-

@ 629c4a12:f822cc1a
2025-02-23 21:50:25
Treasury bonds, once considered the gold standard for conservative investments, have struggled to maintain their appeal in an era of low yields and rising inflation. Governments face mounting pressure to rethink their traditional treasury instruments, especially the long duration bonds. Enter Bitcoin—a neutral, decentralized, scarce, and globally recognized asset. By integrating Bitcoin into treasury bonds, governments have a unique opportunity to breathe new life into their sovereign debt markets and attract a new wave of investors.
### Problem: The decline of long-duration sovereign bonds
Around the world, governments are grappling with declining investor confidence in their long-term debt instruments. Major institutional investors have been reducing their exposure to long-dated sovereign bonds due to rising inflation, unsustainable debt levels, and uncertainty around global monetary policies.
In Europe, countries like Italy and Greece have faced heightened yield spreads, reflecting investor wariness over fiscal sustainability. In Japan, long-term government bonds have seen weak demand, despite interventions by the Bank of Japan to stabilize yields. Emerging markets, too, face significant challenges, with higher borrowing costs and limited foreign investor participation in their sovereign bond markets.
Globally, yields on long-term sovereign bonds have risen as investors demand higher compensation for the perceived risks. This inverse relationship between yields and bond prices highlights a broader issue: governments are finding it increasingly difficult to issue long-term debt at sustainable costs.
### Key factors contributing to this global decline include:
* **Persistent inflation:** Eroding the purchasing power of fixed-income returns across global markets.
* **Increased government borrowing:** Leading to an oversupply of bonds in developed and emerging economies alike.
* **Monetary policy uncertainty:** Central bank actions in response to inflation and slowing economic growth have added volatility to bond markets.
As a result, global investors are increasingly favoring short-term bonds or alternative assets, leaving long-term sovereign bonds struggling to attract sufficient demand.
Solution: Bitcoin as collateral for treasury bonds
Governments can collateralize 10% of their 10-year and 30-year treasury bond offerings with Bitcoin. In practice, this means a portion of the bond’s value would be backed by Bitcoin reserves held securely by the issuing government or a trusted custodian. Investors would gain exposure not only to the guaranteed yield of the bond but also to the potential upside of Bitcoin’s price appreciation.
To sweeten the deal, governments could offer tax-free capital gains on any Bitcoin price appreciation realized through this instrument. This would make Bitcoin-backed treasury bonds not only a conservative, yield-generating investment but also a potentially lucrative one.
### Why this matters for governments
* **Attracting a new investor class:** Bitcoin has a growing base of institutional and retail investors. A Bitcoin-collateralized bond could attract Bitcoin enthusiasts and institutional investors seeking compliant exposure to Bitcoin.
* **Strengthening national bitcoin reserves:** By holding Bitcoin as collateral, governments would gradually build Bitcoin reserves, which could act as a hedge against currency devaluation and macroeconomic instability.
* **Enhancing bond appeal in inflationary environments:** In inflationary periods, traditional bonds struggle to offer real returns. Bitcoin’s historical performance as an inflation hedge could help offset this concern.
* **Diversifying reserve assets:** Bitcoin offers a unique diversification benefit compared to traditional reserve assets like gold and foreign currencies.
### Why this matters for investors
* **Dual upside potential:** Investors not only gain the fixed yield of a treasury bond but also the upside of Bitcoin price appreciation.
* **Tax-gree gains on Bitcoin exposure:** The tax exemption on Bitcoin gains would be a significant incentive for investors looking for capital-efficient exposure to Bitcoin.
* **Low-risk Bitcoin exposure:** For more conservative investors, Bitcoin-backed bonds offer a lower-risk pathway to Bitcoin exposure compared to direct ownership.
### Why focus on 10-Year and 30-year treasuries?
Long-term treasuries, such as 10-year and 30-year bonds, are ideal candidates for Bitcoin collateralization due to their extended maturity periods. These longer timelines allow Bitcoin’s historical price appreciation to play a more significant role in generating value for investors. Additionally, they align better with Bitcoin’s long-term investment thesis, making them more attractive to investors seeking both yield and potential asset growth.
Short-term treasuries, on the other hand, are less suited for Bitcoin collateralization due to Bitcoin’s volatility and shorter investment horizons.
Implementation and challenges
While the concept is innovative, there are several practical and regulatory challenges:
* **Custody and Security:** Governments must establish secure custody solutions for Bitcoin reserves.
* **Volatility Management:** Bitcoin’s price volatility could introduce risk into the bond’s collateral structure.
* **Regulatory Clarity:** Clear regulatory frameworks would need to be established to govern these hybrid financial instruments.
However, with the right infrastructure and governance, these challenges are far from insurmountable.
A win-win opportunity
By collateralizing 10-year and 30-year treasury bonds with Bitcoin, governments around the world can tap into the growing Bitcoin economy, attract a new wave of global investors, and future-proof their financial strategies. Investors, on the other hand, gain access to a secure, regulated, and potentially lucrative investment vehicle.
In a rapidly changing financial landscape, integrating Bitcoin into long-term sovereign bonds is not just an opportunity—it’s a strategic imperative. Governments that act decisively could position themselves at the forefront of a new era in global sovereign finance.
-

@ 629c4a12:f822cc1a
2025-02-23 21:33:31
I’ve always been drawn to minimalism. There’s a certain peace that comes from stripping away the unnecessary, decluttering both physical and mental spaces. Yet, when it comes to finances, I’ve found myself tangled in complexity. As an ‘optimizer,’ I spend an inordinate amount of time thinking about investments, managing risk, and endlessly tinkering with my portfolio. This preoccupation contradicts the minimalist principles I try to live by.
It seems absurd to me that the financial world has become so complicated that we need money managers to simply preserve the value of our money. If investing is so intricate that the average person must hire professionals just to preserve (let alone grow) the value of their savings, then something is fundamentally wrong.
For the past five years, I’ve immersed myself in the history and mechanics of financial systems. The deeper I delved, the clearer it became: Bitcoin is a force of minimalism in an increasingly financialized and complex world.
### The Clutter of Modern Finance
Our financial system has become bloated with complexity. The hyper-securitization of assets has created an environment filled with financial clutter. Derivatives, for example, represent layers upon layers of financial engineering, often so convoluted that even experts struggle to understand them fully.
More troubling is the way nearly everything of value has been financialized. Real estate and art, two things that should embody personal value and cultural significance, have been transformed into mere asset classes. They are bought, sold, and speculated upon not for their intrinsic qualities but as instruments in the game of wealth preservation.
But why has this happened? It’s actually quite simple: our money is constantly losing value. The dollar, for example, debases at a rate of around 7% per year. Holding cash feels like holding melting ice, so it’s only natural for people to seek out scarce assets to preserve their wealth.
The Never-Ending Game of Diversification
This pursuit of scarce assets sets off a complex game—a game that forces people to diversify endlessly:
* Equities
* Bonds
* Real Estate
* Commodities
* Art
* Collectibles
We’re told to spread our investments across these asset classes to mitigate risk and preserve our hard-earned money. Those who can afford to hire money managers generally fare better in this game, as they have access to expertise and strategies designed to navigate this maze of complexity.
Ironically, this system creates an incentive for more complexity. The more convoluted the financial landscape becomes, the more we need money managers, and the more entrenched this cycle of financialization and securitization becomes. It’s a force of ever-increasing entropy—quite the opposite of minimalism.
### Bitcoin: Simplicity in a Complex World
In the midst of this financial chaos, Bitcoin emerges as a beacon of simplicity. It offers a way out of the clutter, a chance to reclaim financial minimalism. Bitcoin embodies the concept of scarcity with a rare kind of perfection: there will only ever be 21 million Bitcoins. No more.
This scarcity makes Bitcoin the perfect savings technology. Unlike traditional currencies, no one can debase your holdings. You don’t need to chase after real estate, art, or other assets to preserve your wealth. You don’t need to constantly diversify and rebalance a portfolio to stay ahead of inflation. Bitcoin’s scarcity gives you a way to hold your wealth securely, without the need for endless tinkering.
I’m not blind to Bitcoin’s short-term price volatility. However, it’s crucial to understand that we’re still in the early stages of adoption. As more people embrace this perfect form of scarcity, Bitcoin’s qualities as savings technology will express itself.
Bitcoin has the potential to de-financialize the housing market. It can de-financialize art.
Ultimately, Bitcoin has the power to replace those aspects of our lives that currently serve as proxies for scarcity.
### A Minimalist Approach to Wealth
Bitcoin allows us to step off the treadmill of constant financial optimization. It offers a simpler way to safeguard the fruits of our labor. Rather than spending our time, energy, and attention on navigating a complex financial system, we can focus on what truly matters: living a meaningful life.
By embracing Bitcoin, we embrace a minimalist approach to wealth. We reject the idea that we must play a never-ending game of diversification to maintain our standard of living. Instead, we adopt a simple, elegant solution that aligns with the principles of minimalism.
### Conclusion
In a world that grows more financially cluttered by the day, Bitcoin stands as a path to financial minimalism. It frees us from the complexities of traditional finance, allowing us to preserve our wealth without the need for constant vigilance and management.
By embodying scarcity and simplicity, Bitcoin gives us a way to reclaim our time and energy. It’s not just a financial tool; it’s a way to simplify our lives, to step back from the chaos, and to focus on what truly matters
-

@ c11cf5f8:4928464d
2025-02-23 20:42:52
Let's hear some of your latest #Bitcoin purchases, feel free to include links to the #shops or #merchants you bought from too. Any good #deal we should know about?
If you missed our last thread, [here](https://stacker.news/items/887305/r/AG) are some of the items stackers recently spent and #zap #sats on.
originally posted at https://stacker.news/items/895134
-

@ 378562cd:a6fc6773
2025-02-23 20:41:59
Social media platforms like Facebook and X (formerly Twitter) have long dominated online communication. However, many people are looking for alternatives due to increasing censorship, algorithmic manipulation, and corporate control over user data. One of the most promising new protocols I have found is Nostr, a decentralized and open-source alternative to traditional social media. But how does Nostr compare, and why should you consider making the switch? If you're reading this, presumably, you already have made the switch, but share this with friends if you like. Let’s dive in.
The Fundamental Differences Between Nostr and Traditional Social Media
1. Decentralization vs. Centralization
Facebook and X are owned and operated by massive corporations that control everything from content moderation to algorithmic visibility. Your posts, followers, and interactions are at the mercy of the company's policies and changes.
Nostr: No single entity owns Nostr. It operates as a protocol where anyone can run a relay (a server that transmits messages). Users are not tied to a single company or platform, ensuring freedom from corporate control.
2. Censorship Resistance
Facebook & X: Heavily moderate content, often removing posts or banning accounts based on internal policies, government pressure, or **advertiser** demands.
Nostr: Built to resist censorship. Since users publish to multiple relays, blocking content on one relay does not remove it from others. You control where your messages are sent, not a centralized authority.
3. User Ownership and Privacy
Facebook & X: Your data is stored on corporate servers and often sold to advertisers. You don’t truly own your content or connections.
Nostr: Users control their private keys, which function like cryptographic signatures. Your identity is yours alone, and no company can take it away.
4. Algorithm-Free Experience
Facebook & X: Content is curated by algorithms that determine what you see based on engagement metrics, often promoting divisive or viral content over meaningful conversations.
Nostr: No forced algorithms. You decide which relays to use and what content to follow. Your feed remains chronological and free from corporate influence.
Pros and Cons of Nostr
✅ Pros:
True freedom of speech: No corporate moderation, allowing open discussion.
User-owned identity: You control your account with a cryptographic key.
No ads or tracking: Your data isn’t harvested or sold to advertisers.
Resilient against shutdowns: Multiple relays ensure content persists even if one relay goes offline.
Customizable experience: Choose the relays and clients that best suit your needs.
❌ Cons (If Any):
Early-stage adoption: Not as many users as Facebook or X (yet!).
Technical learning curve: Requires setting up keys and understanding relays, though improving rapidly.
Lack of centralized moderation: While this is a pro for free speech, it can also mean exposure to spam or undesirable content if it is not filtered properly. However, they are developing hidden or block features to help control your feeds. I don't have a lot of worries here. To be perfectly honest, it seems like a better class of people come here.
Why Should You Leave Facebook and Join Nostr?
If you’re tired of algorithmic manipulation, invasive tracking, and corporate censorship, Nostr offers a fresh start. It’s a place where your voice truly belongs to you, and a centralized authority cannot control your connections.
Yes, it may take some time to adjust to using Nostr, but the benefits far outweigh the minor learning curve. If you value digital freedom, privacy, and resistance to censorship, now is the perfect time to explore the future of social networking.
How to Get Your Friends to Leave Corporate Social Media and Join Nostr
Switching to Nostr is one thing, but convincing your friends to make the leap can be challenging. Here are some practical ways to help them transition:
Explain the benefits: Many people don’t realize how much control corporations have over their online experience. Share this article and highlight the key points.
Make it easy: Walk them through setting up a Nostr account, generating a private key, and connecting to relays.
Show them the community: Introduce them to active Nostr users, groups, and discussions to make the transition feel worthwhile.
Lead by example: Use Nostr consistently and post compelling content that makes it appealing to your friends.
Keep the conversation going. As more people join, Nostr will become even more engaging, making it a true alternative to corporate-controlled platforms.
-

@ badc29af:a92bd071
2025-02-23 20:34:58
**Part I: The First Hour (Blocks 694,200–694,205)**
**Block 694,200: The Coder**\
Sarah Chen sat hunched over her keyboard in her San Francisco apartment, the fog smudging her window. Debugging a fintech app, she watched block 694,200 confirm on the Bitcoin blockchain. Suddenly, its architecture snapped into focus: not just code, but a defiance of artificial abundance.\
"Holy shit," she whispered, easing back from her desk, her monitor casting light on scattered ramen cups. She’d coded financial systems for years, but now she saw money’s true potential—scarce, digital, unbound.
**Block 694,201: The Entrepreneur**\
Ten minutes later, in a steamy Lagos cybercafé, James Okonjo’s world shifted as block 694,201 locked in. Struggling with payment delays under Nigeria’s currency controls, he read about Bitcoin’s borderless flow.\
"No more gatekeepers," he said, startling nearby patrons. His hands shook as he set up his first wallet, already dreaming of a Bitcoin education platform for African developers.
**Block 694,202: The Economist**\
In Caracas, Maria Rodriguez paced before her Universidad Central de Venezuela class, dissecting inflation’s latest surge. As block 694,202 formed, the idea of fixed-supply money hit her like a revelation.\
"Forget this slide," she said, closing her laptop. "Let’s talk proof-of-work." Her students stared, but her mind was already racing with possibilities.
**Block 694,203: The Retiree**\
In Tokyo, Hiroshi Yamamoto sipped tea during his morning portfolio review when block 694,203 confirmed. A retired salaryman, he saw Bitcoin as a shield against decades of yen erosion. Quietly, he began researching wallets, his curiosity ignited.
**Block 694,204: The Prodigy**\
In Toronto, 16-year-old Emma Chen, a coding whiz, stumbled across block 694,204 while tinkering online. The power to program her own money dawned on her. She grinned, diving into Bitcoin’s whitepaper with reckless glee.
**Block 694,205: The Shopkeeper**\
In Buenos Aires, Carlos Mendoza tallied his shop’s dwindling profits as block 694,205 ticked into existence. Sick of the peso’s collapse, he found Bitcoin—an escape from financial quicksand. By nightfall, he’d downloaded a wallet app.
---
**Part II: The First Day (Blocks 694,206–694,343)**
**The Morning Wave (Blocks 694,206–694,247)**\
Over the next 42 blocks—about seven hours—as Asia slept and Europe stirred, the awakenings multiplied:
**Block 694,206**: A Swiss banker questioned her fiat career.
**Block 694,207**: A German programmer marveled at Bitcoin’s consensus beauty.
**Block 694,208**: A Korean gamer saw virtual gold turn real.\
The chain hummed, each block birthing new believers, ten minutes apart.
**The American Session (Blocks 694,248–694,295)**\
As Wall Street woke, blocks 694,248 to 694,295—eight hours—marked a finance-world reckoning:
**Block 694,248**: A Connecticut hedge fund manager saw through fiat’s illusions.
**Block 694,249**: A Chicago commodities trader grasped digital scarcity.
**Block 694,250**: A Texas pension admin envisioned a sounder future.\
Each block stamped a timestamp on their transformation.
**The Global South Rises (Blocks 694,296–694,343)**\
The day’s final stretch—48 blocks, eight more hours—saw the global south ignite:
**Block 694,296**: Brazilian students planned Bitcoin beach hubs.
**Block 694,297**: Indonesian merchants linked Lightning payment loops.
**Block 694,298**: South African miners turned solar power into hash rate.\
The chain pulsed, relentless, binding them all.
---
**Part III: The Network Effect (Beyond Block 694,343)**
**The Teachers (Block 694,344)**\
Sarah quit her job at block 694,344, coding Bitcoin education tools. James’s platform launched, reaching Africa’s devs. Maria’s NOSTR lectures spread, her voice a beacon.
**The Builders (Block 694,345)**\
At block 694,345, innovation bloomed: privacy upgrades, scaling fixes, Lightning finance tools. The awakened built atop the chain.
**The HODLers (Block 694,346)**\
By block 694,346, others simply held—silent sentinels whose faith grew with each block, each halving.
---
**Epilogue: The Endless Chain (Blocks Onward)**
The awakening rolled on, ten minutes at a time. Block 694,347 saw a Mumbai coder join Sarah’s cause. Block 694,348 brought a Nairobi merchant to James’s platform. Block 694,349 swayed a Manila policymaker with Maria’s words.
Every block—144 a day—sparked new stories: dreamers seeking freedom, builders crafting tools, HODLers standing firm. Money, they understood, was too vital to be ruled by power. From block 694,200, the chain stretched forward, a living testament to scarcity, ownership, math over might.
Each block was a birth, each hash a heartbeat, each Bitcoiner a node in a network of financial truth—marching on, block by block, toward a harder, sounder world, forever verified, never permissioned, growing but never diluted, ten minutes at a time.
-

@ 629c4a12:f822cc1a
2025-02-23 20:27:36
This is test 2
-

@ d34e832d:383f78d0
2025-02-23 19:53:32
Hockeypuck is an **OpenPGP keyserver** that allows users to publish, search, and retrieve **PGP public keys** for secure communication. It is designed for **federation** with other keyservers and supports a **high-performance, scalable** architecture.
---
## **🛠️ Usage**
### **1. Public PGP Key Directory**
- Organizations, security researchers, and privacy-focused users can **publish and retrieve PGP keys** for encrypted email and document verification.
- Similar to **SKS Keyserver**, but actively maintained and more scalable.
### **2. Enterprise PGP Key Management**
- Companies can **host a private keyserver** for internal teams to share PGP keys securely.
- Prevents reliance on external keyservers like keys.openpgp.org.
### **3. Decentralized Identity and Key Distribution**
- Used in federated **PGP keyserver networks** like **Hockeypuck & SKS pools** to distribute OpenPGP keys across multiple servers.
- Useful for **distributed trust models** where multiple organizations manage keys collaboratively.
### **4. Bitcoin & Nostr Applications**
- Can be used alongside **Nostr** for key verification, ensuring public keys are retrievable for cryptographic signatures.
- Useful in **Bitcoin** applications where PGP-signed messages confirm identity.
### **5. Software Package Signing**
- Developers and package maintainers can **sign software updates** using OpenPGP, and end users can fetch public keys from Hockeypuck to verify authenticity.
- Example: **Debian and Arch Linux package signing**.
### **6. Secure Messaging**
- Supports secure email systems using **PGP-encrypted mail (e.g., ProtonMail, Thunderbird + Enigmail, Mailpile, etc.)**.
---
## **📌 Key Benefits**
✅ **Docker-Based Deployment** → Easily installable with **Docker** and **docker-compose**.
✅ **Federated Keyserver** → Can join existing **PGP keyserver networks**.
✅ **High-Performance Storage** → Uses PostgreSQL for better performance than older SKS keyservers.
✅ **Supports HTTP & HTTPS** → Can be hosted publicly with **TLS encryption**.
✅ **Fully Open Source** → Maintained as a modern alternative to SKS.
## **🔑 Signing a Nostr Event Using PGP & Verifying It on a Relay**
If Alice wants to **prove she controls `npub1xyz...`** using **PGP**, she can sign a Nostr event and publish both the event and signature.
---
### **🔹 Step 1: Create a Nostr Event (Kind 0)**
Alice generates a **Nostr profile metadata event**:
```json
{
"id": "xxxxxxxxxxxxxxxxxx",
"pubkey": "npub1xyz...",
"created_at": 1700000000,
"kind": 0,
"tags": [],
"content": "{ \"name\": \"Alice\", \"about\": \"PGP Verified Nostr User\" }"
}
```
She saves this as **`nostr_event.json`**.
---
### **🔹 Step 2: Sign the Event with PGP**
Alice uses GnuPG to sign the event:
```bash
gpg --clearsign --armor nostr_event.json
```
This creates **`nostr_event.json.asc`**, which contains the event with a **PGP signature**.
🔹 **Example of the signed event:**
```
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA256
{
"id": "xxxxxxxxxxxxxxxxxx",
"pubkey": "npub1xyz...",
"created_at": 1700000000,
"kind": 0,
"tags": [],
"content": "{ \"name\": \"Alice\", \"about\": \"PGP Verified Nostr User\" }"
}
-----BEGIN PGP SIGNATURE-----
iQIzBAEBCAAdFiEEbGSk4HTlMz5tG0tF0Y8fO3HTQYYFAmS8mOkACgkQ0Y8fO3HT
QYYX4w/+JwzbfM1EZ2F7H3yqbdGBJ2cGd...
-----END PGP SIGNATURE-----
```
---
### **🔹 Step 3: Upload the Signature to a Public Keyserver**
Alice submits her signed Nostr event to the **Hockeypuck keyserver**:
```bash
curl --data-binary @nostr_event.json.asc https://keyserver.example.com/pks/add
```
---
### **🔹 Step 4: Publish the Event to a Nostr Relay**
Alice **publishes the original event** to a Nostr relay:
```bash
curl -X POST https://nostr-relay.example.com/ -d @nostr_event.json
```
---
### **🔹 Step 5: Verification**
Anyone can **fetch Alice’s PGP-signed event** and verify it:
```bash
curl "https://keyserver.example.com/pks/lookup?op=get&search=alice@nostr.example.com" | gpg --verify
```
If successful, it will show:
```
gpg: Good signature from "Alice <alice@nostr.example.com>"
```
---
### **✅ Use Cases**
1. **Proving Ownership of a Nostr Public Key** with PGP.
2. **Bitcoin Applications**: PGP-signed messages can confirm identities for multisig coordination.
3. **Decentralized Web of Trust**: Verifying Nostr users via signed events.
---
Additionally a simple JS or python script could automate signing process.
-

@ 3ffac3a6:2d656657
2025-02-23 19:40:19
## Renoters: Proposal for Anonymous Event Relaying in Nostr
*This document is a proposal and not an official NIP.*
This Document proposes "Renoters," a mechanism for anonymous event relaying in Nostr, inspired by the Mixminion remailer design. Renoters aim to enhance privacy by obscuring the origin of events, making it difficult to trace the author of a message.
### **Motivation**
While Nostr offers a decentralized platform, current relay mechanisms can potentially reveal the source of events. Renoters address this by introducing an onion-routing-like system where events are encrypted and relayed through a series of nodes, making it harder to link the event to its originator. This enhances privacy for users who wish to communicate anonymously or protect their identity.
In some totalitarian regimes, the use of Tor and VPNs is criminalized, making online anonymity dangerous. Even in some democratic countries, merely downloading Tor can mark individuals as suspects. This underscores the need for a decentralized and anonymous communication system that operates independently of commonly surveilled privacy tools.
### **Proposed Solution**
Renoters operate on the principle of "gift-wrapping" events, using asymmetric encryption. A user wishing to send an event anonymously performs the following steps:
1. **Event Creation:** The user creates the Nostr event they wish to publish.
2. **Renoter Path Selection:** The user selects a path of Renoters through which the event will be relayed. This path can be pre-configured or dynamically chosen.
3. **Gift Wrapping (Encryption and Signing):** The user encrypts and signs the event for each Renoter in the path, working in reverse order:
- A *new* random Nostr private key (`sk_wrapper`) is generated.
- The event (or the previously wrapped event) is encrypted using the *next* Renoter's Npub (`npub_next`) using Nostr's standard encryption mechanism (e.g., using shared secrets derived from the private key and the recipient's public key).
- A *new* Nostr event is created. This "wrapper" event's content contains the ciphertext. The wrapper event is signed using the newly generated private key `sk_wrapper`. The wrapper event also includes the next hop's `npub_next` (or the final destination if it's the last renoter) in cleartext, to allow for routing.
4. **Publication:** The user publishes the *first* gift-wrapped event (the one encrypted for the last Renoter in the path). This event is sent to a regular Nostr relay, which then forwards it to the first Renoter in the path.
5. **Renoter Relaying:** Each Renoter in the path receives the gift-wrapped event, verifies the signature using the `sk_wrapper`'s corresponding public key, decrypts it using its own private key, and forwards the decrypted event (now wrapped for the *next* Renoter) to the next Renoter in the path. This process continues until the event reaches the final Renoter.
6. **Final Delivery:** The final Renoter decrypts the event and publishes it to the Nostr network.
### **Example**
Let's say Alice wants to send an event anonymously through Renoters R1, R2, and R3.
1. Alice creates her event.
2. She generates a random private key `sk3` and encrypts the event with R3's public key `npub_r3`.
3. She creates a wrapper event containing the ciphertext and `npub_r3`, signed with `sk3`.
4. She generates a random private key `sk2` and encrypts the previous wrapper event with R2's public key `npub_r2`.
5. She creates a wrapper event containing this ciphertext and `npub_r2`, signed with `sk2`.
6. She generates a random private key `sk1` and encrypts the previous wrapper event with R1's public key `npub_r1`.
7. She creates a final wrapper event containing this ciphertext and `npub_r1`, signed with `sk1`.
8. Alice publishes this final wrapper event.
R1 decrypts with its private key, verifies the signature with the public key corresponding to `sk1`, and forwards to R2. R2 decrypts, verifies the signature with the public key corresponding to `sk2`, and forwards to R3. R3 decrypts, verifies the signature with the public key corresponding to `sk3`, and publishes the original event.
### **Renoter Incentives (using Cashu)**
To incentivize Renoters to participate in the network, this NIP proposes integrating Cashu tokens as a payment mechanism.
- **Token Inclusion:** When a user creates the initial gift-wrapped event (the one sent to the first Renoter), they include a Cashu token *within* the event content. This token is itself encrypted and wrapped along with the original message, so only the receiving Renoter can access it.
- **Renoter Redemption:** Upon receiving a gift-wrapped event, the Renoter decrypts it. If the event contains a Cashu token, the Renoter can decrypt the token and redeem it.
- **Renoter Behavior:** Paid Renoters would be configured *not* to relay events that do *not* contain a valid Cashu token. This ensures that Renoters are compensated for their service. Free Renoters could still exist, but paid Renoters would likely offer faster or more reliable service.
- **Token Value and Tiers:** Different Cashu token denominations could represent different levels of service (e.g., faster relaying, higher priority). This could create a tiered system where users can pay for better anonymity or speed.
- **Token Generation:** Users would need a way to acquire Cashu tokens. This could involve purchasing them from a Cashu mint or earning them through other means.
### **Security Threats and Mitigations**
- **Anonymity Against Correlation Attacks:** Even when using Tor, traffic patterns can still be analyzed to infer the origin of events. To mitigate this risk, Renoters can introduce:
- Random delays in event relaying.
- Dummy packets to complicate statistical analysis by malicious observers.
- **Replay Attacks:** To mitigate replay attacks, each Renoter must store, for a reasonable period, the IDs of received events and the decrypted events that were forwarded. This ensures that duplicate messages are not processed again.
- **Sybil Attacks:** Sybil attacks can be mitigated by requiring payments via Cashu tokens for relaying events, increasing the cost of launching such attacks. By ensuring that each relay operation has a monetary cost, attackers are discouraged from creating large numbers of fake identities to manipulate the network.
- **Traffic Analysis:** Traffic analysis can be mitigated by using Tor for Renoters. Routing events through the Tor network adds an additional layer of anonymity, making it more difficult to track message origins or infer sender-recipient relationships. While Renoters enhance privacy, sophisticated traffic analysis might still be a threat.
### **Operational Considerations**
- **Renoter Reliability:** The reliability of the Renoter network is crucial.
- **Latency:** Relaying through multiple Renoters will introduce latency.
- **Key Management:** While each layer uses a new key, the initial key generation and path selection process need to be secure.
This NIP provides a robust framework for anonymous event relaying in Nostr, leveraging encryption and Cashu-based incentives to enhance privacy and usability.
### **References**
- **Untraceable Electronic Mail, Return Addresses, and Digital Pseudonyms**: David L. Chaum (https://dl.acm.org/doi/10.1145/358549.358563)
- **Mixminion Design**: Mixminion: Design of a Type III Anonymous Remailer (https://www.mixminion.net/minion-design.pdf)
- **Nostr Protocol**: Official Nostr Documentation (https://github.com/nostr-protocol/nostr)
- **Cashu Token System**: Cashu: Ecash for Bitcoin Lightning (https://cashu.space/)
- **Tor Project**: The Tor Project - Anonymity Online (https://www.torproject.org/)
- **Onion Routing**: The Second-Generation Onion Router (https://svn.torproject.org/svn/projects/design-paper/tor-design.pdf)
#Privacy #Nostr #Anonymity #Crypto #CensorshipResistance #OnlinePrivacy #Decentralization #Encryption #Security #ThreatMitigation #Micropayments #CryptoEconomy #NextSteps #Development
-

@ f3873798:24b3f2f3
2025-02-23 19:21:48
A liberdade de expressão e a descentralização do poder estão intimamente ligadas ao avanço do pensamento humano e à construção de uma sociedade mais justa e consciente. A evolução da compreensão sobre o certo e o errado surge da comunicação, da observação empírica e da análise das consequências de ações passadas.
Para que haja uma aproximação real com a verdade e uma relação equilibrada entre a razão da vida e o convívio com o poder, é essencial garantir a liberdade de expressão. Somente por meio do livre debate de ideias é possível avaliar as diversas perspectivas, identificar erros e aprender com eles.
Embora a maioria das pessoas busque o aprendizado e a compreensão do que é correto, o apego cego a uma ideia evidentemente equivocada pode fazer com que percam o real propósito da busca pela verdade. Em vez de refletirem criticamente, muitos acabam apenas defendendo um erro pelo simples fato de se identificarem com ele.
Esse é um dos motivos pelos quais a censura tem se tornado uma ferramenta tão temida e contestada. Ilude-se quem acredita que a censura existe apenas para combater crimes e golpes. Na realidade, quanto maior a censura, mais favorecidos são aqueles que desejam ocultar informações, tornando ainda mais difícil a identificação e o combate a abusos.
Nos países livres, onde a liberdade de expressão é respeitada, há maior autonomia nas decisões políticas e um engajamento mais ativo da população. A participação cidadã fortalece o controle do povo sobre as influências que moldam o convívio social, garantindo que o poder não fique concentrado nas mãos de poucos, mas distribuído de forma mais democrática e justa.
-

@ ef1744f8:96fbc3fe
2025-02-23 19:12:52
6/WRXHyH0NZbnQJ9LX+VZnSZBv5Y3iYgws/SZV0BVXSE4c8GJp9/HVp2ZfUsstNeQ6KDIA2LVlmrnnW7Dwb6rr09Tbh79cQp7LukzkVzjtWJ6FlWkM8iaHW6YgET77s1PfZV0fZ9tVpXo77byWCMI/R8feh2BhQ7Nhr35AnLhWa++0jKtIRSShY+BRKGusyT8zn09pYg4Wg8rDosilrbd4GUX6QqMguLuiBSi7D8VRWAXEkSefV0T04QUeVyvIcIloKAkLqQloVAHGPMJc65GtVc1705lI4aa62aGraGhg1yEXkr5PelI3X1P5PYx29NZbPyeSUBh40dJQFZmYDxV9WSPUtJqIn/1gQUW0jueCuQASpNfKr17F2bHvcIOeOp+ukbWfbYDWt4IammFZCuXw==?iv=r1dw0EG1b8Fvsxm+8ykvRA==
-

@ ef1744f8:96fbc3fe
2025-02-23 19:12:47
UvEa5PR6FF+PYlYXJM9Sqt06t01ARuO5vW2ct5SyIg4+aA4nq38Mofx2NI5YydZJcn9iQO2f0nlgIJaMFuDYBLXQFHklMlq7OfY5UyTnOFZ8Js9NwIMI1I7IVWp6qPEBSp5z0OmKOB1g2Z1jEZrySpkMd53AjaeYXiEyT5IMSDsKjxAbwuLRWaZiCWKtxKJxRdT/VUvYeE9dIfnadSkZdF8oIT6PlZYlgQ836Rt7X4O6hA/ydm1Hrc/1H/eTuKS8ePXZs5E4b/+XtgPclYqMPdUzD5/4rplIRJJXZQZX3cWiGC/0ilWIqyItead3JhwPAb+lNAyycfYelZRNjI10U719a0wjBsc0q7PgjQvSze4=?iv=uIyBfCznssKHgZaTSeUpbw==
-

@ ef1744f8:96fbc3fe
2025-02-23 19:08:09
wleig1qZtQh8+b2BEGuJl1Cug0McB7COckI3WeF/654AXNK2nrxnYZS/p/mZ2JNW4IVEOu8vrhb0w3l8VZP5BUdAqY/Ex3H0XhKTRUKNcwunirweS2DYC+F5P6VC9hUTRaLmhlmnqFU5Hmj/fwSCKfv9wfUOveaTvwV7SJLtH5n5qRrbwfwHyOexJw0e3NTcUvklklroaW7MiQIPcsEVLldQ/BYoLFee6330gfFxAwEEC5JrUR/kSatULlMMfm9WKoPF2CGwD/eVIrpc5CS+yS4meIS2d1YLFy5LmCHpnqcCiLCGOPmBTDW0iJCjWarbDJFcHibwZCvp8rNv4lHxlKpGP26dYDGHp4gUifXgf+U=?iv=XVG/yZf2/q0uHCOAvBxAUQ==
-

@ ef1744f8:96fbc3fe
2025-02-23 19:07:54
/hQoalQuH7Vp8NLH0TwCxIAPmLziuM/rOlXEJw2NkUMnzojVUkDft8aujNYnK2NzWTW6Cj3a8B8F+uvsJiARBQcDWZIEzSnlDe3uk+LBf53yGtn49KTv7Wm6mB1luqC8bCvulLxJquD7KCH3Cum82z1dPxxZ7OeBCAOht0duQToWZ+hZ3nixGKSYl3gBzzvHbxgrpuBpxTxKlG8DqpmaWTqIKvv0qVeJE5/kj1Hsa7RytJyEdXP7IIVXR46IRpmsxUP4yg1zJRwy9oVJz8ZXbdrJqYebVmhyWOdqq6r+T4LzJXuPELlzi5C6bMqAVuO+899r8Ixo/DfYa/QnFw+sHZT95omH6/TSzoVsLW/JPkc=?iv=hBMT+C7DLhHbT2xpaEFeWg==
-

@ ef1744f8:96fbc3fe
2025-02-23 19:07:41
jBiT1F1hY5a3Vq2M4HQw8gzVRLsjgq55R7BiuA27ArQTWpw4IPwLwljsZ5LDgw3GrZLbDXwFJchQxD7uBvMnMJWhyNTCcrrtG+HEwOKI2QNoOuvD/7ilDa6LRkH27dcJkwYykm4m2Z/55OKy/tFlDmuILrVI292kLmYtaM5a9J0BCzEjUYD2y3rsSEao33ffBPr1sguZqJ4v+6+JPI/v2g90RrJx4SUS8rwi4u+JK7NmFZ8kvQ/2q3pkxQlGQwHO6QJvjojhnP1wh10Hfjv55Zy12QCoIFEwfEyXiVgiY28eiLqMmFwuew73/KlDac/7cK46SY8Ctc9XCCVyMIeWrtvAf9Xv/gaXf+Bdma9nFd49ajE0vTu1ek0w/VAjbDMM?iv=0lLA9SdWMNruCC1dP2LLgA==
-

@ ef1744f8:96fbc3fe
2025-02-23 19:07:38
3jqbINLb+Eu6xeXqFoZnxGx1vWAPYzmPDiD7QWXr7gEmomwqlvfMkaP//6lgCfRZWMgQ+CwOy8O87HiQVlKz4S7Or1EJD50aWxSLkPWsIxvP7qbQucBZT4dGJZcfx1roCbmatYwiFsEx82qmbpm8otkry7GI5tCFVMpFzvgW2W03j+ogXmvPgrgrta5RJT6eHX0HlzoRPmUi7MUzulSCnIWWwB+mrSbP5UHsPuwyNAsS5y3o4v0poQKEFEPRhin1x3e+Ng1TaaSvtqS8cDsJbl+MR/Tg+rf5tY7vJYWfE08I7oAu5onu5sPwQxRAdsugUUkHTqV4NFHPtRdUXETzpZWMnMzjRNQQxJxKCvAx1kNQPAawWMmiVm+D2CxTMsQF6ppj7Fy/2k071Atbyo1U24EAxnpe4QKxmRYmqGFi1/8=?iv=putQEJoUu8Jq2j5iMUe+5w==
-

@ ef1744f8:96fbc3fe
2025-02-23 18:57:50
PYb07VjQ46ph8Nm/1ChBV/71d/mvwfdg1JbshVfDENrQm77om+bb4qswyBwZ9Jd7j2ZWbQJZ4RLwEu4UG/kz93RkY7z8/fGDZWp4X2BGQKnayQmlVZW+nVfyQ1EWHiAUSbDZglbFBCM7OfpEA/bSTC0K0hacqvNF/c7OStbcK3rtYAlSoOmOd18uYFaCnZFC20IplacQitbEPRkWbCY7jk1J1n1axFXcYO37n9fR/Phor6TCLx0Mlqdv1AlqCA0Z9kuf9OwqGO/vp7FtdMDNowDFLdFSiYTO+q0Mt40oiGuHbJKdCRXczEnLZiXEuhgIIckFdN0pPHvyl9bfuU5H587nNhIBgkG8uh1U5RVVBCbixHkXGgtXUzUbPE/66AKTkYlXZM85VuOVduEoKzGwBqZCHcD/s33mdKI0eDUXrE5VrgzUFMBP1FKz7R2P6L6d?iv=EwWM5EBKuyRHXzIajYDOkw==
-

@ 2e8970de:63345c7a
2025-02-23 18:38:06
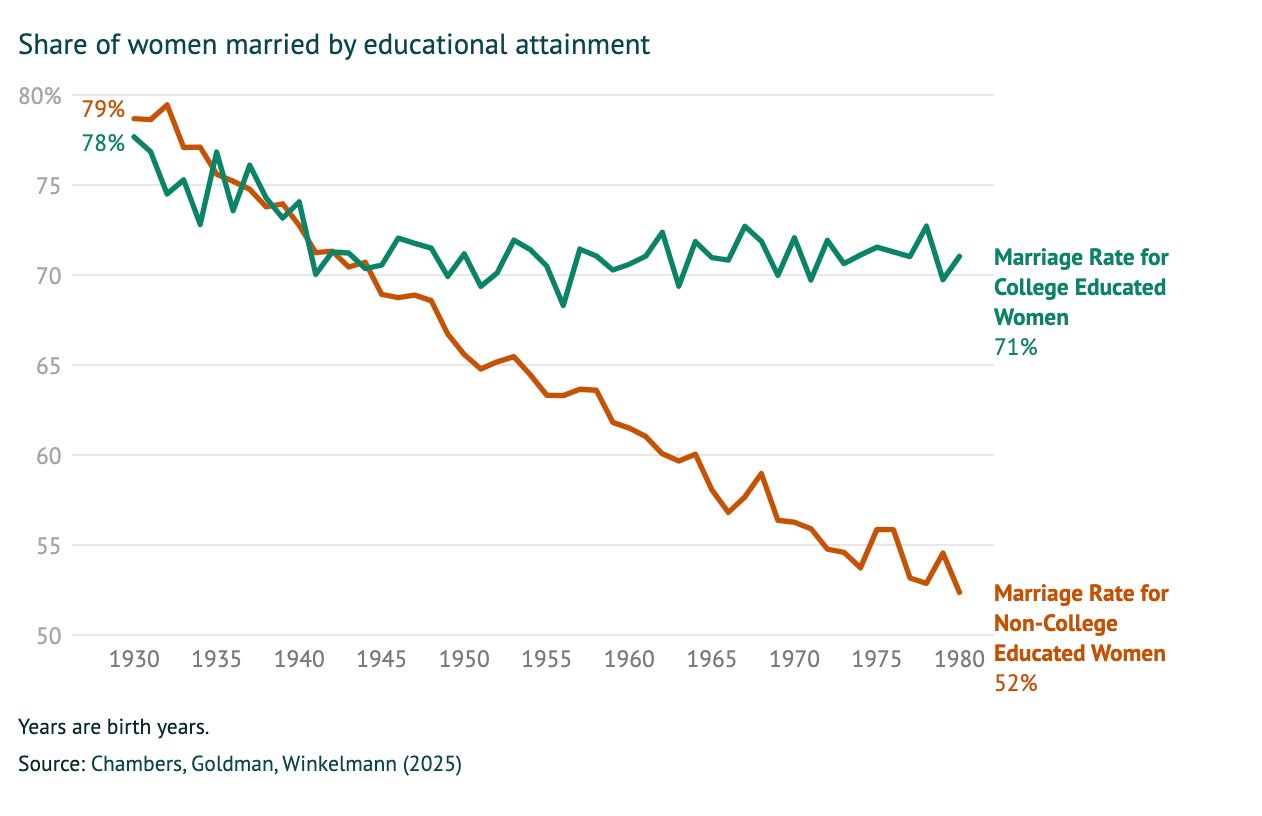
> 1 in 5 women with a BA are willing to marry a man without one
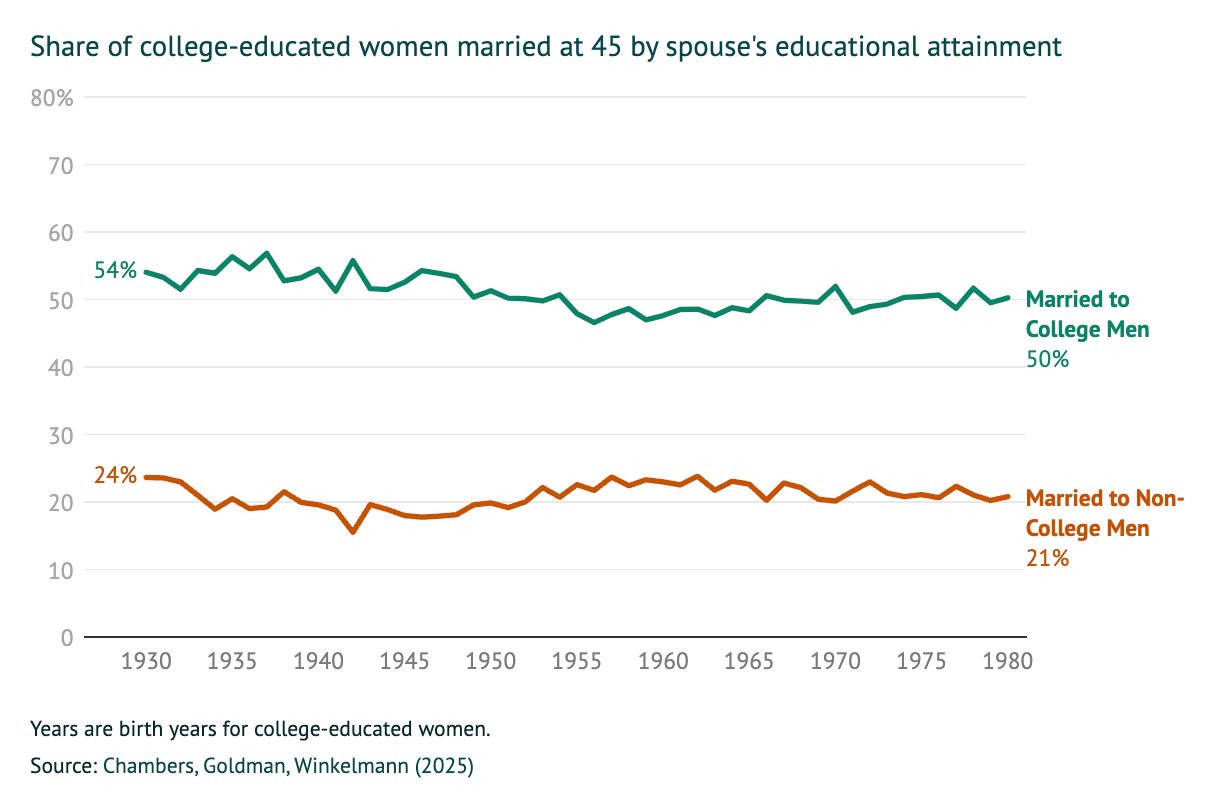
> But crucially, the men without a BA married to women with a BA are those with better earnings. So women "marry down" educationally, not so much economically
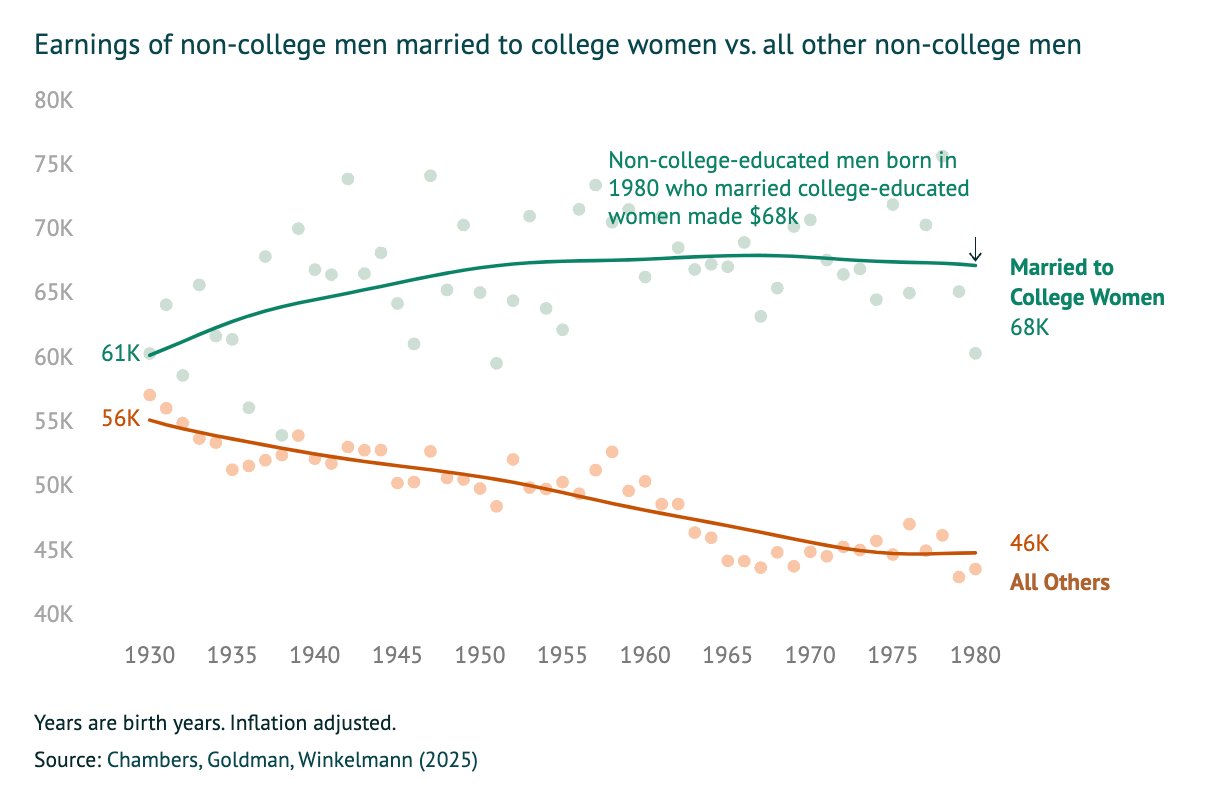
> Why aren't women without a BA marrying men without one? Short answer: economic viability. In areas where men from lower-income backgrounds are doing better. women are more likely to be married

https://aibm.org/research/will-college-educated-women-find-someone-to-marry/
originally posted at https://stacker.news/items/895044
-

@ f7d424b5:618c51e8
2025-02-23 18:01:38
(This was originally posted on melonmancy.net which is a blog on write.as, an ActivityPub based blogging instance)
Listeners rejoice as we are joined today by [ironee212 @ shitposter.world](https://shitposter.world/ironee212)
Another major videogame release happened since we last recorded and it looks like a big stinker, or is it? All that and more in today's episode.
We mentioned a few things in the show you might want to pull up while listening, they are the following:
- [Avowed steam chart](https://steamdb.info/app/2457220/charts/)
- [TF2 SDK news](https://www.teamfortress.com/post.php?id=238809)
Obligatory:
- [Listen to the new episode here!](https://melonmancy.net/listen)
- [Discuss this episode on OUR NEW FORUM](https://melonmancy.cafe/d/103-mp101-my-favorite-body-type-b)
- [Get the RSS and Subscribe](https://feeds.rssblue.com/melonmancy-podcast) (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at [newpodcastapps.com](http://newpodcastapps.com/)
- Or listen to the show on [the forum](https://melonmancy.cafe) using the embedded [Podverse](https://podverse.fm) player!
- [Send your complaints here](https://melonmancy.net/contact-us)
Reminder that this is a [Value4Value](https://value4value.info/) podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
Our podcast is created entirely with free software and is proudly hosted on [RSSBlue!](https://rssblue.com)
-

