
@ 1c19eb1a:e22fb0bc
2025-02-28 07:32:53
After my first major review of [Primal on Android](https://www.nostr-reviews.com/post/1733635103705/), we're going to go a very different direction for this next review. Primal is your standard "Twitter clone" type of kind 1 note client, now branching into long-form. They also have a team of developers working on making it one of the best clients to fill that use-case. By contrast, this review will not be focusing on any client at all. Not even an "other stuff" client.
Instead, we will be reviewing a very useful tool created and maintained by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 called #Amber. For those unfamiliar with Amber, it is an #Android application dedicated to managing your signing keys, and allowing you to log into various #Nostr applications without having to paste in your private key, better known as your #nsec. It is not recommended to paste your nsec into various applications because they each represent another means by which it could be compromised, and anyone who has your nsec can post as you. On Nostr, your #npub is your identity, and your signature using your private key is considered absolute proof that any given note, reaction, follow update, or profile change was authorized by the rightful owner of that identity.
It happens less often these days, but early on, when the only way to try out a new client was by inputting your nsec, users had their nsec compromised from time to time, or they would suspect that their key may have been compromised. When this occurs, there is no way to recover your account, or set a new private key, deprecating the previous one. The only thing you can do is start over from scratch, letting everyone know that your key has been compromised and to follow you on your new npub.
If you use Amber to log into other Nostr apps, you significantly reduce the likelihood that your private key will be compromised, because only one application has access to it, and all other applications reach out to Amber to sign any events. This isn't quite as secure as storing your private key on a separate device that isn't connected to the internet whatsoever, like many of us have grown accustomed to with securing our #Bitcoin, but then again, an online persona isn't nearly as important to secure for most of us as our entire life savings.
Amber is the first application of its kind for managing your Nostr keys on a mobile device. nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 didn't merely develop the application, but literally created the specification for accomplishing external signing on Android which can be found in [NIP-55](https://github.com/nostr-protocol/nips/blob/master/55.md). Unfortunately, Amber is only available for Android. A signer application for iOS is in the works from nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, but is not ready for use at this time. There is also a new mobile signer app for Android and iOS called Nowser, but I have not yet had a chance to try this app out. From a cursory look at the Android version, it is indeed in the very early stages of development and cannot be compared with Amber.
This review of Amber is current as of version 3.2.5.

## Overall Impression
Score: **4.5** / 5
I cannot speak highly enough about Amber as a tool that every Nostr user on Android should start using if they are not already. When the day comes that we have more options for well-developed signer apps on mobile, my opinion may very well change, but until then Amber is what we have available to us. Even so, it is an incredibly well thought-out and reliable tool for securing your nsec.
Despite being the only well-established Android signer available for Android, Amber ***can*** be compared with other external signing methods available on other platforms. Even with more competition in this arena, though, Amber still holds up incredibly well. If you are signing into web applications on a desktop, I still would recommend using a browser extension like #Alby or #Nos2x, as the experience is usually faster, more seamless, and far more web apps support this signing method ([NIP-07](https://github.com/nostr-protocol/nips/blob/master/07.md)) than currently support the two methods employed by Amber. Nevertheless that gap is definitely narrowing.
A running list I created of applications that support login and signing with Amber can be found here: [Nostr Clients with External Signer Support](nostr:naddr1qvzqqqrcvgpzpde8f55w86vrhaeqmd955y4rraw8aunzxgxstsj7eyzgntyev2xtqydhwumn8ghj7un9d3shjtnzwf5kw6r5vfhkcapwdejhgtcpr4mhxue69uhkg6ttv95k7ue3x5cnwtnwdaehgu339e3k7mf0qq4xummnw3ez6cmvd9jkuarn94mkjarg94jhsar9wfhxzmpdwd5kwmn9wgkhxatswphhyaqrcy76t)
I have run into relatively few bugs in my extensive use of Amber for all of my mobile signing needs. Occasionally the application crashes when trying to send it a signing request from a couple of applications, but I would not be surprised if this is no fault of Amber at all, and rather the fault of those specific apps, since it works flawlessly with the vast majority of apps that support either [NIP-55](https://github.com/nostr-protocol/nips/blob/master/55.md) or [NIP-46](https://github.com/nostr-protocol/nips/blob/master/46.md) login.
I also believe that mobile is the ideal platform to use for this type of application. First, because most people use Nostr clients on their phone more than on a desktop. There are, of course, exceptions to that, but in general we spend more time on our phones when interacting online. New users are also more likely to be introduced to Nostr by a friend having them download a Nostr client on their phone than on a PC, and that can be a prime opportunity to introduce the new user to protecting their private key. Finally, I agree with the following assessment from nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn.
nostr:nevent1qqsw0r6gzn05xg67h5q2xkplwsuzedjxw9lf7ntrxjl8ajm350fcyugpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsyg9hyaxj3clfswlhyrd5kjsj5v04clhjvgeq6pwztmysfzdvn93gevpsgqqqye9qd30q62
The one downside to Amber is that it will be quite foreign for new users. That is partially unavoidable with Nostr, since folks are not accustomed to public/private key cryptography in general, let alone using a private key to log into websites or social media apps. However, the initial signup process is a bit cumbersome if Amber is being used as the means of initially generating a key pair. I think some of this could be foregone at start-up in favor of streamlining onboarding, and then encourage the user to back-up their private key at a later time.
## Features
Amber has some features that may surprise you, outside of just storing your private key and signing requests from your favorite Nostr clients. It is a full key management application, supporting multiple accounts, various backup methods, and even the ability to authorize other users to access a Nostr profile you control.
### Android Signing
This is the signing method where Amber really shines in both speed and ease of use. Any Android application that supports this standard, and even some progressive web-apps that can be installed to your Android's home-screen, can very quickly and seamlessly connect with Amber to authorize anything that you need signed with your nsec. All you have to do is select "Login with Amber" in clients like #Amethyst or #0xChat and the app will reach out to Amber for all signing requests from there on out. If you had previously signed into the app with your nsec, you will first need to log out, then choose the option to use Amber when you log back in.

This is a massive deal, because everything you do on Nostr requires a signature from your private key. Log in? Needs a signature. Post a "GM" note? Needs a signature. Follow someone who zapped your note? Needs a signature. Zap them back? You guessed it; needs a signature. When you paste your private key into an application, it will automatically sign a lot of these actions without you ever being asked for approval, but you will quickly realize just how many things the client is doing on your behalf when Amber is asking you to approve them each time.
Now, this can also get quite annoying after a while. I recommend using the setting that allows Amber to automatically sign for basic functions, which will cut down on some of the authorization spam. Once you have been asked to authorize the same type of action a few times, you can also toggle the option to automatically authorize that action in the future. Don't worry, though, you have full control to require Amber to ask you for permission again if you want to be alerted each time, and this toggle is specific to each application, so it's not a blanket approval for all Nostr clients you connect with.

This method of signing is just as fast as signing via browser extension on web clients, which users may be more accustomed to. Everything is happening locally on the device, so it can be very snappy and secure.
### Nostr Connect/Bunker Signing
This next method of signing has a bit of a delay, because it is using a Nostr relay to send encrypted information back and forth between the app the user is interacting with and Amber to obtain signatures remotely. It isn't a significant delay most of the time, but it is just enough to be noticeable.
Also, unlike the previous signing method that would automatically switch to Amber as the active application when a signing request is sent, this method only sends you a notification that you must be watching for. This can lead to situations where you are wondering why something isn't working in a client you signed into remotely, because it is waiting on you to authorize the action and you didn't notice the notification from Amber. As you use the application, you get used to the need to check for such authorization requests from time to time, or when something isn't working as expected.

By default, Amber will use relay.nsec.app to communicate with whichever Nostr app you are connecting to. You can set a different relay for this purpose, if you like, though not just any relay will support the event kinds that Amber uses for remote signing. You can even run your own relay just for your own signing purposes. In fact, the creator of Amber has a relay application you can run on your phone, called Citrine, that can be used for signing with any web app you are using locally on your phone. This is definitely more of an advanced option, but it is there for you if you want it. For most users, sticking with relay.nsec.app will be just fine, especially since the contents of the events sent back and forth for signing are all encrypted.
Something many users may not realize is that this remote signing feature allows for issuing signing permissions to team members. For instance, if anyone ever joined me in writing reviews, I could issue them a connection string from Amber, and limit their permissions to just posting long-form draft events. Anything else they tried to do would require my explicit approval each time. Moreover, I could revoke those permissions if I ever felt they were being abused, without the need to start over with a whole new npub. Of course, this requires that your phone is online whenever a team member is trying to sign using the connection string you issued, and it requires you pay attention to your notifications so you can approve or reject requests you have not set to auto-approve. However, this is probably only useful for small teams, and larger businesses will want to find a more robust solution for managing access to their npub, such as Keycast from nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc.
The method for establishing a connection between Amber and a Nostr app for remote signing can vary for each app. Most, at minimum, will support obtaining a connection string from Amber that starts with "bunker://" and pasting it in at the time of login. Then you just need to approve the connection request from Amber and the client will log you in and send any subsequent signing requests to Amber using the same connection string.

Some clients will also offer the option to scan a QR code to connect the client to Amber. This is quite convenient, but just remember that this also means the client is setting which relay will be used for communication between the two. Clients with this option will also have a connection string you can copy and paste into Amber to achieve the same purpose. For instance, you may need this option if you are trying to connect to an app on your phone and therefore can't scan the QR code using Amber on the same phone.

### Multiple Accounts
Amber does not lock you into using it with only a single set of keys. You can add all of your Nostr "accounts" to Amber and use it for signing events for each independently. Of course, Nostr doesn't actually have "accounts" in the traditional sense. Your identity is simply your key-pair, and Amber stores and accesses each private key as needed.

When first signing in using native Android signing as described above, Amber will default to whichever account was most recently selected, but you can switch to the account that is needed before approving the request. After initial login, Amber will automatically detect the account that the signing request is for.
### Key Backup & Restore
Amber allows multiple ways to back up your private key. As most users would expect, you can get your standard nsec and copy/paste it to a password manager, but you can also obtain your private key as a list of mnemonic seed words, an encrypted version of your key called an ncryptsec, or even a QR code of your nsec or ncryptsec.

Additionally, in order to gain access to this information, Amber requires you to enter your device's PIN or use biometric authentication. This isn't cold-storage level protection for your private key by any means, especially since your phone is an internet connected device and does not store your key within a secure element, but it is about as secure as you can ask for while having your key accessible for signing Nostr events.
### Tor Support
While Amber does not have Tor support within the app itself, it does support connecting to Tor through Orbot. This would be used with remote signing so that Amber would not connect directly over clearnet to the relay used for communication with the Nostr app requesting the signature. Instead, Amber would connect through Tor, so the relay would not see your IP address. This means you can utilize the remote signing option without compromising your anonymity.

### Additional Security
Amber allows the user the option to require either biometric or PIN authentication before approving signing requests. This can provide that extra bit of assurance that no one will be able to sign events using your private key if they happen to gain access to your phone. The PIN you set in Amber is also independent from the PIN to unlock your device, allowing for separation of access.
## Can My Grandma Use It?
Score: **4.0** / 5
At the end of the day, Amber is a tool for those who have some concept of the importance of protecting their private key by not pasting it into every Nostr client that comes along. This concept in itself is not terribly approachable to an average person. They are used to just plugging their password into every service they use, and even worse, they usually have the ***same password*** for everything so they can more readily remember it. The idea that they should never enter their "Nostr password" into any Nostr application would never occur to them unless someone first explained how cryptography works related to public/private key pairs.
That said, I think there can be some improvements made to how users are introduced to these concepts, and that a signer application like Amber might be ideal for the job. Considering Amber as a new user's first touchpoint with Nostr, I think it holds up well, but could be somewhat streamlined.
Upon opening the app, the user is prompted to either use their existing private key or "Create a new Nostr account." This is straightforward enough. "Account" is not a technically correct term with Nostr, but it is a term that new users would be familiar with and understand the basic concept.

The next screen announces that the account is ready, and presents the user with their public key, explaining that it is "a sort of username" that will allow others to find them on Nostr. While it is good to explain this to the user, it is unnecessary information at this point. This screen also prompts the user to set a nickname and set a password to encrypt their private key. Since the backup options also allow the user to set this password, I think this step could be pushed to a later time. This screen would better serve the new user if it simply prompted them to set a nickname and short bio that could be saved to a few default relays.

Of course, Amber is currently prompting for a password to be set up-front because the next screen requires the new user to download a "backup kit" in order to continue. While I do believe it is a good idea to encourage the creation of a backup, it is not crucial to do so immediately upon creation of a new npub that has nothing at stake if the private key is lost. This is something the UI could remind the user to do at a later time, reducing the friction of profile creation, and expediting getting them into the action.

Outside of these minor onboarding friction points, I think Amber does a great job of explaining to the user the purpose of each of its features, all within the app and without any need to reference external documentation. As long as the user understands the basic concept that their private key is being stored by Amber in order to sign requests from other Nostr apps, so they don't have to be given the private key, Amber is very good about explaining the rest without getting too far into the technical weeds.
The most glaring usability issue with Amber is that it isn't available in the Play Store. Average users expect to be able to find applications they can trust in their mobile device's default app store. There is a valid argument to be made that they are incorrect in this assumption, but that doesn't change the fact that this is the assumption most people make. They believe that applications in the Play Store are "safe" and that anything they can't install through the Play Store is suspect. The prompts that the Android operating system requires the user to approve when installing "unknown apps" certainly doesn't help with this impression.
Now, I absolutely ***love*** the Zapstore from nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but it doesn't do much to alleviate this issue. Users will still need to be convinced that it is safe to install the Zapstore from the GitHub repo, and then install Amber from there. Furthermore, this adds yet another step to the onboarding process.
Instead of:
- Install Amber
- Set up your keys
- Install the client you want to use
- Log in with Amber
The process becomes:
- Go to the Zapstore GitHub and download the latest version from the releases page.
- Install the APK you downloaded, allowing any prompt to install unknown apps.
- Open Zapstore and install Amber, allowing any prompt to install unknown apps again.
- Open Amber and set up your keys.
- Install the client you want to use
- Log in with Amber
An application as important as Amber for protecting users' private keys should be as readily available to the new user as possible. New users are the ones most prone to making mistakes that could compromise their private keys. Amber should be available to them in the Play Store.
## How do UI Look?
Score: **4.5** / 5
Amber's UI can be described as clean but utilitarian. But then, Amber is a tool, so this is somewhat expected. It is not an app you will be spending a lot of time in, so the UI just needs to be serviceable. I would say it accomplishes this and then some. UI elements are generally easy to understand what they do, and page headings fill in the gaps where that is not the case.

I am not the biggest fan of the color-scheme, particularly in light-mode, but it is not bad in dark-mode at all, and Amber follows whatever theme you have set for your device in that respect. Additionally, the color choice does make sense given the application's name.

It must also be taken into consideration that Amber is almost entirely the product of a single developer's work. He has done a great job producing an app that is not only useful, but pleasant to interact with. The same cannot be said for most utility apps I have previously used, with interfaces that clearly made good design the lowest priority. While Amber's UI may not be the most beautiful Nostr app I have seen, design was clearly not an afterthought, either, and it is appreciated.
## Relay Management
Score: **4.9** / 5
Even though Amber is not a Nostr client, where users can browse notes from their favorite npubs, it still relies heavily on relays for some of its features. Primarily, it uses relays for communicating with other Nostr apps for remote signing requests. However, it also uses relays to fetch profile data, so that each private key you add to Amber will automatically load your chosen username and profile picture.
In the relay settings, users can choose which relays are being used to fetch profile data, and which relays will be used by default when creating new remote signing connection strings.

