-

@ 6b0a60cf:b952e7d4
2025-03-06 02:45:45
とあるSNSで海外の相互さん(以降、Aさんと呼ぶ)からDMで相談されたことがあって、思ったことをつらつらと書いてみる。
非公開の場での相談なので多少ぼかしを入れるけど。
## 事の経緯
発端は、Aさんの友人が作品に日本人作者の素材を使用しようとしていて、その利用規約を翻訳して読んだらうまく翻訳されなくて理解が正しいのかわからない、なので間違いが無いか確認してほしい、という相談だった。
あー、確かに日本語特有の回りくどい表現があるねー、と思いながらバシッと簡潔に意訳してお伝えしたところ、スッキリ理解していただけたらしく一件落着となった。
## 独自ライセンス文化
しかしまあ、創作界隈における作品・素材の利用規約というものは総じて長くて細かい。
ジャンルによるのかもしれないけれど。
自分は絵や音を創ることは無いがプログラムのコードを書く趣味はあるのでプログラム向けのライセンスを利用している。MITとかGPLとかいうやつ。
創作向けであればCCライセンスが適しているだろう。しかしこれがなかなか広まらない。
杓子定規のライセンスでは表しきれないような特別な希望があるのだろう。
そして独自ライセンスが跋扈することとなる。
## NO MORE 映画泥棒
特に気になるのが、「泥棒をしてはいけません」レベルの注意書きが散見されるのだ。
わざわざライセンスに書くことではない。あなたが警告するまでもなく、違法な行為は処罰される。
でも、たぶん効果があるからこういうのが広まるのだろう。
「泥棒してはいけないって書いてないから泥棒しました」というレベルの利用者が存在するのだろう。
そういう人は書いてあっても読んでないか、理屈をこねて泥棒するんだろうと思うけれども。
## その術はオレに効く
で、そういう警告文が魔除けの札のごとくびっしり貼られていると、こちらにやましい心が無くても、ちょっとこの素材は利用しないほうがよさそうだな……と思って引き返してしまうことがある。
SNSで可愛い絵を見て、作者さんをフォローしようと思ったら「無断転載禁止」みたいなのがプロフにずらずら書いてあって「おっと……」みたいに引き返すことがあるが、それに似ている。
きっと過去によくない体験をしてしまって、そのようにプロフに書くことでそれが改善するという実体験があって、そうなっているのだろうと推測している。
## 異文化の壁を超えて
冒頭で話したAさんはきわめて紳士的な方であり、日本文化に対してもよく理解しようと努めてくれるので、話が通じやすくて助かったし、件の素材についても臆すること無く使用することになりそうだった。
ただ魔除けの札が効かないような魑魅魍魎にはいくら札を貼っても意味がないし、実際の悪魔祓いの効果と善良な利用者をも祓ってしまう機会損失(?)を比べて合理的なのだろうか、と考えたりしたのでした。オチは無い。
## ライセンス
この文章は CC0 1.0 でライセンスします。
Nostrイベントとして公開する以上はNIPsに従う範囲内で自由に利用されることを望みます。
NIPsに違反したご利用は他のクライアントの利用者にご迷惑になるのでご遠慮いただくことを希望します。[^1]
[^1]: Damusを使ってリポストする、等の行為が該当します
-

@ a63655ce:05240c71
2025-03-06 00:48:46
looks really clean. `window.nostr` asked for the key multiple times for some reason
-

@ 6e0ea5d6:0327f353
2025-03-06 00:18:09
Ascolta, amico mio...
There come moments when a grown man looks in the mirror and fails to recognize himself.
Naturally, when this happens, there is nothing more fitting than lighting a cigarette, pouring a glass of fine wine, and toasting to oneself—the birth of a new man, forged in the womb of a harsh and sobering reality.
One cannot scatter thorns along a path walked barefoot, nor allow the tongue to speak what the mind may later pay for—but this, we learn only through years of suffering.
Only now do I realize that, among all the teachers I have had, experience was the harshest of them all, for it first administered the test and only afterward taught me the lesson.
In peaceful moments, one can reflect more easily on the world around him. Imagine, then, the depths of reflection that can be reached in a state of true inner tranquility.
If you have never gazed upon the horizon, taken in all the fortune before your eyes, and declared to yourself, "I will own all of this!", then you have never possessed true ambition. However, blind ambition will leave you waking up hungry for wealth and power but going to sleep with an empty soul.
Walk always with honor, pride, and loyalty—let these principles never depart from you nor fail to steady your steps. In your battles, do not wish for your enemies to be handed to you on their knees; instead, seek to gain the strength and ruthlessness to bring them down while they stand.
Your greatest dilemma is the eternal paradox in the life of a businessman within the sacred Sicilian organization: how to acquire power and wealth without placing both feet in hell?
Be careful not to surrender to arrogance. The man who shouts his virtues to the wind will, when he falls, hear only the echo of his own pride.
Let your greatest legacy be to live in a way that does not shame your mother and makes your father proud.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-

@ b8851a06:9b120ba1
2025-03-05 23:03:00
The U.S. isn't just blocking Gaza's reconstruction—it's ensuring Palestinians have no future there.
This week, Washington rejected the Arab League's $53 billion plan to rebuild Gaza. Not because it was unworkable, but because it was unwanted. #Gaza, they say, is "uninhabitable." The solution? Depopulation, disguised as development.
## The Riviera Plan: Rebuilding Without Its People
National Security Council spokesman Brian Hughes put it bluntly:
"Gaza is uninhabitable."
This isn't a call for humanitarian intervention. It's a pretext for forced displacement.
Trump's vision transforms Gaza into a "Riviera of the #MiddleEast"—after its population has been relocated. Officials have explicitly stated Palestinians "would not be allowed to return" once reconstruction begins. This isn't rebuilding; it's replacement.
## Regional Consensus Rejected
The Arab League's proposal represented rare unity among regional powers. It offered a detailed roadmap for reconstruction while allowing #Palestinians to remain in their homeland.
By dismissing this plan, Washington sent a clear message: **Palestinian self-determination remains subordinate to Western geopolitical interests.**
This isn't new. For over a century, Western capitals have determined Palestinian futures while treating their voices as irrelevant.
## The Fiat War Machine Connection
War and fiat money go hand in hand. Governments don't fund wars through taxes anymore—it's all printed money. Inflation steals from the public silently, financing endless destruction abroad while citizens struggle at home.
As Saifedean Ammous writes in The Fiat Standard: nostr:npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak
"Central banks are essentially war machines, enabling governments to finance endless conflicts through inflation rather than direct taxation."
This system divorces "economic reward from economic productivity, and instead bases it on political allegiance." The result? A world "perpetually lurching from one crisis to another, with devastating consequences for humanity."
## Ukraine Parallels: When Support Is Conditional
The U.S. has now halted military aid to #Ukraine, suspending over $1 billion in arms. #Europe scrambles to fill the gap, suddenly realizing the conditional nature of American protection.
Both conflicts reveal the same truth: **geopolitical support is increasingly transactional rather than values-based.**
As Henry Kissinger observed: "It may be dangerous to be America's enemy, but being America's friend can be fatal."
## The Cycle Continues
The U.S. model is simple: fund destruction, control reconstruction, keep the cycle going.
Fiat money makes it possible. Indifference makes it permanent. And yes #Bitcoin can fix it. But will it?
How long before people wake up #nostr? How long before the cycle breaks?
"Fiat money is a tool for governments to control their citizens" as Saifedean rightly says—and now, through endless war, to control the world.
-

@ f3873798:24b3f2f3
2025-03-05 23:01:12
O café faz parte da rotina de milhões de pessoas, seja para despertar pela manhã, acompanhar uma boa conversa ou até impulsionar a produtividade no trabalho. Mas você já parou para pensar na qualidade do café que consome diariamente? Neste artigo, vamos falar sobre os benefícios do café e as diferenças entre o café extraforte e o café especial.
## ☕ Benefícios do Café no Dia a Dia

O café não é apenas uma bebida saborosa, mas também oferece diversos benefícios para a saúde, como:
Aumento da energia e concentração – A cafeína estimula o sistema nervoso central, ajudando na atenção e no foco.
Melhora do humor – O consumo moderado de café pode estimular a produção de dopamina, contribuindo para uma sensação de bem-estar.
Propriedades antioxidantes – O café é rico em compostos que combatem os radicais livres, ajudando a prevenir o envelhecimento precoce.
Auxílio na digestão – Para muitas pessoas, o café funciona como um leve estimulante do sistema digestivo.
## ☕ Café Extraforte vs. Café Especial: Qual a Diferença?

Na prateleira do supermercado ou na cafeteria, há uma grande variedade de cafés. Mas, afinal, qual é a diferença entre o café extraforte e o café especial?
### ☕Café Extraforte
Produzido a partir de grãos de qualidade inferior, muitas vezes misturados com impurezas.
Possui torra muito escura, o que pode mascarar defeitos do grão.
Tem um sabor mais amargo e intenso, muitas vezes com notas queimadas.
Pode ser mais ácido e difícil de digerir para algumas pessoas.
### ☕Café Especial
Feito com grãos selecionados e de alta qualidade, sem defeitos.
A torra é mais equilibrada, preservando os aromas e sabores naturais.
Possui notas sensoriais diferenciadas (frutadas, achocolatadas, florais, etc.).
Mais suave e menos ácido, proporcionando uma experiência mais agradável ao paladar.
## ☕ Qual Escolher para o Dia a Dia?

Se você busca praticidade e um café forte, o extraforte pode ser uma opção. No entanto, se quiser aproveitar melhor os benefícios do café e sentir sabores mais ricos, vale a pena investir no café especial. Além disso, moer os grãos na hora e preparar a bebida com métodos como coador de pano, prensa francesa ou Hario V60 pode transformar sua experiência com o café.
-

@ b7b1382e:74635e6c
2025-03-05 22:32:18
## Abstract
**By Lamar Wilson**
This white paper examines an alternative taxation framework characterized by three primary components: a uniform 15% flat tax on income, a redistribution mechanism, and a tiered consumption tax structure. The proposed model aims to stimulate economic growth while maintaining social equity through strategic fiscal policy interventions. This paper analyzes the theoretical underpinnings of this approach, its potential macroeconomic implications, distributional effects across income strata, and implementation challenges. The analysis suggests that while the proposed framework offers significant advantages in terms of simplicity and growth incentives, careful consideration must be given to revenue adequacy, wealth concentration effects, and long-term economic sustainability.
## 1. Introduction
Taxation systems fundamentally shape economic incentive structures, income distribution, and government fiscal capacity. Contemporary tax regimes often reflect accumulated historical policy decisions rather than coherent economic theory, resulting in complex systems with varying degrees of progressivity, efficiency, and equity (Mirrlees et al., 2011). This paper examines a potential alternative taxation framework built upon three pillars: a uniform flat tax, redistribution mechanisms, and stratified consumption taxation.
The theoretical foundation of this approach draws upon both supply-side economics, which emphasizes the importance of investment incentives, and demand-side considerations, which recognize the economic significance of broad-based consumption. By synthesizing these perspectives, the proposed framework attempts to create a self-reinforcing economic cycle wherein simplified taxation stimulates both investment and consumption.
## 2. Structural Components of the Proposed Framework
### 2.1 Uniform Flat Income Taxation
The cornerstone of the proposed system is a uniform 15% tax rate applied to income. This component includes two key elements:
- **Individual Taxation**: A 15% flat tax applied to gross income across all individual taxpayers, regardless of income level. This approach eliminates tax brackets, deductions, and exemptions that characterize progressive taxation systems.
- **Business Taxation**: A parallel 15% flat tax on net business income (profits), allowing for business expense deductions while maintaining a uniform rate across business entities regardless of size, industry, or organizational structure.
The flat tax component represents a significant departure from graduated or progressive taxation systems prevalent in many developed economies. This simplification potentially reduces compliance costs, eliminates bracket-based behavioral distortions, and creates uniform incentive structures across income levels (Hall & Rabushka, 2007).
### 2.2 Universal Redistribution Mechanism
The second component involves the pooling and redistribution of tax revenue:
- **Collection Aggregation**: All tax revenues from both individual and business taxation are consolidated into a unified fiscal pool.
- **Equal Per Capita Distribution**: The aggregated tax revenue is redistributed on an equal per capita basis to all individuals within the jurisdiction, functioning as a universal basic income mechanism.
This redistribution mechanism effectively creates a de facto progressive element within the overtly flat system, as redistribution amounts represent a larger percentage of total income for lower-income individuals compared to higher-income individuals (Van Parijs & Vanderborght, 2017).
### 2.3 Tiered Consumption Taxation
The third component introduces a differentiated consumption tax structure:
- **Essential Goods and Services**: A minimal 2% consumption tax applied to essential items including food, healthcare, housing, and utilities.
- **Non-Essential and Luxury Items**: A higher consumption tax rate (suggested at 5% or greater) applied to discretionary purchases and luxury goods.
This differentiated approach to consumption taxation acknowledges consumption patterns that vary across income levels, with lower-income households typically allocating a greater proportion of spending to essential goods (Lustig, 2018).
## 3. Economic Implications Analysis
### 3.1 Distributive Effects Across Income Levels
#### 3.1.1 Lower-Income Households
The model's impact on lower-income households involves several counterbalancing forces:
- The 15% flat income tax represents a potentially higher nominal rate than many lower-income households currently face under progressive systems.
- The universal redistribution component serves as a direct income supplement, with the amount received likely exceeding tax contributions for this demographic.
- The 2% consumption tax on essentials introduces a modest additional cost on necessary expenditures.
Net analysis suggests that lower-income households would likely experience a positive fiscal impact through this system, as the redistributive component would exceed their combined income and consumption tax obligations (Piketty & Saez, 2013).
#### 3.1.2 Higher-Income Households
For higher-income households, the framework produces different effects:
- The 15% flat income tax rate typically represents a reduction from current progressive tax rates applied to higher income brackets.
- The universal redistribution amount constitutes a proportionally smaller income supplement relative to total income.
- Higher consumption taxes on luxury goods create a de facto progressive element based on discretionary spending patterns.
The net impact on higher-income households would likely be a reduced overall tax burden compared to progressive systems, potentially increasing capital availability for investment (Auerbach & Hassett, 2015).
### 3.2 Macroeconomic Implications
#### 3.2.1 Investment and Growth Effects
The framework's reduced taxation on higher incomes and business profits theoretically increases capital availability for investment. This aligns with supply-side economic theories suggesting that lower marginal tax rates stimulate economic expansion through:
- Increased business formation and expansion
- Enhanced capital investment
- Improved labor productivity through capital deepening
- Potential innovation stimulation through retained earnings
Empirical research on flat tax implementations in various jurisdictions provides mixed evidence regarding growth effects, with contextual factors playing significant roles in outcomes (Keen et al., 2008).
#### 3.2.2 Demand Stability and Consumption Patterns
The redistribution component creates a consumption floor that may enhance economic stability through:
- Maintaining baseline consumer demand during economic downturns
- Reducing consumption volatility across business cycles
- Supporting broader-based consumption patterns
- Creating demand-side support for business expansion
This mechanism acknowledges the economic significance of broad-based consumption capacity alongside investment incentives (Stiglitz, 2012).
#### 3.2.3 Labor Market Dynamics
The simplified tax structure potentially influences labor market participation through:
- Elimination of high marginal tax rates that may discourage additional work
- Reduced tax-related work disincentives at lower income levels
- Possible increased labor force participation due to simplified income-benefit calculations
- Potential wage effects as businesses retain higher post-tax profits
The framework's impact on labor markets would likely vary across skill levels, industries, and existing labor market institutions (Card & Krueger, 2015).
## 4. Implementation Challenges and Considerations
### 4.1 Fiscal Revenue Adequacy
A primary challenge involves ensuring sufficient government revenue, particularly during the transition period:
- The overall tax burden reduction (estimated at approximately 50% compared to current systems) creates potential revenue shortfalls.
- Government spending obligations would require adjustment, postponement, or alternative funding mechanisms.
- Transitional provisions may be necessary to align revenue reductions with spending adaptations.
Potential solutions include phased implementation, temporary supplementary revenue sources, or deliberate acceleration of economic growth to expand the tax base (Auerbach, 2006).
### 4.2 Wealth Concentration Effects
Despite redistribution mechanisms, the framework may influence wealth concentration dynamics:
- Reduced taxation on higher incomes could accelerate capital accumulation among wealthy individuals.
- Business owners might experience wealth growth exceeding redistribution effects.
- Global investment patterns could divert economic benefits outside the domestic economy.
Addressing these concerns might require calibration of the redistribution component or implementing complementary policies addressing wealth concentration (Piketty, 2014).
### 4.3 Long-Term Sustainability Considerations
The framework's long-term viability depends on several factors:
- Sustained economic growth sufficient to support government functions with reduced tax rates
- Continued business investment in productive domestic activities rather than financial engineering
- Maintenance of investment-consumption balance to prevent boom-bust cycles
- Evolution of the system in response to changing economic conditions
Supplementary policies supporting research and development, entrepreneurship, and domestic investment may be necessary to ensure the system's sustainability (Acemoglu & Robinson, 2012).
## 5. Comparative Cost-Benefit Analysis: Proposed System vs. Current Tax Structure
### 5.1 Compliance Cost Reduction
The current U.S. tax system imposes substantial compliance costs on individuals and businesses that extend far beyond direct tax payments:
- Americans spend approximately 6.5 billion hours annually on tax compliance activities (Taxpayer Advocate Service, 2022)
- The monetary value of compliance time is estimated at $200-400 billion annually (Laffer et al., 2018)
- Businesses spend an estimated $147 billion annually on tax compliance (Tax Foundation, 2021)
- The Internal Revenue Service budget exceeds $13 billion annually for tax administration and enforcement
The proposed flat tax system would dramatically reduce these costs through:
- Elimination of complex deduction and credit calculations (estimated 90% reduction in form complexity)
- Removal of recordkeeping requirements for numerous tax provisions
- Significant reduction in tax planning expenses for both individuals and businesses
- Decreased need for professional tax preparation services
- Streamlined tax enforcement with fewer provisions to interpret and audit
Quantitative analysis suggests that transitioning to the proposed system could reduce overall compliance costs by approximately 70-80%, representing annual savings of $140-320 billion to the U.S. economy (Greenberg, 2020).
### 5.2 Administrative Efficiency Gains
The current tax administration infrastructure incurs substantial costs:
- The IRS employs approximately 75,000 full-time equivalent positions
- Tax litigation consumes significant judicial resources across multiple court systems
- Regulatory development and guidance require extensive government resources
- Tax enforcement costs represent approximately 35 cents per $100 collected
The proposed system would generate administrative efficiencies through:
- Simplified verification processes requiring fewer personnel
- Reduced need for specialized tax rulings and interpretations
- Lower audit costs due to straightforward compliance requirements
- Streamlined distribution mechanisms leveraging existing payment systems
Conservative estimates suggest administrative cost reductions of 50-60%, representing billions in government savings that could be redirected to essential services or deficit reduction.
### 5.3 Economic Efficiency Improvements
Beyond direct compliance and administrative costs, the current system creates significant economic distortions:
- Taxpayers make economic decisions influenced by tax considerations rather than underlying economic value
- Complex provisions create market inefficiencies and misallocation of resources
- High marginal rates discourage additional productive activity
- International tax complexities influence global investment decisions
The proposed system addresses these inefficiencies through:
- Uniform treatment of income regardless of source
- Elimination of tax-motivated transaction structures
- Reduced incentives for artificial entity structures
- Simplified international transactions with domestic reinvestment incentives
Economic models suggest these efficiency improvements could increase GDP by 0.5-1.0% annually beyond direct compliance savings (Jorgenson & Yun, 2012).
### 5.4 Distributional Cost Analysis
The current system's compliance burden falls disproportionately across income levels:
- Lower-income taxpayers spend a higher percentage of their income on tax compliance
- Small businesses face compliance costs estimated at $1,500-$4,000 per employee
- Middle-income taxpayers navigate complex provisions with limited professional assistance
- High-income taxpayers allocate substantial resources to tax planning and compliance
The proposed system redistributes this burden by:
- Equalizing compliance requirements across income levels
- Substantially reducing small business administrative overhead
- Eliminating the need for complex tax planning strategies
- Providing transparent, predictable tax consequences for economic decisions
This redistribution of compliance costs represents an additional progressive element beyond the direct redistribution component, with estimated financial benefits to lower and middle-income households of $300-500 annually in reduced compliance costs.
## 6. Conclusion
The proposed tripartite taxation framework offers a conceptually coherent alternative to conventional progressive taxation systems. By combining flat income taxation with universal redistribution and differentiated consumption taxes, the approach attempts to simultaneously address supply-side investment incentives and demand-side consumption support.
The theoretical analysis suggests potential advantages in terms of simplicity, economic growth stimulation, and maintenance of social safety net functions. However, significant implementation challenges exist regarding revenue adequacy, wealth concentration effects, and long-term economic sustainability.
Further empirical research, potentially through regional pilot implementations or microsimulation modeling, would enhance understanding of the practical implications of this taxation approach. While the framework presents a promising theoretical model, its successful implementation would require careful calibration to specific economic contexts, thoughtful transition planning, and ongoing adjustment based on observed outcomes.
## References
Acemoglu, D., & Robinson, J. A. (2012). *Why nations fail: The origins of power, prosperity, and poverty*. Crown Business.
Greenberg, S. (2020). *Reforming the U.S. tax system: Evidence on economic growth and distribution*. American Enterprise Institute.
Jorgenson, D. W., & Yun, K. Y. (2012). *Tax reform and the cost of capital*. Oxford University Press.
Laffer, A. B., Moore, S., & Williams, J. (2018). *The wealth of states: How taxes, energy, and worker freedom change everything*. Wiley.
Tax Foundation (2021). *The cost of tax compliance*. Fiscal Fact No. 512.
Taxpayer Advocate Service (2022). *Annual report to Congress*. Internal Revenue Service.
Auerbach, A. J. (2006). The choice between income and consumption taxes: A primer. *NBER Working Paper Series*.
Auerbach, A. J., & Hassett, K. (2015). Capital taxation in the twenty-first century. *American Economic Review*, 105(5), 38-42.
Card, D., & Krueger, A. B. (2015). *Myth and measurement: The new economics of the minimum wage*. Princeton University Press.
Hall, R. E., & Rabushka, A. (2007). *The flat tax*. Hoover Institution Press.
Keen, M., Kim, Y., & Varsano, R. (2008). The "flat tax(es)": Principles and experience. *International Tax and Public Finance*, 15(6), 712-751.
Lustig, N. (2018). Fiscal policy, income redistribution and poverty reduction in low and middle income countries. *Commitment to Equity Handbook*.
Mirrlees, J., Adam, S., Besley, T., Blundell, R., Bond, S., Chote, R., Gammie, M., Johnson, P., Myles, G., & Poterba, J. (2011). *Tax by design*. Oxford University Press.
Piketty, T. (2014). *Capital in the twenty-first century*. Harvard University Press.
Piketty, T., & Saez, E. (2013). Optimal labor income taxation. *Handbook of Public Economics*, 5, 391-474.
Stiglitz, J. E. (2012). *The price of inequality: How today's divided society endangers our future*. W.W. Norton & Company.
Van Parijs, P., & Vanderborght, Y. (2017). *Basic income: A radical proposal for a free society and a sane economy*. Harvard University Press.
# A Tripartite Approach to Fiscal Reform: Analyzing the Economic Impact of a Flat Tax, Redistribution, and Consumption Tax Framework
**Author: Lamar Wilson**
## Abstract
**By Lamar Wilson**
This white paper examines an alternative taxation framework characterized by three primary components: a uniform 15% flat tax on income, a redistribution mechanism, and a tiered consumption tax structure. The proposed model aims to stimulate economic growth while maintaining social equity through strategic fiscal policy interventions. This paper analyzes the theoretical underpinnings of this approach, its potential macroeconomic implications, distributional effects across income strata, and implementation challenges. The analysis suggests that while the proposed framework offers significant advantages in terms of simplicity and growth incentives, careful consideration must be given to revenue adequacy, wealth concentration effects, and long-term economic sustainability.
## 1. Introduction
Taxation systems fundamentally shape economic incentive structures, income distribution, and government fiscal capacity. Contemporary tax regimes often reflect accumulated historical policy decisions rather than coherent economic theory, resulting in complex systems with varying degrees of progressivity, efficiency, and equity (Mirrlees et al., 2011). This paper examines a potential alternative taxation framework built upon three pillars: a uniform flat tax, redistribution mechanisms, and stratified consumption taxation.
The theoretical foundation of this approach draws upon both supply-side economics, which emphasizes the importance of investment incentives, and demand-side considerations, which recognize the economic significance of broad-based consumption. By synthesizing these perspectives, the proposed framework attempts to create a self-reinforcing economic cycle wherein simplified taxation stimulates both investment and consumption.
## 2. Structural Components of the Proposed Framework
### 2.1 Uniform Flat Income Taxation
The cornerstone of the proposed system is a uniform 15% tax rate applied to income. This component includes two key elements:
- **Individual Taxation**: A 15% flat tax applied to gross income across all individual taxpayers, regardless of income level. This approach eliminates tax brackets, deductions, and exemptions that characterize progressive taxation systems.
- **Business Taxation**: A parallel 15% flat tax on net business income (profits), allowing for business expense deductions while maintaining a uniform rate across business entities regardless of size, industry, or organizational structure.
The flat tax component represents a significant departure from graduated or progressive taxation systems prevalent in many developed economies. This simplification potentially reduces compliance costs, eliminates bracket-based behavioral distortions, and creates uniform incentive structures across income levels (Hall & Rabushka, 2007).
### 2.2 Universal Redistribution Mechanism
The second component involves the pooling and redistribution of tax revenue:
- **Collection Aggregation**: All tax revenues from both individual and business taxation are consolidated into a unified fiscal pool.
- **Equal Per Capita Distribution**: The aggregated tax revenue is redistributed on an equal per capita basis to all individuals within the jurisdiction, functioning as a universal basic income mechanism.
This redistribution mechanism effectively creates a de facto progressive element within the overtly flat system, as redistribution amounts represent a larger percentage of total income for lower-income individuals compared to higher-income individuals (Van Parijs & Vanderborght, 2017).
### 2.3 Tiered Consumption Taxation
The third component introduces a differentiated consumption tax structure:
- **Essential Goods and Services**: A minimal 2% consumption tax applied to essential items including food, healthcare, housing, and utilities.
- **Non-Essential and Luxury Items**: A higher consumption tax rate (suggested at 5% or greater) applied to discretionary purchases and luxury goods.
This differentiated approach to consumption taxation acknowledges consumption patterns that vary across income levels, with lower-income households typically allocating a greater proportion of spending to essential goods (Lustig, 2018).
## 3. Economic Implications Analysis
### 3.1 Distributive Effects Across Income Levels
#### 3.1.1 Lower-Income Households
The model's impact on lower-income households involves several counterbalancing forces:
- The 15% flat income tax represents a potentially higher nominal rate than many lower-income households currently face under progressive systems.
- The universal redistribution component serves as a direct income supplement, with the amount received likely exceeding tax contributions for this demographic.
- The 2% consumption tax on essentials introduces a modest additional cost on necessary expenditures.
Net analysis suggests that lower-income households would likely experience a positive fiscal impact through this system, as the redistributive component would exceed their combined income and consumption tax obligations (Piketty & Saez, 2013).
#### 3.1.2 Higher-Income Households
For higher-income households, the framework produces different effects:
- The 15% flat income tax rate typically represents a reduction from current progressive tax rates applied to higher income brackets.
- The universal redistribution amount constitutes a proportionally smaller income supplement relative to total income.
- Higher consumption taxes on luxury goods create a de facto progressive element based on discretionary spending patterns.
The net impact on higher-income households would likely be a reduced overall tax burden compared to progressive systems, potentially increasing capital availability for investment (Auerbach & Hassett, 2015).
### 3.2 Macroeconomic Implications
#### 3.2.1 Investment and Growth Effects
The framework's reduced taxation on higher incomes and business profits theoretically increases capital availability for investment. This aligns with supply-side economic theories suggesting that lower marginal tax rates stimulate economic expansion through:
- Increased business formation and expansion
- Enhanced capital investment
- Improved labor productivity through capital deepening
- Potential innovation stimulation through retained earnings
Empirical research on flat tax implementations in various jurisdictions provides mixed evidence regarding growth effects, with contextual factors playing significant roles in outcomes (Keen et al., 2008).
#### 3.2.2 Demand Stability and Consumption Patterns
The redistribution component creates a consumption floor that may enhance economic stability through:
- Maintaining baseline consumer demand during economic downturns
- Reducing consumption volatility across business cycles
- Supporting broader-based consumption patterns
- Creating demand-side support for business expansion
This mechanism acknowledges the economic significance of broad-based consumption capacity alongside investment incentives (Stiglitz, 2012).
#### 3.2.3 Labor Market Dynamics
The simplified tax structure potentially influences labor market participation through:
- Elimination of high marginal tax rates that may discourage additional work
- Reduced tax-related work disincentives at lower income levels
- Possible increased labor force participation due to simplified income-benefit calculations
- Potential wage effects as businesses retain higher post-tax profits
The framework's impact on labor markets would likely vary across skill levels, industries, and existing labor market institutions (Card & Krueger, 2015).
## 4. Implementation Challenges and Considerations
### 4.1 Fiscal Revenue Adequacy
A primary challenge involves ensuring sufficient government revenue, particularly during the transition period:
- The overall tax burden reduction (estimated at approximately 50% compared to current systems) creates potential revenue shortfalls.
- Government spending obligations would require adjustment, postponement, or alternative funding mechanisms.
- Transitional provisions may be necessary to align revenue reductions with spending adaptations.
Potential solutions include phased implementation, temporary supplementary revenue sources, or deliberate acceleration of economic growth to expand the tax base (Auerbach, 2006).
### 4.2 Wealth Concentration Effects
Despite redistribution mechanisms, the framework may influence wealth concentration dynamics:
- Reduced taxation on higher incomes could accelerate capital accumulation among wealthy individuals.
- Business owners might experience wealth growth exceeding redistribution effects.
- Global investment patterns could divert economic benefits outside the domestic economy.
Addressing these concerns might require calibration of the redistribution component or implementing complementary policies addressing wealth concentration (Piketty, 2014).
### 4.3 Long-Term Sustainability Considerations
The framework's long-term viability depends on several factors:
- Sustained economic growth sufficient to support government functions with reduced tax rates
- Continued business investment in productive domestic activities rather than financial engineering
- Maintenance of investment-consumption balance to prevent boom-bust cycles
- Evolution of the system in response to changing economic conditions
Supplementary policies supporting research and development, entrepreneurship, and domestic investment may be necessary to ensure the system's sustainability (Acemoglu & Robinson, 2012).
## 5. Comparative Cost-Benefit Analysis: Proposed System vs. Current Tax Structure
### 5.1 Compliance Cost Reduction
The current U.S. tax system imposes substantial compliance costs on individuals and businesses that extend far beyond direct tax payments:
- Americans spend approximately 6.5 billion hours annually on tax compliance activities (Taxpayer Advocate Service, 2022)
- The monetary value of compliance time is estimated at $200-400 billion annually (Laffer et al., 2018)
- Businesses spend an estimated $147 billion annually on tax compliance (Tax Foundation, 2021)
- The Internal Revenue Service budget exceeds $13 billion annually for tax administration and enforcement
The proposed flat tax system would dramatically reduce these costs through:
- Elimination of complex deduction and credit calculations (estimated 90% reduction in form complexity)
- Removal of recordkeeping requirements for numerous tax provisions
- Significant reduction in tax planning expenses for both individuals and businesses
- Decreased need for professional tax preparation services
- Streamlined tax enforcement with fewer provisions to interpret and audit
Quantitative analysis suggests that transitioning to the proposed system could reduce overall compliance costs by approximately 70-80%, representing annual savings of $140-320 billion to the U.S. economy (Greenberg, 2020).
### 5.2 Administrative Efficiency Gains
The current tax administration infrastructure incurs substantial costs:
- The IRS employs approximately 75,000 full-time equivalent positions
- Tax litigation consumes significant judicial resources across multiple court systems
- Regulatory development and guidance require extensive government resources
- Tax enforcement costs represent approximately 35 cents per $100 collected
The proposed system would generate administrative efficiencies through:
- Simplified verification processes requiring fewer personnel
- Reduced need for specialized tax rulings and interpretations
- Lower audit costs due to straightforward compliance requirements
- Streamlined distribution mechanisms leveraging existing payment systems
Conservative estimates suggest administrative cost reductions of 50-60%, representing billions in government savings that could be redirected to essential services or deficit reduction.
### 5.3 Economic Efficiency Improvements
Beyond direct compliance and administrative costs, the current system creates significant economic distortions:
- Taxpayers make economic decisions influenced by tax considerations rather than underlying economic value
- Complex provisions create market inefficiencies and misallocation of resources
- High marginal rates discourage additional productive activity
- International tax complexities influence global investment decisions
The proposed system addresses these inefficiencies through:
- Uniform treatment of income regardless of source
- Elimination of tax-motivated transaction structures
- Reduced incentives for artificial entity structures
- Simplified international transactions with domestic reinvestment incentives
Economic models suggest these efficiency improvements could increase GDP by 0.5-1.0% annually beyond direct compliance savings (Jorgenson & Yun, 2012).
### 5.4 Distributional Cost Analysis
The current system's compliance burden falls disproportionately across income levels:
- Lower-income taxpayers spend a higher percentage of their income on tax compliance
- Small businesses face compliance costs estimated at $1,500-$4,000 per employee
- Middle-income taxpayers navigate complex provisions with limited professional assistance
- High-income taxpayers allocate substantial resources to tax planning and compliance
The proposed system redistributes this burden by:
- Equalizing compliance requirements across income levels
- Substantially reducing small business administrative overhead
- Eliminating the need for complex tax planning strategies
- Providing transparent, predictable tax consequences for economic decisions
This redistribution of compliance costs represents an additional progressive element beyond the direct redistribution component, with estimated financial benefits to lower and middle-income households of $300-500 annually in reduced compliance costs.
## 6. Conclusion
The proposed tripartite taxation framework offers a conceptually coherent alternative to conventional progressive taxation systems. By combining flat income taxation with universal redistribution and differentiated consumption taxes, the approach attempts to simultaneously address supply-side investment incentives and demand-side consumption support.
The theoretical analysis suggests potential advantages in terms of simplicity, economic growth stimulation, and maintenance of social safety net functions. However, significant implementation challenges exist regarding revenue adequacy, wealth concentration effects, and long-term economic sustainability.
Further empirical research, potentially through regional pilot implementations or microsimulation modeling, would enhance understanding of the practical implications of this taxation approach. While the framework presents a promising theoretical model, its successful implementation would require careful calibration to specific economic contexts, thoughtful transition planning, and ongoing adjustment based on observed outcomes.
## References
Acemoglu, D., & Robinson, J. A. (2012). *Why nations fail: The origins of power, prosperity, and poverty*. Crown Business.
Greenberg, S. (2020). *Reforming the U.S. tax system: Evidence on economic growth and distribution*. American Enterprise Institute.
Jorgenson, D. W., & Yun, K. Y. (2012). *Tax reform and the cost of capital*. Oxford University Press.
Laffer, A. B., Moore, S., & Williams, J. (2018). *The wealth of states: How taxes, energy, and worker freedom change everything*. Wiley.
Tax Foundation (2021). *The cost of tax compliance*. Fiscal Fact No. 512.
Taxpayer Advocate Service (2022). *Annual report to Congress*. Internal Revenue Service.
Auerbach, A. J. (2006). The choice between income and consumption taxes: A primer. *NBER Working Paper Series*.
Auerbach, A. J., & Hassett, K. (2015). Capital taxation in the twenty-first century. *American Economic Review*, 105(5), 38-42.
Card, D., & Krueger, A. B. (2015). *Myth and measurement: The new economics of the minimum wage*. Princeton University Press.
Hall, R. E., & Rabushka, A. (2007). *The flat tax*. Hoover Institution Press.
Keen, M., Kim, Y., & Varsano, R. (2008). The "flat tax(es)": Principles and experience. *International Tax and Public Finance*, 15(6), 712-751.
Lustig, N. (2018). Fiscal policy, income redistribution and poverty reduction in low and middle income countries. *Commitment to Equity Handbook*.
Mirrlees, J., Adam, S., Besley, T., Blundell, R., Bond, S., Chote, R., Gammie, M., Johnson, P., Myles, G., & Poterba, J. (2011). *Tax by design*. Oxford University Press.
Piketty, T. (2014). *Capital in the twenty-first century*. Harvard University Press.
Piketty, T., & Saez, E. (2013). Optimal labor income taxation. *Handbook of Public Economics*, 5, 391-474.
Stiglitz, J. E. (2012). *The price of inequality: How today's divided society endangers our future*. W.W. Norton & Company.
Van Parijs, P., & Vanderborght, Y. (2017). *Basic income: A radical proposal for a free society and a sane economy*. Harvard University Press.
-

