-

@ bc575705:dba3ed39
2025-03-06 09:32:42
We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
!(image)[https://cdn.pixabay.com/photo/2018/07/16/23/36/puppet-3543246_1280.jpg]
## **The Psychological Warfare of Traditional Social Media**
**The Algorithmic Cage:** These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
**The Illusion of Perfection:** The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
**The Echo Chamber Effect:** Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
**The Toxicity Vortex:** The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
**The Attention Deficit Trap:** The constant stream of notifications, updates, and content creates a state of perpetual distraction, making it difficult to focus, think critically, and engage in meaningful interactions.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
!(image)[https://cdn.pixabay.com/photo/2017/08/06/12/21/web-2592005_1280.jpg]
## **NOSTR: A Sanctuary in the Digital Wasteland**
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
**User-Controlled Feeds:** You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
**Ownership of Your Digital Identity:** Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
**Interoperability:** Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
**Value-Driven Interactions:** The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
**Decentralized Power:** No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
!(image)[https://images.pexels.com/photos/2694434/pexels-photo-2694434.jpeg]
## **Building a Healthier Digital Future**
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
**Cultivating Authentic Connections:** Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
**Supporting Independent Creators:** Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
**Embracing Intellectual Diversity:** Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
**Prioritizing Your Mental Health:** Take control of your digital environment and create a space that supports your well-being.
**Removing the noise:** Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
!(image)[https://images.pexels.com/photos/158826/structure-light-led-movement-158826.jpeg]
## **The Time for Action is Now**
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
!(image)[https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fm.primal.net%2FPKgz.jpg]
## **Join the NOSTR movement.**
Embrace the power of decentralization.
Let's build a digital future that's worthy of our humanity.
Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
**Simple Signup:** Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
**X-like Client:** Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
**Sharing Photos and Videos:** Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
**Creating and Consuming Blogs:** NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
**Live Streaming and Audio Spaces:** Explore platforms like Hivetalk and Zap Stream for live streaming and audio-based interactions.
Get the full overview of these and other apps here: https://nostrapps.com/
**NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.**
-

@ a012dc82:6458a70d
2025-03-06 08:28:23
In a groundbreaking move that could significantly alter the investment landscape, Harvest Fund Management, a prominent Chinese asset manager, has boldly stepped forward with an application for a spot Bitcoin exchange-traded fund (ETF) in Hong Kong. This initiative is not just a leap towards diversifying investment options but also a testament to the evolving acceptance and integration of digital assets into the mainstream financial ecosystem.
**Table of Contents**
- Introduction to Spot Bitcoin ETFs
- Harvest Fund's Strategic Move
- The Significance for Hong Kong
- Regulatory Landscape and Stablecoin Interest
- The Road Ahead
- Conclusion
- FAQs
**Introduction to Spot Bitcoin ETFs**
Spot Bitcoin ETFs represent a bridge between the traditional financial world and the burgeoning realm of cryptocurrencies. By mirroring the current market price of Bitcoin, these ETFs offer investors a straightforward path to participate in the cryptocurrency market without the direct ownership of Bitcoin. This eliminates the need for investors to engage with cryptocurrency exchanges or secure digital wallets, thereby lowering the entry barriers to the Bitcoin market. The significance of spot Bitcoin ETFs extends beyond convenience; they are a symbol of the growing legitimization of cryptocurrencies as a viable asset class. By being listed on conventional stock exchanges, these ETFs are subjected to regulatory scrutiny and standards, offering a layer of security and transparency that is sometimes questioned in the crypto space. This development could potentially attract a new wave of institutional and retail investors, who have been on the sidelines due to concerns over regulatory clarity and the technical challenges associated with cryptocurrency investments.
**Harvest Fund's Strategic Move**
Harvest Fund Management's application for a spot Bitcoin ETF is a calculated strategic move, positioning the firm at the forefront of financial innovation in Hong Kong. By aiming to launch the city's first such ETF, Harvest Fund is not merely expanding its product lineup but is also contributing to the legitimization and institutionalization of Bitcoin as an investable asset. This pioneering effort reflects a deep understanding of market dynamics and a vision for the future of investment, where digital and traditional assets coexist within regulated frameworks. The initiative by Harvest Fund could catalyze a shift in investor sentiment, encouraging more conservative players to consider the potential of Bitcoin and other cryptocurrencies. Furthermore, it sets a benchmark for product innovation and regulatory compliance, potentially influencing the pace and direction of cryptocurrency adoption across the financial sector. As the first mover, Harvest Fund could enjoy a competitive advantage, capturing significant market share among investors eager to explore digital assets within a regulated environment.
**The Significance for Hong Kong**
Hong Kong's financial landscape is on the cusp of transformation, with Harvest Fund's application signaling a broader trend towards the acceptance of digital assets. This move comes at a pivotal moment, as Hong Kong seeks to assert itself as a global hub for cryptocurrency and blockchain technology. The interest from approximately 10 fund companies in launching their own spot crypto ETFs underscores the city's potential to lead in the virtual asset space. This collective momentum could significantly enhance Hong Kong's attractiveness as a financial center, drawing in global investors looking for regulated avenues into the cryptocurrency market. The introduction of spot Bitcoin ETFs would not only diversify the city's financial products but also reinforce its reputation as a jurisdiction that balances innovation with investor protection. By providing a structured and regulated framework for cryptocurrency investments, Hong Kong can set a global standard for how financial centers can adapt to the evolving landscape of digital assets. This development is a key step in the broader journey towards integrating cryptocurrencies into the global financial system, with Hong Kong leading the way.
**Regulatory Landscape and Stablecoin Interest**
The enthusiasm for spot Bitcoin ETFs in Hong Kong is paralleled by an equally significant interest in stablecoins, indicating a comprehensive approach to cryptocurrency regulation and adoption. The discussions between the HKMA and various companies about stablecoin trials reflect a proactive stance towards understanding and integrating digital currencies in a way that supports financial stability and innovation. This balanced approach is crucial, as stablecoins represent a bridge between traditional fiat currencies and cryptocurrencies, offering the potential for more efficient payment systems and financial services. The regulatory efforts around stablecoins, coupled with the move towards spot Bitcoin ETFs, show Hong Kong's commitment to creating a robust framework for digital assets. This not only enhances the city's competitive edge as a financial hub but also provides a blueprint for other jurisdictions navigating the complexities of cryptocurrency regulation. By leading in both areas, Hong Kong is positioning itself at the forefront of financial innovation, setting the stage for a future where digital and traditional finance converge seamlessly.
**The Road Ahead**
The initiative by Harvest Fund Management to launch a spot Bitcoin ETF in Hong Kong marks the beginning of a new era in cryptocurrency investment. This move is more than just an expansion of the financial products available to investors; it is a signal of the maturing relationship between the cryptocurrency industry and the broader financial community. As regulatory frameworks continue to evolve and more players enter the market, the landscape for cryptocurrency investment is set to undergo significant changes. Hong Kong's role in this transition cannot be understated. By fostering an environment that encourages innovation while ensuring investor protection, the city is not just adapting to the rise of digital assets but is actively shaping the future of finance. The success of Harvest Fund's application and the subsequent launch of the city's first spot Bitcoin ETF could serve as a catalyst for other financial centers to follow suit, potentially leading to a global shift in how cryptocurrencies are perceived and utilized within the investment world.
**Conclusion**
Harvest Fund Management's bold step towards launching a spot Bitcoin ETF in Hong Kong is a landmark moment in the integration of digital assets into mainstream finance. This initiative not only opens up new avenues for investment but also underscores Hong Kong's ambition to be at the forefront of financial innovation. As the regulatory landscape evolves and the market for digital assets continues to grow, the efforts of Harvest Fund and like-minded institutions will be crucial in bridging the gap between traditional finance and the digital asset world. The path ahead is promising, and Hong Kong's leadership in this space could pave the way for a new chapter in the global financial narrative, where digital and traditional assets coexist in a regulated, dynamic, and inclusive investment ecosystem.
**FAQs**
**Who has filed for the first spot Bitcoin ETF in Hong Kong?**
Harvest Fund Management, a major Chinese asset manager, has filed an application for the first spot Bitcoin ETF in Hong Kong with the Securities and Futures Commission (SFC).
**Why is a spot Bitcoin ETF significant for investors?**
A spot Bitcoin ETF provides a regulated, accessible, and potentially less risky way for investors to gain exposure to Bitcoin's price movements without dealing with the complexities of cryptocurrency exchanges, digital wallets, and private keys.
**How does a spot Bitcoin ETF work?**
A spot Bitcoin ETF buys and holds actual Bitcoin, and the value of the ETF shares fluctuates with the real-time price of Bitcoin. Investors can buy and sell these shares through traditional stock exchanges.
**What are the benefits of investing in a spot Bitcoin ETF?**
Investing in a spot Bitcoin ETF offers the benefits of trading and owning a stock, including regulatory protection, ease of access, and liquidity, while also providing exposure to Bitcoin's price.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnewsco](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co/](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@thebitcoinlibertarian](https://www.youtube.com/@thebitcoinlibertarian)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
**Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats
link: https://signup.theorangepillapp.com/opa/croxroad**
**Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad”
link: https://bitcoinbook.shop?ref=21croxroad**
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
-

@ bc575705:dba3ed39
2025-03-06 07:55:57
One of the most exciting aspects of music production is blending the organic warmth of acoustic instruments with the limitless possibilities of electronic sounds. Combining these two worlds allows me to create rich, layered compositions that feel both timeless and modern. In this post, I’ll share my process for merging acoustic and electronic elements, offering a glimpse into how I approach this dynamic interplay in my music.
## **Start With a Core Idea**
Every track begins with a central idea that sets the tone for the composition. This could be a melody played on an acoustic piano, a chord progression on a guitar, or a rhythmic motif created with electronic drums. Starting with a strong foundation helps anchor the track, making it easier to integrate acoustic and electronic layers cohesively.
Example: I might record a simple acoustic guitar loop and use it as the backbone of the track. Its natural tone provides a grounding element that contrasts beautifully with the synthetic textures I’ll layer in later.
## **Record Acoustic Elements With Character**
When incorporating acoustic instruments, I focus on capturing their raw, authentic sound. Imperfections—like the creak of a guitar string or the ambient noise of the recording space—add character and depth to the track.
**What I Use:** I often record acoustic elements using a condenser microphone to capture detail and warmth. Instruments like piano, guitar, or even simple percussive hits serve as the organic counterpoint to electronic layers.
**How I Use It:** I’ll sometimes process these recordings with effects like reverb or delay to give them a dreamlike quality, or leave them raw for a more intimate feel.
## **Build Electronic Layers**
With the acoustic elements in place, I begin crafting the electronic components. These can range from deep, evolving synth pads to intricate drum patterns and glitchy textures. The goal is to complement the acoustic elements without overpowering them.
**What I Use:** Tools like Serum, Omnisphere, and analog synths like the Korg Minilogue are my go-to for designing electronic sounds. Drum machines or sample packs provide the rhythmic backbone.
**How I Use It:** I’ll often create electronic layers that echo or contrast with the acoustic parts—for instance, pairing a warm piano melody with shimmering, high-frequency synths to create a sense of balance.
## **Focus on Blending and Balance**
The magic of combining acoustic and electronic elements lies in how they interact. To achieve a cohesive sound, I pay close attention to how each layer fits within the mix.
**Techniques I Use:**
**EQ:** I carve out space in the frequency spectrum for each element. For example, cutting low-end frequencies on a synth pad can make room for the natural resonance of an acoustic bass.
**Compression:** Light compression can help glue the acoustic and electronic layers together, ensuring they feel like part of the same sonic space.
**Reverb and Delay:** Applying similar reverb settings to both acoustic and electronic elements can create a sense of unity and atmosphere.
## **Experiment With Textures and Effects**
One of my favorite parts of the process is experimenting with how acoustic and electronic sounds can interact. Sometimes, this involves processing acoustic recordings through electronic effects, or vice versa.
**Examples:**
*Running an acoustic guitar loop through a granular synthesizer to create glitchy, fragmented textures.*
*Sampling a piano note and pitching it down to create a haunting drone.*
*Adding subtle distortion to electronic drums to give them a more organic, analog feel.*
## **Embrace the Contrast**
Part of what makes this combination so compelling is the contrast between the two elements. Acoustic instruments bring warmth, humanity, and imperfection, while electronic sounds add precision, innovation, and texture. Leaning into these differences can create dynamic and emotionally resonant compositions.
**Example:** Pairing a raw, emotive vocal recording with a pulsating, mechanical bassline creates a tension that keeps the listener engaged.
## **Refine and Iterate**
Once all the elements are in place, I spend time refining the mix and arrangement. **This involves:**
*Adjusting levels to ensure no element overpowers the others.*
*Experimenting with transitions to smoothly blend acoustic and electronic sections.*
*Listening to the track as a whole to ensure it tells a cohesive story.*
## **Why This Approach Inspires Me**
Blending acoustic and electronic elements allows me to explore the dualities of sound—the organic and the synthetic, the familiar and the futuristic. It’s a process that pushes me creatively, challenging me to think beyond genre boundaries and embrace the full spectrum of sonic possibilities.
At its core, this approach is about connection—bridging the past and the present, the human and the technological, to create music that feels both timeless and forward-thinking.
-

@ 1c19eb1a:e22fb0bc
2025-03-06 07:52:32
It's been barely two years since I joined Nostr on my main npub, nostr:npub1kun5628raxpm7usdkj62z2337hr77f3ryrg9cf0vjpyf4jvk9r9smv3lhe, and in just that relatively short time, the amount of development on top of this protocol has been staggering. When nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m first opened the floodgates of adoption by tweeting about Nostr, it felt like most of the available clients were barely serviceable and held together with a prayer and copious amounts of duct tape. Of course, it can sometimes still feel that way, but there are definitely some Nostr apps looking and feeling more polished and providing true innovation when compared with legacy social platforms. Indeed, there are a growing number of Nostr-based applications and tools that have very little to do with social media at all.
One thing we have not had available to the growing Nostr community, and those considering joining it, is a source for application reviews that is thorough, approachable, knowledgeable, and balanced. This is what I hope to begin to provide through this new npub dedicated to reviewing as many of the Nostr clients, apps, and tools as I possibly can, so you the reader can determine which ones will fit your needs, and perhaps help you find new ones you had never heard about.
One of the best parts about Nostr is the portability of your identity and social graph, allowing users to log into any Nostr-based application with their same "account" without some centralized tech giant like Google or Apple owning who you are and all of your data. Leverage this super-power of Nostr with me as we explore the best applications and tools the intrepid developers building on this platform have cooked up.
## What will you review?
My choice of applications to review will be based on a few factors.
First, I will only be reviewing applications that have a production release, or are otherwise considered production ready by the developer. nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s, you won't have to worry that I will be putting NoteDeck under the microscope while it is still very much in alpha. All of us who love to try the new clients as soon as they are available understand well enough that there will be plenty of bugs, UI quirks, and rough edges to look past.
Second, I will generally be reviewing applications that are meant to be user-facing for the average person. That is, apps that your normie friends might soon be using, and then asking you why they can't edit anything they post. I will not be doing reviews of various relay implementations, for instance, unless they are designed to be approachable to the average user to install and manage. nostr:npub10npj3gydmv40m70ehemmal6vsdyfl7tewgvz043g54p0x23y0s8qzztl5h, your project might just be a notable exception.
Third, my reviews will be limited by the operating systems I have available to me at the time. Sorry folks over on iOS, Mac, and Windows. I will only be able to review apps I can run on Android, Linux, or my web browser for the time being.
## How will the apps be rated?
I want to be thorough in my reviews, and yet avoid overloading my readers with information they don't care about. In order to attempt to achieve this, I will break my reviews into several sections, so readers can skip to the sections relevant to their interests.
First, I will provide a basic overview of the type of application I am reviewing, what it is trying to achieve, and why a user might want to try it out.
Next, I will give my overall impression of the application. The good, the bad, and the ugly, as it were, so that those who just want a brief rundown can get the TLDR right out the gate and be on their way.
Then we will begin diving into the nitty-gritty with an in depth look at the main features of the application. What it does well. What features seem lacking. What expected features are absent. What features make it unique and set it apart from other applications with a similar purpose.
For the sake of all the baby Nostriches out there, the next section will be an assessment of how approachable the application would likely be to a normie who is coming to Nostr with no idea what a public and private key are, what relays are, or why they might want to start interacting here instead of on a legacy equivalent. What would someone used to Twitter think of #Snort? What would someone used to Spotify think of #Fountain or #Wavlake?
The next section will be a review of the application's UI. The design and polish. How easy it is to find the things you want in the areas you would expect them. In short, how well the application achieves the goal of making the user feel at home and want to continue using the app just through quality UI design.
If you know me and my contstant harping on developers to include various forms of external signing, it should be no surprise to you that the next section will cover login options. What does the sign-in and sign-up flow look like, and does the user have to expose their private key to the application in order to use it?
A review of virtually any Nostr application would be incomplete without a section dedicated to zap integration. How prominent is zapping in the app? How easy is it to zap or start receiving zaps? Are zaps displayed in a way that encourages users to compete to be top zapper? Is Nostr Wallet Connect supported for using external wallets for one-tap-zapping?
Most Nostr applications, even "other stuff" clients, are designed to present some form of content to the user. The next section will cover how easy it is for the user to find the type of content they may be interested in, or to discover content they didn't know they might be interested in. For social clients, how easy is it to discover other users that they might want to follow?
The backbone of the protocol is the interplay between clients and relays, and the next section of the review will cover how the app manages relays. Are they hidden from the user? Are there sensible defaults? Can users who want to do so select the relays they prefer? Does the app respect relays the user has selected in other apps, or are the app's relays independent of those selected in other apps. Worse, does the app overwrite your selected relays with its defaults?
Finally, I will scour the #AskNostr feed for questions and comments from other users about the app under review to get more perspectives than just my own. What are the common pain-points other users are having? What do they love about the app? What features would they like to see added?
Are there other sections you would like to see me add before I start dropping reviews? Get them to me soon, because I am currently taking notes for my first review, which will be the #Primal #Android client!
PV 🤙
-

@ 1c19eb1a:e22fb0bc
2025-03-06 07:48:38
I am happy to present to you the first full review posted to Nostr Reviews: #Primal for #Android!
Primal has its origins as a micro-blogging, social media client, though it is now expanding its horizons into long-form content. It was first released only as a web client in March of 2023, but has since had a native client released for both iOS and Android. All of Primal's clients recently had an update to Primal 2.0, which included both performance improvements and a number of new features. This review will focus on the Android client specifically, both on phone and tablet.
Since Primal has also added features that are only available to those enrolled in their new premium subscription, it should also be noted that this review will be from the perspective of a free user. This is for two reasons. First, I am using an alternate npub to review the app, and if I were to purchase premium at some time in the future, it would be on my main npub. Second, despite a lot of positive things I have to say about Primal, I am not planning to regularly use any of their apps on my main account for the time being, for reasons that will be discussed later in the review.
The application can be installed through the [Google Play Store](https://play.google.com/store/apps/details?id=net.primal.android&hl=en_US), Zapstore, or by downloading it directly from Primal's [GitHub](https://github.com/PrimalHQ/primal-android-app/releases/). This review is current as of Primal Android version 2.0.21.
In the ecosystem of "notes and other stuff," Primal is predominantly in the "notes" category. It is geared toward users who want a social media experience similar to Twitter or Facebook with an infinite scrolling feed of notes to interact with. However, there is some "other stuff" included to complement this primary focus on short and long form notes including a built-in Lightning wallet powered by #Strike, a robust advanced search, and a media-only feed.

## Overall Impression
Score: **3.8** / 5
Primal may well be the most polished UI of any Nostr client native to Android. It is incredibly well designed and thought out, with all of the icons and settings in the places a user would expect to find them. It is also incredibly easy to get started on Nostr via Primal's sign-up flow. The only two things that will be foreign to new users are the lack of any need to set a password or give an email address, and the prompt to optionally set up the wallet.
Complaints prior to the 2.0 update about Primal being slow and clunky should now be completely alleviated. I only experienced quick load times and snappy UI controls with a couple very minor exceptions.
Primal is not, however, a client that I would recommend for the power-user. Control over preferred relays is minimal and does not allow the user to determine which relays they write to and which they only read from. Though you can use your own wallet, it will not appear within the wallet interface, which only works with the custodial wallet from Strike. Moreover, and most eggregiously, the only way for existing users to log in is by pasting their nsec, as Primal does not support either the Android signer or remote signer options for users to protect their private key at this time. This lack of signer support is the primary reason the client received such a low overall score. If even one form of external signer log in is added to Primal, the score will be amended to 4.2 / 5, and if both Android signer and remote signer support is added, it will increase to 4.5.
Another downside to Primal is that it still utilizes an outdated direct message specification that leaks metadata that can be readily seen by anyone on the network. While the content of your messages remains encrypted, anyone can see who you are messaging with, and when.
That said, the beautiful thing about Nostr as a protocol is that users are not locked into any particular client. You may find Primal to be a great client for your average #bloomscrolling and zapping memes, but opt for a different client for more advanced uses and for direct messaging.
## Features
Primal has a lot of features users would expect from any Nostr client that is focused on short-form notes, but it also packs in a lot of features that set it apart from other clients, and that showcase Primal's obvious prioritization of a top-tier user experience.
### Home Feed
By default, the infinitely scrolling Home feed displays notes from those you currently follow in chronological order. This is traditional Nostr at its finest, and made all the more immersive by the choice to have all distracting UI elements quickly hide themselves from view as the you begin to scroll down the feed. They return just as quickly when you begin to scroll back up.

Scrolling the feed is incredibly fast, with no noticeable choppiness and minimal media pop-in if you are on a decent internet connection.
Helpfully, it is easy to get back to the top of the feed whenever there is a new post to be viewed, as a bubble will appear with the profile pictures of the users who have posted since you started scrolling.

### Interacting With Notes
Interacting with a note in the feed can be done via the very recognizable icons at the bottom of each post. You can comment, zap, like, repost, and/or bookmark the note.
Notably, tapping on the zap icon will immediately zap the note your default amount of sats, making zapping incredibly fast, especially when using the built-in wallet. Long pressing on the zap icon will open up a menu with a variety of amounts, along with the ability to zap a custom amount. All of these amounts, and the messages that are sent with the zap, can be customized in the application settings.

Users who are familiar with Twitter or Instagram will feel right at home with only having one option for "liking" a post. However, users from Facebook or other Nostr clients may wonder why they don't have more options for reactions. This is one of those things where users who are new to Nostr probably won't notice they are missing out on anything at all, while users familiar with clients like #Amethyst or #noStrudel will miss the ability to react with a 🤙 or a 🫂.
It's a similar story with the bookmark option. While this is a nice bit of feature parity for Twitter users, for those already used to the ability to have multiple customized lists of bookmarks, or at minimum have the ability to separate them into public and private, it may be a disappointment that they have no access to the bookmarks they already built up on other clients. Primal offers only one list of bookmarks for short-form notes and they are all visible to the public. However, you are at least presented with a warning about the public nature of your bookmarks before saving your first one.
Yet, I can't dock the Primal team much for making these design choices, as they are understandable for Primal's goal of being a welcoming client for those coming over to Nostr from centralized platforms. They have optimized for the onboarding of new users, rather than for those who have been around for a while, and there is absolutely nothing wrong with that.
### Post Creation
Composing posts in Primal is as simple as it gets. Accessed by tapping the obvious circular button with a "+" on it in the lower right of the Home feed, most of what you could need is included in the interface, and nothing you don't.

Your device's default keyboard loads immediately, and the you can start typing away.
There are options for adding images from your gallery, or taking a picture with your camera, both of which will result in the image being uploaded to Primal's media-hosting server. If you prefer to host your media elsewhere, you can simply paste the link to that media into your post.
There is also an @ icon as a tip-off that you can tag other users. Tapping on this simply types "@" into your note and brings up a list of users. All you have to do to narrow down the user you want to tag is continue typing their handle, Nostr address, or paste in their npub.

This can get mixed results in other clients, which sometimes have a hard time finding particular users when typing in their handle, forcing you to have to remember their Nostr address or go hunt down their npub by another means. Not so with Primal, though. I had no issues tagging anyone I wanted by simply typing in their handle.
Of course, when you are tagging someone well known, you may find that there are multiple users posing as that person. Primal helps you out here, though. Usually the top result is the person you want, as Primal places them in order of how many followers they have. This is quite reliable right now, but there is nothing stopping someone from spinning up an army of bots to follow their fake accounts, rendering follower count useless for determining which account is legitimate. It would be nice to see these results ranked by web-of-trust, or at least an indication of how many users you follow who also follow the users listed in the results.
Once you are satisfied with your note, the "Post" button is easy to find in the top right of the screen.
### Feed Selector and Marketplace
Primal's Home feed really shines when you open up the feed selection interface, and find that there are a plethora of options available for customizing your view. By default, it only shows four options, but tapping "Edit" opens up a new page of available toggles to add to the feed selector.

The options don't end there, though. Tapping "Add Feed" will open up the feed marketplace, where an ever-growing number of custom feeds can be found, some created by Primal and some created by others. This feed marketplace is available to a few other clients, but none have so closely integrated it with their Home feeds like Primal has.

Unfortunately, as great as these custom feeds are, this was also the feature where I ran into the most bugs while testing out the app.
One of these bugs was while selecting custom feeds. Occasionally, these feed menu screens would become unresponsive and I would be unable to confirm my selection, or even use the back button on my device to back out of the screen. However, I was able to pull the screen down to close it and re-open the menu, and everything would be responsive again.
This only seemed to occur when I spent 30 seconds or more on the same screen, so I imagine that most users won't encounter it much in their regular use.
Another UI bug occurred for me while in the feed marketplace. I could scroll down the list of available feeds, but attempting to scroll back up the feed would often close the interface entirely instead, as though I had pulled the screen down from the top, when I was swiping in the middle of the screen.
The last of these bugs occurred when selecting a long-form "Reads" feed while in the menu for the Home feed. The menu would allow me to add this feed and select it to be displayed, but it would fail to load the feed once selected, stating "There is no content in this feed." Going to a different page within the the app and then going back to the Home tab would automatically remove the long-form feed from view, and reset back to the most recently viewed short-form "Notes" feed, though the long-form feed would still be available to select again. The results were similar when selecting a short-form feed for the Reads feed.
I would suggest that if long-form and short-form feeds are going to be displayed in the same list, and yet not be able to be displayed in the same feed, the application should present an error message when attempting to add a long-form feed for the Home feed or a short-form feed for the Reads feed, and encourage the user add it to the proper feed instead.
### Long-Form "Reads" Feed
A brand new feature in Primal 2.0, users can now browse and read long-form content posted to Nostr without having to go to a separate client. Primal now has a dedicated "Reads" feed to browse and interact with these articles.
This feed displays the author and title of each article or blog, along with an image, if available. Quite conveniently, it also lets you know the approximate amount of time it will take to read a given article, so you can decide if you have the time to dive into it now, or come back later.

Noticeably absent from the Reads feed, though, is the ability to compose an article of your own. This is another understandable design choice for a mobile client. Composing a long-form note on a smart-phone screen is not a good time. Better to be done on a larger screen, in a client with a full-featured text editor.
Tapping an article will open up an attractive reading interface, with the ability to bookmark for later. These bookmarks are a separate list from your short-form note bookmarks so you don't have to scroll through a bunch of notes you bookmarked to find the article you told yourself you would read later and it's already been three weeks.
While you can comment on the article or zap it, you will notice that you cannot repost or quote-post it. It's not that you can't do so on Nostr. You absolutely can in other clients. In fact, you can do so on Primal's web client, too. However, Primal on Android does not handle rendering long-form note previews in the Home feed, so they have simply left out the option to share them there. See below for an example of a quote-post of a long-form note in the Primal web client vs the Android client.
Primal Web:

Primal Android:

### The Explore Tab
Another unique feature of the Primal client is the Explore tab, indicated by the compass icon. This tab is dedicated to discovering content from outside your current follow list. You can find the feed marketplace here, and add any of the available feeds to your Home or Reads feed selections. You can also find suggested users to follow in the People tab. The Zaps tab will show you who has been sending and receiving large zaps. Make friends with the generous ones!
The Media tab gives you a chronological feed of just media, displayed in a tile view. This can be great when you are looking for users who post dank memes, or incredible photography on a regular basis. Unfortunately, it appears that there is no way to filter this feed for sensitive content, and so you do not have to scroll far before you see pornographic material.
Indeed, it does not appear that filters for sensitive content are available in Primal for ***any*** feed. The app is kind enough to give a minimal warning that objectionable content may be present when selecting the "Nostr Firehose" option in your Home feed, with a brief "be careful" in the feed description, but there is not even that much of a warning here for the media-only feed.

The media-only feed doesn't appear to be quite as bad as the Nostr Firehose feed, so there must be some form of filtering already taking place, rather than being a truly global feed of all media. Yet, occasional sensitive content still litters the feed and is unavoidable, even for users who would rather not see it. There are, of course, ways to mute particular users who post such content, if you don't want to see it a second time from the same user, but that is a never-ending game of whack-a-mole, so your only realistic choices in Primal are currently to either avoid the Nostr Firehose and media-only feeds, or determine that you can put up with regularly scrolling past often graphic content.
This is probably the only choice Primal has made that is not friendly to new users. Most clients these days will have some protections in place to hide sensitive content by default, but still allow the user to toggle those protections off if they so choose. Some of them hide posts flagged as sensitive content altogether, others just blur the images unless the user taps to reveal them, and others simply blur all images posted by users you don't follow. If Primal wants to target new users who are accustomed to legacy social media platforms, they really should follow suit.
The final tab is titled "Topics," but it is really just a list of popular hashtags, which appear to be arranged by how often they are being used. This can be good for finding things that other users are interested in talking about, or finding specific content you are interested in.
If you tap on any topic in the list, it will display a feed of notes that include that hashtag. What's better, you can add it as a feed option you can select on your Home feed any time you want to see posts with that tag.
The only suggestion I would make to improve this tab is some indication of why the topics are arranged in the order presented. A simple indicator of the number of posts with that hashtag in the last 24 hours, or whatever the interval is for determining their ranking, would more than suffice.
Even with those few shortcomings, Primal's Explore tab makes the client one of the best options for discovering content on Nostr that you are actually interested in seeing and interacting with.
### Built-In Wallet
While this feature is completely optional, the icon to access the wallet is the largest of the icons at the bottom of the screen, making you feel like you are missing out on the most important feature of the app if you don't set it up. I could be critical of this design choice, but in many ways I think it is warranted. The built-in wallet is one of the most unique features that Primal has going for it.

Consider: If you are a new user coming to Nostr, who isn't already a Bitcoiner, and you see that everyone else on the platform is sending and receiving sats for their posts, will you be more likely to go download a separate wallet application or use one that is built-into your client? I would wager the latter option by a long shot. No need to figure out which wallet you should download, whether you should do self-custody or custodial, or make the mistake of choosing a wallet with unexpected setup fees and no Lightning address so you can't even receive zaps to it. nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr often states that he believes more people will be onboarded to Bitcoin through Nostr than by any other means, and by including a wallet into the Primal client, his team has made adopting Bitcoin that much easier for new Nostr users.
Some of us purists may complain that it is custodial and KYC, but that is an unfortunate necessity in order to facilitate onboarding newcoiners to Bitcoin. This is ***not*** intended to be a wallet for those of us who have been using Bitcoin and Lightning regularly already. It is meant for those who are not already familiar with Bitcoin to make it as easy as possible to get off zero, and it accomplishes this better than any other wallet I have ever tried.
In large part, this is because the KYC is very light. It does need the user's legal name, a valid email address, date of birth, and country of residence, but that's it! From there, the user can buy Bitcoin directly through the app, but only in the amount of $4.99 at a time. This is because there is a substantial markup on top of the current market price, due to utilizing whatever payment method the user has set up through their Google Play Store. The markup seemed to be about 19% above the current price, since I could purchase 4,143 sats for $4.99 ($120,415 / Bitcoin), when the current price was about $101,500. But the idea here is not for the Primal wallet to be a user's primary method of stacking sats. Rather, it is intended to get them off zero and have a small amount of sats to experience zapping with, and it accomplishes this with less friction than any other method I know.
Moreover, the Primal wallet has the features one would expect from any Lightning wallet. You can send sats to any Nostr user or Lightning address, receive via invoice, or scan to pay an invoice. It even has the ability to receive via on-chain. This means users who don't want to pay the markup from buying through Primal can easily transfer sats they obtained by other means into the Primal wallet for zapping, or for using it as their daily-driver spending wallet.
Speaking of zapping, once the wallet is activated, sending zaps is automatically set to use the wallet, and they are ***fast***. Primal gives you immediate feedback that the zap was sent and the transaction shows in your wallet history typically before you can open the interface. I can confidently say that Primal wallet's integration is the absolute best zapping experience I have seen in any Nostr client.
One thing to note that may not be immediately apparent to new users is they need to add their Lightning address with Primal into their profile details before they can start receiving zaps. So, sending zaps using the wallet is automatic as soon as you activate it, but receiving is not. Ideally, this could be further streamlined, so that Primal automatically adds the Lightning address to the user's profile when the wallet is set up, so long as there is not currently a Lightning address listed.
Of course, if you already have a Lightning wallet, you can connect it to Primal for zapping, too. We will discuss this further in the section dedicated to zap integration.
### Advanced Search
Search has always been a tough nut to crack on Nostr, since it is highly dependent on which relays the client is pulling information from. Primal has sought to resolve this issue, among others, by running a caching relay that pulls notes from a number of relays to store them locally, and perform some spam filtering. This allows for much faster retrieval of search results, and also makes their advanced search feature possible.
Advanced search can be accessed from most pages by selecting the magnifying glass icon, and then the icon for more options next to the search bar.
As can be seen in the screenshot below, there are a plethora of filters that can be applied to your search terms.

You can immediately see how this advanced search could be a very powerful tool for not just finding a particular previous note that you are looking for, but for creating your own custom feed of notes. Well, wouldn't you know it, Primal allows you to do just that! This search feature, paired with the other features mentioned above related to finding notes you want to see in your feed, makes Primal hands-down the best client for content discovery.
The only downside as a free user is that some of these search options are locked behind the premium membership. Or else you only get to see a certain number of results of your advanced search before you must be a premium member to see more.
## Can My Grandma Use It?
Score: **4.8** / 5
Primal has obviously put a high priority on making their client user-friendly, even for those who have never heard of relays, public/private key cryptography, or Bitcoin. All of that complexity is hidden away. Some of it is available to play around with for the users who care to do so, but it does not at all get in the way of the users who just want to jump in and start posting notes and interacting with other users in a truly open public square.
To begin with, the onboarting experience is incredibly smooth. Tap "Create Account," enter your chosen display name and optional bio information, upload a profile picture, and then choose some topics you are interested in. You are then presented with a preview of your profile, with the ability to add a banner image, if you so choose, and then tap "Create Account Now."

From there you receive confirmation that your account has been created and that your "Nostr key" is available to you in the application settings. No further explanation is given about what this key is for at this point, but the user doesn't really need to know at the moment, either. If they are curious, they will go to the app settings to find out.
At this point, Primal encourages the user to activate Primal Wallet, but also gives the option for the user to do it later.

That's it! The next screen the user sees if they don't opt to set up the wallet is their Home feed with notes listed in chronological order. More impressive, the feed is not empty, because Primal has auto-followed several accounts based on your selected topics.
Now, there has definitely been some legitimate criticism of this practice of following specific accounts based on the topic selection, and I agree. I would much prefer to see Primal follow hashtags based on what was selected, and combine the followed hashtags into a feed titled "My Topics" or something of that nature, and make that the default view when the user finishes onboarding. Following particular users automatically will artificially inflate certain users' exposure, while other users who might be quality follows for that topic aren't seen at all.
The advantage of following particular users over a hashtag, though, is that Primal retains some control over the quality of the posts that new users are exposed to right away. Primal can ensure that new users see people who are actually posting quality photography when they choose it as one of their interests. However, even with that example, I chose photography as one of my interests and while I did get some stunning photography in my Home feed by default based on Primal's chosen follows, I also scrolled through the Photography hashtag for a bit and I really feel like I would have been better served if Primal had simply followed that hashtag rather than a particular set of users.
We've already discussed how simple it is to set up the Primal Wallet. You can see the features section above if you missed it. It is, by far, the most user friendly experience to onboarding onto Lightning and getting a few sats for zapping, and it is the only one I know of that is built directly into a Nostr client. This means new users will have a frictionless introduction to transacting via Lightning, perhaps without even realizing that's what they are doing.
Discovering new content of interest is incredibly intuitive on Primal, and the only thing that new users may struggle with is getting their own notes seen by others. To assist with this, I would suggest Primal encourage users to make their first post to the introductions hashtag and direct any questions to the AskNostr hashtag as part of the onboarding process. This will get them some immediate interactions from other users, and further encouragement to set up their wallet if they haven't already done so.
## How do UI look?
Score: **4.9** / 5
Primal is the most stunningly beautiful Nostr client available, in my honest opinion. Despite some of my hangups about certain functionality, the UI alone makes me ***want*** to use it.

It is clean, attractive, and intuitive. Everything I needed was easy to find, and nothing felt busy or cluttered. There are only a few minor UI glitches that I ran into while testing the app. Some of them were mentioned in the section of the review detailing the feed selector feature, but a couple others occurred during onboarding.
First, my profile picture was not centered in the preview when I uploaded it. This appears to be because it was a low quality image. Uploading a higher quality photo did not have this result.

The other UI bug was related to text instructions that were cut off, and not able to scroll to see the rest of them. This occurred on a few pages during onboarding, and I expect it was due to the size of my phone screen, since it did not occur when I was on a slightly larger phone or tablet.

Speaking of tablets, Primal Android looks really good on a tablet, too! While the client does not have a landscape mode by default, many Android tablets support forcing apps to open in full-screen landscape mode, with mixed results. However, Primal handles it well. I would still like to see a tablet version developed that takes advantage of the increased screen real estate, but it is certainly a passable option.





At this point, I would say the web client probably has a bit better UI for use on a tablet than the Android client does, but you miss out on using the built-in wallet, which is a major selling point of the app.
This lack of a landscape mode for tablets and the few very minor UI bugs I encountered are the only reason Primal doesn't get a perfect score in this category, because the client is absolutely stunning otherwise, both in light and dark modes. There are also two color schemes available for each.

## Log In Options
Score: **1** / 5
Unfortunately, Primal has not included any options for log in outside of pasting your private key into the application. While this is a very simple way to log in for new users to understand, it is also the least secure means to log into Nostr applications.
This is because, even with the most trustworthy client developer, giving the application access to your private key always has the potential for that private key to somehow be exposed or leaked, and on Nostr there is currently no way to rotate to a different private key and keep your identity and social graph. If someone gets your key, they ***are you*** on Nostr for all intents and purposes.
This is not a situation that users should be willing to tolerate from production-release clients at this point. There are much better log in standards that can and should be implemented if you care about your users.
That said, I am happy to report that external signer support is on the roadmap for Primal, as confirmed below:
nostr:note1n59tc8k5l2v30jxuzghg7dy2ns76ld0hqnn8tkahyywpwp47ms5qst8ehl
No word yet on whether this will be Android signer or remote signer support, or both.
This lack of external signer support is why I absolutely will not use my main npub with Primal for Android. I am happy to use the web client, which supports and encourages logging in with a browser extension, but until the Android client allows users to protect their private key, I cannot recommend it for existing Nostr users.
## Zap Integration
Score: **4.8** / 5
As mentioned when discussing Primal's built-in wallet feature, zapping in Primal can be the most seamless experience I have ever seen in a Nostr client. Pairing the wallet with the client is absolutely the path forward for Nostr leading the way to Bitcoin adoption.
But what if you already have a Lightning wallet you want to use for zapping? You have a couple options. If it is an Alby wallet or another wallet that supports Nostr Wallet Connect, you can connect it with Primal to use with one-tap zapping.

How your zapping experience goes with this option will vary greatly based on your particular wallet of choice and is beyond the scope of this review. I used this option with a hosted wallet on my Alby Hub and it worked perfectly. Primal gives you immediate feedback that you have zapped, even though the transaction usually takes a few seconds to process and appear in your wallet's history.
The one major downside to using an external wallet is the lack of integration with the wallet interface. This interface currently only works with Primal's wallet, and therefore the most prominent tab in the entire app goes unused when you connect an external wallet.

An ideal improvement would be for the wallet screen to work similar to Alby Go when you have an external wallet connected via Nostr Wallet Connect, allowing the user to have Primal act as their primary mobile Lightning wallet. It could have balance and transaction history displayed, and allow sending and receiving, just like the integrated Primal wallet, but remove the ability to purchase sats directly through the app when using an external wallet.
## Content Discovery
Score: **4.8** / 5
Primal is the best client to use if you want to discover new content you are interested in. There is no comparison, with only a few caveats.
First, the content must have been posted to Nostr as either a short-form or long-form note. Primal has a limited ability to display other types of content. For instance, discovering video content or streaming content is lacking.
Second, you must be willing to put up with the fact that Primal lacks a means of filtering sensitive content when you are exploring beyond the bounds of your current followers. This may not be an issue for some, but for others it could be a deal-breaker.
Third, it would be preferable for Primal to follow topics you are interested in when you choose them during onboarding, rather than follow specific npubs. Ideally, create a "My Topics" feed that can be edited by selecting your interests in the Topics section of the Explore tab.
## Relay Management
Score: **2.5** / 5
For new users who don't want to mess around with managing relays, Primal is fantastic! There are 7 relays selected by default, in addition to Primal's caching service. For most users who aren't familiar with Nostr's protocol archetecture, they probably won't ever have to change their default relays in order to use the client as they would expect.
However, two of these default relays were consistently unreachable during the week that I tested. These were relay.plebes.fans and remnant.cloud. The first relay seems to be an incorrect URL, as I found nosflare.plebes.fans online and with perfect uptime for the last 12 hours on [nostr.watch](https://nostr.watch). I was unable to find remnant.cloud on nostr.watch at all. A third relay was intermittent, sometimes online and reachable, and other times unreachable: v1250.planz.io/nostr. If Primal is going to have default relays, they should ideally be reliable and with accurate URLs.
That said, users can add other relays that they prefer, and remove relays that they no longer want to use. They can even set a different caching service to use with the client, rather than using Primal's.

However, that is the extent of a user's control over their relays. They cannot choose which relays they want to write to and which they want to read from, nor can they set any private relays, outbox or inbox relays, or general relays. Loading the npub I used for this review into another client with full relay management support revealed that the relays selected in Primal are being added to both the user's public outbox relays and public inbox relays, but not to any other relay type, which leads me to believe the caching relay is acting as the client's only general relay and search relay.
One unique and welcomed addition is the "Enhanced Privacy" feature, which is off by default, but which can be toggled on. I am not sure why this is not on by default, though. Perhaps someone from the Primal team can enlighten me on that choice.
By default, when you post to Nostr, all of your outbox relays will see your IP address. If you turn on the Enhanced Privacy mode, only Primal's caching service will see your IP address, because it will post your note to the other relays on your behalf. In this way, the caching service acts similar to a VPN for posting to Nostr, as long as you trust Primal not to log or leak your IP address.
## Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with a client. Here are some of the most common questions submitted about Primal since the launch of 2.0:
nostr:note1dqv4mwqn7lvpaceg9s7damf932ydv9skv2x99l56ufy3f7q8tkdqpxk0rd
This was a pretty common question, because users expect that they will be able to create the same type of content that they can consume in a particular client. I can understand why this was left out in a mobile client, but perhaps it should be added in the web client.
nostr:note16xnm8a2mmrs7t9pqymwjgd384ynpf098gmemzy49p3572vhwx2mqcqw8xe
This is a more concerning bug, since it appears some users are experiencing their images being replaced with completely different images. I did not experience anything similar in my testing, though.
nostr:note1uhrk30nq0e566kx8ac4qpwrdh0vfaav33rfvckyvlzn04tkuqahsx8e7mr
There hasn't been an answer to this, but I have not been able to find a way. It seems search results will always include replies as well as original notes, so a feed made from the search results will as well. Perhaps a filter can be added to the advanced search to exclude replies? There is already a filter to ***only*** show replies, but there is no corresponding filter to only show original notes.
nostr:note1zlnzua28a5v76jwuakyrf7hham56kx9me9la3dnt3fvymcyaq6eqjfmtq6
Since both mobile platforms support the wallet, users expect that they will be able to access it in their web client, too. At this time, they cannot. The only way to have seamless zapping in the web client is to use the Alby extension, but there is not a way to connect it to your Primal wallet via Nostr Wallet Connect either. This means users must have a separate wallet for zapping on the web client if they use the Primal Wallet on mobile.
nostr:note15tf2u9pffy58y9lk27y245ew792raqc7lc22jezxvqj7xrak9ztqu45wep
It seems that Primal is filtering for spam even for profiles you actively follow. Moreover, exactly what the criteria is for being considered spam is currently opaque.
nostr:note1xexnzv0vrmc8svvduurydwmu43w7dftyqmjh4ps98zksr39ln2qswkuced
For those unaware, Blossom is a protocol for hosting media as blobs identified by a hash, allowing them to be located on and displayed from other servers they have been mirrored to when when the target server isn't available. Primal currently runs a Blossom server (blossom.primal.net) so I would expect we see Blossom support in the future.
nostr:note1unugv7s36e2kxl768ykg0qly7czeplp8qnc207k4pj45rexgqv4sue50y6
Currently, Primal on Android only supports uploading photos to your posts. Users must upload any video to some other hosting service and copy/paste a link to the video into their post on Primal. I would not be surprised to see this feature added in the near future, though.
nostr:note10w6538y58dkd9mdrlkfc8ylhnyqutc56ggdw7gk5y7nsp00rdk4q3qgrex
Many Nostr users have more than one npub for various uses. Users would prefer to have a way to quickly switch between accounts than to have to log all the way out and paste their npub for the other account every time they want to use it.
There is good news on this front, though:
nostr:note17xv632yqfz8nx092lj4sxr7drrqfey6e2373ha00qlq8j8qv6jjs36kxlh
## Wrap Up
All in all, Primal is an excellent client. It won't be for everyone, but that's one of the strengths of Nostr as a protocol. You can choose to use the client that best fits your own needs, and supplement with other clients and tools as necessary.
There are a couple glaring issues I have with Primal that prevent me from using it on my main npub, but it is also an ever-improving client, that already has me hopeful for those issues to be resolved in a future release.
So, what should I review next? Another Android client, such as #Amethyst or #Voyage? Maybe an "other stuff" app, like #Wavlake or #Fountain? Please leave your suggestions in the comments.
I hope this review was valuable to you! If it was, please consider letting me know just how valuable by zapping me some sats and reposting it out to your follows.
Thank you for reading!
PV 🤙
-

@ 1c19eb1a:e22fb0bc
2025-03-06 07:47:42
After my first major review of [Primal on Android](https://www.nostr-reviews.com/post/1733635103705/), we're going to go a very different direction for this next review. Primal is your standard "Twitter clone" type of kind 1 note client, now branching into long-form. They also have a team of developers working on making it one of the best clients to fill that use-case. By contrast, this review will not be focusing on any client at all. Not even an "other stuff" client.
Instead, we will be reviewing a very useful tool created and maintained by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 called #Amber. For those unfamiliar with Amber, it is an #Android application dedicated to managing your signing keys, and allowing you to log into various #Nostr applications without having to paste in your private key, better known as your #nsec. It is not recommended to paste your nsec into various applications because they each represent another means by which it could be compromised, and anyone who has your nsec can post as you. On Nostr, your #npub is your identity, and your signature using your private key is considered absolute proof that any given note, reaction, follow update, or profile change was authorized by the rightful owner of that identity.
It happens less often these days, but early on, when the only way to try out a new client was by inputting your nsec, users had their nsec compromised from time to time, or they would suspect that their key may have been compromised. When this occurs, there is no way to recover your account, or set a new private key, deprecating the previous one. The only thing you can do is start over from scratch, letting everyone know that your key has been compromised and to follow you on your new npub.
If you use Amber to log into other Nostr apps, you significantly reduce the likelihood that your private key will be compromised, because only one application has access to it, and all other applications reach out to Amber to sign any events. This isn't quite as secure as storing your private key on a separate device that isn't connected to the internet whatsoever, like many of us have grown accustomed to with securing our #Bitcoin, but then again, an online persona isn't nearly as important to secure for most of us as our entire life savings.
Amber is the first application of its kind for managing your Nostr keys on a mobile device. nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 didn't merely develop the application, but literally created the specification for accomplishing external signing on Android which can be found in [NIP-55](https://github.com/nostr-protocol/nips/blob/master/55.md). Unfortunately, Amber is only available for Android. A signer application for iOS is in the works from nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, but is not ready for use at this time. There is also a new mobile signer app for Android and iOS called Nowser, but I have not yet had a chance to try this app out. From a cursory look at the Android version, it is indeed in the very early stages of development and cannot be compared with Amber.
This review of Amber is current as of version 3.2.5.

## Overall Impression
Score: **4.5** / 5
I cannot speak highly enough about Amber as a tool that every Nostr user on Android should start using if they are not already. When the day comes that we have more options for well-developed signer apps on mobile, my opinion may very well change, but until then Amber is what we have available to us. Even so, it is an incredibly well thought-out and reliable tool for securing your nsec.
Despite being the only well-established Android signer available for Android, Amber ***can*** be compared with other external signing methods available on other platforms. Even with more competition in this arena, though, Amber still holds up incredibly well. If you are signing into web applications on a desktop, I still would recommend using a browser extension like #Alby or #Nos2x, as the experience is usually faster, more seamless, and far more web apps support this signing method ([NIP-07](https://github.com/nostr-protocol/nips/blob/master/07.md)) than currently support the two methods employed by Amber. Nevertheless that gap is definitely narrowing.
A running list I created of applications that support login and signing with Amber can be found here: [Nostr Clients with External Signer Support](nostr:naddr1qvzqqqrcvgpzpde8f55w86vrhaeqmd955y4rraw8aunzxgxstsj7eyzgntyev2xtqydhwumn8ghj7un9d3shjtnzwf5kw6r5vfhkcapwdejhgtcpr4mhxue69uhkg6ttv95k7ue3x5cnwtnwdaehgu339e3k7mf0qq4xummnw3ez6cmvd9jkuarn94mkjarg94jhsar9wfhxzmpdwd5kwmn9wgkhxatswphhyaqrcy76t)
I have run into relatively few bugs in my extensive use of Amber for all of my mobile signing needs. Occasionally the application crashes when trying to send it a signing request from a couple of applications, but I would not be surprised if this is no fault of Amber at all, and rather the fault of those specific apps, since it works flawlessly with the vast majority of apps that support either [NIP-55](https://github.com/nostr-protocol/nips/blob/master/55.md) or [NIP-46](https://github.com/nostr-protocol/nips/blob/master/46.md) login.
I also believe that mobile is the ideal platform to use for this type of application. First, because most people use Nostr clients on their phone more than on a desktop. There are, of course, exceptions to that, but in general we spend more time on our phones when interacting online. New users are also more likely to be introduced to Nostr by a friend having them download a Nostr client on their phone than on a PC, and that can be a prime opportunity to introduce the new user to protecting their private key. Finally, I agree with the following assessment from nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn.
nostr:nevent1qqsw0r6gzn05xg67h5q2xkplwsuzedjxw9lf7ntrxjl8ajm350fcyugprfmhxue69uhhyetvv9ujumn0wd68yurvv438xtnrdaksyg9hyaxj3clfswlhyrd5kjsj5v04clhjvgeq6pwztmysfzdvn93gev7awu9v
The one downside to Amber is that it will be quite foreign for new users. That is partially unavoidable with Nostr, since folks are not accustomed to public/private key cryptography in general, let alone using a private key to log into websites or social media apps. However, the initial signup process is a bit cumbersome if Amber is being used as the means of initially generating a key pair. I think some of this could be foregone at start-up in favor of streamlining onboarding, and then encourage the user to back-up their private key at a later time.
## Features
Amber has some features that may surprise you, outside of just storing your private key and signing requests from your favorite Nostr clients. It is a full key management application, supporting multiple accounts, various backup methods, and even the ability to authorize other users to access a Nostr profile you control.
### Android Signing
This is the signing method where Amber really shines in both speed and ease of use. Any Android application that supports this standard, and even some progressive web-apps that can be installed to your Android's home-screen, can very quickly and seamlessly connect with Amber to authorize anything that you need signed with your nsec. All you have to do is select "Login with Amber" in clients like #Amethyst or #0xChat and the app will reach out to Amber for all signing requests from there on out. If you had previously signed into the app with your nsec, you will first need to log out, then choose the option to use Amber when you log back in.

This is a massive deal, because everything you do on Nostr requires a signature from your private key. Log in? Needs a signature. Post a "GM" note? Needs a signature. Follow someone who zapped your note? Needs a signature. Zap them back? You guessed it; needs a signature. When you paste your private key into an application, it will automatically sign a lot of these actions without you ever being asked for approval, but you will quickly realize just how many things the client is doing on your behalf when Amber is asking you to approve them each time.
Now, this can also get quite annoying after a while. I recommend using the setting that allows Amber to automatically sign for basic functions, which will cut down on some of the authorization spam. Once you have been asked to authorize the same type of action a few times, you can also toggle the option to automatically authorize that action in the future. Don't worry, though, you have full control to require Amber to ask you for permission again if you want to be alerted each time, and this toggle is specific to each application, so it's not a blanket approval for all Nostr clients you connect with.

This method of signing is just as fast as signing via browser extension on web clients, which users may be more accustomed to. Everything is happening locally on the device, so it can be very snappy and secure.
### Nostr Connect/Bunker Signing
This next method of signing has a bit of a delay, because it is using a Nostr relay to send encrypted information back and forth between the app the user is interacting with and Amber to obtain signatures remotely. It isn't a significant delay most of the time, but it is just enough to be noticeable.
Also, unlike the previous signing method that would automatically switch to Amber as the active application when a signing request is sent, this method only sends you a notification that you must be watching for. This can lead to situations where you are wondering why something isn't working in a client you signed into remotely, because it is waiting on you to authorize the action and you didn't notice the notification from Amber. As you use the application, you get used to the need to check for such authorization requests from time to time, or when something isn't working as expected.

By default, Amber will use relay.nsec.app to communicate with whichever Nostr app you are connecting to. You can set a different relay for this purpose, if you like, though not just any relay will support the event kinds that Amber uses for remote signing. You can even run your own relay just for your own signing purposes. In fact, the creator of Amber has a relay application you can run on your phone, called Citrine, that can be used for signing with any web app you are using locally on your phone. This is definitely more of an advanced option, but it is there for you if you want it. For most users, sticking with relay.nsec.app will be just fine, especially since the contents of the events sent back and forth for signing are all encrypted.
Something many users may not realize is that this remote signing feature allows for issuing signing permissions to team members. For instance, if anyone ever joined me in writing reviews, I could issue them a connection string from Amber, and limit their permissions to just posting long-form draft events. Anything else they tried to do would require my explicit approval each time. Moreover, I could revoke those permissions if I ever felt they were being abused, without the need to start over with a whole new npub. Of course, this requires that your phone is online whenever a team member is trying to sign using the connection string you issued, and it requires you pay attention to your notifications so you can approve or reject requests you have not set to auto-approve. However, this is probably only useful for small teams, and larger businesses will want to find a more robust solution for managing access to their npub, such as Keycast from nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc.
The method for establishing a connection between Amber and a Nostr app for remote signing can vary for each app. Most, at minimum, will support obtaining a connection string from Amber that starts with "bunker://" and pasting it in at the time of login. Then you just need to approve the connection request from Amber and the client will log you in and send any subsequent signing requests to Amber using the same connection string.

Some clients will also offer the option to scan a QR code to connect the client to Amber. This is quite convenient, but just remember that this also means the client is setting which relay will be used for communication between the two. Clients with this option will also have a connection string you can copy and paste into Amber to achieve the same purpose. For instance, you may need this option if you are trying to connect to an app on your phone and therefore can't scan the QR code using Amber on the same phone.

### Multiple Accounts
Amber does not lock you into using it with only a single set of keys. You can add all of your Nostr "accounts" to Amber and use it for signing events for each independently. Of course, Nostr doesn't actually have "accounts" in the traditional sense. Your identity is simply your key-pair, and Amber stores and accesses each private key as needed.

When first signing in using native Android signing as described above, Amber will default to whichever account was most recently selected, but you can switch to the account that is needed before approving the request. After initial login, Amber will automatically detect the account that the signing request is for.
### Key Backup & Restore
Amber allows multiple ways to back up your private key. As most users would expect, you can get your standard nsec and copy/paste it to a password manager, but you can also obtain your private key as a list of mnemonic seed words, an encrypted version of your key called an ncryptsec, or even a QR code of your nsec or ncryptsec.

Additionally, in order to gain access to this information, Amber requires you to enter your device's PIN or use biometric authentication. This isn't cold-storage level protection for your private key by any means, especially since your phone is an internet connected device and does not store your key within a secure element, but it is about as secure as you can ask for while having your key accessible for signing Nostr events.
### Tor Support
While Amber does not have Tor support within the app itself, it does support connecting to Tor through Orbot. This would be used with remote signing so that Amber would not connect directly over clearnet to the relay used for communication with the Nostr app requesting the signature. Instead, Amber would connect through Tor, so the relay would not see your IP address. This means you can utilize the remote signing option without compromising your anonymity.

### Additional Security
Amber allows the user the option to require either biometric or PIN authentication before approving signing requests. This can provide that extra bit of assurance that no one will be able to sign events using your private key if they happen to gain access to your phone. The PIN you set in Amber is also independent from the PIN to unlock your device, allowing for separation of access.
## Can My Grandma Use It?
Score: **4.0** / 5
At the end of the day, Amber is a tool for those who have some concept of the importance of protecting their private key by not pasting it into every Nostr client that comes along. This concept in itself is not terribly approachable to an average person. They are used to just plugging their password into every service they use, and even worse, they usually have the ***same password*** for everything so they can more readily remember it. The idea that they should never enter their "Nostr password" into any Nostr application would never occur to them unless someone first explained how cryptography works related to public/private key pairs.
That said, I think there can be some improvements made to how users are introduced to these concepts, and that a signer application like Amber might be ideal for the job. Considering Amber as a new user's first touchpoint with Nostr, I think it holds up well, but could be somewhat streamlined.
Upon opening the app, the user is prompted to either use their existing private key or "Create a new Nostr account." This is straightforward enough. "Account" is not a technically correct term with Nostr, but it is a term that new users would be familiar with and understand the basic concept.

The next screen announces that the account is ready, and presents the user with their public key, explaining that it is "a sort of username" that will allow others to find them on Nostr. While it is good to explain this to the user, it is unnecessary information at this point. This screen also prompts the user to set a nickname and set a password to encrypt their private key. Since the backup options also allow the user to set this password, I think this step could be pushed to a later time. This screen would better serve the new user if it simply prompted them to set a nickname and short bio that could be saved to a few default relays.

Of course, Amber is currently prompting for a password to be set up-front because the next screen requires the new user to download a "backup kit" in order to continue. While I do believe it is a good idea to encourage the creation of a backup, it is not crucial to do so immediately upon creation of a new npub that has nothing at stake if the private key is lost. This is something the UI could remind the user to do at a later time, reducing the friction of profile creation, and expediting getting them into the action.

Outside of these minor onboarding friction points, I think Amber does a great job of explaining to the user the purpose of each of its features, all within the app and without any need to reference external documentation. As long as the user understands the basic concept that their private key is being stored by Amber in order to sign requests from other Nostr apps, so they don't have to be given the private key, Amber is very good about explaining the rest without getting too far into the technical weeds.
The most glaring usability issue with Amber is that it isn't available in the Play Store. Average users expect to be able to find applications they can trust in their mobile device's default app store. There is a valid argument to be made that they are incorrect in this assumption, but that doesn't change the fact that this is the assumption most people make. They believe that applications in the Play Store are "safe" and that anything they can't install through the Play Store is suspect. The prompts that the Android operating system requires the user to approve when installing "unknown apps" certainly doesn't help with this impression.
Now, I absolutely ***love*** the Zapstore from nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but it doesn't do much to alleviate this issue. Users will still need to be convinced that it is safe to install the Zapstore from the GitHub repo, and then install Amber from there. Furthermore, this adds yet another step to the onboarding process.
Instead of:
- Install Amber
- Set up your keys
- Install the client you want to use
- Log in with Amber
The process becomes:
- Go to the Zapstore GitHub and download the latest version from the releases page.
- Install the APK you downloaded, allowing any prompt to install unknown apps.
- Open Zapstore and install Amber, allowing any prompt to install unknown apps again.
- Open Amber and set up your keys.
- Install the client you want to use
- Log in with Amber
An application as important as Amber for protecting users' private keys should be as readily available to the new user as possible. New users are the ones most prone to making mistakes that could compromise their private keys. Amber should be available to them in the Play Store.
## How do UI Look?
Score: **4.5** / 5
Amber's UI can be described as clean but utilitarian. But then, Amber is a tool, so this is somewhat expected. It is not an app you will be spending a lot of time in, so the UI just needs to be serviceable. I would say it accomplishes this and then some. UI elements are generally easy to understand what they do, and page headings fill in the gaps where that is not the case.

I am not the biggest fan of the color-scheme, particularly in light-mode, but it is not bad in dark-mode at all, and Amber follows whatever theme you have set for your device in that respect. Additionally, the color choice does make sense given the application's name.

It must also be taken into consideration that Amber is almost entirely the product of a single developer's work. He has done a great job producing an app that is not only useful, but pleasant to interact with. The same cannot be said for most utility apps I have previously used, with interfaces that clearly made good design the lowest priority. While Amber's UI may not be the most beautiful Nostr app I have seen, design was clearly not an afterthought, either, and it is appreciated.
## Relay Management
Score: **4.9** / 5
Even though Amber is not a Nostr client, where users can browse notes from their favorite npubs, it still relies heavily on relays for some of its features. Primarily, it uses relays for communicating with other Nostr apps for remote signing requests. However, it also uses relays to fetch profile data, so that each private key you add to Amber will automatically load your chosen username and profile picture.
In the relay settings, users can choose which relays are being used to fetch profile data, and which relays will be used by default when creating new remote signing connection strings.

The user can also see which relays are currently connected to Amber and even look at the information that has been passed back and forth on each of those active relays. This information about actively connected relays is not only available within the application, but also in the notification that Amber has to keep in your device's notification tray in order to continue to operate in the background while you are using other apps.

Optionality is the name of the game when it comes to how Amber handles relay selection. The user can just stick with the default signing relay, use their own relay as the default, or even use a different relay for each Nostr application that they connect to for remote signing. Amber gives the user an incredible amount of flexibility in this regard.
In addition to all of this, because not all relays accept the event types needed for remote signing, when you add a relay address to Amber, it automatically tests that relay to see if it will work. This alone can be a massive time saver, so users aren't trying to use relays that don't support remote signing and wondering why they can't log into noStrudel with the connection string they got from Amber.

The only way I could see relay management being improved would be some means of giving the user relay recommendations, in case they want to use a relay other than relay.nsec.app, but they aren't sure which other relays will accept remote signing events. That said, most users who want to use a different relay for signing remote events will likely be using their own, in which case recommendations aren't needed.
## Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with any Nostr application. Here are some of the most common questions submitted about Amber in the last two months.
nostr:nevent1qqsfrdr68fafgcvl8dgnhm9hxpsjxuks78afxhu8yewhtyf3d7mkg9gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qkgh77xxt7hhtt4u528hecnx69rhagla8jj3tclgyf9wvkxa6dc0sxp0e6m
This is a good example of Amber working correctly, but the app the user is trying to log into not working. In my experience with #Olas in particular, it sometimes allows remote signer login, and sometimes doesn't. Amber will receive the signing request and I will approve it, but Olas remains on the login screen.
If Amber is receiving the signing requests, and you are approving them, the fault is likely with the application you are trying to log into.
That's it. That's all the repeated questions I could find. Oh, there were a few one-off questions where relay.nsec.app wouldn't connect, or where the user's out-of-date web browser was the issue. Outside of that, though, there were no common questions about ***how*** to use Amber, and that is a testament to Amber's ease of use all on its own.
## Wrap Up
If you are on Android and you are not already using Amber to protect your nsec, please do yourself a favor and get it installed. It's not at all complicated to set up, and it will make trying out all the latest Nostr clients a safe and pleasant experience.
If you are a client developer and you have not added support for NIP-55 or NIP-46, do your users the courtesy of respecting the sanctity of their private keys. Even developers who have no intention of compromising their users' keys can inadvertently do so. Make that eventuality impossible by adding support for NIP-55 and NIP-46 signing.
Finally, I apologize for the extended time it took me to get this review finished. The time I have available is scarce, Nostr is distracting, and nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 kept improving Amber even as I was putting it through its paces over the last two months. Keep shipping, my friend! You have made one of the most useful tools we have seen for Nostr to date!
Now... What should I review next?
-

@ 2cb8ae56:84d30cba
2025-03-06 07:40:38
どうも、Nostrまとめ(2024)ぶりですね。
記事として出すのはかなりお久しぶりかも、お名前変わりまして「フェゼレント」でございます。
意味としては以下の通りです
1.Fezer(フェザー)という英単語
2.ent(エント)という造語
2-1. netを崩した形、よくこれに打ち間違えます。
2-2. Entertainment(エンターテイメント)の略語、なんか娯楽とか話題を生み出せる人になりたいですね。
1と2をガッタイ!!!(トムブラウン風)しまして、フェゼレントです。
なんとググってみますと、Fezerent及びフェゼレントの検索結果が0。
これは...一種のチャンスでは!?と思って、使っています。
さて、そこで出てくるのが「薄味のキャルピス」と「IVstrook」の今後ですよね。
後者に至っては3年分の料金を払ってドメインまで取っているわけですし、前者はかなりネットとかラジオでも浸透しています。
というわけで、こんな風に置き換えます。
Nostr、YT、Discordはフェゼレント及びFezerentを使用します。
それ以外(ラジオを含む)では薄味のキャルピス、IVstrookを使用します。
そして、NHKなどAM波を使用して放送を行っているラジオ局用で使用していた「テックジャンカー」ですが、使用を停止します。
あんま浸透しなかったわけですからね
そんな感じでやっていきます
最後に、記事最後に使用する署名のような奴ですが、そちらは変更なく「IVstrook」単体で行います。
また、ニコニコ動画及び各種ポッドキャストサービスにて配信しておりました「Small Room Space」ですが、今後はzap.streamというNostrのシステムを使用したサービスを用い、番組名の変更は行わないものとします。
zap.streamでの配信開始は「4月7日」
ちょうど#1が公開されてから1年が経過した日です
重ねて、当名義を使用したニコニコ動画への投稿は「3月8日」をもって終了とし、zap.streamへ移行します。
以上、今年に入ってからまともにニコニコ動画で投稿できていませんでしたが、そのような運びとさせていただきます。
2025/03/06 IVstrook
-

@ da0b9bc3:4e30a4a9
2025-03-06 06:35:31
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/905374
-

@ 732c6a62:42003da2
2025-03-06 06:00:53
> De acordo com a Forbes, a Ripple (Empresa responsável pela Criptomoeda XRP) tem financiado e apoiado campanhas contra a mineração de Bitcoin.
## **Por que Ripple faz propaganda anti-bitcoin?**
Simples: **eles são o oposto do Bitcoin em quase tudo.** Enquanto o Bitcoin foi criado para ser descentralizado, resistente à censura e independente de instituições, o Ripple é basicamente um serviço bancário 2.0. Eles precisam atacar o Bitcoin para justificar sua própria existência.
## **O que você não sabe:**
1. **Ripple Labs controla a maioria do XRP:** Eles têm um estoque estratégico que pode ser liberado no mercado a qualquer momento. Isso é o oposto de descentralização.
2. **XRP não é uma moeda para "pessoas comuns":** Foi criada para bancos e instituições financeiras. Basicamente, é o "banco central" das criptomoedas.
3. **Ripple não é blockchain no sentido tradicional:** Eles usam um protocolo chamado **Ripple Protocol Consensus Algorithm (RPCA)**, que é mais rápido, mas menos descentralizado.
## **Os principais ataques do Ripple ao Bitcoin:**
1. **Anti-mineração:** O Ripple critica o consumo de energia do Bitcoin, mas esquece que seu próprio sistema depende de servidores centralizados que também consomem energia.
2. **Anti-reserva estratégica:** O Ripple tem um estoque gigante de XRP, mas critica o Bitcoin por ser "deflacionário". Hipocrisia? Nunca ouvi falar.
3. **Anti-descentralização:** O Ripple prega que a descentralização do Bitcoin é "ineficiente", mas o que eles realmente querem é manter o controle nas mãos de poucos.
## **Análise Psicológica Básica (para você que acha que XRP é o futuro):**
- **Síndrome do Underdog:** Acha que apoiar o Ripple te faz um rebelde, mas na verdade você está torcendo para o sistema bancário tradicional.
- **Viés de Confirmação:** Só ouve opiniões que validam sua decisão de comprar XRP.
- **Efeito Dunning-Kruger:** Acha que entender Ripple te torna um especialista em criptomoedas, mas não sabe o que é um *hard fork*.
**Estudo de Caso (Real, mas Você Vai Ignorar):**
Carlos, 30 anos, comprou XRP porque "é o futuro das transações bancárias". Ele não sabe que o Ripple está sendo processado pela SEC por vender XRP como um título não registrado. Carlos agora está esperando o "pump" que nunca vem.
## **Conclusão: ou, "volte para a aula de economia do ensino médio"**
Ripple não é o futuro das finanças. É só mais um player tentando lucrar em um mercado competitivo. E sua propaganda anti-Bitcoin? Essa só prova que **a descentralização assusta quem quer controle**. Agora vá estudar blockchain básico — ou pelo menos pare de compartilhar memes com erros de português.
-

@ 732c6a62:42003da2
2025-03-06 04:33:48
>De ''Dialética do Oprimido'' a ''Like do Oprimido'': A Queda Livre do Debate que Nunca Existiu.
## **A moda do momento**
Fiquei aproximadamente 8 meses sem ter acesso a nenhum dispositivo. Quando consegui novamente o acesso ao smartphone, percebi algo diferente no debate político brasileiro: enquanto a direita estava se engajando em incontáveis números de curtidas e compartilhamentos com memes que demonstravam críticas ao governo e aos seus ainda poucos apoiadores que se humilham para defender o indefensável, a esquerda radical repetia sua imposição intelectual em comentários de vários posts, incluindo textos, vídeos e tweets com frases semelhantes a "vai ler um livro de história" "nunca leu um livro", "eu estou do lado certo da história" e "se eu fosse irracional eu seria de direita". Tudo isso pra tentar passar uma mensagem de que a história é de esquerda. A tese é: será que eles realmente são tão inteligentes como juram?
**Fatos que ignoram enquanto cospem jargões do "lado certo da história":**
1. **A esquerda também tem seus terraplanistas:** Anti-vaxxers de organicafé, terraplanistas do gênero, e os que acham que a Coreia do Norte é uma democracia.
2. **Viés de confirmação não é monopólio da direita:** Eles compartilham estudos "científicos" do Medium como se fossem *peer-reviewed*, mas desdenham de dados que contradizem sua narrativa.
3. **A direita não é um monolito:** Tem desde ancaps que calculam até a última casa decimal até bolsominions que acham que a Terra é plana. Generalizar é... bem, **irracional**.
**Estudo de Caso (Fictício, mas Verdadeiro):**
Larissa, 23 anos, posta sobre "ciência e razão" enquanto defende horóscopo como "ferramenta de autoconhecimento". Acredita que o capitalismo causa depressão, mas não sabe o que é taxa Selic. Larissa é você após três caipirinhas.
### **A Imposição intelectual que ninguém pediu (mas todos recebem de graça)**
A esquerda brasileira, em sua cruzada épica para salvar o mundo dos *"fascistas que ousam discordar"*, adotou uma nova estratégia: **transformar complexidade política em slogans de camiseta de feira**. A frase *"se eu fosse irracional, seria de direita"* não é original — é plágio descarado da cartilha do **Complexo de Deus em Oferta no AliExpress**.
#### **O Quebra-Cabeça da superioridade Auto-Delirante**
A tese esquerdista se sustenta em três pilares frágeis:
1. **A falácia do "lado certo da história":** Como se história fosse um jogo de futebol com narração do João Cléber.
2. **A ilusão de que citar Foucault = ter QI elevado:** Spoiler: decorar *"biopoder"* não te torna imune a acreditar em astrologia.
3. **A crença de que volume de texto = profundidade:** 15 parágrafos no Twitter não equivalem a um semestre de Ciência Política.
**Dado Cruel:** Um estudo da Universidade de Cambridge (2022) mostrou que **extremistas de ambos os lados cometem erros lógicos similares**. A diferença? A esquerda usa palavras mais bonitas para mascarar a burrice.
### **A hipocrisia do "nunca tocou em um livro" (enquanto compartilham resumo de livro no TikTok)**
A acusação preferida — *"você não lê!"* — esconde uma ironia deliciosa:
- 72% dos *"intelectuais de rede social"* citam livros que nunca leram além do título (Fonte: Pesquisa Informal do Twitter, 2023).
- **Obras citadas como troféu:** *"1984"* (para chamar Bolsonaro de Big Brother), *"O Capital"* (para justificar o NFT da Gal Gadot), e *"Feminismo para os 99%"* (para atacar homens heterossexuais que usam sandália de dedo).
**Pergunta Incômoda:** Se ler Marx fosse garantia de racionalidade, por que a União Soviética acabou em pizza (literalmente, considerando a economia deles)?
### **Quando a autoimagem colide com a realidade (Ou: por que nenhum esquerdista lassa no teste de turing da coerência)**
A esquerda adora se pintar como a **Última Trincheira da Razão**, mas pratica o que critica:
- **Exemplo 1:** Defendem *"ciência"* quando convém (vacinas), mas abraçam pseudociência quando é *trendy* (cristais energéticos contra o capitalismo).
- **Exemplo 2:** Chamam a direita de *"terraplanista"*, mas acham que inflação se resolve com tabelamento estatal — a versão econômica de *"a Terra é sustentada por tartarugas"*.
- **Exemplo 3:** Criticam *"fake news"*, mas compartilham teorias de que o agro *"envenena a comida"* (enquanto comem sushi de supermercado).
**Frase-Chave:** *"Racionalidade seletiva é o novo analfabetismo funcional."*
**Pergunta Final:** Se a esquerda é tão racional, por que não usa a *"lógica implacável"* para resolver algo além do enquadro perfeito de stories no Instagram?
# **Enfim**
O debate *"esquerda racional vs. direita irracional"* é só **mais um episódio da novela "Brasil: O País que Confunde Opinião com Ataque de Ego"**. Enquanto uns brincam de *"quem tem o QI mais alto"*, o país queima — literalmente, considerando o Pantanal. Talvez a verdadeira irracionalidade seja gastar energia discutindo superioridade moral enquanto o Wi-Fi cai pela décima vez no dia. Racionalidade não tem lado político. Arrogância, por outro lado, é universal. Sua necessidade de se sentir superior só prova que **a lacração é o último refúgio dos fracos de argumento**. Agora deviam estudar economia básica — ou pelo menos que parem de achar que *"Ah, mas o capitalismo!"* é um contra-argumento.
Saudade da época em que a esquerda não se fingia de intelectual.
-

@ 6b0a60cf:b952e7d4
2025-03-06 02:45:45
とあるSNSで海外の相互さん(以降、Aさんと呼ぶ)からDMで相談されたことがあって、思ったことをつらつらと書いてみる。
非公開の場での相談なので多少ぼかしを入れるけど。
## 事の経緯
発端は、Aさんの友人が作品に日本人作者の素材を使用しようとしていて、その利用規約を翻訳して読んだらうまく翻訳されなくて理解が正しいのかわからない、なので間違いが無いか確認してほしい、という相談だった。
あー、確かに日本語特有の回りくどい表現があるねー、と思いながらバシッと簡潔に意訳してお伝えしたところ、スッキリ理解していただけたらしく一件落着となった。
## 独自ライセンス文化
しかしまあ、創作界隈における作品・素材の利用規約というものは総じて長くて細かい。
ジャンルによるのかもしれないけれど。
自分は絵や音を創ることは無いがプログラムのコードを書く趣味はあるのでプログラム向けのライセンスを利用している。MITとかGPLとかいうやつ。
創作向けであればCCライセンスが適しているだろう。しかしこれがなかなか広まらない。
杓子定規のライセンスでは表しきれないような特別な希望があるのだろう。
そして独自ライセンスが跋扈することとなる。
## NO MORE 映画泥棒
特に気になるのが、「泥棒をしてはいけません」レベルの注意書きが散見されるのだ。
わざわざライセンスに書くことではない。あなたが警告するまでもなく、違法な行為は処罰される。
でも、たぶん効果があるからこういうのが広まるのだろう。
「泥棒してはいけないって書いてないから泥棒しました」というレベルの利用者が存在するのだろう。
そういう人は書いてあっても読んでないか、理屈をこねて泥棒するんだろうと思うけれども。
## その術はオレに効く
で、そういう警告文が魔除けの札のごとくびっしり貼られていると、こちらにやましい心が無くても、ちょっとこの素材は利用しないほうがよさそうだな……と思って引き返してしまうことがある。
SNSで可愛い絵を見て、作者さんをフォローしようと思ったら「無断転載禁止」みたいなのがプロフにずらずら書いてあって「おっと……」みたいに引き返すことがあるが、それに似ている。
きっと過去によくない体験をしてしまって、そのようにプロフに書くことでそれが改善するという実体験があって、そうなっているのだろうと推測している。
## 異文化の壁を超えて
冒頭で話したAさんはきわめて紳士的な方であり、日本文化に対してもよく理解しようと努めてくれるので、話が通じやすくて助かったし、件の素材についても臆すること無く使用することになりそうだった。
ただ魔除けの札が効かないような魑魅魍魎にはいくら札を貼っても意味がないし、実際の悪魔祓いの効果と善良な利用者をも祓ってしまう機会損失(?)を比べて合理的なのだろうか、と考えたりしたのでした。オチは無い。
## ライセンス
この文章は CC0 1.0 でライセンスします。
Nostrイベントとして公開する以上はNIPsに従う範囲内で自由に利用されることを望みます。
NIPsに違反したご利用は他のクライアントの利用者にご迷惑になるのでご遠慮いただくことを希望します。[^1]
[^1]: Damusを使ってリポストする、等の行為が該当します
-

@ a63655ce:05240c71
2025-03-06 00:48:46
looks really clean. `window.nostr` asked for the key multiple times for some reason
-

@ 6e0ea5d6:0327f353
2025-03-06 00:18:09
Ascolta, amico mio...
There come moments when a grown man looks in the mirror and fails to recognize himself.
Naturally, when this happens, there is nothing more fitting than lighting a cigarette, pouring a glass of fine wine, and toasting to oneself—the birth of a new man, forged in the womb of a harsh and sobering reality.
One cannot scatter thorns along a path walked barefoot, nor allow the tongue to speak what the mind may later pay for—but this, we learn only through years of suffering.
Only now do I realize that, among all the teachers I have had, experience was the harshest of them all, for it first administered the test and only afterward taught me the lesson.
In peaceful moments, one can reflect more easily on the world around him. Imagine, then, the depths of reflection that can be reached in a state of true inner tranquility.
If you have never gazed upon the horizon, taken in all the fortune before your eyes, and declared to yourself, "I will own all of this!", then you have never possessed true ambition. However, blind ambition will leave you waking up hungry for wealth and power but going to sleep with an empty soul.
Walk always with honor, pride, and loyalty—let these principles never depart from you nor fail to steady your steps. In your battles, do not wish for your enemies to be handed to you on their knees; instead, seek to gain the strength and ruthlessness to bring them down while they stand.
Your greatest dilemma is the eternal paradox in the life of a businessman within the sacred Sicilian organization: how to acquire power and wealth without placing both feet in hell?
Be careful not to surrender to arrogance. The man who shouts his virtues to the wind will, when he falls, hear only the echo of his own pride.
Let your greatest legacy be to live in a way that does not shame your mother and makes your father proud.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-

@ b8851a06:9b120ba1
2025-03-05 23:03:00
The U.S. isn't just blocking Gaza's reconstruction—it's ensuring Palestinians have no future there.
This week, Washington rejected the Arab League's $53 billion plan to rebuild Gaza. Not because it was unworkable, but because it was unwanted. #Gaza, they say, is "uninhabitable." The solution? Depopulation, disguised as development.
## The Riviera Plan: Rebuilding Without Its People
National Security Council spokesman Brian Hughes put it bluntly:
"Gaza is uninhabitable."
This isn't a call for humanitarian intervention. It's a pretext for forced displacement.
Trump's vision transforms Gaza into a "Riviera of the #MiddleEast"—after its population has been relocated. Officials have explicitly stated Palestinians "would not be allowed to return" once reconstruction begins. This isn't rebuilding; it's replacement.
## Regional Consensus Rejected
The Arab League's proposal represented rare unity among regional powers. It offered a detailed roadmap for reconstruction while allowing #Palestinians to remain in their homeland.
By dismissing this plan, Washington sent a clear message: **Palestinian self-determination remains subordinate to Western geopolitical interests.**
This isn't new. For over a century, Western capitals have determined Palestinian futures while treating their voices as irrelevant.
## The Fiat War Machine Connection
War and fiat money go hand in hand. Governments don't fund wars through taxes anymore—it's all printed money. Inflation steals from the public silently, financing endless destruction abroad while citizens struggle at home.
As Saifedean Ammous writes in The Fiat Standard: nostr:npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak
"Central banks are essentially war machines, enabling governments to finance endless conflicts through inflation rather than direct taxation."
This system divorces "economic reward from economic productivity, and instead bases it on political allegiance." The result? A world "perpetually lurching from one crisis to another, with devastating consequences for humanity."
## Ukraine Parallels: When Support Is Conditional
The U.S. has now halted military aid to #Ukraine, suspending over $1 billion in arms. #Europe scrambles to fill the gap, suddenly realizing the conditional nature of American protection.
Both conflicts reveal the same truth: **geopolitical support is increasingly transactional rather than values-based.**
As Henry Kissinger observed: "It may be dangerous to be America's enemy, but being America's friend can be fatal."
## The Cycle Continues
The U.S. model is simple: fund destruction, control reconstruction, keep the cycle going.
Fiat money makes it possible. Indifference makes it permanent. And yes #Bitcoin can fix it. But will it?
How long before people wake up #nostr? How long before the cycle breaks?
"Fiat money is a tool for governments to control their citizens" as Saifedean rightly says—and now, through endless war, to control the world.
-

@ f3873798:24b3f2f3
2025-03-05 23:01:12
O café faz parte da rotina de milhões de pessoas, seja para despertar pela manhã, acompanhar uma boa conversa ou até impulsionar a produtividade no trabalho. Mas você já parou para pensar na qualidade do café que consome diariamente? Neste artigo, vamos falar sobre os benefícios do café e as diferenças entre o café extraforte e o café especial.
## ☕ Benefícios do Café no Dia a Dia

O café não é apenas uma bebida saborosa, mas também oferece diversos benefícios para a saúde, como:
Aumento da energia e concentração – A cafeína estimula o sistema nervoso central, ajudando na atenção e no foco.
Melhora do humor – O consumo moderado de café pode estimular a produção de dopamina, contribuindo para uma sensação de bem-estar.
Propriedades antioxidantes – O café é rico em compostos que combatem os radicais livres, ajudando a prevenir o envelhecimento precoce.
Auxílio na digestão – Para muitas pessoas, o café funciona como um leve estimulante do sistema digestivo.
## ☕ Café Extraforte vs. Café Especial: Qual a Diferença?

Na prateleira do supermercado ou na cafeteria, há uma grande variedade de cafés. Mas, afinal, qual é a diferença entre o café extraforte e o café especial?
### ☕Café Extraforte
Produzido a partir de grãos de qualidade inferior, muitas vezes misturados com impurezas.
Possui torra muito escura, o que pode mascarar defeitos do grão.
Tem um sabor mais amargo e intenso, muitas vezes com notas queimadas.
Pode ser mais ácido e difícil de digerir para algumas pessoas.
### ☕Café Especial
Feito com grãos selecionados e de alta qualidade, sem defeitos.
A torra é mais equilibrada, preservando os aromas e sabores naturais.
Possui notas sensoriais diferenciadas (frutadas, achocolatadas, florais, etc.).
Mais suave e menos ácido, proporcionando uma experiência mais agradável ao paladar.
## ☕ Qual Escolher para o Dia a Dia?