@ 04ea4f83:210e1713
2025-02-23 17:38:11
Erschienen in [Citadel 21 Vol. 21](https://www.citadel21.com/are-you-tired-of-clown-world?ref=europeanbitcoiners.com) | Veröffentlichung 21.03.2023 \
Autor: [Knut Svanholm](https://twitter.com/knutsvanholm?ref=europeanbitcoiners.com)\
Übersetzt von: [Sinautoshi am 24.03.2023 - 782344](https://twitter.com/Sinautoshi_8_21?ref=europeanbitcoiners.com)\
\
Rückblickend sieht das Jahr 2022 wie eine Art Höhepunkt aus. Während der Großteil der Gesellschaft weitgehend vergessen hat, was die politische Klasse ihren Untertanen während der sogenannten Pandemie angetan hat, kotzte Hollywood weiterhin Inhalte aus, die von „diversen" Regisseuren und Drehbuchautoren produziert wurden und bis zum Rand mit nicht ganz so subtilen Botschaften und Verachtung für ihr Publikum gefüllt waren.
Star Wars und Marvel haben nach der Übernahme durch Disney auf diese Weise Franchise-Mord begangen, und auch das Erbe von *Der Herr der Ringe* wurde von der linken Idiotie vergewaltigt und für immer befleckt. Jetzt gibt es von jedem männlichen Avenger eine weibliche Version. Hugh Jackman, der Schauspieler, der früher die Hauptrolle des X-Men-Mutanten Wolverine spielte, empfahl seinen Anhängern in den sozialen Medien kürzlich Bill Gates' Buch über den Klimawandel.
Als Frauen verkleidete Männer gewinnen Sportmeisterschaften für Frauen, und alle haben so viel Angst davor, als bigott bezeichnet zu werden, dass sich niemand traut, auf die Absurdität hinzuweisen, dass ein Mann alle Mädchen schlägt. Diese so genannten Sportler werden als „mutig" bezeichnet, obwohl sie alles andere als das sind.
Die Tatsache, dass es in einigen Berufen mehr Männer als Frauen gibt, wird als Problem angesehen, aber warum genau das ein Problem ist, wird selten erwähnt. Die Verdienste und die tatsächliche Meinungsvielfalt werden auf dem Altar der „Vielfalt und Integration" geschlachtet.
Die Gesellschaft ist an einem Punkt angelangt, an dem die Verbraucher Ärzten und Anwälten gerade wegen ihrer Hautfarbe misstrauen, da sie vermuten, dass sie deshalb in ihre Positionen gekommen sind und nicht wegen ihrer Kompetenz oder ihrer Verdienste. Noch vor zwanzig Jahren war die normale Bauchreaktion das Gegenteil: „*Wow, ein Arzt aus einer Minderheit! Sie müssen hart gearbeitet haben, um dorthin zu gelangen, wo sie heute sind!*"
Als ich aufgewachsen bin, wurde ein „Rassist" als jemand definiert, der sich einen Dreck um die Hautfarbe oder die ethnische Zugehörigkeit einer anderen Person scherte. Dasselbe galt für das Wort „Sexist" - man war ein Sexist, wenn man das Geschlecht einer Person bei der Beurteilung berücksichtigte.
Ich hatte das Gefühl, dass die Welt seit den Gräueltaten des Zweiten Weltkriegs im Kampf gegen diese Vorurteile einen weiten Weg zurückgelegt hatte und dass jeder eine anständige Karriere in jedem Beruf machen konnte, wenn er sich nur anstrengte und sich Mühe gab. Doch irgendwann in den frühen 2000er Jahren änderte sich etwas.
Plötzlich begannen die Worte das Gegenteil von dem zu bedeuten, was sie ursprünglich bedeuteten. Plötzlich war jeder, der sich einen Dreck um seine Hautfarbe scherte, ein Rassist. Jeder, dem es egal war, ob der CEO eines großen Unternehmens ein Mann oder eine Frau war, war ein Sexist.
Im Jahr 2023 behaupten manche sogar, man sei ein „Transphobe", wenn man nicht gelegentlich Fellatio an einem „weiblichen Penis" betreiben will. Die Tugendwächter laufen in der Tat Amok, und die Medienunternehmen lieben es. Sie lieben es, weil sie alles lieben, was die Kluft zwischen den Menschen schürt. Je verrückter die Aktionen der Clownwelt® sind, desto wütender sind die Reaktionen der leichtgläubigen, verärgerten Menschen auf der „vernünftigen" Seite des politischen Spektrums.
Die Menschheit neigt dazu, sich wie ein Pendel oder eine Abrissbirne zu verhalten, wenn es um politische Meinungen oder „die aktuelle Sache" geht.
Wenn es zu viele blauhaarige, übergewichtige, lesbische, glutenintolerante, vegane Umweltschützer gibt, taucht von irgendwoher eine Welle von Skinheads auf, die mit Steroiden vollgepumpt sind und gegen Samenöl und Fleischfresser sind.
Für jede Hillary Clinton gibt es einen Donald Trump. Für jede Greta Thunberg gibt es einen Andrew Tate. Für jeden CNN-Reporter gibt es einen Alex Jones.
Auch im Bitcoin-Bereich gibt es immer ein „aktuelles Thema", an das man sich klammern kann, wenn auch oft eine männlichere Idee als das „aktuelle Thema" des Mainstreams. Was nur wenige wissen, ist, wie faul diese Art des Denkens ist.
Wissenschaft ist nicht automatisch schlecht, nur weil „die Wissenschaft" schlecht ist.
Nur weil man gelernt hat, dass alles, was die Regierung sagt, eine Lüge ist, ist nicht automatisch auch das Gegenteil wahr. Die Welt ist nuanciert; die meisten Dinge sind nicht schwarz oder weiß.
Was wahr und sehr schwarz-weiß ist, ist das Geld - es gibt Bitcoin und es gibt Shitcoins. Nur wenn wir letztere für erstere aufgeben, können wir die Politik aus dem menschlichen Handeln entfernen und uns auf eine gewisse Wahrheit in der Basisschicht der Zivilisation zurück arbeiten. Bitcoin belohnt weder Rent-Seeking noch faules Denken.
Die positiven Aspekte vieler moderner Technologien werden oft übersehen. Auch wenn sich die Clownwelt® und die lächerlichen Ideen, die ihr folgen, wie ein Lauffeuer verbreiten, gibt es Gründe für einen ungetrübten Optimismus für die Zukunft.
Wir hören oft von den Gefahren der sozialen Medien und wie sie die Gehirne unserer Kinder schädigen, aber wir werden selten an die Kehrseite der Medaille erinnert. Soziale Medien verbinden Menschen in einem Ausmaß, das der Menschheit nie zuvor zugänglich war. Jeder Mensch auf der Welt kann heute mit jedem anderen in Kontakt treten und mit einem Mausklick einen Videoanruf starten. Das ist ein enorm wichtiges Instrument für den Frieden. In Kombination mit Bitcoin haben die Bösewichte keine Chance mehr.
Wenn jeder auf diese Weise vernetzt ist, wird überdeutlich, wie absurd es ist, dass wir in Staaten mit unterschiedlichen Gesetzen und Vorschriften leben. Warum gelten für meine Mitmenschen auf der anderen Seite dieses Teiches, dieses Flusses, dieses Gebirges oder sogar dieser imaginären Linie in der Erde andere Regeln?
Jeden Tag wachen mehr und mehr Menschen auf und erkennen, dass es nur ein einziges Menschenrecht gibt - das Recht, in Ruhe gelassen zu werden.
Immer mehr Menschen erkennen, dass die Geldentwertung kein natürliches Phänomen ist, sondern eine bewusste Politik. Es ist nur eine Frage der Zeit, bis die alte Welt verschwindet. Solange wir kommunizieren dürfen, gibt es Hoffnung. Das Internet hat bewiesen, dass sich jede Kommunikation auf eine Reihe von Einsen und Nullen reduzieren lässt, und Bitcoin hat bewiesen, dass Geld nichts anderes als Information ist.
-

@ dbb19ae0:c3f22d5a
2025-02-23 16:38:41
Derive npub from nsec given as parameter
``` python
import argparse
import asyncio
from nostr_sdk import Keys, init_logger, LogLevel
async def main(nsec):
init_logger(LogLevel.INFO)
keys = Keys.parse(nsec)
public_key = keys.public_key()
print(f"Public key (hex): {public_key.to_hex()}")
print(f"Public key (npub): {public_key.to_bech32()}")
if __name__ == '__main__':
parser = argparse.ArgumentParser(description='Fetch all relay from a given nsec')
parser.add_argument('nsec', type=str, help='The nsec of the user')
args = parser.parse_args()
asyncio.run(main(args.nsec))
```
https://docs.rs/nostr_rust/latest/nostr_rust/keys/fn.get_public_key_from_secret.html
https://github.com/ev3rst/nostr_sdk_examples/blob/main/ns-derive-npub.py
-

@ 2779f3d9:1a7f98d1
2025-02-23 15:20:19
# NOSTR SDK FOR APPLE PLATFORMS
## Progress Report # 2: Nov 2024 - Jan 2025
[Nostr SDK for Apple Platforms](https://github.com/nostr-sdk/nostr-sdk-ios) continued to make progress this quarter. I am still the sole part-time active developer and maintainer of Nostr SDK for Apple Platforms.
Implementations for a few NIPs were added or updated. The CI build pipeline was broken due to deprecated dependencies, which have since been fixed.
I pushed out a (controversial) [proposal](https://github.com/nostr-protocol/nips/pull/1770) to gracefully deprecate stringified JSON in favor of tags on user metadata kind 0 events to the NIPs repo as a pull request to improve consistency and reduce the complexity of reading and writing this commonly used kind. The SDK has become the first to [implement](https://github.com/nostr-sdk/nostr-sdk-ios/pull/212) with the hopes that others will follow.
We have had new external interest in the SDK from developers working on various Nostr clients:
- Damus has [copied the NIP-44 encryption implementation from the SDK](https://github.com/damus-io/damus/pull/2850/files#diff-5eb31bd8e6dc73d21bb3caef975a7f3508765e7f3ab01ecec545635ccb89d17c) for their use in [NIP-37 Draft Events](https://github.com/nostr-protocol/nips/blob/7cc120ecb01963e37f9adcd3b57b8efc1dd9e828/37.md), swapping out their previous usage of rust-nostr due to large binary size issues.
- [Fabian](nostr:npub1n0sturny6w9zn2wwexju3m6asu7zh7jnv2jt2kx6tlmfhs7thq0qnflahe) from Nostur contributed a [NIP-44 encrypt/decrypt example](https://github.com/nostr-sdk/nostr-sdk-ios/pull/204) to the SDK demo project to help him understand how it works and is [currently being used](https://github.com/nostur-com/nostr-essentials/blob/05e5452bb05c4c2e94ec9a78bb0c80d5123919a7/Sources/NostrEssentials/NIP-44/NIP44v2Encrypting.swift) by Nostur
- A new livestreaming Nostr client called [Swae](https://github.com/suhailsaqan/swae) has adopted the SDK, using Comingle as a reference client implementation.
Progress on the SDK this quarter has been slower than the previous quarter due to a shift in emerging priorities in Nostr. This quarter, I focused on building a native iOS Nostr event signer, as none exist today. The problem is that some iOS users do not fully trust pasting their private key into Nostr clients, which they fear could be buggy or malicious in accessing and signing bad data with their private key. A native signer on Android called Amber already exists, and there has been an increase in demand from users for an equivalent solution on iOS. The iOS signer app is called [Yeti](https://github.com/tyiu/Yeti) (credit to [Karnage](nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac) for the name and Figma designs) and I'm using Nostr SDK for Apple Platforms and its demo app as a [test bed](https://github.com/nostr-sdk/nostr-sdk-ios/tree/tyiu/signer-demo) for this experimental cross-app communication protocol that will eventually be proposed as a NIP. I hope iOS clients adopting the SDK will get built-in standardized event signing protocol capabilities, tightening up this attack vector.
This report marks the end of the six-month grant period, as agreed with OpenSats. I thank OpenSats for supporting Nostr SDK for Apple Platforms, other Nostr projects, and the developer community. I will re-apply for a grant at OpenSats for the SDK, Yeti, or other impactful Nostr projects.
## 1) How did you spend your time?
Below is a broken-down summarized bulletpointed list of completed tasks.
### Development of Nostr SDK for Apple Platforms
#### Added
- [NIP-37 Draft Events](https://github.com/nostr-protocol/nips/blob/master/37.md)
- [NIP-44 encrypt/decrypt example to demo project](https://github.com/nostr-sdk/nostr-sdk-ios/pull/204)
### Updated
- [Updated NIP-11 Relay Information Document implementation](https://github.com/nostr-sdk/nostr-sdk-ios/pull/201) to support all the newly added fields
- [Renamed ParameterizedReplaceableEvent to AddressableEvent and NonParameterizedReplaceableEvent to NormalReplaceableEvent](https://github.com/nostr-sdk/nostr-sdk-ios/pull/205) to conform to the [new terminology](https://github.com/nostr-protocol/nips/pull/1418) in the NIPs repo
- Gracefully deprecated stringified JSON in favor of tags on user metadata kind 0 events, being the first to implement the [not-yet-merged proposal](https://github.com/nostr-protocol/nips/pull/1770) to NIP-01/NIP-24
### Fixed
- Fixed broken CI build pipeline
- [Fix GitHub workflow for running build and test](https://github.com/nostr-sdk/nostr-sdk-ios/pull/202)
- [Upgrade upload-pages-artifact from deprecated version to v3 to fix build](https://github.com/nostr-sdk/nostr-sdk-ios/pull/207)
- [Upgrade deploy pages action to v4 to fix build](https://github.com/nostr-sdk/nostr-sdk-ios/pull/208)
#### In Progress
- Native iOS event signing protocol, using the [SDK as a test bed](https://github.com/nostr-sdk/nostr-sdk-ios/tree/tyiu/signer-demo)
## 2) What do you plan to work on next quarter?
The top priorities will be developing the native iOS event signing protocol, building out Yeti, and integrating the iOS signing protocol into the SDK.
I will continue maintaining and developing the SDK, albeit at a slower pace:
- Deprecate EventCreating protocol in favor of NostrEventBuilding protocol for the remaining event kinds
- Add or update implementations for various NIPs where critical or needed
- Support clients as they integrate with parts of the SDK by answering questions, fixing any issues they have, adding requested features, and reviewing pull requests
## 3) How did you make use of the money?
Living expenses.
-

@ 8d34bd24:414be32b
2025-02-23 12:49:20
I recently wrote a post “[What? Do Not Pray For ...](https://trustjesus.substack.com/p/what-do-not-pray-for)” where I shared a passage telling us not to pray for the nation of Israel (at a particular point in time). Before reading this post, I strongly encourage you to read that post first.
The verse in question was:
> “As for you, **do not pray for this people, and do not lift up cry or prayer for them, and do not intercede with Me; for I do not hear you**. Do you not see what they are doing in the cities of Judah and in the streets of Jerusalem? The children gather wood, and the fathers kindle the fire, and the women knead dough to make cakes for the queen of heaven; and *they* pour out drink offerings to other gods in order to spite Me. Do they spite Me?” declares the Lord. “Is it not themselves *they spite,* to their own shame?” (Jeremiah 7:16-19) {emphasis mine}
Jeremiah was told not to pray blessings on Israel because Israel had turned away from God and were serving other Gods.
I was just listening to a “Renewing Your Mind” podcast and the speaker made the statement, “We all want to say, ‘God bless America,’ but we don’t want to hear, ‘God curse America.’” That made me contemplate, “Should we ask God to bless America?”
Over the past decade or more (probably several decades), America has been using its military and economic might to push actions around the globe that are abhorrent to God. We give aid to countries if they legalize and fund abortions, if they promote gay marriage, and if they encourage transgender surgeries and chemical castration. They encourage people and nations to murder unborn children, to redefine marriage as different than what God created it to be, and to sterilize young people confused about their gender, breaking both God’s good creation of male and female and \
His command to be fruitful and multiply. You could make the argument that the US has been the largest purveyor of evil in the world. (It breaks my heart to say this.)
It is true that with the past election, America has turned away from many of these evil actions, but have Americans truly repented and turned back to God? I am convinced that neither our leaders nor most of our people have turned back to God in any significant way. It is like famous atheist, Richard Dawkins, saying he misses Christian culture but continuing to reject God and make fun of actual Christians. We can’t have it both ways. We can’t have God’s blessings without God.
Now I am not saying that we shouldn’t pray for America. It is totally appropriate to pray for revival in America. It is good to pray for Americans to repent of their sins and to trust in Jesus. It is great to pray for God to help us to share the gospel and to produce fruit. The issue is that we shouldn’t pray for America’s blessing while she has turned her back on God.
Obviously there are a decent number of Christians in America. That and the fact that America was founded on Christian principles actually means that America will be punished harsher than those nations where people have had little knowledge of the Bible and Jesus. Those who have been shown the gospel and still rejected God will be held to a higher standard and will be punished harsher than those who have never heard the gospel.
I ask you to pray that God would bring revival to America, that He would turn hearts and minds to Himself, and that He would draw our leaders to submit in full trust and obedience to Him. I also pray that God would help all of believers to be faithful stewards with all of the blessings with which He has already showered us and to use us to shine the light of the gospel with America and the rest of the world. I pray that He would help us to live lives fully devoted to Him and will help us to stand out from the crowd of pseudo-Christians and normal people, so we can be used to draw America back to God.
Unfortunately, we may be in a situation, like Jeremiah and Israel, where the nation has turned so far from God that we will be rejected in the same way they reject Jesus. We may have to look upon the nation we love and let go because our citizenship is in heaven. We need to always be more devoted to God and His kingdom than we are to our earthly citizenship.
> “Son of man, if a country sins against Me by committing unfaithfulness, and I stretch out My hand against it, destroy its supply of bread, send famine against it and cut off from it both man and beast, even though these three men, Noah, Daniel and Job were in its midst, by their own righteousness they could only deliver themselves,” declares the Lord God. (Ezekiel 14:13-14)
May God guide you in your prayers, your actions, and your faith so that you will be a light in the darkness and never forget where your allegiance lies. I pledge allegiance to my God, my Lord, and my Creator, and to Him alone does my allegiance belong.
Trust Jesus
-

@ 95cb4330:96db706c
2025-02-23 12:38:57
Embracing asynchronous work can significantly enhance productivity and reduce burnout by allowing individuals to work according to their own schedules without the pressure of immediate responses. This approach fosters deep, focused work and minimizes unnecessary interruptions.
---
## Understanding Asynchronous Work
- **Definition:**
Asynchronous work refers to a work style where employees complete tasks and communicate on their own time, without the expectation of immediate feedback. This contrasts with synchronous work, which requires real-time interaction.
---
## Benefits of Asynchronous Work
- **Enhanced Productivity:**
By reducing the need for constant real-time communication, employees can focus on tasks without frequent interruptions, leading to improved efficiency.
- **Flexibility:**
Employees can work during their most productive hours, accommodating personal schedules and time zones, which promotes a healthier work-life balance.
- **Reduced Burnout:**
The autonomy to manage one's workload and schedule can decrease stress and prevent burnout.
---
## Implementing Asynchronous Work
1. **Limit Meetings:**
Reduce the number of real-time meetings. When meetings are necessary, keep them concise and focused.
2. **Utilize Asynchronous Communication Tools:**
Employ platforms like email, project management software, and collaborative documents that allow team members to contribute on their own schedules.
3. **Set Clear Expectations:**
Establish guidelines for response times and project deadlines to ensure alignment and accountability.
4. **Encourage Deep Work:**
Promote periods of uninterrupted work to allow employees to engage deeply with complex tasks.
---
## Jeff Bezos's Approach to Time Management
Jeff Bezos, founder of Amazon, is known for his strategic approach to time management, which aligns with asynchronous principles:
- **Morning Routine:**
Bezos avoids early morning meetings, preferring to start his day with personal time that includes having coffee and reading the newspaper.
- **"Two-Pizza Rule":**
He limits meetings to a size that can be fed with two pizzas, ensuring they remain small and focused.
- **Intentional "Do Nothing" Time:**
Bezos schedules periods with no planned activities, allowing for reflection and spontaneous thought, which can lead to innovative ideas.
---
## Action Step
Evaluate your current work processes to identify areas where asynchronous methods can be applied. Start by reducing unnecessary meetings and implementing tools that facilitate communication without requiring immediate responses. This shift can lead to increased productivity, flexibility, and overall job satisfaction.
By adopting asynchronous work practices, you empower yourself and your team to work more efficiently and harmoniously, aligning work schedules with personal productivity peaks and reducing the risk of burnout.
-

@ 04ea4f83:210e1713
2025-02-23 10:43:38
Veröffentlicht auf [Discreetlog.com](https://www.discreetlog.com/no-privacy-no-freedom/?ref=europeanbitcoiners.com) am 17.04.2023\
Originalautor: [Matt Odell](https://twitter.com/ODELL?ref=europeanbitcoiners.com)\
Übersetzt von: [Sinautoshi am 20.05.2023 - 790600](https://twitter.com/Sinautoshi_8_21?ref=europeanbitcoiners.com)
*„Privatsphäre ist für eine offene Gesellschaft im elektronischen Zeitalter notwendig. Privatsphäre ist keine Geheimhaltung. Eine private Angelegenheit ist etwas, von dem man nicht möchte, dass es die ganze Welt erfährt, aber eine geheime Angelegenheit ist etwas, von dem man nicht möchte, dass es irgendjemand erfährt." Privatsphäre ist die Macht, sich der Welt selektiv zu offenbaren.“* **- Eric Hughes, [A Cypherpunk's Manifesto](https://www.activism.net/cypherpunk/manifesto.html?ref=discreetlog.com) , 1993**
**Privatsphäre ist für die Freiheit unerlässlich.** Ohne Privatsphäre ist der Einzelne nicht in der Lage, frei von Überwachung und Kontrolle Entscheidungen zu treffen. Mangelnde Privatsphäre führt zum Verlust der Selbstbestimmung. Wenn Einzelpersonen ständig überwacht werden, schränkt dies unsere Fähigkeit ein, uns auszudrücken und Risiken einzugehen. Alle Entscheidungen, die wir treffen, können negative Auswirkungen auf diejenigen haben, die uns überwachen. Ohne die Freiheit, Entscheidungen zu treffen, kann der Einzelne nicht wirklich frei sein.
**Freiheit ist für den Erwerb und Erhalt von Wohlstand von entscheidender Bedeutung.** Wenn der Einzelne nicht die Freiheit hat, Entscheidungen zu treffen, hindern uns Einschränkungen und Beschränkungen daran, wirtschaftliche Chancen zu nutzen. Wenn es uns in einem solchen Umfeld irgendwie gelingt, Wohlstand zu erlangen, kann mangelnde Freiheit zur direkten Beschlagnahme von Vermögenswerten durch Regierungen oder andere böswillige Organisationen führen. Wenn die Freiheit gefährdet wird, führt dies im großen Maßstab zu weitverbreiteter wirtschaftlicher Stagnation und Armut. Der Schutz der Freiheit ist für den wirtschaftlichen Wohlstand von wesentlicher Bedeutung.
Der Zusammenhang zwischen **Privatsphäre, Freiheit und Wohlstand** ist entscheidend. Ohne Privatsphäre verliert der Einzelne die Freiheit, frei von Überwachung und Kontrolle Entscheidungen zu treffen. Während der Mangel an Freiheit den Einzelnen daran hindert, wirtschaftliche Chancen wahrzunehmen, und den Vermögenserhalt nahezu unmöglich macht. ***Keine Privatsphäre? Keine Freiheit. Keine Freiheit? Kein Wohlstand.***
Rechte werden nicht gewährt. Sie werden eingenommen und verteidigt. Rechte werden oft als Erlaubnis der Machthaber missverstanden, etwas zu tun. Wenn dir jedoch jemand etwas geben kann, kann er es dir grundsätzlich nach Belieben wegnehmen. Im Laufe der Geschichte haben Menschen zwangsläufig für Grundrechte gekämpft, darunter Privatsphäre und Freiheit. Diese Rechte wurden nicht von den Machthabern gegeben, sondern durch Kampf eingefordert und erkämpft. Selbst nachdem diese Rechte erlangt wurden, müssen sie kontinuierlich verteidigt werden, um sicherzustellen, dass sie nicht weggenommen werden. **Rechte werden nicht gewährt – sie werden durch Kampf erworben und durch Opfer verteidigt.**
-

@ 42342239:1d80db24
2025-02-23 10:00:20
Europe's economic framework requires restructuring grounded in realism. The Commission's Competitiveness Compass, alas, reveals dangerous left-hemisphere dominance and risks repeating Mao's mistakes.
The European Commission presented its "competitiveness compass" in January. There will be massive investments in biotechnology, materials technology, medicines, space, and the defence industry. AI gigafactories are to be established, while Europe will "maintain its leadership in quantum technologies" (a leadership that few seem to be aware of). This will be achieved through more environmental labelling schemes, nature credits, procurement rules, platforms, cooperation plans, and coordination systems. Although the report contains some bright spots, such as promises to ease the regulatory burden, **the overall picture is strikingly lacking in creativity**. Instead, we are mainly met with the usual thought patterns of the European technocracy, which manifest in additional centralised frameworks, quantifiable goals, and annual reports. Mao's ghost haunts Brussels.
#### The Missing Half of Europe's Brain
Iain McGilchrist, a British psychiatrist and philosopher, has launched the hemispheric hypothesis (a theory about how the two hemispheres of the brain work). The left hemisphere is more detail- and control-oriented, while the right hemisphere is holistic and creative. A society dominated by the left hemisphere, [like our own according to McGilchrist](https://www.youtube.com/watch?v=WYB7P-xPRsk), "would see it as its task to control everything maximally." **The Commission's compass appears similarly lobotomised , prioritising measurable processes over imaginative solutions.**
In an earlier text, I mentioned that Europe might need to return [to its roots](https://www.affarsvarlden.se/kronika/enlund-lar-av-elon-musk-vi-behover-ett-mer-radikalt-europa) and asked if Europe should have "the same end goal as China." This is still a relevant and justified question. But if we are honest, China has implemented a series of well-thought-out reforms since the 1980s, in addition to its many well-known and large-scale investments. It is not necessarily wrong to be inspired by China, as many believe; it depends on which China you are inspired by.
#### Lessons from the Cat Theory
When Deng Xiaoping returned to power in the late 1970s, he chose a more pragmatic approach than his predecessors. China left Mao Zedong's purges of dissidents behind. Instead, he launched the cat theory: **"it doesn't matter what colour the cat is as long as it catches mice"**, regarding economic development. It was now free to experiment with different models. Instead of ideological conformity, the most important thing was to increase productivity and material prosperity.
What was done in China?
* Companies and individuals were given more freedom
* Provinces and municipalities were given more autonomy
* Special economic zones were established, with different conditions and rules
* Programs to increase the number of banks were introduced
* The banking sector was deregulated
* Property rights and contract law began to be respected
China has since gone from being an economic backwater to not only being the world's largest economy in terms of purchasing power but also a [global tech contender](https://www.aspi.org.au/index.php/report/critical-technology-tracker) (leading in 37 out of 44 key technologies per ASPI).
#### EU's Compliance Obsession vs Chinese Pragmatism
And today, when China is astonishing the world with surprisingly cheap and competent AI systems, which recently set American tech stocks in motion, in the EU one is met with advertisements for yet another compliance training, this time about AI. **Every new compliance training echoes Mao's ghost** – ideological correctness overriding practical results. Is prosperity really built with certifications, directives, requirements, and penalties?
When we compare the Chinese experience with today's EU, the contrast is clear:
* Freedoms are curtailed. The right to privacy is undermined (Chat Control, etc.)
* Member states' ability to self-govern is reduced, year by year
* Streamlining and harmony are popular buzzwords in the bureaucracy
* The ECB is actively working to reduce the number of banks
* The banking sector is being regulated more and more
* Property rights and contract law are being eroded, which can be partly attributed to [developments in payment systems](https://underorion.se/en/posts/freedom_to_transact/)
Deng's cat theory was an example of when the right hemisphere was involved in decision-making. Rather than just focusing on details (the cat's colour), the whole (the result) was important. **The Chinese proverb "cross the river by feeling the stones" is another example of more holistic thinking**. Under Deng's leadership, reforms were first tested in a free zone or a province. After a while, the reforms could be evaluated before they were possibly implemented on a larger scale. "Try before you buy" is also a wise principle that follows from complexity research. In sharp contrast to this approach was Mao's "Great Leap Forward," a part of a disastrous five-year plan that shows what can happen when the left hemisphere is given too much power. A tragedy of historic proportions - a mass famine - resulted. While Deng exorcized Mao's ghost through pragmatic experimentation, Brussels seems determined to resurrect. **Today's EU risks repeating Mao's mistake of letting political abstractions ("green transition! digital decade!") override reality** – Mao's ghost surely smiles at nature credit schemes replacing actual market signals.
#### Mao's ghost trives on the ontological mistake
The serious problems that the EU is facing have been built up over decades and stem from incorrect assumptions. The economy is not complicated. It is complex. The concepts are often confused, but they describe two fundamentally different things. The complicated refers to something composite, but which can still be unfolded and then folded back up again without changing its essence. The complex, on the other hand, refers to something entangled, where every attempt to divide it changes its character. Compare, for example, an airplane engine with a béarnaise sauce. If you mix up the concepts, you make an ontological mistake, a philosopher would say. A programmer would say: garbage in, garbage out. **Mao's ghost thrives on this ontological error**, convincing technocrats they can blueprint society like a Soviet tractor factory.
**When a system is complicated, predictable, and linear, centralised coordination and control by the left hemisphere can work well.** But in complex systems, it can never be a solution because it leads to reduced adaptability and increased system risks. Instead, the goal should be diversity and decentralisation, which provide greater adaptability! The faster the changes of the system or in the environment, the greater the demands on adaptability and flexibility - if the system is to survive, that is. Increased diversity and decentralisation would not only increase adaptability and flexibility but also promote creativity, an ability that will likely become increasingly important in a world where AI and automation are changing the rules.
#### A better path forward
Europe's economic framework requires restructuring grounded in realism. The Commission's competitiveness compass - fixated on metrics and control - reveals dangerous left-hemisphere dominance, echoing Maoist central planning's epistemological errors. Our path forward demands:
* Dual-brain governance (prioritising creativity over control)
* Banishing of category mistakes (acknowledging the complex adaptive nature of the economy)
* Pragmatism over ideology (policy sandboxes inspired by China's special economic zones)
* Anti-fragile design (increased autonomy of EU nations, within states, and decentralised banking)
* Sunset clauses on all bureaucracy (regulators cannot originate breakthroughs)
The alternative? Another technocratic Great Leap Forward - eco-certified, AI-monitored, but economically brittle and fundamentally maladapted to the complex global economy. **As Deng's reformers understood: no institutional architecture, not even the First Emperor's Terracotta Army, can withstand modernity's tide.**
-

@ 41fa852b:af7b7706
2025-02-23 09:41:15
> "Paper money eventually returns to its intrinsic value, zero." --Voltaire
* * *
**Lots happening this coming week for UK Bitcoiners, so there is plenty to report for this edition.**
There are ten meetups for the coming week, two new businesses, and two new events, and we have a new sponsor, [Bitcoin Metalworks](https://bitcoinmetalworks.com/). Check out their amazing Bitcoin-inspired artwork at the bottom of the ad section.
Let's dive in…
* * *
[](https://bitcoinevents.uk/donate/)
* * *
_This week's sponsor is…_
[](https://www.orangepillapp.com/?utm_source=BEUK&utm_medium=email&utm_campaign=BEUK)
* * *
### **Upcoming Bitcoin Meetups**
Happening this week…
1. [**Real Bedford - Home Game**](https://www.realbedford.com/real-bedford-v-aylesbury-united2): Peter MacCormack's boys are at home this Tuesday the 25th, playing Aylesbury United. Join them for a 19:45 kickoff. ⚽️
2. [**Leamington Spa**](https://t.me/leambitcoin): Meetups on the last Tuesday of each month at 7 PM. You'll find them this month at the White Horse, CV32 5PZ on the 25th. 🍻
3. [**Bitcoin Surrey**](https://x.com/bitcoinsurrey/status/1888974122358641007): On Tuesday, February 25th, from 18:00 to 23:00, Bitcoin Surrey is hosting a special meetup focused on Bitcoin art at Yiayias at The Fox, located at 21 Frensham Road, Lower Bourne, Farnham, Surrey GU10 3PH. The event features a fireside chat and talk at 19:00 by artist and curator Rebel Money Art, titled "Bitcoin Art: The New Revolution," discussing the evolution and future of Bitcoin art. Additionally, the venue's upstairs will be transformed into a pop-up Bitcoin art gallery for the evening, showcasing works by various international artists, including Cryptograffiti, RYR, HodlxHold, Flo Montoya, Sham Shad, 2140 Collective, Mr Hansel, Asanoha, No Good, and Rebel Money Art. Bitcoin is accepted at the venue and entry is free. 🍻🖼️🎨
4. [**Brighton Bitcoin**](https://t.me/brighton_btc): Building a bitcoin community in the Brighton & Hove area. A regular informal meetup happens every last Wednesday of the month at [Indian Summer](https://www.indiansummerbrighton.co.uk/) where they accept bitcoin payments. The meetup starts at 20:00, or 19:00 if you'd like to eat first. 🥘🍻
5. [**Manchester Bitcoin**](https://btcmap.org/community/bitcoin-manchester): On the 27th, Manchesters Bitcoin will be at The Smithfield Market Tavern. Join them at 19:00. 🍺
6. [**Cyphermunk House - Constellation Money**](https://btcpay.btc.aw/apps/3KBnXP178MWUvGGizGKsgFQrKoaY/pos): Exploring unconscious blocks and hidden patterns in your relationship to money. At 18:30 on Thursday 27th. 👨🏻🚀
7. [**The Satoshi Society - Southampton**](https://x.com/satssociety): Join a friendly group of bitcoiners at The Maritimo Lounge, Ocean Village on Friday the 28th for food and a Bitcoin chat. 🍺
8. [**Bitcoin Walk - Edinburgh**](https://bitcoinwalk.org/): Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏽♂️🚶🏼♀️🚶🏻
9. [**Leeds Bitcoin Network**](https://t.me/LeedsBTC): The first Sunday of every month the Leeds Bitcoin Network meet at the [Global Tribe Cafe](https://www.globalcrystals.com/), LS1 6LG at 1 PM on Sunday 2nd March. ☕️
10. [**Cyphermunk House - Repair Party**](https://btcpay.btc.aw/apps/3KBnXP178MWUvGGizGKsgFQrKoaY/pos): Watch, learn and get hands-on experience at this community lead electronic repair training workshop. UK Plug, Laptop, Kettle, toaster... On Sunday 2nd March at 10:00. 👨🏻🔧🛠️
* * *
### New Businesses Accepting Bitcoin
- [**Hollins Mill**](https://btcmap.org/merchant/node:236019804): This traditional English Pub in Sowerby Bridge specialises in craft beers and ales, 50+ gins, and has a large beer garden and function room for up to 120 people. Perfect for weddings, christenings and birthday parties. Now accepting bitcoin!
- [**Alema Coffee**](https://www.alemacoffee.com/): Some great work is going on behind the scenes in Bury St Edmunds. Expect some new businesses to appear here as Bitcoin East onboard them. Alema's Coffee is grown on a family farm in Ecuador and sent directly to Alema coffee for roasting. You can visit them at 2 High Baxter Street, Bury St Edmunds, IP33 1ES for some exceptional, hand-crafted coffee, paid for with bitcoin.
* * *
### Upcoming Special Events
These events aren't happening next week, but they're important to add to your calendar now as tickets are selling fast.
- [**Eat and Meet with Joe Bryan**](https://orangepill.app.link/MDg7o8KxcRb): Meet the creator of 'Whats the Problem' and a host of bitcoiners at the Weeping Willow in Bury St Edmunds. Starting at 18:00 on Tuesday March the 4th.
[](https://orangepill.app.link/MDg7o8KxcRb)
- [**CheatCode 2025**](https://www.cheatcode.co.uk/) - Peter McCormack hosts the CheatCode conference, following last year's success. This year, international guest speakers include Preston Pysh, Alex Gladstein, Natalie Brunell, Matthew Pines, Steve Baker, Ben Arc, and Checkmate.
Friday, April 11th, is the main conference day, followed by a huge meetup at Ledger Park for the men's Real Bedford match, and again on Sunday for the women's match. Check out the link for ticket details.
[](https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fbcb0553a-dc8c-4fb7-98dd-4a95085d83a5_1500x500.png)
* * *
**Get Involved**
- **Volunteer Opportunities**: [Bridge2Bitcoin](https://bridge2bitcoin.com/) is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on [Twitter](https://x.com/bridge2bitcoin) or through our [website](https://bridge2bitcoin.com/).
- **Start Your Own Meetup**: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via [Twitter](https://x.com/bitcoineventsuk).
- [**Contribute to BTCMaps**](https://wiki.btcmap.org/general/tagging-instructions.html): BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date.
- **Telegram users**: You might find our [Telegram Channel](https://t.me/BitcoinEventsUKHub) another useful way to keep up-to-date with UK meetups.
- **Feedback and Suggestions**: We value your input! Share your ideas on how we can enhance this newsletter.
* * *
_This week's sponsors are…_
[](https://orangecoinstore.com/)
[](https://bitcoinretreat.co.uk/)
[](https://bitcoinmetalworks.com/)
* * *
Get out and support the meetups where you can, visit [Bitcoin Events UK](https://bitcoinevents.uk/) for more info on each meetup and to find your closest on the interactive map.
Stay tuned for more updates next week!
Simon.
[](https://bitcoinevents.uk/donate/)
-

@ 6a3d3f20:6a569bcc
2025-02-23 08:50:19
Imagina un internet donde tú tienes el control, donde nadie puede silenciarte y donde las conexiones entre personas fluyen sin barreras corporativas. Esto no es un sueño lejano, ¡es la realidad que está tomando forma gracias a Nostr! Este protocolo **descentralizado**, nacido en 2020 de la mente ingeniosa de un desarrollador brasileño conocido como *fiatjaf*, ha surgido como una respuesta vibrante a los desafíos del internet actual. En un mundo donde las redes sociales centralizadas han comenzado a tambalearse bajo el peso de la **censura**, la privacidad comprometida y el control excesivo, Nostr llega como un soplo de aire fresco, prometiendo devolvernos el poder sobre nuestra voz y nuestros datos.
## Cómo surge Nostr
El nacimiento de Nostr no fue un accidente, sino una reacción a un panorama digital que pedía a gritos un cambio. Hacia finales de la década de 2010, plataformas como **Twitter** enfrentaban crecientes críticas por sus políticas de **moderación**, dejando a muchos usuarios frustrados y silenciados. Al mismo tiempo, alternativas como **Mastodon** o **ActivityPub**, aunque descentralizadas, no terminaban de cuajar para todos debido a su complejidad técnica o diferencias culturales. Fue en este caldo de cultivo donde *fiatjaf*, inspirado por la resistencia de **Bitcoin** y su criptografía de clave pública, lanzó **Nostr** en noviembre de 2020. Pero el verdadero punto de inflexión llegó en diciembre de 2022, cuando *Jack Dorsey*, cofundador de Twitter, donó 14 bitcoins (unos 250,000 dólares) al proyecto. ¡Ese fue el momento en que Nostr pasó de ser un secreto de la comunidad *web3* a brillar en el radar global!
## Una evolución que no para de sorprendernos
Desde sus humildes comienzos, Nostr ha crecido a pasos agigantados. Su diseño es simple pero poderoso: "*Notes and Other Stuff Transmitted by Relays*" (Notas y otras cosas transmitidas por relevadores) usa servidores ligeros llamados *relays* para distribuir mensajes firmados criptográficamente por los usuarios. ¿Lo mejor? No depende de un servidor central, lo que lo hace prácticamente ++imposible de censurar++. En sus primeros años, era un terreno experimental, con aplicaciones como **Damus** (un cliente tipo Twitter) abriendo camino. Hoy, en 2025, la escena es vibrante: desde **Primal 2.0**, con búsquedas avanzadas y feeds personalizados, hasta integraciones con la **Lightning Network** de Bitcoin, que permite "**zaps**" (*micropagos*) para apoyar a creadores. Los desarrolladores no paran de innovar, creando desde marketplaces descentralizados hasta sistemas de identidad, demostrando que Nostr es mucho más que una red social: ¡es una base para reinventar el internet!
## La importancia de Nostr hoy y mañana
¿Por qué Nostr importa tanto ahora? Porque está devolviendo la *soberanía* a los usuarios en un momento en que la *privacidad* y la *libertad* en línea están bajo asedio. Con cada relay que se suma y cada cliente que aparece, Nostr construye una red resistente donde las grandes tecnológicas no dictan las reglas. Su integración con Bitcoin está creando una economía circular emocionante: imagina ganar *sats* (fracciones de bitcoin) por tus publicaciones o apoyar directamente a tus creadores favoritos sin intermediarios. En febrero de 2025, ya vemos comunidades activas, desde entusiastas de la tecnología hasta artistas, floreciendo en este ecosistema abierto.
De cara al futuro, Nostr tiene el potencial de ser un pilar del internet que siempre quisimos: descentralizado, transparente y al servicio de las personas. No solo compite con las redes sociales tradicionales, sino que las supera al ofrecer un lienzo en blanco para que cualquiera construya lo que imagine, desde plataformas de comunicación hasta soluciones IoT o mercados globales. Su simplicidad invita a miles de desarrolladores a sumarse, y su resistencia a la censura asegura que las voces marginadas siempre tengan un lugar. Si **Bitcoin** nos dio libertad financiera, **Nostr** nos está dando libertad digital, y juntos podrían ser la dupla que transforme cómo interactuamos en línea.
[[]()]()
## Un gran futuro nos espera
Nostr no es solo un protocolo; es un movimiento, una chispa de optimismo en un mundo digital que a veces parece gris. Cada vez que alguien se une, configura un relay o prueba una nueva app, estamos dando un paso hacia un internet más justo y emocionante. Así que, ¿qué esperas? Nostr no es el futuro lejano, ¡es el presente vibrante que está creciendo hoy! **Únete**, experimenta y sé parte de esta revolución que está poniendo el poder de internet de vuelta en nuestras manos. ¡El mañana digital nunca lució tan prometedor!
-

@ e373ca41:b82abcc5
2025-02-23 08:39:06
*Dieser Artikel wurde mit dem* *[Pareto-Client](https://pareto.space/read)* *geschrieben (lesen Sie ihn dort, um die volle Erfahrung zu machen). Er wurde zuerst auf Deutsch von Milosz Matuschek auf* *["Freischwebende Intelligenz"](https://www.freischwebende-intelligenz.org/p/was-bringt-eine-wahl-wenn-das-system)* *veröffentlicht.*
Zur Demokratur, der vom Souverän losgelösten Demokratie, gehört es zum Ritus, dem Volk regelmäßig den Puls zu fühlen. Heute ist wieder so ein Tag. Doch was wird der Souverän am Ende dieses Tages gewonnen haben?
Zur parlamentarischen Demokratie gehört der Wesentlichkeitsgrundsatz. Alle grundrechtswesentlichen, also den Wesenskern von Grundrechten betreffenden Entscheidungen müssen vom Parlament gefällt werden.
Behandelt der Bundestag die wesentlichen Fragen?
* Was hat man im Gremium des Souveräns bisher über Nordstream herausgefunden?
* Was über Spike-Proteine, die 700 Tage nach der Impfung noch aktiv sind?
* Wie erklärt dieses Gremium dem Souverän, dass Bankenbosse, Bundeskanzler und migrantische Straftäter in diesem Land ungleich schwieriger zu verurteilen sind als Bürger, die einen gefährlich mindertalentierten Politiker „Schwachkopf“ nennen?
Wofür einen Bundestag wählen, der nichts zählt, wenn es darauf ankommt und wenig zustande bringt, was dem Bürger nützt, wenn er mal darf? Eine allgemeine Impfpflicht, die auf Politikerseite erst jeder kategorisch ausschloss und dann jeder ebenso salbungsvoll kategorisch befürwortete, scheiterte nur knapp. Aufarbeitung seither?

