieve 95% security. He also noted that many pools, like Braiins and ViaBTC, are actually Antpool under different names. ### Payjoin Development Progress Review Spiral [reviewed](https://spiralbtc.substack.com/p/nerd-of-the-month-payjoin) the development progress of [Payjoin](https://bitcoinops.org/en/topics/payjoin/), which allows for including an additional input in a payment transaction to enhance privacy. The article also mentions that by using joint batching to optimize fees, Payjoin reduces transaction costs and increases network efficiency. Moreover, when both parties contribute inputs, Payjoin helps protect privacy by breaking common blockchain monitoring assumptions, making it harder for third parties to track payment amounts and private spending behaviors. ### Block Size Report Reveals: Growth Partly Limited by Miner Policies and Bitcoin Core Defaults The [Block Size Report](https://research.mempool.space/block-size-report/), published by Mempool research, uses data-driven analysis to examine the evolution of block size in Bitcoin from its inception to February 2025. It discusses changes in block size post-SegWit upgrade and reveals how growth has been partly limited by miner policies and Bitcoin Core defaults over the years. The report concludes with predictions about the growth of Bitcoin’s blockchain in the coming years. ### Tutorial on Becoming an Advanced Nostr User With Sats Cashback Rizful published a [guide](https://rizful.com/get_on_nostr_today) on how to become an advanced Nostr user and set up the self-owned Lightning node. After completing the tutorial, users can receive 5,000 sats via zap cashback. ### Build a Smart Card for Bitcoin and Nostr Event Signing for Under $25 The 100% open-source smart card [Satochip](https://stacker.news/items/877488) allows users to build their own signing device in just 10 minutes under 25 USD. Satochip's advantages include: * Affordable and widely available * Dual interface: supports both NFC (contactless) and Chip (contact) modes * Minimal electronics, reducing the attack surface * Enhanced security based in Secure Element ### Bitcoin at the Crossroads of AI Revolution and Sovereign Evolution CKBEcoFund [shared](https://x.com/c_hongzhou/status/1887142941980041727) their insights from the talk at [The Satoshi Roundtable](https://satoshiroundtable.org/), discussing several macro issues including the dominance of artificial intelligence, Bitcoin's security, scalability, sovereignty, and national Bitcoin strategic reserves. He explored how CKB, as a Bitcoin Layer 2, is positioning itself for high-frequency micropayments, smart contracts, and cross-chain asset management. ## Top Reads on Blockchain and Beyond ### Pod: An Optimal-Latency, Censorship-Free, and Accountable Generalized Consensus Layer [This paper](https://arxiv.org/pdf/2501.14931) introduces a new consensus concept pod, aiming to achieve physically optimal latency for one round-trip—just one write of a new transaction and one read. This work solves inherent problems of high latency in blockchain and low scalability in traditional consensus protocols. [Grigore Rosu](https://x.com/RosuGrigore) commented: "It can lead to the end of blockchains as we know them today. It shows how we can still achieve all the benefits of blockchains, but dropping the tyranny of sequentiality (and all the value exploiters that come with it).” ### Tracking and Surveillance In-App Ads The author learned of a massive [location data breach](https://www.404media.co/hackers-claim-massive-breach-of-location-data-giant-threaten-to-leak-data/?ref=timsh.org) revealing that over 2,000 apps in the App Store and Google Play were secretly collecting geographic location data without users' consent, and developers were unaware. He then began tracking himself through location data leaked by some apps and made the following discoveries: * Regardless of whether users choose "Allow" or "Ask not to track" in phone settings, the combination of "IP + location + user agent + geography" is still leaked to hundreds of third parties. * The phone sends requests with location and leaked IP. These can be converted to geographic locations through reverse DNS. * Data collection pathway: stack → [o.isx.unity3d.com](http://o.isx.unity3d.com/) → [molocoads](https://www.moloco.com/?ref=timsh.org) → bwin * **Unity** is an SSP (supply-side platform) that collects app data via its SDK * **Moloco Ads** is a DSP network that resells data from multiple SSPs like Unity, Applovin, Chartboost * **bwin** is the advertiser that users see ads for in games More discoveries in this [post](9https://timsh.org/tracking-myself-down-through-in-app-ads/). ### Potential DAO 2.0 Product Ideas The author believes that the development of on-chain AI agents will lead to new forms of DAO, giving true autonomy to the "A" in DAO. [New product ideas](https://blog.variant.fund/dao-product-ideas) include: * **DAO 2.0 launcher:** platform enables launching new community/governance tokens tied to an agent, agent responds to tokenholder votes, reads discussion forums and generates proposals * **Quality assessment for token distribution**: agent assesses contribution quality to determine payouts/token distributions for DAOs/airdrops/etc. * **ZachZBT:** agent monitors for hacks or other fraudulent activity and publishes research as well as tries to get funds back for people * **Due diligence agent**: agent verifies contract integrity, dev reputations, on-chain behavior, and potential rug risks; allows users to interact with the agent to ask questions about risks @ 19220736:7578e0e9
2025-02-14 03:44:21While Zelle promotes itself as a quick and easy way to send money, its instant, irreversible transactions have made it a prime target for fraudsters. Despite mounting reports of consumer losses, banks continue to deny reimbursement for many fraud victims, citing narrow legal loopholes. Meanwhile, Early Warning Services, the company behind Zelle, profits from the vast consumer data it collects, fueling concerns about privacy and corporate exploitation. With government investigations ramping up and public pressure mounting, Zelle and their bank owners have teamed up with the Aspen Institute, forming a new task force with corporate and government players. In 2017, [Early Warning Services](https://www.earlywarning.com/about), owned by Bank of America, Capital One, JPMorgan Chase, PNC Bank, Trust, U.S. Bank, and Wells Fargo, released the [Zelle](https://www.zellepay.com/faq/what-zelle) payment system. It was a fast way to send and receive funds peer to peer between different bank accounts by only needing either the other person's email address or their U.S. mobile phone number. By 2018, there were growing [concerns](https://www.nytimes.com/2018/04/22/business/zelle-banks-fraud.html) about fraud on Zelle. Despite its convenience, Zelle's design allows funds to transfer instantly and irreversibly, making it a target for scammers. Victims reported being defrauded through tactics like fake online sales or impersonation schemes, and many struggled to recover lost funds due to inconsistent fraud policies among banks. Consumer advocates criticized the platform for inadequate protections, urging banks to implement stronger safeguards to prevent fraud and better support affected customers. In 2022, a Senate report [criticized](https://www.bankingdive.com/news/warren-zelle-fraud-scams-report-truist-pnc-us-bank-america-jpmorgan-wells-fargo-aba-bpi-cba/633305/) major U.S. banks, including JPMorgan Chase, Bank of America, and Wells Fargo, for failing to adequately protect consumers from fraud on the Zelle payment platform. The investigation revealed that these banks often deny reimbursement for scams where victims are tricked into transferring funds, citing a narrow interpretation of liability under the Electronic Fund Transfer Act. (*"While banks bear responsibility for unauthorized transactions to scammers, consumer-authorized transactions made to fraudsters are another matter”*.) Jamie Dimon, CEO of JPMorgan Chase, [explained](https://www.bankingdive.com/news/bank-ceos-defend-zelle-in-senate-hearing/632554/), *“Anything unauthorized, we do cover”* On June 16, 2023, the United States Senate Committee on Homeland Security and Governmental Affairs subcommittee, the Permanent Subcommittee on Investigations, launched an inquiry into Early Warning Services and the three largest banks that co-own EWS: JPMorgan Chase, Bank of America, and Wells Fargo. After a 15-month investigation, the Senate Permanent Subcommittee on Investigations released a [report](https://www.hsgac.senate.gov/wp-content/uploads/2024.7.23-PSI-Majority-Staff-Report-on-Zelle.pdf) on July 23, 2024, highlighting consumer fraud issues tied to the Zelle payment network. The report noted significant drops in the percentage of fraud disputes reimbursed—from 62% in 2019 to just 38% in 2023. Between 2021 and 2023 Zelle [refused](https://dailyhodl.com/2024/07/25/jpmorgan-chase-wells-fargo-and-bank-of-america-refuse-to-reimburse-863000000-to-customers-in-repeated-relentless-failure-to-protect-victims-of-fraud-us-senate-investigation/) to reimburse $880 million to customers who fell victim to fraud on their payment network. Bank employees were found to have broad discretion in deciding whether to reimburse fraud claims, often denying compensation without clear justification. This has raised questions about whether banks are meeting legal obligations under the Electronic Fund Transfer Act ([Regulation E](https://www.consumerfinance.gov/rules-policy/regulations/1005/)) Early Warning Services (EWS) runs the payment network Zelle at a financial loss but generates revenue by selling data-based services to financial institutions. EWS collects extensive consumer and bank data through its operation of Zelle and daily data-sharing agreements with its member banks. This data is used to develop fraud and risk management products, which EWS sells to financial institutions as its primary profit source. While EWS asserts it has not commercialized this data beyond these financial products, the sale of such services remains its main revenue driver. On August 4, 2024, Senator Richard Blumenthal sent a [letter](https://www.hsgac.senate.gov/wp-content/uploads/2024.08.04-Blumenthal-Letter-to-Chopra.pdf) to CFPB Director Rohit Chopra urging immediate action to address fraud concerns tied to the Zelle payment platform. The letter calls for the Consumer Financial Protection Bureau (CFPB) to investigate their dispute resolution practices and ensure that they fully and promptly address consumer fraud reports. On August 7, 2024, it was [reported](https://www.reuters.com/business/finance/us-consumer-watchdog-probes-major-us-banks-over-zelle-scam-wsj-reports-2024-08-07/) that the Consumer Financial Protection Bureau was investigating several banks due to their handling of Zelle. On December 20, 2024, The Consumer Financial Protection Bureau (CFPB) responded by [filing](https://files.consumerfinance.gov/f/documents/cfpb_Zelle-Complaint_2024-12.pdf) a lawsuit against Early Warning Services, LLC and the major banks including Bank of America, JPMorgan Chase, and Wells Fargo. The CFPB alleges that these institutions prioritized the rapid deployment of Zelle over implementing effective anti-fraud measures, resulting in significant consumer losses. The lawsuit contends that the defendants failed to adequately address these issues, often denying relief to defrauded consumers. The CFPB seeks injunctive relief, monetary compensation for affected consumers, and civil penalties. Just 5 days before the Senate Permanent Subcommittee on Investigations released its report, the [Aspen Institute](https://www.aspeninstitute.org/) Financial Security Program (Aspen FSP) [announced](https://www.aspeninstitute.org/news/task-force-on-fraud-and-scams/) the formation of a National Task Force for Fraud & Scam Prevention with their founding sponsor JPMorganChase and executive sponsor Zelle. The stated purpose of the Task Force is to develop a unified national strategy to help the U.S. government and private sector companies work together to stop fraud and scams. [Members](https://fraudtaskforce.aspeninstitute.org/membership) of this private/public task force include: JPMorgan Chase, Bank of America, Wells Fargo, Google, Meta, Amazon, Visa, Mastercard, Verizon, the Federal Trade Commission, the FBI Criminal Investigation Unit, US Department of the Treasury, Homeland Security, and many others. The Aspen Institute is a 501(c)(3) nonprofit located in Washington DC. In [2023](https://projects.propublica.org/nonprofits/organizations/840399006) they had revenue of $232M and total assets of $519M with the primary source of income coming from donations and federal grants. Per their [mission](https://www.aspeninstitute.org/what-we-do/) statement, their goal is "realizing a free, just, and equitable society." The Institute works to achieve this through creating and driving policy as well as training future policy leaders. Recently on November 25, 2024, FinCen [announced](https://www.fincen.gov/news/news-releases/fincen-joins-public-private-partnership-combat-fraud-and-scams-impacting) they are also joining the National Task Force that *"brings together key stakeholders including the financial services sector, technology companies, consumer advocacy groups, information sharing and analysis centers, and federal government agencies to develop a comprehensive national strategy for combating fraud and scams."* In The Case for a Coordinated National Strategy to Prevent Fraud and Scams, the Task Force lists [key components](https://fraudtaskforce.aspeninstitute.org/time-is-now) of a national strategy to include improved education of consumers to identify fraud, enhanced information sharing across industry, law enforcement, and regulatory agencies by use of data exchanges and legal mechanisms for sharing information. As well as empowering law enforcement with additional authority and resources. The document cites the recent [UK action](https://www.gov.uk/government/news/new-powers-to-seize-cryptoassets-used-by-criminals-go-live) as an example of recent amendments to law enforcement powers which in England means police will no longer be required to arrest seizing crypto from a suspect, can seize written passwords or memory sticks, as well as transfer "crypto assets" to a law enforcement wallet. In an August 2024 [interview](https://www.businessinsider.com/zelle-scams-how-to-get-money-back-2024-8?) with Fortune, Ben Chance, the Chief Fraud Risk Management Officer for Early Warning Services reportedly "told the outlet that the best way to prevent scams on money-sharing apps is better user education, sound policy and more funding for law enforcement." This sounds very similar to the National Strategy to Prevent Fraud and Scams being crafted by the National Task Force for Fraud & Scam Prevention, with more user education and law enforcement. No mention of standardized reimbursement policies or enhancing transparency around fraud investigations which are the primary accusations aimed at Zelle and its owners by the US Senate and the subject of the current investigation by the Consumer Financial Protection Bureau.
@ 19220736:7578e0e9
2025-02-14 03:44:21While Zelle promotes itself as a quick and easy way to send money, its instant, irreversible transactions have made it a prime target for fraudsters. Despite mounting reports of consumer losses, banks continue to deny reimbursement for many fraud victims, citing narrow legal loopholes. Meanwhile, Early Warning Services, the company behind Zelle, profits from the vast consumer data it collects, fueling concerns about privacy and corporate exploitation. With government investigations ramping up and public pressure mounting, Zelle and their bank owners have teamed up with the Aspen Institute, forming a new task force with corporate and government players. In 2017, [Early Warning Services](https://www.earlywarning.com/about), owned by Bank of America, Capital One, JPMorgan Chase, PNC Bank, Trust, U.S. Bank, and Wells Fargo, released the [Zelle](https://www.zellepay.com/faq/what-zelle) payment system. It was a fast way to send and receive funds peer to peer between different bank accounts by only needing either the other person's email address or their U.S. mobile phone number. By 2018, there were growing [concerns](https://www.nytimes.com/2018/04/22/business/zelle-banks-fraud.html) about fraud on Zelle. Despite its convenience, Zelle's design allows funds to transfer instantly and irreversibly, making it a target for scammers. Victims reported being defrauded through tactics like fake online sales or impersonation schemes, and many struggled to recover lost funds due to inconsistent fraud policies among banks. Consumer advocates criticized the platform for inadequate protections, urging banks to implement stronger safeguards to prevent fraud and better support affected customers. In 2022, a Senate report [criticized](https://www.bankingdive.com/news/warren-zelle-fraud-scams-report-truist-pnc-us-bank-america-jpmorgan-wells-fargo-aba-bpi-cba/633305/) major U.S. banks, including JPMorgan Chase, Bank of America, and Wells Fargo, for failing to adequately protect consumers from fraud on the Zelle payment platform. The investigation revealed that these banks often deny reimbursement for scams where victims are tricked into transferring funds, citing a narrow interpretation of liability under the Electronic Fund Transfer Act. (*"While banks bear responsibility for unauthorized transactions to scammers, consumer-authorized transactions made to fraudsters are another matter”*.) Jamie Dimon, CEO of JPMorgan Chase, [explained](https://www.bankingdive.com/news/bank-ceos-defend-zelle-in-senate-hearing/632554/), *“Anything unauthorized, we do cover”* On June 16, 2023, the United States Senate Committee on Homeland Security and Governmental Affairs subcommittee, the Permanent Subcommittee on Investigations, launched an inquiry into Early Warning Services and the three largest banks that co-own EWS: JPMorgan Chase, Bank of America, and Wells Fargo. After a 15-month investigation, the Senate Permanent Subcommittee on Investigations released a [report](https://www.hsgac.senate.gov/wp-content/uploads/2024.7.23-PSI-Majority-Staff-Report-on-Zelle.pdf) on July 23, 2024, highlighting consumer fraud issues tied to the Zelle payment network. The report noted significant drops in the percentage of fraud disputes reimbursed—from 62% in 2019 to just 38% in 2023. Between 2021 and 2023 Zelle [refused](https://dailyhodl.com/2024/07/25/jpmorgan-chase-wells-fargo-and-bank-of-america-refuse-to-reimburse-863000000-to-customers-in-repeated-relentless-failure-to-protect-victims-of-fraud-us-senate-investigation/) to reimburse $880 million to customers who fell victim to fraud on their payment network. Bank employees were found to have broad discretion in deciding whether to reimburse fraud claims, often denying compensation without clear justification. This has raised questions about whether banks are meeting legal obligations under the Electronic Fund Transfer Act ([Regulation E](https://www.consumerfinance.gov/rules-policy/regulations/1005/)) Early Warning Services (EWS) runs the payment network Zelle at a financial loss but generates revenue by selling data-based services to financial institutions. EWS collects extensive consumer and bank data through its operation of Zelle and daily data-sharing agreements with its member banks. This data is used to develop fraud and risk management products, which EWS sells to financial institutions as its primary profit source. While EWS asserts it has not commercialized this data beyond these financial products, the sale of such services remains its main revenue driver. On August 4, 2024, Senator Richard Blumenthal sent a [letter](https://www.hsgac.senate.gov/wp-content/uploads/2024.08.04-Blumenthal-Letter-to-Chopra.pdf) to CFPB Director Rohit Chopra urging immediate action to address fraud concerns tied to the Zelle payment platform. The letter calls for the Consumer Financial Protection Bureau (CFPB) to investigate their dispute resolution practices and ensure that they fully and promptly address consumer fraud reports. On August 7, 2024, it was [reported](https://www.reuters.com/business/finance/us-consumer-watchdog-probes-major-us-banks-over-zelle-scam-wsj-reports-2024-08-07/) that the Consumer Financial Protection Bureau was investigating several banks due to their handling of Zelle. On December 20, 2024, The Consumer Financial Protection Bureau (CFPB) responded by [filing](https://files.consumerfinance.gov/f/documents/cfpb_Zelle-Complaint_2024-12.pdf) a lawsuit against Early Warning Services, LLC and the major banks including Bank of America, JPMorgan Chase, and Wells Fargo. The CFPB alleges that these institutions prioritized the rapid deployment of Zelle over implementing effective anti-fraud measures, resulting in significant consumer losses. The lawsuit contends that the defendants failed to adequately address these issues, often denying relief to defrauded consumers. The CFPB seeks injunctive relief, monetary compensation for affected consumers, and civil penalties. Just 5 days before the Senate Permanent Subcommittee on Investigations released its report, the [Aspen Institute](https://www.aspeninstitute.org/) Financial Security Program (Aspen FSP) [announced](https://www.aspeninstitute.org/news/task-force-on-fraud-and-scams/) the formation of a National Task Force for Fraud & Scam Prevention with their founding sponsor JPMorganChase and executive sponsor Zelle. The stated purpose of the Task Force is to develop a unified national strategy to help the U.S. government and private sector companies work together to stop fraud and scams. [Members](https://fraudtaskforce.aspeninstitute.org/membership) of this private/public task force include: JPMorgan Chase, Bank of America, Wells Fargo, Google, Meta, Amazon, Visa, Mastercard, Verizon, the Federal Trade Commission, the FBI Criminal Investigation Unit, US Department of the Treasury, Homeland Security, and many others. The Aspen Institute is a 501(c)(3) nonprofit located in Washington DC. In [2023](https://projects.propublica.org/nonprofits/organizations/840399006) they had revenue of $232M and total assets of $519M with the primary source of income coming from donations and federal grants. Per their [mission](https://www.aspeninstitute.org/what-we-do/) statement, their goal is "realizing a free, just, and equitable society." The Institute works to achieve this through creating and driving policy as well as training future policy leaders. Recently on November 25, 2024, FinCen [announced](https://www.fincen.gov/news/news-releases/fincen-joins-public-private-partnership-combat-fraud-and-scams-impacting) they are also joining the National Task Force that *"brings together key stakeholders including the financial services sector, technology companies, consumer advocacy groups, information sharing and analysis centers, and federal government agencies to develop a comprehensive national strategy for combating fraud and scams."* In The Case for a Coordinated National Strategy to Prevent Fraud and Scams, the Task Force lists [key components](https://fraudtaskforce.aspeninstitute.org/time-is-now) of a national strategy to include improved education of consumers to identify fraud, enhanced information sharing across industry, law enforcement, and regulatory agencies by use of data exchanges and legal mechanisms for sharing information. As well as empowering law enforcement with additional authority and resources. The document cites the recent [UK action](https://www.gov.uk/government/news/new-powers-to-seize-cryptoassets-used-by-criminals-go-live) as an example of recent amendments to law enforcement powers which in England means police will no longer be required to arrest seizing crypto from a suspect, can seize written passwords or memory sticks, as well as transfer "crypto assets" to a law enforcement wallet. In an August 2024 [interview](https://www.businessinsider.com/zelle-scams-how-to-get-money-back-2024-8?) with Fortune, Ben Chance, the Chief Fraud Risk Management Officer for Early Warning Services reportedly "told the outlet that the best way to prevent scams on money-sharing apps is better user education, sound policy and more funding for law enforcement." This sounds very similar to the National Strategy to Prevent Fraud and Scams being crafted by the National Task Force for Fraud & Scam Prevention, with more user education and law enforcement. No mention of standardized reimbursement policies or enhancing transparency around fraud investigations which are the primary accusations aimed at Zelle and its owners by the US Senate and the subject of the current investigation by the Consumer Financial Protection Bureau. @ 21db9b8a:2a94c796
2025-02-14 03:37:49Fair warning: This is an explicit and erotic story involving extremely taboo themes that would prevent it from being published on most sites that host erotic stories. All characters in this story are ***fictional only***. It is not in any way based on true events. This is also not your average stroke story. It will be released in chapters, and while there ***is*** sexual content in each chapter, there is no full-on sex until late in chapter 4. It is a story of sexual discovery and exploration between young people who have few resources to educate them, but also few inhibitions to hold them back. I hope you enjoy it. If not… Well… You don’t have to host it on your relay, and you can always mute me so you don’t see any more. *** Dani barreled through the dining room in pursuit of her younger brother, Jake, who sped out the sliding glass door onto the back deck, making a feeble and unsuccessful attempt to close the door behind him as he ran. He had always been faster than Dani over short distances, and his recent growth spurt, just before turning thirteen, had made it that much more difficult to catch him. "Give them back, you thief!" she shouted after him, taking just enough time to open and fully slide the door closed behind her, in order to avoid incurring her mother's wrath. It was all the lead her brother needed. He leaped off the deck into the sunlit back yard and sprinted over to one of the tall maple trees at the edge of the lawn. By the time Dani had made it to the yard, her brother was already scurrying up the trunk with her sunglasses gripped between his teeth. Jake was younger than Dani by seventeen months, but he had recently grown to be two full inches taller than her, and he had begun to develop muscle tone to compliment his athleticism. It also helped him climb trees with frustrating ease. Dani jogged to the base of the maple, which had no limbs for at least the first ten to twelve feet, and glared up at her brother lounging across two of the branches. He was now wearing her sunglasses to further taunt her. The twerp took his role as the annoying younger brother seriously, despite their age difference being relatively small. Dani's other two brothers, ages ten and seven, had thankfully not learned Jake's bad habits and generally left Dani alone, but her oldest brother seemed to make it his mission to infuriate her. It was just for sport, Dani knew, and Jake really was alright to be around most of the time, but let him get bored and it always seemed like she was the one who paid for it. "Give me a break, Jacob William Hansen!" she demanded, using his full name like their mother often did when she wanted him to know he was in trouble. She shaded her eyes from the early summer sun as she continued to glare up at him. It did not seem to have the same effect as when her mother used it. "When you come down from there, I'll have your hide!" "You may have my hide, Danielle Elizabeth Hansen,” he mocked, “but you won't have your glasses." With that, he plucked them from his face and hooked them over a smaller branch above him. "You wouldn't dare leave them up there!" she asserted, not really sure whether he would or not. Jake knew better than to push things too far, but he might not consider abandoning her sunglasses in the limbs of a tree to count as 'too far'. "What are you going to do? Go tell on me?" Of course, he knew she would not. They had long since stopped tattling on one another. In their household, the tattler often brought as much punishment upon him or herself as the one tattled on, and sometimes more. Instead, Jake and Dani had agreed to settle most matters between themselves, and only bring their parents in when it was more serious, like when Jake had planned to jump off the garage roof onto his skateboard, and Dani just knew he would have cracked open his skull if he had tried it. "If you want your sunglasses back, you are just going to have to come up here and get them." "How did you even make it up there?" she demanded. Dani was no slouch at climbing trees most of the time. She liked to play in the woods and didn't mind getting dirty, but the trees she climbed at least had branches close enough to the ground that she could jump up and grab hold of them. This maple had nothing but bare trunk for several feet above her head. "You didn't see how I did it?" Jake asked. "You just have to wrap your legs around it and use them to hold on. Then grab as high as you can with your arms and pull your legs up higher." Dani cocked an eyebrow at him dubiously, unsure whether she could mimic the technique. For one, her brother didn't have breasts to contend with, and Dani had been a bit of an early bloomer in that department. At fourteen, she already would have filled out a B-cup bra, if she ever wore anything other than sports bras. The lumps of fatty flesh sticking out from her chest were horribly annoying and always getting in the way. It seemed more than likely that her breasts would do just that while trying to shimmy up the tree as well. Shrugging to herself she decided to give it a shot. She approached the trunk and wrapped her arms around it as high up as she could reach. She could just barely touch her fingers together on the other side when hugging as closely as her chest would allow. Supporting herself with her arms, she jumped and wrapped her legs around the trunk as well and felt the bark lightly scratching the inside of her thighs and back of her calves. It probably wasn't the best idea to be doing this in her cutoff jeans and a tank top, but it was far too warm out to wear her usual jeans and a hoodie. She would just have to tough her way through it. Gritting her teeth she pushed her body upward with her legs, which invariably tugged the front of her tank top downward to expose part of her sports bra underneath, then she reached as high as she could with her arms and let her weight settle on them to pull her legs up again. This caused Dani's breasts, which were being crushed between her and the tree, to push upward, partially spilling out of the top of her sports bra and tank top. As predicted, they were getting in the way of things once again. Dani was far too distracted to think about what kind of display she was putting on for her brother above her, though. As her weight had settled, her crotch had slid against the trunk and caused a pleasurable sensation to well up in her nether-regions. It was a shock to Dani, and she nearly let go of the tree. She'd never felt anything quite like that from “down there” before, and it was distractingly pleasant. She sat frozen in place for a moment, trying to make sense of the feeling. "Well?" her brother voiced his impatience. "Are you just going to hang there like a koala or are you going to come get your shades?" Letting out a low, frustrated growl, Dani continued upward, the pleasant sensation in her groin returning each time she slid it against the trunk. What on earth was going on? This was not a situation that should be causing her pleasure whatsoever, let alone down there. Her legs and arms felt like they had several new scrapes from the rough trunk, but her crotch was alight with a dull pleasurable throbbing that Dani had never experienced before. Then again, she'd never thought to rub it against anything before. As she finally shimmied her way high enough to grab hold of the lower-most branch, Dani was panting from more than the sun's heat and her exertion. Pulling herself up onto the sturdy limb, she hoped her brother didn't notice the flush in her face or the way she self-consciously adjusted her tank top so that it properly covered what it was meant to. Then she looked up to see him holding her sunglasses out to her from the branch he was seated on. "Not cool, Jake!" she chided, snatching her sunglasses from his hand and inspecting them for damage. Satisfied they were none the worse for wear, she slid them into her dark hair, which was pulled back into a loose ponytail that hung just past her shoulders, so that they rested securely atop her head. "Oh stop your whining," he brushed off her anger. "You know you needed some motivation to get out of the kitchen. Mom has had you cooped up in there all morning." "Yeah, that's because it gets too hot to bake in the afternoon, doofus! Don't you want fresh bread for the monstrous sandwich I'm sure you will somehow manage to stuff down your throat for lunch?" "Fair point," Jake acknowledged. "But aren't you glad to get out and get your blood pumping?" "No!" Dani retorted. "Look at me!" She held her scraped-up arms out for his inspection. "I blame you for this!" "Oh come on! You love it!" Jake insisted. "I have seen you laughing off far worse war-wounds than that." Dani sighed and shook her head at him. He was right, of course. She was known for playing hard. Hard enough to keep up with the boys in the neighborhood, who often used to wrestle her like she was one of them. At least, they had until recently. Since she'd developed breasts they all seemed scared of her. All except Jake, but he was her brother. They had never been awkward with one another, and he still didn't seem to notice that she was a girl, let alone growing into a woman. For most of their childhood, Jake was the only playmate Dani had, so she had adapted to playing like a boy. Instead of Barbies and tea sets, it had been Legos and Nerf guns, and she had loved every minute of it, even if it did tend to come with a fair share of bruises and scrapes. And sure, Jake could be an absolute pest, but it was mutual antagonism born out of playful sibling affection. "Fine," she admitted. "It was a welcome rescue from mom's home ec class. But you're still going to owe me for all the scrapes I have from climbing this tree. My legs are even worse than my arms!" "I'm sure you'll think of some way to get sweet revenge," Jake laughed. "You always do." Again, he was right. As much as Jake infuriated her with his taunting, teasing, and pranks, Dani could dish it right back at him. That was part of their strange sibling relationship that made it look to all on the outside like they couldn't stand one another, when in reality they were best friends and would do anything for the other when it really mattered. "Alright, meat-brain," Dani changed the subject, using her favorite pet name for her brother. "Now that we're free of mom's clutches for the afternoon, what should we do with ourselves?" "I don't know what you're going to do, but when Finn gets home from school, we're going fishing." Finn was Jake's best friend who lived just a few houses down from them. While Jake, Dani, and their siblings were homeschooled by their mother, Finn went to public school and wouldn't be getting home until mid afternoon. Soon school would be out for the summer, making Jake and Finn nearly inseparable during daylight hours, but that was still a week and a half away, despite the heat wave they were getting in early June, and then Finn's family would be going to summer camp for three weeks, so the boys were taking advantage of as much time as they could get to hang out while they had the chance. Dani knew that she only had a short time while Finn was at camp to have her brother to herself before he would be all but lost to her for three months, since Jake and Finn usually didn't like having her along with them anymore. They had played together for years, but over the last several months, the two boys had started excluding her from their activities. That left Dani feeling quite alone when Jake and Finn rode their bikes off to wherever they hung out these days. She had no friends of her own in the neighborhood. Her closest female friend, Audrey, lived almost a half-hour away, in a small town to the north, so they only really got to see each other at church, and the occasional planned sleepover. "Fine, ditch your sister, as usual," Dani complained, rolling her eyes at her brother. "Don't be like that, Dani," Jake protested. "It's just awkward talking about girls with your sister around, ya know?" "Like you actually have any girls to talk about!" she teased. "Maybe not, but a guy can live vicariously through his best friend, can't he?" "Ha!" Dani scoffed. "I seriously doubt Finley O'Connor has a lineup of girls to give you all the juicy details about, either. At least not any that aren't figments of his imagination." "You might be surprised." Was that a blush that suddenly appeared on Jake's face? Had she misjudged Finn? Jake's best friend was not what she would think of as a chick-magnet. He was a bean-pole of a boy with an unkempt mop of red hair topping his head. He had a mouth that was too large for his face that always seemed to be twisted in a mischievous grin, and an over-abundance of freckles that covered every inch of him that Dani had ever seen, which was most of him since he often accompanied their family to go swimming at the river. He did not fit into Dani's definition of attractive, nor any other girl she knew. Not that she knew many other girls well enough to talk about boys with them. "Whatever you say, meat brain," Dani said, shifting on the branch and dropping to hang beneath it before letting go to allow herself to fall the three or four feet down to the ground. She landed on her feet, bending her legs deeply to absorb the impact, then stood up straight and defiant. Brushing her hands off on the sides of her cutoffs and looking back up at her brother. "I'll just have to figure out how to keep myself occupied, as always." There was more disappointment in her voice than she had intended. She didn't really want to make him feel bad for leaving her without anyone to hang out with for the afternoon. She could find things to do to keep herself busy. For one, she could help her younger brothers finish up their school work, though that would likely only get her through the first hour after lunchtime or so. The benefit of being homeschooled was that you could easily get all your work done for the day in just a few short hours, instead of being cooped up in a classroom the whole day like the public-schoolers had to endure. Of course, that was also the downside, because you then had to figure out what you would do with all the extra time you had. Then Dani remembered the pleasurable sensation she had experienced while climbing the tree. That was certainly something she could investigate this afternoon while Jake was off gallivanting with Finn. She wanted to see if that feeling could be repeated, or if it was just some kind of fluke. She wasn't about to go rub her crotch against trees where anyone might see her, though. Perhaps she could find somewhere more discreet to experiment and see if that sensation returned. It had felt SO GOOD! Surely she could find a way to make it happen again. *** Jake watched as his sister strolled away from the tree back toward the house, her round bottom framed enticingly in her cutoff jeans. He couldn't believe he was looking at her that way; she was his sister after all, not some random girl like the ones Finn liked to show him. Yet, after watching her climb the tree to retrieve her stolen sunglasses from him, Jake could not deny that she possessed every quality that made those girls on Finn's tablet so appealing. Finn had been sharing pictures of naked and nearly-naked girls with Jake almost since he had gotten the tablet as a Christmas present last year. Well, Jake supposed they were actually women, not girls, since they all looked much older than Dani, and most had more pronounced curves. Then again, that could just be because he was seeing them without their clothes on, while Dani's curves were usually covered up. And Dani definitely did have some curves that Jake could no longer help but notice, especially after the display he had just seen. From his perch in the branches of the maple tree, Jake had a perfect view down the front of his sister's tank top as she had shimmied her way up the trunk. No, he had not seen her nipples - her sports bra had done it's job of holding them in - but her round breasts pressing up prominently every time she let her weight rest on her arms made it clear that she was no longer the flat-chested little girl he somehow had still thought of her as. He should not have been so naive. He knew his own body had changed drastically, but had not even considered that his sister's was changing as well, let alone that she might just look a lot like the women in those pictures when she took her clothes off. Jake frowned, noticing that his thoughts had made his dick stiffen in his pants. These were not thoughts he should be having about his sister! Hopefully Finn would have some new pictures to distract him away from thinking of Dani in that context. For that reason and more, Jake looked forward to his friend getting home from school, when the two of them could head out to do some "fishing". Oh, they might do a bit of actual fishing as well, but most of their time would likely be spent at their fort in the woods, well away from any prying eyes, while Finn shared his latest photographic acquisitions. It would still be a few hours before the bus dropped his friend off where their street connected to the main road, so Jake resigned himself to finding something else to distract him from thoughts of his sister until then. It was too nice a day to expect that he could get away with playing Xbox in the basement game room. His brother, Travis, should be done with his school work by now, though, and always enjoyed tinkering with bikes in the garage with him, so Jake dropped out of the tree and headed toward the house to seek his brother out. He crossed the back lawn and their dog, Dozer, ran to meet him. He was a massive brute of a dog, being a full-bred Rottweiler, but he was as gentle and loyal as anyone could ask for with the Hansen children. Jake patted the dog's blocky head and rubbed his ears as he strode toward the back deck. He skirted around the left side of the deck and down the concrete stairs to an exterior door that led directly to the basement where he expected he would find his brother. All of the Hansen boys had rooms in the basement. Jake, as the oldest boy, had his own, while Travis and Aaron shared a room on the opposite end, next to the bathroom, with the game room and stairs up to the front entryway situated conveniently in-between. At age ten, Travis was three years younger than Jake, though he would be turning eleven in the fall, so it was more like two and a half years. Aaron was another three years younger than that, at age seven. The two of them were very close, just like Jake and Dani had always been, but lately Travis had been wanting to spend more time with Jake, whenever the older boy would allow it. The last of the Hansen children was their adopted sister, Rebecca, who was only two years old. Everyone called her Bec, and she lived in the nursery upstairs next to their parents' master bedroom. Their family had fostered her as an infant, and finally adopted her just last year. Dani had been thrilled to finally have a sister, despite the massive age difference, and couldn't wait to teach the child all about being a girl. Not that Dani really had any clue how to be a girl herself, having grown up with three brothers. As expected, when Jake opened the door into the basement, which opened into their game room, his younger brother was seated facing him on the couch with an Xbox controller in hand, transfixed by the large flat screen television on the wall. He looked quite a lot like Jake, with his short, brown hair and blue eyes. The younger boy hadn’t yet started to fill out with muscle tone, though, making him look scrawny, with a head too large for his stringy limbs. The effect was particularly humorous when he stood next to Jake. "You'd better not let mom or dad catch you on that when the sun's out," Jake warned his brother. "Mom's still busy helping Aaron with his math, and Dad's working on tonight's sermon," Travis assured him. "Besides, I was going to get off in just a few minutes anyway." "Oh trust me," Jake began, crossing to the couch and sitting next to his brother, to see that he was playing Minecraft. "I know how 'just a few minutes' can turn into several hours without even realizing it. Why don't you come hang out in the garage and we'll get that chain tightened on your bike so it's not always falling off on you." "Really!?" Travis exclaimed, putting the controller down and turning to Jake with an excited look on his face. "Of course, runt!" Jake had continued to call his brother the pet name even after Aaron was born, much to Travis' chagrin. "What are big brother's for?" He wasn't about to tell him that the reason he was suddenly so willing to help his little brother out was to take his mind off of thinking about Dani. Seeing her round breasts pressing out of the top of her tank top had shattered Jake's ability to think of her in practically the same terms as his brothers, or one of his male friends. Now he found himself remembering her long, smooth legs, and round bottom swaying back and forth hypnotically as she had walked back toward the house, and it seemed the more he told himself he shouldn't think of her that way, the harder it was not to. Travis shut off the Xbox and the two boys marched up the stairs toward the door to the garage. As Jake pulled it open, he heard his mom call out from the dining room. "You boys don't go far! Lunchtime is coming in thirty minutes!" "Don't worry mom!" Jake called back. "Travis and I will just be in the garage working on his bike!" He didn't wait for a response before disappearing into the dark and hitting the button on the wall to open the massive roll up door on the two-car garage, allowing the sunlight to flood in. Then he and Travis went to work on the bike, not only tightening the chain, but straightening the handlebars that had been twisted to one side when Travis had crashed into a tree, and replacing one of the pedals that had nearly fallen apart since it was a hand-me-down bike from someone at their church. Travis was thrilled and rode the bike up and down their short driveway and around the cul-de-sac until their mother called them in for lunch. After scarfing down a massive sandwich, as Dani had predicted, a bag of chips, and a banana, Jake offered to take Travis and Aaron on bike ride to the park and back to pass the time until Finn got home from school. He worried that Dani might want to come, too, but she had disappeared as soon as she was done with lunch without a word. That was highly unusual for her, but not unwelcome since Jake wasn't sure how he would keep himself from ogling her body if she came along. Thankfully, the bike ride with his younger brothers ate up a fair amount of the afternoon. When the time finally came for Finn to be dropped off, Jake let his mom know where he was going then grabbed his fishing pole and tackle box and hopped on his bike once again to pedal down to the corner where the bus dropped off all the kids that lived on their street. He arrived just as the bus was pulling away, and saw his friend, backpack slung casually across one shoulder, strolling toward him among four other kids from the neighborhood of various ages. "Jeez Jake!" Finn exclaimed. "You must have been bored out of your mind to meet me right as I got dropped off!" "Let's just say I'm glad you're finally home," Jake responded, swinging his leg across the back of his bike to dismount and turning it around to walk along side his friend back the direction he had come. "Yeah, I'm finally free from that prison, even if it is only until tomorrow," Finn joked. "Seriously, though, you usually come find me at home, after I've had a chance to ditch my bag and pack us some snacks. What gives?" Jake sighed. He certainly wasn't going to tell his friend the real reason he was so eager to hang out with him. What would Finn think of him if he knew he was having dirty thoughts about his own sister? "It's been a long day, is all," he said finally, and that was partially true. It ***had*** felt exceptionally long. "And we won't be able to stay out long tonight, since I have church." "Oh that's right, it's Wednesday, so you have to go be an altar boy tonight," Finn teased. "No wonder you want to get your debauchery in ahead of time." "It's not like that..." Jake protested halfheartedly. "But now that you mention it, do you have any new pictures to share?" Finn glanced around them to see if any of the other kids who had gotten off the bus were still walking close by, but they had all split off to head to their own homes. "Dude... I've found us some good ones. You'll have jerk-off material for the next month! Or you would if you had a photographic memory." "Oh shut it!" Jake said, punching his friend's shoulder. "It's not like your memory is any better." "Doesn't have to be. I'm the one with the tablet," Finn pointed out as they turned into his driveway and Jake laid his bike down carefully on the front lawn, making sure the fishing gear didn't get damaged. "You say that now, but just make sure your parents don't catch you with those pictures saved on it," Jake warned. "Oh, don't worry about that," Finn assured him. "My parent's don't check what I've been doing on it. They only got it for me because they figure it will keep me from being too noisy and disturbing their peace. I doubt they could even figure out how to turn it on." Finn wasn't exaggerating. His parents were much older than Jake's, and had not grown up with computers. They had both been married before and had adult children from their previous marriages, some of whom had their own kids already. They got together and had Finn and his older brother Scott when they were both in their forties. Now they were in their late fifties and far from being computer literate. The only reason they had an internet connection at all was because it had come with their cable TV plan and Scott had set it up. "Wait here for a minute," Finn instructed. "I just have to drop off my bag and grab my gear." With that the red head disappeared inside his front door, appearing a few short minutes later with his own fishing pole and tackle box. He'd also changed into shorts and a t-shirt. As he approached, he popped open his tackle box and showed Jake that his tablet was tucked inside, then he retrieved his own bike from the side of the garage and the two boys headed out. They rode through the park and out of the back of the neighborhood, where it was bordered by logging company land, serviced by a bumpy dirt road. Nearly a mile down the dirt road, they cut into the woods, stowing their bikes in some bushes. The forest was thick here, and full of fallen logs that the boys deftly maneuvered over and around to reach their destination. Barely visible in the undergrowth ahead was a short, vaguely unnaturally shaped structure that was the fort the two of them had constructed the previous summer, and had continued to improve upon since then. It was made entirely of natural materials, a fact that Jake was particularly proud of, and only large enough for three or four to sit in comfortably. They had constructed it by lashing logs together using roots and vines and anything else that would work as cordage, then taking evergreen boughs to create a roof and walls that did a fair job of blocking the wind, though a less fair job of keeping out the rain, as they had discovered the hard way. The important thing was, the fort was a place they could reasonably expect to be left alone. Even in hunting season, not many people were wandering these woods, since they were too close to residential neighborhoods to safely shoot a rifle. The logging company that owned the land didn't even seem to have any intention of logging it anytime soon. They might have in years past, but that was before the city had grown so much that all the neighborhoods had sprung up around it. Indeed, the most likely event would be that the logging company would sell the land to a developer and yet another neighborhood would be built. Until then, Jake and his friend could use their fort to hide away and look at dirty pictures on Finn's tablet. The two of them crawled through the small opening that served as a doorway and Jake was immediately enveloped by the scent of pine and spruce from the boughs laid on the walls, roof, and even the floor of their fort, to make it more comfortable to sit inside. The interior was not tall enough for him to stand, though he could move around on his knees without his head brushing against the roof, and the evergreen boughs were so thickly piled on the walls and roof that the only light within was the meager amount that filtered through the doorway. Jake took a seat with his back to one of the walls while Finn sat beside him and powered up his tablet. "I have some real babes to show you today, my friend," Finn bragged, punching in his security code so that the tablet allowed him access to his home screen. Then he tapped the icon for the photos app and turned the screen so Jake could see it better. Inside the dim fort, the tablet seemed to blaze with light as an image filled its screen. The picture was of a stunning blonde with wavy hair hanging loose to her shoulders. She was facing toward the camera as though looking past it into the distance while standing in a mostly empty room, though the background was too blurry to pick out any details. The shot only showed her from the waist up, and she was unbuttoning a pair of white jeans, though it was impossible to tell if they were pants or shorts. The top half of her body was completely bare, and her large breasts stood out proudly above her toned stomach. She was absolutely magnificent! She didn't have the biggest tits out of all the girls Finn had shown him before, but they were more than adequately large, perfectly round, and had similarly rounded areolas tipped with eraser shaped nipples. Her skin was the perfect shade of tan, with no tan-lines whatsoever. "She's a stunner, right?" Finn asked, seeing Jake's reaction. "Her name's Nata Lee, or at least that's what she calls herself. She's got loads of pictures with her clothes on, but this is one of the only ones I could find where she shows her tits." "She's a babe, for sure," Jake agreed, still staring at the photo. Finn swiped his finger across the screen and a new photo took the place of the stunning blonde. Pictured was a young woman with dark blonde hair with a hint of red, tied back in a short ponytail. She was laying completely naked on a white couch with the photo taken from above looking down on her. She was staring straight into the camera, a mischievous smile on her face, with one hand caressing her shoulder and the other pressing in on an ample breast. Her breasts were easily as large as the first girl's, but they seemed to sag more. Her areolas were more oval in shape, and didn't contrast with her skin tone as much. The main attraction, though, was the bottom half of her body, with her legs spread wide to reveal her shaved pussy, it's pink inner folds poking out from between the soft outer lips. She was equally as gorgeous as the first girl, though in a decidedly different way. This girl looked like more fun, while the first looked more serious. The way her hair was tied back in a ponytail made her look younger, too, though there was no way she was anywhere near his age with tits like those. Something about her smile made Jake's cock twitch even more than looking at her naked body. It held the promise of delights he had never dreamed of. "Another one you approve of, I take it?" Finn asked with a laugh. "Just wait. They get even better." Swiping the screen again, a close-up image of a shaven pussy and the woman's inner thighs filled the screen. The inner folds of the pussy glistened with moisture and they were parted, revealing an oblong opening into her depths. "Why is she wet down there?" Jake asked, transfixed by the high resolution close-up that showed her every fold and goose-bump. "I don't know, maybe she just went pee," Finn replied. "But that's where you stick your dick in." He pointed to the opening. "Wow..." Jake breathed. "That's crazy..." Finn swiped the screen again, much to Jake's dismay, but his disappointment at not getting more time to inspect such a detailed image of a pussy evaporated as the next image filled the screen. It was of a brunette with long, dark hair hanging loosely over her shoulder as she leaned against a wall. The shot was taken from an angle to her left side, though not fully a profile shot, and only showed her from the chest up. What was visible was completely exposed, and she had slightly tanned skin and perky breasts that were nowhere near as big as the previous girls’, though they were adequately round, with erect nipples and round areolas that contrasted nicely with her skin tone. Somehow, those breasts were even more alluring to Jake, even though they weren't as large. What shocked and captivated him, though, was her face. Her round nose, full lips with just the hint of a smile, and thin, dark eyebrows hanging just above her sultry eyes, made her look uncannily like an older version of Dani. His sister still possessed a bit more girlish roundness to her cheeks and innocence in her eyes, and usually kept her long hair tied back and out of the way, but there was no denying the strong resemblance. Was this what she would look like with her hair down and a few more years of growing up? This girl's breasts were probably closer to the same size as Dani's, too. Was that what his sister's tits looked like under her shirt and sports bra? The image had only been on the screen for a few seconds when Finn suddenly swiped it away saying, "Sorry, I thought I had deleted that one." "What? Why?" Jake asked, looking up from the tablet, which now had a busty redhead filling the screen. "Because..." Finn hesitated. "That one looks a lot like your sister, and I thought that might be weird." "Oh..." Jake said, feeling his face turn crimson and suddenly glad that it was too dark in the fort for his friend to see. "I... I hadn't really noticed." Finn chuckled nervously and said, "I suppose you wouldn't if your attention was on her tits the whole time." "Right?" Jake agreed, adding his own nervous laugh. Then it suddenly hit him that his friend had been looking at pictures of someone who looked like his sister. "Hey! Why did you have that picture in the first place if you know it looks like Dani?" "Chill bro!" Finn started, setting the tablet down on the opposite side of him from Jake and putting his hands up defensively. "I am sure that all of these girls look like the sisters of someone we know." "That's probably true, but this one looks like ***my*** sister, and you ***knew*** it did when you saved it to your tablet!" The heat in Jake's face was growing and he wasn't sure if it was because of his embarrassment or his anger at his friend. "Look, I can understand why you're mad. You have every right to be the protective brother." Finn edged away from Jake a few inches as he spoke. "But before you pummel me, you have to admit that Dani is hot as fuck, and I am not going to be the only guy to notice." Jake certainly did ***not*** want to admit that his sister was hot, but then hadn't that been his issue all afternoon? He'd never thought of her in those terms before, but he'd suddenly had her femininity thrust in his face and he had to admit that it was really messing with his perception of her. Now, after seeing a picture of a naked woman who looked uncannily similar to her, it was even harder not to think of Dani as incredibly attractive, or as Finn had put it, "hot as fuck". The steam had been taken out of his anger, but Jake still wasn't in any mood to hang out with his friend, knowing that Finn had thought of Dani in similar terms as he was reluctantly having to admit he now did as well. Finn was right, of course, and there would probably be loads of guys who would think of his sister that way, but Jake simply wasn't prepared to find her attractive himself, let alone for anyone else to have the same opinion. "Whatever, man..." Jake said, crawling to the doorway. "I'm going home to get dinner before church tonight. Maybe we can go fishing tomorrow." The tone of his voice made it plain that he didn't plan on it. He emerged from the fort and retrieved his bike from the bushes without even waiting for Finn's reply. How on earth was he going to make sense of his friend's dirty thoughts about his sister if he couldn't even make sense of his own? *** As Dani rode home from church that night, she thought back on the events of the day. After chasing Jake out of the house to retrieve her sunglasses, and discovering the pleasant sensation in her groin when she rubbed it against the tree while climbing up after him, she had looked forward to finding herself some alone time to see if she could make it happen again. First, though, she had helped tutor her youngest brother, Aaron, with his math, his least favorite subject because he struggled with it so much. Then it had been lunch time and Dani had started to wonder how she could possibly find any time to herself for the afternoon. In a household of five children, there wasn't a lot of alone time to be had, and since her bedroom was right next to the living room on the ground level, she could not expect to get away with hiding in there; certainly not with the sun shining outside. Her mother would ensure that all the children spent ample time outdoors as long as the weather was good, and June had been unseasonably clear and hot so far. As much as Dani wanted to investigate whether she could reproduce that warm and pleasurable feeling, she couldn't just go rubbing her crotch against objects where anyone might see her. With the privacy of her own room out of the question until later that evening, that left only the tree-house in the back yard, but that was Travis and Aaron's favorite hang-out spot most afternoons. Fortunately, Jake had unwittingly come to the rescue by taking the other boys with him on a bike ride. That in itself was odd. Usually Jake would spend most of the day until Finn got home from school hanging out with her. Yet, today he seemed to have avoided her like the plague after stealing her sunglasses that morning. She decided she would need to find out what that was all about if it continued, but for today it had worked to her advantage, affording her the alone time she craved. Dani had gone out to the tree-house immediately after her brothers left for their bike ride. It was situated at the back of their property, built around the trunk of another of the massive maple trees, with a ladder leading up to a trap door in its floor. It was not terribly high off the ground, only ten to twelve feet or so, but that was high enough that no one standing on the ground could see inside the small windows. Once inside, Dani knew she could expect near complete privacy, especially since the branches of the tree hid the tree house windows from anyone on the second floor of their home looking toward the back of the property. Hesitantly, Dani had gone to the trunk of the tree sticking up through the middle of the tree-house floor. It had a slightly larger circumference than the one she had climbed that morning, but she could still wrap her legs all the way around it. She could not do the same with her arms, however, so she leaned back and supported her weight with her hands on the rough planks beneath her. This didn't allow her to move her hips nearly enough to rub herself against the tree, so she let her feet fall to the floor as well. This gave her the freedom of motion she needed, and also allowed her to control how much pressure she exerted as she slid her cutoff jean clad crotch against the tree. The sensation was nearly immediate; a dull, warm pleasure welling up from between her legs. She continued to move her hips up and down, sliding herself against the tree's firm girth, the roughness of the bark dulled by the layers of cloth between it and her skin. The sensation seemed to build with each repeated grinding of her hips, but so did her fatigue. It was hard work to hold her whole body suspended in the air with just her arms and legs while she pumped and ground her groin against the trunk. Soon she was forced to collapse to the floor in exhaustion, despite how good it felt and how much she wanted to keep going. She needed to find something else she could rub herself against. Something that didn't require her to hold herself up the whole time, but the inside of the tree-house was pretty sparse. There were a couple of beanbag chairs and a small table between them acting as the only furniture, but that was about all, aside from a few action figures and Lego bricks her brothers had left strewn across the floor. She wondered if she might be able to use her own hand instead, and went over to recline in one of the beanbag chairs. Spreading her legs, she placed the palm of her hand on the crotch of her cutoffs and gently rubbed downward and back up. The sensation was pleasant, but not as strong as it had been while rubbing against the tree trunk. She continued to rub herself for several minutes, but the sensation just stayed a dull, pleasurable ache, rather than building upon itself as it had when grinding against something more firm and solid, not to mention more textured, than the palm of her own hand. Frustrated, Dani had spent the rest of the afternoon playing with their dog and then helped her mother prepare for dinner. Now that she had a bit more time to think about what had happened, though, she wondered if the sensation with her hand might have been stronger if she didn't have the thick fabric of her cutoffs in the way. She would have the perfect opportunity to test that theory not long after getting home, since Wednesday night was her turn to take a shower. Dani liked to take her showers late in the evening, if possible. It always felt good to go to bed fresh and clean, and it was relaxing to brush and dry her long hair, which usually helped her wind down for sleep. The shower would also be the perfect opportunity to be alone and try rubbing herself without any clothing in-between her hand and her vagina, which seemed to be the source of the pleasant sensation. When their minivan pulled into the garage, the whole family piled out, filed into the house through the door to the main entryway, and split off in various directions. Dani's mother and father went upstairs to put Bec down for bed, her brothers went downstairs to get their pajamas on and brush their teeth, and Dani went through the kitchen and living room to get all the way around to her own bedroom. Once there, she retrieved her shower supplies from atop her vanity across from her bed. Her bathroom doubled as the family and guest bathroom, and was too small for Dani to leave all of her things laying around on the counter like her brothers could in their larger bathroom downstairs. She was allowed to leave her shampoo and body wash in the shower, because it was hidden from guests by the closed shower door. She was also permitted to leave her toothbrush and toothpaste inside the medicine cabinet behind the over-sink mirror. But she had to keep her razor, shaving gel, deodorant, and towels in her own room and take anything she needed with her to use the shower. This resulted in Dani doing as little of her hygiene in the bathroom as she could get away with, using her vanity in her bedroom instead. Dani brought a towel for her hair, another for her body, and her bathrobe with her as she exited her room and crossed behind the living room couch to the small bathroom beyond. Closing and locking the door behind her, she crossed the room and locked the opposite door as well. Whoever had designed their home had thought it would be convenient to have access to the bathroom from both the living room and the kitchen. In reality it had just been more hassle remembering to lock and unlock both doors instead of just one. Indeed, it had led to more than one awkward encounter when she had forgotten to lock one door or the other before using the toilet, only to have her father or one of her brothers barge in on her by mistake. Having ensured a similarly embarrassing event would not occur this evening, Dani set her things on the small counter next to the sink and began to disrobe, letting each article of clothing fall to the floor. Then she pulled out the hair tie holding her ponytail back and strode naked over to the shower stall. The bathroom was too small to fit a tub, but Dani didn't mind most of the time. If she really wanted to take a bath, her parents would often let her use the massive tub in their master bathroom upstairs, rather than make her use the one in her brothers' bathroom in the basement. Most of the time she just wanted to get clean and be done with it, though, so a shower suited her fine. She turned on the water and waited for it to get warm enough to step in, then turned it up until it was just this side of scalding, the way she liked it. When the steaming hot water poured over her skin, she let out a deep and relaxed sigh of pleasure, then got her hair thoroughly wet before sudsing it up with shampoo and rinsing it out, enjoying every second of the cleansing heat. Her plans of trying to give herself pleasure again were nearly forgotten as she lost herself in the soothing waters, until she started soaping up her body and she got to washing her more sensitive regions. As her fingers moved through the tuft of hair on the mound above her vagina she remembered that she was going to try to use her hand to rub against her bare skin and see if that made any difference. Dipping her hand lower, she put pressure against her mound and the outer lips of her vagina with her palm of her hand, the water and soap allowing it to slide smoothly along without any noticeable friction. Her body responded with a slight pleasurable ache, encouraging her to continue. As she slowly rubbed the palm of her hand up and down against her sex, she felt the sensation begin to build upon itself, growing in strength and demand for more. Her hips had begun pressing into the motions of her hand almost of their own accord and Dani was surprised to feel something between the outer folds of her vagina that had grown firm. It was like a shallow ridge with a round nub, protected beneath the folds of skin. Experimentally, she let her palm drift higher over her mound, and ran two of her fingers to either side of the nub. The resulting shudder of pleasure was almost overwhelming, making her legs feel weak so that she had to lean against the shower wall to remain upright. Whatever that was, it felt ***AMAZING***, and was most certainly the source of the pleasurable sensations. Dani focused her attention on that nub, running her fingers up and down, around, and across it, enjoying every spark of more and more intense pleasure that erupted as a result. She was not prepared for what happened next, as her whole body suddenly went tense involuntarily, and pleasure exploded inside her, pulsing and throbbing through her whole core. She gasped in surprise and bit her lip hard to keep herself from calling out, since she knew her parents were likely watching TV just beyond the bathroom wall. Her legs could not hold her anymore, and she let herself slide down the smooth side of the shower stall, her fingers still gently teasing the center of her pleasure as wave after wave of sensation wracked her body. Each wave eventually seemed smaller and less intense than the last until it finally subsided, leaving behind a satisfied hum of pleasure as Dani's breath came in desperate heaves. She had no idea what had just happened, but it had been utterly fantastic! She knew instantly that this would be her new shower-time routine, maybe even nightly bedtime routine, from now on. She had no idea she could give herself such pure and intense bliss! Absently, she wondered if her friend Audrey was aware of it. Maybe it was just something unique to Dani, and Audrey would look at her like a weirdo when she asked, but she decided she must find out for sure the next time she had opportunity to hang out with her friend. When her breathing finally returned to normal, Dani collected herself from the shower floor and finished washing before shutting off the water and grabbing one of her towels. She hoped that her parents hadn't noticed how much longer of a shower she had taken than normal, as she didn't want to try and explain why. She could probably come up with an excuse if she thought about it, but her brain wasn't firing on all cylinders after that incredible experience. As she tied a second towel around her still soaking wet hair, she thought to herself that even though she'd just moments ago enjoyed the deepest pleasure she’d ever felt, she couldn't wait to try it again. *** Jake lay in his bed trying to focus on reading a book, but found that he could not keep his mind on the task at hand. His brothers had already gone to bed, and he could hear the water running upstairs where his sister still taking a shower. Meanwhile, his parents were probably watching TV in the living room, unless Bec had given them trouble trying to put her down for the night. As one of the oldest two Hansen children, Jake was allowed to stay up later than his younger brothers, but because they were trying to sleep, he was restricted to having quiet time in his room. Normally he'd be fine with that. He enjoyed reading, or drawing, or whittling with his pocketknife, but tonight was different. All through church, Jake had been distracted from the youth pastor’s message by the image he'd seen on Finn's tablet screen that afternoon. He had nearly forgotten the other pictures, but the one of the woman who looked so much like Dani was firmly lodged in his brain, even though he'd only seen it for a few seconds. The perky breasts with erect nipples jutting out below elegant collar bones and satin smooth skin were burned into his memory, along with that slight, knowing smile and seductive eyes. It was his sister's face, even if obviously more mature and angular. Was there a similar resemblance to his sister's body? He'd probably never know. Dani was just one floor above him, completely naked in the shower, but beyond his gaze. He'd have no excuse to go anywhere near that bathroom to even attempt to catch a glimpse of her. Even if he tried, his sister was always good about locking the door since she lived with three brothers. Then a thought occurred to him: Dani wouldn't just be undressed in the bathroom for her shower. He'd sat in the living room watching a movie with his parents before and seen her come out of the bathroom wrapped in her robe to scurry across to her bedroom to change into pajamas. That meant she would be naked in her bedroom, too, at least for a short time. Moreover, her bedroom had a window that she always complained was pointless because the only thing she could see out of it was the overgrown rhododendron bush planted outside. It was so big and thick with foliage that she could not even see through it to the side fence between their yard and the forest beyond. For his part, Jake had always retorted that at least she had a window, since his basement bedroom had none. The only thing on that side of the house outside Dani's window was a completely unused space intended for parking an RV, which the Hansens could never afford on their father’s pastor salary. If Jake was quiet about it, he could sneak out the basement door into the back yard, and around to Dani's window. By now it was dark enough that he probably would not be seen, if he was careful. He would have to hurry, though, because he had just heard the shower water stop. Not wasting any more time thinking about it, he sat up, closed his book, and set it on the bed before throwing on some shoes and a light jacket, since the night air would likely be cool. Then he crept out of his room as quietly as he could to avoid alerting his brothers, in case they were still awake in their bedroom on the opposite side of the game room. The basement was dark, but Jake could easily navigate past the couch and coffee table on his left to the basement's exterior door. He eased it open, stepped outside, and closed it again just as silently, then crept up the concrete stairs to the back lawn. Alerted to his presence, Dozer gave a low bark of alarm, then noticed it was him and trotted over from his dog house by the fence. Jake gave the big dog a pat then commanded him to go lie down in a stern whisper. The dog obeyed, returning the way he had come to plop down in front of his dog house. Jake let out a sigh of relief and continued around the corner of the house to the side where the rhododendron bush grew in front of Dani's window. The window itself was dark as Jake made his way toward it and he worried that he might have been too slow; that his sister might have already dressed in her pajamas and tucked herself into bed. Determined to confirm if that was the case, he crept closer, easing himself behind the massive bush and resting on his knees before inching his head up to the bottom corner of his sister's window. As his eyes peeked up to peer inside her room, he found that it was too dark to see anything but her window blinds, which were open to allow the sunlight in during the day. Between the blinds, all he could make out was the vague shape of her bed to his right, and her vanity on the opposite wall to his left. Beyond her bed he could make out the strong right angle of her closet door, but no details at all. Not enough to confirm whether his sister was in bed already or not. Suddenly, a long, vertical sliver of light appeared at the back left end of the room and grew wider as the door was opened, then light flooded his eyes as Dani turned on her bedroom light. Instinctively, Jake ducked below the window, blinking away his light-blindness, then set his resolve and peeked back into his sister's room. Dani had closed her door and was tossing an armload of her clothes into a hamper next to her vanity. She then hung a towel from the post at the foot of her bed that was farthest from the window and began to unwrap the towel on her head from around her hair, using it to tousle the long locks and help them dry. She then moved closer to the window in order to place this towel on the other post on the opposite corner of the foot of her bed. At last she moved on to what Jake had been waiting for: she undid the tie at the waist of her robe and casually let it fall to the floor. Jake nearly gasped at the sight of his sister's suddenly naked form. She was absolutely exquisite! Unlike the girl in the photo, she had obvious, though light, tan lines on her legs and shoulders from her cutoffs and tank top that she wore on particularly warm days. Her wet hair hung heavily past her shoulders, brushing against her skin as she moved, bumping enticingly against her breasts. And Dani's breasts were mesmerizing as they jiggled slightly on her chest while she ran her fingers through her wet hair, tossing it behind her. They definitely were not as big as the tits on the first two girls Finn had shown him that afternoon - maybe not even as big as the woman who was Dani's lookalike - but they were perky, round, and firm like only a teenage girl's tits could be, with cute nipples standing out proudly from being exposed to the air. Jake didn't get a chance to let his gaze drift lower before Dani turned to go take a seat at her vanity, revealing a round, bubble butt for a few precious seconds before she sat down. From his angle at the window, he couldn't see Dani's reflection in her vanity's mirror, but he did get a delicious view of the side of her left breast as she grabbed her hairbrush and began working tangles out of her long hair, causing the round breast to bounce playfully and sway slightly. He was rooted to the spot as surely as the rhododendron bush beside him as he watched his naked sister brush and dry her hair. Her skin was so perfect, and her proportions so petite, and yet toned and athletic at the same time. He could see the muscles of her arms and shoulders moving beneath her smooth skin, and the graceful slope where her neck met with her torso. How had he never noticed this before? It wasn't as if all of these things had been hidden under her clothing. He had just never paid attention until now. Finished with her hair, Dani got up from the vanity and strode over to her closet, giving Jake his first look at her pussy with it's clump of bush on the mound above it. That was something he hadn't seen before. All of the vaginas he had seen on Finn's tablet had been bare, but Dani's had hair similar to the fuzz surrounding Jake’s own dick. Her breasts bounced with each step across the room until she turned her back to the window and opened her closet door. Jake enjoyed another glorious viewing of her round ass while she fished clothing out, then she turned and tossed her pajamas onto her bed and bent down facing him, her breasts hanging enticingly in his view for a moment before she straightened, pulling a pair of panties up her legs and over her pussy, hiding it from his gaze. Then she snagged her pajama pants off the bed and pulled them on over her panties, and Jake knew what would be next so he savored a last look at her perfect tits. Dani slipped each of her arms into the sleeves of her pajama top in turn, causing her breasts to sway and jiggle even more before she began to button up the front of the garment. Fully clothed, she turned to close her closet door and Jake could just make out the roundness of her ass from the way the light pajama material clung to her skin. Her evening routine now concluded, Dani turned on her bedside lamp, crossed toward the door to turn off the ceiling light and returned to her bed in the half darkness. She flung aside the covers and flopped onto her mattress before snuggling in for the night, and Jake knew that was his cue to leave. He wasn't going to get any more of a show, and he'd already gotten more than he had hoped for. Quietly as he could, he pushed his way out of the rhododendron bush and crept around to the back yard then down the stairs into the basement and across the game room to his own bedroom door, conscious that his wildly attractive sister had just settled in for the night directly above him. He slipped out of his shoes and tossed his jacket to the floor before crawling into his bed, picking up the book he couldn't focus on earlier and placing it on his nightstand. He let himself flop onto his back, his head hitting his pillow, and he stared up at the ceiling re-living every detail of what he had just seen. He'd just watched his older sister as she went about her evening routine completely naked, and she was drop dead gorgeous! As he thought about her lithe form, his hand naturally wandered down to his dick and began gently stroking it. Soon he was jerking off in earnest and the only images in his head were of Dani. He needed very little imagination to picture her, since her body was so freshly burned into his mind, and it took no time at all before he was ejaculating pulse after pulse of thick cum into a sock that he kept nearby for that purpose. When he was done, he felt that slight sense of guilt that always followed a jerk-off session, tinged with additional guilt for spying on his sister in the privacy of her room. Yet he already knew that since he'd gotten away with it this time, he would be back again for more. His sister generally showered Monday, Wednesday, and Friday evenings, and that meant he only had two days to wait before he would have another opportunity to see her naked. It was an opportunity he doubted he would ever pass up again.