The user can also see which relays are currently connected to Amber and even look at the information that has been passed back and forth on each of those active relays. This information about actively connected relays is not only available within the application, but also in the notification that Amber has to keep in your device's notification tray in order to continue to operate in the background while you are using other apps.

Optionality is the name of the game when it comes to how Amber handles relay selection. The user can just stick with the default signing relay, use their own relay as the default, or even use a different relay for each Nostr application that they connect to for remote signing. Amber gives the user an incredible amount of flexibility in this regard.
In addition to all of this, because not all relays accept the event types needed for remote signing, when you add a relay address to Amber, it automatically tests that relay to see if it will work. This alone can be a massive time saver, so users aren't trying to use relays that don't support remote signing and wondering why they can't log into noStrudel with the connection string they got from Amber.

The only way I could see relay management being improved would be some means of giving the user relay recommendations, in case they want to use a relay other than relay.nsec.app, but they aren't sure which other relays will accept remote signing events. That said, most users who want to use a different relay for signing remote events will likely be using their own, in which case recommendations aren't needed.
## Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with any Nostr application. Here are some of the most common questions submitted about Amber in the last two months.
nostr:nevent1qvzqqqqqqypzpv30auvvha0wkhteg500n3xd528063l6099zh37sgj2uevdm5mslqythwumn8ghj7ct49eex2mrp09skymr99ehhyee0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcpz9mhxue69uhnzdps9enrw73wd9hj7qpqjx685wn6j3se7w6380ktwvrpydedpu06jd0cwfjawkgnzmahvs2s7t0585
This is a good example of Amber working correctly, but the app the user is trying to log into not working. In my experience with #Olas in particular, it sometimes allows remote signer login, and sometimes doesn't. Amber will receive the signing request and I will approve it, but Olas remains on the login screen.
If Amber is receiving the signing requests, and you are approving them, the fault is likely with the application you are trying to log into.
That's it. That's all the repeated questions I could find. Oh, there were a few one-off questions where relay.nsec.app wouldn't connect, or where the user's out-of-date web browser was the issue. Outside of that, though, there were no common questions about ***how*** to use Amber, and that is a testament to Amber's ease of use all on its own.
## Wrap Up
If you are on Android and you are not already using Amber to protect your nsec, please do yourself a favor and get it installed. It's not at all complicated to set up, and it will make trying out all the latest Nostr clients a safe and pleasant experience.
If you are a client developer and you have not added support for NIP-55 or NIP-46, do your users the courtesy of respecting the sanctity of their private keys. Even developers who have no intention of compromising their users' keys can inadvertently do so. Make that eventuality impossible by adding support for NIP-55 and NIP-46 signing.
Finally, I apologize for the extended time it took me to get this review finished. The time I have available is scarce, Nostr is distracting, and nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 kept improving Amber even as I was putting it through its paces over the last two months. Keep shipping, my friend! You have made one of the most useful tools we have seen for Nostr to date!
Now... What should I review next?