Legitimation des rituellen Umkehrschwungs? (Foto: [Rosenbusch/X](https://x.com/rosenbusch_/status/1893456799728062698))
\
Aus dem Kontrollgremium des Souveräns gegenüber der Regierung ist eine realitätsverweigernde BRD-Volkskammer geworden. Was kann eine Wahl verändern, wenn das System, welches sie alimentiert und perpetuiert, das Problem ist? Nehmen wir einen Motor, der mit Benzin läuft. Der Motor ist „unsere Demokratie“, Wahlen sind der Betankungsvorgang. Der Bürger betankt heute die Maschinerie mit der Legitimation durch seine Stimme. Doch er weiß nicht mehr, welche Hebel und Gerätschaften der Motor eigentlich antreibt. Dieser Teil befindet sich hinter einem schweren Vorhang. Kann im Sinne von Transparenz und Mit-Verantwortung der Betankungsvorgang guten Gewissens vollzogen werden?
Der Wahlvorgang ist ein Paradebeispiel dessen, was der Soziologe Niklas Luhmann mit „Legitimation durch Verfahren“ beschrieben hat. Der prozessuale Akt, die Auszählung und Verkündung schafft neue Realität und legitimiert die neue Ordnung. Aus der Erfahrung der letzten Jahre in einer autoritären parlamentarischen Demokratur bedeutet die Wahlentscheidung jedoch eine de facto Blanko-Einwilligung in die eigene Versklavung. Im Privatrecht wäre das ein sittenwidriges Ziel, das zur Nichtigkeit des Vertrages führen würde. Wieso sollte das auf der Ebene des politischen Gesellschaftsvertrages dann möglich sein? Und wie kann ein solcher Legitimationsvorgang verantwortet werden?
<https://www.youtube.com/watch?v=Ngy05PFUlo8&t=5s>
Der Parlamentarismus in Deutschland ist für mich gescheitert, wieder einmal. Doch warum soll in einem besetzten, globalistisch durchzogenen NATO-EU-WHO-Konglomerat wie Deutschland auch ausgerechnet der Bürger das letzte Wort haben? Die Legitimationskette von Bürger zu Staat hat zu viele blinde Flecken bekommen. Die Rückverfolgung desaströsen politischen Handelns ist nicht mehr möglich. In Deutschland hat keine gesellschaftliche Instanz, nicht die Politik, nicht die Wissenschaft, nicht die Justiz, nicht die Medien, bisher eine Form der Corona-Aufarbeitung hinbekommen, die diesen Namen verdient. Das ist Sache von unabhängigen, versprengten Stimmen und Publikationen.
Wie ist es um die Legitimität der „Partneroganisationen“ Deutschlands bestellt? Die EU ist unlängst vom Friedensbündnis zum Kriegsbündnis geworden, die Nato kann nicht mal Bündnispartner vor Bündnispartnern schützen und die WHO ist ein durch China und Bill Gates unterwandertes Jointventure für globale Impf- und Kontrollexperimente. All das wird heute erneut zementiert und wenn es gesprengt würde, müsste der Wahlvorgang verboten werden. Im besetzten Land darf nur richtig gewählt werden.
Und deshalb gibt es für mich in diesem System keine Wahl.
Wie ist es bei Ihnen?
Wie stehen Sie zu dieser Wahl? Gehen Sie hin und mit welchen Gefühlen, Erwartungen, Intentionen? Ich freue mich auf Ihren Kommentar.
ANZEIGE:
**Sie suchen nach dem einfachsten Weg, Bitcoin zu kaufen und selbst zu verwahren?**\*\*\*\*\*\* *Die* ***[Relai-App](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)*** *ist Europas erfolgreichste Bitcoin-App.* ***[Hier](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)*** *kaufen Sie Bitcoin in wenigen Schritten und können auch Sparpläne einrichten. Niemand hat Zugriff auf Ihre Bitcoin, außer Sie selbst.* ***Relai senkt jetzt die Gebühr auf 1%**, mit dem Referral-Code* ***MILOSZ*** *sparen Sie weitere 10%. (keine Finanzberatung). Disclaimer wg. EU-Mica-Regulierung: Die Dienste von Relai werden ausschließlich für Einwohner der Schweiz und Italiens empfohlen.*
***
***You prefer reading me in English?*** *You can find my first uncensorable articles written with our Pareto client via Nostr,* ***[clicking on this link.](https://pareto.space/u/ashoka@pareto.space)*** *Discover other authors at* ***[Pareto.space/read.](https://pareto.space/read)(click on the Pareto button to see our first authors).*** 
[](https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fc33bfce1-1a89-42ff-a89f-e1fbd7edfac4_2382x1272.png)
***
***Join the marketplace of ideas!** We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the [Pareto Project](https://pareto.space/en)? Zap me, if you want to contribute (all Zaps go to the project).*
*Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to **<team@pareto.space>***
**Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Start.](https://start.njump.me/)**
-

@ e5de992e:4a95ef85
2025-02-23 07:52:00
A trading log isn't just a record of past trades—it's a tool for learning, improving, and achieving consistency. By keeping a detailed log, you gain insights into your decision-making process, identify patterns, and refine your strategy over time.
Here's why and how to maintain a comprehensive trading log effectively.
---
## 1. The Importance of a Trading Log
- **Track Performance Objectively**
Without a log, it's easy to misremember trades or overestimate success. A detailed log provides accurate data to analyze your progress.
- **Understand Your Strengths and Weaknesses**
By reviewing your log, you can identify what works well and where you need improvement. Patterns in losing trades often highlight common mistakes or emotional triggers.
- **Build Confidence and Trust in Your System**
Seeing a record of rule-based, consistent trades reinforces trust in your strategy. Reviewing past successes can boost morale during challenging periods.
---
## 2. What to Include in Your Trading Log
A detailed trading log should cover both objective data and subjective reflections.
### Objective Data
- **Date and Time:** When the trade was entered and exited.
- **Instrument Traded:** Stock, forex pair, crypto, etc.
- **Entry and Exit Prices:** Precise levels where you opened and closed the trade.
- **Position Size:** Number of shares, contracts, or units traded.
- **Stop Loss and Take Profit Levels:** Risk management details.
- **P/L (Profit or Loss):** Outcome of the trade in dollars or percentage terms.
- **Trade Type:** Long, short, scalping, swing, etc.
### Subjective Reflections
- **Reason for Entering the Trade:** What setup or signal prompted the trade?
- **Emotional State:** How did you feel before, during, and after the trade?
- **Execution Notes:** Did you follow your plan? If not, why?
- **Lessons Learned:** What can you take away from this trade to improve next time?
> **Key Insight:** Both data and reflection are essential for meaningful analysis.
---
## 3. How to Analyze Your Trading Log
1. **Identify Patterns**
Look for common themes in your winning and losing trades.
_Examples:_ Winning trades often align with specific setups, while losing trades frequently result from breaking rules or impulsive decisions.
2. **Evaluate Strategy Effectiveness**
Assess whether your system produces consistent results over time.
Use metrics like win rate, risk-reward ratio, and drawdown to evaluate performance.
3. **Address Emotional Triggers**
Reflect on emotional notes to understand what triggers fear, greed, or hesitation.
Develop strategies to manage emotions based on these insights.
---
## 4. Benefits of Keeping a Trading Log
- **Improved Discipline:**
Writing down each trade reinforces the habit of sticking to your plan.
- **Informed Adjustments:**
Logs provide data-driven insights to refine your strategy.
- **Emotional Control:**
Journaling emotions helps you recognize and address psychological pitfalls.
- **Long-Term Growth:**
By tracking your progress, you can measure improvement over months and years.
> **Key Insight:** A trading log turns mistakes into lessons and successes into repeatable actions.
---
## 5. Tools for Logging Trades
### Manual Logs
- Use a notebook or spreadsheet to record trades.
- **Pros:** Highly customizable, forces you to engage deeply with each entry.
- **Cons:** Time-intensive and less automated.
### Software and Platforms
- Tools like Edgewonk, TraderSync, or Tradervue can streamline the process.
- **Pros:** Automated data collection, advanced analytics, and performance tracking.
- **Cons:** May have a learning curve or subscription costs.
> **Key Insight:** Choose a method that aligns with your workflow and trading style.
---
## 6. Tips for Maintaining a Consistent Trading Log
- **Log Every Trade:**
Don't skip trades, even the ones you'd rather forget. They're often the most valuable for learning.
- **Be Honest:**
Record trades exactly as they happened, including mistakes and rule-breaking.
- **Review Regularly:**
Set aside time weekly or monthly to analyze your log and adjust your approach.
- **Stay Disciplined:**
Treat logging as an essential part of your trading routine.
---
## 7. Conclusion: Your Trading Log is Your Mirror
A detailed trading log is more than just a record—it's a roadmap to success. It provides clarity, accountability, and insights that are essential for continuous improvement.
Start today. Keep a detailed log, review it often, and use it to refine both your strategy and your mindset. Your future self will thank you.
-

@ e5de992e:4a95ef85
2025-02-23 07:46:45
China’s M1 increases a lot, it means there’s more money available for people and businesses to buy things. This can help boost spending and economic growth in the short term. However, if there’s too much money chasing the same amount of goods and services, prices can rise, leading to inflation. Sometimes, a rapid increase in M1 can also signal that banks are lending a lot of money, which might eventually create bubbles in things like real estate or stocks if the growth isn’t managed carefully.
https://tradingeconomics.com/china/money-supply-m1
China’s M1 increases a lot, it means there’s more money available for people and businesses to buy things. This can help boost spending and economic growth in the short term.
-

@ da0b9bc3:4e30a4a9
2025-02-23 07:08:22
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/894609
-

@ e3ba5e1a:5e433365
2025-02-23 06:35:51
My wife and I have six children, making our house a household of eight people. Looking just at the eight of us, how many relationships exist? Well, as a first stab, we could look at how many connections exist between two unique individuals in this family. The mathematical term for this is “8 choose 2”, and the answer is 8\*7/2, or 28\.
Even that doesn’t really capture the answer though, because relationships aren’t just between two people. For example, when my wife and two oldest children are the only ones still awake after the younger kids go to bed, we’ll put on my mature TV shows that they’ll appreciate and watch together. It’s our own little subgroup within the group.
Based on that, we could have groups of 2, 3, 4, all the way up to 8, the group of all of us. If you do the math, this comes up to 247 different subgroups of 2 or more people. That’s a lot of groups for just 8 people.
As a father, this means I’ll never be able to fully understand every set of connections within my family. I may have a good understanding of my own relationship with each child. I also am closely aware of the relationship between our two youngest children, since they’re twins. And I could probably list 20 or so other noteworthy relationships. But I’ll never understand all of them.
For example, months ago I bought a game on Steam for my 3rd and 4th kids. I know they like to play games together, so it was a relationship that I thought I understood well. A few days ago I found out that my oldest had joined them in playing one of these games (Brotato). I’d made the purchase, given it to the kids, and it sparked new relationship and interaction structures without my involvement.
There’s no problem with the fact that I can’t track every interaction in my house. That’s healthy\! The kids are able to discover ways of interacting beyond what I can teach them, learn everything from schoolwork to video games from each other, and overall become more healthy and well-adjusted adults (I hope).
And here’s the important part: the growth of the number of connections is *massive* as the number of participants increases. If we add in another participant, we have 502 groupings. At 10 total participants, it jumps to over 1,000. By the time we get to 100, we’re well into the trillions.
A mathematical and software term for this is *combinatoric complexity*, the massive increase in an output value based on a small increase in the input. The analysis I’m providing could be termed as part of graph theory (for connections of 2, looking at people as *vertices* and connections as *edges*) or set theory (unique subsets, allowing for larger group sizes). But regardless, the point is: the increase in complexity is huge as more people join.
Now consider the global economy. It’s over 8 billion people. There are so many people that the number of groupings is absurd to talk about. Nonetheless, massive numbers of these groupings naturally occur. There are family units, friend circles, individual connections, companies, project teams, sports teams, schools, classes, and millions more. These groups of people form new ways of interacting, express vastly different desires for goods and services, and are capable of producing wide varieties of goods and services themselves.
When you allow this system to run free, beauty emerges. Each node in the graph can manage its own connections. Each *person* is free to make his or her own decisions about association, what to spend time on, what to spend money on, and so on. Each person does so on their own judgement and world view.
Some of these people may make “dumb” decisions. They may “waste” their time and money on useless things. Except: who made that value judgement? Clearly not them, they decided it was worth it. No central planner has the right to override their will.
My point in all this is: as yet another of many reasons in the list of “why people should be free,” we have one more data point: pure math. Central planning will never scale. Central planning will never appreciate the individuality and desires of each person. Only by giving people the freedom to explore their connections to others, discover what they can produce and consume, explore their options, and ultimately make their own decisions, can we have any chance of creating a world where everyone can succeed.
-

@ 78c90fc4:4bff983c
2025-02-23 06:25:25
 
Vor dem Prozess kursierten Gerüchte, Maxwell verstecke sich in einem U-Boot oder auf nahe gelegenen Inseln. Sie besitzt ein U-Boot und hat eine Lizenz dafür
Water Island ist eine 500 Hektar große Landzunge auf den U.S. Virgin Islands. Aufnahmen aus dem Jahr 2012 (auch Video) zeigen einen Teil des Untergrunds und seiner Umgebung.
2005: James und Sara Biden kaufen ein Grundstück auf Water Island, in der Mitte der Insel, für 150.000 Euro. Dieser Teil des Grundstücks wurde in drei Teile aufgeteilt und verkauft. Einer von ihnen ist Scott Green.
Scott Green, ein Lobbyist mit engen Beziehungen zu Joe Biden, kaufte das Grundstück auf den Jungferninseln von James Biden und gewährte ihm dann eine private Hypothek.
Nach dem Kauf machte Joe Biden mindestens dreimal Urlaub auf der winzigen Insel, die einst einen nahe gelegenen U-Boot-Stützpunkt und eine unterirdische Anlage schützte, bevor sie zu einem tropischen Rückzugsort wurde.
Die Bedingungen des Darlehens wurden in den Immobilienunterlagen nicht offengelegt.
Green hat auf mehrere Bitten um Stellungnahme nicht reagiert.
Der Anwalt von James Biden, George Mesires, bestätigte den Erhalt von Fragen, beantwortete sie aber nicht.
Green hat Biden 2.300 Dollar gespendet, aber als er um einen Kommentar gebeten wurde, hat er nicht geantwortet.
Und raten Sie mal, was Green in Washington, D.C., als Auftragnehmer für öffentliche Sicherheits- und Strafverfolgungsbehörden als Teil einer Firma arbeitet, die er 1994 mitbegründet hat.
Es wird noch interessanter!! Scotts Lafayette Group erhält 5,8 Millionen Dollar von der FEMA. 3 TAGE SPÄTER gaben sie James und Sara Biden eine Hypothek von 133.000 für Water Island Land. Und es gibt noch so viel mehr, aber das ist ein anderes Kaninchenloch (ein weiterer Zuschuss für 40 Millionen Dollar).
Unten können Sie eine von Bidens zahlreichen Lügen sehen:
„Ich habe nie mit meinem Sohn oder meinem Bruder oder sonst jemandem etwas besprochen, was mit ihren Geschäften zu tun hat.“
Hunter Biden arbeitete als Energieberater ohne jegliche Erfahrung in diesem Bereich.
James Biden trat der Firma HillStone bei. Und wie durch ein Wunder erhielt das Unternehmen zahlreiche Aufträge von der Bundesregierung (USA, Irak, Puerto Rico, Mosambik usw.)
Kredit: Natly Denise, CaptainBirchShow, Politico
\#EpsteinClientList #EpsteinIsland
<https://x.com/SaladMeToday/status/1892971887006810214>
<https://x.com/RealWsiegrist/status/1893543364676522222>
Perplexity:
Der U-Boot-Stützpunkt in der Nähe von Water Island auf St. Thomas auf den US-Jungferninseln war während des Zweiten Weltkriegs aufgrund seiner Rolle bei der Verteidigung der Karibik und der US-Marineoperationen von großer strategischer Bedeutung.\
\
\### \*\*Strategische Bedeutung der U-Boot-Basis\*\*\
\- Die U-Boot-Basis auf St. Thomas wurde 1941 als Teil einer umfassenderen US-Militärstrategie zur Sicherung der Karibik während des Zweiten Weltkriegs eingerichtet. Diese Region war entscheidend für den Schutz der Schifffahrtswege und die Bekämpfung der deutschen U-Boot-Aktivitäten im Atlantik\[1]\[2].\
\- Der Stützpunkt verfügte über eine umfangreiche Infrastruktur mit drei Piers, Unterkünften für fast 1.000 Mitarbeiter, Lagereinrichtungen, einer Torpedoüberholungswerkstatt und einem bombensicheren Maschinenhaus\[1]. Diese Einrichtungen unterstützten den Betrieb und die Wartung von U-Booten in einem strategisch wichtigen Gebiet.\
\
\###\
\- Water Island, südlich von St. Thomas gelegen, wurde 1944 von der US-Regierung erworben, um die Küstenverteidigung zu stärken\[5]. Fort Segarra, eine unterirdische Festung auf Water Island, wurde zum Schutz der nahe gelegenen U-Boot-Basis auf St. Thomas\[2]\[4] errichtet.\
\- Das Fort umfasste Geschützstellungen, Tunnel, unterirdische Kammern, Kasernen und andere militärische Infrastrukturen. Es wurde jedoch nie fertiggestellt oder voll einsatzfähig, da der Zweite Weltkrieg vor Abschluss der Bauarbeiten beendet wurde\[3]\[6].\
\
\*\*Nachkriegsnutzung\*\*\
\- Nach dem Krieg wurden Fort Segarra und Water Island für verschiedene militärische Tests genutzt, darunter Experimente zur chemischen Kriegsführung, die zwischen 1948 und 1950 durchgeführt wurden\[4]\[6]. Später, im Jahr 1952, wurde die Insel unter zivile Kontrolle gestellt.\
\
\###\
\- Heute sind die Überreste von Fort Segarra und seine unterirdischen Strukturen auf Water Island für Besucher zugänglich. Sie erinnern an die Rolle des Forts beim Schutz des U-Boot-Stützpunkts und an seine strategische Bedeutung während des Zweiten Weltkriegs\[3]\[6].\
\
Zusammenfassend lässt sich sagen, dass der U-Boot-Stützpunkt auf St. Thomas und die damit verbundenen Verteidigungsanlagen auf Water Island entscheidende Komponenten der US-Bemühungen zur Sicherung der Karibik während des Zweiten Weltkriegs waren. Obwohl ihre militärische Nutzung vor Jahrzehnten endete, bleiben sie aufgrund ihres historischen und strategischen Erbes von Bedeutung.\
\
Quellen\
\[1] Militärgeschichte von Water Island https\://history.wica.vi/military-history/\
\[2] Fort Segarra - Flamingo Point USVI Water Island http\://flamingopointusvi.com/water-island\
\[3] Fort Segarra - Virgin Islands - VInow\.com https\://www\.vinow\.com/wi/wi-a/fort-segarra/\
\[4] Fort Segarra - Wikipedia https\://en.wikipedia.org/wiki/Fort\_Segarra\
\[5] Fort Segarra - Jacksonville District - Army.mil https\://www\.saj.usace.army.mil/FortSegarra/\
\[6] Water Island, U.S. Virgin Islands - Wikipedia https\://en.wikipedia.org/wiki/Water\_Island,\_U.S.\_Virgin\_Islands\
\[7] Water Island | Seas the Day Charters USVI https\://seasthedayusvi.com/2022/02/11/exploring-water-island-u-s-virgin-islands-best-kept-secret/\
\[8] Water Island: Aktivitäten und Sehenswürdigkeiten - Jungferninseln - VInow\.com https\://www\.vinow\.com/waterisland/attractions\_wi/
Dazu auch die Sammlung
Epstein
<https://waltisiegrist.locals.com/post/1353380/epstein-oder-wie-leicht-sich-die-wissenschaft-kaufen-laesst>
-

@ 52adc2ef:9f4bc0ba
2025-02-23 03:45:10
สวัสดีครับ วันนี้อยากมาเล่าเรื่องเกี่ยวกับ Options
เราได้ไปเรียนกับทาง อ.เอ็ม ติดเล่า เรื่องลงทุน
อยากจะเเชร์สำหรับคนที่สนใจ Options เเต่เพื่อนๆที่ลงทุนมาบ้างน่าจะเคยได้ยิน
เเต่ก่อนอื่นการเทรดลงทุนอยากให้เข้าใจ 3 คำนี้ก่อนนะครับ
**Spot , Futures , options**
**Spot** คือ การซื้อขาย สินทรัพย์ ณ เวลาปัจจุบัน ตามราคาปัจจุบัน เช่น BTC มีราคา 95,000$
ในเวปเทรด เรากดซื้อ จะได้ตามราคา
Futures คือ สัญญาซื้อ ขาย สินทรัพย์ล่วงหน้า จะซื้อขายในราคาที่กำหนด เมื่อถึงเวลากำหนด
จะต้องทำการซื้อขายตามนั้น คล้ายๆสัญญาซื้อที่ดิน ที่เราต้องใช้สิทธิ์กันทั้งผู้ซื้อและผู้ขาย
เช่น สัญญาจะซื้อ BTC ราคา 90,000$ โดยมีอายุสัญญา 3 เดือน ถ้าวันครบสัญญา BTC ราคา 95,000$ จะต้องขายให้ในราคา 90,000$
หรือ สัญญาขาย BTC ราคา 100,000$ โดยมีอายุสัญญา 3 เดือน ถ้าวันครบสัญญา BTC ราคา 95,000$ จะต้องขายให้ในราคา 100,000$
**Options** คือ สัญญาที่ผู้จะซื้อขาย เเบบ futures แต่มีจ่ายค่า Premium เพื่อมีสิทธิ์ที่จะใช้สิทธิ์ซื้อหรือสิทธิ์ขายก็ได้ โดยใช้สิทธิ์ในระยะเวลาที่กำหนด
เช่น สัญญา long call สัญญาใช้สิทธิ์ซื้อ เมื่อ BTC ราคา 98,000$ โดยต้องจ่ายค่า premium 100$ เพื่อLock สิทธิ์
ถ้าราคา BTC = 95,000$ เราไม่จำเป็นต้องใช้สิทธิ์ได้ เพราะซื้อในตลาดถูกกว่า เเต่เราจะต้องเสีย premium ที่เราวางไว้ เป็นต้น
พอจะเห็นภาพใช่มั้ยครับ
ซึ่งจะมาพูดในส่วนของ options กัน
Options มีการใช้สิทธิ์อยู่ 2 แบบ
Call Options โดยมี Long call คือ สิทธิ์ในการซื้อ Long put คือ สิทธิ์ในการขาย
Put Optionsโดยมี Short call คือ ผู้ที่มีหน้าที่ต้องขายจะคู่กับ Long call
Short put คือ ผู้ที่มีหน้าที่ต้องซื้อจะคู่กับ Long put
โดยมีคำศัพท์ควรรู้อีกเล็กน้อย จะได้เข้าใจภาพรวมทั้งหมดกัน
Strike price = ราคาที่จะซื้อจะขาย
maturity=วันสิ้นสัญญา
premium=เบี้ย
time to maturity=ระยะเวลาสัญญา
อาจจะยังงงๆ งั้นเริ่มอธิบายทีละข้อกันมาเริ่มที่
**Long Call Option**

สิทธิ์ในการซื้อ จากรูปจะเห็นว่าถ้าเราคิดว่าราคา สินทรัพย์ที่เราสนใจมีเเนวโน้มที่จะขึ้น
ซึ่งขณะนี้ ราคาอยู่ที่ 90$ เราอาจจะซื้อ Long call ที่ราคาเริ่มใช้สิทธิ์ Strike Price=100$
โดยมีค่า Premium ที่ 5$
จะเห็นว่าถ้าราคาเป็น 80$ เราคงไม่ใช้สิทธิ์ เพราะซื้อปกติถูกกว่า
ราคาใช้สิทธิ์เราจะต้องซื้อที่ 100$
เมื่อไม่ใช้สิทธิ์ เราต้องเสียค่า Premium ให้กับฝั่งที่มีหน้าที่ขาย คือ Short call
ซึ่งเมื่อเทียบกับการ Long Futures ถ้าเกิดลงไปเหลือ 45$ เราจะเสีย 50% เเต่ถ้ามี option จะเสียสุดที่เเค่ค่า Premium

รูปกราฟของ Long Futures
ซึ่ง Long call = Long future ครึ่งเดียวเพราะ Long Future ราคาจะขึ้นไปเรื่อยๆตามกราฟ
Long Call Option เหมาะใช้เมื่อไหร่?
ให้คิดว่าเหมือนซื้อหวย เพราะถ้าราคาไม่ไปตามที่คิดเราจะเสียเเค่ค่า Premium หวยเหมือนเราเสียค่า Premium ไปก่อน 80 บาท หรือวิเคราะห์มาเเล้วว่ามีโอกาสที่ราคาขึ้น
**Short Call Option**

เป็นฝั่งตรงข้ามกับ Long
call เราต้องมีหน้าที่ขายให้ฝั่ง long call ซึ่งฝั่งขายต้องมีสินทรัพย์นั้นๆเพื่อไว้ขาย เพราะมีหน้าที่
ต้องขาย ไม่เหมือนฝั่ง long call ที่มีสามารถเลือกใช้สิทธิ์ได้
เมื่อราคาไม่ถึง Strike Price หลังจากหมดอายุสัญญา ฝั่ง short call ได้ค่า Premium
จากฝั่ง Long call
จากรูป ถ้าสินทรัพย์ ราคา 90$ ราคาที่ต้องขายสินทรัพย์ 100$ ถ้าราคาไม่ถึง 100$ จะได้ค่า Premium เเต่ถ้าราคาเกิน 100$ เป็นต้นไป จะขาดทุนมากขึ้นเรื่อยๆ
ถ้าราคาไปที่ 150$ ต้องมาขายที่ 100$ ตามสัญญา
Short Call Option เหมาะใช้เมื่อไหร่?
เหมาะสำหรับที่เรามีสินทรัพย์ที่อยากจะขายอยู่เเล้วตาม Target ที่เราตั้งไว้
เช่น มีหุ้นที่ถือไว้อยู่เเล้ว ราคา 50$ ตั้งใจจะทำกำไรเมื่อราคา 100$ แทนที่จะรอขายเฉยๆ
มาทำการ Short call
ถ้าราคาไม่ถึงก็ได้กินค่า Premium ไป เเต่ถ้าราคาถึง 100$
เราต้องการที่จะ Take Profit อยู่เเล้ว ก็ขายไป
Long Put Option

หมายถึงเราสิทธ์ในการขายรือไม่ขายก็ได้ จะตรงข้ามกับ Long call
จากรูปถ้าถือสินทรัพย์จากทุน 50$ เเต่ตอนนี้ราคา 80$ เเล้วไม่เเน่ใจว่าราคาจะลงมั้ย เเต่ขึ้นต่อก็ไม่เปนไร
อยากจะ Lock ราคาขาย 70$ ใช้สัญญา Long Put จ่ายค่า Premium ถ้าราคาลงไปที่ 50$ เราใช้สิทธิ์ในการขายที่ ราคา 70$ ได้ ถ้าราคาขึ้นเราก็จะไม่ใช้สิทธิ์เพราะขายในตลาดได้ราคาดีกว่า

รูปกราฟของ Short Futures
ซึ่ง Long put = Short future ครึ่งเดียวเพราะ Short Future ราคาจะลงไปเรื่อยๆตามกราฟ
Long Put Option เหมาะใช้เมื่อไหร่?
ให้คิดว่าเหมือนซื้อประกัน ที่เราจ่ายเบี้ยประกันไปเพื่อที่จะ Lock ความเสี่ยงที่จะเกิด ส่วน Long Put ก็ไม่รู้ว่าราคาที่ถือจะลงมั้ย ยอมที่จ่ายค่า Premium เพื่อที่จะได้ราคาตามมูลค่าเดิมของเรา
**Short Put Option*
*
เป็นฝั่งตรงข้ามกับ Long put เราต้องมีหน้าที่รับซื้อให้ฝั่ง long put ซึ่งฝั่งซื้อต้องมีเงินเพื่อไว้ซื้อ เพราะมีหน้าที่ต้องซื้อ ไม่เหมือนฝั่ง long put ที่มีสามารถเลือกใช้สิทธิ์ได้
เมื่อราคาไม่ถึง Strike Price หลังจากหมดอายุสัญญา ฝั่ง short put ได้ค่า
Premium จากฝั่ง Long put
จากรูป
ราคาสินทรัพย์อยู่ที่ 80$ ราคาที่เรารับซื้อ หรือ Strike Price 70$ ถ้าราคาลงไม่ถึง 70 $ ก็จะได้ค่า Premium ถ้าราคาลงไปต่ำกว่า 70$ ก็ต้องรับซื้อทุกกรณี
ราคาลงไปที่ 50$ เราก็ต้องรับซื้อที่ 70$ ตามสัญญา
Short Put Option เหมาะใช้เมื่อไหร่?
ใช้เมื่อเราอยากจะซื้อสินทรัพย์ราคานั้นๆอยู่เเล้ว เช่น อยากจะซื้อที่ราคา 70 $ แทนที่จะรอเฉยๆ
อาจจะเปิด Short Put เพื่อที่ราคายังไม่ถึง target ก็จะได้ค่า Premium
ถ้าราคาถึงก็ได้ซื้อเหมือนที่ตั้งใจไว้
สรุป
จากที่เล่าทั้งหมดเป็นการอธิบาย Options เบื้องต้นที่อยากให้เพื่อนๆ ที่สนใจการเทรดอยู่เเล้ว
ถ้าเข้าใจเรื่อง Options ด้วยเราคิดว่าน่าจะปรับใช้ในส่วนช่วยใน Port ของเราไม่มากก็น้อย
หวังว่าจะเป็นประโยชน์กับทุกๆคนนะครับขอบคุณครับ
-

@ 5d4b6c8d:8a1c1ee3
2025-02-23 01:06:46
Well, my Wemby pick from last month just went up in flames. It's only getting more difficult to figure out who's getting that last spot, now. I want to take KAT, but that would give me the same exact picks as @gnilma with fewer possible points. I'll take his teammate, Jalen Brunson, and hope NY voters pick the wrong Knick.
Remember, older correct predictions are worth more than recent ones, so don't wait too long to get off your bad predictions.
Also, players must play in at least 65 games to be eligible for awards. Luka, AD, and Wemby are not going to be eligible, so you should swap them out if you still have them.
Here's the current state of the competition with your max possible score next to your nym:
| Contestant | MVP | Champ | All NBA | | | | |
|--------------|------|---------|----------|-|-|-|-|
| @Undisciplined 47| SGA| OKC | Jokic | Giannis |Tatum | SGA | Brunson |
| @grayruby 55| Giannis| Cavs| Jokic | Giannis | Luka | Mitchell| Brunson|
| @gnilma 55| SGA| OKC| Jokic | KAT | Giannis | Tatum| SGA |
| @BitcoinAbhi 70 | Luka| Denver| Jokic | Giannis | Luka | Ant| SGA|
| @Bell_curve 63| SGA| Celtics| Jokic | Giannis | Luka | Ant| SGA|
| @0xbitcoiner 70 | Jokic| Pacers| Jokic | Giannis | Luka | Ant| Brunson|
| @Coinsreporter 49| Giannis| Pacers| Jokic | Giannis | Luka | Ant| Brunson|
| @TheMorningStar 49| Luka| Celtics| Jokic | Giannis | Luka | Ant| SGA|
| @onthedeklein 49| Luka| T-Wolves| Jokic | Giannis | Luka | Wemby| SGA|
| @Carresan 49| Luka| Mavs| Jokic | Giannis | Luka | Wemby| SGA|
| @BTC_Bellzer 34| SGA| Celtics| Jokic| Giannis | Tatum| SGA| Brunson |
| @realBitcoinDog 49| Luka| Lakers| Jokic | Giannis | Luka | Ant| SGA|
| @SimpleStacker 42| SGA| Celtics| Jokic| Tatum| Luka | Brunson| SGA|
| @BlokchainB 42| SGA| Knicks| AD| Giannis | Ant| Brunson| SGA|
**Prize**
At least 6k (I'll keep adding zaps to the pot).
If you want to join this contest, just leave your predictions for MVP, Champion, and All-NBA 1st team in the comments. See the [June post](https://stacker.news/items/585231/r/Undisciplined) for more details.
originally posted at https://stacker.news/items/894412
-

@ 641d8c39:1224c8d3
2025-02-23 00:17:46
A specter is haunting the modern world, the specter of crypto anarchy.
Computer technology is on the verge of providing the ability for individuals and groups to communicate and interact with each other in a totally anonymous manner. Two persons may exchange messages, conduct business, and negotiate electronic contracts without ever knowing the True Name, or legal identity, of the other. Interactions over networks will be untraceable, via extensive re-routing of encrypted packets and tamper-proof boxes which implement cryptographic protocols with nearly perfect assurance against any tampering. Reputations will be of central importance, far more important in dealings than even the credit ratings of today. These developments will alter completely the nature of government regulation, the ability to tax and control economic interactions, the ability to keep information secret, and will even alter the nature of trust and reputation.
The technology for this revolution--and it surely will be both a social and economic revolution--has existed in theory for the past decade. The methods are based upon public-key encryption, zero-knowledge interactive proof systems, and various software protocols for interaction, authentication, and verification. The focus has until now been on academic conferences in Europe and the U.S., conferences monitored closely by the National Security Agency. But only recently have computer networks and personal computers attained sufficient speed to make the ideas practically realizable. And the next ten years will bring enough additional speed to make the ideas economically feasible and essentially unstoppable. High-speed networks, ISDN, tamper-proof boxes, smart cards, satellites, Ku-band transmitters, multi-MIPS personal computers, and encryption chips now under development will be some of the enabling technologies.
The State will of course try to slow or halt the spread of this technology, citing national security concerns, use of the technology by drug dealers and tax evaders, and fears of societal disintegration. Many of these concerns will be valid; crypto anarchy will allow national secrets to be trade freely and will allow illicit and stolen materials to be traded. An anonymous computerized market will even make possible abhorrent markets for assassinations and extortion. Various criminal and foreign elements will be active users of CryptoNet. But this will not halt the spread of crypto anarchy.
Just as the technology of printing altered and reduced the power of medieval guilds and the social power structure, so too will cryptologic methods fundamentally alter the nature of corporations and of government interference in economic transactions. Combined with emerging information markets, crypto anarchy will create a liquid market for any and all material which can be put into words and pictures. And just as a seemingly minor invention like barbed wire made possible the fencing-off of vast ranches and farms, thus altering forever the concepts of land and property rights in the frontier West, so too will the seemingly minor discovery out of an arcane branch of mathematics come to be the wire clippers which dismantle the barbed wire around intellectual property.
Arise, you have nothing to lose but your barbed wire fences!A specter is haunting the modern world, the specter of crypto anarchy.
Computer technology is on the verge of providing the ability for individuals and groups to communicate and interact with each other in a totally anonymous manner. Two persons may exchange messages, conduct business, and negotiate electronic contracts without ever knowing the True Name, or legal identity, of the other. Interactions over networks will be untraceable, via extensive re-routing of encrypted packets and tamper-proof boxes which implement cryptographic protocols with nearly perfect assurance against any tampering. Reputations will be of central importance, far more important in dealings than even the credit ratings of today. These developments will alter completely the nature of government regulation, the ability to tax and control economic interactions, the ability to keep information secret, and will even alter the nature of trust and reputation.
The technology for this revolution--and it surely will be both a social and economic revolution--has existed in theory for the past decade. The methods are based upon public-key encryption, zero-knowledge interactive proof systems, and various software protocols for interaction, authentication, and verification. The focus has until now been on academic conferences in Europe and the U.S., conferences monitored closely by the National Security Agency. But only recently have computer networks and personal computers attained sufficient speed to make the ideas practically realizable. And the next ten years will bring enough additional speed to make the ideas economically feasible and essentially unstoppable. High-speed networks, ISDN, tamper-proof boxes, smart cards, satellites, Ku-band transmitters, multi-MIPS personal computers, and encryption chips now under development will be some of the enabling technologies.
The State will of course try to slow or halt the spread of this technology, citing national security concerns, use of the technology by drug dealers and tax evaders, and fears of societal disintegration. Many of these concerns will be valid; crypto anarchy will allow national secrets to be trade freely and will allow illicit and stolen materials to be traded. An anonymous computerized market will even make possible abhorrent markets for assassinations and extortion. Various criminal and foreign elements will be active users of CryptoNet. But this will not halt the spread of crypto anarchy.
Just as the technology of printing altered and reduced the power of medieval guilds and the social power structure, so too will cryptologic methods fundamentally alter the nature of corporations and of government interference in economic transactions. Combined with emerging information markets, crypto anarchy will create a liquid market for any and all material which can be put into words and pictures. And just as a seemingly minor invention like barbed wire made possible the fencing-off of vast ranches and farms, thus altering forever the concepts of land and property rights in the frontier West, so too will the seemingly minor discovery out of an arcane branch of mathematics come to be the wire clippers which dismantle the barbed wire around intellectual property.
Arise, you have nothing to lose but your barbed wire fences!
https://groups.csail.mit.edu/mac/classes/6.805/articles/crypto/cypherpunks/may-crypto-manifesto.html
-

@ fc481c65:e280e7ba
2025-02-22 22:22:14
**Math is the formalization of a human idea**
Mathematics is a broad field of study that involves the investigation of patterns, quantities, structures, and changes in the abstract form as well as their real-world applications. It is foundational to a variety of disciplines including science, engineering, medicine, and the social sciences, providing a framework for reasoning, problem-solving, and understanding the universe.
<iframe title="The Map of Mathematics" src="https://www.youtube.com/embed/OmJ-4B-mS-Y?feature=oembed" height="113" width="200" allowfullscreen="" allow="fullscreen" style="aspect-ratio: 1.76991 / 1; width: 100%; height: 100%;"></iframe>
Mathematics is composed of many subfields, including but not limited to:
1. **Arithmetic:** The study of numbers and the basic operations on them: addition, subtraction, multiplication, and division.
2. **Algebra:** The study of symbols and the rules for manipulating these symbols; it is a unifying thread of almost all of mathematics.
3. **Geometry:** The study of shapes, sizes, and properties of space.
4. **Calculus:** The study of change in mathematical functions and models, dealing with limits, derivatives, integrals, and infinite series.
5. **Statistics:** The study of data collection, analysis, interpretation, presentation, and organization.
6. **Number Theory:** The study of properties and relationships of numbers, especially the integers.
7. **Topology:** The study of properties that remain constant through continuous deformations, such as stretching and bending, but not tearing or gluing.
8. **Applied Mathematics:** Uses mathematical methods and reasoning to solve real-world problems in business, science, engineering, and other fields.
Mathematics is both ancient and modern; it has a rich history stretching back thousands of years, yet it continues to develop and evolve today, with new theories, discoveries, and applications constantly emerging. It is both a rigorous discipline in its own right and an essential tool used throughout the sciences and beyond.
## Pure and Applied Mathematics
Pure mathematics and applied mathematics represent two broad categories within the field of mathematics, each with its focus, methodologies, and applications. The distinction between them lies in their primary objectives and the way mathematical theories are utilized.
[[Attachments/01233372a59d2dc17b937c38319d672f_MD5.jpeg|Open: Pasted image 20240405125055.png]]
![[Attachments/01233372a59d2dc17b937c38319d672f_MD5.jpeg]]
#### Pure Mathematics
Pure mathematics is concerned with the study of mathematical concepts independent of any application outside mathematics. It is motivated by a desire to understand abstract principles and the properties of mathematical structures. The pursuit in pure mathematics is knowledge for its own sake, not necessarily aiming to find immediate practical applications. Pure mathematicians often focus on proving theorems and exploring theoretical frameworks, driven by curiosity and the aesthetic appeal of mathematics itself.
Key areas within pure mathematics include:
- **Algebra:** The study of symbols and the rules for manipulating these symbols.
- **Geometry:** The investigation of the properties of space and figures.
- **Analysis:** The rigorous formulation of calculus, focusing on limits, continuity, and infinite series.
- **Number Theory:** The study of the properties of numbers, particularly integers.
- **Topology:** The study of properties preserved through deformations, twistings, and stretchings of objects.
#### Applied Mathematics
Applied mathematics, on the other hand, is focused on the development and practical use of mathematical methods to solve problems in other areas, such as science, engineering, technology, economics, business, and industry. Applied mathematics is deeply connected with empirical research and the application of mathematical models to real-world situations. It involves the formulation, study, and use of mathematical models and seeks to make predictions, optimize solutions, and develop new approaches based on mathematical theory.
Key areas within applied mathematics include:
- **Differential Equations:** Used to model rates of change in applied contexts.
- **Statistics and Probability:** The study of data, uncertainty, and the quantification of the likelihood of events.
- **Computational Mathematics:** The use of algorithmic techniques for solving mathematical problems more efficiently, especially those that are too large for human numerical capacity.
- **Mathematical Physics:** The application of mathematics to solve problems in physics and the development of mathematical methods for such applications.
## Is Mathematics discovered or Invented
The question of whether mathematics is discovered or invented is a philosophical one that has sparked debate among mathematicians, philosophers, and scientists for centuries. Both viewpoints offer compelling arguments, and the distinction often hinges on one's perspective on the nature of mathematical objects and the universality of mathematical truths.
<iframe title="Is math discovered or invented? - Jeff Dekofsky" src="https://www.youtube.com/embed/X_xR5Kes4Rs?feature=oembed" height="113" width="200" allowfullscreen="" allow="fullscreen" style="aspect-ratio: 1.76991 / 1; width: 100%; height: 100%;"></iframe>
### Mathematics as Discovered
Those who argue that mathematics is discovered believe that mathematical truths exist independently of human thought and that mathematicians uncover these truths through investigation and reasoning. This viewpoint suggests that mathematical concepts like numbers, geometrical shapes, and even more abstract ideas have a reality that transcends human invention. The consistency of mathematical laws across cultures and times, and their applicability in accurately describing the natural world, supports the notion that mathematics is a universal truth waiting to be discovered. According to this perspective, mathematical structures exist in some abstract realm, and humans merely uncover aspects of this pre-existing world.
#### Mathematics as Invented
On the other hand, the viewpoint that mathematics is invented centers on the idea that mathematical concepts are human creations, designed to describe and understand the world. According to this perspective, mathematical theories and structures are the products of human thought, created to serve specific purposes in science, engineering, and other fields. This view emphasizes the role of creativity and invention in the development of mathematical ideas, suggesting that different cultures or species might develop entirely different mathematical systems depending on their needs and experiences. Proponents of this view point to the variety of mathematical systems (such as different geometries or number systems) that have been invented to solve particular types of problems, arguing that this diversity is evidence of mathematics being a human invention.
#### A Middle Ground
Some argue for a middle ground, suggesting that while the basic elements of mathematics are discovered, the development of complex mathematical theories and the choice of which aspects to study or develop further involve human invention and creativity. This perspective acknowledges the intrinsic properties of mathematical objects while also recognizing the role of human ingenuity in shaping the field of mathematics.
#### Conclusion
The debate between discovery and invention in mathematics may never be conclusively resolved, as it touches on deep philosophical questions about the nature of reality and the human mind's relationship to it. Whether one views mathematics as discovered or invented often reflects deeper beliefs about the world and our place within it.
## Axioms
a particular mathematical system or theory. They serve as the foundational building blocks from which theorems and other mathematical truths are derived. Axioms are assumed to be self-evident, and their selection is based on their ability to produce a coherent and logically consistent framework for a body of mathematical knowledge.
In the context of different branches of mathematics, axioms can vary significantly:
- **In Euclidean geometry,** one of the most famous sets of axioms are Euclid's postulates, which include statements like "A straight line segment can be drawn joining any two points," and "All right angles are congruent."
- **In algebra,** the field axioms define the properties of operations like addition and multiplication over sets of numbers.
- **In set theory,** Zermelo-Fraenkel axioms (with the Axiom of Choice) are a set of axioms used to establish a foundation for much of modern mathematics.
The role of axioms has evolved throughout the history of mathematics. Initially, they were considered self-evident truths, but as mathematics has developed, the emphasis has shifted to viewing axioms more as arbitrary starting points chosen for their usefulness in building a mathematical theory. This shift allows for the creation of different, sometimes non-intuitive, mathematical frameworks such as non-Euclidean geometries, which arise from altering Euclid's original postulates.
**Everything in maths is constructed based on Axioms, not observation of the scientific method!** It's based only on the human logic reasoning. **And the universe doesn't five a fuck to fit inside human logic reasoning.**
<iframe title="The paradox at the heart of mathematics: Gödel's Incompleteness Theorem - Marcus du Sautoy" src="https://www.youtube.com/embed/I4pQbo5MQOs?feature=oembed" height="113" width="200" allowfullscreen="" allow="fullscreen" style="aspect-ratio: 1.76991 / 1; width: 100%; height: 100%;"></iframe>
## Mathematics is not a Science
Mathematics and science are deeply interconnected, but they are distinguished by their fundamental approaches, methodologies, and objectives. The distinction between mathematics as a formal science and other natural or empirical sciences like physics, biology, and chemistry lies in the nature of their inquiry and validation methods.
**Maths doesn't need to prove itself through the scientific method, it only needs axioms, logic, and previous definitions.**
- **Mathematics:** Uses deduction as a primary tool. Starting from axioms and definitions, mathematicians use logical reasoning to derive theorems and propositions. The validity of mathematical statements is determined through proofs, which are arguments that demonstrate their truth within the context of axiomatic systems.
- **Science:** Employs the scientific method, which involves hypothesis formation, experimentation, observation, and the modification of hypotheses based on empirical evidence. Scientific theories and laws are validated by their ability to predict and explain phenomena in the natural world, and they are always subject to revision in light of new evidence.
### Objectives
- **Mathematics:** Aims to create a coherent set of rules and structures that can explain and predict outcomes within abstract systems. Its primary goal is not to describe the physical world but to explore the properties and possibilities of mathematical structures.
- **Science:** Aims to understand and describe the universe. The goal is to produce a body of knowledge that explains natural phenomena and can predict outcomes based on empirical evidence.
In summary, while mathematics is often used as a tool in science to model and solve problems, its focus on abstract reasoning and logical proof distinguishes it from the empirical methodologies of the natural sciences. This fundamental difference in approach and objective is why mathematics is considered a formal science or a branch of knowledge distinct from natural or physical sciences, which are based on empirical evidence and experimental validation.
-