Se você busca praticidade e um café forte, o extraforte pode ser uma opção. No entanto, se quiser aproveitar melhor os benefícios do café e sentir sabores mais ricos, vale a pena investir no café especial. Além disso, moer os grãos na hora e preparar a bebida com métodos como coador de pano, prensa francesa ou Hario V60 pode transformar sua experiência com o café.
-

@ b7b1382e:74635e6c
2025-03-05 22:32:18
## Abstract
**By Lamar Wilson**
This white paper examines an alternative taxation framework characterized by three primary components: a uniform 15% flat tax on income, a redistribution mechanism, and a tiered consumption tax structure. The proposed model aims to stimulate economic growth while maintaining social equity through strategic fiscal policy interventions. This paper analyzes the theoretical underpinnings of this approach, its potential macroeconomic implications, distributional effects across income strata, and implementation challenges. The analysis suggests that while the proposed framework offers significant advantages in terms of simplicity and growth incentives, careful consideration must be given to revenue adequacy, wealth concentration effects, and long-term economic sustainability.
## 1. Introduction
Taxation systems fundamentally shape economic incentive structures, income distribution, and government fiscal capacity. Contemporary tax regimes often reflect accumulated historical policy decisions rather than coherent economic theory, resulting in complex systems with varying degrees of progressivity, efficiency, and equity (Mirrlees et al., 2011). This paper examines a potential alternative taxation framework built upon three pillars: a uniform flat tax, redistribution mechanisms, and stratified consumption taxation.
The theoretical foundation of this approach draws upon both supply-side economics, which emphasizes the importance of investment incentives, and demand-side considerations, which recognize the economic significance of broad-based consumption. By synthesizing these perspectives, the proposed framework attempts to create a self-reinforcing economic cycle wherein simplified taxation stimulates both investment and consumption.
## 2. Structural Components of the Proposed Framework
### 2.1 Uniform Flat Income Taxation
The cornerstone of the proposed system is a uniform 15% tax rate applied to income. This component includes two key elements:
- **Individual Taxation**: A 15% flat tax applied to gross income across all individual taxpayers, regardless of income level. This approach eliminates tax brackets, deductions, and exemptions that characterize progressive taxation systems.
- **Business Taxation**: A parallel 15% flat tax on net business income (profits), allowing for business expense deductions while maintaining a uniform rate across business entities regardless of size, industry, or organizational structure.
The flat tax component represents a significant departure from graduated or progressive taxation systems prevalent in many developed economies. This simplification potentially reduces compliance costs, eliminates bracket-based behavioral distortions, and creates uniform incentive structures across income levels (Hall & Rabushka, 2007).
### 2.2 Universal Redistribution Mechanism
The second component involves the pooling and redistribution of tax revenue:
- **Collection Aggregation**: All tax revenues from both individual and business taxation are consolidated into a unified fiscal pool.
- **Equal Per Capita Distribution**: The aggregated tax revenue is redistributed on an equal per capita basis to all individuals within the jurisdiction, functioning as a universal basic income mechanism.
This redistribution mechanism effectively creates a de facto progressive element within the overtly flat system, as redistribution amounts represent a larger percentage of total income for lower-income individuals compared to higher-income individuals (Van Parijs & Vanderborght, 2017).
### 2.3 Tiered Consumption Taxation
The third component introduces a differentiated consumption tax structure:
- **Essential Goods and Services**: A minimal 2% consumption tax applied to essential items including food, healthcare, housing, and utilities.
- **Non-Essential and Luxury Items**: A higher consumption tax rate (suggested at 5% or greater) applied to discretionary purchases and luxury goods.
This differentiated approach to consumption taxation acknowledges consumption patterns that vary across income levels, with lower-income households typically allocating a greater proportion of spending to essential goods (Lustig, 2018).
## 3. Economic Implications Analysis
### 3.1 Distributive Effects Across Income Levels
#### 3.1.1 Lower-Income Households
The model's impact on lower-income households involves several counterbalancing forces:
- The 15% flat income tax represents a potentially higher nominal rate than many lower-income households currently face under progressive systems.
- The universal redistribution component serves as a direct income supplement, with the amount received likely exceeding tax contributions for this demographic.
- The 2% consumption tax on essentials introduces a modest additional cost on necessary expenditures.
Net analysis suggests that lower-income households would likely experience a positive fiscal impact through this system, as the redistributive component would exceed their combined income and consumption tax obligations (Piketty & Saez, 2013).
#### 3.1.2 Higher-Income Households
For higher-income households, the framework produces different effects:
- The 15% flat income tax rate typically represents a reduction from current progressive tax rates applied to higher income brackets.
- The universal redistribution amount constitutes a proportionally smaller income supplement relative to total income.
- Higher consumption taxes on luxury goods create a de facto progressive element based on discretionary spending patterns.
The net impact on higher-income households would likely be a reduced overall tax burden compared to progressive systems, potentially increasing capital availability for investment (Auerbach & Hassett, 2015).
### 3.2 Macroeconomic Implications
#### 3.2.1 Investment and Growth Effects
The framework's reduced taxation on higher incomes and business profits theoretically increases capital availability for investment. This aligns with supply-side economic theories suggesting that lower marginal tax rates stimulate economic expansion through:
- Increased business formation and expansion
- Enhanced capital investment
- Improved labor productivity through capital deepening
- Potential innovation stimulation through retained earnings
Empirical research on flat tax implementations in various jurisdictions provides mixed evidence regarding growth effects, with contextual factors playing significant roles in outcomes (Keen et al., 2008).
#### 3.2.2 Demand Stability and Consumption Patterns
The redistribution component creates a consumption floor that may enhance economic stability through:
- Maintaining baseline consumer demand during economic downturns
- Reducing consumption volatility across business cycles
- Supporting broader-based consumption patterns
- Creating demand-side support for business expansion
This mechanism acknowledges the economic significance of broad-based consumption capacity alongside investment incentives (Stiglitz, 2012).
#### 3.2.3 Labor Market Dynamics
The simplified tax structure potentially influences labor market participation through:
- Elimination of high marginal tax rates that may discourage additional work
- Reduced tax-related work disincentives at lower income levels
- Possible increased labor force participation due to simplified income-benefit calculations
- Potential wage effects as businesses retain higher post-tax profits
The framework's impact on labor markets would likely vary across skill levels, industries, and existing labor market institutions (Card & Krueger, 2015).
## 4. Implementation Challenges and Considerations
### 4.1 Fiscal Revenue Adequacy
A primary challenge involves ensuring sufficient government revenue, particularly during the transition period:
- The overall tax burden reduction (estimated at approximately 50% compared to current systems) creates potential revenue shortfalls.
- Government spending obligations would require adjustment, postponement, or alternative funding mechanisms.
- Transitional provisions may be necessary to align revenue reductions with spending adaptations.
Potential solutions include phased implementation, temporary supplementary revenue sources, or deliberate acceleration of economic growth to expand the tax base (Auerbach, 2006).
### 4.2 Wealth Concentration Effects
Despite redistribution mechanisms, the framework may influence wealth concentration dynamics:
- Reduced taxation on higher incomes could accelerate capital accumulation among wealthy individuals.
- Business owners might experience wealth growth exceeding redistribution effects.
- Global investment patterns could divert economic benefits outside the domestic economy.
Addressing these concerns might require calibration of the redistribution component or implementing complementary policies addressing wealth concentration (Piketty, 2014).
### 4.3 Long-Term Sustainability Considerations
The framework's long-term viability depends on several factors:
- Sustained economic growth sufficient to support government functions with reduced tax rates
- Continued business investment in productive domestic activities rather than financial engineering
- Maintenance of investment-consumption balance to prevent boom-bust cycles
- Evolution of the system in response to changing economic conditions
Supplementary policies supporting research and development, entrepreneurship, and domestic investment may be necessary to ensure the system's sustainability (Acemoglu & Robinson, 2012).
## 5. Comparative Cost-Benefit Analysis: Proposed System vs. Current Tax Structure
### 5.1 Compliance Cost Reduction
The current U.S. tax system imposes substantial compliance costs on individuals and businesses that extend far beyond direct tax payments:
- Americans spend approximately 6.5 billion hours annually on tax compliance activities (Taxpayer Advocate Service, 2022)
- The monetary value of compliance time is estimated at $200-400 billion annually (Laffer et al., 2018)
- Businesses spend an estimated $147 billion annually on tax compliance (Tax Foundation, 2021)
- The Internal Revenue Service budget exceeds $13 billion annually for tax administration and enforcement
The proposed flat tax system would dramatically reduce these costs through:
- Elimination of complex deduction and credit calculations (estimated 90% reduction in form complexity)
- Removal of recordkeeping requirements for numerous tax provisions
- Significant reduction in tax planning expenses for both individuals and businesses
- Decreased need for professional tax preparation services
- Streamlined tax enforcement with fewer provisions to interpret and audit
Quantitative analysis suggests that transitioning to the proposed system could reduce overall compliance costs by approximately 70-80%, representing annual savings of $140-320 billion to the U.S. economy (Greenberg, 2020).
### 5.2 Administrative Efficiency Gains
The current tax administration infrastructure incurs substantial costs:
- The IRS employs approximately 75,000 full-time equivalent positions
- Tax litigation consumes significant judicial resources across multiple court systems
- Regulatory development and guidance require extensive government resources
- Tax enforcement costs represent approximately 35 cents per $100 collected
The proposed system would generate administrative efficiencies through:
- Simplified verification processes requiring fewer personnel
- Reduced need for specialized tax rulings and interpretations
- Lower audit costs due to straightforward compliance requirements
- Streamlined distribution mechanisms leveraging existing payment systems
Conservative estimates suggest administrative cost reductions of 50-60%, representing billions in government savings that could be redirected to essential services or deficit reduction.
### 5.3 Economic Efficiency Improvements
Beyond direct compliance and administrative costs, the current system creates significant economic distortions:
- Taxpayers make economic decisions influenced by tax considerations rather than underlying economic value
- Complex provisions create market inefficiencies and misallocation of resources
- High marginal rates discourage additional productive activity
- International tax complexities influence global investment decisions
The proposed system addresses these inefficiencies through:
- Uniform treatment of income regardless of source
- Elimination of tax-motivated transaction structures
- Reduced incentives for artificial entity structures
- Simplified international transactions with domestic reinvestment incentives
Economic models suggest these efficiency improvements could increase GDP by 0.5-1.0% annually beyond direct compliance savings (Jorgenson & Yun, 2012).
### 5.4 Distributional Cost Analysis
The current system's compliance burden falls disproportionately across income levels:
- Lower-income taxpayers spend a higher percentage of their income on tax compliance
- Small businesses face compliance costs estimated at $1,500-$4,000 per employee
- Middle-income taxpayers navigate complex provisions with limited professional assistance
- High-income taxpayers allocate substantial resources to tax planning and compliance
The proposed system redistributes this burden by:
- Equalizing compliance requirements across income levels
- Substantially reducing small business administrative overhead
- Eliminating the need for complex tax planning strategies
- Providing transparent, predictable tax consequences for economic decisions
This redistribution of compliance costs represents an additional progressive element beyond the direct redistribution component, with estimated financial benefits to lower and middle-income households of $300-500 annually in reduced compliance costs.
## 6. Conclusion
The proposed tripartite taxation framework offers a conceptually coherent alternative to conventional progressive taxation systems. By combining flat income taxation with universal redistribution and differentiated consumption taxes, the approach attempts to simultaneously address supply-side investment incentives and demand-side consumption support.
The theoretical analysis suggests potential advantages in terms of simplicity, economic growth stimulation, and maintenance of social safety net functions. However, significant implementation challenges exist regarding revenue adequacy, wealth concentration effects, and long-term economic sustainability.
Further empirical research, potentially through regional pilot implementations or microsimulation modeling, would enhance understanding of the practical implications of this taxation approach. While the framework presents a promising theoretical model, its successful implementation would require careful calibration to specific economic contexts, thoughtful transition planning, and ongoing adjustment based on observed outcomes.
## References
Acemoglu, D., & Robinson, J. A. (2012). *Why nations fail: The origins of power, prosperity, and poverty*. Crown Business.
Greenberg, S. (2020). *Reforming the U.S. tax system: Evidence on economic growth and distribution*. American Enterprise Institute.
Jorgenson, D. W., & Yun, K. Y. (2012). *Tax reform and the cost of capital*. Oxford University Press.
Laffer, A. B., Moore, S., & Williams, J. (2018). *The wealth of states: How taxes, energy, and worker freedom change everything*. Wiley.
Tax Foundation (2021). *The cost of tax compliance*. Fiscal Fact No. 512.
Taxpayer Advocate Service (2022). *Annual report to Congress*. Internal Revenue Service.
Auerbach, A. J. (2006). The choice between income and consumption taxes: A primer. *NBER Working Paper Series*.
Auerbach, A. J., & Hassett, K. (2015). Capital taxation in the twenty-first century. *American Economic Review*, 105(5), 38-42.
Card, D., & Krueger, A. B. (2015). *Myth and measurement: The new economics of the minimum wage*. Princeton University Press.
Hall, R. E., & Rabushka, A. (2007). *The flat tax*. Hoover Institution Press.
Keen, M., Kim, Y., & Varsano, R. (2008). The "flat tax(es)": Principles and experience. *International Tax and Public Finance*, 15(6), 712-751.
Lustig, N. (2018). Fiscal policy, income redistribution and poverty reduction in low and middle income countries. *Commitment to Equity Handbook*.
Mirrlees, J., Adam, S., Besley, T., Blundell, R., Bond, S., Chote, R., Gammie, M., Johnson, P., Myles, G., & Poterba, J. (2011). *Tax by design*. Oxford University Press.
Piketty, T. (2014). *Capital in the twenty-first century*. Harvard University Press.
Piketty, T., & Saez, E. (2013). Optimal labor income taxation. *Handbook of Public Economics*, 5, 391-474.
Stiglitz, J. E. (2012). *The price of inequality: How today's divided society endangers our future*. W.W. Norton & Company.
Van Parijs, P., & Vanderborght, Y. (2017). *Basic income: A radical proposal for a free society and a sane economy*. Harvard University Press.
# A Tripartite Approach to Fiscal Reform: Analyzing the Economic Impact of a Flat Tax, Redistribution, and Consumption Tax Framework
**Author: Lamar Wilson**
## Abstract
**By Lamar Wilson**
This white paper examines an alternative taxation framework characterized by three primary components: a uniform 15% flat tax on income, a redistribution mechanism, and a tiered consumption tax structure. The proposed model aims to stimulate economic growth while maintaining social equity through strategic fiscal policy interventions. This paper analyzes the theoretical underpinnings of this approach, its potential macroeconomic implications, distributional effects across income strata, and implementation challenges. The analysis suggests that while the proposed framework offers significant advantages in terms of simplicity and growth incentives, careful consideration must be given to revenue adequacy, wealth concentration effects, and long-term economic sustainability.
## 1. Introduction
Taxation systems fundamentally shape economic incentive structures, income distribution, and government fiscal capacity. Contemporary tax regimes often reflect accumulated historical policy decisions rather than coherent economic theory, resulting in complex systems with varying degrees of progressivity, efficiency, and equity (Mirrlees et al., 2011). This paper examines a potential alternative taxation framework built upon three pillars: a uniform flat tax, redistribution mechanisms, and stratified consumption taxation.
The theoretical foundation of this approach draws upon both supply-side economics, which emphasizes the importance of investment incentives, and demand-side considerations, which recognize the economic significance of broad-based consumption. By synthesizing these perspectives, the proposed framework attempts to create a self-reinforcing economic cycle wherein simplified taxation stimulates both investment and consumption.
## 2. Structural Components of the Proposed Framework
### 2.1 Uniform Flat Income Taxation
The cornerstone of the proposed system is a uniform 15% tax rate applied to income. This component includes two key elements:
- **Individual Taxation**: A 15% flat tax applied to gross income across all individual taxpayers, regardless of income level. This approach eliminates tax brackets, deductions, and exemptions that characterize progressive taxation systems.
- **Business Taxation**: A parallel 15% flat tax on net business income (profits), allowing for business expense deductions while maintaining a uniform rate across business entities regardless of size, industry, or organizational structure.
The flat tax component represents a significant departure from graduated or progressive taxation systems prevalent in many developed economies. This simplification potentially reduces compliance costs, eliminates bracket-based behavioral distortions, and creates uniform incentive structures across income levels (Hall & Rabushka, 2007).
### 2.2 Universal Redistribution Mechanism
The second component involves the pooling and redistribution of tax revenue:
- **Collection Aggregation**: All tax revenues from both individual and business taxation are consolidated into a unified fiscal pool.
- **Equal Per Capita Distribution**: The aggregated tax revenue is redistributed on an equal per capita basis to all individuals within the jurisdiction, functioning as a universal basic income mechanism.
This redistribution mechanism effectively creates a de facto progressive element within the overtly flat system, as redistribution amounts represent a larger percentage of total income for lower-income individuals compared to higher-income individuals (Van Parijs & Vanderborght, 2017).
### 2.3 Tiered Consumption Taxation
The third component introduces a differentiated consumption tax structure:
- **Essential Goods and Services**: A minimal 2% consumption tax applied to essential items including food, healthcare, housing, and utilities.
- **Non-Essential and Luxury Items**: A higher consumption tax rate (suggested at 5% or greater) applied to discretionary purchases and luxury goods.
This differentiated approach to consumption taxation acknowledges consumption patterns that vary across income levels, with lower-income households typically allocating a greater proportion of spending to essential goods (Lustig, 2018).
## 3. Economic Implications Analysis
### 3.1 Distributive Effects Across Income Levels
#### 3.1.1 Lower-Income Households
The model's impact on lower-income households involves several counterbalancing forces:
- The 15% flat income tax represents a potentially higher nominal rate than many lower-income households currently face under progressive systems.
- The universal redistribution component serves as a direct income supplement, with the amount received likely exceeding tax contributions for this demographic.
- The 2% consumption tax on essentials introduces a modest additional cost on necessary expenditures.
Net analysis suggests that lower-income households would likely experience a positive fiscal impact through this system, as the redistributive component would exceed their combined income and consumption tax obligations (Piketty & Saez, 2013).
#### 3.1.2 Higher-Income Households
For higher-income households, the framework produces different effects:
- The 15% flat income tax rate typically represents a reduction from current progressive tax rates applied to higher income brackets.
- The universal redistribution amount constitutes a proportionally smaller income supplement relative to total income.
- Higher consumption taxes on luxury goods create a de facto progressive element based on discretionary spending patterns.
The net impact on higher-income households would likely be a reduced overall tax burden compared to progressive systems, potentially increasing capital availability for investment (Auerbach & Hassett, 2015).
### 3.2 Macroeconomic Implications
#### 3.2.1 Investment and Growth Effects
The framework's reduced taxation on higher incomes and business profits theoretically increases capital availability for investment. This aligns with supply-side economic theories suggesting that lower marginal tax rates stimulate economic expansion through:
- Increased business formation and expansion
- Enhanced capital investment
- Improved labor productivity through capital deepening
- Potential innovation stimulation through retained earnings
Empirical research on flat tax implementations in various jurisdictions provides mixed evidence regarding growth effects, with contextual factors playing significant roles in outcomes (Keen et al., 2008).
#### 3.2.2 Demand Stability and Consumption Patterns
The redistribution component creates a consumption floor that may enhance economic stability through:
- Maintaining baseline consumer demand during economic downturns
- Reducing consumption volatility across business cycles
- Supporting broader-based consumption patterns
- Creating demand-side support for business expansion
This mechanism acknowledges the economic significance of broad-based consumption capacity alongside investment incentives (Stiglitz, 2012).
#### 3.2.3 Labor Market Dynamics
The simplified tax structure potentially influences labor market participation through:
- Elimination of high marginal tax rates that may discourage additional work
- Reduced tax-related work disincentives at lower income levels
- Possible increased labor force participation due to simplified income-benefit calculations
- Potential wage effects as businesses retain higher post-tax profits
The framework's impact on labor markets would likely vary across skill levels, industries, and existing labor market institutions (Card & Krueger, 2015).
## 4. Implementation Challenges and Considerations
### 4.1 Fiscal Revenue Adequacy
A primary challenge involves ensuring sufficient government revenue, particularly during the transition period:
- The overall tax burden reduction (estimated at approximately 50% compared to current systems) creates potential revenue shortfalls.
- Government spending obligations would require adjustment, postponement, or alternative funding mechanisms.
- Transitional provisions may be necessary to align revenue reductions with spending adaptations.
Potential solutions include phased implementation, temporary supplementary revenue sources, or deliberate acceleration of economic growth to expand the tax base (Auerbach, 2006).
### 4.2 Wealth Concentration Effects
Despite redistribution mechanisms, the framework may influence wealth concentration dynamics:
- Reduced taxation on higher incomes could accelerate capital accumulation among wealthy individuals.
- Business owners might experience wealth growth exceeding redistribution effects.
- Global investment patterns could divert economic benefits outside the domestic economy.
Addressing these concerns might require calibration of the redistribution component or implementing complementary policies addressing wealth concentration (Piketty, 2014).
### 4.3 Long-Term Sustainability Considerations
The framework's long-term viability depends on several factors:
- Sustained economic growth sufficient to support government functions with reduced tax rates
- Continued business investment in productive domestic activities rather than financial engineering
- Maintenance of investment-consumption balance to prevent boom-bust cycles
- Evolution of the system in response to changing economic conditions
Supplementary policies supporting research and development, entrepreneurship, and domestic investment may be necessary to ensure the system's sustainability (Acemoglu & Robinson, 2012).
## 5. Comparative Cost-Benefit Analysis: Proposed System vs. Current Tax Structure
### 5.1 Compliance Cost Reduction
The current U.S. tax system imposes substantial compliance costs on individuals and businesses that extend far beyond direct tax payments:
- Americans spend approximately 6.5 billion hours annually on tax compliance activities (Taxpayer Advocate Service, 2022)
- The monetary value of compliance time is estimated at $200-400 billion annually (Laffer et al., 2018)
- Businesses spend an estimated $147 billion annually on tax compliance (Tax Foundation, 2021)
- The Internal Revenue Service budget exceeds $13 billion annually for tax administration and enforcement
The proposed flat tax system would dramatically reduce these costs through:
- Elimination of complex deduction and credit calculations (estimated 90% reduction in form complexity)
- Removal of recordkeeping requirements for numerous tax provisions
- Significant reduction in tax planning expenses for both individuals and businesses
- Decreased need for professional tax preparation services
- Streamlined tax enforcement with fewer provisions to interpret and audit
Quantitative analysis suggests that transitioning to the proposed system could reduce overall compliance costs by approximately 70-80%, representing annual savings of $140-320 billion to the U.S. economy (Greenberg, 2020).
### 5.2 Administrative Efficiency Gains
The current tax administration infrastructure incurs substantial costs:
- The IRS employs approximately 75,000 full-time equivalent positions
- Tax litigation consumes significant judicial resources across multiple court systems
- Regulatory development and guidance require extensive government resources
- Tax enforcement costs represent approximately 35 cents per $100 collected
The proposed system would generate administrative efficiencies through:
- Simplified verification processes requiring fewer personnel
- Reduced need for specialized tax rulings and interpretations
- Lower audit costs due to straightforward compliance requirements
- Streamlined distribution mechanisms leveraging existing payment systems
Conservative estimates suggest administrative cost reductions of 50-60%, representing billions in government savings that could be redirected to essential services or deficit reduction.
### 5.3 Economic Efficiency Improvements
Beyond direct compliance and administrative costs, the current system creates significant economic distortions:
- Taxpayers make economic decisions influenced by tax considerations rather than underlying economic value
- Complex provisions create market inefficiencies and misallocation of resources
- High marginal rates discourage additional productive activity
- International tax complexities influence global investment decisions
The proposed system addresses these inefficiencies through:
- Uniform treatment of income regardless of source
- Elimination of tax-motivated transaction structures
- Reduced incentives for artificial entity structures
- Simplified international transactions with domestic reinvestment incentives
Economic models suggest these efficiency improvements could increase GDP by 0.5-1.0% annually beyond direct compliance savings (Jorgenson & Yun, 2012).
### 5.4 Distributional Cost Analysis
The current system's compliance burden falls disproportionately across income levels:
- Lower-income taxpayers spend a higher percentage of their income on tax compliance
- Small businesses face compliance costs estimated at $1,500-$4,000 per employee
- Middle-income taxpayers navigate complex provisions with limited professional assistance
- High-income taxpayers allocate substantial resources to tax planning and compliance
The proposed system redistributes this burden by:
- Equalizing compliance requirements across income levels
- Substantially reducing small business administrative overhead
- Eliminating the need for complex tax planning strategies
- Providing transparent, predictable tax consequences for economic decisions
This redistribution of compliance costs represents an additional progressive element beyond the direct redistribution component, with estimated financial benefits to lower and middle-income households of $300-500 annually in reduced compliance costs.
## 6. Conclusion
The proposed tripartite taxation framework offers a conceptually coherent alternative to conventional progressive taxation systems. By combining flat income taxation with universal redistribution and differentiated consumption taxes, the approach attempts to simultaneously address supply-side investment incentives and demand-side consumption support.
The theoretical analysis suggests potential advantages in terms of simplicity, economic growth stimulation, and maintenance of social safety net functions. However, significant implementation challenges exist regarding revenue adequacy, wealth concentration effects, and long-term economic sustainability.
Further empirical research, potentially through regional pilot implementations or microsimulation modeling, would enhance understanding of the practical implications of this taxation approach. While the framework presents a promising theoretical model, its successful implementation would require careful calibration to specific economic contexts, thoughtful transition planning, and ongoing adjustment based on observed outcomes.
## References
Acemoglu, D., & Robinson, J. A. (2012). *Why nations fail: The origins of power, prosperity, and poverty*. Crown Business.
Greenberg, S. (2020). *Reforming the U.S. tax system: Evidence on economic growth and distribution*. American Enterprise Institute.
Jorgenson, D. W., & Yun, K. Y. (2012). *Tax reform and the cost of capital*. Oxford University Press.
Laffer, A. B., Moore, S., & Williams, J. (2018). *The wealth of states: How taxes, energy, and worker freedom change everything*. Wiley.
Tax Foundation (2021). *The cost of tax compliance*. Fiscal Fact No. 512.
Taxpayer Advocate Service (2022). *Annual report to Congress*. Internal Revenue Service.
Auerbach, A. J. (2006). The choice between income and consumption taxes: A primer. *NBER Working Paper Series*.
Auerbach, A. J., & Hassett, K. (2015). Capital taxation in the twenty-first century. *American Economic Review*, 105(5), 38-42.
Card, D., & Krueger, A. B. (2015). *Myth and measurement: The new economics of the minimum wage*. Princeton University Press.
Hall, R. E., & Rabushka, A. (2007). *The flat tax*. Hoover Institution Press.
Keen, M., Kim, Y., & Varsano, R. (2008). The "flat tax(es)": Principles and experience. *International Tax and Public Finance*, 15(6), 712-751.
Lustig, N. (2018). Fiscal policy, income redistribution and poverty reduction in low and middle income countries. *Commitment to Equity Handbook*.
Mirrlees, J., Adam, S., Besley, T., Blundell, R., Bond, S., Chote, R., Gammie, M., Johnson, P., Myles, G., & Poterba, J. (2011). *Tax by design*. Oxford University Press.
Piketty, T. (2014). *Capital in the twenty-first century*. Harvard University Press.
Piketty, T., & Saez, E. (2013). Optimal labor income taxation. *Handbook of Public Economics*, 5, 391-474.
Stiglitz, J. E. (2012). *The price of inequality: How today's divided society endangers our future*. W.W. Norton & Company.
Van Parijs, P., & Vanderborght, Y. (2017). *Basic income: A radical proposal for a free society and a sane economy*. Harvard University Press.
-

@ 6389be64:ef439d32
2025-03-05 21:18:52
Carbon is a "Long-Tail" asset: the residual earnings that come from an asset after it has had its initial market impact.
The Carbon Cascade converts labile into recalcitrant carbon.
During transformation power is generated and lands restored.
Total production of biomass per annum is 100 billion tons of carbon and at $500 to $2,000 per ton of biochar that's $100 trillion of potential carbon trading on the open market. (fanciful to be sure)
originally posted at https://stacker.news/items/904996
-

@ 05933d87:81bac46e
2025-03-05 20:17:49
A few months ago, an Uber driver alerted me to [the presence of his rival](https://stacker.news/items/687682/r/k00b?commentId=688882). By that point, [Waymo had been testing in Austin](https://waymo.com/blog/2023/08/waymo-one-heads-to-austin/) for over a year. I hid my excitement during the ride but I applied as a beta tester, noting my belonging to the demographics a PM might test for. My application went ignored until, huzzah, Waymo sent me an email yesterday announcing [their self-driving cars are available directly through Uber in Austin](https://waymo.com/waymo-on-uber/).

I configured my allegiance to our new overlords swearing in on my screened sandwich of silicon.
Without willing it, and having forgot my new religion, I woke earlier than planned today and hailed a ride. The app spoke to me, "if you wait 3 minutes longer, we'll send you a car without a driver." For five minutes, I watched a car but not a driver move in the direction of me and my screen.
The ride was nice. I didn't have to theatrically rush to a waiting human. There was less social weirdness than I would normally sit with on a ride. I could inspect the car without risking the driver sense that I'm inspecting them. The car couldn't look at me buffering, deciphering if I am homeless or merely look it. I got to pick my own music. I got to watch people un-contacted by Waymo watch the car.

But ... it drove a lot more like a robot driving a car than a human driving a car. It pumped the brakes a few times as we passed weirdly parked cars uncertain (apparently) if the car might move into our lane. Once it signaled that we were headed into oncoming traffic as a street widened from one lane to two. Worst of all, it dropped me off near an anomalous stretch of sidewalk where my door opened to a wall, and if I were to climb and get out the other side, I'd arrive in the middle lane of a busy street. Trapped, I pinched myself through the door and, like Laura Croft, navigated the road's edge to a sidewalk.

tbh I'm still excited for my next Waymo ride. I'll just choose a different drop-off address.
originally posted at https://stacker.news/items/904830
-

@ 2e8970de:63345c7a
2025-03-05 19:50:10
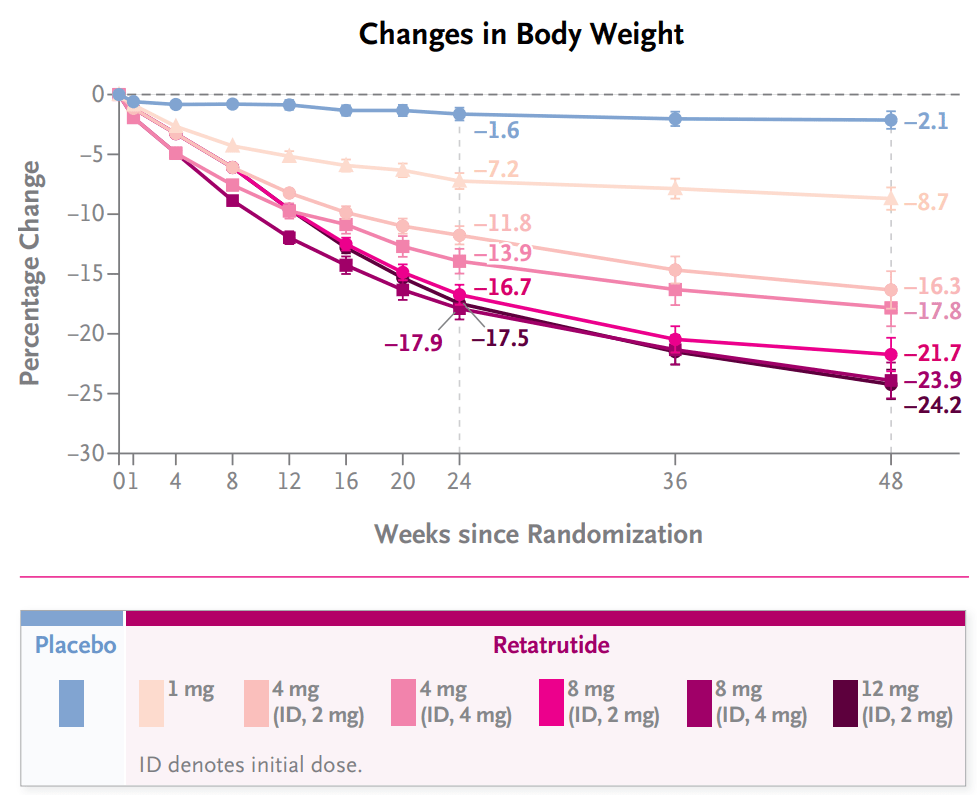
> It leads to fast, and massive weight loss by not just suppressing appetite, but also by upregulating metabolism.
https://www.nejm.org/doi/full/10.1056/NEJMoa2301972
originally posted at https://stacker.news/items/904851
-

@ 4925ea33:025410d8
2025-03-05 19:44:37
De acordo com a Resolução 03/25 do Conselho Federal de Farmácia a Aromaterapia é uma prática terapêutica que utiliza as propriedades dos óleos essenciais para restaurar o equilíbrio e a harmonia do organismo, promovendo a saúde física, mental e emocional. Essa técnica baseia-se no uso dos compostos aromáticos naturais extraídos das plantas para estimular respostas neurológicas e bioquímicas no corpo.
Os óleos essenciais atuam diretamente no sistema límbico, região do cérebro responsável pelas emoções, memórias e comportamentos. Mas seus benefícios vão muito além do bem-estar emocional! Eles possuem propriedades terapêuticas únicas, podendo atuar como cicatrizantes, antifúngicos, antibacterianos, anti-inflamatórios e até auxiliares no alívio de dores e tensões musculares. Além da inalação, os óleos podem ser aplicados topicamente, sendo absorvidos pela pele e interagindo com o organismo de maneira profunda e eficaz.
No entanto, é importante lembrar que os óleos essenciais são altamente concentrados e contêm substâncias que podem causar alergias ou irritações se usados de forma inadequada. Por isso, é essencial buscar orientação de um profissional qualificado para garantir um tratamento seguro e eficaz.
**Quer saber como a Aromaterapia pode transformar seu bem-estar? Agende uma consulta comigo e descubra os benefícios personalizados para você**.
-

@ b4403b24:83542d4e
2025-03-05 19:18:39


I can't believe so many shitcoiners are invited to attend 🫣
originally posted at https://stacker.news/items/904818
-

@ 97c70a44:ad98e322
2025-03-05 18:09:05
So you've decided to join nostr! Some wide-eyed fanatic has convinced you that the "sun shines every day on the birds and the bees and the cigarette trees" in a magical land of decentralized, censorship-resistant freedom of speech - and it's waiting just over the next hill.
But your experience has not been all you hoped. Before you've even had a chance to upload your AI-generated cyberpunk avatar or make up exploit codenames for your pseudonym's bio, you've been confronted with a new concept that has left you completely nonplussed.
It doesn't help that this new idea might be called by any number of strange names. You may have been asked to "paste your nsec", "generate a private key", "enter your seed words", "connect with a bunker", "sign in with extension", or even "generate entropy". Sorry about that.
All these terms are really referring to one concept under many different names: that of "cryptographic identity".
Now, you may have noticed that I just introduced yet another new term which explains exactly nothing. You're absolutely correct. And now I'm going to proceed to ignore your complaints and talk about something completely different. But bear with me, because the juice is worth the squeeze.
# Identity
What is identity? There are many philosophical, political, or technical answers to this question, but for our purposes it's probably best to think of it this way:
> Identity is the essence of a thing. Identity separates one thing from all others, and is itself indivisible.
This definition has three parts:
- Identity is "essential": a thing can change, but its identity cannot. I might re-paint my house, replace its components, sell it, or even burn it down, but its identity as something that can be referred to - "this house" - is durable, even outside the boundaries of its own physical existence.
- Identity is a unit: you can't break an identity into multiple parts. A thing might be _composed_ of multiple parts, but that's only incidental to the identity of a thing, which is a _concept_, not a material thing.
- Identity is distinct: identity is what separates one thing from all others - the concept of an apple can't be mixed with that of an orange; the two ideas are distinct. In the same way, a single concrete apple is distinct in identity from another - even if the component parts of the apple decompose into compost used to grow more apples.
Identity is not a physical thing, but a metaphysical thing. Or, in simpler terms, identity is a "concept".
I (or someone more qualified) could at this point launch into a Scholastic tangent on what "is" is, but that is, fortunately, not necessary here. The kind of identities I want to focus on here are not our _actual_ identities as people, but entirely _fictional_ identities that we use to extend our agency into the digital world.
Think of it this way - your bank login does not represent _you_ as a complete person. It only represents the _access granted to you_ by the bank. This access is in fact an _entirely new identity_ that has been associated with you, and is limited in what it's useful for.
Other examples of fictional identities include:
- The country you live in
- Your social media persona
- Your mortgage
- Geographical coordinates
- A moment in time
- A chess piece
Some of these identites are inert, for example points in space and time. Other identies have agency and so are able to act in the world - even as fictional concepts. In order to do this, they must "authenticate" themselves (which means "to prove they are real"), and act within a system of established rules.
For example, your D&D character exists only within the collective fiction of your D&D group, and can do anything the rules say. Its identity is authenticated simply by your claim as a member of the group that your character in fact exists. Similarly, a lawyer must prove they are a member of the Bar Association before they are allowed to practice law within that collective fiction.
"Cryptographic identity" is simply another way of authenticating a fictional identity within a given system. As we'll see, it has some interesting attributes that set it apart from things like a library card or your latitude and longitude. Before we get there though, let's look in more detail at how identities are authenticated.
# Certificates
Merriam-Webster defines the verb "certify" as meaning "to attest authoritatively". A "certificate" is just a fancy way of saying "because I said so". Certificates are issued by a "certificate authority", someone who has the authority to "say so". Examples include your boss, your mom, or the Pope.
This method of authentication is how almost every institution authenticates the people who associate with it. Colleges issue student ID cards, governments issue passports, and websites allow you to "register an account".
In every case mentioned above, the "authority" creates a closed system in which a document (aka a "certificate") is issued which serves as a claim to a given identity. When someone wants to access some privileged service, location, or information, they present their certificate. The authority then validates it and grants or denies access. In the case of an international airport, the certificate is a little book printed with fancy inks. In the case of a login page, the certificate is a username and password combination.
This pattern for authentication is ubiquitous, and has some very important implications.
First of all, certified authentication implies that the issuer of the certificate has the right to _exclusive control_ of any identity it issues. This identity can be revoked at any time, or its permissions may change. Your social credit score may drop arbitrarily, or money might disappear from your account. When dealing with certificate authorities, you have no inherent rights.
Second, certified authentication depends on the certificate authority continuing to exist. If you store your stuff at a storage facility but the company running it goes out of business, your stuff might disappear along with it.
Usually, authentication via certificate authority works pretty well, since an appeal can always be made to a higher authority (nature, God, the government, etc). Authorities also can't generally dictate their terms with impunity without losing their customers, alienating their constituents, or provoking revolt. But it's also true that certification by authority creates an incentive structure that frequently leads to abuse - arbitrary deplatforming is increasingly common, and the bigger the certificate authority, the less recourse the certificate holder (or "subject") has.
Certificates also put the issuer in a position to intermediate relationships that wouldn't otherwise be subject to their authority. This might take the form of selling user attention to advertisers, taking a cut of financial transactions, or selling surveillance data to third parties.
Proliferation of certificate authorities is not a solution to these problems. Websites and apps frequently often offer multiple "social sign-in" options, allowing their users to choose which certificate authority to appeal to. But this only piles more value into the social platform that issues the certificate - not only can Google shut down your email inbox, they can revoke your ability to log in to every website you used their identity provider to get into.
In every case, certificate issuance results in an asymmetrical power dynamic, where the issuer is able to exert significant control over the certificate holder, even in areas unrelated to the original pretext for the relationship between parties.
# Self-Certification
But what if we could reverse this power dynamic? What if individuals could issue their own certificates and force institutions to accept them?

Ron Swanson's counterexample notwithstanding, there's a reason I can't simply write myself a parking permit and slip it under the windshield wiper. Questions about voluntary submission to legitimate authorities aside, the fact is that we don't have the power to act without impunity - just like any other certificate authority, we have to prove our claims either by the exercise of raw power or by appeal to a higher authority.
So the question becomes: which higher authority can we appeal to in order to issue our own certificates within a given system of identity?
The obvious answer here is to go straight to the top and ask God himself to back our claim to self-sovereignty. However, that's not how he normally works - there's a reason they call direct acts of God "miracles". In fact, Romans 13:1 explicitly says that "the authorities that exist have been appointed by God". God has structured the universe in such a way that we must appeal to the deputies he has put in place to govern various parts of the world.
Another tempting appeal might be to nature - i.e. the material world. This is the realm in which we most frequently have the experience of "self-authenticating" identities. For example, a gold coin can be authenticated by biting it or by burning it with acid. If it quacks like a duck, walks like a duck, and looks like a duck, then it probably is a duck.
In most cases however, the ability to authenticate using physical claims depends on physical access, and so appeals to physical reality have major limitations when it comes to the digital world. Captchas, selfies and other similar tricks are often used to bridge the physical world into the digital, but these are increasingly easy to forge, and hard to verify.
There are exceptions to this rule - an example of self-certification that makes its appeal to the physical world is that of a signature. Signatures are hard to forge - an incredible amount of data is encoded in physical signatures, from strength, to illnesses, to upbringing, to [personality](https://en.wikipedia.org/wiki/Graphology). These can even be scanned and used within the digital world as well. Even today, most contracts are sealed with some simulacrum of a physical signature. Of course, this custom is quickly becoming a mere historical curiosity, since the very act of digitizing a signature makes it trivially forgeable.
So: transcendent reality is too remote to subtantiate our claims, and the material world is too limited to work within the world of information. There is another aspect of reality remaining that we might appeal to: information itself.
Physical signatures authenticate physical identities by encoding unique physical data into an easily recognizable artifact. To transpose this idea to the realm of information, a "digital signature" might authenticate "digital identities" by encoding unique "digital data" into an easily recognizable artifact.
Unfortunately, in the digital world we have the additional challenge that the artifact itself can be copied, undermining any claim to legitimacy. We need something that can be easily verified _and unforgeable_.
# Digital Signatures
In fact such a thing does exist, but calling it a "digital signature" obscures more than it reveals. We might just as well call the thing we're looking for a "digital fingerprint", or a "digital electroencephalogram". Just keep that in mind as we work our way towards defining the term - we are not looking for something _looks like a physical signature_, but for something that _does the same thing as_ a physical signature, in that it allows us to issue ourselves a credential that must be accepted by others by encoding privileged information into a recognizable, unforgeable artifact.
With that, let's get into the weeds.
An important idea in computer science is that of a "function". A function is a sort of information machine that converts data from one form to another. One example is the idea of "incrementing" a number. If you increment 1, you get 2. If you increment 2, you get 3. Incrementing can be reversed, by creating a complementary function that instead subtracts 1 from a number.
A "one-way function" is a function that can't be reversed. A good example of a one-way function is integer rounding. If you round a number and get `5`, what number did you begin with? It's impossible to know - 5.1, 4.81, 5.332794, in fact an infinite number of numbers can be rounded to the number `5`. These numbers can also be infinitely long - for example rounding PI to the nearest integer results in the number `3`.
A real-life example of a useful one-way function is `sha256`. This function is a member of a family of one-way functions called "hash functions". You can feed as much data as you like into `sha256`, and you will always get 256 bits of information out. Hash functions are especially useful because collisions between outputs are very rare - even if you change a single bit in a huge pile of data, you're almost certainly going to get a different output.
Taking this a step further, there is a whole family of cryptographic one-way "trapdoor" functions that act similarly to hash functions, but which maintain a specific mathematical relationship between the input and the output which allows the input/output pair to be used in a variety of useful applications. For example, in Elliptic Curve Cryptography, scalar multiplication on an elliptic curve is used to derive the output.
"Ok", you say, "that's all completely clear and lucidly explained" (thank you). "But what goes _into_ the function?" You might expect that because of our analogy to physical signatures we would have to gather an incredible amount of digital information to cram into our cryptographic trapdoor function, mashing together bank statements, a record of our heartbeat, brain waves and cellular respiration. Well, we _could_ do it that way (maybe), but there's actually a _much_ simpler solution.
Let's play a quick game. What number am I thinking of? Wrong, it's 82,749,283,929,834. Good guess though.
The reason we use signatures to authenticate our identity in the physical world is not because they're backed by a lot of implicit physical information, but because they're hard to forge and easy to validate. Even so, there is a lot of variation in a single person's signature, even from one moment to the next.
Trapdoor functions solve the validation problem - it's trivially simple to compare one 256-bit number to another. And randomness solves the problem of forgeability.
Now, randomness (A.K.A. "entropy") is actually kind of hard to generate. Random numbers that don't have enough "noise" in them are known as "pseudo-random numbers", and are weirdly easy to guess. This is why Cloudflare uses a video stream of their [giant wall of lava lamps](https://blog.cloudflare.com/randomness-101-lavarand-in-production/) to feed the random number generator that powers their CDN. For our purposes though, we can just imagine that our random numbers come from rolling a bunch of dice.
To recap, we can get a digital equivalent of a physical signature (or fingerprint, etc) by 1. coming up with a random number, and 2. feeding it into our chosen trapdoor function. The random number is called the "private" part. The output of the trapdoor function is called the "public" part. These two halves are often called "keys", hence the terms "public key" and "private key".
And now we come full circle - remember about 37 years ago when I introduced the term "cryptographic identity"? Well, we've finally arrived at the point where I explain what that actually is.
A "cryptographic identity" is _identified_ by a public key, and _authenticated_ by the ability to prove that you know the private key.
Notice that I didn't say "authenticated by the private key". If you had to reveal the private key in order to prove you know it, you could only authenticate a public key once without losing exclusive control of the key. But cryptographic identities can be authenticated any number of times because the certification is an _algorithm_ that only someone who knows the private key can execute.
This is the super power that trapdoor functions have that hash functions don't. Within certain cryptosystems, it is possible to mix additional data with your private key to get yet another number in such a way that someone else who only knows the public key can _prove_ that you know the private key.
For example, if my secret number is `12`, and someone tells me the number `37`, I can "combine" the two by adding them together and returning the number `49`. This "proves" that my secret number is `12`. Of course, addition is not a trapdoor function, so it's trivially easy to reverse, which is why cryptography is its own field of knowledge.
# What's it for?
If I haven't completely lost you yet, you might be wondering why this matters. Who cares if I can prove that I made up a random number?
To answer this, let's consider a simple example: that of public social media posts.
Most social media platforms function by issuing credentials and verifying them based on their internal database. When you log in to your Twitter (ok, fine, X) account, you provide X with a phone number (or email) and password. X compares these records to the ones stored in the database when you created your account, and if they match they let you "log in" by issuing yet another credential, called a "session key".
Next, when you "say" something on X, you pass along your session key and your tweet to X's servers. They check that the session key is legit, and if it is they associate your tweet with your account's identity. Later, when someone wants to see the tweet, X vouches for the fact that you created it by saying "trust me" and displaying your name next to the tweet.
In other words, X creates and controls your identity, but they let you use it as long as you can prove that you know the secret that you agreed on when you registered (by giving it to them every time).
Now pretend that X gets bought by someone _even more evil_ than Elon Musk (if such a thing can be imagined). The new owner now has the ability to control _your_ identity, potentially making it say things that you didn't actually say. Someone could be completely banned from the platform, but their account could be made to continue saying whatever the owner of the platform wanted.
In reality, such a breach of trust would quickly result in a complete loss of credibility for the platform, which is why this kind of thing doesn't happen (at least, not that we know of).
But there are other ways of exploiting this system, most notably by censoring speech. As often happens, platforms are able to confiscate user identities, leaving the tenant no recourse except to appeal to the platform itself (or the government, but that doesn't seem to happen for some reason - probably due to some legalese in social platforms' terms of use). The user has to start completely from scratch, either on the same platform or another.
Now suppose that when you signed up for X instead of simply telling X your password you made up a random number and provided a cryptographic proof to X along with your public key. When you're ready to tweet (there's no need to issue a session key, or even to store your public key in their database) you would again prove your ownership of that key with a new piece of data. X could then publish that tweet or not, along with the same proof you provided that it really came from you.
What X _can't_ do in this system is pretend you said something you didn't, because they _don't know your private key_.
X also wouldn't be able to deplatform you as effectively either. While they could choose to ban you from their website and refuse to serve your tweets, they don't control your identity. There's nothing they can do to prevent you from re-using it on another platform. Plus, if the system was set up in such a way that other users followed your key instead of an ID made up by X, you could switch platforms and _keep your followers_. In the same way, it would also be possible to keep a copy of all your tweets in your own database, since their authenticity is determined by _your_ digital signature, not X's "because I say so".
This new power is not just limited to social media either. Here are some other examples of ways that self-issued cryptographic identites transform the power dynamic inherent in digital platforms:
- Banks sometimes freeze accounts or confiscate funds. If your money was stored in a system based on self-issued cryptographic keys rather than custodians, banks would not be able to keep you from accessing or moving your funds. This system exists, and it's called [bitcoin](https://bitcoin.rocks/).
- Identity theft happens when your identifying information is stolen and used to take out a loan in your name, and without your consent. The reason this is so common is because your credentials are not cryptographic - your name, address, and social security number can only be authenticated by being shared, and they are shared so often and with so many counterparties that they frequently end up in data breaches. If credit checks were authenticated by self-issued cryptographic keys, identity theft would cease to exist (unless your private key itself got stolen).
- Cryptographic keys allow credential issuers to protect their subjects' privacy better too. Instead of showing your ID (including your home address, birth date, height, weight, etc), the DMV could sign a message asserting that the holder of a given public key indeed over 21. The liquor store could then validate that claim, and your ownership of the named key, without knowing anything more about you. [Zero-knowledge](https://en.wikipedia.org/wiki/Non-interactive_zero-knowledge_proof) proofs take this a step further.
In each of these cases, the interests of the property owner, loan seeker, or customer are elevated over the interests of those who might seek to control their assets, exploit their hard work, or surveil their activity. Just as with personal privacy, freedom of speech, and Second Amendment rights the individual case is rarely decisive, but in the aggregate realigned incentives can tip the scale in favor of freedom.
# Objections
Now, there are some drawbacks to digital signatures. Systems that rely on digital signatures are frequently less forgiving of errors than their custodial counterparts, and many of their strengths have corresponding weaknesses. Part of this is because people haven't yet developed an intuition for how to use cryptographic identities, and the tools for managing them are still being designed. Other aspects can be mitigated through judicious use of keys fit to the problems they are being used to solve.
Below I'll articulate some of these concerns, and explore ways in which they might be mitigated over time.
## Key Storage
Keeping secrets is hard. "A lie can travel halfway around the world before the truth can get its boots on", and the same goes for gossip. Key storage has become increasingly important as more of our lives move online, to the extent that password managers have become almost a requirement for keeping track of our digital lives. But even with good password management, credentials frequently end up for sale on the dark web as a consequence of poorly secured infrastructure.
Apart from the fact that all of this is an argument _for_ cryptographic identities (since keys are shared with far fewer parties), it's also true that the danger of losing a cryptographic key is severe, especially if that key is used in multiple places. Instead of hackers stealing your Facebook password, they might end up with access to all your other social media accounts too!
Keys should be treated with the utmost care. Using password managers is a good start, but very valuable keys should be stored even more securely - for example in a [hardware signing device](https://nostrsigningdevice.com/). This is a hassle, and something additional to learn, but is an indispensable part of taking advantage of the benefits associated with cryptographic identity.
There are ways to lessen the impact of lost or stolen secrets, however. Lots of different techniques exist for structuring key systems in such a way that keys can be protected, invalidated, or limited. Here are a few:
- [Hierarchical Deterministic Keys](https://www.ietf.org/archive/id/draft-dijkhuis-cfrg-hdkeys-02.html) allow for the creation of a single root key from which multiple child keys can be generated. These keys are hard to link to the parent, which provides additional privacy, but this link can also be proven when necessary. One limitation is that the identity system has to be designed with HD keys in mind.
- [Key Rotation](https://crypto.stackexchange.com/questions/41796/whats-the-purpose-of-key-rotation) allows keys to become expendable. Additional credentials might be attached to a key, allowing the holder to prove they have the right to rotate the key. Social attestations can help with the process as well if the key is embedded in a web of trust.
- Remote Signing is a technique for storing a key on one device, but using it on another. This might take the form of signing using a hardware wallet and transferring an SD card to your computer for broadcasting, or using a mobile app like [Amber](https://github.com/greenart7c3/Amber) to manage sessions with different applications.
- [Key](https://github.com/coracle-social/promenade/tree/master) [sharding](https://www.frostr.org/) takes this to another level by breaking a single key into multiple pieces and storing them separately. A coordinator can then be used to collaboratively sign messages without sharing key material. This dramatically reduces the ability of an attacker to steal a complete key.
## Multi-Factor Authentication
One method for helping users secure their accounts that is becoming increasingly common is "multi-factor authentication". Instead of just providing your email and password, platforms send a one-time use code to your phone number or email, or use "time-based one time passwords" which are stored in a password manager or on a hardware device.
Again, MFA is a solution to a problem inherent in account-based authentication which would not be nearly so prevalent in a cryptographic identity system. Still, theft of keys does happen, and so MFA would be an important improvement - if not for an extra layer of authentication, then as a basis for key rotation.
In a sense, MFA is already being researched - key shards is one way of creating multiple credentials from a single key. However, this doesn't address the issue of key rotation, especially when an identity is tied to the public key that corresponds to a given private key. There are two possible solutions to this problem:
- Introduce a naming system. This would allow identities to use a durable name, assigning it to different keys over time. The downside is that this would require the introduction of either centralized naming authorities (back to the old model), or a blockchain in order to solve [Zooko's trilemma](https://en.wikipedia.org/wiki/Zooko%27s_triangle).
- Establish a chain of keys. This would require a given key to name a successor key in advance and self-invalidate, or some other process like social recovery to invalidate an old key and assign the identity to a new one. This also would significantly increase the complexity of validating messages and associating them with a given identity.
Both solutions are workable, but introduce a lot of complexity that could cause more trouble than it's worth, depending on the identity system we're talking about.
## Surveillance
One of the nice qualities that systems based on cryptographic identities have is that digitally signed data can be passed through any number of untrusted systems and emerge intact. This ability to resist tampering makes it possible to broadcast signed data more widely than would otherwise be the case in a system that relies on a custodian to authenticate information.
The downside of this is that more untrusted systems have access to data. And if information is broadcast publicly, anyone can get access to it.
This problem is compounded by re-use of cryptographic identities across multiple contexts. A benefit of self-issued credentials is that it becomes possible to bring everything attached to your identity with you, including social context and attached credentials. This is convenient and can be quite powerful, but it also means that more context is attached to your activity, making it easier to infer information about you for advertising or surveillance purposes. This is dangerously close to the dystopian ideal of a "Digital ID".
The best way to deal with this risk is to consider identity re-use an option to be used when desirable, but to default to creating a new key for every identity you create. This is no worse than the status quo, and it makes room for the ability to link identities when desired.
Another possible approach to this problem is to avoid broadcasting signed data when possible. This could be done by obscuring your cryptographic identity when data is served from a database, or by encrypting your signed data in order to selectively share it with named counterparties.
Still, this is a real risk, and should be kept in mind when designing and using systems based on cryptographic identity. If you'd like to read more about this, please see [this blog post](https://habla.news/u/hodlbod@coracle.social/1687802006398).
# Making Keys Usable
You might be tempted to look at that list of trade-offs and get the sense that cryptographic identity is not for mere mortals. Key management is hard, and footguns abound - but there is a way forward. With [nostr](https://nostr.com/), some new things are happening in the world of key management that have never really happened before.
Plenty of work over the last 30 years has gone into making key management tractable, but none have really been widely adopted. The reason for this is simple: network effect.
Many of these older key systems only applied the thinnest veneer of humanity over keys. But an identity is much richer than a mere label. Having a real name, social connections, and a corpus of work to attach to a key creates a system of keys that _humans care about_.
By bootstrapping key management within a social context, nostr ensures that the payoff of key management is worth the learning curve. Not only is social engagement a strong incentive to get off the ground, people already on the network are eager to help you get past any roadblocks you might face.
So if I could offer an action item: give nostr a try today. Whether you're in it for the people and their values, or you just want to experiment with cryptographic identity, nostr is a great place to start. For a quick introduction and to securely generate keys, visit [njump.me](https://njump.me/).
Thanks for taking the time to read this post. I hope it's been helpful, and I can't wait to see you on nostr!
-

@ f839fb67:5c930939
2025-03-05 16:54:25
# Relays
| Name | Address | Price (Sats/Year)|
| - | - | - |
| stephen's aegis relay | wss://paid.relay.vanderwarker.family | 42069
| stephen's Outbox | wss://relay.vanderwarker.family | 0 |
| stephen's Inbox | wss://haven.vanderwarker.family/inbox | 0 |
| stephen's DMs | wss://haven.vanderwarker.family/chat | 0 |
| VFam Data Relay | wss://data.relay.vanderwarker.family | 0 |
| [TOR] My Phone Relay | ws://naswsosuewqxyf7ov7gr7igc4tq2rbtqoxxirwyhkbuns4lwc3iowwid.onion | 0 |
---
# My Pubkeys
| Name | hex | nprofile |
| - | - | - |
| Main | f839fb6714598a7233d09dbd42af82cc9781d0faa57474f1841af90b5c930939 | nprofile1qqs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us9mapfx |
| Vanity (Backup) | 82f21be67353c0d68438003fe6e56a35e2a57c49e0899b368b5ca7aa8dde7c23 | nprofile1qqsg9usmuee48sxkssuqq0lxu44rtc4903y7pzvmx694efa23h08cgcpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3ussel49x |
| VFStore | 6416f1e658ba00d42107b05ad9bf485c7e46698217e0c19f0dc2e125de3af0d0 | nprofile1qqsxg9h3uevt5qx5yyrmqkkehay9cljxdxpp0cxpnuxu9cf9mca0p5qpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usaa8plu |
| NostrSMS | 9be1b8315248eeb20f9d9ab2717d1750e4f27489eab1fa531d679dadd34c2f8d | nprofile1qqsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us595d45 |
---
# "Personal Nostr Things"
> [D] = Saves darkmode preferences over nostr
> [A] = Auth over nostr
> [B] = Beta (software)
> [z] = zap enabled
- [[DABz] Main Site](https://vanderwarker.family)
- [[DAB] Contact Site](https://stephen.vanderwarker.family)
- [[DAB] PGP Site](https://pgp.vanderwarker.family)
- [[DAB] VFCA Site](https://ca.vanderwarker.family)
---
# Other Services (Hosted code)
* [Blossom](https://blossom.vanderwarker.family)
* [NostrCheck](https://nostr.vanderwarker.family)
---
# Emojis Packs
* Minecraft
- <code>nostr:naddr1qqy566twv43hyctxwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsd0k5wp</code>
* AIM
- <code>nostr:naddr1qqxxz6tdv4kk7arfvdhkuucpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usyg8c88akw9ze3fer85yah4p2lqkvj7qap749w360rpq6ly94eycf8ypsgqqqw48qe0j2yk</code>
* Blobs
- <code>nostr:naddr1qqz5ymr0vfesz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2wek4ukj</code>
* FavEmojis
- <code>nostr:naddr1qqy5vctkg4kk76nfwvq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsf7sdwt</code>
* Modern Family
- <code>nostr:naddr1qqx56mmyv4exugzxv9kkjmreqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqp65ujlj36n</code>
* nostriches (Amethyst collection)
- <code>nostr:naddr1qq9xummnw3exjcmgv4esz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w2sqg6w</code>
* Pepe
- <code>nostr:naddr1qqz9qetsv5q37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82ns85f6x7</code>
* Minecraft Font
- <code>nostr:naddr1qq8y66twv43hyctxwssyvmmwwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsmzftgr</code>
* Archer Font
- <code>nostr:naddr1qq95zunrdpjhygzxdah8gqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr4fclkyxsh</code>
* SMB Font
- <code>nostr:naddr1qqv4xatsv4ezqntpwf5k7gzzwfhhg6r9wfejq3n0de6qz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w0wqpuk</code>
---
# Git Over Nostr
* NostrSMS
- <code>nostr:naddr1qqyxummnw3e8xmtnqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfrwaehxw309amk7apwwfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqyj8wumn8ghj7urpd9jzuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyxhwumn8ghj7mn0wvhxcmmvqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqaueqp0epk</code>
* nip51backup
- <code>nostr:naddr1qq9ku6tsx5ckyctrdd6hqqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjxamnwvaz7tmhda6zuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfywaehxw309acxz6ty9eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qgdwaehxw309ahx7uewd3hkcq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqpmej4gtqs6</code>
* bukkitstr
- <code>nostr:naddr1qqykyattdd5hgum5wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dspzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqrhnyf6g0n2</code>
---
# Market Places
Please use [Nostr Market](https://market.nostr.com) or somthing simular, to view.
* VFStore
- <code>nostr:naddr1qqjx2v34xe3kxvpn95cnqven956rwvpc95unscn9943kxet98q6nxde58p3ryqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzqeqk78n93wsq6sss0vz6mxl5shr7ge5cy9lqcx0smshpyh0r4uxsqvzqqqr4gve4aen9</code>
---
# Badges
## Created
* paidrelayvf
- <code>nostr:naddr1qq9hqctfv3ex2mrp09mxvqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr48y85v3u3</code>
* iPow
- <code>nostr:naddr1qqzxj5r02uq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgg02u0r</code>
* codmaster
- <code>nostr:naddr1qqykxmmyd4shxar9wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgk3gm4g</code>
* iMine
- <code>nostr:naddr1qqzkjntfdejsz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqafed5s4x5</code>
---
# Clients I Use
* noStrudel
- <code>nostr:naddr1qqxnzd3cxccrvd34xser2dpkqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsygpxdq27pjfppharynrvhg6h8v2taeya5ssf49zkl9yyu5gxe4qg55psgqqq0nmq5mza9n</code>
* nostrsms
- <code>nostr:naddr1qq9rzdejxcunxde4xymqz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgrqsqqql8kjn33qm</code>
-

@ 8d34bd24:414be32b
2025-03-05 16:52:58
Sometimes I wonder why I write posts like this. This is not the way to gain a big following, but then again, that is not my goal. My goal is to share Jesus with anyone who will listen, to faithfully speak whatever truth I feel God is leading me to share, and to teach the inerrant word of God in order to draw people, both believers and not yet believers, closer to Jesus. I trust God to use my words in whatever way He sees best. If it only reaches a few, that is OK by me. If somehow this substack starts reaching a vast audience, then praise God for that!
Today, I am writing about a hard truth. The Bible contains a number of hard truths that most people don’t want to believe, but which our Creator God has stated as truth. None of us likes being called a sinner, but the Bible says:
> as it is written, “There is none righteous, not even one. (Romans 3:10)
As hard as the truth that we are all sinners is, a much harder truth is that not everyone gets to go to Heaven. Some people are destined for Hell. I am going to investigate some verses that illuminate this truth.
Ironically, most people have two contradictory thoughts. Most people wonder why God allows so much evil in the world. If He is truly sovereign, why doesn’t He stop evil? At the same time they wonder why a loving God would send anyone to Hell. We can’t expect God to stop and punish evil, but not send some people to Hell. We can’t have it both ways.
> The Lord is not slow about His promise, as some count slowness, but is patient toward you, not wishing for any to perish but for all to come to repentance. (2 Peter 3:9)
This verse explains the basic facts of how God’s holiness is reconciled with His love and mercy, but of course there is so much more. If God is truly sovereign over all, then why is there any evil? Why does anyone sin? Why is there pain and suffering?
> **The Lord has made everything for its own purpose,\
> Even the wicked for the day of evil**.\
> Everyone who is proud in heart is an abomination to the Lord;\
> Assuredly, he will not be unpunished.\
> By lovingkindness and truth iniquity is atoned for,\
> And by the fear of the Lord one keeps away from evil. (Proverbs 16:4-6) {emphasis mine}
Everyone and everything was made for God’s own purpose. As our Creator, He has the right to make each of us for whatever purpose He desires. The creature has no right to question the Creator and His purpose.
> Then I went down to the potter’s house, and there he was, making something on the wheel. But the vessel that he was making of clay was spoiled in the hand of the potter; so **he remade it into another vessel, as it pleased the potter to make**.
>
> Then the word of the Lord came to me saying, “**Can I not, O house of Israel, deal with you as this potter does?**” declares the Lord. “Behold, like the clay in the potter’s hand, so are you in My hand, O house of Israel. At one moment I might speak concerning a nation or concerning a kingdom to uproot, to pull down, or to destroy it; if that nation against which I have spoken turns from its evil, I will relent concerning the calamity I planned to bring on it. Or at another moment I might speak concerning a nation or concerning a kingdom to build up or to plant it; if it does evil in My sight by not obeying My voice, then I will think better of the good with which I had promised to bless it. (Jeremiah 18:3-10) {emphasis mine}
But the Bible says it even goes beyond God directly responding to our choices. The God of the Bible is creator and sovereign over all. Nothing happens contrary to His will.
> So then **He has mercy on whom He desires, and He hardens whom He desires**.
>
> You **will say to me then, “Why does He still find fault?** For who resists His will?” On the contrary, **who are you, O man, who answers back to God?** **The thing molded will not say to the molder, “Why did you make me like this,” will it? Or does not the potter have a right over the clay, to make from the same lump one vessel for honorable use and another for common use?** What if God, although willing to demonstrate His wrath and to make His power known, endured with much patience **vessels of wrath prepared for destruction**? And He did so to make known the riches of His glory upon **vessels of mercy, which He prepared beforehand for glory**, even us, whom He also called, not from among Jews only, but also from among Gentiles. (Romans 9:18-24) {emphasis mine}
The above passage speaks a very uncomfortable truth. We don’t like thinking we don’t have full and complete free-will to do whatever we want and to determine our future, but it isn’t that simple. The Bible says specifically that some are “*prepared for destruction*” and others are “*prepared beforehand for glory*.”
> For by grace **you have been saved through faith; and that not of yourselves, it is the gift of God; not as a result of works, so that no one may boast**. For we are His workmanship, created in Christ Jesus for good works, which God prepared beforehand so that we would walk in them. (Ephesians 2:8-10) {emphasis mine}
We aren’t saved because we are smarter than all of the people who didn’t choose Jesus. We aren’t wiser than those who chose their own path rather than the path designed by God. We are saved by God as a gift. He called those who were dead in their sins to life in him. The dead can’t choose anything. We all must be made spiritually alive so we can follow Him. Only Jesus does that. We can’t make ourselves alive in Him.
Every believer needs to thank Jesus daily for the miracle of spiritual life in Him that has been given to us despite us not deserving it or choosing it.
> In this is love, not that we loved God, but that He loved us and sent His Son to be the propitiation for our sins. (1 John 4:10)
and
> We love, because He first loved us. (1 John 4:19)
Jesus acted first, choosing us, and we responded, not that we chose Him and He loved us because of our choice.
I’m sure many of my readers are cringing at this Biblical truth. We all try to make God’s word say something else because we don’t like feeling out of control. We don’t like to think that someone else is smarter, stronger, or more in control of our lives than ourselves. Still, being made to follow Jesus is the greatest blessing a person can receive.
> Trust in the Lord with all your heart\
> And do not lean on your own understanding.\
> In all your ways acknowledge Him,\
> And He will make your paths straight.\
> Do not be wise in your own eyes;\
> Fear the Lord and turn away from evil.\
> It will be healing to your body\
> And refreshment to your bones. (Proverbs 3:5-8)
We don’t have to fully understand God’s truth, but we do need to accept it.
May God guide you in the truth through His God breathed word, so we may serve Him faithfully and submit fully to His authority and His will to the glory of His majesty.
Trust Jesus
-

@ 401014b3:59d5476b
2025-03-05 15:37:44
Alright, football fiends, it’s March 2025, and we’re diving into the NFC North like it’s a polar plunge with a side of cheap beer. Free agency’s a free-for-all, the draft’s a crapshoot, and this division’s always a slugfest of grit, guts, and grudges. The Vikings shocked the world with a 14-3 run in 2024, the Lions roared, the Packers stayed scrappy, and the Bears showed flashes. Let’s slap some records on this beast and figure out who’s got the stones to take the North. Here we go, fam—hold my bratwurst.
### **Minnesota Vikings: 11-6 – Darnold’s Encore or Bust**
The Vikings were the NFL’s Cinderella story in 2024, rolling to 14-3 with Sam Darnold slinging it and Brian Flores’ defense eating souls. Justin Jefferson’s still a cheat code, and Aaron Jones keeps the ground game humming. That D-line—Jonathan Greenard, Andrew Van Ginkel—stays nasty, but free agency’s lurking. Danielle Hunter’s long gone, and guys like Harrison Phillips might chase a bag. J.J. McCarthy’s waiting in the wings, but Darnold’s 2024 magic earns him the nod. Regression’s real after a dream season—11-6 feels right, snagging the division. They’re not hitting 14 again, but they’re still a playoff lock.
### **Detroit Lions: 10-7 – Campbell’s Grit Keeps Grinding**
The Lions were a buzzsaw in 2024, and they’re not fading. Jared Goff’s got Amon-Ra St. Brown and Jameson Williams torching secondaries, while David Montgomery and Jahmyr Gibbs bulldoze defenses. Aidan Hutchinson’s a one-man wrecking crew up front, but free agency could nick ‘em—Brian Branch or Alim McNeill might dip. Dan Campbell’s got this team playing with their hair on fire, and that O-line’s still elite. 10-7’s the call, grabbing a wildcard. They’re a hair behind Minnesota but ready to punch someone’s lights out in January.
### **Green Bay Packers: 9-8 – Love’s Rollercoaster Redux**
The Packers are the NFC North’s wild card—literally. Jordan Love’s got that boom-or-bust vibe, Josh Jacobs keeps the run game honest, and the WR trio—Christian Watson, Romeo Doubs, Jayden Reed—is a problem when healthy. Rashan Gary’s a beast on D, but the secondary’s shaky, and Jaire Alexander might bolt if the money’s right. This team’s young, scrappy, and inconsistent—9-8’s where they land. Might sneak a wildcard if the chips fall, but they’re not catching the top dogs yet.
### **Chicago Bears: 6-11 – Caleb’s Sophomore Slump**
The Bears had their moments in 2024, but 2025’s a grind. Caleb Williams has DJ Moore and Rome Odunze to sling it to, and D’Andre Swift’s solid, but that O-line’s still a sieve. The defense—Montez Sweat, Jaylon Johnson—can ball, but depth’s thin, and free agency might swipe Tremaine Edmunds. Williams takes a step, but not a leap—6-11’s the harsh reality. They’re building something, but it’s not playoff-ready. Sorry, Windy City, you’re still in the basement.
### **The Final Roar**
The NFC North in 2025 is a Viking victory lap with a tight chase. The Vikings (11-6) snag the crown because Darnold’s 2024 glow carries over, the Lions (10-7) claw a wildcard with grit, the Packers (9-8) flirt with relevance, and the Bears (6-11) eat turf. Free agency’s the X-factor—lose a star, you’re cooked; keep ‘em, you’re golden. Yell at me on X when I botch this, but this is my NFC North sermon. Let’s ride, degenerates.
-

@ d360efec:14907b5f
2025-03-05 13:58:42
**ภาพรวม:**
จากภาพรวมทั้ง 3 Timeframe (TF) จะเห็นได้ว่า BTC มีแนวโน้มเป็นขาขึ้น (Bullish) อย่างชัดเจน โดยเฉพาะอย่างยิ่งใน TF Day ที่ราคาอยู่เหนือเส้น EMA 50 และ EMA 200 อย่างแข็งแกร่ง อย่างไรก็ตาม ใน TF ที่เล็กลงมา (15m และ 4H) เริ่มเห็นสัญญาณการพักตัวและอาจมีการปรับฐานระยะสั้น
**การวิเคราะห์แยกตาม Timeframe:**
* **TF Day:**
* 
* **SMC:** ราคามีการ Breakout โครงสร้างตลาดขาลงก่อนหน้า และสร้าง Higher High (HH) และ Higher Low (HL) อย่างต่อเนื่อง
* **ICT Buyside & Sellside Liquidity:**
* Buyside Liquidity: อยู่บริเวณ $70,000 (เป็นเป้าหมายถัดไปที่ราคามีโอกาสขึ้นไปทดสอบ)
* Sellside Liquidity: อยู่บริเวณ $60,000 (เป็นแนวรับสำคัญ หากราคาหลุดลงมา อาจมีการปรับฐานที่รุนแรงขึ้น)
* **Money Flow:** เป็นบวก สนับสนุนแนวโน้มขาขึ้น
* **EMA:** EMA 50 (เหลือง) อยู่เหนือ EMA 200 (ขาว) เป็นสัญญาณ Bullish
* **Trend Strength:** เมฆสีเขียวหนาแน่น แสดงถึงแนวโน้มขาขึ้นที่แข็งแกร่ง และมีสัญญาณ Buy
* **Chart Pattern:** ไม่มีรูปแบบ Chart Pattern ที่ชัดเจนใน TF นี้
* **TF 4H:**
* 
* **SMC:** ราคาเริ่มมีการพักตัวและสร้างฐาน (Consolidation)
* **ICT Buyside & Sellside Liquidity:**
* Buyside Liquidity: อยู่บริเวณ $69,000 (แนวต้านย่อย)
* Sellside Liquidity: อยู่บริเวณ $64,000 (แนวรับย่อย)
* **Money Flow:** เริ่มมีสัญญาณการไหลออกของเงิน (Outflow)
* **EMA:** EMA 50 ยังคงอยู่เหนือ EMA 200 แต่เริ่มมีการ Cross กัน อาจเป็นสัญญาณเตือนการพักตัว
* **Trend Strength:** เมฆสีเขียวเริ่มบางลง และมีสัญญาณ Neutral
* **Chart Pattern:** อาจกำลังก่อตัวเป็นรูปแบบ Head and Shoulders (กลับตัว) หรืออาจเป็นเพียงการพักตัวเพื่อไปต่อ
* **TF 15m:**
* 
* **SMC:** ราคาอยู่ในช่วง Sideways แคบๆ
* **ICT Buyside & Sellside Liquidity:**
* Buyside Liquidity: อยู่บริเวณ $68,500
* Sellside Liquidity: อยู่บริเวณ $66,000
* **Money Flow:** เป็นลบ (Outflow)
* **EMA:** EMA 50 และ EMA 200 พันกัน (Cross) บ่งบอกถึงการไม่มี Trend ที่ชัดเจน
* **Trend Strength:** เมฆสีแดง แสดงถึงแนวโน้มขาลงระยะสั้น และมีสัญญาณ Sell
* **Chart Pattern:** ไม่พบรูปแบบ Chart Pattern ที่ชัดเจน
**กลยุทธ์และคำแนะนำ:**
* **Day Trade:**
* **กลยุทธ์:** เน้น Buy on Dip (ซื้อเมื่อราคาอ่อนตัว) ใน TF 15m หรือ 4H โดยรอสัญญาณการกลับตัวของราคา และตั้ง Stop Loss ที่เหมาะสม
* **Setup (SMC):**
1. รอให้ราคาลงมาทดสอบแนวรับ (Demand Zone) ที่ $66,000-$67,000 ใน TF 15m
2. สังเกต Price Action ว่ามีการกลับตัว (เช่น Bullish Engulfing, Hammer) หรือไม่
3. เข้า Buy เมื่อมีสัญญาณยืนยัน และตั้ง Stop Loss ต่ำกว่า Swing Low ล่าสุด
4. Take Profit ที่แนวต้านถัดไป ($68,500) หรือ Buyside Liquidity
* **สิ่งที่ต้องระวัง:**
* ความผันผวนของราคา BTC ที่สูง
* ข่าวหรือเหตุการณ์ที่อาจส่งผลกระทบต่อตลาด
* สัญญาณ Divergence (หากมี) ระหว่างราคาและ Indicator
* **ภาพรวม (ระยะกลาง-ยาว):** ยังคงมีมุมมองเป็น Bullish แต่ควรระมัดระวังการพักตัวหรือปรับฐานระยะสั้น
**สรุป:**
BTC ยังคงมีแนวโน้มเป็นขาขึ้นในระยะกลาง-ยาว แต่ในระยะสั้นอาจมีการพักตัวหรือปรับฐาน Day Trader ควรใช้กลยุทธ์ Buy on Dip และบริหารความเสี่ยงอย่างรอบคอบ
**Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-

@ c1e9ab3a:9cb56b43
2025-03-05 13:54:03
The financial system has long relied on traditional banking methods, but emerging technologies like Bitcoin and Nostr are paving the way for a new era of financial interactions.
## Secure Savings with Bitcoin:
Bitcoin wallets can act as secure savings accounts, offering users control and ownership over their funds without relying on third parties.
## Instant Settlements with the Lightning Network:
The Lightning Network can replace traditional settlement systems, such as ACH or wire transfers, by enabling instant, low-cost transactions.
## Face-to-Face Transactions with Ecash:
Ecash could offer a fee-free option for smaller, everyday transactions, complementing the Lightning Network for larger payments.
## Automated Billing with Nostr Wallet Connect:
Nostr Wallet Connect could revolutionize automated billing, allowing users to set payment limits and offering more control over subscriptions and recurring expenses.
## Conclusion:
Combining Bitcoin and Nostr technologies could create a more efficient, user-centric financial system that empowers individuals and businesses alike.
-

@ d360efec:14907b5f
2025-03-05 13:46:26
**Overview:**
From an overall perspective across all 3 timeframes (TF), BTC shows a clear uptrend (Bullish), especially in the Day TF where the price is firmly above the EMA 50 and EMA 200. However, in the smaller TFs (15m and 4H), there are signs of consolidation and a potential short-term correction.
**Analysis by Timeframe:**
* **Day TF:**
* 
* **SMC:** The price has broken out of the previous downtrend structure and continues to create Higher Highs (HH) and Higher Lows (HL).
* **ICT Buyside & Sellside Liquidity:**
* Buyside Liquidity: Around $70,000 (the next target the price is likely to test).
* Sellside Liquidity: Around $60,000 (a key support level; if the price breaks below this, a deeper correction may occur).
* **Money Flow:** Positive, supporting the uptrend.
* **EMA:** EMA 50 (yellow) is above EMA 200 (white), a bullish signal.
* **Trend Strength:** Thick green cloud, indicating a strong uptrend, and a Buy signal.
* **Chart Pattern:** No clear chart pattern on this TF.
* **4H TF:**
* 
* **SMC:** The price is starting to consolidate and form a base.
* **ICT Buyside & Sellside Liquidity:**
* Buyside Liquidity: Around $69,000 (minor resistance).
* Sellside Liquidity: Around $64,000 (minor support).
* **Money Flow:** Starting to show signs of outflow.
* **EMA:** EMA 50 is still above EMA 200, but they are starting to cross, which could be a warning sign of consolidation.
* **Trend Strength:** The green cloud is starting to thin, and there is a Neutral signal.
* **Chart Pattern:** Potentially forming a Head and Shoulders pattern (reversal) or it may just be a consolidation before continuing higher.
* **15m TF:**
* 
* **SMC:** The price is in a narrow sideways range.
* **ICT Buyside & Sellside Liquidity:**
* Buyside Liquidity: Around $68,500.
* Sellside Liquidity: Around $66,000.
* **Money Flow:** Negative (Outflow).
* **EMA:** EMA 50 and EMA 200 are intertwined (Cross), indicating a lack of a clear trend.
* **Trend Strength:** Red cloud, indicating a short-term downtrend, and a Sell signal.
* **Chart Pattern:** No clear chart pattern found.
**Strategy and Recommendations:**
* **Day Trade:**
* **Strategy:** Focus on Buy on Dip in the 15m or 4H TF, waiting for price reversal signals, and setting appropriate Stop Losses.
* **Setup (SMC):**
1. Wait for the price to test the support (Demand Zone) at $66,000-$67,000 in the 15m TF.
2. Observe Price Action for a reversal (e.g., Bullish Engulfing, Hammer).
3. Enter a Buy when there is a confirmation signal and set a Stop Loss below the latest Swing Low.
4. Take Profit at the next resistance ($68,500) or Buyside Liquidity.
* **Things to watch out for:**
* High volatility of BTC price.
* News or events that may affect the market.
* Divergence signals (if any) between price and indicators.
* **Overall (Medium-Long Term):** Still bullish, but be cautious of short-term consolidations or corrections.
**Summary:**
BTC remains bullish in the medium to long term, but there may be a short-term consolidation or correction. Day traders should use a Buy on Dip strategy and manage risk carefully.
**Disclaimer:** This analysis is a personal opinion and not investment advice. Investors should do their own research and make decisions carefully.
-

@ beb6bdc9:eeb17df3
2025-03-05 13:25:08
https://image.nostr.build/2ad4cf1beb7f1ebaecfe1e011f83c85d09c2c17e4a1f40eac412bb08e03d82c4.jpg
00020126360014BR.GOV.BCB.PIX0114dig@depix.info520400005303986540549.905802BR5923CURSO BITCOIN PARA TDAH6013SATOSHILANDIA62070503***63045C68
↑ COPIE TODO O TEXTO DA CHAVE PIX ACIMA! ↑
Para ter acesso ao guia **BITCOIN PARA TDAH**, pague a chave pix copia e cola acima e apresente o comprovante de pagamento em:
https://t.me/dinopacon
-

@ a58a2663:87bb2918
2025-03-05 12:41:36
After two years of using Standard Notes as my main note-taking app, I’m switching to Obsidian.
The $100 that Standard Notes charges for basic editing capabilities is difficult to justify, especially for someone paying in Brazilian Real and striving to make a living from writing. However, I will certainly miss its simplicity and cleaner interface.
It’s my impression that the developers are missing an opportunity to create a privacy-focused note-taking app tailored to the specific needs of writers, rather than general users.
Substack, for example, achieved such success because it targeted the distribution and monetization of writers’ work. But we need more tools focused not on distribution or monetization, but on the actual process—indeed, the various phases of the process—of creating texts. This is especially true for complex, long-form texts with different levels of argumentation, numerous written and multimedia sources, and cross-references to other works by the author.
It’s crucial that an app like this doesn’t feel overly complex, like Notion or Evernote, or so all-purpose, like Obsidian. And, of course, I’m not talking about a new full-fledged text editor like Scrivener.
Just a thought. Take note.
-

@ 5f3e7e41:81cb07cf
2025-03-05 11:37:27
The question of life’s meaning has long been a central concern in philosophy, debated by existentialists, nihilists, absurdists, and theologians alike. Is there an inherent purpose to human existence, or must we construct our own meaning? This essay explores the philosophical dimensions of the question by examining various perspectives, including existentialism, nihilism, and teleological interpretations. **Existentialist Perspective**
Existentialists argue that meaning is not intrinsic but must be created. Jean-Paul Sartre, for instance, asserts that existence precedes essence—humans exist first and define their own purpose afterward. Unlike an artifact designed for a specific function, human beings are thrown into existence without predetermined meaning. Sartre’s concept of radical freedom suggests that we are entirely responsible for imbuing our lives with purpose through our choices and actions. Albert Camus, while existential in his approach, leans toward absurdism. He argues that human beings seek meaning in a universe that offers none. This fundamental conflict, the absurd, leads to either nihilism or rebellion. Camus advocates for an embrace of the absurd—accepting life’s lack of inherent purpose and living in defiance of this reality, deriving meaning from the act of living itself. **Nihilistic Perspective**
Nihilism, most famously articulated by Friedrich Nietzsche, asserts that life has no objective meaning, purpose, or value. The "death of God" in Nietzsche’s work signifies the collapse of religious and metaphysical sources of meaning, leaving humanity in an existential void. Without a higher order dictating meaning, one might fall into existential despair. However, Nietzsche’s solution is the creation of personal values through the concept of the Übermensch, an individual who forges their own path and meaning without reliance on external validation. **Teleological and Theistic Views**
In contrast, religious and teleological perspectives propose an intrinsic meaning to life, often rooted in divine purpose. Theistic traditions argue that meaning is bestowed upon humanity by a higher power. For example, in Christianity, the purpose of life is to fulfill God’s will, achieve salvation, and cultivate virtue. Similarly, in Aristotelian philosophy, eudaimonia, or human flourishing, is seen as the ultimate telos (end goal) of human existence, achieved through rational activity and moral virtue. **Synthesis: A Constructivist Approach**
Given the divergence in perspectives, one might adopt a constructivist stance that synthesizes elements from each. If no inherent meaning exists, as existentialists and nihilists suggest, and if religious interpretations require faith, then meaning may best be understood as a subjective construction. Humans, as rational and reflective beings, can choose to ascribe significance to their existence based on personal values, relationships, creative endeavors, or contributions to humanity. **Conclusion**
The meaning of life remains an open question, shaped by individual perspectives and cultural influences. Whether meaning is self-created, divinely ordained, or ultimately absent, the inquiry itself underscores a fundamental aspect of human nature: the relentless pursuit of significance. Perhaps the search for meaning is what gives life its greatest meaning.
-

@ bd32f268:22b33966
2025-03-05 11:04:29
Segundo a filosofia Aristotélica quando analisamos uma coisa seja ela um objecto ou um fenómeno devemos ser capazes de observar as suas causas. Podemos dizer que analisar as causas nos permite compreender com outra densidade, a origem, o significado e a finalidade das coisas.
Atualmente, estamos vetados a um reducionismo materialista quando fazemos ciência, sendo portanto nota dominante a nossa fixação na matéria como o fator primordial do conhecimento dos objetos. Ao fixarmo-nos neste aspeto perdemos muitas outras dimensões que compõe as coisas.
Atendamos então a Aristóteles e a quatro causas que este autor identifica para as coisas e fenómenos.
Segundo o filósofo grego as causas dividem-se entre: materiais (relativas ao que algo é feito), as formais (relativas ao que algo é), as eficientes/motoras (relativas ao que as produziu ou quem as produziu) e as finais ( relativas á finalidade, Télos ou para quê; ou seja o que algo visa ou “tem por fim”).
Seguindo esta teoria das quatro das quatro causas podemos descrever as condições de existência tanto de entidades estáticas como em transformação. Quer isto dizer que assim temos meios para explorar o porquê das coisas. Até conhecermos o porquê das coisas não podemos dizer que as conhecemos verdadeiramente.
Analisemos um exemplo para que fique mais claro este método de análise. Uma mesa tem como causa material a madeira que a compõe, a sua causa formal (que diz respeito à forma) é a estrutura, ou seja o seu design; a sua causa eficiente é o trabalho de carpintaria que lhe deu origem e a sua causa final é servir de suporte para as refeições.
\
Destas causas destaco em particular a causa final que creio ser a que mais frequentemente induz confusão nas pessoas. De facto, o conhecimento da finalidade das coisas é fundamental inclusive para que possamos viver de forma harmoniosa com a realidade. É certo que nos podemos sentar numa mesa e jantar na cadeira, contudo automaticamente vamos perceber a desarmonia que advém dessa decisão.
Por vezes essa desarmonia não será tão evidente, no entanto não nos podemos esquecer que tudo o que existe tem um propósito, isto é orienta-se para um fim, cumprindo-nos agir em conformidade com a natureza das coisas para alcançar essa harmonia com a própria realidade.
São muitas as ocasiões na nossa vida que queremos de alguma forma revogar esta inclinação natural das coisas para os seus fins, que funciona também como objeto e fundamento para a lei natural. Vejamos por exemplo a forma como muitas vezes quando comemos, em vez ordenar a nossa ação pelo fim primeiro (alimentar-se) buscamos o prazer como fim primário ao qual os outros estão subordinados resultando em desordem, ou seja num apetite que não está em conformidade com o objetivo último da alimentação. Não quer isto dizer que não se possa ou deva sentir prazer ao comer, quer apenas dizer que o fim último para que existe esse ato não é o prazer, mas sim a subsistência do corpo. Com este exemplo conseguimos perceber que há uma ordenação natural nos fins para que se orientam as coisas, sendo que nessa ordenação há sempre fins primários e secundários. Sendo conscientes dessa hierarquia podemos, de uma forma mais ajustada adaptar as nossas atitudes á realidade, isto é aos preceitos da lei natural.
-

