-

@ c2827524:5f45b2f7
2025-02-13 11:54:16
> innèsto s. m. [der. di innestare]. – 1. In agraria: a. Operazione con cui si fa concrescere sopra una pianta (detta portainnesto o soggetto) una parte di un altro della stessa specie o di specie differenti (detto nesto o oggetto), **al fine di formare un nuovo individuo più pregiato o più produttivo o più giovane**: fare, operare, praticare un innesto.
Le collaborazioni sono di una potenza micidiale.
Quelle che si sviluppano nello spazio #Bitcoin ancora di più.
Non è più una collaborazione, è un #innesto: rami di alberi diversi, destinati da soli a dare grandi frutti, si fondono per **donare ad un intero ecosistema sapori ancora più deliziosi**.
Contributi e suggerimenti vanno e vengono alla velocità della luce, col sorriso, senza sacrificio e sempre con la volontà di migliorarsi e crescere.
Lo spazio #Bitcoin è una fabbrica magica, che accoglie minuscoli semini(*) da chiunque voglia partecipare, volontariamente, alla crescita della cultura Bitcoin. Ma li trasforma in un **incanto**.
In solitaria i semini sarebbero destinati comunque a grandi cose e questo è già, di per sé, meraviglioso. La fabbrica magica, invece, li fa germogliare, fiorire e fruttare in maniera ancora più potente.
Quando la magia è totale, avviene l’*innesto*, **la generazione di una nuova creatura più pregiata**.
Sta succedendo davanti ai miei occhi. Sono onorata di poter assistere a questo mini miracolo della vita e, manco a dirlo, felice di farne parte.
Non è solo cambiare atteggiamento, smussare frizioni e rigidità o correggere la propria visione, è proprio ampliare sé stessi accogliendo gli altri.
Grazie nostr:npub1uhj92lnwh8rrhhuvulfqstk4g0ayx0zx35wj2d62jueqheknkxks5m4zj6 nostr:npub1au23c73cpaq2whtazjf6cdrmvam6nkd4lg928nwmgl78374kn29sq9t53j nostr:npub1awnu9vg352863e7tqlc6urlw7jgdf8vf00tmr76uuhflp4nnn68sjmnnl3 e nostr:npub1lrurmgmlfl4u72258fc4q5ke7tr82kw5xct5vchdmzr9uhmx6j4qn3t72a
(1) Semini, non #seed [non chiamatelo seed, si dice mnemonica (cit.)]
Siccome in italiano la parola **seme** porta alla mente anche *giochini di parole fiat*, se siete qui per perculare fate pure. -> H.F.S.P. 🤣
-

@ d360efec:14907b5f
2025-02-13 11:15:12
**Top-Down Analysis:** กลยุทธ์การเทรดเพื่อมองภาพรวมและจับจังหวะทำกำไร
ในโลกของการเทรดที่เต็มไปด้วยความผันผวน การมีเครื่องมือวิเคราะห์ที่แข็งแกร่งเป็นสิ่งสำคัญอย่างยิ่งที่จะช่วยนำทางให้เทรดเดอร์สามารถตัดสินใจได้อย่างมีหลักการและเพิ่มโอกาสในการทำกำไร หนึ่งในเครื่องมือที่ได้รับความนิยมและมีประสิทธิภาพคือ "Top-Down Analysis" หรือการวิเคราะห์จากบนลงล่าง ซึ่งเป็นวิธีการมองภาพรวมของตลาดก่อนที่จะเจาะจงไปที่สินทรัพย์ที่เราสนใจ บทความนี้จะพาคุณไปทำความเข้าใจกับ Top-Down Analysis อย่างละเอียด พร้อมทั้งแนะนำกลยุทธ์การเทรดที่สามารถนำไปปรับใช้ได้จริง
**Top-Down Analysis คืออะไร?**
Top-Down Analysis เป็นกระบวนการวิเคราะห์ตลาดที่เริ่มต้นจากการพิจารณาภาพรวมในกรอบเวลาที่ใหญ่ขึ้น ก่อนที่จะค่อยๆ ย่อยลงไปในกรอบเวลาที่เล็กลง เพื่อทำความเข้าใจบริบทของตลาดและหาจังหวะการเทรดที่เหมาะสม วิธีการนี้ช่วยให้เทรดเดอร์สามารถมองเห็นทิศทางหลักของตลาด, แนวโน้มที่กำลังเกิดขึ้น, ระดับราคาสำคัญ, และความสมดุลระหว่างอุปสงค์และอุปทาน ก่อนที่จะตัดสินใจเข้าเทรดในกรอบเวลาที่เล็กลง
**องค์ประกอบสำคัญของ Top-Down Analysis (อ้างอิงจากภาพ)**
ภาพ "Top-Down Analysis" ได้สรุปองค์ประกอบสำคัญของการวิเคราะห์นี้ไว้อย่างชัดเจน โดยแบ่งการวิเคราะห์ออกเป็น 3 กรอบเวลาหลัก: 4 ชั่วโมง (4H), 1 ชั่วโมง (1H), และ 15 นาที (15min) แต่ละกรอบเวลามีองค์ประกอบที่ต้องพิจารณาดังนี้:
1. กรอบเวลา 4 ชั่วโมง (4H): ภาพรวมตลาดและทิศทางหลัก
ในกรอบเวลา 4 ชั่วโมง เราจะเน้นการวิเคราะห์ภาพรวมของตลาด เพื่อกำหนดทิศทางหลักและแนวโน้มในระยะกลาง องค์ประกอบสำคัญในกรอบเวลานี้คือ:
* Direction (ทิศทาง): ประเมินทิศทางที่ตลาดกำลังเคลื่อนที่ไป โดยพิจารณาจากแนวโน้มและโครงสร้างราคาในภาพรวม ตลาดกำลังเป็นขาขึ้น, ขาลง หรืออยู่ในช่วง Sideways?
* Trend (แนวโน้ม): ระบุแนวโน้มหลักของตลาด ไม่ว่าจะเป็นแนวโน้มขาขึ้น (Uptrend), แนวโน้มขาลง (Downtrend) หรือ Sideways การเข้าใจแนวโน้มช่วยในการกำหนดกลยุทธ์การเทรดที่เหมาะสม
* Key levels (ระดับราคาสำคัญ): หาระดับราคาแนวรับและแนวต้านที่สำคัญในกรอบเวลา 4 ชั่วโมง ระดับเหล่านี้มักเป็นจุดที่ราคาเคยมีการกลับตัวหรือพักตัวในอดีต และอาจเป็นบริเวณที่ราคาจะตอบสนองอีกครั้งในอนาคต
* Supply & Demand (อุปทานและอุปสงค์): วิเคราะห์ความสมดุลระหว่างแรงซื้อ (Demand) และแรงขาย (Supply) ในตลาด โดยพิจารณาจากพฤติกรรมราคาบริเวณแนวรับแนวต้าน และสัญญาณจากเครื่องมือวิเคราะห์อื่นๆ (ถ้าใช้)
2. กรอบเวลา 1 ชั่วโมง (1H): หาจังหวะและบริเวณที่น่าสนใจ
เมื่อได้ภาพรวมและทิศทางหลักจากกรอบ 4H แล้ว เราจะย่อยลงมาในกรอบ 1 ชั่วโมง เพื่อหาจังหวะการเทรดที่สอดคล้องกับทิศทางหลัก และมองหารูปแบบราคาที่น่าสนใจ องค์ประกอบสำคัญในกรอบเวลานี้คือ:
* Breaks (การทะลุ): สังเกตการทะลุแนวรับแนวต้าน หรือระดับราคาสำคัญในกรอบ 1H ที่สอดคล้องกับทิศทางหลักใน 4H การทะลุเหล่านี้อาจเป็นสัญญาณของการเคลื่อนไหวครั้งใหญ่ของราคา
* Reversals (การกลับตัว): มองหารูปแบบการกลับตัวของราคาที่อาจเกิดขึ้นบริเวณระดับราคาสำคัญในกรอบ 1H ซึ่งบ่งบอกถึงจุดสิ้นสุดของแนวโน้มปัจจุบันและเริ่มต้นแนวโน้มใหม่
* OB (Order Blocks): ระบุบริเวณ Order Blocks ในกรอบ 1H ซึ่งเป็นพื้นที่ที่มีการสั่งซื้อขายจำนวนมากในอดีต Order Blocks เหล่านี้มักจะทำหน้าที่เป็นแนวรับแนวต้านในอนาคต
* FVG (Fair Value Gaps): มองหา Fair Value Gaps ในกรอบ 1H ซึ่งเป็นช่องว่างของราคาที่เกิดจากการเคลื่อนไหวอย่างรวดเร็ว FVG มักจะเป็นเป้าหมายของราคาในอนาคต เนื่องจากราคาอาจจะกลับมาปิดช่องว่างเหล่านี้
* Liquidity (สภาพคล่อง): ประเมินสภาพคล่องบริเวณระดับราคาที่เราสนใจในกรอบ 1H บริเวณที่มีสภาพคล่องสูงมักจะดึงดูดนักลงทุนรายใหญ่ และอาจทำให้เกิดการเคลื่อนไหวของราคาที่รุนแรง
3. กรอบเวลา 15 นาที (15min): ยืนยันสัญญาณและหาจุดเข้าเทรด
ในกรอบเวลา 15 นาที เราจะเน้นการยืนยันสัญญาณการเทรด และหาจุดเข้าเทรดที่แม่นยำ เพื่อลดความเสี่ยงในการเข้าเทรดเร็วเกินไป องค์ประกอบสำคัญในกรอบเวลานี้คือ:
* Confirmation (การยืนยัน): รอสัญญาณยืนยันการเคลื่อนไหวของราคาในกรอบ 15 นาที ที่สอดคล้องกับการวิเคราะห์ในกรอบ 1H และ 4H สัญญาณยืนยันอาจมาในรูปแบบของแท่งเทียนกลับตัว, รูปแบบ Chart Patterns, หรือสัญญาณจาก Indicators
* จุดเข้าเทรด: เมื่อมีสัญญาณยืนยันที่ชัดเจนในกรอบ 15 นาที และสอดคล้องกับการวิเคราะห์ในกรอบเวลาที่ใหญ่ขึ้น จึงตัดสินใจเข้าเทรด โดยกำหนด Stop Loss เพื่อจำกัดความเสี่ยง และ Take Profit เพื่อตั้งเป้าหมายในการทำกำไร
**กลยุทธ์การเทรด Top-Down Analysis: ขั้นตอนสู่ความสำเร็จ**
เพื่อนำ Top-Down Analysis ไปใช้ในการเทรดอย่างมีประสิทธิภาพ เราสามารถทำตามขั้นตอนต่อไปนี้:
1. **เริ่มต้นที่ 4H**: กำหนดทิศทางและแนวโน้มหลัก วิเคราะห์กราฟ 4H เพื่อระบุทิศทางหลักของตลาด แนวโน้ม และระดับราคาสำคัญ ประเมินความสมดุลของ Supply & Demand เพื่อกำหนด Bias การเทรด (เน้นซื้อหรือขาย)
2. **เจาะลึก 1H:** หาจังหวะและบริเวณที่น่าสนใจ เมื่อได้ทิศทางหลักจาก 4H แล้ว ให้ย่อยลงมาดูกราฟ 1H เพื่อหารูปแบบราคาที่น่าสนใจ เช่น การทะลุแนวรับแนวต้าน, รูปแบบการกลับตัว, Order Blocks, Fair Value Gaps และบริเวณที่มีสภาพคล่องสูง
3. **ยืนยันใน 15min:** หาจุดเข้าเทรดที่แม่นยำ รอสัญญาณยืนยันในกรอบ 15 นาที ที่สอดคล้องกับการวิเคราะห์ในกรอบเวลาที่ใหญ่ขึ้น ใช้ Price Action, แท่งเทียน, หรือ Indicators เพื่อยืนยันสัญญาณ และหาจุดเข้าเทรดที่แม่นยำ พร้อมกำหนด Stop Loss และ Take Profit ที่เหมาะสม
**ประโยชน์ของการใช้ Top-Down Analysis**
* มองเห็นภาพรวมตลาด: ช่วยให้เทรดเดอร์เข้าใจบริบทของตลาดในภาพรวม ไม่หลงทางในรายละเอียดเล็กๆ น้อยๆ
* ตัดสินใจเทรดอย่างมีหลักการ: ทำให้การตัดสินใจเทรดมีเหตุผลและมีข้อมูลสนับสนุนมากขึ้น ไม่ใช่แค่การคาดเดา
* เพิ่มความแม่นยำในการเทรด: การวิเคราะห์หลายกรอบเวลาช่วยกรองสัญญาณรบกวน และเพิ่มโอกาสในการเข้าเทรดในทิศทางที่ถูกต้อง
* ลดความเสี่ยง: ช่วยลดโอกาสในการเทรดสวนทางแนวโน้มหลักของตลาด และช่วยในการกำหนด Stop Loss ที่เหมาะสม
**ข้อควรจำและข้อควรระวัง**
* ฝึกฝนและสังเกต: Top-Down Analysis ต้องอาศัยการฝึกฝนและการสังเกตกราฟราคาอย่างสม่ำเสมอ เพื่อพัฒนาความเข้าใจและทักษะในการวิเคราะห์
* ปรับใช้ให้เข้ากับสไตล์: ปรับกลยุทธ์ให้เข้ากับสไตล์การเทรดของคุณ และสินทรัพย์ที่คุณเทรด
* บริหารความเสี่ยง: ให้ความสำคัญกับการบริหารความเสี่ยงเสมอ กำหนดขนาด Position ที่เหมาะสม และใช้ Stop Loss ทุกครั้ง
* ไม่มีกลยุทธ์ใดสมบูรณ์แบบ: Top-Down Analysis เป็นเครื่องมือที่มีประสิทธิภาพ แต่ไม่มีกลยุทธ์ใดที่รับประกันผลกำไร 100% การเทรดมีความเสี่ยง โปรดศึกษาและทำความเข้าใจความเสี่ยงก่อนตัดสินใจลงทุน
**สรุป**
Top-Down Analysis เป็นกลยุทธ์การเทรดที่ทรงพลัง ซึ่งช่วยให้เทรดเดอร์สามารถวิเคราะห์ตลาดอย่างเป็นระบบ มองภาพรวม และจับจังหวะการเทรดได้อย่างแม่นยำ การนำหลักการของ Top-Down Analysis ไปปรับใช้ในการเทรด จะช่วยเพิ่มประสิทธิภาพในการตัดสินใจ และเพิ่มโอกาสในการประสบความสำเร็จในตลาดการเงินได้อย่างยั่งยืน
-

@ e373ca41:b82abcc5
2025-02-13 09:13:10
*This article has been written with the* ***[Pareto client](https://pareto.space/read).*** *(read it there for the full experience). It was first published in German by Milosz Matuschek on* ***["Freischwebende Intelligenz".](https://www.freischwebende-intelligenz.org/p/unterwanderter-journalismus-der-mediale)***
***
It is unmistakable. The hydra of the Deep State is losing a few heads - and this time it's the turn of the media heads. Anyone can look at [USASpending](https://www.usaspending.gov/) to see how much taxpayers' money has gone to whom in the USA.
### When the state pays its advocates
The mainstream media were also among the beneficiaries: Politico (100% Axel Springer) received over [USD 7 million](https://www.usaspending.gov/recipient/fa0cefae-7cfb-881d-29c3-1bd39cc6a49e-C/latest); the New York Times received over USD 40 million. Thousands of (probably not always necessary) government subscriptions flowed to large media houses - paid for with taxpayers' money. A form of covert press financing by the state. At what point can or should we speak of state media?
")
However, this is only the tip of the iceberg. The CIA front organization USAID ([known for its funding of virus research in Wuhan and other questionable activities](https://pareto.space/a/naddr1qqxnzden8quryveexq6rywp3qgswxu72gyq7ykjdfl9j556887jpzwu3mw3v9ez36quas55whq4te3grqsqqqa28qyxhwumn8ghj7mn0wvhxcmmvqyf8wumn8ghj7mmxve3ksctfdch8qatzqythwumn8ghj7urpwfjhgmewdehhxarjxyhxxmmdqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsz9nhwden5te0wfjkccte9ehx7um5wghxyctwvszsxfjh)) - [pumped USD 472.6 million directly into the media landscape via the “Internews Network”.](https://www.zerohedge.com/political/usaid-funded-massive-global-state-propaganda-news-matrix-nearly-billion-people-reach) FAZ journalist Udo Ulfkotte once called this “bought journalists” in a very clear and media-effective way, which was not good for his health. There is ample evidence of the CIA-USAID connections, for example [here](https://timesofindia.indiatimes.com/toi-plus/international/how-usaid-worked-alongside-cia-in-vietnam-a-whistleblowers-account/articleshow/118164225.cms), [here](https://foreignpolicy.com/2014/04/03/cuban-twitter-and-other-times-usaid-pretended-to-be-an-intelligence-agency/) and [here.](https://www.jstor.org/stable/4017728)
")
But this is now over for the time being: USD 268 million, which was to go to “independent media for the free flow of information” (according to the [Columbia Journalism Review](https://www.cjr.org/the_media_today/usaid-and-the-media-in-a-time-of-monsters.php)) in 2025, has been frozen. The largest media influence machine in the Western world is bleeding a little. One has to admit: part of the media-deepstate swamp is actually being drained dry financially. The fact that the Columbia Journalism Review doesn't even seem to notice that “free international journalism”, which, as it writes, is largely funded by USAID, ceases to be “free journalism” speaks volumes about this “hotbed of journalism”. Matt Taibbi of Racket News rightly finds, “The legacy media system is dead. They just don't know it yet.”
***
ADVERTISEMENT:
*Looking for the easiest way to buy Bitcoin and store it yourself? The **[Relai app](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. **[Here you can buy Bitcoin](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees (no financial advice). Disclaimer due to regulatory issues: The services of the Relai App are hereby only recommended to inhabitants of Switzerland or Italy.*
*Need more security? The **[Trezor wallets](https://trezor.io/trezor-safe-5-bitcoin-only?transaction_id=102e192a206d1585e56a2fddef6d83\&offer_id=238\&affiliate_id=35234)** are recommended and easy to use, others are available in the **[store](https://trezor.io/?transaction_id=102bc85bdca2733287749c7f879ebd\&offer_id=133\&affiliate_id=35234)**. Need more advice? Book an **[introductory meeting](https://trezor.io/trezor-expert-session?transaction_id=1020e18dad0aa4b1186289fd22e90f\&offer_id=241\&affiliate_id=35234)** with a wallet expert.*
***
Large-scale media manipulation has become visible. The propaganda matrix, if you will. The disastrous thing about it: if the Overton window is infiltrated, so to speak, the entire institution of journalism cannot be trusted. Every day, readers must expect to be pulled through the nose ring of intelligence service narratives and public agendas by mainstream journalists who pretend to be objective (and are often simply clueless and unsuspecting). The panorama of what we are supposed to see and believe, so to speak.
How many mainstream journalists today are basically mouthpieces for the services? Every mainstream reader must now ask themselves: Is my favorite journalist at NZZ, Welt, SZ, ZEIT or FAZ perhaps just a CIA-IM? There were no major dissenters among them: EU criticism? Vaccination criticism? Criticism of NATO? Criticism of Biden and America? Criticism of Nord Stream? There were brief moments on television when questions about journalists' ties to lobby organizations were still part of the German satire program.
<https://x.com/Spitze_Zunge_/status/1887915509988876786>
### The cards in the media are being reshuffled
The watchdog of the powerful has been infiltrated by the powerful. This means that the Fourth Power is not a power at all, but part of the executive branch, a mouthpiece of the government. The claim that the mainstream is quality journalism, the gold standard for trustworthy information, is therefore the real fake news. It is the last, now crumbling dogma of an infiltrated press sect that has formed a cartel and is subjecting citizens to a permanent psy-op with intelligence-controlled taxpayers' money. A troupe of spokespeople at the work of mental synchronization.
<https://x.com/TopherField/status/1887962959072149989>
### The fight against independent media
But they not only give to one, they also take from the other. While government agencies use taxpayers' money to promote a certain type of journalism, the juice is actively being cut off from the critical part. All it takes is to be classified as a “PEP” (politically exposed person) and the bank account is gone. This is what has just happened to swiss Radio Kontrafunk. The critical Swiss author Stefan Millius was canceled by his publisher. Others have had their monetization via YouTube cut off (Snicklink). Others are harassed by the state media authority (Multipolar, Alexander Wallasch). The next one has a house search. It has been known since the Twitter files that the government and services also intervened massively in social media communication. This is no longer the Cold War. But it is the cold information war.
<https://www.youtube.com/watch?v=kmgWAGDFCZI>
Is this all so outrageous and new? During the Cold War, the CIA systematically infiltrated media outlets in the US. Thousands of agents were deployed as journalists - and wrote what they were told. This “Operation Mockingbird”, which the Church Committee also investigated, never ended, so to speak. It lives on as Operation Mockingbird 2.0.
Intelligence payments to media outlets continue to exist.
USAID distributes millions for “pro-democratic” reporting.
Government subscriptions keep uncritical media alive.
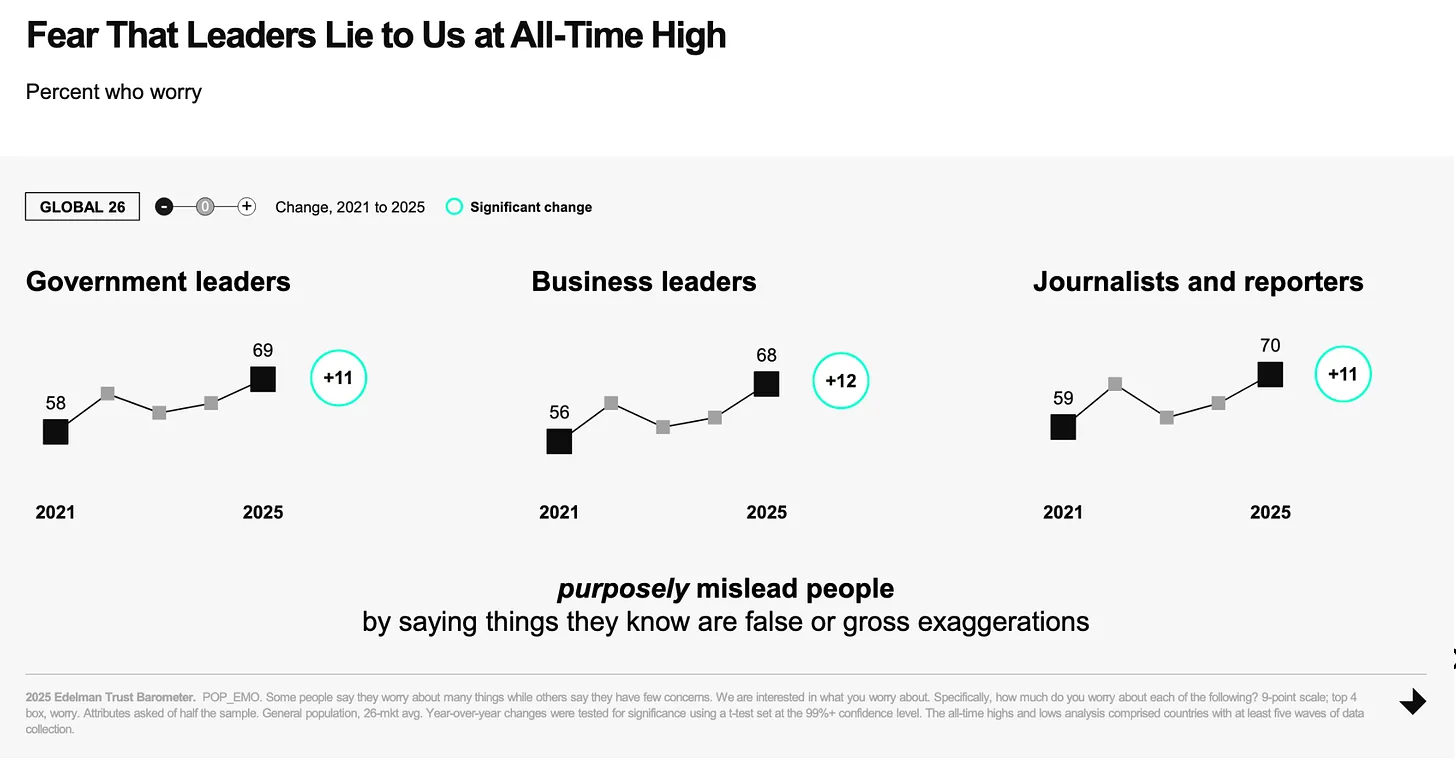
Media control of public opinion is the most important tool of power in a modern “democracy”. The difference to back then? Today, the manipulation is global. However, these revelations come at a time when trust in the media is already at an all-time low. [The fear of being lied to by the powerful is currently the majority opinion at 70%.](https://www.edelman.com/trust/2025/trust-barometer) They are currently in the process of convincing the remaining 30% of their own incompetence.
### Update on the [Pareto project](https://pareto.space/en)

“Half the victory”, says Sun Tsu, ‘lies in the impregnable defense’. Free media now have the opportunity to build their own impregnable bastion and the [Pareto Project](https://pareto.space/read) invites them to do just that: [become uncensorable, be able to scale infinitely and not depend on third parties for all processes of journalistic work](https://pareto.space/a/naddr1qqxnzdenxuerxdpkxycngvpcqgsvlutjpemmkp50p6aa8zwu65yz9hg6erf2czc0tuyqpt57zhr79vsrqsqqqa28qyxhwumn8ghj7mn0wvhxcmmvqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hs33ee7d). It's all possible now. Everyone has to realize that: With other platforms, you build your house on someone else's property. With Nostr/Pareto, there is nothing and no one between author and reader, both in terms of communication and payment (via Bitcoin/Litghtning).
**A brief update on the project, January was very busy.**
* We have about 35 journalists, publications, substackers, bloggers, memers onboarded who publish texts via the Pareto client, and the number is growing all the time.
* The first Telepolis authors, such as Mathias Bröckers and Alexander Unzicker, will soon be able to re-publish their deleted texts with us in a censorship-proof manner, and we are helping with the migration of content.
* We recently successfully tested the newsletter function! We will soon be able to offer all authors and readers the functions of Substack, Steady, Ghost etc. without having to entrust their readers' sensitive data to a platform or expose them to platform tracking.
* We are delighted to have more high-caliber additions to our development team, which now comprises around ten wonderful people, almost all of whom come from this group of readers.
* Our [open source code is now also public.](https://github.com/twenty-eighty/pareto-client)
* We have opened a [crowdfunding on Geyser!](https://geyser.fund/project/pareto)
- Our editor will soon be available to everyone free of charge (atm you have to drop us your npub: <team@pareto.space>)
### What's next?
This opens up a new window of unimagined possibilities: On a strong basis such as that offered by decentralized technology, many critical authors can now publish securely or new publications can be created - worldwide and uncensorable. What kind of publications would you like to see? Where do you see gaps (also in the critical spectrum) that need to be filled, both in terms of formats and topics? What does the journalism of the future look like to you? Feel free to write to me: **<milosz@pareto.space>**
## One last thing
Our funds are coming to an end. If you would like to support us: We have started a [crowdfunding on Geyser](https://geyser.fund/project/pareto), where you can help us with Bitcoin/Lightning donations. 

For traditional donations, you can find our bank account on our **[landingpage.](https://pareto.space/en)**
***
***Join the marketplace of ideas!** We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the [Pareto Project](https://pareto.space/en)? Zap me, if you want to contribute (all Zaps go to the project).*
*Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to **<team@pareto.space>***
**Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Start.](https://start.njump.me/)**
-

@ 3eba5ef4:751f23ae
2025-02-13 09:00:41
Security is fundamental to any blockchain. It ensures that all tokens are secure. When talking about a virtual machine and the smart contract platform it forms, security comes in two main aspects:
* The code running on the virtual machine must be secure
* The virtual machine itself should also be designed to facilitate safer code execution
The first aspect often gets sufficient attention. When it comes to [CKB](https://www.nervos.org/), we now encourage developers to write scripts in Rust for maximum security, reserving pure C code only for those who fully understand its risks. Additionally, higher-level languages have been introduced in CKB to strike a better balance between productivity and security.
Virtual machine security was a major focus when CKB-VM was originally designed. Many potential risks were addressed at the architectural level, though some—despite thorough research—were still left open. One such issue is **Return-Oriented Programming (ROP)**—a rather ingenious attack. It exploits executable code that has been legitimately loaded into memory, making widely effective protections (e.g., [W^X](https://yakihonne.com/write-article)) futile. It spans multiple architectures and is constantly evolving. Although we’ve spent a great deal of effort in the early days on ROP, we did not implement specific countermeasures to prevent it. Now, with new RISC-V extensions now available, it is the perfect time to introduce design-level protections against ROP.
## Acknowledgments
Before diving deeper, we would like to acknowledge Todd Mortimer from the OpenBSD team. His work on ROP mitigations at the OpenBSD kernel in 2018-2019 significantly inspired our research and this article. We highly recommend his [talk](https://www.youtube.com/watch?v=ZvSSHtRv5Mg), slide decks from [AsiaBSDCon 2019](https://www.openbsd.org/papers/asiabsdcon2019-rop-slides.pdf) and [EuroBSD 2018](https://www.openbsd.org/papers/eurobsdcon2018-rop.pdf), and this [paper](https://www.openbsd.org/papers/asiabsdcon2019-rop-paper.pdf) for a deeper understanding of ROP. Several examples on x64 ROP attacks in this post are also drawn from his research.
## Typical Attack Workflow
While there are many sophisticated [ways](https://www.wired.com/2016/06/clever-attack-uses-sound-computers-fan-steal-data/) of attacks, a common attack on a program typically follows this process:
Prepare a [shellcode](https://en.wikipedia.org/wiki/Shellcode)— a piece of binary code to perform specific actions (e.g., running a shell or other programs on the target computer).
Exploit one possible vulnerability in the target system, most commonly a [buffer overflow](https://en.wikipedia.org/wiki/Buffer_overflow) attack. The attack could be initiated via a network protocol (such as HTTP) against a remote system, or via command line input to a target program;
As the result of the attack, the shellcode is inserted to a designated memory region of the target system and gets executed, allowing the attacker to achieve their goal. The consequences vary, like gaining unauthorized access to sensitive data, destroying certain data/machine, planting malicious programs onto the target for further actions, manipulating control flow.
While traditional systems face a wide range of attacks, blockchains run in their own limited and unique runtime environment, rendering many conventional attacks irrelevant. Major blockchain security threats includes:
* **Private key security**: Blockchain wallets rely on private keys, which are prime targets for various attacks.
* **Smart contract vulnerability**: Poorly written smart contracts contain logic flaws that lead to security risks.
* **Virtual machine security**: Attacker may send malicious inputs to a smart contract, causing it to terminate unexpectedly with a success status—despite lacking proper credentials.
This post focuses specifically on attacks targeting the blockchain’s virtual machine—in our case—CKB Virtual Machine (CKB-VM) specifically.
## CKB’s Early Approach
While it is impossible to predict every attack, disrupting the typical attack workflow is an effective defense strategy. From its inception, CKB-VM has implemented [W^X](https://en.wikipedia.org/wiki/W%5EX) protection: at any given time, any memory location in CKB-VM is either writable (allowing data modification) or executable (allowing data execution)—but never both. Once a memory region is marked as **executable**, it cannot be reverted to **writable** throughout the lifecycle of the current CKB-VM instance. Only writable memory location can be **frozen** to executable.
This design significantly disrupts the typical attack workflow. For shellcode to execute on CKB-VM, it must reside in **executable** memory. However, an attacker can only provide shellcode as part of program inputs, which are loaded into **writable** memory. As long as a CKB script does not voluntarily mark input data as **executable** (a highly unlikely scenario), the shellcode remains inert. Additionally, attempting to overwrite existing **executable** shellcode is also futile, since executable memory region is unwritable, and cannot be converted back to writable.
This way, W^X is a well-established security technique widely used in modern hardwares, operating systems, and virtual machines. Although it cannot prevent all possible attacks, W^X effectively shields many by breaking the standard attack workflow. Even if an attacker successfully injects shellcode into a target machine, the attack is incomplete due to the inability to execute it.
## Understanding ROP
While W^X is effective, it does not solve all our problems. This leads to the topic of this post: **Return-oriented Programming (ROP)**. Instead of explicitly injecting new code, ROP exploits executable code that already resides in the target machine’s memory. Essentially, ROP builds a shellcode by chaining existing code snippets together that were never intended to function as such. It may sound like a fantasy, but as we shall see from the following examples, ROP is a practical and effective attack technique.
To understand ROP, we must first examine modern CPU architecture and memory layout. While assembly instructions vary in representations and lengths, they are put together in memory one after another as a stream of bytes:

*Image [Source](https://www.quora.com/Is-assembly-language-a-source-code-or-object-code)*
As seen in the above example, different assembly instructions come in different lengths. For x86-64 ISA, an instruction can range from 1 to 7 bytes (RISC ISAs such as ARM or RISC-V have more uniform instruction lengths—we will discuss it later). But in memory, instructions are stored sequentially without gaps.
This means that with a stream of bytes alone, we really don’t know what instructions the stream of bytes consist of. In the above example, meaningful assembly instructions emerge only when we start decoding from the `B8` byte. In a different occasion, assuming we know elsewhere that `B8 22 11` bytes at the front are for certain magic flags, the decoding would start from `00` byte, yielding a totally different instruction set.

*Image [Source](https://www.quora.com/Is-assembly-language-a-source-code-or-object-code)*
It is really the combination of a special program counter (`PC`) register from the CPU and the current memory stream, jointly determine the instructions the CPU executes. Depending on each different ISA or hardware, a booting process initializes a CPU’s `PC` register to a pre-defined value, then loads up instructions from this pre-defined address, and initializes everything related to the operating system. When a user launches a new program, the metadata for each program will contain an `entrypoint` address, where OS sets the CPU’s `PC` register to, in order to start executing the program. It is suffice to say that maintaining a proper `PC` value is a critical job to ensure a computer’s proper function. An invalid `PC` value might lead to a CPU malfunction at best, or at worst, leaking sensitive information or granting attackers unauthorized access.
### Forming an ROP Attack Via ROP Gadgets
Let’s look at the following byte instruction stream in a x86-64 CPU:
```
8a 5d c3 movb -61(%rbp), %bl
```
This 3-byte represents a `mov` instruction: it takes the address of `rbp` register, adds an offset of `-61`, then uses the result as a memory address to load 1 byte data, and finally sets the loaded data to `bl` register. However, if we ignore `8a` and only look at `5b c3` here, it actually represents a different instruction set:
```
5d popq %rbp
c3 retq
```
This byte sequence contains two instructions:
* Pop 8-byte value from stack, and use it to set `rbp` register
* Pop 8-byte value from stack, and use it to set `PC` register, so we continue executing from the new location
We've briefly discussed that shellcode only fulfills a certain task required by the attacker. In fact, the most common type of shellcode simply construct a new shell, where the attacker can execute more operations. Such shellcode can be represented in the following C pseudocode to run a new command via the `execve` syscall:
```
execve(“/bin/sh”, NULL, NULL);
```
To execute this on an x86-64 CPU, the following actions are needed for a syscall:
* `rax` register: must contain the syscall number, for `execve`, it is `59`
* `rdi`, `rsi`, `rdx` registers: hold the first 3 arguments to the syscall. In this case, `rdi` holds a pointer to the C string `/bin/sh`; `rsi` and `rdx` must be zero.
* The `syscall` instruction (or typically `int 80h` on x64) shall be executed
A typical shellcode would be a packed assembly sequence directly doing all of the above instructions. In contrast, ROP attack looks for the following sequences:
```
# Those can set the value of different registers from values on the stack
pop %rax; ret
pop %rdi; ret
pop %rsi; ret
pop %rdx; ret
# Finally, trigger the syscall
syscall
```
Each of these small code sequences, are conventionally callled **ROP gadgets**. An attacker searches for these gadgets in the target program or system libraries (such as libc). Once these required gadgets are obtained, the attacker pieces together a sequence of data, much like the following:

With the prepared data sequence, the attacker can exploit a vulnerability in the target computer or program, such as typical buffer overflow attack. During this process, the attacker performs three key actions:
* Pushes (or overwrites existing data) the crafted data sequence to the stack
* Sets the stack pointer (top of the stack) to `X + 64`
* Sets the `PC` register to the address of a code sequence, `pop %rax; ret` in the existing program or libc memory space
Now the attack proceeds step by step as follows:
1. The CPU runs `pop %rax; ret`. With the stack pointer pointing to `X + 64`, the CPU pops `59` from the stack and sets `rax` register to `59`. It then pops the address to code sequence `pop %rdi; ret` from the stack, and sets `PC` to this value;
2. The CPU runs `pop %rdi; ret`. With the stack pointer pointing to `X + 48`, the CPU pops value `X`, pointing to the C string `/bin/sh` from the stack, and sets `rdi` register to `X`. It then pops the address to code sequence `pop %rsi; ret` from the stack, and sets `PC` to this value;
3. The CPU runs `pop %rsi; ret`. With the stack pointer pointing to `X + 32`, the CPU pops `0` from the stack and sets `rsi` register to `0`. It then pops the address to code sequence `pop %rdx; ret` from the stack, and sets `PC` to this value;
4. The CPU runs `pop %rdx; ret`. With the stack pointer pointing to `X + 16`, the CPU pops `0` from the stack and sets `rdx` register to `0`. It then pops the address to code sequence `syscall` from the stack, and sets `P`C to this value;
5. The CPU runs `syscall`. At this point, `rax` holds `59`, `rdi` points to `/bin/sh`, and both `rsi` and `rdx` are zero, the CPU invokes `execve("/bin/sh, NULL, NULL);`, granting the attacker a shell for further manipulations.
This sequence of ROP gadgets, referred to as **ROP chains**, demonstrates how a complete ROP attack works. Two key takeaways are:
* **ROP does not inject new code**. Instead, it injects data into the stack and leverages the existing code loaded in memory and marked them as executable. W^X protections hence cannot prevent ROP attacks.
* **Attackers can mine ROP gadgets from the [libc](https://en.wikipedia.org/wiki/C_standard_library) library**. This is because modern computers employs [protection rings](https://en.wikipedia.org/wiki/Protection_ring) as a way for privilege encapsulations: on x86-64 computers, programs normally run at ring level 3, while libc runs at ring level 1. Lower ring levels have higher privileges, meaning that even if a program misbehaves, its capacities are limited at ring level 3. However, by using ROP gadgets in the libc library which runs at ring level 1, ROP attacks can have higher privileges and execute more damaging operations then normal shellcodes.
Note that the above examples simply show the most basic ROP gadgets. In reality, ROP gadgets come in all kinds of forms. Since they come from compiler outputs, they can be combined in the least expected way, and can vary the forms as new compiler optimizations come out. Numerous tools (e.g., [ropper](https://scoding.de/ropper/), [ropr](https://github.com/Ben-Lichtman/ropr)) and research papers (e.g., *[Experiments on ROP Attack with Various Instruction Set Architectures](https://dl.yumulab.org/papers/42/paper.pdf)*, *[ROPGMN](https://www.sciencedirect.com/science/article/abs/pii/S0167739X24005314)*, *[Detecting and Preventing ROP Attacks using Machine Learning on ARM](https://www.infosun.fim.uni-passau.de/ch/publications/compsac23.pdf)*, *[KROP](https://arxiv.org/pdf/2406.11880)* ) keep coming out, making it almost impossible to enumerate all possible ROP gadget combinations.
### ROP on ARM & RISC-V
ROP attacks are not limited to CISC architectures, where instructions vary in length. They also affect RISC designs, such as [ARM](https://developer.arm.com/documentation/102433/0200/Return-oriented-programming) and [RISC-V](https://pure.royalholloway.ac.uk/ws/portalfiles/portal/37157938/ROP_RISCV.pdf). Take the following sequence for example:
```
13 4f 83 23 0b 00
```
Decoding from the start, the first four bytes represent `xori t5,t1,568` following the RISC-V ISA. But if we skip the first two, the latter four represent `lw t2,0(s6)`. This illustrates that a byte stream interpretation also requires `PC` register in a RISC design such as RISC-V. As a result, one can find ROP gadgets from a RISC-V program as well.
### ROP on CKB-VM
CKB’s RISC-V machine operates in a more restricted environment: for programs running on CKB, there are no `execve` syscalls to hijack a running shell, and all runtime states are publicly visible on a public blockchain like CKB. However, ROP attacks can still occur on CKB: one could construct an ROP chain that sets `a0` to `0`, `a7` to `93`, then executes `ecall`. This causes CKB-VM to immediately return with a success code (`0`), potentially allowing a script to pass validation when it should have failed—such as a lock script succeeding without a valid signature.
### Short Recap
Let’s briefly recap what we’ve learned so far:
* ROP attacks utilize existing executable code for malicious purposes. W^X cannot prevent ROP.
* ROP is possible across multiple architecture, including x86-64, ARM, RISC-V, and CKB.
* The landscape of ROP is constantly evolving. With new tools, techniques, and research emerging regularly, it’s impossible to foresee all ROP gadgets.
ROP has been extensively studied over the years, leading to various mitigation strategies, which can be broadly categorized into two main approaches:
* **Software Solutions**: Covering techniques like rewriting code sequences and implementing Retguard to prevent the creation of ROP gadgets
* **Hardware Solutions**: Introducing additional CPU instructions with Control Flow Integrity (CFI) checks to safeguard control flow.
I’ll explore these strategies in greater detail in the following sections.
## Software Solutions to Mitigate ROP
### Rewriting Sequence
Certain instruction sequences are often targeted to form ROP gadgets. To prevent ROP, one approach is to alter the compiler, so that such sequences can never be generated. Take the following example:
```
89 c3 mov %eax,%ebx
90.
```
In x86-64, `c3` represents the `ret` instruction, making it a potential target for ROP gadgets. We can rewrite it into the following equivalent sequence:
```
48 87 d8 xchgq %rbx, %rax
89 d8 movl %ebx, %eax
48 87 d8 xchgq %rbx, %rax
```
The new sequence lacks `c3` byte at the expense of more bytes and more executed instructions. However, it is really up to real benchmarks to see if this causes noticeable overhead.
Further analysis has revealed that the `rbx` register in x86-64 is often the source of ROP gadgets, due to the way Intel encodes x86-64 instructions. Hence, the OpenBSD team decided to avoid `rbx` register wherever possible, reducing the number of potential ROP gadgets.
Again, this approach comes at the cost of having bigger code fragments, more instructions to execute, and an additional patched compiler. While OpenBSD has integrated these changes into its distribution, other environments must weigh the benefits against the costs.
For a deeper dive, I would strongly recommend Todd Mortimer’s [work](https://www.openbsd.org/papers/asiabsdcon2019-rop-slides.pdf).
### Retguard’s Solution: Prologue and Epilogue
Todd Mortimer also introduced Retguard in this [work](https://www.openbsd.org/papers/asiabsdcon2019-rop-slides.pdf) for securing OpenBSD known. ROP attacks typically occur when you enter a function `foo`, but the stack was manipulated, so the CPU exits to another code fragment that is not `foo`. What if to verify that, at each function exit, it is the same function for exiting and entering?
Retguard introduces two components to perform this task:
* **Prologue**: A prologue is inserted to each function’s entry, taking two inputs:
- - A `cookie` value, a random data assigned for this particular function.
- - The return address, where to jump to when current function exits—as inputs.
The prologue computes the XOR value of these two, and stores the result into the current function’s [frame](https://en.wikipedia.org/wiki/Call_stack#Stack_and_frame_pointers) section, a dedicated memory region designated to the current function to hold data, separated from the stack.
* **Epilogue**: An epilogue is inserted to the location where a function might exit. It takes two inputs:
- - The saved XOR value from the prologue in the frame section
- - The return address it now can access to (most likely popped from the stack in x64 machine, or read from a special `RA` register in RISC design)
The epilogue computes the XOR of these two. If the result matches the original `cookie`, execution proceeds. Otherwise, the epilogue halts the program, signaling an error.
This prologue-epilogue mechanism in Retguard guards the call stack from tampering. At a noticeable but acceptable cost (both in performance and code size), Retguard eliminates a significant number of ROP gadgets from the OpenBSD kernel. Like other software-based mitigations, it requires a patched compiler, and it is up to each environment to decide if such technique shall be employed.
## Hardware Advancements to Mitigate ROP
In addition to software solutions, hardware-based defenses have also been developed. For instance, Intel has introduced [Indirect Branch Tracking](https://edc.intel.com/content/www/us/en/design/ipla/software-development-platforms/client/platforms/alder-lake-desktop/12th-generation-intel-core-processors-datasheet-volume-1-of-2/007/indirect-branch-tracking/?language=en) feature starting with its 12th generation core processors, using a new instruction `endbr32` or `endbr64` added at every location the program might jump to or call into. When the CPU executes a jump/call, it asserts that the target location is a proper `endbr32` / `endbr64` instruction, before updating the program counter `PC` register to proper values. Otherwise, the CPU halts to terminate the program. This ensures that all control flows will follow the intended way, preventing ROP attacks from redirecting execution arbitrary locations.
Modern OSes have already extensively leveraged `endbr32` / `endbr64` instructions. Ubuntu 24.04, for instance, has included these instructions in its packages:
```
$ objdump -d /bin/bash | head -n 50
/bin/bash: file format elf64-x86-64
Disassembly of section .init:
0000000000030000 <.init>:
30000: f3 0f 1e fa endbr64
30004: 48 83 ec 08 sub $0x8,%rsp
30008: 48 8b 05 d9 7e 12 00 mov 0x127ed9(%rip),%rax # 157ee8 <__gmon_start__@Base>
3000f: 48 85 c0 test %rax,%rax
30012: 74 02 je 30016 <unlink@plt-0xe1a>
30014: ff d0 call *%rax
30016: 48 83 c4 08 add $0x8,%rsp
3001a: c3 ret
Disassembly of section .plt:
0000000000030020 <.plt>:
30020: ff 35 a2 76 12 00 push 0x1276a2(%rip) # 1576c8 <o_options@@Base+0x1cc8>
30026: ff 25 a4 76 12 00 jmp *0x1276a4(%rip) # 1576d0 <o_options@@Base+0x1cd0>
3002c: 0f 1f 40 00 nopl 0x0(%rax)
30030: f3 0f 1e fa endbr64
30034: 68 00 00 00 00 push $0x0
30039: e9 e2 ff ff ff jmp 30020 <unlink@plt-0xe10>
3003e: 66 90 xchg %ax,%ax
30040: f3 0f 1e fa endbr64
30044: 68 01 00 00 00 push $0x1
30049: e9 d2 ff ff ff jmp 30020 <unlink@plt-0xe10>
3004e: 66 90 xchg %ax,%ax
30050: f3 0f 1e fa endbr64
30054: 68 02 00 00 00 push $0x2
30059: e9 c2 ff ff ff jmp 30020 <unlink@plt-0xe10>
3005e: 66 90 xchg %ax,%ax
30060: f3 0f 1e fa endbr64
30064: 68 03 00 00 00 push $0x3
30069: e9 b2 ff ff ff jmp 30020 <unlink@plt-0xe10>
3006e: 66 90 xchg %ax,%ax
30070: f3 0f 1e fa endbr64
30074: 68 04 00 00 00 push $0x4
30079: e9 a2 ff ff ff jmp 30020 <unlink@plt-0xe10>
3007e: 66 90 xchg %ax,%ax
30080: f3 0f 1e fa endbr64
30084: 68 05 00 00 00 push $0x5
30089: e9 92 ff ff ff jmp 30020 <unlink@plt-0xe10>
3008e: 66 90 xchg %ax,%ax
30090: f3 0f 1e fa endbr64
30094: 68 06 00 00 00 push $0x6
30099: e9 82 ff ff ff jmp 30020 <unlink@plt-0xe10>
3009e: 66 90 xchg %ax,%ax
```
The `endbr32` / `endbr64` instructions has been carefully designed, so they are `nop` instructions—meaning they can do nothing at all—on CPUs prior to their introductions. Having them doesn't have any effect on older CPUs but enhances security on supported hardware.
## RISC-V’s Latest Achievements: CFI Extension
The above mitigations against ROP fall into two categories:
* **Compiler Modifications**: Can generate more secure binary assembly code.
* **Additional CPU instructions**: Coming with Control Flow Integrity (CFI) checks to prevent exploitation
Back to the beginning of designing CKB-VM, we throughly studied ROP and recognized that a vulnerability in a CKB script could potentially open the door to ROP attacks. However, we eventually did not introduce any specific mitigation against ROP in CKB-VM. Our decision was to stay aligned with the RISC-V ecosystem, avoiding shipping any custom RISC-V spec with additional instructions that would require a patched compiler. Nor do we want to maintain our own compiler set, eliminating the potential that any RISC-V-compliant compiler shall be able to produce CKB script. As the result, we shipped the first version of CKB-VM without ROP mitigations, but that does not mean we’ve ignore this issue:
* We’ve [reached out](https://groups.google.com/a/groups.riscv.org/g/isa-dev/c/LyZzjJG7_18/m/pCSnKZPdBAAJ) to the RISC-V community for possible extension similar to Intel’s solution, and kept monitoring advancements in this field;
* We’ve been watching over progress and writing secure CKB scripts. Since ROP relies on existing vulnerabilities, secure CKB scripts can kept ROP purely theoretical.
We were thrilled when the **RISC-V CFI (Control-Flow Integrity) Extension** was officialy [ratified](https://github.com/riscv/riscv-cfi/releases/tag/v1.0) in July 2024. Designed by the brilliant minds from the RISC-V Foundation, this extension directly addresses ROP attacks with two key features:
* `Zicfilp` extension introduces **landing pad**: Resembles Intel’s `endbr32` / `endbr64` to ensure that the CPU can only jump to valid, permitted targets.
* `Zicfiss` extension introduces **shadow stack** with a series of instructions:. Offers a hardware solution similar to Retguard, where CPU ensures the control flow integrity or simply puts the call stack, preventing tampering throughout execution.
Together, these features offer the state-of-the-art mitigations against ROP. More importantly, RISC-V CFI is now an official extension, meaning all future RISC-V CPUs, compilers, and tools will support this extension. In fact, LLVM 19 has already [supported](https://releases.llvm.org/19.1.0/docs/ReleaseNotes.html#changes-to-the-risc-v-backend), and I believe other compilers and tools will follow soon.
Once fully adopted, CKB script developers can simply turn them on like a switch during code compilation. Without modifying the code, they can enjoy the security provided by RISC-V CFI extensions. Even if a vulnerability exists in a CKB script, these built-in enforcements can prevent it from being exploited.
## Final Words
Security is complex. While we strive for maximum security, certain design principles might get in the way from introducing specific mitigations. ROP is a prime example: while we did learn much about it early on, implementing the best mitigations needs proper timing. Now the time has come. We are happy to introduce RISC-V CFI in CKB’s next hardfork, bringing stronger security for everyone.
***
✍🏻 Written by Xuejie Xiao
His previous posts include:
* [A Journey Optimizing CKB Smart Contract: Porting Bitcoin as an Example](https://blog.cryptape.com/a-journey-optimizing-ckb-smart-contract)
* [Optimizing C++ Code for CKB-VM: Porting Bitcoin as an Example](https://blog.cryptape.com/optimizing-c-code-for-ckb-vm)
Find more in his personal website [Less is More](https://xuejie.space/).
-

@ 9967f375:04f9a5e1
2025-02-13 08:39:58
El día 13, primer viernes de Cuaresma asistió su Exc. y Real Audiencia en la Capilla Real del Palacio a la Misa, y Sermón, que predicó el Doctor Don Pedro Ramírez del Castillo, Canónigo Penitenciario de la Metropoltana.
#GacetadeMéxico #Febrero
-

@ bf47c19e:c3d2573b
2025-02-13 08:10:44
Originalni tekst na [dvadesetjedan.com](https://dvadesetjedan.com/blog/bitcoin-privatnost-najbolje-prakse).
###### Autor: [Gigi](https://dergigi.com/2021/03/14/bitcoin-privacy-best-practices/) / Prevod na srpski: [Plumsky](https://t.me/Plumski)
---
> Postoji sveto carstvo privatnosti za svakog čoveka gde on bira i pravi odluke – carstvo stvoreno na bazičnim pravima i slobode koje zakon, generalno, ne sme narušavati. Džefri Fišer, Arhiepiskop Canterberija (1959)
Pre ne toliko dugo, uobičajen režim interneta je bio neenkriptovan običan tekst (plain text). Svi su mogli špiunirati svakoga i mnogi nisu o tome ni razmišljali. Globalno obelodanjivanje nadzora 2013. je to promenilo i danas se koriste mnogo bezbedniji protokoli i end-to-end enkripcija postaje standard sve više. Iako bitcoin postaje tinejdžer, mi smo – metaforično govoreći – i dalje u dobu običnog teksta narandžastog novčića. Bitcoin je radikalno providljiv protokol sam po sebi, ali postoje značajni načini da korisnik zaštiti svoju privatnost. U ovom članku želimo da istaknemo neke od ovih strategija, prodiskutujemo najbolje prakse, i damo preporuke koje mogu primeniti i bitcoin novajlije i veterani.
#### Zašto je privatnost bitna
> Privatnost je potrebna da bi otvoreno društvo moglo da funkcioniše u digitalnoj eri. Privatnost nije isto što i tajanstvenost. Privatna stvar je nešto što neko ne želi da ceo svet zna, a tajna stvar je nešto što neko ne želi bilo ko da zna. Privatnost je moć da se čovek selektivno otkriva svom okruženju.
Ovim snažnim rečima Erik Hjus je započeo svoj tekst Sajferpankov Manifesto (Cypherpunk's Manifesto) 1993. Razlika između privatnosti i tajanstvenosti je suptilna ali jako važna. Odlučiti se za privatnost ne znači da neko ima tajne koje želi sakriti. Da ovo ilustrujemo shvatite samo da ono što obavljate u svom toaletu ili u spavaćoj sobi nije niti ilegalno niti tajna (u mnogim slučajevima), ali vi svejedno odlučujete da zatvorite vrata i navučete zavese.
Slično tome, koliko para imate i gde ih trošite nije naručito tajna stvar. Ipak, to bi trebalo biti privatan slučaj. Mnogi bi se složili da vaš šef ne treba da zna gde vi trošite vašu platu. Privatnosti je čak zaštićena od strane mnogobrojnih internacionalnih nadležnih organa. Iz Američke Deklaracije Prava i Dužnosti Čoveka (American Declaration of the Rights and Duties of Man) Ujedinjenim Nacijama, napisano je da je privatnost fundamentalno prava gradjana širom sveta.
> Niko ne sme biti podvrgnut smetnjama njegovoj privatnosti, porodici, rezidenciji ili komunikacijama, niti napadnuta njegova čast i reputacija. Svi imaju pravo da se štite zakonom protiv takvih smetnja ili napada. Artikal 12, Deklaracija Ljudskih Prava Ujedinjenih Nacija
#### Bitcoin i privatnost
Iako je bitcoin često opisivan kao anoniman način plaćanja medijima, on u stvari poseduje potpuno suprotne osobine. On je poluanoniman u najboljem slučaju i danas mnogima nije ni malo lako primeniti taktike da bi bili sigurni da njihov poluanonimni identitet na bitcoin mreži ne bude povezan sa legalnim identitetom u stvarnom svetu.
Bitcoin je otvoren sistem. On je javna baza podataka koju svako može da proučava i analizira. Znači, svaka transakcija koja je upisana u tu bazu kroz dokaz rada (proof-of-work) postojaće i biće otkrivena dokle god bitcoin postoji, što znači - zauvek. Ne primenjivati najbolje prakse privatnosti može imati štetne posledice u dalekoj budućnosti.
Privatnost, kao sigurnost, je proces koji je težak, ali nije nemoguć. Alatke nastavljaju da se razvijaju koje čuvaju privatnost kad se koristi bitcoin and srećom mnoge od tih alatki su sve lakše za korišćenje. Nažalost ne postoji panacea u ovom pristupu. Mora se biti svesan svih kompromisa i usavršavati te prakse dok se one menjaju.
#### Najbolje prakse privatnosti
Kao i sve u bitcoinu, kontrola privatnosti je postepena, korak po korak, procedura. Naučiti i primeniti ove najbolje prakse zahteva strpljivost i odgovornost, tako da ne budite obeshrabreni ako vam se čini da je to sve previše. Svaki korak, koliko god bio mali, je korak u dobrom pravcu.
Koje korake preduzeti da bi uvećali svoju privatnost:
* Budite u vlasništvu sami svojih novčića
* Nikad ne ponavljajte korišćenje istih adresa
* Minimizirajte korišćenje servisa koji zahtevaju identitet (Know your customer - KYC)
* Minimizirajte sve izloženosti trećim licima
* Upravljajte svojim nodom
* Koristite Lightning mrežu za male transakcije
* Nemojte koristiti javne blok pretraživače za svoje transakcije
* Koristite metodu CoinJoin često i rano pri nabavljanju svojih novčića
**Budite u vlasništvu sami svojih novčića**: Ako ključevi nisu tvoji, onda nije ni bitcoin. Ako neko drugo drži vaš bitcoin za vas, oni znaju sve što se može znati: količinu, istoriju transakcija pa i sve buduće transakcije, itd. Preuzimanje vlasništva bitcoina u svoje ruke je prvi i najvažniji korak.
**Nikad ne kroistite istu adresu dvaput**: Ponavljanje adresa poništava privatnost pošiljalca i primaoca bitcoina. Ovo se treba izbegavati pod svaku cenu.
**Minimizirajte korišćenje servisa koji zahtevaju identitet (KYC)**: Vezivati svoj legalni identitet za svoje bitcoin adrese je zlo koje se zahteva od strane mnogih državnih nadležnosti. Dok je efektivnost ovih zakona i regulacija disputabilno, posledice njihovog primenjivanja su uglavnom štetne po korisnicima. Ovo je očigledno pošto je česta pojava da se te informacije često izlivaju iz slabo obezbeđenih digitalnih servera. Ako izaberete da koristite KYC servise da bi nabavljali bitcoin, proučite i razumite odnos između vas i tog biznisa. Vi ste poverljivi tom biznisu za sve vaše lične podatke, pa i buduće obezbeđenje tih podataka. Ako i dalje zarađujete kroz fiat novčani sistem, mi preporučujemo da koristite samo bitcoin ekskluzivne servise koji vam dozvoljavaju da autamatski kupujete bitcoin s vremena na vreme. Ako zelite da potpuno da izbegnete KYC, pregledajte https://bitcoinqna.github.io/noKYConly/.
**Minimizirajte sve izloženosti trećim licima**: Poverljivost trećim licima je bezbednosna rupa (https://nakamotoinstitute.org/trusted-third-parties/). Ako možete biti poverljivi samo sebi, onda bi to tako trebalo da bude.
**Upravljajte svojim nodom**: Ako nod nije tvoj, onda nisu ni pravila. Upravljanje svojim nodom je suštinska potreba da bi se bitcoin koristio na privatan način. Svaka interakcija sa bitcoin mrežom je posrednjena nodom. Ako vi taj nod ne upravljate, čiji god nod koristite može da vidi sve što vi radite. Ova upustva (https://bitcoiner.guide/node/) su jako korisna da bi započeli proces korišćenja svog noda.
**Koristite Lightning mrežu za male transakcije**: Pošto Lightning protokol ne koristi glavnu bitcoin mrežu za trasakcije onda je i samim tim povećana privatnost korišćenja bez dodatnog truda. Iako je i dalje rano, oni apsolutno bezobzirni periodi Lightning mreže su verovatno daleko iza nas. Korišćenje Lightning-a za transakcije malih i srednjih veličina će vam pomoći da uvećate privatnost a da smanjite naplate svojih pojedinačnih bitcoin transakcija.
**Nemojte koristiti javne blok pretraživače za svoje transakcije**: Proveravanje adresa na javnim blok pretraživačima povezuje te adrese sa vašim IP podacima, koji se onda mogu koristiti da se otkrije vaš identitet. Softveri kao Umbrel i myNode vam omogućavaju da lako koristite sami svoj blok pretraživač. Ako morate koristiti javne pretraživače, uradite to uz VPN ili Tor.
**Koristite CoinJoin često i rano pri nabavljanju svojih novčića**: Pošto je bitcoin večan, primenjivanje saradničkih CoinJoin praksa će vam obezbediti privatnost u budućnosti. Dok su CoinJoin transakcije svakovrsne, softveri koji su laki za korišćenje već sad postoje koji mogu automatizovati ovu vrstu transakcija. Samourai Whirlpool (https://samouraiwallet.com/whirlpool) je odličan izbor za Android korisnike. Joinmarket (https://github.com/joinmarket-webui/jam) se može koristiti na vašem nodu. A servisi postoje koji pri snabdevanju vašeg bitcoina istog trenutka obave CoinJoin tranzakciju automatski.
#### Zaključak
Svi bi trebalo da se potrude da koriste bitcoin na što privatniji način. Privatnost nije isto što i tajanstvenost. Privatnost je ljudsko pravo i mi svi trebamo da branimo i primenljujemo to pravo. Teško je izbrisati postojeće informacije sa interneta; a izbrisati ih sa bitcoin baze podataka je nemoguće. Iako su daleko od savršenih, alatke postoje danas koje vam omogućavaju da najbolje prakse privatnosti i vi sami primenite. Mi smo vam naglasili neke od njih i - kroz poboljšanje u bitcoin protokolu kroz Taproot i Schnorr - one će postajati sve usavršenije.
Bitcoin postupci se ne mogu lako opisati korišćenjem tradicionalnim konceptima. Pitanja kao što su "Ko je vlasnik ovog novca?" ili "Odakle taj novac potiče?" postaju sve teža da se odgovore a u nekim okolnostima postaju potpuno beznačajna.
Satoši je dizajnirao bitcoin misleći na privatnost. Na nivou protokola svaka bitcoin transakcija je proces "topljenja" koji za sobom samo ostavlja heuristične mrvice hleba. Protokolu nije bitno odakle se pojavio bilo koji bitcoin ili satoši. Niti je njega briga ko je legalan identitet vlasnika. Protokolu je samo važno da li su digitalni potpisi validni. Dokle god je govor slobodan, potpisivanje poruka - privatno ili ne - ne sme biti kriminalan postupak.
Dodatni Resursi
[This Month in Bitcoin Privacy](https://enegnei.github.io/This-Month-In-Bitcoin-Privacy/) | Janine
[Hodl Privacy FAQ](https://6102bitcoin.com/faq-hodl-privacy/) | 6102
[Digital Privacy](https://6102bitcoin.com/blog/digital-privacy/) | 6102
[UseWhirlpool.com](http://usewhirlpool.com/) | Bitcoin Q+A
[Bitcoin Privacy Guide](https://bitcoiner.guide/privacy/) | Bitcoin Q+A
Ovaj članak napisan je u saradnji sa Matt Odellom, nezavisnim bitcoin istraživačem. Nađite njegove preporuke za privatnost na [werunbtc.com](https://werunbtc.com/)
[Originalni tekst](https://dergigi.com/2021/03/14/bitcoin-privacy-best-practices/)
-

@ 04ed2b8f:75be6756
2025-02-13 08:02:39
Freedom. It’s the word on everyone’s lips, the dream of every soul. We long for it, we chase it, we believe that if we can break free from this chain or that constraint, we will finally be free. **But true freedom is not about external circumstances—it’s about control.**
The truth is, **the most powerful chains are the ones we place on ourselves**. The world can throw its challenges at you, life can dish out its unfair blows, but **if you cannot control yourself, your thoughts, your emotions, your reactions, then you are no different than a prisoner.**
There is no freedom in chaos. There is no freedom in losing control. **Freedom is mastery—mastery of the self.**
## **Freedom Begins Within**
You can have all the money in the world, live in the most luxurious place, and have every material possession your heart desires, but **if you cannot control your impulses, your habits, your desires—none of that will matter.** You are still a slave to your cravings. You are still a puppet to your own emotions, and that is **no real freedom.**
What does freedom look like?
- **It’s the power to act with purpose, not to react out of emotion.**
- **It’s the strength to stay disciplined when every part of you wants to quit.**
- **It’s the courage to say ‘no’ to distractions, to temptation, to things that steer you off course.**
- **It’s the clarity to make choices that serve your growth, not your immediate desires.**
True freedom is the ability to say, “I am in control of myself. I do not let my circumstances control me, nor my emotions rule me. I dictate my actions, my thoughts, my destiny.”
## **Self-Control: The Ultimate Weapon**
The power to control yourself is your greatest weapon. Without it, **you are at the mercy of every challenge, every temptation, and every fleeting emotion**. You may feel like you are “free,” but without self-discipline, you are just a puppet swaying in the wind, vulnerable to every whim that blows your way.
- **The impulse to procrastinate? You overcome it.**
- **The desire to give up? You push through it.**
- **The craving for comfort? You choose growth.**
In the face of any storm, a man with self-control remains grounded, focused, and clear. He doesn’t react in anger or fear—he acts with purpose, with precision, and with vision.
A man who cannot control himself is a man who is owned by his emotions, his desires, his distractions. But the man who conquers his mind, his body, his impulses—he is the one who **owns his life.**
## **The Price of Freedom**
It’s not easy to control yourself. It requires constant effort, relentless discipline, and the courage to face yourself head-on. It means saying ‘no’ to what feels good now, to invest in what will make you stronger later. It means constantly improving, constantly fighting the urge to quit, to give in, to indulge in comfort.
But the price of freedom is worth it. **For when you have control over yourself, no one can take your power.** You become the master of your fate. **You become unshakable.**
## **Freedom Through Discipline**
So, ask yourself: **Are you truly free, or are you simply a slave to your impulses?**
- **Do you control your actions, or do your actions control you?**
- **Are you the master of your emotions, or are they the masters of you?**
Freedom isn’t just about having no chains; it’s about not letting anything control you—least of all yourself. **And when you control yourself, there’s nothing you can’t accomplish.**
A man who cannot control himself is never truly free. But a man who conquers his mind, his habits, his emotions—he is unstoppable.
**Now go and choose to control yourself, and unlock the freedom that’s waiting for you. Or remain a prisoner to your impulses, forever shackled by the chains of your own making. The choice is yours.**
-

@ bf47c19e:c3d2573b
2025-02-13 07:56:50
Originalni tekst na [dvadesetjedan.com](https://dvadesetjedan.com/blog/niko-ne-moze-zabraniti-bitcoin)
###### Autor: [Parker Lewis](https://x.com/parkeralewis) / Prevod na srpski: [Plumsky](https://t.me/Plumski)
---
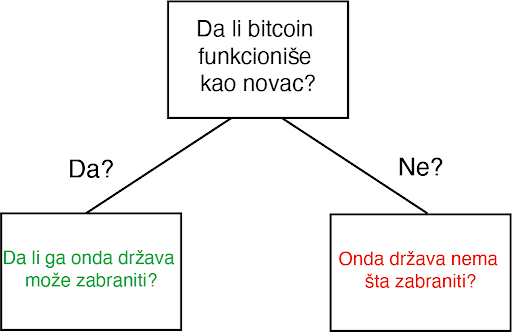
Ideja da država može nekako zabraniti bitcoin je jedna od poslednjih faza tuge, tačno pred prihvatanje realnosti. Posledica ove rečenice je priznanje da bitcoin “funkcioniše”. U stvari, ona predstavlja činjenicu da bitcoin funkcioniše toliko dobro da on preti postojećim državnim monopolima nad novcem i da će zbog toga države da ga unište kroz regulativne prepreke da bi eliminisale tu pretnju. Gledajte na tvrdnju da će države zabraniti bitcoin kao kondicionalnu logiku. Da li bitcoin funkcioniše kao novac? Ako je odgovor „ne“, onda države nemaju šta da zabrane. Ako je odgovor „da“, onda će države da probaju da ga zabrane. Znači, glavna poenta ovog razmišljanja je pretpostavka da bitcoin funkcioiniše kao novac. Onda je sledeće logično pitanje da li intervencija od strane države može uspešno da uništi upravo taj funkcionalan bitcoin.
Za početak, svako ko pokušava da razume kako, zašto, ili da li bitcoin funkcioniše mora da proceni ta pitanja potpuno nezavisno od prouzrekovanja državne regulacije ili intervencije. Iako je nesumnjivo da bitcoin mora da postoji uzgred državnih regulativa, zamislite na momenat da države ne postoje. Sam od sebe, da li bi bitcoin funkcionisao kao novac, kad bi se prepustio slobodnom tržištu? Ovo pitanje se širi u dodatna pitanja i ubrzo se pretvara u bunar bez dna. Šta je novac? Šta su svojstva koja čine jednu vrstu novca bolje od druge? Da li bitcoin poseduje ta svojstva? Da li je bitcoin bolja verzija novca po takvim osobinama? Ako je finalni zaključak da bitcoin ne funkcioniše kao novac, implikacije državne intervencije su nebitne. Ali, ako je bitcoin funkcionalan kao novac, ta pitanja onda postaju bitna u ovoj debati, i svako ko o tome razmišlja bi morao imati taj početnički kontekst da bi mogao proceniti da li je uopšte moguće zabraniti. Po svom dizajnu, bitcoin postoji van države. Ali bitcoin nije samo van kontrole države, on u stvari funkcioniše bez bilo kakve saradnje centralizovanih identiteta. On je globalan i decentralizovan. Svako može pristupiti bitcoinu bez potrebe saglasnosti bilo koga i što se više širi sve je teže cenzurisati celokupnu mrežu. Arhitektura bitcoina je namerno izmišljena da bude otporna na bilo koje pokušaje države da ga zabrane. Ovo ne znači da države širom sveta neće pokušavati da ga regulišu, oporezuju ili čak da potpuno zabrane njegovo korišćenje. Naravno da će biti puno bitki i otpora protiv usvajanja bitcoina među građanima. Federal Reserve i Američki Treasury (i njihovi globalni suparnici) se neće ležeći predati dok bitcoin sve više i više ugrožava njihove monopole prihvatljivog novca. Doduše, pre nego što se odbaci ideja da države mogu potpuno zabraniti bitcoin, mora se prvo razumeti posledice tog stava i njegovog glasnika.
#### Progresija poricanja i stepeni tuge
Pripovesti skeptičara se neprestano menjaju kroz vreme. Prvi stepen tuge: bitcoin nikad ne može funkcionisati-njegova vrednost je osnovana ni na čemu. On je moderna verzija tulip manije. Sa svakim ciklusom uzbuđenja, vrednost bitcoina skače i onda vrlo brzo se vraća na dole. Često nazvano kao kraj njegove vrednosti, bitcoin svaki put odbija da umre i njegova vrednost pronađe nivo koji je uvek viši od prethodnih ciklusa globalne usvajanja. Tulip pripovetka postaje stara i dosadna i skeptičari pređu na više nijansirane teme, i time menjaju bazu debate. Drugi stepen tuge predstoji: bitcoin je manjkav kao novac. On je previše volatilan da bi bio valuta, ili je suviše spor da bi se koristio kao sistem plaćanja, ili se ne može proširiti dovoljno da zadovolji sve promete plaćanja na svetu, ili troši isuviše struje. Taj niz kritike ide sve dalje i dalje. Ovaj drugi stepen je progresija poricanja i dosta je udaljen od ideje da je bitcoin ništa više od bukvalno bezvrednog ničega.
Uprkos tim pretpostavnim manjcima, vrednost bitcoin mreže nastavje da raste vremenom. Svaki put, ona ne umire, nasuprot, ona postaje sve veća i jača. Dok se skeptičari bave ukazivanjem na manjke, bitcoin ne prestaje. Rast u vrednosti je prouzrokovan jednostavnom dinamikom tržišta: postoji više kupca nego prodavca. To je sve i to je razlog rasta u adopciji. Sve više i više ljudi shvata zašto postoji fundamentalna potražnja za bitcoinom i zašto/kako on funkcioniše. To je razlog njegovog dugotrajnog rasta. Dokle god ga sve više ljudi koristi za čuvanje vrednosti, neće pasti cena snabdevanja. Zauvek će postojati samo 21 milion bitcoina. Nebitno je koliko ljudi zahtevaju bitcoin, njegova cela količina je uvek ista i neelastična. Dok skeptičari nastavljaju sa svojom starom pričom, mase ljudi nastavljaju da eliminišu zabludu i zahtevaju bitcoin zbog njegovih prednosti u smislu novčanih svojstva. Između ostalog, ne postoji grupa ljudi koja je više upoznata sa svim argumentima protiv bitcoina od samih bitcoinera.

Očajanje počinje da se stvara i onda se debata još jedanput pomera. Sada nije više činjenica je vrednost bitcoina osnovana ni na čemu niti da ima manjke kao valuta; sada se debata centrira na regulaciji državnih autoriteta. U ovom zadnjem stepenu tuge, bitcoin se predstavlja kao u stvari isuviše uspešnom alatkom i zbog toga države ne smeju dozvoliti da on postoji. Zaista? Znači da je genijalnost čoveka ponovo ostvarila funkcionalan novac u tehnološko superiornoj formi, čije su posledice zaista neshvatljive, i da će države upravo taj izum nekako zabraniti. Primetite da tom izjavom skeptičari praktično priznaju svoj poraz. Ovo su poslednji pokušaji u seriji promašenih argumenata. Skeptičari u isto vreme prihvataju da postoji fundamentalna potražnja za bitcoinom a onda se premeštaju na neosnovan stav da ga države mogu zabraniti.
Ajde da se poigramo i tim pitanjem. Kada bih zapravo razvijene države nastupile na scenu i pokušale da zabrane bitcoin? Trenutno, Federal Reserve i Treasury ne smatraju bitcoin kao ozbiljnu pretnju superiornosti dolara. Po njihovom celokupnom mišljenju, bitcoin je slatka mala igračka i ne može da funkcioniše kao novac. Sadašnja kompletna kupovna moć bitcoina je manja od $200 milijardi. Sa druge strane, zlato ima celokupnu vrednost od $8 triliona (40X veću od bitcoina) i količina odštampanog novca (M2) je otprilike 15 triliona (75X veličine bitcoinove vrednosti). Kada će Federal Reserve i Treasury da počne da smatra bitcoin kao ozbiljnu pretnju? Kad bitcoin poraste na $1, $2 ili $3 triliona? Možete i sami da izaberete nivo, ali implikacija je da će bitcoin biti mnogo vredniji, i posedovaće ga sve više ljudi širom sveta, pre nego što će ga državne vlasti shvatiti kao obiljnog protivnika.
Predsednik Tramp & Treasury Sekretar Mnučin o Bitcoinu (2019):
> „Ja neću pričati o bitcoinu za 10 godina, u to možete biti sigurni {…} Ja bi se kladio da čak za 5 ili 6 godina neću više pričati o bitcoinu kao sekretar Trusury-a. Imaću preča posla {…} Mogu vam obećati da ja lično neću biti pun bitcoina.“ – Sekretar Treasury-a Stiv Mnučin
> „Ja nisam ljubitelj bitcoina {…}, koji nije novac i čija vrednost je jako volatilna i osnovana na praznom vazduhu.“ – Predsednik Donald J. Tramp
Znači, logika skeptika ide ovako: bitcoin ne funkcioniše, ali ako funkcioniše, onda će ga država zabraniti. Ali, države slobodnog sveta neće pokušati da ga zabrane dokle god se on ne pokaže kao ozbiljna pretnja. U tom trenutku, bitcoin će biti vredniji i sigurno teži da se zabrani, pošto će ga više ljudi posedovati na mnogo širem geografskom prostoru. Ignorišite fundamentalne činjenice i asimetriju koja je urođena u globalnom dešavanju monetizacije zato što u slučaju da ste u pravu, države će taj proces zabraniti. Na kojoj strani tog argumenta bi radije stajao racionalan ekonomski učesnik? Posedovanje finansijske imovine kojoj vrednost toliko raste da preti globalnoj rezervnoj valuti, ili nasuprot – nemati tu imovinu? Sa pretpostavkom da individualci razumeju zašto je mogućnost (a sve više i verovatnoća) ove realnosti, koji stav je logičniji u ovom scenariju? Asimetrija dve strane ovog argumenta sama od sebe zahteva da je prvi stav onaj istinit i da fundamentalno razumevanje potražnje bitcoina samo još više ojačava to mišljenje.
#### Niko ne moze zabraniti bitcoin
Razmislite šta bitcoin u stvari predstavlja pa onda šta bi predstavljala njegova zabrana. Bitcoin je konverzija subjektivne vrednosti, stvorena i razmenjena u realnošću, u digitalne potpise. Jednostavno rečeno, to je konverzija ljudskog vremena u novac. Kad neko zahteva bitcoin, oni u isto vreme ne zahtevaju neki drugi posed, nek to bio dolar, kuća, auto ili hrana itd. Bitcoin predstavlja novčanu štednju koja sa sobom žrtvuje druge imovine i servise. Zabrana bitcoina bi bio napad na najosnovnije ljudske slobode koje je on upravo stvoren da brani. Zamislite reakciju svih onih koji su prihvatili bitcoin: „Bilo je zabavno, alatka za koju su svi eksperti tvrdili da neće nikad funkcionisati, sada toliko dobro radi i sad ti isti eksperti i autoriteti kažu da mi to nemožemo koristiti. Svi idite kući, predstava je gotova.“verovanje da će svi ljudi koji su učestvovali u bitcoin usvajanju, suverenitetu koji nudi i finansiskoj slobodi, odjednom samo da se predaju osnovnom rušenju njihovih prava je potpuno iracionalna pozicija.
> Novac je jedan od najbitnijih instrumenata za slobodu koji je ikad izmišljen. Novac je to što u postojećem društvu ostvaruje mogućnosti siromašnom čoveku – čiji je domet veći nego onaj koji je bio dostižan bogatim ljudima pre ne toliko puno generacija.“ – F. A. Hajek
Države nisu uspele da zabrane konzumiranje alkohola, droga, kupovinu vatrenog oružja, pa ni posedovanje zlata. Država može samo pomalo da uspori pristup ili da deklariše posedovanje ilegalnim, ali ne može da uništi nešto što veliki broj raznovrsnih ljudi smatra vrednim. Kada je SAD zabranila privatno posedovanje zlata 1933., zlato nije palo u vrednosti ili nestalo sa finansijskog tržišta. Ono je u stvari poraslo u vrednosti u poređenju sa dolarom, i samo trideset godina kasnije, zabrana je bila ukinuta. Ne samo da bitcoin nudi veću vrednosno obećanje od bilo kog drugog dobra koje su države pokušale da zabrane (uključujući i zlato); nego po svojim osobinama, njega je mnogo teže zabraniti. Bitcoin je globalan i decentralizovan. On ne poštuje granice i osiguran je mnoštvom nodova i kriptografskim potpisima. Sam postupak zabrane bi zahtevao da se u isto vreme zaustavi „open source“ softver koji emituje i izvršava slanje i potvrđivanje digitalno enkriptovanih ključeva i potpisa. Ta zabrana bi morala biti koordinisana između velikog broja zemalja, sa tim da je nemoguće znati gde se ti nodovi i softver nalazi ili da se zaustavi instaliranje novih nodova u drugim pravnim nadležnostima. Da ne pominjemo i ustavske pitanja, bilo bi tehnički neizvodljivo da se takva zabrana primeni na bilo kakav značajan način.
Čak kada bih sve zemlje iz G-20 grupe koordinisale takvu zabranu u isto vreme, to ne bi uništilo bitcoin. U stvari, to bi bilo samoubistvo za fiat novčani sistem. To bi još više prikazalo masama da je bitcoin u stvari novac koji treba shvatiti ozbiljno, i to bi samo od sebe započelo globalnu igru vatanje mačke za rep. Bitcoin nema centralnu tačku za napad; bitcoin rudari, nodovi i digitalni potpisi su rasejani po celom svetu. Svaki aspekt bitcoina je decentralizovan, zato su glavni stubovi njegove arhitekture da učesnici uvek treba kontrolisati svoje potpise i upravljati svojim nodom. Što više digitalnih potpisa i nodova koji postoje, to je više bitcoin decentralizovan, i to je više odbranjiva njegova mreža od strane neprijatelja. Što je više zemalja gde rudari izvršavaju svoj posao, to je manji rizik da jedan nadležni identitet može uticati na njegov bezbednosni sistem. Koordinisan internacionalni napad na bitcoin bi samo koristio da bitcoin još više ojača svoj imuni sistem. Na kraju krajeva, to bi ubrzalo seobu iz tradicionalnog finansijskog sistema (i njegovih valuta) a i inovaciju koja postoji u bitcoin ekosistemu. Sa svakom bivšom pretnjom, bitcoin je maštovito pronalazio način da ih neutrališe pa i koordinisan napad od strane država ne bi bio ništa drugačiji.
Inovacija u ovoj oblasti koja se odlikuje svojom „permissionless“ (bez dozvole centralnih identiteta) osobinom, omogućava odbranu od svakojakih napada. Sve varijante napada koje su bile predvidjene je upravo to što zahteva konstantnu inovaciju bitcoina. To je ona Adam Smitova nevidljiva ruka, ali dopingovana. Pojedinačni učesnici mogu da veruju da su motivisani nekim većim uzrokom, ali u stvari, korisnost kaja je ugrađena u bitcoin stvara kod učesnika dovoljno snažan podsticaj da omogući svoje preživljavanje. Sopstveni interes milione, ako ne milijarde, nekoordinisanih ljudi koji se jedino slažu u svojom međusobnom potrebom za funkcionalnim novcem podstiče inovacije u bitcoinu. Danas, možda to izgleda kao neka kul nova tehnologija ili neki dobar investment u finansijskom portfoliju, ali čak i ako to mnogi ne razumeju, bitcoin je apsolutna nužnost u svetu. To je tako zato što je novac nužnost a historijski priznate valute se fundamentalno raspadaju. Pre dva meseca, tržište američkih državnih obveznica je doživeo kolaps na šta je Federal Reserve reagovao time što je povećao celokupnu količinu dolara u postojanju za $250 milijardi, a još više u bliskoj budućnosti. Tačno ovo je razlog zašto je bitcoin nužnost a ne samo luksuzni dodatak. Kada inovacija omogućava bazično funkcionisanje ekonomije ne postoji ni jedna država na svetu koja može da zaustavi njenu adopciju i rast. Novac je nužnost a bitcoin znatno poboljšava sistem novca koji je ikada postojao pre njega.
Sa više praktične strane, pokušaj zabranjivanja bitcoina ili njegove velike regulacije od nadležnosti bi direktno bilo u korist susedne nadležnih organa. Podsticaj da se odustane od koordinisanog napada na bitcoin bi bio isuviše veliki da bi takvi dogovori bili uspešni. Kada bi SAD deklarisovale posed bitcoina ilegalnim sutra, da li bi to zaustavilo njegov rast, razvoj i adopciji i da li bi to smanjilo vrednost celokupne mreže? Verovatno. Da li bi to uništilo bitcoin? Ne bi. Bitcoin predstavlja najpokretljivije kapitalno sredstvo na svetu. Zemlje i nadležne strukture koje kreiraju regulativnu strukturu koja najmanje ustručava korišćenje bitcoina će biti dobitnici velike količine uliva kapitala u svoje države.
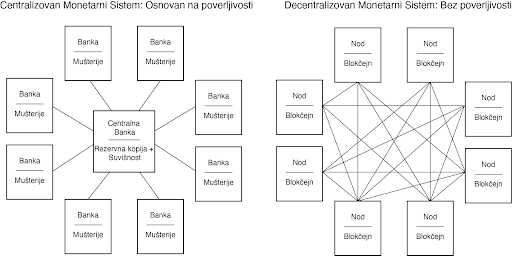
#### Zabrana Bitcoinove Zatvoreničke Dileme
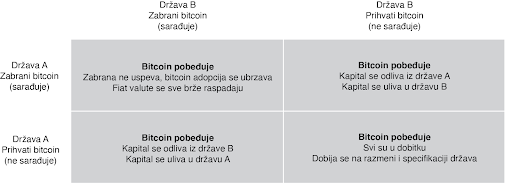
U praksi, zatvorenička dilema nije igra jedan na jedan. Ona je multidimenzijska i uključuje mnoštvo nadležnosti, čiji se interesi nadmeću međusobno, i to uskraćuje mogućnosti bilo kakve mogućnosti zabrane. Ljudski kapital, fizički kapital i novčani kapital će sav ići u pravcu država i nadležnosti koje najmanje ustručuju bitcoin. To se možda neće desiti sve odjednom, ali pokušaji zabrane su isto za badava koliko bi bilo odseći sebi nos u inat svom licu. To ne znači da države to neće pokušati. India je već probala da zabrani bitcoin. Kina je uvela puno restrikcija. Drugi će da prate njihove tragove. Ali svaki put kada država preduzme takve korake, to ima nepredvidljive efekte povećanja bitcoin adopcije. Pokušaji zabranjivanja bitcoina su jako efektivne marketing kampanje. Bitcoin postoji kao sistem nevezan za jednu suverenu državu i kao novac je otporan na cenzuru. On je dizajniran da postoji van državne kontrole. Pokušaji da se taj koncept zabrani samo još više daje njemu razlog i logiku za postojanje.
#### Jedini Pobednički Potez je da se Uključiš u Igru
Zabrana bitcoina je trošenje vremena. Neki će to pokušati; ali svi će biti neuspešni. Sami ti pokušaji će još više ubrzati njegovu adopciju i širenje. Biće to vetar od 100 km/h koji raspaljuje vatru. To će ojačati bitcoin sve više i doprineće njegovoj pouzdanosti. U svakom slučaju, verovanje da će države zabraniti bitcoin u momentu kada on postane dovoljno velika pretnja rezervnim valutam sveta, je iracionalan razlog da se on no poseduje kao instrument štednje novca. To ne samo da podrazumeva da je bitcoin novac, ali u isto vreme i ignoriše glavne razloge zašto je to tako: on je decentralizovan i otporan na cenzure. Zamislite da razumete jednu od nojvećih tajni današnjice i da u isto vreme tu tajnu asimetrije koju bitcoin nudi ne primenjujete u svoju korist zbog straha od države. Pre će biti, neko ko razume zašto bitcoin funkcioniše i da ga država ne može zaustaviti, ili nepuno znanje postoji u razumevanju kako bitcoin uopšte funckioniše. Počnite sa razmatranjem fundamentalnih pitanja, a onda primenite to kao temelj da bi procenili bilo koji potencijalan rizik od strane budućih regulacija ili restrikcija državnih organa. I nikad nemojte da zaboravite na vrednost asimetrije između dve strane ovde prezentiranih argumenata. Jedini pobednički potez je da se uključite u igru.
Stavovi ovde prezentirani su samo moji i ne predstavljaju Unchained Capital ili moje kolege. Zahvaljujem se Fil Gajgeru za razmatranje teksta i primedbe.
[Originalni tekst](https://unchained.com/blog/bitcoin-cannot-be-banned/)
-