@ 6389be64:ef439d32
2025-03-05 21:18:52
Carbon is a "Long-Tail" asset: the residual earnings that come from an asset after it has had its initial market impact.
The Carbon Cascade converts labile into recalcitrant carbon.
During transformation power is generated and lands restored.
Total production of biomass per annum is 100 billion tons of carbon and at $500 to $2,000 per ton of biochar that's $100 trillion of potential carbon trading on the open market. (fanciful to be sure)
originally posted at https://stacker.news/items/904996
-

@ 878dff7c:037d18bc
2025-03-05 20:37:35
# Overview
Tropical Cyclone Alfred, currently a Category 2 system, is approaching Australia's eastern coast, with landfall anticipated between the Sunshine Coast and Gold Coast early Friday. This rare event has prompted widespread preparations and warnings across Queensland and New South Wales. Authorities are urging residents in vulnerable areas to evacuate and brace for destructive winds, heavy rainfall, and potential life-threatening flooding. [TROPICAL CYCLONE FORECAST TRACK MAP](http://www.bom.gov.au/products/IDQ65002.shtml)
(Cover photo thanks to our 'unfortunately on the ground' photographer Sean. Stay safe mate!)
## Queensland and New South Wales Brace for Cyclone Alfred's Impact
### Summary:
Residents in Queensland and northern New South Wales are preparing for Tropical Cyclone Alfred, expected to make landfall early Friday between the Sunshine Coast and Gold Coast. The Category 2 storm is forecasted to bring severe winds and heavy rain, with potential for major flooding. Emergency measures include power outages, flight cancellations, school closures, and activation of emergency centers. The Australian Defence Force has been engaged to assist with response efforts.
Sources: [The Guardian - 6 March 2025](https://www.theguardian.com/australia-news/2025/mar/05/afternoon-update-wednesday-ntwnfb)
## Authorities Issue Evacuation Warnings Ahead of Cyclone Alfred
### Summary:
Australian authorities have issued major evacuation warnings ahead of Tropical Cyclone Alfred's expected landfall on Friday morning. The cyclone, categorized as Category 2, is anticipated to bring winds of 155 km/h and 800 mm of rainfall, potentially leading to dangerous and life-threatening conditions. Areas like Brisbane, the Gold Coast, and Sunshine Coast are in the cyclone's projected path. Residents in flood-prone and coastal areas are urged to evacuate and make necessary preparations, including stocking up on water and non-perishable food. The Australian government has declared a state of emergency and engaged the Australian Defence Force to assist with evacuation and disaster response efforts.
Sources: [The Sun - 6 March 2025](https://www.thesun.ie/news/14823247/tropical-cyclone-alfred-irish-people-evacuate-warning-australia/)
## Residents Prepare for First Cyclone in Over Five Decades
### Summary:
Residents in Brisbane and the Gold Coast are preparing for Tropical Cyclone Alfred, the first cyclone in 51 years to hit the Australian east coast near Brisbane. The cyclone is predicted to make landfall late Thursday or early Friday, bringing destructive winds, large swells, and potential life-threatening flooding. Brisbane, with over 3 million residents, may see up to 20,000 homes affected by flooding. The government has provided 250,000 sandbags and established cyclone refuge centers. Schools, public transport, and non-urgent hospital surgeries will be suspended. Queensland Premier David Crisafulli has urged residents to prepare their homes and plan evacuation routes.
Sources: [AP News - 6 March 2025](https://apnews.com/article/f40a46f400f42d7d94dc5a91cb11c11a)
## Cyclone Alfred's Approach Prompts Widespread Preparations
### Summary:
Cyclone Alfred, a Category 2 storm, is approaching the Tweed Coast near Brisbane, expected to make landfall late Thursday or early Friday. As tension mounts, residents are bracing for potential disaster with power outages and water contamination being the main concerns. Supermarkets are emptied of essential supplies, and emergency preparations, such as sandbagging and securing properties, are in full swing. The community displays remarkable solidarity, with neighbors helping one another and sharing real-time updates. Surfers are taking advantage of the monster swells, enjoying the waves despite the looming threat. Families face difficult decisions on whether to stay or evacuate, while prioritizing the safety and well-being of their loved ones. With a keen sense of unity and preparedness, the community waits in hope that their efforts will withstand the upcoming storm.
Sources: [News.com.au - 6 March 2025](https://www.news.com.au/technology/environment/every-nerve-jangling-queenslanders-prepare-for-disaster-as-cyclone-alfred-nears/news-story/23e6cd554103de012374c1ce238ba8c7)
## Cyclone Alfred's Unusual Path Raises Concerns
### Summary:
Australia is preparing for a rare tropical cyclone, named Alfred, approaching Brisbane. Authorities are urging residents in flood-prone suburbs to evacuate due to potential destructive wind gusts up to 155 kph and significant rainfall that could lead to life-threatening flash flooding. The storm is expected to land as a Category 2 cyclone early on Friday. Evacuation efforts are in place, with heavy-lift helicopters deployed and evacuation centers being opened. Schools and public transport will shut down, and flights have been canceled in the affected regions. This area of southeast Queensland and northern New South Wales has not experienced such a cyclone for over fifty years.
Sources: [Reuters - 6 March 2025](https://www.reuters.com/business/environment/australias-east-coast-braces-cyclone-alfred-2025-03-04/)
## Ice Cube Shares Experience Amid Cyclone Alfred
### Summary:
Ice Cube is currently staying at a beachfront hotel in Australia as Cyclone Alfred intensifies. The 55-year-old rapper and actor, who is there for upcoming performances, humorously commented about experiencing a cyclone for the first time. Residents in flood-prone regions have been advised to evacuate, with heavy rains and strong winds expected to cause potentially life-threatening flash floods and severe storm conditions. The cyclone is particularly significant for Queensland, which hasn't seen such severe weather in decades. Ice Cube also denied rumors of his involvement in an 'Anaconda' reboot being filmed in Australia, stating he was only there for his Sydney show.
Sources: [People - 6 March 2025](https://people.com/ice-cube-australian-hotel-cyclone-alfred-11691119)
## Cyclone Alfred's Impact on Northern New South Wales
### Summary:
Residents in Northern New South Wales are preparing for the impacts of Cyclone Alfred, with rainfalls of up to 400 millimeters expected, alongside winds of up to 150 kilometers per hour and likely flooding. The cyclone's approach has led to heightened concerns and preparations in the region.
Sources: [ABC News - 6 March 2025](https://www.abc.net.au/news/2025-03-06/tropical-cyclone-alfred-northern-nsw/105014292)
## Authorities Urge Evacuations as Cyclone Alfred Nears
### Summary:
Residents in flood-prone suburbs of Brisbane and the Gold Coast are being urged to evacuate as Cyclone Alfred approaches. The storm is expected to bring destructive winds and heavy rainfall, leading to life-threatening flash flooding. Evacuation centers have been established, and emergency services are on high alert to assist those in need.
Sources: [The Guardian - 6 March 2025](https://www.theguardian.com/australia-news/live/2025/mar/06/tropical-cylone-alfred-live-update-brisbane-queensland-nsw-suburbs-weather-bom-forecast-path-track-map-school-closures)
-

@ 05933d87:81bac46e
2025-03-05 20:17:49
A few months ago, an Uber driver alerted me to [the presence of his rival](https://stacker.news/items/687682/r/k00b?commentId=688882). By that point, [Waymo had been testing in Austin](https://waymo.com/blog/2023/08/waymo-one-heads-to-austin/) for over a year. I hid my excitement during the ride but I applied as a beta tester, noting my belonging to the demographics a PM might test for. My application went ignored until, huzzah, Waymo sent me an email yesterday announcing [their self-driving cars are available directly through Uber in Austin](https://waymo.com/waymo-on-uber/).

I configured my allegiance to our new overlords swearing in on my screened sandwich of silicon.
Without willing it, and having forgot my new religion, I woke earlier than planned today and hailed a ride. The app spoke to me, "if you wait 3 minutes longer, we'll send you a car without a driver." For five minutes, I watched a car but not a driver move in the direction of me and my screen.
The ride was nice. I didn't have to theatrically rush to a waiting human. There was less social weirdness than I would normally sit with on a ride. I could inspect the car without risking the driver sense that I'm inspecting them. The car couldn't look at me buffering, deciphering if I am homeless or merely look it. I got to pick my own music. I got to watch people un-contacted by Waymo watch the car.

But ... it drove a lot more like a robot driving a car than a human driving a car. It pumped the brakes a few times as we passed weirdly parked cars uncertain (apparently) if the car might move into our lane. Once it signaled that we were headed into oncoming traffic as a street widened from one lane to two. Worst of all, it dropped me off near an anomalous stretch of sidewalk where my door opened to a wall, and if I were to climb and get out the other side, I'd arrive in the middle lane of a busy street. Trapped, I pinched myself through the door and, like Laura Croft, navigated the road's edge to a sidewalk.

tbh I'm still excited for my next Waymo ride. I'll just choose a different drop-off address.
originally posted at https://stacker.news/items/904830
-

@ 878dff7c:037d18bc
2025-03-05 20:12:53
## Queensland Premier Urges Immediate Preparations Ahead of Cyclone Alfred
### Summary:
Queensland Premier David Crisafulli has urged residents to complete their preparations immediately as Tropical Cyclone Alfred approaches. The Category 2 cyclone is expected to bring heavy rainfall, destructive winds, and potential flooding to South-East Queensland and Northern New South Wales. Public transport services and elective surgeries have been canceled, and hundreds of schools will remain closed through the week. Residents are advised to stay indoors and ensure their safety during the cyclone's landfall.
Sources: [The Guardian - March 5, 2025](https://www.theguardian.com/australia-news/live/2025/mar/05/australia-news-live-tropical-cyclone-alfred-brisbane-gold-coast-floods-storm-election-anthony-albanese-peter-dutton-ntwnfb), [News.com.au - March 6, 2025](https://www.news.com.au/technology/environment/1000km-warning-zone-alfred-set-to-hit-millions/news-story/6faff4d5aeb7a2c962dd94d46655fcea)
## Evacuation Orders Issued as Cyclone Alfred Approaches
### Summary:
Authorities have issued evacuation orders for residents in Northern New South Wales, particularly in areas from Tweed to Yamba, as Cyclone Alfred intensifies. The cyclone is expected to bring gale-force winds, heavy rainfall up to 400 mm, and significant flooding. Schools and flights have been disrupted, with widespread closures and cancellations in the region. Coastal areas are experiencing high winds and massive waves, increasing the risk of flash floods. Emergency services are on high alert, preparing residents and reinforcing infrastructure to manage imminent threats.
Sources: [The Daily Telegraph - March 6, 2025](https://www.dailytelegraph.com.au/news/regional/latest-on-tropical-cyclone-alfred-fears-for-northern-nsw-as-system-intensifies/news-story/b52b74b763dc895afa9fedcb33063925), [News.com.au - March 6, 2025](https://www.news.com.au/technology/environment/1000km-warning-zone-alfred-set-to-hit-millions/news-story/6faff4d5aeb7a2c962dd94d46655fcea)
## Liberal Senator Alex Antic's Rise Signals Shift to Conservatism in South Australia
### Summary:
Liberal Senator Alex Antic has ascended to the top position on South Australia's Senate ticket, marking a significant shift from the state's traditionally moderate Liberal stance to a more conservative direction. This change follows the resignation of veteran moderate Simon Birmingham and an influx of social conservatives and libertarians into the party. Antic, known for his controversial views, believes that conservative values are gaining traction as the world reaches "peak woke." He emphasizes the importance of adhering to traditional conservative principles to appeal to families concerned about social issues and younger individuals focused on economic matters. Despite past conflicts with party moderates, Antic is optimistic about the party's future under leaders like Peter Dutton, noting similar conservative movements globally.
Sources: [The Australian - March 5, 2025](https://www.theaustralian.com.au/nation/politics/antiwoke-warrior-welcomes-libs-step-to-the-right/news-story/6ce80aadb64afecc0b1744141671a5c1)
## Government's $130k Weekly Legal Fees for Toll Reform Under Scrutiny
### Summary:
The Minns government's efforts to reform Sydney's toll network have cost taxpayers over $8 million, with legal advice alone amounting to $130,000 per week since February 5, 2025. Despite these expenditures, significant changes have yet to be implemented, leading to criticism over the prioritization of consultancy fees over actionable toll reforms.
Sources: [The Daily Telegraph - March 6, 2025](https://www.dailytelegraph.com.au/news/nsw/taxpayers-slugged-130k-per-week-for-legal-advice-on-toll-reform/news-story/01d7ef103b0e6af03e92ee39de667326)
## Tech Giants Generate $27 Billion Annually from Australian Consumers
### Summary:
An analysis by the Parliamentary Budget Office reveals that the top 16 tech companies, including Google, Microsoft, Meta, and Amazon, collectively earn $26.7 billion annually from Australian consumers. The Greens propose a 3% tax on these companies' revenues exceeding $20 million, potentially generating $11.5 billion for the government to fund essential services like dental care in Medicare. However, this proposal faces challenges due to potential retaliatory measures from the U.S. government.
Sources: [The Guardian - 6 March 2025](https://www.theguardian.com/technology/2025/mar/06/google-microsoft-meta-and-amazon-among-tech-companies-making-27bn-from-australians)
## Melioidosis Outbreak in Queensland
### Summary:
Queensland is experiencing a significant outbreak of melioidosis, a serious disease caused by the bacteria *Burkholderia pseudomallei*, typically found in soil and freshwater. The bacteria can infect humans and animals through cuts, contaminated water, or inhalation. Symptoms include fever, headache, respiratory issues, and muscle pain. This year, there have been over 90 confirmed cases and 15 deaths in Queensland, higher than usual. The outbreak is believed to be linked to heavy rainfall and flooding, increasing the bacteria's prevalence. Preventative measures include wearing protective gear in wet areas and seeking early medical attention for symptoms like fever and breathing difficulties.
Sources: [The Advertiser - 3 March 2025](https://www.adelaidenow.com.au/lifestyle/what-is-melioidosis-the-deadly-disease-spreading-in-australia/news-story/05448740ef803a0ead29f8175670474b)
## Philippine Defense Chief Warns Against Chinese Restrictions in South China Sea
### Summary:
Philippine Defense Secretary Gilberto Teodoro warned that the Philippines and its allies would respond to any Chinese attempt to impose an air defense zone or restrict flights over the South China Sea. Teodoro highlighted China's growing aggression in the disputed waters, which has led to increased confrontations involving Chinese and Philippine forces, as well as incidents with U.S. and Australian military aircraft. Recent encounters have included close flybys and warning flares from Chinese aircraft. Teodoro emphasized that China's actions pose a major threat to both Philippine and global security due to the region's critical trade routes. He stated that defense officials are preparing contingency measures and could act alone or with international partners to counter potential Chinese aggression. Teodoro noted the possibility of a broader coalition forming to resist China's attempts to reshape international law and norms.
Sources: [Associated Press - 6 March 2025](https://apnews.com/article/4c63b28b674c63b1730a22dc9faa5f22)
## Amazon Joins Quantum Computing Race with 'Cat Qubit' Chip
### Summary:
Amazon has unveiled its new quantum computing chip, Ocelot, which utilizes "cat qubit" technology to significantly reduce quantum errors—a major hurdle in developing commercially viable quantum systems. This advancement positions Amazon alongside other tech giants like Google and Microsoft in the quest for functional quantum computers.
Sources: [SHRM - March 6, 2025](https://www.shrm.org/enterprise-solutions/insights/other-tomorrowist-trends-news-march-6-2025)
## New $1 Billion Fund Launched to Boost Australia's Circular Economy
### Summary:
Planet Ark and Boston Global have partnered to launch the BG Planet Ark Circular Future Fund, aiming to raise $1 billion by 2030 to invest in businesses promoting sustainability, reducing carbon emissions, and enhancing the circular economy. This initiative aligns with Australia's Circular Economy Framework, which seeks to double circularity by 2035 and add $26 billion annually to the GDP. Initial funding of $100 million has been secured, targeting sectors like regenerative farming and waste-to-energy solutions.
Sources: [The Australian - March 6, 2025](https://www.theaustralian.com.au/business/renewable-energy-economy/planet-ark-and-boston-global-join-forces-on-1bn-investment-fund-targeting-waste-reduction/news-story/067a6b67d9a3e51e61d5155e472e2bb6)
## Australia's Foreign Minister Comments on Trump's Second Term
### Summary:
Foreign Minister Penny Wong has remarked that Donald Trump's second presidency is already more disruptive than his first. She noted that Australia's government is dealing with a very different American administration, reflecting concerns about potential shifts in international relations and policies affecting Australia's strategic interests.
Sources: [Reuters - March 5, 2025](https://www.reuters.com/world/trumps-second-term-already-more-disruptive-than-his-first-australias-foreign-2025-03-05/)
-

@ 2e8970de:63345c7a
2025-03-05 19:50:10
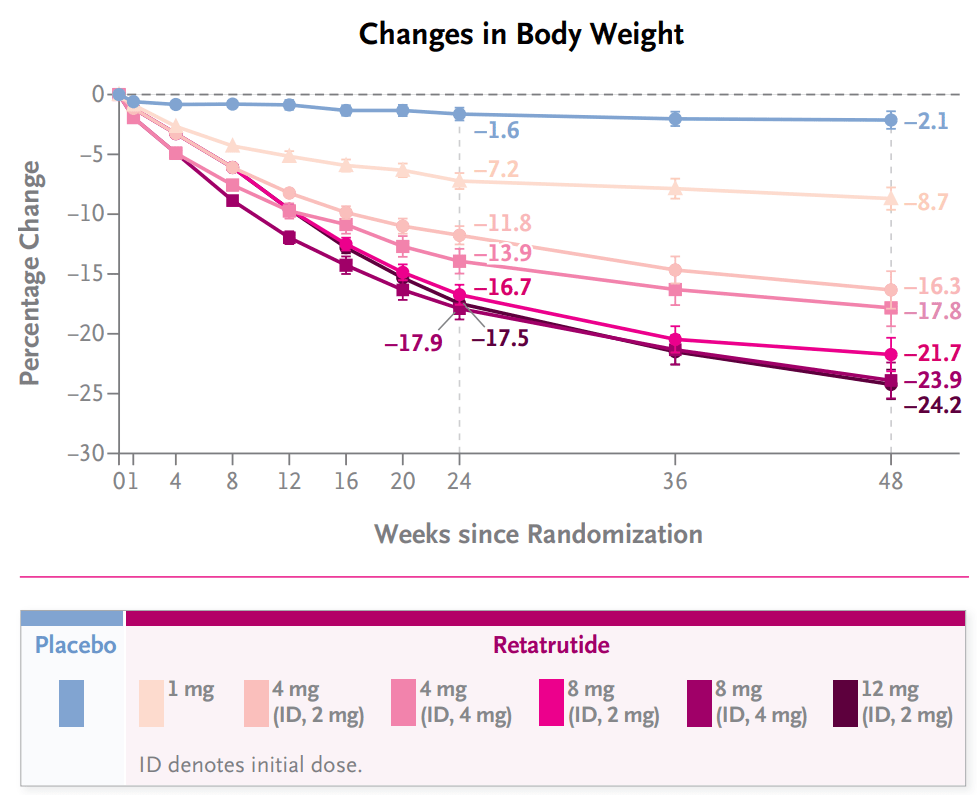
> It leads to fast, and massive weight loss by not just suppressing appetite, but also by upregulating metabolism.
https://www.nejm.org/doi/full/10.1056/NEJMoa2301972
originally posted at https://stacker.news/items/904851
-

@ 4925ea33:025410d8
2025-03-05 19:44:37
De acordo com a Resolução 03/25 do Conselho Federal de Farmácia a Aromaterapia é uma prática terapêutica que utiliza as propriedades dos óleos essenciais para restaurar o equilíbrio e a harmonia do organismo, promovendo a saúde física, mental e emocional. Essa técnica baseia-se no uso dos compostos aromáticos naturais extraídos das plantas para estimular respostas neurológicas e bioquímicas no corpo.
Os óleos essenciais atuam diretamente no sistema límbico, região do cérebro responsável pelas emoções, memórias e comportamentos. Mas seus benefícios vão muito além do bem-estar emocional! Eles possuem propriedades terapêuticas únicas, podendo atuar como cicatrizantes, antifúngicos, antibacterianos, anti-inflamatórios e até auxiliares no alívio de dores e tensões musculares. Além da inalação, os óleos podem ser aplicados topicamente, sendo absorvidos pela pele e interagindo com o organismo de maneira profunda e eficaz.
No entanto, é importante lembrar que os óleos essenciais são altamente concentrados e contêm substâncias que podem causar alergias ou irritações se usados de forma inadequada. Por isso, é essencial buscar orientação de um profissional qualificado para garantir um tratamento seguro e eficaz.
**Quer saber como a Aromaterapia pode transformar seu bem-estar? Agende uma consulta comigo e descubra os benefícios personalizados para você**.
-

@ b4403b24:83542d4e
2025-03-05 19:18:39


I can't believe so many shitcoiners are invited to attend 🫣
originally posted at https://stacker.news/items/904818
-

@ a296b972:e5a7a2e8
2025-03-05 18:34:49
Von Egon Bahr stammt der Satz: „Wir können politisch alles Mögliche ändern, nur nicht die Geografie.“ Er scheint der letzte deutsche Politiker gewesen zu sein, der wusste, dass Europa zwischen den USA im Westen und Russland im Osten liegt. Die tektonische Plattenverschiebung wird daran über kurz oder lang auch nichts ändern.
 
Europa, besonders Deutschland, wird erneut von der Weltgeschichte die Möglichkeit gegeben, seine ihm ureigenste Rolle anzunehmen, nämlich endlich eine neutrale, vermittelnde Rolle zwischen West und Ost zu ergreifen. Stattdessen verscherzt Europa es sich derzeit mit beiden Weltmächten. Das muss man erst einmal hinbekommen. Wie doof kann man sein? Brücken bauen scheint man in Deutschland nicht mehr zu können. Sieht man ja in Dresden.
Deutschland scheint diese Chance erneut nicht zu erkennen, da es spätestens seit dem C-Ereignis, entgegen den USA zumindest teilweise, bis heute nicht wieder zu Verstand gekommen ist. Eigentlich schon früher, nur da hat man es noch nicht so gemerkt.
Bis auf wenige Ausnahmen wird ganz Europa derzeit von Verrückten und deren Erfüllungsgehilfen geleitet. Allein die Aussage der CDU in Deutschland einen Tag nach der Wahl, „Die Ukraine muss den Krieg gewinnen“, zeigt, dass weiterhin nicht alle Porzellan-Trinkgefäße in dem dafür vorgesehenen Küchenmöbel vorhanden sind.
Es werden „Kriegs-Konferenzen“ einberufen, wie man die Ukraine weiter mit Geld und Waffen unterstützen kann, statt zu erkennen, dass sich der Wind Richtung Frieden gedreht hat. Europa hat zwar nichts zu sagen, dennoch kann Dummheit gefährlich werden. Es können Teller zerdeppert werden, die man besser nicht angerührt hätte.
Jeder Banker schüttelt den Kopf und drückt auf den Alarmknopf unter der Schreibtischplatte, wenn man zu ihm geht und um ein Sondervermögen ansucht. Hexenmeister Deutschland kann Geld herbeizaubern, allein durch seinen politischen Willen, Kraft seiner Gedanken. Schöpfung aus dem Nichts. Und warum drängt sich gerade Deutschland schon wieder so nach vorne? Was steht im Zeugnis von Deutschland? Geschichtsunterricht: nicht teilgenommen
Alles, wofür Deutschland einmal stand, für Frieden und Diplomatie, scheint einer allgemeinen Kriegslüsternheit des Polit-Büros gewichen zu sein, obwohl die Arsenale leer sind (Gottseidank!). Eine Aufrüstung sowohl logistisch, personell als auch materialmäßig würde mindestens 10 Jahre dauern. Da kann man nur hoffen, dass Putin so lange wartet, wo doch aus allen Propagandarohren geschossen wird, dass er seine imperialistischen Phantasien nach der Ukraine weiter in Richtung Europa ausleben will. Erst nach Polen und dann mit dem Trampolin von Brandenburg aus direkt nach Berlin. Das war’s. Dabei brauchen wir gar keinen Feind von außen. Deutschland ist ja bereits mit der BRD im Krieg.
Man spekuliert auf einen europäischen Schutzschild mit Frankreich als Land mit Atomwaffen. Wie lächerlich ist das denn? Das erinnert an einen Yorkshire-Terrier, der ein Pferd anbellt. Die immer noch gültige Feindstaaten-Klausel scheint für alle zu gelten, nur nicht für die, die sie betrifft, also Deutschland. Sie ist durch den 2 + 4 – Vertrag nicht aufgehoben worden, weil der kein Friedensvertrag ist.
Trump spricht davon, seine Truppen aus Europa, aus Deutschland abzuziehen. Es kursieren Gerüchte, dass er gar die NATO verlassen könnte. Dann steht Deutschland völlig blank da – stets aufs Äußerste zur Entschlossenheit bereit! Panik im Hühnerstall, weil der Fuchs in der Nähe gesehen wurde. Und statt Überlegungen in Richtung Neutralität anzustellen, was gut zu Deutschland, im Verbund mit Österreich und der Schweiz als deutschsprachigen Kulturraum passen würde, überlegt man, wie man die Arbeiter der niedergehenden Autoindustrie in der Rüstungsindustrie anschlussverwenden kann. Es ist alles nur noch irre.
Wer Pazifist und für den Frieden ist, delegitimiert den Staat, ist reeeeechts. Ja, wo sind wir denn inzwischen gelandet? Im Emsland macht die Polizei folgende Ansage durch einen Lautsprecher: „Beachten Sie die Beschränkungen. Ausrufe, wie „Stoppt das Morden“, „Stoppt den Krieg“ und weiterfolgend, haben zu unterbleiben.“
Vielleicht spekuliert man ja darauf, dass es eine neue Migrationswelle nach Europa gibt. Diesmal von denen, die von der US-Regierung als Deep State-Angehörige aufgespürt werden. Mit ihrem Geld und Einfluss kämen sie den Großmanns-Phantasien der Europäer gerade recht. Herzlich Willkommen, ihr Deep-State-Fachkräfte!
Mit den zukünftig in der deutschen Regierung befindlichen Alt-Parteien wird es ein „Weiter so“ in Richtung Niedergang geben. Ein weiteres Zeichen dafür, dass Deutschland von Masochisten gelenkt wird. Wie man an den Wahlergebnissen sehen kann, befindet sich ein großer Teil der Bevölkerung immer noch im Dauer-Tiefschlaf. Und der wache Rest schaut ohnmächtig zu, wie die Katastrophe weiter ihren Lauf nimmt. Die einzige friedliche Möglichkeit, diesem schadenbringenden Treiben ein Ende zu bereiten, wäre dem Staat den Geldhahn zuzudrehen: Steuerzahlungs-Verweigerung, Einstellung der Zwangsgebühren für den Staats-Propaganda-Funk, Verweigerung der Kammer-Zwangs-Beiträge, doch da landet man im Knast. Da stößt die vielgepriesene Freiheit in „Unseredemokratie“ an ihre Grenzen.
Und dass all die Missstände ja nicht an die breite Öffentlichkeit gelangen, wird fleißig zensiert und zum Denunzieren angeregt, wozu es Menschen braucht, die sich dafür hergeben, und die es aber offensichtlich zu geben scheint. Der Digital Services Act ist nichts weiter, als die Weiterentwicklung des Fernsehens der DDR, oder noch schlimmeres. Jüngst erst wurde eine Telefonseelsorge für diejenigen eingerichtet, die auf dem Pfad des tugendhaft betreuten Denkens vom Weg abgekommen sind. Bereue und Dir wird vergeben!
Bei den vorletzten Wahlen mussten die Bürger einen Maulkorb tragen, bei der jüngsten Bundestagswahl hatten sie diesen bereits in den Kopf implantiert, da fast die Hälfte der Deutschen meint, ihre Meinung nicht mehr frei äußern zu können. Wenn das mal keinen Einfluss auf die Wahlentscheidung hatte.
Man kann recht pessimistisch sein, dass in absehbarer Zeit wieder die Vernunft Einzug in die Köpfe der Verantwortlichen hält, daher ist zu vermuten, dass Europa erst komplett implodieren muss, bevor ein Neuanfang möglich sein wird. Man kann aber auch optimistisch sein, da Deutschland, in der EU der größte Geldgeber, derzeit fleißig daran arbeitet, dass der Karren tiefst möglich in den Dreck gefahren wird. Fein, weg mit dem Brüsseler Bürokratie-Monster und zurück zur Europäischen Wirtschaftsgemeinschaft. Die Sommerzeit, die Gurken-Krümmungs-Verordnung und die Tetra-Pak-Deckel-Ehe würde man wohl kaum vermissen.
Die zahlreichen Universal-Dilettanten und Kriegs-Maulhelden in ganz Europa werden ihren Teil dazu beitragen, den Deppen-Status in der Welt zu manifestieren.
Nicht ganz so rosig wäre es, wenn die US-Deep-State-Migranten auf die Idee kämen, in Europa Fuß fassen zu wollen. Das wäre dann eher ein Neuanfang mit einer E-ID, dem digitalen Bargeld, einem Social-Credit-System, also den feuchten Träumen des WEFs, 15-Minuten-Städten, KI-gesteuerter Mobilität und totaler Versklavung durch 24/7/365-Überwachung. Die Kriminell-Kommissarin, das Röschen in Brüssel, arbeitet auch hier schon emsig wie ein Bienchen. Wenn hinter all dem Trump-Getöse dasselbe steckt, haben wir sowieso verloren.
Europa befindet sich am Scheideweg. Quo vadis?
Die breite Masse fühlt sich in ihrem Weltbild „verunsichert“. Eingeschüchtert von Messer-Fachkräften und Autos, die trotz Fahrer einfach so in Menschenmengen rasen, weil sie es wollen. Ob ein System hinter den Anschlägen steckt, oder nicht, spielt gar keine Rolle. Es passiert. Was, wenn der Staat sagt, jetzt ist Schluss, wir greifen durch. Zum Schutze und zur Sicherheit der Bevölkerung führen wir eine persönliche ID ein, als Abschreckungsmaßnahme, damit ja kein Irrer mehr auch nur auf die Idee kommt, so einen Anschlag verüben zu wollen.
Wollt ihr zu eurem eigenen Schutz die totale Überwachung? „JAAAAAAA!“
Die positiv Gestimmten behaupten zwar, es würden immer mehr Menschen wach werden, doch obwohl die Wecker nun schon seit 5 Jahren ununterbrochen laut klingeln, geht das viel zu langsam. Bis auch Lieschen Müller aus Hinterdeppendorf verstanden hat, dass wir nach allen Regeln der Kunst belogen und betrogen werden, ist es wahrscheinlich schon längst soweit, dass die Falle zugeschnappt ist.
Und dann wird das Geheule groß sein: „Ach hätten wir doch mal…“ Ja, wenn so viele nicht immer noch viel zu bequem, behäbig und träge wären, hätten wir schon längst die Pfeifen in unseren europäischen Parlamenten inklusive des Affen-Zirkus in Brüssel in die Wüste geschickt.
Ja, wir brauchen eine Revolution, aber eine geistige! Wie bekommen wir die Denkvergiftung durch jahrzehntelanges Starren auf die Inhalte der öffentlich-rechtlichen Anstalt für Propaganda und Volksverblödung als Gehirnwaschanlage aus den Köpfen der Leute wieder heraus?
Lieber wartet man auf den Erlöser, der es schon richten wird. Ich habe ja schließlich gewählt, mehr kann ich nicht tun. Nein, der kommt nicht. Der Fritzefanzler ist es leider auch nicht. Der wechselt seine Meinung schneller, als man ein Paar Socken an- und ausgezogen hat. Da nutzen auch seine markig akzentuierten Sprechabsonderungen nichts. Schon jetzt muss man sein Bild umdrehen, damit die Mundwinkel einmal nach oben zeigen. Warum ist er traurig? Geht es dem Sauerländer nicht schnell genug, den Rest von Deutschland in Essig einzulegen, damit dieses Land vollkommen in ein trefflich schmeckendes Glas Gewürzgurken verwandelt wird?
Es wäre an uns, uns unserer Kraft als Souverän bewusst zu werden und die Schritte einzuleiten, die nötig sind, um ein friedliches und einträgliches miteinander der Nationen zu leben. Die Menschen wollen keinen Krieg, es sind immer die Staaten. In Rumänien, in Bulgarien sind die Menschen massenweise auf der Straße und drücken ihren Protest aus. In Deutschland geht das nicht. Man hat ja noch die Kartoffeln auf dem Herd und kann solange nicht weg. Es sei denn, man kann ein paar Euro dazuverdienen, das ist dann was anderes. Und endlich ist dann auch noch einmal was im Leben der enkellosen Großmutter los.
Krieg ist nur die Durchsetzung von Politik mit anderen Mitteln. Es ging und geht nie um Menschenleben, sondern um das erbarmungslose Durchsetzen von staatlichen Interessen, die gefälligst im schlimmsten Fall vom dämlichen Volk als Kanonenfutter umzusetzen sind.
Nach den Impfverweigerern kommen vielleicht bald die Kriegsdienstverweigerer in den Fokus. Ich soll mein Leben für ein Land auf’s Spiel setzen, das einen Bockmist nach dem anderen baut? Bin ich lebensmüde?
Und obendrein zahlt der brave Bürger auch noch die Zeche, mit seinem sauer verdienten Geld durch legalisierten Steuerraub. Jeder würde wohl gerne Steuern zahlen, wenn das Geld sinnvoll verwendet würde. Ein Hochrüsten gehört ganz sicher nicht dazu. Geschickteres Ausbeuten von Staatsseite geht nicht, und dümmer nicht von Seiten der Bevölkerung, die sich das gefallen lässt.
Die Demokratie-Simulation hat bislang recht gut funktioniert. Es bleibt zu hoffen, dass es ein guter Wind ist, der da von Westen über den Atlantik nach Europa weht und diese ganzen verklebten Gehirne einmal so richtig durchbläst. Die Ereignisse überschlagen sich derzeit, wer weiß?
-

