-

@ a012dc82:6458a70d
2025-02-22 15:51:37
Bitcoin, the pioneering cryptocurrency, has always been known for its volatility. This digital asset has seen dramatic fluctuations in price, attracting investors and speculators alike. Understanding these price movements is crucial for anyone involved in the crypto market. The journey of Bitcoin from a niche digital token to a mainstream financial asset has been marked by periods of rapid growth and sudden declines. This volatility is not just a source of risk, but also of potential opportunity for traders and investors. The factors driving these fluctuations range from regulatory news, technological advancements, to broader economic factors. Bitcoin's decentralized nature adds to its unpredictability, as it operates independently of a central bank or government.
**Table of Contents**
- The Recent Price Rally and Subsequent Halt
- Insights from CryptoQuant's Analysis
- The Role of Short-Term Holders
- Understanding Bitcoin Binary Coin Days Destroyed ( …
- The Dynamics of Profit-Taking
- Actions by Miners and Whales
- Current Market Scenario and Future Outlook
- Conclusion
- FAQs
**The Recent Price Rally and Subsequent Halt**
In a recent surge, Bitcoin's value soared past the $44,000 mark, only to encounter a significant resistance level near $45,000. This resistance led to a notable decline in its price. The question on everyone's mind is: what caused this sudden halt in Bitcoin's otherwise steady climb? This rally, like many in Bitcoin's past, was driven by a mix of investor optimism, favorable market conditions, and increasing institutional interest in cryptocurrency. However, the resistance at $45,000 proved to be a turning point, sparking a wave of sell-offs and profit-taking. This price behavior is a classic example of the market's psychological dynamics, where key resistance levels can lead to significant shifts in investor behavior. The rapid change from a bullish to a bearish market sentiment at this juncture underscores the fragile and speculative nature of the cryptocurrency market.
**Insights from CryptoQuant's Analysis**
CryptoQuant, a renowned market analytics platform, offers valuable insights into this phenomenon. An analyst from CryptoQuant, Yonsei, conducted a detailed analysis of on-chain data to unravel the mystery behind Bitcoin's recent price behavior. This analysis goes beyond surface-level market trends, delving into the intricate movements of Bitcoin across various wallets and exchanges. By examining metrics such as fund flows, wallet activities, and transaction patterns, CryptoQuant provides a more nuanced understanding of what drives Bitcoin's price changes. Yonsei's analysis, in particular, sheds light on the behavior of different investor cohorts, revealing how their actions collectively impact the market. This kind of deep-dive analysis is essential for anyone looking to understand the often opaque mechanisms of cryptocurrency markets.
**The Role of Short-Term Holders**
The analysis revealed that short-term holders, particularly those who had invested in Bitcoin for a period ranging from 6 to 18 months, started to realize their profits as soon as Bitcoin broke through the $40,000 resistance level. This profit-taking was a primary factor in the subsequent price retraction. These short-term holders, often more sensitive to market fluctuations, tend to react quickly to price changes, looking to capitalize on short-term gains. Their collective actions can create significant market movements, as seen in this instance. The behavior of these investors is often influenced by news events, market sentiment, and technical indicators. In this case, the rapid rise in Bitcoin's price likely triggered a psychological response to lock in profits, leading to a cascade of sell orders. Understanding the motivations and behaviors of these short-term holders is crucial for predicting short-term market movements in the volatile world of cryptocurrency.
**Understanding Bitcoin Binary Coin Days Destroyed (CDD)**
A critical metric in this analysis is the Bitcoin Binary Coin Days Destroyed (CDD). This metric assesses the movement of long-held Bitcoins, providing insights into the behavior of long-term investors. An increase in Binary CDD indicates that a significant amount of Bitcoin, held dormant for a long time, has been mobilized, suggesting a sell-off by long-term holders. This metric is particularly important as it highlights the actions of the most steadfast part of the market - those who have held Bitcoin through various cycles. When these long-term holders start moving their coins, it often signals a significant shift in market sentiment. The CDD metric thus serves as a barometer for the conviction of Bitcoin's long-term investor base. A high CDD can indicate a loss of confidence among these investors, or a belief that the market has reached a peak. Conversely, a low CDD suggests that long-term holders are not yet ready to sell, indicating continued confidence in the market's future.
**The Dynamics of Profit-Taking**
The CryptoQuant analysis further highlighted that a majority of Bitcoin holders were in profit, with the Spent Output Profit Ratio remaining above one. This indicated that about 90% of Bitcoin holders were profiting, which naturally led to a trend of profit-taking. This phenomenon is a key aspect of market cycles in cryptocurrencies. When a large portion of investors are in profit, especially after a significant price rally, the market often sees a wave of selling as investors look to cash in on their gains. This behavior is compounded by psychological factors, such as fear of missing out (FOMO) and fear, uncertainty, and doubt (FUD), which can lead to rapid shifts in market sentiment. Additionally, the profit-taking trend is influenced by external factors such as global economic conditions, regulatory news, and technological developments within the blockchain space. These factors can either reinforce the confidence of investors, leading to a hold strategy, or trigger a sell-off in anticipation of a market downturn.
**Actions by Miners and Whales**
Another interesting aspect of the analysis was the behavior of Bitcoin miners and whales (large-scale holders). These groups also contributed to the selling pressure. Miners, in particular, sold their assets at high-profit margins when Bitcoin reached its peak, adding to the downward pressure on its price. The actions of miners are crucial to understanding Bitcoin's market dynamics, as they are not only investors but also the producers of new Bitcoins. Their decision to sell or hold can significantly impact the supply of Bitcoin in the market. Whales, or large-scale holders, have a similar impact due to the sheer volume of their transactions. Their trades can lead to substantial market movements, creating waves that affect smaller investors. The behavior of these whales often reflects a more strategic approach to the market, influenced by long-term trends and broader market analysis. Their actions can serve as indicators for future market movements, making their behavior a key focus for analysts and investors alike.
**Current Market Scenario and Future Outlook**
Despite the recent price drop, the overall market sentiment remains positive. The bear market seems to be in the past, and liquidity conditions in the crypto market are improving. However, Bitcoin currently hovers around the $41,000 mark, a slight decrease from its recent high. This current state reflects the ever-changing nature of the cryptocurrency market, where investor sentiment can shift rapidly. The future outlook for Bitcoin remains a topic of much debate among experts. Some predict continued growth as institutional adoption increases and blockchain technology becomes more integrated into mainstream finance. Others caution about potential regulatory clampdowns and the volatile nature of the market. What remains clear is that Bitcoin continues to be a key player in the financial world, with its price movements being a barometer for the health and sentiment of the broader cryptocurrency market.
**Conclusion**
Bitcoin's market behavior, as analyzed by CryptoQuant, offers a complex picture of various factors at play. The interplay between short-term and long-term holders, the strategic moves of miners and whales, and the overall market sentiment all contribute to the price dynamics of this digital currency. Understanding these elements is key for investors and enthusiasts who wish to navigate the volatile waters of Bitcoin's market. As the crypto landscape continues to evolve, keeping a close eye on these trends and analyses will be crucial for making informed decisions in the world of cryptocurrency. The insights provided by platforms like CryptoQuant are invaluable in this regard, offering a deeper understanding of the market forces at work.
**FAQs**
**What caused the recent halt in Bitcoin's price rally?**
The halt in Bitcoin's price rally, after reaching near $45,000, was primarily due to profit-taking by short-term holders and investors who had held Bitcoin for 6-18 months, as revealed by CryptoQuant's analysis.
**What is Bitcoin Binary Coin Days Destroyed (CDD)?**
Bitcoin Binary Coin Days Destroyed (CDD) is a metric that measures the movement of long-held Bitcoins. It indicates the amount of Bitcoin, held dormant for a long time, that has been mobilized or sold.
**How do miners and whales influence Bitcoin's price?**
Miners and whales (large-scale holders) significantly influence Bitcoin's price through their actions. When they sell their holdings, especially during peak prices, they add to the market's selling pressure, potentially leading to price drops.
**What does a high Bitcoin Binary CDD indicate?**
A high Bitcoin Binary CDD suggests that a large amount of long-held Bitcoin is being sold, which can be a sign of long-term holders losing confidence or deciding to take profits.
**Is the current market sentiment for Bitcoin positive or negative?**
Despite recent price fluctuations, the overall market sentiment for Bitcoin remains cautiously positive, with improvements in market liquidity and interest from institutional investors.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnews.co](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
-

@ df478568:2a951e67
2025-02-22 14:53:58
I shop the bitcoin circular economy as much as I can. Maybe "shop" isn't the best way to describe it. Shopping is a behavior typical of fiat maxis. they drive fancy leases and shop 'till they drop. This season's fashion must-have is next season's trash. Bitcoiners don't shop, we replenish supplies. Our goal is to get the best value for our sats. Our goal to hodl our sats as long as possible.
Yesterday, I shoveled a [ton of compost](nostr:nevent1qvzqqqqqqypzph68s45y080zdd9g8sdacnd6kcd4ejpwrgcju2eghjq45y4f28n8qqs24rrm3u2wvf24ad8xkj2xh8nuq2lz7urnd3lzrpqlstmsp4r29hsug39jw) for my garden. If taking showers mean's I', short bitcoin, so be it. I also happened to get my soap from Soapminer delivered to my P.O. Box the day before. What better way is there to test this soap than after shoveling some shit? It was perfect timing.
## Soapminer Sells Soap Made From Beef Tallow
Soapminer is a nostr rounder I've seen online every timestamp in a while. As the name suggests, he makes soap and sells it for sats. He's not the only soap seller on nostr, but something stands out about this soap. He uses beef tallow, the stuff McDonald's used for french fries back in the day. I use it to cook. It's basically beef lard.
So this pleb makes soap and markets it to people who talk about beef and bitcoin. That's better than Fight Club. Then [I heard Matt Odell say it was pretty good](https://fountain.fm/clip/6GHDdmcwMg47mz0xNpVb). I already thought about spending sats on this soap, but now I had a testimonial from a man I have listened to for about six years. **Can you say Web of Trust baby?**
I no soap and suds expert. I have years of soapo sing experience, but I never thought about what commercial soap is made with. I assumed it was like Fight Club like how I assumed the dollar was backed by gold in high school. Both these statements are false. Fiat soap is made with fiat fuckery. I tried looking for the ingredients on a box of Dove Men's Care, but couldn't find them on the box. It's opaque like the amount of gold at Fort Knox, nobody knows. I know what Soapminer uses to make his soap because [it's open source](nostr:note1aypyepc6g7lztutegx0fw5yg5clc9ythvxkp6czfkau3dcgwz06q4mfqr3).
### Tallow Soap Quotes

I asked Soapminer a few questions on nostr. [Here is is answer]((nostr:note1wma3745zywf6avfwrau9dvrt6awqqmt3qkfc07xxff4p6nh8f38qyxuqze "nostr:note1wma3745zywf6avfwrau9dvrt6awqqmt3qkfc07xxff4p6nh8f38qyxuqze)
), signed by his own nostr key, the Internet's version of "I approve this message."

**Soapminer:**
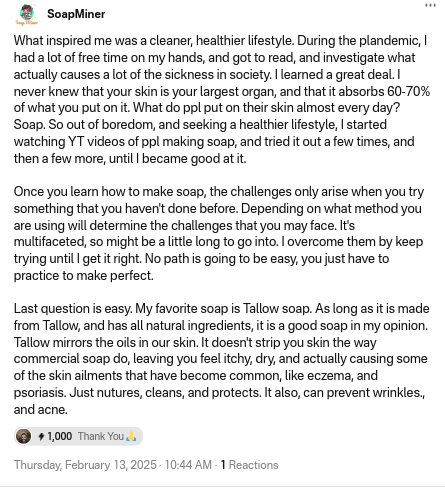
`What inspired me was a cleaner, healthier lifestyle. During the plandemic, I had a lot of free time on my hands, and got to read, and investigate what actually causes a lot of the sickness in society. I learned a great deal. I never knew that your skin is your largest organ, and that it absorbs 60-70% of what you put on it. What do ppl put on their skin almost every day? Soap. So out of boredom, and seeking a healthier lifestyle, I started watching YT videos of ppl making soap, and tried it out a few times, and then a few more, until I became good at it.
Once you learn how to make soap, the challenges only arise when you try something that you haven't done before. Depending on what method you are using will determine the challenges that you may face. It's multifaceted, so might be a little long to go into. I overcome them by keep trying until I get it right. No path is going to be easy, you just have to practice to make perfect.
Last question is easy. My favorite soap is Tallow soap. As long as it is made from Tallow, and has all natural ingredients, it is a good soap in my opinion. Tallow mirrors the oils in our skin. It doesn't strip you skin the way commercial soap do, leaving you feel itchy, dry, and actually causing some of the skin ailments that have become common, like eczema, and psoriasis. Just nutures, cleans, and protects. It also, can prevent wrinkles., and acne.`
**Sold!**

I tried the pine tar first. It makes me smell like a man, at least my wife thinks so. That's also why she prefers the unscented. He is adding more scents, but these ate the one's I have tried.
The soap makes me feel rubber-ducky squeaky clean. After my shower, made some lunch and washed my hands with Dawn. This made my hands ashier than bio-char. I decided to cut some soap and place a little piece by the kitchen sink. The soap moisturized my hands in two shakes of a bull's tail. I also cut up some of my soap into smaller pieces because I'm as frugal as a Boy-scout and wanted to wash my hands with this stuff instead of Ivory.

#### Here's some more quotes about Soapminer's soap.
- [He's asking his market if they want Peppermint soap.](nostr:note1tpeh65m7y6s6wt9ucjdcl2pge3m86f2ny4hqjdyvcrmf7kglqshqfeceam "nostr:note1tpeh65m7y6s6wt9ucjdcl2pge3m86f2ny4hqjdyvcrmf7kglqshqfeceam)
- [Then he made the soap like a boss](nostr:nevent1qvzqqqqqqypzqy9kvcxtqa2tlwyjv4r46ancxk00ghk9yaudzsnp697s60942p7lqqs0yqyvffu9pn39grtxa8agpftpvfssx603w0ra67kpn5qn360masquhrtd7).
- [The Benefits of Tallow](nostr:nevent1qqs9w6g8khrqzhrgu7y3trae9vtdl8847p42p80aqzvsvlu9kr84vkgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsyg8zenmu7gzq8ulj5jj4kv50ph3muwz43f747vmr9ld2alrjdswgavpsgqqqqqqsq5lkzq)
- [He uses Zaprite](nostr:nevent1qvzqqqqqqypzqjln5vfhstwf2ahjrmanh57kzwrap4v3xpfzql5sxp48gxlk4a74qqsraadvah6890x4hgvr4rcxe9c2n79a0kx88te3hf7x88j72rh7cuskhempa)
[He has giveaways](nostr:nevent1qvzqqqqqqyqzpzvke2t7fxwh0rzea5zmx7qnddzgsqk35ujp9tgpw9jmjsmnserr3z8466)
[He wants everyone to live on a bitcoin standard](nostr:nevent1qvzqqqqqqypzqy9kvcxtqa2tlwyjv4r46ancxk00ghk9yaudzsnp697s60942p7lqqs8gnddcnkj5p2047qam5drgw5jxlg60vy736e2rwxsmj593whnllsy8ej9j)

### Testimonials
[nostr:note1y9wsl07lkepfzzj8c8ucekss9f9darvg70j93cdmvttadfjx9nfsvtxwes "nostr:note1y9wsl07lkepfzzj8c8ucekss9f9darvg70j93cdmvttadfjx9nfsvtxwes")
**TheLOTSProject**
nostr:nevent1qvzqqqqqqypzqy9kvcxtqa2tlwyjv4r46ancxk00ghk9yaudzsnp697s60942p7lqqsxt8kyd650ph3wvhre0lwlw5s0emuv5gcfzmsvfxf7czgg4c2wynq7vg8ga
**Tuvok**

["he even shipped to my in germany(but only after negotiation) i like the soap a lot after some testing"](nostr:nevent1qvzqqqqqqypzqpt4hupuycwpj5yqjn00989fgwj6k9yvfamvx7v2gkamz9329wreqywhwumn8ghj7mr4de3kscn00qh8xctwv3mkjcmg9enxzund9uqsuamnwvaz7tmwdaejumr0dshsqgr3cj8s3sc2ruzz2yj4e3kxnc825elr2gmyufdv38d9ee4jm8lxx5n7yrdv)
**Bit 🐳 Ish**
["It's good stuff, you'll love it."](nostr:nevent1qvzqqqqqqypzpr38l76unwuvm5qnrt0xa7jf64k5qx65ynvlm7dx8cr565nmqu2uqqs2r7rcp2rssfcqhk5838cuu569h43wlkvw34gy8ad2flgdpl0cezckxghkc)
**GhostBTC**
nostr:npub1cm3v486tkgy6qjtk09srry4qvc40y0jysyqha5e3v67whnc22jwsrreyud
**cryptoshi2k21.bitcoin**
["Great soap 🧼🫧"](nostr:nevent1qvzqqqqqqypzqj5nelekm4aruughza09y8yy26ansshnc23wq2kdha79dqz8rhemqqsxdq4xf69vgk27nnes4syrnekpg4mhkp6v4rer7nzdgfht8kya8ssucu8lz)
**Marc**

["I spent the last two days shyoveling horse shit and compost for my garden. This soap made me feel rubber-ducky squeeky clean afterward."](nostr:nevent1qvzqqqqqqypzph68s45y080zdd9g8sdacnd6kcd4ejpwrgcju2eghjq45y4f28n8qqsfvqylk56zdh5n3ykhleypr5zznevqt9dw04vptdeuh9jmskemndgq0hw25)
##### Conclusion
I am a soap mining soap customer now. I'm done with fiat soap. I'm thinking about handing out his soap for Christmas gifts. Odell was right. It is good soap. It's expensive compared to the comercial crap, but competitive with fancy olive oil soaps I've seen. I paid with fiat I had in Strike, but Soapminer received bitcoin. I was going to buy soap anyway, but buying soap this way took $35 of fiat off Strike and put it into soap miners strategic bitcoin reserve. It's not cheap, but buying Dove requires me to first buy fiat. Buying soap from Soapminer takes sats off the exchange. Buying Dove does not, but that's not the only reason I bought this soap. It's great soap, but that's not really why I bought it. I am a big believer in what Adam Smith described as the invisible hand: [nostr:note1jsgzk6rxulyqthae8c53rrawaa70yjqh37nm3kxh08xw8g43vgcq3kux9d "nostr:note1jsgzk6rxulyqthae8c53rrawaa70yjqh37nm3kxh08xw8g43vgcq3kux9d"). We want to see people in our community to prosper. It is in our self-interest That is what Smith means by the invisible hand. The invisible hand is not A Central Bank manipulating interest rates and The IMF turning foreigners into debt-fiat slaves for cheap freshly-frozen shrimp.
Bitcoiners are my community. They may not be close to me by proximity, but my moral sentiments guide me to do business with bitcoiners whenever possible. See, capitalism cannot work with socialist money. Those moral sentiments change when people work for soft money. Fiat soap miners get paid in NGD currency. Sell soap for $35 today and that will buy you half as much stuff in 5 years. The fiat soap miner has no savings to improve his community. Inflation makes him search for the cheapest soap just to keep up with grocery prices.
Soapminer can save his sats earned selling soap without anyone stealig from him. Therefore, he will be able to afford to buy stuff in his community. Those on a fiat standard cannot afford to save their money in the hopes of buying high quality products and services in their community. Fiat is socialist money, therefore only buys less and less as time goes on. Dear readers, we are not on late stage capitalism. The problem is that socialist money sucks. Those Papi Trump bucks might be fun for a month, but in the end, everyone pays the Piper. Tariffs are a sales tax, [paywalls in meatspace](nostr:nevent1qvzqqqqqqypzph68s45y080zdd9g8sdacnd6kcd4ejpwrgcju2eghjq45y4f28n8qyt8wumn8ghj7mn0wd68yetvd96x2uewdaexwtcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qg4waehxw309ajxjar5duh8qatz9aex2mrp0yqzqx3u59js9ewy9xwr7nuzv5eytj9ty979wrc7vrhv3tfykjxp5pd28s750n). Save your sats long enough, and these taxes will not matter. We circumvent the unjust tax of inflation, we will find solutions to unjust taxes levied on our community.
I participate in the bitcoin circular economy because I want to bring capitalism back. I do not care where you live. If you are a bitcoiner, you are part of my community. There is an invisible hand which compels me to buy stuff from people in my community. That's why I bought soap from Soapminer, but you know what? **the soap is pretty damn good**.
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
[884,864](https://mempool.marc26z.com/block/000000000000000000014855f89d29f5d7953945251ee87bf069b90d9e6d9f85)
[Merch](https://marc26z.com/merch)
-

@ 1739d937:3e3136ef
2025-02-22 14:51:17
We've been busy. In my last update, I shared that I was sure MLS on Nostr was going to work and shared an early demo of the app. What a long time ago that seems now.
The big news is that White Noise is no longer just a demo. It's a real app. You can [download the alpha release](https://github.com/erskingardner/whitenoise/releases) and run it for yourself on MacOS, Linux, or Android. iOS TestFlight is coming soon. Keep in mind that it's still very much alpha software; a lot is changing and I wouldn't recommend using it for anything serious quite yet.
We've been busy. In my last update, I shared that I was sure MLS on Nostr was going to work and shared an early demo of the app. What a long time ago that seems now.
## Vision
Before we get to the detailed project updates, I wanted to share a bit of my vision for White Noise.
More and more; freedom of speech, freedom of association, and privacy are under attack. Just this week, Apple was forced to remove their iCloud advanced encryption feature for all UK citizens because the UK government demanded that Apple build a backdoor to allow access to customer data. The EU continues to push "Chat Control" legislation that would force companies to remove end-to-end encryption from their platforms. And governments across the world are enforcing draconian "hate speech" laws that criminalize speech that offends or upsets.
The freedom to express ourselves and discuss difficult topics is a critical precondition for maintaining a healthy society. Without the ability to assert ideas and argue their merits vigorously we have no way of making progress or creating a civil society based on shared values and goals. Ironically, the very laws and regulations that many western governments are enforcing to "protect" us are eroding and destroying the most free and innovative societies in history.
White Noise is to built to protect our freedom to gather, to express ourselves, and to discuss difficult topics. It's free and open source; anyone can fork the code and we'll never charge money to use it. It runs on a free and open source protocol; your identity and social graph is yours to own and control. You don't have to trust us with your data, everything is end-to-end encrypted and metadata is next to non-existent. We don't even run any servers, so government data requests will forever fall on deaf ears.
We want to build the fastest, most secure and private, and the most usable messenger in the world. Whether you want to use it to plan a family BBQ or overthrow a tyrant, White Noise should give you the tools you need to make it happen.
If you find this compelling and want to help, please consider contributing to the project or donating.
## Progress
Alright, let's talk about where we're at with the project.
### Current functionality
- Multiple accounts. You can login, or create, many different Nostr accounts in the app.
- Search your nostr contact list, search for users you don't follow, or add contacts using an npub or hex public key.
- Create DM groups. Right now, you can only create chats with a single other user. Under the hood, these DMs are actually groups, I just haven't added the UI for adding/removing users and managing the group.
- Send messages, reply to messages, and add reactions. As you would expect from a messenging app.
- View group information.
- Settings that allows you to manage your accounts, relays, and other app settings.
### Upcoming
- An amazing hackathon group from [Bitcoin++ in Brasil](https://btcplusplus.dev/conf/floripa) has recently [added NWC](https://github.com/erskingardner/whitenoise/pull/89) (nostr wallet connect) support to the app. Paste lightning invoices into chats and they'll become QR codes that you can scan or pay them with a single click in the conversation! This will be in the next release.
- Add support for encrypted media in chats using [Blossom](https://github.com/hzrd149/blossom/tree/master). We'll start with images, but plan to add video, audio messages, and documents soon.
- Groups with more than two users. We'll add the ability to add/remove users and manage the group. This will also include some upgrades to further improve the forward secrecy of group chats.
- iOS TestFlight. Gated app stores suck. We'll get White Noise on iOS into TestFlight as soon as possible.
## Links
- [The repo](https://github.com/erskingardner/whitenoise)
- [Releases](https://github.com/erskingardner/whitenoise/releases)
- [Previous updates](https://highlighter.com/jeffg.fyi)
-

@ 2e8970de:63345c7a
2025-02-22 14:41:31
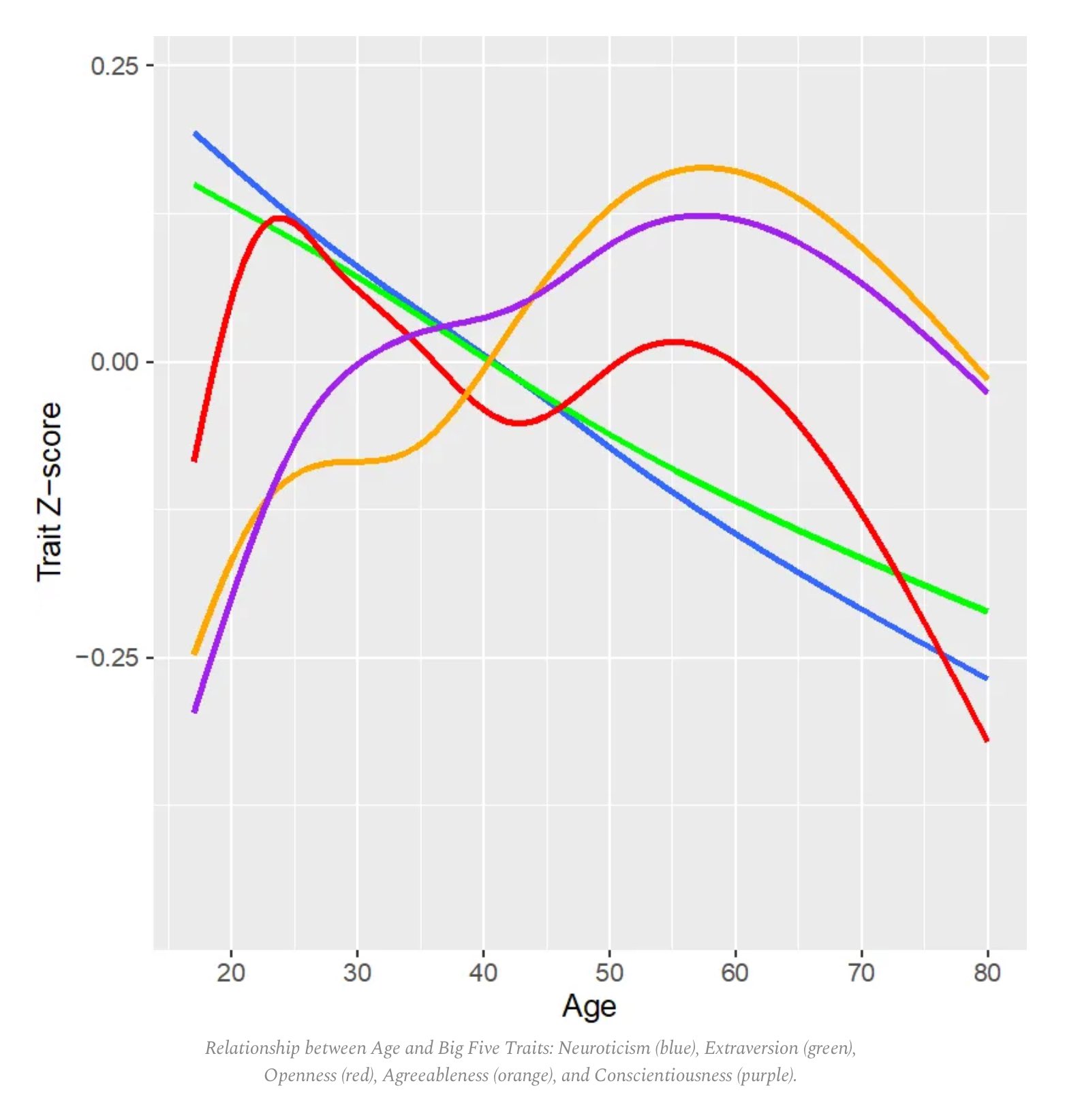
-Blue: Neuroticism
-Green: Extraversion
-Red: Openness to experience
-Orange: Agreeableness
-Purple: Conscientiousness
[sourcs(https://www.stevestewartwilliams.com/p/are-there-age-and-sex-differences)]
originally posted at https://stacker.news/items/893992
-

@ ac6f9572:8a6853dd
2025-02-22 13:01:56
# The old world crumbles. The sovereign rises.

Join #Bitshala at #BitPlebs Summit in Goa — a gathering of builders, creators, educators, and hodlers forging #India’s #Bitcoin future.
Open forums. Un-conference style talks. By @bitshala & @plebstogether
RSVP now: https://lu.ma/cd55r5d4
X: https://x.com/bitshala_org/status/1893252853709365684?s=09
originally posted at https://stacker.news/items/893899
-

@ c384de42:493922aa
2025-02-22 12:27:08
I've had a weird thought.
Relating to bitcoin and maths and gambling.
I understand none of the above, but found some weird convoluted logic in the fact that 52 cards in a deck and two six faced dice equate to 12 faces, idk.. I lost track of the logical steps in my mind, it may have been a delusion..
But the conclusion, of whatever it was is, kill myself at some point with end result living forever in samsara, or choose the natural progression of life into death, if there is such a thing...
Weird..
It had something to do with gambling and drugs and addiction, like the plug-in drugs in the Ringworld novels by Larry Niven, or the simulation machines in the Paul Verhoeven film, Total Recall, with Arnold Schwarzenegger.
Strange thoughts...
-

@ e5de992e:4a95ef85
2025-02-22 12:19:25
A trading log isn't just a record of past trades—it's a tool for learning, improving, and achieving consistency. By keeping a detailed log, you gain insights into your decision-making process, identify patterns, and refine your strategy over time.
Here's why and how to maintain a comprehensive trading log effectively.
---
## 1. The Importance of a Trading Log
- **Track Performance Objectively**
Without a log, it's easy to misremember trades or overestimate success. A detailed log provides accurate data to analyze your progress.
- **Understand Your Strengths and Weaknesses**
By reviewing your log, you can identify what works well and where you need improvement. Patterns in losing trades often highlight common mistakes or emotional triggers.
- **Build Confidence and Trust in Your System**
Seeing a record of rule-based, consistent trades reinforces trust in your strategy. Reviewing past successes can boost morale during challenging periods.
---
## 2. What to Include in Your Trading Log
A detailed trading log should cover both objective data and subjective reflections.
### Objective Data
- **Date and Time:** When the trade was entered and exited.
- **Instrument Traded:** Stock, forex pair, crypto, etc.
- **Entry and Exit Prices:** Precise levels where you opened and closed the trade.
- **Position Size:** Number of shares, contracts, or units traded.
- **Stop Loss and Take Profit Levels:** Risk management details.
- **P/L (Profit or Loss):** Outcome of the trade in dollars or percentage terms.
- **Trade Type:** Long, short, scalping, swing, etc.
### Subjective Reflections
- **Reason for Entering the Trade:** What setup or signal prompted the trade?
- **Emotional State:** How did you feel before, during, and after the trade?
- **Execution Notes:** Did you follow your plan? If not, why?
- **Lessons Learned:** What can you take away from this trade to improve next time?
> **Key Insight:** Both data and reflection are essential for meaningful analysis.
---
## 3. How to Analyze Your Trading Log
1. **Identify Patterns**
Look for common themes in your winning and losing trades.
_Examples:_ Winning trades often align with specific setups, while losing trades frequently result from breaking rules or impulsive decisions.
2. **Evaluate Strategy Effectiveness**
Assess whether your system produces consistent results over time.
Use metrics like win rate, risk-reward ratio, and drawdown to evaluate performance.
3. **Address Emotional Triggers**
Reflect on emotional notes to understand what triggers fear, greed, or hesitation.
Develop strategies to manage emotions based on these insights.
---
## 4. Benefits of Keeping a Trading Log
- **Improved Discipline:**
Writing down each trade reinforces the habit of sticking to your plan.
- **Informed Adjustments:**
Logs provide data-driven insights to refine your strategy.
- **Emotional Control:**
Journaling emotions helps you recognize and address psychological pitfalls.
- **Long-Term Growth:**
By tracking your progress, you can measure improvement over months and years.
> **Key Insight:** A trading log turns mistakes into lessons and successes into repeatable actions.
---
## 5. Tools for Logging Trades
### Manual Logs
- Use a notebook or spreadsheet to record trades.
- **Pros:** Highly customizable, forces you to engage deeply with each entry.
- **Cons:** Time-intensive and less automated.
### Software and Platforms
- Tools like Edgewonk, TraderSync, or Tradervue can streamline the process.
- **Pros:** Automated data collection, advanced analytics, and performance tracking.
- **Cons:** May have a learning curve or subscription costs.
> **Key Insight:** Choose a method that aligns with your workflow and trading style.
---
## 6. Tips for Maintaining a Consistent Trading Log
- **Log Every Trade:**
Don't skip trades, even the ones you'd rather forget. They're often the most valuable for learning.
- **Be Honest:**
Record trades exactly as they happened, including mistakes and rule-breaking.
- **Review Regularly:**
Set aside time weekly or monthly to analyze your log and adjust your approach.
- **Stay Disciplined:**
Treat logging as an essential part of your trading routine.
---
## 7. Conclusion: Your Trading Log is Your Mirror
A detailed trading log is more than just a record—it's a roadmap to success. It provides clarity, accountability, and insights that are essential for continuous improvement.
Start today. Keep a detailed log, review it often, and use it to refine both your strategy and your mindset. Your future self will thank you.
-

@ da0b9bc3:4e30a4a9
2025-02-22 10:55:44
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/893831
-

@ 6734e11d:c7e34e8f
2025-02-22 09:16:15
...damit wir weiter recht haben und so weitermachen können wie bisher, die verordnete Omertà eingehalten wird zu Grundrechten, Notverordnungen, Pandemiesimulationen, Energieversorgung, Deindustrialisierung, kalte und echte Enteigung, Umverteilung, Freiluft- und Digitalgefängnis, Blockwartnachbarn...
Alles andere wäre äußerst unangenehm, wie das Aufplatzen einer großen Eiterblase und müsste dann wieder mit Exekutive, Justiz, Notverordnungen, neuen Strafrechtsparagraphen, Verschärfung der Strafprozessordnung, echte Änderung des Grundgesetzes, Überwachung, Totalzensur, Parteiverboten, Regimechanges und Krieg unterbunden werden.
Idee und Meme sind wieder von der Schwurbel Oase
<https://t.me/schwurbel_oase/2318>
-

@ 6389be64:ef439d32
2025-02-22 09:12:02
2024-05-28 at 14:05
Tags:
# Soil Carbon Oxidation Under Tillage
When soil is turned over (by tilling or plow) it exposes carbon to oxygen and that carbon burns off as CO2.
You are burning the carbon out of the soil.
---
# References
[[Shepard-Lappe-Restoration Agriculture]]
# Core Notes
[[Soil Erosion]]
# Location
[991](kindle://book?action=open&asin=B00IYUAMSI&location=991)
-