@ a012dc82:6458a70d
2025-03-05 10:24:56
In the dynamic and often unpredictable realm of cryptocurrency, the actions of Bitcoin whales—investors who hold large amounts of BTC—can significantly influence market trends and investor sentiment. A recent transaction, involving the transfer of over $1.5 billion worth of Bitcoin, has once again highlighted the profound impact these entities can have on the digital currency landscape. This article delves into the details of this massive move, exploring its implications and the broader context of whale activity in the cryptocurrency market.
**Table of Contents**
- The Billion-Dollar Transaction: A Deep Dive
- Other Significant Whale Movements
- Analyzing the Impact of Whale Activity
- Market Volatility and Speculation
- Psychological Impact on Investors
- The Role of Whales in the Cryptocurrency Ecosystem
- Liquidity and Market Depth
- Influence on Adoption and Perception
- The Billion-Dollar Transfer in Context
- Bitcoin's Market Position
- Historical Whale Activity
- Future Implications and the Evolving Role of Whale …
- Regulatory Environment
- Institutional Investors and Market Stability
- Technological Advances and Market Monitoring
- Conclusion
- FAQs
**The Billion-Dollar Transaction: A Deep Dive**
On January 31st, the cryptocurrency community was abuzz with news of a monumental Bitcoin transfer. A whale moved 35,049 BTC, valued at approximately $1,518,020,170, from one unknown wallet to another. This transaction not only stood out due to its sheer size but also because it underscored the significant liquidity and wealth concentrated in the hands of a few within the Bitcoin ecosystem.
**Other Significant Whale Movements**
The billion-dollar transfer was part of a series of large transactions that day, which included:
- 25,266 BTC ($1,099,679,062) transferred between unknown wallets.
- 929 BTC ($39,562,024) moved from Coinbase to Gemini.
- 2,500 BTC ($106,647,312) sent to PayPal.
- 1,736 BTC ($73,943,008) transferred to Gemini.
- 34,300 BTC ($1,476,690,397) moved between unknown wallets.
These transactions, totaling around $4.5 billion, highlight the enormous sums that whales can mobilize, influencing the Bitcoin market's liquidity and volatility.
**Analyzing the Impact of Whale Activity**
The actions of Bitcoin whales can lead to significant market movements. Large-scale transfers and trades can signal potential sales or acquisitions, prompting widespread speculation and reactive trading among smaller investors.
**Market Volatility and Speculation**
The recent billion-dollar transaction has sparked intense speculation regarding the whale's motives and the potential repercussions for Bitcoin's price stability. Such movements can create uncertainty, leading to price volatility as the market reacts to perceived changes in supply and demand.
**Psychological Impact on Investors**
Whale activity can also have a psychological impact on retail investors. The knowledge that a single entity or group can move the market might lead to caution, fear, or even panic selling, exacerbating price fluctuations and potentially leading to market manipulation accusations.
**The Role of Whales in the Cryptocurrency Ecosystem**
Bitcoin whales play a crucial role in the cryptocurrency ecosystem. Their significant holdings give them considerable influence over market dynamics, liquidity, and even the adoption and perception of Bitcoin as a digital asset.
**Liquidity and Market Depth**
Whales contribute to market liquidity and depth by providing substantial capital. Their trades, though potentially disruptive in the short term, help create a more liquid market, enabling other investors to execute large transactions more smoothly.
**Influence on Adoption and Perception**
The actions of whales can influence the broader perception of Bitcoin. Significant investments or divestments by these entities can signal confidence or concern regarding Bitcoin's future, influencing the sentiment of smaller investors and the general public.
**The Billion-Dollar Transfer in Context**
To fully understand the implications of the billion-dollar transfer, it's essential to consider the broader context of Bitcoin's market position and the historical activity of whales.
**Bitcoin's Market Position**
At the time of the transfer, Bitcoin was trading at $42,647, experiencing a slight decrease from its previous values. This period of relative stability makes the timing of the whale's move particularly noteworthy, as it suggests strategic positioning rather than a reaction to short-term market trends.
**Historical Whale Activity**
Historically, whale movements have preceded significant market movements, both bullish and bearish. By analyzing past transactions, investors attempt to predict future market directions based on whale behavior. However, the opaque nature of these entities and their motivations makes such predictions speculative at best.
**Future Implications and the Evolving Role of Whales**
As the cryptocurrency market matures, the role and impact of whales may evolve. Regulatory changes, the growing adoption of Bitcoin, and the entrance of institutional investors could all influence whale behavior and their impact on the market.
**Regulatory Environment**
Increased regulatory scrutiny could lead to more transparency in whale transactions, potentially mitigating some of the market volatility associated with these moves. However, it could also lead to more sophisticated strategies by whales to conceal their actions or to manipulate the market within legal boundaries.
**Institutional Investors and Market Stability**
The entrance of more institutional investors into the cryptocurrency market could dilute the relative influence of individual whales, leading to greater market stability. Institutional investors typically employ more conservative strategies and are subject to stricter regulatory oversight, which could help moderate the impact of large-scale transactions.
**Technological Advances and Market Monitoring**
Advancements in blockchain analytics and monitoring tools are making it easier to track whale activity in real-time. This increased transparency could help demystify whale actions, allowing smaller investors to make more informed decisions and potentially leveling the playing field.
**Conclusion**
The recent billion-dollar Bitcoin transfer by a whale is a stark reminder of the significant influence these entities hold over the cryptocurrency market. While their actions can lead to market volatility and speculation, they also play a crucial role in providing liquidity and depth to the market. As the cryptocurrency ecosystem continues to evolve, understanding the motivations and implications of whale activity will remain a critical aspect of navigating the digital asset landscape.
**FAQs**
**What is a Bitcoin whale?**
A Bitcoin whale is an individual or entity that holds a large amount of Bitcoin. These investors have enough capital to influence market movements significantly when they buy or sell large quantities of BTC.
**How much Bitcoin was moved by the whale?**
The whale moved 35,049 BTC, which was valued at approximately $1,518,020,170 at the time of the transaction.
**Where was the Bitcoin transferred?**
The Bitcoin was transferred from one unknown wallet to another. The identities of the parties involved and the purpose of the transfer remain undisclosed.
**Were there other significant transactions on the same day?**
Yes, there were several other significant transactions on the same day, including transfers worth hundreds of millions and billions of dollars, contributing to a total movement of about $4.5 billion in Bitcoin by whales.
**How do whale movements affect the Bitcoin market?**
Whale movements can lead to increased volatility in the Bitcoin market. Large transactions can signal potential sales or purchases to other traders, influencing the market price and leading to speculative trading.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: @croxroadnewsco**
**Instagram: @croxroadnews.co/**
**Youtube: @thebitcoinlibertarian**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
**Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats
link: https://signup.theorangepillapp.com/opa/croxroad**
**Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad”
link: https://bitcoinbook.shop?ref=21croxroad**
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
-

@ e31e84c4:77bbabc0
2025-03-05 10:23:47
The IMF’s $1.4 Billion Shackle *was Written By Kudzai Kutukwa. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: **muggyarch11@walletofsatoshi.com***
The recent $1.4 billion Extended Fund Facility (EFF) agreement between the International Monetary Fund (IMF) and El Salvador marks a significant turning point in the nation's economic and monetary policy. The IMF’s $1.4 billion “lifeline” is a sly Trojan horse, gutting El Salvador’s sovereignty and kneecapping its 2021 Bitcoin law— which represented a bold step toward monetary freedom and economic self-determination— all to prop up the same economic mess it pretends to fix. Brilliant, right?
**The IMF’s Colonialist Agenda: A Historical Precedent**
In 2021, El Salvador made history by adopting Bitcoin as legal tender, positioning itself at the forefront of financial innovation and offering its citizens an alternative to the U.S. dollar. This move was a bold step toward monetary independence and as a pathway toward individual financial sovereignty by reducing remittance costs for Salvadorans and bypassing the predatory international banking system. By making Bitcoin legal tender, El Salvador was taking steps to free itself from financial colonialism.
The IMF’s response to El Salvador’s Bitcoin law was predictably hostile from day one. The institution repeatedly warned of the “risks” associated with Bitcoin, framing it as a threat to financial stability rather than a tool for economic empowerment. Hypocrisy drips from every word—the IMF’s own debt traps and inflationary schemes have fueled the chaos it now “rescues” El Salvador from.
The Bretton Woods institution has long been the enforcer of the global financial elite, ensuring that nations remain shackled to the U.S. dollar-dominated system. Through predatory loans and stringent conditions, the IMF perpetuates economic subjugation. Now, facing pressure from these same institutions, El Salvador finds itself caught in the classic IMF trap: accepting loans with strings attached that further cement dependency.
This aid package isn't a solution to El Salvador's problems; it's leverage to force compliance with the global banking cartel's agenda. Under the IMF agreement, El Salvador has been compelled to amend its Bitcoin law, revoking Bitcoin's status as legal tender and making its acceptance by businesses voluntary. Additionally, tax obligations must now be settled exclusively in U.S. dollars. This gut-wrenching retreat from its bold Bitcoin rebellion represents a diabolical masterpiece of oppression—stripping citizens of financial freedom and forcing them to forever bow before the fiat gods.
**Why the IMF Must Destroy Bitcoin’s Medium of Exchange Use Case**
To understand why the IMF is so determined to undermine Bitcoin’s role as a medium of exchange in El Salvador, it’s important to revisit the fundamental nature of money. The widely cited “three functions” of money—medium of exchange, store of value, and unit of account—are often misunderstood. These are not rigid definitions, but empirical observations of how money functions in practice.
Money is, first and foremost, the generally accepted medium of exchange. The other functions tend to follow, but they are not exclusive to money. For example, gold can serve as a store of value but is no longer a commonly accepted medium of exchange, and other commodities can also act as units of account, but neither is money unless it is widely accepted as a medium of exchange. Bitcoin’s rise as a store of value (akin to “digital gold”) is not as threatening to the fiat system as its potential to function as a widely accepted medium of exchange. A strong store of value can exist within a system that is still dominated by fiat currencies.
If Bitcoin were to become a dominant medium of exchange, it would directly challenge the monopoly of central banks and the control that institutions like the IMF exert over global financial systems. That is why the IMF’s primary goal in El Salvador is not necessarily to stop Bitcoin’s adoption altogether but rather to strip Bitcoin of its medium of exchange function, thus effectively relegating Bitcoin to a speculative asset or store of value.
Furthermore, this Bitcoin experiment was the first real-world test of Bitcoin as a medium of exchange at the nation-state level. If it had succeeded, other countries—especially those in the Global South struggling with inflation, currency devaluation, and IMF-imposed austerity—might have followed suit. The IMF couldn't afford to let that happen. By neutralizing Bitcoin's role as money, it ensures that alternative financial systems do not gain traction outside the fiat-based global order. In other words, as long as Bitcoin can't be used freely as a medium of exchange, it cannot fulfill its role as money, and the fiat gods' grip on the global monetary system remains unchallenged—at least for now.
**The $1.4 Billion Faustian Bargain**
El Salvador’s decision to seek IMF funding is a reflection of the immense pressure it faces from global financial markets and institutions. The country’s high debt levels and weak external buffers are, in large part, a consequence of its integration into a global financial system that prioritizes short-term capital flows over long-term economic stability. By accepting the IMF’s terms, El Salvador has effectively traded its sovereignty for temporary financial relief.
What is even more surprising is that El Salvador had an alternative to this Faustian bargain: the issuance of Bitcoin bonds. While initially proposed as a way to finance Bitcoin City and geothermal Bitcoin mining infrastructure, the volcano bonds the country could have raised the $1.4 billion needed without sacrificing its monetary sovereignty. This represents a missed opportunity for El Salvador to bolster its financial independence, attract global capital, and solidify its position as a pioneer in the adoption of decentralized money.
Instead of falling back into the IMF’s debt trap—complete with austerity measures, restrictions on Bitcoin use, and financial surveillance—El Salvador could have embraced a Bitcoin-native financial strategy that aligned with its long-term vision of economic independence.
So why didn't El Salvador go through with the Bitcoin bond issuance? I don't know, but if I were to speculate, I would say the answer likely lies in political and institutional inertia, coupled with external pressures from the IMF and its allied institutions, or worse. If El Salvador had raised capital through Bitcoin bonds, it would have sent shockwaves through the financial world, proving that a nation-state could operate independently of the IMF.
**The Long-Term Consequences for El Salvador**
While the IMF’s program may provide short-term relief, its long-term consequences are likely to be detrimental to the Salvadoran people. The emphasis on fiscal consolidation and debt reduction will inevitably lead to cuts in public spending, particularly in areas such as social services and infrastructure. These measures will disproportionately affect the most vulnerable segments of society, exacerbating inequality and undermining the country’s social fabric.
Moreover, the IMF’s focus on “strengthening governance and transparency” is a thinly veiled attempt to impose external control over El Salvador’s domestic policies. The requirement to enhance Anti-Money Laundering and Countering the Financing of Terrorism (AML/CFT) frameworks, while ostensibly aimed at combating illicit activities, will likely be used to surveil and restrict the financial activities of ordinary citizens. This represents a gross violation of individual rights and a further erosion of economic freedom.
**Conclusion**
The IMF's $1.4 billion arrangement with El Salvador represents not economic salvation but a calculated reassertion of control. By forcing El Salvador to retreat from its Bitcoin initiative, the IMF is protecting the very system that has kept developing nations financially subjugated for decades.
For Salvadorans, this means their bold experiment in monetary sovereignty has been curtailed, not by market forces or technological limitations, but by the deliberate intervention of the guardians of the old financial order.
Those who believe in true financial freedom must recognize this for what it is: not assistance, but suppression; not aid, but control. The battle for monetary sovereignty continues, and despite this setback, Bitcoin's promise of financial liberation remains as vital as ever—not just for El Salvador, but for all those seeking escape from the oppressive machinery of central banking.
---
The IMF’s $1.4 Billion Shackle *was Written By Kudzai Kutukwa. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: **muggyarch11@walletofsatoshi.com***
-

@ 220522c2:61e18cb4
2025-03-05 09:53:59
# How to package a macOS Desktop App
## Introduction
Creating and distributing macOS desktop applications is a huge pain in the ass and can be very confusing. I'm writing this article as a reference for myself as well as any other developer who wants to package a desktop app for macOS.
## Join the Apple Developer Program
- Go to [developer.apple.com](https://developer.apple.com) and sign in with your Apple ID
- Enroll in an individual ($99/year) or organization ($299/year) membership
- Complete the enrollment process and wait for approval
## Setup Xcode for some reason
- Download Xcode from from the Mac App Store
- Go to Xcode -> Settings -> Accounts
- Click the "+" button and add your Apple Developer Account
Check if Xcode Command Line Tools are installed
```
xcode-select -p
```
If they are not installed for some reason you can install them with
```
xcode-select --install
```
## Generate a Certificate Signing Request (CSR)
- Open Keychain Access
- Go to Keychain Access > Certificate Assistant > Request a Certificate From a Certificate Authority
- Enter your email address and a common name (e.g., your name or company name)
- Leave "CA Email Address" blank, select Saved to disk, and click Continue
- Save the `.certSigningRequest` file somewhere
## Request Certificate
- Log in to [developer.apple.com/account](https://developer.apple.com/account)
- Go to Certificates, Identifiers & Profiles > Certificates
- Click the + button to add a new certificate
- Under "Software," select **Developer ID Application**, then Continue
- Choose **G2 Sub-CA (Xcode 11.4.1 or later)**
- Upload the `.certSigningRequest` file you just created, then Continue
- Download the `.cer` file (e.g., `developerID_application.cer`)
## Install the Certificate
- Double-click the downloaded `.cer` file to add it to your Keychain Access under "My Certificates"
- Verify it’s there with a private key, after selecting the cert look at the top tabs, select "My Certificates" expand the certificate to see the key icon
## Sign your Application
You can now try signing your application, if you run into issues check out the troubleshooting section at the bottom of this article.
```
codesign --deep --force --verify --verbose --sign "Developer ID Application: Your Name (TeamID)" --options=runtime --timestamp /path/to/YourApp.app
```
## Package Your App
Most apps distributed via websites are packaged in a `.dmg` (disk image) for a polished user experience:
- Use Disk Utility or a tool like `create-dmg` (install via Homebrew: `brew install create-dmg`)
```
create-dmg --volname "YourApp" --app-drop-link 600 185 --window-pos 200 120 --window-size 800 400 "YourApp.dmg" /path/to/YourApp.app
```
This will setup the drag and drop thing for you app into the applications folder, when you run this command that drag and drop ui will pop up, ignore it.
You really should use a tool like this, if you try to do it on your own you'll need to deal with symlinks, applescript and other nonsense. I've done it this way and if there's interest I can write a part two for a more manual approach.
- Sign the `.dmg`
```
codesign --deep --force --verify --verbose --sign "Developer ID Application: Your Name (TeamID)" --options=runtime --timestamp YourApp.dmg
```
## Notarize your App
Apple requires notarization to confirm your app isn’t malicious. You’ll need an app-specific password (not your Apple ID password)
Create and App-Specific Password:
- Go to [appleid.apple.com](https://appleid.apple.com), sign in, and under "Sign-In and Security," select App-Specific Passwords
- Generate a new password (name it whatever you like) and save it
Submit for Notarization
- Use the `notarytool` command
```
xcrun notarytool submit /path/to/YourApp.dmg --apple-id "your@email.com" --password "app-specific-password" --team-id "YourTeamID" --wait
```
- Replace placeholders with your Apple ID, the app-specific password, and your Team ID
- The `--wait` flag shows the result immediately (takes a few minutes). You’ll get a "Success" message or a log ID with issues to fix
Staple the Notarization Ticket:
- After approval, attach the notarization ticket to your `.dmg`
```
xcrun stapler staple /path/to/YourApp.dmg
```
- This ensures [Gatekeeper](https://support.apple.com/guide/security/gatekeeper-and-runtime-protection-sec5599b66df/web) can verify it offline
## Upload and Distribute
- Upload the notarized `.dmg` to your GitHub or your website
- Provide a download link (preferably HTTPS for security)
- Users might see a Gatekeeper prompt on first launch; they can right-click > Open or allow it in System Settings > Security & Privacy
## Troubleshooting
I have had countless issues when trying to sign applications
### Unable to build chain to self-signed root
One issue that I've run into on both of my macbooks is:
`Warning: unable to build chain to self-signed root for signer`
Something I usually have to do is open the Developer Certificate, expand the trust section and set "When using this certificate:" to "Use System Defaults" Then I restart my laptop once or twice and eventually it works.
### Can't delete cert in GUI
I have also had an issue where I can't delete the certs in the gui, in this case run the command to list the certs:
```
security find-identity -v -p codesigning
```
and delete it based on the hash in the beginning:
```
security delete-certificate -Z ABC123...
```
### Notarization fails
This is usually due to not passing the hardened runtime option so try resigning the app and dmg with `--options runtime`
You can use the command below to see what's wrong
```
xcrun notarytool log "notary id" --apple-id "your@email.com" --password "app-specific-password" --team-id "HGGSBC8HJF"
```
## Conclusion
Having an article like this would have saved me a lot of time debugging.
npub1ygzj9skr9val9yqxkf67yf9jshtyhvvl0x76jp5er09nsc0p3j6qr260k2
Posted at [notestack.com](https://notestack.com)
-

@ fd78c37f:a0ec0833
2025-03-05 09:50:19
In this edition, we invited njump.me/npub134d6jtyveg74cuuj7qun4v2m6r7x7c6ryk69z4q7pa7f43kran2sl2yggk from Bitcoin Junior Club to share how she empowers children, teenagers, and families through Bitcoin education. She emphasizes that in the Bitcoin ecosystem, education should come before mass adoption.
**YakiHonne**: Şelale, thank you for being here! Before we dive into the interview questions, I'd like to introduce YakiHonne, the hosting platform for today’s discussion. YakiHonne is a decentralized media client built on Nostr—a protocol designed to empower freedom of speech through technology. It enables creators to own their voices and assets while offering innovative tools like smart widgets, verified notes, and support for long-form content. With YakiHonne, individuals can express themselves freely, without the fear of censorship, bans, or restrictions. Today, we’ll be exploring more about your community,Şelale. So, let’s start with an introduction—could you tell us a bit about yourself and your community?
**Şelale**:Thank you! I'm actually a big fan of YakiHonne. Nostr is my second biggest passion, right after Bitcoin. And within this ecosystem, everything YakiHonne has done—whether empowering communities or supporting creators—looks truly incredible. I could represent many different communities, but today, I want to focus on a recent project I started together with my husband—[Bitcoin Junior Club](https://www.bitcoin4youth.com/shortly-about-us-bitcoin-junior-club/). It's a fun and educational space designed for children, teenagers, and entire families.
My Bitcoin journey dates back to around 2017 when I started diving deeper into Bitcoin. During the block size controversy. I found myself repeatedly reading the Whitepaper, trying to understand why some people were attempting to manipulate the rules and why the debate was gaining so much traction in the mass media. As I often say, the Bitcoin journey is a dynamic process—over the years, my experiences, perspectives, and areas of focus have continuously evolved. Right now, one of my key priorities are families and education. The Bitcoin ecosystem had already seen various emerging trends, such as the rise of female-oriented communities, hence the need for children related topics as well. Overall, the last few years have brought more creative minds building up their projects, which is very nice to see. A good example here would be [Bitcoin FilmFest](https://bitcoinfilmfest.com/), another dynamic initiative I’m involved in. These are all signs of Bitcoin's ever-expanding and evolving landscape.
**YakiHonne**: I would like to know, what sparked your interest in Bitcoin? And what motivated you to create Bitcoin Junior Club? What inspired you to create a whole community around it?
**Şelale**:There were many different aspects that drew me to Bitcoin, but I would say the most important one is the aspect of freedom, Bitcoin is the best form of money humanity has ever had. No middlemen, no one setting the rules. For the first time, people who have always been unprivileged and unbanked now have a real alternative—a way to opt out of the system they were born into. At the same time, when we look at developed countries, we see increasing surveillance, restrictions, and privacy constraints. Once again, Bitcoin serves a crucial role here. It is freedom money, a freedom tool, and that’s what hooked me the most.
On the other hand, what truly motivated me to launch our project was the realization that money is just a tool. If people stop thinking critically, if they don’t truly understand its potential, even something as revolutionary as Bitcoin can be misused or even turned against us.
Together with my husband, we believe that education is essential, especially for younger generations. We want to help them develop critical and creative thinking skills, to keep questioning topics they come across, and to think for themselves. This is the core reason we started this community. Along the way, I’ve come across many family-friendly projects with a similar mission. But most of such resources are scattered and difficult to locate. That’s why, one of our main goals is to create a comprehensive database—a place where people can find all kinds of educational resources, from the content we produce to information about existing initiatives in areas like: homeschooling, unschooling, Bitcoin, financial education, and more.
At the heart of it all, our focus remains on fostering creativity and independent thinking, because without it, we risk heading toward a future I personally don’t want to see. In the end, our mission is to help raise sovereign generations— individuals who truly understand and embrace financial and personal freedom.

([source: interactive game for kids and families, “Bitcoin Calendar, Part 01”](https://www.bitcoin4youth.com/))
**YakiHonne**: Yes, absolutely! I really appreciate your recognition of Bitcoin’s freedom aspect, as that is its very core—sovereignty. I also deeply admire your dedication to educating the next generation—it’s truly essential. We need to nurture and guide these young minds so that when they step into this space, they can help maintain the stability of the Bitcoin ecosystem and safeguard the communities that have been built around it. Could you share with us how your community was founded and how you initially attracted members?
**Şelale**:Well, to make a long story short, it all started as a way for me to relax at night. I work on several projects within the Bitcoin ecosystem, and when I feel mentally exhausted, I like to unwind by designing and drawing. That’s how it all began—I started designing various creative worksheets, such as logic puzzles, coloring pages, and other engaging activities targeted at younger audiences.
My husband and I are also nomads, so a few years ago, we began distributing these materials to different homes during our travels. The response was overwhelmingly positive—kids were excited and, interestingly, it also turned out to be a subtle "orange pill" tool for their parents. Quite often, when they noticed the Bitcoin logo in these materials, it sparked their curiosity and triggered many questions.
At first, I simply wanted to share these resources freely with the community, allowing anyone interested to use them. Over time, I came across many other family-friendly Bitcoin-themed materials such as books, videos, and games. I wanted to create a space where these things could be seen and heard. That’s when I decided to build a website, which could be described more as a database rather than a community.
Since I’m involved in multiple projects and have limited time, I don’t want to focus entirely on building a community around Bitcoin Junior Club—at least not for now. Instead, my priority is to expand the database, continue creating creative educational materials, and connect with other family-friendly Bitcoin projects to give them extra visibility.

([source: a snapshot from the home-page of Bitcoin Junior Club](https://www.bitcoin4youth.com/))
**YakiHonne**: What challenges did you encounter while creating this project?
**Şelale**:If we were to shift more towards community-building, I would say the biggest challenge lies in the diverse target audience—especially across different age groups. If you want to engage very young children, aged 2 to 3.5 years, you also need to involve their parents or mentors. If you want to reach teenagers and young adults (aged 11 to 20+), their interests, perspectives, and learning preferences are entirely different. To truly engage all these different groups, you need a wide range of tools that cater to their needs and interests. That is a significant challenge.
I’ve noticed that when people discover Bitcoin Junior Club, they often feel excited and relieved, realizing that such an initiative exists. But at the same time, it’s a fragmented process—it takes time to plant the seed and let people know, this resource is available if you or someone you know might need it.
These are the biggest challenges. But nothing to worry about. The project is naturally and organically growing, and the community will likely develop on its own over time.

(source: Selected photos from Adopting Bitcoin El Salvador, Nov 2024, where a 2-day event for families, co-organized by Bitcoin Junior Club, was run in parallel to the entire conference)
**YakiHonne**: Yeah, that’s very true. The age gap and diverse target audience can indeed be a challenge for many communities. It’s a key factor to consider. However, I really admire the way you’ve been able to navigate this challenge and still effectively reach out to them despite the difficulties. That’s truly something worth recognizing.
**Şelale**:Thank you, that’s true. What I see here, once again, is the power of Nostr. On other social media platforms and across the Internet, there is so much noise—it’s an overwhelming space. But Nostr is different. The community is still relatively small, which means the audience is more specific and targeted. This also makes it faster and easier to understand their needs. Compared to three, four, or five years ago, this is a huge advantage when it comes to reaching specific groups and learning from them.
**YakiHonne**: What advice would you give to someone looking to start or grow a Bitcoin-focused community in today's landscape?
**Şelale**: Overall, don’t overthink it, and don’t try to build something too big from the start. Whatever you envision at the beginning will likely evolve over time. If you know your skills and have an idea that could bring value to the community, start with a high-level roadmap. Avoid over-planning—don’t try to monetize everything or map out years ahead, especially in the early stages, unless you’re working on a large-scale project in a bigger group.
Start with smaller steps and learn from the feedback. As we often say in the Bitcoin world, “don’t ask for permission, just do it”.
I would also emphasize: Learn and adapt along the way, because the feedback you receive from people is the best teacher. As I mentioned earlier, your initial idea may evolve into something different—so don’t give up, and don’t get discouraged. Just keep building. Also, especially for non-technical people, remember that contributing to the Bitcoin ecosystem isn’t just about tech. Of course, technology is at the core of our freedom-oriented future, and it’s incredibly important. But you don’t need technical skills to contribute—there are many ways to add value. It can be anything.
**YakiHonne**: Yes, I really love the last part of what you just said—it’s so important. Many people tend to believe that if you don’t have technical skills, you can’t contribute to the Bitcoin ecosystem, and this is a very common misconception. The more we educate people and help them understand that Bitcoin needs contributions beyond just the technical side, the stronger the community will become. It’s a crucial point and absolutely true. I’d love to know—does your community focus more on the technical or non-technical aspects of Bitcoin? Or do you cover both?
**Şelale**:I would say both, but more indirectly. Bitcoin Junior Club is not only a fun and educational space, but also an online resource providing a wide variety of materials, and so it naturally covers both technical and non-technical aspects.
There are many excellent technical projects out there, such as those related to Lightning Network, which are more technical fields, and these can target young generations as well. [Lightning Piggy](https://www.lightningpiggy.com/) is a great example to use here.
Also, during my recent time in El Salvador, I came across an amazing project, [Node Nation](https://x.com/nodenationsv), that teaches teenagers how to run their own Bitcoin nodes—a clearly technical-focused initiative.
In the future, if we continue to expand and place more emphasis on family-friendly gatherings in person, where practical activities are the core, the technical aspect may naturally grow as well. I have some ideas related to coding courses, interactive games, and other technical aspects that teenagers could be interested in. However, for now, our main focus remains on education and sharing existing resources with more people online. All in all, Bitcoin Junior Club is indirectly engaging with both technical and non-technical content.
**YakiHonne**: Sounds like a lot of work, but what you guys are doing is truly amazing. I can already see the large-scale impact this will have in the coming years. Since you are involved in the technical side as well, what advice would you give to technically inclined individuals or organizations looking to contribute meaningfully to the Bitcoin ecosystem?
**Şelale**:My advice would be: go out and speak up. Try to join different meetups—not necessarily large conferences, but smaller local meetups, hackathons, and co-working spaces. These environments will help you connect with others who also have technical skills. You may meet people who are already working on something related to your field, and eventually can guide you toward bigger areas of contribution.
Face to face meetings are the best options to find potential collaborators, and to build something together, as well as to strengthen your skills, and to motivate you to start building on your own.
Also, don’t hesitate to share your ideas and ask questions publicly—for example, on Nostr, or through platforms like YakiHonne.
Simply, speak up, and see if anyone is working on something similar or wants to collaborate.
Most importantly, don’t be shy. Don’t isolate yourself in your own bubble. Just like creative people, technical people too, sometimes tend to stay in their own world, hesitant to step out. The truth is, it’s not that difficult to get involved—you just need to let people know you exist and what you can contribute.
**YakiHonne**: You know, many people tend to believe that only large conferences are worthwhile, thinking they won’t gain much from local meetups. But in reality, starting with local gatherings often leads to stronger connections. That’s a crucial point. So, my next question, Selale—how do you see the role of Bitcoin communities evolving as the technology matures, particularly in areas like scalability, privacy, and adaptability with other systems?
**Şelale**:What I’m about to say might be a bit of an unpopular opinion, but this is how I genuinely feel—especially in the past few years, there has been a lot of noise around mass adoption and scaling up, with a strong focus on doing things on a huge scale for everyone.
However, I believe there is a more important step before that—which is mass education and awareness. If we truly want to protect privacy and ensure the conscious use of Bitcoin, so that it remains a freedom technology, we need to prioritize education before expansion.
I hope that Bitcoin communities will become more aware of this and continue building on core values—the real Bitcoin ethos, such as truth, long-trem progress, privacy, and sovereignty, rather than just repeating hype-driven trends. I hope the community moves in this direction or, at the very least, remains strong enough to keep spreading the message of privacy and scalability as tools for freedom, rather than just chasing mass adoption and making everything overly simple.
Of course, user experience matters—I absolutely support improving UX across different areas because it’s necessary for broader adoption. However, before that, we need to raise awareness and ensure that people—whoever they are—truly understand Bitcoin’s potential along with the risks that come with losing sovereignty, overexposing personal data, and rushing into oversimplification.
For me, Proof of Work is not just about mining—it also means that understanding Bitcoin requires effort. You have to invest time, energy, and thought into learning about it. Making things too easy, too big, and too flashy isn’t necessarily something I believe in or support.
**YakiHonne**: Though it’s true that Bitcoin communities will play an increasingly significant role as time goes on and as the technology matures, they will also evolve in terms of scalability, privacy, and adaptability. These aspects align with the core values that most Bitcoin communities uphold, especially given Bitcoin’s decentralized nature. So, we’ve now come to our last question for today, and I must say, it’s one of my favorite questions. Is the government in your region supportive or opposed to Bitcoin? And how has that impacted the community?
**Şelale**:That’s an interesting question, because as a nomad, I don’t stay under the influence of any single government for long—usually not more than one to three months. We are constantly changing locations. However, we mostly stay within the European Union, and just using it as an example, with its centralized structure, it’s fundamentally opposite to what Bitcoin stands for. It operates against nation-states, encouraging people to think and act not as individuals, but as a collective.
I don’t see any direct threats or actions taken against Bitcoin Junior Club or any other communities I’m involved in. However, I do believe that the narratives pushed by certain jurisdictions can create obstacles—or, maybe on the other hand, they can actually awaken more people. These days, it has become popular among politicians to claim they are pro-Bitcoin, using it as a low-hanging fruit to gain attention. Hence, it’s hard to say whether some governments are truly pro- or anti-Bitcoin. From my personal journey I see them rather having a neutral approach, but it could change in the next few months, as supporting Bitcoin has suddenly become trendy. Probably a topic for a longer chat.
At the same time, I’ve seen areas in which ruling parties are officially anti-Bitcoin, yet people still find ways to work within the ecosystem and continue spreading the message of freedom.
**YakiHonne**: Just an outside the box question. Did anyone around your area or towards your community consider Bitcoin to be a scam?
**Şelale**:I had those experiences many years ago, in the very beginning. Currently, I’ve just consciously stopped spending time around people who hold such opinions, so I don’t see or hear it as often. ItThat said, it still happens occasionally—especially in Western countries. If I talk to someone new and they ask, “What do you do?” and I mention Bitcoin, sometimes they respond with:"Oh, that’s a Ponzi scheme." It’s very rare, but it still happens. For me, it just shows that those people are still too influenced by mainstream narratives—the same way people repeat things like "Bitcoin consumes too much energy" without fully understanding the subject. However, compared to five to ten years ago, these misconceptions have definitely become less common.
As a site note, I’ve reached a stage where instead of overwhelming others with Bitcoin-themed conversations, I prefer to keep building- i.e. working on various resources that will be easy enough to find to learn from. If somebody later wants to ask questions or debate, still doubting whether Bitcoin is good or bad for humanity, I am ready to join. All in all, instead of actively trying to convince people, I focus my energy on projects like Bitcoin Junior Club, Bitcoin Film Fest, and other initiatives that provide content for freedom-seekers at heart.
**YakiHonne**: Thank you so much. We've reached the end of today's interview, and it has truly been a fantastic conversation. I’ve gained a lot of valuable insights from you, and I genuinely appreciate the incredible work that you and your community are doing in the European Union. It’s truly inspiring. I’m certain that Europe is privileged to have you and your team contributing to this space.
**Şelale**: The pleasure is mine. Thank you very much for this conversation. Once again, kudos to all you are bullying at Yaki Honne.
-

@ 95cb4330:96db706c
2025-03-05 08:39:40
Embracing a **Long-Term Thinking Mindset**, as exemplified by leaders like Jeff Bezos and Peter Thiel, involves making decisions that prioritize enduring success over immediate gains. This approach fosters sustainable growth and innovation by focusing on strategies that yield compounded benefits over time.
---
## Understanding the Long-Term Thinking Mindset
- **Definition:**
A strategic perspective that emphasizes planning and decision-making with a focus on achieving substantial, lasting outcomes—often at the expense of short-term profits or conveniences.
---
## Examples in Practice
- **Jeff Bezos and Amazon:**
Bezos structured Amazon to prioritize long-term customer trust over quarterly profits, leading to its dominance. He believes that long-term thinking leverages existing abilities and supports the failure and iteration required for invention.
- **Peter Thiel's Investment Strategy:**
Thiel invests in startups with unique, superior products and a 10+ year vision, rather than chasing short-term competition. His contrarian investment strategy focuses on long-term tech investments.
---
## Implementing Long-Term Thinking
1. **Set Visionary Goals:**
Define objectives that align with enduring values and aspirations, guiding sustained efforts toward meaningful achievements.
2. **Prioritize Sustainable Practices:**
Adopt strategies that ensure environmental, social, and economic sustainability, contributing to long-term viability.
3. **Embrace Delayed Gratification:**
Recognize that significant rewards often require patience and persistent effort, avoiding the allure of immediate but fleeting benefits.
---
## Benefits of Long-Term Thinking
- **Resilience:**
Organizations and individuals become better equipped to navigate challenges and adapt to changing circumstances.
- **Reputation:**
A commitment to long-term goals fosters trust and credibility among stakeholders, enhancing relationships and opportunities.
- **Innovation:**
Focusing on enduring success encourages continuous improvement and the development of groundbreaking solutions.
---
## Action Step
Identify a current decision or project and assess whether your approach favors short-term comfort or long-term success. If it leans toward immediate gratification, consider realigning your strategy to prioritize enduring benefits—ensuring that today's choices contribute positively to your future goals.
---
By adopting a long-term thinking mindset, you position yourself and your organization to achieve sustained success and make a lasting impact.
For further insights into Jeff Bezos's perspective on long-term thinking, consider watching this discussion:
[JEFF BEZOS - THINK LONG TERM](https://www.youtube.com/watch?v=y-lbBrbfmDw)
---
-

@ da0b9bc3:4e30a4a9
2025-03-05 07:20:21
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/904251
-

@ 1d7ff02a:d042b5be
2025-03-05 06:02:55
### ມະນຸດມີຄວາມຈະເລີນໄດ້ຍ້ອນຮູ້ຈັກສ້າງຄວາມຫມັ້ນຄົງໃນອະນາຄົດ
ມະນຸດເຮົາສ້າງຄວາມຈະເລີນຮຸ່ງຮອງໄດ້ກໍຍ້ອນການສ້າງຄວາມຫມັ້ນຄົງໃນກະນາຄົດ ເຊິ່ງສະແດງອອກຢູ່ໃນ ຈາກແຕ່ກ່ອນຕ້ອງອອກໄປ ຫາອາຫານ ລ່າສັດ ເພື່ອເປັນພະລັງງານໃນການມີຊີວິດ ຈົນຮູ້ເຮົາຮູ້ຈັກການເກັບດອງອາຫານໃຫ້ກິນຍາວນານຂຶ້ນ, ຈາການຫາອາຫານເພື່ອຕົວເອງຢ່າງດຽວ ກໍຮູ້ຈັກການແລກປ່ຽນ (barter trade) ເຮັດໃຫ້ໄດ້ສິນຄ້າທີ່ຕົວເອງຕ້ອງການ ໂດຍບໍ່ຕ້ອງໃຊ້ເວລາທັງຫມົດໄປກັບການຫາ ຫລື ຜະລິດສິ່ງນັ້ນ ແລະ ສຸດທ້າຍເຮົາກໍຮູ້ຈັກເລືອກສິນຄ້າທີ່ມີຄວາມຫມັ້ນຄົງ ແລະ ຜະລິດຍາກ ມາເປັນເງິນ ເພື່ອໃຊ້ເປັນ ສື່ກາງ ໃນການແລກປ່ຽນ ຈົນແຕ່ລະຄົນມີເວລາໃນການໂຟກັສ ພັດທະນາທັກສະທີ່ຕົວເອງສົນໃຈຈົນມີຄວາມຊຳນານກວ່າຄົນທົ່ວໄປ ເຮັດໃຫ້ສາມາດຜະລິດສິນຄ້າ ແລະ ບໍລິການ ທີ່ມີຄຸນນະພາບ ແລະ ລາຄາຖືກລົງ. ປະກົດການເຫລົ່ານີ້ເກີດຂຶ້ນໄດ້ຍ້ອນເຮົາມີຄວາມຫມັ້ນຄົງໃນອະນາຄົດດ້ວຍເງິນເກັບ ຈົນມີເວລາຈະລອງຜິດລອງຖືກໄດ້.
ແຕ່ຫລັງຈາກທີ່ເຮົາອອກຈາກ ມາດຕະຖານທອງຄຳ ກໍເຮັດໃຫ້ເງິນມັນເຊື່ອມຄ່າລົງໄປຕາມການເວລາ ຈົນເຮັດໃຫ້ຄົນເຫັນແກ່ເວລາອັນສັ້ນ, ຜະລິດສິນຄ້າ ແລະ ບໍລິການ ທີ່ບໍ່ໄດ້ຄຸນນະພາບ ເພາະຄິດແຕ່ວ່າຈະເຮັດແນວໃດເພື່ອຈະໄດ້ເງິນຫລາຍຂຶ້ນ ເພາະເງິນມັນເຊື່ອມມູນຄ່າລົງເລື່ອຍໆ ຈົນລືມຄິດໄປວ່າສິ່ງໃດແທ້ ທີ່ສຳຄັນໃນຊີວິດ ຈົນເກີດບັນຫາຕ່າງໆ ບໍ່ວ່າຈະເປັນສັງຄົມ ແລະ ເສດຖະກິດ.
> ບິດຄອຍ ບໍ່ໄດ້ເຮັດໃຫ້ທ່ານລວຍໄວຂຶ້ນ ແຕ່ມັນກຳລັງແກ້ບັນຫາພື້ນຖານຢ່າງການ ເກັບເງິນ ຢູ່ ເພາະປະຈຸບັນມະນຸດເກັບເງິນບໍ່ໄດ້ແລ້ວ ເພາະມູນຄ່າຂອງມັນຫລຸດລົງເລື່ອຍໆ
### ການ DCA ບິດຄອຍ
<img src="https://blossom.primal.net/7899fb7c4ccc478027ca38f12cf21730f46dbc8def7dec5a023f30539121b2ff.png">
ບິດຄອຍມີຄວາມຜັນຜວນເລື່ອງລາຄາຫລາຍ ກໍຍ້ອນເຮົາເບິ່ງໃນໄລຍະສັ້ນ ແຕ່ຖ້າເຮົາເບິ່ງມັນເປັນເຄື່ອງມືເກັບອອມເຮົາຈະເຫັນຄວາມຈິງ ບິດຄອຍຄືຄວາມຫມັ້ນຄົງ ແລະ ຕໍ່ຕ້ານການເຟີ້ຂອງເງິນ. ຕົວຢ່າງລຸ່ມນີ້ເປັນການຄຳນວນວ່າ ຖ້າເຮົາເກັບບິດຄອຍ ທຸກເດືອນ ຜ່ານໄປ 8 ປີ ມັນຈະມີມູນຄ່າເພີ່ມຂຶ້ນ 617% ຫລື ປະມານປີລະ 77% ໂດຍສະເລ່ຍ ເຊິ່ງມັນກໍບໍ່ໄດ້ເປັນໂຕເລກໂອເວີຫຍັງຫລາຍ ແຕ່ສາມາດເອົາຊະນະເງິນເພີ້ໄດ້ແລ້ວ ພຽງແຕ່ເກັບ ແລະ ບໍ່ຕ້ອງຄິດຫຍັງ.
### ເມື່ອເຮົາມີເງິນເກັບທີ່ຮັກສາມູນຄ່າໄດ້ ມັນເປັນຄົນລະເລື່ອງເລີຍໃນການໃຊ້ຊີວິດ ແລະ ວິທີຄິດ
ຄົນຈະມີຄວາມຄິດການໄກຫລາຍຂຶ້ນ, ມີເວລາຄິດທົບທວນເລື່ອງຕ່າງໆໃນຊີວິດຢ່າງລະອຽດຖີ່ຖ້ວນ ແລະ ຕັດສິນໃຈແບບມີເຫດມີຜົນ. ຄົນຈະເລືອກເຮັດວຽກມີຢາກເຮັດ ເຖິງວ່າລາຍໄດ້ອາດຈະຫນ້ອຍ ແຕ່ເງິນເກັບສາມາດຮັກສາມູນຄ່າຂຶ້ນໄດ້ເລື່ອຍໆ, ເຮົາຈະມີເວລາໃຫ້ກັບຄອບຄົວຫລາຍກວ່າ ເພາະບໍ່ໄດ້ແລ່ນຕາມວຽກເພື່ອຈະໄດ້ລາຍຮັບເພີ່ມຂຶ້ນຕາມການເຊື່ອມຄ່າຂອງເງິນ. ຄົນຈະໃຫ້ຄວາມສຳຄັນກັບສຸຂະພາບຫລາຍຂຶ້ນ ເພາະສຸດທ້າຍແລ້ວເຮົາຈະເຂົ້າໃຈວ່າສຸຂະພາບນີ້ແລະ ສຳຄັນສຸດ.
ຈາກຄວາມຮູ້ສຶກຂອງຕົວຂ້ອຍເອງມັນເຮັດໃຫ້ ມີຄວາມຫວັງ ແລະ ຕື່ນເຕັ້ນທີ່ຈະໄດ້ໃຊ້ຊີວິດໄປໃນການນາຄົດ ເພາະຮູ້ສຶກວ່າມີຄວາມຫມັ້ນຄົງ ຈາກການຄ່ອຍໆເກັບ ບິດຄອຍ ໂດຍມີເປົ້າຫມາຍເຮັດແນວໃດ ຈະໄດ້ໃຊ້ເວລາທີ່ເຫລືອຢູ່ ເກັບຄົນທີ່ເຮົາຮັກ, ເຮັດສິ່ງທີ່ມັກ ແລະ ມີສຸຂະພາບດີຈົນຈາກໂລກນີ້ໄປໃຫ້ເຈັບປວດຫນ້ອຍທີ່ສຸດ.
-

@ 9ea10fd4:011d3b15
2025-03-05 02:09:11
(Le français suit) Scott Ritter discusses Trump’s willingness to end the war in Ukraine, highlighting his desire for peace (although other analysts suggest that the United States is shifting its strategic focus toward China).
Ritter claims that the United States could consider leaving NATO by the end of the summer but provides no explanation. The U.S. takes a utilitarian approach toward its allies. Ritter believes that, unlike the Democrats, Trump does not align with the military-industrial complex. He is seen as an outsider to this complex, seeking to shift American policy toward trade and the economy rather than militarism (however, military spending increased during his first term). This complex, which developed during World War II and the Cold War, has an increasing need for conflicts to sustain itself, potentially leading to nuclear war.
Europe, under U.S. influence, is compared to a Frankenstein’s monster—believing it is America’s ally while actually being a replaceable tool. A global transition is underway, marked by closer ties between the U.S., Russia, China, and India, excluding Europe for ideological and practical reasons—if I understand correctly, because it is characterized as knowing only war (I note that European diplomacy has recently turned toward India as an alternative to the U.S. and China). This shift, as described by Ritter, could signify the end of the transatlantic order.
Obstacles remain for Trump, notably the issue of Gaza, which is complicated by pressure from the pro-Israel lobby and the positioning of Arab countries.
Finally, it is suggested that Trump might want to reduce the size of the military and rethink the role of the United Nations, seen as a legacy of past conflicts—an intriguing idea but not fully developed.
**
“In this perspective, Trump’s imposition of tariffs would serve as a key element of a strategy aimed at prioritizing the economy over militarism, marginalizing Europe while fostering pragmatic ties with powers like Russia and China, and redefining American power in a post-transatlantic world. This would reflect a break from the military-industrial complex and a utilitarian view of international relations, where tariffs replace tanks as tools of domination or negotiation. However, their success would depend on Trump’s ability to navigate internal pressures (the pro-Israel lobby) and external reactions (from trade partners).” (Grok 3 Beta)
(On Telegram)
[FIRST IMPRESSION ON TRUMP ZELENSKY FIASCO
Interview for India & Global Left](https://t.me/ScottRitter/3761)
****
Scott Ritter évoque la volonté de Trump de mettre fin à la guerre en Ukraine, soulignant son désir de paix (cela bien que d’autres analystes disent que les États-Unis sont en train de réorienter leur stratégie vers la Chine).
Ritter avance que les États-Unis pourraient envisager de quitter l’OTAN d’ici à la fin de l’été mais ne fournit aucune explication. Les États-Unis adoptent une approche utilitaire vis-à-vis de leurs alliés. Ritter estime que Trump ne se positionne pas en faveur du complexe militaro-industriel, contrairement aux démocrates. Trump est perçu comme un acteur extérieur à ce complexe, cherchant à réorienter la politique américaine vers le commerce et l’économie plutôt que le militarisme (cependant les dépenses militaires avaient augmenté lors de son premier mandat). Ce complexe, qui s'est développé pendant la Seconde Guerre mondiale et la guerre froide, a un besoin croissant de conflits pour perdurer, menant éventuellement à une guerre nucléaire.
L’Europe, sous l’influence des États-Unis, est comparée à un monstre de Frankenstein, croyant être l’alliée des États-Unis alors qu’elle n’est qu’un outil remplaçable. Une transition mondiale est en cours, marquée par un rapprochement entre les États-Unis, la Russie, la Chine et l’Inde, en excluant l’Europe pour des raisons idéologiques et pratiques si j’ai bien compris, car elle est caractérisée comme ne connaissant que la guerre (je remarque que la diplomatie européenne s'est récemment tournée vers l'Inde présentée comme une alternative aux États-Unis et à Chine). Ce changement tel que décrit par Ritter pourrait signifier la fin de l’ordre transatlantique.
Des obstacles subsisteraient pour Trump, notamment la question de Gaza, compliquée par les pressions exercées par le lobby pro-Israël et le positionnement des pays arabes.
Enfin, il est suggéré que Trump pourrait vouloir réduire la taille de l’armée et repenser le rôle des Nations Unies, perçues comme un héritage des conflits passés, une idée suggestive mais peu développée.
**
« Dans cette perspective, l’imposition de tarifs douaniers par Trump s’insérerait comme une pièce maîtresse d’une stratégie visant à privilégier l’économie sur le militarisme, à marginaliser l’Europe tout en se rapprochant de puissances comme la Russie ou la Chine sur des bases pragmatiques, et à redéfinir la puissance américaine dans un monde post-transatlantique. Cela refléterait une rupture avec le complexe militaro-industriel et une vision utilitaire des relations internationales, où les tarifs remplacent les tanks comme outils de domination ou de négociation. Toutefois, leur succès dépendrait de la capacité de Trump à naviguer entre des pressions internes (lobby pro-Israël) et externes (réactions des partenaires commerciaux). » (Grok 3 bêta)
(Sur Telegram)
[FIRST IMPRESSION ON TRUMP ZELENSKY FIASCO
Interview for India & Global Left](https://t.me/ScottRitter/3761)
-

@ 401014b3:59d5476b
2025-03-05 01:39:21
Alright, football freaks, it’s March 2025, and we’re slinging some half-baked AFC East predictions like it’s a tailgate wing-eating contest. Free agency’s a madhouse, the draft’s a blind stab, and this division’s always a mix of fireworks and faceplants. The Bills ran the show in 2024, the Dolphins teased us, the Jets are jetting Rodgers out the door, and the Pats have a new sheriff in town. Let’s slap records on this chaos and see who’s got the cajones to take the crown. Strap in—this one’s a banger.
### **Buffalo Bills: 12-5 – Josh Allen’s Reign of Pain**
The Bills owned the AFC East in 2024, and 2025’s looking like a victory lap. Josh Allen’s a goddamn force of nature—cannon arm, truck-stick legs—and he’s got James Cook tearing up the ground game even without a stud WR1. That O-line’s a top-10 crew, and the defense, despite some roster churn, still hits hard with Greg Rousseau leading the charge. Free agency might nibble at the edges—Matt Milano’s return could be clutch—but this squad’s a bully. 12-5’s the vibe, division locked up again. Good luck stopping ‘em.
### **Miami Dolphins: 9-8 – Tua’s Hot-and-Cold Hustle**
The Dolphins are the AFC East’s rollercoaster—thrilling ‘til they puke. Tua Tagovailoa’s slinging to Tyreek Hill and Jaylen Waddle, but that O-line’s still a question mark, and they fold like lawn chairs in December. The defense stepped up in 2024 with Jalen Ramsey locking down receivers, but free agency could sting—Jaelan Phillips might chase a bag elsewhere. If Tua stays healthy and the core holds, 9-8’s on the table. Wildcard’s their best shot—Buffalo’s still the big brother they can’t shake.
### **New York Jets: 8-9 – New QB, Same Jets Jinx**
The Jets are ditching Aaron Rodgers—old man’s outta here—and rolling with a new QB (TBD, but let’s say a rookie or a vet like Tyrod Taylor for kicks). Garrett Wilson and Breece Hall are studs, but that O-line’s a disaster, and the defense might take a hit if Sauce Gardner starts sniffing bigger paychecks. New coach, fresh start, same Jets curse? They’ve got enough talent to flirt with 8-9, maybe sniff a wildcard if the QB doesn’t totally tank. Still feels like classic Jets—almost there, never quite.
### **New England Patriots: 5-12 – Vrabel’s Rough Rebuild**
The Pats are a work in progress, but Mike Vrabel’s the new head honcho, and that’s worth a damn shout. The ex-Titans tough guy’s got Drake Maye at QB—bright future, brutal present. 2025’s gonna be a grind; Maye’s taking rookie lumps behind a shaky O-line with no real weapons to speak of. Christian Gonzalez is a lockdown corner, but the defense ain’t what it was without Belichick’s wizardry. Vrabel’s a culture guy—he’ll keep ‘em scrappy—but 5-12’s the reality. They’re building, not winning, in Foxboro this year.
### **The Final Buzzer**
The AFC East in 2025 is Buffalo’s playground with a dash of dysfunction. The Bills (12-5) snag the crown because Josh Allen’s a beast, the Dolphins (9-8) tease a wildcard, the Jets (8-9) stumble sans Rodgers, and the Pats (5-12) grit it out under Vrabel. That’s 34 wins, 34 losses—math’s tight when you factor in the division’s slugfest with the NFL’s other suckers. Free agency’s the X-factor—lose a star, you’re screwed; snag a gem, you’re golden. Yell at me on X when I botch this, but for now, this is my story, and I’m sticking to it. Let’s ride, degenerates.
-