@ 97c70a44:ad98e322
2025-03-05 18:09:05
So you've decided to join nostr! Some wide-eyed fanatic has convinced you that the "sun shines every day on the birds and the bees and the cigarette trees" in a magical land of decentralized, censorship-resistant freedom of speech - and it's waiting just over the next hill.
But your experience has not been all you hoped. Before you've even had a chance to upload your AI-generated cyberpunk avatar or make up exploit codenames for your pseudonym's bio, you've been confronted with a new concept that has left you completely nonplussed.
It doesn't help that this new idea might be called by any number of strange names. You may have been asked to "paste your nsec", "generate a private key", "enter your seed words", "connect with a bunker", "sign in with extension", or even "generate entropy". Sorry about that.
All these terms are really referring to one concept under many different names: that of "cryptographic identity".
Now, you may have noticed that I just introduced yet another new term which explains exactly nothing. You're absolutely correct. And now I'm going to proceed to ignore your complaints and talk about something completely different. But bear with me, because the juice is worth the squeeze.
# Identity
What is identity? There are many philosophical, political, or technical answers to this question, but for our purposes it's probably best to think of it this way:
> Identity is the essence of a thing. Identity separates one thing from all others, and is itself indivisible.
This definition has three parts:
- Identity is "essential": a thing can change, but its identity cannot. I might re-paint my house, replace its components, sell it, or even burn it down, but its identity as something that can be referred to - "this house" - is durable, even outside the boundaries of its own physical existence.
- Identity is a unit: you can't break an identity into multiple parts. A thing might be _composed_ of multiple parts, but that's only incidental to the identity of a thing, which is a _concept_, not a material thing.
- Identity is distinct: identity is what separates one thing from all others - the concept of an apple can't be mixed with that of an orange; the two ideas are distinct. In the same way, a single concrete apple is distinct in identity from another - even if the component parts of the apple decompose into compost used to grow more apples.
Identity is not a physical thing, but a metaphysical thing. Or, in simpler terms, identity is a "concept".
I (or someone more qualified) could at this point launch into a Scholastic tangent on what "is" is, but that is, fortunately, not necessary here. The kind of identities I want to focus on here are not our _actual_ identities as people, but entirely _fictional_ identities that we use to extend our agency into the digital world.
Think of it this way - your bank login does not represent _you_ as a complete person. It only represents the _access granted to you_ by the bank. This access is in fact an _entirely new identity_ that has been associated with you, and is limited in what it's useful for.
Other examples of fictional identities include:
- The country you live in
- Your social media persona
- Your mortgage
- Geographical coordinates
- A moment in time
- A chess piece
Some of these identites are inert, for example points in space and time. Other identies have agency and so are able to act in the world - even as fictional concepts. In order to do this, they must "authenticate" themselves (which means "to prove they are real"), and act within a system of established rules.
For example, your D&D character exists only within the collective fiction of your D&D group, and can do anything the rules say. Its identity is authenticated simply by your claim as a member of the group that your character in fact exists. Similarly, a lawyer must prove they are a member of the Bar Association before they are allowed to practice law within that collective fiction.
"Cryptographic identity" is simply another way of authenticating a fictional identity within a given system. As we'll see, it has some interesting attributes that set it apart from things like a library card or your latitude and longitude. Before we get there though, let's look in more detail at how identities are authenticated.
# Certificates
Merriam-Webster defines the verb "certify" as meaning "to attest authoritatively". A "certificate" is just a fancy way of saying "because I said so". Certificates are issued by a "certificate authority", someone who has the authority to "say so". Examples include your boss, your mom, or the Pope.
This method of authentication is how almost every institution authenticates the people who associate with it. Colleges issue student ID cards, governments issue passports, and websites allow you to "register an account".
In every case mentioned above, the "authority" creates a closed system in which a document (aka a "certificate") is issued which serves as a claim to a given identity. When someone wants to access some privileged service, location, or information, they present their certificate. The authority then validates it and grants or denies access. In the case of an international airport, the certificate is a little book printed with fancy inks. In the case of a login page, the certificate is a username and password combination.
This pattern for authentication is ubiquitous, and has some very important implications.
First of all, certified authentication implies that the issuer of the certificate has the right to _exclusive control_ of any identity it issues. This identity can be revoked at any time, or its permissions may change. Your social credit score may drop arbitrarily, or money might disappear from your account. When dealing with certificate authorities, you have no inherent rights.
Second, certified authentication depends on the certificate authority continuing to exist. If you store your stuff at a storage facility but the company running it goes out of business, your stuff might disappear along with it.
Usually, authentication via certificate authority works pretty well, since an appeal can always be made to a higher authority (nature, God, the government, etc). Authorities also can't generally dictate their terms with impunity without losing their customers, alienating their constituents, or provoking revolt. But it's also true that certification by authority creates an incentive structure that frequently leads to abuse - arbitrary deplatforming is increasingly common, and the bigger the certificate authority, the less recourse the certificate holder (or "subject") has.
Certificates also put the issuer in a position to intermediate relationships that wouldn't otherwise be subject to their authority. This might take the form of selling user attention to advertisers, taking a cut of financial transactions, or selling surveillance data to third parties.
Proliferation of certificate authorities is not a solution to these problems. Websites and apps frequently often offer multiple "social sign-in" options, allowing their users to choose which certificate authority to appeal to. But this only piles more value into the social platform that issues the certificate - not only can Google shut down your email inbox, they can revoke your ability to log in to every website you used their identity provider to get into.
In every case, certificate issuance results in an asymmetrical power dynamic, where the issuer is able to exert significant control over the certificate holder, even in areas unrelated to the original pretext for the relationship between parties.
# Self-Certification
But what if we could reverse this power dynamic? What if individuals could issue their own certificates and force institutions to accept them?