@ fc481c65:e280e7ba
2025-02-22 22:09:56
Starting with the basics, #statistics is a branch of #mathematics that deals with collecting, analysing, interpreting, presenting, and organising #data. It provides a way to make sense of data, see patterns, and make decisions based on data analysis. Here's a brief overview of some fundamental concepts in statistics:
### 1. Types of Statistics
- **Descriptive Statistics**: Involves summarising and organising data so it can be easily understood. Common measures include mean (average), median (middle value), mode (most frequent value), variance (measure of how spread out numbers are), and standard deviation (average distance from the mean).
- **Inferential Statistics**: Involves making predictions or inferences about a population based on a sample. This includes hypothesis testing, confidence intervals, and regression analysis.
### 2. Types of Data
- **Qualitative Data** (Categorical): Data that describes qualities or characteristics that cannot be measured with numbers, such as colors, names, labels, and yes/no responses.
- **Quantitative Data**: Data that can be measured and expressed numerically, including age, height, salary, and temperature. It can be further divided into discrete data (countable items, like the number of students in a class) and continuous data (measurable items, like height).
### 3. Measures of Central Tendency
- **Mean**: The average of a data set, found by adding all numbers and dividing by the count of numbers.
- **Median**: The middle value when a data set is ordered from least to greatest; if there’s an even number of observations, it is the average of the two middle numbers.
- **Mode**: The most frequently occurring value in a data set.
### 4. Measures of Spread
- **Range**: The difference between the highest and lowest values in a data set.
- **Variance**: Measures how far each number in the set is from the mean and thus from every other number in the set.
- **Standard Deviation**: The square root of the variance, providing a measure of the spread of a distribution of values.
### 5. Probability
Probability measures the likelihood of an event occurring, ranging from 0 (impossible) to 1 (certain). Understanding probability is essential for inferential statistics and making predictions based on data.
### 6. Sampling and Data Collection
- **Population**: The entire group that you want to draw conclusions about.
- **Sample**: A subset of the population, selected for the actual study. It’s crucial for the sample to be representative of the population to make accurate inferences.
### 7. Hypothesis Testing
This is a method of making decisions or inferences about population parameters based on sample statistics. It involves:
- Formulating a null hypothesis (no effect) and an alternative hypothesis (some effect).
- Calculating a test statistic based on the sample data.
- Using the test statistic to decide whether to reject the null hypothesis in favor of the alternative.
 @ 629c4a12:f822cc1a
2025-02-23 21:50:25Treasury bonds, once considered the gold standard for conservative investments, have struggled to maintain their appeal in an era of low yields and rising inflation. Governments face mounting pressure to rethink their traditional treasury instruments, especially the long duration bonds. Enter Bitcoin—a neutral, decentralized, scarce, and globally recognized asset. By integrating Bitcoin into treasury bonds, governments have a unique opportunity to breathe new life into their sovereign debt markets and attract a new wave of investors. ### Problem: The decline of long-duration sovereign bonds Around the world, governments are grappling with declining investor confidence in their long-term debt instruments. Major institutional investors have been reducing their exposure to long-dated sovereign bonds due to rising inflation, unsustainable debt levels, and uncertainty around global monetary policies. In Europe, countries like Italy and Greece have faced heightened yield spreads, reflecting investor wariness over fiscal sustainability. In Japan, long-term government bonds have seen weak demand, despite interventions by the Bank of Japan to stabilize yields. Emerging markets, too, face significant challenges, with higher borrowing costs and limited foreign investor participation in their sovereign bond markets. Globally, yields on long-term sovereign bonds have risen as investors demand higher compensation for the perceived risks. This inverse relationship between yields and bond prices highlights a broader issue: governments are finding it increasingly difficult to issue long-term debt at sustainable costs. ### Key factors contributing to this global decline include: * **Persistent inflation:** Eroding the purchasing power of fixed-income returns across global markets. * **Increased government borrowing:** Leading to an oversupply of bonds in developed and emerging economies alike. * **Monetary policy uncertainty:** Central bank actions in response to inflation and slowing economic growth have added volatility to bond markets. As a result, global investors are increasingly favoring short-term bonds or alternative assets, leaving long-term sovereign bonds struggling to attract sufficient demand. Solution: Bitcoin as collateral for treasury bonds Governments can collateralize 10% of their 10-year and 30-year treasury bond offerings with Bitcoin. In practice, this means a portion of the bond’s value would be backed by Bitcoin reserves held securely by the issuing government or a trusted custodian. Investors would gain exposure not only to the guaranteed yield of the bond but also to the potential upside of Bitcoin’s price appreciation. To sweeten the deal, governments could offer tax-free capital gains on any Bitcoin price appreciation realized through this instrument. This would make Bitcoin-backed treasury bonds not only a conservative, yield-generating investment but also a potentially lucrative one. ### Why this matters for governments * **Attracting a new investor class:** Bitcoin has a growing base of institutional and retail investors. A Bitcoin-collateralized bond could attract Bitcoin enthusiasts and institutional investors seeking compliant exposure to Bitcoin. * **Strengthening national bitcoin reserves:** By holding Bitcoin as collateral, governments would gradually build Bitcoin reserves, which could act as a hedge against currency devaluation and macroeconomic instability. * **Enhancing bond appeal in inflationary environments:** In inflationary periods, traditional bonds struggle to offer real returns. Bitcoin’s historical performance as an inflation hedge could help offset this concern. * **Diversifying reserve assets:** Bitcoin offers a unique diversification benefit compared to traditional reserve assets like gold and foreign currencies. ### Why this matters for investors * **Dual upside potential:** Investors not only gain the fixed yield of a treasury bond but also the upside of Bitcoin price appreciation. * **Tax-gree gains on Bitcoin exposure:** The tax exemption on Bitcoin gains would be a significant incentive for investors looking for capital-efficient exposure to Bitcoin. * **Low-risk Bitcoin exposure:** For more conservative investors, Bitcoin-backed bonds offer a lower-risk pathway to Bitcoin exposure compared to direct ownership. ### Why focus on 10-Year and 30-year treasuries? Long-term treasuries, such as 10-year and 30-year bonds, are ideal candidates for Bitcoin collateralization due to their extended maturity periods. These longer timelines allow Bitcoin’s historical price appreciation to play a more significant role in generating value for investors. Additionally, they align better with Bitcoin’s long-term investment thesis, making them more attractive to investors seeking both yield and potential asset growth. Short-term treasuries, on the other hand, are less suited for Bitcoin collateralization due to Bitcoin’s volatility and shorter investment horizons. Implementation and challenges While the concept is innovative, there are several practical and regulatory challenges: * **Custody and Security:** Governments must establish secure custody solutions for Bitcoin reserves. * **Volatility Management:** Bitcoin’s price volatility could introduce risk into the bond’s collateral structure. * **Regulatory Clarity:** Clear regulatory frameworks would need to be established to govern these hybrid financial instruments. However, with the right infrastructure and governance, these challenges are far from insurmountable. A win-win opportunity By collateralizing 10-year and 30-year treasury bonds with Bitcoin, governments around the world can tap into the growing Bitcoin economy, attract a new wave of global investors, and future-proof their financial strategies. Investors, on the other hand, gain access to a secure, regulated, and potentially lucrative investment vehicle. In a rapidly changing financial landscape, integrating Bitcoin into long-term sovereign bonds is not just an opportunity—it’s a strategic imperative. Governments that act decisively could position themselves at the forefront of a new era in global sovereign finance.
@ 629c4a12:f822cc1a
2025-02-23 21:50:25Treasury bonds, once considered the gold standard for conservative investments, have struggled to maintain their appeal in an era of low yields and rising inflation. Governments face mounting pressure to rethink their traditional treasury instruments, especially the long duration bonds. Enter Bitcoin—a neutral, decentralized, scarce, and globally recognized asset. By integrating Bitcoin into treasury bonds, governments have a unique opportunity to breathe new life into their sovereign debt markets and attract a new wave of investors. ### Problem: The decline of long-duration sovereign bonds Around the world, governments are grappling with declining investor confidence in their long-term debt instruments. Major institutional investors have been reducing their exposure to long-dated sovereign bonds due to rising inflation, unsustainable debt levels, and uncertainty around global monetary policies. In Europe, countries like Italy and Greece have faced heightened yield spreads, reflecting investor wariness over fiscal sustainability. In Japan, long-term government bonds have seen weak demand, despite interventions by the Bank of Japan to stabilize yields. Emerging markets, too, face significant challenges, with higher borrowing costs and limited foreign investor participation in their sovereign bond markets. Globally, yields on long-term sovereign bonds have risen as investors demand higher compensation for the perceived risks. This inverse relationship between yields and bond prices highlights a broader issue: governments are finding it increasingly difficult to issue long-term debt at sustainable costs. ### Key factors contributing to this global decline include: * **Persistent inflation:** Eroding the purchasing power of fixed-income returns across global markets. * **Increased government borrowing:** Leading to an oversupply of bonds in developed and emerging economies alike. * **Monetary policy uncertainty:** Central bank actions in response to inflation and slowing economic growth have added volatility to bond markets. As a result, global investors are increasingly favoring short-term bonds or alternative assets, leaving long-term sovereign bonds struggling to attract sufficient demand. Solution: Bitcoin as collateral for treasury bonds Governments can collateralize 10% of their 10-year and 30-year treasury bond offerings with Bitcoin. In practice, this means a portion of the bond’s value would be backed by Bitcoin reserves held securely by the issuing government or a trusted custodian. Investors would gain exposure not only to the guaranteed yield of the bond but also to the potential upside of Bitcoin’s price appreciation. To sweeten the deal, governments could offer tax-free capital gains on any Bitcoin price appreciation realized through this instrument. This would make Bitcoin-backed treasury bonds not only a conservative, yield-generating investment but also a potentially lucrative one. ### Why this matters for governments * **Attracting a new investor class:** Bitcoin has a growing base of institutional and retail investors. A Bitcoin-collateralized bond could attract Bitcoin enthusiasts and institutional investors seeking compliant exposure to Bitcoin. * **Strengthening national bitcoin reserves:** By holding Bitcoin as collateral, governments would gradually build Bitcoin reserves, which could act as a hedge against currency devaluation and macroeconomic instability. * **Enhancing bond appeal in inflationary environments:** In inflationary periods, traditional bonds struggle to offer real returns. Bitcoin’s historical performance as an inflation hedge could help offset this concern. * **Diversifying reserve assets:** Bitcoin offers a unique diversification benefit compared to traditional reserve assets like gold and foreign currencies. ### Why this matters for investors * **Dual upside potential:** Investors not only gain the fixed yield of a treasury bond but also the upside of Bitcoin price appreciation. * **Tax-gree gains on Bitcoin exposure:** The tax exemption on Bitcoin gains would be a significant incentive for investors looking for capital-efficient exposure to Bitcoin. * **Low-risk Bitcoin exposure:** For more conservative investors, Bitcoin-backed bonds offer a lower-risk pathway to Bitcoin exposure compared to direct ownership. ### Why focus on 10-Year and 30-year treasuries? Long-term treasuries, such as 10-year and 30-year bonds, are ideal candidates for Bitcoin collateralization due to their extended maturity periods. These longer timelines allow Bitcoin’s historical price appreciation to play a more significant role in generating value for investors. Additionally, they align better with Bitcoin’s long-term investment thesis, making them more attractive to investors seeking both yield and potential asset growth. Short-term treasuries, on the other hand, are less suited for Bitcoin collateralization due to Bitcoin’s volatility and shorter investment horizons. Implementation and challenges While the concept is innovative, there are several practical and regulatory challenges: * **Custody and Security:** Governments must establish secure custody solutions for Bitcoin reserves. * **Volatility Management:** Bitcoin’s price volatility could introduce risk into the bond’s collateral structure. * **Regulatory Clarity:** Clear regulatory frameworks would need to be established to govern these hybrid financial instruments. However, with the right infrastructure and governance, these challenges are far from insurmountable. A win-win opportunity By collateralizing 10-year and 30-year treasury bonds with Bitcoin, governments around the world can tap into the growing Bitcoin economy, attract a new wave of global investors, and future-proof their financial strategies. Investors, on the other hand, gain access to a secure, regulated, and potentially lucrative investment vehicle. In a rapidly changing financial landscape, integrating Bitcoin into long-term sovereign bonds is not just an opportunity—it’s a strategic imperative. Governments that act decisively could position themselves at the forefront of a new era in global sovereign finance. @ 629c4a12:f822cc1a
2025-02-23 21:33:31I’ve always been drawn to minimalism. There’s a certain peace that comes from stripping away the unnecessary, decluttering both physical and mental spaces. Yet, when it comes to finances, I’ve found myself tangled in complexity. As an ‘optimizer,’ I spend an inordinate amount of time thinking about investments, managing risk, and endlessly tinkering with my portfolio. This preoccupation contradicts the minimalist principles I try to live by. It seems absurd to me that the financial world has become so complicated that we need money managers to simply preserve the value of our money. If investing is so intricate that the average person must hire professionals just to preserve (let alone grow) the value of their savings, then something is fundamentally wrong. For the past five years, I’ve immersed myself in the history and mechanics of financial systems. The deeper I delved, the clearer it became: Bitcoin is a force of minimalism in an increasingly financialized and complex world. ### The Clutter of Modern Finance Our financial system has become bloated with complexity. The hyper-securitization of assets has created an environment filled with financial clutter. Derivatives, for example, represent layers upon layers of financial engineering, often so convoluted that even experts struggle to understand them fully. More troubling is the way nearly everything of value has been financialized. Real estate and art, two things that should embody personal value and cultural significance, have been transformed into mere asset classes. They are bought, sold, and speculated upon not for their intrinsic qualities but as instruments in the game of wealth preservation. But why has this happened? It’s actually quite simple: our money is constantly losing value. The dollar, for example, debases at a rate of around 7% per year. Holding cash feels like holding melting ice, so it’s only natural for people to seek out scarce assets to preserve their wealth. The Never-Ending Game of Diversification This pursuit of scarce assets sets off a complex game—a game that forces people to diversify endlessly: * Equities * Bonds * Real Estate * Commodities * Art * Collectibles We’re told to spread our investments across these asset classes to mitigate risk and preserve our hard-earned money. Those who can afford to hire money managers generally fare better in this game, as they have access to expertise and strategies designed to navigate this maze of complexity. Ironically, this system creates an incentive for more complexity. The more convoluted the financial landscape becomes, the more we need money managers, and the more entrenched this cycle of financialization and securitization becomes. It’s a force of ever-increasing entropy—quite the opposite of minimalism. ### Bitcoin: Simplicity in a Complex World In the midst of this financial chaos, Bitcoin emerges as a beacon of simplicity. It offers a way out of the clutter, a chance to reclaim financial minimalism. Bitcoin embodies the concept of scarcity with a rare kind of perfection: there will only ever be 21 million Bitcoins. No more. This scarcity makes Bitcoin the perfect savings technology. Unlike traditional currencies, no one can debase your holdings. You don’t need to chase after real estate, art, or other assets to preserve your wealth. You don’t need to constantly diversify and rebalance a portfolio to stay ahead of inflation. Bitcoin’s scarcity gives you a way to hold your wealth securely, without the need for endless tinkering. I’m not blind to Bitcoin’s short-term price volatility. However, it’s crucial to understand that we’re still in the early stages of adoption. As more people embrace this perfect form of scarcity, Bitcoin’s qualities as savings technology will express itself. Bitcoin has the potential to de-financialize the housing market. It can de-financialize art. Ultimately, Bitcoin has the power to replace those aspects of our lives that currently serve as proxies for scarcity. ### A Minimalist Approach to Wealth Bitcoin allows us to step off the treadmill of constant financial optimization. It offers a simpler way to safeguard the fruits of our labor. Rather than spending our time, energy, and attention on navigating a complex financial system, we can focus on what truly matters: living a meaningful life. By embracing Bitcoin, we embrace a minimalist approach to wealth. We reject the idea that we must play a never-ending game of diversification to maintain our standard of living. Instead, we adopt a simple, elegant solution that aligns with the principles of minimalism. ### Conclusion In a world that grows more financially cluttered by the day, Bitcoin stands as a path to financial minimalism. It frees us from the complexities of traditional finance, allowing us to preserve our wealth without the need for constant vigilance and management. By embodying scarcity and simplicity, Bitcoin gives us a way to reclaim our time and energy. It’s not just a financial tool; it’s a way to simplify our lives, to step back from the chaos, and to focus on what truly matters
@ 629c4a12:f822cc1a
2025-02-23 21:33:31I’ve always been drawn to minimalism. There’s a certain peace that comes from stripping away the unnecessary, decluttering both physical and mental spaces. Yet, when it comes to finances, I’ve found myself tangled in complexity. As an ‘optimizer,’ I spend an inordinate amount of time thinking about investments, managing risk, and endlessly tinkering with my portfolio. This preoccupation contradicts the minimalist principles I try to live by. It seems absurd to me that the financial world has become so complicated that we need money managers to simply preserve the value of our money. If investing is so intricate that the average person must hire professionals just to preserve (let alone grow) the value of their savings, then something is fundamentally wrong. For the past five years, I’ve immersed myself in the history and mechanics of financial systems. The deeper I delved, the clearer it became: Bitcoin is a force of minimalism in an increasingly financialized and complex world. ### The Clutter of Modern Finance Our financial system has become bloated with complexity. The hyper-securitization of assets has created an environment filled with financial clutter. Derivatives, for example, represent layers upon layers of financial engineering, often so convoluted that even experts struggle to understand them fully. More troubling is the way nearly everything of value has been financialized. Real estate and art, two things that should embody personal value and cultural significance, have been transformed into mere asset classes. They are bought, sold, and speculated upon not for their intrinsic qualities but as instruments in the game of wealth preservation. But why has this happened? It’s actually quite simple: our money is constantly losing value. The dollar, for example, debases at a rate of around 7% per year. Holding cash feels like holding melting ice, so it’s only natural for people to seek out scarce assets to preserve their wealth. The Never-Ending Game of Diversification This pursuit of scarce assets sets off a complex game—a game that forces people to diversify endlessly: * Equities * Bonds * Real Estate * Commodities * Art * Collectibles We’re told to spread our investments across these asset classes to mitigate risk and preserve our hard-earned money. Those who can afford to hire money managers generally fare better in this game, as they have access to expertise and strategies designed to navigate this maze of complexity. Ironically, this system creates an incentive for more complexity. The more convoluted the financial landscape becomes, the more we need money managers, and the more entrenched this cycle of financialization and securitization becomes. It’s a force of ever-increasing entropy—quite the opposite of minimalism. ### Bitcoin: Simplicity in a Complex World In the midst of this financial chaos, Bitcoin emerges as a beacon of simplicity. It offers a way out of the clutter, a chance to reclaim financial minimalism. Bitcoin embodies the concept of scarcity with a rare kind of perfection: there will only ever be 21 million Bitcoins. No more. This scarcity makes Bitcoin the perfect savings technology. Unlike traditional currencies, no one can debase your holdings. You don’t need to chase after real estate, art, or other assets to preserve your wealth. You don’t need to constantly diversify and rebalance a portfolio to stay ahead of inflation. Bitcoin’s scarcity gives you a way to hold your wealth securely, without the need for endless tinkering. I’m not blind to Bitcoin’s short-term price volatility. However, it’s crucial to understand that we’re still in the early stages of adoption. As more people embrace this perfect form of scarcity, Bitcoin’s qualities as savings technology will express itself. Bitcoin has the potential to de-financialize the housing market. It can de-financialize art. Ultimately, Bitcoin has the power to replace those aspects of our lives that currently serve as proxies for scarcity. ### A Minimalist Approach to Wealth Bitcoin allows us to step off the treadmill of constant financial optimization. It offers a simpler way to safeguard the fruits of our labor. Rather than spending our time, energy, and attention on navigating a complex financial system, we can focus on what truly matters: living a meaningful life. By embracing Bitcoin, we embrace a minimalist approach to wealth. We reject the idea that we must play a never-ending game of diversification to maintain our standard of living. Instead, we adopt a simple, elegant solution that aligns with the principles of minimalism. ### Conclusion In a world that grows more financially cluttered by the day, Bitcoin stands as a path to financial minimalism. It frees us from the complexities of traditional finance, allowing us to preserve our wealth without the need for constant vigilance and management. By embodying scarcity and simplicity, Bitcoin gives us a way to reclaim our time and energy. It’s not just a financial tool; it’s a way to simplify our lives, to step back from the chaos, and to focus on what truly matters @ c11cf5f8:4928464d
2025-02-23 20:42:52Let's hear some of your latest #Bitcoin purchases, feel free to include links to the #shops or #merchants you bought from too. Any good #deal we should know about? If you missed our last thread, [here](https://stacker.news/items/887305/r/AG) are some of the items stackers recently spent and #zap #sats on. originally posted at https://stacker.news/items/895134
@ c11cf5f8:4928464d
2025-02-23 20:42:52Let's hear some of your latest #Bitcoin purchases, feel free to include links to the #shops or #merchants you bought from too. Any good #deal we should know about? If you missed our last thread, [here](https://stacker.news/items/887305/r/AG) are some of the items stackers recently spent and #zap #sats on. originally posted at https://stacker.news/items/895134 @ 378562cd:a6fc6773
2025-02-23 20:41:59Social media platforms like Facebook and X (formerly Twitter) have long dominated online communication. However, many people are looking for alternatives due to increasing censorship, algorithmic manipulation, and corporate control over user data. One of the most promising new protocols I have found is Nostr, a decentralized and open-source alternative to traditional social media. But how does Nostr compare, and why should you consider making the switch? If you're reading this, presumably, you already have made the switch, but share this with friends if you like. Let’s dive in. The Fundamental Differences Between Nostr and Traditional Social Media 1. Decentralization vs. Centralization Facebook and X are owned and operated by massive corporations that control everything from content moderation to algorithmic visibility. Your posts, followers, and interactions are at the mercy of the company's policies and changes. Nostr: No single entity owns Nostr. It operates as a protocol where anyone can run a relay (a server that transmits messages). Users are not tied to a single company or platform, ensuring freedom from corporate control. 2. Censorship Resistance Facebook & X: Heavily moderate content, often removing posts or banning accounts based on internal policies, government pressure, or **advertiser** demands. Nostr: Built to resist censorship. Since users publish to multiple relays, blocking content on one relay does not remove it from others. You control where your messages are sent, not a centralized authority. 3. User Ownership and Privacy Facebook & X: Your data is stored on corporate servers and often sold to advertisers. You don’t truly own your content or connections. Nostr: Users control their private keys, which function like cryptographic signatures. Your identity is yours alone, and no company can take it away. 4. Algorithm-Free Experience Facebook & X: Content is curated by algorithms that determine what you see based on engagement metrics, often promoting divisive or viral content over meaningful conversations. Nostr: No forced algorithms. You decide which relays to use and what content to follow. Your feed remains chronological and free from corporate influence. Pros and Cons of Nostr ✅ Pros: True freedom of speech: No corporate moderation, allowing open discussion. User-owned identity: You control your account with a cryptographic key. No ads or tracking: Your data isn’t harvested or sold to advertisers. Resilient against shutdowns: Multiple relays ensure content persists even if one relay goes offline. Customizable experience: Choose the relays and clients that best suit your needs. ❌ Cons (If Any): Early-stage adoption: Not as many users as Facebook or X (yet!). Technical learning curve: Requires setting up keys and understanding relays, though improving rapidly. Lack of centralized moderation: While this is a pro for free speech, it can also mean exposure to spam or undesirable content if it is not filtered properly. However, they are developing hidden or block features to help control your feeds. I don't have a lot of worries here. To be perfectly honest, it seems like a better class of people come here. Why Should You Leave Facebook and Join Nostr? If you’re tired of algorithmic manipulation, invasive tracking, and corporate censorship, Nostr offers a fresh start. It’s a place where your voice truly belongs to you, and a centralized authority cannot control your connections. Yes, it may take some time to adjust to using Nostr, but the benefits far outweigh the minor learning curve. If you value digital freedom, privacy, and resistance to censorship, now is the perfect time to explore the future of social networking. How to Get Your Friends to Leave Corporate Social Media and Join Nostr Switching to Nostr is one thing, but convincing your friends to make the leap can be challenging. Here are some practical ways to help them transition: Explain the benefits: Many people don’t realize how much control corporations have over their online experience. Share this article and highlight the key points. Make it easy: Walk them through setting up a Nostr account, generating a private key, and connecting to relays. Show them the community: Introduce them to active Nostr users, groups, and discussions to make the transition feel worthwhile. Lead by example: Use Nostr consistently and post compelling content that makes it appealing to your friends. Keep the conversation going. As more people join, Nostr will become even more engaging, making it a true alternative to corporate-controlled platforms.
@ 378562cd:a6fc6773
2025-02-23 20:41:59Social media platforms like Facebook and X (formerly Twitter) have long dominated online communication. However, many people are looking for alternatives due to increasing censorship, algorithmic manipulation, and corporate control over user data. One of the most promising new protocols I have found is Nostr, a decentralized and open-source alternative to traditional social media. But how does Nostr compare, and why should you consider making the switch? If you're reading this, presumably, you already have made the switch, but share this with friends if you like. Let’s dive in. The Fundamental Differences Between Nostr and Traditional Social Media 1. Decentralization vs. Centralization Facebook and X are owned and operated by massive corporations that control everything from content moderation to algorithmic visibility. Your posts, followers, and interactions are at the mercy of the company's policies and changes. Nostr: No single entity owns Nostr. It operates as a protocol where anyone can run a relay (a server that transmits messages). Users are not tied to a single company or platform, ensuring freedom from corporate control. 2. Censorship Resistance Facebook & X: Heavily moderate content, often removing posts or banning accounts based on internal policies, government pressure, or **advertiser** demands. Nostr: Built to resist censorship. Since users publish to multiple relays, blocking content on one relay does not remove it from others. You control where your messages are sent, not a centralized authority. 3. User Ownership and Privacy Facebook & X: Your data is stored on corporate servers and often sold to advertisers. You don’t truly own your content or connections. Nostr: Users control their private keys, which function like cryptographic signatures. Your identity is yours alone, and no company can take it away. 4. Algorithm-Free Experience Facebook & X: Content is curated by algorithms that determine what you see based on engagement metrics, often promoting divisive or viral content over meaningful conversations. Nostr: No forced algorithms. You decide which relays to use and what content to follow. Your feed remains chronological and free from corporate influence. Pros and Cons of Nostr ✅ Pros: True freedom of speech: No corporate moderation, allowing open discussion. User-owned identity: You control your account with a cryptographic key. No ads or tracking: Your data isn’t harvested or sold to advertisers. Resilient against shutdowns: Multiple relays ensure content persists even if one relay goes offline. Customizable experience: Choose the relays and clients that best suit your needs. ❌ Cons (If Any): Early-stage adoption: Not as many users as Facebook or X (yet!). Technical learning curve: Requires setting up keys and understanding relays, though improving rapidly. Lack of centralized moderation: While this is a pro for free speech, it can also mean exposure to spam or undesirable content if it is not filtered properly. However, they are developing hidden or block features to help control your feeds. I don't have a lot of worries here. To be perfectly honest, it seems like a better class of people come here. Why Should You Leave Facebook and Join Nostr? If you’re tired of algorithmic manipulation, invasive tracking, and corporate censorship, Nostr offers a fresh start. It’s a place where your voice truly belongs to you, and a centralized authority cannot control your connections. Yes, it may take some time to adjust to using Nostr, but the benefits far outweigh the minor learning curve. If you value digital freedom, privacy, and resistance to censorship, now is the perfect time to explore the future of social networking. How to Get Your Friends to Leave Corporate Social Media and Join Nostr Switching to Nostr is one thing, but convincing your friends to make the leap can be challenging. Here are some practical ways to help them transition: Explain the benefits: Many people don’t realize how much control corporations have over their online experience. Share this article and highlight the key points. Make it easy: Walk them through setting up a Nostr account, generating a private key, and connecting to relays. Show them the community: Introduce them to active Nostr users, groups, and discussions to make the transition feel worthwhile. Lead by example: Use Nostr consistently and post compelling content that makes it appealing to your friends. Keep the conversation going. As more people join, Nostr will become even more engaging, making it a true alternative to corporate-controlled platforms. @ badc29af:a92bd071
2025-02-23 20:34:58**Part I: The First Hour (Blocks 694,200–694,205)** **Block 694,200: The Coder**\ Sarah Chen sat hunched over her keyboard in her San Francisco apartment, the fog smudging her window. Debugging a fintech app, she watched block 694,200 confirm on the Bitcoin blockchain. Suddenly, its architecture snapped into focus: not just code, but a defiance of artificial abundance.\ "Holy shit," she whispered, easing back from her desk, her monitor casting light on scattered ramen cups. She’d coded financial systems for years, but now she saw money’s true potential—scarce, digital, unbound. **Block 694,201: The Entrepreneur**\ Ten minutes later, in a steamy Lagos cybercafé, James Okonjo’s world shifted as block 694,201 locked in. Struggling with payment delays under Nigeria’s currency controls, he read about Bitcoin’s borderless flow.\ "No more gatekeepers," he said, startling nearby patrons. His hands shook as he set up his first wallet, already dreaming of a Bitcoin education platform for African developers. **Block 694,202: The Economist**\ In Caracas, Maria Rodriguez paced before her Universidad Central de Venezuela class, dissecting inflation’s latest surge. As block 694,202 formed, the idea of fixed-supply money hit her like a revelation.\ "Forget this slide," she said, closing her laptop. "Let’s talk proof-of-work." Her students stared, but her mind was already racing with possibilities. **Block 694,203: The Retiree**\ In Tokyo, Hiroshi Yamamoto sipped tea during his morning portfolio review when block 694,203 confirmed. A retired salaryman, he saw Bitcoin as a shield against decades of yen erosion. Quietly, he began researching wallets, his curiosity ignited. **Block 694,204: The Prodigy**\ In Toronto, 16-year-old Emma Chen, a coding whiz, stumbled across block 694,204 while tinkering online. The power to program her own money dawned on her. She grinned, diving into Bitcoin’s whitepaper with reckless glee. **Block 694,205: The Shopkeeper**\ In Buenos Aires, Carlos Mendoza tallied his shop’s dwindling profits as block 694,205 ticked into existence. Sick of the peso’s collapse, he found Bitcoin—an escape from financial quicksand. By nightfall, he’d downloaded a wallet app. --- **Part II: The First Day (Blocks 694,206–694,343)** **The Morning Wave (Blocks 694,206–694,247)**\ Over the next 42 blocks—about seven hours—as Asia slept and Europe stirred, the awakenings multiplied: **Block 694,206**: A Swiss banker questioned her fiat career. **Block 694,207**: A German programmer marveled at Bitcoin’s consensus beauty. **Block 694,208**: A Korean gamer saw virtual gold turn real.\ The chain hummed, each block birthing new believers, ten minutes apart. **The American Session (Blocks 694,248–694,295)**\ As Wall Street woke, blocks 694,248 to 694,295—eight hours—marked a finance-world reckoning: **Block 694,248**: A Connecticut hedge fund manager saw through fiat’s illusions. **Block 694,249**: A Chicago commodities trader grasped digital scarcity. **Block 694,250**: A Texas pension admin envisioned a sounder future.\ Each block stamped a timestamp on their transformation. **The Global South Rises (Blocks 694,296–694,343)**\ The day’s final stretch—48 blocks, eight more hours—saw the global south ignite: **Block 694,296**: Brazilian students planned Bitcoin beach hubs. **Block 694,297**: Indonesian merchants linked Lightning payment loops. **Block 694,298**: South African miners turned solar power into hash rate.\ The chain pulsed, relentless, binding them all. --- **Part III: The Network Effect (Beyond Block 694,343)** **The Teachers (Block 694,344)**\ Sarah quit her job at block 694,344, coding Bitcoin education tools. James’s platform launched, reaching Africa’s devs. Maria’s NOSTR lectures spread, her voice a beacon. **The Builders (Block 694,345)**\ At block 694,345, innovation bloomed: privacy upgrades, scaling fixes, Lightning finance tools. The awakened built atop the chain. **The HODLers (Block 694,346)**\ By block 694,346, others simply held—silent sentinels whose faith grew with each block, each halving. --- **Epilogue: The Endless Chain (Blocks Onward)** The awakening rolled on, ten minutes at a time. Block 694,347 saw a Mumbai coder join Sarah’s cause. Block 694,348 brought a Nairobi merchant to James’s platform. Block 694,349 swayed a Manila policymaker with Maria’s words. Every block—144 a day—sparked new stories: dreamers seeking freedom, builders crafting tools, HODLers standing firm. Money, they understood, was too vital to be ruled by power. From block 694,200, the chain stretched forward, a living testament to scarcity, ownership, math over might. Each block was a birth, each hash a heartbeat, each Bitcoiner a node in a network of financial truth—marching on, block by block, toward a harder, sounder world, forever verified, never permissioned, growing but never diluted, ten minutes at a time.
@ badc29af:a92bd071
2025-02-23 20:34:58**Part I: The First Hour (Blocks 694,200–694,205)** **Block 694,200: The Coder**\ Sarah Chen sat hunched over her keyboard in her San Francisco apartment, the fog smudging her window. Debugging a fintech app, she watched block 694,200 confirm on the Bitcoin blockchain. Suddenly, its architecture snapped into focus: not just code, but a defiance of artificial abundance.\ "Holy shit," she whispered, easing back from her desk, her monitor casting light on scattered ramen cups. She’d coded financial systems for years, but now she saw money’s true potential—scarce, digital, unbound. **Block 694,201: The Entrepreneur**\ Ten minutes later, in a steamy Lagos cybercafé, James Okonjo’s world shifted as block 694,201 locked in. Struggling with payment delays under Nigeria’s currency controls, he read about Bitcoin’s borderless flow.\ "No more gatekeepers," he said, startling nearby patrons. His hands shook as he set up his first wallet, already dreaming of a Bitcoin education platform for African developers. **Block 694,202: The Economist**\ In Caracas, Maria Rodriguez paced before her Universidad Central de Venezuela class, dissecting inflation’s latest surge. As block 694,202 formed, the idea of fixed-supply money hit her like a revelation.\ "Forget this slide," she said, closing her laptop. "Let’s talk proof-of-work." Her students stared, but her mind was already racing with possibilities. **Block 694,203: The Retiree**\ In Tokyo, Hiroshi Yamamoto sipped tea during his morning portfolio review when block 694,203 confirmed. A retired salaryman, he saw Bitcoin as a shield against decades of yen erosion. Quietly, he began researching wallets, his curiosity ignited. **Block 694,204: The Prodigy**\ In Toronto, 16-year-old Emma Chen, a coding whiz, stumbled across block 694,204 while tinkering online. The power to program her own money dawned on her. She grinned, diving into Bitcoin’s whitepaper with reckless glee. **Block 694,205: The Shopkeeper**\ In Buenos Aires, Carlos Mendoza tallied his shop’s dwindling profits as block 694,205 ticked into existence. Sick of the peso’s collapse, he found Bitcoin—an escape from financial quicksand. By nightfall, he’d downloaded a wallet app. --- **Part II: The First Day (Blocks 694,206–694,343)** **The Morning Wave (Blocks 694,206–694,247)**\ Over the next 42 blocks—about seven hours—as Asia slept and Europe stirred, the awakenings multiplied: **Block 694,206**: A Swiss banker questioned her fiat career. **Block 694,207**: A German programmer marveled at Bitcoin’s consensus beauty. **Block 694,208**: A Korean gamer saw virtual gold turn real.\ The chain hummed, each block birthing new believers, ten minutes apart. **The American Session (Blocks 694,248–694,295)**\ As Wall Street woke, blocks 694,248 to 694,295—eight hours—marked a finance-world reckoning: **Block 694,248**: A Connecticut hedge fund manager saw through fiat’s illusions. **Block 694,249**: A Chicago commodities trader grasped digital scarcity. **Block 694,250**: A Texas pension admin envisioned a sounder future.\ Each block stamped a timestamp on their transformation. **The Global South Rises (Blocks 694,296–694,343)**\ The day’s final stretch—48 blocks, eight more hours—saw the global south ignite: **Block 694,296**: Brazilian students planned Bitcoin beach hubs. **Block 694,297**: Indonesian merchants linked Lightning payment loops. **Block 694,298**: South African miners turned solar power into hash rate.\ The chain pulsed, relentless, binding them all. --- **Part III: The Network Effect (Beyond Block 694,343)** **The Teachers (Block 694,344)**\ Sarah quit her job at block 694,344, coding Bitcoin education tools. James’s platform launched, reaching Africa’s devs. Maria’s NOSTR lectures spread, her voice a beacon. **The Builders (Block 694,345)**\ At block 694,345, innovation bloomed: privacy upgrades, scaling fixes, Lightning finance tools. The awakened built atop the chain. **The HODLers (Block 694,346)**\ By block 694,346, others simply held—silent sentinels whose faith grew with each block, each halving. --- **Epilogue: The Endless Chain (Blocks Onward)** The awakening rolled on, ten minutes at a time. Block 694,347 saw a Mumbai coder join Sarah’s cause. Block 694,348 brought a Nairobi merchant to James’s platform. Block 694,349 swayed a Manila policymaker with Maria’s words. Every block—144 a day—sparked new stories: dreamers seeking freedom, builders crafting tools, HODLers standing firm. Money, they understood, was too vital to be ruled by power. From block 694,200, the chain stretched forward, a living testament to scarcity, ownership, math over might. Each block was a birth, each hash a heartbeat, each Bitcoiner a node in a network of financial truth—marching on, block by block, toward a harder, sounder world, forever verified, never permissioned, growing but never diluted, ten minutes at a time. @ 629c4a12:f822cc1a
2025-02-23 20:27:36This is test 2
@ 629c4a12:f822cc1a
2025-02-23 20:27:36This is test 2 @ d34e832d:383f78d0
2025-02-23 19:53:32Hockeypuck is an **OpenPGP keyserver** that allows users to publish, search, and retrieve **PGP public keys** for secure communication. It is designed for **federation** with other keyservers and supports a **high-performance, scalable** architecture. --- ## **🛠️ Usage** ### **1. Public PGP Key Directory** - Organizations, security researchers, and privacy-focused users can **publish and retrieve PGP keys** for encrypted email and document verification. - Similar to **SKS Keyserver**, but actively maintained and more scalable. ### **2. Enterprise PGP Key Management** - Companies can **host a private keyserver** for internal teams to share PGP keys securely. - Prevents reliance on external keyservers like keys.openpgp.org. ### **3. Decentralized Identity and Key Distribution** - Used in federated **PGP keyserver networks** like **Hockeypuck & SKS pools** to distribute OpenPGP keys across multiple servers. - Useful for **distributed trust models** where multiple organizations manage keys collaboratively. ### **4. Bitcoin & Nostr Applications** - Can be used alongside **Nostr** for key verification, ensuring public keys are retrievable for cryptographic signatures. - Useful in **Bitcoin** applications where PGP-signed messages confirm identity. ### **5. Software Package Signing** - Developers and package maintainers can **sign software updates** using OpenPGP, and end users can fetch public keys from Hockeypuck to verify authenticity. - Example: **Debian and Arch Linux package signing**. ### **6. Secure Messaging** - Supports secure email systems using **PGP-encrypted mail (e.g., ProtonMail, Thunderbird + Enigmail, Mailpile, etc.)**. --- ## **📌 Key Benefits** ✅ **Docker-Based Deployment** → Easily installable with **Docker** and **docker-compose**. ✅ **Federated Keyserver** → Can join existing **PGP keyserver networks**. ✅ **High-Performance Storage** → Uses PostgreSQL for better performance than older SKS keyservers. ✅ **Supports HTTP & HTTPS** → Can be hosted publicly with **TLS encryption**. ✅ **Fully Open Source** → Maintained as a modern alternative to SKS. ## **🔑 Signing a Nostr Event Using PGP & Verifying It on a Relay** If Alice wants to **prove she controls `npub1xyz...`** using **PGP**, she can sign a Nostr event and publish both the event and signature. --- ### **🔹 Step 1: Create a Nostr Event (Kind 0)** Alice generates a **Nostr profile metadata event**: ```json { "id": "xxxxxxxxxxxxxxxxxx", "pubkey": "npub1xyz...", "created_at": 1700000000, "kind": 0, "tags": [], "content": "{ \"name\": \"Alice\", \"about\": \"PGP Verified Nostr User\" }" } ``` She saves this as **`nostr_event.json`**. --- ### **🔹 Step 2: Sign the Event with PGP** Alice uses GnuPG to sign the event: ```bash gpg --clearsign --armor nostr_event.json ``` This creates **`nostr_event.json.asc`**, which contains the event with a **PGP signature**. 🔹 **Example of the signed event:** ``` -----BEGIN PGP SIGNED MESSAGE----- Hash: SHA256 { "id": "xxxxxxxxxxxxxxxxxx", "pubkey": "npub1xyz...", "created_at": 1700000000, "kind": 0, "tags": [], "content": "{ \"name\": \"Alice\", \"about\": \"PGP Verified Nostr User\" }" } -----BEGIN PGP SIGNATURE----- iQIzBAEBCAAdFiEEbGSk4HTlMz5tG0tF0Y8fO3HTQYYFAmS8mOkACgkQ0Y8fO3HT QYYX4w/+JwzbfM1EZ2F7H3yqbdGBJ2cGd... -----END PGP SIGNATURE----- ``` --- ### **🔹 Step 3: Upload the Signature to a Public Keyserver** Alice submits her signed Nostr event to the **Hockeypuck keyserver**: ```bash curl --data-binary @nostr_event.json.asc https://keyserver.example.com/pks/add ``` --- ### **🔹 Step 4: Publish the Event to a Nostr Relay** Alice **publishes the original event** to a Nostr relay: ```bash curl -X POST https://nostr-relay.example.com/ -d @nostr_event.json ``` --- ### **🔹 Step 5: Verification** Anyone can **fetch Alice’s PGP-signed event** and verify it: ```bash curl "https://keyserver.example.com/pks/lookup?op=get&search=alice@nostr.example.com" | gpg --verify ``` If successful, it will show: ``` gpg: Good signature from "Alice <alice@nostr.example.com>" ``` --- ### **✅ Use Cases** 1. **Proving Ownership of a Nostr Public Key** with PGP. 2. **Bitcoin Applications**: PGP-signed messages can confirm identities for multisig coordination. 3. **Decentralized Web of Trust**: Verifying Nostr users via signed events. --- Additionally a simple JS or python script could automate signing process.
@ d34e832d:383f78d0
2025-02-23 19:53:32Hockeypuck is an **OpenPGP keyserver** that allows users to publish, search, and retrieve **PGP public keys** for secure communication. It is designed for **federation** with other keyservers and supports a **high-performance, scalable** architecture. --- ## **🛠️ Usage** ### **1. Public PGP Key Directory** - Organizations, security researchers, and privacy-focused users can **publish and retrieve PGP keys** for encrypted email and document verification. - Similar to **SKS Keyserver**, but actively maintained and more scalable. ### **2. Enterprise PGP Key Management** - Companies can **host a private keyserver** for internal teams to share PGP keys securely. - Prevents reliance on external keyservers like keys.openpgp.org. ### **3. Decentralized Identity and Key Distribution** - Used in federated **PGP keyserver networks** like **Hockeypuck & SKS pools** to distribute OpenPGP keys across multiple servers. - Useful for **distributed trust models** where multiple organizations manage keys collaboratively. ### **4. Bitcoin & Nostr Applications** - Can be used alongside **Nostr** for key verification, ensuring public keys are retrievable for cryptographic signatures. - Useful in **Bitcoin** applications where PGP-signed messages confirm identity. ### **5. Software Package Signing** - Developers and package maintainers can **sign software updates** using OpenPGP, and end users can fetch public keys from Hockeypuck to verify authenticity. - Example: **Debian and Arch Linux package signing**. ### **6. Secure Messaging** - Supports secure email systems using **PGP-encrypted mail (e.g., ProtonMail, Thunderbird + Enigmail, Mailpile, etc.)**. --- ## **📌 Key Benefits** ✅ **Docker-Based Deployment** → Easily installable with **Docker** and **docker-compose**. ✅ **Federated Keyserver** → Can join existing **PGP keyserver networks**. ✅ **High-Performance Storage** → Uses PostgreSQL for better performance than older SKS keyservers. ✅ **Supports HTTP & HTTPS** → Can be hosted publicly with **TLS encryption**. ✅ **Fully Open Source** → Maintained as a modern alternative to SKS. ## **🔑 Signing a Nostr Event Using PGP & Verifying It on a Relay** If Alice wants to **prove she controls `npub1xyz...`** using **PGP**, she can sign a Nostr event and publish both the event and signature. --- ### **🔹 Step 1: Create a Nostr Event (Kind 0)** Alice generates a **Nostr profile metadata event**: ```json { "id": "xxxxxxxxxxxxxxxxxx", "pubkey": "npub1xyz...", "created_at": 1700000000, "kind": 0, "tags": [], "content": "{ \"name\": \"Alice\", \"about\": \"PGP Verified Nostr User\" }" } ``` She saves this as **`nostr_event.json`**. --- ### **🔹 Step 2: Sign the Event with PGP** Alice uses GnuPG to sign the event: ```bash gpg --clearsign --armor nostr_event.json ``` This creates **`nostr_event.json.asc`**, which contains the event with a **PGP signature**. 🔹 **Example of the signed event:** ``` -----BEGIN PGP SIGNED MESSAGE----- Hash: SHA256 { "id": "xxxxxxxxxxxxxxxxxx", "pubkey": "npub1xyz...", "created_at": 1700000000, "kind": 0, "tags": [], "content": "{ \"name\": \"Alice\", \"about\": \"PGP Verified Nostr User\" }" } -----BEGIN PGP SIGNATURE----- iQIzBAEBCAAdFiEEbGSk4HTlMz5tG0tF0Y8fO3HTQYYFAmS8mOkACgkQ0Y8fO3HT QYYX4w/+JwzbfM1EZ2F7H3yqbdGBJ2cGd... -----END PGP SIGNATURE----- ``` --- ### **🔹 Step 3: Upload the Signature to a Public Keyserver** Alice submits her signed Nostr event to the **Hockeypuck keyserver**: ```bash curl --data-binary @nostr_event.json.asc https://keyserver.example.com/pks/add ``` --- ### **🔹 Step 4: Publish the Event to a Nostr Relay** Alice **publishes the original event** to a Nostr relay: ```bash curl -X POST https://nostr-relay.example.com/ -d @nostr_event.json ``` --- ### **🔹 Step 5: Verification** Anyone can **fetch Alice’s PGP-signed event** and verify it: ```bash curl "https://keyserver.example.com/pks/lookup?op=get&search=alice@nostr.example.com" | gpg --verify ``` If successful, it will show: ``` gpg: Good signature from "Alice <alice@nostr.example.com>" ``` --- ### **✅ Use Cases** 1. **Proving Ownership of a Nostr Public Key** with PGP. 2. **Bitcoin Applications**: PGP-signed messages can confirm identities for multisig coordination. 3. **Decentralized Web of Trust**: Verifying Nostr users via signed events. --- Additionally a simple JS or python script could automate signing process. @ 3ffac3a6:2d656657