@ 62a6a41e:b12acb43
2025-03-04 22:19:29
War is rarely (or if ever) the will of the people. Throughout history, wars have been orchestrated by political and economic elites, while the media plays a key role in shaping public opinion. World War I is a clear example of how propaganda was used to glorify war, silence dissent, and demonize the enemy.
Today, we see similar tactics being used in the Ukrainian War. The media spreads one-sided narratives, censors alternative views, and manipulates public sentiment. This article argues that **wars are decided from the top**, and media is used to justify them.
---
## How the Media Glorified and Propagated WW1
### The Media Sold War as an Adventure
Before WW1, newspapers and propaganda made war seem noble and exciting. Young men were encouraged to enlist for honor and glory. Posters displayed slogans like *“Your Country Needs You”*, making war look like a duty rather than a tragedy.
### Demonization of the Enemy
Governments and media portrayed Germans as "barbaric Huns," spreading exaggerated stories like the "Rape of Belgium," where German soldiers were accused of horrific war crimes—many later proven false. Today, Russia is painted as purely evil, while NATO’s role and Ukraine’s internal conflicts are ignored.
### Social Pressure & Nationalism
Anyone who opposed WW1 was labeled a traitor. Conscientious objectors were shamed, jailed, or even executed. The same happens today—if you question support for Ukraine, you are called "pro-Russian" or "anti-European." In the U.S., opposing war is falsely linked to supporting Trump or extremism.
### Fabricated Stories
During WW1, fake reports of German soldiers killing babies were widely spread. In Ukraine, reports of massacres and war crimes often circulate without verification, while Ukrainian war crimes receive little coverage.
---
## How the Media Promotes War Today: The Case of Ukraine
### One-Sided Narratives
The media presents Ukraine as a heroic struggle against an evil invader, ignoring the 2014 coup, the Donbas conflict, and NATO expansion. By simplifying the issue, people are discouraged from questioning the full story.
### Censorship and Suppression of Dissent
During WW1, anti-war activists were jailed. Today, journalists and commentators questioning NATO’s role face censorship, deplatforming, or cancellation.
### Selective Coverage
Media highlights civilian deaths in Ukraine but ignores similar suffering in Yemen, Syria, or Palestine. Coverage depends on political interests, not humanitarian concern.
### Glorification of War Efforts
Ukrainian soldiers—even extremist groups—are painted as heroes. Meanwhile, peace negotiations and diplomatic efforts receive little attention.
---
## War is a Top-Down Decision, Not the Will of the People
### People Don’t Want Wars
If given a choice, most people would reject war. Examples:
- **Before WW1:** Many workers and socialists opposed war, but governments ignored them.
- **Vietnam War:** Protests grew, but the war continued.
- **Iraq War (2003):** Millions protested, yet the invasion went ahead.
### Small Elites Decide War
Wars benefit arms manufacturers, politicians, and corporate interests—not ordinary people. Public opposition is often ignored or crushed.
### Manipulation Through Fear
Governments use fear to justify war: *“If we don’t act now, it will be too late.”* This tactic was used in WW1, the Iraq War, and is used today in Ukraine.
---
## Violence vs. War: A Manufactured Conflict
### Violence Happens, But War is Manufactured
Conflicts and disputes are natural, but large-scale war is **deliberately planned** using propaganda and logistical preparation.
### War Requires Justification
If war were natural, why does it need **massive media campaigns** to convince people to fight? Just like in WW1, today’s wars rely on media narratives to gain support.
---
## The Crimea Referendum: A Case of Ignored Democracy
### Crimea’s 2014 Referendum
- Over **90% of Crimeans voted to join Russia** in 2014.
- Western governments called it "illegitimate," while similar referendums (like in Kosovo) were accepted.
### The Contradiction in Democracy
- If democracy is sacred, why ignore a **clear vote** in Crimea?
- Other examples: Brexit was resisted, Catalonia’s referendum was shut down, and peace referendums were dismissed when they didn’t fit political interests.
- **Democracy is used as a tool when convenient.**
---
## VII. The Libertarian Case Against War
### The Non-Aggression Principle (NAP)
Libertarianism is fundamentally opposed to war because it violates the **Non-Aggression Principle (NAP)**—the idea that no person or institution has the right to initiate force against another. War, by its very nature, is the **ultimate violation of the NAP**, as it involves mass killing, destruction, and theft under the guise of national interest.
### War is State Aggression
- Governments wage wars, not individuals. No private citizen would naturally start a conflict with another country.
- The state **forces people to fund wars through taxation**, violating their economic freedom.
- **Conscription**, used in many wars, is nothing more than **state-sponsored slavery**, forcing individuals to fight and die for political goals they may not support.
### War Creates Bigger Government
- War expands state power, **eroding civil liberties** (e.g., WW1's Espionage Act, the Patriot Act after 9/11).
- The **military-industrial complex** grows richer while taxpayers foot the bill.
- **Emergency powers granted during wars rarely get repealed** after conflicts end, leaving citizens with fewer freedoms.
### Peaceful Trade vs. War
- Libertarians advocate for **free trade** as a means of cooperation. Countries that trade are **less likely to go to war**.
- Wars **destroy wealth and infrastructure**, while peaceful trade **increases prosperity** for all.
- Many wars have been fought **not for defense, but for economic interests**, such as securing **oil, resources, or geopolitical power**.
### Who Benefits from War?
- **Not the people**, who suffer death, destruction, and economic hardship.
- **Not small businesses or workers**, who bear the burden of inflation and taxes to fund wars.
- **Not individual liberty**, as war leads to **greater state control and surveillance**.
- **Only the elites**, including **defense contractors, politicians, and bankers**, who profit from war and use it to consolidate power.
## Conclusion: The Media’s Role in War is Crucial
Wars don’t happen naturally—they are **carefully planned and sold to the public** using propaganda, fear, and nationalism.
- **WW1 and Ukraine prove that media is key to war-making.**
- **The media silences peace efforts and glorifies conflict.**
- **If people truly had a choice, most wars would never happen.**
To resist this, we must **recognize how we are manipulated** and reject the forced narratives that push us toward war.
 @ bc575705:dba3ed39
2025-03-06 09:32:42We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away. I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays). !(image)[https://cdn.pixabay.com/photo/2018/07/16/23/36/puppet-3543246_1280.jpg] ## **The Psychological Warfare of Traditional Social Media** **The Algorithmic Cage:** These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division. **The Illusion of Perfection:** The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt. **The Echo Chamber Effect:** Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance. **The Toxicity Vortex:** The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust. **The Attention Deficit Trap:** The constant stream of notifications, updates, and content creates a state of perpetual distraction, making it difficult to focus, think critically, and engage in meaningful interactions. This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back. !(image)[https://cdn.pixabay.com/photo/2017/08/06/12/21/web-2592005_1280.jpg] ## **NOSTR: A Sanctuary in the Digital Wasteland** NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty. **User-Controlled Feeds:** You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you. **Ownership of Your Digital Identity:** Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder. **Interoperability:** Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs. **Value-Driven Interactions:** The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation. **Decentralized Power:** No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords. !(image)[https://images.pexels.com/photos/2694434/pexels-photo-2694434.jpeg] ## **Building a Healthier Digital Future** NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience. **Cultivating Authentic Connections:** Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers. **Supporting Independent Creators:** Use "zaps" to directly support the artists, writers, and thinkers who inspire you. **Embracing Intellectual Diversity:** Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions. **Prioritizing Your Mental Health:** Take control of your digital environment and create a space that supports your well-being. **Removing the noise:** Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes. !(image)[https://images.pexels.com/photos/158826/structure-light-led-movement-158826.jpeg] ## **The Time for Action is Now** NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity. We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy. !(image)[https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fm.primal.net%2FPKgz.jpg] ## **Join the NOSTR movement.** Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us. In addition to the points above, here are some examples/links of how NOSTR can be used: **Simple Signup:** Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem. **X-like Client:** Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms. **Sharing Photos and Videos:** Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers. **Creating and Consuming Blogs:** NOSTR can be used to publish and share blog posts, fostering a community of independent creators. **Live Streaming and Audio Spaces:** Explore platforms like Hivetalk and Zap Stream for live streaming and audio-based interactions. Get the full overview of these and other apps here: https://nostrapps.com/ **NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.**
@ bc575705:dba3ed39
2025-03-06 09:32:42We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away. I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays). !(image)[https://cdn.pixabay.com/photo/2018/07/16/23/36/puppet-3543246_1280.jpg] ## **The Psychological Warfare of Traditional Social Media** **The Algorithmic Cage:** These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division. **The Illusion of Perfection:** The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt. **The Echo Chamber Effect:** Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance. **The Toxicity Vortex:** The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust. **The Attention Deficit Trap:** The constant stream of notifications, updates, and content creates a state of perpetual distraction, making it difficult to focus, think critically, and engage in meaningful interactions. This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back. !(image)[https://cdn.pixabay.com/photo/2017/08/06/12/21/web-2592005_1280.jpg] ## **NOSTR: A Sanctuary in the Digital Wasteland** NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty. **User-Controlled Feeds:** You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you. **Ownership of Your Digital Identity:** Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder. **Interoperability:** Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs. **Value-Driven Interactions:** The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation. **Decentralized Power:** No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords. !(image)[https://images.pexels.com/photos/2694434/pexels-photo-2694434.jpeg] ## **Building a Healthier Digital Future** NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience. **Cultivating Authentic Connections:** Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers. **Supporting Independent Creators:** Use "zaps" to directly support the artists, writers, and thinkers who inspire you. **Embracing Intellectual Diversity:** Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions. **Prioritizing Your Mental Health:** Take control of your digital environment and create a space that supports your well-being. **Removing the noise:** Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes. !(image)[https://images.pexels.com/photos/158826/structure-light-led-movement-158826.jpeg] ## **The Time for Action is Now** NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity. We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy. !(image)[https://primal.b-cdn.net/media-cache?s=o&a=1&u=https%3A%2F%2Fm.primal.net%2FPKgz.jpg] ## **Join the NOSTR movement.** Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us. In addition to the points above, here are some examples/links of how NOSTR can be used: **Simple Signup:** Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem. **X-like Client:** Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms. **Sharing Photos and Videos:** Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers. **Creating and Consuming Blogs:** NOSTR can be used to publish and share blog posts, fostering a community of independent creators. **Live Streaming and Audio Spaces:** Explore platforms like Hivetalk and Zap Stream for live streaming and audio-based interactions. Get the full overview of these and other apps here: https://nostrapps.com/ **NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.** @ a012dc82:6458a70d
2025-03-06 08:28:23In a groundbreaking move that could significantly alter the investment landscape, Harvest Fund Management, a prominent Chinese asset manager, has boldly stepped forward with an application for a spot Bitcoin exchange-traded fund (ETF) in Hong Kong. This initiative is not just a leap towards diversifying investment options but also a testament to the evolving acceptance and integration of digital assets into the mainstream financial ecosystem. **Table of Contents** - Introduction to Spot Bitcoin ETFs - Harvest Fund's Strategic Move - The Significance for Hong Kong - Regulatory Landscape and Stablecoin Interest - The Road Ahead - Conclusion - FAQs **Introduction to Spot Bitcoin ETFs** Spot Bitcoin ETFs represent a bridge between the traditional financial world and the burgeoning realm of cryptocurrencies. By mirroring the current market price of Bitcoin, these ETFs offer investors a straightforward path to participate in the cryptocurrency market without the direct ownership of Bitcoin. This eliminates the need for investors to engage with cryptocurrency exchanges or secure digital wallets, thereby lowering the entry barriers to the Bitcoin market. The significance of spot Bitcoin ETFs extends beyond convenience; they are a symbol of the growing legitimization of cryptocurrencies as a viable asset class. By being listed on conventional stock exchanges, these ETFs are subjected to regulatory scrutiny and standards, offering a layer of security and transparency that is sometimes questioned in the crypto space. This development could potentially attract a new wave of institutional and retail investors, who have been on the sidelines due to concerns over regulatory clarity and the technical challenges associated with cryptocurrency investments. **Harvest Fund's Strategic Move** Harvest Fund Management's application for a spot Bitcoin ETF is a calculated strategic move, positioning the firm at the forefront of financial innovation in Hong Kong. By aiming to launch the city's first such ETF, Harvest Fund is not merely expanding its product lineup but is also contributing to the legitimization and institutionalization of Bitcoin as an investable asset. This pioneering effort reflects a deep understanding of market dynamics and a vision for the future of investment, where digital and traditional assets coexist within regulated frameworks. The initiative by Harvest Fund could catalyze a shift in investor sentiment, encouraging more conservative players to consider the potential of Bitcoin and other cryptocurrencies. Furthermore, it sets a benchmark for product innovation and regulatory compliance, potentially influencing the pace and direction of cryptocurrency adoption across the financial sector. As the first mover, Harvest Fund could enjoy a competitive advantage, capturing significant market share among investors eager to explore digital assets within a regulated environment. **The Significance for Hong Kong** Hong Kong's financial landscape is on the cusp of transformation, with Harvest Fund's application signaling a broader trend towards the acceptance of digital assets. This move comes at a pivotal moment, as Hong Kong seeks to assert itself as a global hub for cryptocurrency and blockchain technology. The interest from approximately 10 fund companies in launching their own spot crypto ETFs underscores the city's potential to lead in the virtual asset space. This collective momentum could significantly enhance Hong Kong's attractiveness as a financial center, drawing in global investors looking for regulated avenues into the cryptocurrency market. The introduction of spot Bitcoin ETFs would not only diversify the city's financial products but also reinforce its reputation as a jurisdiction that balances innovation with investor protection. By providing a structured and regulated framework for cryptocurrency investments, Hong Kong can set a global standard for how financial centers can adapt to the evolving landscape of digital assets. This development is a key step in the broader journey towards integrating cryptocurrencies into the global financial system, with Hong Kong leading the way. **Regulatory Landscape and Stablecoin Interest** The enthusiasm for spot Bitcoin ETFs in Hong Kong is paralleled by an equally significant interest in stablecoins, indicating a comprehensive approach to cryptocurrency regulation and adoption. The discussions between the HKMA and various companies about stablecoin trials reflect a proactive stance towards understanding and integrating digital currencies in a way that supports financial stability and innovation. This balanced approach is crucial, as stablecoins represent a bridge between traditional fiat currencies and cryptocurrencies, offering the potential for more efficient payment systems and financial services. The regulatory efforts around stablecoins, coupled with the move towards spot Bitcoin ETFs, show Hong Kong's commitment to creating a robust framework for digital assets. This not only enhances the city's competitive edge as a financial hub but also provides a blueprint for other jurisdictions navigating the complexities of cryptocurrency regulation. By leading in both areas, Hong Kong is positioning itself at the forefront of financial innovation, setting the stage for a future where digital and traditional finance converge seamlessly. **The Road Ahead** The initiative by Harvest Fund Management to launch a spot Bitcoin ETF in Hong Kong marks the beginning of a new era in cryptocurrency investment. This move is more than just an expansion of the financial products available to investors; it is a signal of the maturing relationship between the cryptocurrency industry and the broader financial community. As regulatory frameworks continue to evolve and more players enter the market, the landscape for cryptocurrency investment is set to undergo significant changes. Hong Kong's role in this transition cannot be understated. By fostering an environment that encourages innovation while ensuring investor protection, the city is not just adapting to the rise of digital assets but is actively shaping the future of finance. The success of Harvest Fund's application and the subsequent launch of the city's first spot Bitcoin ETF could serve as a catalyst for other financial centers to follow suit, potentially leading to a global shift in how cryptocurrencies are perceived and utilized within the investment world. **Conclusion** Harvest Fund Management's bold step towards launching a spot Bitcoin ETF in Hong Kong is a landmark moment in the integration of digital assets into mainstream finance. This initiative not only opens up new avenues for investment but also underscores Hong Kong's ambition to be at the forefront of financial innovation. As the regulatory landscape evolves and the market for digital assets continues to grow, the efforts of Harvest Fund and like-minded institutions will be crucial in bridging the gap between traditional finance and the digital asset world. The path ahead is promising, and Hong Kong's leadership in this space could pave the way for a new chapter in the global financial narrative, where digital and traditional assets coexist in a regulated, dynamic, and inclusive investment ecosystem. **FAQs** **Who has filed for the first spot Bitcoin ETF in Hong Kong?** Harvest Fund Management, a major Chinese asset manager, has filed an application for the first spot Bitcoin ETF in Hong Kong with the Securities and Futures Commission (SFC). **Why is a spot Bitcoin ETF significant for investors?** A spot Bitcoin ETF provides a regulated, accessible, and potentially less risky way for investors to gain exposure to Bitcoin's price movements without dealing with the complexities of cryptocurrency exchanges, digital wallets, and private keys. **How does a spot Bitcoin ETF work?** A spot Bitcoin ETF buys and holds actual Bitcoin, and the value of the ETF shares fluctuates with the real-time price of Bitcoin. Investors can buy and sell these shares through traditional stock exchanges. **What are the benefits of investing in a spot Bitcoin ETF?** Investing in a spot Bitcoin ETF offers the benefits of trading and owning a stock, including regulatory protection, ease of access, and liquidity, while also providing exposure to Bitcoin's price. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnewsco](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co/](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@thebitcoinlibertarian](https://www.youtube.com/@thebitcoinlibertarian)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** **Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad** **Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
@ a012dc82:6458a70d
2025-03-06 08:28:23In a groundbreaking move that could significantly alter the investment landscape, Harvest Fund Management, a prominent Chinese asset manager, has boldly stepped forward with an application for a spot Bitcoin exchange-traded fund (ETF) in Hong Kong. This initiative is not just a leap towards diversifying investment options but also a testament to the evolving acceptance and integration of digital assets into the mainstream financial ecosystem. **Table of Contents** - Introduction to Spot Bitcoin ETFs - Harvest Fund's Strategic Move - The Significance for Hong Kong - Regulatory Landscape and Stablecoin Interest - The Road Ahead - Conclusion - FAQs **Introduction to Spot Bitcoin ETFs** Spot Bitcoin ETFs represent a bridge between the traditional financial world and the burgeoning realm of cryptocurrencies. By mirroring the current market price of Bitcoin, these ETFs offer investors a straightforward path to participate in the cryptocurrency market without the direct ownership of Bitcoin. This eliminates the need for investors to engage with cryptocurrency exchanges or secure digital wallets, thereby lowering the entry barriers to the Bitcoin market. The significance of spot Bitcoin ETFs extends beyond convenience; they are a symbol of the growing legitimization of cryptocurrencies as a viable asset class. By being listed on conventional stock exchanges, these ETFs are subjected to regulatory scrutiny and standards, offering a layer of security and transparency that is sometimes questioned in the crypto space. This development could potentially attract a new wave of institutional and retail investors, who have been on the sidelines due to concerns over regulatory clarity and the technical challenges associated with cryptocurrency investments. **Harvest Fund's Strategic Move** Harvest Fund Management's application for a spot Bitcoin ETF is a calculated strategic move, positioning the firm at the forefront of financial innovation in Hong Kong. By aiming to launch the city's first such ETF, Harvest Fund is not merely expanding its product lineup but is also contributing to the legitimization and institutionalization of Bitcoin as an investable asset. This pioneering effort reflects a deep understanding of market dynamics and a vision for the future of investment, where digital and traditional assets coexist within regulated frameworks. The initiative by Harvest Fund could catalyze a shift in investor sentiment, encouraging more conservative players to consider the potential of Bitcoin and other cryptocurrencies. Furthermore, it sets a benchmark for product innovation and regulatory compliance, potentially influencing the pace and direction of cryptocurrency adoption across the financial sector. As the first mover, Harvest Fund could enjoy a competitive advantage, capturing significant market share among investors eager to explore digital assets within a regulated environment. **The Significance for Hong Kong** Hong Kong's financial landscape is on the cusp of transformation, with Harvest Fund's application signaling a broader trend towards the acceptance of digital assets. This move comes at a pivotal moment, as Hong Kong seeks to assert itself as a global hub for cryptocurrency and blockchain technology. The interest from approximately 10 fund companies in launching their own spot crypto ETFs underscores the city's potential to lead in the virtual asset space. This collective momentum could significantly enhance Hong Kong's attractiveness as a financial center, drawing in global investors looking for regulated avenues into the cryptocurrency market. The introduction of spot Bitcoin ETFs would not only diversify the city's financial products but also reinforce its reputation as a jurisdiction that balances innovation with investor protection. By providing a structured and regulated framework for cryptocurrency investments, Hong Kong can set a global standard for how financial centers can adapt to the evolving landscape of digital assets. This development is a key step in the broader journey towards integrating cryptocurrencies into the global financial system, with Hong Kong leading the way. **Regulatory Landscape and Stablecoin Interest** The enthusiasm for spot Bitcoin ETFs in Hong Kong is paralleled by an equally significant interest in stablecoins, indicating a comprehensive approach to cryptocurrency regulation and adoption. The discussions between the HKMA and various companies about stablecoin trials reflect a proactive stance towards understanding and integrating digital currencies in a way that supports financial stability and innovation. This balanced approach is crucial, as stablecoins represent a bridge between traditional fiat currencies and cryptocurrencies, offering the potential for more efficient payment systems and financial services. The regulatory efforts around stablecoins, coupled with the move towards spot Bitcoin ETFs, show Hong Kong's commitment to creating a robust framework for digital assets. This not only enhances the city's competitive edge as a financial hub but also provides a blueprint for other jurisdictions navigating the complexities of cryptocurrency regulation. By leading in both areas, Hong Kong is positioning itself at the forefront of financial innovation, setting the stage for a future where digital and traditional finance converge seamlessly. **The Road Ahead** The initiative by Harvest Fund Management to launch a spot Bitcoin ETF in Hong Kong marks the beginning of a new era in cryptocurrency investment. This move is more than just an expansion of the financial products available to investors; it is a signal of the maturing relationship between the cryptocurrency industry and the broader financial community. As regulatory frameworks continue to evolve and more players enter the market, the landscape for cryptocurrency investment is set to undergo significant changes. Hong Kong's role in this transition cannot be understated. By fostering an environment that encourages innovation while ensuring investor protection, the city is not just adapting to the rise of digital assets but is actively shaping the future of finance. The success of Harvest Fund's application and the subsequent launch of the city's first spot Bitcoin ETF could serve as a catalyst for other financial centers to follow suit, potentially leading to a global shift in how cryptocurrencies are perceived and utilized within the investment world. **Conclusion** Harvest Fund Management's bold step towards launching a spot Bitcoin ETF in Hong Kong is a landmark moment in the integration of digital assets into mainstream finance. This initiative not only opens up new avenues for investment but also underscores Hong Kong's ambition to be at the forefront of financial innovation. As the regulatory landscape evolves and the market for digital assets continues to grow, the efforts of Harvest Fund and like-minded institutions will be crucial in bridging the gap between traditional finance and the digital asset world. The path ahead is promising, and Hong Kong's leadership in this space could pave the way for a new chapter in the global financial narrative, where digital and traditional assets coexist in a regulated, dynamic, and inclusive investment ecosystem. **FAQs** **Who has filed for the first spot Bitcoin ETF in Hong Kong?** Harvest Fund Management, a major Chinese asset manager, has filed an application for the first spot Bitcoin ETF in Hong Kong with the Securities and Futures Commission (SFC). **Why is a spot Bitcoin ETF significant for investors?** A spot Bitcoin ETF provides a regulated, accessible, and potentially less risky way for investors to gain exposure to Bitcoin's price movements without dealing with the complexities of cryptocurrency exchanges, digital wallets, and private keys. **How does a spot Bitcoin ETF work?** A spot Bitcoin ETF buys and holds actual Bitcoin, and the value of the ETF shares fluctuates with the real-time price of Bitcoin. Investors can buy and sell these shares through traditional stock exchanges. **What are the benefits of investing in a spot Bitcoin ETF?** Investing in a spot Bitcoin ETF offers the benefits of trading and owning a stock, including regulatory protection, ease of access, and liquidity, while also providing exposure to Bitcoin's price. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnewsco](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co/](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@thebitcoinlibertarian](https://www.youtube.com/@thebitcoinlibertarian)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** **Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad** **Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.* @ bc575705:dba3ed39
2025-03-06 07:55:57One of the most exciting aspects of music production is blending the organic warmth of acoustic instruments with the limitless possibilities of electronic sounds. Combining these two worlds allows me to create rich, layered compositions that feel both timeless and modern. In this post, I’ll share my process for merging acoustic and electronic elements, offering a glimpse into how I approach this dynamic interplay in my music. ## **Start With a Core Idea** Every track begins with a central idea that sets the tone for the composition. This could be a melody played on an acoustic piano, a chord progression on a guitar, or a rhythmic motif created with electronic drums. Starting with a strong foundation helps anchor the track, making it easier to integrate acoustic and electronic layers cohesively. Example: I might record a simple acoustic guitar loop and use it as the backbone of the track. Its natural tone provides a grounding element that contrasts beautifully with the synthetic textures I’ll layer in later. ## **Record Acoustic Elements With Character** When incorporating acoustic instruments, I focus on capturing their raw, authentic sound. Imperfections—like the creak of a guitar string or the ambient noise of the recording space—add character and depth to the track. **What I Use:** I often record acoustic elements using a condenser microphone to capture detail and warmth. Instruments like piano, guitar, or even simple percussive hits serve as the organic counterpoint to electronic layers. **How I Use It:** I’ll sometimes process these recordings with effects like reverb or delay to give them a dreamlike quality, or leave them raw for a more intimate feel. ## **Build Electronic Layers** With the acoustic elements in place, I begin crafting the electronic components. These can range from deep, evolving synth pads to intricate drum patterns and glitchy textures. The goal is to complement the acoustic elements without overpowering them. **What I Use:** Tools like Serum, Omnisphere, and analog synths like the Korg Minilogue are my go-to for designing electronic sounds. Drum machines or sample packs provide the rhythmic backbone. **How I Use It:** I’ll often create electronic layers that echo or contrast with the acoustic parts—for instance, pairing a warm piano melody with shimmering, high-frequency synths to create a sense of balance. ## **Focus on Blending and Balance** The magic of combining acoustic and electronic elements lies in how they interact. To achieve a cohesive sound, I pay close attention to how each layer fits within the mix. **Techniques I Use:** **EQ:** I carve out space in the frequency spectrum for each element. For example, cutting low-end frequencies on a synth pad can make room for the natural resonance of an acoustic bass. **Compression:** Light compression can help glue the acoustic and electronic layers together, ensuring they feel like part of the same sonic space. **Reverb and Delay:** Applying similar reverb settings to both acoustic and electronic elements can create a sense of unity and atmosphere. ## **Experiment With Textures and Effects** One of my favorite parts of the process is experimenting with how acoustic and electronic sounds can interact. Sometimes, this involves processing acoustic recordings through electronic effects, or vice versa. **Examples:** *Running an acoustic guitar loop through a granular synthesizer to create glitchy, fragmented textures.* *Sampling a piano note and pitching it down to create a haunting drone.* *Adding subtle distortion to electronic drums to give them a more organic, analog feel.* ## **Embrace the Contrast** Part of what makes this combination so compelling is the contrast between the two elements. Acoustic instruments bring warmth, humanity, and imperfection, while electronic sounds add precision, innovation, and texture. Leaning into these differences can create dynamic and emotionally resonant compositions. **Example:** Pairing a raw, emotive vocal recording with a pulsating, mechanical bassline creates a tension that keeps the listener engaged. ## **Refine and Iterate** Once all the elements are in place, I spend time refining the mix and arrangement. **This involves:** *Adjusting levels to ensure no element overpowers the others.* *Experimenting with transitions to smoothly blend acoustic and electronic sections.* *Listening to the track as a whole to ensure it tells a cohesive story.* ## **Why This Approach Inspires Me** Blending acoustic and electronic elements allows me to explore the dualities of sound—the organic and the synthetic, the familiar and the futuristic. It’s a process that pushes me creatively, challenging me to think beyond genre boundaries and embrace the full spectrum of sonic possibilities. At its core, this approach is about connection—bridging the past and the present, the human and the technological, to create music that feels both timeless and forward-thinking.
@ bc575705:dba3ed39
2025-03-06 07:55:57One of the most exciting aspects of music production is blending the organic warmth of acoustic instruments with the limitless possibilities of electronic sounds. Combining these two worlds allows me to create rich, layered compositions that feel both timeless and modern. In this post, I’ll share my process for merging acoustic and electronic elements, offering a glimpse into how I approach this dynamic interplay in my music. ## **Start With a Core Idea** Every track begins with a central idea that sets the tone for the composition. This could be a melody played on an acoustic piano, a chord progression on a guitar, or a rhythmic motif created with electronic drums. Starting with a strong foundation helps anchor the track, making it easier to integrate acoustic and electronic layers cohesively. Example: I might record a simple acoustic guitar loop and use it as the backbone of the track. Its natural tone provides a grounding element that contrasts beautifully with the synthetic textures I’ll layer in later. ## **Record Acoustic Elements With Character** When incorporating acoustic instruments, I focus on capturing their raw, authentic sound. Imperfections—like the creak of a guitar string or the ambient noise of the recording space—add character and depth to the track. **What I Use:** I often record acoustic elements using a condenser microphone to capture detail and warmth. Instruments like piano, guitar, or even simple percussive hits serve as the organic counterpoint to electronic layers. **How I Use It:** I’ll sometimes process these recordings with effects like reverb or delay to give them a dreamlike quality, or leave them raw for a more intimate feel. ## **Build Electronic Layers** With the acoustic elements in place, I begin crafting the electronic components. These can range from deep, evolving synth pads to intricate drum patterns and glitchy textures. The goal is to complement the acoustic elements without overpowering them. **What I Use:** Tools like Serum, Omnisphere, and analog synths like the Korg Minilogue are my go-to for designing electronic sounds. Drum machines or sample packs provide the rhythmic backbone. **How I Use It:** I’ll often create electronic layers that echo or contrast with the acoustic parts—for instance, pairing a warm piano melody with shimmering, high-frequency synths to create a sense of balance. ## **Focus on Blending and Balance** The magic of combining acoustic and electronic elements lies in how they interact. To achieve a cohesive sound, I pay close attention to how each layer fits within the mix. **Techniques I Use:** **EQ:** I carve out space in the frequency spectrum for each element. For example, cutting low-end frequencies on a synth pad can make room for the natural resonance of an acoustic bass. **Compression:** Light compression can help glue the acoustic and electronic layers together, ensuring they feel like part of the same sonic space. **Reverb and Delay:** Applying similar reverb settings to both acoustic and electronic elements can create a sense of unity and atmosphere. ## **Experiment With Textures and Effects** One of my favorite parts of the process is experimenting with how acoustic and electronic sounds can interact. Sometimes, this involves processing acoustic recordings through electronic effects, or vice versa. **Examples:** *Running an acoustic guitar loop through a granular synthesizer to create glitchy, fragmented textures.* *Sampling a piano note and pitching it down to create a haunting drone.* *Adding subtle distortion to electronic drums to give them a more organic, analog feel.* ## **Embrace the Contrast** Part of what makes this combination so compelling is the contrast between the two elements. Acoustic instruments bring warmth, humanity, and imperfection, while electronic sounds add precision, innovation, and texture. Leaning into these differences can create dynamic and emotionally resonant compositions. **Example:** Pairing a raw, emotive vocal recording with a pulsating, mechanical bassline creates a tension that keeps the listener engaged. ## **Refine and Iterate** Once all the elements are in place, I spend time refining the mix and arrangement. **This involves:** *Adjusting levels to ensure no element overpowers the others.* *Experimenting with transitions to smoothly blend acoustic and electronic sections.* *Listening to the track as a whole to ensure it tells a cohesive story.* ## **Why This Approach Inspires Me** Blending acoustic and electronic elements allows me to explore the dualities of sound—the organic and the synthetic, the familiar and the futuristic. It’s a process that pushes me creatively, challenging me to think beyond genre boundaries and embrace the full spectrum of sonic possibilities. At its core, this approach is about connection—bridging the past and the present, the human and the technological, to create music that feels both timeless and forward-thinking. @ 1c19eb1a:e22fb0bc
2025-03-06 07:52:32It's been barely two years since I joined Nostr on my main npub, nostr:npub1kun5628raxpm7usdkj62z2337hr77f3ryrg9cf0vjpyf4jvk9r9smv3lhe, and in just that relatively short time, the amount of development on top of this protocol has been staggering. When nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m first opened the floodgates of adoption by tweeting about Nostr, it felt like most of the available clients were barely serviceable and held together with a prayer and copious amounts of duct tape. Of course, it can sometimes still feel that way, but there are definitely some Nostr apps looking and feeling more polished and providing true innovation when compared with legacy social platforms. Indeed, there are a growing number of Nostr-based applications and tools that have very little to do with social media at all. One thing we have not had available to the growing Nostr community, and those considering joining it, is a source for application reviews that is thorough, approachable, knowledgeable, and balanced. This is what I hope to begin to provide through this new npub dedicated to reviewing as many of the Nostr clients, apps, and tools as I possibly can, so you the reader can determine which ones will fit your needs, and perhaps help you find new ones you had never heard about. One of the best parts about Nostr is the portability of your identity and social graph, allowing users to log into any Nostr-based application with their same "account" without some centralized tech giant like Google or Apple owning who you are and all of your data. Leverage this super-power of Nostr with me as we explore the best applications and tools the intrepid developers building on this platform have cooked up. ## What will you review? My choice of applications to review will be based on a few factors. First, I will only be reviewing applications that have a production release, or are otherwise considered production ready by the developer. nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s, you won't have to worry that I will be putting NoteDeck under the microscope while it is still very much in alpha. All of us who love to try the new clients as soon as they are available understand well enough that there will be plenty of bugs, UI quirks, and rough edges to look past. Second, I will generally be reviewing applications that are meant to be user-facing for the average person. That is, apps that your normie friends might soon be using, and then asking you why they can't edit anything they post. I will not be doing reviews of various relay implementations, for instance, unless they are designed to be approachable to the average user to install and manage. nostr:npub10npj3gydmv40m70ehemmal6vsdyfl7tewgvz043g54p0x23y0s8qzztl5h, your project might just be a notable exception. Third, my reviews will be limited by the operating systems I have available to me at the time. Sorry folks over on iOS, Mac, and Windows. I will only be able to review apps I can run on Android, Linux, or my web browser for the time being. ## How will the apps be rated? I want to be thorough in my reviews, and yet avoid overloading my readers with information they don't care about. In order to attempt to achieve this, I will break my reviews into several sections, so readers can skip to the sections relevant to their interests. First, I will provide a basic overview of the type of application I am reviewing, what it is trying to achieve, and why a user might want to try it out. Next, I will give my overall impression of the application. The good, the bad, and the ugly, as it were, so that those who just want a brief rundown can get the TLDR right out the gate and be on their way. Then we will begin diving into the nitty-gritty with an in depth look at the main features of the application. What it does well. What features seem lacking. What expected features are absent. What features make it unique and set it apart from other applications with a similar purpose. For the sake of all the baby Nostriches out there, the next section will be an assessment of how approachable the application would likely be to a normie who is coming to Nostr with no idea what a public and private key are, what relays are, or why they might want to start interacting here instead of on a legacy equivalent. What would someone used to Twitter think of #Snort? What would someone used to Spotify think of #Fountain or #Wavlake? The next section will be a review of the application's UI. The design and polish. How easy it is to find the things you want in the areas you would expect them. In short, how well the application achieves the goal of making the user feel at home and want to continue using the app just through quality UI design. If you know me and my contstant harping on developers to include various forms of external signing, it should be no surprise to you that the next section will cover login options. What does the sign-in and sign-up flow look like, and does the user have to expose their private key to the application in order to use it? A review of virtually any Nostr application would be incomplete without a section dedicated to zap integration. How prominent is zapping in the app? How easy is it to zap or start receiving zaps? Are zaps displayed in a way that encourages users to compete to be top zapper? Is Nostr Wallet Connect supported for using external wallets for one-tap-zapping? Most Nostr applications, even "other stuff" clients, are designed to present some form of content to the user. The next section will cover how easy it is for the user to find the type of content they may be interested in, or to discover content they didn't know they might be interested in. For social clients, how easy is it to discover other users that they might want to follow? The backbone of the protocol is the interplay between clients and relays, and the next section of the review will cover how the app manages relays. Are they hidden from the user? Are there sensible defaults? Can users who want to do so select the relays they prefer? Does the app respect relays the user has selected in other apps, or are the app's relays independent of those selected in other apps. Worse, does the app overwrite your selected relays with its defaults? Finally, I will scour the #AskNostr feed for questions and comments from other users about the app under review to get more perspectives than just my own. What are the common pain-points other users are having? What do they love about the app? What features would they like to see added? Are there other sections you would like to see me add before I start dropping reviews? Get them to me soon, because I am currently taking notes for my first review, which will be the #Primal #Android client! PV 🤙
@ 1c19eb1a:e22fb0bc
2025-03-06 07:52:32It's been barely two years since I joined Nostr on my main npub, nostr:npub1kun5628raxpm7usdkj62z2337hr77f3ryrg9cf0vjpyf4jvk9r9smv3lhe, and in just that relatively short time, the amount of development on top of this protocol has been staggering. When nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m first opened the floodgates of adoption by tweeting about Nostr, it felt like most of the available clients were barely serviceable and held together with a prayer and copious amounts of duct tape. Of course, it can sometimes still feel that way, but there are definitely some Nostr apps looking and feeling more polished and providing true innovation when compared with legacy social platforms. Indeed, there are a growing number of Nostr-based applications and tools that have very little to do with social media at all. One thing we have not had available to the growing Nostr community, and those considering joining it, is a source for application reviews that is thorough, approachable, knowledgeable, and balanced. This is what I hope to begin to provide through this new npub dedicated to reviewing as many of the Nostr clients, apps, and tools as I possibly can, so you the reader can determine which ones will fit your needs, and perhaps help you find new ones you had never heard about. One of the best parts about Nostr is the portability of your identity and social graph, allowing users to log into any Nostr-based application with their same "account" without some centralized tech giant like Google or Apple owning who you are and all of your data. Leverage this super-power of Nostr with me as we explore the best applications and tools the intrepid developers building on this platform have cooked up. ## What will you review? My choice of applications to review will be based on a few factors. First, I will only be reviewing applications that have a production release, or are otherwise considered production ready by the developer. nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s, you won't have to worry that I will be putting NoteDeck under the microscope while it is still very much in alpha. All of us who love to try the new clients as soon as they are available understand well enough that there will be plenty of bugs, UI quirks, and rough edges to look past. Second, I will generally be reviewing applications that are meant to be user-facing for the average person. That is, apps that your normie friends might soon be using, and then asking you why they can't edit anything they post. I will not be doing reviews of various relay implementations, for instance, unless they are designed to be approachable to the average user to install and manage. nostr:npub10npj3gydmv40m70ehemmal6vsdyfl7tewgvz043g54p0x23y0s8qzztl5h, your project might just be a notable exception. Third, my reviews will be limited by the operating systems I have available to me at the time. Sorry folks over on iOS, Mac, and Windows. I will only be able to review apps I can run on Android, Linux, or my web browser for the time being. ## How will the apps be rated? I want to be thorough in my reviews, and yet avoid overloading my readers with information they don't care about. In order to attempt to achieve this, I will break my reviews into several sections, so readers can skip to the sections relevant to their interests. First, I will provide a basic overview of the type of application I am reviewing, what it is trying to achieve, and why a user might want to try it out. Next, I will give my overall impression of the application. The good, the bad, and the ugly, as it were, so that those who just want a brief rundown can get the TLDR right out the gate and be on their way. Then we will begin diving into the nitty-gritty with an in depth look at the main features of the application. What it does well. What features seem lacking. What expected features are absent. What features make it unique and set it apart from other applications with a similar purpose. For the sake of all the baby Nostriches out there, the next section will be an assessment of how approachable the application would likely be to a normie who is coming to Nostr with no idea what a public and private key are, what relays are, or why they might want to start interacting here instead of on a legacy equivalent. What would someone used to Twitter think of #Snort? What would someone used to Spotify think of #Fountain or #Wavlake? The next section will be a review of the application's UI. The design and polish. How easy it is to find the things you want in the areas you would expect them. In short, how well the application achieves the goal of making the user feel at home and want to continue using the app just through quality UI design. If you know me and my contstant harping on developers to include various forms of external signing, it should be no surprise to you that the next section will cover login options. What does the sign-in and sign-up flow look like, and does the user have to expose their private key to the application in order to use it? A review of virtually any Nostr application would be incomplete without a section dedicated to zap integration. How prominent is zapping in the app? How easy is it to zap or start receiving zaps? Are zaps displayed in a way that encourages users to compete to be top zapper? Is Nostr Wallet Connect supported for using external wallets for one-tap-zapping? Most Nostr applications, even "other stuff" clients, are designed to present some form of content to the user. The next section will cover how easy it is for the user to find the type of content they may be interested in, or to discover content they didn't know they might be interested in. For social clients, how easy is it to discover other users that they might want to follow? The backbone of the protocol is the interplay between clients and relays, and the next section of the review will cover how the app manages relays. Are they hidden from the user? Are there sensible defaults? Can users who want to do so select the relays they prefer? Does the app respect relays the user has selected in other apps, or are the app's relays independent of those selected in other apps. Worse, does the app overwrite your selected relays with its defaults? Finally, I will scour the #AskNostr feed for questions and comments from other users about the app under review to get more perspectives than just my own. What are the common pain-points other users are having? What do they love about the app? What features would they like to see added? Are there other sections you would like to see me add before I start dropping reviews? Get them to me soon, because I am currently taking notes for my first review, which will be the #Primal #Android client! PV 🤙 @ 1c19eb1a:e22fb0bc
2025-03-06 07:48:38I am happy to present to you the first full review posted to Nostr Reviews: #Primal for #Android! Primal has its origins as a micro-blogging, social media client, though it is now expanding its horizons into long-form content. It was first released only as a web client in March of 2023, but has since had a native client released for both iOS and Android. All of Primal's clients recently had an update to Primal 2.0, which included both performance improvements and a number of new features. This review will focus on the Android client specifically, both on phone and tablet. Since Primal has also added features that are only available to those enrolled in their new premium subscription, it should also be noted that this review will be from the perspective of a free user. This is for two reasons. First, I am using an alternate npub to review the app, and if I were to purchase premium at some time in the future, it would be on my main npub. Second, despite a lot of positive things I have to say about Primal, I am not planning to regularly use any of their apps on my main account for the time being, for reasons that will be discussed later in the review. The application can be installed through the [Google Play Store](https://play.google.com/store/apps/details?id=net.primal.android&hl=en_US), Zapstore, or by downloading it directly from Primal's [GitHub](https://github.com/PrimalHQ/primal-android-app/releases/). This review is current as of Primal Android version 2.0.21. In the ecosystem of "notes and other stuff," Primal is predominantly in the "notes" category. It is geared toward users who want a social media experience similar to Twitter or Facebook with an infinite scrolling feed of notes to interact with. However, there is some "other stuff" included to complement this primary focus on short and long form notes including a built-in Lightning wallet powered by #Strike, a robust advanced search, and a media-only feed.  ## Overall Impression Score: **3.8** / 5 Primal may well be the most polished UI of any Nostr client native to Android. It is incredibly well designed and thought out, with all of the icons and settings in the places a user would expect to find them. It is also incredibly easy to get started on Nostr via Primal's sign-up flow. The only two things that will be foreign to new users are the lack of any need to set a password or give an email address, and the prompt to optionally set up the wallet. Complaints prior to the 2.0 update about Primal being slow and clunky should now be completely alleviated. I only experienced quick load times and snappy UI controls with a couple very minor exceptions. Primal is not, however, a client that I would recommend for the power-user. Control over preferred relays is minimal and does not allow the user to determine which relays they write to and which they only read from. Though you can use your own wallet, it will not appear within the wallet interface, which only works with the custodial wallet from Strike. Moreover, and most eggregiously, the only way for existing users to log in is by pasting their nsec, as Primal does not support either the Android signer or remote signer options for users to protect their private key at this time. This lack of signer support is the primary reason the client received such a low overall score. If even one form of external signer log in is added to Primal, the score will be amended to 4.2 / 5, and if both Android signer and remote signer support is added, it will increase to 4.5. Another downside to Primal is that it still utilizes an outdated direct message specification that leaks metadata that can be readily seen by anyone on the network. While the content of your messages remains encrypted, anyone can see who you are messaging with, and when. That said, the beautiful thing about Nostr as a protocol is that users are not locked into any particular client. You may find Primal to be a great client for your average #bloomscrolling and zapping memes, but opt for a different client for more advanced uses and for direct messaging. ## Features Primal has a lot of features users would expect from any Nostr client that is focused on short-form notes, but it also packs in a lot of features that set it apart from other clients, and that showcase Primal's obvious prioritization of a top-tier user experience. ### Home Feed By default, the infinitely scrolling Home feed displays notes from those you currently follow in chronological order. This is traditional Nostr at its finest, and made all the more immersive by the choice to have all distracting UI elements quickly hide themselves from view as the you begin to scroll down the feed. They return just as quickly when you begin to scroll back up.  Scrolling the feed is incredibly fast, with no noticeable choppiness and minimal media pop-in if you are on a decent internet connection. Helpfully, it is easy to get back to the top of the feed whenever there is a new post to be viewed, as a bubble will appear with the profile pictures of the users who have posted since you started scrolling.  ### Interacting With Notes Interacting with a note in the feed can be done via the very recognizable icons at the bottom of each post. You can comment, zap, like, repost, and/or bookmark the note. Notably, tapping on the zap icon will immediately zap the note your default amount of sats, making zapping incredibly fast, especially when using the built-in wallet. Long pressing on the zap icon will open up a menu with a variety of amounts, along with the ability to zap a custom amount. All of these amounts, and the messages that are sent with the zap, can be customized in the application settings.  Users who are familiar with Twitter or Instagram will feel right at home with only having one option for "liking" a post. However, users from Facebook or other Nostr clients may wonder why they don't have more options for reactions. This is one of those things where users who are new to Nostr probably won't notice they are missing out on anything at all, while users familiar with clients like #Amethyst or #noStrudel will miss the ability to react with a 🤙 or a 🫂. It's a similar story with the bookmark option. While this is a nice bit of feature parity for Twitter users, for those already used to the ability to have multiple customized lists of bookmarks, or at minimum have the ability to separate them into public and private, it may be a disappointment that they have no access to the bookmarks they already built up on other clients. Primal offers only one list of bookmarks for short-form notes and they are all visible to the public. However, you are at least presented with a warning about the public nature of your bookmarks before saving your first one. Yet, I can't dock the Primal team much for making these design choices, as they are understandable for Primal's goal of being a welcoming client for those coming over to Nostr from centralized platforms. They have optimized for the onboarding of new users, rather than for those who have been around for a while, and there is absolutely nothing wrong with that. ### Post Creation Composing posts in Primal is as simple as it gets. Accessed by tapping the obvious circular button with a "+" on it in the lower right of the Home feed, most of what you could need is included in the interface, and nothing you don't.  Your device's default keyboard loads immediately, and the you can start typing away. There are options for adding images from your gallery, or taking a picture with your camera, both of which will result in the image being uploaded to Primal's media-hosting server. If you prefer to host your media elsewhere, you can simply paste the link to that media into your post. There is also an @ icon as a tip-off that you can tag other users. Tapping on this simply types "@" into your note and brings up a list of users. All you have to do to narrow down the user you want to tag is continue typing their handle, Nostr address, or paste in their npub.  This can get mixed results in other clients, which sometimes have a hard time finding particular users when typing in their handle, forcing you to have to remember their Nostr address or go hunt down their npub by another means. Not so with Primal, though. I had no issues tagging anyone I wanted by simply typing in their handle. Of course, when you are tagging someone well known, you may find that there are multiple users posing as that person. Primal helps you out here, though. Usually the top result is the person you want, as Primal places them in order of how many followers they have. This is quite reliable right now, but there is nothing stopping someone from spinning up an army of bots to follow their fake accounts, rendering follower count useless for determining which account is legitimate. It would be nice to see these results ranked by web-of-trust, or at least an indication of how many users you follow who also follow the users listed in the results. Once you are satisfied with your note, the "Post" button is easy to find in the top right of the screen. ### Feed Selector and Marketplace Primal's Home feed really shines when you open up the feed selection interface, and find that there are a plethora of options available for customizing your view. By default, it only shows four options, but tapping "Edit" opens up a new page of available toggles to add to the feed selector.  The options don't end there, though. Tapping "Add Feed" will open up the feed marketplace, where an ever-growing number of custom feeds can be found, some created by Primal and some created by others. This feed marketplace is available to a few other clients, but none have so closely integrated it with their Home feeds like Primal has.  Unfortunately, as great as these custom feeds are, this was also the feature where I ran into the most bugs while testing out the app. One of these bugs was while selecting custom feeds. Occasionally, these feed menu screens would become unresponsive and I would be unable to confirm my selection, or even use the back button on my device to back out of the screen. However, I was able to pull the screen down to close it and re-open the menu, and everything would be responsive again. This only seemed to occur when I spent 30 seconds or more on the same screen, so I imagine that most users won't encounter it much in their regular use. Another UI bug occurred for me while in the feed marketplace. I could scroll down the list of available feeds, but attempting to scroll back up the feed would often close the interface entirely instead, as though I had pulled the screen down from the top, when I was swiping in the middle of the screen. The last of these bugs occurred when selecting a long-form "Reads" feed while in the menu for the Home feed. The menu would allow me to add this feed and select it to be displayed, but it would fail to load the feed once selected, stating "There is no content in this feed." Going to a different page within the the app and then going back to the Home tab would automatically remove the long-form feed from view, and reset back to the most recently viewed short-form "Notes" feed, though the long-form feed would still be available to select again. The results were similar when selecting a short-form feed for the Reads feed. I would suggest that if long-form and short-form feeds are going to be displayed in the same list, and yet not be able to be displayed in the same feed, the application should present an error message when attempting to add a long-form feed for the Home feed or a short-form feed for the Reads feed, and encourage the user add it to the proper feed instead. ### Long-Form "Reads" Feed A brand new feature in Primal 2.0, users can now browse and read long-form content posted to Nostr without having to go to a separate client. Primal now has a dedicated "Reads" feed to browse and interact with these articles. This feed displays the author and title of each article or blog, along with an image, if available. Quite conveniently, it also lets you know the approximate amount of time it will take to read a given article, so you can decide if you have the time to dive into it now, or come back later.  Noticeably absent from the Reads feed, though, is the ability to compose an article of your own. This is another understandable design choice for a mobile client. Composing a long-form note on a smart-phone screen is not a good time. Better to be done on a larger screen, in a client with a full-featured text editor. Tapping an article will open up an attractive reading interface, with the ability to bookmark for later. These bookmarks are a separate list from your short-form note bookmarks so you don't have to scroll through a bunch of notes you bookmarked to find the article you told yourself you would read later and it's already been three weeks. While you can comment on the article or zap it, you will notice that you cannot repost or quote-post it. It's not that you can't do so on Nostr. You absolutely can in other clients. In fact, you can do so on Primal's web client, too. However, Primal on Android does not handle rendering long-form note previews in the Home feed, so they have simply left out the option to share them there. See below for an example of a quote-post of a long-form note in the Primal web client vs the Android client. Primal Web:  Primal Android:  ### The Explore Tab Another unique feature of the Primal client is the Explore tab, indicated by the compass icon. This tab is dedicated to discovering content from outside your current follow list. You can find the feed marketplace here, and add any of the available feeds to your Home or Reads feed selections. You can also find suggested users to follow in the People tab. The Zaps tab will show you who has been sending and receiving large zaps. Make friends with the generous ones! The Media tab gives you a chronological feed of just media, displayed in a tile view. This can be great when you are looking for users who post dank memes, or incredible photography on a regular basis. Unfortunately, it appears that there is no way to filter this feed for sensitive content, and so you do not have to scroll far before you see pornographic material. Indeed, it does not appear that filters for sensitive content are available in Primal for ***any*** feed. The app is kind enough to give a minimal warning that objectionable content may be present when selecting the "Nostr Firehose" option in your Home feed, with a brief "be careful" in the feed description, but there is not even that much of a warning here for the media-only feed.  The media-only feed doesn't appear to be quite as bad as the Nostr Firehose feed, so there must be some form of filtering already taking place, rather than being a truly global feed of all media. Yet, occasional sensitive content still litters the feed and is unavoidable, even for users who would rather not see it. There are, of course, ways to mute particular users who post such content, if you don't want to see it a second time from the same user, but that is a never-ending game of whack-a-mole, so your only realistic choices in Primal are currently to either avoid the Nostr Firehose and media-only feeds, or determine that you can put up with regularly scrolling past often graphic content. This is probably the only choice Primal has made that is not friendly to new users. Most clients these days will have some protections in place to hide sensitive content by default, but still allow the user to toggle those protections off if they so choose. Some of them hide posts flagged as sensitive content altogether, others just blur the images unless the user taps to reveal them, and others simply blur all images posted by users you don't follow. If Primal wants to target new users who are accustomed to legacy social media platforms, they really should follow suit. The final tab is titled "Topics," but it is really just a list of popular hashtags, which appear to be arranged by how often they are being used. This can be good for finding things that other users are interested in talking about, or finding specific content you are interested in. If you tap on any topic in the list, it will display a feed of notes that include that hashtag. What's better, you can add it as a feed option you can select on your Home feed any time you want to see posts with that tag. The only suggestion I would make to improve this tab is some indication of why the topics are arranged in the order presented. A simple indicator of the number of posts with that hashtag in the last 24 hours, or whatever the interval is for determining their ranking, would more than suffice. Even with those few shortcomings, Primal's Explore tab makes the client one of the best options for discovering content on Nostr that you are actually interested in seeing and interacting with. ### Built-In Wallet While this feature is completely optional, the icon to access the wallet is the largest of the icons at the bottom of the screen, making you feel like you are missing out on the most important feature of the app if you don't set it up. I could be critical of this design choice, but in many ways I think it is warranted. The built-in wallet is one of the most unique features that Primal has going for it.  Consider: If you are a new user coming to Nostr, who isn't already a Bitcoiner, and you see that everyone else on the platform is sending and receiving sats for their posts, will you be more likely to go download a separate wallet application or use one that is built-into your client? I would wager the latter option by a long shot. No need to figure out which wallet you should download, whether you should do self-custody or custodial, or make the mistake of choosing a wallet with unexpected setup fees and no Lightning address so you can't even receive zaps to it. nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr often states that he believes more people will be onboarded to Bitcoin through Nostr than by any other means, and by including a wallet into the Primal client, his team has made adopting Bitcoin that much easier for new Nostr users. Some of us purists may complain that it is custodial and KYC, but that is an unfortunate necessity in order to facilitate onboarding newcoiners to Bitcoin. This is ***not*** intended to be a wallet for those of us who have been using Bitcoin and Lightning regularly already. It is meant for those who are not already familiar with Bitcoin to make it as easy as possible to get off zero, and it accomplishes this better than any other wallet I have ever tried. In large part, this is because the KYC is very light. It does need the user's legal name, a valid email address, date of birth, and country of residence, but that's it! From there, the user can buy Bitcoin directly through the app, but only in the amount of $4.99 at a time. This is because there is a substantial markup on top of the current market price, due to utilizing whatever payment method the user has set up through their Google Play Store. The markup seemed to be about 19% above the current price, since I could purchase 4,143 sats for $4.99 ($120,415 / Bitcoin), when the current price was about $101,500. But the idea here is not for the Primal wallet to be a user's primary method of stacking sats. Rather, it is intended to get them off zero and have a small amount of sats to experience zapping with, and it accomplishes this with less friction than any other method I know. Moreover, the Primal wallet has the features one would expect from any Lightning wallet. You can send sats to any Nostr user or Lightning address, receive via invoice, or scan to pay an invoice. It even has the ability to receive via on-chain. This means users who don't want to pay the markup from buying through Primal can easily transfer sats they obtained by other means into the Primal wallet for zapping, or for using it as their daily-driver spending wallet. Speaking of zapping, once the wallet is activated, sending zaps is automatically set to use the wallet, and they are ***fast***. Primal gives you immediate feedback that the zap was sent and the transaction shows in your wallet history typically before you can open the interface. I can confidently say that Primal wallet's integration is the absolute best zapping experience I have seen in any Nostr client. One thing to note that may not be immediately apparent to new users is they need to add their Lightning address with Primal into their profile details before they can start receiving zaps. So, sending zaps using the wallet is automatic as soon as you activate it, but receiving is not. Ideally, this could be further streamlined, so that Primal automatically adds the Lightning address to the user's profile when the wallet is set up, so long as there is not currently a Lightning address listed. Of course, if you already have a Lightning wallet, you can connect it to Primal for zapping, too. We will discuss this further in the section dedicated to zap integration. ### Advanced Search Search has always been a tough nut to crack on Nostr, since it is highly dependent on which relays the client is pulling information from. Primal has sought to resolve this issue, among others, by running a caching relay that pulls notes from a number of relays to store them locally, and perform some spam filtering. This allows for much faster retrieval of search results, and also makes their advanced search feature possible. Advanced search can be accessed from most pages by selecting the magnifying glass icon, and then the icon for more options next to the search bar. As can be seen in the screenshot below, there are a plethora of filters that can be applied to your search terms.  You can immediately see how this advanced search could be a very powerful tool for not just finding a particular previous note that you are looking for, but for creating your own custom feed of notes. Well, wouldn't you know it, Primal allows you to do just that! This search feature, paired with the other features mentioned above related to finding notes you want to see in your feed, makes Primal hands-down the best client for content discovery. The only downside as a free user is that some of these search options are locked behind the premium membership. Or else you only get to see a certain number of results of your advanced search before you must be a premium member to see more. ## Can My Grandma Use It? Score: **4.8** / 5 Primal has obviously put a high priority on making their client user-friendly, even for those who have never heard of relays, public/private key cryptography, or Bitcoin. All of that complexity is hidden away. Some of it is available to play around with for the users who care to do so, but it does not at all get in the way of the users who just want to jump in and start posting notes and interacting with other users in a truly open public square. To begin with, the onboarting experience is incredibly smooth. Tap "Create Account," enter your chosen display name and optional bio information, upload a profile picture, and then choose some topics you are interested in. You are then presented with a preview of your profile, with the ability to add a banner image, if you so choose, and then tap "Create Account Now."  From there you receive confirmation that your account has been created and that your "Nostr key" is available to you in the application settings. No further explanation is given about what this key is for at this point, but the user doesn't really need to know at the moment, either. If they are curious, they will go to the app settings to find out. At this point, Primal encourages the user to activate Primal Wallet, but also gives the option for the user to do it later.  That's it! The next screen the user sees if they don't opt to set up the wallet is their Home feed with notes listed in chronological order. More impressive, the feed is not empty, because Primal has auto-followed several accounts based on your selected topics. Now, there has definitely been some legitimate criticism of this practice of following specific accounts based on the topic selection, and I agree. I would much prefer to see Primal follow hashtags based on what was selected, and combine the followed hashtags into a feed titled "My Topics" or something of that nature, and make that the default view when the user finishes onboarding. Following particular users automatically will artificially inflate certain users' exposure, while other users who might be quality follows for that topic aren't seen at all. The advantage of following particular users over a hashtag, though, is that Primal retains some control over the quality of the posts that new users are exposed to right away. Primal can ensure that new users see people who are actually posting quality photography when they choose it as one of their interests. However, even with that example, I chose photography as one of my interests and while I did get some stunning photography in my Home feed by default based on Primal's chosen follows, I also scrolled through the Photography hashtag for a bit and I really feel like I would have been better served if Primal had simply followed that hashtag rather than a particular set of users. We've already discussed how simple it is to set up the Primal Wallet. You can see the features section above if you missed it. It is, by far, the most user friendly experience to onboarding onto Lightning and getting a few sats for zapping, and it is the only one I know of that is built directly into a Nostr client. This means new users will have a frictionless introduction to transacting via Lightning, perhaps without even realizing that's what they are doing. Discovering new content of interest is incredibly intuitive on Primal, and the only thing that new users may struggle with is getting their own notes seen by others. To assist with this, I would suggest Primal encourage users to make their first post to the introductions hashtag and direct any questions to the AskNostr hashtag as part of the onboarding process. This will get them some immediate interactions from other users, and further encouragement to set up their wallet if they haven't already done so. ## How do UI look? Score: **4.9** / 5 Primal is the most stunningly beautiful Nostr client available, in my honest opinion. Despite some of my hangups about certain functionality, the UI alone makes me ***want*** to use it.  It is clean, attractive, and intuitive. Everything I needed was easy to find, and nothing felt busy or cluttered. There are only a few minor UI glitches that I ran into while testing the app. Some of them were mentioned in the section of the review detailing the feed selector feature, but a couple others occurred during onboarding. First, my profile picture was not centered in the preview when I uploaded it. This appears to be because it was a low quality image. Uploading a higher quality photo did not have this result.  The other UI bug was related to text instructions that were cut off, and not able to scroll to see the rest of them. This occurred on a few pages during onboarding, and I expect it was due to the size of my phone screen, since it did not occur when I was on a slightly larger phone or tablet.  Speaking of tablets, Primal Android looks really good on a tablet, too! While the client does not have a landscape mode by default, many Android tablets support forcing apps to open in full-screen landscape mode, with mixed results. However, Primal handles it well. I would still like to see a tablet version developed that takes advantage of the increased screen real estate, but it is certainly a passable option.      At this point, I would say the web client probably has a bit better UI for use on a tablet than the Android client does, but you miss out on using the built-in wallet, which is a major selling point of the app. This lack of a landscape mode for tablets and the few very minor UI bugs I encountered are the only reason Primal doesn't get a perfect score in this category, because the client is absolutely stunning otherwise, both in light and dark modes. There are also two color schemes available for each.  ## Log In Options Score: **1** / 5 Unfortunately, Primal has not included any options for log in outside of pasting your private key into the application. While this is a very simple way to log in for new users to understand, it is also the least secure means to log into Nostr applications. This is because, even with the most trustworthy client developer, giving the application access to your private key always has the potential for that private key to somehow be exposed or leaked, and on Nostr there is currently no way to rotate to a different private key and keep your identity and social graph. If someone gets your key, they ***are you*** on Nostr for all intents and purposes. This is not a situation that users should be willing to tolerate from production-release clients at this point. There are much better log in standards that can and should be implemented if you care about your users. That said, I am happy to report that external signer support is on the roadmap for Primal, as confirmed below: nostr:note1n59tc8k5l2v30jxuzghg7dy2ns76ld0hqnn8tkahyywpwp47ms5qst8ehl No word yet on whether this will be Android signer or remote signer support, or both. This lack of external signer support is why I absolutely will not use my main npub with Primal for Android. I am happy to use the web client, which supports and encourages logging in with a browser extension, but until the Android client allows users to protect their private key, I cannot recommend it for existing Nostr users. ## Zap Integration Score: **4.8** / 5 As mentioned when discussing Primal's built-in wallet feature, zapping in Primal can be the most seamless experience I have ever seen in a Nostr client. Pairing the wallet with the client is absolutely the path forward for Nostr leading the way to Bitcoin adoption. But what if you already have a Lightning wallet you want to use for zapping? You have a couple options. If it is an Alby wallet or another wallet that supports Nostr Wallet Connect, you can connect it with Primal to use with one-tap zapping.  How your zapping experience goes with this option will vary greatly based on your particular wallet of choice and is beyond the scope of this review. I used this option with a hosted wallet on my Alby Hub and it worked perfectly. Primal gives you immediate feedback that you have zapped, even though the transaction usually takes a few seconds to process and appear in your wallet's history. The one major downside to using an external wallet is the lack of integration with the wallet interface. This interface currently only works with Primal's wallet, and therefore the most prominent tab in the entire app goes unused when you connect an external wallet.  An ideal improvement would be for the wallet screen to work similar to Alby Go when you have an external wallet connected via Nostr Wallet Connect, allowing the user to have Primal act as their primary mobile Lightning wallet. It could have balance and transaction history displayed, and allow sending and receiving, just like the integrated Primal wallet, but remove the ability to purchase sats directly through the app when using an external wallet. ## Content Discovery Score: **4.8** / 5 Primal is the best client to use if you want to discover new content you are interested in. There is no comparison, with only a few caveats. First, the content must have been posted to Nostr as either a short-form or long-form note. Primal has a limited ability to display other types of content. For instance, discovering video content or streaming content is lacking. Second, you must be willing to put up with the fact that Primal lacks a means of filtering sensitive content when you are exploring beyond the bounds of your current followers. This may not be an issue for some, but for others it could be a deal-breaker. Third, it would be preferable for Primal to follow topics you are interested in when you choose them during onboarding, rather than follow specific npubs. Ideally, create a "My Topics" feed that can be edited by selecting your interests in the Topics section of the Explore tab. ## Relay Management Score: **2.5** / 5 For new users who don't want to mess around with managing relays, Primal is fantastic! There are 7 relays selected by default, in addition to Primal's caching service. For most users who aren't familiar with Nostr's protocol archetecture, they probably won't ever have to change their default relays in order to use the client as they would expect. However, two of these default relays were consistently unreachable during the week that I tested. These were relay.plebes.fans and remnant.cloud. The first relay seems to be an incorrect URL, as I found nosflare.plebes.fans online and with perfect uptime for the last 12 hours on [nostr.watch](https://nostr.watch). I was unable to find remnant.cloud on nostr.watch at all. A third relay was intermittent, sometimes online and reachable, and other times unreachable: v1250.planz.io/nostr. If Primal is going to have default relays, they should ideally be reliable and with accurate URLs. That said, users can add other relays that they prefer, and remove relays that they no longer want to use. They can even set a different caching service to use with the client, rather than using Primal's.  However, that is the extent of a user's control over their relays. They cannot choose which relays they want to write to and which they want to read from, nor can they set any private relays, outbox or inbox relays, or general relays. Loading the npub I used for this review into another client with full relay management support revealed that the relays selected in Primal are being added to both the user's public outbox relays and public inbox relays, but not to any other relay type, which leads me to believe the caching relay is acting as the client's only general relay and search relay. One unique and welcomed addition is the "Enhanced Privacy" feature, which is off by default, but which can be toggled on. I am not sure why this is not on by default, though. Perhaps someone from the Primal team can enlighten me on that choice. By default, when you post to Nostr, all of your outbox relays will see your IP address. If you turn on the Enhanced Privacy mode, only Primal's caching service will see your IP address, because it will post your note to the other relays on your behalf. In this way, the caching service acts similar to a VPN for posting to Nostr, as long as you trust Primal not to log or leak your IP address. ## Current Users' Questions The AskNostr hashtag can be a good indication of the pain points that other users are currently having with a client. Here are some of the most common questions submitted about Primal since the launch of 2.0: nostr:note1dqv4mwqn7lvpaceg9s7damf932ydv9skv2x99l56ufy3f7q8tkdqpxk0rd This was a pretty common question, because users expect that they will be able to create the same type of content that they can consume in a particular client. I can understand why this was left out in a mobile client, but perhaps it should be added in the web client. nostr:note16xnm8a2mmrs7t9pqymwjgd384ynpf098gmemzy49p3572vhwx2mqcqw8xe This is a more concerning bug, since it appears some users are experiencing their images being replaced with completely different images. I did not experience anything similar in my testing, though. nostr:note1uhrk30nq0e566kx8ac4qpwrdh0vfaav33rfvckyvlzn04tkuqahsx8e7mr There hasn't been an answer to this, but I have not been able to find a way. It seems search results will always include replies as well as original notes, so a feed made from the search results will as well. Perhaps a filter can be added to the advanced search to exclude replies? There is already a filter to ***only*** show replies, but there is no corresponding filter to only show original notes. nostr:note1zlnzua28a5v76jwuakyrf7hham56kx9me9la3dnt3fvymcyaq6eqjfmtq6 Since both mobile platforms support the wallet, users expect that they will be able to access it in their web client, too. At this time, they cannot. The only way to have seamless zapping in the web client is to use the Alby extension, but there is not a way to connect it to your Primal wallet via Nostr Wallet Connect either. This means users must have a separate wallet for zapping on the web client if they use the Primal Wallet on mobile. nostr:note15tf2u9pffy58y9lk27y245ew792raqc7lc22jezxvqj7xrak9ztqu45wep It seems that Primal is filtering for spam even for profiles you actively follow. Moreover, exactly what the criteria is for being considered spam is currently opaque. nostr:note1xexnzv0vrmc8svvduurydwmu43w7dftyqmjh4ps98zksr39ln2qswkuced For those unaware, Blossom is a protocol for hosting media as blobs identified by a hash, allowing them to be located on and displayed from other servers they have been mirrored to when when the target server isn't available. Primal currently runs a Blossom server (blossom.primal.net) so I would expect we see Blossom support in the future. nostr:note1unugv7s36e2kxl768ykg0qly7czeplp8qnc207k4pj45rexgqv4sue50y6 Currently, Primal on Android only supports uploading photos to your posts. Users must upload any video to some other hosting service and copy/paste a link to the video into their post on Primal. I would not be surprised to see this feature added in the near future, though. nostr:note10w6538y58dkd9mdrlkfc8ylhnyqutc56ggdw7gk5y7nsp00rdk4q3qgrex Many Nostr users have more than one npub for various uses. Users would prefer to have a way to quickly switch between accounts than to have to log all the way out and paste their npub for the other account every time they want to use it. There is good news on this front, though: nostr:note17xv632yqfz8nx092lj4sxr7drrqfey6e2373ha00qlq8j8qv6jjs36kxlh ## Wrap Up All in all, Primal is an excellent client. It won't be for everyone, but that's one of the strengths of Nostr as a protocol. You can choose to use the client that best fits your own needs, and supplement with other clients and tools as necessary. There are a couple glaring issues I have with Primal that prevent me from using it on my main npub, but it is also an ever-improving client, that already has me hopeful for those issues to be resolved in a future release. So, what should I review next? Another Android client, such as #Amethyst or #Voyage? Maybe an "other stuff" app, like #Wavlake or #Fountain? Please leave your suggestions in the comments. I hope this review was valuable to you! If it was, please consider letting me know just how valuable by zapping me some sats and reposting it out to your follows. Thank you for reading! PV 🤙
@ 1c19eb1a:e22fb0bc