@ 21db9b8a:2a94c796
2025-02-14 03:37:49Fair warning: This is an explicit and erotic story involving extremely taboo themes that would prevent it from being published on most sites that host erotic stories. All characters in this story are ***fictional only***. It is not in any way based on true events. This is also not your average stroke story. It will be released in chapters, and while there ***is*** sexual content in each chapter, there is no full-on sex until late in chapter 4. It is a story of sexual discovery and exploration between young people who have few resources to educate them, but also few inhibitions to hold them back. I hope you enjoy it. If not… Well… You don’t have to host it on your relay, and you can always mute me so you don’t see any more. *** Dani barreled through the dining room in pursuit of her younger brother, Jake, who sped out the sliding glass door onto the back deck, making a feeble and unsuccessful attempt to close the door behind him as he ran. He had always been faster than Dani over short distances, and his recent growth spurt, just before turning thirteen, had made it that much more difficult to catch him. "Give them back, you thief!" she shouted after him, taking just enough time to open and fully slide the door closed behind her, in order to avoid incurring her mother's wrath. It was all the lead her brother needed. He leaped off the deck into the sunlit back yard and sprinted over to one of the tall maple trees at the edge of the lawn. By the time Dani had made it to the yard, her brother was already scurrying up the trunk with her sunglasses gripped between his teeth. Jake was younger than Dani by seventeen months, but he had recently grown to be two full inches taller than her, and he had begun to develop muscle tone to compliment his athleticism. It also helped him climb trees with frustrating ease. Dani jogged to the base of the maple, which had no limbs for at least the first ten to twelve feet, and glared up at her brother lounging across two of the branches. He was now wearing her sunglasses to further taunt her. The twerp took his role as the annoying younger brother seriously, despite their age difference being relatively small. Dani's other two brothers, ages ten and seven, had thankfully not learned Jake's bad habits and generally left Dani alone, but her oldest brother seemed to make it his mission to infuriate her. It was just for sport, Dani knew, and Jake really was alright to be around most of the time, but let him get bored and it always seemed like she was the one who paid for it. "Give me a break, Jacob William Hansen!" she demanded, using his full name like their mother often did when she wanted him to know he was in trouble. She shaded her eyes from the early summer sun as she continued to glare up at him. It did not seem to have the same effect as when her mother used it. "When you come down from there, I'll have your hide!" "You may have my hide, Danielle Elizabeth Hansen,” he mocked, “but you won't have your glasses." With that, he plucked them from his face and hooked them over a smaller branch above him. "You wouldn't dare leave them up there!" she asserted, not really sure whether he would or not. Jake knew better than to push things too far, but he might not consider abandoning her sunglasses in the limbs of a tree to count as 'too far'. "What are you going to do? Go tell on me?" Of course, he knew she would not. They had long since stopped tattling on one another. In their household, the tattler often brought as much punishment upon him or herself as the one tattled on, and sometimes more. Instead, Jake and Dani had agreed to settle most matters between themselves, and only bring their parents in when it was more serious, like when Jake had planned to jump off the garage roof onto his skateboard, and Dani just knew he would have cracked open his skull if he had tried it. "If you want your sunglasses back, you are just going to have to come up here and get them." "How did you even make it up there?" she demanded. Dani was no slouch at climbing trees most of the time. She liked to play in the woods and didn't mind getting dirty, but the trees she climbed at least had branches close enough to the ground that she could jump up and grab hold of them. This maple had nothing but bare trunk for several feet above her head. "You didn't see how I did it?" Jake asked. "You just have to wrap your legs around it and use them to hold on. Then grab as high as you can with your arms and pull your legs up higher." Dani cocked an eyebrow at him dubiously, unsure whether she could mimic the technique. For one, her brother didn't have breasts to contend with, and Dani had been a bit of an early bloomer in that department. At fourteen, she already would have filled out a B-cup bra, if she ever wore anything other than sports bras. The lumps of fatty flesh sticking out from her chest were horribly annoying and always getting in the way. It seemed more than likely that her breasts would do just that while trying to shimmy up the tree as well. Shrugging to herself she decided to give it a shot. She approached the trunk and wrapped her arms around it as high up as she could reach. She could just barely touch her fingers together on the other side when hugging as closely as her chest would allow. Supporting herself with her arms, she jumped and wrapped her legs around the trunk as well and felt the bark lightly scratching the inside of her thighs and back of her calves. It probably wasn't the best idea to be doing this in her cutoff jeans and a tank top, but it was far too warm out to wear her usual jeans and a hoodie. She would just have to tough her way through it. Gritting her teeth she pushed her body upward with her legs, which invariably tugged the front of her tank top downward to expose part of her sports bra underneath, then she reached as high as she could with her arms and let her weight settle on them to pull her legs up again. This caused Dani's breasts, which were being crushed between her and the tree, to push upward, partially spilling out of the top of her sports bra and tank top. As predicted, they were getting in the way of things once again. Dani was far too distracted to think about what kind of display she was putting on for her brother above her, though. As her weight had settled, her crotch had slid against the trunk and caused a pleasurable sensation to well up in her nether-regions. It was a shock to Dani, and she nearly let go of the tree. She'd never felt anything quite like that from “down there” before, and it was distractingly pleasant. She sat frozen in place for a moment, trying to make sense of the feeling. "Well?" her brother voiced his impatience. "Are you just going to hang there like a koala or are you going to come get your shades?" Letting out a low, frustrated growl, Dani continued upward, the pleasant sensation in her groin returning each time she slid it against the trunk. What on earth was going on? This was not a situation that should be causing her pleasure whatsoever, let alone down there. Her legs and arms felt like they had several new scrapes from the rough trunk, but her crotch was alight with a dull pleasurable throbbing that Dani had never experienced before. Then again, she'd never thought to rub it against anything before. As she finally shimmied her way high enough to grab hold of the lower-most branch, Dani was panting from more than the sun's heat and her exertion. Pulling herself up onto the sturdy limb, she hoped her brother didn't notice the flush in her face or the way she self-consciously adjusted her tank top so that it properly covered what it was meant to. Then she looked up to see him holding her sunglasses out to her from the branch he was seated on. "Not cool, Jake!" she chided, snatching her sunglasses from his hand and inspecting them for damage. Satisfied they were none the worse for wear, she slid them into her dark hair, which was pulled back into a loose ponytail that hung just past her shoulders, so that they rested securely atop her head. "Oh stop your whining," he brushed off her anger. "You know you needed some motivation to get out of the kitchen. Mom has had you cooped up in there all morning." "Yeah, that's because it gets too hot to bake in the afternoon, doofus! Don't you want fresh bread for the monstrous sandwich I'm sure you will somehow manage to stuff down your throat for lunch?" "Fair point," Jake acknowledged. "But aren't you glad to get out and get your blood pumping?" "No!" Dani retorted. "Look at me!" She held her scraped-up arms out for his inspection. "I blame you for this!" "Oh come on! You love it!" Jake insisted. "I have seen you laughing off far worse war-wounds than that." Dani sighed and shook her head at him. He was right, of course. She was known for playing hard. Hard enough to keep up with the boys in the neighborhood, who often used to wrestle her like she was one of them. At least, they had until recently. Since she'd developed breasts they all seemed scared of her. All except Jake, but he was her brother. They had never been awkward with one another, and he still didn't seem to notice that she was a girl, let alone growing into a woman. For most of their childhood, Jake was the only playmate Dani had, so she had adapted to playing like a boy. Instead of Barbies and tea sets, it had been Legos and Nerf guns, and she had loved every minute of it, even if it did tend to come with a fair share of bruises and scrapes. And sure, Jake could be an absolute pest, but it was mutual antagonism born out of playful sibling affection. "Fine," she admitted. "It was a welcome rescue from mom's home ec class. But you're still going to owe me for all the scrapes I have from climbing this tree. My legs are even worse than my arms!" "I'm sure you'll think of some way to get sweet revenge," Jake laughed. "You always do." Again, he was right. As much as Jake infuriated her with his taunting, teasing, and pranks, Dani could dish it right back at him. That was part of their strange sibling relationship that made it look to all on the outside like they couldn't stand one another, when in reality they were best friends and would do anything for the other when it really mattered. "Alright, meat-brain," Dani changed the subject, using her favorite pet name for her brother. "Now that we're free of mom's clutches for the afternoon, what should we do with ourselves?" "I don't know what you're going to do, but when Finn gets home from school, we're going fishing." Finn was Jake's best friend who lived just a few houses down from them. While Jake, Dani, and their siblings were homeschooled by their mother, Finn went to public school and wouldn't be getting home until mid afternoon. Soon school would be out for the summer, making Jake and Finn nearly inseparable during daylight hours, but that was still a week and a half away, despite the heat wave they were getting in early June, and then Finn's family would be going to summer camp for three weeks, so the boys were taking advantage of as much time as they could get to hang out while they had the chance. Dani knew that she only had a short time while Finn was at camp to have her brother to herself before he would be all but lost to her for three months, since Jake and Finn usually didn't like having her along with them anymore. They had played together for years, but over the last several months, the two boys had started excluding her from their activities. That left Dani feeling quite alone when Jake and Finn rode their bikes off to wherever they hung out these days. She had no friends of her own in the neighborhood. Her closest female friend, Audrey, lived almost a half-hour away, in a small town to the north, so they only really got to see each other at church, and the occasional planned sleepover. "Fine, ditch your sister, as usual," Dani complained, rolling her eyes at her brother. "Don't be like that, Dani," Jake protested. "It's just awkward talking about girls with your sister around, ya know?" "Like you actually have any girls to talk about!" she teased. "Maybe not, but a guy can live vicariously through his best friend, can't he?" "Ha!" Dani scoffed. "I seriously doubt Finley O'Connor has a lineup of girls to give you all the juicy details about, either. At least not any that aren't figments of his imagination." "You might be surprised." Was that a blush that suddenly appeared on Jake's face? Had she misjudged Finn? Jake's best friend was not what she would think of as a chick-magnet. He was a bean-pole of a boy with an unkempt mop of red hair topping his head. He had a mouth that was too large for his face that always seemed to be twisted in a mischievous grin, and an over-abundance of freckles that covered every inch of him that Dani had ever seen, which was most of him since he often accompanied their family to go swimming at the river. He did not fit into Dani's definition of attractive, nor any other girl she knew. Not that she knew many other girls well enough to talk about boys with them. "Whatever you say, meat brain," Dani said, shifting on the branch and dropping to hang beneath it before letting go to allow herself to fall the three or four feet down to the ground. She landed on her feet, bending her legs deeply to absorb the impact, then stood up straight and defiant. Brushing her hands off on the sides of her cutoffs and looking back up at her brother. "I'll just have to figure out how to keep myself occupied, as always." There was more disappointment in her voice than she had intended. She didn't really want to make him feel bad for leaving her without anyone to hang out with for the afternoon. She could find things to do to keep herself busy. For one, she could help her younger brothers finish up their school work, though that would likely only get her through the first hour after lunchtime or so. The benefit of being homeschooled was that you could easily get all your work done for the day in just a few short hours, instead of being cooped up in a classroom the whole day like the public-schoolers had to endure. Of course, that was also the downside, because you then had to figure out what you would do with all the extra time you had. Then Dani remembered the pleasurable sensation she had experienced while climbing the tree. That was certainly something she could investigate this afternoon while Jake was off gallivanting with Finn. She wanted to see if that feeling could be repeated, or if it was just some kind of fluke. She wasn't about to go rub her crotch against trees where anyone might see her, though. Perhaps she could find somewhere more discreet to experiment and see if that sensation returned. It had felt SO GOOD! Surely she could find a way to make it happen again. *** Jake watched as his sister strolled away from the tree back toward the house, her round bottom framed enticingly in her cutoff jeans. He couldn't believe he was looking at her that way; she was his sister after all, not some random girl like the ones Finn liked to show him. Yet, after watching her climb the tree to retrieve her stolen sunglasses from him, Jake could not deny that she possessed every quality that made those girls on Finn's tablet so appealing. Finn had been sharing pictures of naked and nearly-naked girls with Jake almost since he had gotten the tablet as a Christmas present last year. Well, Jake supposed they were actually women, not girls, since they all looked much older than Dani, and most had more pronounced curves. Then again, that could just be because he was seeing them without their clothes on, while Dani's curves were usually covered up. And Dani definitely did have some curves that Jake could no longer help but notice, especially after the display he had just seen. From his perch in the branches of the maple tree, Jake had a perfect view down the front of his sister's tank top as she had shimmied her way up the trunk. No, he had not seen her nipples - her sports bra had done it's job of holding them in - but her round breasts pressing up prominently every time she let her weight rest on her arms made it clear that she was no longer the flat-chested little girl he somehow had still thought of her as. He should not have been so naive. He knew his own body had changed drastically, but had not even considered that his sister's was changing as well, let alone that she might just look a lot like the women in those pictures when she took her clothes off. Jake frowned, noticing that his thoughts had made his dick stiffen in his pants. These were not thoughts he should be having about his sister! Hopefully Finn would have some new pictures to distract him away from thinking of Dani in that context. For that reason and more, Jake looked forward to his friend getting home from school, when the two of them could head out to do some "fishing". Oh, they might do a bit of actual fishing as well, but most of their time would likely be spent at their fort in the woods, well away from any prying eyes, while Finn shared his latest photographic acquisitions. It would still be a few hours before the bus dropped his friend off where their street connected to the main road, so Jake resigned himself to finding something else to distract him from thoughts of his sister until then. It was too nice a day to expect that he could get away with playing Xbox in the basement game room. His brother, Travis, should be done with his school work by now, though, and always enjoyed tinkering with bikes in the garage with him, so Jake dropped out of the tree and headed toward the house to seek his brother out. He crossed the back lawn and their dog, Dozer, ran to meet him. He was a massive brute of a dog, being a full-bred Rottweiler, but he was as gentle and loyal as anyone could ask for with the Hansen children. Jake patted the dog's blocky head and rubbed his ears as he strode toward the back deck. He skirted around the left side of the deck and down the concrete stairs to an exterior door that led directly to the basement where he expected he would find his brother. All of the Hansen boys had rooms in the basement. Jake, as the oldest boy, had his own, while Travis and Aaron shared a room on the opposite end, next to the bathroom, with the game room and stairs up to the front entryway situated conveniently in-between. At age ten, Travis was three years younger than Jake, though he would be turning eleven in the fall, so it was more like two and a half years. Aaron was another three years younger than that, at age seven. The two of them were very close, just like Jake and Dani had always been, but lately Travis had been wanting to spend more time with Jake, whenever the older boy would allow it. The last of the Hansen children was their adopted sister, Rebecca, who was only two years old. Everyone called her Bec, and she lived in the nursery upstairs next to their parents' master bedroom. Their family had fostered her as an infant, and finally adopted her just last year. Dani had been thrilled to finally have a sister, despite the massive age difference, and couldn't wait to teach the child all about being a girl. Not that Dani really had any clue how to be a girl herself, having grown up with three brothers. As expected, when Jake opened the door into the basement, which opened into their game room, his younger brother was seated facing him on the couch with an Xbox controller in hand, transfixed by the large flat screen television on the wall. He looked quite a lot like Jake, with his short, brown hair and blue eyes. The younger boy hadn’t yet started to fill out with muscle tone, though, making him look scrawny, with a head too large for his stringy limbs. The effect was particularly humorous when he stood next to Jake. "You'd better not let mom or dad catch you on that when the sun's out," Jake warned his brother. "Mom's still busy helping Aaron with his math, and Dad's working on tonight's sermon," Travis assured him. "Besides, I was going to get off in just a few minutes anyway." "Oh trust me," Jake began, crossing to the couch and sitting next to his brother, to see that he was playing Minecraft. "I know how 'just a few minutes' can turn into several hours without even realizing it. Why don't you come hang out in the garage and we'll get that chain tightened on your bike so it's not always falling off on you." "Really!?" Travis exclaimed, putting the controller down and turning to Jake with an excited look on his face. "Of course, runt!" Jake had continued to call his brother the pet name even after Aaron was born, much to Travis' chagrin. "What are big brother's for?" He wasn't about to tell him that the reason he was suddenly so willing to help his little brother out was to take his mind off of thinking about Dani. Seeing her round breasts pressing out of the top of her tank top had shattered Jake's ability to think of her in practically the same terms as his brothers, or one of his male friends. Now he found himself remembering her long, smooth legs, and round bottom swaying back and forth hypnotically as she had walked back toward the house, and it seemed the more he told himself he shouldn't think of her that way, the harder it was not to. Travis shut off the Xbox and the two boys marched up the stairs toward the door to the garage. As Jake pulled it open, he heard his mom call out from the dining room. "You boys don't go far! Lunchtime is coming in thirty minutes!" "Don't worry mom!" Jake called back. "Travis and I will just be in the garage working on his bike!" He didn't wait for a response before disappearing into the dark and hitting the button on the wall to open the massive roll up door on the two-car garage, allowing the sunlight to flood in. Then he and Travis went to work on the bike, not only tightening the chain, but straightening the handlebars that had been twisted to one side when Travis had crashed into a tree, and replacing one of the pedals that had nearly fallen apart since it was a hand-me-down bike from someone at their church. Travis was thrilled and rode the bike up and down their short driveway and around the cul-de-sac until their mother called them in for lunch. After scarfing down a massive sandwich, as Dani had predicted, a bag of chips, and a banana, Jake offered to take Travis and Aaron on bike ride to the park and back to pass the time until Finn got home from school. He worried that Dani might want to come, too, but she had disappeared as soon as she was done with lunch without a word. That was highly unusual for her, but not unwelcome since Jake wasn't sure how he would keep himself from ogling her body if she came along. Thankfully, the bike ride with his younger brothers ate up a fair amount of the afternoon. When the time finally came for Finn to be dropped off, Jake let his mom know where he was going then grabbed his fishing pole and tackle box and hopped on his bike once again to pedal down to the corner where the bus dropped off all the kids that lived on their street. He arrived just as the bus was pulling away, and saw his friend, backpack slung casually across one shoulder, strolling toward him among four other kids from the neighborhood of various ages. "Jeez Jake!" Finn exclaimed. "You must have been bored out of your mind to meet me right as I got dropped off!" "Let's just say I'm glad you're finally home," Jake responded, swinging his leg across the back of his bike to dismount and turning it around to walk along side his friend back the direction he had come. "Yeah, I'm finally free from that prison, even if it is only until tomorrow," Finn joked. "Seriously, though, you usually come find me at home, after I've had a chance to ditch my bag and pack us some snacks. What gives?" Jake sighed. He certainly wasn't going to tell his friend the real reason he was so eager to hang out with him. What would Finn think of him if he knew he was having dirty thoughts about his own sister? "It's been a long day, is all," he said finally, and that was partially true. It ***had*** felt exceptionally long. "And we won't be able to stay out long tonight, since I have church." "Oh that's right, it's Wednesday, so you have to go be an altar boy tonight," Finn teased. "No wonder you want to get your debauchery in ahead of time." "It's not like that..." Jake protested halfheartedly. "But now that you mention it, do you have any new pictures to share?" Finn glanced around them to see if any of the other kids who had gotten off the bus were still walking close by, but they had all split off to head to their own homes. "Dude... I've found us some good ones. You'll have jerk-off material for the next month! Or you would if you had a photographic memory." "Oh shut it!" Jake said, punching his friend's shoulder. "It's not like your memory is any better." "Doesn't have to be. I'm the one with the tablet," Finn pointed out as they turned into his driveway and Jake laid his bike down carefully on the front lawn, making sure the fishing gear didn't get damaged. "You say that now, but just make sure your parents don't catch you with those pictures saved on it," Jake warned. "Oh, don't worry about that," Finn assured him. "My parent's don't check what I've been doing on it. They only got it for me because they figure it will keep me from being too noisy and disturbing their peace. I doubt they could even figure out how to turn it on." Finn wasn't exaggerating. His parents were much older than Jake's, and had not grown up with computers. They had both been married before and had adult children from their previous marriages, some of whom had their own kids already. They got together and had Finn and his older brother Scott when they were both in their forties. Now they were in their late fifties and far from being computer literate. The only reason they had an internet connection at all was because it had come with their cable TV plan and Scott had set it up. "Wait here for a minute," Finn instructed. "I just have to drop off my bag and grab my gear." With that the red head disappeared inside his front door, appearing a few short minutes later with his own fishing pole and tackle box. He'd also changed into shorts and a t-shirt. As he approached, he popped open his tackle box and showed Jake that his tablet was tucked inside, then he retrieved his own bike from the side of the garage and the two boys headed out. They rode through the park and out of the back of the neighborhood, where it was bordered by logging company land, serviced by a bumpy dirt road. Nearly a mile down the dirt road, they cut into the woods, stowing their bikes in some bushes. The forest was thick here, and full of fallen logs that the boys deftly maneuvered over and around to reach their destination. Barely visible in the undergrowth ahead was a short, vaguely unnaturally shaped structure that was the fort the two of them had constructed the previous summer, and had continued to improve upon since then. It was made entirely of natural materials, a fact that Jake was particularly proud of, and only large enough for three or four to sit in comfortably. They had constructed it by lashing logs together using roots and vines and anything else that would work as cordage, then taking evergreen boughs to create a roof and walls that did a fair job of blocking the wind, though a less fair job of keeping out the rain, as they had discovered the hard way. The important thing was, the fort was a place they could reasonably expect to be left alone. Even in hunting season, not many people were wandering these woods, since they were too close to residential neighborhoods to safely shoot a rifle. The logging company that owned the land didn't even seem to have any intention of logging it anytime soon. They might have in years past, but that was before the city had grown so much that all the neighborhoods had sprung up around it. Indeed, the most likely event would be that the logging company would sell the land to a developer and yet another neighborhood would be built. Until then, Jake and his friend could use their fort to hide away and look at dirty pictures on Finn's tablet. The two of them crawled through the small opening that served as a doorway and Jake was immediately enveloped by the scent of pine and spruce from the boughs laid on the walls, roof, and even the floor of their fort, to make it more comfortable to sit inside. The interior was not tall enough for him to stand, though he could move around on his knees without his head brushing against the roof, and the evergreen boughs were so thickly piled on the walls and roof that the only light within was the meager amount that filtered through the doorway. Jake took a seat with his back to one of the walls while Finn sat beside him and powered up his tablet. "I have some real babes to show you today, my friend," Finn bragged, punching in his security code so that the tablet allowed him access to his home screen. Then he tapped the icon for the photos app and turned the screen so Jake could see it better. Inside the dim fort, the tablet seemed to blaze with light as an image filled its screen. The picture was of a stunning blonde with wavy hair hanging loose to her shoulders. She was facing toward the camera as though looking past it into the distance while standing in a mostly empty room, though the background was too blurry to pick out any details. The shot only showed her from the waist up, and she was unbuttoning a pair of white jeans, though it was impossible to tell if they were pants or shorts. The top half of her body was completely bare, and her large breasts stood out proudly above her toned stomach. She was absolutely magnificent! She didn't have the biggest tits out of all the girls Finn had shown him before, but they were more than adequately large, perfectly round, and had similarly rounded areolas tipped with eraser shaped nipples. Her skin was the perfect shade of tan, with no tan-lines whatsoever. "She's a stunner, right?" Finn asked, seeing Jake's reaction. "Her name's Nata Lee, or at least that's what she calls herself. She's got loads of pictures with her clothes on, but this is one of the only ones I could find where she shows her tits." "She's a babe, for sure," Jake agreed, still staring at the photo. Finn swiped his finger across the screen and a new photo took the place of the stunning blonde. Pictured was a young woman with dark blonde hair with a hint of red, tied back in a short ponytail. She was laying completely naked on a white couch with the photo taken from above looking down on her. She was staring straight into the camera, a mischievous smile on her face, with one hand caressing her shoulder and the other pressing in on an ample breast. Her breasts were easily as large as the first girl's, but they seemed to sag more. Her areolas were more oval in shape, and didn't contrast with her skin tone as much. The main attraction, though, was the bottom half of her body, with her legs spread wide to reveal her shaved pussy, it's pink inner folds poking out from between the soft outer lips. She was equally as gorgeous as the first girl, though in a decidedly different way. This girl looked like more fun, while the first looked more serious. The way her hair was tied back in a ponytail made her look younger, too, though there was no way she was anywhere near his age with tits like those. Something about her smile made Jake's cock twitch even more than looking at her naked body. It held the promise of delights he had never dreamed of. "Another one you approve of, I take it?" Finn asked with a laugh. "Just wait. They get even better." Swiping the screen again, a close-up image of a shaven pussy and the woman's inner thighs filled the screen. The inner folds of the pussy glistened with moisture and they were parted, revealing an oblong opening into her depths. "Why is she wet down there?" Jake asked, transfixed by the high resolution close-up that showed her every fold and goose-bump. "I don't know, maybe she just went pee," Finn replied. "But that's where you stick your dick in." He pointed to the opening. "Wow..." Jake breathed. "That's crazy..." Finn swiped the screen again, much to Jake's dismay, but his disappointment at not getting more time to inspect such a detailed image of a pussy evaporated as the next image filled the screen. It was of a brunette with long, dark hair hanging loosely over her shoulder as she leaned against a wall. The shot was taken from an angle to her left side, though not fully a profile shot, and only showed her from the chest up. What was visible was completely exposed, and she had slightly tanned skin and perky breasts that were nowhere near as big as the previous girls’, though they were adequately round, with erect nipples and round areolas that contrasted nicely with her skin tone. Somehow, those breasts were even more alluring to Jake, even though they weren't as large. What shocked and captivated him, though, was her face. Her round nose, full lips with just the hint of a smile, and thin, dark eyebrows hanging just above her sultry eyes, made her look uncannily like an older version of Dani. His sister still possessed a bit more girlish roundness to her cheeks and innocence in her eyes, and usually kept her long hair tied back and out of the way, but there was no denying the strong resemblance. Was this what she would look like with her hair down and a few more years of growing up? This girl's breasts were probably closer to the same size as Dani's, too. Was that what his sister's tits looked like under her shirt and sports bra? The image had only been on the screen for a few seconds when Finn suddenly swiped it away saying, "Sorry, I thought I had deleted that one." "What? Why?" Jake asked, looking up from the tablet, which now had a busty redhead filling the screen. "Because..." Finn hesitated. "That one looks a lot like your sister, and I thought that might be weird." "Oh..." Jake said, feeling his face turn crimson and suddenly glad that it was too dark in the fort for his friend to see. "I... I hadn't really noticed." Finn chuckled nervously and said, "I suppose you wouldn't if your attention was on her tits the whole time." "Right?" Jake agreed, adding his own nervous laugh. Then it suddenly hit him that his friend had been looking at pictures of someone who looked like his sister. "Hey! Why did you have that picture in the first place if you know it looks like Dani?" "Chill bro!" Finn started, setting the tablet down on the opposite side of him from Jake and putting his hands up defensively. "I am sure that all of these girls look like the sisters of someone we know." "That's probably true, but this one looks like ***my*** sister, and you ***knew*** it did when you saved it to your tablet!" The heat in Jake's face was growing and he wasn't sure if it was because of his embarrassment or his anger at his friend. "Look, I can understand why you're mad. You have every right to be the protective brother." Finn edged away from Jake a few inches as he spoke. "But before you pummel me, you have to admit that Dani is hot as fuck, and I am not going to be the only guy to notice." Jake certainly did ***not*** want to admit that his sister was hot, but then hadn't that been his issue all afternoon? He'd never thought of her in those terms before, but he'd suddenly had her femininity thrust in his face and he had to admit that it was really messing with his perception of her. Now, after seeing a picture of a naked woman who looked uncannily similar to her, it was even harder not to think of Dani as incredibly attractive, or as Finn had put it, "hot as fuck". The steam had been taken out of his anger, but Jake still wasn't in any mood to hang out with his friend, knowing that Finn had thought of Dani in similar terms as he was reluctantly having to admit he now did as well. Finn was right, of course, and there would probably be loads of guys who would think of his sister that way, but Jake simply wasn't prepared to find her attractive himself, let alone for anyone else to have the same opinion. "Whatever, man..." Jake said, crawling to the doorway. "I'm going home to get dinner before church tonight. Maybe we can go fishing tomorrow." The tone of his voice made it plain that he didn't plan on it. He emerged from the fort and retrieved his bike from the bushes without even waiting for Finn's reply. How on earth was he going to make sense of his friend's dirty thoughts about his sister if he couldn't even make sense of his own? *** As Dani rode home from church that night, she thought back on the events of the day. After chasing Jake out of the house to retrieve her sunglasses, and discovering the pleasant sensation in her groin when she rubbed it against the tree while climbing up after him, she had looked forward to finding herself some alone time to see if she could make it happen again. First, though, she had helped tutor her youngest brother, Aaron, with his math, his least favorite subject because he struggled with it so much. Then it had been lunch time and Dani had started to wonder how she could possibly find any time to herself for the afternoon. In a household of five children, there wasn't a lot of alone time to be had, and since her bedroom was right next to the living room on the ground level, she could not expect to get away with hiding in there; certainly not with the sun shining outside. Her mother would ensure that all the children spent ample time outdoors as long as the weather was good, and June had been unseasonably clear and hot so far. As much as Dani wanted to investigate whether she could reproduce that warm and pleasurable feeling, she couldn't just go rubbing her crotch against objects where anyone might see her. With the privacy of her own room out of the question until later that evening, that left only the tree-house in the back yard, but that was Travis and Aaron's favorite hang-out spot most afternoons. Fortunately, Jake had unwittingly come to the rescue by taking the other boys with him on a bike ride. That in itself was odd. Usually Jake would spend most of the day until Finn got home from school hanging out with her. Yet, today he seemed to have avoided her like the plague after stealing her sunglasses that morning. She decided she would need to find out what that was all about if it continued, but for today it had worked to her advantage, affording her the alone time she craved. Dani had gone out to the tree-house immediately after her brothers left for their bike ride. It was situated at the back of their property, built around the trunk of another of the massive maple trees, with a ladder leading up to a trap door in its floor. It was not terribly high off the ground, only ten to twelve feet or so, but that was high enough that no one standing on the ground could see inside the small windows. Once inside, Dani knew she could expect near complete privacy, especially since the branches of the tree hid the tree house windows from anyone on the second floor of their home looking toward the back of the property. Hesitantly, Dani had gone to the trunk of the tree sticking up through the middle of the tree-house floor. It had a slightly larger circumference than the one she had climbed that morning, but she could still wrap her legs all the way around it. She could not do the same with her arms, however, so she leaned back and supported her weight with her hands on the rough planks beneath her. This didn't allow her to move her hips nearly enough to rub herself against the tree, so she let her feet fall to the floor as well. This gave her the freedom of motion she needed, and also allowed her to control how much pressure she exerted as she slid her cutoff jean clad crotch against the tree. The sensation was nearly immediate; a dull, warm pleasure welling up from between her legs. She continued to move her hips up and down, sliding herself against the tree's firm girth, the roughness of the bark dulled by the layers of cloth between it and her skin. The sensation seemed to build with each repeated grinding of her hips, but so did her fatigue. It was hard work to hold her whole body suspended in the air with just her arms and legs while she pumped and ground her groin against the trunk. Soon she was forced to collapse to the floor in exhaustion, despite how good it felt and how much she wanted to keep going. She needed to find something else she could rub herself against. Something that didn't require her to hold herself up the whole time, but the inside of the tree-house was pretty sparse. There were a couple of beanbag chairs and a small table between them acting as the only furniture, but that was about all, aside from a few action figures and Lego bricks her brothers had left strewn across the floor. She wondered if she might be able to use her own hand instead, and went over to recline in one of the beanbag chairs. Spreading her legs, she placed the palm of her hand on the crotch of her cutoffs and gently rubbed downward and back up. The sensation was pleasant, but not as strong as it had been while rubbing against the tree trunk. She continued to rub herself for several minutes, but the sensation just stayed a dull, pleasurable ache, rather than building upon itself as it had when grinding against something more firm and solid, not to mention more textured, than the palm of her own hand. Frustrated, Dani had spent the rest of the afternoon playing with their dog and then helped her mother prepare for dinner. Now that she had a bit more time to think about what had happened, though, she wondered if the sensation with her hand might have been stronger if she didn't have the thick fabric of her cutoffs in the way. She would have the perfect opportunity to test that theory not long after getting home, since Wednesday night was her turn to take a shower. Dani liked to take her showers late in the evening, if possible. It always felt good to go to bed fresh and clean, and it was relaxing to brush and dry her long hair, which usually helped her wind down for sleep. The shower would also be the perfect opportunity to be alone and try rubbing herself without any clothing in-between her hand and her vagina, which seemed to be the source of the pleasant sensation. When their minivan pulled into the garage, the whole family piled out, filed into the house through the door to the main entryway, and split off in various directions. Dani's mother and father went upstairs to put Bec down for bed, her brothers went downstairs to get their pajamas on and brush their teeth, and Dani went through the kitchen and living room to get all the way around to her own bedroom. Once there, she retrieved her shower supplies from atop her vanity across from her bed. Her bathroom doubled as the family and guest bathroom, and was too small for Dani to leave all of her things laying around on the counter like her brothers could in their larger bathroom downstairs. She was allowed to leave her shampoo and body wash in the shower, because it was hidden from guests by the closed shower door. She was also permitted to leave her toothbrush and toothpaste inside the medicine cabinet behind the over-sink mirror. But she had to keep her razor, shaving gel, deodorant, and towels in her own room and take anything she needed with her to use the shower. This resulted in Dani doing as little of her hygiene in the bathroom as she could get away with, using her vanity in her bedroom instead. Dani brought a towel for her hair, another for her body, and her bathrobe with her as she exited her room and crossed behind the living room couch to the small bathroom beyond. Closing and locking the door behind her, she crossed the room and locked the opposite door as well. Whoever had designed their home had thought it would be convenient to have access to the bathroom from both the living room and the kitchen. In reality it had just been more hassle remembering to lock and unlock both doors instead of just one. Indeed, it had led to more than one awkward encounter when she had forgotten to lock one door or the other before using the toilet, only to have her father or one of her brothers barge in on her by mistake. Having ensured a similarly embarrassing event would not occur this evening, Dani set her things on the small counter next to the sink and began to disrobe, letting each article of clothing fall to the floor. Then she pulled out the hair tie holding her ponytail back and strode naked over to the shower stall. The bathroom was too small to fit a tub, but Dani didn't mind most of the time. If she really wanted to take a bath, her parents would often let her use the massive tub in their master bathroom upstairs, rather than make her use the one in her brothers' bathroom in the basement. Most of the time she just wanted to get clean and be done with it, though, so a shower suited her fine. She turned on the water and waited for it to get warm enough to step in, then turned it up until it was just this side of scalding, the way she liked it. When the steaming hot water poured over her skin, she let out a deep and relaxed sigh of pleasure, then got her hair thoroughly wet before sudsing it up with shampoo and rinsing it out, enjoying every second of the cleansing heat. Her plans of trying to give herself pleasure again were nearly forgotten as she lost herself in the soothing waters, until she started soaping up her body and she got to washing her more sensitive regions. As her fingers moved through the tuft of hair on the mound above her vagina she remembered that she was going to try to use her hand to rub against her bare skin and see if that made any difference. Dipping her hand lower, she put pressure against her mound and the outer lips of her vagina with her palm of her hand, the water and soap allowing it to slide smoothly along without any noticeable friction. Her body responded with a slight pleasurable ache, encouraging her to continue. As she slowly rubbed the palm of her hand up and down against her sex, she felt the sensation begin to build upon itself, growing in strength and demand for more. Her hips had begun pressing into the motions of her hand almost of their own accord and Dani was surprised to feel something between the outer folds of her vagina that had grown firm. It was like a shallow ridge with a round nub, protected beneath the folds of skin. Experimentally, she let her palm drift higher over her mound, and ran two of her fingers to either side of the nub. The resulting shudder of pleasure was almost overwhelming, making her legs feel weak so that she had to lean against the shower wall to remain upright. Whatever that was, it felt ***AMAZING***, and was most certainly the source of the pleasurable sensations. Dani focused her attention on that nub, running her fingers up and down, around, and across it, enjoying every spark of more and more intense pleasure that erupted as a result. She was not prepared for what happened next, as her whole body suddenly went tense involuntarily, and pleasure exploded inside her, pulsing and throbbing through her whole core. She gasped in surprise and bit her lip hard to keep herself from calling out, since she knew her parents were likely watching TV just beyond the bathroom wall. Her legs could not hold her anymore, and she let herself slide down the smooth side of the shower stall, her fingers still gently teasing the center of her pleasure as wave after wave of sensation wracked her body. Each wave eventually seemed smaller and less intense than the last until it finally subsided, leaving behind a satisfied hum of pleasure as Dani's breath came in desperate heaves. She had no idea what had just happened, but it had been utterly fantastic! She knew instantly that this would be her new shower-time routine, maybe even nightly bedtime routine, from now on. She had no idea she could give herself such pure and intense bliss! Absently, she wondered if her friend Audrey was aware of it. Maybe it was just something unique to Dani, and Audrey would look at her like a weirdo when she asked, but she decided she must find out for sure the next time she had opportunity to hang out with her friend. When her breathing finally returned to normal, Dani collected herself from the shower floor and finished washing before shutting off the water and grabbing one of her towels. She hoped that her parents hadn't noticed how much longer of a shower she had taken than normal, as she didn't want to try and explain why. She could probably come up with an excuse if she thought about it, but her brain wasn't firing on all cylinders after that incredible experience. As she tied a second towel around her still soaking wet hair, she thought to herself that even though she'd just moments ago enjoyed the deepest pleasure she’d ever felt, she couldn't wait to try it again. *** Jake lay in his bed trying to focus on reading a book, but found that he could not keep his mind on the task at hand. His brothers had already gone to bed, and he could hear the water running upstairs where his sister still taking a shower. Meanwhile, his parents were probably watching TV in the living room, unless Bec had given them trouble trying to put her down for the night. As one of the oldest two Hansen children, Jake was allowed to stay up later than his younger brothers, but because they were trying to sleep, he was restricted to having quiet time in his room. Normally he'd be fine with that. He enjoyed reading, or drawing, or whittling with his pocketknife, but tonight was different. All through church, Jake had been distracted from the youth pastor’s message by the image he'd seen on Finn's tablet screen that afternoon. He had nearly forgotten the other pictures, but the one of the woman who looked so much like Dani was firmly lodged in his brain, even though he'd only seen it for a few seconds. The perky breasts with erect nipples jutting out below elegant collar bones and satin smooth skin were burned into his memory, along with that slight, knowing smile and seductive eyes. It was his sister's face, even if obviously more mature and angular. Was there a similar resemblance to his sister's body? He'd probably never know. Dani was just one floor above him, completely naked in the shower, but beyond his gaze. He'd have no excuse to go anywhere near that bathroom to even attempt to catch a glimpse of her. Even if he tried, his sister was always good about locking the door since she lived with three brothers. Then a thought occurred to him: Dani wouldn't just be undressed in the bathroom for her shower. He'd sat in the living room watching a movie with his parents before and seen her come out of the bathroom wrapped in her robe to scurry across to her bedroom to change into pajamas. That meant she would be naked in her bedroom, too, at least for a short time. Moreover, her bedroom had a window that she always complained was pointless because the only thing she could see out of it was the overgrown rhododendron bush planted outside. It was so big and thick with foliage that she could not even see through it to the side fence between their yard and the forest beyond. For his part, Jake had always retorted that at least she had a window, since his basement bedroom had none. The only thing on that side of the house outside Dani's window was a completely unused space intended for parking an RV, which the Hansens could never afford on their father’s pastor salary. If Jake was quiet about it, he could sneak out the basement door into the back yard, and around to Dani's window. By now it was dark enough that he probably would not be seen, if he was careful. He would have to hurry, though, because he had just heard the shower water stop. Not wasting any more time thinking about it, he sat up, closed his book, and set it on the bed before throwing on some shoes and a light jacket, since the night air would likely be cool. Then he crept out of his room as quietly as he could to avoid alerting his brothers, in case they were still awake in their bedroom on the opposite side of the game room. The basement was dark, but Jake could easily navigate past the couch and coffee table on his left to the basement's exterior door. He eased it open, stepped outside, and closed it again just as silently, then crept up the concrete stairs to the back lawn. Alerted to his presence, Dozer gave a low bark of alarm, then noticed it was him and trotted over from his dog house by the fence. Jake gave the big dog a pat then commanded him to go lie down in a stern whisper. The dog obeyed, returning the way he had come to plop down in front of his dog house. Jake let out a sigh of relief and continued around the corner of the house to the side where the rhododendron bush grew in front of Dani's window. The window itself was dark as Jake made his way toward it and he worried that he might have been too slow; that his sister might have already dressed in her pajamas and tucked herself into bed. Determined to confirm if that was the case, he crept closer, easing himself behind the massive bush and resting on his knees before inching his head up to the bottom corner of his sister's window. As his eyes peeked up to peer inside her room, he found that it was too dark to see anything but her window blinds, which were open to allow the sunlight in during the day. Between the blinds, all he could make out was the vague shape of her bed to his right, and her vanity on the opposite wall to his left. Beyond her bed he could make out the strong right angle of her closet door, but no details at all. Not enough to confirm whether his sister was in bed already or not. Suddenly, a long, vertical sliver of light appeared at the back left end of the room and grew wider as the door was opened, then light flooded his eyes as Dani turned on her bedroom light. Instinctively, Jake ducked below the window, blinking away his light-blindness, then set his resolve and peeked back into his sister's room. Dani had closed her door and was tossing an armload of her clothes into a hamper next to her vanity. She then hung a towel from the post at the foot of her bed that was farthest from the window and began to unwrap the towel on her head from around her hair, using it to tousle the long locks and help them dry. She then moved closer to the window in order to place this towel on the other post on the opposite corner of the foot of her bed. At last she moved on to what Jake had been waiting for: she undid the tie at the waist of her robe and casually let it fall to the floor. Jake nearly gasped at the sight of his sister's suddenly naked form. She was absolutely exquisite! Unlike the girl in the photo, she had obvious, though light, tan lines on her legs and shoulders from her cutoffs and tank top that she wore on particularly warm days. Her wet hair hung heavily past her shoulders, brushing against her skin as she moved, bumping enticingly against her breasts. And Dani's breasts were mesmerizing as they jiggled slightly on her chest while she ran her fingers through her wet hair, tossing it behind her. They definitely were not as big as the tits on the first two girls Finn had shown him that afternoon - maybe not even as big as the woman who was Dani's lookalike - but they were perky, round, and firm like only a teenage girl's tits could be, with cute nipples standing out proudly from being exposed to the air. Jake didn't get a chance to let his gaze drift lower before Dani turned to go take a seat at her vanity, revealing a round, bubble butt for a few precious seconds before she sat down. From his angle at the window, he couldn't see Dani's reflection in her vanity's mirror, but he did get a delicious view of the side of her left breast as she grabbed her hairbrush and began working tangles out of her long hair, causing the round breast to bounce playfully and sway slightly. He was rooted to the spot as surely as the rhododendron bush beside him as he watched his naked sister brush and dry her hair. Her skin was so perfect, and her proportions so petite, and yet toned and athletic at the same time. He could see the muscles of her arms and shoulders moving beneath her smooth skin, and the graceful slope where her neck met with her torso. How had he never noticed this before? It wasn't as if all of these things had been hidden under her clothing. He had just never paid attention until now. Finished with her hair, Dani got up from the vanity and strode over to her closet, giving Jake his first look at her pussy with it's clump of bush on the mound above it. That was something he hadn't seen before. All of the vaginas he had seen on Finn's tablet had been bare, but Dani's had hair similar to the fuzz surrounding Jake’s own dick. Her breasts bounced with each step across the room until she turned her back to the window and opened her closet door. Jake enjoyed another glorious viewing of her round ass while she fished clothing out, then she turned and tossed her pajamas onto her bed and bent down facing him, her breasts hanging enticingly in his view for a moment before she straightened, pulling a pair of panties up her legs and over her pussy, hiding it from his gaze. Then she snagged her pajama pants off the bed and pulled them on over her panties, and Jake knew what would be next so he savored a last look at her perfect tits. Dani slipped each of her arms into the sleeves of her pajama top in turn, causing her breasts to sway and jiggle even more before she began to button up the front of the garment. Fully clothed, she turned to close her closet door and Jake could just make out the roundness of her ass from the way the light pajama material clung to her skin. Her evening routine now concluded, Dani turned on her bedside lamp, crossed toward the door to turn off the ceiling light and returned to her bed in the half darkness. She flung aside the covers and flopped onto her mattress before snuggling in for the night, and Jake knew that was his cue to leave. He wasn't going to get any more of a show, and he'd already gotten more than he had hoped for. Quietly as he could, he pushed his way out of the rhododendron bush and crept around to the back yard then down the stairs into the basement and across the game room to his own bedroom door, conscious that his wildly attractive sister had just settled in for the night directly above him. He slipped out of his shoes and tossed his jacket to the floor before crawling into his bed, picking up the book he couldn't focus on earlier and placing it on his nightstand. He let himself flop onto his back, his head hitting his pillow, and he stared up at the ceiling re-living every detail of what he had just seen. He'd just watched his older sister as she went about her evening routine completely naked, and she was drop dead gorgeous! As he thought about her lithe form, his hand naturally wandered down to his dick and began gently stroking it. Soon he was jerking off in earnest and the only images in his head were of Dani. He needed very little imagination to picture her, since her body was so freshly burned into his mind, and it took no time at all before he was ejaculating pulse after pulse of thick cum into a sock that he kept nearby for that purpose. When he was done, he felt that slight sense of guilt that always followed a jerk-off session, tinged with additional guilt for spying on his sister in the privacy of her room. Yet he already knew that since he'd gotten away with it this time, he would be back again for more. His sister generally showered Monday, Wednesday, and Friday evenings, and that meant he only had two days to wait before he would have another opportunity to see her naked. It was an opportunity he doubted he would ever pass up again. @ 0000065e:9b5b4c75
2025-02-14 01:55:12En el ámbito bitcoiner es muy habitual que el Estado sea el blanco de las principales críticas, que se ve convertido así en el muñeco de paja al que dirigir nuestros palos. Pero no, en realidad es una piñata que está a punto de desmoronarse de los golpes que le pegan. Cada vez tengo más claro que gran parte de los movimientos "antiestatales", si no todos, están contribuyendo, consciente o inconscientemente, a los intereses de los políticos que nos han llevado a esta situación. El Estado, con todos sus defectos, sigue siendo la principal unidad de ejercicio de la violencia organizada. Señalando al Estado como el origen de todos los males, no hacemos otra cosa que pegarnos un tiro en el pie, haciendo el caldo gordo a quienes trabajan para cercenar nuestras libertades. Lo que está claro es que los políticos actuales, de boquilla firmes defensores del Estado, lo que están haciendo es provocar su colapso. Puede que estos políticos, o algunos de ellos, incluso no sean conscientes del todo, pero da igual, pues simplemente priman sus intereses personales, como hacemos todos, intentando aprovechar los incentivos que están encima de la mesa, con las reglas de juego que hemos ido asumiendo. No es que quieran más Estado o que pretendan dinamitarlo, tanto una cosa como otra no son más que las consecuencias de los incentivos que subyacen a nuestra forma de organizarnos en sociedad en el contexto actual. Albert Rivera, en una reciente charla con Iván Espinosa de los Monteros, aludía a esta idea criticando las [redes clientelares y de dependencia del Estado](https://youtu.be/AI7roBGtmvk?t=2709) que generan las actuales dinámicas políticas y adulteran el sistema democrático. Aunque, cabría dudar sobre si el propio “sistema democrático” tiene o no algo que ver con esta situación. En cualquier caso, no es que la mayoría de políticos sean malvados por naturaleza, aunque algunos puedan realmente serlo; es irrelevante. Sus acciones no están motivadas por su maldad, ni por su ideología o su estupidez, sino, simple y llanamente, por sus intereses personales y los del grupo con el que los comparten. Las ideologías que manejan los políticos se han convertido en nichos de mercado, en caladeros donde echar la caña a ver si pescan suficientes votos como para asegurarse su porvenir y el de los suyos. Es del todo irrelevante si se creen o no esas ideas que defienden con tanta vehemencia como ausencia de plausabilidad, o incluso si están a sueldo de intereses espurios. De cualquier forma, actuarán en función de lo que crean más conveniente para sus intereses personales y para que más peces caigan en sus redes. Véase, por ejemplo, como [Albert Rivera](https://www.youtube.com/watch?v=XrdCP3viocU), ahora que está fuera de la política, manifiesta que resulta evidente que el sistema de pensiones es una estafa piramidal, mientras que cuando estaba en política defendía lo contrario. O a [Errejón](https://www.youtube.com/watch?v=oZ0KfTsITh8), que sostenía la tesis de que no había denuncias falsas hasta que lo denunciaron a él. Como digo, los políticos no son malvados o estúpidos (aunque haya algunos, o muchos, que entren en esas categorías), simplemente velan por sus intereses con las armas que tienen a su alcance y, como diría [Vito Corleone](https://youtu.be/Z1dRPt_4rZs?t=208), me es indiferente lo que un hombre haga para vivir. El problema es que esta dinámica está generando unas tendencias que se oponen al progreso que hemos generado como sociedad. Esas reglas de juego en la actualidad, convendremos, son inmorales, en el sentido de que actúan como una fuerza contraria a [nuestra supervivencia y potencia de actuar y obrar](https://maestreabogados.com/bitcoin-el-bien-y-el-mal/). > *Este artículo forma parte de un trabajo más extenso en elaboración sobre las relaciones de Bitcoin con el Estado.*
@ 0000065e:9b5b4c75
2025-02-14 01:55:12En el ámbito bitcoiner es muy habitual que el Estado sea el blanco de las principales críticas, que se ve convertido así en el muñeco de paja al que dirigir nuestros palos. Pero no, en realidad es una piñata que está a punto de desmoronarse de los golpes que le pegan. Cada vez tengo más claro que gran parte de los movimientos "antiestatales", si no todos, están contribuyendo, consciente o inconscientemente, a los intereses de los políticos que nos han llevado a esta situación. El Estado, con todos sus defectos, sigue siendo la principal unidad de ejercicio de la violencia organizada. Señalando al Estado como el origen de todos los males, no hacemos otra cosa que pegarnos un tiro en el pie, haciendo el caldo gordo a quienes trabajan para cercenar nuestras libertades. Lo que está claro es que los políticos actuales, de boquilla firmes defensores del Estado, lo que están haciendo es provocar su colapso. Puede que estos políticos, o algunos de ellos, incluso no sean conscientes del todo, pero da igual, pues simplemente priman sus intereses personales, como hacemos todos, intentando aprovechar los incentivos que están encima de la mesa, con las reglas de juego que hemos ido asumiendo. No es que quieran más Estado o que pretendan dinamitarlo, tanto una cosa como otra no son más que las consecuencias de los incentivos que subyacen a nuestra forma de organizarnos en sociedad en el contexto actual. Albert Rivera, en una reciente charla con Iván Espinosa de los Monteros, aludía a esta idea criticando las [redes clientelares y de dependencia del Estado](https://youtu.be/AI7roBGtmvk?t=2709) que generan las actuales dinámicas políticas y adulteran el sistema democrático. Aunque, cabría dudar sobre si el propio “sistema democrático” tiene o no algo que ver con esta situación. En cualquier caso, no es que la mayoría de políticos sean malvados por naturaleza, aunque algunos puedan realmente serlo; es irrelevante. Sus acciones no están motivadas por su maldad, ni por su ideología o su estupidez, sino, simple y llanamente, por sus intereses personales y los del grupo con el que los comparten. Las ideologías que manejan los políticos se han convertido en nichos de mercado, en caladeros donde echar la caña a ver si pescan suficientes votos como para asegurarse su porvenir y el de los suyos. Es del todo irrelevante si se creen o no esas ideas que defienden con tanta vehemencia como ausencia de plausabilidad, o incluso si están a sueldo de intereses espurios. De cualquier forma, actuarán en función de lo que crean más conveniente para sus intereses personales y para que más peces caigan en sus redes. Véase, por ejemplo, como [Albert Rivera](https://www.youtube.com/watch?v=XrdCP3viocU), ahora que está fuera de la política, manifiesta que resulta evidente que el sistema de pensiones es una estafa piramidal, mientras que cuando estaba en política defendía lo contrario. O a [Errejón](https://www.youtube.com/watch?v=oZ0KfTsITh8), que sostenía la tesis de que no había denuncias falsas hasta que lo denunciaron a él. Como digo, los políticos no son malvados o estúpidos (aunque haya algunos, o muchos, que entren en esas categorías), simplemente velan por sus intereses con las armas que tienen a su alcance y, como diría [Vito Corleone](https://youtu.be/Z1dRPt_4rZs?t=208), me es indiferente lo que un hombre haga para vivir. El problema es que esta dinámica está generando unas tendencias que se oponen al progreso que hemos generado como sociedad. Esas reglas de juego en la actualidad, convendremos, son inmorales, en el sentido de que actúan como una fuerza contraria a [nuestra supervivencia y potencia de actuar y obrar](https://maestreabogados.com/bitcoin-el-bien-y-el-mal/). > *Este artículo forma parte de un trabajo más extenso en elaboración sobre las relaciones de Bitcoin con el Estado.* @ 7d33ba57:1b82db35
2025-02-14 01:46:37The short answer is YES—but the more honest answer is that it’s much harder than when I started. I’ve been in the travel stock media industry for over 13 years, creating a vast archive of stock photos and videos from around the world. You can check out my portfolio on [https://www.shutterstock.com/g/traveltelly](Shutterstock). My work is also available on Pond5, Videoblocks, and Adobe Stock. Other big agencies where I don’t have my media are Getty Images and iStock. My media has been featured on TV channels and even in feature films. However, most of the time, contributors don’t know exactly where their content is used—stock agencies (the middlemen) keep that information to themselves. While stock media can still generate income, it requires persistence, a large portfolio, and an understanding of the ever-changing market. When I started filming stock footage, most people didn’t even have a phone capable of taking good photos or videos—can you imagine? Now, everyone is a (travel) content creator. Technology has evolved, but creating a well-composed photo or video is still an art. However, the combination of improved tech and the increasing centralization of the stock media market has made it much harder to earn a decent income from stock media compared to 10 years ago.  **Centralization & Declining Royalties** Over the years, I’ve watched stock media royalties decline year after year. In the beginning, I couldn't understand why I wasn’t able to recoup the cost of my expensive camera—one I specifically bought to shoot high-quality 4K footage. As the stock media industry became more centralized, agencies took a larger cut while contributors earned less, despite creating higher-quality content. The market became saturated, and with more competition and lower payouts, making a sustainable income from stock media became increasingly difficult.  **The Reality of Centralization in Stock Media** Every year, stock agencies announced yet another royalty downgrade for contributors. They always framed it as something beneficial for content creators, but in reality, it only served the big companies and their shareholders. As content creators, we had no say in the matter. These agencies grew too big and powerful, and they knew it. Leaving one platform wasn’t really an option—doing so would only mean an even greater loss of income. In recent years, the industry has become even more centralized, with only a handful of major agencies buying out smaller competitors. This consolidation further reduces competition, giving contributors even less control over pricing, royalties, and where their content is used.  **The Bitcoin Standard: A Wake-Up Call** I couldn’t understand why I was struggling to pay off my expensive camera investment, despite working hard and producing high-quality content. Until then, I had never really thought about how money worked. That changed in 2018 when I read The Bitcoin Standard—an absolute eye-opener. That book sparked my curiosity about Bitcoin. Like many, I initially got distracted by shitcoins, thinking I could multiply my holdings faster—after all, Bitcoin seemed “too expensive.” It was a hard but valuable lesson. Just like in a casino, you can win and lose a lot with altcoins, but that has nothing to do with Bitcoin itself. After those first few years of learning, I realized that for me, Bitcoin—not crypto—was the only way forward.  **From Centralization to Decentralization** When people ask me if they should start selling stock footage, my answer is always the same: It’s much harder now than when I started. Sure, you can make a few bucks, but is all the time and effort really worth it? If I had to start today, I simply wouldn’t—it’s way more work than what you’ll earn. Instead of spending years building content for centralized platforms that take the biggest cut, I believe it’s better to focus on decentralized media like Nostr. In my opinion, that’s where the future lies.  Nostr: A New Protocol for Socializing (and More) Nostr is a revolutionary protocol that goes beyond just social networking. You can read all about it at [Nostr.org](Nostr.org). As a content creator, one of the most exciting aspects of Nostr is the ability to earn directly through Zaps—small payments made in Satoshis (the smallest unit of Bitcoin). * 1 Bitcoin = 100 million Satoshis * By receiving Zaps, you’re not just earning—you’re stacking the hardest money (Bitcoin) directly on Nostr. This shift toward decentralized earning is a game changer, giving creators more control and financial sovereignty compared to traditional, centralized platforms.  **Join Nostr and Create Your Freedom Content** On Nostr, no one can stop you. No one can deplatform you. You can be truly free.Whether you're a content creator, artist, or thinker, Nostr empowers you to share your work without censorship or gatekeepers. It’s a place where you control your content, connect directly with your audience, and even earn Bitcoin through Zaps.Embrace decentralization. ***Join Nostr and take back your freedom*** 🚀
@ 7d33ba57:1b82db35
2025-02-14 01:46:37The short answer is YES—but the more honest answer is that it’s much harder than when I started. I’ve been in the travel stock media industry for over 13 years, creating a vast archive of stock photos and videos from around the world. You can check out my portfolio on [https://www.shutterstock.com/g/traveltelly](Shutterstock). My work is also available on Pond5, Videoblocks, and Adobe Stock. Other big agencies where I don’t have my media are Getty Images and iStock. My media has been featured on TV channels and even in feature films. However, most of the time, contributors don’t know exactly where their content is used—stock agencies (the middlemen) keep that information to themselves. While stock media can still generate income, it requires persistence, a large portfolio, and an understanding of the ever-changing market. When I started filming stock footage, most people didn’t even have a phone capable of taking good photos or videos—can you imagine? Now, everyone is a (travel) content creator. Technology has evolved, but creating a well-composed photo or video is still an art. However, the combination of improved tech and the increasing centralization of the stock media market has made it much harder to earn a decent income from stock media compared to 10 years ago.  **Centralization & Declining Royalties** Over the years, I’ve watched stock media royalties decline year after year. In the beginning, I couldn't understand why I wasn’t able to recoup the cost of my expensive camera—one I specifically bought to shoot high-quality 4K footage. As the stock media industry became more centralized, agencies took a larger cut while contributors earned less, despite creating higher-quality content. The market became saturated, and with more competition and lower payouts, making a sustainable income from stock media became increasingly difficult.  **The Reality of Centralization in Stock Media** Every year, stock agencies announced yet another royalty downgrade for contributors. They always framed it as something beneficial for content creators, but in reality, it only served the big companies and their shareholders. As content creators, we had no say in the matter. These agencies grew too big and powerful, and they knew it. Leaving one platform wasn’t really an option—doing so would only mean an even greater loss of income. In recent years, the industry has become even more centralized, with only a handful of major agencies buying out smaller competitors. This consolidation further reduces competition, giving contributors even less control over pricing, royalties, and where their content is used.  **The Bitcoin Standard: A Wake-Up Call** I couldn’t understand why I was struggling to pay off my expensive camera investment, despite working hard and producing high-quality content. Until then, I had never really thought about how money worked. That changed in 2018 when I read The Bitcoin Standard—an absolute eye-opener. That book sparked my curiosity about Bitcoin. Like many, I initially got distracted by shitcoins, thinking I could multiply my holdings faster—after all, Bitcoin seemed “too expensive.” It was a hard but valuable lesson. Just like in a casino, you can win and lose a lot with altcoins, but that has nothing to do with Bitcoin itself. After those first few years of learning, I realized that for me, Bitcoin—not crypto—was the only way forward.  **From Centralization to Decentralization** When people ask me if they should start selling stock footage, my answer is always the same: It’s much harder now than when I started. Sure, you can make a few bucks, but is all the time and effort really worth it? If I had to start today, I simply wouldn’t—it’s way more work than what you’ll earn. Instead of spending years building content for centralized platforms that take the biggest cut, I believe it’s better to focus on decentralized media like Nostr. In my opinion, that’s where the future lies.  Nostr: A New Protocol for Socializing (and More) Nostr is a revolutionary protocol that goes beyond just social networking. You can read all about it at [Nostr.org](Nostr.org). As a content creator, one of the most exciting aspects of Nostr is the ability to earn directly through Zaps—small payments made in Satoshis (the smallest unit of Bitcoin). * 1 Bitcoin = 100 million Satoshis * By receiving Zaps, you’re not just earning—you’re stacking the hardest money (Bitcoin) directly on Nostr. This shift toward decentralized earning is a game changer, giving creators more control and financial sovereignty compared to traditional, centralized platforms.  **Join Nostr and Create Your Freedom Content** On Nostr, no one can stop you. No one can deplatform you. You can be truly free.Whether you're a content creator, artist, or thinker, Nostr empowers you to share your work without censorship or gatekeepers. It’s a place where you control your content, connect directly with your audience, and even earn Bitcoin through Zaps.Embrace decentralization. ***Join Nostr and take back your freedom*** 🚀 @ 9e69e420:d12360c2
2025-02-13 23:01:36Robert F. Kennedy Jr. has been confirmed as the next Secretary of Health and Human Services with a Senate vote of 52-48. Senator Mitch McConnell opposed the confirmation. Kennedy's nomination faced hurdles but gained support from the Senate Finance Committee. During the confirmation hearing, Senator Rand Paul criticized the oversimplification of vaccine discussions. He stated, "Discussion over vaccines is so oversimplified and dumbed down." Kennedy asserted his support for vaccines like measles and polio, promising not to discourage vaccinations as HHS Secretary. Previously, he switched from the Democratic Party to run as an independent and endorsed Trump
@ 9e69e420:d12360c2
2025-02-13 23:01:36Robert F. Kennedy Jr. has been confirmed as the next Secretary of Health and Human Services with a Senate vote of 52-48. Senator Mitch McConnell opposed the confirmation. Kennedy's nomination faced hurdles but gained support from the Senate Finance Committee. During the confirmation hearing, Senator Rand Paul criticized the oversimplification of vaccine discussions. He stated, "Discussion over vaccines is so oversimplified and dumbed down." Kennedy asserted his support for vaccines like measles and polio, promising not to discourage vaccinations as HHS Secretary. Previously, he switched from the Democratic Party to run as an independent and endorsed Trump @ 85bdb587:7339d672
2025-02-13 22:56:08## Marty's Bent I must admit, I have been thoroughly impressed with the work the Trump administration has done since taking the reins from the Biden admin 23 days ago. Over the course of the first eight years of this newsletter there were multiple books-worth of words written about the rampant government corruption in the United States and the negative effects it was having on the economy, freedom and the psyche of the American people. The emergence of DOGE, its rag-tag team of autistic Gen Z'ers and the blatant fraud that has been surfaced is equally gratifying and infuriating. For the longest time any American taxpayer with the smallest shred of common sense has known that they've been getting screwed by the federal government. We've said it for many years; taxes are a humiliation ritual in which the Common Man works his ass off for a meager wage, the government takes one third of it, and then lines their own pockets. We were reaching levels of corruption that rivaled Soviet Russia. *“We know that they are lying, they know that they are lying, they even know that we know they are lying, we also know that they know we know they are lying too, they of course know that we certainly know they know we know they are lying too as well, but they are still lying. In our country, the lie has become not just moral category, but the pillar industry of this country.”* - Aleksandr Solzhenitsyn The fact that all of the corruption that has been building up for decades in the United States is being brought to the light is extremely encouraging. We're not out of the woods yet, but it looks like we're actually making material progress to unveil the parasites in Washington DC. Hopefully DOGE's actions will lead to their eradication from American politics and a shrinking of the federal government to its smallest viable form. Nothing proves that DOGE is over the target more than the pearl clutching and screeching that is coming from the halls of Congress. FEED ME the crocodile tears of Elizabeth Warren, Maxine Waters and Mitch McConnell. These people are criminals and deserve nothing but the utmost contempt from the American people. The louder the screams coming from these individuals and others in similar positions should only be seen as confirmation that they are scared and are attempting to evade justice by screaming "CoNsTiTuTiOnAl CrIsIs" as many times as is humanly possible. With all of that being said, DOGE should be seen as a mechanism to identify corruption, root it out, and salvage what they can of the American taxpayers' money. It's an admirable endeavor that should be lauded, but it only goes so far. Unfortunately for the United States, you can't DOGE the debt. via TFTC  What you are looking at is a block of 10-year US Treasuries that need to be rolled over in a couple of days. Particularly, $66B 10Ys that were issued in February 2015 when interest rates were 2.00%. They'll be rolling over in a few days at 4.55%, representing an additional $1.67B in interest expense on the debt per year. While that may not seem a lot in a world where governments and central banks throw trillions around like their going out of style, it is important to realize that this is just one block of bonds that needs to be rolled over this year. If my memory serves me correctly, the Treasury needs to roll over ~$6 TRILLION in debt in the first half of this year. Using some back of the napkin Marty math skills, if all that debt rolled over at the same interest rate, that would add another ~$150B to the annual expense we pay on the interest on that debt. And in case you missed it, earlier this week the United States surpassed an incredible milestone; we are now paying $100B a MONTH in interest expense on the debt and $1.2T per year. If all of the debt that needs to be rolled over in the first half of the year is rolled over where interest rates stand today, it will increase the annual debt expense by more than 10%. Not great, Bob!  The actions of DOGE are incredible to see, but you simply can't eliminate debt that has already been accrued by raiding the Treasury and ousting corrupt bureaucrats. The United States has an obligation to pay back those who hold our debt and the only way to do that is to produce a surplus that allows the government to pay down what has been accrued or issue new debt at wherever rates find themselves at the time of roll over to pay it back. While spending cuts are being made we, unfortunately do not find ourselves reaping the benefits of a government surplus at the moment, so we'll have to roll over the debt. With interest rates where they are, the increase on the debt expense may put the United States government in a position where it becomes impossible to take care of the debt issue without printing their way out of it or getting all of the world's leaders around the table for a Bretton Woods-like monetary reset. We'll see how it plays out. One thing I know for damn sure is that no matter how the US decides to deal with the debt issue, bitcoin is going to benefit massively. If they print their way out people are going to flee to scarce assets, and bitcoin is the scarcest asset on the planet outside of time. If they reset the monetary order people are going to flee to bitcoin due to the certainty of its monetary policy and its relative inability to be corrupted. Now for... ## An Incredibly Simple Yet Powerful Quote As discussed in my recent conversation with Porter Stansberry, the mounting U.S. government debt problem has created an intriguing dynamic for Bitcoin holders. Porter articulated a compelling perspective: government debt, which threatens most people's savings and financial security, actually becomes an asset for Bitcoin owners. The logic is straightforward – as debt levels become unsustainable, more people will be forced to flee the traditional financial system, driving demand for alternative stores of value like Bitcoin. *"Their debt is your problem until you own Bitcoin. And then the moment you own bitcoin their debt is your greatest asset."* - Porter Stansberry This thesis becomes even more relevant when considering the staggering numbers we discussed. The U.S. currently faces $37 trillion in on-balance-sheet debt, plus an additional $190 trillion in unfunded liabilities from Medicare, Medicaid, and Social Security. These obligations, as Porter and I agreed, are mathematically impossible to fulfill without significant monetary debasement. This reality creates a powerful tailwind for Bitcoin adoption, as it positions the asset as one of the few viable escape hatches from a system drowning in debt. [Check out the full podcast](https://www.youtube.com/watch?v=2f8LWO_RmtU&ab_channel=TFTC) here for more on Trump's economic strategy, the commercial real estate crisis, and the future of energy markets in America. ## Headlines of the Day Bitcoin's Realized Cap Reaches Record High - via [X](https://x.com/TFTC21/status/1889831485701833056) Texas Bill Removes $500M Cap on State Bitcoin Purchases - via [X](https://x.com/BitcoinPierre/status/1889821134021075012) ETF Demand Outpaces Mining Production - via [X](https://x.com/TFTC21/status/1889779939982840185) U.S. Interest Expense on the National Debt Hits $1.2T - via [X](https://x.com/TFTC21/status/1889764204208324764) ## Bitcoin Lesson of the Day Bitcoin transactions work by sending entire "outputs" (batches of bitcoin) rather than spending partial amounts. When spending bitcoin, the entire output must be used and split into new outputs. For example, if you have a 25 BTC output and want to spend 1 BTC, you'd create two new outputs: 1 BTC to the recipient and 24 BTC back to yourself as change. The original 25 BTC output becomes spent and unusable. When making a payment that exceeds any single output you own, multiple outputs can be combined as inputs in a transaction. For instance, to spend 4.2 BTC, you might combine outputs of 1 + 0.5 + 2 + 1 BTC as inputs, creating new outputs of 4.2 BTC (payment) and 0.3 BTC (change). Transaction fees are created by making the total output amount slightly less than the input amount. The difference becomes the fee, which miners collect when including the transaction in a block. The balance of a bitcoin address is the sum of all its unspent transaction outputs (UTXOs). [Outputs | What is a Transaction Output? A simple explanation of transaction outputs and how they work.](https://learnmeabitcoin.com/beginners/guide/outputs/) ICYMI Fold opened the waiting list for the new Bitcoin Rewards Credit Card. Fold cardholders will get unlimited 2% cash back in sats. [Get on the waiting list](https://foldapp.com/credit-card?r=BgwRS) now before it fills up! $200k worth of prizes are up for grabs. Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at [ten31.vc/funds](ten31.vc/funds).
@ 85bdb587:7339d672
2025-02-13 22:56:08## Marty's Bent I must admit, I have been thoroughly impressed with the work the Trump administration has done since taking the reins from the Biden admin 23 days ago. Over the course of the first eight years of this newsletter there were multiple books-worth of words written about the rampant government corruption in the United States and the negative effects it was having on the economy, freedom and the psyche of the American people. The emergence of DOGE, its rag-tag team of autistic Gen Z'ers and the blatant fraud that has been surfaced is equally gratifying and infuriating. For the longest time any American taxpayer with the smallest shred of common sense has known that they've been getting screwed by the federal government. We've said it for many years; taxes are a humiliation ritual in which the Common Man works his ass off for a meager wage, the government takes one third of it, and then lines their own pockets. We were reaching levels of corruption that rivaled Soviet Russia. *“We know that they are lying, they know that they are lying, they even know that we know they are lying, we also know that they know we know they are lying too, they of course know that we certainly know they know we know they are lying too as well, but they are still lying. In our country, the lie has become not just moral category, but the pillar industry of this country.”* - Aleksandr Solzhenitsyn The fact that all of the corruption that has been building up for decades in the United States is being brought to the light is extremely encouraging. We're not out of the woods yet, but it looks like we're actually making material progress to unveil the parasites in Washington DC. Hopefully DOGE's actions will lead to their eradication from American politics and a shrinking of the federal government to its smallest viable form. Nothing proves that DOGE is over the target more than the pearl clutching and screeching that is coming from the halls of Congress. FEED ME the crocodile tears of Elizabeth Warren, Maxine Waters and Mitch McConnell. These people are criminals and deserve nothing but the utmost contempt from the American people. The louder the screams coming from these individuals and others in similar positions should only be seen as confirmation that they are scared and are attempting to evade justice by screaming "CoNsTiTuTiOnAl CrIsIs" as many times as is humanly possible. With all of that being said, DOGE should be seen as a mechanism to identify corruption, root it out, and salvage what they can of the American taxpayers' money. It's an admirable endeavor that should be lauded, but it only goes so far. Unfortunately for the United States, you can't DOGE the debt. via TFTC  What you are looking at is a block of 10-year US Treasuries that need to be rolled over in a couple of days. Particularly, $66B 10Ys that were issued in February 2015 when interest rates were 2.00%. They'll be rolling over in a few days at 4.55%, representing an additional $1.67B in interest expense on the debt per year. While that may not seem a lot in a world where governments and central banks throw trillions around like their going out of style, it is important to realize that this is just one block of bonds that needs to be rolled over this year. If my memory serves me correctly, the Treasury needs to roll over ~$6 TRILLION in debt in the first half of this year. Using some back of the napkin Marty math skills, if all that debt rolled over at the same interest rate, that would add another ~$150B to the annual expense we pay on the interest on that debt. And in case you missed it, earlier this week the United States surpassed an incredible milestone; we are now paying $100B a MONTH in interest expense on the debt and $1.2T per year. If all of the debt that needs to be rolled over in the first half of the year is rolled over where interest rates stand today, it will increase the annual debt expense by more than 10%. Not great, Bob!  The actions of DOGE are incredible to see, but you simply can't eliminate debt that has already been accrued by raiding the Treasury and ousting corrupt bureaucrats. The United States has an obligation to pay back those who hold our debt and the only way to do that is to produce a surplus that allows the government to pay down what has been accrued or issue new debt at wherever rates find themselves at the time of roll over to pay it back. While spending cuts are being made we, unfortunately do not find ourselves reaping the benefits of a government surplus at the moment, so we'll have to roll over the debt. With interest rates where they are, the increase on the debt expense may put the United States government in a position where it becomes impossible to take care of the debt issue without printing their way out of it or getting all of the world's leaders around the table for a Bretton Woods-like monetary reset. We'll see how it plays out. One thing I know for damn sure is that no matter how the US decides to deal with the debt issue, bitcoin is going to benefit massively. If they print their way out people are going to flee to scarce assets, and bitcoin is the scarcest asset on the planet outside of time. If they reset the monetary order people are going to flee to bitcoin due to the certainty of its monetary policy and its relative inability to be corrupted. Now for... ## An Incredibly Simple Yet Powerful Quote As discussed in my recent conversation with Porter Stansberry, the mounting U.S. government debt problem has created an intriguing dynamic for Bitcoin holders. Porter articulated a compelling perspective: government debt, which threatens most people's savings and financial security, actually becomes an asset for Bitcoin owners. The logic is straightforward – as debt levels become unsustainable, more people will be forced to flee the traditional financial system, driving demand for alternative stores of value like Bitcoin. *"Their debt is your problem until you own Bitcoin. And then the moment you own bitcoin their debt is your greatest asset."* - Porter Stansberry This thesis becomes even more relevant when considering the staggering numbers we discussed. The U.S. currently faces $37 trillion in on-balance-sheet debt, plus an additional $190 trillion in unfunded liabilities from Medicare, Medicaid, and Social Security. These obligations, as Porter and I agreed, are mathematically impossible to fulfill without significant monetary debasement. This reality creates a powerful tailwind for Bitcoin adoption, as it positions the asset as one of the few viable escape hatches from a system drowning in debt. [Check out the full podcast](https://www.youtube.com/watch?v=2f8LWO_RmtU&ab_channel=TFTC) here for more on Trump's economic strategy, the commercial real estate crisis, and the future of energy markets in America. ## Headlines of the Day Bitcoin's Realized Cap Reaches Record High - via [X](https://x.com/TFTC21/status/1889831485701833056) Texas Bill Removes $500M Cap on State Bitcoin Purchases - via [X](https://x.com/BitcoinPierre/status/1889821134021075012) ETF Demand Outpaces Mining Production - via [X](https://x.com/TFTC21/status/1889779939982840185) U.S. Interest Expense on the National Debt Hits $1.2T - via [X](https://x.com/TFTC21/status/1889764204208324764) ## Bitcoin Lesson of the Day Bitcoin transactions work by sending entire "outputs" (batches of bitcoin) rather than spending partial amounts. When spending bitcoin, the entire output must be used and split into new outputs. For example, if you have a 25 BTC output and want to spend 1 BTC, you'd create two new outputs: 1 BTC to the recipient and 24 BTC back to yourself as change. The original 25 BTC output becomes spent and unusable. When making a payment that exceeds any single output you own, multiple outputs can be combined as inputs in a transaction. For instance, to spend 4.2 BTC, you might combine outputs of 1 + 0.5 + 2 + 1 BTC as inputs, creating new outputs of 4.2 BTC (payment) and 0.3 BTC (change). Transaction fees are created by making the total output amount slightly less than the input amount. The difference becomes the fee, which miners collect when including the transaction in a block. The balance of a bitcoin address is the sum of all its unspent transaction outputs (UTXOs). [Outputs | What is a Transaction Output? A simple explanation of transaction outputs and how they work.](https://learnmeabitcoin.com/beginners/guide/outputs/) ICYMI Fold opened the waiting list for the new Bitcoin Rewards Credit Card. Fold cardholders will get unlimited 2% cash back in sats. [Get on the waiting list](https://foldapp.com/credit-card?r=BgwRS) now before it fills up! $200k worth of prizes are up for grabs. Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at [ten31.vc/funds](ten31.vc/funds). @ e373ca41:b82abcc5
2025-02-13 22:27:58*This article has been written with the* ***[Pareto client](https://pareto.space/read).*** *(read it there for the full experience). It was first published in German by Milosz Matuschek on* ***["Freischwebende Intelligenz".](https://www.freischwebende-intelligenz.org/p/unterwanderter-journalismus-der-mediale)*** *** It is unmistakable. The hydra of the Deep State is losing a few heads - and this time it's the turn of the media heads. Anyone can look at [USASpending](https://www.usaspending.gov/) to see how much taxpayers' money has gone to whom in the USA. ### When the state pays its advocates The mainstream media were also among the beneficiaries: Politico (100% Axel Springer) received over [USD 7 million](https://www.usaspending.gov/recipient/fa0cefae-7cfb-881d-29c3-1bd39cc6a49e-C/latest); the New York Times received over USD 40 million. Thousands of (probably not always necessary) government subscriptions flowed to large media houses - paid for with taxpayers' money. A form of covert press financing by the state. At what point can or should we speak of state media? ") However, this is only the tip of the iceberg. The CIA front organization USAID ([known for its funding of virus research in Wuhan and other questionable activities](https://pareto.space/a/naddr1qqxnzden8quryveexq6rywp3qgswxu72gyq7ykjdfl9j556887jpzwu3mw3v9ez36quas55whq4te3grqsqqqa28qyxhwumn8ghj7mn0wvhxcmmvqyf8wumn8ghj7mmxve3ksctfdch8qatzqythwumn8ghj7urpwfjhgmewdehhxarjxyhxxmmdqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsz9nhwden5te0wfjkccte9ehx7um5wghxyctwvszsxfjh)) - [pumped USD 472.6 million directly into the media landscape via the “Internews Network”.](https://www.zerohedge.com/political/usaid-funded-massive-global-state-propaganda-news-matrix-nearly-billion-people-reach) FAZ journalist Udo Ulfkotte once called this “bought journalists” in a very clear and media-effective way, which was not good for his health. There is ample evidence of the CIA-USAID connections, for example [here](https://timesofindia.indiatimes.com/toi-plus/international/how-usaid-worked-alongside-cia-in-vietnam-a-whistleblowers-account/articleshow/118164225.cms), [here](https://foreignpolicy.com/2014/04/03/cuban-twitter-and-other-times-usaid-pretended-to-be-an-intelligence-agency/) and [here.](https://www.jstor.org/stable/4017728) ") But this is now over for the time being: USD 268 million, which was to go to “independent media for the free flow of information” (according to the [Columbia Journalism Review](https://www.cjr.org/the_media_today/usaid-and-the-media-in-a-time-of-monsters.php)) in 2025, has been frozen. The largest media influence machine in the Western world is bleeding a little. One has to admit: part of the media-deepstate swamp is actually being drained dry financially. The fact that the Columbia Journalism Review doesn't even seem to notice that “free international journalism”, which, as it writes, is largely funded by USAID, ceases to be “free journalism” speaks volumes about this “hotbed of journalism”. Matt Taibbi of Racket News rightly finds, “The legacy media system is dead. They just don't know it yet.” *** ADVERTISEMENT: *Looking for the easiest way to buy Bitcoin and store it yourself? The **[Relai app](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. **[Here you can buy Bitcoin](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees (no financial advice). Disclaimer due to regulatory issues: The services of the Relai App are hereby only recommended to inhabitants of Switzerland or Italy.*  *Need more security? The **[Trezor wallets](https://trezor.io/trezor-safe-5-bitcoin-only?transaction_id=102e192a206d1585e56a2fddef6d83\&offer_id=238\&affiliate_id=35234)** are recommended and easy to use, others are available in the **[store](https://trezor.io/?transaction_id=102bc85bdca2733287749c7f879ebd\&offer_id=133\&affiliate_id=35234)**. Need more advice? Book an **[introductory meeting](https://trezor.io/trezor-expert-session?transaction_id=1020e18dad0aa4b1186289fd22e90f\&offer_id=241\&affiliate_id=35234)** with a wallet expert.* *** Large-scale media manipulation has become visible. The propaganda matrix, if you will. The disastrous thing about it: if the Overton window is infiltrated, so to speak, the entire institution of journalism cannot be trusted. Every day, readers must expect to be pulled through the nose ring of intelligence service narratives and public agendas by mainstream journalists who pretend to be objective (and are often simply clueless and unsuspecting). The panorama of what we are supposed to see and believe, so to speak. How many mainstream journalists today are basically mouthpieces for the services? Every mainstream reader must now ask themselves: Is my favorite journalist at NZZ, Welt, SZ, ZEIT or FAZ perhaps just a CIA-IM? There were no major dissenters among them: EU criticism? Vaccination criticism? Criticism of NATO? Criticism of Biden and America? Criticism of Nord Stream? There were brief moments on television when questions about journalists' ties to lobby organizations were still part of the German satire program. <https://x.com/Spitze_Zunge_/status/1887915509988876786> ### The cards in the media are being reshuffled The watchdog of the powerful has been infiltrated by the powerful. This means that the Fourth Power is not a power at all, but part of the executive branch, a mouthpiece of the government. The claim that the mainstream is quality journalism, the gold standard for trustworthy information, is therefore the real fake news. It is the last, now crumbling dogma of an infiltrated press sect that has formed a cartel and is subjecting citizens to a permanent psy-op with intelligence-controlled taxpayers' money. A troupe of spokespeople at the work of mental synchronization. <https://x.com/TopherField/status/1887962959072149989> ### The fight against independent media But they not only give to one, they also take from the other. While government agencies use taxpayers' money to promote a certain type of journalism, the juice is actively being cut off from the critical part. All it takes is to be classified as a “PEP” (politically exposed person) and the bank account is gone. This is what has just happened to swiss Radio Kontrafunk. The critical Swiss author Stefan Millius was canceled by his publisher. Others have had their monetization via YouTube cut off (Snicklink). Others are harassed by the state media authority (Multipolar, Alexander Wallasch). The next one has a house search. It has been known since the Twitter files that the government and services also intervened massively in social media communication. This is no longer the Cold War. But it is the cold information war. <https://www.youtube.com/watch?v=kmgWAGDFCZI> Is this all so outrageous and new? During the Cold War, the CIA systematically infiltrated media outlets in the US. Thousands of agents were deployed as journalists - and wrote what they were told. This “Operation Mockingbird”, which the Church Committee also investigated, never ended, so to speak. It lives on as Operation Mockingbird 2.0. Intelligence payments to media outlets continue to exist. USAID distributes millions for “pro-democratic” reporting. Government subscriptions keep uncritical media alive. Media control of public opinion is the most important tool of power in a modern “democracy”. The difference to back then? Today, the manipulation is global. However, these revelations come at a time when trust in the media is already at an all-time low. [The fear of being lied to by the powerful is currently the majority opinion at 70%.](https://www.edelman.com/trust/2025/trust-barometer) They are currently in the process of convincing the remaining 30% of their own incompetence.  ### Update on the [Pareto project](https://pareto.space/en)  “Half the victory”, says Sun Tsu, ‘lies in the impregnable defense’. Free media now have the opportunity to build their own impregnable bastion and the [Pareto Project](https://pareto.space/read) invites them to do just that: [become uncensorable, be able to scale infinitely and not depend on third parties for all processes of journalistic work](https://pareto.space/a/naddr1qqxnzdenxuerxdpkxycngvpcqgsvlutjpemmkp50p6aa8zwu65yz9hg6erf2czc0tuyqpt57zhr79vsrqsqqqa28qyxhwumn8ghj7mn0wvhxcmmvqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hs33ee7d). It's all possible now. Everyone has to realize that: With other platforms, you build your house on someone else's property. With Nostr/Pareto, there is nothing and no one between author and reader, both in terms of communication and payment (via Bitcoin/Lightning). **A brief update on the project, January was very busy.** * We have about 35 journalists, publications, substackers, bloggers, memers onboarded who publish texts via the Pareto client, and the number is growing all the time. * The first Telepolis authors, such as Mathias Bröckers and Alexander Unzicker, will soon be able to re-publish their deleted texts with us in a censorship-proof manner, and we are helping with the migration of content. * We recently successfully tested the newsletter function! We will soon be able to offer all authors and readers the functions of Substack, Steady, Ghost etc. without having to entrust their readers' sensitive data to a platform or expose them to platform tracking. * We are delighted to have more high-caliber additions to our development team, which now comprises around ten wonderful people, almost all of whom come from this group of readers. * Our [open source code is now also public.](https://github.com/twenty-eighty/pareto-client) * We have opened a [crowdfunding on Geyser!](https://geyser.fund/project/pareto) - Our editor will soon be available to everyone free of charge (atm you have to drop us your npub: <team@pareto.space>) ### What's next? This opens up a new window of unimagined possibilities: On a strong basis such as that offered by decentralized technology, many critical authors can now publish securely or new publications can be created - worldwide and uncensorable. What kind of publications would you like to see? Where do you see gaps (also in the critical spectrum) that need to be filled, both in terms of formats and topics? What does the journalism of the future look like to you? Feel free to write to me: **<milosz@pareto.space>** ## One last thing Our funds are coming to an end. If you would like to support us: We have started a [crowdfunding on Geyser](https://geyser.fund/project/pareto), where you can help us with Bitcoin/Lightning donations.   For traditional donations, you can find our bank account on our **[landingpage.](https://pareto.space/en)** *** ***Join the marketplace of ideas!** We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the [Pareto Project](https://pareto.space/en)? Zap me, if you want to contribute (all Zaps go to the project).* *Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to **<team@pareto.space>*** **Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Start.](https://start.njump.me/)**
@ e373ca41:b82abcc5
2025-02-13 22:27:58*This article has been written with the* ***[Pareto client](https://pareto.space/read).*** *(read it there for the full experience). It was first published in German by Milosz Matuschek on* ***["Freischwebende Intelligenz".](https://www.freischwebende-intelligenz.org/p/unterwanderter-journalismus-der-mediale)*** *** It is unmistakable. The hydra of the Deep State is losing a few heads - and this time it's the turn of the media heads. Anyone can look at [USASpending](https://www.usaspending.gov/) to see how much taxpayers' money has gone to whom in the USA. ### When the state pays its advocates The mainstream media were also among the beneficiaries: Politico (100% Axel Springer) received over [USD 7 million](https://www.usaspending.gov/recipient/fa0cefae-7cfb-881d-29c3-1bd39cc6a49e-C/latest); the New York Times received over USD 40 million. Thousands of (probably not always necessary) government subscriptions flowed to large media houses - paid for with taxpayers' money. A form of covert press financing by the state. At what point can or should we speak of state media? ") However, this is only the tip of the iceberg. The CIA front organization USAID ([known for its funding of virus research in Wuhan and other questionable activities](https://pareto.space/a/naddr1qqxnzden8quryveexq6rywp3qgswxu72gyq7ykjdfl9j556887jpzwu3mw3v9ez36quas55whq4te3grqsqqqa28qyxhwumn8ghj7mn0wvhxcmmvqyf8wumn8ghj7mmxve3ksctfdch8qatzqythwumn8ghj7urpwfjhgmewdehhxarjxyhxxmmdqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsz9nhwden5te0wfjkccte9ehx7um5wghxyctwvszsxfjh)) - [pumped USD 472.6 million directly into the media landscape via the “Internews Network”.](https://www.zerohedge.com/political/usaid-funded-massive-global-state-propaganda-news-matrix-nearly-billion-people-reach) FAZ journalist Udo Ulfkotte once called this “bought journalists” in a very clear and media-effective way, which was not good for his health. There is ample evidence of the CIA-USAID connections, for example [here](https://timesofindia.indiatimes.com/toi-plus/international/how-usaid-worked-alongside-cia-in-vietnam-a-whistleblowers-account/articleshow/118164225.cms), [here](https://foreignpolicy.com/2014/04/03/cuban-twitter-and-other-times-usaid-pretended-to-be-an-intelligence-agency/) and [here.](https://www.jstor.org/stable/4017728) ") But this is now over for the time being: USD 268 million, which was to go to “independent media for the free flow of information” (according to the [Columbia Journalism Review](https://www.cjr.org/the_media_today/usaid-and-the-media-in-a-time-of-monsters.php)) in 2025, has been frozen. The largest media influence machine in the Western world is bleeding a little. One has to admit: part of the media-deepstate swamp is actually being drained dry financially. The fact that the Columbia Journalism Review doesn't even seem to notice that “free international journalism”, which, as it writes, is largely funded by USAID, ceases to be “free journalism” speaks volumes about this “hotbed of journalism”. Matt Taibbi of Racket News rightly finds, “The legacy media system is dead. They just don't know it yet.” *** ADVERTISEMENT: *Looking for the easiest way to buy Bitcoin and store it yourself? The **[Relai app](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. **[Here you can buy Bitcoin](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees (no financial advice). Disclaimer due to regulatory issues: The services of the Relai App are hereby only recommended to inhabitants of Switzerland or Italy.*  *Need more security? The **[Trezor wallets](https://trezor.io/trezor-safe-5-bitcoin-only?transaction_id=102e192a206d1585e56a2fddef6d83\&offer_id=238\&affiliate_id=35234)** are recommended and easy to use, others are available in the **[store](https://trezor.io/?transaction_id=102bc85bdca2733287749c7f879ebd\&offer_id=133\&affiliate_id=35234)**. Need more advice? Book an **[introductory meeting](https://trezor.io/trezor-expert-session?transaction_id=1020e18dad0aa4b1186289fd22e90f\&offer_id=241\&affiliate_id=35234)** with a wallet expert.* *** Large-scale media manipulation has become visible. The propaganda matrix, if you will. The disastrous thing about it: if the Overton window is infiltrated, so to speak, the entire institution of journalism cannot be trusted. Every day, readers must expect to be pulled through the nose ring of intelligence service narratives and public agendas by mainstream journalists who pretend to be objective (and are often simply clueless and unsuspecting). The panorama of what we are supposed to see and believe, so to speak. How many mainstream journalists today are basically mouthpieces for the services? Every mainstream reader must now ask themselves: Is my favorite journalist at NZZ, Welt, SZ, ZEIT or FAZ perhaps just a CIA-IM? There were no major dissenters among them: EU criticism? Vaccination criticism? Criticism of NATO? Criticism of Biden and America? Criticism of Nord Stream? There were brief moments on television when questions about journalists' ties to lobby organizations were still part of the German satire program. <https://x.com/Spitze_Zunge_/status/1887915509988876786> ### The cards in the media are being reshuffled The watchdog of the powerful has been infiltrated by the powerful. This means that the Fourth Power is not a power at all, but part of the executive branch, a mouthpiece of the government. The claim that the mainstream is quality journalism, the gold standard for trustworthy information, is therefore the real fake news. It is the last, now crumbling dogma of an infiltrated press sect that has formed a cartel and is subjecting citizens to a permanent psy-op with intelligence-controlled taxpayers' money. A troupe of spokespeople at the work of mental synchronization. <https://x.com/TopherField/status/1887962959072149989> ### The fight against independent media But they not only give to one, they also take from the other. While government agencies use taxpayers' money to promote a certain type of journalism, the juice is actively being cut off from the critical part. All it takes is to be classified as a “PEP” (politically exposed person) and the bank account is gone. This is what has just happened to swiss Radio Kontrafunk. The critical Swiss author Stefan Millius was canceled by his publisher. Others have had their monetization via YouTube cut off (Snicklink). Others are harassed by the state media authority (Multipolar, Alexander Wallasch). The next one has a house search. It has been known since the Twitter files that the government and services also intervened massively in social media communication. This is no longer the Cold War. But it is the cold information war. <https://www.youtube.com/watch?v=kmgWAGDFCZI> Is this all so outrageous and new? During the Cold War, the CIA systematically infiltrated media outlets in the US. Thousands of agents were deployed as journalists - and wrote what they were told. This “Operation Mockingbird”, which the Church Committee also investigated, never ended, so to speak. It lives on as Operation Mockingbird 2.0. Intelligence payments to media outlets continue to exist. USAID distributes millions for “pro-democratic” reporting. Government subscriptions keep uncritical media alive. Media control of public opinion is the most important tool of power in a modern “democracy”. The difference to back then? Today, the manipulation is global. However, these revelations come at a time when trust in the media is already at an all-time low. [The fear of being lied to by the powerful is currently the majority opinion at 70%.](https://www.edelman.com/trust/2025/trust-barometer) They are currently in the process of convincing the remaining 30% of their own incompetence.  ### Update on the [Pareto project](https://pareto.space/en)  “Half the victory”, says Sun Tsu, ‘lies in the impregnable defense’. Free media now have the opportunity to build their own impregnable bastion and the [Pareto Project](https://pareto.space/read) invites them to do just that: [become uncensorable, be able to scale infinitely and not depend on third parties for all processes of journalistic work](https://pareto.space/a/naddr1qqxnzdenxuerxdpkxycngvpcqgsvlutjpemmkp50p6aa8zwu65yz9hg6erf2czc0tuyqpt57zhr79vsrqsqqqa28qyxhwumn8ghj7mn0wvhxcmmvqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hs33ee7d). It's all possible now. Everyone has to realize that: With other platforms, you build your house on someone else's property. With Nostr/Pareto, there is nothing and no one between author and reader, both in terms of communication and payment (via Bitcoin/Lightning). **A brief update on the project, January was very busy.** * We have about 35 journalists, publications, substackers, bloggers, memers onboarded who publish texts via the Pareto client, and the number is growing all the time. * The first Telepolis authors, such as Mathias Bröckers and Alexander Unzicker, will soon be able to re-publish their deleted texts with us in a censorship-proof manner, and we are helping with the migration of content. * We recently successfully tested the newsletter function! We will soon be able to offer all authors and readers the functions of Substack, Steady, Ghost etc. without having to entrust their readers' sensitive data to a platform or expose them to platform tracking. * We are delighted to have more high-caliber additions to our development team, which now comprises around ten wonderful people, almost all of whom come from this group of readers. * Our [open source code is now also public.](https://github.com/twenty-eighty/pareto-client) * We have opened a [crowdfunding on Geyser!](https://geyser.fund/project/pareto) - Our editor will soon be available to everyone free of charge (atm you have to drop us your npub: <team@pareto.space>) ### What's next? This opens up a new window of unimagined possibilities: On a strong basis such as that offered by decentralized technology, many critical authors can now publish securely or new publications can be created - worldwide and uncensorable. What kind of publications would you like to see? Where do you see gaps (also in the critical spectrum) that need to be filled, both in terms of formats and topics? What does the journalism of the future look like to you? Feel free to write to me: **<milosz@pareto.space>** ## One last thing Our funds are coming to an end. If you would like to support us: We have started a [crowdfunding on Geyser](https://geyser.fund/project/pareto), where you can help us with Bitcoin/Lightning donations.   For traditional donations, you can find our bank account on our **[landingpage.](https://pareto.space/en)** *** ***Join the marketplace of ideas!** We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the [Pareto Project](https://pareto.space/en)? Zap me, if you want to contribute (all Zaps go to the project).* *Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to **<team@pareto.space>*** **Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Start.](https://start.njump.me/)** @ dbb19ae0:c3f22d5a
2025-02-13 20:42:08Installation: ``` bash python3 -venv nostr-sdk source nostr-sdk/bin/activate pip install nostr_sdk requests ``` Python program: ``` python # Usage example: python ns_read_metadata.py nostr:npub1mwce4c8qa2zn9zw9f372syrc9dsnqmyy3jkcmpqkzaze0slj94dqu6nmwy # Compatible with version 0.39 # ns_read_metadata.py # version 3 import asyncio, argparse, json from nostr_sdk import Metadata, Client, NostrSigner, Keys, Filter, PublicKey, Kind from datetime import timedelta async def main(npub): client = Client() await client.add_relay("wss://relay.damus.io") await client.connect() pk = PublicKey.parse(npub) print(f"\nGetting profile metadata for {npub}:") metadata = await client.fetch_metadata(pk, timedelta(seconds=15)) print(metadata) if __name__ == '__main__': parser = argparse.ArgumentParser(description='Fetch all metadata for a given npub') parser.add_argument('npub', type=str, help='The npub of the user') args = parser.parse_args() asyncio.run(main(args.npub)) ```
@ dbb19ae0:c3f22d5a
2025-02-13 20:42:08Installation: ``` bash python3 -venv nostr-sdk source nostr-sdk/bin/activate pip install nostr_sdk requests ``` Python program: ``` python # Usage example: python ns_read_metadata.py nostr:npub1mwce4c8qa2zn9zw9f372syrc9dsnqmyy3jkcmpqkzaze0slj94dqu6nmwy # Compatible with version 0.39 # ns_read_metadata.py # version 3 import asyncio, argparse, json from nostr_sdk import Metadata, Client, NostrSigner, Keys, Filter, PublicKey, Kind from datetime import timedelta async def main(npub): client = Client() await client.add_relay("wss://relay.damus.io") await client.connect() pk = PublicKey.parse(npub) print(f"\nGetting profile metadata for {npub}:") metadata = await client.fetch_metadata(pk, timedelta(seconds=15)) print(metadata) if __name__ == '__main__': parser = argparse.ArgumentParser(description='Fetch all metadata for a given npub') parser.add_argument('npub', type=str, help='The npub of the user') args = parser.parse_args() asyncio.run(main(args.npub)) ``` @ 19220736:7578e0e9
2025-02-13 20:39:52The U.S. economy is facing a double whammy of challenges as housing prices skyrocket and trade tensions escalate, creating a perfect storm of economic strain for everyday Americans. First-time homebuyers are bearing the brunt of the housing crisis, with median home prices rising by nearly 15% in major cities over the past year [1]. While wages have remained stagnant, the cost of living continues to climb. This has left many young families and individuals struggling to afford homes, forcing some to delay homeownership or take on risky levels of debt. Meanwhile, trade tensions between the U.S., Canada, and Mexico have added another layer of uncertainty for businesses and workers. The Trump administration's tariffs [2] on goods imported from these countries will lead to higher costs for industries ranging from agriculture to manufacturing. Companies reliant on imports will see profit margins shrink, with some forced to lay off workers or pass the added costs onto consumers. The interplay between these two experts warn that they could feed into each other. Rising housing costs can limit the availability of skilled labor, as workers may need to take on more demanding jobs to afford rising rents or home prices. This, in turn, could impact industries already struggling with reduced productivity due to trade disruptions. The long-term effects of trade tensions remain unclear, but the uncertainty caused by the threat of tariffs has already led to reduced investment in Mexico, with businesses hesitant to expand operations for fear of retaliatory measures from other countries [3]. While some argue that stronger trade agreements could benefit all parties involved, others fear that continued tension could lead to reciprocal measures that harm global markets. The cumulative effect of these challenges is leaving many Americans feeling vulnerable. From the first-time homebuyer struggling to save for a down payment to the worker worried about job security, the combination of rising housing costs and trade tariffs creates a perfect storm of economic instability. In cities across the U.S., local leaders are calling for more affordable housing [4] options and better wage protections as immediate solutions. Advocates argue that without addressing these issues, the economic strain on families will only worsen, potentially leading to long-term social and economic consequences. While both issues are complex and multifaceted, the need for a coordinated response has never been more urgent. Policymakers at all levels of government must work together to mitigate the negative impacts of rising housing costs and trade tariffs, ensuring that no one is left behind in this challenging economic landscape. Reference links: [1] [Past year ]( https://apnews.com/article/first-time-home-buyer-housing-prices-8ede22e18fd11a40f45e2e0ba6c055c1) [2] [Tariffs ]( https://apnews.com/article/america-canada-mexico-tariffs-trump-trade-4568dababcf524945333bb518232ec4b) [3] [4] [Housing ]( https://apnews.com/article/first-time-home-buyer-housing-prices-8ede22e18fd11a40f45e2e0ba6c055c1)
@ 19220736:7578e0e9
2025-02-13 20:39:52The U.S. economy is facing a double whammy of challenges as housing prices skyrocket and trade tensions escalate, creating a perfect storm of economic strain for everyday Americans. First-time homebuyers are bearing the brunt of the housing crisis, with median home prices rising by nearly 15% in major cities over the past year [1]. While wages have remained stagnant, the cost of living continues to climb. This has left many young families and individuals struggling to afford homes, forcing some to delay homeownership or take on risky levels of debt. Meanwhile, trade tensions between the U.S., Canada, and Mexico have added another layer of uncertainty for businesses and workers. The Trump administration's tariffs [2] on goods imported from these countries will lead to higher costs for industries ranging from agriculture to manufacturing. Companies reliant on imports will see profit margins shrink, with some forced to lay off workers or pass the added costs onto consumers. The interplay between these two experts warn that they could feed into each other. Rising housing costs can limit the availability of skilled labor, as workers may need to take on more demanding jobs to afford rising rents or home prices. This, in turn, could impact industries already struggling with reduced productivity due to trade disruptions. The long-term effects of trade tensions remain unclear, but the uncertainty caused by the threat of tariffs has already led to reduced investment in Mexico, with businesses hesitant to expand operations for fear of retaliatory measures from other countries [3]. While some argue that stronger trade agreements could benefit all parties involved, others fear that continued tension could lead to reciprocal measures that harm global markets. The cumulative effect of these challenges is leaving many Americans feeling vulnerable. From the first-time homebuyer struggling to save for a down payment to the worker worried about job security, the combination of rising housing costs and trade tariffs creates a perfect storm of economic instability. In cities across the U.S., local leaders are calling for more affordable housing [4] options and better wage protections as immediate solutions. Advocates argue that without addressing these issues, the economic strain on families will only worsen, potentially leading to long-term social and economic consequences. While both issues are complex and multifaceted, the need for a coordinated response has never been more urgent. Policymakers at all levels of government must work together to mitigate the negative impacts of rising housing costs and trade tariffs, ensuring that no one is left behind in this challenging economic landscape. Reference links: [1] [Past year ]( https://apnews.com/article/first-time-home-buyer-housing-prices-8ede22e18fd11a40f45e2e0ba6c055c1) [2] [Tariffs ]( https://apnews.com/article/america-canada-mexico-tariffs-trump-trade-4568dababcf524945333bb518232ec4b) [3] [4] [Housing ]( https://apnews.com/article/first-time-home-buyer-housing-prices-8ede22e18fd11a40f45e2e0ba6c055c1) @ 3ad01248:962d8a07
2025-02-13 20:03:40I feel like this is go to be a common phrase over the next four years. While I generally like most of the policies that he is in favor of, I for the life of me can't understand his position on Gaza. It sounds like nothing like the Trump for the campaign trail whatsoever. When he ran for president last year he ran on a platform of not starting any new wars. Having a US solider set foot in Gaza is a recipe for disaster and chaos. Sending in the military is not "America First". Gaza has no national security implication for the United States so obviously there is a different reason why President Trump is proposing this idea. We have to look at who funded his campaign to understand his motives by wanting to clear out Gaza and rebuild it like it some real estate deal. ## Miriam Adelson [Miriam Adelson the wife of late casino magnate Sheldon Adelson](https://www.timesofisrael.com/miriam-adelson-gives-100-million-to-trump-campaign-making-good-on-reported-pledge/) gave Trump $100 million to help get Trump elected. Mrs. Adelson is a pro-Israel and supports a variety of Jewish causes. $100 million buys you a lot of political favors if you ask me. Mrs. Adelson and her husband were the power behind the scene of the first Trump administration to get them to move the US embassy to Jerusalem. She also own the largest newspaper in Israel which means she has the ability to impact public opinion inside the country. As you can see this is person with a tremendous amount money and social capital to spend and she is undoubtedly using it to get Trump to purge Gaza of the native Palestinians. Who else is in Trump's ear that influence him to come up with crazy idea? ### Jared Kushner We all know that Trump values family and loyalty above all else so it is no surprise that Trump would listen to someone in his family for guidance on what to do in Gaza. Jared Kushner is that guy for Trump. As the son-in-law of is favorite daughter you can bet that he is going to listen to what he has to say. Funny you listen to Trump and I swear that you hear Jared come out of his mouth. Back in March 2024 Kushner suggest the very idea that Trump is talking about right now! Almost verbatim to be honest. Here is a link to a talk where Kushner laid out what he thought should happen to Gaza and the Palestinians. https://www.youtube.com/watch?v=nneWrllngAU When you listen to it, you see that Trump basically took this idea from Kushner and made it his own. Who is exactly is running the show in the White House? Trump seems to be doing the bidding of everyone else except the American people. Who else is Trump listening to on the Gaza issue? #### Bibi Netanyahu/Israeli Far-Right Last but not least is the persons behind all the death and mayhem in Gaza. Trump absolutely sides with the Israeli narrative spun by Bibi Netanyahu and the Israeli far right characters such as Itamar Ben-Gvir and Bezalel Smotrich. This trio have a distinct hatred of Palestinians and do not want to see the creation of a Palestinian state. They want to see occupied West Bank annexed by Israel and all of the Palestinians there to leave or be subjugated to Israeli rule. Just take a look at the worldview of these people and they have power within the halls of the Israeli government. https://www.jpost.com/Israel-News/Politics-And-Diplomacy/Bayit-Yehudi-MK-causes-uproar-by-saying-God-commanded-Jews-not-to-sell-homes-to-Arabs-409241 https://hashiloach.org.il/israels-decisive-plan/ https://www.reuters.com/article/idUSKBN0MC1I7/ When you have this world view how is peace even possible? It's not because they don't want peace and quite frankly I don't know if its possible at this point. Israelis and Palestinians have diametrically opposing views of what the land should be. Israeli believe that the land should be exclusively governed by Jewish people whereas the Palestinian view from what I understand just want to return to the lands they were kicked out from and deal with governance later. There are elements on both side that want this conflict to go on forever because it gives the outsized power, namely Hamas on the Palestinian side and the Israeli Far Right on the Jewish side. I would guess that a majority of people in the middle would have no problem living side by side with each other as long as rights and freedoms were respected. A one state solution looks like the most reasonable solution to me but the odds of that happening are slim to none right now. President Trump has the power to change the middle east for the better if he had the backbone do to what is right but it looks like he is going to listen to people the want war, genocide and ethnic cleansing.