@ da0b9bc3:4e30a4a9
2025-02-13 06:36:12
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/884478
-

@ e3ba5e1a:5e433365
2025-02-13 06:16:49
My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get [this line](https://www.youtube.com/shorts/kqsomjpz7ok):
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song [Devil Went Down to Georgia](https://youtu.be/ut8UqFlWdDc) that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” *is*, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people *should* be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is *freedom*. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are *definitionally* better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In *Devil Went Down to Georgia*, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
*Libertas magnitudo est*
-

@ d360efec:14907b5f
2025-02-13 05:54:17

**ภาพรวม LUNCUSDT (OKX):**
LUNCUSDT กำลังอยู่ในช่วงที่ *มีความผันผวนสูงและมีความไม่แน่นอนมาก* แม้ว่าในอดีต (TF Day) จะเคยมีสัญญาณของการพยายามกลับตัวเป็นขาขึ้น (Breakout EMA 50 และเกิด Golden Cross) แต่ปัจจุบันแรงซื้อเหล่านั้นเริ่มอ่อนแรงลง และมีแรงขายเข้ามาในตลาดมากขึ้น ทำให้เกิดความขัดแย้งระหว่าง Timeframes ต่างๆ

**สถานะปัจจุบัน:**
* **แนวโน้ม:**
* **TF Day:** เริ่มไม่แน่นอน (จากเดิมที่เป็น Early Uptrend) - แม้ว่าราคาจะยังอยู่เหนือ EMA 50/200 แต่ Money Flow เริ่มแสดงสัญญาณเตือน
* **TF4H:** เริ่มไม่แน่นอน (พักตัว, ทดสอบแนวรับ EMA 50) - Money Flow บ่งบอกถึงแรงขายที่เข้ามา
* **TF15:** ผันผวนสูง, ไม่มีทิศทางชัดเจน (Sideways) - Money Flow แสดงถึงแรงขาย แต่ก็มีแรงซื้อกลับเข้ามาบ้าง
* **Money Flow (LuxAlgo):**
* **TF Day:** แรงซื้อเริ่มอ่อนแรงลงอย่างมีนัยสำคัญ, มีแรงขายเข้ามา
* **TF4H:** แรงขายมีมากกว่าแรงซื้อ
* **TF15:** แรงขายและแรงซื้อผสมกัน, โดยรวมแรงขายยังมากกว่า
* **EMA:**
* **TF Day:** EMA 50/200 เป็นแนวรับ/แนวต้าน
* **TF4H:** EMA 50 กำลังถูกทดสอบ, EMA 200 เป็นแนวต้าน
* **TF15:** EMA 50/200 เป็นแนวต้าน
**โครงสร้างราคา (SMC):**
| Timeframe | Break of Structure (BOS) | Change of Character (CHoCH) | Higher High (HH) & Higher Low (HL) | Equal Highs (EQH) / Equal Lows (EQL) |
| :-------- | :----------------------- | :--------------------------- | :----------------------------------- | :------------------------------------- |
| Day | ด้านบนและล่าง | ด้านบน | เริ่มก่อตัว (แต่ไม่แข็งแกร่ง) | - |
| 4H | ด้านบน | ด้านบน | เริ่มก่อตัว (แต่ไม่ชัดเจน) | มี EQH หลายจุด |
| 15m | ด้านบนและล่าง | มีทั้งบนและล่าง | Lower Highs (LH) & Lower Lows (LL) | มี EQH และ EQL หลายจุด |
**แนวรับ-แนวต้านสำคัญ:**
| Timeframe | แนวรับ | แนวต้าน |
| :-------- | :----------------------------------------------------------- | :--------------------------------------------------------------------- |
| Day | EMA 50 (≈0.00010000), EMA 200 (≈0.00008000), 0.00006000-0.00007000 | 0.00017953 (High ล่าสุด), 0.00014000 (Volume Profile) |
| 4H | EMA 50 (≈0.00007000), 0.00006000-0.00007000 | EMA 200 (≈0.00008000), 0.00008132, บริเวณ 0.00010000-0.00012000 (EQH) |
| 15m | บริเวณ Low ล่าสุด | EMA 50, EMA 200, บริเวณ 0.000075-0.000076 (EQH) |
**กลยุทธ์ (LUNCUSDT):**
1. **Wait & See (ทางเลือกที่ดีที่สุด):**
* **เหตุผล:** ความขัดแย้งระหว่าง Timeframes สูงมาก, แนวโน้มไม่ชัดเจน, Money Flow ใน TF4H และ TF15 เป็นลบ
* รอให้ราคาแสดงทิศทางที่ชัดเจนกว่านี้ (ยืนเหนือ EMA 50 ใน TF4H ได้, Breakout แนวต้านใน TF15)
2. **Buy on Dip (Day, 4H) - *ความเสี่ยงสูงมาก ไม่แนะนำ*:**
* **เหตุผล:** แนวโน้มระยะยาวอาจจะยังเป็นขาขึ้นได้ (ถ้าไม่หลุดแนวรับสำคัญ)
* **เงื่อนไข:** *ต้อง* รอสัญญาณการกลับตัวใน TF15 ก่อน
* **จุดเข้า:** พิจารณาเฉพาะบริเวณแนวรับที่แข็งแกร่งมากๆ (EMA ของ Day/4H) *และต้องดู TF15 ประกอบ*
* **Stop Loss:** ต่ำกว่า Low ล่าสุดของ TF15
3. **Short (15, ความเสี่ยงสูงมาก):**
* **เหตุผล:** แนวโน้ม TF15 เป็นขาลง, Money Flow เป็นลบ
* **เงื่อนไข:** ราคาไม่สามารถ Breakout EMA หรือแนวต้านอื่นๆ ใน TF15 ได้
* **จุดเข้า:** บริเวณ EMA หรือแนวต้านของ TF15
* **Stop Loss:** เหนือ High ล่าสุดของ TF15
**คำแนะนำ (เน้นย้ำ):**
* **LUNC เป็นเหรียญที่มีความเสี่ยงสูงมาก (High Risk):** มีความผันผวนสูง และอาจมีการเปลี่ยนแปลงอย่างรวดเร็ว
* **ความขัดแย้งของ Timeframes:** สถานการณ์ของ LUNCUSDT มีความขัดแย้งสูงมาก และมีความเสี่ยงสูง
* **Money Flow:** บ่งบอกถึงแรงขายที่เริ่มเข้ามา และแนวโน้มขาขึ้น (ระยะกลาง-ยาว) ที่อ่อนแอลง
* **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด:** "รอ" เป็นกลยุทธ์ที่ดีที่สุด
* **Risk Management:** สำคัญที่สุด ไม่ว่าจะเลือกกลยุทธ์ใด ต้องมีการบริหารความเสี่ยงที่ดี
**สรุป:** LUNCUSDT กำลังอยู่ในช่วงเวลาที่ยากลำบากและมีความเสี่ยงสูงมากที่สุดในบรรดา 3 เหรียญที่เราวิเคราะห์กันมา การตัดสินใจที่ผิดพลาดอาจนำไปสู่การขาดทุนได้ ควรพิจารณาอย่างรอบคอบก่อนเข้าเทรดทุกครั้ง และ "รอ" จนกว่าจะมีสัญญาณที่ชัดเจนกว่านี้ เป็นทางเลือกที่ปลอดภัยที่สุดสำหรับนักลงทุนส่วนใหญ่ค่ะ
**Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-

@ d360efec:14907b5f
2025-02-13 05:27:39

**ภาพรวม XRPUSDT (OKX):**
XRPUSDT กำลังอยู่ในช่วงสำคัญ แนวโน้มระยะยาว (TF Day) เริ่มมีสัญญาณบวกของการเป็นขาขึ้น (Early Uptrend) หลังราคา Breakout EMA 50 และ Money Flow สนับสนุน อย่างไรก็ตาม แนวโน้มระยะกลาง (TF4H) เริ่มแสดงความอ่อนแอลง โดยราคาพักตัวลงมาทดสอบแนวรับสำคัญ และ Money Flow บ่งชี้ถึงแรงซื้อที่ลดลงและแรงขายที่เพิ่มขึ้น ส่วนแนวโน้มระยะสั้นมาก (TF15) เป็นขาลงชัดเจน

**แนวโน้ม:**
* **TF Day:** เริ่มเป็นขาขึ้น (Early Uptrend) - Breakout EMA 50, Money Flow เป็นบวก
* **TF4H:** เริ่มไม่แน่นอน (พักตัว, ทดสอบแนวรับ EMA 50 และ EQL) - Money Flow เริ่มเป็นลบ
* **TF15:** ขาลง (Downtrend) ระยะสั้นมาก - ราคาหลุด EMA, โครงสร้างราคาเป็น Lower Highs/Lows, Money Flow เป็นลบ
**โครงสร้างราคา (SMC):**
| Timeframe | Break of Structure (BOS) | Change of Character (CHoCH) | Higher High (HH) & Higher Low (HL) | Equal Highs (EQH) / Equal Lows (EQL) |
| :-------- | :----------------------- | :--------------------------- | :----------------------------------- | :------------------------------------- |
| Day | ด้านบน (Breakout EMA 50) | ไม่ชัดเจน | เริ่มก่อตัว (แต่ยังไม่ชัดเจน) | - |
| 4H | ด้านบน | ไม่ชัดเจน | เริ่มก่อตัว (แต่ไม่ชัดเจน) | EQH: 3.00-3.20, EQL: 2.2667 |
| 15m | ด้านล่าง | มีทั้งบนและล่าง | Lower Highs (LH) & Lower Lows (LL) | EQH: 2.48-2.50, EQL: 2.38 |

**Money Flow (LuxAlgo):**
* **TF Day:** แรงซื้อแข็งแกร่ง
* **TF4H:** แรงซื้อเริ่มอ่อนแรงลง, แรงขายเริ่มเข้ามา
* **TF15:** แรงขายมีอิทธิพลเหนือกว่า
**EMA (Exponential Moving Average):**
* **TF Day:** EMA 50 & 200 เป็นแนวรับ
* **TF4H:** EMA 50 กำลังถูกทดสอบ, EMA 200 เป็นแนวรับถัดไป
* **TF15:** EMA 50 & 200 เป็นแนวต้าน
**แนวรับ-แนวต้านสำคัญ:**
| Timeframe | แนวรับ | แนวต้าน |
| :-------- | :----------------------------------------------------- | :----------------------------------------------------------------------- |
| Day | EMA 50 (≈1.56), EMA 200 (≈1.08) | 3.4049 (High), 3.00-3.20 (EQH) |
| 4H | EMA 50 (≈2.20), *2.2667 (EQL)*, EMA 200, 1.7820 | 3.4049, 2.3987 (Volume Profile), 3.00-3.20 (EQH) |
| 15m | 2.38 (EQL, Volume Profile), 2.3274 | EMA 50, EMA 200, 2.4196, Equilibrium (≈2.44), 2.48-2.50 (EQH) |
**กลยุทธ์ (XRPUSDT):**
1. **Wait & See (ทางเลือกที่ดีที่สุด):**
* **เหตุผล:** ความขัดแย้งระหว่าง Timeframes สูง, TF4H กำลังทดสอบแนวรับสำคัญ, Money Flow ใน TF4H และ TF15 เป็นลบ
* รอให้ราคาแสดงทิศทางที่ชัดเจน (ยืนเหนือ EMA 50 ใน TF4H ได้ หรือ Breakout แนวต้านใน TF15)
2. **Buy on Dip (Day, 4H) - *ความเสี่ยงสูงมาก*:**
* **เหตุผล:** แนวโน้มระยะยาวยังมีโอกาสเป็นขาขึ้น, Money Flow ใน TF Day เป็นบวก
* **เงื่อนไข (สำคัญมาก):** *ต้อง* รอสัญญาณการกลับตัวใน TF15 ก่อน เช่น:
* Breakout แนวต้านย่อยๆ พร้อม Volume
* Money Flow (TF15) เปลี่ยนเป็นสีเขียว
* Bullish Candlestick Patterns
* **จุดเข้า (Day):** EMA 50, EMA 200 (*ดู TF15 ประกอบ*)
* **จุดเข้า (4H):** EMA 50, *2.2667 (EQL)* (*ดู TF15 ประกอบ*)
* **Stop Loss:** ต่ำกว่า Low ล่าสุดของ TF15 หรือต่ำกว่าแนวรับที่เข้าซื้อ
3. **Short (15, ความเสี่ยงสูงมาก):**
* **เหตุผล:** แนวโน้ม TF15 เป็นขาลง, Money Flow เป็นลบ
* **เงื่อนไข:** ราคาไม่สามารถกลับขึ้นไปยืนเหนือ EMA ของ TF15 ได้
* **จุดเข้า:** บริเวณ EMA ของ TF15 หรือแนวต้านอื่นๆ
* **Stop Loss:** เหนือ High ล่าสุดของ TF15
**คำแนะนำ:**
* **ความขัดแย้งของ Timeframes:** XRPUSDT มีความขัดแย้งสูงมาก และมีความเสี่ยงสูง
* **Money Flow:** Day เป็นบวก, 4H เริ่มเป็นลบ, 15m เป็นลบ
* **EMA 50 (TF4H) & EQL 2.2667:** จุดชี้ชะตา
* **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด:** "รอ" ดีที่สุด
* **Risk Management:** สำคัญที่สุด
**สรุป:** สถานการณ์ของ XRPUSDT ตอนนี้มีความเสี่ยงสูงมาก และไม่เหมาะกับนักลงทุนที่รับความเสี่ยงได้ต่ำ การ "รอ" จนกว่าจะมีสัญญาณที่ชัดเจนกว่านี้ เป็นทางเลือกที่ปลอดภัยที่สุดค่ะ
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-

@ d360efec:14907b5f
2025-02-13 04:47:20

**ภาพรวม BTCUSDT :**
Bitcoin (BTCUSDT) กำลังอยู่ในช่วงสำคัญ แม้ว่าแนวโน้มหลักในระยะกลางถึงยาว (TF Day & 4H) จะยังคงเป็นขาขึ้นที่แข็งแกร่ง แต่ในระยะสั้นมาก (TF15) กลับแสดงสัญญาณของความอ่อนแอและการปรับฐานลงมา ทำให้เกิดความไม่แน่นอนในทิศทางของราคา อย่างไรก็ตาม *Money Flow ใน TF Day บ่งชี้ว่าแรงซื้อโดยรวมยังคงแข็งแกร่ง*

**แนวโน้ม:**
* **TF Day:** ขาขึ้น (Uptrend) แข็งแกร่ง – ราคาอยู่เหนือ EMA 50 และ EMA 200, โครงสร้างราคาเป็น Higher Highs (HH) และ Higher Lows (HL), *Money Flow เป็นบวก (แรงซื้อ)*
* **TF4H:** ขาขึ้น (Uptrend) – ราคาอยู่เหนือ EMA, มีการพักตัวลงมา (Pullback) แต่ยังไม่เสียโครงสร้างขาขึ้น, *Money Flow เริ่มอ่อนแรง (แรงซื้อลดลง, แรงขายเพิ่มขึ้น)*
* **TF15:** ขาลง (Downtrend) ระยะสั้นมาก – ราคาหลุด EMA และแนวรับย่อย, โครงสร้างราคาเป็น Lower Highs (LH) และ Lower Lows (LL), *Money Flow เป็นลบ (แรงขาย)*
**โครงสร้างราคา (SMC):**
* **TF Day:** ยืนยันแนวโน้มขาขึ้น (HH, HL, BOS)
* **TF4H:** ยืนยันแนวโน้มขาขึ้น (HH, HL, BOS), มี Equal Highs (EQH) ที่เป็นแนวต้าน
* **TF15:** บ่งบอกถึงแนวโน้มขาลงระยะสั้น (BOS ด้านล่าง, LH, LL), มี EQH เป็นแนวต้าน
**Money Flow (LuxAlgo) - สรุป:**
* **TF Day:** แรงซื้อยังคงแข็งแกร่งอย่างชัดเจน
* **TF4H:** แรงซื้อเริ่มอ่อนแรงลง, มีแรงขายเข้ามา
* **TF15:** แรงขายมีอิทธิพลเหนือกว่า

**EMA (Exponential Moving Average):**
* **TF Day & 4H:** EMA 50 & 200 เป็นแนวรับสำคัญ
* **TF15:** EMA 50 & 200 กลายเป็นแนวต้าน
**แนวรับ-แนวต้านสำคัญ:**
| Timeframe | แนวรับ | แนวต้าน |
| :-------- | :------------------------------------------------------------------------- | :-------------------------------------------------------------- |
| Day | EMA 50, EMA 200, 96,000-98,000, 85,724.7 | 109,998.9 (High เดิม) |
| 4H | EMA 50, EMA 200, 96,000-98,000, 89,037.0 | 109,998.9 (EQH, High เดิม) |
| 15m | 95,200 (Low ล่าสุด), 94,707.4 (Low ก่อนหน้า) | EMA 50, EMA 200, บริเวณ 96,000, 96,807.8, 97,000-97,200 |
**กลยุทธ์ (BTCUSDT):**
1. **Buy on Dip (Day, 4H) - *มีความน่าเชื่อถือมากขึ้น แต่ยังคงต้องระมัดระวัง*:**
* **เหตุผล:** แนวโน้มหลักยังเป็นขาขึ้น, Money Flow ใน TF Day แข็งแกร่ง
* **เงื่อนไข:** *ยังคงต้องรอสัญญาณการกลับตัวของราคาใน TF15 ก่อน* (Breakout แนวต้านย่อย, Money Flow TF15 เป็นบวก, Bullish Candlestick Patterns)
* **จุดเข้า (Day):** EMA 50, EMA 200, บริเวณ 96,000-98,000
* **จุดเข้า (4H):** EMA 50
* **Stop Loss:** ต่ำกว่า Low ล่าสุดของ TF15 หรือต่ำกว่าแนวรับที่เข้าซื้อ
2. **Short (15, ความเสี่ยงสูงมาก):**
* **เหตุผล:** แนวโน้ม TF15 เป็นขาลง, Money Flow TF15 เป็นลบ
* **เงื่อนไข:** ราคาไม่สามารถกลับขึ้นไปยืนเหนือ EMA ของ TF15 ได้
* **จุดเข้า:** บริเวณ EMA ของ TF15 หรือแนวต้านอื่นๆ
* **Stop Loss:** เหนือ High ล่าสุดของ TF15
3. **Wait & See (ทางเลือกที่ปลอดภัย):**
* **เหตุผล:** ความขัดแย้งระหว่าง Timeframes ยังคงมีอยู่
* รอให้ตลาดเฉลยทิศทางที่ชัดเจนกว่านี้
**คำแนะนำ (เน้นย้ำ):**
* **Money Flow ใน TF Day:** เป็นปัจจัยบวกที่สำคัญ ทำให้กลยุทธ์ Buy on Dip มีน้ำหนักมากขึ้น
* **ความขัดแย้งของ Timeframes:** ยังคงต้องระวัง TF15 ที่เป็นขาลง
* **Volume:** การ Breakout/Breakdown ใดๆ ควรมี Volume สนับสนุน
* **Risk Management:** สำคัญที่สุด
**สรุป:**
สถานการณ์ของ BTCUSDT โดยรวมยังคงเป็นบวก (ขาขึ้น) แต่มีความเสี่ยงในระยะสั้นจาก TF15 การตัดสินใจลงทุนควรพิจารณาจาก Timeframe ที่เหมาะสมกับสไตล์การเทรดของคุณ และอย่าลืมบริหารความเสี่ยงเสมอค่ะ
**Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-

@ 2183e947:f497b975
2025-02-13 04:44:45
# How Coinpools Improve Bitcoin
# Problems with bitcoin
UX problems with base layer payments include:
- Mining fees are sometimes high
- Confirmations usually take several minutes
- Using it privately requires running a coinjoin server
UX problems with lightning payments include:
- Setup fees are sometimes high
- Payments frequently fail
- Payments aren't asynchronous (the recipient has to stand there with their device open waiting to do a revoke_and_ack on their old state -- unless they use a custodian)
- Payments that *do* succeed occasionally take more than 30 seconds (due to stuck payments, automatic retries, and no ability to say "stop retrying" in any existing wallets that I'm aware of)
- Using it privately requires manual channel management
# Solutions
A lot of my recent work focuses on non-interactive coinpools. I figured out a way to do them on bitcoin if we had CTV + CSFS, and then, with a bit more thought, I figured out that my model didn't actually require those things, so I am now working on an implementation. But my model does benefit a lot from CTV (less sure about CSFS at this point) so let me outline how non-interactive coinpools fix the above problems and along the way I will share how CTV specifically improves coinpools.
## "Mining fees are sometimes high"
Coinpools improve the problem of "mining fees are sometimes high" by letting you bypass them in more cases. If you're in a coinpool and pay someone else in the same coinpool, your payment does not show up on the base layer, it just involves modifying some unilateral withdrawal transactions such that the sender can withdraw less and the recipient can withdraw more. The transactions are off-chain, like LN transactions, so you can do that without paying a base layer fee.
## "Confirmations usually take several minutes"
Coinpools improve the problem of "confirmations usually take several minutes" in a similar manner. Payments *inside* a coinpool (i.e. to another pool user) merely involve modifying off-chain data (and revoking an old state), so they can be as fast as lightning. In most cases I expect them to be a bit faster because there's less need for pathfinding or negotiating with a variety of routing nodes. If the sender and the recipient are in the same pool, they only need to talk to each other and, in my model, a coordinator.
## "Using the base layer privately requires running a coinjoin server"
Coinpools improve the problem of "using the base layer privately requires running a coinjoin server" in two ways: first, if you're in a coinpool and you send money to a bitcoin address, the blockchain doesn't know which coinpool user sent that payment. Analysts might be able to trace the payment to the coinpool, but from the blockchain's perspective, that's just a multisig; the actual person *inside* the multisig who sent the money is not revealed. However, my model uses a coordinator, and the coordinator probably knows which user sent the payment. Still, only 1 person knowing is better than having everyone on the blockchain know.
Second, if you send money to someone *inside* the coinpool, in my model, the only people who know about your payment are the sender, the recipient, and the coordinator, and the recipient does not know who the sender is. Moreover, my model allows users to act as bridges from LN to other pool users, so even the coordinator doesn't know if the person who *looks* like the sender was the *real* sender or just a bridge node, with the *real* sender being someone on lightning.
## "Setup fees on lightning are sometimes high"
Coinpools improve the problem of "setup fees are sometimes high" by having multiple users share the setup cost. My model allows a single bitcoin transaction to fund a coinpool with a number of members between 1 and probably about 100. (The max I've actually successfully tested is 11.) If the users share the cost of that transaction, then even in a high fee scenario, where bitcoin transactions cost $50, each user only has to pay a fraction of that, where the fraction is determined by how many users are joining the pool. If 10 people are joining, each user would pay $5 instead of $50. If 50 people are joining, each user would pay $1. If 100 people are joining, each user would pay 50¢.
## Sidebar: how CTV improves my coinpool model
The setup is also where CTV greatly improves my model. For my model to work, the users have to coordinate to create the pool in something I call a "signing ceremony," which is very similar to a coinjoin. The signing ceremony has to be scheduled and each user has to show up for it or they won't get into the pool. With CTV, you could fix this: instead of a signing ceremony, an exchange could autosend your money into a coinpool on e.g. a monthly basis and email you the data you need to perform your unilateral exit. All they need from you is a pubkey, and they can do everything else.
## "Lightning payments frequently fail"
Coinpools improve the problem of "payments frequently fail" by reducing the need for pathfinding, which is a typical cause of failure on lightning. If you are paying someone in the same pool as you, you always know an exact path: it will be you -> coordinator -> recipient. These short paths also reduce the likelihood of routing nodes having insufficient capacity to forward the payment. You've only got one "routing node" to worry about -- the coordinator.
## "Lightning payments aren't asynchronous"
Coinpools *in general* don't improve the problem of "payments aren't asynchronous" but my model in particular *does* improve that problem because I am combining it with my hedgehog protocol from last year, which *does* allow for asynchronous lightning-like payments. Relatedly, my coinpool model technically has a network model, it's just a hub-and-spoke network: the coordinator is connected to every user of the pool and can forward asynchronous hedgehog payments to them. This means you can send money to someone when they are offline; they'll get it whenever they *do* get online, even if *you* went offline in the meantime.
## "Lightning payments sometimes take too long"
Coinpools improve the problem of "stuck" lightning payments by reducing the number of hops along the route. As above, a payment inside the pool (per my model) is always just sender -> coordinator -> recipient. Due to only having 1 hop, there are fewer opportunities for a node to have a network issue and cause a delay.
## "Channel management is a pain"
Coinpools have multiple ways of improving the problem of manual channel management. In particular, not all coinpool models *have* channels, so channel management is not always needed in a coinpool. My model, however, does have channels, so channel management is still a thing.
Nonetheless, my model improves channel management in two ways: first, the setup costs are lower for the reasons given above. Second, payment asynchronicity helps for the following reason:
The worst pain point in channel management *today* occurs when someone sends you a payment but it fails because you didn't have enough inbound capacity. That doesn't happen in my coinpool model because payments are asynchronous. If you don't have enough inbound capacity, the payment doesn't fail, it just remains pending. So all you have to do is open a new channel (i.e. enter a new pool) and *then* finalize the payment.
## Zap me
I hope this essay clarifies why coinpools improve the problems I outlined and why CTV improves coinpools. I also hope this gets you a bit excited for my latest coinpool invention, which I hope to release soon :D (It really is very close to demo-ready.) If you liked this essay, consider zapping me: supertestnet@coinos.io
-