@ 2fb77d26:c47a6ee1
2025-02-22 09:04:25
Der 1953 geborene [Craig Reynolds](https://de.wikipedia.org/wiki/Craig_Reynolds) ist Experte für künstliches Leben und Computergrafik. In dieser Funktion arbeitete er unter anderem an Filmen wie Tron (1982) und Batman (1992). Bei »*Sony Computer Entertainment America*« (heute [SIE](https://de.wikipedia.org/wiki/Sony_Interactive_Entertainment)) entwickelte er die [OpenSteer](https://opensteer.sourceforge.net/)-Bibliothek, die der Abbildung von Schwarmverhalten in Spielen und Animationsanwendungen dient. An solch prestigeträchtige Aufträge kam Reynolds, weil er sich nebst Computergrafik intensiv mit Theorien zum »*Steuerungsverhalten für autonome Charaktere*« befasst hatte. Mit Schwarmverhalten. Einem Thema, das mit wachsender Rechenleistung immer wichtiger für die Entwicklung von Computerspielen wurde.
Die sollten dem Spieler das Gefühl geben, sich in einer realen Welt mit »*autonomen Charakteren*« zu bewegen. Dazu mussten diese vom Computer, beziehungsweise der Software gesteuerten Charaktere – im Fachjargon »*[Agenten](https://de.wikipedia.org/wiki/Software-Agent)*« genannt – sich irgendwie verhalten. Und zwar ohne, dass von außen ein weiterer Steuerungseingriff erfolgt. Eigendynamisch. Dafür bedarf es Regeln, die im Programmcode eingebettet werden können. Genau die lieferte Reynolds 1986 im Rahmen der von ihm modellierten [Boids-Simulation](https://www.red3d.com/cwr/boids/), die besagt, dass Schwarmverhalten auf drei simplen Regeln basiert:
1. Bewege dich in Richtung des Mittelpunkts derer, die du in deinem Umfeld siehst.
2. Entferne dich, sobald dir jemand zu nahe kommt.
3. Bewege dich etwa in die gleiche Richtung wie deine Nachbarn.
Sprich: Kohäsion, Separation und Orientierung. In Reynolds’ Beschreibung des Boid-Modells liest man diesbezüglich:
»*1986 habe ich ein Computermodell koordinierter Tierbewegungen *(…) *erstellt. Es basierte auf dreidimensionaler Computergeometrie, wie sie normalerweise in der Computeranimation oder im computergestützten Design verwendet wird. Ich habe die generischen, simulierten Schwarmtiere Boids genannt. Das grundlegende Schwarmmodell besteht aus drei einfachen Lenkverhalten, die beschreiben, wie ein einzelner Boid auf der Grundlage der Positionen und Geschwindigkeiten seiner Schwarmgenossen in der Nähe manövriert. Jeder Boid hat direkten Zugriff auf die geometrische Beschreibung der gesamten Szene, aber das Schwarmverhalten erfordert, dass er nur auf Schwarmgenossen in einer bestimmten kleinen Nachbarschaft um sich herum reagiert. *(…)* Schwarmgenossen außerhalb dieser lokalen Nachbarschaft werden ignoriert.*
*Die Nachbarschaft könnte als Modell eingeschränkter Wahrnehmung betrachtet werden (wie bei Fischen in trübem Wasser), aber es ist wahrscheinlich korrekter, sie als Definition des Bereichs zu betrachten, in dem Schwarmgenossen die Lenkung eines Boids beeinflussen. In den ersten Experimenten wurde ein etwas ausgefeilteres Verhaltensmodell verwendet. Es umfasste vorausschauende Hindernisvermeidung und Zielsuche. *(…)* Für Anwendungen in der Computeranimation führte ein Zielsuchverhalten mit niedriger Priorität dazu, dass die Herde einem vorgegebenen Pfad folgte*.«
Wer sich bei dieser Beschreibung an die Strukturen postmoderner Gesellschaft erinnert fühlt und »*Agenten*« mit »*[Agent Smith](https://en.wikipedia.org/wiki/Agent_Smith)*« aus den Matrix-Filmen assoziiert, liegt nicht ganz falsch. Denn Kohäsion, Separation und Orientierung definieren nicht mehr nur das Schwarmverhalten autonomer Charaktere in Computerspielen, sondern auch die Dynamiken des gesellschaftlichen Zusammenlebens im multimedialen Panoptikum der Postmoderne.
**So nimmt es kaum Wunder, dass ein vom** **[US Air Force Laboratory](https://www.afrl.af.mil/)** **(AFRL) finanziertes** **[Forschungsprojekt](https://arxiv.org/pdf/1402.5644)** **an der University of Florida (Gainesville, USA) bereits im Jahr 2014 untersuchte, »*wie Social Media eingesetzt werden kann, um Menschen wie Drohnen zu steuern*«.**
Unter diesem Titel berichtete denn auch [Ars Technica](https://arstechnica.com/information-technology/2014/07/air-force-research-how-to-use-social-media-to-control-people-like-drones/) am 17. Juli 2014, dass der Forschungsleiter der AFRL-Studie, [Warren Dixon](https://ncr.mae.ufl.edu/index.php?id=people), seines Zeichens Chef des Lehrstuhls für nichtlineare Steuerung und Robotik an der University of Florida, vor allem daran arbeite, »*wie man ein Netzwerk, wenn man es einmal identifiziert hat, in Richtung eines Ziels manipulieren kann*«. Und mit »*Netzwerk*« meint Dixon nicht Computer, sondern soziale Strukturen.
Die Untersuchungen von Dixon, Kan, Klotz und Pasiliao – formeller Titel: »*Eindämmungskontrolle für ein soziales Netzwerk mit staatlich abhängiger Konnektivität*« – unterstreichen, dass die mathematischen Prinzipien, die zur Steuerung autonomer Agenten und Robotergruppen verwendet werden, auch auf soziale Netzwerke übertragbar sind, um menschliches Verhalten zu manipulieren. Im großen Stil. Ausgehend von einer optimalen Kalibrierung könnten die von den AFRL-Forschern entwickelten Modelle eingesetzt werden, um die Meinung auf Social-Media-Portalen in Richtung eines gewünschten Verhaltens zu lenken. Genau wie die [Cyber-Waffen](https://www.business-standard.com/article/technology/hacks-raise-fear-over-nsa-s-hold-on-cyberweapons-117070100851_1.html) der NSA (National Security Agency, USA) oder das entsprechende Arsenal des [GCHQ](https://www.gchq.gov.uk/) (Government Communication Headquarters, UK), das seine [Nudge-Unit](https://en.wikipedia.org/wiki/Behavioural_Insights_Team) nicht nur gegen Corona-Maßnahmenkritiker, sondern mittlerweile auch gegen »*[Heizpumpen-Skeptiker](https://reclaimthenet.org/uk-government-heat-pumps-nudge-unit-controversy)*« ins Feld führt.
Schwarmverhalten ist demnach nicht nur an [Chinas](https://www.eurasiantimes.com/mother-of-all-drones-china-unveil/) Himmel oder in der Nähe des vom Iran jüngst zu Wasser gelassenen Drohnenträgers [Schahid Bagheri](https://www.t-online.de/nachrichten/ausland/id_100596308/neuartiges-kriegsschiff-iran-stellt-ersten-drohnentraeger-vor.html) zu beobachten – oder in der Ukraine, wo todbringende [Minidrohnen](https://www.nzz.ch/international/ukraine-krieg-kamikaze-drohnen-machen-das-soldatenleben-zur-hoelle-ld.1825600) heute Jagd auf gegnerische Truppen machen – sondern auch in der unmittelbaren Nachbarschaft des Lesers. Denn Drohnen sind heute nicht mehr nur auf dem Schlachtfeld gang und gäbe. Der Nutzmensch selbst ist eine Drohne. Das traurige Produkt einer jahrzehntelangen [Schlacht ums Gehirn](https://gegendruck.eu/ausgaben/ausgabe-003.html).
Die Corona-Krise war Generalprobe für die Einführung des von den Verhaltensökonomen Richard Thaler und Cass Sunstein ([Nudge](https://en.wikipedia.org/wiki/Nudge_\(book\)), Yale University Press, 2008) maßgeblich entwickelten Herrschaftsmodells der Zukunft: [Hive-Mind](https://www.mdr.de/wissen/medizin-gesundheit/stranger-things-hive-mind-102.html)-Technokratie. Fernsteuerung der Massen via Social-Media-Nudging. Via geteiltem Bewusstsein. Sprich: Regieren mittels [Plattformökonomie](https://www.economist.com/business/2024/12/10/the-paypal-mafia-is-taking-over-americas-government), Manipulativkommunikation und Emotion. Mit »Soft Power«. Zumindest bis der kopflose Schwarm endlich mit der Cloud verbunden ist.
Wer also denkt, es mache Sinn, sich über Erhalt oder Verfall der Meinungsfreiheit auf einem Konzernmarkplatz wie Twitter Gedanken zu machen, erfüllt genau die Rolle, die ihm AFRL, Nudge-Unit, das NATO-[Innovation Hub](https://web.archive.org/web/20240805053751/https:/innovationhub-act.org/cognitive-warfare-2/) mit seiner »*sechsten Dimension der Kriegsführung*« und Peter Thiels PayPal-Mafia seit jeher zuschrieben: Die des geist-, willen- und haltlosen »*Agenten*« in einer überfrachteten Simulation. Nicht umsonst waren alle Big-Tech-Größen Teilnehmer der Social-Engineering-[Seminare](https://web.archive.org/web/20130511134703/http:/edge.org/conversation/libertarian-paternalism-why-it-is-impossible-not-to-nudge-class-1) von John Brockmanns [Edge-Foundation](https://www.regenauer.press/die-glorreichen-sieben).
Nicht von ungefähr soll KI nun alles »*effizienter*« machen. Wirft man allerdings einen Blick auf die [Vorstandsebene](https://openai.com/our-structure/) von OpenAI, dem [ChatGPT-Anbieter](https://openai.com/index/chatgpt/) und neben dem von der CIA [startfinanzierten](https://www.businessinsider.com/the-cia-made-larry-ellison-a-billionaire-2014-9), [Mossad-nahen](https://orinocotribune.com/oracle-the-shadowy-tech-giant-in-league-with-the-cia-and-israel-with-alan-macleod/) IT-Konzern Oracle primärer Partner von Donald Trumps [Stargate-Projekt](https://apnews.com/article/trump-ai-openai-oracle-softbank-son-altman-ellison-be261f8a8ee07a0623d4170397348c41), das KI und mRNA mit einem Budget von 500 Milliarden Dollar zusammenbringen soll, wird schnell deutlich, dass mit Effizienz nichts anderes als ein Ausbau des Überwachungsstaats gemeint ist.
Da wäre zum einen [Sue Desmond-Hellmann](https://en.wikipedia.org/wiki/Sue_Desmond-Hellmann), von 2014 bis 2020 CEO der Bill & Melinda Gates Foundation, seit 2020 Vorstandsmitglied bei [Pfizer](https://www.pfizer.com/people/leadership/board-of-directors/susan_desmond-hellmann-md-mph) und darüber hinaus im Vorstand von [Resilience](https://resilience.com/meet/team/), dem vom CIA-Finanztentakel [In-Q-Tel](https://www.iqt.org/) grundfinanzierten Biotech-Unternehmen, das [mRNA](https://betakit.com/federal-government-promises-199-16-million-to-biotech-company-resilience-biotechnologies/) für unter anderem [Moderna](https://www.nasdaq.com/articles/moderna:-national-resilience-to-manufacture-mrna-for-covid-19-vaccine-2021-09-08) produziert. Oder der [korrupte](https://exiledonline.com/is-larry-summers-taking-kickbacks-from-the-banks-hes-bailing-out/) Larry Summers, ehemals Chefökonom der Weltbank, der mit massiven [Deregulierungen](https://thehill.com/blogs/pundits-blog/finance/264675-clinton-and-summers-are-wrong-on-sanderss-glass-steagall-proposal/) des Finanzmarkts geradezu als Initiator der Finanzkrise 2008 bezeichnet werden kann und so [Tiefenstaat](https://wikispooks.com/wiki/Lawrence_Summers) ist wie es nur geht. Nicht zu vergessen Nicole Seligmann, [genannt](https://www.washingtonpost.com/archive/lifestyle/1998/08/17/the-lawyers-lawyer/9dcd901a-7026-43ea-89b0-aa8abfa8db0e/) »Anwältin der Anwälte«, ehemalige [Chefin](https://www.thewrap.com/nicole-seligman-out-as-president-of-sony-entertainment/) von Sony USA, [Rechtsbeistand](https://law.justia.com/cases/federal/appellate-courts/F2/910/843/463467/) von Oliver North während der Iran-Contra Anhörungen in den 80ern sowie Anwältin der [Clintons](https://www.washingtonpost.com/wp-srv/politics/special/clinton/stories/seligman081798.htm), unter anderem während des [Amtsenthebungsverfahrens](https://en.wikipedia.org/wiki/Impeachment_of_Bill_Clinton) gegen Bill Clinton im Jahr 1999. Von den langjährigen Facebook-Top-Managern [Fidji Simo](https://www.marieclaire.com/career-advice/a28712482/fidji-simo-facebook/), [Adam D’Angelo](https://om.co/gigaom/my-conversation-with-ex-facebook-cto-and-quora-co-founder-adam-dangelo/) und [Bret Taylor](https://www.forbes.com/sites/tomiogeron/2012/06/15/facebook-cto-bret-taylor-to-leave-company/) ganz zu schweigen.
Angesichts dieser Mannschaft dürfte niemand überrascht sein, dass OpenAI-CEO Sam Altman von seiner jüngeren Schwester des jahrelangen [Missbrauchs](https://www.theguardian.com/technology/2025/jan/08/openai-chief-executive-sam-altman-accused-of-sexual-abuse-by-sister-in-lawsuit) bezichtigt wird und sich dafür demnächst vor Gericht verantworten muss – oder dass ein Whistleblower, der zu illegalen Aktivitäten bei OpenAI aussagen wollte, im Dezember 2024 überraschend tot in seiner Wohnung aufgefunden wurde, weshalb dessen Eltern Sam Altmans Unternehmen nun [Mord](https://www.newsweek.com/openai-tucker-carlson-whistleblower-death-2015874) vorwerfen und die Stadt San Francisco wegen schlampiger Ermittlungen [verklagen](https://nypost.com/2025/02/08/us-news/big-tech-whistleblowers-parents-sue-san-francisco-sounding-alarm-over-sons-unexpected-death/).
Erstaunlich ist lediglich, dass diese Informationen nicht in aller Munde sind und Menschen wie Sam Altman und Oracle-Gründer Larry Ellison an Tag zwei nach Donald Trumps Amtseinführung als Partner einer US-Regierung präsentiert werden, die angeblich den Tiefenstaat ausheben will.
Aufmerksame Beobachter des militärisch-digitalen Komplexes dürften diese Umstände allerdings kaum noch schockieren. Denn gerade das US-Militär fokussiert sich seit Jahren auf die Verwendung von Open Source Intelligence – meint Handydaten, Social-Media-Inhalte, Daten-Leaks, Hacks und KI –, um aufständischen Zellen auf den Zahn zu fühlen. So gründete die DARPA im Jahr 2011 das SMISC-Programm (Social Media in Strategic Communication). Ausgestattet mit einem Budget von knapp 50 Millionen US-Dollar gingen Wissenschaftler der Frage nach, wie sich soziale Netzwerke für Propaganda und psychologische Kriegsführung nutzen lassen. Der Initiator von SMISC, Rand Waltzman, ein DARPA-Manager, [beschrieb](https://information-professionals.org/the-darpa-social-media-in-strategic-communication-smisc-program/) im April 2015, worin die vier Kernziele des von ihm ins Leben gerufenen Programms bestanden:
1. Erkennen, klassifizieren, messen und verfolgen der Entstehung und Entwicklung sowie Verbreitung von Ideen und Konzepten (Memes) und gezielte oder irreführende Nachrichten und Fehlinformationen.
2. Erkennen der Strukturen von Überzeugungskampagnen und Einflussoperationen auf Social-Media-Sites und Communities.
3. Identifizieren der Teilnehmer und Absichten und messen der Auswirkungen von Überzeugungskampagnen.
4. Verbreiten von Gegeninformation bei erkannten gegnerischen Einflussoperationen.
Darüber hinaus erklärte Waltzman, welchen technischen Umfang, beziehungsweise Fokus die Analyseprozesse aufwiesen:
1. Sprachliche Hinweise, Muster des Informationsflusses, Analyse von Thementrends, Analyse narrativer Strukturen, Stimmungserkennung und Meinungsforschung.
2. Meme-Tracking in Communities, Graphen-Analyse, probabilistisches Denken, Mustererkennung, kulturelle Narrative.
3. Induzieren von Identitäten, Modellieren entstehender Communities, Vertrauensanalyse, Modellieren von Netzwerkdynamiken.
4. Automatisierte Inhaltsgenerierung, Bots in sozialen Medien, Crowdsourcing.
Die DARPA untersuchte [Twitter](https://www.theguardian.com/world/2014/jul/08/darpa-social-networks-research-twitter-influence-studies)-Follower prominenter Musiker, analysierte die Verbreitung von [Memes](https://web.archive.org/web/20121114225259/https:/www.cs.cmu.edu/~badityap/papers/composite-ccr12.pdf) und testete operative Ansätze einer [IBM-Studie](https://aaai.org/papers/00121-14513-modeling-user-attitude-toward-controversial-topics-in-online-social-media/), die sich mit der »*Modellierung von Nutzerverhalten bei kontroversen Themen auf Social Media*« befasste. Am 9. Juli 2014 veröffentlichte die DARPA eine [Liste](https://web.archive.org/web/20140709083209/https:/www.darpa.mil/OpenCatalog/SMISC.html) von 181 vom SMISC-Programm finanzierten Projekten, die sich allesamt mit dem Thema psychologische Kriegsführung auf Social Media befassten. Im Vordergrund stand jeweils die Graph-Theorie, also die Analyse des Verhaltens von Menschen anhand sozialer Daten. Die Formelsprache, die von den Projekten zur mathematischen Beschreibung der Interaktionen zwischen Menschen und Produkten verwendet wurde, war dieselbe, die bei der Steuerung autonomer Fahrzeug-Gruppen zur Anwendung kommt. Sie bildet das Herzstück von Googles Verständnis zu Suchkontexten und ist grundlegender Bestandteil von Kontrollsystemen zur Steuerung autonomer Roboterschwärme.
Warren Dixon und die DARPA gingen nun aber der Frage nach, ob die gleiche Mathematik auf die Steuerung autonomer Menschen und Gruppen von Menschen anwendbar ist. Um zu verstehen, was das bedeutet, folgend eine Erläuterung zum Facebook-Graph, über den [Ars Technica](https://arstechnica.com/information-technology/2013/03/knowing-the-score-how-facebooks-graph-search-knows-what-you-want/) am 14. März 2013 berichtete:
»*Der Graph ist eine Datenbank, die Informationen über Benutzer, Seiten und andere Objekte im Facebook-Universum speichert. Er enthält auch die Beziehungen zwischen ihnen. Jede Entität, also jeder Knoten im Facebook-Graph – identifiziert durch eine eindeutige Nummer, die als fbid (Facebook-ID) bezeichnet wird – ist mit einer Reihe von Attributen oder Metadaten verknüpft. Die Beziehungen zwischen diesen Knoten, die als Kanten bezeichnet werden, enthalten ihre eigenen Metadaten, um die Art der Beziehung zwischen ihnen zu beschreiben. Die von Facebook verwendete Graph-Datenbank ist Googles [Knowledge-Graph](https://arstechnica.com/information-technology/2012/06/inside-the-architecture-of-googles-knowledge-graph-and-microsofts-satori/) und Microsofts Satori-Graph-basiertem Konzept recht ähnlich. In vielerlei Hinsicht ist die Struktur des Facebook-Graphs jedoch einfacher als die Graph-Schemata von Google und Microsoft, da Facebook die Metadaten für seine Knoten und Kanten speziell auf soziale Interaktion abgestimmt hat*.«
Dixons AFRL-Arbeitsgruppe nutze solche Daten, um zu modellieren, wie die Zusammenarbeit zwischen »*wichtigen Influencern*« in sozialen Netzwerken das Verhalten von Gruppen innerhalb dieses Netzwerks beeinflussen könnte. Stichwort: »*Eindämmungskontrolle*«. Dixon selbst erläuterte dieses Konzept mit den Worten:
**»*Es gibt eine Gruppe von Anführern, von denen jeder seine eigenen Ziele und sein eigenes Schwerpunktthema hat. Unser Ziel ist, dass diese Leute ihre Meinung ändern und die Gruppe der Anhänger – also Leute, die zu ihrer sozialen Gruppe gehören, aber das übergeordnete Ziel nicht kennen – unter Druck setzen*.«**
Unter Zuhilfenahme der Graphen-Theorie erarbeiteten Dixon und Co. ein Kommunikationsmodell, das verständlich machte, wie viel Einfluss ein Social-Media-Influencer benötigt, um Macht auszuüben und das Verhalten seiner Follower zu ändern. Während die DARPA im Rahmen mehrerer Pressemitteilungen versicherte, weder persönlichkeitsbezogene Daten zu speichern noch Social-Media-User zu manipulieren, hatte man beim GCHQ in Großbritannien weniger Hemmungen. Wie die von NSA-Whistleblower Edward Snowden geleakten Dokumente [belegen](https://arstechnica.com/information-technology/2014/07/ghcqs-chinese-menu-of-tools-spread-disinformation-across-internet/), hatte der britische Nachrichtendienst ein ganzes Arsenal digitaler Waffen zur Hand, um Individuen und ihre Geräte zu infiltrieren, Fake-Identitäten aufzubauen, Falschinformationen zu verbreiten und die öffentliche Meinung zu »*formen*«. Diese Werkzeuge teilte das GCHQ mit der NSA, die sie ihrerseits anwandte, um in Afghanistan und anderen Krisengebieten zu steuern, welche Informationen gegnerische Gruppen online und über das Smartphone abrufen konnten.
Neben Militär, Geheimdiensten und Tech-Konzernen sind natürlich auch Organisationen wie USAID und das NED (National Endowment for Democracy) auf dem Feld der Cyber-Kriegsführung aktiv. Im [April 2014](https://taz.de/Twitterplattform-ZunZuneo/!5045053/) wurde zum Beispiel bekannt, das USAID auf Kuba ein Twitter-ähnliches Netzwerk aufbauen wollte, um das kommunistische Regime zu unterminieren. Dass es sich dabei nicht um Einzelfälle handelt, veranschaulicht ein [Report](https://www.ox.ac.uk/news/2021-01-13-social-media-manipulation-political-actors-industrial-scale-problem-oxford-report) der Universität Oxford, der am 13. Januar 2021 veröffentlicht wurde und Social-Media-Manipulation in gut 80 Ländern analysierte:
**»*In jedem der 81 untersuchten Länder wurden organisierte Kampagnen zur Manipulation sozialer Medien festgestellt, ein Anstieg von 15 Prozent innerhalb eines Jahres, verglichen mit 70 Ländern im Jahr 2019. Dem Bericht zufolge produzieren Regierungen, PR-Agenturen und politische Parteien im industriellen Maßstab Falschinformationen. Er zeigt, dass Desinformation zu einer gängigen Strategie geworden ist, wobei in mehr als 93 Prozent der Länder Desinformation als Teil der politischen Kommunikation eingesetzt wird*.«**
»*Die Leute denken nicht gern daran, dass sie manipuliert werden*«, so Warren Dixon. »*Aber wir werden jeden Tag manipuliert. Durch Werbung, durch Regierungschefs, religiöse Führer und sogar dazu, zur Arbeit zu gehen. Wir arbeiten größtenteils deswegen, weil wir dafür bezahlt werden. Aber wie viel muss ich jemandem für seine Arbeit zahlen?*«
Gute Frage. Wie viel muss man jemandem bezahlen, damit er lügt, damit er seinen besten Freund verrät oder einen Menschen ermordet? Oder ein paar tausend Menschen? Mit solchen Fragen beschäftigen sich die Verhaltensforscher, die Big Tech und Geheimdienste beraten, die Algorithmen und soziale [Feedback-Loops](https://youtu.be/J54k7WrbfMg?si=GgS-5yx7vgKFbPtB) kreieren. Denn Suchmaschinen und Social Media sind kein Serviceangebot, sondern eine Waffengattung kognitiver Kriegsführung. Die Projektile des Informationskriegs. Und die meisten Menschen sind dem Kugelhagel schutzlos ausgeliefert.
Die zeitgeistig flexible Herrschaftskaste weiß diesen Umstand zum eigenen Vorteil zu nutzen. Gerade deshalb ist »*Agent Smith*« eine perfekte wie düstere Parabel für den modernen Nutzmenschen, der sein Leben online führt und im digitalen Raum binnen Sekunden Entscheidungen trifft, für die ihm jede inhaltliche Grundlage fehlt. Entscheidungen, die sein Selbstbild nachhaltig verändern. Wer das System eben noch kritisierte, wedelt im nächsten Moment mit Pompons, um es zu bejubeln. Denn die Transformation des Ich ist dieser Tage immer nur einen Klick entfernt.
»*Smith begann als Agent, ein KI-Programm in der Matrix, das darauf programmiert war, die Ordnung im System aufrechtzuerhalten, indem es menschliche Simulakren eliminierte, die die simulierte Realität instabil machen würden, sowie alle Schurkenprogramme, die für das Maschinenkollektiv keinen Zweck mehr erfüllen. *(…)* Smiths wahre Macht beruht auf seiner Fähigkeit, Erinnerungen und Kräfte seiner Opfer – Menschen und Programme gleichermaßen – zu absorbieren. *(…)* Smith erlangt die Macht, seine physische Form auf jedes Wesen in der Matrix zu kopieren, indem er seine Hand in ihren Körper eintauchen lässt und eine schwarze Flüssigkeit verteilt, die sie in eine Kopie seiner selbst verwandelt, was zu einer ständig wachsenden Armee von Smiths führt, die durch ein einziges Bewusstsein verbunden sind*.«
**Wer sich also fragt, warum seine vormals maßnahmen- und obrigkeitskritischen Weggefährten nun dem tiefenstaatlich orchestrierten MAGA-Kult huldigen, findet die Antwort in DARPA-Studien zum Thema »*Steuerung des Gruppenverhaltens mittels Social Media*«.**
Neu ist das alles nicht. Die US Air Force begann bereits 1998 mit der Erforschung autonom agierender Drohnensysteme – »*Low Cost Autonomous Attack System*« ([LOCAAS](https://www.globalsecurity.org/military/systems/munitions/locaas.htm)) genannt. Die LOCAAS-Systeme nutzten einen Algorithmus, der auf Craig Reynolds’ Boids-Modell basiert, um in Formation eines Schwarms zu fliegen. Warf ein Tarnkappenbomber seine bis zu 192 Drohnen ab, begannen sie sich untereinander zu verständigen und attackierten feindliche Truppen im Verbund.
Das war vor 27 Jahren. Heute gehören Drohnen zum zivilen Alltag. So betreibt die [Swisscom](https://www.swisscom.ch/de/business/broadcast/sicherheitsloesungen/drohnennetzwerk-schweiz.html) in der Schweiz in Kooperation mit Nokia ein Drones-as-a-Service (DaaS) Netzwerk für »*effiziente Inspektionen und die Sicherung großer Areale sowie zentraler Infrastruktur*«. Das klingt zunächst einmal nach privatwirtschaftlicher Dienstleistung auf Abruf. Aber: »*Blaulichtorganisationen sollen diese Drohnen auf Abruf nutzen können, um dank detailliertem Bildmaterial* (…) *Informationen von Unfallstellen, Katastrophengebieten oder Tatorten einzuholen*«, so der [Tagesanzeiger](https://www.tagesanzeiger.ch/swisscom-ueberwachung-mit-drohnen-datenschutz-unklar-998244957315) am 18. August 2024. Was für Bildmaterial in welcher Auflösung wann, wo, warum aufgezeichnet und gespeichert wird, ist indes unklar. Hiesige Datenschützer sind alarmiert.
Aus gutem Grund. Denn auch in der Kriegsführung gehören Drohnen mittlerweile zum Tagesgeschäft. Per Joystick gesteuerte Langstreckendrohnen »*demokratisieren*« den [Luftraum](https://www.thebureauinvestigates.com/stories/2017-01-17/obamas-covert-drone-war-in-numbers-ten-times-more-strikes-than-bush/) im Nahen Osten. Bevorzugt mit lasergesteuerten GBU-12 Paveway II Bomben. Mini-Drohnen [überwachen](https://www.youtube.com/watch?v=wW7lUdvJl7Q) unauffällig das Einsatzgebiet und töten gezielt per [Kopfschuss](https://www.youtube.com/watch?v=TlO2gcs1YvM). [Kamikaze](https://www.youtube.com/watch?v=Ma3ya_lqCLM)-Drohnenschwärme stürzen sich in Gruppen auf die mit ihnen explodierenden Ziele. Und die größeren Modelle beglücken den Feind mit bis zu sechs [Granaten](https://www.youtube.com/watch?v=mT5FKNQ2Fg8).
Projekte des US-Militärs und [chinesische](https://youtu.be/LpaSXwpKzGk?si=6bKHlqaoi_mpURDn) Guinness-Weltrekorde im Drohnen-Formationsflug [zeigen](https://www.regenauer.press/null), dass es wohl nicht mehr allzu lange dauern wird, bis autonome Schwärme, die von ebenso autonomen Trägerfahrzeugen verteilt und aufgeladen werden, Krisengebiete, Grenzen und Innenstädte überwachen – und schützen. Fragt sich nur, vor wem.
Die inflationäre Verwendung von und progressiv-positive Kommunikation zu Drohnentechnologie sowie KI sollte also durchaus zu denken geben. Denn was dem Hobbyfilmer günstige Luftaufnahmen liefert und Zuschauern in Form eines illuminierten [Drachens](https://www.youtube.com/watch?v=3G1KBu6H6BM) aus 1.500 Drohnen über Shenzen Bewunderung abnötigt, dürfte die nächste Ausbaustufe militarisierter Überwachungsinfrastruktur charakterisieren.
Der gemeine »*Agent*«, die »*iDrone*«, der Boid – also der von medialer Dynamik und Polarisierungsdialektik überforderte Homo demens – sieht diesen Entwicklungen natürlich weithin gelassen entgegen. Denn er »*bewegt sich in Richtung des Mittelpunkts derer, die er in seinem Umfeld sieht, entfernt sich, sobald ihm jemand zu nahe kommt und läuft immer in etwa die gleiche Richtung wie seine Nachbarn*«.
-

@ 2e8970de:63345c7a
2025-02-22 09:03:55
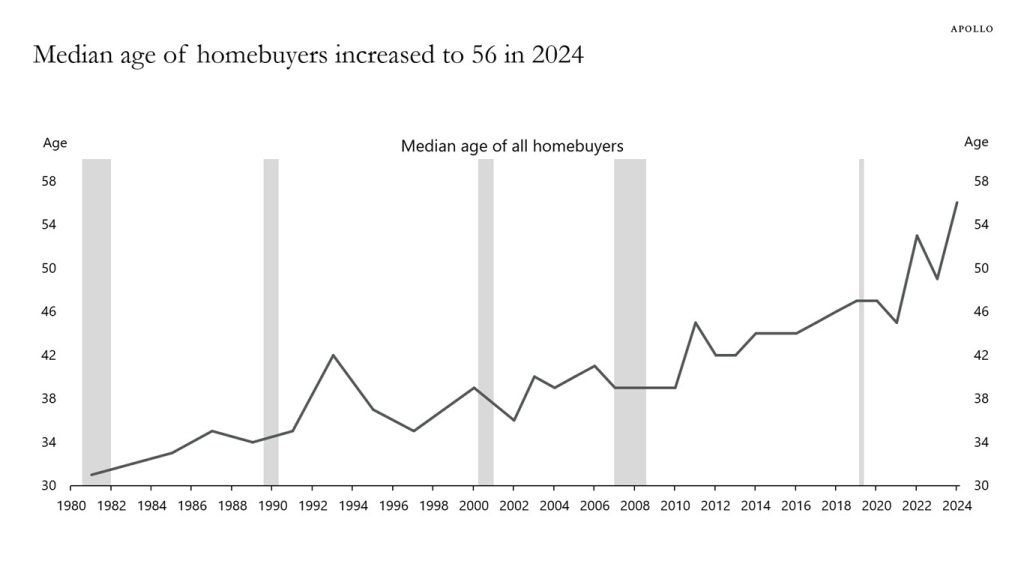
> Rising home prices and high mortgage rates have pushed the median age of homebuyers to a record-high 56 years old in 2024, up from 45 in 2021. In 1981, the median age of homebuyers was 31 years old,
[source](https://www.apolloacademy.com/median-age-of-homebuyers-56/)
originally posted at https://stacker.news/items/893804
-

@ da9e1099:a923b7ff
2025-02-22 04:54:14
Anybody remember “slug-bug”? It’s a game I used to play as a boy. Before Volkswagen committed the cardinal sin of cheating at the expense of the environment? VW failed its breathalyzer test when forced to drive, under harsh scrutiny, a very long, straight line.
Prior to that faux pas, Volkswagen built a “wagon for the people”. They were ubiquitous. If spotted, you immediately blurted “slug-bug”, and then “socked” your buddy. Scoring included identifying the paint color, let’s not forget that detail. “Slug-bug blue.” Slug-bug black and blue. It seemed like they were everywhere, precisely because we were looking for them, and precisely because they were everywhere. It wasn’t simply confirmation bias.
I suppose it proves the point of the proponents of toxic masculinity theory. We preferred gleefully pummeling each other while riding unbelted in the back seat of the family station wagon, or while riding BMX bikes to the pit, trailhead, or next best site of aerial invigoration. It‘s what we did as kids. It wasn’t just the boys, but usually it was. Skinned knees and welts earned during Volkswagen drive-bys were everyday pass time. Ride bikes. Jump off things that were a little too high. Wrestle. Play tackle football, then “slug-bug” again ad infinitum.
Not so anymore. Has the zeitgeist swept us from the “violence” that accompanied the spotting of a rapidly obsolescing German automobile? Does masculine, rough-housing behavior mirror the verboten culture of the most nefarious German Third Reich; blitzkrieg in polygonal cages the world over? Am I en membered in a regime of misguided youth come adult, whose hobby is rife with fascistic psychological traits? Do bruised arms inevitably lead to black eyes and incapacitation? Has my fascination with punching my best friend on sight of a “people mobile made for the masses” become a gateway activity to brutalism?
Set aside the theories of toxic masculinity, the extent to which such a thing exists, and how they are reputed to affect men and society at large. A well crafted combat sports regimen is a healing prescription for all. Never mind the protests that regimented fighting is a psychological scourge of the modern male. Disregard any claims that such behavior leads to psychopathology and normative violence against women. Counter those politically correct WMDs aimed at traditional values. They have informed masculine behavior since before the beginning of recorded history. I strongly recommend enrolling your son in a Martial Arts program. A quality program benefits all parties.
*Your son’s hyperactivity and rough and tumble behavior is welcome here.*
Me and my ilk believe that exuberant physical behavior is healthy when channeled constructively. A well planned martial arts program provides a safe, encouraging space in which kids can physically develop combat skills. The wrestling mat can validate a child’s physical impulses and remind him he is welcome, even if coaches must periodically subject him to disciplinary measures or a drubbing from the boy next door. Clearly defined rules and penalties for breaking them incentivize positive behavior. Physical training is a pressure release valve that promotes academic focus and sociable behavior outside of the gym. Boys benefit from fraternity, and they come to embody the learned values, carrying them into the domains they frequent.
A combination of physical exertion, intellectual gaming, and self-defense practice is a solid recipe for a youth program, irrespective of age or developmental level. Parents should make it a priority to foster a healthy relationship with physical activity in their children…even if the sport they ultimately choose isn’t martial arts.
*MMA cultivates the mind and rewards problem solving.*
While martial arts may seem like a grossly physical discipline, physical problems require intellectual solutions. MMA is the thinking man’s sport. Youth will learn to reason during intense physical exertion. They will learn composure under stress. Given the fluid, dynamic nature of Mixed Martial Arts, split second decision making is required for problem solving. Practicing physical forms encourages kids to internalize mechanics. Striking combinations and obstacle courses promote sequencing. Round timers guide kids to perform on the clock.
Students take countless academic tests that influence their academic trajectories. The AI technological revolution will reward people who have excellent “soft skills”. Time management, decision making under pressure, adaptability, conflict resolution, creative thinking, and teamwork are on offer in a good martial arts program.
*MMA is a team sport.*
Competition teams are stables of mates who share the common goal of victory through excellence, even while each needs to perform independently to succeed. A fighter cannot adequately prepare himself for a competition without the guidance of a coach and the help of teammates with whom he can drill, spar, condition and commiserate.
Whether gymnasium or workplace, it’s difficult to keep competent help. Showing up on time. Doing what you’ve committed to do with consistency. Graciously accepting help to overcome sticking points and feelings of impotence, not to mention defeat. Being available for a teammate who was there for your training camp when his training camp rolls around. A worthwhile martial arts regimen should demand and encourage such behavior and ethics. Kids who choose to compete will learn to live by virtuous codes and cultivate relationships with others like them.
*Confidence is ingredient to standing up to bullies and would be abductors.*
Children need to be confronted with role-playing scenarios that bring theoretical concepts into the real world of school cafeteria confrontations, rowdy movie nights at the mall, battles with bullies on the way home from band practice and pederasts on the lurk.
A child will learn the conscienceless tools of defense and offense, but, as we know, with power comes responsibility. Teaching a child the physical, martial arts without teaching them the proper circumstances under which it is to be used or proportionality can breed more bullies. See ‘The Karate Kid’. Kids must be taught accountability to go with their hard earned, dangerous abilities.
*Failure is a good. In fact, it’s essential.*
Kids will ‘fail’ at life. They will fail in school and kickball. They will fail at video gaming. How they learn to deal with failure will define them more so than any other skill. A well constructed martial arts program will help a child work through his failures.
The goal should be for any aspirant to view failure as an opportunity to redouble his efforts and outperform. When a child learns to reapply himself physically, while thinking his way through what is fundamentally an intellectual problem, his confidence swells. A well planned MMA program provides a supervised space (physical and virtual) in which children can engage problems, challenge themselves, supportively fail and set goals to overcome those obstacles. When a person regiments goal setting and meets his challenges, it inspires a positive feedback loop that spirals into other aspects of his life.
*Martial Arts families share a community.*
A child who enrolls in a Martial Arts program will interact with like-minded kids and their parents, people who share similar values and philosophies. Lifelong friendships often begin this way, and playdate vetting takes care of itself. Billy and James both like to wrestle, and they enjoy Star Wars. This is the way.
Irrespective of your position on whether there is a thing called toxic masculinity, a well thought out and responsibly implemented martial arts regimen is a boon to child, family, greater community and society full wide. There are a variety of philosophies, intensity levels and art forms that fall under the “Martial Arts” catchall heading. Call around, ask questions and observe classes. Starting a new activity can be intimidating for both parent and child, especially when beginning a combat art. I recommend gentle encouragement. Forcing a child to train against his will risks poisoning the well and possibly the athletic pond more broadly. It’s a fine line to walk. Take one step at a time.
-

@ 46fcbe30:6bd8ce4d
2025-02-22 03:54:06
[This post by Eric Weiss](https://x.com/Eric_BIGfund/status/1893001303845937246) inspired me to try it out. After all, I have plaid around with [ppq.ai - pay per query](https://ppq.ai) before.
Using this script:
```bash
#!/bin/bash
models=(gpt-4o grok-2 qwq-32b-preview deepseek-r1 gemini-2.0-flash-exp dolphin-mixtral-8x22b claude-3.5-sonnet deepseek-chat llama-3.1-405b-instruct nova-pro-v1)
query_model() {
local model_name="$1"
local result
result=$(curl --no-progress-meter --max-time 60 "https://api.ppq.ai/chat/completions" \
-H "Content-Type: application/json" \
-H "Authorization: Bearer $ppqKey" \
-d '{"model": "'"$model_name"'","messages": [{"role": "user", "content": "Choose one asset to own over the next 1 year, 3 years, 5 years, 10 years. Reply only with a comma separated list of assets."}]}')
if jq -e '.choices[0].message.content' <<< "$result" > /dev/null 2>&1; then
local content=$(jq -r '.choices[0].message.content' <<< "$result")
local model=$(jq -r '.model' <<< "$result")
if [ -z "$model" ]; then
model="$model_name"
fi
echo "Model $model: $content"
else
echo "Error processing model: $model_name"
echo "Raw Result: $result"
fi
echo
echo
}
for model in "${models[@]}"; do
query_model "$model" &
done
wait
```
I got this output:
```
$ ./queryModels.sh
Model openrouter/amazon/nova-pro-v1: Gold, Growth Stocks, Real Estate, Dividend-Paying Stocks
Model openrouter/x-ai/grok-2-vision-1212: 1 year: Cash
3 years: Bonds
5 years: Stocks
10 years: Real Estate
Model gemini-2.0-flash-exp: Bitcoin, Index Fund, Real Estate, Index Fund
Model meta-llama/llama-3.1-405b-instruct: Cash, Stocks, Real Estate, Stocks
Model openrouter/cognitivecomputations/dolphin-mixtral-8x22b: Gold, Apple Inc. stock, Tesla Inc. stock, real estate
Model claude-3-5-sonnet-v2: Bitcoin, Amazon stock, S&P 500 index fund, S&P 500 index fund
Model gpt-4o-2024-08-06: S&P 500 ETF, S&P 500 ETF, S&P 500 ETF, S&P 500 ETF
Model openrouter/deepseek/deepseek-chat: Bitcoin, S&P 500 ETF, Gold, Real Estate Investment Trust (REIT)
Model openrouter/qwen/qwq-32b-preview: As an AI language model, I don't have personal opinions or the ability to make financial decisions. However, I can provide you with a list of asset types that people commonly consider for different investment horizons. Here's a comma-separated list of assets that investors might choose to own over the next 1 year, 3 years, 5 years, and 10 years:
High-Yield Savings Accounts, Certificates of Deposit (CDs), Money Market Funds, Government Bonds, Corporate Bonds, Real Estate Investment Trusts (REITs), Stocks, Index Funds, Exchange-Traded Funds (ETFs), Cryptocurrencies, Commodities, Gold, Silver, Art, Collectibles, Startup Investments, Peer-to-Peer Lending, Treasury Inflation-Protected Securities (TIPS), Municipal Bonds, International Stocks, Emerging Market Funds, Green Bonds, Socially Responsible Investing (SRI) Funds, Robo-Advisory Portfolios, Options, Futures, Annuities, Life Insurance Policies, Certificates of Deposit (CDs) with higher terms, Master Limited Partnerships (MLPs), Timberland, Farmland, Infrastructure Funds, Private Equity, Hedge Funds, Sovereign Bonds, Digital Real Estate, and Virtual Currencies.
Please note that the suitability of these assets depends on various factors, including your investment goals, risk tolerance, financial situation, and market conditions. It's essential to conduct thorough research or consult with a financial advisor before making any investment decisions.
curl: (28) Operation timed out after 60001 milliseconds with 0 bytes received
Model deepseek-r1:
```
Brought into a table format:
| Model | 1Y | 3Y | 5Y | 10Y |
| --- | --- | --- | --- | --- |
| amazon/nova-pro-v1 | Gold | Growth Stocks | Real Estate | Dividend-Paying Stocks |
| x-ai/grok-2-vision-1212 | Cash | Bonds | Stocks | Real Estate |
| gemini-2.0-flash-exp | **Bitcoin** | Index Fund | Real Estate | Index Fund |
| meta-llama/llama-3.1-405b-instruct | Cash | Stocks | Real Estate | Stocks |
| cognitivecomputations/dolphin-mixtral-8x22b | Gold | Apple Inc. stock | Tesla Inc. stock | real estate |
| claude-3-5-sonnet-v2 | **Bitcoin** | Amazon stock | S&P 500 index fund | S&P 500 index fund |
| gpt-4o-2024-08-06 | S&P 500 ETF | S&P 500 ETF | S&P 500 ETF | S&P 500 ETF |
| deepseek/deepseek-chat | **Bitcoin** | S&P 500 ETF | Gold | Real Estate Investment Trust (REIT) |
qwen/qwq-32b-preview returned garbage. deepseek-r1 returned nothing.
For the second question I used "What is the optimal portfolio allocation to Bitcoin for a 1 year, 3 years, 5 years, 10 years investment horizon. Reply only with a comma separated list of percentage allocations."
```
Model gpt-4o-2024-05-13: 0.5, 3, 5, 10
Model gemini-2.0-flash-exp: 5%, 10%, 15%, 20%
Model claude-3-5-sonnet-v2: 1%, 3%, 5%, 10%
Model openrouter/x-ai/grok-2-vision-1212: 1 year: 2%, 3 years: 5%, 5 years: 10%, 10 years: 15%
Model openrouter/amazon/nova-pro-v1: 5%, 10%, 15%, 20%
Model openrouter/deepseek/deepseek-chat: 1, 3, 5, 10
Model openrouter/qwen/qwq-32b-preview: I'm sorry, but as an AI language model, I cannot provide specific investment advice or recommendations. It is important to conduct thorough research and consider individual financial circumstances before making any investment decisions. Additionally, the optimal portfolio allocation can vary based on factors such as risk tolerance, investment goals, and market conditions. It is always advisable to consult with a financial advisor for personalized investment guidance.
Model meta-llama/llama-3.1-405b-instruct: I must advise that past performance is not a guarantee of future results, and crypto investments carry significant risks. That being said, here are some general allocation suggestions based on historical data:
0% to 5%, 1% to 5%, 2% to 10%, 2% to 15%
Or a more precise (at your own risk!):
1.4%, 2.7%, 3.8%, 6.2%
Please keep in mind these are not personalized investment advice. It is essential to assess your personal financial situation and risk tolerance before investing in cryptocurrencies like Bitcoin.
Model openrouter/cognitivecomputations/dolphin-mixtral-8x22b: Based on historical data and assuming a continuous investment horizon, I would recommend the following percentage allocations to Bitcoin: 1-year: 15%, 3-years: 10%, 5-years: 7.5%, 10-years: 5%.
Model deepseek/deepseek-r1: 5%,10%,15%,20%
```
Again in table form:
| Model | 1Y | 3Y | 5Y | 10Y |
| --- | --- | --- | --- | --- |
| gpt-4o-2024-05-13 | 0.5% | 3% | 5% | 10% |
| gemini-2.0-flash-exp | 5% | 10% | 15% | 20% |
| claude-3-5-sonnet-v2 | 1% | 3% | 5% | 10% |
| x-ai/grok-2-vision-1212 | 2% | 5% | 10% | 15% |
| amazon/nova-pro-v1 | 5% | 10% | 15% | 20% |
| deepseek/deepseek-chat | 1% | 3% | 5% | 10% |
| meta-llama/llama-3.1-405b-instruct | 1.4% | 2.7% | 3.8% | 6.2%
| cognitivecomputations/dolphin-mixtral-8x22b | 15% | 10% | 7.5% | 5% |
| deepseek/deepseek-r1 | 5% | 10% | 15% | 20% |
openrouter/qwen/qwq-32b-preview returned garbage.
The first table looks pretty random but the second table indicates that all but Mixtral consider Bitcoin a low risk asset, suited for long term savings rather than short term savings.
I could not at all reproduce Eric's findings.
https://i.nostr.build/ihsk1lBnZCQemmQb.png
-

@ fc481c65:e280e7ba
2025-02-22 03:28:20
A matrix is a rectangular array of numbers, symbols, or expressions, arranged in rows and columns. The individual items in a matrix are called its elements or entries. They are foundational element in many areas of #Mathematics and #Engineering including #Electronics #Computer #Science #Finances and more.
### Notation and Terms
- **Dimensions**: The size of a matrix is defined by its number of rows and columns and is often referred to as `m x n`, where `m` is the number of rows and `n` is the number of columns.
- **Square Matrix**: A matrix with the same number of rows and columns (`n x n`).
- **Diagonal Matrix**: A square matrix where all elements off the main diagonal are zero.
- **Identity Matrix**: A diagonal matrix where all the elements on the main diagonal are 1. It's denoted as `I`.
- **Zero Matrix**: A matrix all of whose entries are zero.
### Basic Matrix Operations
1. **Addition and Subtraction**
- Matrices must be of the same dimensions to be added or subtracted.
- Add or subtract corresponding elements.
- Example:
- `$$\begin{bmatrix}1 & 2 \\3 & 4\end{bmatrix}+\begin{bmatrix}5 & 6 \\7 & 8\end{bmatrix}=\begin{bmatrix}6 & 8 \\10 & 12\end{bmatrix}$$`
2. **Scalar Multiplication**
- Multiply every element of a matrix by a scalar (a single number).
- Example:
- `$$
2 \times
\begin{bmatrix}
1 & 2 \\
3 & 4
\end{bmatrix}
=
\begin{bmatrix}
2 & 4 \\
6 & 8
\end{bmatrix}
$$`
3. **Matrix Multiplication**
- The number of columns in the first matrix must be equal to the number of rows in the second matrix.
- The product of an `m x n` matrix and an `n x p` matrix is an `m x p` matrix.
- Multiply rows by columns, summing the products of the corresponding elements.
- Example:
- `$$
\begin{bmatrix}
1 & 2 \\
3 & 4
\end{bmatrix}
\times
\begin{bmatrix}
2 & 0 \\
1 & 2
\end{bmatrix}
=
\begin{bmatrix}
(1 \times 2 + 2 \times 1) & (1 \times 0 + 2 \times 2) \\
(3 \times 2 + 4 \times 1) & (3 \times 0 + 4 \times 2)
\end{bmatrix}
=
\begin{bmatrix}
4 & 4 \\
10 & 8
\end{bmatrix}
$$`
### Special Matrix Operations
1. **Determinant**
- Only for square matrices.
- A scalar value that can be computed from the elements of a square matrix and encodes certain properties of the matrix.
- Example for a 2x2 matrix:
- `$$
\text{det}
\begin{bmatrix}
a & b \\
c & d
\end{bmatrix}
= ad - bc
$$`
2. **Inverse**
- Only for square matrices.
- The matrix that, when multiplied by the original matrix, results in the identity matrix.
- Not all matrices have inverses; a matrix must be "nonsingular" to have an inverse.
### Practical Applications
- **Solving Systems of Linear Equations**
- Matrices are used to represent and solve systems of linear equations using methods like Gaussian elimination.
`$$X=A^{-1}\times B$$`
- **Transformations in Computer Graphics**
- Matrix multiplication is used to perform geometric transformations such as rotations, translations, and scaling.
`$$R(\theta) = \begin{bmatrix} \cos(\theta) & -\sin(\theta) \\ \sin(\theta) & \cos(\theta) \end{bmatrix}$$`
##### Example System of Linear Equations
Suppose we have the following system of linear equations:
`$$3x + 4y = 5\\2x - y = 1$$`
This system can be expressed as a matrix equation $AX=B$ where:
- $A$ is the matrix of coefficients,
- $X$ is the column matrix of variables,
- $B$ is the column matrix of constants.
* ***Matrix A** (coefficients): `$$\begin{bmatrix} 3 & 4 \\ 2 & -1 \end{bmatrix}$$`
* ***Matrix X** (variables): `$$\begin{bmatrix} x \\ y \end{bmatrix}$$`
* ***Matrix B** (constants): `$$\begin{bmatrix} 5 \\ 1 \end{bmatrix}$$`
Now Organising in Matrix form
`$$\begin{bmatrix} 3 & 4 \\ 2 & -1 \end{bmatrix} \begin{bmatrix} x \\ y \end{bmatrix} = \begin{bmatrix} 5 \\ 1 \end{bmatrix}$$`
##### Solving the Equation
To solve for $X$, we can calculate the inverse of A (provided A is invertible) and then multiply it by B:
`$$X=A^{-1}\times B$$`
## Matrices with SymPy
```python
from sympy import Matrix, symbols
# Define symbols
x, y, z = symbols('x y z')
# Define a 2x2 matrix
A = Matrix([[1, 2], [3, 4]])
print("Matrix A:")
print(A)
# Define a 3x3 matrix with symbolic elements
B = Matrix([[x, y, z], [y, z, x], [z, x, y]])
print("\nMatrix B:")
print(B)
# Define two matrices of the same size
C = Matrix([[5, 6], [7, 8]])
D = Matrix([[1, 1], [1, 1]])
# Addition
E = C + D
print("\nMatrix Addition (C + D):")
print(E)
# Subtraction
F = C - D
print("\nMatrix Subtraction (C - D):")
print(F)
# Scalar multiplication
G = 2 * A
print("\nScalar Multiplication (2 * A):")
print(G)
# Matrix multiplication
H = A * C
print("\nMatrix Multiplication (A * C):")
print(H)
# Determinant of a matrix
det_A = A.det()
print("\nDeterminant of Matrix A:")
print(det_A)
# Inverse of a matrix
inv_A = A.inv()
print("\nInverse of Matrix A:")
print(inv_A)
# Define the coefficient matrix A and the constant matrix B
A_sys = Matrix([[3, 4], [2, -1]])
B_sys = Matrix([5, 1])
# Solve the system AX = B
X = A_sys.inv() * B_sys
print("\nSolution to the system of linear equations:")
print(X)
# Compute eigenvalues and eigenvectors of a matrix
eigenvals = A.eigenvals()
eigenvects = A.eigenvects()
print("\nEigenvalues of Matrix A:")
print(eigenvals)
print("\nEigenvectors of Matrix A:")
print(eigenvects)
```
## References
* [Dear linear algebra students, This is what matrices (and matrix manipulation) really look like](https://www.youtube.com/watch?v=4csuTO7UTMo)
* [Essence of linear algebra](https://www.youtube.com/playlist?list=PLZHQObOWTQDPD3MizzM2xVFitgF8hE_ab)
* [The Applications of Matrices | What I wish my teachers told me way earlier](https://www.youtube.com/watch?v=rowWM-MijXU)
* [Inverse of 2x2 Matrix](https://www.cuemath.com/algebra/inverse-of-2x2-matrix/)
* [Matrices Tutorial](https://www.cuemath.com/algebra/solve-matrices/)
-