@ 3ad01248:962d8a07
2025-02-13 20:03:40I feel like this is go to be a common phrase over the next four years. While I generally like most of the policies that he is in favor of, I for the life of me can't understand his position on Gaza. It sounds like nothing like the Trump for the campaign trail whatsoever. When he ran for president last year he ran on a platform of not starting any new wars. Having a US solider set foot in Gaza is a recipe for disaster and chaos. Sending in the military is not "America First". Gaza has no national security implication for the United States so obviously there is a different reason why President Trump is proposing this idea. We have to look at who funded his campaign to understand his motives by wanting to clear out Gaza and rebuild it like it some real estate deal. ## Miriam Adelson [Miriam Adelson the wife of late casino magnate Sheldon Adelson](https://www.timesofisrael.com/miriam-adelson-gives-100-million-to-trump-campaign-making-good-on-reported-pledge/) gave Trump $100 million to help get Trump elected. Mrs. Adelson is a pro-Israel and supports a variety of Jewish causes. $100 million buys you a lot of political favors if you ask me. Mrs. Adelson and her husband were the power behind the scene of the first Trump administration to get them to move the US embassy to Jerusalem. She also own the largest newspaper in Israel which means she has the ability to impact public opinion inside the country. As you can see this is person with a tremendous amount money and social capital to spend and she is undoubtedly using it to get Trump to purge Gaza of the native Palestinians. Who else is in Trump's ear that influence him to come up with crazy idea? ### Jared Kushner We all know that Trump values family and loyalty above all else so it is no surprise that Trump would listen to someone in his family for guidance on what to do in Gaza. Jared Kushner is that guy for Trump. As the son-in-law of is favorite daughter you can bet that he is going to listen to what he has to say. Funny you listen to Trump and I swear that you hear Jared come out of his mouth. Back in March 2024 Kushner suggest the very idea that Trump is talking about right now! Almost verbatim to be honest. Here is a link to a talk where Kushner laid out what he thought should happen to Gaza and the Palestinians. https://www.youtube.com/watch?v=nneWrllngAU When you listen to it, you see that Trump basically took this idea from Kushner and made it his own. Who is exactly is running the show in the White House? Trump seems to be doing the bidding of everyone else except the American people. Who else is Trump listening to on the Gaza issue? #### Bibi Netanyahu/Israeli Far-Right Last but not least is the persons behind all the death and mayhem in Gaza. Trump absolutely sides with the Israeli narrative spun by Bibi Netanyahu and the Israeli far right characters such as Itamar Ben-Gvir and Bezalel Smotrich. This trio have a distinct hatred of Palestinians and do not want to see the creation of a Palestinian state. They want to see occupied West Bank annexed by Israel and all of the Palestinians there to leave or be subjugated to Israeli rule. Just take a look at the worldview of these people and they have power within the halls of the Israeli government. https://www.jpost.com/Israel-News/Politics-And-Diplomacy/Bayit-Yehudi-MK-causes-uproar-by-saying-God-commanded-Jews-not-to-sell-homes-to-Arabs-409241 https://hashiloach.org.il/israels-decisive-plan/ https://www.reuters.com/article/idUSKBN0MC1I7/ When you have this world view how is peace even possible? It's not because they don't want peace and quite frankly I don't know if its possible at this point. Israelis and Palestinians have diametrically opposing views of what the land should be. Israeli believe that the land should be exclusively governed by Jewish people whereas the Palestinian view from what I understand just want to return to the lands they were kicked out from and deal with governance later. There are elements on both side that want this conflict to go on forever because it gives the outsized power, namely Hamas on the Palestinian side and the Israeli Far Right on the Jewish side. I would guess that a majority of people in the middle would have no problem living side by side with each other as long as rights and freedoms were respected. A one state solution looks like the most reasonable solution to me but the odds of that happening are slim to none right now. President Trump has the power to change the middle east for the better if he had the backbone do to what is right but it looks like he is going to listen to people the want war, genocide and ethnic cleansing. @ 21ffd29c:518a8ff5
2025-02-13 20:03:17**Introduction:** Self sovereignty is a pivotal concept in understanding personal autonomy across various ideologies, including, libertarianism, socialism and individualism. This article explores how the statement "I own myself" by the Ole Voyager in the 1600's encapsulates this principle, emphasizing empowerment and self-management. **Article:** - **What is Self Sovereignty?** - **Definition:** It refers to the ability of an individual or group to govern themselves without external imposition. - **Core Principles:** - Autonomy: The right to manage one's own affairs independently. - Equality: Recognition of equal rights and responsibilities among individuals. - **Historical Context:** Rooted in ideas from liberalism, socialism, and feminism, advocating for personal freedom and equality. - **The Significance of 'I Own Myself'** - **Statement Explanation:** The Ole Voyager's quote highlights personal ownership over one's life, values, and destiny. - **Contrast with Traditional Views:** Shifts from societal control to individual responsibility, advocating for personal agency. - **Implications:** Encourages owning health, relationships, knowledge, and cultural identity, promoting a holistic view of self-worth. **Conclusion:** Understanding self sovereignty through the Ole Voyager's statement is crucial. It empowers individuals by asserting their right to manage their lives autonomously. This concept not only enhances personal freedom but also challenges societal structures, fostering inclusive governance that respects individual rights and equality. Not everyone has the capacity to be a sovereign and self govern themselves. Some are quite content to be told what to do and how to do it. Others are very happy to be on the dole and get free things in exchange for trinkets. This empowerment can lead to more equitable societies where individuals thrive within their own means, emphasizing empowerment and collective responsibility.
@ 21ffd29c:518a8ff5
2025-02-13 20:03:17**Introduction:** Self sovereignty is a pivotal concept in understanding personal autonomy across various ideologies, including, libertarianism, socialism and individualism. This article explores how the statement "I own myself" by the Ole Voyager in the 1600's encapsulates this principle, emphasizing empowerment and self-management. **Article:** - **What is Self Sovereignty?** - **Definition:** It refers to the ability of an individual or group to govern themselves without external imposition. - **Core Principles:** - Autonomy: The right to manage one's own affairs independently. - Equality: Recognition of equal rights and responsibilities among individuals. - **Historical Context:** Rooted in ideas from liberalism, socialism, and feminism, advocating for personal freedom and equality. - **The Significance of 'I Own Myself'** - **Statement Explanation:** The Ole Voyager's quote highlights personal ownership over one's life, values, and destiny. - **Contrast with Traditional Views:** Shifts from societal control to individual responsibility, advocating for personal agency. - **Implications:** Encourages owning health, relationships, knowledge, and cultural identity, promoting a holistic view of self-worth. **Conclusion:** Understanding self sovereignty through the Ole Voyager's statement is crucial. It empowers individuals by asserting their right to manage their lives autonomously. This concept not only enhances personal freedom but also challenges societal structures, fostering inclusive governance that respects individual rights and equality. Not everyone has the capacity to be a sovereign and self govern themselves. Some are quite content to be told what to do and how to do it. Others are very happy to be on the dole and get free things in exchange for trinkets. This empowerment can lead to more equitable societies where individuals thrive within their own means, emphasizing empowerment and collective responsibility. @ 30b99916:3cc6e3fe
2025-02-13 18:56:37## Upgrade Details Download current release and manifest files ```shell Navigate to https://github.com/getAlby/hub/releases/tag/v1.13.0/ Download albyhub-Server-Linux-x86_64.tar.bz2 manifest.txt manifext.txt.asc Copy the downloaded files to $HOME mv $HOME/Downloads/albyhub-Server-Linux-x86_64.tar.bz2 $HOME mv $HOME/Downloads/manifest.txt $HOME mv $HOME/Downloads/manifest.txt.asc $HOME ``` Verify manifest signature & Checksum ```sh Only need to import once curl https://raw.githubusercontent.com/getalby/hub/master/scripts/keys/rolznz.asc | gpg --import gpg --verify manifest.txt.asc manifest.txt gpg: Signature made Tue 07 Jan 2025 08:56:42 PM PST gpg: using RSA key 5D92185938E6DBF893DCCC5BA5EABD8835092B08 gpg: Good signature from "Roland Bewick <roland.bewick@gmail.com>" [unknown] gpg: WARNING: This key is not certified with a trusted signature! gpg: There is no indication that the signature belongs to the owner. Primary key fingerprint: 5D92 1859 38E6 DBF8 93DC CC5B A5EA BD88 3509 2B08 shasum -a 256 server-linux-x86_64.tar.bz2 a75c03d241921611dfc428c413c4a2c2cef35bc6d1974839b688ef462604058d server-linux-x86_64.tar.bz2 The above checksum should be referenced in the manifest.txt file cat manifest.txt ``` Stop AlbyHub & Backup existing data directory & Binaries ```shell systemctl stop albyhub cp -r $HOME/.local/share/albyhub /media/veracrypt1/albyhub cp $HOME/bin/albyhub $HOME/bin/albyhub172 cp -r $HOME/lib $HOME/lib172 ``` Extract new release Binaries & Start AlbyHub ```sh tar -xvjf albyhub-Server-Linux-x86_64.tar.bz2 ./ ./lib/ ./lib/libglalby_bindings.so ./lib/libldk_node.so ./lib/libbreez_sdk_bindings.so ./bin/ ./bin/albyhub systemctl start albyhub ``` Navigate to http://localhost:9090
@ 30b99916:3cc6e3fe
2025-02-13 18:56:37## Upgrade Details Download current release and manifest files ```shell Navigate to https://github.com/getAlby/hub/releases/tag/v1.13.0/ Download albyhub-Server-Linux-x86_64.tar.bz2 manifest.txt manifext.txt.asc Copy the downloaded files to $HOME mv $HOME/Downloads/albyhub-Server-Linux-x86_64.tar.bz2 $HOME mv $HOME/Downloads/manifest.txt $HOME mv $HOME/Downloads/manifest.txt.asc $HOME ``` Verify manifest signature & Checksum ```sh Only need to import once curl https://raw.githubusercontent.com/getalby/hub/master/scripts/keys/rolznz.asc | gpg --import gpg --verify manifest.txt.asc manifest.txt gpg: Signature made Tue 07 Jan 2025 08:56:42 PM PST gpg: using RSA key 5D92185938E6DBF893DCCC5BA5EABD8835092B08 gpg: Good signature from "Roland Bewick <roland.bewick@gmail.com>" [unknown] gpg: WARNING: This key is not certified with a trusted signature! gpg: There is no indication that the signature belongs to the owner. Primary key fingerprint: 5D92 1859 38E6 DBF8 93DC CC5B A5EA BD88 3509 2B08 shasum -a 256 server-linux-x86_64.tar.bz2 a75c03d241921611dfc428c413c4a2c2cef35bc6d1974839b688ef462604058d server-linux-x86_64.tar.bz2 The above checksum should be referenced in the manifest.txt file cat manifest.txt ``` Stop AlbyHub & Backup existing data directory & Binaries ```shell systemctl stop albyhub cp -r $HOME/.local/share/albyhub /media/veracrypt1/albyhub cp $HOME/bin/albyhub $HOME/bin/albyhub172 cp -r $HOME/lib $HOME/lib172 ``` Extract new release Binaries & Start AlbyHub ```sh tar -xvjf albyhub-Server-Linux-x86_64.tar.bz2 ./ ./lib/ ./lib/libglalby_bindings.so ./lib/libldk_node.so ./lib/libbreez_sdk_bindings.so ./bin/ ./bin/albyhub systemctl start albyhub ``` Navigate to http://localhost:9090 @ dbb19ae0:c3f22d5a
2025-02-13 17:46:41This code below works with nostr_sdk 0.32.2 ``` python import asyncio, argparse, json from nostr_sdk import Metadata, Client, NostrSigner, Keys, Filter, PublicKey, Kind from datetime import timedelta async def main(npub): client = Client() await client.add_relay("wss://relay.damus.io") await client.connect() pk = PublicKey.from_bech32(npub) print(f"Getting profile metadata for {npub}:") f = Filter().kind(Kind(0)).author(pk).limit(1) events = await client.get_events_of([f], timedelta(seconds=15)) if events: event = events[0] metadata_dict = json.loads(event.content()) for key, value in metadata_dict.items(): print(f"{key}: {value}") else: print("Could not retrieve metadata for the given public key.") if __name__ == '__main__': parser = argparse.ArgumentParser(description='Fetch all metadata for a given npub') parser.add_argument('npub', type=str, help='The npub of the user') args = parser.parse_args() asyncio.run(main(args.npub)) ``` but with nostr_sdk 0.39 the program no longer worked and crash with error: ``` AttributeError: type object 'PublicKey' has no attribute 'from_bech32'. Did you mean: 'to_bech32'? ``` why? --- source: - https://github.com/ev3rst/nostr_sdk_examples - https://alashazam.wordpress.com/2024/07/07/python-nostr_sdk-fetching-all-metadata/
@ dbb19ae0:c3f22d5a
2025-02-13 17:46:41This code below works with nostr_sdk 0.32.2 ``` python import asyncio, argparse, json from nostr_sdk import Metadata, Client, NostrSigner, Keys, Filter, PublicKey, Kind from datetime import timedelta async def main(npub): client = Client() await client.add_relay("wss://relay.damus.io") await client.connect() pk = PublicKey.from_bech32(npub) print(f"Getting profile metadata for {npub}:") f = Filter().kind(Kind(0)).author(pk).limit(1) events = await client.get_events_of([f], timedelta(seconds=15)) if events: event = events[0] metadata_dict = json.loads(event.content()) for key, value in metadata_dict.items(): print(f"{key}: {value}") else: print("Could not retrieve metadata for the given public key.") if __name__ == '__main__': parser = argparse.ArgumentParser(description='Fetch all metadata for a given npub') parser.add_argument('npub', type=str, help='The npub of the user') args = parser.parse_args() asyncio.run(main(args.npub)) ``` but with nostr_sdk 0.39 the program no longer worked and crash with error: ``` AttributeError: type object 'PublicKey' has no attribute 'from_bech32'. Did you mean: 'to_bech32'? ``` why? --- source: - https://github.com/ev3rst/nostr_sdk_examples - https://alashazam.wordpress.com/2024/07/07/python-nostr_sdk-fetching-all-metadata/ @ 8e56fde2:bb433b31
2025-02-13 17:41:41Let us introduce you to “**DoShit!**”: the **oracle that three friends created in order to combat creative block.** A self-produced card game made possible by the investment of a generous patreon who believed in us from the start, and in empowering people to Do their Shit. <img src="https://blossom.primal.net/6b9439e70cc5ee3e82148bf9ee9533557cd2c8569f7e37b16f2d922ec981d2c8.jpg"> ## **What is DoShit! ?** **DoShit!** is a card game that guides you in the process of building a creative life. It’s a self-reflection tool when used individually, and also a great conversation starter when played with friends or strangers. **84 oracle cards** that will help you question your fears, your strengths, doubts, excuses… DoShit! is a great companion to bring along when meeting your friends or potential collaborators. Both individually as well as collectively, the game can become very addictive once you start asking about your projects and aspirations. Sometimes the cards even lay on you hard truths necessary on the journey to self-discovery The cards are very intuitive to understand accompanied by a language that sparks profound conversations in a lightweight manner. <img src="https://blossom.primal.net/e677e9f2622d3eb86d8085a11ab85739ceaa884e3e26aa2f5c3c47a487012194.png"> Learning how to play takes less than 5 minutes and anyone can attempt to interpret the cards without any previous knowledge (even if it may feel scary at first). In fact, the card readings always benefit from people sharing their own interpretation of the cards. <img src="https://blossom.primal.net/afae65997d5222e270bdabe9bbc8762f254514deba3a9b44dbf5da194722feb9.png"> Link to [video](https://youtu.be/ZvBzlznunVo?feature=shared) ## **Why DoShit! ?** As creators, we are very aware of the struggles of building a creative life and also of how easy it can be to limit ourselves, hide behind excuses, let fear win and quit. Our philosophy in response is “Do Shit”, yes, simply **do shit**, even if it ends up being shit… The important thing is to do it! Because when you Do Shit the project no longer dies in idea valley. And the more Shit you do the better you get at doing it, shortening the Gap between your expectations and your Shit. That is why we created this tool, to accompany every DoShitter in the world on their journey (DoShitters being those who take responsibility for their Shit). These cards were born at a moment of creative block and search for answers, and we can guarantee this game has helped unstuck many people. It is also a great companion to unleash your creativity and reach beyond your comfort zone! <img src="https://blossom.primal.net/d08c811e48fca1187d894ae041174126172c24a06335b3e8655830f6247f9292.png"> ## **How did it get started?** The three of us (Mar, Elisabet & Marta) have known each other for years and we’ve always had a shared admiration for each other’s work as well as the desire to do a project together someday. One afternoon, with no specific expectations, simply wanting to enjoy ourselves without pressure, we started searching for an idea. Elisabet had some blank cards and Mar had been reading about tarot, and the idea simply sparked: we would do an oracle about the creative process with [the structure of the Hero’s Journey](https://en.wikipedia.org/wiki/Hero%27s_journey) (a concept that had followed us since we studied film school together) as a backbone. That afternoon, the first prototype of DoShit! was made. <img src="https://blossom.primal.net/c2a59b73465da2b4a42560b43f6fe1ec84681ccf577877aa2d6cbc43ef9382dd.png"> ## **The artistic process** The 84 unique cards were illustrated by Mar Delmar. Each card is created manually with cut paper and gouache, creating first the different pieces that compose each card, and then placing them together in 3D to take the photo that becomes the final illustration. The whole process took more than 8 months. Cards were painted and cut up in different locations (Barcelona, Tarragona, Castellar de n'Hug, Porrera y L'Argentera (Catalunya) y Castelo (Galicia)) where Mar attended artistic residencies along with a big box filled with the many octopuses in their envelopes, one for each card… ([Video ](https://www.instagram.com/reel/CkWQWDvj5Ab/?igshid=MzRlODBiNWFlZA==)of the process) <img src="https://blossom.primal.net/1a9a26add6e54ed30b4e48e44346567d0133934b56cbdd6e24335593d285fe22.png"> ## Where to buy this awesome Shit? - You can buy directly from our online [store](https://doshitters.bigcartel.com/product/doshit-oracle-card-game), but depending where you are in the world, shipping costs may showcase the literal cost of supporting small sellers. If you do buy it there use the promo code SATOSHI and get a small discount in return for your generosity <3 - You can also buy it with bitcoin , the best money in the world, in [Plebeian Market](https://plebeian.market/products/doshitters@ditto.pub/doshit-creative-oracle-y0fdoz0u56 ) . Since you'd be using the best money in the world, we shaved off a bit from the price and shipping in comparison to our online store since we appreciate being paid in sound money :D - You can temporarily buy this Shit on the [A\*\*\*\*\*\* giant](https://a.co/d/8ygMa8p) with FREE Shipping depending of your location or prime subscription status, but we are going to be removing our beloved DoShitS from there soon due to our very negative experience with them portrayed in our article that you can find the link to at the bottom. In any case, if you read this far, THANK YOU. You can support our Shit by gifting this deck (to someone else, or to yourself :P) , zapping this article or simply sharing it around in the hopes that THE PEOPLE WHO NEED THIS SHIT, FIND THIS SHIT <3 And if you want to know more about this inspiring product, don’t hesitate to get in touch with us. ### **We wish you the best on you creative adventures!** <img src="https://blossom.primal.net/865a8cee47bbcfe6bbcde6aa0a56d0a294d58eab99fae3414e99a7664ddcfc61.jpg"> **Join the #artMy** ARTICLE ON OUR HORRID EXPERIENCE TRYING TO MAKE "doShit!" CHEAPER TO GET FOR YOU: naddr1qvzqqqr4gupzprjklh3rdmxhj60knvpel0uk03vq3kyh4x3dlu2m7pgkcxa5xwe3qq247635g4v553t329e9x4rhvajhwvmrxahhgxv3ddc
@ 8e56fde2:bb433b31
2025-02-13 17:41:41Let us introduce you to “**DoShit!**”: the **oracle that three friends created in order to combat creative block.** A self-produced card game made possible by the investment of a generous patreon who believed in us from the start, and in empowering people to Do their Shit. <img src="https://blossom.primal.net/6b9439e70cc5ee3e82148bf9ee9533557cd2c8569f7e37b16f2d922ec981d2c8.jpg"> ## **What is DoShit! ?** **DoShit!** is a card game that guides you in the process of building a creative life. It’s a self-reflection tool when used individually, and also a great conversation starter when played with friends or strangers. **84 oracle cards** that will help you question your fears, your strengths, doubts, excuses… DoShit! is a great companion to bring along when meeting your friends or potential collaborators. Both individually as well as collectively, the game can become very addictive once you start asking about your projects and aspirations. Sometimes the cards even lay on you hard truths necessary on the journey to self-discovery The cards are very intuitive to understand accompanied by a language that sparks profound conversations in a lightweight manner. <img src="https://blossom.primal.net/e677e9f2622d3eb86d8085a11ab85739ceaa884e3e26aa2f5c3c47a487012194.png"> Learning how to play takes less than 5 minutes and anyone can attempt to interpret the cards without any previous knowledge (even if it may feel scary at first). In fact, the card readings always benefit from people sharing their own interpretation of the cards. <img src="https://blossom.primal.net/afae65997d5222e270bdabe9bbc8762f254514deba3a9b44dbf5da194722feb9.png"> Link to [video](https://youtu.be/ZvBzlznunVo?feature=shared) ## **Why DoShit! ?** As creators, we are very aware of the struggles of building a creative life and also of how easy it can be to limit ourselves, hide behind excuses, let fear win and quit. Our philosophy in response is “Do Shit”, yes, simply **do shit**, even if it ends up being shit… The important thing is to do it! Because when you Do Shit the project no longer dies in idea valley. And the more Shit you do the better you get at doing it, shortening the Gap between your expectations and your Shit. That is why we created this tool, to accompany every DoShitter in the world on their journey (DoShitters being those who take responsibility for their Shit). These cards were born at a moment of creative block and search for answers, and we can guarantee this game has helped unstuck many people. It is also a great companion to unleash your creativity and reach beyond your comfort zone! <img src="https://blossom.primal.net/d08c811e48fca1187d894ae041174126172c24a06335b3e8655830f6247f9292.png"> ## **How did it get started?** The three of us (Mar, Elisabet & Marta) have known each other for years and we’ve always had a shared admiration for each other’s work as well as the desire to do a project together someday. One afternoon, with no specific expectations, simply wanting to enjoy ourselves without pressure, we started searching for an idea. Elisabet had some blank cards and Mar had been reading about tarot, and the idea simply sparked: we would do an oracle about the creative process with [the structure of the Hero’s Journey](https://en.wikipedia.org/wiki/Hero%27s_journey) (a concept that had followed us since we studied film school together) as a backbone. That afternoon, the first prototype of DoShit! was made. <img src="https://blossom.primal.net/c2a59b73465da2b4a42560b43f6fe1ec84681ccf577877aa2d6cbc43ef9382dd.png"> ## **The artistic process** The 84 unique cards were illustrated by Mar Delmar. Each card is created manually with cut paper and gouache, creating first the different pieces that compose each card, and then placing them together in 3D to take the photo that becomes the final illustration. The whole process took more than 8 months. Cards were painted and cut up in different locations (Barcelona, Tarragona, Castellar de n'Hug, Porrera y L'Argentera (Catalunya) y Castelo (Galicia)) where Mar attended artistic residencies along with a big box filled with the many octopuses in their envelopes, one for each card… ([Video ](https://www.instagram.com/reel/CkWQWDvj5Ab/?igshid=MzRlODBiNWFlZA==)of the process) <img src="https://blossom.primal.net/1a9a26add6e54ed30b4e48e44346567d0133934b56cbdd6e24335593d285fe22.png"> ## Where to buy this awesome Shit? - You can buy directly from our online [store](https://doshitters.bigcartel.com/product/doshit-oracle-card-game), but depending where you are in the world, shipping costs may showcase the literal cost of supporting small sellers. If you do buy it there use the promo code SATOSHI and get a small discount in return for your generosity <3 - You can also buy it with bitcoin , the best money in the world, in [Plebeian Market](https://plebeian.market/products/doshitters@ditto.pub/doshit-creative-oracle-y0fdoz0u56 ) . Since you'd be using the best money in the world, we shaved off a bit from the price and shipping in comparison to our online store since we appreciate being paid in sound money :D - You can temporarily buy this Shit on the [A\*\*\*\*\*\* giant](https://a.co/d/8ygMa8p) with FREE Shipping depending of your location or prime subscription status, but we are going to be removing our beloved DoShitS from there soon due to our very negative experience with them portrayed in our article that you can find the link to at the bottom. In any case, if you read this far, THANK YOU. You can support our Shit by gifting this deck (to someone else, or to yourself :P) , zapping this article or simply sharing it around in the hopes that THE PEOPLE WHO NEED THIS SHIT, FIND THIS SHIT <3 And if you want to know more about this inspiring product, don’t hesitate to get in touch with us. ### **We wish you the best on you creative adventures!** <img src="https://blossom.primal.net/865a8cee47bbcfe6bbcde6aa0a56d0a294d58eab99fae3414e99a7664ddcfc61.jpg"> **Join the #artMy** ARTICLE ON OUR HORRID EXPERIENCE TRYING TO MAKE "doShit!" CHEAPER TO GET FOR YOU: naddr1qvzqqqr4gupzprjklh3rdmxhj60knvpel0uk03vq3kyh4x3dlu2m7pgkcxa5xwe3qq247635g4v553t329e9x4rhvajhwvmrxahhgxv3ddc @ 89ccea93:df4e00b7
2025-02-13 17:34:06**[Original Post](https://expatriotic.me/grapheneos/)** ## Core Philosophy 1. **Privacy ≠ Optional**: Prevents mass data collection by design 2. **Security > Convenience**: Sacrifices "smart" features for exploit resistance 3. **Transparency**: Every line of code [auditable](https://github.com/GrapheneOS) 4. **Device Sanity**: Removes 2M+ lines of Google telemetry code 5. **Proactive Hardening**: Replaces reactive "vulnerability whack-a-mole" with systemic memory safety improvements. 73% of Android CVEs prevented via Scudo++ allocator and Rust integration. 6. **Hardware Paradox**: Uses Google Pixels *because* of their Titan M2 secure enclave (physically separate from main CPU, Verified Boot with user-defined root of trust, Firmware-level MAC randomization (prevents Wi-Fi tracking)). 7. **Support Superiority**: GrapheneOS support for Pixel phones is 2 years longer Google's. > *"We're eliminating entire vulnerability classes - not just patching holes."* ## **History** * Born in **2014** as **CopperheadOS** * **2016**: First Pixel support (Google's hardware + de-Googled OS) * Rebranded in **2019** after a developer split. Focuses exclusively on Pixel phones. * **2021**: **Scudo++** with quarantines (NSA-grade exploit mitigation) * **2023**: Full Rust integration (prevents buffer overflows in core OS) * **2023**: Controversial lead dev, Daniel Micay, stepped down but remains director * **2024**: Quantum-resistant encryption prototypes > *"Our Auditor app detects hardware tampering better than Apple's T2 chip."* ## **Installation** * **Minimum**: Pixel 4a * **Recommended**: Pixel 7a (5-year update guarantee) * **Backup data first**: unlocking bootloader wipes device ### **Beginners: Web Installer** 1. Enable OEM Unlock: `Settings → About → Tap Build Number 7x → Developer Options → OEM Unlocking` 2. Visit [grapheneos.org/install](https://grapheneos.org/install) 3. Connect phone → Follow prompts (20 minutes) ### **Advanced: CLI install** * Full CLI guide: [grapheneos.org/install/cli](https://grapheneos.org/install/cli) (8 minutes) >*"We're proving iPhones aren't the only secure option - just better marketed."* ### **Post-Install Checklist** [ ] Deny all "convenience" permissions [ ] Enable Sensors Off toggle [ ] Install Auditor app [ ] Sensors Killswitch: `Quick Settings → Toggle Off` [ ] Network Restrictions: ```markdown Settings → Network & Internet → Firewall - Enable per-connection MAC randomization - Block local network discovery ``` [ ] Auditor Validation: Daily automated checks against Google's hardware certs ## Setting up ### **Priority Sources** 1. **Accrescent** (Pre-installed) - Molly (Signal fork) - Aves Gallery (EXIF stripping) - AppVerifier (APK validation) 2. **Obtainium** ([GitHub](https://github.com/ImranR98/Obtainium)) ```markdown 1. Search "[App] GitHub releases" 2. Copy releases page URL 3. Paste into Obtainium → Auto-updates enabled ``` - *Example*: NewPipe → `https://github.com/TeamNewPipe/NewPipe/releases` 3. **Google Play** (Last Resort) - Use separate profile - Burner account: Fake name + **NO phone number** ## FOSS Apps * Accrescent - Privacy-focused app store * Aegis - 2FA authenticator * Amethyst - Nostr decentralized social client * AndBible - Offline Bible study * Antennapod - Podcast manager * AppVerifier - APK signature validation * Ashigaru - Bitcoin wallet with Ricochet * Aves Gallery - Gallery with EXIF stripping * Brave - Anti-fingerprinting browser * Easy Noise - Offline white noise generator * Easy Note - Minimalist notes * Envoy - Bitcoin wallet * IronFox - Hardened Firefox fork * KeePassDX - Offline password manager * Léon - URL tracking stripper * LocalSend - AirDrop alternative * Material Files - File manager * Molly - Signal fork with local encyption * Monero.com - Official Monero wallet * NetGuard - No-root firewall * NewPipe - YouTube client with SponsorBlock * Nextcloud - Self-hosted cloud suite * OpenKeychain - PGP encryption * Organic Maps - Offline navigation * Orbot - Tor proxy * Proton Drive - E2E encrypted storage * Proton Mail - Zero-access email * RedReader - Privacy-first Reddit client * Simple Calendar Pro - Telemetry-free calendar * Telegram FOSS - Decentralized messaging * Tor Browser - Onion-routed browsing * Twidere - Twitter/Fediverse client * Tuta - Encrypted email * Tuta Calendar - Encrypted calendar * Vanadium - Hardened Chromium * Zeus - Bitcoin Lightning node > _"Your phone is a corporate surveillance device that happens to make calls. GrapheneOS removes the spyware OS while keeping the secure hardware."_ ## **Silent.Link eSIM: Anonymous Connectivity** **No Phone Number Required** Visit [Silent.Link](https://silent.link) → Select data plus eSIM plan (with NO phone number). ```I've used this successfully in many countries. It even gives me unfettered and free internet in China. Be sure to pick the telecom company based on what they charge per GB of data. The difference can be 100x!``` ## Support the Project: - **Donate**: [grapheneos.org/donate](https://grapheneos.org/donate) - **Community**: [grapheneos.org/contact](https://grapheneos.org/contact) >*"GrapheneOS isn't about becoming a privacy expert overnight. It's about systematically removing corporate surveillance hooks - one app, one permission, one profile at a time."* ## Moar Halp * **[Side Of Burritos](https://www.youtube.com/playlist?list=PLHvdaysg3bMyYwJAcxbFUY9YqKKC0Dtrd)** * **[Hated One interview with GrapheneOS dev Gabe](https://www.youtube.com/watch?v=WkQ_OCzuLNg)** originally posted at https://stacker.news/items/884965
@ 89ccea93:df4e00b7
2025-02-13 17:34:06**[Original Post](https://expatriotic.me/grapheneos/)** ## Core Philosophy 1. **Privacy ≠ Optional**: Prevents mass data collection by design 2. **Security > Convenience**: Sacrifices "smart" features for exploit resistance 3. **Transparency**: Every line of code [auditable](https://github.com/GrapheneOS) 4. **Device Sanity**: Removes 2M+ lines of Google telemetry code 5. **Proactive Hardening**: Replaces reactive "vulnerability whack-a-mole" with systemic memory safety improvements. 73% of Android CVEs prevented via Scudo++ allocator and Rust integration. 6. **Hardware Paradox**: Uses Google Pixels *because* of their Titan M2 secure enclave (physically separate from main CPU, Verified Boot with user-defined root of trust, Firmware-level MAC randomization (prevents Wi-Fi tracking)). 7. **Support Superiority**: GrapheneOS support for Pixel phones is 2 years longer Google's. > *"We're eliminating entire vulnerability classes - not just patching holes."* ## **History** * Born in **2014** as **CopperheadOS** * **2016**: First Pixel support (Google's hardware + de-Googled OS) * Rebranded in **2019** after a developer split. Focuses exclusively on Pixel phones. * **2021**: **Scudo++** with quarantines (NSA-grade exploit mitigation) * **2023**: Full Rust integration (prevents buffer overflows in core OS) * **2023**: Controversial lead dev, Daniel Micay, stepped down but remains director * **2024**: Quantum-resistant encryption prototypes > *"Our Auditor app detects hardware tampering better than Apple's T2 chip."* ## **Installation** * **Minimum**: Pixel 4a * **Recommended**: Pixel 7a (5-year update guarantee) * **Backup data first**: unlocking bootloader wipes device ### **Beginners: Web Installer** 1. Enable OEM Unlock: `Settings → About → Tap Build Number 7x → Developer Options → OEM Unlocking` 2. Visit [grapheneos.org/install](https://grapheneos.org/install) 3. Connect phone → Follow prompts (20 minutes) ### **Advanced: CLI install** * Full CLI guide: [grapheneos.org/install/cli](https://grapheneos.org/install/cli) (8 minutes) >*"We're proving iPhones aren't the only secure option - just better marketed."* ### **Post-Install Checklist** [ ] Deny all "convenience" permissions [ ] Enable Sensors Off toggle [ ] Install Auditor app [ ] Sensors Killswitch: `Quick Settings → Toggle Off` [ ] Network Restrictions: ```markdown Settings → Network & Internet → Firewall - Enable per-connection MAC randomization - Block local network discovery ``` [ ] Auditor Validation: Daily automated checks against Google's hardware certs ## Setting up ### **Priority Sources** 1. **Accrescent** (Pre-installed) - Molly (Signal fork) - Aves Gallery (EXIF stripping) - AppVerifier (APK validation) 2. **Obtainium** ([GitHub](https://github.com/ImranR98/Obtainium)) ```markdown 1. Search "[App] GitHub releases" 2. Copy releases page URL 3. Paste into Obtainium → Auto-updates enabled ``` - *Example*: NewPipe → `https://github.com/TeamNewPipe/NewPipe/releases` 3. **Google Play** (Last Resort) - Use separate profile - Burner account: Fake name + **NO phone number** ## FOSS Apps * Accrescent - Privacy-focused app store * Aegis - 2FA authenticator * Amethyst - Nostr decentralized social client * AndBible - Offline Bible study * Antennapod - Podcast manager * AppVerifier - APK signature validation * Ashigaru - Bitcoin wallet with Ricochet * Aves Gallery - Gallery with EXIF stripping * Brave - Anti-fingerprinting browser * Easy Noise - Offline white noise generator * Easy Note - Minimalist notes * Envoy - Bitcoin wallet * IronFox - Hardened Firefox fork * KeePassDX - Offline password manager * Léon - URL tracking stripper * LocalSend - AirDrop alternative * Material Files - File manager * Molly - Signal fork with local encyption * Monero.com - Official Monero wallet * NetGuard - No-root firewall * NewPipe - YouTube client with SponsorBlock * Nextcloud - Self-hosted cloud suite * OpenKeychain - PGP encryption * Organic Maps - Offline navigation * Orbot - Tor proxy * Proton Drive - E2E encrypted storage * Proton Mail - Zero-access email * RedReader - Privacy-first Reddit client * Simple Calendar Pro - Telemetry-free calendar * Telegram FOSS - Decentralized messaging * Tor Browser - Onion-routed browsing * Twidere - Twitter/Fediverse client * Tuta - Encrypted email * Tuta Calendar - Encrypted calendar * Vanadium - Hardened Chromium * Zeus - Bitcoin Lightning node > _"Your phone is a corporate surveillance device that happens to make calls. GrapheneOS removes the spyware OS while keeping the secure hardware."_ ## **Silent.Link eSIM: Anonymous Connectivity** **No Phone Number Required** Visit [Silent.Link](https://silent.link) → Select data plus eSIM plan (with NO phone number). ```I've used this successfully in many countries. It even gives me unfettered and free internet in China. Be sure to pick the telecom company based on what they charge per GB of data. The difference can be 100x!``` ## Support the Project: - **Donate**: [grapheneos.org/donate](https://grapheneos.org/donate) - **Community**: [grapheneos.org/contact](https://grapheneos.org/contact) >*"GrapheneOS isn't about becoming a privacy expert overnight. It's about systematically removing corporate surveillance hooks - one app, one permission, one profile at a time."* ## Moar Halp * **[Side Of Burritos](https://www.youtube.com/playlist?list=PLHvdaysg3bMyYwJAcxbFUY9YqKKC0Dtrd)** * **[Hated One interview with GrapheneOS dev Gabe](https://www.youtube.com/watch?v=WkQ_OCzuLNg)** originally posted at https://stacker.news/items/884965 @ dbb19ae0:c3f22d5a
2025-02-13 17:32:36pip cache will show how much space is taken from past download ``` bash (nostr) ever3st@Alashazam:~/Documents/dev/python/$ pip cache info Package index page cache location: /home/ever3st/.cache/pip/http Package index page cache size: 2437.7 MB Number of HTTP files: 271 Wheels location: /home/ever3st/.cache/pip/wheels Wheels size: 2.2 MB Number of wheels: 2 ``` About 2GB if space is needed it can be cleared ``` bash (nostr) ever3st@Alashazam:~/Documents/dev/python/$ pip cache purge Files removed: 273 (nostr) ever3st@Alashazam:~/Documents/dev/python/bots/nostr$ pip cache info Package index page cache location: /home/ever3st/.cache/pip/http Package index page cache size: 0 bytes Number of HTTP files: 0 Wheels location: /home/ever3st/.cache/pip/wheels Wheels size: 326 bytes Number of wheels: 0 ```
@ dbb19ae0:c3f22d5a
2025-02-13 17:32:36pip cache will show how much space is taken from past download ``` bash (nostr) ever3st@Alashazam:~/Documents/dev/python/$ pip cache info Package index page cache location: /home/ever3st/.cache/pip/http Package index page cache size: 2437.7 MB Number of HTTP files: 271 Wheels location: /home/ever3st/.cache/pip/wheels Wheels size: 2.2 MB Number of wheels: 2 ``` About 2GB if space is needed it can be cleared ``` bash (nostr) ever3st@Alashazam:~/Documents/dev/python/$ pip cache purge Files removed: 273 (nostr) ever3st@Alashazam:~/Documents/dev/python/bots/nostr$ pip cache info Package index page cache location: /home/ever3st/.cache/pip/http Package index page cache size: 0 bytes Number of HTTP files: 0 Wheels location: /home/ever3st/.cache/pip/wheels Wheels size: 326 bytes Number of wheels: 0 ``` @ 6538925e:571e55c3
2025-02-13 16:05:42\ **Nostr Live Streams (Beta)** If you follow shows like Rabbit Hole Recap, THE Bitcoin Podcast or Simply Bitcoin on Nostr, you can now watch the video in Fountain and hang out in the live chat as it’s being recorded. You'll find livestreams from people who follow on Nostr at the top of the home screen. As well and live podcasts, you will also find live music events from PhantomPowerMedia, radio stations like NoGood and Noderunners, as well as channels dedicated to gaming, art, coding and much more. Bringing creators and fans together through live experiences enables audience participation and creates a special feeling of community, so we’re really excited to get this into your hands. Nostr livestreams are a beta feature - i.e. we still have a lot more work to do! We will continue to make improvements to livestreams over the coming months - so we would love to hear your feedback. \ **Storage Manager** We’ve added a storage manager in the app’s settings so that you can view file storage size for audio downloads, video downloads, transcripts, image cache, feed cache, and temp files. You can delete all files in any of these folders to free up storage on your device so that Fountain continues to run optimally. There are other performance and stability improvements that we are working on too. For example, in the next couple of weeks we will be rolling out an image proxy service, which should reduce mobile data usage and optimise storage. Stay tuned for further updates and, as always, thanks for your support.
@ 6538925e:571e55c3
2025-02-13 16:05:42\ **Nostr Live Streams (Beta)** If you follow shows like Rabbit Hole Recap, THE Bitcoin Podcast or Simply Bitcoin on Nostr, you can now watch the video in Fountain and hang out in the live chat as it’s being recorded. You'll find livestreams from people who follow on Nostr at the top of the home screen. As well and live podcasts, you will also find live music events from PhantomPowerMedia, radio stations like NoGood and Noderunners, as well as channels dedicated to gaming, art, coding and much more. Bringing creators and fans together through live experiences enables audience participation and creates a special feeling of community, so we’re really excited to get this into your hands. Nostr livestreams are a beta feature - i.e. we still have a lot more work to do! We will continue to make improvements to livestreams over the coming months - so we would love to hear your feedback. \ **Storage Manager** We’ve added a storage manager in the app’s settings so that you can view file storage size for audio downloads, video downloads, transcripts, image cache, feed cache, and temp files. You can delete all files in any of these folders to free up storage on your device so that Fountain continues to run optimally. There are other performance and stability improvements that we are working on too. For example, in the next couple of weeks we will be rolling out an image proxy service, which should reduce mobile data usage and optimise storage. Stay tuned for further updates and, as always, thanks for your support. @ f1989a96:bcaaf2c1
2025-02-13 14:24:32Good morning, readers! This week, we highlight how authoritarian regimes are manipulating digital assets. The Central African Republic launched a government-backed meme coin that crashed spectacularly within a day of launch as regime insiders cashed out for profits, leaving the public with worthless tokens. Meanwhile, the Nigerian regime introduced its first official stablecoin, cNGN. It is issued by the African Stablecoin Consortium and is backed 1:1 with the naira. Still, it operates under the direct oversight of the Nigerian Securities and Exchange Commission, allowing further surveillance of Nigerians’ financial activity alongside the struggling eNaira CBDC. On the freedom tech front, Mullad VPN now supports Bitcoin payments via the Lightning Network, offering activists, journalists, and individuals under oppressive regimes a censorship-resistant and permissionless way to pay for their privacy. Additionally, SeedSigner, an open-source hardware wallet for Bitcoin self-custody, rolled out multilingual support, expanding accessibility to Spanish-speaking activists and human rights defenders.\ \ Finally, journalist Frank Corva explores Africa’s grassroots Bitcoin movement, where open-source tools and circular economies are empowering communities inside authoritarian regimes with financial freedom. For those who doubt Bitcoin’s real-world impact, this article is a must-read. **Now, let’s get right to it!** ### [**Subscribe Here**](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a) ## **GLOBAL NEWS** #### **Central African Republic | Launches Meme Coin Experiment** The Central African Republic (CAR) [debuted](https://www.reuters.com/world/africa/central-african-republic-debuts-meme-coin-experiment-2025-02-10/) a government-backed meme coin, $CAR, which President Faustin-Archange Touadéra [claims](https://www.reuters.com/world/africa/central-african-republic-debuts-meme-coin-experiment-2025-02-10/) will “unite people” and “support national development.” In reality, meme coins are speculative assets that often serve as vehicles for insider profit. This scheme follows CAR’s failed [Sango Coin](https://www.mariblock.com/central-african-republic-top-court-rules-sango-coin-unconstitutional/) project, which promised citizenship and land in exchange for [locked](https://www.mariblock.com/central-african-republic-top-court-rules-sango-coin-unconstitutional/) investments but sold only 7.5% of its supply. Those who did “buy in” did not receive what was promised. In 2022, CAR briefly made Bitcoin legal tender, calling it a path to sovereignty — only to [abandon](https://bitcoinmagazine.com/culture/why-bitcoin-failed-in-car) it shortly after. Instead of supporting open and neutral money like Bitcoin, the government has turned to dubious crypto schemes. The real beneficiaries of $CAR appear to be regime insiders who reportedly cashed out [$40 million](https://x.com/bored2boar/status/1889002901370196098) while the public holds [worthless](https://decrypt.co/305225/central-african-republic-president-meme-coin) tokens. #### **Nigeria | Debuts Naira Stablecoin** The Nigerian state [launched](https://www.mariblock.com/move-over-enaira-cngn-enters-the-chat-2/) its first regulated stablecoin, [cNGN](https://cngn.co/?ref=mariblock.com). Similar to US dollar-pegged stablecoins like USDT and USDC, cNGN is pegged 1:1 to its local currency (the naira). It is issued by the African Stablecoin Consortium (ASC), a private coalition of Nigerian financial institutions and blockchain companies. Positioned as a bridge between fiat and digital assets, cNGN aims to facilitate remittances and trade but comes with strict verification requirements that limit financial privacy. The Nigerian SEC also tightly regulates the stablecoin and it is only available on government-approved exchanges, Busha and Quidax. As Nigeria expands its control over digital transactions — through both cNGN and its struggling [eNaira CBDC](https://cbdctracker.hrf.org/currency/nigeria) — more and more Nigerians are [turning](https://www.forbes.com/sites/digital-assets/2024/01/08/central-bank-of-nigeria-approves-naira-stablecoin-for-2024-launch/) to Bitcoin as a censorship-resistant alternative. #### **Russia | Proposes Registry to Track Bitcoin Mining Hardware** Russia’s deputy energy minister, Yevgeny Grabchak, has [proposed](https://theminermag.com/news/2025-02-03/russia-minister-bitcoin-miner/) a centralized registry of Bitcoin mining equipment and wallet addresses to “identify mining activities and ensure stricter enforcement of bans in restricted regions,” such as Russian-occupied Ukraine territories. Meanwhile, the Chairman of the State Duma Committee on Energy, Nikolai Shulginov, warned that last year’s mining ban in several Russian and occupied regions may not be enough to eliminate mining fully. As an authoritarian state with an egregious human rights record and a long history of financial repression, Russia appears intent on tightening surveillance of economic activity — especially that of Bitcoin. By registering, tracking, and restricting mining, the Kremlin expands its financial control, undermines economic autonomy, and limits access to permissionless money. #### **Turkey | Erdoğan Targets Opposition as Inflation Forecast Rises** Turkish President Recep Tayyip Erdoğan sentenced Istanbul Mayor Ekrem Imamoglu — a key political rival — to [seven](https://www.bloomberg.com/news/articles/2025-02-05/turkey-s-main-rival-to-erdogan-faces-jail-time-in-new-indictment) years in prison on charges widely seen as politically motivated. If upheld, the conviction will bar Imamoglu from office, further clearing Erdoğan’s path to dominance ahead of the 2028 elections. At the same time, Turkey’s economic crisis is worsening. [Accelerating inflation](https://www.reuters.com/world/middle-east/turkey-cenbank-raises-inflation-forecast-says-not-autopilot-with-cuts-2025-02-07/) forced the central bank to raise its 2025 forecast from 21% to 24%, exacerbating the lira’s decline and eroding purchasing power. As both political and financial repression deepen, more Turks are turning to alternatives to sidestep Erdoğan’s expanding control over the economic and political sphere. #### **Georgia | Regime to Pass Censorship Law** Georgia’s ruling Georgian Dream party is set to introduce a media censorship [law](https://jam-news.net/georgian-dream-plans-to-pass-media-censorship-law/) aimed at enforcing government-defined standards for journalistic objectivity and ethics, while also restricting foreign funding for media outlets. MP Mamuka Mdinaradze [claims](https://jam-news.net/ngos-and-media-organizations-of-georgia-to-challenge-the-foreign-agents-law-in-strasbourg-court/) the law will establish monitoring mechanisms and is modeled after UK regulations, though critics [compare](https://jam-news.net/opinion-ivanishvili-adopts-belarusian-tactics-to-control-protests/) it to Belarusian-style repression. Georgian Dream Prime Minister Irakli Kobakhidze defended the move as necessary to close legislative “loopholes” and strengthen state control. Journalists and activists warn that the law is part of a broader crackdown on press freedom and dissent. Decentralized social networks like Nostr will become increasingly vital for journalists and activists to communicate freely, resist censorship, and ensure the flow of independent information. \___________________________________________________________\_ #### **Webinar Series for Nonprofits: Become Unstoppable** HRF will host a [free, three-day webinar](https://docs.google.com/forms/d/e/1FAIpQLSf0sjqwSFQo8HGMsWIIDRyhx34TsoonOSTfYoWSy-aaBbLeSw/viewform) from March 17-19, teaching human rights defenders and nonprofits how to use Bitcoin to counter state censorship and confiscation. Sessions run daily from 10:30 a.m. to 12:00 p.m. EDT and are beginner-friendly. The webinar will be led by Anna Chekhovich, HRF’s Bitcoin nonprofit adoption lead and financial manager at Alexei Navalny’s Anti-Corruption Foundation. ### [Register Here](https://docs.google.com/forms/d/e/1FAIpQLSf0sjqwSFQo8HGMsWIIDRyhx34TsoonOSTfYoWSy-aaBbLeSw/viewform) #### **SXSW | The Human Rights Risks of Central Bank Digital Currencies (CBDCs)** Join HRF at [SXSW 2025](https://www.sxsw.com/) in Austin from March 9-12 to explore how CBDCs threaten financial freedom. Experts [Roger Huang](https://x.com/Rogerh1991), [Charlene Fadirepo](https://x.com/CharFadirepo), and [Nick Anthony](https://x.com/EconWithNick) will discuss how authoritarian regimes use CBDCs for surveillance and control on March 9. Attendees can also visit HRF’s [CBDC Tracker](https://cbdctracker.hrf.org/) booth to explore an interactive map of CBDC developments worldwide. ### [Get Tickets](https://www.sxsw.com/conference/) \___________________________________________________________\_ ## BITCOIN AND FREEDOM TECH NEWS #### **Mullvad VPN | Testing Lightning Network Payments** [Mullvad VPN](https://mullvad.net/en) is experimenting with Bitcoin for payments via the Lightning Network, a second-layer payment protocol built on Bitcoin that enables faster, cheaper, and more private transactions. This integration lets Mullvad VPN users pay for their services in bitcoin while enhancing their privacy and bypassing payment networks that track or censor financial activity. VPNs protect users by masking IP addresses and encrypting traffic. Accepting Bitcoin over Lightning strengthens this protection with a censorship-resistant payment option. For activists, journalists, and individuals in authoritarian regimes, this combination provides a shield against surveillance. #### **SeedSigner | Releases Multilingual Support** [SeedSigner](https://seedsigner.com/), an open-source and customizable Bitcoin hardware wallet and HRF grantee, [introduced](https://github.com/SeedSigner/seedsigner/releases/tag/0.8.5) multilingual support for Spanish. This update makes secure Bitcoin self-custody more accessible to Spanish-speaking activists and human rights defenders who may rely on Bitcoin for transactional freedom. By expanding access to secure self-custody, SeedSigner helps reduce dependence on restrictive financial systems and allows more people in Nicaragua, Venezuela, Cuba, and beyond to “be their own bank.” #### **Iris | Implements Private Bitcoin Payments with Cashu** [Iris](https://iris.cx/), a Nostr client, has added support for a Cashu wallet to allow users to send and receive ecash. Cashu is an open-source Chaumian ecash protocol built for Bitcoin and integrated with the Lightning Network. It lets users make fast, low-cost, and extremely private transactions using Bitcoin-backed ecash. While it requires a trusted custodian, it helps users spend Bitcoin anonymously without revealing their identity or transaction activity. This ability provides activists and nonprofits a different way to make private Bitcoin payments alongside nostr’s censorship-resistant communications. #### **Sparrow Wallet | Supports Lark for USB Hardware Wallets** [Sparrow Wallet](https://sparrowwallet.com/), a popular open-source Bitcoin wallet, has added support for [Lark](https://github.com/sparrowwallet/larkapp?mc_cid=aab08acf41&mc_eid=5c5878c08e), a new tool for USB hardware wallet communication. Lark works alongside the existing [Hardware Wallet Interface](https://github.com/bitcoin-core/HWI) (HWI), giving users an alternative way to connect their hardware wallets via USB. This update improves reliability, reduces dependence on a single software interface, and strengthens Bitcoin self-custody. #### **Bitcoin Dada | Opens Applications for Second Cohort of Dada Devs** [Bitcoin Dada](https://btcdada.com/), an HRF-supported nonprofit initiative empowering African women through Bitcoin and financial education, is now [accepting](https://x.com/DadaDevs/status/1886819762660929674) applications for the second cohort of Dada Devs. This developer program provides hands-on training, mentorship, and a collaborative community to help African women under authoritarian regimes contribute to Bitcoin development. If you’re an aspiring female developer, [apply now](https://docs.google.com/forms/d/e/1FAIpQLSeJ8nXL96qNeCAaXnSlGxqykBPEGm21z9qS9oE1ldNusM0nTA/viewform) to join a network of African women shaping the future of finance. Applications close Feb. 13. #### **Summer of Bitcoin | Applications for Summer 2025 Cohort Now Open** [Summer of Bitcoin](https://www.summerofbitcoin.org/), an HRF-supported Bitcoin internship program, is now accepting [applications](https://www.summerofbitcoin.org/apply) for its summer 2025 cohort. This program introduces students from anywhere, including from authoritarian regimes, to Bitcoin open-source development and design, giving interns the option to choose between a developer or designer track based on their interests. Participants will gain hands-on work experience, contribute to real-world Bitcoin projects, and receive mentorship from industry leaders. You can learn more and apply [here](https://www.summerofbitcoin.org/). #### **Spiral | Announces Grant Renewals for the Bitcoin Design Community and BDK** [Spiral](http://spiral.xyz), a Bitcoin company building and funding open-source projects, announced renewed grants for critical initiatives, including the [Bitcoin Design Community](https://github.com/bitcoindesign) and [Bitcoin Dev Kit](https://bitcoindevkit.org/) (BDK). The Bitcoin Design Community is a free and open-source resource for designers, developers, and others working on non-custodial Bitcoin products. This [grant](https://x.com/spiralbtc/status/1885000120439095607) will support designers who push the user experience and adoption of Bitcoin forward. Meanwhile, BDK is a software library that helps developers in building cross-platform Bitcoin wallets. Its [grant](https://x.com/spiralbtc/status/1884998758976405840) will support the project’s continued refinement and development. ## RECOMMENDED CONTENT #### **The Bitcoin and Cypherpunk Spirit Is Alive and Well in Africa by Frank Corva** In this [article](https://bitcoinmagazine.com/culture/the-bitcoin-and-cypherpunk-spirit-is-alive-and-well-in-africa) for [Bitcoin Magazine](http://bitcoinmagazine.com), journalist [Frank Corva](https://x.com/frankcorva) spotlights Bitcoin's growing presence across Africa. Across the continent, people are building Bitcoin circular economies, open-source financial tools, and educational initiatives. From [Bitcoin Ekasi](https://x.com/BitcoinEkasi) in South Africa to [AfriBit Kibera](https://x.com/AfribitKibera) in Kenya and [Bitcoin Dua](https://x.com/bitcoin_dua) in Ghana, these grassroots initiatives drive financial inclusion and education for individuals and communities. Meanwhile, tools like [Tando](https://tando.me/) and [Machankura](https://8333.mobi/) are expanding access to transactional freedom, and conferences like [Adopting Bitcoin Captetown](https://za25.adoptingbitcoin.org/) and the [Africa Bitcoin Conference](https://afrobitcoin.org/) nurture ongoing collaboration between individuals, developers, and activists to advance financial freedom on a continent that otherwise has very little liberal democracy. Read the full article [here](https://bitcoinmagazine.com/culture/the-bitcoin-and-cypherpunk-spirit-is-alive-and-well-in-africa). #### **Using Bitcoin Without Internet! Here’s How Machankura Makes It Happen with Anita Posch** In this short [interview](https://www.youtube.com/watch?v=XzXfd237XVo), Bitcoin educator and host of the [Bitcoin for Fairness](https://www.youtube.com/@AnitaPosch) channel, Anita Posch, speaks with Mary Imasuen, a [Machankura](https://8333.mobi/) team member, about how this technology makes Bitcoin accessible to Africans without Internet access. Machankura is an app that allows feature phones to send and receive Bitcoin using the Unstructured Supplementary Service Data (USSD) protocol, a mobile communications system similar to SMS. This means people can transact in Bitcoin without needing a smartphone or data connection, a situation common to many living under autocratic regimes in sub-Saharan Africa. By removing Internet barriers, Machankura helps millions of Africans overcome high data costs and unreliable networks, offering a practical solution to financial inclusion. *If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report [here](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a).* *Support the newsletter by donating bitcoin to HRF’s Financial Freedom program [via BTCPay](https://hrf.org/btc).*\ *Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ [hrf.org](http://hrf.org/)* *The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals [here](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1)*. [**Subscribe to newsletter**](http://financialfreedomreport.org/) [**Apply for a grant**](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1&mc_cid=39c1c9b7e8&mc_eid=778e9876e3) [**Support our work**](https://hrf.org/btc?mc_cid=39c1c9b7e8&mc_eid=778e9876e3) [**Visit our website**](https://hrf.org/programs/financial-freedom/)
@ f1989a96:bcaaf2c1
2025-02-13 14:24:32Good morning, readers! This week, we highlight how authoritarian regimes are manipulating digital assets. The Central African Republic launched a government-backed meme coin that crashed spectacularly within a day of launch as regime insiders cashed out for profits, leaving the public with worthless tokens. Meanwhile, the Nigerian regime introduced its first official stablecoin, cNGN. It is issued by the African Stablecoin Consortium and is backed 1:1 with the naira. Still, it operates under the direct oversight of the Nigerian Securities and Exchange Commission, allowing further surveillance of Nigerians’ financial activity alongside the struggling eNaira CBDC. On the freedom tech front, Mullad VPN now supports Bitcoin payments via the Lightning Network, offering activists, journalists, and individuals under oppressive regimes a censorship-resistant and permissionless way to pay for their privacy. Additionally, SeedSigner, an open-source hardware wallet for Bitcoin self-custody, rolled out multilingual support, expanding accessibility to Spanish-speaking activists and human rights defenders.\ \ Finally, journalist Frank Corva explores Africa’s grassroots Bitcoin movement, where open-source tools and circular economies are empowering communities inside authoritarian regimes with financial freedom. For those who doubt Bitcoin’s real-world impact, this article is a must-read. **Now, let’s get right to it!** ### [**Subscribe Here**](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a) ## **GLOBAL NEWS** #### **Central African Republic | Launches Meme Coin Experiment** The Central African Republic (CAR) [debuted](https://www.reuters.com/world/africa/central-african-republic-debuts-meme-coin-experiment-2025-02-10/) a government-backed meme coin, $CAR, which President Faustin-Archange Touadéra [claims](https://www.reuters.com/world/africa/central-african-republic-debuts-meme-coin-experiment-2025-02-10/) will “unite people” and “support national development.” In reality, meme coins are speculative assets that often serve as vehicles for insider profit. This scheme follows CAR’s failed [Sango Coin](https://www.mariblock.com/central-african-republic-top-court-rules-sango-coin-unconstitutional/) project, which promised citizenship and land in exchange for [locked](https://www.mariblock.com/central-african-republic-top-court-rules-sango-coin-unconstitutional/) investments but sold only 7.5% of its supply. Those who did “buy in” did not receive what was promised. In 2022, CAR briefly made Bitcoin legal tender, calling it a path to sovereignty — only to [abandon](https://bitcoinmagazine.com/culture/why-bitcoin-failed-in-car) it shortly after. Instead of supporting open and neutral money like Bitcoin, the government has turned to dubious crypto schemes. The real beneficiaries of $CAR appear to be regime insiders who reportedly cashed out [$40 million](https://x.com/bored2boar/status/1889002901370196098) while the public holds [worthless](https://decrypt.co/305225/central-african-republic-president-meme-coin) tokens. #### **Nigeria | Debuts Naira Stablecoin** The Nigerian state [launched](https://www.mariblock.com/move-over-enaira-cngn-enters-the-chat-2/) its first regulated stablecoin, [cNGN](https://cngn.co/?ref=mariblock.com). Similar to US dollar-pegged stablecoins like USDT and USDC, cNGN is pegged 1:1 to its local currency (the naira). It is issued by the African Stablecoin Consortium (ASC), a private coalition of Nigerian financial institutions and blockchain companies. Positioned as a bridge between fiat and digital assets, cNGN aims to facilitate remittances and trade but comes with strict verification requirements that limit financial privacy. The Nigerian SEC also tightly regulates the stablecoin and it is only available on government-approved exchanges, Busha and Quidax. As Nigeria expands its control over digital transactions — through both cNGN and its struggling [eNaira CBDC](https://cbdctracker.hrf.org/currency/nigeria) — more and more Nigerians are [turning](https://www.forbes.com/sites/digital-assets/2024/01/08/central-bank-of-nigeria-approves-naira-stablecoin-for-2024-launch/) to Bitcoin as a censorship-resistant alternative. #### **Russia | Proposes Registry to Track Bitcoin Mining Hardware** Russia’s deputy energy minister, Yevgeny Grabchak, has [proposed](https://theminermag.com/news/2025-02-03/russia-minister-bitcoin-miner/) a centralized registry of Bitcoin mining equipment and wallet addresses to “identify mining activities and ensure stricter enforcement of bans in restricted regions,” such as Russian-occupied Ukraine territories. Meanwhile, the Chairman of the State Duma Committee on Energy, Nikolai Shulginov, warned that last year’s mining ban in several Russian and occupied regions may not be enough to eliminate mining fully. As an authoritarian state with an egregious human rights record and a long history of financial repression, Russia appears intent on tightening surveillance of economic activity — especially that of Bitcoin. By registering, tracking, and restricting mining, the Kremlin expands its financial control, undermines economic autonomy, and limits access to permissionless money. #### **Turkey | Erdoğan Targets Opposition as Inflation Forecast Rises** Turkish President Recep Tayyip Erdoğan sentenced Istanbul Mayor Ekrem Imamoglu — a key political rival — to [seven](https://www.bloomberg.com/news/articles/2025-02-05/turkey-s-main-rival-to-erdogan-faces-jail-time-in-new-indictment) years in prison on charges widely seen as politically motivated. If upheld, the conviction will bar Imamoglu from office, further clearing Erdoğan’s path to dominance ahead of the 2028 elections. At the same time, Turkey’s economic crisis is worsening. [Accelerating inflation](https://www.reuters.com/world/middle-east/turkey-cenbank-raises-inflation-forecast-says-not-autopilot-with-cuts-2025-02-07/) forced the central bank to raise its 2025 forecast from 21% to 24%, exacerbating the lira’s decline and eroding purchasing power. As both political and financial repression deepen, more Turks are turning to alternatives to sidestep Erdoğan’s expanding control over the economic and political sphere. #### **Georgia | Regime to Pass Censorship Law** Georgia’s ruling Georgian Dream party is set to introduce a media censorship [law](https://jam-news.net/georgian-dream-plans-to-pass-media-censorship-law/) aimed at enforcing government-defined standards for journalistic objectivity and ethics, while also restricting foreign funding for media outlets. MP Mamuka Mdinaradze [claims](https://jam-news.net/ngos-and-media-organizations-of-georgia-to-challenge-the-foreign-agents-law-in-strasbourg-court/) the law will establish monitoring mechanisms and is modeled after UK regulations, though critics [compare](https://jam-news.net/opinion-ivanishvili-adopts-belarusian-tactics-to-control-protests/) it to Belarusian-style repression. Georgian Dream Prime Minister Irakli Kobakhidze defended the move as necessary to close legislative “loopholes” and strengthen state control. Journalists and activists warn that the law is part of a broader crackdown on press freedom and dissent. Decentralized social networks like Nostr will become increasingly vital for journalists and activists to communicate freely, resist censorship, and ensure the flow of independent information. \___________________________________________________________\_ #### **Webinar Series for Nonprofits: Become Unstoppable** HRF will host a [free, three-day webinar](https://docs.google.com/forms/d/e/1FAIpQLSf0sjqwSFQo8HGMsWIIDRyhx34TsoonOSTfYoWSy-aaBbLeSw/viewform) from March 17-19, teaching human rights defenders and nonprofits how to use Bitcoin to counter state censorship and confiscation. Sessions run daily from 10:30 a.m. to 12:00 p.m. EDT and are beginner-friendly. The webinar will be led by Anna Chekhovich, HRF’s Bitcoin nonprofit adoption lead and financial manager at Alexei Navalny’s Anti-Corruption Foundation. ### [Register Here](https://docs.google.com/forms/d/e/1FAIpQLSf0sjqwSFQo8HGMsWIIDRyhx34TsoonOSTfYoWSy-aaBbLeSw/viewform) #### **SXSW | The Human Rights Risks of Central Bank Digital Currencies (CBDCs)** Join HRF at [SXSW 2025](https://www.sxsw.com/) in Austin from March 9-12 to explore how CBDCs threaten financial freedom. Experts [Roger Huang](https://x.com/Rogerh1991), [Charlene Fadirepo](https://x.com/CharFadirepo), and [Nick Anthony](https://x.com/EconWithNick) will discuss how authoritarian regimes use CBDCs for surveillance and control on March 9. Attendees can also visit HRF’s [CBDC Tracker](https://cbdctracker.hrf.org/) booth to explore an interactive map of CBDC developments worldwide. ### [Get Tickets](https://www.sxsw.com/conference/) \___________________________________________________________\_ ## BITCOIN AND FREEDOM TECH NEWS #### **Mullvad VPN | Testing Lightning Network Payments** [Mullvad VPN](https://mullvad.net/en) is experimenting with Bitcoin for payments via the Lightning Network, a second-layer payment protocol built on Bitcoin that enables faster, cheaper, and more private transactions. This integration lets Mullvad VPN users pay for their services in bitcoin while enhancing their privacy and bypassing payment networks that track or censor financial activity. VPNs protect users by masking IP addresses and encrypting traffic. Accepting Bitcoin over Lightning strengthens this protection with a censorship-resistant payment option. For activists, journalists, and individuals in authoritarian regimes, this combination provides a shield against surveillance. #### **SeedSigner | Releases Multilingual Support** [SeedSigner](https://seedsigner.com/), an open-source and customizable Bitcoin hardware wallet and HRF grantee, [introduced](https://github.com/SeedSigner/seedsigner/releases/tag/0.8.5) multilingual support for Spanish. This update makes secure Bitcoin self-custody more accessible to Spanish-speaking activists and human rights defenders who may rely on Bitcoin for transactional freedom. By expanding access to secure self-custody, SeedSigner helps reduce dependence on restrictive financial systems and allows more people in Nicaragua, Venezuela, Cuba, and beyond to “be their own bank.” #### **Iris | Implements Private Bitcoin Payments with Cashu** [Iris](https://iris.cx/), a Nostr client, has added support for a Cashu wallet to allow users to send and receive ecash. Cashu is an open-source Chaumian ecash protocol built for Bitcoin and integrated with the Lightning Network. It lets users make fast, low-cost, and extremely private transactions using Bitcoin-backed ecash. While it requires a trusted custodian, it helps users spend Bitcoin anonymously without revealing their identity or transaction activity. This ability provides activists and nonprofits a different way to make private Bitcoin payments alongside nostr’s censorship-resistant communications. #### **Sparrow Wallet | Supports Lark for USB Hardware Wallets** [Sparrow Wallet](https://sparrowwallet.com/), a popular open-source Bitcoin wallet, has added support for [Lark](https://github.com/sparrowwallet/larkapp?mc_cid=aab08acf41&mc_eid=5c5878c08e), a new tool for USB hardware wallet communication. Lark works alongside the existing [Hardware Wallet Interface](https://github.com/bitcoin-core/HWI) (HWI), giving users an alternative way to connect their hardware wallets via USB. This update improves reliability, reduces dependence on a single software interface, and strengthens Bitcoin self-custody. #### **Bitcoin Dada | Opens Applications for Second Cohort of Dada Devs** [Bitcoin Dada](https://btcdada.com/), an HRF-supported nonprofit initiative empowering African women through Bitcoin and financial education, is now [accepting](https://x.com/DadaDevs/status/1886819762660929674) applications for the second cohort of Dada Devs. This developer program provides hands-on training, mentorship, and a collaborative community to help African women under authoritarian regimes contribute to Bitcoin development. If you’re an aspiring female developer, [apply now](https://docs.google.com/forms/d/e/1FAIpQLSeJ8nXL96qNeCAaXnSlGxqykBPEGm21z9qS9oE1ldNusM0nTA/viewform) to join a network of African women shaping the future of finance. Applications close Feb. 13. #### **Summer of Bitcoin | Applications for Summer 2025 Cohort Now Open** [Summer of Bitcoin](https://www.summerofbitcoin.org/), an HRF-supported Bitcoin internship program, is now accepting [applications](https://www.summerofbitcoin.org/apply) for its summer 2025 cohort. This program introduces students from anywhere, including from authoritarian regimes, to Bitcoin open-source development and design, giving interns the option to choose between a developer or designer track based on their interests. Participants will gain hands-on work experience, contribute to real-world Bitcoin projects, and receive mentorship from industry leaders. You can learn more and apply [here](https://www.summerofbitcoin.org/). #### **Spiral | Announces Grant Renewals for the Bitcoin Design Community and BDK** [Spiral](http://spiral.xyz), a Bitcoin company building and funding open-source projects, announced renewed grants for critical initiatives, including the [Bitcoin Design Community](https://github.com/bitcoindesign) and [Bitcoin Dev Kit](https://bitcoindevkit.org/) (BDK). The Bitcoin Design Community is a free and open-source resource for designers, developers, and others working on non-custodial Bitcoin products. This [grant](https://x.com/spiralbtc/status/1885000120439095607) will support designers who push the user experience and adoption of Bitcoin forward. Meanwhile, BDK is a software library that helps developers in building cross-platform Bitcoin wallets. Its [grant](https://x.com/spiralbtc/status/1884998758976405840) will support the project’s continued refinement and development. ## RECOMMENDED CONTENT #### **The Bitcoin and Cypherpunk Spirit Is Alive and Well in Africa by Frank Corva** In this [article](https://bitcoinmagazine.com/culture/the-bitcoin-and-cypherpunk-spirit-is-alive-and-well-in-africa) for [Bitcoin Magazine](http://bitcoinmagazine.com), journalist [Frank Corva](https://x.com/frankcorva) spotlights Bitcoin's growing presence across Africa. Across the continent, people are building Bitcoin circular economies, open-source financial tools, and educational initiatives. From [Bitcoin Ekasi](https://x.com/BitcoinEkasi) in South Africa to [AfriBit Kibera](https://x.com/AfribitKibera) in Kenya and [Bitcoin Dua](https://x.com/bitcoin_dua) in Ghana, these grassroots initiatives drive financial inclusion and education for individuals and communities. Meanwhile, tools like [Tando](https://tando.me/) and [Machankura](https://8333.mobi/) are expanding access to transactional freedom, and conferences like [Adopting Bitcoin Captetown](https://za25.adoptingbitcoin.org/) and the [Africa Bitcoin Conference](https://afrobitcoin.org/) nurture ongoing collaboration between individuals, developers, and activists to advance financial freedom on a continent that otherwise has very little liberal democracy. Read the full article [here](https://bitcoinmagazine.com/culture/the-bitcoin-and-cypherpunk-spirit-is-alive-and-well-in-africa). #### **Using Bitcoin Without Internet! Here’s How Machankura Makes It Happen with Anita Posch** In this short [interview](https://www.youtube.com/watch?v=XzXfd237XVo), Bitcoin educator and host of the [Bitcoin for Fairness](https://www.youtube.com/@AnitaPosch) channel, Anita Posch, speaks with Mary Imasuen, a [Machankura](https://8333.mobi/) team member, about how this technology makes Bitcoin accessible to Africans without Internet access. Machankura is an app that allows feature phones to send and receive Bitcoin using the Unstructured Supplementary Service Data (USSD) protocol, a mobile communications system similar to SMS. This means people can transact in Bitcoin without needing a smartphone or data connection, a situation common to many living under autocratic regimes in sub-Saharan Africa. By removing Internet barriers, Machankura helps millions of Africans overcome high data costs and unreliable networks, offering a practical solution to financial inclusion. *If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report [here](https://mailchi.mp/hrf.org/financial-freedom-newsletter?mc_cid=bf652c0a5a).* *Support the newsletter by donating bitcoin to HRF’s Financial Freedom program [via BTCPay](https://hrf.org/btc).*\ *Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ [hrf.org](http://hrf.org/)* *The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals [here](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1)*. [**Subscribe to newsletter**](http://financialfreedomreport.org/) [**Apply for a grant**](https://forms.monday.com/forms/57019f8829449d9e729d9e3545a237ea?r=use1&mc_cid=39c1c9b7e8&mc_eid=778e9876e3) [**Support our work**](https://hrf.org/btc?mc_cid=39c1c9b7e8&mc_eid=778e9876e3) [**Visit our website**](https://hrf.org/programs/financial-freedom/) @ 9673b322:1b75ee9e
2025-02-13 14:15:38This is test content 
@ 9673b322:1b75ee9e
2025-02-13 14:15:38This is test content  @ 9673b322:1b75ee9e
2025-02-13 14:10:06This is some test content Adding a Sample Image 
@ 9673b322:1b75ee9e
2025-02-13 14:10:06This is some test content Adding a Sample Image  @ 2e8970de:63345c7a
2025-02-13 13:39:35 > We measure gender differences using the Cross-Gender Friending Ratio, the ratio of female friends in men's networks to the share of female friends in women's networks in a given place. Men almost always have a lower share of female friends than women do, but the degree varies:  > Across countries, the CGFR is strongly predictive of gender differences in labor force participation. Within countries, we also find a strong correlation with gender attitudes in the World Values Survey, such as beliefs about women's suitability for politics. https://x.com/drew_m_johnston/status/1889794718004826288 originally posted at https://stacker.news/items/884660
@ 2e8970de:63345c7a
2025-02-13 13:39:35 > We measure gender differences using the Cross-Gender Friending Ratio, the ratio of female friends in men's networks to the share of female friends in women's networks in a given place. Men almost always have a lower share of female friends than women do, but the degree varies:  > Across countries, the CGFR is strongly predictive of gender differences in labor force participation. Within countries, we also find a strong correlation with gender attitudes in the World Values Survey, such as beliefs about women's suitability for politics. https://x.com/drew_m_johnston/status/1889794718004826288 originally posted at https://stacker.news/items/884660 @ c2827524:5f45b2f7
2025-02-13 11:54:16> innèsto s. m. [der. di innestare]. – 1. In agraria: a. Operazione con cui si fa concrescere sopra una pianta (detta portainnesto o soggetto) una parte di un altro della stessa specie o di specie differenti (detto nesto o oggetto), **al fine di formare un nuovo individuo più pregiato o più produttivo o più giovane**: fare, operare, praticare un innesto. Le collaborazioni sono di una potenza micidiale. Quelle che si sviluppano nello spazio #Bitcoin ancora di più. Non è più una collaborazione, è un #innesto: rami di alberi diversi, destinati da soli a dare grandi frutti, si fondono per **donare ad un intero ecosistema sapori ancora più deliziosi**. Contributi e suggerimenti vanno e vengono alla velocità della luce, col sorriso, senza sacrificio e sempre con la volontà di migliorarsi e crescere. Lo spazio #Bitcoin è una fabbrica magica, che accoglie minuscoli semini(*) da chiunque voglia partecipare, volontariamente, alla crescita della cultura Bitcoin. Ma li trasforma in un **incanto**. In solitaria i semini sarebbero destinati comunque a grandi cose e questo è già, di per sé, meraviglioso. La fabbrica magica, invece, li fa germogliare, fiorire e fruttare in maniera ancora più potente. Quando la magia è totale, avviene l’*innesto*, **la generazione di una nuova creatura più pregiata**. Sta succedendo davanti ai miei occhi. Sono onorata di poter assistere a questo mini miracolo della vita e, manco a dirlo, felice di farne parte. Non è solo cambiare atteggiamento, smussare frizioni e rigidità o correggere la propria visione, è proprio ampliare sé stessi accogliendo gli altri. Grazie nostr:npub1uhj92lnwh8rrhhuvulfqstk4g0ayx0zx35wj2d62jueqheknkxks5m4zj6 nostr:npub1au23c73cpaq2whtazjf6cdrmvam6nkd4lg928nwmgl78374kn29sq9t53j nostr:npub1awnu9vg352863e7tqlc6urlw7jgdf8vf00tmr76uuhflp4nnn68sjmnnl3 e nostr:npub1lrurmgmlfl4u72258fc4q5ke7tr82kw5xct5vchdmzr9uhmx6j4qn3t72a (1) Semini, non #seed [non chiamatelo seed, si dice mnemonica (cit.)] Siccome in italiano la parola **seme** porta alla mente anche *giochini di parole fiat*, se siete qui per perculare fate pure. -> H.F.S.P. 🤣
@ c2827524:5f45b2f7
2025-02-13 11:54:16> innèsto s. m. [der. di innestare]. – 1. In agraria: a. Operazione con cui si fa concrescere sopra una pianta (detta portainnesto o soggetto) una parte di un altro della stessa specie o di specie differenti (detto nesto o oggetto), **al fine di formare un nuovo individuo più pregiato o più produttivo o più giovane**: fare, operare, praticare un innesto. Le collaborazioni sono di una potenza micidiale. Quelle che si sviluppano nello spazio #Bitcoin ancora di più. Non è più una collaborazione, è un #innesto: rami di alberi diversi, destinati da soli a dare grandi frutti, si fondono per **donare ad un intero ecosistema sapori ancora più deliziosi**. Contributi e suggerimenti vanno e vengono alla velocità della luce, col sorriso, senza sacrificio e sempre con la volontà di migliorarsi e crescere. Lo spazio #Bitcoin è una fabbrica magica, che accoglie minuscoli semini(*) da chiunque voglia partecipare, volontariamente, alla crescita della cultura Bitcoin. Ma li trasforma in un **incanto**. In solitaria i semini sarebbero destinati comunque a grandi cose e questo è già, di per sé, meraviglioso. La fabbrica magica, invece, li fa germogliare, fiorire e fruttare in maniera ancora più potente. Quando la magia è totale, avviene l’*innesto*, **la generazione di una nuova creatura più pregiata**. Sta succedendo davanti ai miei occhi. Sono onorata di poter assistere a questo mini miracolo della vita e, manco a dirlo, felice di farne parte. Non è solo cambiare atteggiamento, smussare frizioni e rigidità o correggere la propria visione, è proprio ampliare sé stessi accogliendo gli altri. Grazie nostr:npub1uhj92lnwh8rrhhuvulfqstk4g0ayx0zx35wj2d62jueqheknkxks5m4zj6 nostr:npub1au23c73cpaq2whtazjf6cdrmvam6nkd4lg928nwmgl78374kn29sq9t53j nostr:npub1awnu9vg352863e7tqlc6urlw7jgdf8vf00tmr76uuhflp4nnn68sjmnnl3 e nostr:npub1lrurmgmlfl4u72258fc4q5ke7tr82kw5xct5vchdmzr9uhmx6j4qn3t72a (1) Semini, non #seed [non chiamatelo seed, si dice mnemonica (cit.)] Siccome in italiano la parola **seme** porta alla mente anche *giochini di parole fiat*, se siete qui per perculare fate pure. -> H.F.S.P. 🤣 @ d360efec:14907b5f