@ d830ee7b:4e61cd62
2025-02-28 05:07:17
In our daily lives, we often measure the value of things using familiar monetary units such as baht or dollars. We feel delighted when our investments **"increase"** in these units.
However, few people stop to consider how stable the measuring stick itself is. If the ruler we use to measure value keeps shrinking, the objects we measure may appear longer, even though their actual size remains unchanged. This concept reflects the way we assess economic value in constantly changing monetary units, leading us to the principle of opportunity cost in investment: when we choose to hold one type of asset, we are always giving up the opportunity to earn returns from another.
Understanding what serves as our standard measure and the opportunity costs that come with it is the first step toward exploring a new perspective on wealth assessment.
In this context, Bitcoin has been proposed as a new **"standard"** for measuring value, much like gold once served as the global financial standard in the past. Some view Bitcoin as the "digital gold standard" that could support the international financial system in the future.
A key reason Bitcoin is considered **"sound money"** is its rarity—something modern currencies lack. Its supply is permanently capped at 21 million units, meaning no central bank can print more at will. This contrasts with fiat money, such as the dollar or baht, which constantly increases in supply due to government policies.
As a result, Bitcoin is resistant to inflation-induced depreciation and can retain its value over the long term, much like gold in the past. Many therefore consider it **"sound money"**—a form of currency that is stable and reliable in preserving value over time.
This idea opens the door to using Bitcoin as a benchmark for comparing the value of other assets, offering a fresh perspective on the economy.
Imagine a graph that compares the leading stock index, **the S&P 500, in Bitcoin terms instead of dollars.**
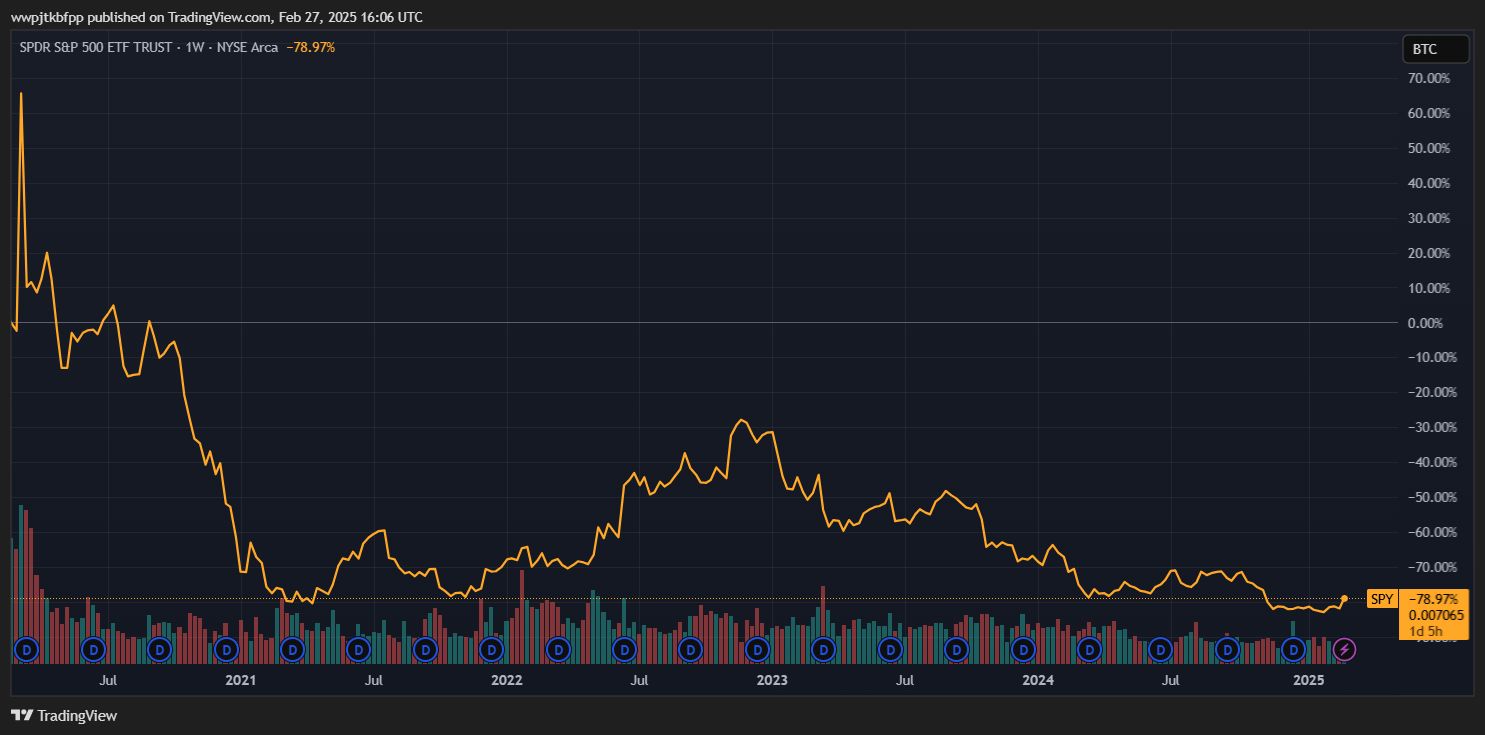
This graph would reveal a drastically different picture from the conventional charts we are familiar with. Looking back to 2011, the S&P 500 was around 1,300 points, while Bitcoin was priced at less than $1.
This means the S&P 500 index was valued at approximately 1,300 BTC at the time. However, as Bitcoin's price surged over the years—reaching tens of thousands of dollars per BTC in 2021–2022—the value of the S&P 500, when measured in BTC, shrank dramatically.
Suppose the S&P 500 currently stands at around 4,000 points, while Bitcoin is priced at six figures in dollars. The entire S&P 500 index might be worth less than 0.05 BTC.
The resulting graph would show a consistent downward trend in the S&P 500's value **(when measured in BTC)** over the past decade.
This means Bitcoin has appreciated relative to traditional financial assets like stocks—to the extent that simply holding Bitcoin has outperformed investing in major stock indices.
As surprising as this may seem, the data tells this story: from the perspective of a Bitcoin standard, even the high-performing U.S. stock market appears lackluster.
Data from the past decade reinforces this view. Bitcoin has outperformed nearly every asset class known today. In numerical terms, Bitcoin delivered an average annual return of **approximately 230% from 2011 to 2021**, whereas the S&P 500, which is renowned for its consistent performance, achieved an average annual return of just over 10%.
When compounded over time, this means Bitcoin's value increased by tens of thousands of percent over the past decade, while the S&P 500's value rose by only a few hundred percent.
The magnitude of this difference is significant enough to reshape how we perceive investment success. Observations also indicate that in just **the past five years, the S&P 500 has lost nearly 90% of its value when measured in Bitcoin.**
In other words, for someone using Bitcoin as their benchmark, a 100-baht investment in stocks at the beginning of this period would be worth only about 10 baht today—the remaining 90 baht representing the opportunity cost of not holding Bitcoin.
This perspective challenges our assumptions about the stability of supposedly safe assets when evaluated under a new standard.
This comparison also highlights the issue of fiat currency depreciation—something we are familiar with but often underestimate. The U.S. dollar, the world's primary reserve currency, has **lost over 96% of its purchasing power since 1913**.
This means that what $1 could buy back then now requires nearly $30. This ongoing depreciation implies that prices in fiat terms may rise even when real value does not. For example, the S&P 500 frequently reaches all-time highs in U.S. dollar terms.
However, when adjusted for inflation or money supply expansion, its real value has not increased as much as it seems. Some analyses suggest that since the 2008 financial crisis, although the S&P 500's nominal value has surged, when divided by the expanding money supply (such as M3), its graph remains largely unchanged from pre-crisis levels.
This suggests that stock prices have risen primarily in response to liquidity injections rather than genuine economic growth. Inflation and monetary expansion act like a **"fog,"** obscuring our ability to discern real value from mere numerical increases.
When Bitcoin is used as a comparative unit, it acts as a clear lens that removes this inflationary fog, revealing a completely different picture.
The same applies when comparing commodity prices in BTC. A notable experiment by the St. Louis Federal Reserve once examined the price of **"a dozen eggs"** in both dollars and Bitcoin. While the study aimed to highlight Bitcoin’s volatility, it inadvertently reinforced the point that during periods of high inflation, the price of eggs, which seemed to rise continuously in dollars, actually remained stable or even declined in BTC terms.
This amusing example illustrates the profound impact of measurement standards.
Of course, Bitcoin itself is highly volatile and still in its early stages compared to traditional assets. Its meteoric rise over the past decade does not guarantee that all asset graphs in BTC terms will continue declining indefinitely. However, what has already transpired provides deep financial insights.
**The first takeaway** is the concept of opportunity cost mentioned earlier—every financial decision has an inherent cost, even if we do not always recognize it. Holding cash in a bank carries the opportunity cost of the returns one could earn by investing elsewhere. Investing in asset A means missing out on asset B, and if B delivers higher returns, we incur that loss.
Over the past decade, Bitcoin has outperformed all other assets by a wide margin, making the opportunity cost of not holding Bitcoin extremely high. Investors looking back on this period might regret not having bought Bitcoin earlier, but the key lesson is not about dwelling on past decisions—it is about becoming aware of **opportunity costs** and their long-term impact on wealth.
On a deeper level, this discussion raises questions about whether our current valuation framework is truly appropriate. If using a depreciating fiat currency as a benchmark distorts our perception of value, our economic decisions may be misaligned in the long run.
Imagine a scenario where money retains or even appreciates in value in line with real economic productivity (as Bitcoin was designed to do). In such a system, people would not need to chase high returns merely to preserve their savings from inflation. They could plan finances with a longer-term perspective. Concepts like **"time preference"** and **"discounting the future"** would shift.
It is often argued that sound money encourages saving and long-term investment, whereas inflationary systems push people toward short-term spending or speculation out of fear that their money will lose value.
This is not just a matter of personal finance but a fundamental influence on the quality of economic growth and innovation. **A sound money standard** like **Bitcoin** might enforce stricter investment discipline, as liquidity injections could no longer be used as a safety net for unsustainable projects.
At this point, readers may not conclude that they should immediately hold Bitcoin instead of investing in other assets—and this article is not intended as investment advice. Its real purpose is to provoke thought about how we measure value.
**Ask yourself:** What unit do we use to gauge wealth and economic progress? Is that unit reliable?
If the money we use for measurement loses value every year, how can we be sure that increasing numbers on paper reflect true wealth growth?
Using Bitcoin as a reference standard is like measuring with a new ruler—one that may be more accurate. In many cases, it reveals unexpected insights and challenges long-held beliefs.
Ultimately, whether or not one believes in the **"Bitcoin standard"** is less important than the ability to critically examine the system we rely on daily.
Perhaps the greatest value Bitcoin and new financial philosophies offer is not a definitive answer but the impetus to look at the bigger economic picture with fresh eyes.
Thank you, Thai Ratel, for enlightening me on this topic!
Jakk Goodday.
 @ da0b9bc3:4e30a4a9
2025-02-28 08:39:58Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/899482
@ da0b9bc3:4e30a4a9
2025-02-28 08:39:58Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/899482 @ 1c19eb1a:e22fb0bc
2025-02-28 07:32:53After my first major review of [Primal on Android](https://www.nostr-reviews.com/post/1733635103705/), we're going to go a very different direction for this next review. Primal is your standard "Twitter clone" type of kind 1 note client, now branching into long-form. They also have a team of developers working on making it one of the best clients to fill that use-case. By contrast, this review will not be focusing on any client at all. Not even an "other stuff" client. Instead, we will be reviewing a very useful tool created and maintained by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 called #Amber. For those unfamiliar with Amber, it is an #Android application dedicated to managing your signing keys, and allowing you to log into various #Nostr applications without having to paste in your private key, better known as your #nsec. It is not recommended to paste your nsec into various applications because they each represent another means by which it could be compromised, and anyone who has your nsec can post as you. On Nostr, your #npub is your identity, and your signature using your private key is considered absolute proof that any given note, reaction, follow update, or profile change was authorized by the rightful owner of that identity. It happens less often these days, but early on, when the only way to try out a new client was by inputting your nsec, users had their nsec compromised from time to time, or they would suspect that their key may have been compromised. When this occurs, there is no way to recover your account, or set a new private key, deprecating the previous one. The only thing you can do is start over from scratch, letting everyone know that your key has been compromised and to follow you on your new npub. If you use Amber to log into other Nostr apps, you significantly reduce the likelihood that your private key will be compromised, because only one application has access to it, and all other applications reach out to Amber to sign any events. This isn't quite as secure as storing your private key on a separate device that isn't connected to the internet whatsoever, like many of us have grown accustomed to with securing our #Bitcoin, but then again, an online persona isn't nearly as important to secure for most of us as our entire life savings. Amber is the first application of its kind for managing your Nostr keys on a mobile device. nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 didn't merely develop the application, but literally created the specification for accomplishing external signing on Android which can be found in [NIP-55](https://github.com/nostr-protocol/nips/blob/master/55.md). Unfortunately, Amber is only available for Android. A signer application for iOS is in the works from nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, but is not ready for use at this time. There is also a new mobile signer app for Android and iOS called Nowser, but I have not yet had a chance to try this app out. From a cursory look at the Android version, it is indeed in the very early stages of development and cannot be compared with Amber. This review of Amber is current as of version 3.2.5.  ## Overall Impression Score: **4.5** / 5 I cannot speak highly enough about Amber as a tool that every Nostr user on Android should start using if they are not already. When the day comes that we have more options for well-developed signer apps on mobile, my opinion may very well change, but until then Amber is what we have available to us. Even so, it is an incredibly well thought-out and reliable tool for securing your nsec. Despite being the only well-established Android signer available for Android, Amber ***can*** be compared with other external signing methods available on other platforms. Even with more competition in this arena, though, Amber still holds up incredibly well. If you are signing into web applications on a desktop, I still would recommend using a browser extension like #Alby or #Nos2x, as the experience is usually faster, more seamless, and far more web apps support this signing method ([NIP-07](https://github.com/nostr-protocol/nips/blob/master/07.md)) than currently support the two methods employed by Amber. Nevertheless that gap is definitely narrowing. A running list I created of applications that support login and signing with Amber can be found here: [Nostr Clients with External Signer Support](nostr:naddr1qvzqqqrcvgpzpde8f55w86vrhaeqmd955y4rraw8aunzxgxstsj7eyzgntyev2xtqydhwumn8ghj7un9d3shjtnzwf5kw6r5vfhkcapwdejhgtcpr4mhxue69uhkg6ttv95k7ue3x5cnwtnwdaehgu339e3k7mf0qq4xummnw3ez6cmvd9jkuarn94mkjarg94jhsar9wfhxzmpdwd5kwmn9wgkhxatswphhyaqrcy76t) I have run into relatively few bugs in my extensive use of Amber for all of my mobile signing needs. Occasionally the application crashes when trying to send it a signing request from a couple of applications, but I would not be surprised if this is no fault of Amber at all, and rather the fault of those specific apps, since it works flawlessly with the vast majority of apps that support either [NIP-55](https://github.com/nostr-protocol/nips/blob/master/55.md) or [NIP-46](https://github.com/nostr-protocol/nips/blob/master/46.md) login. I also believe that mobile is the ideal platform to use for this type of application. First, because most people use Nostr clients on their phone more than on a desktop. There are, of course, exceptions to that, but in general we spend more time on our phones when interacting online. New users are also more likely to be introduced to Nostr by a friend having them download a Nostr client on their phone than on a PC, and that can be a prime opportunity to introduce the new user to protecting their private key. Finally, I agree with the following assessment from nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn. nostr:nevent1qqsw0r6gzn05xg67h5q2xkplwsuzedjxw9lf7ntrxjl8ajm350fcyugpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsyg9hyaxj3clfswlhyrd5kjsj5v04clhjvgeq6pwztmysfzdvn93gevpsgqqqye9qd30q62 The one downside to Amber is that it will be quite foreign for new users. That is partially unavoidable with Nostr, since folks are not accustomed to public/private key cryptography in general, let alone using a private key to log into websites or social media apps. However, the initial signup process is a bit cumbersome if Amber is being used as the means of initially generating a key pair. I think some of this could be foregone at start-up in favor of streamlining onboarding, and then encourage the user to back-up their private key at a later time. ## Features Amber has some features that may surprise you, outside of just storing your private key and signing requests from your favorite Nostr clients. It is a full key management application, supporting multiple accounts, various backup methods, and even the ability to authorize other users to access a Nostr profile you control. ### Android Signing This is the signing method where Amber really shines in both speed and ease of use. Any Android application that supports this standard, and even some progressive web-apps that can be installed to your Android's home-screen, can very quickly and seamlessly connect with Amber to authorize anything that you need signed with your nsec. All you have to do is select "Login with Amber" in clients like #Amethyst or #0xChat and the app will reach out to Amber for all signing requests from there on out. If you had previously signed into the app with your nsec, you will first need to log out, then choose the option to use Amber when you log back in.  