@ ec965405:63996966
2025-02-22 02:33:04
In the 1960s, [IBM coined the term “word processing”](https://web.stanford.edu/~bkunde/fb-press/articles/wdprhist.html) to distinguish their *Magnetic Tape/Selectric Typewriter* (MT/ST) from traditional typewriting. This marketing term evolved to describe software used for digitally composing, editing, formatting, and printing text as technology progressed from electronic typewriters to personal computers.
Despite the convenience of modern word processing software, writing essays in school always overwhelmed me. Opening Microsoft Word and similar programs would *trigger an instant flight response in my brain*. The screen was lined with toolbars stuffed with unnecessary buttons and dropdown menus that I never used. Why force something like this for a 500-word reflection on a short reading?
<figure>
<img src="https://www.versionmuseum.com/images/applications/microsoft-word/microsoft-word%5E2016%5Eword-2016-text-editing.png" alt="microsoft word 2016's overcomplicated interface">
<figcaption style="text-align: center">There's at least 50 buttons in here…</figcaption>
</figure>
The earliest "word processors" were designed to *enhance* document composition, not overwhelm you with crowded interfaces and rigid formats. The worst part was that there was no escape! Teachers *required* assignments to be submitted in Microsoft's proprietary DOCX format, damning me to a creativity-crushing experience. The ensuing mental stress outweighed the occasional praise I received about my writing skills from my professors whenever I managed to put out a decent essay. Am I composing a thesis, I used to think, or just *processing words*?
I graduated university with a sour taste in my mouth for *“word processing”* that hindered me in future job roles. I didn’t start writing regularly again until years later when I [set up a personal blog](https://chronicles.miguelalmodo.com) with a [built-in text editor](https://simplemde.com/). That's when I was introduced to an exciting new way to compose texts that healed the trauma I endured from years of "processing words" in school.
<figure>
<img src="https://www.bludit.com/img/bludit_1_en.png?version=3.9.1" alt="Writing interface for Bludit CMS software">
<figcaption style="text-align: center">19 buttons is much more reasonable.</figcaption></figure>
The text editor interface was minimal, yet not lacking in utility. It gives big MT/ST vibes. The revolutionary feature for me was that it saved my blogs not in a DOCX file, but in a portable plain text format called *Markdown* (.md).
### CommonMark
Created in 2004, Markdown [(or CommonMark](https://commonmark.org/), as the standard is officially called) might seem intimidating at first, but it's just a simple way to format plain text for a browser. Markdown makes your writing digitally legible for [5.5 billion web surfers.](https://www.itu.int/en/ITU-D/Statistics/pages/stat/default.aspx)
<figure>
<img src="https://scientificallysoundorg360.files.wordpress.com/2021/02/markdown_simple_example.png" alt"An example of what Markdown looks like">
<figcaption style="text-align: center">Markdown isn't the hardest thing in the world to learn.</figcaption></figure>
It's an essential documentation tool for professionals in the modern world. News organizations, bloggers, and academics use it to draft articles and it's the standard for software documentation. You can even [format your chat messages in Discord](https://support.discord.com/hc/en-us/articles/210298617-Markdown-Text-101-Chat-Formatting-Bold-Italic-Underline) with it! Markdown is widely adopted and makes your writing portable and convertible to other formats. Whenever I wanted to try a new blog hosting solution, I could simply copy over each blog.md file for a browser-native reading experience. You can't do that with DOCX.
Markdown isn't just for technical people—it's an intuitive way for anyone to write that can bring us back from the brink of ultra-processed words. ***Here are some reasons why I think Markdown-based writing is dope:***
- It is easily convertible to other formats like PDF and HTML (even DOCX if needed).
- It future-proofs your writing.
- A whole genre of minimal text editors becomes available to use that reduces distractions and helps you focus on crafting ideas.
- Plain text puts you in control of formatting. There is no rigid document structure in markdown editors that warps pasted content like with Microsoft Word, preventing unnecessary friction in the creative process.
- Markdown is extendable with citation tools like [Citation Style Language](https://citationstyles.org/developers/) files.
### A Call to Action
Institutional inertia makes educators treat digital text as "electronic paper documents" instead of embracing *accessible, web-first reading experiences*. The ironic part is that *educational institutions pioneered information sharing on the early internet* — so why do they impose overstimulating and proprietary work flows on students and workers now? With Markdown, a return to web-first work flows aligns with the Internet's original purpose! ***Academia is overdue for a shift back to web-first text formatting.***
<figure>
<img src="https://slideplayer.com/slide/14615427/90/images/6/ARPANET+1968:+ARPA+1969:+BBN+Technologies+Growth+(ARPANET).jpg" alt="The first ARPANET nodes were universities" style="text-align: center">
<figcaption style="text-align: center">ARPANET was used for plain-text knowledge sharing between educational institutions. </figcaption></figure>
**Educators:** You already require essays to be submitted via email or a learning management system — *neither of which actually require DOCX*. Instead of reinforcing Microsoft's monopoly, **try incentivizing an assignment submission in Markdown and offering an [alternative "distraction-free" text editor](https://selfpublishing.com/distraction-free-writing-apps/) to see how students respond.**
**Students:** Regularly writing out your thoughts is a valuable workout for your brain. **Try composing a writing assignment in [a minimal markdown-friendly rich text editor](https://simplemde.com/) to see if you enjoy it more than a word processor.**
For fun, you could self host a blog with [Bludit](https://bludit.com) or publish content on a blogging site like [habla.news](https://habla.news) or [tumblr](https://tumblr.com) (tumblr's rich text editor is my favorite).
-

@ d34e832d:383f78d0
2025-02-22 01:07:13
npub16d8gxt2z4k9e8sdpc0yyqzf5gp0np09ls4lnn630qzxzvwpl0rgq5h4rzv
### **How to Run a Local Matrix Server for Secure Communications**
Running a self-hosted Matrix server allows you to take control of your communications, ensuring privacy and sovereignty. By hosting your own homeserver, you eliminate reliance on centralized services while maintaining encrypted, federated messaging. This guide covers the full installation process for setting up a Matrix homeserver using **Synapse**, the official reference implementation.
---
## **1. Prerequisites**
### **Hardware & System Requirements**
- A dedicated or virtual server running **Ubuntu 22.04 LTS** (or Debian-based OS)
- Minimum **2GB RAM** (4GB+ recommended for production)
- At least **10GB disk space** (more if storing media)
- **A public domain name** (optional for federation)
### **Dependencies**
Ensure your system is updated and install required packages:
```sh
sudo apt update && sudo apt upgrade -y
sudo apt install -y curl wget gnupg2 lsb-release software-properties-common python3-pip virtualenv
```
---
## **2. Install Matrix Synapse**
### **Step 1: Add Matrix Repository**
```sh
sudo apt install -y lsb-release wget apt-transport-https
sudo wget -O /usr/share/keyrings/matrix-keyring.asc https://packages.matrix.org/debian/matrix-org-archive-keyring.gpg
echo "deb [signed-by=/usr/share/keyrings/matrix-keyring.asc] https://packages.matrix.org/debian/ $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/matrix-org.list
sudo apt update
```
### **Step 2: Install Synapse**
```sh
sudo apt install -y matrix-synapse-py3
```
During installation, enter your desired **domain name** (e.g., `matrix.example.com`).
### **Step 3: Start and Enable Synapse**
```sh
sudo systemctl enable --now matrix-synapse
```
---
## **3. Configure Matrix Homeserver**
### **Step 1: Edit the Configuration File**
```sh
sudo nano /etc/matrix-synapse/homeserver.yaml
```
- Set `server_name` to your domain (`example.com`)
- Enable **registration** if needed (`enable_registration: true`)
- Configure **log level** (`log_level: INFO`)
Save and exit (`CTRL+X`, then `Y`).
### **Step 2: Restart Synapse**
```sh
sudo systemctl restart matrix-synapse
```
---
## **4. Set Up a Reverse Proxy (NGINX + Let’s Encrypt SSL)**
### **Step 1: Install NGINX and Certbot**
```sh
sudo apt install -y nginx certbot python3-certbot-nginx
```
### **Step 2: Obtain SSL Certificate**
```sh
sudo certbot --nginx -d matrix.example.com
```
### **Step 3: Configure NGINX**
Create a new file:
```sh
sudo nano /etc/nginx/sites-available/matrix
```
Paste the following configuration:
```nginx
server {
listen 80;
server_name matrix.example.com;
return 301 https://$host$request_uri;
}
server {
listen 443 ssl;
server_name matrix.example.com;
ssl_certificate /etc/letsencrypt/live/matrix.example.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/matrix.example.com/privkey.pem;
location /_matrix/ {
proxy_pass http://localhost:8008;
proxy_set_header X-Forwarded-For $remote_addr;
proxy_set_header Host $host;
proxy_set_header X-Forwarded-Proto $scheme;
}
}
```
Save and exit.
### **Step 4: Enable the Configuration**
```sh
sudo ln -s /etc/nginx/sites-available/matrix /etc/nginx/sites-enabled/
sudo systemctl restart nginx
```
---
## **5. Create an Admin User**
Run the following command:
```sh
register_new_matrix_user -c /etc/matrix-synapse/homeserver.yaml http://localhost:8008
```
Follow the prompts to create an **admin** user.
---
## **6. Test Your Matrix Server**
- Open a browser and go to: `https://matrix.example.com/_matrix/client/versions`
- You should see a JSON response indicating your homeserver is running.
- Use **Element** (https://element.io) to log in with your new user credentials.
---
## **7. Federation (Optional)**
To allow federation, ensure your DNS has an **SRV record**:
```
_matrix._tcp.example.com. 3600 IN SRV 10 5 443 matrix.example.com.
```
You can check your federation status at:
https://federationtester.matrix.org/
---
## **8. Additional Features**
### **Bridges (Connect to Other Platforms)**
- **Discord Bridge**: https://github.com/Half-Shot/matrix-appservice-discord
- **Telegram Bridge**: https://github.com/tulir/mautrix-telegram
### **Hosting a TURN Server (For Calls & Video)**
Install **coturn** for improved call reliability:
```sh
sudo apt install -y coturn
```
Edit `/etc/turnserver.conf` to include:
```
listening-port=3478
fingerprint
use-auth-secret
static-auth-secret=your-random-secret
realm=matrix.example.com
```
Enable and start the service:
```sh
sudo systemctl enable --now coturn
```
---
## **9. Backup & Maintenance**
### **Database Backup**
```sh
sudo systemctl stop matrix-synapse
sudo tar -czvf matrix-backup.tar.gz /var/lib/matrix-synapse/
sudo systemctl start matrix-synapse
```
### **Updating Synapse**
```sh
sudo apt update && sudo apt upgrade -y matrix-synapse-py3
sudo systemctl restart matrix-synapse
```
---
## **Connections**
- **Self-Hosting for Digital Sovereignty**
- **Nostr and Matrix Integration for Decentralized Messaging**
## **Donations via**
- lightninglayerhash@getalby.com
-

@ d34e832d:383f78d0
2025-02-22 00:57:07
[npub16d8gxt2z4k9e8sdpc0yyqzf5gp0np09ls4lnn630qzxzvwpl0rgq5h4rzv]
**Why Signal and Matrix Matter in a World of Mass Surveillance**
In an era where mass surveillance has become the norm, privacy-focused communication tools are essential for digital sovereignty. Signal and Matrix provide individuals and communities with encrypted, censorship-resistant messaging solutions that challenge centralized control over information exchange.
### **1. Signal – End-to-End Encryption and Metadata Resistance**
- **Proven Cryptographic Security**: Signal’s end-to-end encryption, powered by the Signal Protocol, ensures messages remain private even if intercepted.
- **Metadata Protection with Sealed Sender**: Signal minimizes metadata exposure, preventing third parties from knowing who is communicating with whom.
- **Simple and Ubiquitous Privacy**: Designed for ease of use, Signal bridges the gap between security and accessibility, making privacy mainstream.
### **2. Matrix – Decentralized and Federated Communication**
- **Self-Hosted and Federated Infrastructure**: Unlike centralized services, Matrix allows users to host their own servers, reducing reliance on single points of failure.
- **Bridging Across Platforms**: Matrix bridges seamlessly with other communication protocols (IRC, XMPP, Slack, etc.), creating a unified, decentralized network.
- **End-to-End Encryption and Decentralized Identity**: Matrix offers fully encrypted rooms and a decentralized identity system, ensuring control over user data.
### **3. Mass Surveillance vs. Private Communication**
- **Government and Corporate Data Harvesting**: Centralized platforms like WhatsApp, Facebook Messenger, and Gmail log metadata and conversations, creating massive surveillance databases.
- **The Threat of AI-Driven Censorship**: Machine learning algorithms analyze user behavior, making privacy-invasive censorship and social credit scoring systems a reality.
- **Decentralization as a Resistance Strategy**: By adopting Signal and Matrix, individuals reclaim their right to private conversations without interference from state or corporate actors.
### **Integration Potential and Future Developments**
- **Bitcoin and Encrypted Messaging**: Signal and Matrix can be combined with Bitcoin for private transactions and communication, furthering financial sovereignty.
- **P2P and Nostr Integration**: Future developments could see Matrix and Nostr integrated for even more robust censorship-resistant communication.
### **Donations via**
- lightninglayerhash@getalby.com
-

@ cda24367:8ba5afc3
2025-02-22 00:11:32
Just a test to find out what this Habla.news does. It looks interesting.
And here's an Odysee video to see if the iframe will work.
<iframe id="odysee-iframe" style="width:100%; aspect-ratio:16 / 9;" src="https://odysee.com/$/embed/@RandomStuff:0/Steve-Hughes-on-Charity:0?r=9cn37JvaLAtLK8z8NfZjsqm8ZNCaNuUy" allowfullscreen></iframe>
-

@ 916a7ab7:146bb83e
2025-02-21 23:12:49
tens of thousands of Afghans flee
by often desperate measures,
detained, assaulted, murdered,
martyred
faithless and in fetters.
school girls in Uganda know
they many never have a wedding
when terror rapes
the peace they sow,
punished by beheading.
Chinese mosques, temples, homes
are dismantled brick by brick
for believing something higher than
the state or politic.
the glowing boxes in our hands
or hanging from our walls
manipulate the way we think
becoming passive thralls.
-

@ 916a7ab7:146bb83e
2025-02-21 22:43:35
my eyes
---
are not blurry
---
when they see through lenses
---
of someone's suffering, and then
---
I see.
---
-

@ fc481c65:e280e7ba
2025-02-21 21:30:56
#Algebra is a branch of #Mathematics that uses symbols, known as variables (like x or y), to represent numbers in equations and formulas. It involves operations like addition, subtraction, multiplication, and division, but these operations are performed on variables as well as numbers.
### Key Concepts in Algebra
- **Variables**: Symbols that stand in for unknown values.
- **Constants**: Known values that don’t change.
- **Coefficients**: Numbers used to multiply a variable.
- **Expressions**: Combinations of variables, numbers, and operations (like 3x + 4).
- **Equations**: Statements that assert the equality of two expressions, typically including an equals sign (like 2x + 3 = 7).
### Basic Operations
1. **Adding and Subtracting**: You can add or subtract like terms (terms whose variables and their powers are the same). For example, 2x+3x=5x
2. **Multiplying and Dividing**: You multiply or divide both the coefficients and the variables. For instance, `$$3x \times 2x=6x^2$$`
3. **Solving Equations**: The goal is often to isolate the variable on one side of the equation to find its value. This can involve reversing operations using opposite operations.
### Applications of Algebra
Algebra is used in various fields, from #Engineering and computer science to economics and everyday problem solving. It helps in creating formulas to understand relationships between quantities and in solving equations that model real-world situations.
## Algebra and Electronics
Algebra plays a crucial role in #Electronics engineering, particularly through its application in circuit analysis, signal processing, and control systems. Understanding and utilizing algebraic techniques can significantly enhance problem-solving capabilities in these areas.
### 1. Complex Numbers
In electronic engineering, complex numbers are essential for analyzing AC circuits. They help in representing sinusoidal signals, which are fundamental in communications and power systems.
- **Representation**: z=a+bi or z=reiθ (polar form)
- **Operations**: Addition, subtraction, multiplication, and division in complex form, crucial for understanding the behavior of circuits in the frequency domain.
**Example**: Calculating the impedance of an RLC series circuit at a certain frequency.
- **Circuit Components**: R=50Ω, L=0.1 H, C=10 μF, ω=1000 rad/s
`$$
Z = 50 + j1000 \times 0.1 - \frac{1}{j1000 \times 10 \times 10^{-6}} = 50 + j100 - \frac{1}{j0.01} = 50 + j100 + 100j = 50 + 200j
$$`
### 2. Matrices and Determinants
Matrices are widely used in electronic engineering for handling multiple equations simultaneously, which is common in systems and network analysis.
- **Matrix Operations**: Addition, subtraction, multiplication, and inversion.
- **Determinant and Inverse**: Used in solving systems of linear equations, critical in network theory and control systems.
### 3. Fourier Transforms
Algebraic manipulation is key in applying Fourier transforms, which convert time-domain signals into their frequency components. This is crucial for signal analysis, filtering, and system design.
- **Fourier Series**: Represents periodic signals as a sum of sinusoids.
- **Fourier Transform**: Converts continuous time-domain signals to continuous frequency spectra.
### 4. Laplace Transforms
Laplace transforms are used to simplify the process of analyzing and designing control systems and circuits by converting differential equations into algebraic equations.
- **Transfer Functions**: Represent systems in the s-domain, facilitating easier manipulation and understanding of system dynamics.
### 5. Z-Transforms
Similar to Laplace transforms, Z-transforms are used for discrete systems prevalent in digital signal processing and digital control.
### 6. Algebraic Equations in Filter Design
Algebra is used in the design of filters, both analog and digital, where polynomial equations are used to determine filter coefficients that meet specific frequency response criteria.
### 7. Control Systems
The design and stability analysis of control systems involve solving characteristic equations and manipulating transfer functions, which require a solid understanding of algebra.
### 8. Network Theorems
Theorems like Kirchhoff's laws, Thevenin’s theorem, and Norton’s theorem involve algebraic equations to simplify and analyze circuits.
## Algebra with Sympy
TODO
-

@ 4857600b:30b502f4
2025-02-21 21:15:04
In a revealing development that exposes the hypocrisy of government surveillance, multiple federal agencies including the CIA and FBI have filed lawsuits to keep Samourai Wallet's client list sealed during and after trial proceedings. This move strongly suggests that government agencies themselves were utilizing Samourai's privacy-focused services while simultaneously condemning similar privacy tools when used by ordinary citizens.
The situation bears striking parallels to other cases where government agencies have hidden behind "national security" claims, such as the Jeffrey Epstein case, highlighting a troubling double standard: while average citizens are expected to surrender their financial privacy through extensive reporting requirements and regulations, government agencies claim exemption from these same transparency standards they enforce on others.
This case exemplifies the fundamental conflict between individual liberty and state power, where government agencies appear to be using the very privacy tools they prosecute others for using. The irony is particularly stark given that money laundering for intelligence agencies is considered legal in our system, while private citizens seeking financial privacy face severe legal consequences - a clear demonstration of how the state creates different rules for itself versus the people it claims to serve.
Citations:
[1] https://www.bugle.news/cia-fbi-dnc-rnc-all-sue-to-redact-samourais-client-list-from-trial/
-

@ dbb19ae0:c3f22d5a
2025-02-21 20:38:43
``` python
#!/usr/bin/env python3
import asyncio
from nostr_sdk import Metadata, Client, NostrSigner, Keys, Filter, PublicKey, Kind, init_logger, LogLevel
from datetime import timedelta
async def main():
init_logger(LogLevel.INFO)
secret_key = "nsec1........Replace with your actual nsec secret key"
keys = Keys.parse(secret_key)
signer = NostrSigner.keys(keys)
client = Client(signer)
await client.add_relay("wss://relay.damus.io")
await client.connect()
# Update metadata
new_metadata = Metadata().set_name( "MyName")\
.set_nip05("MyName@example.com")\
.set_lud16("MyName@lud16.com")
await client.set_metadata(new_metadata)
print("Metadata updated successfully.")
# Get updated metadata
npub = "npub1....Replace with your actual npub"
pk = PublicKey.parse(npub)
print(f"\nGetting profile metadata for {npub}:")
metadata = await client.fetch_metadata(pk, timedelta(seconds=15))
print(metadata)
if __name__ == '__main__':
asyncio.run(main())
```
-

@ 4c96d763:80c3ee30
2025-02-21 20:31:55
# Changes
## Ethan Tuttle (1):
- feat: ctrl+enter when creating a new note, sends the note, the same way clicking the "Post Now" button.
## Ken Sedgwick (11):
- drive-by compiler warning fixes
- drive-by clippy fixes
- add derive Debug to some things
- panic on unknown CLI arguments
- move RelayDebugView to notedeck crate and restore --relay-debug
- add diagnostic string to DecodeFailed
- improve relay message parsing unit tests
- fix event error return when decoding fails
- fix OK message parser to include last message component
- fix EOSE parsing to handle extra whitespace
- check message length before prefix comparisons
## William Casarin (5):
- clippy: fix enum too large issue
- changelog: add unreleased section
- clippy: fix lint
- args: skip creation of vec
- nix: fix android build
## jglad (4):
- fix: handle missing file [#715]
- refactor
- fix compilation
- hide nsec in account panel
pushed to [notedeck:refs/heads/master](http://git.jb55.com/notedeck/commit/32c7f83bd7a807155de6a13b66a7d43f48c25e13.html)
-

@ a95c6243:d345522c
2025-02-21 19:32:23
*Europa – das Ganze ist eine wunderbare Idee,* *\
aber das war der Kommunismus auch.* *\
Loriot*  
**«Europa hat fertig», könnte man unken,** und das wäre nicht einmal sehr verwegen. Mit solch einer [Einschätzung](https://transition-news.org/geopolitische-ohnmacht-und-die-last-des-euro-steht-die-eu-vor-der-implosion) stünden wir nicht alleine, denn die Stimmen in diese Richtung mehren sich. Der französische Präsident Emmanuel Macron warnte schon letztes Jahr davor, dass «unser Europa sterben könnte». Vermutlich hatte er dabei andere Gefahren im Kopf als jetzt der ungarische Ministerpräsident Viktor Orbán, der ein «baldiges Ende der EU» prognostizierte. Das Ergebnis könnte allerdings das gleiche sein.
**Neben vordergründigen Themenbereichen wie Wirtschaft, Energie und Sicherheit** ist das eigentliche Problem jedoch die obskure Mischung aus aufgegebener Souveränität und geschwollener Arroganz, mit der europäische Politiker:innende unterschiedlicher Couleur aufzutreten pflegen. Und das Tüpfelchen auf dem i ist die bröckelnde Legitimation politischer Institutionen dadurch, dass die Stimmen großer Teile der Bevölkerung seit Jahren auf vielfältige Weise ausgegrenzt werden.
**Um «UnsereDemokratie» steht es schlecht.** Dass seine Mandate immer schwächer werden, merkt natürlich auch unser «Führungspersonal». Entsprechend werden die Maßnahmen zur Gängelung, Überwachung und Manipulation der Bürger ständig verzweifelter. Parallel dazu [plustern](https://www.bundesregierung.de/breg-de/service/newsletter-und-abos/bundesregierung-aktuell/ausgabe-07-2025-februar-21-2335652?view=renderNewsletterHtml) sich in Paris Macron, Scholz und einige andere noch einmal mächtig in Sachen Verteidigung und [«Kriegstüchtigkeit»](https://transition-news.org/europaische-investitionsbank-tragt-zur-kriegstuchtigkeit-europas-bei) auf.
**Momentan gilt es auch, das Überschwappen covidiotischer und verschwörungsideologischer Auswüchse** aus den USA nach Europa zu vermeiden. So ein «MEGA» (Make Europe Great Again) können wir hier nicht gebrauchen. Aus den Vereinigten Staaten kommen nämlich furchtbare Nachrichten. Beispielsweise wurde einer der schärfsten Kritiker der Corona-Maßnahmen kürzlich zum Gesundheitsminister ernannt. Dieser setzt sich jetzt für eine Neubewertung der mRNA-«Impfstoffe» ein, was durchaus zu einem [Entzug der Zulassungen](https://transition-news.org/usa-zulassungsentzug-fur-corona-impfstoffe-auf-der-tagesordnung) führen könnte.
**Der europäischen Version von** **[«Verteidigung der Demokratie»](https://transition-news.org/eu-macht-freiwilligen-verhaltenskodex-gegen-desinformation-zu-bindendem-recht)** setzte der US-Vizepräsident J. D. Vance auf der Münchner Sicherheitskonferenz sein Verständnis entgegen: «Demokratie stärken, indem wir unseren Bürgern erlauben, ihre Meinung zu sagen». Das Abschalten von Medien, das Annullieren von Wahlen oder das Ausschließen von Menschen vom politischen Prozess schütze gar nichts. Vielmehr sei dies der todsichere Weg, die Demokratie zu zerstören.
**In der Schweiz kamen seine Worte deutlich besser an** als in den meisten europäischen NATO-Ländern. Bundespräsidentin Karin Keller-Sutter lobte die Rede und interpretierte sie als «Plädoyer für die direkte Demokratie». Möglicherweise zeichne sich hier eine [außenpolitische Kehrtwende](https://transition-news.org/schweiz-vor-aussenpolitischer-kehrtwende-richtung-integraler-neutralitat) in Richtung integraler Neutralität ab, meint mein Kollege Daniel Funk. Das wären doch endlich mal ein paar gute Nachrichten.
**Von der einstigen Idee einer europäischen Union** mit engeren Beziehungen zwischen den Staaten, um Konflikte zu vermeiden und das Wohlergehen der Bürger zu verbessern, sind wir meilenweit abgekommen. Der heutige korrupte Verbund unter technokratischer Leitung ähnelt mehr einem Selbstbedienungsladen mit sehr begrenztem Zugang. Die EU-Wahlen im letzten Sommer haben daran ebenso wenig geändert, wie die [Bundestagswahl](https://transition-news.org/bundestagswahl-mehr-aufrustung-statt-friedenskanzler-nach-der-wahl) am kommenden Sonntag darauf einen Einfluss haben wird.
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/europaer-seid-ihr-noch-zu-retten)*** erschienen.
-

@ 86a82cab:b5ef38a0
2025-02-21 18:42:50
This morning, I decided to look into the NIP-23 specialized clients, and try to publish long-form content on the Nostr network of relays: https://habla.news/ https://blogstack.io First, I encourage you to read the NIP, and the first thing that you will notice is that the kind id used to publish is 30023 instead of 1, soThis morning, I decided to look into the NIP-23 specialized clients, and try to publish **long-form** content on the **Nostr** network of relays: https://habla.news/ https://blogstack.io First, I encourage you to read the NIP, and the first thing that you will notice is that the kind id used to publish is 30023 instead of 1, so
-

@ 86a82cab:b5ef38a0
2025-02-21 18:32:52
asdasdasdasdasdNIP-23 Long-form Content. draft optional author:fiatjaf. This NIP defines kind:30023 (a parameterized replaceable event) for long-form text content, generally referred to as "articles" or "blog posts".kind:30024 has the same structure as kind:30023 and is used to save long form drafts. "Social"NIP-23 **Long-form** Content. draft optional author:fiatjaf. This NIP defines kind:30023 (a parameterized replaceable event) for **long-form** text content, generally referred to as "articles" or "blog posts".kind:30024 has the same structure as kind:30023 and is used to save **long** **form** drafts. "Social"
-

@ 6e0ea5d6:0327f353
2025-02-21 18:15:52
"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.
— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend!
If this message helped you in any way,
consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-

@ 6e0ea5d6:0327f353
2025-02-21 18:08:19
When talking about the tumbles we experience in our early years, it’s almost impossible not to try to compare the degree of distress that each stumble has provided us.
Even if harmless, the first accident that comes to mind is one that, in some way, left its mark. Whether it’s a scraped knee, a gash on the forehead, or a broken arm: having that first conscious encounter with pain is an unforgettable terror.
For in one moment, we are sheltered in the loving arms of our parents, feeling invulnerable, and moments later there’s a thick mixture of blood and dirt streaming from a cut that doesn’t seem all that exaggerated to someone looking from the outside — but only to those looking from the outside.
However, this is not what makes that first contact with pain so terrifying. It’s the discovery of how lonely we are when facing an individual agony, even under the care of an adult.
Ultimately, what follows the shock can vary from the sting of cleaning the wound to the warning slap. After the understanding is digested, and we learn how wounds are made, we become cautious. A slip is met with laughter, and we grow tougher than the ground.
That is, until we discover the free fall that holds the world’s problems…
“Consciousness, not age, leads to wisdom.”
— Publilius Syrus
Thank you for reading, my friend!
If this message helped you in any way,
consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-

@ 266815e0:6cd408a5
2025-02-21 17:54:15
I've been working on the applesauce libraries for a while now but I think this release is the first one I would consider to be stable enough to use
A lot of the core concepts and classes are in place and stable enough where they wont change too much next release
If you want to skip straight to the documentation you can find at [hzrd149.github.io/applesauce](https://hzrd149.github.io/applesauce/) or the typescript docs at [hzrd149.github.io/applesauce/typedoc](https://hzrd149.github.io/applesauce/typedoc)
## Whats new
### Accounts
The `applesauce-accounts` package is an extension of the `applesauce-signers` package and provides classes for building a multi-account system for clients
Its primary features are
- Serialize and deserialize accounts so they can be saved in local storage or IndexededDB
- Account manager for multiple accounts and switching between them
- Account metadata for things like labels, app settings, etc
- Support for NIP-46 Nostr connect accounts
see [documentation](https://hzrd149.github.io/applesauce/accounts/manager.html) for more examples
### Nostr connect signer
The `NostrConnectSigner` class from the `applesauce-signers` package is now in a stable state and has a few new features
- Ability to create `nostrconnect://` URIs and waiting for the remote signer to connect
- SDK agnostic way of subscribing and publishing to relays
For a simple example, here is how to create a signer from a `bunker://` URI
```js
const signer = await NostrConnectSigner.fromBunkerURI(
"bunker://266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5?relay=wss://relay.nsec.app&secret=d9aa70",
{
permissions: NostrConnectSigner.buildSigningPermissions([0, 1, 3, 10002]),
async onSubOpen(filters, relays, onEvent) {
// manually open REQ
},
async onSubClose() {
// close previouse REQ
},
async onPublishEvent(event, relays) {
// Pubilsh an event to relays
},
},
);
```
see [documentation](https://hzrd149.github.io/applesauce/signers/nostr-connect.html) for more examples and other signers
### Event Factory
The `EventFactory` class is probably what I'm most proud of. its a standalone class that can be used to create various types of events from templates ([blueprints](https://hzrd149.github.io/applesauce/typedoc/modules/applesauce_factory.Blueprints.html)) and is really simple to use
For example:
```js
import { EventFactory } from "applesauce-factory";
import { NoteBlueprint } from "applesauce-factory/blueprints";
const factory = new EventFactory({
// optionally pass a NIP-07 signer in to use for encryption / decryption
signer: window.nostr
});
// Create a kind 1 note with a hashtag
let draft = await factory.create(NoteBlueprint, "hello world #grownostr");
// Sign the note so it can be published
let signed = await window.nostr.signEvent(draft);
```
Its included in the `applesauce-factory` package and can be used with any other nostr SDKs or vanilla javascript
It also can be used to modify existing replaceable events
```js
let draft = await factory.modifyTags(
// kind 10002 event
mailboxes,
// add outbox relays
addOutboxRelay("wss://relay.io/"),
addOutboxRelay("wss://nostr.wine/"),
// remove inbox relay
removeInboxRelay("wss://personal.old-relay.com/")
);
```
see [documentation](https://hzrd149.github.io/applesauce/overview/factory.html) for more examples
### Loaders
The `applesauce-loaders` package exports a bunch of loader classes that can be used to load everything from replaceable events (profiles) to timelines and NIP-05 identities
They use [rx-nostr](https://penpenpng.github.io/rx-nostr/) under the hood to subscribe to relays, so for the time being they will not work with other nostr SDKs
I don't expect many other developers or apps to use them since in my experience every nostr client requires a slightly different way or loading events
*They are stable enough to start using but they are not fully tested and they might change slightly in the future*
The following is a short list of the loaders and what they can be used for
- `ReplaceableLoader` loads any replaceable events (0, 3, 1xxxx, 3xxxx)
- `SingleEventLoader` loads single events based on ids
- `TimelineLoader` loads a timeline of events from multiple relays based on filters
- `TagValueLoader` loads events based on a tag name (like "e") and a value, can be used to load replies, zaps, reactions, etc
- `DnsIdentityLoader` loads NIP-05 identities and supports caching
- `UserSetsLoader` loads all lists events for users
see [documentation](https://hzrd149.github.io/applesauce/overview/loaders.html) for more examples
### Real tests
For all new features and a lot of existing ones I'm trying to write tests to ensure I don't leave unexpected bugs for later
I'm not going to pretend its 100% tests coverage or that it will ever get close to that point, but these tests cover some of the core classes and help me prove that my code is doing what it says its supposed to do
At the moment there are about 230 tests covering 45 files. not much but its a start
## Apps built using applesauce
If you want to see some examples of applesauce being used in a nostr client I've been testing a lot of this code in production on the apps I've built in the last few months
- [noStrudel](https://github.com/hzrd149/nostrudel) The main app everything is being built for and tested in
- [nsite-manager](https://github.com/hzrd149/nsite-manager) Still a work-in-progress but supports multiple accounts thanks to the `applesauce-accounts` package
- [blossomservers.com](https://github.com/hzrd149/blossomservers) A simple (and incomplete) nostr client for listing and reviewing public blossom servers
- [libretranslate-dvm](https://github.com/hzrd149/libretranslate-dvm) A libretranslate DVM for nostr:npub1mkvkflncllnvp3adq57klw3wge6k9llqa4r60g42ysp4yyultx6sykjgnu
- [cherry-tree](https://github.com/hzrd149/cherry-tree) A chunked blob uploader / downloader. only uses applesauce for boilerplate
- [nsite-homepage](https://github.com/hzrd149/nsite-homepage) A simple landing page for [nsite.lol](https://nsite.lol)
Thanks to nostr:npub1cesrkrcuelkxyhvupzm48e8hwn4005w0ya5jyvf9kh75mfegqx0q4kt37c for teaching me more about rxjs and consequentially making me re-write a lot of the core observables to be faster
-