2025-03-06 07:48:38I am happy to present to you the first full review posted to Nostr Reviews: #Primal for #Android! Primal has its origins as a micro-blogging, social media client, though it is now expanding its horizons into long-form content. It was first released only as a web client in March of 2023, but has since had a native client released for both iOS and Android. All of Primal's clients recently had an update to Primal 2.0, which included both performance improvements and a number of new features. This review will focus on the Android client specifically, both on phone and tablet. Since Primal has also added features that are only available to those enrolled in their new premium subscription, it should also be noted that this review will be from the perspective of a free user. This is for two reasons. First, I am using an alternate npub to review the app, and if I were to purchase premium at some time in the future, it would be on my main npub. Second, despite a lot of positive things I have to say about Primal, I am not planning to regularly use any of their apps on my main account for the time being, for reasons that will be discussed later in the review. The application can be installed through the [Google Play Store](https://play.google.com/store/apps/details?id=net.primal.android&hl=en_US), Zapstore, or by downloading it directly from Primal's [GitHub](https://github.com/PrimalHQ/primal-android-app/releases/). This review is current as of Primal Android version 2.0.21. In the ecosystem of "notes and other stuff," Primal is predominantly in the "notes" category. It is geared toward users who want a social media experience similar to Twitter or Facebook with an infinite scrolling feed of notes to interact with. However, there is some "other stuff" included to complement this primary focus on short and long form notes including a built-in Lightning wallet powered by #Strike, a robust advanced search, and a media-only feed.  ## Overall Impression Score: **3.8** / 5 Primal may well be the most polished UI of any Nostr client native to Android. It is incredibly well designed and thought out, with all of the icons and settings in the places a user would expect to find them. It is also incredibly easy to get started on Nostr via Primal's sign-up flow. The only two things that will be foreign to new users are the lack of any need to set a password or give an email address, and the prompt to optionally set up the wallet. Complaints prior to the 2.0 update about Primal being slow and clunky should now be completely alleviated. I only experienced quick load times and snappy UI controls with a couple very minor exceptions. Primal is not, however, a client that I would recommend for the power-user. Control over preferred relays is minimal and does not allow the user to determine which relays they write to and which they only read from. Though you can use your own wallet, it will not appear within the wallet interface, which only works with the custodial wallet from Strike. Moreover, and most eggregiously, the only way for existing users to log in is by pasting their nsec, as Primal does not support either the Android signer or remote signer options for users to protect their private key at this time. This lack of signer support is the primary reason the client received such a low overall score. If even one form of external signer log in is added to Primal, the score will be amended to 4.2 / 5, and if both Android signer and remote signer support is added, it will increase to 4.5. Another downside to Primal is that it still utilizes an outdated direct message specification that leaks metadata that can be readily seen by anyone on the network. While the content of your messages remains encrypted, anyone can see who you are messaging with, and when. That said, the beautiful thing about Nostr as a protocol is that users are not locked into any particular client. You may find Primal to be a great client for your average #bloomscrolling and zapping memes, but opt for a different client for more advanced uses and for direct messaging. ## Features Primal has a lot of features users would expect from any Nostr client that is focused on short-form notes, but it also packs in a lot of features that set it apart from other clients, and that showcase Primal's obvious prioritization of a top-tier user experience. ### Home Feed By default, the infinitely scrolling Home feed displays notes from those you currently follow in chronological order. This is traditional Nostr at its finest, and made all the more immersive by the choice to have all distracting UI elements quickly hide themselves from view as the you begin to scroll down the feed. They return just as quickly when you begin to scroll back up.  Scrolling the feed is incredibly fast, with no noticeable choppiness and minimal media pop-in if you are on a decent internet connection. Helpfully, it is easy to get back to the top of the feed whenever there is a new post to be viewed, as a bubble will appear with the profile pictures of the users who have posted since you started scrolling.  ### Interacting With Notes Interacting with a note in the feed can be done via the very recognizable icons at the bottom of each post. You can comment, zap, like, repost, and/or bookmark the note. Notably, tapping on the zap icon will immediately zap the note your default amount of sats, making zapping incredibly fast, especially when using the built-in wallet. Long pressing on the zap icon will open up a menu with a variety of amounts, along with the ability to zap a custom amount. All of these amounts, and the messages that are sent with the zap, can be customized in the application settings.  Users who are familiar with Twitter or Instagram will feel right at home with only having one option for "liking" a post. However, users from Facebook or other Nostr clients may wonder why they don't have more options for reactions. This is one of those things where users who are new to Nostr probably won't notice they are missing out on anything at all, while users familiar with clients like #Amethyst or #noStrudel will miss the ability to react with a 🤙 or a 🫂. It's a similar story with the bookmark option. While this is a nice bit of feature parity for Twitter users, for those already used to the ability to have multiple customized lists of bookmarks, or at minimum have the ability to separate them into public and private, it may be a disappointment that they have no access to the bookmarks they already built up on other clients. Primal offers only one list of bookmarks for short-form notes and they are all visible to the public. However, you are at least presented with a warning about the public nature of your bookmarks before saving your first one. Yet, I can't dock the Primal team much for making these design choices, as they are understandable for Primal's goal of being a welcoming client for those coming over to Nostr from centralized platforms. They have optimized for the onboarding of new users, rather than for those who have been around for a while, and there is absolutely nothing wrong with that. ### Post Creation Composing posts in Primal is as simple as it gets. Accessed by tapping the obvious circular button with a "+" on it in the lower right of the Home feed, most of what you could need is included in the interface, and nothing you don't.  Your device's default keyboard loads immediately, and the you can start typing away. There are options for adding images from your gallery, or taking a picture with your camera, both of which will result in the image being uploaded to Primal's media-hosting server. If you prefer to host your media elsewhere, you can simply paste the link to that media into your post. There is also an @ icon as a tip-off that you can tag other users. Tapping on this simply types "@" into your note and brings up a list of users. All you have to do to narrow down the user you want to tag is continue typing their handle, Nostr address, or paste in their npub.  This can get mixed results in other clients, which sometimes have a hard time finding particular users when typing in their handle, forcing you to have to remember their Nostr address or go hunt down their npub by another means. Not so with Primal, though. I had no issues tagging anyone I wanted by simply typing in their handle. Of course, when you are tagging someone well known, you may find that there are multiple users posing as that person. Primal helps you out here, though. Usually the top result is the person you want, as Primal places them in order of how many followers they have. This is quite reliable right now, but there is nothing stopping someone from spinning up an army of bots to follow their fake accounts, rendering follower count useless for determining which account is legitimate. It would be nice to see these results ranked by web-of-trust, or at least an indication of how many users you follow who also follow the users listed in the results. Once you are satisfied with your note, the "Post" button is easy to find in the top right of the screen. ### Feed Selector and Marketplace Primal's Home feed really shines when you open up the feed selection interface, and find that there are a plethora of options available for customizing your view. By default, it only shows four options, but tapping "Edit" opens up a new page of available toggles to add to the feed selector.  The options don't end there, though. Tapping "Add Feed" will open up the feed marketplace, where an ever-growing number of custom feeds can be found, some created by Primal and some created by others. This feed marketplace is available to a few other clients, but none have so closely integrated it with their Home feeds like Primal has.  Unfortunately, as great as these custom feeds are, this was also the feature where I ran into the most bugs while testing out the app. One of these bugs was while selecting custom feeds. Occasionally, these feed menu screens would become unresponsive and I would be unable to confirm my selection, or even use the back button on my device to back out of the screen. However, I was able to pull the screen down to close it and re-open the menu, and everything would be responsive again. This only seemed to occur when I spent 30 seconds or more on the same screen, so I imagine that most users won't encounter it much in their regular use. Another UI bug occurred for me while in the feed marketplace. I could scroll down the list of available feeds, but attempting to scroll back up the feed would often close the interface entirely instead, as though I had pulled the screen down from the top, when I was swiping in the middle of the screen. The last of these bugs occurred when selecting a long-form "Reads" feed while in the menu for the Home feed. The menu would allow me to add this feed and select it to be displayed, but it would fail to load the feed once selected, stating "There is no content in this feed." Going to a different page within the the app and then going back to the Home tab would automatically remove the long-form feed from view, and reset back to the most recently viewed short-form "Notes" feed, though the long-form feed would still be available to select again. The results were similar when selecting a short-form feed for the Reads feed. I would suggest that if long-form and short-form feeds are going to be displayed in the same list, and yet not be able to be displayed in the same feed, the application should present an error message when attempting to add a long-form feed for the Home feed or a short-form feed for the Reads feed, and encourage the user add it to the proper feed instead. ### Long-Form "Reads" Feed A brand new feature in Primal 2.0, users can now browse and read long-form content posted to Nostr without having to go to a separate client. Primal now has a dedicated "Reads" feed to browse and interact with these articles. This feed displays the author and title of each article or blog, along with an image, if available. Quite conveniently, it also lets you know the approximate amount of time it will take to read a given article, so you can decide if you have the time to dive into it now, or come back later.  Noticeably absent from the Reads feed, though, is the ability to compose an article of your own. This is another understandable design choice for a mobile client. Composing a long-form note on a smart-phone screen is not a good time. Better to be done on a larger screen, in a client with a full-featured text editor. Tapping an article will open up an attractive reading interface, with the ability to bookmark for later. These bookmarks are a separate list from your short-form note bookmarks so you don't have to scroll through a bunch of notes you bookmarked to find the article you told yourself you would read later and it's already been three weeks. While you can comment on the article or zap it, you will notice that you cannot repost or quote-post it. It's not that you can't do so on Nostr. You absolutely can in other clients. In fact, you can do so on Primal's web client, too. However, Primal on Android does not handle rendering long-form note previews in the Home feed, so they have simply left out the option to share them there. See below for an example of a quote-post of a long-form note in the Primal web client vs the Android client. Primal Web:  Primal Android:  ### The Explore Tab Another unique feature of the Primal client is the Explore tab, indicated by the compass icon. This tab is dedicated to discovering content from outside your current follow list. You can find the feed marketplace here, and add any of the available feeds to your Home or Reads feed selections. You can also find suggested users to follow in the People tab. The Zaps tab will show you who has been sending and receiving large zaps. Make friends with the generous ones! The Media tab gives you a chronological feed of just media, displayed in a tile view. This can be great when you are looking for users who post dank memes, or incredible photography on a regular basis. Unfortunately, it appears that there is no way to filter this feed for sensitive content, and so you do not have to scroll far before you see pornographic material. Indeed, it does not appear that filters for sensitive content are available in Primal for ***any*** feed. The app is kind enough to give a minimal warning that objectionable content may be present when selecting the "Nostr Firehose" option in your Home feed, with a brief "be careful" in the feed description, but there is not even that much of a warning here for the media-only feed.  The media-only feed doesn't appear to be quite as bad as the Nostr Firehose feed, so there must be some form of filtering already taking place, rather than being a truly global feed of all media. Yet, occasional sensitive content still litters the feed and is unavoidable, even for users who would rather not see it. There are, of course, ways to mute particular users who post such content, if you don't want to see it a second time from the same user, but that is a never-ending game of whack-a-mole, so your only realistic choices in Primal are currently to either avoid the Nostr Firehose and media-only feeds, or determine that you can put up with regularly scrolling past often graphic content. This is probably the only choice Primal has made that is not friendly to new users. Most clients these days will have some protections in place to hide sensitive content by default, but still allow the user to toggle those protections off if they so choose. Some of them hide posts flagged as sensitive content altogether, others just blur the images unless the user taps to reveal them, and others simply blur all images posted by users you don't follow. If Primal wants to target new users who are accustomed to legacy social media platforms, they really should follow suit. The final tab is titled "Topics," but it is really just a list of popular hashtags, which appear to be arranged by how often they are being used. This can be good for finding things that other users are interested in talking about, or finding specific content you are interested in. If you tap on any topic in the list, it will display a feed of notes that include that hashtag. What's better, you can add it as a feed option you can select on your Home feed any time you want to see posts with that tag. The only suggestion I would make to improve this tab is some indication of why the topics are arranged in the order presented. A simple indicator of the number of posts with that hashtag in the last 24 hours, or whatever the interval is for determining their ranking, would more than suffice. Even with those few shortcomings, Primal's Explore tab makes the client one of the best options for discovering content on Nostr that you are actually interested in seeing and interacting with. ### Built-In Wallet While this feature is completely optional, the icon to access the wallet is the largest of the icons at the bottom of the screen, making you feel like you are missing out on the most important feature of the app if you don't set it up. I could be critical of this design choice, but in many ways I think it is warranted. The built-in wallet is one of the most unique features that Primal has going for it.  Consider: If you are a new user coming to Nostr, who isn't already a Bitcoiner, and you see that everyone else on the platform is sending and receiving sats for their posts, will you be more likely to go download a separate wallet application or use one that is built-into your client? I would wager the latter option by a long shot. No need to figure out which wallet you should download, whether you should do self-custody or custodial, or make the mistake of choosing a wallet with unexpected setup fees and no Lightning address so you can't even receive zaps to it. nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr often states that he believes more people will be onboarded to Bitcoin through Nostr than by any other means, and by including a wallet into the Primal client, his team has made adopting Bitcoin that much easier for new Nostr users. Some of us purists may complain that it is custodial and KYC, but that is an unfortunate necessity in order to facilitate onboarding newcoiners to Bitcoin. This is ***not*** intended to be a wallet for those of us who have been using Bitcoin and Lightning regularly already. It is meant for those who are not already familiar with Bitcoin to make it as easy as possible to get off zero, and it accomplishes this better than any other wallet I have ever tried. In large part, this is because the KYC is very light. It does need the user's legal name, a valid email address, date of birth, and country of residence, but that's it! From there, the user can buy Bitcoin directly through the app, but only in the amount of $4.99 at a time. This is because there is a substantial markup on top of the current market price, due to utilizing whatever payment method the user has set up through their Google Play Store. The markup seemed to be about 19% above the current price, since I could purchase 4,143 sats for $4.99 ($120,415 / Bitcoin), when the current price was about $101,500. But the idea here is not for the Primal wallet to be a user's primary method of stacking sats. Rather, it is intended to get them off zero and have a small amount of sats to experience zapping with, and it accomplishes this with less friction than any other method I know. Moreover, the Primal wallet has the features one would expect from any Lightning wallet. You can send sats to any Nostr user or Lightning address, receive via invoice, or scan to pay an invoice. It even has the ability to receive via on-chain. This means users who don't want to pay the markup from buying through Primal can easily transfer sats they obtained by other means into the Primal wallet for zapping, or for using it as their daily-driver spending wallet. Speaking of zapping, once the wallet is activated, sending zaps is automatically set to use the wallet, and they are ***fast***. Primal gives you immediate feedback that the zap was sent and the transaction shows in your wallet history typically before you can open the interface. I can confidently say that Primal wallet's integration is the absolute best zapping experience I have seen in any Nostr client. One thing to note that may not be immediately apparent to new users is they need to add their Lightning address with Primal into their profile details before they can start receiving zaps. So, sending zaps using the wallet is automatic as soon as you activate it, but receiving is not. Ideally, this could be further streamlined, so that Primal automatically adds the Lightning address to the user's profile when the wallet is set up, so long as there is not currently a Lightning address listed. Of course, if you already have a Lightning wallet, you can connect it to Primal for zapping, too. We will discuss this further in the section dedicated to zap integration. ### Advanced Search Search has always been a tough nut to crack on Nostr, since it is highly dependent on which relays the client is pulling information from. Primal has sought to resolve this issue, among others, by running a caching relay that pulls notes from a number of relays to store them locally, and perform some spam filtering. This allows for much faster retrieval of search results, and also makes their advanced search feature possible. Advanced search can be accessed from most pages by selecting the magnifying glass icon, and then the icon for more options next to the search bar. As can be seen in the screenshot below, there are a plethora of filters that can be applied to your search terms.  You can immediately see how this advanced search could be a very powerful tool for not just finding a particular previous note that you are looking for, but for creating your own custom feed of notes. Well, wouldn't you know it, Primal allows you to do just that! This search feature, paired with the other features mentioned above related to finding notes you want to see in your feed, makes Primal hands-down the best client for content discovery. The only downside as a free user is that some of these search options are locked behind the premium membership. Or else you only get to see a certain number of results of your advanced search before you must be a premium member to see more. ## Can My Grandma Use It? Score: **4.8** / 5 Primal has obviously put a high priority on making their client user-friendly, even for those who have never heard of relays, public/private key cryptography, or Bitcoin. All of that complexity is hidden away. Some of it is available to play around with for the users who care to do so, but it does not at all get in the way of the users who just want to jump in and start posting notes and interacting with other users in a truly open public square. To begin with, the onboarting experience is incredibly smooth. Tap "Create Account," enter your chosen display name and optional bio information, upload a profile picture, and then choose some topics you are interested in. You are then presented with a preview of your profile, with the ability to add a banner image, if you so choose, and then tap "Create Account Now."  From there you receive confirmation that your account has been created and that your "Nostr key" is available to you in the application settings. No further explanation is given about what this key is for at this point, but the user doesn't really need to know at the moment, either. If they are curious, they will go to the app settings to find out. At this point, Primal encourages the user to activate Primal Wallet, but also gives the option for the user to do it later.  That's it! The next screen the user sees if they don't opt to set up the wallet is their Home feed with notes listed in chronological order. More impressive, the feed is not empty, because Primal has auto-followed several accounts based on your selected topics. Now, there has definitely been some legitimate criticism of this practice of following specific accounts based on the topic selection, and I agree. I would much prefer to see Primal follow hashtags based on what was selected, and combine the followed hashtags into a feed titled "My Topics" or something of that nature, and make that the default view when the user finishes onboarding. Following particular users automatically will artificially inflate certain users' exposure, while other users who might be quality follows for that topic aren't seen at all. The advantage of following particular users over a hashtag, though, is that Primal retains some control over the quality of the posts that new users are exposed to right away. Primal can ensure that new users see people who are actually posting quality photography when they choose it as one of their interests. However, even with that example, I chose photography as one of my interests and while I did get some stunning photography in my Home feed by default based on Primal's chosen follows, I also scrolled through the Photography hashtag for a bit and I really feel like I would have been better served if Primal had simply followed that hashtag rather than a particular set of users. We've already discussed how simple it is to set up the Primal Wallet. You can see the features section above if you missed it. It is, by far, the most user friendly experience to onboarding onto Lightning and getting a few sats for zapping, and it is the only one I know of that is built directly into a Nostr client. This means new users will have a frictionless introduction to transacting via Lightning, perhaps without even realizing that's what they are doing. Discovering new content of interest is incredibly intuitive on Primal, and the only thing that new users may struggle with is getting their own notes seen by others. To assist with this, I would suggest Primal encourage users to make their first post to the introductions hashtag and direct any questions to the AskNostr hashtag as part of the onboarding process. This will get them some immediate interactions from other users, and further encouragement to set up their wallet if they haven't already done so. ## How do UI look? Score: **4.9** / 5 Primal is the most stunningly beautiful Nostr client available, in my honest opinion. Despite some of my hangups about certain functionality, the UI alone makes me ***want*** to use it.  It is clean, attractive, and intuitive. Everything I needed was easy to find, and nothing felt busy or cluttered. There are only a few minor UI glitches that I ran into while testing the app. Some of them were mentioned in the section of the review detailing the feed selector feature, but a couple others occurred during onboarding. First, my profile picture was not centered in the preview when I uploaded it. This appears to be because it was a low quality image. Uploading a higher quality photo did not have this result.  The other UI bug was related to text instructions that were cut off, and not able to scroll to see the rest of them. This occurred on a few pages during onboarding, and I expect it was due to the size of my phone screen, since it did not occur when I was on a slightly larger phone or tablet.  Speaking of tablets, Primal Android looks really good on a tablet, too! While the client does not have a landscape mode by default, many Android tablets support forcing apps to open in full-screen landscape mode, with mixed results. However, Primal handles it well. I would still like to see a tablet version developed that takes advantage of the increased screen real estate, but it is certainly a passable option.      At this point, I would say the web client probably has a bit better UI for use on a tablet than the Android client does, but you miss out on using the built-in wallet, which is a major selling point of the app. This lack of a landscape mode for tablets and the few very minor UI bugs I encountered are the only reason Primal doesn't get a perfect score in this category, because the client is absolutely stunning otherwise, both in light and dark modes. There are also two color schemes available for each.  ## Log In Options Score: **1** / 5 Unfortunately, Primal has not included any options for log in outside of pasting your private key into the application. While this is a very simple way to log in for new users to understand, it is also the least secure means to log into Nostr applications. This is because, even with the most trustworthy client developer, giving the application access to your private key always has the potential for that private key to somehow be exposed or leaked, and on Nostr there is currently no way to rotate to a different private key and keep your identity and social graph. If someone gets your key, they ***are you*** on Nostr for all intents and purposes. This is not a situation that users should be willing to tolerate from production-release clients at this point. There are much better log in standards that can and should be implemented if you care about your users. That said, I am happy to report that external signer support is on the roadmap for Primal, as confirmed below: nostr:note1n59tc8k5l2v30jxuzghg7dy2ns76ld0hqnn8tkahyywpwp47ms5qst8ehl No word yet on whether this will be Android signer or remote signer support, or both. This lack of external signer support is why I absolutely will not use my main npub with Primal for Android. I am happy to use the web client, which supports and encourages logging in with a browser extension, but until the Android client allows users to protect their private key, I cannot recommend it for existing Nostr users. ## Zap Integration Score: **4.8** / 5 As mentioned when discussing Primal's built-in wallet feature, zapping in Primal can be the most seamless experience I have ever seen in a Nostr client. Pairing the wallet with the client is absolutely the path forward for Nostr leading the way to Bitcoin adoption. But what if you already have a Lightning wallet you want to use for zapping? You have a couple options. If it is an Alby wallet or another wallet that supports Nostr Wallet Connect, you can connect it with Primal to use with one-tap zapping.  How your zapping experience goes with this option will vary greatly based on your particular wallet of choice and is beyond the scope of this review. I used this option with a hosted wallet on my Alby Hub and it worked perfectly. Primal gives you immediate feedback that you have zapped, even though the transaction usually takes a few seconds to process and appear in your wallet's history. The one major downside to using an external wallet is the lack of integration with the wallet interface. This interface currently only works with Primal's wallet, and therefore the most prominent tab in the entire app goes unused when you connect an external wallet.  An ideal improvement would be for the wallet screen to work similar to Alby Go when you have an external wallet connected via Nostr Wallet Connect, allowing the user to have Primal act as their primary mobile Lightning wallet. It could have balance and transaction history displayed, and allow sending and receiving, just like the integrated Primal wallet, but remove the ability to purchase sats directly through the app when using an external wallet. ## Content Discovery Score: **4.8** / 5 Primal is the best client to use if you want to discover new content you are interested in. There is no comparison, with only a few caveats. First, the content must have been posted to Nostr as either a short-form or long-form note. Primal has a limited ability to display other types of content. For instance, discovering video content or streaming content is lacking. Second, you must be willing to put up with the fact that Primal lacks a means of filtering sensitive content when you are exploring beyond the bounds of your current followers. This may not be an issue for some, but for others it could be a deal-breaker. Third, it would be preferable for Primal to follow topics you are interested in when you choose them during onboarding, rather than follow specific npubs. Ideally, create a "My Topics" feed that can be edited by selecting your interests in the Topics section of the Explore tab. ## Relay Management Score: **2.5** / 5 For new users who don't want to mess around with managing relays, Primal is fantastic! There are 7 relays selected by default, in addition to Primal's caching service. For most users who aren't familiar with Nostr's protocol archetecture, they probably won't ever have to change their default relays in order to use the client as they would expect. However, two of these default relays were consistently unreachable during the week that I tested. These were relay.plebes.fans and remnant.cloud. The first relay seems to be an incorrect URL, as I found nosflare.plebes.fans online and with perfect uptime for the last 12 hours on [nostr.watch](https://nostr.watch). I was unable to find remnant.cloud on nostr.watch at all. A third relay was intermittent, sometimes online and reachable, and other times unreachable: v1250.planz.io/nostr. If Primal is going to have default relays, they should ideally be reliable and with accurate URLs. That said, users can add other relays that they prefer, and remove relays that they no longer want to use. They can even set a different caching service to use with the client, rather than using Primal's.  However, that is the extent of a user's control over their relays. They cannot choose which relays they want to write to and which they want to read from, nor can they set any private relays, outbox or inbox relays, or general relays. Loading the npub I used for this review into another client with full relay management support revealed that the relays selected in Primal are being added to both the user's public outbox relays and public inbox relays, but not to any other relay type, which leads me to believe the caching relay is acting as the client's only general relay and search relay. One unique and welcomed addition is the "Enhanced Privacy" feature, which is off by default, but which can be toggled on. I am not sure why this is not on by default, though. Perhaps someone from the Primal team can enlighten me on that choice. By default, when you post to Nostr, all of your outbox relays will see your IP address. If you turn on the Enhanced Privacy mode, only Primal's caching service will see your IP address, because it will post your note to the other relays on your behalf. In this way, the caching service acts similar to a VPN for posting to Nostr, as long as you trust Primal not to log or leak your IP address. ## Current Users' Questions The AskNostr hashtag can be a good indication of the pain points that other users are currently having with a client. Here are some of the most common questions submitted about Primal since the launch of 2.0: nostr:note1dqv4mwqn7lvpaceg9s7damf932ydv9skv2x99l56ufy3f7q8tkdqpxk0rd This was a pretty common question, because users expect that they will be able to create the same type of content that they can consume in a particular client. I can understand why this was left out in a mobile client, but perhaps it should be added in the web client. nostr:note16xnm8a2mmrs7t9pqymwjgd384ynpf098gmemzy49p3572vhwx2mqcqw8xe This is a more concerning bug, since it appears some users are experiencing their images being replaced with completely different images. I did not experience anything similar in my testing, though. nostr:note1uhrk30nq0e566kx8ac4qpwrdh0vfaav33rfvckyvlzn04tkuqahsx8e7mr There hasn't been an answer to this, but I have not been able to find a way. It seems search results will always include replies as well as original notes, so a feed made from the search results will as well. Perhaps a filter can be added to the advanced search to exclude replies? There is already a filter to ***only*** show replies, but there is no corresponding filter to only show original notes. nostr:note1zlnzua28a5v76jwuakyrf7hham56kx9me9la3dnt3fvymcyaq6eqjfmtq6 Since both mobile platforms support the wallet, users expect that they will be able to access it in their web client, too. At this time, they cannot. The only way to have seamless zapping in the web client is to use the Alby extension, but there is not a way to connect it to your Primal wallet via Nostr Wallet Connect either. This means users must have a separate wallet for zapping on the web client if they use the Primal Wallet on mobile. nostr:note15tf2u9pffy58y9lk27y245ew792raqc7lc22jezxvqj7xrak9ztqu45wep It seems that Primal is filtering for spam even for profiles you actively follow. Moreover, exactly what the criteria is for being considered spam is currently opaque. nostr:note1xexnzv0vrmc8svvduurydwmu43w7dftyqmjh4ps98zksr39ln2qswkuced For those unaware, Blossom is a protocol for hosting media as blobs identified by a hash, allowing them to be located on and displayed from other servers they have been mirrored to when when the target server isn't available. Primal currently runs a Blossom server (blossom.primal.net) so I would expect we see Blossom support in the future. nostr:note1unugv7s36e2kxl768ykg0qly7czeplp8qnc207k4pj45rexgqv4sue50y6 Currently, Primal on Android only supports uploading photos to your posts. Users must upload any video to some other hosting service and copy/paste a link to the video into their post on Primal. I would not be surprised to see this feature added in the near future, though. nostr:note10w6538y58dkd9mdrlkfc8ylhnyqutc56ggdw7gk5y7nsp00rdk4q3qgrex Many Nostr users have more than one npub for various uses. Users would prefer to have a way to quickly switch between accounts than to have to log all the way out and paste their npub for the other account every time they want to use it. There is good news on this front, though: nostr:note17xv632yqfz8nx092lj4sxr7drrqfey6e2373ha00qlq8j8qv6jjs36kxlh ## Wrap Up All in all, Primal is an excellent client. It won't be for everyone, but that's one of the strengths of Nostr as a protocol. You can choose to use the client that best fits your own needs, and supplement with other clients and tools as necessary. There are a couple glaring issues I have with Primal that prevent me from using it on my main npub, but it is also an ever-improving client, that already has me hopeful for those issues to be resolved in a future release. So, what should I review next? Another Android client, such as #Amethyst or #Voyage? Maybe an "other stuff" app, like #Wavlake or #Fountain? Please leave your suggestions in the comments. I hope this review was valuable to you! If it was, please consider letting me know just how valuable by zapping me some sats and reposting it out to your follows. Thank you for reading! PV 🤙 @ 1c19eb1a:e22fb0bc
2025-03-06 07:47:42After my first major review of [Primal on Android](https://www.nostr-reviews.com/post/1733635103705/), we're going to go a very different direction for this next review. Primal is your standard "Twitter clone" type of kind 1 note client, now branching into long-form. They also have a team of developers working on making it one of the best clients to fill that use-case. By contrast, this review will not be focusing on any client at all. Not even an "other stuff" client. Instead, we will be reviewing a very useful tool created and maintained by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 called #Amber. For those unfamiliar with Amber, it is an #Android application dedicated to managing your signing keys, and allowing you to log into various #Nostr applications without having to paste in your private key, better known as your #nsec. It is not recommended to paste your nsec into various applications because they each represent another means by which it could be compromised, and anyone who has your nsec can post as you. On Nostr, your #npub is your identity, and your signature using your private key is considered absolute proof that any given note, reaction, follow update, or profile change was authorized by the rightful owner of that identity. It happens less often these days, but early on, when the only way to try out a new client was by inputting your nsec, users had their nsec compromised from time to time, or they would suspect that their key may have been compromised. When this occurs, there is no way to recover your account, or set a new private key, deprecating the previous one. The only thing you can do is start over from scratch, letting everyone know that your key has been compromised and to follow you on your new npub. If you use Amber to log into other Nostr apps, you significantly reduce the likelihood that your private key will be compromised, because only one application has access to it, and all other applications reach out to Amber to sign any events. This isn't quite as secure as storing your private key on a separate device that isn't connected to the internet whatsoever, like many of us have grown accustomed to with securing our #Bitcoin, but then again, an online persona isn't nearly as important to secure for most of us as our entire life savings. Amber is the first application of its kind for managing your Nostr keys on a mobile device. nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 didn't merely develop the application, but literally created the specification for accomplishing external signing on Android which can be found in [NIP-55](https://github.com/nostr-protocol/nips/blob/master/55.md). Unfortunately, Amber is only available for Android. A signer application for iOS is in the works from nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, but is not ready for use at this time. There is also a new mobile signer app for Android and iOS called Nowser, but I have not yet had a chance to try this app out. From a cursory look at the Android version, it is indeed in the very early stages of development and cannot be compared with Amber. This review of Amber is current as of version 3.2.5.  ## Overall Impression Score: **4.5** / 5 I cannot speak highly enough about Amber as a tool that every Nostr user on Android should start using if they are not already. When the day comes that we have more options for well-developed signer apps on mobile, my opinion may very well change, but until then Amber is what we have available to us. Even so, it is an incredibly well thought-out and reliable tool for securing your nsec. Despite being the only well-established Android signer available for Android, Amber ***can*** be compared with other external signing methods available on other platforms. Even with more competition in this arena, though, Amber still holds up incredibly well. If you are signing into web applications on a desktop, I still would recommend using a browser extension like #Alby or #Nos2x, as the experience is usually faster, more seamless, and far more web apps support this signing method ([NIP-07](https://github.com/nostr-protocol/nips/blob/master/07.md)) than currently support the two methods employed by Amber. Nevertheless that gap is definitely narrowing. A running list I created of applications that support login and signing with Amber can be found here: [Nostr Clients with External Signer Support](nostr:naddr1qvzqqqrcvgpzpde8f55w86vrhaeqmd955y4rraw8aunzxgxstsj7eyzgntyev2xtqydhwumn8ghj7un9d3shjtnzwf5kw6r5vfhkcapwdejhgtcpr4mhxue69uhkg6ttv95k7ue3x5cnwtnwdaehgu339e3k7mf0qq4xummnw3ez6cmvd9jkuarn94mkjarg94jhsar9wfhxzmpdwd5kwmn9wgkhxatswphhyaqrcy76t) I have run into relatively few bugs in my extensive use of Amber for all of my mobile signing needs. Occasionally the application crashes when trying to send it a signing request from a couple of applications, but I would not be surprised if this is no fault of Amber at all, and rather the fault of those specific apps, since it works flawlessly with the vast majority of apps that support either [NIP-55](https://github.com/nostr-protocol/nips/blob/master/55.md) or [NIP-46](https://github.com/nostr-protocol/nips/blob/master/46.md) login. I also believe that mobile is the ideal platform to use for this type of application. First, because most people use Nostr clients on their phone more than on a desktop. There are, of course, exceptions to that, but in general we spend more time on our phones when interacting online. New users are also more likely to be introduced to Nostr by a friend having them download a Nostr client on their phone than on a PC, and that can be a prime opportunity to introduce the new user to protecting their private key. Finally, I agree with the following assessment from nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn. nostr:nevent1qqsw0r6gzn05xg67h5q2xkplwsuzedjxw9lf7ntrxjl8ajm350fcyugprfmhxue69uhhyetvv9ujumn0wd68yurvv438xtnrdaksyg9hyaxj3clfswlhyrd5kjsj5v04clhjvgeq6pwztmysfzdvn93gev7awu9v The one downside to Amber is that it will be quite foreign for new users. That is partially unavoidable with Nostr, since folks are not accustomed to public/private key cryptography in general, let alone using a private key to log into websites or social media apps. However, the initial signup process is a bit cumbersome if Amber is being used as the means of initially generating a key pair. I think some of this could be foregone at start-up in favor of streamlining onboarding, and then encourage the user to back-up their private key at a later time. ## Features Amber has some features that may surprise you, outside of just storing your private key and signing requests from your favorite Nostr clients. It is a full key management application, supporting multiple accounts, various backup methods, and even the ability to authorize other users to access a Nostr profile you control. ### Android Signing This is the signing method where Amber really shines in both speed and ease of use. Any Android application that supports this standard, and even some progressive web-apps that can be installed to your Android's home-screen, can very quickly and seamlessly connect with Amber to authorize anything that you need signed with your nsec. All you have to do is select "Login with Amber" in clients like #Amethyst or #0xChat and the app will reach out to Amber for all signing requests from there on out. If you had previously signed into the app with your nsec, you will first need to log out, then choose the option to use Amber when you log back in.  This is a massive deal, because everything you do on Nostr requires a signature from your private key. Log in? Needs a signature. Post a "GM" note? Needs a signature. Follow someone who zapped your note? Needs a signature. Zap them back? You guessed it; needs a signature. When you paste your private key into an application, it will automatically sign a lot of these actions without you ever being asked for approval, but you will quickly realize just how many things the client is doing on your behalf when Amber is asking you to approve them each time. Now, this can also get quite annoying after a while. I recommend using the setting that allows Amber to automatically sign for basic functions, which will cut down on some of the authorization spam. Once you have been asked to authorize the same type of action a few times, you can also toggle the option to automatically authorize that action in the future. Don't worry, though, you have full control to require Amber to ask you for permission again if you want to be alerted each time, and this toggle is specific to each application, so it's not a blanket approval for all Nostr clients you connect with.  This method of signing is just as fast as signing via browser extension on web clients, which users may be more accustomed to. Everything is happening locally on the device, so it can be very snappy and secure. ### Nostr Connect/Bunker Signing This next method of signing has a bit of a delay, because it is using a Nostr relay to send encrypted information back and forth between the app the user is interacting with and Amber to obtain signatures remotely. It isn't a significant delay most of the time, but it is just enough to be noticeable. Also, unlike the previous signing method that would automatically switch to Amber as the active application when a signing request is sent, this method only sends you a notification that you must be watching for. This can lead to situations where you are wondering why something isn't working in a client you signed into remotely, because it is waiting on you to authorize the action and you didn't notice the notification from Amber. As you use the application, you get used to the need to check for such authorization requests from time to time, or when something isn't working as expected.  By default, Amber will use relay.nsec.app to communicate with whichever Nostr app you are connecting to. You can set a different relay for this purpose, if you like, though not just any relay will support the event kinds that Amber uses for remote signing. You can even run your own relay just for your own signing purposes. In fact, the creator of Amber has a relay application you can run on your phone, called Citrine, that can be used for signing with any web app you are using locally on your phone. This is definitely more of an advanced option, but it is there for you if you want it. For most users, sticking with relay.nsec.app will be just fine, especially since the contents of the events sent back and forth for signing are all encrypted. Something many users may not realize is that this remote signing feature allows for issuing signing permissions to team members. For instance, if anyone ever joined me in writing reviews, I could issue them a connection string from Amber, and limit their permissions to just posting long-form draft events. Anything else they tried to do would require my explicit approval each time. Moreover, I could revoke those permissions if I ever felt they were being abused, without the need to start over with a whole new npub. Of course, this requires that your phone is online whenever a team member is trying to sign using the connection string you issued, and it requires you pay attention to your notifications so you can approve or reject requests you have not set to auto-approve. However, this is probably only useful for small teams, and larger businesses will want to find a more robust solution for managing access to their npub, such as Keycast from nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc. The method for establishing a connection between Amber and a Nostr app for remote signing can vary for each app. Most, at minimum, will support obtaining a connection string from Amber that starts with "bunker://" and pasting it in at the time of login. Then you just need to approve the connection request from Amber and the client will log you in and send any subsequent signing requests to Amber using the same connection string.  Some clients will also offer the option to scan a QR code to connect the client to Amber. This is quite convenient, but just remember that this also means the client is setting which relay will be used for communication between the two. Clients with this option will also have a connection string you can copy and paste into Amber to achieve the same purpose. For instance, you may need this option if you are trying to connect to an app on your phone and therefore can't scan the QR code using Amber on the same phone.  ### Multiple Accounts Amber does not lock you into using it with only a single set of keys. You can add all of your Nostr "accounts" to Amber and use it for signing events for each independently. Of course, Nostr doesn't actually have "accounts" in the traditional sense. Your identity is simply your key-pair, and Amber stores and accesses each private key as needed.  When first signing in using native Android signing as described above, Amber will default to whichever account was most recently selected, but you can switch to the account that is needed before approving the request. After initial login, Amber will automatically detect the account that the signing request is for. ### Key Backup & Restore Amber allows multiple ways to back up your private key. As most users would expect, you can get your standard nsec and copy/paste it to a password manager, but you can also obtain your private key as a list of mnemonic seed words, an encrypted version of your key called an ncryptsec, or even a QR code of your nsec or ncryptsec.  Additionally, in order to gain access to this information, Amber requires you to enter your device's PIN or use biometric authentication. This isn't cold-storage level protection for your private key by any means, especially since your phone is an internet connected device and does not store your key within a secure element, but it is about as secure as you can ask for while having your key accessible for signing Nostr events. ### Tor Support While Amber does not have Tor support within the app itself, it does support connecting to Tor through Orbot. This would be used with remote signing so that Amber would not connect directly over clearnet to the relay used for communication with the Nostr app requesting the signature. Instead, Amber would connect through Tor, so the relay would not see your IP address. This means you can utilize the remote signing option without compromising your anonymity.  ### Additional Security Amber allows the user the option to require either biometric or PIN authentication before approving signing requests. This can provide that extra bit of assurance that no one will be able to sign events using your private key if they happen to gain access to your phone. The PIN you set in Amber is also independent from the PIN to unlock your device, allowing for separation of access. ## Can My Grandma Use It? Score: **4.0** / 5 At the end of the day, Amber is a tool for those who have some concept of the importance of protecting their private key by not pasting it into every Nostr client that comes along. This concept in itself is not terribly approachable to an average person. They are used to just plugging their password into every service they use, and even worse, they usually have the ***same password*** for everything so they can more readily remember it. The idea that they should never enter their "Nostr password" into any Nostr application would never occur to them unless someone first explained how cryptography works related to public/private key pairs. That said, I think there can be some improvements made to how users are introduced to these concepts, and that a signer application like Amber might be ideal for the job. Considering Amber as a new user's first touchpoint with Nostr, I think it holds up well, but could be somewhat streamlined. Upon opening the app, the user is prompted to either use their existing private key or "Create a new Nostr account." This is straightforward enough. "Account" is not a technically correct term with Nostr, but it is a term that new users would be familiar with and understand the basic concept.  The next screen announces that the account is ready, and presents the user with their public key, explaining that it is "a sort of username" that will allow others to find them on Nostr. While it is good to explain this to the user, it is unnecessary information at this point. This screen also prompts the user to set a nickname and set a password to encrypt their private key. Since the backup options also allow the user to set this password, I think this step could be pushed to a later time. This screen would better serve the new user if it simply prompted them to set a nickname and short bio that could be saved to a few default relays.  Of course, Amber is currently prompting for a password to be set up-front because the next screen requires the new user to download a "backup kit" in order to continue. While I do believe it is a good idea to encourage the creation of a backup, it is not crucial to do so immediately upon creation of a new npub that has nothing at stake if the private key is lost. This is something the UI could remind the user to do at a later time, reducing the friction of profile creation, and expediting getting them into the action.  Outside of these minor onboarding friction points, I think Amber does a great job of explaining to the user the purpose of each of its features, all within the app and without any need to reference external documentation. As long as the user understands the basic concept that their private key is being stored by Amber in order to sign requests from other Nostr apps, so they don't have to be given the private key, Amber is very good about explaining the rest without getting too far into the technical weeds. The most glaring usability issue with Amber is that it isn't available in the Play Store. Average users expect to be able to find applications they can trust in their mobile device's default app store. There is a valid argument to be made that they are incorrect in this assumption, but that doesn't change the fact that this is the assumption most people make. They believe that applications in the Play Store are "safe" and that anything they can't install through the Play Store is suspect. The prompts that the Android operating system requires the user to approve when installing "unknown apps" certainly doesn't help with this impression. Now, I absolutely ***love*** the Zapstore from nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but it doesn't do much to alleviate this issue. Users will still need to be convinced that it is safe to install the Zapstore from the GitHub repo, and then install Amber from there. Furthermore, this adds yet another step to the onboarding process. Instead of: - Install Amber - Set up your keys - Install the client you want to use - Log in with Amber The process becomes: - Go to the Zapstore GitHub and download the latest version from the releases page. - Install the APK you downloaded, allowing any prompt to install unknown apps. - Open Zapstore and install Amber, allowing any prompt to install unknown apps again. - Open Amber and set up your keys. - Install the client you want to use - Log in with Amber An application as important as Amber for protecting users' private keys should be as readily available to the new user as possible. New users are the ones most prone to making mistakes that could compromise their private keys. Amber should be available to them in the Play Store. ## How do UI Look? Score: **4.5** / 5 Amber's UI can be described as clean but utilitarian. But then, Amber is a tool, so this is somewhat expected. It is not an app you will be spending a lot of time in, so the UI just needs to be serviceable. I would say it accomplishes this and then some. UI elements are generally easy to understand what they do, and page headings fill in the gaps where that is not the case.  I am not the biggest fan of the color-scheme, particularly in light-mode, but it is not bad in dark-mode at all, and Amber follows whatever theme you have set for your device in that respect. Additionally, the color choice does make sense given the application's name.  It must also be taken into consideration that Amber is almost entirely the product of a single developer's work. He has done a great job producing an app that is not only useful, but pleasant to interact with. The same cannot be said for most utility apps I have previously used, with interfaces that clearly made good design the lowest priority. While Amber's UI may not be the most beautiful Nostr app I have seen, design was clearly not an afterthought, either, and it is appreciated. ## Relay Management Score: **4.9** / 5 Even though Amber is not a Nostr client, where users can browse notes from their favorite npubs, it still relies heavily on relays for some of its features. Primarily, it uses relays for communicating with other Nostr apps for remote signing requests. However, it also uses relays to fetch profile data, so that each private key you add to Amber will automatically load your chosen username and profile picture. In the relay settings, users can choose which relays are being used to fetch profile data, and which relays will be used by default when creating new remote signing connection strings.  The user can also see which relays are currently connected to Amber and even look at the information that has been passed back and forth on each of those active relays. This information about actively connected relays is not only available within the application, but also in the notification that Amber has to keep in your device's notification tray in order to continue to operate in the background while you are using other apps.  Optionality is the name of the game when it comes to how Amber handles relay selection. The user can just stick with the default signing relay, use their own relay as the default, or even use a different relay for each Nostr application that they connect to for remote signing. Amber gives the user an incredible amount of flexibility in this regard. In addition to all of this, because not all relays accept the event types needed for remote signing, when you add a relay address to Amber, it automatically tests that relay to see if it will work. This alone can be a massive time saver, so users aren't trying to use relays that don't support remote signing and wondering why they can't log into noStrudel with the connection string they got from Amber.  The only way I could see relay management being improved would be some means of giving the user relay recommendations, in case they want to use a relay other than relay.nsec.app, but they aren't sure which other relays will accept remote signing events. That said, most users who want to use a different relay for signing remote events will likely be using their own, in which case recommendations aren't needed. ## Current Users' Questions The AskNostr hashtag can be a good indication of the pain points that other users are currently having with any Nostr application. Here are some of the most common questions submitted about Amber in the last two months. nostr:nevent1qqsfrdr68fafgcvl8dgnhm9hxpsjxuks78afxhu8yewhtyf3d7mkg9gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qkgh77xxt7hhtt4u528hecnx69rhagla8jj3tclgyf9wvkxa6dc0sxp0e6m This is a good example of Amber working correctly, but the app the user is trying to log into not working. In my experience with #Olas in particular, it sometimes allows remote signer login, and sometimes doesn't. Amber will receive the signing request and I will approve it, but Olas remains on the login screen. If Amber is receiving the signing requests, and you are approving them, the fault is likely with the application you are trying to log into. That's it. That's all the repeated questions I could find. Oh, there were a few one-off questions where relay.nsec.app wouldn't connect, or where the user's out-of-date web browser was the issue. Outside of that, though, there were no common questions about ***how*** to use Amber, and that is a testament to Amber's ease of use all on its own. ## Wrap Up If you are on Android and you are not already using Amber to protect your nsec, please do yourself a favor and get it installed. It's not at all complicated to set up, and it will make trying out all the latest Nostr clients a safe and pleasant experience. If you are a client developer and you have not added support for NIP-55 or NIP-46, do your users the courtesy of respecting the sanctity of their private keys. Even developers who have no intention of compromising their users' keys can inadvertently do so. Make that eventuality impossible by adding support for NIP-55 and NIP-46 signing. Finally, I apologize for the extended time it took me to get this review finished. The time I have available is scarce, Nostr is distracting, and nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 kept improving Amber even as I was putting it through its paces over the last two months. Keep shipping, my friend! You have made one of the most useful tools we have seen for Nostr to date! Now... What should I review next?
@ 1c19eb1a:e22fb0bc
2025-03-06 07:47:42After my first major review of [Primal on Android](https://www.nostr-reviews.com/post/1733635103705/), we're going to go a very different direction for this next review. Primal is your standard "Twitter clone" type of kind 1 note client, now branching into long-form. They also have a team of developers working on making it one of the best clients to fill that use-case. By contrast, this review will not be focusing on any client at all. Not even an "other stuff" client. Instead, we will be reviewing a very useful tool created and maintained by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 called #Amber. For those unfamiliar with Amber, it is an #Android application dedicated to managing your signing keys, and allowing you to log into various #Nostr applications without having to paste in your private key, better known as your #nsec. It is not recommended to paste your nsec into various applications because they each represent another means by which it could be compromised, and anyone who has your nsec can post as you. On Nostr, your #npub is your identity, and your signature using your private key is considered absolute proof that any given note, reaction, follow update, or profile change was authorized by the rightful owner of that identity. It happens less often these days, but early on, when the only way to try out a new client was by inputting your nsec, users had their nsec compromised from time to time, or they would suspect that their key may have been compromised. When this occurs, there is no way to recover your account, or set a new private key, deprecating the previous one. The only thing you can do is start over from scratch, letting everyone know that your key has been compromised and to follow you on your new npub. If you use Amber to log into other Nostr apps, you significantly reduce the likelihood that your private key will be compromised, because only one application has access to it, and all other applications reach out to Amber to sign any events. This isn't quite as secure as storing your private key on a separate device that isn't connected to the internet whatsoever, like many of us have grown accustomed to with securing our #Bitcoin, but then again, an online persona isn't nearly as important to secure for most of us as our entire life savings. Amber is the first application of its kind for managing your Nostr keys on a mobile device. nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 didn't merely develop the application, but literally created the specification for accomplishing external signing on Android which can be found in [NIP-55](https://github.com/nostr-protocol/nips/blob/master/55.md). Unfortunately, Amber is only available for Android. A signer application for iOS is in the works from nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, but is not ready for use at this time. There is also a new mobile signer app for Android and iOS called Nowser, but I have not yet had a chance to try this app out. From a cursory look at the Android version, it is indeed in the very early stages of development and cannot be compared with Amber. This review of Amber is current as of version 3.2.5.  ## Overall Impression Score: **4.5** / 5 I cannot speak highly enough about Amber as a tool that every Nostr user on Android should start using if they are not already. When the day comes that we have more options for well-developed signer apps on mobile, my opinion may very well change, but until then Amber is what we have available to us. Even so, it is an incredibly well thought-out and reliable tool for securing your nsec. Despite being the only well-established Android signer available for Android, Amber ***can*** be compared with other external signing methods available on other platforms. Even with more competition in this arena, though, Amber still holds up incredibly well. If you are signing into web applications on a desktop, I still would recommend using a browser extension like #Alby or #Nos2x, as the experience is usually faster, more seamless, and far more web apps support this signing method ([NIP-07](https://github.com/nostr-protocol/nips/blob/master/07.md)) than currently support the two methods employed by Amber. Nevertheless that gap is definitely narrowing. A running list I created of applications that support login and signing with Amber can be found here: [Nostr Clients with External Signer Support](nostr:naddr1qvzqqqrcvgpzpde8f55w86vrhaeqmd955y4rraw8aunzxgxstsj7eyzgntyev2xtqydhwumn8ghj7un9d3shjtnzwf5kw6r5vfhkcapwdejhgtcpr4mhxue69uhkg6ttv95k7ue3x5cnwtnwdaehgu339e3k7mf0qq4xummnw3ez6cmvd9jkuarn94mkjarg94jhsar9wfhxzmpdwd5kwmn9wgkhxatswphhyaqrcy76t) I have run into relatively few bugs in my extensive use of Amber for all of my mobile signing needs. Occasionally the application crashes when trying to send it a signing request from a couple of applications, but I would not be surprised if this is no fault of Amber at all, and rather the fault of those specific apps, since it works flawlessly with the vast majority of apps that support either [NIP-55](https://github.com/nostr-protocol/nips/blob/master/55.md) or [NIP-46](https://github.com/nostr-protocol/nips/blob/master/46.md) login. I also believe that mobile is the ideal platform to use for this type of application. First, because most people use Nostr clients on their phone more than on a desktop. There are, of course, exceptions to that, but in general we spend more time on our phones when interacting online. New users are also more likely to be introduced to Nostr by a friend having them download a Nostr client on their phone than on a PC, and that can be a prime opportunity to introduce the new user to protecting their private key. Finally, I agree with the following assessment from nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn. nostr:nevent1qqsw0r6gzn05xg67h5q2xkplwsuzedjxw9lf7ntrxjl8ajm350fcyugprfmhxue69uhhyetvv9ujumn0wd68yurvv438xtnrdaksyg9hyaxj3clfswlhyrd5kjsj5v04clhjvgeq6pwztmysfzdvn93gev7awu9v The one downside to Amber is that it will be quite foreign for new users. That is partially unavoidable with Nostr, since folks are not accustomed to public/private key cryptography in general, let alone using a private key to log into websites or social media apps. However, the initial signup process is a bit cumbersome if Amber is being used as the means of initially generating a key pair. I think some of this could be foregone at start-up in favor of streamlining onboarding, and then encourage the user to back-up their private key at a later time. ## Features Amber has some features that may surprise you, outside of just storing your private key and signing requests from your favorite Nostr clients. It is a full key management application, supporting multiple accounts, various backup methods, and even the ability to authorize other users to access a Nostr profile you control. ### Android Signing This is the signing method where Amber really shines in both speed and ease of use. Any Android application that supports this standard, and even some progressive web-apps that can be installed to your Android's home-screen, can very quickly and seamlessly connect with Amber to authorize anything that you need signed with your nsec. All you have to do is select "Login with Amber" in clients like #Amethyst or #0xChat and the app will reach out to Amber for all signing requests from there on out. If you had previously signed into the app with your nsec, you will first need to log out, then choose the option to use Amber when you log back in.  This is a massive deal, because everything you do on Nostr requires a signature from your private key. Log in? Needs a signature. Post a "GM" note? Needs a signature. Follow someone who zapped your note? Needs a signature. Zap them back? You guessed it; needs a signature. When you paste your private key into an application, it will automatically sign a lot of these actions without you ever being asked for approval, but you will quickly realize just how many things the client is doing on your behalf when Amber is asking you to approve them each time. Now, this can also get quite annoying after a while. I recommend using the setting that allows Amber to automatically sign for basic functions, which will cut down on some of the authorization spam. Once you have been asked to authorize the same type of action a few times, you can also toggle the option to automatically authorize that action in the future. Don't worry, though, you have full control to require Amber to ask you for permission again if you want to be alerted each time, and this toggle is specific to each application, so it's not a blanket approval for all Nostr clients you connect with.  This method of signing is just as fast as signing via browser extension on web clients, which users may be more accustomed to. Everything is happening locally on the device, so it can be very snappy and secure. ### Nostr Connect/Bunker Signing This next method of signing has a bit of a delay, because it is using a Nostr relay to send encrypted information back and forth between the app the user is interacting with and Amber to obtain signatures remotely. It isn't a significant delay most of the time, but it is just enough to be noticeable. Also, unlike the previous signing method that would automatically switch to Amber as the active application when a signing request is sent, this method only sends you a notification that you must be watching for. This can lead to situations where you are wondering why something isn't working in a client you signed into remotely, because it is waiting on you to authorize the action and you didn't notice the notification from Amber. As you use the application, you get used to the need to check for such authorization requests from time to time, or when something isn't working as expected.  By default, Amber will use relay.nsec.app to communicate with whichever Nostr app you are connecting to. You can set a different relay for this purpose, if you like, though not just any relay will support the event kinds that Amber uses for remote signing. You can even run your own relay just for your own signing purposes. In fact, the creator of Amber has a relay application you can run on your phone, called Citrine, that can be used for signing with any web app you are using locally on your phone. This is definitely more of an advanced option, but it is there for you if you want it. For most users, sticking with relay.nsec.app will be just fine, especially since the contents of the events sent back and forth for signing are all encrypted. Something many users may not realize is that this remote signing feature allows for issuing signing permissions to team members. For instance, if anyone ever joined me in writing reviews, I could issue them a connection string from Amber, and limit their permissions to just posting long-form draft events. Anything else they tried to do would require my explicit approval each time. Moreover, I could revoke those permissions if I ever felt they were being abused, without the need to start over with a whole new npub. Of course, this requires that your phone is online whenever a team member is trying to sign using the connection string you issued, and it requires you pay attention to your notifications so you can approve or reject requests you have not set to auto-approve. However, this is probably only useful for small teams, and larger businesses will want to find a more robust solution for managing access to their npub, such as Keycast from nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc. The method for establishing a connection between Amber and a Nostr app for remote signing can vary for each app. Most, at minimum, will support obtaining a connection string from Amber that starts with "bunker://" and pasting it in at the time of login. Then you just need to approve the connection request from Amber and the client will log you in and send any subsequent signing requests to Amber using the same connection string.  Some clients will also offer the option to scan a QR code to connect the client to Amber. This is quite convenient, but just remember that this also means the client is setting which relay will be used for communication between the two. Clients with this option will also have a connection string you can copy and paste into Amber to achieve the same purpose. For instance, you may need this option if you are trying to connect to an app on your phone and therefore can't scan the QR code using Amber on the same phone.  ### Multiple Accounts Amber does not lock you into using it with only a single set of keys. You can add all of your Nostr "accounts" to Amber and use it for signing events for each independently. Of course, Nostr doesn't actually have "accounts" in the traditional sense. Your identity is simply your key-pair, and Amber stores and accesses each private key as needed.  When first signing in using native Android signing as described above, Amber will default to whichever account was most recently selected, but you can switch to the account that is needed before approving the request. After initial login, Amber will automatically detect the account that the signing request is for. ### Key Backup & Restore Amber allows multiple ways to back up your private key. As most users would expect, you can get your standard nsec and copy/paste it to a password manager, but you can also obtain your private key as a list of mnemonic seed words, an encrypted version of your key called an ncryptsec, or even a QR code of your nsec or ncryptsec.  Additionally, in order to gain access to this information, Amber requires you to enter your device's PIN or use biometric authentication. This isn't cold-storage level protection for your private key by any means, especially since your phone is an internet connected device and does not store your key within a secure element, but it is about as secure as you can ask for while having your key accessible for signing Nostr events. ### Tor Support While Amber does not have Tor support within the app itself, it does support connecting to Tor through Orbot. This would be used with remote signing so that Amber would not connect directly over clearnet to the relay used for communication with the Nostr app requesting the signature. Instead, Amber would connect through Tor, so the relay would not see your IP address. This means you can utilize the remote signing option without compromising your anonymity.  ### Additional Security Amber allows the user the option to require either biometric or PIN authentication before approving signing requests. This can provide that extra bit of assurance that no one will be able to sign events using your private key if they happen to gain access to your phone. The PIN you set in Amber is also independent from the PIN to unlock your device, allowing for separation of access. ## Can My Grandma Use It? Score: **4.0** / 5 At the end of the day, Amber is a tool for those who have some concept of the importance of protecting their private key by not pasting it into every Nostr client that comes along. This concept in itself is not terribly approachable to an average person. They are used to just plugging their password into every service they use, and even worse, they usually have the ***same password*** for everything so they can more readily remember it. The idea that they should never enter their "Nostr password" into any Nostr application would never occur to them unless someone first explained how cryptography works related to public/private key pairs. That said, I think there can be some improvements made to how users are introduced to these concepts, and that a signer application like Amber might be ideal for the job. Considering Amber as a new user's first touchpoint with Nostr, I think it holds up well, but could be somewhat streamlined. Upon opening the app, the user is prompted to either use their existing private key or "Create a new Nostr account." This is straightforward enough. "Account" is not a technically correct term with Nostr, but it is a term that new users would be familiar with and understand the basic concept.  The next screen announces that the account is ready, and presents the user with their public key, explaining that it is "a sort of username" that will allow others to find them on Nostr. While it is good to explain this to the user, it is unnecessary information at this point. This screen also prompts the user to set a nickname and set a password to encrypt their private key. Since the backup options also allow the user to set this password, I think this step could be pushed to a later time. This screen would better serve the new user if it simply prompted them to set a nickname and short bio that could be saved to a few default relays.  Of course, Amber is currently prompting for a password to be set up-front because the next screen requires the new user to download a "backup kit" in order to continue. While I do believe it is a good idea to encourage the creation of a backup, it is not crucial to do so immediately upon creation of a new npub that has nothing at stake if the private key is lost. This is something the UI could remind the user to do at a later time, reducing the friction of profile creation, and expediting getting them into the action.  Outside of these minor onboarding friction points, I think Amber does a great job of explaining to the user the purpose of each of its features, all within the app and without any need to reference external documentation. As long as the user understands the basic concept that their private key is being stored by Amber in order to sign requests from other Nostr apps, so they don't have to be given the private key, Amber is very good about explaining the rest without getting too far into the technical weeds. The most glaring usability issue with Amber is that it isn't available in the Play Store. Average users expect to be able to find applications they can trust in their mobile device's default app store. There is a valid argument to be made that they are incorrect in this assumption, but that doesn't change the fact that this is the assumption most people make. They believe that applications in the Play Store are "safe" and that anything they can't install through the Play Store is suspect. The prompts that the Android operating system requires the user to approve when installing "unknown apps" certainly doesn't help with this impression. Now, I absolutely ***love*** the Zapstore from nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but it doesn't do much to alleviate this issue. Users will still need to be convinced that it is safe to install the Zapstore from the GitHub repo, and then install Amber from there. Furthermore, this adds yet another step to the onboarding process. Instead of: - Install Amber - Set up your keys - Install the client you want to use - Log in with Amber The process becomes: - Go to the Zapstore GitHub and download the latest version from the releases page. - Install the APK you downloaded, allowing any prompt to install unknown apps. - Open Zapstore and install Amber, allowing any prompt to install unknown apps again. - Open Amber and set up your keys. - Install the client you want to use - Log in with Amber An application as important as Amber for protecting users' private keys should be as readily available to the new user as possible. New users are the ones most prone to making mistakes that could compromise their private keys. Amber should be available to them in the Play Store. ## How do UI Look? Score: **4.5** / 5 Amber's UI can be described as clean but utilitarian. But then, Amber is a tool, so this is somewhat expected. It is not an app you will be spending a lot of time in, so the UI just needs to be serviceable. I would say it accomplishes this and then some. UI elements are generally easy to understand what they do, and page headings fill in the gaps where that is not the case.  I am not the biggest fan of the color-scheme, particularly in light-mode, but it is not bad in dark-mode at all, and Amber follows whatever theme you have set for your device in that respect. Additionally, the color choice does make sense given the application's name.  It must also be taken into consideration that Amber is almost entirely the product of a single developer's work. He has done a great job producing an app that is not only useful, but pleasant to interact with. The same cannot be said for most utility apps I have previously used, with interfaces that clearly made good design the lowest priority. While Amber's UI may not be the most beautiful Nostr app I have seen, design was clearly not an afterthought, either, and it is appreciated. ## Relay Management Score: **4.9** / 5 Even though Amber is not a Nostr client, where users can browse notes from their favorite npubs, it still relies heavily on relays for some of its features. Primarily, it uses relays for communicating with other Nostr apps for remote signing requests. However, it also uses relays to fetch profile data, so that each private key you add to Amber will automatically load your chosen username and profile picture. In the relay settings, users can choose which relays are being used to fetch profile data, and which relays will be used by default when creating new remote signing connection strings.  The user can also see which relays are currently connected to Amber and even look at the information that has been passed back and forth on each of those active relays. This information about actively connected relays is not only available within the application, but also in the notification that Amber has to keep in your device's notification tray in order to continue to operate in the background while you are using other apps.  Optionality is the name of the game when it comes to how Amber handles relay selection. The user can just stick with the default signing relay, use their own relay as the default, or even use a different relay for each Nostr application that they connect to for remote signing. Amber gives the user an incredible amount of flexibility in this regard. In addition to all of this, because not all relays accept the event types needed for remote signing, when you add a relay address to Amber, it automatically tests that relay to see if it will work. This alone can be a massive time saver, so users aren't trying to use relays that don't support remote signing and wondering why they can't log into noStrudel with the connection string they got from Amber.  The only way I could see relay management being improved would be some means of giving the user relay recommendations, in case they want to use a relay other than relay.nsec.app, but they aren't sure which other relays will accept remote signing events. That said, most users who want to use a different relay for signing remote events will likely be using their own, in which case recommendations aren't needed. ## Current Users' Questions The AskNostr hashtag can be a good indication of the pain points that other users are currently having with any Nostr application. Here are some of the most common questions submitted about Amber in the last two months. nostr:nevent1qqsfrdr68fafgcvl8dgnhm9hxpsjxuks78afxhu8yewhtyf3d7mkg9gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qkgh77xxt7hhtt4u528hecnx69rhagla8jj3tclgyf9wvkxa6dc0sxp0e6m This is a good example of Amber working correctly, but the app the user is trying to log into not working. In my experience with #Olas in particular, it sometimes allows remote signer login, and sometimes doesn't. Amber will receive the signing request and I will approve it, but Olas remains on the login screen. If Amber is receiving the signing requests, and you are approving them, the fault is likely with the application you are trying to log into. That's it. That's all the repeated questions I could find. Oh, there were a few one-off questions where relay.nsec.app wouldn't connect, or where the user's out-of-date web browser was the issue. Outside of that, though, there were no common questions about ***how*** to use Amber, and that is a testament to Amber's ease of use all on its own. ## Wrap Up If you are on Android and you are not already using Amber to protect your nsec, please do yourself a favor and get it installed. It's not at all complicated to set up, and it will make trying out all the latest Nostr clients a safe and pleasant experience. If you are a client developer and you have not added support for NIP-55 or NIP-46, do your users the courtesy of respecting the sanctity of their private keys. Even developers who have no intention of compromising their users' keys can inadvertently do so. Make that eventuality impossible by adding support for NIP-55 and NIP-46 signing. Finally, I apologize for the extended time it took me to get this review finished. The time I have available is scarce, Nostr is distracting, and nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 kept improving Amber even as I was putting it through its paces over the last two months. Keep shipping, my friend! You have made one of the most useful tools we have seen for Nostr to date! Now... What should I review next? @ 2cb8ae56:84d30cba
2025-03-06 07:40:38どうも、Nostrまとめ(2024)ぶりですね。 記事として出すのはかなりお久しぶりかも、お名前変わりまして「フェゼレント」でございます。 意味としては以下の通りです 1.Fezer(フェザー)という英単語 2.ent(エント)という造語 2-1. netを崩した形、よくこれに打ち間違えます。 2-2. Entertainment(エンターテイメント)の略語、なんか娯楽とか話題を生み出せる人になりたいですね。 1と2をガッタイ!!!(トムブラウン風)しまして、フェゼレントです。 なんとググってみますと、Fezerent及びフェゼレントの検索結果が0。 これは...一種のチャンスでは!?と思って、使っています。 さて、そこで出てくるのが「薄味のキャルピス」と「IVstrook」の今後ですよね。 後者に至っては3年分の料金を払ってドメインまで取っているわけですし、前者はかなりネットとかラジオでも浸透しています。 というわけで、こんな風に置き換えます。 Nostr、YT、Discordはフェゼレント及びFezerentを使用します。 それ以外(ラジオを含む)では薄味のキャルピス、IVstrookを使用します。 そして、NHKなどAM波を使用して放送を行っているラジオ局用で使用していた「テックジャンカー」ですが、使用を停止します。 あんま浸透しなかったわけですからね そんな感じでやっていきます 最後に、記事最後に使用する署名のような奴ですが、そちらは変更なく「IVstrook」単体で行います。 また、ニコニコ動画及び各種ポッドキャストサービスにて配信しておりました「Small Room Space」ですが、今後はzap.streamというNostrのシステムを使用したサービスを用い、番組名の変更は行わないものとします。 zap.streamでの配信開始は「4月7日」 ちょうど#1が公開されてから1年が経過した日です 重ねて、当名義を使用したニコニコ動画への投稿は「3月8日」をもって終了とし、zap.streamへ移行します。 以上、今年に入ってからまともにニコニコ動画で投稿できていませんでしたが、そのような運びとさせていただきます。 2025/03/06 IVstrook
@ 2cb8ae56:84d30cba
2025-03-06 07:40:38どうも、Nostrまとめ(2024)ぶりですね。 記事として出すのはかなりお久しぶりかも、お名前変わりまして「フェゼレント」でございます。 意味としては以下の通りです 1.Fezer(フェザー)という英単語 2.ent(エント)という造語 2-1. netを崩した形、よくこれに打ち間違えます。 2-2. Entertainment(エンターテイメント)の略語、なんか娯楽とか話題を生み出せる人になりたいですね。 1と2をガッタイ!!!(トムブラウン風)しまして、フェゼレントです。 なんとググってみますと、Fezerent及びフェゼレントの検索結果が0。 これは...一種のチャンスでは!?と思って、使っています。 さて、そこで出てくるのが「薄味のキャルピス」と「IVstrook」の今後ですよね。 後者に至っては3年分の料金を払ってドメインまで取っているわけですし、前者はかなりネットとかラジオでも浸透しています。 というわけで、こんな風に置き換えます。 Nostr、YT、Discordはフェゼレント及びFezerentを使用します。 それ以外(ラジオを含む)では薄味のキャルピス、IVstrookを使用します。 そして、NHKなどAM波を使用して放送を行っているラジオ局用で使用していた「テックジャンカー」ですが、使用を停止します。 あんま浸透しなかったわけですからね そんな感じでやっていきます 最後に、記事最後に使用する署名のような奴ですが、そちらは変更なく「IVstrook」単体で行います。 また、ニコニコ動画及び各種ポッドキャストサービスにて配信しておりました「Small Room Space」ですが、今後はzap.streamというNostrのシステムを使用したサービスを用い、番組名の変更は行わないものとします。 zap.streamでの配信開始は「4月7日」 ちょうど#1が公開されてから1年が経過した日です 重ねて、当名義を使用したニコニコ動画への投稿は「3月8日」をもって終了とし、zap.streamへ移行します。 以上、今年に入ってからまともにニコニコ動画で投稿できていませんでしたが、そのような運びとさせていただきます。 2025/03/06 IVstrook @ da0b9bc3:4e30a4a9
2025-03-06 06:35:31Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/905374
@ da0b9bc3:4e30a4a9
2025-03-06 06:35:31Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/905374 @ 732c6a62:42003da2
2025-03-06 06:00:53> De acordo com a Forbes, a Ripple (Empresa responsável pela Criptomoeda XRP) tem financiado e apoiado campanhas contra a mineração de Bitcoin. ## **Por que Ripple faz propaganda anti-bitcoin?** Simples: **eles são o oposto do Bitcoin em quase tudo.** Enquanto o Bitcoin foi criado para ser descentralizado, resistente à censura e independente de instituições, o Ripple é basicamente um serviço bancário 2.0. Eles precisam atacar o Bitcoin para justificar sua própria existência. ## **O que você não sabe:** 1. **Ripple Labs controla a maioria do XRP:** Eles têm um estoque estratégico que pode ser liberado no mercado a qualquer momento. Isso é o oposto de descentralização. 2. **XRP não é uma moeda para "pessoas comuns":** Foi criada para bancos e instituições financeiras. Basicamente, é o "banco central" das criptomoedas. 3. **Ripple não é blockchain no sentido tradicional:** Eles usam um protocolo chamado **Ripple Protocol Consensus Algorithm (RPCA)**, que é mais rápido, mas menos descentralizado. ## **Os principais ataques do Ripple ao Bitcoin:** 1. **Anti-mineração:** O Ripple critica o consumo de energia do Bitcoin, mas esquece que seu próprio sistema depende de servidores centralizados que também consomem energia. 2. **Anti-reserva estratégica:** O Ripple tem um estoque gigante de XRP, mas critica o Bitcoin por ser "deflacionário". Hipocrisia? Nunca ouvi falar. 3. **Anti-descentralização:** O Ripple prega que a descentralização do Bitcoin é "ineficiente", mas o que eles realmente querem é manter o controle nas mãos de poucos. ## **Análise Psicológica Básica (para você que acha que XRP é o futuro):** - **Síndrome do Underdog:** Acha que apoiar o Ripple te faz um rebelde, mas na verdade você está torcendo para o sistema bancário tradicional. - **Viés de Confirmação:** Só ouve opiniões que validam sua decisão de comprar XRP. - **Efeito Dunning-Kruger:** Acha que entender Ripple te torna um especialista em criptomoedas, mas não sabe o que é um *hard fork*. **Estudo de Caso (Real, mas Você Vai Ignorar):** Carlos, 30 anos, comprou XRP porque "é o futuro das transações bancárias". Ele não sabe que o Ripple está sendo processado pela SEC por vender XRP como um título não registrado. Carlos agora está esperando o "pump" que nunca vem. ## **Conclusão: ou, "volte para a aula de economia do ensino médio"** Ripple não é o futuro das finanças. É só mais um player tentando lucrar em um mercado competitivo. E sua propaganda anti-Bitcoin? Essa só prova que **a descentralização assusta quem quer controle**. Agora vá estudar blockchain básico — ou pelo menos pare de compartilhar memes com erros de português.
@ 732c6a62:42003da2
2025-03-06 06:00:53> De acordo com a Forbes, a Ripple (Empresa responsável pela Criptomoeda XRP) tem financiado e apoiado campanhas contra a mineração de Bitcoin. ## **Por que Ripple faz propaganda anti-bitcoin?** Simples: **eles são o oposto do Bitcoin em quase tudo.** Enquanto o Bitcoin foi criado para ser descentralizado, resistente à censura e independente de instituições, o Ripple é basicamente um serviço bancário 2.0. Eles precisam atacar o Bitcoin para justificar sua própria existência. ## **O que você não sabe:** 1. **Ripple Labs controla a maioria do XRP:** Eles têm um estoque estratégico que pode ser liberado no mercado a qualquer momento. Isso é o oposto de descentralização. 2. **XRP não é uma moeda para "pessoas comuns":** Foi criada para bancos e instituições financeiras. Basicamente, é o "banco central" das criptomoedas. 3. **Ripple não é blockchain no sentido tradicional:** Eles usam um protocolo chamado **Ripple Protocol Consensus Algorithm (RPCA)**, que é mais rápido, mas menos descentralizado. ## **Os principais ataques do Ripple ao Bitcoin:** 1. **Anti-mineração:** O Ripple critica o consumo de energia do Bitcoin, mas esquece que seu próprio sistema depende de servidores centralizados que também consomem energia. 2. **Anti-reserva estratégica:** O Ripple tem um estoque gigante de XRP, mas critica o Bitcoin por ser "deflacionário". Hipocrisia? Nunca ouvi falar. 3. **Anti-descentralização:** O Ripple prega que a descentralização do Bitcoin é "ineficiente", mas o que eles realmente querem é manter o controle nas mãos de poucos. ## **Análise Psicológica Básica (para você que acha que XRP é o futuro):** - **Síndrome do Underdog:** Acha que apoiar o Ripple te faz um rebelde, mas na verdade você está torcendo para o sistema bancário tradicional. - **Viés de Confirmação:** Só ouve opiniões que validam sua decisão de comprar XRP. - **Efeito Dunning-Kruger:** Acha que entender Ripple te torna um especialista em criptomoedas, mas não sabe o que é um *hard fork*. **Estudo de Caso (Real, mas Você Vai Ignorar):** Carlos, 30 anos, comprou XRP porque "é o futuro das transações bancárias". Ele não sabe que o Ripple está sendo processado pela SEC por vender XRP como um título não registrado. Carlos agora está esperando o "pump" que nunca vem. ## **Conclusão: ou, "volte para a aula de economia do ensino médio"** Ripple não é o futuro das finanças. É só mais um player tentando lucrar em um mercado competitivo. E sua propaganda anti-Bitcoin? Essa só prova que **a descentralização assusta quem quer controle**. Agora vá estudar blockchain básico — ou pelo menos pare de compartilhar memes com erros de português. @ 732c6a62:42003da2
2025-03-06 04:33:48>De ''Dialética do Oprimido'' a ''Like do Oprimido'': A Queda Livre do Debate que Nunca Existiu. ## **A moda do momento** Fiquei aproximadamente 8 meses sem ter acesso a nenhum dispositivo. Quando consegui novamente o acesso ao smartphone, percebi algo diferente no debate político brasileiro: enquanto a direita estava se engajando em incontáveis números de curtidas e compartilhamentos com memes que demonstravam críticas ao governo e aos seus ainda poucos apoiadores que se humilham para defender o indefensável, a esquerda radical repetia sua imposição intelectual em comentários de vários posts, incluindo textos, vídeos e tweets com frases semelhantes a "vai ler um livro de história" "nunca leu um livro", "eu estou do lado certo da história" e "se eu fosse irracional eu seria de direita". Tudo isso pra tentar passar uma mensagem de que a história é de esquerda. A tese é: será que eles realmente são tão inteligentes como juram? **Fatos que ignoram enquanto cospem jargões do "lado certo da história":** 1. **A esquerda também tem seus terraplanistas:** Anti-vaxxers de organicafé, terraplanistas do gênero, e os que acham que a Coreia do Norte é uma democracia. 2. **Viés de confirmação não é monopólio da direita:** Eles compartilham estudos "científicos" do Medium como se fossem *peer-reviewed*, mas desdenham de dados que contradizem sua narrativa. 3. **A direita não é um monolito:** Tem desde ancaps que calculam até a última casa decimal até bolsominions que acham que a Terra é plana. Generalizar é... bem, **irracional**. **Estudo de Caso (Fictício, mas Verdadeiro):** Larissa, 23 anos, posta sobre "ciência e razão" enquanto defende horóscopo como "ferramenta de autoconhecimento". Acredita que o capitalismo causa depressão, mas não sabe o que é taxa Selic. Larissa é você após três caipirinhas. ### **A Imposição intelectual que ninguém pediu (mas todos recebem de graça)** A esquerda brasileira, em sua cruzada épica para salvar o mundo dos *"fascistas que ousam discordar"*, adotou uma nova estratégia: **transformar complexidade política em slogans de camiseta de feira**. A frase *"se eu fosse irracional, seria de direita"* não é original — é plágio descarado da cartilha do **Complexo de Deus em Oferta no AliExpress**. #### **O Quebra-Cabeça da superioridade Auto-Delirante** A tese esquerdista se sustenta em três pilares frágeis: 1. **A falácia do "lado certo da história":** Como se história fosse um jogo de futebol com narração do João Cléber. 2. **A ilusão de que citar Foucault = ter QI elevado:** Spoiler: decorar *"biopoder"* não te torna imune a acreditar em astrologia. 3. **A crença de que volume de texto = profundidade:** 15 parágrafos no Twitter não equivalem a um semestre de Ciência Política. **Dado Cruel:** Um estudo da Universidade de Cambridge (2022) mostrou que **extremistas de ambos os lados cometem erros lógicos similares**. A diferença? A esquerda usa palavras mais bonitas para mascarar a burrice. ### **A hipocrisia do "nunca tocou em um livro" (enquanto compartilham resumo de livro no TikTok)** A acusação preferida — *"você não lê!"* — esconde uma ironia deliciosa: - 72% dos *"intelectuais de rede social"* citam livros que nunca leram além do título (Fonte: Pesquisa Informal do Twitter, 2023). - **Obras citadas como troféu:** *"1984"* (para chamar Bolsonaro de Big Brother), *"O Capital"* (para justificar o NFT da Gal Gadot), e *"Feminismo para os 99%"* (para atacar homens heterossexuais que usam sandália de dedo). **Pergunta Incômoda:** Se ler Marx fosse garantia de racionalidade, por que a União Soviética acabou em pizza (literalmente, considerando a economia deles)? ### **Quando a autoimagem colide com a realidade (Ou: por que nenhum esquerdista lassa no teste de turing da coerência)** A esquerda adora se pintar como a **Última Trincheira da Razão**, mas pratica o que critica: - **Exemplo 1:** Defendem *"ciência"* quando convém (vacinas), mas abraçam pseudociência quando é *trendy* (cristais energéticos contra o capitalismo). - **Exemplo 2:** Chamam a direita de *"terraplanista"*, mas acham que inflação se resolve com tabelamento estatal — a versão econômica de *"a Terra é sustentada por tartarugas"*. - **Exemplo 3:** Criticam *"fake news"*, mas compartilham teorias de que o agro *"envenena a comida"* (enquanto comem sushi de supermercado). **Frase-Chave:** *"Racionalidade seletiva é o novo analfabetismo funcional."* **Pergunta Final:** Se a esquerda é tão racional, por que não usa a *"lógica implacável"* para resolver algo além do enquadro perfeito de stories no Instagram? # **Enfim** O debate *"esquerda racional vs. direita irracional"* é só **mais um episódio da novela "Brasil: O País que Confunde Opinião com Ataque de Ego"**. Enquanto uns brincam de *"quem tem o QI mais alto"*, o país queima — literalmente, considerando o Pantanal. Talvez a verdadeira irracionalidade seja gastar energia discutindo superioridade moral enquanto o Wi-Fi cai pela décima vez no dia. Racionalidade não tem lado político. Arrogância, por outro lado, é universal. Sua necessidade de se sentir superior só prova que **a lacração é o último refúgio dos fracos de argumento**. Agora deviam estudar economia básica — ou pelo menos que parem de achar que *"Ah, mas o capitalismo!"* é um contra-argumento. Saudade da época em que a esquerda não se fingia de intelectual.
@ 732c6a62:42003da2
2025-03-06 04:33:48>De ''Dialética do Oprimido'' a ''Like do Oprimido'': A Queda Livre do Debate que Nunca Existiu. ## **A moda do momento** Fiquei aproximadamente 8 meses sem ter acesso a nenhum dispositivo. Quando consegui novamente o acesso ao smartphone, percebi algo diferente no debate político brasileiro: enquanto a direita estava se engajando em incontáveis números de curtidas e compartilhamentos com memes que demonstravam críticas ao governo e aos seus ainda poucos apoiadores que se humilham para defender o indefensável, a esquerda radical repetia sua imposição intelectual em comentários de vários posts, incluindo textos, vídeos e tweets com frases semelhantes a "vai ler um livro de história" "nunca leu um livro", "eu estou do lado certo da história" e "se eu fosse irracional eu seria de direita". Tudo isso pra tentar passar uma mensagem de que a história é de esquerda. A tese é: será que eles realmente são tão inteligentes como juram? **Fatos que ignoram enquanto cospem jargões do "lado certo da história":** 1. **A esquerda também tem seus terraplanistas:** Anti-vaxxers de organicafé, terraplanistas do gênero, e os que acham que a Coreia do Norte é uma democracia. 2. **Viés de confirmação não é monopólio da direita:** Eles compartilham estudos "científicos" do Medium como se fossem *peer-reviewed*, mas desdenham de dados que contradizem sua narrativa. 3. **A direita não é um monolito:** Tem desde ancaps que calculam até a última casa decimal até bolsominions que acham que a Terra é plana. Generalizar é... bem, **irracional**. **Estudo de Caso (Fictício, mas Verdadeiro):** Larissa, 23 anos, posta sobre "ciência e razão" enquanto defende horóscopo como "ferramenta de autoconhecimento". Acredita que o capitalismo causa depressão, mas não sabe o que é taxa Selic. Larissa é você após três caipirinhas. ### **A Imposição intelectual que ninguém pediu (mas todos recebem de graça)** A esquerda brasileira, em sua cruzada épica para salvar o mundo dos *"fascistas que ousam discordar"*, adotou uma nova estratégia: **transformar complexidade política em slogans de camiseta de feira**. A frase *"se eu fosse irracional, seria de direita"* não é original — é plágio descarado da cartilha do **Complexo de Deus em Oferta no AliExpress**. #### **O Quebra-Cabeça da superioridade Auto-Delirante** A tese esquerdista se sustenta em três pilares frágeis: 1. **A falácia do "lado certo da história":** Como se história fosse um jogo de futebol com narração do João Cléber. 2. **A ilusão de que citar Foucault = ter QI elevado:** Spoiler: decorar *"biopoder"* não te torna imune a acreditar em astrologia. 3. **A crença de que volume de texto = profundidade:** 15 parágrafos no Twitter não equivalem a um semestre de Ciência Política. **Dado Cruel:** Um estudo da Universidade de Cambridge (2022) mostrou que **extremistas de ambos os lados cometem erros lógicos similares**. A diferença? A esquerda usa palavras mais bonitas para mascarar a burrice. ### **A hipocrisia do "nunca tocou em um livro" (enquanto compartilham resumo de livro no TikTok)** A acusação preferida — *"você não lê!"* — esconde uma ironia deliciosa: - 72% dos *"intelectuais de rede social"* citam livros que nunca leram além do título (Fonte: Pesquisa Informal do Twitter, 2023). - **Obras citadas como troféu:** *"1984"* (para chamar Bolsonaro de Big Brother), *"O Capital"* (para justificar o NFT da Gal Gadot), e *"Feminismo para os 99%"* (para atacar homens heterossexuais que usam sandália de dedo). **Pergunta Incômoda:** Se ler Marx fosse garantia de racionalidade, por que a União Soviética acabou em pizza (literalmente, considerando a economia deles)? ### **Quando a autoimagem colide com a realidade (Ou: por que nenhum esquerdista lassa no teste de turing da coerência)** A esquerda adora se pintar como a **Última Trincheira da Razão**, mas pratica o que critica: - **Exemplo 1:** Defendem *"ciência"* quando convém (vacinas), mas abraçam pseudociência quando é *trendy* (cristais energéticos contra o capitalismo). - **Exemplo 2:** Chamam a direita de *"terraplanista"*, mas acham que inflação se resolve com tabelamento estatal — a versão econômica de *"a Terra é sustentada por tartarugas"*. - **Exemplo 3:** Criticam *"fake news"*, mas compartilham teorias de que o agro *"envenena a comida"* (enquanto comem sushi de supermercado). **Frase-Chave:** *"Racionalidade seletiva é o novo analfabetismo funcional."* **Pergunta Final:** Se a esquerda é tão racional, por que não usa a *"lógica implacável"* para resolver algo além do enquadro perfeito de stories no Instagram? # **Enfim** O debate *"esquerda racional vs. direita irracional"* é só **mais um episódio da novela "Brasil: O País que Confunde Opinião com Ataque de Ego"**. Enquanto uns brincam de *"quem tem o QI mais alto"*, o país queima — literalmente, considerando o Pantanal. Talvez a verdadeira irracionalidade seja gastar energia discutindo superioridade moral enquanto o Wi-Fi cai pela décima vez no dia. Racionalidade não tem lado político. Arrogância, por outro lado, é universal. Sua necessidade de se sentir superior só prova que **a lacração é o último refúgio dos fracos de argumento**. Agora deviam estudar economia básica — ou pelo menos que parem de achar que *"Ah, mas o capitalismo!"* é um contra-argumento. Saudade da época em que a esquerda não se fingia de intelectual. @ 6b0a60cf:b952e7d4
2025-03-06 02:45:45とあるSNSで海外の相互さん(以降、Aさんと呼ぶ)からDMで相談されたことがあって、思ったことをつらつらと書いてみる。 非公開の場での相談なので多少ぼかしを入れるけど。 ## 事の経緯 発端は、Aさんの友人が作品に日本人作者の素材を使用しようとしていて、その利用規約を翻訳して読んだらうまく翻訳されなくて理解が正しいのかわからない、なので間違いが無いか確認してほしい、という相談だった。 あー、確かに日本語特有の回りくどい表現があるねー、と思いながらバシッと簡潔に意訳してお伝えしたところ、スッキリ理解していただけたらしく一件落着となった。 ## 独自ライセンス文化 しかしまあ、創作界隈における作品・素材の利用規約というものは総じて長くて細かい。 ジャンルによるのかもしれないけれど。 自分は絵や音を創ることは無いがプログラムのコードを書く趣味はあるのでプログラム向けのライセンスを利用している。MITとかGPLとかいうやつ。 創作向けであればCCライセンスが適しているだろう。しかしこれがなかなか広まらない。 杓子定規のライセンスでは表しきれないような特別な希望があるのだろう。 そして独自ライセンスが跋扈することとなる。 ## NO MORE 映画泥棒 特に気になるのが、「泥棒をしてはいけません」レベルの注意書きが散見されるのだ。 わざわざライセンスに書くことではない。あなたが警告するまでもなく、違法な行為は処罰される。 でも、たぶん効果があるからこういうのが広まるのだろう。 「泥棒してはいけないって書いてないから泥棒しました」というレベルの利用者が存在するのだろう。 そういう人は書いてあっても読んでないか、理屈をこねて泥棒するんだろうと思うけれども。 ## その術はオレに効く で、そういう警告文が魔除けの札のごとくびっしり貼られていると、こちらにやましい心が無くても、ちょっとこの素材は利用しないほうがよさそうだな……と思って引き返してしまうことがある。 SNSで可愛い絵を見て、作者さんをフォローしようと思ったら「無断転載禁止」みたいなのがプロフにずらずら書いてあって「おっと……」みたいに引き返すことがあるが、それに似ている。 きっと過去によくない体験をしてしまって、そのようにプロフに書くことでそれが改善するという実体験があって、そうなっているのだろうと推測している。 ## 異文化の壁を超えて 冒頭で話したAさんはきわめて紳士的な方であり、日本文化に対してもよく理解しようと努めてくれるので、話が通じやすくて助かったし、件の素材についても臆すること無く使用することになりそうだった。 ただ魔除けの札が効かないような魑魅魍魎にはいくら札を貼っても意味がないし、実際の悪魔祓いの効果と善良な利用者をも祓ってしまう機会損失(?)を比べて合理的なのだろうか、と考えたりしたのでした。オチは無い。 ## ライセンス この文章は CC0 1.0 でライセンスします。 Nostrイベントとして公開する以上はNIPsに従う範囲内で自由に利用されることを望みます。 NIPsに違反したご利用は他のクライアントの利用者にご迷惑になるのでご遠慮いただくことを希望します。[^1] [^1]: Damusを使ってリポストする、等の行為が該当します
@ 6b0a60cf:b952e7d4
2025-03-06 02:45:45とあるSNSで海外の相互さん(以降、Aさんと呼ぶ)からDMで相談されたことがあって、思ったことをつらつらと書いてみる。 非公開の場での相談なので多少ぼかしを入れるけど。 ## 事の経緯 発端は、Aさんの友人が作品に日本人作者の素材を使用しようとしていて、その利用規約を翻訳して読んだらうまく翻訳されなくて理解が正しいのかわからない、なので間違いが無いか確認してほしい、という相談だった。 あー、確かに日本語特有の回りくどい表現があるねー、と思いながらバシッと簡潔に意訳してお伝えしたところ、スッキリ理解していただけたらしく一件落着となった。 ## 独自ライセンス文化 しかしまあ、創作界隈における作品・素材の利用規約というものは総じて長くて細かい。 ジャンルによるのかもしれないけれど。 自分は絵や音を創ることは無いがプログラムのコードを書く趣味はあるのでプログラム向けのライセンスを利用している。MITとかGPLとかいうやつ。 創作向けであればCCライセンスが適しているだろう。しかしこれがなかなか広まらない。 杓子定規のライセンスでは表しきれないような特別な希望があるのだろう。 そして独自ライセンスが跋扈することとなる。 ## NO MORE 映画泥棒 特に気になるのが、「泥棒をしてはいけません」レベルの注意書きが散見されるのだ。 わざわざライセンスに書くことではない。あなたが警告するまでもなく、違法な行為は処罰される。 でも、たぶん効果があるからこういうのが広まるのだろう。 「泥棒してはいけないって書いてないから泥棒しました」というレベルの利用者が存在するのだろう。 そういう人は書いてあっても読んでないか、理屈をこねて泥棒するんだろうと思うけれども。 ## その術はオレに効く で、そういう警告文が魔除けの札のごとくびっしり貼られていると、こちらにやましい心が無くても、ちょっとこの素材は利用しないほうがよさそうだな……と思って引き返してしまうことがある。 SNSで可愛い絵を見て、作者さんをフォローしようと思ったら「無断転載禁止」みたいなのがプロフにずらずら書いてあって「おっと……」みたいに引き返すことがあるが、それに似ている。 きっと過去によくない体験をしてしまって、そのようにプロフに書くことでそれが改善するという実体験があって、そうなっているのだろうと推測している。 ## 異文化の壁を超えて 冒頭で話したAさんはきわめて紳士的な方であり、日本文化に対してもよく理解しようと努めてくれるので、話が通じやすくて助かったし、件の素材についても臆すること無く使用することになりそうだった。 ただ魔除けの札が効かないような魑魅魍魎にはいくら札を貼っても意味がないし、実際の悪魔祓いの効果と善良な利用者をも祓ってしまう機会損失(?)を比べて合理的なのだろうか、と考えたりしたのでした。オチは無い。 ## ライセンス この文章は CC0 1.0 でライセンスします。 Nostrイベントとして公開する以上はNIPsに従う範囲内で自由に利用されることを望みます。 NIPsに違反したご利用は他のクライアントの利用者にご迷惑になるのでご遠慮いただくことを希望します。[^1] [^1]: Damusを使ってリポストする、等の行為が該当します @ a63655ce:05240c71
2025-03-06 00:48:46looks really clean. `window.nostr` asked for the key multiple times for some reason
@ a63655ce:05240c71
2025-03-06 00:48:46looks really clean. `window.nostr` asked for the key multiple times for some reason @ 6e0ea5d6:0327f353
2025-03-06 00:18:09Ascolta, amico mio... There come moments when a grown man looks in the mirror and fails to recognize himself. Naturally, when this happens, there is nothing more fitting than lighting a cigarette, pouring a glass of fine wine, and toasting to oneself—the birth of a new man, forged in the womb of a harsh and sobering reality. One cannot scatter thorns along a path walked barefoot, nor allow the tongue to speak what the mind may later pay for—but this, we learn only through years of suffering. Only now do I realize that, among all the teachers I have had, experience was the harshest of them all, for it first administered the test and only afterward taught me the lesson. In peaceful moments, one can reflect more easily on the world around him. Imagine, then, the depths of reflection that can be reached in a state of true inner tranquility. If you have never gazed upon the horizon, taken in all the fortune before your eyes, and declared to yourself, "I will own all of this!", then you have never possessed true ambition. However, blind ambition will leave you waking up hungry for wealth and power but going to sleep with an empty soul. Walk always with honor, pride, and loyalty—let these principles never depart from you nor fail to steady your steps. In your battles, do not wish for your enemies to be handed to you on their knees; instead, seek to gain the strength and ruthlessness to bring them down while they stand. Your greatest dilemma is the eternal paradox in the life of a businessman within the sacred Sicilian organization: how to acquire power and wealth without placing both feet in hell? Be careful not to surrender to arrogance. The man who shouts his virtues to the wind will, when he falls, hear only the echo of his own pride. Let your greatest legacy be to live in a way that does not shame your mother and makes your father proud. Thank you for reading, my friend! If this message resonated with you, consider leaving your "🥃" as a token of appreciation. A toast to our family!
@ 6e0ea5d6:0327f353
2025-03-06 00:18:09Ascolta, amico mio... There come moments when a grown man looks in the mirror and fails to recognize himself. Naturally, when this happens, there is nothing more fitting than lighting a cigarette, pouring a glass of fine wine, and toasting to oneself—the birth of a new man, forged in the womb of a harsh and sobering reality. One cannot scatter thorns along a path walked barefoot, nor allow the tongue to speak what the mind may later pay for—but this, we learn only through years of suffering. Only now do I realize that, among all the teachers I have had, experience was the harshest of them all, for it first administered the test and only afterward taught me the lesson. In peaceful moments, one can reflect more easily on the world around him. Imagine, then, the depths of reflection that can be reached in a state of true inner tranquility. If you have never gazed upon the horizon, taken in all the fortune before your eyes, and declared to yourself, "I will own all of this!", then you have never possessed true ambition. However, blind ambition will leave you waking up hungry for wealth and power but going to sleep with an empty soul. Walk always with honor, pride, and loyalty—let these principles never depart from you nor fail to steady your steps. In your battles, do not wish for your enemies to be handed to you on their knees; instead, seek to gain the strength and ruthlessness to bring them down while they stand. Your greatest dilemma is the eternal paradox in the life of a businessman within the sacred Sicilian organization: how to acquire power and wealth without placing both feet in hell? Be careful not to surrender to arrogance. The man who shouts his virtues to the wind will, when he falls, hear only the echo of his own pride. Let your greatest legacy be to live in a way that does not shame your mother and makes your father proud. Thank you for reading, my friend! If this message resonated with you, consider leaving your "🥃" as a token of appreciation. A toast to our family! @ b8851a06:9b120ba1
2025-03-05 23:03:00The U.S. isn't just blocking Gaza's reconstruction—it's ensuring Palestinians have no future there. This week, Washington rejected the Arab League's $53 billion plan to rebuild Gaza. Not because it was unworkable, but because it was unwanted. #Gaza, they say, is "uninhabitable." The solution? Depopulation, disguised as development. ## The Riviera Plan: Rebuilding Without Its People National Security Council spokesman Brian Hughes put it bluntly: "Gaza is uninhabitable." This isn't a call for humanitarian intervention. It's a pretext for forced displacement. Trump's vision transforms Gaza into a "Riviera of the #MiddleEast"—after its population has been relocated. Officials have explicitly stated Palestinians "would not be allowed to return" once reconstruction begins. This isn't rebuilding; it's replacement. ## Regional Consensus Rejected The Arab League's proposal represented rare unity among regional powers. It offered a detailed roadmap for reconstruction while allowing #Palestinians to remain in their homeland. By dismissing this plan, Washington sent a clear message: **Palestinian self-determination remains subordinate to Western geopolitical interests.** This isn't new. For over a century, Western capitals have determined Palestinian futures while treating their voices as irrelevant. ## The Fiat War Machine Connection War and fiat money go hand in hand. Governments don't fund wars through taxes anymore—it's all printed money. Inflation steals from the public silently, financing endless destruction abroad while citizens struggle at home. As Saifedean Ammous writes in The Fiat Standard: nostr:npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak "Central banks are essentially war machines, enabling governments to finance endless conflicts through inflation rather than direct taxation." This system divorces "economic reward from economic productivity, and instead bases it on political allegiance." The result? A world "perpetually lurching from one crisis to another, with devastating consequences for humanity." ## Ukraine Parallels: When Support Is Conditional The U.S. has now halted military aid to #Ukraine, suspending over $1 billion in arms. #Europe scrambles to fill the gap, suddenly realizing the conditional nature of American protection. Both conflicts reveal the same truth: **geopolitical support is increasingly transactional rather than values-based.** As Henry Kissinger observed: "It may be dangerous to be America's enemy, but being America's friend can be fatal." ## The Cycle Continues The U.S. model is simple: fund destruction, control reconstruction, keep the cycle going. Fiat money makes it possible. Indifference makes it permanent. And yes #Bitcoin can fix it. But will it? How long before people wake up #nostr? How long before the cycle breaks? "Fiat money is a tool for governments to control their citizens" as Saifedean rightly says—and now, through endless war, to control the world.
@ b8851a06:9b120ba1
2025-03-05 23:03:00The U.S. isn't just blocking Gaza's reconstruction—it's ensuring Palestinians have no future there. This week, Washington rejected the Arab League's $53 billion plan to rebuild Gaza. Not because it was unworkable, but because it was unwanted. #Gaza, they say, is "uninhabitable." The solution? Depopulation, disguised as development. ## The Riviera Plan: Rebuilding Without Its People National Security Council spokesman Brian Hughes put it bluntly: "Gaza is uninhabitable." This isn't a call for humanitarian intervention. It's a pretext for forced displacement. Trump's vision transforms Gaza into a "Riviera of the #MiddleEast"—after its population has been relocated. Officials have explicitly stated Palestinians "would not be allowed to return" once reconstruction begins. This isn't rebuilding; it's replacement. ## Regional Consensus Rejected The Arab League's proposal represented rare unity among regional powers. It offered a detailed roadmap for reconstruction while allowing #Palestinians to remain in their homeland. By dismissing this plan, Washington sent a clear message: **Palestinian self-determination remains subordinate to Western geopolitical interests.** This isn't new. For over a century, Western capitals have determined Palestinian futures while treating their voices as irrelevant. ## The Fiat War Machine Connection War and fiat money go hand in hand. Governments don't fund wars through taxes anymore—it's all printed money. Inflation steals from the public silently, financing endless destruction abroad while citizens struggle at home. As Saifedean Ammous writes in The Fiat Standard: nostr:npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak "Central banks are essentially war machines, enabling governments to finance endless conflicts through inflation rather than direct taxation." This system divorces "economic reward from economic productivity, and instead bases it on political allegiance." The result? A world "perpetually lurching from one crisis to another, with devastating consequences for humanity." ## Ukraine Parallels: When Support Is Conditional The U.S. has now halted military aid to #Ukraine, suspending over $1 billion in arms. #Europe scrambles to fill the gap, suddenly realizing the conditional nature of American protection. Both conflicts reveal the same truth: **geopolitical support is increasingly transactional rather than values-based.** As Henry Kissinger observed: "It may be dangerous to be America's enemy, but being America's friend can be fatal." ## The Cycle Continues The U.S. model is simple: fund destruction, control reconstruction, keep the cycle going. Fiat money makes it possible. Indifference makes it permanent. And yes #Bitcoin can fix it. But will it? How long before people wake up #nostr? How long before the cycle breaks? "Fiat money is a tool for governments to control their citizens" as Saifedean rightly says—and now, through endless war, to control the world. @ f3873798:24b3f2f3
2025-03-05 23:01:12O café faz parte da rotina de milhões de pessoas, seja para despertar pela manhã, acompanhar uma boa conversa ou até impulsionar a produtividade no trabalho. Mas você já parou para pensar na qualidade do café que consome diariamente? Neste artigo, vamos falar sobre os benefícios do café e as diferenças entre o café extraforte e o café especial. ## ☕ Benefícios do Café no Dia a Dia  O café não é apenas uma bebida saborosa, mas também oferece diversos benefícios para a saúde, como: Aumento da energia e concentração – A cafeína estimula o sistema nervoso central, ajudando na atenção e no foco. Melhora do humor – O consumo moderado de café pode estimular a produção de dopamina, contribuindo para uma sensação de bem-estar. Propriedades antioxidantes – O café é rico em compostos que combatem os radicais livres, ajudando a prevenir o envelhecimento precoce. Auxílio na digestão – Para muitas pessoas, o café funciona como um leve estimulante do sistema digestivo. ## ☕ Café Extraforte vs. Café Especial: Qual a Diferença?  Na prateleira do supermercado ou na cafeteria, há uma grande variedade de cafés. Mas, afinal, qual é a diferença entre o café extraforte e o café especial? ### ☕Café Extraforte Produzido a partir de grãos de qualidade inferior, muitas vezes misturados com impurezas. Possui torra muito escura, o que pode mascarar defeitos do grão. Tem um sabor mais amargo e intenso, muitas vezes com notas queimadas. Pode ser mais ácido e difícil de digerir para algumas pessoas. ### ☕Café Especial Feito com grãos selecionados e de alta qualidade, sem defeitos. A torra é mais equilibrada, preservando os aromas e sabores naturais. Possui notas sensoriais diferenciadas (frutadas, achocolatadas, florais, etc.). Mais suave e menos ácido, proporcionando uma experiência mais agradável ao paladar. ## ☕ Qual Escolher para o Dia a Dia?  Se você busca praticidade e um café forte, o extraforte pode ser uma opção. No entanto, se quiser aproveitar melhor os benefícios do café e sentir sabores mais ricos, vale a pena investir no café especial. Além disso, moer os grãos na hora e preparar a bebida com métodos como coador de pano, prensa francesa ou Hario V60 pode transformar sua experiência com o café.
@ f3873798:24b3f2f3
2025-03-05 23:01:12O café faz parte da rotina de milhões de pessoas, seja para despertar pela manhã, acompanhar uma boa conversa ou até impulsionar a produtividade no trabalho. Mas você já parou para pensar na qualidade do café que consome diariamente? Neste artigo, vamos falar sobre os benefícios do café e as diferenças entre o café extraforte e o café especial. ## ☕ Benefícios do Café no Dia a Dia  O café não é apenas uma bebida saborosa, mas também oferece diversos benefícios para a saúde, como: Aumento da energia e concentração – A cafeína estimula o sistema nervoso central, ajudando na atenção e no foco. Melhora do humor – O consumo moderado de café pode estimular a produção de dopamina, contribuindo para uma sensação de bem-estar. Propriedades antioxidantes – O café é rico em compostos que combatem os radicais livres, ajudando a prevenir o envelhecimento precoce. Auxílio na digestão – Para muitas pessoas, o café funciona como um leve estimulante do sistema digestivo. ## ☕ Café Extraforte vs. Café Especial: Qual a Diferença?  Na prateleira do supermercado ou na cafeteria, há uma grande variedade de cafés. Mas, afinal, qual é a diferença entre o café extraforte e o café especial? ### ☕Café Extraforte Produzido a partir de grãos de qualidade inferior, muitas vezes misturados com impurezas. Possui torra muito escura, o que pode mascarar defeitos do grão. Tem um sabor mais amargo e intenso, muitas vezes com notas queimadas. Pode ser mais ácido e difícil de digerir para algumas pessoas. ### ☕Café Especial Feito com grãos selecionados e de alta qualidade, sem defeitos. A torra é mais equilibrada, preservando os aromas e sabores naturais. Possui notas sensoriais diferenciadas (frutadas, achocolatadas, florais, etc.). Mais suave e menos ácido, proporcionando uma experiência mais agradável ao paladar. ## ☕ Qual Escolher para o Dia a Dia?  Se você busca praticidade e um café forte, o extraforte pode ser uma opção. No entanto, se quiser aproveitar melhor os benefícios do café e sentir sabores mais ricos, vale a pena investir no café especial. Além disso, moer os grãos na hora e preparar a bebida com métodos como coador de pano, prensa francesa ou Hario V60 pode transformar sua experiência com o café. @ b7b1382e:74635e6c