This is a massive deal, because everything you do on Nostr requires a signature from your private key. Log in? Needs a signature. Post a "GM" note? Needs a signature. Follow someone who zapped your note? Needs a signature. Zap them back? You guessed it; needs a signature. When you paste your private key into an application, it will automatically sign a lot of these actions without you ever being asked for approval, but you will quickly realize just how many things the client is doing on your behalf when Amber is asking you to approve them each time. Now, this can also get quite annoying after a while. I recommend using the setting that allows Amber to automatically sign for basic functions, which will cut down on some of the authorization spam. Once you have been asked to authorize the same type of action a few times, you can also toggle the option to automatically authorize that action in the future. Don't worry, though, you have full control to require Amber to ask you for permission again if you want to be alerted each time, and this toggle is specific to each application, so it's not a blanket approval for all Nostr clients you connect with.  This method of signing is just as fast as signing via browser extension on web clients, which users may be more accustomed to. Everything is happening locally on the device, so it can be very snappy and secure. ### Nostr Connect/Bunker Signing This next method of signing has a bit of a delay, because it is using a Nostr relay to send encrypted information back and forth between the app the user is interacting with and Amber to obtain signatures remotely. It isn't a significant delay most of the time, but it is just enough to be noticeable. Also, unlike the previous signing method that would automatically switch to Amber as the active application when a signing request is sent, this method only sends you a notification that you must be watching for. This can lead to situations where you are wondering why something isn't working in a client you signed into remotely, because it is waiting on you to authorize the action and you didn't notice the notification from Amber. As you use the application, you get used to the need to check for such authorization requests from time to time, or when something isn't working as expected.  By default, Amber will use relay.nsec.app to communicate with whichever Nostr app you are connecting to. You can set a different relay for this purpose, if you like, though not just any relay will support the event kinds that Amber uses for remote signing. You can even run your own relay just for your own signing purposes. In fact, the creator of Amber has a relay application you can run on your phone, called Citrine, that can be used for signing with any web app you are using locally on your phone. This is definitely more of an advanced option, but it is there for you if you want it. For most users, sticking with relay.nsec.app will be just fine, especially since the contents of the events sent back and forth for signing are all encrypted. Something many users may not realize is that this remote signing feature allows for issuing signing permissions to team members. For instance, if anyone ever joined me in writing reviews, I could issue them a connection string from Amber, and limit their permissions to just posting long-form draft events. Anything else they tried to do would require my explicit approval each time. Moreover, I could revoke those permissions if I ever felt they were being abused, without the need to start over with a whole new npub. Of course, this requires that your phone is online whenever a team member is trying to sign using the connection string you issued, and it requires you pay attention to your notifications so you can approve or reject requests you have not set to auto-approve. However, this is probably only useful for small teams, and larger businesses will want to find a more robust solution for managing access to their npub, such as Keycast from nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc. The method for establishing a connection between Amber and a Nostr app for remote signing can vary for each app. Most, at minimum, will support obtaining a connection string from Amber that starts with "bunker://" and pasting it in at the time of login. Then you just need to approve the connection request from Amber and the client will log you in and send any subsequent signing requests to Amber using the same connection string.  Some clients will also offer the option to scan a QR code to connect the client to Amber. This is quite convenient, but just remember that this also means the client is setting which relay will be used for communication between the two. Clients with this option will also have a connection string you can copy and paste into Amber to achieve the same purpose. For instance, you may need this option if you are trying to connect to an app on your phone and therefore can't scan the QR code using Amber on the same phone.  ### Multiple Accounts Amber does not lock you into using it with only a single set of keys. You can add all of your Nostr "accounts" to Amber and use it for signing events for each independently. Of course, Nostr doesn't actually have "accounts" in the traditional sense. Your identity is simply your key-pair, and Amber stores and accesses each private key as needed.  When first signing in using native Android signing as described above, Amber will default to whichever account was most recently selected, but you can switch to the account that is needed before approving the request. After initial login, Amber will automatically detect the account that the signing request is for. ### Key Backup & Restore Amber allows multiple ways to back up your private key. As most users would expect, you can get your standard nsec and copy/paste it to a password manager, but you can also obtain your private key as a list of mnemonic seed words, an encrypted version of your key called an ncryptsec, or even a QR code of your nsec or ncryptsec.  Additionally, in order to gain access to this information, Amber requires you to enter your device's PIN or use biometric authentication. This isn't cold-storage level protection for your private key by any means, especially since your phone is an internet connected device and does not store your key within a secure element, but it is about as secure as you can ask for while having your key accessible for signing Nostr events. ### Tor Support While Amber does not have Tor support within the app itself, it does support connecting to Tor through Orbot. This would be used with remote signing so that Amber would not connect directly over clearnet to the relay used for communication with the Nostr app requesting the signature. Instead, Amber would connect through Tor, so the relay would not see your IP address. This means you can utilize the remote signing option without compromising your anonymity.  ### Additional Security Amber allows the user the option to require either biometric or PIN authentication before approving signing requests. This can provide that extra bit of assurance that no one will be able to sign events using your private key if they happen to gain access to your phone. The PIN you set in Amber is also independent from the PIN to unlock your device, allowing for separation of access. ## Can My Grandma Use It? Score: **4.0** / 5 At the end of the day, Amber is a tool for those who have some concept of the importance of protecting their private key by not pasting it into every Nostr client that comes along. This concept in itself is not terribly approachable to an average person. They are used to just plugging their password into every service they use, and even worse, they usually have the ***same password*** for everything so they can more readily remember it. The idea that they should never enter their "Nostr password" into any Nostr application would never occur to them unless someone first explained how cryptography works related to public/private key pairs. That said, I think there can be some improvements made to how users are introduced to these concepts, and that a signer application like Amber might be ideal for the job. Considering Amber as a new user's first touchpoint with Nostr, I think it holds up well, but could be somewhat streamlined. Upon opening the app, the user is prompted to either use their existing private key or "Create a new Nostr account." This is straightforward enough. "Account" is not a technically correct term with Nostr, but it is a term that new users would be familiar with and understand the basic concept.  The next screen announces that the account is ready, and presents the user with their public key, explaining that it is "a sort of username" that will allow others to find them on Nostr. While it is good to explain this to the user, it is unnecessary information at this point. This screen also prompts the user to set a nickname and set a password to encrypt their private key. Since the backup options also allow the user to set this password, I think this step could be pushed to a later time. This screen would better serve the new user if it simply prompted them to set a nickname and short bio that could be saved to a few default relays.  Of course, Amber is currently prompting for a password to be set up-front because the next screen requires the new user to download a "backup kit" in order to continue. While I do believe it is a good idea to encourage the creation of a backup, it is not crucial to do so immediately upon creation of a new npub that has nothing at stake if the private key is lost. This is something the UI could remind the user to do at a later time, reducing the friction of profile creation, and expediting getting them into the action.  Outside of these minor onboarding friction points, I think Amber does a great job of explaining to the user the purpose of each of its features, all within the app and without any need to reference external documentation. As long as the user understands the basic concept that their private key is being stored by Amber in order to sign requests from other Nostr apps, so they don't have to be given the private key, Amber is very good about explaining the rest without getting too far into the technical weeds. The most glaring usability issue with Amber is that it isn't available in the Play Store. Average users expect to be able to find applications they can trust in their mobile device's default app store. There is a valid argument to be made that they are incorrect in this assumption, but that doesn't change the fact that this is the assumption most people make. They believe that applications in the Play Store are "safe" and that anything they can't install through the Play Store is suspect. The prompts that the Android operating system requires the user to approve when installing "unknown apps" certainly doesn't help with this impression. Now, I absolutely ***love*** the Zapstore from nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but it doesn't do much to alleviate this issue. Users will still need to be convinced that it is safe to install the Zapstore from the GitHub repo, and then install Amber from there. Furthermore, this adds yet another step to the onboarding process. Instead of: - Install Amber - Set up your keys - Install the client you want to use - Log in with Amber The process becomes: - Go to the Zapstore GitHub and download the latest version from the releases page. - Install the APK you downloaded, allowing any prompt to install unknown apps. - Open Zapstore and install Amber, allowing any prompt to install unknown apps again. - Open Amber and set up your keys. - Install the client you want to use - Log in with Amber An application as important as Amber for protecting users' private keys should be as readily available to the new user as possible. New users are the ones most prone to making mistakes that could compromise their private keys. Amber should be available to them in the Play Store. ## How do UI Look? Score: **4.5** / 5 Amber's UI can be described as clean but utilitarian. But then, Amber is a tool, so this is somewhat expected. It is not an app you will be spending a lot of time in, so the UI just needs to be serviceable. I would say it accomplishes this and then some. UI elements are generally easy to understand what they do, and page headings fill in the gaps where that is not the case.  I am not the biggest fan of the color-scheme, particularly in light-mode, but it is not bad in dark-mode at all, and Amber follows whatever theme you have set for your device in that respect. Additionally, the color choice does make sense given the application's name.  It must also be taken into consideration that Amber is almost entirely the product of a single developer's work. He has done a great job producing an app that is not only useful, but pleasant to interact with. The same cannot be said for most utility apps I have previously used, with interfaces that clearly made good design the lowest priority. While Amber's UI may not be the most beautiful Nostr app I have seen, design was clearly not an afterthought, either, and it is appreciated. ## Relay Management Score: **4.9** / 5 Even though Amber is not a Nostr client, where users can browse notes from their favorite npubs, it still relies heavily on relays for some of its features. Primarily, it uses relays for communicating with other Nostr apps for remote signing requests. However, it also uses relays to fetch profile data, so that each private key you add to Amber will automatically load your chosen username and profile picture. In the relay settings, users can choose which relays are being used to fetch profile data, and which relays will be used by default when creating new remote signing connection strings.  The user can also see which relays are currently connected to Amber and even look at the information that has been passed back and forth on each of those active relays. This information about actively connected relays is not only available within the application, but also in the notification that Amber has to keep in your device's notification tray in order to continue to operate in the background while you are using other apps.  Optionality is the name of the game when it comes to how Amber handles relay selection. The user can just stick with the default signing relay, use their own relay as the default, or even use a different relay for each Nostr application that they connect to for remote signing. Amber gives the user an incredible amount of flexibility in this regard. In addition to all of this, because not all relays accept the event types needed for remote signing, when you add a relay address to Amber, it automatically tests that relay to see if it will work. This alone can be a massive time saver, so users aren't trying to use relays that don't support remote signing and wondering why they can't log into noStrudel with the connection string they got from Amber.  The only way I could see relay management being improved would be some means of giving the user relay recommendations, in case they want to use a relay other than relay.nsec.app, but they aren't sure which other relays will accept remote signing events. That said, most users who want to use a different relay for signing remote events will likely be using their own, in which case recommendations aren't needed. ## Current Users' Questions The AskNostr hashtag can be a good indication of the pain points that other users are currently having with any Nostr application. Here are some of the most common questions submitted about Amber in the last two months. nostr:nevent1qvzqqqqqqypzpv30auvvha0wkhteg500n3xd528063l6099zh37sgj2uevdm5mslqythwumn8ghj7ct49eex2mrp09skymr99ehhyee0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcpz9mhxue69uhnzdps9enrw73wd9hj7qpqjx685wn6j3se7w6380ktwvrpydedpu06jd0cwfjawkgnzmahvs2s7t0585 This is a good example of Amber working correctly, but the app the user is trying to log into not working. In my experience with #Olas in particular, it sometimes allows remote signer login, and sometimes doesn't. Amber will receive the signing request and I will approve it, but Olas remains on the login screen. If Amber is receiving the signing requests, and you are approving them, the fault is likely with the application you are trying to log into. That's it. That's all the repeated questions I could find. Oh, there were a few one-off questions where relay.nsec.app wouldn't connect, or where the user's out-of-date web browser was the issue. Outside of that, though, there were no common questions about ***how*** to use Amber, and that is a testament to Amber's ease of use all on its own. ## Wrap Up If you are on Android and you are not already using Amber to protect your nsec, please do yourself a favor and get it installed. It's not at all complicated to set up, and it will make trying out all the latest Nostr clients a safe and pleasant experience. If you are a client developer and you have not added support for NIP-55 or NIP-46, do your users the courtesy of respecting the sanctity of their private keys. Even developers who have no intention of compromising their users' keys can inadvertently do so. Make that eventuality impossible by adding support for NIP-55 and NIP-46 signing. Finally, I apologize for the extended time it took me to get this review finished. The time I have available is scarce, Nostr is distracting, and nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 kept improving Amber even as I was putting it through its paces over the last two months. Keep shipping, my friend! You have made one of the most useful tools we have seen for Nostr to date! Now... What should I review next?