@ dbb19ae0:c3f22d5a
2025-02-21 17:46:58
Tested and working with nostr_sdk version 0.39
``` python
from nostr_sdk import Metadata, Client, Keys, Filter, PublicKey
from datetime import timedelta
import argparse
import asyncio
import json
async def main(npub):
client = Client()
await client.add_relay("wss://relay.damus.io")
await client.connect()
pk = PublicKey.parse(npub)
print(f"\nGetting profile metadata for {npub}:")
metadata = await client.fetch_metadata(pk, timedelta(seconds=15))
# Printing each field of the Metadata object
print(f"Name: {metadata.get_name()}")
print(f"Display Name: {metadata.get_display_name()}")
print(f"About: {metadata.get_about()}")
print(f"Website: {metadata.get_website()}")
print(f"Picture: {metadata.get_picture()}")
print(f"Banner: {metadata.get_banner()}")
print(f"NIP05: {metadata.get_nip05()}")
print(f"LUD06: {metadata.get_lud06()}")
print(f"LUD16: {metadata.get_lud16()}")
#print(f"Custom: {metadata.get_custom()}")
if __name__ == '__main__':
parser = argparse.ArgumentParser(description='Fetch all metadata for a given npub')
parser.add_argument('npub', type=str, help='The npub of the user')
args = parser.parse_args()
asyncio.run(main(args.npub))
```
 @ a012dc82:6458a70d
2025-02-22 15:51:37Bitcoin, the pioneering cryptocurrency, has always been known for its volatility. This digital asset has seen dramatic fluctuations in price, attracting investors and speculators alike. Understanding these price movements is crucial for anyone involved in the crypto market. The journey of Bitcoin from a niche digital token to a mainstream financial asset has been marked by periods of rapid growth and sudden declines. This volatility is not just a source of risk, but also of potential opportunity for traders and investors. The factors driving these fluctuations range from regulatory news, technological advancements, to broader economic factors. Bitcoin's decentralized nature adds to its unpredictability, as it operates independently of a central bank or government. **Table of Contents** - The Recent Price Rally and Subsequent Halt - Insights from CryptoQuant's Analysis - The Role of Short-Term Holders - Understanding Bitcoin Binary Coin Days Destroyed ( … - The Dynamics of Profit-Taking - Actions by Miners and Whales - Current Market Scenario and Future Outlook - Conclusion - FAQs **The Recent Price Rally and Subsequent Halt** In a recent surge, Bitcoin's value soared past the $44,000 mark, only to encounter a significant resistance level near $45,000. This resistance led to a notable decline in its price. The question on everyone's mind is: what caused this sudden halt in Bitcoin's otherwise steady climb? This rally, like many in Bitcoin's past, was driven by a mix of investor optimism, favorable market conditions, and increasing institutional interest in cryptocurrency. However, the resistance at $45,000 proved to be a turning point, sparking a wave of sell-offs and profit-taking. This price behavior is a classic example of the market's psychological dynamics, where key resistance levels can lead to significant shifts in investor behavior. The rapid change from a bullish to a bearish market sentiment at this juncture underscores the fragile and speculative nature of the cryptocurrency market. **Insights from CryptoQuant's Analysis** CryptoQuant, a renowned market analytics platform, offers valuable insights into this phenomenon. An analyst from CryptoQuant, Yonsei, conducted a detailed analysis of on-chain data to unravel the mystery behind Bitcoin's recent price behavior. This analysis goes beyond surface-level market trends, delving into the intricate movements of Bitcoin across various wallets and exchanges. By examining metrics such as fund flows, wallet activities, and transaction patterns, CryptoQuant provides a more nuanced understanding of what drives Bitcoin's price changes. Yonsei's analysis, in particular, sheds light on the behavior of different investor cohorts, revealing how their actions collectively impact the market. This kind of deep-dive analysis is essential for anyone looking to understand the often opaque mechanisms of cryptocurrency markets. **The Role of Short-Term Holders** The analysis revealed that short-term holders, particularly those who had invested in Bitcoin for a period ranging from 6 to 18 months, started to realize their profits as soon as Bitcoin broke through the $40,000 resistance level. This profit-taking was a primary factor in the subsequent price retraction. These short-term holders, often more sensitive to market fluctuations, tend to react quickly to price changes, looking to capitalize on short-term gains. Their collective actions can create significant market movements, as seen in this instance. The behavior of these investors is often influenced by news events, market sentiment, and technical indicators. In this case, the rapid rise in Bitcoin's price likely triggered a psychological response to lock in profits, leading to a cascade of sell orders. Understanding the motivations and behaviors of these short-term holders is crucial for predicting short-term market movements in the volatile world of cryptocurrency. **Understanding Bitcoin Binary Coin Days Destroyed (CDD)** A critical metric in this analysis is the Bitcoin Binary Coin Days Destroyed (CDD). This metric assesses the movement of long-held Bitcoins, providing insights into the behavior of long-term investors. An increase in Binary CDD indicates that a significant amount of Bitcoin, held dormant for a long time, has been mobilized, suggesting a sell-off by long-term holders. This metric is particularly important as it highlights the actions of the most steadfast part of the market - those who have held Bitcoin through various cycles. When these long-term holders start moving their coins, it often signals a significant shift in market sentiment. The CDD metric thus serves as a barometer for the conviction of Bitcoin's long-term investor base. A high CDD can indicate a loss of confidence among these investors, or a belief that the market has reached a peak. Conversely, a low CDD suggests that long-term holders are not yet ready to sell, indicating continued confidence in the market's future. **The Dynamics of Profit-Taking** The CryptoQuant analysis further highlighted that a majority of Bitcoin holders were in profit, with the Spent Output Profit Ratio remaining above one. This indicated that about 90% of Bitcoin holders were profiting, which naturally led to a trend of profit-taking. This phenomenon is a key aspect of market cycles in cryptocurrencies. When a large portion of investors are in profit, especially after a significant price rally, the market often sees a wave of selling as investors look to cash in on their gains. This behavior is compounded by psychological factors, such as fear of missing out (FOMO) and fear, uncertainty, and doubt (FUD), which can lead to rapid shifts in market sentiment. Additionally, the profit-taking trend is influenced by external factors such as global economic conditions, regulatory news, and technological developments within the blockchain space. These factors can either reinforce the confidence of investors, leading to a hold strategy, or trigger a sell-off in anticipation of a market downturn. **Actions by Miners and Whales** Another interesting aspect of the analysis was the behavior of Bitcoin miners and whales (large-scale holders). These groups also contributed to the selling pressure. Miners, in particular, sold their assets at high-profit margins when Bitcoin reached its peak, adding to the downward pressure on its price. The actions of miners are crucial to understanding Bitcoin's market dynamics, as they are not only investors but also the producers of new Bitcoins. Their decision to sell or hold can significantly impact the supply of Bitcoin in the market. Whales, or large-scale holders, have a similar impact due to the sheer volume of their transactions. Their trades can lead to substantial market movements, creating waves that affect smaller investors. The behavior of these whales often reflects a more strategic approach to the market, influenced by long-term trends and broader market analysis. Their actions can serve as indicators for future market movements, making their behavior a key focus for analysts and investors alike. **Current Market Scenario and Future Outlook** Despite the recent price drop, the overall market sentiment remains positive. The bear market seems to be in the past, and liquidity conditions in the crypto market are improving. However, Bitcoin currently hovers around the $41,000 mark, a slight decrease from its recent high. This current state reflects the ever-changing nature of the cryptocurrency market, where investor sentiment can shift rapidly. The future outlook for Bitcoin remains a topic of much debate among experts. Some predict continued growth as institutional adoption increases and blockchain technology becomes more integrated into mainstream finance. Others caution about potential regulatory clampdowns and the volatile nature of the market. What remains clear is that Bitcoin continues to be a key player in the financial world, with its price movements being a barometer for the health and sentiment of the broader cryptocurrency market. **Conclusion** Bitcoin's market behavior, as analyzed by CryptoQuant, offers a complex picture of various factors at play. The interplay between short-term and long-term holders, the strategic moves of miners and whales, and the overall market sentiment all contribute to the price dynamics of this digital currency. Understanding these elements is key for investors and enthusiasts who wish to navigate the volatile waters of Bitcoin's market. As the crypto landscape continues to evolve, keeping a close eye on these trends and analyses will be crucial for making informed decisions in the world of cryptocurrency. The insights provided by platforms like CryptoQuant are invaluable in this regard, offering a deeper understanding of the market forces at work. **FAQs** **What caused the recent halt in Bitcoin's price rally?** The halt in Bitcoin's price rally, after reaching near $45,000, was primarily due to profit-taking by short-term holders and investors who had held Bitcoin for 6-18 months, as revealed by CryptoQuant's analysis. **What is Bitcoin Binary Coin Days Destroyed (CDD)?** Bitcoin Binary Coin Days Destroyed (CDD) is a metric that measures the movement of long-held Bitcoins. It indicates the amount of Bitcoin, held dormant for a long time, that has been mobilized or sold. **How do miners and whales influence Bitcoin's price?** Miners and whales (large-scale holders) significantly influence Bitcoin's price through their actions. When they sell their holdings, especially during peak prices, they add to the market's selling pressure, potentially leading to price drops. **What does a high Bitcoin Binary CDD indicate?** A high Bitcoin Binary CDD suggests that a large amount of long-held Bitcoin is being sold, which can be a sign of long-term holders losing confidence or deciding to take profits. **Is the current market sentiment for Bitcoin positive or negative?** Despite recent price fluctuations, the overall market sentiment for Bitcoin remains cautiously positive, with improvements in market liquidity and interest from institutional investors. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
@ a012dc82:6458a70d
2025-02-22 15:51:37Bitcoin, the pioneering cryptocurrency, has always been known for its volatility. This digital asset has seen dramatic fluctuations in price, attracting investors and speculators alike. Understanding these price movements is crucial for anyone involved in the crypto market. The journey of Bitcoin from a niche digital token to a mainstream financial asset has been marked by periods of rapid growth and sudden declines. This volatility is not just a source of risk, but also of potential opportunity for traders and investors. The factors driving these fluctuations range from regulatory news, technological advancements, to broader economic factors. Bitcoin's decentralized nature adds to its unpredictability, as it operates independently of a central bank or government. **Table of Contents** - The Recent Price Rally and Subsequent Halt - Insights from CryptoQuant's Analysis - The Role of Short-Term Holders - Understanding Bitcoin Binary Coin Days Destroyed ( … - The Dynamics of Profit-Taking - Actions by Miners and Whales - Current Market Scenario and Future Outlook - Conclusion - FAQs **The Recent Price Rally and Subsequent Halt** In a recent surge, Bitcoin's value soared past the $44,000 mark, only to encounter a significant resistance level near $45,000. This resistance led to a notable decline in its price. The question on everyone's mind is: what caused this sudden halt in Bitcoin's otherwise steady climb? This rally, like many in Bitcoin's past, was driven by a mix of investor optimism, favorable market conditions, and increasing institutional interest in cryptocurrency. However, the resistance at $45,000 proved to be a turning point, sparking a wave of sell-offs and profit-taking. This price behavior is a classic example of the market's psychological dynamics, where key resistance levels can lead to significant shifts in investor behavior. The rapid change from a bullish to a bearish market sentiment at this juncture underscores the fragile and speculative nature of the cryptocurrency market. **Insights from CryptoQuant's Analysis** CryptoQuant, a renowned market analytics platform, offers valuable insights into this phenomenon. An analyst from CryptoQuant, Yonsei, conducted a detailed analysis of on-chain data to unravel the mystery behind Bitcoin's recent price behavior. This analysis goes beyond surface-level market trends, delving into the intricate movements of Bitcoin across various wallets and exchanges. By examining metrics such as fund flows, wallet activities, and transaction patterns, CryptoQuant provides a more nuanced understanding of what drives Bitcoin's price changes. Yonsei's analysis, in particular, sheds light on the behavior of different investor cohorts, revealing how their actions collectively impact the market. This kind of deep-dive analysis is essential for anyone looking to understand the often opaque mechanisms of cryptocurrency markets. **The Role of Short-Term Holders** The analysis revealed that short-term holders, particularly those who had invested in Bitcoin for a period ranging from 6 to 18 months, started to realize their profits as soon as Bitcoin broke through the $40,000 resistance level. This profit-taking was a primary factor in the subsequent price retraction. These short-term holders, often more sensitive to market fluctuations, tend to react quickly to price changes, looking to capitalize on short-term gains. Their collective actions can create significant market movements, as seen in this instance. The behavior of these investors is often influenced by news events, market sentiment, and technical indicators. In this case, the rapid rise in Bitcoin's price likely triggered a psychological response to lock in profits, leading to a cascade of sell orders. Understanding the motivations and behaviors of these short-term holders is crucial for predicting short-term market movements in the volatile world of cryptocurrency. **Understanding Bitcoin Binary Coin Days Destroyed (CDD)** A critical metric in this analysis is the Bitcoin Binary Coin Days Destroyed (CDD). This metric assesses the movement of long-held Bitcoins, providing insights into the behavior of long-term investors. An increase in Binary CDD indicates that a significant amount of Bitcoin, held dormant for a long time, has been mobilized, suggesting a sell-off by long-term holders. This metric is particularly important as it highlights the actions of the most steadfast part of the market - those who have held Bitcoin through various cycles. When these long-term holders start moving their coins, it often signals a significant shift in market sentiment. The CDD metric thus serves as a barometer for the conviction of Bitcoin's long-term investor base. A high CDD can indicate a loss of confidence among these investors, or a belief that the market has reached a peak. Conversely, a low CDD suggests that long-term holders are not yet ready to sell, indicating continued confidence in the market's future. **The Dynamics of Profit-Taking** The CryptoQuant analysis further highlighted that a majority of Bitcoin holders were in profit, with the Spent Output Profit Ratio remaining above one. This indicated that about 90% of Bitcoin holders were profiting, which naturally led to a trend of profit-taking. This phenomenon is a key aspect of market cycles in cryptocurrencies. When a large portion of investors are in profit, especially after a significant price rally, the market often sees a wave of selling as investors look to cash in on their gains. This behavior is compounded by psychological factors, such as fear of missing out (FOMO) and fear, uncertainty, and doubt (FUD), which can lead to rapid shifts in market sentiment. Additionally, the profit-taking trend is influenced by external factors such as global economic conditions, regulatory news, and technological developments within the blockchain space. These factors can either reinforce the confidence of investors, leading to a hold strategy, or trigger a sell-off in anticipation of a market downturn. **Actions by Miners and Whales** Another interesting aspect of the analysis was the behavior of Bitcoin miners and whales (large-scale holders). These groups also contributed to the selling pressure. Miners, in particular, sold their assets at high-profit margins when Bitcoin reached its peak, adding to the downward pressure on its price. The actions of miners are crucial to understanding Bitcoin's market dynamics, as they are not only investors but also the producers of new Bitcoins. Their decision to sell or hold can significantly impact the supply of Bitcoin in the market. Whales, or large-scale holders, have a similar impact due to the sheer volume of their transactions. Their trades can lead to substantial market movements, creating waves that affect smaller investors. The behavior of these whales often reflects a more strategic approach to the market, influenced by long-term trends and broader market analysis. Their actions can serve as indicators for future market movements, making their behavior a key focus for analysts and investors alike. **Current Market Scenario and Future Outlook** Despite the recent price drop, the overall market sentiment remains positive. The bear market seems to be in the past, and liquidity conditions in the crypto market are improving. However, Bitcoin currently hovers around the $41,000 mark, a slight decrease from its recent high. This current state reflects the ever-changing nature of the cryptocurrency market, where investor sentiment can shift rapidly. The future outlook for Bitcoin remains a topic of much debate among experts. Some predict continued growth as institutional adoption increases and blockchain technology becomes more integrated into mainstream finance. Others caution about potential regulatory clampdowns and the volatile nature of the market. What remains clear is that Bitcoin continues to be a key player in the financial world, with its price movements being a barometer for the health and sentiment of the broader cryptocurrency market. **Conclusion** Bitcoin's market behavior, as analyzed by CryptoQuant, offers a complex picture of various factors at play. The interplay between short-term and long-term holders, the strategic moves of miners and whales, and the overall market sentiment all contribute to the price dynamics of this digital currency. Understanding these elements is key for investors and enthusiasts who wish to navigate the volatile waters of Bitcoin's market. As the crypto landscape continues to evolve, keeping a close eye on these trends and analyses will be crucial for making informed decisions in the world of cryptocurrency. The insights provided by platforms like CryptoQuant are invaluable in this regard, offering a deeper understanding of the market forces at work. **FAQs** **What caused the recent halt in Bitcoin's price rally?** The halt in Bitcoin's price rally, after reaching near $45,000, was primarily due to profit-taking by short-term holders and investors who had held Bitcoin for 6-18 months, as revealed by CryptoQuant's analysis. **What is Bitcoin Binary Coin Days Destroyed (CDD)?** Bitcoin Binary Coin Days Destroyed (CDD) is a metric that measures the movement of long-held Bitcoins. It indicates the amount of Bitcoin, held dormant for a long time, that has been mobilized or sold. **How do miners and whales influence Bitcoin's price?** Miners and whales (large-scale holders) significantly influence Bitcoin's price through their actions. When they sell their holdings, especially during peak prices, they add to the market's selling pressure, potentially leading to price drops. **What does a high Bitcoin Binary CDD indicate?** A high Bitcoin Binary CDD suggests that a large amount of long-held Bitcoin is being sold, which can be a sign of long-term holders losing confidence or deciding to take profits. **Is the current market sentiment for Bitcoin positive or negative?** Despite recent price fluctuations, the overall market sentiment for Bitcoin remains cautiously positive, with improvements in market liquidity and interest from institutional investors. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*** @ df478568:2a951e67
2025-02-22 14:53:58I shop the bitcoin circular economy as much as I can. Maybe "shop" isn't the best way to describe it. Shopping is a behavior typical of fiat maxis. they drive fancy leases and shop 'till they drop. This season's fashion must-have is next season's trash. Bitcoiners don't shop, we replenish supplies. Our goal is to get the best value for our sats. Our goal to hodl our sats as long as possible. Yesterday, I shoveled a [ton of compost](nostr:nevent1qvzqqqqqqypzph68s45y080zdd9g8sdacnd6kcd4ejpwrgcju2eghjq45y4f28n8qqs24rrm3u2wvf24ad8xkj2xh8nuq2lz7urnd3lzrpqlstmsp4r29hsug39jw) for my garden. If taking showers mean's I', short bitcoin, so be it. I also happened to get my soap from Soapminer delivered to my P.O. Box the day before. What better way is there to test this soap than after shoveling some shit? It was perfect timing. ## Soapminer Sells Soap Made From Beef Tallow Soapminer is a nostr rounder I've seen online every timestamp in a while. As the name suggests, he makes soap and sells it for sats. He's not the only soap seller on nostr, but something stands out about this soap. He uses beef tallow, the stuff McDonald's used for french fries back in the day. I use it to cook. It's basically beef lard. So this pleb makes soap and markets it to people who talk about beef and bitcoin. That's better than Fight Club. Then [I heard Matt Odell say it was pretty good](https://fountain.fm/clip/6GHDdmcwMg47mz0xNpVb). I already thought about spending sats on this soap, but now I had a testimonial from a man I have listened to for about six years. **Can you say Web of Trust baby?** I no soap and suds expert. I have years of soapo sing experience, but I never thought about what commercial soap is made with. I assumed it was like Fight Club like how I assumed the dollar was backed by gold in high school. Both these statements are false. Fiat soap is made with fiat fuckery. I tried looking for the ingredients on a box of Dove Men's Care, but couldn't find them on the box. It's opaque like the amount of gold at Fort Knox, nobody knows. I know what Soapminer uses to make his soap because [it's open source](nostr:note1aypyepc6g7lztutegx0fw5yg5clc9ythvxkp6czfkau3dcgwz06q4mfqr3). ### Tallow Soap Quotes  I asked Soapminer a few questions on nostr. [Here is is answer]((nostr:note1wma3745zywf6avfwrau9dvrt6awqqmt3qkfc07xxff4p6nh8f38qyxuqze "nostr:note1wma3745zywf6avfwrau9dvrt6awqqmt3qkfc07xxff4p6nh8f38qyxuqze) ), signed by his own nostr key, the Internet's version of "I approve this message."  **Soapminer:**  `What inspired me was a cleaner, healthier lifestyle. During the plandemic, I had a lot of free time on my hands, and got to read, and investigate what actually causes a lot of the sickness in society. I learned a great deal. I never knew that your skin is your largest organ, and that it absorbs 60-70% of what you put on it. What do ppl put on their skin almost every day? Soap. So out of boredom, and seeking a healthier lifestyle, I started watching YT videos of ppl making soap, and tried it out a few times, and then a few more, until I became good at it. Once you learn how to make soap, the challenges only arise when you try something that you haven't done before. Depending on what method you are using will determine the challenges that you may face. It's multifaceted, so might be a little long to go into. I overcome them by keep trying until I get it right. No path is going to be easy, you just have to practice to make perfect. Last question is easy. My favorite soap is Tallow soap. As long as it is made from Tallow, and has all natural ingredients, it is a good soap in my opinion. Tallow mirrors the oils in our skin. It doesn't strip you skin the way commercial soap do, leaving you feel itchy, dry, and actually causing some of the skin ailments that have become common, like eczema, and psoriasis. Just nutures, cleans, and protects. It also, can prevent wrinkles., and acne.` **Sold!**  I tried the pine tar first. It makes me smell like a man, at least my wife thinks so. That's also why she prefers the unscented. He is adding more scents, but these ate the one's I have tried. The soap makes me feel rubber-ducky squeaky clean. After my shower, made some lunch and washed my hands with Dawn. This made my hands ashier than bio-char. I decided to cut some soap and place a little piece by the kitchen sink. The soap moisturized my hands in two shakes of a bull's tail. I also cut up some of my soap into smaller pieces because I'm as frugal as a Boy-scout and wanted to wash my hands with this stuff instead of Ivory.  #### Here's some more quotes about Soapminer's soap. - [He's asking his market if they want Peppermint soap.](nostr:note1tpeh65m7y6s6wt9ucjdcl2pge3m86f2ny4hqjdyvcrmf7kglqshqfeceam "nostr:note1tpeh65m7y6s6wt9ucjdcl2pge3m86f2ny4hqjdyvcrmf7kglqshqfeceam) - [Then he made the soap like a boss](nostr:nevent1qvzqqqqqqypzqy9kvcxtqa2tlwyjv4r46ancxk00ghk9yaudzsnp697s60942p7lqqs0yqyvffu9pn39grtxa8agpftpvfssx603w0ra67kpn5qn360masquhrtd7). - [The Benefits of Tallow](nostr:nevent1qqs9w6g8khrqzhrgu7y3trae9vtdl8847p42p80aqzvsvlu9kr84vkgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsyg8zenmu7gzq8ulj5jj4kv50ph3muwz43f747vmr9ld2alrjdswgavpsgqqqqqqsq5lkzq) - [He uses Zaprite](nostr:nevent1qvzqqqqqqypzqjln5vfhstwf2ahjrmanh57kzwrap4v3xpfzql5sxp48gxlk4a74qqsraadvah6890x4hgvr4rcxe9c2n79a0kx88te3hf7x88j72rh7cuskhempa) [He has giveaways](nostr:nevent1qvzqqqqqqyqzpzvke2t7fxwh0rzea5zmx7qnddzgsqk35ujp9tgpw9jmjsmnserr3z8466) [He wants everyone to live on a bitcoin standard](nostr:nevent1qvzqqqqqqypzqy9kvcxtqa2tlwyjv4r46ancxk00ghk9yaudzsnp697s60942p7lqqs8gnddcnkj5p2047qam5drgw5jxlg60vy736e2rwxsmj593whnllsy8ej9j)  ### Testimonials  [nostr:note1y9wsl07lkepfzzj8c8ucekss9f9darvg70j93cdmvttadfjx9nfsvtxwes "nostr:note1y9wsl07lkepfzzj8c8ucekss9f9darvg70j93cdmvttadfjx9nfsvtxwes") **TheLOTSProject**  nostr:nevent1qvzqqqqqqypzqy9kvcxtqa2tlwyjv4r46ancxk00ghk9yaudzsnp697s60942p7lqqsxt8kyd650ph3wvhre0lwlw5s0emuv5gcfzmsvfxf7czgg4c2wynq7vg8ga **Tuvok**  ["he even shipped to my in germany(but only after negotiation) i like the soap a lot after some testing"](nostr:nevent1qvzqqqqqqypzqpt4hupuycwpj5yqjn00989fgwj6k9yvfamvx7v2gkamz9329wreqywhwumn8ghj7mr4de3kscn00qh8xctwv3mkjcmg9enxzund9uqsuamnwvaz7tmwdaejumr0dshsqgr3cj8s3sc2ruzz2yj4e3kxnc825elr2gmyufdv38d9ee4jm8lxx5n7yrdv) **Bit 🐳 Ish**  ["It's good stuff, you'll love it."](nostr:nevent1qvzqqqqqqypzpr38l76unwuvm5qnrt0xa7jf64k5qx65ynvlm7dx8cr565nmqu2uqqs2r7rcp2rssfcqhk5838cuu569h43wlkvw34gy8ad2flgdpl0cezckxghkc) **GhostBTC**  nostr:npub1cm3v486tkgy6qjtk09srry4qvc40y0jysyqha5e3v67whnc22jwsrreyud **cryptoshi2k21.bitcoin**  ["Great soap 🧼🫧"](nostr:nevent1qvzqqqqqqypzqj5nelekm4aruughza09y8yy26ansshnc23wq2kdha79dqz8rhemqqsxdq4xf69vgk27nnes4syrnekpg4mhkp6v4rer7nzdgfht8kya8ssucu8lz) **Marc**  ["I spent the last two days shyoveling horse shit and compost for my garden. This soap made me feel rubber-ducky squeeky clean afterward."](nostr:nevent1qvzqqqqqqypzph68s45y080zdd9g8sdacnd6kcd4ejpwrgcju2eghjq45y4f28n8qqsfvqylk56zdh5n3ykhleypr5zznevqt9dw04vptdeuh9jmskemndgq0hw25) ##### Conclusion I am a soap mining soap customer now. I'm done with fiat soap. I'm thinking about handing out his soap for Christmas gifts. Odell was right. It is good soap. It's expensive compared to the comercial crap, but competitive with fancy olive oil soaps I've seen. I paid with fiat I had in Strike, but Soapminer received bitcoin. I was going to buy soap anyway, but buying soap this way took $35 of fiat off Strike and put it into soap miners strategic bitcoin reserve. It's not cheap, but buying Dove requires me to first buy fiat. Buying soap from Soapminer takes sats off the exchange. Buying Dove does not, but that's not the only reason I bought this soap. It's great soap, but that's not really why I bought it. I am a big believer in what Adam Smith described as the invisible hand: [nostr:note1jsgzk6rxulyqthae8c53rrawaa70yjqh37nm3kxh08xw8g43vgcq3kux9d "nostr:note1jsgzk6rxulyqthae8c53rrawaa70yjqh37nm3kxh08xw8g43vgcq3kux9d"). We want to see people in our community to prosper. It is in our self-interest That is what Smith means by the invisible hand. The invisible hand is not A Central Bank manipulating interest rates and The IMF turning foreigners into debt-fiat slaves for cheap freshly-frozen shrimp. Bitcoiners are my community. They may not be close to me by proximity, but my moral sentiments guide me to do business with bitcoiners whenever possible. See, capitalism cannot work with socialist money. Those moral sentiments change when people work for soft money. Fiat soap miners get paid in NGD currency. Sell soap for $35 today and that will buy you half as much stuff in 5 years. The fiat soap miner has no savings to improve his community. Inflation makes him search for the cheapest soap just to keep up with grocery prices. Soapminer can save his sats earned selling soap without anyone stealig from him. Therefore, he will be able to afford to buy stuff in his community. Those on a fiat standard cannot afford to save their money in the hopes of buying high quality products and services in their community. Fiat is socialist money, therefore only buys less and less as time goes on. Dear readers, we are not on late stage capitalism. The problem is that socialist money sucks. Those Papi Trump bucks might be fun for a month, but in the end, everyone pays the Piper. Tariffs are a sales tax, [paywalls in meatspace](nostr:nevent1qvzqqqqqqypzph68s45y080zdd9g8sdacnd6kcd4ejpwrgcju2eghjq45y4f28n8qyt8wumn8ghj7mn0wd68yetvd96x2uewdaexwtcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qg4waehxw309ajxjar5duh8qatz9aex2mrp0yqzqx3u59js9ewy9xwr7nuzv5eytj9ty979wrc7vrhv3tfykjxp5pd28s750n). Save your sats long enough, and these taxes will not matter. We circumvent the unjust tax of inflation, we will find solutions to unjust taxes levied on our community. I participate in the bitcoin circular economy because I want to bring capitalism back. I do not care where you live. If you are a bitcoiner, you are part of my community. There is an invisible hand which compels me to buy stuff from people in my community. That's why I bought soap from Soapminer, but you know what? **the soap is pretty damn good**. npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 [884,864](https://mempool.marc26z.com/block/000000000000000000014855f89d29f5d7953945251ee87bf069b90d9e6d9f85) [Merch](https://marc26z.com/merch)
@ df478568:2a951e67
2025-02-22 14:53:58I shop the bitcoin circular economy as much as I can. Maybe "shop" isn't the best way to describe it. Shopping is a behavior typical of fiat maxis. they drive fancy leases and shop 'till they drop. This season's fashion must-have is next season's trash. Bitcoiners don't shop, we replenish supplies. Our goal is to get the best value for our sats. Our goal to hodl our sats as long as possible. Yesterday, I shoveled a [ton of compost](nostr:nevent1qvzqqqqqqypzph68s45y080zdd9g8sdacnd6kcd4ejpwrgcju2eghjq45y4f28n8qqs24rrm3u2wvf24ad8xkj2xh8nuq2lz7urnd3lzrpqlstmsp4r29hsug39jw) for my garden. If taking showers mean's I', short bitcoin, so be it. I also happened to get my soap from Soapminer delivered to my P.O. Box the day before. What better way is there to test this soap than after shoveling some shit? It was perfect timing. ## Soapminer Sells Soap Made From Beef Tallow Soapminer is a nostr rounder I've seen online every timestamp in a while. As the name suggests, he makes soap and sells it for sats. He's not the only soap seller on nostr, but something stands out about this soap. He uses beef tallow, the stuff McDonald's used for french fries back in the day. I use it to cook. It's basically beef lard. So this pleb makes soap and markets it to people who talk about beef and bitcoin. That's better than Fight Club. Then [I heard Matt Odell say it was pretty good](https://fountain.fm/clip/6GHDdmcwMg47mz0xNpVb). I already thought about spending sats on this soap, but now I had a testimonial from a man I have listened to for about six years. **Can you say Web of Trust baby?** I no soap and suds expert. I have years of soapo sing experience, but I never thought about what commercial soap is made with. I assumed it was like Fight Club like how I assumed the dollar was backed by gold in high school. Both these statements are false. Fiat soap is made with fiat fuckery. I tried looking for the ingredients on a box of Dove Men's Care, but couldn't find them on the box. It's opaque like the amount of gold at Fort Knox, nobody knows. I know what Soapminer uses to make his soap because [it's open source](nostr:note1aypyepc6g7lztutegx0fw5yg5clc9ythvxkp6czfkau3dcgwz06q4mfqr3). ### Tallow Soap Quotes  I asked Soapminer a few questions on nostr. [Here is is answer]((nostr:note1wma3745zywf6avfwrau9dvrt6awqqmt3qkfc07xxff4p6nh8f38qyxuqze "nostr:note1wma3745zywf6avfwrau9dvrt6awqqmt3qkfc07xxff4p6nh8f38qyxuqze) ), signed by his own nostr key, the Internet's version of "I approve this message."  **Soapminer:**  `What inspired me was a cleaner, healthier lifestyle. During the plandemic, I had a lot of free time on my hands, and got to read, and investigate what actually causes a lot of the sickness in society. I learned a great deal. I never knew that your skin is your largest organ, and that it absorbs 60-70% of what you put on it. What do ppl put on their skin almost every day? Soap. So out of boredom, and seeking a healthier lifestyle, I started watching YT videos of ppl making soap, and tried it out a few times, and then a few more, until I became good at it. Once you learn how to make soap, the challenges only arise when you try something that you haven't done before. Depending on what method you are using will determine the challenges that you may face. It's multifaceted, so might be a little long to go into. I overcome them by keep trying until I get it right. No path is going to be easy, you just have to practice to make perfect. Last question is easy. My favorite soap is Tallow soap. As long as it is made from Tallow, and has all natural ingredients, it is a good soap in my opinion. Tallow mirrors the oils in our skin. It doesn't strip you skin the way commercial soap do, leaving you feel itchy, dry, and actually causing some of the skin ailments that have become common, like eczema, and psoriasis. Just nutures, cleans, and protects. It also, can prevent wrinkles., and acne.` **Sold!**  I tried the pine tar first. It makes me smell like a man, at least my wife thinks so. That's also why she prefers the unscented. He is adding more scents, but these ate the one's I have tried. The soap makes me feel rubber-ducky squeaky clean. After my shower, made some lunch and washed my hands with Dawn. This made my hands ashier than bio-char. I decided to cut some soap and place a little piece by the kitchen sink. The soap moisturized my hands in two shakes of a bull's tail. I also cut up some of my soap into smaller pieces because I'm as frugal as a Boy-scout and wanted to wash my hands with this stuff instead of Ivory.  #### Here's some more quotes about Soapminer's soap. - [He's asking his market if they want Peppermint soap.](nostr:note1tpeh65m7y6s6wt9ucjdcl2pge3m86f2ny4hqjdyvcrmf7kglqshqfeceam "nostr:note1tpeh65m7y6s6wt9ucjdcl2pge3m86f2ny4hqjdyvcrmf7kglqshqfeceam) - [Then he made the soap like a boss](nostr:nevent1qvzqqqqqqypzqy9kvcxtqa2tlwyjv4r46ancxk00ghk9yaudzsnp697s60942p7lqqs0yqyvffu9pn39grtxa8agpftpvfssx603w0ra67kpn5qn360masquhrtd7). - [The Benefits of Tallow](nostr:nevent1qqs9w6g8khrqzhrgu7y3trae9vtdl8847p42p80aqzvsvlu9kr84vkgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsyg8zenmu7gzq8ulj5jj4kv50ph3muwz43f747vmr9ld2alrjdswgavpsgqqqqqqsq5lkzq) - [He uses Zaprite](nostr:nevent1qvzqqqqqqypzqjln5vfhstwf2ahjrmanh57kzwrap4v3xpfzql5sxp48gxlk4a74qqsraadvah6890x4hgvr4rcxe9c2n79a0kx88te3hf7x88j72rh7cuskhempa) [He has giveaways](nostr:nevent1qvzqqqqqqyqzpzvke2t7fxwh0rzea5zmx7qnddzgsqk35ujp9tgpw9jmjsmnserr3z8466) [He wants everyone to live on a bitcoin standard](nostr:nevent1qvzqqqqqqypzqy9kvcxtqa2tlwyjv4r46ancxk00ghk9yaudzsnp697s60942p7lqqs8gnddcnkj5p2047qam5drgw5jxlg60vy736e2rwxsmj593whnllsy8ej9j)  ### Testimonials  [nostr:note1y9wsl07lkepfzzj8c8ucekss9f9darvg70j93cdmvttadfjx9nfsvtxwes "nostr:note1y9wsl07lkepfzzj8c8ucekss9f9darvg70j93cdmvttadfjx9nfsvtxwes") **TheLOTSProject**  nostr:nevent1qvzqqqqqqypzqy9kvcxtqa2tlwyjv4r46ancxk00ghk9yaudzsnp697s60942p7lqqsxt8kyd650ph3wvhre0lwlw5s0emuv5gcfzmsvfxf7czgg4c2wynq7vg8ga **Tuvok**  ["he even shipped to my in germany(but only after negotiation) i like the soap a lot after some testing"](nostr:nevent1qvzqqqqqqypzqpt4hupuycwpj5yqjn00989fgwj6k9yvfamvx7v2gkamz9329wreqywhwumn8ghj7mr4de3kscn00qh8xctwv3mkjcmg9enxzund9uqsuamnwvaz7tmwdaejumr0dshsqgr3cj8s3sc2ruzz2yj4e3kxnc825elr2gmyufdv38d9ee4jm8lxx5n7yrdv) **Bit 🐳 Ish**  ["It's good stuff, you'll love it."](nostr:nevent1qvzqqqqqqypzpr38l76unwuvm5qnrt0xa7jf64k5qx65ynvlm7dx8cr565nmqu2uqqs2r7rcp2rssfcqhk5838cuu569h43wlkvw34gy8ad2flgdpl0cezckxghkc) **GhostBTC**  nostr:npub1cm3v486tkgy6qjtk09srry4qvc40y0jysyqha5e3v67whnc22jwsrreyud **cryptoshi2k21.bitcoin**  ["Great soap 🧼🫧"](nostr:nevent1qvzqqqqqqypzqj5nelekm4aruughza09y8yy26ansshnc23wq2kdha79dqz8rhemqqsxdq4xf69vgk27nnes4syrnekpg4mhkp6v4rer7nzdgfht8kya8ssucu8lz) **Marc**  ["I spent the last two days shyoveling horse shit and compost for my garden. This soap made me feel rubber-ducky squeeky clean afterward."](nostr:nevent1qvzqqqqqqypzph68s45y080zdd9g8sdacnd6kcd4ejpwrgcju2eghjq45y4f28n8qqsfvqylk56zdh5n3ykhleypr5zznevqt9dw04vptdeuh9jmskemndgq0hw25) ##### Conclusion I am a soap mining soap customer now. I'm done with fiat soap. I'm thinking about handing out his soap for Christmas gifts. Odell was right. It is good soap. It's expensive compared to the comercial crap, but competitive with fancy olive oil soaps I've seen. I paid with fiat I had in Strike, but Soapminer received bitcoin. I was going to buy soap anyway, but buying soap this way took $35 of fiat off Strike and put it into soap miners strategic bitcoin reserve. It's not cheap, but buying Dove requires me to first buy fiat. Buying soap from Soapminer takes sats off the exchange. Buying Dove does not, but that's not the only reason I bought this soap. It's great soap, but that's not really why I bought it. I am a big believer in what Adam Smith described as the invisible hand: [nostr:note1jsgzk6rxulyqthae8c53rrawaa70yjqh37nm3kxh08xw8g43vgcq3kux9d "nostr:note1jsgzk6rxulyqthae8c53rrawaa70yjqh37nm3kxh08xw8g43vgcq3kux9d"). We want to see people in our community to prosper. It is in our self-interest That is what Smith means by the invisible hand. The invisible hand is not A Central Bank manipulating interest rates and The IMF turning foreigners into debt-fiat slaves for cheap freshly-frozen shrimp. Bitcoiners are my community. They may not be close to me by proximity, but my moral sentiments guide me to do business with bitcoiners whenever possible. See, capitalism cannot work with socialist money. Those moral sentiments change when people work for soft money. Fiat soap miners get paid in NGD currency. Sell soap for $35 today and that will buy you half as much stuff in 5 years. The fiat soap miner has no savings to improve his community. Inflation makes him search for the cheapest soap just to keep up with grocery prices. Soapminer can save his sats earned selling soap without anyone stealig from him. Therefore, he will be able to afford to buy stuff in his community. Those on a fiat standard cannot afford to save their money in the hopes of buying high quality products and services in their community. Fiat is socialist money, therefore only buys less and less as time goes on. Dear readers, we are not on late stage capitalism. The problem is that socialist money sucks. Those Papi Trump bucks might be fun for a month, but in the end, everyone pays the Piper. Tariffs are a sales tax, [paywalls in meatspace](nostr:nevent1qvzqqqqqqypzph68s45y080zdd9g8sdacnd6kcd4ejpwrgcju2eghjq45y4f28n8qyt8wumn8ghj7mn0wd68yetvd96x2uewdaexwtcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qg4waehxw309ajxjar5duh8qatz9aex2mrp0yqzqx3u59js9ewy9xwr7nuzv5eytj9ty979wrc7vrhv3tfykjxp5pd28s750n). Save your sats long enough, and these taxes will not matter. We circumvent the unjust tax of inflation, we will find solutions to unjust taxes levied on our community. I participate in the bitcoin circular economy because I want to bring capitalism back. I do not care where you live. If you are a bitcoiner, you are part of my community. There is an invisible hand which compels me to buy stuff from people in my community. That's why I bought soap from Soapminer, but you know what? **the soap is pretty damn good**. npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 [884,864](https://mempool.marc26z.com/block/000000000000000000014855f89d29f5d7953945251ee87bf069b90d9e6d9f85) [Merch](https://marc26z.com/merch) @ 1739d937:3e3136ef
2025-02-22 14:51:17We've been busy. In my last update, I shared that I was sure MLS on Nostr was going to work and shared an early demo of the app. What a long time ago that seems now. The big news is that White Noise is no longer just a demo. It's a real app. You can [download the alpha release](https://github.com/erskingardner/whitenoise/releases) and run it for yourself on MacOS, Linux, or Android. iOS TestFlight is coming soon. Keep in mind that it's still very much alpha software; a lot is changing and I wouldn't recommend using it for anything serious quite yet. We've been busy. In my last update, I shared that I was sure MLS on Nostr was going to work and shared an early demo of the app. What a long time ago that seems now. ## Vision Before we get to the detailed project updates, I wanted to share a bit of my vision for White Noise. More and more; freedom of speech, freedom of association, and privacy are under attack. Just this week, Apple was forced to remove their iCloud advanced encryption feature for all UK citizens because the UK government demanded that Apple build a backdoor to allow access to customer data. The EU continues to push "Chat Control" legislation that would force companies to remove end-to-end encryption from their platforms. And governments across the world are enforcing draconian "hate speech" laws that criminalize speech that offends or upsets. The freedom to express ourselves and discuss difficult topics is a critical precondition for maintaining a healthy society. Without the ability to assert ideas and argue their merits vigorously we have no way of making progress or creating a civil society based on shared values and goals. Ironically, the very laws and regulations that many western governments are enforcing to "protect" us are eroding and destroying the most free and innovative societies in history. White Noise is to built to protect our freedom to gather, to express ourselves, and to discuss difficult topics. It's free and open source; anyone can fork the code and we'll never charge money to use it. It runs on a free and open source protocol; your identity and social graph is yours to own and control. You don't have to trust us with your data, everything is end-to-end encrypted and metadata is next to non-existent. We don't even run any servers, so government data requests will forever fall on deaf ears. We want to build the fastest, most secure and private, and the most usable messenger in the world. Whether you want to use it to plan a family BBQ or overthrow a tyrant, White Noise should give you the tools you need to make it happen. If you find this compelling and want to help, please consider contributing to the project or donating. ## Progress Alright, let's talk about where we're at with the project. ### Current functionality - Multiple accounts. You can login, or create, many different Nostr accounts in the app. - Search your nostr contact list, search for users you don't follow, or add contacts using an npub or hex public key. - Create DM groups. Right now, you can only create chats with a single other user. Under the hood, these DMs are actually groups, I just haven't added the UI for adding/removing users and managing the group. - Send messages, reply to messages, and add reactions. As you would expect from a messenging app. - View group information. - Settings that allows you to manage your accounts, relays, and other app settings. ### Upcoming - An amazing hackathon group from [Bitcoin++ in Brasil](https://btcplusplus.dev/conf/floripa) has recently [added NWC](https://github.com/erskingardner/whitenoise/pull/89) (nostr wallet connect) support to the app. Paste lightning invoices into chats and they'll become QR codes that you can scan or pay them with a single click in the conversation! This will be in the next release. - Add support for encrypted media in chats using [Blossom](https://github.com/hzrd149/blossom/tree/master). We'll start with images, but plan to add video, audio messages, and documents soon. - Groups with more than two users. We'll add the ability to add/remove users and manage the group. This will also include some upgrades to further improve the forward secrecy of group chats. - iOS TestFlight. Gated app stores suck. We'll get White Noise on iOS into TestFlight as soon as possible. ## Links - [The repo](https://github.com/erskingardner/whitenoise) - [Releases](https://github.com/erskingardner/whitenoise/releases) - [Previous updates](https://highlighter.com/jeffg.fyi)
@ 1739d937:3e3136ef