2025-02-23 19:40:19## Renoters: Proposal for Anonymous Event Relaying in Nostr *This document is a proposal and not an official NIP.* This Document proposes "Renoters," a mechanism for anonymous event relaying in Nostr, inspired by the Mixminion remailer design. Renoters aim to enhance privacy by obscuring the origin of events, making it difficult to trace the author of a message. ### **Motivation** While Nostr offers a decentralized platform, current relay mechanisms can potentially reveal the source of events. Renoters address this by introducing an onion-routing-like system where events are encrypted and relayed through a series of nodes, making it harder to link the event to its originator. This enhances privacy for users who wish to communicate anonymously or protect their identity. In some totalitarian regimes, the use of Tor and VPNs is criminalized, making online anonymity dangerous. Even in some democratic countries, merely downloading Tor can mark individuals as suspects. This underscores the need for a decentralized and anonymous communication system that operates independently of commonly surveilled privacy tools. ### **Proposed Solution** Renoters operate on the principle of "gift-wrapping" events, using asymmetric encryption. A user wishing to send an event anonymously performs the following steps: 1. **Event Creation:** The user creates the Nostr event they wish to publish. 2. **Renoter Path Selection:** The user selects a path of Renoters through which the event will be relayed. This path can be pre-configured or dynamically chosen. 3. **Gift Wrapping (Encryption and Signing):** The user encrypts and signs the event for each Renoter in the path, working in reverse order: - A *new* random Nostr private key (`sk_wrapper`) is generated. - The event (or the previously wrapped event) is encrypted using the *next* Renoter's Npub (`npub_next`) using Nostr's standard encryption mechanism (e.g., using shared secrets derived from the private key and the recipient's public key). - A *new* Nostr event is created. This "wrapper" event's content contains the ciphertext. The wrapper event is signed using the newly generated private key `sk_wrapper`. The wrapper event also includes the next hop's `npub_next` (or the final destination if it's the last renoter) in cleartext, to allow for routing. 4. **Publication:** The user publishes the *first* gift-wrapped event (the one encrypted for the last Renoter in the path). This event is sent to a regular Nostr relay, which then forwards it to the first Renoter in the path. 5. **Renoter Relaying:** Each Renoter in the path receives the gift-wrapped event, verifies the signature using the `sk_wrapper`'s corresponding public key, decrypts it using its own private key, and forwards the decrypted event (now wrapped for the *next* Renoter) to the next Renoter in the path. This process continues until the event reaches the final Renoter. 6. **Final Delivery:** The final Renoter decrypts the event and publishes it to the Nostr network. ### **Example** Let's say Alice wants to send an event anonymously through Renoters R1, R2, and R3. 1. Alice creates her event. 2. She generates a random private key `sk3` and encrypts the event with R3's public key `npub_r3`. 3. She creates a wrapper event containing the ciphertext and `npub_r3`, signed with `sk3`. 4. She generates a random private key `sk2` and encrypts the previous wrapper event with R2's public key `npub_r2`. 5. She creates a wrapper event containing this ciphertext and `npub_r2`, signed with `sk2`. 6. She generates a random private key `sk1` and encrypts the previous wrapper event with R1's public key `npub_r1`. 7. She creates a final wrapper event containing this ciphertext and `npub_r1`, signed with `sk1`. 8. Alice publishes this final wrapper event. R1 decrypts with its private key, verifies the signature with the public key corresponding to `sk1`, and forwards to R2. R2 decrypts, verifies the signature with the public key corresponding to `sk2`, and forwards to R3. R3 decrypts, verifies the signature with the public key corresponding to `sk3`, and publishes the original event. ### **Renoter Incentives (using Cashu)** To incentivize Renoters to participate in the network, this NIP proposes integrating Cashu tokens as a payment mechanism. - **Token Inclusion:** When a user creates the initial gift-wrapped event (the one sent to the first Renoter), they include a Cashu token *within* the event content. This token is itself encrypted and wrapped along with the original message, so only the receiving Renoter can access it. - **Renoter Redemption:** Upon receiving a gift-wrapped event, the Renoter decrypts it. If the event contains a Cashu token, the Renoter can decrypt the token and redeem it. - **Renoter Behavior:** Paid Renoters would be configured *not* to relay events that do *not* contain a valid Cashu token. This ensures that Renoters are compensated for their service. Free Renoters could still exist, but paid Renoters would likely offer faster or more reliable service. - **Token Value and Tiers:** Different Cashu token denominations could represent different levels of service (e.g., faster relaying, higher priority). This could create a tiered system where users can pay for better anonymity or speed. - **Token Generation:** Users would need a way to acquire Cashu tokens. This could involve purchasing them from a Cashu mint or earning them through other means. ### **Security Threats and Mitigations** - **Anonymity Against Correlation Attacks:** Even when using Tor, traffic patterns can still be analyzed to infer the origin of events. To mitigate this risk, Renoters can introduce: - Random delays in event relaying. - Dummy packets to complicate statistical analysis by malicious observers. - **Replay Attacks:** To mitigate replay attacks, each Renoter must store, for a reasonable period, the IDs of received events and the decrypted events that were forwarded. This ensures that duplicate messages are not processed again. - **Sybil Attacks:** Sybil attacks can be mitigated by requiring payments via Cashu tokens for relaying events, increasing the cost of launching such attacks. By ensuring that each relay operation has a monetary cost, attackers are discouraged from creating large numbers of fake identities to manipulate the network. - **Traffic Analysis:** Traffic analysis can be mitigated by using Tor for Renoters. Routing events through the Tor network adds an additional layer of anonymity, making it more difficult to track message origins or infer sender-recipient relationships. While Renoters enhance privacy, sophisticated traffic analysis might still be a threat. ### **Operational Considerations** - **Renoter Reliability:** The reliability of the Renoter network is crucial. - **Latency:** Relaying through multiple Renoters will introduce latency. - **Key Management:** While each layer uses a new key, the initial key generation and path selection process need to be secure. This NIP provides a robust framework for anonymous event relaying in Nostr, leveraging encryption and Cashu-based incentives to enhance privacy and usability. ### **References** - **Untraceable Electronic Mail, Return Addresses, and Digital Pseudonyms**: David L. Chaum (https://dl.acm.org/doi/10.1145/358549.358563) - **Mixminion Design**: Mixminion: Design of a Type III Anonymous Remailer (https://www.mixminion.net/minion-design.pdf) - **Nostr Protocol**: Official Nostr Documentation (https://github.com/nostr-protocol/nostr) - **Cashu Token System**: Cashu: Ecash for Bitcoin Lightning (https://cashu.space/) - **Tor Project**: The Tor Project - Anonymity Online (https://www.torproject.org/) - **Onion Routing**: The Second-Generation Onion Router (https://svn.torproject.org/svn/projects/design-paper/tor-design.pdf) #Privacy #Nostr #Anonymity #Crypto #CensorshipResistance #OnlinePrivacy #Decentralization #Encryption #Security #ThreatMitigation #Micropayments #CryptoEconomy #NextSteps #Development
@ 3ffac3a6:2d656657
2025-02-23 19:40:19## Renoters: Proposal for Anonymous Event Relaying in Nostr *This document is a proposal and not an official NIP.* This Document proposes "Renoters," a mechanism for anonymous event relaying in Nostr, inspired by the Mixminion remailer design. Renoters aim to enhance privacy by obscuring the origin of events, making it difficult to trace the author of a message. ### **Motivation** While Nostr offers a decentralized platform, current relay mechanisms can potentially reveal the source of events. Renoters address this by introducing an onion-routing-like system where events are encrypted and relayed through a series of nodes, making it harder to link the event to its originator. This enhances privacy for users who wish to communicate anonymously or protect their identity. In some totalitarian regimes, the use of Tor and VPNs is criminalized, making online anonymity dangerous. Even in some democratic countries, merely downloading Tor can mark individuals as suspects. This underscores the need for a decentralized and anonymous communication system that operates independently of commonly surveilled privacy tools. ### **Proposed Solution** Renoters operate on the principle of "gift-wrapping" events, using asymmetric encryption. A user wishing to send an event anonymously performs the following steps: 1. **Event Creation:** The user creates the Nostr event they wish to publish. 2. **Renoter Path Selection:** The user selects a path of Renoters through which the event will be relayed. This path can be pre-configured or dynamically chosen. 3. **Gift Wrapping (Encryption and Signing):** The user encrypts and signs the event for each Renoter in the path, working in reverse order: - A *new* random Nostr private key (`sk_wrapper`) is generated. - The event (or the previously wrapped event) is encrypted using the *next* Renoter's Npub (`npub_next`) using Nostr's standard encryption mechanism (e.g., using shared secrets derived from the private key and the recipient's public key). - A *new* Nostr event is created. This "wrapper" event's content contains the ciphertext. The wrapper event is signed using the newly generated private key `sk_wrapper`. The wrapper event also includes the next hop's `npub_next` (or the final destination if it's the last renoter) in cleartext, to allow for routing. 4. **Publication:** The user publishes the *first* gift-wrapped event (the one encrypted for the last Renoter in the path). This event is sent to a regular Nostr relay, which then forwards it to the first Renoter in the path. 5. **Renoter Relaying:** Each Renoter in the path receives the gift-wrapped event, verifies the signature using the `sk_wrapper`'s corresponding public key, decrypts it using its own private key, and forwards the decrypted event (now wrapped for the *next* Renoter) to the next Renoter in the path. This process continues until the event reaches the final Renoter. 6. **Final Delivery:** The final Renoter decrypts the event and publishes it to the Nostr network. ### **Example** Let's say Alice wants to send an event anonymously through Renoters R1, R2, and R3. 1. Alice creates her event. 2. She generates a random private key `sk3` and encrypts the event with R3's public key `npub_r3`. 3. She creates a wrapper event containing the ciphertext and `npub_r3`, signed with `sk3`. 4. She generates a random private key `sk2` and encrypts the previous wrapper event with R2's public key `npub_r2`. 5. She creates a wrapper event containing this ciphertext and `npub_r2`, signed with `sk2`. 6. She generates a random private key `sk1` and encrypts the previous wrapper event with R1's public key `npub_r1`. 7. She creates a final wrapper event containing this ciphertext and `npub_r1`, signed with `sk1`. 8. Alice publishes this final wrapper event. R1 decrypts with its private key, verifies the signature with the public key corresponding to `sk1`, and forwards to R2. R2 decrypts, verifies the signature with the public key corresponding to `sk2`, and forwards to R3. R3 decrypts, verifies the signature with the public key corresponding to `sk3`, and publishes the original event. ### **Renoter Incentives (using Cashu)** To incentivize Renoters to participate in the network, this NIP proposes integrating Cashu tokens as a payment mechanism. - **Token Inclusion:** When a user creates the initial gift-wrapped event (the one sent to the first Renoter), they include a Cashu token *within* the event content. This token is itself encrypted and wrapped along with the original message, so only the receiving Renoter can access it. - **Renoter Redemption:** Upon receiving a gift-wrapped event, the Renoter decrypts it. If the event contains a Cashu token, the Renoter can decrypt the token and redeem it. - **Renoter Behavior:** Paid Renoters would be configured *not* to relay events that do *not* contain a valid Cashu token. This ensures that Renoters are compensated for their service. Free Renoters could still exist, but paid Renoters would likely offer faster or more reliable service. - **Token Value and Tiers:** Different Cashu token denominations could represent different levels of service (e.g., faster relaying, higher priority). This could create a tiered system where users can pay for better anonymity or speed. - **Token Generation:** Users would need a way to acquire Cashu tokens. This could involve purchasing them from a Cashu mint or earning them through other means. ### **Security Threats and Mitigations** - **Anonymity Against Correlation Attacks:** Even when using Tor, traffic patterns can still be analyzed to infer the origin of events. To mitigate this risk, Renoters can introduce: - Random delays in event relaying. - Dummy packets to complicate statistical analysis by malicious observers. - **Replay Attacks:** To mitigate replay attacks, each Renoter must store, for a reasonable period, the IDs of received events and the decrypted events that were forwarded. This ensures that duplicate messages are not processed again. - **Sybil Attacks:** Sybil attacks can be mitigated by requiring payments via Cashu tokens for relaying events, increasing the cost of launching such attacks. By ensuring that each relay operation has a monetary cost, attackers are discouraged from creating large numbers of fake identities to manipulate the network. - **Traffic Analysis:** Traffic analysis can be mitigated by using Tor for Renoters. Routing events through the Tor network adds an additional layer of anonymity, making it more difficult to track message origins or infer sender-recipient relationships. While Renoters enhance privacy, sophisticated traffic analysis might still be a threat. ### **Operational Considerations** - **Renoter Reliability:** The reliability of the Renoter network is crucial. - **Latency:** Relaying through multiple Renoters will introduce latency. - **Key Management:** While each layer uses a new key, the initial key generation and path selection process need to be secure. This NIP provides a robust framework for anonymous event relaying in Nostr, leveraging encryption and Cashu-based incentives to enhance privacy and usability. ### **References** - **Untraceable Electronic Mail, Return Addresses, and Digital Pseudonyms**: David L. Chaum (https://dl.acm.org/doi/10.1145/358549.358563) - **Mixminion Design**: Mixminion: Design of a Type III Anonymous Remailer (https://www.mixminion.net/minion-design.pdf) - **Nostr Protocol**: Official Nostr Documentation (https://github.com/nostr-protocol/nostr) - **Cashu Token System**: Cashu: Ecash for Bitcoin Lightning (https://cashu.space/) - **Tor Project**: The Tor Project - Anonymity Online (https://www.torproject.org/) - **Onion Routing**: The Second-Generation Onion Router (https://svn.torproject.org/svn/projects/design-paper/tor-design.pdf) #Privacy #Nostr #Anonymity #Crypto #CensorshipResistance #OnlinePrivacy #Decentralization #Encryption #Security #ThreatMitigation #Micropayments #CryptoEconomy #NextSteps #Development @ f3873798:24b3f2f3
2025-02-23 19:21:48A liberdade de expressão e a descentralização do poder estão intimamente ligadas ao avanço do pensamento humano e à construção de uma sociedade mais justa e consciente. A evolução da compreensão sobre o certo e o errado surge da comunicação, da observação empírica e da análise das consequências de ações passadas. Para que haja uma aproximação real com a verdade e uma relação equilibrada entre a razão da vida e o convívio com o poder, é essencial garantir a liberdade de expressão. Somente por meio do livre debate de ideias é possível avaliar as diversas perspectivas, identificar erros e aprender com eles. Embora a maioria das pessoas busque o aprendizado e a compreensão do que é correto, o apego cego a uma ideia evidentemente equivocada pode fazer com que percam o real propósito da busca pela verdade. Em vez de refletirem criticamente, muitos acabam apenas defendendo um erro pelo simples fato de se identificarem com ele. Esse é um dos motivos pelos quais a censura tem se tornado uma ferramenta tão temida e contestada. Ilude-se quem acredita que a censura existe apenas para combater crimes e golpes. Na realidade, quanto maior a censura, mais favorecidos são aqueles que desejam ocultar informações, tornando ainda mais difícil a identificação e o combate a abusos. Nos países livres, onde a liberdade de expressão é respeitada, há maior autonomia nas decisões políticas e um engajamento mais ativo da população. A participação cidadã fortalece o controle do povo sobre as influências que moldam o convívio social, garantindo que o poder não fique concentrado nas mãos de poucos, mas distribuído de forma mais democrática e justa.
@ f3873798:24b3f2f3
2025-02-23 19:21:48A liberdade de expressão e a descentralização do poder estão intimamente ligadas ao avanço do pensamento humano e à construção de uma sociedade mais justa e consciente. A evolução da compreensão sobre o certo e o errado surge da comunicação, da observação empírica e da análise das consequências de ações passadas. Para que haja uma aproximação real com a verdade e uma relação equilibrada entre a razão da vida e o convívio com o poder, é essencial garantir a liberdade de expressão. Somente por meio do livre debate de ideias é possível avaliar as diversas perspectivas, identificar erros e aprender com eles. Embora a maioria das pessoas busque o aprendizado e a compreensão do que é correto, o apego cego a uma ideia evidentemente equivocada pode fazer com que percam o real propósito da busca pela verdade. Em vez de refletirem criticamente, muitos acabam apenas defendendo um erro pelo simples fato de se identificarem com ele. Esse é um dos motivos pelos quais a censura tem se tornado uma ferramenta tão temida e contestada. Ilude-se quem acredita que a censura existe apenas para combater crimes e golpes. Na realidade, quanto maior a censura, mais favorecidos são aqueles que desejam ocultar informações, tornando ainda mais difícil a identificação e o combate a abusos. Nos países livres, onde a liberdade de expressão é respeitada, há maior autonomia nas decisões políticas e um engajamento mais ativo da população. A participação cidadã fortalece o controle do povo sobre as influências que moldam o convívio social, garantindo que o poder não fique concentrado nas mãos de poucos, mas distribuído de forma mais democrática e justa. @ ef1744f8:96fbc3fe
2025-02-23 19:12:526/WRXHyH0NZbnQJ9LX+VZnSZBv5Y3iYgws/SZV0BVXSE4c8GJp9/HVp2ZfUsstNeQ6KDIA2LVlmrnnW7Dwb6rr09Tbh79cQp7LukzkVzjtWJ6FlWkM8iaHW6YgET77s1PfZV0fZ9tVpXo77byWCMI/R8feh2BhQ7Nhr35AnLhWa++0jKtIRSShY+BRKGusyT8zn09pYg4Wg8rDosilrbd4GUX6QqMguLuiBSi7D8VRWAXEkSefV0T04QUeVyvIcIloKAkLqQloVAHGPMJc65GtVc1705lI4aa62aGraGhg1yEXkr5PelI3X1P5PYx29NZbPyeSUBh40dJQFZmYDxV9WSPUtJqIn/1gQUW0jueCuQASpNfKr17F2bHvcIOeOp+ukbWfbYDWt4IammFZCuXw==?iv=r1dw0EG1b8Fvsxm+8ykvRA==
@ ef1744f8:96fbc3fe
2025-02-23 19:12:526/WRXHyH0NZbnQJ9LX+VZnSZBv5Y3iYgws/SZV0BVXSE4c8GJp9/HVp2ZfUsstNeQ6KDIA2LVlmrnnW7Dwb6rr09Tbh79cQp7LukzkVzjtWJ6FlWkM8iaHW6YgET77s1PfZV0fZ9tVpXo77byWCMI/R8feh2BhQ7Nhr35AnLhWa++0jKtIRSShY+BRKGusyT8zn09pYg4Wg8rDosilrbd4GUX6QqMguLuiBSi7D8VRWAXEkSefV0T04QUeVyvIcIloKAkLqQloVAHGPMJc65GtVc1705lI4aa62aGraGhg1yEXkr5PelI3X1P5PYx29NZbPyeSUBh40dJQFZmYDxV9WSPUtJqIn/1gQUW0jueCuQASpNfKr17F2bHvcIOeOp+ukbWfbYDWt4IammFZCuXw==?iv=r1dw0EG1b8Fvsxm+8ykvRA== @ ef1744f8:96fbc3fe
2025-02-23 19:12:47UvEa5PR6FF+PYlYXJM9Sqt06t01ARuO5vW2ct5SyIg4+aA4nq38Mofx2NI5YydZJcn9iQO2f0nlgIJaMFuDYBLXQFHklMlq7OfY5UyTnOFZ8Js9NwIMI1I7IVWp6qPEBSp5z0OmKOB1g2Z1jEZrySpkMd53AjaeYXiEyT5IMSDsKjxAbwuLRWaZiCWKtxKJxRdT/VUvYeE9dIfnadSkZdF8oIT6PlZYlgQ836Rt7X4O6hA/ydm1Hrc/1H/eTuKS8ePXZs5E4b/+XtgPclYqMPdUzD5/4rplIRJJXZQZX3cWiGC/0ilWIqyItead3JhwPAb+lNAyycfYelZRNjI10U719a0wjBsc0q7PgjQvSze4=?iv=uIyBfCznssKHgZaTSeUpbw==
@ ef1744f8:96fbc3fe
2025-02-23 19:12:47UvEa5PR6FF+PYlYXJM9Sqt06t01ARuO5vW2ct5SyIg4+aA4nq38Mofx2NI5YydZJcn9iQO2f0nlgIJaMFuDYBLXQFHklMlq7OfY5UyTnOFZ8Js9NwIMI1I7IVWp6qPEBSp5z0OmKOB1g2Z1jEZrySpkMd53AjaeYXiEyT5IMSDsKjxAbwuLRWaZiCWKtxKJxRdT/VUvYeE9dIfnadSkZdF8oIT6PlZYlgQ836Rt7X4O6hA/ydm1Hrc/1H/eTuKS8ePXZs5E4b/+XtgPclYqMPdUzD5/4rplIRJJXZQZX3cWiGC/0ilWIqyItead3JhwPAb+lNAyycfYelZRNjI10U719a0wjBsc0q7PgjQvSze4=?iv=uIyBfCznssKHgZaTSeUpbw== @ ef1744f8:96fbc3fe
2025-02-23 19:08:09wleig1qZtQh8+b2BEGuJl1Cug0McB7COckI3WeF/654AXNK2nrxnYZS/p/mZ2JNW4IVEOu8vrhb0w3l8VZP5BUdAqY/Ex3H0XhKTRUKNcwunirweS2DYC+F5P6VC9hUTRaLmhlmnqFU5Hmj/fwSCKfv9wfUOveaTvwV7SJLtH5n5qRrbwfwHyOexJw0e3NTcUvklklroaW7MiQIPcsEVLldQ/BYoLFee6330gfFxAwEEC5JrUR/kSatULlMMfm9WKoPF2CGwD/eVIrpc5CS+yS4meIS2d1YLFy5LmCHpnqcCiLCGOPmBTDW0iJCjWarbDJFcHibwZCvp8rNv4lHxlKpGP26dYDGHp4gUifXgf+U=?iv=XVG/yZf2/q0uHCOAvBxAUQ==
@ ef1744f8:96fbc3fe
2025-02-23 19:08:09wleig1qZtQh8+b2BEGuJl1Cug0McB7COckI3WeF/654AXNK2nrxnYZS/p/mZ2JNW4IVEOu8vrhb0w3l8VZP5BUdAqY/Ex3H0XhKTRUKNcwunirweS2DYC+F5P6VC9hUTRaLmhlmnqFU5Hmj/fwSCKfv9wfUOveaTvwV7SJLtH5n5qRrbwfwHyOexJw0e3NTcUvklklroaW7MiQIPcsEVLldQ/BYoLFee6330gfFxAwEEC5JrUR/kSatULlMMfm9WKoPF2CGwD/eVIrpc5CS+yS4meIS2d1YLFy5LmCHpnqcCiLCGOPmBTDW0iJCjWarbDJFcHibwZCvp8rNv4lHxlKpGP26dYDGHp4gUifXgf+U=?iv=XVG/yZf2/q0uHCOAvBxAUQ== @ ef1744f8:96fbc3fe
2025-02-23 19:07:54/hQoalQuH7Vp8NLH0TwCxIAPmLziuM/rOlXEJw2NkUMnzojVUkDft8aujNYnK2NzWTW6Cj3a8B8F+uvsJiARBQcDWZIEzSnlDe3uk+LBf53yGtn49KTv7Wm6mB1luqC8bCvulLxJquD7KCH3Cum82z1dPxxZ7OeBCAOht0duQToWZ+hZ3nixGKSYl3gBzzvHbxgrpuBpxTxKlG8DqpmaWTqIKvv0qVeJE5/kj1Hsa7RytJyEdXP7IIVXR46IRpmsxUP4yg1zJRwy9oVJz8ZXbdrJqYebVmhyWOdqq6r+T4LzJXuPELlzi5C6bMqAVuO+899r8Ixo/DfYa/QnFw+sHZT95omH6/TSzoVsLW/JPkc=?iv=hBMT+C7DLhHbT2xpaEFeWg==
@ ef1744f8:96fbc3fe
2025-02-23 19:07:54/hQoalQuH7Vp8NLH0TwCxIAPmLziuM/rOlXEJw2NkUMnzojVUkDft8aujNYnK2NzWTW6Cj3a8B8F+uvsJiARBQcDWZIEzSnlDe3uk+LBf53yGtn49KTv7Wm6mB1luqC8bCvulLxJquD7KCH3Cum82z1dPxxZ7OeBCAOht0duQToWZ+hZ3nixGKSYl3gBzzvHbxgrpuBpxTxKlG8DqpmaWTqIKvv0qVeJE5/kj1Hsa7RytJyEdXP7IIVXR46IRpmsxUP4yg1zJRwy9oVJz8ZXbdrJqYebVmhyWOdqq6r+T4LzJXuPELlzi5C6bMqAVuO+899r8Ixo/DfYa/QnFw+sHZT95omH6/TSzoVsLW/JPkc=?iv=hBMT+C7DLhHbT2xpaEFeWg== @ ef1744f8:96fbc3fe
2025-02-23 19:07:41jBiT1F1hY5a3Vq2M4HQw8gzVRLsjgq55R7BiuA27ArQTWpw4IPwLwljsZ5LDgw3GrZLbDXwFJchQxD7uBvMnMJWhyNTCcrrtG+HEwOKI2QNoOuvD/7ilDa6LRkH27dcJkwYykm4m2Z/55OKy/tFlDmuILrVI292kLmYtaM5a9J0BCzEjUYD2y3rsSEao33ffBPr1sguZqJ4v+6+JPI/v2g90RrJx4SUS8rwi4u+JK7NmFZ8kvQ/2q3pkxQlGQwHO6QJvjojhnP1wh10Hfjv55Zy12QCoIFEwfEyXiVgiY28eiLqMmFwuew73/KlDac/7cK46SY8Ctc9XCCVyMIeWrtvAf9Xv/gaXf+Bdma9nFd49ajE0vTu1ek0w/VAjbDMM?iv=0lLA9SdWMNruCC1dP2LLgA==
@ ef1744f8:96fbc3fe
2025-02-23 19:07:41jBiT1F1hY5a3Vq2M4HQw8gzVRLsjgq55R7BiuA27ArQTWpw4IPwLwljsZ5LDgw3GrZLbDXwFJchQxD7uBvMnMJWhyNTCcrrtG+HEwOKI2QNoOuvD/7ilDa6LRkH27dcJkwYykm4m2Z/55OKy/tFlDmuILrVI292kLmYtaM5a9J0BCzEjUYD2y3rsSEao33ffBPr1sguZqJ4v+6+JPI/v2g90RrJx4SUS8rwi4u+JK7NmFZ8kvQ/2q3pkxQlGQwHO6QJvjojhnP1wh10Hfjv55Zy12QCoIFEwfEyXiVgiY28eiLqMmFwuew73/KlDac/7cK46SY8Ctc9XCCVyMIeWrtvAf9Xv/gaXf+Bdma9nFd49ajE0vTu1ek0w/VAjbDMM?iv=0lLA9SdWMNruCC1dP2LLgA== @ ef1744f8:96fbc3fe
2025-02-23 19:07:383jqbINLb+Eu6xeXqFoZnxGx1vWAPYzmPDiD7QWXr7gEmomwqlvfMkaP//6lgCfRZWMgQ+CwOy8O87HiQVlKz4S7Or1EJD50aWxSLkPWsIxvP7qbQucBZT4dGJZcfx1roCbmatYwiFsEx82qmbpm8otkry7GI5tCFVMpFzvgW2W03j+ogXmvPgrgrta5RJT6eHX0HlzoRPmUi7MUzulSCnIWWwB+mrSbP5UHsPuwyNAsS5y3o4v0poQKEFEPRhin1x3e+Ng1TaaSvtqS8cDsJbl+MR/Tg+rf5tY7vJYWfE08I7oAu5onu5sPwQxRAdsugUUkHTqV4NFHPtRdUXETzpZWMnMzjRNQQxJxKCvAx1kNQPAawWMmiVm+D2CxTMsQF6ppj7Fy/2k071Atbyo1U24EAxnpe4QKxmRYmqGFi1/8=?iv=putQEJoUu8Jq2j5iMUe+5w==
@ ef1744f8:96fbc3fe
2025-02-23 19:07:383jqbINLb+Eu6xeXqFoZnxGx1vWAPYzmPDiD7QWXr7gEmomwqlvfMkaP//6lgCfRZWMgQ+CwOy8O87HiQVlKz4S7Or1EJD50aWxSLkPWsIxvP7qbQucBZT4dGJZcfx1roCbmatYwiFsEx82qmbpm8otkry7GI5tCFVMpFzvgW2W03j+ogXmvPgrgrta5RJT6eHX0HlzoRPmUi7MUzulSCnIWWwB+mrSbP5UHsPuwyNAsS5y3o4v0poQKEFEPRhin1x3e+Ng1TaaSvtqS8cDsJbl+MR/Tg+rf5tY7vJYWfE08I7oAu5onu5sPwQxRAdsugUUkHTqV4NFHPtRdUXETzpZWMnMzjRNQQxJxKCvAx1kNQPAawWMmiVm+D2CxTMsQF6ppj7Fy/2k071Atbyo1U24EAxnpe4QKxmRYmqGFi1/8=?iv=putQEJoUu8Jq2j5iMUe+5w== @ ef1744f8:96fbc3fe
2025-02-23 18:57:50PYb07VjQ46ph8Nm/1ChBV/71d/mvwfdg1JbshVfDENrQm77om+bb4qswyBwZ9Jd7j2ZWbQJZ4RLwEu4UG/kz93RkY7z8/fGDZWp4X2BGQKnayQmlVZW+nVfyQ1EWHiAUSbDZglbFBCM7OfpEA/bSTC0K0hacqvNF/c7OStbcK3rtYAlSoOmOd18uYFaCnZFC20IplacQitbEPRkWbCY7jk1J1n1axFXcYO37n9fR/Phor6TCLx0Mlqdv1AlqCA0Z9kuf9OwqGO/vp7FtdMDNowDFLdFSiYTO+q0Mt40oiGuHbJKdCRXczEnLZiXEuhgIIckFdN0pPHvyl9bfuU5H587nNhIBgkG8uh1U5RVVBCbixHkXGgtXUzUbPE/66AKTkYlXZM85VuOVduEoKzGwBqZCHcD/s33mdKI0eDUXrE5VrgzUFMBP1FKz7R2P6L6d?iv=EwWM5EBKuyRHXzIajYDOkw==
@ ef1744f8:96fbc3fe
2025-02-23 18:57:50PYb07VjQ46ph8Nm/1ChBV/71d/mvwfdg1JbshVfDENrQm77om+bb4qswyBwZ9Jd7j2ZWbQJZ4RLwEu4UG/kz93RkY7z8/fGDZWp4X2BGQKnayQmlVZW+nVfyQ1EWHiAUSbDZglbFBCM7OfpEA/bSTC0K0hacqvNF/c7OStbcK3rtYAlSoOmOd18uYFaCnZFC20IplacQitbEPRkWbCY7jk1J1n1axFXcYO37n9fR/Phor6TCLx0Mlqdv1AlqCA0Z9kuf9OwqGO/vp7FtdMDNowDFLdFSiYTO+q0Mt40oiGuHbJKdCRXczEnLZiXEuhgIIckFdN0pPHvyl9bfuU5H587nNhIBgkG8uh1U5RVVBCbixHkXGgtXUzUbPE/66AKTkYlXZM85VuOVduEoKzGwBqZCHcD/s33mdKI0eDUXrE5VrgzUFMBP1FKz7R2P6L6d?iv=EwWM5EBKuyRHXzIajYDOkw== @ 2e8970de:63345c7a
2025-02-23 18:38:06 > 1 in 5 women with a BA are willing to marry a man without one  > But crucially, the men without a BA married to women with a BA are those with better earnings. So women "marry down" educationally, not so much economically  > Why aren't women without a BA marrying men without one? Short answer: economic viability. In areas where men from lower-income backgrounds are doing better. women are more likely to be married  https://aibm.org/research/will-college-educated-women-find-someone-to-marry/ originally posted at https://stacker.news/items/895044
@ 2e8970de:63345c7a
2025-02-23 18:38:06 > 1 in 5 women with a BA are willing to marry a man without one  > But crucially, the men without a BA married to women with a BA are those with better earnings. So women "marry down" educationally, not so much economically  > Why aren't women without a BA marrying men without one? Short answer: economic viability. In areas where men from lower-income backgrounds are doing better. women are more likely to be married  https://aibm.org/research/will-college-educated-women-find-someone-to-marry/ originally posted at https://stacker.news/items/895044 @ f7d424b5:618c51e8
2025-02-23 18:01:38(This was originally posted on melonmancy.net which is a blog on write.as, an ActivityPub based blogging instance) Listeners rejoice as we are joined today by [ironee212 @ shitposter.world](https://shitposter.world/ironee212) Another major videogame release happened since we last recorded and it looks like a big stinker, or is it? All that and more in today's episode. We mentioned a few things in the show you might want to pull up while listening, they are the following: - [Avowed steam chart](https://steamdb.info/app/2457220/charts/) - [TF2 SDK news](https://www.teamfortress.com/post.php?id=238809) Obligatory: - [Listen to the new episode here!](https://melonmancy.net/listen) - [Discuss this episode on OUR NEW FORUM](https://melonmancy.cafe/d/103-mp101-my-favorite-body-type-b) - [Get the RSS and Subscribe](https://feeds.rssblue.com/melonmancy-podcast) (this is a new feed URL, but the old one redirects here too!) - Get a modern podcast app to use that RSS feed on at [newpodcastapps.com](http://newpodcastapps.com/) - Or listen to the show on [the forum](https://melonmancy.cafe) using the embedded [Podverse](https://podverse.fm) player! - [Send your complaints here](https://melonmancy.net/contact-us) Reminder that this is a [Value4Value](https://value4value.info/) podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors! Our podcast is created entirely with free software and is proudly hosted on [RSSBlue!](https://rssblue.com)
@ f7d424b5:618c51e8
2025-02-23 18:01:38(This was originally posted on melonmancy.net which is a blog on write.as, an ActivityPub based blogging instance) Listeners rejoice as we are joined today by [ironee212 @ shitposter.world](https://shitposter.world/ironee212) Another major videogame release happened since we last recorded and it looks like a big stinker, or is it? All that and more in today's episode. We mentioned a few things in the show you might want to pull up while listening, they are the following: - [Avowed steam chart](https://steamdb.info/app/2457220/charts/) - [TF2 SDK news](https://www.teamfortress.com/post.php?id=238809) Obligatory: - [Listen to the new episode here!](https://melonmancy.net/listen) - [Discuss this episode on OUR NEW FORUM](https://melonmancy.cafe/d/103-mp101-my-favorite-body-type-b) - [Get the RSS and Subscribe](https://feeds.rssblue.com/melonmancy-podcast) (this is a new feed URL, but the old one redirects here too!) - Get a modern podcast app to use that RSS feed on at [newpodcastapps.com](http://newpodcastapps.com/) - Or listen to the show on [the forum](https://melonmancy.cafe) using the embedded [Podverse](https://podverse.fm) player! - [Send your complaints here](https://melonmancy.net/contact-us) Reminder that this is a [Value4Value](https://value4value.info/) podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors! Our podcast is created entirely with free software and is proudly hosted on [RSSBlue!](https://rssblue.com) @ 04ea4f83:210e1713
2025-02-23 17:38:11Erschienen in [Citadel 21 Vol. 21](https://www.citadel21.com/are-you-tired-of-clown-world?ref=europeanbitcoiners.com) | Veröffentlichung 21.03.2023 \ Autor: [Knut Svanholm](https://twitter.com/knutsvanholm?ref=europeanbitcoiners.com)\ Übersetzt von: [Sinautoshi am 24.03.2023 - 782344](https://twitter.com/Sinautoshi_8_21?ref=europeanbitcoiners.com)\ \ Rückblickend sieht das Jahr 2022 wie eine Art Höhepunkt aus. Während der Großteil der Gesellschaft weitgehend vergessen hat, was die politische Klasse ihren Untertanen während der sogenannten Pandemie angetan hat, kotzte Hollywood weiterhin Inhalte aus, die von „diversen" Regisseuren und Drehbuchautoren produziert wurden und bis zum Rand mit nicht ganz so subtilen Botschaften und Verachtung für ihr Publikum gefüllt waren. Star Wars und Marvel haben nach der Übernahme durch Disney auf diese Weise Franchise-Mord begangen, und auch das Erbe von *Der Herr der Ringe* wurde von der linken Idiotie vergewaltigt und für immer befleckt. Jetzt gibt es von jedem männlichen Avenger eine weibliche Version. Hugh Jackman, der Schauspieler, der früher die Hauptrolle des X-Men-Mutanten Wolverine spielte, empfahl seinen Anhängern in den sozialen Medien kürzlich Bill Gates' Buch über den Klimawandel. Als Frauen verkleidete Männer gewinnen Sportmeisterschaften für Frauen, und alle haben so viel Angst davor, als bigott bezeichnet zu werden, dass sich niemand traut, auf die Absurdität hinzuweisen, dass ein Mann alle Mädchen schlägt. Diese so genannten Sportler werden als „mutig" bezeichnet, obwohl sie alles andere als das sind. Die Tatsache, dass es in einigen Berufen mehr Männer als Frauen gibt, wird als Problem angesehen, aber warum genau das ein Problem ist, wird selten erwähnt. Die Verdienste und die tatsächliche Meinungsvielfalt werden auf dem Altar der „Vielfalt und Integration" geschlachtet. Die Gesellschaft ist an einem Punkt angelangt, an dem die Verbraucher Ärzten und Anwälten gerade wegen ihrer Hautfarbe misstrauen, da sie vermuten, dass sie deshalb in ihre Positionen gekommen sind und nicht wegen ihrer Kompetenz oder ihrer Verdienste. Noch vor zwanzig Jahren war die normale Bauchreaktion das Gegenteil: „*Wow, ein Arzt aus einer Minderheit! Sie müssen hart gearbeitet haben, um dorthin zu gelangen, wo sie heute sind!*" Als ich aufgewachsen bin, wurde ein „Rassist" als jemand definiert, der sich einen Dreck um die Hautfarbe oder die ethnische Zugehörigkeit einer anderen Person scherte. Dasselbe galt für das Wort „Sexist" - man war ein Sexist, wenn man das Geschlecht einer Person bei der Beurteilung berücksichtigte. Ich hatte das Gefühl, dass die Welt seit den Gräueltaten des Zweiten Weltkriegs im Kampf gegen diese Vorurteile einen weiten Weg zurückgelegt hatte und dass jeder eine anständige Karriere in jedem Beruf machen konnte, wenn er sich nur anstrengte und sich Mühe gab. Doch irgendwann in den frühen 2000er Jahren änderte sich etwas. Plötzlich begannen die Worte das Gegenteil von dem zu bedeuten, was sie ursprünglich bedeuteten. Plötzlich war jeder, der sich einen Dreck um seine Hautfarbe scherte, ein Rassist. Jeder, dem es egal war, ob der CEO eines großen Unternehmens ein Mann oder eine Frau war, war ein Sexist. Im Jahr 2023 behaupten manche sogar, man sei ein „Transphobe", wenn man nicht gelegentlich Fellatio an einem „weiblichen Penis" betreiben will. Die Tugendwächter laufen in der Tat Amok, und die Medienunternehmen lieben es. Sie lieben es, weil sie alles lieben, was die Kluft zwischen den Menschen schürt. Je verrückter die Aktionen der Clownwelt® sind, desto wütender sind die Reaktionen der leichtgläubigen, verärgerten Menschen auf der „vernünftigen" Seite des politischen Spektrums. Die Menschheit neigt dazu, sich wie ein Pendel oder eine Abrissbirne zu verhalten, wenn es um politische Meinungen oder „die aktuelle Sache" geht. Wenn es zu viele blauhaarige, übergewichtige, lesbische, glutenintolerante, vegane Umweltschützer gibt, taucht von irgendwoher eine Welle von Skinheads auf, die mit Steroiden vollgepumpt sind und gegen Samenöl und Fleischfresser sind. Für jede Hillary Clinton gibt es einen Donald Trump. Für jede Greta Thunberg gibt es einen Andrew Tate. Für jeden CNN-Reporter gibt es einen Alex Jones. Auch im Bitcoin-Bereich gibt es immer ein „aktuelles Thema", an das man sich klammern kann, wenn auch oft eine männlichere Idee als das „aktuelle Thema" des Mainstreams. Was nur wenige wissen, ist, wie faul diese Art des Denkens ist. Wissenschaft ist nicht automatisch schlecht, nur weil „die Wissenschaft" schlecht ist. Nur weil man gelernt hat, dass alles, was die Regierung sagt, eine Lüge ist, ist nicht automatisch auch das Gegenteil wahr. Die Welt ist nuanciert; die meisten Dinge sind nicht schwarz oder weiß. Was wahr und sehr schwarz-weiß ist, ist das Geld - es gibt Bitcoin und es gibt Shitcoins. Nur wenn wir letztere für erstere aufgeben, können wir die Politik aus dem menschlichen Handeln entfernen und uns auf eine gewisse Wahrheit in der Basisschicht der Zivilisation zurück arbeiten. Bitcoin belohnt weder Rent-Seeking noch faules Denken. Die positiven Aspekte vieler moderner Technologien werden oft übersehen. Auch wenn sich die Clownwelt® und die lächerlichen Ideen, die ihr folgen, wie ein Lauffeuer verbreiten, gibt es Gründe für einen ungetrübten Optimismus für die Zukunft. Wir hören oft von den Gefahren der sozialen Medien und wie sie die Gehirne unserer Kinder schädigen, aber wir werden selten an die Kehrseite der Medaille erinnert. Soziale Medien verbinden Menschen in einem Ausmaß, das der Menschheit nie zuvor zugänglich war. Jeder Mensch auf der Welt kann heute mit jedem anderen in Kontakt treten und mit einem Mausklick einen Videoanruf starten. Das ist ein enorm wichtiges Instrument für den Frieden. In Kombination mit Bitcoin haben die Bösewichte keine Chance mehr. Wenn jeder auf diese Weise vernetzt ist, wird überdeutlich, wie absurd es ist, dass wir in Staaten mit unterschiedlichen Gesetzen und Vorschriften leben. Warum gelten für meine Mitmenschen auf der anderen Seite dieses Teiches, dieses Flusses, dieses Gebirges oder sogar dieser imaginären Linie in der Erde andere Regeln? Jeden Tag wachen mehr und mehr Menschen auf und erkennen, dass es nur ein einziges Menschenrecht gibt - das Recht, in Ruhe gelassen zu werden. Immer mehr Menschen erkennen, dass die Geldentwertung kein natürliches Phänomen ist, sondern eine bewusste Politik. Es ist nur eine Frage der Zeit, bis die alte Welt verschwindet. Solange wir kommunizieren dürfen, gibt es Hoffnung. Das Internet hat bewiesen, dass sich jede Kommunikation auf eine Reihe von Einsen und Nullen reduzieren lässt, und Bitcoin hat bewiesen, dass Geld nichts anderes als Information ist.
@ 04ea4f83:210e1713
2025-02-23 17:38:11Erschienen in [Citadel 21 Vol. 21](https://www.citadel21.com/are-you-tired-of-clown-world?ref=europeanbitcoiners.com) | Veröffentlichung 21.03.2023 \ Autor: [Knut Svanholm](https://twitter.com/knutsvanholm?ref=europeanbitcoiners.com)\ Übersetzt von: [Sinautoshi am 24.03.2023 - 782344](https://twitter.com/Sinautoshi_8_21?ref=europeanbitcoiners.com)\ \ Rückblickend sieht das Jahr 2022 wie eine Art Höhepunkt aus. Während der Großteil der Gesellschaft weitgehend vergessen hat, was die politische Klasse ihren Untertanen während der sogenannten Pandemie angetan hat, kotzte Hollywood weiterhin Inhalte aus, die von „diversen" Regisseuren und Drehbuchautoren produziert wurden und bis zum Rand mit nicht ganz so subtilen Botschaften und Verachtung für ihr Publikum gefüllt waren. Star Wars und Marvel haben nach der Übernahme durch Disney auf diese Weise Franchise-Mord begangen, und auch das Erbe von *Der Herr der Ringe* wurde von der linken Idiotie vergewaltigt und für immer befleckt. Jetzt gibt es von jedem männlichen Avenger eine weibliche Version. Hugh Jackman, der Schauspieler, der früher die Hauptrolle des X-Men-Mutanten Wolverine spielte, empfahl seinen Anhängern in den sozialen Medien kürzlich Bill Gates' Buch über den Klimawandel. Als Frauen verkleidete Männer gewinnen Sportmeisterschaften für Frauen, und alle haben so viel Angst davor, als bigott bezeichnet zu werden, dass sich niemand traut, auf die Absurdität hinzuweisen, dass ein Mann alle Mädchen schlägt. Diese so genannten Sportler werden als „mutig" bezeichnet, obwohl sie alles andere als das sind. Die Tatsache, dass es in einigen Berufen mehr Männer als Frauen gibt, wird als Problem angesehen, aber warum genau das ein Problem ist, wird selten erwähnt. Die Verdienste und die tatsächliche Meinungsvielfalt werden auf dem Altar der „Vielfalt und Integration" geschlachtet. Die Gesellschaft ist an einem Punkt angelangt, an dem die Verbraucher Ärzten und Anwälten gerade wegen ihrer Hautfarbe misstrauen, da sie vermuten, dass sie deshalb in ihre Positionen gekommen sind und nicht wegen ihrer Kompetenz oder ihrer Verdienste. Noch vor zwanzig Jahren war die normale Bauchreaktion das Gegenteil: „*Wow, ein Arzt aus einer Minderheit! Sie müssen hart gearbeitet haben, um dorthin zu gelangen, wo sie heute sind!*" Als ich aufgewachsen bin, wurde ein „Rassist" als jemand definiert, der sich einen Dreck um die Hautfarbe oder die ethnische Zugehörigkeit einer anderen Person scherte. Dasselbe galt für das Wort „Sexist" - man war ein Sexist, wenn man das Geschlecht einer Person bei der Beurteilung berücksichtigte. Ich hatte das Gefühl, dass die Welt seit den Gräueltaten des Zweiten Weltkriegs im Kampf gegen diese Vorurteile einen weiten Weg zurückgelegt hatte und dass jeder eine anständige Karriere in jedem Beruf machen konnte, wenn er sich nur anstrengte und sich Mühe gab. Doch irgendwann in den frühen 2000er Jahren änderte sich etwas. Plötzlich begannen die Worte das Gegenteil von dem zu bedeuten, was sie ursprünglich bedeuteten. Plötzlich war jeder, der sich einen Dreck um seine Hautfarbe scherte, ein Rassist. Jeder, dem es egal war, ob der CEO eines großen Unternehmens ein Mann oder eine Frau war, war ein Sexist. Im Jahr 2023 behaupten manche sogar, man sei ein „Transphobe", wenn man nicht gelegentlich Fellatio an einem „weiblichen Penis" betreiben will. Die Tugendwächter laufen in der Tat Amok, und die Medienunternehmen lieben es. Sie lieben es, weil sie alles lieben, was die Kluft zwischen den Menschen schürt. Je verrückter die Aktionen der Clownwelt® sind, desto wütender sind die Reaktionen der leichtgläubigen, verärgerten Menschen auf der „vernünftigen" Seite des politischen Spektrums. Die Menschheit neigt dazu, sich wie ein Pendel oder eine Abrissbirne zu verhalten, wenn es um politische Meinungen oder „die aktuelle Sache" geht. Wenn es zu viele blauhaarige, übergewichtige, lesbische, glutenintolerante, vegane Umweltschützer gibt, taucht von irgendwoher eine Welle von Skinheads auf, die mit Steroiden vollgepumpt sind und gegen Samenöl und Fleischfresser sind. Für jede Hillary Clinton gibt es einen Donald Trump. Für jede Greta Thunberg gibt es einen Andrew Tate. Für jeden CNN-Reporter gibt es einen Alex Jones. Auch im Bitcoin-Bereich gibt es immer ein „aktuelles Thema", an das man sich klammern kann, wenn auch oft eine männlichere Idee als das „aktuelle Thema" des Mainstreams. Was nur wenige wissen, ist, wie faul diese Art des Denkens ist. Wissenschaft ist nicht automatisch schlecht, nur weil „die Wissenschaft" schlecht ist. Nur weil man gelernt hat, dass alles, was die Regierung sagt, eine Lüge ist, ist nicht automatisch auch das Gegenteil wahr. Die Welt ist nuanciert; die meisten Dinge sind nicht schwarz oder weiß. Was wahr und sehr schwarz-weiß ist, ist das Geld - es gibt Bitcoin und es gibt Shitcoins. Nur wenn wir letztere für erstere aufgeben, können wir die Politik aus dem menschlichen Handeln entfernen und uns auf eine gewisse Wahrheit in der Basisschicht der Zivilisation zurück arbeiten. Bitcoin belohnt weder Rent-Seeking noch faules Denken. Die positiven Aspekte vieler moderner Technologien werden oft übersehen. Auch wenn sich die Clownwelt® und die lächerlichen Ideen, die ihr folgen, wie ein Lauffeuer verbreiten, gibt es Gründe für einen ungetrübten Optimismus für die Zukunft. Wir hören oft von den Gefahren der sozialen Medien und wie sie die Gehirne unserer Kinder schädigen, aber wir werden selten an die Kehrseite der Medaille erinnert. Soziale Medien verbinden Menschen in einem Ausmaß, das der Menschheit nie zuvor zugänglich war. Jeder Mensch auf der Welt kann heute mit jedem anderen in Kontakt treten und mit einem Mausklick einen Videoanruf starten. Das ist ein enorm wichtiges Instrument für den Frieden. In Kombination mit Bitcoin haben die Bösewichte keine Chance mehr. Wenn jeder auf diese Weise vernetzt ist, wird überdeutlich, wie absurd es ist, dass wir in Staaten mit unterschiedlichen Gesetzen und Vorschriften leben. Warum gelten für meine Mitmenschen auf der anderen Seite dieses Teiches, dieses Flusses, dieses Gebirges oder sogar dieser imaginären Linie in der Erde andere Regeln? Jeden Tag wachen mehr und mehr Menschen auf und erkennen, dass es nur ein einziges Menschenrecht gibt - das Recht, in Ruhe gelassen zu werden. Immer mehr Menschen erkennen, dass die Geldentwertung kein natürliches Phänomen ist, sondern eine bewusste Politik. Es ist nur eine Frage der Zeit, bis die alte Welt verschwindet. Solange wir kommunizieren dürfen, gibt es Hoffnung. Das Internet hat bewiesen, dass sich jede Kommunikation auf eine Reihe von Einsen und Nullen reduzieren lässt, und Bitcoin hat bewiesen, dass Geld nichts anderes als Information ist. @ dbb19ae0:c3f22d5a
2025-02-23 16:38:41Derive npub from nsec given as parameter ``` python import argparse import asyncio from nostr_sdk import Keys, init_logger, LogLevel async def main(nsec): init_logger(LogLevel.INFO) keys = Keys.parse(nsec) public_key = keys.public_key() print(f"Public key (hex): {public_key.to_hex()}") print(f"Public key (npub): {public_key.to_bech32()}") if __name__ == '__main__': parser = argparse.ArgumentParser(description='Fetch all relay from a given nsec') parser.add_argument('nsec', type=str, help='The nsec of the user') args = parser.parse_args() asyncio.run(main(args.nsec)) ``` https://docs.rs/nostr_rust/latest/nostr_rust/keys/fn.get_public_key_from_secret.html https://github.com/ev3rst/nostr_sdk_examples/blob/main/ns-derive-npub.py
@ dbb19ae0:c3f22d5a
2025-02-23 16:38:41Derive npub from nsec given as parameter ``` python import argparse import asyncio from nostr_sdk import Keys, init_logger, LogLevel async def main(nsec): init_logger(LogLevel.INFO) keys = Keys.parse(nsec) public_key = keys.public_key() print(f"Public key (hex): {public_key.to_hex()}") print(f"Public key (npub): {public_key.to_bech32()}") if __name__ == '__main__': parser = argparse.ArgumentParser(description='Fetch all relay from a given nsec') parser.add_argument('nsec', type=str, help='The nsec of the user') args = parser.parse_args() asyncio.run(main(args.nsec)) ``` https://docs.rs/nostr_rust/latest/nostr_rust/keys/fn.get_public_key_from_secret.html https://github.com/ev3rst/nostr_sdk_examples/blob/main/ns-derive-npub.py @ 2779f3d9:1a7f98d1
2025-02-23 15:20:19# NOSTR SDK FOR APPLE PLATFORMS ## Progress Report # 2: Nov 2024 - Jan 2025 [Nostr SDK for Apple Platforms](https://github.com/nostr-sdk/nostr-sdk-ios) continued to make progress this quarter. I am still the sole part-time active developer and maintainer of Nostr SDK for Apple Platforms. Implementations for a few NIPs were added or updated. The CI build pipeline was broken due to deprecated dependencies, which have since been fixed. I pushed out a (controversial) [proposal](https://github.com/nostr-protocol/nips/pull/1770) to gracefully deprecate stringified JSON in favor of tags on user metadata kind 0 events to the NIPs repo as a pull request to improve consistency and reduce the complexity of reading and writing this commonly used kind. The SDK has become the first to [implement](https://github.com/nostr-sdk/nostr-sdk-ios/pull/212) with the hopes that others will follow. We have had new external interest in the SDK from developers working on various Nostr clients: - Damus has [copied the NIP-44 encryption implementation from the SDK](https://github.com/damus-io/damus/pull/2850/files#diff-5eb31bd8e6dc73d21bb3caef975a7f3508765e7f3ab01ecec545635ccb89d17c) for their use in [NIP-37 Draft Events](https://github.com/nostr-protocol/nips/blob/7cc120ecb01963e37f9adcd3b57b8efc1dd9e828/37.md), swapping out their previous usage of rust-nostr due to large binary size issues. - [Fabian](nostr:npub1n0sturny6w9zn2wwexju3m6asu7zh7jnv2jt2kx6tlmfhs7thq0qnflahe) from Nostur contributed a [NIP-44 encrypt/decrypt example](https://github.com/nostr-sdk/nostr-sdk-ios/pull/204) to the SDK demo project to help him understand how it works and is [currently being used](https://github.com/nostur-com/nostr-essentials/blob/05e5452bb05c4c2e94ec9a78bb0c80d5123919a7/Sources/NostrEssentials/NIP-44/NIP44v2Encrypting.swift) by Nostur - A new livestreaming Nostr client called [Swae](https://github.com/suhailsaqan/swae) has adopted the SDK, using Comingle as a reference client implementation. Progress on the SDK this quarter has been slower than the previous quarter due to a shift in emerging priorities in Nostr. This quarter, I focused on building a native iOS Nostr event signer, as none exist today. The problem is that some iOS users do not fully trust pasting their private key into Nostr clients, which they fear could be buggy or malicious in accessing and signing bad data with their private key. A native signer on Android called Amber already exists, and there has been an increase in demand from users for an equivalent solution on iOS. The iOS signer app is called [Yeti](https://github.com/tyiu/Yeti) (credit to [Karnage](nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac) for the name and Figma designs) and I'm using Nostr SDK for Apple Platforms and its demo app as a [test bed](https://github.com/nostr-sdk/nostr-sdk-ios/tree/tyiu/signer-demo) for this experimental cross-app communication protocol that will eventually be proposed as a NIP. I hope iOS clients adopting the SDK will get built-in standardized event signing protocol capabilities, tightening up this attack vector. This report marks the end of the six-month grant period, as agreed with OpenSats. I thank OpenSats for supporting Nostr SDK for Apple Platforms, other Nostr projects, and the developer community. I will re-apply for a grant at OpenSats for the SDK, Yeti, or other impactful Nostr projects. ## 1) How did you spend your time? Below is a broken-down summarized bulletpointed list of completed tasks. ### Development of Nostr SDK for Apple Platforms #### Added - [NIP-37 Draft Events](https://github.com/nostr-protocol/nips/blob/master/37.md) - [NIP-44 encrypt/decrypt example to demo project](https://github.com/nostr-sdk/nostr-sdk-ios/pull/204) ### Updated - [Updated NIP-11 Relay Information Document implementation](https://github.com/nostr-sdk/nostr-sdk-ios/pull/201) to support all the newly added fields - [Renamed ParameterizedReplaceableEvent to AddressableEvent and NonParameterizedReplaceableEvent to NormalReplaceableEvent](https://github.com/nostr-sdk/nostr-sdk-ios/pull/205) to conform to the [new terminology](https://github.com/nostr-protocol/nips/pull/1418) in the NIPs repo - Gracefully deprecated stringified JSON in favor of tags on user metadata kind 0 events, being the first to implement the [not-yet-merged proposal](https://github.com/nostr-protocol/nips/pull/1770) to NIP-01/NIP-24 ### Fixed - Fixed broken CI build pipeline - [Fix GitHub workflow for running build and test](https://github.com/nostr-sdk/nostr-sdk-ios/pull/202) - [Upgrade upload-pages-artifact from deprecated version to v3 to fix build](https://github.com/nostr-sdk/nostr-sdk-ios/pull/207) - [Upgrade deploy pages action to v4 to fix build](https://github.com/nostr-sdk/nostr-sdk-ios/pull/208) #### In Progress - Native iOS event signing protocol, using the [SDK as a test bed](https://github.com/nostr-sdk/nostr-sdk-ios/tree/tyiu/signer-demo) ## 2) What do you plan to work on next quarter? The top priorities will be developing the native iOS event signing protocol, building out Yeti, and integrating the iOS signing protocol into the SDK. I will continue maintaining and developing the SDK, albeit at a slower pace: - Deprecate EventCreating protocol in favor of NostrEventBuilding protocol for the remaining event kinds - Add or update implementations for various NIPs where critical or needed - Support clients as they integrate with parts of the SDK by answering questions, fixing any issues they have, adding requested features, and reviewing pull requests ## 3) How did you make use of the money? Living expenses.
@ 2779f3d9:1a7f98d1
2025-02-23 15:20:19# NOSTR SDK FOR APPLE PLATFORMS ## Progress Report # 2: Nov 2024 - Jan 2025 [Nostr SDK for Apple Platforms](https://github.com/nostr-sdk/nostr-sdk-ios) continued to make progress this quarter. I am still the sole part-time active developer and maintainer of Nostr SDK for Apple Platforms. Implementations for a few NIPs were added or updated. The CI build pipeline was broken due to deprecated dependencies, which have since been fixed. I pushed out a (controversial) [proposal](https://github.com/nostr-protocol/nips/pull/1770) to gracefully deprecate stringified JSON in favor of tags on user metadata kind 0 events to the NIPs repo as a pull request to improve consistency and reduce the complexity of reading and writing this commonly used kind. The SDK has become the first to [implement](https://github.com/nostr-sdk/nostr-sdk-ios/pull/212) with the hopes that others will follow. We have had new external interest in the SDK from developers working on various Nostr clients: - Damus has [copied the NIP-44 encryption implementation from the SDK](https://github.com/damus-io/damus/pull/2850/files#diff-5eb31bd8e6dc73d21bb3caef975a7f3508765e7f3ab01ecec545635ccb89d17c) for their use in [NIP-37 Draft Events](https://github.com/nostr-protocol/nips/blob/7cc120ecb01963e37f9adcd3b57b8efc1dd9e828/37.md), swapping out their previous usage of rust-nostr due to large binary size issues. - [Fabian](nostr:npub1n0sturny6w9zn2wwexju3m6asu7zh7jnv2jt2kx6tlmfhs7thq0qnflahe) from Nostur contributed a [NIP-44 encrypt/decrypt example](https://github.com/nostr-sdk/nostr-sdk-ios/pull/204) to the SDK demo project to help him understand how it works and is [currently being used](https://github.com/nostur-com/nostr-essentials/blob/05e5452bb05c4c2e94ec9a78bb0c80d5123919a7/Sources/NostrEssentials/NIP-44/NIP44v2Encrypting.swift) by Nostur - A new livestreaming Nostr client called [Swae](https://github.com/suhailsaqan/swae) has adopted the SDK, using Comingle as a reference client implementation. Progress on the SDK this quarter has been slower than the previous quarter due to a shift in emerging priorities in Nostr. This quarter, I focused on building a native iOS Nostr event signer, as none exist today. The problem is that some iOS users do not fully trust pasting their private key into Nostr clients, which they fear could be buggy or malicious in accessing and signing bad data with their private key. A native signer on Android called Amber already exists, and there has been an increase in demand from users for an equivalent solution on iOS. The iOS signer app is called [Yeti](https://github.com/tyiu/Yeti) (credit to [Karnage](nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac) for the name and Figma designs) and I'm using Nostr SDK for Apple Platforms and its demo app as a [test bed](https://github.com/nostr-sdk/nostr-sdk-ios/tree/tyiu/signer-demo) for this experimental cross-app communication protocol that will eventually be proposed as a NIP. I hope iOS clients adopting the SDK will get built-in standardized event signing protocol capabilities, tightening up this attack vector. This report marks the end of the six-month grant period, as agreed with OpenSats. I thank OpenSats for supporting Nostr SDK for Apple Platforms, other Nostr projects, and the developer community. I will re-apply for a grant at OpenSats for the SDK, Yeti, or other impactful Nostr projects. ## 1) How did you spend your time? Below is a broken-down summarized bulletpointed list of completed tasks. ### Development of Nostr SDK for Apple Platforms #### Added - [NIP-37 Draft Events](https://github.com/nostr-protocol/nips/blob/master/37.md) - [NIP-44 encrypt/decrypt example to demo project](https://github.com/nostr-sdk/nostr-sdk-ios/pull/204) ### Updated - [Updated NIP-11 Relay Information Document implementation](https://github.com/nostr-sdk/nostr-sdk-ios/pull/201) to support all the newly added fields - [Renamed ParameterizedReplaceableEvent to AddressableEvent and NonParameterizedReplaceableEvent to NormalReplaceableEvent](https://github.com/nostr-sdk/nostr-sdk-ios/pull/205) to conform to the [new terminology](https://github.com/nostr-protocol/nips/pull/1418) in the NIPs repo - Gracefully deprecated stringified JSON in favor of tags on user metadata kind 0 events, being the first to implement the [not-yet-merged proposal](https://github.com/nostr-protocol/nips/pull/1770) to NIP-01/NIP-24 ### Fixed - Fixed broken CI build pipeline - [Fix GitHub workflow for running build and test](https://github.com/nostr-sdk/nostr-sdk-ios/pull/202) - [Upgrade upload-pages-artifact from deprecated version to v3 to fix build](https://github.com/nostr-sdk/nostr-sdk-ios/pull/207) - [Upgrade deploy pages action to v4 to fix build](https://github.com/nostr-sdk/nostr-sdk-ios/pull/208) #### In Progress - Native iOS event signing protocol, using the [SDK as a test bed](https://github.com/nostr-sdk/nostr-sdk-ios/tree/tyiu/signer-demo) ## 2) What do you plan to work on next quarter? The top priorities will be developing the native iOS event signing protocol, building out Yeti, and integrating the iOS signing protocol into the SDK. I will continue maintaining and developing the SDK, albeit at a slower pace: - Deprecate EventCreating protocol in favor of NostrEventBuilding protocol for the remaining event kinds - Add or update implementations for various NIPs where critical or needed - Support clients as they integrate with parts of the SDK by answering questions, fixing any issues they have, adding requested features, and reviewing pull requests ## 3) How did you make use of the money? Living expenses. @ 8d34bd24:414be32b