@ a012dc82:6458a70d
2025-02-13 04:00:01
In the dynamic world of global finance, the interplay between traditional monetary policy and the burgeoning digital asset market is becoming increasingly prominent. The U.S. Federal Reserve's recent pivot towards a more accommodative monetary policy has sparked intense discussion among investors, economists, and cryptocurrency enthusiasts. This shift, characterized by an expected reduction in interest rates, is not just a routine adjustment but a significant move that could have far-reaching implications for various asset classes, including cryptocurrencies like Bitcoin. As we delve into this topic, we aim to unravel the complexities of the Fed's policy change and its potential ripple effects on Bitcoin, a digital asset that has been a subject of much intrigue and speculation.
**Table Of Content**
- Understanding the Fed's Policy Shift
- Impact on Traditional Financial Markets
- Bitcoin's Response to Monetary Easing
- Analyzing the Economic Backdrop
- Bitcoin: A Safe Haven or Risk Asset?
- Risks and Opportunities
- Conclusion
- FAQs
**Understanding the Fed's Policy Shift**
The Federal Reserve, the guardian of the U.S. monetary system, wields immense influence over global financial markets. Its recent signaling of a dovish turn – an expectation of 75 basis points in rate cuts by 2024 – marks a significant departure from its previous stance. This change is reflective of the Fed's response to a confluence of macroeconomic factors, such as fluctuating inflation rates, global economic uncertainties, and domestic financial stability concerns. The Fed's decisions are closely monitored as they set the tone for economic growth, inflation control, and financial market stability. In this context, the anticipated rate cuts suggest a strategic move to stimulate economic activity by making borrowing cheaper, thereby potentially boosting investment and consumption. However, this policy shift is not without its complexities and nuances, as it must balance the fine line between stimulating growth and controlling inflation.
**Impact on Traditional Financial Markets**
The ripple effects of the Fed's policy announcement were immediately felt across traditional financial markets. Stock markets, often seen as a barometer of economic sentiment, reacted positively, with indices like the Dow Jones Industrial Average reaching new heights. This surge reflects investors' optimism about the potential for increased corporate profits and economic growth in a lower interest rate environment. Similarly, the bond market experienced a significant rally, with yields on government securities falling as bond prices rose. This movement in the bond market is indicative of investors' expectations of a more accommodative monetary policy, which typically leads to lower yields on fixed-income securities. These market reactions underscore the pivotal role of central bank policies in shaping investor sentiment and the direction of financial markets. They also highlight the interconnectedness of various asset classes, as changes in monetary policy can have cascading effects across different sectors of the economy.
**Bitcoin's Response to Monetary Easing**
Bitcoin's reaction to the Fed's dovish turn has been a subject of keen interest. The cryptocurrency, which had been experiencing volatility, showed signs of recovery following the Fed's announcement. This response is indicative of Bitcoin's increasing correlation with broader financial market trends, a significant development given its history as an uncorrelated asset. Bitcoin's sensitivity to macroeconomic factors like central bank policies points to its growing integration into the mainstream financial ecosystem. However, this integration also means that Bitcoin is increasingly exposed to the same macroeconomic risks and uncertainties that affect traditional assets. The Fed's policy shift could potentially make Bitcoin more attractive to investors seeking non-traditional assets in a low-interest-rate environment. However, Bitcoin's complex dynamics, including its decentralized nature, limited supply, and regulatory landscape, add layers of complexity to its response to monetary policy changes.
**Analyzing the Economic Backdrop**
The economic backdrop against which the Fed's policy shift occurs is multifaceted and dynamic. On one hand, the U.S. economy has demonstrated resilience, with robust GDP growth and positive retail sales figures suggesting underlying strength. On the other hand, inflation, though moderated from its peak, remains a concern, hovering above the Fed's target. This economic duality presents a challenging scenario for policymakers, who must navigate the delicate balance between stimulating growth and containing inflation. For investors and market participants, this creates an environment of uncertainty, as they must decipher mixed signals from economic data and policy announcements. In this context, Bitcoin's role and response become even more intriguing, as it operates at the intersection of technology, finance, and macroeconomics.
**Bitcoin: A Safe Haven or Risk Asset?**
The debate over Bitcoin's classification as a safe haven or a risk asset is intensified by the Fed's easing stance. Traditionally, in a low-interest-rate environment, investors seek assets that can serve as hedges against inflation and currency devaluation. Gold has historically played this role, and Bitcoin, with its fixed supply and digital scarcity, has drawn comparisons to gold. However, Bitcoin's relatively short history and high volatility make it a more complex and potentially riskier asset. The Fed's dovish policy could enhance Bitcoin's appeal as an alternative investment, especially if traditional assets like bonds offer lower returns. However, Bitcoin's classification as a safe haven is still a matter of debate, with opinions divided on its long-term stability and value retention capabilities.
**Risks and Opportunities**
Investors considering Bitcoin in light of the Fed's policy change face a landscape filled with both risks and opportunities. The potential for a Bitcoin rally in a low-interest-rate environment is counterbalanced by the cryptocurrency's inherent volatility and regulatory uncertainties. Bitcoin's price movements can be dramatic and unpredictable, influenced by a range of factors from technological developments to geopolitical events. Additionally, the regulatory environment for cryptocurrencies is still evolving, with potential changes posing risks to Bitcoin's accessibility and value. Investors must also consider the broader global economic context, including actions by other central banks and international trade dynamics, which can impact Bitcoin's market movement.
**Conclusion**
The Federal Reserve's shift towards a more accommodative monetary policy in 2024 presents a fascinating scenario for Bitcoin and the broader cryptocurrency market. This development underscores the increasing relevance of digital assets in the global financial landscape and highlights the complex interplay between traditional monetary policies and emerging financial technologies. As Bitcoin continues to evolve and gain acceptance, its response to macroeconomic factors like central bank policies will be a critical area of focus for investors. In navigating this dynamic and uncertain environment, a cautious and well-informed approach is essential for those looking to explore the opportunities and navigate the challenges of cryptocurrency investments. The coming years promise to be a pivotal period in the maturation of Bitcoin as it responds to the shifting tides of global finance.
**FAQs**
**How does the Federal Reserve's easing stance impact Bitcoin?**
The Fed's shift towards lower interest rates can make riskier assets like Bitcoin more attractive to investors. This is because lower rates often lead to reduced yields on traditional investments, prompting investors to seek higher returns elsewhere.
**What is the significance of the Fed's 'dot plot' for Bitcoin investors?**
The 'dot plot' is a projection of interest rate movements by Federal Reserve members. A shift towards lower rates, as indicated in the recent dot plot, can signal a more accommodative monetary policy, potentially impacting Bitcoin's market as investors adjust their portfolios.
**Can Bitcoin be considered a safe haven asset in light of the Fed's policy?**
Bitcoin's role as a safe haven asset is debated. While its fixed supply and digital nature offer some safe haven characteristics, its volatility and regulatory uncertainties make it a complex choice compared to traditional safe havens like gold.
**What risks should Bitcoin investors consider in the context of the Fed's easing policy?**
Investors should be aware of Bitcoin's volatility, regulatory changes, and its sensitivity to macroeconomic factors. Additionally, global economic conditions and actions by other central banks can also influence Bitcoin's market.
**How does the economic backdrop influence Bitcoin's response to the Fed's policy?**
Economic factors like GDP growth, inflation rates, and retail sales impact investor sentiment and risk appetite, which in turn can affect Bitcoin's market. A strong economy might reduce the appeal of risk assets like Bitcoin, while economic uncertainties can increase their attractiveness.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: @croxroadnews.co**
**Instagram: @croxroadnews.co**
**Youtube: @croxroadnews**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
 @ c2827524:5f45b2f7
2025-02-13 11:54:16> innèsto s. m. [der. di innestare]. – 1. In agraria: a. Operazione con cui si fa concrescere sopra una pianta (detta portainnesto o soggetto) una parte di un altro della stessa specie o di specie differenti (detto nesto o oggetto), **al fine di formare un nuovo individuo più pregiato o più produttivo o più giovane**: fare, operare, praticare un innesto. Le collaborazioni sono di una potenza micidiale. Quelle che si sviluppano nello spazio #Bitcoin ancora di più. Non è più una collaborazione, è un #innesto: rami di alberi diversi, destinati da soli a dare grandi frutti, si fondono per **donare ad un intero ecosistema sapori ancora più deliziosi**. Contributi e suggerimenti vanno e vengono alla velocità della luce, col sorriso, senza sacrificio e sempre con la volontà di migliorarsi e crescere. Lo spazio #Bitcoin è una fabbrica magica, che accoglie minuscoli semini(*) da chiunque voglia partecipare, volontariamente, alla crescita della cultura Bitcoin. Ma li trasforma in un **incanto**. In solitaria i semini sarebbero destinati comunque a grandi cose e questo è già, di per sé, meraviglioso. La fabbrica magica, invece, li fa germogliare, fiorire e fruttare in maniera ancora più potente. Quando la magia è totale, avviene l’*innesto*, **la generazione di una nuova creatura più pregiata**. Sta succedendo davanti ai miei occhi. Sono onorata di poter assistere a questo mini miracolo della vita e, manco a dirlo, felice di farne parte. Non è solo cambiare atteggiamento, smussare frizioni e rigidità o correggere la propria visione, è proprio ampliare sé stessi accogliendo gli altri. Grazie nostr:npub1uhj92lnwh8rrhhuvulfqstk4g0ayx0zx35wj2d62jueqheknkxks5m4zj6 nostr:npub1au23c73cpaq2whtazjf6cdrmvam6nkd4lg928nwmgl78374kn29sq9t53j nostr:npub1awnu9vg352863e7tqlc6urlw7jgdf8vf00tmr76uuhflp4nnn68sjmnnl3 e nostr:npub1lrurmgmlfl4u72258fc4q5ke7tr82kw5xct5vchdmzr9uhmx6j4qn3t72a (1) Semini, non #seed [non chiamatelo seed, si dice mnemonica (cit.)] Siccome in italiano la parola **seme** porta alla mente anche *giochini di parole fiat*, se siete qui per perculare fate pure. -> H.F.S.P. 🤣
@ c2827524:5f45b2f7
2025-02-13 11:54:16> innèsto s. m. [der. di innestare]. – 1. In agraria: a. Operazione con cui si fa concrescere sopra una pianta (detta portainnesto o soggetto) una parte di un altro della stessa specie o di specie differenti (detto nesto o oggetto), **al fine di formare un nuovo individuo più pregiato o più produttivo o più giovane**: fare, operare, praticare un innesto. Le collaborazioni sono di una potenza micidiale. Quelle che si sviluppano nello spazio #Bitcoin ancora di più. Non è più una collaborazione, è un #innesto: rami di alberi diversi, destinati da soli a dare grandi frutti, si fondono per **donare ad un intero ecosistema sapori ancora più deliziosi**. Contributi e suggerimenti vanno e vengono alla velocità della luce, col sorriso, senza sacrificio e sempre con la volontà di migliorarsi e crescere. Lo spazio #Bitcoin è una fabbrica magica, che accoglie minuscoli semini(*) da chiunque voglia partecipare, volontariamente, alla crescita della cultura Bitcoin. Ma li trasforma in un **incanto**. In solitaria i semini sarebbero destinati comunque a grandi cose e questo è già, di per sé, meraviglioso. La fabbrica magica, invece, li fa germogliare, fiorire e fruttare in maniera ancora più potente. Quando la magia è totale, avviene l’*innesto*, **la generazione di una nuova creatura più pregiata**. Sta succedendo davanti ai miei occhi. Sono onorata di poter assistere a questo mini miracolo della vita e, manco a dirlo, felice di farne parte. Non è solo cambiare atteggiamento, smussare frizioni e rigidità o correggere la propria visione, è proprio ampliare sé stessi accogliendo gli altri. Grazie nostr:npub1uhj92lnwh8rrhhuvulfqstk4g0ayx0zx35wj2d62jueqheknkxks5m4zj6 nostr:npub1au23c73cpaq2whtazjf6cdrmvam6nkd4lg928nwmgl78374kn29sq9t53j nostr:npub1awnu9vg352863e7tqlc6urlw7jgdf8vf00tmr76uuhflp4nnn68sjmnnl3 e nostr:npub1lrurmgmlfl4u72258fc4q5ke7tr82kw5xct5vchdmzr9uhmx6j4qn3t72a (1) Semini, non #seed [non chiamatelo seed, si dice mnemonica (cit.)] Siccome in italiano la parola **seme** porta alla mente anche *giochini di parole fiat*, se siete qui per perculare fate pure. -> H.F.S.P. 🤣 @ d360efec:14907b5f
2025-02-13 11:15:12**Top-Down Analysis:** กลยุทธ์การเทรดเพื่อมองภาพรวมและจับจังหวะทำกำไร ในโลกของการเทรดที่เต็มไปด้วยความผันผวน การมีเครื่องมือวิเคราะห์ที่แข็งแกร่งเป็นสิ่งสำคัญอย่างยิ่งที่จะช่วยนำทางให้เทรดเดอร์สามารถตัดสินใจได้อย่างมีหลักการและเพิ่มโอกาสในการทำกำไร หนึ่งในเครื่องมือที่ได้รับความนิยมและมีประสิทธิภาพคือ "Top-Down Analysis" หรือการวิเคราะห์จากบนลงล่าง ซึ่งเป็นวิธีการมองภาพรวมของตลาดก่อนที่จะเจาะจงไปที่สินทรัพย์ที่เราสนใจ บทความนี้จะพาคุณไปทำความเข้าใจกับ Top-Down Analysis อย่างละเอียด พร้อมทั้งแนะนำกลยุทธ์การเทรดที่สามารถนำไปปรับใช้ได้จริง **Top-Down Analysis คืออะไร?** Top-Down Analysis เป็นกระบวนการวิเคราะห์ตลาดที่เริ่มต้นจากการพิจารณาภาพรวมในกรอบเวลาที่ใหญ่ขึ้น ก่อนที่จะค่อยๆ ย่อยลงไปในกรอบเวลาที่เล็กลง เพื่อทำความเข้าใจบริบทของตลาดและหาจังหวะการเทรดที่เหมาะสม วิธีการนี้ช่วยให้เทรดเดอร์สามารถมองเห็นทิศทางหลักของตลาด, แนวโน้มที่กำลังเกิดขึ้น, ระดับราคาสำคัญ, และความสมดุลระหว่างอุปสงค์และอุปทาน ก่อนที่จะตัดสินใจเข้าเทรดในกรอบเวลาที่เล็กลง **องค์ประกอบสำคัญของ Top-Down Analysis (อ้างอิงจากภาพ)** ภาพ "Top-Down Analysis" ได้สรุปองค์ประกอบสำคัญของการวิเคราะห์นี้ไว้อย่างชัดเจน โดยแบ่งการวิเคราะห์ออกเป็น 3 กรอบเวลาหลัก: 4 ชั่วโมง (4H), 1 ชั่วโมง (1H), และ 15 นาที (15min) แต่ละกรอบเวลามีองค์ประกอบที่ต้องพิจารณาดังนี้: 1. กรอบเวลา 4 ชั่วโมง (4H): ภาพรวมตลาดและทิศทางหลัก ในกรอบเวลา 4 ชั่วโมง เราจะเน้นการวิเคราะห์ภาพรวมของตลาด เพื่อกำหนดทิศทางหลักและแนวโน้มในระยะกลาง องค์ประกอบสำคัญในกรอบเวลานี้คือ: * Direction (ทิศทาง): ประเมินทิศทางที่ตลาดกำลังเคลื่อนที่ไป โดยพิจารณาจากแนวโน้มและโครงสร้างราคาในภาพรวม ตลาดกำลังเป็นขาขึ้น, ขาลง หรืออยู่ในช่วง Sideways? * Trend (แนวโน้ม): ระบุแนวโน้มหลักของตลาด ไม่ว่าจะเป็นแนวโน้มขาขึ้น (Uptrend), แนวโน้มขาลง (Downtrend) หรือ Sideways การเข้าใจแนวโน้มช่วยในการกำหนดกลยุทธ์การเทรดที่เหมาะสม * Key levels (ระดับราคาสำคัญ): หาระดับราคาแนวรับและแนวต้านที่สำคัญในกรอบเวลา 4 ชั่วโมง ระดับเหล่านี้มักเป็นจุดที่ราคาเคยมีการกลับตัวหรือพักตัวในอดีต และอาจเป็นบริเวณที่ราคาจะตอบสนองอีกครั้งในอนาคต * Supply & Demand (อุปทานและอุปสงค์): วิเคราะห์ความสมดุลระหว่างแรงซื้อ (Demand) และแรงขาย (Supply) ในตลาด โดยพิจารณาจากพฤติกรรมราคาบริเวณแนวรับแนวต้าน และสัญญาณจากเครื่องมือวิเคราะห์อื่นๆ (ถ้าใช้) 2. กรอบเวลา 1 ชั่วโมง (1H): หาจังหวะและบริเวณที่น่าสนใจ เมื่อได้ภาพรวมและทิศทางหลักจากกรอบ 4H แล้ว เราจะย่อยลงมาในกรอบ 1 ชั่วโมง เพื่อหาจังหวะการเทรดที่สอดคล้องกับทิศทางหลัก และมองหารูปแบบราคาที่น่าสนใจ องค์ประกอบสำคัญในกรอบเวลานี้คือ: * Breaks (การทะลุ): สังเกตการทะลุแนวรับแนวต้าน หรือระดับราคาสำคัญในกรอบ 1H ที่สอดคล้องกับทิศทางหลักใน 4H การทะลุเหล่านี้อาจเป็นสัญญาณของการเคลื่อนไหวครั้งใหญ่ของราคา * Reversals (การกลับตัว): มองหารูปแบบการกลับตัวของราคาที่อาจเกิดขึ้นบริเวณระดับราคาสำคัญในกรอบ 1H ซึ่งบ่งบอกถึงจุดสิ้นสุดของแนวโน้มปัจจุบันและเริ่มต้นแนวโน้มใหม่ * OB (Order Blocks): ระบุบริเวณ Order Blocks ในกรอบ 1H ซึ่งเป็นพื้นที่ที่มีการสั่งซื้อขายจำนวนมากในอดีต Order Blocks เหล่านี้มักจะทำหน้าที่เป็นแนวรับแนวต้านในอนาคต * FVG (Fair Value Gaps): มองหา Fair Value Gaps ในกรอบ 1H ซึ่งเป็นช่องว่างของราคาที่เกิดจากการเคลื่อนไหวอย่างรวดเร็ว FVG มักจะเป็นเป้าหมายของราคาในอนาคต เนื่องจากราคาอาจจะกลับมาปิดช่องว่างเหล่านี้ * Liquidity (สภาพคล่อง): ประเมินสภาพคล่องบริเวณระดับราคาที่เราสนใจในกรอบ 1H บริเวณที่มีสภาพคล่องสูงมักจะดึงดูดนักลงทุนรายใหญ่ และอาจทำให้เกิดการเคลื่อนไหวของราคาที่รุนแรง 3. กรอบเวลา 15 นาที (15min): ยืนยันสัญญาณและหาจุดเข้าเทรด ในกรอบเวลา 15 นาที เราจะเน้นการยืนยันสัญญาณการเทรด และหาจุดเข้าเทรดที่แม่นยำ เพื่อลดความเสี่ยงในการเข้าเทรดเร็วเกินไป องค์ประกอบสำคัญในกรอบเวลานี้คือ: * Confirmation (การยืนยัน): รอสัญญาณยืนยันการเคลื่อนไหวของราคาในกรอบ 15 นาที ที่สอดคล้องกับการวิเคราะห์ในกรอบ 1H และ 4H สัญญาณยืนยันอาจมาในรูปแบบของแท่งเทียนกลับตัว, รูปแบบ Chart Patterns, หรือสัญญาณจาก Indicators * จุดเข้าเทรด: เมื่อมีสัญญาณยืนยันที่ชัดเจนในกรอบ 15 นาที และสอดคล้องกับการวิเคราะห์ในกรอบเวลาที่ใหญ่ขึ้น จึงตัดสินใจเข้าเทรด โดยกำหนด Stop Loss เพื่อจำกัดความเสี่ยง และ Take Profit เพื่อตั้งเป้าหมายในการทำกำไร **กลยุทธ์การเทรด Top-Down Analysis: ขั้นตอนสู่ความสำเร็จ** เพื่อนำ Top-Down Analysis ไปใช้ในการเทรดอย่างมีประสิทธิภาพ เราสามารถทำตามขั้นตอนต่อไปนี้: 1. **เริ่มต้นที่ 4H**: กำหนดทิศทางและแนวโน้มหลัก วิเคราะห์กราฟ 4H เพื่อระบุทิศทางหลักของตลาด แนวโน้ม และระดับราคาสำคัญ ประเมินความสมดุลของ Supply & Demand เพื่อกำหนด Bias การเทรด (เน้นซื้อหรือขาย) 2. **เจาะลึก 1H:** หาจังหวะและบริเวณที่น่าสนใจ เมื่อได้ทิศทางหลักจาก 4H แล้ว ให้ย่อยลงมาดูกราฟ 1H เพื่อหารูปแบบราคาที่น่าสนใจ เช่น การทะลุแนวรับแนวต้าน, รูปแบบการกลับตัว, Order Blocks, Fair Value Gaps และบริเวณที่มีสภาพคล่องสูง 3. **ยืนยันใน 15min:** หาจุดเข้าเทรดที่แม่นยำ รอสัญญาณยืนยันในกรอบ 15 นาที ที่สอดคล้องกับการวิเคราะห์ในกรอบเวลาที่ใหญ่ขึ้น ใช้ Price Action, แท่งเทียน, หรือ Indicators เพื่อยืนยันสัญญาณ และหาจุดเข้าเทรดที่แม่นยำ พร้อมกำหนด Stop Loss และ Take Profit ที่เหมาะสม **ประโยชน์ของการใช้ Top-Down Analysis** * มองเห็นภาพรวมตลาด: ช่วยให้เทรดเดอร์เข้าใจบริบทของตลาดในภาพรวม ไม่หลงทางในรายละเอียดเล็กๆ น้อยๆ * ตัดสินใจเทรดอย่างมีหลักการ: ทำให้การตัดสินใจเทรดมีเหตุผลและมีข้อมูลสนับสนุนมากขึ้น ไม่ใช่แค่การคาดเดา * เพิ่มความแม่นยำในการเทรด: การวิเคราะห์หลายกรอบเวลาช่วยกรองสัญญาณรบกวน และเพิ่มโอกาสในการเข้าเทรดในทิศทางที่ถูกต้อง * ลดความเสี่ยง: ช่วยลดโอกาสในการเทรดสวนทางแนวโน้มหลักของตลาด และช่วยในการกำหนด Stop Loss ที่เหมาะสม **ข้อควรจำและข้อควรระวัง** * ฝึกฝนและสังเกต: Top-Down Analysis ต้องอาศัยการฝึกฝนและการสังเกตกราฟราคาอย่างสม่ำเสมอ เพื่อพัฒนาความเข้าใจและทักษะในการวิเคราะห์ * ปรับใช้ให้เข้ากับสไตล์: ปรับกลยุทธ์ให้เข้ากับสไตล์การเทรดของคุณ และสินทรัพย์ที่คุณเทรด * บริหารความเสี่ยง: ให้ความสำคัญกับการบริหารความเสี่ยงเสมอ กำหนดขนาด Position ที่เหมาะสม และใช้ Stop Loss ทุกครั้ง * ไม่มีกลยุทธ์ใดสมบูรณ์แบบ: Top-Down Analysis เป็นเครื่องมือที่มีประสิทธิภาพ แต่ไม่มีกลยุทธ์ใดที่รับประกันผลกำไร 100% การเทรดมีความเสี่ยง โปรดศึกษาและทำความเข้าใจความเสี่ยงก่อนตัดสินใจลงทุน **สรุป** Top-Down Analysis เป็นกลยุทธ์การเทรดที่ทรงพลัง ซึ่งช่วยให้เทรดเดอร์สามารถวิเคราะห์ตลาดอย่างเป็นระบบ มองภาพรวม และจับจังหวะการเทรดได้อย่างแม่นยำ การนำหลักการของ Top-Down Analysis ไปปรับใช้ในการเทรด จะช่วยเพิ่มประสิทธิภาพในการตัดสินใจ และเพิ่มโอกาสในการประสบความสำเร็จในตลาดการเงินได้อย่างยั่งยืน
@ d360efec:14907b5f
2025-02-13 11:15:12**Top-Down Analysis:** กลยุทธ์การเทรดเพื่อมองภาพรวมและจับจังหวะทำกำไร ในโลกของการเทรดที่เต็มไปด้วยความผันผวน การมีเครื่องมือวิเคราะห์ที่แข็งแกร่งเป็นสิ่งสำคัญอย่างยิ่งที่จะช่วยนำทางให้เทรดเดอร์สามารถตัดสินใจได้อย่างมีหลักการและเพิ่มโอกาสในการทำกำไร หนึ่งในเครื่องมือที่ได้รับความนิยมและมีประสิทธิภาพคือ "Top-Down Analysis" หรือการวิเคราะห์จากบนลงล่าง ซึ่งเป็นวิธีการมองภาพรวมของตลาดก่อนที่จะเจาะจงไปที่สินทรัพย์ที่เราสนใจ บทความนี้จะพาคุณไปทำความเข้าใจกับ Top-Down Analysis อย่างละเอียด พร้อมทั้งแนะนำกลยุทธ์การเทรดที่สามารถนำไปปรับใช้ได้จริง **Top-Down Analysis คืออะไร?** Top-Down Analysis เป็นกระบวนการวิเคราะห์ตลาดที่เริ่มต้นจากการพิจารณาภาพรวมในกรอบเวลาที่ใหญ่ขึ้น ก่อนที่จะค่อยๆ ย่อยลงไปในกรอบเวลาที่เล็กลง เพื่อทำความเข้าใจบริบทของตลาดและหาจังหวะการเทรดที่เหมาะสม วิธีการนี้ช่วยให้เทรดเดอร์สามารถมองเห็นทิศทางหลักของตลาด, แนวโน้มที่กำลังเกิดขึ้น, ระดับราคาสำคัญ, และความสมดุลระหว่างอุปสงค์และอุปทาน ก่อนที่จะตัดสินใจเข้าเทรดในกรอบเวลาที่เล็กลง **องค์ประกอบสำคัญของ Top-Down Analysis (อ้างอิงจากภาพ)** ภาพ "Top-Down Analysis" ได้สรุปองค์ประกอบสำคัญของการวิเคราะห์นี้ไว้อย่างชัดเจน โดยแบ่งการวิเคราะห์ออกเป็น 3 กรอบเวลาหลัก: 4 ชั่วโมง (4H), 1 ชั่วโมง (1H), และ 15 นาที (15min) แต่ละกรอบเวลามีองค์ประกอบที่ต้องพิจารณาดังนี้: 1. กรอบเวลา 4 ชั่วโมง (4H): ภาพรวมตลาดและทิศทางหลัก ในกรอบเวลา 4 ชั่วโมง เราจะเน้นการวิเคราะห์ภาพรวมของตลาด เพื่อกำหนดทิศทางหลักและแนวโน้มในระยะกลาง องค์ประกอบสำคัญในกรอบเวลานี้คือ: * Direction (ทิศทาง): ประเมินทิศทางที่ตลาดกำลังเคลื่อนที่ไป โดยพิจารณาจากแนวโน้มและโครงสร้างราคาในภาพรวม ตลาดกำลังเป็นขาขึ้น, ขาลง หรืออยู่ในช่วง Sideways? * Trend (แนวโน้ม): ระบุแนวโน้มหลักของตลาด ไม่ว่าจะเป็นแนวโน้มขาขึ้น (Uptrend), แนวโน้มขาลง (Downtrend) หรือ Sideways การเข้าใจแนวโน้มช่วยในการกำหนดกลยุทธ์การเทรดที่เหมาะสม * Key levels (ระดับราคาสำคัญ): หาระดับราคาแนวรับและแนวต้านที่สำคัญในกรอบเวลา 4 ชั่วโมง ระดับเหล่านี้มักเป็นจุดที่ราคาเคยมีการกลับตัวหรือพักตัวในอดีต และอาจเป็นบริเวณที่ราคาจะตอบสนองอีกครั้งในอนาคต * Supply & Demand (อุปทานและอุปสงค์): วิเคราะห์ความสมดุลระหว่างแรงซื้อ (Demand) และแรงขาย (Supply) ในตลาด โดยพิจารณาจากพฤติกรรมราคาบริเวณแนวรับแนวต้าน และสัญญาณจากเครื่องมือวิเคราะห์อื่นๆ (ถ้าใช้) 2. กรอบเวลา 1 ชั่วโมง (1H): หาจังหวะและบริเวณที่น่าสนใจ เมื่อได้ภาพรวมและทิศทางหลักจากกรอบ 4H แล้ว เราจะย่อยลงมาในกรอบ 1 ชั่วโมง เพื่อหาจังหวะการเทรดที่สอดคล้องกับทิศทางหลัก และมองหารูปแบบราคาที่น่าสนใจ องค์ประกอบสำคัญในกรอบเวลานี้คือ: * Breaks (การทะลุ): สังเกตการทะลุแนวรับแนวต้าน หรือระดับราคาสำคัญในกรอบ 1H ที่สอดคล้องกับทิศทางหลักใน 4H การทะลุเหล่านี้อาจเป็นสัญญาณของการเคลื่อนไหวครั้งใหญ่ของราคา * Reversals (การกลับตัว): มองหารูปแบบการกลับตัวของราคาที่อาจเกิดขึ้นบริเวณระดับราคาสำคัญในกรอบ 1H ซึ่งบ่งบอกถึงจุดสิ้นสุดของแนวโน้มปัจจุบันและเริ่มต้นแนวโน้มใหม่ * OB (Order Blocks): ระบุบริเวณ Order Blocks ในกรอบ 1H ซึ่งเป็นพื้นที่ที่มีการสั่งซื้อขายจำนวนมากในอดีต Order Blocks เหล่านี้มักจะทำหน้าที่เป็นแนวรับแนวต้านในอนาคต * FVG (Fair Value Gaps): มองหา Fair Value Gaps ในกรอบ 1H ซึ่งเป็นช่องว่างของราคาที่เกิดจากการเคลื่อนไหวอย่างรวดเร็ว FVG มักจะเป็นเป้าหมายของราคาในอนาคต เนื่องจากราคาอาจจะกลับมาปิดช่องว่างเหล่านี้ * Liquidity (สภาพคล่อง): ประเมินสภาพคล่องบริเวณระดับราคาที่เราสนใจในกรอบ 1H บริเวณที่มีสภาพคล่องสูงมักจะดึงดูดนักลงทุนรายใหญ่ และอาจทำให้เกิดการเคลื่อนไหวของราคาที่รุนแรง 3. กรอบเวลา 15 นาที (15min): ยืนยันสัญญาณและหาจุดเข้าเทรด ในกรอบเวลา 15 นาที เราจะเน้นการยืนยันสัญญาณการเทรด และหาจุดเข้าเทรดที่แม่นยำ เพื่อลดความเสี่ยงในการเข้าเทรดเร็วเกินไป องค์ประกอบสำคัญในกรอบเวลานี้คือ: * Confirmation (การยืนยัน): รอสัญญาณยืนยันการเคลื่อนไหวของราคาในกรอบ 15 นาที ที่สอดคล้องกับการวิเคราะห์ในกรอบ 1H และ 4H สัญญาณยืนยันอาจมาในรูปแบบของแท่งเทียนกลับตัว, รูปแบบ Chart Patterns, หรือสัญญาณจาก Indicators * จุดเข้าเทรด: เมื่อมีสัญญาณยืนยันที่ชัดเจนในกรอบ 15 นาที และสอดคล้องกับการวิเคราะห์ในกรอบเวลาที่ใหญ่ขึ้น จึงตัดสินใจเข้าเทรด โดยกำหนด Stop Loss เพื่อจำกัดความเสี่ยง และ Take Profit เพื่อตั้งเป้าหมายในการทำกำไร **กลยุทธ์การเทรด Top-Down Analysis: ขั้นตอนสู่ความสำเร็จ** เพื่อนำ Top-Down Analysis ไปใช้ในการเทรดอย่างมีประสิทธิภาพ เราสามารถทำตามขั้นตอนต่อไปนี้: 1. **เริ่มต้นที่ 4H**: กำหนดทิศทางและแนวโน้มหลัก วิเคราะห์กราฟ 4H เพื่อระบุทิศทางหลักของตลาด แนวโน้ม และระดับราคาสำคัญ ประเมินความสมดุลของ Supply & Demand เพื่อกำหนด Bias การเทรด (เน้นซื้อหรือขาย) 2. **เจาะลึก 1H:** หาจังหวะและบริเวณที่น่าสนใจ เมื่อได้ทิศทางหลักจาก 4H แล้ว ให้ย่อยลงมาดูกราฟ 1H เพื่อหารูปแบบราคาที่น่าสนใจ เช่น การทะลุแนวรับแนวต้าน, รูปแบบการกลับตัว, Order Blocks, Fair Value Gaps และบริเวณที่มีสภาพคล่องสูง 3. **ยืนยันใน 15min:** หาจุดเข้าเทรดที่แม่นยำ รอสัญญาณยืนยันในกรอบ 15 นาที ที่สอดคล้องกับการวิเคราะห์ในกรอบเวลาที่ใหญ่ขึ้น ใช้ Price Action, แท่งเทียน, หรือ Indicators เพื่อยืนยันสัญญาณ และหาจุดเข้าเทรดที่แม่นยำ พร้อมกำหนด Stop Loss และ Take Profit ที่เหมาะสม **ประโยชน์ของการใช้ Top-Down Analysis** * มองเห็นภาพรวมตลาด: ช่วยให้เทรดเดอร์เข้าใจบริบทของตลาดในภาพรวม ไม่หลงทางในรายละเอียดเล็กๆ น้อยๆ * ตัดสินใจเทรดอย่างมีหลักการ: ทำให้การตัดสินใจเทรดมีเหตุผลและมีข้อมูลสนับสนุนมากขึ้น ไม่ใช่แค่การคาดเดา * เพิ่มความแม่นยำในการเทรด: การวิเคราะห์หลายกรอบเวลาช่วยกรองสัญญาณรบกวน และเพิ่มโอกาสในการเข้าเทรดในทิศทางที่ถูกต้อง * ลดความเสี่ยง: ช่วยลดโอกาสในการเทรดสวนทางแนวโน้มหลักของตลาด และช่วยในการกำหนด Stop Loss ที่เหมาะสม **ข้อควรจำและข้อควรระวัง** * ฝึกฝนและสังเกต: Top-Down Analysis ต้องอาศัยการฝึกฝนและการสังเกตกราฟราคาอย่างสม่ำเสมอ เพื่อพัฒนาความเข้าใจและทักษะในการวิเคราะห์ * ปรับใช้ให้เข้ากับสไตล์: ปรับกลยุทธ์ให้เข้ากับสไตล์การเทรดของคุณ และสินทรัพย์ที่คุณเทรด * บริหารความเสี่ยง: ให้ความสำคัญกับการบริหารความเสี่ยงเสมอ กำหนดขนาด Position ที่เหมาะสม และใช้ Stop Loss ทุกครั้ง * ไม่มีกลยุทธ์ใดสมบูรณ์แบบ: Top-Down Analysis เป็นเครื่องมือที่มีประสิทธิภาพ แต่ไม่มีกลยุทธ์ใดที่รับประกันผลกำไร 100% การเทรดมีความเสี่ยง โปรดศึกษาและทำความเข้าใจความเสี่ยงก่อนตัดสินใจลงทุน **สรุป** Top-Down Analysis เป็นกลยุทธ์การเทรดที่ทรงพลัง ซึ่งช่วยให้เทรดเดอร์สามารถวิเคราะห์ตลาดอย่างเป็นระบบ มองภาพรวม และจับจังหวะการเทรดได้อย่างแม่นยำ การนำหลักการของ Top-Down Analysis ไปปรับใช้ในการเทรด จะช่วยเพิ่มประสิทธิภาพในการตัดสินใจ และเพิ่มโอกาสในการประสบความสำเร็จในตลาดการเงินได้อย่างยั่งยืน @ e373ca41:b82abcc5
2025-02-13 09:13:10*This article has been written with the* ***[Pareto client](https://pareto.space/read).*** *(read it there for the full experience). It was first published in German by Milosz Matuschek on* ***["Freischwebende Intelligenz".](https://www.freischwebende-intelligenz.org/p/unterwanderter-journalismus-der-mediale)*** *** It is unmistakable. The hydra of the Deep State is losing a few heads - and this time it's the turn of the media heads. Anyone can look at [USASpending](https://www.usaspending.gov/) to see how much taxpayers' money has gone to whom in the USA. ### When the state pays its advocates The mainstream media were also among the beneficiaries: Politico (100% Axel Springer) received over [USD 7 million](https://www.usaspending.gov/recipient/fa0cefae-7cfb-881d-29c3-1bd39cc6a49e-C/latest); the New York Times received over USD 40 million. Thousands of (probably not always necessary) government subscriptions flowed to large media houses - paid for with taxpayers' money. A form of covert press financing by the state. At what point can or should we speak of state media? ") However, this is only the tip of the iceberg. The CIA front organization USAID ([known for its funding of virus research in Wuhan and other questionable activities](https://pareto.space/a/naddr1qqxnzden8quryveexq6rywp3qgswxu72gyq7ykjdfl9j556887jpzwu3mw3v9ez36quas55whq4te3grqsqqqa28qyxhwumn8ghj7mn0wvhxcmmvqyf8wumn8ghj7mmxve3ksctfdch8qatzqythwumn8ghj7urpwfjhgmewdehhxarjxyhxxmmdqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsz9nhwden5te0wfjkccte9ehx7um5wghxyctwvszsxfjh)) - [pumped USD 472.6 million directly into the media landscape via the “Internews Network”.](https://www.zerohedge.com/political/usaid-funded-massive-global-state-propaganda-news-matrix-nearly-billion-people-reach) FAZ journalist Udo Ulfkotte once called this “bought journalists” in a very clear and media-effective way, which was not good for his health. There is ample evidence of the CIA-USAID connections, for example [here](https://timesofindia.indiatimes.com/toi-plus/international/how-usaid-worked-alongside-cia-in-vietnam-a-whistleblowers-account/articleshow/118164225.cms), [here](https://foreignpolicy.com/2014/04/03/cuban-twitter-and-other-times-usaid-pretended-to-be-an-intelligence-agency/) and [here.](https://www.jstor.org/stable/4017728) ") But this is now over for the time being: USD 268 million, which was to go to “independent media for the free flow of information” (according to the [Columbia Journalism Review](https://www.cjr.org/the_media_today/usaid-and-the-media-in-a-time-of-monsters.php)) in 2025, has been frozen. The largest media influence machine in the Western world is bleeding a little. One has to admit: part of the media-deepstate swamp is actually being drained dry financially. The fact that the Columbia Journalism Review doesn't even seem to notice that “free international journalism”, which, as it writes, is largely funded by USAID, ceases to be “free journalism” speaks volumes about this “hotbed of journalism”. Matt Taibbi of Racket News rightly finds, “The legacy media system is dead. They just don't know it yet.” *** ADVERTISEMENT: *Looking for the easiest way to buy Bitcoin and store it yourself? The **[Relai app](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. **[Here you can buy Bitcoin](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees (no financial advice). Disclaimer due to regulatory issues: The services of the Relai App are hereby only recommended to inhabitants of Switzerland or Italy.*  *Need more security? The **[Trezor wallets](https://trezor.io/trezor-safe-5-bitcoin-only?transaction_id=102e192a206d1585e56a2fddef6d83\&offer_id=238\&affiliate_id=35234)** are recommended and easy to use, others are available in the **[store](https://trezor.io/?transaction_id=102bc85bdca2733287749c7f879ebd\&offer_id=133\&affiliate_id=35234)**. Need more advice? Book an **[introductory meeting](https://trezor.io/trezor-expert-session?transaction_id=1020e18dad0aa4b1186289fd22e90f\&offer_id=241\&affiliate_id=35234)** with a wallet expert.* *** Large-scale media manipulation has become visible. The propaganda matrix, if you will. The disastrous thing about it: if the Overton window is infiltrated, so to speak, the entire institution of journalism cannot be trusted. Every day, readers must expect to be pulled through the nose ring of intelligence service narratives and public agendas by mainstream journalists who pretend to be objective (and are often simply clueless and unsuspecting). The panorama of what we are supposed to see and believe, so to speak. How many mainstream journalists today are basically mouthpieces for the services? Every mainstream reader must now ask themselves: Is my favorite journalist at NZZ, Welt, SZ, ZEIT or FAZ perhaps just a CIA-IM? There were no major dissenters among them: EU criticism? Vaccination criticism? Criticism of NATO? Criticism of Biden and America? Criticism of Nord Stream? There were brief moments on television when questions about journalists' ties to lobby organizations were still part of the German satire program. <https://x.com/Spitze_Zunge_/status/1887915509988876786> ### The cards in the media are being reshuffled The watchdog of the powerful has been infiltrated by the powerful. This means that the Fourth Power is not a power at all, but part of the executive branch, a mouthpiece of the government. The claim that the mainstream is quality journalism, the gold standard for trustworthy information, is therefore the real fake news. It is the last, now crumbling dogma of an infiltrated press sect that has formed a cartel and is subjecting citizens to a permanent psy-op with intelligence-controlled taxpayers' money. A troupe of spokespeople at the work of mental synchronization. <https://x.com/TopherField/status/1887962959072149989> ### The fight against independent media But they not only give to one, they also take from the other. While government agencies use taxpayers' money to promote a certain type of journalism, the juice is actively being cut off from the critical part. All it takes is to be classified as a “PEP” (politically exposed person) and the bank account is gone. This is what has just happened to swiss Radio Kontrafunk. The critical Swiss author Stefan Millius was canceled by his publisher. Others have had their monetization via YouTube cut off (Snicklink). Others are harassed by the state media authority (Multipolar, Alexander Wallasch). The next one has a house search. It has been known since the Twitter files that the government and services also intervened massively in social media communication. This is no longer the Cold War. But it is the cold information war. <https://www.youtube.com/watch?v=kmgWAGDFCZI> Is this all so outrageous and new? During the Cold War, the CIA systematically infiltrated media outlets in the US. Thousands of agents were deployed as journalists - and wrote what they were told. This “Operation Mockingbird”, which the Church Committee also investigated, never ended, so to speak. It lives on as Operation Mockingbird 2.0. Intelligence payments to media outlets continue to exist. USAID distributes millions for “pro-democratic” reporting. Government subscriptions keep uncritical media alive. Media control of public opinion is the most important tool of power in a modern “democracy”. The difference to back then? Today, the manipulation is global. However, these revelations come at a time when trust in the media is already at an all-time low. [The fear of being lied to by the powerful is currently the majority opinion at 70%.](https://www.edelman.com/trust/2025/trust-barometer) They are currently in the process of convincing the remaining 30% of their own incompetence.  ### Update on the [Pareto project](https://pareto.space/en)  “Half the victory”, says Sun Tsu, ‘lies in the impregnable defense’. Free media now have the opportunity to build their own impregnable bastion and the [Pareto Project](https://pareto.space/read) invites them to do just that: [become uncensorable, be able to scale infinitely and not depend on third parties for all processes of journalistic work](https://pareto.space/a/naddr1qqxnzdenxuerxdpkxycngvpcqgsvlutjpemmkp50p6aa8zwu65yz9hg6erf2czc0tuyqpt57zhr79vsrqsqqqa28qyxhwumn8ghj7mn0wvhxcmmvqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hs33ee7d). It's all possible now. Everyone has to realize that: With other platforms, you build your house on someone else's property. With Nostr/Pareto, there is nothing and no one between author and reader, both in terms of communication and payment (via Bitcoin/Litghtning). **A brief update on the project, January was very busy.** * We have about 35 journalists, publications, substackers, bloggers, memers onboarded who publish texts via the Pareto client, and the number is growing all the time. * The first Telepolis authors, such as Mathias Bröckers and Alexander Unzicker, will soon be able to re-publish their deleted texts with us in a censorship-proof manner, and we are helping with the migration of content. * We recently successfully tested the newsletter function! We will soon be able to offer all authors and readers the functions of Substack, Steady, Ghost etc. without having to entrust their readers' sensitive data to a platform or expose them to platform tracking. * We are delighted to have more high-caliber additions to our development team, which now comprises around ten wonderful people, almost all of whom come from this group of readers. * Our [open source code is now also public.](https://github.com/twenty-eighty/pareto-client) * We have opened a [crowdfunding on Geyser!](https://geyser.fund/project/pareto) - Our editor will soon be available to everyone free of charge (atm you have to drop us your npub: <team@pareto.space>) ### What's next? This opens up a new window of unimagined possibilities: On a strong basis such as that offered by decentralized technology, many critical authors can now publish securely or new publications can be created - worldwide and uncensorable. What kind of publications would you like to see? Where do you see gaps (also in the critical spectrum) that need to be filled, both in terms of formats and topics? What does the journalism of the future look like to you? Feel free to write to me: **<milosz@pareto.space>** ## One last thing Our funds are coming to an end. If you would like to support us: We have started a [crowdfunding on Geyser](https://geyser.fund/project/pareto), where you can help us with Bitcoin/Lightning donations.   For traditional donations, you can find our bank account on our **[landingpage.](https://pareto.space/en)** *** ***Join the marketplace of ideas!** We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the [Pareto Project](https://pareto.space/en)? Zap me, if you want to contribute (all Zaps go to the project).* *Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to **<team@pareto.space>*** **Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Start.](https://start.njump.me/)**
@ e373ca41:b82abcc5
2025-02-13 09:13:10*This article has been written with the* ***[Pareto client](https://pareto.space/read).*** *(read it there for the full experience). It was first published in German by Milosz Matuschek on* ***["Freischwebende Intelligenz".](https://www.freischwebende-intelligenz.org/p/unterwanderter-journalismus-der-mediale)*** *** It is unmistakable. The hydra of the Deep State is losing a few heads - and this time it's the turn of the media heads. Anyone can look at [USASpending](https://www.usaspending.gov/) to see how much taxpayers' money has gone to whom in the USA. ### When the state pays its advocates The mainstream media were also among the beneficiaries: Politico (100% Axel Springer) received over [USD 7 million](https://www.usaspending.gov/recipient/fa0cefae-7cfb-881d-29c3-1bd39cc6a49e-C/latest); the New York Times received over USD 40 million. Thousands of (probably not always necessary) government subscriptions flowed to large media houses - paid for with taxpayers' money. A form of covert press financing by the state. At what point can or should we speak of state media? ") However, this is only the tip of the iceberg. The CIA front organization USAID ([known for its funding of virus research in Wuhan and other questionable activities](https://pareto.space/a/naddr1qqxnzden8quryveexq6rywp3qgswxu72gyq7ykjdfl9j556887jpzwu3mw3v9ez36quas55whq4te3grqsqqqa28qyxhwumn8ghj7mn0wvhxcmmvqyf8wumn8ghj7mmxve3ksctfdch8qatzqythwumn8ghj7urpwfjhgmewdehhxarjxyhxxmmdqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsz9nhwden5te0wfjkccte9ehx7um5wghxyctwvszsxfjh)) - [pumped USD 472.6 million directly into the media landscape via the “Internews Network”.](https://www.zerohedge.com/political/usaid-funded-massive-global-state-propaganda-news-matrix-nearly-billion-people-reach) FAZ journalist Udo Ulfkotte once called this “bought journalists” in a very clear and media-effective way, which was not good for his health. There is ample evidence of the CIA-USAID connections, for example [here](https://timesofindia.indiatimes.com/toi-plus/international/how-usaid-worked-alongside-cia-in-vietnam-a-whistleblowers-account/articleshow/118164225.cms), [here](https://foreignpolicy.com/2014/04/03/cuban-twitter-and-other-times-usaid-pretended-to-be-an-intelligence-agency/) and [here.](https://www.jstor.org/stable/4017728) ") But this is now over for the time being: USD 268 million, which was to go to “independent media for the free flow of information” (according to the [Columbia Journalism Review](https://www.cjr.org/the_media_today/usaid-and-the-media-in-a-time-of-monsters.php)) in 2025, has been frozen. The largest media influence machine in the Western world is bleeding a little. One has to admit: part of the media-deepstate swamp is actually being drained dry financially. The fact that the Columbia Journalism Review doesn't even seem to notice that “free international journalism”, which, as it writes, is largely funded by USAID, ceases to be “free journalism” speaks volumes about this “hotbed of journalism”. Matt Taibbi of Racket News rightly finds, “The legacy media system is dead. They just don't know it yet.” *** ADVERTISEMENT: *Looking for the easiest way to buy Bitcoin and store it yourself? The **[Relai app](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. **[Here you can buy Bitcoin](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees (no financial advice). Disclaimer due to regulatory issues: The services of the Relai App are hereby only recommended to inhabitants of Switzerland or Italy.*  *Need more security? The **[Trezor wallets](https://trezor.io/trezor-safe-5-bitcoin-only?transaction_id=102e192a206d1585e56a2fddef6d83\&offer_id=238\&affiliate_id=35234)** are recommended and easy to use, others are available in the **[store](https://trezor.io/?transaction_id=102bc85bdca2733287749c7f879ebd\&offer_id=133\&affiliate_id=35234)**. Need more advice? Book an **[introductory meeting](https://trezor.io/trezor-expert-session?transaction_id=1020e18dad0aa4b1186289fd22e90f\&offer_id=241\&affiliate_id=35234)** with a wallet expert.* *** Large-scale media manipulation has become visible. The propaganda matrix, if you will. The disastrous thing about it: if the Overton window is infiltrated, so to speak, the entire institution of journalism cannot be trusted. Every day, readers must expect to be pulled through the nose ring of intelligence service narratives and public agendas by mainstream journalists who pretend to be objective (and are often simply clueless and unsuspecting). The panorama of what we are supposed to see and believe, so to speak. How many mainstream journalists today are basically mouthpieces for the services? Every mainstream reader must now ask themselves: Is my favorite journalist at NZZ, Welt, SZ, ZEIT or FAZ perhaps just a CIA-IM? There were no major dissenters among them: EU criticism? Vaccination criticism? Criticism of NATO? Criticism of Biden and America? Criticism of Nord Stream? There were brief moments on television when questions about journalists' ties to lobby organizations were still part of the German satire program. <https://x.com/Spitze_Zunge_/status/1887915509988876786> ### The cards in the media are being reshuffled The watchdog of the powerful has been infiltrated by the powerful. This means that the Fourth Power is not a power at all, but part of the executive branch, a mouthpiece of the government. The claim that the mainstream is quality journalism, the gold standard for trustworthy information, is therefore the real fake news. It is the last, now crumbling dogma of an infiltrated press sect that has formed a cartel and is subjecting citizens to a permanent psy-op with intelligence-controlled taxpayers' money. A troupe of spokespeople at the work of mental synchronization. <https://x.com/TopherField/status/1887962959072149989> ### The fight against independent media But they not only give to one, they also take from the other. While government agencies use taxpayers' money to promote a certain type of journalism, the juice is actively being cut off from the critical part. All it takes is to be classified as a “PEP” (politically exposed person) and the bank account is gone. This is what has just happened to swiss Radio Kontrafunk. The critical Swiss author Stefan Millius was canceled by his publisher. Others have had their monetization via YouTube cut off (Snicklink). Others are harassed by the state media authority (Multipolar, Alexander Wallasch). The next one has a house search. It has been known since the Twitter files that the government and services also intervened massively in social media communication. This is no longer the Cold War. But it is the cold information war. <https://www.youtube.com/watch?v=kmgWAGDFCZI> Is this all so outrageous and new? During the Cold War, the CIA systematically infiltrated media outlets in the US. Thousands of agents were deployed as journalists - and wrote what they were told. This “Operation Mockingbird”, which the Church Committee also investigated, never ended, so to speak. It lives on as Operation Mockingbird 2.0. Intelligence payments to media outlets continue to exist. USAID distributes millions for “pro-democratic” reporting. Government subscriptions keep uncritical media alive. Media control of public opinion is the most important tool of power in a modern “democracy”. The difference to back then? Today, the manipulation is global. However, these revelations come at a time when trust in the media is already at an all-time low. [The fear of being lied to by the powerful is currently the majority opinion at 70%.](https://www.edelman.com/trust/2025/trust-barometer) They are currently in the process of convincing the remaining 30% of their own incompetence.  ### Update on the [Pareto project](https://pareto.space/en)  “Half the victory”, says Sun Tsu, ‘lies in the impregnable defense’. Free media now have the opportunity to build their own impregnable bastion and the [Pareto Project](https://pareto.space/read) invites them to do just that: [become uncensorable, be able to scale infinitely and not depend on third parties for all processes of journalistic work](https://pareto.space/a/naddr1qqxnzdenxuerxdpkxycngvpcqgsvlutjpemmkp50p6aa8zwu65yz9hg6erf2czc0tuyqpt57zhr79vsrqsqqqa28qyxhwumn8ghj7mn0wvhxcmmvqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hs33ee7d). It's all possible now. Everyone has to realize that: With other platforms, you build your house on someone else's property. With Nostr/Pareto, there is nothing and no one between author and reader, both in terms of communication and payment (via Bitcoin/Litghtning). **A brief update on the project, January was very busy.** * We have about 35 journalists, publications, substackers, bloggers, memers onboarded who publish texts via the Pareto client, and the number is growing all the time. * The first Telepolis authors, such as Mathias Bröckers and Alexander Unzicker, will soon be able to re-publish their deleted texts with us in a censorship-proof manner, and we are helping with the migration of content. * We recently successfully tested the newsletter function! We will soon be able to offer all authors and readers the functions of Substack, Steady, Ghost etc. without having to entrust their readers' sensitive data to a platform or expose them to platform tracking. * We are delighted to have more high-caliber additions to our development team, which now comprises around ten wonderful people, almost all of whom come from this group of readers. * Our [open source code is now also public.](https://github.com/twenty-eighty/pareto-client) * We have opened a [crowdfunding on Geyser!](https://geyser.fund/project/pareto) - Our editor will soon be available to everyone free of charge (atm you have to drop us your npub: <team@pareto.space>) ### What's next? This opens up a new window of unimagined possibilities: On a strong basis such as that offered by decentralized technology, many critical authors can now publish securely or new publications can be created - worldwide and uncensorable. What kind of publications would you like to see? Where do you see gaps (also in the critical spectrum) that need to be filled, both in terms of formats and topics? What does the journalism of the future look like to you? Feel free to write to me: **<milosz@pareto.space>** ## One last thing Our funds are coming to an end. If you would like to support us: We have started a [crowdfunding on Geyser](https://geyser.fund/project/pareto), where you can help us with Bitcoin/Lightning donations.   For traditional donations, you can find our bank account on our **[landingpage.](https://pareto.space/en)** *** ***Join the marketplace of ideas!** We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the [Pareto Project](https://pareto.space/en)? Zap me, if you want to contribute (all Zaps go to the project).* *Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to **<team@pareto.space>*** **Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Start.](https://start.njump.me/)** @ 3eba5ef4:751f23ae