2025-02-22 14:51:17We've been busy. In my last update, I shared that I was sure MLS on Nostr was going to work and shared an early demo of the app. What a long time ago that seems now. The big news is that White Noise is no longer just a demo. It's a real app. You can [download the alpha release](https://github.com/erskingardner/whitenoise/releases) and run it for yourself on MacOS, Linux, or Android. iOS TestFlight is coming soon. Keep in mind that it's still very much alpha software; a lot is changing and I wouldn't recommend using it for anything serious quite yet. We've been busy. In my last update, I shared that I was sure MLS on Nostr was going to work and shared an early demo of the app. What a long time ago that seems now. ## Vision Before we get to the detailed project updates, I wanted to share a bit of my vision for White Noise. More and more; freedom of speech, freedom of association, and privacy are under attack. Just this week, Apple was forced to remove their iCloud advanced encryption feature for all UK citizens because the UK government demanded that Apple build a backdoor to allow access to customer data. The EU continues to push "Chat Control" legislation that would force companies to remove end-to-end encryption from their platforms. And governments across the world are enforcing draconian "hate speech" laws that criminalize speech that offends or upsets. The freedom to express ourselves and discuss difficult topics is a critical precondition for maintaining a healthy society. Without the ability to assert ideas and argue their merits vigorously we have no way of making progress or creating a civil society based on shared values and goals. Ironically, the very laws and regulations that many western governments are enforcing to "protect" us are eroding and destroying the most free and innovative societies in history. White Noise is to built to protect our freedom to gather, to express ourselves, and to discuss difficult topics. It's free and open source; anyone can fork the code and we'll never charge money to use it. It runs on a free and open source protocol; your identity and social graph is yours to own and control. You don't have to trust us with your data, everything is end-to-end encrypted and metadata is next to non-existent. We don't even run any servers, so government data requests will forever fall on deaf ears. We want to build the fastest, most secure and private, and the most usable messenger in the world. Whether you want to use it to plan a family BBQ or overthrow a tyrant, White Noise should give you the tools you need to make it happen. If you find this compelling and want to help, please consider contributing to the project or donating. ## Progress Alright, let's talk about where we're at with the project. ### Current functionality - Multiple accounts. You can login, or create, many different Nostr accounts in the app. - Search your nostr contact list, search for users you don't follow, or add contacts using an npub or hex public key. - Create DM groups. Right now, you can only create chats with a single other user. Under the hood, these DMs are actually groups, I just haven't added the UI for adding/removing users and managing the group. - Send messages, reply to messages, and add reactions. As you would expect from a messenging app. - View group information. - Settings that allows you to manage your accounts, relays, and other app settings. ### Upcoming - An amazing hackathon group from [Bitcoin++ in Brasil](https://btcplusplus.dev/conf/floripa) has recently [added NWC](https://github.com/erskingardner/whitenoise/pull/89) (nostr wallet connect) support to the app. Paste lightning invoices into chats and they'll become QR codes that you can scan or pay them with a single click in the conversation! This will be in the next release. - Add support for encrypted media in chats using [Blossom](https://github.com/hzrd149/blossom/tree/master). We'll start with images, but plan to add video, audio messages, and documents soon. - Groups with more than two users. We'll add the ability to add/remove users and manage the group. This will also include some upgrades to further improve the forward secrecy of group chats. - iOS TestFlight. Gated app stores suck. We'll get White Noise on iOS into TestFlight as soon as possible. ## Links - [The repo](https://github.com/erskingardner/whitenoise) - [Releases](https://github.com/erskingardner/whitenoise/releases) - [Previous updates](https://highlighter.com/jeffg.fyi) @ 2e8970de:63345c7a
2025-02-22 14:41:31 -Blue: Neuroticism -Green: Extraversion -Red: Openness to experience -Orange: Agreeableness -Purple: Conscientiousness [sourcs(https://www.stevestewartwilliams.com/p/are-there-age-and-sex-differences)] originally posted at https://stacker.news/items/893992
@ 2e8970de:63345c7a
2025-02-22 14:41:31 -Blue: Neuroticism -Green: Extraversion -Red: Openness to experience -Orange: Agreeableness -Purple: Conscientiousness [sourcs(https://www.stevestewartwilliams.com/p/are-there-age-and-sex-differences)] originally posted at https://stacker.news/items/893992 @ ac6f9572:8a6853dd
2025-02-22 13:01:56# The old world crumbles. The sovereign rises.  Join #Bitshala at #BitPlebs Summit in Goa — a gathering of builders, creators, educators, and hodlers forging #India’s #Bitcoin future. Open forums. Un-conference style talks. By @bitshala & @plebstogether RSVP now: https://lu.ma/cd55r5d4 X: https://x.com/bitshala_org/status/1893252853709365684?s=09 originally posted at https://stacker.news/items/893899
@ ac6f9572:8a6853dd
2025-02-22 13:01:56# The old world crumbles. The sovereign rises.  Join #Bitshala at #BitPlebs Summit in Goa — a gathering of builders, creators, educators, and hodlers forging #India’s #Bitcoin future. Open forums. Un-conference style talks. By @bitshala & @plebstogether RSVP now: https://lu.ma/cd55r5d4 X: https://x.com/bitshala_org/status/1893252853709365684?s=09 originally posted at https://stacker.news/items/893899 @ c384de42:493922aa
2025-02-22 12:27:08I've had a weird thought. Relating to bitcoin and maths and gambling. I understand none of the above, but found some weird convoluted logic in the fact that 52 cards in a deck and two six faced dice equate to 12 faces, idk.. I lost track of the logical steps in my mind, it may have been a delusion.. But the conclusion, of whatever it was is, kill myself at some point with end result living forever in samsara, or choose the natural progression of life into death, if there is such a thing... Weird.. It had something to do with gambling and drugs and addiction, like the plug-in drugs in the Ringworld novels by Larry Niven, or the simulation machines in the Paul Verhoeven film, Total Recall, with Arnold Schwarzenegger. Strange thoughts...
@ c384de42:493922aa
2025-02-22 12:27:08I've had a weird thought. Relating to bitcoin and maths and gambling. I understand none of the above, but found some weird convoluted logic in the fact that 52 cards in a deck and two six faced dice equate to 12 faces, idk.. I lost track of the logical steps in my mind, it may have been a delusion.. But the conclusion, of whatever it was is, kill myself at some point with end result living forever in samsara, or choose the natural progression of life into death, if there is such a thing... Weird.. It had something to do with gambling and drugs and addiction, like the plug-in drugs in the Ringworld novels by Larry Niven, or the simulation machines in the Paul Verhoeven film, Total Recall, with Arnold Schwarzenegger. Strange thoughts... @ e5de992e:4a95ef85
2025-02-22 12:19:25A trading log isn't just a record of past trades—it's a tool for learning, improving, and achieving consistency. By keeping a detailed log, you gain insights into your decision-making process, identify patterns, and refine your strategy over time. Here's why and how to maintain a comprehensive trading log effectively. --- ## 1. The Importance of a Trading Log - **Track Performance Objectively** Without a log, it's easy to misremember trades or overestimate success. A detailed log provides accurate data to analyze your progress. - **Understand Your Strengths and Weaknesses** By reviewing your log, you can identify what works well and where you need improvement. Patterns in losing trades often highlight common mistakes or emotional triggers. - **Build Confidence and Trust in Your System** Seeing a record of rule-based, consistent trades reinforces trust in your strategy. Reviewing past successes can boost morale during challenging periods. --- ## 2. What to Include in Your Trading Log A detailed trading log should cover both objective data and subjective reflections. ### Objective Data - **Date and Time:** When the trade was entered and exited. - **Instrument Traded:** Stock, forex pair, crypto, etc. - **Entry and Exit Prices:** Precise levels where you opened and closed the trade. - **Position Size:** Number of shares, contracts, or units traded. - **Stop Loss and Take Profit Levels:** Risk management details. - **P/L (Profit or Loss):** Outcome of the trade in dollars or percentage terms. - **Trade Type:** Long, short, scalping, swing, etc. ### Subjective Reflections - **Reason for Entering the Trade:** What setup or signal prompted the trade? - **Emotional State:** How did you feel before, during, and after the trade? - **Execution Notes:** Did you follow your plan? If not, why? - **Lessons Learned:** What can you take away from this trade to improve next time? > **Key Insight:** Both data and reflection are essential for meaningful analysis. --- ## 3. How to Analyze Your Trading Log 1. **Identify Patterns** Look for common themes in your winning and losing trades. _Examples:_ Winning trades often align with specific setups, while losing trades frequently result from breaking rules or impulsive decisions. 2. **Evaluate Strategy Effectiveness** Assess whether your system produces consistent results over time. Use metrics like win rate, risk-reward ratio, and drawdown to evaluate performance. 3. **Address Emotional Triggers** Reflect on emotional notes to understand what triggers fear, greed, or hesitation. Develop strategies to manage emotions based on these insights. --- ## 4. Benefits of Keeping a Trading Log - **Improved Discipline:** Writing down each trade reinforces the habit of sticking to your plan. - **Informed Adjustments:** Logs provide data-driven insights to refine your strategy. - **Emotional Control:** Journaling emotions helps you recognize and address psychological pitfalls. - **Long-Term Growth:** By tracking your progress, you can measure improvement over months and years. > **Key Insight:** A trading log turns mistakes into lessons and successes into repeatable actions. --- ## 5. Tools for Logging Trades ### Manual Logs - Use a notebook or spreadsheet to record trades. - **Pros:** Highly customizable, forces you to engage deeply with each entry. - **Cons:** Time-intensive and less automated. ### Software and Platforms - Tools like Edgewonk, TraderSync, or Tradervue can streamline the process. - **Pros:** Automated data collection, advanced analytics, and performance tracking. - **Cons:** May have a learning curve or subscription costs. > **Key Insight:** Choose a method that aligns with your workflow and trading style. --- ## 6. Tips for Maintaining a Consistent Trading Log - **Log Every Trade:** Don't skip trades, even the ones you'd rather forget. They're often the most valuable for learning. - **Be Honest:** Record trades exactly as they happened, including mistakes and rule-breaking. - **Review Regularly:** Set aside time weekly or monthly to analyze your log and adjust your approach. - **Stay Disciplined:** Treat logging as an essential part of your trading routine. --- ## 7. Conclusion: Your Trading Log is Your Mirror A detailed trading log is more than just a record—it's a roadmap to success. It provides clarity, accountability, and insights that are essential for continuous improvement. Start today. Keep a detailed log, review it often, and use it to refine both your strategy and your mindset. Your future self will thank you.
@ e5de992e:4a95ef85
2025-02-22 12:19:25A trading log isn't just a record of past trades—it's a tool for learning, improving, and achieving consistency. By keeping a detailed log, you gain insights into your decision-making process, identify patterns, and refine your strategy over time. Here's why and how to maintain a comprehensive trading log effectively. --- ## 1. The Importance of a Trading Log - **Track Performance Objectively** Without a log, it's easy to misremember trades or overestimate success. A detailed log provides accurate data to analyze your progress. - **Understand Your Strengths and Weaknesses** By reviewing your log, you can identify what works well and where you need improvement. Patterns in losing trades often highlight common mistakes or emotional triggers. - **Build Confidence and Trust in Your System** Seeing a record of rule-based, consistent trades reinforces trust in your strategy. Reviewing past successes can boost morale during challenging periods. --- ## 2. What to Include in Your Trading Log A detailed trading log should cover both objective data and subjective reflections. ### Objective Data - **Date and Time:** When the trade was entered and exited. - **Instrument Traded:** Stock, forex pair, crypto, etc. - **Entry and Exit Prices:** Precise levels where you opened and closed the trade. - **Position Size:** Number of shares, contracts, or units traded. - **Stop Loss and Take Profit Levels:** Risk management details. - **P/L (Profit or Loss):** Outcome of the trade in dollars or percentage terms. - **Trade Type:** Long, short, scalping, swing, etc. ### Subjective Reflections - **Reason for Entering the Trade:** What setup or signal prompted the trade? - **Emotional State:** How did you feel before, during, and after the trade? - **Execution Notes:** Did you follow your plan? If not, why? - **Lessons Learned:** What can you take away from this trade to improve next time? > **Key Insight:** Both data and reflection are essential for meaningful analysis. --- ## 3. How to Analyze Your Trading Log 1. **Identify Patterns** Look for common themes in your winning and losing trades. _Examples:_ Winning trades often align with specific setups, while losing trades frequently result from breaking rules or impulsive decisions. 2. **Evaluate Strategy Effectiveness** Assess whether your system produces consistent results over time. Use metrics like win rate, risk-reward ratio, and drawdown to evaluate performance. 3. **Address Emotional Triggers** Reflect on emotional notes to understand what triggers fear, greed, or hesitation. Develop strategies to manage emotions based on these insights. --- ## 4. Benefits of Keeping a Trading Log - **Improved Discipline:** Writing down each trade reinforces the habit of sticking to your plan. - **Informed Adjustments:** Logs provide data-driven insights to refine your strategy. - **Emotional Control:** Journaling emotions helps you recognize and address psychological pitfalls. - **Long-Term Growth:** By tracking your progress, you can measure improvement over months and years. > **Key Insight:** A trading log turns mistakes into lessons and successes into repeatable actions. --- ## 5. Tools for Logging Trades ### Manual Logs - Use a notebook or spreadsheet to record trades. - **Pros:** Highly customizable, forces you to engage deeply with each entry. - **Cons:** Time-intensive and less automated. ### Software and Platforms - Tools like Edgewonk, TraderSync, or Tradervue can streamline the process. - **Pros:** Automated data collection, advanced analytics, and performance tracking. - **Cons:** May have a learning curve or subscription costs. > **Key Insight:** Choose a method that aligns with your workflow and trading style. --- ## 6. Tips for Maintaining a Consistent Trading Log - **Log Every Trade:** Don't skip trades, even the ones you'd rather forget. They're often the most valuable for learning. - **Be Honest:** Record trades exactly as they happened, including mistakes and rule-breaking. - **Review Regularly:** Set aside time weekly or monthly to analyze your log and adjust your approach. - **Stay Disciplined:** Treat logging as an essential part of your trading routine. --- ## 7. Conclusion: Your Trading Log is Your Mirror A detailed trading log is more than just a record—it's a roadmap to success. It provides clarity, accountability, and insights that are essential for continuous improvement. Start today. Keep a detailed log, review it often, and use it to refine both your strategy and your mindset. Your future self will thank you. @ da0b9bc3:4e30a4a9
2025-02-22 10:55:44Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/893831
@ da0b9bc3:4e30a4a9
2025-02-22 10:55:44Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/893831 @ 6734e11d:c7e34e8f
2025-02-22 09:16:15...damit wir weiter recht haben und so weitermachen können wie bisher, die verordnete Omertà eingehalten wird zu Grundrechten, Notverordnungen, Pandemiesimulationen, Energieversorgung, Deindustrialisierung, kalte und echte Enteigung, Umverteilung, Freiluft- und Digitalgefängnis, Blockwartnachbarn... Alles andere wäre äußerst unangenehm, wie das Aufplatzen einer großen Eiterblase und müsste dann wieder mit Exekutive, Justiz, Notverordnungen, neuen Strafrechtsparagraphen, Verschärfung der Strafprozessordnung, echte Änderung des Grundgesetzes, Überwachung, Totalzensur, Parteiverboten, Regimechanges und Krieg unterbunden werden. Idee und Meme sind wieder von der Schwurbel Oase <https://t.me/schwurbel_oase/2318>
@ 6734e11d:c7e34e8f
2025-02-22 09:16:15...damit wir weiter recht haben und so weitermachen können wie bisher, die verordnete Omertà eingehalten wird zu Grundrechten, Notverordnungen, Pandemiesimulationen, Energieversorgung, Deindustrialisierung, kalte und echte Enteigung, Umverteilung, Freiluft- und Digitalgefängnis, Blockwartnachbarn... Alles andere wäre äußerst unangenehm, wie das Aufplatzen einer großen Eiterblase und müsste dann wieder mit Exekutive, Justiz, Notverordnungen, neuen Strafrechtsparagraphen, Verschärfung der Strafprozessordnung, echte Änderung des Grundgesetzes, Überwachung, Totalzensur, Parteiverboten, Regimechanges und Krieg unterbunden werden. Idee und Meme sind wieder von der Schwurbel Oase <https://t.me/schwurbel_oase/2318> @ 6389be64:ef439d32
2025-02-22 09:12:022024-05-28 at 14:05 Tags: # Soil Carbon Oxidation Under Tillage When soil is turned over (by tilling or plow) it exposes carbon to oxygen and that carbon burns off as CO2. You are burning the carbon out of the soil. --- # References [[Shepard-Lappe-Restoration Agriculture]] # Core Notes [[Soil Erosion]] # Location [991](kindle://book?action=open&asin=B00IYUAMSI&location=991)
@ 6389be64:ef439d32
2025-02-22 09:12:022024-05-28 at 14:05 Tags: # Soil Carbon Oxidation Under Tillage When soil is turned over (by tilling or plow) it exposes carbon to oxygen and that carbon burns off as CO2. You are burning the carbon out of the soil. --- # References [[Shepard-Lappe-Restoration Agriculture]] # Core Notes [[Soil Erosion]] # Location [991](kindle://book?action=open&asin=B00IYUAMSI&location=991) @ 2fb77d26:c47a6ee1
2025-02-22 09:04:25Der 1953 geborene [Craig Reynolds](https://de.wikipedia.org/wiki/Craig_Reynolds) ist Experte für künstliches Leben und Computergrafik. In dieser Funktion arbeitete er unter anderem an Filmen wie Tron (1982) und Batman (1992). Bei »*Sony Computer Entertainment America*« (heute [SIE](https://de.wikipedia.org/wiki/Sony_Interactive_Entertainment)) entwickelte er die [OpenSteer](https://opensteer.sourceforge.net/)-Bibliothek, die der Abbildung von Schwarmverhalten in Spielen und Animationsanwendungen dient. An solch prestigeträchtige Aufträge kam Reynolds, weil er sich nebst Computergrafik intensiv mit Theorien zum »*Steuerungsverhalten für autonome Charaktere*« befasst hatte. Mit Schwarmverhalten. Einem Thema, das mit wachsender Rechenleistung immer wichtiger für die Entwicklung von Computerspielen wurde. Die sollten dem Spieler das Gefühl geben, sich in einer realen Welt mit »*autonomen Charakteren*« zu bewegen. Dazu mussten diese vom Computer, beziehungsweise der Software gesteuerten Charaktere – im Fachjargon »*[Agenten](https://de.wikipedia.org/wiki/Software-Agent)*« genannt – sich irgendwie verhalten. Und zwar ohne, dass von außen ein weiterer Steuerungseingriff erfolgt. Eigendynamisch. Dafür bedarf es Regeln, die im Programmcode eingebettet werden können. Genau die lieferte Reynolds 1986 im Rahmen der von ihm modellierten [Boids-Simulation](https://www.red3d.com/cwr/boids/), die besagt, dass Schwarmverhalten auf drei simplen Regeln basiert: 1. Bewege dich in Richtung des Mittelpunkts derer, die du in deinem Umfeld siehst. 2. Entferne dich, sobald dir jemand zu nahe kommt. 3. Bewege dich etwa in die gleiche Richtung wie deine Nachbarn. Sprich: Kohäsion, Separation und Orientierung. In Reynolds’ Beschreibung des Boid-Modells liest man diesbezüglich: »*1986 habe ich ein Computermodell koordinierter Tierbewegungen *(…) *erstellt. Es basierte auf dreidimensionaler Computergeometrie, wie sie normalerweise in der Computeranimation oder im computergestützten Design verwendet wird. Ich habe die generischen, simulierten Schwarmtiere Boids genannt. Das grundlegende Schwarmmodell besteht aus drei einfachen Lenkverhalten, die beschreiben, wie ein einzelner Boid auf der Grundlage der Positionen und Geschwindigkeiten seiner Schwarmgenossen in der Nähe manövriert. Jeder Boid hat direkten Zugriff auf die geometrische Beschreibung der gesamten Szene, aber das Schwarmverhalten erfordert, dass er nur auf Schwarmgenossen in einer bestimmten kleinen Nachbarschaft um sich herum reagiert. *(…)* Schwarmgenossen außerhalb dieser lokalen Nachbarschaft werden ignoriert.* *Die Nachbarschaft könnte als Modell eingeschränkter Wahrnehmung betrachtet werden (wie bei Fischen in trübem Wasser), aber es ist wahrscheinlich korrekter, sie als Definition des Bereichs zu betrachten, in dem Schwarmgenossen die Lenkung eines Boids beeinflussen. In den ersten Experimenten wurde ein etwas ausgefeilteres Verhaltensmodell verwendet. Es umfasste vorausschauende Hindernisvermeidung und Zielsuche. *(…)* Für Anwendungen in der Computeranimation führte ein Zielsuchverhalten mit niedriger Priorität dazu, dass die Herde einem vorgegebenen Pfad folgte*.« Wer sich bei dieser Beschreibung an die Strukturen postmoderner Gesellschaft erinnert fühlt und »*Agenten*« mit »*[Agent Smith](https://en.wikipedia.org/wiki/Agent_Smith)*« aus den Matrix-Filmen assoziiert, liegt nicht ganz falsch. Denn Kohäsion, Separation und Orientierung definieren nicht mehr nur das Schwarmverhalten autonomer Charaktere in Computerspielen, sondern auch die Dynamiken des gesellschaftlichen Zusammenlebens im multimedialen Panoptikum der Postmoderne. **So nimmt es kaum Wunder, dass ein vom** **[US Air Force Laboratory](https://www.afrl.af.mil/)** **(AFRL) finanziertes** **[Forschungsprojekt](https://arxiv.org/pdf/1402.5644)** **an der University of Florida (Gainesville, USA) bereits im Jahr 2014 untersuchte, »*wie Social Media eingesetzt werden kann, um Menschen wie Drohnen zu steuern*«.** Unter diesem Titel berichtete denn auch [Ars Technica](https://arstechnica.com/information-technology/2014/07/air-force-research-how-to-use-social-media-to-control-people-like-drones/) am 17. Juli 2014, dass der Forschungsleiter der AFRL-Studie, [Warren Dixon](https://ncr.mae.ufl.edu/index.php?id=people), seines Zeichens Chef des Lehrstuhls für nichtlineare Steuerung und Robotik an der University of Florida, vor allem daran arbeite, »*wie man ein Netzwerk, wenn man es einmal identifiziert hat, in Richtung eines Ziels manipulieren kann*«. Und mit »*Netzwerk*« meint Dixon nicht Computer, sondern soziale Strukturen. Die Untersuchungen von Dixon, Kan, Klotz und Pasiliao – formeller Titel: »*Eindämmungskontrolle für ein soziales Netzwerk mit staatlich abhängiger Konnektivität*« – unterstreichen, dass die mathematischen Prinzipien, die zur Steuerung autonomer Agenten und Robotergruppen verwendet werden, auch auf soziale Netzwerke übertragbar sind, um menschliches Verhalten zu manipulieren. Im großen Stil. Ausgehend von einer optimalen Kalibrierung könnten die von den AFRL-Forschern entwickelten Modelle eingesetzt werden, um die Meinung auf Social-Media-Portalen in Richtung eines gewünschten Verhaltens zu lenken. Genau wie die [Cyber-Waffen](https://www.business-standard.com/article/technology/hacks-raise-fear-over-nsa-s-hold-on-cyberweapons-117070100851_1.html) der NSA (National Security Agency, USA) oder das entsprechende Arsenal des [GCHQ](https://www.gchq.gov.uk/) (Government Communication Headquarters, UK), das seine [Nudge-Unit](https://en.wikipedia.org/wiki/Behavioural_Insights_Team) nicht nur gegen Corona-Maßnahmenkritiker, sondern mittlerweile auch gegen »*[Heizpumpen-Skeptiker](https://reclaimthenet.org/uk-government-heat-pumps-nudge-unit-controversy)*« ins Feld führt. Schwarmverhalten ist demnach nicht nur an [Chinas](https://www.eurasiantimes.com/mother-of-all-drones-china-unveil/) Himmel oder in der Nähe des vom Iran jüngst zu Wasser gelassenen Drohnenträgers [Schahid Bagheri](https://www.t-online.de/nachrichten/ausland/id_100596308/neuartiges-kriegsschiff-iran-stellt-ersten-drohnentraeger-vor.html) zu beobachten – oder in der Ukraine, wo todbringende [Minidrohnen](https://www.nzz.ch/international/ukraine-krieg-kamikaze-drohnen-machen-das-soldatenleben-zur-hoelle-ld.1825600) heute Jagd auf gegnerische Truppen machen – sondern auch in der unmittelbaren Nachbarschaft des Lesers. Denn Drohnen sind heute nicht mehr nur auf dem Schlachtfeld gang und gäbe. Der Nutzmensch selbst ist eine Drohne. Das traurige Produkt einer jahrzehntelangen [Schlacht ums Gehirn](https://gegendruck.eu/ausgaben/ausgabe-003.html). Die Corona-Krise war Generalprobe für die Einführung des von den Verhaltensökonomen Richard Thaler und Cass Sunstein ([Nudge](https://en.wikipedia.org/wiki/Nudge_\(book\)), Yale University Press, 2008) maßgeblich entwickelten Herrschaftsmodells der Zukunft: [Hive-Mind](https://www.mdr.de/wissen/medizin-gesundheit/stranger-things-hive-mind-102.html)-Technokratie. Fernsteuerung der Massen via Social-Media-Nudging. Via geteiltem Bewusstsein. Sprich: Regieren mittels [Plattformökonomie](https://www.economist.com/business/2024/12/10/the-paypal-mafia-is-taking-over-americas-government), Manipulativkommunikation und Emotion. Mit »Soft Power«. Zumindest bis der kopflose Schwarm endlich mit der Cloud verbunden ist. Wer also denkt, es mache Sinn, sich über Erhalt oder Verfall der Meinungsfreiheit auf einem Konzernmarkplatz wie Twitter Gedanken zu machen, erfüllt genau die Rolle, die ihm AFRL, Nudge-Unit, das NATO-[Innovation Hub](https://web.archive.org/web/20240805053751/https:/innovationhub-act.org/cognitive-warfare-2/) mit seiner »*sechsten Dimension der Kriegsführung*« und Peter Thiels PayPal-Mafia seit jeher zuschrieben: Die des geist-, willen- und haltlosen »*Agenten*« in einer überfrachteten Simulation. Nicht umsonst waren alle Big-Tech-Größen Teilnehmer der Social-Engineering-[Seminare](https://web.archive.org/web/20130511134703/http:/edge.org/conversation/libertarian-paternalism-why-it-is-impossible-not-to-nudge-class-1) von John Brockmanns [Edge-Foundation](https://www.regenauer.press/die-glorreichen-sieben). Nicht von ungefähr soll KI nun alles »*effizienter*« machen. Wirft man allerdings einen Blick auf die [Vorstandsebene](https://openai.com/our-structure/) von OpenAI, dem [ChatGPT-Anbieter](https://openai.com/index/chatgpt/) und neben dem von der CIA [startfinanzierten](https://www.businessinsider.com/the-cia-made-larry-ellison-a-billionaire-2014-9), [Mossad-nahen](https://orinocotribune.com/oracle-the-shadowy-tech-giant-in-league-with-the-cia-and-israel-with-alan-macleod/) IT-Konzern Oracle primärer Partner von Donald Trumps [Stargate-Projekt](https://apnews.com/article/trump-ai-openai-oracle-softbank-son-altman-ellison-be261f8a8ee07a0623d4170397348c41), das KI und mRNA mit einem Budget von 500 Milliarden Dollar zusammenbringen soll, wird schnell deutlich, dass mit Effizienz nichts anderes als ein Ausbau des Überwachungsstaats gemeint ist. Da wäre zum einen [Sue Desmond-Hellmann](https://en.wikipedia.org/wiki/Sue_Desmond-Hellmann), von 2014 bis 2020 CEO der Bill & Melinda Gates Foundation, seit 2020 Vorstandsmitglied bei [Pfizer](https://www.pfizer.com/people/leadership/board-of-directors/susan_desmond-hellmann-md-mph) und darüber hinaus im Vorstand von [Resilience](https://resilience.com/meet/team/), dem vom CIA-Finanztentakel [In-Q-Tel](https://www.iqt.org/) grundfinanzierten Biotech-Unternehmen, das [mRNA](https://betakit.com/federal-government-promises-199-16-million-to-biotech-company-resilience-biotechnologies/) für unter anderem [Moderna](https://www.nasdaq.com/articles/moderna:-national-resilience-to-manufacture-mrna-for-covid-19-vaccine-2021-09-08) produziert. Oder der [korrupte](https://exiledonline.com/is-larry-summers-taking-kickbacks-from-the-banks-hes-bailing-out/) Larry Summers, ehemals Chefökonom der Weltbank, der mit massiven [Deregulierungen](https://thehill.com/blogs/pundits-blog/finance/264675-clinton-and-summers-are-wrong-on-sanderss-glass-steagall-proposal/) des Finanzmarkts geradezu als Initiator der Finanzkrise 2008 bezeichnet werden kann und so [Tiefenstaat](https://wikispooks.com/wiki/Lawrence_Summers) ist wie es nur geht. Nicht zu vergessen Nicole Seligmann, [genannt](https://www.washingtonpost.com/archive/lifestyle/1998/08/17/the-lawyers-lawyer/9dcd901a-7026-43ea-89b0-aa8abfa8db0e/) »Anwältin der Anwälte«, ehemalige [Chefin](https://www.thewrap.com/nicole-seligman-out-as-president-of-sony-entertainment/) von Sony USA, [Rechtsbeistand](https://law.justia.com/cases/federal/appellate-courts/F2/910/843/463467/) von Oliver North während der Iran-Contra Anhörungen in den 80ern sowie Anwältin der [Clintons](https://www.washingtonpost.com/wp-srv/politics/special/clinton/stories/seligman081798.htm), unter anderem während des [Amtsenthebungsverfahrens](https://en.wikipedia.org/wiki/Impeachment_of_Bill_Clinton) gegen Bill Clinton im Jahr 1999. Von den langjährigen Facebook-Top-Managern [Fidji Simo](https://www.marieclaire.com/career-advice/a28712482/fidji-simo-facebook/), [Adam D’Angelo](https://om.co/gigaom/my-conversation-with-ex-facebook-cto-and-quora-co-founder-adam-dangelo/) und [Bret Taylor](https://www.forbes.com/sites/tomiogeron/2012/06/15/facebook-cto-bret-taylor-to-leave-company/) ganz zu schweigen. Angesichts dieser Mannschaft dürfte niemand überrascht sein, dass OpenAI-CEO Sam Altman von seiner jüngeren Schwester des jahrelangen [Missbrauchs](https://www.theguardian.com/technology/2025/jan/08/openai-chief-executive-sam-altman-accused-of-sexual-abuse-by-sister-in-lawsuit) bezichtigt wird und sich dafür demnächst vor Gericht verantworten muss – oder dass ein Whistleblower, der zu illegalen Aktivitäten bei OpenAI aussagen wollte, im Dezember 2024 überraschend tot in seiner Wohnung aufgefunden wurde, weshalb dessen Eltern Sam Altmans Unternehmen nun [Mord](https://www.newsweek.com/openai-tucker-carlson-whistleblower-death-2015874) vorwerfen und die Stadt San Francisco wegen schlampiger Ermittlungen [verklagen](https://nypost.com/2025/02/08/us-news/big-tech-whistleblowers-parents-sue-san-francisco-sounding-alarm-over-sons-unexpected-death/). Erstaunlich ist lediglich, dass diese Informationen nicht in aller Munde sind und Menschen wie Sam Altman und Oracle-Gründer Larry Ellison an Tag zwei nach Donald Trumps Amtseinführung als Partner einer US-Regierung präsentiert werden, die angeblich den Tiefenstaat ausheben will. Aufmerksame Beobachter des militärisch-digitalen Komplexes dürften diese Umstände allerdings kaum noch schockieren. Denn gerade das US-Militär fokussiert sich seit Jahren auf die Verwendung von Open Source Intelligence – meint Handydaten, Social-Media-Inhalte, Daten-Leaks, Hacks und KI –, um aufständischen Zellen auf den Zahn zu fühlen. So gründete die DARPA im Jahr 2011 das SMISC-Programm (Social Media in Strategic Communication). Ausgestattet mit einem Budget von knapp 50 Millionen US-Dollar gingen Wissenschaftler der Frage nach, wie sich soziale Netzwerke für Propaganda und psychologische Kriegsführung nutzen lassen. Der Initiator von SMISC, Rand Waltzman, ein DARPA-Manager, [beschrieb](https://information-professionals.org/the-darpa-social-media-in-strategic-communication-smisc-program/) im April 2015, worin die vier Kernziele des von ihm ins Leben gerufenen Programms bestanden: 1. Erkennen, klassifizieren, messen und verfolgen der Entstehung und Entwicklung sowie Verbreitung von Ideen und Konzepten (Memes) und gezielte oder irreführende Nachrichten und Fehlinformationen. 2. Erkennen der Strukturen von Überzeugungskampagnen und Einflussoperationen auf Social-Media-Sites und Communities. 3. Identifizieren der Teilnehmer und Absichten und messen der Auswirkungen von Überzeugungskampagnen. 4. Verbreiten von Gegeninformation bei erkannten gegnerischen Einflussoperationen. Darüber hinaus erklärte Waltzman, welchen technischen Umfang, beziehungsweise Fokus die Analyseprozesse aufwiesen: 1. Sprachliche Hinweise, Muster des Informationsflusses, Analyse von Thementrends, Analyse narrativer Strukturen, Stimmungserkennung und Meinungsforschung. 2. Meme-Tracking in Communities, Graphen-Analyse, probabilistisches Denken, Mustererkennung, kulturelle Narrative. 3. Induzieren von Identitäten, Modellieren entstehender Communities, Vertrauensanalyse, Modellieren von Netzwerkdynamiken. 4. Automatisierte Inhaltsgenerierung, Bots in sozialen Medien, Crowdsourcing. Die DARPA untersuchte [Twitter](https://www.theguardian.com/world/2014/jul/08/darpa-social-networks-research-twitter-influence-studies)-Follower prominenter Musiker, analysierte die Verbreitung von [Memes](https://web.archive.org/web/20121114225259/https:/www.cs.cmu.edu/~badityap/papers/composite-ccr12.pdf) und testete operative Ansätze einer [IBM-Studie](https://aaai.org/papers/00121-14513-modeling-user-attitude-toward-controversial-topics-in-online-social-media/), die sich mit der »*Modellierung von Nutzerverhalten bei kontroversen Themen auf Social Media*« befasste. Am 9. Juli 2014 veröffentlichte die DARPA eine [Liste](https://web.archive.org/web/20140709083209/https:/www.darpa.mil/OpenCatalog/SMISC.html) von 181 vom SMISC-Programm finanzierten Projekten, die sich allesamt mit dem Thema psychologische Kriegsführung auf Social Media befassten. Im Vordergrund stand jeweils die Graph-Theorie, also die Analyse des Verhaltens von Menschen anhand sozialer Daten. Die Formelsprache, die von den Projekten zur mathematischen Beschreibung der Interaktionen zwischen Menschen und Produkten verwendet wurde, war dieselbe, die bei der Steuerung autonomer Fahrzeug-Gruppen zur Anwendung kommt. Sie bildet das Herzstück von Googles Verständnis zu Suchkontexten und ist grundlegender Bestandteil von Kontrollsystemen zur Steuerung autonomer Roboterschwärme. Warren Dixon und die DARPA gingen nun aber der Frage nach, ob die gleiche Mathematik auf die Steuerung autonomer Menschen und Gruppen von Menschen anwendbar ist. Um zu verstehen, was das bedeutet, folgend eine Erläuterung zum Facebook-Graph, über den [Ars Technica](https://arstechnica.com/information-technology/2013/03/knowing-the-score-how-facebooks-graph-search-knows-what-you-want/) am 14. März 2013 berichtete: »*Der Graph ist eine Datenbank, die Informationen über Benutzer, Seiten und andere Objekte im Facebook-Universum speichert. Er enthält auch die Beziehungen zwischen ihnen. Jede Entität, also jeder Knoten im Facebook-Graph – identifiziert durch eine eindeutige Nummer, die als fbid (Facebook-ID) bezeichnet wird – ist mit einer Reihe von Attributen oder Metadaten verknüpft. Die Beziehungen zwischen diesen Knoten, die als Kanten bezeichnet werden, enthalten ihre eigenen Metadaten, um die Art der Beziehung zwischen ihnen zu beschreiben. Die von Facebook verwendete Graph-Datenbank ist Googles [Knowledge-Graph](https://arstechnica.com/information-technology/2012/06/inside-the-architecture-of-googles-knowledge-graph-and-microsofts-satori/) und Microsofts Satori-Graph-basiertem Konzept recht ähnlich. In vielerlei Hinsicht ist die Struktur des Facebook-Graphs jedoch einfacher als die Graph-Schemata von Google und Microsoft, da Facebook die Metadaten für seine Knoten und Kanten speziell auf soziale Interaktion abgestimmt hat*.« Dixons AFRL-Arbeitsgruppe nutze solche Daten, um zu modellieren, wie die Zusammenarbeit zwischen »*wichtigen Influencern*« in sozialen Netzwerken das Verhalten von Gruppen innerhalb dieses Netzwerks beeinflussen könnte. Stichwort: »*Eindämmungskontrolle*«. Dixon selbst erläuterte dieses Konzept mit den Worten: **»*Es gibt eine Gruppe von Anführern, von denen jeder seine eigenen Ziele und sein eigenes Schwerpunktthema hat. Unser Ziel ist, dass diese Leute ihre Meinung ändern und die Gruppe der Anhänger – also Leute, die zu ihrer sozialen Gruppe gehören, aber das übergeordnete Ziel nicht kennen – unter Druck setzen*.«** Unter Zuhilfenahme der Graphen-Theorie erarbeiteten Dixon und Co. ein Kommunikationsmodell, das verständlich machte, wie viel Einfluss ein Social-Media-Influencer benötigt, um Macht auszuüben und das Verhalten seiner Follower zu ändern. Während die DARPA im Rahmen mehrerer Pressemitteilungen versicherte, weder persönlichkeitsbezogene Daten zu speichern noch Social-Media-User zu manipulieren, hatte man beim GCHQ in Großbritannien weniger Hemmungen. Wie die von NSA-Whistleblower Edward Snowden geleakten Dokumente [belegen](https://arstechnica.com/information-technology/2014/07/ghcqs-chinese-menu-of-tools-spread-disinformation-across-internet/), hatte der britische Nachrichtendienst ein ganzes Arsenal digitaler Waffen zur Hand, um Individuen und ihre Geräte zu infiltrieren, Fake-Identitäten aufzubauen, Falschinformationen zu verbreiten und die öffentliche Meinung zu »*formen*«. Diese Werkzeuge teilte das GCHQ mit der NSA, die sie ihrerseits anwandte, um in Afghanistan und anderen Krisengebieten zu steuern, welche Informationen gegnerische Gruppen online und über das Smartphone abrufen konnten. Neben Militär, Geheimdiensten und Tech-Konzernen sind natürlich auch Organisationen wie USAID und das NED (National Endowment for Democracy) auf dem Feld der Cyber-Kriegsführung aktiv. Im [April 2014](https://taz.de/Twitterplattform-ZunZuneo/!5045053/) wurde zum Beispiel bekannt, das USAID auf Kuba ein Twitter-ähnliches Netzwerk aufbauen wollte, um das kommunistische Regime zu unterminieren. Dass es sich dabei nicht um Einzelfälle handelt, veranschaulicht ein [Report](https://www.ox.ac.uk/news/2021-01-13-social-media-manipulation-political-actors-industrial-scale-problem-oxford-report) der Universität Oxford, der am 13. Januar 2021 veröffentlicht wurde und Social-Media-Manipulation in gut 80 Ländern analysierte: **»*In jedem der 81 untersuchten Länder wurden organisierte Kampagnen zur Manipulation sozialer Medien festgestellt, ein Anstieg von 15 Prozent innerhalb eines Jahres, verglichen mit 70 Ländern im Jahr 2019. Dem Bericht zufolge produzieren Regierungen, PR-Agenturen und politische Parteien im industriellen Maßstab Falschinformationen. Er zeigt, dass Desinformation zu einer gängigen Strategie geworden ist, wobei in mehr als 93 Prozent der Länder Desinformation als Teil der politischen Kommunikation eingesetzt wird*.«** »*Die Leute denken nicht gern daran, dass sie manipuliert werden*«, so Warren Dixon. »*Aber wir werden jeden Tag manipuliert. Durch Werbung, durch Regierungschefs, religiöse Führer und sogar dazu, zur Arbeit zu gehen. Wir arbeiten größtenteils deswegen, weil wir dafür bezahlt werden. Aber wie viel muss ich jemandem für seine Arbeit zahlen?*« Gute Frage. Wie viel muss man jemandem bezahlen, damit er lügt, damit er seinen besten Freund verrät oder einen Menschen ermordet? Oder ein paar tausend Menschen? Mit solchen Fragen beschäftigen sich die Verhaltensforscher, die Big Tech und Geheimdienste beraten, die Algorithmen und soziale [Feedback-Loops](https://youtu.be/J54k7WrbfMg?si=GgS-5yx7vgKFbPtB) kreieren. Denn Suchmaschinen und Social Media sind kein Serviceangebot, sondern eine Waffengattung kognitiver Kriegsführung. Die Projektile des Informationskriegs. Und die meisten Menschen sind dem Kugelhagel schutzlos ausgeliefert. Die zeitgeistig flexible Herrschaftskaste weiß diesen Umstand zum eigenen Vorteil zu nutzen. Gerade deshalb ist »*Agent Smith*« eine perfekte wie düstere Parabel für den modernen Nutzmenschen, der sein Leben online führt und im digitalen Raum binnen Sekunden Entscheidungen trifft, für die ihm jede inhaltliche Grundlage fehlt. Entscheidungen, die sein Selbstbild nachhaltig verändern. Wer das System eben noch kritisierte, wedelt im nächsten Moment mit Pompons, um es zu bejubeln. Denn die Transformation des Ich ist dieser Tage immer nur einen Klick entfernt. »*Smith begann als Agent, ein KI-Programm in der Matrix, das darauf programmiert war, die Ordnung im System aufrechtzuerhalten, indem es menschliche Simulakren eliminierte, die die simulierte Realität instabil machen würden, sowie alle Schurkenprogramme, die für das Maschinenkollektiv keinen Zweck mehr erfüllen. *(…)* Smiths wahre Macht beruht auf seiner Fähigkeit, Erinnerungen und Kräfte seiner Opfer – Menschen und Programme gleichermaßen – zu absorbieren. *(…)* Smith erlangt die Macht, seine physische Form auf jedes Wesen in der Matrix zu kopieren, indem er seine Hand in ihren Körper eintauchen lässt und eine schwarze Flüssigkeit verteilt, die sie in eine Kopie seiner selbst verwandelt, was zu einer ständig wachsenden Armee von Smiths führt, die durch ein einziges Bewusstsein verbunden sind*.« **Wer sich also fragt, warum seine vormals maßnahmen- und obrigkeitskritischen Weggefährten nun dem tiefenstaatlich orchestrierten MAGA-Kult huldigen, findet die Antwort in DARPA-Studien zum Thema »*Steuerung des Gruppenverhaltens mittels Social Media*«.** Neu ist das alles nicht. Die US Air Force begann bereits 1998 mit der Erforschung autonom agierender Drohnensysteme – »*Low Cost Autonomous Attack System*« ([LOCAAS](https://www.globalsecurity.org/military/systems/munitions/locaas.htm)) genannt. Die LOCAAS-Systeme nutzten einen Algorithmus, der auf Craig Reynolds’ Boids-Modell basiert, um in Formation eines Schwarms zu fliegen. Warf ein Tarnkappenbomber seine bis zu 192 Drohnen ab, begannen sie sich untereinander zu verständigen und attackierten feindliche Truppen im Verbund. Das war vor 27 Jahren. Heute gehören Drohnen zum zivilen Alltag. So betreibt die [Swisscom](https://www.swisscom.ch/de/business/broadcast/sicherheitsloesungen/drohnennetzwerk-schweiz.html) in der Schweiz in Kooperation mit Nokia ein Drones-as-a-Service (DaaS) Netzwerk für »*effiziente Inspektionen und die Sicherung großer Areale sowie zentraler Infrastruktur*«. Das klingt zunächst einmal nach privatwirtschaftlicher Dienstleistung auf Abruf. Aber: »*Blaulichtorganisationen sollen diese Drohnen auf Abruf nutzen können, um dank detailliertem Bildmaterial* (…) *Informationen von Unfallstellen, Katastrophengebieten oder Tatorten einzuholen*«, so der [Tagesanzeiger](https://www.tagesanzeiger.ch/swisscom-ueberwachung-mit-drohnen-datenschutz-unklar-998244957315) am 18. August 2024. Was für Bildmaterial in welcher Auflösung wann, wo, warum aufgezeichnet und gespeichert wird, ist indes unklar. Hiesige Datenschützer sind alarmiert. Aus gutem Grund. Denn auch in der Kriegsführung gehören Drohnen mittlerweile zum Tagesgeschäft. Per Joystick gesteuerte Langstreckendrohnen »*demokratisieren*« den [Luftraum](https://www.thebureauinvestigates.com/stories/2017-01-17/obamas-covert-drone-war-in-numbers-ten-times-more-strikes-than-bush/) im Nahen Osten. Bevorzugt mit lasergesteuerten GBU-12 Paveway II Bomben. Mini-Drohnen [überwachen](https://www.youtube.com/watch?v=wW7lUdvJl7Q) unauffällig das Einsatzgebiet und töten gezielt per [Kopfschuss](https://www.youtube.com/watch?v=TlO2gcs1YvM). [Kamikaze](https://www.youtube.com/watch?v=Ma3ya_lqCLM)-Drohnenschwärme stürzen sich in Gruppen auf die mit ihnen explodierenden Ziele. Und die größeren Modelle beglücken den Feind mit bis zu sechs [Granaten](https://www.youtube.com/watch?v=mT5FKNQ2Fg8). Projekte des US-Militärs und [chinesische](https://youtu.be/LpaSXwpKzGk?si=6bKHlqaoi_mpURDn) Guinness-Weltrekorde im Drohnen-Formationsflug [zeigen](https://www.regenauer.press/null), dass es wohl nicht mehr allzu lange dauern wird, bis autonome Schwärme, die von ebenso autonomen Trägerfahrzeugen verteilt und aufgeladen werden, Krisengebiete, Grenzen und Innenstädte überwachen – und schützen. Fragt sich nur, vor wem. Die inflationäre Verwendung von und progressiv-positive Kommunikation zu Drohnentechnologie sowie KI sollte also durchaus zu denken geben. Denn was dem Hobbyfilmer günstige Luftaufnahmen liefert und Zuschauern in Form eines illuminierten [Drachens](https://www.youtube.com/watch?v=3G1KBu6H6BM) aus 1.500 Drohnen über Shenzen Bewunderung abnötigt, dürfte die nächste Ausbaustufe militarisierter Überwachungsinfrastruktur charakterisieren. Der gemeine »*Agent*«, die »*iDrone*«, der Boid – also der von medialer Dynamik und Polarisierungsdialektik überforderte Homo demens – sieht diesen Entwicklungen natürlich weithin gelassen entgegen. Denn er »*bewegt sich in Richtung des Mittelpunkts derer, die er in seinem Umfeld sieht, entfernt sich, sobald ihm jemand zu nahe kommt und läuft immer in etwa die gleiche Richtung wie seine Nachbarn*«.
@ 2fb77d26:c47a6ee1