2025-03-05 22:32:18## Abstract **By Lamar Wilson** This white paper examines an alternative taxation framework characterized by three primary components: a uniform 15% flat tax on income, a redistribution mechanism, and a tiered consumption tax structure. The proposed model aims to stimulate economic growth while maintaining social equity through strategic fiscal policy interventions. This paper analyzes the theoretical underpinnings of this approach, its potential macroeconomic implications, distributional effects across income strata, and implementation challenges. The analysis suggests that while the proposed framework offers significant advantages in terms of simplicity and growth incentives, careful consideration must be given to revenue adequacy, wealth concentration effects, and long-term economic sustainability. ## 1. Introduction Taxation systems fundamentally shape economic incentive structures, income distribution, and government fiscal capacity. Contemporary tax regimes often reflect accumulated historical policy decisions rather than coherent economic theory, resulting in complex systems with varying degrees of progressivity, efficiency, and equity (Mirrlees et al., 2011). This paper examines a potential alternative taxation framework built upon three pillars: a uniform flat tax, redistribution mechanisms, and stratified consumption taxation. The theoretical foundation of this approach draws upon both supply-side economics, which emphasizes the importance of investment incentives, and demand-side considerations, which recognize the economic significance of broad-based consumption. By synthesizing these perspectives, the proposed framework attempts to create a self-reinforcing economic cycle wherein simplified taxation stimulates both investment and consumption. ## 2. Structural Components of the Proposed Framework ### 2.1 Uniform Flat Income Taxation The cornerstone of the proposed system is a uniform 15% tax rate applied to income. This component includes two key elements: - **Individual Taxation**: A 15% flat tax applied to gross income across all individual taxpayers, regardless of income level. This approach eliminates tax brackets, deductions, and exemptions that characterize progressive taxation systems. - **Business Taxation**: A parallel 15% flat tax on net business income (profits), allowing for business expense deductions while maintaining a uniform rate across business entities regardless of size, industry, or organizational structure. The flat tax component represents a significant departure from graduated or progressive taxation systems prevalent in many developed economies. This simplification potentially reduces compliance costs, eliminates bracket-based behavioral distortions, and creates uniform incentive structures across income levels (Hall & Rabushka, 2007). ### 2.2 Universal Redistribution Mechanism The second component involves the pooling and redistribution of tax revenue: - **Collection Aggregation**: All tax revenues from both individual and business taxation are consolidated into a unified fiscal pool. - **Equal Per Capita Distribution**: The aggregated tax revenue is redistributed on an equal per capita basis to all individuals within the jurisdiction, functioning as a universal basic income mechanism. This redistribution mechanism effectively creates a de facto progressive element within the overtly flat system, as redistribution amounts represent a larger percentage of total income for lower-income individuals compared to higher-income individuals (Van Parijs & Vanderborght, 2017). ### 2.3 Tiered Consumption Taxation The third component introduces a differentiated consumption tax structure: - **Essential Goods and Services**: A minimal 2% consumption tax applied to essential items including food, healthcare, housing, and utilities. - **Non-Essential and Luxury Items**: A higher consumption tax rate (suggested at 5% or greater) applied to discretionary purchases and luxury goods. This differentiated approach to consumption taxation acknowledges consumption patterns that vary across income levels, with lower-income households typically allocating a greater proportion of spending to essential goods (Lustig, 2018). ## 3. Economic Implications Analysis ### 3.1 Distributive Effects Across Income Levels #### 3.1.1 Lower-Income Households The model's impact on lower-income households involves several counterbalancing forces: - The 15% flat income tax represents a potentially higher nominal rate than many lower-income households currently face under progressive systems. - The universal redistribution component serves as a direct income supplement, with the amount received likely exceeding tax contributions for this demographic. - The 2% consumption tax on essentials introduces a modest additional cost on necessary expenditures. Net analysis suggests that lower-income households would likely experience a positive fiscal impact through this system, as the redistributive component would exceed their combined income and consumption tax obligations (Piketty & Saez, 2013). #### 3.1.2 Higher-Income Households For higher-income households, the framework produces different effects: - The 15% flat income tax rate typically represents a reduction from current progressive tax rates applied to higher income brackets. - The universal redistribution amount constitutes a proportionally smaller income supplement relative to total income. - Higher consumption taxes on luxury goods create a de facto progressive element based on discretionary spending patterns. The net impact on higher-income households would likely be a reduced overall tax burden compared to progressive systems, potentially increasing capital availability for investment (Auerbach & Hassett, 2015). ### 3.2 Macroeconomic Implications #### 3.2.1 Investment and Growth Effects The framework's reduced taxation on higher incomes and business profits theoretically increases capital availability for investment. This aligns with supply-side economic theories suggesting that lower marginal tax rates stimulate economic expansion through: - Increased business formation and expansion - Enhanced capital investment - Improved labor productivity through capital deepening - Potential innovation stimulation through retained earnings Empirical research on flat tax implementations in various jurisdictions provides mixed evidence regarding growth effects, with contextual factors playing significant roles in outcomes (Keen et al., 2008). #### 3.2.2 Demand Stability and Consumption Patterns The redistribution component creates a consumption floor that may enhance economic stability through: - Maintaining baseline consumer demand during economic downturns - Reducing consumption volatility across business cycles - Supporting broader-based consumption patterns - Creating demand-side support for business expansion This mechanism acknowledges the economic significance of broad-based consumption capacity alongside investment incentives (Stiglitz, 2012). #### 3.2.3 Labor Market Dynamics The simplified tax structure potentially influences labor market participation through: - Elimination of high marginal tax rates that may discourage additional work - Reduced tax-related work disincentives at lower income levels - Possible increased labor force participation due to simplified income-benefit calculations - Potential wage effects as businesses retain higher post-tax profits The framework's impact on labor markets would likely vary across skill levels, industries, and existing labor market institutions (Card & Krueger, 2015). ## 4. Implementation Challenges and Considerations ### 4.1 Fiscal Revenue Adequacy A primary challenge involves ensuring sufficient government revenue, particularly during the transition period: - The overall tax burden reduction (estimated at approximately 50% compared to current systems) creates potential revenue shortfalls. - Government spending obligations would require adjustment, postponement, or alternative funding mechanisms. - Transitional provisions may be necessary to align revenue reductions with spending adaptations. Potential solutions include phased implementation, temporary supplementary revenue sources, or deliberate acceleration of economic growth to expand the tax base (Auerbach, 2006). ### 4.2 Wealth Concentration Effects Despite redistribution mechanisms, the framework may influence wealth concentration dynamics: - Reduced taxation on higher incomes could accelerate capital accumulation among wealthy individuals. - Business owners might experience wealth growth exceeding redistribution effects. - Global investment patterns could divert economic benefits outside the domestic economy. Addressing these concerns might require calibration of the redistribution component or implementing complementary policies addressing wealth concentration (Piketty, 2014). ### 4.3 Long-Term Sustainability Considerations The framework's long-term viability depends on several factors: - Sustained economic growth sufficient to support government functions with reduced tax rates - Continued business investment in productive domestic activities rather than financial engineering - Maintenance of investment-consumption balance to prevent boom-bust cycles - Evolution of the system in response to changing economic conditions Supplementary policies supporting research and development, entrepreneurship, and domestic investment may be necessary to ensure the system's sustainability (Acemoglu & Robinson, 2012). ## 5. Comparative Cost-Benefit Analysis: Proposed System vs. Current Tax Structure ### 5.1 Compliance Cost Reduction The current U.S. tax system imposes substantial compliance costs on individuals and businesses that extend far beyond direct tax payments: - Americans spend approximately 6.5 billion hours annually on tax compliance activities (Taxpayer Advocate Service, 2022) - The monetary value of compliance time is estimated at $200-400 billion annually (Laffer et al., 2018) - Businesses spend an estimated $147 billion annually on tax compliance (Tax Foundation, 2021) - The Internal Revenue Service budget exceeds $13 billion annually for tax administration and enforcement The proposed flat tax system would dramatically reduce these costs through: - Elimination of complex deduction and credit calculations (estimated 90% reduction in form complexity) - Removal of recordkeeping requirements for numerous tax provisions - Significant reduction in tax planning expenses for both individuals and businesses - Decreased need for professional tax preparation services - Streamlined tax enforcement with fewer provisions to interpret and audit Quantitative analysis suggests that transitioning to the proposed system could reduce overall compliance costs by approximately 70-80%, representing annual savings of $140-320 billion to the U.S. economy (Greenberg, 2020). ### 5.2 Administrative Efficiency Gains The current tax administration infrastructure incurs substantial costs: - The IRS employs approximately 75,000 full-time equivalent positions - Tax litigation consumes significant judicial resources across multiple court systems - Regulatory development and guidance require extensive government resources - Tax enforcement costs represent approximately 35 cents per $100 collected The proposed system would generate administrative efficiencies through: - Simplified verification processes requiring fewer personnel - Reduced need for specialized tax rulings and interpretations - Lower audit costs due to straightforward compliance requirements - Streamlined distribution mechanisms leveraging existing payment systems Conservative estimates suggest administrative cost reductions of 50-60%, representing billions in government savings that could be redirected to essential services or deficit reduction. ### 5.3 Economic Efficiency Improvements Beyond direct compliance and administrative costs, the current system creates significant economic distortions: - Taxpayers make economic decisions influenced by tax considerations rather than underlying economic value - Complex provisions create market inefficiencies and misallocation of resources - High marginal rates discourage additional productive activity - International tax complexities influence global investment decisions The proposed system addresses these inefficiencies through: - Uniform treatment of income regardless of source - Elimination of tax-motivated transaction structures - Reduced incentives for artificial entity structures - Simplified international transactions with domestic reinvestment incentives Economic models suggest these efficiency improvements could increase GDP by 0.5-1.0% annually beyond direct compliance savings (Jorgenson & Yun, 2012). ### 5.4 Distributional Cost Analysis The current system's compliance burden falls disproportionately across income levels: - Lower-income taxpayers spend a higher percentage of their income on tax compliance - Small businesses face compliance costs estimated at $1,500-$4,000 per employee - Middle-income taxpayers navigate complex provisions with limited professional assistance - High-income taxpayers allocate substantial resources to tax planning and compliance The proposed system redistributes this burden by: - Equalizing compliance requirements across income levels - Substantially reducing small business administrative overhead - Eliminating the need for complex tax planning strategies - Providing transparent, predictable tax consequences for economic decisions This redistribution of compliance costs represents an additional progressive element beyond the direct redistribution component, with estimated financial benefits to lower and middle-income households of $300-500 annually in reduced compliance costs. ## 6. Conclusion The proposed tripartite taxation framework offers a conceptually coherent alternative to conventional progressive taxation systems. By combining flat income taxation with universal redistribution and differentiated consumption taxes, the approach attempts to simultaneously address supply-side investment incentives and demand-side consumption support. The theoretical analysis suggests potential advantages in terms of simplicity, economic growth stimulation, and maintenance of social safety net functions. However, significant implementation challenges exist regarding revenue adequacy, wealth concentration effects, and long-term economic sustainability. Further empirical research, potentially through regional pilot implementations or microsimulation modeling, would enhance understanding of the practical implications of this taxation approach. While the framework presents a promising theoretical model, its successful implementation would require careful calibration to specific economic contexts, thoughtful transition planning, and ongoing adjustment based on observed outcomes. ## References Acemoglu, D., & Robinson, J. A. (2012). *Why nations fail: The origins of power, prosperity, and poverty*. Crown Business. Greenberg, S. (2020). *Reforming the U.S. tax system: Evidence on economic growth and distribution*. American Enterprise Institute. Jorgenson, D. W., & Yun, K. Y. (2012). *Tax reform and the cost of capital*. Oxford University Press. Laffer, A. B., Moore, S., & Williams, J. (2018). *The wealth of states: How taxes, energy, and worker freedom change everything*. Wiley. Tax Foundation (2021). *The cost of tax compliance*. Fiscal Fact No. 512. Taxpayer Advocate Service (2022). *Annual report to Congress*. Internal Revenue Service. Auerbach, A. J. (2006). The choice between income and consumption taxes: A primer. *NBER Working Paper Series*. Auerbach, A. J., & Hassett, K. (2015). Capital taxation in the twenty-first century. *American Economic Review*, 105(5), 38-42. Card, D., & Krueger, A. B. (2015). *Myth and measurement: The new economics of the minimum wage*. Princeton University Press. Hall, R. E., & Rabushka, A. (2007). *The flat tax*. Hoover Institution Press. Keen, M., Kim, Y., & Varsano, R. (2008). The "flat tax(es)": Principles and experience. *International Tax and Public Finance*, 15(6), 712-751. Lustig, N. (2018). Fiscal policy, income redistribution and poverty reduction in low and middle income countries. *Commitment to Equity Handbook*. Mirrlees, J., Adam, S., Besley, T., Blundell, R., Bond, S., Chote, R., Gammie, M., Johnson, P., Myles, G., & Poterba, J. (2011). *Tax by design*. Oxford University Press. Piketty, T. (2014). *Capital in the twenty-first century*. Harvard University Press. Piketty, T., & Saez, E. (2013). Optimal labor income taxation. *Handbook of Public Economics*, 5, 391-474. Stiglitz, J. E. (2012). *The price of inequality: How today's divided society endangers our future*. W.W. Norton & Company. Van Parijs, P., & Vanderborght, Y. (2017). *Basic income: A radical proposal for a free society and a sane economy*. Harvard University Press. # A Tripartite Approach to Fiscal Reform: Analyzing the Economic Impact of a Flat Tax, Redistribution, and Consumption Tax Framework **Author: Lamar Wilson** ## Abstract **By Lamar Wilson** This white paper examines an alternative taxation framework characterized by three primary components: a uniform 15% flat tax on income, a redistribution mechanism, and a tiered consumption tax structure. The proposed model aims to stimulate economic growth while maintaining social equity through strategic fiscal policy interventions. This paper analyzes the theoretical underpinnings of this approach, its potential macroeconomic implications, distributional effects across income strata, and implementation challenges. The analysis suggests that while the proposed framework offers significant advantages in terms of simplicity and growth incentives, careful consideration must be given to revenue adequacy, wealth concentration effects, and long-term economic sustainability. ## 1. Introduction Taxation systems fundamentally shape economic incentive structures, income distribution, and government fiscal capacity. Contemporary tax regimes often reflect accumulated historical policy decisions rather than coherent economic theory, resulting in complex systems with varying degrees of progressivity, efficiency, and equity (Mirrlees et al., 2011). This paper examines a potential alternative taxation framework built upon three pillars: a uniform flat tax, redistribution mechanisms, and stratified consumption taxation. The theoretical foundation of this approach draws upon both supply-side economics, which emphasizes the importance of investment incentives, and demand-side considerations, which recognize the economic significance of broad-based consumption. By synthesizing these perspectives, the proposed framework attempts to create a self-reinforcing economic cycle wherein simplified taxation stimulates both investment and consumption. ## 2. Structural Components of the Proposed Framework ### 2.1 Uniform Flat Income Taxation The cornerstone of the proposed system is a uniform 15% tax rate applied to income. This component includes two key elements: - **Individual Taxation**: A 15% flat tax applied to gross income across all individual taxpayers, regardless of income level. This approach eliminates tax brackets, deductions, and exemptions that characterize progressive taxation systems. - **Business Taxation**: A parallel 15% flat tax on net business income (profits), allowing for business expense deductions while maintaining a uniform rate across business entities regardless of size, industry, or organizational structure. The flat tax component represents a significant departure from graduated or progressive taxation systems prevalent in many developed economies. This simplification potentially reduces compliance costs, eliminates bracket-based behavioral distortions, and creates uniform incentive structures across income levels (Hall & Rabushka, 2007). ### 2.2 Universal Redistribution Mechanism The second component involves the pooling and redistribution of tax revenue: - **Collection Aggregation**: All tax revenues from both individual and business taxation are consolidated into a unified fiscal pool. - **Equal Per Capita Distribution**: The aggregated tax revenue is redistributed on an equal per capita basis to all individuals within the jurisdiction, functioning as a universal basic income mechanism. This redistribution mechanism effectively creates a de facto progressive element within the overtly flat system, as redistribution amounts represent a larger percentage of total income for lower-income individuals compared to higher-income individuals (Van Parijs & Vanderborght, 2017). ### 2.3 Tiered Consumption Taxation The third component introduces a differentiated consumption tax structure: - **Essential Goods and Services**: A minimal 2% consumption tax applied to essential items including food, healthcare, housing, and utilities. - **Non-Essential and Luxury Items**: A higher consumption tax rate (suggested at 5% or greater) applied to discretionary purchases and luxury goods. This differentiated approach to consumption taxation acknowledges consumption patterns that vary across income levels, with lower-income households typically allocating a greater proportion of spending to essential goods (Lustig, 2018). ## 3. Economic Implications Analysis ### 3.1 Distributive Effects Across Income Levels #### 3.1.1 Lower-Income Households The model's impact on lower-income households involves several counterbalancing forces: - The 15% flat income tax represents a potentially higher nominal rate than many lower-income households currently face under progressive systems. - The universal redistribution component serves as a direct income supplement, with the amount received likely exceeding tax contributions for this demographic. - The 2% consumption tax on essentials introduces a modest additional cost on necessary expenditures. Net analysis suggests that lower-income households would likely experience a positive fiscal impact through this system, as the redistributive component would exceed their combined income and consumption tax obligations (Piketty & Saez, 2013). #### 3.1.2 Higher-Income Households For higher-income households, the framework produces different effects: - The 15% flat income tax rate typically represents a reduction from current progressive tax rates applied to higher income brackets. - The universal redistribution amount constitutes a proportionally smaller income supplement relative to total income. - Higher consumption taxes on luxury goods create a de facto progressive element based on discretionary spending patterns. The net impact on higher-income households would likely be a reduced overall tax burden compared to progressive systems, potentially increasing capital availability for investment (Auerbach & Hassett, 2015). ### 3.2 Macroeconomic Implications #### 3.2.1 Investment and Growth Effects The framework's reduced taxation on higher incomes and business profits theoretically increases capital availability for investment. This aligns with supply-side economic theories suggesting that lower marginal tax rates stimulate economic expansion through: - Increased business formation and expansion - Enhanced capital investment - Improved labor productivity through capital deepening - Potential innovation stimulation through retained earnings Empirical research on flat tax implementations in various jurisdictions provides mixed evidence regarding growth effects, with contextual factors playing significant roles in outcomes (Keen et al., 2008). #### 3.2.2 Demand Stability and Consumption Patterns The redistribution component creates a consumption floor that may enhance economic stability through: - Maintaining baseline consumer demand during economic downturns - Reducing consumption volatility across business cycles - Supporting broader-based consumption patterns - Creating demand-side support for business expansion This mechanism acknowledges the economic significance of broad-based consumption capacity alongside investment incentives (Stiglitz, 2012). #### 3.2.3 Labor Market Dynamics The simplified tax structure potentially influences labor market participation through: - Elimination of high marginal tax rates that may discourage additional work - Reduced tax-related work disincentives at lower income levels - Possible increased labor force participation due to simplified income-benefit calculations - Potential wage effects as businesses retain higher post-tax profits The framework's impact on labor markets would likely vary across skill levels, industries, and existing labor market institutions (Card & Krueger, 2015). ## 4. Implementation Challenges and Considerations ### 4.1 Fiscal Revenue Adequacy A primary challenge involves ensuring sufficient government revenue, particularly during the transition period: - The overall tax burden reduction (estimated at approximately 50% compared to current systems) creates potential revenue shortfalls. - Government spending obligations would require adjustment, postponement, or alternative funding mechanisms. - Transitional provisions may be necessary to align revenue reductions with spending adaptations. Potential solutions include phased implementation, temporary supplementary revenue sources, or deliberate acceleration of economic growth to expand the tax base (Auerbach, 2006). ### 4.2 Wealth Concentration Effects Despite redistribution mechanisms, the framework may influence wealth concentration dynamics: - Reduced taxation on higher incomes could accelerate capital accumulation among wealthy individuals. - Business owners might experience wealth growth exceeding redistribution effects. - Global investment patterns could divert economic benefits outside the domestic economy. Addressing these concerns might require calibration of the redistribution component or implementing complementary policies addressing wealth concentration (Piketty, 2014). ### 4.3 Long-Term Sustainability Considerations The framework's long-term viability depends on several factors: - Sustained economic growth sufficient to support government functions with reduced tax rates - Continued business investment in productive domestic activities rather than financial engineering - Maintenance of investment-consumption balance to prevent boom-bust cycles - Evolution of the system in response to changing economic conditions Supplementary policies supporting research and development, entrepreneurship, and domestic investment may be necessary to ensure the system's sustainability (Acemoglu & Robinson, 2012). ## 5. Comparative Cost-Benefit Analysis: Proposed System vs. Current Tax Structure ### 5.1 Compliance Cost Reduction The current U.S. tax system imposes substantial compliance costs on individuals and businesses that extend far beyond direct tax payments: - Americans spend approximately 6.5 billion hours annually on tax compliance activities (Taxpayer Advocate Service, 2022) - The monetary value of compliance time is estimated at $200-400 billion annually (Laffer et al., 2018) - Businesses spend an estimated $147 billion annually on tax compliance (Tax Foundation, 2021) - The Internal Revenue Service budget exceeds $13 billion annually for tax administration and enforcement The proposed flat tax system would dramatically reduce these costs through: - Elimination of complex deduction and credit calculations (estimated 90% reduction in form complexity) - Removal of recordkeeping requirements for numerous tax provisions - Significant reduction in tax planning expenses for both individuals and businesses - Decreased need for professional tax preparation services - Streamlined tax enforcement with fewer provisions to interpret and audit Quantitative analysis suggests that transitioning to the proposed system could reduce overall compliance costs by approximately 70-80%, representing annual savings of $140-320 billion to the U.S. economy (Greenberg, 2020). ### 5.2 Administrative Efficiency Gains The current tax administration infrastructure incurs substantial costs: - The IRS employs approximately 75,000 full-time equivalent positions - Tax litigation consumes significant judicial resources across multiple court systems - Regulatory development and guidance require extensive government resources - Tax enforcement costs represent approximately 35 cents per $100 collected The proposed system would generate administrative efficiencies through: - Simplified verification processes requiring fewer personnel - Reduced need for specialized tax rulings and interpretations - Lower audit costs due to straightforward compliance requirements - Streamlined distribution mechanisms leveraging existing payment systems Conservative estimates suggest administrative cost reductions of 50-60%, representing billions in government savings that could be redirected to essential services or deficit reduction. ### 5.3 Economic Efficiency Improvements Beyond direct compliance and administrative costs, the current system creates significant economic distortions: - Taxpayers make economic decisions influenced by tax considerations rather than underlying economic value - Complex provisions create market inefficiencies and misallocation of resources - High marginal rates discourage additional productive activity - International tax complexities influence global investment decisions The proposed system addresses these inefficiencies through: - Uniform treatment of income regardless of source - Elimination of tax-motivated transaction structures - Reduced incentives for artificial entity structures - Simplified international transactions with domestic reinvestment incentives Economic models suggest these efficiency improvements could increase GDP by 0.5-1.0% annually beyond direct compliance savings (Jorgenson & Yun, 2012). ### 5.4 Distributional Cost Analysis The current system's compliance burden falls disproportionately across income levels: - Lower-income taxpayers spend a higher percentage of their income on tax compliance - Small businesses face compliance costs estimated at $1,500-$4,000 per employee - Middle-income taxpayers navigate complex provisions with limited professional assistance - High-income taxpayers allocate substantial resources to tax planning and compliance The proposed system redistributes this burden by: - Equalizing compliance requirements across income levels - Substantially reducing small business administrative overhead - Eliminating the need for complex tax planning strategies - Providing transparent, predictable tax consequences for economic decisions This redistribution of compliance costs represents an additional progressive element beyond the direct redistribution component, with estimated financial benefits to lower and middle-income households of $300-500 annually in reduced compliance costs. ## 6. Conclusion The proposed tripartite taxation framework offers a conceptually coherent alternative to conventional progressive taxation systems. By combining flat income taxation with universal redistribution and differentiated consumption taxes, the approach attempts to simultaneously address supply-side investment incentives and demand-side consumption support. The theoretical analysis suggests potential advantages in terms of simplicity, economic growth stimulation, and maintenance of social safety net functions. However, significant implementation challenges exist regarding revenue adequacy, wealth concentration effects, and long-term economic sustainability. Further empirical research, potentially through regional pilot implementations or microsimulation modeling, would enhance understanding of the practical implications of this taxation approach. While the framework presents a promising theoretical model, its successful implementation would require careful calibration to specific economic contexts, thoughtful transition planning, and ongoing adjustment based on observed outcomes. ## References Acemoglu, D., & Robinson, J. A. (2012). *Why nations fail: The origins of power, prosperity, and poverty*. Crown Business. Greenberg, S. (2020). *Reforming the U.S. tax system: Evidence on economic growth and distribution*. American Enterprise Institute. Jorgenson, D. W., & Yun, K. Y. (2012). *Tax reform and the cost of capital*. Oxford University Press. Laffer, A. B., Moore, S., & Williams, J. (2018). *The wealth of states: How taxes, energy, and worker freedom change everything*. Wiley. Tax Foundation (2021). *The cost of tax compliance*. Fiscal Fact No. 512. Taxpayer Advocate Service (2022). *Annual report to Congress*. Internal Revenue Service. Auerbach, A. J. (2006). The choice between income and consumption taxes: A primer. *NBER Working Paper Series*. Auerbach, A. J., & Hassett, K. (2015). Capital taxation in the twenty-first century. *American Economic Review*, 105(5), 38-42. Card, D., & Krueger, A. B. (2015). *Myth and measurement: The new economics of the minimum wage*. Princeton University Press. Hall, R. E., & Rabushka, A. (2007). *The flat tax*. Hoover Institution Press. Keen, M., Kim, Y., & Varsano, R. (2008). The "flat tax(es)": Principles and experience. *International Tax and Public Finance*, 15(6), 712-751. Lustig, N. (2018). Fiscal policy, income redistribution and poverty reduction in low and middle income countries. *Commitment to Equity Handbook*. Mirrlees, J., Adam, S., Besley, T., Blundell, R., Bond, S., Chote, R., Gammie, M., Johnson, P., Myles, G., & Poterba, J. (2011). *Tax by design*. Oxford University Press. Piketty, T. (2014). *Capital in the twenty-first century*. Harvard University Press. Piketty, T., & Saez, E. (2013). Optimal labor income taxation. *Handbook of Public Economics*, 5, 391-474. Stiglitz, J. E. (2012). *The price of inequality: How today's divided society endangers our future*. W.W. Norton & Company. Van Parijs, P., & Vanderborght, Y. (2017). *Basic income: A radical proposal for a free society and a sane economy*. Harvard University Press.
@ b7b1382e:74635e6c
2025-03-05 22:32:18## Abstract **By Lamar Wilson** This white paper examines an alternative taxation framework characterized by three primary components: a uniform 15% flat tax on income, a redistribution mechanism, and a tiered consumption tax structure. The proposed model aims to stimulate economic growth while maintaining social equity through strategic fiscal policy interventions. This paper analyzes the theoretical underpinnings of this approach, its potential macroeconomic implications, distributional effects across income strata, and implementation challenges. The analysis suggests that while the proposed framework offers significant advantages in terms of simplicity and growth incentives, careful consideration must be given to revenue adequacy, wealth concentration effects, and long-term economic sustainability. ## 1. Introduction Taxation systems fundamentally shape economic incentive structures, income distribution, and government fiscal capacity. Contemporary tax regimes often reflect accumulated historical policy decisions rather than coherent economic theory, resulting in complex systems with varying degrees of progressivity, efficiency, and equity (Mirrlees et al., 2011). This paper examines a potential alternative taxation framework built upon three pillars: a uniform flat tax, redistribution mechanisms, and stratified consumption taxation. The theoretical foundation of this approach draws upon both supply-side economics, which emphasizes the importance of investment incentives, and demand-side considerations, which recognize the economic significance of broad-based consumption. By synthesizing these perspectives, the proposed framework attempts to create a self-reinforcing economic cycle wherein simplified taxation stimulates both investment and consumption. ## 2. Structural Components of the Proposed Framework ### 2.1 Uniform Flat Income Taxation The cornerstone of the proposed system is a uniform 15% tax rate applied to income. This component includes two key elements: - **Individual Taxation**: A 15% flat tax applied to gross income across all individual taxpayers, regardless of income level. This approach eliminates tax brackets, deductions, and exemptions that characterize progressive taxation systems. - **Business Taxation**: A parallel 15% flat tax on net business income (profits), allowing for business expense deductions while maintaining a uniform rate across business entities regardless of size, industry, or organizational structure. The flat tax component represents a significant departure from graduated or progressive taxation systems prevalent in many developed economies. This simplification potentially reduces compliance costs, eliminates bracket-based behavioral distortions, and creates uniform incentive structures across income levels (Hall & Rabushka, 2007). ### 2.2 Universal Redistribution Mechanism The second component involves the pooling and redistribution of tax revenue: - **Collection Aggregation**: All tax revenues from both individual and business taxation are consolidated into a unified fiscal pool. - **Equal Per Capita Distribution**: The aggregated tax revenue is redistributed on an equal per capita basis to all individuals within the jurisdiction, functioning as a universal basic income mechanism. This redistribution mechanism effectively creates a de facto progressive element within the overtly flat system, as redistribution amounts represent a larger percentage of total income for lower-income individuals compared to higher-income individuals (Van Parijs & Vanderborght, 2017). ### 2.3 Tiered Consumption Taxation The third component introduces a differentiated consumption tax structure: - **Essential Goods and Services**: A minimal 2% consumption tax applied to essential items including food, healthcare, housing, and utilities. - **Non-Essential and Luxury Items**: A higher consumption tax rate (suggested at 5% or greater) applied to discretionary purchases and luxury goods. This differentiated approach to consumption taxation acknowledges consumption patterns that vary across income levels, with lower-income households typically allocating a greater proportion of spending to essential goods (Lustig, 2018). ## 3. Economic Implications Analysis ### 3.1 Distributive Effects Across Income Levels #### 3.1.1 Lower-Income Households The model's impact on lower-income households involves several counterbalancing forces: - The 15% flat income tax represents a potentially higher nominal rate than many lower-income households currently face under progressive systems. - The universal redistribution component serves as a direct income supplement, with the amount received likely exceeding tax contributions for this demographic. - The 2% consumption tax on essentials introduces a modest additional cost on necessary expenditures. Net analysis suggests that lower-income households would likely experience a positive fiscal impact through this system, as the redistributive component would exceed their combined income and consumption tax obligations (Piketty & Saez, 2013). #### 3.1.2 Higher-Income Households For higher-income households, the framework produces different effects: - The 15% flat income tax rate typically represents a reduction from current progressive tax rates applied to higher income brackets. - The universal redistribution amount constitutes a proportionally smaller income supplement relative to total income. - Higher consumption taxes on luxury goods create a de facto progressive element based on discretionary spending patterns. The net impact on higher-income households would likely be a reduced overall tax burden compared to progressive systems, potentially increasing capital availability for investment (Auerbach & Hassett, 2015). ### 3.2 Macroeconomic Implications #### 3.2.1 Investment and Growth Effects The framework's reduced taxation on higher incomes and business profits theoretically increases capital availability for investment. This aligns with supply-side economic theories suggesting that lower marginal tax rates stimulate economic expansion through: - Increased business formation and expansion - Enhanced capital investment - Improved labor productivity through capital deepening - Potential innovation stimulation through retained earnings Empirical research on flat tax implementations in various jurisdictions provides mixed evidence regarding growth effects, with contextual factors playing significant roles in outcomes (Keen et al., 2008). #### 3.2.2 Demand Stability and Consumption Patterns The redistribution component creates a consumption floor that may enhance economic stability through: - Maintaining baseline consumer demand during economic downturns - Reducing consumption volatility across business cycles - Supporting broader-based consumption patterns - Creating demand-side support for business expansion This mechanism acknowledges the economic significance of broad-based consumption capacity alongside investment incentives (Stiglitz, 2012). #### 3.2.3 Labor Market Dynamics The simplified tax structure potentially influences labor market participation through: - Elimination of high marginal tax rates that may discourage additional work - Reduced tax-related work disincentives at lower income levels - Possible increased labor force participation due to simplified income-benefit calculations - Potential wage effects as businesses retain higher post-tax profits The framework's impact on labor markets would likely vary across skill levels, industries, and existing labor market institutions (Card & Krueger, 2015). ## 4. Implementation Challenges and Considerations ### 4.1 Fiscal Revenue Adequacy A primary challenge involves ensuring sufficient government revenue, particularly during the transition period: - The overall tax burden reduction (estimated at approximately 50% compared to current systems) creates potential revenue shortfalls. - Government spending obligations would require adjustment, postponement, or alternative funding mechanisms. - Transitional provisions may be necessary to align revenue reductions with spending adaptations. Potential solutions include phased implementation, temporary supplementary revenue sources, or deliberate acceleration of economic growth to expand the tax base (Auerbach, 2006). ### 4.2 Wealth Concentration Effects Despite redistribution mechanisms, the framework may influence wealth concentration dynamics: - Reduced taxation on higher incomes could accelerate capital accumulation among wealthy individuals. - Business owners might experience wealth growth exceeding redistribution effects. - Global investment patterns could divert economic benefits outside the domestic economy. Addressing these concerns might require calibration of the redistribution component or implementing complementary policies addressing wealth concentration (Piketty, 2014). ### 4.3 Long-Term Sustainability Considerations The framework's long-term viability depends on several factors: - Sustained economic growth sufficient to support government functions with reduced tax rates - Continued business investment in productive domestic activities rather than financial engineering - Maintenance of investment-consumption balance to prevent boom-bust cycles - Evolution of the system in response to changing economic conditions Supplementary policies supporting research and development, entrepreneurship, and domestic investment may be necessary to ensure the system's sustainability (Acemoglu & Robinson, 2012). ## 5. Comparative Cost-Benefit Analysis: Proposed System vs. Current Tax Structure ### 5.1 Compliance Cost Reduction The current U.S. tax system imposes substantial compliance costs on individuals and businesses that extend far beyond direct tax payments: - Americans spend approximately 6.5 billion hours annually on tax compliance activities (Taxpayer Advocate Service, 2022) - The monetary value of compliance time is estimated at $200-400 billion annually (Laffer et al., 2018) - Businesses spend an estimated $147 billion annually on tax compliance (Tax Foundation, 2021) - The Internal Revenue Service budget exceeds $13 billion annually for tax administration and enforcement The proposed flat tax system would dramatically reduce these costs through: - Elimination of complex deduction and credit calculations (estimated 90% reduction in form complexity) - Removal of recordkeeping requirements for numerous tax provisions - Significant reduction in tax planning expenses for both individuals and businesses - Decreased need for professional tax preparation services - Streamlined tax enforcement with fewer provisions to interpret and audit Quantitative analysis suggests that transitioning to the proposed system could reduce overall compliance costs by approximately 70-80%, representing annual savings of $140-320 billion to the U.S. economy (Greenberg, 2020). ### 5.2 Administrative Efficiency Gains The current tax administration infrastructure incurs substantial costs: - The IRS employs approximately 75,000 full-time equivalent positions - Tax litigation consumes significant judicial resources across multiple court systems - Regulatory development and guidance require extensive government resources - Tax enforcement costs represent approximately 35 cents per $100 collected The proposed system would generate administrative efficiencies through: - Simplified verification processes requiring fewer personnel - Reduced need for specialized tax rulings and interpretations - Lower audit costs due to straightforward compliance requirements - Streamlined distribution mechanisms leveraging existing payment systems Conservative estimates suggest administrative cost reductions of 50-60%, representing billions in government savings that could be redirected to essential services or deficit reduction. ### 5.3 Economic Efficiency Improvements Beyond direct compliance and administrative costs, the current system creates significant economic distortions: - Taxpayers make economic decisions influenced by tax considerations rather than underlying economic value - Complex provisions create market inefficiencies and misallocation of resources - High marginal rates discourage additional productive activity - International tax complexities influence global investment decisions The proposed system addresses these inefficiencies through: - Uniform treatment of income regardless of source - Elimination of tax-motivated transaction structures - Reduced incentives for artificial entity structures - Simplified international transactions with domestic reinvestment incentives Economic models suggest these efficiency improvements could increase GDP by 0.5-1.0% annually beyond direct compliance savings (Jorgenson & Yun, 2012). ### 5.4 Distributional Cost Analysis The current system's compliance burden falls disproportionately across income levels: - Lower-income taxpayers spend a higher percentage of their income on tax compliance - Small businesses face compliance costs estimated at $1,500-$4,000 per employee - Middle-income taxpayers navigate complex provisions with limited professional assistance - High-income taxpayers allocate substantial resources to tax planning and compliance The proposed system redistributes this burden by: - Equalizing compliance requirements across income levels - Substantially reducing small business administrative overhead - Eliminating the need for complex tax planning strategies - Providing transparent, predictable tax consequences for economic decisions This redistribution of compliance costs represents an additional progressive element beyond the direct redistribution component, with estimated financial benefits to lower and middle-income households of $300-500 annually in reduced compliance costs. ## 6. Conclusion The proposed tripartite taxation framework offers a conceptually coherent alternative to conventional progressive taxation systems. By combining flat income taxation with universal redistribution and differentiated consumption taxes, the approach attempts to simultaneously address supply-side investment incentives and demand-side consumption support. The theoretical analysis suggests potential advantages in terms of simplicity, economic growth stimulation, and maintenance of social safety net functions. However, significant implementation challenges exist regarding revenue adequacy, wealth concentration effects, and long-term economic sustainability. Further empirical research, potentially through regional pilot implementations or microsimulation modeling, would enhance understanding of the practical implications of this taxation approach. While the framework presents a promising theoretical model, its successful implementation would require careful calibration to specific economic contexts, thoughtful transition planning, and ongoing adjustment based on observed outcomes. ## References Acemoglu, D., & Robinson, J. A. (2012). *Why nations fail: The origins of power, prosperity, and poverty*. Crown Business. Greenberg, S. (2020). *Reforming the U.S. tax system: Evidence on economic growth and distribution*. American Enterprise Institute. Jorgenson, D. W., & Yun, K. Y. (2012). *Tax reform and the cost of capital*. Oxford University Press. Laffer, A. B., Moore, S., & Williams, J. (2018). *The wealth of states: How taxes, energy, and worker freedom change everything*. Wiley. Tax Foundation (2021). *The cost of tax compliance*. Fiscal Fact No. 512. Taxpayer Advocate Service (2022). *Annual report to Congress*. Internal Revenue Service. Auerbach, A. J. (2006). The choice between income and consumption taxes: A primer. *NBER Working Paper Series*. Auerbach, A. J., & Hassett, K. (2015). Capital taxation in the twenty-first century. *American Economic Review*, 105(5), 38-42. Card, D., & Krueger, A. B. (2015). *Myth and measurement: The new economics of the minimum wage*. Princeton University Press. Hall, R. E., & Rabushka, A. (2007). *The flat tax*. Hoover Institution Press. Keen, M., Kim, Y., & Varsano, R. (2008). The "flat tax(es)": Principles and experience. *International Tax and Public Finance*, 15(6), 712-751. Lustig, N. (2018). Fiscal policy, income redistribution and poverty reduction in low and middle income countries. *Commitment to Equity Handbook*. Mirrlees, J., Adam, S., Besley, T., Blundell, R., Bond, S., Chote, R., Gammie, M., Johnson, P., Myles, G., & Poterba, J. (2011). *Tax by design*. Oxford University Press. Piketty, T. (2014). *Capital in the twenty-first century*. Harvard University Press. Piketty, T., & Saez, E. (2013). Optimal labor income taxation. *Handbook of Public Economics*, 5, 391-474. Stiglitz, J. E. (2012). *The price of inequality: How today's divided society endangers our future*. W.W. Norton & Company. Van Parijs, P., & Vanderborght, Y. (2017). *Basic income: A radical proposal for a free society and a sane economy*. Harvard University Press. # A Tripartite Approach to Fiscal Reform: Analyzing the Economic Impact of a Flat Tax, Redistribution, and Consumption Tax Framework **Author: Lamar Wilson** ## Abstract **By Lamar Wilson** This white paper examines an alternative taxation framework characterized by three primary components: a uniform 15% flat tax on income, a redistribution mechanism, and a tiered consumption tax structure. The proposed model aims to stimulate economic growth while maintaining social equity through strategic fiscal policy interventions. This paper analyzes the theoretical underpinnings of this approach, its potential macroeconomic implications, distributional effects across income strata, and implementation challenges. The analysis suggests that while the proposed framework offers significant advantages in terms of simplicity and growth incentives, careful consideration must be given to revenue adequacy, wealth concentration effects, and long-term economic sustainability. ## 1. Introduction Taxation systems fundamentally shape economic incentive structures, income distribution, and government fiscal capacity. Contemporary tax regimes often reflect accumulated historical policy decisions rather than coherent economic theory, resulting in complex systems with varying degrees of progressivity, efficiency, and equity (Mirrlees et al., 2011). This paper examines a potential alternative taxation framework built upon three pillars: a uniform flat tax, redistribution mechanisms, and stratified consumption taxation. The theoretical foundation of this approach draws upon both supply-side economics, which emphasizes the importance of investment incentives, and demand-side considerations, which recognize the economic significance of broad-based consumption. By synthesizing these perspectives, the proposed framework attempts to create a self-reinforcing economic cycle wherein simplified taxation stimulates both investment and consumption. ## 2. Structural Components of the Proposed Framework ### 2.1 Uniform Flat Income Taxation The cornerstone of the proposed system is a uniform 15% tax rate applied to income. This component includes two key elements: - **Individual Taxation**: A 15% flat tax applied to gross income across all individual taxpayers, regardless of income level. This approach eliminates tax brackets, deductions, and exemptions that characterize progressive taxation systems. - **Business Taxation**: A parallel 15% flat tax on net business income (profits), allowing for business expense deductions while maintaining a uniform rate across business entities regardless of size, industry, or organizational structure. The flat tax component represents a significant departure from graduated or progressive taxation systems prevalent in many developed economies. This simplification potentially reduces compliance costs, eliminates bracket-based behavioral distortions, and creates uniform incentive structures across income levels (Hall & Rabushka, 2007). ### 2.2 Universal Redistribution Mechanism The second component involves the pooling and redistribution of tax revenue: - **Collection Aggregation**: All tax revenues from both individual and business taxation are consolidated into a unified fiscal pool. - **Equal Per Capita Distribution**: The aggregated tax revenue is redistributed on an equal per capita basis to all individuals within the jurisdiction, functioning as a universal basic income mechanism. This redistribution mechanism effectively creates a de facto progressive element within the overtly flat system, as redistribution amounts represent a larger percentage of total income for lower-income individuals compared to higher-income individuals (Van Parijs & Vanderborght, 2017). ### 2.3 Tiered Consumption Taxation The third component introduces a differentiated consumption tax structure: - **Essential Goods and Services**: A minimal 2% consumption tax applied to essential items including food, healthcare, housing, and utilities. - **Non-Essential and Luxury Items**: A higher consumption tax rate (suggested at 5% or greater) applied to discretionary purchases and luxury goods. This differentiated approach to consumption taxation acknowledges consumption patterns that vary across income levels, with lower-income households typically allocating a greater proportion of spending to essential goods (Lustig, 2018). ## 3. Economic Implications Analysis ### 3.1 Distributive Effects Across Income Levels #### 3.1.1 Lower-Income Households The model's impact on lower-income households involves several counterbalancing forces: - The 15% flat income tax represents a potentially higher nominal rate than many lower-income households currently face under progressive systems. - The universal redistribution component serves as a direct income supplement, with the amount received likely exceeding tax contributions for this demographic. - The 2% consumption tax on essentials introduces a modest additional cost on necessary expenditures. Net analysis suggests that lower-income households would likely experience a positive fiscal impact through this system, as the redistributive component would exceed their combined income and consumption tax obligations (Piketty & Saez, 2013). #### 3.1.2 Higher-Income Households For higher-income households, the framework produces different effects: - The 15% flat income tax rate typically represents a reduction from current progressive tax rates applied to higher income brackets. - The universal redistribution amount constitutes a proportionally smaller income supplement relative to total income. - Higher consumption taxes on luxury goods create a de facto progressive element based on discretionary spending patterns. The net impact on higher-income households would likely be a reduced overall tax burden compared to progressive systems, potentially increasing capital availability for investment (Auerbach & Hassett, 2015). ### 3.2 Macroeconomic Implications #### 3.2.1 Investment and Growth Effects The framework's reduced taxation on higher incomes and business profits theoretically increases capital availability for investment. This aligns with supply-side economic theories suggesting that lower marginal tax rates stimulate economic expansion through: - Increased business formation and expansion - Enhanced capital investment - Improved labor productivity through capital deepening - Potential innovation stimulation through retained earnings Empirical research on flat tax implementations in various jurisdictions provides mixed evidence regarding growth effects, with contextual factors playing significant roles in outcomes (Keen et al., 2008). #### 3.2.2 Demand Stability and Consumption Patterns The redistribution component creates a consumption floor that may enhance economic stability through: - Maintaining baseline consumer demand during economic downturns - Reducing consumption volatility across business cycles - Supporting broader-based consumption patterns - Creating demand-side support for business expansion This mechanism acknowledges the economic significance of broad-based consumption capacity alongside investment incentives (Stiglitz, 2012). #### 3.2.3 Labor Market Dynamics The simplified tax structure potentially influences labor market participation through: - Elimination of high marginal tax rates that may discourage additional work - Reduced tax-related work disincentives at lower income levels - Possible increased labor force participation due to simplified income-benefit calculations - Potential wage effects as businesses retain higher post-tax profits The framework's impact on labor markets would likely vary across skill levels, industries, and existing labor market institutions (Card & Krueger, 2015). ## 4. Implementation Challenges and Considerations ### 4.1 Fiscal Revenue Adequacy A primary challenge involves ensuring sufficient government revenue, particularly during the transition period: - The overall tax burden reduction (estimated at approximately 50% compared to current systems) creates potential revenue shortfalls. - Government spending obligations would require adjustment, postponement, or alternative funding mechanisms. - Transitional provisions may be necessary to align revenue reductions with spending adaptations. Potential solutions include phased implementation, temporary supplementary revenue sources, or deliberate acceleration of economic growth to expand the tax base (Auerbach, 2006). ### 4.2 Wealth Concentration Effects Despite redistribution mechanisms, the framework may influence wealth concentration dynamics: - Reduced taxation on higher incomes could accelerate capital accumulation among wealthy individuals. - Business owners might experience wealth growth exceeding redistribution effects. - Global investment patterns could divert economic benefits outside the domestic economy. Addressing these concerns might require calibration of the redistribution component or implementing complementary policies addressing wealth concentration (Piketty, 2014). ### 4.3 Long-Term Sustainability Considerations The framework's long-term viability depends on several factors: - Sustained economic growth sufficient to support government functions with reduced tax rates - Continued business investment in productive domestic activities rather than financial engineering - Maintenance of investment-consumption balance to prevent boom-bust cycles - Evolution of the system in response to changing economic conditions Supplementary policies supporting research and development, entrepreneurship, and domestic investment may be necessary to ensure the system's sustainability (Acemoglu & Robinson, 2012). ## 5. Comparative Cost-Benefit Analysis: Proposed System vs. Current Tax Structure ### 5.1 Compliance Cost Reduction The current U.S. tax system imposes substantial compliance costs on individuals and businesses that extend far beyond direct tax payments: - Americans spend approximately 6.5 billion hours annually on tax compliance activities (Taxpayer Advocate Service, 2022) - The monetary value of compliance time is estimated at $200-400 billion annually (Laffer et al., 2018) - Businesses spend an estimated $147 billion annually on tax compliance (Tax Foundation, 2021) - The Internal Revenue Service budget exceeds $13 billion annually for tax administration and enforcement The proposed flat tax system would dramatically reduce these costs through: - Elimination of complex deduction and credit calculations (estimated 90% reduction in form complexity) - Removal of recordkeeping requirements for numerous tax provisions - Significant reduction in tax planning expenses for both individuals and businesses - Decreased need for professional tax preparation services - Streamlined tax enforcement with fewer provisions to interpret and audit Quantitative analysis suggests that transitioning to the proposed system could reduce overall compliance costs by approximately 70-80%, representing annual savings of $140-320 billion to the U.S. economy (Greenberg, 2020). ### 5.2 Administrative Efficiency Gains The current tax administration infrastructure incurs substantial costs: - The IRS employs approximately 75,000 full-time equivalent positions - Tax litigation consumes significant judicial resources across multiple court systems - Regulatory development and guidance require extensive government resources - Tax enforcement costs represent approximately 35 cents per $100 collected The proposed system would generate administrative efficiencies through: - Simplified verification processes requiring fewer personnel - Reduced need for specialized tax rulings and interpretations - Lower audit costs due to straightforward compliance requirements - Streamlined distribution mechanisms leveraging existing payment systems Conservative estimates suggest administrative cost reductions of 50-60%, representing billions in government savings that could be redirected to essential services or deficit reduction. ### 5.3 Economic Efficiency Improvements Beyond direct compliance and administrative costs, the current system creates significant economic distortions: - Taxpayers make economic decisions influenced by tax considerations rather than underlying economic value - Complex provisions create market inefficiencies and misallocation of resources - High marginal rates discourage additional productive activity - International tax complexities influence global investment decisions The proposed system addresses these inefficiencies through: - Uniform treatment of income regardless of source - Elimination of tax-motivated transaction structures - Reduced incentives for artificial entity structures - Simplified international transactions with domestic reinvestment incentives Economic models suggest these efficiency improvements could increase GDP by 0.5-1.0% annually beyond direct compliance savings (Jorgenson & Yun, 2012). ### 5.4 Distributional Cost Analysis The current system's compliance burden falls disproportionately across income levels: - Lower-income taxpayers spend a higher percentage of their income on tax compliance - Small businesses face compliance costs estimated at $1,500-$4,000 per employee - Middle-income taxpayers navigate complex provisions with limited professional assistance - High-income taxpayers allocate substantial resources to tax planning and compliance The proposed system redistributes this burden by: - Equalizing compliance requirements across income levels - Substantially reducing small business administrative overhead - Eliminating the need for complex tax planning strategies - Providing transparent, predictable tax consequences for economic decisions This redistribution of compliance costs represents an additional progressive element beyond the direct redistribution component, with estimated financial benefits to lower and middle-income households of $300-500 annually in reduced compliance costs. ## 6. Conclusion The proposed tripartite taxation framework offers a conceptually coherent alternative to conventional progressive taxation systems. By combining flat income taxation with universal redistribution and differentiated consumption taxes, the approach attempts to simultaneously address supply-side investment incentives and demand-side consumption support. The theoretical analysis suggests potential advantages in terms of simplicity, economic growth stimulation, and maintenance of social safety net functions. However, significant implementation challenges exist regarding revenue adequacy, wealth concentration effects, and long-term economic sustainability. Further empirical research, potentially through regional pilot implementations or microsimulation modeling, would enhance understanding of the practical implications of this taxation approach. While the framework presents a promising theoretical model, its successful implementation would require careful calibration to specific economic contexts, thoughtful transition planning, and ongoing adjustment based on observed outcomes. ## References Acemoglu, D., & Robinson, J. A. (2012). *Why nations fail: The origins of power, prosperity, and poverty*. Crown Business. Greenberg, S. (2020). *Reforming the U.S. tax system: Evidence on economic growth and distribution*. American Enterprise Institute. Jorgenson, D. W., & Yun, K. Y. (2012). *Tax reform and the cost of capital*. Oxford University Press. Laffer, A. B., Moore, S., & Williams, J. (2018). *The wealth of states: How taxes, energy, and worker freedom change everything*. Wiley. Tax Foundation (2021). *The cost of tax compliance*. Fiscal Fact No. 512. Taxpayer Advocate Service (2022). *Annual report to Congress*. Internal Revenue Service. Auerbach, A. J. (2006). The choice between income and consumption taxes: A primer. *NBER Working Paper Series*. Auerbach, A. J., & Hassett, K. (2015). Capital taxation in the twenty-first century. *American Economic Review*, 105(5), 38-42. Card, D., & Krueger, A. B. (2015). *Myth and measurement: The new economics of the minimum wage*. Princeton University Press. Hall, R. E., & Rabushka, A. (2007). *The flat tax*. Hoover Institution Press. Keen, M., Kim, Y., & Varsano, R. (2008). The "flat tax(es)": Principles and experience. *International Tax and Public Finance*, 15(6), 712-751. Lustig, N. (2018). Fiscal policy, income redistribution and poverty reduction in low and middle income countries. *Commitment to Equity Handbook*. Mirrlees, J., Adam, S., Besley, T., Blundell, R., Bond, S., Chote, R., Gammie, M., Johnson, P., Myles, G., & Poterba, J. (2011). *Tax by design*. Oxford University Press. Piketty, T. (2014). *Capital in the twenty-first century*. Harvard University Press. Piketty, T., & Saez, E. (2013). Optimal labor income taxation. *Handbook of Public Economics*, 5, 391-474. Stiglitz, J. E. (2012). *The price of inequality: How today's divided society endangers our future*. W.W. Norton & Company. Van Parijs, P., & Vanderborght, Y. (2017). *Basic income: A radical proposal for a free society and a sane economy*. Harvard University Press. @ 6389be64:ef439d32
2025-03-05 21:18:52Carbon is a "Long-Tail" asset: the residual earnings that come from an asset after it has had its initial market impact. The Carbon Cascade converts labile into recalcitrant carbon. During transformation power is generated and lands restored. Total production of biomass per annum is 100 billion tons of carbon and at $500 to $2,000 per ton of biochar that's $100 trillion of potential carbon trading on the open market. (fanciful to be sure) originally posted at https://stacker.news/items/904996
@ 6389be64:ef439d32
2025-03-05 21:18:52Carbon is a "Long-Tail" asset: the residual earnings that come from an asset after it has had its initial market impact. The Carbon Cascade converts labile into recalcitrant carbon. During transformation power is generated and lands restored. Total production of biomass per annum is 100 billion tons of carbon and at $500 to $2,000 per ton of biochar that's $100 trillion of potential carbon trading on the open market. (fanciful to be sure) originally posted at https://stacker.news/items/904996 @ 05933d87:81bac46e
2025-03-05 20:17:49A few months ago, an Uber driver alerted me to [the presence of his rival](https://stacker.news/items/687682/r/k00b?commentId=688882). By that point, [Waymo had been testing in Austin](https://waymo.com/blog/2023/08/waymo-one-heads-to-austin/) for over a year. I hid my excitement during the ride but I applied as a beta tester, noting my belonging to the demographics a PM might test for. My application went ignored until, huzzah, Waymo sent me an email yesterday announcing [their self-driving cars are available directly through Uber in Austin](https://waymo.com/waymo-on-uber/).  I configured my allegiance to our new overlords swearing in on my screened sandwich of silicon. Without willing it, and having forgot my new religion, I woke earlier than planned today and hailed a ride. The app spoke to me, "if you wait 3 minutes longer, we'll send you a car without a driver." For five minutes, I watched a car but not a driver move in the direction of me and my screen. The ride was nice. I didn't have to theatrically rush to a waiting human. There was less social weirdness than I would normally sit with on a ride. I could inspect the car without risking the driver sense that I'm inspecting them. The car couldn't look at me buffering, deciphering if I am homeless or merely look it. I got to pick my own music. I got to watch people un-contacted by Waymo watch the car.  But ... it drove a lot more like a robot driving a car than a human driving a car. It pumped the brakes a few times as we passed weirdly parked cars uncertain (apparently) if the car might move into our lane. Once it signaled that we were headed into oncoming traffic as a street widened from one lane to two. Worst of all, it dropped me off near an anomalous stretch of sidewalk where my door opened to a wall, and if I were to climb and get out the other side, I'd arrive in the middle lane of a busy street. Trapped, I pinched myself through the door and, like Laura Croft, navigated the road's edge to a sidewalk.  tbh I'm still excited for my next Waymo ride. I'll just choose a different drop-off address. originally posted at https://stacker.news/items/904830
@ 05933d87:81bac46e
2025-03-05 20:17:49A few months ago, an Uber driver alerted me to [the presence of his rival](https://stacker.news/items/687682/r/k00b?commentId=688882). By that point, [Waymo had been testing in Austin](https://waymo.com/blog/2023/08/waymo-one-heads-to-austin/) for over a year. I hid my excitement during the ride but I applied as a beta tester, noting my belonging to the demographics a PM might test for. My application went ignored until, huzzah, Waymo sent me an email yesterday announcing [their self-driving cars are available directly through Uber in Austin](https://waymo.com/waymo-on-uber/).  I configured my allegiance to our new overlords swearing in on my screened sandwich of silicon. Without willing it, and having forgot my new religion, I woke earlier than planned today and hailed a ride. The app spoke to me, "if you wait 3 minutes longer, we'll send you a car without a driver." For five minutes, I watched a car but not a driver move in the direction of me and my screen. The ride was nice. I didn't have to theatrically rush to a waiting human. There was less social weirdness than I would normally sit with on a ride. I could inspect the car without risking the driver sense that I'm inspecting them. The car couldn't look at me buffering, deciphering if I am homeless or merely look it. I got to pick my own music. I got to watch people un-contacted by Waymo watch the car.  But ... it drove a lot more like a robot driving a car than a human driving a car. It pumped the brakes a few times as we passed weirdly parked cars uncertain (apparently) if the car might move into our lane. Once it signaled that we were headed into oncoming traffic as a street widened from one lane to two. Worst of all, it dropped me off near an anomalous stretch of sidewalk where my door opened to a wall, and if I were to climb and get out the other side, I'd arrive in the middle lane of a busy street. Trapped, I pinched myself through the door and, like Laura Croft, navigated the road's edge to a sidewalk.  tbh I'm still excited for my next Waymo ride. I'll just choose a different drop-off address. originally posted at https://stacker.news/items/904830 @ 2e8970de:63345c7a
2025-03-05 19:50:10 > It leads to fast, and massive weight loss by not just suppressing appetite, but also by upregulating metabolism. https://www.nejm.org/doi/full/10.1056/NEJMoa2301972 originally posted at https://stacker.news/items/904851
@ 2e8970de:63345c7a
2025-03-05 19:50:10 > It leads to fast, and massive weight loss by not just suppressing appetite, but also by upregulating metabolism. https://www.nejm.org/doi/full/10.1056/NEJMoa2301972 originally posted at https://stacker.news/items/904851 @ 4925ea33:025410d8
2025-03-05 19:44:37De acordo com a Resolução 03/25 do Conselho Federal de Farmácia a Aromaterapia é uma prática terapêutica que utiliza as propriedades dos óleos essenciais para restaurar o equilíbrio e a harmonia do organismo, promovendo a saúde física, mental e emocional. Essa técnica baseia-se no uso dos compostos aromáticos naturais extraídos das plantas para estimular respostas neurológicas e bioquímicas no corpo. Os óleos essenciais atuam diretamente no sistema límbico, região do cérebro responsável pelas emoções, memórias e comportamentos. Mas seus benefícios vão muito além do bem-estar emocional! Eles possuem propriedades terapêuticas únicas, podendo atuar como cicatrizantes, antifúngicos, antibacterianos, anti-inflamatórios e até auxiliares no alívio de dores e tensões musculares. Além da inalação, os óleos podem ser aplicados topicamente, sendo absorvidos pela pele e interagindo com o organismo de maneira profunda e eficaz. No entanto, é importante lembrar que os óleos essenciais são altamente concentrados e contêm substâncias que podem causar alergias ou irritações se usados de forma inadequada. Por isso, é essencial buscar orientação de um profissional qualificado para garantir um tratamento seguro e eficaz. **Quer saber como a Aromaterapia pode transformar seu bem-estar? Agende uma consulta comigo e descubra os benefícios personalizados para você**.
@ 4925ea33:025410d8
2025-03-05 19:44:37De acordo com a Resolução 03/25 do Conselho Federal de Farmácia a Aromaterapia é uma prática terapêutica que utiliza as propriedades dos óleos essenciais para restaurar o equilíbrio e a harmonia do organismo, promovendo a saúde física, mental e emocional. Essa técnica baseia-se no uso dos compostos aromáticos naturais extraídos das plantas para estimular respostas neurológicas e bioquímicas no corpo. Os óleos essenciais atuam diretamente no sistema límbico, região do cérebro responsável pelas emoções, memórias e comportamentos. Mas seus benefícios vão muito além do bem-estar emocional! Eles possuem propriedades terapêuticas únicas, podendo atuar como cicatrizantes, antifúngicos, antibacterianos, anti-inflamatórios e até auxiliares no alívio de dores e tensões musculares. Além da inalação, os óleos podem ser aplicados topicamente, sendo absorvidos pela pele e interagindo com o organismo de maneira profunda e eficaz. No entanto, é importante lembrar que os óleos essenciais são altamente concentrados e contêm substâncias que podem causar alergias ou irritações se usados de forma inadequada. Por isso, é essencial buscar orientação de um profissional qualificado para garantir um tratamento seguro e eficaz. **Quer saber como a Aromaterapia pode transformar seu bem-estar? Agende uma consulta comigo e descubra os benefícios personalizados para você**. @ b4403b24:83542d4e
2025-03-05 19:18:39  I can't believe so many shitcoiners are invited to attend 🫣 originally posted at https://stacker.news/items/904818
@ b4403b24:83542d4e
2025-03-05 19:18:39  I can't believe so many shitcoiners are invited to attend 🫣 originally posted at https://stacker.news/items/904818 @ 97c70a44:ad98e322
2025-03-05 18:09:05So you've decided to join nostr! Some wide-eyed fanatic has convinced you that the "sun shines every day on the birds and the bees and the cigarette trees" in a magical land of decentralized, censorship-resistant freedom of speech - and it's waiting just over the next hill. But your experience has not been all you hoped. Before you've even had a chance to upload your AI-generated cyberpunk avatar or make up exploit codenames for your pseudonym's bio, you've been confronted with a new concept that has left you completely nonplussed. It doesn't help that this new idea might be called by any number of strange names. You may have been asked to "paste your nsec", "generate a private key", "enter your seed words", "connect with a bunker", "sign in with extension", or even "generate entropy". Sorry about that. All these terms are really referring to one concept under many different names: that of "cryptographic identity". Now, you may have noticed that I just introduced yet another new term which explains exactly nothing. You're absolutely correct. And now I'm going to proceed to ignore your complaints and talk about something completely different. But bear with me, because the juice is worth the squeeze. # Identity What is identity? There are many philosophical, political, or technical answers to this question, but for our purposes it's probably best to think of it this way: > Identity is the essence of a thing. Identity separates one thing from all others, and is itself indivisible. This definition has three parts: - Identity is "essential": a thing can change, but its identity cannot. I might re-paint my house, replace its components, sell it, or even burn it down, but its identity as something that can be referred to - "this house" - is durable, even outside the boundaries of its own physical existence. - Identity is a unit: you can't break an identity into multiple parts. A thing might be _composed_ of multiple parts, but that's only incidental to the identity of a thing, which is a _concept_, not a material thing. - Identity is distinct: identity is what separates one thing from all others - the concept of an apple can't be mixed with that of an orange; the two ideas are distinct. In the same way, a single concrete apple is distinct in identity from another - even if the component parts of the apple decompose into compost used to grow more apples. Identity is not a physical thing, but a metaphysical thing. Or, in simpler terms, identity is a "concept". I (or someone more qualified) could at this point launch into a Scholastic tangent on what "is" is, but that is, fortunately, not necessary here. The kind of identities I want to focus on here are not our _actual_ identities as people, but entirely _fictional_ identities that we use to extend our agency into the digital world. Think of it this way - your bank login does not represent _you_ as a complete person. It only represents the _access granted to you_ by the bank. This access is in fact an _entirely new identity_ that has been associated with you, and is limited in what it's useful for. Other examples of fictional identities include: - The country you live in - Your social media persona - Your mortgage - Geographical coordinates - A moment in time - A chess piece Some of these identites are inert, for example points in space and time. Other identies have agency and so are able to act in the world - even as fictional concepts. In order to do this, they must "authenticate" themselves (which means "to prove they are real"), and act within a system of established rules. For example, your D&D character exists only within the collective fiction of your D&D group, and can do anything the rules say. Its identity is authenticated simply by your claim as a member of the group that your character in fact exists. Similarly, a lawyer must prove they are a member of the Bar Association before they are allowed to practice law within that collective fiction. "Cryptographic identity" is simply another way of authenticating a fictional identity within a given system. As we'll see, it has some interesting attributes that set it apart from things like a library card or your latitude and longitude. Before we get there though, let's look in more detail at how identities are authenticated. # Certificates Merriam-Webster defines the verb "certify" as meaning "to attest authoritatively". A "certificate" is just a fancy way of saying "because I said so". Certificates are issued by a "certificate authority", someone who has the authority to "say so". Examples include your boss, your mom, or the Pope. This method of authentication is how almost every institution authenticates the people who associate with it. Colleges issue student ID cards, governments issue passports, and websites allow you to "register an account". In every case mentioned above, the "authority" creates a closed system in which a document (aka a "certificate") is issued which serves as a claim to a given identity. When someone wants to access some privileged service, location, or information, they present their certificate. The authority then validates it and grants or denies access. In the case of an international airport, the certificate is a little book printed with fancy inks. In the case of a login page, the certificate is a username and password combination. This pattern for authentication is ubiquitous, and has some very important implications. First of all, certified authentication implies that the issuer of the certificate has the right to _exclusive control_ of any identity it issues. This identity can be revoked at any time, or its permissions may change. Your social credit score may drop arbitrarily, or money might disappear from your account. When dealing with certificate authorities, you have no inherent rights. Second, certified authentication depends on the certificate authority continuing to exist. If you store your stuff at a storage facility but the company running it goes out of business, your stuff might disappear along with it. Usually, authentication via certificate authority works pretty well, since an appeal can always be made to a higher authority (nature, God, the government, etc). Authorities also can't generally dictate their terms with impunity without losing their customers, alienating their constituents, or provoking revolt. But it's also true that certification by authority creates an incentive structure that frequently leads to abuse - arbitrary deplatforming is increasingly common, and the bigger the certificate authority, the less recourse the certificate holder (or "subject") has. Certificates also put the issuer in a position to intermediate relationships that wouldn't otherwise be subject to their authority. This might take the form of selling user attention to advertisers, taking a cut of financial transactions, or selling surveillance data to third parties. Proliferation of certificate authorities is not a solution to these problems. Websites and apps frequently often offer multiple "social sign-in" options, allowing their users to choose which certificate authority to appeal to. But this only piles more value into the social platform that issues the certificate - not only can Google shut down your email inbox, they can revoke your ability to log in to every website you used their identity provider to get into. In every case, certificate issuance results in an asymmetrical power dynamic, where the issuer is able to exert significant control over the certificate holder, even in areas unrelated to the original pretext for the relationship between parties. # Self-Certification But what if we could reverse this power dynamic? What if individuals could issue their own certificates and force institutions to accept them?  Ron Swanson's counterexample notwithstanding, there's a reason I can't simply write myself a parking permit and slip it under the windshield wiper. Questions about voluntary submission to legitimate authorities aside, the fact is that we don't have the power to act without impunity - just like any other certificate authority, we have to prove our claims either by the exercise of raw power or by appeal to a higher authority. So the question becomes: which higher authority can we appeal to in order to issue our own certificates within a given system of identity? The obvious answer here is to go straight to the top and ask God himself to back our claim to self-sovereignty. However, that's not how he normally works - there's a reason they call direct acts of God "miracles". In fact, Romans 13:1 explicitly says that "the authorities that exist have been appointed by God". God has structured the universe in such a way that we must appeal to the deputies he has put in place to govern various parts of the world. Another tempting appeal might be to nature - i.e. the material world. This is the realm in which we most frequently have the experience of "self-authenticating" identities. For example, a gold coin can be authenticated by biting it or by burning it with acid. If it quacks like a duck, walks like a duck, and looks like a duck, then it probably is a duck. In most cases however, the ability to authenticate using physical claims depends on physical access, and so appeals to physical reality have major limitations when it comes to the digital world. Captchas, selfies and other similar tricks are often used to bridge the physical world into the digital, but these are increasingly easy to forge, and hard to verify. There are exceptions to this rule - an example of self-certification that makes its appeal to the physical world is that of a signature. Signatures are hard to forge - an incredible amount of data is encoded in physical signatures, from strength, to illnesses, to upbringing, to [personality](https://en.wikipedia.org/wiki/Graphology). These can even be scanned and used within the digital world as well. Even today, most contracts are sealed with some simulacrum of a physical signature. Of course, this custom is quickly becoming a mere historical curiosity, since the very act of digitizing a signature makes it trivially forgeable. So: transcendent reality is too remote to subtantiate our claims, and the material world is too limited to work within the world of information. There is another aspect of reality remaining that we might appeal to: information itself. Physical signatures authenticate physical identities by encoding unique physical data into an easily recognizable artifact. To transpose this idea to the realm of information, a "digital signature" might authenticate "digital identities" by encoding unique "digital data" into an easily recognizable artifact. Unfortunately, in the digital world we have the additional challenge that the artifact itself can be copied, undermining any claim to legitimacy. We need something that can be easily verified _and unforgeable_. # Digital Signatures In fact such a thing does exist, but calling it a "digital signature" obscures more than it reveals. We might just as well call the thing we're looking for a "digital fingerprint", or a "digital electroencephalogram". Just keep that in mind as we work our way towards defining the term - we are not looking for something _looks like a physical signature_, but for something that _does the same thing as_ a physical signature, in that it allows us to issue ourselves a credential that must be accepted by others by encoding privileged information into a recognizable, unforgeable artifact. With that, let's get into the weeds. An important idea in computer science is that of a "function". A function is a sort of information machine that converts data from one form to another. One example is the idea of "incrementing" a number. If you increment 1, you get 2. If you increment 2, you get 3. Incrementing can be reversed, by creating a complementary function that instead subtracts 1 from a number. A "one-way function" is a function that can't be reversed. A good example of a one-way function is integer rounding. If you round a number and get `5`, what number did you begin with? It's impossible to know - 5.1, 4.81, 5.332794, in fact an infinite number of numbers can be rounded to the number `5`. These numbers can also be infinitely long - for example rounding PI to the nearest integer results in the number `3`. A real-life example of a useful one-way function is `sha256`. This function is a member of a family of one-way functions called "hash functions". You can feed as much data as you like into `sha256`, and you will always get 256 bits of information out. Hash functions are especially useful because collisions between outputs are very rare - even if you change a single bit in a huge pile of data, you're almost certainly going to get a different output. Taking this a step further, there is a whole family of cryptographic one-way "trapdoor" functions that act similarly to hash functions, but which maintain a specific mathematical relationship between the input and the output which allows the input/output pair to be used in a variety of useful applications. For example, in Elliptic Curve Cryptography, scalar multiplication on an elliptic curve is used to derive the output. "Ok", you say, "that's all completely clear and lucidly explained" (thank you). "But what goes _into_ the function?" You might expect that because of our analogy to physical signatures we would have to gather an incredible amount of digital information to cram into our cryptographic trapdoor function, mashing together bank statements, a record of our heartbeat, brain waves and cellular respiration. Well, we _could_ do it that way (maybe), but there's actually a _much_ simpler solution. Let's play a quick game. What number am I thinking of? Wrong, it's 82,749,283,929,834. Good guess though. The reason we use signatures to authenticate our identity in the physical world is not because they're backed by a lot of implicit physical information, but because they're hard to forge and easy to validate. Even so, there is a lot of variation in a single person's signature, even from one moment to the next. Trapdoor functions solve the validation problem - it's trivially simple to compare one 256-bit number to another. And randomness solves the problem of forgeability. Now, randomness (A.K.A. "entropy") is actually kind of hard to generate. Random numbers that don't have enough "noise" in them are known as "pseudo-random numbers", and are weirdly easy to guess. This is why Cloudflare uses a video stream of their [giant wall of lava lamps](https://blog.cloudflare.com/randomness-101-lavarand-in-production/) to feed the random number generator that powers their CDN. For our purposes though, we can just imagine that our random numbers come from rolling a bunch of dice. To recap, we can get a digital equivalent of a physical signature (or fingerprint, etc) by 1. coming up with a random number, and 2. feeding it into our chosen trapdoor function. The random number is called the "private" part. The output of the trapdoor function is called the "public" part. These two halves are often called "keys", hence the terms "public key" and "private key". And now we come full circle - remember about 37 years ago when I introduced the term "cryptographic identity"? Well, we've finally arrived at the point where I explain what that actually is. A "cryptographic identity" is _identified_ by a public key, and _authenticated_ by the ability to prove that you know the private key. Notice that I didn't say "authenticated by the private key". If you had to reveal the private key in order to prove you know it, you could only authenticate a public key once without losing exclusive control of the key. But cryptographic identities can be authenticated any number of times because the certification is an _algorithm_ that only someone who knows the private key can execute. This is the super power that trapdoor functions have that hash functions don't. Within certain cryptosystems, it is possible to mix additional data with your private key to get yet another number in such a way that someone else who only knows the public key can _prove_ that you know the private key. For example, if my secret number is `12`, and someone tells me the number `37`, I can "combine" the two by adding them together and returning the number `49`. This "proves" that my secret number is `12`. Of course, addition is not a trapdoor function, so it's trivially easy to reverse, which is why cryptography is its own field of knowledge. # What's it for? If I haven't completely lost you yet, you might be wondering why this matters. Who cares if I can prove that I made up a random number? To answer this, let's consider a simple example: that of public social media posts. Most social media platforms function by issuing credentials and verifying them based on their internal database. When you log in to your Twitter (ok, fine, X) account, you provide X with a phone number (or email) and password. X compares these records to the ones stored in the database when you created your account, and if they match they let you "log in" by issuing yet another credential, called a "session key". Next, when you "say" something on X, you pass along your session key and your tweet to X's servers. They check that the session key is legit, and if it is they associate your tweet with your account's identity. Later, when someone wants to see the tweet, X vouches for the fact that you created it by saying "trust me" and displaying your name next to the tweet. In other words, X creates and controls your identity, but they let you use it as long as you can prove that you know the secret that you agreed on when you registered (by giving it to them every time). Now pretend that X gets bought by someone _even more evil_ than Elon Musk (if such a thing can be imagined). The new owner now has the ability to control _your_ identity, potentially making it say things that you didn't actually say. Someone could be completely banned from the platform, but their account could be made to continue saying whatever the owner of the platform wanted. In reality, such a breach of trust would quickly result in a complete loss of credibility for the platform, which is why this kind of thing doesn't happen (at least, not that we know of). But there are other ways of exploiting this system, most notably by censoring speech. As often happens, platforms are able to confiscate user identities, leaving the tenant no recourse except to appeal to the platform itself (or the government, but that doesn't seem to happen for some reason - probably due to some legalese in social platforms' terms of use). The user has to start completely from scratch, either on the same platform or another. Now suppose that when you signed up for X instead of simply telling X your password you made up a random number and provided a cryptographic proof to X along with your public key. When you're ready to tweet (there's no need to issue a session key, or even to store your public key in their database) you would again prove your ownership of that key with a new piece of data. X could then publish that tweet or not, along with the same proof you provided that it really came from you. What X _can't_ do in this system is pretend you said something you didn't, because they _don't know your private key_. X also wouldn't be able to deplatform you as effectively either. While they could choose to ban you from their website and refuse to serve your tweets, they don't control your identity. There's nothing they can do to prevent you from re-using it on another platform. Plus, if the system was set up in such a way that other users followed your key instead of an ID made up by X, you could switch platforms and _keep your followers_. In the same way, it would also be possible to keep a copy of all your tweets in your own database, since their authenticity is determined by _your_ digital signature, not X's "because I say so". This new power is not just limited to social media either. Here are some other examples of ways that self-issued cryptographic identites transform the power dynamic inherent in digital platforms: - Banks sometimes freeze accounts or confiscate funds. If your money was stored in a system based on self-issued cryptographic keys rather than custodians, banks would not be able to keep you from accessing or moving your funds. This system exists, and it's called [bitcoin](https://bitcoin.rocks/). - Identity theft happens when your identifying information is stolen and used to take out a loan in your name, and without your consent. The reason this is so common is because your credentials are not cryptographic - your name, address, and social security number can only be authenticated by being shared, and they are shared so often and with so many counterparties that they frequently end up in data breaches. If credit checks were authenticated by self-issued cryptographic keys, identity theft would cease to exist (unless your private key itself got stolen). - Cryptographic keys allow credential issuers to protect their subjects' privacy better too. Instead of showing your ID (including your home address, birth date, height, weight, etc), the DMV could sign a message asserting that the holder of a given public key indeed over 21. The liquor store could then validate that claim, and your ownership of the named key, without knowing anything more about you. [Zero-knowledge](https://en.wikipedia.org/wiki/Non-interactive_zero-knowledge_proof) proofs take this a step further. In each of these cases, the interests of the property owner, loan seeker, or customer are elevated over the interests of those who might seek to control their assets, exploit their hard work, or surveil their activity. Just as with personal privacy, freedom of speech, and Second Amendment rights the individual case is rarely decisive, but in the aggregate realigned incentives can tip the scale in favor of freedom. # Objections Now, there are some drawbacks to digital signatures. Systems that rely on digital signatures are frequently less forgiving of errors than their custodial counterparts, and many of their strengths have corresponding weaknesses. Part of this is because people haven't yet developed an intuition for how to use cryptographic identities, and the tools for managing them are still being designed. Other aspects can be mitigated through judicious use of keys fit to the problems they are being used to solve. Below I'll articulate some of these concerns, and explore ways in which they might be mitigated over time. ## Key Storage Keeping secrets is hard. "A lie can travel halfway around the world before the truth can get its boots on", and the same goes for gossip. Key storage has become increasingly important as more of our lives move online, to the extent that password managers have become almost a requirement for keeping track of our digital lives. But even with good password management, credentials frequently end up for sale on the dark web as a consequence of poorly secured infrastructure. Apart from the fact that all of this is an argument _for_ cryptographic identities (since keys are shared with far fewer parties), it's also true that the danger of losing a cryptographic key is severe, especially if that key is used in multiple places. Instead of hackers stealing your Facebook password, they might end up with access to all your other social media accounts too! Keys should be treated with the utmost care. Using password managers is a good start, but very valuable keys should be stored even more securely - for example in a [hardware signing device](https://nostrsigningdevice.com/). This is a hassle, and something additional to learn, but is an indispensable part of taking advantage of the benefits associated with cryptographic identity. There are ways to lessen the impact of lost or stolen secrets, however. Lots of different techniques exist for structuring key systems in such a way that keys can be protected, invalidated, or limited. Here are a few: - [Hierarchical Deterministic Keys](https://www.ietf.org/archive/id/draft-dijkhuis-cfrg-hdkeys-02.html) allow for the creation of a single root key from which multiple child keys can be generated. These keys are hard to link to the parent, which provides additional privacy, but this link can also be proven when necessary. One limitation is that the identity system has to be designed with HD keys in mind. - [Key Rotation](https://crypto.stackexchange.com/questions/41796/whats-the-purpose-of-key-rotation) allows keys to become expendable. Additional credentials might be attached to a key, allowing the holder to prove they have the right to rotate the key. Social attestations can help with the process as well if the key is embedded in a web of trust. - Remote Signing is a technique for storing a key on one device, but using it on another. This might take the form of signing using a hardware wallet and transferring an SD card to your computer for broadcasting, or using a mobile app like [Amber](https://github.com/greenart7c3/Amber) to manage sessions with different applications. - [Key](https://github.com/coracle-social/promenade/tree/master) [sharding](https://www.frostr.org/) takes this to another level by breaking a single key into multiple pieces and storing them separately. A coordinator can then be used to collaboratively sign messages without sharing key material. This dramatically reduces the ability of an attacker to steal a complete key. ## Multi-Factor Authentication One method for helping users secure their accounts that is becoming increasingly common is "multi-factor authentication". Instead of just providing your email and password, platforms send a one-time use code to your phone number or email, or use "time-based one time passwords" which are stored in a password manager or on a hardware device. Again, MFA is a solution to a problem inherent in account-based authentication which would not be nearly so prevalent in a cryptographic identity system. Still, theft of keys does happen, and so MFA would be an important improvement - if not for an extra layer of authentication, then as a basis for key rotation. In a sense, MFA is already being researched - key shards is one way of creating multiple credentials from a single key. However, this doesn't address the issue of key rotation, especially when an identity is tied to the public key that corresponds to a given private key. There are two possible solutions to this problem: - Introduce a naming system. This would allow identities to use a durable name, assigning it to different keys over time. The downside is that this would require the introduction of either centralized naming authorities (back to the old model), or a blockchain in order to solve [Zooko's trilemma](https://en.wikipedia.org/wiki/Zooko%27s_triangle). - Establish a chain of keys. This would require a given key to name a successor key in advance and self-invalidate, or some other process like social recovery to invalidate an old key and assign the identity to a new one. This also would significantly increase the complexity of validating messages and associating them with a given identity. Both solutions are workable, but introduce a lot of complexity that could cause more trouble than it's worth, depending on the identity system we're talking about. ## Surveillance One of the nice qualities that systems based on cryptographic identities have is that digitally signed data can be passed through any number of untrusted systems and emerge intact. This ability to resist tampering makes it possible to broadcast signed data more widely than would otherwise be the case in a system that relies on a custodian to authenticate information. The downside of this is that more untrusted systems have access to data. And if information is broadcast publicly, anyone can get access to it. This problem is compounded by re-use of cryptographic identities across multiple contexts. A benefit of self-issued credentials is that it becomes possible to bring everything attached to your identity with you, including social context and attached credentials. This is convenient and can be quite powerful, but it also means that more context is attached to your activity, making it easier to infer information about you for advertising or surveillance purposes. This is dangerously close to the dystopian ideal of a "Digital ID". The best way to deal with this risk is to consider identity re-use an option to be used when desirable, but to default to creating a new key for every identity you create. This is no worse than the status quo, and it makes room for the ability to link identities when desired. Another possible approach to this problem is to avoid broadcasting signed data when possible. This could be done by obscuring your cryptographic identity when data is served from a database, or by encrypting your signed data in order to selectively share it with named counterparties. Still, this is a real risk, and should be kept in mind when designing and using systems based on cryptographic identity. If you'd like to read more about this, please see [this blog post](https://habla.news/u/hodlbod@coracle.social/1687802006398). # Making Keys Usable You might be tempted to look at that list of trade-offs and get the sense that cryptographic identity is not for mere mortals. Key management is hard, and footguns abound - but there is a way forward. With [nostr](https://nostr.com/), some new things are happening in the world of key management that have never really happened before. Plenty of work over the last 30 years has gone into making key management tractable, but none have really been widely adopted. The reason for this is simple: network effect. Many of these older key systems only applied the thinnest veneer of humanity over keys. But an identity is much richer than a mere label. Having a real name, social connections, and a corpus of work to attach to a key creates a system of keys that _humans care about_. By bootstrapping key management within a social context, nostr ensures that the payoff of key management is worth the learning curve. Not only is social engagement a strong incentive to get off the ground, people already on the network are eager to help you get past any roadblocks you might face. So if I could offer an action item: give nostr a try today. Whether you're in it for the people and their values, or you just want to experiment with cryptographic identity, nostr is a great place to start. For a quick introduction and to securely generate keys, visit [njump.me](https://njump.me/). Thanks for taking the time to read this post. I hope it's been helpful, and I can't wait to see you on nostr!
@ 97c70a44:ad98e322