2025-02-13 09:00:41Security is fundamental to any blockchain. It ensures that all tokens are secure. When talking about a virtual machine and the smart contract platform it forms, security comes in two main aspects: * The code running on the virtual machine must be secure * The virtual machine itself should also be designed to facilitate safer code execution The first aspect often gets sufficient attention. When it comes to [CKB](https://www.nervos.org/), we now encourage developers to write scripts in Rust for maximum security, reserving pure C code only for those who fully understand its risks. Additionally, higher-level languages have been introduced in CKB to strike a better balance between productivity and security. Virtual machine security was a major focus when CKB-VM was originally designed. Many potential risks were addressed at the architectural level, though some—despite thorough research—were still left open. One such issue is **Return-Oriented Programming (ROP)**—a rather ingenious attack. It exploits executable code that has been legitimately loaded into memory, making widely effective protections (e.g., [W^X](https://yakihonne.com/write-article)) futile. It spans multiple architectures and is constantly evolving. Although we’ve spent a great deal of effort in the early days on ROP, we did not implement specific countermeasures to prevent it. Now, with new RISC-V extensions now available, it is the perfect time to introduce design-level protections against ROP. ## Acknowledgments Before diving deeper, we would like to acknowledge Todd Mortimer from the OpenBSD team. His work on ROP mitigations at the OpenBSD kernel in 2018-2019 significantly inspired our research and this article. We highly recommend his [talk](https://www.youtube.com/watch?v=ZvSSHtRv5Mg), slide decks from [AsiaBSDCon 2019](https://www.openbsd.org/papers/asiabsdcon2019-rop-slides.pdf) and [EuroBSD 2018](https://www.openbsd.org/papers/eurobsdcon2018-rop.pdf), and this [paper](https://www.openbsd.org/papers/asiabsdcon2019-rop-paper.pdf) for a deeper understanding of ROP. Several examples on x64 ROP attacks in this post are also drawn from his research. ## Typical Attack Workflow While there are many sophisticated [ways](https://www.wired.com/2016/06/clever-attack-uses-sound-computers-fan-steal-data/) of attacks, a common attack on a program typically follows this process: Prepare a [shellcode](https://en.wikipedia.org/wiki/Shellcode)— a piece of binary code to perform specific actions (e.g., running a shell or other programs on the target computer). Exploit one possible vulnerability in the target system, most commonly a [buffer overflow](https://en.wikipedia.org/wiki/Buffer_overflow) attack. The attack could be initiated via a network protocol (such as HTTP) against a remote system, or via command line input to a target program; As the result of the attack, the shellcode is inserted to a designated memory region of the target system and gets executed, allowing the attacker to achieve their goal. The consequences vary, like gaining unauthorized access to sensitive data, destroying certain data/machine, planting malicious programs onto the target for further actions, manipulating control flow. While traditional systems face a wide range of attacks, blockchains run in their own limited and unique runtime environment, rendering many conventional attacks irrelevant. Major blockchain security threats includes: * **Private key security**: Blockchain wallets rely on private keys, which are prime targets for various attacks. * **Smart contract vulnerability**: Poorly written smart contracts contain logic flaws that lead to security risks. * **Virtual machine security**: Attacker may send malicious inputs to a smart contract, causing it to terminate unexpectedly with a success status—despite lacking proper credentials. This post focuses specifically on attacks targeting the blockchain’s virtual machine—in our case—CKB Virtual Machine (CKB-VM) specifically. ## CKB’s Early Approach While it is impossible to predict every attack, disrupting the typical attack workflow is an effective defense strategy. From its inception, CKB-VM has implemented [W^X](https://en.wikipedia.org/wiki/W%5EX) protection: at any given time, any memory location in CKB-VM is either writable (allowing data modification) or executable (allowing data execution)—but never both. Once a memory region is marked as **executable**, it cannot be reverted to **writable** throughout the lifecycle of the current CKB-VM instance. Only writable memory location can be **frozen** to executable. This design significantly disrupts the typical attack workflow. For shellcode to execute on CKB-VM, it must reside in **executable** memory. However, an attacker can only provide shellcode as part of program inputs, which are loaded into **writable** memory. As long as a CKB script does not voluntarily mark input data as **executable** (a highly unlikely scenario), the shellcode remains inert. Additionally, attempting to overwrite existing **executable** shellcode is also futile, since executable memory region is unwritable, and cannot be converted back to writable. This way, W^X is a well-established security technique widely used in modern hardwares, operating systems, and virtual machines. Although it cannot prevent all possible attacks, W^X effectively shields many by breaking the standard attack workflow. Even if an attacker successfully injects shellcode into a target machine, the attack is incomplete due to the inability to execute it. ## Understanding ROP While W^X is effective, it does not solve all our problems. This leads to the topic of this post: **Return-oriented Programming (ROP)**. Instead of explicitly injecting new code, ROP exploits executable code that already resides in the target machine’s memory. Essentially, ROP builds a shellcode by chaining existing code snippets together that were never intended to function as such. It may sound like a fantasy, but as we shall see from the following examples, ROP is a practical and effective attack technique. To understand ROP, we must first examine modern CPU architecture and memory layout. While assembly instructions vary in representations and lengths, they are put together in memory one after another as a stream of bytes:  *Image [Source](https://www.quora.com/Is-assembly-language-a-source-code-or-object-code)* As seen in the above example, different assembly instructions come in different lengths. For x86-64 ISA, an instruction can range from 1 to 7 bytes (RISC ISAs such as ARM or RISC-V have more uniform instruction lengths—we will discuss it later). But in memory, instructions are stored sequentially without gaps. This means that with a stream of bytes alone, we really don’t know what instructions the stream of bytes consist of. In the above example, meaningful assembly instructions emerge only when we start decoding from the `B8` byte. In a different occasion, assuming we know elsewhere that `B8 22 11` bytes at the front are for certain magic flags, the decoding would start from `00` byte, yielding a totally different instruction set.  *Image [Source](https://www.quora.com/Is-assembly-language-a-source-code-or-object-code)* It is really the combination of a special program counter (`PC`) register from the CPU and the current memory stream, jointly determine the instructions the CPU executes. Depending on each different ISA or hardware, a booting process initializes a CPU’s `PC` register to a pre-defined value, then loads up instructions from this pre-defined address, and initializes everything related to the operating system. When a user launches a new program, the metadata for each program will contain an `entrypoint` address, where OS sets the CPU’s `PC` register to, in order to start executing the program. It is suffice to say that maintaining a proper `PC` value is a critical job to ensure a computer’s proper function. An invalid `PC` value might lead to a CPU malfunction at best, or at worst, leaking sensitive information or granting attackers unauthorized access. ### Forming an ROP Attack Via ROP Gadgets Let’s look at the following byte instruction stream in a x86-64 CPU: ``` 8a 5d c3 movb -61(%rbp), %bl ``` This 3-byte represents a `mov` instruction: it takes the address of `rbp` register, adds an offset of `-61`, then uses the result as a memory address to load 1 byte data, and finally sets the loaded data to `bl` register. However, if we ignore `8a` and only look at `5b c3` here, it actually represents a different instruction set: ``` 5d popq %rbp c3 retq ``` This byte sequence contains two instructions: * Pop 8-byte value from stack, and use it to set `rbp` register * Pop 8-byte value from stack, and use it to set `PC` register, so we continue executing from the new location We've briefly discussed that shellcode only fulfills a certain task required by the attacker. In fact, the most common type of shellcode simply construct a new shell, where the attacker can execute more operations. Such shellcode can be represented in the following C pseudocode to run a new command via the `execve` syscall: ``` execve(“/bin/sh”, NULL, NULL); ``` To execute this on an x86-64 CPU, the following actions are needed for a syscall: * `rax` register: must contain the syscall number, for `execve`, it is `59` * `rdi`, `rsi`, `rdx` registers: hold the first 3 arguments to the syscall. In this case, `rdi` holds a pointer to the C string `/bin/sh`; `rsi` and `rdx` must be zero. * The `syscall` instruction (or typically `int 80h` on x64) shall be executed A typical shellcode would be a packed assembly sequence directly doing all of the above instructions. In contrast, ROP attack looks for the following sequences: ``` # Those can set the value of different registers from values on the stack pop %rax; ret pop %rdi; ret pop %rsi; ret pop %rdx; ret # Finally, trigger the syscall syscall ``` Each of these small code sequences, are conventionally callled **ROP gadgets**. An attacker searches for these gadgets in the target program or system libraries (such as libc). Once these required gadgets are obtained, the attacker pieces together a sequence of data, much like the following:  With the prepared data sequence, the attacker can exploit a vulnerability in the target computer or program, such as typical buffer overflow attack. During this process, the attacker performs three key actions: * Pushes (or overwrites existing data) the crafted data sequence to the stack * Sets the stack pointer (top of the stack) to `X + 64` * Sets the `PC` register to the address of a code sequence, `pop %rax; ret` in the existing program or libc memory space Now the attack proceeds step by step as follows: 1. The CPU runs `pop %rax; ret`. With the stack pointer pointing to `X + 64`, the CPU pops `59` from the stack and sets `rax` register to `59`. It then pops the address to code sequence `pop %rdi; ret` from the stack, and sets `PC` to this value; 2. The CPU runs `pop %rdi; ret`. With the stack pointer pointing to `X + 48`, the CPU pops value `X`, pointing to the C string `/bin/sh` from the stack, and sets `rdi` register to `X`. It then pops the address to code sequence `pop %rsi; ret` from the stack, and sets `PC` to this value; 3. The CPU runs `pop %rsi; ret`. With the stack pointer pointing to `X + 32`, the CPU pops `0` from the stack and sets `rsi` register to `0`. It then pops the address to code sequence `pop %rdx; ret` from the stack, and sets `PC` to this value; 4. The CPU runs `pop %rdx; ret`. With the stack pointer pointing to `X + 16`, the CPU pops `0` from the stack and sets `rdx` register to `0`. It then pops the address to code sequence `syscall` from the stack, and sets `P`C to this value; 5. The CPU runs `syscall`. At this point, `rax` holds `59`, `rdi` points to `/bin/sh`, and both `rsi` and `rdx` are zero, the CPU invokes `execve("/bin/sh, NULL, NULL);`, granting the attacker a shell for further manipulations. This sequence of ROP gadgets, referred to as **ROP chains**, demonstrates how a complete ROP attack works. Two key takeaways are: * **ROP does not inject new code**. Instead, it injects data into the stack and leverages the existing code loaded in memory and marked them as executable. W^X protections hence cannot prevent ROP attacks. * **Attackers can mine ROP gadgets from the [libc](https://en.wikipedia.org/wiki/C_standard_library) library**. This is because modern computers employs [protection rings](https://en.wikipedia.org/wiki/Protection_ring) as a way for privilege encapsulations: on x86-64 computers, programs normally run at ring level 3, while libc runs at ring level 1. Lower ring levels have higher privileges, meaning that even if a program misbehaves, its capacities are limited at ring level 3. However, by using ROP gadgets in the libc library which runs at ring level 1, ROP attacks can have higher privileges and execute more damaging operations then normal shellcodes. Note that the above examples simply show the most basic ROP gadgets. In reality, ROP gadgets come in all kinds of forms. Since they come from compiler outputs, they can be combined in the least expected way, and can vary the forms as new compiler optimizations come out. Numerous tools (e.g., [ropper](https://scoding.de/ropper/), [ropr](https://github.com/Ben-Lichtman/ropr)) and research papers (e.g., *[Experiments on ROP Attack with Various Instruction Set Architectures](https://dl.yumulab.org/papers/42/paper.pdf)*, *[ROPGMN](https://www.sciencedirect.com/science/article/abs/pii/S0167739X24005314)*, *[Detecting and Preventing ROP Attacks using Machine Learning on ARM](https://www.infosun.fim.uni-passau.de/ch/publications/compsac23.pdf)*, *[KROP](https://arxiv.org/pdf/2406.11880)* ) keep coming out, making it almost impossible to enumerate all possible ROP gadget combinations. ### ROP on ARM & RISC-V ROP attacks are not limited to CISC architectures, where instructions vary in length. They also affect RISC designs, such as [ARM](https://developer.arm.com/documentation/102433/0200/Return-oriented-programming) and [RISC-V](https://pure.royalholloway.ac.uk/ws/portalfiles/portal/37157938/ROP_RISCV.pdf). Take the following sequence for example: ``` 13 4f 83 23 0b 00 ``` Decoding from the start, the first four bytes represent `xori t5,t1,568` following the RISC-V ISA. But if we skip the first two, the latter four represent `lw t2,0(s6)`. This illustrates that a byte stream interpretation also requires `PC` register in a RISC design such as RISC-V. As a result, one can find ROP gadgets from a RISC-V program as well. ### ROP on CKB-VM CKB’s RISC-V machine operates in a more restricted environment: for programs running on CKB, there are no `execve` syscalls to hijack a running shell, and all runtime states are publicly visible on a public blockchain like CKB. However, ROP attacks can still occur on CKB: one could construct an ROP chain that sets `a0` to `0`, `a7` to `93`, then executes `ecall`. This causes CKB-VM to immediately return with a success code (`0`), potentially allowing a script to pass validation when it should have failed—such as a lock script succeeding without a valid signature. ### Short Recap Let’s briefly recap what we’ve learned so far: * ROP attacks utilize existing executable code for malicious purposes. W^X cannot prevent ROP. * ROP is possible across multiple architecture, including x86-64, ARM, RISC-V, and CKB. * The landscape of ROP is constantly evolving. With new tools, techniques, and research emerging regularly, it’s impossible to foresee all ROP gadgets. ROP has been extensively studied over the years, leading to various mitigation strategies, which can be broadly categorized into two main approaches: * **Software Solutions**: Covering techniques like rewriting code sequences and implementing Retguard to prevent the creation of ROP gadgets * **Hardware Solutions**: Introducing additional CPU instructions with Control Flow Integrity (CFI) checks to safeguard control flow. I’ll explore these strategies in greater detail in the following sections. ## Software Solutions to Mitigate ROP ### Rewriting Sequence Certain instruction sequences are often targeted to form ROP gadgets. To prevent ROP, one approach is to alter the compiler, so that such sequences can never be generated. Take the following example: ``` 89 c3 mov %eax,%ebx 90. ``` In x86-64, `c3` represents the `ret` instruction, making it a potential target for ROP gadgets. We can rewrite it into the following equivalent sequence: ``` 48 87 d8 xchgq %rbx, %rax 89 d8 movl %ebx, %eax 48 87 d8 xchgq %rbx, %rax ``` The new sequence lacks `c3` byte at the expense of more bytes and more executed instructions. However, it is really up to real benchmarks to see if this causes noticeable overhead. Further analysis has revealed that the `rbx` register in x86-64 is often the source of ROP gadgets, due to the way Intel encodes x86-64 instructions. Hence, the OpenBSD team decided to avoid `rbx` register wherever possible, reducing the number of potential ROP gadgets. Again, this approach comes at the cost of having bigger code fragments, more instructions to execute, and an additional patched compiler. While OpenBSD has integrated these changes into its distribution, other environments must weigh the benefits against the costs. For a deeper dive, I would strongly recommend Todd Mortimer’s [work](https://www.openbsd.org/papers/asiabsdcon2019-rop-slides.pdf). ### Retguard’s Solution: Prologue and Epilogue Todd Mortimer also introduced Retguard in this [work](https://www.openbsd.org/papers/asiabsdcon2019-rop-slides.pdf) for securing OpenBSD known. ROP attacks typically occur when you enter a function `foo`, but the stack was manipulated, so the CPU exits to another code fragment that is not `foo`. What if to verify that, at each function exit, it is the same function for exiting and entering? Retguard introduces two components to perform this task: * **Prologue**: A prologue is inserted to each function’s entry, taking two inputs: - - A `cookie` value, a random data assigned for this particular function. - - The return address, where to jump to when current function exits—as inputs. The prologue computes the XOR value of these two, and stores the result into the current function’s [frame](https://en.wikipedia.org/wiki/Call_stack#Stack_and_frame_pointers) section, a dedicated memory region designated to the current function to hold data, separated from the stack. * **Epilogue**: An epilogue is inserted to the location where a function might exit. It takes two inputs: - - The saved XOR value from the prologue in the frame section - - The return address it now can access to (most likely popped from the stack in x64 machine, or read from a special `RA` register in RISC design) The epilogue computes the XOR of these two. If the result matches the original `cookie`, execution proceeds. Otherwise, the epilogue halts the program, signaling an error. This prologue-epilogue mechanism in Retguard guards the call stack from tampering. At a noticeable but acceptable cost (both in performance and code size), Retguard eliminates a significant number of ROP gadgets from the OpenBSD kernel. Like other software-based mitigations, it requires a patched compiler, and it is up to each environment to decide if such technique shall be employed. ## Hardware Advancements to Mitigate ROP In addition to software solutions, hardware-based defenses have also been developed. For instance, Intel has introduced [Indirect Branch Tracking](https://edc.intel.com/content/www/us/en/design/ipla/software-development-platforms/client/platforms/alder-lake-desktop/12th-generation-intel-core-processors-datasheet-volume-1-of-2/007/indirect-branch-tracking/?language=en) feature starting with its 12th generation core processors, using a new instruction `endbr32` or `endbr64` added at every location the program might jump to or call into. When the CPU executes a jump/call, it asserts that the target location is a proper `endbr32` / `endbr64` instruction, before updating the program counter `PC` register to proper values. Otherwise, the CPU halts to terminate the program. This ensures that all control flows will follow the intended way, preventing ROP attacks from redirecting execution arbitrary locations. Modern OSes have already extensively leveraged `endbr32` / `endbr64` instructions. Ubuntu 24.04, for instance, has included these instructions in its packages: ``` $ objdump -d /bin/bash | head -n 50 /bin/bash: file format elf64-x86-64 Disassembly of section .init: 0000000000030000 <.init>: 30000: f3 0f 1e fa endbr64 30004: 48 83 ec 08 sub $0x8,%rsp 30008: 48 8b 05 d9 7e 12 00 mov 0x127ed9(%rip),%rax # 157ee8 <__gmon_start__@Base> 3000f: 48 85 c0 test %rax,%rax 30012: 74 02 je 30016 <unlink@plt-0xe1a> 30014: ff d0 call *%rax 30016: 48 83 c4 08 add $0x8,%rsp 3001a: c3 ret Disassembly of section .plt: 0000000000030020 <.plt>: 30020: ff 35 a2 76 12 00 push 0x1276a2(%rip) # 1576c8 <o_options@@Base+0x1cc8> 30026: ff 25 a4 76 12 00 jmp *0x1276a4(%rip) # 1576d0 <o_options@@Base+0x1cd0> 3002c: 0f 1f 40 00 nopl 0x0(%rax) 30030: f3 0f 1e fa endbr64 30034: 68 00 00 00 00 push $0x0 30039: e9 e2 ff ff ff jmp 30020 <unlink@plt-0xe10> 3003e: 66 90 xchg %ax,%ax 30040: f3 0f 1e fa endbr64 30044: 68 01 00 00 00 push $0x1 30049: e9 d2 ff ff ff jmp 30020 <unlink@plt-0xe10> 3004e: 66 90 xchg %ax,%ax 30050: f3 0f 1e fa endbr64 30054: 68 02 00 00 00 push $0x2 30059: e9 c2 ff ff ff jmp 30020 <unlink@plt-0xe10> 3005e: 66 90 xchg %ax,%ax 30060: f3 0f 1e fa endbr64 30064: 68 03 00 00 00 push $0x3 30069: e9 b2 ff ff ff jmp 30020 <unlink@plt-0xe10> 3006e: 66 90 xchg %ax,%ax 30070: f3 0f 1e fa endbr64 30074: 68 04 00 00 00 push $0x4 30079: e9 a2 ff ff ff jmp 30020 <unlink@plt-0xe10> 3007e: 66 90 xchg %ax,%ax 30080: f3 0f 1e fa endbr64 30084: 68 05 00 00 00 push $0x5 30089: e9 92 ff ff ff jmp 30020 <unlink@plt-0xe10> 3008e: 66 90 xchg %ax,%ax 30090: f3 0f 1e fa endbr64 30094: 68 06 00 00 00 push $0x6 30099: e9 82 ff ff ff jmp 30020 <unlink@plt-0xe10> 3009e: 66 90 xchg %ax,%ax ``` The `endbr32` / `endbr64` instructions has been carefully designed, so they are `nop` instructions—meaning they can do nothing at all—on CPUs prior to their introductions. Having them doesn't have any effect on older CPUs but enhances security on supported hardware. ## RISC-V’s Latest Achievements: CFI Extension The above mitigations against ROP fall into two categories: * **Compiler Modifications**: Can generate more secure binary assembly code. * **Additional CPU instructions**: Coming with Control Flow Integrity (CFI) checks to prevent exploitation Back to the beginning of designing CKB-VM, we throughly studied ROP and recognized that a vulnerability in a CKB script could potentially open the door to ROP attacks. However, we eventually did not introduce any specific mitigation against ROP in CKB-VM. Our decision was to stay aligned with the RISC-V ecosystem, avoiding shipping any custom RISC-V spec with additional instructions that would require a patched compiler. Nor do we want to maintain our own compiler set, eliminating the potential that any RISC-V-compliant compiler shall be able to produce CKB script. As the result, we shipped the first version of CKB-VM without ROP mitigations, but that does not mean we’ve ignore this issue: * We’ve [reached out](https://groups.google.com/a/groups.riscv.org/g/isa-dev/c/LyZzjJG7_18/m/pCSnKZPdBAAJ) to the RISC-V community for possible extension similar to Intel’s solution, and kept monitoring advancements in this field; * We’ve been watching over progress and writing secure CKB scripts. Since ROP relies on existing vulnerabilities, secure CKB scripts can kept ROP purely theoretical. We were thrilled when the **RISC-V CFI (Control-Flow Integrity) Extension** was officialy [ratified](https://github.com/riscv/riscv-cfi/releases/tag/v1.0) in July 2024. Designed by the brilliant minds from the RISC-V Foundation, this extension directly addresses ROP attacks with two key features: * `Zicfilp` extension introduces **landing pad**: Resembles Intel’s `endbr32` / `endbr64` to ensure that the CPU can only jump to valid, permitted targets. * `Zicfiss` extension introduces **shadow stack** with a series of instructions:. Offers a hardware solution similar to Retguard, where CPU ensures the control flow integrity or simply puts the call stack, preventing tampering throughout execution. Together, these features offer the state-of-the-art mitigations against ROP. More importantly, RISC-V CFI is now an official extension, meaning all future RISC-V CPUs, compilers, and tools will support this extension. In fact, LLVM 19 has already [supported](https://releases.llvm.org/19.1.0/docs/ReleaseNotes.html#changes-to-the-risc-v-backend), and I believe other compilers and tools will follow soon. Once fully adopted, CKB script developers can simply turn them on like a switch during code compilation. Without modifying the code, they can enjoy the security provided by RISC-V CFI extensions. Even if a vulnerability exists in a CKB script, these built-in enforcements can prevent it from being exploited. ## Final Words Security is complex. While we strive for maximum security, certain design principles might get in the way from introducing specific mitigations. ROP is a prime example: while we did learn much about it early on, implementing the best mitigations needs proper timing. Now the time has come. We are happy to introduce RISC-V CFI in CKB’s next hardfork, bringing stronger security for everyone. *** ✍🏻 Written by Xuejie Xiao His previous posts include: * [A Journey Optimizing CKB Smart Contract: Porting Bitcoin as an Example](https://blog.cryptape.com/a-journey-optimizing-ckb-smart-contract) * [Optimizing C++ Code for CKB-VM: Porting Bitcoin as an Example](https://blog.cryptape.com/optimizing-c-code-for-ckb-vm) Find more in his personal website [Less is More](https://xuejie.space/).
@ 3eba5ef4:751f23ae
2025-02-13 09:00:41Security is fundamental to any blockchain. It ensures that all tokens are secure. When talking about a virtual machine and the smart contract platform it forms, security comes in two main aspects: * The code running on the virtual machine must be secure * The virtual machine itself should also be designed to facilitate safer code execution The first aspect often gets sufficient attention. When it comes to [CKB](https://www.nervos.org/), we now encourage developers to write scripts in Rust for maximum security, reserving pure C code only for those who fully understand its risks. Additionally, higher-level languages have been introduced in CKB to strike a better balance between productivity and security. Virtual machine security was a major focus when CKB-VM was originally designed. Many potential risks were addressed at the architectural level, though some—despite thorough research—were still left open. One such issue is **Return-Oriented Programming (ROP)**—a rather ingenious attack. It exploits executable code that has been legitimately loaded into memory, making widely effective protections (e.g., [W^X](https://yakihonne.com/write-article)) futile. It spans multiple architectures and is constantly evolving. Although we’ve spent a great deal of effort in the early days on ROP, we did not implement specific countermeasures to prevent it. Now, with new RISC-V extensions now available, it is the perfect time to introduce design-level protections against ROP. ## Acknowledgments Before diving deeper, we would like to acknowledge Todd Mortimer from the OpenBSD team. His work on ROP mitigations at the OpenBSD kernel in 2018-2019 significantly inspired our research and this article. We highly recommend his [talk](https://www.youtube.com/watch?v=ZvSSHtRv5Mg), slide decks from [AsiaBSDCon 2019](https://www.openbsd.org/papers/asiabsdcon2019-rop-slides.pdf) and [EuroBSD 2018](https://www.openbsd.org/papers/eurobsdcon2018-rop.pdf), and this [paper](https://www.openbsd.org/papers/asiabsdcon2019-rop-paper.pdf) for a deeper understanding of ROP. Several examples on x64 ROP attacks in this post are also drawn from his research. ## Typical Attack Workflow While there are many sophisticated [ways](https://www.wired.com/2016/06/clever-attack-uses-sound-computers-fan-steal-data/) of attacks, a common attack on a program typically follows this process: Prepare a [shellcode](https://en.wikipedia.org/wiki/Shellcode)— a piece of binary code to perform specific actions (e.g., running a shell or other programs on the target computer). Exploit one possible vulnerability in the target system, most commonly a [buffer overflow](https://en.wikipedia.org/wiki/Buffer_overflow) attack. The attack could be initiated via a network protocol (such as HTTP) against a remote system, or via command line input to a target program; As the result of the attack, the shellcode is inserted to a designated memory region of the target system and gets executed, allowing the attacker to achieve their goal. The consequences vary, like gaining unauthorized access to sensitive data, destroying certain data/machine, planting malicious programs onto the target for further actions, manipulating control flow. While traditional systems face a wide range of attacks, blockchains run in their own limited and unique runtime environment, rendering many conventional attacks irrelevant. Major blockchain security threats includes: * **Private key security**: Blockchain wallets rely on private keys, which are prime targets for various attacks. * **Smart contract vulnerability**: Poorly written smart contracts contain logic flaws that lead to security risks. * **Virtual machine security**: Attacker may send malicious inputs to a smart contract, causing it to terminate unexpectedly with a success status—despite lacking proper credentials. This post focuses specifically on attacks targeting the blockchain’s virtual machine—in our case—CKB Virtual Machine (CKB-VM) specifically. ## CKB’s Early Approach While it is impossible to predict every attack, disrupting the typical attack workflow is an effective defense strategy. From its inception, CKB-VM has implemented [W^X](https://en.wikipedia.org/wiki/W%5EX) protection: at any given time, any memory location in CKB-VM is either writable (allowing data modification) or executable (allowing data execution)—but never both. Once a memory region is marked as **executable**, it cannot be reverted to **writable** throughout the lifecycle of the current CKB-VM instance. Only writable memory location can be **frozen** to executable. This design significantly disrupts the typical attack workflow. For shellcode to execute on CKB-VM, it must reside in **executable** memory. However, an attacker can only provide shellcode as part of program inputs, which are loaded into **writable** memory. As long as a CKB script does not voluntarily mark input data as **executable** (a highly unlikely scenario), the shellcode remains inert. Additionally, attempting to overwrite existing **executable** shellcode is also futile, since executable memory region is unwritable, and cannot be converted back to writable. This way, W^X is a well-established security technique widely used in modern hardwares, operating systems, and virtual machines. Although it cannot prevent all possible attacks, W^X effectively shields many by breaking the standard attack workflow. Even if an attacker successfully injects shellcode into a target machine, the attack is incomplete due to the inability to execute it. ## Understanding ROP While W^X is effective, it does not solve all our problems. This leads to the topic of this post: **Return-oriented Programming (ROP)**. Instead of explicitly injecting new code, ROP exploits executable code that already resides in the target machine’s memory. Essentially, ROP builds a shellcode by chaining existing code snippets together that were never intended to function as such. It may sound like a fantasy, but as we shall see from the following examples, ROP is a practical and effective attack technique. To understand ROP, we must first examine modern CPU architecture and memory layout. While assembly instructions vary in representations and lengths, they are put together in memory one after another as a stream of bytes:  *Image [Source](https://www.quora.com/Is-assembly-language-a-source-code-or-object-code)* As seen in the above example, different assembly instructions come in different lengths. For x86-64 ISA, an instruction can range from 1 to 7 bytes (RISC ISAs such as ARM or RISC-V have more uniform instruction lengths—we will discuss it later). But in memory, instructions are stored sequentially without gaps. This means that with a stream of bytes alone, we really don’t know what instructions the stream of bytes consist of. In the above example, meaningful assembly instructions emerge only when we start decoding from the `B8` byte. In a different occasion, assuming we know elsewhere that `B8 22 11` bytes at the front are for certain magic flags, the decoding would start from `00` byte, yielding a totally different instruction set.  *Image [Source](https://www.quora.com/Is-assembly-language-a-source-code-or-object-code)* It is really the combination of a special program counter (`PC`) register from the CPU and the current memory stream, jointly determine the instructions the CPU executes. Depending on each different ISA or hardware, a booting process initializes a CPU’s `PC` register to a pre-defined value, then loads up instructions from this pre-defined address, and initializes everything related to the operating system. When a user launches a new program, the metadata for each program will contain an `entrypoint` address, where OS sets the CPU’s `PC` register to, in order to start executing the program. It is suffice to say that maintaining a proper `PC` value is a critical job to ensure a computer’s proper function. An invalid `PC` value might lead to a CPU malfunction at best, or at worst, leaking sensitive information or granting attackers unauthorized access. ### Forming an ROP Attack Via ROP Gadgets Let’s look at the following byte instruction stream in a x86-64 CPU: ``` 8a 5d c3 movb -61(%rbp), %bl ``` This 3-byte represents a `mov` instruction: it takes the address of `rbp` register, adds an offset of `-61`, then uses the result as a memory address to load 1 byte data, and finally sets the loaded data to `bl` register. However, if we ignore `8a` and only look at `5b c3` here, it actually represents a different instruction set: ``` 5d popq %rbp c3 retq ``` This byte sequence contains two instructions: * Pop 8-byte value from stack, and use it to set `rbp` register * Pop 8-byte value from stack, and use it to set `PC` register, so we continue executing from the new location We've briefly discussed that shellcode only fulfills a certain task required by the attacker. In fact, the most common type of shellcode simply construct a new shell, where the attacker can execute more operations. Such shellcode can be represented in the following C pseudocode to run a new command via the `execve` syscall: ``` execve(“/bin/sh”, NULL, NULL); ``` To execute this on an x86-64 CPU, the following actions are needed for a syscall: * `rax` register: must contain the syscall number, for `execve`, it is `59` * `rdi`, `rsi`, `rdx` registers: hold the first 3 arguments to the syscall. In this case, `rdi` holds a pointer to the C string `/bin/sh`; `rsi` and `rdx` must be zero. * The `syscall` instruction (or typically `int 80h` on x64) shall be executed A typical shellcode would be a packed assembly sequence directly doing all of the above instructions. In contrast, ROP attack looks for the following sequences: ``` # Those can set the value of different registers from values on the stack pop %rax; ret pop %rdi; ret pop %rsi; ret pop %rdx; ret # Finally, trigger the syscall syscall ``` Each of these small code sequences, are conventionally callled **ROP gadgets**. An attacker searches for these gadgets in the target program or system libraries (such as libc). Once these required gadgets are obtained, the attacker pieces together a sequence of data, much like the following:  With the prepared data sequence, the attacker can exploit a vulnerability in the target computer or program, such as typical buffer overflow attack. During this process, the attacker performs three key actions: * Pushes (or overwrites existing data) the crafted data sequence to the stack * Sets the stack pointer (top of the stack) to `X + 64` * Sets the `PC` register to the address of a code sequence, `pop %rax; ret` in the existing program or libc memory space Now the attack proceeds step by step as follows: 1. The CPU runs `pop %rax; ret`. With the stack pointer pointing to `X + 64`, the CPU pops `59` from the stack and sets `rax` register to `59`. It then pops the address to code sequence `pop %rdi; ret` from the stack, and sets `PC` to this value; 2. The CPU runs `pop %rdi; ret`. With the stack pointer pointing to `X + 48`, the CPU pops value `X`, pointing to the C string `/bin/sh` from the stack, and sets `rdi` register to `X`. It then pops the address to code sequence `pop %rsi; ret` from the stack, and sets `PC` to this value; 3. The CPU runs `pop %rsi; ret`. With the stack pointer pointing to `X + 32`, the CPU pops `0` from the stack and sets `rsi` register to `0`. It then pops the address to code sequence `pop %rdx; ret` from the stack, and sets `PC` to this value; 4. The CPU runs `pop %rdx; ret`. With the stack pointer pointing to `X + 16`, the CPU pops `0` from the stack and sets `rdx` register to `0`. It then pops the address to code sequence `syscall` from the stack, and sets `P`C to this value; 5. The CPU runs `syscall`. At this point, `rax` holds `59`, `rdi` points to `/bin/sh`, and both `rsi` and `rdx` are zero, the CPU invokes `execve("/bin/sh, NULL, NULL);`, granting the attacker a shell for further manipulations. This sequence of ROP gadgets, referred to as **ROP chains**, demonstrates how a complete ROP attack works. Two key takeaways are: * **ROP does not inject new code**. Instead, it injects data into the stack and leverages the existing code loaded in memory and marked them as executable. W^X protections hence cannot prevent ROP attacks. * **Attackers can mine ROP gadgets from the [libc](https://en.wikipedia.org/wiki/C_standard_library) library**. This is because modern computers employs [protection rings](https://en.wikipedia.org/wiki/Protection_ring) as a way for privilege encapsulations: on x86-64 computers, programs normally run at ring level 3, while libc runs at ring level 1. Lower ring levels have higher privileges, meaning that even if a program misbehaves, its capacities are limited at ring level 3. However, by using ROP gadgets in the libc library which runs at ring level 1, ROP attacks can have higher privileges and execute more damaging operations then normal shellcodes. Note that the above examples simply show the most basic ROP gadgets. In reality, ROP gadgets come in all kinds of forms. Since they come from compiler outputs, they can be combined in the least expected way, and can vary the forms as new compiler optimizations come out. Numerous tools (e.g., [ropper](https://scoding.de/ropper/), [ropr](https://github.com/Ben-Lichtman/ropr)) and research papers (e.g., *[Experiments on ROP Attack with Various Instruction Set Architectures](https://dl.yumulab.org/papers/42/paper.pdf)*, *[ROPGMN](https://www.sciencedirect.com/science/article/abs/pii/S0167739X24005314)*, *[Detecting and Preventing ROP Attacks using Machine Learning on ARM](https://www.infosun.fim.uni-passau.de/ch/publications/compsac23.pdf)*, *[KROP](https://arxiv.org/pdf/2406.11880)* ) keep coming out, making it almost impossible to enumerate all possible ROP gadget combinations. ### ROP on ARM & RISC-V ROP attacks are not limited to CISC architectures, where instructions vary in length. They also affect RISC designs, such as [ARM](https://developer.arm.com/documentation/102433/0200/Return-oriented-programming) and [RISC-V](https://pure.royalholloway.ac.uk/ws/portalfiles/portal/37157938/ROP_RISCV.pdf). Take the following sequence for