2025-02-13 11:15:12**Top-Down Analysis:** กลยุทธ์การเทรดเพื่อมองภาพรวมและจับจังหวะทำกำไร ในโลกของการเทรดที่เต็มไปด้วยความผันผวน การมีเครื่องมือวิเคราะห์ที่แข็งแกร่งเป็นสิ่งสำคัญอย่างยิ่งที่จะช่วยนำทางให้เทรดเดอร์สามารถตัดสินใจได้อย่างมีหลักการและเพิ่มโอกาสในการทำกำไร หนึ่งในเครื่องมือที่ได้รับความนิยมและมีประสิทธิภาพคือ "Top-Down Analysis" หรือการวิเคราะห์จากบนลงล่าง ซึ่งเป็นวิธีการมองภาพรวมของตลาดก่อนที่จะเจาะจงไปที่สินทรัพย์ที่เราสนใจ บทความนี้จะพาคุณไปทำความเข้าใจกับ Top-Down Analysis อย่างละเอียด พร้อมทั้งแนะนำกลยุทธ์การเทรดที่สามารถนำไปปรับใช้ได้จริง **Top-Down Analysis คืออะไร?** Top-Down Analysis เป็นกระบวนการวิเคราะห์ตลาดที่เริ่มต้นจากการพิจารณาภาพรวมในกรอบเวลาที่ใหญ่ขึ้น ก่อนที่จะค่อยๆ ย่อยลงไปในกรอบเวลาที่เล็กลง เพื่อทำความเข้าใจบริบทของตลาดและหาจังหวะการเทรดที่เหมาะสม วิธีการนี้ช่วยให้เทรดเดอร์สามารถมองเห็นทิศทางหลักของตลาด, แนวโน้มที่กำลังเกิดขึ้น, ระดับราคาสำคัญ, และความสมดุลระหว่างอุปสงค์และอุปทาน ก่อนที่จะตัดสินใจเข้าเทรดในกรอบเวลาที่เล็กลง **องค์ประกอบสำคัญของ Top-Down Analysis (อ้างอิงจากภาพ)** ภาพ "Top-Down Analysis" ได้สรุปองค์ประกอบสำคัญของการวิเคราะห์นี้ไว้อย่างชัดเจน โดยแบ่งการวิเคราะห์ออกเป็น 3 กรอบเวลาหลัก: 4 ชั่วโมง (4H), 1 ชั่วโมง (1H), และ 15 นาที (15min) แต่ละกรอบเวลามีองค์ประกอบที่ต้องพิจารณาดังนี้: 1. กรอบเวลา 4 ชั่วโมง (4H): ภาพรวมตลาดและทิศทางหลัก ในกรอบเวลา 4 ชั่วโมง เราจะเน้นการวิเคราะห์ภาพรวมของตลาด เพื่อกำหนดทิศทางหลักและแนวโน้มในระยะกลาง องค์ประกอบสำคัญในกรอบเวลานี้คือ: * Direction (ทิศทาง): ประเมินทิศทางที่ตลาดกำลังเคลื่อนที่ไป โดยพิจารณาจากแนวโน้มและโครงสร้างราคาในภาพรวม ตลาดกำลังเป็นขาขึ้น, ขาลง หรืออยู่ในช่วง Sideways? * Trend (แนวโน้ม): ระบุแนวโน้มหลักของตลาด ไม่ว่าจะเป็นแนวโน้มขาขึ้น (Uptrend), แนวโน้มขาลง (Downtrend) หรือ Sideways การเข้าใจแนวโน้มช่วยในการกำหนดกลยุทธ์การเทรดที่เหมาะสม * Key levels (ระดับราคาสำคัญ): หาระดับราคาแนวรับและแนวต้านที่สำคัญในกรอบเวลา 4 ชั่วโมง ระดับเหล่านี้มักเป็นจุดที่ราคาเคยมีการกลับตัวหรือพักตัวในอดีต และอาจเป็นบริเวณที่ราคาจะตอบสนองอีกครั้งในอนาคต * Supply & Demand (อุปทานและอุปสงค์): วิเคราะห์ความสมดุลระหว่างแรงซื้อ (Demand) และแรงขาย (Supply) ในตลาด โดยพิจารณาจากพฤติกรรมราคาบริเวณแนวรับแนวต้าน และสัญญาณจากเครื่องมือวิเคราะห์อื่นๆ (ถ้าใช้) 2. กรอบเวลา 1 ชั่วโมง (1H): หาจังหวะและบริเวณที่น่าสนใจ เมื่อได้ภาพรวมและทิศทางหลักจากกรอบ 4H แล้ว เราจะย่อยลงมาในกรอบ 1 ชั่วโมง เพื่อหาจังหวะการเทรดที่สอดคล้องกับทิศทางหลัก และมองหารูปแบบราคาที่น่าสนใจ องค์ประกอบสำคัญในกรอบเวลานี้คือ: * Breaks (การทะลุ): สังเกตการทะลุแนวรับแนวต้าน หรือระดับราคาสำคัญในกรอบ 1H ที่สอดคล้องกับทิศทางหลักใน 4H การทะลุเหล่านี้อาจเป็นสัญญาณของการเคลื่อนไหวครั้งใหญ่ของราคา * Reversals (การกลับตัว): มองหารูปแบบการกลับตัวของราคาที่อาจเกิดขึ้นบริเวณระดับราคาสำคัญในกรอบ 1H ซึ่งบ่งบอกถึงจุดสิ้นสุดของแนวโน้มปัจจุบันและเริ่มต้นแนวโน้มใหม่ * OB (Order Blocks): ระบุบริเวณ Order Blocks ในกรอบ 1H ซึ่งเป็นพื้นที่ที่มีการสั่งซื้อขายจำนวนมากในอดีต Order Blocks เหล่านี้มักจะทำหน้าที่เป็นแนวรับแนวต้านในอนาคต * FVG (Fair Value Gaps): มองหา Fair Value Gaps ในกรอบ 1H ซึ่งเป็นช่องว่างของราคาที่เกิดจากการเคลื่อนไหวอย่างรวดเร็ว FVG มักจะเป็นเป้าหมายของราคาในอนาคต เนื่องจากราคาอาจจะกลับมาปิดช่องว่างเหล่านี้ * Liquidity (สภาพคล่อง): ประเมินสภาพคล่องบริเวณระดับราคาที่เราสนใจในกรอบ 1H บริเวณที่มีสภาพคล่องสูงมักจะดึงดูดนักลงทุนรายใหญ่ และอาจทำให้เกิดการเคลื่อนไหวของราคาที่รุนแรง 3. กรอบเวลา 15 นาที (15min): ยืนยันสัญญาณและหาจุดเข้าเทรด ในกรอบเวลา 15 นาที เราจะเน้นการยืนยันสัญญาณการเทรด และหาจุดเข้าเทรดที่แม่นยำ เพื่อลดความเสี่ยงในการเข้าเทรดเร็วเกินไป องค์ประกอบสำคัญในกรอบเวลานี้คือ: * Confirmation (การยืนยัน): รอสัญญาณยืนยันการเคลื่อนไหวของราคาในกรอบ 15 นาที ที่สอดคล้องกับการวิเคราะห์ในกรอบ 1H และ 4H สัญญาณยืนยันอาจมาในรูปแบบของแท่งเทียนกลับตัว, รูปแบบ Chart Patterns, หรือสัญญาณจาก Indicators * จุดเข้าเทรด: เมื่อมีสัญญาณยืนยันที่ชัดเจนในกรอบ 15 นาที และสอดคล้องกับการวิเคราะห์ในกรอบเวลาที่ใหญ่ขึ้น จึงตัดสินใจเข้าเทรด โดยกำหนด Stop Loss เพื่อจำกัดความเสี่ยง และ Take Profit เพื่อตั้งเป้าหมายในการทำกำไร **กลยุทธ์การเทรด Top-Down Analysis: ขั้นตอนสู่ความสำเร็จ** เพื่อนำ Top-Down Analysis ไปใช้ในการเทรดอย่างมีประสิทธิภาพ เราสามารถทำตามขั้นตอนต่อไปนี้: 1. **เริ่มต้นที่ 4H**: กำหนดทิศทางและแนวโน้มหลัก วิเคราะห์กราฟ 4H เพื่อระบุทิศทางหลักของตลาด แนวโน้ม และระดับราคาสำคัญ ประเมินความสมดุลของ Supply & Demand เพื่อกำหนด Bias การเทรด (เน้นซื้อหรือขาย) 2. **เจาะลึก 1H:** หาจังหวะและบริเวณที่น่าสนใจ เมื่อได้ทิศทางหลักจาก 4H แล้ว ให้ย่อยลงมาดูกราฟ 1H เพื่อหารูปแบบราคาที่น่าสนใจ เช่น การทะลุแนวรับแนวต้าน, รูปแบบการกลับตัว, Order Blocks, Fair Value Gaps และบริเวณที่มีสภาพคล่องสูง 3. **ยืนยันใน 15min:** หาจุดเข้าเทรดที่แม่นยำ รอสัญญาณยืนยันในกรอบ 15 นาที ที่สอดคล้องกับการวิเคราะห์ในกรอบเวลาที่ใหญ่ขึ้น ใช้ Price Action, แท่งเทียน, หรือ Indicators เพื่อยืนยันสัญญาณ และหาจุดเข้าเทรดที่แม่นยำ พร้อมกำหนด Stop Loss และ Take Profit ที่เหมาะสม **ประโยชน์ของการใช้ Top-Down Analysis** * มองเห็นภาพรวมตลาด: ช่วยให้เทรดเดอร์เข้าใจบริบทของตลาดในภาพรวม ไม่หลงทางในรายละเอียดเล็กๆ น้อยๆ * ตัดสินใจเทรดอย่างมีหลักการ: ทำให้การตัดสินใจเทรดมีเหตุผลและมีข้อมูลสนับสนุนมากขึ้น ไม่ใช่แค่การคาดเดา * เพิ่มความแม่นยำในการเทรด: การวิเคราะห์หลายกรอบเวลาช่วยกรองสัญญาณรบกวน และเพิ่มโอกาสในการเข้าเทรดในทิศทางที่ถูกต้อง * ลดความเสี่ยง: ช่วยลดโอกาสในการเทรดสวนทางแนวโน้มหลักของตลาด และช่วยในการกำหนด Stop Loss ที่เหมาะสม **ข้อควรจำและข้อควรระวัง** * ฝึกฝนและสังเกต: Top-Down Analysis ต้องอาศัยการฝึกฝนและการสังเกตกราฟราคาอย่างสม่ำเสมอ เพื่อพัฒนาความเข้าใจและทักษะในการวิเคราะห์ * ปรับใช้ให้เข้ากับสไตล์: ปรับกลยุทธ์ให้เข้ากับสไตล์การเทรดของคุณ และสินทรัพย์ที่คุณเทรด * บริหารความเสี่ยง: ให้ความสำคัญกับการบริหารความเสี่ยงเสมอ กำหนดขนาด Position ที่เหมาะสม และใช้ Stop Loss ทุกครั้ง * ไม่มีกลยุทธ์ใดสมบูรณ์แบบ: Top-Down Analysis เป็นเครื่องมือที่มีประสิทธิภาพ แต่ไม่มีกลยุทธ์ใดที่รับประกันผลกำไร 100% การเทรดมีความเสี่ยง โปรดศึกษาและทำความเข้าใจความเสี่ยงก่อนตัดสินใจลงทุน **สรุป** Top-Down Analysis เป็นกลยุทธ์การเทรดที่ทรงพลัง ซึ่งช่วยให้เทรดเดอร์สามารถวิเคราะห์ตลาดอย่างเป็นระบบ มองภาพรวม และจับจังหวะการเทรดได้อย่างแม่นยำ การนำหลักการของ Top-Down Analysis ไปปรับใช้ในการเทรด จะช่วยเพิ่มประสิทธิภาพในการตัดสินใจ และเพิ่มโอกาสในการประสบความสำเร็จในตลาดการเงินได้อย่างยั่งยืน
@ d360efec:14907b5f
2025-02-13 11:15:12**Top-Down Analysis:** กลยุทธ์การเทรดเพื่อมองภาพรวมและจับจังหวะทำกำไร ในโลกของการเทรดที่เต็มไปด้วยความผันผวน การมีเครื่องมือวิเคราะห์ที่แข็งแกร่งเป็นสิ่งสำคัญอย่างยิ่งที่จะช่วยนำทางให้เทรดเดอร์สามารถตัดสินใจได้อย่างมีหลักการและเพิ่มโอกาสในการทำกำไร หนึ่งในเครื่องมือที่ได้รับความนิยมและมีประสิทธิภาพคือ "Top-Down Analysis" หรือการวิเคราะห์จากบนลงล่าง ซึ่งเป็นวิธีการมองภาพรวมของตลาดก่อนที่จะเจาะจงไปที่สินทรัพย์ที่เราสนใจ บทความนี้จะพาคุณไปทำความเข้าใจกับ Top-Down Analysis อย่างละเอียด พร้อมทั้งแนะนำกลยุทธ์การเทรดที่สามารถนำไปปรับใช้ได้จริง **Top-Down Analysis คืออะไร?** Top-Down Analysis เป็นกระบวนการวิเคราะห์ตลาดที่เริ่มต้นจากการพิจารณาภาพรวมในกรอบเวลาที่ใหญ่ขึ้น ก่อนที่จะค่อยๆ ย่อยลงไปในกรอบเวลาที่เล็กลง เพื่อทำความเข้าใจบริบทของตลาดและหาจังหวะการเทรดที่เหมาะสม วิธีการนี้ช่วยให้เทรดเดอร์สามารถมองเห็นทิศทางหลักของตลาด, แนวโน้มที่กำลังเกิดขึ้น, ระดับราคาสำคัญ, และความสมดุลระหว่างอุปสงค์และอุปทาน ก่อนที่จะตัดสินใจเข้าเทรดในกรอบเวลาที่เล็กลง **องค์ประกอบสำคัญของ Top-Down Analysis (อ้างอิงจากภาพ)** ภาพ "Top-Down Analysis" ได้สรุปองค์ประกอบสำคัญของการวิเคราะห์นี้ไว้อย่างชัดเจน โดยแบ่งการวิเคราะห์ออกเป็น 3 กรอบเวลาหลัก: 4 ชั่วโมง (4H), 1 ชั่วโมง (1H), และ 15 นาที (15min) แต่ละกรอบเวลามีองค์ประกอบที่ต้องพิจารณาดังนี้: 1. กรอบเวลา 4 ชั่วโมง (4H): ภาพรวมตลาดและทิศทางหลัก ในกรอบเวลา 4 ชั่วโมง เราจะเน้นการวิเคราะห์ภาพรวมของตลาด เพื่อกำหนดทิศทางหลักและแนวโน้มในระยะกลาง องค์ประกอบสำคัญในกรอบเวลานี้คือ: * Direction (ทิศทาง): ประเมินทิศทางที่ตลาดกำลังเคลื่อนที่ไป โดยพิจารณาจากแนวโน้มและโครงสร้างราคาในภาพรวม ตลาดกำลังเป็นขาขึ้น, ขาลง หรืออยู่ในช่วง Sideways? * Trend (แนวโน้ม): ระบุแนวโน้มหลักของตลาด ไม่ว่าจะเป็นแนวโน้มขาขึ้น (Uptrend), แนวโน้มขาลง (Downtrend) หรือ Sideways การเข้าใจแนวโน้มช่วยในการกำหนดกลยุทธ์การเทรดที่เหมาะสม * Key levels (ระดับราคาสำคัญ): หาระดับราคาแนวรับและแนวต้านที่สำคัญในกรอบเวลา 4 ชั่วโมง ระดับเหล่านี้มักเป็นจุดที่ราคาเคยมีการกลับตัวหรือพักตัวในอดีต และอาจเป็นบริเวณที่ราคาจะตอบสนองอีกครั้งในอนาคต * Supply & Demand (อุปทานและอุปสงค์): วิเคราะห์ความสมดุลระหว่างแรงซื้อ (Demand) และแรงขาย (Supply) ในตลาด โดยพิจารณาจากพฤติกรรมราคาบริเวณแนวรับแนวต้าน และสัญญาณจากเครื่องมือวิเคราะห์อื่นๆ (ถ้าใช้) 2. กรอบเวลา 1 ชั่วโมง (1H): หาจังหวะและบริเวณที่น่าสนใจ เมื่อได้ภาพรวมและทิศทางหลักจากกรอบ 4H แล้ว เราจะย่อยลงมาในกรอบ 1 ชั่วโมง เพื่อหาจังหวะการเทรดที่สอดคล้องกับทิศทางหลัก และมองหารูปแบบราคาที่น่าสนใจ องค์ประกอบสำคัญในกรอบเวลานี้คือ: * Breaks (การทะลุ): สังเกตการทะลุแนวรับแนวต้าน หรือระดับราคาสำคัญในกรอบ 1H ที่สอดคล้องกับทิศทางหลักใน 4H การทะลุเหล่านี้อาจเป็นสัญญาณของการเคลื่อนไหวครั้งใหญ่ของราคา * Reversals (การกลับตัว): มองหารูปแบบการกลับตัวของราคาที่อาจเกิดขึ้นบริเวณระดับราคาสำคัญในกรอบ 1H ซึ่งบ่งบอกถึงจุดสิ้นสุดของแนวโน้มปัจจุบันและเริ่มต้นแนวโน้มใหม่ * OB (Order Blocks): ระบุบริเวณ Order Blocks ในกรอบ 1H ซึ่งเป็นพื้นที่ที่มีการสั่งซื้อขายจำนวนมากในอดีต Order Blocks เหล่านี้มักจะทำหน้าที่เป็นแนวรับแนวต้านในอนาคต * FVG (Fair Value Gaps): มองหา Fair Value Gaps ในกรอบ 1H ซึ่งเป็นช่องว่างของราคาที่เกิดจากการเคลื่อนไหวอย่างรวดเร็ว FVG มักจะเป็นเป้าหมายของราคาในอนาคต เนื่องจากราคาอาจจะกลับมาปิดช่องว่างเหล่านี้ * Liquidity (สภาพคล่อง): ประเมินสภาพคล่องบริเวณระดับราคาที่เราสนใจในกรอบ 1H บริเวณที่มีสภาพคล่องสูงมักจะดึงดูดนักลงทุนรายใหญ่ และอาจทำให้เกิดการเคลื่อนไหวของราคาที่รุนแรง 3. กรอบเวลา 15 นาที (15min): ยืนยันสัญญาณและหาจุดเข้าเทรด ในกรอบเวลา 15 นาที เราจะเน้นการยืนยันสัญญาณการเทรด และหาจุดเข้าเทรดที่แม่นยำ เพื่อลดความเสี่ยงในการเข้าเทรดเร็วเกินไป องค์ประกอบสำคัญในกรอบเวลานี้คือ: * Confirmation (การยืนยัน): รอสัญญาณยืนยันการเคลื่อนไหวของราคาในกรอบ 15 นาที ที่สอดคล้องกับการวิเคราะห์ในกรอบ 1H และ 4H สัญญาณยืนยันอาจมาในรูปแบบของแท่งเทียนกลับตัว, รูปแบบ Chart Patterns, หรือสัญญาณจาก Indicators * จุดเข้าเทรด: เมื่อมีสัญญาณยืนยันที่ชัดเจนในกรอบ 15 นาที และสอดคล้องกับการวิเคราะห์ในกรอบเวลาที่ใหญ่ขึ้น จึงตัดสินใจเข้าเทรด โดยกำหนด Stop Loss เพื่อจำกัดความเสี่ยง และ Take Profit เพื่อตั้งเป้าหมายในการทำกำไร **กลยุทธ์การเทรด Top-Down Analysis: ขั้นตอนสู่ความสำเร็จ** เพื่อนำ Top-Down Analysis ไปใช้ในการเทรดอย่างมีประสิทธิภาพ เราสามารถทำตามขั้นตอนต่อไปนี้: 1. **เริ่มต้นที่ 4H**: กำหนดทิศทางและแนวโน้มหลัก วิเคราะห์กราฟ 4H เพื่อระบุทิศทางหลักของตลาด แนวโน้ม และระดับราคาสำคัญ ประเมินความสมดุลของ Supply & Demand เพื่อกำหนด Bias การเทรด (เน้นซื้อหรือขาย) 2. **เจาะลึก 1H:** หาจังหวะและบริเวณที่น่าสนใจ เมื่อได้ทิศทางหลักจาก 4H แล้ว ให้ย่อยลงมาดูกราฟ 1H เพื่อหารูปแบบราคาที่น่าสนใจ เช่น การทะลุแนวรับแนวต้าน, รูปแบบการกลับตัว, Order Blocks, Fair Value Gaps และบริเวณที่มีสภาพคล่องสูง 3. **ยืนยันใน 15min:** หาจุดเข้าเทรดที่แม่นยำ รอสัญญาณยืนยันในกรอบ 15 นาที ที่สอดคล้องกับการวิเคราะห์ในกรอบเวลาที่ใหญ่ขึ้น ใช้ Price Action, แท่งเทียน, หรือ Indicators เพื่อยืนยันสัญญาณ และหาจุดเข้าเทรดที่แม่นยำ พร้อมกำหนด Stop Loss และ Take Profit ที่เหมาะสม **ประโยชน์ของการใช้ Top-Down Analysis** * มองเห็นภาพรวมตลาด: ช่วยให้เทรดเดอร์เข้าใจบริบทของตลาดในภาพรวม ไม่หลงทางในรายละเอียดเล็กๆ น้อยๆ * ตัดสินใจเทรดอย่างมีหลักการ: ทำให้การตัดสินใจเทรดมีเหตุผลและมีข้อมูลสนับสนุนมากขึ้น ไม่ใช่แค่การคาดเดา * เพิ่มความแม่นยำในการเทรด: การวิเคราะห์หลายกรอบเวลาช่วยกรองสัญญาณรบกวน และเพิ่มโอกาสในการเข้าเทรดในทิศทางที่ถูกต้อง * ลดความเสี่ยง: ช่วยลดโอกาสในการเทรดสวนทางแนวโน้มหลักของตลาด และช่วยในการกำหนด Stop Loss ที่เหมาะสม **ข้อควรจำและข้อควรระวัง** * ฝึกฝนและสังเกต: Top-Down Analysis ต้องอาศัยการฝึกฝนและการสังเกตกราฟราคาอย่างสม่ำเสมอ เพื่อพัฒนาความเข้าใจและทักษะในการวิเคราะห์ * ปรับใช้ให้เข้ากับสไตล์: ปรับกลยุทธ์ให้เข้ากับสไตล์การเทรดของคุณ และสินทรัพย์ที่คุณเทรด * บริหารความเสี่ยง: ให้ความสำคัญกับการบริหารความเสี่ยงเสมอ กำหนดขนาด Position ที่เหมาะสม และใช้ Stop Loss ทุกครั้ง * ไม่มีกลยุทธ์ใดสมบูรณ์แบบ: Top-Down Analysis เป็นเครื่องมือที่มีประสิทธิภาพ แต่ไม่มีกลยุทธ์ใดที่รับประกันผลกำไร 100% การเทรดมีความเสี่ยง โปรดศึกษาและทำความเข้าใจความเสี่ยงก่อนตัดสินใจลงทุน **สรุป** Top-Down Analysis เป็นกลยุทธ์การเทรดที่ทรงพลัง ซึ่งช่วยให้เทรดเดอร์สามารถวิเคราะห์ตลาดอย่างเป็นระบบ มองภาพรวม และจับจังหวะการเทรดได้อย่างแม่นยำ การนำหลักการของ Top-Down Analysis ไปปรับใช้ในการเทรด จะช่วยเพิ่มประสิทธิภาพในการตัดสินใจ และเพิ่มโอกาสในการประสบความสำเร็จในตลาดการเงินได้อย่างยั่งยืน @ 3eba5ef4:751f23ae
2025-02-13 09:00:41Security is fundamental to any blockchain. It ensures that all tokens are secure. When talking about a virtual machine and the smart contract platform it forms, security comes in two main aspects: * The code running on the virtual machine must be secure * The virtual machine itself should also be designed to facilitate safer code execution The first aspect often gets sufficient attention. When it comes to [CKB](https://www.nervos.org/), we now encourage developers to write scripts in Rust for maximum security, reserving pure C code only for those who fully understand its risks. Additionally, higher-level languages have been introduced in CKB to strike a better balance between productivity and security. Virtual machine security was a major focus when CKB-VM was originally designed. Many potential risks were addressed at the architectural level, though some—despite thorough research—were still left open. One such issue is **Return-Oriented Programming (ROP)**—a rather ingenious attack. It exploits executable code that has been legitimately loaded into memory, making widely effective protections (e.g., [W^X](https://yakihonne.com/write-article)) futile. It spans multiple architectures and is constantly evolving. Although we’ve spent a great deal of effort in the early days on ROP, we did not implement specific countermeasures to prevent it. Now, with new RISC-V extensions now available, it is the perfect time to introduce design-level protections against ROP. ## Acknowledgments Before diving deeper, we would like to acknowledge Todd Mortimer from the OpenBSD team. His work on ROP mitigations at the OpenBSD kernel in 2018-2019 significantly inspired our research and this article. We highly recommend his [talk](https://www.youtube.com/watch?v=ZvSSHtRv5Mg), slide decks from [AsiaBSDCon 2019](https://www.openbsd.org/papers/asiabsdcon2019-rop-slides.pdf) and [EuroBSD 2018](https://www.openbsd.org/papers/eurobsdcon2018-rop.pdf), and this [paper](https://www.openbsd.org/papers/asiabsdcon2019-rop-paper.pdf) for a deeper understanding of ROP. Several examples on x64 ROP attacks in this post are also drawn from his research. ## Typical Attack Workflow While there are many sophisticated [ways](https://www.wired.com/2016/06/clever-attack-uses-sound-computers-fan-steal-data/) of attacks, a common attack on a program typically follows this process: Prepare a [shellcode](https://en.wikipedia.org/wiki/Shellcode)— a piece of binary code to perform specific actions (e.g., running a shell or other programs on the target computer). Exploit one possible vulnerability in the target system, most commonly a [buffer overflow](https://en.wikipedia.org/wiki/Buffer_overflow) attack. The attack could be initiated via a network protocol (such as HTTP) against a remote system, or via command line input to a target program; As the result of the attack, the shellcode is inserted to a designated memory region of the target system and gets executed, allowing the attacker to achieve their goal. The consequences vary, like gaining unauthorized access to sensitive data, destroying certain data/machine, planting malicious programs onto the target for further actions, manipulating control flow. While traditional systems face a wide range of attacks, blockchains run in their own limited and unique runtime environment, rendering many conventional attacks irrelevant. Major blockchain security threats includes: * **Private key security**: Blockchain wallets rely on private keys, which are prime targets for various attacks. * **Smart contract vulnerability**: Poorly written smart contracts contain logic flaws that lead to security risks. * **Virtual machine security**: Attacker may send malicious inputs to a smart contract, causing it to terminate unexpectedly with a success status—despite lacking proper credentials. This post focuses specifically on attacks targeting the blockchain’s virtual machine—in our case—CKB Virtual Machine (CKB-VM) specifically. ## CKB’s Early Approach While it is impossible to predict every attack, disrupting the typical attack workflow is an effective defense strategy. From its inception, CKB-VM has implemented [W^X](https://en.wikipedia.org/wiki/W%5EX) protection: at any given time, any memory location in CKB-VM is either writable (allowing data modification) or executable (allowing data execution)—but never both. Once a memory region is marked as **executable**, it cannot be reverted to **writable** throughout the lifecycle of the current CKB-VM instance. Only writable memory location can be **frozen** to executable. This design significantly disrupts the typical attack workflow. For shellcode to execute on CKB-VM, it must reside in **executable** memory. However, an attacker can only provide shellcode as part of program inputs, which are loaded into **writable** memory. As long as a CKB script does not voluntarily mark input data as **executable** (a highly unlikely scenario), the shellcode remains inert. Additionally, attempting to overwrite existing **executable** shellcode is also futile, since executable memory region is unwritable, and cannot be converted back to writable. This way, W^X is a well-established security technique widely used in modern hardwares, operating systems, and virtual machines. Although it cannot prevent all possible attacks, W^X effectively shields many by breaking the standard attack workflow. Even if an attacker successfully injects shellcode into a target machine, the attack is incomplete due to the inability to execute it. ## Understanding ROP While W^X is effective, it does not solve all our problems. This leads to the topic of this post: **Return-oriented Programming (ROP)**. Instead of explicitly injecting new code, ROP exploits executable code that already resides in the target machine’s memory. Essentially, ROP builds a shellcode by chaining existing code snippets together that were never intended to function as such. It may sound like a fantasy, but as we shall see from the following examples, ROP is a practical and effective attack technique. To understand ROP, we must first examine modern CPU architecture and memory layout. While assembly instructions vary in representations and lengths, they are put together in memory one after another as a stream of bytes:  *Image [Source](https://www.quora.com/Is-assembly-language-a-source-code-or-object-code)* As seen in the above example, different assembly instructions come in different lengths. For x86-64 ISA, an instruction can range from 1 to 7 bytes (RISC ISAs such as ARM or RISC-V have more uniform instruction lengths—we will discuss it later). But in memory, instructions are stored sequentially without gaps. This means that with a stream of bytes alone, we really don’t know what instructions the stream of bytes consist of. In the above example, meaningful assembly instructions emerge only when we start decoding from the `B8` byte. In a different occasion, assuming we know elsewhere that `B8 22 11` bytes at the front are for certain magic flags, the decoding would start from `00` byte, yielding a totally different instruction set.  *Image [Source](https://www.quora.com/Is-assembly-language-a-source-code-or-object-code)* It is really the combination of a special program counter (`PC`) register from the CPU and the current memory stream, jointly determine the instructions the CPU executes. Depending on each different ISA or hardware, a booting process initializes a CPU’s `PC` register to a pre-defined value, then loads up instructions from this pre-defined address, and initializes everything related to the operating system. When a user launches a new program, the metadata for each program will contain an `entrypoint` address, where OS sets the CPU’s `PC` register to, in order to start executing the program. It is suffice to say that maintaining a proper `PC` value is a critical job to ensure a computer’s proper function. An invalid `PC` value might lead to a CPU malfunction at best, or at worst, leaking sensitive information or granting attackers unauthorized access. ### Forming an ROP Attack Via ROP Gadgets Let’s look at the following byte instruction stream in a x86-64 CPU: ``` 8a 5d c3 movb -61(%rbp), %bl ``` This 3-byte represents a `mov` instruction: it takes the address of `rbp` register, adds an offset of `-61`, then uses the result as a memory address to load 1 byte data, and finally sets the loaded data to `bl` register. However, if we ignore `8a` and only look at `5b c3` here, it actually represents a different instruction set: ``` 5d popq %rbp c3 retq ``` This byte sequence contains two instructions: * Pop 8-byte value from stack, and use it to set `rbp` register * Pop 8-byte value from stack, and use it to set `PC` register, so we continue executing from the new location We've briefly discussed that shellcode only fulfills a certain task required by the attacker. In fact, the most common type of shellcode simply construct a new shell, where the attacker can execute more operations. Such shellcode can be represented in the following C pseudocode to run a new command via the `execve` syscall: ``` execve(“/bin/sh”, NULL, NULL); ``` To execute this on an x86-64 CPU, the following actions are needed for a syscall: * `rax` register: must contain the syscall number, for `execve`, it is `59` * `rdi`, `rsi`, `rdx` registers: hold the first 3 arguments to the syscall. In this case, `rdi` holds a pointer to the C string `/bin/sh`; `rsi` and `rdx` must be zero. * The `syscall` instruction (or typically `int 80h` on x64) shall be executed A typical shellcode would be a packed assembly sequence directly doing all of the above instructions. In contrast, ROP attack looks for the following sequences: ``` # Those can set the value of different registers from values on the stack pop %rax; ret pop %rdi; ret pop %rsi; ret pop %rdx; ret # Finally, trigger the syscall syscall ``` Each of these small code sequences, are conventionally callled **ROP gadgets**. An attacker searches for these gadgets in the target program or system libraries (such as libc). Once these required gadgets are obtained, the attacker pieces together a sequence of data, much like the following:  With the prepared data sequence, the attacker can exploit a vulnerability in the target computer or program, such as typical buffer overflow attack. During this process, the attacker performs three key actions: * Pushes (or overwrites existing data) the crafted data sequence to the stack * Sets the stack pointer (top of the stack) to `X + 64` * Sets the `PC` register to the address of a code sequence, `pop %rax; ret` in the existing program or libc memory space Now the attack proceeds step by step as follows: 1. The CPU runs `pop %rax; ret`. With the stack pointer pointing to `X + 64`, the CPU pops `59` from the stack and sets `rax` register to `59`. It then pops the address to code sequence `pop %rdi; ret` from the stack, and sets `PC` to this value; 2. The CPU runs `pop %rdi; ret`. With the stack pointer pointing to `X + 48`, the CPU pops value `X`, pointing to the C string `/bin/sh` from the stack, and sets `rdi` register to `X`. It then pops the address to code sequence `pop %rsi; ret` from the stack, and sets `PC` to this value; 3. The CPU runs `pop %rsi; ret`. With the stack pointer pointing to `X + 32`, the CPU pops `0` from the stack and sets `rsi` register to `0`. It then pops the address to code sequence `pop %rdx; ret` from the stack, and sets `PC` to this value; 4. The CPU runs `pop %rdx; ret`. With the stack pointer pointing to `X + 16`, the CPU pops `0` from the stack and sets `rdx` register to `0`. It then pops the address to code sequence `syscall` from the stack, and sets `P`C to this value; 5. The CPU runs `syscall`. At this point, `rax` holds `59`, `rdi` points to `/bin/sh`, and both `rsi` and `rdx` are zero, the CPU invokes `execve("/bin/sh, NULL, NULL);`, granting the attacker a shell for further manipulations. This sequence of ROP gadgets, referred to as **ROP chains**, demonstrates how a complete ROP attack works. Two key takeaways are: * **ROP does not inject new code**. Instead, it injects data into the stack and leverages the existing code loaded in memory and marked them as executable. W^X protections hence cannot prevent ROP attacks. * **Attackers can mine ROP gadgets from the [libc](https://en.wikipedia.org/wiki/C_standard_library) library**. This is because modern computers employs [protection rings](https://en.wikipedia.org/wiki/Protection_ring) as a way for privilege encapsulations: on x86-64 computers, programs normally run at ring level 3, while libc runs at ring level 1. Lower ring levels have higher privileges, meaning that even if a program misbehaves, its capacities are limited at ring level 3. However, by using ROP gadgets in the libc library which runs at ring level 1, ROP attacks can have higher privileges and execute more damaging operations then normal shellcodes. Note that the above examples simply show the most basic ROP gadgets. In reality, ROP gadgets come in all kinds of forms. Since they come from compiler outputs, they can be combined in the least expected way, and can vary the forms as new compiler optimizations come out. Numerous tools (e.g., [ropper](https://scoding.de/ropper/), [ropr](https://github.com/Ben-Lichtman/ropr)) and research papers (e.g., *[Experiments on ROP Attack with Various Instruction Set Architectures](https://dl.yumulab.org/papers/42/paper.pdf)*, *[ROPGMN](https://www.sciencedirect.com/science/article/abs/pii/S0167739X24005314)*, *[Detecting and Preventing ROP Attacks using Machine Learning on ARM](https://www.infosun.fim.uni-passau.de/ch/publications/compsac23.pdf)*, *[KROP](https://arxiv.org/pdf/2406.11880)* ) keep coming out, making it almost impossible to enumerate all possible ROP gadget combinations. ### ROP on ARM & RISC-V ROP attacks are not limited to CISC architectures, where instructions vary in length. They also affect RISC designs, such as [ARM](https://developer.arm.com/documentation/102433/0200/Return-oriented-programming) and [RISC-V](https://pure.royalholloway.ac.uk/ws/portalfiles/portal/37157938/ROP_RISCV.pdf). Take the following sequence for example: ``` 13 4f 83 23 0b 00 ``` Decoding from the start, the first four bytes represent `xori t5,t1,568` following the RISC-V ISA. But if we skip the first two, the latter four represent `lw t2,0(s6)`. This illustrates that a byte stream interpretation also requires `PC` register in a RISC design such as RISC-V. As a result, one can find ROP gadgets from a RISC-V program as well. ### ROP on CKB-VM CKB’s RISC-V machine operates in a more restricted environment: for programs running on CKB, there are no `execve` syscalls to hijack a running shell, and all runtime states are publicly visible on a public blockchain like CKB. However, ROP attacks can still occur on CKB: one could construct an ROP chain that sets `a0` to `0`, `a7` to `93`, then executes `ecall`. This causes CKB-VM to immediately return with a success code (`0`), potentially allowing a script to pass validation when it should have failed—such as a lock script succeeding without a valid signature. ### Short Recap Let’s briefly recap what we’ve learned so far: * ROP attacks utilize existing executable code for malicious purposes. W^X cannot prevent ROP. * ROP is possible across multiple architecture, including x86-64, ARM, RISC-V, and CKB. * The landscape of ROP is constantly evolving. With new tools, techniques, and research emerging regularly, it’s impossible to foresee all ROP gadgets. ROP has been extensively studied over the years, leading to various mitigation strategies, which can be broadly categorized into two main approaches: * **Software Solutions**: Covering techniques like rewriting code sequences and implementing Retguard to prevent the creation of ROP gadgets * **Hardware Solutions**: Introducing additional CPU instructions with Control Flow Integrity (CFI) checks to safeguard control flow. I’ll explore these strategies in greater detail in the following sections. ## Software Solutions to Mitigate ROP ### Rewriting Sequence Certain instruction sequences are often targeted to form ROP gadgets. To prevent ROP, one approach is to alter the compiler, so that such sequences can never be generated. Take the following example: ``` 89 c3 mov %eax,%ebx 90. ``` In x86-64, `c3` represents the `ret` instruction, making it a potential target for ROP gadgets. We can rewrite it into the following equivalent sequence: ``` 48 87 d8 xchgq %rbx, %rax 89 d8 movl %ebx, %eax 48 87 d8 xchgq %rbx, %rax ``` The new sequence lacks `c3` byte at the expense of more bytes and more executed instructions. However, it is really up to real benchmarks to see if this causes noticeable overhead. Further analysis has revealed that the `rbx` register in x86-64 is often the source of ROP gadgets, due to the way Intel encodes x86-64 instructions. Hence, the OpenBSD team decided to avoid `rbx` register wherever possible, reducing the number of potential ROP gadgets. Again, this approach comes at the cost of having bigger code fragments, more instructions to execute, and an additional patched compiler. While OpenBSD has integrated these changes into its distribution, other environments must weigh the benefits against the costs. For a deeper dive, I would strongly recommend Todd Mortimer’s [work](https://www.openbsd.org/papers/asiabsdcon2019-rop-slides.pdf). ### Retguard’s Solution: Prologue and Epilogue Todd Mortimer also introduced Retguard in this [work](https://www.openbsd.org/papers/asiabsdcon2019-rop-slides.pdf) for securing OpenBSD known. ROP attacks typically occur when you enter a function `foo`, but the stack was manipulated, so the CPU exits to another code fragment that is not `foo`. What if to verify that, at each function exit, it is the same function for exiting and entering? Retguard introduces two components to perform this task: * **Prologue**: A prologue is inserted to each function’s entry, taking two inputs: - - A `cookie` value, a random data assigned for this particular function. - - The return address, where to jump to when current function exits—as inputs. The prologue computes the XOR value of these two, and stores the result into the current function’s [frame](https://en.wikipedia.org/wiki/Call_stack#Stack_and_frame_pointers) section, a dedicated memory region designated to the current function to hold data, separated from the stack. * **Epilogue**: An epilogue is inserted to the location where a function might exit. It takes two inputs: - - The saved XOR value from the prologue in the frame section - - The return address it now can access to (most likely popped from the stack in x64 machine, or read from a special `RA` register in RISC design) The epilogue computes the XOR of these two. If the result matches the original `cookie`, execution proceeds. Otherwise, the epilogue halts the program, signaling an error. This prologue-epilogue mechanism in Retguard guards the call stack from tampering. At a noticeable but acceptable cost (both in performance and code size), Retguard eliminates a significant number of ROP gadgets from the OpenBSD kernel. Like other software-based mitigations, it requires a patched compiler, and it is up to each environment to decide if such technique shall be employed. ## Hardware Advancements to Mitigate ROP In addition to software solutions, hardware-based defenses have also been developed. For instance, Intel has introduced [Indirect Branch Tracking](https://edc.intel.com/content/www/us/en/design/ipla/software-development-platforms/client/platforms/alder-lake-desktop/12th-generation-intel-core-processors-datasheet-volume-1-of-2/007/indirect-branch-tracking/?language=en) feature starting with its 12th generation core processors, using a new instruction `endbr32` or `endbr64` added at every location the program might jump to or call into. When the CPU executes a jump/call, it asserts that the target location is a proper `endbr32` / `endbr64` instruction, before updating the program counter `PC` register to proper values. Otherwise, the CPU halts to terminate the program. This ensures that all control flows will follow the intended way, preventing ROP attacks from redirecting execution arbitrary locations. Modern OSes have already extensively leveraged `endbr32` / `endbr64` instructions. Ubuntu 24.04, for instance, has included these instructions in its packages: ``` $ objdump -d /bin/bash | head -n 50 /bin/bash: file format elf64-x86-64 Disassembly of section .init: 0000000000030000 <.init>: 30000: f3 0f 1e fa endbr64 30004: 48 83 ec 08 sub $0x8,%rsp 30008: 48 8b 05 d9 7e 12 00 mov 0x127ed9(%rip),%rax # 157ee8 <__gmon_start__@Base> 3000f: 48 85 c0 test %rax,%rax 30012: 74 02 je 30016 <unlink@plt-0xe1a> 30014: ff d0 call *%rax 30016: 48 83 c4 08 add $0x8,%rsp 3001a: c3 ret Disassembly of section .plt: 0000000000030020 <.plt>: 30020: ff 35 a2 76 12 00 push 0x1276a2(%rip) # 1576c8 <o_options@@Base+0x1cc8> 30026: ff 25 a4 76 12 00 jmp *0x1276a4(%rip) # 1576d0 <o_options@@Base+0x1cd0> 3002c: 0f 1f 40 00 nopl 0x0(%rax) 30030: f3 0f 1e fa endbr64 30034: 68 00 00 00 00 push $0x0 30039: e9 e2 ff ff ff jmp 30020 <unlink@plt-0xe10> 3003e: 66 90 xchg %ax,%ax 30040: f3 0f 1e fa endbr64 30044: 68 01 00 00 00 push $0x1 30049: e9 d2 ff ff ff jmp 30020 <unlink@plt-0xe10> 3004e: 66 90 xchg %ax,%ax 30050: f3 0f 1e fa endbr64 30054: 68 02 00 00 00 push $0x2 30059: e9 c2 ff ff ff jmp 30020 <unlink@plt-0xe10> 3005e: 66 90 xchg %ax,%ax 30060: f3 0f 1e fa endbr64 30064: 68 03 00 00 00 push $0x3 30069: e9 b2 ff ff ff jmp 30020 <unlink@plt-0xe10> 3006e: 66 90 xchg %ax,%ax 30070: f3 0f 1e fa endbr64 30074: 68 04 00 00 00 push $0x4 30079: e9 a2 ff ff ff jmp 30020 <unlink@plt-0xe10> 3007e: 66 90 xchg %ax,%ax 30080: f3 0f 1e fa endbr64 30084: 68 05 00 00 00 push $0x5 30089: e9 92 ff ff ff jmp 30020 <unlink@plt-0xe10> 3008e: 66 90 xchg %ax,%ax 30090: f3 0f 1e fa endbr64 30094: 68 06 00 00 00 push $0x6 30099: e9 82 ff ff ff jmp 30020 <unlink@plt-0xe10> 3009e: 66 90 xchg %ax,%ax ``` The `endbr32` / `endbr64` instructions has been carefully designed, so they are `nop` instructions—meaning they can do nothing at all—on CPUs prior to their introductions. Having them doesn't have any effect on older CPUs but enhances security on supported hardware. ## RISC-V’s Latest Achievements: CFI Extension The above mitigations against ROP fall into two categories: * **Compiler Modifications**: Can generate more secure binary assembly code. * **Additional CPU instructions**: Coming with Control Flow Integrity (CFI) checks to prevent exploitation Back to the beginning of designing CKB-VM, we throughly studied ROP and recognized that a vulnerability in a CKB script could potentially open the door to ROP attacks. However, we eventually did not introduce any specific mitigation against ROP in CKB-VM. Our decision was to stay aligned with the RISC-V ecosystem, avoiding shipping any custom RISC-V spec with additional instructions that would require a patched compiler. Nor do we want to maintain our own compiler set, eliminating the potential that any RISC-V-compliant compiler shall be able to produce CKB script. As the result, we shipped the first version of CKB-VM without ROP mitigations, but that does not mean we’ve ignore this issue: * We’ve [reached out](https://groups.google.com/a/groups.riscv.org/g/isa-dev/c/LyZzjJG7_18/m/pCSnKZPdBAAJ) to the RISC-V community for possible extension similar to Intel’s solution, and kept monitoring advancements in this field; * We’ve been watching over progress and writing secure CKB scripts. Since ROP relies on existing vulnerabilities, secure CKB scripts can kept ROP purely theoretical. We were thrilled when the **RISC-V CFI (Control-Flow Integrity) Extension** was officialy [ratified](https://github.com/riscv/riscv-cfi/releases/tag/v1.0) in July 2024. Designed by the brilliant minds from the RISC-V Foundation, this extension directly addresses ROP attacks with two key features: * `Zicfilp` extension introduces **landing pad**: Resembles Intel’s `endbr32` / `endbr64` to ensure that the CPU can only jump to valid, permitted targets. * `Zicfiss` extension introduces **shadow stack** with a series of instructions:. Offers a hardware solution similar to Retguard, where CPU ensures the control flow integrity or simply puts the call stack, preventing tampering throughout execution. Together, these features offer the state-of-the-art mitigations against ROP. More importantly, RISC-V CFI is now an official extension, meaning all future RISC-V CPUs, compilers, and tools will support this extension. In fact, LLVM 19 has already [supported](https://releases.llvm.org/19.1.0/docs/ReleaseNotes.html#changes-to-the-risc-v-backend), and I believe other compilers and tools will follow soon. Once fully adopted, CKB script developers can simply turn them on like a switch during code compilation. Without modifying the code, they can enjoy the security provided by RISC-V CFI extensions. Even if a vulnerability exists in a CKB script, these built-in enforcements can prevent it from being exploited. ## Final Words Security is complex. While we strive for maximum security, certain design principles might get in the way from introducing specific mitigations. ROP is a prime example: while we did learn much about it early on, implementing the best mitigations needs proper timing. Now the time has come. We are happy to introduce RISC-V CFI in CKB’s next hardfork, bringing stronger security for everyone. *** ✍🏻 Written by Xuejie Xiao His previous posts include: * [A Journey Optimizing CKB Smart Contract: Porting Bitcoin as an Example](https://blog.cryptape.com/a-journey-optimizing-ckb-smart-contract) * [Optimizing C++ Code for CKB-VM: Porting Bitcoin as an Example](https://blog.cryptape.com/optimizing-c-code-for-ckb-vm) Find more in his personal website [Less is More](https://xuejie.space/).
@ 3eba5ef4:751f23ae
2025-02-13 09:00:41Security is fundamental to any blockchain. It ensures that all tokens are secure. When talking about a virtual machine and the smart contract platform it forms, security comes in two main aspects: * The code running on the virtual machine must be secure * The virtual machine itself should also be designed to facilitate safer code execution The first aspect often gets sufficient attention. When it comes to [CKB](https://www.nervos.org/), we now encourage developers to write scripts in Rust for maximum security, reserving pure C code only for those who fully understand its risks. Additionally, higher-level languages have been introduced in CKB to strike a better balance between productivity and security. Virtual machine security was a major focus when CKB-VM was originally designed. Many potential risks were addressed at the architectural level, though some—despite thorough research—were still left open. One such issue is **Return-Oriented Programming (ROP)**—a rather ingenious attack. It exploits executable code that has been legitimately loaded into memory, making widely effective protections (e.g., [W^X](https://yakihonne.com/write-article)) futile. It spans multiple architectures and is constantly evolving. Although we’ve spent a great deal of effort in the early days on ROP, we did not implement specific countermeasures to prevent it. Now, with new RISC-V extensions now available, it is the perfect time to introduce design-level protections against ROP. ## Acknowledgments Before diving deeper, we would like to acknowledge Todd Mortimer from the OpenBSD team. His work on ROP mitigations at the OpenBSD kernel in 2018-2019 significantly inspired our research and this article. We highly recommend his [talk](https://www.youtube.com/watch?v=ZvSSHtRv5Mg), slide decks from [AsiaBSDCon 2019](https://www.openbsd.org/papers/asiabsdcon2019-rop-slides.pdf) and [EuroBSD 2018](https://www.openbsd.org/papers/eurobsdcon2018-rop.pdf), and this [paper](https://www.openbsd.org/papers/asiabsdcon2019-rop-paper.pdf) for a deeper understanding of ROP. Several examples on x64 ROP attacks in this post are also drawn from his research. ## Typical Attack Workflow While there are many sophisticated [ways](https://www.wired.com/2016/06/clever-attack-uses-sound-computers-fan-steal-data/) of attacks, a common attack on a program typically follows this process: Prepare a [shellcode](https://en.wikipedia.org/wiki/Shellcode)— a piece of binary code to perform specific actions (e.g., running a shell or other programs on the target computer). Exploit one possible vulnerability in the target system, most commonly a [buffer overflow](https://en.wikipedia.org/wiki/Buffer_overflow) attack. The attack could be initiated via a network protocol (such as HTTP) against a remote system, or via command line input to a target program; As the result of the attack, the shellcode is inserted to a designated memory region of the target system and gets executed, allowing the attacker to achieve their goal. The consequences vary, like gaining unauthorized access to sensitive data, destroying certain data/machine, planting malicious programs onto the target for further actions, manipulating control flow. While traditional systems face a wide range of attacks, blockchains run in their own limited and unique runtime environment, rendering many conventional attacks irrelevant. Major blockchain security threats includes: * **Private key security**: Blockchain wallets rely on private keys, which are prime targets for various attacks. * **Smart contract vulnerability**: Poorly written smart contracts contain logic flaws that lead to security risks. * **Virtual machine security**: Attacker may send malicious inputs to a smart contract, causing it to terminate unexpectedly with a success status—despite lacking proper credentials. This post focuses specifically on attacks targeting the blockchain’s virtual machine—in our case—CKB Virtual Machine (CKB-VM) specifically. ## CKB’s Early Approach While it is impossible to predict every attack, disrupting the typical attack workflow is an effective defense strategy. From its inception, CKB-VM has implemented [W^X](https://en.wikipedia.org/wiki/W%5EX) protection: at any given time, any memory location in CKB-VM is either writable (allowing data modification) or executable (allowing data execution)—but never both. Once a memory region is marked as **executable**, it cannot be reverted to **writable** throughout the lifecycle of the current CKB-VM instance. Only writable memory location can be **frozen** to executable. This design significantly disrupts the typical attack workflow. For shellcode to execute on CKB-VM, it must reside in **executable** memory. However, an attacker can only provide shellcode as part of program inputs, which are loaded into **writable** memory. As long as a CKB script does not voluntarily mark input data as **executable** (a highly unlikely scenario), the shellcode remains inert. Additionally, attempting to overwrite existing **executable** shellcode is also futile, since executable memory region is unwritable, and cannot be converted back to writable. This way, W^X is a well-established security technique widely used in modern hardwares, operating systems, and virtual machines. Although it cannot prevent all possible attacks, W^X effectively shields many by breaking the standard attack workflow. Even if an attacker successfully injects shellcode into a target machine, the attack is incomplete due to the inability to execute it. ## Understanding ROP While W^X is effective, it does not solve all our problems. This leads to the topic of this post: **Return-oriented Programming (ROP)**. Instead of explicitly injecting new code, ROP exploits executable code that already resides in the target machine’s memory. Essentially, ROP builds a shellcode by chaining existing code snippets together that were never intended to function as such. It may sound like a fantasy, but as we shall see from the following examples, ROP is a practical and effective attack technique. To understand ROP, we must first examine modern CPU architecture and memory layout. While assembly instructions vary in representations and lengths, they are put together in memory one after another as a stream of bytes:  *Image [Source](https://www.quora.com/Is-assembly-language-a-source-code-or-object-code)* As seen in the above example, different assembly instructions come in different lengths. For x86-64 ISA, an instruction can range from 1 to 7 bytes (RISC ISAs such as ARM or RISC-V have more uniform instruction lengths—we will discuss it later). But in memory, instructions are stored sequentially without gaps. This means that with a stream of bytes alone, we really don’t know what instructions the stream of bytes consist of. In the above example, meaningful assembly instructions emerge only when we start decoding from the `B8` byte. In a different occasion, assuming we know elsewhere that `B8 22 11` bytes at the front are for certain magic flags, the decoding would start from `00` byte, yielding a totally different instruction set.  *Image [Source](https://www.quora.com/Is-assembly-language-a-source-code-or-object-code)* It is really the combination of a special program counter (`PC`) register from the CPU and the current memory stream, jointly determine the instructions the CPU executes. Depending on each different ISA or hardware, a booting process initializes a CPU’s `PC` register to a pre-defined value, then loads up instructions from this pre-defined address, and initializes everything related to the operating system. When a user launches a new program, the metadata for each program will contain an `entrypoint` address, where OS sets the CPU’s `PC` register to, in order to start executing the program. It is suffice to say that maintaining a proper `PC` value is a critical job to ensure a computer’s proper function. An invalid `PC` value might lead to a CPU malfunction at best, or at worst, leaking sensitive information or granting attackers unauthorized access. ### Forming an ROP Attack Via ROP Gadgets Let’s look at the following byte instruction stream in a x86-64 CPU: ``` 8a 5d c3 movb -61(%rbp), %bl ``` This 3-byte represents a `mov` instruction: it takes the address of `rbp` register, adds an offset of `-61`, then uses the result as a memory address to load 1 byte data, and finally sets the loaded data to `bl` register. However, if we ignore `8a` and only look at `5b c3` here, it actually represents a different instruction set: ``` 5d popq %rbp c3 retq ``` This byte sequence contains two instructions: * Pop 8-byte value from stack, and use it to set `rbp` register * Pop 8-byte value from stack, and use it to set `PC` register, so we continue executing from the new location We've briefly discussed that shellcode only fulfills a certain task required by the attacker. In fact, the most common type of shellcode simply construct a new shell, where the attacker can execute more operations. Such shellcode can be represented in the following C pseudocode to run a new command via the `execve` syscall: ``` execve(“/bin/sh”, NULL, NULL); ``` To execute this on an x86-64 CPU, the following actions are needed for a syscall: * `rax` register: must contain the syscall number, for `execve`, it is `59` * `rdi`, `rsi`, `rdx` registers: hold the first 3 arguments to the syscall. In this case, `rdi` holds a pointer to the C string `/bin/sh`; `rsi` and `rdx` must be zero. * The `syscall` instruction (or typically `int 80h` on x64) shall be executed A typical shellcode would be a packed assembly sequence directly doing all of the above instructions. In contrast, ROP attack looks for the following sequences: ``` # Those can set the value of different registers from values on the stack pop %rax; ret pop %rdi; ret pop %rsi; ret pop %rdx; ret # Finally, trigger the syscall syscall ``` Each of these small code sequences, are conventionally callled **ROP gadgets**. An attacker searches for these gadgets in the target program or system libraries (such as libc). Once these required gadgets are obtained, the attacker pieces together a sequence of data, much like the following:  With the prepared data sequence, the attacker can exploit a vulnerability in the target computer or program, such as typical buffer overflow attack. During this process, the attacker performs three key actions: * Pushes (or overwrites existing data) the crafted data sequence to the stack * Sets the stack pointer (top of the stack) to `X + 64` * Sets the `PC` register to the address of a code sequence, `pop %rax; ret` in the existing program or libc memory space Now the attack proceeds step by step as follows: 1. The CPU runs `pop %rax; ret`. With the stack pointer pointing to `X + 64`, the CPU pops `59` from the stack and sets `rax` register to `59`. It then pops the address to code sequence `pop %rdi; ret` from the stack, and sets `PC` to this value; 2. The CPU runs `pop %rdi; ret`. With the stack pointer pointing to `X + 48`, the CPU pops value `X`, pointing to the C string `/bin/sh` from the stack, and sets `rdi` register to `X`. It then pops the address to code sequence `pop %rsi; ret` from the stack, and sets `PC` to this value; 3. The CPU runs `pop %rsi; ret`. With the stack pointer pointing to `X + 32`, the CPU pops `0` from the stack and sets `rsi` register to `0`. It then pops the address to code sequence `pop %rdx; ret` from the stack, and sets `PC` to this value; 4. The CPU runs `pop %rdx; ret`. With the stack pointer pointing to `X + 16`, the CPU pops `0` from the stack and sets `rdx` register to `0`. It then pops the address to code sequence `syscall` from the stack, and sets `P`C to this value; 5. The CPU runs `syscall`. At this point, `rax` holds `59`, `rdi` points to `/bin/sh`, and both `rsi` and `rdx` are zero, the CPU invokes `execve("/bin/sh, NULL, NULL);`, granting the attacker a shell for further manipulations. This sequence of ROP gadgets, referred to as **ROP chains**, demonstrates how a complete ROP attack works. Two key takeaways are: * **ROP does not inject new code**. Instead, it injects data into the stack and leverages the existing code loaded in memory and marked them as executable. W^X protections hence cannot prevent ROP attacks. * **Attackers can mine ROP gadgets from the [libc](https://en.wikipedia.org/wiki/C_standard_library) library**. This is because modern computers employs [protection rings](https://en.wikipedia.org/wiki/Protection_ring) as a way for privilege encapsulations: on x86-64 computers, programs normally run at ring level 3, while libc runs at ring level 1. Lower ring levels have higher privileges, meaning that even if a program misbehaves, its capacities are limited at ring level 3. However, by using ROP gadgets in the libc library which runs at ring level 1, ROP attacks can have higher privileges and execute more damaging operations then normal shellcodes. Note that the above examples simply show the most basic ROP gadgets. In reality, ROP gadgets come in all kinds of forms. Since they come from compiler outputs, they can be combined in the least expected way, and can vary the forms as new compiler optimizations come out. Numerous tools (e.g., [ropper](https://scoding.de/ropper/), [ropr](https://github.com/Ben-Lichtman/ropr)) and research papers (e.g., *[Experiments on ROP Attack with Various Instruction Set Architectures](https://dl.yumulab.org/papers/42/paper.pdf)*, *[ROPGMN](https://www.sciencedirect.com/science/article/abs/pii/S0167739X24005314)*, *[Detecting and Preventing ROP Attacks using Machine Learning on ARM](https://www.infosun.fim.uni-passau.de/ch/publications/compsac23.pdf)*, *[KROP](https://arxiv.org/pdf/2406.11880)* ) keep coming out, making it almost impossible to enumerate all possible ROP gadget combinations. ### ROP on ARM & RISC-V ROP attacks are not limited to CISC architectures, where instructions vary in length. They also affect RISC designs, such as [ARM](https://developer.arm.com/documentation/102433/0200/Return-oriented-programming) and [RISC-V](https://pure.royalholloway.ac.uk/ws/portalfiles/portal/37157938/ROP_RISCV.pdf). Take the following sequence for example: ``` 13 4f 83 23 0b 00 ``` Decoding from the start, the first four bytes represent `xori t5,t1,568` following the RISC-V ISA. But if we skip the first two, the latter four represent `lw t2,0(s6)`. This illustrates that a byte stream interpretation also requires `PC` register in a RISC design such as RISC-V. As a result, one can find ROP gadgets from a RISC-V program as well. ### ROP on CKB-VM CKB’s RISC-V machine operates in a more restricted environment: for programs running on CKB, there are no `execve` syscalls to hijack a running shell, and all runtime states are publicly visible on a public blockchain like CKB. However, ROP attacks can still occur on CKB: one could construct an ROP chain that sets `a0` to `0`, `a7` to `93`, then executes `ecall`. This causes CKB-VM to immediately return with a success code (`0`), potentially allowing a script to pass validation when it should have failed—such as a lock script succeeding without a valid signature. ### Short Recap Let’s briefly recap what we’ve learned so far: * ROP attacks utilize existing executable code for malicious purposes. W^X cannot prevent ROP. * ROP is possible across multiple architecture, including x86-64, ARM, RISC-V, and CKB. * The landscape of ROP is constantly evolving. With new tools, techniques, and research emerging regularly, it’s impossible to foresee all ROP gadgets. ROP has been extensively studied over the years, leading to various mitigation strategies, which can be broadly categorized into two main approaches: * **Software Solutions**: Covering techniques like rewriting code sequences and implementing Retguard to prevent the creation of ROP gadgets * **Hardware Solutions**: Introducing additional CPU instructions with Control Flow Integrity (CFI) checks to safeguard control flow. I’ll explore these strategies in greater detail in the following sections. ## Software Solutions to Mitigate ROP ### Rewriting Sequence Certain instruction sequences are often targeted to form ROP gadgets. To prevent ROP, one approach is to alter the compiler, so that such sequences can never be generated. Take the following example: ``` 89 c3 mov %eax,%ebx 90. ``` In x86-64, `c3` represents the `ret` instruction, making it a potential target for ROP gadgets. We can rewrite it into the following equivalent sequence: ``` 48 87 d8 xchgq %rbx, %rax 89 d8 movl %ebx, %eax 48 87 d8 xchgq %rbx, %rax ``` The new sequence lacks `c3` byte at the expense of more bytes and more executed instructions. However, it is really up to real benchmarks to see if this causes noticeable overhead. Further analysis has revealed that the `rbx` register in x86-64 is often the source of ROP gadgets, due to the way Intel encodes x86-64 instructions. Hence, the OpenBSD team decided to avoid `rbx` register wherever possible, reducing the number of potential ROP gadgets. Again, this approach comes at the cost of having bigger code fragments, more instructions to execute, and an additional patched compiler. While OpenBSD has integrated these changes into its distribution, other environments must weigh the benefits against the costs. For a deeper dive, I would strongly recommend Todd Mortimer’s [work](https://www.openbsd.org/papers/asiabsdcon2019-rop-slides.pdf). ### Retguard’s Solution: Prologue and Epilogue Todd Mortimer also introduced Retguard in this [work](https://www.openbsd.org/papers/asiabsdcon2019-rop-slides.pdf) for securing OpenBSD known. ROP attacks typically occur when you enter a function `foo`, but the stack was manipulated, so the CPU exits to another code fragment that is not `foo`. What if to verify that, at each function exit, it is the same function for exiting and entering? Retguard introduces two components to perform this task: * **Prologue**: A prologue is inserted to each function’s entry, taking two inputs: - - A `cookie` value, a random data assigned for this particular function. - - The return address, where to jump to when current function exits—as inputs. The prologue computes the XOR value of these two, and stores the result into the current function’s [frame](https://en.wikipedia.org/wiki/Call_stack#Stack_and_frame_pointers) section, a dedicated memory region designated to the current function to hold data, separated from the stack. * **Epilogue**: An epilogue is inserted to the location where a function might exit. It takes two inputs: - - The saved XOR value from the prologue in the frame section - - The return address it now can access to (most likely popped from the stack in x64 machine, or read from a special `RA` register in RISC design) The epilogue computes the XOR of these two. If the result matches the original `cookie`, execution proceeds. Otherwise, the epilogue halts the program, signaling an error. This prologue-epilogue mechanism in Retguard guards the call stack from tampering. At a noticeable but acceptable cost (both in performance and code size), Retguard eliminates a significant number of ROP gadgets from the OpenBSD kernel. Like other software-based mitigations, it requires a patched compiler, and it is up to each environment to decide if such technique shall be employed. ## Hardware Advancements to Mitigate ROP In addition to software solutions, hardware-based defenses have also been developed. For instance, Intel has introduced [Indirect Branch Tracking](https://edc.intel.com/content/www/us/en/design/ipla/software-development-platforms/client/platforms/alder-lake-desktop/12th-generation-intel-core-processors-datasheet-volume-1-of-2/007/indirect-branch-tracking/?language=en) feature starting with its 12th generation core processors, using a new instruction `endbr32` or `endbr64` added at every location the program might jump to or call into. When the CPU executes a jump/call, it asserts that the target location is a proper `endbr32` / `endbr64` instruction, before updating the program counter `PC` register to proper values. Otherwise, the CPU halts to terminate the program. This ensures that all control flows will follow the intended way, preventing ROP attacks from redirecting execution arbitrary locations. Modern OSes have already extensively leveraged `endbr32` / `endbr64` instructions. Ubuntu 24.04, for instance, has included these instructions in its packages: ``` $ objdump -d /bin/bash | head -n 50 /bin/bash: file format elf64-x86-64 Disassembly of section .init: 0000000000030000 <.init>: 30000: f3 0f 1e fa endbr64 30004: 48 83 ec 08 sub $0x8,%rsp 30008: 48 8b 05 d9 7e 12 00 mov 0x127ed9(%rip),%rax # 157ee8 <__gmon_start__@Base> 3000f: 48 85 c0 test %rax,%rax 30012: 74 02 je 30016 <unlink@plt-0xe1a> 30014: ff d0 call *%rax 30016: 48 83 c4 08 add $0x8,%rsp 3001a: c3 ret Disassembly of section .plt: 0000000000030020 <.plt>: 30020: ff 35 a2 76 12 00 push 0x1276a2(%rip) # 1576c8 <o_options@@Base+0x1cc8> 30026: ff 25 a4 76 12 00 jmp *0x1276a4(%rip) # 1576d0 <o_options@@Base+0x1cd0> 3002c: 0f 1f 40 00 nopl 0x0(%rax) 30030: f3 0f 1e fa endbr64 30034: 68 00 00 00 00 push $0x0 30039: e9 e2 ff ff ff jmp 30020 <unlink@plt-0xe10> 3003e: 66 90 xchg %ax,%ax 30040: f3 0f 1e fa endbr64 30044: 68 01 00 00 00 push $0x1 30049: e9 d2 ff ff ff jmp 30020 <unlink@plt-0xe10> 3004e: 66 90 xchg %ax,%ax 30050: f3 0f 1e fa endbr64 30054: 68 02 00 00 00 push $0x2 30059: e9 c2 ff ff ff jmp 30020 <unlink@plt-0xe10> 3005e: 66 90 xchg %ax,%ax 30060: f3 0f 1e fa endbr64 30064: 68 03 00 00 00 push $0x3 30069: e9 b2 ff ff ff jmp 30020 <unlink@plt-0xe10> 3006e: 66 90 xchg %ax,%ax 30070: f3 0f 1e fa endbr64 30074: 68 04 00 00 00 push $0x4 30079: e9 a2 ff ff ff jmp 30020 <unlink@plt-0xe10> 3007e: 66 90 xchg %ax,%ax 30080: f3 0f 1e fa endbr64 30084: 68 05 00 00 00 push $0x5 30089: e9 92 ff ff ff jmp 30020 <unlink@plt-0xe10> 3008e: 66 90 xchg %ax,%ax 30090: f3 0f 1e fa endbr64 30094: 68 06 00 00 00 push $0x6 30099: e9 82 ff ff ff jmp 30020 <unlink@plt-0xe10> 3009e: 66 90 xchg %ax,%ax ``` The `endbr32` / `endbr64` instructions has been carefully designed, so they are `nop` instructions—meaning they can do nothing at all—on CPUs prior to their introductions. Having them doesn't have any effect on older CPUs but enhances security on supported hardware. ## RISC-V’s Latest Achievements: CFI Extension The above mitigations against ROP fall into two categories: * **Compiler Modifications**: Can generate more secure binary assembly code. * **Additional CPU instructions**: Coming with Control Flow Integrity (CFI) checks to prevent exploitation Back to the beginning of designing CKB-VM, we throughly studied ROP and recognized that a vulnerability in a CKB script could potentially open the door to ROP attacks. However, we eventually did not introduce any specific mitigation against ROP in CKB-VM. Our decision was to stay aligned with the RISC-V ecosystem, avoiding shipping any custom RISC-V spec with additional instructions that would require a patched compiler. Nor do we want to maintain our own compiler set, eliminating the potential that any RISC-V-compliant compiler shall be able to produce CKB script. As the result, we shipped the first version of CKB-VM without ROP mitigations, but that does not mean we’ve ignore this issue: * We’ve [reached out](https://groups.google.com/a/groups.riscv.org/g/isa-dev/c/LyZzjJG7_18/m/pCSnKZPdBAAJ) to the RISC-V community for possible extension similar to Intel’s solution, and kept monitoring advancements in this field; * We’ve been watching over progress and writing secure CKB scripts. Since ROP relies on existing vulnerabilities, secure CKB scripts can kept ROP purely theoretical. We were thrilled when the **RISC-V CFI (Control-Flow Integrity) Extension** was officialy [ratified](https://github.com/riscv/riscv-cfi/releases/tag/v1.0) in July 2024. Designed by the brilliant minds from the RISC-V Foundation, this extension directly addresses ROP attacks with two key features: * `Zicfilp` extension introduces **landing pad**: Resembles Intel’s `endbr32` / `endbr64` to ensure that the CPU can only jump to valid, permitted targets. * `Zicfiss` extension introduces **shadow stack** with a series of instructions:. Offers a hardware solution similar to Retguard, where CPU ensures the control flow integrity or simply puts the call stack, preventing tampering throughout execution. Together, these features offer the state-of-the-art mitigations against ROP. More importantly, RISC-V CFI is now an official extension, meaning all future RISC-V CPUs, compilers, and tools will support this extension. In fact, LLVM 19 has already [supported](https://releases.llvm.org/19.1.0/docs/ReleaseNotes.html#changes-to-the-risc-v-backend), and I believe other compilers and tools will follow soon. Once fully adopted, CKB script developers can simply turn them on like a switch during code compilation. Without modifying the code, they can enjoy the security provided by RISC-V CFI extensions. Even if a vulnerability exists in a CKB script, these built-in enforcements can prevent it from being exploited. ## Final Words Security is complex. While we strive for maximum security, certain design principles might get in the way from introducing specific mitigations. ROP is a prime example: while we did learn much about it early on, implementing the best mitigations needs proper timing. Now the time has come. We are happy to introduce RISC-V CFI in CKB’s next hardfork, bringing stronger security for everyone. *** ✍🏻 Written by Xuejie Xiao His previous posts include: * [A Journey Optimizing CKB Smart Contract: Porting Bitcoin as an Example](https://blog.cryptape.com/a-journey-optimizing-ckb-smart-contract) * [Optimizing C++ Code for CKB-VM: Porting Bitcoin as an Example](https://blog.cryptape.com/optimizing-c-code-for-ckb-vm) Find more in his personal website [Less is More](https://xuejie.space/). @ 9967f375:04f9a5e1
2025-02-13 08:39:58El día 13, primer viernes de Cuaresma asistió su Exc. y Real Audiencia en la Capilla Real del Palacio a la Misa, y Sermón, que predicó el Doctor Don Pedro Ramírez del Castillo, Canónigo Penitenciario de la Metropoltana. #GacetadeMéxico #Febrero
@ 9967f375:04f9a5e1
2025-02-13 08:39:58El día 13, primer viernes de Cuaresma asistió su Exc. y Real Audiencia en la Capilla Real del Palacio a la Misa, y Sermón, que predicó el Doctor Don Pedro Ramírez del Castillo, Canónigo Penitenciario de la Metropoltana. #GacetadeMéxico #Febrero @ bf47c19e:c3d2573b
2025-02-13 08:10:44Originalni tekst na [dvadesetjedan.com](https://dvadesetjedan.com/blog/bitcoin-privatnost-najbolje-prakse). ###### Autor: [Gigi](https://dergigi.com/2021/03/14/bitcoin-privacy-best-practices/) / Prevod na srpski: [Plumsky](https://t.me/Plumski) --- > Postoji sveto carstvo privatnosti za svakog čoveka gde on bira i pravi odluke – carstvo stvoreno na bazičnim pravima i slobode koje zakon, generalno, ne sme narušavati. Džefri Fišer, Arhiepiskop Canterberija (1959) Pre ne toliko dugo, uobičajen režim interneta je bio neenkriptovan običan tekst (plain text). Svi su mogli špiunirati svakoga i mnogi nisu o tome ni razmišljali. Globalno obelodanjivanje nadzora 2013. je to promenilo i danas se koriste mnogo bezbedniji protokoli i end-to-end enkripcija postaje standard sve više. Iako bitcoin postaje tinejdžer, mi smo – metaforično govoreći – i dalje u dobu običnog teksta narandžastog novčića. Bitcoin je radikalno providljiv protokol sam po sebi, ali postoje značajni načini da korisnik zaštiti svoju privatnost. U ovom članku želimo da istaknemo neke od ovih strategija, prodiskutujemo najbolje prakse, i damo preporuke koje mogu primeniti i bitcoin novajlije i veterani. #### Zašto je privatnost bitna > Privatnost je potrebna da bi otvoreno društvo moglo da funkcioniše u digitalnoj eri. Privatnost nije isto što i tajanstvenost. Privatna stvar je nešto što neko ne želi da ceo svet zna, a tajna stvar je nešto što neko ne želi bilo ko da zna. Privatnost je moć da se čovek selektivno otkriva svom okruženju. Ovim snažnim rečima Erik Hjus je započeo svoj tekst Sajferpankov Manifesto (Cypherpunk's Manifesto) 1993. Razlika između privatnosti i tajanstvenosti je suptilna ali jako važna. Odlučiti se za privatnost ne znači da neko ima tajne koje želi sakriti. Da ovo ilustrujemo shvatite samo da ono što obavljate u svom toaletu ili u spavaćoj sobi nije niti ilegalno niti tajna (u mnogim slučajevima), ali vi svejedno odlučujete da zatvorite vrata i navučete zavese. Slično tome, koliko para imate i gde ih trošite nije naručito tajna stvar. Ipak, to bi trebalo biti privatan slučaj. Mnogi bi se složili da vaš šef ne treba da zna gde vi trošite vašu platu. Privatnosti je čak zaštićena od strane mnogobrojnih internacionalnih nadležnih organa. Iz Američke Deklaracije Prava i Dužnosti Čoveka (American Declaration of the Rights and Duties of Man) Ujedinjenim Nacijama, napisano je da je privatnost fundamentalno prava gradjana širom sveta. > Niko ne sme biti podvrgnut smetnjama njegovoj privatnosti, porodici, rezidenciji ili komunikacijama, niti napadnuta njegova čast i reputacija. Svi imaju pravo da se štite zakonom protiv takvih smetnja ili napada. Artikal 12, Deklaracija Ljudskih Prava Ujedinjenih Nacija #### Bitcoin i privatnost Iako je bitcoin često opisivan kao anoniman način plaćanja medijima, on u stvari poseduje potpuno suprotne osobine. On je poluanoniman u najboljem slučaju i danas mnogima nije ni malo lako primeniti taktike da bi bili sigurni da njihov poluanonimni identitet na bitcoin mreži ne bude povezan sa legalnim identitetom u stvarnom svetu. Bitcoin je otvoren sistem. On je javna baza podataka koju svako može da proučava i analizira. Znači, svaka transakcija koja je upisana u tu bazu kroz dokaz rada (proof-of-work) postojaće i biće otkrivena dokle god bitcoin postoji, što znači - zauvek. Ne primenjivati najbolje prakse privatnosti može imati štetne posledice u dalekoj budućnosti. Privatnost, kao sigurnost, je proces koji je težak, ali nije nemoguć. Alatke nastavljaju da se razvijaju koje čuvaju privatnost kad se koristi bitcoin and srećom mnoge od tih alatki su sve lakše za korišćenje. Nažalost ne postoji panacea u ovom pristupu. Mora se biti svesan svih kompromisa i usavršavati te prakse dok se one menjaju. #### Najbolje prakse privatnosti Kao i sve u bitcoinu, kontrola privatnosti je postepena, korak po korak, procedura. Naučiti i primeniti ove najbolje prakse zahteva strpljivost i odgovornost, tako da ne budite obeshrabreni ako vam se čini da je to sve previše. Svaki korak, koliko god bio mali, je korak u dobrom pravcu. Koje korake preduzeti da bi uvećali svoju privatnost: * Budite u vlasništvu sami svojih novčića * Nikad ne ponavljajte korišćenje istih adresa * Minimizirajte korišćenje servisa koji zahtevaju identitet (Know your customer - KYC) * Minimizirajte sve izloženosti trećim licima * Upravljajte svojim nodom * Koristite Lightning mrežu za male transakcije * Nemojte koristiti javne blok pretraživače za svoje transakcije * Koristite metodu CoinJoin često i rano pri nabavljanju svojih novčića **Budite u vlasništvu sami svojih novčića**: Ako ključevi nisu tvoji, onda nije ni bitcoin. Ako neko drugo drži vaš bitcoin za vas, oni znaju sve što se može znati: količinu, istoriju transakcija pa i sve buduće transakcije, itd. Preuzimanje vlasništva bitcoina u svoje ruke je prvi i najvažniji korak. **Nikad ne kroistite istu adresu dvaput**: Ponavljanje adresa poništava privatnost pošiljalca i primaoca bitcoina. Ovo se treba izbegavati pod svaku cenu. **Minimizirajte korišćenje servisa koji zahtevaju identitet (KYC)**: Vezivati svoj legalni identitet za svoje bitcoin adrese je zlo koje se zahteva od strane mnogih državnih nadležnosti. Dok je efektivnost ovih zakona i regulacija disputabilno, posledice njihovog primenjivanja su uglavnom štetne po korisnicima. Ovo je očigledno pošto je česta pojava da se te informacije često izlivaju iz slabo obezbeđenih digitalnih servera. Ako izaberete da koristite KYC servise da bi nabavljali bitcoin, proučite i razumite odnos između vas i tog biznisa. Vi ste poverljivi tom biznisu za sve vaše lične podatke, pa i buduće obezbeđenje tih podataka. Ako i dalje zarađujete kroz fiat novčani sistem, mi preporučujemo da koristite samo bitcoin ekskluzivne servise koji vam dozvoljavaju da autamatski kupujete bitcoin s vremena na vreme. Ako zelite da potpuno da izbegnete KYC, pregledajte https://bitcoinqna.github.io/noKYConly/. **Minimizirajte sve izloženosti trećim licima**: Poverljivost trećim licima je bezbednosna rupa (https://nakamotoinstitute.org/trusted-third-parties/). Ako možete biti poverljivi samo sebi, onda bi to tako trebalo da bude. **Upravljajte svojim nodom**: Ako nod nije tvoj, onda nisu ni pravila. Upravljanje svojim nodom je suštinska potreba da bi se bitcoin koristio na privatan način. Svaka interakcija sa bitcoin mrežom je posrednjena nodom. Ako vi taj nod ne upravljate, čiji god nod koristite može da vidi sve što vi radite. Ova upustva (https://bitcoiner.guide/node/) su jako korisna da bi započeli proces korišćenja svog noda. **Koristite Lightning mrežu za male transakcije**: Pošto Lightning protokol ne koristi glavnu bitcoin mrežu za trasakcije onda je i samim tim povećana privatnost korišćenja bez dodatnog truda. Iako je i dalje rano, oni apsolutno bezobzirni periodi Lightning mreže su verovatno daleko iza nas. Korišćenje Lightning-a za transakcije malih i srednjih veličina će vam pomoći da uvećate privatnost a da smanjite naplate svojih pojedinačnih bitcoin transakcija. **Nemojte koristiti javne blok pretraživače za svoje transakcije**: Proveravanje adresa na javnim blok pretraživačima povezuje te adrese sa vašim IP podacima, koji se onda mogu koristiti da se otkrije vaš identitet. Softveri kao Umbrel i myNode vam omogućavaju da lako koristite sami svoj blok pretraživač. Ako morate koristiti javne pretraživače, uradite to uz VPN ili Tor. **Koristite CoinJoin često i rano pri nabavljanju svojih novčića**: Pošto je bitcoin večan, primenjivanje saradničkih CoinJoin praksa će vam obezbediti privatnost u budućnosti. Dok su CoinJoin transakcije svakovrsne, softveri koji su laki za korišćenje već sad postoje koji mogu automatizovati ovu vrstu transakcija. Samourai Whirlpool (https://samouraiwallet.com/whirlpool) je odličan izbor za Android korisnike. Joinmarket (https://github.com/joinmarket-webui/jam) se može koristiti na vašem nodu. A servisi postoje koji pri snabdevanju vašeg bitcoina istog trenutka obave CoinJoin tranzakciju automatski. #### Zaključak Svi bi trebalo da se potrude da koriste bitcoin na što privatniji način. Privatnost nije isto što i tajanstvenost. Privatnost je ljudsko pravo i mi svi trebamo da branimo i primenljujemo to pravo. Teško je izbrisati postojeće informacije sa interneta; a izbrisati ih sa bitcoin baze podataka je nemoguće. Iako su daleko od savršenih, alatke postoje danas koje vam omogućavaju da najbolje prakse privatnosti i vi sami primenite. Mi smo vam naglasili neke od njih i - kroz poboljšanje u bitcoin protokolu kroz Taproot i Schnorr - one će postajati sve usavršenije. Bitcoin postupci se ne mogu lako opisati korišćenjem tradicionalnim konceptima. Pitanja kao što su "Ko je vlasnik ovog novca?" ili "Odakle taj novac potiče?" postaju sve teža da se odgovore a u nekim okolnostima postaju potpuno beznačajna. Satoši je dizajnirao bitcoin misleći na privatnost. Na nivou protokola svaka bitcoin transakcija je proces "topljenja" koji za sobom samo ostavlja heuristične mrvice hleba. Protokolu nije bitno odakle se pojavio bilo koji bitcoin ili satoši. Niti je njega briga ko je legalan identitet vlasnika. Protokolu je samo važno da li su digitalni potpisi validni. Dokle god je govor slobodan, potpisivanje poruka - privatno ili ne - ne sme biti kriminalan postupak. Dodatni Resursi [This Month in Bitcoin Privacy](https://enegnei.github.io/This-Month-In-Bitcoin-Privacy/) | Janine [Hodl Privacy FAQ](https://6102bitcoin.com/faq-hodl-privacy/) | 6102 [Digital Privacy](https://6102bitcoin.com/blog/digital-privacy/) | 6102 [UseWhirlpool.com](http://usewhirlpool.com/) | Bitcoin Q+A [Bitcoin Privacy Guide](https://bitcoiner.guide/privacy/) | Bitcoin Q+A Ovaj članak napisan je u saradnji sa Matt Odellom, nezavisnim bitcoin istraživačem. Nađite njegove preporuke za privatnost na [werunbtc.com](https://werunbtc.com/) [Originalni tekst](https://dergigi.com/2021/03/14/bitcoin-privacy-best-practices/)
@ bf47c19e:c3d2573b
2025-02-13 08:10:44Originalni tekst na [dvadesetjedan.com](https://dvadesetjedan.com/blog/bitcoin-privatnost-najbolje-prakse). ###### Autor: [Gigi](https://dergigi.com/2021/03/14/bitcoin-privacy-best-practices/) / Prevod na srpski: [Plumsky](https://t.me/Plumski) --- > Postoji sveto carstvo privatnosti za svakog čoveka gde on bira i pravi odluke – carstvo stvoreno na bazičnim pravima i slobode koje zakon, generalno, ne sme narušavati. Džefri Fišer, Arhiepiskop Canterberija (1959) Pre ne toliko dugo, uobičajen režim interneta je bio neenkriptovan običan tekst (plain text). Svi su mogli špiunirati svakoga i mnogi nisu o tome ni razmišljali. Globalno obelodanjivanje nadzora 2013. je to promenilo i danas se koriste mnogo bezbedniji protokoli i end-to-end enkripcija postaje standard sve više. Iako bitcoin postaje tinejdžer, mi smo – metaforično govoreći – i dalje u dobu običnog teksta narandžastog novčića. Bitcoin je radikalno providljiv protokol sam po sebi, ali postoje značajni načini da korisnik zaštiti svoju privatnost. U ovom članku želimo da istaknemo neke od ovih strategija, prodiskutujemo najbolje prakse, i damo preporuke koje mogu primeniti i bitcoin novajlije i veterani. #### Zašto je privatnost bitna > Privatnost je potrebna da bi otvoreno društvo moglo da funkcioniše u digitalnoj eri. Privatnost nije isto što i tajanstvenost. Privatna stvar je nešto što neko ne želi da ceo svet zna, a tajna stvar je nešto što neko ne želi bilo ko da zna. Privatnost je moć da se čovek selektivno otkriva svom okruženju. Ovim snažnim rečima Erik Hjus je započeo svoj tekst Sajferpankov Manifesto (Cypherpunk's Manifesto) 1993. Razlika između privatnosti i tajanstvenosti je suptilna ali jako važna. Odlučiti se za privatnost ne znači da neko ima tajne koje želi sakriti. Da ovo ilustrujemo shvatite samo da ono što obavljate u svom toaletu ili u spavaćoj sobi nije niti ilegalno niti tajna (u mnogim slučajevima), ali vi svejedno odlučujete da zatvorite vrata i navučete zavese. Slično tome, koliko para imate i gde ih trošite nije naručito tajna stvar. Ipak, to bi trebalo biti privatan slučaj. Mnogi bi se složili da vaš šef ne treba da zna gde vi trošite vašu platu. Privatnosti je čak zaštićena od strane mnogobrojnih internacionalnih nadležnih organa. Iz Američke Deklaracije Prava i Dužnosti Čoveka (American Declaration of the Rights and Duties of Man) Ujedinjenim Nacijama, napisano je da je privatnost fundamentalno prava gradjana širom sveta. > Niko ne sme biti podvrgnut smetnjama njegovoj privatnosti, porodici, rezidenciji ili komunikacijama, niti napadnuta njegova čast i reputacija. Svi imaju pravo da se štite zakonom protiv takvih smetnja ili napada. Artikal 12, Deklaracija Ljudskih Prava Ujedinjenih Nacija #### Bitcoin i privatnost Iako je bitcoin često opisivan kao anoniman način plaćanja medijima, on u stvari poseduje potpuno suprotne osobine. On je poluanoniman u najboljem slučaju i danas mnogima nije ni malo lako primeniti taktike da bi bili sigurni da njihov poluanonimni identitet na bitcoin mreži ne bude povezan sa legalnim identitetom u stvarnom svetu. Bitcoin je otvoren sistem. On je javna baza podataka koju svako može da proučava i analizira. Znači, svaka transakcija koja je upisana u tu bazu kroz dokaz rada (proof-of-work) postojaće i biće otkrivena dokle god bitcoin postoji, što znači - zauvek. Ne primenjivati najbolje prakse privatnosti može imati štetne posledice u dalekoj budućnosti. Privatnost, kao sigurnost, je proces koji je težak, ali nije nemoguć. Alatke nastavljaju da se razvijaju koje čuvaju privatnost kad se koristi bitcoin and srećom mnoge od tih alatki su sve lakše za korišćenje. Nažalost ne postoji panacea u ovom pristupu. Mora se biti svesan svih kompromisa i usavršavati te prakse dok se one menjaju. #### Najbolje prakse privatnosti Kao i sve u bitcoinu, kontrola privatnosti je postepena, korak po korak, procedura. Naučiti i primeniti ove najbolje prakse zahteva strpljivost i odgovornost, tako da ne budite obeshrabreni ako vam se čini da je to sve previše. Svaki korak, koliko god bio mali, je korak u dobrom pravcu. Koje korake preduzeti da bi uvećali svoju privatnost: * Budite u vlasništvu sami svojih novčića * Nikad ne ponavljajte korišćenje istih adresa * Minimizirajte korišćenje servisa koji zahtevaju identitet (Know your customer - KYC) * Minimizirajte sve izloženosti trećim licima * Upravljajte svojim nodom * Koristite Lightning mrežu za male transakcije * Nemojte koristiti javne blok pretraživače za svoje transakcije * Koristite metodu CoinJoin često i rano pri nabavljanju svojih novčića **Budite u vlasništvu sami svojih novčića**: Ako ključevi nisu tvoji, onda nije ni bitcoin. Ako neko drugo drži vaš bitcoin za vas, oni znaju sve što se može znati: količinu, istoriju transakcija pa i sve buduće transakcije, itd. Preuzimanje vlasništva bitcoina u svoje ruke je prvi i najvažniji korak. **Nikad ne kroistite istu adresu dvaput**: Ponavljanje adresa poništava privatnost pošiljalca i primaoca bitcoina. Ovo se treba izbegavati pod svaku cenu. **Minimizirajte korišćenje servisa koji zahtevaju identitet (KYC)**: Vezivati svoj legalni identitet za svoje bitcoin adrese je zlo koje se zahteva od strane mnogih državnih nadležnosti. Dok je efektivnost ovih zakona i regulacija disputabilno, posledice njihovog primenjivanja su uglavnom štetne po korisnicima. Ovo je očigledno pošto je česta pojava da se te informacije često izlivaju iz slabo obezbeđenih digitalnih servera. Ako izaberete da koristite KYC servise da bi nabavljali bitcoin, proučite i razumite odnos između vas i tog biznisa. Vi ste poverljivi tom biznisu za sve vaše lične podatke, pa i buduće obezbeđenje tih podataka. Ako i dalje zarađujete kroz fiat novčani sistem, mi preporučujemo da koristite samo bitcoin ekskluzivne servise koji vam dozvoljavaju da autamatski kupujete bitcoin s vremena na vreme. Ako zelite da potpuno da izbegnete KYC, pregledajte https://bitcoinqna.github.io/noKYConly/. **Minimizirajte sve izloženosti trećim licima**: Poverljivost trećim licima je bezbednosna rupa (https://nakamotoinstitute.org/trusted-third-parties/). Ako možete biti poverljivi samo sebi, onda bi to tako trebalo da bude. **Upravljajte svojim nodom**: Ako nod nije tvoj, onda nisu ni pravila. Upravljanje svojim nodom je suštinska potreba da bi se bitcoin koristio na privatan način. Svaka interakcija sa bitcoin mrežom je posrednjena nodom. Ako vi taj nod ne upravljate, čiji god nod koristite može da vidi sve što vi radite. Ova upustva (https://bitcoiner.guide/node/) su jako korisna da bi započeli proces korišćenja svog noda. **Koristite Lightning mrežu za male transakcije**: Pošto Lightning protokol ne koristi glavnu bitcoin mrežu za trasakcije onda je i samim tim povećana privatnost korišćenja bez dodatnog truda. Iako je i dalje rano, oni apsolutno bezobzirni periodi Lightning mreže su verovatno daleko iza nas. Korišćenje Lightning-a za transakcije malih i srednjih veličina će vam pomoći da uvećate privatnost a da smanjite naplate svojih pojedinačnih bitcoin transakcija. **Nemojte koristiti javne blok pretraživače za svoje transakcije**: Proveravanje adresa na javnim blok pretraživačima povezuje te adrese sa vašim IP podacima, koji se onda mogu koristiti da se otkrije vaš identitet. Softveri kao Umbrel i myNode vam omogućavaju da lako koristite sami svoj blok pretraživač. Ako morate koristiti javne pretraživače, uradite to uz VPN ili Tor. **Koristite CoinJoin često i rano pri nabavljanju svojih novčića**: Pošto je bitcoin večan, primenjivanje saradničkih CoinJoin praksa će vam obezbediti privatnost u budućnosti. Dok su CoinJoin transakcije svakovrsne, softveri koji su laki za korišćenje već sad postoje koji mogu automatizovati ovu vrstu transakcija. Samourai Whirlpool (https://samouraiwallet.com/whirlpool) je odličan izbor za Android korisnike. Joinmarket (https://github.com/joinmarket-webui/jam) se može koristiti na vašem nodu. A servisi postoje koji pri snabdevanju vašeg bitcoina istog trenutka obave CoinJoin tranzakciju automatski. #### Zaključak Svi bi trebalo da se potrude da koriste bitcoin na što privatniji način. Privatnost nije isto što i tajanstvenost. Privatnost je ljudsko pravo i mi svi trebamo da branimo i primenljujemo to pravo. Teško je izbrisati postojeće informacije sa interneta; a izbrisati ih sa bitcoin baze podataka je nemoguće. Iako su daleko od savršenih, alatke postoje danas koje vam omogućavaju da najbolje prakse privatnosti i vi sami primenite. Mi smo vam naglasili neke od njih i - kroz poboljšanje u bitcoin protokolu kroz Taproot i Schnorr - one će postajati sve usavršenije. Bitcoin postupci se ne mogu lako opisati korišćenjem tradicionalnim konceptima. Pitanja kao što su "Ko je vlasnik ovog novca?" ili "Odakle taj novac potiče?" postaju sve teža da se odgovore a u nekim okolnostima postaju potpuno beznačajna. Satoši je dizajnirao bitcoin misleći na privatnost. Na nivou protokola svaka bitcoin transakcija je proces "topljenja" koji za sobom samo ostavlja heuristične mrvice hleba. Protokolu nije bitno odakle se pojavio bilo koji bitcoin ili satoši. Niti je njega briga ko je legalan identitet vlasnika. Protokolu je samo važno da li su digitalni potpisi validni. Dokle god je govor slobodan, potpisivanje poruka - privatno ili ne - ne sme biti kriminalan postupak. Dodatni Resursi [This Month in Bitcoin Privacy](https://enegnei.github.io/This-Month-In-Bitcoin-Privacy/) | Janine [Hodl Privacy FAQ](https://6102bitcoin.com/faq-hodl-privacy/) | 6102 [Digital Privacy](https://6102bitcoin.com/blog/digital-privacy/) | 6102 [UseWhirlpool.com](http://usewhirlpool.com/) | Bitcoin Q+A [Bitcoin Privacy Guide](https://bitcoiner.guide/privacy/) | Bitcoin Q+A Ovaj članak napisan je u saradnji sa Matt Odellom, nezavisnim bitcoin istraživačem. Nađite njegove preporuke za privatnost na [werunbtc.com](https://werunbtc.com/) [Originalni tekst](https://dergigi.com/2021/03/14/bitcoin-privacy-best-practices/) @ 04ed2b8f:75be6756
2025-02-13 08:02:39Freedom. It’s the word on everyone’s lips, the dream of every soul. We long for it, we chase it, we believe that if we can break free from this chain or that constraint, we will finally be free. **But true freedom is not about external circumstances—it’s about control.** The truth is, **the most powerful chains are the ones we place on ourselves**. The world can throw its challenges at you, life can dish out its unfair blows, but **if you cannot control yourself, your thoughts, your emotions, your reactions, then you are no different than a prisoner.** There is no freedom in chaos. There is no freedom in losing control. **Freedom is mastery—mastery of the self.** ## **Freedom Begins Within** You can have all the money in the world, live in the most luxurious place, and have every material possession your heart desires, but **if you cannot control your impulses, your habits, your desires—none of that will matter.** You are still a slave to your cravings. You are still a puppet to your own emotions, and that is **no real freedom.** What does freedom look like? - **It’s the power to act with purpose, not to react out of emotion.** - **It’s the strength to stay disciplined when every part of you wants to quit.** - **It’s the courage to say ‘no’ to distractions, to temptation, to things that steer you off course.** - **It’s the clarity to make choices that serve your growth, not your immediate desires.** True freedom is the ability to say, “I am in control of myself. I do not let my circumstances control me, nor my emotions rule me. I dictate my actions, my thoughts, my destiny.” ## **Self-Control: The Ultimate Weapon** The power to control yourself is your greatest weapon. Without it, **you are at the mercy of every challenge, every temptation, and every fleeting emotion**. You may feel like you are “free,” but without self-discipline, you are just a puppet swaying in the wind, vulnerable to every whim that blows your way. - **The impulse to procrastinate? You overcome it.** - **The desire to give up? You push through it.** - **The craving for comfort? You choose growth.** In the face of any storm, a man with self-control remains grounded, focused, and clear. He doesn’t react in anger or fear—he acts with purpose, with precision, and with vision. A man who cannot control himself is a man who is owned by his emotions, his desires, his distractions. But the man who conquers his mind, his body, his impulses—he is the one who **owns his life.** ## **The Price of Freedom** It’s not easy to control yourself. It requires constant effort, relentless discipline, and the courage to face yourself head-on. It means saying ‘no’ to what feels good now, to invest in what will make you stronger later. It means constantly improving, constantly fighting the urge to quit, to give in, to indulge in comfort. But the price of freedom is worth it. **For when you have control over yourself, no one can take your power.** You become the master of your fate. **You become unshakable.** ## **Freedom Through Discipline** So, ask yourself: **Are you truly free, or are you simply a slave to your impulses?** - **Do you control your actions, or do your actions control you?** - **Are you the master of your emotions, or are they the masters of you?** Freedom isn’t just about having no chains; it’s about not letting anything control you—least of all yourself. **And when you control yourself, there’s nothing you can’t accomplish.** A man who cannot control himself is never truly free. But a man who conquers his mind, his habits, his emotions—he is unstoppable. **Now go and choose to control yourself, and unlock the freedom that’s waiting for you. Or remain a prisoner to your impulses, forever shackled by the chains of your own making. The choice is yours.**