2025-03-05 18:09:05So you've decided to join nostr! Some wide-eyed fanatic has convinced you that the "sun shines every day on the birds and the bees and the cigarette trees" in a magical land of decentralized, censorship-resistant freedom of speech - and it's waiting just over the next hill. But your experience has not been all you hoped. Before you've even had a chance to upload your AI-generated cyberpunk avatar or make up exploit codenames for your pseudonym's bio, you've been confronted with a new concept that has left you completely nonplussed. It doesn't help that this new idea might be called by any number of strange names. You may have been asked to "paste your nsec", "generate a private key", "enter your seed words", "connect with a bunker", "sign in with extension", or even "generate entropy". Sorry about that. All these terms are really referring to one concept under many different names: that of "cryptographic identity". Now, you may have noticed that I just introduced yet another new term which explains exactly nothing. You're absolutely correct. And now I'm going to proceed to ignore your complaints and talk about something completely different. But bear with me, because the juice is worth the squeeze. # Identity What is identity? There are many philosophical, political, or technical answers to this question, but for our purposes it's probably best to think of it this way: > Identity is the essence of a thing. Identity separates one thing from all others, and is itself indivisible. This definition has three parts: - Identity is "essential": a thing can change, but its identity cannot. I might re-paint my house, replace its components, sell it, or even burn it down, but its identity as something that can be referred to - "this house" - is durable, even outside the boundaries of its own physical existence. - Identity is a unit: you can't break an identity into multiple parts. A thing might be _composed_ of multiple parts, but that's only incidental to the identity of a thing, which is a _concept_, not a material thing. - Identity is distinct: identity is what separates one thing from all others - the concept of an apple can't be mixed with that of an orange; the two ideas are distinct. In the same way, a single concrete apple is distinct in identity from another - even if the component parts of the apple decompose into compost used to grow more apples. Identity is not a physical thing, but a metaphysical thing. Or, in simpler terms, identity is a "concept". I (or someone more qualified) could at this point launch into a Scholastic tangent on what "is" is, but that is, fortunately, not necessary here. The kind of identities I want to focus on here are not our _actual_ identities as people, but entirely _fictional_ identities that we use to extend our agency into the digital world. Think of it this way - your bank login does not represent _you_ as a complete person. It only represents the _access granted to you_ by the bank. This access is in fact an _entirely new identity_ that has been associated with you, and is limited in what it's useful for. Other examples of fictional identities include: - The country you live in - Your social media persona - Your mortgage - Geographical coordinates - A moment in time - A chess piece Some of these identites are inert, for example points in space and time. Other identies have agency and so are able to act in the world - even as fictional concepts. In order to do this, they must "authenticate" themselves (which means "to prove they are real"), and act within a system of established rules. For example, your D&D character exists only within the collective fiction of your D&D group, and can do anything the rules say. Its identity is authenticated simply by your claim as a member of the group that your character in fact exists. Similarly, a lawyer must prove they are a member of the Bar Association before they are allowed to practice law within that collective fiction. "Cryptographic identity" is simply another way of authenticating a fictional identity within a given system. As we'll see, it has some interesting attributes that set it apart from things like a library card or your latitude and longitude. Before we get there though, let's look in more detail at how identities are authenticated. # Certificates Merriam-Webster defines the verb "certify" as meaning "to attest authoritatively". A "certificate" is just a fancy way of saying "because I said so". Certificates are issued by a "certificate authority", someone who has the authority to "say so". Examples include your boss, your mom, or the Pope. This method of authentication is how almost every institution authenticates the people who associate with it. Colleges issue student ID cards, governments issue passports, and websites allow you to "register an account". In every case mentioned above, the "authority" creates a closed system in which a document (aka a "certificate") is issued which serves as a claim to a given identity. When someone wants to access some privileged service, location, or information, they present their certificate. The authority then validates it and grants or denies access. In the case of an international airport, the certificate is a little book printed with fancy inks. In the case of a login page, the certificate is a username and password combination. This pattern for authentication is ubiquitous, and has some very important implications. First of all, certified authentication implies that the issuer of the certificate has the right to _exclusive control_ of any identity it issues. This identity can be revoked at any time, or its permissions may change. Your social credit score may drop arbitrarily, or money might disappear from your account. When dealing with certificate authorities, you have no inherent rights. Second, certified authentication depends on the certificate authority continuing to exist. If you store your stuff at a storage facility but the company running it goes out of business, your stuff might disappear along with it. Usually, authentication via certificate authority works pretty well, since an appeal can always be made to a higher authority (nature, God, the government, etc). Authorities also can't generally dictate their terms with impunity without losing their customers, alienating their constituents, or provoking revolt. But it's also true that certification by authority creates an incentive structure that frequently leads to abuse - arbitrary deplatforming is increasingly common, and the bigger the certificate authority, the less recourse the certificate holder (or "subject") has. Certificates also put the issuer in a position to intermediate relationships that wouldn't otherwise be subject to their authority. This might take the form of selling user attention to advertisers, taking a cut of financial transactions, or selling surveillance data to third parties. Proliferation of certificate authorities is not a solution to these problems. Websites and apps frequently often offer multiple "social sign-in" options, allowing their users to choose which certificate authority to appeal to. But this only piles more value into the social platform that issues the certificate - not only can Google shut down your email inbox, they can revoke your ability to log in to every website you used their identity provider to get into. In every case, certificate issuance results in an asymmetrical power dynamic, where the issuer is able to exert significant control over the certificate holder, even in areas unrelated to the original pretext for the relationship between parties. # Self-Certification But what if we could reverse this power dynamic? What if individuals could issue their own certificates and force institutions to accept them?  Ron Swanson's counterexample notwithstanding, there's a reason I can't simply write myself a parking permit and slip it under the windshield wiper. Questions about voluntary submission to legitimate authorities aside, the fact is that we don't have the power to act without impunity - just like any other certificate authority, we have to prove our claims either by the exercise of raw power or by appeal to a higher authority. So the question becomes: which higher authority can we appeal to in order to issue our own certificates within a given system of identity? The obvious answer here is to go straight to the top and ask God himself to back our claim to self-sovereignty. However, that's not how he normally works - there's a reason they call direct acts of God "miracles". In fact, Romans 13:1 explicitly says that "the authorities that exist have been appointed by God". God has structured the universe in such a way that we must appeal to the deputies he has put in place to govern various parts of the world. Another tempting appeal might be to nature - i.e. the material world. This is the realm in which we most frequently have the experience of "self-authenticating" identities. For example, a gold coin can be authenticated by biting it or by burning it with acid. If it quacks like a duck, walks like a duck, and looks like a duck, then it probably is a duck. In most cases however, the ability to authenticate using physical claims depends on physical access, and so appeals to physical reality have major limitations when it comes to the digital world. Captchas, selfies and other similar tricks are often used to bridge the physical world into the digital, but these are increasingly easy to forge, and hard to verify. There are exceptions to this rule - an example of self-certification that makes its appeal to the physical world is that of a signature. Signatures are hard to forge - an incredible amount of data is encoded in physical signatures, from strength, to illnesses, to upbringing, to [personality](https://en.wikipedia.org/wiki/Graphology). These can even be scanned and used within the digital world as well. Even today, most contracts are sealed with some simulacrum of a physical signature. Of course, this custom is quickly becoming a mere historical curiosity, since the very act of digitizing a signature makes it trivially forgeable. So: transcendent reality is too remote to subtantiate our claims, and the material world is too limited to work within the world of information. There is another aspect of reality remaining that we might appeal to: information itself. Physical signatures authenticate physical identities by encoding unique physical data into an easily recognizable artifact. To transpose this idea to the realm of information, a "digital signature" might authenticate "digital identities" by encoding unique "digital data" into an easily recognizable artifact. Unfortunately, in the digital world we have the additional challenge that the artifact itself can be copied, undermining any claim to legitimacy. We need something that can be easily verified _and unforgeable_. # Digital Signatures In fact such a thing does exist, but calling it a "digital signature" obscures more than it reveals. We might just as well call the thing we're looking for a "digital fingerprint", or a "digital electroencephalogram". Just keep that in mind as we work our way towards defining the term - we are not looking for something _looks like a physical signature_, but for something that _does the same thing as_ a physical signature, in that it allows us to issue ourselves a credential that must be accepted by others by encoding privileged information into a recognizable, unforgeable artifact. With that, let's get into the weeds. An important idea in computer science is that of a "function". A function is a sort of information machine that converts data from one form to another. One example is the idea of "incrementing" a number. If you increment 1, you get 2. If you increment 2, you get 3. Incrementing can be reversed, by creating a complementary function that instead subtracts 1 from a number. A "one-way function" is a function that can't be reversed. A good example of a one-way function is integer rounding. If you round a number and get `5`, what number did you begin with? It's impossible to know - 5.1, 4.81, 5.332794, in fact an infinite number of numbers can be rounded to the number `5`. These numbers can also be infinitely long - for example rounding PI to the nearest integer results in the number `3`. A real-life example of a useful one-way function is `sha256`. This function is a member of a family of one-way functions called "hash functions". You can feed as much data as you like into `sha256`, and you will always get 256 bits of information out. Hash functions are especially useful because collisions between outputs are very rare - even if you change a single bit in a huge pile of data, you're almost certainly going to get a different output. Taking this a step further, there is a whole family of cryptographic one-way "trapdoor" functions that act similarly to hash functions, but which maintain a specific mathematical relationship between the input and the output which allows the input/output pair to be used in a variety of useful applications. For example, in Elliptic Curve Cryptography, scalar multiplication on an elliptic curve is used to derive the output. "Ok", you say, "that's all completely clear and lucidly explained" (thank you). "But what goes _into_ the function?" You might expect that because of our analogy to physical signatures we would have to gather an incredible amount of digital information to cram into our cryptographic trapdoor function, mashing together bank statements, a record of our heartbeat, brain waves and cellular respiration. Well, we _could_ do it that way (maybe), but there's actually a _much_ simpler solution. Let's play a quick game. What number am I thinking of? Wrong, it's 82,749,283,929,834. Good guess though. The reason we use signatures to authenticate our identity in the physical world is not because they're backed by a lot of implicit physical information, but because they're hard to forge and easy to validate. Even so, there is a lot of variation in a single person's signature, even from one moment to the next. Trapdoor functions solve the validation problem - it's trivially simple to compare one 256-bit number to another. And randomness solves the problem of forgeability. Now, randomness (A.K.A. "entropy") is actually kind of hard to generate. Random numbers that don't have enough "noise" in them are known as "pseudo-random numbers", and are weirdly easy to guess. This is why Cloudflare uses a video stream of their [giant wall of lava lamps](https://blog.cloudflare.com/randomness-101-lavarand-in-production/) to feed the random number generator that powers their CDN. For our purposes though, we can just imagine that our random numbers come from rolling a bunch of dice. To recap, we can get a digital equivalent of a physical signature (or fingerprint, etc) by 1. coming up with a random number, and 2. feeding it into our chosen trapdoor function. The random number is called the "private" part. The output of the trapdoor function is called the "public" part. These two halves are often called "keys", hence the terms "public key" and "private key". And now we come full circle - remember about 37 years ago when I introduced the term "cryptographic identity"? Well, we've finally arrived at the point where I explain what that actually is. A "cryptographic identity" is _identified_ by a public key, and _authenticated_ by the ability to prove that you know the private key. Notice that I didn't say "authenticated by the private key". If you had to reveal the private key in order to prove you know it, you could only authenticate a public key once without losing exclusive control of the key. But cryptographic identities can be authenticated any number of times because the certification is an _algorithm_ that only someone who knows the private key can execute. This is the super power that trapdoor functions have that hash functions don't. Within certain cryptosystems, it is possible to mix additional data with your private key to get yet another number in such a way that someone else who only knows the public key can _prove_ that you know the private key. For example, if my secret number is `12`, and someone tells me the number `37`, I can "combine" the two by adding them together and returning the number `49`. This "proves" that my secret number is `12`. Of course, addition is not a trapdoor function, so it's trivially easy to reverse, which is why cryptography is its own field of knowledge. # What's it for? If I haven't completely lost you yet, you might be wondering why this matters. Who cares if I can prove that I made up a random number? To answer this, let's consider a simple example: that of public social media posts. Most social media platforms function by issuing credentials and verifying them based on their internal database. When you log in to your Twitter (ok, fine, X) account, you provide X with a phone number (or email) and password. X compares these records to the ones stored in the database when you created your account, and if they match they let you "log in" by issuing yet another credential, called a "session key". Next, when you "say" something on X, you pass along your session key and your tweet to X's servers. They check that the session key is legit, and if it is they associate your tweet with your account's identity. Later, when someone wants to see the tweet, X vouches for the fact that you created it by saying "trust me" and displaying your name next to the tweet. In other words, X creates and controls your identity, but they let you use it as long as you can prove that you know the secret that you agreed on when you registered (by giving it to them every time). Now pretend that X gets bought by someone _even more evil_ than Elon Musk (if such a thing can be imagined). The new owner now has the ability to control _your_ identity, potentially making it say things that you didn't actually say. Someone could be completely banned from the platform, but their account could be made to continue saying whatever the owner of the platform wanted. In reality, such a breach of trust would quickly result in a complete loss of credibility for the platform, which is why this kind of thing doesn't happen (at least, not that we know of). But there are other ways of exploiting this system, most notably by censoring speech. As often happens, platforms are able to confiscate user identities, leaving the tenant no recourse except to appeal to the platform itself (or the government, but that doesn't seem to happen for some reason - probably due to some legalese in social platforms' terms of use). The user has to start completely from scratch, either on the same platform or another. Now suppose that when you signed up for X instead of simply telling X your password you made up a random number and provided a cryptographic proof to X along with your public key. When you're ready to tweet (there's no need to issue a session key, or even to store your public key in their database) you would again prove your ownership of that key with a new piece of data. X could then publish that tweet or not, along with the same proof you provided that it really came from you. What X _can't_ do in this system is pretend you said something you didn't, because they _don't know your private key_. X also wouldn't be able to deplatform you as effectively either. While they could choose to ban you from their website and refuse to serve your tweets, they don't control your identity. There's nothing they can do to prevent you from re-using it on another platform. Plus, if the system was set up in such a way that other users followed your key instead of an ID made up by X, you could switch platforms and _keep your followers_. In the same way, it would also be possible to keep a copy of all your tweets in your own database, since their authenticity is determined by _your_ digital signature, not X's "because I say so". This new power is not just limited to social media either. Here are some other examples of ways that self-issued cryptographic identites transform the power dynamic inherent in digital platforms: - Banks sometimes freeze accounts or confiscate funds. If your money was stored in a system based on self-issued cryptographic keys rather than custodians, banks would not be able to keep you from accessing or moving your funds. This system exists, and it's called [bitcoin](https://bitcoin.rocks/). - Identity theft happens when your identifying information is stolen and used to take out a loan in your name, and without your consent. The reason this is so common is because your credentials are not cryptographic - your name, address, and social security number can only be authenticated by being shared, and they are shared so often and with so many counterparties that they frequently end up in data breaches. If credit checks were authenticated by self-issued cryptographic keys, identity theft would cease to exist (unless your private key itself got stolen). - Cryptographic keys allow credential issuers to protect their subjects' privacy better too. Instead of showing your ID (including your home address, birth date, height, weight, etc), the DMV could sign a message asserting that the holder of a given public key indeed over 21. The liquor store could then validate that claim, and your ownership of the named key, without knowing anything more about you. [Zero-knowledge](https://en.wikipedia.org/wiki/Non-interactive_zero-knowledge_proof) proofs take this a step further. In each of these cases, the interests of the property owner, loan seeker, or customer are elevated over the interests of those who might seek to control their assets, exploit their hard work, or surveil their activity. Just as with personal privacy, freedom of speech, and Second Amendment rights the individual case is rarely decisive, but in the aggregate realigned incentives can tip the scale in favor of freedom. # Objections Now, there are some drawbacks to digital signatures. Systems that rely on digital signatures are frequently less forgiving of errors than their custodial counterparts, and many of their strengths have corresponding weaknesses. Part of this is because people haven't yet developed an intuition for how to use cryptographic identities, and the tools for managing them are still being designed. Other aspects can be mitigated through judicious use of keys fit to the problems they are being used to solve. Below I'll articulate some of these concerns, and explore ways in which they might be mitigated over time. ## Key Storage Keeping secrets is hard. "A lie can travel halfway around the world before the truth can get its boots on", and the same goes for gossip. Key storage has become increasingly important as more of our lives move online, to the extent that password managers have become almost a requirement for keeping track of our digital lives. But even with good password management, credentials frequently end up for sale on the dark web as a consequence of poorly secured infrastructure. Apart from the fact that all of this is an argument _for_ cryptographic identities (since keys are shared with far fewer parties), it's also true that the danger of losing a cryptographic key is severe, especially if that key is used in multiple places. Instead of hackers stealing your Facebook password, they might end up with access to all your other social media accounts too! Keys should be treated with the utmost care. Using password managers is a good start, but very valuable keys should be stored even more securely - for example in a [hardware signing device](https://nostrsigningdevice.com/). This is a hassle, and something additional to learn, but is an indispensable part of taking advantage of the benefits associated with cryptographic identity. There are ways to lessen the impact of lost or stolen secrets, however. Lots of different techniques exist for structuring key systems in such a way that keys can be protected, invalidated, or limited. Here are a few: - [Hierarchical Deterministic Keys](https://www.ietf.org/archive/id/draft-dijkhuis-cfrg-hdkeys-02.html) allow for the creation of a single root key from which multiple child keys can be generated. These keys are hard to link to the parent, which provides additional privacy, but this link can also be proven when necessary. One limitation is that the identity system has to be designed with HD keys in mind. - [Key Rotation](https://crypto.stackexchange.com/questions/41796/whats-the-purpose-of-key-rotation) allows keys to become expendable. Additional credentials might be attached to a key, allowing the holder to prove they have the right to rotate the key. Social attestations can help with the process as well if the key is embedded in a web of trust. - Remote Signing is a technique for storing a key on one device, but using it on another. This might take the form of signing using a hardware wallet and transferring an SD card to your computer for broadcasting, or using a mobile app like [Amber](https://github.com/greenart7c3/Amber) to manage sessions with different applications. - [Key](https://github.com/coracle-social/promenade/tree/master) [sharding](https://www.frostr.org/) takes this to another level by breaking a single key into multiple pieces and storing them separately. A coordinator can then be used to collaboratively sign messages without sharing key material. This dramatically reduces the ability of an attacker to steal a complete key. ## Multi-Factor Authentication One method for helping users secure their accounts that is becoming increasingly common is "multi-factor authentication". Instead of just providing your email and password, platforms send a one-time use code to your phone number or email, or use "time-based one time passwords" which are stored in a password manager or on a hardware device. Again, MFA is a solution to a problem inherent in account-based authentication which would not be nearly so prevalent in a cryptographic identity system. Still, theft of keys does happen, and so MFA would be an important improvement - if not for an extra layer of authentication, then as a basis for key rotation. In a sense, MFA is already being researched - key shards is one way of creating multiple credentials from a single key. However, this doesn't address the issue of key rotation, especially when an identity is tied to the public key that corresponds to a given private key. There are two possible solutions to this problem: - Introduce a naming system. This would allow identities to use a durable name, assigning it to different keys over time. The downside is that this would require the introduction of either centralized naming authorities (back to the old model), or a blockchain in order to solve [Zooko's trilemma](https://en.wikipedia.org/wiki/Zooko%27s_triangle). - Establish a chain of keys. This would require a given key to name a successor key in advance and self-invalidate, or some other process like social recovery to invalidate an old key and assign the identity to a new one. This also would significantly increase the complexity of validating messages and associating them with a given identity. Both solutions are workable, but introduce a lot of complexity that could cause more trouble than it's worth, depending on the identity system we're talking about. ## Surveillance One of the nice qualities that systems based on cryptographic identities have is that digitally signed data can be passed through any number of untrusted systems and emerge intact. This ability to resist tampering makes it possible to broadcast signed data more widely than would otherwise be the case in a system that relies on a custodian to authenticate information. The downside of this is that more untrusted systems have access to data. And if information is broadcast publicly, anyone can get access to it. This problem is compounded by re-use of cryptographic identities across multiple contexts. A benefit of self-issued credentials is that it becomes possible to bring everything attached to your identity with you, including social context and attached credentials. This is convenient and can be quite powerful, but it also means that more context is attached to your activity, making it easier to infer information about you for advertising or surveillance purposes. This is dangerously close to the dystopian ideal of a "Digital ID". The best way to deal with this risk is to consider identity re-use an option to be used when desirable, but to default to creating a new key for every identity you create. This is no worse than the status quo, and it makes room for the ability to link identities when desired. Another possible approach to this problem is to avoid broadcasting signed data when possible. This could be done by obscuring your cryptographic identity when data is served from a database, or by encrypting your signed data in order to selectively share it with named counterparties. Still, this is a real risk, and should be kept in mind when designing and using systems based on cryptographic identity. If you'd like to read more about this, please see [this blog post](https://habla.news/u/hodlbod@coracle.social/1687802006398). # Making Keys Usable You might be tempted to look at that list of trade-offs and get the sense that cryptographic identity is not for mere mortals. Key management is hard, and footguns abound - but there is a way forward. With [nostr](https://nostr.com/), some new things are happening in the world of key management that have never really happened before. Plenty of work over the last 30 years has gone into making key management tractable, but none have really been widely adopted. The reason for this is simple: network effect. Many of these older key systems only applied the thinnest veneer of humanity over keys. But an identity is much richer than a mere label. Having a real name, social connections, and a corpus of work to attach to a key creates a system of keys that _humans care about_. By bootstrapping key management within a social context, nostr ensures that the payoff of key management is worth the learning curve. Not only is social engagement a strong incentive to get off the ground, people already on the network are eager to help you get past any roadblocks you might face. So if I could offer an action item: give nostr a try today. Whether you're in it for the people and their values, or you just want to experiment with cryptographic identity, nostr is a great place to start. For a quick introduction and to securely generate keys, visit [njump.me](https://njump.me/). Thanks for taking the time to read this post. I hope it's been helpful, and I can't wait to see you on nostr! @ f839fb67:5c930939
2025-03-05 16:54:25# Relays | Name | Address | Price (Sats/Year)| | - | - | - | | stephen's aegis relay | wss://paid.relay.vanderwarker.family | 42069 | stephen's Outbox | wss://relay.vanderwarker.family | 0 | | stephen's Inbox | wss://haven.vanderwarker.family/inbox | 0 | | stephen's DMs | wss://haven.vanderwarker.family/chat | 0 | | VFam Data Relay | wss://data.relay.vanderwarker.family | 0 | | [TOR] My Phone Relay | ws://naswsosuewqxyf7ov7gr7igc4tq2rbtqoxxirwyhkbuns4lwc3iowwid.onion | 0 | --- # My Pubkeys | Name | hex | nprofile | | - | - | - | | Main | f839fb6714598a7233d09dbd42af82cc9781d0faa57474f1841af90b5c930939 | nprofile1qqs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us9mapfx | | Vanity (Backup) | 82f21be67353c0d68438003fe6e56a35e2a57c49e0899b368b5ca7aa8dde7c23 | nprofile1qqsg9usmuee48sxkssuqq0lxu44rtc4903y7pzvmx694efa23h08cgcpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3ussel49x | | VFStore | 6416f1e658ba00d42107b05ad9bf485c7e46698217e0c19f0dc2e125de3af0d0 | nprofile1qqsxg9h3uevt5qx5yyrmqkkehay9cljxdxpp0cxpnuxu9cf9mca0p5qpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usaa8plu | | NostrSMS | 9be1b8315248eeb20f9d9ab2717d1750e4f27489eab1fa531d679dadd34c2f8d | nprofile1qqsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us595d45 | --- # "Personal Nostr Things" > [D] = Saves darkmode preferences over nostr > [A] = Auth over nostr > [B] = Beta (software) > [z] = zap enabled - [[DABz] Main Site](https://vanderwarker.family) - [[DAB] Contact Site](https://stephen.vanderwarker.family) - [[DAB] PGP Site](https://pgp.vanderwarker.family) - [[DAB] VFCA Site](https://ca.vanderwarker.family) --- # Other Services (Hosted code) * [Blossom](https://blossom.vanderwarker.family) * [NostrCheck](https://nostr.vanderwarker.family) --- # Emojis Packs * Minecraft - <code>nostr:naddr1qqy566twv43hyctxwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsd0k5wp</code> * AIM - <code>nostr:naddr1qqxxz6tdv4kk7arfvdhkuucpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usyg8c88akw9ze3fer85yah4p2lqkvj7qap749w360rpq6ly94eycf8ypsgqqqw48qe0j2yk</code> * Blobs - <code>nostr:naddr1qqz5ymr0vfesz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2wek4ukj</code> * FavEmojis - <code>nostr:naddr1qqy5vctkg4kk76nfwvq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsf7sdwt</code> * Modern Family - <code>nostr:naddr1qqx56mmyv4exugzxv9kkjmreqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqp65ujlj36n</code> * nostriches (Amethyst collection) - <code>nostr:naddr1qq9xummnw3exjcmgv4esz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w2sqg6w</code> * Pepe - <code>nostr:naddr1qqz9qetsv5q37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82ns85f6x7</code> * Minecraft Font - <code>nostr:naddr1qq8y66twv43hyctxwssyvmmwwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsmzftgr</code> * Archer Font - <code>nostr:naddr1qq95zunrdpjhygzxdah8gqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr4fclkyxsh</code> * SMB Font - <code>nostr:naddr1qqv4xatsv4ezqntpwf5k7gzzwfhhg6r9wfejq3n0de6qz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w0wqpuk</code> --- # Git Over Nostr * NostrSMS - <code>nostr:naddr1qqyxummnw3e8xmtnqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfrwaehxw309amk7apwwfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqyj8wumn8ghj7urpd9jzuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyxhwumn8ghj7mn0wvhxcmmvqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqaueqp0epk</code> * nip51backup - <code>nostr:naddr1qq9ku6tsx5ckyctrdd6hqqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjxamnwvaz7tmhda6zuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfywaehxw309acxz6ty9eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qgdwaehxw309ahx7uewd3hkcq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqpmej4gtqs6</code> * bukkitstr - <code>nostr:naddr1qqykyattdd5hgum5wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dspzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqrhnyf6g0n2</code> --- # Market Places Please use [Nostr Market](https://market.nostr.com) or somthing simular, to view. * VFStore - <code>nostr:naddr1qqjx2v34xe3kxvpn95cnqven956rwvpc95unscn9943kxet98q6nxde58p3ryqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzqeqk78n93wsq6sss0vz6mxl5shr7ge5cy9lqcx0smshpyh0r4uxsqvzqqqr4gve4aen9</code> --- # Badges ## Created * paidrelayvf - <code>nostr:naddr1qq9hqctfv3ex2mrp09mxvqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr48y85v3u3</code> * iPow - <code>nostr:naddr1qqzxj5r02uq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgg02u0r</code> * codmaster - <code>nostr:naddr1qqykxmmyd4shxar9wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgk3gm4g</code> * iMine - <code>nostr:naddr1qqzkjntfdejsz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqafed5s4x5</code> --- # Clients I Use * noStrudel - <code>nostr:naddr1qqxnzd3cxccrvd34xser2dpkqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsygpxdq27pjfppharynrvhg6h8v2taeya5ssf49zkl9yyu5gxe4qg55psgqqq0nmq5mza9n</code> * nostrsms - <code>nostr:naddr1qq9rzdejxcunxde4xymqz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgrqsqqql8kjn33qm</code>
@ f839fb67:5c930939
2025-03-05 16:54:25# Relays | Name | Address | Price (Sats/Year)| | - | - | - | | stephen's aegis relay | wss://paid.relay.vanderwarker.family | 42069 | stephen's Outbox | wss://relay.vanderwarker.family | 0 | | stephen's Inbox | wss://haven.vanderwarker.family/inbox | 0 | | stephen's DMs | wss://haven.vanderwarker.family/chat | 0 | | VFam Data Relay | wss://data.relay.vanderwarker.family | 0 | | [TOR] My Phone Relay | ws://naswsosuewqxyf7ov7gr7igc4tq2rbtqoxxirwyhkbuns4lwc3iowwid.onion | 0 | --- # My Pubkeys | Name | hex | nprofile | | - | - | - | | Main | f839fb6714598a7233d09dbd42af82cc9781d0faa57474f1841af90b5c930939 | nprofile1qqs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us9mapfx | | Vanity (Backup) | 82f21be67353c0d68438003fe6e56a35e2a57c49e0899b368b5ca7aa8dde7c23 | nprofile1qqsg9usmuee48sxkssuqq0lxu44rtc4903y7pzvmx694efa23h08cgcpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3ussel49x | | VFStore | 6416f1e658ba00d42107b05ad9bf485c7e46698217e0c19f0dc2e125de3af0d0 | nprofile1qqsxg9h3uevt5qx5yyrmqkkehay9cljxdxpp0cxpnuxu9cf9mca0p5qpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usaa8plu | | NostrSMS | 9be1b8315248eeb20f9d9ab2717d1750e4f27489eab1fa531d679dadd34c2f8d | nprofile1qqsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us595d45 | --- # "Personal Nostr Things" > [D] = Saves darkmode preferences over nostr > [A] = Auth over nostr > [B] = Beta (software) > [z] = zap enabled - [[DABz] Main Site](https://vanderwarker.family) - [[DAB] Contact Site](https://stephen.vanderwarker.family) - [[DAB] PGP Site](https://pgp.vanderwarker.family) - [[DAB] VFCA Site](https://ca.vanderwarker.family) --- # Other Services (Hosted code) * [Blossom](https://blossom.vanderwarker.family) * [NostrCheck](https://nostr.vanderwarker.family) --- # Emojis Packs * Minecraft - <code>nostr:naddr1qqy566twv43hyctxwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsd0k5wp</code> * AIM - <code>nostr:naddr1qqxxz6tdv4kk7arfvdhkuucpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usyg8c88akw9ze3fer85yah4p2lqkvj7qap749w360rpq6ly94eycf8ypsgqqqw48qe0j2yk</code> * Blobs - <code>nostr:naddr1qqz5ymr0vfesz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2wek4ukj</code> * FavEmojis - <code>nostr:naddr1qqy5vctkg4kk76nfwvq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsf7sdwt</code> * Modern Family - <code>nostr:naddr1qqx56mmyv4exugzxv9kkjmreqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqp65ujlj36n</code> * nostriches (Amethyst collection) - <code>nostr:naddr1qq9xummnw3exjcmgv4esz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w2sqg6w</code> * Pepe - <code>nostr:naddr1qqz9qetsv5q37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82ns85f6x7</code> * Minecraft Font - <code>nostr:naddr1qq8y66twv43hyctxwssyvmmwwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsmzftgr</code> * Archer Font - <code>nostr:naddr1qq95zunrdpjhygzxdah8gqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr4fclkyxsh</code> * SMB Font - <code>nostr:naddr1qqv4xatsv4ezqntpwf5k7gzzwfhhg6r9wfejq3n0de6qz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w0wqpuk</code> --- # Git Over Nostr * NostrSMS - <code>nostr:naddr1qqyxummnw3e8xmtnqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfrwaehxw309amk7apwwfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqyj8wumn8ghj7urpd9jzuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyxhwumn8ghj7mn0wvhxcmmvqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqaueqp0epk</code> * nip51backup - <code>nostr:naddr1qq9ku6tsx5ckyctrdd6hqqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjxamnwvaz7tmhda6zuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfywaehxw309acxz6ty9eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qgdwaehxw309ahx7uewd3hkcq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqpmej4gtqs6</code> * bukkitstr - <code>nostr:naddr1qqykyattdd5hgum5wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dspzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqrhnyf6g0n2</code> --- # Market Places Please use [Nostr Market](https://market.nostr.com) or somthing simular, to view. * VFStore - <code>nostr:naddr1qqjx2v34xe3kxvpn95cnqven956rwvpc95unscn9943kxet98q6nxde58p3ryqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzqeqk78n93wsq6sss0vz6mxl5shr7ge5cy9lqcx0smshpyh0r4uxsqvzqqqr4gve4aen9</code> --- # Badges ## Created * paidrelayvf - <code>nostr:naddr1qq9hqctfv3ex2mrp09mxvqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr48y85v3u3</code> * iPow - <code>nostr:naddr1qqzxj5r02uq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgg02u0r</code> * codmaster - <code>nostr:naddr1qqykxmmyd4shxar9wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgk3gm4g</code> * iMine - <code>nostr:naddr1qqzkjntfdejsz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqafed5s4x5</code> --- # Clients I Use * noStrudel - <code>nostr:naddr1qqxnzd3cxccrvd34xser2dpkqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsygpxdq27pjfppharynrvhg6h8v2taeya5ssf49zkl9yyu5gxe4qg55psgqqq0nmq5mza9n</code> * nostrsms - <code>nostr:naddr1qq9rzdejxcunxde4xymqz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgrqsqqql8kjn33qm</code> @ 8d34bd24:414be32b
2025-03-05 16:52:58Sometimes I wonder why I write posts like this. This is not the way to gain a big following, but then again, that is not my goal. My goal is to share Jesus with anyone who will listen, to faithfully speak whatever truth I feel God is leading me to share, and to teach the inerrant word of God in order to draw people, both believers and not yet believers, closer to Jesus. I trust God to use my words in whatever way He sees best. If it only reaches a few, that is OK by me. If somehow this substack starts reaching a vast audience, then praise God for that! Today, I am writing about a hard truth. The Bible contains a number of hard truths that most people don’t want to believe, but which our Creator God has stated as truth. None of us likes being called a sinner, but the Bible says: > as it is written, “There is none righteous, not even one. (Romans 3:10) As hard as the truth that we are all sinners is, a much harder truth is that not everyone gets to go to Heaven. Some people are destined for Hell. I am going to investigate some verses that illuminate this truth. Ironically, most people have two contradictory thoughts. Most people wonder why God allows so much evil in the world. If He is truly sovereign, why doesn’t He stop evil? At the same time they wonder why a loving God would send anyone to Hell. We can’t expect God to stop and punish evil, but not send some people to Hell. We can’t have it both ways. > The Lord is not slow about His promise, as some count slowness, but is patient toward you, not wishing for any to perish but for all to come to repentance. (2 Peter 3:9) This verse explains the basic facts of how God’s holiness is reconciled with His love and mercy, but of course there is so much more. If God is truly sovereign over all, then why is there any evil? Why does anyone sin? Why is there pain and suffering? > **The Lord has made everything for its own purpose,\ > Even the wicked for the day of evil**.\ > Everyone who is proud in heart is an abomination to the Lord;\ > Assuredly, he will not be unpunished.\ > By lovingkindness and truth iniquity is atoned for,\ > And by the fear of the Lord one keeps away from evil. (Proverbs 16:4-6) {emphasis mine} Everyone and everything was made for God’s own purpose. As our Creator, He has the right to make each of us for whatever purpose He desires. The creature has no right to question the Creator and His purpose. > Then I went down to the potter’s house, and there he was, making something on the wheel. But the vessel that he was making of clay was spoiled in the hand of the potter; so **he remade it into another vessel, as it pleased the potter to make**. > > Then the word of the Lord came to me saying, “**Can I not, O house of Israel, deal with you as this potter does?**” declares the Lord. “Behold, like the clay in the potter’s hand, so are you in My hand, O house of Israel. At one moment I might speak concerning a nation or concerning a kingdom to uproot, to pull down, or to destroy it; if that nation against which I have spoken turns from its evil, I will relent concerning the calamity I planned to bring on it. Or at another moment I might speak concerning a nation or concerning a kingdom to build up or to plant it; if it does evil in My sight by not obeying My voice, then I will think better of the good with which I had promised to bless it. (Jeremiah 18:3-10) {emphasis mine} But the Bible says it even goes beyond God directly responding to our choices. The God of the Bible is creator and sovereign over all. Nothing happens contrary to His will. > So then **He has mercy on whom He desires, and He hardens whom He desires**. > > You **will say to me then, “Why does He still find fault?** For who resists His will?” On the contrary, **who are you, O man, who answers back to God?** **The thing molded will not say to the molder, “Why did you make me like this,” will it? Or does not the potter have a right over the clay, to make from the same lump one vessel for honorable use and another for common use?** What if God, although willing to demonstrate His wrath and to make His power known, endured with much patience **vessels of wrath prepared for destruction**? And He did so to make known the riches of His glory upon **vessels of mercy, which He prepared beforehand for glory**, even us, whom He also called, not from among Jews only, but also from among Gentiles. (Romans 9:18-24) {emphasis mine} The above passage speaks a very uncomfortable truth. We don’t like thinking we don’t have full and complete free-will to do whatever we want and to determine our future, but it isn’t that simple. The Bible says specifically that some are “*prepared for destruction*” and others are “*prepared beforehand for glory*.” > For by grace **you have been saved through faith; and that not of yourselves, it is the gift of God; not as a result of works, so that no one may boast**. For we are His workmanship, created in Christ Jesus for good works, which God prepared beforehand so that we would walk in them. (Ephesians 2:8-10) {emphasis mine} We aren’t saved because we are smarter than all of the people who didn’t choose Jesus. We aren’t wiser than those who chose their own path rather than the path designed by God. We are saved by God as a gift. He called those who were dead in their sins to life in him. The dead can’t choose anything. We all must be made spiritually alive so we can follow Him. Only Jesus does that. We can’t make ourselves alive in Him. Every believer needs to thank Jesus daily for the miracle of spiritual life in Him that has been given to us despite us not deserving it or choosing it. > In this is love, not that we loved God, but that He loved us and sent His Son to be the propitiation for our sins. (1 John 4:10) and > We love, because He first loved us. (1 John 4:19) Jesus acted first, choosing us, and we responded, not that we chose Him and He loved us because of our choice. I’m sure many of my readers are cringing at this Biblical truth. We all try to make God’s word say something else because we don’t like feeling out of control. We don’t like to think that someone else is smarter, stronger, or more in control of our lives than ourselves. Still, being made to follow Jesus is the greatest blessing a person can receive. > Trust in the Lord with all your heart\ > And do not lean on your own understanding.\ > In all your ways acknowledge Him,\ > And He will make your paths straight.\ > Do not be wise in your own eyes;\ > Fear the Lord and turn away from evil.\ > It will be healing to your body\ > And refreshment to your bones. (Proverbs 3:5-8) We don’t have to fully understand God’s truth, but we do need to accept it. May God guide you in the truth through His God breathed word, so we may serve Him faithfully and submit fully to His authority and His will to the glory of His majesty. Trust Jesus
@ 8d34bd24:414be32b
2025-03-05 16:52:58Sometimes I wonder why I write posts like this. This is not the way to gain a big following, but then again, that is not my goal. My goal is to share Jesus with anyone who will listen, to faithfully speak whatever truth I feel God is leading me to share, and to teach the inerrant word of God in order to draw people, both believers and not yet believers, closer to Jesus. I trust God to use my words in whatever way He sees best. If it only reaches a few, that is OK by me. If somehow this substack starts reaching a vast audience, then praise God for that! Today, I am writing about a hard truth. The Bible contains a number of hard truths that most people don’t want to believe, but which our Creator God has stated as truth. None of us likes being called a sinner, but the Bible says: > as it is written, “There is none righteous, not even one. (Romans 3:10) As hard as the truth that we are all sinners is, a much harder truth is that not everyone gets to go to Heaven. Some people are destined for Hell. I am going to investigate some verses that illuminate this truth. Ironically, most people have two contradictory thoughts. Most people wonder why God allows so much evil in the world. If He is truly sovereign, why doesn’t He stop evil? At the same time they wonder why a loving God would send anyone to Hell. We can’t expect God to stop and punish evil, but not send some people to Hell. We can’t have it both ways. > The Lord is not slow about His promise, as some count slowness, but is patient toward you, not wishing for any to perish but for all to come to repentance. (2 Peter 3:9) This verse explains the basic facts of how God’s holiness is reconciled with His love and mercy, but of course there is so much more. If God is truly sovereign over all, then why is there any evil? Why does anyone sin? Why is there pain and suffering? > **The Lord has made everything for its own purpose,\ > Even the wicked for the day of evil**.\ > Everyone who is proud in heart is an abomination to the Lord;\ > Assuredly, he will not be unpunished.\ > By lovingkindness and truth iniquity is atoned for,\ > And by the fear of the Lord one keeps away from evil. (Proverbs 16:4-6) {emphasis mine} Everyone and everything was made for God’s own purpose. As our Creator, He has the right to make each of us for whatever purpose He desires. The creature has no right to question the Creator and His purpose. > Then I went down to the potter’s house, and there he was, making something on the wheel. But the vessel that he was making of clay was spoiled in the hand of the potter; so **he remade it into another vessel, as it pleased the potter to make**. > > Then the word of the Lord came to me saying, “**Can I not, O house of Israel, deal with you as this potter does?**” declares the Lord. “Behold, like the clay in the potter’s hand, so are you in My hand, O house of Israel. At one moment I might speak concerning a nation or concerning a kingdom to uproot, to pull down, or to destroy it; if that nation against which I have spoken turns from its evil, I will relent concerning the calamity I planned to bring on it. Or at another moment I might speak concerning a nation or concerning a kingdom to build up or to plant it; if it does evil in My sight by not obeying My voice, then I will think better of the good with which I had promised to bless it. (Jeremiah 18:3-10) {emphasis mine} But the Bible says it even goes beyond God directly responding to our choices. The God of the Bible is creator and sovereign over all. Nothing happens contrary to His will. > So then **He has mercy on whom He desires, and He hardens whom He desires**. > > You **will say to me then, “Why does He still find fault?** For who resists His will?” On the contrary, **who are you, O man, who answers back to God?** **The thing molded will not say to the molder, “Why did you make me like this,” will it? Or does not the potter have a right over the clay, to make from the same lump one vessel for honorable use and another for common use?** What if God, although willing to demonstrate His wrath and to make His power known, endured with much patience **vessels of wrath prepared for destruction**? And He did so to make known the riches of His glory upon **vessels of mercy, which He prepared beforehand for glory**, even us, whom He also called, not from among Jews only, but also from among Gentiles. (Romans 9:18-24) {emphasis mine} The above passage speaks a very uncomfortable truth. We don’t like thinking we don’t have full and complete free-will to do whatever we want and to determine our future, but it isn’t that simple. The Bible says specifically that some are “*prepared for destruction*” and others are “*prepared beforehand for glory*.” > For by grace **you have been saved through faith; and that not of yourselves, it is the gift of God; not as a result of works, so that no one may boast**. For we are His workmanship, created in Christ Jesus for good works, which God prepared beforehand so that we would walk in them. (Ephesians 2:8-10) {emphasis mine} We aren’t saved because we are smarter than all of the people who didn’t choose Jesus. We aren’t wiser than those who chose their own path rather than the path designed by God. We are saved by God as a gift. He called those who were dead in their sins to life in him. The dead can’t choose anything. We all must be made spiritually alive so we can follow Him. Only Jesus does that. We can’t make ourselves alive in Him. Every believer needs to thank Jesus daily for the miracle of spiritual life in Him that has been given to us despite us not deserving it or choosing it. > In this is love, not that we loved God, but that He loved us and sent His Son to be the propitiation for our sins. (1 John 4:10) and > We love, because He first loved us. (1 John 4:19) Jesus acted first, choosing us, and we responded, not that we chose Him and He loved us because of our choice. I’m sure many of my readers are cringing at this Biblical truth. We all try to make God’s word say something else because we don’t like feeling out of control. We don’t like to think that someone else is smarter, stronger, or more in control of our lives than ourselves. Still, being made to follow Jesus is the greatest blessing a person can receive. > Trust in the Lord with all your heart\ > And do not lean on your own understanding.\ > In all your ways acknowledge Him,\ > And He will make your paths straight.\ > Do not be wise in your own eyes;\ > Fear the Lord and turn away from evil.\ > It will be healing to your body\ > And refreshment to your bones. (Proverbs 3:5-8) We don’t have to fully understand God’s truth, but we do need to accept it. May God guide you in the truth through His God breathed word, so we may serve Him faithfully and submit fully to His authority and His will to the glory of His majesty. Trust Jesus @ 401014b3:59d5476b
2025-03-05 15:37:44Alright, football fiends, it’s March 2025, and we’re diving into the NFC North like it’s a polar plunge with a side of cheap beer. Free agency’s a free-for-all, the draft’s a crapshoot, and this division’s always a slugfest of grit, guts, and grudges. The Vikings shocked the world with a 14-3 run in 2024, the Lions roared, the Packers stayed scrappy, and the Bears showed flashes. Let’s slap some records on this beast and figure out who’s got the stones to take the North. Here we go, fam—hold my bratwurst. ### **Minnesota Vikings: 11-6 – Darnold’s Encore or Bust** The Vikings were the NFL’s Cinderella story in 2024, rolling to 14-3 with Sam Darnold slinging it and Brian Flores’ defense eating souls. Justin Jefferson’s still a cheat code, and Aaron Jones keeps the ground game humming. That D-line—Jonathan Greenard, Andrew Van Ginkel—stays nasty, but free agency’s lurking. Danielle Hunter’s long gone, and guys like Harrison Phillips might chase a bag. J.J. McCarthy’s waiting in the wings, but Darnold’s 2024 magic earns him the nod. Regression’s real after a dream season—11-6 feels right, snagging the division. They’re not hitting 14 again, but they’re still a playoff lock. ### **Detroit Lions: 10-7 – Campbell’s Grit Keeps Grinding** The Lions were a buzzsaw in 2024, and they’re not fading. Jared Goff’s got Amon-Ra St. Brown and Jameson Williams torching secondaries, while David Montgomery and Jahmyr Gibbs bulldoze defenses. Aidan Hutchinson’s a one-man wrecking crew up front, but free agency could nick ‘em—Brian Branch or Alim McNeill might dip. Dan Campbell’s got this team playing with their hair on fire, and that O-line’s still elite. 10-7’s the call, grabbing a wildcard. They’re a hair behind Minnesota but ready to punch someone’s lights out in January. ### **Green Bay Packers: 9-8 – Love’s Rollercoaster Redux** The Packers are the NFC North’s wild card—literally. Jordan Love’s got that boom-or-bust vibe, Josh Jacobs keeps the run game honest, and the WR trio—Christian Watson, Romeo Doubs, Jayden Reed—is a problem when healthy. Rashan Gary’s a beast on D, but the secondary’s shaky, and Jaire Alexander might bolt if the money’s right. This team’s young, scrappy, and inconsistent—9-8’s where they land. Might sneak a wildcard if the chips fall, but they’re not catching the top dogs yet. ### **Chicago Bears: 6-11 – Caleb’s Sophomore Slump** The Bears had their moments in 2024, but 2025’s a grind. Caleb Williams has DJ Moore and Rome Odunze to sling it to, and D’Andre Swift’s solid, but that O-line’s still a sieve. The defense—Montez Sweat, Jaylon Johnson—can ball, but depth’s thin, and free agency might swipe Tremaine Edmunds. Williams takes a step, but not a leap—6-11’s the harsh reality. They’re building something, but it’s not playoff-ready. Sorry, Windy City, you’re still in the basement. ### **The Final Roar** The NFC North in 2025 is a Viking victory lap with a tight chase. The Vikings (11-6) snag the crown because Darnold’s 2024 glow carries over, the Lions (10-7) claw a wildcard with grit, the Packers (9-8) flirt with relevance, and the Bears (6-11) eat turf. Free agency’s the X-factor—lose a star, you’re cooked; keep ‘em, you’re golden. Yell at me on X when I botch this, but this is my NFC North sermon. Let’s ride, degenerates.
@ 401014b3:59d5476b
2025-03-05 15:37:44Alright, football fiends, it’s March 2025, and we’re diving into the NFC North like it’s a polar plunge with a side of cheap beer. Free agency’s a free-for-all, the draft’s a crapshoot, and this division’s always a slugfest of grit, guts, and grudges. The Vikings shocked the world with a 14-3 run in 2024, the Lions roared, the Packers stayed scrappy, and the Bears showed flashes. Let’s slap some records on this beast and figure out who’s got the stones to take the North. Here we go, fam—hold my bratwurst. ### **Minnesota Vikings: 11-6 – Darnold’s Encore or Bust** The Vikings were the NFL’s Cinderella story in 2024, rolling to 14-3 with Sam Darnold slinging it and Brian Flores’ defense eating souls. Justin Jefferson’s still a cheat code, and Aaron Jones keeps the ground game humming. That D-line—Jonathan Greenard, Andrew Van Ginkel—stays nasty, but free agency’s lurking. Danielle Hunter’s long gone, and guys like Harrison Phillips might chase a bag. J.J. McCarthy’s waiting in the wings, but Darnold’s 2024 magic earns him the nod. Regression’s real after a dream season—11-6 feels right, snagging the division. They’re not hitting 14 again, but they’re still a playoff lock. ### **Detroit Lions: 10-7 – Campbell’s Grit Keeps Grinding** The Lions were a buzzsaw in 2024, and they’re not fading. Jared Goff’s got Amon-Ra St. Brown and Jameson Williams torching secondaries, while David Montgomery and Jahmyr Gibbs bulldoze defenses. Aidan Hutchinson’s a one-man wrecking crew up front, but free agency could nick ‘em—Brian Branch or Alim McNeill might dip. Dan Campbell’s got this team playing with their hair on fire, and that O-line’s still elite. 10-7’s the call, grabbing a wildcard. They’re a hair behind Minnesota but ready to punch someone’s lights out in January. ### **Green Bay Packers: 9-8 – Love’s Rollercoaster Redux** The Packers are the NFC North’s wild card—literally. Jordan Love’s got that boom-or-bust vibe, Josh Jacobs keeps the run game honest, and the WR trio—Christian Watson, Romeo Doubs, Jayden Reed—is a problem when healthy. Rashan Gary’s a beast on D, but the secondary’s shaky, and Jaire Alexander might bolt if the money’s right. This team’s young, scrappy, and inconsistent—9-8’s where they land. Might sneak a wildcard if the chips fall, but they’re not catching the top dogs yet. ### **Chicago Bears: 6-11 – Caleb’s Sophomore Slump** The Bears had their moments in 2024, but 2025’s a grind. Caleb Williams has DJ Moore and Rome Odunze to sling it to, and D’Andre Swift’s solid, but that O-line’s still a sieve. The defense—Montez Sweat, Jaylon Johnson—can ball, but depth’s thin, and free agency might swipe Tremaine Edmunds. Williams takes a step, but not a leap—6-11’s the harsh reality. They’re building something, but it’s not playoff-ready. Sorry, Windy City, you’re still in the basement. ### **The Final Roar** The NFC North in 2025 is a Viking victory lap with a tight chase. The Vikings (11-6) snag the crown because Darnold’s 2024 glow carries over, the Lions (10-7) claw a wildcard with grit, the Packers (9-8) flirt with relevance, and the Bears (6-11) eat turf. Free agency’s the X-factor—lose a star, you’re cooked; keep ‘em, you’re golden. Yell at me on X when I botch this, but this is my NFC North sermon. Let’s ride, degenerates. @ d360efec:14907b5f
2025-03-05 13:58:42**ภาพรวม:** จากภาพรวมทั้ง 3 Timeframe (TF) จะเห็นได้ว่า BTC มีแนวโน้มเป็นขาขึ้น (Bullish) อย่างชัดเจน โดยเฉพาะอย่างยิ่งใน TF Day ที่ราคาอยู่เหนือเส้น EMA 50 และ EMA 200 อย่างแข็งแกร่ง อย่างไรก็ตาม ใน TF ที่เล็กลงมา (15m และ 4H) เริ่มเห็นสัญญาณการพักตัวและอาจมีการปรับฐานระยะสั้น **การวิเคราะห์แยกตาม Timeframe:** * **TF Day:** *  * **SMC:** ราคามีการ Breakout โครงสร้างตลาดขาลงก่อนหน้า และสร้าง Higher High (HH) และ Higher Low (HL) อย่างต่อเนื่อง * **ICT Buyside & Sellside Liquidity:** * Buyside Liquidity: อยู่บริเวณ $70,000 (เป็นเป้าหมายถัดไปที่ราคามีโอกาสขึ้นไปทดสอบ) * Sellside Liquidity: อยู่บริเวณ $60,000 (เป็นแนวรับสำคัญ หากราคาหลุดลงมา อาจมีการปรับฐานที่รุนแรงขึ้น) * **Money Flow:** เป็นบวก สนับสนุนแนวโน้มขาขึ้น * **EMA:** EMA 50 (เหลือง) อยู่เหนือ EMA 200 (ขาว) เป็นสัญญาณ Bullish * **Trend Strength:** เมฆสีเขียวหนาแน่น แสดงถึงแนวโน้มขาขึ้นที่แข็งแกร่ง และมีสัญญาณ Buy * **Chart Pattern:** ไม่มีรูปแบบ Chart Pattern ที่ชัดเจนใน TF นี้ * **TF 4H:** *  * **SMC:** ราคาเริ่มมีการพักตัวและสร้างฐาน (Consolidation) * **ICT Buyside & Sellside Liquidity:** * Buyside Liquidity: อยู่บริเวณ $69,000 (แนวต้านย่อย) * Sellside Liquidity: อยู่บริเวณ $64,000 (แนวรับย่อย) * **Money Flow:** เริ่มมีสัญญาณการไหลออกของเงิน (Outflow) * **EMA:** EMA 50 ยังคงอยู่เหนือ EMA 200 แต่เริ่มมีการ Cross กัน อาจเป็นสัญญาณเตือนการพักตัว * **Trend Strength:** เมฆสีเขียวเริ่มบางลง และมีสัญญาณ Neutral * **Chart Pattern:** อาจกำลังก่อตัวเป็นรูปแบบ Head and Shoulders (กลับตัว) หรืออาจเป็นเพียงการพักตัวเพื่อไปต่อ * **TF 15m:** *  * **SMC:** ราคาอยู่ในช่วง Sideways แคบๆ * **ICT Buyside & Sellside Liquidity:** * Buyside Liquidity: อยู่บริเวณ $68,500 * Sellside Liquidity: อยู่บริเวณ $66,000 * **Money Flow:** เป็นลบ (Outflow) * **EMA:** EMA 50 และ EMA 200 พันกัน (Cross) บ่งบอกถึงการไม่มี Trend ที่ชัดเจน * **Trend Strength:** เมฆสีแดง แสดงถึงแนวโน้มขาลงระยะสั้น และมีสัญญาณ Sell * **Chart Pattern:** ไม่พบรูปแบบ Chart Pattern ที่ชัดเจน **กลยุทธ์และคำแนะนำ:** * **Day Trade:** * **กลยุทธ์:** เน้น Buy on Dip (ซื้อเมื่อราคาอ่อนตัว) ใน TF 15m หรือ 4H โดยรอสัญญาณการกลับตัวของราคา และตั้ง Stop Loss ที่เหมาะสม * **Setup (SMC):** 1. รอให้ราคาลงมาทดสอบแนวรับ (Demand Zone) ที่ $66,000-$67,000 ใน TF 15m 2. สังเกต Price Action ว่ามีการกลับตัว (เช่น Bullish Engulfing, Hammer) หรือไม่ 3. เข้า Buy เมื่อมีสัญญาณยืนยัน และตั้ง Stop Loss ต่ำกว่า Swing Low ล่าสุด 4. Take Profit ที่แนวต้านถัดไป ($68,500) หรือ Buyside Liquidity * **สิ่งที่ต้องระวัง:** * ความผันผวนของราคา BTC ที่สูง * ข่าวหรือเหตุการณ์ที่อาจส่งผลกระทบต่อตลาด * สัญญาณ Divergence (หากมี) ระหว่างราคาและ Indicator * **ภาพรวม (ระยะกลาง-ยาว):** ยังคงมีมุมมองเป็น Bullish แต่ควรระมัดระวังการพักตัวหรือปรับฐานระยะสั้น **สรุป:** BTC ยังคงมีแนวโน้มเป็นขาขึ้นในระยะกลาง-ยาว แต่ในระยะสั้นอาจมีการพักตัวหรือปรับฐาน Day Trader ควรใช้กลยุทธ์ Buy on Dip และบริหารความเสี่ยงอย่างรอบคอบ **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
@ d360efec:14907b5f
2025-03-05 13:58:42**ภาพรวม:** จากภาพรวมทั้ง 3 Timeframe (TF) จะเห็นได้ว่า BTC มีแนวโน้มเป็นขาขึ้น (Bullish) อย่างชัดเจน โดยเฉพาะอย่างยิ่งใน TF Day ที่ราคาอยู่เหนือเส้น EMA 50 และ EMA 200 อย่างแข็งแกร่ง อย่างไรก็ตาม ใน TF ที่เล็กลงมา (15m และ 4H) เริ่มเห็นสัญญาณการพักตัวและอาจมีการปรับฐานระยะสั้น **การวิเคราะห์แยกตาม Timeframe:** * **TF Day:** *  * **SMC:** ราคามีการ Breakout โครงสร้างตลาดขาลงก่อนหน้า และสร้าง Higher High (HH) และ Higher Low (HL) อย่างต่อเนื่อง * **ICT Buyside & Sellside Liquidity:** * Buyside Liquidity: อยู่บริเวณ $70,000 (เป็นเป้าหมายถัดไปที่ราคามีโอกาสขึ้นไปทดสอบ) * Sellside Liquidity: อยู่บริเวณ $60,000 (เป็นแนวรับสำคัญ หากราคาหลุดลงมา อาจมีการปรับฐานที่รุนแรงขึ้น) * **Money Flow:** เป็นบวก สนับสนุนแนวโน้มขาขึ้น * **EMA:** EMA 50 (เหลือง) อยู่เหนือ EMA 200 (ขาว) เป็นสัญญาณ Bullish * **Trend Strength:** เมฆสีเขียวหนาแน่น แสดงถึงแนวโน้มขาขึ้นที่แข็งแกร่ง และมีสัญญาณ Buy * **Chart Pattern:** ไม่มีรูปแบบ Chart Pattern ที่ชัดเจนใน TF นี้ * **TF 4H:** *  * **SMC:** ราคาเริ่มมีการพักตัวและสร้างฐาน (Consolidation) * **ICT Buyside & Sellside Liquidity:** * Buyside Liquidity: อยู่บริเวณ $69,000 (แนวต้านย่อย) * Sellside Liquidity: อยู่บริเวณ $64,000 (แนวรับย่อย) * **Money Flow:** เริ่มมีสัญญาณการไหลออกของเงิน (Outflow) * **EMA:** EMA 50 ยังคงอยู่เหนือ EMA 200 แต่เริ่มมีการ Cross กัน อาจเป็นสัญญาณเตือนการพักตัว * **Trend Strength:** เมฆสีเขียวเริ่มบางลง และมีสัญญาณ Neutral * **Chart Pattern:** อาจกำลังก่อตัวเป็นรูปแบบ Head and Shoulders (กลับตัว) หรืออาจเป็นเพียงการพักตัวเพื่อไปต่อ * **TF 15m:** *  * **SMC:** ราคาอยู่ในช่วง Sideways แคบๆ * **ICT Buyside & Sellside Liquidity:** * Buyside Liquidity: อยู่บริเวณ $68,500 * Sellside Liquidity: อยู่บริเวณ $66,000 * **Money Flow:** เป็นลบ (Outflow) * **EMA:** EMA 50 และ EMA 200 พันกัน (Cross) บ่งบอกถึงการไม่มี Trend ที่ชัดเจน * **Trend Strength:** เมฆสีแดง แสดงถึงแนวโน้มขาลงระยะสั้น และมีสัญญาณ Sell * **Chart Pattern:** ไม่พบรูปแบบ Chart Pattern ที่ชัดเจน **กลยุทธ์และคำแนะนำ:** * **Day Trade:** * **กลยุทธ์:** เน้น Buy on Dip (ซื้อเมื่อราคาอ่อนตัว) ใน TF 15m หรือ 4H โดยรอสัญญาณการกลับตัวของราคา และตั้ง Stop Loss ที่เหมาะสม * **Setup (SMC):** 1. รอให้ราคาลงมาทดสอบแนวรับ (Demand Zone) ที่ $66,000-$67,000 ใน TF 15m 2. สังเกต Price Action ว่ามีการกลับตัว (เช่น Bullish Engulfing, Hammer) หรือไม่ 3. เข้า Buy เมื่อมีสัญญาณยืนยัน และตั้ง Stop Loss ต่ำกว่า Swing Low ล่าสุด 4. Take Profit ที่แนวต้านถัดไป ($68,500) หรือ Buyside Liquidity * **สิ่งที่ต้องระวัง:** * ความผันผวนของราคา BTC ที่สูง * ข่าวหรือเหตุการณ์ที่อาจส่งผลกระทบต่อตลาด * สัญญาณ Divergence (หากมี) ระหว่างราคาและ Indicator * **ภาพรวม (ระยะกลาง-ยาว):** ยังคงมีมุมมองเป็น Bullish แต่ควรระมัดระวังการพักตัวหรือปรับฐานระยะสั้น **สรุป:** BTC ยังคงมีแนวโน้มเป็นขาขึ้นในระยะกลาง-ยาว แต่ในระยะสั้นอาจมีการพักตัวหรือปรับฐาน Day Trader ควรใช้กลยุทธ์ Buy on Dip และบริหารความเสี่ยงอย่างรอบคอบ **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ @ c1e9ab3a:9cb56b43
2025-03-05 13:54:03The financial system has long relied on traditional banking methods, but emerging technologies like Bitcoin and Nostr are paving the way for a new era of financial interactions. ## Secure Savings with Bitcoin: Bitcoin wallets can act as secure savings accounts, offering users control and ownership over their funds without relying on third parties. ## Instant Settlements with the Lightning Network: The Lightning Network can replace traditional settlement systems, such as ACH or wire transfers, by enabling instant, low-cost transactions. ## Face-to-Face Transactions with Ecash: Ecash could offer a fee-free option for smaller, everyday transactions, complementing the Lightning Network for larger payments. ## Automated Billing with Nostr Wallet Connect: Nostr Wallet Connect could revolutionize automated billing, allowing users to set payment limits and offering more control over subscriptions and recurring expenses. ## Conclusion: Combining Bitcoin and Nostr technologies could create a more efficient, user-centric financial system that empowers individuals and businesses alike.
@ c1e9ab3a:9cb56b43
2025-03-05 13:54:03The financial system has long relied on traditional banking methods, but emerging technologies like Bitcoin and Nostr are paving the way for a new era of financial interactions. ## Secure Savings with Bitcoin: Bitcoin wallets can act as secure savings accounts, offering users control and ownership over their funds without relying on third parties. ## Instant Settlements with the Lightning Network: The Lightning Network can replace traditional settlement systems, such as ACH or wire transfers, by enabling instant, low-cost transactions. ## Face-to-Face Transactions with Ecash: Ecash could offer a fee-free option for smaller, everyday transactions, complementing the Lightning Network for larger payments. ## Automated Billing with Nostr Wallet Connect: Nostr Wallet Connect could revolutionize automated billing, allowing users to set payment limits and offering more control over subscriptions and recurring expenses. ## Conclusion: Combining Bitcoin and Nostr technologies could create a more efficient, user-centric financial system that empowers individuals and businesses alike. @ d360efec:14907b5f
2025-03-05 13:46:26**Overview:** From an overall perspective across all 3 timeframes (TF), BTC shows a clear uptrend (Bullish), especially in the Day TF where the price is firmly above the EMA 50 and EMA 200. However, in the smaller TFs (15m and 4H), there are signs of consolidation and a potential short-term correction. **Analysis by Timeframe:** * **Day TF:** *  * **SMC:** The price has broken out of the previous downtrend structure and continues to create Higher Highs (HH) and Higher Lows (HL). * **ICT Buyside & Sellside Liquidity:** * Buyside Liquidity: Around $70,000 (the next target the price is likely to test). * Sellside Liquidity: Around $60,000 (a key support level; if the price breaks below this, a deeper correction may occur). * **Money Flow:** Positive, supporting the uptrend. * **EMA:** EMA 50 (yellow) is above EMA 200 (white), a bullish signal. * **Trend Strength:** Thick green cloud, indicating a strong uptrend, and a Buy signal. * **Chart Pattern:** No clear chart pattern on this TF. * **4H TF:** *  * **SMC:** The price is starting to consolidate and form a base. * **ICT Buyside & Sellside Liquidity:** * Buyside Liquidity: Around $69,000 (minor resistance). * Sellside Liquidity: Around $64,000 (minor support). * **Money Flow:** Starting to show signs of outflow. * **EMA:** EMA 50 is still above EMA 200, but they are starting to cross, which could be a warning sign of consolidation. * **Trend Strength:** The green cloud is starting to thin, and there is a Neutral signal. * **Chart Pattern:** Potentially forming a Head and Shoulders pattern (reversal) or it may just be a consolidation before continuing higher. * **15m TF:** *  * **SMC:** The price is in a narrow sideways range. * **ICT Buyside & Sellside Liquidity:** * Buyside Liquidity: Around $68,500. * Sellside Liquidity: Around $66,000. * **Money Flow:** Negative (Outflow). * **EMA:** EMA 50 and EMA 200 are intertwined (Cross), indicating a lack of a clear trend. * **Trend Strength:** Red cloud, indicating a short-term downtrend, and a Sell signal. * **Chart Pattern:** No clear chart pattern found. **Strategy and Recommendations:** * **Day Trade:** * **Strategy:** Focus on Buy on Dip in the 15m or 4H TF, waiting for price reversal signals, and setting appropriate Stop Losses. * **Setup (SMC):** 1. Wait for the price to test the support (Demand Zone) at $66,000-$67,000 in the 15m TF. 2. Observe Price Action for a reversal (e.g., Bullish Engulfing, Hammer). 3. Enter a Buy when there is a confirmation signal and set a Stop Loss below the latest Swing Low. 4. Take Profit at the next resistance ($68,500) or Buyside Liquidity. * **Things to watch out for:** * High volatility of BTC price. * News or events that may affect the market. * Divergence signals (if any) between price and indicators. * **Overall (Medium-Long Term):** Still bullish, but be cautious of short-term consolidations or corrections. **Summary:** BTC remains bullish in the medium to long term, but there may be a short-term consolidation or correction. Day traders should use a Buy on Dip strategy and manage risk carefully. **Disclaimer:** This analysis is a personal opinion and not investment advice. Investors should do their own research and make decisions carefully.
@ d360efec:14907b5f
2025-03-05 13:46:26**Overview:** From an overall perspective across all 3 timeframes (TF), BTC shows a clear uptrend (Bullish), especially in the Day TF where the price is firmly above the EMA 50 and EMA 200. However, in the smaller TFs (15m and 4H), there are signs of consolidation and a potential short-term correction. **Analysis by Timeframe:** * **Day TF:** *  * **SMC:** The price has broken out of the previous downtrend structure and continues to create Higher Highs (HH) and Higher Lows (HL). * **ICT Buyside & Sellside Liquidity:** * Buyside Liquidity: Around $70,000 (the next target the price is likely to test). * Sellside Liquidity: Around $60,000 (a key support level; if the price breaks below this, a deeper correction may occur). * **Money Flow:** Positive, supporting the uptrend. * **EMA:** EMA 50 (yellow) is above EMA 200 (white), a bullish signal. * **Trend Strength:** Thick green cloud, indicating a strong uptrend, and a Buy signal. * **Chart Pattern:** No clear chart pattern on this TF. * **4H TF:** *  * **SMC:** The price is starting to consolidate and form a base. * **ICT Buyside & Sellside Liquidity:** * Buyside Liquidity: Around $69,000 (minor resistance). * Sellside Liquidity: Around $64,000 (minor support). * **Money Flow:** Starting to show signs of outflow. * **EMA:** EMA 50 is still above EMA 200, but they are starting to cross, which could be a warning sign of consolidation. * **Trend Strength:** The green cloud is starting to thin, and there is a Neutral signal. * **Chart Pattern:** Potentially forming a Head and Shoulders pattern (reversal) or it may just be a consolidation before continuing higher. * **15m TF:** *  * **SMC:** The price is in a narrow sideways range. * **ICT Buyside & Sellside Liquidity:** * Buyside Liquidity: Around $68,500. * Sellside Liquidity: Around $66,000. * **Money Flow:** Negative (Outflow). * **EMA:** EMA 50 and EMA 200 are intertwined (Cross), indicating a lack of a clear trend. * **Trend Strength:** Red cloud, indicating a short-term downtrend, and a Sell signal. * **Chart Pattern:** No clear chart pattern found. **Strategy and Recommendations:** * **Day Trade:** * **Strategy:** Focus on Buy on Dip in the 15m or 4H TF, waiting for price reversal signals, and setting appropriate Stop Losses. * **Setup (SMC):** 1. Wait for the price to test the support (Demand Zone) at $66,000-$67,000 in the 15m TF. 2. Observe Price Action for a reversal (e.g., Bullish Engulfing, Hammer). 3. Enter a Buy when there is a confirmation signal and set a Stop Loss below the latest Swing Low. 4. Take Profit at the next resistance ($68,500) or Buyside Liquidity. * **Things to watch out for:** * High volatility of BTC price. * News or events that may affect the market. * Divergence signals (if any) between price and indicators. * **Overall (Medium-Long Term):** Still bullish, but be cautious of short-term consolidations or corrections. **Summary:** BTC remains bullish in the medium to long term, but there may be a short-term consolidation or correction. Day traders should use a Buy on Dip strategy and manage risk carefully. **Disclaimer:** This analysis is a personal opinion and not investment advice. Investors should do their own research and make decisions carefully. @ beb6bdc9:eeb17df3
2025-03-05 13:25:08https://image.nostr.build/2ad4cf1beb7f1ebaecfe1e011f83c85d09c2c17e4a1f40eac412bb08e03d82c4.jpg 00020126360014BR.GOV.BCB.PIX0114dig@depix.info520400005303986540549.905802BR5923CURSO BITCOIN PARA TDAH6013SATOSHILANDIA62070503***63045C68 ↑ COPIE TODO O TEXTO DA CHAVE PIX ACIMA! ↑ Para ter acesso ao guia **BITCOIN PARA TDAH**, pague a chave pix copia e cola acima e apresente o comprovante de pagamento em: https://t.me/dinopacon
@ beb6bdc9:eeb17df3
2025-03-05 13:25:08https://image.nostr.build/2ad4cf1beb7f1ebaecfe1e011f83c85d09c2c17e4a1f40eac412bb08e03d82c4.jpg 00020126360014BR.GOV.BCB.PIX0114dig@depix.info520400005303986540549.905802BR5923CURSO BITCOIN PARA TDAH6013SATOSHILANDIA62070503***63045C68 ↑ COPIE TODO O TEXTO DA CHAVE PIX ACIMA! ↑ Para ter acesso ao guia **BITCOIN PARA TDAH**, pague a chave pix copia e cola acima e apresente o comprovante de pagamento em: https://t.me/dinopacon @ a58a2663:87bb2918
2025-03-05 12:41:36After two years of using Standard Notes as my main note-taking app, I’m switching to Obsidian. The $100 that Standard Notes charges for basic editing capabilities is difficult to justify, especially for someone paying in Brazilian Real and striving to make a living from writing. However, I will certainly miss its simplicity and cleaner interface. It’s my impression that the developers are missing an opportunity to create a privacy-focused note-taking app tailored to the specific needs of writers, rather than general users. Substack, for example, achieved such success because it targeted the distribution and monetization of writers’ work. But we need more tools focused not on distribution or monetization, but on the actual process—indeed, the various phases of the process—of creating texts. This is especially true for complex, long-form texts with different levels of argumentation, numerous written and multimedia sources, and cross-references to other works by the author. It’s crucial that an app like this doesn’t feel overly complex, like Notion or Evernote, or so all-purpose, like Obsidian. And, of course, I’m not talking about a new full-fledged text editor like Scrivener. Just a thought. Take note.
@ a58a2663:87bb2918
2025-03-05 12:41:36After two years of using Standard Notes as my main note-taking app, I’m switching to Obsidian. The $100 that Standard Notes charges for basic editing capabilities is difficult to justify, especially for someone paying in Brazilian Real and striving to make a living from writing. However, I will certainly miss its simplicity and cleaner interface. It’s my impression that the developers are missing an opportunity to create a privacy-focused note-taking app tailored to the specific needs of writers, rather than general users. Substack, for example, achieved such success because it targeted the distribution and monetization of writers’ work. But we need more tools focused not on distribution or monetization, but on the actual process—indeed, the various phases of the process—of creating texts. This is especially true for complex, long-form texts with different levels of argumentation, numerous written and multimedia sources, and cross-references to other works by the author. It’s crucial that an app like this doesn’t feel overly complex, like Notion or Evernote, or so all-purpose, like Obsidian. And, of course, I’m not talking about a new full-fledged text editor like Scrivener. Just a thought. Take note. @ 5f3e7e41:81cb07cf
2025-03-05 11:37:27The question of life’s meaning has long been a central concern in philosophy, debated by existentialists, nihilists, absurdists, and theologians alike. Is there an inherent purpose to human existence, or must we construct our own meaning? This essay explores the philosophical dimensions of the question by examining various perspectives, including existentialism, nihilism, and teleological interpretations. **Existentialist Perspective** Existentialists argue that meaning is not intrinsic but must be created. Jean-Paul Sartre, for instance, asserts that existence precedes essence—humans exist first and define their own purpose afterward. Unlike an artifact designed for a specific function, human beings are thrown into existence without predetermined meaning. Sartre’s concept of radical freedom suggests that we are entirely responsible for imbuing our lives with purpose through our choices and actions. Albert Camus, while existential in his approach, leans toward absurdism. He argues that human beings seek meaning in a universe that offers none. This fundamental conflict, the absurd, leads to either nihilism or rebellion. Camus advocates for an embrace of the absurd—accepting life’s lack of inherent purpose and living in defiance of this reality, deriving meaning from the act of living itself. **Nihilistic Perspective** Nihilism, most famously articulated by Friedrich Nietzsche, asserts that life has no objective meaning, purpose, or value. The "death of God" in Nietzsche’s work signifies the collapse of religious and metaphysical sources of meaning, leaving humanity in an existential void. Without a higher order dictating meaning, one might fall into existential despair. However, Nietzsche’s solution is the creation of personal values through the concept of the Übermensch, an individual who forges their own path and meaning without reliance on external validation. **Teleological and Theistic Views** In contrast, religious and teleological perspectives propose an intrinsic meaning to life, often rooted in divine purpose. Theistic traditions argue that meaning is bestowed upon humanity by a higher power. For example, in Christianity, the purpose of life is to fulfill God’s will, achieve salvation, and cultivate virtue. Similarly, in Aristotelian philosophy, eudaimonia, or human flourishing, is seen as the ultimate telos (end goal) of human existence, achieved through rational activity and moral virtue. **Synthesis: A Constructivist Approach** Given the divergence in perspectives, one might adopt a constructivist stance that synthesizes elements from each. If no inherent meaning exists, as existentialists and nihilists suggest, and if religious interpretations require faith, then meaning may best be understood as a subjective construction. Humans, as rational and reflective beings, can choose to ascribe significance to their existence based on personal values, relationships, creative endeavors, or contributions to humanity. **Conclusion** The meaning of life remains an open question, shaped by individual perspectives and cultural influences. Whether meaning is self-created, divinely ordained, or ultimately absent, the inquiry itself underscores a fundamental aspect of human nature: the relentless pursuit of significance. Perhaps the search for meaning is what gives life its greatest meaning.
@ 5f3e7e41:81cb07cf
2025-03-05 11:37:27The question of life’s meaning has long been a central concern in philosophy, debated by existentialists, nihilists, absurdists, and theologians alike. Is there an inherent purpose to human existence, or must we construct our own meaning? This essay explores the philosophical dimensions of the question by examining various perspectives, including existentialism, nihilism, and teleological interpretations. **Existentialist Perspective** Existentialists argue that meaning is not intrinsic but must be created. Jean-Paul Sartre, for instance, asserts that existence precedes essence—humans exist first and define their own purpose afterward. Unlike an artifact designed for a specific function, human beings are thrown into existence without predetermined meaning. Sartre’s concept of radical freedom suggests that we are entirely responsible for imbuing our lives with purpose through our choices and actions. Albert Camus, while existential in his approach, leans toward absurdism. He argues that human beings seek meaning in a universe that offers none. This fundamental conflict, the absurd, leads to either nihilism or rebellion. Camus advocates for an embrace of the absurd—accepting life’s lack of inherent purpose and living in defiance of this reality, deriving meaning from the act of living itself. **Nihilistic Perspective** Nihilism, most famously articulated by Friedrich Nietzsche, asserts that life has no objective meaning, purpose, or value. The "death of God" in Nietzsche’s work signifies the collapse of religious and metaphysical sources of meaning, leaving humanity in an existential void. Without a higher order dictating meaning, one might fall into existential despair. However, Nietzsche’s solution is the creation of personal values through the concept of the Übermensch, an individual who forges their own path and meaning without reliance on external validation. **Teleological and Theistic Views** In contrast, religious and teleological perspectives propose an intrinsic meaning to life, often rooted in divine purpose. Theistic traditions argue that meaning is bestowed upon humanity by a higher power. For example, in Christianity, the purpose of life is to fulfill God’s will, achieve salvation, and cultivate virtue. Similarly, in Aristotelian philosophy, eudaimonia, or human flourishing, is seen as the ultimate telos (end goal) of human existence, achieved through rational activity and moral virtue. **Synthesis: A Constructivist Approach** Given the divergence in perspectives, one might adopt a constructivist stance that synthesizes elements from each. If no inherent meaning exists, as existentialists and nihilists suggest, and if religious interpretations require faith, then meaning may best be understood as a subjective construction. Humans, as rational and reflective beings, can choose to ascribe significance to their existence based on personal values, relationships, creative endeavors, or contributions to humanity. **Conclusion** The meaning of life remains an open question, shaped by individual perspectives and cultural influences. Whether meaning is self-created, divinely ordained, or ultimately absent, the inquiry itself underscores a fundamental aspect of human nature: the relentless pursuit of significance. Perhaps the search for meaning is what gives life its greatest meaning. @ bd32f268:22b33966
2025-03-05 11:04:29Segundo a filosofia Aristotélica quando analisamos uma coisa seja ela um objecto ou um fenómeno devemos ser capazes de observar as suas causas. Podemos dizer que analisar as causas nos permite compreender com outra densidade, a origem, o significado e a finalidade das coisas. Atualmente, estamos vetados a um reducionismo materialista quando fazemos ciência, sendo portanto nota dominante a nossa fixação na matéria como o fator primordial do conhecimento dos objetos. Ao fixarmo-nos neste aspeto perdemos muitas outras dimensões que compõe as coisas. Atendamos então a Aristóteles e a quatro causas que este autor identifica para as coisas e fenómenos. Segundo o filósofo grego as causas dividem-se entre: materiais (relativas ao que algo é feito), as formais (relativas ao que algo é), as eficientes/motoras (relativas ao que as produziu ou quem as produziu) e as finais ( relativas á finalidade, Télos ou para quê; ou seja o que algo visa ou “tem por fim”). Seguindo esta teoria das quatro das quatro causas podemos descrever as condições de existência tanto de entidades estáticas como em transformação. Quer isto dizer que assim temos meios para explorar o porquê das coisas. Até conhecermos o porquê das coisas não podemos dizer que as conhecemos verdadeiramente. Analisemos um exemplo para que fique mais claro este método de análise. Uma mesa tem como causa material a madeira que a compõe, a sua causa formal (que diz respeito à forma) é a estrutura, ou seja o seu design; a sua causa eficiente é o trabalho de carpintaria que lhe deu origem e a sua causa final é servir de suporte para as refeições. \ Destas causas destaco em particular a causa final que creio ser a que mais frequentemente induz confusão nas pessoas. De facto, o conhecimento da finalidade das coisas é fundamental inclusive para que possamos viver de forma harmoniosa com a realidade. É certo que nos podemos sentar numa mesa e jantar na cadeira, contudo automaticamente vamos perceber a desarmonia que advém dessa decisão. Por vezes essa desarmonia não será tão evidente, no entanto não nos podemos esquecer que tudo o que existe tem um propósito, isto é orienta-se para um fim, cumprindo-nos agir em conformidade com a natureza das coisas para alcançar essa harmonia com a própria realidade. São muitas as ocasiões na nossa vida que queremos de alguma forma revogar esta inclinação natural das coisas para os seus fins, que funciona também como objeto e fundamento para a lei natural. Vejamos por exemplo a forma como muitas vezes quando comemos, em vez ordenar a nossa ação pelo fim primeiro (alimentar-se) buscamos o prazer como fim primário ao qual os outros estão subordinados resultando em desordem, ou seja num apetite que não está em conformidade com o objetivo último da alimentação. Não quer isto dizer que não se possa ou deva sentir prazer ao comer, quer apenas dizer que o fim último para que existe esse ato não é o prazer, mas sim a subsistência do corpo. Com este exemplo conseguimos perceber que há uma ordenação natural nos fins para que se orientam as coisas, sendo que nessa ordenação há sempre fins primários e secundários. Sendo conscientes dessa hierarquia podemos, de uma forma mais ajustada adaptar as nossas atitudes á realidade, isto é aos preceitos da lei natural.
@ bd32f268:22b33966
2025-03-05 11:04:29Segundo a filosofia Aristotélica quando analisamos uma coisa seja ela um objecto ou um fenómeno devemos ser capazes de observar as suas causas. Podemos dizer que analisar as causas nos permite compreender com outra densidade, a origem, o significado e a finalidade das coisas. Atualmente, estamos vetados a um reducionismo materialista quando fazemos ciência, sendo portanto nota dominante a nossa fixação na matéria como o fator primordial do conhecimento dos objetos. Ao fixarmo-nos neste aspeto perdemos muitas outras dimensões que compõe as coisas. Atendamos então a Aristóteles e a quatro causas que este autor identifica para as coisas e fenómenos. Segundo o filósofo grego as causas dividem-se entre: materiais (relativas ao que algo é feito), as formais (relativas ao que algo é), as eficientes/motoras (relativas ao que as produziu ou quem as produziu) e as finais ( relativas á finalidade, Télos ou para quê; ou seja o que algo visa ou “tem por fim”). Seguindo esta teoria das quatro das quatro causas podemos descrever as condições de existência tanto de entidades estáticas como em transformação. Quer isto dizer que assim temos meios para explorar o porquê das coisas. Até conhecermos o porquê das coisas não podemos dizer que as conhecemos verdadeiramente. Analisemos um exemplo para que fique mais claro este método de análise. Uma mesa tem como causa material a madeira que a compõe, a sua causa formal (que diz respeito à forma) é a estrutura, ou seja o seu design; a sua causa eficiente é o trabalho de carpintaria que lhe deu origem e a sua causa final é servir de suporte para as refeições. \ Destas causas destaco em particular a causa final que creio ser a que mais frequentemente induz confusão nas pessoas. De facto, o conhecimento da finalidade das coisas é fundamental inclusive para que possamos viver de forma harmoniosa com a realidade. É certo que nos podemos sentar numa mesa e jantar na cadeira, contudo automaticamente vamos perceber a desarmonia que advém dessa decisão. Por vezes essa desarmonia não será tão evidente, no entanto não nos podemos esquecer que tudo o que existe tem um propósito, isto é orienta-se para um fim, cumprindo-nos agir em conformidade com a natureza das coisas para alcançar essa harmonia com a própria realidade. São muitas as ocasiões na nossa vida que queremos de alguma forma revogar esta inclinação natural das coisas para os seus fins, que funciona também como objeto e fundamento para a lei natural. Vejamos por exemplo a forma como muitas vezes quando comemos, em vez ordenar a nossa ação pelo fim primeiro (alimentar-se) buscamos o prazer como fim primário ao qual os outros estão subordinados resultando em desordem, ou seja num apetite que não está em conformidade com o objetivo último da alimentação. Não quer isto dizer que não se possa ou deva sentir prazer ao comer, quer apenas dizer que o fim último para que existe esse ato não é o prazer, mas sim a subsistência do corpo. Com este exemplo conseguimos perceber que há uma ordenação natural nos fins para que se orientam as coisas, sendo que nessa ordenação há sempre fins primários e secundários. Sendo conscientes dessa hierarquia podemos, de uma forma mais ajustada adaptar as nossas atitudes á realidade, isto é aos preceitos da lei natural. @ a012dc82:6458a70d
2025-03-05 10:24:56In the dynamic and often unpredictable realm of cryptocurrency, the actions of Bitcoin whales—investors who hold large amounts of BTC—can significantly influence market trends and investor sentiment. A recent transaction, involving the transfer of over $1.5 billion worth of Bitcoin, has once again highlighted the profound impact these entities can have on the digital currency landscape. This article delves into the details of this massive move, exploring its implications and the broader context of whale activity in the cryptocurrency market. **Table of Contents** - The Billion-Dollar Transaction: A Deep Dive - Other Significant Whale Movements - Analyzing the Impact of Whale Activity - Market Volatility and Speculation - Psychological Impact on Investors - The Role of Whales in the Cryptocurrency Ecosystem - Liquidity and Market Depth - Influence on Adoption and Perception - The Billion-Dollar Transfer in Context - Bitcoin's Market Position - Historical Whale Activity - Future Implications and the Evolving Role of Whale … - Regulatory Environment - Institutional Investors and Market Stability - Technological Advances and Market Monitoring - Conclusion - FAQs **The Billion-Dollar Transaction: A Deep Dive** On January 31st, the cryptocurrency community was abuzz with news of a monumental Bitcoin transfer. A whale moved 35,049 BTC, valued at approximately $1,518,020,170, from one unknown wallet to another. This transaction not only stood out due to its sheer size but also because it underscored the significant liquidity and wealth concentrated in the hands of a few within the Bitcoin ecosystem. **Other Significant Whale Movements** The billion-dollar transfer was part of a series of large transactions that day, which included: - 25,266 BTC ($1,099,679,062) transferred between unknown wallets. - 929 BTC ($39,562,024) moved from Coinbase to Gemini. - 2,500 BTC ($106,647,312) sent to PayPal. - 1,736 BTC ($73,943,008) transferred to Gemini. - 34,300 BTC ($1,476,690,397) moved between unknown wallets. These transactions, totaling around $4.5 billion, highlight the enormous sums that whales can mobilize, influencing the Bitcoin market's liquidity and volatility. **Analyzing the Impact of Whale Activity** The actions of Bitcoin whales can lead to significant market movements. Large-scale transfers and trades can signal potential sales or acquisitions, prompting widespread speculation and reactive trading among smaller investors. **Market Volatility and Speculation** The recent billion-dollar transaction has sparked intense speculation regarding the whale's motives and the potential repercussions for Bitcoin's price stability. Such movements can create uncertainty, leading to price volatility as the market reacts to perceived changes in supply and demand. **Psychological Impact on Investors** Whale activity can also have a psychological impact on retail investors. The knowledge that a single entity or group can move the market might lead to caution, fear, or even panic selling, exacerbating price fluctuations and potentially leading to market manipulation accusations. **The Role of Whales in the Cryptocurrency Ecosystem** Bitcoin whales play a crucial role in the cryptocurrency ecosystem. Their significant holdings give them considerable influence over market dynamics, liquidity, and even the adoption and perception of Bitcoin as a digital asset. **Liquidity and Market Depth** Whales contribute to market liquidity and depth by providing substantial capital. Their trades, though potentially disruptive in the short term, help create a more liquid market, enabling other investors to execute large transactions more smoothly. **Influence on Adoption and Perception** The actions of whales can influence the broader perception of Bitcoin. Significant investments or divestments by these entities can signal confidence or concern regarding Bitcoin's future, influencing the sentiment of smaller investors and the general public. **The Billion-Dollar Transfer in Context** To fully understand the implications of the billion-dollar transfer, it's essential to consider the broader context of Bitcoin's market position and the historical activity of whales. **Bitcoin's Market Position** At the time of the transfer, Bitcoin was trading at $42,647, experiencing a slight decrease from its previous values. This period of relative stability makes the timing of the whale's move particularly noteworthy, as it suggests strategic positioning rather than a reaction to short-term market trends. **Historical Whale Activity** Historically, whale movements have preceded significant market movements, both bullish and bearish. By analyzing past transactions, investors attempt to predict future market directions based on whale behavior. However, the opaque nature of these entities and their motivations makes such predictions speculative at best. **Future Implications and the Evolving Role of Whales** As the cryptocurrency market matures, the role and impact of whales may evolve. Regulatory changes, the growing adoption of Bitcoin, and the entrance of institutional investors could all influence whale behavior and their impact on the market. **Regulatory Environment** Increased regulatory scrutiny could lead to more transparency in whale transactions, potentially mitigating some of the market volatility associated with these moves. However, it could also lead to more sophisticated strategies by whales to conceal their actions or to manipulate the market within legal boundaries. **Institutional Investors and Market Stability** The entrance of more institutional investors into the cryptocurrency market could dilute the relative influence of individual whales, leading to greater market stability. Institutional investors typically employ more conservative strategies and are subject to stricter regulatory oversight, which could help moderate the impact of large-scale transactions. **Technological Advances and Market Monitoring** Advancements in blockchain analytics and monitoring tools are making it easier to track whale activity in real-time. This increased transparency could help demystify whale actions, allowing smaller investors to make more informed decisions and potentially leveling the playing field. **Conclusion** The recent billion-dollar Bitcoin transfer by a whale is a stark reminder of the significant influence these entities hold over the cryptocurrency market. While their actions can lead to market volatility and speculation, they also play a crucial role in providing liquidity and depth to the market. As the cryptocurrency ecosystem continues to evolve, understanding the motivations and implications of whale activity will remain a critical aspect of navigating the digital asset landscape. **FAQs** **What is a Bitcoin whale?** A Bitcoin whale is an individual or entity that holds a large amount of Bitcoin. These investors have enough capital to influence market movements significantly when they buy or sell large quantities of BTC. **How much Bitcoin was moved by the whale?** The whale moved 35,049 BTC, which was valued at approximately $1,518,020,170 at the time of the transaction. **Where was the Bitcoin transferred?** The Bitcoin was transferred from one unknown wallet to another. The identities of the parties involved and the purpose of the transfer remain undisclosed. **Were there other significant transactions on the same day?** Yes, there were several other significant transactions on the same day, including transfers worth hundreds of millions and billions of dollars, contributing to a total movement of about $4.5 billion in Bitcoin by whales. **How do whale movements affect the Bitcoin market?** Whale movements can lead to increased volatility in the Bitcoin market. Large transactions can signal potential sales or purchases to other traders, influencing the market price and leading to speculative trading. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: @croxroadnewsco** **Instagram: @croxroadnews.co/** **Youtube: @thebitcoinlibertarian** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** **Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad** **Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
@ a012dc82:6458a70d
2025-03-05 10:24:56In the dynamic and often unpredictable realm of cryptocurrency, the actions of Bitcoin whales—investors who hold large amounts of BTC—can significantly influence market trends and investor sentiment. A recent transaction, involving the transfer of over $1.5 billion worth of Bitcoin, has once again highlighted the profound impact these entities can have on the digital currency landscape. This article delves into the details of this massive move, exploring its implications and the broader context of whale activity in the cryptocurrency market. **Table of Contents** - The Billion-Dollar Transaction: A Deep Dive - Other Significant Whale Movements - Analyzing the Impact of Whale Activity - Market Volatility and Speculation - Psychological Impact on Investors - The Role of Whales in the Cryptocurrency Ecosystem - Liquidity and Market Depth - Influence on Adoption and Perception - The Billion-Dollar Transfer in Context - Bitcoin's Market Position - Historical Whale Activity - Future Implications and the Evolving Role of Whale … - Regulatory Environment - Institutional Investors and Market Stability - Technological Advances and Market Monitoring - Conclusion - FAQs **The Billion-Dollar Transaction: A Deep Dive** On January 31st, the cryptocurrency community was abuzz with news of a monumental Bitcoin transfer. A whale moved 35,049 BTC, valued at approximately $1,518,020,170, from one unknown wallet to another. This transaction not only stood out due to its sheer size but also because it underscored the significant liquidity and wealth concentrated in the hands of a few within the Bitcoin ecosystem. **Other Significant Whale Movements** The billion-dollar transfer was part of a series of large transactions that day, which included: - 25,266 BTC ($1,099,679,062) transferred between unknown wallets. - 929 BTC ($39,562,024) moved from Coinbase to Gemini. - 2,500 BTC ($106,647,312) sent to PayPal. - 1,736 BTC ($73,943,008) transferred to Gemini. - 34,300 BTC ($1,476,690,397) moved between unknown wallets. These transactions, totaling around $4.5 billion, highlight the enormous sums that whales can mobilize, influencing the Bitcoin market's liquidity and volatility. **Analyzing the Impact of Whale Activity** The actions of Bitcoin whales can lead to significant market movements. Large-scale transfers and trades can signal potential sales or acquisitions, prompting widespread speculation and reactive trading among smaller investors. **Market Volatility and Speculation** The recent billion-dollar transaction has sparked intense speculation regarding the whale's motives and the potential repercussions for Bitcoin's price stability. Such movements can create uncertainty, leading to price volatility as the market reacts to perceived changes in supply and demand. **Psychological Impact on Investors** Whale activity can also have a psychological impact on retail investors. The knowledge that a single entity or group can move the market might lead to caution, fear, or even panic selling, exacerbating price fluctuations and potentially leading to market manipulation accusations. **The Role of Whales in the Cryptocurrency Ecosystem** Bitcoin whales play a crucial role in the cryptocurrency ecosystem. Their significant holdings give them considerable influence over market dynamics, liquidity, and even the adoption and perception of Bitcoin as a digital asset. **Liquidity and Market Depth** Whales contribute to market liquidity and depth by providing substantial capital. Their trades, though potentially disruptive in the short term, help create a more liquid market, enabling other investors to execute large transactions more smoothly. **Influence on Adoption and Perception** The actions of whales can influence the broader perception of Bitcoin. Significant investments or divestments by these entities can signal confidence or concern regarding Bitcoin's future, influencing the sentiment of smaller investors and the general public. **The Billion-Dollar Transfer in Context** To fully understand the implications of the billion-dollar transfer, it's essential to consider the broader context of Bitcoin's market position and the historical activity of whales. **Bitcoin's Market Position** At the time of the transfer, Bitcoin was trading at $42,647, experiencing a slight decrease from its previous values. This period of relative stability makes the timing of the whale's move particularly noteworthy, as it suggests strategic positioning rather than a reaction to short-term market trends. **Historical Whale Activity** Historically, whale movements have preceded significant market movements, both bullish and bearish. By analyzing past transactions, investors attempt to predict future market directions based on whale behavior. However, the opaque nature of these entities and their motivations makes such predictions speculative at best. **Future Implications and the Evolving Role of Whales** As the cryptocurrency market matures, the role and impact of whales may evolve. Regulatory changes, the growing adoption of Bitcoin, and the entrance of institutional investors could all influence whale behavior and their impact on the market. **Regulatory Environment** Increased regulatory scrutiny could lead to more transparency in whale transactions, potentially mitigating some of the market volatility associated with these moves. However, it could also lead to more sophisticated strategies by whales to conceal their actions or to manipulate the market within legal boundaries. **Institutional Investors and Market Stability** The entrance of more institutional investors into the cryptocurrency market could dilute the relative influence of individual whales, leading to greater market stability. Institutional investors typically employ more conservative strategies and are subject to stricter regulatory oversight, which could help moderate the impact of large-scale transactions. **Technological Advances and Market Monitoring** Advancements in blockchain analytics and monitoring tools are making it easier to track whale activity in real-time. This increased transparency could help demystify whale actions, allowing smaller investors to make more informed decisions and potentially leveling the playing field. **Conclusion** The recent billion-dollar Bitcoin transfer by a whale is a stark reminder of the significant influence these entities hold over the cryptocurrency market. While their actions can lead to market volatility and speculation, they also play a crucial role in providing liquidity and depth to the market. As the cryptocurrency ecosystem continues to evolve, understanding the motivations and implications of whale activity will remain a critical aspect of navigating the digital asset landscape. **FAQs** **What is a Bitcoin whale?** A Bitcoin whale is an individual or entity that holds a large amount of Bitcoin. These investors have enough capital to influence market movements significantly when they buy or sell large quantities of BTC. **How much Bitcoin was moved by the whale?** The whale moved 35,049 BTC, which was valued at approximately $1,518,020,170 at the time of the transaction. **Where was the Bitcoin transferred?** The Bitcoin was transferred from one unknown wallet to another. The identities of the parties involved and the purpose of the transfer remain undisclosed. **Were there other significant transactions on the same day?** Yes, there were several other significant transactions on the same day, including transfers worth hundreds of millions and billions of dollars, contributing to a total movement of about $4.5 billion in Bitcoin by whales. **How do whale movements affect the Bitcoin market?** Whale movements can lead to increased volatility in the Bitcoin market. Large transactions can signal potential sales or purchases to other traders, influencing the market price and leading to speculative trading. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: @croxroadnewsco** **Instagram: @croxroadnews.co/** **Youtube: @thebitcoinlibertarian** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** **Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad** **Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.* @ e31e84c4:77bbabc0