example: ``` 13 4f 83 23 0b 00 ``` Decoding from the start, the first four bytes represent `xori t5,t1,568` following the RISC-V ISA. But if we skip the first two, the latter four represent `lw t2,0(s6)`. This illustrates that a byte stream interpretation also requires `PC` register in a RISC design such as RISC-V. As a result, one can find ROP gadgets from a RISC-V program as well. ### ROP on CKB-VM CKB’s RISC-V machine operates in a more restricted environment: for programs running on CKB, there are no `execve` syscalls to hijack a running shell, and all runtime states are publicly visible on a public blockchain like CKB. However, ROP attacks can still occur on CKB: one could construct an ROP chain that sets `a0` to `0`, `a7` to `93`, then executes `ecall`. This causes CKB-VM to immediately return with a success code (`0`), potentially allowing a script to pass validation when it should have failed—such as a lock script succeeding without a valid signature. ### Short Recap Let’s briefly recap what we’ve learned so far: * ROP attacks utilize existing executable code for malicious purposes. W^X cannot prevent ROP. * ROP is possible across multiple architecture, including x86-64, ARM, RISC-V, and CKB. * The landscape of ROP is constantly evolving. With new tools, techniques, and research emerging regularly, it’s impossible to foresee all ROP gadgets. ROP has been extensively studied over the years, leading to various mitigation strategies, which can be broadly categorized into two main approaches: * **Software Solutions**: Covering techniques like rewriting code sequences and implementing Retguard to prevent the creation of ROP gadgets * **Hardware Solutions**: Introducing additional CPU instructions with Control Flow Integrity (CFI) checks to safeguard control flow. I’ll explore these strategies in greater detail in the following sections. ## Software Solutions to Mitigate ROP ### Rewriting Sequence Certain instruction sequences are often targeted to form ROP gadgets. To prevent ROP, one approach is to alter the compiler, so that such sequences can never be generated. Take the following example: ``` 89 c3 mov %eax,%ebx 90. ``` In x86-64, `c3` represents the `ret` instruction, making it a potential target for ROP gadgets. We can rewrite it into the following equivalent sequence: ``` 48 87 d8 xchgq %rbx, %rax 89 d8 movl %ebx, %eax 48 87 d8 xchgq %rbx, %rax ``` The new sequence lacks `c3` byte at the expense of more bytes and more executed instructions. However, it is really up to real benchmarks to see if this causes noticeable overhead. Further analysis has revealed that the `rbx` register in x86-64 is often the source of ROP gadgets, due to the way Intel encodes x86-64 instructions. Hence, the OpenBSD team decided to avoid `rbx` register wherever possible, reducing the number of potential ROP gadgets. Again, this approach comes at the cost of having bigger code fragments, more instructions to execute, and an additional patched compiler. While OpenBSD has integrated these changes into its distribution, other environments must weigh the benefits against the costs. For a deeper dive, I would strongly recommend Todd Mortimer’s [work](https://www.openbsd.org/papers/asiabsdcon2019-rop-slides.pdf). ### Retguard’s Solution: Prologue and Epilogue Todd Mortimer also introduced Retguard in this [work](https://www.openbsd.org/papers/asiabsdcon2019-rop-slides.pdf) for securing OpenBSD known. ROP attacks typically occur when you enter a function `foo`, but the stack was manipulated, so the CPU exits to another code fragment that is not `foo`. What if to verify that, at each function exit, it is the same function for exiting and entering? Retguard introduces two components to perform this task: * **Prologue**: A prologue is inserted to each function’s entry, taking two inputs: - - A `cookie` value, a random data assigned for this particular function. - - The return address, where to jump to when current function exits—as inputs. The prologue computes the XOR value of these two, and stores the result into the current function’s [frame](https://en.wikipedia.org/wiki/Call_stack#Stack_and_frame_pointers) section, a dedicated memory region designated to the current function to hold data, separated from the stack. * **Epilogue**: An epilogue is inserted to the location where a function might exit. It takes two inputs: - - The saved XOR value from the prologue in the frame section - - The return address it now can access to (most likely popped from the stack in x64 machine, or read from a special `RA` register in RISC design) The epilogue computes the XOR of these two. If the result matches the original `cookie`, execution proceeds. Otherwise, the epilogue halts the program, signaling an error. This prologue-epilogue mechanism in Retguard guards the call stack from tampering. At a noticeable but acceptable cost (both in performance and code size), Retguard eliminates a significant number of ROP gadgets from the OpenBSD kernel. Like other software-based mitigations, it requires a patched compiler, and it is up to each environment to decide if such technique shall be employed. ## Hardware Advancements to Mitigate ROP In addition to software solutions, hardware-based defenses have also been developed. For instance, Intel has introduced [Indirect Branch Tracking](https://edc.intel.com/content/www/us/en/design/ipla/software-development-platforms/client/platforms/alder-lake-desktop/12th-generation-intel-core-processors-datasheet-volume-1-of-2/007/indirect-branch-tracking/?language=en) feature starting with its 12th generation core processors, using a new instruction `endbr32` or `endbr64` added at every location the program might jump to or call into. When the CPU executes a jump/call, it asserts that the target location is a proper `endbr32` / `endbr64` instruction, before updating the program counter `PC` register to proper values. Otherwise, the CPU halts to terminate the program. This ensures that all control flows will follow the intended way, preventing ROP attacks from redirecting execution arbitrary locations. Modern OSes have already extensively leveraged `endbr32` / `endbr64` instructions. Ubuntu 24.04, for instance, has included these instructions in its packages: ``` $ objdump -d /bin/bash | head -n 50 /bin/bash: file format elf64-x86-64 Disassembly of section .init: 0000000000030000 <.init>: 30000: f3 0f 1e fa endbr64 30004: 48 83 ec 08 sub $0x8,%rsp 30008: 48 8b 05 d9 7e 12 00 mov 0x127ed9(%rip),%rax # 157ee8 <__gmon_start__@Base> 3000f: 48 85 c0 test %rax,%rax 30012: 74 02 je 30016 <unlink@plt-0xe1a> 30014: ff d0 call *%rax 30016: 48 83 c4 08 add $0x8,%rsp 3001a: c3 ret Disassembly of section .plt: 0000000000030020 <.plt>: 30020: ff 35 a2 76 12 00 push 0x1276a2(%rip) # 1576c8 <o_options@@Base+0x1cc8> 30026: ff 25 a4 76 12 00 jmp *0x1276a4(%rip) # 1576d0 <o_options@@Base+0x1cd0> 3002c: 0f 1f 40 00 nopl 0x0(%rax) 30030: f3 0f 1e fa endbr64 30034: 68 00 00 00 00 push $0x0 30039: e9 e2 ff ff ff jmp 30020 <unlink@plt-0xe10> 3003e: 66 90 xchg %ax,%ax 30040: f3 0f 1e fa endbr64 30044: 68 01 00 00 00 push $0x1 30049: e9 d2 ff ff ff jmp 30020 <unlink@plt-0xe10> 3004e: 66 90 xchg %ax,%ax 30050: f3 0f 1e fa endbr64 30054: 68 02 00 00 00 push $0x2 30059: e9 c2 ff ff ff jmp 30020 <unlink@plt-0xe10> 3005e: 66 90 xchg %ax,%ax 30060: f3 0f 1e fa endbr64 30064: 68 03 00 00 00 push $0x3 30069: e9 b2 ff ff ff jmp 30020 <unlink@plt-0xe10> 3006e: 66 90 xchg %ax,%ax 30070: f3 0f 1e fa endbr64 30074: 68 04 00 00 00 push $0x4 30079: e9 a2 ff ff ff jmp 30020 <unlink@plt-0xe10> 3007e: 66 90 xchg %ax,%ax 30080: f3 0f 1e fa endbr64 30084: 68 05 00 00 00 push $0x5 30089: e9 92 ff ff ff jmp 30020 <unlink@plt-0xe10> 3008e: 66 90 xchg %ax,%ax 30090: f3 0f 1e fa endbr64 30094: 68 06 00 00 00 push $0x6 30099: e9 82 ff ff ff jmp 30020 <unlink@plt-0xe10> 3009e: 66 90 xchg %ax,%ax ``` The `endbr32` / `endbr64` instructions has been carefully designed, so they are `nop` instructions—meaning they can do nothing at all—on CPUs prior to their introductions. Having them doesn't have any effect on older CPUs but enhances security on supported hardware. ## RISC-V’s Latest Achievements: CFI Extension The above mitigations against ROP fall into two categories: * **Compiler Modifications**: Can generate more secure binary assembly code. * **Additional CPU instructions**: Coming with Control Flow Integrity (CFI) checks to prevent exploitation Back to the beginning of designing CKB-VM, we throughly studied ROP and recognized that a vulnerability in a CKB script could potentially open the door to ROP attacks. However, we eventually did not introduce any specific mitigation against ROP in CKB-VM. Our decision was to stay aligned with the RISC-V ecosystem, avoiding shipping any custom RISC-V spec with additional instructions that would require a patched compiler. Nor do we want to maintain our own compiler set, eliminating the potential that any RISC-V-compliant compiler shall be able to produce CKB script. As the result, we shipped the first version of CKB-VM without ROP mitigations, but that does not mean we’ve ignore this issue: * We’ve [reached out](https://groups.google.com/a/groups.riscv.org/g/isa-dev/c/LyZzjJG7_18/m/pCSnKZPdBAAJ) to the RISC-V community for possible extension similar to Intel’s solution, and kept monitoring advancements in this field; * We’ve been watching over progress and writing secure CKB scripts. Since ROP relies on existing vulnerabilities, secure CKB scripts can kept ROP purely theoretical. We were thrilled when the **RISC-V CFI (Control-Flow Integrity) Extension** was officialy [ratified](https://github.com/riscv/riscv-cfi/releases/tag/v1.0) in July 2024. Designed by the brilliant minds from the RISC-V Foundation, this extension directly addresses ROP attacks with two key features: * `Zicfilp` extension introduces **landing pad**: Resembles Intel’s `endbr32` / `endbr64` to ensure that the CPU can only jump to valid, permitted targets. * `Zicfiss` extension introduces **shadow stack** with a series of instructions:. Offers a hardware solution similar to Retguard, where CPU ensures the control flow integrity or simply puts the call stack, preventing tampering throughout execution. Together, these features offer the state-of-the-art mitigations against ROP. More importantly, RISC-V CFI is now an official extension, meaning all future RISC-V CPUs, compilers, and tools will support this extension. In fact, LLVM 19 has already [supported](https://releases.llvm.org/19.1.0/docs/ReleaseNotes.html#changes-to-the-risc-v-backend), and I believe other compilers and tools will follow soon. Once fully adopted, CKB script developers can simply turn them on like a switch during code compilation. Without modifying the code, they can enjoy the security provided by RISC-V CFI extensions. Even if a vulnerability exists in a CKB script, these built-in enforcements can prevent it from being exploited. ## Final Words Security is complex. While we strive for maximum security, certain design principles might get in the way from introducing specific mitigations. ROP is a prime example: while we did learn much about it early on, implementing the best mitigations needs proper timing. Now the time has come. We are happy to introduce RISC-V CFI in CKB’s next hardfork, bringing stronger security for everyone. *** ✍🏻 Written by Xuejie Xiao His previous posts include: * [A Journey Optimizing CKB Smart Contract: Porting Bitcoin as an Example](https://blog.cryptape.com/a-journey-optimizing-ckb-smart-contract) * [Optimizing C++ Code for CKB-VM: Porting Bitcoin as an Example](https://blog.cryptape.com/optimizing-c-code-for-ckb-vm) Find more in his personal website [Less is More](https://xuejie.space/). @ 9967f375:04f9a5e1
2025-02-13 08:39:58El día 13, primer viernes de Cuaresma asistió su Exc. y Real Audiencia en la Capilla Real del Palacio a la Misa, y Sermón, que predicó el Doctor Don Pedro Ramírez del Castillo, Canónigo Penitenciario de la Metropoltana. #GacetadeMéxico #Febrero
@ 9967f375:04f9a5e1
2025-02-13 08:39:58El día 13, primer viernes de Cuaresma asistió su Exc. y Real Audiencia en la Capilla Real del Palacio a la Misa, y Sermón, que predicó el Doctor Don Pedro Ramírez del Castillo, Canónigo Penitenciario de la Metropoltana. #GacetadeMéxico #Febrero @ bf47c19e:c3d2573b
2025-02-13 08:10:44Originalni tekst na [dvadesetjedan.com](https://dvadesetjedan.com/blog/bitcoin-privatnost-najbolje-prakse). ###### Autor: [Gigi](https://dergigi.com/2021/03/14/bitcoin-privacy-best-practices/) / Prevod na srpski: [Plumsky](https://t.me/Plumski) --- > Postoji sveto carstvo privatnosti za svakog čoveka gde on bira i pravi odluke – carstvo stvoreno na bazičnim pravima i slobode koje zakon, generalno, ne sme narušavati. Džefri Fišer, Arhiepiskop Canterberija (1959) Pre ne toliko dugo, uobičajen režim interneta je bio neenkriptovan običan tekst (plain text). Svi su mogli špiunirati svakoga i mnogi nisu o tome ni razmišljali. Globalno obelodanjivanje nadzora 2013. je to promenilo i danas se koriste mnogo bezbedniji protokoli i end-to-end enkripcija postaje standard sve više. Iako bitcoin postaje tinejdžer, mi smo – metaforično govoreći – i dalje u dobu običnog teksta narandžastog novčića. Bitcoin je radikalno providljiv protokol sam po sebi, ali postoje značajni načini da korisnik zaštiti svoju privatnost. U ovom članku želimo da istaknemo neke od ovih strategija, prodiskutujemo najbolje prakse, i damo preporuke koje mogu primeniti i bitcoin novajlije i veterani. #### Zašto je privatnost bitna > Privatnost je potrebna da bi otvoreno društvo moglo da funkcioniše u digitalnoj eri. Privatnost nije isto što i tajanstvenost. Privatna stvar je nešto što neko ne želi da ceo svet zna, a tajna stvar je nešto što neko ne želi bilo ko da zna. Privatnost je moć da se čovek selektivno otkriva svom okruženju. Ovim snažnim rečima Erik Hjus je započeo svoj tekst Sajferpankov Manifesto (Cypherpunk's Manifesto) 1993. Razlika između privatnosti i tajanstvenosti je suptilna ali jako važna. Odlučiti se za privatnost ne znači da neko ima tajne koje želi sakriti. Da ovo ilustrujemo shvatite samo da ono što obavljate u svom toaletu ili u spavaćoj sobi nije niti ilegalno niti tajna (u mnogim slučajevima), ali vi svejedno odlučujete da zatvorite vrata i navučete zavese. Slično tome, koliko para imate i gde ih trošite nije naručito tajna stvar. Ipak, to bi trebalo biti privatan slučaj. Mnogi bi se složili da vaš šef ne treba da zna gde vi trošite vašu platu. Privatnosti je čak zaštićena od strane mnogobrojnih internacionalnih nadležnih organa. Iz Američke Deklaracije Prava i Dužnosti Čoveka (American Declaration of the Rights and Duties of Man) Ujedinjenim Nacijama, napisano je da je privatnost fundamentalno prava gradjana širom sveta. > Niko ne sme biti podvrgnut smetnjama njegovoj privatnosti, porodici, rezidenciji ili komunikacijama, niti napadnuta njegova čast i reputacija. Svi imaju pravo da se štite zakonom protiv takvih smetnja ili napada. Artikal 12, Deklaracija Ljudskih Prava Ujedinjenih Nacija #### Bitcoin i privatnost Iako je bitcoin često opisivan kao anoniman način plaćanja medijima, on u stvari poseduje potpuno suprotne osobine. On je poluanoniman u najboljem slučaju i danas mnogima nije ni malo lako primeniti taktike da bi bili sigurni da njihov poluanonimni identitet na bitcoin mreži ne bude povezan sa legalnim identitetom u stvarnom svetu. Bitcoin je otvoren sistem. On je javna baza podataka koju svako može da proučava i analizira. Znači, svaka transakcija koja je upisana u tu bazu kroz dokaz rada (proof-of-work) postojaće i biće otkrivena dokle god bitcoin postoji, što znači - zauvek. Ne primenjivati najbolje prakse privatnosti može imati štetne posledice u dalekoj budućnosti. Privatnost, kao sigurnost, je proces koji je težak, ali nije nemoguć. Alatke nastavljaju da se razvijaju koje čuvaju privatnost kad se koristi bitcoin and srećom mnoge od tih alatki su sve lakše za korišćenje. Nažalost ne postoji panacea u ovom pristupu. Mora se biti svesan svih kompromisa i usavršavati te prakse dok se one menjaju. #### Najbolje prakse privatnosti Kao i sve u bitcoinu, kontrola privatnosti je postepena, korak po korak, procedura. Naučiti i primeniti ove najbolje prakse zahteva strpljivost i odgovornost, tako da ne budite obeshrabreni ako vam se čini da je to sve previše. Svaki korak, koliko god bio mali, je korak u dobrom pravcu. Koje korake preduzeti da bi uvećali svoju privatnost: * Budite u vlasništvu sami svojih novčića * Nikad ne ponavljajte korišćenje istih adresa * Minimizirajte korišćenje servisa koji zahtevaju identitet (Know your customer - KYC) * Minimizirajte sve izloženosti trećim licima * Upravljajte svojim nodom * Koristite Lightning mrežu za male transakcije * Nemojte koristiti javne blok pretraživače za svoje transakcije * Koristite metodu CoinJoin često i rano pri nabavljanju svojih novčića **Budite u vlasništvu sami svojih novčića**: Ako ključevi nisu tvoji, onda nije ni bitcoin. Ako neko drugo drži vaš bitcoin za vas, oni znaju sve što se može znati: količinu, istoriju transakcija pa i sve buduće transakcije, itd. Preuzimanje vlasništva bitcoina u svoje ruke je prvi i najvažniji korak. **Nikad ne kroistite istu adresu dvaput**: Ponavljanje adresa poništava privatnost pošiljalca i primaoca bitcoina. Ovo se treba izbegavati pod svaku cenu. **Minimizirajte korišćenje servisa koji zahtevaju identitet (KYC)**: Vezivati svoj legalni identitet za svoje bitcoin adrese je zlo koje se zahteva od strane mnogih državnih nadležnosti. Dok je efektivnost ovih zakona i regulacija disputabilno, posledice njihovog primenjivanja su uglavnom štetne po korisnicima. Ovo je očigledno pošto je česta pojava da se te informacije često izlivaju iz slabo obezbeđenih digitalnih servera. Ako izaberete da koristite KYC servise da bi nabavljali bitcoin, proučite i razumite odnos između vas i tog biznisa. Vi ste poverljivi tom biznisu za sve vaše lične podatke, pa i buduće obezbeđenje tih podataka. Ako i dalje zarađujete kroz fiat novčani sistem, mi preporučujemo da koristite samo bitcoin ekskluzivne servise koji vam dozvoljavaju da autamatski kupujete bitcoin s vremena na vreme. Ako zelite da potpuno da izbegnete KYC, pregledajte https://bitcoinqna.github.io/noKYConly/. **Minimizirajte sve izloženosti trećim licima**: Poverljivost trećim licima je bezbednosna rupa (https://nakamotoinstitute.org/trusted-third-parties/). Ako možete biti poverljivi samo sebi, onda bi to tako trebalo da bude. **Upravljajte svojim nodom**: Ako nod nije tvoj, onda nisu ni pravila. Upravljanje svojim nodom je suštinska potreba da bi se bitcoin koristio na privatan način. Svaka interakcija sa bitcoin mrežom je posrednjena nodom. Ako vi taj nod ne upravljate, čiji god nod koristite može da vidi sve što vi radite. Ova upustva (https://bitcoiner.guide/node/) su jako korisna da bi započeli proces korišćenja svog noda. **Koristite Lightning mrežu za male transakcije**: Pošto Lightning protokol ne koristi glavnu bitcoin mrežu za trasakcije onda je i samim tim povećana privatnost korišćenja bez dodatnog truda. Iako je i dalje rano, oni apsolutno bezobzirni periodi Lightning mreže su verovatno daleko iza nas. Korišćenje Lightning-a za transakcije malih i srednjih veličina će vam pomoći da uvećate privatnost a da smanjite naplate svojih pojedinačnih bitcoin transakcija. **Nemojte koristiti javne blok pretraživače za svoje transakcije**: Proveravanje adresa na javnim blok pretraživačima povezuje te adrese sa vašim IP podacima, koji se onda mogu koristiti da se otkrije vaš identitet. Softveri kao Umbrel i myNode vam omogućavaju da lako koristite sami svoj blok pretraživač. Ako morate koristiti javne pretraživače, uradite to uz VPN ili Tor. **Koristite CoinJoin često i rano pri nabavljanju svojih novčića**: Pošto je bitcoin večan, primenjivanje saradničkih CoinJoin praksa će vam obezbediti privatnost u budućnosti. Dok su CoinJoin transakcije svakovrsne, softveri koji su laki za korišćenje već sad postoje koji mogu automatizovati ovu vrstu transakcija. Samourai Whirlpool (https://samouraiwallet.com/whirlpool) je odličan izbor za Android korisnike. Joinmarket (https://github.com/joinmarket-webui/jam) se može koristiti na vašem nodu. A servisi postoje koji pri snabdevanju vašeg bitcoina istog trenutka obave CoinJoin tranzakciju automatski. #### Zaključak Svi bi trebalo da se potrude da koriste bitcoin na što privatniji način. Privatnost nije isto što i tajanstvenost. Privatnost je ljudsko pravo i mi svi trebamo da branimo i primenljujemo to pravo. Teško je izbrisati postojeće informacije sa interneta; a izbrisati ih sa bitcoin baze podataka je nemoguće. Iako su daleko od savršenih, alatke postoje danas koje vam omogućavaju da najbolje prakse privatnosti i vi sami primenite. Mi smo vam naglasili neke od njih i - kroz poboljšanje u bitcoin protokolu kroz Taproot i Schnorr - one će postajati sve usavršenije. Bitcoin postupci se ne mogu lako opisati korišćenjem tradicionalnim konceptima. Pitanja kao što su "Ko je vlasnik ovog novca?" ili "Odakle taj novac potiče?" postaju sve teža da se odgovore a u nekim okolnostima postaju potpuno beznačajna. Satoši je dizajnirao bitcoin misleći na privatnost. Na nivou protokola svaka bitcoin transakcija je proces "topljenja" koji za sobom samo ostavlja heuristične mrvice hleba. Protokolu nije bitno odakle se pojavio bilo koji bitcoin ili satoši. Niti je njega briga ko je legalan identitet vlasnika. Protokolu je samo važno da li su digitalni potpisi validni. Dokle god je govor slobodan, potpisivanje poruka - privatno ili ne - ne sme biti kriminalan postupak. Dodatni Resursi [This Month in Bitcoin Privacy](https://enegnei.github.io/This-Month-In-Bitcoin-Privacy/) | Janine [Hodl Privacy FAQ](https://6102bitcoin.com/faq-hodl-privacy/) | 6102 [Digital Privacy](https://6102bitcoin.com/blog/digital-privacy/) | 6102 [UseWhirlpool.com](http://usewhirlpool.com/) | Bitcoin Q+A [Bitcoin Privacy Guide](https://bitcoiner.guide/privacy/) | Bitcoin Q+A Ovaj članak napisan je u saradnji sa Matt Odellom, nezavisnim bitcoin istraživačem. Nađite njegove preporuke za privatnost na [werunbtc.com](https://werunbtc.com/) [Originalni tekst](https://dergigi.com/2021/03/14/bitcoin-privacy-best-practices/)
@ bf47c19e:c3d2573b
2025-02-13 08:10:44Originalni tekst na [dvadesetjedan.com](https://dvadesetjedan.com/blog/bitcoin-privatnost-najbolje-prakse). ###### Autor: [Gigi](https://dergigi.com/2021/03/14/bitcoin-privacy-best-practices/) / Prevod na srpski: [Plumsky](https://t.me/Plumski) --- > Postoji sveto carstvo privatnosti za svakog čoveka gde on bira i pravi odluke – carstvo stvoreno na bazičnim pravima i slobode koje zakon, generalno, ne sme narušavati. Džefri Fišer, Arhiepiskop Canterberija (1959) Pre ne toliko dugo, uobičajen režim interneta je bio neenkriptovan običan tekst (plain text). Svi su mogli špiunirati svakoga i mnogi nisu o tome ni razmišljali. Globalno obelodanjivanje nadzora 2013. je to promenilo i danas se koriste mnogo bezbedniji protokoli i end-to-end enkripcija postaje standard sve više. Iako bitcoin postaje tinejdžer, mi smo – metaforično govoreći – i dalje u dobu običnog teksta narandžastog novčića. Bitcoin je radikalno providljiv protokol sam po sebi, ali postoje značajni načini da korisnik zaštiti svoju privatnost. U ovom članku želimo da istaknemo neke od ovih strategija, prodiskutujemo najbolje prakse, i damo preporuke koje mogu primeniti i bitcoin novajlije i veterani. #### Zašto je privatnost bitna > Privatnost je potrebna da bi otvoreno društvo moglo da funkcioniše u digitalnoj eri. Privatnost nije isto što i tajanstvenost. Privatna stvar je nešto što neko ne želi da ceo svet zna, a tajna stvar je nešto što neko ne želi bilo ko da zna. Privatnost je moć da se čovek selektivno otkriva svom okruženju. Ovim snažnim rečima Erik Hjus je započeo svoj tekst Sajferpankov Manifesto (Cypherpunk's Manifesto) 1993. Razlika između privatnosti i tajanstvenosti je suptilna ali jako važna. Odlučiti se za privatnost ne znači da neko ima tajne koje želi sakriti. Da ovo ilustrujemo shvatite samo da ono što obavljate u svom toaletu ili u spavaćoj sobi nije niti ilegalno niti tajna (u mnogim slučajevima), ali vi svejedno odlučujete da zatvorite vrata i navučete zavese. Slično tome, koliko para imate i gde ih trošite nije naručito tajna stvar. Ipak, to bi trebalo biti privatan slučaj. Mnogi bi se složili da vaš šef ne treba da zna gde vi trošite vašu platu. Privatnosti je čak zaštićena od strane mnogobrojnih internacionalnih nadležnih organa. Iz Američke Deklaracije Prava i Dužnosti Čoveka (American Declaration of the Rights and Duties of Man) Ujedinjenim Nacijama, napisano je da je privatnost fundamentalno prava gradjana širom sveta. > Niko ne sme biti podvrgnut smetnjama njegovoj privatnosti, porodici, rezidenciji ili komunikacijama, niti napadnuta njegova čast i reputacija. Svi imaju pravo da se štite zakonom protiv takvih smetnja ili napada. Artikal 12, Deklaracija Ljudskih Prava Ujedinjenih Nacija #### Bitcoin i privatnost Iako je bitcoin često opisivan kao anoniman način plaćanja medijima, on u stvari poseduje potpuno suprotne osobine. On je poluanoniman u najboljem slučaju i danas mnogima nije ni malo lako primeniti taktike da bi bili sigurni da njihov poluanonimni identitet na bitcoin mreži ne bude povezan sa legalnim identitetom u stvarnom svetu. Bitcoin je otvoren sistem. On je javna baza podataka koju svako može da proučava i analizira. Znači, svaka transakcija koja je upisana u tu bazu kroz dokaz rada (proof-of-work) postojaće i biće otkrivena dokle god bitcoin postoji, što znači - zauvek. Ne primenjivati najbolje prakse privatnosti može imati štetne posledice u dalekoj budućnosti. Privatnost, kao sigurnost, je proces koji je težak, ali nije nemoguć. Alatke nastavljaju da se razvijaju koje čuvaju privatnost kad se koristi bitcoin and srećom mnoge od tih alatki su sve lakše za korišćenje. Nažalost ne postoji panacea u ovom pristupu. Mora se biti svesan svih kompromisa i usavršavati te prakse dok se one menjaju. #### Najbolje prakse privatnosti Kao i sve u bitcoinu, kontrola privatnosti je postepena, korak po korak, procedura. Naučiti i primeniti ove najbolje prakse zahteva strpljivost i odgovornost, tako da ne budite obeshrabreni ako vam se čini da je to sve previše. Svaki korak, koliko god bio mali, je korak u dobrom pravcu. Koje korake preduzeti da bi uvećali svoju privatnost: * Budite u vlasništvu sami svojih novčića * Nikad ne ponavljajte korišćenje istih adresa * Minimizirajte korišćenje servisa koji zahtevaju identitet (Know your customer - KYC) * Minimizirajte sve izloženosti trećim licima * Upravljajte svojim nodom * Koristite Lightning mrežu za male transakcije * Nemojte koristiti javne blok pretraživače za svoje transakcije * Koristite metodu CoinJoin često i rano pri nabavljanju svojih novčića **Budite u vlasništvu sami svojih novčića**: Ako ključevi nisu tvoji, onda nije ni bitcoin. Ako neko drugo drži vaš bitcoin za vas, oni znaju sve što se može znati: količinu, istoriju transakcija pa i sve buduće transakcije, itd. Preuzimanje vlasništva bitcoina u svoje ruke je prvi i najvažniji korak. **Nikad ne kroistite istu adresu dvaput**: Ponavljanje adresa poništava privatnost pošiljalca i primaoca bitcoina. Ovo se treba izbegavati pod svaku cenu. **Minimizirajte korišćenje servisa koji zahtevaju identitet (KYC)**: Vezivati svoj legalni identitet za svoje bitcoin adrese je zlo koje se zahteva od strane mnogih državnih nadležnosti. Dok je efektivnost ovih zakona i regulacija disputabilno, posledice njihovog primenjivanja su uglavnom štetne po korisnicima. Ovo je očigledno pošto je česta pojava da se te informacije često izlivaju iz slabo obezbeđenih digitalnih servera. Ako izaberete da koristite KYC servise da bi nabavljali bitcoin, proučite i razumite odnos između vas i tog biznisa. Vi ste poverljivi tom biznisu za sve vaše lične podatke, pa i buduće obezbeđenje tih podataka. Ako i dalje zarađujete kroz fiat novčani sistem, mi preporučujemo da koristite samo bitcoin ekskluzivne servise koji vam dozvoljavaju da autamatski kupujete bitcoin s vremena na vreme. Ako zelite da potpuno da izbegnete KYC, pregledajte https://bitcoinqna.github.io/noKYConly/. **Minimizirajte sve izloženosti trećim licima**: Poverljivost trećim licima je bezbednosna rupa (https://nakamotoinstitute.org/trusted-third-parties/). Ako možete biti poverljivi samo sebi, onda bi to tako trebalo da bude. **Upravljajte svojim nodom**: Ako nod nije tvoj, onda nisu ni pravila. Upravljanje svojim nodom je suštinska potreba da bi se bitcoin koristio na privatan način. Svaka interakcija sa bitcoin mrežom je posrednjena nodom. Ako vi taj nod ne upravljate, čiji god nod koristite može da vidi sve što vi radite. Ova upustva (https://bitcoiner.guide/node/) su jako korisna da bi započeli proces korišćenja svog noda. **Koristite Lightning mrežu za male transakcije**: Pošto Lightning protokol ne koristi glavnu bitcoin mrežu za trasakcije onda je i samim tim povećana privatnost korišćenja bez dodatnog truda. Iako je i dalje rano, oni apsolutno bezobzirni periodi Lightning mreže su verovatno daleko iza nas. Korišćenje Lightning-a za transakcije malih i srednjih veličina će vam pomoći da uvećate privatnost a da smanjite naplate svojih pojedinačnih bitcoin transakcija. **Nemojte koristiti javne blok pretraživače za svoje transakcije**: Proveravanje adresa na javnim blok pretraživačima povezuje te adrese sa vašim IP podacima, koji se onda mogu koristiti da se otkrije vaš identitet. Softveri kao Umbrel i myNode vam omogućavaju da lako koristite sami svoj blok pretraživač. Ako morate koristiti javne pretraživače, uradite to uz VPN ili Tor. **Koristite CoinJoin često i rano pri nabavljanju svojih novčića**: Pošto je bitcoin večan, primenjivanje saradničkih CoinJoin praksa će vam obezbediti privatnost u budućnosti. Dok su CoinJoin transakcije svakovrsne, softveri koji su laki za korišćenje već sad postoje koji mogu automatizovati ovu vrstu transakcija. Samourai Whirlpool (https://samouraiwallet.com/whirlpool) je odličan izbor za Android korisnike. Joinmarket (https://github.com/joinmarket-webui/jam) se može koristiti na vašem nodu. A servisi postoje koji pri snabdevanju vašeg bitcoina istog trenutka obave CoinJoin tranzakciju automatski. #### Zaključak Svi bi trebalo da se potrude da koriste bitcoin na što privatniji način. Privatnost nije isto što i tajanstvenost. Privatnost je ljudsko pravo i mi svi trebamo da branimo i primenljujemo to pravo. Teško je izbrisati postojeće informacije sa interneta; a izbrisati ih sa bitcoin baze podataka je nemoguće. Iako su daleko od savršenih, alatke postoje danas koje vam omogućavaju da najbolje prakse privatnosti i vi sami primenite. Mi smo vam naglasili neke od njih i - kroz poboljšanje u bitcoin protokolu kroz Taproot i Schnorr - one će postajati sve usavršenije. Bitcoin postupci se ne mogu lako opisati korišćenjem tradicionalnim konceptima. Pitanja kao što su "Ko je vlasnik ovog novca?" ili "Odakle taj novac potiče?" postaju sve teža da se odgovore a u nekim okolnostima postaju potpuno beznačajna. Satoši je dizajnirao bitcoin misleći na privatnost. Na nivou protokola svaka bitcoin transakcija je proces "topljenja" koji za sobom samo ostavlja heuristične mrvice hleba. Protokolu nije bitno odakle se pojavio bilo koji bitcoin ili satoši. Niti je njega briga ko je legalan identitet vlasnika. Protokolu je samo važno da li su digitalni potpisi validni. Dokle god je govor slobodan, potpisivanje poruka - privatno ili ne - ne sme biti kriminalan postupak. Dodatni Resursi [This Month in Bitcoin Privacy](https://enegnei.github.io/This-Month-In-Bitcoin-Privacy/) | Janine [Hodl Privacy FAQ](https://6102bitcoin.com/faq-hodl-privacy/) | 6102 [Digital Privacy](https://6102bitcoin.com/blog/digital-privacy/) | 6102 [UseWhirlpool.com](http://usewhirlpool.com/) | Bitcoin Q+A [Bitcoin Privacy Guide](https://bitcoiner.guide/privacy/) | Bitcoin Q+A Ovaj članak napisan je u saradnji sa Matt Odellom, nezavisnim bitcoin istraživačem. Nađite njegove preporuke za privatnost na [werunbtc.com](https://werunbtc.com/) [Originalni tekst](https://dergigi.com/2021/03/14/bitcoin-privacy-best-practices/) @ 04ed2b8f:75be6756
2025-02-13 08:02:39Freedom. It’s the word on everyone’s lips, the dream of every soul. We long for it, we chase it, we believe that if we can break free from this chain or that constraint, we will finally be free. **But true freedom is not about external circumstances—it’s about control.** The truth is, **the most powerful chains are the ones we place on ourselves**. The world can throw its challenges at you, life can dish out its unfair blows, but **if you cannot control yourself, your thoughts, your emotions, your reactions, then you are no different than a prisoner.** There is no freedom in chaos. There is no freedom in losing control. **Freedom is mastery—mastery of the self.** ## **Freedom Begins Within** You can have all the money in the world, live in the most luxurious place, and have every material possession your heart desires, but **if you cannot control your impulses, your habits, your desires—none of that will matter.** You are still a slave to your cravings. You are still a puppet to your own emotions, and that is **no real freedom.** What does freedom look like? - **It’s the power to act with purpose, not to react out of emotion.** - **It’s the strength to stay disciplined when every part of you wants to quit.** - **It’s the courage to say ‘no’ to distractions, to temptation, to things that steer you off course.** - **It’s the clarity to make choices that serve your growth, not your immediate desires.** True freedom is the ability to say, “I am in control of myself. I do not let my circumstances control me, nor my emotions rule me. I dictate my actions, my thoughts, my destiny.” ## **Self-Control: The Ultimate Weapon** The power to control yourself is your greatest weapon. Without it, **you are at the mercy of every challenge, every temptation, and every fleeting emotion**. You may feel like you are “free,” but without self-discipline, you are just a puppet swaying in the wind, vulnerable to every whim that blows your way. - **The impulse to procrastinate? You overcome it.** - **The desire to give up? You push through it.** - **The craving for comfort? You choose growth.** In the face of any storm, a man with self-control remains grounded, focused, and clear. He doesn’t react in anger or fear—he acts with purpose, with precision, and with vision. A man who cannot control himself is a man who is owned by his emotions, his desires, his distractions. But the man who conquers his mind, his body, his impulses—he is the one who **owns his life.** ## **The Price of Freedom** It’s not easy to control yourself. It requires constant effort, relentless discipline, and the courage to face yourself head-on. It means saying ‘no’ to what feels good now, to invest in what will make you stronger later. It means constantly improving, constantly fighting the urge to quit, to give in, to indulge in comfort. But the price of freedom is worth it. **For when you have control over yourself, no one can take your power.** You become the master of your fate. **You become unshakable.** ## **Freedom Through Discipline** So, ask yourself: **Are you truly free, or are you simply a slave to your impulses?** - **Do you control your actions, or do your actions control you?** - **Are you the master of your emotions, or are they the masters of you?** Freedom isn’t just about having no chains; it’s about not letting anything control you—least of all yourself. **And when you control yourself, there’s nothing you can’t accomplish.** A man who cannot control himself is never truly free. But a man who conquers his mind, his habits, his emotions—he is unstoppable. **Now go and choose to control yourself, and unlock the freedom that’s waiting for you. Or remain a prisoner to your impulses, forever shackled by the chains of your own making. The choice is yours.**
@ 04ed2b8f:75be6756
2025-02-13 08:02:39Freedom. It’s the word on everyone’s lips, the dream of every soul. We long for it, we chase it, we believe that if we can break free from this chain or that constraint, we will finally be free. **But true freedom is not about external circumstances—it’s about control.** The truth is, **the most powerful chains are the ones we place on ourselves**. The world can throw its challenges at you, life can dish out its unfair blows, but **if you cannot control yourself, your thoughts, your emotions, your reactions, then you are no different than a prisoner.** There is no freedom in chaos. There is no freedom in losing control. **Freedom is mastery—mastery of the self.** ## **Freedom Begins Within** You can have all the money in the world, live in the most luxurious place, and have every material possession your heart desires, but **if you cannot control your impulses, your habits, your desires—none of that will matter.** You are still a slave to your cravings. You are still a puppet to your own emotions, and that is **no real freedom.** What does freedom look like? - **It’s the power to act with purpose, not to react out of emotion.** - **It’s the strength to stay disciplined when every part of you wants to quit.** - **It’s the courage to say ‘no’ to distractions, to temptation, to things that steer you off course.** - **It’s the clarity to make choices that serve your growth, not your immediate desires.** True freedom is the ability to say, “I am in control of myself. I do not let my circumstances control me, nor my emotions rule me. I dictate my actions, my thoughts, my destiny.” ## **Self-Control: The Ultimate Weapon** The power to control yourself is your greatest weapon. Without it, **you are at the mercy of every challenge, every temptation, and every fleeting emotion**. You may feel like you are “free,” but without self-discipline, you are just a puppet swaying in the wind, vulnerable to every whim that blows your way. - **The impulse to procrastinate? You overcome it.** - **The desire to give up? You push through it.** - **The craving for comfort? You choose growth.** In the face of any storm, a man with self-control remains grounded, focused, and clear. He doesn’t react in anger or fear—he acts with purpose, with precision, and with vision. A man who cannot control himself is a man who is owned by his emotions, his desires, his distractions. But the man who conquers his mind, his body, his impulses—he is the one who **owns his life.** ## **The Price of Freedom** It’s not easy to control yourself. It requires constant effort, relentless discipline, and the courage to face yourself head-on. It means saying ‘no’ to what feels good now, to invest in what will make you stronger later. It means constantly improving, constantly fighting the urge to quit, to give in, to indulge in comfort. But the price of freedom is worth it. **For when you have control over yourself, no one can take your power.** You become the master of your fate. **You become unshakable.** ## **Freedom Through Discipline** So, ask yourself: **Are you truly free, or are you simply a slave to your impulses?** - **Do you control your actions, or do your actions control you?** - **Are you the master of your emotions, or are they the masters of you?** Freedom isn’t just about having no chains; it’s about not letting anything control you—least of all yourself. **And when you control yourself, there’s nothing you can’t accomplish.** A man who cannot control himself is never truly free. But a man who conquers his mind, his habits, his emotions—he is unstoppable. **Now go and choose to control yourself, and unlock the freedom that’s waiting for you. Or remain a prisoner to your impulses, forever shackled by the chains of your own making. The choice is yours.** @ bf47c19e:c3d2573b