@ 1c19eb1a:e22fb0bc
2025-02-28 07:32:53After my first major review of [Primal on Android](https://www.nostr-reviews.com/post/1733635103705/), we're going to go a very different direction for this next review. Primal is your standard "Twitter clone" type of kind 1 note client, now branching into long-form. They also have a team of developers working on making it one of the best clients to fill that use-case. By contrast, this review will not be focusing on any client at all. Not even an "other stuff" client. Instead, we will be reviewing a very useful tool created and maintained by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 called #Amber. For those unfamiliar with Amber, it is an #Android application dedicated to managing your signing keys, and allowing you to log into various #Nostr applications without having to paste in your private key, better known as your #nsec. It is not recommended to paste your nsec into various applications because they each represent another means by which it could be compromised, and anyone who has your nsec can post as you. On Nostr, your #npub is your identity, and your signature using your private key is considered absolute proof that any given note, reaction, follow update, or profile change was authorized by the rightful owner of that identity. It happens less often these days, but early on, when the only way to try out a new client was by inputting your nsec, users had their nsec compromised from time to time, or they would suspect that their key may have been compromised. When this occurs, there is no way to recover your account, or set a new private key, deprecating the previous one. The only thing you can do is start over from scratch, letting everyone know that your key has been compromised and to follow you on your new npub. If you use Amber to log into other Nostr apps, you significantly reduce the likelihood that your private key will be compromised, because only one application has access to it, and all other applications reach out to Amber to sign any events. This isn't quite as secure as storing your private key on a separate device that isn't connected to the internet whatsoever, like many of us have grown accustomed to with securing our #Bitcoin, but then again, an online persona isn't nearly as important to secure for most of us as our entire life savings. Amber is the first application of its kind for managing your Nostr keys on a mobile device. nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 didn't merely develop the application, but literally created the specification for accomplishing external signing on Android which can be found in [NIP-55](https://github.com/nostr-protocol/nips/blob/master/55.md). Unfortunately, Amber is only available for Android. A signer application for iOS is in the works from nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, but is not ready for use at this time. There is also a new mobile signer app for Android and iOS called Nowser, but I have not yet had a chance to try this app out. From a cursory look at the Android version, it is indeed in the very early stages of development and cannot be compared with Amber. This review of Amber is current as of version 3.2.5.  ## Overall Impression Score: **4.5** / 5 I cannot speak highly enough about Amber as a tool that every Nostr user on Android should start using if they are not already. When the day comes that we have more options for well-developed signer apps on mobile, my opinion may very well change, but until then Amber is what we have available to us. Even so, it is an incredibly well thought-out and reliable tool for securing your nsec. Despite being the only well-established Android signer available for Android, Amber ***can*** be compared with other external signing methods available on other platforms. Even with more competition in this arena, though, Amber still holds up incredibly well. If you are signing into web applications on a desktop, I still would recommend using a browser extension like #Alby or #Nos2x, as the experience is usually faster, more seamless, and far more web apps support this signing method ([NIP-07](https://github.com/nostr-protocol/nips/blob/master/07.md)) than currently support the two methods employed by Amber. Nevertheless that gap is definitely narrowing. A running list I created of applications that support login and signing with Amber can be found here: [Nostr Clients with External Signer Support](nostr:naddr1qvzqqqrcvgpzpde8f55w86vrhaeqmd955y4rraw8aunzxgxstsj7eyzgntyev2xtqydhwumn8ghj7un9d3shjtnzwf5kw6r5vfhkcapwdejhgtcpr4mhxue69uhkg6ttv95k7ue3x5cnwtnwdaehgu339e3k7mf0qq4xummnw3ez6cmvd9jkuarn94mkjarg94jhsar9wfhxzmpdwd5kwmn9wgkhxatswphhyaqrcy76t) I have run into relatively few bugs in my extensive use of Amber for all of my mobile signing needs. Occasionally the application crashes when trying to send it a signing request from a couple of applications, but I would not be surprised if this is no fault of Amber at all, and rather the fault of those specific apps, since it works flawlessly with the vast majority of apps that support either [NIP-55](https://github.com/nostr-protocol/nips/blob/master/55.md) or [NIP-46](https://github.com/nostr-protocol/nips/blob/master/46.md) login. I also believe that mobile is the ideal platform to use for this type of application. First, because most people use Nostr clients on their phone more than on a desktop. There are, of course, exceptions to that, but in general we spend more time on our phones when interacting online. New users are also more likely to be introduced to Nostr by a friend having them download a Nostr client on their phone than on a PC, and that can be a prime opportunity to introduce the new user to protecting their private key. Finally, I agree with the following assessment from nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn. nostr:nevent1qqsw0r6gzn05xg67h5q2xkplwsuzedjxw9lf7ntrxjl8ajm350fcyugpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsyg9hyaxj3clfswlhyrd5kjsj5v04clhjvgeq6pwztmysfzdvn93gevpsgqqqye9qd30q62 The one downside to Amber is that it will be quite foreign for new users. That is partially unavoidable with Nostr, since folks are not accustomed to public/private key cryptography in general, let alone using a private key to log into websites or social media apps. However, the initial signup process is a bit cumbersome if Amber is being used as the means of initially generating a key pair. I think some of this could be foregone at start-up in favor of streamlining onboarding, and then encourage the user to back-up their private key at a later time. ## Features Amber has some features that may surprise you, outside of just storing your private key and signing requests from your favorite Nostr clients. It is a full key management application, supporting multiple accounts, various backup methods, and even the ability to authorize other users to access a Nostr profile you control. ### Android Signing This is the signing method where Amber really shines in both speed and ease of use. Any Android application that supports this standard, and even some progressive web-apps that can be installed to your Android's home-screen, can very quickly and seamlessly connect with Amber to authorize anything that you need signed with your nsec. All you have to do is select "Login with Amber" in clients like #Amethyst or #0xChat and the app will reach out to Amber for all signing requests from there on out. If you had previously signed into the app with your nsec, you will first need to log out, then choose the option to use Amber when you log back in.  This is a massive deal, because everything you do on Nostr requires a signature from your private key. Log in? Needs a signature. Post a "GM" note? Needs a signature. Follow someone who zapped your note? Needs a signature. Zap them back? You guessed it; needs a signature. When you paste your private key into an application, it will automatically sign a lot of these actions without you ever being asked for approval, but you will quickly realize just how many things the client is doing on your behalf when Amber is asking you to approve them each time. Now, this can also get quite annoying after a while. I recommend using the setting that allows Amber to automatically sign for basic functions, which will cut down on some of the authorization spam. Once you have been asked to authorize the same type of action a few times, you can also toggle the option to automatically authorize that action in the future. Don't worry, though, you have full control to require Amber to ask you for permission again if you want to be alerted each time, and this toggle is specific to each application, so it's not a blanket approval for all Nostr clients you connect with.  This method of signing is just as fast as signing via browser extension on web clients, which users may be more accustomed to. Everything is happening locally on the device, so it can be very snappy and secure. ### Nostr Connect/Bunker Signing This next method of signing has a bit of a delay, because it is using a Nostr relay to send encrypted information back and forth between the app the user is interacting with and Amber to obtain signatures remotely. It isn't a significant delay most of the time, but it is just enough to be noticeable. Also, unlike the previous signing method that would automatically switch to Amber as the active application when a signing request is sent, this method only sends you a notification that you must be watching for. This can lead to situations where you are wondering why something isn't working in a client you signed into remotely, because it is waiting on you to authorize the action and you didn't notice the notification from Amber. As you use the application, you get used to the need to check for such authorization requests from time to time, or when something isn't working as expected.  By default, Amber will use relay.nsec.app to communicate with whichever Nostr app you are connecting to. You can set a different relay for this purpose, if you like, though not just any relay will support the event kinds that Amber uses for remote signing. You can even run your own relay just for your own signing purposes. In fact, the creator of Amber has a relay application you can run on your phone, called Citrine, that can be used for signing with any web app you are using locally on your phone. This is definitely more of an advanced option, but it is there for you if you want it. For most users, sticking with relay.nsec.app will be just fine, especially since the contents of the events sent back and forth for signing are all encrypted. Something many users may not realize is that this remote signing feature allows for issuing signing permissions to team members. For instance, if anyone ever joined me in writing reviews, I could issue them a connection string from Amber, and limit their permissions to just posting long-form draft events. Anything else they tried to do would require my explicit approval each time. Moreover, I could revoke those permissions if I ever felt they were being abused, without the need to start over with a whole new npub. Of course, this requires that your phone is online whenever a team member is trying to sign using the connection string you issued, and it requires you pay attention to your notifications so you can approve or reject requests you have not set to auto-approve. However, this is probably only useful for small teams, and larger businesses will want to find a more robust solution for managing access to their npub, such as Keycast from nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc. The method for establishing a connection between Amber and a Nostr app for remote signing can vary for each app. Most, at minimum, will support obtaining a connection string from Amber that starts with "bunker://" and pasting it in at the time of login. Then you just need to approve the connection request from Amber and the client will log you in and send any subsequent signing requests to Amber using the same connection string.  Some clients will also offer the option to scan a QR code to connect the client to Amber. This is quite convenient, but just remember that this also means the client is setting which relay will be used for communication between the two. Clients with this option will also have a connection string you can copy and paste into Amber to achieve the same purpose. For instance, you may need this option if you are trying to connect to an app on your phone and therefore can't scan the QR code using Amber on the same phone.  ### Multiple Accounts Amber does not lock you into using it with only a single set of keys. You can add all of your Nostr "accounts" to Amber and use it for signing events for each independently. Of course, Nostr doesn't actually have "accounts" in the traditional sense. Your identity is simply your key-pair, and Amber stores and accesses each private key as needed.  When first signing in using native Android signing as described above, Amber will default to whichever account was most recently selected, but you can switch to the account that is needed before approving the request. After initial login, Amber will automatically detect the account that the signing request is for. ### Key Backup & Restore Amber allows multiple ways to back up your private key. As most users would expect, you can get your standard nsec and copy/paste it to a password manager, but you can also obtain your private key as a list of mnemonic seed words, an encrypted version of your key called an ncryptsec, or even a QR code of your nsec or ncryptsec.  Additionally, in order to gain access to this information, Amber requires you to enter your device's PIN or use biometric authentication. This isn't cold-storage level protection for your private key by any means, especially since your phone is an internet connected device and does not store your key within a secure element, but it is about as secure as you can ask for while having your key accessible for signing Nostr events. ### Tor Support While Amber does not have Tor support within the app itself, it does support connecting to Tor through Orbot. This would be used with remote signing so that Amber would not connect directly over clearnet to the relay used for communication with the Nostr app requesting the signature. Instead, Amber would connect through Tor, so the relay would not see your IP address. This means you can utilize the remote signing option without compromising your anonymity.  ### Additional Security Amber allows the user the option to require either biometric or PIN authentication before approving signing requests. This can provide that extra bit of assurance that no one will be able to sign events using your private key if they happen to gain access to your phone. The PIN you set in Amber is also independent from the PIN to unlock your device, allowing for separation of access. ## Can My Grandma Use It? Score: **4.0** / 5 At the end of the day, Amber is a tool for those who have some concept of the importance of protecting their private key by not pasting it into every Nostr client that comes along. This concept in itself is not terribly approachable to an average person. They are used to just plugging their password into every service they use, and even worse, they usually have the ***same password*** for everything so they can more readily remember it. The idea that they should never enter their "Nostr password" into any Nostr application would never occur to them unless someone first explained how cryptography works related to public/private key pairs. That said, I think there can be some improvements made to how users are introduced to these concepts, and that a signer application like Amber might be ideal for the job. Considering Amber as a new user's first touchpoint with Nostr, I think it holds up well, but could be somewhat streamlined. Upon opening the app, the user is prompted to either use their existing private key or "Create a new Nostr account." This is straightforward enough. "Account" is not a technically correct term with Nostr, but it is a term that new users would be familiar with and understand the basic concept.  The next screen announces that the account is ready, and presents the user with their public key, explaining that it is "a sort of username" that will allow others to find them on Nostr. While it is good to explain this to the user, it is unnecessary information at this point. This screen also prompts the user to set a nickname and set a password to encrypt their private key. Since the backup options also allow the user to set this password, I think this step could be pushed to a later time. This screen would better serve the new user if it simply prompted them to set a nickname and short bio that could be saved to a few default relays.  Of course, Amber is currently prompting for a password to be set up-front because the next screen requires the new user to download a "backup kit" in order to continue. While I do believe it is a good idea to encourage the creation of a backup, it is not crucial to do so immediately upon creation of a new npub that has nothing at stake if the private key is lost. This is something the UI could remind the user to do at a later time, reducing the friction of profile creation, and expediting getting them into the action.  Outside of these minor onboarding friction points, I think Amber does a great job of explaining to the user the purpose of each of its features, all within the app and without any need to reference external documentation. As long as the user understands the basic concept that their private key is being stored by Amber in order to sign requests from other Nostr apps, so they don't have to be given the private key, Amber is very good about explaining the rest without getting too far into the technical weeds. The most glaring usability issue with Amber is that it isn't available in the Play Store. Average users expect to be able to find applications they can trust in their mobile device's default app store. There is a valid argument to be made that they are incorrect in this assumption, but that doesn't change the fact that this is the assumption most people make. They believe that applications in the Play Store are "safe" and that anything they can't install through the Play Store is suspect. The prompts that the Android operating system requires the user to approve when installing "unknown apps" certainly doesn't help with this impression. Now, I absolutely ***love*** the Zapstore from nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but it doesn't do much to alleviate this issue. Users will still need to be convinced that it is safe to install the Zapstore from the GitHub repo, and then install Amber from there. Furthermore, this adds yet another step to the onboarding process. Instead of: - Install Amber - Set up your keys - Install the client you want to use - Log in with Amber The process becomes: - Go to the Zapstore GitHub and download the latest version from the releases page. - Install the APK you downloaded, allowing any prompt to install unknown apps. - Open Zapstore and install Amber, allowing any prompt to install unknown apps again. - Open Amber and set up your keys. - Install the client you want to use - Log in with Amber An application as important as Amber for protecting users' private keys should be as readily available to the new user as possible. New users are the ones most prone to making mistakes that could compromise their private keys. Amber should be available to them in the Play Store. ## How do UI Look? Score: **4.5** / 5 Amber's UI can be described as clean but utilitarian. But then, Amber is a tool, so this is somewhat expected. It is not an app you will be spending a lot of time in, so the UI just needs to be serviceable. I would say it accomplishes this and then some. UI elements are generally easy to understand what they do, and page headings fill in the gaps where that is not the case.  I am not the biggest fan of the color-scheme, particularly in light-mode, but it is not bad in dark-mode at all, and Amber follows whatever theme you have set for your device in that respect. Additionally, the color choice does make sense given the application's name.  It must also be taken into consideration that Amber is almost entirely the product of a single developer's work. He has done a great job producing an app that is not only useful, but pleasant to interact with. The same cannot be said for most utility apps I have previously used, with interfaces that clearly made good design the lowest priority. While Amber's UI may not be the most beautiful Nostr app I have seen, design was clearly not an afterthought, either, and it is appreciated. ## Relay Management Score: **4.9** / 5 Even though Amber is not a Nostr client, where users can browse notes from their favorite npubs, it still relies heavily on relays for some of its features. Primarily, it uses relays for communicating with other Nostr apps for remote signing requests. However, it also uses relays to fetch profile data, so that each private key you add to Amber will automatically load your chosen username and profile picture. In the relay settings, users can choose which relays are being used to fetch profile data, and which relays will be used by default when creating new remote signing connection strings.  The user can also see which relays are currently connected to Amber and even look at the information that has been passed back and forth on each of those active relays. This information about actively connected relays is not only available within the application, but also in the notification that Amber has to keep in your device's notification tray in order to continue to operate in the background while you are using other apps.  Optionality is the name of the game when it comes to how Amber handles relay selection. The user can just stick with the default signing relay, use their own relay as the default, or even use a different relay for each Nostr application that they connect to for remote signing. Amber gives the user an incredible amount of flexibility in this regard. In addition to all of this, because not all relays accept the event types needed for remote signing, when you add a relay address to Amber, it automatically tests that relay to see if it will work. This alone can be a massive time saver, so users aren't trying to use relays that don't support remote signing and wondering why they can't log into noStrudel with the connection string they got from Amber.  The only way I could see relay management being improved would be some means of giving the user relay recommendations, in case they want to use a relay other than relay.nsec.app, but they aren't sure which other relays will accept remote signing events. That said, most users who want to use a different relay for signing remote events will likely be using their own, in which case recommendations aren't needed. ## Current Users' Questions The AskNostr hashtag can be a good indication of the pain points that other users are currently having with any Nostr application. Here are some of the most common questions submitted about Amber in the last two months. nostr:nevent1qvzqqqqqqypzpv30auvvha0wkhteg500n3xd528063l6099zh37sgj2uevdm5mslqythwumn8ghj7ct49eex2mrp09skymr99ehhyee0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcpz9mhxue69uhnzdps9enrw73wd9hj7qpqjx685wn6j3se7w6380ktwvrpydedpu06jd0cwfjawkgnzmahvs2s7t0585 This is a good example of Amber working correctly, but the app the user is trying to log into not working. In my experience with #Olas in particular, it sometimes allows remote signer login, and sometimes doesn't. Amber will receive the signing request and I will approve it, but Olas remains on the login screen. If Amber is receiving the signing requests, and you are approving them, the fault is likely with the application you are trying to log into. That's it. That's all the repeated questions I could find. Oh, there were a few one-off questions where relay.nsec.app wouldn't connect, or where the user's out-of-date web browser was the issue. Outside of that, though, there were no common questions about ***how*** to use Amber, and that is a testament to Amber's ease of use all on its own. ## Wrap Up If you are on Android and you are not already using Amber to protect your nsec, please do yourself a favor and get it installed. It's not at all complicated to set up, and it will make trying out all the latest Nostr clients a safe and pleasant experience. If you are a client developer and you have not added support for NIP-55 or NIP-46, do your users the courtesy of respecting the sanctity of their private keys. Even developers who have no intention of compromising their users' keys can inadvertently do so. Make that eventuality impossible by adding support for NIP-55 and NIP-46 signing. Finally, I apologize for the extended time it took me to get this review finished. The time I have available is scarce, Nostr is distracting, and nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 kept improving Amber even as I was putting it through its paces over the last two months. Keep shipping, my friend! You have made one of the most useful tools we have seen for Nostr to date! Now... What should I review next? @ d830ee7b:4e61cd62
2025-02-28 05:45:17ในชีวิตประจำวัน เรามักวัดมูลค่าของสิ่งต่างๆ ด้วยหน่วยเงินที่เราคุ้นเคย เช่น บาทหรือดอลลาร์ เราดีใจเมื่อการลงทุนของเรา **“เพิ่มขึ้น”** ในหน่วยเงินเหล่านั้น ..แต่น้อยคนนักจะหยุดคิดว่าไม้บรรทัดที่เราใช้วัดมูลค่านั้นมีความมั่นคงเพียงใด หากไม้บรรทัดเองหดสั้นลงเรื่อยๆ สิ่งของที่เราวัดอาจดูเหมือนยาวขึ้นทั้งที่ความจริงไม่ได้เปลี่ยนไปเลย แนวคิดนี้สะท้อนถึงการวัดมูลค่าทางเศรษฐกิจในหน่วยเงินที่เปลี่ยนแปลงตลอดเวลา และนำเราไปสู่หลักการเรื่อง **"ค่าเสียโอกาส" (opportunity cost)** ในการลงทุน เมื่อเราเลือกถือสินทรัพย์ชนิดหนึ่ง เรากำลังสละโอกาสที่จะได้ผลตอบแทนจากอีกชนิดหนึ่งเสมอ การทำความเข้าใจว่าอะไรเป็นตัววัดมาตรฐานของเราและค่าเสียโอกาสที่ตามมา จึงเป็นจุดเริ่มต้นในการสำรวจมุมมองใหม่ของการประเมินความมั่งคั่ง ในบริบทนี้.. **บิตคอยน์** (Bitcoin) ได้ถูกเสนอขึ้นมาเป็น **“มาตรฐาน”** ใหม่ในการวัดมูลค่ว เสมือนกับที่ทองคำเคยเป็นมาตรฐานการเงินของโลกในอดีต หนังสือ **The Bitcoin Standard** ของ Saifedean Ammous ชวนเราคิดว่า Bitcoin อาจกลายเป็นเหมือน **“มาตรฐานทองคำ”** ยุคดิจิทัล ที่มารองรับระบบการเงินสากลในอนาคต เหตุผลสำคัญที่ Bitcoin ถูกมองว่าเป็นเงินตราที่มีความแข็งแกร่ง (sound money) คือคุณสมบัติที่หาได้ยากในเงินสกุลปัจจุบัน มันมีปริมาณจำกัดตายตัว 21 ล้านหน่วย ไม่มีธนาคารกลางใดสามารถพิมพ์เพิ่มได้ตามใจชอบ ต่างจากเงินเฟียต (Fiat money) อย่างดอลลาร์ ที่จำนวนเพิ่มขึ้นตลอดเวลาจากนโยบายรัฐ ผลคือ Bitcoin มีความทนทานต่อภาวะค่าเงินเสื่อมค่าจากเงินเฟ้อ และสามารถรักษามูลค่าได้ในระยะยาวดุจทองคำในอดีต หลายคนจึงยกให้มันเป็น **“Sound Money”** หรือเงินที่มั่นคง เชื่อถือได้ในด้านมูลค่าเมื่อเวลาผ่านไป แนวคิดนี้เองเปิดประตูไปสู่การใช้ Bitcoin เป็นหน่วยวัดเปรียบเทียบมูลค่าสินทรัพย์อื่นๆ เพื่อมองภาพเศรษฐกิจในมุมใหม่ - - - ลองจินตนาการกราฟหนึ่งที่นำดัชนีหุ้นชั้นนำอย่าง S&P 500 มาเปรียบเทียบในหน่วย Bitcoin แทนที่จะเป็นดอลลาร์ กราฟนี้จะแสดงให้เราเห็นภาพที่ต่างออกไปอย่างมากจากกราฟปกติที่คุ้นเคย https://nostr.download/e344db050a8f6b023b2a9c7883560ad8a7be3fc4154d3908cbae3471b970272a.webp หากย้อนไปช่วงปี 2011 หุ้น S&P 500 อยู่ที่ราว 1,300 จุด ขณะที่บิตคอยน์มีราคายังไม่ถึง 1 ดอลลาร์ นั่นหมายความว่าดัชนี S&P 500 ในเวลานั้นมีมูลค่าประมาณ 1,300 BTC แต่เมื่อเวลาผ่านไป Bitcoin มีราคาสูงขึ้นมหาศาล ในปี 2021–2022 Bitcoin (เคยพุ่งขึ้นไปแตะหลักหลายหมื่นดอลลาร์ต่อ 1 BTC) ทำให้มูลค่าของ S&P 500 เมื่อวัดในหน่วย BTC กลับกลายเป็นเพียงเศษเสี้ยวของที่เคยเป็น สมมติ S&P 500 ล่าสุดอยู่แถว 4,000 จุด และราคา BTC อยู่หลักแสนดอลลาร์ ดัชนี S&P 500 ทั้งดัชนีอาจมีค่าไม่ถึง 0.05 BTC ด้วยซ้ำ ผลลัพธ์ที่สะท้อนออกมาบนกราฟคือเส้นค่าของ S&P 500 (เมื่อวัดด้วย BTC) ที่มีแนวโน้มลดลงเรื่อยๆ ตลอดทศวรรษที่ผ่านมา แปลความได้ว่า.. บิตคอยน์มีมูลค่าเพิ่มขึ้นเมื่อเทียบกับสินทรัพย์การเงินดั้งเดิมอย่างหุ้น ถึงขั้นที่... **การถือ Bitcoin ไว้ให้ผลตอบแทนดีกว่าการลงทุนในดัชนีหุ้นใหญ่เสียอีกในช่วงเวลาที่ผ่านมา** แม้จะฟังดูเหลือเชื่อ แต่นี่คือภาพที่ข้อมูลได้บอกเรา.. ในมุมมองของมาตรฐาน Bitcoin ตลาดหุ้นสหรัฐฯ ที่ว่าทำผลตอบแทนโดดเด่น ยังดูซีดเซียวลงในทันที ข้อมูลในช่วงสิบปีให้หลังตอกย้ำภาพนี้อย่างชัดเจน ผลตอบแทนของ Bitcoin เหนือกว่าสินทรัพย์แทบทุกชนิดที่เรารู้จักในยุคปัจจุบัน ในเชิงตัวเลข Bitcoin ให้ผลตอบแทนเฉลี่ยต่อปีราว 230% ตลอดทศวรรษ 2011–2021 ขณะที่ดัชนี S&P 500 ซึ่งขึ้นชื่อว่าให้ผลตอบแทนดีสม่ำเสมอ ยังมีค่าเฉลี่ยผลตอบแทนต่อปีประมาณ 10% กว่าๆ เท่านั้นเอง เมื่อนำมาคำนวณทบต้น นั่นหมายความว่า.. ในช่วงเวลาประมาณ 10 ปีที่ผ่านมา มูลค่าของ Bitcoin เพิ่มขึ้นหลักหลายหมื่นเปอร์เซ็นต์ ในขณะที่ S&P 500 เพิ่มขึ้นเพียงไม่กี่ร้อยเปอร์เซ็นต์ **ผลต่างระดับนี้ใหญ่พอที่จะเปลี่ยนวิธีที่เรามองความสำเร็จในการลงทุนไปเลยทีเดียว** มีการสังเกตด้วยว่าเพียงช่วงห้าปีหลังสุด ดัชนี S&P 500 สูญเสียมูลค่าประมาณเกือบ 90% หากวัดในหน่วยของบิตคอยน์ พูดอีกอย่างคือ.. ในสายตาของคนที่ถือ Bitcoin ไว้เป็นเกณฑ์ *"เงิน 100 บาทที่ลงทุนในหุ้นเมื่อต้นช่วงเวลาดังกล่าว จะเหลือมูลค่าเพียงประมาณ 10 บาทเท่านั้นในปัจจุบัน** (เพราะ 90 บาทที่เหลือคือค่าเสียโอกาสที่หายไปเมื่อเทียบกับการถือ Bitcoin) มุมมองแบบนี้ชวนให้เราตั้งคำถามว่า ที่ผ่านมาสินทรัพย์ที่ดูเหมือนมั่นคงปลอดภัย อาจไม่ปลอดภัยอย่างที่คิดเมื่อประเมินด้วยบรรทัดฐานใหม่ การเปรียบเทียบข้างต้นยังสะท้อนถึง ปัญหาการเสื่อมค่าของเงินเฟียต ซึ่งเราคุ้นเคยแต่บางครั้งมองข้ามความร้ายกาจของมัน เงินดอลลาร์สหรัฐซึ่งเป็นสกุลเงินหลักของโลก สูญเสียอำนาจซื้อไปแล้วกว่า 96% ตั้งแต่ปี 1913 จนถึงปัจจุบัน (กล่าวคือ เงิน 1 ดอลลาร์ในสมัยนั้นมีค่าพอๆ กับเงินเกือบ 30 ดอลลาร์ในปัจจุบัน) การที่ค่าเงินด้อยค่าลงเรื่อยๆ แบบนี้หมายความว่า **ตัวเลขราคาในหน่วยเงินเฟียตอาจเพิ่มขึ้นทั้งที่มูลค่าที่แท้จริงไม่เพิ่ม** ยกตัวอย่างเช่น ดัชนี S&P 500 ทำจุดสูงสุดใหม่เป็นประวัติการณ์ในหน่วยดอลลาร์สหรัฐอยู่บ่อยครั้ง แต่หากปรับค่าด้วยปัจจัยเงินเฟ้อหรือปริมาณเงินที่พิมพ์เพิ่มเข้าไป เราจะพบว่ามูลค่าที่แท้จริงของดัชนีนี้ไม่ได้เพิ่มขึ้นมากอย่างที่เห็น บางการวิเคราะห์ชี้ว่าหลังวิกฤตการเงินปี 2008 เป็นต้นมา แม้ดัชนี S&P 500 ในตัวเลขจะพุ่งขึ้นไม่หยุด แต่เมื่อหารด้วยปริมาณเงินที่เพิ่มขึ้น (เช่น M3) เส้นกราฟที่ได้กลับแทบไม่สูงไปกว่าจุดก่อนวิกฤตเลยด้วยซ้ำ หมายความว่า.. ที่ราคาหุ้นสูงขึ้น ส่วนใหญ่ก็เพื่อไล่ตามสภาพคล่องเงินที่ไหลเข้าระบบเท่านั้น ไม่ได้สะท้อนการเติบโตแท้จริงของเศรษฐกิจมากนัก เงินเฟ้อและการขยายตัวของปริมาณเงินจึงเปรียบเสมือน **“หมอก”** ที่บังตา ทำให้เรามองไม่ชัดว่าสิ่งใดเพิ่มมูลค่าแท้จริง สิ่งใดแค่ตัวเลขฟูขึ้นตามสกุลเงินที่ด้อยค่าลง เมื่อ Bitcoin ถูกใช้เป็นหน่วยวัดเปรียบเทียบ มันทำหน้าที่เสมือนกระจกใสที่กวาดเอาหมอกเงินเฟ้อนั้นออกไป เราจึงเห็นภาพที่ต่างไปโดยสิ้นเชิง เช่นเดียวกับกรณีที่เราเปรียบเทียบราคาสินค้าโภคภัณฑ์บางอย่างในหน่วย BTC ผลลัพธ์ก็อาจกลับทิศ การทดลองหนึ่งของธนาคารเฟด สาขาเซนต์หลุยส์ เคยเล่นเปรียบเทียบราคา **“ไข่ไก่หนึ่งโหล”** ในหน่วยดอลลาร์กับในหน่วยบิตคอยน์ ปรากฏว่า... แม้ต้องการจะชี้ให้เห็นความผันผวนของ Bitcoin แต่ดันกลับตอกย้ำความจริงที่ว่า ในช่วงเงินเฟ้อสูง ราคาฟองไข่ที่ดูเพิ่มขึ้นเรื่อยๆ ในหน่วยดอลลาร์ จริงๆ แล้วทรงตัวหรือลดลงด้วยซ้ำเมื่อคิดเป็น BTC นี่เป็นตัวอย่างสนุกๆ ที่บอกเราว่า กรอบอ้างอิง (frame of reference) ในการวัดมูลค่านั้นสำคัญเพียงใด แน่นอนว่า Bitcoin เองก็มีความผันผวนสูงและยังอยู่ในช่วงเริ่มต้นเมื่อเทียบกับสินทรัพย์ดั้งเดิม การที่มันพุ่งทะยานหลายหมื่นเปอร์เซ็นต์ที่ผ่านมาไม่ได้รับประกันว่ากราฟในหน่วย BTC ของสินทรัพย์ต่างๆ จะดิ่งลงอย่างนี้ไปตลอด แต่สิ่งที่เกิดขึ้นแล้วได้ให้แง่คิดทางปรัชญาการเงินที่ลึกซึ้งกับเรา อย่างแรกคือเรื่อง **ค่าเสียโอกาส** ที่กล่าวถึงตอนต้น ทุกการตัดสินใจทางการเงินมีต้นทุนค่าเสียโอกาสแฝงอยู่เสมอ เพียงแต่เมื่อก่อนเราอาจไม่เห็นมันชัดเจน การเก็บออมเงินสดไว้เฉยๆ ในธนาคารมีต้นทุนคือผลตอบแทนที่สูญไปหากเราเลือกลงทุนอย่างอื่น การลงทุนในสินทรัพย์ A ก็ย่อมหมายถึงการไม่ได้ลงทุนในสินทรัพย์ B หาก B นั้นให้ผลตอบแทนสูงกว่า เราก็สูญเสียส่วนต่างนั้นไป สิบกว่าปีที่ผ่านมา Bitcoin ทำผลงานได้เหนือชั้นกว่าสินทรัพย์อื่นๆ มาก ค่าเสียโอกาสของการไม่ถือ Bitcoin จึงสูงลิ่วในช่วงนี้ สำหรับนักลงทุนที่มองย้อนกลับไป นี่คือบทเรียนราคาแพง บางคนอาจนึกเสียดายว่า **“รู้งี้ซื้อบิตคอยน์ไว้ตั้งแต่แรกซะก็ดี”** แต่ประเด็นไม่ได้อยู่ที่การเสียดายอดีต แต่อยู่ที่ **การตระหนักรู้ถึงค่าเสียโอกาสและผลกระทบของมันที่มีต่อความมั่งคั่งของเราในระยะยาว** ต่างหาก อีกแง่หนึ่งที่ลึกกว่านั้นคือเรื่อง **กรอบในการวัดมูลค่า** ของเราทุกวันนี้ว่าเหมาะสมแล้วหรือไม่ หากการที่เราใช้เงินเฟียตที่เสื่อมค่าเป็นตัววัด ทำให้เราประเมินค่าของสิ่งต่างๆ ผิดเพี้ยนไป การตัดสินใจทางเศรษฐกิจของเราก็อาจผิดทิศทางในระยะยาวได้ ลองนึกภาพว่า.. ถ้าเงินที่เราใช้อยู่มีมูลค่าเสถียรหรือเพิ่มขึ้นตามประสิทธิภาพการผลิตจริงๆ ของเศรษฐกิจ (เหมือนที่เงิน Bitcoin ถูกออกแบบมาให้ไม่เสื่อมค่าไปตามกาลเวลา) เราอาจไม่จำเป็นต้องวิ่งไล่หาผลตอบแทนสูงๆ เพียงเพื่อรักษามูลค่าเงินออมของตัวเองให้ทันเงินเฟ้อ ผู้คนอาจวางแผนการเงินระยะยาวขึ้น แนวคิดเรื่อง **“เวลาที่ต้องใช้”** กับ **“อัตราส่วนลดของอนาคต”** (time preference) ก็จะเปลี่ยนไป ดังที่ Ammous กล่าวไว้ใน The Bitcoin Standard ว่าเงินที่มีเสถียรภาพจะส่งเสริมให้คนออมและลงทุนในโครงการระยะยาวมากขึ้น ผิดกับระบบเงินเฟ้อที่ชักจูงให้ผู้คนรีบใช้จ่ายหรือเข้าร่วมเก็งกำไรระยะสั้นเพราะกลัวว่าเงินจะด้อยค่าไป นี่ไม่ใช่แค่เรื่องการเงินส่วนบุคคล แต่สะท้อนถึงคุณภาพของการเติบโตทางเศรษฐกิจและนวัตกรรมในสังคมโดยรวมด้วย หากเรามีหน่วยวัดมูลค่าที่เที่ยงตรง ไม่บิดเบือนไปตามนโยบายการเงินรายวัน เราก็อาจประเมินโครงการต่างๆ ได้ตามศักยภาพที่แท้จริงมากขึ้น เงินเฟ้อและการพิมพ์เงินจำนวนมากมักทำให้เกิดการลงทุนผิดที่ผิดทาง (malinvestment) เพราะสัญญาณราคาถูกบิดเบือน เช่น ดอกเบี้ยที่ต่ำผิดปกติอาจทำให้เกิดหนี้ล้นเกินหรือลงทุนในโครงการที่ไม่ยั่งยืน ในขณะที่มาตรฐานเงินที่เข้มงวดอย่าง Bitcoin อาจบังคับให้ทุกการลงทุนต้องมีเหตุผลรองรับที่แข็งแรงขึ้น เนื่องจากไม่สามารถอาศัยการอัดฉีดสภาพคล่องมาช่วยพยุงได้ง่ายๆ เมื่อมาถึงตรงนี้.. เราอาจไม่ได้ข้อสรุปทันทีว่า **“ต่อไปนี้ฉันควรถือ Bitcoin แทนที่จะลงทุนอย่างอื่น”** และบทความนี้ก็ไม่ได้มีเจตนาจะชี้นำการลงทุนเช่นนั้น เป้าหมายแท้จริงคือการเปิดมุมมองใหม่ว่า เราประเมินคุณค่าของสิ่งต่างๆ อย่างไร ลองตั้งคำถามกับตัวเองว่า.. ทุกวันนี้เราวัดความร่ำรวยหรือความก้าวหน้าทางเศรษฐกิจด้วยหน่วยอะไร หน่วยนั้นวัดได้เที่ยงตรงหรือเปล่า? หากเงินที่เราใช้วัดเองลดค่าลงทุกปีๆ เราจะมั่นใจได้อย่างไรว่าตัวเลขที่เพิ่มขึ้นบนกระดาษคือความมั่งคั่งที่เพิ่มขึ้นจริง? การใช้ Bitcoin เป็นมาตรฐานเทียบเคียง เป็นเสมือนการลองวัดด้วยไม้บรรทัดอีกอันที่อาจตรงกว่าเดิม ในหลายกรณีมันเผยให้เห็นภาพที่เราคาดไม่ถึงและท้าทายความเชื่อเดิมๆ ของเรา บทเรียนที่ได้รับไม่ใช่ให้เราทุกคนเปลี่ยนไปคิดเป็น BTC ในชีวิตประจำวันทันที แต่คือการตระหนักว่า **หน่วยวัดมีความหมาย** และการมองโลกการเงินด้วยหน่วยวัดที่ต่างออกไปสามารถให้ข้อคิดที่ลึกซึ้งได้อย่างไร ท้ายที่สุด ไม่ว่าจะเชื่อใน **“มาตรฐานบิตคอยน์”** หรือไม่นั้น ไม่สำคัญเท่ากับการที่เราได้ฉุกคิดและตั้งคำถามกับระบบที่เราใช้อยู่ทุกเมื่อเชื่อวัน บางทีสิ่งที่ Bitcoin และปรัชญาการเงินแบบใหม่ๆ นำมาให้เรา อาจไม่ใช่คำตอบสำเร็จรูป แต่คือแรงกระตุ้นให้เราเปิดใจมองภาพใหญ่ของเศรษฐกิจในมุมที่กว้างขึ้น ลองพิจารณาปัจจัยพื้นฐานอย่างค่าเงิน เวลา และโอกาสที่สูญเสียไปกับการตัดสินใจต่างๆ อย่างรอบด้านขึ้น เมื่อเราเริ่มมองเห็นว่าการวัดมูลค่าของสิ่งต่างๆ ด้วย **ไม้บรรทัดที่ต่างออกไป** ให้อะไรเราได้บ้าง เราก็จะพร้อมที่จะปรับมุมมองและกลยุทธ์การเงินของตนเองให้เท่าทันโลกที่เปลี่ยนแปลงเสมอ ไม่แน่ว่าในอนาคต เราอาจได้เห็นผู้คนพูดถึงราคาบ้านหรือดัชนีหุ้นในหน่วยบิตคอยน์อย่างเป็นเรื่องปกติ และการคิดเช่นนั้นอาจไม่ใช่เรื่องแปลกใหม่อีกต่อไป เพราะเราได้เรียนรู้ที่จะมองผ่านเปลือกของหน่วยเงิน ไปสู่แก่นแท้ของมูลค่าจริงๆ ที่อยู่เบื้องหลังนั่นเอง ขอบคุณ Thai Ratel สำหรับความกระจ่างในการวัดมูลค่าสินทรัพย์ต่าง ๆ ด้วยบิตคอยน์
@ d830ee7b:4e61cd62
2025-02-28 05:45:17ในชีวิตประจำวัน เรามักวัดมูลค่าของสิ่งต่างๆ ด้วยหน่วยเงินที่เราคุ้นเคย เช่น บาทหรือดอลลาร์ เราดีใจเมื่อการลงทุนของเรา **“เพิ่มขึ้น”** ในหน่วยเงินเหล่านั้น ..แต่น้อยคนนักจะหยุดคิดว่าไม้บรรทัดที่เราใช้วัดมูลค่านั้นมีความมั่นคงเพียงใด หากไม้บรรทัดเองหดสั้นลงเรื่อยๆ สิ่งของที่เราวัดอาจดูเหมือนยาวขึ้นทั้งที่ความจริงไม่ได้เปลี่ยนไปเลย แนวคิดนี้สะท้อนถึงการวัดมูลค่าทางเศรษฐกิจในหน่วยเงินที่เปลี่ยนแปลงตลอดเวลา และนำเราไปสู่หลักการเรื่อง **"ค่าเสียโอกาส" (opportunity cost)** ในการลงทุน เมื่อเราเลือกถือสินทรัพย์ชนิดหนึ่ง เรากำลังสละโอกาสที่จะได้ผลตอบแทนจากอีกชนิดหนึ่งเสมอ การทำความเข้าใจว่าอะไรเป็นตัววัดมาตรฐานของเราและค่าเสียโอกาสที่ตามมา จึงเป็นจุดเริ่มต้นในการสำรวจมุมมองใหม่ของการประเมินความมั่งคั่ง ในบริบทนี้.. **บิตคอยน์** (Bitcoin) ได้ถูกเสนอขึ้นมาเป็น **“มาตรฐาน”** ใหม่ในการวัดมูลค่ว เสมือนกับที่ทองคำเคยเป็นมาตรฐานการเงินของโลกในอดีต หนังสือ **The Bitcoin Standard** ของ Saifedean Ammous ชวนเราคิดว่า Bitcoin อาจกลายเป็นเหมือน **“มาตรฐานทองคำ”** ยุคดิจิทัล ที่มารองรับระบบการเงินสากลในอนาคต เหตุผลสำคัญที่ Bitcoin ถูกมองว่าเป็นเงินตราที่มีความแข็งแกร่ง (sound money) คือคุณสมบัติที่หาได้ยากในเงินสกุลปัจจุบัน มันมีปริมาณจำกัดตายตัว 21 ล้านหน่วย ไม่มีธนาคารกลางใดสามารถพิมพ์เพิ่มได้ตามใจชอบ ต่างจากเงินเฟียต (Fiat money) อย่างดอลลาร์ ที่จำนวนเพิ่มขึ้นตลอดเวลาจากนโยบายรัฐ ผลคือ Bitcoin มีความทนทานต่อภาวะค่าเงินเสื่อมค่าจากเงินเฟ้อ และสามารถรักษามูลค่าได้ในระยะยาวดุจทองคำในอดีต หลายคนจึงยกให้มันเป็น **“Sound Money”** หรือเงินที่มั่นคง เชื่อถือได้ในด้านมูลค่าเมื่อเวลาผ่านไป แนวคิดนี้เองเปิดประตูไปสู่การใช้ Bitcoin เป็นหน่วยวัดเปรียบเทียบมูลค่าสินทรัพย์อื่นๆ เพื่อมองภาพเศรษฐกิจในมุมใหม่ - - - ลองจินตนาการกราฟหนึ่งที่นำดัชนีหุ้นชั้นนำอย่าง S&P 500 มาเปรียบเทียบในหน่วย Bitcoin แทนที่จะเป็นดอลลาร์ กราฟนี้จะแสดงให้เราเห็นภาพที่ต่างออกไปอย่างมากจากกราฟปกติที่คุ้นเคย https://nostr.download/e344db050a8f6b023b2a9c7883560ad8a7be3fc4154d3908cbae3471b970272a.webp หากย้อนไปช่วงปี 2011 หุ้น S&P 500 อยู่ที่ราว 1,300 จุด ขณะที่บิตคอยน์มีราคายังไม่ถึง 1 ดอลลาร์ นั่นหมายความว่าดัชนี S&P 500 ในเวลานั้นมีมูลค่าประมาณ 1,300 BTC แต่เมื่อเวลาผ่านไป Bitcoin มีราคาสูงขึ้นมหาศาล ในปี 2021–2022 Bitcoin (เคยพุ่งขึ้นไปแตะหลักหลายหมื่นดอลลาร์ต่อ 1 BTC) ทำให้มูลค่าของ S&P 500 เมื่อวัดในหน่วย BTC กลับกลายเป็นเพียงเศษเสี้ยวของที่เคยเป็น สมมติ S&P 500 ล่าสุดอยู่แถว 4,000 จุด และราคา BTC อยู่หลักแสนดอลลาร์ ดัชนี S&P 500 ทั้งดัชนีอาจมีค่าไม่ถึง 0.05 BTC ด้วยซ้ำ ผลลัพธ์ที่สะท้อนออกมาบนกราฟคือเส้นค่าของ S&P 500 (เมื่อวัดด้วย BTC) ที่มีแนวโน้มลดลงเรื่อยๆ ตลอดทศวรรษที่ผ่านมา แปลความได้ว่า.. บิตคอยน์มีมูลค่าเพิ่มขึ้นเมื่อเทียบกับสินทรัพย์การเงินดั้งเดิมอย่างหุ้น ถึงขั้นที่... **การถือ Bitcoin ไว้ให้ผลตอบแทนดีกว่าการลงทุนในดัชนีหุ้นใหญ่เสียอีกในช่วงเวลาที่ผ่านมา** แม้จะฟังดูเหลือเชื่อ แต่นี่คือภาพที่ข้อมูลได้บอกเรา.. ในมุมมองของมาตรฐาน Bitcoin ตลาดหุ้นสหรัฐฯ ที่ว่าทำผลตอบแทนโดดเด่น ยังดูซีดเซียวลงในทันที ข้อมูลในช่วงสิบปีให้หลังตอกย้ำภาพนี้อย่างชัดเจน ผลตอบแทนของ Bitcoin เหนือกว่าสินทรัพย์แทบทุกชนิดที่เรารู้จักในยุคปัจจุบัน ในเชิงตัวเลข Bitcoin ให้ผลตอบแทนเฉลี่ยต่อปีราว 230% ตลอดทศวรรษ 2011–2021 ขณะที่ดัชนี S&P 500 ซึ่งขึ้นชื่อว่าให้ผลตอบแทนดีสม่ำเสมอ ยังมีค่าเฉลี่ยผลตอบแทนต่อปีประมาณ 10% กว่าๆ เท่านั้นเอง เมื่อนำมาคำนวณทบต้น นั่นหมายความว่า.. ในช่วงเวลาประมาณ 10 ปีที่ผ่านมา มูลค่าของ Bitcoin เพิ่มขึ้นหลักหลายหมื่นเปอร์เซ็นต์ ในขณะที่ S&P 500 เพิ่มขึ้นเพียงไม่กี่ร้อยเปอร์เซ็นต์ **ผลต่างระดับนี้ใหญ่พอที่จะเปลี่ยนวิธีที่เรามองความสำเร็จในการลงทุนไปเลยทีเดียว** มีการสังเกตด้วยว่าเพียงช่วงห้าปีหลังสุด ดัชนี S&P 500 สูญเสียมูลค่าประมาณเกือบ 90% หากวัดในหน่วยของบิตคอยน์ พูดอีกอย่างคือ.. ในสายตาของคนที่ถือ Bitcoin ไว้เป็นเกณฑ์ *"เงิน 100 บาทที่ลงทุนในหุ้นเมื่อต้นช่วงเวลาดังกล่าว จะเหลือมูลค่าเพียงประมาณ 10 บาทเท่านั้นในปัจจุบัน** (เพราะ 90 บาทที่เหลือคือค่าเสียโอกาสที่หายไปเมื่อเทียบกับการถือ Bitcoin) มุมมองแบบนี้ชวนให้เราตั้งคำถามว่า ที่ผ่านมาสินทรัพย์ที่ดูเหมือนมั่นคงปลอดภัย อาจไม่ปลอดภัยอย่างที่คิดเมื่อประเมินด้วยบรรทัดฐานใหม่ การเปรียบเทียบข้างต้นยังสะท้อนถึง ปัญหาการเสื่อมค่าของเงินเฟียต ซึ่งเราคุ้นเคยแต่บางครั้งมองข้ามความร้ายกาจของมัน เงินดอลลาร์สหรัฐซึ่งเป็นสกุลเงินหลักของโลก สูญเสียอำนาจซื้อไปแล้วกว่า 96% ตั้งแต่ปี 1913 จนถึงปัจจุบัน (กล่าวคือ เงิน 1 ดอลลาร์ในสมัยนั้นมีค่าพอๆ กับเงินเกือบ 30 ดอลลาร์ในปัจจุบัน) การที่ค่าเงินด้อยค่าลงเรื่อยๆ แบบนี้หมายความว่า **ตัวเลขราคาในหน่วยเงินเฟียตอาจเพิ่มขึ้นทั้งที่มูลค่าที่แท้จริงไม่เพิ่ม** ยกตัวอย่างเช่น ดัชนี S&P 500 ทำจุดสูงสุดใหม่เป็นประวัติการณ์ในหน่วยดอลลาร์สหรัฐอยู่บ่อยครั้ง แต่หากปรับค่าด้วยปัจจัยเงินเฟ้อหรือปริมาณเงินที่พิมพ์เพิ่มเข้าไป เราจะพบว่ามูลค่าที่แท้จริงของดัชนีนี้ไม่ได้เพิ่มขึ้นมากอย่างที่เห็น บางการวิเคราะห์ชี้ว่าหลังวิกฤตการเงินปี 2008 เป็นต้นมา แม้ดัชนี S&P 500 ในตัวเลขจะพุ่งขึ้นไม่หยุด แต่เมื่อหารด้วยปริมาณเงินที่เพิ่มขึ้น (เช่น M3) เส้นกราฟที่ได้กลับแทบไม่สูงไปกว่าจุดก่อนวิกฤตเลยด้วยซ้ำ หมายความว่า.. ที่ราคาหุ้นสูงขึ้น ส่วนใหญ่ก็เพื่อไล่ตามสภาพคล่องเงินที่ไหลเข้าระบบเท่านั้น ไม่ได้สะท้อนการเติบโตแท้จริงของเศรษฐกิจมากนัก เงินเฟ้อและการขยายตัวของปริมาณเงินจึงเปรียบเสมือน **“หมอก”** ที่บังตา ทำให้เรามองไม่ชัดว่าสิ่งใดเพิ่มมูลค่าแท้จริง สิ่งใดแค่ตัวเลขฟูขึ้นตามสกุลเงินที่ด้อยค่าลง เมื่อ Bitcoin ถูกใช้เป็นหน่วยวัดเปรียบเทียบ มันทำหน้าที่เสมือนกระจกใสที่กวาดเอาหมอกเงินเฟ้อนั้นออกไป เราจึงเห็นภาพที่ต่างไปโดยสิ้นเชิง เช่นเดียวกับกรณีที่เราเปรียบเทียบราคาสินค้าโภคภัณฑ์บางอย่างในหน่วย BTC ผลลัพธ์ก็อาจกลับทิศ การทดลองหนึ่งของธนาคารเฟด สาขาเซนต์หลุยส์ เคยเล่นเปรียบเทียบราคา **“ไข่ไก่หนึ่งโหล”** ในหน่วยดอลลาร์กับในหน่วยบิตคอยน์ ปรากฏว่า... แม้ต้องการจะชี้ให้เห็นความผันผวนของ Bitcoin แต่ดันกลับตอกย้ำความจริงที่ว่า ในช่วงเงินเฟ้อสูง ราคาฟองไข่ที่ดูเพิ่มขึ้นเรื่อยๆ ในหน่วยดอลลาร์ จริงๆ แล้วทรงตัวหรือลดลงด้วยซ้ำเมื่อคิดเป็น BTC นี่เป็นตัวอย่างสนุกๆ ที่บอกเราว่า กรอบอ้างอิง (frame of reference) ในการวัดมูลค่านั้นสำคัญเพียงใด แน่นอนว่า Bitcoin เองก็มีความผันผวนสูงและยังอยู่ในช่วงเริ่มต้นเมื่อเทียบกับสินทรัพย์ดั้งเดิม การที่มันพุ่งทะยานหลายหมื่นเปอร์เซ็นต์ที่ผ่านมาไม่ได้รับประกันว่ากราฟในหน่วย BTC ของสินทรัพย์ต่างๆ จะดิ่งลงอย่างนี้ไปตลอด แต่สิ่งที่เกิดขึ้นแล้วได้ให้แง่คิดทางปรัชญาการเงินที่ลึกซึ้งกับเรา อย่างแรกคือเรื่อง **ค่าเสียโอกาส** ที่กล่าวถึงตอนต้น ทุกการตัดสินใจทางการเงินมีต้นทุนค่าเสียโอกาสแฝงอยู่เสมอ เพียงแต่เมื่อก่อนเราอาจไม่เห็นมันชัดเจน การเก็บออมเงินสดไว้เฉยๆ ในธนาคารมีต้นทุนคือผลตอบแทนที่สูญไปหากเราเลือกลงทุนอย่างอื่น การลงทุนในสินทรัพย์ A ก็ย่อมหมายถึงการไม่ได้ลงทุนในสินทรัพย์ B หาก B นั้นให้ผลตอบแทนสูงกว่า เราก็สูญเสียส่วนต่างนั้นไป สิบกว่าปีที่ผ่านมา Bitcoin ทำผลงานได้เหนือชั้นกว่าสินทรัพย์อื่นๆ มาก ค่าเสียโอกาสของการไม่ถือ Bitcoin จึงสูงลิ่วในช่วงนี้ สำหรับนักลงทุนที่มองย้อนกลับไป นี่คือบทเรียนราคาแพง บางคนอาจนึกเสียดายว่า **“รู้งี้ซื้อบิตคอยน์ไว้ตั้งแต่แรกซะก็ดี”** แต่ประเด็นไม่ได้อยู่ที่การเสียดายอดีต แต่อยู่ที่ **การตระหนักรู้ถึงค่าเสียโอกาสและผลกระทบของมันที่มีต่อความมั่งคั่งของเราในระยะยาว** ต่างหาก อีกแง่หนึ่งที่ลึกกว่านั้นคือเรื่อง **กรอบในการวัดมูลค่า** ของเราทุกวันนี้ว่าเหมาะสมแล้วหรือไม่ หากการที่เราใช้เงินเฟียตที่เสื่อมค่าเป็นตัววัด ทำให้เราประเมินค่าของสิ่งต่างๆ ผิดเพี้ยนไป การตัดสินใจทางเศรษฐกิจของเราก็อาจผิดทิศทางในระยะยาวได้ ลองนึกภาพว่า.. ถ้าเงินที่เราใช้อยู่มีมูลค่าเสถียรหรือเพิ่มขึ้นตามประสิทธิภาพการผลิตจริงๆ ของเศรษฐกิจ (เหมือนที่เงิน Bitcoin ถูกออกแบบมาให้ไม่เสื่อมค่าไปตามกาลเวลา) เราอาจไม่จำเป็นต้องวิ่งไล่หาผลตอบแทนสูงๆ เพียงเพื่อรักษามูลค่าเงินออมของตัวเองให้ทันเงินเฟ้อ ผู้คนอาจวางแผนการเงินระยะยาวขึ้น แนวคิดเรื่อง **“เวลาที่ต้องใช้”** กับ **“อัตราส่วนลดของอนาคต”** (time preference) ก็จะเปลี่ยนไป ดังที่ Ammous กล่าวไว้ใน The Bitcoin Standard ว่าเงินที่มีเสถียรภาพจะส่งเสริมให้คนออมและลงทุนในโครงการระยะยาวมากขึ้น ผิดกับระบบเงินเฟ้อที่ชักจูงให้ผู้คนรีบใช้จ่ายหรือเข้าร่วมเก็งกำไรระยะสั้นเพราะกลัวว่าเงินจะด้อยค่าไป นี่ไม่ใช่แค่เรื่องการเงินส่วนบุคคล แต่สะท้อนถึงคุณภาพของการเติบโตทางเศรษฐกิจและนวัตกรรมในสังคมโดยรวมด้วย หากเรามีหน่วยวัดมูลค่าที่เที่ยงตรง ไม่บิดเบือนไปตามนโยบายการเงินรายวัน เราก็อาจประเมินโครงการต่างๆ ได้ตามศักยภาพที่แท้จริงมากขึ้น เงินเฟ้อและการพิมพ์เงินจำนวนมากมักทำให้เกิดการลงทุนผิดที่ผิดทาง (malinvestment) เพราะสัญญาณราคาถูกบิดเบือน เช่น ดอกเบี้ยที่ต่ำผิดปกติอาจทำให้เกิดหนี้ล้นเกินหรือลงทุนในโครงการที่ไม่ยั่งยืน ในขณะที่มาตรฐานเงินที่เข้มงวดอย่าง Bitcoin อาจบังคับให้ทุกการลงทุนต้องมีเหตุผลรองรับที่แข็งแรงขึ้น เนื่องจากไม่สามารถอาศัยการอัดฉีดสภาพคล่องมาช่วยพยุงได้ง่ายๆ เมื่อมาถึงตรงนี้.. เราอาจไม่ได้ข้อสรุปทันทีว่า **“ต่อไปนี้ฉันควรถือ Bitcoin แทนที่จะลงทุนอย่างอื่น”** และบทความนี้ก็ไม่ได้มีเจตนาจะชี้นำการลงทุนเช่นนั้น เป้าหมายแท้จริงคือการเปิดมุมมองใหม่ว่า เราประเมินคุณค่าของสิ่งต่างๆ อย่างไร ลองตั้งคำถามกับตัวเองว่า.. ทุกวันนี้เราวัดความร่ำรวยหรือความก้าวหน้าทางเศรษฐกิจด้วยหน่วยอะไร หน่วยนั้นวัดได้เที่ยงตรงหรือเปล่า? หากเงินที่เราใช้วัดเองลดค่าลงทุกปีๆ เราจะมั่นใจได้อย่างไรว่าตัวเลขที่เพิ่มขึ้นบนกระดาษคือความมั่งคั่งที่เพิ่มขึ้นจริง? การใช้ Bitcoin เป็นมาตรฐานเทียบเคียง เป็นเสมือนการลองวัดด้วยไม้บรรทัดอีกอันที่อาจตรงกว่าเดิม ในหลายกรณีมันเผยให้เห็นภาพที่เราคาดไม่ถึงและท้าทายความเชื่อเดิมๆ ของเรา บทเรียนที่ได้รับไม่ใช่ให้เราทุกคนเปลี่ยนไปคิดเป็น BTC ในชีวิตประจำวันทันที แต่คือการตระหนักว่า **หน่วยวัดมีความหมาย** และการมองโลกการเงินด้วยหน่วยวัดที่ต่างออกไปสามารถให้ข้อคิดที่ลึกซึ้งได้อย่างไร ท้ายที่สุด ไม่ว่าจะเชื่อใน **“มาตรฐานบิตคอยน์”** หรือไม่นั้น ไม่สำคัญเท่ากับการที่เราได้ฉุกคิดและตั้งคำถามกับระบบที่เราใช้อยู่ทุกเมื่อเชื่อวัน บางทีสิ่งที่ Bitcoin และปรัชญาการเงินแบบใหม่ๆ นำมาให้เรา อาจไม่ใช่คำตอบสำเร็จรูป แต่คือแรงกระตุ้นให้เราเปิดใจมองภาพใหญ่ของเศรษฐกิจในมุมที่กว้างขึ้น ลองพิจารณาปัจจัยพื้นฐานอย่างค่าเงิน เวลา และโอกาสที่สูญเสียไปกับการตัดสินใจต่างๆ อย่างรอบด้านขึ้น เมื่อเราเริ่มมองเห็นว่าการวัดมูลค่าของสิ่งต่างๆ ด้วย **ไม้บรรทัดที่ต่างออกไป** ให้อะไรเราได้บ้าง เราก็จะพร้อมที่จะปรับมุมมองและกลยุทธ์การเงินของตนเองให้เท่าทันโลกที่เปลี่ยนแปลงเสมอ ไม่แน่ว่าในอนาคต เราอาจได้เห็นผู้คนพูดถึงราคาบ้านหรือดัชนีหุ้นในหน่วยบิตคอยน์อย่างเป็นเรื่องปกติ และการคิดเช่นนั้นอาจไม่ใช่เรื่องแปลกใหม่อีกต่อไป เพราะเราได้เรียนรู้ที่จะมองผ่านเปลือกของหน่วยเงิน ไปสู่แก่นแท้ของมูลค่าจริงๆ ที่อยู่เบื้องหลังนั่นเอง ขอบคุณ Thai Ratel สำหรับความกระจ่างในการวัดมูลค่าสินทรัพย์ต่าง ๆ ด้วยบิตคอยน์ @ d830ee7b:4e61cd62