@ 04ed2b8f:75be6756
2025-02-13 08:02:39Freedom. It’s the word on everyone’s lips, the dream of every soul. We long for it, we chase it, we believe that if we can break free from this chain or that constraint, we will finally be free. **But true freedom is not about external circumstances—it’s about control.** The truth is, **the most powerful chains are the ones we place on ourselves**. The world can throw its challenges at you, life can dish out its unfair blows, but **if you cannot control yourself, your thoughts, your emotions, your reactions, then you are no different than a prisoner.** There is no freedom in chaos. There is no freedom in losing control. **Freedom is mastery—mastery of the self.** ## **Freedom Begins Within** You can have all the money in the world, live in the most luxurious place, and have every material possession your heart desires, but **if you cannot control your impulses, your habits, your desires—none of that will matter.** You are still a slave to your cravings. You are still a puppet to your own emotions, and that is **no real freedom.** What does freedom look like? - **It’s the power to act with purpose, not to react out of emotion.** - **It’s the strength to stay disciplined when every part of you wants to quit.** - **It’s the courage to say ‘no’ to distractions, to temptation, to things that steer you off course.** - **It’s the clarity to make choices that serve your growth, not your immediate desires.** True freedom is the ability to say, “I am in control of myself. I do not let my circumstances control me, nor my emotions rule me. I dictate my actions, my thoughts, my destiny.” ## **Self-Control: The Ultimate Weapon** The power to control yourself is your greatest weapon. Without it, **you are at the mercy of every challenge, every temptation, and every fleeting emotion**. You may feel like you are “free,” but without self-discipline, you are just a puppet swaying in the wind, vulnerable to every whim that blows your way. - **The impulse to procrastinate? You overcome it.** - **The desire to give up? You push through it.** - **The craving for comfort? You choose growth.** In the face of any storm, a man with self-control remains grounded, focused, and clear. He doesn’t react in anger or fear—he acts with purpose, with precision, and with vision. A man who cannot control himself is a man who is owned by his emotions, his desires, his distractions. But the man who conquers his mind, his body, his impulses—he is the one who **owns his life.** ## **The Price of Freedom** It’s not easy to control yourself. It requires constant effort, relentless discipline, and the courage to face yourself head-on. It means saying ‘no’ to what feels good now, to invest in what will make you stronger later. It means constantly improving, constantly fighting the urge to quit, to give in, to indulge in comfort. But the price of freedom is worth it. **For when you have control over yourself, no one can take your power.** You become the master of your fate. **You become unshakable.** ## **Freedom Through Discipline** So, ask yourself: **Are you truly free, or are you simply a slave to your impulses?** - **Do you control your actions, or do your actions control you?** - **Are you the master of your emotions, or are they the masters of you?** Freedom isn’t just about having no chains; it’s about not letting anything control you—least of all yourself. **And when you control yourself, there’s nothing you can’t accomplish.** A man who cannot control himself is never truly free. But a man who conquers his mind, his habits, his emotions—he is unstoppable. **Now go and choose to control yourself, and unlock the freedom that’s waiting for you. Or remain a prisoner to your impulses, forever shackled by the chains of your own making. The choice is yours.** @ bf47c19e:c3d2573b
2025-02-13 07:56:50Originalni tekst na [dvadesetjedan.com](https://dvadesetjedan.com/blog/niko-ne-moze-zabraniti-bitcoin) ###### Autor: [Parker Lewis](https://x.com/parkeralewis) / Prevod na srpski: [Plumsky](https://t.me/Plumski) --- Ideja da država može nekako zabraniti bitcoin je jedna od poslednjih faza tuge, tačno pred prihvatanje realnosti. Posledica ove rečenice je priznanje da bitcoin “funkcioniše”. U stvari, ona predstavlja činjenicu da bitcoin funkcioniše toliko dobro da on preti postojećim državnim monopolima nad novcem i da će zbog toga države da ga unište kroz regulativne prepreke da bi eliminisale tu pretnju. Gledajte na tvrdnju da će države zabraniti bitcoin kao kondicionalnu logiku. Da li bitcoin funkcioniše kao novac? Ako je odgovor „ne“, onda države nemaju šta da zabrane. Ako je odgovor „da“, onda će države da probaju da ga zabrane. Znači, glavna poenta ovog razmišljanja je pretpostavka da bitcoin funkcioiniše kao novac. Onda je sledeće logično pitanje da li intervencija od strane države može uspešno da uništi upravo taj funkcionalan bitcoin.  Za početak, svako ko pokušava da razume kako, zašto, ili da li bitcoin funkcioniše mora da proceni ta pitanja potpuno nezavisno od prouzrekovanja državne regulacije ili intervencije. Iako je nesumnjivo da bitcoin mora da postoji uzgred državnih regulativa, zamislite na momenat da države ne postoje. Sam od sebe, da li bi bitcoin funkcionisao kao novac, kad bi se prepustio slobodnom tržištu? Ovo pitanje se širi u dodatna pitanja i ubrzo se pretvara u bunar bez dna. Šta je novac? Šta su svojstva koja čine jednu vrstu novca bolje od druge? Da li bitcoin poseduje ta svojstva? Da li je bitcoin bolja verzija novca po takvim osobinama? Ako je finalni zaključak da bitcoin ne funkcioniše kao novac, implikacije državne intervencije su nebitne. Ali, ako je bitcoin funkcionalan kao novac, ta pitanja onda postaju bitna u ovoj debati, i svako ko o tome razmišlja bi morao imati taj početnički kontekst da bi mogao proceniti da li je uopšte moguće zabraniti. Po svom dizajnu, bitcoin postoji van države. Ali bitcoin nije samo van kontrole države, on u stvari funkcioniše bez bilo kakve saradnje centralizovanih identiteta. On je globalan i decentralizovan. Svako može pristupiti bitcoinu bez potrebe saglasnosti bilo koga i što se više širi sve je teže cenzurisati celokupnu mrežu. Arhitektura bitcoina je namerno izmišljena da bude otporna na bilo koje pokušaje države da ga zabrane. Ovo ne znači da države širom sveta neće pokušavati da ga regulišu, oporezuju ili čak da potpuno zabrane njegovo korišćenje. Naravno da će biti puno bitki i otpora protiv usvajanja bitcoina među građanima. Federal Reserve i Američki Treasury (i njihovi globalni suparnici) se neće ležeći predati dok bitcoin sve više i više ugrožava njihove monopole prihvatljivog novca. Doduše, pre nego što se odbaci ideja da države mogu potpuno zabraniti bitcoin, mora se prvo razumeti posledice tog stava i njegovog glasnika. #### Progresija poricanja i stepeni tuge Pripovesti skeptičara se neprestano menjaju kroz vreme. Prvi stepen tuge: bitcoin nikad ne može funkcionisati-njegova vrednost je osnovana ni na čemu. On je moderna verzija tulip manije. Sa svakim ciklusom uzbuđenja, vrednost bitcoina skače i onda vrlo brzo se vraća na dole. Često nazvano kao kraj njegove vrednosti, bitcoin svaki put odbija da umre i njegova vrednost pronađe nivo koji je uvek viši od prethodnih ciklusa globalne usvajanja. Tulip pripovetka postaje stara i dosadna i skeptičari pređu na više nijansirane teme, i time menjaju bazu debate. Drugi stepen tuge predstoji: bitcoin je manjkav kao novac. On je previše volatilan da bi bio valuta, ili je suviše spor da bi se koristio kao sistem plaćanja, ili se ne može proširiti dovoljno da zadovolji sve promete plaćanja na svetu, ili troši isuviše struje. Taj niz kritike ide sve dalje i dalje. Ovaj drugi stepen je progresija poricanja i dosta je udaljen od ideje da je bitcoin ništa više od bukvalno bezvrednog ničega. Uprkos tim pretpostavnim manjcima, vrednost bitcoin mreže nastavje da raste vremenom. Svaki put, ona ne umire, nasuprot, ona postaje sve veća i jača. Dok se skeptičari bave ukazivanjem na manjke, bitcoin ne prestaje. Rast u vrednosti je prouzrokovan jednostavnom dinamikom tržišta: postoji više kupca nego prodavca. To je sve i to je razlog rasta u adopciji. Sve više i više ljudi shvata zašto postoji fundamentalna potražnja za bitcoinom i zašto/kako on funkcioniše. To je razlog njegovog dugotrajnog rasta. Dokle god ga sve više ljudi koristi za čuvanje vrednosti, neće pasti cena snabdevanja. Zauvek će postojati samo 21 milion bitcoina. Nebitno je koliko ljudi zahtevaju bitcoin, njegova cela količina je uvek ista i neelastična. Dok skeptičari nastavljaju sa svojom starom pričom, mase ljudi nastavljaju da eliminišu zabludu i zahtevaju bitcoin zbog njegovih prednosti u smislu novčanih svojstva. Između ostalog, ne postoji grupa ljudi koja je više upoznata sa svim argumentima protiv bitcoina od samih bitcoinera.  Očajanje počinje da se stvara i onda se debata još jedanput pomera. Sada nije više činjenica je vrednost bitcoina osnovana ni na čemu niti da ima manjke kao valuta; sada se debata centrira na regulaciji državnih autoriteta. U ovom zadnjem stepenu tuge, bitcoin se predstavlja kao u stvari isuviše uspešnom alatkom i zbog toga države ne smeju dozvoliti da on postoji. Zaista? Znači da je genijalnost čoveka ponovo ostvarila funkcionalan novac u tehnološko superiornoj formi, čije su posledice zaista neshvatljive, i da će države upravo taj izum nekako zabraniti. Primetite da tom izjavom skeptičari praktično priznaju svoj poraz. Ovo su poslednji pokušaji u seriji promašenih argumenata. Skeptičari u isto vreme prihvataju da postoji fundamentalna potražnja za bitcoinom a onda se premeštaju na neosnovan stav da ga države mogu zabraniti. Ajde da se poigramo i tim pitanjem. Kada bih zapravo razvijene države nastupile na scenu i pokušale da zabrane bitcoin? Trenutno, Federal Reserve i Treasury ne smatraju bitcoin kao ozbiljnu pretnju superiornosti dolara. Po njihovom celokupnom mišljenju, bitcoin je slatka mala igračka i ne može da funkcioniše kao novac. Sadašnja kompletna kupovna moć bitcoina je manja od $200 milijardi. Sa druge strane, zlato ima celokupnu vrednost od $8 triliona (40X veću od bitcoina) i količina odštampanog novca (M2) je otprilike 15 triliona (75X veličine bitcoinove vrednosti). Kada će Federal Reserve i Treasury da počne da smatra bitcoin kao ozbiljnu pretnju? Kad bitcoin poraste na $1, $2 ili $3 triliona? Možete i sami da izaberete nivo, ali implikacija je da će bitcoin biti mnogo vredniji, i posedovaće ga sve više ljudi širom sveta, pre nego što će ga državne vlasti shvatiti kao obiljnog protivnika. Predsednik Tramp & Treasury Sekretar Mnučin o Bitcoinu (2019): > „Ja neću pričati o bitcoinu za 10 godina, u to možete biti sigurni {…} Ja bi se kladio da čak za 5 ili 6 godina neću više pričati o bitcoinu kao sekretar Trusury-a. Imaću preča posla {…} Mogu vam obećati da ja lično neću biti pun bitcoina.“ – Sekretar Treasury-a Stiv Mnučin > „Ja nisam ljubitelj bitcoina {…}, koji nije novac i čija vrednost je jako volatilna i osnovana na praznom vazduhu.“ – Predsednik Donald J. Tramp Znači, logika skeptika ide ovako: bitcoin ne funkcioniše, ali ako funkcioniše, onda će ga država zabraniti. Ali, države slobodnog sveta neće pokušati da ga zabrane dokle god se on ne pokaže kao ozbiljna pretnja. U tom trenutku, bitcoin će biti vredniji i sigurno teži da se zabrani, pošto će ga više ljudi posedovati na mnogo širem geografskom prostoru. Ignorišite fundamentalne činjenice i asimetriju koja je urođena u globalnom dešavanju monetizacije zato što u slučaju da ste u pravu, države će taj proces zabraniti. Na kojoj strani tog argumenta bi radije stajao racionalan ekonomski učesnik? Posedovanje finansijske imovine kojoj vrednost toliko raste da preti globalnoj rezervnoj valuti, ili nasuprot – nemati tu imovinu? Sa pretpostavkom da individualci razumeju zašto je mogućnost (a sve više i verovatnoća) ove realnosti, koji stav je logičniji u ovom scenariju? Asimetrija dve strane ovog argumenta sama od sebe zahteva da je prvi stav onaj istinit i da fundamentalno razumevanje potražnje bitcoina samo još više ojačava to mišljenje. #### Niko ne moze zabraniti bitcoin Razmislite šta bitcoin u stvari predstavlja pa onda šta bi predstavljala njegova zabrana. Bitcoin je konverzija subjektivne vrednosti, stvorena i razmenjena u realnošću, u digitalne potpise. Jednostavno rečeno, to je konverzija ljudskog vremena u novac. Kad neko zahteva bitcoin, oni u isto vreme ne zahtevaju neki drugi posed, nek to bio dolar, kuća, auto ili hrana itd. Bitcoin predstavlja novčanu štednju koja sa sobom žrtvuje druge imovine i servise. Zabrana bitcoina bi bio napad na najosnovnije ljudske slobode koje je on upravo stvoren da brani. Zamislite reakciju svih onih koji su prihvatili bitcoin: „Bilo je zabavno, alatka za koju su svi eksperti tvrdili da neće nikad funkcionisati, sada toliko dobro radi i sad ti isti eksperti i autoriteti kažu da mi to nemožemo koristiti. Svi idite kući, predstava je gotova.“verovanje da će svi ljudi koji su učestvovali u bitcoin usvajanju, suverenitetu koji nudi i finansiskoj slobodi, odjednom samo da se predaju osnovnom rušenju njihovih prava je potpuno iracionalna pozicija. > Novac je jedan od najbitnijih instrumenata za slobodu koji je ikad izmišljen. Novac je to što u postojećem društvu ostvaruje mogućnosti siromašnom čoveku – čiji je domet veći nego onaj koji je bio dostižan bogatim ljudima pre ne toliko puno generacija.“ – F. A. Hajek Države nisu uspele da zabrane konzumiranje alkohola, droga, kupovinu vatrenog oružja, pa ni posedovanje zlata. Država može samo pomalo da uspori pristup ili da deklariše posedovanje ilegalnim, ali ne može da uništi nešto što veliki broj raznovrsnih ljudi smatra vrednim. Kada je SAD zabranila privatno posedovanje zlata 1933., zlato nije palo u vrednosti ili nestalo sa finansijskog tržišta. Ono je u stvari poraslo u vrednosti u poređenju sa dolarom, i samo trideset godina kasnije, zabrana je bila ukinuta. Ne samo da bitcoin nudi veću vrednosno obećanje od bilo kog drugog dobra koje su države pokušale da zabrane (uključujući i zlato); nego po svojim osobinama, njega je mnogo teže zabraniti. Bitcoin je globalan i decentralizovan. On ne poštuje granice i osiguran je mnoštvom nodova i kriptografskim potpisima. Sam postupak zabrane bi zahtevao da se u isto vreme zaustavi „open source“ softver koji emituje i izvršava slanje i potvrđivanje digitalno enkriptovanih ključeva i potpisa. Ta zabrana bi morala biti koordinisana između velikog broja zemalja, sa tim da je nemoguće znati gde se ti nodovi i softver nalazi ili da se zaustavi instaliranje novih nodova u drugim pravnim nadležnostima. Da ne pominjemo i ustavske pitanja, bilo bi tehnički neizvodljivo da se takva zabrana primeni na bilo kakav značajan način.  Čak kada bih sve zemlje iz G-20 grupe koordinisale takvu zabranu u isto vreme, to ne bi uništilo bitcoin. U stvari, to bi bilo samoubistvo za fiat novčani sistem. To bi još više prikazalo masama da je bitcoin u stvari novac koji treba shvatiti ozbiljno, i to bi samo od sebe započelo globalnu igru vatanje mačke za rep. Bitcoin nema centralnu tačku za napad; bitcoin rudari, nodovi i digitalni potpisi su rasejani po celom svetu. Svaki aspekt bitcoina je decentralizovan, zato su glavni stubovi njegove arhitekture da učesnici uvek treba kontrolisati svoje potpise i upravljati svojim nodom. Što više digitalnih potpisa i nodova koji postoje, to je više bitcoin decentralizovan, i to je više odbranjiva njegova mreža od strane neprijatelja. Što je više zemalja gde rudari izvršavaju svoj posao, to je manji rizik da jedan nadležni identitet može uticati na njegov bezbednosni sistem. Koordinisan internacionalni napad na bitcoin bi samo koristio da bitcoin još više ojača svoj imuni sistem. Na kraju krajeva, to bi ubrzalo seobu iz tradicionalnog finansijskog sistema (i njegovih valuta) a i inovaciju koja postoji u bitcoin ekosistemu. Sa svakom bivšom pretnjom, bitcoin je maštovito pronalazio način da ih neutrališe pa i koordinisan napad od strane država ne bi bio ništa drugačiji.  Inovacija u ovoj oblasti koja se odlikuje svojom „permissionless“ (bez dozvole centralnih identiteta) osobinom, omogućava odbranu od svakojakih napada. Sve varijante napada koje su bile predvidjene je upravo to što zahteva konstantnu inovaciju bitcoina. To je ona Adam Smitova nevidljiva ruka, ali dopingovana. Pojedinačni učesnici mogu da veruju da su motivisani nekim većim uzrokom, ali u stvari, korisnost kaja je ugrađena u bitcoin stvara kod učesnika dovoljno snažan podsticaj da omogući svoje preživljavanje. Sopstveni interes milione, ako ne milijarde, nekoordinisanih ljudi koji se jedino slažu u svojom međusobnom potrebom za funkcionalnim novcem podstiče inovacije u bitcoinu. Danas, možda to izgleda kao neka kul nova tehnologija ili neki dobar investment u finansijskom portfoliju, ali čak i ako to mnogi ne razumeju, bitcoin je apsolutna nužnost u svetu. To je tako zato što je novac nužnost a historijski priznate valute se fundamentalno raspadaju. Pre dva meseca, tržište američkih državnih obveznica je doživeo kolaps na šta je Federal Reserve reagovao time što je povećao celokupnu količinu dolara u postojanju za $250 milijardi, a još više u bliskoj budućnosti. Tačno ovo je razlog zašto je bitcoin nužnost a ne samo luksuzni dodatak. Kada inovacija omogućava bazično funkcionisanje ekonomije ne postoji ni jedna država na svetu koja može da zaustavi njenu adopciju i rast. Novac je nužnost a bitcoin znatno poboljšava sistem novca koji je ikada postojao pre njega. Sa više praktične strane, pokušaj zabranjivanja bitcoina ili njegove velike regulacije od nadležnosti bi direktno bilo u korist susedne nadležnih organa. Podsticaj da se odustane od koordinisanog napada na bitcoin bi bio isuviše veliki da bi takvi dogovori bili uspešni. Kada bi SAD deklarisovale posed bitcoina ilegalnim sutra, da li bi to zaustavilo njegov rast, razvoj i adopciji i da li bi to smanjilo vrednost celokupne mreže? Verovatno. Da li bi to uništilo bitcoin? Ne bi. Bitcoin predstavlja najpokretljivije kapitalno sredstvo na svetu. Zemlje i nadležne strukture koje kreiraju regulativnu strukturu koja najmanje ustručava korišćenje bitcoina će biti dobitnici velike količine uliva kapitala u svoje države. #### Zabrana Bitcoinove Zatvoreničke Dileme  U praksi, zatvorenička dilema nije igra jedan na jedan. Ona je multidimenzijska i uključuje mnoštvo nadležnosti, čiji se interesi nadmeću međusobno, i to uskraćuje mogućnosti bilo kakve mogućnosti zabrane. Ljudski kapital, fizički kapital i novčani kapital će sav ići u pravcu država i nadležnosti koje najmanje ustručuju bitcoin. To se možda neće desiti sve odjednom, ali pokušaji zabrane su isto za badava koliko bi bilo odseći sebi nos u inat svom licu. To ne znači da države to neće pokušati. India je već probala da zabrani bitcoin. Kina je uvela puno restrikcija. Drugi će da prate njihove tragove. Ali svaki put kada država preduzme takve korake, to ima nepredvidljive efekte povećanja bitcoin adopcije. Pokušaji zabranjivanja bitcoina su jako efektivne marketing kampanje. Bitcoin postoji kao sistem nevezan za jednu suverenu državu i kao novac je otporan na cenzuru. On je dizajniran da postoji van državne kontrole. Pokušaji da se taj koncept zabrani samo još više daje njemu razlog i logiku za postojanje. #### Jedini Pobednički Potez je da se Uključiš u Igru Zabrana bitcoina je trošenje vremena. Neki će to pokušati; ali svi će biti neuspešni. Sami ti pokušaji će još više ubrzati njegovu adopciju i širenje. Biće to vetar od 100 km/h koji raspaljuje vatru. To će ojačati bitcoin sve više i doprineće njegovoj pouzdanosti. U svakom slučaju, verovanje da će države zabraniti bitcoin u momentu kada on postane dovoljno velika pretnja rezervnim valutam sveta, je iracionalan razlog da se on no poseduje kao instrument štednje novca. To ne samo da podrazumeva da je bitcoin novac, ali u isto vreme i ignoriše glavne razloge zašto je to tako: on je decentralizovan i otporan na cenzure. Zamislite da razumete jednu od nojvećih tajni današnjice i da u isto vreme tu tajnu asimetrije koju bitcoin nudi ne primenjujete u svoju korist zbog straha od države. Pre će biti, neko ko razume zašto bitcoin funkcioniše i da ga država ne može zaustaviti, ili nepuno znanje postoji u razumevanju kako bitcoin uopšte funckioniše. Počnite sa razmatranjem fundamentalnih pitanja, a onda primenite to kao temelj da bi procenili bilo koji potencijalan rizik od strane budućih regulacija ili restrikcija državnih organa. I nikad nemojte da zaboravite na vrednost asimetrije između dve strane ovde prezentiranih argumenata. Jedini pobednički potez je da se uključite u igru. Stavovi ovde prezentirani su samo moji i ne predstavljaju Unchained Capital ili moje kolege. Zahvaljujem se Fil Gajgeru za razmatranje teksta i primedbe. [Originalni tekst](https://unchained.com/blog/bitcoin-cannot-be-banned/)
@ bf47c19e:c3d2573b
2025-02-13 07:56:50Originalni tekst na [dvadesetjedan.com](https://dvadesetjedan.com/blog/niko-ne-moze-zabraniti-bitcoin) ###### Autor: [Parker Lewis](https://x.com/parkeralewis) / Prevod na srpski: [Plumsky](https://t.me/Plumski) --- Ideja da država može nekako zabraniti bitcoin je jedna od poslednjih faza tuge, tačno pred prihvatanje realnosti. Posledica ove rečenice je priznanje da bitcoin “funkcioniše”. U stvari, ona predstavlja činjenicu da bitcoin funkcioniše toliko dobro da on preti postojećim državnim monopolima nad novcem i da će zbog toga države da ga unište kroz regulativne prepreke da bi eliminisale tu pretnju. Gledajte na tvrdnju da će države zabraniti bitcoin kao kondicionalnu logiku. Da li bitcoin funkcioniše kao novac? Ako je odgovor „ne“, onda države nemaju šta da zabrane. Ako je odgovor „da“, onda će države da probaju da ga zabrane. Znači, glavna poenta ovog razmišljanja je pretpostavka da bitcoin funkcioiniše kao novac. Onda je sledeće logično pitanje da li intervencija od strane države može uspešno da uništi upravo taj funkcionalan bitcoin.  Za početak, svako ko pokušava da razume kako, zašto, ili da li bitcoin funkcioniše mora da proceni ta pitanja potpuno nezavisno od prouzrekovanja državne regulacije ili intervencije. Iako je nesumnjivo da bitcoin mora da postoji uzgred državnih regulativa, zamislite na momenat da države ne postoje. Sam od sebe, da li bi bitcoin funkcionisao kao novac, kad bi se prepustio slobodnom tržištu? Ovo pitanje se širi u dodatna pitanja i ubrzo se pretvara u bunar bez dna. Šta je novac? Šta su svojstva koja čine jednu vrstu novca bolje od druge? Da li bitcoin poseduje ta svojstva? Da li je bitcoin bolja verzija novca po takvim osobinama? Ako je finalni zaključak da bitcoin ne funkcioniše kao novac, implikacije državne intervencije su nebitne. Ali, ako je bitcoin funkcionalan kao novac, ta pitanja onda postaju bitna u ovoj debati, i svako ko o tome razmišlja bi morao imati taj početnički kontekst da bi mogao proceniti da li je uopšte moguće zabraniti. Po svom dizajnu, bitcoin postoji van države. Ali bitcoin nije samo van kontrole države, on u stvari funkcioniše bez bilo kakve saradnje centralizovanih identiteta. On je globalan i decentralizovan. Svako može pristupiti bitcoinu bez potrebe saglasnosti bilo koga i što se više širi sve je teže cenzurisati celokupnu mrežu. Arhitektura bitcoina je namerno izmišljena da bude otporna na bilo koje pokušaje države da ga zabrane. Ovo ne znači da države širom sveta neće pokušavati da ga regulišu, oporezuju ili čak da potpuno zabrane njegovo korišćenje. Naravno da će biti puno bitki i otpora protiv usvajanja bitcoina među građanima. Federal Reserve i Američki Treasury (i njihovi globalni suparnici) se neće ležeći predati dok bitcoin sve više i više ugrožava njihove monopole prihvatljivog novca. Doduše, pre nego što se odbaci ideja da države mogu potpuno zabraniti bitcoin, mora se prvo razumeti posledice tog stava i njegovog glasnika. #### Progresija poricanja i stepeni tuge Pripovesti skeptičara se neprestano menjaju kroz vreme. Prvi stepen tuge: bitcoin nikad ne može funkcionisati-njegova vrednost je osnovana ni na čemu. On je moderna verzija tulip manije. Sa svakim ciklusom uzbuđenja, vrednost bitcoina skače i onda vrlo brzo se vraća na dole. Često nazvano kao kraj njegove vrednosti, bitcoin svaki put odbija da umre i njegova vrednost pronađe nivo koji je uvek viši od prethodnih ciklusa globalne usvajanja. Tulip pripovetka postaje stara i dosadna i skeptičari pređu na više nijansirane teme, i time menjaju bazu debate. Drugi stepen tuge predstoji: bitcoin je manjkav kao novac. On je previše volatilan da bi bio valuta, ili je suviše spor da bi se koristio kao sistem plaćanja, ili se ne može proširiti dovoljno da zadovolji sve promete plaćanja na svetu, ili troši isuviše struje. Taj niz kritike ide sve dalje i dalje. Ovaj drugi stepen je progresija poricanja i dosta je udaljen od ideje da je bitcoin ništa više od bukvalno bezvrednog ničega. Uprkos tim pretpostavnim manjcima, vrednost bitcoin mreže nastavje da raste vremenom. Svaki put, ona ne umire, nasuprot, ona postaje sve veća i jača. Dok se skeptičari bave ukazivanjem na manjke, bitcoin ne prestaje. Rast u vrednosti je prouzrokovan jednostavnom dinamikom tržišta: postoji više kupca nego prodavca. To je sve i to je razlog rasta u adopciji. Sve više i više ljudi shvata zašto postoji fundamentalna potražnja za bitcoinom i zašto/kako on funkcioniše. To je razlog njegovog dugotrajnog rasta. Dokle god ga sve više ljudi koristi za čuvanje vrednosti, neće pasti cena snabdevanja. Zauvek će postojati samo 21 milion bitcoina. Nebitno je koliko ljudi zahtevaju bitcoin, njegova cela količina je uvek ista i neelastična. Dok skeptičari nastavljaju sa svojom starom pričom, mase ljudi nastavljaju da eliminišu zabludu i zahtevaju bitcoin zbog njegovih prednosti u smislu novčanih svojstva. Između ostalog, ne postoji grupa ljudi koja je više upoznata sa svim argumentima protiv bitcoina od samih bitcoinera.  Očajanje počinje da se stvara i onda se debata još jedanput pomera. Sada nije više činjenica je vrednost bitcoina osnovana ni na čemu niti da ima manjke kao valuta; sada se debata centrira na regulaciji državnih autoriteta. U ovom zadnjem stepenu tuge, bitcoin se predstavlja kao u stvari isuviše uspešnom alatkom i zbog toga države ne smeju dozvoliti da on postoji. Zaista? Znači da je genijalnost čoveka ponovo ostvarila funkcionalan novac u tehnološko superiornoj formi, čije su posledice zaista neshvatljive, i da će države upravo taj izum nekako zabraniti. Primetite da tom izjavom skeptičari praktično priznaju svoj poraz. Ovo su poslednji pokušaji u seriji promašenih argumenata. Skeptičari u isto vreme prihvataju da postoji fundamentalna potražnja za bitcoinom a onda se premeštaju na neosnovan stav da ga države mogu zabraniti. Ajde da se poigramo i tim pitanjem. Kada bih zapravo razvijene države nastupile na scenu i pokušale da zabrane bitcoin? Trenutno, Federal Reserve i Treasury ne smatraju bitcoin kao ozbiljnu pretnju superiornosti dolara. Po njihovom celokupnom mišljenju, bitcoin je slatka mala igračka i ne može da funkcioniše kao novac. Sadašnja kompletna kupovna moć bitcoina je manja od $200 milijardi. Sa druge strane, zlato ima celokupnu vrednost od $8 triliona (40X veću od bitcoina) i količina odštampanog novca (M2) je otprilike 15 triliona (75X veličine bitcoinove vrednosti). Kada će Federal Reserve i Treasury da počne da smatra bitcoin kao ozbiljnu pretnju? Kad bitcoin poraste na $1, $2 ili $3 triliona? Možete i sami da izaberete nivo, ali implikacija je da će bitcoin biti mnogo vredniji, i posedovaće ga sve više ljudi širom sveta, pre nego što će ga državne vlasti shvatiti kao obiljnog protivnika. Predsednik Tramp & Treasury Sekretar Mnučin o Bitcoinu (2019): > „Ja neću pričati o bitcoinu za 10 godina, u to možete biti sigurni {…} Ja bi se kladio da čak za 5 ili 6 godina neću više pričati o bitcoinu kao sekretar Trusury-a. Imaću preča posla {…} Mogu vam obećati da ja lično neću biti pun bitcoina.“ – Sekretar Treasury-a Stiv Mnučin > „Ja nisam ljubitelj bitcoina {…}, koji nije novac i čija vrednost je jako volatilna i osnovana na praznom vazduhu.“ – Predsednik Donald J. Tramp Znači, logika skeptika ide ovako: bitcoin ne funkcioniše, ali ako funkcioniše, onda će ga država zabraniti. Ali, države slobodnog sveta neće pokušati da ga zabrane dokle god se on ne pokaže kao ozbiljna pretnja. U tom trenutku, bitcoin će biti vredniji i sigurno teži da se zabrani, pošto će ga više ljudi posedovati na mnogo širem geografskom prostoru. Ignorišite fundamentalne činjenice i asimetriju koja je urođena u globalnom dešavanju monetizacije zato što u slučaju da ste u pravu, države će taj proces zabraniti. Na kojoj strani tog argumenta bi radije stajao racionalan ekonomski učesnik? Posedovanje finansijske imovine kojoj vrednost toliko raste da preti globalnoj rezervnoj valuti, ili nasuprot – nemati tu imovinu? Sa pretpostavkom da individualci razumeju zašto je mogućnost (a sve više i verovatnoća) ove realnosti, koji stav je logičniji u ovom scenariju? Asimetrija dve strane ovog argumenta sama od sebe zahteva da je prvi stav onaj istinit i da fundamentalno razumevanje potražnje bitcoina samo još više ojačava to mišljenje. #### Niko ne moze zabraniti bitcoin Razmislite šta bitcoin u stvari predstavlja pa onda šta bi predstavljala njegova zabrana. Bitcoin je konverzija subjektivne vrednosti, stvorena i razmenjena u realnošću, u digitalne potpise. Jednostavno rečeno, to je konverzija ljudskog vremena u novac. Kad neko zahteva bitcoin, oni u isto vreme ne zahtevaju neki drugi posed, nek to bio dolar, kuća, auto ili hrana itd. Bitcoin predstavlja novčanu štednju koja sa sobom žrtvuje druge imovine i servise. Zabrana bitcoina bi bio napad na najosnovnije ljudske slobode koje je on upravo stvoren da brani. Zamislite reakciju svih onih koji su prihvatili bitcoin: „Bilo je zabavno, alatka za koju su svi eksperti tvrdili da neće nikad funkcionisati, sada toliko dobro radi i sad ti isti eksperti i autoriteti kažu da mi to nemožemo koristiti. Svi idite kući, predstava je gotova.“verovanje da će svi ljudi koji su učestvovali u bitcoin usvajanju, suverenitetu koji nudi i finansiskoj slobodi, odjednom samo da se predaju osnovnom rušenju njihovih prava je potpuno iracionalna pozicija. > Novac je jedan od najbitnijih instrumenata za slobodu koji je ikad izmišljen. Novac je to što u postojećem društvu ostvaruje mogućnosti siromašnom čoveku – čiji je domet veći nego onaj koji je bio dostižan bogatim ljudima pre ne toliko puno generacija.“ – F. A. Hajek Države nisu uspele da zabrane konzumiranje alkohola, droga, kupovinu vatrenog oružja, pa ni posedovanje zlata. Država može samo pomalo da uspori pristup ili da deklariše posedovanje ilegalnim, ali ne može da uništi nešto što veliki broj raznovrsnih ljudi smatra vrednim. Kada je SAD zabranila privatno posedovanje zlata 1933., zlato nije palo u vrednosti ili nestalo sa finansijskog tržišta. Ono je u stvari poraslo u vrednosti u poređenju sa dolarom, i samo trideset godina kasnije, zabrana je bila ukinuta. Ne samo da bitcoin nudi veću vrednosno obećanje od bilo kog drugog dobra koje su države pokušale da zabrane (uključujući i zlato); nego po svojim osobinama, njega je mnogo teže zabraniti. Bitcoin je globalan i decentralizovan. On ne poštuje granice i osiguran je mnoštvom nodova i kriptografskim potpisima. Sam postupak zabrane bi zahtevao da se u isto vreme zaustavi „open source“ softver koji emituje i izvršava slanje i potvrđivanje digitalno enkriptovanih ključeva i potpisa. Ta zabrana bi morala biti koordinisana između velikog broja zemalja, sa tim da je nemoguće znati gde se ti nodovi i softver nalazi ili da se zaustavi instaliranje novih nodova u drugim pravnim nadležnostima. Da ne pominjemo i ustavske pitanja, bilo bi tehnički neizvodljivo da se takva zabrana primeni na bilo kakav značajan način.  Čak kada bih sve zemlje iz G-20 grupe koordinisale takvu zabranu u isto vreme, to ne bi uništilo bitcoin. U stvari, to bi bilo samoubistvo za fiat novčani sistem. To bi još više prikazalo masama da je bitcoin u stvari novac koji treba shvatiti ozbiljno, i to bi samo od sebe započelo globalnu igru vatanje mačke za rep. Bitcoin nema centralnu tačku za napad; bitcoin rudari, nodovi i digitalni potpisi su rasejani po celom svetu. Svaki aspekt bitcoina je decentralizovan, zato su glavni stubovi njegove arhitekture da učesnici uvek treba kontrolisati svoje potpise i upravljati svojim nodom. Što više digitalnih potpisa i nodova koji postoje, to je više bitcoin decentralizovan, i to je više odbranjiva njegova mreža od strane neprijatelja. Što je više zemalja gde rudari izvršavaju svoj posao, to je manji rizik da jedan nadležni identitet može uticati na njegov bezbednosni sistem. Koordinisan internacionalni napad na bitcoin bi samo koristio da bitcoin još više ojača svoj imuni sistem. Na kraju krajeva, to bi ubrzalo seobu iz tradicionalnog finansijskog sistema (i njegovih valuta) a i inovaciju koja postoji u bitcoin ekosistemu. Sa svakom bivšom pretnjom, bitcoin je maštovito pronalazio način da ih neutrališe pa i koordinisan napad od strane država ne bi bio ništa drugačiji.  Inovacija u ovoj oblasti koja se odlikuje svojom „permissionless“ (bez dozvole centralnih identiteta) osobinom, omogućava odbranu od svakojakih napada. Sve varijante napada koje su bile predvidjene je upravo to što zahteva konstantnu inovaciju bitcoina. To je ona Adam Smitova nevidljiva ruka, ali dopingovana. Pojedinačni učesnici mogu da veruju da su motivisani nekim većim uzrokom, ali u stvari, korisnost kaja je ugrađena u bitcoin stvara kod učesnika dovoljno snažan podsticaj da omogući svoje preživljavanje. Sopstveni interes milione, ako ne milijarde, nekoordinisanih ljudi koji se jedino slažu u svojom međusobnom potrebom za funkcionalnim novcem podstiče inovacije u bitcoinu. Danas, možda to izgleda kao neka kul nova tehnologija ili neki dobar investment u finansijskom portfoliju, ali čak i ako to mnogi ne razumeju, bitcoin je apsolutna nužnost u svetu. To je tako zato što je novac nužnost a historijski priznate valute se fundamentalno raspadaju. Pre dva meseca, tržište američkih državnih obveznica je doživeo kolaps na šta je Federal Reserve reagovao time što je povećao celokupnu količinu dolara u postojanju za $250 milijardi, a još više u bliskoj budućnosti. Tačno ovo je razlog zašto je bitcoin nužnost a ne samo luksuzni dodatak. Kada inovacija omogućava bazično funkcionisanje ekonomije ne postoji ni jedna država na svetu koja može da zaustavi njenu adopciju i rast. Novac je nužnost a bitcoin znatno poboljšava sistem novca koji je ikada postojao pre njega. Sa više praktične strane, pokušaj zabranjivanja bitcoina ili njegove velike regulacije od nadležnosti bi direktno bilo u korist susedne nadležnih organa. Podsticaj da se odustane od koordinisanog napada na bitcoin bi bio isuviše veliki da bi takvi dogovori bili uspešni. Kada bi SAD deklarisovale posed bitcoina ilegalnim sutra, da li bi to zaustavilo njegov rast, razvoj i adopciji i da li bi to smanjilo vrednost celokupne mreže? Verovatno. Da li bi to uništilo bitcoin? Ne bi. Bitcoin predstavlja najpokretljivije kapitalno sredstvo na svetu. Zemlje i nadležne strukture koje kreiraju regulativnu strukturu koja najmanje ustručava korišćenje bitcoina će biti dobitnici velike količine uliva kapitala u svoje države. #### Zabrana Bitcoinove Zatvoreničke Dileme  U praksi, zatvorenička dilema nije igra jedan na jedan. Ona je multidimenzijska i uključuje mnoštvo nadležnosti, čiji se interesi nadmeću međusobno, i to uskraćuje mogućnosti bilo kakve mogućnosti zabrane. Ljudski kapital, fizički kapital i novčani kapital će sav ići u pravcu država i nadležnosti koje najmanje ustručuju bitcoin. To se možda neće desiti sve odjednom, ali pokušaji zabrane su isto za badava koliko bi bilo odseći sebi nos u inat svom licu. To ne znači da države to neće pokušati. India je već probala da zabrani bitcoin. Kina je uvela puno restrikcija. Drugi će da prate njihove tragove. Ali svaki put kada država preduzme takve korake, to ima nepredvidljive efekte povećanja bitcoin adopcije. Pokušaji zabranjivanja bitcoina su jako efektivne marketing kampanje. Bitcoin postoji kao sistem nevezan za jednu suverenu državu i kao novac je otporan na cenzuru. On je dizajniran da postoji van državne kontrole. Pokušaji da se taj koncept zabrani samo još više daje njemu razlog i logiku za postojanje. #### Jedini Pobednički Potez je da se Uključiš u Igru Zabrana bitcoina je trošenje vremena. Neki će to pokušati; ali svi će biti neuspešni. Sami ti pokušaji će još više ubrzati njegovu adopciju i širenje. Biće to vetar od 100 km/h koji raspaljuje vatru. To će ojačati bitcoin sve više i doprineće njegovoj pouzdanosti. U svakom slučaju, verovanje da će države zabraniti bitcoin u momentu kada on postane dovoljno velika pretnja rezervnim valutam sveta, je iracionalan razlog da se on no poseduje kao instrument štednje novca. To ne samo da podrazumeva da je bitcoin novac, ali u isto vreme i ignoriše glavne razloge zašto je to tako: on je decentralizovan i otporan na cenzure. Zamislite da razumete jednu od nojvećih tajni današnjice i da u isto vreme tu tajnu asimetrije koju bitcoin nudi ne primenjujete u svoju korist zbog straha od države. Pre će biti, neko ko razume zašto bitcoin funkcioniše i da ga država ne može zaustaviti, ili nepuno znanje postoji u razumevanju kako bitcoin uopšte funckioniše. Počnite sa razmatranjem fundamentalnih pitanja, a onda primenite to kao temelj da bi procenili bilo koji potencijalan rizik od strane budućih regulacija ili restrikcija državnih organa. I nikad nemojte da zaboravite na vrednost asimetrije između dve strane ovde prezentiranih argumenata. Jedini pobednički potez je da se uključite u igru. Stavovi ovde prezentirani su samo moji i ne predstavljaju Unchained Capital ili moje kolege. Zahvaljujem se Fil Gajgeru za razmatranje teksta i primedbe. [Originalni tekst](https://unchained.com/blog/bitcoin-cannot-be-banned/) @ da0b9bc3:4e30a4a9
2025-02-13 06:36:12Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/884478
@ da0b9bc3:4e30a4a9
2025-02-13 06:36:12Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/884478 @ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get [this line](https://www.youtube.com/shorts/kqsomjpz7ok): “Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.” Yesterday, I came across a comment on the song [Devil Went Down to Georgia](https://youtu.be/ut8UqFlWdDc) that had a very similar feel to it:  America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans. That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form. For most countries, saying “our nation is the greatest” *is*, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people *should* be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence. But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America. That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is *freedom*. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit. American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are *definitionally* better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.) In *Devil Went Down to Georgia*, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.” *Libertas magnitudo est*
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get [this line](https://www.youtube.com/shorts/kqsomjpz7ok): “Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.” Yesterday, I came across a comment on the song [Devil Went Down to Georgia](https://youtu.be/ut8UqFlWdDc) that had a very similar feel to it:  America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans. That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form. For most countries, saying “our nation is the greatest” *is*, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people *should* be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence. But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America. That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is *freedom*. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit. American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are *definitionally* better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.) In *Devil Went Down to Georgia*, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.” *Libertas magnitudo est* @ d360efec:14907b5f
2025-02-13 05:54:17 **ภาพรวม LUNCUSDT (OKX):** LUNCUSDT กำลังอยู่ในช่วงที่ *มีความผันผวนสูงและมีความไม่แน่นอนมาก* แม้ว่าในอดีต (TF Day) จะเคยมีสัญญาณของการพยายามกลับตัวเป็นขาขึ้น (Breakout EMA 50 และเกิด Golden Cross) แต่ปัจจุบันแรงซื้อเหล่านั้นเริ่มอ่อนแรงลง และมีแรงขายเข้ามาในตลาดมากขึ้น ทำให้เกิดความขัดแย้งระหว่าง Timeframes ต่างๆ  **สถานะปัจจุบัน:** * **แนวโน้ม:** * **TF Day:** เริ่มไม่แน่นอน (จากเดิมที่เป็น Early Uptrend) - แม้ว่าราคาจะยังอยู่เหนือ EMA 50/200 แต่ Money Flow เริ่มแสดงสัญญาณเตือน * **TF4H:** เริ่มไม่แน่นอน (พักตัว, ทดสอบแนวรับ EMA 50) - Money Flow บ่งบอกถึงแรงขายที่เข้ามา * **TF15:** ผันผวนสูง, ไม่มีทิศทางชัดเจน (Sideways) - Money Flow แสดงถึงแรงขาย แต่ก็มีแรงซื้อกลับเข้ามาบ้าง * **Money Flow (LuxAlgo):** * **TF Day:** แรงซื้อเริ่มอ่อนแรงลงอย่างมีนัยสำคัญ, มีแรงขายเข้ามา * **TF4H:** แรงขายมีมากกว่าแรงซื้อ * **TF15:** แรงขายและแรงซื้อผสมกัน, โดยรวมแรงขายยังมากกว่า * **EMA:** * **TF Day:** EMA 50/200 เป็นแนวรับ/แนวต้าน * **TF4H:** EMA 50 กำลังถูกทดสอบ, EMA 200 เป็นแนวต้าน * **TF15:** EMA 50/200 เป็นแนวต้าน **โครงสร้างราคา (SMC):** | Timeframe | Break of Structure (BOS) | Change of Character (CHoCH) | Higher High (HH) & Higher Low (HL) | Equal Highs (EQH) / Equal Lows (EQL) | | :-------- | :----------------------- | :--------------------------- | :----------------------------------- | :------------------------------------- | | Day | ด้านบนและล่าง | ด้านบน | เริ่มก่อตัว (แต่ไม่แข็งแกร่ง) | - | | 4H | ด้านบน | ด้านบน | เริ่มก่อตัว (แต่ไม่ชัดเจน) | มี EQH หลายจุด | | 15m | ด้านบนและล่าง | มีทั้งบนและล่าง | Lower Highs (LH) & Lower Lows (LL) | มี EQH และ EQL หลายจุด | **แนวรับ-แนวต้านสำคัญ:** | Timeframe | แนวรับ | แนวต้าน | | :-------- | :----------------------------------------------------------- | :--------------------------------------------------------------------- | | Day | EMA 50 (≈0.00010000), EMA 200 (≈0.00008000), 0.00006000-0.00007000 | 0.00017953 (High ล่าสุด), 0.00014000 (Volume Profile) | | 4H | EMA 50 (≈0.00007000), 0.00006000-0.00007000 | EMA 200 (≈0.00008000), 0.00008132, บริเวณ 0.00010000-0.00012000 (EQH) | | 15m | บริเวณ Low ล่าสุด | EMA 50, EMA 200, บริเวณ 0.000075-0.000076 (EQH) | **กลยุทธ์ (LUNCUSDT):** 1. **Wait & See (ทางเลือกที่ดีที่สุด):** * **เหตุผล:** ความขัดแย้งระหว่าง Timeframes สูงมาก, แนวโน้มไม่ชัดเจน, Money Flow ใน TF4H และ TF15 เป็นลบ * รอให้ราคาแสดงทิศทางที่ชัดเจนกว่านี้ (ยืนเหนือ EMA 50 ใน TF4H ได้, Breakout แนวต้านใน TF15) 2. **Buy on Dip (Day, 4H) - *ความเสี่ยงสูงมาก ไม่แนะนำ*:** * **เหตุผล:** แนวโน้มระยะยาวอาจจะยังเป็นขาขึ้นได้ (ถ้าไม่หลุดแนวรับสำคัญ) * **เงื่อนไข:** *ต้อง* รอสัญญาณการกลับตัวใน TF15 ก่อน * **จุดเข้า:** พิจารณาเฉพาะบริเวณแนวรับที่แข็งแกร่งมากๆ (EMA ของ Day/4H) *และต้องดู TF15 ประกอบ* * **Stop Loss:** ต่ำกว่า Low ล่าสุดของ TF15 3. **Short (15, ความเสี่ยงสูงมาก):** * **เหตุผล:** แนวโน้ม TF15 เป็นขาลง, Money Flow เป็นลบ * **เงื่อนไข:** ราคาไม่สามารถ Breakout EMA หรือแนวต้านอื่นๆ ใน TF15 ได้ * **จุดเข้า:** บริเวณ EMA หรือแนวต้านของ TF15 * **Stop Loss:** เหนือ High ล่าสุดของ TF15 **คำแนะนำ (เน้นย้ำ):** * **LUNC เป็นเหรียญที่มีความเสี่ยงสูงมาก (High Risk):** มีความผันผวนสูง และอาจมีการเปลี่ยนแปลงอย่างรวดเร็ว * **ความขัดแย้งของ Timeframes:** สถานการณ์ของ LUNCUSDT มีความขัดแย้งสูงมาก และมีความเสี่ยงสูง * **Money Flow:** บ่งบอกถึงแรงขายที่เริ่มเข้ามา และแนวโน้มขาขึ้น (ระยะกลาง-ยาว) ที่อ่อนแอลง * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด:** "รอ" เป็นกลยุทธ์ที่ดีที่สุด * **Risk Management:** สำคัญที่สุด ไม่ว่าจะเลือกกลยุทธ์ใด ต้องมีการบริหารความเสี่ยงที่ดี **สรุป:** LUNCUSDT กำลังอยู่ในช่วงเวลาที่ยากลำบากและมีความเสี่ยงสูงมากที่สุดในบรรดา 3 เหรียญที่เราวิเคราะห์กันมา การตัดสินใจที่ผิดพลาดอาจนำไปสู่การขาดทุนได้ ควรพิจารณาอย่างรอบคอบก่อนเข้าเทรดทุกครั้ง และ "รอ" จนกว่าจะมีสัญญาณที่ชัดเจนกว่านี้ เป็นทางเลือกที่ปลอดภัยที่สุดสำหรับนักลงทุนส่วนใหญ่ค่ะ **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
@ d360efec:14907b5f
2025-02-13 05:54:17 **ภาพรวม LUNCUSDT (OKX):** LUNCUSDT กำลังอยู่ในช่วงที่ *มีความผันผวนสูงและมีความไม่แน่นอนมาก* แม้ว่าในอดีต (TF Day) จะเคยมีสัญญาณของการพยายามกลับตัวเป็นขาขึ้น (Breakout EMA 50 และเกิด Golden Cross) แต่ปัจจุบันแรงซื้อเหล่านั้นเริ่มอ่อนแรงลง และมีแรงขายเข้ามาในตลาดมากขึ้น ทำให้เกิดความขัดแย้งระหว่าง Timeframes ต่างๆ  **สถานะปัจจุบัน:** * **แนวโน้ม:** * **TF Day:** เริ่มไม่แน่นอน (จากเดิมที่เป็น Early Uptrend) - แม้ว่าราคาจะยังอยู่เหนือ EMA 50/200 แต่ Money Flow เริ่มแสดงสัญญาณเตือน * **TF4H:** เริ่มไม่แน่นอน (พักตัว, ทดสอบแนวรับ EMA 50) - Money Flow บ่งบอกถึงแรงขายที่เข้ามา * **TF15:** ผันผวนสูง, ไม่มีทิศทางชัดเจน (Sideways) - Money Flow แสดงถึงแรงขาย แต่ก็มีแรงซื้อกลับเข้ามาบ้าง * **Money Flow (LuxAlgo):** * **TF Day:** แรงซื้อเริ่มอ่อนแรงลงอย่างมีนัยสำคัญ, มีแรงขายเข้ามา * **TF4H:** แรงขายมีมากกว่าแรงซื้อ * **TF15:** แรงขายและแรงซื้อผสมกัน, โดยรวมแรงขายยังมากกว่า * **EMA:** * **TF Day:** EMA 50/200 เป็นแนวรับ/แนวต้าน * **TF4H:** EMA 50 กำลังถูกทดสอบ, EMA 200 เป็นแนวต้าน * **TF15:** EMA 50/200 เป็นแนวต้าน **โครงสร้างราคา (SMC):** | Timeframe | Break of Structure (BOS) | Change of Character (CHoCH) | Higher High (HH) & Higher Low (HL) | Equal Highs (EQH) / Equal Lows (EQL) | | :-------- | :----------------------- | :--------------------------- | :----------------------------------- | :------------------------------------- | | Day | ด้านบนและล่าง | ด้านบน | เริ่มก่อตัว (แต่ไม่แข็งแกร่ง) | - | | 4H | ด้านบน | ด้านบน | เริ่มก่อตัว (แต่ไม่ชัดเจน) | มี EQH หลายจุด | | 15m | ด้านบนและล่าง | มีทั้งบนและล่าง | Lower Highs (LH) & Lower Lows (LL) | มี EQH และ EQL หลายจุด | **แนวรับ-แนวต้านสำคัญ:** | Timeframe | แนวรับ | แนวต้าน | | :-------- | :----------------------------------------------------------- | :--------------------------------------------------------------------- | | Day | EMA 50 (≈0.00010000), EMA 200 (≈0.00008000), 0.00006000-0.00007000 | 0.00017953 (High ล่าสุด), 0.00014000 (Volume Profile) | | 4H | EMA 50 (≈0.00007000), 0.00006000-0.00007000 | EMA 200 (≈0.00008000), 0.00008132, บริเวณ 0.00010000-0.00012000 (EQH) | | 15m | บริเวณ Low ล่าสุด | EMA 50, EMA 200, บริเวณ 0.000075-0.000076 (EQH) | **กลยุทธ์ (LUNCUSDT):** 1. **Wait & See (ทางเลือกที่ดีที่สุด):** * **เหตุผล:** ความขัดแย้งระหว่าง Timeframes สูงมาก, แนวโน้มไม่ชัดเจน, Money Flow ใน TF4H และ TF15 เป็นลบ * รอให้ราคาแสดงทิศทางที่ชัดเจนกว่านี้ (ยืนเหนือ EMA 50 ใน TF4H ได้, Breakout แนวต้านใน TF15) 2. **Buy on Dip (Day, 4H) - *ความเสี่ยงสูงมาก ไม่แนะนำ*:** * **เหตุผล:** แนวโน้มระยะยาวอาจจะยังเป็นขาขึ้นได้ (ถ้าไม่หลุดแนวรับสำคัญ) * **เงื่อนไข:** *ต้อง* รอสัญญาณการกลับตัวใน TF15 ก่อน * **จุดเข้า:** พิจารณาเฉพาะบริเวณแนวรับที่แข็งแกร่งมากๆ (EMA ของ Day/4H) *และต้องดู TF15 ประกอบ* * **Stop Loss:** ต่ำกว่า Low ล่าสุดของ TF15 3. **Short (15, ความเสี่ยงสูงมาก):** * **เหตุผล:** แนวโน้ม TF15 เป็นขาลง, Money Flow เป็นลบ * **เงื่อนไข:** ราคาไม่สามารถ Breakout EMA หรือแนวต้านอื่นๆ ใน TF15 ได้ * **จุดเข้า:** บริเวณ EMA หรือแนวต้านของ TF15 * **Stop Loss:** เหนือ High ล่าสุดของ TF15 **คำแนะนำ (เน้นย้ำ):** * **LUNC เป็นเหรียญที่มีความเสี่ยงสูงมาก (High Risk):** มีความผันผวนสูง และอาจมีการเปลี่ยนแปลงอย่างรวดเร็ว * **ความขัดแย้งของ Timeframes:** สถานการณ์ของ LUNCUSDT มีความขัดแย้งสูงมาก และมีความเสี่ยงสูง * **Money Flow:** บ่งบอกถึงแรงขายที่เริ่มเข้ามา และแนวโน้มขาขึ้น (ระยะกลาง-ยาว) ที่อ่อนแอลง * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด:** "รอ" เป็นกลยุทธ์ที่ดีที่สุด * **Risk Management:** สำคัญที่สุด ไม่ว่าจะเลือกกลยุทธ์ใด ต้องมีการบริหารความเสี่ยงที่ดี **สรุป:** LUNCUSDT กำลังอยู่ในช่วงเวลาที่ยากลำบากและมีความเสี่ยงสูงมากที่สุดในบรรดา 3 เหรียญที่เราวิเคราะห์กันมา การตัดสินใจที่ผิดพลาดอาจนำไปสู่การขาดทุนได้ ควรพิจารณาอย่างรอบคอบก่อนเข้าเทรดทุกครั้ง และ "รอ" จนกว่าจะมีสัญญาณที่ชัดเจนกว่านี้ เป็นทางเลือกที่ปลอดภัยที่สุดสำหรับนักลงทุนส่วนใหญ่ค่ะ **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ @ d360efec:14907b5f
2025-02-13 05:27:39 **ภาพรวม XRPUSDT (OKX):** XRPUSDT กำลังอยู่ในช่วงสำคัญ แนวโน้มระยะยาว (TF Day) เริ่มมีสัญญาณบวกของการเป็นขาขึ้น (Early Uptrend) หลังราคา Breakout EMA 50 และ Money Flow สนับสนุน อย่างไรก็ตาม แนวโน้มระยะกลาง (TF4H) เริ่มแสดงความอ่อนแอลง โดยราคาพักตัวลงมาทดสอบแนวรับสำคัญ และ Money Flow บ่งชี้ถึงแรงซื้อที่ลดลงและแรงขายที่เพิ่มขึ้น ส่วนแนวโน้มระยะสั้นมาก (TF15) เป็นขาลงชัดเจน  **แนวโน้ม:** * **TF Day:** เริ่มเป็นขาขึ้น (Early Uptrend) - Breakout EMA 50, Money Flow เป็นบวก * **TF4H:** เริ่มไม่แน่นอน (พักตัว, ทดสอบแนวรับ EMA 50 และ EQL) - Money Flow เริ่มเป็นลบ * **TF15:** ขาลง (Downtrend) ระยะสั้นมาก - ราคาหลุด EMA, โครงสร้างราคาเป็น Lower Highs/Lows, Money Flow เป็นลบ **โครงสร้างราคา (SMC):** | Timeframe | Break of Structure (BOS) | Change of Character (CHoCH) | Higher High (HH) & Higher Low (HL) | Equal Highs (EQH) / Equal Lows (EQL) | | :-------- | :----------------------- | :--------------------------- | :----------------------------------- | :------------------------------------- | | Day | ด้านบน (Breakout EMA 50) | ไม่ชัดเจน | เริ่มก่อตัว (แต่ยังไม่ชัดเจน) | - | | 4H | ด้านบน | ไม่ชัดเจน | เริ่มก่อตัว (แต่ไม่ชัดเจน) | EQH: 3.00-3.20, EQL: 2.2667 | | 15m | ด้านล่าง | มีทั้งบนและล่าง | Lower Highs (LH) & Lower Lows (LL) | EQH: 2.48-2.50, EQL: 2.38 |   **Money Flow (LuxAlgo):** * **TF Day:** แรงซื้อแข็งแกร่ง * **TF4H:** แรงซื้อเริ่มอ่อนแรงลง, แรงขายเริ่มเข้ามา * **TF15:** แรงขายมีอิทธิพลเหนือกว่า **EMA (Exponential Moving Average):** * **TF Day:** EMA 50 & 200 เป็นแนวรับ * **TF4H:** EMA 50 กำลังถูกทดสอบ, EMA 200 เป็นแนวรับถัดไป * **TF15:** EMA 50 & 200 เป็นแนวต้าน **แนวรับ-แนวต้านสำคัญ:** | Timeframe | แนวรับ | แนวต้าน | | :-------- | :----------------------------------------------------- | :----------------------------------------------------------------------- | | Day | EMA 50 (≈1.56), EMA 200 (≈1.08) | 3.4049 (High), 3.00-3.20 (EQH) | | 4H | EMA 50 (≈2.20), *2.2667 (EQL)*, EMA 200, 1.7820 | 3.4049, 2.3987 (Volume Profile), 3.00-3.20 (EQH) | | 15m | 2.38 (EQL, Volume Profile), 2.3274 | EMA 50, EMA 200, 2.4196, Equilibrium (≈2.44), 2.48-2.50 (EQH) | **กลยุทธ์ (XRPUSDT):** 1. **Wait & See (ทางเลือกที่ดีที่สุด):** * **เหตุผล:** ความขัดแย้งระหว่าง Timeframes สูง, TF4H กำลังทดสอบแนวรับสำคัญ, Money Flow ใน TF4H และ TF15 เป็นลบ * รอให้ราคาแสดงทิศทางที่ชัดเจน (ยืนเหนือ EMA 50 ใน TF4H ได้ หรือ Breakout แนวต้านใน TF15) 2. **Buy on Dip (Day, 4H) - *ความเสี่ยงสูงมาก*:** * **เหตุผล:** แนวโน้มระยะยาวยังมีโอกาสเป็นขาขึ้น, Money Flow ใน TF Day เป็นบวก * **เงื่อนไข (สำคัญมาก):** *ต้อง* รอสัญญาณการกลับตัวใน TF15 ก่อน เช่น: * Breakout แนวต้านย่อยๆ พร้อม Volume * Money Flow (TF15) เปลี่ยนเป็นสีเขียว * Bullish Candlestick Patterns * **จุดเข้า (Day):** EMA 50, EMA 200 (*ดู TF15 ประกอบ*) * **จุดเข้า (4H):** EMA 50, *2.2667 (EQL)* (*ดู TF15 ประกอบ*) * **Stop Loss:** ต่ำกว่า Low ล่าสุดของ TF15 หรือต่ำกว่าแนวรับที่เข้าซื้อ 3. **Short (15, ความเสี่ยงสูงมาก):** * **เหตุผล:** แนวโน้ม TF15 เป็นขาลง, Money Flow เป็นลบ * **เงื่อนไข:** ราคาไม่สามารถกลับขึ้นไปยืนเหนือ EMA ของ TF15 ได้ * **จุดเข้า:** บริเวณ EMA ของ TF15 หรือแนวต้านอื่นๆ * **Stop Loss:** เหนือ High ล่าสุดของ TF15 **คำแนะนำ:** * **ความขัดแย้งของ Timeframes:** XRPUSDT มีความขัดแย้งสูงมาก และมีความเสี่ยงสูง * **Money Flow:** Day เป็นบวก, 4H เริ่มเป็นลบ, 15m เป็นลบ * **EMA 50 (TF4H) & EQL 2.2667:** จุดชี้ชะตา * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด:** "รอ" ดีที่สุด * **Risk Management:** สำคัญที่สุด **สรุป:** สถานการณ์ของ XRPUSDT ตอนนี้มีความเสี่ยงสูงมาก และไม่เหมาะกับนักลงทุนที่รับความเสี่ยงได้ต่ำ การ "รอ" จนกว่าจะมีสัญญาณที่ชัดเจนกว่านี้ เป็นทางเลือกที่ปลอดภัยที่สุดค่ะ Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
@ d360efec:14907b5f
2025-02-13 05:27:39 **ภาพรวม XRPUSDT (OKX):** XRPUSDT กำลังอยู่ในช่วงสำคัญ แนวโน้มระยะยาว (TF Day) เริ่มมีสัญญาณบวกของการเป็นขาขึ้น (Early Uptrend) หลังราคา Breakout EMA 50 และ Money Flow สนับสนุน อย่างไรก็ตาม แนวโน้มระยะกลาง (TF4H) เริ่มแสดงความอ่อนแอลง โดยราคาพักตัวลงมาทดสอบแนวรับสำคัญ และ Money Flow บ่งชี้ถึงแรงซื้อที่ลดลงและแรงขายที่เพิ่มขึ้น ส่วนแนวโน้มระยะสั้นมาก (TF15) เป็นขาลงชัดเจน  **แนวโน้ม:** * **TF Day:** เริ่มเป็นขาขึ้น (Early Uptrend) - Breakout EMA 50, Money Flow เป็นบวก * **TF4H:** เริ่มไม่แน่นอน (พักตัว, ทดสอบแนวรับ EMA 50 และ EQL) - Money Flow เริ่มเป็นลบ * **TF15:** ขาลง (Downtrend) ระยะสั้นมาก - ราคาหลุด EMA, โครงสร้างราคาเป็น Lower Highs/Lows, Money Flow เป็นลบ **โครงสร้างราคา (SMC):** | Timeframe | Break of Structure (BOS) | Change of Character (CHoCH) | Higher High (HH) & Higher Low (HL) | Equal Highs (EQH) / Equal Lows (EQL) | | :-------- | :----------------------- | :--------------------------- | :----------------------------------- | :------------------------------------- | | Day | ด้านบน (Breakout EMA 50) | ไม่ชัดเจน | เริ่มก่อตัว (แต่ยังไม่ชัดเจน) | - | | 4H | ด้านบน | ไม่ชัดเจน | เริ่มก่อตัว (แต่ไม่ชัดเจน) | EQH: 3.00-3.20, EQL: 2.2667 | | 15m | ด้านล่าง | มีทั้งบนและล่าง | Lower Highs (LH) & Lower Lows (LL) | EQH: 2.48-2.50, EQL: 2.38 |   **Money Flow (LuxAlgo):** * **TF Day:** แรงซื้อแข็งแกร่ง * **TF4H:** แรงซื้อเริ่มอ่อนแรงลง, แรงขายเริ่มเข้ามา * **TF15:** แรงขายมีอิทธิพลเหนือกว่า **EMA (Exponential Moving Average):** * **TF Day:** EMA 50 & 200 เป็นแนวรับ * **TF4H:** EMA 50 กำลังถูกทดสอบ, EMA 200 เป็นแนวรับถัดไป * **TF15:** EMA 50 & 200 เป็นแนวต้าน **แนวรับ-แนวต้านสำคัญ:** | Timeframe | แนวรับ | แนวต้าน | | :-------- | :----------------------------------------------------- | :----------------------------------------------------------------------- | | Day | EMA 50 (≈1.56), EMA 200 (≈1.08) | 3.4049 (High), 3.00-3.20 (EQH) | | 4H | EMA 50 (≈2.20), *2.2667 (EQL)*, EMA 200, 1.7820 | 3.4049, 2.3987 (Volume Profile), 3.00-3.20 (EQH) | | 15m | 2.38 (EQL, Volume Profile), 2.3274 | EMA 50, EMA 200, 2.4196, Equilibrium (≈2.44), 2.48-2.50 (EQH) | **กลยุทธ์ (XRPUSDT):** 1. **Wait & See (ทางเลือกที่ดีที่สุด):** * **เหตุผล:** ความขัดแย้งระหว่าง Timeframes สูง, TF4H กำลังทดสอบแนวรับสำคัญ, Money Flow ใน TF4H และ TF15 เป็นลบ * รอให้ราคาแสดงทิศทางที่ชัดเจน (ยืนเหนือ EMA 50 ใน TF4H ได้ หรือ Breakout แนวต้านใน TF15) 2. **Buy on Dip (Day, 4H) - *ความเสี่ยงสูงมาก*:** * **เหตุผล:** แนวโน้มระยะยาวยังมีโอกาสเป็นขาขึ้น, Money Flow ใน TF Day เป็นบวก * **เงื่อนไข (สำคัญมาก):** *ต้อง* รอสัญญาณการกลับตัวใน TF15 ก่อน เช่น: * Breakout แนวต้านย่อยๆ พร้อม Volume * Money Flow (TF15) เปลี่ยนเป็นสีเขียว * Bullish Candlestick Patterns * **จุดเข้า (Day):** EMA 50, EMA 200 (*ดู TF15 ประกอบ*) * **จุดเข้า (4H):** EMA 50, *2.2667 (EQL)* (*ดู TF15 ประกอบ*) * **Stop Loss:** ต่ำกว่า Low ล่าสุดของ TF15 หรือต่ำกว่าแนวรับที่เข้าซื้อ 3. **Short (15, ความเสี่ยงสูงมาก):** * **เหตุผล:** แนวโน้ม TF15 เป็นขาลง, Money Flow เป็นลบ * **เงื่อนไข:** ราคาไม่สามารถกลับขึ้นไปยืนเหนือ EMA ของ TF15 ได้ * **จุดเข้า:** บริเวณ EMA ของ TF15 หรือแนวต้านอื่นๆ * **Stop Loss:** เหนือ High ล่าสุดของ TF15 **คำแนะนำ:** * **ความขัดแย้งของ Timeframes:** XRPUSDT มีความขัดแย้งสูงมาก และมีความเสี่ยงสูง * **Money Flow:** Day เป็นบวก, 4H เริ่มเป็นลบ, 15m เป็นลบ * **EMA 50 (TF4H) & EQL 2.2667:** จุดชี้ชะตา * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด:** "รอ" ดีที่สุด * **Risk Management:** สำคัญที่สุด **สรุป:** สถานการณ์ของ XRPUSDT ตอนนี้มีความเสี่ยงสูงมาก และไม่เหมาะกับนักลงทุนที่รับความเสี่ยงได้ต่ำ การ "รอ" จนกว่าจะมีสัญญาณที่ชัดเจนกว่านี้ เป็นทางเลือกที่ปลอดภัยที่สุดค่ะ Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ @ d360efec:14907b5f
2025-02-13 04:47:20 **ภาพรวม BTCUSDT :** Bitcoin (BTCUSDT) กำลังอยู่ในช่วงสำคัญ แม้ว่าแนวโน้มหลักในระยะกลางถึงยาว (TF Day & 4H) จะยังคงเป็นขาขึ้นที่แข็งแกร่ง แต่ในระยะสั้นมาก (TF15) กลับแสดงสัญญาณของความอ่อนแอและการปรับฐานลงมา ทำให้เกิดความไม่แน่นอนในทิศทางของราคา อย่างไรก็ตาม *Money Flow ใน TF Day บ่งชี้ว่าแรงซื้อโดยรวมยังคงแข็งแกร่ง*  **แนวโน้ม:** * **TF Day:** ขาขึ้น (Uptrend) แข็งแกร่ง – ราคาอยู่เหนือ EMA 50 และ EMA 200, โครงสร้างราคาเป็น Higher Highs (HH) และ Higher Lows (HL), *Money Flow เป็นบวก (แรงซื้อ)* * **TF4H:** ขาขึ้น (Uptrend) – ราคาอยู่เหนือ EMA, มีการพักตัวลงมา (Pullback) แต่ยังไม่เสียโครงสร้างขาขึ้น, *Money Flow เริ่มอ่อนแรง (แรงซื้อลดลง, แรงขายเพิ่มขึ้น)* * **TF15:** ขาลง (Downtrend) ระยะสั้นมาก – ราคาหลุด EMA และแนวรับย่อย, โครงสร้างราคาเป็น Lower Highs (LH) และ Lower Lows (LL), *Money Flow เป็นลบ (แรงขาย)* **โครงสร้างราคา (SMC):** * **TF Day:** ยืนยันแนวโน้มขาขึ้น (HH, HL, BOS) * **TF4H:** ยืนยันแนวโน้มขาขึ้น (HH, HL, BOS), มี Equal Highs (EQH) ที่เป็นแนวต้าน * **TF15:** บ่งบอกถึงแนวโน้มขาลงระยะสั้น (BOS ด้านล่าง, LH, LL), มี EQH เป็นแนวต้าน **Money Flow (LuxAlgo) - สรุป:** * **TF Day:** แรงซื้อยังคงแข็งแกร่งอย่างชัดเจน * **TF4H:** แรงซื้อเริ่มอ่อนแรงลง, มีแรงขายเข้ามา * **TF15:** แรงขายมีอิทธิพลเหนือกว่า  **EMA (Exponential Moving Average):** * **TF Day & 4H:** EMA 50 & 200 เป็นแนวรับสำคัญ * **TF15:** EMA 50 & 200 กลายเป็นแนวต้าน **แนวรับ-แนวต้านสำคัญ:** | Timeframe | แนวรับ | แนวต้าน | | :-------- | :------------------------------------------------------------------------- | :-------------------------------------------------------------- | | Day | EMA 50, EMA 200, 96,000-98,000, 85,724.7 | 109,998.9 (High เดิม) | | 4H | EMA 50, EMA 200, 96,000-98,000, 89,037.0 | 109,998.9 (EQH, High เดิม) | | 15m | 95,200 (Low ล่าสุด), 94,707.4 (Low ก่อนหน้า) | EMA 50, EMA 200, บริเวณ 96,000, 96,807.8, 97,000-97,200 | **กลยุทธ์ (BTCUSDT):** 1. **Buy on Dip (Day, 4H) - *มีความน่าเชื่อถือมากขึ้น แต่ยังคงต้องระมัดระวัง*:** * **เหตุผล:** แนวโน้มหลักยังเป็นขาขึ้น, Money Flow ใน TF Day แข็งแกร่ง * **เงื่อนไข:** *ยังคงต้องรอสัญญาณการกลับตัวของราคาใน TF15 ก่อน* (Breakout แนวต้านย่อย, Money Flow TF15 เป็นบวก, Bullish Candlestick Patterns) * **จุดเข้า (Day):** EMA 50, EMA 200, บริเวณ 96,000-98,000 * **จุดเข้า (4H):** EMA 50 * **Stop Loss:** ต่ำกว่า Low ล่าสุดของ TF15 หรือต่ำกว่าแนวรับที่เข้าซื้อ 2. **Short (15, ความเสี่ยงสูงมาก):** * **เหตุผล:** แนวโน้ม TF15 เป็นขาลง, Money Flow TF15 เป็นลบ * **เงื่อนไข:** ราคาไม่สามารถกลับขึ้นไปยืนเหนือ EMA ของ TF15 ได้ * **จุดเข้า:** บริเวณ EMA ของ TF15 หรือแนวต้านอื่นๆ * **Stop Loss:** เหนือ High ล่าสุดของ TF15 3. **Wait & See (ทางเลือกที่ปลอดภัย):** * **เหตุผล:** ความขัดแย้งระหว่าง Timeframes ยังคงมีอยู่ * รอให้ตลาดเฉลยทิศทางที่ชัดเจนกว่านี้ **คำแนะนำ (เน้นย้ำ):** * **Money Flow ใน TF Day:** เป็นปัจจัยบวกที่สำคัญ ทำให้กลยุทธ์ Buy on Dip มีน้ำหนักมากขึ้น * **ความขัดแย้งของ Timeframes:** ยังคงต้องระวัง TF15 ที่เป็นขาลง * **Volume:** การ Breakout/Breakdown ใดๆ ควรมี Volume สนับสนุน * **Risk Management:** สำคัญที่สุด **สรุป:** สถานการณ์ของ BTCUSDT โดยรวมยังคงเป็นบวก (ขาขึ้น) แต่มีความเสี่ยงในระยะสั้นจาก TF15 การตัดสินใจลงทุนควรพิจารณาจาก Timeframe ที่เหมาะสมกับสไตล์การเทรดของคุณ และอย่าลืมบริหารความเสี่ยงเสมอค่ะ **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
@ d360efec:14907b5f
2025-02-13 04:47:20 **ภาพรวม BTCUSDT :** Bitcoin (BTCUSDT) กำลังอยู่ในช่วงสำคัญ แม้ว่าแนวโน้มหลักในระยะกลางถึงยาว (TF Day & 4H) จะยังคงเป็นขาขึ้นที่แข็งแกร่ง แต่ในระยะสั้นมาก (TF15) กลับแสดงสัญญาณของความอ่อนแอและการปรับฐานลงมา ทำให้เกิดความไม่แน่นอนในทิศทางของราคา อย่างไรก็ตาม *Money Flow ใน TF Day บ่งชี้ว่าแรงซื้อโดยรวมยังคงแข็งแกร่ง*  **แนวโน้ม:** * **TF Day:** ขาขึ้น (Uptrend) แข็งแกร่ง – ราคาอยู่เหนือ EMA 50 และ EMA 200, โครงสร้างราคาเป็น Higher Highs (HH) และ Higher Lows (HL), *Money Flow เป็นบวก (แรงซื้อ)* * **TF4H:** ขาขึ้น (Uptrend) – ราคาอยู่เหนือ EMA, มีการพักตัวลงมา (Pullback) แต่ยังไม่เสียโครงสร้างขาขึ้น, *Money Flow เริ่มอ่อนแรง (แรงซื้อลดลง, แรงขายเพิ่มขึ้น)* * **TF15:** ขาลง (Downtrend) ระยะสั้นมาก – ราคาหลุด EMA และแนวรับย่อย, โครงสร้างราคาเป็น Lower Highs (LH) และ Lower Lows (LL), *Money Flow เป็นลบ (แรงขาย)* **โครงสร้างราคา (SMC):** * **TF Day:** ยืนยันแนวโน้มขาขึ้น (HH, HL, BOS) * **TF4H:** ยืนยันแนวโน้มขาขึ้น (HH, HL, BOS), มี Equal Highs (EQH) ที่เป็นแนวต้าน * **TF15:** บ่งบอกถึงแนวโน้มขาลงระยะสั้น (BOS ด้านล่าง, LH, LL), มี EQH เป็นแนวต้าน **Money Flow (LuxAlgo) - สรุป:** * **TF Day:** แรงซื้อยังคงแข็งแกร่งอย่างชัดเจน * **TF4H:** แรงซื้อเริ่มอ่อนแรงลง, มีแรงขายเข้ามา * **TF15:** แรงขายมีอิทธิพลเหนือกว่า  **EMA (Exponential Moving Average):** * **TF Day & 4H:** EMA 50 & 200 เป็นแนวรับสำคัญ * **TF15:** EMA 50 & 200 กลายเป็นแนวต้าน **แนวรับ-แนวต้านสำคัญ:** | Timeframe | แนวรับ | แนวต้าน | | :-------- | :------------------------------------------------------------------------- | :-------------------------------------------------------------- | | Day | EMA 50, EMA 200, 96,000-98,000, 85,724.7 | 109,998.9 (High เดิม) | | 4H | EMA 50, EMA 200, 96,000-98,000, 89,037.0 | 109,998.9 (EQH, High เดิม) | | 15m | 95,200 (Low ล่าสุด), 94,707.4 (Low ก่อนหน้า) | EMA 50, EMA 200, บริเวณ 96,000, 96,807.8, 97,000-97,200 | **กลยุทธ์ (BTCUSDT):** 1. **Buy on Dip (Day, 4H) - *มีความน่าเชื่อถือมากขึ้น แต่ยังคงต้องระมัดระวัง*:** * **เหตุผล:** แนวโน้มหลักยังเป็นขาขึ้น, Money Flow ใน TF Day แข็งแกร่ง * **เงื่อนไข:** *ยังคงต้องรอสัญญาณการกลับตัวของราคาใน TF15 ก่อน* (Breakout แนวต้านย่อย, Money Flow TF15 เป็นบวก, Bullish Candlestick Patterns) * **จุดเข้า (Day):** EMA 50, EMA 200, บริเวณ 96,000-98,000 * **จุดเข้า (4H):** EMA 50 * **Stop Loss:** ต่ำกว่า Low ล่าสุดของ TF15 หรือต่ำกว่าแนวรับที่เข้าซื้อ 2. **Short (15, ความเสี่ยงสูงมาก):** * **เหตุผล:** แนวโน้ม TF15 เป็นขาลง, Money Flow TF15 เป็นลบ * **เงื่อนไข:** ราคาไม่สามารถกลับขึ้นไปยืนเหนือ EMA ของ TF15 ได้ * **จุดเข้า:** บริเวณ EMA ของ TF15 หรือแนวต้านอื่นๆ * **Stop Loss:** เหนือ High ล่าสุดของ TF15 3. **Wait & See (ทางเลือกที่ปลอดภัย):** * **เหตุผล:** ความขัดแย้งระหว่าง Timeframes ยังคงมีอยู่ * รอให้ตลาดเฉลยทิศทางที่ชัดเจนกว่านี้ **คำแนะนำ (เน้นย้ำ):** * **Money Flow ใน TF Day:** เป็นปัจจัยบวกที่สำคัญ ทำให้กลยุทธ์ Buy on Dip มีน้ำหนักมากขึ้น * **ความขัดแย้งของ Timeframes:** ยังคงต้องระวัง TF15 ที่เป็นขาลง * **Volume:** การ Breakout/Breakdown ใดๆ ควรมี Volume สนับสนุน * **Risk Management:** สำคัญที่สุด **สรุป:** สถานการณ์ของ BTCUSDT โดยรวมยังคงเป็นบวก (ขาขึ้น) แต่มีความเสี่ยงในระยะสั้นจาก TF15 การตัดสินใจลงทุนควรพิจารณาจาก Timeframe ที่เหมาะสมกับสไตล์การเทรดของคุณ และอย่าลืมบริหารความเสี่ยงเสมอค่ะ **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ @ 2183e947:f497b975
2025-02-13 04:44:45# How Coinpools Improve Bitcoin # Problems with bitcoin UX problems with base layer payments include: - Mining fees are sometimes high - Confirmations usually take several minutes - Using it privately requires running a coinjoin server UX problems with lightning payments include: - Setup fees are sometimes high - Payments frequently fail - Payments aren't asynchronous (the recipient has to stand there with their device open waiting to do a revoke_and_ack on their old state -- unless they use a custodian) - Payments that *do* succeed occasionally take more than 30 seconds (due to stuck payments, automatic retries, and no ability to say "stop retrying" in any existing wallets that I'm aware of) - Using it privately requires manual channel management # Solutions A lot of my recent work focuses on non-interactive coinpools. I figured out a way to do them on bitcoin if we had CTV + CSFS, and then, with a bit more thought, I figured out that my model didn't actually require those things, so I am now working on an implementation. But my model does benefit a lot from CTV (less sure about CSFS at this point) so let me outline how non-interactive coinpools fix the above problems and along the way I will share how CTV specifically improves coinpools. ## "Mining fees are sometimes high" Coinpools improve the problem of "mining fees are sometimes high" by letting you bypass them in more cases. If you're in a coinpool and pay someone else in the same coinpool, your payment does not show up on the base layer, it just involves modifying some unilateral withdrawal transactions such that the sender can withdraw less and the recipient can withdraw more. The transactions are off-chain, like LN transactions, so you can do that without paying a base layer fee. ## "Confirmations usually take several minutes" Coinpools improve the problem of "confirmations usually take several minutes" in a similar manner. Payments *inside* a coinpool (i.e. to another pool user) merely involve modifying off-chain data (and revoking an old state), so they can be as fast as lightning. In most cases I expect them to be a bit faster because there's less need for pathfinding or negotiating with a variety of routing nodes. If the sender and the recipient are in the same pool, they only need to talk to each other and, in my model, a coordinator. ## "Using the base layer privately requires running a coinjoin server" Coinpools improve the problem of "using the base layer privately requires running a coinjoin server" in two ways: first, if you're in a coinpool and you send money to a bitcoin address, the blockchain doesn't know which coinpool user sent that payment. Analysts might be able to trace the payment to the coinpool, but from the blockchain's perspective, that's just a multisig; the actual person *inside* the multisig who sent the money is not revealed. However, my model uses a coordinator, and the coordinator probably knows which user sent the payment. Still, only 1 person knowing is better than having everyone on the blockchain know. Second, if you send money to someone *inside* the coinpool, in my model, the only people who know about your payment are the sender, the recipient, and the coordinator, and the recipient does not know who the sender is. Moreover, my model allows users to act as bridges from LN to other pool users, so even the coordinator doesn't know if the person who *looks* like the sender was the *real* sender or just a bridge node, with the *real* sender being someone on lightning. ## "Setup fees on lightning are sometimes high" Coinpools improve the problem of "setup fees are sometimes high" by having multiple users share the setup cost. My model allows a single bitcoin transaction to fund a coinpool with a number of members between 1 and probably about 100. (The max I've actually successfully tested is 11.) If the users share the cost of that transaction, then even in a high fee scenario, where bitcoin transactions cost $50, each user only has to pay a fraction of that, where the fraction is determined by how many users are joining the pool. If 10 people are joining, each user would pay $5 instead of $50. If 50 people are joining, each user would pay $1. If 100 people are joining, each user would pay 50¢. ## Sidebar: how CTV improves my coinpool model The setup is also where CTV greatly improves my model. For my model to work, the users have to coordinate to create the pool in something I call a "signing ceremony," which is very similar to a coinjoin. The signing ceremony has to be scheduled and each user has to show up for it or they won't get into the pool. With CTV, you could fix this: instead of a signing ceremony, an exchange could autosend your money into a coinpool on e.g. a monthly basis and email you the data you need to perform your unilateral exit. All they need from you is a pubkey, and they can do everything else. ## "Lightning payments frequently fail" Coinpools improve the problem of "payments frequently fail" by reducing the need for pathfinding, which is a typical cause of failure on lightning. If you are paying someone in the same pool as you, you always know an exact path: it will be you -> coordinator -> recipient. These short paths also reduce the likelihood of routing nodes having insufficient capacity to forward the payment. You've only got one "routing node" to worry about -- the coordinator. ## "Lightning payments aren't asynchronous" Coinpools *in general* don't improve the problem of "payments aren't asynchronous" but my model in particular *does* improve that problem because I am combining it with my hedgehog protocol from last year, which *does* allow for asynchronous lightning-like payments. Relatedly, my coinpool model technically has a network model, it's just a hub-and-spoke network: the coordinator is connected to every user of the pool and can forward asynchronous hedgehog payments to them. This means you can send money to someone when they are offline; they'll get it whenever they *do* get online, even if *you* went offline in the meantime. ## "Lightning payments sometimes take too long" Coinpools improve the problem of "stuck" lightning payments by reducing the number of hops along the route. As above, a payment inside the pool (per my model) is always just sender -> coordinator -> recipient. Due to only having 1 hop, there are fewer opportunities for a node to have a network issue and cause a delay. ## "Channel management is a pain" Coinpools have multiple ways of improving the problem of manual channel management. In particular, not all coinpool models *have* channels, so channel management is not always needed in a coinpool. My model, however, does have channels, so channel management is still a thing. Nonetheless, my model improves channel management in two ways: first, the setup costs are lower for the reasons given above. Second, payment asynchronicity helps for the following reason: The worst pain point in channel management *today* occurs when someone sends you a payment but it fails because you didn't have enough inbound capacity. That doesn't happen in my coinpool model because payments are asynchronous. If you don't have enough inbound capacity, the payment doesn't fail, it just remains pending. So all you have to do is open a new channel (i.e. enter a new pool) and *then* finalize the payment. ## Zap me I hope this essay clarifies why coinpools improve the problems I outlined and why CTV improves coinpools. I also hope this gets you a bit excited for my latest coinpool invention, which I hope to release soon :D (It really is very close to demo-ready.) If you liked this essay, consider zapping me: supertestnet@coinos.io
@ 2183e947:f497b975
2025-02-13 04:44:45# How Coinpools Improve Bitcoin # Problems with bitcoin UX problems with base layer payments include: - Mining fees are sometimes high - Confirmations usually take several minutes - Using it privately requires running a coinjoin server UX problems with lightning payments include: - Setup fees are sometimes high - Payments frequently fail - Payments aren't asynchronous (the recipient has to stand there with their device open waiting to do a revoke_and_ack on their old state -- unless they use a custodian) - Payments that *do* succeed occasionally take more than 30 seconds (due to stuck payments, automatic retries, and no ability to say "stop retrying" in any existing wallets that I'm aware of) - Using it privately requires manual channel management # Solutions A lot of my recent work focuses on non-interactive coinpools. I figured out a way to do them on bitcoin if we had CTV + CSFS, and then, with a bit more thought, I figured out that my model didn't actually require those things, so I am now working on an implementation. But my model does benefit a lot from CTV (less sure about CSFS at this point) so let me outline how non-interactive coinpools fix the above problems and along the way I will share how CTV specifically improves coinpools. ## "Mining fees are sometimes high" Coinpools improve the problem of "mining fees are sometimes high" by letting you bypass them in more cases. If you're in a coinpool and pay someone else in the same coinpool, your payment does not show up on the base layer, it just involves modifying some unilateral withdrawal transactions such that the sender can withdraw less and the recipient can withdraw more. The transactions are off-chain, like LN transactions, so you can do that without paying a base layer fee. ## "Confirmations usually take several minutes" Coinpools improve the problem of "confirmations usually take several minutes" in a similar manner. Payments *inside* a coinpool (i.e. to another pool user) merely involve modifying off-chain data (and revoking an old state), so they can be as fast as lightning. In most cases I expect them to be a bit faster because there's less need for pathfinding or negotiating with a variety of routing nodes. If the sender and the recipient are in the same pool, they only need to talk to each other and, in my model, a coordinator. ## "Using the base layer privately requires running a coinjoin server" Coinpools improve the problem of "using the base layer privately requires running a coinjoin server" in two ways: first, if you're in a coinpool and you send money to a bitcoin address, the blockchain doesn't know which coinpool user sent that payment. Analysts might be able to trace the payment to the coinpool, but from the blockchain's perspective, that's just a multisig; the actual person *inside* the multisig who sent the money is not revealed. However, my model uses a coordinator, and the coordinator probably knows which user sent the payment. Still, only 1 person knowing is better than having everyone on the blockchain know. Second, if you send money to someone *inside* the coinpool, in my model, the only people who know about your payment are the sender, the recipient, and the coordinator, and the recipient does not know who the sender is. Moreover, my model allows users to act as bridges from LN to other pool users, so even the coordinator doesn't know if the person who *looks* like the sender was the *real* sender or just a bridge node, with the *real* sender being someone on lightning. ## "Setup fees on lightning are sometimes high" Coinpools improve the problem of "setup fees are sometimes high" by having multiple users share the setup cost. My model allows a single bitcoin transaction to fund a coinpool with a number of members between 1 and probably about 100. (The max I've actually successfully tested is 11.) If the users share the cost of that transaction, then even in a high fee scenario, where bitcoin transactions cost $50, each user only has to pay a fraction of that, where the fraction is determined by how many users are joining the pool. If 10 people are joining, each user would pay $5 instead of $50. If 50 people are joining, each user would pay $1. If 100 people are joining, each user would pay 50¢. ## Sidebar: how CTV improves my coinpool model The setup is also where CTV greatly improves my model. For my model to work, the users have to coordinate to create the pool in something I call a "signing ceremony," which is very similar to a coinjoin. The signing ceremony has to be scheduled and each user has to show up for it or they won't get into the pool. With CTV, you could fix this: instead of a signing ceremony, an exchange could autosend your money into a coinpool on e.g. a monthly basis and email you the data you need to perform your unilateral exit. All they need from you is a pubkey, and they can do everything else. ## "Lightning payments frequently fail" Coinpools improve the problem of "payments frequently fail" by reducing the need for pathfinding, which is a typical cause of failure on lightning. If you are paying someone in the same pool as you, you always know an exact path: it will be you -> coordinator -> recipient. These short paths also reduce the likelihood of routing nodes having insufficient capacity to forward the payment. You've only got one "routing node" to worry about -- the coordinator. ## "Lightning payments aren't asynchronous" Coinpools *in general* don't improve the problem of "payments aren't asynchronous" but my model in particular *does* improve that problem because I am combining it with my hedgehog protocol from last year, which *does* allow for asynchronous lightning-like payments. Relatedly, my coinpool model technically has a network model, it's just a hub-and-spoke network: the coordinator is connected to every user of the pool and can forward asynchronous hedgehog payments to them. This means you can send money to someone when they are offline; they'll get it whenever they *do* get online, even if *you* went offline in the meantime. ## "Lightning payments sometimes take too long" Coinpools improve the problem of "stuck" lightning payments by reducing the number of hops along the route. As above, a payment inside the pool (per my model) is always just sender -> coordinator -> recipient. Due to only having 1 hop, there are fewer opportunities for a node to have a network issue and cause a delay. ## "Channel management is a pain" Coinpools have multiple ways of improving the problem of manual channel management. In particular, not all coinpool models *have* channels, so channel management is not always needed in a coinpool. My model, however, does have channels, so channel management is still a thing. Nonetheless, my model improves channel management in two ways: first, the setup costs are lower for the reasons given above. Second, payment asynchronicity helps for the following reason: The worst pain point in channel management *today* occurs when someone sends you a payment but it fails because you didn't have enough inbound capacity. That doesn't happen in my coinpool model because payments are asynchronous. If you don't have enough inbound capacity, the payment doesn't fail, it just remains pending. So all you have to do is open a new channel (i.e. enter a new pool) and *then* finalize the payment. ## Zap me I hope this essay clarifies why coinpools improve the problems I outlined and why CTV improves coinpools. I also hope this gets you a bit excited for my latest coinpool invention, which I hope to release soon :D (It really is very close to demo-ready.) If you liked this essay, consider zapping me: supertestnet@coinos.io @ a012dc82:6458a70d
2025-02-13 04:00:01In the dynamic world of global finance, the interplay between traditional monetary policy and the burgeoning digital asset market is becoming increasingly prominent. The U.S. Federal Reserve's recent pivot towards a more accommodative monetary policy has sparked intense discussion among investors, economists, and cryptocurrency enthusiasts. This shift, characterized by an expected reduction in interest rates, is not just a routine adjustment but a significant move that could have far-reaching implications for various asset classes, including cryptocurrencies like Bitcoin. As we delve into this topic, we aim to unravel the complexities of the Fed's policy change and its potential ripple effects on Bitcoin, a digital asset that has been a subject of much intrigue and speculation. **Table Of Content** - Understanding the Fed's Policy Shift - Impact on Traditional Financial Markets - Bitcoin's Response to Monetary Easing - Analyzing the Economic Backdrop - Bitcoin: A Safe Haven or Risk Asset? - Risks and Opportunities - Conclusion - FAQs **Understanding the Fed's Policy Shift** The Federal Reserve, the guardian of the U.S. monetary system, wields immense influence over global financial markets. Its recent signaling of a dovish turn – an expectation of 75 basis points in rate cuts by 2024 – marks a significant departure from its previous stance. This change is reflective of the Fed's response to a confluence of macroeconomic factors, such as fluctuating inflation rates, global economic uncertainties, and domestic financial stability concerns. The Fed's decisions are closely monitored as they set the tone for economic growth, inflation control, and financial market stability. In this context, the anticipated rate cuts suggest a strategic move to stimulate economic activity by making borrowing cheaper, thereby potentially boosting investment and consumption. However, this policy shift is not without its complexities and nuances, as it must balance the fine line between stimulating growth and controlling inflation. **Impact on Traditional Financial Markets** The ripple effects of the Fed's policy announcement were immediately felt across traditional financial markets. Stock markets, often seen as a barometer of economic sentiment, reacted positively, with indices like the Dow Jones Industrial Average reaching new heights. This surge reflects investors' optimism about the potential for increased corporate profits and economic growth in a lower interest rate environment. Similarly, the bond market experienced a significant rally, with yields on government securities falling as bond prices rose. This movement in the bond market is indicative of investors' expectations of a more accommodative monetary policy, which typically leads to lower yields on fixed-income securities. These market reactions underscore the pivotal role of central bank policies in shaping investor sentiment and the direction of financial markets. They also highlight the interconnectedness of various asset classes, as changes in monetary policy can have cascading effects across different sectors of the economy. **Bitcoin's Response to Monetary Easing** Bitcoin's reaction to the Fed's dovish turn has been a subject of keen interest. The cryptocurrency, which had been experiencing volatility, showed signs of recovery following the Fed's announcement. This response is indicative of Bitcoin's increasing correlation with broader financial market trends, a significant development given its history as an uncorrelated asset. Bitcoin's sensitivity to macroeconomic factors like central bank policies points to its growing integration into the mainstream financial ecosystem. However, this integration also means that Bitcoin is increasingly exposed to the same macroeconomic risks and uncertainties that affect traditional assets. The Fed's policy shift could potentially make Bitcoin more attractive to investors seeking non-traditional assets in a low-interest-rate environment. However, Bitcoin's complex dynamics, including its decentralized nature, limited supply, and regulatory landscape, add layers of complexity to its response to monetary policy changes. **Analyzing the Economic Backdrop** The economic backdrop against which the Fed's policy shift occurs is multifaceted and dynamic. On one hand, the U.S. economy has demonstrated resilience, with robust GDP growth and positive retail sales figures suggesting underlying strength. On the other hand, inflation, though moderated from its peak, remains a concern, hovering above the Fed's target. This economic duality presents a challenging scenario for policymakers, who must navigate the delicate balance between stimulating growth and containing inflation. For investors and market participants, this creates an environment of uncertainty, as they must decipher mixed signals from economic data and policy announcements. In this context, Bitcoin's role and response become even more intriguing, as it operates at the intersection of technology, finance, and macroeconomics. **Bitcoin: A Safe Haven or Risk Asset?** The debate over Bitcoin's classification as a safe haven or a risk asset is intensified by the Fed's easing stance. Traditionally, in a low-interest-rate environment, investors seek assets that can serve as hedges against inflation and currency devaluation. Gold has historically played this role, and Bitcoin, with its fixed supply and digital scarcity, has drawn comparisons to gold. However, Bitcoin's relatively short history and high volatility make it a more complex and potentially riskier asset. The Fed's dovish policy could enhance Bitcoin's appeal as an alternative investment, especially if traditional assets like bonds offer lower returns. However, Bitcoin's classification as a safe haven is still a matter of debate, with opinions divided on its long-term stability and value retention capabilities. **Risks and Opportunities** Investors considering Bitcoin in light of the Fed's policy change face a landscape filled with both risks and opportunities. The potential for a Bitcoin rally in a low-interest-rate environment is counterbalanced by the cryptocurrency's inherent volatility and regulatory uncertainties. Bitcoin's price movements can be dramatic and unpredictable, influenced by a range of factors from technological developments to geopolitical events. Additionally, the regulatory environment for cryptocurrencies is still evolving, with potential changes posing risks to Bitcoin's accessibility and value. Investors must also consider the broader global economic context, including actions by other central banks and international trade dynamics, which can impact Bitcoin's market movement. **Conclusion** The Federal Reserve's shift towards a more accommodative monetary policy in 2024 presents a fascinating scenario for Bitcoin and the broader cryptocurrency market. This development underscores the increasing relevance of digital assets in the global financial landscape and highlights the complex interplay between traditional monetary policies and emerging financial technologies. As Bitcoin continues to evolve and gain acceptance, its response to macroeconomic factors like central bank policies will be a critical area of focus for investors. In navigating this dynamic and uncertain environment, a cautious and well-informed approach is essential for those looking to explore the opportunities and navigate the challenges of cryptocurrency investments. The coming years promise to be a pivotal period in the maturation of Bitcoin as it responds to the shifting tides of global finance. **FAQs** **How does the Federal Reserve's easing stance impact Bitcoin?** The Fed's shift towards lower interest rates can make riskier assets like Bitcoin more attractive to investors. This is because lower rates often lead to reduced yields on traditional investments, prompting investors to seek higher returns elsewhere. **What is the significance of the Fed's 'dot plot' for Bitcoin investors?** The 'dot plot' is a projection of interest rate movements by Federal Reserve members. A shift towards lower rates, as indicated in the recent dot plot, can signal a more accommodative monetary policy, potentially impacting Bitcoin's market as investors adjust their portfolios. **Can Bitcoin be considered a safe haven asset in light of the Fed's policy?** Bitcoin's role as a safe haven asset is debated. While its fixed supply and digital nature offer some safe haven characteristics, its volatility and regulatory uncertainties make it a complex choice compared to traditional safe havens like gold. **What risks should Bitcoin investors consider in the context of the Fed's easing policy?** Investors should be aware of Bitcoin's volatility, regulatory changes, and its sensitivity to macroeconomic factors. Additionally, global economic conditions and actions by other central banks can also influence Bitcoin's market. **How does the economic backdrop influence Bitcoin's response to the Fed's policy?** Economic factors like GDP growth, inflation rates, and retail sales impact investor sentiment and risk appetite, which in turn can affect Bitcoin's market. A strong economy might reduce the appeal of risk assets like Bitcoin, while economic uncertainties can increase their attractiveness. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: @croxroadnews.co** **Instagram: @croxroadnews.co** **Youtube: @croxroadnews** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