2025-02-13 07:56:50Originalni tekst na [dvadesetjedan.com](https://dvadesetjedan.com/blog/niko-ne-moze-zabraniti-bitcoin) ###### Autor: [Parker Lewis](https://x.com/parkeralewis) / Prevod na srpski: [Plumsky](https://t.me/Plumski) --- Ideja da država može nekako zabraniti bitcoin je jedna od poslednjih faza tuge, tačno pred prihvatanje realnosti. Posledica ove rečenice je priznanje da bitcoin “funkcioniše”. U stvari, ona predstavlja činjenicu da bitcoin funkcioniše toliko dobro da on preti postojećim državnim monopolima nad novcem i da će zbog toga države da ga unište kroz regulativne prepreke da bi eliminisale tu pretnju. Gledajte na tvrdnju da će države zabraniti bitcoin kao kondicionalnu logiku. Da li bitcoin funkcioniše kao novac? Ako je odgovor „ne“, onda države nemaju šta da zabrane. Ako je odgovor „da“, onda će države da probaju da ga zabrane. Znači, glavna poenta ovog razmišljanja je pretpostavka da bitcoin funkcioiniše kao novac. Onda je sledeće logično pitanje da li intervencija od strane države može uspešno da uništi upravo taj funkcionalan bitcoin.  Za početak, svako ko pokušava da razume kako, zašto, ili da li bitcoin funkcioniše mora da proceni ta pitanja potpuno nezavisno od prouzrekovanja državne regulacije ili intervencije. Iako je nesumnjivo da bitcoin mora da postoji uzgred državnih regulativa, zamislite na momenat da države ne postoje. Sam od sebe, da li bi bitcoin funkcionisao kao novac, kad bi se prepustio slobodnom tržištu? Ovo pitanje se širi u dodatna pitanja i ubrzo se pretvara u bunar bez dna. Šta je novac? Šta su svojstva koja čine jednu vrstu novca bolje od druge? Da li bitcoin poseduje ta svojstva? Da li je bitcoin bolja verzija novca po takvim osobinama? Ako je finalni zaključak da bitcoin ne funkcioniše kao novac, implikacije državne intervencije su nebitne. Ali, ako je bitcoin funkcionalan kao novac, ta pitanja onda postaju bitna u ovoj debati, i svako ko o tome razmišlja bi morao imati taj početnički kontekst da bi mogao proceniti da li je uopšte moguće zabraniti. Po svom dizajnu, bitcoin postoji van države. Ali bitcoin nije samo van kontrole države, on u stvari funkcioniše bez bilo kakve saradnje centralizovanih identiteta. On je globalan i decentralizovan. Svako može pristupiti bitcoinu bez potrebe saglasnosti bilo koga i što se više širi sve je teže cenzurisati celokupnu mrežu. Arhitektura bitcoina je namerno izmišljena da bude otporna na bilo koje pokušaje države da ga zabrane. Ovo ne znači da države širom sveta neće pokušavati da ga regulišu, oporezuju ili čak da potpuno zabrane njegovo korišćenje. Naravno da će biti puno bitki i otpora protiv usvajanja bitcoina među građanima. Federal Reserve i Američki Treasury (i njihovi globalni suparnici) se neće ležeći predati dok bitcoin sve više i više ugrožava njihove monopole prihvatljivog novca. Doduše, pre nego što se odbaci ideja da države mogu potpuno zabraniti bitcoin, mora se prvo razumeti posledice tog stava i njegovog glasnika. #### Progresija poricanja i stepeni tuge Pripovesti skeptičara se neprestano menjaju kroz vreme. Prvi stepen tuge: bitcoin nikad ne može funkcionisati-njegova vrednost je osnovana ni na čemu. On je moderna verzija tulip manije. Sa svakim ciklusom uzbuđenja, vrednost bitcoina skače i onda vrlo brzo se vraća na dole. Često nazvano kao kraj njegove vrednosti, bitcoin svaki put odbija da umre i njegova vrednost pronađe nivo koji je uvek viši od prethodnih ciklusa globalne usvajanja. Tulip pripovetka postaje stara i dosadna i skeptičari pređu na više nijansirane teme, i time menjaju bazu debate. Drugi stepen tuge predstoji: bitcoin je manjkav kao novac. On je previše volatilan da bi bio valuta, ili je suviše spor da bi se koristio kao sistem plaćanja, ili se ne može proširiti dovoljno da zadovolji sve promete plaćanja na svetu, ili troši isuviše struje. Taj niz kritike ide sve dalje i dalje. Ovaj drugi stepen je progresija poricanja i dosta je udaljen od ideje da je bitcoin ništa više od bukvalno bezvrednog ničega. Uprkos tim pretpostavnim manjcima, vrednost bitcoin mreže nastavje da raste vremenom. Svaki put, ona ne umire, nasuprot, ona postaje sve veća i jača. Dok se skeptičari bave ukazivanjem na manjke, bitcoin ne prestaje. Rast u vrednosti je prouzrokovan jednostavnom dinamikom tržišta: postoji više kupca nego prodavca. To je sve i to je razlog rasta u adopciji. Sve više i više ljudi shvata zašto postoji fundamentalna potražnja za bitcoinom i zašto/kako on funkcioniše. To je razlog njegovog dugotrajnog rasta. Dokle god ga sve više ljudi koristi za čuvanje vrednosti, neće pasti cena snabdevanja. Zauvek će postojati samo 21 milion bitcoina. Nebitno je koliko ljudi zahtevaju bitcoin, njegova cela količina je uvek ista i neelastična. Dok skeptičari nastavljaju sa svojom starom pričom, mase ljudi nastavljaju da eliminišu zabludu i zahtevaju bitcoin zbog njegovih prednosti u smislu novčanih svojstva. Između ostalog, ne postoji grupa ljudi koja je više upoznata sa svim argumentima protiv bitcoina od samih bitcoinera.  Očajanje počinje da se stvara i onda se debata još jedanput pomera. Sada nije više činjenica je vrednost bitcoina osnovana ni na čemu niti da ima manjke kao valuta; sada se debata centrira na regulaciji državnih autoriteta. U ovom zadnjem stepenu tuge, bitcoin se predstavlja kao u stvari isuviše uspešnom alatkom i zbog toga države ne smeju dozvoliti da on postoji. Zaista? Znači da je genijalnost čoveka ponovo ostvarila funkcionalan novac u tehnološko superiornoj formi, čije su posledice zaista neshvatljive, i da će države upravo taj izum nekako zabraniti. Primetite da tom izjavom skeptičari praktično priznaju svoj poraz. Ovo su poslednji pokušaji u seriji promašenih argumenata. Skeptičari u isto vreme prihvataju da postoji fundamentalna potražnja za bitcoinom a onda se premeštaju na neosnovan stav da ga države mogu zabraniti. Ajde da se poigramo i tim pitanjem. Kada bih zapravo razvijene države nastupile na scenu i pokušale da zabrane bitcoin? Trenutno, Federal Reserve i Treasury ne smatraju bitcoin kao ozbiljnu pretnju superiornosti dolara. Po njihovom celokupnom mišljenju, bitcoin je slatka mala igračka i ne može da funkcioniše kao novac. Sadašnja kompletna kupovna moć bitcoina je manja od $200 milijardi. Sa druge strane, zlato ima celokupnu vrednost od $8 triliona (40X veću od bitcoina) i količina odštampanog novca (M2) je otprilike 15 triliona (75X veličine bitcoinove vrednosti). Kada će Federal Reserve i Treasury da počne da smatra bitcoin kao ozbiljnu pretnju? Kad bitcoin poraste na $1, $2 ili $3 triliona? Možete i sami da izaberete nivo, ali implikacija je da će bitcoin biti mnogo vredniji, i posedovaće ga sve više ljudi širom sveta, pre nego što će ga državne vlasti shvatiti kao obiljnog protivnika. Predsednik Tramp & Treasury Sekretar Mnučin o Bitcoinu (2019): > „Ja neću pričati o bitcoinu za 10 godina, u to možete biti sigurni {…} Ja bi se kladio da čak za 5 ili 6 godina neću više pričati o bitcoinu kao sekretar Trusury-a. Imaću preča posla {…} Mogu vam obećati da ja lično neću biti pun bitcoina.“ – Sekretar Treasury-a Stiv Mnučin > „Ja nisam ljubitelj bitcoina {…}, koji nije novac i čija vrednost je jako volatilna i osnovana na praznom vazduhu.“ – Predsednik Donald J. Tramp Znači, logika skeptika ide ovako: bitcoin ne funkcioniše, ali ako funkcioniše, onda će ga država zabraniti. Ali, države slobodnog sveta neće pokušati da ga zabrane dokle god se on ne pokaže kao ozbiljna pretnja. U tom trenutku, bitcoin će biti vredniji i sigurno teži da se zabrani, pošto će ga više ljudi posedovati na mnogo širem geografskom prostoru. Ignorišite fundamentalne činjenice i asimetriju koja je urođena u globalnom dešavanju monetizacije zato što u slučaju da ste u pravu, države će taj proces zabraniti. Na kojoj strani tog argumenta bi radije stajao racionalan ekonomski učesnik? Posedovanje finansijske imovine kojoj vrednost toliko raste da preti globalnoj rezervnoj valuti, ili nasuprot – nemati tu imovinu? Sa pretpostavkom da individualci razumeju zašto je mogućnost (a sve više i verovatnoća) ove realnosti, koji stav je logičniji u ovom scenariju? Asimetrija dve strane ovog argumenta sama od sebe zahteva da je prvi stav onaj istinit i da fundamentalno razumevanje potražnje bitcoina samo još više ojačava to mišljenje. #### Niko ne moze zabraniti bitcoin Razmislite šta bitcoin u stvari predstavlja pa onda šta bi predstavljala njegova zabrana. Bitcoin je konverzija subjektivne vrednosti, stvorena i razmenjena u realnošću, u digitalne potpise. Jednostavno rečeno, to je konverzija ljudskog vremena u novac. Kad neko zahteva bitcoin, oni u isto vreme ne zahtevaju neki drugi posed, nek to bio dolar, kuća, auto ili hrana itd. Bitcoin predstavlja novčanu štednju koja sa sobom žrtvuje druge imovine i servise. Zabrana bitcoina bi bio napad na najosnovnije ljudske slobode koje je on upravo stvoren da brani. Zamislite reakciju svih onih koji su prihvatili bitcoin: „Bilo je zabavno, alatka za koju su svi eksperti tvrdili da neće nikad funkcionisati, sada toliko dobro radi i sad ti isti eksperti i autoriteti kažu da mi to nemožemo koristiti. Svi idite kući, predstava je gotova.“verovanje da će svi ljudi koji su učestvovali u bitcoin usvajanju, suverenitetu koji nudi i finansiskoj slobodi, odjednom samo da se predaju osnovnom rušenju njihovih prava je potpuno iracionalna pozicija. > Novac je jedan od najbitnijih instrumenata za slobodu koji je ikad izmišljen. Novac je to što u postojećem društvu ostvaruje mogućnosti siromašnom čoveku – čiji je domet veći nego onaj koji je bio dostižan bogatim ljudima pre ne toliko puno generacija.“ – F. A. Hajek Države nisu uspele da zabrane konzumiranje alkohola, droga, kupovinu vatrenog oružja, pa ni posedovanje zlata. Država može samo pomalo da uspori pristup ili da deklariše posedovanje ilegalnim, ali ne može da uništi nešto što veliki broj raznovrsnih ljudi smatra vrednim. Kada je SAD zabranila privatno posedovanje zlata 1933., zlato nije palo u vrednosti ili nestalo sa finansijskog tržišta. Ono je u stvari poraslo u vrednosti u poređenju sa dolarom, i samo trideset godina kasnije, zabrana je bila ukinuta. Ne samo da bitcoin nudi veću vrednosno obećanje od bilo kog drugog dobra koje su države pokušale da zabrane (uključujući i zlato); nego po svojim osobinama, njega je mnogo teže zabraniti. Bitcoin je globalan i decentralizovan. On ne poštuje granice i osiguran je mnoštvom nodova i kriptografskim potpisima. Sam postupak zabrane bi zahtevao da se u isto vreme zaustavi „open source“ softver koji emituje i izvršava slanje i potvrđivanje digitalno enkriptovanih ključeva i potpisa. Ta zabrana bi morala biti koordinisana između velikog broja zemalja, sa tim da je nemoguće znati gde se ti nodovi i softver nalazi ili da se zaustavi instaliranje novih nodova u drugim pravnim nadležnostima. Da ne pominjemo i ustavske pitanja, bilo bi tehnički neizvodljivo da se takva zabrana primeni na bilo kakav značajan način.  Čak kada bih sve zemlje iz G-20 grupe koordinisale takvu zabranu u isto vreme, to ne bi uništilo bitcoin. U stvari, to bi bilo samoubistvo za fiat novčani sistem. To bi još više prikazalo masama da je bitcoin u stvari novac koji treba shvatiti ozbiljno, i to bi samo od sebe započelo globalnu igru vatanje mačke za rep. Bitcoin nema centralnu tačku za napad; bitcoin rudari, nodovi i digitalni potpisi su rasejani po celom svetu. Svaki aspekt bitcoina je decentralizovan, zato su glavni stubovi njegove arhitekture da učesnici uvek treba kontrolisati svoje potpise i upravljati svojim nodom. Što više digitalnih potpisa i nodova koji postoje, to je više bitcoin decentralizovan, i to je više odbranjiva njegova mreža od strane neprijatelja. Što je više zemalja gde rudari izvršavaju svoj posao, to je manji rizik da jedan nadležni identitet može uticati na njegov bezbednosni sistem. Koordinisan internacionalni napad na bitcoin bi samo koristio da bitcoin još više ojača svoj imuni sistem. Na kraju krajeva, to bi ubrzalo seobu iz tradicionalnog finansijskog sistema (i njegovih valuta) a i inovaciju koja postoji u bitcoin ekosistemu. Sa svakom bivšom pretnjom, bitcoin je maštovito pronalazio način da ih neutrališe pa i koordinisan napad od strane država ne bi bio ništa drugačiji.  Inovacija u ovoj oblasti koja se odlikuje svojom „permissionless“ (bez dozvole centralnih identiteta) osobinom, omogućava odbranu od svakojakih napada. Sve varijante napada koje su bile predvidjene je upravo to što zahteva konstantnu inovaciju bitcoina. To je ona Adam Smitova nevidljiva ruka, ali dopingovana. Pojedinačni učesnici mogu da veruju da su motivisani nekim većim uzrokom, ali u stvari, korisnost kaja je ugrađena u bitcoin stvara kod učesnika dovoljno snažan podsticaj da omogući svoje preživljavanje. Sopstveni interes milione, ako ne milijarde, nekoordinisanih ljudi koji se jedino slažu u svojom međusobnom potrebom za funkcionalnim novcem podstiče inovacije u bitcoinu. Danas, možda to izgleda kao neka kul nova tehnologija ili neki dobar investment u finansijskom portfoliju, ali čak i ako to mnogi ne razumeju, bitcoin je apsolutna nužnost u svetu. To je tako zato što je novac nužnost a historijski priznate valute se fundamentalno raspadaju. Pre dva meseca, tržište američkih državnih obveznica je doživeo kolaps na šta je Federal Reserve reagovao time što je povećao celokupnu količinu dolara u postojanju za $250 milijardi, a još više u bliskoj budućnosti. Tačno ovo je razlog zašto je bitcoin nužnost a ne samo luksuzni dodatak. Kada inovacija omogućava bazično funkcionisanje ekonomije ne postoji ni jedna država na svetu koja može da zaustavi njenu adopciju i rast. Novac je nužnost a bitcoin znatno poboljšava sistem novca koji je ikada postojao pre njega. Sa više praktične strane, pokušaj zabranjivanja bitcoina ili njegove velike regulacije od nadležnosti bi direktno bilo u korist susedne nadležnih organa. Podsticaj da se odustane od koordinisanog napada na bitcoin bi bio isuviše veliki da bi takvi dogovori bili uspešni. Kada bi SAD deklarisovale posed bitcoina ilegalnim sutra, da li bi to zaustavilo njegov rast, razvoj i adopciji i da li bi to smanjilo vrednost celokupne mreže? Verovatno. Da li bi to uništilo bitcoin? Ne bi. Bitcoin predstavlja najpokretljivije kapitalno sredstvo na svetu. Zemlje i nadležne strukture koje kreiraju regulativnu strukturu koja najmanje ustručava korišćenje bitcoina će biti dobitnici velike količine uliva kapitala u svoje države. #### Zabrana Bitcoinove Zatvoreničke Dileme  U praksi, zatvorenička dilema nije igra jedan na jedan. Ona je multidimenzijska i uključuje mnoštvo nadležnosti, čiji se interesi nadmeću međusobno, i to uskraćuje mogućnosti bilo kakve mogućnosti zabrane. Ljudski kapital, fizički kapital i novčani kapital će sav ići u pravcu država i nadležnosti koje najmanje ustručuju bitcoin. To se možda neće desiti sve odjednom, ali pokušaji zabrane su isto za badava koliko bi bilo odseći sebi nos u inat svom licu. To ne znači da države to neće pokušati. India je već probala da zabrani bitcoin. Kina je uvela puno restrikcija. Drugi će da prate njihove tragove. Ali svaki put kada država preduzme takve korake, to ima nepredvidljive efekte povećanja bitcoin adopcije. Pokušaji zabranjivanja bitcoina su jako efektivne marketing kampanje. Bitcoin postoji kao sistem nevezan za jednu suverenu državu i kao novac je otporan na cenzuru. On je dizajniran da postoji van državne kontrole. Pokušaji da se taj koncept zabrani samo još više daje njemu razlog i logiku za postojanje. #### Jedini Pobednički Potez je da se Uključiš u Igru Zabrana bitcoina je trošenje vremena. Neki će to pokušati; ali svi će biti neuspešni. Sami ti pokušaji će još više ubrzati njegovu adopciju i širenje. Biće to vetar od 100 km/h koji raspaljuje vatru. To će ojačati bitcoin sve više i doprineće njegovoj pouzdanosti. U svakom slučaju, verovanje da će države zabraniti bitcoin u momentu kada on postane dovoljno velika pretnja rezervnim valutam sveta, je iracionalan razlog da se on no poseduje kao instrument štednje novca. To ne samo da podrazumeva da je bitcoin novac, ali u isto vreme i ignoriše glavne razloge zašto je to tako: on je decentralizovan i otporan na cenzure. Zamislite da razumete jednu od nojvećih tajni današnjice i da u isto vreme tu tajnu asimetrije koju bitcoin nudi ne primenjujete u svoju korist zbog straha od države. Pre će biti, neko ko razume zašto bitcoin funkcioniše i da ga država ne može zaustaviti, ili nepuno znanje postoji u razumevanju kako bitcoin uopšte funckioniše. Počnite sa razmatranjem fundamentalnih pitanja, a onda primenite to kao temelj da bi procenili bilo koji potencijalan rizik od strane budućih regulacija ili restrikcija državnih organa. I nikad nemojte da zaboravite na vrednost asimetrije između dve strane ovde prezentiranih argumenata. Jedini pobednički potez je da se uključite u igru. Stavovi ovde prezentirani su samo moji i ne predstavljaju Unchained Capital ili moje kolege. Zahvaljujem se Fil Gajgeru za razmatranje teksta i primedbe. [Originalni tekst](https://unchained.com/blog/bitcoin-cannot-be-banned/)
@ bf47c19e:c3d2573b
2025-02-13 07:56:50Originalni tekst na [dvadesetjedan.com](https://dvadesetjedan.com/blog/niko-ne-moze-zabraniti-bitcoin) ###### Autor: [Parker Lewis](https://x.com/parkeralewis) / Prevod na srpski: [Plumsky](https://t.me/Plumski) --- Ideja da država može nekako zabraniti bitcoin je jedna od poslednjih faza tuge, tačno pred prihvatanje realnosti. Posledica ove rečenice je priznanje da bitcoin “funkcioniše”. U stvari, ona predstavlja činjenicu da bitcoin funkcioniše toliko dobro da on preti postojećim državnim monopolima nad novcem i da će zbog toga države da ga unište kroz regulativne prepreke da bi eliminisale tu pretnju. Gledajte na tvrdnju da će države zabraniti bitcoin kao kondicionalnu logiku. Da li bitcoin funkcioniše kao novac? Ako je odgovor „ne“, onda države nemaju šta da zabrane. Ako je odgovor „da“, onda će države da probaju da ga zabrane. Znači, glavna poenta ovog razmišljanja je pretpostavka da bitcoin funkcioiniše kao novac. Onda je sledeće logično pitanje da li intervencija od strane države može uspešno da uništi upravo taj funkcionalan bitcoin.  Za početak, svako ko pokušava da razume kako, zašto, ili da li bitcoin funkcioniše mora da proceni ta pitanja potpuno nezavisno od prouzrekovanja državne regulacije ili intervencije. Iako je nesumnjivo da bitcoin mora da postoji uzgred državnih regulativa, zamislite na momenat da države ne postoje. Sam od sebe, da li bi bitcoin funkcionisao kao novac, kad bi se prepustio slobodnom tržištu? Ovo pitanje se širi u dodatna pitanja i ubrzo se pretvara u bunar bez dna. Šta je novac? Šta su svojstva koja čine jednu vrstu novca bolje od druge? Da li bitcoin poseduje ta svojstva? Da li je bitcoin bolja verzija novca po takvim osobinama? Ako je finalni zaključak da bitcoin ne funkcioniše kao novac, implikacije državne intervencije su nebitne. Ali, ako je bitcoin funkcionalan kao novac, ta pitanja onda postaju bitna u ovoj debati, i svako ko o tome razmišlja bi morao imati taj početnički kontekst da bi mogao proceniti da li je uopšte moguće zabraniti. Po svom dizajnu, bitcoin postoji van države. Ali bitcoin nije samo van kontrole države, on u stvari funkcioniše bez bilo kakve saradnje centralizovanih identiteta. On je globalan i decentralizovan. Svako može pristupiti bitcoinu bez potrebe saglasnosti bilo koga i što se više širi sve je teže cenzurisati celokupnu mrežu. Arhitektura bitcoina je namerno izmišljena da bude otporna na bilo koje pokušaje države da ga zabrane. Ovo ne znači da države širom sveta neće pokušavati da ga regulišu, oporezuju ili čak da potpuno zabrane njegovo korišćenje. Naravno da će biti puno bitki i otpora protiv usvajanja bitcoina među građanima. Federal Reserve i Američki Treasury (i njihovi globalni suparnici) se neće ležeći predati dok bitcoin sve više i više ugrožava njihove monopole prihvatljivog novca. Doduše, pre nego što se odbaci ideja da države mogu potpuno zabraniti bitcoin, mora se prvo razumeti posledice tog stava i njegovog glasnika. #### Progresija poricanja i stepeni tuge Pripovesti skeptičara se neprestano menjaju kroz vreme. Prvi stepen tuge: bitcoin nikad ne može funkcionisati-njegova vrednost je osnovana ni na čemu. On je moderna verzija tulip manije. Sa svakim ciklusom uzbuđenja, vrednost bitcoina skače i onda vrlo brzo se vraća na dole. Često nazvano kao kraj njegove vrednosti, bitcoin svaki put odbija da umre i njegova vrednost pronađe nivo koji je uvek viši od prethodnih ciklusa globalne usvajanja. Tulip pripovetka postaje stara i dosadna i skeptičari pređu na više nijansirane teme, i time menjaju bazu debate. Drugi stepen tuge predstoji: bitcoin je manjkav kao novac. On je previše volatilan da bi bio valuta, ili je suviše spor da bi se koristio kao sistem plaćanja, ili se ne može proširiti dovoljno da zadovolji sve promete plaćanja na svetu, ili troši isuviše struje. Taj niz kritike ide sve dalje i dalje. Ovaj drugi stepen je progresija poricanja i dosta je udaljen od ideje da je bitcoin ništa više od bukvalno bezvrednog ničega. Uprkos tim pretpostavnim manjcima, vrednost bitcoin mreže nastavje da raste vremenom. Svaki put, ona ne umire, nasuprot, ona postaje sve veća i jača. Dok se skeptičari bave ukazivanjem na manjke, bitcoin ne prestaje. Rast u vrednosti je prouzrokovan jednostavnom dinamikom tržišta: postoji više kupca nego prodavca. To je sve i to je razlog rasta u adopciji. Sve više i više ljudi shvata zašto postoji fundamentalna potražnja za bitcoinom i zašto/kako on funkcioniše. To je razlog njegovog dugotrajnog rasta. Dokle god ga sve više ljudi koristi za čuvanje vrednosti, neće pasti cena snabdevanja. Zauvek će postojati samo 21 milion bitcoina. Nebitno je koliko ljudi zahtevaju bitcoin, njegova cela količina je uvek ista i neelastična. Dok skeptičari nastavljaju sa svojom starom pričom, mase ljudi nastavljaju da eliminišu zabludu i zahtevaju bitcoin zbog njegovih prednosti u smislu novčanih svojstva. Između ostalog, ne postoji grupa ljudi koja je više upoznata sa svim argumentima protiv bitcoina od samih bitcoinera.  Očajanje počinje da se stvara i onda se debata još jedanput pomera. Sada nije više činjenica je vrednost bitcoina osnovana ni na čemu niti da ima manjke kao valuta; sada se debata centrira na regulaciji državnih autoriteta. U ovom zadnjem stepenu tuge, bitcoin se predstavlja kao u stvari isuviše uspešnom alatkom i zbog toga države ne smeju dozvoliti da on postoji. Zaista? Znači da je genijalnost čoveka ponovo ostvarila funkcionalan novac u tehnološko superiornoj formi, čije su posledice zaista neshvatljive, i da će države upravo taj izum nekako zabraniti. Primetite da tom izjavom skeptičari praktično priznaju svoj poraz. Ovo su poslednji pokušaji u seriji promašenih argumenata. Skeptičari u isto vreme prihvataju da postoji fundamentalna potražnja za bitcoinom a onda se premeštaju na neosnovan stav da ga države mogu zabraniti. Ajde da se poigramo i tim pitanjem. Kada bih zapravo razvijene države nastupile na scenu i pokušale da zabrane bitcoin? Trenutno, Federal Reserve i Treasury ne smatraju bitcoin kao ozbiljnu pretnju superiornosti dolara. Po njihovom celokupnom mišljenju, bitcoin je slatka mala igračka i ne može da funkcioniše kao novac. Sadašnja kompletna kupovna moć bitcoina je manja od $200 milijardi. Sa druge strane, zlato ima celokupnu vrednost od $8 triliona (40X veću od bitcoina) i količina odštampanog novca (M2) je otprilike 15 triliona (75X veličine bitcoinove vrednosti). Kada će Federal Reserve i Treasury da počne da smatra bitcoin kao ozbiljnu pretnju? Kad bitcoin poraste na $1, $2 ili $3 triliona? Možete i sami da izaberete nivo, ali implikacija je da će bitcoin biti mnogo vredniji, i posedovaće ga sve više ljudi širom sveta, pre nego što će ga državne vlasti shvatiti kao obiljnog protivnika. Predsednik Tramp & Treasury Sekretar Mnučin o Bitcoinu (2019): > „Ja neću pričati o bitcoinu za 10 godina, u to možete biti sigurni {…} Ja bi se kladio da čak za 5 ili 6 godina neću više pričati o bitcoinu kao sekretar Trusury-a. Imaću preča posla {…} Mogu vam obećati da ja lično neću biti pun bitcoina.“ – Sekretar Treasury-a Stiv Mnučin > „Ja nisam ljubitelj bitcoina {…}, koji nije novac i čija vrednost je jako volatilna i osnovana na praznom vazduhu.“ – Predsednik Donald J. Tramp Znači, logika skeptika ide ovako: bitcoin ne funkcioniše, ali ako funkcioniše, onda će ga država zabraniti. Ali, države slobodnog sveta neće pokušati da ga zabrane dokle god se on ne pokaže kao ozbiljna pretnja. U tom trenutku, bitcoin će biti vredniji i sigurno teži da se zabrani, pošto će ga više ljudi posedovati na mnogo širem geografskom prostoru. Ignorišite fundamentalne činjenice i asimetriju koja je urođena u globalnom dešavanju monetizacije zato što u slučaju da ste u pravu, države će taj proces zabraniti. Na kojoj strani tog argumenta bi radije stajao racionalan ekonomski učesnik? Posedovanje finansijske imovine kojoj vrednost toliko raste da preti globalnoj rezervnoj valuti, ili nasuprot – nemati tu imovinu? Sa pretpostavkom da individualci razumeju zašto je mogućnost (a sve više i verovatnoća) ove realnosti, koji stav je logičniji u ovom scenariju? Asimetrija dve strane ovog argumenta sama od sebe zahteva da je prvi stav onaj istinit i da fundamentalno razumevanje potražnje bitcoina samo još više ojačava to mišljenje. #### Niko ne moze zabraniti bitcoin Razmislite šta bitcoin u stvari predstavlja pa onda šta bi predstavljala njegova zabrana. Bitcoin je konverzija subjektivne vrednosti, stvorena i razmenjena u realnošću, u digitalne potpise. Jednostavno rečeno, to je konverzija ljudskog vremena u novac. Kad neko zahteva bitcoin, oni u isto vreme ne zahtevaju neki drugi posed, nek to bio dolar, kuća, auto ili hrana itd. Bitcoin predstavlja novčanu štednju koja sa sobom žrtvuje druge imovine i servise. Zabrana bitcoina bi bio napad na najosnovnije ljudske slobode koje je on upravo stvoren da brani. Zamislite reakciju svih onih koji su prihvatili bitcoin: „Bilo je zabavno, alatka za koju su svi eksperti tvrdili da neće nikad funkcionisati, sada toliko dobro radi i sad ti isti eksperti i autoriteti kažu da mi to nemožemo koristiti. Svi idite kući, predstava je gotova.“verovanje da će svi ljudi koji su učestvovali u bitcoin usvajanju, suverenitetu koji nudi i finansiskoj slobodi, odjednom samo da se predaju osnovnom rušenju njihovih prava je potpuno iracionalna pozicija. > Novac je jedan od najbitnijih instrumenata za slobodu koji je ikad izmišljen. Novac je to što u postojećem društvu ostvaruje mogućnosti siromašnom čoveku – čiji je domet veći nego onaj koji je bio dostižan bogatim ljudima pre ne toliko puno generacija.“ – F. A. Hajek Države nisu uspele da zabrane konzumiranje alkohola, droga, kupovinu vatrenog oružja, pa ni posedovanje zlata. Država može samo pomalo da uspori pristup ili da deklariše posedovanje ilegalnim, ali ne može da uništi nešto što veliki broj raznovrsnih ljudi smatra vrednim. Kada je SAD zabranila privatno posedovanje zlata 1933., zlato nije palo u vrednosti ili nestalo sa finansijskog tržišta. Ono je u stvari poraslo u vrednosti u poređenju sa dolarom, i samo trideset godina kasnije, zabrana je bila ukinuta. Ne samo da bitcoin nudi veću vrednosno obećanje od bilo kog drugog dobra koje su države pokušale da zabrane (uključujući i zlato); nego po svojim osobinama, njega je mnogo teže zabraniti. Bitcoin je globalan i decentralizovan. On ne poštuje granice i osiguran je mnoštvom nodova i kriptografskim potpisima. Sam postupak zabrane bi zahtevao da se u isto vreme zaustavi „open source“ softver koji emituje i izvršava slanje i potvrđivanje digitalno enkriptovanih ključeva i potpisa. Ta zabrana bi morala biti koordinisana između velikog broja zemalja, sa tim da je nemoguće znati gde se ti nodovi i softver nalazi ili da se zaustavi instaliranje novih nodova u drugim pravnim nadležnostima. Da ne pominjemo i ustavske pitanja, bilo bi tehnički neizvodljivo da se takva zabrana primeni na bilo kakav značajan način.  Čak kada bih sve zemlje iz G-20 grupe koordinisale takvu zabranu u isto vreme, to ne bi uništilo bitcoin. U stvari, to bi bilo samoubistvo za fiat novčani sistem. To bi još više prikazalo masama da je bitcoin u stvari novac koji treba shvatiti ozbiljno, i to bi samo od sebe započelo globalnu igru vatanje mačke za rep. Bitcoin nema centralnu tačku za napad; bitcoin rudari, nodovi i digitalni potpisi su rasejani po celom svetu. Svaki aspekt bitcoina je decentralizovan, zato su glavni stubovi njegove arhitekture da učesnici uvek treba kontrolisati svoje potpise i upravljati svojim nodom. Što više digitalnih potpisa i nodova koji postoje, to je više bitcoin decentralizovan, i to je više odbranjiva njegova mreža od strane neprijatelja. Što je više zemalja gde rudari izvršavaju svoj posao, to je manji rizik da jedan nadležni identitet može uticati na njegov bezbednosni sistem. Koordinisan internacionalni napad na bitcoin bi samo koristio da bitcoin još više ojača svoj imuni sistem. Na kraju krajeva, to bi ubrzalo seobu iz tradicionalnog finansijskog sistema (i njegovih valuta) a i inovaciju koja postoji u bitcoin ekosistemu. Sa svakom bivšom pretnjom, bitcoin je maštovito pronalazio način da ih neutrališe pa i koordinisan napad od strane država ne bi bio ništa drugačiji.  Inovacija u ovoj oblasti koja se odlikuje svojom „permissionless“ (bez dozvole centralnih identiteta) osobinom, omogućava odbranu od svakojakih napada. Sve varijante napada koje su bile predvidjene je upravo to što zahteva konstantnu inovaciju bitcoina. To je ona Adam Smitova nevidljiva ruka, ali dopingovana. Pojedinačni učesnici mogu da veruju da su motivisani nekim većim uzrokom, ali u stvari, korisnost kaja je ugrađena u bitcoin stvara kod učesnika dovoljno snažan podsticaj da omogući svoje preživljavanje. Sopstveni interes milione, ako ne milijarde, nekoordinisanih ljudi koji se jedino slažu u svojom međusobnom potrebom za funkcionalnim novcem podstiče inovacije u bitcoinu. Danas, možda to izgleda kao neka kul nova tehnologija ili neki dobar investment u finansijskom portfoliju, ali čak i ako to mnogi ne razumeju, bitcoin je apsolutna nužnost u svetu. To je tako zato što je novac nužnost a historijski priznate valute se fundamentalno raspadaju. Pre dva meseca, tržište američkih državnih obveznica je doživeo kolaps na šta je Federal Reserve reagovao time što je povećao celokupnu količinu dolara u postojanju za $250 milijardi, a još više u bliskoj budućnosti. Tačno ovo je razlog zašto je bitcoin nužnost a ne samo luksuzni dodatak. Kada inovacija omogućava bazično funkcionisanje ekonomije ne postoji ni jedna država na svetu koja može da zaustavi njenu adopciju i rast. Novac je nužnost a bitcoin znatno poboljšava sistem novca koji je ikada postojao pre njega. Sa više praktične strane, pokušaj zabranjivanja bitcoina ili njegove velike regulacije od nadležnosti bi direktno bilo u korist susedne nadležnih organa. Podsticaj da se odustane od koordinisanog napada na bitcoin bi bio isuviše veliki da bi takvi dogovori bili uspešni. Kada bi SAD deklarisovale posed bitcoina ilegalnim sutra, da li bi to zaustavilo njegov rast, razvoj i adopciji i da li bi to smanjilo vrednost celokupne mreže? Verovatno. Da li bi to uništilo bitcoin? Ne bi. Bitcoin predstavlja najpokretljivije kapitalno sredstvo na svetu. Zemlje i nadležne strukture koje kreiraju regulativnu strukturu koja najmanje ustručava korišćenje bitcoina će biti dobitnici velike količine uliva kapitala u svoje države. #### Zabrana Bitcoinove Zatvoreničke Dileme  U praksi, zatvorenička dilema nije igra jedan na jedan. Ona je multidimenzijska i uključuje mnoštvo nadležnosti, čiji se interesi nadmeću međusobno, i to uskraćuje mogućnosti bilo kakve mogućnosti zabrane. Ljudski kapital, fizički kapital i novčani kapital će sav ići u pravcu država i nadležnosti koje najmanje ustručuju bitcoin. To se možda neće desiti sve odjednom, ali pokušaji zabrane su isto za badava koliko bi bilo odseći sebi nos u inat svom licu. To ne znači da države to neće pokušati. India je već probala da zabrani bitcoin. Kina je uvela puno restrikcija. Drugi će da prate njihove tragove. Ali svaki put kada država preduzme takve korake, to ima nepredvidljive efekte povećanja bitcoin adopcije. Pokušaji zabranjivanja bitcoina su jako efektivne marketing kampanje. Bitcoin postoji kao sistem nevezan za jednu suverenu državu i kao novac je otporan na cenzuru. On je dizajniran da postoji van državne kontrole. Pokušaji da se taj koncept zabrani samo još više daje njemu razlog i logiku za postojanje. #### Jedini Pobednički Potez je da se Uključiš u Igru Zabrana bitcoina je trošenje vremena. Neki će to pokušati; ali svi će biti neuspešni. Sami ti pokušaji će još više ubrzati njegovu adopciju i širenje. Biće to vetar od 100 km/h koji raspaljuje vatru. To će ojačati bitcoin sve više i doprineće njegovoj pouzdanosti. U svakom slučaju, verovanje da će države zabraniti bitcoin u momentu kada on postane dovoljno velika pretnja rezervnim valutam sveta, je iracionalan razlog da se on no poseduje kao instrument štednje novca. To ne samo da podrazumeva da je bitcoin novac, ali u isto vreme i ignoriše glavne razloge zašto je to tako: on je decentralizovan i otporan na cenzure. Zamislite da razumete jednu od nojvećih tajni današnjice i da u isto vreme tu tajnu asimetrije koju bitcoin nudi ne primenjujete u svoju korist zbog straha od države. Pre će biti, neko ko razume zašto bitcoin funkcioniše i da ga država ne može zaustaviti, ili nepuno znanje postoji u razumevanju kako bitcoin uopšte funckioniše. Počnite sa razmatranjem fundamentalnih pitanja, a onda primenite to kao temelj da bi procenili bilo koji potencijalan rizik od strane budućih regulacija ili restrikcija državnih organa. I nikad nemojte da zaboravite na vrednost asimetrije između dve strane ovde prezentiranih argumenata. Jedini pobednički potez je da se uključite u igru. Stavovi ovde prezentirani su samo moji i ne predstavljaju Unchained Capital ili moje kolege. Zahvaljujem se Fil Gajgeru za razmatranje teksta i primedbe. [Originalni tekst](https://unchained.com/blog/bitcoin-cannot-be-banned/) @ da0b9bc3:4e30a4a9
2025-02-13 06:36:12Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/884478
@ da0b9bc3:4e30a4a9
2025-02-13 06:36:12Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/884478 @ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get [this line](https://www.youtube.com/shorts/kqsomjpz7ok): “Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.” Yesterday, I came across a comment on the song [Devil Went Down to Georgia](https://youtu.be/ut8UqFlWdDc) that had a very similar feel to it:  America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans. That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form. For most countries, saying “our nation is the greatest” *is*, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people *should* be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence. But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America. That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is *freedom*. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit. American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are *definitionally* better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.) In *Devil Went Down to Georgia*, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.” *Libertas magnitudo est*
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get [this line](https://www.youtube.com/shorts/kqsomjpz7ok): “Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.” Yesterday, I came across a comment on the song [Devil Went Down to Georgia](https://youtu.be/ut8UqFlWdDc) that had a very similar feel to it:  America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans. That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form. For most countries, saying “our nation is the greatest” *is*, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people *should* be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence. But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America. That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is *freedom*. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit. American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are *definitionally* better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.) In *Devil Went Down to Georgia*, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.” *Libertas magnitudo est* @ d360efec:14907b5f
2025-02-13 05:54:17 **ภาพรวม LUNCUSDT (OKX):** LUNCUSDT กำลังอยู่ในช่วงที่ *มีความผันผวนสูงและมีความไม่แน่นอนมาก* แม้ว่าในอดีต (TF Day) จะเคยมีสัญญาณของการพยายามกลับตัวเป็นขาขึ้น (Breakout EMA 50 และเกิด Golden Cross) แต่ปัจจุบันแรงซื้อเหล่านั้นเริ่มอ่อนแรงลง และมีแรงขายเข้ามาในตลาดมากขึ้น ทำให้เกิดความขัดแย้งระหว่าง Timeframes ต่างๆ  **สถานะปัจจุบัน:** * **แนวโน้ม:** * **TF Day:** เริ่มไม่แน่นอน (จากเดิมที่เป็น Early Uptrend) - แม้ว่าราคาจะยังอยู่เหนือ EMA 50/200 แต่ Money Flow เริ่มแสดงสัญญาณเตือน * **TF4H:** เริ่มไม่แน่นอน (พักตัว, ทดสอบแนวรับ EMA 50) - Money Flow บ่งบอกถึงแรงขายที่เข้ามา * **TF15:** ผันผวนสูง, ไม่มีทิศทางชัดเจน (Sideways) - Money Flow แสดงถึงแรงขาย แต่ก็มีแรงซื้อกลับเข้ามาบ้าง * **Money Flow (LuxAlgo):** * **TF Day:** แรงซื้อเริ่มอ่อนแรงลงอย่างมีนัยสำคัญ, มีแรงขายเข้ามา * **TF4H:** แรงขายมีมากกว่าแรงซื้อ * **TF15:** แรงขายและแรงซื้อผสมกัน, โดยรวมแรงขายยังมากกว่า * **EMA:** * **TF Day:** EMA 50/200 เป็นแนวรับ/แนวต้าน * **TF4H:** EMA 50 กำลังถูกทดสอบ, EMA 200 เป็นแนวต้าน * **TF15:** EMA 50/200 เป็นแนวต้าน **โครงสร้างราคา (SMC):** | Timeframe | Break of Structure (BOS) | Change of Character (CHoCH) | Higher High (HH) & Higher Low (HL) | Equal Highs (EQH) / Equal Lows (EQL) | | :-------- | :----------------------- | :--------------------------- | :----------------------------------- | :------------------------------------- | | Day | ด้านบนและล่าง | ด้านบน | เริ่มก่อตัว (แต่ไม่แข็งแกร่ง) | - | | 4H | ด้านบน | ด้านบน | เริ่มก่อตัว (แต่ไม่ชัดเจน) | มี EQH หลายจุด | | 15m | ด้านบนและล่าง | มีทั้งบนและล่าง | Lower Highs (LH) & Lower Lows (LL) | มี EQH และ EQL หลายจุด | **แนวรับ-แนวต้านสำคัญ:** | Timeframe | แนวรับ | แนวต้าน | | :-------- | :----------------------------------------------------------- | :--------------------------------------------------------------------- | | Day | EMA 50 (≈0.00010000), EMA 200 (≈0.00008000), 0.00006000-0.00007000 | 0.00017953 (High ล่าสุด), 0.00014000 (Volume Profile) | | 4H | EMA 50 (≈0.00007000), 0.00006000-0.00007000 | EMA 200 (≈0.00008000), 0.00008132, บริเวณ 0.00010000-0.00012000 (EQH) | | 15m | บริเวณ Low ล่าสุด | EMA 50, EMA 200, บริเวณ 0.000075-0.000076 (EQH) | **กลยุทธ์ (LUNCUSDT):** 1. **Wait & See (ทางเลือกที่ดีที่สุด):** * **เหตุผล:** ความขัดแย้งระหว่าง Timeframes สูงมาก, แนวโน้มไม่ชัดเจน, Money Flow ใน TF4H และ TF15 เป็นลบ * รอให้ราคาแสดงทิศทางที่ชัดเจนกว่านี้ (ยืนเหนือ EMA 50 ใน TF4H ได้, Breakout แนวต้านใน TF15) 2. **Buy on Dip (Day, 4H) - *ความเสี่ยงสูงมาก ไม่แนะนำ*:** * **เหตุผล:** แนวโน้มระยะยาวอาจจะยังเป็นขาขึ้นได้ (ถ้าไม่หลุดแนวรับสำคัญ) * **เงื่อนไข:** *ต้อง* รอสัญญาณการกลับตัวใน TF15 ก่อน * **จุดเข้า:** พิจารณาเฉพาะบริเวณแนวรับที่แข็งแกร่งมากๆ (EMA ของ Day/4H) *และต้องดู TF15 ประกอบ* * **Stop Loss:** ต่ำกว่า Low ล่าสุดของ TF15 3. **Short (15, ความเสี่ยงสูงมาก):** * **เหตุผล:** แนวโน้ม TF15 เป็นขาลง, Money Flow เป็นลบ * **เงื่อนไข:** ราคาไม่สามารถ Breakout EMA หรือแนวต้านอื่นๆ ใน TF15 ได้ * **จุดเข้า:** บริเวณ EMA หรือแนวต้านของ TF15 * **Stop Loss:** เหนือ High ล่าสุดของ TF15 **คำแนะนำ (เน้นย้ำ):** * **LUNC เป็นเหรียญที่มีความเสี่ยงสูงมาก (High Risk):** มีความผันผวนสูง และอาจมีการเปลี่ยนแปลงอย่างรวดเร็ว * **ความขัดแย้งของ Timeframes:** สถานการณ์ของ LUNCUSDT มีความขัดแย้งสูงมาก และมีความเสี่ยงสูง * **Money Flow:** บ่งบอกถึงแรงขายที่เริ่มเข้ามา และแนวโน้มขาขึ้น (ระยะกลาง-ยาว) ที่อ่อนแอลง * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด:** "รอ" เป็นกลยุทธ์ที่ดีที่สุด * **Risk Management:** สำคัญที่สุด ไม่ว่าจะเลือกกลยุทธ์ใด ต้องมีการบริหารความเสี่ยงที่ดี **สรุป:** LUNCUSDT กำลังอยู่ในช่วงเวลาที่ยากลำบากและมีความเสี่ยงสูงมากที่สุดในบรรดา 3 เหรียญที่เราวิเคราะห์กันมา การตัดสินใจที่ผิดพลาดอาจนำไปสู่การขาดทุนได้ ควรพิจารณาอย่างรอบคอบก่อนเข้าเทรดทุกครั้ง และ "รอ" จนกว่าจะมีสัญญาณที่ชัดเจนกว่านี้ เป็นทางเลือกที่ปลอดภัยที่สุดสำหรับนักลงทุนส่วนใหญ่ค่ะ **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
@ d360efec:14907b5f
2025-02-13 05:54:17 **ภาพรวม LUNCUSDT (OKX):** LUNCUSDT กำลังอยู่ในช่วงที่ *มีความผันผวนสูงและมีความไม่แน่นอนมาก* แม้ว่าในอดีต (TF Day) จะเคยมีสัญญาณของการพยายามกลับตัวเป็นขาขึ้น (Breakout EMA 50 และเกิด Golden Cross) แต่ปัจจุบันแรงซื้อเหล่านั้นเริ่มอ่อนแรงลง และมีแรงขายเข้ามาในตลาดมากขึ้น ทำให้เกิดความขัดแย้งระหว่าง Timeframes ต่างๆ  **สถานะปัจจุบัน:** * **แนวโน้ม:** * **TF Day:** เริ่มไม่แน่นอน (จากเดิมที่เป็น Early Uptrend) - แม้ว่าราคาจะยังอยู่เหนือ EMA 50/200 แต่ Money Flow เริ่มแสดงสัญญาณเตือน * **TF4H:** เริ่มไม่แน่นอน (พักตัว, ทดสอบแนวรับ EMA 50) - Money Flow บ่งบอกถึงแรงขายที่เข้ามา * **TF15:** ผันผวนสูง, ไม่มีทิศทางชัดเจน (Sideways) - Money Flow แสดงถึงแรงขาย แต่ก็มีแรงซื้อกลับเข้ามาบ้าง * **Money Flow (LuxAlgo):** * **TF Day:** แรงซื้อเริ่มอ่อนแรงลงอย่างมีนัยสำคัญ, มีแรงขายเข้ามา * **TF4H:** แรงขายมีมากกว่าแรงซื้อ * **TF15:** แรงขายและแรงซื้อผสมกัน, โดยรวมแรงขายยังมากกว่า * **EMA:** * **TF Day:** EMA 50/200 เป็นแนวรับ/แนวต้าน * **TF4H:** EMA 50 กำลังถูกทดสอบ, EMA 200 เป็นแนวต้าน * **TF15:** EMA 50/200 เป็นแนวต้าน **โครงสร้างราคา (SMC):** | Timeframe | Break of Structure (BOS) | Change of Character (CHoCH) | Higher High (HH) & Higher Low (HL) | Equal Highs (EQH) / Equal Lows (EQL) | | :-------- | :----------------------- | :--------------------------- | :----------------------------------- | :------------------------------------- | | Day | ด้านบนและล่าง | ด้านบน | เริ่มก่อตัว (แต่ไม่แข็งแกร่ง) | - | | 4H | ด้านบน | ด้านบน | เริ่มก่อตัว (แต่ไม่ชัดเจน) | มี EQH หลายจุด | | 15m | ด้านบนและล่าง | มีทั้งบนและล่าง | Lower Highs (LH) & Lower Lows (LL) | มี EQH และ EQL หลายจุด | **แนวรับ-แนวต้านสำคัญ:** | Timeframe | แนวรับ | แนวต้าน | | :-------- | :----------------------------------------------------------- | :--------------------------------------------------------------------- | | Day | EMA 50 (≈0.00010000), EMA 200 (≈0.00008000), 0.00006000-0.00007000 | 0.00017953 (High ล่าสุด), 0.00014000 (Volume Profile) | | 4H | EMA 50 (≈0.00007000), 0.00006000-0.00007000 | EMA 200 (≈0.00008000), 0.00008132, บริเวณ 0.00010000-0.00012000 (EQH) | | 15m | บริเวณ Low ล่าสุด | EMA 50, EMA 200, บริเวณ 0.000075-0.000076 (EQH) | **กลยุทธ์ (LUNCUSDT):** 1. **Wait & See (ทางเลือกที่ดีที่สุด):** * **เหตุผล:** ความขัดแย้งระหว่าง Timeframes สูงมาก, แนวโน้มไม่ชัดเจน, Money Flow ใน TF4H และ TF15 เป็นลบ * รอให้ราคาแสดงทิศทางที่ชัดเจนกว่านี้ (ยืนเหนือ EMA 50 ใน TF4H ได้, Breakout แนวต้านใน TF15) 2. **Buy on Dip (Day, 4H) - *ความเสี่ยงสูงมาก ไม่แนะนำ*:** * **เหตุผล:** แนวโน้มระยะยาวอาจจะยังเป็นขาขึ้นได้ (ถ้าไม่หลุดแนวรับสำคัญ) * **เงื่อนไข:** *ต้อง* รอสัญญาณการกลับตัวใน TF15 ก่อน * **จุดเข้า:** พิจารณาเฉพาะบริเวณแนวรับที่แข็งแกร่งมากๆ (EMA ของ Day/4H) *และต้องดู TF15 ประกอบ* * **Stop Loss:** ต่ำกว่า Low ล่าสุดของ TF15 3. **Short (15, ความเสี่ยงสูงมาก):** * **เหตุผล:** แนวโน้ม TF15 เป็นขาลง, Money Flow เป็นลบ * **เงื่อนไข:** ราคาไม่สามารถ Breakout EMA หรือแนวต้านอื่นๆ ใน TF15 ได้ * **จุดเข้า:** บริเวณ EMA หรือแนวต้านของ TF15 * **Stop Loss:** เหนือ High ล่าสุดของ TF15 **คำแนะนำ (เน้นย้ำ):** * **LUNC เป็นเหรียญที่มีความเสี่ยงสูงมาก (High Risk):** มีความผันผวนสูง และอาจมีการเปลี่ยนแปลงอย่างรวดเร็ว * **ความขัดแย้งของ Timeframes:** สถานการณ์ของ LUNCUSDT มีความขัดแย้งสูงมาก และมีความเสี่ยงสูง * **Money Flow:** บ่งบอกถึงแรงขายที่เริ่มเข้ามา และแนวโน้มขาขึ้น (ระยะกลาง-ยาว) ที่อ่อนแอลง * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด:** "รอ" เป็นกลยุทธ์ที่ดีที่สุด * **Risk Management:** สำคัญที่สุด ไม่ว่าจะเลือกกลยุทธ์ใด ต้องมีการบริหารความเสี่ยงที่ดี **สรุป:** LUNCUSDT กำลังอยู่ในช่วงเวลาที่ยากลำบากและมีความเสี่ยงสูงมากที่สุดในบรรดา 3 เหรียญที่เราวิเคราะห์กันมา การตัดสินใจที่ผิดพลาดอาจนำไปสู่การขาดทุนได้ ควรพิจารณาอย่างรอบคอบก่อนเข้าเทรดทุกครั้ง และ "รอ" จนกว่าจะมีสัญญาณที่ชัดเจนกว่านี้ เป็นทางเลือกที่ปลอดภัยที่สุดสำหรับนักลงทุนส่วนใหญ่ค่ะ **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ @ d360efec:14907b5f
2025-02-13 05:27:39 **ภาพรวม XRPUSDT (OKX):** XRPUSDT กำลังอยู่ในช่วงสำคัญ แนวโน้มระยะยาว (TF Day) เริ่มมีสัญญาณบวกของการเป็นขาขึ้น (Early Uptrend) หลังราคา Breakout EMA 50 และ Money Flow สนับสนุน อย่างไรก็ตาม แนวโน้มระยะกลาง (TF4H) เริ่มแสดงความอ่อนแอลง โดยราคาพักตัวลงมาทดสอบแนวรับสำคัญ และ Money Flow บ่งชี้ถึงแรงซื้อที่ลดลงและแรงขายที่เพิ่มขึ้น ส่วนแนวโน้มระยะสั้นมาก (TF15) เป็นขาลงชัดเจน  **แนวโน้ม:** * **TF Day:** เริ่มเป็นขาขึ้น (Early Uptrend) - Breakout EMA 50, Money Flow เป็นบวก * **TF4H:** เริ่มไม่แน่นอน (พักตัว, ทดสอบแนวรับ EMA 50 และ EQL) - Money Flow เริ่มเป็นลบ * **TF15:** ขาลง (Downtrend) ระยะสั้นมาก - ราคาหลุด EMA, โครงสร้างราคาเป็น Lower Highs/Lows, Money Flow เป็นลบ **โครงสร้างราคา (SMC):** | Timeframe | Break of Structure (BOS) | Change of Character (CHoCH) | Higher High (HH) & Higher Low (HL) | Equal Highs (EQH) / Equal Lows (EQL) | | :-------- | :----------------------- | :--------------------------- | :----------------------------------- | :------------------------------------- | | Day | ด้านบน (Breakout EMA 50) | ไม่ชัดเจน | เริ่มก่อตัว (แต่ยังไม่ชัดเจน) | - | | 4H | ด้านบน | ไม่ชัดเจน | เริ่มก่อตัว (แต่ไม่ชัดเจน) | EQH: 3.00-3.20, EQL: 2.2667 | | 15m | ด้านล่าง | มีทั้งบนและล่าง | Lower Highs (LH) & Lower Lows (LL) | EQH: 2.48-2.50, EQL: 2.38 |   **Money Flow (LuxAlgo):** * **TF Day:** แรงซื้อแข็งแกร่ง * **TF4H:** แรงซื้อเริ่มอ่อนแรงลง, แรงขายเริ่มเข้ามา * **TF15:** แรงขายมีอิทธิพลเหนือกว่า **EMA (Exponential Moving Average):** * **TF Day:** EMA 50 & 200 เป็นแนวรับ * **TF4H:** EMA 50 กำลังถูกทดสอบ, EMA 200 เป็นแนวรับถัดไป * **TF15:** EMA 50 & 200 เป็นแนวต้าน **แนวรับ-แนวต้านสำคัญ:** | Timeframe | แนวรับ | แนวต้าน | | :-------- | :----------------------------------------------------- | :----------------------------------------------------------------------- | | Day | EMA 50 (≈1.56), EMA 200 (≈1.08) | 3.4049 (High), 3.00-3.20 (EQH) | | 4H | EMA 50 (≈2.20), *2.2667 (EQL)*, EMA 200, 1.7820 | 3.4049, 2.3987 (Volume Profile), 3.00-3.20 (EQH) | | 15m | 2.38 (EQL, Volume Profile), 2.3274 | EMA 50, EMA 200, 2.4196, Equilibrium (≈2.44), 2.48-2.50 (EQH) | **กลยุทธ์ (XRPUSDT):** 1. **Wait & See (ทางเลือกที่ดีที่สุด):** * **เหตุผล:** ความขัดแย้งระหว่าง Timeframes สูง, TF4H กำลังทดสอบแนวรับสำคัญ, Money Flow ใน TF4H และ TF15 เป็นลบ * รอให้ราคาแสดงทิศทางที่ชัดเจน (ยืนเหนือ EMA 50 ใน TF4H ได้ หรือ Breakout แนวต้านใน TF15) 2. **Buy on Dip (Day, 4H) - *ความเสี่ยงสูงมาก*:** * **เหตุผล:** แนวโน้มระยะยาวยังมีโอกาสเป็นขาขึ้น, Money Flow ใน TF Day เป็นบวก * **เงื่อนไข (สำคัญมาก):** *ต้อง* รอสัญญาณการกลับตัวใน TF15 ก่อน เช่น: * Breakout แนวต้านย่อยๆ พร้อม Volume * Money Flow (TF15) เปลี่ยนเป็นสีเขียว * Bullish Candlestick Patterns * **จุดเข้า (Day):** EMA 50, EMA 200 (*ดู TF15 ประกอบ*) * **จุดเข้า (4H):** EMA 50, *2.2667 (EQL)* (*ดู TF15 ประกอบ*) * **Stop Loss:** ต่ำกว่า Low ล่าสุดของ TF15 หรือต่ำกว่าแนวรับที่เข้าซื้อ 3. **Short (15, ความเสี่ยงสูงมาก):** * **เหตุผล:** แนวโน้ม TF15 เป็นขาลง, Money Flow เป็นลบ * **เงื่อนไข:** ราคาไม่สามารถกลับขึ้นไปยืนเหนือ EMA ของ TF15 ได้ * **จุดเข้า:** บริเวณ EMA ของ TF15 หรือแนวต้านอื่นๆ * **Stop Loss:** เหนือ High ล่าสุดของ TF15 **คำแนะนำ:** * **ความขัดแย้งของ Timeframes:** XRPUSDT มีความขัดแย้งสูงมาก และมีความเสี่ยงสูง * **Money Flow:** Day เป็นบวก, 4H เริ่มเป็นลบ, 15m เป็นลบ * **EMA 50 (TF4H) & EQL 2.2667:** จุดชี้ชะตา * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด:** "รอ" ดีที่สุด * **Risk Management:** สำคัญที่สุด **สรุป:** สถานการณ์ของ XRPUSDT ตอนนี้มีความเสี่ยงสูงมาก และไม่เหมาะกับนักลงทุนที่รับความเสี่ยงได้ต่ำ การ "รอ" จนกว่าจะมีสัญญาณที่ชัดเจนกว่านี้ เป็นทางเลือกที่ปลอดภัยที่สุดค่ะ Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
@ d360efec:14907b5f