2025-02-23 12:49:20I recently wrote a post “[What? Do Not Pray For ...](https://trustjesus.substack.com/p/what-do-not-pray-for)” where I shared a passage telling us not to pray for the nation of Israel (at a particular point in time). Before reading this post, I strongly encourage you to read that post first. The verse in question was: > “As for you, **do not pray for this people, and do not lift up cry or prayer for them, and do not intercede with Me; for I do not hear you**. Do you not see what they are doing in the cities of Judah and in the streets of Jerusalem? The children gather wood, and the fathers kindle the fire, and the women knead dough to make cakes for the queen of heaven; and *they* pour out drink offerings to other gods in order to spite Me. Do they spite Me?” declares the Lord. “Is it not themselves *they spite,* to their own shame?” (Jeremiah 7:16-19) {emphasis mine} Jeremiah was told not to pray blessings on Israel because Israel had turned away from God and were serving other Gods. I was just listening to a “Renewing Your Mind” podcast and the speaker made the statement, “We all want to say, ‘God bless America,’ but we don’t want to hear, ‘God curse America.’” That made me contemplate, “Should we ask God to bless America?” Over the past decade or more (probably several decades), America has been using its military and economic might to push actions around the globe that are abhorrent to God. We give aid to countries if they legalize and fund abortions, if they promote gay marriage, and if they encourage transgender surgeries and chemical castration. They encourage people and nations to murder unborn children, to redefine marriage as different than what God created it to be, and to sterilize young people confused about their gender, breaking both God’s good creation of male and female and \ His command to be fruitful and multiply. You could make the argument that the US has been the largest purveyor of evil in the world. (It breaks my heart to say this.) It is true that with the past election, America has turned away from many of these evil actions, but have Americans truly repented and turned back to God? I am convinced that neither our leaders nor most of our people have turned back to God in any significant way. It is like famous atheist, Richard Dawkins, saying he misses Christian culture but continuing to reject God and make fun of actual Christians. We can’t have it both ways. We can’t have God’s blessings without God. Now I am not saying that we shouldn’t pray for America. It is totally appropriate to pray for revival in America. It is good to pray for Americans to repent of their sins and to trust in Jesus. It is great to pray for God to help us to share the gospel and to produce fruit. The issue is that we shouldn’t pray for America’s blessing while she has turned her back on God. Obviously there are a decent number of Christians in America. That and the fact that America was founded on Christian principles actually means that America will be punished harsher than those nations where people have had little knowledge of the Bible and Jesus. Those who have been shown the gospel and still rejected God will be held to a higher standard and will be punished harsher than those who have never heard the gospel. I ask you to pray that God would bring revival to America, that He would turn hearts and minds to Himself, and that He would draw our leaders to submit in full trust and obedience to Him. I also pray that God would help all of believers to be faithful stewards with all of the blessings with which He has already showered us and to use us to shine the light of the gospel with America and the rest of the world. I pray that He would help us to live lives fully devoted to Him and will help us to stand out from the crowd of pseudo-Christians and normal people, so we can be used to draw America back to God. Unfortunately, we may be in a situation, like Jeremiah and Israel, where the nation has turned so far from God that we will be rejected in the same way they reject Jesus. We may have to look upon the nation we love and let go because our citizenship is in heaven. We need to always be more devoted to God and His kingdom than we are to our earthly citizenship. > “Son of man, if a country sins against Me by committing unfaithfulness, and I stretch out My hand against it, destroy its supply of bread, send famine against it and cut off from it both man and beast, even though these three men, Noah, Daniel and Job were in its midst, by their own righteousness they could only deliver themselves,” declares the Lord God. (Ezekiel 14:13-14) May God guide you in your prayers, your actions, and your faith so that you will be a light in the darkness and never forget where your allegiance lies. I pledge allegiance to my God, my Lord, and my Creator, and to Him alone does my allegiance belong. Trust Jesus
@ 8d34bd24:414be32b
2025-02-23 12:49:20I recently wrote a post “[What? Do Not Pray For ...](https://trustjesus.substack.com/p/what-do-not-pray-for)” where I shared a passage telling us not to pray for the nation of Israel (at a particular point in time). Before reading this post, I strongly encourage you to read that post first. The verse in question was: > “As for you, **do not pray for this people, and do not lift up cry or prayer for them, and do not intercede with Me; for I do not hear you**. Do you not see what they are doing in the cities of Judah and in the streets of Jerusalem? The children gather wood, and the fathers kindle the fire, and the women knead dough to make cakes for the queen of heaven; and *they* pour out drink offerings to other gods in order to spite Me. Do they spite Me?” declares the Lord. “Is it not themselves *they spite,* to their own shame?” (Jeremiah 7:16-19) {emphasis mine} Jeremiah was told not to pray blessings on Israel because Israel had turned away from God and were serving other Gods. I was just listening to a “Renewing Your Mind” podcast and the speaker made the statement, “We all want to say, ‘God bless America,’ but we don’t want to hear, ‘God curse America.’” That made me contemplate, “Should we ask God to bless America?” Over the past decade or more (probably several decades), America has been using its military and economic might to push actions around the globe that are abhorrent to God. We give aid to countries if they legalize and fund abortions, if they promote gay marriage, and if they encourage transgender surgeries and chemical castration. They encourage people and nations to murder unborn children, to redefine marriage as different than what God created it to be, and to sterilize young people confused about their gender, breaking both God’s good creation of male and female and \ His command to be fruitful and multiply. You could make the argument that the US has been the largest purveyor of evil in the world. (It breaks my heart to say this.) It is true that with the past election, America has turned away from many of these evil actions, but have Americans truly repented and turned back to God? I am convinced that neither our leaders nor most of our people have turned back to God in any significant way. It is like famous atheist, Richard Dawkins, saying he misses Christian culture but continuing to reject God and make fun of actual Christians. We can’t have it both ways. We can’t have God’s blessings without God. Now I am not saying that we shouldn’t pray for America. It is totally appropriate to pray for revival in America. It is good to pray for Americans to repent of their sins and to trust in Jesus. It is great to pray for God to help us to share the gospel and to produce fruit. The issue is that we shouldn’t pray for America’s blessing while she has turned her back on God. Obviously there are a decent number of Christians in America. That and the fact that America was founded on Christian principles actually means that America will be punished harsher than those nations where people have had little knowledge of the Bible and Jesus. Those who have been shown the gospel and still rejected God will be held to a higher standard and will be punished harsher than those who have never heard the gospel. I ask you to pray that God would bring revival to America, that He would turn hearts and minds to Himself, and that He would draw our leaders to submit in full trust and obedience to Him. I also pray that God would help all of believers to be faithful stewards with all of the blessings with which He has already showered us and to use us to shine the light of the gospel with America and the rest of the world. I pray that He would help us to live lives fully devoted to Him and will help us to stand out from the crowd of pseudo-Christians and normal people, so we can be used to draw America back to God. Unfortunately, we may be in a situation, like Jeremiah and Israel, where the nation has turned so far from God that we will be rejected in the same way they reject Jesus. We may have to look upon the nation we love and let go because our citizenship is in heaven. We need to always be more devoted to God and His kingdom than we are to our earthly citizenship. > “Son of man, if a country sins against Me by committing unfaithfulness, and I stretch out My hand against it, destroy its supply of bread, send famine against it and cut off from it both man and beast, even though these three men, Noah, Daniel and Job were in its midst, by their own righteousness they could only deliver themselves,” declares the Lord God. (Ezekiel 14:13-14) May God guide you in your prayers, your actions, and your faith so that you will be a light in the darkness and never forget where your allegiance lies. I pledge allegiance to my God, my Lord, and my Creator, and to Him alone does my allegiance belong. Trust Jesus @ 95cb4330:96db706c
2025-02-23 12:38:57Embracing asynchronous work can significantly enhance productivity and reduce burnout by allowing individuals to work according to their own schedules without the pressure of immediate responses. This approach fosters deep, focused work and minimizes unnecessary interruptions. --- ## Understanding Asynchronous Work - **Definition:** Asynchronous work refers to a work style where employees complete tasks and communicate on their own time, without the expectation of immediate feedback. This contrasts with synchronous work, which requires real-time interaction. --- ## Benefits of Asynchronous Work - **Enhanced Productivity:** By reducing the need for constant real-time communication, employees can focus on tasks without frequent interruptions, leading to improved efficiency. - **Flexibility:** Employees can work during their most productive hours, accommodating personal schedules and time zones, which promotes a healthier work-life balance. - **Reduced Burnout:** The autonomy to manage one's workload and schedule can decrease stress and prevent burnout. --- ## Implementing Asynchronous Work 1. **Limit Meetings:** Reduce the number of real-time meetings. When meetings are necessary, keep them concise and focused. 2. **Utilize Asynchronous Communication Tools:** Employ platforms like email, project management software, and collaborative documents that allow team members to contribute on their own schedules. 3. **Set Clear Expectations:** Establish guidelines for response times and project deadlines to ensure alignment and accountability. 4. **Encourage Deep Work:** Promote periods of uninterrupted work to allow employees to engage deeply with complex tasks. --- ## Jeff Bezos's Approach to Time Management Jeff Bezos, founder of Amazon, is known for his strategic approach to time management, which aligns with asynchronous principles: - **Morning Routine:** Bezos avoids early morning meetings, preferring to start his day with personal time that includes having coffee and reading the newspaper. - **"Two-Pizza Rule":** He limits meetings to a size that can be fed with two pizzas, ensuring they remain small and focused. - **Intentional "Do Nothing" Time:** Bezos schedules periods with no planned activities, allowing for reflection and spontaneous thought, which can lead to innovative ideas. --- ## Action Step Evaluate your current work processes to identify areas where asynchronous methods can be applied. Start by reducing unnecessary meetings and implementing tools that facilitate communication without requiring immediate responses. This shift can lead to increased productivity, flexibility, and overall job satisfaction. By adopting asynchronous work practices, you empower yourself and your team to work more efficiently and harmoniously, aligning work schedules with personal productivity peaks and reducing the risk of burnout.
@ 95cb4330:96db706c
2025-02-23 12:38:57Embracing asynchronous work can significantly enhance productivity and reduce burnout by allowing individuals to work according to their own schedules without the pressure of immediate responses. This approach fosters deep, focused work and minimizes unnecessary interruptions. --- ## Understanding Asynchronous Work - **Definition:** Asynchronous work refers to a work style where employees complete tasks and communicate on their own time, without the expectation of immediate feedback. This contrasts with synchronous work, which requires real-time interaction. --- ## Benefits of Asynchronous Work - **Enhanced Productivity:** By reducing the need for constant real-time communication, employees can focus on tasks without frequent interruptions, leading to improved efficiency. - **Flexibility:** Employees can work during their most productive hours, accommodating personal schedules and time zones, which promotes a healthier work-life balance. - **Reduced Burnout:** The autonomy to manage one's workload and schedule can decrease stress and prevent burnout. --- ## Implementing Asynchronous Work 1. **Limit Meetings:** Reduce the number of real-time meetings. When meetings are necessary, keep them concise and focused. 2. **Utilize Asynchronous Communication Tools:** Employ platforms like email, project management software, and collaborative documents that allow team members to contribute on their own schedules. 3. **Set Clear Expectations:** Establish guidelines for response times and project deadlines to ensure alignment and accountability. 4. **Encourage Deep Work:** Promote periods of uninterrupted work to allow employees to engage deeply with complex tasks. --- ## Jeff Bezos's Approach to Time Management Jeff Bezos, founder of Amazon, is known for his strategic approach to time management, which aligns with asynchronous principles: - **Morning Routine:** Bezos avoids early morning meetings, preferring to start his day with personal time that includes having coffee and reading the newspaper. - **"Two-Pizza Rule":** He limits meetings to a size that can be fed with two pizzas, ensuring they remain small and focused. - **Intentional "Do Nothing" Time:** Bezos schedules periods with no planned activities, allowing for reflection and spontaneous thought, which can lead to innovative ideas. --- ## Action Step Evaluate your current work processes to identify areas where asynchronous methods can be applied. Start by reducing unnecessary meetings and implementing tools that facilitate communication without requiring immediate responses. This shift can lead to increased productivity, flexibility, and overall job satisfaction. By adopting asynchronous work practices, you empower yourself and your team to work more efficiently and harmoniously, aligning work schedules with personal productivity peaks and reducing the risk of burnout. @ 04ea4f83:210e1713
2025-02-23 10:43:38Veröffentlicht auf [Discreetlog.com](https://www.discreetlog.com/no-privacy-no-freedom/?ref=europeanbitcoiners.com) am 17.04.2023\ Originalautor: [Matt Odell](https://twitter.com/ODELL?ref=europeanbitcoiners.com)\ Übersetzt von: [Sinautoshi am 20.05.2023 - 790600](https://twitter.com/Sinautoshi_8_21?ref=europeanbitcoiners.com) *„Privatsphäre ist für eine offene Gesellschaft im elektronischen Zeitalter notwendig. Privatsphäre ist keine Geheimhaltung. Eine private Angelegenheit ist etwas, von dem man nicht möchte, dass es die ganze Welt erfährt, aber eine geheime Angelegenheit ist etwas, von dem man nicht möchte, dass es irgendjemand erfährt." Privatsphäre ist die Macht, sich der Welt selektiv zu offenbaren.“* **- Eric Hughes, [A Cypherpunk's Manifesto](https://www.activism.net/cypherpunk/manifesto.html?ref=discreetlog.com) , 1993** **Privatsphäre ist für die Freiheit unerlässlich.** Ohne Privatsphäre ist der Einzelne nicht in der Lage, frei von Überwachung und Kontrolle Entscheidungen zu treffen. Mangelnde Privatsphäre führt zum Verlust der Selbstbestimmung. Wenn Einzelpersonen ständig überwacht werden, schränkt dies unsere Fähigkeit ein, uns auszudrücken und Risiken einzugehen. Alle Entscheidungen, die wir treffen, können negative Auswirkungen auf diejenigen haben, die uns überwachen. Ohne die Freiheit, Entscheidungen zu treffen, kann der Einzelne nicht wirklich frei sein. **Freiheit ist für den Erwerb und Erhalt von Wohlstand von entscheidender Bedeutung.** Wenn der Einzelne nicht die Freiheit hat, Entscheidungen zu treffen, hindern uns Einschränkungen und Beschränkungen daran, wirtschaftliche Chancen zu nutzen. Wenn es uns in einem solchen Umfeld irgendwie gelingt, Wohlstand zu erlangen, kann mangelnde Freiheit zur direkten Beschlagnahme von Vermögenswerten durch Regierungen oder andere böswillige Organisationen führen. Wenn die Freiheit gefährdet wird, führt dies im großen Maßstab zu weitverbreiteter wirtschaftlicher Stagnation und Armut. Der Schutz der Freiheit ist für den wirtschaftlichen Wohlstand von wesentlicher Bedeutung. Der Zusammenhang zwischen **Privatsphäre, Freiheit und Wohlstand** ist entscheidend. Ohne Privatsphäre verliert der Einzelne die Freiheit, frei von Überwachung und Kontrolle Entscheidungen zu treffen. Während der Mangel an Freiheit den Einzelnen daran hindert, wirtschaftliche Chancen wahrzunehmen, und den Vermögenserhalt nahezu unmöglich macht. ***Keine Privatsphäre? Keine Freiheit. Keine Freiheit? Kein Wohlstand.*** Rechte werden nicht gewährt. Sie werden eingenommen und verteidigt. Rechte werden oft als Erlaubnis der Machthaber missverstanden, etwas zu tun. Wenn dir jedoch jemand etwas geben kann, kann er es dir grundsätzlich nach Belieben wegnehmen. Im Laufe der Geschichte haben Menschen zwangsläufig für Grundrechte gekämpft, darunter Privatsphäre und Freiheit. Diese Rechte wurden nicht von den Machthabern gegeben, sondern durch Kampf eingefordert und erkämpft. Selbst nachdem diese Rechte erlangt wurden, müssen sie kontinuierlich verteidigt werden, um sicherzustellen, dass sie nicht weggenommen werden. **Rechte werden nicht gewährt – sie werden durch Kampf erworben und durch Opfer verteidigt.**
@ 04ea4f83:210e1713
2025-02-23 10:43:38Veröffentlicht auf [Discreetlog.com](https://www.discreetlog.com/no-privacy-no-freedom/?ref=europeanbitcoiners.com) am 17.04.2023\ Originalautor: [Matt Odell](https://twitter.com/ODELL?ref=europeanbitcoiners.com)\ Übersetzt von: [Sinautoshi am 20.05.2023 - 790600](https://twitter.com/Sinautoshi_8_21?ref=europeanbitcoiners.com) *„Privatsphäre ist für eine offene Gesellschaft im elektronischen Zeitalter notwendig. Privatsphäre ist keine Geheimhaltung. Eine private Angelegenheit ist etwas, von dem man nicht möchte, dass es die ganze Welt erfährt, aber eine geheime Angelegenheit ist etwas, von dem man nicht möchte, dass es irgendjemand erfährt." Privatsphäre ist die Macht, sich der Welt selektiv zu offenbaren.“* **- Eric Hughes, [A Cypherpunk's Manifesto](https://www.activism.net/cypherpunk/manifesto.html?ref=discreetlog.com) , 1993** **Privatsphäre ist für die Freiheit unerlässlich.** Ohne Privatsphäre ist der Einzelne nicht in der Lage, frei von Überwachung und Kontrolle Entscheidungen zu treffen. Mangelnde Privatsphäre führt zum Verlust der Selbstbestimmung. Wenn Einzelpersonen ständig überwacht werden, schränkt dies unsere Fähigkeit ein, uns auszudrücken und Risiken einzugehen. Alle Entscheidungen, die wir treffen, können negative Auswirkungen auf diejenigen haben, die uns überwachen. Ohne die Freiheit, Entscheidungen zu treffen, kann der Einzelne nicht wirklich frei sein. **Freiheit ist für den Erwerb und Erhalt von Wohlstand von entscheidender Bedeutung.** Wenn der Einzelne nicht die Freiheit hat, Entscheidungen zu treffen, hindern uns Einschränkungen und Beschränkungen daran, wirtschaftliche Chancen zu nutzen. Wenn es uns in einem solchen Umfeld irgendwie gelingt, Wohlstand zu erlangen, kann mangelnde Freiheit zur direkten Beschlagnahme von Vermögenswerten durch Regierungen oder andere böswillige Organisationen führen. Wenn die Freiheit gefährdet wird, führt dies im großen Maßstab zu weitverbreiteter wirtschaftlicher Stagnation und Armut. Der Schutz der Freiheit ist für den wirtschaftlichen Wohlstand von wesentlicher Bedeutung. Der Zusammenhang zwischen **Privatsphäre, Freiheit und Wohlstand** ist entscheidend. Ohne Privatsphäre verliert der Einzelne die Freiheit, frei von Überwachung und Kontrolle Entscheidungen zu treffen. Während der Mangel an Freiheit den Einzelnen daran hindert, wirtschaftliche Chancen wahrzunehmen, und den Vermögenserhalt nahezu unmöglich macht. ***Keine Privatsphäre? Keine Freiheit. Keine Freiheit? Kein Wohlstand.*** Rechte werden nicht gewährt. Sie werden eingenommen und verteidigt. Rechte werden oft als Erlaubnis der Machthaber missverstanden, etwas zu tun. Wenn dir jedoch jemand etwas geben kann, kann er es dir grundsätzlich nach Belieben wegnehmen. Im Laufe der Geschichte haben Menschen zwangsläufig für Grundrechte gekämpft, darunter Privatsphäre und Freiheit. Diese Rechte wurden nicht von den Machthabern gegeben, sondern durch Kampf eingefordert und erkämpft. Selbst nachdem diese Rechte erlangt wurden, müssen sie kontinuierlich verteidigt werden, um sicherzustellen, dass sie nicht weggenommen werden. **Rechte werden nicht gewährt – sie werden durch Kampf erworben und durch Opfer verteidigt.** @ 42342239:1d80db24
2025-02-23 10:00:20Europe's economic framework requires restructuring grounded in realism. The Commission's Competitiveness Compass, alas, reveals dangerous left-hemisphere dominance and risks repeating Mao's mistakes. The European Commission presented its "competitiveness compass" in January. There will be massive investments in biotechnology, materials technology, medicines, space, and the defence industry. AI gigafactories are to be established, while Europe will "maintain its leadership in quantum technologies" (a leadership that few seem to be aware of). This will be achieved through more environmental labelling schemes, nature credits, procurement rules, platforms, cooperation plans, and coordination systems. Although the report contains some bright spots, such as promises to ease the regulatory burden, **the overall picture is strikingly lacking in creativity**. Instead, we are mainly met with the usual thought patterns of the European technocracy, which manifest in additional centralised frameworks, quantifiable goals, and annual reports. Mao's ghost haunts Brussels. #### The Missing Half of Europe's Brain Iain McGilchrist, a British psychiatrist and philosopher, has launched the hemispheric hypothesis (a theory about how the two hemispheres of the brain work). The left hemisphere is more detail- and control-oriented, while the right hemisphere is holistic and creative. A society dominated by the left hemisphere, [like our own according to McGilchrist](https://www.youtube.com/watch?v=WYB7P-xPRsk), "would see it as its task to control everything maximally." **The Commission's compass appears similarly lobotomised , prioritising measurable processes over imaginative solutions.** In an earlier text, I mentioned that Europe might need to return [to its roots](https://www.affarsvarlden.se/kronika/enlund-lar-av-elon-musk-vi-behover-ett-mer-radikalt-europa) and asked if Europe should have "the same end goal as China." This is still a relevant and justified question. But if we are honest, China has implemented a series of well-thought-out reforms since the 1980s, in addition to its many well-known and large-scale investments. It is not necessarily wrong to be inspired by China, as many believe; it depends on which China you are inspired by. #### Lessons from the Cat Theory When Deng Xiaoping returned to power in the late 1970s, he chose a more pragmatic approach than his predecessors. China left Mao Zedong's purges of dissidents behind. Instead, he launched the cat theory: **"it doesn't matter what colour the cat is as long as it catches mice"**, regarding economic development. It was now free to experiment with different models. Instead of ideological conformity, the most important thing was to increase productivity and material prosperity. What was done in China? * Companies and individuals were given more freedom * Provinces and municipalities were given more autonomy * Special economic zones were established, with different conditions and rules * Programs to increase the number of banks were introduced * The banking sector was deregulated * Property rights and contract law began to be respected China has since gone from being an economic backwater to not only being the world's largest economy in terms of purchasing power but also a [global tech contender](https://www.aspi.org.au/index.php/report/critical-technology-tracker) (leading in 37 out of 44 key technologies per ASPI). #### EU's Compliance Obsession vs Chinese Pragmatism And today, when China is astonishing the world with surprisingly cheap and competent AI systems, which recently set American tech stocks in motion, in the EU one is met with advertisements for yet another compliance training, this time about AI. **Every new compliance training echoes Mao's ghost** – ideological correctness overriding practical results. Is prosperity really built with certifications, directives, requirements, and penalties? When we compare the Chinese experience with today's EU, the contrast is clear: * Freedoms are curtailed. The right to privacy is undermined (Chat Control, etc.) * Member states' ability to self-govern is reduced, year by year * Streamlining and harmony are popular buzzwords in the bureaucracy * The ECB is actively working to reduce the number of banks * The banking sector is being regulated more and more * Property rights and contract law are being eroded, which can be partly attributed to [developments in payment systems](https://underorion.se/en/posts/freedom_to_transact/) Deng's cat theory was an example of when the right hemisphere was involved in decision-making. Rather than just focusing on details (the cat's colour), the whole (the result) was important. **The Chinese proverb "cross the river by feeling the stones" is another example of more holistic thinking**. Under Deng's leadership, reforms were first tested in a free zone or a province. After a while, the reforms could be evaluated before they were possibly implemented on a larger scale. "Try before you buy" is also a wise principle that follows from complexity research. In sharp contrast to this approach was Mao's "Great Leap Forward," a part of a disastrous five-year plan that shows what can happen when the left hemisphere is given too much power. A tragedy of historic proportions - a mass famine - resulted. While Deng exorcized Mao's ghost through pragmatic experimentation, Brussels seems determined to resurrect. **Today's EU risks repeating Mao's mistake of letting political abstractions ("green transition! digital decade!") override reality** – Mao's ghost surely smiles at nature credit schemes replacing actual market signals. #### Mao's ghost trives on the ontological mistake The serious problems that the EU is facing have been built up over decades and stem from incorrect assumptions. The economy is not complicated. It is complex. The concepts are often confused, but they describe two fundamentally different things. The complicated refers to something composite, but which can still be unfolded and then folded back up again without changing its essence. The complex, on the other hand, refers to something entangled, where every attempt to divide it changes its character. Compare, for example, an airplane engine with a béarnaise sauce. If you mix up the concepts, you make an ontological mistake, a philosopher would say. A programmer would say: garbage in, garbage out. **Mao's ghost thrives on this ontological error**, convincing technocrats they can blueprint society like a Soviet tractor factory. **When a system is complicated, predictable, and linear, centralised coordination and control by the left hemisphere can work well.** But in complex systems, it can never be a solution because it leads to reduced adaptability and increased system risks. Instead, the goal should be diversity and decentralisation, which provide greater adaptability! The faster the changes of the system or in the environment, the greater the demands on adaptability and flexibility - if the system is to survive, that is. Increased diversity and decentralisation would not only increase adaptability and flexibility but also promote creativity, an ability that will likely become increasingly important in a world where AI and automation are changing the rules. #### A better path forward Europe's economic framework requires restructuring grounded in realism. The Commission's competitiveness compass - fixated on metrics and control - reveals dangerous left-hemisphere dominance, echoing Maoist central planning's epistemological errors. Our path forward demands: * Dual-brain governance (prioritising creativity over control) * Banishing of category mistakes (acknowledging the complex adaptive nature of the economy) * Pragmatism over ideology (policy sandboxes inspired by China's special economic zones) * Anti-fragile design (increased autonomy of EU nations, within states, and decentralised banking) * Sunset clauses on all bureaucracy (regulators cannot originate breakthroughs) The alternative? Another technocratic Great Leap Forward - eco-certified, AI-monitored, but economically brittle and fundamentally maladapted to the complex global economy. **As Deng's reformers understood: no institutional architecture, not even the First Emperor's Terracotta Army, can withstand modernity's tide.**
@ 42342239:1d80db24
2025-02-23 10:00:20Europe's economic framework requires restructuring grounded in realism. The Commission's Competitiveness Compass, alas, reveals dangerous left-hemisphere dominance and risks repeating Mao's mistakes. The European Commission presented its "competitiveness compass" in January. There will be massive investments in biotechnology, materials technology, medicines, space, and the defence industry. AI gigafactories are to be established, while Europe will "maintain its leadership in quantum technologies" (a leadership that few seem to be aware of). This will be achieved through more environmental labelling schemes, nature credits, procurement rules, platforms, cooperation plans, and coordination systems. Although the report contains some bright spots, such as promises to ease the regulatory burden, **the overall picture is strikingly lacking in creativity**. Instead, we are mainly met with the usual thought patterns of the European technocracy, which manifest in additional centralised frameworks, quantifiable goals, and annual reports. Mao's ghost haunts Brussels. #### The Missing Half of Europe's Brain Iain McGilchrist, a British psychiatrist and philosopher, has launched the hemispheric hypothesis (a theory about how the two hemispheres of the brain work). The left hemisphere is more detail- and control-oriented, while the right hemisphere is holistic and creative. A society dominated by the left hemisphere, [like our own according to McGilchrist](https://www.youtube.com/watch?v=WYB7P-xPRsk), "would see it as its task to control everything maximally." **The Commission's compass appears similarly lobotomised , prioritising measurable processes over imaginative solutions.** In an earlier text, I mentioned that Europe might need to return [to its roots](https://www.affarsvarlden.se/kronika/enlund-lar-av-elon-musk-vi-behover-ett-mer-radikalt-europa) and asked if Europe should have "the same end goal as China." This is still a relevant and justified question. But if we are honest, China has implemented a series of well-thought-out reforms since the 1980s, in addition to its many well-known and large-scale investments. It is not necessarily wrong to be inspired by China, as many believe; it depends on which China you are inspired by. #### Lessons from the Cat Theory When Deng Xiaoping returned to power in the late 1970s, he chose a more pragmatic approach than his predecessors. China left Mao Zedong's purges of dissidents behind. Instead, he launched the cat theory: **"it doesn't matter what colour the cat is as long as it catches mice"**, regarding economic development. It was now free to experiment with different models. Instead of ideological conformity, the most important thing was to increase productivity and material prosperity. What was done in China? * Companies and individuals were given more freedom * Provinces and municipalities were given more autonomy * Special economic zones were established, with different conditions and rules * Programs to increase the number of banks were introduced * The banking sector was deregulated * Property rights and contract law began to be respected China has since gone from being an economic backwater to not only being the world's largest economy in terms of purchasing power but also a [global tech contender](https://www.aspi.org.au/index.php/report/critical-technology-tracker) (leading in 37 out of 44 key technologies per ASPI). #### EU's Compliance Obsession vs Chinese Pragmatism And today, when China is astonishing the world with surprisingly cheap and competent AI systems, which recently set American tech stocks in motion, in the EU one is met with advertisements for yet another compliance training, this time about AI. **Every new compliance training echoes Mao's ghost** – ideological correctness overriding practical results. Is prosperity really built with certifications, directives, requirements, and penalties? When we compare the Chinese experience with today's EU, the contrast is clear: * Freedoms are curtailed. The right to privacy is undermined (Chat Control, etc.) * Member states' ability to self-govern is reduced, year by year * Streamlining and harmony are popular buzzwords in the bureaucracy * The ECB is actively working to reduce the number of banks * The banking sector is being regulated more and more * Property rights and contract law are being eroded, which can be partly attributed to [developments in payment systems](https://underorion.se/en/posts/freedom_to_transact/) Deng's cat theory was an example of when the right hemisphere was involved in decision-making. Rather than just focusing on details (the cat's colour), the whole (the result) was important. **The Chinese proverb "cross the river by feeling the stones" is another example of more holistic thinking**. Under Deng's leadership, reforms were first tested in a free zone or a province. After a while, the reforms could be evaluated before they were possibly implemented on a larger scale. "Try before you buy" is also a wise principle that follows from complexity research. In sharp contrast to this approach was Mao's "Great Leap Forward," a part of a disastrous five-year plan that shows what can happen when the left hemisphere is given too much power. A tragedy of historic proportions - a mass famine - resulted. While Deng exorcized Mao's ghost through pragmatic experimentation, Brussels seems determined to resurrect. **Today's EU risks repeating Mao's mistake of letting political abstractions ("green transition! digital decade!") override reality** – Mao's ghost surely smiles at nature credit schemes replacing actual market signals. #### Mao's ghost trives on the ontological mistake The serious problems that the EU is facing have been built up over decades and stem from incorrect assumptions. The economy is not complicated. It is complex. The concepts are often confused, but they describe two fundamentally different things. The complicated refers to something composite, but which can still be unfolded and then folded back up again without changing its essence. The complex, on the other hand, refers to something entangled, where every attempt to divide it changes its character. Compare, for example, an airplane engine with a béarnaise sauce. If you mix up the concepts, you make an ontological mistake, a philosopher would say. A programmer would say: garbage in, garbage out. **Mao's ghost thrives on this ontological error**, convincing technocrats they can blueprint society like a Soviet tractor factory. **When a system is complicated, predictable, and linear, centralised coordination and control by the left hemisphere can work well.** But in complex systems, it can never be a solution because it leads to reduced adaptability and increased system risks. Instead, the goal should be diversity and decentralisation, which provide greater adaptability! The faster the changes of the system or in the environment, the greater the demands on adaptability and flexibility - if the system is to survive, that is. Increased diversity and decentralisation would not only increase adaptability and flexibility but also promote creativity, an ability that will likely become increasingly important in a world where AI and automation are changing the rules. #### A better path forward Europe's economic framework requires restructuring grounded in realism. The Commission's competitiveness compass - fixated on metrics and control - reveals dangerous left-hemisphere dominance, echoing Maoist central planning's epistemological errors. Our path forward demands: * Dual-brain governance (prioritising creativity over control) * Banishing of category mistakes (acknowledging the complex adaptive nature of the economy) * Pragmatism over ideology (policy sandboxes inspired by China's special economic zones) * Anti-fragile design (increased autonomy of EU nations, within states, and decentralised banking) * Sunset clauses on all bureaucracy (regulators cannot originate breakthroughs) The alternative? Another technocratic Great Leap Forward - eco-certified, AI-monitored, but economically brittle and fundamentally maladapted to the complex global economy. **As Deng's reformers understood: no institutional architecture, not even the First Emperor's Terracotta Army, can withstand modernity's tide.** @ 41fa852b:af7b7706
2025-02-23 09:41:15> "Paper money eventually returns to its intrinsic value, zero." --Voltaire * * * **Lots happening this coming week for UK Bitcoiners, so there is plenty to report for this edition.** There are ten meetups for the coming week, two new businesses, and two new events, and we have a new sponsor, [Bitcoin Metalworks](https://bitcoinmetalworks.com/). Check out their amazing Bitcoin-inspired artwork at the bottom of the ad section. Let's dive in… * * * [](https://bitcoinevents.uk/donate/) * * * _This week's sponsor is…_ [](https://www.orangepillapp.com/?utm_source=BEUK&utm_medium=email&utm_campaign=BEUK) * * * ### **Upcoming Bitcoin Meetups** Happening this week… 1. [**Real Bedford - Home Game**](https://www.realbedford.com/real-bedford-v-aylesbury-united2): Peter MacCormack's boys are at home this Tuesday the 25th, playing Aylesbury United. Join them for a 19:45 kickoff. ⚽️ 2. [**Leamington Spa**](https://t.me/leambitcoin): Meetups on the last Tuesday of each month at 7 PM. You'll find them this month at the White Horse, CV32 5PZ on the 25th. 🍻 3. [**Bitcoin Surrey**](https://x.com/bitcoinsurrey/status/1888974122358641007): On Tuesday, February 25th, from 18:00 to 23:00, Bitcoin Surrey is hosting a special meetup focused on Bitcoin art at Yiayias at The Fox, located at 21 Frensham Road, Lower Bourne, Farnham, Surrey GU10 3PH. The event features a fireside chat and talk at 19:00 by artist and curator Rebel Money Art, titled "Bitcoin Art: The New Revolution," discussing the evolution and future of Bitcoin art. Additionally, the venue's upstairs will be transformed into a pop-up Bitcoin art gallery for the evening, showcasing works by various international artists, including Cryptograffiti, RYR, HodlxHold, Flo Montoya, Sham Shad, 2140 Collective, Mr Hansel, Asanoha, No Good, and Rebel Money Art. Bitcoin is accepted at the venue and entry is free. 🍻🖼️🎨 4. [**Brighton Bitcoin**](https://t.me/brighton_btc): Building a bitcoin community in the Brighton & Hove area. A regular informal meetup happens every last Wednesday of the month at [Indian Summer](https://www.indiansummerbrighton.co.uk/) where they accept bitcoin payments. The meetup starts at 20:00, or 19:00 if you'd like to eat first. 🥘🍻 5. [**Manchester Bitcoin**](https://btcmap.org/community/bitcoin-manchester): On the 27th, Manchesters Bitcoin will be at The Smithfield Market Tavern. Join them at 19:00. 🍺 6. [**Cyphermunk House - Constellation Money**](https://btcpay.btc.aw/apps/3KBnXP178MWUvGGizGKsgFQrKoaY/pos): Exploring unconscious blocks and hidden patterns in your relationship to money. At 18:30 on Thursday 27th. 👨🏻🚀 7. [**The Satoshi Society - Southampton**](https://x.com/satssociety): Join a friendly group of bitcoiners at The Maritimo Lounge, Ocean Village on Friday the 28th for food and a Bitcoin chat. 🍺 8. [**Bitcoin Walk - Edinburgh**](https://bitcoinwalk.org/): Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏽♂️🚶🏼♀️🚶🏻 9. [**Leeds Bitcoin Network**](https://t.me/LeedsBTC): The first Sunday of every month the Leeds Bitcoin Network meet at the [Global Tribe Cafe](https://www.globalcrystals.com/), LS1 6LG at 1 PM on Sunday 2nd March. ☕️ 10. [**Cyphermunk House - Repair Party**](https://btcpay.btc.aw/apps/3KBnXP178MWUvGGizGKsgFQrKoaY/pos): Watch, learn and get hands-on experience at this community lead electronic repair training workshop. UK Plug, Laptop, Kettle, toaster... On Sunday 2nd March at 10:00. 👨🏻🔧🛠️ * * * ### New Businesses Accepting Bitcoin - [**Hollins Mill**](https://btcmap.org/merchant/node:236019804): This traditional English Pub in Sowerby Bridge specialises in craft beers and ales, 50+ gins, and has a large beer garden and function room for up to 120 people. Perfect for weddings, christenings and birthday parties. Now accepting bitcoin! - [**Alema Coffee**](https://www.alemacoffee.com/): Some great work is going on behind the scenes in Bury St Edmunds. Expect some new businesses to appear here as Bitcoin East onboard them. Alema's Coffee is grown on a family farm in Ecuador and sent directly to Alema coffee for roasting. You can visit them at 2 High Baxter Street, Bury St Edmunds, IP33 1ES for some exceptional, hand-crafted coffee, paid for with bitcoin. * * * ### Upcoming Special Events These events aren't happening next week, but they're important to add to your calendar now as tickets are selling fast. - [**Eat and Meet with Joe Bryan**](https://orangepill.app.link/MDg7o8KxcRb): Meet the creator of 'Whats the Problem' and a host of bitcoiners at the Weeping Willow in Bury St Edmunds. Starting at 18:00 on Tuesday March the 4th. [](https://orangepill.app.link/MDg7o8KxcRb) - [**CheatCode 2025**](https://www.cheatcode.co.uk/) - Peter McCormack hosts the CheatCode conference, following last year's success. This year, international guest speakers include Preston Pysh, Alex Gladstein, Natalie Brunell, Matthew Pines, Steve Baker, Ben Arc, and Checkmate. Friday, April 11th, is the main conference day, followed by a huge meetup at Ledger Park for the men's Real Bedford match, and again on Sunday for the women's match. Check out the link for ticket details. [](https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fbcb0553a-dc8c-4fb7-98dd-4a95085d83a5_1500x500.png) * * * **Get Involved** - **Volunteer Opportunities**: [Bridge2Bitcoin](https://bridge2bitcoin.com/) is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on [Twitter](https://x.com/bridge2bitcoin) or through our [website](https://bridge2bitcoin.com/). - **Start Your Own Meetup**: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via [Twitter](https://x.com/bitcoineventsuk). - [**Contribute to BTCMaps**](https://wiki.btcmap.org/general/tagging-instructions.html): BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date. - **Telegram users**: You might find our [Telegram Channel](https://t.me/BitcoinEventsUKHub) another useful way to keep up-to-date with UK meetups. - **Feedback and Suggestions**: We value your input! Share your ideas on how we can enhance this newsletter. * * * _This week's sponsors are…_ [](https://orangecoinstore.com/) [](https://bitcoinretreat.co.uk/) [](https://bitcoinmetalworks.com/) * * * Get out and support the meetups where you can, visit [Bitcoin Events UK](https://bitcoinevents.uk/) for more info on each meetup and to find your closest on the interactive map. Stay tuned for more updates next week! Simon. [](https://bitcoinevents.uk/donate/)
@ 41fa852b:af7b7706
2025-02-23 09:41:15> "Paper money eventually returns to its intrinsic value, zero." --Voltaire * * * **Lots happening this coming week for UK Bitcoiners, so there is plenty to report for this edition.** There are ten meetups for the coming week, two new businesses, and two new events, and we have a new sponsor, [Bitcoin Metalworks](https://bitcoinmetalworks.com/). Check out their amazing Bitcoin-inspired artwork at the bottom of the ad section. Let's dive in… * * * [](https://bitcoinevents.uk/donate/) * * * _This week's sponsor is…_ [](https://www.orangepillapp.com/?utm_source=BEUK&utm_medium=email&utm_campaign=BEUK) * * * ### **Upcoming Bitcoin Meetups** Happening this week… 1. [**Real Bedford - Home Game**](https://www.realbedford.com/real-bedford-v-aylesbury-united2): Peter MacCormack's boys are at home this Tuesday the 25th, playing Aylesbury United. Join them for a 19:45 kickoff. ⚽️ 2. [**Leamington Spa**](https://t.me/leambitcoin): Meetups on the last Tuesday of each month at 7 PM. You'll find them this month at the White Horse, CV32 5PZ on the 25th. 🍻 3. [**Bitcoin Surrey**](https://x.com/bitcoinsurrey/status/1888974122358641007): On Tuesday, February 25th, from 18:00 to 23:00, Bitcoin Surrey is hosting a special meetup focused on Bitcoin art at Yiayias at The Fox, located at 21 Frensham Road, Lower Bourne, Farnham, Surrey GU10 3PH. The event features a fireside chat and talk at 19:00 by artist and curator Rebel Money Art, titled "Bitcoin Art: The New Revolution," discussing the evolution and future of Bitcoin art. Additionally, the venue's upstairs will be transformed into a pop-up Bitcoin art gallery for the evening, showcasing works by various international artists, including Cryptograffiti, RYR, HodlxHold, Flo Montoya, Sham Shad, 2140 Collective, Mr Hansel, Asanoha, No Good, and Rebel Money Art. Bitcoin is accepted at the venue and entry is free. 🍻🖼️🎨 4. [**Brighton Bitcoin**](https://t.me/brighton_btc): Building a bitcoin community in the Brighton & Hove area. A regular informal meetup happens every last Wednesday of the month at [Indian Summer](https://www.indiansummerbrighton.co.uk/) where they accept bitcoin payments. The meetup starts at 20:00, or 19:00 if you'd like to eat first. 🥘🍻 5. [**Manchester Bitcoin**](https://btcmap.org/community/bitcoin-manchester): On the 27th, Manchesters Bitcoin will be at The Smithfield Market Tavern. Join them at 19:00. 🍺 6. [**Cyphermunk House - Constellation Money**](https://btcpay.btc.aw/apps/3KBnXP178MWUvGGizGKsgFQrKoaY/pos): Exploring unconscious blocks and hidden patterns in your relationship to money. At 18:30 on Thursday 27th. 👨🏻🚀 7. [**The Satoshi Society - Southampton**](https://x.com/satssociety): Join a friendly group of bitcoiners at The Maritimo Lounge, Ocean Village on Friday the 28th for food and a Bitcoin chat. 🍺 8. [**Bitcoin Walk - Edinburgh**](https://bitcoinwalk.org/): Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏽♂️🚶🏼♀️🚶🏻 9. [**Leeds Bitcoin Network**](https://t.me/LeedsBTC): The first Sunday of every month the Leeds Bitcoin Network meet at the [Global Tribe Cafe](https://www.globalcrystals.com/), LS1 6LG at 1 PM on Sunday 2nd March. ☕️ 10. [**Cyphermunk House - Repair Party**](https://btcpay.btc.aw/apps/3KBnXP178MWUvGGizGKsgFQrKoaY/pos): Watch, learn and get hands-on experience at this community lead electronic repair training workshop. UK Plug, Laptop, Kettle, toaster... On Sunday 2nd March at 10:00. 👨🏻🔧🛠️ * * * ### New Businesses Accepting Bitcoin - [**Hollins Mill**](https://btcmap.org/merchant/node:236019804): This traditional English Pub in Sowerby Bridge specialises in craft beers and ales, 50+ gins, and has a large beer garden and function room for up to 120 people. Perfect for weddings, christenings and birthday parties. Now accepting bitcoin! - [**Alema Coffee**](https://www.alemacoffee.com/): Some great work is going on behind the scenes in Bury St Edmunds. Expect some new businesses to appear here as Bitcoin East onboard them. Alema's Coffee is grown on a family farm in Ecuador and sent directly to Alema coffee for roasting. You can visit them at 2 High Baxter Street, Bury St Edmunds, IP33 1ES for some exceptional, hand-crafted coffee, paid for with bitcoin. * * * ### Upcoming Special Events These events aren't happening next week, but they're important to add to your calendar now as tickets are selling fast. - [**Eat and Meet with Joe Bryan**](https://orangepill.app.link/MDg7o8KxcRb): Meet the creator of 'Whats the Problem' and a host of bitcoiners at the Weeping Willow in Bury St Edmunds. Starting at 18:00 on Tuesday March the 4th. [](https://orangepill.app.link/MDg7o8KxcRb) - [**CheatCode 2025**](https://www.cheatcode.co.uk/) - Peter McCormack hosts the CheatCode conference, following last year's success. This year, international guest speakers include Preston Pysh, Alex Gladstein, Natalie Brunell, Matthew Pines, Steve Baker, Ben Arc, and Checkmate. Friday, April 11th, is the main conference day, followed by a huge meetup at Ledger Park for the men's Real Bedford match, and again on Sunday for the women's match. Check out the link for ticket details. [](https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fbcb0553a-dc8c-4fb7-98dd-4a95085d83a5_1500x500.png) * * * **Get Involved** - **Volunteer Opportunities**: [Bridge2Bitcoin](https://bridge2bitcoin.com/) is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on [Twitter](https://x.com/bridge2bitcoin) or through our [website](https://bridge2bitcoin.com/). - **Start Your Own Meetup**: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via [Twitter](https://x.com/bitcoineventsuk). - [**Contribute to BTCMaps**](https://wiki.btcmap.org/general/tagging-instructions.html): BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date. - **Telegram users**: You might find our [Telegram Channel](https://t.me/BitcoinEventsUKHub) another useful way to keep up-to-date with UK meetups. - **Feedback and Suggestions**: We value your input! Share your ideas on how we can enhance this newsletter. * * * _This week's sponsors are…_ [](https://orangecoinstore.com/) [](https://bitcoinretreat.co.uk/) [](https://bitcoinmetalworks.com/) * * * Get out and support the meetups where you can, visit [Bitcoin Events UK](https://bitcoinevents.uk/) for more info on each meetup and to find your closest on the interactive map. Stay tuned for more updates next week! Simon. [](https://bitcoinevents.uk/donate/) @ 6a3d3f20:6a569bcc