Ron Swanson's counterexample notwithstanding, there's a reason I can't simply write myself a parking permit and slip it under the windshield wiper. Questions about voluntary submission to legitimate authorities aside, the fact is that we don't have the power to act without impunity - just like any other certificate authority, we have to prove our claims either by the exercise of raw power or by appeal to a higher authority.
So the question becomes: which higher authority can we appeal to in order to issue our own certificates within a given system of identity?
The obvious answer here is to go straight to the top and ask God himself to back our claim to self-sovereignty. However, that's not how he normally works - there's a reason they call direct acts of God "miracles". In fact, Romans 13:1 explicitly says that "the authorities that exist have been appointed by God". God has structured the universe in such a way that we must appeal to the deputies he has put in place to govern various parts of the world.
Another tempting appeal might be to nature - i.e. the material world. This is the realm in which we most frequently have the experience of "self-authenticating" identities. For example, a gold coin can be authenticated by biting it or by burning it with acid. If it quacks like a duck, walks like a duck, and looks like a duck, then it probably is a duck.
In most cases however, the ability to authenticate using physical claims depends on physical access, and so appeals to physical reality have major limitations when it comes to the digital world. Captchas, selfies and other similar tricks are often used to bridge the physical world into the digital, but these are increasingly easy to forge, and hard to verify.
There are exceptions to this rule - an example of self-certification that makes its appeal to the physical world is that of a signature. Signatures are hard to forge - an incredible amount of data is encoded in physical signatures, from strength, to illnesses, to upbringing, to [personality](https://en.wikipedia.org/wiki/Graphology). These can even be scanned and used within the digital world as well. Even today, most contracts are sealed with some simulacrum of a physical signature. Of course, this custom is quickly becoming a mere historical curiosity, since the very act of digitizing a signature makes it trivially forgeable.
So: transcendent reality is too remote to subtantiate our claims, and the material world is too limited to work within the world of information. There is another aspect of reality remaining that we might appeal to: information itself.
Physical signatures authenticate physical identities by encoding unique physical data into an easily recognizable artifact. To transpose this idea to the realm of information, a "digital signature" might authenticate "digital identities" by encoding unique "digital data" into an easily recognizable artifact.
Unfortunately, in the digital world we have the additional challenge that the artifact itself can be copied, undermining any claim to legitimacy. We need something that can be easily verified _and unforgeable_.
# Digital Signatures
In fact such a thing does exist, but calling it a "digital signature" obscures more than it reveals. We might just as well call the thing we're looking for a "digital fingerprint", or a "digital electroencephalogram". Just keep that in mind as we work our way towards defining the term - we are not looking for something _looks like a physical signature_, but for something that _does the same thing as_ a physical signature, in that it allows us to issue ourselves a credential that must be accepted by others by encoding privileged information into a recognizable, unforgeable artifact.
With that, let's get into the weeds.
An important idea in computer science is that of a "function". A function is a sort of information machine that converts data from one form to another. One example is the idea of "incrementing" a number. If you increment 1, you get 2. If you increment 2, you get 3. Incrementing can be reversed, by creating a complementary function that instead subtracts 1 from a number.
A "one-way function" is a function that can't be reversed. A good example of a one-way function is integer rounding. If you round a number and get `5`, what number did you begin with? It's impossible to know - 5.1, 4.81, 5.332794, in fact an infinite number of numbers can be rounded to the number `5`. These numbers can also be infinitely long - for example rounding PI to the nearest integer results in the number `3`.
A real-life example of a useful one-way function is `sha256`. This function is a member of a family of one-way functions called "hash functions". You can feed as much data as you like into `sha256`, and you will always get 256 bits of information out. Hash functions are especially useful because collisions between outputs are very rare - even if you change a single bit in a huge pile of data, you're almost certainly going to get a different output.
Taking this a step further, there is a whole family of cryptographic one-way "trapdoor" functions that act similarly to hash functions, but which maintain a specific mathematical relationship between the input and the output which allows the input/output pair to be used in a variety of useful applications. For example, in Elliptic Curve Cryptography, scalar multiplication on an elliptic curve is used to derive the output.
"Ok", you say, "that's all completely clear and lucidly explained" (thank you). "But what goes _into_ the function?" You might expect that because of our analogy to physical signatures we would have to gather an incredible amount of digital information to cram into our cryptographic trapdoor function, mashing together bank statements, a record of our heartbeat, brain waves and cellular respiration. Well, we _could_ do it that way (maybe), but there's actually a _much_ simpler solution.
Let's play a quick game. What number am I thinking of? Wrong, it's 82,749,283,929,834. Good guess though.
The reason we use signatures to authenticate our identity in the physical world is not because they're backed by a lot of implicit physical information, but because they're hard to forge and easy to validate. Even so, there is a lot of variation in a single person's signature, even from one moment to the next.
Trapdoor functions solve the validation problem - it's trivially simple to compare one 256-bit number to another. And randomness solves the problem of forgeability.
Now, randomness (A.K.A. "entropy") is actually kind of hard to generate. Random numbers that don't have enough "noise" in them are known as "pseudo-random numbers", and are weirdly easy to guess. This is why Cloudflare uses a video stream of their [giant wall of lava lamps](https://blog.cloudflare.com/randomness-101-lavarand-in-production/) to feed the random number generator that powers their CDN. For our purposes though, we can just imagine that our random numbers come from rolling a bunch of dice.
To recap, we can get a digital equivalent of a physical signature (or fingerprint, etc) by 1. coming up with a random number, and 2. feeding it into our chosen trapdoor function. The random number is called the "private" part. The output of the trapdoor function is called the "public" part. These two halves are often called "keys", hence the terms "public key" and "private key".
And now we come full circle - remember about 37 years ago when I introduced the term "cryptographic identity"? Well, we've finally arrived at the point where I explain what that actually is.
A "cryptographic identity" is _identified_ by a public key, and _authenticated_ by the ability to prove that you know the private key.
Notice that I didn't say "authenticated by the private key". If you had to reveal the private key in order to prove you know it, you could only authenticate a public key once without losing exclusive control of the key. But cryptographic identities can be authenticated any number of times because the certification is an _algorithm_ that only someone who knows the private key can execute.
This is the super power that trapdoor functions have that hash functions don't. Within certain cryptosystems, it is possible to mix additional data with your private key to get yet another number in such a way that someone else who only knows the public key can _prove_ that you know the private key.
For example, if my secret number is `12`, and someone tells me the number `37`, I can "combine" the two by adding them together and returning the number `49`. This "proves" that my secret number is `12`. Of course, addition is not a trapdoor function, so it's trivially easy to reverse, which is why cryptography is its own field of knowledge.
# What's it for?
If I haven't completely lost you yet, you might be wondering why this matters. Who cares if I can prove that I made up a random number?
To answer this, let's consider a simple example: that of public social media posts.
Most social media platforms function by issuing credentials and verifying them based on their internal database. When you log in to your Twitter (ok, fine, X) account, you provide X with a phone number (or email) and password. X compares these records to the ones stored in the database when you created your account, and if they match they let you "log in" by issuing yet another credential, called a "session key".
Next, when you "say" something on X, you pass along your session key and your tweet to X's servers. They check that the session key is legit, and if it is they associate your tweet with your account's identity. Later, when someone wants to see the tweet, X vouches for the fact that you created it by saying "trust me" and displaying your name next to the tweet.
In other words, X creates and controls your identity, but they let you use it as long as you can prove that you know the secret that you agreed on when you registered (by giving it to them every time).
Now pretend that X gets bought by someone _even more evil_ than Elon Musk (if such a thing can be imagined). The new owner now has the ability to control _your_ identity, potentially making it say things that you didn't actually say. Someone could be completely banned from the platform, but their account could be made to continue saying whatever the owner of the platform wanted.
In reality, such a breach of trust would quickly result in a complete loss of credibility for the platform, which is why this kind of thing doesn't happen (at least, not that we know of).
But there are other ways of exploiting this system, most notably by censoring speech. As often happens, platforms are able to confiscate user identities, leaving the tenant no recourse except to appeal to the platform itself (or the government, but that doesn't seem to happen for some reason - probably due to some legalese in social platforms' terms of use). The user has to start completely from scratch, either on the same platform or another.
Now suppose that when you signed up for X instead of simply telling X your password you made up a random number and provided a cryptographic proof to X along with your public key. When you're ready to tweet (there's no need to issue a session key, or even to store your public key in their database) you would again prove your ownership of that key with a new piece of data. X could then publish that tweet or not, along with the same proof you provided that it really came from you.
What X _can't_ do in this system is pretend you said something you didn't, because they _don't know your private key_.
X also wouldn't be able to deplatform you as effectively either. While they could choose to ban you from their website and refuse to serve your tweets, they don't control your identity. There's nothing they can do to prevent you from re-using it on another platform. Plus, if the system was set up in such a way that other users followed your key instead of an ID made up by X, you could switch platforms and _keep your followers_. In the same way, it would also be possible to keep a copy of all your tweets in your own database, since their authenticity is determined by _your_ digital signature, not X's "because I say so".
This new power is not just limited to social media either. Here are some other examples of ways that self-issued cryptographic identites transform the power dynamic inherent in digital platforms:
- Banks sometimes freeze accounts or confiscate funds. If your money was stored in a system based on self-issued cryptographic keys rather than custodians, banks would not be able to keep you from accessing or moving your funds. This system exists, and it's called [bitcoin](https://bitcoin.rocks/).
- Identity theft happens when your identifying information is stolen and used to take out a loan in your name, and without your consent. The reason this is so common is because your credentials are not cryptographic - your name, address, and social security number can only be authenticated by being shared, and they are shared so often and with so many counterparties that they frequently end up in data breaches. If credit checks were authenticated by self-issued cryptographic keys, identity theft would cease to exist (unless your private key itself got stolen).
- Cryptographic keys allow credential issuers to protect their subjects' privacy better too. Instead of showing your ID (including your home address, birth date, height, weight, etc), the DMV could sign a message asserting that the holder of a given public key indeed over 21. The liquor store could then validate that claim, and your ownership of the named key, without knowing anything more about you. [Zero-knowledge](https://en.wikipedia.org/wiki/Non-interactive_zero-knowledge_proof) proofs take this a step further.
In each of these cases, the interests of the property owner, loan seeker, or customer are elevated over the interests of those who might seek to control their assets, exploit their hard work, or surveil their activity. Just as with personal privacy, freedom of speech, and Second Amendment rights the individual case is rarely decisive, but in the aggregate realigned incentives can tip the scale in favor of freedom.
# Objections
Now, there are some drawbacks to digital signatures. Systems that rely on digital signatures are frequently less forgiving of errors than their custodial counterparts, and many of their strengths have corresponding weaknesses. Part of this is because people haven't yet developed an intuition for how to use cryptographic identities, and the tools for managing them are still being designed. Other aspects can be mitigated through judicious use of keys fit to the problems they are being used to solve.
Below I'll articulate some of these concerns, and explore ways in which they might be mitigated over time.
## Key Storage
Keeping secrets is hard. "A lie can travel halfway around the world before the truth can get its boots on", and the same goes for gossip. Key storage has become increasingly important as more of our lives move online, to the extent that password managers have become almost a requirement for keeping track of our digital lives. But even with good password management, credentials frequently end up for sale on the dark web as a consequence of poorly secured infrastructure.
Apart from the fact that all of this is an argument _for_ cryptographic identities (since keys are shared with far fewer parties), it's also true that the danger of losing a cryptographic key is severe, especially if that key is used in multiple places. Instead of hackers stealing your Facebook password, they might end up with access to all your other social media accounts too!
Keys should be treated with the utmost care. Using password managers is a good start, but very valuable keys should be stored even more securely - for example in a [hardware signing device](https://nostrsigningdevice.com/). This is a hassle, and something additional to learn, but is an indispensable part of taking advantage of the benefits associated with cryptographic identity.
There are ways to lessen the impact of lost or stolen secrets, however. Lots of different techniques exist for structuring key systems in such a way that keys can be protected, invalidated, or limited. Here are a few:
- [Hierarchical Deterministic Keys](https://www.ietf.org/archive/id/draft-dijkhuis-cfrg-hdkeys-02.html) allow for the creation of a single root key from which multiple child keys can be generated. These keys are hard to link to the parent, which provides additional privacy, but this link can also be proven when necessary. One limitation is that the identity system has to be designed with HD keys in mind.
- [Key Rotation](https://crypto.stackexchange.com/questions/41796/whats-the-purpose-of-key-rotation) allows keys to become expendable. Additional credentials might be attached to a key, allowing the holder to prove they have the right to rotate the key. Social attestations can help with the process as well if the key is embedded in a web of trust.
- Remote Signing is a technique for storing a key on one device, but using it on another. This might take the form of signing using a hardware wallet and transferring an SD card to your computer for broadcasting, or using a mobile app like [Amber](https://github.com/greenart7c3/Amber) to manage sessions with different applications.
- [Key](https://github.com/coracle-social/promenade/tree/master) [sharding](https://www.frostr.org/) takes this to another level by breaking a single key into multiple pieces and storing them separately. A coordinator can then be used to collaboratively sign messages without sharing key material. This dramatically reduces the ability of an attacker to steal a complete key.
## Multi-Factor Authentication
One method for helping users secure their accounts that is becoming increasingly common is "multi-factor authentication". Instead of just providing your email and password, platforms send a one-time use code to your phone number or email, or use "time-based one time passwords" which are stored in a password manager or on a hardware device.
Again, MFA is a solution to a problem inherent in account-based authentication which would not be nearly so prevalent in a cryptographic identity system. Still, theft of keys does happen, and so MFA would be an important improvement - if not for an extra layer of authentication, then as a basis for key rotation.
In a sense, MFA is already being researched - key shards is one way of creating multiple credentials from a single key. However, this doesn't address the issue of key rotation, especially when an identity is tied to the public key that corresponds to a given private key. There are two possible solutions to this problem:
- Introduce a naming system. This would allow identities to use a durable name, assigning it to different keys over time. The downside is that this would require the introduction of either centralized naming authorities (back to the old model), or a blockchain in order to solve [Zooko's trilemma](https://en.wikipedia.org/wiki/Zooko%27s_triangle).
- Establish a chain of keys. This would require a given key to name a successor key in advance and self-invalidate, or some other process like social recovery to invalidate an old key and assign the identity to a new one. This also would significantly increase the complexity of validating messages and associating them with a given identity.
Both solutions are workable, but introduce a lot of complexity that could cause more trouble than it's worth, depending on the identity system we're talking about.
## Surveillance
One of the nice qualities that systems based on cryptographic identities have is that digitally signed data can be passed through any number of untrusted systems and emerge intact. This ability to resist tampering makes it possible to broadcast signed data more widely than would otherwise be the case in a system that relies on a custodian to authenticate information.
The downside of this is that more untrusted systems have access to data. And if information is broadcast publicly, anyone can get access to it.
This problem is compounded by re-use of cryptographic identities across multiple contexts. A benefit of self-issued credentials is that it becomes possible to bring everything attached to your identity with you, including social context and attached credentials. This is convenient and can be quite powerful, but it also means that more context is attached to your activity, making it easier to infer information about you for advertising or surveillance purposes. This is dangerously close to the dystopian ideal of a "Digital ID".
The best way to deal with this risk is to consider identity re-use an option to be used when desirable, but to default to creating a new key for every identity you create. This is no worse than the status quo, and it makes room for the ability to link identities when desired.
Another possible approach to this problem is to avoid broadcasting signed data when possible. This could be done by obscuring your cryptographic identity when data is served from a database, or by encrypting your signed data in order to selectively share it with named counterparties.
Still, this is a real risk, and should be kept in mind when designing and using systems based on cryptographic identity. If you'd like to read more about this, please see [this blog post](https://habla.news/u/hodlbod@coracle.social/1687802006398).
# Making Keys Usable
You might be tempted to look at that list of trade-offs and get the sense that cryptographic identity is not for mere mortals. Key management is hard, and footguns abound - but there is a way forward. With [nostr](https://nostr.com/), some new things are happening in the world of key management that have never really happened before.
Plenty of work over the last 30 years has gone into making key management tractable, but none have really been widely adopted. The reason for this is simple: network effect.
Many of these older key systems only applied the thinnest veneer of humanity over keys. But an identity is much richer than a mere label. Having a real name, social connections, and a corpus of work to attach to a key creates a system of keys that _humans care about_.
By bootstrapping key management within a social context, nostr ensures that the payoff of key management is worth the learning curve. Not only is social engagement a strong incentive to get off the ground, people already on the network are eager to help you get past any roadblocks you might face.
So if I could offer an action item: give nostr a try today. Whether you're in it for the people and their values, or you just want to experiment with cryptographic identity, nostr is a great place to start. For a quick introduction and to securely generate keys, visit [njump.me](https://njump.me/).
Thanks for taking the time to read this post. I hope it's been helpful, and I can't wait to see you on nostr!
 @ 6b0a60cf:b952e7d4
2025-03-06 02:45:45とあるSNSで海外の相互さん(以降、Aさんと呼ぶ)からDMで相談されたことがあって、思ったことをつらつらと書いてみる。 非公開の場での相談なので多少ぼかしを入れるけど。 ## 事の経緯 発端は、Aさんの友人が作品に日本人作者の素材を使用しようとしていて、その利用規約を翻訳して読んだらうまく翻訳されなくて理解が正しいのかわからない、なので間違いが無いか確認してほしい、という相談だった。 あー、確かに日本語特有の回りくどい表現があるねー、と思いながらバシッと簡潔に意訳してお伝えしたところ、スッキリ理解していただけたらしく一件落着となった。 ## 独自ライセンス文化 しかしまあ、創作界隈における作品・素材の利用規約というものは総じて長くて細かい。 ジャンルによるのかもしれないけれど。 自分は絵や音を創ることは無いがプログラムのコードを書く趣味はあるのでプログラム向けのライセンスを利用している。MITとかGPLとかいうやつ。 創作向けであればCCライセンスが適しているだろう。しかしこれがなかなか広まらない。 杓子定規のライセンスでは表しきれないような特別な希望があるのだろう。 そして独自ライセンスが跋扈することとなる。 ## NO MORE 映画泥棒 特に気になるのが、「泥棒をしてはいけません」レベルの注意書きが散見されるのだ。 わざわざライセンスに書くことではない。あなたが警告するまでもなく、違法な行為は処罰される。 でも、たぶん効果があるからこういうのが広まるのだろう。 「泥棒してはいけないって書いてないから泥棒しました」というレベルの利用者が存在するのだろう。 そういう人は書いてあっても読んでないか、理屈をこねて泥棒するんだろうと思うけれども。 ## その術はオレに効く で、そういう警告文が魔除けの札のごとくびっしり貼られていると、こちらにやましい心が無くても、ちょっとこの素材は利用しないほうがよさそうだな……と思って引き返してしまうことがある。 SNSで可愛い絵を見て、作者さんをフォローしようと思ったら「無断転載禁止」みたいなのがプロフにずらずら書いてあって「おっと……」みたいに引き返すことがあるが、それに似ている。 きっと過去によくない体験をしてしまって、そのようにプロフに書くことでそれが改善するという実体験があって、そうなっているのだろうと推測している。 ## 異文化の壁を超えて 冒頭で話したAさんはきわめて紳士的な方であり、日本文化に対してもよく理解しようと努めてくれるので、話が通じやすくて助かったし、件の素材についても臆すること無く使用することになりそうだった。 ただ魔除けの札が効かないような魑魅魍魎にはいくら札を貼っても意味がないし、実際の悪魔祓いの効果と善良な利用者をも祓ってしまう機会損失(?)を比べて合理的なのだろうか、と考えたりしたのでした。オチは無い。 ## ライセンス この文章は CC0 1.0 でライセンスします。 Nostrイベントとして公開する以上はNIPsに従う範囲内で自由に利用されることを望みます。 NIPsに違反したご利用は他のクライアントの利用者にご迷惑になるのでご遠慮いただくことを希望します。[^1] [^1]: Damusを使ってリポストする、等の行為が該当します
@ 6b0a60cf:b952e7d4
2025-03-06 02:45:45とあるSNSで海外の相互さん(以降、Aさんと呼ぶ)からDMで相談されたことがあって、思ったことをつらつらと書いてみる。 非公開の場での相談なので多少ぼかしを入れるけど。 ## 事の経緯 発端は、Aさんの友人が作品に日本人作者の素材を使用しようとしていて、その利用規約を翻訳して読んだらうまく翻訳されなくて理解が正しいのかわからない、なので間違いが無いか確認してほしい、という相談だった。 あー、確かに日本語特有の回りくどい表現があるねー、と思いながらバシッと簡潔に意訳してお伝えしたところ、スッキリ理解していただけたらしく一件落着となった。 ## 独自ライセンス文化 しかしまあ、創作界隈における作品・素材の利用規約というものは総じて長くて細かい。 ジャンルによるのかもしれないけれど。 自分は絵や音を創ることは無いがプログラムのコードを書く趣味はあるのでプログラム向けのライセンスを利用している。MITとかGPLとかいうやつ。 創作向けであればCCライセンスが適しているだろう。しかしこれがなかなか広まらない。 杓子定規のライセンスでは表しきれないような特別な希望があるのだろう。 そして独自ライセンスが跋扈することとなる。 ## NO MORE 映画泥棒 特に気になるのが、「泥棒をしてはいけません」レベルの注意書きが散見されるのだ。 わざわざライセンスに書くことではない。あなたが警告するまでもなく、違法な行為は処罰される。 でも、たぶん効果があるからこういうのが広まるのだろう。 「泥棒してはいけないって書いてないから泥棒しました」というレベルの利用者が存在するのだろう。 そういう人は書いてあっても読んでないか、理屈をこねて泥棒するんだろうと思うけれども。 ## その術はオレに効く で、そういう警告文が魔除けの札のごとくびっしり貼られていると、こちらにやましい心が無くても、ちょっとこの素材は利用しないほうがよさそうだな……と思って引き返してしまうことがある。 SNSで可愛い絵を見て、作者さんをフォローしようと思ったら「無断転載禁止」みたいなのがプロフにずらずら書いてあって「おっと……」みたいに引き返すことがあるが、それに似ている。 きっと過去によくない体験をしてしまって、そのようにプロフに書くことでそれが改善するという実体験があって、そうなっているのだろうと推測している。 ## 異文化の壁を超えて 冒頭で話したAさんはきわめて紳士的な方であり、日本文化に対してもよく理解しようと努めてくれるので、話が通じやすくて助かったし、件の素材についても臆すること無く使用することになりそうだった。 ただ魔除けの札が効かないような魑魅魍魎にはいくら札を貼っても意味がないし、実際の悪魔祓いの効果と善良な利用者をも祓ってしまう機会損失(?)を比べて合理的なのだろうか、と考えたりしたのでした。オチは無い。 ## ライセンス この文章は CC0 1.0 でライセンスします。 Nostrイベントとして公開する以上はNIPsに従う範囲内で自由に利用されることを望みます。 NIPsに違反したご利用は他のクライアントの利用者にご迷惑になるのでご遠慮いただくことを希望します。[^1] [^1]: Damusを使ってリポストする、等の行為が該当します @ a63655ce:05240c71
2025-03-06 00:48:46looks really clean. `window.nostr` asked for the key multiple times for some reason
@ a63655ce:05240c71
2025-03-06 00:48:46looks really clean. `window.nostr` asked for the key multiple times for some reason @ 6e0ea5d6:0327f353
2025-03-06 00:18:09Ascolta, amico mio... There come moments when a grown man looks in the mirror and fails to recognize himself. Naturally, when this happens, there is nothing more fitting than lighting a cigarette, pouring a glass of fine wine, and toasting to oneself—the birth of a new man, forged in the womb of a harsh and sobering reality. One cannot scatter thorns along a path walked barefoot, nor allow the tongue to speak what the mind may later pay for—but this, we learn only through years of suffering. Only now do I realize that, among all the teachers I have had, experience was the harshest of them all, for it first administered the test and only afterward taught me the lesson. In peaceful moments, one can reflect more easily on the world around him. Imagine, then, the depths of reflection that can be reached in a state of true inner tranquility. If you have never gazed upon the horizon, taken in all the fortune before your eyes, and declared to yourself, "I will own all of this!", then you have never possessed true ambition. However, blind ambition will leave you waking up hungry for wealth and power but going to sleep with an empty soul. Walk always with honor, pride, and loyalty—let these principles never depart from you nor fail to steady your steps. In your battles, do not wish for your enemies to be handed to you on their knees; instead, seek to gain the strength and ruthlessness to bring them down while they stand. Your greatest dilemma is the eternal paradox in the life of a businessman within the sacred Sicilian organization: how to acquire power and wealth without placing both feet in hell? Be careful not to surrender to arrogance. The man who shouts his virtues to the wind will, when he falls, hear only the echo of his own pride. Let your greatest legacy be to live in a way that does not shame your mother and makes your father proud. Thank you for reading, my friend! If this message resonated with you, consider leaving your "🥃" as a token of appreciation. A toast to our family!
@ 6e0ea5d6:0327f353
2025-03-06 00:18:09Ascolta, amico mio... There come moments when a grown man looks in the mirror and fails to recognize himself. Naturally, when this happens, there is nothing more fitting than lighting a cigarette, pouring a glass of fine wine, and toasting to oneself—the birth of a new man, forged in the womb of a harsh and sobering reality. One cannot scatter thorns along a path walked barefoot, nor allow the tongue to speak what the mind may later pay for—but this, we learn only through years of suffering. Only now do I realize that, among all the teachers I have had, experience was the harshest of them all, for it first administered the test and only afterward taught me the lesson. In peaceful moments, one can reflect more easily on the world around him. Imagine, then, the depths of reflection that can be reached in a state of true inner tranquility. If you have never gazed upon the horizon, taken in all the fortune before your eyes, and declared to yourself, "I will own all of this!", then you have never possessed true ambition. However, blind ambition will leave you waking up hungry for wealth and power but going to sleep with an empty soul. Walk always with honor, pride, and loyalty—let these principles never depart from you nor fail to steady your steps. In your battles, do not wish for your enemies to be handed to you on their knees; instead, seek to gain the strength and ruthlessness to bring them down while they stand. Your greatest dilemma is the eternal paradox in the life of a businessman within the sacred Sicilian organization: how to acquire power and wealth without placing both feet in hell? Be careful not to surrender to arrogance. The man who shouts his virtues to the wind will, when he falls, hear only the echo of his own pride. Let your greatest legacy be to live in a way that does not shame your mother and makes your father proud. Thank you for reading, my friend! If this message resonated with you, consider leaving your "🥃" as a token of appreciation. A toast to our family! @ b8851a06:9b120ba1
2025-03-05 23:03:00The U.S. isn't just blocking Gaza's reconstruction—it's ensuring Palestinians have no future there. This week, Washington rejected the Arab League's $53 billion plan to rebuild Gaza. Not because it was unworkable, but because it was unwanted. #Gaza, they say, is "uninhabitable." The solution? Depopulation, disguised as development. ## The Riviera Plan: Rebuilding Without Its People National Security Council spokesman Brian Hughes put it bluntly: "Gaza is uninhabitable." This isn't a call for humanitarian intervention. It's a pretext for forced displacement. Trump's vision transforms Gaza into a "Riviera of the #MiddleEast"—after its population has been relocated. Officials have explicitly stated Palestinians "would not be allowed to return" once reconstruction begins. This isn't rebuilding; it's replacement. ## Regional Consensus Rejected The Arab League's proposal represented rare unity among regional powers. It offered a detailed roadmap for reconstruction while allowing #Palestinians to remain in their homeland. By dismissing this plan, Washington sent a clear message: **Palestinian self-determination remains subordinate to Western geopolitical interests.** This isn't new. For over a century, Western capitals have determined Palestinian futures while treating their voices as irrelevant. ## The Fiat War Machine Connection War and fiat money go hand in hand. Governments don't fund wars through taxes anymore—it's all printed money. Inflation steals from the public silently, financing endless destruction abroad while citizens struggle at home. As Saifedean Ammous writes in The Fiat Standard: nostr:npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak "Central banks are essentially war machines, enabling governments to finance endless conflicts through inflation rather than direct taxation." This system divorces "economic reward from economic productivity, and instead bases it on political allegiance." The result? A world "perpetually lurching from one crisis to another, with devastating consequences for humanity." ## Ukraine Parallels: When Support Is Conditional The U.S. has now halted military aid to #Ukraine, suspending over $1 billion in arms. #Europe scrambles to fill the gap, suddenly realizing the conditional nature of American protection. Both conflicts reveal the same truth: **geopolitical support is increasingly transactional rather than values-based.** As Henry Kissinger observed: "It may be dangerous to be America's enemy, but being America's friend can be fatal." ## The Cycle Continues The U.S. model is simple: fund destruction, control reconstruction, keep the cycle going. Fiat money makes it possible. Indifference makes it permanent. And yes #Bitcoin can fix it. But will it? How long before people wake up #nostr? How long before the cycle breaks? "Fiat money is a tool for governments to control their citizens" as Saifedean rightly says—and now, through endless war, to control the world.
@ b8851a06:9b120ba1
2025-03-05 23:03:00The U.S. isn't just blocking Gaza's reconstruction—it's ensuring Palestinians have no future there. This week, Washington rejected the Arab League's $53 billion plan to rebuild Gaza. Not because it was unworkable, but because it was unwanted. #Gaza, they say, is "uninhabitable." The solution? Depopulation, disguised as development. ## The Riviera Plan: Rebuilding Without Its People National Security Council spokesman Brian Hughes put it bluntly: "Gaza is uninhabitable." This isn't a call for humanitarian intervention. It's a pretext for forced displacement. Trump's vision transforms Gaza into a "Riviera of the #MiddleEast"—after its population has been relocated. Officials have explicitly stated Palestinians "would not be allowed to return" once reconstruction begins. This isn't rebuilding; it's replacement. ## Regional Consensus Rejected The Arab League's proposal represented rare unity among regional powers. It offered a detailed roadmap for reconstruction while allowing #Palestinians to remain in their homeland. By dismissing this plan, Washington sent a clear message: **Palestinian self-determination remains subordinate to Western geopolitical interests.** This isn't new. For over a century, Western capitals have determined Palestinian futures while treating their voices as irrelevant. ## The Fiat War Machine Connection War and fiat money go hand in hand. Governments don't fund wars through taxes anymore—it's all printed money. Inflation steals from the public silently, financing endless destruction abroad while citizens struggle at home. As Saifedean Ammous writes in The Fiat Standard: nostr:npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak "Central banks are essentially war machines, enabling governments to finance endless conflicts through inflation rather than direct taxation." This system divorces "economic reward from economic productivity, and instead bases it on political allegiance." The result? A world "perpetually lurching from one crisis to another, with devastating consequences for humanity." ## Ukraine Parallels: When Support Is Conditional The U.S. has now halted military aid to #Ukraine, suspending over $1 billion in arms. #Europe scrambles to fill the gap, suddenly realizing the conditional nature of American protection. Both conflicts reveal the same truth: **geopolitical support is increasingly transactional rather than values-based.** As Henry Kissinger observed: "It may be dangerous to be America's enemy, but being America's friend can be fatal." ## The Cycle Continues The U.S. model is simple: fund destruction, control reconstruction, keep the cycle going. Fiat money makes it possible. Indifference makes it permanent. And yes #Bitcoin can fix it. But will it? How long before people wake up #nostr? How long before the cycle breaks? "Fiat money is a tool for governments to control their citizens" as Saifedean rightly says—and now, through endless war, to control the world. @ f3873798:24b3f2f3
2025-03-05 23:01:12O café faz parte da rotina de milhões de pessoas, seja para despertar pela manhã, acompanhar uma boa conversa ou até impulsionar a produtividade no trabalho. Mas você já parou para pensar na qualidade do café que consome diariamente? Neste artigo, vamos falar sobre os benefícios do café e as diferenças entre o café extraforte e o café especial. ## ☕ Benefícios do Café no Dia a Dia  O café não é apenas uma bebida saborosa, mas também oferece diversos benefícios para a saúde, como: Aumento da energia e concentração – A cafeína estimula o sistema nervoso central, ajudando na atenção e no foco. Melhora do humor – O consumo moderado de café pode estimular a produção de dopamina, contribuindo para uma sensação de bem-estar. Propriedades antioxidantes – O café é rico em compostos que combatem os radicais livres, ajudando a prevenir o envelhecimento precoce. Auxílio na digestão – Para muitas pessoas, o café funciona como um leve estimulante do sistema digestivo. ## ☕ Café Extraforte vs. Café Especial: Qual a Diferença?  Na prateleira do supermercado ou na cafeteria, há uma grande variedade de cafés. Mas, afinal, qual é a diferença entre o café extraforte e o café especial? ### ☕Café Extraforte Produzido a partir de grãos de qualidade inferior, muitas vezes misturados com impurezas. Possui torra muito escura, o que pode mascarar defeitos do grão. Tem um sabor mais amargo e intenso, muitas vezes com notas queimadas. Pode ser mais ácido e difícil de digerir para algumas pessoas. ### ☕Café Especial Feito com grãos selecionados e de alta qualidade, sem defeitos. A torra é mais equilibrada, preservando os aromas e sabores naturais. Possui notas sensoriais diferenciadas (frutadas, achocolatadas, florais, etc.). Mais suave e menos ácido, proporcionando uma experiência mais agradável ao paladar. ## ☕ Qual Escolher para o Dia a Dia?  Se você busca praticidade e um café forte, o extraforte pode ser uma opção. No entanto, se quiser aproveitar melhor os benefícios do café e sentir sabores mais ricos, vale a pena investir no café especial. Além disso, moer os grãos na hora e preparar a bebida com métodos como coador de pano, prensa francesa ou Hario V60 pode transformar sua experiência com o café.
@ f3873798:24b3f2f3
2025-03-05 23:01:12O café faz parte da rotina de milhões de pessoas, seja para despertar pela manhã, acompanhar uma boa conversa ou até impulsionar a produtividade no trabalho. Mas você já parou para pensar na qualidade do café que consome diariamente? Neste artigo, vamos falar sobre os benefícios do café e as diferenças entre o café extraforte e o café especial. ## ☕ Benefícios do Café no Dia a Dia  O café não é apenas uma bebida saborosa, mas também oferece diversos benefícios para a saúde, como: Aumento da energia e concentração – A cafeína estimula o sistema nervoso central, ajudando na atenção e no foco. Melhora do humor – O consumo moderado de café pode estimular a produção de dopamina, contribuindo para uma sensação de bem-estar. Propriedades antioxidantes – O café é rico em compostos que combatem os radicais livres, ajudando a prevenir o envelhecimento precoce. Auxílio na digestão – Para muitas pessoas, o café funciona como um leve estimulante do sistema digestivo. ## ☕ Café Extraforte vs. Café Especial: Qual a Diferença?  Na prateleira do supermercado ou na cafeteria, há uma grande variedade de cafés. Mas, afinal, qual é a diferença entre o café extraforte e o café especial? ### ☕Café Extraforte Produzido a partir de grãos de qualidade inferior, muitas vezes misturados com impurezas. Possui torra muito escura, o que pode mascarar defeitos do grão. Tem um sabor mais amargo e intenso, muitas vezes com notas queimadas. Pode ser mais ácido e difícil de digerir para algumas pessoas. ### ☕Café Especial Feito com grãos selecionados e de alta qualidade, sem defeitos. A torra é mais equilibrada, preservando os aromas e sabores naturais. Possui notas sensoriais diferenciadas (frutadas, achocolatadas, florais, etc.). Mais suave e menos ácido, proporcionando uma experiência mais agradável ao paladar. ## ☕ Qual Escolher para o Dia a Dia?  Se você busca praticidade e um café forte, o extraforte pode ser uma opção. No entanto, se quiser aproveitar melhor os benefícios do café e sentir sabores mais ricos, vale a pena investir no café especial. Além disso, moer os grãos na hora e preparar a bebida com métodos como coador de pano, prensa francesa ou Hario V60 pode transformar sua experiência com o café. @ b7b1382e:74635e6c