2025-02-13 05:27:39 **ภาพรวม XRPUSDT (OKX):** XRPUSDT กำลังอยู่ในช่วงสำคัญ แนวโน้มระยะยาว (TF Day) เริ่มมีสัญญาณบวกของการเป็นขาขึ้น (Early Uptrend) หลังราคา Breakout EMA 50 และ Money Flow สนับสนุน อย่างไรก็ตาม แนวโน้มระยะกลาง (TF4H) เริ่มแสดงความอ่อนแอลง โดยราคาพักตัวลงมาทดสอบแนวรับสำคัญ และ Money Flow บ่งชี้ถึงแรงซื้อที่ลดลงและแรงขายที่เพิ่มขึ้น ส่วนแนวโน้มระยะสั้นมาก (TF15) เป็นขาลงชัดเจน  **แนวโน้ม:** * **TF Day:** เริ่มเป็นขาขึ้น (Early Uptrend) - Breakout EMA 50, Money Flow เป็นบวก * **TF4H:** เริ่มไม่แน่นอน (พักตัว, ทดสอบแนวรับ EMA 50 และ EQL) - Money Flow เริ่มเป็นลบ * **TF15:** ขาลง (Downtrend) ระยะสั้นมาก - ราคาหลุด EMA, โครงสร้างราคาเป็น Lower Highs/Lows, Money Flow เป็นลบ **โครงสร้างราคา (SMC):** | Timeframe | Break of Structure (BOS) | Change of Character (CHoCH) | Higher High (HH) & Higher Low (HL) | Equal Highs (EQH) / Equal Lows (EQL) | | :-------- | :----------------------- | :--------------------------- | :----------------------------------- | :------------------------------------- | | Day | ด้านบน (Breakout EMA 50) | ไม่ชัดเจน | เริ่มก่อตัว (แต่ยังไม่ชัดเจน) | - | | 4H | ด้านบน | ไม่ชัดเจน | เริ่มก่อตัว (แต่ไม่ชัดเจน) | EQH: 3.00-3.20, EQL: 2.2667 | | 15m | ด้านล่าง | มีทั้งบนและล่าง | Lower Highs (LH) & Lower Lows (LL) | EQH: 2.48-2.50, EQL: 2.38 |   **Money Flow (LuxAlgo):** * **TF Day:** แรงซื้อแข็งแกร่ง * **TF4H:** แรงซื้อเริ่มอ่อนแรงลง, แรงขายเริ่มเข้ามา * **TF15:** แรงขายมีอิทธิพลเหนือกว่า **EMA (Exponential Moving Average):** * **TF Day:** EMA 50 & 200 เป็นแนวรับ * **TF4H:** EMA 50 กำลังถูกทดสอบ, EMA 200 เป็นแนวรับถัดไป * **TF15:** EMA 50 & 200 เป็นแนวต้าน **แนวรับ-แนวต้านสำคัญ:** | Timeframe | แนวรับ | แนวต้าน | | :-------- | :----------------------------------------------------- | :----------------------------------------------------------------------- | | Day | EMA 50 (≈1.56), EMA 200 (≈1.08) | 3.4049 (High), 3.00-3.20 (EQH) | | 4H | EMA 50 (≈2.20), *2.2667 (EQL)*, EMA 200, 1.7820 | 3.4049, 2.3987 (Volume Profile), 3.00-3.20 (EQH) | | 15m | 2.38 (EQL, Volume Profile), 2.3274 | EMA 50, EMA 200, 2.4196, Equilibrium (≈2.44), 2.48-2.50 (EQH) | **กลยุทธ์ (XRPUSDT):** 1. **Wait & See (ทางเลือกที่ดีที่สุด):** * **เหตุผล:** ความขัดแย้งระหว่าง Timeframes สูง, TF4H กำลังทดสอบแนวรับสำคัญ, Money Flow ใน TF4H และ TF15 เป็นลบ * รอให้ราคาแสดงทิศทางที่ชัดเจน (ยืนเหนือ EMA 50 ใน TF4H ได้ หรือ Breakout แนวต้านใน TF15) 2. **Buy on Dip (Day, 4H) - *ความเสี่ยงสูงมาก*:** * **เหตุผล:** แนวโน้มระยะยาวยังมีโอกาสเป็นขาขึ้น, Money Flow ใน TF Day เป็นบวก * **เงื่อนไข (สำคัญมาก):** *ต้อง* รอสัญญาณการกลับตัวใน TF15 ก่อน เช่น: * Breakout แนวต้านย่อยๆ พร้อม Volume * Money Flow (TF15) เปลี่ยนเป็นสีเขียว * Bullish Candlestick Patterns * **จุดเข้า (Day):** EMA 50, EMA 200 (*ดู TF15 ประกอบ*) * **จุดเข้า (4H):** EMA 50, *2.2667 (EQL)* (*ดู TF15 ประกอบ*) * **Stop Loss:** ต่ำกว่า Low ล่าสุดของ TF15 หรือต่ำกว่าแนวรับที่เข้าซื้อ 3. **Short (15, ความเสี่ยงสูงมาก):** * **เหตุผล:** แนวโน้ม TF15 เป็นขาลง, Money Flow เป็นลบ * **เงื่อนไข:** ราคาไม่สามารถกลับขึ้นไปยืนเหนือ EMA ของ TF15 ได้ * **จุดเข้า:** บริเวณ EMA ของ TF15 หรือแนวต้านอื่นๆ * **Stop Loss:** เหนือ High ล่าสุดของ TF15 **คำแนะนำ:** * **ความขัดแย้งของ Timeframes:** XRPUSDT มีความขัดแย้งสูงมาก และมีความเสี่ยงสูง * **Money Flow:** Day เป็นบวก, 4H เริ่มเป็นลบ, 15m เป็นลบ * **EMA 50 (TF4H) & EQL 2.2667:** จุดชี้ชะตา * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด:** "รอ" ดีที่สุด * **Risk Management:** สำคัญที่สุด **สรุป:** สถานการณ์ของ XRPUSDT ตอนนี้มีความเสี่ยงสูงมาก และไม่เหมาะกับนักลงทุนที่รับความเสี่ยงได้ต่ำ การ "รอ" จนกว่าจะมีสัญญาณที่ชัดเจนกว่านี้ เป็นทางเลือกที่ปลอดภัยที่สุดค่ะ Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ @ d360efec:14907b5f
2025-02-13 04:47:20 **ภาพรวม BTCUSDT :** Bitcoin (BTCUSDT) กำลังอยู่ในช่วงสำคัญ แม้ว่าแนวโน้มหลักในระยะกลางถึงยาว (TF Day & 4H) จะยังคงเป็นขาขึ้นที่แข็งแกร่ง แต่ในระยะสั้นมาก (TF15) กลับแสดงสัญญาณของความอ่อนแอและการปรับฐานลงมา ทำให้เกิดความไม่แน่นอนในทิศทางของราคา อย่างไรก็ตาม *Money Flow ใน TF Day บ่งชี้ว่าแรงซื้อโดยรวมยังคงแข็งแกร่ง*  **แนวโน้ม:** * **TF Day:** ขาขึ้น (Uptrend) แข็งแกร่ง – ราคาอยู่เหนือ EMA 50 และ EMA 200, โครงสร้างราคาเป็น Higher Highs (HH) และ Higher Lows (HL), *Money Flow เป็นบวก (แรงซื้อ)* * **TF4H:** ขาขึ้น (Uptrend) – ราคาอยู่เหนือ EMA, มีการพักตัวลงมา (Pullback) แต่ยังไม่เสียโครงสร้างขาขึ้น, *Money Flow เริ่มอ่อนแรง (แรงซื้อลดลง, แรงขายเพิ่มขึ้น)* * **TF15:** ขาลง (Downtrend) ระยะสั้นมาก – ราคาหลุด EMA และแนวรับย่อย, โครงสร้างราคาเป็น Lower Highs (LH) และ Lower Lows (LL), *Money Flow เป็นลบ (แรงขาย)* **โครงสร้างราคา (SMC):** * **TF Day:** ยืนยันแนวโน้มขาขึ้น (HH, HL, BOS) * **TF4H:** ยืนยันแนวโน้มขาขึ้น (HH, HL, BOS), มี Equal Highs (EQH) ที่เป็นแนวต้าน * **TF15:** บ่งบอกถึงแนวโน้มขาลงระยะสั้น (BOS ด้านล่าง, LH, LL), มี EQH เป็นแนวต้าน **Money Flow (LuxAlgo) - สรุป:** * **TF Day:** แรงซื้อยังคงแข็งแกร่งอย่างชัดเจน * **TF4H:** แรงซื้อเริ่มอ่อนแรงลง, มีแรงขายเข้ามา * **TF15:** แรงขายมีอิทธิพลเหนือกว่า  **EMA (Exponential Moving Average):** * **TF Day & 4H:** EMA 50 & 200 เป็นแนวรับสำคัญ * **TF15:** EMA 50 & 200 กลายเป็นแนวต้าน **แนวรับ-แนวต้านสำคัญ:** | Timeframe | แนวรับ | แนวต้าน | | :-------- | :------------------------------------------------------------------------- | :-------------------------------------------------------------- | | Day | EMA 50, EMA 200, 96,000-98,000, 85,724.7 | 109,998.9 (High เดิม) | | 4H | EMA 50, EMA 200, 96,000-98,000, 89,037.0 | 109,998.9 (EQH, High เดิม) | | 15m | 95,200 (Low ล่าสุด), 94,707.4 (Low ก่อนหน้า) | EMA 50, EMA 200, บริเวณ 96,000, 96,807.8, 97,000-97,200 | **กลยุทธ์ (BTCUSDT):** 1. **Buy on Dip (Day, 4H) - *มีความน่าเชื่อถือมากขึ้น แต่ยังคงต้องระมัดระวัง*:** * **เหตุผล:** แนวโน้มหลักยังเป็นขาขึ้น, Money Flow ใน TF Day แข็งแกร่ง * **เงื่อนไข:** *ยังคงต้องรอสัญญาณการกลับตัวของราคาใน TF15 ก่อน* (Breakout แนวต้านย่อย, Money Flow TF15 เป็นบวก, Bullish Candlestick Patterns) * **จุดเข้า (Day):** EMA 50, EMA 200, บริเวณ 96,000-98,000 * **จุดเข้า (4H):** EMA 50 * **Stop Loss:** ต่ำกว่า Low ล่าสุดของ TF15 หรือต่ำกว่าแนวรับที่เข้าซื้อ 2. **Short (15, ความเสี่ยงสูงมาก):** * **เหตุผล:** แนวโน้ม TF15 เป็นขาลง, Money Flow TF15 เป็นลบ * **เงื่อนไข:** ราคาไม่สามารถกลับขึ้นไปยืนเหนือ EMA ของ TF15 ได้ * **จุดเข้า:** บริเวณ EMA ของ TF15 หรือแนวต้านอื่นๆ * **Stop Loss:** เหนือ High ล่าสุดของ TF15 3. **Wait & See (ทางเลือกที่ปลอดภัย):** * **เหตุผล:** ความขัดแย้งระหว่าง Timeframes ยังคงมีอยู่ * รอให้ตลาดเฉลยทิศทางที่ชัดเจนกว่านี้ **คำแนะนำ (เน้นย้ำ):** * **Money Flow ใน TF Day:** เป็นปัจจัยบวกที่สำคัญ ทำให้กลยุทธ์ Buy on Dip มีน้ำหนักมากขึ้น * **ความขัดแย้งของ Timeframes:** ยังคงต้องระวัง TF15 ที่เป็นขาลง * **Volume:** การ Breakout/Breakdown ใดๆ ควรมี Volume สนับสนุน * **Risk Management:** สำคัญที่สุด **สรุป:** สถานการณ์ของ BTCUSDT โดยรวมยังคงเป็นบวก (ขาขึ้น) แต่มีความเสี่ยงในระยะสั้นจาก TF15 การตัดสินใจลงทุนควรพิจารณาจาก Timeframe ที่เหมาะสมกับสไตล์การเทรดของคุณ และอย่าลืมบริหารความเสี่ยงเสมอค่ะ **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
@ d360efec:14907b5f
2025-02-13 04:47:20 **ภาพรวม BTCUSDT :** Bitcoin (BTCUSDT) กำลังอยู่ในช่วงสำคัญ แม้ว่าแนวโน้มหลักในระยะกลางถึงยาว (TF Day & 4H) จะยังคงเป็นขาขึ้นที่แข็งแกร่ง แต่ในระยะสั้นมาก (TF15) กลับแสดงสัญญาณของความอ่อนแอและการปรับฐานลงมา ทำให้เกิดความไม่แน่นอนในทิศทางของราคา อย่างไรก็ตาม *Money Flow ใน TF Day บ่งชี้ว่าแรงซื้อโดยรวมยังคงแข็งแกร่ง*  **แนวโน้ม:** * **TF Day:** ขาขึ้น (Uptrend) แข็งแกร่ง – ราคาอยู่เหนือ EMA 50 และ EMA 200, โครงสร้างราคาเป็น Higher Highs (HH) และ Higher Lows (HL), *Money Flow เป็นบวก (แรงซื้อ)* * **TF4H:** ขาขึ้น (Uptrend) – ราคาอยู่เหนือ EMA, มีการพักตัวลงมา (Pullback) แต่ยังไม่เสียโครงสร้างขาขึ้น, *Money Flow เริ่มอ่อนแรง (แรงซื้อลดลง, แรงขายเพิ่มขึ้น)* * **TF15:** ขาลง (Downtrend) ระยะสั้นมาก – ราคาหลุด EMA และแนวรับย่อย, โครงสร้างราคาเป็น Lower Highs (LH) และ Lower Lows (LL), *Money Flow เป็นลบ (แรงขาย)* **โครงสร้างราคา (SMC):** * **TF Day:** ยืนยันแนวโน้มขาขึ้น (HH, HL, BOS) * **TF4H:** ยืนยันแนวโน้มขาขึ้น (HH, HL, BOS), มี Equal Highs (EQH) ที่เป็นแนวต้าน * **TF15:** บ่งบอกถึงแนวโน้มขาลงระยะสั้น (BOS ด้านล่าง, LH, LL), มี EQH เป็นแนวต้าน **Money Flow (LuxAlgo) - สรุป:** * **TF Day:** แรงซื้อยังคงแข็งแกร่งอย่างชัดเจน * **TF4H:** แรงซื้อเริ่มอ่อนแรงลง, มีแรงขายเข้ามา * **TF15:** แรงขายมีอิทธิพลเหนือกว่า  **EMA (Exponential Moving Average):** * **TF Day & 4H:** EMA 50 & 200 เป็นแนวรับสำคัญ * **TF15:** EMA 50 & 200 กลายเป็นแนวต้าน **แนวรับ-แนวต้านสำคัญ:** | Timeframe | แนวรับ | แนวต้าน | | :-------- | :------------------------------------------------------------------------- | :-------------------------------------------------------------- | | Day | EMA 50, EMA 200, 96,000-98,000, 85,724.7 | 109,998.9 (High เดิม) | | 4H | EMA 50, EMA 200, 96,000-98,000, 89,037.0 | 109,998.9 (EQH, High เดิม) | | 15m | 95,200 (Low ล่าสุด), 94,707.4 (Low ก่อนหน้า) | EMA 50, EMA 200, บริเวณ 96,000, 96,807.8, 97,000-97,200 | **กลยุทธ์ (BTCUSDT):** 1. **Buy on Dip (Day, 4H) - *มีความน่าเชื่อถือมากขึ้น แต่ยังคงต้องระมัดระวัง*:** * **เหตุผล:** แนวโน้มหลักยังเป็นขาขึ้น, Money Flow ใน TF Day แข็งแกร่ง * **เงื่อนไข:** *ยังคงต้องรอสัญญาณการกลับตัวของราคาใน TF15 ก่อน* (Breakout แนวต้านย่อย, Money Flow TF15 เป็นบวก, Bullish Candlestick Patterns) * **จุดเข้า (Day):** EMA 50, EMA 200, บริเวณ 96,000-98,000 * **จุดเข้า (4H):** EMA 50 * **Stop Loss:** ต่ำกว่า Low ล่าสุดของ TF15 หรือต่ำกว่าแนวรับที่เข้าซื้อ 2. **Short (15, ความเสี่ยงสูงมาก):** * **เหตุผล:** แนวโน้ม TF15 เป็นขาลง, Money Flow TF15 เป็นลบ * **เงื่อนไข:** ราคาไม่สามารถกลับขึ้นไปยืนเหนือ EMA ของ TF15 ได้ * **จุดเข้า:** บริเวณ EMA ของ TF15 หรือแนวต้านอื่นๆ * **Stop Loss:** เหนือ High ล่าสุดของ TF15 3. **Wait & See (ทางเลือกที่ปลอดภัย):** * **เหตุผล:** ความขัดแย้งระหว่าง Timeframes ยังคงมีอยู่ * รอให้ตลาดเฉลยทิศทางที่ชัดเจนกว่านี้ **คำแนะนำ (เน้นย้ำ):** * **Money Flow ใน TF Day:** เป็นปัจจัยบวกที่สำคัญ ทำให้กลยุทธ์ Buy on Dip มีน้ำหนักมากขึ้น * **ความขัดแย้งของ Timeframes:** ยังคงต้องระวัง TF15 ที่เป็นขาลง * **Volume:** การ Breakout/Breakdown ใดๆ ควรมี Volume สนับสนุน * **Risk Management:** สำคัญที่สุด **สรุป:** สถานการณ์ของ BTCUSDT โดยรวมยังคงเป็นบวก (ขาขึ้น) แต่มีความเสี่ยงในระยะสั้นจาก TF15 การตัดสินใจลงทุนควรพิจารณาจาก Timeframe ที่เหมาะสมกับสไตล์การเทรดของคุณ และอย่าลืมบริหารความเสี่ยงเสมอค่ะ **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ @ 2183e947:f497b975
2025-02-13 04:44:45# How Coinpools Improve Bitcoin # Problems with bitcoin UX problems with base layer payments include: - Mining fees are sometimes high - Confirmations usually take several minutes - Using it privately requires running a coinjoin server UX problems with lightning payments include: - Setup fees are sometimes high - Payments frequently fail - Payments aren't asynchronous (the recipient has to stand there with their device open waiting to do a revoke_and_ack on their old state -- unless they use a custodian) - Payments that *do* succeed occasionally take more than 30 seconds (due to stuck payments, automatic retries, and no ability to say "stop retrying" in any existing wallets that I'm aware of) - Using it privately requires manual channel management # Solutions A lot of my recent work focuses on non-interactive coinpools. I figured out a way to do them on bitcoin if we had CTV + CSFS, and then, with a bit more thought, I figured out that my model didn't actually require those things, so I am now working on an implementation. But my model does benefit a lot from CTV (less sure about CSFS at this point) so let me outline how non-interactive coinpools fix the above problems and along the way I will share how CTV specifically improves coinpools. ## "Mining fees are sometimes high" Coinpools improve the problem of "mining fees are sometimes high" by letting you bypass them in more cases. If you're in a coinpool and pay someone else in the same coinpool, your payment does not show up on the base layer, it just involves modifying some unilateral withdrawal transactions such that the sender can withdraw less and the recipient can withdraw more. The transactions are off-chain, like LN transactions, so you can do that without paying a base layer fee. ## "Confirmations usually take several minutes" Coinpools improve the problem of "confirmations usually take several minutes" in a similar manner. Payments *inside* a coinpool (i.e. to another pool user) merely involve modifying off-chain data (and revoking an old state), so they can be as fast as lightning. In most cases I expect them to be a bit faster because there's less need for pathfinding or negotiating with a variety of routing nodes. If the sender and the recipient are in the same pool, they only need to talk to each other and, in my model, a coordinator. ## "Using the base layer privately requires running a coinjoin server" Coinpools improve the problem of "using the base layer privately requires running a coinjoin server" in two ways: first, if you're in a coinpool and you send money to a bitcoin address, the blockchain doesn't know which coinpool user sent that payment. Analysts might be able to trace the payment to the coinpool, but from the blockchain's perspective, that's just a multisig; the actual person *inside* the multisig who sent the money is not revealed. However, my model uses a coordinator, and the coordinator probably knows which user sent the payment. Still, only 1 person knowing is better than having everyone on the blockchain know. Second, if you send money to someone *inside* the coinpool, in my model, the only people who know about your payment are the sender, the recipient, and the coordinator, and the recipient does not know who the sender is. Moreover, my model allows users to act as bridges from LN to other pool users, so even the coordinator doesn't know if the person who *looks* like the sender was the *real* sender or just a bridge node, with the *real* sender being someone on lightning. ## "Setup fees on lightning are sometimes high" Coinpools improve the problem of "setup fees are sometimes high" by having multiple users share the setup cost. My model allows a single bitcoin transaction to fund a coinpool with a number of members between 1 and probably about 100. (The max I've actually successfully tested is 11.) If the users share the cost of that transaction, then even in a high fee scenario, where bitcoin transactions cost $50, each user only has to pay a fraction of that, where the fraction is determined by how many users are joining the pool. If 10 people are joining, each user would pay $5 instead of $50. If 50 people are joining, each user would pay $1. If 100 people are joining, each user would pay 50¢. ## Sidebar: how CTV improves my coinpool model The setup is also where CTV greatly improves my model. For my model to work, the users have to coordinate to create the pool in something I call a "signing ceremony," which is very similar to a coinjoin. The signing ceremony has to be scheduled and each user has to show up for it or they won't get into the pool. With CTV, you could fix this: instead of a signing ceremony, an exchange could autosend your money into a coinpool on e.g. a monthly basis and email you the data you need to perform your unilateral exit. All they need from you is a pubkey, and they can do everything else. ## "Lightning payments frequently fail" Coinpools improve the problem of "payments frequently fail" by reducing the need for pathfinding, which is a typical cause of failure on lightning. If you are paying someone in the same pool as you, you always know an exact path: it will be you -> coordinator -> recipient. These short paths also reduce the likelihood of routing nodes having insufficient capacity to forward the payment. You've only got one "routing node" to worry about -- the coordinator. ## "Lightning payments aren't asynchronous" Coinpools *in general* don't improve the problem of "payments aren't asynchronous" but my model in particular *does* improve that problem because I am combining it with my hedgehog protocol from last year, which *does* allow for asynchronous lightning-like payments. Relatedly, my coinpool model technically has a network model, it's just a hub-and-spoke network: the coordinator is connected to every user of the pool and can forward asynchronous hedgehog payments to them. This means you can send money to someone when they are offline; they'll get it whenever they *do* get online, even if *you* went offline in the meantime. ## "Lightning payments sometimes take too long" Coinpools improve the problem of "stuck" lightning payments by reducing the number of hops along the route. As above, a payment inside the pool (per my model) is always just sender -> coordinator -> recipient. Due to only having 1 hop, there are fewer opportunities for a node to have a network issue and cause a delay. ## "Channel management is a pain" Coinpools have multiple ways of improving the problem of manual channel management. In particular, not all coinpool models *have* channels, so channel management is not always needed in a coinpool. My model, however, does have channels, so channel management is still a thing. Nonetheless, my model improves channel management in two ways: first, the setup costs are lower for the reasons given above. Second, payment asynchronicity helps for the following reason: The worst pain point in channel management *today* occurs when someone sends you a payment but it fails because you didn't have enough inbound capacity. That doesn't happen in my coinpool model because payments are asynchronous. If you don't have enough inbound capacity, the payment doesn't fail, it just remains pending. So all you have to do is open a new channel (i.e. enter a new pool) and *then* finalize the payment. ## Zap me I hope this essay clarifies why coinpools improve the problems I outlined and why CTV improves coinpools. I also hope this gets you a bit excited for my latest coinpool invention, which I hope to release soon :D (It really is very close to demo-ready.) If you liked this essay, consider zapping me: supertestnet@coinos.io
@ 2183e947:f497b975
2025-02-13 04:44:45# How Coinpools Improve Bitcoin # Problems with bitcoin UX problems with base layer payments include: - Mining fees are sometimes high - Confirmations usually take several minutes - Using it privately requires running a coinjoin server UX problems with lightning payments include: - Setup fees are sometimes high - Payments frequently fail - Payments aren't asynchronous (the recipient has to stand there with their device open waiting to do a revoke_and_ack on their old state -- unless they use a custodian) - Payments that *do* succeed occasionally take more than 30 seconds (due to stuck payments, automatic retries, and no ability to say "stop retrying" in any existing wallets that I'm aware of) - Using it privately requires manual channel management # Solutions A lot of my recent work focuses on non-interactive coinpools. I figured out a way to do them on bitcoin if we had CTV + CSFS, and then, with a bit more thought, I figured out that my model didn't actually require those things, so I am now working on an implementation. But my model does benefit a lot from CTV (less sure about CSFS at this point) so let me outline how non-interactive coinpools fix the above problems and along the way I will share how CTV specifically improves coinpools. ## "Mining fees are sometimes high" Coinpools improve the problem of "mining fees are sometimes high" by letting you bypass them in more cases. If you're in a coinpool and pay someone else in the same coinpool, your payment does not show up on the base layer, it just involves modifying some unilateral withdrawal transactions such that the sender can withdraw less and the recipient can withdraw more. The transactions are off-chain, like LN transactions, so you can do that without paying a base layer fee. ## "Confirmations usually take several minutes" Coinpools improve the problem of "confirmations usually take several minutes" in a similar manner. Payments *inside* a coinpool (i.e. to another pool user) merely involve modifying off-chain data (and revoking an old state), so they can be as fast as lightning. In most cases I expect them to be a bit faster because there's less need for pathfinding or negotiating with a variety of routing nodes. If the sender and the recipient are in the same pool, they only need to talk to each other and, in my model, a coordinator. ## "Using the base layer privately requires running a coinjoin server" Coinpools improve the problem of "using the base layer privately requires running a coinjoin server" in two ways: first, if you're in a coinpool and you send money to a bitcoin address, the blockchain doesn't know which coinpool user sent that payment. Analysts might be able to trace the payment to the coinpool, but from the blockchain's perspective, that's just a multisig; the actual person *inside* the multisig who sent the money is not revealed. However, my model uses a coordinator, and the coordinator probably knows which user sent the payment. Still, only 1 person knowing is better than having everyone on the blockchain know. Second, if you send money to someone *inside* the coinpool, in my model, the only people who know about your payment are the sender, the recipient, and the coordinator, and the recipient does not know who the sender is. Moreover, my model allows users to act as bridges from LN to other pool users, so even the coordinator doesn't know if the person who *looks* like the sender was the *real* sender or just a bridge node, with the *real* sender being someone on lightning. ## "Setup fees on lightning are sometimes high" Coinpools improve the problem of "setup fees are sometimes high" by having multiple users share the setup cost. My model allows a single bitcoin transaction to fund a coinpool with a number of members between 1 and probably about 100. (The max I've actually successfully tested is 11.) If the users share the cost of that transaction, then even in a high fee scenario, where bitcoin transactions cost $50, each user only has to pay a fraction of that, where the fraction is determined by how many users are joining the pool. If 10 people are joining, each user would pay $5 instead of $50. If 50 people are joining, each user would pay $1. If 100 people are joining, each user would pay 50¢. ## Sidebar: how CTV improves my coinpool model The setup is also where CTV greatly improves my model. For my model to work, the users have to coordinate to create the pool in something I call a "signing ceremony," which is very similar to a coinjoin. The signing ceremony has to be scheduled and each user has to show up for it or they won't get into the pool. With CTV, you could fix this: instead of a signing ceremony, an exchange could autosend your money into a coinpool on e.g. a monthly basis and email you the data you need to perform your unilateral exit. All they need from you is a pubkey, and they can do everything else. ## "Lightning payments frequently fail" Coinpools improve the problem of "payments frequently fail" by reducing the need for pathfinding, which is a typical cause of failure on lightning. If you are paying someone in the same pool as you, you always know an exact path: it will be you -> coordinator -> recipient. These short paths also reduce the likelihood of routing nodes having insufficient capacity to forward the payment. You've only got one "routing node" to worry about -- the coordinator. ## "Lightning payments aren't asynchronous" Coinpools *in general* don't improve the problem of "payments aren't asynchronous" but my model in particular *does* improve that problem because I am combining it with my hedgehog protocol from last year, which *does* allow for asynchronous lightning-like payments. Relatedly, my coinpool model technically has a network model, it's just a hub-and-spoke network: the coordinator is connected to every user of the pool and can forward asynchronous hedgehog payments to them. This means you can send money to someone when they are offline; they'll get it whenever they *do* get online, even if *you* went offline in the meantime. ## "Lightning payments sometimes take too long" Coinpools improve the problem of "stuck" lightning payments by reducing the number of hops along the route. As above, a payment inside the pool (per my model) is always just sender -> coordinator -> recipient. Due to only having 1 hop, there are fewer opportunities for a node to have a network issue and cause a delay. ## "Channel management is a pain" Coinpools have multiple ways of improving the problem of manual channel management. In particular, not all coinpool models *have* channels, so channel management is not always needed in a coinpool. My model, however, does have channels, so channel management is still a thing. Nonetheless, my model improves channel management in two ways: first, the setup costs are lower for the reasons given above. Second, payment asynchronicity helps for the following reason: The worst pain point in channel management *today* occurs when someone sends you a payment but it fails because you didn't have enough inbound capacity. That doesn't happen in my coinpool model because payments are asynchronous. If you don't have enough inbound capacity, the payment doesn't fail, it just remains pending. So all you have to do is open a new channel (i.e. enter a new pool) and *then* finalize the payment. ## Zap me I hope this essay clarifies why coinpools improve the problems I outlined and why CTV improves coinpools. I also hope this gets you a bit excited for my latest coinpool invention, which I hope to release soon :D (It really is very close to demo-ready.) If you liked this essay, consider zapping me: supertestnet@coinos.io @ a012dc82:6458a70d
2025-02-13 04:00:01In the dynamic world of global finance, the interplay between traditional monetary policy and the burgeoning digital asset market is becoming increasingly prominent. The U.S. Federal Reserve's recent pivot towards a more accommodative monetary policy has sparked intense discussion among investors, economists, and cryptocurrency enthusiasts. This shift, characterized by an expected reduction in interest rates, is not just a routine adjustment but a significant move that could have far-reaching implications for various asset classes, including cryptocurrencies like Bitcoin. As we delve into this topic, we aim to unravel the complexities of the Fed's policy change and its potential ripple effects on Bitcoin, a digital asset that has been a subject of much intrigue and speculation. **Table Of Content** - Understanding the Fed's Policy Shift - Impact on Traditional Financial Markets - Bitcoin's Response to Monetary Easing - Analyzing the Economic Backdrop - Bitcoin: A Safe Haven or Risk Asset? - Risks and Opportunities - Conclusion - FAQs **Understanding the Fed's Policy Shift** The Federal Reserve, the guardian of the U.S. monetary system, wields immense influence over global financial markets. Its recent signaling of a dovish turn – an expectation of 75 basis points in rate cuts by 2024 – marks a significant departure from its previous stance. This change is reflective of the Fed's response to a confluence of macroeconomic factors, such as fluctuating inflation rates, global economic uncertainties, and domestic financial stability concerns. The Fed's decisions are closely monitored as they set the tone for economic growth, inflation control, and financial market stability. In this context, the anticipated rate cuts suggest a strategic move to stimulate economic activity by making borrowing cheaper, thereby potentially boosting investment and consumption. However, this policy shift is not without its complexities and nuances, as it must balance the fine line between stimulating growth and controlling inflation. **Impact on Traditional Financial Markets** The ripple effects of the Fed's policy announcement were immediately felt across traditional financial markets. Stock markets, often seen as a barometer of economic sentiment, reacted positively, with indices like the Dow Jones Industrial Average reaching new heights. This surge reflects investors' optimism about the potential for increased corporate profits and economic growth in a lower interest rate environment. Similarly, the bond market experienced a significant rally, with yields on government securities falling as bond prices rose. This movement in the bond market is indicative of investors' expectations of a more accommodative monetary policy, which typically leads to lower yields on fixed-income securities. These market reactions underscore the pivotal role of central bank policies in shaping investor sentiment and the direction of financial markets. They also highlight the interconnectedness of various asset classes, as changes in monetary policy can have cascading effects across different sectors of the economy. **Bitcoin's Response to Monetary Easing** Bitcoin's reaction to the Fed's dovish turn has been a subject of keen interest. The cryptocurrency, which had been experiencing volatility, showed signs of recovery following the Fed's announcement. This response is indicative of Bitcoin's increasing correlation with broader financial market trends, a significant development given its history as an uncorrelated asset. Bitcoin's sensitivity to macroeconomic factors like central bank policies points to its growing integration into the mainstream financial ecosystem. However, this integration also means that Bitcoin is increasingly exposed to the same macroeconomic risks and uncertainties that affect traditional assets. The Fed's policy shift could potentially make Bitcoin more attractive to investors seeking non-traditional assets in a low-interest-rate environment. However, Bitcoin's complex dynamics, including its decentralized nature, limited supply, and regulatory landscape, add layers of complexity to its response to monetary policy changes. **Analyzing the Economic Backdrop** The economic backdrop against which the Fed's policy shift occurs is multifaceted and dynamic. On one hand, the U.S. economy has demonstrated resilience, with robust GDP growth and positive retail sales figures suggesting underlying strength. On the other hand, inflation, though moderated from its peak, remains a concern, hovering above the Fed's target. This economic duality presents a challenging scenario for policymakers, who must navigate the delicate balance between stimulating growth and containing inflation. For investors and market participants, this creates an environment of uncertainty, as they must decipher mixed signals from economic data and policy announcements. In this context, Bitcoin's role and response become even more intriguing, as it operates at the intersection of technology, finance, and macroeconomics. **Bitcoin: A Safe Haven or Risk Asset?** The debate over Bitcoin's classification as a safe haven or a risk asset is intensified by the Fed's easing stance. Traditionally, in a low-interest-rate environment, investors seek assets that can serve as hedges against inflation and currency devaluation. Gold has historically played this role, and Bitcoin, with its fixed supply and digital scarcity, has drawn comparisons to gold. However, Bitcoin's relatively short history and high volatility make it a more complex and potentially riskier asset. The Fed's dovish policy could enhance Bitcoin's appeal as an alternative investment, especially if traditional assets like bonds offer lower returns. However, Bitcoin's classification as a safe haven is still a matter of debate, with opinions divided on its long-term stability and value retention capabilities. **Risks and Opportunities** Investors considering Bitcoin in light of the Fed's policy change face a landscape filled with both risks and opportunities. The potential for a Bitcoin rally in a low-interest-rate environment is counterbalanced by the cryptocurrency's inherent volatility and regulatory uncertainties. Bitcoin's price movements can be dramatic and unpredictable, influenced by a range of factors from technological developments to geopolitical events. Additionally, the regulatory environment for cryptocurrencies is still evolving, with potential changes posing risks to Bitcoin's accessibility and value. Investors must also consider the broader global economic context, including actions by other central banks and international trade dynamics, which can impact Bitcoin's market movement. **Conclusion** The Federal Reserve's shift towards a more accommodative monetary policy in 2024 presents a fascinating scenario for Bitcoin and the broader cryptocurrency market. This development underscores the increasing relevance of digital assets in the global financial landscape and highlights the complex interplay between traditional monetary policies and emerging financial technologies. As Bitcoin continues to evolve and gain acceptance, its response to macroeconomic factors like central bank policies will be a critical area of focus for investors. In navigating this dynamic and uncertain environment, a cautious and well-informed approach is essential for those looking to explore the opportunities and navigate the challenges of cryptocurrency investments. The coming years promise to be a pivotal period in the maturation of Bitcoin as it responds to the shifting tides of global finance. **FAQs** **How does the Federal Reserve's easing stance impact Bitcoin?** The Fed's shift towards lower interest rates can make riskier assets like Bitcoin more attractive to investors. This is because lower rates often lead to reduced yields on traditional investments, prompting investors to seek higher returns elsewhere. **What is the significance of the Fed's 'dot plot' for Bitcoin investors?** The 'dot plot' is a projection of interest rate movements by Federal Reserve members. A shift towards lower rates, as indicated in the recent dot plot, can signal a more accommodative monetary policy, potentially impacting Bitcoin's market as investors adjust their portfolios. **Can Bitcoin be considered a safe haven asset in light of the Fed's policy?** Bitcoin's role as a safe haven asset is debated. While its fixed supply and digital nature offer some safe haven characteristics, its volatility and regulatory uncertainties make it a complex choice compared to traditional safe havens like gold. **What risks should Bitcoin investors consider in the context of the Fed's easing policy?** Investors should be aware of Bitcoin's volatility, regulatory changes, and its sensitivity to macroeconomic factors. Additionally, global economic conditions and actions by other central banks can also influence Bitcoin's market. **How does the economic backdrop influence Bitcoin's response to the Fed's policy?** Economic factors like GDP growth, inflation rates, and retail sales impact investor sentiment and risk appetite, which in turn can affect Bitcoin's market. A strong economy might reduce the appeal of risk assets like Bitcoin, while economic uncertainties can increase their attractiveness. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: @croxroadnews.co** **Instagram: @croxroadnews.co** **Youtube: @croxroadnews** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
@ a012dc82:6458a70d
2025-02-13 04:00:01In the dynamic world of global finance, the interplay between traditional monetary policy and the burgeoning digital asset market is becoming increasingly prominent. The U.S. Federal Reserve's recent pivot towards a more accommodative monetary policy has sparked intense discussion among investors, economists, and cryptocurrency enthusiasts. This shift, characterized by an expected reduction in interest rates, is not just a routine adjustment but a significant move that could have far-reaching implications for various asset classes, including cryptocurrencies like Bitcoin. As we delve into this topic, we aim to unravel the complexities of the Fed's policy change and its potential ripple effects on Bitcoin, a digital asset that has been a subject of much intrigue and speculation. **Table Of Content** - Understanding the Fed's Policy Shift - Impact on Traditional Financial Markets - Bitcoin's Response to Monetary Easing - Analyzing the Economic Backdrop - Bitcoin: A Safe Haven or Risk Asset? - Risks and Opportunities - Conclusion - FAQs **Understanding the Fed's Policy Shift** The Federal Reserve, the guardian of the U.S. monetary system, wields immense influence over global financial markets. Its recent signaling of a dovish turn – an expectation of 75 basis points in rate cuts by 2024 – marks a significant departure from its previous stance. This change is reflective of the Fed's response to a confluence of macroeconomic factors, such as fluctuating inflation rates, global economic uncertainties, and domestic financial stability concerns. The Fed's decisions are closely monitored as they set the tone for economic growth, inflation control, and financial market stability. In this context, the anticipated rate cuts suggest a strategic move to stimulate economic activity by making borrowing cheaper, thereby potentially boosting investment and consumption. However, this policy shift is not without its complexities and nuances, as it must balance the fine line between stimulating growth and controlling inflation. **Impact on Traditional Financial Markets** The ripple effects of the Fed's policy announcement were immediately felt across traditional financial markets. Stock markets, often seen as a barometer of economic sentiment, reacted positively, with indices like the Dow Jones Industrial Average reaching new heights. This surge reflects investors' optimism about the potential for increased corporate profits and economic growth in a lower interest rate environment. Similarly, the bond market experienced a significant rally, with yields on government securities falling as bond prices rose. This movement in the bond market is indicative of investors' expectations of a more accommodative monetary policy, which typically leads to lower yields on fixed-income securities. These market reactions underscore the pivotal role of central bank policies in shaping investor sentiment and the direction of financial markets. They also highlight the interconnectedness of various asset classes, as changes in monetary policy can have cascading effects across different sectors of the economy. **Bitcoin's Response to Monetary Easing** Bitcoin's reaction to the Fed's dovish turn has been a subject of keen interest. The cryptocurrency, which had been experiencing volatility, showed signs of recovery following the Fed's announcement. This response is indicative of Bitcoin's increasing correlation with broader financial market trends, a significant development given its history as an uncorrelated asset. Bitcoin's sensitivity to macroeconomic factors like central bank policies points to its growing integration into the mainstream financial ecosystem. However, this integration also means that Bitcoin is increasingly exposed to the same macroeconomic risks and uncertainties that affect traditional assets. The Fed's policy shift could potentially make Bitcoin more attractive to investors seeking non-traditional assets in a low-interest-rate environment. However, Bitcoin's complex dynamics, including its decentralized nature, limited supply, and regulatory landscape, add layers of complexity to its response to monetary policy changes. **Analyzing the Economic Backdrop** The economic backdrop against which the Fed's policy shift occurs is multifaceted and dynamic. On one hand, the U.S. economy has demonstrated resilience, with robust GDP growth and positive retail sales figures suggesting underlying strength. On the other hand, inflation, though moderated from its peak, remains a concern, hovering above the Fed's target. This economic duality presents a challenging scenario for policymakers, who must navigate the delicate balance between stimulating growth and containing inflation. For investors and market participants, this creates an environment of uncertainty, as they must decipher mixed signals from economic data and policy announcements. In this context, Bitcoin's role and response become even more intriguing, as it operates at the intersection of technology, finance, and macroeconomics. **Bitcoin: A Safe Haven or Risk Asset?** The debate over Bitcoin's classification as a safe haven or a risk asset is intensified by the Fed's easing stance. Traditionally, in a low-interest-rate environment, investors seek assets that can serve as hedges against inflation and currency devaluation. Gold has historically played this role, and Bitcoin, with its fixed supply and digital scarcity, has drawn comparisons to gold. However, Bitcoin's relatively short history and high volatility make it a more complex and potentially riskier asset. The Fed's dovish policy could enhance Bitcoin's appeal as an alternative investment, especially if traditional assets like bonds offer lower returns. However, Bitcoin's classification as a safe haven is still a matter of debate, with opinions divided on its long-term stability and value retention capabilities. **Risks and Opportunities** Investors considering Bitcoin in light of the Fed's policy change face a landscape filled with both risks and opportunities. The potential for a Bitcoin rally in a low-interest-rate environment is counterbalanced by the cryptocurrency's inherent volatility and regulatory uncertainties. Bitcoin's price movements can be dramatic and unpredictable, influenced by a range of factors from technological developments to geopolitical events. Additionally, the regulatory environment for cryptocurrencies is still evolving, with potential changes posing risks to Bitcoin's accessibility and value. Investors must also consider the broader global economic context, including actions by other central banks and international trade dynamics, which can impact Bitcoin's market movement. **Conclusion** The Federal Reserve's shift towards a more accommodative monetary policy in 2024 presents a fascinating scenario for Bitcoin and the broader cryptocurrency market. This development underscores the increasing relevance of digital assets in the global financial landscape and highlights the complex interplay between traditional monetary policies and emerging financial technologies. As Bitcoin continues to evolve and gain acceptance, its response to macroeconomic factors like central bank policies will be a critical area of focus for investors. In navigating this dynamic and uncertain environment, a cautious and well-informed approach is essential for those looking to explore the opportunities and navigate the challenges of cryptocurrency investments. The coming years promise to be a pivotal period in the maturation of Bitcoin as it responds to the shifting tides of global finance. **FAQs** **How does the Federal Reserve's easing stance impact Bitcoin?** The Fed's shift towards lower interest rates can make riskier assets like Bitcoin more attractive to investors. This is because lower rates often lead to reduced yields on traditional investments, prompting investors to seek higher returns elsewhere. **What is the significance of the Fed's 'dot plot' for Bitcoin investors?** The 'dot plot' is a projection of interest rate movements by Federal Reserve members. A shift towards lower rates, as indicated in the recent dot plot, can signal a more accommodative monetary policy, potentially impacting Bitcoin's market as investors adjust their portfolios. **Can Bitcoin be considered a safe haven asset in light of the Fed's policy?** Bitcoin's role as a safe haven asset is debated. While its fixed supply and digital nature offer some safe haven characteristics, its volatility and regulatory uncertainties make it a complex choice compared to traditional safe havens like gold. **What risks should Bitcoin investors consider in the context of the Fed's easing policy?** Investors should be aware of Bitcoin's volatility, regulatory changes, and its sensitivity to macroeconomic factors. Additionally, global economic conditions and actions by other central banks can also influence Bitcoin's market. **How does the economic backdrop influence Bitcoin's response to the Fed's policy?** Economic factors like GDP growth, inflation rates, and retail sales impact investor sentiment and risk appetite, which in turn can affect Bitcoin's market. A strong economy might reduce the appeal of risk assets like Bitcoin, while economic uncertainties can increase their attractiveness. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: @croxroadnews.co** **Instagram: @croxroadnews.co** **Youtube: @croxroadnews** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***