2025-02-28 05:07:17In our daily lives, we often measure the value of things using familiar monetary units such as baht or dollars. We feel delighted when our investments **"increase"** in these units. However, few people stop to consider how stable the measuring stick itself is. If the ruler we use to measure value keeps shrinking, the objects we measure may appear longer, even though their actual size remains unchanged. This concept reflects the way we assess economic value in constantly changing monetary units, leading us to the principle of opportunity cost in investment: when we choose to hold one type of asset, we are always giving up the opportunity to earn returns from another. Understanding what serves as our standard measure and the opportunity costs that come with it is the first step toward exploring a new perspective on wealth assessment. In this context, Bitcoin has been proposed as a new **"standard"** for measuring value, much like gold once served as the global financial standard in the past. Some view Bitcoin as the "digital gold standard" that could support the international financial system in the future. A key reason Bitcoin is considered **"sound money"** is its rarity—something modern currencies lack. Its supply is permanently capped at 21 million units, meaning no central bank can print more at will. This contrasts with fiat money, such as the dollar or baht, which constantly increases in supply due to government policies. As a result, Bitcoin is resistant to inflation-induced depreciation and can retain its value over the long term, much like gold in the past. Many therefore consider it **"sound money"**—a form of currency that is stable and reliable in preserving value over time. This idea opens the door to using Bitcoin as a benchmark for comparing the value of other assets, offering a fresh perspective on the economy. Imagine a graph that compares the leading stock index, **the S&P 500, in Bitcoin terms instead of dollars.**  This graph would reveal a drastically different picture from the conventional charts we are familiar with. Looking back to 2011, the S&P 500 was around 1,300 points, while Bitcoin was priced at less than $1. This means the S&P 500 index was valued at approximately 1,300 BTC at the time. However, as Bitcoin's price surged over the years—reaching tens of thousands of dollars per BTC in 2021–2022—the value of the S&P 500, when measured in BTC, shrank dramatically. Suppose the S&P 500 currently stands at around 4,000 points, while Bitcoin is priced at six figures in dollars. The entire S&P 500 index might be worth less than 0.05 BTC. The resulting graph would show a consistent downward trend in the S&P 500's value **(when measured in BTC)** over the past decade. This means Bitcoin has appreciated relative to traditional financial assets like stocks—to the extent that simply holding Bitcoin has outperformed investing in major stock indices. As surprising as this may seem, the data tells this story: from the perspective of a Bitcoin standard, even the high-performing U.S. stock market appears lackluster. Data from the past decade reinforces this view. Bitcoin has outperformed nearly every asset class known today. In numerical terms, Bitcoin delivered an average annual return of **approximately 230% from 2011 to 2021**, whereas the S&P 500, which is renowned for its consistent performance, achieved an average annual return of just over 10%. When compounded over time, this means Bitcoin's value increased by tens of thousands of percent over the past decade, while the S&P 500's value rose by only a few hundred percent. The magnitude of this difference is significant enough to reshape how we perceive investment success. Observations also indicate that in just **the past five years, the S&P 500 has lost nearly 90% of its value when measured in Bitcoin.** In other words, for someone using Bitcoin as their benchmark, a 100-baht investment in stocks at the beginning of this period would be worth only about 10 baht today—the remaining 90 baht representing the opportunity cost of not holding Bitcoin. This perspective challenges our assumptions about the stability of supposedly safe assets when evaluated under a new standard. This comparison also highlights the issue of fiat currency depreciation—something we are familiar with but often underestimate. The U.S. dollar, the world's primary reserve currency, has **lost over 96% of its purchasing power since 1913**. This means that what $1 could buy back then now requires nearly $30. This ongoing depreciation implies that prices in fiat terms may rise even when real value does not. For example, the S&P 500 frequently reaches all-time highs in U.S. dollar terms. However, when adjusted for inflation or money supply expansion, its real value has not increased as much as it seems. Some analyses suggest that since the 2008 financial crisis, although the S&P 500's nominal value has surged, when divided by the expanding money supply (such as M3), its graph remains largely unchanged from pre-crisis levels. This suggests that stock prices have risen primarily in response to liquidity injections rather than genuine economic growth. Inflation and monetary expansion act like a **"fog,"** obscuring our ability to discern real value from mere numerical increases. When Bitcoin is used as a comparative unit, it acts as a clear lens that removes this inflationary fog, revealing a completely different picture. The same applies when comparing commodity prices in BTC. A notable experiment by the St. Louis Federal Reserve once examined the price of **"a dozen eggs"** in both dollars and Bitcoin. While the study aimed to highlight Bitcoin’s volatility, it inadvertently reinforced the point that during periods of high inflation, the price of eggs, which seemed to rise continuously in dollars, actually remained stable or even declined in BTC terms. This amusing example illustrates the profound impact of measurement standards. Of course, Bitcoin itself is highly volatile and still in its early stages compared to traditional assets. Its meteoric rise over the past decade does not guarantee that all asset graphs in BTC terms will continue declining indefinitely. However, what has already transpired provides deep financial insights. **The first takeaway** is the concept of opportunity cost mentioned earlier—every financial decision has an inherent cost, even if we do not always recognize it. Holding cash in a bank carries the opportunity cost of the returns one could earn by investing elsewhere. Investing in asset A means missing out on asset B, and if B delivers higher returns, we incur that loss. Over the past decade, Bitcoin has outperformed all other assets by a wide margin, making the opportunity cost of not holding Bitcoin extremely high. Investors looking back on this period might regret not having bought Bitcoin earlier, but the key lesson is not about dwelling on past decisions—it is about becoming aware of **opportunity costs** and their long-term impact on wealth. On a deeper level, this discussion raises questions about whether our current valuation framework is truly appropriate. If using a depreciating fiat currency as a benchmark distorts our perception of value, our economic decisions may be misaligned in the long run. Imagine a scenario where money retains or even appreciates in value in line with real economic productivity (as Bitcoin was designed to do). In such a system, people would not need to chase high returns merely to preserve their savings from inflation. They could plan finances with a longer-term perspective. Concepts like **"time preference"** and **"discounting the future"** would shift. It is often argued that sound money encourages saving and long-term investment, whereas inflationary systems push people toward short-term spending or speculation out of fear that their money will lose value. This is not just a matter of personal finance but a fundamental influence on the quality of economic growth and innovation. **A sound money standard** like **Bitcoin** might enforce stricter investment discipline, as liquidity injections could no longer be used as a safety net for unsustainable projects. At this point, readers may not conclude that they should immediately hold Bitcoin instead of investing in other assets—and this article is not intended as investment advice. Its real purpose is to provoke thought about how we measure value. **Ask yourself:** What unit do we use to gauge wealth and economic progress? Is that unit reliable? If the money we use for measurement loses value every year, how can we be sure that increasing numbers on paper reflect true wealth growth? Using Bitcoin as a reference standard is like measuring with a new ruler—one that may be more accurate. In many cases, it reveals unexpected insights and challenges long-held beliefs. Ultimately, whether or not one believes in the **"Bitcoin standard"** is less important than the ability to critically examine the system we rely on daily. Perhaps the greatest value Bitcoin and new financial philosophies offer is not a definitive answer but the impetus to look at the bigger economic picture with fresh eyes. Thank you, Thai Ratel, for enlightening me on this topic! Jakk Goodday.
@ d830ee7b:4e61cd62
2025-02-28 05:07:17In our daily lives, we often measure the value of things using familiar monetary units such as baht or dollars. We feel delighted when our investments **"increase"** in these units. However, few people stop to consider how stable the measuring stick itself is. If the ruler we use to measure value keeps shrinking, the objects we measure may appear longer, even though their actual size remains unchanged. This concept reflects the way we assess economic value in constantly changing monetary units, leading us to the principle of opportunity cost in investment: when we choose to hold one type of asset, we are always giving up the opportunity to earn returns from another. Understanding what serves as our standard measure and the opportunity costs that come with it is the first step toward exploring a new perspective on wealth assessment. In this context, Bitcoin has been proposed as a new **"standard"** for measuring value, much like gold once served as the global financial standard in the past. Some view Bitcoin as the "digital gold standard" that could support the international financial system in the future. A key reason Bitcoin is considered **"sound money"** is its rarity—something modern currencies lack. Its supply is permanently capped at 21 million units, meaning no central bank can print more at will. This contrasts with fiat money, such as the dollar or baht, which constantly increases in supply due to government policies. As a result, Bitcoin is resistant to inflation-induced depreciation and can retain its value over the long term, much like gold in the past. Many therefore consider it **"sound money"**—a form of currency that is stable and reliable in preserving value over time. This idea opens the door to using Bitcoin as a benchmark for comparing the value of other assets, offering a fresh perspective on the economy. Imagine a graph that compares the leading stock index, **the S&P 500, in Bitcoin terms instead of dollars.**  This graph would reveal a drastically different picture from the conventional charts we are familiar with. Looking back to 2011, the S&P 500 was around 1,300 points, while Bitcoin was priced at less than $1. This means the S&P 500 index was valued at approximately 1,300 BTC at the time. However, as Bitcoin's price surged over the years—reaching tens of thousands of dollars per BTC in 2021–2022—the value of the S&P 500, when measured in BTC, shrank dramatically. Suppose the S&P 500 currently stands at around 4,000 points, while Bitcoin is priced at six figures in dollars. The entire S&P 500 index might be worth less than 0.05 BTC. The resulting graph would show a consistent downward trend in the S&P 500's value **(when measured in BTC)** over the past decade. This means Bitcoin has appreciated relative to traditional financial assets like stocks—to the extent that simply holding Bitcoin has outperformed investing in major stock indices. As surprising as this may seem, the data tells this story: from the perspective of a Bitcoin standard, even the high-performing U.S. stock market appears lackluster. Data from the past decade reinforces this view. Bitcoin has outperformed nearly every asset class known today. In numerical terms, Bitcoin delivered an average annual return of **approximately 230% from 2011 to 2021**, whereas the S&P 500, which is renowned for its consistent performance, achieved an average annual return of just over 10%. When compounded over time, this means Bitcoin's value increased by tens of thousands of percent over the past decade, while the S&P 500's value rose by only a few hundred percent. The magnitude of this difference is significant enough to reshape how we perceive investment success. Observations also indicate that in just **the past five years, the S&P 500 has lost nearly 90% of its value when measured in Bitcoin.** In other words, for someone using Bitcoin as their benchmark, a 100-baht investment in stocks at the beginning of this period would be worth only about 10 baht today—the remaining 90 baht representing the opportunity cost of not holding Bitcoin. This perspective challenges our assumptions about the stability of supposedly safe assets when evaluated under a new standard. This comparison also highlights the issue of fiat currency depreciation—something we are familiar with but often underestimate. The U.S. dollar, the world's primary reserve currency, has **lost over 96% of its purchasing power since 1913**. This means that what $1 could buy back then now requires nearly $30. This ongoing depreciation implies that prices in fiat terms may rise even when real value does not. For example, the S&P 500 frequently reaches all-time highs in U.S. dollar terms. However, when adjusted for inflation or money supply expansion, its real value has not increased as much as it seems. Some analyses suggest that since the 2008 financial crisis, although the S&P 500's nominal value has surged, when divided by the expanding money supply (such as M3), its graph remains largely unchanged from pre-crisis levels. This suggests that stock prices have risen primarily in response to liquidity injections rather than genuine economic growth. Inflation and monetary expansion act like a **"fog,"** obscuring our ability to discern real value from mere numerical increases. When Bitcoin is used as a comparative unit, it acts as a clear lens that removes this inflationary fog, revealing a completely different picture. The same applies when comparing commodity prices in BTC. A notable experiment by the St. Louis Federal Reserve once examined the price of **"a dozen eggs"** in both dollars and Bitcoin. While the study aimed to highlight Bitcoin’s volatility, it inadvertently reinforced the point that during periods of high inflation, the price of eggs, which seemed to rise continuously in dollars, actually remained stable or even declined in BTC terms. This amusing example illustrates the profound impact of measurement standards. Of course, Bitcoin itself is highly volatile and still in its early stages compared to traditional assets. Its meteoric rise over the past decade does not guarantee that all asset graphs in BTC terms will continue declining indefinitely. However, what has already transpired provides deep financial insights. **The first takeaway** is the concept of opportunity cost mentioned earlier—every financial decision has an inherent cost, even if we do not always recognize it. Holding cash in a bank carries the opportunity cost of the returns one could earn by investing elsewhere. Investing in asset A means missing out on asset B, and if B delivers higher returns, we incur that loss. Over the past decade, Bitcoin has outperformed all other assets by a wide margin, making the opportunity cost of not holding Bitcoin extremely high. Investors looking back on this period might regret not having bought Bitcoin earlier, but the key lesson is not about dwelling on past decisions—it is about becoming aware of **opportunity costs** and their long-term impact on wealth. On a deeper level, this discussion raises questions about whether our current valuation framework is truly appropriate. If using a depreciating fiat currency as a benchmark distorts our perception of value, our economic decisions may be misaligned in the long run. Imagine a scenario where money retains or even appreciates in value in line with real economic productivity (as Bitcoin was designed to do). In such a system, people would not need to chase high returns merely to preserve their savings from inflation. They could plan finances with a longer-term perspective. Concepts like **"time preference"** and **"discounting the future"** would shift. It is often argued that sound money encourages saving and long-term investment, whereas inflationary systems push people toward short-term spending or speculation out of fear that their money will lose value. This is not just a matter of personal finance but a fundamental influence on the quality of economic growth and innovation. **A sound money standard** like **Bitcoin** might enforce stricter investment discipline, as liquidity injections could no longer be used as a safety net for unsustainable projects. At this point, readers may not conclude that they should immediately hold Bitcoin instead of investing in other assets—and this article is not intended as investment advice. Its real purpose is to provoke thought about how we measure value. **Ask yourself:** What unit do we use to gauge wealth and economic progress? Is that unit reliable? If the money we use for measurement loses value every year, how can we be sure that increasing numbers on paper reflect true wealth growth? Using Bitcoin as a reference standard is like measuring with a new ruler—one that may be more accurate. In many cases, it reveals unexpected insights and challenges long-held beliefs. Ultimately, whether or not one believes in the **"Bitcoin standard"** is less important than the ability to critically examine the system we rely on daily. Perhaps the greatest value Bitcoin and new financial philosophies offer is not a definitive answer but the impetus to look at the bigger economic picture with fresh eyes. Thank you, Thai Ratel, for enlightening me on this topic! Jakk Goodday.