2025-03-05 22:32:18## Abstract **By Lamar Wilson** This white paper examines an alternative taxation framework characterized by three primary components: a uniform 15% flat tax on income, a redistribution mechanism, and a tiered consumption tax structure. The proposed model aims to stimulate economic growth while maintaining social equity through strategic fiscal policy interventions. This paper analyzes the theoretical underpinnings of this approach, its potential macroeconomic implications, distributional effects across income strata, and implementation challenges. The analysis suggests that while the proposed framework offers significant advantages in terms of simplicity and growth incentives, careful consideration must be given to revenue adequacy, wealth concentration effects, and long-term economic sustainability. ## 1. Introduction Taxation systems fundamentally shape economic incentive structures, income distribution, and government fiscal capacity. Contemporary tax regimes often reflect accumulated historical policy decisions rather than coherent economic theory, resulting in complex systems with varying degrees of progressivity, efficiency, and equity (Mirrlees et al., 2011). This paper examines a potential alternative taxation framework built upon three pillars: a uniform flat tax, redistribution mechanisms, and stratified consumption taxation. The theoretical foundation of this approach draws upon both supply-side economics, which emphasizes the importance of investment incentives, and demand-side considerations, which recognize the economic significance of broad-based consumption. By synthesizing these perspectives, the proposed framework attempts to create a self-reinforcing economic cycle wherein simplified taxation stimulates both investment and consumption. ## 2. Structural Components of the Proposed Framework ### 2.1 Uniform Flat Income Taxation The cornerstone of the proposed system is a uniform 15% tax rate applied to income. This component includes two key elements: - **Individual Taxation**: A 15% flat tax applied to gross income across all individual taxpayers, regardless of income level. This approach eliminates tax brackets, deductions, and exemptions that characterize progressive taxation systems. - **Business Taxation**: A parallel 15% flat tax on net business income (profits), allowing for business expense deductions while maintaining a uniform rate across business entities regardless of size, industry, or organizational structure. The flat tax component represents a significant departure from graduated or progressive taxation systems prevalent in many developed economies. This simplification potentially reduces compliance costs, eliminates bracket-based behavioral distortions, and creates uniform incentive structures across income levels (Hall & Rabushka, 2007). ### 2.2 Universal Redistribution Mechanism The second component involves the pooling and redistribution of tax revenue: - **Collection Aggregation**: All tax revenues from both individual and business taxation are consolidated into a unified fiscal pool. - **Equal Per Capita Distribution**: The aggregated tax revenue is redistributed on an equal per capita basis to all individuals within the jurisdiction, functioning as a universal basic income mechanism. This redistribution mechanism effectively creates a de facto progressive element within the overtly flat system, as redistribution amounts represent a larger percentage of total income for lower-income individuals compared to higher-income individuals (Van Parijs & Vanderborght, 2017). ### 2.3 Tiered Consumption Taxation The third component introduces a differentiated consumption tax structure: - **Essential Goods and Services**: A minimal 2% consumption tax applied to essential items including food, healthcare, housing, and utilities. - **Non-Essential and Luxury Items**: A higher consumption tax rate (suggested at 5% or greater) applied to discretionary purchases and luxury goods. This differentiated approach to consumption taxation acknowledges consumption patterns that vary across income levels, with lower-income households typically allocating a greater proportion of spending to essential goods (Lustig, 2018). ## 3. Economic Implications Analysis ### 3.1 Distributive Effects Across Income Levels #### 3.1.1 Lower-Income Households The model's impact on lower-income households involves several counterbalancing forces: - The 15% flat income tax represents a potentially higher nominal rate than many lower-income households currently face under progressive systems. - The universal redistribution component serves as a direct income supplement, with the amount received likely exceeding tax contributions for this demographic. - The 2% consumption tax on essentials introduces a modest additional cost on necessary expenditures. Net analysis suggests that lower-income households would likely experience a positive fiscal impact through this system, as the redistributive component would exceed their combined income and consumption tax obligations (Piketty & Saez, 2013). #### 3.1.2 Higher-Income Households For higher-income households, the framework produces different effects: - The 15% flat income tax rate typically represents a reduction from current progressive tax rates applied to higher income brackets. - The universal redistribution amount constitutes a proportionally smaller income supplement relative to total income. - Higher consumption taxes on luxury goods create a de facto progressive element based on discretionary spending patterns. The net impact on higher-income households would likely be a reduced overall tax burden compared to progressive systems, potentially increasing capital availability for investment (Auerbach & Hassett, 2015). ### 3.2 Macroeconomic Implications #### 3.2.1 Investment and Growth Effects The framework's reduced taxation on higher incomes and business profits theoretically increases capital availability for investment. This aligns with supply-side economic theories suggesting that lower marginal tax rates stimulate economic expansion through: - Increased business formation and expansion - Enhanced capital investment - Improved labor productivity through capital deepening - Potential innovation stimulation through retained earnings Empirical research on flat tax implementations in various jurisdictions provides mixed evidence regarding growth effects, with contextual factors playing significant roles in outcomes (Keen et al., 2008). #### 3.2.2 Demand Stability and Consumption Patterns The redistribution component creates a consumption floor that may enhance economic stability through: - Maintaining baseline consumer demand during economic downturns - Reducing consumption volatility across business cycles - Supporting broader-based consumption patterns - Creating demand-side support for business expansion This mechanism acknowledges the economic significance of broad-based consumption capacity alongside investment incentives (Stiglitz, 2012). #### 3.2.3 Labor Market Dynamics The simplified tax structure potentially influences labor market participation through: - Elimination of high marginal tax rates that may discourage additional work - Reduced tax-related work disincentives at lower income levels - Possible increased labor force participation due to simplified income-benefit calculations - Potential wage effects as businesses retain higher post-tax profits The framework's impact on labor markets would likely vary across skill levels, industries, and existing labor market institutions (Card & Krueger, 2015). ## 4. Implementation Challenges and Considerations ### 4.1 Fiscal Revenue Adequacy A primary challenge involves ensuring sufficient government revenue, particularly during the transition period: - The overall tax burden reduction (estimated at approximately 50% compared to current systems) creates potential revenue shortfalls. - Government spending obligations would require adjustment, postponement, or alternative funding mechanisms. - Transitional provisions may be necessary to align revenue reductions with spending adaptations. Potential solutions include phased implementation, temporary supplementary revenue sources, or deliberate acceleration of economic growth to expand the tax base (Auerbach, 2006). ### 4.2 Wealth Concentration Effects Despite redistribution mechanisms, the framework may influence wealth concentration dynamics: - Reduced taxation on higher incomes could accelerate capital accumulation among wealthy individuals. - Business owners might experience wealth growth exceeding redistribution effects. - Global investment patterns could divert economic benefits outside the domestic economy. Addressing these concerns might require calibration of the redistribution component or implementing complementary policies addressing wealth concentration (Piketty, 2014). ### 4.3 Long-Term Sustainability Considerations The framework's long-term viability depends on several factors: - Sustained economic growth sufficient to support government functions with reduced tax rates - Continued business investment in productive domestic activities rather than financial engineering - Maintenance of investment-consumption balance to prevent boom-bust cycles - Evolution of the system in response to changing economic conditions Supplementary policies supporting research and development, entrepreneurship, and domestic investment may be necessary to ensure the system's sustainability (Acemoglu & Robinson, 2012). ## 5. Comparative Cost-Benefit Analysis: Proposed System vs. Current Tax Structure ### 5.1 Compliance Cost Reduction The current U.S. tax system imposes substantial compliance costs on individuals and businesses that extend far beyond direct tax payments: - Americans spend approximately 6.5 billion hours annually on tax compliance activities (Taxpayer Advocate Service, 2022) - The monetary value of compliance time is estimated at $200-400 billion annually (Laffer et al., 2018) - Businesses spend an estimated $147 billion annually on tax compliance (Tax Foundation, 2021) - The Internal Revenue Service budget exceeds $13 billion annually for tax administration and enforcement The proposed flat tax system would dramatically reduce these costs through: - Elimination of complex deduction and credit calculations (estimated 90% reduction in form complexity) - Removal of recordkeeping requirements for numerous tax provisions - Significant reduction in tax planning expenses for both individuals and businesses - Decreased need for professional tax preparation services - Streamlined tax enforcement with fewer provisions to interpret and audit Quantitative analysis suggests that transitioning to the proposed system could reduce overall compliance costs by approximately 70-80%, representing annual savings of $140-320 billion to the U.S. economy (Greenberg, 2020). ### 5.2 Administrative Efficiency Gains The current tax administration infrastructure incurs substantial costs: - The IRS employs approximately 75,000 full-time equivalent positions - Tax litigation consumes significant judicial resources across multiple court systems - Regulatory development and guidance require extensive government resources - Tax enforcement costs represent approximately 35 cents per $100 collected The proposed system would generate administrative efficiencies through: - Simplified verification processes requiring fewer personnel - Reduced need for specialized tax rulings and interpretations - Lower audit costs due to straightforward compliance requirements - Streamlined distribution mechanisms leveraging existing payment systems Conservative estimates suggest administrative cost reductions of 50-60%, representing billions in government savings that could be redirected to essential services or deficit reduction. ### 5.3 Economic Efficiency Improvements Beyond direct compliance and administrative costs, the current system creates significant economic distortions: - Taxpayers make economic decisions influenced by tax considerations rather than underlying economic value - Complex provisions create market inefficiencies and misallocation of resources - High marginal rates discourage additional productive activity - International tax complexities influence global investment decisions The proposed system addresses these inefficiencies through: - Uniform treatment of income regardless of source - Elimination of tax-motivated transaction structures - Reduced incentives for artificial entity structures - Simplified international transactions with domestic reinvestment incentives Economic models suggest these efficiency improvements could increase GDP by 0.5-1.0% annually beyond direct compliance savings (Jorgenson & Yun, 2012). ### 5.4 Distributional Cost Analysis The current system's compliance burden falls disproportionately across income levels: - Lower-income taxpayers spend a higher percentage of their income on tax compliance - Small businesses face compliance costs estimated at $1,500-$4,000 per employee - Middle-income taxpayers navigate complex provisions with limited professional assistance - High-income taxpayers allocate substantial resources to tax planning and compliance The proposed system redistributes this burden by: - Equalizing compliance requirements across income levels - Substantially reducing small business administrative overhead - Eliminating the need for complex tax planning strategies - Providing transparent, predictable tax consequences for economic decisions This redistribution of compliance costs represents an additional progressive element beyond the direct redistribution component, with estimated financial benefits to lower and middle-income households of $300-500 annually in reduced compliance costs. ## 6. Conclusion The proposed tripartite taxation framework offers a conceptually coherent alternative to conventional progressive taxation systems. By combining flat income taxation with universal redistribution and differentiated consumption taxes, the approach attempts to simultaneously address supply-side investment incentives and demand-side consumption support. The theoretical analysis suggests potential advantages in terms of simplicity, economic growth stimulation, and maintenance of social safety net functions. However, significant implementation challenges exist regarding revenue adequacy, wealth concentration effects, and long-term economic sustainability. Further empirical research, potentially through regional pilot implementations or microsimulation modeling, would enhance understanding of the practical implications of this taxation approach. While the framework presents a promising theoretical model, its successful implementation would require careful calibration to specific economic contexts, thoughtful transition planning, and ongoing adjustment based on observed outcomes. ## References Acemoglu, D., & Robinson, J. A. (2012). *Why nations fail: The origins of power, prosperity, and poverty*. Crown Business. Greenberg, S. (2020). *Reforming the U.S. tax system: Evidence on economic growth and distribution*. American Enterprise Institute. Jorgenson, D. W., & Yun, K. Y. (2012). *Tax reform and the cost of capital*. Oxford University Press. Laffer, A. B., Moore, S., & Williams, J. (2018). *The wealth of states: How taxes, energy, and worker freedom change everything*. Wiley. Tax Foundation (2021). *The cost of tax compliance*. Fiscal Fact No. 512. Taxpayer Advocate Service (2022). *Annual report to Congress*. Internal Revenue Service. Auerbach, A. J. (2006). The choice between income and consumption taxes: A primer. *NBER Working Paper Series*. Auerbach, A. J., & Hassett, K. (2015). Capital taxation in the twenty-first century. *American Economic Review*, 105(5), 38-42. Card, D., & Krueger, A. B. (2015). *Myth and measurement: The new economics of the minimum wage*. Princeton University Press. Hall, R. E., & Rabushka, A. (2007). *The flat tax*. Hoover Institution Press. Keen, M., Kim, Y., & Varsano, R. (2008). The "flat tax(es)": Principles and experience. *International Tax and Public Finance*, 15(6), 712-751. Lustig, N. (2018). Fiscal policy, income redistribution and poverty reduction in low and middle income countries. *Commitment to Equity Handbook*. Mirrlees, J., Adam, S., Besley, T., Blundell, R., Bond, S., Chote, R., Gammie, M., Johnson, P., Myles, G., & Poterba, J. (2011). *Tax by design*. Oxford University Press. Piketty, T. (2014). *Capital in the twenty-first century*. Harvard University Press. Piketty, T., & Saez, E. (2013). Optimal labor income taxation. *Handbook of Public Economics*, 5, 391-474. Stiglitz, J. E. (2012). *The price of inequality: How today's divided society endangers our future*. W.W. Norton & Company. Van Parijs, P., & Vanderborght, Y. (2017). *Basic income: A radical proposal for a free society and a sane economy*. Harvard University Press. # A Tripartite Approach to Fiscal Reform: Analyzing the Economic Impact of a Flat Tax, Redistribution, and Consumption Tax Framework **Author: Lamar Wilson** ## Abstract **By Lamar Wilson** This white paper examines an alternative taxation framework characterized by three primary components: a uniform 15% flat tax on income, a redistribution mechanism, and a tiered consumption tax structure. The proposed model aims to stimulate economic growth while maintaining social equity through strategic fiscal policy interventions. This paper analyzes the theoretical underpinnings of this approach, its potential macroeconomic implications, distributional effects across income strata, and implementation challenges. The analysis suggests that while the proposed framework offers significant advantages in terms of simplicity and growth incentives, careful consideration must be given to revenue adequacy, wealth concentration effects, and long-term economic sustainability. ## 1. Introduction Taxation systems fundamentally shape economic incentive structures, income distribution, and government fiscal capacity. Contemporary tax regimes often reflect accumulated historical policy decisions rather than coherent economic theory, resulting in complex systems with varying degrees of progressivity, efficiency, and equity (Mirrlees et al., 2011). This paper examines a potential alternative taxation framework built upon three pillars: a uniform flat tax, redistribution mechanisms, and stratified consumption taxation. The theoretical foundation of this approach draws upon both supply-side economics, which emphasizes the importance of investment incentives, and demand-side considerations, which recognize the economic significance of broad-based consumption. By synthesizing these perspectives, the proposed framework attempts to create a self-reinforcing economic cycle wherein simplified taxation stimulates both investment and consumption. ## 2. Structural Components of the Proposed Framework ### 2.1 Uniform Flat Income Taxation The cornerstone of the proposed system is a uniform 15% tax rate applied to income. This component includes two key elements: - **Individual Taxation**: A 15% flat tax applied to gross income across all individual taxpayers, regardless of income level. This approach eliminates tax brackets, deductions, and exemptions that characterize progressive taxation systems. - **Business Taxation**: A parallel 15% flat tax on net business income (profits), allowing for business expense deductions while maintaining a uniform rate across business entities regardless of size, industry, or organizational structure. The flat tax component represents a significant departure from graduated or progressive taxation systems prevalent in many developed economies. This simplification potentially reduces compliance costs, eliminates bracket-based behavioral distortions, and creates uniform incentive structures across income levels (Hall & Rabushka, 2007). ### 2.2 Universal Redistribution Mechanism The second component involves the pooling and redistribution of tax revenue: - **Collection Aggregation**: All tax revenues from both individual and business taxation are consolidated into a unified fiscal pool. - **Equal Per Capita Distribution**: The aggregated tax revenue is redistributed on an equal per capita basis to all individuals within the jurisdiction, functioning as a universal basic income mechanism. This redistribution mechanism effectively creates a de facto progressive element within the overtly flat system, as redistribution amounts represent a larger percentage of total income for lower-income individuals compared to higher-income individuals (Van Parijs & Vanderborght, 2017). ### 2.3 Tiered Consumption Taxation The third component introduces a differentiated consumption tax structure: - **Essential Goods and Services**: A minimal 2% consumption tax applied to essential items including food, healthcare, housing, and utilities. - **Non-Essential and Luxury Items**: A higher consumption tax rate (suggested at 5% or greater) applied to discretionary purchases and luxury goods. This differentiated approach to consumption taxation acknowledges consumption patterns that vary across income levels, with lower-income households typically allocating a greater proportion of spending to essential goods (Lustig, 2018). ## 3. Economic Implications Analysis ### 3.1 Distributive Effects Across Income Levels #### 3.1.1 Lower-Income Households The model's impact on lower-income households involves several counterbalancing forces: - The 15% flat income tax represents a potentially higher nominal rate than many lower-income households currently face under progressive systems. - The universal redistribution component serves as a direct income supplement, with the amount received likely exceeding tax contributions for this demographic. - The 2% consumption tax on essentials introduces a modest additional cost on necessary expenditures. Net analysis suggests that lower-income households would likely experience a positive fiscal impact through this system, as the redistributive component would exceed their combined income and consumption tax obligations (Piketty & Saez, 2013). #### 3.1.2 Higher-Income Households For higher-income households, the framework produces different effects: - The 15% flat income tax rate typically represents a reduction from current progressive tax rates applied to higher income brackets. - The universal redistribution amount constitutes a proportionally smaller income supplement relative to total income. - Higher consumption taxes on luxury goods create a de facto progressive element based on discretionary spending patterns. The net impact on higher-income households would likely be a reduced overall tax burden compared to progressive systems, potentially increasing capital availability for investment (Auerbach & Hassett, 2015). ### 3.2 Macroeconomic Implications #### 3.2.1 Investment and Growth Effects The framework's reduced taxation on higher incomes and business profits theoretically increases capital availability for investment. This aligns with supply-side economic theories suggesting that lower marginal tax rates stimulate economic expansion through: - Increased business formation and expansion - Enhanced capital investment - Improved labor productivity through capital deepening - Potential innovation stimulation through retained earnings Empirical research on flat tax implementations in various jurisdictions provides mixed evidence regarding growth effects, with contextual factors playing significant roles in outcomes (Keen et al., 2008). #### 3.2.2 Demand Stability and Consumption Patterns The redistribution component creates a consumption floor that may enhance economic stability through: - Maintaining baseline consumer demand during economic downturns - Reducing consumption volatility across business cycles - Supporting broader-based consumption patterns - Creating demand-side support for business expansion This mechanism acknowledges the economic significance of broad-based consumption capacity alongside investment incentives (Stiglitz, 2012). #### 3.2.3 Labor Market Dynamics The simplified tax structure potentially influences labor market participation through: - Elimination of high marginal tax rates that may discourage additional work - Reduced tax-related work disincentives at lower income levels - Possible increased labor force participation due to simplified income-benefit calculations - Potential wage effects as businesses retain higher post-tax profits The framework's impact on labor markets would likely vary across skill levels, industries, and existing labor market institutions (Card & Krueger, 2015). ## 4. Implementation Challenges and Considerations ### 4.1 Fiscal Revenue Adequacy A primary challenge involves ensuring sufficient government revenue, particularly during the transition period: - The overall tax burden reduction (estimated at approximately 50% compared to current systems) creates potential revenue shortfalls. - Government spending obligations would require adjustment, postponement, or alternative funding mechanisms. - Transitional provisions may be necessary to align revenue reductions with spending adaptations. Potential solutions include phased implementation, temporary supplementary revenue sources, or deliberate acceleration of economic growth to expand the tax base (Auerbach, 2006). ### 4.2 Wealth Concentration Effects Despite redistribution mechanisms, the framework may influence wealth concentration dynamics: - Reduced taxation on higher incomes could accelerate capital accumulation among wealthy individuals. - Business owners might experience wealth growth exceeding redistribution effects. - Global investment patterns could divert economic benefits outside the domestic economy. Addressing these concerns might require calibration of the redistribution component or implementing complementary policies addressing wealth concentration (Piketty, 2014). ### 4.3 Long-Term Sustainability Considerations The framework's long-term viability depends on several factors: - Sustained economic growth sufficient to support government functions with reduced tax rates - Continued business investment in productive domestic activities rather than financial engineering - Maintenance of investment-consumption balance to prevent boom-bust cycles - Evolution of the system in response to changing economic conditions Supplementary policies supporting research and development, entrepreneurship, and domestic investment may be necessary to ensure the system's sustainability (Acemoglu & Robinson, 2012). ## 5. Comparative Cost-Benefit Analysis: Proposed System vs. Current Tax Structure ### 5.1 Compliance Cost Reduction The current U.S. tax system imposes substantial compliance costs on individuals and businesses that extend far beyond direct tax payments: - Americans spend approximately 6.5 billion hours annually on tax compliance activities (Taxpayer Advocate Service, 2022) - The monetary value of compliance time is estimated at $200-400 billion annually (Laffer et al., 2018) - Businesses spend an estimated $147 billion annually on tax compliance (Tax Foundation, 2021) - The Internal Revenue Service budget exceeds $13 billion annually for tax administration and enforcement The proposed flat tax system would dramatically reduce these costs through: - Elimination of complex deduction and credit calculations (estimated 90% reduction in form complexity) - Removal of recordkeeping requirements for numerous tax provisions - Significant reduction in tax planning expenses for both individuals and businesses - Decreased need for professional tax preparation services - Streamlined tax enforcement with fewer provisions to interpret and audit Quantitative analysis suggests that transitioning to the proposed system could reduce overall compliance costs by approximately 70-80%, representing annual savings of $140-320 billion to the U.S. economy (Greenberg, 2020). ### 5.2 Administrative Efficiency Gains The current tax administration infrastructure incurs substantial costs: - The IRS employs approximately 75,000 full-time equivalent positions - Tax litigation consumes significant judicial resources across multiple court systems - Regulatory development and guidance require extensive government resources - Tax enforcement costs represent approximately 35 cents per $100 collected The proposed system would generate administrative efficiencies through: - Simplified verification processes requiring fewer personnel - Reduced need for specialized tax rulings and interpretations - Lower audit costs due to straightforward compliance requirements - Streamlined distribution mechanisms leveraging existing payment systems Conservative estimates suggest administrative cost reductions of 50-60%, representing billions in government savings that could be redirected to essential services or deficit reduction. ### 5.3 Economic Efficiency Improvements Beyond direct compliance and administrative costs, the current system creates significant economic distortions: - Taxpayers make economic decisions influenced by tax considerations rather than underlying economic value - Complex provisions create market inefficiencies and misallocation of resources - High marginal rates discourage additional productive activity - International tax complexities influence global investment decisions The proposed system addresses these inefficiencies through: - Uniform treatment of income regardless of source - Elimination of tax-motivated transaction structures - Reduced incentives for artificial entity structures - Simplified international transactions with domestic reinvestment incentives Economic models suggest these efficiency improvements could increase GDP by 0.5-1.0% annually beyond direct compliance savings (Jorgenson & Yun, 2012). ### 5.4 Distributional Cost Analysis The current system's compliance burden falls disproportionately across income levels: - Lower-income taxpayers spend a higher percentage of their income on tax compliance - Small businesses face compliance costs estimated at $1,500-$4,000 per employee - Middle-income taxpayers navigate complex provisions with limited professional assistance - High-income taxpayers allocate substantial resources to tax planning and compliance The proposed system redistributes this burden by: - Equalizing compliance requirements across income levels - Substantially reducing small business administrative overhead - Eliminating the need for complex tax planning strategies - Providing transparent, predictable tax consequences for economic decisions This redistribution of compliance costs represents an additional progressive element beyond the direct redistribution component, with estimated financial benefits to lower and middle-income households of $300-500 annually in reduced compliance costs. ## 6. Conclusion The proposed tripartite taxation framework offers a conceptually coherent alternative to conventional progressive taxation systems. By combining flat income taxation with universal redistribution and differentiated consumption taxes, the approach attempts to simultaneously address supply-side investment incentives and demand-side consumption support. The theoretical analysis suggests potential advantages in terms of simplicity, economic growth stimulation, and maintenance of social safety net functions. However, significant implementation challenges exist regarding revenue adequacy, wealth concentration effects, and long-term economic sustainability. Further empirical research, potentially through regional pilot implementations or microsimulation modeling, would enhance understanding of the practical implications of this taxation approach. While the framework presents a promising theoretical model, its successful implementation would require careful calibration to specific economic contexts, thoughtful transition planning, and ongoing adjustment based on observed outcomes. ## References Acemoglu, D., & Robinson, J. A. (2012). *Why nations fail: The origins of power, prosperity, and poverty*. Crown Business. Greenberg, S. (2020). *Reforming the U.S. tax system: Evidence on economic growth and distribution*. American Enterprise Institute. Jorgenson, D. W., & Yun, K. Y. (2012). *Tax reform and the cost of capital*. Oxford University Press. Laffer, A. B., Moore, S., & Williams, J. (2018). *The wealth of states: How taxes, energy, and worker freedom change everything*. Wiley. Tax Foundation (2021). *The cost of tax compliance*. Fiscal Fact No. 512. Taxpayer Advocate Service (2022). *Annual report to Congress*. Internal Revenue Service. Auerbach, A. J. (2006). The choice between income and consumption taxes: A primer. *NBER Working Paper Series*. Auerbach, A. J., & Hassett, K. (2015). Capital taxation in the twenty-first century. *American Economic Review*, 105(5), 38-42. Card, D., & Krueger, A. B. (2015). *Myth and measurement: The new economics of the minimum wage*. Princeton University Press. Hall, R. E., & Rabushka, A. (2007). *The flat tax*. Hoover Institution Press. Keen, M., Kim, Y., & Varsano, R. (2008). The "flat tax(es)": Principles and experience. *International Tax and Public Finance*, 15(6), 712-751. Lustig, N. (2018). Fiscal policy, income redistribution and poverty reduction in low and middle income countries. *Commitment to Equity Handbook*. Mirrlees, J., Adam, S., Besley, T., Blundell, R., Bond, S., Chote, R., Gammie, M., Johnson, P., Myles, G., & Poterba, J. (2011). *Tax by design*. Oxford University Press. Piketty, T. (2014). *Capital in the twenty-first century*. Harvard University Press. Piketty, T., & Saez, E. (2013). Optimal labor income taxation. *Handbook of Public Economics*, 5, 391-474. Stiglitz, J. E. (2012). *The price of inequality: How today's divided society endangers our future*. W.W. Norton & Company. Van Parijs, P., & Vanderborght, Y. (2017). *Basic income: A radical proposal for a free society and a sane economy*. Harvard University Press.
@ b7b1382e:74635e6c
2025-03-05 22:32:18## Abstract **By Lamar Wilson** This white paper examines an alternative taxation framework characterized by three primary components: a uniform 15% flat tax on income, a redistribution mechanism, and a tiered consumption tax structure. The proposed model aims to stimulate economic growth while maintaining social equity through strategic fiscal policy interventions. This paper analyzes the theoretical underpinnings of this approach, its potential macroeconomic implications, distributional effects across income strata, and implementation challenges. The analysis suggests that while the proposed framework offers significant advantages in terms of simplicity and growth incentives, careful consideration must be given to revenue adequacy, wealth concentration effects, and long-term economic sustainability. ## 1. Introduction Taxation systems fundamentally shape economic incentive structures, income distribution, and government fiscal capacity. Contemporary tax regimes often reflect accumulated historical policy decisions rather than coherent economic theory, resulting in complex systems with varying degrees of progressivity, efficiency, and equity (Mirrlees et al., 2011). This paper examines a potential alternative taxation framework built upon three pillars: a uniform flat tax, redistribution mechanisms, and stratified consumption taxation. The theoretical foundation of this approach draws upon both supply-side economics, which emphasizes the importance of investment incentives, and demand-side considerations, which recognize the economic significance of broad-based consumption. By synthesizing these perspectives, the proposed framework attempts to create a self-reinforcing economic cycle wherein simplified taxation stimulates both investment and consumption. ## 2. Structural Components of the Proposed Framework ### 2.1 Uniform Flat Income Taxation The cornerstone of the proposed system is a uniform 15% tax rate applied to income. This component includes two key elements: - **Individual Taxation**: A 15% flat tax applied to gross income across all individual taxpayers, regardless of income level. This approach eliminates tax brackets, deductions, and exemptions that characterize progressive taxation systems. - **Business Taxation**: A parallel 15% flat tax on net business income (profits), allowing for business expense deductions while maintaining a uniform rate across business entities regardless of size, industry, or organizational structure. The flat tax component represents a significant departure from graduated or progressive taxation systems prevalent in many developed economies. This simplification potentially reduces compliance costs, eliminates bracket-based behavioral distortions, and creates uniform incentive structures across income levels (Hall & Rabushka, 2007). ### 2.2 Universal Redistribution Mechanism The second component involves the pooling and redistribution of tax revenue: - **Collection Aggregation**: All tax revenues from both individual and business taxation are consolidated into a unified fiscal pool. - **Equal Per Capita Distribution**: The aggregated tax revenue is redistributed on an equal per capita basis to all individuals within the jurisdiction, functioning as a universal basic income mechanism. This redistribution mechanism effectively creates a de facto progressive element within the overtly flat system, as redistribution amounts represent a larger percentage of total income for lower-income individuals compared to higher-income individuals (Van Parijs & Vanderborght, 2017). ### 2.3 Tiered Consumption Taxation The third component introduces a differentiated consumption tax structure: - **Essential Goods and Services**: A minimal 2% consumption tax applied to essential items including food, healthcare, housing, and utilities. - **Non-Essential and Luxury Items**: A higher consumption tax rate (suggested at 5% or greater) applied to discretionary purchases and luxury goods. This differentiated approach to consumption taxation acknowledges consumption patterns that vary across income levels, with lower-income households typically allocating a greater proportion of spending to essential goods (Lustig, 2018). ## 3. Economic Implications Analysis ### 3.1 Distributive Effects Across Income Levels #### 3.1.1 Lower-Income Households The model's impact on lower-income households involves several counterbalancing forces: - The 15% flat income tax represents a potentially higher nominal rate than many lower-income households currently face under progressive systems. - The universal redistribution component serves as a direct income supplement, with the amount received likely exceeding tax contributions for this demographic. - The 2% consumption tax on essentials introduces a modest additional cost on necessary expenditures. Net analysis suggests that lower-income households would likely experience a positive fiscal impact through this system, as the redistributive component would exceed their combined income and consumption tax obligations (Piketty & Saez, 2013). #### 3.1.2 Higher-Income Households For higher-income households, the framework produces different effects: - The 15% flat income tax rate typically represents a reduction from current progressive tax rates applied to higher income brackets. - The universal redistribution amount constitutes a proportionally smaller income supplement relative to total income. - Higher consumption taxes on luxury goods create a de facto progressive element based on discretionary spending patterns. The net impact on higher-income households would likely be a reduced overall tax burden compared to progressive systems, potentially increasing capital availability for investment (Auerbach & Hassett, 2015). ### 3.2 Macroeconomic Implications #### 3.2.1 Investment and Growth Effects The framework's reduced taxation on higher incomes and business profits theoretically increases capital availability for investment. This aligns with supply-side economic theories suggesting that lower marginal tax rates stimulate economic expansion through: - Increased business formation and expansion - Enhanced capital investment - Improved labor productivity through capital deepening - Potential innovation stimulation through retained earnings Empirical research on flat tax implementations in various jurisdictions provides mixed evidence regarding growth effects, with contextual factors playing significant roles in outcomes (Keen et al., 2008). #### 3.2.2 Demand Stability and Consumption Patterns The redistribution component creates a consumption floor that may enhance economic stability through: - Maintaining baseline consumer demand during economic downturns - Reducing consumption volatility across business cycles - Supporting broader-based consumption patterns - Creating demand-side support for business expansion This mechanism acknowledges the economic significance of broad-based consumption capacity alongside investment incentives (Stiglitz, 2012). #### 3.2.3 Labor Market Dynamics The simplified tax structure potentially influences labor market participation through: - Elimination of high marginal tax rates that may discourage additional work - Reduced tax-related work disincentives at lower income levels - Possible increased labor force participation due to simplified income-benefit calculations - Potential wage effects as businesses retain higher post-tax profits The framework's impact on labor markets would likely vary across skill levels, industries, and existing labor market institutions (Card & Krueger, 2015). ## 4. Implementation Challenges and Considerations ### 4.1 Fiscal Revenue Adequacy A primary challenge involves ensuring sufficient government revenue, particularly during the transition period: - The overall tax burden reduction (estimated at approximately 50% compared to current systems) creates potential revenue shortfalls. - Government spending obligations would require adjustment, postponement, or alternative funding mechanisms. - Transitional provisions may be necessary to align revenue reductions with spending adaptations. Potential solutions include phased implementation, temporary supplementary revenue sources, or deliberate acceleration of economic growth to expand the tax base (Auerbach, 2006). ### 4.2 Wealth Concentration Effects Despite redistribution mechanisms, the framework may influence wealth concentration dynamics: - Reduced taxation on higher incomes could accelerate capital accumulation among wealthy individuals. - Business owners might experience wealth growth exceeding redistribution effects. - Global investment patterns could divert economic benefits outside the domestic economy. Addressing these concerns might require calibration of the redistribution component or implementing complementary policies addressing wealth concentration (Piketty, 2014). ### 4.3 Long-Term Sustainability Considerations The framework's long-term viability depends on several factors: - Sustained economic growth sufficient to support government functions with reduced tax rates - Continued business investment in productive domestic activities rather than financial engineering - Maintenance of investment-consumption balance to prevent boom-bust cycles - Evolution of the system in response to changing economic conditions Supplementary policies supporting research and development, entrepreneurship, and domestic investment may be necessary to ensure the system's sustainability (Acemoglu & Robinson, 2012). ## 5. Comparative Cost-Benefit Analysis: Proposed System vs. Current Tax Structure ### 5.1 Compliance Cost Reduction The current U.S. tax system imposes substantial compliance costs on individuals and businesses that extend far beyond direct tax payments: - Americans spend approximately 6.5 billion hours annually on tax compliance activities (Taxpayer Advocate Service, 2022) - The monetary value of compliance time is estimated at $200-400 billion annually (Laffer et al., 2018) - Businesses spend an estimated $147 billion annually on tax compliance (Tax Foundation, 2021) - The Internal Revenue Service budget exceeds $13 billion annually for tax administration and enforcement The proposed flat tax system would dramatically reduce these costs through: - Elimination of complex deduction and credit calculations (estimated 90% reduction in form complexity) - Removal of recordkeeping requirements for numerous tax provisions - Significant reduction in tax planning expenses for both individuals and businesses - Decreased need for professional tax preparation services - Streamlined tax enforcement with fewer provisions to interpret and audit Quantitative analysis suggests that transitioning to the proposed system could reduce overall compliance costs by approximately 70-80%, representing annual savings of $140-320 billion to the U.S. economy (Greenberg, 2020). ### 5.2 Administrative Efficiency Gains The current tax administration infrastructure incurs substantial costs: - The IRS employs approximately 75,000 full-time equivalent positions - Tax litigation consumes significant judicial resources across multiple court systems - Regulatory development and guidance require extensive government resources - Tax enforcement costs represent approximately 35 cents per $100 collected The proposed system would generate administrative efficiencies through: - Simplified verification processes requiring fewer personnel - Reduced need for specialized tax rulings and interpretations - Lower audit costs due to straightforward compliance requirements - Streamlined distribution mechanisms leveraging existing payment systems Conservative estimates suggest administrative cost reductions of 50-60%, representing billions in government savings that could be redirected to essential services or deficit reduction. ### 5.3 Economic Efficiency Improvements Beyond direct compliance and administrative costs, the current system creates significant economic distortions: - Taxpayers make economic decisions influenced by tax considerations rather than underlying economic value - Complex provisions create market inefficiencies and misallocation of resources - High marginal rates discourage additional productive activity - International tax complexities influence global investment decisions The proposed system addresses these inefficiencies through: - Uniform treatment of income regardless of source - Elimination of tax-motivated transaction structures - Reduced incentives for artificial entity structures - Simplified international transactions with domestic reinvestment incentives Economic models suggest these efficiency improvements could increase GDP by 0.5-1.0% annually beyond direct compliance savings (Jorgenson & Yun, 2012). ### 5.4 Distributional Cost Analysis The current system's compliance burden falls disproportionately across income levels: - Lower-income taxpayers spend a higher percentage of their income on tax compliance - Small businesses face compliance costs estimated at $1,500-$4,000 per employee - Middle-income taxpayers navigate complex provisions with limited professional assistance - High-income taxpayers allocate substantial resources to tax planning and compliance The proposed system redistributes this burden by: - Equalizing compliance requirements across income levels - Substantially reducing small business administrative overhead - Eliminating the need for complex tax planning strategies - Providing transparent, predictable tax consequences for economic decisions This redistribution of compliance costs represents an additional progressive element beyond the direct redistribution component, with estimated financial benefits to lower and middle-income households of $300-500 annually in reduced compliance costs. ## 6. Conclusion The proposed tripartite taxation framework offers a conceptually coherent alternative to conventional progressive taxation systems. By combining flat income taxation with universal redistribution and differentiated consumption taxes, the approach attempts to simultaneously address supply-side investment incentives and demand-side consumption support. The theoretical analysis suggests potential advantages in terms of simplicity, economic growth stimulation, and maintenance of social safety net functions. However, significant implementation challenges exist regarding revenue adequacy, wealth concentration effects, and long-term economic sustainability. Further empirical research, potentially through regional pilot implementations or microsimulation modeling, would enhance understanding of the practical implications of this taxation approach. While the framework presents a promising theoretical model, its successful implementation would require careful calibration to specific economic contexts, thoughtful transition planning, and ongoing adjustment based on observed outcomes. ## References Acemoglu, D., & Robinson, J. A. (2012). *Why nations fail: The origins of power, prosperity, and poverty*. Crown Business. Greenberg, S. (2020). *Reforming the U.S. tax system: Evidence on economic growth and distribution*. American Enterprise Institute. Jorgenson, D. W., & Yun, K. Y. (2012). *Tax reform and the cost of capital*. Oxford University Press. Laffer, A. B., Moore, S., & Williams, J. (2018). *The wealth of states: How taxes, energy, and worker freedom change everything*. Wiley. Tax Foundation (2021). *The cost of tax compliance*. Fiscal Fact No. 512. Taxpayer Advocate Service (2022). *Annual report to Congress*. Internal Revenue Service. Auerbach, A. J. (2006). The choice between income and consumption taxes: A primer. *NBER Working Paper Series*. Auerbach, A. J., & Hassett, K. (2015). Capital taxation in the twenty-first century. *American Economic Review*, 105(5), 38-42. Card, D., & Krueger, A. B. (2015). *Myth and measurement: The new economics of the minimum wage*. Princeton University Press. Hall, R. E., & Rabushka, A. (2007). *The flat tax*. Hoover Institution Press. Keen, M., Kim, Y., & Varsano, R. (2008). The "flat tax(es)": Principles and experience. *International Tax and Public Finance*, 15(6), 712-751. Lustig, N. (2018). Fiscal policy, income redistribution and poverty reduction in low and middle income countries. *Commitment to Equity Handbook*. Mirrlees, J., Adam, S., Besley, T., Blundell, R., Bond, S., Chote, R., Gammie, M., Johnson, P., Myles, G., & Poterba, J. (2011). *Tax by design*. Oxford University Press. Piketty, T. (2014). *Capital in the twenty-first century*. Harvard University Press. Piketty, T., & Saez, E. (2013). Optimal labor income taxation. *Handbook of Public Economics*, 5, 391-474. Stiglitz, J. E. (2012). *The price of inequality: How today's divided society endangers our future*. W.W. Norton & Company. Van Parijs, P., & Vanderborght, Y. (2017). *Basic income: A radical proposal for a free society and a sane economy*. Harvard University Press. # A Tripartite Approach to Fiscal Reform: Analyzing the Economic Impact of a Flat Tax, Redistribution, and Consumption Tax Framework **Author: Lamar Wilson** ## Abstract **By Lamar Wilson** This white paper examines an alternative taxation framework characterized by three primary components: a uniform 15% flat tax on income, a redistribution mechanism, and a tiered consumption tax structure. The proposed model aims to stimulate economic growth while maintaining social equity through strategic fiscal policy interventions. This paper analyzes the theoretical underpinnings of this approach, its potential macroeconomic implications, distributional effects across income strata, and implementation challenges. The analysis suggests that while the proposed framework offers significant advantages in terms of simplicity and growth incentives, careful consideration must be given to revenue adequacy, wealth concentration effects, and long-term economic sustainability. ## 1. Introduction Taxation systems fundamentally shape economic incentive structures, income distribution, and government fiscal capacity. Contemporary tax regimes often reflect accumulated historical policy decisions rather than coherent economic theory, resulting in complex systems with varying degrees of progressivity, efficiency, and equity (Mirrlees et al., 2011). This paper examines a potential alternative taxation framework built upon three pillars: a uniform flat tax, redistribution mechanisms, and stratified consumption taxation. The theoretical foundation of this approach draws upon both supply-side economics, which emphasizes the importance of investment incentives, and demand-side considerations, which recognize the economic significance of broad-based consumption. By synthesizing these