2025-02-23 08:50:19Imagina un internet donde tú tienes el control, donde nadie puede silenciarte y donde las conexiones entre personas fluyen sin barreras corporativas. Esto no es un sueño lejano, ¡es la realidad que está tomando forma gracias a Nostr! Este protocolo **descentralizado**, nacido en 2020 de la mente ingeniosa de un desarrollador brasileño conocido como *fiatjaf*, ha surgido como una respuesta vibrante a los desafíos del internet actual. En un mundo donde las redes sociales centralizadas han comenzado a tambalearse bajo el peso de la **censura**, la privacidad comprometida y el control excesivo, Nostr llega como un soplo de aire fresco, prometiendo devolvernos el poder sobre nuestra voz y nuestros datos. ## Cómo surge Nostr El nacimiento de Nostr no fue un accidente, sino una reacción a un panorama digital que pedía a gritos un cambio. Hacia finales de la década de 2010, plataformas como **Twitter** enfrentaban crecientes críticas por sus políticas de **moderación**, dejando a muchos usuarios frustrados y silenciados. Al mismo tiempo, alternativas como **Mastodon** o **ActivityPub**, aunque descentralizadas, no terminaban de cuajar para todos debido a su complejidad técnica o diferencias culturales. Fue en este caldo de cultivo donde *fiatjaf*, inspirado por la resistencia de **Bitcoin** y su criptografía de clave pública, lanzó **Nostr** en noviembre de 2020. Pero el verdadero punto de inflexión llegó en diciembre de 2022, cuando *Jack Dorsey*, cofundador de Twitter, donó 14 bitcoins (unos 250,000 dólares) al proyecto. ¡Ese fue el momento en que Nostr pasó de ser un secreto de la comunidad *web3* a brillar en el radar global! ## Una evolución que no para de sorprendernos Desde sus humildes comienzos, Nostr ha crecido a pasos agigantados. Su diseño es simple pero poderoso: "*Notes and Other Stuff Transmitted by Relays*" (Notas y otras cosas transmitidas por relevadores) usa servidores ligeros llamados *relays* para distribuir mensajes firmados criptográficamente por los usuarios. ¿Lo mejor? No depende de un servidor central, lo que lo hace prácticamente ++imposible de censurar++. En sus primeros años, era un terreno experimental, con aplicaciones como **Damus** (un cliente tipo Twitter) abriendo camino. Hoy, en 2025, la escena es vibrante: desde **Primal 2.0**, con búsquedas avanzadas y feeds personalizados, hasta integraciones con la **Lightning Network** de Bitcoin, que permite "**zaps**" (*micropagos*) para apoyar a creadores. Los desarrolladores no paran de innovar, creando desde marketplaces descentralizados hasta sistemas de identidad, demostrando que Nostr es mucho más que una red social: ¡es una base para reinventar el internet! ## La importancia de Nostr hoy y mañana ¿Por qué Nostr importa tanto ahora? Porque está devolviendo la *soberanía* a los usuarios en un momento en que la *privacidad* y la *libertad* en línea están bajo asedio. Con cada relay que se suma y cada cliente que aparece, Nostr construye una red resistente donde las grandes tecnológicas no dictan las reglas. Su integración con Bitcoin está creando una economía circular emocionante: imagina ganar *sats* (fracciones de bitcoin) por tus publicaciones o apoyar directamente a tus creadores favoritos sin intermediarios. En febrero de 2025, ya vemos comunidades activas, desde entusiastas de la tecnología hasta artistas, floreciendo en este ecosistema abierto. De cara al futuro, Nostr tiene el potencial de ser un pilar del internet que siempre quisimos: descentralizado, transparente y al servicio de las personas. No solo compite con las redes sociales tradicionales, sino que las supera al ofrecer un lienzo en blanco para que cualquiera construya lo que imagine, desde plataformas de comunicación hasta soluciones IoT o mercados globales. Su simplicidad invita a miles de desarrolladores a sumarse, y su resistencia a la censura asegura que las voces marginadas siempre tengan un lugar. Si **Bitcoin** nos dio libertad financiera, **Nostr** nos está dando libertad digital, y juntos podrían ser la dupla que transforme cómo interactuamos en línea. [[]()]() ## Un gran futuro nos espera Nostr no es solo un protocolo; es un movimiento, una chispa de optimismo en un mundo digital que a veces parece gris. Cada vez que alguien se une, configura un relay o prueba una nueva app, estamos dando un paso hacia un internet más justo y emocionante. Así que, ¿qué esperas? Nostr no es el futuro lejano, ¡es el presente vibrante que está creciendo hoy! **Únete**, experimenta y sé parte de esta revolución que está poniendo el poder de internet de vuelta en nuestras manos. ¡El mañana digital nunca lució tan prometedor!
@ 6a3d3f20:6a569bcc
2025-02-23 08:50:19Imagina un internet donde tú tienes el control, donde nadie puede silenciarte y donde las conexiones entre personas fluyen sin barreras corporativas. Esto no es un sueño lejano, ¡es la realidad que está tomando forma gracias a Nostr! Este protocolo **descentralizado**, nacido en 2020 de la mente ingeniosa de un desarrollador brasileño conocido como *fiatjaf*, ha surgido como una respuesta vibrante a los desafíos del internet actual. En un mundo donde las redes sociales centralizadas han comenzado a tambalearse bajo el peso de la **censura**, la privacidad comprometida y el control excesivo, Nostr llega como un soplo de aire fresco, prometiendo devolvernos el poder sobre nuestra voz y nuestros datos. ## Cómo surge Nostr El nacimiento de Nostr no fue un accidente, sino una reacción a un panorama digital que pedía a gritos un cambio. Hacia finales de la década de 2010, plataformas como **Twitter** enfrentaban crecientes críticas por sus políticas de **moderación**, dejando a muchos usuarios frustrados y silenciados. Al mismo tiempo, alternativas como **Mastodon** o **ActivityPub**, aunque descentralizadas, no terminaban de cuajar para todos debido a su complejidad técnica o diferencias culturales. Fue en este caldo de cultivo donde *fiatjaf*, inspirado por la resistencia de **Bitcoin** y su criptografía de clave pública, lanzó **Nostr** en noviembre de 2020. Pero el verdadero punto de inflexión llegó en diciembre de 2022, cuando *Jack Dorsey*, cofundador de Twitter, donó 14 bitcoins (unos 250,000 dólares) al proyecto. ¡Ese fue el momento en que Nostr pasó de ser un secreto de la comunidad *web3* a brillar en el radar global! ## Una evolución que no para de sorprendernos Desde sus humildes comienzos, Nostr ha crecido a pasos agigantados. Su diseño es simple pero poderoso: "*Notes and Other Stuff Transmitted by Relays*" (Notas y otras cosas transmitidas por relevadores) usa servidores ligeros llamados *relays* para distribuir mensajes firmados criptográficamente por los usuarios. ¿Lo mejor? No depende de un servidor central, lo que lo hace prácticamente ++imposible de censurar++. En sus primeros años, era un terreno experimental, con aplicaciones como **Damus** (un cliente tipo Twitter) abriendo camino. Hoy, en 2025, la escena es vibrante: desde **Primal 2.0**, con búsquedas avanzadas y feeds personalizados, hasta integraciones con la **Lightning Network** de Bitcoin, que permite "**zaps**" (*micropagos*) para apoyar a creadores. Los desarrolladores no paran de innovar, creando desde marketplaces descentralizados hasta sistemas de identidad, demostrando que Nostr es mucho más que una red social: ¡es una base para reinventar el internet! ## La importancia de Nostr hoy y mañana ¿Por qué Nostr importa tanto ahora? Porque está devolviendo la *soberanía* a los usuarios en un momento en que la *privacidad* y la *libertad* en línea están bajo asedio. Con cada relay que se suma y cada cliente que aparece, Nostr construye una red resistente donde las grandes tecnológicas no dictan las reglas. Su integración con Bitcoin está creando una economía circular emocionante: imagina ganar *sats* (fracciones de bitcoin) por tus publicaciones o apoyar directamente a tus creadores favoritos sin intermediarios. En febrero de 2025, ya vemos comunidades activas, desde entusiastas de la tecnología hasta artistas, floreciendo en este ecosistema abierto. De cara al futuro, Nostr tiene el potencial de ser un pilar del internet que siempre quisimos: descentralizado, transparente y al servicio de las personas. No solo compite con las redes sociales tradicionales, sino que las supera al ofrecer un lienzo en blanco para que cualquiera construya lo que imagine, desde plataformas de comunicación hasta soluciones IoT o mercados globales. Su simplicidad invita a miles de desarrolladores a sumarse, y su resistencia a la censura asegura que las voces marginadas siempre tengan un lugar. Si **Bitcoin** nos dio libertad financiera, **Nostr** nos está dando libertad digital, y juntos podrían ser la dupla que transforme cómo interactuamos en línea. [[]()]() ## Un gran futuro nos espera Nostr no es solo un protocolo; es un movimiento, una chispa de optimismo en un mundo digital que a veces parece gris. Cada vez que alguien se une, configura un relay o prueba una nueva app, estamos dando un paso hacia un internet más justo y emocionante. Así que, ¿qué esperas? Nostr no es el futuro lejano, ¡es el presente vibrante que está creciendo hoy! **Únete**, experimenta y sé parte de esta revolución que está poniendo el poder de internet de vuelta en nuestras manos. ¡El mañana digital nunca lució tan prometedor! @ e373ca41:b82abcc5
2025-02-23 08:39:06*Dieser Artikel wurde mit dem* *[Pareto-Client](https://pareto.space/read)* *geschrieben (lesen Sie ihn dort, um die volle Erfahrung zu machen). Er wurde zuerst auf Deutsch von Milosz Matuschek auf* *["Freischwebende Intelligenz"](https://www.freischwebende-intelligenz.org/p/was-bringt-eine-wahl-wenn-das-system)* *veröffentlicht.* Zur Demokratur, der vom Souverän losgelösten Demokratie, gehört es zum Ritus, dem Volk regelmäßig den Puls zu fühlen. Heute ist wieder so ein Tag. Doch was wird der Souverän am Ende dieses Tages gewonnen haben? Zur parlamentarischen Demokratie gehört der Wesentlichkeitsgrundsatz. Alle grundrechtswesentlichen, also den Wesenskern von Grundrechten betreffenden Entscheidungen müssen vom Parlament gefällt werden. Behandelt der Bundestag die wesentlichen Fragen? * Was hat man im Gremium des Souveräns bisher über Nordstream herausgefunden? * Was über Spike-Proteine, die 700 Tage nach der Impfung noch aktiv sind? * Wie erklärt dieses Gremium dem Souverän, dass Bankenbosse, Bundeskanzler und migrantische Straftäter in diesem Land ungleich schwieriger zu verurteilen sind als Bürger, die einen gefährlich mindertalentierten Politiker „Schwachkopf“ nennen? Wofür einen Bundestag wählen, der nichts zählt, wenn es darauf ankommt und wenig zustande bringt, was dem Bürger nützt, wenn er mal darf? Eine allgemeine Impfpflicht, die auf Politikerseite erst jeder kategorisch ausschloss und dann jeder ebenso salbungsvoll kategorisch befürwortete, scheiterte nur knapp. Aufarbeitung seither?  Legitimation des rituellen Umkehrschwungs? (Foto: [Rosenbusch/X](https://x.com/rosenbusch_/status/1893456799728062698)) \ Aus dem Kontrollgremium des Souveräns gegenüber der Regierung ist eine realitätsverweigernde BRD-Volkskammer geworden. Was kann eine Wahl verändern, wenn das System, welches sie alimentiert und perpetuiert, das Problem ist? Nehmen wir einen Motor, der mit Benzin läuft. Der Motor ist „unsere Demokratie“, Wahlen sind der Betankungsvorgang. Der Bürger betankt heute die Maschinerie mit der Legitimation durch seine Stimme. Doch er weiß nicht mehr, welche Hebel und Gerätschaften der Motor eigentlich antreibt. Dieser Teil befindet sich hinter einem schweren Vorhang. Kann im Sinne von Transparenz und Mit-Verantwortung der Betankungsvorgang guten Gewissens vollzogen werden? Der Wahlvorgang ist ein Paradebeispiel dessen, was der Soziologe Niklas Luhmann mit „Legitimation durch Verfahren“ beschrieben hat. Der prozessuale Akt, die Auszählung und Verkündung schafft neue Realität und legitimiert die neue Ordnung. Aus der Erfahrung der letzten Jahre in einer autoritären parlamentarischen Demokratur bedeutet die Wahlentscheidung jedoch eine de facto Blanko-Einwilligung in die eigene Versklavung. Im Privatrecht wäre das ein sittenwidriges Ziel, das zur Nichtigkeit des Vertrages führen würde. Wieso sollte das auf der Ebene des politischen Gesellschaftsvertrages dann möglich sein? Und wie kann ein solcher Legitimationsvorgang verantwortet werden? <https://www.youtube.com/watch?v=Ngy05PFUlo8&t=5s> Der Parlamentarismus in Deutschland ist für mich gescheitert, wieder einmal. Doch warum soll in einem besetzten, globalistisch durchzogenen NATO-EU-WHO-Konglomerat wie Deutschland auch ausgerechnet der Bürger das letzte Wort haben? Die Legitimationskette von Bürger zu Staat hat zu viele blinde Flecken bekommen. Die Rückverfolgung desaströsen politischen Handelns ist nicht mehr möglich. In Deutschland hat keine gesellschaftliche Instanz, nicht die Politik, nicht die Wissenschaft, nicht die Justiz, nicht die Medien, bisher eine Form der Corona-Aufarbeitung hinbekommen, die diesen Namen verdient. Das ist Sache von unabhängigen, versprengten Stimmen und Publikationen. Wie ist es um die Legitimität der „Partneroganisationen“ Deutschlands bestellt? Die EU ist unlängst vom Friedensbündnis zum Kriegsbündnis geworden, die Nato kann nicht mal Bündnispartner vor Bündnispartnern schützen und die WHO ist ein durch China und Bill Gates unterwandertes Jointventure für globale Impf- und Kontrollexperimente. All das wird heute erneut zementiert und wenn es gesprengt würde, müsste der Wahlvorgang verboten werden. Im besetzten Land darf nur richtig gewählt werden. Und deshalb gibt es für mich in diesem System keine Wahl. Wie ist es bei Ihnen? Wie stehen Sie zu dieser Wahl? Gehen Sie hin und mit welchen Gefühlen, Erwartungen, Intentionen? Ich freue mich auf Ihren Kommentar. ANZEIGE: **Sie suchen nach dem einfachsten Weg, Bitcoin zu kaufen und selbst zu verwahren?**\*\*\*\*\*\* *Die* ***[Relai-App](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)*** *ist Europas erfolgreichste Bitcoin-App.* ***[Hier](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)*** *kaufen Sie Bitcoin in wenigen Schritten und können auch Sparpläne einrichten. Niemand hat Zugriff auf Ihre Bitcoin, außer Sie selbst.* ***Relai senkt jetzt die Gebühr auf 1%**, mit dem Referral-Code* ***MILOSZ*** *sparen Sie weitere 10%. (keine Finanzberatung). Disclaimer wg. EU-Mica-Regulierung: Die Dienste von Relai werden ausschließlich für Einwohner der Schweiz und Italiens empfohlen.* *** ***You prefer reading me in English?*** *You can find my first uncensorable articles written with our Pareto client via Nostr,* ***[clicking on this link.](https://pareto.space/u/ashoka@pareto.space)*** *Discover other authors at* ***[Pareto.space/read.](https://pareto.space/read)(click on the Pareto button to see our first authors).***  [](https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fc33bfce1-1a89-42ff-a89f-e1fbd7edfac4_2382x1272.png) *** ***Join the marketplace of ideas!** We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the [Pareto Project](https://pareto.space/en)? Zap me, if you want to contribute (all Zaps go to the project).* *Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to **<team@pareto.space>*** **Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Start.](https://start.njump.me/)**
@ e373ca41:b82abcc5
2025-02-23 08:39:06*Dieser Artikel wurde mit dem* *[Pareto-Client](https://pareto.space/read)* *geschrieben (lesen Sie ihn dort, um die volle Erfahrung zu machen). Er wurde zuerst auf Deutsch von Milosz Matuschek auf* *["Freischwebende Intelligenz"](https://www.freischwebende-intelligenz.org/p/was-bringt-eine-wahl-wenn-das-system)* *veröffentlicht.* Zur Demokratur, der vom Souverän losgelösten Demokratie, gehört es zum Ritus, dem Volk regelmäßig den Puls zu fühlen. Heute ist wieder so ein Tag. Doch was wird der Souverän am Ende dieses Tages gewonnen haben? Zur parlamentarischen Demokratie gehört der Wesentlichkeitsgrundsatz. Alle grundrechtswesentlichen, also den Wesenskern von Grundrechten betreffenden Entscheidungen müssen vom Parlament gefällt werden. Behandelt der Bundestag die wesentlichen Fragen? * Was hat man im Gremium des Souveräns bisher über Nordstream herausgefunden? * Was über Spike-Proteine, die 700 Tage nach der Impfung noch aktiv sind? * Wie erklärt dieses Gremium dem Souverän, dass Bankenbosse, Bundeskanzler und migrantische Straftäter in diesem Land ungleich schwieriger zu verurteilen sind als Bürger, die einen gefährlich mindertalentierten Politiker „Schwachkopf“ nennen? Wofür einen Bundestag wählen, der nichts zählt, wenn es darauf ankommt und wenig zustande bringt, was dem Bürger nützt, wenn er mal darf? Eine allgemeine Impfpflicht, die auf Politikerseite erst jeder kategorisch ausschloss und dann jeder ebenso salbungsvoll kategorisch befürwortete, scheiterte nur knapp. Aufarbeitung seither?  Legitimation des rituellen Umkehrschwungs? (Foto: [Rosenbusch/X](https://x.com/rosenbusch_/status/1893456799728062698)) \ Aus dem Kontrollgremium des Souveräns gegenüber der Regierung ist eine realitätsverweigernde BRD-Volkskammer geworden. Was kann eine Wahl verändern, wenn das System, welches sie alimentiert und perpetuiert, das Problem ist? Nehmen wir einen Motor, der mit Benzin läuft. Der Motor ist „unsere Demokratie“, Wahlen sind der Betankungsvorgang. Der Bürger betankt heute die Maschinerie mit der Legitimation durch seine Stimme. Doch er weiß nicht mehr, welche Hebel und Gerätschaften der Motor eigentlich antreibt. Dieser Teil befindet sich hinter einem schweren Vorhang. Kann im Sinne von Transparenz und Mit-Verantwortung der Betankungsvorgang guten Gewissens vollzogen werden? Der Wahlvorgang ist ein Paradebeispiel dessen, was der Soziologe Niklas Luhmann mit „Legitimation durch Verfahren“ beschrieben hat. Der prozessuale Akt, die Auszählung und Verkündung schafft neue Realität und legitimiert die neue Ordnung. Aus der Erfahrung der letzten Jahre in einer autoritären parlamentarischen Demokratur bedeutet die Wahlentscheidung jedoch eine de facto Blanko-Einwilligung in die eigene Versklavung. Im Privatrecht wäre das ein sittenwidriges Ziel, das zur Nichtigkeit des Vertrages führen würde. Wieso sollte das auf der Ebene des politischen Gesellschaftsvertrages dann möglich sein? Und wie kann ein solcher Legitimationsvorgang verantwortet werden? <https://www.youtube.com/watch?v=Ngy05PFUlo8&t=5s> Der Parlamentarismus in Deutschland ist für mich gescheitert, wieder einmal. Doch warum soll in einem besetzten, globalistisch durchzogenen NATO-EU-WHO-Konglomerat wie Deutschland auch ausgerechnet der Bürger das letzte Wort haben? Die Legitimationskette von Bürger zu Staat hat zu viele blinde Flecken bekommen. Die Rückverfolgung desaströsen politischen Handelns ist nicht mehr möglich. In Deutschland hat keine gesellschaftliche Instanz, nicht die Politik, nicht die Wissenschaft, nicht die Justiz, nicht die Medien, bisher eine Form der Corona-Aufarbeitung hinbekommen, die diesen Namen verdient. Das ist Sache von unabhängigen, versprengten Stimmen und Publikationen. Wie ist es um die Legitimität der „Partneroganisationen“ Deutschlands bestellt? Die EU ist unlängst vom Friedensbündnis zum Kriegsbündnis geworden, die Nato kann nicht mal Bündnispartner vor Bündnispartnern schützen und die WHO ist ein durch China und Bill Gates unterwandertes Jointventure für globale Impf- und Kontrollexperimente. All das wird heute erneut zementiert und wenn es gesprengt würde, müsste der Wahlvorgang verboten werden. Im besetzten Land darf nur richtig gewählt werden. Und deshalb gibt es für mich in diesem System keine Wahl. Wie ist es bei Ihnen? Wie stehen Sie zu dieser Wahl? Gehen Sie hin und mit welchen Gefühlen, Erwartungen, Intentionen? Ich freue mich auf Ihren Kommentar. ANZEIGE: **Sie suchen nach dem einfachsten Weg, Bitcoin zu kaufen und selbst zu verwahren?**\*\*\*\*\*\* *Die* ***[Relai-App](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)*** *ist Europas erfolgreichste Bitcoin-App.* ***[Hier](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)*** *kaufen Sie Bitcoin in wenigen Schritten und können auch Sparpläne einrichten. Niemand hat Zugriff auf Ihre Bitcoin, außer Sie selbst.* ***Relai senkt jetzt die Gebühr auf 1%**, mit dem Referral-Code* ***MILOSZ*** *sparen Sie weitere 10%. (keine Finanzberatung). Disclaimer wg. EU-Mica-Regulierung: Die Dienste von Relai werden ausschließlich für Einwohner der Schweiz und Italiens empfohlen.* *** ***You prefer reading me in English?*** *You can find my first uncensorable articles written with our Pareto client via Nostr,* ***[clicking on this link.](https://pareto.space/u/ashoka@pareto.space)*** *Discover other authors at* ***[Pareto.space/read.](https://pareto.space/read)(click on the Pareto button to see our first authors).***  [](https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fc33bfce1-1a89-42ff-a89f-e1fbd7edfac4_2382x1272.png) *** ***Join the marketplace of ideas!** We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the [Pareto Project](https://pareto.space/en)? Zap me, if you want to contribute (all Zaps go to the project).* *Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to **<team@pareto.space>*** **Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Start.](https://start.njump.me/)** @ e5de992e:4a95ef85
2025-02-23 07:52:00A trading log isn't just a record of past trades—it's a tool for learning, improving, and achieving consistency. By keeping a detailed log, you gain insights into your decision-making process, identify patterns, and refine your strategy over time. Here's why and how to maintain a comprehensive trading log effectively. --- ## 1. The Importance of a Trading Log - **Track Performance Objectively** Without a log, it's easy to misremember trades or overestimate success. A detailed log provides accurate data to analyze your progress. - **Understand Your Strengths and Weaknesses** By reviewing your log, you can identify what works well and where you need improvement. Patterns in losing trades often highlight common mistakes or emotional triggers. - **Build Confidence and Trust in Your System** Seeing a record of rule-based, consistent trades reinforces trust in your strategy. Reviewing past successes can boost morale during challenging periods. --- ## 2. What to Include in Your Trading Log A detailed trading log should cover both objective data and subjective reflections. ### Objective Data - **Date and Time:** When the trade was entered and exited. - **Instrument Traded:** Stock, forex pair, crypto, etc. - **Entry and Exit Prices:** Precise levels where you opened and closed the trade. - **Position Size:** Number of shares, contracts, or units traded. - **Stop Loss and Take Profit Levels:** Risk management details. - **P/L (Profit or Loss):** Outcome of the trade in dollars or percentage terms. - **Trade Type:** Long, short, scalping, swing, etc. ### Subjective Reflections - **Reason for Entering the Trade:** What setup or signal prompted the trade? - **Emotional State:** How did you feel before, during, and after the trade? - **Execution Notes:** Did you follow your plan? If not, why? - **Lessons Learned:** What can you take away from this trade to improve next time? > **Key Insight:** Both data and reflection are essential for meaningful analysis. --- ## 3. How to Analyze Your Trading Log 1. **Identify Patterns** Look for common themes in your winning and losing trades. _Examples:_ Winning trades often align with specific setups, while losing trades frequently result from breaking rules or impulsive decisions. 2. **Evaluate Strategy Effectiveness** Assess whether your system produces consistent results over time. Use metrics like win rate, risk-reward ratio, and drawdown to evaluate performance. 3. **Address Emotional Triggers** Reflect on emotional notes to understand what triggers fear, greed, or hesitation. Develop strategies to manage emotions based on these insights. --- ## 4. Benefits of Keeping a Trading Log - **Improved Discipline:** Writing down each trade reinforces the habit of sticking to your plan. - **Informed Adjustments:** Logs provide data-driven insights to refine your strategy. - **Emotional Control:** Journaling emotions helps you recognize and address psychological pitfalls. - **Long-Term Growth:** By tracking your progress, you can measure improvement over months and years. > **Key Insight:** A trading log turns mistakes into lessons and successes into repeatable actions. --- ## 5. Tools for Logging Trades ### Manual Logs - Use a notebook or spreadsheet to record trades. - **Pros:** Highly customizable, forces you to engage deeply with each entry. - **Cons:** Time-intensive and less automated. ### Software and Platforms - Tools like Edgewonk, TraderSync, or Tradervue can streamline the process. - **Pros:** Automated data collection, advanced analytics, and performance tracking. - **Cons:** May have a learning curve or subscription costs. > **Key Insight:** Choose a method that aligns with your workflow and trading style. --- ## 6. Tips for Maintaining a Consistent Trading Log - **Log Every Trade:** Don't skip trades, even the ones you'd rather forget. They're often the most valuable for learning. - **Be Honest:** Record trades exactly as they happened, including mistakes and rule-breaking. - **Review Regularly:** Set aside time weekly or monthly to analyze your log and adjust your approach. - **Stay Disciplined:** Treat logging as an essential part of your trading routine. --- ## 7. Conclusion: Your Trading Log is Your Mirror A detailed trading log is more than just a record—it's a roadmap to success. It provides clarity, accountability, and insights that are essential for continuous improvement. Start today. Keep a detailed log, review it often, and use it to refine both your strategy and your mindset. Your future self will thank you.
@ e5de992e:4a95ef85
2025-02-23 07:52:00A trading log isn't just a record of past trades—it's a tool for learning, improving, and achieving consistency. By keeping a detailed log, you gain insights into your decision-making process, identify patterns, and refine your strategy over time. Here's why and how to maintain a comprehensive trading log effectively. --- ## 1. The Importance of a Trading Log - **Track Performance Objectively** Without a log, it's easy to misremember trades or overestimate success. A detailed log provides accurate data to analyze your progress. - **Understand Your Strengths and Weaknesses** By reviewing your log, you can identify what works well and where you need improvement. Patterns in losing trades often highlight common mistakes or emotional triggers. - **Build Confidence and Trust in Your System** Seeing a record of rule-based, consistent trades reinforces trust in your strategy. Reviewing past successes can boost morale during challenging periods. --- ## 2. What to Include in Your Trading Log A detailed trading log should cover both objective data and subjective reflections. ### Objective Data - **Date and Time:** When the trade was entered and exited. - **Instrument Traded:** Stock, forex pair, crypto, etc. - **Entry and Exit Prices:** Precise levels where you opened and closed the trade. - **Position Size:** Number of shares, contracts, or units traded. - **Stop Loss and Take Profit Levels:** Risk management details. - **P/L (Profit or Loss):** Outcome of the trade in dollars or percentage terms. - **Trade Type:** Long, short, scalping, swing, etc. ### Subjective Reflections - **Reason for Entering the Trade:** What setup or signal prompted the trade? - **Emotional State:** How did you feel before, during, and after the trade? - **Execution Notes:** Did you follow your plan? If not, why? - **Lessons Learned:** What can you take away from this trade to improve next time? > **Key Insight:** Both data and reflection are essential for meaningful analysis. --- ## 3. How to Analyze Your Trading Log 1. **Identify Patterns** Look for common themes in your winning and losing trades. _Examples:_ Winning trades often align with specific setups, while losing trades frequently result from breaking rules or impulsive decisions. 2. **Evaluate Strategy Effectiveness** Assess whether your system produces consistent results over time. Use metrics like win rate, risk-reward ratio, and drawdown to evaluate performance. 3. **Address Emotional Triggers** Reflect on emotional notes to understand what triggers fear, greed, or hesitation. Develop strategies to manage emotions based on these insights. --- ## 4. Benefits of Keeping a Trading Log - **Improved Discipline:** Writing down each trade reinforces the habit of sticking to your plan. - **Informed Adjustments:** Logs provide data-driven insights to refine your strategy. - **Emotional Control:** Journaling emotions helps you recognize and address psychological pitfalls. - **Long-Term Growth:** By tracking your progress, you can measure improvement over months and years. > **Key Insight:** A trading log turns mistakes into lessons and successes into repeatable actions. --- ## 5. Tools for Logging Trades ### Manual Logs - Use a notebook or spreadsheet to record trades. - **Pros:** Highly customizable, forces you to engage deeply with each entry. - **Cons:** Time-intensive and less automated. ### Software and Platforms - Tools like Edgewonk, TraderSync, or Tradervue can streamline the process. - **Pros:** Automated data collection, advanced analytics, and performance tracking. - **Cons:** May have a learning curve or subscription costs. > **Key Insight:** Choose a method that aligns with your workflow and trading style. --- ## 6. Tips for Maintaining a Consistent Trading Log - **Log Every Trade:** Don't skip trades, even the ones you'd rather forget. They're often the most valuable for learning. - **Be Honest:** Record trades exactly as they happened, including mistakes and rule-breaking. - **Review Regularly:** Set aside time weekly or monthly to analyze your log and adjust your approach. - **Stay Disciplined:** Treat logging as an essential part of your trading routine. --- ## 7. Conclusion: Your Trading Log is Your Mirror A detailed trading log is more than just a record—it's a roadmap to success. It provides clarity, accountability, and insights that are essential for continuous improvement. Start today. Keep a detailed log, review it often, and use it to refine both your strategy and your mindset. Your future self will thank you. @ e5de992e:4a95ef85
2025-02-23 07:46:45China’s M1 increases a lot, it means there’s more money available for people and businesses to buy things. This can help boost spending and economic growth in the short term. However, if there’s too much money chasing the same amount of goods and services, prices can rise, leading to inflation. Sometimes, a rapid increase in M1 can also signal that banks are lending a lot of money, which might eventually create bubbles in things like real estate or stocks if the growth isn’t managed carefully. https://tradingeconomics.com/china/money-supply-m1 China’s M1 increases a lot, it means there’s more money available for people and businesses to buy things. This can help boost spending and economic growth in the short term.
@ e5de992e:4a95ef85
2025-02-23 07:46:45China’s M1 increases a lot, it means there’s more money available for people and businesses to buy things. This can help boost spending and economic growth in the short term. However, if there’s too much money chasing the same amount of goods and services, prices can rise, leading to inflation. Sometimes, a rapid increase in M1 can also signal that banks are lending a lot of money, which might eventually create bubbles in things like real estate or stocks if the growth isn’t managed carefully. https://tradingeconomics.com/china/money-supply-m1 China’s M1 increases a lot, it means there’s more money available for people and businesses to buy things. This can help boost spending and economic growth in the short term. @ da0b9bc3:4e30a4a9
2025-02-23 07:08:22Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/894609
@ da0b9bc3:4e30a4a9
2025-02-23 07:08:22Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/894609 @ e3ba5e1a:5e433365
2025-02-23 06:35:51My wife and I have six children, making our house a household of eight people. Looking just at the eight of us, how many relationships exist? Well, as a first stab, we could look at how many connections exist between two unique individuals in this family. The mathematical term for this is “8 choose 2”, and the answer is 8\*7/2, or 28\. Even that doesn’t really capture the answer though, because relationships aren’t just between two people. For example, when my wife and two oldest children are the only ones still awake after the younger kids go to bed, we’ll put on my mature TV shows that they’ll appreciate and watch together. It’s our own little subgroup within the group. Based on that, we could have groups of 2, 3, 4, all the way up to 8, the group of all of us. If you do the math, this comes up to 247 different subgroups of 2 or more people. That’s a lot of groups for just 8 people. As a father, this means I’ll never be able to fully understand every set of connections within my family. I may have a good understanding of my own relationship with each child. I also am closely aware of the relationship between our two youngest children, since they’re twins. And I could probably list 20 or so other noteworthy relationships. But I’ll never understand all of them. For example, months ago I bought a game on Steam for my 3rd and 4th kids. I know they like to play games together, so it was a relationship that I thought I understood well. A few days ago I found out that my oldest had joined them in playing one of these games (Brotato). I’d made the purchase, given it to the kids, and it sparked new relationship and interaction structures without my involvement. There’s no problem with the fact that I can’t track every interaction in my house. That’s healthy\! The kids are able to discover ways of interacting beyond what I can teach them, learn everything from schoolwork to video games from each other, and overall become more healthy and well-adjusted adults (I hope). And here’s the important part: the growth of the number of connections is *massive* as the number of participants increases. If we add in another participant, we have 502 groupings. At 10 total participants, it jumps to over 1,000. By the time we get to 100, we’re well into the trillions. A mathematical and software term for this is *combinatoric complexity*, the massive increase in an output value based on a small increase in the input. The analysis I’m providing could be termed as part of graph theory (for connections of 2, looking at people as *vertices* and connections as *edges*) or set theory (unique subsets, allowing for larger group sizes). But regardless, the point is: the increase in complexity is huge as more people join. Now consider the global economy. It’s over 8 billion people. There are so many people that the number of groupings is absurd to talk about. Nonetheless, massive numbers of these groupings naturally occur. There are family units, friend circles, individual connections, companies, project teams, sports teams, schools, classes, and millions more. These groups of people form new ways of interacting, express vastly different desires for goods and services, and are capable of producing wide varieties of goods and services themselves. When you allow this system to run free, beauty emerges. Each node in the graph can manage its own connections. Each *person* is free to make his or her own decisions about association, what to spend time on, what to spend money on, and so on. Each person does so on their own judgement and world view. Some of these people may make “dumb” decisions. They may “waste” their time and money on useless things. Except: who made that value judgement? Clearly not them, they decided it was worth it. No central planner has the right to override their will. My point in all this is: as yet another of many reasons in the list of “why people should be free,” we have one more data point: pure math. Central planning will never scale. Central planning will never appreciate the individuality and desires of each person. Only by giving people the freedom to explore their connections to others, discover what they can produce and consume, explore their options, and ultimately make their own decisions, can we have any chance of creating a world where everyone can succeed.
@ e3ba5e1a:5e433365
2025-02-23 06:35:51My wife and I have six children, making our house a household of eight people. Looking just at the eight of us, how many relationships exist? Well, as a first stab, we could look at how many connections exist between two unique individuals in this family. The mathematical term for this is “8 choose 2”, and the answer is 8\*7/2, or 28\. Even that doesn’t really capture the answer though, because relationships aren’t just between two people. For example, when my wife and two oldest children are the only ones still awake after the younger kids go to bed, we’ll put on my mature TV shows that they’ll appreciate and watch together. It’s our own little subgroup within the group. Based on that, we could have groups of 2, 3, 4, all the way up to 8, the group of all of us. If you do the math, this comes up to 247 different subgroups of 2 or more people. That’s a lot of groups for just 8 people. As a father, this means I’ll never be able to fully understand every set of connections within my family. I may have a good understanding of my own relationship with each child. I also am closely aware of the relationship between our two youngest children, since they’re twins. And I could probably list 20 or so other noteworthy relationships. But I’ll never understand all of them. For example, months ago I bought a game on Steam for my 3rd and 4th kids. I know they like to play games together, so it was a relationship that I thought I understood well. A few days ago I found out that my oldest had joined them in playing one of these games (Brotato). I’d made the purchase, given it to the kids, and it sparked new relationship and interaction structures without my involvement. There’s no problem with the fact that I can’t track every interaction in my house. That’s healthy\! The kids are able to discover ways of interacting beyond what I can teach them, learn everything from schoolwork to video games from each other, and overall become more healthy and well-adjusted adults (I hope). And here’s the important part: the growth of the number of connections is *massive* as the number of participants increases. If we add in another participant, we have 502 groupings. At 10 total participants, it jumps to over 1,000. By the time we get to 100, we’re well into the trillions. A mathematical and software term for this is *combinatoric complexity*, the massive increase in an output value based on a small increase in the input. The analysis I’m providing could be termed as part of graph theory (for connections of 2, looking at people as *vertices* and connections as *edges*) or set theory (unique subsets, allowing for larger group sizes). But regardless, the point is: the increase in complexity is huge as more people join. Now consider the global economy. It’s over 8 billion people. There are so many people that the number of groupings is absurd to talk about. Nonetheless, massive numbers of these groupings naturally occur. There are family units, friend circles, individual connections, companies, project teams, sports teams, schools, classes, and millions more. These groups of people form new ways of interacting, express vastly different desires for goods and services, and are capable of producing wide varieties of goods and services themselves. When you allow this system to run free, beauty emerges. Each node in the graph can manage its own connections. Each *person* is free to make his or her own decisions about association, what to spend time on, what to spend money on, and so on. Each person does so on their own judgement and world view. Some of these people may make “dumb” decisions. They may “waste” their time and money on useless things. Except: who made that value judgement? Clearly not them, they decided it was worth it. No central planner has the right to override their will. My point in all this is: as yet another of many reasons in the list of “why people should be free,” we have one more data point: pure math. Central planning will never scale. Central planning will never appreciate the individuality and desires of each person. Only by giving people the freedom to explore their connections to others, discover what they can produce and consume, explore their options, and ultimately make their own decisions, can we have any chance of creating a world where everyone can succeed. @ 78c90fc4:4bff983c
2025-02-23 06:25:25  Vor dem Prozess kursierten Gerüchte, Maxwell verstecke sich in einem U-Boot oder auf nahe gelegenen Inseln. Sie besitzt ein U-Boot und hat eine Lizenz dafür Water Island ist eine 500 Hektar große Landzunge auf den U.S. Virgin Islands. Aufnahmen aus dem Jahr 2012 (auch Video) zeigen einen Teil des Untergrunds und seiner Umgebung. 2005: James und Sara Biden kaufen ein Grundstück auf Water Island, in der Mitte der Insel, für 150.000 Euro. Dieser Teil des Grundstücks wurde in drei Teile aufgeteilt und verkauft. Einer von ihnen ist Scott Green. Scott Green, ein Lobbyist mit engen Beziehungen zu Joe Biden, kaufte das Grundstück auf den Jungferninseln von James Biden und gewährte ihm dann eine private Hypothek. Nach dem Kauf machte Joe Biden mindestens dreimal Urlaub auf der winzigen Insel, die einst einen nahe gelegenen U-Boot-Stützpunkt und eine unterirdische Anlage schützte, bevor sie zu einem tropischen Rückzugsort wurde. Die Bedingungen des Darlehens wurden in den Immobilienunterlagen nicht offengelegt. Green hat auf mehrere Bitten um Stellungnahme nicht reagiert. Der Anwalt von James Biden, George Mesires, bestätigte den Erhalt von Fragen, beantwortete sie aber nicht. Green hat Biden 2.300 Dollar gespendet, aber als er um einen Kommentar gebeten wurde, hat er nicht geantwortet. Und raten Sie mal, was Green in Washington, D.C., als Auftragnehmer für öffentliche Sicherheits- und Strafverfolgungsbehörden als Teil einer Firma arbeitet, die er 1994 mitbegründet hat. Es wird noch interessanter!! Scotts Lafayette Group erhält 5,8 Millionen Dollar von der FEMA. 3 TAGE SPÄTER gaben sie James und Sara Biden eine Hypothek von 133.000 für Water Island Land. Und es gibt noch so viel mehr, aber das ist ein anderes Kaninchenloch (ein weiterer Zuschuss für 40 Millionen Dollar). Unten können Sie eine von Bidens zahlreichen Lügen sehen: „Ich habe nie mit meinem Sohn oder meinem Bruder oder sonst jemandem etwas besprochen, was mit ihren Geschäften zu tun hat.“ Hunter Biden arbeitete als Energieberater ohne jegliche Erfahrung in diesem Bereich. James Biden trat der Firma HillStone bei. Und wie durch ein Wunder erhielt das Unternehmen zahlreiche Aufträge von der Bundesregierung (USA, Irak, Puerto Rico, Mosambik usw.) Kredit: Natly Denise, CaptainBirchShow, Politico \#EpsteinClientList #EpsteinIsland <https://x.com/SaladMeToday/status/1892971887006810214> <https://x.com/RealWsiegrist/status/1893543364676522222> Perplexity: Der U-Boot-Stützpunkt in der Nähe von Water Island auf St. Thomas auf den US-Jungferninseln war während des Zweiten Weltkriegs aufgrund seiner Rolle bei der Verteidigung der Karibik und der US-Marineoperationen von großer strategischer Bedeutung.\ \ \### \*\*Strategische Bedeutung der U-Boot-Basis\*\*\ \- Die U-Boot-Basis auf St. Thomas wurde 1941 als Teil einer umfassenderen US-Militärstrategie zur Sicherung der Karibik während des Zweiten Weltkriegs eingerichtet. Diese Region war entscheidend für den Schutz der Schifffahrtswege und die Bekämpfung der deutschen U-Boot-Aktivitäten im Atlantik\[1]\[2].\ \- Der Stützpunkt verfügte über eine umfangreiche Infrastruktur mit drei Piers, Unterkünften für fast 1.000 Mitarbeiter, Lagereinrichtungen, einer Torpedoüberholungswerkstatt und einem bombensicheren Maschinenhaus\[1]. Diese Einrichtungen unterstützten den Betrieb und die Wartung von U-Booten in einem strategisch wichtigen Gebiet.\ \ \###\ \- Water Island, südlich von St. Thomas gelegen, wurde 1944 von der US-Regierung erworben, um die Küstenverteidigung zu stärken\[5]. Fort Segarra, eine unterirdische Festung auf Water Island, wurde zum Schutz der nahe gelegenen U-Boot-Basis auf St. Thomas\[2]\[4] errichtet.\ \- Das Fort umfasste Geschützstellungen, Tunnel, unterirdische Kammern, Kasernen und andere militärische Infrastrukturen. Es wurde jedoch nie fertiggestellt oder voll einsatzfähig, da der Zweite Weltkrieg vor Abschluss der Bauarbeiten beendet wurde\[3]\[6].\ \ \*\*Nachkriegsnutzung\*\*\ \- Nach dem Krieg wurden Fort Segarra und Water Island für verschiedene militärische Tests genutzt, darunter Experimente zur chemischen Kriegsführung, die zwischen 1948 und 1950 durchgeführt wurden\[4]\[6]. Später, im Jahr 1952, wurde die Insel unter zivile Kontrolle gestellt.\ \ \###\ \- Heute sind die Überreste von Fort Segarra und seine unterirdischen Strukturen auf Water Island für Besucher zugänglich. Sie erinnern an die Rolle des Forts beim Schutz des U-Boot-Stützpunkts und an seine strategische Bedeutung während des Zweiten Weltkriegs\[3]\[6].\ \ Zusammenfassend lässt sich sagen, dass der U-Boot-Stützpunkt auf St. Thomas und die damit verbundenen Verteidigungsanlagen auf Water Island entscheidende Komponenten der US-Bemühungen zur Sicherung der Karibik während des Zweiten Weltkriegs waren. Obwohl ihre militärische Nutzung vor Jahrzehnten endete, bleiben sie aufgrund ihres historischen und strategischen Erbes von Bedeutung.\ \ Quellen\ \[1] Militärgeschichte von Water Island https\://history.wica.vi/military-history/\ \[2] Fort Segarra - Flamingo Point USVI Water Island http\://flamingopointusvi.com/water-island\ \[3] Fort Segarra - Virgin Islands - VInow\.com https\://www\.vinow\.com/wi/wi-a/fort-segarra/\ \[4] Fort Segarra - Wikipedia https\://en.wikipedia.org/wiki/Fort\_Segarra\ \[5] Fort Segarra - Jacksonville District - Army.mil https\://www\.saj.usace.army.mil/FortSegarra/\ \[6] Water Island, U.S. Virgin Islands - Wikipedia https\://en.wikipedia.org/wiki/Water\_Island,\_U.S.\_Virgin\_Islands\ \[7] Water Island | Seas the Day Charters USVI https\://seasthedayusvi.com/2022/02/11/exploring-water-island-u-s-virgin-islands-best-kept-secret/\ \[8] Water Island: Aktivitäten und Sehenswürdigkeiten - Jungferninseln - VInow\.com https\://www\.vinow\.com/waterisland/attractions\_wi/ Dazu auch die Sammlung Epstein <https://waltisiegrist.locals.com/post/1353380/epstein-oder-wie-leicht-sich-die-wissenschaft-kaufen-laesst>
@ 78c90fc4:4bff983c
2025-02-23 06:25:25  Vor dem Prozess kursierten Gerüchte, Maxwell verstecke sich in einem U-Boot oder auf nahe gelegenen Inseln. Sie besitzt ein U-Boot und hat eine Lizenz dafür Water Island ist eine 500 Hektar große Landzunge auf den U.S. Virgin Islands. Aufnahmen aus dem Jahr 2012 (auch Video) zeigen einen Teil des Untergrunds und seiner Umgebung. 2005: James und Sara Biden kaufen ein Grundstück auf Water Island, in der Mitte der Insel, für 150.000 Euro. Dieser Teil des Grundstücks wurde in drei Teile aufgeteilt und verkauft. Einer von ihnen ist Scott Green. Scott Green, ein Lobbyist mit engen Beziehungen zu Joe Biden, kaufte das Grundstück auf den Jungferninseln von James Biden und gewährte ihm dann eine private Hypothek. Nach dem Kauf machte Joe Biden mindestens dreimal Urlaub auf der winzigen Insel, die einst einen nahe gelegenen U-Boot-Stützpunkt und eine unterirdische Anlage schützte, bevor sie zu einem tropischen Rückzugsort wurde. Die Bedingungen des Darlehens wurden in den Immobilienunterlagen nicht offengelegt. Green hat auf mehrere Bitten um Stellungnahme nicht reagiert. Der Anwalt von James Biden, George Mesires, bestätigte den Erhalt von Fragen, beantwortete sie aber nicht. Green hat Biden 2.300 Dollar gespendet, aber als er um einen Kommentar gebeten wurde, hat er nicht geantwortet. Und raten Sie mal, was Green in Washington, D.C., als Auftragnehmer für öffentliche Sicherheits- und Strafverfolgungsbehörden als Teil einer Firma arbeitet, die er 1994 mitbegründet hat. Es wird noch interessanter!! Scotts Lafayette Group erhält 5,8 Millionen Dollar von der FEMA. 3 TAGE SPÄTER gaben sie James und Sara Biden eine Hypothek von 133.000 für Water Island Land. Und es gibt noch so viel mehr, aber das ist ein anderes Kaninchenloch (ein weiterer Zuschuss für 40 Millionen Dollar). Unten können Sie eine von Bidens zahlreichen Lügen sehen: „Ich habe nie mit meinem Sohn oder meinem Bruder oder sonst jemandem etwas besprochen, was mit ihren Geschäften zu tun hat.“ Hunter Biden arbeitete als Energieberater ohne jegliche Erfahrung in diesem Bereich. James Biden trat der Firma HillStone bei. Und wie durch ein Wunder erhielt das Unternehmen zahlreiche Aufträge von der Bundesregierung (USA, Irak, Puerto Rico, Mosambik usw.) Kredit: Natly Denise, CaptainBirchShow, Politico \#EpsteinClientList #EpsteinIsland <https://x.com/SaladMeToday/status/1892971887006810214> <https://x.com/RealWsiegrist/status/1893543364676522222> Perplexity: Der U-Boot-Stützpunkt in der Nähe von Water Island auf St. Thomas auf den US-Jungferninseln war während des Zweiten Weltkriegs aufgrund seiner Rolle bei der Verteidigung der Karibik und der US-Marineoperationen von großer strategischer Bedeutung.\ \ \### \*\*Strategische Bedeutung der U-Boot-Basis\*\*\ \- Die U-Boot-Basis auf St. Thomas wurde 1941 als Teil einer umfassenderen US-Militärstrategie zur Sicherung der Karibik während des Zweiten Weltkriegs eingerichtet. Diese Region war entscheidend für den Schutz der Schifffahrtswege und die Bekämpfung der deutschen U-Boot-Aktivitäten im Atlantik\[1]\[2].\ \- Der Stützpunkt verfügte über eine umfangreiche Infrastruktur mit drei Piers, Unterkünften für fast 1.000 Mitarbeiter, Lagereinrichtungen, einer Torpedoüberholungswerkstatt und einem bombensicheren Maschinenhaus\[1]. Diese Einrichtungen unterstützten den Betrieb und die Wartung von U-Booten in einem strategisch wichtigen Gebiet.\ \ \###\ \- Water Island, südlich von St. Thomas gelegen, wurde 1944 von der US-Regierung erworben, um die Küstenverteidigung zu stärken\[5]. Fort Segarra, eine unterirdische Festung auf Water Island, wurde zum Schutz der nahe gelegenen U-Boot-Basis auf St. Thomas\[2]\[4] errichtet.\ \- Das Fort umfasste Geschützstellungen, Tunnel, unterirdische Kammern, Kasernen und andere militärische Infrastrukturen. Es wurde jedoch nie fertiggestellt oder voll einsatzfähig, da der Zweite Weltkrieg vor Abschluss der Bauarbeiten beendet wurde\[3]\[6].\ \ \*\*Nachkriegsnutzung\*\*\ \- Nach dem Krieg wurden Fort Segarra und Water Island für verschiedene militärische Tests genutzt, darunter Experimente zur chemischen Kriegsführung, die zwischen 1948 und 1950 durchgeführt wurden\[4]\[6]. Später, im Jahr 1952, wurde die Insel unter zivile Kontrolle gestellt.\ \ \###\ \- Heute sind die Überreste von Fort Segarra und seine unterirdischen Strukturen auf Water Island für Besucher zugänglich. Sie erinnern an die Rolle des Forts beim Schutz des U-Boot-Stützpunkts und an seine strategische Bedeutung während des Zweiten Weltkriegs\[3]\[6].\ \ Zusammenfassend lässt sich sagen, dass der U-Boot-Stützpunkt auf St. Thomas und die damit verbundenen Verteidigungsanlagen auf Water Island entscheidende Komponenten der US-Bemühungen zur Sicherung der Karibik während des Zweiten Weltkriegs waren. Obwohl ihre militärische Nutzung vor Jahrzehnten endete, bleiben sie aufgrund ihres historischen und strategischen Erbes von Bedeutung.\ \ Quellen\ \[1] Militärgeschichte von Water Island https\://history.wica.vi/military-history/\ \[2] Fort Segarra - Flamingo Point USVI Water Island http\://flamingopointusvi.com/water-island\ \[3] Fort Segarra - Virgin Islands - VInow\.com https\://www\.vinow\.com/wi/wi-a/fort-segarra/\ \[4] Fort Segarra - Wikipedia https\://en.wikipedia.org/wiki/Fort\_Segarra\ \[5] Fort Segarra - Jacksonville District - Army.mil https\://www\.saj.usace.army.mil/FortSegarra/\ \[6] Water Island, U.S. Virgin Islands - Wikipedia https\://en.wikipedia.org/wiki/Water\_Island,\_U.S.\_Virgin\_Islands\ \[7] Water Island | Seas the Day Charters USVI https\://seasthedayusvi.com/2022/02/11/exploring-water-island-u-s-virgin-islands-best-kept-secret/\ \[8] Water Island: Aktivitäten und Sehenswürdigkeiten - Jungferninseln - VInow\.com https\://www\.vinow\.com/waterisland/attractions\_wi/ Dazu auch die Sammlung Epstein <https://waltisiegrist.locals.com/post/1353380/epstein-oder-wie-leicht-sich-die-wissenschaft-kaufen-laesst> @ 52adc2ef:9f4bc0ba
2025-02-23 03:45:10สวัสดีครับ วันนี้อยากมาเล่าเรื่องเกี่ยวกับ Options เราได้ไปเรียนกับทาง อ.เอ็ม ติดเล่า เรื่องลงทุน อยากจะเเชร์สำหรับคนที่สนใจ Options เเต่เพื่อนๆที่ลงทุนมาบ้างน่าจะเคยได้ยิน เเต่ก่อนอื่นการเทรดลงทุนอยากให้เข้าใจ 3 คำนี้ก่อนนะครับ **Spot , Futures , options** **Spot** คือ การซื้อขาย สินทรัพย์ ณ เวลาปัจจุบัน ตามราคาปัจจุบัน เช่น BTC มีราคา 95,000$ ในเวปเทรด เรากดซื้อ จะได้ตามราคา Futures คือ สัญญาซื้อ ขาย สินทรัพย์ล่วงหน้า จะซื้อขายในราคาที่กำหนด เมื่อถึงเวลากำหนด จะต้องทำการซื้อขายตามนั้น คล้ายๆสัญญาซื้อที่ดิน ที่เราต้องใช้สิทธิ์กันทั้งผู้ซื้อและผู้ขาย เช่น สัญญาจะซื้อ BTC ราคา 90,000$ โดยมีอายุสัญญา 3 เดือน ถ้าวันครบสัญญา BTC ราคา 95,000$ จะต้องขายให้ในราคา 90,000$ หรือ สัญญาขาย BTC ราคา 100,000$ โดยมีอายุสัญญา 3 เดือน ถ้าวันครบสัญญา BTC ราคา 95,000$ จะต้องขายให้ในราคา 100,000$ **Options** คือ สัญญาที่ผู้จะซื้อขาย เเบบ futures แต่มีจ่ายค่า Premium เพื่อมีสิทธิ์ที่จะใช้สิทธิ์ซื้อหรือสิทธิ์ขายก็ได้ โดยใช้สิทธิ์ในระยะเวลาที่กำหนด เช่น สัญญา long call สัญญาใช้สิทธิ์ซื้อ เมื่อ BTC ราคา 98,000$ โดยต้องจ่ายค่า premium 100$ เพื่อLock สิทธิ์ ถ้าราคา BTC = 95,000$ เราไม่จำเป็นต้องใช้สิทธิ์ได้ เพราะซื้อในตลาดถูกกว่า เเต่เราจะต้องเสีย premium ที่เราวางไว้ เป็นต้น พอจะเห็นภาพใช่มั้ยครับ ซึ่งจะมาพูดในส่วนของ options กัน Options มีการใช้สิทธิ์อยู่ 2 แบบ Call Options โดยมี Long call คือ สิทธิ์ในการซื้อ Long put คือ สิทธิ์ในการขาย Put Optionsโดยมี Short call คือ ผู้ที่มีหน้าที่ต้องขายจะคู่กับ Long call Short put คือ ผู้ที่มีหน้าที่ต้องซื้อจะคู่กับ Long put โดยมีคำศัพท์ควรรู้อีกเล็กน้อย จะได้เข้าใจภาพรวมทั้งหมดกัน Strike price = ราคาที่จะซื้อจะขาย maturity=วันสิ้นสัญญา premium=เบี้ย time to maturity=ระยะเวลาสัญญา อาจจะยังงงๆ งั้นเริ่มอธิบายทีละข้อกันมาเริ่มที่ **Long Call Option**  สิทธิ์ในการซื้อ จากรูปจะเห็นว่าถ้าเราคิดว่าราคา สินทรัพย์ที่เราสนใจมีเเนวโน้มที่จะขึ้น ซึ่งขณะนี้ ราคาอยู่ที่ 90$ เราอาจจะซื้อ Long call ที่ราคาเริ่มใช้สิทธิ์ Strike Price=100$ โดยมีค่า Premium ที่ 5$ จะเห็นว่าถ้าราคาเป็น 80$ เราคงไม่ใช้สิทธิ์ เพราะซื้อปกติถูกกว่า ราคาใช้สิทธิ์เราจะต้องซื้อที่ 100$ เมื่อไม่ใช้สิทธิ์ เราต้องเสียค่า Premium ให้กับฝั่งที่มีหน้าที่ขาย คือ Short call ซึ่งเมื่อเทียบกับการ Long Futures ถ้าเกิดลงไปเหลือ 45$ เราจะเสีย 50% เเต่ถ้ามี option จะเสียสุดที่เเค่ค่า Premium  รูปกราฟของ Long Futures ซึ่ง Long call = Long future ครึ่งเดียวเพราะ Long Future ราคาจะขึ้นไปเรื่อยๆตามกราฟ Long Call Option เหมาะใช้เมื่อไหร่? ให้คิดว่าเหมือนซื้อหวย เพราะถ้าราคาไม่ไปตามที่คิดเราจะเสียเเค่ค่า Premium หวยเหมือนเราเสียค่า Premium ไปก่อน 80 บาท หรือวิเคราะห์มาเเล้วว่ามีโอกาสที่ราคาขึ้น **Short Call Option**  เป็นฝั่งตรงข้ามกับ Long call เราต้องมีหน้าที่ขายให้ฝั่ง long call ซึ่งฝั่งขายต้องมีสินทรัพย์นั้นๆเพื่อไว้ขาย เพราะมีหน้าที่ ต้องขาย ไม่เหมือนฝั่ง long call ที่มีสามารถเลือกใช้สิทธิ์ได้ เมื่อราคาไม่ถึง Strike Price หลังจากหมดอายุสัญญา ฝั่ง short call ได้ค่า Premium จากฝั่ง Long call จากรูป ถ้าสินทรัพย์ ราคา 90$ ราคาที่ต้องขายสินทรัพย์ 100$ ถ้าราคาไม่ถึง 100$ จะได้ค่า Premium เเต่ถ้าราคาเกิน 100$ เป็นต้นไป จะขาดทุนมากขึ้นเรื่อยๆ ถ้าราคาไปที่ 150$ ต้องมาขายที่ 100$ ตามสัญญา Short Call Option เหมาะใช้เมื่อไหร่? เหมาะสำหรับที่เรามีสินทรัพย์ที่อยากจะขายอยู่เเล้วตาม Target ที่เราตั้งไว้ เช่น มีหุ้นที่ถือไว้อยู่เเล้ว ราคา 50$ ตั้งใจจะทำกำไรเมื่อราคา 100$ แทนที่จะรอขายเฉยๆ มาทำการ Short call ถ้าราคาไม่ถึงก็ได้กินค่า Premium ไป เเต่ถ้าราคาถึง 100$ เราต้องการที่จะ Take Profit อยู่เเล้ว ก็ขายไป Long Put Option  หมายถึงเราสิทธ์ในการขายรือไม่ขายก็ได้ จะตรงข้ามกับ Long call จากรูปถ้าถือสินทรัพย์จากทุน 50$ เเต่ตอนนี้ราคา 80$ เเล้วไม่เเน่ใจว่าราคาจะลงมั้ย เเต่ขึ้นต่อก็ไม่เปนไร อยากจะ Lock ราคาขาย 70$ ใช้สัญญา Long Put จ่ายค่า Premium ถ้าราคาลงไปที่ 50$ เราใช้สิทธิ์ในการขายที่ ราคา 70$ ได้ ถ้าราคาขึ้นเราก็จะไม่ใช้สิทธิ์เพราะขายในตลาดได้ราคาดีกว่า  รูปกราฟของ Short Futures ซึ่ง Long put = Short future ครึ่งเดียวเพราะ Short Future ราคาจะลงไปเรื่อยๆตามกราฟ Long Put Option เหมาะใช้เมื่อไหร่? ให้คิดว่าเหมือนซื้อประกัน ที่เราจ่ายเบี้ยประกันไปเพื่อที่จะ Lock ความเสี่ยงที่จะเกิด ส่วน Long Put ก็ไม่รู้ว่าราคาที่ถือจะลงมั้ย ยอมที่จ่ายค่า Premium เพื่อที่จะได้ราคาตามมูลค่าเดิมของเรา **Short Put Option* * เป็นฝั่งตรงข้ามกับ Long put เราต้องมีหน้าที่รับซื้อให้ฝั่ง long put ซึ่งฝั่งซื้อต้องมีเงินเพื่อไว้ซื้อ เพราะมีหน้าที่ต้องซื้อ ไม่เหมือนฝั่ง long put ที่มีสามารถเลือกใช้สิทธิ์ได้ เมื่อราคาไม่ถึง Strike Price หลังจากหมดอายุสัญญา ฝั่ง short put ได้ค่า Premium จากฝั่ง Long put จากรูป ราคาสินทรัพย์อยู่ที่ 80$ ราคาที่เรารับซื้อ หรือ Strike Price 70$ ถ้าราคาลงไม่ถึง 70 $ ก็จะได้ค่า Premium ถ้าราคาลงไปต่ำกว่า 70$ ก็ต้องรับซื้อทุกกรณี ราคาลงไปที่ 50$ เราก็ต้องรับซื้อที่ 70$ ตามสัญญา Short Put Option เหมาะใช้เมื่อไหร่? ใช้เมื่อเราอยากจะซื้อสินทรัพย์ราคานั้นๆอยู่เเล้ว เช่น อยากจะซื้อที่ราคา 70 $ แทนที่จะรอเฉยๆ อาจจะเปิด Short Put เพื่อที่ราคายังไม่ถึง target ก็จะได้ค่า Premium ถ้าราคาถึงก็ได้ซื้อเหมือนที่ตั้งใจไว้ สรุป จากที่เล่าทั้งหมดเป็นการอธิบาย Options เบื้องต้นที่อยากให้เพื่อนๆ ที่สนใจการเทรดอยู่เเล้ว ถ้าเข้าใจเรื่อง Options ด้วยเราคิดว่าน่าจะปรับใช้ในส่วนช่วยใน Port ของเราไม่มากก็น้อย หวังว่าจะเป็นประโยชน์กับทุกๆคนนะครับขอบคุณครับ