@ a012dc82:6458a70d
2025-02-13 04:00:01In the dynamic world of global finance, the interplay between traditional monetary policy and the burgeoning digital asset market is becoming increasingly prominent. The U.S. Federal Reserve's recent pivot towards a more accommodative monetary policy has sparked intense discussion among investors, economists, and cryptocurrency enthusiasts. This shift, characterized by an expected reduction in interest rates, is not just a routine adjustment but a significant move that could have far-reaching implications for various asset classes, including cryptocurrencies like Bitcoin. As we delve into this topic, we aim to unravel the complexities of the Fed's policy change and its potential ripple effects on Bitcoin, a digital asset that has been a subject of much intrigue and speculation. **Table Of Content** - Understanding the Fed's Policy Shift - Impact on Traditional Financial Markets - Bitcoin's Response to Monetary Easing - Analyzing the Economic Backdrop - Bitcoin: A Safe Haven or Risk Asset? - Risks and Opportunities - Conclusion - FAQs **Understanding the Fed's Policy Shift** The Federal Reserve, the guardian of the U.S. monetary system, wields immense influence over global financial markets. Its recent signaling of a dovish turn – an expectation of 75 basis points in rate cuts by 2024 – marks a significant departure from its previous stance. This change is reflective of the Fed's response to a confluence of macroeconomic factors, such as fluctuating inflation rates, global economic uncertainties, and domestic financial stability concerns. The Fed's decisions are closely monitored as they set the tone for economic growth, inflation control, and financial market stability. In this context, the anticipated rate cuts suggest a strategic move to stimulate economic activity by making borrowing cheaper, thereby potentially boosting investment and consumption. However, this policy shift is not without its complexities and nuances, as it must balance the fine line between stimulating growth and controlling inflation. **Impact on Traditional Financial Markets** The ripple effects of the Fed's policy announcement were immediately felt across traditional financial markets. Stock markets, often seen as a barometer of economic sentiment, reacted positively, with indices like the Dow Jones Industrial Average reaching new heights. This surge reflects investors' optimism about the potential for increased corporate profits and economic growth in a lower interest rate environment. Similarly, the bond market experienced a significant rally, with yields on government securities falling as bond prices rose. This movement in the bond market is indicative of investors' expectations of a more accommodative monetary policy, which typically leads to lower yields on fixed-income securities. These market reactions underscore the pivotal role of central bank policies in shaping investor sentiment and the direction of financial markets. They also highlight the interconnectedness of various asset classes, as changes in monetary policy can have cascading effects across different sectors of the economy. **Bitcoin's Response to Monetary Easing** Bitcoin's reaction to the Fed's dovish turn has been a subject of keen interest. The cryptocurrency, which had been experiencing volatility, showed signs of recovery following the Fed's announcement. This response is indicative of Bitcoin's increasing correlation with broader financial market trends, a significant development given its history as an uncorrelated asset. Bitcoin's sensitivity to macroeconomic factors like central bank policies points to its growing integration into the mainstream financial ecosystem. However, this integration also means that Bitcoin is increasingly exposed to the same macroeconomic risks and uncertainties that affect traditional assets. The Fed's policy shift could potentially make Bitcoin more attractive to investors seeking non-traditional assets in a low-interest-rate environment. However, Bitcoin's complex dynamics, including its decentralized nature, limited supply, and regulatory landscape, add layers of complexity to its response to monetary policy changes. **Analyzing the Economic Backdrop** The economic backdrop against which the Fed's policy shift occurs is multifaceted and dynamic. On one hand, the U.S. economy has demonstrated resilience, with robust GDP growth and positive retail sales figures suggesting underlying strength. On the other hand, inflation, though moderated from its peak, remains a concern, hovering above the Fed's target. This economic duality presents a challenging scenario for policymakers, who must navigate the delicate balance between stimulating growth and containing inflation. For investors and market participants, this creates an environment of uncertainty, as they must decipher mixed signals from economic data and policy announcements. In this context, Bitcoin's role and response become even more intriguing, as it operates at the intersection of technology, finance, and macroeconomics. **Bitcoin: A Safe Haven or Risk Asset?** The debate over Bitcoin's classification as a safe haven or a risk asset is intensified by the Fed's easing stance. Traditionally, in a low-interest-rate environment, investors seek assets that can serve as hedges against inflation and currency devaluation. Gold has historically played this role, and Bitcoin, with its fixed supply and digital scarcity, has drawn comparisons to gold. However, Bitcoin's relatively short history and high volatility make it a more complex and potentially riskier asset. The Fed's dovish policy could enhance Bitcoin's appeal as an alternative investment, especially if traditional assets like bonds offer lower returns. However, Bitcoin's classification as a safe haven is still a matter of debate, with opinions divided on its long-term stability and value retention capabilities. **Risks and Opportunities** Investors considering Bitcoin in light of the Fed's policy change face a landscape filled with both risks and opportunities. The potential for a Bitcoin rally in a low-interest-rate environment is counterbalanced by the cryptocurrency's inherent volatility and regulatory uncertainties. Bitcoin's price movements can be dramatic and unpredictable, influenced by a range of factors from technological developments to geopolitical events. Additionally, the regulatory environment for cryptocurrencies is still evolving, with potential changes posing risks to Bitcoin's accessibility and value. Investors must also consider the broader global economic context, including actions by other central banks and international trade dynamics, which can impact Bitcoin's market movement. **Conclusion** The Federal Reserve's shift towards a more accommodative monetary policy in 2024 presents a fascinating scenario for Bitcoin and the broader cryptocurrency market. This development underscores the increasing relevance of digital assets in the global financial landscape and highlights the complex interplay between traditional monetary policies and emerging financial technologies. As Bitcoin continues to evolve and gain acceptance, its response to macroeconomic factors like central bank policies will be a critical area of focus for investors. In navigating this dynamic and uncertain environment, a cautious and well-informed approach is essential for those looking to explore the opportunities and navigate the challenges of cryptocurrency investments. The coming years promise to be a pivotal period in the maturation of Bitcoin as it responds to the shifting tides of global finance. **FAQs** **How does the Federal Reserve's easing stance impact Bitcoin?** The Fed's shift towards lower interest rates can make riskier assets like Bitcoin more attractive to investors. This is because lower rates often lead to reduced yields on traditional investments, prompting investors to seek higher returns elsewhere. **What is the significance of the Fed's 'dot plot' for Bitcoin investors?** The 'dot plot' is a projection of interest rate movements by Federal Reserve members. A shift towards lower rates, as indicated in the recent dot plot, can signal a more accommodative monetary policy, potentially impacting Bitcoin's market as investors adjust their portfolios. **Can Bitcoin be considered a safe haven asset in light of the Fed's policy?** Bitcoin's role as a safe haven asset is debated. While its fixed supply and digital nature offer some safe haven characteristics, its volatility and regulatory uncertainties make it a complex choice compared to traditional safe havens like gold. **What risks should Bitcoin investors consider in the context of the Fed's easing policy?** Investors should be aware of Bitcoin's volatility, regulatory changes, and its sensitivity to macroeconomic factors. Additionally, global economic conditions and actions by other central banks can also influence Bitcoin's market. **How does the economic backdrop influence Bitcoin's response to the Fed's policy?** Economic factors like GDP growth, inflation rates, and retail sales impact investor sentiment and risk appetite, which in turn can affect Bitcoin's market. A strong economy might reduce the appeal of risk assets like Bitcoin, while economic uncertainties can increase their attractiveness. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: @croxroadnews.co** **Instagram: @croxroadnews.co** **Youtube: @croxroadnews** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*** @ 57d1a264:69f1fee1
2025-02-13 03:45:23 **What You Will Learn:** - Understanding the concept of cybersecurity - Networking Basics - Operating Systems Overview - Introduction to Kali Linux - Threat Actors and Cyber Threats - Ethical Hacking Techniques and Tools. **How to Register:** Use this link to Register. https://forms.gle/L8AGLCWU4djwUXxz9 originally posted at https://stacker.news/items/884407
@ 57d1a264:69f1fee1
2025-02-13 03:45:23 **What You Will Learn:** - Understanding the concept of cybersecurity - Networking Basics - Operating Systems Overview - Introduction to Kali Linux - Threat Actors and Cyber Threats - Ethical Hacking Techniques and Tools. **How to Register:** Use this link to Register. https://forms.gle/L8AGLCWU4djwUXxz9 originally posted at https://stacker.news/items/884407 @ f6488c62:c929299d
2025-02-13 02:39:41Lowering interest rates is one of the tools that central banks use to manage the economy, especially during periods of inflation, which causes the prices of goods and services to rise. Lowering interest rates not only helps stimulate spending but can also foster sustainable growth in businesses and labor markets. Access to Capital and Economic Stimulation When interest rates are lowered, the public can access capital more easily. With lower interest rates, borrowing becomes less burdensome, giving individuals and businesses the opportunity to start new ventures or expand existing businesses. This leads to increased investment and spending, which in turn keeps the economy circulating and growing. For instance, when people can easily borrow money to start a new business—such as an online store or a product manufacturing business—the increase in entrepreneurs and the availability of goods in the market will ensure that the supply is sufficient to meet consumer demand. This, in turn, prevents prices from rising too much due to a lack of supply. Reducing Inflation by Increasing Supply Increasing the supply of goods and services in the market can significantly help in controlling inflation. When there are more goods or services available to meet market demand, competition among producers will naturally drive prices down. This is the basic principle of market dynamics: when there’s enough supply, prices are less likely to increase, even in times of high demand. In addition, increasing supply helps address shortages, which are one of the key drivers of rising prices. When there is enough product available to satisfy demand, inflationary pressures can be relieved, and prices can stabilize. Redistributing Income and Reducing Inequality Lower interest rates also play a crucial role in redistributing income within society. By making access to capital easier, especially for those with lower or middle incomes, the public’s purchasing power increases, which can stimulate spending on essential goods and services. When people have more money in hand, they are better able to access necessary products. This boosts demand in the market. However, alongside this increased demand, sufficient supply is needed to prevent prices from rising uncontrollably, which can lead to inflation. Moreover, supporting the population through welfare programs or initiatives that allow everyone to access education and investment opportunities helps individuals create products and value in the market. A diverse market with a variety of products increases production efficiency and helps mitigate economic inequality, ensuring a more balanced and inclusive economy. Conclusion Lowering interest rates and redistributing income effectively can stimulate economic growth and reduce inflation. This works by ensuring there is sufficient supply to meet market demand, while also providing capital that allows the public to start new businesses and generate new products in the market. For sustainable long-term economic growth, managing inflation should go hand in hand with investing in infrastructure and ensuring wealth distribution. This ensures that everyone has equal access to opportunities, leading to steady economic growth without negatively impacting the majority of society. In summary, lowering interest rates is a key tool in stimulating the economy and reducing inflation, especially when the economy faces imbalances. It not only increases supply, but also promotes income redistribution and the creation of an economy that is more equitable in the long run.
@ f6488c62:c929299d
2025-02-13 02:39:41Lowering interest rates is one of the tools that central banks use to manage the economy, especially during periods of inflation, which causes the prices of goods and services to rise. Lowering interest rates not only helps stimulate spending but can also foster sustainable growth in businesses and labor markets. Access to Capital and Economic Stimulation When interest rates are lowered, the public can access capital more easily. With lower interest rates, borrowing becomes less burdensome, giving individuals and businesses the opportunity to start new ventures or expand existing businesses. This leads to increased investment and spending, which in turn keeps the economy circulating and growing. For instance, when people can easily borrow money to start a new business—such as an online store or a product manufacturing business—the increase in entrepreneurs and the availability of goods in the market will ensure that the supply is sufficient to meet consumer demand. This, in turn, prevents prices from rising too much due to a lack of supply. Reducing Inflation by Increasing Supply Increasing the supply of goods and services in the market can significantly help in controlling inflation. When there are more goods or services available to meet market demand, competition among producers will naturally drive prices down. This is the basic principle of market dynamics: when there’s enough supply, prices are less likely to increase, even in times of high demand. In addition, increasing supply helps address shortages, which are one of the key drivers of rising prices. When there is enough product available to satisfy demand, inflationary pressures can be relieved, and prices can stabilize. Redistributing Income and Reducing Inequality Lower interest rates also play a crucial role in redistributing income within society. By making access to capital easier, especially for those with lower or middle incomes, the public’s purchasing power increases, which can stimulate spending on essential goods and services. When people have more money in hand, they are better able to access necessary products. This boosts demand in the market. However, alongside this increased demand, sufficient supply is needed to prevent prices from rising uncontrollably, which can lead to inflation. Moreover, supporting the population through welfare programs or initiatives that allow everyone to access education and investment opportunities helps individuals create products and value in the market. A diverse market with a variety of products increases production efficiency and helps mitigate economic inequality, ensuring a more balanced and inclusive economy. Conclusion Lowering interest rates and redistributing income effectively can stimulate economic growth and reduce inflation. This works by ensuring there is sufficient supply to meet market demand, while also providing capital that allows the public to start new businesses and generate new products in the market. For sustainable long-term economic growth, managing inflation should go hand in hand with investing in infrastructure and ensuring wealth distribution. This ensures that everyone has equal access to opportunities, leading to steady economic growth without negatively impacting the majority of society. In summary, lowering interest rates is a key tool in stimulating the economy and reducing inflation, especially when the economy faces imbalances. It not only increases supply, but also promotes income redistribution and the creation of an economy that is more equitable in the long run. @ 3b7fc823:e194354f
2025-02-13 02:25:42site:example.com intitle:"index of" inurl:admin intext:"password" site:example.com site:.gov site:.edu site:*.mil inurl:login inurl:admin inurl:dashboard inurl:portal intitle:"admin login" intitle:"index of /" intitle:"index of" "parent directory" intitle:"index of" "backup" filetype:pdf "confidential" filetype:xls "username | password" filetype:doc "top secret" filetype:sql "database" intext:"username" intext:"password" intext:"login" intext:"password" filetype:txt "passwords" inurl:"viewerframe?mode=" inurl:"/view.shtml" inurl:"/view/index.shtml" intitle:"index of" "wp-config.php" inurl:".git" filetype:xls intext:"email" filetype:csv intext:"email" inurl:"/setup.cgi?next_file=netgear.cfg" inurl:"/wificonf.html"
@ 3b7fc823:e194354f
2025-02-13 02:25:42site:example.com intitle:"index of" inurl:admin intext:"password" site:example.com site:.gov site:.edu site:*.mil inurl:login inurl:admin inurl:dashboard inurl:portal intitle:"admin login" intitle:"index of /" intitle:"index of" "parent directory" intitle:"index of" "backup" filetype:pdf "confidential" filetype:xls "username | password" filetype:doc "top secret" filetype:sql "database" intext:"username" intext:"password" intext:"login" intext:"password" filetype:txt "passwords" inurl:"viewerframe?mode=" inurl:"/view.shtml" inurl:"/view/index.shtml" intitle:"index of" "wp-config.php" inurl:".git" filetype:xls intext:"email" filetype:csv intext:"email" inurl:"/setup.cgi?next_file=netgear.cfg" inurl:"/wificonf.html" @ fd78c37f:a0ec0833
2025-02-13 02:24:48In this edition, we invited Rafael from Bitcoin É Aqui to share the development of his community and its efforts in promoting Bitcoin adoption. From establishing a Bitcoin-friendly environment in Rolante to organizing and supporting events like the Bitcoin Spring Festival and KuchenFest, Rafael highlighted Bitcoin's impact on the local economy and tourism industry. **YakiHonne**: Today, we are honored to invite Rafael from Bitcoin é Aqui to join us. Before we dive in, I'd like to take a moment to introduce YakiHonne and share a bit about what we do. YakiHonne is a decentralized media client built on the Nostr protocol that enables freedom of speech through technology. It empowers creators to create their own voice, assets, and features. It also allows features like smart widgets, verified notes, and focuses on long-form articles. Now today we'll be exploring more about the Bitcoin community. Rafael, could you please briefly introduce what sparked your interest in Bitcoin, and what motivated you to create this community? **Rafael**:Like many, Stim's and his wife Camila's initial interest was in technology— a completely new way to transfer money with full self-custody. From the beginning, the project focused on the payment network, and at the time, they didn’t realize it would evolve into “A Project.” **YakiHonne**: Could you share how your community got started, the strategies you used to attract members, and the early challenges you encountered? **Rafael**:From the start, we were all about building a payment network. We began by paying our barber, gardener, and other service providers with Bitcoin. After a few close friends joined, word started to spread—even though some were worried about scams and Bitcoin's legality. To address these concerns, we held a talk at the City's Trade Association on how merchants could legally accept Bitcoin. We expected 5 to 10 friends, but over 60 merchants attended! Today, we’re proud to say that our city is the most Bitcoin-friendly in the world, with more than 40% of stores accepting it. From plumbers to supermarkets, it’s amazing to see our community featured on the BitcoinMap website.  **YakiHonne**: What principles guide the community, and how do you maintain trust and reliability in discussions? **Rafael**:Like Bitcoin itself, decentralization is our core principle. The project "Bitcoin É Aqui" (loosely translated as "Bitcoin is Here") assists merchants in setting up Lightning wallets and offers best practices. However, every merchant is free to operate as they see fit—choosing whether to follow our advice or to use any wallet they prefer. Moreover, many experienced merchants help onboard newcomers, building trust through established networks and reinforcing our decentralized approach. **YakiHonne**: How do you educate members and keep them updated on Bitcoin developments? **Rafael**:We have a group chat where we post some news, but in Brazil, almost everyone already uses WhatsApp for communication, and news usually spreads through these groups, again highlighting the decentralized nature of the Project. **YakiHonne**: What initiatives has the community undertaken to promote Bitcoin adoption, and what results have you seen? **Rafael**:Of course, the rising coin value draws attention, but the main attraction is tourists coming to Rolante to learn about the project. Rolante was already famed for its natural wonders—majestic mountains and breathtaking waterfalls. Combined with Bitcoin’s innovative acceptance as a payment method, it has become an even stronger magnet for visitors. **Rafael**:In Rolante, living completely on Bitcoin is a reality. Here, you'll find travel agencies, professional tour guides, and a variety of services—from department stores and opticians to real estate agents, construction companies, architects, furniture stores, building materials suppliers, and solar energy providers. In the healthcare sector, you can rely on pharmacies, massage therapists, physiotherapists, and advanced dental services; even the city hospital accepts Bitcoin as payment.  **YakiHonne**: What are the community’s goals for the next 6-12 months, and how do you see it evolving with Bitcoin’s growth? **Rafael**:As a project, Bitcoin É Aqui doesn’t dictate what the community should do, but we support many events like Pizza Day, Bitcoin Spring Festival, Bier Rock, KuchenFest. One major event is the biennial Bitcoin Spring Festival (BSF). The Bitcoin Spring Festival (BSF) is a key event in the Rolante Bitcoin community, aimed at promoting Bitcoin adoption and circular economy development. This year, the festival focuses on "Bitcoinization," bringing together notable figures in the Bitcoin space to showcase a real Bitcoin economic ecosystem. During the event, all transactions will be conducted via the Lightning Network, with Coinos.io and Wallet Of Satoshi recommended. BSF is not just a celebration but a movement toward financial freedom.  **Rafael**:This March, Rolante will host its most traditional event, KuchenFest, celebrating the local traditional bread delicacy. The event centers around the sweet bread Cuca, bringing together candy makers and Cuca enthusiasts to share recipes, techniques, and stories. Additionally, the festival features live music, folk dances, and family activities, showcasing rich cultural traditions. We will help the event accept and promote the use of Bitcoin.
@ fd78c37f:a0ec0833
2025-02-13 02:24:48In this edition, we invited Rafael from Bitcoin É Aqui to share the development of his community and its efforts in promoting Bitcoin adoption. From establishing a Bitcoin-friendly environment in Rolante to organizing and supporting events like the Bitcoin Spring Festival and KuchenFest, Rafael highlighted Bitcoin's impact on the local economy and tourism industry. **YakiHonne**: Today, we are honored to invite Rafael from Bitcoin é Aqui to join us. Before we dive in, I'd like to take a moment to introduce YakiHonne and share a bit about what we do. YakiHonne is a decentralized media client built on the Nostr protocol that enables freedom of speech through technology. It empowers creators to create their own voice, assets, and features. It also allows features like smart widgets, verified notes, and focuses on long-form articles. Now today we'll be exploring more about the Bitcoin community. Rafael, could you please briefly introduce what sparked your interest in Bitcoin, and what motivated you to create this community? **Rafael**:Like many, Stim's and his wife Camila's initial interest was in technology— a completely new way to transfer money with full self-custody. From the beginning, the project focused on the payment network, and at the time, they didn’t realize it would evolve into “A Project.” **YakiHonne**: Could you share how your community got started, the strategies you used to attract members, and the early challenges you encountered? **Rafael**:From the start, we were all about building a payment network. We began by paying our barber, gardener, and other service providers with Bitcoin. After a few close friends joined, word started to spread—even though some were worried about scams and Bitcoin's legality. To address these concerns, we held a talk at the City's Trade Association on how merchants could legally accept Bitcoin. We expected 5 to 10 friends, but over 60 merchants attended! Today, we’re proud to say that our city is the most Bitcoin-friendly in the world, with more than 40% of stores accepting it. From plumbers to supermarkets, it’s amazing to see our community featured on the BitcoinMap website.  **YakiHonne**: What principles guide the community, and how do you maintain trust and reliability in discussions? **Rafael**:Like Bitcoin itself, decentralization is our core principle. The project "Bitcoin É Aqui" (loosely translated as "Bitcoin is Here") assists merchants in setting up Lightning wallets and offers best practices. However, every merchant is free to operate as they see fit—choosing whether to follow our advice or to use any wallet they prefer. Moreover, many experienced merchants help onboard newcomers, building trust through established networks and reinforcing our decentralized approach. **YakiHonne**: How do you educate members and keep them updated on Bitcoin developments? **Rafael**:We have a group chat where we post some news, but in Brazil, almost everyone already uses WhatsApp for communication, and news usually spreads through these groups, again highlighting the decentralized nature of the Project. **YakiHonne**: What initiatives has the community undertaken to promote Bitcoin adoption, and what results have you seen? **Rafael**:Of course, the rising coin value draws attention, but the main attraction is tourists coming to Rolante to learn about the project. Rolante was already famed for its natural wonders—majestic mountains and breathtaking waterfalls. Combined with Bitcoin’s innovative acceptance as a payment method, it has become an even stronger magnet for visitors. **Rafael**:In Rolante, living completely on Bitcoin is a reality. Here, you'll find travel agencies, professional tour guides, and a variety of services—from department stores and opticians to real estate agents, construction companies, architects, furniture stores, building materials suppliers, and solar energy providers. In the healthcare sector, you can rely on pharmacies, massage therapists, physiotherapists, and advanced dental services; even the city hospital accepts Bitcoin as payment.  **YakiHonne**: What are the community’s goals for the next 6-12 months, and how do you see it evolving with Bitcoin’s growth? **Rafael**:As a project, Bitcoin É Aqui doesn’t dictate what the community should do, but we support many events like Pizza Day, Bitcoin Spring Festival, Bier Rock, KuchenFest. One major event is the biennial Bitcoin Spring Festival (BSF). The Bitcoin Spring Festival (BSF) is a key event in the Rolante Bitcoin community, aimed at promoting Bitcoin adoption and circular economy development. This year, the festival focuses on "Bitcoinization," bringing together notable figures in the Bitcoin space to showcase a real Bitcoin economic ecosystem. During the event, all transactions will be conducted via the Lightning Network, with Coinos.io and Wallet Of Satoshi recommended. BSF is not just a celebration but a movement toward financial freedom.  **Rafael**:This March, Rolante will host its most traditional event, KuchenFest, celebrating the local traditional bread delicacy. The event centers around the sweet bread Cuca, bringing together candy makers and Cuca enthusiasts to share recipes, techniques, and stories. Additionally, the festival features live music, folk dances, and family activities, showcasing rich cultural traditions. We will help the event accept and promote the use of Bitcoin. @ ac6f9572:8a6853dd
2025-02-13 02:05:22I attended Sats ‘n’ Facts to share my art, joining other Nostr artists in exhibiting our work at the event’s very first venue. It was a great opportunity to connect with fellow creatives, including Siritravelsketch, whose work I’ve admired on Nostr for some time. Meeting other artists in real life is always inspiring—there’s an undeniable creative bond that comes from sharing our passion in person.  Sats ‘n’ Facts is an Unconference, meaning there’s no strict schedule—everything is open for participants. It’s all about the connections made, the synergy shared, and, for the developers attending, the excitement of a hackathon. (A hackathon is an event where people collaborate intensively on engineering projects, often within 24 to 48 hours.)  My goal as an artist is to become a bridge between the Bitcoin tech world and the Bitcoin art and design space. Bitcoin empowers us by providing greater (financial) freedom, and with that freedom comes more time to pursue what we truly love—so in a way, you never have to “work” again. 😊  Nostr is a great example of how bubbles 🫧 POP, leading to new collaborations. Without tech, artists wouldn’t have a way to share their work, and without artists, creatives, and plebs, developers would have no one to build for. Both sides are essential for organic growth. This kind of synergy can only thrive in a decentralized system—otherwise, it risks being captured by big corporations. And that single point of failure is one of the biggest challenges we face in the world today.  Decentralization is freedom. Events like Sats ‘n’ Facts give us the opportunity to collaborate, create, and contribute to a more decentralized world—one where more people can truly become free.  Can’t wait to join the next Sats’n’facts. Maybe Barcelona!? * * * Originally article published by @BitPopArt on @YakiHonne: https://yakihonne.com/article/naddr1qvzqqqr4gupzqsa64uxz3ek0kx2mzlhqs0seavay4l06c4xek6a0zup8pmge8c6vqq242en0tukk7u2fwe8kkjrpv3ykgjtzwfsk5hmmfyp #art #nostr #ThaiNostrich #artonnostr #artstr originally posted at https://stacker.news/items/884327
@ ac6f9572:8a6853dd
2025-02-13 02:05:22I attended Sats ‘n’ Facts to share my art, joining other Nostr artists in exhibiting our work at the event’s very first venue. It was a great opportunity to connect with fellow creatives, including Siritravelsketch, whose work I’ve admired on Nostr for some time. Meeting other artists in real life is always inspiring—there’s an undeniable creative bond that comes from sharing our passion in person.  Sats ‘n’ Facts is an Unconference, meaning there’s no strict schedule—everything is open for participants. It’s all about the connections made, the synergy shared, and, for the developers attending, the excitement of a hackathon. (A hackathon is an event where people collaborate intensively on engineering projects, often within 24 to 48 hours.)  My goal as an artist is to become a bridge between the Bitcoin tech world and the Bitcoin art and design space. Bitcoin empowers us by providing greater (financial) freedom, and with that freedom comes more time to pursue what we truly love—so in a way, you never have to “work” again. 😊  Nostr is a great example of how bubbles 🫧 POP, leading to new collaborations. Without tech, artists wouldn’t have a way to share their work, and without artists, creatives, and plebs, developers would have no one to build for. Both sides are essential for organic growth. This kind of synergy can only thrive in a decentralized system—otherwise, it risks being captured by big corporations. And that single point of failure is one of the biggest challenges we face in the world today.  Decentralization is freedom. Events like Sats ‘n’ Facts give us the opportunity to collaborate, create, and contribute to a more decentralized world—one where more people can truly become free.  Can’t wait to join the next Sats’n’facts. Maybe Barcelona!? * * * Originally article published by @BitPopArt on @YakiHonne: https://yakihonne.com/article/naddr1qvzqqqr4gupzqsa64uxz3ek0kx2mzlhqs0seavay4l06c4xek6a0zup8pmge8c6vqq242en0tukk7u2fwe8kkjrpv3ykgjtzwfsk5hmmfyp #art #nostr #ThaiNostrich #artonnostr #artstr originally posted at https://stacker.news/items/884327 @ df478568:2a951e67
2025-02-13 02:04:30In the very early days, Nostr was pretty much troll-free. It was one of my favorite things about it, but I suspected this was only the case because only hardcore bitcoiners were on there. Now that the network is growing, there is more diversity of ideas. Ideology tends to make people mean. Mean people suck, so I try to remain respectful even when I disagree with others. I am not a fan of communism, but enjoy reading other perspectives. I do not wish to censor any speech at all, especially speech I do not agree with. The freedom of speech is not about the First Amendment to me. It's about creating a space that is safe for free speech. Platforms are not a safe space for free speech. The safety of free speech is in peril on platforms. Nostr is a space where people can speak freely in an open Internet-connected society. There is some speech I would rather not see. I wish some people did not say certain things, but I do not want to stop them. If we censor the worst speech, the speech does not go away. It merely goes underground and creates bad speech silos where people hide their true selves and go only speak to people just like them. Censorship is like prison for ideas. Prisoners improve their robbery skills because they exchange ideas with other criminals. It's like a conference for criminals. Fascists get more fascist when they only have permission to talk to fellow fascists. Communists get more communist when they can only talk to other communists. Ideas are a marketplace. May the best ideas win. Nostr allows me to speak with people about topics I might not otherwise get a chance to speak about. I never see any pro-communist posts on Twitter. That's a problem because communists also don't see me. I also never saw sex workers talk about anything other than kinky-boinky talk on Twitter. Nostr brings the humanity back to sex workers. Sex workers are people too. They have interesting ideas and take [interesting photos]([take interesting pictures](nostr:note1svl3ne6l7dkxx4gckqsttx24nva7m37ynam7rvgq4zu83u9wl2ks86ahwx). ) On the [What is Money Show](https://fountain.fm/episode/DYPKRSkN11EmYDhrhH0H), Rabble says he wants to have Christians have a Christian-only Nostr network and sex workers to have a sex worker-only network. It's a fun idea, but I'm not convinced this would be a good thing. What if Jesus was on the Christian Nostr, but Mary Magdalen was on sex worker Nostr? I suspect Christians talking to sex workers is not such a bad thing. **What would Jesus do?** Here is a conversation I had with a stripper on nostr. You can read the original [here](nostr:note1wxalrm6tpftrrs9rmzvv4e5gpnamkmfuu6fpwu9gs3wtudeegd7qpd5l0r) but I have reprinted it on the Habla and Substack. I don't believe it's possible for a community or state to abolish private property when the private property can be distilled into 12 secret random words. Ironically, bitcoin does give the means of monetary production to the people, but this is a moot point given that individual people do not have equal ability. Very few people had sufficient knowledge to mine bitcoin when the block reward was 50 bitcoin every 10 minutes. Therefore, even though anybody could technically produce bitcoin blocks, very few people can. The same is true for saving. Even if we could defy human nature with schemes such as this, it would not solve wealth inequality. Most people spend money like drunken sailors. If everyone had the same income that could not be debased or stolen, broke people would still exist because people do not have equal money management skills. That is why I prefer capitalism with a non-socialist monetary system. The United States, contrary to popular belief, is not a capitalist economic system. It's a mixed economy where some people (banks and government) get money without doing any work aside from fudging numbers. A bank does not save capital to buy a house. Banks print money to buy homes and collect rent from homeowners. It's an accounting trick, not capitalism. Here's how capitalism works according to economist, Russ Roberts. https://youtu.be/ljULutAUL7o?si=bLPY5IvwwMQvfXJK npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 https://mempool.marc26z.com/block/00000000000000000001fa33d3d7750ed315d94e3c1def6512281b33bece333b
@ df478568:2a951e67
2025-02-13 02:04:30In the very early days, Nostr was pretty much troll-free. It was one of my favorite things about it, but I suspected this was only the case because only hardcore bitcoiners were on there. Now that the network is growing, there is more diversity of ideas. Ideology tends to make people mean. Mean people suck, so I try to remain respectful even when I disagree with others. I am not a fan of communism, but enjoy reading other perspectives. I do not wish to censor any speech at all, especially speech I do not agree with. The freedom of speech is not about the First Amendment to me. It's about creating a space that is safe for free speech. Platforms are not a safe space for free speech. The safety of free speech is in peril on platforms. Nostr is a space where people can speak freely in an open Internet-connected society. There is some speech I would rather not see. I wish some people did not say certain things, but I do not want to stop them. If we censor the worst speech, the speech does not go away. It merely goes underground and creates bad speech silos where people hide their true selves and go only speak to people just like them. Censorship is like prison for ideas. Prisoners improve their robbery skills because they exchange ideas with other criminals. It's like a conference for criminals. Fascists get more fascist when they only have permission to talk to fellow fascists. Communists get more communist when they can only talk to other communists. Ideas are a marketplace. May the best ideas win. Nostr allows me to speak with people about topics I might not otherwise get a chance to speak about. I never see any pro-communist posts on Twitter. That's a problem because communists also don't see me. I also never saw sex workers talk about anything other than kinky-boinky talk on Twitter. Nostr brings the humanity back to sex workers. Sex workers are people too. They have interesting ideas and take [interesting photos]([take interesting pictures](nostr:note1svl3ne6l7dkxx4gckqsttx24nva7m37ynam7rvgq4zu83u9wl2ks86ahwx). ) On the [What is Money Show](https://fountain.fm/episode/DYPKRSkN11EmYDhrhH0H), Rabble says he wants to have Christians have a Christian-only Nostr network and sex workers to have a sex worker-only network. It's a fun idea, but I'm not convinced this would be a good thing. What if Jesus was on the Christian Nostr, but Mary Magdalen was on sex worker Nostr? I suspect Christians talking to sex workers is not such a bad thing. **What would Jesus do?** Here is a conversation I had with a stripper on nostr. You can read the original [here](nostr:note1wxalrm6tpftrrs9rmzvv4e5gpnamkmfuu6fpwu9gs3wtudeegd7qpd5l0r) but I have reprinted it on the Habla and Substack. I don't believe it's possible for a community or state to abolish private property when the private property can be distilled into 12 secret random words. Ironically, bitcoin does give the means of monetary production to the people, but this is a moot point given that individual people do not have equal ability. Very few people had sufficient knowledge to mine bitcoin when the block reward was 50 bitcoin every 10 minutes. Therefore, even though anybody could technically produce bitcoin blocks, very few people can. The same is true for saving. Even if we could defy human nature with schemes such as this, it would not solve wealth inequality. Most people spend money like drunken sailors. If everyone had the same income that could not be debased or stolen, broke people would still exist because people do not have equal money management skills. That is why I prefer capitalism with a non-socialist monetary system. The United States, contrary to popular belief, is not a capitalist economic system. It's a mixed economy where some people (banks and government) get money without doing any work aside from fudging numbers. A bank does not save capital to buy a house. Banks print money to buy homes and collect rent from homeowners. It's an accounting trick, not capitalism. Here's how capitalism works according to economist, Russ Roberts. https://youtu.be/ljULutAUL7o?si=bLPY5IvwwMQvfXJK npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 https://mempool.marc26z.com/block/00000000000000000001fa33d3d7750ed315d94e3c1def6512281b33bece333b @ 97c70a44:ad98e322
2025-02-13 02:03:33Everyone knows that relays are central to how nostr works - they're even in the name: Notes and Other Stuff Transmitted by *Relays*. As time goes on though, there are three other letters which are becoming conspicuously absent from our beloved and ambiguously pronounceable acronym - "D", "V", and "M". The hype cycle for DVMs seems to have reached escape velocity in a way few other things have - zaps being the possible exception. But *what* exactly DVMs are remains something of a mystery to many nostr developers - and how to build one may as well be written on clay tablets. This blog post is designed to address that - below is a soup to nuts (no nutzaps though) guide to building a DVM flow, both from the client and the server side. Here's what we'll be covering: - Discovering DVM metadata - Basic request/response flow - Implementing a minimal example Let's get started! # DVM Metadata First of all, it's helpful to know how DVMs are reified on the nostr network. While not strictly necessary, this can be useful for discovering DVMs and presenting them to users, and for targeting specific DVMs we want a response from. [NIP 89](https://github.com/nostr-protocol/nips/blob/master/89.md) goes into this in more detail, but the basic idea is that anyone can create a `kind 31990` "application handler" event and publish it to the network with their own (or a dedicated) public key. This handler was originally intended to advertise clients, but has been re-purposed for DVM listings as well. Here's what the "Fluffy Frens" handler looks like: ```json { "content": "{\"name\": \"Fluffy Frens\", \"picture\": \"https://image.nostr.build/f609311532c470f663e129510a76c9a1912ae9bc4aaaf058e5ba21cfb512c88e.jpg\", \"about\": \"I show recent notes about animals\", \"lud16\": \"discovery_content_fluffy@nostrdvm.com\", \"supportsEncryption\": true, \"acceptsNutZaps\": false, \"personalized\": false, \"amount\": \"free\", \"nip90Params\": {\"max_results\": {\"required\": false, \"values\": [], \"description\": \"The number of maximum results to return (default currently 100)\"}}}", "created_at": 1738874694, "id": "0aa8d1f19cfe17e00ce55ca86fea487c83be39a1813601f56f869abdfa776b3c", "kind": 31990, "pubkey": "7b7373dd58554ff4c0d28b401b9eae114bd92e30d872ae843b9a217375d66f9d", "sig": "22403a7996147da607cf215994ab3b893176e5302a44a245e9c0d91214e4c56fae40d2239dce58ea724114591e8f95caed2ba1a231d09a6cd06c9f0980e1abd5", "tags": [ ["k", "5300"], ["d", "198650843898570c"] ] } ``` This event is rendered in various clients using the kind-0-style metadata contained in the `content` field, allowing users to browse DVMs and pick one for their use case. If a user likes using a particular DVM, they might publish a `kind 31989` "application recommendation", which other users can use to find DVMs that are in use within their network. Note the `k` tag in the handler event - this allows DVMs to advertise support only for specific job types. It's also important to note that even though the spec doesn't cover relay selection, most clients use the publisher's `kind 10002` event to find out where the DVM listens for events. If this looks messy to you, you're right. See [this PR](https://github.com/nostr-protocol/nips/pull/1728) for a proposal to split DVMs out into their own handler kind, give them a dedicated pubkey along with dedicated metadata and relay selections, and clean up the data model a bit. # DVM Flow Now that we know what a DVM looks like, we can start to address how they work. My explanation below will elide some of the detail involved in [NIP 90](https://github.com/nostr-protocol/nips/blob/master/90.md) for simplicity, so I encourage you to read the complete spec. The basic DVM flow can be a little (very) confusing to work with, because in essence it's a request/response paradigm, but it has some additional wrinkles. First of all, the broker for the request isn't abstracted away as is usually the case with request/response flows. Regular HTTP requests involve all kinds of work in the background - from resolving domain names to traversing routers, VPNs, and ISP infrastructure. But developers don't generally have to care about all these intermediaries. With DVMs, on the other hand, the essential complexity of relay selection can't simply be ignored. DVMs often advertise their own relay selections, which should be used rather than a hard-coded or randomly chosen relay to ensure messages are delivered. The benefit of this is that DVMs can avoid censorship, just as users can, by choosing relays that are willing to broker their activity. DVMs can even select multiple relays to broker requests, which means that clients might receive multiple copies of the same response. Secondly, the DVM request/response model is far more fluid than is usually the case with request/response flows. There are a set of standard practices, but the flow is flexible enough to admit exceptions to these conventions for special use cases. Here are some examples: - Normally, clients p-tag the DVM they wish to address. But if a client isn't picky about where a response comes from, they may choose to send an open request to the network and collect responses from multiple DVMs simultaneously. - Normally, a client creates a request before collecting responses using a subscription with an e-tag filter matching the request event. But clients may choose to skip the request step entirely and collect responses from the network that have already been created. This can be useful for computationally intensive tasks or common queries, where a single result can be re-used multiple times. - Sometimes, a DVM may respond with a `kind 7000` job status event to let clients know they're working on the request. This is particularly useful for longer-running tasks, where feedback is useful for building a responsive UX. - There are also some details in the spec regarding monetization, parameterization, error codes, encryption, etc. # Example DVM implementation For the purposes of this blog post, I'll keep things simple by illustrating the most common kind of DVM flow: a `kind 5300` [content discovery](https://www.data-vending-machines.org/kinds/5300/) request, addressed to a particular DVM. If you're interested in other use cases, please visit [data-vending-machines.org](https://data-vending-machines.org) for additional documented kinds. The basic flow looks like this: - The DVM starts by listening for `kind 5300` job requests on some relays it has selected and advertised via NIP 89 (more on that later) - A client creates a request event of `kind 5300`, p-tagged with the DVM's pubkey and sends it to the DVM's relay selections. - The DVM receives the event and processes it, issuing optional `kind 7000` job status events, and eventually issuing a `kind 6300` job result event (job result event kinds are always 1000 greater than the request's kind). - The client listens to the same relays for a response, and when it comes through does whatever it wants to with it. Here's a swimlane diagram of that flow:  To avoid massive code samples, I'm going to implement our DVM entirely using nak (backed by the power of the human mind). The first step is to start our DVM listening for requests that it wants to respond to. Nak's default pubkey is `79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798`, so we'll only listen for requests sent to nak. ```bash nak req -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 ``` This gives us the following filter: ```json ["REQ","nak",{"kinds":[5300],"#p":["79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"]}] ``` To open a subscription to `nos.lol` and stream job requests, add `--stream wss://nos.lol` to the previous request and leave it running. Next, open a new terminal window for our "client" and create a job request. In this case, there's nothing we need to provide as `input`, but we'll include it just for illustration. It's also good practice to include an `expiration` tag so we're not asking relays to keep our ephemeral requests forever. ```bash nak event -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 -t expiration=$(( $(date +%s) + 30 )) -t input=hello ``` Here's what comes out: ```json { "kind": 5300, "id": "0e419d0b3c5d29f86d2132a38ca29cdfb81a246e1a649cb2fe1b9ed6144ebe30", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739407684, "tags": [ ["p", "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"], ["expiration", "1739407683"], ["input", "hello"] ], "content": "", "sig": "560807548a75779a7a68c0ea73c6f097583e2807f4bb286c39931e99a4e377c0a64af664fa90f43e01ddd1de2e9405acd4e268f1bf3bc66f0ed5a866ea093966" } ``` Now go ahead and publish this event by adding `nos.lol` to the end of your `nak` command. If all goes well, you should see your event pop up in your "dvm" subscription. If so, great! That's half of the flow. Next, we'll want our client to start listening for `kind 6300` responses to the request. In your "client" terminal window, run: ```bash nak req -k 6300 -t e=<your-eventid-here> --stream nos.lol ``` Note that if you only want to accept responses from the specified DVM (a good policy in general to avoid spam) you would include a `p` tag here. I've omitted it for brevity. Also notice the `k` tag specifies the request kind plus `1000` - this is just a convention for what kinds requests and responses use. Now, according to [data-vending-machines.org](https://www.data-vending-machines.org/kinds/5300/), `kind 5300` responses are supposed to put a JSON-encoded list of e-tags in the `content` field of the response. Weird, but ok. Stop the subscription in your "dvm" terminal and respond to your "client" with a recommendation to read my first note: ```bash nak event -k 6300 -t e=a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf -c '[["e","214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08","wss://nos.lol/"]]' nos.lol ``` Here's the response event we're sending: ```json { "kind": 6300, "id": "bb5f38920cbca15d3c79021f7d0051e82337254a84c56e0f4182578e4025232e", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739408411, "tags": [ ["e", "a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf"] ], "content": "[[\"e\",\"214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08\",\"wss://nos.lol/\"]]", "sig": "a0fe2c3419c5c54cf2a6d9a2a5726b2a5b766d3c9e55d55568140979354003aacb038e90bdead43becf5956faa54e3b60ff18c0ea4d8e7dfdf0c8dd97fb24ff9" } ``` Notice the `e` tag targets our original request. This should result in the job result event showing up in our "client" terminal. Success! If something isn't working, I've also create a video of the full process with some commentary which you can find [here](https://coracle-media.us-southeast-1.linodeobjects.com/nakflow.mov). Note that in practice, DVMs can be much more picky about the requests they will respond to, due to implementations failing to follow [Postel's law](https://en.wikipedia.org/wiki/Robustness_principle). Hopefully that will improve over time. For now, here are a few resources that are useful when working with or developing DVMs: - [dvmdash](https://dvmdash.live) - [data-vending-machines.org](https://data-vending-machines.org) - [noogle](https://noogle.lol/) - [nostrdvm](https://github.com/believethehype/nostrdvm) # Conclusion I started this post by hinting that DVMs might be as fundamental as relays are to making nostr work. But (apart from the fact that we'd end up with an acronym like DVMNOSTRZ+*, which would only exascerbate the pronounciation wars (if such a thing were possible)), that's not exactly true. DVMs have emerged as a central paradigm in the nostr world because they're a generalization of a design pattern unique to nostr's architecture - but which exists in many other places, including NIP 46 signer flows and NIP 47 wallet connect. Each of these sub-protocols works by using relays as neutral brokers for requests in order to avoid coupling services to web addresses. This approach has all kinds of neat benefits, not least of which is allowing service providers to host their software without having to accept incoming TCP connections. But it's really an emergent property of relays, which not only are useful for brokering communication between users (aka storing events), but also brokering communication between machines. The possibilities of this architecture have only started to emerge, so be on the lookout for new applications, and don't be afraid to experiment - just please, don't serialize json inside json 🤦♂️
@ 97c70a44:ad98e322
2025-02-13 02:03:33Everyone knows that relays are central to how nostr works - they're even in the name: Notes and Other Stuff Transmitted by *Relays*. As time goes on though, there are three other letters which are becoming conspicuously absent from our beloved and ambiguously pronounceable acronym - "D", "V", and "M". The hype cycle for DVMs seems to have reached escape velocity in a way few other things have - zaps being the possible exception. But *what* exactly DVMs are remains something of a mystery to many nostr developers - and how to build one may as well be written on clay tablets. This blog post is designed to address that - below is a soup to nuts (no nutzaps though) guide to building a DVM flow, both from the client and the server side. Here's what we'll be covering: - Discovering DVM metadata - Basic request/response flow - Implementing a minimal example Let's get started! # DVM Metadata First of all, it's helpful to know how DVMs are reified on the nostr network. While not strictly necessary, this can be useful for discovering DVMs and presenting them to users, and for targeting specific DVMs we want a response from. [NIP 89](https://github.com/nostr-protocol/nips/blob/master/89.md) goes into this in more detail, but the basic idea is that anyone can create a `kind 31990` "application handler" event and publish it to the network with their own (or a dedicated) public key. This handler was originally intended to advertise clients, but has been re-purposed for DVM listings as well. Here's what the "Fluffy Frens" handler looks like: ```json { "content": "{\"name\": \"Fluffy Frens\", \"picture\": \"https://image.nostr.build/f609311532c470f663e129510a76c9a1912ae9bc4aaaf058e5ba21cfb512c88e.jpg\", \"about\": \"I show recent notes about animals\", \"lud16\": \"discovery_content_fluffy@nostrdvm.com\", \"supportsEncryption\": true, \"acceptsNutZaps\": false, \"personalized\": false, \"amount\": \"free\", \"nip90Params\": {\"max_results\": {\"required\": false, \"values\": [], \"description\": \"The number of maximum results to return (default currently 100)\"}}}", "created_at": 1738874694, "id": "0aa8d1f19cfe17e00ce55ca86fea487c83be39a1813601f56f869abdfa776b3c", "kind": 31990, "pubkey": "7b7373dd58554ff4c0d28b401b9eae114bd92e30d872ae843b9a217375d66f9d", "sig": "22403a7996147da607cf215994ab3b893176e5302a44a245e9c0d91214e4c56fae40d2239dce58ea724114591e8f95caed2ba1a231d09a6cd06c9f0980e1abd5", "tags": [ ["k", "5300"], ["d", "198650843898570c"] ] } ``` This event is rendered in various clients using the kind-0-style metadata contained in the `content` field, allowing users to browse DVMs and pick one for their use case. If a user likes using a particular DVM, they might publish a `kind 31989` "application recommendation", which other users can use to find DVMs that are in use within their network. Note the `k` tag in the handler event - this allows DVMs to advertise support only for specific job types. It's also important to note that even though the spec doesn't cover relay selection, most clients use the publisher's `kind 10002` event to find out where the DVM listens for events. If this looks messy to you, you're right. See [this PR](https://github.com/nostr-protocol/nips/pull/1728) for a proposal to split DVMs out into their own handler kind, give them a dedicated pubkey along with dedicated metadata and relay selections, and clean up the data model a bit. # DVM Flow Now that we know what a DVM looks like, we can start to address how they work. My explanation below will elide some of the detail involved in [NIP 90](https://github.com/nostr-protocol/nips/blob/master/90.md) for simplicity, so I encourage you to read the complete spec. The basic DVM flow can be a little (very) confusing to work with, because in essence it's a request/response paradigm, but it has some additional wrinkles. First of all, the broker for the request isn't abstracted away as is usually the case with request/response flows. Regular HTTP requests involve all kinds of work in the background - from resolving domain names to traversing routers, VPNs, and ISP infrastructure. But developers don't generally have to care about all these intermediaries. With DVMs, on the other hand, the essential complexity of relay selection can't simply be ignored. DVMs often advertise their own relay selections, which should be used rather than a hard-coded or randomly chosen relay to ensure messages are delivered. The benefit of this is that DVMs can avoid censorship, just as users can, by choosing relays that are willing to broker their activity. DVMs can even select multiple relays to broker requests, which means that clients might receive multiple copies of the same response. Secondly, the DVM request/response model is far more fluid than is usually the case with request/response flows. There are a set of standard practices, but the flow is flexible enough to admit exceptions to these conventions for special use cases. Here are some examples: - Normally, clients p-tag the DVM they wish to address. But if a client isn't picky about where a response comes from, they may choose to send an open request to the network and collect responses from multiple DVMs simultaneously. - Normally, a client creates a request before collecting responses using a subscription with an e-tag filter matching the request event. But clients may choose to skip the request step entirely and collect responses from the network that have already been created. This can be useful for computationally intensive tasks or common queries, where a single result can be re-used multiple times. - Sometimes, a DVM may respond with a `kind 7000` job status event to let clients know they're working on the request. This is particularly useful for longer-running tasks, where feedback is useful for building a responsive UX. - There are also some details in the spec regarding monetization, parameterization, error codes, encryption, etc. # Example DVM implementation For the purposes of this blog post, I'll keep things simple by illustrating the most common kind of DVM flow: a `kind 5300` [content discovery](https://www.data-vending-machines.org/kinds/5300/) request, addressed to a particular DVM. If you're interested in other use cases, please visit [data-vending-machines.org](https://data-vending-machines.org) for additional documented kinds. The basic flow looks like this: - The DVM starts by listening for `kind 5300` job requests on some relays it has selected and advertised via NIP 89 (more on that later) - A client creates a request event of `kind 5300`, p-tagged with the DVM's pubkey and sends it to the DVM's relay selections. - The DVM receives the event and processes it, issuing optional `kind 7000` job status events, and eventually issuing a `kind 6300` job result event (job result event kinds are always 1000 greater than the request's kind). - The client listens to the same relays for a response, and when it comes through does whatever it wants to with it. Here's a swimlane diagram of that flow:  To avoid massive code samples, I'm going to implement our DVM entirely using nak (backed by the power of the human mind). The first step is to start our DVM listening for requests that it wants to respond to. Nak's default pubkey is `79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798`, so we'll only listen for requests sent to nak. ```bash nak req -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 ``` This gives us the following filter: ```json ["REQ","nak",{"kinds":[5300],"#p":["79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"]}] ``` To open a subscription to `nos.lol` and stream job requests, add `--stream wss://nos.lol` to the previous request and leave it running. Next, open a new terminal window for our "client" and create a job request. In this case, there's nothing we need to provide as `input`, but we'll include it just for illustration. It's also good practice to include an `expiration` tag so we're not asking relays to keep our ephemeral requests forever. ```bash nak event -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 -t expiration=$(( $(date +%s) + 30 )) -t input=hello ``` Here's what comes out: ```json { "kind": 5300, "id": "0e419d0b3c5d29f86d2132a38ca29cdfb81a246e1a649cb2fe1b9ed6144ebe30", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739407684, "tags": [ ["p", "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"], ["expiration", "1739407683"], ["input", "hello"] ], "content": "", "sig": "560807548a75779a7a68c0ea73c6f097583e2807f4bb286c39931e99a4e377c0a64af664fa90f43e01ddd1de2e9405acd4e268f1bf3bc66f0ed5a866ea093966" } ``` Now go ahead and publish this event by adding `nos.lol` to the end of your `nak` command. If all goes well, you should see your event pop up in your "dvm" subscription. If so, great! That's half of the flow. Next, we'll want our client to start listening for `kind 6300` responses to the request. In your "client" terminal window, run: ```bash nak req -k 6300 -t e=<your-eventid-here> --stream nos.lol ``` Note that if you only want to accept responses from the specified DVM (a good policy in general to avoid spam) you would include a `p` tag here. I've omitted it for brevity. Also notice the `k` tag specifies the request kind plus `1000` - this is just a convention for what kinds requests and responses use. Now, according to [data-vending-machines.org](https://www.data-vending-machines.org/kinds/5300/), `kind 5300` responses are supposed to put a JSON-encoded list of e-tags in the `content` field of the response. Weird, but ok. Stop the subscription in your "dvm" terminal and respond to your "client" with a recommendation to read my first note: ```bash nak event -k 6300 -t e=a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf -c '[["e","214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08","wss://nos.lol/"]]' nos.lol ``` Here's the response event we're sending: ```json { "kind": 6300, "id": "bb5f38920cbca15d3c79021f7d0051e82337254a84c56e0f4182578e4025232e", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739408411, "tags": [ ["e", "a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf"] ], "content": "[[\"e\",\"214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08\",\"wss://nos.lol/\"]]", "sig": "a0fe2c3419c5c54cf2a6d9a2a5726b2a5b766d3c9e55d55568140979354003aacb038e90bdead43becf5956faa54e3b60ff18c0ea4d8e7dfdf0c8dd97fb24ff9" } ``` Notice the `e` tag targets our original request. This should result in the job result event showing up in our "client" terminal. Success! If something isn't working, I've also create a video of the full process with some commentary which you can find [here](https://coracle-media.us-southeast-1.linodeobjects.com/nakflow.mov). Note that in practice, DVMs can be much more picky about the requests they will respond to, due to implementations failing to follow [Postel's law](https://en.wikipedia.org/wiki/Robustness_principle). Hopefully that will improve over time. For now, here are a few resources that are useful when working with or developing DVMs: - [dvmdash](https://dvmdash.live) - [data-vending-machines.org](https://data-vending-machines.org) - [noogle](https://noogle.lol/) - [nostrdvm](https://github.com/believethehype/nostrdvm) # Conclusion I started this post by hinting that DVMs might be as fundamental as relays are to making nostr work. But (apart from the fact that we'd end up with an acronym like DVMNOSTRZ+*, which would only exascerbate the pronounciation wars (if such a thing were possible)), that's not exactly true. DVMs have emerged as a central paradigm in the nostr world because they're a generalization of a design pattern unique to nostr's architecture - but which exists in many other places, including NIP 46 signer flows and NIP 47 wallet connect. Each of these sub-protocols works by using relays as neutral brokers for requests in order to avoid coupling services to web addresses. This approach has all kinds of neat benefits, not least of which is allowing service providers to host their software without having to accept incoming TCP connections. But it's really an emergent property of relays, which not only are useful for brokering communication between users (aka storing events), but also brokering communication between machines. The possibilities of this architecture have only started to emerge, so be on the lookout for new applications, and don't be afraid to experiment - just please, don't serialize json inside json 🤦♂️ @ ac6f9572:8a6853dd
2025-02-13 01:56:23 Date: 02/12/2025 One of the most efficient options to expand your knowledge and truly connect with people actively working in the space is through direct interactions, whether they’re happening at large conferences or smaller, semi-official meetups. But let’s be honest: finding all meaningful events can be a mess. Take, for example, the '[BTC Events Map](https://docs.google.com/spreadsheets/d/1oni0QAHb2XYOL5gFVKHHGhG8w_HY5GDGBhdQ4SSrCZg/edit?gid=0&ref=europeanbitcoiners.com#gid=0),’ which already lists over 550 Bitcoin-only gatherings worldwide. This simple but very useful resource, put together by Satlantis, can help many of us plan our trips throughout the year. However, if you don’t know about its existence and rely solely on a search engine—whether Google or Brave—you’ll likely end up frustrated (and unfortunately missing many great opportunities to meet with others and learn). Search for '_bitcoin events_,' and you’ll get a mix of irrelevant crypto, fintech, and Web3 results, with Bitcoin-related stuff buried somewhere in the middle, if at all.. Well, it’s really tough to find what you’re actually looking for. That’s why word of mouth and trusted communities are so important. Sometimes, the best way to hear about an event is directly from people you know. **One of those that flew under my radar was** [**SatsNFacts**](https://satsnfacts.btc.pub/?ref=europeanbitcoiners.com)**.** It wasn’t listed on many typical event aggregators or any big news-promo sites. It mostly spread peer-to-peer and through the main channels on [Nostr](https://njump.me/npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx?ref=europeanbitcoiners.com). I was ‘_lucky_’ enough to hear about it just in time to plan the trip from Europe to Thailand. Now, I’d like to briefly share my experience with you—everything that, in my opinion, made this event truly stand out. **A Journey to Southeast Asia: Where Builders and Artists Collide.** -------------------------------------------------------------------- Approximately 10,176 kilometers, 14 hours of travel, and finally three days spent at SatsNFacts—"Thailand’s first Bitcoin Technical Unconference”. The event ran from February 8 to 10 in Chiang Mai (the largest city in northern Thailand). Held at Weave Artisan Society, a 700 sq.m venue that used to be an ice factory, it smoothly combined pleasant outdoors with an industrial-style, two-floor indoor area, creating a unique and very practical setup. While its was billed as a “_Technical Unconference_,” in practice it nicely connected the developer-based ecosystem with different aspects of culture and art. Each day, from 10 am to 6 pm, the agenda—shaped directly by attendees—was packed with various presentations, group chats, learning session, hackathons, and actionable workshops. With many options available (around 10-20 topics per day), I couldn’t attend everything, but here are a few more technical sessions I joined and found especially worthwhile: * **Liana Workshop** (long-term security, recovery, and inheritance), * **TollGates** ([streaming sats for internet access](https://primal.net/e/naddr1qvzqqqr4gupzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qq2nz63h0969vn2xwse9j3n5ge4xsdr2ddc4j0g960h?ref=europeanbitcoiners.com)), * **Open Vault** (enterprise wallet interface), * **Yaki Honne** ([decentralized media](https://yakihonne.com/?ref=europeanbitcoiners.com)), * **Nostr Proxies** (Epoxy, WebSocket and relay monetization). * **Silent payments** (simplified payment experiences without compromising privacy). As mentioned earlier, SatsNFacts wasn’t just about Bitcoin tech. Some topics focused on community aspects as well. Two discussions I joined highlighted Bitcoin adoption ⚡ in for example Bali and Thailand, showing how sound money, integrity, and consistent work can solve real problems in these regions. Impressive stuff! Here you can learn more: * [HuaiPhueng](https://geyser.fund/project/huaiphuengproject?hero=geyser&ref=europeanbitcoiners.com) on Geyser + "Bitcoin City" (their [short video](https://www.youtube.com/watch?feature=shared&v=211meP4liIo&ref=europeanbitcoiners.com)). * Bitcoin Indonesia & Bitcoin House Bali ([all in one on GitHub](https://github.com/bitcoinindo21?ref=europeanbitcoiners.com)) Now, the art gallery, to continue with less technical aspects of SatsNFacts 🎨 This nicely-organized space located on the ground floor, near cozy coworking and networking spots, was for me a real gem. Indeed, adding a creative vibe to the entire event. Around 30 unique works from local and international artists were on display, all inspired by themes of freedom and privacy. Though I don’t see myself as a typical _'artist_', I was honored to have some of my own pieces exhibited there as well (a short video below). * * * One of the highlights was meeting local Thai artists, especially [Siritravelsketch](https://njump.me/npub14lqzjhfvdc9psgxzznq8xys8pfq8p4fqsvtr6llyzraq90u9m8fqevhssu?ref=europeanbitcoiners.com), who travelled six hours by train just one way to attend two days of the event. Her stunning paintings, created using just a bamboo stick and ink, are deeply inspired by Thai architecture and culture. While some of her pre-prepared pieces hung in the gallery, she also painted a few new works on the spot during her visit. Truly spectacular!  * * * I also had the chance to reconnect with [Satoshi Builds](https://njump.me/npub19m7m3rs66pfdn4ewhrm8slh60ukyxgrylaa03m73wa40j39lc03syq4gfu?ref=europeanbitcoiners.com), who made many great sketches during this event, and with [BitPopArt](https://njump.me/npub1gwa27rpgum8mr9d30msg8cv7kwj2lhav2nvmdwh3wqnsa5vnudxqlta2sz?ref=europeanbitcoiners.com), a Dutch artist who, just like me, chosen a nomadic lifestyle yet has been clearly considering Thailand his 'second home' as well for several years now. By the way, ✍️ here's his short summary of the event, focusing more on the artistic side of SatsNFacts: "[Art exhibition in Chiang Mai](https://bitpopart.com/2025/02/11/art-exhibition-in-chiang-mai/?ref=europeanbitcoiners.com)". All in all, spending my time in many meaningful conversations and seeing so many deep artworks in one place filled me with hope and positive energy. THANK YOU, EVERYONE!  * * * (presented artworks by for example: [Agi Choote](https://njump.me/npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7?ref=europeanbitcoiners.com), [Samhain](https://njump.me/npub1df47g7a39usamq83aula72zdz23fx9xw5rrfmd0v6p9t20n5u0ss2eqez9?ref=europeanbitcoiners.com), [Zed Erwan](https://njump.me/npub1r2sah0htqnw7xrs70gq00m48vp25neu8ym2n2ghrny92dqqf7sest8hth0?ref=europeanbitcoiners.com), [Existing Sprinkles](https://njump.me/npub1f5kc2agn63ecv2ua4909z9ahgmr2x9263na36jh6r908ql0926jq3nvk2u?ref=europeanbitcoiners.com), AZA 21m, BitPopArt.) * * * Mr. Rabbit in Thailand... ------------------------- Monday, the final evening, and SatsNFacts got one more item on its agenda rooted in creative expression and independent art. Representing [Bitcoin FilmFest](https://x.com/bitcoinfilmfest?ref=europeanbitcoiners.com) (a grassroots project created by an amazing group of freedom fighters and activists 🐇🧡), since I was the only one from our team in Thailand, in one of the rooms upstairs, I put together a mini cinematic experience. Seven trailers and eleven shorts, including for example: * NO MORE INFLATION, HUMMINGBIRD, PARALLEL SPACE, UNBANKABLE, THE LEGEND OF LANDI (🎬 some of the trailers). * BITCOIN A NEW HOPE, SATOSHI NAKAMOTO - THE CREATOR OF BITCOIN, MAXIS CLUB SHOW - CHAPTER ONE, THE GREATEST HEIST IN HISTORY, HODL, THE ANATOMY OF BITCOIN – GENESIS BLOCK (📺 some of the presented shorts) With around 10-15 participants, the response was positive, and we ended up spending an extra 10-maybe-20 minutes discussing the challenges and opportunities in Bitcoin-powered filmmaking, as well as the upcoming edition of [BFF25](https://bitcoinfilmfest.com/bff25/?ref=europeanbitcoiners.com) (the annual festival we're organizing this May in Warsaw, Poland).  **Substance Over Hype. Gatherings That Matter.** ------------------------------------------------ SatsNFacts made a solid reminder that Bitcoin events can help build a truly sovereign future while bringing together developers and artistic souls alike. The mix of technical depth and creative energy—free from the shiny gossip that floods many social channels—made it a truly meaningful experience. > SatsNFacts set a high standard, and I hope to see more events like it in the future. More unconferences, more cultural and community-driven gatherings. **Here's to more signal, less noise!!!** Big congrats to everyone who made the first SatsNFacts happen 👏 Respect especially to the organizers! You pulled off something truly special! * * * _BTC Your Mind. Let it Beat._ _Şela_ @AZA_21M 💡 Did you enjoy this article? Zap me some sats. No amount is small :) Lightning wallet: `aza21m@getalby.com` - - - Original Article: https://europeanbitcoiners.com/sats-and-facts-short-coverage-of-the-first-bitcoin-unconference-in-thailand/ #english #opinion #events #bitcoin #nostr #freedom #conference #siamstr #asia #thailand
@ ac6f9572:8a6853dd
2025-02-13 01:56:23 Date: 02/12/2025 One of the most efficient options to expand your knowledge and truly connect with people actively working in the space is through direct interactions, whether they’re happening at large conferences or smaller, semi-official meetups. But let’s be honest: finding all meaningful events can be a mess. Take, for example, the '[BTC Events Map](https://docs.google.com/spreadsheets/d/1oni0QAHb2XYOL5gFVKHHGhG8w_HY5GDGBhdQ4SSrCZg/edit?gid=0&ref=europeanbitcoiners.com#gid=0),’ which already lists over 550 Bitcoin-only gatherings worldwide. This simple but very useful resource, put together by Satlantis, can help many of us plan our trips throughout the year. However, if you don’t know about its existence and rely solely on a search engine—whether Google or Brave—you’ll likely end up frustrated (and unfortunately missing many great opportunities to meet with others and learn). Search for '_bitcoin events_,' and you’ll get a mix of irrelevant crypto, fintech, and Web3 results, with Bitcoin-related stuff buried somewhere in the middle, if at all.. Well, it’s really tough to find what you’re actually looking for. That’s why word of mouth and trusted communities are so important. Sometimes, the best way to hear about an event is directly from people you know. **One of those that flew under my radar was** [**SatsNFacts**](https://satsnfacts.btc.pub/?ref=europeanbitcoiners.com)**.** It wasn’t listed on many typical event aggregators or any big news-promo sites. It mostly spread peer-to-peer and through the main channels on [Nostr](https://njump.me/npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx?ref=europeanbitcoiners.com). I was ‘_lucky_’ enough to hear about it just in time to plan the trip from Europe to Thailand. Now, I’d like to briefly share my experience with you—everything that, in my opinion, made this event truly stand out. **A Journey to Southeast Asia: Where Builders and Artists Collide.** -------------------------------------------------------------------- Approximately 10,176 kilometers, 14 hours of travel, and finally three days spent at SatsNFacts—"Thailand’s first Bitcoin Technical Unconference”. The event ran from February 8 to 10 in Chiang Mai (the largest city in northern Thailand). Held at Weave Artisan Society, a 700 sq.m venue that used to be an ice factory, it smoothly combined pleasant outdoors with an industrial-style, two-floor indoor area, creating a unique and very practical setup. While its was billed as a “_Technical Unconference_,” in practice it nicely connected the developer-based ecosystem with different aspects of culture and art. Each day, from 10 am to 6 pm, the agenda—shaped directly by attendees—was packed with various presentations, group chats, learning session, hackathons, and actionable workshops. With many options available (around 10-20 topics per day), I couldn’t attend everything, but here are a few more technical sessions I joined and found especially worthwhile: * **Liana Workshop** (long-term security, recovery, and inheritance), * **TollGates** ([streaming sats for internet access](https://primal.net/e/naddr1qvzqqqr4gupzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qq2nz63h0969vn2xwse9j3n5ge4xsdr2ddc4j0g960h?ref=europeanbitcoiners.com)), * **Open Vault** (enterprise wallet interface), * **Yaki Honne** ([decentralized media](https://yakihonne.com/?ref=europeanbitcoiners.com)), * **Nostr Proxies** (Epoxy, WebSocket and relay monetization). * **Silent payments** (simplified payment experiences without compromising privacy). As mentioned earlier, SatsNFacts wasn’t just about Bitcoin tech. Some topics focused on community aspects as well. Two discussions I joined highlighted Bitcoin adoption ⚡ in for example Bali and Thailand, showing how sound money, integrity, and consistent work can solve real problems in these regions. Impressive stuff! Here you can learn more: * [HuaiPhueng](https://geyser.fund/project/huaiphuengproject?hero=geyser&ref=europeanbitcoiners.com) on Geyser + "Bitcoin City" (their [short video](https://www.youtube.com/watch?feature=shared&v=211meP4liIo&ref=europeanbitcoiners.com)). * Bitcoin Indonesia & Bitcoin House Bali ([all in one on GitHub](https://github.com/bitcoinindo21?ref=europeanbitcoiners.com)) Now, the art gallery, to continue with less technical aspects of SatsNFacts 🎨 This nicely-organized space located on the ground floor, near cozy coworking and networking spots, was for me a real gem. Indeed, adding a creative vibe to the entire event. Around 30 unique works from local and international artists were on display, all inspired by themes of freedom and privacy. Though I don’t see myself as a typical _'artist_', I was honored to have some of my own pieces exhibited there as well (a short video below). * * * One of the highlights was meeting local Thai artists, especially [Siritravelsketch](https://njump.me/npub14lqzjhfvdc9psgxzznq8xys8pfq8p4fqsvtr6llyzraq90u9m8fqevhssu?ref=europeanbitcoiners.com), who travelled six hours by train just one way to attend two days of the event. Her stunning paintings, created using just a bamboo stick and ink, are deeply inspired by Thai architecture and culture. While some of her pre-prepared pieces hung in the gallery, she also painted a few new works on the spot during her visit. Truly spectacular!  * * * I also had the chance to reconnect with [Satoshi Builds](https://njump.me/npub19m7m3rs66pfdn4ewhrm8slh60ukyxgrylaa03m73wa40j39lc03syq4gfu?ref=europeanbitcoiners.com), who made many great sketches during this event, and with [BitPopArt](https://njump.me/npub1gwa27rpgum8mr9d30msg8cv7kwj2lhav2nvmdwh3wqnsa5vnudxqlta2sz?ref=europeanbitcoiners.com), a Dutch artist who, just like me, chosen a nomadic lifestyle yet has been clearly considering Thailand his 'second home' as well for several years now. By the way, ✍️ here's his short summary of the event, focusing more on the artistic side of SatsNFacts: "[Art exhibition in Chiang Mai](https://bitpopart.com/2025/02/11/art-exhibition-in-chiang-mai/?ref=europeanbitcoiners.com)". All in all, spending my time in many meaningful conversations and seeing so many deep artworks in one place filled me with hope and positive energy. THANK YOU, EVERYONE!  * * * (presented artworks by for example: [Agi Choote](https://njump.me/npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7?ref=europeanbitcoiners.com), [Samhain](https://njump.me/npub1df47g7a39usamq83aula72zdz23fx9xw5rrfmd0v6p9t20n5u0ss2eqez9?ref=europeanbitcoiners.com), [Zed Erwan](https://njump.me/npub1r2sah0htqnw7xrs70gq00m48vp25neu8ym2n2ghrny92dqqf7sest8hth0?ref=europeanbitcoiners.com), [Existing Sprinkles](https://njump.me/npub1f5kc2agn63ecv2ua4909z9ahgmr2x9263na36jh6r908ql0926jq3nvk2u?ref=europeanbitcoiners.com), AZA 21m, BitPopArt.) * * * Mr. Rabbit in Thailand... ------------------------- Monday, the final evening, and SatsNFacts got one more item on its agenda rooted in creative expression and independent art. Representing [Bitcoin FilmFest](https://x.com/bitcoinfilmfest?ref=europeanbitcoiners.com) (a grassroots project created by an amazing group of freedom fighters and activists 🐇🧡), since I was the only one from our team in Thailand, in one of the rooms upstairs, I put together a mini cinematic experience. Seven trailers and eleven shorts, including for example: * NO MORE INFLATION, HUMMINGBIRD, PARALLEL SPACE, UNBANKABLE, THE LEGEND OF LANDI (🎬 some of the trailers). * BITCOIN A NEW HOPE, SATOSHI NAKAMOTO - THE CREATOR OF BITCOIN, MAXIS CLUB SHOW - CHAPTER ONE, THE GREATEST HEIST IN HISTORY, HODL, THE ANATOMY OF BITCOIN – GENESIS BLOCK (📺 some of the presented shorts) With around 10-15 participants, the response was positive, and we ended up spending an extra 10-maybe-20 minutes discussing the challenges and opportunities in Bitcoin-powered filmmaking, as well as the upcoming edition of [BFF25](https://bitcoinfilmfest.com/bff25/?ref=europeanbitcoiners.com) (the annual festival we're organizing this May in Warsaw, Poland).  **Substance Over Hype. Gatherings That Matter.** ------------------------------------------------ SatsNFacts made a solid reminder that Bitcoin events can help build a truly sovereign future while bringing together developers and artistic souls alike. The mix of technical depth and creative energy—free from the shiny gossip that floods many social channels—made it a truly meaningful experience. > SatsNFacts set a high standard, and I hope to see more events like it in the future. More unconferences, more cultural and community-driven gatherings. **Here's to more signal, less noise!!!** Big congrats to everyone who made the first SatsNFacts happen 👏 Respect especially to the organizers! You pulled off something truly special! * * * _BTC Your Mind. Let it Beat._ _Şela_ @AZA_21M 💡 Did you enjoy this article? Zap me some sats. No amount is small :) Lightning wallet: `aza21m@getalby.com` - - - Original Article: https://europeanbitcoiners.com/sats-and-facts-short-coverage-of-the-first-bitcoin-unconference-in-thailand/ #english #opinion #events #bitcoin #nostr #freedom #conference #siamstr #asia #thailand @ ac6f9572:8a6853dd