2025-03-05 10:23:47The IMF’s $1.4 Billion Shackle *was Written By Kudzai Kutukwa. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: **muggyarch11@walletofsatoshi.com*** The recent $1.4 billion Extended Fund Facility (EFF) agreement between the International Monetary Fund (IMF) and El Salvador marks a significant turning point in the nation's economic and monetary policy. The IMF’s $1.4 billion “lifeline” is a sly Trojan horse, gutting El Salvador’s sovereignty and kneecapping its 2021 Bitcoin law— which represented a bold step toward monetary freedom and economic self-determination— all to prop up the same economic mess it pretends to fix. Brilliant, right? **The IMF’s Colonialist Agenda: A Historical Precedent** In 2021, El Salvador made history by adopting Bitcoin as legal tender, positioning itself at the forefront of financial innovation and offering its citizens an alternative to the U.S. dollar. This move was a bold step toward monetary independence and as a pathway toward individual financial sovereignty by reducing remittance costs for Salvadorans and bypassing the predatory international banking system. By making Bitcoin legal tender, El Salvador was taking steps to free itself from financial colonialism. The IMF’s response to El Salvador’s Bitcoin law was predictably hostile from day one. The institution repeatedly warned of the “risks” associated with Bitcoin, framing it as a threat to financial stability rather than a tool for economic empowerment. Hypocrisy drips from every word—the IMF’s own debt traps and inflationary schemes have fueled the chaos it now “rescues” El Salvador from. The Bretton Woods institution has long been the enforcer of the global financial elite, ensuring that nations remain shackled to the U.S. dollar-dominated system. Through predatory loans and stringent conditions, the IMF perpetuates economic subjugation. Now, facing pressure from these same institutions, El Salvador finds itself caught in the classic IMF trap: accepting loans with strings attached that further cement dependency. This aid package isn't a solution to El Salvador's problems; it's leverage to force compliance with the global banking cartel's agenda. Under the IMF agreement, El Salvador has been compelled to amend its Bitcoin law, revoking Bitcoin's status as legal tender and making its acceptance by businesses voluntary. Additionally, tax obligations must now be settled exclusively in U.S. dollars. This gut-wrenching retreat from its bold Bitcoin rebellion represents a diabolical masterpiece of oppression—stripping citizens of financial freedom and forcing them to forever bow before the fiat gods. **Why the IMF Must Destroy Bitcoin’s Medium of Exchange Use Case** To understand why the IMF is so determined to undermine Bitcoin’s role as a medium of exchange in El Salvador, it’s important to revisit the fundamental nature of money. The widely cited “three functions” of money—medium of exchange, store of value, and unit of account—are often misunderstood. These are not rigid definitions, but empirical observations of how money functions in practice. Money is, first and foremost, the generally accepted medium of exchange. The other functions tend to follow, but they are not exclusive to money. For example, gold can serve as a store of value but is no longer a commonly accepted medium of exchange, and other commodities can also act as units of account, but neither is money unless it is widely accepted as a medium of exchange. Bitcoin’s rise as a store of value (akin to “digital gold”) is not as threatening to the fiat system as its potential to function as a widely accepted medium of exchange. A strong store of value can exist within a system that is still dominated by fiat currencies. If Bitcoin were to become a dominant medium of exchange, it would directly challenge the monopoly of central banks and the control that institutions like the IMF exert over global financial systems. That is why the IMF’s primary goal in El Salvador is not necessarily to stop Bitcoin’s adoption altogether but rather to strip Bitcoin of its medium of exchange function, thus effectively relegating Bitcoin to a speculative asset or store of value. Furthermore, this Bitcoin experiment was the first real-world test of Bitcoin as a medium of exchange at the nation-state level. If it had succeeded, other countries—especially those in the Global South struggling with inflation, currency devaluation, and IMF-imposed austerity—might have followed suit. The IMF couldn't afford to let that happen. By neutralizing Bitcoin's role as money, it ensures that alternative financial systems do not gain traction outside the fiat-based global order. In other words, as long as Bitcoin can't be used freely as a medium of exchange, it cannot fulfill its role as money, and the fiat gods' grip on the global monetary system remains unchallenged—at least for now. **The $1.4 Billion Faustian Bargain** El Salvador’s decision to seek IMF funding is a reflection of the immense pressure it faces from global financial markets and institutions. The country’s high debt levels and weak external buffers are, in large part, a consequence of its integration into a global financial system that prioritizes short-term capital flows over long-term economic stability. By accepting the IMF’s terms, El Salvador has effectively traded its sovereignty for temporary financial relief. What is even more surprising is that El Salvador had an alternative to this Faustian bargain: the issuance of Bitcoin bonds. While initially proposed as a way to finance Bitcoin City and geothermal Bitcoin mining infrastructure, the volcano bonds the country could have raised the $1.4 billion needed without sacrificing its monetary sovereignty. This represents a missed opportunity for El Salvador to bolster its financial independence, attract global capital, and solidify its position as a pioneer in the adoption of decentralized money. Instead of falling back into the IMF’s debt trap—complete with austerity measures, restrictions on Bitcoin use, and financial surveillance—El Salvador could have embraced a Bitcoin-native financial strategy that aligned with its long-term vision of economic independence. So why didn't El Salvador go through with the Bitcoin bond issuance? I don't know, but if I were to speculate, I would say the answer likely lies in political and institutional inertia, coupled with external pressures from the IMF and its allied institutions, or worse. If El Salvador had raised capital through Bitcoin bonds, it would have sent shockwaves through the financial world, proving that a nation-state could operate independently of the IMF. **The Long-Term Consequences for El Salvador** While the IMF’s program may provide short-term relief, its long-term consequences are likely to be detrimental to the Salvadoran people. The emphasis on fiscal consolidation and debt reduction will inevitably lead to cuts in public spending, particularly in areas such as social services and infrastructure. These measures will disproportionately affect the most vulnerable segments of society, exacerbating inequality and undermining the country’s social fabric. Moreover, the IMF’s focus on “strengthening governance and transparency” is a thinly veiled attempt to impose external control over El Salvador’s domestic policies. The requirement to enhance Anti-Money Laundering and Countering the Financing of Terrorism (AML/CFT) frameworks, while ostensibly aimed at combating illicit activities, will likely be used to surveil and restrict the financial activities of ordinary citizens. This represents a gross violation of individual rights and a further erosion of economic freedom. **Conclusion** The IMF's $1.4 billion arrangement with El Salvador represents not economic salvation but a calculated reassertion of control. By forcing El Salvador to retreat from its Bitcoin initiative, the IMF is protecting the very system that has kept developing nations financially subjugated for decades. For Salvadorans, this means their bold experiment in monetary sovereignty has been curtailed, not by market forces or technological limitations, but by the deliberate intervention of the guardians of the old financial order. Those who believe in true financial freedom must recognize this for what it is: not assistance, but suppression; not aid, but control. The battle for monetary sovereignty continues, and despite this setback, Bitcoin's promise of financial liberation remains as vital as ever—not just for El Salvador, but for all those seeking escape from the oppressive machinery of central banking. --- The IMF’s $1.4 Billion Shackle *was Written By Kudzai Kutukwa. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: **muggyarch11@walletofsatoshi.com***
@ e31e84c4:77bbabc0
2025-03-05 10:23:47The IMF’s $1.4 Billion Shackle *was Written By Kudzai Kutukwa. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: **muggyarch11@walletofsatoshi.com*** The recent $1.4 billion Extended Fund Facility (EFF) agreement between the International Monetary Fund (IMF) and El Salvador marks a significant turning point in the nation's economic and monetary policy. The IMF’s $1.4 billion “lifeline” is a sly Trojan horse, gutting El Salvador’s sovereignty and kneecapping its 2021 Bitcoin law— which represented a bold step toward monetary freedom and economic self-determination— all to prop up the same economic mess it pretends to fix. Brilliant, right? **The IMF’s Colonialist Agenda: A Historical Precedent** In 2021, El Salvador made history by adopting Bitcoin as legal tender, positioning itself at the forefront of financial innovation and offering its citizens an alternative to the U.S. dollar. This move was a bold step toward monetary independence and as a pathway toward individual financial sovereignty by reducing remittance costs for Salvadorans and bypassing the predatory international banking system. By making Bitcoin legal tender, El Salvador was taking steps to free itself from financial colonialism. The IMF’s response to El Salvador’s Bitcoin law was predictably hostile from day one. The institution repeatedly warned of the “risks” associated with Bitcoin, framing it as a threat to financial stability rather than a tool for economic empowerment. Hypocrisy drips from every word—the IMF’s own debt traps and inflationary schemes have fueled the chaos it now “rescues” El Salvador from. The Bretton Woods institution has long been the enforcer of the global financial elite, ensuring that nations remain shackled to the U.S. dollar-dominated system. Through predatory loans and stringent conditions, the IMF perpetuates economic subjugation. Now, facing pressure from these same institutions, El Salvador finds itself caught in the classic IMF trap: accepting loans with strings attached that further cement dependency. This aid package isn't a solution to El Salvador's problems; it's leverage to force compliance with the global banking cartel's agenda. Under the IMF agreement, El Salvador has been compelled to amend its Bitcoin law, revoking Bitcoin's status as legal tender and making its acceptance by businesses voluntary. Additionally, tax obligations must now be settled exclusively in U.S. dollars. This gut-wrenching retreat from its bold Bitcoin rebellion represents a diabolical masterpiece of oppression—stripping citizens of financial freedom and forcing them to forever bow before the fiat gods. **Why the IMF Must Destroy Bitcoin’s Medium of Exchange Use Case** To understand why the IMF is so determined to undermine Bitcoin’s role as a medium of exchange in El Salvador, it’s important to revisit the fundamental nature of money. The widely cited “three functions” of money—medium of exchange, store of value, and unit of account—are often misunderstood. These are not rigid definitions, but empirical observations of how money functions in practice. Money is, first and foremost, the generally accepted medium of exchange. The other functions tend to follow, but they are not exclusive to money. For example, gold can serve as a store of value but is no longer a commonly accepted medium of exchange, and other commodities can also act as units of account, but neither is money unless it is widely accepted as a medium of exchange. Bitcoin’s rise as a store of value (akin to “digital gold”) is not as threatening to the fiat system as its potential to function as a widely accepted medium of exchange. A strong store of value can exist within a system that is still dominated by fiat currencies. If Bitcoin were to become a dominant medium of exchange, it would directly challenge the monopoly of central banks and the control that institutions like the IMF exert over global financial systems. That is why the IMF’s primary goal in El Salvador is not necessarily to stop Bitcoin’s adoption altogether but rather to strip Bitcoin of its medium of exchange function, thus effectively relegating Bitcoin to a speculative asset or store of value. Furthermore, this Bitcoin experiment was the first real-world test of Bitcoin as a medium of exchange at the nation-state level. If it had succeeded, other countries—especially those in the Global South struggling with inflation, currency devaluation, and IMF-imposed austerity—might have followed suit. The IMF couldn't afford to let that happen. By neutralizing Bitcoin's role as money, it ensures that alternative financial systems do not gain traction outside the fiat-based global order. In other words, as long as Bitcoin can't be used freely as a medium of exchange, it cannot fulfill its role as money, and the fiat gods' grip on the global monetary system remains unchallenged—at least for now. **The $1.4 Billion Faustian Bargain** El Salvador’s decision to seek IMF funding is a reflection of the immense pressure it faces from global financial markets and institutions. The country’s high debt levels and weak external buffers are, in large part, a consequence of its integration into a global financial system that prioritizes short-term capital flows over long-term economic stability. By accepting the IMF’s terms, El Salvador has effectively traded its sovereignty for temporary financial relief. What is even more surprising is that El Salvador had an alternative to this Faustian bargain: the issuance of Bitcoin bonds. While initially proposed as a way to finance Bitcoin City and geothermal Bitcoin mining infrastructure, the volcano bonds the country could have raised the $1.4 billion needed without sacrificing its monetary sovereignty. This represents a missed opportunity for El Salvador to bolster its financial independence, attract global capital, and solidify its position as a pioneer in the adoption of decentralized money. Instead of falling back into the IMF’s debt trap—complete with austerity measures, restrictions on Bitcoin use, and financial surveillance—El Salvador could have embraced a Bitcoin-native financial strategy that aligned with its long-term vision of economic independence. So why didn't El Salvador go through with the Bitcoin bond issuance? I don't know, but if I were to speculate, I would say the answer likely lies in political and institutional inertia, coupled with external pressures from the IMF and its allied institutions, or worse. If El Salvador had raised capital through Bitcoin bonds, it would have sent shockwaves through the financial world, proving that a nation-state could operate independently of the IMF. **The Long-Term Consequences for El Salvador** While the IMF’s program may provide short-term relief, its long-term consequences are likely to be detrimental to the Salvadoran people. The emphasis on fiscal consolidation and debt reduction will inevitably lead to cuts in public spending, particularly in areas such as social services and infrastructure. These measures will disproportionately affect the most vulnerable segments of society, exacerbating inequality and undermining the country’s social fabric. Moreover, the IMF’s focus on “strengthening governance and transparency” is a thinly veiled attempt to impose external control over El Salvador’s domestic policies. The requirement to enhance Anti-Money Laundering and Countering the Financing of Terrorism (AML/CFT) frameworks, while ostensibly aimed at combating illicit activities, will likely be used to surveil and restrict the financial activities of ordinary citizens. This represents a gross violation of individual rights and a further erosion of economic freedom. **Conclusion** The IMF's $1.4 billion arrangement with El Salvador represents not economic salvation but a calculated reassertion of control. By forcing El Salvador to retreat from its Bitcoin initiative, the IMF is protecting the very system that has kept developing nations financially subjugated for decades. For Salvadorans, this means their bold experiment in monetary sovereignty has been curtailed, not by market forces or technological limitations, but by the deliberate intervention of the guardians of the old financial order. Those who believe in true financial freedom must recognize this for what it is: not assistance, but suppression; not aid, but control. The battle for monetary sovereignty continues, and despite this setback, Bitcoin's promise of financial liberation remains as vital as ever—not just for El Salvador, but for all those seeking escape from the oppressive machinery of central banking. --- The IMF’s $1.4 Billion Shackle *was Written By Kudzai Kutukwa. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: **muggyarch11@walletofsatoshi.com*** @ 220522c2:61e18cb4
2025-03-05 09:53:59# How to package a macOS Desktop App  ## Introduction Creating and distributing macOS desktop applications is a huge pain in the ass and can be very confusing. I'm writing this article as a reference for myself as well as any other developer who wants to package a desktop app for macOS. ## Join the Apple Developer Program - Go to [developer.apple.com](https://developer.apple.com) and sign in with your Apple ID - Enroll in an individual ($99/year) or organization ($299/year) membership - Complete the enrollment process and wait for approval ## Setup Xcode for some reason - Download Xcode from from the Mac App Store - Go to Xcode -> Settings -> Accounts - Click the "+" button and add your Apple Developer Account Check if Xcode Command Line Tools are installed ``` xcode-select -p ``` If they are not installed for some reason you can install them with ``` xcode-select --install ``` ## Generate a Certificate Signing Request (CSR) - Open Keychain Access - Go to Keychain Access > Certificate Assistant > Request a Certificate From a Certificate Authority - Enter your email address and a common name (e.g., your name or company name) - Leave "CA Email Address" blank, select Saved to disk, and click Continue - Save the `.certSigningRequest` file somewhere ## Request Certificate - Log in to [developer.apple.com/account](https://developer.apple.com/account) - Go to Certificates, Identifiers & Profiles > Certificates - Click the + button to add a new certificate - Under "Software," select **Developer ID Application**, then Continue - Choose **G2 Sub-CA (Xcode 11.4.1 or later)** - Upload the `.certSigningRequest` file you just created, then Continue - Download the `.cer` file (e.g., `developerID_application.cer`) ## Install the Certificate - Double-click the downloaded `.cer` file to add it to your Keychain Access under "My Certificates" - Verify it’s there with a private key, after selecting the cert look at the top tabs, select "My Certificates" expand the certificate to see the key icon ## Sign your Application You can now try signing your application, if you run into issues check out the troubleshooting section at the bottom of this article. ``` codesign --deep --force --verify --verbose --sign "Developer ID Application: Your Name (TeamID)" --options=runtime --timestamp /path/to/YourApp.app ``` ## Package Your App Most apps distributed via websites are packaged in a `.dmg` (disk image) for a polished user experience: - Use Disk Utility or a tool like `create-dmg` (install via Homebrew: `brew install create-dmg`) ``` create-dmg --volname "YourApp" --app-drop-link 600 185 --window-pos 200 120 --window-size 800 400 "YourApp.dmg" /path/to/YourApp.app ``` This will setup the drag and drop thing for you app into the applications folder, when you run this command that drag and drop ui will pop up, ignore it. You really should use a tool like this, if you try to do it on your own you'll need to deal with symlinks, applescript and other nonsense. I've done it this way and if there's interest I can write a part two for a more manual approach. - Sign the `.dmg` ``` codesign --deep --force --verify --verbose --sign "Developer ID Application: Your Name (TeamID)" --options=runtime --timestamp YourApp.dmg ``` ## Notarize your App Apple requires notarization to confirm your app isn’t malicious. You’ll need an app-specific password (not your Apple ID password) Create and App-Specific Password: - Go to [appleid.apple.com](https://appleid.apple.com), sign in, and under "Sign-In and Security," select App-Specific Passwords - Generate a new password (name it whatever you like) and save it Submit for Notarization - Use the `notarytool` command ``` xcrun notarytool submit /path/to/YourApp.dmg --apple-id "your@email.com" --password "app-specific-password" --team-id "YourTeamID" --wait ``` - Replace placeholders with your Apple ID, the app-specific password, and your Team ID - The `--wait` flag shows the result immediately (takes a few minutes). You’ll get a "Success" message or a log ID with issues to fix Staple the Notarization Ticket: - After approval, attach the notarization ticket to your `.dmg` ``` xcrun stapler staple /path/to/YourApp.dmg ``` - This ensures [Gatekeeper](https://support.apple.com/guide/security/gatekeeper-and-runtime-protection-sec5599b66df/web) can verify it offline ## Upload and Distribute - Upload the notarized `.dmg` to your GitHub or your website - Provide a download link (preferably HTTPS for security) - Users might see a Gatekeeper prompt on first launch; they can right-click > Open or allow it in System Settings > Security & Privacy ## Troubleshooting I have had countless issues when trying to sign applications ### Unable to build chain to self-signed root One issue that I've run into on both of my macbooks is: `Warning: unable to build chain to self-signed root for signer` Something I usually have to do is open the Developer Certificate, expand the trust section and set "When using this certificate:" to "Use System Defaults" Then I restart my laptop once or twice and eventually it works. ### Can't delete cert in GUI I have also had an issue where I can't delete the certs in the gui, in this case run the command to list the certs: ``` security find-identity -v -p codesigning ``` and delete it based on the hash in the beginning: ``` security delete-certificate -Z ABC123... ``` ### Notarization fails This is usually due to not passing the hardened runtime option so try resigning the app and dmg with `--options runtime` You can use the command below to see what's wrong ``` xcrun notarytool log "notary id" --apple-id "your@email.com" --password "app-specific-password" --team-id "HGGSBC8HJF" ``` ## Conclusion Having an article like this would have saved me a lot of time debugging. npub1ygzj9skr9val9yqxkf67yf9jshtyhvvl0x76jp5er09nsc0p3j6qr260k2 Posted at [notestack.com](https://notestack.com)
@ 220522c2:61e18cb4
2025-03-05 09:53:59# How to package a macOS Desktop App  ## Introduction Creating and distributing macOS desktop applications is a huge pain in the ass and can be very confusing. I'm writing this article as a reference for myself as well as any other developer who wants to package a desktop app for macOS. ## Join the Apple Developer Program - Go to [developer.apple.com](https://developer.apple.com) and sign in with your Apple ID - Enroll in an individual ($99/year) or organization ($299/year) membership - Complete the enrollment process and wait for approval ## Setup Xcode for some reason - Download Xcode from from the Mac App Store - Go to Xcode -> Settings -> Accounts - Click the "+" button and add your Apple Developer Account Check if Xcode Command Line Tools are installed ``` xcode-select -p ``` If they are not installed for some reason you can install them with ``` xcode-select --install ``` ## Generate a Certificate Signing Request (CSR) - Open Keychain Access - Go to Keychain Access > Certificate Assistant > Request a Certificate From a Certificate Authority - Enter your email address and a common name (e.g., your name or company name) - Leave "CA Email Address" blank, select Saved to disk, and click Continue - Save the `.certSigningRequest` file somewhere ## Request Certificate - Log in to [developer.apple.com/account](https://developer.apple.com/account) - Go to Certificates, Identifiers & Profiles > Certificates - Click the + button to add a new certificate - Under "Software," select **Developer ID Application**, then Continue - Choose **G2 Sub-CA (Xcode 11.4.1 or later)** - Upload the `.certSigningRequest` file you just created, then Continue - Download the `.cer` file (e.g., `developerID_application.cer`) ## Install the Certificate - Double-click the downloaded `.cer` file to add it to your Keychain Access under "My Certificates" - Verify it’s there with a private key, after selecting the cert look at the top tabs, select "My Certificates" expand the certificate to see the key icon ## Sign your Application You can now try signing your application, if you run into issues check out the troubleshooting section at the bottom of this article. ``` codesign --deep --force --verify --verbose --sign "Developer ID Application: Your Name (TeamID)" --options=runtime --timestamp /path/to/YourApp.app ``` ## Package Your App Most apps distributed via websites are packaged in a `.dmg` (disk image) for a polished user experience: - Use Disk Utility or a tool like `create-dmg` (install via Homebrew: `brew install create-dmg`) ``` create-dmg --volname "YourApp" --app-drop-link 600 185 --window-pos 200 120 --window-size 800 400 "YourApp.dmg" /path/to/YourApp.app ``` This will setup the drag and drop thing for you app into the applications folder, when you run this command that drag and drop ui will pop up, ignore it. You really should use a tool like this, if you try to do it on your own you'll need to deal with symlinks, applescript and other nonsense. I've done it this way and if there's interest I can write a part two for a more manual approach. - Sign the `.dmg` ``` codesign --deep --force --verify --verbose --sign "Developer ID Application: Your Name (TeamID)" --options=runtime --timestamp YourApp.dmg ``` ## Notarize your App Apple requires notarization to confirm your app isn’t malicious. You’ll need an app-specific password (not your Apple ID password) Create and App-Specific Password: - Go to [appleid.apple.com](https://appleid.apple.com), sign in, and under "Sign-In and Security," select App-Specific Passwords - Generate a new password (name it whatever you like) and save it Submit for Notarization - Use the `notarytool` command ``` xcrun notarytool submit /path/to/YourApp.dmg --apple-id "your@email.com" --password "app-specific-password" --team-id "YourTeamID" --wait ``` - Replace placeholders with your Apple ID, the app-specific password, and your Team ID - The `--wait` flag shows the result immediately (takes a few minutes). You’ll get a "Success" message or a log ID with issues to fix Staple the Notarization Ticket: - After approval, attach the notarization ticket to your `.dmg` ``` xcrun stapler staple /path/to/YourApp.dmg ``` - This ensures [Gatekeeper](https://support.apple.com/guide/security/gatekeeper-and-runtime-protection-sec5599b66df/web) can verify it offline ## Upload and Distribute - Upload the notarized `.dmg` to your GitHub or your website - Provide a download link (preferably HTTPS for security) - Users might see a Gatekeeper prompt on first launch; they can right-click > Open or allow it in System Settings > Security & Privacy ## Troubleshooting I have had countless issues when trying to sign applications ### Unable to build chain to self-signed root One issue that I've run into on both of my macbooks is: `Warning: unable to build chain to self-signed root for signer` Something I usually have to do is open the Developer Certificate, expand the trust section and set "When using this certificate:" to "Use System Defaults" Then I restart my laptop once or twice and eventually it works. ### Can't delete cert in GUI I have also had an issue where I can't delete the certs in the gui, in this case run the command to list the certs: ``` security find-identity -v -p codesigning ``` and delete it based on the hash in the beginning: ``` security delete-certificate -Z ABC123... ``` ### Notarization fails This is usually due to not passing the hardened runtime option so try resigning the app and dmg with `--options runtime` You can use the command below to see what's wrong ``` xcrun notarytool log "notary id" --apple-id "your@email.com" --password "app-specific-password" --team-id "HGGSBC8HJF" ``` ## Conclusion Having an article like this would have saved me a lot of time debugging. npub1ygzj9skr9val9yqxkf67yf9jshtyhvvl0x76jp5er09nsc0p3j6qr260k2 Posted at [notestack.com](https://notestack.com) @ fd78c37f:a0ec0833
2025-03-05 09:50:19In this edition, we invited njump.me/npub134d6jtyveg74cuuj7qun4v2m6r7x7c6ryk69z4q7pa7f43kran2sl2yggk from Bitcoin Junior Club to share how she empowers children, teenagers, and families through Bitcoin education. She emphasizes that in the Bitcoin ecosystem, education should come before mass adoption. **YakiHonne**: Şelale, thank you for being here! Before we dive into the interview questions, I'd like to introduce YakiHonne, the hosting platform for today’s discussion. YakiHonne is a decentralized media client built on Nostr—a protocol designed to empower freedom of speech through technology. It enables creators to own their voices and assets while offering innovative tools like smart widgets, verified notes, and support for long-form content. With YakiHonne, individuals can express themselves freely, without the fear of censorship, bans, or restrictions. Today, we’ll be exploring more about your community,Şelale. So, let’s start with an introduction—could you tell us a bit about yourself and your community? **Şelale**:Thank you! I'm actually a big fan of YakiHonne. Nostr is my second biggest passion, right after Bitcoin. And within this ecosystem, everything YakiHonne has done—whether empowering communities or supporting creators—looks truly incredible. I could represent many different communities, but today, I want to focus on a recent project I started together with my husband—[Bitcoin Junior Club](https://www.bitcoin4youth.com/shortly-about-us-bitcoin-junior-club/). It's a fun and educational space designed for children, teenagers, and entire families. My Bitcoin journey dates back to around 2017 when I started diving deeper into Bitcoin. During the block size controversy. I found myself repeatedly reading the Whitepaper, trying to understand why some people were attempting to manipulate the rules and why the debate was gaining so much traction in the mass media. As I often say, the Bitcoin journey is a dynamic process—over the years, my experiences, perspectives, and areas of focus have continuously evolved. Right now, one of my key priorities are families and education. The Bitcoin ecosystem had already seen various emerging trends, such as the rise of female-oriented communities, hence the need for children related topics as well. Overall, the last few years have brought more creative minds building up their projects, which is very nice to see. A good example here would be [Bitcoin FilmFest](https://bitcoinfilmfest.com/), another dynamic initiative I’m involved in. These are all signs of Bitcoin's ever-expanding and evolving landscape. **YakiHonne**: I would like to know, what sparked your interest in Bitcoin? And what motivated you to create Bitcoin Junior Club? What inspired you to create a whole community around it? **Şelale**:There were many different aspects that drew me to Bitcoin, but I would say the most important one is the aspect of freedom, Bitcoin is the best form of money humanity has ever had. No middlemen, no one setting the rules. For the first time, people who have always been unprivileged and unbanked now have a real alternative—a way to opt out of the system they were born into. At the same time, when we look at developed countries, we see increasing surveillance, restrictions, and privacy constraints. Once again, Bitcoin serves a crucial role here. It is freedom money, a freedom tool, and that’s what hooked me the most. On the other hand, what truly motivated me to launch our project was the realization that money is just a tool. If people stop thinking critically, if they don’t truly understand its potential, even something as revolutionary as Bitcoin can be misused or even turned against us. Together with my husband, we believe that education is essential, especially for younger generations. We want to help them develop critical and creative thinking skills, to keep questioning topics they come across, and to think for themselves. This is the core reason we started this community. Along the way, I’ve come across many family-friendly projects with a similar mission. But most of such resources are scattered and difficult to locate. That’s why, one of our main goals is to create a comprehensive database—a place where people can find all kinds of educational resources, from the content we produce to information about existing initiatives in areas like: homeschooling, unschooling, Bitcoin, financial education, and more. At the heart of it all, our focus remains on fostering creativity and independent thinking, because without it, we risk heading toward a future I personally don’t want to see. In the end, our mission is to help raise sovereign generations— individuals who truly understand and embrace financial and personal freedom.  ([source: interactive game for kids and families, “Bitcoin Calendar, Part 01”](https://www.bitcoin4youth.com/)) **YakiHonne**: Yes, absolutely! I really appreciate your recognition of Bitcoin’s freedom aspect, as that is its very core—sovereignty. I also deeply admire your dedication to educating the next generation—it’s truly essential. We need to nurture and guide these young minds so that when they step into this space, they can help maintain the stability of the Bitcoin ecosystem and safeguard the communities that have been built around it. Could you share with us how your community was founded and how you initially attracted members? **Şelale**:Well, to make a long story short, it all started as a way for me to relax at night. I work on several projects within the Bitcoin ecosystem, and when I feel mentally exhausted, I like to unwind by designing and drawing. That’s how it all began—I started designing various creative worksheets, such as logic puzzles, coloring pages, and other engaging activities targeted at younger audiences. My husband and I are also nomads, so a few years ago, we began distributing these materials to different homes during our travels. The response was overwhelmingly positive—kids were excited and, interestingly, it also turned out to be a subtle "orange pill" tool for their parents. Quite often, when they noticed the Bitcoin logo in these materials, it sparked their curiosity and triggered many questions. At first, I simply wanted to share these resources freely with the community, allowing anyone interested to use them. Over time, I came across many other family-friendly Bitcoin-themed materials such as books, videos, and games. I wanted to create a space where these things could be seen and heard. That’s when I decided to build a website, which could be described more as a database rather than a community. Since I’m involved in multiple projects and have limited time, I don’t want to focus entirely on building a community around Bitcoin Junior Club—at least not for now. Instead, my priority is to expand the database, continue creating creative educational materials, and connect with other family-friendly Bitcoin projects to give them extra visibility.  ([source: a snapshot from the home-page of Bitcoin Junior Club](https://www.bitcoin4youth.com/)) **YakiHonne**: What challenges did you encounter while creating this project? **Şelale**:If we were to shift more towards community-building, I would say the biggest challenge lies in the diverse target audience—especially across different age groups. If you want to engage very young children, aged 2 to 3.5 years, you also need to involve their parents or mentors. If you want to reach teenagers and young adults (aged 11 to 20+), their interests, perspectives, and learning preferences are entirely different. To truly engage all these different groups, you need a wide range of tools that cater to their needs and interests. That is a significant challenge. I’ve noticed that when people discover Bitcoin Junior Club, they often feel excited and relieved, realizing that such an initiative exists. But at the same time, it’s a fragmented process—it takes time to plant the seed and let people know, this resource is available if you or someone you know might need it. These are the biggest challenges. But nothing to worry about. The project is naturally and organically growing, and the community will likely develop on its own over time.  (source: Selected photos from Adopting Bitcoin El Salvador, Nov 2024, where a 2-day event for families, co-organized by Bitcoin Junior Club, was run in parallel to the entire conference) **YakiHonne**: Yeah, that’s very true. The age gap and diverse target audience can indeed be a challenge for many communities. It’s a key factor to consider. However, I really admire the way you’ve been able to navigate this challenge and still effectively reach out to them despite the difficulties. That’s truly something worth recognizing. **Şelale**:Thank you, that’s true. What I see here, once again, is the power of Nostr. On other social media platforms and across the Internet, there is so much noise—it’s an overwhelming space. But Nostr is different. The community is still relatively small, which means the audience is more specific and targeted. This also makes it faster and easier to understand their needs. Compared to three, four, or five years ago, this is a huge advantage when it comes to reaching specific groups and learning from them. **YakiHonne**: What advice would you give to someone looking to start or grow a Bitcoin-focused community in today's landscape? **Şelale**: Overall, don’t overthink it, and don’t try to build something too big from the start. Whatever you envision at the beginning will likely evolve over time. If you know your skills and have an idea that could bring value to the community, start with a high-level roadmap. Avoid over-planning—don’t try to monetize everything or map out years ahead, especially in the early stages, unless you’re working on a large-scale project in a bigger group. Start with smaller steps and learn from the feedback. As we often say in the Bitcoin world, “don’t ask for permission, just do it”. I would also emphasize: Learn and adapt along the way, because the feedback you receive from people is the best teacher. As I mentioned earlier, your initial idea may evolve into something different—so don’t give up, and don’t get discouraged. Just keep building. Also, especially for non-technical people, remember that contributing to the Bitcoin ecosystem isn’t just about tech. Of course, technology is at the core of our freedom-oriented future, and it’s incredibly important. But you don’t need technical skills to contribute—there are many ways to add value. It can be anything. **YakiHonne**: Yes, I really love the last part of what you just said—it’s so important. Many people tend to believe that if you don’t have technical skills, you can’t contribute to the Bitcoin ecosystem, and this is a very common misconception. The more we educate people and help them understand that Bitcoin needs contributions beyond just the technical side, the stronger the community will become. It’s a crucial point and absolutely true. I’d love to know—does your community focus more on the technical or non-technical aspects of Bitcoin? Or do you cover both? **Şelale**:I would say both, but more indirectly. Bitcoin Junior Club is not only a fun and educational space, but also an online resource providing a wide variety of materials, and so it naturally covers both technical and non-technical aspects. There are many excellent technical projects out there, such as those related to Lightning Network, which are more technical fields, and these can target young generations as well. [Lightning Piggy](https://www.lightningpiggy.com/) is a great example to use here. Also, during my recent time in El Salvador, I came across an amazing project, [Node Nation](https://x.com/nodenationsv), that teaches teenagers how to run their own Bitcoin nodes—a clearly technical-focused initiative. In the future, if we continue to expand and place more emphasis on family-friendly gatherings in person, where practical activities are the core, the technical aspect may naturally grow as well. I have some ideas related to coding courses, interactive games, and other technical aspects that teenagers could be interested in. However, for now, our main focus remains on education and sharing existing resources with more people online. All in all, Bitcoin Junior Club is indirectly engaging with both technical and non-technical content. **YakiHonne**: Sounds like a lot of work, but what you guys are doing is truly amazing. I can already see the large-scale impact this will have in the coming years. Since you are involved in the technical side as well, what advice would you give to technically inclined individuals or organizations looking to contribute meaningfully to the Bitcoin ecosystem? **Şelale**:My advice would be: go out and speak up. Try to join different meetups—not necessarily large conferences, but smaller local meetups, hackathons, and co-working spaces. These environments will help you connect with others who also have technical skills. You may meet people who are already working on something related to your field, and eventually can guide you toward bigger areas of contribution. Face to face meetings are the best options to find potential collaborators, and to build something together, as well as to strengthen your skills, and to motivate you to start building on your own. Also, don’t hesitate to share your ideas and ask questions publicly—for example, on Nostr, or through platforms like YakiHonne. Simply, speak up, and see if anyone is working on something similar or wants to collaborate. Most importantly, don’t be shy. Don’t isolate yourself in your own bubble. Just like creative people, technical people too, sometimes tend to stay in their own world, hesitant to step out. The truth is, it’s not that difficult to get involved—you just need to let people know you exist and what you can contribute. **YakiHonne**: You know, many people tend to believe that only large conferences are worthwhile, thinking they won’t gain much from local meetups. But in reality, starting with local gatherings often leads to stronger connections. That’s a crucial point. So, my next question, Selale—how do you see the role of Bitcoin communities evolving as the technology matures, particularly in areas like scalability, privacy, and adaptability with other systems? **Şelale**:What I’m about to say might be a bit of an unpopular opinion, but this is how I genuinely feel—especially in the past few years, there has been a lot of noise around mass adoption and scaling up, with a strong focus on doing things on a huge scale for everyone. However, I believe there is a more important step before that—which is mass education and awareness. If we truly want to protect privacy and ensure the conscious use of Bitcoin, so that it remains a freedom technology, we need to prioritize education before expansion. I hope that Bitcoin communities will become more aware of this and continue building on core values—the real Bitcoin ethos, such as truth, long-trem progress, privacy, and sovereignty, rather than just repeating hype-driven trends. I hope the community moves in this direction or, at the very least, remains strong enough to keep spreading the message of privacy and scalability as tools for freedom, rather than just chasing mass adoption and making everything overly simple. Of course, user experience matters—I absolutely support improving UX across different areas because it’s necessary for broader adoption. However, before that, we need to raise awareness and ensure that people—whoever they are—truly understand Bitcoin’s potential along with the risks that come with losing sovereignty, overexposing personal data, and rushing into oversimplification. For me, Proof of Work is not just about mining—it also means that understanding Bitcoin requires effort. You have to invest time, energy, and thought into learning about it. Making things too easy, too big, and too flashy isn’t necessarily something I believe in or support. **YakiHonne**: Though it’s true that Bitcoin communities will play an increasingly significant role as time goes on and as the technology matures, they will also evolve in terms of scalability, privacy, and adaptability. These aspects align with the core values that most Bitcoin communities uphold, especially given Bitcoin’s decentralized nature. So, we’ve now come to our last question for today, and I must say, it’s one of my favorite questions. Is the government in your region supportive or opposed to Bitcoin? And how has that impacted the community? **Şelale**:That’s an interesting question, because as a nomad, I don’t stay under the influence of any single government for long—usually not more than one to three months. We are constantly changing locations. However, we mostly stay within the European Union, and just using it as an example, with its centralized structure, it’s fundamentally opposite to what Bitcoin stands for. It operates against nation-states, encouraging people to think and act not as individuals, but as a collective. I don’t see any direct threats or actions taken against Bitcoin Junior Club or any other communities I’m involved in. However, I do believe that the narratives pushed by certain jurisdictions can create obstacles—or, maybe on the other hand, they can actually awaken more people. These days, it has become popular among politicians to claim they are pro-Bitcoin, using it as a low-hanging fruit to gain attention. Hence, it’s hard to say whether some governments are truly pro- or anti-Bitcoin. From my personal journey I see them rather having a neutral approach, but it could change in the next few months, as supporting Bitcoin has suddenly become trendy. Probably a topic for a longer chat. At the same time, I’ve seen areas in which ruling parties are officially anti-Bitcoin, yet people still find ways to work within the ecosystem and continue spreading the message of freedom. **YakiHonne**: Just an outside the box question. Did anyone around your area or towards your community consider Bitcoin to be a scam? **Şelale**:I had those experiences many years ago, in the very beginning. Currently, I’ve just consciously stopped spending time around people who hold such opinions, so I don’t see or hear it as often. ItThat said, it still happens occasionally—especially in Western countries. If I talk to someone new and they ask, “What do you do?” and I mention Bitcoin, sometimes they respond with:"Oh, that’s a Ponzi scheme." It’s very rare, but it still happens. For me, it just shows that those people are still too influenced by mainstream narratives—the same way people repeat things like "Bitcoin consumes too much energy" without fully understanding the subject. However, compared to five to ten years ago, these misconceptions have definitely become less common. As a site note, I’ve reached a stage where instead of overwhelming others with Bitcoin-themed conversations, I prefer to keep building- i.e. working on various resources that will be easy enough to find to learn from. If somebody later wants to ask questions or debate, still doubting whether Bitcoin is good or bad for humanity, I am ready to join. All in all, instead of actively trying to convince people, I focus my energy on projects like Bitcoin Junior Club, Bitcoin Film Fest, and other initiatives that provide content for freedom-seekers at heart. **YakiHonne**: Thank you so much. We've reached the end of today's interview, and it has truly been a fantastic conversation. I’ve gained a lot of valuable insights from you, and I genuinely appreciate the incredible work that you and your community are doing in the European Union. It’s truly inspiring. I’m certain that Europe is privileged to have you and your team contributing to this space. **Şelale**: The pleasure is mine. Thank you very much for this conversation. Once again, kudos to all you are bullying at Yaki Honne.
@ fd78c37f:a0ec0833
2025-03-05 09:50:19In this edition, we invited njump.me/npub134d6jtyveg74cuuj7qun4v2m6r7x7c6ryk69z4q7pa7f43kran2sl2yggk from Bitcoin Junior Club to share how she empowers children, teenagers, and families through Bitcoin education. She emphasizes that in the Bitcoin ecosystem, education should come before mass adoption. **YakiHonne**: Şelale, thank you for being here! Before we dive into the interview questions, I'd like to introduce YakiHonne, the hosting platform for today’s discussion. YakiHonne is a decentralized media client built on Nostr—a protocol designed to empower freedom of speech through technology. It enables creators to own their voices and assets while offering innovative tools like smart widgets, verified notes, and support for long-form content. With YakiHonne, individuals can express themselves freely, without the fear of censorship, bans, or restrictions. Today, we’ll be exploring more about your community,Şelale. So, let’s start with an introduction—could you tell us a bit about yourself and your community? **Şelale**:Thank you! I'm actually a big fan of YakiHonne. Nostr is my second biggest passion, right after Bitcoin. And within this ecosystem, everything YakiHonne has done—whether empowering communities or supporting creators—looks truly incredible. I could represent many different communities, but today, I want to focus on a recent project I started together with my husband—[Bitcoin Junior Club](https://www.bitcoin4youth.com/shortly-about-us-bitcoin-junior-club/). It's a fun and educational space designed for children, teenagers, and entire families. My Bitcoin journey dates back to around 2017 when I started diving deeper into Bitcoin. During the block size controversy. I found myself repeatedly reading the Whitepaper, trying to understand why some people were attempting to manipulate the rules and why the debate was gaining so much traction in the mass media. As I often say, the Bitcoin journey is a dynamic process—over the years, my experiences, perspectives, and areas of focus have continuously evolved. Right now, one of my key priorities are families and education. The Bitcoin ecosystem had already seen various emerging trends, such as the rise of female-oriented communities, hence the need for children related topics as well. Overall, the last few years have brought more creative minds building up their projects, which is very nice to see. A good example here would be [Bitcoin FilmFest](https://bitcoinfilmfest.com/), another dynamic initiative I’m involved in. These are all signs of Bitcoin's ever-expanding and evolving landscape. **YakiHonne**: I would like to know, what sparked your interest in Bitcoin? And what motivated you to create Bitcoin Junior Club? What inspired you to create a whole community around it? **Şelale**:There were many different aspects that drew me to Bitcoin, but I would say the most important one is the aspect of freedom, Bitcoin is the best form of money humanity has ever had. No middlemen, no one setting the rules. For the first time, people who have always been unprivileged and unbanked now have a real alternative—a way to opt out of the system they were born into. At the same time, when we look at developed countries, we see increasing surveillance, restrictions, and privacy constraints. Once again, Bitcoin serves a crucial role here. It is freedom money, a freedom tool, and that’s what hooked me the most. On the other hand, what truly motivated me to launch our project was the realization that money is just a tool. If people stop thinking critically, if they don’t truly understand its potential, even something as revolutionary as Bitcoin can be misused or even turned against us. Together with my husband, we believe that education is essential, especially for younger generations. We want to help them develop critical and creative thinking skills, to keep questioning topics they come across, and to think for themselves. This is the core reason we started this community. Along the way, I’ve come across many family-friendly projects with a similar mission. But most of such resources are scattered and difficult to locate. That’s why, one of our main goals is to create a comprehensive database—a place where people can find all kinds of educational resources, from the content we produce to information about existing initiatives in areas like: homeschooling, unschooling, Bitcoin, financial education, and more. At the heart of it all, our focus remains on fostering creativity and independent thinking, because without it, we risk heading toward a future I personally don’t want to see. In the end, our mission is to help raise sovereign generations— individuals who truly understand and embrace financial and personal freedom.  ([source: interactive game for kids and families, “Bitcoin Calendar, Part 01”](https://www.bitcoin4youth.com/)) **YakiHonne**: Yes, absolutely! I really appreciate your recognition of Bitcoin’s freedom aspect, as that is its very core—sovereignty. I also deeply admire your dedication to educating the next generation—it’s truly essential. We need to nurture and guide these young minds so that when they step into this space, they can help maintain the stability of the Bitcoin ecosystem and safeguard the communities that have been built around it. Could you share with us how your community was founded and how you initially attracted members? **Şelale**:Well, to make a long story short, it all started as a way for me to relax at night. I work on several projects within the Bitcoin ecosystem, and when I feel mentally exhausted, I like to unwind by designing and drawing. That’s how it all began—I started designing various creative worksheets, such as logic puzzles, coloring pages, and other engaging activities targeted at younger audiences. My husband and I are also nomads, so a few years ago, we began distributing these materials to different homes during our travels. The response was overwhelmingly positive—kids were excited and, interestingly, it also turned out to be a subtle "orange pill" tool for their parents. Quite often, when they noticed the Bitcoin logo in these materials, it sparked their curiosity and triggered many questions. At first, I simply wanted to share these resources freely with the community, allowing anyone interested to use them. Over time, I came across many other family-friendly Bitcoin-themed materials such as books, videos, and games. I wanted to create a space where these things could be seen and heard. That’s when I decided to build a website, which could be described more as a database rather than a community. Since I’m involved in multiple projects and have limited time, I don’t want to focus entirely on building a community around Bitcoin Junior Club—at least not for now. Instead, my priority is to expand the database, continue creating creative educational materials, and connect with other family-friendly Bitcoin projects to give them extra visibility.  ([source: a snapshot from the home-page of Bitcoin Junior Club](https://www.bitcoin4youth.com/)) **YakiHonne**: What challenges did you encounter while creating this project? **Şelale**:If we were to shift more towards community-building, I would say the biggest challenge lies in the diverse target audience—especially across different age groups. If you want to engage very young children, aged 2 to 3.5 years, you also need to involve their parents or mentors. If you want to reach teenagers and young adults (aged 11 to 20+), their interests, perspectives, and learning preferences are entirely different. To truly engage all these different groups, you need a wide range of tools that cater to their needs and interests. That is a significant challenge. I’ve noticed that when people discover Bitcoin Junior Club, they often feel excited and relieved, realizing that such an initiative exists. But at the same time, it’s a fragmented process—it takes time to plant the seed and let people know, this resource is available if you or someone you know might need it. These are the biggest challenges. But nothing to worry about. The project is naturally and organically growing, and the community will likely develop on its own over time.  (source: Selected photos from Adopting Bitcoin El Salvador, Nov 2024, where a 2-day event for families, co-organized by Bitcoin Junior Club, was run in parallel to the entire conference) **YakiHonne**: Yeah, that’s very true. The age gap and diverse target audience can indeed be a challenge for many communities. It’s a key factor to consider. However, I really admire the way you’ve been able to navigate this challenge and still effectively reach out to them despite the difficulties. That’s truly something worth recognizing. **Şelale**:Thank you, that’s true. What I see here, once again, is the power of Nostr. On other social media platforms and across the Internet, there is so much noise—it’s an overwhelming space. But Nostr is different. The community is still relatively small, which means the audience is more specific and targeted. This also makes it faster and easier to understand their needs. Compared to three, four, or five years ago, this is a huge advantage when it comes to reaching specific groups and learning from them. **YakiHonne**: What advice would you give to someone looking to start or grow a Bitcoin-focused community in today's landscape? **Şelale**: Overall, don’t overthink it, and don’t try to build something too big from the start. Whatever you envision at the beginning will likely evolve over time. If you know your skills and have an idea that could bring value to the community, start with a high-level roadmap. Avoid over-planning—don’t try to monetize everything or map out years ahead, especially in the early stages, unless you’re working on a large-scale project in a bigger group. Start with smaller steps and learn from the feedback. As we often say in the Bitcoin world, “don’t ask for permission, just do it”. I would also emphasize: Learn and adapt along the way, because the feedback you receive from people is the best teacher. As I mentioned earlier, your initial idea may evolve into something different—so don’t give up, and don’t get discouraged. Just keep building. Also, especially for non-technical people, remember that contributing to the Bitcoin ecosystem isn’t just about tech. Of course, technology is at the core of our freedom-oriented future, and it’s incredibly important. But you don’t need technical skills to contribute—there are many ways to add value. It can be anything. **YakiHonne**: Yes, I really love the last part of what you just said—it’s so important. Many people tend to believe that if you don’t have technical skills, you can’t contribute to the Bitcoin ecosystem, and this is a very common misconception. The more we educate people and help them understand that Bitcoin needs contributions beyond just the technical side, the stronger the community will become. It’s a crucial point and absolutely true. I’d love to know—does your community focus more on the technical or non-technical aspects of Bitcoin? Or do you cover both? **Şelale**:I would say both, but more indirectly. Bitcoin Junior Club is not only a fun and educational space, but also an online resource providing a wide variety of materials, and so it naturally covers both technical and non-technical aspects. There are many excellent technical projects out there, such as those related to Lightning Network, which are more technical fields, and these can target young generations as well. [Lightning Piggy](https://www.lightningpiggy.com/) is a great example to use here. Also, during my recent time in El Salvador, I came across an amazing project, [Node Nation](https://x.com/nodenationsv), that teaches teenagers how to run their own Bitcoin nodes—a clearly technical-focused initiative. In the future, if we continue to expand and place more emphasis on family-friendly gatherings in person, where practical activities are the core, the technical aspect may naturally grow as well. I have some ideas related to coding courses, interactive games, and other technical aspects that teenagers could be interested in. However, for now, our main focus remains on education and sharing existing resources with more people online. All in all, Bitcoin Junior Club is indirectly engaging with both technical and non-technical content. **YakiHonne**: Sounds like a lot of work, but what you guys are doing is truly amazing. I can already see the large-scale impact this will have in the coming years. Since you are involved in the technical side as well, what advice would you give to technically inclined individuals or organizations looking to contribute meaningfully to the Bitcoin ecosystem? **Şelale**:My advice would be: go out and speak up. Try to join different meetups—not necessarily large conferences, but smaller local meetups, hackathons, and co-working spaces. These environments will help you connect with others who also have technical skills. You may meet people who are already working on something related to your field, and eventually can guide you toward bigger areas of contribution. Face to face meetings are the best options to find potential collaborators, and to build something together, as well as to strengthen your skills, and to motivate you to start building on your own. Also, don’t hesitate to share your ideas and ask questions publicly—for example, on Nostr, or through platforms like YakiHonne. Simply, speak up, and see if anyone is working on something similar or wants to collaborate. Most importantly, don’t be shy. Don’t isolate yourself in your own bubble. Just like creative people, technical people too, sometimes tend to stay in their own world, hesitant to step out. The truth is, it’s not that difficult to get involved—you just need to let people know you exist and what you can contribute. **YakiHonne**: You know, many people tend to believe that only large conferences are worthwhile, thinking they won’t gain much from local meetups. But in reality, starting with local gatherings often leads to stronger connections. That’s a crucial point. So, my next question, Selale—how do you see the role of Bitcoin communities evolving as the technology matures, particularly in areas like scalability, privacy, and adaptability with other systems? **Şelale**:What I’m about to say might be a bit of an unpopular opinion, but this is how I genuinely feel—especially in the past few years, there has been a lot of noise around mass adoption and scaling up, with a strong focus on doing things on a huge scale for everyone. However, I believe there is a more important step before that—which is mass education and awareness. If we truly want to protect privacy and ensure the conscious use of Bitcoin, so that it remains a freedom technology, we need to prioritize education before expansion. I hope that Bitcoin communities will become more aware of this and continue building on core values—the real Bitcoin ethos, such as truth, long-trem progress, privacy, and sovereignty, rather than just repeating hype-driven trends. I hope the community moves in this direction or, at the very least, remains strong enough to keep spreading the message of privacy and scalability as tools for freedom, rather than just chasing mass adoption and making everything overly simple. Of course, user experience matters—I absolutely support improving UX across different areas because it’s necessary for broader adoption. However, before that, we need to raise awareness and ensure that people—whoever they are—truly understand Bitcoin’s potential along with the risks that come with losing sovereignty, overexposing personal data, and rushing into oversimplification. For me, Proof of Work is not just about mining—it also means that understanding Bitcoin requires effort. You have to invest time, energy, and thought into learning about it. Making things too easy, too big, and too flashy isn’t necessarily something I believe in or support. **YakiHonne**: Though it’s true that Bitcoin communities will play an increasingly significant role as time goes on and as the technology matures, they will also evolve in terms of scalability, privacy, and adaptability. These aspects align with the core values that most Bitcoin communities uphold, especially given Bitcoin’s decentralized nature. So, we’ve now come to our last question for today, and I must say, it’s one of my favorite questions. Is the government in your region supportive or opposed to Bitcoin? And how has that impacted the community? **Şelale**:That’s an interesting question, because as a nomad, I don’t stay under the influence of any single government for long—usually not more than one to three months. We are constantly changing locations. However, we mostly stay within the European Union, and just using it as an example, with its centralized structure, it’s fundamentally opposite to what Bitcoin stands for. It operates against nation-states, encouraging people to think and act not as individuals, but as a collective. I don’t see any direct threats or actions taken against Bitcoin Junior Club or any other communities I’m involved in. However, I do believe that the narratives pushed by certain jurisdictions can create obstacles—or, maybe on the other hand, they can actually awaken more people. These days, it has become popular among politicians to claim they are pro-Bitcoin, using it as a low-hanging fruit to gain attention. Hence, it’s hard to say whether some governments are truly pro- or anti-Bitcoin. From my personal journey I see them rather having a neutral approach, but it could change in the next few months, as supporting Bitcoin has suddenly become trendy. Probably a topic for a longer chat. At the same time, I’ve seen areas in which ruling parties are officially anti-Bitcoin, yet people still find ways to work within the ecosystem and continue spreading the message of freedom. **YakiHonne**: Just an outside the box question. Did anyone around your area or towards your community consider Bitcoin to be a scam? **Şelale**:I had those experiences many years ago, in the very beginning. Currently, I’ve just consciously stopped spending time around people who hold such opinions, so I don’t see or hear it as often. ItThat said, it still happens occasionally—especially in Western countries. If I talk to someone new and they ask, “What do you do?” and I mention Bitcoin, sometimes they respond with:"Oh, that’s a Ponzi scheme." It’s very rare, but it still happens. For me, it just shows that those people are still too influenced by mainstream narratives—the same way people repeat things like "Bitcoin consumes too much energy" without fully understanding the subject. However, compared to five to ten years ago, these misconceptions have definitely become less common. As a site note, I’ve reached a stage where instead of overwhelming others with Bitcoin-themed conversations, I prefer to keep building- i.e. working on various resources that will be easy enough to find to learn from. If somebody later wants to ask questions or debate, still doubting whether Bitcoin is good or bad for humanity, I am ready to join. All in all, instead of actively trying to convince people, I focus my energy on projects like Bitcoin Junior Club, Bitcoin Film Fest, and other initiatives that provide content for freedom-seekers at heart. **YakiHonne**: Thank you so much. We've reached the end of today's interview, and it has truly been a fantastic conversation. I’ve gained a lot of valuable insights from you, and I genuinely appreciate the incredible work that you and your community are doing in the European Union. It’s truly inspiring. I’m certain that Europe is privileged to have you and your team contributing to this space. **Şelale**: The pleasure is mine. Thank you very much for this conversation. Once again, kudos to all you are bullying at Yaki Honne. @ 95cb4330:96db706c
2025-03-05 08:39:40Embracing a **Long-Term Thinking Mindset**, as exemplified by leaders like Jeff Bezos and Peter Thiel, involves making decisions that prioritize enduring success over immediate gains. This approach fosters sustainable growth and innovation by focusing on strategies that yield compounded benefits over time. --- ## Understanding the Long-Term Thinking Mindset - **Definition:** A strategic perspective that emphasizes planning and decision-making with a focus on achieving substantial, lasting outcomes—often at the expense of short-term profits or conveniences. --- ## Examples in Practice - **Jeff Bezos and Amazon:** Bezos structured Amazon to prioritize long-term customer trust over quarterly profits, leading to its dominance. He believes that long-term thinking leverages existing abilities and supports the failure and iteration required for invention. - **Peter Thiel's Investment Strategy:** Thiel invests in startups with unique, superior products and a 10+ year vision, rather than chasing short-term competition. His contrarian investment strategy focuses on long-term tech investments. --- ## Implementing Long-Term Thinking 1. **Set Visionary Goals:** Define objectives that align with enduring values and aspirations, guiding sustained efforts toward meaningful achievements. 2. **Prioritize Sustainable Practices:** Adopt strategies that ensure environmental, social, and economic sustainability, contributing to long-term viability. 3. **Embrace Delayed Gratification:** Recognize that significant rewards often require patience and persistent effort, avoiding the allure of immediate but fleeting benefits. --- ## Benefits of Long-Term Thinking - **Resilience:** Organizations and individuals become better equipped to navigate challenges and adapt to changing circumstances. - **Reputation:** A commitment to long-term goals fosters trust and credibility among stakeholders, enhancing relationships and opportunities. - **Innovation:** Focusing on enduring success encourages continuous improvement and the development of groundbreaking solutions. --- ## Action Step Identify a current decision or project and assess whether your approach favors short-term comfort or long-term success. If it leans toward immediate gratification, consider realigning your strategy to prioritize enduring benefits—ensuring that today's choices contribute positively to your future goals. --- By adopting a long-term thinking mindset, you position yourself and your organization to achieve sustained success and make a lasting impact. For further insights into Jeff Bezos's perspective on long-term thinking, consider watching this discussion: [JEFF BEZOS - THINK LONG TERM](https://www.youtube.com/watch?v=y-lbBrbfmDw) ---
@ 95cb4330:96db706c
2025-03-05 08:39:40Embracing a **Long-Term Thinking Mindset**, as exemplified by leaders like Jeff Bezos and Peter Thiel, involves making decisions that prioritize enduring success over immediate gains. This approach fosters sustainable growth and innovation by focusing on strategies that yield compounded benefits over time. --- ## Understanding the Long-Term Thinking Mindset - **Definition:** A strategic perspective that emphasizes planning and decision-making with a focus on achieving substantial, lasting outcomes—often at the expense of short-term profits or conveniences. --- ## Examples in Practice - **Jeff Bezos and Amazon:** Bezos structured Amazon to prioritize long-term customer trust over quarterly profits, leading to its dominance. He believes that long-term thinking leverages existing abilities and supports the failure and iteration required for invention. - **Peter Thiel's Investment Strategy:** Thiel invests in startups with unique, superior products and a 10+ year vision, rather than chasing short-term competition. His contrarian investment strategy focuses on long-term tech investments. --- ## Implementing Long-Term Thinking 1. **Set Visionary Goals:** Define objectives that align with enduring values and aspirations, guiding sustained efforts toward meaningful achievements. 2. **Prioritize Sustainable Practices:** Adopt strategies that ensure environmental, social, and economic sustainability, contributing to long-term viability. 3. **Embrace Delayed Gratification:** Recognize that significant rewards often require patience and persistent effort, avoiding the allure of immediate but fleeting benefits. --- ## Benefits of Long-Term Thinking - **Resilience:** Organizations and individuals become better equipped to navigate challenges and adapt to changing circumstances. - **Reputation:** A commitment to long-term goals fosters trust and credibility among stakeholders, enhancing relationships and opportunities. - **Innovation:** Focusing on enduring success encourages continuous improvement and the development of groundbreaking solutions. --- ## Action Step Identify a current decision or project and assess whether your approach favors short-term comfort or long-term success. If it leans toward immediate gratification, consider realigning your strategy to prioritize enduring benefits—ensuring that today's choices contribute positively to your future goals. --- By adopting a long-term thinking mindset, you position yourself and your organization to achieve sustained success and make a lasting impact. For further insights into Jeff Bezos's perspective on long-term thinking, consider watching this discussion: [JEFF BEZOS - THINK LONG TERM](https://www.youtube.com/watch?v=y-lbBrbfmDw) --- @ da0b9bc3:4e30a4a9
2025-03-05 07:20:21Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/904251
@ da0b9bc3:4e30a4a9
2025-03-05 07:20:21Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/904251 @ 1d7ff02a:d042b5be
2025-03-05 06:02:55### ມະນຸດມີຄວາມຈະເລີນໄດ້ຍ້ອນຮູ້ຈັກສ້າງຄວາມຫມັ້ນຄົງໃນອະນາຄົດ ມະນຸດເຮົາສ້າງຄວາມຈະເລີນຮຸ່ງຮອງໄດ້ກໍຍ້ອນການສ້າງຄວາມຫມັ້ນຄົງໃນກະນາຄົດ ເຊິ່ງສະແດງອອກຢູ່ໃນ ຈາກແຕ່ກ່ອນຕ້ອງອອກໄປ ຫາອາຫານ ລ່າສັດ ເພື່ອເປັນພະລັງງານໃນການມີຊີວິດ ຈົນຮູ້ເຮົາຮູ້ຈັກການເກັບດອງອາຫານໃຫ້ກິນຍາວນານຂຶ້ນ, ຈາການຫາອາຫານເພື່ອຕົວເອງຢ່າງດຽວ ກໍຮູ້ຈັກການແລກປ່ຽນ (barter trade) ເຮັດໃຫ້ໄດ້ສິນຄ້າທີ່ຕົວເອງຕ້ອງການ ໂດຍບໍ່ຕ້ອງໃຊ້ເວລາທັງຫມົດໄປກັບການຫາ ຫລື ຜະລິດສິ່ງນັ້ນ ແລະ ສຸດທ້າຍເຮົາກໍຮູ້ຈັກເລືອກສິນຄ້າທີ່ມີຄວາມຫມັ້ນຄົງ ແລະ ຜະລິດຍາກ ມາເປັນເງິນ ເພື່ອໃຊ້ເປັນ ສື່ກາງ ໃນການແລກປ່ຽນ ຈົນແຕ່ລະຄົນມີເວລາໃນການໂຟກັສ ພັດທະນາທັກສະທີ່ຕົວເອງສົນໃຈຈົນມີຄວາມຊຳນານກວ່າຄົນທົ່ວໄປ ເຮັດໃຫ້ສາມາດຜະລິດສິນຄ້າ ແລະ ບໍລິການ ທີ່ມີຄຸນນະພາບ ແລະ ລາຄາຖືກລົງ. ປະກົດການເຫລົ່ານີ້ເກີດຂຶ້ນໄດ້ຍ້ອນເຮົາມີຄວາມຫມັ້ນຄົງໃນອະນາຄົດດ້ວຍເງິນເກັບ ຈົນມີເວລາຈະລອງຜິດລອງຖືກໄດ້. ແຕ່ຫລັງຈາກທີ່ເຮົາອອກຈາກ ມາດຕະຖານທອງຄຳ ກໍເຮັດໃຫ້ເງິນມັນເຊື່ອມຄ່າລົງໄປຕາມການເວລາ ຈົນເຮັດໃຫ້ຄົນເຫັນແກ່ເວລາອັນສັ້ນ, ຜະລິດສິນຄ້າ ແລະ ບໍລິການ ທີ່ບໍ່ໄດ້ຄຸນນະພາບ ເພາະຄິດແຕ່ວ່າຈະເຮັດແນວໃດເພື່ອຈະໄດ້ເງິນຫລາຍຂຶ້ນ ເພາະເງິນມັນເຊື່ອມມູນຄ່າລົງເລື່ອຍໆ ຈົນລືມຄິດໄປວ່າສິ່ງໃດແທ້ ທີ່ສຳຄັນໃນຊີວິດ ຈົນເກີດບັນຫາຕ່າງໆ ບໍ່ວ່າຈະເປັນສັງຄົມ ແລະ ເສດຖະກິດ. > ບິດຄອຍ ບໍ່ໄດ້ເຮັດໃຫ້ທ່ານລວຍໄວຂຶ້ນ ແຕ່ມັນກຳລັງແກ້ບັນຫາພື້ນຖານຢ່າງການ ເກັບເງິນ ຢູ່ ເພາະປະຈຸບັນມະນຸດເກັບເງິນບໍ່ໄດ້ແລ້ວ ເພາະມູນຄ່າຂອງມັນຫລຸດລົງເລື່ອຍໆ ### ການ DCA ບິດຄອຍ <img src="https://blossom.primal.net/7899fb7c4ccc478027ca38f12cf21730f46dbc8def7dec5a023f30539121b2ff.png"> ບິດຄອຍມີຄວາມຜັນຜວນເລື່ອງລາຄາຫລາຍ ກໍຍ້ອນເຮົາເບິ່ງໃນໄລຍະສັ້ນ ແຕ່ຖ້າເຮົາເບິ່ງມັນເປັນເຄື່ອງມືເກັບອອມເຮົາຈະເຫັນຄວາມຈິງ ບິດຄອຍຄືຄວາມຫມັ້ນຄົງ ແລະ ຕໍ່ຕ້ານການເຟີ້ຂອງເງິນ. ຕົວຢ່າງລຸ່ມນີ້ເປັນການຄຳນວນວ່າ ຖ້າເຮົາເກັບບິດຄອຍ ທຸກເດືອນ ຜ່ານໄປ 8 ປີ ມັນຈະມີມູນຄ່າເພີ່ມຂຶ້ນ 617% ຫລື ປະມານປີລະ 77% ໂດຍສະເລ່ຍ ເຊິ່ງມັນກໍບໍ່ໄດ້ເປັນໂຕເລກໂອເວີຫຍັງຫລາຍ ແຕ່ສາມາດເອົາຊະນະເງິນເພີ້ໄດ້ແລ້ວ ພຽງແຕ່ເກັບ ແລະ ບໍ່ຕ້ອງຄິດຫຍັງ. ### ເມື່ອເຮົາມີເງິນເກັບທີ່ຮັກສາມູນຄ່າໄດ້ ມັນເປັນຄົນລະເລື່ອງເລີຍໃນການໃຊ້ຊີວິດ ແລະ ວິທີຄິດ ຄົນຈະມີຄວາມຄິດການໄກຫລາຍຂຶ້ນ, ມີເວລາຄິດທົບທວນເລື່ອງຕ່າງໆໃນຊີວິດຢ່າງລະອຽດຖີ່ຖ້ວນ ແລະ ຕັດສິນໃຈແບບມີເຫດມີຜົນ. ຄົນຈະເລືອກເຮັດວຽກມີຢາກເຮັດ ເຖິງວ່າລາຍໄດ້ອາດຈະຫນ້ອຍ ແຕ່ເງິນເກັບສາມາດຮັກສາມູນຄ່າຂຶ້ນໄດ້ເລື່ອຍໆ, ເຮົາຈະມີເວລາໃຫ້ກັບຄອບຄົວຫລາຍກວ່າ ເພາະບໍ່ໄດ້ແລ່ນຕາມວຽກເພື່ອຈະໄດ້ລາຍຮັບເພີ່ມຂຶ້ນຕາມການເຊື່ອມຄ່າຂອງເງິນ. ຄົນຈະໃຫ້ຄວາມສຳຄັນກັບສຸຂະພາບຫລາຍຂຶ້ນ ເພາະສຸດທ້າຍແລ້ວເຮົາຈະເຂົ້າໃຈວ່າສຸຂະພາບນີ້ແລະ ສຳຄັນສຸດ. ຈາກຄວາມຮູ້ສຶກຂອງຕົວຂ້ອຍເອງມັນເຮັດໃຫ້ ມີຄວາມຫວັງ ແລະ ຕື່ນເຕັ້ນທີ່ຈະໄດ້ໃຊ້ຊີວິດໄປໃນການນາຄົດ ເພາະຮູ້ສຶກວ່າມີຄວາມຫມັ້ນຄົງ ຈາກການຄ່ອຍໆເກັບ ບິດຄອຍ ໂດຍມີເປົ້າຫມາຍເຮັດແນວໃດ ຈະໄດ້ໃຊ້ເວລາທີ່ເຫລືອຢູ່ ເກັບຄົນທີ່ເຮົາຮັກ, ເຮັດສິ່ງທີ່ມັກ ແລະ ມີສຸຂະພາບດີຈົນຈາກໂລກນີ້ໄປໃຫ້ເຈັບປວດຫນ້ອຍທີ່ສຸດ.
@ 1d7ff02a:d042b5be
2025-03-05 06:02:55### ມະນຸດມີຄວາມຈະເລີນໄດ້ຍ້ອນຮູ້ຈັກສ້າງຄວາມຫມັ້ນຄົງໃນອະນາຄົດ ມະນຸດເຮົາສ້າງຄວາມຈະເລີນຮຸ່ງຮອງໄດ້ກໍຍ້ອນການສ້າງຄວາມຫມັ້ນຄົງໃນກະນາຄົດ ເຊິ່ງສະແດງອອກຢູ່ໃນ ຈາກແຕ່ກ່ອນຕ້ອງອອກໄປ ຫາອາຫານ ລ່າສັດ ເພື່ອເປັນພະລັງງານໃນການມີຊີວິດ ຈົນຮູ້ເຮົາຮູ້ຈັກການເກັບດອງອາຫານໃຫ້ກິນຍາວນານຂຶ້ນ, ຈາການຫາອາຫານເພື່ອຕົວເອງຢ່າງດຽວ ກໍຮູ້ຈັກການແລກປ່ຽນ (barter trade) ເຮັດໃຫ້ໄດ້ສິນຄ້າທີ່ຕົວເອງຕ້ອງການ ໂດຍບໍ່ຕ້ອງໃຊ້ເວລາທັງຫມົດໄປກັບການຫາ ຫລື ຜະລິດສິ່ງນັ້ນ ແລະ ສຸດທ້າຍເຮົາກໍຮູ້ຈັກເລືອກສິນຄ້າທີ່ມີຄວາມຫມັ້ນຄົງ ແລະ ຜະລິດຍາກ ມາເປັນເງິນ ເພື່ອໃຊ້ເປັນ ສື່ກາງ ໃນການແລກປ່ຽນ ຈົນແຕ່ລະຄົນມີເວລາໃນການໂຟກັສ ພັດທະນາທັກສະທີ່ຕົວເອງສົນໃຈຈົນມີຄວາມຊຳນານກວ່າຄົນທົ່ວໄປ ເຮັດໃຫ້ສາມາດຜະລິດສິນຄ້າ ແລະ ບໍລິການ ທີ່ມີຄຸນນະພາບ ແລະ ລາຄາຖືກລົງ. ປະກົດການເຫລົ່ານີ້ເກີດຂຶ້ນໄດ້ຍ້ອນເຮົາມີຄວາມຫມັ້ນຄົງໃນອະນາຄົດດ້ວຍເງິນເກັບ ຈົນມີເວລາຈະລອງຜິດລອງຖືກໄດ້. ແຕ່ຫລັງຈາກທີ່ເຮົາອອກຈາກ ມາດຕະຖານທອງຄຳ ກໍເຮັດໃຫ້ເງິນມັນເຊື່ອມຄ່າລົງໄປຕາມການເວລາ ຈົນເຮັດໃຫ້ຄົນເຫັນແກ່ເວລາອັນສັ້ນ, ຜະລິດສິນຄ້າ ແລະ ບໍລິການ ທີ່ບໍ່ໄດ້ຄຸນນະພາບ ເພາະຄິດແຕ່ວ່າຈະເຮັດແນວໃດເພື່ອຈະໄດ້ເງິນຫລາຍຂຶ້ນ ເພາະເງິນມັນເຊື່ອມມູນຄ່າລົງເລື່ອຍໆ ຈົນລືມຄິດໄປວ່າສິ່ງໃດແທ້ ທີ່ສຳຄັນໃນຊີວິດ ຈົນເກີດບັນຫາຕ່າງໆ ບໍ່ວ່າຈະເປັນສັງຄົມ ແລະ ເສດຖະກິດ. > ບິດຄອຍ ບໍ່ໄດ້ເຮັດໃຫ້ທ່ານລວຍໄວຂຶ້ນ ແຕ່ມັນກຳລັງແກ້ບັນຫາພື້ນຖານຢ່າງການ ເກັບເງິນ ຢູ່ ເພາະປະຈຸບັນມະນຸດເກັບເງິນບໍ່ໄດ້ແລ້ວ ເພາະມູນຄ່າຂອງມັນຫລຸດລົງເລື່ອຍໆ ### ການ DCA ບິດຄອຍ <img src="https://blossom.primal.net/7899fb7c4ccc478027ca38f12cf21730f46dbc8def7dec5a023f30539121b2ff.png"> ບິດຄອຍມີຄວາມຜັນຜວນເລື່ອງລາຄາຫລາຍ ກໍຍ້ອນເຮົາເບິ່ງໃນໄລຍະສັ້ນ ແຕ່ຖ້າເຮົາເບິ່ງມັນເປັນເຄື່ອງມືເກັບອອມເຮົາຈະເຫັນຄວາມຈິງ ບິດຄອຍຄືຄວາມຫມັ້ນຄົງ ແລະ ຕໍ່ຕ້ານການເຟີ້ຂອງເງິນ. ຕົວຢ່າງລຸ່ມນີ້ເປັນການຄຳນວນວ່າ ຖ້າເຮົາເກັບບິດຄອຍ ທຸກເດືອນ ຜ່ານໄປ 8 ປີ ມັນຈະມີມູນຄ່າເພີ່ມຂຶ້ນ 617% ຫລື ປະມານປີລະ 77% ໂດຍສະເລ່ຍ ເຊິ່ງມັນກໍບໍ່ໄດ້ເປັນໂຕເລກໂອເວີຫຍັງຫລາຍ ແຕ່ສາມາດເອົາຊະນະເງິນເພີ້ໄດ້ແລ້ວ ພຽງແຕ່ເກັບ ແລະ ບໍ່ຕ້ອງຄິດຫຍັງ. ### ເມື່ອເຮົາມີເງິນເກັບທີ່ຮັກສາມູນຄ່າໄດ້ ມັນເປັນຄົນລະເລື່ອງເລີຍໃນການໃຊ້ຊີວິດ ແລະ ວິທີຄິດ ຄົນຈະມີຄວາມຄິດການໄກຫລາຍຂຶ້ນ, ມີເວລາຄິດທົບທວນເລື່ອງຕ່າງໆໃນຊີວິດຢ່າງລະອຽດຖີ່ຖ້ວນ ແລະ ຕັດສິນໃຈແບບມີເຫດມີຜົນ. ຄົນຈະເລືອກເຮັດວຽກມີຢາກເຮັດ ເຖິງວ່າລາຍໄດ້ອາດຈະຫນ້ອຍ ແຕ່ເງິນເກັບສາມາດຮັກສາມູນຄ່າຂຶ້ນໄດ້ເລື່ອຍໆ, ເຮົາຈະມີເວລາໃຫ້ກັບຄອບຄົວຫລາຍກວ່າ ເພາະບໍ່ໄດ້ແລ່ນຕາມວຽກເພື່ອຈະໄດ້ລາຍຮັບເພີ່ມຂຶ້ນຕາມການເຊື່ອມຄ່າຂອງເງິນ. ຄົນຈະໃຫ້ຄວາມສຳຄັນກັບສຸຂະພາບຫລາຍຂຶ້ນ ເພາະສຸດທ້າຍແລ້ວເຮົາຈະເຂົ້າໃຈວ່າສຸຂະພາບນີ້ແລະ ສຳຄັນສຸດ. ຈາກຄວາມຮູ້ສຶກຂອງຕົວຂ້ອຍເອງມັນເຮັດໃຫ້ ມີຄວາມຫວັງ ແລະ ຕື່ນເຕັ້ນທີ່ຈະໄດ້ໃຊ້ຊີວິດໄປໃນການນາຄົດ ເພາະຮູ້ສຶກວ່າມີຄວາມຫມັ້ນຄົງ ຈາກການຄ່ອຍໆເກັບ ບິດຄອຍ ໂດຍມີເປົ້າຫມາຍເຮັດແນວໃດ ຈະໄດ້ໃຊ້ເວລາທີ່ເຫລືອຢູ່ ເກັບຄົນທີ່ເຮົາຮັກ, ເຮັດສິ່ງທີ່ມັກ ແລະ ມີສຸຂະພາບດີຈົນຈາກໂລກນີ້ໄປໃຫ້ເຈັບປວດຫນ້ອຍທີ່ສຸດ. @ 9ea10fd4:011d3b15
2025-03-05 02:09:11(Le français suit) Scott Ritter discusses Trump’s willingness to end the war in Ukraine, highlighting his desire for peace (although other analysts suggest that the United States is shifting its strategic focus toward China). Ritter claims that the United States could consider leaving NATO by the end of the summer but provides no explanation. The U.S. takes a utilitarian approach toward its allies. Ritter believes that, unlike the Democrats, Trump does not align with the military-industrial complex. He is seen as an outsider to this complex, seeking to shift American policy toward trade and the economy rather than militarism (however, military spending increased during his first term). This complex, which developed during World War II and the Cold War, has an increasing need for conflicts to sustain itself, potentially leading to nuclear war. Europe, under U.S. influence, is compared to a Frankenstein’s monster—believing it is America’s ally while actually being a replaceable tool. A global transition is underway, marked by closer ties between the U.S., Russia, China, and India, excluding Europe for ideological and practical reasons—if I understand correctly, because it is characterized as knowing only war (I note that European diplomacy has recently turned toward India as an alternative to the U.S. and China). This shift, as described by Ritter, could signify the end of the transatlantic order. Obstacles remain for Trump, notably the issue of Gaza, which is complicated by pressure from the pro-Israel lobby and the positioning of Arab countries. Finally, it is suggested that Trump might want to reduce the size of the military and rethink the role of the United Nations, seen as a legacy of past conflicts—an intriguing idea but not fully developed. ** “In this perspective, Trump’s imposition of tariffs would serve as a key element of a strategy aimed at prioritizing the economy over militarism, marginalizing Europe while fostering pragmatic ties with powers like Russia and China, and redefining American power in a post-transatlantic world. This would reflect a break from the military-industrial complex and a utilitarian view of international relations, where tariffs replace tanks as tools of domination or negotiation. However, their success would depend on Trump’s ability to navigate internal pressures (the pro-Israel lobby) and external reactions (from trade partners).” (Grok 3 Beta) (On Telegram) [FIRST IMPRESSION ON TRUMP ZELENSKY FIASCO Interview for India & Global Left](https://t.me/ScottRitter/3761) **** Scott Ritter évoque la volonté de Trump de mettre fin à la guerre en Ukraine, soulignant son désir de paix (cela bien que d’autres analystes disent que les États-Unis sont en train de réorienter leur stratégie vers la Chine). Ritter avance que les États-Unis pourraient envisager de quitter l’OTAN d’ici à la fin de l’été mais ne fournit aucune explication. Les États-Unis adoptent une approche utilitaire vis-à-vis de leurs alliés. Ritter estime que Trump ne se positionne pas en faveur du complexe militaro-industriel, contrairement aux démocrates. Trump est perçu comme un acteur extérieur à ce complexe, cherchant à réorienter la politique américaine vers le commerce et l’économie plutôt que le militarisme (cependant les dépenses militaires avaient augmenté lors de son premier mandat). Ce complexe, qui s'est développé pendant la Seconde Guerre mondiale et la guerre froide, a un besoin croissant de conflits pour perdurer, menant éventuellement à une guerre nucléaire. L’Europe, sous l’influence des États-Unis, est comparée à un monstre de Frankenstein, croyant être l’alliée des États-Unis alors qu’elle n’est qu’un outil remplaçable. Une transition mondiale est en cours, marquée par un rapprochement entre les États-Unis, la Russie, la Chine et l’Inde, en excluant l’Europe pour des raisons idéologiques et pratiques si j’ai bien compris, car elle est caractérisée comme ne connaissant que la guerre (je remarque que la diplomatie européenne s'est récemment tournée vers l'Inde présentée comme une alternative aux États-Unis et à Chine). Ce changement tel que décrit par Ritter pourrait signifier la fin de l’ordre transatlantique. Des obstacles subsisteraient pour Trump, notamment la question de Gaza, compliquée par les pressions exercées par le lobby pro-Israël et le positionnement des pays arabes. Enfin, il est suggéré que Trump pourrait vouloir réduire la taille de l’armée et repenser le rôle des Nations Unies, perçues comme un héritage des conflits passés, une idée suggestive mais peu développée. ** « Dans cette perspective, l’imposition de tarifs douaniers par Trump s’insérerait comme une pièce maîtresse d’une stratégie visant à privilégier l’économie sur le militarisme, à marginaliser l’Europe tout en se rapprochant de puissances comme la Russie ou la Chine sur des bases pragmatiques, et à redéfinir la puissance américaine dans un monde post-transatlantique. Cela refléterait une rupture avec le complexe militaro-industriel et une vision utilitaire des relations internationales, où les tarifs remplacent les tanks comme outils de domination ou de négociation. Toutefois, leur succès dépendrait de la capacité de Trump à naviguer entre des pressions internes (lobby pro-Israël) et externes (réactions des partenaires commerciaux). » (Grok 3 bêta) (Sur Telegram) [FIRST IMPRESSION ON TRUMP ZELENSKY FIASCO Interview for India & Global Left](https://t.me/ScottRitter/3761)
@ 9ea10fd4:011d3b15
2025-03-05 02:09:11(Le français suit) Scott Ritter discusses Trump’s willingness to end the war in Ukraine, highlighting his desire for peace (although other analysts suggest that the United States is shifting its strategic focus toward China). Ritter claims that the United States could consider leaving NATO by the end of the summer but provides no explanation. The U.S. takes a utilitarian approach toward its allies. Ritter believes that, unlike the Democrats, Trump does not align with the military-industrial complex. He is seen as an outsider to this complex, seeking to shift American policy toward trade and the economy rather than militarism (however, military spending increased during his first term). This complex, which developed during World War II and the Cold War, has an increasing need for conflicts to sustain itself, potentially leading to nuclear war. Europe, under U.S. influence, is compared to a Frankenstein’s monster—believing it is America’s ally while actually being a replaceable tool. A global transition is underway, marked by closer ties between the U.S., Russia, China, and India, excluding Europe for ideological and practical reasons—if I understand correctly, because it is characterized as knowing only war (I note that European diplomacy has recently turned toward India as an alternative to the U.S. and China). This shift, as described by Ritter, could signify the end of the transatlantic order. Obstacles remain for Trump, notably the issue of Gaza, which is complicated by pressure from the pro-Israel lobby and the positioning of Arab countries. Finally, it is suggested that Trump might want to reduce the size of the military and rethink the role of the United Nations, seen as a legacy of past conflicts—an intriguing idea but not fully developed. ** “In this perspective, Trump’s imposition of tariffs would serve as a key element of a strategy aimed at prioritizing the economy over militarism, marginalizing Europe while fostering pragmatic ties with powers like Russia and China, and redefining American power in a post-transatlantic world. This would reflect a break from the military-industrial complex and a utilitarian view of international relations, where tariffs replace tanks as tools of domination or negotiation. However, their success would depend on Trump’s ability to navigate internal pressures (the pro-Israel lobby) and external reactions (from trade partners).” (Grok 3 Beta) (On Telegram) [FIRST IMPRESSION ON TRUMP ZELENSKY FIASCO Interview for India & Global Left](https://t.me/ScottRitter/3761) **** Scott Ritter évoque la volonté de Trump de mettre fin à la guerre en Ukraine, soulignant son désir de paix (cela bien que d’autres analystes disent que les États-Unis sont en train de réorienter leur stratégie vers la Chine). Ritter avance que les États-Unis pourraient envisager de quitter l’OTAN d’ici à la fin de l’été mais ne fournit aucune explication. Les États-Unis adoptent une approche utilitaire vis-à-vis de leurs alliés. Ritter estime que Trump ne se positionne pas en faveur du complexe militaro-industriel, contrairement aux démocrates. Trump est perçu comme un acteur extérieur à ce complexe, cherchant à réorienter la politique américaine vers le commerce et l’économie plutôt que le militarisme (cependant les dépenses militaires avaient augmenté lors de son premier mandat). Ce complexe, qui s'est développé pendant la Seconde Guerre mondiale et la guerre froide, a un besoin croissant de conflits pour perdurer, menant éventuellement à une guerre nucléaire. L’Europe, sous l’influence des États-Unis, est comparée à un monstre de Frankenstein, croyant être l’alliée des États-Unis alors qu’elle n’est qu’un outil remplaçable. Une transition mondiale est en cours, marquée par un rapprochement entre les États-Unis, la Russie, la Chine et l’Inde, en excluant l’Europe pour des raisons idéologiques et pratiques si j’ai bien compris, car elle est caractérisée comme ne connaissant que la guerre (je remarque que la diplomatie européenne s'est récemment tournée vers l'Inde présentée comme une alternative aux États-Unis et à Chine). Ce changement tel que décrit par Ritter pourrait signifier la fin de l’ordre transatlantique. Des obstacles subsisteraient pour Trump, notamment la question de Gaza, compliquée par les pressions exercées par le lobby pro-Israël et le positionnement des pays arabes. Enfin, il est suggéré que Trump pourrait vouloir réduire la taille de l’armée et repenser le rôle des Nations Unies, perçues comme un héritage des conflits passés, une idée suggestive mais peu développée. ** « Dans cette perspective, l’imposition de tarifs douaniers par Trump s’insérerait comme une pièce maîtresse d’une stratégie visant à privilégier l’économie sur le militarisme, à marginaliser l’Europe tout en se rapprochant de puissances comme la Russie ou la Chine sur des bases pragmatiques, et à redéfinir la puissance américaine dans un monde post-transatlantique. Cela refléterait une rupture avec le complexe militaro-industriel et une vision utilitaire des relations internationales, où les tarifs remplacent les tanks comme outils de domination ou de négociation. Toutefois, leur succès dépendrait de la capacité de Trump à naviguer entre des pressions internes (lobby pro-Israël) et externes (réactions des partenaires commerciaux). » (Grok 3 bêta) (Sur Telegram) [FIRST IMPRESSION ON TRUMP ZELENSKY FIASCO Interview for India & Global Left](https://t.me/ScottRitter/3761) @ 401014b3:59d5476b
2025-03-05 01:39:21Alright, football freaks, it’s March 2025, and we’re slinging some half-baked AFC East predictions like it’s a tailgate wing-eating contest. Free agency’s a madhouse, the draft’s a blind stab, and this division’s always a mix of fireworks and faceplants. The Bills ran the show in 2024, the Dolphins teased us, the Jets are jetting Rodgers out the door, and the Pats have a new sheriff in town. Let’s slap records on this chaos and see who’s got the cajones to take the crown. Strap in—this one’s a banger. ### **Buffalo Bills: 12-5 – Josh Allen’s Reign of Pain** The Bills owned the AFC East in 2024, and 2025’s looking like a victory lap. Josh Allen’s a goddamn force of nature—cannon arm, truck-stick legs—and he’s got James Cook tearing up the ground game even without a stud WR1. That O-line’s a top-10 crew, and the defense, despite some roster churn, still hits hard with Greg Rousseau leading the charge. Free agency might nibble at the edges—Matt Milano’s return could be clutch—but this squad’s a bully. 12-5’s the vibe, division locked up again. Good luck stopping ‘em. ### **Miami Dolphins: 9-8 – Tua’s Hot-and-Cold Hustle** The Dolphins are the AFC East’s rollercoaster—thrilling ‘til they puke. Tua Tagovailoa’s slinging to Tyreek Hill and Jaylen Waddle, but that O-line’s still a question mark, and they fold like lawn chairs in December. The defense stepped up in 2024 with Jalen Ramsey locking down receivers, but free agency could sting—Jaelan Phillips might chase a bag elsewhere. If Tua stays healthy and the core holds, 9-8’s on the table. Wildcard’s their best shot—Buffalo’s still the big brother they can’t shake. ### **New York Jets: 8-9 – New QB, Same Jets Jinx** The Jets are ditching Aaron Rodgers—old man’s outta here—and rolling with a new QB (TBD, but let’s say a rookie or a vet like Tyrod Taylor for kicks). Garrett Wilson and Breece Hall are studs, but that O-line’s a disaster, and the defense might take a hit if Sauce Gardner starts sniffing bigger paychecks. New coach, fresh start, same Jets curse? They’ve got enough talent to flirt with 8-9, maybe sniff a wildcard if the QB doesn’t totally tank. Still feels like classic Jets—almost there, never quite. ### **New England Patriots: 5-12 – Vrabel’s Rough Rebuild** The Pats are a work in progress, but Mike Vrabel’s the new head honcho, and that’s worth a damn shout. The ex-Titans tough guy’s got Drake Maye at QB—bright future, brutal present. 2025’s gonna be a grind; Maye’s taking rookie lumps behind a shaky O-line with no real weapons to speak of. Christian Gonzalez is a lockdown corner, but the defense ain’t what it was without Belichick’s wizardry. Vrabel’s a culture guy—he’ll keep ‘em scrappy—but 5-12’s the reality. They’re building, not winning, in Foxboro this year. ### **The Final Buzzer** The AFC East in 2025 is Buffalo’s playground with a dash of dysfunction. The Bills (12-5) snag the crown because Josh Allen’s a beast, the Dolphins (9-8) tease a wildcard, the Jets (8-9) stumble sans Rodgers, and the Pats (5-12) grit it out under Vrabel. That’s 34 wins, 34 losses—math’s tight when you factor in the division’s slugfest with the NFL’s other suckers. Free agency’s the X-factor—lose a star, you’re screwed; snag a gem, you’re golden. Yell at me on X when I botch this, but for now, this is my story, and I’m sticking to it. Let’s ride, degenerates.
@ 401014b3:59d5476b
2025-03-05 01:39:21Alright, football freaks, it’s March 2025, and we’re slinging some half-baked AFC East predictions like it’s a tailgate wing-eating contest. Free agency’s a madhouse, the draft’s a blind stab, and this division’s always a mix of fireworks and faceplants. The Bills ran the show in 2024, the Dolphins teased us, the Jets are jetting Rodgers out the door, and the Pats have a new sheriff in town. Let’s slap records on this chaos and see who’s got the cajones to take the crown. Strap in—this one’s a banger. ### **Buffalo Bills: 12-5 – Josh Allen’s Reign of Pain** The Bills owned the AFC East in 2024, and 2025’s looking like a victory lap. Josh Allen’s a goddamn force of nature—cannon arm, truck-stick legs—and he’s got James Cook tearing up the ground game even without a stud WR1. That O-line’s a top-10 crew, and the defense, despite some roster churn, still hits hard with Greg Rousseau leading the charge. Free agency might nibble at the edges—Matt Milano’s return could be clutch—but this squad’s a bully. 12-5’s the vibe, division locked up again. Good luck stopping ‘em. ### **Miami Dolphins: 9-8 – Tua’s Hot-and-Cold Hustle** The Dolphins are the AFC East’s rollercoaster—thrilling ‘til they puke. Tua Tagovailoa’s slinging to Tyreek Hill and Jaylen Waddle, but that O-line’s still a question mark, and they fold like lawn chairs in December. The defense stepped up in 2024 with Jalen Ramsey locking down receivers, but free agency could sting—Jaelan Phillips might chase a bag elsewhere. If Tua stays healthy and the core holds, 9-8’s on the table. Wildcard’s their best shot—Buffalo’s still the big brother they can’t shake. ### **New York Jets: 8-9 – New QB, Same Jets Jinx** The Jets are ditching Aaron Rodgers—old man’s outta here—and rolling with a new QB (TBD, but let’s say a rookie or a vet like Tyrod Taylor for kicks). Garrett Wilson and Breece Hall are studs, but that O-line’s a disaster, and the defense might take a hit if Sauce Gardner starts sniffing bigger paychecks. New coach, fresh start, same Jets curse? They’ve got enough talent to flirt with 8-9, maybe sniff a wildcard if the QB doesn’t totally tank. Still feels like classic Jets—almost there, never quite. ### **New England Patriots: 5-12 – Vrabel’s Rough Rebuild** The Pats are a work in progress, but Mike Vrabel’s the new head honcho, and that’s worth a damn shout. The ex-Titans tough guy’s got Drake Maye at QB—bright future, brutal present. 2025’s gonna be a grind; Maye’s taking rookie lumps behind a shaky O-line with no real weapons to speak of. Christian Gonzalez is a lockdown corner, but the defense ain’t what it was without Belichick’s wizardry. Vrabel’s a culture guy—he’ll keep ‘em scrappy—but 5-12’s the reality. They’re building, not winning, in Foxboro this year. ### **The Final Buzzer** The AFC East in 2025 is Buffalo’s playground with a dash of dysfunction. The Bills (12-5) snag the crown because Josh Allen’s a beast, the Dolphins (9-8) tease a wildcard, the Jets (8-9) stumble sans Rodgers, and the Pats (5-12) grit it out under Vrabel. That’s 34 wins, 34 losses—math’s tight when you factor in the division’s slugfest with the NFL’s other suckers. Free agency’s the X-factor—lose a star, you’re screwed; snag a gem, you’re golden. Yell at me on X when I botch this, but for now, this is my story, and I’m sticking to it. Let’s ride, degenerates. @ 62a6a41e:b12acb43
2025-03-04 22:19:29War is rarely (or if ever) the will of the people. Throughout history, wars have been orchestrated by political and economic elites, while the media plays a key role in shaping public opinion. World War I is a clear example of how propaganda was used to glorify war, silence dissent, and demonize the enemy. Today, we see similar tactics being used in the Ukrainian War. The media spreads one-sided narratives, censors alternative views, and manipulates public sentiment. This article argues that **wars are decided from the top**, and media is used to justify them. --- ## How the Media Glorified and Propagated WW1 ### The Media Sold War as an Adventure Before WW1, newspapers and propaganda made war seem noble and exciting. Young men were encouraged to enlist for honor and glory. Posters displayed slogans like *“Your Country Needs You”*, making war look like a duty rather than a tragedy. ### Demonization of the Enemy Governments and media portrayed Germans as "barbaric Huns," spreading exaggerated stories like the "Rape of Belgium," where German soldiers were accused of horrific war crimes—many later proven false. Today, Russia is painted as purely evil, while NATO’s role and Ukraine’s internal conflicts are ignored. ### Social Pressure & Nationalism Anyone who opposed WW1 was labeled a traitor. Conscientious objectors were shamed, jailed, or even executed. The same happens today—if you question support for Ukraine, you are called "pro-Russian" or "anti-European." In the U.S., opposing war is falsely linked to supporting Trump or extremism. ### Fabricated Stories During WW1, fake reports of German soldiers killing babies were widely spread. In Ukraine, reports of massacres and war crimes often circulate without verification, while Ukrainian war crimes receive little coverage. --- ## How the Media Promotes War Today: The Case of Ukraine ### One-Sided Narratives The media presents Ukraine as a heroic struggle against an evil invader, ignoring the 2014 coup, the Donbas conflict, and NATO expansion. By simplifying the issue, people are discouraged from questioning the full story. ### Censorship and Suppression of Dissent During WW1, anti-war activists were jailed. Today, journalists and commentators questioning NATO’s role face censorship, deplatforming, or cancellation. ### Selective Coverage Media highlights civilian deaths in Ukraine but ignores similar suffering in Yemen, Syria, or Palestine. Coverage depends on political interests, not humanitarian concern. ### Glorification of War Efforts Ukrainian soldiers—even extremist groups—are painted as heroes. Meanwhile, peace negotiations and diplomatic efforts receive little attention. --- ## War is a Top-Down Decision, Not the Will of the People ### People Don’t Want Wars If given a choice, most people would reject war. Examples: - **Before WW1:** Many workers and socialists opposed war, but governments ignored them. - **Vietnam War:** Protests grew, but the war continued. - **Iraq War (2003):** Millions protested, yet the invasion went ahead. ### Small Elites Decide War Wars benefit arms manufacturers, politicians, and corporate interests—not ordinary people. Public opposition is often ignored or crushed. ### Manipulation Through Fear Governments use fear to justify war: *“If we don’t act now, it will be too late.”* This tactic was used in WW1, the Iraq War, and is used today in Ukraine. --- ## Violence vs. War: A Manufactured Conflict ### Violence Happens, But War is Manufactured Conflicts and disputes are natural, but large-scale war is **deliberately planned** using propaganda and logistical preparation. ### War Requires Justification If war were natural, why does it need **massive media campaigns** to convince people to fight? Just like in WW1, today’s wars rely on media narratives to gain support. --- ## The Crimea Referendum: A Case of Ignored Democracy ### Crimea’s 2014 Referendum - Over **90% of Crimeans voted to join Russia** in 2014. - Western governments called it "illegitimate," while similar referendums (like in Kosovo) were accepted. ### The Contradiction in Democracy - If democracy is sacred, why ignore a **clear vote** in Crimea? - Other examples: Brexit was resisted, Catalonia’s referendum was shut down, and peace referendums were dismissed when they didn’t fit political interests. - **Democracy is used as a tool when convenient.** --- ## VII. The Libertarian Case Against War ### The Non-Aggression Principle (NAP) Libertarianism is fundamentally opposed to war because it violates the **Non-Aggression Principle (NAP)**—the idea that no person or institution has the right to initiate force against another. War, by its very nature, is the **ultimate violation of the NAP**, as it involves mass killing, destruction, and theft under the guise of national interest. ### War is State Aggression - Governments wage wars, not individuals. No private citizen would naturally start a conflict with another country. - The state **forces people to fund wars through taxation**, violating their economic freedom. - **Conscription**, used in many wars, is nothing more than **state-sponsored slavery**, forcing individuals to fight and die for political goals they may not support. ### War Creates Bigger Government - War expands state power, **eroding civil liberties** (e.g., WW1's Espionage Act, the Patriot Act after 9/11). - The **military-industrial complex** grows richer while taxpayers foot the bill. - **Emergency powers granted during wars rarely get repealed** after conflicts end, leaving citizens with fewer freedoms. ### Peaceful Trade vs. War - Libertarians advocate for **free trade** as a means of cooperation. Countries that trade are **less likely to go to war**. - Wars **destroy wealth and infrastructure**, while peaceful trade **increases prosperity** for all. - Many wars have been fought **not for defense, but for economic interests**, such as securing **oil, resources, or geopolitical power**. ### Who Benefits from War? - **Not the people**, who suffer death, destruction, and economic hardship. - **Not small businesses or workers**, who bear the burden of inflation and taxes to fund wars. - **Not individual liberty**, as war leads to **greater state control and surveillance**. - **Only the elites**, including **defense contractors, politicians, and bankers**, who profit from war and use it to consolidate power. ## Conclusion: The Media’s Role in War is Crucial Wars don’t happen naturally—they are **carefully planned and sold to the public** using propaganda, fear, and nationalism. - **WW1 and Ukraine prove that media is key to war-making.** - **The media silences peace efforts and glorifies conflict.** - **If people truly had a choice, most wars would never happen.** To resist this, we must **recognize how we are manipulated** and reject the forced narratives that push us toward war.
@ 62a6a41e:b12acb43
2025-03-04 22:19:29War is rarely (or if ever) the will of the people. Throughout history, wars have been orchestrated by political and economic elites, while the media plays a key role in shaping public opinion. World War I is a clear example of how propaganda was used to glorify war, silence dissent, and demonize the enemy. Today, we see similar tactics being used in the Ukrainian War. The media spreads one-sided narratives, censors alternative views, and manipulates public sentiment. This article argues that **wars are decided from the top**, and media is used to justify them. --- ## How the Media Glorified and Propagated WW1 ### The Media Sold War as an Adventure Before WW1, newspapers and propaganda made war seem noble and exciting. Young men were encouraged to enlist for honor and glory. Posters displayed slogans like *“Your Country Needs You”*, making war look like a duty rather than a tragedy. ### Demonization of the Enemy Governments and media portrayed Germans as "barbaric Huns," spreading exaggerated stories like the "Rape of Belgium," where German soldiers were accused of horrific war crimes—many later proven false. Today, Russia is painted as purely evil, while NATO’s role and Ukraine’s internal conflicts are ignored. ### Social Pressure & Nationalism Anyone who opposed WW1 was labeled a traitor. Conscientious objectors were shamed, jailed, or even executed. The same happens today—if you question support for Ukraine, you are called "pro-Russian" or "anti-European." In the U.S., opposing war is falsely linked to supporting Trump or extremism. ### Fabricated Stories During WW1, fake reports of German soldiers killing babies were widely spread. In Ukraine, reports of massacres and war crimes often circulate without verification, while Ukrainian war crimes receive little coverage. --- ## How the Media Promotes War Today: The Case of Ukraine ### One-Sided Narratives The media presents Ukraine as a heroic struggle against an evil invader, ignoring the 2014 coup, the Donbas conflict, and NATO expansion. By simplifying the issue, people are discouraged from questioning the full story. ### Censorship and Suppression of Dissent During WW1, anti-war activists were jailed. Today, journalists and commentators questioning NATO’s role face censorship, deplatforming, or cancellation. ### Selective Coverage Media highlights civilian deaths in Ukraine but ignores similar suffering in Yemen, Syria, or Palestine. Coverage depends on political interests, not humanitarian concern. ### Glorification of War Efforts Ukrainian soldiers—even extremist groups—are painted as heroes. Meanwhile, peace negotiations and diplomatic efforts receive little attention. --- ## War is a Top-Down Decision, Not the Will of the People ### People Don’t Want Wars If given a choice, most people would reject war. Examples: - **Before WW1:** Many workers and socialists opposed war, but governments ignored them. - **Vietnam War:** Protests grew, but the war continued. - **Iraq War (2003):** Millions protested, yet the invasion went ahead. ### Small Elites Decide War Wars benefit arms manufacturers, politicians, and corporate interests—not ordinary people. Public opposition is often ignored or crushed. ### Manipulation Through Fear Governments use fear to justify war: *“If we don’t act now, it will be too late.”* This tactic was used in WW1, the Iraq War, and is used today in Ukraine. --- ## Violence vs. War: A Manufactured Conflict ### Violence Happens, But War is Manufactured Conflicts and disputes are natural, but large-scale war is **deliberately planned** using propaganda and logistical preparation. ### War Requires Justification If war were natural, why does it need **massive media campaigns** to convince people to fight? Just like in WW1, today’s wars rely on media narratives to gain support. --- ## The Crimea Referendum: A Case of Ignored Democracy ### Crimea’s 2014 Referendum - Over **90% of Crimeans voted to join Russia** in 2014. - Western governments called it "illegitimate," while similar referendums (like in Kosovo) were accepted. ### The Contradiction in Democracy - If democracy is sacred, why ignore a **clear vote** in Crimea? - Other examples: Brexit was resisted, Catalonia’s referendum was shut down, and peace referendums were dismissed when they didn’t fit political interests. - **Democracy is used as a tool when convenient.** --- ## VII. The Libertarian Case Against War ### The Non-Aggression Principle (NAP) Libertarianism is fundamentally opposed to war because it violates the **Non-Aggression Principle (NAP)**—the idea that no person or institution has the right to initiate force against another. War, by its very nature, is the **ultimate violation of the NAP**, as it involves mass killing, destruction, and theft under the guise of national interest. ### War is State Aggression - Governments wage wars, not individuals. No private citizen would naturally start a conflict with another country. - The state **forces people to fund wars through taxation**, violating their economic freedom. - **Conscription**, used in many wars, is nothing more than **state-sponsored slavery**, forcing individuals to fight and die for political goals they may not support. ### War Creates Bigger Government - War expands state power, **eroding civil liberties** (e.g., WW1's Espionage Act, the Patriot Act after 9/11). - The **military-industrial complex** grows richer while taxpayers foot the bill. - **Emergency powers granted during wars rarely get repealed** after conflicts end, leaving citizens with fewer freedoms. ### Peaceful Trade vs. War - Libertarians advocate for **free trade** as a means of cooperation. Countries that trade are **less likely to go to war**. - Wars **destroy wealth and infrastructure**, while peaceful trade **increases prosperity** for all. - Many wars have been fought **not for defense, but for economic interests**, such as securing **oil, resources, or geopolitical power**. ### Who Benefits from War? - **Not the people**, who suffer death, destruction, and economic hardship. - **Not small businesses or workers**, who bear the burden of inflation and taxes to fund wars. - **Not individual liberty**, as war leads to **greater state control and surveillance**. - **Only the elites**, including **defense contractors, politicians, and bankers**, who profit from war and use it to consolidate power. ## Conclusion: The Media’s Role in War is Crucial Wars don’t happen naturally—they are **carefully planned and sold to the public** using propaganda, fear, and nationalism. - **WW1 and Ukraine prove that media is key to war-making.** - **The media silences peace efforts and glorifies conflict.** - **If people truly had a choice, most wars would never happen.** To resist this, we must **recognize how we are manipulated** and reject the forced narratives that push us toward war.