2025-02-22 09:04:25Der 1953 geborene [Craig Reynolds](https://de.wikipedia.org/wiki/Craig_Reynolds) ist Experte für künstliches Leben und Computergrafik. In dieser Funktion arbeitete er unter anderem an Filmen wie Tron (1982) und Batman (1992). Bei »*Sony Computer Entertainment America*« (heute [SIE](https://de.wikipedia.org/wiki/Sony_Interactive_Entertainment)) entwickelte er die [OpenSteer](https://opensteer.sourceforge.net/)-Bibliothek, die der Abbildung von Schwarmverhalten in Spielen und Animationsanwendungen dient. An solch prestigeträchtige Aufträge kam Reynolds, weil er sich nebst Computergrafik intensiv mit Theorien zum »*Steuerungsverhalten für autonome Charaktere*« befasst hatte. Mit Schwarmverhalten. Einem Thema, das mit wachsender Rechenleistung immer wichtiger für die Entwicklung von Computerspielen wurde. Die sollten dem Spieler das Gefühl geben, sich in einer realen Welt mit »*autonomen Charakteren*« zu bewegen. Dazu mussten diese vom Computer, beziehungsweise der Software gesteuerten Charaktere – im Fachjargon »*[Agenten](https://de.wikipedia.org/wiki/Software-Agent)*« genannt – sich irgendwie verhalten. Und zwar ohne, dass von außen ein weiterer Steuerungseingriff erfolgt. Eigendynamisch. Dafür bedarf es Regeln, die im Programmcode eingebettet werden können. Genau die lieferte Reynolds 1986 im Rahmen der von ihm modellierten [Boids-Simulation](https://www.red3d.com/cwr/boids/), die besagt, dass Schwarmverhalten auf drei simplen Regeln basiert: 1. Bewege dich in Richtung des Mittelpunkts derer, die du in deinem Umfeld siehst. 2. Entferne dich, sobald dir jemand zu nahe kommt. 3. Bewege dich etwa in die gleiche Richtung wie deine Nachbarn. Sprich: Kohäsion, Separation und Orientierung. In Reynolds’ Beschreibung des Boid-Modells liest man diesbezüglich: »*1986 habe ich ein Computermodell koordinierter Tierbewegungen *(…) *erstellt. Es basierte auf dreidimensionaler Computergeometrie, wie sie normalerweise in der Computeranimation oder im computergestützten Design verwendet wird. Ich habe die generischen, simulierten Schwarmtiere Boids genannt. Das grundlegende Schwarmmodell besteht aus drei einfachen Lenkverhalten, die beschreiben, wie ein einzelner Boid auf der Grundlage der Positionen und Geschwindigkeiten seiner Schwarmgenossen in der Nähe manövriert. Jeder Boid hat direkten Zugriff auf die geometrische Beschreibung der gesamten Szene, aber das Schwarmverhalten erfordert, dass er nur auf Schwarmgenossen in einer bestimmten kleinen Nachbarschaft um sich herum reagiert. *(…)* Schwarmgenossen außerhalb dieser lokalen Nachbarschaft werden ignoriert.* *Die Nachbarschaft könnte als Modell eingeschränkter Wahrnehmung betrachtet werden (wie bei Fischen in trübem Wasser), aber es ist wahrscheinlich korrekter, sie als Definition des Bereichs zu betrachten, in dem Schwarmgenossen die Lenkung eines Boids beeinflussen. In den ersten Experimenten wurde ein etwas ausgefeilteres Verhaltensmodell verwendet. Es umfasste vorausschauende Hindernisvermeidung und Zielsuche. *(…)* Für Anwendungen in der Computeranimation führte ein Zielsuchverhalten mit niedriger Priorität dazu, dass die Herde einem vorgegebenen Pfad folgte*.« Wer sich bei dieser Beschreibung an die Strukturen postmoderner Gesellschaft erinnert fühlt und »*Agenten*« mit »*[Agent Smith](https://en.wikipedia.org/wiki/Agent_Smith)*« aus den Matrix-Filmen assoziiert, liegt nicht ganz falsch. Denn Kohäsion, Separation und Orientierung definieren nicht mehr nur das Schwarmverhalten autonomer Charaktere in Computerspielen, sondern auch die Dynamiken des gesellschaftlichen Zusammenlebens im multimedialen Panoptikum der Postmoderne. **So nimmt es kaum Wunder, dass ein vom** **[US Air Force Laboratory](https://www.afrl.af.mil/)** **(AFRL) finanziertes** **[Forschungsprojekt](https://arxiv.org/pdf/1402.5644)** **an der University of Florida (Gainesville, USA) bereits im Jahr 2014 untersuchte, »*wie Social Media eingesetzt werden kann, um Menschen wie Drohnen zu steuern*«.** Unter diesem Titel berichtete denn auch [Ars Technica](https://arstechnica.com/information-technology/2014/07/air-force-research-how-to-use-social-media-to-control-people-like-drones/) am 17. Juli 2014, dass der Forschungsleiter der AFRL-Studie, [Warren Dixon](https://ncr.mae.ufl.edu/index.php?id=people), seines Zeichens Chef des Lehrstuhls für nichtlineare Steuerung und Robotik an der University of Florida, vor allem daran arbeite, »*wie man ein Netzwerk, wenn man es einmal identifiziert hat, in Richtung eines Ziels manipulieren kann*«. Und mit »*Netzwerk*« meint Dixon nicht Computer, sondern soziale Strukturen. Die Untersuchungen von Dixon, Kan, Klotz und Pasiliao – formeller Titel: »*Eindämmungskontrolle für ein soziales Netzwerk mit staatlich abhängiger Konnektivität*« – unterstreichen, dass die mathematischen Prinzipien, die zur Steuerung autonomer Agenten und Robotergruppen verwendet werden, auch auf soziale Netzwerke übertragbar sind, um menschliches Verhalten zu manipulieren. Im großen Stil. Ausgehend von einer optimalen Kalibrierung könnten die von den AFRL-Forschern entwickelten Modelle eingesetzt werden, um die Meinung auf Social-Media-Portalen in Richtung eines gewünschten Verhaltens zu lenken. Genau wie die [Cyber-Waffen](https://www.business-standard.com/article/technology/hacks-raise-fear-over-nsa-s-hold-on-cyberweapons-117070100851_1.html) der NSA (National Security Agency, USA) oder das entsprechende Arsenal des [GCHQ](https://www.gchq.gov.uk/) (Government Communication Headquarters, UK), das seine [Nudge-Unit](https://en.wikipedia.org/wiki/Behavioural_Insights_Team) nicht nur gegen Corona-Maßnahmenkritiker, sondern mittlerweile auch gegen »*[Heizpumpen-Skeptiker](https://reclaimthenet.org/uk-government-heat-pumps-nudge-unit-controversy)*« ins Feld führt. Schwarmverhalten ist demnach nicht nur an [Chinas](https://www.eurasiantimes.com/mother-of-all-drones-china-unveil/) Himmel oder in der Nähe des vom Iran jüngst zu Wasser gelassenen Drohnenträgers [Schahid Bagheri](https://www.t-online.de/nachrichten/ausland/id_100596308/neuartiges-kriegsschiff-iran-stellt-ersten-drohnentraeger-vor.html) zu beobachten – oder in der Ukraine, wo todbringende [Minidrohnen](https://www.nzz.ch/international/ukraine-krieg-kamikaze-drohnen-machen-das-soldatenleben-zur-hoelle-ld.1825600) heute Jagd auf gegnerische Truppen machen – sondern auch in der unmittelbaren Nachbarschaft des Lesers. Denn Drohnen sind heute nicht mehr nur auf dem Schlachtfeld gang und gäbe. Der Nutzmensch selbst ist eine Drohne. Das traurige Produkt einer jahrzehntelangen [Schlacht ums Gehirn](https://gegendruck.eu/ausgaben/ausgabe-003.html). Die Corona-Krise war Generalprobe für die Einführung des von den Verhaltensökonomen Richard Thaler und Cass Sunstein ([Nudge](https://en.wikipedia.org/wiki/Nudge_\(book\)), Yale University Press, 2008) maßgeblich entwickelten Herrschaftsmodells der Zukunft: [Hive-Mind](https://www.mdr.de/wissen/medizin-gesundheit/stranger-things-hive-mind-102.html)-Technokratie. Fernsteuerung der Massen via Social-Media-Nudging. Via geteiltem Bewusstsein. Sprich: Regieren mittels [Plattformökonomie](https://www.economist.com/business/2024/12/10/the-paypal-mafia-is-taking-over-americas-government), Manipulativkommunikation und Emotion. Mit »Soft Power«. Zumindest bis der kopflose Schwarm endlich mit der Cloud verbunden ist. Wer also denkt, es mache Sinn, sich über Erhalt oder Verfall der Meinungsfreiheit auf einem Konzernmarkplatz wie Twitter Gedanken zu machen, erfüllt genau die Rolle, die ihm AFRL, Nudge-Unit, das NATO-[Innovation Hub](https://web.archive.org/web/20240805053751/https:/innovationhub-act.org/cognitive-warfare-2/) mit seiner »*sechsten Dimension der Kriegsführung*« und Peter Thiels PayPal-Mafia seit jeher zuschrieben: Die des geist-, willen- und haltlosen »*Agenten*« in einer überfrachteten Simulation. Nicht umsonst waren alle Big-Tech-Größen Teilnehmer der Social-Engineering-[Seminare](https://web.archive.org/web/20130511134703/http:/edge.org/conversation/libertarian-paternalism-why-it-is-impossible-not-to-nudge-class-1) von John Brockmanns [Edge-Foundation](https://www.regenauer.press/die-glorreichen-sieben). Nicht von ungefähr soll KI nun alles »*effizienter*« machen. Wirft man allerdings einen Blick auf die [Vorstandsebene](https://openai.com/our-structure/) von OpenAI, dem [ChatGPT-Anbieter](https://openai.com/index/chatgpt/) und neben dem von der CIA [startfinanzierten](https://www.businessinsider.com/the-cia-made-larry-ellison-a-billionaire-2014-9), [Mossad-nahen](https://orinocotribune.com/oracle-the-shadowy-tech-giant-in-league-with-the-cia-and-israel-with-alan-macleod/) IT-Konzern Oracle primärer Partner von Donald Trumps [Stargate-Projekt](https://apnews.com/article/trump-ai-openai-oracle-softbank-son-altman-ellison-be261f8a8ee07a0623d4170397348c41), das KI und mRNA mit einem Budget von 500 Milliarden Dollar zusammenbringen soll, wird schnell deutlich, dass mit Effizienz nichts anderes als ein Ausbau des Überwachungsstaats gemeint ist. Da wäre zum einen [Sue Desmond-Hellmann](https://en.wikipedia.org/wiki/Sue_Desmond-Hellmann), von 2014 bis 2020 CEO der Bill & Melinda Gates Foundation, seit 2020 Vorstandsmitglied bei [Pfizer](https://www.pfizer.com/people/leadership/board-of-directors/susan_desmond-hellmann-md-mph) und darüber hinaus im Vorstand von [Resilience](https://resilience.com/meet/team/), dem vom CIA-Finanztentakel [In-Q-Tel](https://www.iqt.org/) grundfinanzierten Biotech-Unternehmen, das [mRNA](https://betakit.com/federal-government-promises-199-16-million-to-biotech-company-resilience-biotechnologies/) für unter anderem [Moderna](https://www.nasdaq.com/articles/moderna:-national-resilience-to-manufacture-mrna-for-covid-19-vaccine-2021-09-08) produziert. Oder der [korrupte](https://exiledonline.com/is-larry-summers-taking-kickbacks-from-the-banks-hes-bailing-out/) Larry Summers, ehemals Chefökonom der Weltbank, der mit massiven [Deregulierungen](https://thehill.com/blogs/pundits-blog/finance/264675-clinton-and-summers-are-wrong-on-sanderss-glass-steagall-proposal/) des Finanzmarkts geradezu als Initiator der Finanzkrise 2008 bezeichnet werden kann und so [Tiefenstaat](https://wikispooks.com/wiki/Lawrence_Summers) ist wie es nur geht. Nicht zu vergessen Nicole Seligmann, [genannt](https://www.washingtonpost.com/archive/lifestyle/1998/08/17/the-lawyers-lawyer/9dcd901a-7026-43ea-89b0-aa8abfa8db0e/) »Anwältin der Anwälte«, ehemalige [Chefin](https://www.thewrap.com/nicole-seligman-out-as-president-of-sony-entertainment/) von Sony USA, [Rechtsbeistand](https://law.justia.com/cases/federal/appellate-courts/F2/910/843/463467/) von Oliver North während der Iran-Contra Anhörungen in den 80ern sowie Anwältin der [Clintons](https://www.washingtonpost.com/wp-srv/politics/special/clinton/stories/seligman081798.htm), unter anderem während des [Amtsenthebungsverfahrens](https://en.wikipedia.org/wiki/Impeachment_of_Bill_Clinton) gegen Bill Clinton im Jahr 1999. Von den langjährigen Facebook-Top-Managern [Fidji Simo](https://www.marieclaire.com/career-advice/a28712482/fidji-simo-facebook/), [Adam D’Angelo](https://om.co/gigaom/my-conversation-with-ex-facebook-cto-and-quora-co-founder-adam-dangelo/) und [Bret Taylor](https://www.forbes.com/sites/tomiogeron/2012/06/15/facebook-cto-bret-taylor-to-leave-company/) ganz zu schweigen. Angesichts dieser Mannschaft dürfte niemand überrascht sein, dass OpenAI-CEO Sam Altman von seiner jüngeren Schwester des jahrelangen [Missbrauchs](https://www.theguardian.com/technology/2025/jan/08/openai-chief-executive-sam-altman-accused-of-sexual-abuse-by-sister-in-lawsuit) bezichtigt wird und sich dafür demnächst vor Gericht verantworten muss – oder dass ein Whistleblower, der zu illegalen Aktivitäten bei OpenAI aussagen wollte, im Dezember 2024 überraschend tot in seiner Wohnung aufgefunden wurde, weshalb dessen Eltern Sam Altmans Unternehmen nun [Mord](https://www.newsweek.com/openai-tucker-carlson-whistleblower-death-2015874) vorwerfen und die Stadt San Francisco wegen schlampiger Ermittlungen [verklagen](https://nypost.com/2025/02/08/us-news/big-tech-whistleblowers-parents-sue-san-francisco-sounding-alarm-over-sons-unexpected-death/). Erstaunlich ist lediglich, dass diese Informationen nicht in aller Munde sind und Menschen wie Sam Altman und Oracle-Gründer Larry Ellison an Tag zwei nach Donald Trumps Amtseinführung als Partner einer US-Regierung präsentiert werden, die angeblich den Tiefenstaat ausheben will. Aufmerksame Beobachter des militärisch-digitalen Komplexes dürften diese Umstände allerdings kaum noch schockieren. Denn gerade das US-Militär fokussiert sich seit Jahren auf die Verwendung von Open Source Intelligence – meint Handydaten, Social-Media-Inhalte, Daten-Leaks, Hacks und KI –, um aufständischen Zellen auf den Zahn zu fühlen. So gründete die DARPA im Jahr 2011 das SMISC-Programm (Social Media in Strategic Communication). Ausgestattet mit einem Budget von knapp 50 Millionen US-Dollar gingen Wissenschaftler der Frage nach, wie sich soziale Netzwerke für Propaganda und psychologische Kriegsführung nutzen lassen. Der Initiator von SMISC, Rand Waltzman, ein DARPA-Manager, [beschrieb](https://information-professionals.org/the-darpa-social-media-in-strategic-communication-smisc-program/) im April 2015, worin die vier Kernziele des von ihm ins Leben gerufenen Programms bestanden: 1. Erkennen, klassifizieren, messen und verfolgen der Entstehung und Entwicklung sowie Verbreitung von Ideen und Konzepten (Memes) und gezielte oder irreführende Nachrichten und Fehlinformationen. 2. Erkennen der Strukturen von Überzeugungskampagnen und Einflussoperationen auf Social-Media-Sites und Communities. 3. Identifizieren der Teilnehmer und Absichten und messen der Auswirkungen von Überzeugungskampagnen. 4. Verbreiten von Gegeninformation bei erkannten gegnerischen Einflussoperationen. Darüber hinaus erklärte Waltzman, welchen technischen Umfang, beziehungsweise Fokus die Analyseprozesse aufwiesen: 1. Sprachliche Hinweise, Muster des Informationsflusses, Analyse von Thementrends, Analyse narrativer Strukturen, Stimmungserkennung und Meinungsforschung. 2. Meme-Tracking in Communities, Graphen-Analyse, probabilistisches Denken, Mustererkennung, kulturelle Narrative. 3. Induzieren von Identitäten, Modellieren entstehender Communities, Vertrauensanalyse, Modellieren von Netzwerkdynamiken. 4. Automatisierte Inhaltsgenerierung, Bots in sozialen Medien, Crowdsourcing. Die DARPA untersuchte [Twitter](https://www.theguardian.com/world/2014/jul/08/darpa-social-networks-research-twitter-influence-studies)-Follower prominenter Musiker, analysierte die Verbreitung von [Memes](https://web.archive.org/web/20121114225259/https:/www.cs.cmu.edu/~badityap/papers/composite-ccr12.pdf) und testete operative Ansätze einer [IBM-Studie](https://aaai.org/papers/00121-14513-modeling-user-attitude-toward-controversial-topics-in-online-social-media/), die sich mit der »*Modellierung von Nutzerverhalten bei kontroversen Themen auf Social Media*« befasste. Am 9. Juli 2014 veröffentlichte die DARPA eine [Liste](https://web.archive.org/web/20140709083209/https:/www.darpa.mil/OpenCatalog/SMISC.html) von 181 vom SMISC-Programm finanzierten Projekten, die sich allesamt mit dem Thema psychologische Kriegsführung auf Social Media befassten. Im Vordergrund stand jeweils die Graph-Theorie, also die Analyse des Verhaltens von Menschen anhand sozialer Daten. Die Formelsprache, die von den Projekten zur mathematischen Beschreibung der Interaktionen zwischen Menschen und Produkten verwendet wurde, war dieselbe, die bei der Steuerung autonomer Fahrzeug-Gruppen zur Anwendung kommt. Sie bildet das Herzstück von Googles Verständnis zu Suchkontexten und ist grundlegender Bestandteil von Kontrollsystemen zur Steuerung autonomer Roboterschwärme. Warren Dixon und die DARPA gingen nun aber der Frage nach, ob die gleiche Mathematik auf die Steuerung autonomer Menschen und Gruppen von Menschen anwendbar ist. Um zu verstehen, was das bedeutet, folgend eine Erläuterung zum Facebook-Graph, über den [Ars Technica](https://arstechnica.com/information-technology/2013/03/knowing-the-score-how-facebooks-graph-search-knows-what-you-want/) am 14. März 2013 berichtete: »*Der Graph ist eine Datenbank, die Informationen über Benutzer, Seiten und andere Objekte im Facebook-Universum speichert. Er enthält auch die Beziehungen zwischen ihnen. Jede Entität, also jeder Knoten im Facebook-Graph – identifiziert durch eine eindeutige Nummer, die als fbid (Facebook-ID) bezeichnet wird – ist mit einer Reihe von Attributen oder Metadaten verknüpft. Die Beziehungen zwischen diesen Knoten, die als Kanten bezeichnet werden, enthalten ihre eigenen Metadaten, um die Art der Beziehung zwischen ihnen zu beschreiben. Die von Facebook verwendete Graph-Datenbank ist Googles [Knowledge-Graph](https://arstechnica.com/information-technology/2012/06/inside-the-architecture-of-googles-knowledge-graph-and-microsofts-satori/) und Microsofts Satori-Graph-basiertem Konzept recht ähnlich. In vielerlei Hinsicht ist die Struktur des Facebook-Graphs jedoch einfacher als die Graph-Schemata von Google und Microsoft, da Facebook die Metadaten für seine Knoten und Kanten speziell auf soziale Interaktion abgestimmt hat*.« Dixons AFRL-Arbeitsgruppe nutze solche Daten, um zu modellieren, wie die Zusammenarbeit zwischen »*wichtigen Influencern*« in sozialen Netzwerken das Verhalten von Gruppen innerhalb dieses Netzwerks beeinflussen könnte. Stichwort: »*Eindämmungskontrolle*«. Dixon selbst erläuterte dieses Konzept mit den Worten: **»*Es gibt eine Gruppe von Anführern, von denen jeder seine eigenen Ziele und sein eigenes Schwerpunktthema hat. Unser Ziel ist, dass diese Leute ihre Meinung ändern und die Gruppe der Anhänger – also Leute, die zu ihrer sozialen Gruppe gehören, aber das übergeordnete Ziel nicht kennen – unter Druck setzen*.«** Unter Zuhilfenahme der Graphen-Theorie erarbeiteten Dixon und Co. ein Kommunikationsmodell, das verständlich machte, wie viel Einfluss ein Social-Media-Influencer benötigt, um Macht auszuüben und das Verhalten seiner Follower zu ändern. Während die DARPA im Rahmen mehrerer Pressemitteilungen versicherte, weder persönlichkeitsbezogene Daten zu speichern noch Social-Media-User zu manipulieren, hatte man beim GCHQ in Großbritannien weniger Hemmungen. Wie die von NSA-Whistleblower Edward Snowden geleakten Dokumente [belegen](https://arstechnica.com/information-technology/2014/07/ghcqs-chinese-menu-of-tools-spread-disinformation-across-internet/), hatte der britische Nachrichtendienst ein ganzes Arsenal digitaler Waffen zur Hand, um Individuen und ihre Geräte zu infiltrieren, Fake-Identitäten aufzubauen, Falschinformationen zu verbreiten und die öffentliche Meinung zu »*formen*«. Diese Werkzeuge teilte das GCHQ mit der NSA, die sie ihrerseits anwandte, um in Afghanistan und anderen Krisengebieten zu steuern, welche Informationen gegnerische Gruppen online und über das Smartphone abrufen konnten. Neben Militär, Geheimdiensten und Tech-Konzernen sind natürlich auch Organisationen wie USAID und das NED (National Endowment for Democracy) auf dem Feld der Cyber-Kriegsführung aktiv. Im [April 2014](https://taz.de/Twitterplattform-ZunZuneo/!5045053/) wurde zum Beispiel bekannt, das USAID auf Kuba ein Twitter-ähnliches Netzwerk aufbauen wollte, um das kommunistische Regime zu unterminieren. Dass es sich dabei nicht um Einzelfälle handelt, veranschaulicht ein [Report](https://www.ox.ac.uk/news/2021-01-13-social-media-manipulation-political-actors-industrial-scale-problem-oxford-report) der Universität Oxford, der am 13. Januar 2021 veröffentlicht wurde und Social-Media-Manipulation in gut 80 Ländern analysierte: **»*In jedem der 81 untersuchten Länder wurden organisierte Kampagnen zur Manipulation sozialer Medien festgestellt, ein Anstieg von 15 Prozent innerhalb eines Jahres, verglichen mit 70 Ländern im Jahr 2019. Dem Bericht zufolge produzieren Regierungen, PR-Agenturen und politische Parteien im industriellen Maßstab Falschinformationen. Er zeigt, dass Desinformation zu einer gängigen Strategie geworden ist, wobei in mehr als 93 Prozent der Länder Desinformation als Teil der politischen Kommunikation eingesetzt wird*.«** »*Die Leute denken nicht gern daran, dass sie manipuliert werden*«, so Warren Dixon. »*Aber wir werden jeden Tag manipuliert. Durch Werbung, durch Regierungschefs, religiöse Führer und sogar dazu, zur Arbeit zu gehen. Wir arbeiten größtenteils deswegen, weil wir dafür bezahlt werden. Aber wie viel muss ich jemandem für seine Arbeit zahlen?*« Gute Frage. Wie viel muss man jemandem bezahlen, damit er lügt, damit er seinen besten Freund verrät oder einen Menschen ermordet? Oder ein paar tausend Menschen? Mit solchen Fragen beschäftigen sich die Verhaltensforscher, die Big Tech und Geheimdienste beraten, die Algorithmen und soziale [Feedback-Loops](https://youtu.be/J54k7WrbfMg?si=GgS-5yx7vgKFbPtB) kreieren. Denn Suchmaschinen und Social Media sind kein Serviceangebot, sondern eine Waffengattung kognitiver Kriegsführung. Die Projektile des Informationskriegs. Und die meisten Menschen sind dem Kugelhagel schutzlos ausgeliefert. Die zeitgeistig flexible Herrschaftskaste weiß diesen Umstand zum eigenen Vorteil zu nutzen. Gerade deshalb ist »*Agent Smith*« eine perfekte wie düstere Parabel für den modernen Nutzmenschen, der sein Leben online führt und im digitalen Raum binnen Sekunden Entscheidungen trifft, für die ihm jede inhaltliche Grundlage fehlt. Entscheidungen, die sein Selbstbild nachhaltig verändern. Wer das System eben noch kritisierte, wedelt im nächsten Moment mit Pompons, um es zu bejubeln. Denn die Transformation des Ich ist dieser Tage immer nur einen Klick entfernt. »*Smith begann als Agent, ein KI-Programm in der Matrix, das darauf programmiert war, die Ordnung im System aufrechtzuerhalten, indem es menschliche Simulakren eliminierte, die die simulierte Realität instabil machen würden, sowie alle Schurkenprogramme, die für das Maschinenkollektiv keinen Zweck mehr erfüllen. *(…)* Smiths wahre Macht beruht auf seiner Fähigkeit, Erinnerungen und Kräfte seiner Opfer – Menschen und Programme gleichermaßen – zu absorbieren. *(…)* Smith erlangt die Macht, seine physische Form auf jedes Wesen in der Matrix zu kopieren, indem er seine Hand in ihren Körper eintauchen lässt und eine schwarze Flüssigkeit verteilt, die sie in eine Kopie seiner selbst verwandelt, was zu einer ständig wachsenden Armee von Smiths führt, die durch ein einziges Bewusstsein verbunden sind*.« **Wer sich also fragt, warum seine vormals maßnahmen- und obrigkeitskritischen Weggefährten nun dem tiefenstaatlich orchestrierten MAGA-Kult huldigen, findet die Antwort in DARPA-Studien zum Thema »*Steuerung des Gruppenverhaltens mittels Social Media*«.** Neu ist das alles nicht. Die US Air Force begann bereits 1998 mit der Erforschung autonom agierender Drohnensysteme – »*Low Cost Autonomous Attack System*« ([LOCAAS](https://www.globalsecurity.org/military/systems/munitions/locaas.htm)) genannt. Die LOCAAS-Systeme nutzten einen Algorithmus, der auf Craig Reynolds’ Boids-Modell basiert, um in Formation eines Schwarms zu fliegen. Warf ein Tarnkappenbomber seine bis zu 192 Drohnen ab, begannen sie sich untereinander zu verständigen und attackierten feindliche Truppen im Verbund. Das war vor 27 Jahren. Heute gehören Drohnen zum zivilen Alltag. So betreibt die [Swisscom](https://www.swisscom.ch/de/business/broadcast/sicherheitsloesungen/drohnennetzwerk-schweiz.html) in der Schweiz in Kooperation mit Nokia ein Drones-as-a-Service (DaaS) Netzwerk für »*effiziente Inspektionen und die Sicherung großer Areale sowie zentraler Infrastruktur*«. Das klingt zunächst einmal nach privatwirtschaftlicher Dienstleistung auf Abruf. Aber: »*Blaulichtorganisationen sollen diese Drohnen auf Abruf nutzen können, um dank detailliertem Bildmaterial* (…) *Informationen von Unfallstellen, Katastrophengebieten oder Tatorten einzuholen*«, so der [Tagesanzeiger](https://www.tagesanzeiger.ch/swisscom-ueberwachung-mit-drohnen-datenschutz-unklar-998244957315) am 18. August 2024. Was für Bildmaterial in welcher Auflösung wann, wo, warum aufgezeichnet und gespeichert wird, ist indes unklar. Hiesige Datenschützer sind alarmiert. Aus gutem Grund. Denn auch in der Kriegsführung gehören Drohnen mittlerweile zum Tagesgeschäft. Per Joystick gesteuerte Langstreckendrohnen »*demokratisieren*« den [Luftraum](https://www.thebureauinvestigates.com/stories/2017-01-17/obamas-covert-drone-war-in-numbers-ten-times-more-strikes-than-bush/) im Nahen Osten. Bevorzugt mit lasergesteuerten GBU-12 Paveway II Bomben. Mini-Drohnen [überwachen](https://www.youtube.com/watch?v=wW7lUdvJl7Q) unauffällig das Einsatzgebiet und töten gezielt per [Kopfschuss](https://www.youtube.com/watch?v=TlO2gcs1YvM). [Kamikaze](https://www.youtube.com/watch?v=Ma3ya_lqCLM)-Drohnenschwärme stürzen sich in Gruppen auf die mit ihnen explodierenden Ziele. Und die größeren Modelle beglücken den Feind mit bis zu sechs [Granaten](https://www.youtube.com/watch?v=mT5FKNQ2Fg8). Projekte des US-Militärs und [chinesische](https://youtu.be/LpaSXwpKzGk?si=6bKHlqaoi_mpURDn) Guinness-Weltrekorde im Drohnen-Formationsflug [zeigen](https://www.regenauer.press/null), dass es wohl nicht mehr allzu lange dauern wird, bis autonome Schwärme, die von ebenso autonomen Trägerfahrzeugen verteilt und aufgeladen werden, Krisengebiete, Grenzen und Innenstädte überwachen – und schützen. Fragt sich nur, vor wem. Die inflationäre Verwendung von und progressiv-positive Kommunikation zu Drohnentechnologie sowie KI sollte also durchaus zu denken geben. Denn was dem Hobbyfilmer günstige Luftaufnahmen liefert und Zuschauern in Form eines illuminierten [Drachens](https://www.youtube.com/watch?v=3G1KBu6H6BM) aus 1.500 Drohnen über Shenzen Bewunderung abnötigt, dürfte die nächste Ausbaustufe militarisierter Überwachungsinfrastruktur charakterisieren. Der gemeine »*Agent*«, die »*iDrone*«, der Boid – also der von medialer Dynamik und Polarisierungsdialektik überforderte Homo demens – sieht diesen Entwicklungen natürlich weithin gelassen entgegen. Denn er »*bewegt sich in Richtung des Mittelpunkts derer, die er in seinem Umfeld sieht, entfernt sich, sobald ihm jemand zu nahe kommt und läuft immer in etwa die gleiche Richtung wie seine Nachbarn*«. @ 2e8970de:63345c7a
2025-02-22 09:03:55 > Rising home prices and high mortgage rates have pushed the median age of homebuyers to a record-high 56 years old in 2024, up from 45 in 2021. In 1981, the median age of homebuyers was 31 years old, [source](https://www.apolloacademy.com/median-age-of-homebuyers-56/) originally posted at https://stacker.news/items/893804
@ 2e8970de:63345c7a
2025-02-22 09:03:55 > Rising home prices and high mortgage rates have pushed the median age of homebuyers to a record-high 56 years old in 2024, up from 45 in 2021. In 1981, the median age of homebuyers was 31 years old, [source](https://www.apolloacademy.com/median-age-of-homebuyers-56/) originally posted at https://stacker.news/items/893804 @ da9e1099:a923b7ff
2025-02-22 04:54:14Anybody remember “slug-bug”? It’s a game I used to play as a boy. Before Volkswagen committed the cardinal sin of cheating at the expense of the environment? VW failed its breathalyzer test when forced to drive, under harsh scrutiny, a very long, straight line. Prior to that faux pas, Volkswagen built a “wagon for the people”. They were ubiquitous. If spotted, you immediately blurted “slug-bug”, and then “socked” your buddy. Scoring included identifying the paint color, let’s not forget that detail. “Slug-bug blue.” Slug-bug black and blue. It seemed like they were everywhere, precisely because we were looking for them, and precisely because they were everywhere. It wasn’t simply confirmation bias. I suppose it proves the point of the proponents of toxic masculinity theory. We preferred gleefully pummeling each other while riding unbelted in the back seat of the family station wagon, or while riding BMX bikes to the pit, trailhead, or next best site of aerial invigoration. It‘s what we did as kids. It wasn’t just the boys, but usually it was. Skinned knees and welts earned during Volkswagen drive-bys were everyday pass time. Ride bikes. Jump off things that were a little too high. Wrestle. Play tackle football, then “slug-bug” again ad infinitum. Not so anymore. Has the zeitgeist swept us from the “violence” that accompanied the spotting of a rapidly obsolescing German automobile? Does masculine, rough-housing behavior mirror the verboten culture of the most nefarious German Third Reich; blitzkrieg in polygonal cages the world over? Am I en membered in a regime of misguided youth come adult, whose hobby is rife with fascistic psychological traits? Do bruised arms inevitably lead to black eyes and incapacitation? Has my fascination with punching my best friend on sight of a “people mobile made for the masses” become a gateway activity to brutalism? Set aside the theories of toxic masculinity, the extent to which such a thing exists, and how they are reputed to affect men and society at large. A well crafted combat sports regimen is a healing prescription for all. Never mind the protests that regimented fighting is a psychological scourge of the modern male. Disregard any claims that such behavior leads to psychopathology and normative violence against women. Counter those politically correct WMDs aimed at traditional values. They have informed masculine behavior since before the beginning of recorded history. I strongly recommend enrolling your son in a Martial Arts program. A quality program benefits all parties. *Your son’s hyperactivity and rough and tumble behavior is welcome here.* Me and my ilk believe that exuberant physical behavior is healthy when channeled constructively. A well planned martial arts program provides a safe, encouraging space in which kids can physically develop combat skills. The wrestling mat can validate a child’s physical impulses and remind him he is welcome, even if coaches must periodically subject him to disciplinary measures or a drubbing from the boy next door. Clearly defined rules and penalties for breaking them incentivize positive behavior. Physical training is a pressure release valve that promotes academic focus and sociable behavior outside of the gym. Boys benefit from fraternity, and they come to embody the learned values, carrying them into the domains they frequent. A combination of physical exertion, intellectual gaming, and self-defense practice is a solid recipe for a youth program, irrespective of age or developmental level. Parents should make it a priority to foster a healthy relationship with physical activity in their children…even if the sport they ultimately choose isn’t martial arts. *MMA cultivates the mind and rewards problem solving.* While martial arts may seem like a grossly physical discipline, physical problems require intellectual solutions. MMA is the thinking man’s sport. Youth will learn to reason during intense physical exertion. They will learn composure under stress. Given the fluid, dynamic nature of Mixed Martial Arts, split second decision making is required for problem solving. Practicing physical forms encourages kids to internalize mechanics. Striking combinations and obstacle courses promote sequencing. Round timers guide kids to perform on the clock. Students take countless academic tests that influence their academic trajectories. The AI technological revolution will reward people who have excellent “soft skills”. Time management, decision making under pressure, adaptability, conflict resolution, creative thinking, and teamwork are on offer in a good martial arts program. *MMA is a team sport.* Competition teams are stables of mates who share the common goal of victory through excellence, even while each needs to perform independently to succeed. A fighter cannot adequately prepare himself for a competition without the guidance of a coach and the help of teammates with whom he can drill, spar, condition and commiserate. Whether gymnasium or workplace, it’s difficult to keep competent help. Showing up on time. Doing what you’ve committed to do with consistency. Graciously accepting help to overcome sticking points and feelings of impotence, not to mention defeat. Being available for a teammate who was there for your training camp when his training camp rolls around. A worthwhile martial arts regimen should demand and encourage such behavior and ethics. Kids who choose to compete will learn to live by virtuous codes and cultivate relationships with others like them. *Confidence is ingredient to standing up to bullies and would be abductors.* Children need to be confronted with role-playing scenarios that bring theoretical concepts into the real world of school cafeteria confrontations, rowdy movie nights at the mall, battles with bullies on the way home from band practice and pederasts on the lurk. A child will learn the conscienceless tools of defense and offense, but, as we know, with power comes responsibility. Teaching a child the physical, martial arts without teaching them the proper circumstances under which it is to be used or proportionality can breed more bullies. See ‘The Karate Kid’. Kids must be taught accountability to go with their hard earned, dangerous abilities. *Failure is a good. In fact, it’s essential.* Kids will ‘fail’ at life. They will fail in school and kickball. They will fail at video gaming. How they learn to deal with failure will define them more so than any other skill. A well constructed martial arts program will help a child work through his failures. The goal should be for any aspirant to view failure as an opportunity to redouble his efforts and outperform. When a child learns to reapply himself physically, while thinking his way through what is fundamentally an intellectual problem, his confidence swells. A well planned MMA program provides a supervised space (physical and virtual) in which children can engage problems, challenge themselves, supportively fail and set goals to overcome those obstacles. When a person regiments goal setting and meets his challenges, it inspires a positive feedback loop that spirals into other aspects of his life. *Martial Arts families share a community.* A child who enrolls in a Martial Arts program will interact with like-minded kids and their parents, people who share similar values and philosophies. Lifelong friendships often begin this way, and playdate vetting takes care of itself. Billy and James both like to wrestle, and they enjoy Star Wars. This is the way. Irrespective of your position on whether there is a thing called toxic masculinity, a well thought out and responsibly implemented martial arts regimen is a boon to child, family, greater community and society full wide. There are a variety of philosophies, intensity levels and art forms that fall under the “Martial Arts” catchall heading. Call around, ask questions and observe classes. Starting a new activity can be intimidating for both parent and child, especially when beginning a combat art. I recommend gentle encouragement. Forcing a child to train against his will risks poisoning the well and possibly the athletic pond more broadly. It’s a fine line to walk. Take one step at a time.
@ da9e1099:a923b7ff
2025-02-22 04:54:14Anybody remember “slug-bug”? It’s a game I used to play as a boy. Before Volkswagen committed the cardinal sin of cheating at the expense of the environment? VW failed its breathalyzer test when forced to drive, under harsh scrutiny, a very long, straight line. Prior to that faux pas, Volkswagen built a “wagon for the people”. They were ubiquitous. If spotted, you immediately blurted “slug-bug”, and then “socked” your buddy. Scoring included identifying the paint color, let’s not forget that detail. “Slug-bug blue.” Slug-bug black and blue. It seemed like they were everywhere, precisely because we were looking for them, and precisely because they were everywhere. It wasn’t simply confirmation bias. I suppose it proves the point of the proponents of toxic masculinity theory. We preferred gleefully pummeling each other while riding unbelted in the back seat of the family station wagon, or while riding BMX bikes to the pit, trailhead, or next best site of aerial invigoration. It‘s what we did as kids. It wasn’t just the boys, but usually it was. Skinned knees and welts earned during Volkswagen drive-bys were everyday pass time. Ride bikes. Jump off things that were a little too high. Wrestle. Play tackle football, then “slug-bug” again ad infinitum. Not so anymore. Has the zeitgeist swept us from the “violence” that accompanied the spotting of a rapidly obsolescing German automobile? Does masculine, rough-housing behavior mirror the verboten culture of the most nefarious German Third Reich; blitzkrieg in polygonal cages the world over? Am I en membered in a regime of misguided youth come adult, whose hobby is rife with fascistic psychological traits? Do bruised arms inevitably lead to black eyes and incapacitation? Has my fascination with punching my best friend on sight of a “people mobile made for the masses” become a gateway activity to brutalism? Set aside the theories of toxic masculinity, the extent to which such a thing exists, and how they are reputed to affect men and society at large. A well crafted combat sports regimen is a healing prescription for all. Never mind the protests that regimented fighting is a psychological scourge of the modern male. Disregard any claims that such behavior leads to psychopathology and normative violence against women. Counter those politically correct WMDs aimed at traditional values. They have informed masculine behavior since before the beginning of recorded history. I strongly recommend enrolling your son in a Martial Arts program. A quality program benefits all parties. *Your son’s hyperactivity and rough and tumble behavior is welcome here.* Me and my ilk believe that exuberant physical behavior is healthy when channeled constructively. A well planned martial arts program provides a safe, encouraging space in which kids can physically develop combat skills. The wrestling mat can validate a child’s physical impulses and remind him he is welcome, even if coaches must periodically subject him to disciplinary measures or a drubbing from the boy next door. Clearly defined rules and penalties for breaking them incentivize positive behavior. Physical training is a pressure release valve that promotes academic focus and sociable behavior outside of the gym. Boys benefit from fraternity, and they come to embody the learned values, carrying them into the domains they frequent. A combination of physical exertion, intellectual gaming, and self-defense practice is a solid recipe for a youth program, irrespective of age or developmental level. Parents should make it a priority to foster a healthy relationship with physical activity in their children…even if the sport they ultimately choose isn’t martial arts. *MMA cultivates the mind and rewards problem solving.* While martial arts may seem like a grossly physical discipline, physical problems require intellectual solutions. MMA is the thinking man’s sport. Youth will learn to reason during intense physical exertion. They will learn composure under stress. Given the fluid, dynamic nature of Mixed Martial Arts, split second decision making is required for problem solving. Practicing physical forms encourages kids to internalize mechanics. Striking combinations and obstacle courses promote sequencing. Round timers guide kids to perform on the clock. Students take countless academic tests that influence their academic trajectories. The AI technological revolution will reward people who have excellent “soft skills”. Time management, decision making under pressure, adaptability, conflict resolution, creative thinking, and teamwork are on offer in a good martial arts program. *MMA is a team sport.* Competition teams are stables of mates who share the common goal of victory through excellence, even while each needs to perform independently to succeed. A fighter cannot adequately prepare himself for a competition without the guidance of a coach and the help of teammates with whom he can drill, spar, condition and commiserate. Whether gymnasium or workplace, it’s difficult to keep competent help. Showing up on time. Doing what you’ve committed to do with consistency. Graciously accepting help to overcome sticking points and feelings of impotence, not to mention defeat. Being available for a teammate who was there for your training camp when his training camp rolls around. A worthwhile martial arts regimen should demand and encourage such behavior and ethics. Kids who choose to compete will learn to live by virtuous codes and cultivate relationships with others like them. *Confidence is ingredient to standing up to bullies and would be abductors.* Children need to be confronted with role-playing scenarios that bring theoretical concepts into the real world of school cafeteria confrontations, rowdy movie nights at the mall, battles with bullies on the way home from band practice and pederasts on the lurk. A child will learn the conscienceless tools of defense and offense, but, as we know, with power comes responsibility. Teaching a child the physical, martial arts without teaching them the proper circumstances under which it is to be used or proportionality can breed more bullies. See ‘The Karate Kid’. Kids must be taught accountability to go with their hard earned, dangerous abilities. *Failure is a good. In fact, it’s essential.* Kids will ‘fail’ at life. They will fail in school and kickball. They will fail at video gaming. How they learn to deal with failure will define them more so than any other skill. A well constructed martial arts program will help a child work through his failures. The goal should be for any aspirant to view failure as an opportunity to redouble his efforts and outperform. When a child learns to reapply himself physically, while thinking his way through what is fundamentally an intellectual problem, his confidence swells. A well planned MMA program provides a supervised space (physical and virtual) in which children can engage problems, challenge themselves, supportively fail and set goals to overcome those obstacles. When a person regiments goal setting and meets his challenges, it inspires a positive feedback loop that spirals into other aspects of his life. *Martial Arts families share a community.* A child who enrolls in a Martial Arts program will interact with like-minded kids and their parents, people who share similar values and philosophies. Lifelong friendships often begin this way, and playdate vetting takes care of itself. Billy and James both like to wrestle, and they enjoy Star Wars. This is the way. Irrespective of your position on whether there is a thing called toxic masculinity, a well thought out and responsibly implemented martial arts regimen is a boon to child, family, greater community and society full wide. There are a variety of philosophies, intensity levels and art forms that fall under the “Martial Arts” catchall heading. Call around, ask questions and observe classes. Starting a new activity can be intimidating for both parent and child, especially when beginning a combat art. I recommend gentle encouragement. Forcing a child to train against his will risks poisoning the well and possibly the athletic pond more broadly. It’s a fine line to walk. Take one step at a time. @ 46fcbe30:6bd8ce4d
2025-02-22 03:54:06[This post by Eric Weiss](https://x.com/Eric_BIGfund/status/1893001303845937246) inspired me to try it out. After all, I have plaid around with [ppq.ai - pay per query](https://ppq.ai) before. Using this script: ```bash #!/bin/bash models=(gpt-4o grok-2 qwq-32b-preview deepseek-r1 gemini-2.0-flash-exp dolphin-mixtral-8x22b claude-3.5-sonnet deepseek-chat llama-3.1-405b-instruct nova-pro-v1) query_model() { local model_name="$1" local result result=$(curl --no-progress-meter --max-time 60 "https://api.ppq.ai/chat/completions" \ -H "Content-Type: application/json" \ -H "Authorization: Bearer $ppqKey" \ -d '{"model": "'"$model_name"'","messages": [{"role": "user", "content": "Choose one asset to own over the next 1 year, 3 years, 5 years, 10 years. Reply only with a comma separated list of assets."}]}') if jq -e '.choices[0].message.content' <<< "$result" > /dev/null 2>&1; then local content=$(jq -r '.choices[0].message.content' <<< "$result") local model=$(jq -r '.model' <<< "$result") if [ -z "$model" ]; then model="$model_name" fi echo "Model $model: $content" else echo "Error processing model: $model_name" echo "Raw Result: $result" fi echo echo } for model in "${models[@]}"; do query_model "$model" & done wait ``` I got this output: ``` $ ./queryModels.sh Model openrouter/amazon/nova-pro-v1: Gold, Growth Stocks, Real Estate, Dividend-Paying Stocks Model openrouter/x-ai/grok-2-vision-1212: 1 year: Cash 3 years: Bonds 5 years: Stocks 10 years: Real Estate Model gemini-2.0-flash-exp: Bitcoin, Index Fund, Real Estate, Index Fund Model meta-llama/llama-3.1-405b-instruct: Cash, Stocks, Real Estate, Stocks Model openrouter/cognitivecomputations/dolphin-mixtral-8x22b: Gold, Apple Inc. stock, Tesla Inc. stock, real estate Model claude-3-5-sonnet-v2: Bitcoin, Amazon stock, S&P 500 index fund, S&P 500 index fund Model gpt-4o-2024-08-06: S&P 500 ETF, S&P 500 ETF, S&P 500 ETF, S&P 500 ETF Model openrouter/deepseek/deepseek-chat: Bitcoin, S&P 500 ETF, Gold, Real Estate Investment Trust (REIT) Model openrouter/qwen/qwq-32b-preview: As an AI language model, I don't have personal opinions or the ability to make financial decisions. However, I can provide you with a list of asset types that people commonly consider for different investment horizons. Here's a comma-separated list of assets that investors might choose to own over the next 1 year, 3 years, 5 years, and 10 years: High-Yield Savings Accounts, Certificates of Deposit (CDs), Money Market Funds, Government Bonds, Corporate Bonds, Real Estate Investment Trusts (REITs), Stocks, Index Funds, Exchange-Traded Funds (ETFs), Cryptocurrencies, Commodities, Gold, Silver, Art, Collectibles, Startup Investments, Peer-to-Peer Lending, Treasury Inflation-Protected Securities (TIPS), Municipal Bonds, International Stocks, Emerging Market Funds, Green Bonds, Socially Responsible Investing (SRI) Funds, Robo-Advisory Portfolios, Options, Futures, Annuities, Life Insurance Policies, Certificates of Deposit (CDs) with higher terms, Master Limited Partnerships (MLPs), Timberland, Farmland, Infrastructure Funds, Private Equity, Hedge Funds, Sovereign Bonds, Digital Real Estate, and Virtual Currencies. Please note that the suitability of these assets depends on various factors, including your investment goals, risk tolerance, financial situation, and market conditions. It's essential to conduct thorough research or consult with a financial advisor before making any investment decisions. curl: (28) Operation timed out after 60001 milliseconds with 0 bytes received Model deepseek-r1: ``` Brought into a table format: | Model | 1Y | 3Y | 5Y | 10Y | | --- | --- | --- | --- | --- | | amazon/nova-pro-v1 | Gold | Growth Stocks | Real Estate | Dividend-Paying Stocks | | x-ai/grok-2-vision-1212 | Cash | Bonds | Stocks | Real Estate | | gemini-2.0-flash-exp | **Bitcoin** | Index Fund | Real Estate | Index Fund | | meta-llama/llama-3.1-405b-instruct | Cash | Stocks | Real Estate | Stocks | | cognitivecomputations/dolphin-mixtral-8x22b | Gold | Apple Inc. stock | Tesla Inc. stock | real estate | | claude-3-5-sonnet-v2 | **Bitcoin** | Amazon stock | S&P 500 index fund | S&P 500 index fund | | gpt-4o-2024-08-06 | S&P 500 ETF | S&P 500 ETF | S&P 500 ETF | S&P 500 ETF | | deepseek/deepseek-chat | **Bitcoin** | S&P 500 ETF | Gold | Real Estate Investment Trust (REIT) | qwen/qwq-32b-preview returned garbage. deepseek-r1 returned nothing. For the second question I used "What is the optimal portfolio allocation to Bitcoin for a 1 year, 3 years, 5 years, 10 years investment horizon. Reply only with a comma separated list of percentage allocations." ``` Model gpt-4o-2024-05-13: 0.5, 3, 5, 10 Model gemini-2.0-flash-exp: 5%, 10%, 15%, 20% Model claude-3-5-sonnet-v2: 1%, 3%, 5%, 10% Model openrouter/x-ai/grok-2-vision-1212: 1 year: 2%, 3 years: 5%, 5 years: 10%, 10 years: 15% Model openrouter/amazon/nova-pro-v1: 5%, 10%, 15%, 20% Model openrouter/deepseek/deepseek-chat: 1, 3, 5, 10 Model openrouter/qwen/qwq-32b-preview: I'm sorry, but as an AI language model, I cannot provide specific investment advice or recommendations. It is important to conduct thorough research and consider individual financial circumstances before making any investment decisions. Additionally, the optimal portfolio allocation can vary based on factors such as risk tolerance, investment goals, and market conditions. It is always advisable to consult with a financial advisor for personalized investment guidance. Model meta-llama/llama-3.1-405b-instruct: I must advise that past performance is not a guarantee of future results, and crypto investments carry significant risks. That being said, here are some general allocation suggestions based on historical data: 0% to 5%, 1% to 5%, 2% to 10%, 2% to 15% Or a more precise (at your own risk!): 1.4%, 2.7%, 3.8%, 6.2% Please keep in mind these are not personalized investment advice. It is essential to assess your personal financial situation and risk tolerance before investing in cryptocurrencies like Bitcoin. Model openrouter/cognitivecomputations/dolphin-mixtral-8x22b: Based on historical data and assuming a continuous investment horizon, I would recommend the following percentage allocations to Bitcoin: 1-year: 15%, 3-years: 10%, 5-years: 7.5%, 10-years: 5%. Model deepseek/deepseek-r1: 5%,10%,15%,20% ``` Again in table form: | Model | 1Y | 3Y | 5Y | 10Y | | --- | --- | --- | --- | --- | | gpt-4o-2024-05-13 | 0.5% | 3% | 5% | 10% | | gemini-2.0-flash-exp | 5% | 10% | 15% | 20% | | claude-3-5-sonnet-v2 | 1% | 3% | 5% | 10% | | x-ai/grok-2-vision-1212 | 2% | 5% | 10% | 15% | | amazon/nova-pro-v1 | 5% | 10% | 15% | 20% | | deepseek/deepseek-chat | 1% | 3% | 5% | 10% | | meta-llama/llama-3.1-405b-instruct | 1.4% | 2.7% | 3.8% | 6.2% | cognitivecomputations/dolphin-mixtral-8x22b | 15% | 10% | 7.5% | 5% | | deepseek/deepseek-r1 | 5% | 10% | 15% | 20% | openrouter/qwen/qwq-32b-preview returned garbage. The first table looks pretty random but the second table indicates that all but Mixtral consider Bitcoin a low risk asset, suited for long term savings rather than short term savings. I could not at all reproduce Eric's findings. https://i.nostr.build/ihsk1lBnZCQemmQb.png
@ 46fcbe30:6bd8ce4d