2025-02-13 01:55:20# Freedom Tech, Privacy, Sound Money, and Culture: How to Find Your Tribe? > Keeping up with everything happening in Bitcoin isn’t easy, even if you’ve been around for a while. The pace is relentless: stream of events, discussions, projects, and updates, not to mention the noise on social media...  Date: 02/12/2025 One of the most efficient options to expand your knowledge and truly connect with people actively working in the space is through direct interactions, whether they’re happening at large conferences or smaller, semi-official meetups. But let’s be honest: finding all meaningful events can be a mess. Take, for example, the '[BTC Events Map](https://docs.google.com/spreadsheets/d/1oni0QAHb2XYOL5gFVKHHGhG8w_HY5GDGBhdQ4SSrCZg/edit?gid=0&ref=europeanbitcoiners.com#gid=0),’ which already lists over 550 Bitcoin-only gatherings worldwide. This simple but very useful resource, put together by Satlantis, can help many of us plan our trips throughout the year. However, if you don’t know about its existence and rely solely on a search engine—whether Google or Brave—you’ll likely end up frustrated (and unfortunately missing many great opportunities to meet with others and learn). Search for '_bitcoin events_,' and you’ll get a mix of irrelevant crypto, fintech, and Web3 results, with Bitcoin-related stuff buried somewhere in the middle, if at all.. Well, it’s really tough to find what you’re actually looking for. That’s why word of mouth and trusted communities are so important. Sometimes, the best way to hear about an event is directly from people you know. **One of those that flew under my radar was** [**SatsNFacts**](https://satsnfacts.btc.pub/?ref=europeanbitcoiners.com)**.** It wasn’t listed on many typical event aggregators or any big news-promo sites. It mostly spread peer-to-peer and through the main channels on [Nostr](https://njump.me/npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx?ref=europeanbitcoiners.com). I was ‘_lucky_’ enough to hear about it just in time to plan the trip from Europe to Thailand. Now, I’d like to briefly share my experience with you—everything that, in my opinion, made this event truly stand out. **A Journey to Southeast Asia: Where Builders and Artists Collide.** -------------------------------------------------------------------- Approximately 10,176 kilometers, 14 hours of travel, and finally three days spent at SatsNFacts—"Thailand’s first Bitcoin Technical Unconference”. The event ran from February 8 to 10 in Chiang Mai (the largest city in northern Thailand). Held at Weave Artisan Society, a 700 sq.m venue that used to be an ice factory, it smoothly combined pleasant outdoors with an industrial-style, two-floor indoor area, creating a unique and very practical setup. While its was billed as a “_Technical Unconference_,” in practice it nicely connected the developer-based ecosystem with different aspects of culture and art. Each day, from 10 am to 6 pm, the agenda—shaped directly by attendees—was packed with various presentations, group chats, learning session, hackathons, and actionable workshops. With many options available (around 10-20 topics per day), I couldn’t attend everything, but here are a few more technical sessions I joined and found especially worthwhile: * **Liana Workshop** (long-term security, recovery, and inheritance), * **TollGates** ([streaming sats for internet access](https://primal.net/e/naddr1qvzqqqr4gupzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qq2nz63h0969vn2xwse9j3n5ge4xsdr2ddc4j0g960h?ref=europeanbitcoiners.com)), * **Open Vault** (enterprise wallet interface), * **Yaki Honne** ([decentralized media](https://yakihonne.com/?ref=europeanbitcoiners.com)), * **Nostr Proxies** (Epoxy, WebSocket and relay monetization). * **Silent payments** (simplified payment experiences without compromising privacy). As mentioned earlier, SatsNFacts wasn’t just about Bitcoin tech. Some topics focused on community aspects as well. Two discussions I joined highlighted Bitcoin adoption ⚡ in for example Bali and Thailand, showing how sound money, integrity, and consistent work can solve real problems in these regions. Impressive stuff! Here you can learn more: * [HuaiPhueng](https://geyser.fund/project/huaiphuengproject?hero=geyser&ref=europeanbitcoiners.com) on Geyser + "Bitcoin City" (their [short video](https://www.youtube.com/watch?feature=shared&v=211meP4liIo&ref=europeanbitcoiners.com)). * Bitcoin Indonesia & Bitcoin House Bali ([all in one on GitHub](https://github.com/bitcoinindo21?ref=europeanbitcoiners.com)) Now, the art gallery, to continue with less technical aspects of SatsNFacts 🎨 This nicely-organized space located on the ground floor, near cozy coworking and networking spots, was for me a real gem. Indeed, adding a creative vibe to the entire event. Around 30 unique works from local and international artists were on display, all inspired by themes of freedom and privacy. Though I don’t see myself as a typical _'artist_', I was honored to have some of my own pieces exhibited there as well (a short video below). * * * One of the highlights was meeting local Thai artists, especially [Siritravelsketch](https://njump.me/npub14lqzjhfvdc9psgxzznq8xys8pfq8p4fqsvtr6llyzraq90u9m8fqevhssu?ref=europeanbitcoiners.com), who travelled six hours by train just one way to attend two days of the event. Her stunning paintings, created using just a bamboo stick and ink, are deeply inspired by Thai architecture and culture. While some of her pre-prepared pieces hung in the gallery, she also painted a few new works on the spot during her visit. Truly spectacular!  * * * I also had the chance to reconnect with [Satoshi Builds](https://njump.me/npub19m7m3rs66pfdn4ewhrm8slh60ukyxgrylaa03m73wa40j39lc03syq4gfu?ref=europeanbitcoiners.com), who made many great sketches during this event, and with [BitPopArt](https://njump.me/npub1gwa27rpgum8mr9d30msg8cv7kwj2lhav2nvmdwh3wqnsa5vnudxqlta2sz?ref=europeanbitcoiners.com), a Dutch artist who, just like me, chosen a nomadic lifestyle yet has been clearly considering Thailand his 'second home' as well for several years now. By the way, ✍️ here's his short summary of the event, focusing more on the artistic side of SatsNFacts: "[Art exhibition in Chiang Mai](https://bitpopart.com/2025/02/11/art-exhibition-in-chiang-mai/?ref=europeanbitcoiners.com)". All in all, spending my time in many meaningful conversations and seeing so many deep artworks in one place filled me with hope and positive energy. THANK YOU, EVERYONE!  * * * (presented artworks by for example: [Agi Choote](https://njump.me/npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7?ref=europeanbitcoiners.com), [Samhain](https://njump.me/npub1df47g7a39usamq83aula72zdz23fx9xw5rrfmd0v6p9t20n5u0ss2eqez9?ref=europeanbitcoiners.com), [Zed Erwan](https://njump.me/npub1r2sah0htqnw7xrs70gq00m48vp25neu8ym2n2ghrny92dqqf7sest8hth0?ref=europeanbitcoiners.com), [Existing Sprinkles](https://njump.me/npub1f5kc2agn63ecv2ua4909z9ahgmr2x9263na36jh6r908ql0926jq3nvk2u?ref=europeanbitcoiners.com), AZA 21m, BitPopArt.) * * * Mr. Rabbit in Thailand... ------------------------- Monday, the final evening, and SatsNFacts got one more item on its agenda rooted in creative expression and independent art. Representing [Bitcoin FilmFest](https://x.com/bitcoinfilmfest?ref=europeanbitcoiners.com) (a grassroots project created by an amazing group of freedom fighters and activists 🐇🧡), since I was the only one from our team in Thailand, in one of the rooms upstairs, I put together a mini cinematic experience. Seven trailers and eleven shorts, including for example: * NO MORE INFLATION, HUMMINGBIRD, PARALLEL SPACE, UNBANKABLE, THE LEGEND OF LANDI (🎬 some of the trailers). * BITCOIN A NEW HOPE, SATOSHI NAKAMOTO - THE CREATOR OF BITCOIN, MAXIS CLUB SHOW - CHAPTER ONE, THE GREATEST HEIST IN HISTORY, HODL, THE ANATOMY OF BITCOIN – GENESIS BLOCK (📺 some of the presented shorts) With around 10-15 participants, the response was positive, and we ended up spending an extra 10-maybe-20 minutes discussing the challenges and opportunities in Bitcoin-powered filmmaking, as well as the upcoming edition of [BFF25](https://bitcoinfilmfest.com/bff25/?ref=europeanbitcoiners.com) (the annual festival we're organizing this May in Warsaw, Poland).  **Substance Over Hype. Gatherings That Matter.** ------------------------------------------------ SatsNFacts made a solid reminder that Bitcoin events can help build a truly sovereign future while bringing together developers and artistic souls alike. The mix of technical depth and creative energy—free from the shiny gossip that floods many social channels—made it a truly meaningful experience. > SatsNFacts set a high standard, and I hope to see more events like it in the future. More unconferences, more cultural and community-driven gatherings. **Here's to more signal, less noise!!!** Big congrats to everyone who made the first SatsNFacts happen 👏 Respect especially to the organizers! You pulled off something truly special! * * * _BTC Your Mind. Let it Beat._ _Şela_ @AZA_21M 💡 Did you enjoy this article? Zap me some sats. No amount is small :) Lightning wallet: `aza21m@getalby.com` - - - Original Article: https://europeanbitcoiners.com/sats-and-facts-short-coverage-of-the-first-bitcoin-unconference-in-thailand/ #english #opinion #events #bitcoin #nostr #freedom #conference #siamstr #asia #thailand originally posted at https://stacker.news/items/884317
@ ac6f9572:8a6853dd
2025-02-13 01:55:20# Freedom Tech, Privacy, Sound Money, and Culture: How to Find Your Tribe? > Keeping up with everything happening in Bitcoin isn’t easy, even if you’ve been around for a while. The pace is relentless: stream of events, discussions, projects, and updates, not to mention the noise on social media...  Date: 02/12/2025 One of the most efficient options to expand your knowledge and truly connect with people actively working in the space is through direct interactions, whether they’re happening at large conferences or smaller, semi-official meetups. But let’s be honest: finding all meaningful events can be a mess. Take, for example, the '[BTC Events Map](https://docs.google.com/spreadsheets/d/1oni0QAHb2XYOL5gFVKHHGhG8w_HY5GDGBhdQ4SSrCZg/edit?gid=0&ref=europeanbitcoiners.com#gid=0),’ which already lists over 550 Bitcoin-only gatherings worldwide. This simple but very useful resource, put together by Satlantis, can help many of us plan our trips throughout the year. However, if you don’t know about its existence and rely solely on a search engine—whether Google or Brave—you’ll likely end up frustrated (and unfortunately missing many great opportunities to meet with others and learn). Search for '_bitcoin events_,' and you’ll get a mix of irrelevant crypto, fintech, and Web3 results, with Bitcoin-related stuff buried somewhere in the middle, if at all.. Well, it’s really tough to find what you’re actually looking for. That’s why word of mouth and trusted communities are so important. Sometimes, the best way to hear about an event is directly from people you know. **One of those that flew under my radar was** [**SatsNFacts**](https://satsnfacts.btc.pub/?ref=europeanbitcoiners.com)**.** It wasn’t listed on many typical event aggregators or any big news-promo sites. It mostly spread peer-to-peer and through the main channels on [Nostr](https://njump.me/npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx?ref=europeanbitcoiners.com). I was ‘_lucky_’ enough to hear about it just in time to plan the trip from Europe to Thailand. Now, I’d like to briefly share my experience with you—everything that, in my opinion, made this event truly stand out. **A Journey to Southeast Asia: Where Builders and Artists Collide.** -------------------------------------------------------------------- Approximately 10,176 kilometers, 14 hours of travel, and finally three days spent at SatsNFacts—"Thailand’s first Bitcoin Technical Unconference”. The event ran from February 8 to 10 in Chiang Mai (the largest city in northern Thailand). Held at Weave Artisan Society, a 700 sq.m venue that used to be an ice factory, it smoothly combined pleasant outdoors with an industrial-style, two-floor indoor area, creating a unique and very practical setup. While its was billed as a “_Technical Unconference_,” in practice it nicely connected the developer-based ecosystem with different aspects of culture and art. Each day, from 10 am to 6 pm, the agenda—shaped directly by attendees—was packed with various presentations, group chats, learning session, hackathons, and actionable workshops. With many options available (around 10-20 topics per day), I couldn’t attend everything, but here are a few more technical sessions I joined and found especially worthwhile: * **Liana Workshop** (long-term security, recovery, and inheritance), * **TollGates** ([streaming sats for internet access](https://primal.net/e/naddr1qvzqqqr4gupzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qq2nz63h0969vn2xwse9j3n5ge4xsdr2ddc4j0g960h?ref=europeanbitcoiners.com)), * **Open Vault** (enterprise wallet interface), * **Yaki Honne** ([decentralized media](https://yakihonne.com/?ref=europeanbitcoiners.com)), * **Nostr Proxies** (Epoxy, WebSocket and relay monetization). * **Silent payments** (simplified payment experiences without compromising privacy). As mentioned earlier, SatsNFacts wasn’t just about Bitcoin tech. Some topics focused on community aspects as well. Two discussions I joined highlighted Bitcoin adoption ⚡ in for example Bali and Thailand, showing how sound money, integrity, and consistent work can solve real problems in these regions. Impressive stuff! Here you can learn more: * [HuaiPhueng](https://geyser.fund/project/huaiphuengproject?hero=geyser&ref=europeanbitcoiners.com) on Geyser + "Bitcoin City" (their [short video](https://www.youtube.com/watch?feature=shared&v=211meP4liIo&ref=europeanbitcoiners.com)). * Bitcoin Indonesia & Bitcoin House Bali ([all in one on GitHub](https://github.com/bitcoinindo21?ref=europeanbitcoiners.com)) Now, the art gallery, to continue with less technical aspects of SatsNFacts 🎨 This nicely-organized space located on the ground floor, near cozy coworking and networking spots, was for me a real gem. Indeed, adding a creative vibe to the entire event. Around 30 unique works from local and international artists were on display, all inspired by themes of freedom and privacy. Though I don’t see myself as a typical _'artist_', I was honored to have some of my own pieces exhibited there as well (a short video below). * * * One of the highlights was meeting local Thai artists, especially [Siritravelsketch](https://njump.me/npub14lqzjhfvdc9psgxzznq8xys8pfq8p4fqsvtr6llyzraq90u9m8fqevhssu?ref=europeanbitcoiners.com), who travelled six hours by train just one way to attend two days of the event. Her stunning paintings, created using just a bamboo stick and ink, are deeply inspired by Thai architecture and culture. While some of her pre-prepared pieces hung in the gallery, she also painted a few new works on the spot during her visit. Truly spectacular!  * * * I also had the chance to reconnect with [Satoshi Builds](https://njump.me/npub19m7m3rs66pfdn4ewhrm8slh60ukyxgrylaa03m73wa40j39lc03syq4gfu?ref=europeanbitcoiners.com), who made many great sketches during this event, and with [BitPopArt](https://njump.me/npub1gwa27rpgum8mr9d30msg8cv7kwj2lhav2nvmdwh3wqnsa5vnudxqlta2sz?ref=europeanbitcoiners.com), a Dutch artist who, just like me, chosen a nomadic lifestyle yet has been clearly considering Thailand his 'second home' as well for several years now. By the way, ✍️ here's his short summary of the event, focusing more on the artistic side of SatsNFacts: "[Art exhibition in Chiang Mai](https://bitpopart.com/2025/02/11/art-exhibition-in-chiang-mai/?ref=europeanbitcoiners.com)". All in all, spending my time in many meaningful conversations and seeing so many deep artworks in one place filled me with hope and positive energy. THANK YOU, EVERYONE!  * * * (presented artworks by for example: [Agi Choote](https://njump.me/npub1tlacuxmtv2wqud9qz0ujnr4mqavmnz3ayspfj93jr40tgf2mvu6seax3y7?ref=europeanbitcoiners.com), [Samhain](https://njump.me/npub1df47g7a39usamq83aula72zdz23fx9xw5rrfmd0v6p9t20n5u0ss2eqez9?ref=europeanbitcoiners.com), [Zed Erwan](https://njump.me/npub1r2sah0htqnw7xrs70gq00m48vp25neu8ym2n2ghrny92dqqf7sest8hth0?ref=europeanbitcoiners.com), [Existing Sprinkles](https://njump.me/npub1f5kc2agn63ecv2ua4909z9ahgmr2x9263na36jh6r908ql0926jq3nvk2u?ref=europeanbitcoiners.com), AZA 21m, BitPopArt.) * * * Mr. Rabbit in Thailand... ------------------------- Monday, the final evening, and SatsNFacts got one more item on its agenda rooted in creative expression and independent art. Representing [Bitcoin FilmFest](https://x.com/bitcoinfilmfest?ref=europeanbitcoiners.com) (a grassroots project created by an amazing group of freedom fighters and activists 🐇🧡), since I was the only one from our team in Thailand, in one of the rooms upstairs, I put together a mini cinematic experience. Seven trailers and eleven shorts, including for example: * NO MORE INFLATION, HUMMINGBIRD, PARALLEL SPACE, UNBANKABLE, THE LEGEND OF LANDI (🎬 some of the trailers). * BITCOIN A NEW HOPE, SATOSHI NAKAMOTO - THE CREATOR OF BITCOIN, MAXIS CLUB SHOW - CHAPTER ONE, THE GREATEST HEIST IN HISTORY, HODL, THE ANATOMY OF BITCOIN – GENESIS BLOCK (📺 some of the presented shorts) With around 10-15 participants, the response was positive, and we ended up spending an extra 10-maybe-20 minutes discussing the challenges and opportunities in Bitcoin-powered filmmaking, as well as the upcoming edition of [BFF25](https://bitcoinfilmfest.com/bff25/?ref=europeanbitcoiners.com) (the annual festival we're organizing this May in Warsaw, Poland).  **Substance Over Hype. Gatherings That Matter.** ------------------------------------------------ SatsNFacts made a solid reminder that Bitcoin events can help build a truly sovereign future while bringing together developers and artistic souls alike. The mix of technical depth and creative energy—free from the shiny gossip that floods many social channels—made it a truly meaningful experience. > SatsNFacts set a high standard, and I hope to see more events like it in the future. More unconferences, more cultural and community-driven gatherings. **Here's to more signal, less noise!!!** Big congrats to everyone who made the first SatsNFacts happen 👏 Respect especially to the organizers! You pulled off something truly special! * * * _BTC Your Mind. Let it Beat._ _Şela_ @AZA_21M 💡 Did you enjoy this article? Zap me some sats. No amount is small :) Lightning wallet: `aza21m@getalby.com` - - - Original Article: https://europeanbitcoiners.com/sats-and-facts-short-coverage-of-the-first-bitcoin-unconference-in-thailand/ #english #opinion #events #bitcoin #nostr #freedom #conference #siamstr #asia #thailand originally posted at https://stacker.news/items/884317 @ 1cb14ab3:95d52462
2025-02-13 01:30:00**Dirt, body weight. [125' x 2']** *This project was exhibited in 2015 in Boulder, Colorado.* --- ### Artist Statement “A Line Made By Walking” (2015) is a site-specific piece created in Boulder, CO, where my body weight etched a temporary line into the earth. This work pays homage to Richard Long’s seminal 1967 piece, where a simple act of walking through the landscape left a profound trace. In my version, the line created by my movement forces the viewer to engage with the impermanence of human intervention on the land. The project prompts a reflection on the subtle yet lasting impacts we have on the environment, even through seemingly minimal actions. As part of my larger “[Rockway](https://hes.npub.pro/post/1708400183541/)” project, this case study explores the concept of ‘line’ in both literal and metaphorical ways. The line is not just a physical mark, but also a representation of time, movement, and the dialogue between the body and the land. Walking, in this context, becomes a way of marking time—an act that is as ephemeral as the mark it leaves behind. The work questions the tension between permanence and transience, asking the viewer to consider how we interact with the land, both intentionally and unknowingly, and how those interactions leave traces that may soon fade but never completely disappear. --- ### Photos        --- #### More Land Art: [Earth Lens Series](https://hes.npub.pro/post/1731091744332/) ["Looking Glass"](https://hes.npub.pro/post/1736304563962/) ["Het Bonhe"](https://hes.npub.pro/post/1720242458557/) ["Rockway"](https://hes.npub.pro/post/1708400183541/) ["Invasive"](https://hes.npub.pro/post/1719722211094/) --- #### More from Hes [Full Portfolio](https://hesart.npub.pro) [Online Store](https://plebeian.market/community/hes@nostrplebs.com/hesmart-ym3fcufdfz) [Artist Statements](https://hes.npub.pro/tag/art/) [Travel Guides](https://hes.npub.pro/tag/travel/) [Photography](https://hes.npub.pro/tag/photography) [Writings](https://hes.npub.pro/tag/money) --- *All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.*
@ 1cb14ab3:95d52462
2025-02-13 01:30:00**Dirt, body weight. [125' x 2']** *This project was exhibited in 2015 in Boulder, Colorado.* --- ### Artist Statement “A Line Made By Walking” (2015) is a site-specific piece created in Boulder, CO, where my body weight etched a temporary line into the earth. This work pays homage to Richard Long’s seminal 1967 piece, where a simple act of walking through the landscape left a profound trace. In my version, the line created by my movement forces the viewer to engage with the impermanence of human intervention on the land. The project prompts a reflection on the subtle yet lasting impacts we have on the environment, even through seemingly minimal actions. As part of my larger “[Rockway](https://hes.npub.pro/post/1708400183541/)” project, this case study explores the concept of ‘line’ in both literal and metaphorical ways. The line is not just a physical mark, but also a representation of time, movement, and the dialogue between the body and the land. Walking, in this context, becomes a way of marking time—an act that is as ephemeral as the mark it leaves behind. The work questions the tension between permanence and transience, asking the viewer to consider how we interact with the land, both intentionally and unknowingly, and how those interactions leave traces that may soon fade but never completely disappear. --- ### Photos        --- #### More Land Art: [Earth Lens Series](https://hes.npub.pro/post/1731091744332/) ["Looking Glass"](https://hes.npub.pro/post/1736304563962/) ["Het Bonhe"](https://hes.npub.pro/post/1720242458557/) ["Rockway"](https://hes.npub.pro/post/1708400183541/) ["Invasive"](https://hes.npub.pro/post/1719722211094/) --- #### More from Hes [Full Portfolio](https://hesart.npub.pro) [Online Store](https://plebeian.market/community/hes@nostrplebs.com/hesmart-ym3fcufdfz) [Artist Statements](https://hes.npub.pro/tag/art/) [Travel Guides](https://hes.npub.pro/tag/travel/) [Photography](https://hes.npub.pro/tag/photography) [Writings](https://hes.npub.pro/tag/money) --- *All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.* @ 20e7c953:3b8bcb21
2025-02-13 01:15:42Biggest takeaway? We needed more hands to cover key roles - something to improve for next time, if there is any! That said, the strongest point was the organic networking and building, which set this apart from more structured, commercial conferences. For future events - if any! - Hackathons will need dedicated time slots in the future, given the time constraints. The art side of things isn’t over yet—the exhibition will keep going for another month. The event started a bit messy, but the quality of people made it flow naturally, creating a unique and engaging atmosphere. Overall, a great experience, and we’ll keep iterating for the next one. We’ll send out a survey soon to gather more feedback. Huge thanks to our sponsors and media partners for making this happen - appreciate the support. On Communities: Lastly, while both commercial and less commercial events are needed there is something that doesn't beat Bitcoin Culture which are Bitcoin-only Meetups. If we are in a position to give some advice: Make sure you engage with your local community since people behind it are most likely the ones who can able to bootstrap new comers while keeping trust and accountability in place. Luckily today we have most tools to filter out those who are leeching off others PoW and the genuine ones trailblazing on their own terms. On our side definitely one of the biggest lessons learnt was to work with the local Communities for future events - regardless - this time we managed to get it done with our hands, will and not much else since *most* tools used have been FOSS and that's why we are here for ! With that said and while continuously gathering more feedback these coming days.... WHAT DID YOU ENJOYED THE MOST? ANYTHING YOU DISLIKED? **WHERE SHOULD WE HOST SATS N FACTS NEXT ?👀** SUGGESTIONS AND FEEDBACK MAILBOX IS OPEN 📬 Onwards 🫡
@ 20e7c953:3b8bcb21
2025-02-13 01:15:42Biggest takeaway? We needed more hands to cover key roles - something to improve for next time, if there is any! That said, the strongest point was the organic networking and building, which set this apart from more structured, commercial conferences. For future events - if any! - Hackathons will need dedicated time slots in the future, given the time constraints. The art side of things isn’t over yet—the exhibition will keep going for another month. The event started a bit messy, but the quality of people made it flow naturally, creating a unique and engaging atmosphere. Overall, a great experience, and we’ll keep iterating for the next one. We’ll send out a survey soon to gather more feedback. Huge thanks to our sponsors and media partners for making this happen - appreciate the support. On Communities: Lastly, while both commercial and less commercial events are needed there is something that doesn't beat Bitcoin Culture which are Bitcoin-only Meetups. If we are in a position to give some advice: Make sure you engage with your local community since people behind it are most likely the ones who can able to bootstrap new comers while keeping trust and accountability in place. Luckily today we have most tools to filter out those who are leeching off others PoW and the genuine ones trailblazing on their own terms. On our side definitely one of the biggest lessons learnt was to work with the local Communities for future events - regardless - this time we managed to get it done with our hands, will and not much else since *most* tools used have been FOSS and that's why we are here for ! With that said and while continuously gathering more feedback these coming days.... WHAT DID YOU ENJOYED THE MOST? ANYTHING YOU DISLIKED? **WHERE SHOULD WE HOST SATS N FACTS NEXT ?👀** SUGGESTIONS AND FEEDBACK MAILBOX IS OPEN 📬 Onwards 🫡 @ c582af78:698069cc
2025-02-13 01:04:26# **The Nine Orders of Angels: A Guide to the Celestial Hierarchy** When we think of angels, we often picture winged figures in flowing robes, guiding and protecting humanity. But the biblical and theological reality is far more complex—and often stranger—than these familiar depictions. The word *angel* comes from the Greek *angelos*, meaning “messenger,” but in scripture, angels serve a wide range of roles beyond delivering divine messages. Some are warriors wielding swords and leading celestial armies, others uphold the very throne of God, and some appear as multi-winged, multi-eyed beings beyond human comprehension. To bring order to this celestial realm, theologians—most notably Thomas Aquinas—classified angels into a hierarchy of **nine types**, divided into **three orders** based on their function and proximity to God. - **The lowest order** interacts with humanity. - **The middle order** governs spiritual and cosmic forces. - **The highest order** exists solely to serve and glorify God. Today, we explore these **nine ranks of angels**—from the familiar to the truly otherworldly. --- ## **I. The Third Order: Angels Who Interact with Humanity** *(The lowest tier of angels, closest to humans, acting as messengers and protectors.)* ### **1. Angels – The Messengers** https://image.nostr.build/b6462b67e14c8780896f465b664a521cdcdef7eb4b4314669b8d219aa36964c5.jpg These are the angels most commonly associated with divine guidance. According to Aquinas, every person has a **guardian angel**—an unseen protector guiding them through life. In *Genesis 28:12*, Jacob’s vision of a ladder stretching to Heaven shows angels ascending and descending, delivering messages and fulfilling divine commands. Some, like those who visited Abraham, even appeared as ordinary men, without wings or supernatural radiance. ### **2. Archangels – The Divine Enforcers** https://image.nostr.build/af8799efb61c5a64e958450bcd5aee55d2cade931cfc5ca7f0ae8745ccd4c45a.jpg Archangels carry out the most crucial missions in scripture. Gabriel announced the birth of Jesus to Mary, while Michael led the charge against Satan in the war for Heaven. Though only **Michael** is explicitly called an archangel in the Bible, tradition assigns this title to others, including **Raphael** and **Uriel**. Archangels serve as warriors and heralds, executing God’s most urgent decrees. ### **3. Principalities – Guardians of Nations** https://image.nostr.build/bc7cd78acb656be6c946da32244bfb9ecdfe9a7d1bd80e47eca764cae4a88b95.jpg Principalities oversee nations, cities, and communities, influencing their spiritual well-being. While they are not explicitly named in scripture, *Colossians 1:16* references “thrones, dominions, principalities, and powers.” Tradition suggests that Principalities guide earthly leaders, strengthening them in times of crisis—and perhaps even aiding biblical figures like King David in battle. --- ## **II. The Second Order: The Heavenly Governors** *(These angels reside in Heaven but influence earthly affairs, ensuring divine order is maintained.)* ### **4. Powers – The Celestial Warriors** https://image.nostr.build/1768abcbaefb2d1d21654a869b356d86a45d76a82197b9568528d4d4b9f0ef69.jpg Powers act as Heaven’s **military defenders**, guarding the spiritual realm from demonic forces. They are often depicted in armor, wielding weapons as they engage in cosmic battles. According to Christian tradition, Powers also **escort souls to Heaven**, ensuring their safe passage after death. Some believe that the battle between good and evil plays out, in part, through these celestial warriors. ### **5. Virtues – The Miracle Workers** https://image.nostr.build/b9a1e52f1dd4ef0f7e7dd198d81e7cd171eede8a64a40cac8176e12a5419aeba.jpg Virtues are associated with **miracles and nature**, regulating celestial phenomena and assisting in divine interventions. In Christian tradition, the two angels present at **Christ’s Ascension** are often considered Virtues, manifesting God’s power on Earth. ### **6. Dominions – The Angelic Rulers** https://image.nostr.build/0900d97bf545736e5edc1521f46a8afbf0e93fd81e472c88a56744ff0f56ce48.jpg Dominions do not typically interact with humans directly. Instead, they act as **commanders**, overseeing lower angels and ensuring divine order is maintained. They are described as serene, wise beings, often depicted holding golden staffs and orbs, symbolizing their authority and their close relationship with God. --- ## **III. The First Order: The Angels Closest to God** *(These angels exist solely to worship and serve God, residing in the highest realms of Heaven.)* ### **7. Thrones – The Wheels of God’s Chariot** https://image.nostr.build/d9f1e465129b138f4f960ee43ee9e06ceb3fd6f57e9658cd275e1ac1576b3c02.jpg Among the most mysterious angelic beings, Thrones are described in *Ezekiel’s vision* as **wheels covered in eyes, spinning within wheels**: > *“As I looked, I saw a wheel on the ground beside each creature with its four faces... Their rims were full of eyes all around. Wherever the spirit would go, they would go, because the spirit of the living creatures was in the wheels.”* > — *Ezekiel 1:15-21* Thrones serve as **God’s chariot**, supporting His throne and executing divine justice. Their strange, abstract form symbolizes stability and divine order. ### **8. Cherubim – The Guardians of Glory** https://image.nostr.build/e921ad4c32f56ebbb8f1bcb1ca2bc6eed1c736ec896429e008fc5b71cf2fd151.jpg Cherubim have been drastically misrepresented in art. Far from the **plump, childlike figures** seen in Renaissance paintings, the **biblical Cherubim** are **fearsome beings**. In *Ezekiel 10*, they are described as having **four faces**—a man, a lion, an ox, and an eagle—along with **four wings**. They also appear in *Genesis 3:24*, where they **guard the entrance to Eden with flaming swords** after Adam and Eve’s expulsion. https://image.nostr.build/f51286d4f35d9d6e85d8559600188ecc89a0969c3985814cae56cd230ea5db00.jpg Aquinas even suggested that **Satan himself was a fallen Cherub**. This theory is supported by *Ezekiel 28*, which describes an angelic being cast down from God’s presence: > *“You were anointed as a guardian cherub... You were blameless in your ways until wickedness was found in you... So I drove you in disgrace from the mount of God, and I expelled you, guardian cherub.”* > — *Ezekiel 28:14-17* ### **9. Seraphim – The Highest & Holiest** Seraphim stand **at the very throne of God**, continuously worshiping Him. In *Isaiah’s vision* (*Isaiah 6:1-7*), they are described as having **six wings**—two to fly, two to cover their feet, and two to cover their faces, symbolizing their humility before God. They sing: > **“Holy, holy, holy is the Lord of hosts; the whole earth is full of His glory.”** When Seraphim reappear in *Revelation*, their wings are now **covered in eyes**, representing divine omniscience. Their song shifts slightly: > *“Holy, holy, holy is the Lord God Almighty, who was and is and is to come!”* > — *Revelation 4:8* https://image.nostr.build/3495ccf6c0ba26b42d3e2b438ec19232cca148f6fbf29e5edd4129f5a198d05b.jpg Unlike other angelic beings, Seraphim do not interact with humans—they exist purely to **glorify God**. --- ## **“Be Not Afraid”** The angelic hierarchy provides a glimpse into the vast celestial order governing God’s universe. From the lowest messengers to the highest divine worshippers, each angelic being plays a unique role in the unfolding story of creation and salvation. Yet, despite their differences, there is one striking similarity across biblical encounters with angels: They often begin with a single phrase— **“Be not afraid.”**
@ c582af78:698069cc
2025-02-13 01:04:26# **The Nine Orders of Angels: A Guide to the Celestial Hierarchy** When we think of angels, we often picture winged figures in flowing robes, guiding and protecting humanity. But the biblical and theological reality is far more complex—and often stranger—than these familiar depictions. The word *angel* comes from the Greek *angelos*, meaning “messenger,” but in scripture, angels serve a wide range of roles beyond delivering divine messages. Some are warriors wielding swords and leading celestial armies, others uphold the very throne of God, and some appear as multi-winged, multi-eyed beings beyond human comprehension. To bring order to this celestial realm, theologians—most notably Thomas Aquinas—classified angels into a hierarchy of **nine types**, divided into **three orders** based on their function and proximity to God. - **The lowest order** interacts with humanity. - **The middle order** governs spiritual and cosmic forces. - **The highest order** exists solely to serve and glorify God. Today, we explore these **nine ranks of angels**—from the familiar to the truly otherworldly. --- ## **I. The Third Order: Angels Who Interact with Humanity** *(The lowest tier of angels, closest to humans, acting as messengers and protectors.)* ### **1. Angels – The Messengers** https://image.nostr.build/b6462b67e14c8780896f465b664a521cdcdef7eb4b4314669b8d219aa36964c5.jpg These are the angels most commonly associated with divine guidance. According to Aquinas, every person has a **guardian angel**—an unseen protector guiding them through life. In *Genesis 28:12*, Jacob’s vision of a ladder stretching to Heaven shows angels ascending and descending, delivering messages and fulfilling divine commands. Some, like those who visited Abraham, even appeared as ordinary men, without wings or supernatural radiance. ### **2. Archangels – The Divine Enforcers** https://image.nostr.build/af8799efb61c5a64e958450bcd5aee55d2cade931cfc5ca7f0ae8745ccd4c45a.jpg Archangels carry out the most crucial missions in scripture. Gabriel announced the birth of Jesus to Mary, while Michael led the charge against Satan in the war for Heaven. Though only **Michael** is explicitly called an archangel in the Bible, tradition assigns this title to others, including **Raphael** and **Uriel**. Archangels serve as warriors and heralds, executing God’s most urgent decrees. ### **3. Principalities – Guardians of Nations** https://image.nostr.build/bc7cd78acb656be6c946da32244bfb9ecdfe9a7d1bd80e47eca764cae4a88b95.jpg Principalities oversee nations, cities, and communities, influencing their spiritual well-being. While they are not explicitly named in scripture, *Colossians 1:16* references “thrones, dominions, principalities, and powers.” Tradition suggests that Principalities guide earthly leaders, strengthening them in times of crisis—and perhaps even aiding biblical figures like King David in battle. --- ## **II. The Second Order: The Heavenly Governors** *(These angels reside in Heaven but influence earthly affairs, ensuring divine order is maintained.)* ### **4. Powers – The Celestial Warriors** https://image.nostr.build/1768abcbaefb2d1d21654a869b356d86a45d76a82197b9568528d4d4b9f0ef69.jpg Powers act as Heaven’s **military defenders**, guarding the spiritual realm from demonic forces. They are often depicted in armor, wielding weapons as they engage in cosmic battles. According to Christian tradition, Powers also **escort souls to Heaven**, ensuring their safe passage after death. Some believe that the battle between good and evil plays out, in part, through these celestial warriors. ### **5. Virtues – The Miracle Workers** https://image.nostr.build/b9a1e52f1dd4ef0f7e7dd198d81e7cd171eede8a64a40cac8176e12a5419aeba.jpg Virtues are associated with **miracles and nature**, regulating celestial phenomena and assisting in divine interventions. In Christian tradition, the two angels present at **Christ’s Ascension** are often considered Virtues, manifesting God’s power on Earth. ### **6. Dominions – The Angelic Rulers** https://image.nostr.build/0900d97bf545736e5edc1521f46a8afbf0e93fd81e472c88a56744ff0f56ce48.jpg Dominions do not typically interact with humans directly. Instead, they act as **commanders**, overseeing lower angels and ensuring divine order is maintained. They are described as serene, wise beings, often depicted holding golden staffs and orbs, symbolizing their authority and their close relationship with God. --- ## **III. The First Order: The Angels Closest to God** *(These angels exist solely to worship and serve God, residing in the highest realms of Heaven.)* ### **7. Thrones – The Wheels of God’s Chariot** https://image.nostr.build/d9f1e465129b138f4f960ee43ee9e06ceb3fd6f57e9658cd275e1ac1576b3c02.jpg Among the most mysterious angelic beings, Thrones are described in *Ezekiel’s vision* as **wheels covered in eyes, spinning within wheels**: > *“As I looked, I saw a wheel on the ground beside each creature with its four faces... Their rims were full of eyes all around. Wherever the spirit would go, they would go, because the spirit of the living creatures was in the wheels.”* > — *Ezekiel 1:15-21* Thrones serve as **God’s chariot**, supporting His throne and executing divine justice. Their strange, abstract form symbolizes stability and divine order. ### **8. Cherubim – The Guardians of Glory** https://image.nostr.build/e921ad4c32f56ebbb8f1bcb1ca2bc6eed1c736ec896429e008fc5b71cf2fd151.jpg Cherubim have been drastically misrepresented in art. Far from the **plump, childlike figures** seen in Renaissance paintings, the **biblical Cherubim** are **fearsome beings**. In *Ezekiel 10*, they are described as having **four faces**—a man, a lion, an ox, and an eagle—along with **four wings**. They also appear in *Genesis 3:24*, where they **guard the entrance to Eden with flaming swords** after Adam and Eve’s expulsion. https://image.nostr.build/f51286d4f35d9d6e85d8559600188ecc89a0969c3985814cae56cd230ea5db00.jpg Aquinas even suggested that **Satan himself was a fallen Cherub**. This theory is supported by *Ezekiel 28*, which describes an angelic being cast down from God’s presence: > *“You were anointed as a guardian cherub... You were blameless in your ways until wickedness was found in you... So I drove you in disgrace from the mount of God, and I expelled you, guardian cherub.”* > — *Ezekiel 28:14-17* ### **9. Seraphim – The Highest & Holiest** Seraphim stand **at the very throne of God**, continuously worshiping Him. In *Isaiah’s vision* (*Isaiah 6:1-7*), they are described as having **six wings**—two to fly, two to cover their feet, and two to cover their faces, symbolizing their humility before God. They sing: > **“Holy, holy, holy is the Lord of hosts; the whole earth is full of His glory.”** When Seraphim reappear in *Revelation*, their wings are now **covered in eyes**, representing divine omniscience. Their song shifts slightly: > *“Holy, holy, holy is the Lord God Almighty, who was and is and is to come!”* > — *Revelation 4:8* https://image.nostr.build/3495ccf6c0ba26b42d3e2b438ec19232cca148f6fbf29e5edd4129f5a198d05b.jpg Unlike other angelic beings, Seraphim do not interact with humans—they exist purely to **glorify God**. --- ## **“Be Not Afraid”** The angelic hierarchy provides a glimpse into the vast celestial order governing God’s universe. From the lowest messengers to the highest divine worshippers, each angelic being plays a unique role in the unfolding story of creation and salvation. Yet, despite their differences, there is one striking similarity across biblical encounters with angels: They often begin with a single phrase— **“Be not afraid.”** @ c582af78:698069cc
2025-02-13 01:03:50## **How to Be Happy: Aristotle’s Blueprint for a Flourishing Life** Everyone wants happiness. The problem? Most people don’t actually know what happiness is. Ask someone what would make them happy, and they’ll likely mention wealth, pleasure, success, or recognition. Over 2,000 years ago, Aristotle heard the same answers—and he rejected them. According to Aristotle, happiness isn’t something you *have*, but something you *do*. True happiness—what he called *eudaimonia*—isn’t about fleeting pleasures or external rewards. It’s about living well, cultivating virtue, and engaging deeply in life’s highest pursuits. So, what’s Aristotle’s formula for happiness? It comes down to three essential steps. --- ### **The False Paths to Happiness** Aristotle observed that most people chase happiness in three common ways: **wealth, pleasure, and honor**. While each has its appeal, none can sustain true fulfillment. Take **wealth**, for example. Money provides security and opportunity, but it doesn’t guarantee satisfaction. Aristotle noted that many people who seek wealth become obsessed with accumulating it rather than using it wisely. The result? An endless chase with no real contentment. **Pleasure** is even trickier. Aristotle acknowledged that pleasure is a natural good, but he warned against making it life’s ultimate goal. Living only for pleasure leads to a cycle of chasing temporary highs without ever achieving deeper fulfillment. As Aristotle put it, this is the life of *“fatted cattle”*—comfortable, but lacking excellence. Then there’s **honor**. Recognition feels good, but it depends on the approval of others. If you live solely for status, you risk valuing recognition over real achievement. Honor for its own sake is empty unless it’s tied to genuine virtue. **Aristotle’s conclusion?** These paths don’t lead to true happiness. They are distractions, not destinations. --- ### **The True Meaning of Happiness** If wealth, pleasure, and honor aren’t enough, then what *is* happiness? To answer that, we need to understand Aristotle’s term *eudaimonia*. Unlike our modern idea of happiness as a feeling, *eudaimonia* means **flourishing**—a life of purpose, virtue, and excellence. The key difference is that **wealth, pleasure, and honor are passive**—they happen *to* you. But *eudaimonia* is **active**—it’s something you cultivate through action. In his *Nicomachean Ethics*, Aristotle defines happiness as *“the activity of the soul in accordance with virtue.”* It’s not a prize to be won, but a way of living. A great example comes from sports. A skilled athlete doesn’t just sit around feeling happy—his joy comes from being *in motion*: training, competing, improving, and fully engaging in his craft. For Aristotle, happiness works the same way. It comes from actively developing your best qualities, not passively indulging in comfort. But how do you put this into practice? --- ## **Aristotle’s 3-Step Blueprint for a Good Life** Aristotle’s guide to happiness is surprisingly practical. Here’s how to apply it: ### **1. Cultivate Virtue Through Habit** Virtue isn’t something you’re born with—it’s something you practice. Just as an athlete trains for competition, you develop virtue by repeatedly choosing good actions. Courage, patience, and wisdom don’t just appear; they become part of you through habit. As Aristotle famously said: > **“We are what we repeatedly do. Excellence, then, is not an act, but a habit.”** Want to be generous? **Give more often.** Want to be disciplined? **Practice restraint.** Over time, these actions shape your character—and character shapes happiness. ### **2. Engage Fully in Meaningful Work** Happiness isn’t found in passivity, but in action. Aristotle believed that true fulfillment comes from using your talents to their fullest extent. This applies to everything from philosophy to craftsmanship to leadership. The key is **engagement**. Think of the satisfaction a musician feels while playing at their best, or the pride of a craftsman perfecting their work. These moments—where skill, effort, and purpose align—are true happiness in action. Contrary to popular belief, happiness isn’t about doing less. **It’s about doing the right things, with full commitment.** ### **3. Seek the Right Kind of Pleasure** Aristotle didn’t reject pleasure—he just emphasized choosing the *right* kind. Lower pleasures—like eating, drinking, or binge-watching TV—may feel good in the moment but often leave you feeling empty afterward. Higher pleasures—such as learning, mastering a craft, or cultivating meaningful relationships—lead to lasting fulfillment. The goal isn’t to reject pleasure, but to **align it with virtue**. Instead of chasing immediate gratification, seek pleasures that contribute to long-term flourishing. --- ## **Happiness as a Way of Life** It’s important to understand that happiness isn’t a destination—it’s a **practice**. It’s something cultivated daily by engaging in meaningful work, growing in virtue, and living with purpose. But most importantly, **happiness isn’t about what happens to you—it’s about who you become**. By cultivating *eudaimonia*, you change the essence of your being—just as a farmer who nurtures his crops becomes stronger through his labor. True happiness isn’t a fleeting emotion, but the natural result of a life well lived. The more you nurture virtue through action, the more deeply happiness takes root—until it becomes not just something you seek, but something you embody.
@ c582af78:698069cc
2025-02-13 01:03:50## **How to Be Happy: Aristotle’s Blueprint for a Flourishing Life** Everyone wants happiness. The problem? Most people don’t actually know what happiness is. Ask someone what would make them happy, and they’ll likely mention wealth, pleasure, success, or recognition. Over 2,000 years ago, Aristotle heard the same answers—and he rejected them. According to Aristotle, happiness isn’t something you *have*, but something you *do*. True happiness—what he called *eudaimonia*—isn’t about fleeting pleasures or external rewards. It’s about living well, cultivating virtue, and engaging deeply in life’s highest pursuits. So, what’s Aristotle’s formula for happiness? It comes down to three essential steps. --- ### **The False Paths to Happiness** Aristotle observed that most people chase happiness in three common ways: **wealth, pleasure, and honor**. While each has its appeal, none can sustain true fulfillment. Take **wealth**, for example. Money provides security and opportunity, but it doesn’t guarantee satisfaction. Aristotle noted that many people who seek wealth become obsessed with accumulating it rather than using it wisely. The result? An endless chase with no real contentment. **Pleasure** is even trickier. Aristotle acknowledged that pleasure is a natural good, but he warned against making it life’s ultimate goal. Living only for pleasure leads to a cycle of chasing temporary highs without ever achieving deeper fulfillment. As Aristotle put it, this is the life of *“fatted cattle”*—comfortable, but lacking excellence. Then there’s **honor**. Recognition feels good, but it depends on the approval of others. If you live solely for status, you risk valuing recognition over real achievement. Honor for its own sake is empty unless it’s tied to genuine virtue. **Aristotle’s conclusion?** These paths don’t lead to true happiness. They are distractions, not destinations. --- ### **The True Meaning of Happiness** If wealth, pleasure, and honor aren’t enough, then what *is* happiness? To answer that, we need to understand Aristotle’s term *eudaimonia*. Unlike our modern idea of happiness as a feeling, *eudaimonia* means **flourishing**—a life of purpose, virtue, and excellence. The key difference is that **wealth, pleasure, and honor are passive**—they happen *to* you. But *eudaimonia* is **active**—it’s something you cultivate through action. In his *Nicomachean Ethics*, Aristotle defines happiness as *“the activity of the soul in accordance with virtue.”* It’s not a prize to be won, but a way of living. A great example comes from sports. A skilled athlete doesn’t just sit around feeling happy—his joy comes from being *in motion*: training, competing, improving, and fully engaging in his craft. For Aristotle, happiness works the same way. It comes from actively developing your best qualities, not passively indulging in comfort. But how do you put this into practice? --- ## **Aristotle’s 3-Step Blueprint for a Good Life** Aristotle’s guide to happiness is surprisingly practical. Here’s how to apply it: ### **1. Cultivate Virtue Through Habit** Virtue isn’t something you’re born with—it’s something you practice. Just as an athlete trains for competition, you develop virtue by repeatedly choosing good actions. Courage, patience, and wisdom don’t just appear; they become part of you through habit. As Aristotle famously said: > **“We are what we repeatedly do. Excellence, then, is not an act, but a habit.”** Want to be generous? **Give more often.** Want to be disciplined? **Practice restraint.** Over time, these actions shape your character—and character shapes happiness. ### **2. Engage Fully in Meaningful Work** Happiness isn’t found in passivity, but in action. Aristotle believed that true fulfillment comes from using your talents to their fullest extent. This applies to everything from philosophy to craftsmanship to leadership. The key is **engagement**. Think of the satisfaction a musician feels while playing at their best, or the pride of a craftsman perfecting their work. These moments—where skill, effort, and purpose align—are true happiness in action. Contrary to popular belief, happiness isn’t about doing less. **It’s about doing the right things, with full commitment.** ### **3. Seek the Right Kind of Pleasure** Aristotle didn’t reject pleasure—he just emphasized choosing the *right* kind. Lower pleasures—like eating, drinking, or binge-watching TV—may feel good in the moment but often leave you feeling empty afterward. Higher pleasures—such as learning, mastering a craft, or cultivating meaningful relationships—lead to lasting fulfillment. The goal isn’t to reject pleasure, but to **align it with virtue**. Instead of chasing immediate gratification, seek pleasures that contribute to long-term flourishing. --- ## **Happiness as a Way of Life** It’s important to understand that happiness isn’t a destination—it’s a **practice**. It’s something cultivated daily by engaging in meaningful work, growing in virtue, and living with purpose. But most importantly, **happiness isn’t about what happens to you—it’s about who you become**. By cultivating *eudaimonia*, you change the essence of your being—just as a farmer who nurtures his crops becomes stronger through his labor. True happiness isn’t a fleeting emotion, but the natural result of a life well lived. The more you nurture virtue through action, the more deeply happiness takes root—until it becomes not just something you seek, but something you embody. @ 57d1a264:69f1fee1
2025-02-13 00:28:45This past week, @erik_ and @Sushant have been working on improving the onboarding flow for [Sovran](https://sovranbitcoin.com/) bitcoin wallet. First revision on thee figma file below, would appreciate any feedback.   https://www.figma.com/design/inNLo6AaPMX26D3GumcXGC/UI%2FUX-Audit--Onboarding-User-Flow?node-id=0-1&t=Wl0EVhH5fJgYYSJI-1 If you want to review the UX audit of the current flow, see the feedback provided, and check Sushant's initial suggestions, you can do so here:  https://www.figma.com/board/Jfo4nLIKyR6lacokXze4Mv/Sovran-Onboarding-UX-Audit?node-id=0-1&t=gOZyo57zfeqxFXeB-1 originally posted at https://stacker.news/items/884272
@ 57d1a264:69f1fee1
2025-02-13 00:28:45This past week, @erik_ and @Sushant have been working on improving the onboarding flow for [Sovran](https://sovranbitcoin.com/) bitcoin wallet. First revision on thee figma file below, would appreciate any feedback.   https://www.figma.com/design/inNLo6AaPMX26D3GumcXGC/UI%2FUX-Audit--Onboarding-User-Flow?node-id=0-1&t=Wl0EVhH5fJgYYSJI-1 If you want to review the UX audit of the current flow, see the feedback provided, and check Sushant's initial suggestions, you can do so here:  https://www.figma.com/board/Jfo4nLIKyR6lacokXze4Mv/Sovran-Onboarding-UX-Audit?node-id=0-1&t=gOZyo57zfeqxFXeB-1 originally posted at https://stacker.news/items/884272 @ 4c96d763:80c3ee30
2025-02-12 23:49:24# Changes ## Daniel D’Aquino (2): - Remove rust-nostr dependency - Fix unwanted auto-scrolls related to draft saving mechanism ## William Casarin (3): - driveby compile warning fixes - home: dont show reposts for the same note more than once - reposts: add links to repost listing in timeline ## emir yorulmaz (1): - Change 'twitter' to 'X/Twitter' on README.md pushed to [damus:refs/heads/master](http://git.jb55.com/damus/commit/ec9a89ee4d388f4c706db47d2b73c298f1e268cc.html)
@ 4c96d763:80c3ee30
2025-02-12 23:49:24# Changes ## Daniel D’Aquino (2): - Remove rust-nostr dependency - Fix unwanted auto-scrolls related to draft saving mechanism ## William Casarin (3): - driveby compile warning fixes - home: dont show reposts for the same note more than once - reposts: add links to repost listing in timeline ## emir yorulmaz (1): - Change 'twitter' to 'X/Twitter' on README.md pushed to [damus:refs/heads/master](http://git.jb55.com/damus/commit/ec9a89ee4d388f4c706db47d2b73c298f1e268cc.html) @ 5579d5c0:db104ded
2025-02-12 23:41:09Most people think their metabolism is "broken" because they can't lose weight, feel sluggish, or gain fat easily. The truth? **Your metabolism isn’t broken, it’s just out of sync.** Your body doesn’t just burn calories randomly. It follows a natural **24-hour rhythm**, dictated by light exposure, movement, meal timing, and sleep. When these cues are off, your metabolism becomes dysfunctional. The good news? You don’t need to diet harder or exercise more. **You need to realign your metabolism with your body’s natural rhythm.** --- ### Why your metabolism feels “broken” Your body is designed to run on **timing signals, when to eat, when to move, when to rest**. Modern life disrupts these natural rhythms, leading to: **→ Low energy & afternoon crashes**: Skipping morning sunlight and staying indoors all day. **→ Stubborn belly fat & slow fat loss**: Eating at the wrong times, late-night snacking, and chronic stress. **→ Constant cravings & hunger:** Poor meal timing and eating foods that spike blood sugar too often. **→ Poor sleep & recovery**: Late night screen use, artificial light, and erratic bedtimes. The problem **isn’t your metabolism, it’s your environment and habits.** --- ### How to reset your metabolism naturally You don’t need extreme diets, calorie counting, or hours in the gym. Instead, **align your metabolism with your body’s natural timing signals** by focusing on these fundamentals: ### 1. Get natural light first thing in the morning Light in the first 30 minutes after waking sets your circadian rhythm (body clock), kickstarts hormone production, and improves insulin sensitivity. This simple habit helps to regulate hunger, energy, and fat-burning. **Action step:** Step outside for at least 5–10 minutes within 30 minutes of waking, no sunglasses, no contacts, only natural light exposure and take regular outdoor breaks during the day. --- ### 2. Stop eating late at night Eating late, especially high-carb/high-fat meals, signals your body to store fat instead of burning it. Late-night eating also disrupts sleep, which further impairs fat loss. **Action step:** Keep meals within a **10-12 hour eating window**, preferably between sunrise and sunset. **No snacking**. Finish your last meal **at least 3 hours before bed**. --- ### 3. Move throughout the day (Not just at the gym) Your metabolism isn’t just about burning calories, it’s about **how efficiently your body uses energy**. Sitting for long hours disrupts metabolic function, even if you work out later. **Action step:** Take a **5-minute movement break** every 1–2 hours. Stand, stretch, or better still go for a quick walk outside. --- ### 4. Prioritise deep, uninterrupted sleep Your body **burns fat and repairs muscle while you sleep**. Poor sleep increases hunger hormones (Ghrelin), prevents Leptin from working properly, and makes you crave junk food the next day. **Action step:** Dim lights after sunset, wear blue light blocking glasses, avoid screens 30-60 minutes before bed, and aim for **7.5-9 hours of quality sleep**. --- ### 5. Eat nutrient-dense foods What you eat matters, but **when** you eat it matters just as much. Front-loading protein and nutrients earlier in the day supports fat-burning and stabilises energy. **Action step:** Eat a **high-protein, nutrient-dense breakfast** and **avoid refined carbs & sugar, especially in the morning,** to prevent cravings later. --- Your metabolism isn’t broken, it’s just out of sync. Instead of obsessing over calories, **focus on realigning your body with its natural rhythms**: → **Morning sunlight** to set your metabolism for the day. → **Aligned meal timing** by eating during daylight & avoiding late-night eating. → **Frequent movement** to prevents metabolic slowdown from sitting. → **Quality sleep** which regulates fat-burning and hunger hormones. → **Nutrient-dense eating** giving your body what it needs. Fix your metabolism without dieting harder, just live in sync with how your body is designed to function. \-Chris --- If you want a simple methodical approach to fixing your metabolism, Let’s talk. **Book a free call here:** [**https://calendly.com/hello-chrispatrick**](https://calendly.com/hello-chrispatrick) **Follow me on Nostr**: [**https://primal.net/chrispatrick**](https://primal.net/chrispatrick) or [***nostr:npub124uatsq6pv74trzwvt34y4sx2z0uflhse7tkrv0pl69e8kcsfhkse30zsu***](https://primal.net/chrispatrick/npub124uatsq6pv74trzwvt34y4sx2z0uflhse7tkrv0pl69e8kcsfhkse30zsu)
@ 5579d5c0:db104ded
2025-02-12 23:41:09Most people think their metabolism is "broken" because they can't lose weight, feel sluggish, or gain fat easily. The truth? **Your metabolism isn’t broken, it’s just out of sync.** Your body doesn’t just burn calories randomly. It follows a natural **24-hour rhythm**, dictated by light exposure, movement, meal timing, and sleep. When these cues are off, your metabolism becomes dysfunctional. The good news? You don’t need to diet harder or exercise more. **You need to realign your metabolism with your body’s natural rhythm.** --- ### Why your metabolism feels “broken” Your body is designed to run on **timing signals, when to eat, when to move, when to rest**. Modern life disrupts these natural rhythms, leading to: **→ Low energy & afternoon crashes**: Skipping morning sunlight and staying indoors all day. **→ Stubborn belly fat & slow fat loss**: Eating at the wrong times, late-night snacking, and chronic stress. **→ Constant cravings & hunger:** Poor meal timing and eating foods that spike blood sugar too often. **→ Poor sleep & recovery**: Late night screen use, artificial light, and erratic bedtimes. The problem **isn’t your metabolism, it’s your environment and habits.** --- ### How to reset your metabolism naturally You don’t need extreme diets, calorie counting, or hours in the gym. Instead, **align your metabolism with your body’s natural timing signals** by focusing on these fundamentals: ### 1. Get natural light first thing in the morning Light in the first 30 minutes after waking sets your circadian rhythm (body clock), kickstarts hormone production, and improves insulin sensitivity. This simple habit helps to regulate hunger, energy, and fat-burning. **Action step:** Step outside for at least 5–10 minutes within 30 minutes of waking, no sunglasses, no contacts, only natural light exposure and take regular outdoor breaks during the day. --- ### 2. Stop eating late at night Eating late, especially high-carb/high-fat meals, signals your body to store fat instead of burning it. Late-night eating also disrupts sleep, which further impairs fat loss. **Action step:** Keep meals within a **10-12 hour eating window**, preferably between sunrise and sunset. **No snacking**. Finish your last meal **at least 3 hours before bed**. --- ### 3. Move throughout the day (Not just at the gym) Your metabolism isn’t just about burning calories, it’s about **how efficiently your body uses energy**. Sitting for long hours disrupts metabolic function, even if you work out later. **Action step:** Take a **5-minute movement break** every 1–2 hours. Stand, stretch, or better still go for a quick walk outside. --- ### 4. Prioritise deep, uninterrupted sleep Your body **burns fat and repairs muscle while you sleep**. Poor sleep increases hunger hormones (Ghrelin), prevents Leptin from working properly, and makes you crave junk food the next day. **Action step:** Dim lights after sunset, wear blue light blocking glasses, avoid screens 30-60 minutes before bed, and aim for **7.5-9 hours of quality sleep**. --- ### 5. Eat nutrient-dense foods What you eat matters, but **when** you eat it matters just as much. Front-loading protein and nutrients earlier in the day supports fat-burning and stabilises energy. **Action step:** Eat a **high-protein, nutrient-dense breakfast** and **avoid refined carbs & sugar, especially in the morning,** to prevent cravings later. --- Your metabolism isn’t broken, it’s just out of sync. Instead of obsessing over calories, **focus on realigning your body with its natural rhythms**: → **Morning sunlight** to set your metabolism for the day. → **Aligned meal timing** by eating during daylight & avoiding late-night eating. → **Frequent movement** to prevents metabolic slowdown from sitting. → **Quality sleep** which regulates fat-burning and hunger hormones. → **Nutrient-dense eating** giving your body what it needs. Fix your metabolism without dieting harder, just live in sync with how your body is designed to function. \-Chris --- If you want a simple methodical approach to fixing your metabolism, Let’s talk. **Book a free call here:** [**https://calendly.com/hello-chrispatrick**](https://calendly.com/hello-chrispatrick) **Follow me on Nostr**: [**https://primal.net/chrispatrick**](https://primal.net/chrispatrick) or [***nostr:npub124uatsq6pv74trzwvt34y4sx2z0uflhse7tkrv0pl69e8kcsfhkse30zsu***](https://primal.net/chrispatrick/npub124uatsq6pv74trzwvt34y4sx2z0uflhse7tkrv0pl69e8kcsfhkse30zsu) @ 3b7fc823:e194354f
2025-02-12 23:13:57**Staying Digitally Safe in Airports: A Comprehensive Guide** Airports are hubs of activity, but they’re also places where your digital security can be at risk. From public Wi-Fi to potential device thefts, staying safe while traveling can feel overwhelming. However, with the right knowledge and precautions, you can protect yourself and enjoy your journey stress-free. Let’s dive into how to stay digitally safe in airports while traveling. --- ### **Understanding the Risks** 1. **Public Wi-Fi Vulnerabilities:** - Airports often offer free Wi-Fi, but these networks can be unsecured or insecure. Hackers may use these networks to intercept sensitive data. - Avoid using public Wi-Fi for personal banking, shopping, or handling sensitive information. 2. **Device Theft:** - High-traffic areas like security checkpoints, gates, and lounges are hotspots for device thefts. Always keep your devices in secure locations, such as carry-on bags or locked briefcases. 3. **Malware and Phishing Attacks:** - Some airports may have phishing attempts or malware distributed via pop-ups, email, or malicious websites. 4. **Physical Surveillance:** - In some cases, law enforcement or security personnel may monitor your activities. Always be mindful of your surroundings to avoid unintended data exposure. --- ### **Best Practices for Staying Digitally Safe in Airports** 1. **Use a VPN for Extra Security:** - Even secure airport Wi-Fi can expose your data if not encrypted. Use a reputable Virtual Private Network (VPN) to encrypt your internet traffic and protect your privacy. - Always ensure your VPN is active when using public Wi-Fi. 2. **Minimize Sensitive Data on Public Devices:** - Avoid carrying devices with sensitive information like passwords, credit card details, or personal identification numbers (PIIs). 3. **Encrypt Your Data:** - Enable encryption for all your devices to protect data stored locally or in the cloud. Ensure your operating system and apps are updated with the latest security patches. 4. **Secure Your Devices:** - Use cable locks or secure cases to lock down laptops, tablets, and smartphones when not in use. - Remove screensavers that display your device passcode to prevent unauthorized access. 5. **Keep Antivirus Software Updated:** - Install and maintain up-to-date antivirus software on all devices. This helps detect and remove malicious software (malware) that may be installed through compromised networks or phishing attempts. 6. **Avoid Plugging Into Public USB charging stations:** - Refrain from using public USB ports or charging stations unless you know they’re secure. Malware can spread via these points. 7. **Use Caution With Lost and Found:** - If you find a device or drop one accidentally, avoid using lost and found kiosks to pick it up. Instead, contact airport security for assistance in safely retrieving your property without exposing it to potential thieves. 8. **Stay Alert to Security Alerts:** - Pay attention to announcements over the airport’s PA system regarding suspicious activity or security alerts. Follow any instructions provided by airport staff. 9. **Monitor Your Accounts Remotely:** - If you suspect something is wrong (e.g., unusual transactions on your credit card), check your financial accounts immediately upon arriving at your destination. Notify your bank of potential fraudulent activity and report it to the authorities if necessary. --- ### **Additional Tips for Airport Safety** 1. **Use a Portable Power Bank:** - Keep your devices charged so you don’t rely on public charging stations, which may be compromised. 2. **Travel with Backup Devices:** - Always bring an extra SIM card, USB drive, or cloud storage to backup important data. This ensures you can access critical information even if your primary device is lost or damaged. 3. **Avoid Sharing Personal Information Over Earphone Rentals:** - Refrain from using earphones rented from airport kiosks that may record or intercept your conversations. Stick to your own headphones or those provided by the airline. 4. **Use Airport Lounges Wisely:** - If you’re using an airline lounge, avoid discussing sensitive information in public areas where it could be overheard. 5. **Keep Your Luggage in Sight:** - Never leave your checked luggage unattended, as it may contain devices or documents with sensitive information. 6. **Plan for Data Loss:** - Before leaving home, make a backup of all important files and photos on an external drive or cloud storage. This way, you can restore them if something goes wrong during your trip. --- ### **What to Do If Something Goes Wrong** 1. **Report Suspected Security Incidents:** - If you notice unusual activity on your devices or suspect a security breach, inform airport security immediately. 2. **Contact Your Financial Institutions:** - If you believe your financial information has been compromised, contact your bank or credit card provider to freeze your account and monitor for fraudulent charges. 3. **File a Police Report:** - In cases of theft or suspected unauthorized access, file a report with local authorities and provide evidence (if available). 4. **Use Travel Insurance:** - Check if your travel insurance covers theft, fraud, or data breaches. Submit a claim if you’re covered. --- ### **Extra Security Measures forTech-Savvy Travelers** - **Two-Factor Authentication (2FA):** Enable 2FA for all your critical accounts before leaving home. - **Biometric Locks:** Use biometric locks on your devices to add an extra layer of security. - **Incident Response Plan:** Create a plan in advance for what to do if your devices are lost or compromised. --- ### **Final Tips** - Always prioritize secure practices, even in seemingly safe environments like airports. - Travel light but keep your important documents and devices close at hand. - Remember that staying digitally safe is just as important as physical safety during your travels. By following these tips, you can enjoy your trip with peace of mind, knowing your data and devices are protected. Happy traveling! --- Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero 82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
@ 3b7fc823:e194354f
2025-02-12 23:13:57**Staying Digitally Safe in Airports: A Comprehensive Guide** Airports are hubs of activity, but they’re also places where your digital security can be at risk. From public Wi-Fi to potential device thefts, staying safe while traveling can feel overwhelming. However, with the right knowledge and precautions, you can protect yourself and enjoy your journey stress-free. Let’s dive into how to stay digitally safe in airports while traveling. --- ### **Understanding the Risks** 1. **Public Wi-Fi Vulnerabilities:** - Airports often offer free Wi-Fi, but these networks can be unsecured or insecure. Hackers may use these networks to intercept sensitive data. - Avoid using public Wi-Fi for personal banking, shopping, or handling sensitive information. 2. **Device Theft:** - High-traffic areas like security checkpoints, gates, and lounges are hotspots for device thefts. Always keep your devices in secure locations, such as carry-on bags or locked briefcases. 3. **Malware and Phishing Attacks:** - Some airports may have phishing attempts or malware distributed via pop-ups, email, or malicious websites. 4. **Physical Surveillance:** - In some cases, law enforcement or security personnel may monitor your activities. Always be mindful of your surroundings to avoid unintended data exposure. --- ### **Best Practices for Staying Digitally Safe in Airports** 1. **Use a VPN for Extra Security:** - Even secure airport Wi-Fi can expose your data if not encrypted. Use a reputable Virtual Private Network (VPN) to encrypt your internet traffic and protect your privacy. - Always ensure your VPN is active when using public Wi-Fi. 2. **Minimize Sensitive Data on Public Devices:** - Avoid carrying devices with sensitive information like passwords, credit card details, or personal identification numbers (PIIs). 3. **Encrypt Your Data:** - Enable encryption for all your devices to protect data stored locally or in the cloud. Ensure your operating system and apps are updated with the latest security patches. 4. **Secure Your Devices:** - Use cable locks or secure cases to lock down laptops, tablets, and smartphones when not in use. - Remove screensavers that display your device passcode to prevent unauthorized access. 5. **Keep Antivirus Software Updated:** - Install and maintain up-to-date antivirus software on all devices. This helps detect and remove malicious software (malware) that may be installed through compromised networks or phishing attempts. 6. **Avoid Plugging Into Public USB charging stations:** - Refrain from using public USB ports or charging stations unless you know they’re secure. Malware can spread via these points. 7. **Use Caution With Lost and Found:** - If you find a device or drop one accidentally, avoid using lost and found kiosks to pick it up. Instead, contact airport security for assistance in safely retrieving your property without exposing it to potential thieves. 8. **Stay Alert to Security Alerts:** - Pay attention to announcements over the airport’s PA system regarding suspicious activity or security alerts. Follow any instructions provided by airport staff. 9. **Monitor Your Accounts Remotely:** - If you suspect something is wrong (e.g., unusual transactions on your credit card), check your financial accounts immediately upon arriving at your destination. Notify your bank of potential fraudulent activity and report it to the authorities if necessary. --- ### **Additional Tips for Airport Safety** 1. **Use a Portable Power Bank:** - Keep your devices charged so you don’t rely on public charging stations, which may be compromised. 2. **Travel with Backup Devices:** - Always bring an extra SIM card, USB drive, or cloud storage to backup important data. This ensures you can access critical information even if your primary device is lost or damaged. 3. **Avoid Sharing Personal Information Over Earphone Rentals:** - Refrain from using earphones rented from airport kiosks that may record or intercept your conversations. Stick to your own headphones or those provided by the airline. 4. **Use Airport Lounges Wisely:** - If you’re using an airline lounge, avoid discussing sensitive information in public areas where it could be overheard. 5. **Keep Your Luggage in Sight:** - Never leave your checked luggage unattended, as it may contain devices or documents with sensitive information. 6. **Plan for Data Loss:** - Before leaving home, make a backup of all important files and photos on an external drive or cloud storage. This way, you can restore them if something goes wrong during your trip. --- ### **What to Do If Something Goes Wrong** 1. **Report Suspected Security Incidents:** - If you notice unusual activity on your devices or suspect a security breach, inform airport security immediately. 2. **Contact Your Financial Institutions:** - If you believe your financial information has been compromised, contact your bank or credit card provider to freeze your account and monitor for fraudulent charges. 3. **File a Police Report:** - In cases of theft or suspected unauthorized access, file a report with local authorities and provide evidence (if available). 4. **Use Travel Insurance:** - Check if your travel insurance covers theft, fraud, or data breaches. Submit a claim if you’re covered. --- ### **Extra Security Measures forTech-Savvy Travelers** - **Two-Factor Authentication (2FA):** Enable 2FA for all your critical accounts before leaving home. - **Biometric Locks:** Use biometric locks on your devices to add an extra layer of security. - **Incident Response Plan:** Create a plan in advance for what to do if your devices are lost or compromised. --- ### **Final Tips** - Always prioritize secure practices, even in seemingly safe environments like airports. - Travel light but keep your important documents and devices close at hand. - Remember that staying digitally safe is just as important as physical safety during your travels. By following these tips, you can enjoy your trip with peace of mind, knowing your data and devices are protected. Happy traveling! --- Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero 82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1 @ 000002de:c05780a7
2025-02-12 22:41:17The absolute embarrassment the Chiefs were subjected to... is the end of the their dominance? Of course they have a ton of talent and will win and maybe get back the Super Bowl this game really exposed them. Its one thing to lose to a great team like the Eagles. Its another to be destroyed so fully. When I think about this game its not just on one person. Its coaching and players. I'm just wondering about the impact on the league watching this. Anyone who has played sports knows that a ton of it is mental. Teams can defeat themselves mentally. Does this defeat tell the league, yeah they aren't that good. What do you think? Edit: When I say "done", I mean the dynasty. I don't mean they are gonna have a losing record next year. originally posted at https://stacker.news/items/884169
@ 000002de:c05780a7
2025-02-12 22:41:17The absolute embarrassment the Chiefs were subjected to... is the end of the their dominance? Of course they have a ton of talent and will win and maybe get back the Super Bowl this game really exposed them. Its one thing to lose to a great team like the Eagles. Its another to be destroyed so fully. When I think about this game its not just on one person. Its coaching and players. I'm just wondering about the impact on the league watching this. Anyone who has played sports knows that a ton of it is mental. Teams can defeat themselves mentally. Does this defeat tell the league, yeah they aren't that good. What do you think? Edit: When I say "done", I mean the dynasty. I don't mean they are gonna have a losing record next year. originally posted at https://stacker.news/items/884169 @ 000002de:c05780a7
2025-02-12 22:25:06Honest question. I think he's a great TE but... haven't watched him a ton. I get a feeling he's overrated. Maybe not though. I watched him during the big game and was kinda surprised by his lack luster performance. He really seemed different to me. Since then I've seen video of him not blocking for his QB and not really playing hard. Like he gave up. Does he really have a rep of not blocking? He looks pretty terrible on film. Now, I know I'm a Kittle fan and he is famously great at blocking and takes pride in it. Maybe I'm just using Kittle as the ruler and maybe that's not fair. Also, I loved watching KC get destroyed so factor that in :) originally posted at https://stacker.news/items/884156
@ 000002de:c05780a7
2025-02-12 22:25:06Honest question. I think he's a great TE but... haven't watched him a ton. I get a feeling he's overrated. Maybe not though. I watched him during the big game and was kinda surprised by his lack luster performance. He really seemed different to me. Since then I've seen video of him not blocking for his QB and not really playing hard. Like he gave up. Does he really have a rep of not blocking? He looks pretty terrible on film. Now, I know I'm a Kittle fan and he is famously great at blocking and takes pride in it. Maybe I'm just using Kittle as the ruler and maybe that's not fair. Also, I loved watching KC get destroyed so factor that in :) originally posted at https://stacker.news/items/884156 @ 9673b322:1b75ee9e
2025-02-12 21:50:25This is my test document for nostr publish Although Sainsbury's was already in the midst of a plan to save £1bn over the next few years, the rise in employer's National Insurance contributions set out in the Budget has also been a factor in this latest restructuring plan. ### Add some text this is is a test 
@ 9673b322:1b75ee9e
2025-02-12 21:50:25This is my test document for nostr publish Although Sainsbury's was already in the midst of a plan to save £1bn over the next few years, the rise in employer's National Insurance contributions set out in the Budget has also been a factor in this latest restructuring plan. ### Add some text this is is a test  @ d57360cb:4fe7d935
2025-02-12 19:10:53What’s the difference between the mind that dreams and the mind that you experience reality with? This is a question that floored me when I first began to contemplate it. When I’m in my waking life going about my day to day, I have millions of thoughts flowing through my brain. These thoughts are creating the reality I inhabit. I follow them and live in my version of the world. These thoughts construct my world, they revolve around society, my place in it, the people around me, and the entire world. In that world are millions of stories that connect one structure to another. This is how we live our lives, we create stories, fantasies, heroes, and villains. One person could paint someone as a hero and another can paint them as a villain. So what is the difference between my dreams and reality? When I dream I’m met with vivid images, structures and stories that seem as real as the life I live. I’ve experienced the same features in dreams as I have in reality. In Lucid dreaming a person has the ability to control a dream, they can alter it and mentally experience whatever their mind conjures up. What if it’s the same in ‘reality’. What if reality is as flimsy as dreams. What if the stories you currently told yourself about your life, or the world you live in were wrong. What if you pushed on the flimsy walls of this ‘reality’. Maybe you should give them a push and see if they crumble or stand tall.