@ 52adc2ef:9f4bc0ba
2025-02-23 03:45:10สวัสดีครับ วันนี้อยากมาเล่าเรื่องเกี่ยวกับ Options เราได้ไปเรียนกับทาง อ.เอ็ม ติดเล่า เรื่องลงทุน อยากจะเเชร์สำหรับคนที่สนใจ Options เเต่เพื่อนๆที่ลงทุนมาบ้างน่าจะเคยได้ยิน เเต่ก่อนอื่นการเทรดลงทุนอยากให้เข้าใจ 3 คำนี้ก่อนนะครับ **Spot , Futures , options** **Spot** คือ การซื้อขาย สินทรัพย์ ณ เวลาปัจจุบัน ตามราคาปัจจุบัน เช่น BTC มีราคา 95,000$ ในเวปเทรด เรากดซื้อ จะได้ตามราคา Futures คือ สัญญาซื้อ ขาย สินทรัพย์ล่วงหน้า จะซื้อขายในราคาที่กำหนด เมื่อถึงเวลากำหนด จะต้องทำการซื้อขายตามนั้น คล้ายๆสัญญาซื้อที่ดิน ที่เราต้องใช้สิทธิ์กันทั้งผู้ซื้อและผู้ขาย เช่น สัญญาจะซื้อ BTC ราคา 90,000$ โดยมีอายุสัญญา 3 เดือน ถ้าวันครบสัญญา BTC ราคา 95,000$ จะต้องขายให้ในราคา 90,000$ หรือ สัญญาขาย BTC ราคา 100,000$ โดยมีอายุสัญญา 3 เดือน ถ้าวันครบสัญญา BTC ราคา 95,000$ จะต้องขายให้ในราคา 100,000$ **Options** คือ สัญญาที่ผู้จะซื้อขาย เเบบ futures แต่มีจ่ายค่า Premium เพื่อมีสิทธิ์ที่จะใช้สิทธิ์ซื้อหรือสิทธิ์ขายก็ได้ โดยใช้สิทธิ์ในระยะเวลาที่กำหนด เช่น สัญญา long call สัญญาใช้สิทธิ์ซื้อ เมื่อ BTC ราคา 98,000$ โดยต้องจ่ายค่า premium 100$ เพื่อLock สิทธิ์ ถ้าราคา BTC = 95,000$ เราไม่จำเป็นต้องใช้สิทธิ์ได้ เพราะซื้อในตลาดถูกกว่า เเต่เราจะต้องเสีย premium ที่เราวางไว้ เป็นต้น พอจะเห็นภาพใช่มั้ยครับ ซึ่งจะมาพูดในส่วนของ options กัน Options มีการใช้สิทธิ์อยู่ 2 แบบ Call Options โดยมี Long call คือ สิทธิ์ในการซื้อ Long put คือ สิทธิ์ในการขาย Put Optionsโดยมี Short call คือ ผู้ที่มีหน้าที่ต้องขายจะคู่กับ Long call Short put คือ ผู้ที่มีหน้าที่ต้องซื้อจะคู่กับ Long put โดยมีคำศัพท์ควรรู้อีกเล็กน้อย จะได้เข้าใจภาพรวมทั้งหมดกัน Strike price = ราคาที่จะซื้อจะขาย maturity=วันสิ้นสัญญา premium=เบี้ย time to maturity=ระยะเวลาสัญญา อาจจะยังงงๆ งั้นเริ่มอธิบายทีละข้อกันมาเริ่มที่ **Long Call Option**  สิทธิ์ในการซื้อ จากรูปจะเห็นว่าถ้าเราคิดว่าราคา สินทรัพย์ที่เราสนใจมีเเนวโน้มที่จะขึ้น ซึ่งขณะนี้ ราคาอยู่ที่ 90$ เราอาจจะซื้อ Long call ที่ราคาเริ่มใช้สิทธิ์ Strike Price=100$ โดยมีค่า Premium ที่ 5$ จะเห็นว่าถ้าราคาเป็น 80$ เราคงไม่ใช้สิทธิ์ เพราะซื้อปกติถูกกว่า ราคาใช้สิทธิ์เราจะต้องซื้อที่ 100$ เมื่อไม่ใช้สิทธิ์ เราต้องเสียค่า Premium ให้กับฝั่งที่มีหน้าที่ขาย คือ Short call ซึ่งเมื่อเทียบกับการ Long Futures ถ้าเกิดลงไปเหลือ 45$ เราจะเสีย 50% เเต่ถ้ามี option จะเสียสุดที่เเค่ค่า Premium  รูปกราฟของ Long Futures ซึ่ง Long call = Long future ครึ่งเดียวเพราะ Long Future ราคาจะขึ้นไปเรื่อยๆตามกราฟ Long Call Option เหมาะใช้เมื่อไหร่? ให้คิดว่าเหมือนซื้อหวย เพราะถ้าราคาไม่ไปตามที่คิดเราจะเสียเเค่ค่า Premium หวยเหมือนเราเสียค่า Premium ไปก่อน 80 บาท หรือวิเคราะห์มาเเล้วว่ามีโอกาสที่ราคาขึ้น **Short Call Option**  เป็นฝั่งตรงข้ามกับ Long call เราต้องมีหน้าที่ขายให้ฝั่ง long call ซึ่งฝั่งขายต้องมีสินทรัพย์นั้นๆเพื่อไว้ขาย เพราะมีหน้าที่ ต้องขาย ไม่เหมือนฝั่ง long call ที่มีสามารถเลือกใช้สิทธิ์ได้ เมื่อราคาไม่ถึง Strike Price หลังจากหมดอายุสัญญา ฝั่ง short call ได้ค่า Premium จากฝั่ง Long call จากรูป ถ้าสินทรัพย์ ราคา 90$ ราคาที่ต้องขายสินทรัพย์ 100$ ถ้าราคาไม่ถึง 100$ จะได้ค่า Premium เเต่ถ้าราคาเกิน 100$ เป็นต้นไป จะขาดทุนมากขึ้นเรื่อยๆ ถ้าราคาไปที่ 150$ ต้องมาขายที่ 100$ ตามสัญญา Short Call Option เหมาะใช้เมื่อไหร่? เหมาะสำหรับที่เรามีสินทรัพย์ที่อยากจะขายอยู่เเล้วตาม Target ที่เราตั้งไว้ เช่น มีหุ้นที่ถือไว้อยู่เเล้ว ราคา 50$ ตั้งใจจะทำกำไรเมื่อราคา 100$ แทนที่จะรอขายเฉยๆ มาทำการ Short call ถ้าราคาไม่ถึงก็ได้กินค่า Premium ไป เเต่ถ้าราคาถึง 100$ เราต้องการที่จะ Take Profit อยู่เเล้ว ก็ขายไป Long Put Option  หมายถึงเราสิทธ์ในการขายรือไม่ขายก็ได้ จะตรงข้ามกับ Long call จากรูปถ้าถือสินทรัพย์จากทุน 50$ เเต่ตอนนี้ราคา 80$ เเล้วไม่เเน่ใจว่าราคาจะลงมั้ย เเต่ขึ้นต่อก็ไม่เปนไร อยากจะ Lock ราคาขาย 70$ ใช้สัญญา Long Put จ่ายค่า Premium ถ้าราคาลงไปที่ 50$ เราใช้สิทธิ์ในการขายที่ ราคา 70$ ได้ ถ้าราคาขึ้นเราก็จะไม่ใช้สิทธิ์เพราะขายในตลาดได้ราคาดีกว่า  รูปกราฟของ Short Futures ซึ่ง Long put = Short future ครึ่งเดียวเพราะ Short Future ราคาจะลงไปเรื่อยๆตามกราฟ Long Put Option เหมาะใช้เมื่อไหร่? ให้คิดว่าเหมือนซื้อประกัน ที่เราจ่ายเบี้ยประกันไปเพื่อที่จะ Lock ความเสี่ยงที่จะเกิด ส่วน Long Put ก็ไม่รู้ว่าราคาที่ถือจะลงมั้ย ยอมที่จ่ายค่า Premium เพื่อที่จะได้ราคาตามมูลค่าเดิมของเรา **Short Put Option* * เป็นฝั่งตรงข้ามกับ Long put เราต้องมีหน้าที่รับซื้อให้ฝั่ง long put ซึ่งฝั่งซื้อต้องมีเงินเพื่อไว้ซื้อ เพราะมีหน้าที่ต้องซื้อ ไม่เหมือนฝั่ง long put ที่มีสามารถเลือกใช้สิทธิ์ได้ เมื่อราคาไม่ถึง Strike Price หลังจากหมดอายุสัญญา ฝั่ง short put ได้ค่า Premium จากฝั่ง Long put จากรูป ราคาสินทรัพย์อยู่ที่ 80$ ราคาที่เรารับซื้อ หรือ Strike Price 70$ ถ้าราคาลงไม่ถึง 70 $ ก็จะได้ค่า Premium ถ้าราคาลงไปต่ำกว่า 70$ ก็ต้องรับซื้อทุกกรณี ราคาลงไปที่ 50$ เราก็ต้องรับซื้อที่ 70$ ตามสัญญา Short Put Option เหมาะใช้เมื่อไหร่? ใช้เมื่อเราอยากจะซื้อสินทรัพย์ราคานั้นๆอยู่เเล้ว เช่น อยากจะซื้อที่ราคา 70 $ แทนที่จะรอเฉยๆ อาจจะเปิด Short Put เพื่อที่ราคายังไม่ถึง target ก็จะได้ค่า Premium ถ้าราคาถึงก็ได้ซื้อเหมือนที่ตั้งใจไว้ สรุป จากที่เล่าทั้งหมดเป็นการอธิบาย Options เบื้องต้นที่อยากให้เพื่อนๆ ที่สนใจการเทรดอยู่เเล้ว ถ้าเข้าใจเรื่อง Options ด้วยเราคิดว่าน่าจะปรับใช้ในส่วนช่วยใน Port ของเราไม่มากก็น้อย หวังว่าจะเป็นประโยชน์กับทุกๆคนนะครับขอบคุณครับ @ 5d4b6c8d:8a1c1ee3
2025-02-23 01:06:46Well, my Wemby pick from last month just went up in flames. It's only getting more difficult to figure out who's getting that last spot, now. I want to take KAT, but that would give me the same exact picks as @gnilma with fewer possible points. I'll take his teammate, Jalen Brunson, and hope NY voters pick the wrong Knick. Remember, older correct predictions are worth more than recent ones, so don't wait too long to get off your bad predictions. Also, players must play in at least 65 games to be eligible for awards. Luka, AD, and Wemby are not going to be eligible, so you should swap them out if you still have them. Here's the current state of the competition with your max possible score next to your nym: | Contestant | MVP | Champ | All NBA | | | | | |--------------|------|---------|----------|-|-|-|-| | @Undisciplined 47| SGA| OKC | Jokic | Giannis |Tatum | SGA | Brunson | | @grayruby 55| Giannis| Cavs| Jokic | Giannis | Luka | Mitchell| Brunson| | @gnilma 55| SGA| OKC| Jokic | KAT | Giannis | Tatum| SGA | | @BitcoinAbhi 70 | Luka| Denver| Jokic | Giannis | Luka | Ant| SGA| | @Bell_curve 63| SGA| Celtics| Jokic | Giannis | Luka | Ant| SGA| | @0xbitcoiner 70 | Jokic| Pacers| Jokic | Giannis | Luka | Ant| Brunson| | @Coinsreporter 49| Giannis| Pacers| Jokic | Giannis | Luka | Ant| Brunson| | @TheMorningStar 49| Luka| Celtics| Jokic | Giannis | Luka | Ant| SGA| | @onthedeklein 49| Luka| T-Wolves| Jokic | Giannis | Luka | Wemby| SGA| | @Carresan 49| Luka| Mavs| Jokic | Giannis | Luka | Wemby| SGA| | @BTC_Bellzer 34| SGA| Celtics| Jokic| Giannis | Tatum| SGA| Brunson | | @realBitcoinDog 49| Luka| Lakers| Jokic | Giannis | Luka | Ant| SGA| | @SimpleStacker 42| SGA| Celtics| Jokic| Tatum| Luka | Brunson| SGA| | @BlokchainB 42| SGA| Knicks| AD| Giannis | Ant| Brunson| SGA| **Prize** At least 6k (I'll keep adding zaps to the pot). If you want to join this contest, just leave your predictions for MVP, Champion, and All-NBA 1st team in the comments. See the [June post](https://stacker.news/items/585231/r/Undisciplined) for more details. originally posted at https://stacker.news/items/894412
@ 5d4b6c8d:8a1c1ee3
2025-02-23 01:06:46Well, my Wemby pick from last month just went up in flames. It's only getting more difficult to figure out who's getting that last spot, now. I want to take KAT, but that would give me the same exact picks as @gnilma with fewer possible points. I'll take his teammate, Jalen Brunson, and hope NY voters pick the wrong Knick. Remember, older correct predictions are worth more than recent ones, so don't wait too long to get off your bad predictions. Also, players must play in at least 65 games to be eligible for awards. Luka, AD, and Wemby are not going to be eligible, so you should swap them out if you still have them. Here's the current state of the competition with your max possible score next to your nym: | Contestant | MVP | Champ | All NBA | | | | | |--------------|------|---------|----------|-|-|-|-| | @Undisciplined 47| SGA| OKC | Jokic | Giannis |Tatum | SGA | Brunson | | @grayruby 55| Giannis| Cavs| Jokic | Giannis | Luka | Mitchell| Brunson| | @gnilma 55| SGA| OKC| Jokic | KAT | Giannis | Tatum| SGA | | @BitcoinAbhi 70 | Luka| Denver| Jokic | Giannis | Luka | Ant| SGA| | @Bell_curve 63| SGA| Celtics| Jokic | Giannis | Luka | Ant| SGA| | @0xbitcoiner 70 | Jokic| Pacers| Jokic | Giannis | Luka | Ant| Brunson| | @Coinsreporter 49| Giannis| Pacers| Jokic | Giannis | Luka | Ant| Brunson| | @TheMorningStar 49| Luka| Celtics| Jokic | Giannis | Luka | Ant| SGA| | @onthedeklein 49| Luka| T-Wolves| Jokic | Giannis | Luka | Wemby| SGA| | @Carresan 49| Luka| Mavs| Jokic | Giannis | Luka | Wemby| SGA| | @BTC_Bellzer 34| SGA| Celtics| Jokic| Giannis | Tatum| SGA| Brunson | | @realBitcoinDog 49| Luka| Lakers| Jokic | Giannis | Luka | Ant| SGA| | @SimpleStacker 42| SGA| Celtics| Jokic| Tatum| Luka | Brunson| SGA| | @BlokchainB 42| SGA| Knicks| AD| Giannis | Ant| Brunson| SGA| **Prize** At least 6k (I'll keep adding zaps to the pot). If you want to join this contest, just leave your predictions for MVP, Champion, and All-NBA 1st team in the comments. See the [June post](https://stacker.news/items/585231/r/Undisciplined) for more details. originally posted at https://stacker.news/items/894412 @ 641d8c39:1224c8d3
2025-02-23 00:17:46A specter is haunting the modern world, the specter of crypto anarchy. Computer technology is on the verge of providing the ability for individuals and groups to communicate and interact with each other in a totally anonymous manner. Two persons may exchange messages, conduct business, and negotiate electronic contracts without ever knowing the True Name, or legal identity, of the other. Interactions over networks will be untraceable, via extensive re-routing of encrypted packets and tamper-proof boxes which implement cryptographic protocols with nearly perfect assurance against any tampering. Reputations will be of central importance, far more important in dealings than even the credit ratings of today. These developments will alter completely the nature of government regulation, the ability to tax and control economic interactions, the ability to keep information secret, and will even alter the nature of trust and reputation. The technology for this revolution--and it surely will be both a social and economic revolution--has existed in theory for the past decade. The methods are based upon public-key encryption, zero-knowledge interactive proof systems, and various software protocols for interaction, authentication, and verification. The focus has until now been on academic conferences in Europe and the U.S., conferences monitored closely by the National Security Agency. But only recently have computer networks and personal computers attained sufficient speed to make the ideas practically realizable. And the next ten years will bring enough additional speed to make the ideas economically feasible and essentially unstoppable. High-speed networks, ISDN, tamper-proof boxes, smart cards, satellites, Ku-band transmitters, multi-MIPS personal computers, and encryption chips now under development will be some of the enabling technologies. The State will of course try to slow or halt the spread of this technology, citing national security concerns, use of the technology by drug dealers and tax evaders, and fears of societal disintegration. Many of these concerns will be valid; crypto anarchy will allow national secrets to be trade freely and will allow illicit and stolen materials to be traded. An anonymous computerized market will even make possible abhorrent markets for assassinations and extortion. Various criminal and foreign elements will be active users of CryptoNet. But this will not halt the spread of crypto anarchy. Just as the technology of printing altered and reduced the power of medieval guilds and the social power structure, so too will cryptologic methods fundamentally alter the nature of corporations and of government interference in economic transactions. Combined with emerging information markets, crypto anarchy will create a liquid market for any and all material which can be put into words and pictures. And just as a seemingly minor invention like barbed wire made possible the fencing-off of vast ranches and farms, thus altering forever the concepts of land and property rights in the frontier West, so too will the seemingly minor discovery out of an arcane branch of mathematics come to be the wire clippers which dismantle the barbed wire around intellectual property. Arise, you have nothing to lose but your barbed wire fences!A specter is haunting the modern world, the specter of crypto anarchy. Computer technology is on the verge of providing the ability for individuals and groups to communicate and interact with each other in a totally anonymous manner. Two persons may exchange messages, conduct business, and negotiate electronic contracts without ever knowing the True Name, or legal identity, of the other. Interactions over networks will be untraceable, via extensive re-routing of encrypted packets and tamper-proof boxes which implement cryptographic protocols with nearly perfect assurance against any tampering. Reputations will be of central importance, far more important in dealings than even the credit ratings of today. These developments will alter completely the nature of government regulation, the ability to tax and control economic interactions, the ability to keep information secret, and will even alter the nature of trust and reputation. The technology for this revolution--and it surely will be both a social and economic revolution--has existed in theory for the past decade. The methods are based upon public-key encryption, zero-knowledge interactive proof systems, and various software protocols for interaction, authentication, and verification. The focus has until now been on academic conferences in Europe and the U.S., conferences monitored closely by the National Security Agency. But only recently have computer networks and personal computers attained sufficient speed to make the ideas practically realizable. And the next ten years will bring enough additional speed to make the ideas economically feasible and essentially unstoppable. High-speed networks, ISDN, tamper-proof boxes, smart cards, satellites, Ku-band transmitters, multi-MIPS personal computers, and encryption chips now under development will be some of the enabling technologies. The State will of course try to slow or halt the spread of this technology, citing national security concerns, use of the technology by drug dealers and tax evaders, and fears of societal disintegration. Many of these concerns will be valid; crypto anarchy will allow national secrets to be trade freely and will allow illicit and stolen materials to be traded. An anonymous computerized market will even make possible abhorrent markets for assassinations and extortion. Various criminal and foreign elements will be active users of CryptoNet. But this will not halt the spread of crypto anarchy. Just as the technology of printing altered and reduced the power of medieval guilds and the social power structure, so too will cryptologic methods fundamentally alter the nature of corporations and of government interference in economic transactions. Combined with emerging information markets, crypto anarchy will create a liquid market for any and all material which can be put into words and pictures. And just as a seemingly minor invention like barbed wire made possible the fencing-off of vast ranches and farms, thus altering forever the concepts of land and property rights in the frontier West, so too will the seemingly minor discovery out of an arcane branch of mathematics come to be the wire clippers which dismantle the barbed wire around intellectual property. Arise, you have nothing to lose but your barbed wire fences! https://groups.csail.mit.edu/mac/classes/6.805/articles/crypto/cypherpunks/may-crypto-manifesto.html
@ 641d8c39:1224c8d3
2025-02-23 00:17:46A specter is haunting the modern world, the specter of crypto anarchy. Computer technology is on the verge of providing the ability for individuals and groups to communicate and interact with each other in a totally anonymous manner. Two persons may exchange messages, conduct business, and negotiate electronic contracts without ever knowing the True Name, or legal identity, of the other. Interactions over networks will be untraceable, via extensive re-routing of encrypted packets and tamper-proof boxes which implement cryptographic protocols with nearly perfect assurance against any tampering. Reputations will be of central importance, far more important in dealings than even the credit ratings of today. These developments will alter completely the nature of government regulation, the ability to tax and control economic interactions, the ability to keep information secret, and will even alter the nature of trust and reputation. The technology for this revolution--and it surely will be both a social and economic revolution--has existed in theory for the past decade. The methods are based upon public-key encryption, zero-knowledge interactive proof systems, and various software protocols for interaction, authentication, and verification. The focus has until now been on academic conferences in Europe and the U.S., conferences monitored closely by the National Security Agency. But only recently have computer networks and personal computers attained sufficient speed to make the ideas practically realizable. And the next ten years will bring enough additional speed to make the ideas economically feasible and essentially unstoppable. High-speed networks, ISDN, tamper-proof boxes, smart cards, satellites, Ku-band transmitters, multi-MIPS personal computers, and encryption chips now under development will be some of the enabling technologies. The State will of course try to slow or halt the spread of this technology, citing national security concerns, use of the technology by drug dealers and tax evaders, and fears of societal disintegration. Many of these concerns will be valid; crypto anarchy will allow national secrets to be trade freely and will allow illicit and stolen materials to be traded. An anonymous computerized market will even make possible abhorrent markets for assassinations and extortion. Various criminal and foreign elements will be active users of CryptoNet. But this will not halt the spread of crypto anarchy. Just as the technology of printing altered and reduced the power of medieval guilds and the social power structure, so too will cryptologic methods fundamentally alter the nature of corporations and of government interference in economic transactions. Combined with emerging information markets, crypto anarchy will create a liquid market for any and all material which can be put into words and pictures. And just as a seemingly minor invention like barbed wire made possible the fencing-off of vast ranches and farms, thus altering forever the concepts of land and property rights in the frontier West, so too will the seemingly minor discovery out of an arcane branch of mathematics come to be the wire clippers which dismantle the barbed wire around intellectual property. Arise, you have nothing to lose but your barbed wire fences!A specter is haunting the modern world, the specter of crypto anarchy. Computer technology is on the verge of providing the ability for individuals and groups to communicate and interact with each other in a totally anonymous manner. Two persons may exchange messages, conduct business, and negotiate electronic contracts without ever knowing the True Name, or legal identity, of the other. Interactions over networks will be untraceable, via extensive re-routing of encrypted packets and tamper-proof boxes which implement cryptographic protocols with nearly perfect assurance against any tampering. Reputations will be of central importance, far more important in dealings than even the credit ratings of today. These developments will alter completely the nature of government regulation, the ability to tax and control economic interactions, the ability to keep information secret, and will even alter the nature of trust and reputation. The technology for this revolution--and it surely will be both a social and economic revolution--has existed in theory for the past decade. The methods are based upon public-key encryption, zero-knowledge interactive proof systems, and various software protocols for interaction, authentication, and verification. The focus has until now been on academic conferences in Europe and the U.S., conferences monitored closely by the National Security Agency. But only recently have computer networks and personal computers attained sufficient speed to make the ideas practically realizable. And the next ten years will bring enough additional speed to make the ideas economically feasible and essentially unstoppable. High-speed networks, ISDN, tamper-proof boxes, smart cards, satellites, Ku-band transmitters, multi-MIPS personal computers, and encryption chips now under development will be some of the enabling technologies. The State will of course try to slow or halt the spread of this technology, citing national security concerns, use of the technology by drug dealers and tax evaders, and fears of societal disintegration. Many of these concerns will be valid; crypto anarchy will allow national secrets to be trade freely and will allow illicit and stolen materials to be traded. An anonymous computerized market will even make possible abhorrent markets for assassinations and extortion. Various criminal and foreign elements will be active users of CryptoNet. But this will not halt the spread of crypto anarchy. Just as the technology of printing altered and reduced the power of medieval guilds and the social power structure, so too will cryptologic methods fundamentally alter the nature of corporations and of government interference in economic transactions. Combined with emerging information markets, crypto anarchy will create a liquid market for any and all material which can be put into words and pictures. And just as a seemingly minor invention like barbed wire made possible the fencing-off of vast ranches and farms, thus altering forever the concepts of land and property rights in the frontier West, so too will the seemingly minor discovery out of an arcane branch of mathematics come to be the wire clippers which dismantle the barbed wire around intellectual property. Arise, you have nothing to lose but your barbed wire fences! https://groups.csail.mit.edu/mac/classes/6.805/articles/crypto/cypherpunks/may-crypto-manifesto.html @ fc481c65:e280e7ba
2025-02-22 22:22:14**Math is the formalization of a human idea** Mathematics is a broad field of study that involves the investigation of patterns, quantities, structures, and changes in the abstract form as well as their real-world applications. It is foundational to a variety of disciplines including science, engineering, medicine, and the social sciences, providing a framework for reasoning, problem-solving, and understanding the universe. <iframe title="The Map of Mathematics" src="https://www.youtube.com/embed/OmJ-4B-mS-Y?feature=oembed" height="113" width="200" allowfullscreen="" allow="fullscreen" style="aspect-ratio: 1.76991 / 1; width: 100%; height: 100%;"></iframe> Mathematics is composed of many subfields, including but not limited to: 1. **Arithmetic:** The study of numbers and the basic operations on them: addition, subtraction, multiplication, and division. 2. **Algebra:** The study of symbols and the rules for manipulating these symbols; it is a unifying thread of almost all of mathematics. 3. **Geometry:** The study of shapes, sizes, and properties of space. 4. **Calculus:** The study of change in mathematical functions and models, dealing with limits, derivatives, integrals, and infinite series. 5. **Statistics:** The study of data collection, analysis, interpretation, presentation, and organization. 6. **Number Theory:** The study of properties and relationships of numbers, especially the integers. 7. **Topology:** The study of properties that remain constant through continuous deformations, such as stretching and bending, but not tearing or gluing. 8. **Applied Mathematics:** Uses mathematical methods and reasoning to solve real-world problems in business, science, engineering, and other fields. Mathematics is both ancient and modern; it has a rich history stretching back thousands of years, yet it continues to develop and evolve today, with new theories, discoveries, and applications constantly emerging. It is both a rigorous discipline in its own right and an essential tool used throughout the sciences and beyond. ## Pure and Applied Mathematics Pure mathematics and applied mathematics represent two broad categories within the field of mathematics, each with its focus, methodologies, and applications. The distinction between them lies in their primary objectives and the way mathematical theories are utilized. [[Attachments/01233372a59d2dc17b937c38319d672f_MD5.jpeg|Open: Pasted image 20240405125055.png]] ![[Attachments/01233372a59d2dc17b937c38319d672f_MD5.jpeg]] #### Pure Mathematics Pure mathematics is concerned with the study of mathematical concepts independent of any application outside mathematics. It is motivated by a desire to understand abstract principles and the properties of mathematical structures. The pursuit in pure mathematics is knowledge for its own sake, not necessarily aiming to find immediate practical applications. Pure mathematicians often focus on proving theorems and exploring theoretical frameworks, driven by curiosity and the aesthetic appeal of mathematics itself. Key areas within pure mathematics include: - **Algebra:** The study of symbols and the rules for manipulating these symbols. - **Geometry:** The investigation of the properties of space and figures. - **Analysis:** The rigorous formulation of calculus, focusing on limits, continuity, and infinite series. - **Number Theory:** The study of the properties of numbers, particularly integers. - **Topology:** The study of properties preserved through deformations, twistings, and stretchings of objects. #### Applied Mathematics Applied mathematics, on the other hand, is focused on the development and practical use of mathematical methods to solve problems in other areas, such as science, engineering, technology, economics, business, and industry. Applied mathematics is deeply connected with empirical research and the application of mathematical models to real-world situations. It involves the formulation, study, and use of mathematical models and seeks to make predictions, optimize solutions, and develop new approaches based on mathematical theory. Key areas within applied mathematics include: - **Differential Equations:** Used to model rates of change in applied contexts. - **Statistics and Probability:** The study of data, uncertainty, and the quantification of the likelihood of events. - **Computational Mathematics:** The use of algorithmic techniques for solving mathematical problems more efficiently, especially those that are too large for human numerical capacity. - **Mathematical Physics:** The application of mathematics to solve problems in physics and the development of mathematical methods for such applications. ## Is Mathematics discovered or Invented The question of whether mathematics is discovered or invented is a philosophical one that has sparked debate among mathematicians, philosophers, and scientists for centuries. Both viewpoints offer compelling arguments, and the distinction often hinges on one's perspective on the nature of mathematical objects and the universality of mathematical truths. <iframe title="Is math discovered or invented? - Jeff Dekofsky" src="https://www.youtube.com/embed/X_xR5Kes4Rs?feature=oembed" height="113" width="200" allowfullscreen="" allow="fullscreen" style="aspect-ratio: 1.76991 / 1; width: 100%; height: 100%;"></iframe> ### Mathematics as Discovered Those who argue that mathematics is discovered believe that mathematical truths exist independently of human thought and that mathematicians uncover these truths through investigation and reasoning. This viewpoint suggests that mathematical concepts like numbers, geometrical shapes, and even more abstract ideas have a reality that transcends human invention. The consistency of mathematical laws across cultures and times, and their applicability in accurately describing the natural world, supports the notion that mathematics is a universal truth waiting to be discovered. According to this perspective, mathematical structures exist in some abstract realm, and humans merely uncover aspects of this pre-existing world. #### Mathematics as Invented On the other hand, the viewpoint that mathematics is invented centers on the idea that mathematical concepts are human creations, designed to describe and understand the world. According to this perspective, mathematical theories and structures are the products of human thought, created to serve specific purposes in science, engineering, and other fields. This view emphasizes the role of creativity and invention in the development of mathematical ideas, suggesting that different cultures or species might develop entirely different mathematical systems depending on their needs and experiences. Proponents of this view point to the variety of mathematical systems (such as different geometries or number systems) that have been invented to solve particular types of problems, arguing that this diversity is evidence of mathematics being a human invention. #### A Middle Ground Some argue for a middle ground, suggesting that while the basic elements of mathematics are discovered, the development of complex mathematical theories and the choice of which aspects to study or develop further involve human invention and creativity. This perspective acknowledges the intrinsic properties of mathematical objects while also recognizing the role of human ingenuity in shaping the field of mathematics. #### Conclusion The debate between discovery and invention in mathematics may never be conclusively resolved, as it touches on deep philosophical questions about the nature of reality and the human mind's relationship to it. Whether one views mathematics as discovered or invented often reflects deeper beliefs about the world and our place within it. ## Axioms a particular mathematical system or theory. They serve as the foundational building blocks from which theorems and other mathematical truths are derived. Axioms are assumed to be self-evident, and their selection is based on their ability to produce a coherent and logically consistent framework for a body of mathematical knowledge. In the context of different branches of mathematics, axioms can vary significantly: - **In Euclidean geometry,** one of the most famous sets of axioms are Euclid's postulates, which include statements like "A straight line segment can be drawn joining any two points," and "All right angles are congruent." - **In algebra,** the field axioms define the properties of operations like addition and multiplication over sets of numbers. - **In set theory,** Zermelo-Fraenkel axioms (with the Axiom of Choice) are a set of axioms used to establish a foundation for much of modern mathematics. The role of axioms has evolved throughout the history of mathematics. Initially, they were considered self-evident truths, but as mathematics has developed, the emphasis has shifted to viewing axioms more as arbitrary starting points chosen for their usefulness in building a mathematical theory. This shift allows for the creation of different, sometimes non-intuitive, mathematical frameworks such as non-Euclidean geometries, which arise from altering Euclid's original postulates. **Everything in maths is constructed based on Axioms, not observation of the scientific method!** It's based only on the human logic reasoning. **And the universe doesn't five a fuck to fit inside human logic reasoning.** <iframe title="The paradox at the heart of mathematics: Gödel's Incompleteness Theorem - Marcus du Sautoy" src="https://www.youtube.com/embed/I4pQbo5MQOs?feature=oembed" height="113" width="200" allowfullscreen="" allow="fullscreen" style="aspect-ratio: 1.76991 / 1; width: 100%; height: 100%;"></iframe> ## Mathematics is not a Science Mathematics and science are deeply interconnected, but they are distinguished by their fundamental approaches, methodologies, and objectives. The distinction between mathematics as a formal science and other natural or empirical sciences like physics, biology, and chemistry lies in the nature of their inquiry and validation methods. **Maths doesn't need to prove itself through the scientific method, it only needs axioms, logic, and previous definitions.** - **Mathematics:** Uses deduction as a primary tool. Starting from axioms and definitions, mathematicians use logical reasoning to derive theorems and propositions. The validity of mathematical statements is determined through proofs, which are arguments that demonstrate their truth within the context of axiomatic systems. - **Science:** Employs the scientific method, which involves hypothesis formation, experimentation, observation, and the modification of hypotheses based on empirical evidence. Scientific theories and laws are validated by their ability to predict and explain phenomena in the natural world, and they are always subject to revision in light of new evidence. ### Objectives - **Mathematics:** Aims to create a coherent set of rules and structures that can explain and predict outcomes within abstract systems. Its primary goal is not to describe the physical world but to explore the properties and possibilities of mathematical structures. - **Science:** Aims to understand and describe the universe. The goal is to produce a body of knowledge that explains natural phenomena and can predict outcomes based on empirical evidence. In summary, while mathematics is often used as a tool in science to model and solve problems, its focus on abstract reasoning and logical proof distinguishes it from the empirical methodologies of the natural sciences. This fundamental difference in approach and objective is why mathematics is considered a formal science or a branch of knowledge distinct from natural or physical sciences, which are based on empirical evidence and experimental validation.
@ fc481c65:e280e7ba
2025-02-22 22:22:14**Math is the formalization of a human idea** Mathematics is a broad field of study that involves the investigation of patterns, quantities, structures, and changes in the abstract form as well as their real-world applications. It is foundational to a variety of disciplines including science, engineering, medicine, and the social sciences, providing a framework for reasoning, problem-solving, and understanding the universe. <iframe title="The Map of Mathematics" src="https://www.youtube.com/embed/OmJ-4B-mS-Y?feature=oembed" height="113" width="200" allowfullscreen="" allow="fullscreen" style="aspect-ratio: 1.76991 / 1; width: 100%; height: 100%;"></iframe> Mathematics is composed of many subfields, including but not limited to: 1. **Arithmetic:** The study of numbers and the basic operations on them: addition, subtraction, multiplication, and division. 2. **Algebra:** The study of symbols and the rules for manipulating these symbols; it is a unifying thread of almost all of mathematics. 3. **Geometry:** The study of shapes, sizes, and properties of space. 4. **Calculus:** The study of change in mathematical functions and models, dealing with limits, derivatives, integrals, and infinite series. 5. **Statistics:** The study of data collection, analysis, interpretation, presentation, and organization. 6. **Number Theory:** The study of properties and relationships of numbers, especially the integers. 7. **Topology:** The study of properties that remain constant through continuous deformations, such as stretching and bending, but not tearing or gluing. 8. **Applied Mathematics:** Uses mathematical methods and reasoning to solve real-world problems in business, science, engineering, and other fields. Mathematics is both ancient and modern; it has a rich history stretching back thousands of years, yet it continues to develop and evolve today, with new theories, discoveries, and applications constantly emerging. It is both a rigorous discipline in its own right and an essential tool used throughout the sciences and beyond. ## Pure and Applied Mathematics Pure mathematics and applied mathematics represent two broad categories within the field of mathematics, each with its focus, methodologies, and applications. The distinction between them lies in their primary objectives and the way mathematical theories are utilized. [[Attachments/01233372a59d2dc17b937c38319d672f_MD5.jpeg|Open: Pasted image 20240405125055.png]] ![[Attachments/01233372a59d2dc17b937c38319d672f_MD5.jpeg]] #### Pure Mathematics Pure mathematics is concerned with the study of mathematical concepts independent of any application outside mathematics. It is motivated by a desire to understand abstract principles and the properties of mathematical structures. The pursuit in pure mathematics is knowledge for its own sake, not necessarily aiming to find immediate practical applications. Pure mathematicians often focus on proving theorems and exploring theoretical frameworks, driven by curiosity and the aesthetic appeal of mathematics itself. Key areas within pure mathematics include: - **Algebra:** The study of symbols and the rules for manipulating these symbols. - **Geometry:** The investigation of the properties of space and figures. - **Analysis:** The rigorous formulation of calculus, focusing on limits, continuity, and infinite series. - **Number Theory:** The study of the properties of numbers, particularly integers. - **Topology:** The study of properties preserved through deformations, twistings, and stretchings of objects. #### Applied Mathematics Applied mathematics, on the other hand, is focused on the development and practical use of mathematical methods to solve problems in other areas, such as science, engineering, technology, economics, business, and industry. Applied mathematics is deeply connected with empirical research and the application of mathematical models to real-world situations. It involves the formulation, study, and use of mathematical models and seeks to make predictions, optimize solutions, and develop new approaches based on mathematical theory. Key areas within applied mathematics include: - **Differential Equations:** Used to model rates of change in applied contexts. - **Statistics and Probability:** The study of data, uncertainty, and the quantification of the likelihood of events. - **Computational Mathematics:** The use of algorithmic techniques for solving mathematical problems more efficiently, especially those that are too large for human numerical capacity. - **Mathematical Physics:** The application of mathematics to solve problems in physics and the development of mathematical methods for such applications. ## Is Mathematics discovered or Invented The question of whether mathematics is discovered or invented is a philosophical one that has sparked debate among mathematicians, philosophers, and scientists for centuries. Both viewpoints offer compelling arguments, and the distinction often hinges on one's perspective on the nature of mathematical objects and the universality of mathematical truths. <iframe title="Is math discovered or invented? - Jeff Dekofsky" src="https://www.youtube.com/embed/X_xR5Kes4Rs?feature=oembed" height="113" width="200" allowfullscreen="" allow="fullscreen" style="aspect-ratio: 1.76991 / 1; width: 100%; height: 100%;"></iframe> ### Mathematics as Discovered Those who argue that mathematics is discovered believe that mathematical truths exist independently of human thought and that mathematicians uncover these truths through investigation and reasoning. This viewpoint suggests that mathematical concepts like numbers, geometrical shapes, and even more abstract ideas have a reality that transcends human invention. The consistency of mathematical laws across cultures and times, and their applicability in accurately describing the natural world, supports the notion that mathematics is a universal truth waiting to be discovered. According to this perspective, mathematical structures exist in some abstract realm, and humans merely uncover aspects of this pre-existing world. #### Mathematics as Invented On the other hand, the viewpoint that mathematics is invented centers on the idea that mathematical concepts are human creations, designed to describe and understand the world. According to this perspective, mathematical theories and structures are the products of human thought, created to serve specific purposes in science, engineering, and other fields. This view emphasizes the role of creativity and invention in the development of mathematical ideas, suggesting that different cultures or species might develop entirely different mathematical systems depending on their needs and experiences. Proponents of this view point to the variety of mathematical systems (such as different geometries or number systems) that have been invented to solve particular types of problems, arguing that this diversity is evidence of mathematics being a human invention. #### A Middle Ground Some argue for a middle ground, suggesting that while the basic elements of mathematics are discovered, the development of complex mathematical theories and the choice of which aspects to study or develop further involve human invention and creativity. This perspective acknowledges the intrinsic properties of mathematical objects while also recognizing the role of human ingenuity in shaping the field of mathematics. #### Conclusion The debate between discovery and invention in mathematics may never be conclusively resolved, as it touches on deep philosophical questions about the nature of reality and the human mind's relationship to it. Whether one views mathematics as discovered or invented often reflects deeper beliefs about the world and our place within it. ## Axioms a particular mathematical system or theory. They serve as the foundational building blocks from which theorems and other mathematical truths are derived. Axioms are assumed to be self-evident, and their selection is based on their ability to produce a coherent and logically consistent framework for a body of mathematical knowledge. In the context of different branches of mathematics, axioms can vary significantly: - **In Euclidean geometry,** one of the most famous sets of axioms are Euclid's postulates, which include statements like "A straight line segment can be drawn joining any two points," and "All right angles are congruent." - **In algebra,** the field axioms define the properties of operations like addition and multiplication over sets of numbers. - **In set theory,** Zermelo-Fraenkel axioms (with the Axiom of Choice) are a set of axioms used to establish a foundation for much of modern mathematics. The role of axioms has evolved throughout the history of mathematics. Initially, they were considered self-evident truths, but as mathematics has developed, the emphasis has shifted to viewing axioms more as arbitrary starting points chosen for their usefulness in building a mathematical theory. This shift allows for the creation of different, sometimes non-intuitive, mathematical frameworks such as non-Euclidean geometries, which arise from altering Euclid's original postulates. **Everything in maths is constructed based on Axioms, not observation of the scientific method!** It's based only on the human logic reasoning. **And the universe doesn't five a fuck to fit inside human logic reasoning.** <iframe title="The paradox at the heart of mathematics: Gödel's Incompleteness Theorem - Marcus du Sautoy" src="https://www.youtube.com/embed/I4pQbo5MQOs?feature=oembed" height="113" width="200" allowfullscreen="" allow="fullscreen" style="aspect-ratio: 1.76991 / 1; width: 100%; height: 100%;"></iframe> ## Mathematics is not a Science Mathematics and science are deeply interconnected, but they are distinguished by their fundamental approaches, methodologies, and objectives. The distinction between mathematics as a formal science and other natural or empirical sciences like physics, biology, and chemistry lies in the nature of their inquiry and validation methods. **Maths doesn't need to prove itself through the scientific method, it only needs axioms, logic, and previous definitions.** - **Mathematics:** Uses deduction as a primary tool. Starting from axioms and definitions, mathematicians use logical reasoning to derive theorems and propositions. The validity of mathematical statements is determined through proofs, which are arguments that demonstrate their truth within the context of axiomatic systems. - **Science:** Employs the scientific method, which involves hypothesis formation, experimentation, observation, and the modification of hypotheses based on empirical evidence. Scientific theories and laws are validated by their ability to predict and explain phenomena in the natural world, and they are always subject to revision in light of new evidence. ### Objectives - **Mathematics:** Aims to create a coherent set of rules and structures that can explain and predict outcomes within abstract systems. Its primary goal is not to describe the physical world but to explore the properties and possibilities of mathematical structures. - **Science:** Aims to understand and describe the universe. The goal is to produce a body of knowledge that explains natural phenomena and can predict outcomes based on empirical evidence. In summary, while mathematics is often used as a tool in science to model and solve problems, its focus on abstract reasoning and logical proof distinguishes it from the empirical methodologies of the natural sciences. This fundamental difference in approach and objective is why mathematics is considered a formal science or a branch of knowledge distinct from natural or physical sciences, which are based on empirical evidence and experimental validation. @ fc481c65:e280e7ba
2025-02-22 22:09:56Starting with the basics, #statistics is a branch of #mathematics that deals with collecting, analysing, interpreting, presenting, and organising #data. It provides a way to make sense of data, see patterns, and make decisions based on data analysis. Here's a brief overview of some fundamental concepts in statistics: ### 1. Types of Statistics - **Descriptive Statistics**: Involves summarising and organising data so it can be easily understood. Common measures include mean (average), median (middle value), mode (most frequent value), variance (measure of how spread out numbers are), and standard deviation (average distance from the mean). - **Inferential Statistics**: Involves making predictions or inferences about a population based on a sample. This includes hypothesis testing, confidence intervals, and regression analysis. ### 2. Types of Data - **Qualitative Data** (Categorical): Data that describes qualities or characteristics that cannot be measured with numbers, such as colors, names, labels, and yes/no responses. - **Quantitative Data**: Data that can be measured and expressed numerically, including age, height, salary, and temperature. It can be further divided into discrete data (countable items, like the number of students in a class) and continuous data (measurable items, like height). ### 3. Measures of Central Tendency - **Mean**: The average of a data set, found by adding all numbers and dividing by the count of numbers. - **Median**: The middle value when a data set is ordered from least to greatest; if there’s an even number of observations, it is the average of the two middle numbers. - **Mode**: The most frequently occurring value in a data set. ### 4. Measures of Spread - **Range**: The difference between the highest and lowest values in a data set. - **Variance**: Measures how far each number in the set is from the mean and thus from every other number in the set. - **Standard Deviation**: The square root of the variance, providing a measure of the spread of a distribution of values. ### 5. Probability Probability measures the likelihood of an event occurring, ranging from 0 (impossible) to 1 (certain). Understanding probability is essential for inferential statistics and making predictions based on data. ### 6. Sampling and Data Collection - **Population**: The entire group that you want to draw conclusions about. - **Sample**: A subset of the population, selected for the actual study. It’s crucial for the sample to be representative of the population to make accurate inferences. ### 7. Hypothesis Testing This is a method of making decisions or inferences about population parameters based on sample statistics. It involves: - Formulating a null hypothesis (no effect) and an alternative hypothesis (some effect). - Calculating a test statistic based on the sample data. - Using the test statistic to decide whether to reject the null hypothesis in favor of the alternative.
@ fc481c65:e280e7ba
2025-02-22 22:09:56Starting with the basics, #statistics is a branch of #mathematics that deals with collecting, analysing, interpreting, presenting, and organising #data. It provides a way to make sense of data, see patterns, and make decisions based on data analysis. Here's a brief overview of some fundamental concepts in statistics: ### 1. Types of Statistics - **Descriptive Statistics**: Involves summarising and organising data so it can be easily understood. Common measures include mean (average), median (middle value), mode (most frequent value), variance (measure of how spread out numbers are), and standard deviation (average distance from the mean). - **Inferential Statistics**: Involves making predictions or inferences about a population based on a sample. This includes hypothesis testing, confidence intervals, and regression analysis. ### 2. Types of Data - **Qualitative Data** (Categorical): Data that describes qualities or characteristics that cannot be measured with numbers, such as colors, names, labels, and yes/no responses. - **Quantitative Data**: Data that can be measured and expressed numerically, including age, height, salary, and temperature. It can be further divided into discrete data (countable items, like the number of students in a class) and continuous data (measurable items, like height). ### 3. Measures of Central Tendency - **Mean**: The average of a data set, found by adding all numbers and dividing by the count of numbers. - **Median**: The middle value when a data set is ordered from least to greatest; if there’s an even number of observations, it is the average of the two middle numbers. - **Mode**: The most frequently occurring value in a data set. ### 4. Measures of Spread - **Range**: The difference between the highest and lowest values in a data set. - **Variance**: Measures how far each number in the set is from the mean and thus from every other number in the set. - **Standard Deviation**: The square root of the variance, providing a measure of the spread of a distribution of values. ### 5. Probability Probability measures the likelihood of an event occurring, ranging from 0 (impossible) to 1 (certain). Understanding probability is essential for inferential statistics and making predictions based on data. ### 6. Sampling and Data Collection - **Population**: The entire group that you want to draw conclusions about. - **Sample**: A subset of the population, selected for the actual study. It’s crucial for the sample to be representative of the population to make accurate inferences. ### 7. Hypothesis Testing This is a method of making decisions or inferences about population parameters based on sample statistics. It involves: - Formulating a null hypothesis (no effect) and an alternative hypothesis (some effect). - Calculating a test statistic based on the sample data. - Using the test statistic to decide whether to reject the null hypothesis in favor of the alternative.