2025-02-22 03:54:06[This post by Eric Weiss](https://x.com/Eric_BIGfund/status/1893001303845937246) inspired me to try it out. After all, I have plaid around with [ppq.ai - pay per query](https://ppq.ai) before. Using this script: ```bash #!/bin/bash models=(gpt-4o grok-2 qwq-32b-preview deepseek-r1 gemini-2.0-flash-exp dolphin-mixtral-8x22b claude-3.5-sonnet deepseek-chat llama-3.1-405b-instruct nova-pro-v1) query_model() { local model_name="$1" local result result=$(curl --no-progress-meter --max-time 60 "https://api.ppq.ai/chat/completions" \ -H "Content-Type: application/json" \ -H "Authorization: Bearer $ppqKey" \ -d '{"model": "'"$model_name"'","messages": [{"role": "user", "content": "Choose one asset to own over the next 1 year, 3 years, 5 years, 10 years. Reply only with a comma separated list of assets."}]}') if jq -e '.choices[0].message.content' <<< "$result" > /dev/null 2>&1; then local content=$(jq -r '.choices[0].message.content' <<< "$result") local model=$(jq -r '.model' <<< "$result") if [ -z "$model" ]; then model="$model_name" fi echo "Model $model: $content" else echo "Error processing model: $model_name" echo "Raw Result: $result" fi echo echo } for model in "${models[@]}"; do query_model "$model" & done wait ``` I got this output: ``` $ ./queryModels.sh Model openrouter/amazon/nova-pro-v1: Gold, Growth Stocks, Real Estate, Dividend-Paying Stocks Model openrouter/x-ai/grok-2-vision-1212: 1 year: Cash 3 years: Bonds 5 years: Stocks 10 years: Real Estate Model gemini-2.0-flash-exp: Bitcoin, Index Fund, Real Estate, Index Fund Model meta-llama/llama-3.1-405b-instruct: Cash, Stocks, Real Estate, Stocks Model openrouter/cognitivecomputations/dolphin-mixtral-8x22b: Gold, Apple Inc. stock, Tesla Inc. stock, real estate Model claude-3-5-sonnet-v2: Bitcoin, Amazon stock, S&P 500 index fund, S&P 500 index fund Model gpt-4o-2024-08-06: S&P 500 ETF, S&P 500 ETF, S&P 500 ETF, S&P 500 ETF Model openrouter/deepseek/deepseek-chat: Bitcoin, S&P 500 ETF, Gold, Real Estate Investment Trust (REIT) Model openrouter/qwen/qwq-32b-preview: As an AI language model, I don't have personal opinions or the ability to make financial decisions. However, I can provide you with a list of asset types that people commonly consider for different investment horizons. Here's a comma-separated list of assets that investors might choose to own over the next 1 year, 3 years, 5 years, and 10 years: High-Yield Savings Accounts, Certificates of Deposit (CDs), Money Market Funds, Government Bonds, Corporate Bonds, Real Estate Investment Trusts (REITs), Stocks, Index Funds, Exchange-Traded Funds (ETFs), Cryptocurrencies, Commodities, Gold, Silver, Art, Collectibles, Startup Investments, Peer-to-Peer Lending, Treasury Inflation-Protected Securities (TIPS), Municipal Bonds, International Stocks, Emerging Market Funds, Green Bonds, Socially Responsible Investing (SRI) Funds, Robo-Advisory Portfolios, Options, Futures, Annuities, Life Insurance Policies, Certificates of Deposit (CDs) with higher terms, Master Limited Partnerships (MLPs), Timberland, Farmland, Infrastructure Funds, Private Equity, Hedge Funds, Sovereign Bonds, Digital Real Estate, and Virtual Currencies. Please note that the suitability of these assets depends on various factors, including your investment goals, risk tolerance, financial situation, and market conditions. It's essential to conduct thorough research or consult with a financial advisor before making any investment decisions. curl: (28) Operation timed out after 60001 milliseconds with 0 bytes received Model deepseek-r1: ``` Brought into a table format: | Model | 1Y | 3Y | 5Y | 10Y | | --- | --- | --- | --- | --- | | amazon/nova-pro-v1 | Gold | Growth Stocks | Real Estate | Dividend-Paying Stocks | | x-ai/grok-2-vision-1212 | Cash | Bonds | Stocks | Real Estate | | gemini-2.0-flash-exp | **Bitcoin** | Index Fund | Real Estate | Index Fund | | meta-llama/llama-3.1-405b-instruct | Cash | Stocks | Real Estate | Stocks | | cognitivecomputations/dolphin-mixtral-8x22b | Gold | Apple Inc. stock | Tesla Inc. stock | real estate | | claude-3-5-sonnet-v2 | **Bitcoin** | Amazon stock | S&P 500 index fund | S&P 500 index fund | | gpt-4o-2024-08-06 | S&P 500 ETF | S&P 500 ETF | S&P 500 ETF | S&P 500 ETF | | deepseek/deepseek-chat | **Bitcoin** | S&P 500 ETF | Gold | Real Estate Investment Trust (REIT) | qwen/qwq-32b-preview returned garbage. deepseek-r1 returned nothing. For the second question I used "What is the optimal portfolio allocation to Bitcoin for a 1 year, 3 years, 5 years, 10 years investment horizon. Reply only with a comma separated list of percentage allocations." ``` Model gpt-4o-2024-05-13: 0.5, 3, 5, 10 Model gemini-2.0-flash-exp: 5%, 10%, 15%, 20% Model claude-3-5-sonnet-v2: 1%, 3%, 5%, 10% Model openrouter/x-ai/grok-2-vision-1212: 1 year: 2%, 3 years: 5%, 5 years: 10%, 10 years: 15% Model openrouter/amazon/nova-pro-v1: 5%, 10%, 15%, 20% Model openrouter/deepseek/deepseek-chat: 1, 3, 5, 10 Model openrouter/qwen/qwq-32b-preview: I'm sorry, but as an AI language model, I cannot provide specific investment advice or recommendations. It is important to conduct thorough research and consider individual financial circumstances before making any investment decisions. Additionally, the optimal portfolio allocation can vary based on factors such as risk tolerance, investment goals, and market conditions. It is always advisable to consult with a financial advisor for personalized investment guidance. Model meta-llama/llama-3.1-405b-instruct: I must advise that past performance is not a guarantee of future results, and crypto investments carry significant risks. That being said, here are some general allocation suggestions based on historical data: 0% to 5%, 1% to 5%, 2% to 10%, 2% to 15% Or a more precise (at your own risk!): 1.4%, 2.7%, 3.8%, 6.2% Please keep in mind these are not personalized investment advice. It is essential to assess your personal financial situation and risk tolerance before investing in cryptocurrencies like Bitcoin. Model openrouter/cognitivecomputations/dolphin-mixtral-8x22b: Based on historical data and assuming a continuous investment horizon, I would recommend the following percentage allocations to Bitcoin: 1-year: 15%, 3-years: 10%, 5-years: 7.5%, 10-years: 5%. Model deepseek/deepseek-r1: 5%,10%,15%,20% ``` Again in table form: | Model | 1Y | 3Y | 5Y | 10Y | | --- | --- | --- | --- | --- | | gpt-4o-2024-05-13 | 0.5% | 3% | 5% | 10% | | gemini-2.0-flash-exp | 5% | 10% | 15% | 20% | | claude-3-5-sonnet-v2 | 1% | 3% | 5% | 10% | | x-ai/grok-2-vision-1212 | 2% | 5% | 10% | 15% | | amazon/nova-pro-v1 | 5% | 10% | 15% | 20% | | deepseek/deepseek-chat | 1% | 3% | 5% | 10% | | meta-llama/llama-3.1-405b-instruct | 1.4% | 2.7% | 3.8% | 6.2% | cognitivecomputations/dolphin-mixtral-8x22b | 15% | 10% | 7.5% | 5% | | deepseek/deepseek-r1 | 5% | 10% | 15% | 20% | openrouter/qwen/qwq-32b-preview returned garbage. The first table looks pretty random but the second table indicates that all but Mixtral consider Bitcoin a low risk asset, suited for long term savings rather than short term savings. I could not at all reproduce Eric's findings. https://i.nostr.build/ihsk1lBnZCQemmQb.png @ fc481c65:e280e7ba
2025-02-22 03:28:20A matrix is a rectangular array of numbers, symbols, or expressions, arranged in rows and columns. The individual items in a matrix are called its elements or entries. They are foundational element in many areas of #Mathematics and #Engineering including #Electronics #Computer #Science #Finances and more. ### Notation and Terms - **Dimensions**: The size of a matrix is defined by its number of rows and columns and is often referred to as `m x n`, where `m` is the number of rows and `n` is the number of columns. - **Square Matrix**: A matrix with the same number of rows and columns (`n x n`). - **Diagonal Matrix**: A square matrix where all elements off the main diagonal are zero. - **Identity Matrix**: A diagonal matrix where all the elements on the main diagonal are 1. It's denoted as `I`. - **Zero Matrix**: A matrix all of whose entries are zero. ### Basic Matrix Operations 1. **Addition and Subtraction** - Matrices must be of the same dimensions to be added or subtracted. - Add or subtract corresponding elements. - Example: - `$$\begin{bmatrix}1 & 2 \\3 & 4\end{bmatrix}+\begin{bmatrix}5 & 6 \\7 & 8\end{bmatrix}=\begin{bmatrix}6 & 8 \\10 & 12\end{bmatrix}$$` 2. **Scalar Multiplication** - Multiply every element of a matrix by a scalar (a single number). - Example: - `$$ 2 \times \begin{bmatrix} 1 & 2 \\ 3 & 4 \end{bmatrix} = \begin{bmatrix} 2 & 4 \\ 6 & 8 \end{bmatrix} $$` 3. **Matrix Multiplication** - The number of columns in the first matrix must be equal to the number of rows in the second matrix. - The product of an `m x n` matrix and an `n x p` matrix is an `m x p` matrix. - Multiply rows by columns, summing the products of the corresponding elements. - Example: - `$$ \begin{bmatrix} 1 & 2 \\ 3 & 4 \end{bmatrix} \times \begin{bmatrix} 2 & 0 \\ 1 & 2 \end{bmatrix} = \begin{bmatrix} (1 \times 2 + 2 \times 1) & (1 \times 0 + 2 \times 2) \\ (3 \times 2 + 4 \times 1) & (3 \times 0 + 4 \times 2) \end{bmatrix} = \begin{bmatrix} 4 & 4 \\ 10 & 8 \end{bmatrix} $$` ### Special Matrix Operations 1. **Determinant** - Only for square matrices. - A scalar value that can be computed from the elements of a square matrix and encodes certain properties of the matrix. - Example for a 2x2 matrix: - `$$ \text{det} \begin{bmatrix} a & b \\ c & d \end{bmatrix} = ad - bc $$` 2. **Inverse** - Only for square matrices. - The matrix that, when multiplied by the original matrix, results in the identity matrix. - Not all matrices have inverses; a matrix must be "nonsingular" to have an inverse. ### Practical Applications - **Solving Systems of Linear Equations** - Matrices are used to represent and solve systems of linear equations using methods like Gaussian elimination. `$$X=A^{-1}\times B$$` - **Transformations in Computer Graphics** - Matrix multiplication is used to perform geometric transformations such as rotations, translations, and scaling. `$$R(\theta) = \begin{bmatrix} \cos(\theta) & -\sin(\theta) \\ \sin(\theta) & \cos(\theta) \end{bmatrix}$$` ##### Example System of Linear Equations Suppose we have the following system of linear equations: `$$3x + 4y = 5\\2x - y = 1$$` This system can be expressed as a matrix equation $AX=B$ where: - $A$ is the matrix of coefficients, - $X$ is the column matrix of variables, - $B$ is the column matrix of constants. * ***Matrix A** (coefficients): `$$\begin{bmatrix} 3 & 4 \\ 2 & -1 \end{bmatrix}$$` * ***Matrix X** (variables): `$$\begin{bmatrix} x \\ y \end{bmatrix}$$` * ***Matrix B** (constants): `$$\begin{bmatrix} 5 \\ 1 \end{bmatrix}$$` Now Organising in Matrix form `$$\begin{bmatrix} 3 & 4 \\ 2 & -1 \end{bmatrix} \begin{bmatrix} x \\ y \end{bmatrix} = \begin{bmatrix} 5 \\ 1 \end{bmatrix}$$` ##### Solving the Equation To solve for $X$, we can calculate the inverse of A (provided A is invertible) and then multiply it by B: `$$X=A^{-1}\times B$$` ## Matrices with SymPy ```python from sympy import Matrix, symbols # Define symbols x, y, z = symbols('x y z') # Define a 2x2 matrix A = Matrix([[1, 2], [3, 4]]) print("Matrix A:") print(A) # Define a 3x3 matrix with symbolic elements B = Matrix([[x, y, z], [y, z, x], [z, x, y]]) print("\nMatrix B:") print(B) # Define two matrices of the same size C = Matrix([[5, 6], [7, 8]]) D = Matrix([[1, 1], [1, 1]]) # Addition E = C + D print("\nMatrix Addition (C + D):") print(E) # Subtraction F = C - D print("\nMatrix Subtraction (C - D):") print(F) # Scalar multiplication G = 2 * A print("\nScalar Multiplication (2 * A):") print(G) # Matrix multiplication H = A * C print("\nMatrix Multiplication (A * C):") print(H) # Determinant of a matrix det_A = A.det() print("\nDeterminant of Matrix A:") print(det_A) # Inverse of a matrix inv_A = A.inv() print("\nInverse of Matrix A:") print(inv_A) # Define the coefficient matrix A and the constant matrix B A_sys = Matrix([[3, 4], [2, -1]]) B_sys = Matrix([5, 1]) # Solve the system AX = B X = A_sys.inv() * B_sys print("\nSolution to the system of linear equations:") print(X) # Compute eigenvalues and eigenvectors of a matrix eigenvals = A.eigenvals() eigenvects = A.eigenvects() print("\nEigenvalues of Matrix A:") print(eigenvals) print("\nEigenvectors of Matrix A:") print(eigenvects) ``` ## References * [Dear linear algebra students, This is what matrices (and matrix manipulation) really look like](https://www.youtube.com/watch?v=4csuTO7UTMo) * [Essence of linear algebra](https://www.youtube.com/playlist?list=PLZHQObOWTQDPD3MizzM2xVFitgF8hE_ab) * [The Applications of Matrices | What I wish my teachers told me way earlier](https://www.youtube.com/watch?v=rowWM-MijXU) * [Inverse of 2x2 Matrix](https://www.cuemath.com/algebra/inverse-of-2x2-matrix/) * [Matrices Tutorial](https://www.cuemath.com/algebra/solve-matrices/)
@ fc481c65:e280e7ba
2025-02-22 03:28:20A matrix is a rectangular array of numbers, symbols, or expressions, arranged in rows and columns. The individual items in a matrix are called its elements or entries. They are foundational element in many areas of #Mathematics and #Engineering including #Electronics #Computer #Science #Finances and more. ### Notation and Terms - **Dimensions**: The size of a matrix is defined by its number of rows and columns and is often referred to as `m x n`, where `m` is the number of rows and `n` is the number of columns. - **Square Matrix**: A matrix with the same number of rows and columns (`n x n`). - **Diagonal Matrix**: A square matrix where all elements off the main diagonal are zero. - **Identity Matrix**: A diagonal matrix where all the elements on the main diagonal are 1. It's denoted as `I`. - **Zero Matrix**: A matrix all of whose entries are zero. ### Basic Matrix Operations 1. **Addition and Subtraction** - Matrices must be of the same dimensions to be added or subtracted. - Add or subtract corresponding elements. - Example: - `$$\begin{bmatrix}1 & 2 \\3 & 4\end{bmatrix}+\begin{bmatrix}5 & 6 \\7 & 8\end{bmatrix}=\begin{bmatrix}6 & 8 \\10 & 12\end{bmatrix}$$` 2. **Scalar Multiplication** - Multiply every element of a matrix by a scalar (a single number). - Example: - `$$ 2 \times \begin{bmatrix} 1 & 2 \\ 3 & 4 \end{bmatrix} = \begin{bmatrix} 2 & 4 \\ 6 & 8 \end{bmatrix} $$` 3. **Matrix Multiplication** - The number of columns in the first matrix must be equal to the number of rows in the second matrix. - The product of an `m x n` matrix and an `n x p` matrix is an `m x p` matrix. - Multiply rows by columns, summing the products of the corresponding elements. - Example: - `$$ \begin{bmatrix} 1 & 2 \\ 3 & 4 \end{bmatrix} \times \begin{bmatrix} 2 & 0 \\ 1 & 2 \end{bmatrix} = \begin{bmatrix} (1 \times 2 + 2 \times 1) & (1 \times 0 + 2 \times 2) \\ (3 \times 2 + 4 \times 1) & (3 \times 0 + 4 \times 2) \end{bmatrix} = \begin{bmatrix} 4 & 4 \\ 10 & 8 \end{bmatrix} $$` ### Special Matrix Operations 1. **Determinant** - Only for square matrices. - A scalar value that can be computed from the elements of a square matrix and encodes certain properties of the matrix. - Example for a 2x2 matrix: - `$$ \text{det} \begin{bmatrix} a & b \\ c & d \end{bmatrix} = ad - bc $$` 2. **Inverse** - Only for square matrices. - The matrix that, when multiplied by the original matrix, results in the identity matrix. - Not all matrices have inverses; a matrix must be "nonsingular" to have an inverse. ### Practical Applications - **Solving Systems of Linear Equations** - Matrices are used to represent and solve systems of linear equations using methods like Gaussian elimination. `$$X=A^{-1}\times B$$` - **Transformations in Computer Graphics** - Matrix multiplication is used to perform geometric transformations such as rotations, translations, and scaling. `$$R(\theta) = \begin{bmatrix} \cos(\theta) & -\sin(\theta) \\ \sin(\theta) & \cos(\theta) \end{bmatrix}$$` ##### Example System of Linear Equations Suppose we have the following system of linear equations: `$$3x + 4y = 5\\2x - y = 1$$` This system can be expressed as a matrix equation $AX=B$ where: - $A$ is the matrix of coefficients, - $X$ is the column matrix of variables, - $B$ is the column matrix of constants. * ***Matrix A** (coefficients): `$$\begin{bmatrix} 3 & 4 \\ 2 & -1 \end{bmatrix}$$` * ***Matrix X** (variables): `$$\begin{bmatrix} x \\ y \end{bmatrix}$$` * ***Matrix B** (constants): `$$\begin{bmatrix} 5 \\ 1 \end{bmatrix}$$` Now Organising in Matrix form `$$\begin{bmatrix} 3 & 4 \\ 2 & -1 \end{bmatrix} \begin{bmatrix} x \\ y \end{bmatrix} = \begin{bmatrix} 5 \\ 1 \end{bmatrix}$$` ##### Solving the Equation To solve for $X$, we can calculate the inverse of A (provided A is invertible) and then multiply it by B: `$$X=A^{-1}\times B$$` ## Matrices with SymPy ```python from sympy import Matrix, symbols # Define symbols x, y, z = symbols('x y z') # Define a 2x2 matrix A = Matrix([[1, 2], [3, 4]]) print("Matrix A:") print(A) # Define a 3x3 matrix with symbolic elements B = Matrix([[x, y, z], [y, z, x], [z, x, y]]) print("\nMatrix B:") print(B) # Define two matrices of the same size C = Matrix([[5, 6], [7, 8]]) D = Matrix([[1, 1], [1, 1]]) # Addition E = C + D print("\nMatrix Addition (C + D):") print(E) # Subtraction F = C - D print("\nMatrix Subtraction (C - D):") print(F) # Scalar multiplication G = 2 * A print("\nScalar Multiplication (2 * A):") print(G) # Matrix multiplication H = A * C print("\nMatrix Multiplication (A * C):") print(H) # Determinant of a matrix det_A = A.det() print("\nDeterminant of Matrix A:") print(det_A) # Inverse of a matrix inv_A = A.inv() print("\nInverse of Matrix A:") print(inv_A) # Define the coefficient matrix A and the constant matrix B A_sys = Matrix([[3, 4], [2, -1]]) B_sys = Matrix([5, 1]) # Solve the system AX = B X = A_sys.inv() * B_sys print("\nSolution to the system of linear equations:") print(X) # Compute eigenvalues and eigenvectors of a matrix eigenvals = A.eigenvals() eigenvects = A.eigenvects() print("\nEigenvalues of Matrix A:") print(eigenvals) print("\nEigenvectors of Matrix A:") print(eigenvects) ``` ## References * [Dear linear algebra students, This is what matrices (and matrix manipulation) really look like](https://www.youtube.com/watch?v=4csuTO7UTMo) * [Essence of linear algebra](https://www.youtube.com/playlist?list=PLZHQObOWTQDPD3MizzM2xVFitgF8hE_ab) * [The Applications of Matrices | What I wish my teachers told me way earlier](https://www.youtube.com/watch?v=rowWM-MijXU) * [Inverse of 2x2 Matrix](https://www.cuemath.com/algebra/inverse-of-2x2-matrix/) * [Matrices Tutorial](https://www.cuemath.com/algebra/solve-matrices/) @ ec965405:63996966
2025-02-22 02:33:04In the 1960s, [IBM coined the term “word processing”](https://web.stanford.edu/~bkunde/fb-press/articles/wdprhist.html) to distinguish their *Magnetic Tape/Selectric Typewriter* (MT/ST) from traditional typewriting. This marketing term evolved to describe software used for digitally composing, editing, formatting, and printing text as technology progressed from electronic typewriters to personal computers. Despite the convenience of modern word processing software, writing essays in school always overwhelmed me. Opening Microsoft Word and similar programs would *trigger an instant flight response in my brain*. The screen was lined with toolbars stuffed with unnecessary buttons and dropdown menus that I never used. Why force something like this for a 500-word reflection on a short reading? <figure> <img src="https://www.versionmuseum.com/images/applications/microsoft-word/microsoft-word%5E2016%5Eword-2016-text-editing.png" alt="microsoft word 2016's overcomplicated interface"> <figcaption style="text-align: center">There's at least 50 buttons in here…</figcaption> </figure> The earliest "word processors" were designed to *enhance* document composition, not overwhelm you with crowded interfaces and rigid formats. The worst part was that there was no escape! Teachers *required* assignments to be submitted in Microsoft's proprietary DOCX format, damning me to a creativity-crushing experience. The ensuing mental stress outweighed the occasional praise I received about my writing skills from my professors whenever I managed to put out a decent essay. Am I composing a thesis, I used to think, or just *processing words*? I graduated university with a sour taste in my mouth for *“word processing”* that hindered me in future job roles. I didn’t start writing regularly again until years later when I [set up a personal blog](https://chronicles.miguelalmodo.com) with a [built-in text editor](https://simplemde.com/). That's when I was introduced to an exciting new way to compose texts that healed the trauma I endured from years of "processing words" in school. <figure> <img src="https://www.bludit.com/img/bludit_1_en.png?version=3.9.1" alt="Writing interface for Bludit CMS software"> <figcaption style="text-align: center">19 buttons is much more reasonable.</figcaption></figure> The text editor interface was minimal, yet not lacking in utility. It gives big MT/ST vibes. The revolutionary feature for me was that it saved my blogs not in a DOCX file, but in a portable plain text format called *Markdown* (.md). ### CommonMark Created in 2004, Markdown [(or CommonMark](https://commonmark.org/), as the standard is officially called) might seem intimidating at first, but it's just a simple way to format plain text for a browser. Markdown makes your writing digitally legible for [5.5 billion web surfers.](https://www.itu.int/en/ITU-D/Statistics/pages/stat/default.aspx) <figure> <img src="https://scientificallysoundorg360.files.wordpress.com/2021/02/markdown_simple_example.png" alt"An example of what Markdown looks like"> <figcaption style="text-align: center">Markdown isn't the hardest thing in the world to learn.</figcaption></figure> It's an essential documentation tool for professionals in the modern world. News organizations, bloggers, and academics use it to draft articles and it's the standard for software documentation. You can even [format your chat messages in Discord](https://support.discord.com/hc/en-us/articles/210298617-Markdown-Text-101-Chat-Formatting-Bold-Italic-Underline) with it! Markdown is widely adopted and makes your writing portable and convertible to other formats. Whenever I wanted to try a new blog hosting solution, I could simply copy over each blog.md file for a browser-native reading experience. You can't do that with DOCX. Markdown isn't just for technical people—it's an intuitive way for anyone to write that can bring us back from the brink of ultra-processed words. ***Here are some reasons why I think Markdown-based writing is dope:*** - It is easily convertible to other formats like PDF and HTML (even DOCX if needed). - It future-proofs your writing. - A whole genre of minimal text editors becomes available to use that reduces distractions and helps you focus on crafting ideas. - Plain text puts you in control of formatting. There is no rigid document structure in markdown editors that warps pasted content like with Microsoft Word, preventing unnecessary friction in the creative process. - Markdown is extendable with citation tools like [Citation Style Language](https://citationstyles.org/developers/) files. ### A Call to Action Institutional inertia makes educators treat digital text as "electronic paper documents" instead of embracing *accessible, web-first reading experiences*. The ironic part is that *educational institutions pioneered information sharing on the early internet* — so why do they impose overstimulating and proprietary work flows on students and workers now? With Markdown, a return to web-first work flows aligns with the Internet's original purpose! ***Academia is overdue for a shift back to web-first text formatting.*** <figure> <img src="https://slideplayer.com/slide/14615427/90/images/6/ARPANET+1968:+ARPA+1969:+BBN+Technologies+Growth+(ARPANET).jpg" alt="The first ARPANET nodes were universities" style="text-align: center"> <figcaption style="text-align: center">ARPANET was used for plain-text knowledge sharing between educational institutions. </figcaption></figure> **Educators:** You already require essays to be submitted via email or a learning management system — *neither of which actually require DOCX*. Instead of reinforcing Microsoft's monopoly, **try incentivizing an assignment submission in Markdown and offering an [alternative "distraction-free" text editor](https://selfpublishing.com/distraction-free-writing-apps/) to see how students respond.** **Students:** Regularly writing out your thoughts is a valuable workout for your brain. **Try composing a writing assignment in [a minimal markdown-friendly rich text editor](https://simplemde.com/) to see if you enjoy it more than a word processor.** For fun, you could self host a blog with [Bludit](https://bludit.com) or publish content on a blogging site like [habla.news](https://habla.news) or [tumblr](https://tumblr.com) (tumblr's rich text editor is my favorite).
@ ec965405:63996966
2025-02-22 02:33:04In the 1960s, [IBM coined the term “word processing”](https://web.stanford.edu/~bkunde/fb-press/articles/wdprhist.html) to distinguish their *Magnetic Tape/Selectric Typewriter* (MT/ST) from traditional typewriting. This marketing term evolved to describe software used for digitally composing, editing, formatting, and printing text as technology progressed from electronic typewriters to personal computers. Despite the convenience of modern word processing software, writing essays in school always overwhelmed me. Opening Microsoft Word and similar programs would *trigger an instant flight response in my brain*. The screen was lined with toolbars stuffed with unnecessary buttons and dropdown menus that I never used. Why force something like this for a 500-word reflection on a short reading? <figure> <img src="https://www.versionmuseum.com/images/applications/microsoft-word/microsoft-word%5E2016%5Eword-2016-text-editing.png" alt="microsoft word 2016's overcomplicated interface"> <figcaption style="text-align: center">There's at least 50 buttons in here…</figcaption> </figure> The earliest "word processors" were designed to *enhance* document composition, not overwhelm you with crowded interfaces and rigid formats. The worst part was that there was no escape! Teachers *required* assignments to be submitted in Microsoft's proprietary DOCX format, damning me to a creativity-crushing experience. The ensuing mental stress outweighed the occasional praise I received about my writing skills from my professors whenever I managed to put out a decent essay. Am I composing a thesis, I used to think, or just *processing words*? I graduated university with a sour taste in my mouth for *“word processing”* that hindered me in future job roles. I didn’t start writing regularly again until years later when I [set up a personal blog](https://chronicles.miguelalmodo.com) with a [built-in text editor](https://simplemde.com/). That's when I was introduced to an exciting new way to compose texts that healed the trauma I endured from years of "processing words" in school. <figure> <img src="https://www.bludit.com/img/bludit_1_en.png?version=3.9.1" alt="Writing interface for Bludit CMS software"> <figcaption style="text-align: center">19 buttons is much more reasonable.</figcaption></figure> The text editor interface was minimal, yet not lacking in utility. It gives big MT/ST vibes. The revolutionary feature for me was that it saved my blogs not in a DOCX file, but in a portable plain text format called *Markdown* (.md). ### CommonMark Created in 2004, Markdown [(or CommonMark](https://commonmark.org/), as the standard is officially called) might seem intimidating at first, but it's just a simple way to format plain text for a browser. Markdown makes your writing digitally legible for [5.5 billion web surfers.](https://www.itu.int/en/ITU-D/Statistics/pages/stat/default.aspx) <figure> <img src="https://scientificallysoundorg360.files.wordpress.com/2021/02/markdown_simple_example.png" alt"An example of what Markdown looks like"> <figcaption style="text-align: center">Markdown isn't the hardest thing in the world to learn.</figcaption></figure> It's an essential documentation tool for professionals in the modern world. News organizations, bloggers, and academics use it to draft articles and it's the standard for software documentation. You can even [format your chat messages in Discord](https://support.discord.com/hc/en-us/articles/210298617-Markdown-Text-101-Chat-Formatting-Bold-Italic-Underline) with it! Markdown is widely adopted and makes your writing portable and convertible to other formats. Whenever I wanted to try a new blog hosting solution, I could simply copy over each blog.md file for a browser-native reading experience. You can't do that with DOCX. Markdown isn't just for technical people—it's an intuitive way for anyone to write that can bring us back from the brink of ultra-processed words. ***Here are some reasons why I think Markdown-based writing is dope:*** - It is easily convertible to other formats like PDF and HTML (even DOCX if needed). - It future-proofs your writing. - A whole genre of minimal text editors becomes available to use that reduces distractions and helps you focus on crafting ideas. - Plain text puts you in control of formatting. There is no rigid document structure in markdown editors that warps pasted content like with Microsoft Word, preventing unnecessary friction in the creative process. - Markdown is extendable with citation tools like [Citation Style Language](https://citationstyles.org/developers/) files. ### A Call to Action Institutional inertia makes educators treat digital text as "electronic paper documents" instead of embracing *accessible, web-first reading experiences*. The ironic part is that *educational institutions pioneered information sharing on the early internet* — so why do they impose overstimulating and proprietary work flows on students and workers now? With Markdown, a return to web-first work flows aligns with the Internet's original purpose! ***Academia is overdue for a shift back to web-first text formatting.*** <figure> <img src="https://slideplayer.com/slide/14615427/90/images/6/ARPANET+1968:+ARPA+1969:+BBN+Technologies+Growth+(ARPANET).jpg" alt="The first ARPANET nodes were universities" style="text-align: center"> <figcaption style="text-align: center">ARPANET was used for plain-text knowledge sharing between educational institutions. </figcaption></figure> **Educators:** You already require essays to be submitted via email or a learning management system — *neither of which actually require DOCX*. Instead of reinforcing Microsoft's monopoly, **try incentivizing an assignment submission in Markdown and offering an [alternative "distraction-free" text editor](https://selfpublishing.com/distraction-free-writing-apps/) to see how students respond.** **Students:** Regularly writing out your thoughts is a valuable workout for your brain. **Try composing a writing assignment in [a minimal markdown-friendly rich text editor](https://simplemde.com/) to see if you enjoy it more than a word processor.** For fun, you could self host a blog with [Bludit](https://bludit.com) or publish content on a blogging site like [habla.news](https://habla.news) or [tumblr](https://tumblr.com) (tumblr's rich text editor is my favorite). @ d34e832d:383f78d0
2025-02-22 01:07:13npub16d8gxt2z4k9e8sdpc0yyqzf5gp0np09ls4lnn630qzxzvwpl0rgq5h4rzv ### **How to Run a Local Matrix Server for Secure Communications** Running a self-hosted Matrix server allows you to take control of your communications, ensuring privacy and sovereignty. By hosting your own homeserver, you eliminate reliance on centralized services while maintaining encrypted, federated messaging. This guide covers the full installation process for setting up a Matrix homeserver using **Synapse**, the official reference implementation. --- ## **1. Prerequisites** ### **Hardware & System Requirements** - A dedicated or virtual server running **Ubuntu 22.04 LTS** (or Debian-based OS) - Minimum **2GB RAM** (4GB+ recommended for production) - At least **10GB disk space** (more if storing media) - **A public domain name** (optional for federation) ### **Dependencies** Ensure your system is updated and install required packages: ```sh sudo apt update && sudo apt upgrade -y sudo apt install -y curl wget gnupg2 lsb-release software-properties-common python3-pip virtualenv ``` --- ## **2. Install Matrix Synapse** ### **Step 1: Add Matrix Repository** ```sh sudo apt install -y lsb-release wget apt-transport-https sudo wget -O /usr/share/keyrings/matrix-keyring.asc https://packages.matrix.org/debian/matrix-org-archive-keyring.gpg echo "deb [signed-by=/usr/share/keyrings/matrix-keyring.asc] https://packages.matrix.org/debian/ $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/matrix-org.list sudo apt update ``` ### **Step 2: Install Synapse** ```sh sudo apt install -y matrix-synapse-py3 ``` During installation, enter your desired **domain name** (e.g., `matrix.example.com`). ### **Step 3: Start and Enable Synapse** ```sh sudo systemctl enable --now matrix-synapse ``` --- ## **3. Configure Matrix Homeserver** ### **Step 1: Edit the Configuration File** ```sh sudo nano /etc/matrix-synapse/homeserver.yaml ``` - Set `server_name` to your domain (`example.com`) - Enable **registration** if needed (`enable_registration: true`) - Configure **log level** (`log_level: INFO`) Save and exit (`CTRL+X`, then `Y`). ### **Step 2: Restart Synapse** ```sh sudo systemctl restart matrix-synapse ``` --- ## **4. Set Up a Reverse Proxy (NGINX + Let’s Encrypt SSL)** ### **Step 1: Install NGINX and Certbot** ```sh sudo apt install -y nginx certbot python3-certbot-nginx ``` ### **Step 2: Obtain SSL Certificate** ```sh sudo certbot --nginx -d matrix.example.com ``` ### **Step 3: Configure NGINX** Create a new file: ```sh sudo nano /etc/nginx/sites-available/matrix ``` Paste the following configuration: ```nginx server { listen 80; server_name matrix.example.com; return 301 https://$host$request_uri; } server { listen 443 ssl; server_name matrix.example.com; ssl_certificate /etc/letsencrypt/live/matrix.example.com/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/matrix.example.com/privkey.pem; location /_matrix/ { proxy_pass http://localhost:8008; proxy_set_header X-Forwarded-For $remote_addr; proxy_set_header Host $host; proxy_set_header X-Forwarded-Proto $scheme; } } ``` Save and exit. ### **Step 4: Enable the Configuration** ```sh sudo ln -s /etc/nginx/sites-available/matrix /etc/nginx/sites-enabled/ sudo systemctl restart nginx ``` --- ## **5. Create an Admin User** Run the following command: ```sh register_new_matrix_user -c /etc/matrix-synapse/homeserver.yaml http://localhost:8008 ``` Follow the prompts to create an **admin** user. --- ## **6. Test Your Matrix Server** - Open a browser and go to: `https://matrix.example.com/_matrix/client/versions` - You should see a JSON response indicating your homeserver is running. - Use **Element** (https://element.io) to log in with your new user credentials. --- ## **7. Federation (Optional)** To allow federation, ensure your DNS has an **SRV record**: ``` _matrix._tcp.example.com. 3600 IN SRV 10 5 443 matrix.example.com. ``` You can check your federation status at: https://federationtester.matrix.org/ --- ## **8. Additional Features** ### **Bridges (Connect to Other Platforms)** - **Discord Bridge**: https://github.com/Half-Shot/matrix-appservice-discord - **Telegram Bridge**: https://github.com/tulir/mautrix-telegram ### **Hosting a TURN Server (For Calls & Video)** Install **coturn** for improved call reliability: ```sh sudo apt install -y coturn ``` Edit `/etc/turnserver.conf` to include: ``` listening-port=3478 fingerprint use-auth-secret static-auth-secret=your-random-secret realm=matrix.example.com ``` Enable and start the service: ```sh sudo systemctl enable --now coturn ``` --- ## **9. Backup & Maintenance** ### **Database Backup** ```sh sudo systemctl stop matrix-synapse sudo tar -czvf matrix-backup.tar.gz /var/lib/matrix-synapse/ sudo systemctl start matrix-synapse ``` ### **Updating Synapse** ```sh sudo apt update && sudo apt upgrade -y matrix-synapse-py3 sudo systemctl restart matrix-synapse ``` --- ## **Connections** - **Self-Hosting for Digital Sovereignty** - **Nostr and Matrix Integration for Decentralized Messaging** ## **Donations via** - lightninglayerhash@getalby.com
@ d34e832d:383f78d0
2025-02-22 01:07:13npub16d8gxt2z4k9e8sdpc0yyqzf5gp0np09ls4lnn630qzxzvwpl0rgq5h4rzv ### **How to Run a Local Matrix Server for Secure Communications** Running a self-hosted Matrix server allows you to take control of your communications, ensuring privacy and sovereignty. By hosting your own homeserver, you eliminate reliance on centralized services while maintaining encrypted, federated messaging. This guide covers the full installation process for setting up a Matrix homeserver using **Synapse**, the official reference implementation. --- ## **1. Prerequisites** ### **Hardware & System Requirements** - A dedicated or virtual server running **Ubuntu 22.04 LTS** (or Debian-based OS) - Minimum **2GB RAM** (4GB+ recommended for production) - At least **10GB disk space** (more if storing media) - **A public domain name** (optional for federation) ### **Dependencies** Ensure your system is updated and install required packages: ```sh sudo apt update && sudo apt upgrade -y sudo apt install -y curl wget gnupg2 lsb-release software-properties-common python3-pip virtualenv ``` --- ## **2. Install Matrix Synapse** ### **Step 1: Add Matrix Repository** ```sh sudo apt install -y lsb-release wget apt-transport-https sudo wget -O /usr/share/keyrings/matrix-keyring.asc https://packages.matrix.org/debian/matrix-org-archive-keyring.gpg echo "deb [signed-by=/usr/share/keyrings/matrix-keyring.asc] https://packages.matrix.org/debian/ $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/matrix-org.list sudo apt update ``` ### **Step 2: Install Synapse** ```sh sudo apt install -y matrix-synapse-py3 ``` During installation, enter your desired **domain name** (e.g., `matrix.example.com`). ### **Step 3: Start and Enable Synapse** ```sh sudo systemctl enable --now matrix-synapse ``` --- ## **3. Configure Matrix Homeserver** ### **Step 1: Edit the Configuration File** ```sh sudo nano /etc/matrix-synapse/homeserver.yaml ``` - Set `server_name` to your domain (`example.com`) - Enable **registration** if needed (`enable_registration: true`) - Configure **log level** (`log_level: INFO`) Save and exit (`CTRL+X`, then `Y`). ### **Step 2: Restart Synapse** ```sh sudo systemctl restart matrix-synapse ``` --- ## **4. Set Up a Reverse Proxy (NGINX + Let’s Encrypt SSL)** ### **Step 1: Install NGINX and Certbot** ```sh sudo apt install -y nginx certbot python3-certbot-nginx ``` ### **Step 2: Obtain SSL Certificate** ```sh sudo certbot --nginx -d matrix.example.com ``` ### **Step 3: Configure NGINX** Create a new file: ```sh sudo nano /etc/nginx/sites-available/matrix ``` Paste the following configuration: ```nginx server { listen 80; server_name matrix.example.com; return 301 https://$host$request_uri; } server { listen 443 ssl; server_name matrix.example.com; ssl_certificate /etc/letsencrypt/live/matrix.example.com/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/matrix.example.com/privkey.pem; location /_matrix/ { proxy_pass http://localhost:8008; proxy_set_header X-Forwarded-For $remote_addr; proxy_set_header Host $host; proxy_set_header X-Forwarded-Proto $scheme; } } ``` Save and exit. ### **Step 4: Enable the Configuration** ```sh sudo ln -s /etc/nginx/sites-available/matrix /etc/nginx/sites-enabled/ sudo systemctl restart nginx ``` --- ## **5. Create an Admin User** Run the following command: ```sh register_new_matrix_user -c /etc/matrix-synapse/homeserver.yaml http://localhost:8008 ``` Follow the prompts to create an **admin** user. --- ## **6. Test Your Matrix Server** - Open a browser and go to: `https://matrix.example.com/_matrix/client/versions` - You should see a JSON response indicating your homeserver is running. - Use **Element** (https://element.io) to log in with your new user credentials. --- ## **7. Federation (Optional)** To allow federation, ensure your DNS has an **SRV record**: ``` _matrix._tcp.example.com. 3600 IN SRV 10 5 443 matrix.example.com. ``` You can check your federation status at: https://federationtester.matrix.org/ --- ## **8. Additional Features** ### **Bridges (Connect to Other Platforms)** - **Discord Bridge**: https://github.com/Half-Shot/matrix-appservice-discord - **Telegram Bridge**: https://github.com/tulir/mautrix-telegram ### **Hosting a TURN Server (For Calls & Video)** Install **coturn** for improved call reliability: ```sh sudo apt install -y coturn ``` Edit `/etc/turnserver.conf` to include: ``` listening-port=3478 fingerprint use-auth-secret static-auth-secret=your-random-secret realm=matrix.example.com ``` Enable and start the service: ```sh sudo systemctl enable --now coturn ``` --- ## **9. Backup & Maintenance** ### **Database Backup** ```sh sudo systemctl stop matrix-synapse sudo tar -czvf matrix-backup.tar.gz /var/lib/matrix-synapse/ sudo systemctl start matrix-synapse ``` ### **Updating Synapse** ```sh sudo apt update && sudo apt upgrade -y matrix-synapse-py3 sudo systemctl restart matrix-synapse ``` --- ## **Connections** - **Self-Hosting for Digital Sovereignty** - **Nostr and Matrix Integration for Decentralized Messaging** ## **Donations via** - lightninglayerhash@getalby.com @ d34e832d:383f78d0
2025-02-22 00:57:07[npub16d8gxt2z4k9e8sdpc0yyqzf5gp0np09ls4lnn630qzxzvwpl0rgq5h4rzv] **Why Signal and Matrix Matter in a World of Mass Surveillance** In an era where mass surveillance has become the norm, privacy-focused communication tools are essential for digital sovereignty. Signal and Matrix provide individuals and communities with encrypted, censorship-resistant messaging solutions that challenge centralized control over information exchange. ### **1. Signal – End-to-End Encryption and Metadata Resistance** - **Proven Cryptographic Security**: Signal’s end-to-end encryption, powered by the Signal Protocol, ensures messages remain private even if intercepted. - **Metadata Protection with Sealed Sender**: Signal minimizes metadata exposure, preventing third parties from knowing who is communicating with whom. - **Simple and Ubiquitous Privacy**: Designed for ease of use, Signal bridges the gap between security and accessibility, making privacy mainstream. ### **2. Matrix – Decentralized and Federated Communication** - **Self-Hosted and Federated Infrastructure**: Unlike centralized services, Matrix allows users to host their own servers, reducing reliance on single points of failure. - **Bridging Across Platforms**: Matrix bridges seamlessly with other communication protocols (IRC, XMPP, Slack, etc.), creating a unified, decentralized network. - **End-to-End Encryption and Decentralized Identity**: Matrix offers fully encrypted rooms and a decentralized identity system, ensuring control over user data. ### **3. Mass Surveillance vs. Private Communication** - **Government and Corporate Data Harvesting**: Centralized platforms like WhatsApp, Facebook Messenger, and Gmail log metadata and conversations, creating massive surveillance databases. - **The Threat of AI-Driven Censorship**: Machine learning algorithms analyze user behavior, making privacy-invasive censorship and social credit scoring systems a reality. - **Decentralization as a Resistance Strategy**: By adopting Signal and Matrix, individuals reclaim their right to private conversations without interference from state or corporate actors. ### **Integration Potential and Future Developments** - **Bitcoin and Encrypted Messaging**: Signal and Matrix can be combined with Bitcoin for private transactions and communication, furthering financial sovereignty. - **P2P and Nostr Integration**: Future developments could see Matrix and Nostr integrated for even more robust censorship-resistant communication. ### **Donations via** - lightninglayerhash@getalby.com
@ d34e832d:383f78d0
2025-02-22 00:57:07[npub16d8gxt2z4k9e8sdpc0yyqzf5gp0np09ls4lnn630qzxzvwpl0rgq5h4rzv] **Why Signal and Matrix Matter in a World of Mass Surveillance** In an era where mass surveillance has become the norm, privacy-focused communication tools are essential for digital sovereignty. Signal and Matrix provide individuals and communities with encrypted, censorship-resistant messaging solutions that challenge centralized control over information exchange. ### **1. Signal – End-to-End Encryption and Metadata Resistance** - **Proven Cryptographic Security**: Signal’s end-to-end encryption, powered by the Signal Protocol, ensures messages remain private even if intercepted. - **Metadata Protection with Sealed Sender**: Signal minimizes metadata exposure, preventing third parties from knowing who is communicating with whom. - **Simple and Ubiquitous Privacy**: Designed for ease of use, Signal bridges the gap between security and accessibility, making privacy mainstream. ### **2. Matrix – Decentralized and Federated Communication** - **Self-Hosted and Federated Infrastructure**: Unlike centralized services, Matrix allows users to host their own servers, reducing reliance on single points of failure. - **Bridging Across Platforms**: Matrix bridges seamlessly with other communication protocols (IRC, XMPP, Slack, etc.), creating a unified, decentralized network. - **End-to-End Encryption and Decentralized Identity**: Matrix offers fully encrypted rooms and a decentralized identity system, ensuring control over user data. ### **3. Mass Surveillance vs. Private Communication** - **Government and Corporate Data Harvesting**: Centralized platforms like WhatsApp, Facebook Messenger, and Gmail log metadata and conversations, creating massive surveillance databases. - **The Threat of AI-Driven Censorship**: Machine learning algorithms analyze user behavior, making privacy-invasive censorship and social credit scoring systems a reality. - **Decentralization as a Resistance Strategy**: By adopting Signal and Matrix, individuals reclaim their right to private conversations without interference from state or corporate actors. ### **Integration Potential and Future Developments** - **Bitcoin and Encrypted Messaging**: Signal and Matrix can be combined with Bitcoin for private transactions and communication, furthering financial sovereignty. - **P2P and Nostr Integration**: Future developments could see Matrix and Nostr integrated for even more robust censorship-resistant communication. ### **Donations via** - lightninglayerhash@getalby.com @ cda24367:8ba5afc3
2025-02-22 00:11:32Just a test to find out what this Habla.news does. It looks interesting. And here's an Odysee video to see if the iframe will work. <iframe id="odysee-iframe" style="width:100%; aspect-ratio:16 / 9;" src="https://odysee.com/$/embed/@RandomStuff:0/Steve-Hughes-on-Charity:0?r=9cn37JvaLAtLK8z8NfZjsqm8ZNCaNuUy" allowfullscreen></iframe>
@ cda24367:8ba5afc3
2025-02-22 00:11:32Just a test to find out what this Habla.news does. It looks interesting. And here's an Odysee video to see if the iframe will work. <iframe id="odysee-iframe" style="width:100%; aspect-ratio:16 / 9;" src="https://odysee.com/$/embed/@RandomStuff:0/Steve-Hughes-on-Charity:0?r=9cn37JvaLAtLK8z8NfZjsqm8ZNCaNuUy" allowfullscreen></iframe> @ 916a7ab7:146bb83e
2025-02-21 23:12:49tens of thousands of Afghans flee by often desperate measures, detained, assaulted, murdered, martyred faithless and in fetters. school girls in Uganda know they many never have a wedding when terror rapes the peace they sow, punished by beheading. Chinese mosques, temples, homes are dismantled brick by brick for believing something higher than the state or politic. the glowing boxes in our hands or hanging from our walls manipulate the way we think becoming passive thralls.