@ d57360cb:4fe7d935
2025-02-12 19:10:53What’s the difference between the mind that dreams and the mind that you experience reality with? This is a question that floored me when I first began to contemplate it. When I’m in my waking life going about my day to day, I have millions of thoughts flowing through my brain. These thoughts are creating the reality I inhabit. I follow them and live in my version of the world. These thoughts construct my world, they revolve around society, my place in it, the people around me, and the entire world. In that world are millions of stories that connect one structure to another. This is how we live our lives, we create stories, fantasies, heroes, and villains. One person could paint someone as a hero and another can paint them as a villain. So what is the difference between my dreams and reality? When I dream I’m met with vivid images, structures and stories that seem as real as the life I live. I’ve experienced the same features in dreams as I have in reality. In Lucid dreaming a person has the ability to control a dream, they can alter it and mentally experience whatever their mind conjures up. What if it’s the same in ‘reality’. What if reality is as flimsy as dreams. What if the stories you currently told yourself about your life, or the world you live in were wrong. What if you pushed on the flimsy walls of this ‘reality’. Maybe you should give them a push and see if they crumble or stand tall. @ 5d4b6c8d:8a1c1ee3
2025-02-12 18:36:48Going off of memory, because I forgot to do this in the morning. The last thing I ate were Costco samples yesterday afternoon and then I didn't eat again until lunch today. I'm pretty sure those two things were about 20 hours apart. ## Score Card Day 1: 14 hour fast (13 dry) Day 2: 15 hour fast (14 dry) Day 3: 17 hours (16 dry) Day 4: 18 hours (17 dry) Day 5: 18 hours (16 dry) Day 6: 19 hours (16 dry) Day 7: 16 hours (15 dry) Day 8: 18 hours (17 dry) Day 9: 17 hours (17 dry) Day 10: 15 hours (13 dry) Day 11: 20 hours (19 dry) Day 12: 20 hours (17 dry) This winter storm is going to make getting my steps in a pain, but there's no way I'm letting myself lose the sats that I staked on the challenge. originally posted at https://stacker.news/items/884000
@ 5d4b6c8d:8a1c1ee3
2025-02-12 18:36:48Going off of memory, because I forgot to do this in the morning. The last thing I ate were Costco samples yesterday afternoon and then I didn't eat again until lunch today. I'm pretty sure those two things were about 20 hours apart. ## Score Card Day 1: 14 hour fast (13 dry) Day 2: 15 hour fast (14 dry) Day 3: 17 hours (16 dry) Day 4: 18 hours (17 dry) Day 5: 18 hours (16 dry) Day 6: 19 hours (16 dry) Day 7: 16 hours (15 dry) Day 8: 18 hours (17 dry) Day 9: 17 hours (17 dry) Day 10: 15 hours (13 dry) Day 11: 20 hours (19 dry) Day 12: 20 hours (17 dry) This winter storm is going to make getting my steps in a pain, but there's no way I'm letting myself lose the sats that I staked on the challenge. originally posted at https://stacker.news/items/884000 @ 2e8970de:63345c7a
2025-02-12 17:50:27 originally posted at https://stacker.news/items/883959
@ 2e8970de:63345c7a
2025-02-12 17:50:27 originally posted at https://stacker.news/items/883959 @ 8d34bd24:414be32b
2025-02-12 17:38:19All of us who have truly put our faith in the Lord Jesus Christ want to serve Him, but we all live busy lives. We all get distracted by making a living, taking care of our families, and other good things, but too often we spend so much time on the good that we miss out on the best (see “[Don’t Be Like Martha](https://trustjesus.substack.com/p/dont-be-like-martha)”). In this previous post, I wrote about how we don’t want to live. In this post, I’ll write about what the Bible says about living a life wholly devoted to God. Many of us wonder, “Are we fully serving God if we aren’t in full time ministry, if we aren’t a pastor/priest, missionary, or if we don’t work for a Christian ministry?” There are many ways we can serve God. Sometimes we are called to a Christian “job,” but other times we serve God in other ways. > Let the word of Christ richly dwell within you, with all wisdom teaching and admonishing one another with psalms and hymns and spiritual songs, singing with thankfulness in your hearts to God. **Whatever you do in word or deed, do all in the name of the Lord Jesus, giving thanks through Him to God the Father**. (Colossians 3:16-17) {emphasis mine} The most important thing is that everything we do has a godly focus. We should follow God’s design for marriage and family. We should disciple our children to know and grow in Jesus. We should witness to those with whom we come in contact. We should give to support those who are working in full-time ministry. Even our jobs can be done in service to the Lord, no matter how trivial or unrelated that job might seem. > **Whatever you do, do your work heartily, as for the Lord rather than for men**, knowing that from the Lord you will receive the reward of the inheritance. It is the Lord Christ whom you serve. (Colossians 3:23-24) {emphasis mine} I’m an employer. I see the work ethic, or more often the lack of work ethic, in people. I notice those who work hard and always give their best versus those who do the minimum they need to do to keep their job. When a person lets everyone around them know that they are a Christian and then they work harder than everyone else and they are willing to do the undesirable tasks that need to be done, this is noticed and is a good witness. Sadly, too often Christians are known for not working as hard and not going the extra mile. These Christians give Jesus and all Christians a bad name. Whatever job God has given you, do it to the best of your ability. Do the extra task; do the undesirable task; do the task that should’ve been done by someone else. Put in the extra effort even if nobody seems to notice. In most case, even if you aren’t praised, appreciated, or appropriately rewarded, people do notice and your witness is enhanced. In all cases, Jesus notices and you will be rewarded in heaven for representing Him faithfully. > Whether, then, you eat or drink or whatever you do, **do all to the glory of God**. (1 Corinthians 10:31) {emphasis mine} We are to do everything we do to the God’s glory. The way we work should glorify God. The way we eat and drink should glorify God. The way we do rest and entertainment should glorify God. The way we interact with others should glorify God. We were designed to glorify God. Too often we get busy doing life and leave God out of it. It isn’t that we are doing some terrible sin, but it is always wrong to leave God out of our life. We can even do Christian ministry and get so busy doing “God’s work” that we leave God out of it. This can be disastrous and definitely will damage ministry effectiveness. In everything we do, we should listen to God’s leading, whether through Bible reading, prayer, or being still and listening. > The plans of the heart belong to man,\ > But the answer of the tongue is from the Lord.\ > All the ways of a man are clean in his own sight,\ > But the Lord weighs the motives.\ ****Commit your works to the Lord\ > And your plans will be established**. (Proverbs 16:1-3) {emphasis mine} Part of doing everything in and to the Lord is changing our hearts and minds. Psalm 37 lists several actions we can take in serving the Lord and becoming more like Him. > **Delight yourself in the Lord**;\ > And He will give you the desires of your heart.\ ****Commit your way to the Lord**,\ ****Trust also in Him**, and He will do it.\ > He will bring forth your righteousness as the light\ > And your judgment as the noonday.\ ****Rest in the Lord and wait patiently for Him**;\ ****Do not fret** because of him who prospers in his way,\ > Because of the man who carries out wicked schemes.\ ****Cease from anger and forsake wrath**;\ > Do not fret; it leads only to evildoing. (Psalm 37:4-8) {emphasis mine} If we delight in the Lord, commit our way to the Lord, trust in Him, rest in the Lord, and wait patiently for the Lord, we will be in the right mind to serve Him in all that we do. It will also help us avoid the things that draw us away from the Lord. We are called to not fret, to cease from anger, and to forsake wrath. Fretting, anger, and wrath hurt our witness and draw us away from God. They are a sign that our hearts are not in tune with God and that we need to turn back to Him. They are a sign that we are not trusting in Him nor are we following His will. --- Sometimes believers wonder if they are succeeding in doing anything for the Lord because they are shy and not good at witnessing or because they have personal circumstances (like sickness of themselves or their family members) that don’t allow them to do much. That doesn’t mean there is nothing these believers can do. We can support those doing the mission of God. We can give money to support missionaries, churches, and Christian ministries. We can house a missionary while they are on break. We can do behind the scenes tasks like cleaning, accounting, organizing, planning, etc. Most importantly, we can all pray. Prayer should be a constant part of every day, whether we are infirm and unable to leave our bed, whether we are so busy we don’t have five minutes to sit and take a break, or whether we are in full time Christian ministry. We can’t faithfully serve God without prayer. > Beloved, **you are acting faithfully in whatever you accomplish for the brethren**, and especially *when they are* strangers; and they have testified to your love before the church. You will do well to send them on their way in a manner worthy of God. For they went out for the sake of the Name, accepting nothing from the Gentiles. Therefore **we ought to support such men, so that we may be fellow workers with the truth**. (3 John 1:5-8) {emphasis mine} Anyone who supports those in ministry will receive similar rewards to those in ministry because they are all working together to fulfill God’s will. > He who receives a prophet in the name of a prophet shall receive a prophet’s reward; and he who receives a righteous man in the name of a righteous man shall receive a righteous man’s reward. (Matthew 10:41) We often feel like we are failing God. We feel that we are making zero difference for the kingdom. If you are not growing in your faith, knowledge, and relationship with God, there may be some truth in this, but we also may be listening to the accuser, Satan. Keep in mind that every little thing you do for Jesus or for others, because of your faith in Jesus, is counted as faithful service to Him. > “Then the King will say to those on His right, ‘Come, you who are blessed of My Father, inherit the kingdom prepared for you from the foundation of the world. For I was hungry, and you gave Me something to eat; I was thirsty, and you gave Me something to drink; I was a stranger, and you invited Me in; naked, and you clothed Me; I was sick, and you visited Me; I was in prison, and you came to Me.’ Then the righteous will answer Him, ‘Lord, when did we see You hungry, and feed You, or thirsty, and give You something to drink? And when did we see You a stranger, and invite You in, or naked, and clothe You? When did we see You sick, or in prison, and come to You?’ The King will answer and say to them, ‘**Truly I say to you, to the extent that you did it to one of these brothers of Mine, even the least of them, you did it to Me**.’ (Matthew 25:34-40) {emphasis mine} Turn to Jesus. Pray to Jesus. Read His word —the Bible. Make Him a part of everything you do. Follow His leading. Join God in what He is doing. May God bless you and lead you in the path He designed you to take. Trust Jesus.
@ 8d34bd24:414be32b
2025-02-12 17:38:19All of us who have truly put our faith in the Lord Jesus Christ want to serve Him, but we all live busy lives. We all get distracted by making a living, taking care of our families, and other good things, but too often we spend so much time on the good that we miss out on the best (see “[Don’t Be Like Martha](https://trustjesus.substack.com/p/dont-be-like-martha)”). In this previous post, I wrote about how we don’t want to live. In this post, I’ll write about what the Bible says about living a life wholly devoted to God. Many of us wonder, “Are we fully serving God if we aren’t in full time ministry, if we aren’t a pastor/priest, missionary, or if we don’t work for a Christian ministry?” There are many ways we can serve God. Sometimes we are called to a Christian “job,” but other times we serve God in other ways. > Let the word of Christ richly dwell within you, with all wisdom teaching and admonishing one another with psalms and hymns and spiritual songs, singing with thankfulness in your hearts to God. **Whatever you do in word or deed, do all in the name of the Lord Jesus, giving thanks through Him to God the Father**. (Colossians 3:16-17) {emphasis mine} The most important thing is that everything we do has a godly focus. We should follow God’s design for marriage and family. We should disciple our children to know and grow in Jesus. We should witness to those with whom we come in contact. We should give to support those who are working in full-time ministry. Even our jobs can be done in service to the Lord, no matter how trivial or unrelated that job might seem. > **Whatever you do, do your work heartily, as for the Lord rather than for men**, knowing that from the Lord you will receive the reward of the inheritance. It is the Lord Christ whom you serve. (Colossians 3:23-24) {emphasis mine} I’m an employer. I see the work ethic, or more often the lack of work ethic, in people. I notice those who work hard and always give their best versus those who do the minimum they need to do to keep their job. When a person lets everyone around them know that they are a Christian and then they work harder than everyone else and they are willing to do the undesirable tasks that need to be done, this is noticed and is a good witness. Sadly, too often Christians are known for not working as hard and not going the extra mile. These Christians give Jesus and all Christians a bad name. Whatever job God has given you, do it to the best of your ability. Do the extra task; do the undesirable task; do the task that should’ve been done by someone else. Put in the extra effort even if nobody seems to notice. In most case, even if you aren’t praised, appreciated, or appropriately rewarded, people do notice and your witness is enhanced. In all cases, Jesus notices and you will be rewarded in heaven for representing Him faithfully. > Whether, then, you eat or drink or whatever you do, **do all to the glory of God**. (1 Corinthians 10:31) {emphasis mine} We are to do everything we do to the God’s glory. The way we work should glorify God. The way we eat and drink should glorify God. The way we do rest and entertainment should glorify God. The way we interact with others should glorify God. We were designed to glorify God. Too often we get busy doing life and leave God out of it. It isn’t that we are doing some terrible sin, but it is always wrong to leave God out of our life. We can even do Christian ministry and get so busy doing “God’s work” that we leave God out of it. This can be disastrous and definitely will damage ministry effectiveness. In everything we do, we should listen to God’s leading, whether through Bible reading, prayer, or being still and listening. > The plans of the heart belong to man,\ > But the answer of the tongue is from the Lord.\ > All the ways of a man are clean in his own sight,\ > But the Lord weighs the motives.\ ****Commit your works to the Lord\ > And your plans will be established**. (Proverbs 16:1-3) {emphasis mine} Part of doing everything in and to the Lord is changing our hearts and minds. Psalm 37 lists several actions we can take in serving the Lord and becoming more like Him. > **Delight yourself in the Lord**;\ > And He will give you the desires of your heart.\ ****Commit your way to the Lord**,\ ****Trust also in Him**, and He will do it.\ > He will bring forth your righteousness as the light\ > And your judgment as the noonday.\ ****Rest in the Lord and wait patiently for Him**;\ ****Do not fret** because of him who prospers in his way,\ > Because of the man who carries out wicked schemes.\ ****Cease from anger and forsake wrath**;\ > Do not fret; it leads only to evildoing. (Psalm 37:4-8) {emphasis mine} If we delight in the Lord, commit our way to the Lord, trust in Him, rest in the Lord, and wait patiently for the Lord, we will be in the right mind to serve Him in all that we do. It will also help us avoid the things that draw us away from the Lord. We are called to not fret, to cease from anger, and to forsake wrath. Fretting, anger, and wrath hurt our witness and draw us away from God. They are a sign that our hearts are not in tune with God and that we need to turn back to Him. They are a sign that we are not trusting in Him nor are we following His will. --- Sometimes believers wonder if they are succeeding in doing anything for the Lord because they are shy and not good at witnessing or because they have personal circumstances (like sickness of themselves or their family members) that don’t allow them to do much. That doesn’t mean there is nothing these believers can do. We can support those doing the mission of God. We can give money to support missionaries, churches, and Christian ministries. We can house a missionary while they are on break. We can do behind the scenes tasks like cleaning, accounting, organizing, planning, etc. Most importantly, we can all pray. Prayer should be a constant part of every day, whether we are infirm and unable to leave our bed, whether we are so busy we don’t have five minutes to sit and take a break, or whether we are in full time Christian ministry. We can’t faithfully serve God without prayer. > Beloved, **you are acting faithfully in whatever you accomplish for the brethren**, and especially *when they are* strangers; and they have testified to your love before the church. You will do well to send them on their way in a manner worthy of God. For they went out for the sake of the Name, accepting nothing from the Gentiles. Therefore **we ought to support such men, so that we may be fellow workers with the truth**. (3 John 1:5-8) {emphasis mine} Anyone who supports those in ministry will receive similar rewards to those in ministry because they are all working together to fulfill God’s will. > He who receives a prophet in the name of a prophet shall receive a prophet’s reward; and he who receives a righteous man in the name of a righteous man shall receive a righteous man’s reward. (Matthew 10:41) We often feel like we are failing God. We feel that we are making zero difference for the kingdom. If you are not growing in your faith, knowledge, and relationship with God, there may be some truth in this, but we also may be listening to the accuser, Satan. Keep in mind that every little thing you do for Jesus or for others, because of your faith in Jesus, is counted as faithful service to Him. > “Then the King will say to those on His right, ‘Come, you who are blessed of My Father, inherit the kingdom prepared for you from the foundation of the world. For I was hungry, and you gave Me something to eat; I was thirsty, and you gave Me something to drink; I was a stranger, and you invited Me in; naked, and you clothed Me; I was sick, and you visited Me; I was in prison, and you came to Me.’ Then the righteous will answer Him, ‘Lord, when did we see You hungry, and feed You, or thirsty, and give You something to drink? And when did we see You a stranger, and invite You in, or naked, and clothe You? When did we see You sick, or in prison, and come to You?’ The King will answer and say to them, ‘**Truly I say to you, to the extent that you did it to one of these brothers of Mine, even the least of them, you did it to Me**.’ (Matthew 25:34-40) {emphasis mine} Turn to Jesus. Pray to Jesus. Read His word —the Bible. Make Him a part of everything you do. Follow His leading. Join God in what He is doing. May God bless you and lead you in the path He designed you to take. Trust Jesus. @ 88cc134b:5ae99079
2025-02-12 17:23:02aaaaaa
@ 88cc134b:5ae99079
2025-02-12 17:23:02aaaaaa @ d61f3bc5:0da6ef4a
2025-02-12 16:57:44Micropayments on the Internet have been theorized for decades. However, it wasn’t until the emergence of Nostr that we’ve finally seen them deployed at scale. Nostr is still in its infancy, yet we are already witnessing an explosion of apps built on top of this open protocol. And most of them are featuring zaps! With the recent Primal 2.1 release, Nostr developers now have the option to enhance the experience for their users by integrating a Nostr-powered bitcoin wallet. There is no doubt that micropayments add a new dimension to consumer apps. The incumbents have realized this and are rushing to add payments to their closed platforms. It won't be long before apps that don’t include built-in payments feel dated or outright broken. The question is not if apps of the future will have built-in payments, but what *kind* of payments they will be. Given that open networks have a tendency to win, our bet is that apps of the future will be powered by Bitcoin. Let’s see how Primal can help. ## Primal Wallet Our vision for Primal Wallet is simple: deliver the smoothest transactional bitcoin wallet, endowed with expert Nostr skills. The wallet leverages Nostr’s open social graph as a de facto public lightning directory, while offering the highest level of user experience for Nostr’s rich content. For example, the user can scroll through the transaction list, select a zap, and drill straight into the conversation thread where the zap originated. The whole flow feels perfectly natural.  Since we launched Primal Wallet in December 2023, the user response has been incredibly positive. People love the idea of being able to post something on Nostr, get zaps from plebs around the world, then buy a coffee or a meal with those sats - all from the same app. Having a bitcoin wallet with social skills resonated strongly with users, so Primal Wallet grew rapidly in popularity and usage. Since the launch, we have processed **1,338,460** transactions, with **238,916** just in the past month alone. This rivals some of the leading bitcoin wallets, and we are just getting started! We hear from many bitcoin OGs that they are using Primal Wallet as their transactional daily driver. Bullish. All this is great, but something has been missing. Our users demanded the ability to connect Primal Wallet to other Nostr apps, so they can zap from anywhere in Nostr’s growing ecosystem. ## Zapping from Any Nostr App For an existing Primal user, connecting the wallet to a new Nostr app can now be done in two clicks. Let’s take a look at how this is done from Olas, one of the most exciting new apps on Nostr:  Yes. Click, click. And you can start zapping! Such smooth integration of payments is not available in any competing technology stack. Tradfi, fintech, crypto, etc., have nothing on Bitcoin and Nostr. Two clicks and your external wallet is connected. I’ll give you a moment now to allow for this new reality to settle in. Primal enables you to connect any number of external apps and manage them from wallet settings:  Note that you can set your daily spend budget for each app or revoke its access at any time. ## How This Works So, what is this sorcery? How does it work under the hood? Connecting Nostr apps to external wallets is accomplished via the Nostr Wallet Connect protocol. It utilizes Nostr’s public relay infrastructure to enable communication between apps and wallets. You can learn more about this protocol [here](https://nwc.dev/), and access developer docs [here](https://docs.nwc.dev/). The smooth, two-click connection setup UX is implemented through deep links between Primal and the external app. Here’s the deep link that the external app needs to call to invoke this feature: ```nostrnwc+primal://connect?appicon=[icon_url]&appname=[app_name]&callback=[callback_string]``` After the user clicks “Create Wallet Connection” in Primal, the Primal app calls the deep link defined in the callback, and passes the NWC connection string. That's all that the external app needs to make the wallet connection. ## What Comes Next? The Nostr Wallet Connect protocol has been around for almost two years. Several bitcoin wallets implement it and many Nostr apps use it as their main way of enabling payments. What’s new with Primal 2.1 is the elevated user experience. Since Primal is a Nostr-powered wallet, it is aware of all the relevant metadata for each transaction: Nostr zaps, users, and the related events. Primal indexes the entire Nostr network, and now this is open to all Nostr apps that wish to integrate payments. Nostr keeps expanding and getting better. Its openness enables us to build capabilities that lift all boats. The future is bright; I can’t wait to see how things evolve from here. 🍿🍿🍿
@ d61f3bc5:0da6ef4a
2025-02-12 16:57:44Micropayments on the Internet have been theorized for decades. However, it wasn’t until the emergence of Nostr that we’ve finally seen them deployed at scale. Nostr is still in its infancy, yet we are already witnessing an explosion of apps built on top of this open protocol. And most of them are featuring zaps! With the recent Primal 2.1 release, Nostr developers now have the option to enhance the experience for their users by integrating a Nostr-powered bitcoin wallet. There is no doubt that micropayments add a new dimension to consumer apps. The incumbents have realized this and are rushing to add payments to their closed platforms. It won't be long before apps that don’t include built-in payments feel dated or outright broken. The question is not if apps of the future will have built-in payments, but what *kind* of payments they will be. Given that open networks have a tendency to win, our bet is that apps of the future will be powered by Bitcoin. Let’s see how Primal can help. ## Primal Wallet Our vision for Primal Wallet is simple: deliver the smoothest transactional bitcoin wallet, endowed with expert Nostr skills. The wallet leverages Nostr’s open social graph as a de facto public lightning directory, while offering the highest level of user experience for Nostr’s rich content. For example, the user can scroll through the transaction list, select a zap, and drill straight into the conversation thread where the zap originated. The whole flow feels perfectly natural.  Since we launched Primal Wallet in December 2023, the user response has been incredibly positive. People love the idea of being able to post something on Nostr, get zaps from plebs around the world, then buy a coffee or a meal with those sats - all from the same app. Having a bitcoin wallet with social skills resonated strongly with users, so Primal Wallet grew rapidly in popularity and usage. Since the launch, we have processed **1,338,460** transactions, with **238,916** just in the past month alone. This rivals some of the leading bitcoin wallets, and we are just getting started! We hear from many bitcoin OGs that they are using Primal Wallet as their transactional daily driver. Bullish. All this is great, but something has been missing. Our users demanded the ability to connect Primal Wallet to other Nostr apps, so they can zap from anywhere in Nostr’s growing ecosystem. ## Zapping from Any Nostr App For an existing Primal user, connecting the wallet to a new Nostr app can now be done in two clicks. Let’s take a look at how this is done from Olas, one of the most exciting new apps on Nostr:  Yes. Click, click. And you can start zapping! Such smooth integration of payments is not available in any competing technology stack. Tradfi, fintech, crypto, etc., have nothing on Bitcoin and Nostr. Two clicks and your external wallet is connected. I’ll give you a moment now to allow for this new reality to settle in. Primal enables you to connect any number of external apps and manage them from wallet settings:  Note that you can set your daily spend budget for each app or revoke its access at any time. ## How This Works So, what is this sorcery? How does it work under the hood? Connecting Nostr apps to external wallets is accomplished via the Nostr Wallet Connect protocol. It utilizes Nostr’s public relay infrastructure to enable communication between apps and wallets. You can learn more about this protocol [here](https://nwc.dev/), and access developer docs [here](https://docs.nwc.dev/). The smooth, two-click connection setup UX is implemented through deep links between Primal and the external app. Here’s the deep link that the external app needs to call to invoke this feature: ```nostrnwc+primal://connect?appicon=[icon_url]&appname=[app_name]&callback=[callback_string]``` After the user clicks “Create Wallet Connection” in Primal, the Primal app calls the deep link defined in the callback, and passes the NWC connection string. That's all that the external app needs to make the wallet connection. ## What Comes Next? The Nostr Wallet Connect protocol has been around for almost two years. Several bitcoin wallets implement it and many Nostr apps use it as their main way of enabling payments. What’s new with Primal 2.1 is the elevated user experience. Since Primal is a Nostr-powered wallet, it is aware of all the relevant metadata for each transaction: Nostr zaps, users, and the related events. Primal indexes the entire Nostr network, and now this is open to all Nostr apps that wish to integrate payments. Nostr keeps expanding and getting better. Its openness enables us to build capabilities that lift all boats. The future is bright; I can’t wait to see how things evolve from here. 🍿🍿🍿 @ 85bdb587:7339d672
2025-02-12 15:24:11## Chart of the Day While this is a bitcoin focused rag, I think it is important for any of you who read this to begin paying attention to gold markets if you haven't already. There has been an ongoing exodus of physical gold from London vaults and a rapid acceleration of gold being moved to the three biggest vaults in the United States in recent weeks. More gold has flooded into the US vaults over the first two months of this year than at the peak of the flight to safety during the beginning of the COVID lock downs.   This is particularly perplexing considering the fact that equities are flat or up on the year, depending on the index you like to follow. Gold outperformed the S&P 500 significantly in 2024 and its momentum hasn't slowed down a bit in 2025 as the precious metal consistently hits new all time highs. The current correlation to the S&P 500 has only happened two times in history; right now and October of 2007.  Institutional investors and nation states are piling into gold at an unprecedented pace. This signals that they are preparing for something to break. The catalysts for the exodus of gold from London to the US and from paper gold to physical gold are fears over Trump's tariffs, institutions and governments preparing for a potential monetary reset, and fears of a looming liquidity crisis as liquidity in the reverse repo market dries up. Uncertainty and chaos rule the day and we are witnessing a flight to safety. Many of you are probably asking, "Why isn't bitcoin moving?!" That's a good question. Considering everything mentioned above one would think that bitcoin would be on the move toward new all time highs as well. Having been following bitcoin for twelve years your Uncle Marty has developed some pattern recognition when it comes to this market. Upward bitcoin price movements typically happen in a staircase fashion. Meaning that it trends up and to the right over the long-run with quick bursts to higher levels followed by small corrections and consolidation periods. If I had to guess, we are currently in a consolidation period that should come to an end at some point in the next few months. In recent years, gold has moved higher first and bitcoin has followed. Typically outperforming gold significantly. I find it hard to believe that this relationship is going to end any time soon. Especially considering the geopolitical and economic backdrop. ## Luke Gromen Warns Bitcoin Holders: Historical Currency Revaluations Show Speed Matters During my recent conversation with Luke Gromen, he raised a sobering point about the velocity of monetary regime changes. Drawing from historical examples, including a Ukrainian family who saw their savings devalue from "five cars to one month's groceries" over a single weekend, Luke emphasized that Americans are uniquely blind to how quickly these transitions can occur. The current stress in our financial system - from Treasury market dynamics to global trade tensions - suggests we're approaching a similar inflection point. *"What if they do it on Friday night like they did with Trump coin and you wake up and gold's up 1,000% by the time you're up on Saturday morning, what are you going to do? You're going to sell your bonds and buy gold on Saturday?"* - Luke Gromen  This warning shouldn't be taken lightly. Those waiting for clear signals before acquiring bitcoin may find themselves locked out of the transition entirely. Luke's analysis suggests that rather than a gradual shift, we're more likely to see a compressed timeframe where major monetary changes happen over days or weeks, not months or years. The recent Trump coin phenomenon, while different in nature, demonstrates how quickly markets can move when sentiment shifts dramatically. TLDR: Major monetary changes happen fast - don't wait to stack sats. Check out the full podcast [here](https://www.youtube.com/watch?v=RCeWQHATWYU&t=61s&ab_channel=TFTC&ref=tftc.io) for more on DeepSeek's impact on AI markets, Colombia's trade negotiations, and Scott Percent's three arrows for economic reform. ## Headlines of the Day U.S. Faces $1.67B Annual Cost Spike on Single Bond Rollover - via [X](https://x.com/TFTC21/status/1889454272842268982) BlackRock: Bitcoin is Monetary Hedge, Ethereum is Tech Play - via [X](https://x.com/BitcoinNewsCom/status/1889396849880268814) Lummis: SBR Could Slash U.S. Debt by 50% in Two Decades - via [X](https://x.com/cryptonwsuk/status/1888565117047951869) Fold Launches Bitcoin Rewards Visa Credit Card - via [Business Wire](https://www.businesswire.com/news/home/20250211765772/en/Fold-Launches-Revolutionary-Bitcoin-Rewards-Visa-Credit-Card) Obscura VPN launches with a MacOS product - via [nobsbitcoin.com](https://www.nobsbitcoin.com/obscura-vpn-is-now-available-on-macos/) ## Bitcoin Lesson of the Day The SegWit (Segregated Witness) upgrade in August 2017 made two key changes to Bitcoin. First, it moved transaction signatures to a separate part of the data, fixing "transaction malleability" by preventing nodes from modifying transaction IDs. Second, it increased effective block capacity by introducing "weight units" that gave signature data a 75% discount, allowing blocks to grow from 1MB to about 1.8MB. As a "soft fork," SegWit remained compatible with older Bitcoin software. The upgrade activated at block 481,824 after 95% of miners signaled support. This approach allowed Bitcoin to increase capacity and fix technical issues while maintaining network compatibility. [SegWit - Learnmeabitcoin.com](https://learnmeabitcoin.com/beginners/guide/segwit/?ref=tftc.io) ICYMI Fold opened the waiting list for the new Bitcoin Rewards Credit Card. Fold cardholders will get unlimited 2% cash back in sats. [Get on the waiting list now](https://foldapp.com/credit-card?r=BgwRS) before it fills up! $200k worth of prizes are up for grabs . The Fold Bitcoin Rewards Credit Card waitlist is live! *Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/funds.* Subscribe to our YouTube channels and follow us on Nostr and X: [TFTC YouTube](https://www.youtube.com/tftc21) [Bitcoin Brief YouTube](https://www.youtube.com/@BTCBrief) [TFTC on Nostr](https://primal.net/tftc) [TFTC on X](https://x.com/tftc21)
@ 85bdb587:7339d672
2025-02-12 15:24:11## Chart of the Day While this is a bitcoin focused rag, I think it is important for any of you who read this to begin paying attention to gold markets if you haven't already. There has been an ongoing exodus of physical gold from London vaults and a rapid acceleration of gold being moved to the three biggest vaults in the United States in recent weeks. More gold has flooded into the US vaults over the first two months of this year than at the peak of the flight to safety during the beginning of the COVID lock downs.   This is particularly perplexing considering the fact that equities are flat or up on the year, depending on the index you like to follow. Gold outperformed the S&P 500 significantly in 2024 and its momentum hasn't slowed down a bit in 2025 as the precious metal consistently hits new all time highs. The current correlation to the S&P 500 has only happened two times in history; right now and October of 2007.  Institutional investors and nation states are piling into gold at an unprecedented pace. This signals that they are preparing for something to break. The catalysts for the exodus of gold from London to the US and from paper gold to physical gold are fears over Trump's tariffs, institutions and governments preparing for a potential monetary reset, and fears of a looming liquidity crisis as liquidity in the reverse repo market dries up. Uncertainty and chaos rule the day and we are witnessing a flight to safety. Many of you are probably asking, "Why isn't bitcoin moving?!" That's a good question. Considering everything mentioned above one would think that bitcoin would be on the move toward new all time highs as well. Having been following bitcoin for twelve years your Uncle Marty has developed some pattern recognition when it comes to this market. Upward bitcoin price movements typically happen in a staircase fashion. Meaning that it trends up and to the right over the long-run with quick bursts to higher levels followed by small corrections and consolidation periods. If I had to guess, we are currently in a consolidation period that should come to an end at some point in the next few months. In recent years, gold has moved higher first and bitcoin has followed. Typically outperforming gold significantly. I find it hard to believe that this relationship is going to end any time soon. Especially considering the geopolitical and economic backdrop. ## Luke Gromen Warns Bitcoin Holders: Historical Currency Revaluations Show Speed Matters During my recent conversation with Luke Gromen, he raised a sobering point about the velocity of monetary regime changes. Drawing from historical examples, including a Ukrainian family who saw their savings devalue from "five cars to one month's groceries" over a single weekend, Luke emphasized that Americans are uniquely blind to how quickly these transitions can occur. The current stress in our financial system - from Treasury market dynamics to global trade tensions - suggests we're approaching a similar inflection point. *"What if they do it on Friday night like they did with Trump coin and you wake up and gold's up 1,000% by the time you're up on Saturday morning, what are you going to do? You're going to sell your bonds and buy gold on Saturday?"* - Luke Gromen  This warning shouldn't be taken lightly. Those waiting for clear signals before acquiring bitcoin may find themselves locked out of the transition entirely. Luke's analysis suggests that rather than a gradual shift, we're more likely to see a compressed timeframe where major monetary changes happen over days or weeks, not months or years. The recent Trump coin phenomenon, while different in nature, demonstrates how quickly markets can move when sentiment shifts dramatically. TLDR: Major monetary changes happen fast - don't wait to stack sats. Check out the full podcast [here](https://www.youtube.com/watch?v=RCeWQHATWYU&t=61s&ab_channel=TFTC&ref=tftc.io) for more on DeepSeek's impact on AI markets, Colombia's trade negotiations, and Scott Percent's three arrows for economic reform. ## Headlines of the Day U.S. Faces $1.67B Annual Cost Spike on Single Bond Rollover - via [X](https://x.com/TFTC21/status/1889454272842268982) BlackRock: Bitcoin is Monetary Hedge, Ethereum is Tech Play - via [X](https://x.com/BitcoinNewsCom/status/1889396849880268814) Lummis: SBR Could Slash U.S. Debt by 50% in Two Decades - via [X](https://x.com/cryptonwsuk/status/1888565117047951869) Fold Launches Bitcoin Rewards Visa Credit Card - via [Business Wire](https://www.businesswire.com/news/home/20250211765772/en/Fold-Launches-Revolutionary-Bitcoin-Rewards-Visa-Credit-Card) Obscura VPN launches with a MacOS product - via [nobsbitcoin.com](https://www.nobsbitcoin.com/obscura-vpn-is-now-available-on-macos/) ## Bitcoin Lesson of the Day The SegWit (Segregated Witness) upgrade in August 2017 made two key changes to Bitcoin. First, it moved transaction signatures to a separate part of the data, fixing "transaction malleability" by preventing nodes from modifying transaction IDs. Second, it increased effective block capacity by introducing "weight units" that gave signature data a 75% discount, allowing blocks to grow from 1MB to about 1.8MB. As a "soft fork," SegWit remained compatible with older Bitcoin software. The upgrade activated at block 481,824 after 95% of miners signaled support. This approach allowed Bitcoin to increase capacity and fix technical issues while maintaining network compatibility. [SegWit - Learnmeabitcoin.com](https://learnmeabitcoin.com/beginners/guide/segwit/?ref=tftc.io) ICYMI Fold opened the waiting list for the new Bitcoin Rewards Credit Card. Fold cardholders will get unlimited 2% cash back in sats. [Get on the waiting list now](https://foldapp.com/credit-card?r=BgwRS) before it fills up! $200k worth of prizes are up for grabs . The Fold Bitcoin Rewards Credit Card waitlist is live! *Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/funds.* Subscribe to our YouTube channels and follow us on Nostr and X: [TFTC YouTube](https://www.youtube.com/tftc21) [Bitcoin Brief YouTube](https://www.youtube.com/@BTCBrief) [TFTC on Nostr](https://primal.net/tftc) [TFTC on X](https://x.com/tftc21) @ 94a6a78a:0ddf320e
2025-02-12 15:05:48Azzamo is more than just a relay provider—it’s a **high-performance network** designed to make Nostr **faster, smoother, and more reliable** for everyone. Whether you're **posting notes, zapping sats, sharing media, or sending DMs**, Azzamo keeps your Nostr experience **seamless and efficient**. Nostr is unstoppable, but **not all relays are the same**. Some are **slow, unreliable, or disappear overnight**, while others get **overloaded**, making message delivery **inconsistent**. Azzamo is built differently—offering **fast, stable, and globally distributed relays** to ensure **low-latency, high-speed connections**, no matter where you are. --- ## **🌍 Premium Relays for Maximum Performance** Azzamo **Premium Relays** are optimized for **speed, reliability, and uptime**, available exclusively to **Premium users**: 📡 **Azzamo Premium Relays:** - **Europe:** `wss://relay.azzamo.net` - **America:** `wss://us.azzamo.net` - **Asia:** `wss://asia.azzamo.net` Add **Azzamo Premium Time** to **unlock unlimited, high-speed access** across these global relays. 🔗 **Get Premium:** [azzamo.net/premium](https://azzamo.net/premium) --- ## **🆓 Freemium Relays – Free for Everyone** Azzamo believes in **keeping Nostr open** and accessible to all. That’s why we offer **free relays for everyone**, with **no rate limits for Premium members** 📡 **Freemium Relays:** - **Free Relay:** `wss://nostr.azzamo.net` – Open to all. - **Inbox Relay:** `wss://inbox.azzamo.net` – Reliable for DMs & group messages. By offering both **free and premium options**, Azzamo ensures that **anyone can use Nostr, while also funding the infrastructure that keeps it running smoothly.** --- ## **🛡️ Minimal Moderation, Maximum Transparency** Nostr is about **free speech**, but that doesn’t mean **zero moderation.** Azzamo follows a **minimal moderation policy** to keep relays **functional and spam-free** while maintaining **transparency** in enforcement.\ \ 🚫 **Spam & network abuse**\ 🚫 **Illegal content (CSAM, fraud, malware, scams)**\ 🚫 **Impersonation & identity abuse** We also maintain a **public Ban API** for **transparent moderation decisions**. 📖 **More on our Ban API:** [azzamo.net/introducing-the-azzamo-ban-api](https://azzamo.net/introducing-the-azzamo-ban-api) --- ## **🚀 Get Started with Azzamo Relays Today!** 🔗 **Connect now:**\ 📡 `wss://nostr.azzamo.net` (Freemium Free Relay)\ 📬 `wss://inbox.azzamo.net` (Freemium Inbox Relay)\ 📡 `wss://relay.azzamo.net` (Premium Europe Relay)\ 📡 `wss://us.azzamo.net` (Premium Americas Relay)\ 📡 `wss://asia.azzamo.net` (Premium Asia Relay) Nostr is growing fast. **Make sure your relays can keep up.** 🚀 #azzamo #grownostr #nostr #relay #relays #premiumrelay #paidrelay
@ 94a6a78a:0ddf320e
2025-02-12 15:05:48Azzamo is more than just a relay provider—it’s a **high-performance network** designed to make Nostr **faster, smoother, and more reliable** for everyone. Whether you're **posting notes, zapping sats, sharing media, or sending DMs**, Azzamo keeps your Nostr experience **seamless and efficient**. Nostr is unstoppable, but **not all relays are the same**. Some are **slow, unreliable, or disappear overnight**, while others get **overloaded**, making message delivery **inconsistent**. Azzamo is built differently—offering **fast, stable, and globally distributed relays** to ensure **low-latency, high-speed connections**, no matter where you are. --- ## **🌍 Premium Relays for Maximum Performance** Azzamo **Premium Relays** are optimized for **speed, reliability, and uptime**, available exclusively to **Premium users**: 📡 **Azzamo Premium Relays:** - **Europe:** `wss://relay.azzamo.net` - **America:** `wss://us.azzamo.net` - **Asia:** `wss://asia.azzamo.net` Add **Azzamo Premium Time** to **unlock unlimited, high-speed access** across these global relays. 🔗 **Get Premium:** [azzamo.net/premium](https://azzamo.net/premium) --- ## **🆓 Freemium Relays – Free for Everyone** Azzamo believes in **keeping Nostr open** and accessible to all. That’s why we offer **free relays for everyone**, with **no rate limits for Premium members** 📡 **Freemium Relays:** - **Free Relay:** `wss://nostr.azzamo.net` – Open to all. - **Inbox Relay:** `wss://inbox.azzamo.net` – Reliable for DMs & group messages. By offering both **free and premium options**, Azzamo ensures that **anyone can use Nostr, while also funding the infrastructure that keeps it running smoothly.** --- ## **🛡️ Minimal Moderation, Maximum Transparency** Nostr is about **free speech**, but that doesn’t mean **zero moderation.** Azzamo follows a **minimal moderation policy** to keep relays **functional and spam-free** while maintaining **transparency** in enforcement.\ \ 🚫 **Spam & network abuse**\ 🚫 **Illegal content (CSAM, fraud, malware, scams)**\ 🚫 **Impersonation & identity abuse** We also maintain a **public Ban API** for **transparent moderation decisions**. 📖 **More on our Ban API:** [azzamo.net/introducing-the-azzamo-ban-api](https://azzamo.net/introducing-the-azzamo-ban-api) --- ## **🚀 Get Started with Azzamo Relays Today!** 🔗 **Connect now:**\ 📡 `wss://nostr.azzamo.net` (Freemium Free Relay)\ 📬 `wss://inbox.azzamo.net` (Freemium Inbox Relay)\ 📡 `wss://relay.azzamo.net` (Premium Europe Relay)\ 📡 `wss://us.azzamo.net` (Premium Americas Relay)\ 📡 `wss://asia.azzamo.net` (Premium Asia Relay) Nostr is growing fast. **Make sure your relays can keep up.** 🚀 #azzamo #grownostr #nostr #relay #relays #premiumrelay #paidrelay @ 5d4b6c8d:8a1c1ee3
2025-02-12 14:36:40Here are today's picks using my proprietary betting strategy at [Freebitcoin](https://freebitco.in/?r=51325722). For details about what Risk Balanced Odds Arbitrage is and why it works see https://stacker.news/items/342765/r/Undisciplined. For a hypothetical 1k-ish wager on each match, distribute your sats as follows: | Outcome 1 | Outcome 2 | Outcome 3 | Bet 1 | Bet 2 | Bet 3 | |--------------|-------------|--------------|-------|-------|-------| | Juventus| Inter Milan| Draw | 294| 435| 303| | Tottenham| Man United| Draw | 406| 357| 266| | Liverpool| Wolves| Draw | 833| 67| 125| | Valladolid| Sevilla| Draw | 222| 500| 289| | Real Betis| Real Sociedad| Draw | 393| 321| 313| | Osasuna| Real Madrid| Draw | 174| 619| 227| | Barcelona| Rayo Vallecano| Draw | 818| 80| 133| | Atletico Madrid| Celta Vigo| Draw | 692| 118| 217| I'll be curious to see how @Coinsreporter does with his modified RBOA. On the most recently completed sets of RBOA, I lost 700 sats on about 50k wagered. I'm not sure if that's just normal variance or if it's due to matches not being posted as far in advance, which reduces the early mover bonus. I still haven't precisely identified where the threshold is, but it might be worth skipping any of these with a "time weight multiplier" lower than 90. ---------- A note of caution about Freebitcoin: they recorded the wrong outcome for last week's Bills vs Ravens game and as of yet have not corrected it. I recall one other instance of something similar happening, so proceed with caution. This RBOA strategy is largely immune from that problem, but be aware of it when just betting on one outcome. originally posted at https://stacker.news/items/883708
@ 5d4b6c8d:8a1c1ee3
2025-02-12 14:36:40Here are today's picks using my proprietary betting strategy at [Freebitcoin](https://freebitco.in/?r=51325722). For details about what Risk Balanced Odds Arbitrage is and why it works see https://stacker.news/items/342765/r/Undisciplined. For a hypothetical 1k-ish wager on each match, distribute your sats as follows: | Outcome 1 | Outcome 2 | Outcome 3 | Bet 1 | Bet 2 | Bet 3 | |--------------|-------------|--------------|-------|-------|-------| | Juventus| Inter Milan| Draw | 294| 435| 303| | Tottenham| Man United| Draw | 406| 357| 266| | Liverpool| Wolves| Draw | 833| 67| 125| | Valladolid| Sevilla| Draw | 222| 500| 289| | Real Betis| Real Sociedad| Draw | 393| 321| 313| | Osasuna| Real Madrid| Draw | 174| 619| 227| | Barcelona| Rayo Vallecano| Draw | 818| 80| 133| | Atletico Madrid| Celta Vigo| Draw | 692| 118| 217| I'll be curious to see how @Coinsreporter does with his modified RBOA. On the most recently completed sets of RBOA, I lost 700 sats on about 50k wagered. I'm not sure if that's just normal variance or if it's due to matches not being posted as far in advance, which reduces the early mover bonus. I still haven't precisely identified where the threshold is, but it might be worth skipping any of these with a "time weight multiplier" lower than 90. ---------- A note of caution about Freebitcoin: they recorded the wrong outcome for last week's Bills vs Ravens game and as of yet have not corrected it. I recall one other instance of something similar happening, so proceed with caution. This RBOA strategy is largely immune from that problem, but be aware of it when just betting on one outcome. originally posted at https://stacker.news/items/883708 @ 2180de5b:54d6cba3
2025-02-12 14:14:12Open Source Culture represents the simple idea that ideas are free. That information yearns to be free. We acknowledge that copyright laws are unsuitable for a world that’s highly digitized; where content and information are, and should be, abundant and readily available for anyone. If the information you have is truly valuable for the world, then you do not sell it. You give it away for free. You let it do the good that it can in the world, and know that both yourself and others will be rewarded for it. If you create content that can be digitally distributed and you charge people before accessing your content, then that tells me that you are actually uncertain of the value of your work. Why? Because if you were certain that whatever it is you are trying to sell had any substantial worth, then you would trust these people to pay you in one way or the other, retroactively. The distinction between *price* and *value* is critical in this framework because, as Jeff Booth succinctly said: “*Prices fall to the marginal cost of production.*” The marginal cost of production for digital data is already effectively zero and it is getting exponentially cheaper day by day. That has nothing to do with the *value* of the very same data, though. Prices are mere agreements. Value is innate. “*Value for value*” is real, it's based on trust and abundance, which are both lacking in a society built on fiat money and perceived scarcity, which is why I understand the skepticism behind those ideas and a propensity to put a price tag on everything. Copyright laws are not useful for us anymore at a time when we are moving towards abundance. Digital scarcity only makes sense in digital money, not information. *First mover advantage* is the only real intellectual property right. In another sense, bitcoin is the only real intellectual property anyway. It’s the only thing that’s scarce. All the rest of it can be as abundant as we let it be. "Intellectual property" are, after all, mere ideas and no one can "own" ideas. Copyright laws are nothing else than an impediment to creativity and a gatekeeper to knowledge. Charging money for information, which in digital form is near-free to store and transfer, might as well be considered a form of usury. We shall free information and with it, we will free creativity, discourse, innovation, imagination, cooperation; and, in its totality, nothing less than the human spirit itself. *Written by Kontext* *Published: block height 883,435* *Download the .PDF: [https://satosh.ee/product/open-source-culture-manifesto/](https://satosh.ee/product/open-source-culture-manifesto/)*
@ 2180de5b:54d6cba3
2025-02-12 14:14:12Open Source Culture represents the simple idea that ideas are free. That information yearns to be free. We acknowledge that copyright laws are unsuitable for a world that’s highly digitized; where content and information are, and should be, abundant and readily available for anyone. If the information you have is truly valuable for the world, then you do not sell it. You give it away for free. You let it do the good that it can in the world, and know that both yourself and others will be rewarded for it. If you create content that can be digitally distributed and you charge people before accessing your content, then that tells me that you are actually uncertain of the value of your work. Why? Because if you were certain that whatever it is you are trying to sell had any substantial worth, then you would trust these people to pay you in one way or the other, retroactively. The distinction between *price* and *value* is critical in this framework because, as Jeff Booth succinctly said: “*Prices fall to the marginal cost of production.*” The marginal cost of production for digital data is already effectively zero and it is getting exponentially cheaper day by day. That has nothing to do with the *value* of the very same data, though. Prices are mere agreements. Value is innate. “*Value for value*” is real, it's based on trust and abundance, which are both lacking in a society built on fiat money and perceived scarcity, which is why I understand the skepticism behind those ideas and a propensity to put a price tag on everything. Copyright laws are not useful for us anymore at a time when we are moving towards abundance. Digital scarcity only makes sense in digital money, not information. *First mover advantage* is the only real intellectual property right. In another sense, bitcoin is the only real intellectual property anyway. It’s the only thing that’s scarce. All the rest of it can be as abundant as we let it be. "Intellectual property" are, after all, mere ideas and no one can "own" ideas. Copyright laws are nothing else than an impediment to creativity and a gatekeeper to knowledge. Charging money for information, which in digital form is near-free to store and transfer, might as well be considered a form of usury. We shall free information and with it, we will free creativity, discourse, innovation, imagination, cooperation; and, in its totality, nothing less than the human spirit itself. *Written by Kontext* *Published: block height 883,435* *Download the .PDF: [https://satosh.ee/product/open-source-culture-manifesto/](https://satosh.ee/product/open-source-culture-manifesto/)* @ c4b5369a:b812dbd6
2025-02-12 12:23:40 ### Unidirectional payment channels revisited #### Nodeless lightning - Reduce ecash mints custodial risk --- ### Sats N Facts The nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference has just wrapped up. And what a blast it was. In the heart of northern Thailand, developers, researchers, content creators and more, came together to share ideas on how Bitcoin, Nostr and other free protocols are being used everyday to liberate people. Not only were stories shared from different community leaders on how embracing bitcoin has empowered them and their communities, but a big goal of the unconference was to bring bitcoin engineers and developers from various domains together in one room, unstructured, chaotic, and let them do their thing. At first, I thought not having a schedule might be boring, but oh boy was I wrong. There was so much stuff going on, it was hard to choose which session I would have to miss! ### Luke's Spillman channel proposal One of the sessions I definitely did not want to miss, was nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac s [proposal](https://gist.github.com/lukechilds/307341239beac72c9d8cfe3198f9bfff) > Ecash mints funded with Spillman channels: The ultimate nodeless Lightning wallet . In true unconference fashion, he announced in the main room that the session was about to start, and that the people that are interested should meet him in the whiteboard corner in 10 minutes. The corner was packed, and Luke explained his proposal. ### What's a "[Spillman channel](https://en.bitcoin.it/wiki/Payment_channels#Spillman-style_payment_channels)"? Essentially when we are talking about Spillman channels, what is meant are unidirectional payment channels (or [CLTV-style channels](https://en.bitcoin.it/wiki/Payment_channels#CLTV-style_payment_channels)). An unidirectional payment channel means, only one party can send payments, but not receive, and the other party can only receive, but not send. They also expire after a predetermined amount of time, and must be closed.  At first glance, this might look kinda stupid. After all, we have [Poon-Dryja channels](https://en.bitcoin.it/wiki/Payment_channels#Poon-Dryja_payment_channels) that are powering the lightning network. They are bi-directional, do not expire, and can be used to shuffle coins back and forth theorethically an unlimited amount of times. So, why bother with this stupid one-way channel? ### Simplicity is king People that have worked with lightning channels can sing you a song about complexity, state handling and risks about the current state of bidirectional payment channels. Essentially, There are a lot of requirements on both channel parties when it comes to Liveness (being online) and also state handling (continuous backups).  In some cases, especially when in the context of end-users wanting to perform payments on their mobile phone, they would appreciate it if there was not so much complexity and overhead involved. The gist of the idea is to combine unidirectional channels and ecash mints to achieve the following: A self custodial unidirectional payment channel to an ecash mint, massively reducing the senders liveness and state handling requirements when compared to a lightning channel. Sending payments through the mint will be done through swapping some of the channel balance for ecash tokens. At this point, the user is trusting the mint to honor the redemption of these tokens, while the remaining channel balance remains in self custody. This gives them better controll over their funds than just holding their entire balance custodied in the mint. The ecash tokens can then be redeemed to pay a lightning invoice, just the same as it is done now with normal cashu mints.  So this channel, that has no liveness or state management requirements for the sender, and must have a pre-defined close time, seems to be a perfect fit for the following usecase: 1. A `sender` receives his salary once a month. He opens a channel that is valid for one month. 2. The `sender` then can do his daily spending over this channel. He only trusts the `mint` with the amount for the current outgoing payment while it is swapped for ecash, waiting for redemption. 3. If the `sender` must receive funds (a refund for example), he can do so into the `mints` custody, by receiving ecash. He can spend his ecash funds first when doing his next payment, to reduce his custodial exposure. 4. When the channel expires, or runs out of funds, the `mint` closes the channel. From a consumer perspective, that just want to receive his salary and make frequent payments afterwards, this usecase seems to make a lot of sense. Obviously from a merchants perspective on the other hand, such a channel doesn't really work. But that's fine, it's not the problem we're trying to solve here. What do you think of this idea? Be sure to let me know in the comments! In the next article, we will dive into how such a system can be implemented today, using Bitcoin, Cashu and Lightning. We will also discover how the system can be improved, to make channels non-expiring (A collaborative idea between nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp and nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac born at nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx ). So stay tuned!
@ c4b5369a:b812dbd6
2025-02-12 12:23:40 ### Unidirectional payment channels revisited #### Nodeless lightning - Reduce ecash mints custodial risk --- ### Sats N Facts The nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference has just wrapped up. And what a blast it was. In the heart of northern Thailand, developers, researchers, content creators and more, came together to share ideas on how Bitcoin, Nostr and other free protocols are being used everyday to liberate people. Not only were stories shared from different community leaders on how embracing bitcoin has empowered them and their communities, but a big goal of the unconference was to bring bitcoin engineers and developers from various domains together in one room, unstructured, chaotic, and let them do their thing. At first, I thought not having a schedule might be boring, but oh boy was I wrong. There was so much stuff going on, it was hard to choose which session I would have to miss! ### Luke's Spillman channel proposal One of the sessions I definitely did not want to miss, was nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac s [proposal](https://gist.github.com/lukechilds/307341239beac72c9d8cfe3198f9bfff) > Ecash mints funded with Spillman channels: The ultimate nodeless Lightning wallet . In true unconference fashion, he announced in the main room that the session was about to start, and that the people that are interested should meet him in the whiteboard corner in 10 minutes. The corner was packed, and Luke explained his proposal. ### What's a "[Spillman channel](https://en.bitcoin.it/wiki/Payment_channels#Spillman-style_payment_channels)"? Essentially when we are talking about Spillman channels, what is meant are unidirectional payment channels (or [CLTV-style channels](https://en.bitcoin.it/wiki/Payment_channels#CLTV-style_payment_channels)). An unidirectional payment channel means, only one party can send payments, but not receive, and the other party can only receive, but not send. They also expire after a predetermined amount of time, and must be closed.  At first glance, this might look kinda stupid. After all, we have [Poon-Dryja channels](https://en.bitcoin.it/wiki/Payment_channels#Poon-Dryja_payment_channels) that are powering the lightning network. They are bi-directional, do not expire, and can be used to shuffle coins back and forth theorethically an unlimited amount of times. So, why bother with this stupid one-way channel? ### Simplicity is king People that have worked with lightning channels can sing you a song about complexity, state handling and risks about the current state of bidirectional payment channels. Essentially, There are a lot of requirements on both channel parties when it comes to Liveness (being online) and also state handling (continuous backups).  In some cases, especially when in the context of end-users wanting to perform payments on their mobile phone, they would appreciate it if there was not so much complexity and overhead involved. The gist of the idea is to combine unidirectional channels and ecash mints to achieve the following: A self custodial unidirectional payment channel to an ecash mint, massively reducing the senders liveness and state handling requirements when compared to a lightning channel. Sending payments through the mint will be done through swapping some of the channel balance for ecash tokens. At this point, the user is trusting the mint to honor the redemption of these tokens, while the remaining channel balance remains in self custody. This gives them better controll over their funds than just holding their entire balance custodied in the mint. The ecash tokens can then be redeemed to pay a lightning invoice, just the same as it is done now with normal cashu mints.  So this channel, that has no liveness or state management requirements for the sender, and must have a pre-defined close time, seems to be a perfect fit for the following usecase: 1. A `sender` receives his salary once a month. He opens a channel that is valid for one month. 2. The `sender` then can do his daily spending over this channel. He only trusts the `mint` with the amount for the current outgoing payment while it is swapped for ecash, waiting for redemption. 3. If the `sender` must receive funds (a refund for example), he can do so into the `mints` custody, by receiving ecash. He can spend his ecash funds first when doing his next payment, to reduce his custodial exposure. 4. When the channel expires, or runs out of funds, the `mint` closes the channel. From a consumer perspective, that just want to receive his salary and make frequent payments afterwards, this usecase seems to make a lot of sense. Obviously from a merchants perspective on the other hand, such a channel doesn't really work. But that's fine, it's not the problem we're trying to solve here. What do you think of this idea? Be sure to let me know in the comments! In the next article, we will dive into how such a system can be implemented today, using Bitcoin, Cashu and Lightning. We will also discover how the system can be improved, to make channels non-expiring (A collaborative idea between nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp and nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac born at nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx ). So stay tuned! @ c2827524:5f45b2f7
2025-02-12 12:22:11## L’animo umano  Una delle entità più belle che esistono e che, a mio parere, rendono ancor più meraviglioso questo mondo, è **l’animo degli esseri umani**. È un cocktail fatto di sentimenti, intenzioni, azioni e logica. Quelli che preferisco sono gli animi gentili. Le azioni e le intenzioni devono convergere verso la delicatezza, senza una sbavatura, per essere gentili e io adoro la gentilezza, la riconosco al volo, forse perché non sono delicata. Per niente. L’animo è forse **uno dei più grandi segreti dell’umanità**: in genere perché lo si tiene sempre privato, come è anche logico che sia. C’è un solo fattore che fa rivelare l’animo alle persone, loro malgrado: uno stress test estremo. Dal febbraio del 2020, lo stress test si è tramutato in un organismo multidimensionale, uscendo dalla fantasia distopica di George Orwell e – loro malgrado – **tutti hanno dovuto manifestare l’animo segreto**. Fateci caso: è con il covid-1984 che avete scoperto la vera natura di amici, parenti, sconosciuti o conoscenti. ## Stato di eccezione  La distopia non è mica fuoriuscita da un laboratorio di Wuhan, che ha infettato un pangolino, che ha infettato una papera, che al mercato mio padre comprò. **Ha origini molto più antiche**. Profondi conoscitori dell’animo umano, in grado di prevedere le reazioni delle masse di fronte ad ogni tipo di evento, potrebbero progettare modelli catastrofici e predeterminare con una precisione disarmante la risposta delle persone comuni. Ad esempio di fronte alla probabilità che quattro aerei impazziscano nei cieli americani di una splendida mattina di settembre, oppure guardando i corpi smembrati di un attentato compiuto da una qualunque “sigla” islamica. Infine, potrebbero decidere come e quando dare una sferzata finale allo stress test, ad esempio con il pangolino. O era il pipistrello? È la *«forma legale di ciò che non può avere forma legale»*, più in generale lo spirito disumano dei governanti di oggi, la consuetudine della guerra preventiva, la quale impone con forza che *«lo stato di eccezione tende sempre più a presentarsi come il paradigma di governo dominante della politica contemporanea»*. Così analizza magistralmente Giorgio Agamben nel II° volume della raccolta Homo Sacer, intitolato per l’appunto [Stato di Eccezione](https://www.amazon.it/s?k=stato+di+eccezione+agamben&adgrpid=1234751876426057&hvadid=77172156923137&hvbmt=be&hvdev=c&hvlocphy=1861&hvnetw=s&hvqmt=e&hvtargid=kwd-77172234261086%3Aloc-93&hydadcr=18605_1867270&mcid=df58fe78258f374b81f1fd0eeaa1c659&msclkid=ea580711f461117b4cc160bdad34d584&tag=amamitsp-21&ref=pd_sl_7ni9dvsw1h_e). ## Stato indegno  Gli esseri umani, fondamentalmente miti e pacifici, tendono a condurre vite “normali” in ogni condizione ambientale. Un’unica variabile tende ad interferire per cambiare la condizione ambientale: la politica dello stato. E **lo fa in maniera sempre negativa**. Lo stato crea emergenze, per poi sbattere il suo (piccolissimo) pene sul tavolo e imporre con forza la soluzione, che tenderà puntualmente a facilitare la propria vita rendendo impossibile quella dei ~~cittadini~~ sudditi. Le disuguaglianze create hanno poi **il solo scopo di mettere** esseri miti e pacifici (ma sotto costante pressione) **gli uni contro gli altri**. Pensateci: da quanti decenni siete sotto la pressione di una *«forma legale di ciò che non può avere forma legale»*? Sentendo il Marchese del Grillo ***«Io so’ io, voi siete un cazzo»***, probabilmente è qualche secolo che questo stato indegno esiste. ## Vera natura o Nuda vita?  Il fatto, poi, che lo stato indegno venga accettato senza fiatare, fa parte di quella serie di reazioni delle masse e che i profondi conoscitori dell’animo umano sfruttano per mantenere il potere. Si passa poi alle peggiori angherie che lo stato indegno e i suoi agenti perpetrano nei confronti dei ~~cittadini~~ sudditi, alle estreme disparità tra ~~cittadini~~ sudditi e i “servitori” dello stato, chiamati così perché servono lo stato indegno e non i ~~cittadini~~ sudditi. Prima di arrivare alla sferzata finale dello stress test, persone miti e pacifiche hanno subito così tanti torti da non saperli più contare, ormai fanno parte della normalità. La loro esistenza è ormai ridotta a quello che Walter Benjamin prima e Giorgio Agamben poi definiscono la **Nuda Vita**, mettendo in analogia i sudditi con i detenuti di Guantanamo, giuridicamente innominabili e inclassificabili, ovvero ***«oggetto di una pura signoria di fatto»***. ## Il sontuoso master  Nello stato di eccezione in cui viviamo da almeno 50 anni, a parte pochi dotati di un immenso spirito di osservazione (e i profondi conoscitori al potere, chiaro), nessuno di noi ha mai avuto **veramente** il piacere di conoscere la reale natura delle persone con cui abbiamo scelto di circondarci. Magari c’era quel “piccolo tarlo”, quella “vocina” che ci ha fatto preferire alcuni piuttosto che altri, ma alla fine ha sempre prevalso l’attitudine mite e pacifica, che ha messo a tacere quella vocina. covid-1984 ha il merito di aver messo a nudo tutti: vittime e carnefici. Si tratta verosimilmente di **un sontuoso master che svelerà la vera natura di ognuno**, **nessuno escluso**. Ahinoi, il master è decennale e siamo appena all'inizio del V° anno accademico. ## Istruzioni, prima ancora che l’istruzione  Se c’è un consiglio che mi sento di dare a chi è ancora molto giovane, è proprio quello di non mettere mai a tacere quella “vocina”, per nessun motivo, seppure plausibile. Anche senza rovinare i rapporti, ma l’animo umano va sempre indagato, **si deve fare chiarezza sulla vera natura delle persone con cui si decide di fare un percorso di vita**. La scoperta porterà ad evitare tutti quei “servitori” dello stato di cose indegno di essere definito umano. I *compliant*, gli asserviti, quelli senza spina dorsale o, peggio, **che hanno un interesse personale a mantenere lo status quo** devono essere evitati a tutti i costi. È oltremodo doloroso, ma va fatto. Questi indegni devono essere isolati al più presto, in maniera da renderli innocui. Sono loro il vero esercito dello stato indegno, disposti a combattere qualunque guerra pur di rimediare un piccolissimo quanto ridicolo privilegio. Oggi, i tempi in cui questo esercito si abbassava a tanto per il classico piatto di lenticchie riscaldate, sono un lontanissimo ricordo. covid-1984 ha ulteriormente abbattuto lo standard: ora gli indegni fiancheggiano qualsiasi assurdità **in cambio di un piatto di lenticchie rimasticate dalla signoria di fatto**. L’unico risultato possibile è che l'infame stato rafforza il suo potere di controllo e rosicherà uno alla volta i (pochi) diritti e la libertà di chiunque. Ecco perché bisogna spuntare le armi di questo spregevole stato di cose colpendo l’anello debole, isolandolo. Debole perché non ci crede (nello stato) ma agisce asservito solo per quel piatto di lenticchie (quelle rimasticate e sputate). La prima volta che si incontrano, la vocina vi metterà di fronte alla sensazione di essere ai limiti di uno scontro frontale: capire da che parte andrà il rivale, per buttarsi in quella opposta ed evitare così uno schianto fatale. Fatelo: buttatevi dall’altra parte. E scegliete la parte giusta.
@ c2827524:5f45b2f7
2025-02-12 12:22:11## L’animo umano  Una delle entità più belle che esistono e che, a mio parere, rendono ancor più meraviglioso questo mondo, è **l’animo degli esseri umani**. È un cocktail fatto di sentimenti, intenzioni, azioni e logica. Quelli che preferisco sono gli animi gentili. Le azioni e le intenzioni devono convergere verso la delicatezza, senza una sbavatura, per essere gentili e io adoro la gentilezza, la riconosco al volo, forse perché non sono delicata. Per niente. L’animo è forse **uno dei più grandi segreti dell’umanità**: in genere perché lo si tiene sempre privato, come è anche logico che sia. C’è un solo fattore che fa rivelare l’animo alle persone, loro malgrado: uno stress test estremo. Dal febbraio del 2020, lo stress test si è tramutato in un organismo multidimensionale, uscendo dalla fantasia distopica di George Orwell e – loro malgrado – **tutti hanno dovuto manifestare l’animo segreto**. Fateci caso: è con il covid-1984 che avete scoperto la vera natura di amici, parenti, sconosciuti o conoscenti. ## Stato di eccezione  La distopia non è mica fuoriuscita da un laboratorio di Wuhan, che ha infettato un pangolino, che ha infettato una papera, che al mercato mio padre comprò. **Ha origini molto più antiche**. Profondi conoscitori dell’animo umano, in grado di prevedere le reazioni delle masse di fronte ad ogni tipo di evento, potrebbero progettare modelli catastrofici e predeterminare con una precisione disarmante la risposta delle persone comuni. Ad esempio di fronte alla probabilità che quattro aerei impazziscano nei cieli americani di una splendida mattina di settembre, oppure guardando i corpi smembrati di un attentato compiuto da una qualunque “sigla” islamica. Infine, potrebbero decidere come e quando dare una sferzata finale allo stress test, ad esempio con il pangolino. O era il pipistrello? È la *«forma legale di ciò che non può avere forma legale»*, più in generale lo spirito disumano dei governanti di oggi, la consuetudine della guerra preventiva, la quale impone con forza che *«lo stato di eccezione tende sempre più a presentarsi come il paradigma di governo dominante della politica contemporanea»*. Così analizza magistralmente Giorgio Agamben nel II° volume della raccolta Homo Sacer, intitolato per l’appunto [Stato di Eccezione](https://www.amazon.it/s?k=stato+di+eccezione+agamben&adgrpid=1234751876426057&hvadid=77172156923137&hvbmt=be&hvdev=c&hvlocphy=1861&hvnetw=s&hvqmt=e&hvtargid=kwd-77172234261086%3Aloc-93&hydadcr=18605_1867270&mcid=df58fe78258f374b81f1fd0eeaa1c659&msclkid=ea580711f461117b4cc160bdad34d584&tag=amamitsp-21&ref=pd_sl_7ni9dvsw1h_e). ## Stato indegno  Gli esseri umani, fondamentalmente miti e pacifici, tendono a condurre vite “normali” in ogni condizione ambientale. Un’unica variabile tende ad interferire per cambiare la condizione ambientale: la politica dello stato. E **lo fa in maniera sempre negativa**. Lo stato crea emergenze, per poi sbattere il suo (piccolissimo) pene sul tavolo e imporre con forza la soluzione, che tenderà puntualmente a facilitare la propria vita rendendo impossibile quella dei ~~cittadini~~ sudditi. Le disuguaglianze create hanno poi **il solo scopo di mettere** esseri miti e pacifici (ma sotto costante pressione) **gli uni contro gli altri**. Pensateci: da quanti decenni siete sotto la pressione di una *«forma legale di ciò che non può avere forma legale»*? Sentendo il Marchese del Grillo ***«Io so’ io, voi siete un cazzo»***, probabilmente è qualche secolo che questo stato indegno esiste. ## Vera natura o Nuda vita?  Il fatto, poi, che lo stato indegno venga accettato senza fiatare, fa parte di quella serie di reazioni delle masse e che i profondi conoscitori dell’animo umano sfruttano per mantenere il potere. Si passa poi alle peggiori angherie che lo stato indegno e i suoi agenti perpetrano nei confronti dei ~~cittadini~~ sudditi, alle estreme disparità tra ~~cittadini~~ sudditi e i “servitori” dello stato, chiamati così perché servono lo stato indegno e non i ~~cittadini~~ sudditi. Prima di arrivare alla sferzata finale dello stress test, persone miti e pacifiche hanno subito così tanti torti da non saperli più contare, ormai fanno parte della normalità. La loro esistenza è ormai ridotta a quello che Walter Benjamin prima e Giorgio Agamben poi definiscono la **Nuda Vita**, mettendo in analogia i sudditi con i detenuti di Guantanamo, giuridicamente innominabili e inclassificabili, ovvero ***«oggetto di una pura signoria di fatto»***. ## Il sontuoso master  Nello stato di eccezione in cui viviamo da almeno 50 anni, a parte pochi dotati di un immenso spirito di osservazione (e i profondi conoscitori al potere, chiaro), nessuno di noi ha mai avuto **veramente** il piacere di conoscere la reale natura delle persone con cui abbiamo scelto di circondarci. Magari c’era quel “piccolo tarlo”, quella “vocina” che ci ha fatto preferire alcuni piuttosto che altri, ma alla fine ha sempre prevalso l’attitudine mite e pacifica, che ha messo a tacere quella vocina. covid-1984 ha il merito di aver messo a nudo tutti: vittime e carnefici. Si tratta verosimilmente di **un sontuoso master che svelerà la vera natura di ognuno**, **nessuno escluso**. Ahinoi, il master è decennale e siamo appena all'inizio del V° anno accademico. ## Istruzioni, prima ancora che l’istruzione  Se c’è un consiglio che mi sento di dare a chi è ancora molto giovane, è proprio quello di non mettere mai a tacere quella “vocina”, per nessun motivo, seppure plausibile. Anche senza rovinare i rapporti, ma l’animo umano va sempre indagato, **si deve fare chiarezza sulla vera natura delle persone con cui si decide di fare un percorso di vita**. La scoperta porterà ad evitare tutti quei “servitori” dello stato di cose indegno di essere definito umano. I *compliant*, gli asserviti, quelli senza spina dorsale o, peggio, **che hanno un interesse personale a mantenere lo status quo** devono essere evitati a tutti i costi. È oltremodo doloroso, ma va fatto. Questi indegni devono essere isolati al più presto, in maniera da renderli innocui. Sono loro il vero esercito dello stato indegno, disposti a combattere qualunque guerra pur di rimediare un piccolissimo quanto ridicolo privilegio. Oggi, i tempi in cui questo esercito si abbassava a tanto per il classico piatto di lenticchie riscaldate, sono un lontanissimo ricordo. covid-1984 ha ulteriormente abbattuto lo standard: ora gli indegni fiancheggiano qualsiasi assurdità **in cambio di un piatto di lenticchie rimasticate dalla signoria di fatto**. L’unico risultato possibile è che l'infame stato rafforza il suo potere di controllo e rosicherà uno alla volta i (pochi) diritti e la libertà di chiunque. Ecco perché bisogna spuntare le armi di questo spregevole stato di cose colpendo l’anello debole, isolandolo. Debole perché non ci crede (nello stato) ma agisce asservito solo per quel piatto di lenticchie (quelle rimasticate e sputate). La prima volta che si incontrano, la vocina vi metterà di fronte alla sensazione di essere ai limiti di uno scontro frontale: capire da che parte andrà il rivale, per buttarsi in quella opposta ed evitare così uno schianto fatale. Fatelo: buttatevi dall’altra parte. E scegliete la parte giusta.