perspectives, the proposed framework attempts to create a self-reinforcing economic cycle wherein simplified taxation stimulates both investment and consumption. ## 2. Structural Components of the Proposed Framework ### 2.1 Uniform Flat Income Taxation The cornerstone of the proposed system is a uniform 15% tax rate applied to income. This component includes two key elements: - **Individual Taxation**: A 15% flat tax applied to gross income across all individual taxpayers, regardless of income level. This approach eliminates tax brackets, deductions, and exemptions that characterize progressive taxation systems. - **Business Taxation**: A parallel 15% flat tax on net business income (profits), allowing for business expense deductions while maintaining a uniform rate across business entities regardless of size, industry, or organizational structure. The flat tax component represents a significant departure from graduated or progressive taxation systems prevalent in many developed economies. This simplification potentially reduces compliance costs, eliminates bracket-based behavioral distortions, and creates uniform incentive structures across income levels (Hall & Rabushka, 2007). ### 2.2 Universal Redistribution Mechanism The second component involves the pooling and redistribution of tax revenue: - **Collection Aggregation**: All tax revenues from both individual and business taxation are consolidated into a unified fiscal pool. - **Equal Per Capita Distribution**: The aggregated tax revenue is redistributed on an equal per capita basis to all individuals within the jurisdiction, functioning as a universal basic income mechanism. This redistribution mechanism effectively creates a de facto progressive element within the overtly flat system, as redistribution amounts represent a larger percentage of total income for lower-income individuals compared to higher-income individuals (Van Parijs & Vanderborght, 2017). ### 2.3 Tiered Consumption Taxation The third component introduces a differentiated consumption tax structure: - **Essential Goods and Services**: A minimal 2% consumption tax applied to essential items including food, healthcare, housing, and utilities. - **Non-Essential and Luxury Items**: A higher consumption tax rate (suggested at 5% or greater) applied to discretionary purchases and luxury goods. This differentiated approach to consumption taxation acknowledges consumption patterns that vary across income levels, with lower-income households typically allocating a greater proportion of spending to essential goods (Lustig, 2018). ## 3. Economic Implications Analysis ### 3.1 Distributive Effects Across Income Levels #### 3.1.1 Lower-Income Households The model's impact on lower-income households involves several counterbalancing forces: - The 15% flat income tax represents a potentially higher nominal rate than many lower-income households currently face under progressive systems. - The universal redistribution component serves as a direct income supplement, with the amount received likely exceeding tax contributions for this demographic. - The 2% consumption tax on essentials introduces a modest additional cost on necessary expenditures. Net analysis suggests that lower-income households would likely experience a positive fiscal impact through this system, as the redistributive component would exceed their combined income and consumption tax obligations (Piketty & Saez, 2013). #### 3.1.2 Higher-Income Households For higher-income households, the framework produces different effects: - The 15% flat income tax rate typically represents a reduction from current progressive tax rates applied to higher income brackets. - The universal redistribution amount constitutes a proportionally smaller income supplement relative to total income. - Higher consumption taxes on luxury goods create a de facto progressive element based on discretionary spending patterns. The net impact on higher-income households would likely be a reduced overall tax burden compared to progressive systems, potentially increasing capital availability for investment (Auerbach & Hassett, 2015). ### 3.2 Macroeconomic Implications #### 3.2.1 Investment and Growth Effects The framework's reduced taxation on higher incomes and business profits theoretically increases capital availability for investment. This aligns with supply-side economic theories suggesting that lower marginal tax rates stimulate economic expansion through: - Increased business formation and expansion - Enhanced capital investment - Improved labor productivity through capital deepening - Potential innovation stimulation through retained earnings Empirical research on flat tax implementations in various jurisdictions provides mixed evidence regarding growth effects, with contextual factors playing significant roles in outcomes (Keen et al., 2008). #### 3.2.2 Demand Stability and Consumption Patterns The redistribution component creates a consumption floor that may enhance economic stability through: - Maintaining baseline consumer demand during economic downturns - Reducing consumption volatility across business cycles - Supporting broader-based consumption patterns - Creating demand-side support for business expansion This mechanism acknowledges the economic significance of broad-based consumption capacity alongside investment incentives (Stiglitz, 2012). #### 3.2.3 Labor Market Dynamics The simplified tax structure potentially influences labor market participation through: - Elimination of high marginal tax rates that may discourage additional work - Reduced tax-related work disincentives at lower income levels - Possible increased labor force participation due to simplified income-benefit calculations - Potential wage effects as businesses retain higher post-tax profits The framework's impact on labor markets would likely vary across skill levels, industries, and existing labor market institutions (Card & Krueger, 2015). ## 4. Implementation Challenges and Considerations ### 4.1 Fiscal Revenue Adequacy A primary challenge involves ensuring sufficient government revenue, particularly during the transition period: - The overall tax burden reduction (estimated at approximately 50% compared to current systems) creates potential revenue shortfalls. - Government spending obligations would require adjustment, postponement, or alternative funding mechanisms. - Transitional provisions may be necessary to align revenue reductions with spending adaptations. Potential solutions include phased implementation, temporary supplementary revenue sources, or deliberate acceleration of economic growth to expand the tax base (Auerbach, 2006). ### 4.2 Wealth Concentration Effects Despite redistribution mechanisms, the framework may influence wealth concentration dynamics: - Reduced taxation on higher incomes could accelerate capital accumulation among wealthy individuals. - Business owners might experience wealth growth exceeding redistribution effects. - Global investment patterns could divert economic benefits outside the domestic economy. Addressing these concerns might require calibration of the redistribution component or implementing complementary policies addressing wealth concentration (Piketty, 2014). ### 4.3 Long-Term Sustainability Considerations The framework's long-term viability depends on several factors: - Sustained economic growth sufficient to support government functions with reduced tax rates - Continued business investment in productive domestic activities rather than financial engineering - Maintenance of investment-consumption balance to prevent boom-bust cycles - Evolution of the system in response to changing economic conditions Supplementary policies supporting research and development, entrepreneurship, and domestic investment may be necessary to ensure the system's sustainability (Acemoglu & Robinson, 2012). ## 5. Comparative Cost-Benefit Analysis: Proposed System vs. Current Tax Structure ### 5.1 Compliance Cost Reduction The current U.S. tax system imposes substantial compliance costs on individuals and businesses that extend far beyond direct tax payments: - Americans spend approximately 6.5 billion hours annually on tax compliance activities (Taxpayer Advocate Service, 2022) - The monetary value of compliance time is estimated at $200-400 billion annually (Laffer et al., 2018) - Businesses spend an estimated $147 billion annually on tax compliance (Tax Foundation, 2021) - The Internal Revenue Service budget exceeds $13 billion annually for tax administration and enforcement The proposed flat tax system would dramatically reduce these costs through: - Elimination of complex deduction and credit calculations (estimated 90% reduction in form complexity) - Removal of recordkeeping requirements for numerous tax provisions - Significant reduction in tax planning expenses for both individuals and businesses - Decreased need for professional tax preparation services - Streamlined tax enforcement with fewer provisions to interpret and audit Quantitative analysis suggests that transitioning to the proposed system could reduce overall compliance costs by approximately 70-80%, representing annual savings of $140-320 billion to the U.S. economy (Greenberg, 2020). ### 5.2 Administrative Efficiency Gains The current tax administration infrastructure incurs substantial costs: - The IRS employs approximately 75,000 full-time equivalent positions - Tax litigation consumes significant judicial resources across multiple court systems - Regulatory development and guidance require extensive government resources - Tax enforcement costs represent approximately 35 cents per $100 collected The proposed system would generate administrative efficiencies through: - Simplified verification processes requiring fewer personnel - Reduced need for specialized tax rulings and interpretations - Lower audit costs due to straightforward compliance requirements - Streamlined distribution mechanisms leveraging existing payment systems Conservative estimates suggest administrative cost reductions of 50-60%, representing billions in government savings that could be redirected to essential services or deficit reduction. ### 5.3 Economic Efficiency Improvements Beyond direct compliance and administrative costs, the current system creates significant economic distortions: - Taxpayers make economic decisions influenced by tax considerations rather than underlying economic value - Complex provisions create market inefficiencies and misallocation of resources - High marginal rates discourage additional productive activity - International tax complexities influence global investment decisions The proposed system addresses these inefficiencies through: - Uniform treatment of income regardless of source - Elimination of tax-motivated transaction structures - Reduced incentives for artificial entity structures - Simplified international transactions with domestic reinvestment incentives Economic models suggest these efficiency improvements could increase GDP by 0.5-1.0% annually beyond direct compliance savings (Jorgenson & Yun, 2012). ### 5.4 Distributional Cost Analysis The current system's compliance burden falls disproportionately across income levels: - Lower-income taxpayers spend a higher percentage of their income on tax compliance - Small businesses face compliance costs estimated at $1,500-$4,000 per employee - Middle-income taxpayers navigate complex provisions with limited professional assistance - High-income taxpayers allocate substantial resources to tax planning and compliance The proposed system redistributes this burden by: - Equalizing compliance requirements across income levels - Substantially reducing small business administrative overhead - Eliminating the need for complex tax planning strategies - Providing transparent, predictable tax consequences for economic decisions This redistribution of compliance costs represents an additional progressive element beyond the direct redistribution component, with estimated financial benefits to lower and middle-income households of $300-500 annually in reduced compliance costs. ## 6. Conclusion The proposed tripartite taxation framework offers a conceptually coherent alternative to conventional progressive taxation systems. By combining flat income taxation with universal redistribution and differentiated consumption taxes, the approach attempts to simultaneously address supply-side investment incentives and demand-side consumption support. The theoretical analysis suggests potential advantages in terms of simplicity, economic growth stimulation, and maintenance of social safety net functions. However, significant implementation challenges exist regarding revenue adequacy, wealth concentration effects, and long-term economic sustainability. Further empirical research, potentially through regional pilot implementations or microsimulation modeling, would enhance understanding of the practical implications of this taxation approach. While the framework presents a promising theoretical model, its successful implementation would require careful calibration to specific economic contexts, thoughtful transition planning, and ongoing adjustment based on observed outcomes. ## References Acemoglu, D., & Robinson, J. A. (2012). *Why nations fail: The origins of power, prosperity, and poverty*. Crown Business. Greenberg, S. (2020). *Reforming the U.S. tax system: Evidence on economic growth and distribution*. American Enterprise Institute. Jorgenson, D. W., & Yun, K. Y. (2012). *Tax reform and the cost of capital*. Oxford University Press. Laffer, A. B., Moore, S., & Williams, J. (2018). *The wealth of states: How taxes, energy, and worker freedom change everything*. Wiley. Tax Foundation (2021). *The cost of tax compliance*. Fiscal Fact No. 512. Taxpayer Advocate Service (2022). *Annual report to Congress*. Internal Revenue Service. Auerbach, A. J. (2006). The choice between income and consumption taxes: A primer. *NBER Working Paper Series*. Auerbach, A. J., & Hassett, K. (2015). Capital taxation in the twenty-first century. *American Economic Review*, 105(5), 38-42. Card, D., & Krueger, A. B. (2015). *Myth and measurement: The new economics of the minimum wage*. Princeton University Press. Hall, R. E., & Rabushka, A. (2007). *The flat tax*. Hoover Institution Press. Keen, M., Kim, Y., & Varsano, R. (2008). The "flat tax(es)": Principles and experience. *International Tax and Public Finance*, 15(6), 712-751. Lustig, N. (2018). Fiscal policy, income redistribution and poverty reduction in low and middle income countries. *Commitment to Equity Handbook*. Mirrlees, J., Adam, S., Besley, T., Blundell, R., Bond, S., Chote, R., Gammie, M., Johnson, P., Myles, G., & Poterba, J. (2011). *Tax by design*. Oxford University Press. Piketty, T. (2014). *Capital in the twenty-first century*. Harvard University Press. Piketty, T., & Saez, E. (2013). Optimal labor income taxation. *Handbook of Public Economics*, 5, 391-474. Stiglitz, J. E. (2012). *The price of inequality: How today's divided society endangers our future*. W.W. Norton & Company. Van Parijs, P., & Vanderborght, Y. (2017). *Basic income: A radical proposal for a free society and a sane economy*. Harvard University Press. @ 6389be64:ef439d32
2025-03-05 21:18:52Carbon is a "Long-Tail" asset: the residual earnings that come from an asset after it has had its initial market impact. The Carbon Cascade converts labile into recalcitrant carbon. During transformation power is generated and lands restored. Total production of biomass per annum is 100 billion tons of carbon and at $500 to $2,000 per ton of biochar that's $100 trillion of potential carbon trading on the open market. (fanciful to be sure) originally posted at https://stacker.news/items/904996
@ 6389be64:ef439d32
2025-03-05 21:18:52Carbon is a "Long-Tail" asset: the residual earnings that come from an asset after it has had its initial market impact. The Carbon Cascade converts labile into recalcitrant carbon. During transformation power is generated and lands restored. Total production of biomass per annum is 100 billion tons of carbon and at $500 to $2,000 per ton of biochar that's $100 trillion of potential carbon trading on the open market. (fanciful to be sure) originally posted at https://stacker.news/items/904996 @ 878dff7c:037d18bc
2025-03-05 20:37:35# Overview Tropical Cyclone Alfred, currently a Category 2 system, is approaching Australia's eastern coast, with landfall anticipated between the Sunshine Coast and Gold Coast early Friday. This rare event has prompted widespread preparations and warnings across Queensland and New South Wales. Authorities are urging residents in vulnerable areas to evacuate and brace for destructive winds, heavy rainfall, and potential life-threatening flooding. [TROPICAL CYCLONE FORECAST TRACK MAP](http://www.bom.gov.au/products/IDQ65002.shtml) (Cover photo thanks to our 'unfortunately on the ground' photographer Sean. Stay safe mate!) ## Queensland and New South Wales Brace for Cyclone Alfred's Impact ### Summary: Residents in Queensland and northern New South Wales are preparing for Tropical Cyclone Alfred, expected to make landfall early Friday between the Sunshine Coast and Gold Coast. The Category 2 storm is forecasted to bring severe winds and heavy rain, with potential for major flooding. Emergency measures include power outages, flight cancellations, school closures, and activation of emergency centers. The Australian Defence Force has been engaged to assist with response efforts. Sources: [The Guardian - 6 March 2025](https://www.theguardian.com/australia-news/2025/mar/05/afternoon-update-wednesday-ntwnfb) ## Authorities Issue Evacuation Warnings Ahead of Cyclone Alfred ### Summary: Australian authorities have issued major evacuation warnings ahead of Tropical Cyclone Alfred's expected landfall on Friday morning. The cyclone, categorized as Category 2, is anticipated to bring winds of 155 km/h and 800 mm of rainfall, potentially leading to dangerous and life-threatening conditions. Areas like Brisbane, the Gold Coast, and Sunshine Coast are in the cyclone's projected path. Residents in flood-prone and coastal areas are urged to evacuate and make necessary preparations, including stocking up on water and non-perishable food. The Australian government has declared a state of emergency and engaged the Australian Defence Force to assist with evacuation and disaster response efforts. Sources: [The Sun - 6 March 2025](https://www.thesun.ie/news/14823247/tropical-cyclone-alfred-irish-people-evacuate-warning-australia/) ## Residents Prepare for First Cyclone in Over Five Decades ### Summary: Residents in Brisbane and the Gold Coast are preparing for Tropical Cyclone Alfred, the first cyclone in 51 years to hit the Australian east coast near Brisbane. The cyclone is predicted to make landfall late Thursday or early Friday, bringing destructive winds, large swells, and potential life-threatening flooding. Brisbane, with over 3 million residents, may see up to 20,000 homes affected by flooding. The government has provided 250,000 sandbags and established cyclone refuge centers. Schools, public transport, and non-urgent hospital surgeries will be suspended. Queensland Premier David Crisafulli has urged residents to prepare their homes and plan evacuation routes. Sources: [AP News - 6 March 2025](https://apnews.com/article/f40a46f400f42d7d94dc5a91cb11c11a) ## Cyclone Alfred's Approach Prompts Widespread Preparations ### Summary: Cyclone Alfred, a Category 2 storm, is approaching the Tweed Coast near Brisbane, expected to make landfall late Thursday or early Friday. As tension mounts, residents are bracing for potential disaster with power outages and water contamination being the main concerns. Supermarkets are emptied of essential supplies, and emergency preparations, such as sandbagging and securing properties, are in full swing. The community displays remarkable solidarity, with neighbors helping one another and sharing real-time updates. Surfers are taking advantage of the monster swells, enjoying the waves despite the looming threat. Families face difficult decisions on whether to stay or evacuate, while prioritizing the safety and well-being of their loved ones. With a keen sense of unity and preparedness, the community waits in hope that their efforts will withstand the upcoming storm. Sources: [News.com.au - 6 March 2025](https://www.news.com.au/technology/environment/every-nerve-jangling-queenslanders-prepare-for-disaster-as-cyclone-alfred-nears/news-story/23e6cd554103de012374c1ce238ba8c7) ## Cyclone Alfred's Unusual Path Raises Concerns ### Summary: Australia is preparing for a rare tropical cyclone, named Alfred, approaching Brisbane. Authorities are urging residents in flood-prone suburbs to evacuate due to potential destructive wind gusts up to 155 kph and significant rainfall that could lead to life-threatening flash flooding. The storm is expected to land as a Category 2 cyclone early on Friday. Evacuation efforts are in place, with heavy-lift helicopters deployed and evacuation centers being opened. Schools and public transport will shut down, and flights have been canceled in the affected regions. This area of southeast Queensland and northern New South Wales has not experienced such a cyclone for over fifty years. Sources: [Reuters - 6 March 2025](https://www.reuters.com/business/environment/australias-east-coast-braces-cyclone-alfred-2025-03-04/) ## Ice Cube Shares Experience Amid Cyclone Alfred ### Summary: Ice Cube is currently staying at a beachfront hotel in Australia as Cyclone Alfred intensifies. The 55-year-old rapper and actor, who is there for upcoming performances, humorously commented about experiencing a cyclone for the first time. Residents in flood-prone regions have been advised to evacuate, with heavy rains and strong winds expected to cause potentially life-threatening flash floods and severe storm conditions. The cyclone is particularly significant for Queensland, which hasn't seen such severe weather in decades. Ice Cube also denied rumors of his involvement in an 'Anaconda' reboot being filmed in Australia, stating he was only there for his Sydney show. Sources: [People - 6 March 2025](https://people.com/ice-cube-australian-hotel-cyclone-alfred-11691119) ## Cyclone Alfred's Impact on Northern New South Wales ### Summary: Residents in Northern New South Wales are preparing for the impacts of Cyclone Alfred, with rainfalls of up to 400 millimeters expected, alongside winds of up to 150 kilometers per hour and likely flooding. The cyclone's approach has led to heightened concerns and preparations in the region. Sources: [ABC News - 6 March 2025](https://www.abc.net.au/news/2025-03-06/tropical-cyclone-alfred-northern-nsw/105014292) ## Authorities Urge Evacuations as Cyclone Alfred Nears ### Summary: Residents in flood-prone suburbs of Brisbane and the Gold Coast are being urged to evacuate as Cyclone Alfred approaches. The storm is expected to bring destructive winds and heavy rainfall, leading to life-threatening flash flooding. Evacuation centers have been established, and emergency services are on high alert to assist those in need. Sources: [The Guardian - 6 March 2025](https://www.theguardian.com/australia-news/live/2025/mar/06/tropical-cylone-alfred-live-update-brisbane-queensland-nsw-suburbs-weather-bom-forecast-path-track-map-school-closures)
@ 878dff7c:037d18bc
2025-03-05 20:37:35# Overview Tropical Cyclone Alfred, currently a Category 2 system, is approaching Australia's eastern coast, with landfall anticipated between the Sunshine Coast and Gold Coast early Friday. This rare event has prompted widespread preparations and warnings across Queensland and New South Wales. Authorities are urging residents in vulnerable areas to evacuate and brace for destructive winds, heavy rainfall, and potential life-threatening flooding. [TROPICAL CYCLONE FORECAST TRACK MAP](http://www.bom.gov.au/products/IDQ65002.shtml) (Cover photo thanks to our 'unfortunately on the ground' photographer Sean. Stay safe mate!) ## Queensland and New South Wales Brace for Cyclone Alfred's Impact ### Summary: Residents in Queensland and northern New South Wales are preparing for Tropical Cyclone Alfred, expected to make landfall early Friday between the Sunshine Coast and Gold Coast. The Category 2 storm is forecasted to bring severe winds and heavy rain, with potential for major flooding. Emergency measures include power outages, flight cancellations, school closures, and activation of emergency centers. The Australian Defence Force has been engaged to assist with response efforts. Sources: [The Guardian - 6 March 2025](https://www.theguardian.com/australia-news/2025/mar/05/afternoon-update-wednesday-ntwnfb) ## Authorities Issue Evacuation Warnings Ahead of Cyclone Alfred ### Summary: Australian authorities have issued major evacuation warnings ahead of Tropical Cyclone Alfred's expected landfall on Friday morning. The cyclone, categorized as Category 2, is anticipated to bring winds of 155 km/h and 800 mm of rainfall, potentially leading to dangerous and life-threatening conditions. Areas like Brisbane, the Gold Coast, and Sunshine Coast are in the cyclone's projected path. Residents in flood-prone and coastal areas are urged to evacuate and make necessary preparations, including stocking up on water and non-perishable food. The Australian government has declared a state of emergency and engaged the Australian Defence Force to assist with evacuation and disaster response efforts. Sources: [The Sun - 6 March 2025](https://www.thesun.ie/news/14823247/tropical-cyclone-alfred-irish-people-evacuate-warning-australia/) ## Residents Prepare for First Cyclone in Over Five Decades ### Summary: Residents in Brisbane and the Gold Coast are preparing for Tropical Cyclone Alfred, the first cyclone in 51 years to hit the Australian east coast near Brisbane. The cyclone is predicted to make landfall late Thursday or early Friday, bringing destructive winds, large swells, and potential life-threatening flooding. Brisbane, with over 3 million residents, may see up to 20,000 homes affected by flooding. The government has provided 250,000 sandbags and established cyclone refuge centers. Schools, public transport, and non-urgent hospital surgeries will be suspended. Queensland Premier David Crisafulli has urged residents to prepare their homes and plan evacuation routes. Sources: [AP News - 6 March 2025](https://apnews.com/article/f40a46f400f42d7d94dc5a91cb11c11a) ## Cyclone Alfred's Approach Prompts Widespread Preparations ### Summary: Cyclone Alfred, a Category 2 storm, is approaching the Tweed Coast near Brisbane, expected to make landfall late Thursday or early Friday. As tension mounts, residents are bracing for potential disaster with power outages and water contamination being the main concerns. Supermarkets are emptied of essential supplies, and emergency preparations, such as sandbagging and securing properties, are in full swing. The community displays remarkable solidarity, with neighbors helping one another and sharing real-time updates. Surfers are taking advantage of the monster swells, enjoying the waves despite the looming threat. Families face difficult decisions on whether to stay or evacuate, while prioritizing the safety and well-being of their loved ones. With a keen sense of unity and preparedness, the community waits in hope that their efforts will withstand the upcoming storm. Sources: [News.com.au - 6 March 2025](https://www.news.com.au/technology/environment/every-nerve-jangling-queenslanders-prepare-for-disaster-as-cyclone-alfred-nears/news-story/23e6cd554103de012374c1ce238ba8c7) ## Cyclone Alfred's Unusual Path Raises Concerns ### Summary: Australia is preparing for a rare tropical cyclone, named Alfred, approaching Brisbane. Authorities are urging residents in flood-prone suburbs to evacuate due to potential destructive wind gusts up to 155 kph and significant rainfall that could lead to life-threatening flash flooding. The storm is expected to land as a Category 2 cyclone early on Friday. Evacuation efforts are in place, with heavy-lift helicopters deployed and evacuation centers being opened. Schools and public transport will shut down, and flights have been canceled in the affected regions. This area of southeast Queensland and northern New South Wales has not experienced such a cyclone for over fifty years. Sources: [Reuters - 6 March 2025](https://www.reuters.com/business/environment/australias-east-coast-braces-cyclone-alfred-2025-03-04/) ## Ice Cube Shares Experience Amid Cyclone Alfred ### Summary: Ice Cube is currently staying at a beachfront hotel in Australia as Cyclone Alfred intensifies. The 55-year-old rapper and actor, who is there for upcoming performances, humorously commented about experiencing a cyclone for the first time. Residents in flood-prone regions have been advised to evacuate, with heavy rains and strong winds expected to cause potentially life-threatening flash floods and severe storm conditions. The cyclone is particularly significant for Queensland, which hasn't seen such severe weather in decades. Ice Cube also denied rumors of his involvement in an 'Anaconda' reboot being filmed in Australia, stating he was only there for his Sydney show. Sources: [People - 6 March 2025](https://people.com/ice-cube-australian-hotel-cyclone-alfred-11691119) ## Cyclone Alfred's Impact on Northern New South Wales ### Summary: Residents in Northern New South Wales are preparing for the impacts of Cyclone Alfred, with rainfalls of up to 400 millimeters expected, alongside winds of up to 150 kilometers per hour and likely flooding. The cyclone's approach has led to heightened concerns and preparations in the region. Sources: [ABC News - 6 March 2025](https://www.abc.net.au/news/2025-03-06/tropical-cyclone-alfred-northern-nsw/105014292) ## Authorities Urge Evacuations as Cyclone Alfred Nears ### Summary: Residents in flood-prone suburbs of Brisbane and the Gold Coast are being urged to evacuate as Cyclone Alfred approaches. The storm is expected to bring destructive winds and heavy rainfall, leading to life-threatening flash flooding. Evacuation centers have been established, and emergency services are on high alert to assist those in need. Sources: [The Guardian - 6 March 2025](https://www.theguardian.com/australia-news/live/2025/mar/06/tropical-cylone-alfred-live-update-brisbane-queensland-nsw-suburbs-weather-bom-forecast-path-track-map-school-closures) @ 05933d87:81bac46e
2025-03-05 20:17:49A few months ago, an Uber driver alerted me to [the presence of his rival](https://stacker.news/items/687682/r/k00b?commentId=688882). By that point, [Waymo had been testing in Austin](https://waymo.com/blog/2023/08/waymo-one-heads-to-austin/) for over a year. I hid my excitement during the ride but I applied as a beta tester, noting my belonging to the demographics a PM might test for. My application went ignored until, huzzah, Waymo sent me an email yesterday announcing [their self-driving cars are available directly through Uber in Austin](https://waymo.com/waymo-on-uber/).  I configured my allegiance to our new overlords swearing in on my screened sandwich of silicon. Without willing it, and having forgot my new religion, I woke earlier than planned today and hailed a ride. The app spoke to me, "if you wait 3 minutes longer, we'll send you a car without a driver." For five minutes, I watched a car but not a driver move in the direction of me and my screen. The ride was nice. I didn't have to theatrically rush to a waiting human. There was less social weirdness than I would normally sit with on a ride. I could inspect the car without risking the driver sense that I'm inspecting them. The car couldn't look at me buffering, deciphering if I am homeless or merely look it. I got to pick my own music. I got to watch people un-contacted by Waymo watch the car.  But ... it drove a lot more like a robot driving a car than a human driving a car. It pumped the brakes a few times as we passed weirdly parked cars uncertain (apparently) if the car might move into our lane. Once it signaled that we were headed into oncoming traffic as a street widened from one lane to two. Worst of all, it dropped me off near an anomalous stretch of sidewalk where my door opened to a wall, and if I were to climb and get out the other side, I'd arrive in the middle lane of a busy street. Trapped, I pinched myself through the door and, like Laura Croft, navigated the road's edge to a sidewalk.  tbh I'm still excited for my next Waymo ride. I'll just choose a different drop-off address. originally posted at https://stacker.news/items/904830
@ 05933d87:81bac46e
2025-03-05 20:17:49A few months ago, an Uber driver alerted me to [the presence of his rival](https://stacker.news/items/687682/r/k00b?commentId=688882). By that point, [Waymo had been testing in Austin](https://waymo.com/blog/2023/08/waymo-one-heads-to-austin/) for over a year. I hid my excitement during the ride but I applied as a beta tester, noting my belonging to the demographics a PM might test for. My application went ignored until, huzzah, Waymo sent me an email yesterday announcing [their self-driving cars are available directly through Uber in Austin](https://waymo.com/waymo-on-uber/).  I configured my allegiance to our new overlords swearing in on my screened sandwich of silicon. Without willing it, and having forgot my new religion, I woke earlier than planned today and hailed a ride. The app spoke to me, "if you wait 3 minutes longer, we'll send you a car without a driver." For five minutes, I watched a car but not a driver move in the direction of me and my screen. The ride was nice. I didn't have to theatrically rush to a waiting human. There was less social weirdness than I would normally sit with on a ride. I could inspect the car without risking the driver sense that I'm inspecting them. The car couldn't look at me buffering, deciphering if I am homeless or merely look it. I got to pick my own music. I got to watch people un-contacted by Waymo watch the car.  But ... it drove a lot more like a robot driving a car than a human driving a car. It pumped the brakes a few times as we passed weirdly parked cars uncertain (apparently) if the car might move into our lane. Once it signaled that we were headed into oncoming traffic as a street widened from one lane to two. Worst of all, it dropped me off near an anomalous stretch of sidewalk where my door opened to a wall, and if I were to climb and get out the other side, I'd arrive in the middle lane of a busy street. Trapped, I pinched myself through the door and, like Laura Croft, navigated the road's edge to a sidewalk.  tbh I'm still excited for my next Waymo ride. I'll just choose a different drop-off address. originally posted at https://stacker.news/items/904830 @ 878dff7c:037d18bc
2025-03-05 20:12:53## Queensland Premier Urges Immediate Preparations Ahead of Cyclone Alfred ### Summary: Queensland Premier David Crisafulli has urged residents to complete their preparations immediately as Tropical Cyclone Alfred approaches. The Category 2 cyclone is expected to bring heavy rainfall, destructive winds, and potential flooding to South-East Queensland and Northern New South Wales. Public transport services and elective surgeries have been canceled, and hundreds of schools will remain closed through the week. Residents are advised to stay indoors and ensure their safety during the cyclone's landfall. Sources: [The Guardian - March 5, 2025](https://www.theguardian.com/australia-news/live/2025/mar/05/australia-news-live-tropical-cyclone-alfred-brisbane-gold-coast-floods-storm-election-anthony-albanese-peter-dutton-ntwnfb), [News.com.au - March 6, 2025](https://www.news.com.au/technology/environment/1000km-warning-zone-alfred-set-to-hit-millions/news-story/6faff4d5aeb7a2c962dd94d46655fcea) ## Evacuation Orders Issued as Cyclone Alfred Approaches ### Summary: Authorities have issued evacuation orders for residents in Northern New South Wales, particularly in areas from Tweed to Yamba, as Cyclone Alfred intensifies. The cyclone is expected to bring gale-force winds, heavy rainfall up to 400 mm, and significant flooding. Schools and flights have been disrupted, with widespread closures and cancellations in the region. Coastal areas are experiencing high winds and massive waves, increasing the risk of flash floods. Emergency services are on high alert, preparing residents and reinforcing infrastructure to manage imminent threats. Sources: [The Daily Telegraph - March 6, 2025](https://www.dailytelegraph.com.au/news/regional/latest-on-tropical-cyclone-alfred-fears-for-northern-nsw-as-system-intensifies/news-story/b52b74b763dc895afa9fedcb33063925), [News.com.au - March 6, 2025](https://www.news.com.au/technology/environment/1000km-warning-zone-alfred-set-to-hit-millions/news-story/6faff4d5aeb7a2c962dd94d46655fcea) ## Liberal Senator Alex Antic's Rise Signals Shift to Conservatism in South Australia ### Summary: Liberal Senator Alex Antic has ascended to the top position on South Australia's Senate ticket, marking a significant shift from the state's traditionally moderate Liberal stance to a more conservative direction. This change follows the resignation of veteran moderate Simon Birmingham and an influx of social conservatives and libertarians into the party. Antic, known for his controversial views, believes that conservative values are gaining traction as the world reaches "peak woke." He emphasizes the importance of adhering to traditional conservative principles to appeal to families concerned about social issues and younger individuals focused on economic matters. Despite past conflicts with party moderates, Antic is optimistic about the party's future under leaders like Peter Dutton, noting similar conservative movements globally. Sources: [The Australian - March 5, 2025](https://www.theaustralian.com.au/nation/politics/antiwoke-warrior-welcomes-libs-step-to-the-right/news-story/6ce80aadb64afecc0b1744141671a5c1) ## Government's $130k Weekly Legal Fees for Toll Reform Under Scrutiny ### Summary: The Minns government's efforts to reform Sydney's toll network have cost taxpayers over $8 million, with legal advice alone amounting to $130,000 per week since February 5, 2025. Despite these expenditures, significant changes have yet to be implemented, leading to criticism over the prioritization of consultancy fees over actionable toll reforms. Sources: [The Daily Telegraph - March 6, 2025](https://www.dailytelegraph.com.au/news/nsw/taxpayers-slugged-130k-per-week-for-legal-advice-on-toll-reform/news-story/01d7ef103b0e6af03e92ee39de667326) ## Tech Giants Generate $27 Billion Annually from Australian Consumers ### Summary: An analysis by the Parliamentary Budget Office reveals that the top 16 tech companies, including Google, Microsoft, Meta, and Amazon, collectively earn $26.7 billion annually from Australian consumers. The Greens propose a 3% tax on these companies' revenues exceeding $20 million, potentially generating $11.5 billion for the government to fund essential services like dental care in Medicare. However, this proposal faces challenges due to potential retaliatory measures from the U.S. government. Sources: [The Guardian - 6 March 2025](https://www.theguardian.com/technology/2025/mar/06/google-microsoft-meta-and-amazon-among-tech-companies-making-27bn-from-australians) ## Melioidosis Outbreak in Queensland ### Summary: Queensland is experiencing a significant outbreak of melioidosis, a serious disease caused by the bacteria *Burkholderia pseudomallei*, typically found in soil and freshwater. The bacteria can infect humans and animals through cuts, contaminated water, or inhalation. Symptoms include fever, headache, respiratory issues, and muscle pain. This year, there have been over 90 confirmed cases and 15 deaths in Queensland, higher than usual. The outbreak is believed to be linked to heavy rainfall and flooding, increasing the bacteria's prevalence. Preventative measures include wearing protective gear in wet areas and seeking early medical attention for symptoms like fever and breathing difficulties. Sources: [The Advertiser - 3 March 2025](https://www.adelaidenow.com.au/lifestyle/what-is-melioidosis-the-deadly-disease-spreading-in-australia/news-story/05448740ef803a0ead29f8175670474b) ## Philippine Defense Chief Warns Against Chinese Restrictions in South China Sea ### Summary: Philippine Defense Secretary Gilberto Teodoro warned that the Philippines and its allies would respond to any Chinese attempt to impose an air defense zone or restrict flights over the South China Sea. Teodoro highlighted China's growing aggression in the disputed waters, which has led to increased confrontations involving Chinese and Philippine forces, as well as incidents with U.S. and Australian military aircraft. Recent encounters have included close flybys and warning flares from Chinese aircraft. Teodoro emphasized that China's actions pose a major threat to both Philippine and global security due to the region's critical trade routes. He stated that defense officials are preparing contingency measures and could act alone or with international partners to counter potential Chinese aggression. Teodoro noted the possibility of a broader coalition forming to resist China's attempts to reshape international law and norms. Sources: [Associated Press - 6 March 2025](https://apnews.com/article/4c63b28b674c63b1730a22dc9faa5f22) ## Amazon Joins Quantum Computing Race with 'Cat Qubit' Chip ### Summary: Amazon has unveiled its new quantum computing chip, Ocelot, which utilizes "cat qubit" technology to significantly reduce quantum errors—a major hurdle in developing commercially viable quantum systems. This advancement positions Amazon alongside other tech giants like Google and Microsoft in the quest for functional quantum computers. Sources: [SHRM - March 6, 2025](https://www.shrm.org/enterprise-solutions/insights/other-tomorrowist-trends-news-march-6-2025) ## New $1 Billion Fund Launched to Boost Australia's Circular Economy ### Summary: Planet Ark and Boston Global have partnered to launch the BG Planet Ark Circular Future Fund, aiming to raise $1 billion by 2030 to invest in businesses promoting sustainability, reducing carbon emissions, and enhancing the circular economy. This initiative aligns with Australia's Circular Economy Framework, which seeks to double circularity by 2035 and add $26 billion annually to the GDP. Initial funding of $100 million has been secured, targeting sectors like regenerative farming and waste-to-energy solutions. Sources: [The Australian - March 6, 2025](https://www.theaustralian.com.au/business/renewable-energy-economy/planet-ark-and-boston-global-join-forces-on-1bn-investment-fund-targeting-waste-reduction/news-story/067a6b67d9a3e51e61d5155e472e2bb6) ## Australia's Foreign Minister Comments on Trump's Second Term ### Summary: Foreign Minister Penny Wong has remarked that Donald Trump's second presidency is already more disruptive than his first. She noted that Australia's government is dealing with a very different American administration, reflecting concerns about potential shifts in international relations and policies affecting Australia's strategic interests. Sources: [Reuters - March 5, 2025](https://www.reuters.com/world/trumps-second-term-already-more-disruptive-than-his-first-australias-foreign-2025-03-05/)
@ 878dff7c:037d18bc