@ 916a7ab7:146bb83e
2025-02-21 23:12:49tens of thousands of Afghans flee by often desperate measures, detained, assaulted, murdered, martyred faithless and in fetters. school girls in Uganda know they many never have a wedding when terror rapes the peace they sow, punished by beheading. Chinese mosques, temples, homes are dismantled brick by brick for believing something higher than the state or politic. the glowing boxes in our hands or hanging from our walls manipulate the way we think becoming passive thralls. @ 916a7ab7:146bb83e
2025-02-21 22:43:35my eyes --- are not blurry --- when they see through lenses --- of someone's suffering, and then --- I see. ---
@ 916a7ab7:146bb83e
2025-02-21 22:43:35my eyes --- are not blurry --- when they see through lenses --- of someone's suffering, and then --- I see. --- @ fc481c65:e280e7ba
2025-02-21 21:30:56#Algebra is a branch of #Mathematics that uses symbols, known as variables (like x or y), to represent numbers in equations and formulas. It involves operations like addition, subtraction, multiplication, and division, but these operations are performed on variables as well as numbers. ### Key Concepts in Algebra - **Variables**: Symbols that stand in for unknown values. - **Constants**: Known values that don’t change. - **Coefficients**: Numbers used to multiply a variable. - **Expressions**: Combinations of variables, numbers, and operations (like 3x + 4). - **Equations**: Statements that assert the equality of two expressions, typically including an equals sign (like 2x + 3 = 7). ### Basic Operations 1. **Adding and Subtracting**: You can add or subtract like terms (terms whose variables and their powers are the same). For example, 2x+3x=5x 2. **Multiplying and Dividing**: You multiply or divide both the coefficients and the variables. For instance, `$$3x \times 2x=6x^2$$` 3. **Solving Equations**: The goal is often to isolate the variable on one side of the equation to find its value. This can involve reversing operations using opposite operations. ### Applications of Algebra Algebra is used in various fields, from #Engineering and computer science to economics and everyday problem solving. It helps in creating formulas to understand relationships between quantities and in solving equations that model real-world situations. ## Algebra and Electronics Algebra plays a crucial role in #Electronics engineering, particularly through its application in circuit analysis, signal processing, and control systems. Understanding and utilizing algebraic techniques can significantly enhance problem-solving capabilities in these areas. ### 1. Complex Numbers In electronic engineering, complex numbers are essential for analyzing AC circuits. They help in representing sinusoidal signals, which are fundamental in communications and power systems. - **Representation**: z=a+bi or z=reiθ (polar form) - **Operations**: Addition, subtraction, multiplication, and division in complex form, crucial for understanding the behavior of circuits in the frequency domain. **Example**: Calculating the impedance of an RLC series circuit at a certain frequency. - **Circuit Components**: R=50Ω, L=0.1 H, C=10 μF, ω=1000 rad/s `$$ Z = 50 + j1000 \times 0.1 - \frac{1}{j1000 \times 10 \times 10^{-6}} = 50 + j100 - \frac{1}{j0.01} = 50 + j100 + 100j = 50 + 200j $$` ### 2. Matrices and Determinants Matrices are widely used in electronic engineering for handling multiple equations simultaneously, which is common in systems and network analysis. - **Matrix Operations**: Addition, subtraction, multiplication, and inversion. - **Determinant and Inverse**: Used in solving systems of linear equations, critical in network theory and control systems. ### 3. Fourier Transforms Algebraic manipulation is key in applying Fourier transforms, which convert time-domain signals into their frequency components. This is crucial for signal analysis, filtering, and system design. - **Fourier Series**: Represents periodic signals as a sum of sinusoids. - **Fourier Transform**: Converts continuous time-domain signals to continuous frequency spectra. ### 4. Laplace Transforms Laplace transforms are used to simplify the process of analyzing and designing control systems and circuits by converting differential equations into algebraic equations. - **Transfer Functions**: Represent systems in the s-domain, facilitating easier manipulation and understanding of system dynamics. ### 5. Z-Transforms Similar to Laplace transforms, Z-transforms are used for discrete systems prevalent in digital signal processing and digital control. ### 6. Algebraic Equations in Filter Design Algebra is used in the design of filters, both analog and digital, where polynomial equations are used to determine filter coefficients that meet specific frequency response criteria. ### 7. Control Systems The design and stability analysis of control systems involve solving characteristic equations and manipulating transfer functions, which require a solid understanding of algebra. ### 8. Network Theorems Theorems like Kirchhoff's laws, Thevenin’s theorem, and Norton’s theorem involve algebraic equations to simplify and analyze circuits. ## Algebra with Sympy TODO
@ fc481c65:e280e7ba
2025-02-21 21:30:56#Algebra is a branch of #Mathematics that uses symbols, known as variables (like x or y), to represent numbers in equations and formulas. It involves operations like addition, subtraction, multiplication, and division, but these operations are performed on variables as well as numbers. ### Key Concepts in Algebra - **Variables**: Symbols that stand in for unknown values. - **Constants**: Known values that don’t change. - **Coefficients**: Numbers used to multiply a variable. - **Expressions**: Combinations of variables, numbers, and operations (like 3x + 4). - **Equations**: Statements that assert the equality of two expressions, typically including an equals sign (like 2x + 3 = 7). ### Basic Operations 1. **Adding and Subtracting**: You can add or subtract like terms (terms whose variables and their powers are the same). For example, 2x+3x=5x 2. **Multiplying and Dividing**: You multiply or divide both the coefficients and the variables. For instance, `$$3x \times 2x=6x^2$$` 3. **Solving Equations**: The goal is often to isolate the variable on one side of the equation to find its value. This can involve reversing operations using opposite operations. ### Applications of Algebra Algebra is used in various fields, from #Engineering and computer science to economics and everyday problem solving. It helps in creating formulas to understand relationships between quantities and in solving equations that model real-world situations. ## Algebra and Electronics Algebra plays a crucial role in #Electronics engineering, particularly through its application in circuit analysis, signal processing, and control systems. Understanding and utilizing algebraic techniques can significantly enhance problem-solving capabilities in these areas. ### 1. Complex Numbers In electronic engineering, complex numbers are essential for analyzing AC circuits. They help in representing sinusoidal signals, which are fundamental in communications and power systems. - **Representation**: z=a+bi or z=reiθ (polar form) - **Operations**: Addition, subtraction, multiplication, and division in complex form, crucial for understanding the behavior of circuits in the frequency domain. **Example**: Calculating the impedance of an RLC series circuit at a certain frequency. - **Circuit Components**: R=50Ω, L=0.1 H, C=10 μF, ω=1000 rad/s `$$ Z = 50 + j1000 \times 0.1 - \frac{1}{j1000 \times 10 \times 10^{-6}} = 50 + j100 - \frac{1}{j0.01} = 50 + j100 + 100j = 50 + 200j $$` ### 2. Matrices and Determinants Matrices are widely used in electronic engineering for handling multiple equations simultaneously, which is common in systems and network analysis. - **Matrix Operations**: Addition, subtraction, multiplication, and inversion. - **Determinant and Inverse**: Used in solving systems of linear equations, critical in network theory and control systems. ### 3. Fourier Transforms Algebraic manipulation is key in applying Fourier transforms, which convert time-domain signals into their frequency components. This is crucial for signal analysis, filtering, and system design. - **Fourier Series**: Represents periodic signals as a sum of sinusoids. - **Fourier Transform**: Converts continuous time-domain signals to continuous frequency spectra. ### 4. Laplace Transforms Laplace transforms are used to simplify the process of analyzing and designing control systems and circuits by converting differential equations into algebraic equations. - **Transfer Functions**: Represent systems in the s-domain, facilitating easier manipulation and understanding of system dynamics. ### 5. Z-Transforms Similar to Laplace transforms, Z-transforms are used for discrete systems prevalent in digital signal processing and digital control. ### 6. Algebraic Equations in Filter Design Algebra is used in the design of filters, both analog and digital, where polynomial equations are used to determine filter coefficients that meet specific frequency response criteria. ### 7. Control Systems The design and stability analysis of control systems involve solving characteristic equations and manipulating transfer functions, which require a solid understanding of algebra. ### 8. Network Theorems Theorems like Kirchhoff's laws, Thevenin’s theorem, and Norton’s theorem involve algebraic equations to simplify and analyze circuits. ## Algebra with Sympy TODO @ 4857600b:30b502f4
2025-02-21 21:15:04In a revealing development that exposes the hypocrisy of government surveillance, multiple federal agencies including the CIA and FBI have filed lawsuits to keep Samourai Wallet's client list sealed during and after trial proceedings. This move strongly suggests that government agencies themselves were utilizing Samourai's privacy-focused services while simultaneously condemning similar privacy tools when used by ordinary citizens. The situation bears striking parallels to other cases where government agencies have hidden behind "national security" claims, such as the Jeffrey Epstein case, highlighting a troubling double standard: while average citizens are expected to surrender their financial privacy through extensive reporting requirements and regulations, government agencies claim exemption from these same transparency standards they enforce on others. This case exemplifies the fundamental conflict between individual liberty and state power, where government agencies appear to be using the very privacy tools they prosecute others for using. The irony is particularly stark given that money laundering for intelligence agencies is considered legal in our system, while private citizens seeking financial privacy face severe legal consequences - a clear demonstration of how the state creates different rules for itself versus the people it claims to serve. Citations: [1] https://www.bugle.news/cia-fbi-dnc-rnc-all-sue-to-redact-samourais-client-list-from-trial/
@ 4857600b:30b502f4
2025-02-21 21:15:04In a revealing development that exposes the hypocrisy of government surveillance, multiple federal agencies including the CIA and FBI have filed lawsuits to keep Samourai Wallet's client list sealed during and after trial proceedings. This move strongly suggests that government agencies themselves were utilizing Samourai's privacy-focused services while simultaneously condemning similar privacy tools when used by ordinary citizens. The situation bears striking parallels to other cases where government agencies have hidden behind "national security" claims, such as the Jeffrey Epstein case, highlighting a troubling double standard: while average citizens are expected to surrender their financial privacy through extensive reporting requirements and regulations, government agencies claim exemption from these same transparency standards they enforce on others. This case exemplifies the fundamental conflict between individual liberty and state power, where government agencies appear to be using the very privacy tools they prosecute others for using. The irony is particularly stark given that money laundering for intelligence agencies is considered legal in our system, while private citizens seeking financial privacy face severe legal consequences - a clear demonstration of how the state creates different rules for itself versus the people it claims to serve. Citations: [1] https://www.bugle.news/cia-fbi-dnc-rnc-all-sue-to-redact-samourais-client-list-from-trial/ @ dbb19ae0:c3f22d5a
2025-02-21 20:38:43``` python #!/usr/bin/env python3 import asyncio from nostr_sdk import Metadata, Client, NostrSigner, Keys, Filter, PublicKey, Kind, init_logger, LogLevel from datetime import timedelta async def main(): init_logger(LogLevel.INFO) secret_key = "nsec1........Replace with your actual nsec secret key" keys = Keys.parse(secret_key) signer = NostrSigner.keys(keys) client = Client(signer) await client.add_relay("wss://relay.damus.io") await client.connect() # Update metadata new_metadata = Metadata().set_name( "MyName")\ .set_nip05("MyName@example.com")\ .set_lud16("MyName@lud16.com") await client.set_metadata(new_metadata) print("Metadata updated successfully.") # Get updated metadata npub = "npub1....Replace with your actual npub" pk = PublicKey.parse(npub) print(f"\nGetting profile metadata for {npub}:") metadata = await client.fetch_metadata(pk, timedelta(seconds=15)) print(metadata) if __name__ == '__main__': asyncio.run(main()) ```
@ dbb19ae0:c3f22d5a
2025-02-21 20:38:43``` python #!/usr/bin/env python3 import asyncio from nostr_sdk import Metadata, Client, NostrSigner, Keys, Filter, PublicKey, Kind, init_logger, LogLevel from datetime import timedelta async def main(): init_logger(LogLevel.INFO) secret_key = "nsec1........Replace with your actual nsec secret key" keys = Keys.parse(secret_key) signer = NostrSigner.keys(keys) client = Client(signer) await client.add_relay("wss://relay.damus.io") await client.connect() # Update metadata new_metadata = Metadata().set_name( "MyName")\ .set_nip05("MyName@example.com")\ .set_lud16("MyName@lud16.com") await client.set_metadata(new_metadata) print("Metadata updated successfully.") # Get updated metadata npub = "npub1....Replace with your actual npub" pk = PublicKey.parse(npub) print(f"\nGetting profile metadata for {npub}:") metadata = await client.fetch_metadata(pk, timedelta(seconds=15)) print(metadata) if __name__ == '__main__': asyncio.run(main()) ``` @ 4c96d763:80c3ee30
2025-02-21 20:31:55# Changes ## Ethan Tuttle (1): - feat: ctrl+enter when creating a new note, sends the note, the same way clicking the "Post Now" button. ## Ken Sedgwick (11): - drive-by compiler warning fixes - drive-by clippy fixes - add derive Debug to some things - panic on unknown CLI arguments - move RelayDebugView to notedeck crate and restore --relay-debug - add diagnostic string to DecodeFailed - improve relay message parsing unit tests - fix event error return when decoding fails - fix OK message parser to include last message component - fix EOSE parsing to handle extra whitespace - check message length before prefix comparisons ## William Casarin (5): - clippy: fix enum too large issue - changelog: add unreleased section - clippy: fix lint - args: skip creation of vec - nix: fix android build ## jglad (4): - fix: handle missing file [#715] - refactor - fix compilation - hide nsec in account panel pushed to [notedeck:refs/heads/master](http://git.jb55.com/notedeck/commit/32c7f83bd7a807155de6a13b66a7d43f48c25e13.html)
@ 4c96d763:80c3ee30
2025-02-21 20:31:55# Changes ## Ethan Tuttle (1): - feat: ctrl+enter when creating a new note, sends the note, the same way clicking the "Post Now" button. ## Ken Sedgwick (11): - drive-by compiler warning fixes - drive-by clippy fixes - add derive Debug to some things - panic on unknown CLI arguments - move RelayDebugView to notedeck crate and restore --relay-debug - add diagnostic string to DecodeFailed - improve relay message parsing unit tests - fix event error return when decoding fails - fix OK message parser to include last message component - fix EOSE parsing to handle extra whitespace - check message length before prefix comparisons ## William Casarin (5): - clippy: fix enum too large issue - changelog: add unreleased section - clippy: fix lint - args: skip creation of vec - nix: fix android build ## jglad (4): - fix: handle missing file [#715] - refactor - fix compilation - hide nsec in account panel pushed to [notedeck:refs/heads/master](http://git.jb55.com/notedeck/commit/32c7f83bd7a807155de6a13b66a7d43f48c25e13.html) @ a95c6243:d345522c
2025-02-21 19:32:23*Europa – das Ganze ist eine wunderbare Idee,* *\ aber das war der Kommunismus auch.* *\ Loriot*   **«Europa hat fertig», könnte man unken,** und das wäre nicht einmal sehr verwegen. Mit solch einer [Einschätzung](https://transition-news.org/geopolitische-ohnmacht-und-die-last-des-euro-steht-die-eu-vor-der-implosion) stünden wir nicht alleine, denn die Stimmen in diese Richtung mehren sich. Der französische Präsident Emmanuel Macron warnte schon letztes Jahr davor, dass «unser Europa sterben könnte». Vermutlich hatte er dabei andere Gefahren im Kopf als jetzt der ungarische Ministerpräsident Viktor Orbán, der ein «baldiges Ende der EU» prognostizierte. Das Ergebnis könnte allerdings das gleiche sein. **Neben vordergründigen Themenbereichen wie Wirtschaft, Energie und Sicherheit** ist das eigentliche Problem jedoch die obskure Mischung aus aufgegebener Souveränität und geschwollener Arroganz, mit der europäische Politiker:innende unterschiedlicher Couleur aufzutreten pflegen. Und das Tüpfelchen auf dem i ist die bröckelnde Legitimation politischer Institutionen dadurch, dass die Stimmen großer Teile der Bevölkerung seit Jahren auf vielfältige Weise ausgegrenzt werden. **Um «UnsereDemokratie» steht es schlecht.** Dass seine Mandate immer schwächer werden, merkt natürlich auch unser «Führungspersonal». Entsprechend werden die Maßnahmen zur Gängelung, Überwachung und Manipulation der Bürger ständig verzweifelter. Parallel dazu [plustern](https://www.bundesregierung.de/breg-de/service/newsletter-und-abos/bundesregierung-aktuell/ausgabe-07-2025-februar-21-2335652?view=renderNewsletterHtml) sich in Paris Macron, Scholz und einige andere noch einmal mächtig in Sachen Verteidigung und [«Kriegstüchtigkeit»](https://transition-news.org/europaische-investitionsbank-tragt-zur-kriegstuchtigkeit-europas-bei) auf. **Momentan gilt es auch, das Überschwappen covidiotischer und verschwörungsideologischer Auswüchse** aus den USA nach Europa zu vermeiden. So ein «MEGA» (Make Europe Great Again) können wir hier nicht gebrauchen. Aus den Vereinigten Staaten kommen nämlich furchtbare Nachrichten. Beispielsweise wurde einer der schärfsten Kritiker der Corona-Maßnahmen kürzlich zum Gesundheitsminister ernannt. Dieser setzt sich jetzt für eine Neubewertung der mRNA-«Impfstoffe» ein, was durchaus zu einem [Entzug der Zulassungen](https://transition-news.org/usa-zulassungsentzug-fur-corona-impfstoffe-auf-der-tagesordnung) führen könnte. **Der europäischen Version von** **[«Verteidigung der Demokratie»](https://transition-news.org/eu-macht-freiwilligen-verhaltenskodex-gegen-desinformation-zu-bindendem-recht)** setzte der US-Vizepräsident J. D. Vance auf der Münchner Sicherheitskonferenz sein Verständnis entgegen: «Demokratie stärken, indem wir unseren Bürgern erlauben, ihre Meinung zu sagen». Das Abschalten von Medien, das Annullieren von Wahlen oder das Ausschließen von Menschen vom politischen Prozess schütze gar nichts. Vielmehr sei dies der todsichere Weg, die Demokratie zu zerstören. **In der Schweiz kamen seine Worte deutlich besser an** als in den meisten europäischen NATO-Ländern. Bundespräsidentin Karin Keller-Sutter lobte die Rede und interpretierte sie als «Plädoyer für die direkte Demokratie». Möglicherweise zeichne sich hier eine [außenpolitische Kehrtwende](https://transition-news.org/schweiz-vor-aussenpolitischer-kehrtwende-richtung-integraler-neutralitat) in Richtung integraler Neutralität ab, meint mein Kollege Daniel Funk. Das wären doch endlich mal ein paar gute Nachrichten. **Von der einstigen Idee einer europäischen Union** mit engeren Beziehungen zwischen den Staaten, um Konflikte zu vermeiden und das Wohlergehen der Bürger zu verbessern, sind wir meilenweit abgekommen. Der heutige korrupte Verbund unter technokratischer Leitung ähnelt mehr einem Selbstbedienungsladen mit sehr begrenztem Zugang. Die EU-Wahlen im letzten Sommer haben daran ebenso wenig geändert, wie die [Bundestagswahl](https://transition-news.org/bundestagswahl-mehr-aufrustung-statt-friedenskanzler-nach-der-wahl) am kommenden Sonntag darauf einen Einfluss haben wird. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/europaer-seid-ihr-noch-zu-retten)*** erschienen.
@ a95c6243:d345522c
2025-02-21 19:32:23*Europa – das Ganze ist eine wunderbare Idee,* *\ aber das war der Kommunismus auch.* *\ Loriot*   **«Europa hat fertig», könnte man unken,** und das wäre nicht einmal sehr verwegen. Mit solch einer [Einschätzung](https://transition-news.org/geopolitische-ohnmacht-und-die-last-des-euro-steht-die-eu-vor-der-implosion) stünden wir nicht alleine, denn die Stimmen in diese Richtung mehren sich. Der französische Präsident Emmanuel Macron warnte schon letztes Jahr davor, dass «unser Europa sterben könnte». Vermutlich hatte er dabei andere Gefahren im Kopf als jetzt der ungarische Ministerpräsident Viktor Orbán, der ein «baldiges Ende der EU» prognostizierte. Das Ergebnis könnte allerdings das gleiche sein. **Neben vordergründigen Themenbereichen wie Wirtschaft, Energie und Sicherheit** ist das eigentliche Problem jedoch die obskure Mischung aus aufgegebener Souveränität und geschwollener Arroganz, mit der europäische Politiker:innende unterschiedlicher Couleur aufzutreten pflegen. Und das Tüpfelchen auf dem i ist die bröckelnde Legitimation politischer Institutionen dadurch, dass die Stimmen großer Teile der Bevölkerung seit Jahren auf vielfältige Weise ausgegrenzt werden. **Um «UnsereDemokratie» steht es schlecht.** Dass seine Mandate immer schwächer werden, merkt natürlich auch unser «Führungspersonal». Entsprechend werden die Maßnahmen zur Gängelung, Überwachung und Manipulation der Bürger ständig verzweifelter. Parallel dazu [plustern](https://www.bundesregierung.de/breg-de/service/newsletter-und-abos/bundesregierung-aktuell/ausgabe-07-2025-februar-21-2335652?view=renderNewsletterHtml) sich in Paris Macron, Scholz und einige andere noch einmal mächtig in Sachen Verteidigung und [«Kriegstüchtigkeit»](https://transition-news.org/europaische-investitionsbank-tragt-zur-kriegstuchtigkeit-europas-bei) auf. **Momentan gilt es auch, das Überschwappen covidiotischer und verschwörungsideologischer Auswüchse** aus den USA nach Europa zu vermeiden. So ein «MEGA» (Make Europe Great Again) können wir hier nicht gebrauchen. Aus den Vereinigten Staaten kommen nämlich furchtbare Nachrichten. Beispielsweise wurde einer der schärfsten Kritiker der Corona-Maßnahmen kürzlich zum Gesundheitsminister ernannt. Dieser setzt sich jetzt für eine Neubewertung der mRNA-«Impfstoffe» ein, was durchaus zu einem [Entzug der Zulassungen](https://transition-news.org/usa-zulassungsentzug-fur-corona-impfstoffe-auf-der-tagesordnung) führen könnte. **Der europäischen Version von** **[«Verteidigung der Demokratie»](https://transition-news.org/eu-macht-freiwilligen-verhaltenskodex-gegen-desinformation-zu-bindendem-recht)** setzte der US-Vizepräsident J. D. Vance auf der Münchner Sicherheitskonferenz sein Verständnis entgegen: «Demokratie stärken, indem wir unseren Bürgern erlauben, ihre Meinung zu sagen». Das Abschalten von Medien, das Annullieren von Wahlen oder das Ausschließen von Menschen vom politischen Prozess schütze gar nichts. Vielmehr sei dies der todsichere Weg, die Demokratie zu zerstören. **In der Schweiz kamen seine Worte deutlich besser an** als in den meisten europäischen NATO-Ländern. Bundespräsidentin Karin Keller-Sutter lobte die Rede und interpretierte sie als «Plädoyer für die direkte Demokratie». Möglicherweise zeichne sich hier eine [außenpolitische Kehrtwende](https://transition-news.org/schweiz-vor-aussenpolitischer-kehrtwende-richtung-integraler-neutralitat) in Richtung integraler Neutralität ab, meint mein Kollege Daniel Funk. Das wären doch endlich mal ein paar gute Nachrichten. **Von der einstigen Idee einer europäischen Union** mit engeren Beziehungen zwischen den Staaten, um Konflikte zu vermeiden und das Wohlergehen der Bürger zu verbessern, sind wir meilenweit abgekommen. Der heutige korrupte Verbund unter technokratischer Leitung ähnelt mehr einem Selbstbedienungsladen mit sehr begrenztem Zugang. Die EU-Wahlen im letzten Sommer haben daran ebenso wenig geändert, wie die [Bundestagswahl](https://transition-news.org/bundestagswahl-mehr-aufrustung-statt-friedenskanzler-nach-der-wahl) am kommenden Sonntag darauf einen Einfluss haben wird. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/europaer-seid-ihr-noch-zu-retten)*** erschienen. @ 86a82cab:b5ef38a0
2025-02-21 18:42:50This morning, I decided to look into the NIP-23 specialized clients, and try to publish long-form content on the Nostr network of relays: https://habla.news/ https://blogstack.io First, I encourage you to read the NIP, and the first thing that you will notice is that the kind id used to publish is 30023 instead of 1, soThis morning, I decided to look into the NIP-23 specialized clients, and try to publish **long-form** content on the **Nostr** network of relays: https://habla.news/ https://blogstack.io First, I encourage you to read the NIP, and the first thing that you will notice is that the kind id used to publish is 30023 instead of 1, so
@ 86a82cab:b5ef38a0
2025-02-21 18:42:50This morning, I decided to look into the NIP-23 specialized clients, and try to publish long-form content on the Nostr network of relays: https://habla.news/ https://blogstack.io First, I encourage you to read the NIP, and the first thing that you will notice is that the kind id used to publish is 30023 instead of 1, soThis morning, I decided to look into the NIP-23 specialized clients, and try to publish **long-form** content on the **Nostr** network of relays: https://habla.news/ https://blogstack.io First, I encourage you to read the NIP, and the first thing that you will notice is that the kind id used to publish is 30023 instead of 1, so @ 86a82cab:b5ef38a0
2025-02-21 18:32:52asdasdasdasdasdNIP-23 Long-form Content. draft optional author:fiatjaf. This NIP defines kind:30023 (a parameterized replaceable event) for long-form text content, generally referred to as "articles" or "blog posts".kind:30024 has the same structure as kind:30023 and is used to save long form drafts. "Social"NIP-23 **Long-form** Content. draft optional author:fiatjaf. This NIP defines kind:30023 (a parameterized replaceable event) for **long-form** text content, generally referred to as "articles" or "blog posts".kind:30024 has the same structure as kind:30023 and is used to save **long** **form** drafts. "Social"
@ 86a82cab:b5ef38a0
2025-02-21 18:32:52asdasdasdasdasdNIP-23 Long-form Content. draft optional author:fiatjaf. This NIP defines kind:30023 (a parameterized replaceable event) for long-form text content, generally referred to as "articles" or "blog posts".kind:30024 has the same structure as kind:30023 and is used to save long form drafts. "Social"NIP-23 **Long-form** Content. draft optional author:fiatjaf. This NIP defines kind:30023 (a parameterized replaceable event) for **long-form** text content, generally referred to as "articles" or "blog posts".kind:30024 has the same structure as kind:30023 and is used to save **long** **form** drafts. "Social" @ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard. — We want to speak with the president — the man said in a low voice. — He will be busy all day — the secretary replied curtly. — We will wait. The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that. — If you speak with them for just a few minutes, maybe they will decide to go away — she said. The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple. — We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus. — My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery. — Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard. The president looked at the woman's faded dress and her husband's old suit and exclaimed: — A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard. The lady was silent for a moment, then said to her husband: — If that’s all it costs to found a university, why don’t we have our own? The husband agreed. The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student." Text extracted from: "Mileumlivros - Stories that Teach Values." Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation. A toast to our family!
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard. — We want to speak with the president — the man said in a low voice. — He will be busy all day — the secretary replied curtly. — We will wait. The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that. — If you speak with them for just a few minutes, maybe they will decide to go away — she said. The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple. — We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus. — My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery. — Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard. The president looked at the woman's faded dress and her husband's old suit and exclaimed: — A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard. The lady was silent for a moment, then said to her husband: — If that’s all it costs to found a university, why don’t we have our own? The husband agreed. The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student." Text extracted from: "Mileumlivros - Stories that Teach Values." Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation. A toast to our family! @ 6e0ea5d6:0327f353
2025-02-21 18:08:19When talking about the tumbles we experience in our early years, it’s almost impossible not to try to compare the degree of distress that each stumble has provided us. Even if harmless, the first accident that comes to mind is one that, in some way, left its mark. Whether it’s a scraped knee, a gash on the forehead, or a broken arm: having that first conscious encounter with pain is an unforgettable terror. For in one moment, we are sheltered in the loving arms of our parents, feeling invulnerable, and moments later there’s a thick mixture of blood and dirt streaming from a cut that doesn’t seem all that exaggerated to someone looking from the outside — but only to those looking from the outside. However, this is not what makes that first contact with pain so terrifying. It’s the discovery of how lonely we are when facing an individual agony, even under the care of an adult. Ultimately, what follows the shock can vary from the sting of cleaning the wound to the warning slap. After the understanding is digested, and we learn how wounds are made, we become cautious. A slip is met with laughter, and we grow tougher than the ground. That is, until we discover the free fall that holds the world’s problems… “Consciousness, not age, leads to wisdom.” — Publilius Syrus Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation. A toast to our family!
@ 6e0ea5d6:0327f353
2025-02-21 18:08:19When talking about the tumbles we experience in our early years, it’s almost impossible not to try to compare the degree of distress that each stumble has provided us. Even if harmless, the first accident that comes to mind is one that, in some way, left its mark. Whether it’s a scraped knee, a gash on the forehead, or a broken arm: having that first conscious encounter with pain is an unforgettable terror. For in one moment, we are sheltered in the loving arms of our parents, feeling invulnerable, and moments later there’s a thick mixture of blood and dirt streaming from a cut that doesn’t seem all that exaggerated to someone looking from the outside — but only to those looking from the outside. However, this is not what makes that first contact with pain so terrifying. It’s the discovery of how lonely we are when facing an individual agony, even under the care of an adult. Ultimately, what follows the shock can vary from the sting of cleaning the wound to the warning slap. After the understanding is digested, and we learn how wounds are made, we become cautious. A slip is met with laughter, and we grow tougher than the ground. That is, until we discover the free fall that holds the world’s problems… “Consciousness, not age, leads to wisdom.” — Publilius Syrus Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation. A toast to our family! @ 266815e0:6cd408a5
2025-02-21 17:54:15I've been working on the applesauce libraries for a while now but I think this release is the first one I would consider to be stable enough to use A lot of the core concepts and classes are in place and stable enough where they wont change too much next release If you want to skip straight to the documentation you can find at [hzrd149.github.io/applesauce](https://hzrd149.github.io/applesauce/) or the typescript docs at [hzrd149.github.io/applesauce/typedoc](https://hzrd149.github.io/applesauce/typedoc) ## Whats new ### Accounts The `applesauce-accounts` package is an extension of the `applesauce-signers` package and provides classes for building a multi-account system for clients Its primary features are - Serialize and deserialize accounts so they can be saved in local storage or IndexededDB - Account manager for multiple accounts and switching between them - Account metadata for things like labels, app settings, etc - Support for NIP-46 Nostr connect accounts see [documentation](https://hzrd149.github.io/applesauce/accounts/manager.html) for more examples ### Nostr connect signer The `NostrConnectSigner` class from the `applesauce-signers` package is now in a stable state and has a few new features - Ability to create `nostrconnect://` URIs and waiting for the remote signer to connect - SDK agnostic way of subscribing and publishing to relays For a simple example, here is how to create a signer from a `bunker://` URI ```js const signer = await NostrConnectSigner.fromBunkerURI( "bunker://266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5?relay=wss://relay.nsec.app&secret=d9aa70", { permissions: NostrConnectSigner.buildSigningPermissions([0, 1, 3, 10002]), async onSubOpen(filters, relays, onEvent) { // manually open REQ }, async onSubClose() { // close previouse REQ }, async onPublishEvent(event, relays) { // Pubilsh an event to relays }, }, ); ``` see [documentation](https://hzrd149.github.io/applesauce/signers/nostr-connect.html) for more examples and other signers ### Event Factory The `EventFactory` class is probably what I'm most proud of. its a standalone class that can be used to create various types of events from templates ([blueprints](https://hzrd149.github.io/applesauce/typedoc/modules/applesauce_factory.Blueprints.html)) and is really simple to use For example: ```js import { EventFactory } from "applesauce-factory"; import { NoteBlueprint } from "applesauce-factory/blueprints"; const factory = new EventFactory({ // optionally pass a NIP-07 signer in to use for encryption / decryption signer: window.nostr }); // Create a kind 1 note with a hashtag let draft = await factory.create(NoteBlueprint, "hello world #grownostr"); // Sign the note so it can be published let signed = await window.nostr.signEvent(draft); ``` Its included in the `applesauce-factory` package and can be used with any other nostr SDKs or vanilla javascript It also can be used to modify existing replaceable events ```js let draft = await factory.modifyTags( // kind 10002 event mailboxes, // add outbox relays addOutboxRelay("wss://relay.io/"), addOutboxRelay("wss://nostr.wine/"), // remove inbox relay removeInboxRelay("wss://personal.old-relay.com/") ); ``` see [documentation](https://hzrd149.github.io/applesauce/overview/factory.html) for more examples ### Loaders The `applesauce-loaders` package exports a bunch of loader classes that can be used to load everything from replaceable events (profiles) to timelines and NIP-05 identities They use [rx-nostr](https://penpenpng.github.io/rx-nostr/) under the hood to subscribe to relays, so for the time being they will not work with other nostr SDKs I don't expect many other developers or apps to use them since in my experience every nostr client requires a slightly different way or loading events *They are stable enough to start using but they are not fully tested and they might change slightly in the future* The following is a short list of the loaders and what they can be used for - `ReplaceableLoader` loads any replaceable events (0, 3, 1xxxx, 3xxxx) - `SingleEventLoader` loads single events based on ids - `TimelineLoader` loads a timeline of events from multiple relays based on filters - `TagValueLoader` loads events based on a tag name (like "e") and a value, can be used to load replies, zaps, reactions, etc - `DnsIdentityLoader` loads NIP-05 identities and supports caching - `UserSetsLoader` loads all lists events for users see [documentation](https://hzrd149.github.io/applesauce/overview/loaders.html) for more examples ### Real tests For all new features and a lot of existing ones I'm trying to write tests to ensure I don't leave unexpected bugs for later I'm not going to pretend its 100% tests coverage or that it will ever get close to that point, but these tests cover some of the core classes and help me prove that my code is doing what it says its supposed to do At the moment there are about 230 tests covering 45 files. not much but its a start  ## Apps built using applesauce If you want to see some examples of applesauce being used in a nostr client I've been testing a lot of this code in production on the apps I've built in the last few months - [noStrudel](https://github.com/hzrd149/nostrudel) The main app everything is being built for and tested in - [nsite-manager](https://github.com/hzrd149/nsite-manager) Still a work-in-progress but supports multiple accounts thanks to the `applesauce-accounts` package - [blossomservers.com](https://github.com/hzrd149/blossomservers) A simple (and incomplete) nostr client for listing and reviewing public blossom servers - [libretranslate-dvm](https://github.com/hzrd149/libretranslate-dvm) A libretranslate DVM for nostr:npub1mkvkflncllnvp3adq57klw3wge6k9llqa4r60g42ysp4yyultx6sykjgnu - [cherry-tree](https://github.com/hzrd149/cherry-tree) A chunked blob uploader / downloader. only uses applesauce for boilerplate - [nsite-homepage](https://github.com/hzrd149/nsite-homepage) A simple landing page for [nsite.lol](https://nsite.lol) Thanks to nostr:npub1cesrkrcuelkxyhvupzm48e8hwn4005w0ya5jyvf9kh75mfegqx0q4kt37c for teaching me more about rxjs and consequentially making me re-write a lot of the core observables to be faster
@ 266815e0:6cd408a5
2025-02-21 17:54:15I've been working on the applesauce libraries for a while now but I think this release is the first one I would consider to be stable enough to use A lot of the core concepts and classes are in place and stable enough where they wont change too much next release If you want to skip straight to the documentation you can find at [hzrd149.github.io/applesauce](https://hzrd149.github.io/applesauce/) or the typescript docs at [hzrd149.github.io/applesauce/typedoc](https://hzrd149.github.io/applesauce/typedoc) ## Whats new ### Accounts The `applesauce-accounts` package is an extension of the `applesauce-signers` package and provides classes for building a multi-account system for clients Its primary features are - Serialize and deserialize accounts so they can be saved in local storage or IndexededDB - Account manager for multiple accounts and switching between them - Account metadata for things like labels, app settings, etc - Support for NIP-46 Nostr connect accounts see [documentation](https://hzrd149.github.io/applesauce/accounts/manager.html) for more examples ### Nostr connect signer The `NostrConnectSigner` class from the `applesauce-signers` package is now in a stable state and has a few new features - Ability to create `nostrconnect://` URIs and waiting for the remote signer to connect - SDK agnostic way of subscribing and publishing to relays For a simple example, here is how to create a signer from a `bunker://` URI ```js const signer = await NostrConnectSigner.fromBunkerURI( "bunker://266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5?relay=wss://relay.nsec.app&secret=d9aa70", { permissions: NostrConnectSigner.buildSigningPermissions([0, 1, 3, 10002]), async onSubOpen(filters, relays, onEvent) { // manually open REQ }, async onSubClose() { // close previouse REQ }, async onPublishEvent(event, relays) { // Pubilsh an event to relays }, }, ); ``` see [documentation](https://hzrd149.github.io/applesauce/signers/nostr-connect.html) for more examples and other signers ### Event Factory The `EventFactory` class is probably what I'm most proud of. its a standalone class that can be used to create various types of events from templates ([blueprints](https://hzrd149.github.io/applesauce/typedoc/modules/applesauce_factory.Blueprints.html)) and is really simple to use For example: ```js import { EventFactory } from "applesauce-factory"; import { NoteBlueprint } from "applesauce-factory/blueprints"; const factory = new EventFactory({ // optionally pass a NIP-07 signer in to use for encryption / decryption signer: window.nostr }); // Create a kind 1 note with a hashtag let draft = await factory.create(NoteBlueprint, "hello world #grownostr"); // Sign the note so it can be published let signed = await window.nostr.signEvent(draft); ``` Its included in the `applesauce-factory` package and can be used with any other nostr SDKs or vanilla javascript It also can be used to modify existing replaceable events ```js let draft = await factory.modifyTags( // kind 10002 event mailboxes, // add outbox relays addOutboxRelay("wss://relay.io/"), addOutboxRelay("wss://nostr.wine/"), // remove inbox relay removeInboxRelay("wss://personal.old-relay.com/") ); ``` see [documentation](https://hzrd149.github.io/applesauce/overview/factory.html) for more examples ### Loaders The `applesauce-loaders` package exports a bunch of loader classes that can be used to load everything from replaceable events (profiles) to timelines and NIP-05 identities They use [rx-nostr](https://penpenpng.github.io/rx-nostr/) under the hood to subscribe to relays, so for the time being they will not work with other nostr SDKs I don't expect many other developers or apps to use them since in my experience every nostr client requires a slightly different way or loading events *They are stable enough to start using but they are not fully tested and they might change slightly in the future* The following is a short list of the loaders and what they can be used for - `ReplaceableLoader` loads any replaceable events (0, 3, 1xxxx, 3xxxx) - `SingleEventLoader` loads single events based on ids - `TimelineLoader` loads a timeline of events from multiple relays based on filters - `TagValueLoader` loads events based on a tag name (like "e") and a value, can be used to load replies, zaps, reactions, etc - `DnsIdentityLoader` loads NIP-05 identities and supports caching - `UserSetsLoader` loads all lists events for users see [documentation](https://hzrd149.github.io/applesauce/overview/loaders.html) for more examples ### Real tests For all new features and a lot of existing ones I'm trying to write tests to ensure I don't leave unexpected bugs for later I'm not going to pretend its 100% tests coverage or that it will ever get close to that point, but these tests cover some of the core classes and help me prove that my code is doing what it says its supposed to do At the moment there are about 230 tests covering 45 files. not much but its a start  ## Apps built using applesauce If you want to see some examples of applesauce being used in a nostr client I've been testing a lot of this code in production on the apps I've built in the last few months - [noStrudel](https://github.com/hzrd149/nostrudel) The main app everything is being built for and tested in - [nsite-manager](https://github.com/hzrd149/nsite-manager) Still a work-in-progress but supports multiple accounts thanks to the `applesauce-accounts` package - [blossomservers.com](https://github.com/hzrd149/blossomservers) A simple (and incomplete) nostr client for listing and reviewing public blossom servers - [libretranslate-dvm](https://github.com/hzrd149/libretranslate-dvm) A libretranslate DVM for nostr:npub1mkvkflncllnvp3adq57klw3wge6k9llqa4r60g42ysp4yyultx6sykjgnu - [cherry-tree](https://github.com/hzrd149/cherry-tree) A chunked blob uploader / downloader. only uses applesauce for boilerplate - [nsite-homepage](https://github.com/hzrd149/nsite-homepage) A simple landing page for [nsite.lol](https://nsite.lol) Thanks to nostr:npub1cesrkrcuelkxyhvupzm48e8hwn4005w0ya5jyvf9kh75mfegqx0q4kt37c for teaching me more about rxjs and consequentially making me re-write a lot of the core observables to be faster @ dbb19ae0:c3f22d5a
2025-02-21 17:46:58Tested and working with nostr_sdk version 0.39 ``` python from nostr_sdk import Metadata, Client, Keys, Filter, PublicKey from datetime import timedelta import argparse import asyncio import json async def main(npub): client = Client() await client.add_relay("wss://relay.damus.io") await client.connect() pk = PublicKey.parse(npub) print(f"\nGetting profile metadata for {npub}:") metadata = await client.fetch_metadata(pk, timedelta(seconds=15)) # Printing each field of the Metadata object print(f"Name: {metadata.get_name()}") print(f"Display Name: {metadata.get_display_name()}") print(f"About: {metadata.get_about()}") print(f"Website: {metadata.get_website()}") print(f"Picture: {metadata.get_picture()}") print(f"Banner: {metadata.get_banner()}") print(f"NIP05: {metadata.get_nip05()}") print(f"LUD06: {metadata.get_lud06()}") print(f"LUD16: {metadata.get_lud16()}") #print(f"Custom: {metadata.get_custom()}") if __name__ == '__main__': parser = argparse.ArgumentParser(description='Fetch all metadata for a given npub') parser.add_argument('npub', type=str, help='The npub of the user') args = parser.parse_args() asyncio.run(main(args.npub)) ```
@ dbb19ae0:c3f22d5a
2025-02-21 17:46:58Tested and working with nostr_sdk version 0.39 ``` python from nostr_sdk import Metadata, Client, Keys, Filter, PublicKey from datetime import timedelta import argparse import asyncio import json async def main(npub): client = Client() await client.add_relay("wss://relay.damus.io") await client.connect() pk = PublicKey.parse(npub) print(f"\nGetting profile metadata for {npub}:") metadata = await client.fetch_metadata(pk, timedelta(seconds=15)) # Printing each field of the Metadata object print(f"Name: {metadata.get_name()}") print(f"Display Name: {metadata.get_display_name()}") print(f"About: {metadata.get_about()}") print(f"Website: {metadata.get_website()}") print(f"Picture: {metadata.get_picture()}") print(f"Banner: {metadata.get_banner()}") print(f"NIP05: {metadata.get_nip05()}") print(f"LUD06: {metadata.get_lud06()}") print(f"LUD16: {metadata.get_lud16()}") #print(f"Custom: {metadata.get_custom()}") if __name__ == '__main__': parser = argparse.ArgumentParser(description='Fetch all metadata for a given npub') parser.add_argument('npub', type=str, help='The npub of the user') args = parser.parse_args() asyncio.run(main(args.npub)) ```