2025-03-05 20:12:53## Queensland Premier Urges Immediate Preparations Ahead of Cyclone Alfred ### Summary: Queensland Premier David Crisafulli has urged residents to complete their preparations immediately as Tropical Cyclone Alfred approaches. The Category 2 cyclone is expected to bring heavy rainfall, destructive winds, and potential flooding to South-East Queensland and Northern New South Wales. Public transport services and elective surgeries have been canceled, and hundreds of schools will remain closed through the week. Residents are advised to stay indoors and ensure their safety during the cyclone's landfall. Sources: [The Guardian - March 5, 2025](https://www.theguardian.com/australia-news/live/2025/mar/05/australia-news-live-tropical-cyclone-alfred-brisbane-gold-coast-floods-storm-election-anthony-albanese-peter-dutton-ntwnfb), [News.com.au - March 6, 2025](https://www.news.com.au/technology/environment/1000km-warning-zone-alfred-set-to-hit-millions/news-story/6faff4d5aeb7a2c962dd94d46655fcea) ## Evacuation Orders Issued as Cyclone Alfred Approaches ### Summary: Authorities have issued evacuation orders for residents in Northern New South Wales, particularly in areas from Tweed to Yamba, as Cyclone Alfred intensifies. The cyclone is expected to bring gale-force winds, heavy rainfall up to 400 mm, and significant flooding. Schools and flights have been disrupted, with widespread closures and cancellations in the region. Coastal areas are experiencing high winds and massive waves, increasing the risk of flash floods. Emergency services are on high alert, preparing residents and reinforcing infrastructure to manage imminent threats. Sources: [The Daily Telegraph - March 6, 2025](https://www.dailytelegraph.com.au/news/regional/latest-on-tropical-cyclone-alfred-fears-for-northern-nsw-as-system-intensifies/news-story/b52b74b763dc895afa9fedcb33063925), [News.com.au - March 6, 2025](https://www.news.com.au/technology/environment/1000km-warning-zone-alfred-set-to-hit-millions/news-story/6faff4d5aeb7a2c962dd94d46655fcea) ## Liberal Senator Alex Antic's Rise Signals Shift to Conservatism in South Australia ### Summary: Liberal Senator Alex Antic has ascended to the top position on South Australia's Senate ticket, marking a significant shift from the state's traditionally moderate Liberal stance to a more conservative direction. This change follows the resignation of veteran moderate Simon Birmingham and an influx of social conservatives and libertarians into the party. Antic, known for his controversial views, believes that conservative values are gaining traction as the world reaches "peak woke." He emphasizes the importance of adhering to traditional conservative principles to appeal to families concerned about social issues and younger individuals focused on economic matters. Despite past conflicts with party moderates, Antic is optimistic about the party's future under leaders like Peter Dutton, noting similar conservative movements globally. Sources: [The Australian - March 5, 2025](https://www.theaustralian.com.au/nation/politics/antiwoke-warrior-welcomes-libs-step-to-the-right/news-story/6ce80aadb64afecc0b1744141671a5c1) ## Government's $130k Weekly Legal Fees for Toll Reform Under Scrutiny ### Summary: The Minns government's efforts to reform Sydney's toll network have cost taxpayers over $8 million, with legal advice alone amounting to $130,000 per week since February 5, 2025. Despite these expenditures, significant changes have yet to be implemented, leading to criticism over the prioritization of consultancy fees over actionable toll reforms. Sources: [The Daily Telegraph - March 6, 2025](https://www.dailytelegraph.com.au/news/nsw/taxpayers-slugged-130k-per-week-for-legal-advice-on-toll-reform/news-story/01d7ef103b0e6af03e92ee39de667326) ## Tech Giants Generate $27 Billion Annually from Australian Consumers ### Summary: An analysis by the Parliamentary Budget Office reveals that the top 16 tech companies, including Google, Microsoft, Meta, and Amazon, collectively earn $26.7 billion annually from Australian consumers. The Greens propose a 3% tax on these companies' revenues exceeding $20 million, potentially generating $11.5 billion for the government to fund essential services like dental care in Medicare. However, this proposal faces challenges due to potential retaliatory measures from the U.S. government. Sources: [The Guardian - 6 March 2025](https://www.theguardian.com/technology/2025/mar/06/google-microsoft-meta-and-amazon-among-tech-companies-making-27bn-from-australians) ## Melioidosis Outbreak in Queensland ### Summary: Queensland is experiencing a significant outbreak of melioidosis, a serious disease caused by the bacteria *Burkholderia pseudomallei*, typically found in soil and freshwater. The bacteria can infect humans and animals through cuts, contaminated water, or inhalation. Symptoms include fever, headache, respiratory issues, and muscle pain. This year, there have been over 90 confirmed cases and 15 deaths in Queensland, higher than usual. The outbreak is believed to be linked to heavy rainfall and flooding, increasing the bacteria's prevalence. Preventative measures include wearing protective gear in wet areas and seeking early medical attention for symptoms like fever and breathing difficulties. Sources: [The Advertiser - 3 March 2025](https://www.adelaidenow.com.au/lifestyle/what-is-melioidosis-the-deadly-disease-spreading-in-australia/news-story/05448740ef803a0ead29f8175670474b) ## Philippine Defense Chief Warns Against Chinese Restrictions in South China Sea ### Summary: Philippine Defense Secretary Gilberto Teodoro warned that the Philippines and its allies would respond to any Chinese attempt to impose an air defense zone or restrict flights over the South China Sea. Teodoro highlighted China's growing aggression in the disputed waters, which has led to increased confrontations involving Chinese and Philippine forces, as well as incidents with U.S. and Australian military aircraft. Recent encounters have included close flybys and warning flares from Chinese aircraft. Teodoro emphasized that China's actions pose a major threat to both Philippine and global security due to the region's critical trade routes. He stated that defense officials are preparing contingency measures and could act alone or with international partners to counter potential Chinese aggression. Teodoro noted the possibility of a broader coalition forming to resist China's attempts to reshape international law and norms. Sources: [Associated Press - 6 March 2025](https://apnews.com/article/4c63b28b674c63b1730a22dc9faa5f22) ## Amazon Joins Quantum Computing Race with 'Cat Qubit' Chip ### Summary: Amazon has unveiled its new quantum computing chip, Ocelot, which utilizes "cat qubit" technology to significantly reduce quantum errors—a major hurdle in developing commercially viable quantum systems. This advancement positions Amazon alongside other tech giants like Google and Microsoft in the quest for functional quantum computers. Sources: [SHRM - March 6, 2025](https://www.shrm.org/enterprise-solutions/insights/other-tomorrowist-trends-news-march-6-2025) ## New $1 Billion Fund Launched to Boost Australia's Circular Economy ### Summary: Planet Ark and Boston Global have partnered to launch the BG Planet Ark Circular Future Fund, aiming to raise $1 billion by 2030 to invest in businesses promoting sustainability, reducing carbon emissions, and enhancing the circular economy. This initiative aligns with Australia's Circular Economy Framework, which seeks to double circularity by 2035 and add $26 billion annually to the GDP. Initial funding of $100 million has been secured, targeting sectors like regenerative farming and waste-to-energy solutions. Sources: [The Australian - March 6, 2025](https://www.theaustralian.com.au/business/renewable-energy-economy/planet-ark-and-boston-global-join-forces-on-1bn-investment-fund-targeting-waste-reduction/news-story/067a6b67d9a3e51e61d5155e472e2bb6) ## Australia's Foreign Minister Comments on Trump's Second Term ### Summary: Foreign Minister Penny Wong has remarked that Donald Trump's second presidency is already more disruptive than his first. She noted that Australia's government is dealing with a very different American administration, reflecting concerns about potential shifts in international relations and policies affecting Australia's strategic interests. Sources: [Reuters - March 5, 2025](https://www.reuters.com/world/trumps-second-term-already-more-disruptive-than-his-first-australias-foreign-2025-03-05/) @ 2e8970de:63345c7a
2025-03-05 19:50:10 > It leads to fast, and massive weight loss by not just suppressing appetite, but also by upregulating metabolism. https://www.nejm.org/doi/full/10.1056/NEJMoa2301972 originally posted at https://stacker.news/items/904851
@ 2e8970de:63345c7a
2025-03-05 19:50:10 > It leads to fast, and massive weight loss by not just suppressing appetite, but also by upregulating metabolism. https://www.nejm.org/doi/full/10.1056/NEJMoa2301972 originally posted at https://stacker.news/items/904851 @ 4925ea33:025410d8
2025-03-05 19:44:37De acordo com a Resolução 03/25 do Conselho Federal de Farmácia a Aromaterapia é uma prática terapêutica que utiliza as propriedades dos óleos essenciais para restaurar o equilíbrio e a harmonia do organismo, promovendo a saúde física, mental e emocional. Essa técnica baseia-se no uso dos compostos aromáticos naturais extraídos das plantas para estimular respostas neurológicas e bioquímicas no corpo. Os óleos essenciais atuam diretamente no sistema límbico, região do cérebro responsável pelas emoções, memórias e comportamentos. Mas seus benefícios vão muito além do bem-estar emocional! Eles possuem propriedades terapêuticas únicas, podendo atuar como cicatrizantes, antifúngicos, antibacterianos, anti-inflamatórios e até auxiliares no alívio de dores e tensões musculares. Além da inalação, os óleos podem ser aplicados topicamente, sendo absorvidos pela pele e interagindo com o organismo de maneira profunda e eficaz. No entanto, é importante lembrar que os óleos essenciais são altamente concentrados e contêm substâncias que podem causar alergias ou irritações se usados de forma inadequada. Por isso, é essencial buscar orientação de um profissional qualificado para garantir um tratamento seguro e eficaz. **Quer saber como a Aromaterapia pode transformar seu bem-estar? Agende uma consulta comigo e descubra os benefícios personalizados para você**.
@ 4925ea33:025410d8
2025-03-05 19:44:37De acordo com a Resolução 03/25 do Conselho Federal de Farmácia a Aromaterapia é uma prática terapêutica que utiliza as propriedades dos óleos essenciais para restaurar o equilíbrio e a harmonia do organismo, promovendo a saúde física, mental e emocional. Essa técnica baseia-se no uso dos compostos aromáticos naturais extraídos das plantas para estimular respostas neurológicas e bioquímicas no corpo. Os óleos essenciais atuam diretamente no sistema límbico, região do cérebro responsável pelas emoções, memórias e comportamentos. Mas seus benefícios vão muito além do bem-estar emocional! Eles possuem propriedades terapêuticas únicas, podendo atuar como cicatrizantes, antifúngicos, antibacterianos, anti-inflamatórios e até auxiliares no alívio de dores e tensões musculares. Além da inalação, os óleos podem ser aplicados topicamente, sendo absorvidos pela pele e interagindo com o organismo de maneira profunda e eficaz. No entanto, é importante lembrar que os óleos essenciais são altamente concentrados e contêm substâncias que podem causar alergias ou irritações se usados de forma inadequada. Por isso, é essencial buscar orientação de um profissional qualificado para garantir um tratamento seguro e eficaz. **Quer saber como a Aromaterapia pode transformar seu bem-estar? Agende uma consulta comigo e descubra os benefícios personalizados para você**. @ b4403b24:83542d4e
2025-03-05 19:18:39  I can't believe so many shitcoiners are invited to attend 🫣 originally posted at https://stacker.news/items/904818
@ b4403b24:83542d4e
2025-03-05 19:18:39  I can't believe so many shitcoiners are invited to attend 🫣 originally posted at https://stacker.news/items/904818 @ a296b972:e5a7a2e8
2025-03-05 18:34:49Von Egon Bahr stammt der Satz: „Wir können politisch alles Mögliche ändern, nur nicht die Geografie.“ Er scheint der letzte deutsche Politiker gewesen zu sein, der wusste, dass Europa zwischen den USA im Westen und Russland im Osten liegt. Die tektonische Plattenverschiebung wird daran über kurz oder lang auch nichts ändern.   Europa, besonders Deutschland, wird erneut von der Weltgeschichte die Möglichkeit gegeben, seine ihm ureigenste Rolle anzunehmen, nämlich endlich eine neutrale, vermittelnde Rolle zwischen West und Ost zu ergreifen. Stattdessen verscherzt Europa es sich derzeit mit beiden Weltmächten. Das muss man erst einmal hinbekommen. Wie doof kann man sein? Brücken bauen scheint man in Deutschland nicht mehr zu können. Sieht man ja in Dresden. Deutschland scheint diese Chance erneut nicht zu erkennen, da es spätestens seit dem C-Ereignis, entgegen den USA zumindest teilweise, bis heute nicht wieder zu Verstand gekommen ist. Eigentlich schon früher, nur da hat man es noch nicht so gemerkt. Bis auf wenige Ausnahmen wird ganz Europa derzeit von Verrückten und deren Erfüllungsgehilfen geleitet. Allein die Aussage der CDU in Deutschland einen Tag nach der Wahl, „Die Ukraine muss den Krieg gewinnen“, zeigt, dass weiterhin nicht alle Porzellan-Trinkgefäße in dem dafür vorgesehenen Küchenmöbel vorhanden sind. Es werden „Kriegs-Konferenzen“ einberufen, wie man die Ukraine weiter mit Geld und Waffen unterstützen kann, statt zu erkennen, dass sich der Wind Richtung Frieden gedreht hat. Europa hat zwar nichts zu sagen, dennoch kann Dummheit gefährlich werden. Es können Teller zerdeppert werden, die man besser nicht angerührt hätte. Jeder Banker schüttelt den Kopf und drückt auf den Alarmknopf unter der Schreibtischplatte, wenn man zu ihm geht und um ein Sondervermögen ansucht. Hexenmeister Deutschland kann Geld herbeizaubern, allein durch seinen politischen Willen, Kraft seiner Gedanken. Schöpfung aus dem Nichts. Und warum drängt sich gerade Deutschland schon wieder so nach vorne? Was steht im Zeugnis von Deutschland? Geschichtsunterricht: nicht teilgenommen Alles, wofür Deutschland einmal stand, für Frieden und Diplomatie, scheint einer allgemeinen Kriegslüsternheit des Polit-Büros gewichen zu sein, obwohl die Arsenale leer sind (Gottseidank!). Eine Aufrüstung sowohl logistisch, personell als auch materialmäßig würde mindestens 10 Jahre dauern. Da kann man nur hoffen, dass Putin so lange wartet, wo doch aus allen Propagandarohren geschossen wird, dass er seine imperialistischen Phantasien nach der Ukraine weiter in Richtung Europa ausleben will. Erst nach Polen und dann mit dem Trampolin von Brandenburg aus direkt nach Berlin. Das war’s. Dabei brauchen wir gar keinen Feind von außen. Deutschland ist ja bereits mit der BRD im Krieg. Man spekuliert auf einen europäischen Schutzschild mit Frankreich als Land mit Atomwaffen. Wie lächerlich ist das denn? Das erinnert an einen Yorkshire-Terrier, der ein Pferd anbellt. Die immer noch gültige Feindstaaten-Klausel scheint für alle zu gelten, nur nicht für die, die sie betrifft, also Deutschland. Sie ist durch den 2 + 4 – Vertrag nicht aufgehoben worden, weil der kein Friedensvertrag ist. Trump spricht davon, seine Truppen aus Europa, aus Deutschland abzuziehen. Es kursieren Gerüchte, dass er gar die NATO verlassen könnte. Dann steht Deutschland völlig blank da – stets aufs Äußerste zur Entschlossenheit bereit! Panik im Hühnerstall, weil der Fuchs in der Nähe gesehen wurde. Und statt Überlegungen in Richtung Neutralität anzustellen, was gut zu Deutschland, im Verbund mit Österreich und der Schweiz als deutschsprachigen Kulturraum passen würde, überlegt man, wie man die Arbeiter der niedergehenden Autoindustrie in der Rüstungsindustrie anschlussverwenden kann. Es ist alles nur noch irre. Wer Pazifist und für den Frieden ist, delegitimiert den Staat, ist reeeeechts. Ja, wo sind wir denn inzwischen gelandet? Im Emsland macht die Polizei folgende Ansage durch einen Lautsprecher: „Beachten Sie die Beschränkungen. Ausrufe, wie „Stoppt das Morden“, „Stoppt den Krieg“ und weiterfolgend, haben zu unterbleiben.“ Vielleicht spekuliert man ja darauf, dass es eine neue Migrationswelle nach Europa gibt. Diesmal von denen, die von der US-Regierung als Deep State-Angehörige aufgespürt werden. Mit ihrem Geld und Einfluss kämen sie den Großmanns-Phantasien der Europäer gerade recht. Herzlich Willkommen, ihr Deep-State-Fachkräfte! Mit den zukünftig in der deutschen Regierung befindlichen Alt-Parteien wird es ein „Weiter so“ in Richtung Niedergang geben. Ein weiteres Zeichen dafür, dass Deutschland von Masochisten gelenkt wird. Wie man an den Wahlergebnissen sehen kann, befindet sich ein großer Teil der Bevölkerung immer noch im Dauer-Tiefschlaf. Und der wache Rest schaut ohnmächtig zu, wie die Katastrophe weiter ihren Lauf nimmt. Die einzige friedliche Möglichkeit, diesem schadenbringenden Treiben ein Ende zu bereiten, wäre dem Staat den Geldhahn zuzudrehen: Steuerzahlungs-Verweigerung, Einstellung der Zwangsgebühren für den Staats-Propaganda-Funk, Verweigerung der Kammer-Zwangs-Beiträge, doch da landet man im Knast. Da stößt die vielgepriesene Freiheit in „Unseredemokratie“ an ihre Grenzen. Und dass all die Missstände ja nicht an die breite Öffentlichkeit gelangen, wird fleißig zensiert und zum Denunzieren angeregt, wozu es Menschen braucht, die sich dafür hergeben, und die es aber offensichtlich zu geben scheint. Der Digital Services Act ist nichts weiter, als die Weiterentwicklung des Fernsehens der DDR, oder noch schlimmeres. Jüngst erst wurde eine Telefonseelsorge für diejenigen eingerichtet, die auf dem Pfad des tugendhaft betreuten Denkens vom Weg abgekommen sind. Bereue und Dir wird vergeben! Bei den vorletzten Wahlen mussten die Bürger einen Maulkorb tragen, bei der jüngsten Bundestagswahl hatten sie diesen bereits in den Kopf implantiert, da fast die Hälfte der Deutschen meint, ihre Meinung nicht mehr frei äußern zu können. Wenn das mal keinen Einfluss auf die Wahlentscheidung hatte. Man kann recht pessimistisch sein, dass in absehbarer Zeit wieder die Vernunft Einzug in die Köpfe der Verantwortlichen hält, daher ist zu vermuten, dass Europa erst komplett implodieren muss, bevor ein Neuanfang möglich sein wird. Man kann aber auch optimistisch sein, da Deutschland, in der EU der größte Geldgeber, derzeit fleißig daran arbeitet, dass der Karren tiefst möglich in den Dreck gefahren wird. Fein, weg mit dem Brüsseler Bürokratie-Monster und zurück zur Europäischen Wirtschaftsgemeinschaft. Die Sommerzeit, die Gurken-Krümmungs-Verordnung und die Tetra-Pak-Deckel-Ehe würde man wohl kaum vermissen. Die zahlreichen Universal-Dilettanten und Kriegs-Maulhelden in ganz Europa werden ihren Teil dazu beitragen, den Deppen-Status in der Welt zu manifestieren. Nicht ganz so rosig wäre es, wenn die US-Deep-State-Migranten auf die Idee kämen, in Europa Fuß fassen zu wollen. Das wäre dann eher ein Neuanfang mit einer E-ID, dem digitalen Bargeld, einem Social-Credit-System, also den feuchten Träumen des WEFs, 15-Minuten-Städten, KI-gesteuerter Mobilität und totaler Versklavung durch 24/7/365-Überwachung. Die Kriminell-Kommissarin, das Röschen in Brüssel, arbeitet auch hier schon emsig wie ein Bienchen. Wenn hinter all dem Trump-Getöse dasselbe steckt, haben wir sowieso verloren. Europa befindet sich am Scheideweg. Quo vadis? Die breite Masse fühlt sich in ihrem Weltbild „verunsichert“. Eingeschüchtert von Messer-Fachkräften und Autos, die trotz Fahrer einfach so in Menschenmengen rasen, weil sie es wollen. Ob ein System hinter den Anschlägen steckt, oder nicht, spielt gar keine Rolle. Es passiert. Was, wenn der Staat sagt, jetzt ist Schluss, wir greifen durch. Zum Schutze und zur Sicherheit der Bevölkerung führen wir eine persönliche ID ein, als Abschreckungsmaßnahme, damit ja kein Irrer mehr auch nur auf die Idee kommt, so einen Anschlag verüben zu wollen. Wollt ihr zu eurem eigenen Schutz die totale Überwachung? „JAAAAAAA!“ Die positiv Gestimmten behaupten zwar, es würden immer mehr Menschen wach werden, doch obwohl die Wecker nun schon seit 5 Jahren ununterbrochen laut klingeln, geht das viel zu langsam. Bis auch Lieschen Müller aus Hinterdeppendorf verstanden hat, dass wir nach allen Regeln der Kunst belogen und betrogen werden, ist es wahrscheinlich schon längst soweit, dass die Falle zugeschnappt ist. Und dann wird das Geheule groß sein: „Ach hätten wir doch mal…“ Ja, wenn so viele nicht immer noch viel zu bequem, behäbig und träge wären, hätten wir schon längst die Pfeifen in unseren europäischen Parlamenten inklusive des Affen-Zirkus in Brüssel in die Wüste geschickt. Ja, wir brauchen eine Revolution, aber eine geistige! Wie bekommen wir die Denkvergiftung durch jahrzehntelanges Starren auf die Inhalte der öffentlich-rechtlichen Anstalt für Propaganda und Volksverblödung als Gehirnwaschanlage aus den Köpfen der Leute wieder heraus? Lieber wartet man auf den Erlöser, der es schon richten wird. Ich habe ja schließlich gewählt, mehr kann ich nicht tun. Nein, der kommt nicht. Der Fritzefanzler ist es leider auch nicht. Der wechselt seine Meinung schneller, als man ein Paar Socken an- und ausgezogen hat. Da nutzen auch seine markig akzentuierten Sprechabsonderungen nichts. Schon jetzt muss man sein Bild umdrehen, damit die Mundwinkel einmal nach oben zeigen. Warum ist er traurig? Geht es dem Sauerländer nicht schnell genug, den Rest von Deutschland in Essig einzulegen, damit dieses Land vollkommen in ein trefflich schmeckendes Glas Gewürzgurken verwandelt wird? Es wäre an uns, uns unserer Kraft als Souverän bewusst zu werden und die Schritte einzuleiten, die nötig sind, um ein friedliches und einträgliches miteinander der Nationen zu leben. Die Menschen wollen keinen Krieg, es sind immer die Staaten. In Rumänien, in Bulgarien sind die Menschen massenweise auf der Straße und drücken ihren Protest aus. In Deutschland geht das nicht. Man hat ja noch die Kartoffeln auf dem Herd und kann solange nicht weg. Es sei denn, man kann ein paar Euro dazuverdienen, das ist dann was anderes. Und endlich ist dann auch noch einmal was im Leben der enkellosen Großmutter los. Krieg ist nur die Durchsetzung von Politik mit anderen Mitteln. Es ging und geht nie um Menschenleben, sondern um das erbarmungslose Durchsetzen von staatlichen Interessen, die gefälligst im schlimmsten Fall vom dämlichen Volk als Kanonenfutter umzusetzen sind. Nach den Impfverweigerern kommen vielleicht bald die Kriegsdienstverweigerer in den Fokus. Ich soll mein Leben für ein Land auf’s Spiel setzen, das einen Bockmist nach dem anderen baut? Bin ich lebensmüde? Und obendrein zahlt der brave Bürger auch noch die Zeche, mit seinem sauer verdienten Geld durch legalisierten Steuerraub. Jeder würde wohl gerne Steuern zahlen, wenn das Geld sinnvoll verwendet würde. Ein Hochrüsten gehört ganz sicher nicht dazu. Geschickteres Ausbeuten von Staatsseite geht nicht, und dümmer nicht von Seiten der Bevölkerung, die sich das gefallen lässt. Die Demokratie-Simulation hat bislang recht gut funktioniert. Es bleibt zu hoffen, dass es ein guter Wind ist, der da von Westen über den Atlantik nach Europa weht und diese ganzen verklebten Gehirne einmal so richtig durchbläst. Die Ereignisse überschlagen sich derzeit, wer weiß?
@ a296b972:e5a7a2e8
2025-03-05 18:34:49Von Egon Bahr stammt der Satz: „Wir können politisch alles Mögliche ändern, nur nicht die Geografie.“ Er scheint der letzte deutsche Politiker gewesen zu sein, der wusste, dass Europa zwischen den USA im Westen und Russland im Osten liegt. Die tektonische Plattenverschiebung wird daran über kurz oder lang auch nichts ändern.   Europa, besonders Deutschland, wird erneut von der Weltgeschichte die Möglichkeit gegeben, seine ihm ureigenste Rolle anzunehmen, nämlich endlich eine neutrale, vermittelnde Rolle zwischen West und Ost zu ergreifen. Stattdessen verscherzt Europa es sich derzeit mit beiden Weltmächten. Das muss man erst einmal hinbekommen. Wie doof kann man sein? Brücken bauen scheint man in Deutschland nicht mehr zu können. Sieht man ja in Dresden. Deutschland scheint diese Chance erneut nicht zu erkennen, da es spätestens seit dem C-Ereignis, entgegen den USA zumindest teilweise, bis heute nicht wieder zu Verstand gekommen ist. Eigentlich schon früher, nur da hat man es noch nicht so gemerkt. Bis auf wenige Ausnahmen wird ganz Europa derzeit von Verrückten und deren Erfüllungsgehilfen geleitet. Allein die Aussage der CDU in Deutschland einen Tag nach der Wahl, „Die Ukraine muss den Krieg gewinnen“, zeigt, dass weiterhin nicht alle Porzellan-Trinkgefäße in dem dafür vorgesehenen Küchenmöbel vorhanden sind. Es werden „Kriegs-Konferenzen“ einberufen, wie man die Ukraine weiter mit Geld und Waffen unterstützen kann, statt zu erkennen, dass sich der Wind Richtung Frieden gedreht hat. Europa hat zwar nichts zu sagen, dennoch kann Dummheit gefährlich werden. Es können Teller zerdeppert werden, die man besser nicht angerührt hätte. Jeder Banker schüttelt den Kopf und drückt auf den Alarmknopf unter der Schreibtischplatte, wenn man zu ihm geht und um ein Sondervermögen ansucht. Hexenmeister Deutschland kann Geld herbeizaubern, allein durch seinen politischen Willen, Kraft seiner Gedanken. Schöpfung aus dem Nichts. Und warum drängt sich gerade Deutschland schon wieder so nach vorne? Was steht im Zeugnis von Deutschland? Geschichtsunterricht: nicht teilgenommen Alles, wofür Deutschland einmal stand, für Frieden und Diplomatie, scheint einer allgemeinen Kriegslüsternheit des Polit-Büros gewichen zu sein, obwohl die Arsenale leer sind (Gottseidank!). Eine Aufrüstung sowohl logistisch, personell als auch materialmäßig würde mindestens 10 Jahre dauern. Da kann man nur hoffen, dass Putin so lange wartet, wo doch aus allen Propagandarohren geschossen wird, dass er seine imperialistischen Phantasien nach der Ukraine weiter in Richtung Europa ausleben will. Erst nach Polen und dann mit dem Trampolin von Brandenburg aus direkt nach Berlin. Das war’s. Dabei brauchen wir gar keinen Feind von außen. Deutschland ist ja bereits mit der BRD im Krieg. Man spekuliert auf einen europäischen Schutzschild mit Frankreich als Land mit Atomwaffen. Wie lächerlich ist das denn? Das erinnert an einen Yorkshire-Terrier, der ein Pferd anbellt. Die immer noch gültige Feindstaaten-Klausel scheint für alle zu gelten, nur nicht für die, die sie betrifft, also Deutschland. Sie ist durch den 2 + 4 – Vertrag nicht aufgehoben worden, weil der kein Friedensvertrag ist. Trump spricht davon, seine Truppen aus Europa, aus Deutschland abzuziehen. Es kursieren Gerüchte, dass er gar die NATO verlassen könnte. Dann steht Deutschland völlig blank da – stets aufs Äußerste zur Entschlossenheit bereit! Panik im Hühnerstall, weil der Fuchs in der Nähe gesehen wurde. Und statt Überlegungen in Richtung Neutralität anzustellen, was gut zu Deutschland, im Verbund mit Österreich und der Schweiz als deutschsprachigen Kulturraum passen würde, überlegt man, wie man die Arbeiter der niedergehenden Autoindustrie in der Rüstungsindustrie anschlussverwenden kann. Es ist alles nur noch irre. Wer Pazifist und für den Frieden ist, delegitimiert den Staat, ist reeeeechts. Ja, wo sind wir denn inzwischen gelandet? Im Emsland macht die Polizei folgende Ansage durch einen Lautsprecher: „Beachten Sie die Beschränkungen. Ausrufe, wie „Stoppt das Morden“, „Stoppt den Krieg“ und weiterfolgend, haben zu unterbleiben.“ Vielleicht spekuliert man ja darauf, dass es eine neue Migrationswelle nach Europa gibt. Diesmal von denen, die von der US-Regierung als Deep State-Angehörige aufgespürt werden. Mit ihrem Geld und Einfluss kämen sie den Großmanns-Phantasien der Europäer gerade recht. Herzlich Willkommen, ihr Deep-State-Fachkräfte! Mit den zukünftig in der deutschen Regierung befindlichen Alt-Parteien wird es ein „Weiter so“ in Richtung Niedergang geben. Ein weiteres Zeichen dafür, dass Deutschland von Masochisten gelenkt wird. Wie man an den Wahlergebnissen sehen kann, befindet sich ein großer Teil der Bevölkerung immer noch im Dauer-Tiefschlaf. Und der wache Rest schaut ohnmächtig zu, wie die Katastrophe weiter ihren Lauf nimmt. Die einzige friedliche Möglichkeit, diesem schadenbringenden Treiben ein Ende zu bereiten, wäre dem Staat den Geldhahn zuzudrehen: Steuerzahlungs-Verweigerung, Einstellung der Zwangsgebühren für den Staats-Propaganda-Funk, Verweigerung der Kammer-Zwangs-Beiträge, doch da landet man im Knast. Da stößt die vielgepriesene Freiheit in „Unseredemokratie“ an ihre Grenzen. Und dass all die Missstände ja nicht an die breite Öffentlichkeit gelangen, wird fleißig zensiert und zum Denunzieren angeregt, wozu es Menschen braucht, die sich dafür hergeben, und die es aber offensichtlich zu geben scheint. Der Digital Services Act ist nichts weiter, als die Weiterentwicklung des Fernsehens der DDR, oder noch schlimmeres. Jüngst erst wurde eine Telefonseelsorge für diejenigen eingerichtet, die auf dem Pfad des tugendhaft betreuten Denkens vom Weg abgekommen sind. Bereue und Dir wird vergeben! Bei den vorletzten Wahlen mussten die Bürger einen Maulkorb tragen, bei der jüngsten Bundestagswahl hatten sie diesen bereits in den Kopf implantiert, da fast die Hälfte der Deutschen meint, ihre Meinung nicht mehr frei äußern zu können. Wenn das mal keinen Einfluss auf die Wahlentscheidung hatte. Man kann recht pessimistisch sein, dass in absehbarer Zeit wieder die Vernunft Einzug in die Köpfe der Verantwortlichen hält, daher ist zu vermuten, dass Europa erst komplett implodieren muss, bevor ein Neuanfang möglich sein wird. Man kann aber auch optimistisch sein, da Deutschland, in der EU der größte Geldgeber, derzeit fleißig daran arbeitet, dass der Karren tiefst möglich in den Dreck gefahren wird. Fein, weg mit dem Brüsseler Bürokratie-Monster und zurück zur Europäischen Wirtschaftsgemeinschaft. Die Sommerzeit, die Gurken-Krümmungs-Verordnung und die Tetra-Pak-Deckel-Ehe würde man wohl kaum vermissen. Die zahlreichen Universal-Dilettanten und Kriegs-Maulhelden in ganz Europa werden ihren Teil dazu beitragen, den Deppen-Status in der Welt zu manifestieren. Nicht ganz so rosig wäre es, wenn die US-Deep-State-Migranten auf die Idee kämen, in Europa Fuß fassen zu wollen. Das wäre dann eher ein Neuanfang mit einer E-ID, dem digitalen Bargeld, einem Social-Credit-System, also den feuchten Träumen des WEFs, 15-Minuten-Städten, KI-gesteuerter Mobilität und totaler Versklavung durch 24/7/365-Überwachung. Die Kriminell-Kommissarin, das Röschen in Brüssel, arbeitet auch hier schon emsig wie ein Bienchen. Wenn hinter all dem Trump-Getöse dasselbe steckt, haben wir sowieso verloren. Europa befindet sich am Scheideweg. Quo vadis? Die breite Masse fühlt sich in ihrem Weltbild „verunsichert“. Eingeschüchtert von Messer-Fachkräften und Autos, die trotz Fahrer einfach so in Menschenmengen rasen, weil sie es wollen. Ob ein System hinter den Anschlägen steckt, oder nicht, spielt gar keine Rolle. Es passiert. Was, wenn der Staat sagt, jetzt ist Schluss, wir greifen durch. Zum Schutze und zur Sicherheit der Bevölkerung führen wir eine persönliche ID ein, als Abschreckungsmaßnahme, damit ja kein Irrer mehr auch nur auf die Idee kommt, so einen Anschlag verüben zu wollen. Wollt ihr zu eurem eigenen Schutz die totale Überwachung? „JAAAAAAA!“ Die positiv Gestimmten behaupten zwar, es würden immer mehr Menschen wach werden, doch obwohl die Wecker nun schon seit 5 Jahren ununterbrochen laut klingeln, geht das viel zu langsam. Bis auch Lieschen Müller aus Hinterdeppendorf verstanden hat, dass wir nach allen Regeln der Kunst belogen und betrogen werden, ist es wahrscheinlich schon längst soweit, dass die Falle zugeschnappt ist. Und dann wird das Geheule groß sein: „Ach hätten wir doch mal…“ Ja, wenn so viele nicht immer noch viel zu bequem, behäbig und träge wären, hätten wir schon längst die Pfeifen in unseren europäischen Parlamenten inklusive des Affen-Zirkus in Brüssel in die Wüste geschickt. Ja, wir brauchen eine Revolution, aber eine geistige! Wie bekommen wir die Denkvergiftung durch jahrzehntelanges Starren auf die Inhalte der öffentlich-rechtlichen Anstalt für Propaganda und Volksverblödung als Gehirnwaschanlage aus den Köpfen der Leute wieder heraus? Lieber wartet man auf den Erlöser, der es schon richten wird. Ich habe ja schließlich gewählt, mehr kann ich nicht tun. Nein, der kommt nicht. Der Fritzefanzler ist es leider auch nicht. Der wechselt seine Meinung schneller, als man ein Paar Socken an- und ausgezogen hat. Da nutzen auch seine markig akzentuierten Sprechabsonderungen nichts. Schon jetzt muss man sein Bild umdrehen, damit die Mundwinkel einmal nach oben zeigen. Warum ist er traurig? Geht es dem Sauerländer nicht schnell genug, den Rest von Deutschland in Essig einzulegen, damit dieses Land vollkommen in ein trefflich schmeckendes Glas Gewürzgurken verwandelt wird? Es wäre an uns, uns unserer Kraft als Souverän bewusst zu werden und die Schritte einzuleiten, die nötig sind, um ein friedliches und einträgliches miteinander der Nationen zu leben. Die Menschen wollen keinen Krieg, es sind immer die Staaten. In Rumänien, in Bulgarien sind die Menschen massenweise auf der Straße und drücken ihren Protest aus. In Deutschland geht das nicht. Man hat ja noch die Kartoffeln auf dem Herd und kann solange nicht weg. Es sei denn, man kann ein paar Euro dazuverdienen, das ist dann was anderes. Und endlich ist dann auch noch einmal was im Leben der enkellosen Großmutter los. Krieg ist nur die Durchsetzung von Politik mit anderen Mitteln. Es ging und geht nie um Menschenleben, sondern um das erbarmungslose Durchsetzen von staatlichen Interessen, die gefälligst im schlimmsten Fall vom dämlichen Volk als Kanonenfutter umzusetzen sind. Nach den Impfverweigerern kommen vielleicht bald die Kriegsdienstverweigerer in den Fokus. Ich soll mein Leben für ein Land auf’s Spiel setzen, das einen Bockmist nach dem anderen baut? Bin ich lebensmüde? Und obendrein zahlt der brave Bürger auch noch die Zeche, mit seinem sauer verdienten Geld durch legalisierten Steuerraub. Jeder würde wohl gerne Steuern zahlen, wenn das Geld sinnvoll verwendet würde. Ein Hochrüsten gehört ganz sicher nicht dazu. Geschickteres Ausbeuten von Staatsseite geht nicht, und dümmer nicht von Seiten der Bevölkerung, die sich das gefallen lässt. Die Demokratie-Simulation hat bislang recht gut funktioniert. Es bleibt zu hoffen, dass es ein guter Wind ist, der da von Westen über den Atlantik nach Europa weht und diese ganzen verklebten Gehirne einmal so richtig durchbläst. Die Ereignisse überschlagen sich derzeit, wer weiß? @ 97c70a44:ad98e322
2025-03-05 18:09:05So you've decided to join nostr! Some wide-eyed fanatic has convinced you that the "sun shines every day on the birds and the bees and the cigarette trees" in a magical land of decentralized, censorship-resistant freedom of speech - and it's waiting just over the next hill. But your experience has not been all you hoped. Before you've even had a chance to upload your AI-generated cyberpunk avatar or make up exploit codenames for your pseudonym's bio, you've been confronted with a new concept that has left you completely nonplussed. It doesn't help that this new idea might be called by any number of strange names. You may have been asked to "paste your nsec", "generate a private key", "enter your seed words", "connect with a bunker", "sign in with extension", or even "generate entropy". Sorry about that. All these terms are really referring to one concept under many different names: that of "cryptographic identity". Now, you may have noticed that I just introduced yet another new term which explains exactly nothing. You're absolutely correct. And now I'm going to proceed to ignore your complaints and talk about something completely different. But bear with me, because the juice is worth the squeeze. # Identity What is identity? There are many philosophical, political, or technical answers to this question, but for our purposes it's probably best to think of it this way: > Identity is the essence of a thing. Identity separates one thing from all others, and is itself indivisible. This definition has three parts: - Identity is "essential": a thing can change, but its identity cannot. I might re-paint my house, replace its components, sell it, or even burn it down, but its identity as something that can be referred to - "this house" - is durable, even outside the boundaries of its own physical existence. - Identity is a unit: you can't break an identity into multiple parts. A thing might be _composed_ of multiple parts, but that's only incidental to the identity of a thing, which is a _concept_, not a material thing. - Identity is distinct: identity is what separates one thing from all others - the concept of an apple can't be mixed with that of an orange; the two ideas are distinct. In the same way, a single concrete apple is distinct in identity from another - even if the component parts of the apple decompose into compost used to grow more apples. Identity is not a physical thing, but a metaphysical thing. Or, in simpler terms, identity is a "concept". I (or someone more qualified) could at this point launch into a Scholastic tangent on what "is" is, but that is, fortunately, not necessary here. The kind of identities I want to focus on here are not our _actual_ identities as people, but entirely _fictional_ identities that we use to extend our agency into the digital world. Think of it this way - your bank login does not represent _you_ as a complete person. It only represents the _access granted to you_ by the bank. This access is in fact an _entirely new identity_ that has been associated with you, and is limited in what it's useful for. Other examples of fictional identities include: - The country you live in - Your social media persona - Your mortgage - Geographical coordinates - A moment in time - A chess piece Some of these identites are inert, for example points in space and time. Other identies have agency and so are able to act in the world - even as fictional concepts. In order to do this, they must "authenticate" themselves (which means "to prove they are real"), and act within a system of established rules. For example, your D&D character exists only within the collective fiction of your D&D group, and can do anything the rules say. Its identity is authenticated simply by your claim as a member of the group that your character in fact exists. Similarly, a lawyer must prove they are a member of the Bar Association before they are allowed to practice law within that collective fiction. "Cryptographic identity" is simply another way of authenticating a fictional identity within a given system. As we'll see, it has some interesting attributes that set it apart from things like a library card or your latitude and longitude. Before we get there though, let's look in more detail at how identities are authenticated. # Certificates Merriam-Webster defines the verb "certify" as meaning "to attest authoritatively". A "certificate" is just a fancy way of saying "because I said so". Certificates are issued by a "certificate authority", someone who has the authority to "say so". Examples include your boss, your mom, or the Pope. This method of authentication is how almost every institution authenticates the people who associate with it. Colleges issue student ID cards, governments issue passports, and websites allow you to "register an account". In every case mentioned above, the "authority" creates a closed system in which a document (aka a "certificate") is issued which serves as a claim to a given identity. When someone wants to access some privileged service, location, or information, they present their certificate. The authority then validates it and grants or denies access. In the case of an international airport, the certificate is a little book printed with fancy inks. In the case of a login page, the certificate is a username and password combination. This pattern for authentication is ubiquitous, and has some very important implications. First of all, certified authentication implies that the issuer of the certificate has the right to _exclusive control_ of any identity it issues. This identity can be revoked at any time, or its permissions may change. Your social credit score may drop arbitrarily, or money might disappear from your account. When dealing with certificate authorities, you have no inherent rights. Second, certified authentication depends on the certificate authority continuing to exist. If you store your stuff at a storage facility but the company running it goes out of business, your stuff might disappear along with it. Usually, authentication via certificate authority works pretty well, since an appeal can always be made to a higher authority (nature, God, the government, etc). Authorities also can't generally dictate their terms with impunity without losing their customers, alienating their constituents, or provoking revolt. But it's also true that certification by authority creates an incentive structure that frequently leads to abuse - arbitrary deplatforming is increasingly common, and the bigger the certificate authority, the less recourse the certificate holder (or "subject") has. Certificates also put the issuer in a position to intermediate relationships that wouldn't otherwise be subject to their authority. This might take the form of selling user attention to advertisers, taking a cut of financial transactions, or selling surveillance data to third parties. Proliferation of certificate authorities is not a solution to these problems. Websites and apps frequently often offer multiple "social sign-in" options, allowing their users to choose which certificate authority to appeal to. But this only piles more value into the social platform that issues the certificate - not only can Google shut down your email inbox, they can revoke your ability to log in to every website you used their identity provider to get into. In every case, certificate issuance results in an asymmetrical power dynamic, where the issuer is able to exert significant control over the certificate holder, even in areas unrelated to the original pretext for the relationship between parties. # Self-Certification But what if we could reverse this power dynamic? What if individuals could issue their own certificates and force institutions to accept them?  Ron Swanson's counterexample notwithstanding, there's a reason I can't simply write myself a parking permit and slip it under the windshield wiper. Questions about voluntary submission to legitimate authorities aside, the fact is that we don't have the power to act without impunity - just like any other certificate authority, we have to prove our claims either by the exercise of raw power or by appeal to a higher authority. So the question becomes: which higher authority can we appeal to in order to issue our own certificates within a given system of identity? The obvious answer here is to go straight to the top and ask God himself to back our claim to self-sovereignty. However, that's not how he normally works - there's a reason they call direct acts of God "miracles". In fact, Romans 13:1 explicitly says that "the authorities that exist have been appointed by God". God has structured the universe in such a way that we must appeal to the deputies he has put in place to govern various parts of the world. Another tempting appeal might be to nature - i.e. the material world. This is the realm in which we most frequently have the experience of "self-authenticating" identities. For example, a gold coin can be authenticated by biting it or by burning it with acid. If it quacks like a duck, walks like a duck, and looks like a duck, then it probably is a duck. In most cases however, the ability to authenticate using physical claims depends on physical access, and so appeals to physical reality have major limitations when it comes to the digital world. Captchas, selfies and other similar tricks are often used to bridge the physical world into the digital, but these are increasingly easy to forge, and hard to verify. There are exceptions to this rule - an example of self-certification that makes its appeal to the physical world is that of a signature. Signatures are hard to forge - an incredible amount of data is encoded in physical signatures, from strength, to illnesses, to upbringing, to [personality](https://en.wikipedia.org/wiki/Graphology). These can even be scanned and used within the digital world as well. Even today, most contracts are sealed with some simulacrum of a physical signature. Of course, this custom is quickly becoming a mere historical curiosity, since the very act of digitizing a signature makes it trivially forgeable. So: transcendent reality is too remote to subtantiate our claims, and the material world is too limited to work within the world of information. There is another aspect of reality remaining that we might appeal to: information itself. Physical signatures authenticate physical identities by encoding unique physical data into an easily recognizable artifact. To transpose this idea to the realm of information, a "digital signature" might authenticate "digital identities" by encoding unique "digital data" into an easily recognizable artifact. Unfortunately, in the digital world we have the additional challenge that the artifact itself can be copied, undermining any claim to legitimacy. We need something that can be easily verified _and unforgeable_. # Digital Signatures In fact such a thing does exist, but calling it a "digital signature" obscures more than it reveals. We might just as well call the thing we're looking for a "digital fingerprint", or a "digital electroencephalogram". Just keep that in mind as we work our way towards defining the term - we are not looking for something _looks like a physical signature_, but for something that _does the same thing as_ a physical signature, in that it allows us to issue ourselves a credential that must be accepted by others by encoding privileged information into a recognizable, unforgeable artifact. With that, let's get into the weeds. An important idea in computer science is that of a "function". A function is a sort of information machine that converts data from one form to another. One example is the idea of "incrementing" a number. If you increment 1, you get 2. If you increment 2, you get 3. Incrementing can be reversed, by creating a complementary function that instead subtracts 1 from a number. A "one-way function" is a function that can't be reversed. A good example of a one-way function is integer rounding. If you round a number and get `5`, what number did you begin with? It's impossible to know - 5.1, 4.81, 5.332794, in fact an infinite number of numbers can be rounded to the number `5`. These numbers can also be infinitely long - for example rounding PI to the nearest integer results in the number `3`. A real-life example of a useful one-way function is `sha256`. This function is a member of a family of one-way functions called "hash functions". You can feed as much data as you like into `sha256`, and you will always get 256 bits of information out. Hash functions are especially useful because collisions between outputs are very rare - even if you change a single bit in a huge pile of data, you're almost certainly going to get a different output. Taking this a step further, there is a whole family of cryptographic one-way "trapdoor" functions that act similarly to hash functions, but which maintain a specific mathematical relationship between the input and the output which allows the input/output pair to be used in a variety of useful applications. For example, in Elliptic Curve Cryptography, scalar multiplication on an elliptic curve is used to derive the output. "Ok", you say, "that's all completely clear and lucidly explained" (thank you). "But what goes _into_ the function?" You might expect that because of our analogy to physical signatures we would have to gather an incredible amount of digital information to cram into our cryptographic trapdoor function, mashing together bank statements, a record of our heartbeat, brain waves and cellular respiration. Well, we _could_ do it that way (maybe), but there's actually a _much_ simpler solution. Let's play a quick game. What number am I thinking of? Wrong, it's 82,749,283,929,834. Good guess though. The reason we use signatures to authenticate our identity in the physical world is not because they're backed by a lot of implicit physical information, but because they're hard to forge and easy to validate. Even so, there is a lot of variation in a single person's signature, even from one moment to the next. Trapdoor functions solve the validation problem - it's trivially simple to compare one 256-bit number to another. And randomness solves the problem of forgeability. Now, randomness (A.K.A. "entropy") is actually kind of hard to generate. Random numbers that don't have enough "noise" in them are known as "pseudo-random numbers", and are weirdly easy to guess. This is why Cloudflare uses a video stream of their [giant wall of lava lamps](https://blog.cloudflare.com/randomness-101-lavarand-in-production/) to feed the random number generator that powers their CDN. For our purposes though, we can just imagine that our random numbers come from rolling a bunch of dice. To recap, we can get a digital equivalent of a physical signature (or fingerprint, etc) by 1. coming up with a random number, and 2. feeding it into our chosen trapdoor function. The random number is called the "private" part. The output of the trapdoor function is called the "public" part. These two halves are often called "keys", hence the terms "public key" and "private key". And now we come full circle - remember about 37 years ago when I introduced the term "cryptographic identity"? Well, we've finally arrived at the point where I explain what that actually is. A "cryptographic identity" is _identified_ by a public key, and _authenticated_ by the ability to prove that you know the private key. Notice that I didn't say "authenticated by the private key". If you had to reveal the private key in order to prove you know it, you could only authenticate a public key once without losing exclusive control of the key. But cryptographic identities can be authenticated any number of times because the certification is an _algorithm_ that only someone who knows the private key can execute. This is the super power that trapdoor functions have that hash functions don't. Within certain cryptosystems, it is possible to mix additional data with your private key to get yet another number in such a way that someone else who only knows the public key can _prove_ that you know the private key. For example, if my secret number is `12`, and someone tells me the number `37`, I can "combine" the two by adding them together and returning the number `49`. This "proves" that my secret number is `12`. Of course, addition is not a trapdoor function, so it's trivially easy to reverse, which is why cryptography is its own field of knowledge. # What's it for? If I haven't completely lost you yet, you might be wondering why this matters. Who cares if I can prove that I made up a random number? To answer this, let's consider a simple example: that of public social media posts. Most social media platforms function by issuing credentials and verifying them based on their internal database. When you log in to your Twitter (ok, fine, X) account, you provide X with a phone number (or email) and password. X compares these records to the ones stored in the database when you created your account, and if they match they let you "log in" by issuing yet another credential, called a "session key". Next, when you "say" something on X, you pass along your session key and your tweet to X's servers. They check that the session key is legit, and if it is they associate your tweet with your account's identity. Later, when someone wants to see the tweet, X vouches for the fact that you created it by saying "trust me" and displaying your name next to the tweet. In other words, X creates and controls your identity, but they let you use it as long as you can prove that you know the secret that you agreed on when you registered (by giving it to them every time). Now pretend that X gets bought by someone _even more evil_ than Elon Musk (if such a thing can be imagined). The new owner now has the ability to control _your_ identity, potentially making it say things that you didn't actually say. Someone could be completely banned from the platform, but their account could be made to continue saying whatever the owner of the platform wanted. In reality, such a breach of trust would quickly result in a complete loss of credibility for the platform, which is why this kind of thing doesn't happen (at least, not that we know of). But there are other ways of exploiting this system, most notably by censoring speech. As often happens, platforms are able to confiscate user identities, leaving the tenant no recourse except to appeal to the platform itself (or the government, but that doesn't seem to happen for some reason - probably due to some legalese in social platforms' terms of use). The user has to start completely from scratch, either on the same platform or another. Now suppose that when you signed up for X instead of simply telling X your password you made up a random number and provided a cryptographic proof to X along with your public key. When you're ready to tweet (there's no need to issue a session key, or even to store your public key in their database) you would again prove your ownership of that key with a new piece of data. X could then publish that tweet or not, along with the same proof you provided that it really came from you. What X _can't_ do in this system is pretend you said something you didn't, because they _don't know your private key_. X also wouldn't be able to deplatform you as effectively either. While they could choose to ban you from their website and refuse to serve your tweets, they don't control your identity. There's nothing they can do to prevent you from re-using it on another platform. Plus, if the system was set up in such a way that other users followed your key instead of an ID made up by X, you could switch platforms and _keep your followers_. In the same way, it would also be possible to keep a copy of all your tweets in your own database, since their authenticity is determined by _your_ digital signature, not X's "because I say so". This new power is not just limited to social media either. Here are some other examples of ways that self-issued cryptographic identites transform the power dynamic inherent in digital platforms: - Banks sometimes freeze accounts or confiscate funds. If your money was stored in a system based on self-issued cryptographic keys rather than custodians, banks would not be able to keep you from accessing or moving your funds. This system exists, and it's called [bitcoin](https://bitcoin.rocks/). - Identity theft happens when your identifying information is stolen and used to take out a loan in your name, and without your consent. The reason this is so common is because your credentials are not cryptographic - your name, address, and social security number can only be authenticated by being shared, and they are shared so often and with so many counterparties that they frequently end up in data breaches. If credit checks were authenticated by self-issued cryptographic keys, identity theft would cease to exist (unless your private key itself got stolen). - Cryptographic keys allow credential issuers to protect their subjects' privacy better too. Instead of showing your ID (including your home address, birth date, height, weight, etc), the DMV could sign a message asserting that the holder of a given public key indeed over 21. The liquor store could then validate that claim, and your ownership of the named key, without knowing anything more about you. [Zero-knowledge](https://en.wikipedia.org/wiki/Non-interactive_zero-knowledge_proof) proofs take this a step further. In each of these cases, the interests of the property owner, loan seeker, or customer are elevated over the interests of those who might seek to control their assets, exploit their hard work, or surveil their activity. Just as with personal privacy, freedom of speech, and Second Amendment rights the individual case is rarely decisive, but in the aggregate realigned incentives can tip the scale in favor of freedom. # Objections Now, there are some drawbacks to digital signatures. Systems that rely on digital signatures are frequently less forgiving of errors than their custodial counterparts, and many of their strengths have corresponding weaknesses. Part of this is because people haven't yet developed an intuition for how to use cryptographic identities, and the tools for managing them are still being designed. Other aspects can be mitigated through judicious use of keys fit to the problems they are being used to solve. Below I'll articulate some of these concerns, and explore ways in which they might be mitigated over time. ## Key Storage Keeping secrets is hard. "A lie can travel halfway around the world before the truth can get its boots on", and the same goes for gossip. Key storage has become increasingly important as more of our lives move online, to the extent that password managers have become almost a requirement for keeping track of our digital lives. But even with good password management, credentials frequently end up for sale on the dark web as a consequence of poorly secured infrastructure. Apart from the fact that all of this is an argument _for_ cryptographic identities (since keys are shared with far fewer parties), it's also true that the danger of losing a cryptographic key is severe, especially if that key is used in multiple places. Instead of hackers stealing your Facebook password, they might end up with access to all your other social media accounts too! Keys should be treated with the utmost care. Using password managers is a good start, but very valuable keys should be stored even more securely - for example in a [hardware signing device](https://nostrsigningdevice.com/). This is a hassle, and something additional to learn, but is an indispensable part of taking advantage of the benefits associated with cryptographic identity. There are ways to lessen the impact of lost or stolen secrets, however. Lots of different techniques exist for structuring key systems in such a way that keys can be protected, invalidated, or limited. Here are a few: - [Hierarchical Deterministic Keys](https://www.ietf.org/archive/id/draft-dijkhuis-cfrg-hdkeys-02.html) allow for the creation of a single root key from which multiple child keys can be generated. These keys are hard to link to the parent, which provides additional privacy, but this link can also be proven when necessary. One limitation is that the identity system has to be designed with HD keys in mind. - [Key Rotation](https://crypto.stackexchange.com/questions/41796/whats-the-purpose-of-key-rotation) allows keys to become expendable. Additional credentials might be attached to a key, allowing the holder to prove they have the right to rotate the key. Social attestations can help with the process as well if the key is embedded in a web of trust. - Remote Signing is a technique for storing a key on one device, but using it on another. This might take the form of signing using a hardware wallet and transferring an SD card to your computer for broadcasting, or using a mobile app like [Amber](https://github.com/greenart7c3/Amber) to manage sessions with different applications. - [Key](https://github.com/coracle-social/promenade/tree/master) [sharding](https://www.frostr.org/) takes this to another level by breaking a single key into multiple pieces and storing them separately. A coordinator can then be used to collaboratively sign messages without sharing key material. This dramatically reduces the ability of an attacker to steal a complete key. ## Multi-Factor Authentication One method for helping users secure their accounts that is becoming increasingly common is "multi-factor authentication". Instead of just providing your email and password, platforms send a one-time use code to your phone number or email, or use "time-based one time passwords" which are stored in a password manager or on a hardware device. Again, MFA is a solution to a problem inherent in account-based authentication which would not be nearly so prevalent in a cryptographic identity system. Still, theft of keys does happen, and so MFA would be an important improvement - if not for an extra layer of authentication, then as a basis for key rotation. In a sense, MFA is already being researched - key shards is one way of creating multiple credentials from a single key. However, this doesn't address the issue of key rotation, especially when an identity is tied to the public key that corresponds to a given private key. There are two possible solutions to this problem: - Introduce a naming system. This would allow identities to use a durable name, assigning it to different keys over time. The downside is that this would require the introduction of either centralized naming authorities (back to the old model), or a blockchain in order to solve [Zooko's trilemma](https://en.wikipedia.org/wiki/Zooko%27s_triangle). - Establish a chain of keys. This would require a given key to name a successor key in advance and self-invalidate, or some other process like social recovery to invalidate an old key and assign the identity to a new one. This also would significantly increase the complexity of validating messages and associating them with a given identity. Both solutions are workable, but introduce a lot of complexity that could cause more trouble than it's worth, depending on the identity system we're talking about. ## Surveillance One of the nice qualities that systems based on cryptographic identities have is that digitally signed data can be passed through any number of untrusted systems and emerge intact. This ability to resist tampering makes it possible to broadcast signed data more widely than would otherwise be the case in a system that relies on a custodian to authenticate information. The downside of this is that more untrusted systems have access to data. And if information is broadcast publicly, anyone can get access to it. This problem is compounded by re-use of cryptographic identities across multiple contexts. A benefit of self-issued credentials is that it becomes possible to bring everything attached to your identity with you, including social context and attached credentials. This is convenient and can be quite powerful, but it also means that more context is attached to your activity, making it easier to infer information about you for advertising or surveillance purposes. This is dangerously close to the dystopian ideal of a "Digital ID". The best way to deal with this risk is to consider identity re-use an option to be used when desirable, but to default to creating a new key for every identity you create. This is no worse than the status quo, and it makes room for the ability to link identities when desired. Another possible approach to this problem is to avoid broadcasting signed data when possible. This could be done by obscuring your cryptographic identity when data is served from a database, or by encrypting your signed data in order to selectively share it with named counterparties. Still, this is a real risk, and should be kept in mind when designing and using systems based on cryptographic identity. If you'd like to read more about this, please see [this blog post](https://habla.news/u/hodlbod@coracle.social/1687802006398). # Making Keys Usable You might be tempted to look at that list of trade-offs and get the sense that cryptographic identity is not for mere mortals. Key management is hard, and footguns abound - but there is a way forward. With [nostr](https://nostr.com/), some new things are happening in the world of key management that have never really happened before. Plenty of work over the last 30 years has gone into making key management tractable, but none have really been widely adopted. The reason for this is simple: network effect. Many of these older key systems only applied the thinnest veneer of humanity over keys. But an identity is much richer than a mere label. Having a real name, social connections, and a corpus of work to attach to a key creates a system of keys that _humans care about_. By bootstrapping key management within a social context, nostr ensures that the payoff of key management is worth the learning curve. Not only is social engagement a strong incentive to get off the ground, people already on the network are eager to help you get past any roadblocks you might face. So if I could offer an action item: give nostr a try today. Whether you're in it for the people and their values, or you just want to experiment with cryptographic identity, nostr is a great place to start. For a quick introduction and to securely generate keys, visit [njump.me](https://njump.me/). Thanks for taking the time to read this post. I hope it's been helpful, and I can't wait to see you on nostr!
@ 97c70a44:ad98e322
2025-03-05 18:09:05So you've decided to join nostr! Some wide-eyed fanatic has convinced you that the "sun shines every day on the birds and the bees and the cigarette trees" in a magical land of decentralized, censorship-resistant freedom of speech - and it's waiting just over the next hill. But your experience has not been all you hoped. Before you've even had a chance to upload your AI-generated cyberpunk avatar or make up exploit codenames for your pseudonym's bio, you've been confronted with a new concept that has left you completely nonplussed. It doesn't help that this new idea might be called by any number of strange names. You may have been asked to "paste your nsec", "generate a private key", "enter your seed words", "connect with a bunker", "sign in with extension", or even "generate entropy". Sorry about that. All these terms are really referring to one concept under many different names: that of "cryptographic identity". Now, you may have noticed that I just introduced yet another new term which explains exactly nothing. You're absolutely correct. And now I'm going to proceed to ignore your complaints and talk about something completely different. But bear with me, because the juice is worth the squeeze. # Identity What is identity? There are many philosophical, political, or technical answers to this question, but for our purposes it's probably best to think of it this way: > Identity is the essence of a thing. Identity separates one thing from all others, and is itself indivisible. This definition has three parts: - Identity is "essential": a thing can change, but its identity cannot. I might re-paint my house, replace its components, sell it, or even burn it down, but its identity as something that can be referred to - "this house" - is durable, even outside the boundaries of its own physical existence. - Identity is a unit: you can't break an identity into multiple parts. A thing might be _composed_ of multiple parts, but that's only incidental to the identity of a thing, which is a _concept_, not a material thing. - Identity is distinct: identity is what separates one thing from all others - the concept of an apple can't be mixed with that of an orange; the two ideas are distinct. In the same way, a single concrete apple is distinct in identity from another - even if the component parts of the apple decompose into compost used to grow more apples. Identity is not a physical thing, but a metaphysical thing. Or, in simpler terms, identity is a "concept". I (or someone more qualified) could at this point launch into a Scholastic tangent on what "is" is, but that is, fortunately, not necessary here. The kind of identities I want to focus on here are not our _actual_ identities as people, but entirely _fictional_ identities that we use to extend our agency into the digital world. Think of it this way - your bank login does not represent _you_ as a complete person. It only represents the _access granted to you_ by the bank. This access is in fact an _entirely new identity_ that has been associated with you, and is limited in what it's useful for. Other examples of fictional identities include: - The country you live in - Your social media persona - Your mortgage - Geographical coordinates - A moment in time - A chess piece Some of these identites are inert, for example points in space and time. Other identies have agency and so are able to act in the world - even as fictional concepts. In order to do this, they must "authenticate" themselves (which means "to prove they are real"), and act within a system of established rules. For example, your D&D character exists only within the collective fiction of your D&D group, and can do anything the rules say. Its identity is authenticated simply by your claim as a member of the group that your character in fact exists. Similarly, a lawyer must prove they are a member of the Bar Association before they are allowed to practice law within that collective fiction. "Cryptographic identity" is simply another way of authenticating a fictional identity within a given system. As we'll see, it has some interesting attributes that set it apart from things like a library card or your latitude and longitude. Before we get there though, let's look in more detail at how identities are authenticated. # Certificates Merriam-Webster defines the verb "certify" as meaning "to attest authoritatively". A "certificate" is just a fancy way of saying "because I said so". Certificates are issued by a "certificate authority", someone who has the authority to "say so". Examples include your boss, your mom, or the Pope. This method of authentication is how almost every institution authenticates the people who associate with it. Colleges issue student ID cards, governments issue passports, and websites allow you to "register an account". In every case mentioned above, the "authority" creates a closed system in which a document (aka a "certificate") is issued which serves as a claim to a given identity. When someone wants to access some privileged service, location, or information, they present their certificate. The authority then validates it and grants or denies access. In the case of an international airport, the certificate is a little book printed with fancy inks. In the case of a login page, the certificate is a username and password combination. This pattern for authentication is ubiquitous, and has some very important implications. First of all, certified authentication implies that the issuer of the certificate has the right to _exclusive control_ of any identity it issues. This identity can be revoked at any time, or its permissions may change. Your social credit score may drop arbitrarily, or money might disappear from your account. When dealing with certificate authorities, you have no inherent rights. Second, certified authentication depends on the certificate authority continuing to exist. If you store your stuff at a storage facility but the company running it goes out of business, your stuff might disappear along with it. Usually, authentication via certificate authority works pretty well, since an appeal can always be made to a higher authority (nature, God, the government, etc). Authorities also can't generally dictate their terms with impunity without losing their customers, alienating their constituents, or provoking revolt. But it's also true that certification by authority creates an incentive structure that frequently leads to abuse - arbitrary deplatforming is increasingly common, and the bigger the certificate authority, the less recourse the certificate holder (or "subject") has. Certificates also put the issuer in a position to intermediate relationships that wouldn't otherwise be subject to their authority. This might take the form of selling user attention to advertisers, taking a cut of financial transactions, or selling surveillance data to third parties. Proliferation of certificate authorities is not a solution to these problems. Websites and apps frequently often offer multiple "social sign-in" options, allowing their users to choose which certificate authority to appeal to. But this only piles more value into the social platform that issues the certificate - not only can Google shut down your email inbox, they can revoke your ability to log in to every website you used their identity provider to get into. In every case, certificate issuance results in an asymmetrical power dynamic, where the issuer is able to exert significant control over the certificate holder, even in areas unrelated to the original pretext for the relationship between parties. # Self-Certification But what if we could reverse this power dynamic? What if individuals could issue their own certificates and force institutions to accept them?  Ron Swanson's counterexample notwithstanding, there's a reason I can't simply write myself a parking permit and slip it under the windshield wiper. Questions about voluntary submission to legitimate authorities aside, the fact is that we don't have the power to act without impunity - just like any other certificate authority, we have to prove our claims either by the exercise of raw power or by appeal to a higher authority. So the question becomes: which higher authority can we appeal to in order to issue our own certificates within a given system of identity? The obvious answer here is to go straight to the top and ask God himself to back our claim to self-sovereignty. However, that's not how he normally works - there's a reason they call direct acts of God "miracles". In fact, Romans 13:1 explicitly says that "the authorities that exist have been appointed by God". God has structured the universe in such a way that we must appeal to the deputies he has put in place to govern various parts of the world. Another tempting appeal might be to nature - i.e. the material world. This is the realm in which we most frequently have the experience of "self-authenticating" identities. For example, a gold coin can be authenticated by biting it or by burning it with acid. If it quacks like a duck, walks like a duck, and looks like a duck, then it probably is a duck. In most cases however, the ability to authenticate using physical claims depends on physical access, and so appeals to physical reality have major limitations when it comes to the digital world. Captchas, selfies and other similar tricks are often used to bridge the physical world into the digital, but these are increasingly easy to forge, and hard to verify. There are exceptions to this rule - an example of self-certification that makes its appeal to the physical world is that of a signature. Signatures are hard to forge - an incredible amount of data is encoded in physical signatures, from strength, to illnesses, to upbringing, to [personality](https://en.wikipedia.org/wiki/Graphology). These can even be scanned and used within the digital world as well. Even today, most contracts are sealed with some simulacrum of a physical signature. Of course, this custom is quickly becoming a mere historical curiosity, since the very act of digitizing a signature makes it trivially forgeable. So: transcendent reality is too remote to subtantiate our claims, and the material world is too limited to work within the world of information. There is another aspect of reality remaining that we might appeal to: information itself. Physical signatures authenticate physical identities by encoding unique physical data into an easily recognizable artifact. To transpose this idea to the realm of information, a "digital signature" might authenticate "digital identities" by encoding unique "digital data" into an easily recognizable artifact. Unfortunately, in the digital world we have the additional challenge that the artifact itself can be copied, undermining any claim to legitimacy. We need something that can be easily verified _and unforgeable_. # Digital Signatures In fact such a thing does exist, but calling it a "digital signature" obscures more than it reveals. We might just as well call the thing we're looking for a "digital fingerprint", or a "digital electroencephalogram". Just keep that in mind as we work our way towards defining the term - we are not looking for something _looks like a physical signature_, but for something that _does the same thing as_ a physical signature, in that it allows us to issue ourselves a credential that must be accepted by others by encoding privileged information into a recognizable, unforgeable artifact. With that, let's get into the weeds. An important idea in computer science is that of a "function". A function is a sort of information machine that converts data from one form to another. One example is the idea of "incrementing" a number. If you increment 1, you get 2. If you increment 2, you get 3. Incrementing can be reversed, by creating a complementary function that instead subtracts 1 from a number. A "one-way function" is a function that can't be reversed. A good example of a one-way function is integer rounding. If you round a number and get `5`, what number did you begin with? It's impossible to know - 5.1, 4.81, 5.332794, in fact an infinite number of numbers can be rounded to the number `5`. These numbers can also be infinitely long - for example rounding PI to the nearest integer results in the number `3`. A real-life example of a useful one-way function is `sha256`. This function is a member of a family of one-way functions called "hash functions". You can feed as much data as you like into `sha256`, and you will always get 256 bits of information out. Hash functions are especially useful because collisions between outputs are very rare - even if you change a single bit in a huge pile of data, you're almost certainly going to get a different output. Taking this a step further, there is a whole family of cryptographic one-way "trapdoor" functions that act similarly to hash functions, but which maintain a specific mathematical relationship between the input and the output which allows the input/output pair to be used in a variety of useful applications. For example, in Elliptic Curve Cryptography, scalar multiplication on an elliptic curve is used to derive the output. "Ok", you say, "that's all completely clear and lucidly explained" (thank you). "But what goes _into_ the function?" You might expect that because of our analogy to physical signatures we would have to gather an incredible amount of digital information to cram into our cryptographic trapdoor function, mashing together bank statements, a record of our heartbeat, brain waves and cellular respiration. Well, we _could_ do it that way (maybe), but there's actually a _much_ simpler solution. Let's play a quick game. What number am I thinking of? Wrong, it's 82,749,283,929,834. Good guess though. The reason we use signatures to authenticate our identity in the physical world is not because they're backed by a lot of implicit physical information, but because they're hard to forge and easy to validate. Even so, there is a lot of variation in a single person's signature, even from one moment to the next. Trapdoor functions solve the validation problem - it's trivially simple to compare one 256-bit number to another. And randomness solves the problem of forgeability. Now, randomness (A.K.A. "entropy") is actually kind of hard to generate. Random numbers that don't have enough "noise" in them are known as "pseudo-random numbers", and are weirdly easy to guess. This is why Cloudflare uses a video stream of their [giant wall of lava lamps](https://blog.cloudflare.com/randomness-101-lavarand-in-production/) to feed the random number generator that powers their CDN. For our purposes though, we can just imagine that our random numbers come from rolling a bunch of dice. To recap, we can get a digital equivalent of a physical signature (or fingerprint, etc) by 1. coming up with a random number, and 2. feeding it into our chosen trapdoor function. The random number is called the "private" part. The output of the trapdoor function is called the "public" part. These two halves are often called "keys", hence the terms "public key" and "private key". And now we come full circle - remember about 37 years ago when I introduced the term "cryptographic identity"? Well, we've finally arrived at the point where I explain what that actually is. A "cryptographic identity" is _identified_ by a public key, and _authenticated_ by the ability to prove that you know the private key. Notice that I didn't say "authenticated by the private key". If you had to reveal the private key in order to prove you know it, you could only authenticate a public key once without losing exclusive control of the key. But cryptographic identities can be authenticated any number of times because the certification is an _algorithm_ that only someone who knows the private key can execute. This is the super power that trapdoor functions have that hash functions don't. Within certain cryptosystems, it is possible to mix additional data with your private key to get yet another number in such a way that someone else who only knows the public key can _prove_ that you know the private key. For example, if my secret number is `12`, and someone tells me the number `37`, I can "combine" the two by adding them together and returning the number `49`. This "proves" that my secret number is `12`. Of course, addition is not a trapdoor function, so it's trivially easy to reverse, which is why cryptography is its own field of knowledge. # What's it for? If I haven't completely lost you yet, you might be wondering why this matters. Who cares if I can prove that I made up a random number? To answer this, let's consider a simple example: that of public social media posts. Most social media platforms function by issuing credentials and verifying them based on their internal database. When you log in to your Twitter (ok, fine, X) account, you provide X with a phone number (or email) and password. X compares these records to the ones stored in the database when you created your account, and if they match they let you "log in" by issuing yet another credential, called a "session key". Next, when you "say" something on X, you pass along your session key and your tweet to X's servers. They check that the session key is legit, and if it is they associate your tweet with your account's identity. Later, when someone wants to see the tweet, X vouches for the fact that you created it by saying "trust me" and displaying your name next to the tweet. In other words, X creates and controls your identity, but they let you use it as long as you can prove that you know the secret that you agreed on when you registered (by giving it to them every time). Now pretend that X gets bought by someone _even more evil_ than Elon Musk (if such a thing can be imagined). The new owner now has the ability to control _your_ identity, potentially making it say things that you didn't actually say. Someone could be completely banned from the platform, but their account could be made to continue saying whatever the owner of the platform wanted. In reality, such a breach of trust would quickly result in a complete loss of credibility for the platform, which is why this kind of thing doesn't happen (at least, not that we know of). But there are other ways of exploiting this system, most notably by censoring speech. As often happens, platforms are able to confiscate user identities, leaving the tenant no recourse except to appeal to the platform itself (or the government, but that doesn't seem to happen for some reason - probably due to some legalese in social platforms' terms of use). The user has to start completely from scratch, either on the same platform or another. Now suppose that when you signed up for X instead of simply telling X your password you made up a random number and provided a cryptographic proof to X along with your public key. When you're ready to tweet (there's no need to issue a session key, or even to store your public key in their database) you would again prove your ownership of that key with a new piece of data. X could then publish that tweet or not, along with the same proof you provided that it really came from you. What X _can't_ do in this system is pretend you said something you didn't, because they _don't know your private key_. X also wouldn't be able to deplatform you as effectively either. While they could choose to ban you from their website and refuse to serve your tweets, they don't control your identity. There's nothing they can do to prevent you from re-using it on another platform. Plus, if the system was set up in such a way that other users followed your key instead of an ID made up by X, you could switch platforms and _keep your followers_. In the same way, it would also be possible to keep a copy of all your tweets in your own database, since their authenticity is determined by _your_ digital signature, not X's "because I say so". This new power is not just limited to social media either. Here are some other examples of ways that self-issued cryptographic identites transform the power dynamic inherent in digital platforms: - Banks sometimes freeze accounts or confiscate funds. If your money was stored in a system based on self-issued cryptographic keys rather than custodians, banks would not be able to keep you from accessing or moving your funds. This system exists, and it's called [bitcoin](https://bitcoin.rocks/). - Identity theft happens when your identifying information is stolen and used to take out a loan in your name, and without your consent. The reason this is so common is because your credentials are not cryptographic - your name, address, and social security number can only be authenticated by being shared, and they are shared so often and with so many counterparties that they frequently end up in data breaches. If credit checks were authenticated by self-issued cryptographic keys, identity theft would cease to exist (unless your private key itself got stolen). - Cryptographic keys allow credential issuers to protect their subjects' privacy better too. Instead of showing your ID (including your home address, birth date, height, weight, etc), the DMV could sign a message asserting that the holder of a given public key indeed over 21. The liquor store could then validate that claim, and your ownership of the named key, without knowing anything more about you. [Zero-knowledge](https://en.wikipedia.org/wiki/Non-interactive_zero-knowledge_proof) proofs take this a step further. In each of these cases, the interests of the property owner, loan seeker, or customer are elevated over the interests of those who might seek to control their assets, exploit their hard work, or surveil their activity. Just as with personal privacy, freedom of speech, and Second Amendment rights the individual case is rarely decisive, but in the aggregate realigned incentives can tip the scale in favor of freedom. # Objections Now, there are some drawbacks to digital signatures. Systems that rely on digital signatures are frequently less forgiving of errors than their custodial counterparts, and many of their strengths have corresponding weaknesses. Part of this is because people haven't yet developed an intuition for how to use cryptographic identities, and the tools for managing them are still being designed. Other aspects can be mitigated through judicious use of keys fit to the problems they are being used to solve. Below I'll articulate some of these concerns, and explore ways in which they might be mitigated over time. ## Key Storage Keeping secrets is hard. "A lie can travel halfway around the world before the truth can get its boots on", and the same goes for gossip. Key storage has become increasingly important as more of our lives move online, to the extent that password managers have become almost a requirement for keeping track of our digital lives. But even with good password management, credentials frequently end up for sale on the dark web as a consequence of poorly secured infrastructure. Apart from the fact that all of this is an argument _for_ cryptographic identities (since keys are shared with far fewer parties), it's also true that the danger of losing a cryptographic key is severe, especially if that key is used in multiple places. Instead of hackers stealing your Facebook password, they might end up with access to all your other social media accounts too! Keys should be treated with the utmost care. Using password managers is a good start, but very valuable keys should be stored even more securely - for example in a [hardware signing device](https://nostrsigningdevice.com/). This is a hassle, and something additional to learn, but is an indispensable part of taking advantage of the benefits associated with cryptographic identity. There are ways to lessen the impact of lost or stolen secrets, however. Lots of different techniques exist for structuring key systems in such a way that keys can be protected, invalidated, or limited. Here are a few: - [Hierarchical Deterministic Keys](https://www.ietf.org/archive/id/draft-dijkhuis-cfrg-hdkeys-02.html) allow for the creation of a single root key from which multiple child keys can be generated. These keys are hard to link to the parent, which provides additional privacy, but this link can also be proven when necessary. One limitation is that the identity system has to be designed with HD keys in mind. - [Key Rotation](https://crypto.stackexchange.com/questions/41796/whats-the-purpose-of-key-rotation) allows keys to become expendable. Additional credentials might be attached to a key, allowing the holder to prove they have the right to rotate the key. Social attestations can help with the process as well if the key is embedded in a web of trust. - Remote Signing is a technique for storing a key on one device, but using it on another. This might take the form of signing using a hardware wallet and transferring an SD card to your computer for broadcasting, or using a mobile app like [Amber](https://github.com/greenart7c3/Amber) to manage sessions with different applications. - [Key](https://github.com/coracle-social/promenade/tree/master) [sharding](https://www.frostr.org/) takes this to another level by breaking a single key into multiple pieces and storing them separately. A coordinator can then be used to collaboratively sign messages without sharing key material. This dramatically reduces the ability of an attacker to steal a complete key. ## Multi-Factor Authentication One method for helping users secure their accounts that is becoming increasingly common is "multi-factor authentication". Instead of just providing your email and password, platforms send a one-time use code to your phone number or email, or use "time-based one time passwords" which are stored in a password manager or on a hardware device. Again, MFA is a solution to a problem inherent in account-based authentication which would not be nearly so prevalent in a cryptographic identity system. Still, theft of keys does happen, and so MFA would be an important improvement - if not for an extra layer of authentication, then as a basis for key rotation. In a sense, MFA is already being researched - key shards is one way of creating multiple credentials from a single key. However, this doesn't address the issue of key rotation, especially when an identity is tied to the public key that corresponds to a given private key. There are two possible solutions to this problem: - Introduce a naming system. This would allow identities to use a durable name, assigning it to different keys over time. The downside is that this would require the introduction of either centralized naming authorities (back to the old model), or a blockchain in order to solve [Zooko's trilemma](https://en.wikipedia.org/wiki/Zooko%27s_triangle). - Establish a chain of keys. This would require a given key to name a successor key in advance and self-invalidate, or some other process like social recovery to invalidate an old key and assign the identity to a new one. This also would significantly increase the complexity of validating messages and associating them with a given identity. Both solutions are workable, but introduce a lot of complexity that could cause more trouble than it's worth, depending on the identity system we're talking about. ## Surveillance One of the nice qualities that systems based on cryptographic identities have is that digitally signed data can be passed through any number of untrusted systems and emerge intact. This ability to resist tampering makes it possible to broadcast signed data more widely than would otherwise be the case in a system that relies on a custodian to authenticate information. The downside of this is that more untrusted systems have access to data. And if information is broadcast publicly, anyone can get access to it. This problem is compounded by re-use of cryptographic identities across multiple contexts. A benefit of self-issued credentials is that it becomes possible to bring everything attached to your identity with you, including social context and attached credentials. This is convenient and can be quite powerful, but it also means that more context is attached to your activity, making it easier to infer information about you for advertising or surveillance purposes. This is dangerously close to the dystopian ideal of a "Digital ID". The best way to deal with this risk is to consider identity re-use an option to be used when desirable, but to default to creating a new key for every identity you create. This is no worse than the status quo, and it makes room for the ability to link identities when desired. Another possible approach to this problem is to avoid broadcasting signed data when possible. This could be done by obscuring your cryptographic identity when data is served from a database, or by encrypting your signed data in order to selectively share it with named counterparties. Still, this is a real risk, and should be kept in mind when designing and using systems based on cryptographic identity. If you'd like to read more about this, please see [this blog post](https://habla.news/u/hodlbod@coracle.social/1687802006398). # Making Keys Usable You might be tempted to look at that list of trade-offs and get the sense that cryptographic identity is not for mere mortals. Key management is hard, and footguns abound - but there is a way forward. With [nostr](https://nostr.com/), some new things are happening in the world of key management that have never really happened before. Plenty of work over the last 30 years has gone into making key management tractable, but none have really been widely adopted. The reason for this is simple: network effect. Many of these older key systems only applied the thinnest veneer of humanity over keys. But an identity is much richer than a mere label. Having a real name, social connections, and a corpus of work to attach to a key creates a system of keys that _humans care about_. By bootstrapping key management within a social context, nostr ensures that the payoff of key management is worth the learning curve. Not only is social engagement a strong incentive to get off the ground, people already on the network are eager to help you get past any roadblocks you might face. So if I could offer an action item: give nostr a try today. Whether you're in it for the people and their values, or you just want to experiment with cryptographic identity, nostr is a great place to start. For a quick introduction and to securely generate keys, visit [njump.me](https://njump.me/). Thanks for taking the time to read this post. I hope it's been helpful, and I can't wait to see you on nostr!