-

@ e3ba5e1a:5e433365
2025-02-04 08:29:00
President Trump has started rolling out his tariffs, something I [blogged about in November](https://www.snoyman.com/blog/2024/11/steelmanning-tariffs/). People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I [put up a poll on X](https://x.com/snoyberg/status/1886035800019599808) to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.

For purposes of this blog post, our ultimate question will be the following:
* Suppose apples currently sell for $1 each in the entire United States.
* There are domestic sellers and foreign sellers of apples, all receiving the same price.
* There are no taxes or tariffs on the purchase of apples.
* The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following:
* Number of apples bought in the US
* Price paid by buyers for apples in the US
* Post-tax price received by domestic apple producers
* Post-tax price received by foreign apple producers
Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1?
And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why:
1. The number of apples bought will go down
2. The buyers will pay more for each apple they buy, but not the full amount of the tariff
3. Domestic apple sellers will receive a *higher* price per apple
4. Foreign apple sellers will receive a *lower* price per apple, but not lowered by the full amount of the tariff
In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit.
## Marginal benefit
All of the numbers discussed below are part of a [helper Google Sheet](https://docs.google.com/spreadsheets/d/14ZbkWpw1B9Q1UDB9Yh47DmdKQfIafVVBKbDUsSIfGZw/edit?usp=sharing) I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are [some difficulties with creating supply and demand charts in Google Sheets](https://superuser.com/questions/1359731/how-to-create-a-supply-demand-style-chart).
Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B.
But that’s not what I mean. What I mean is: how high would the price of apples have to go *everywhere* so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5.
How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot.
The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called *marginal benefit*: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal *demand curve*. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:

Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples.
## Marginal cost
Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product.
Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right?
Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of *sunk costs*. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further.
Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price\!
However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with:
* Total expenditure: $100 \+ $70 \* 8 hours a day \* 5 days \== $2900
* Total revenue: $5000 (10,000 apples at $0.50 each)
* Total profit: $2100
So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money.
This kind of analysis is called *marginal cost*. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:

## Equilibrium price
We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:

You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the *surplus* created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example:
* When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point.
* When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point.
Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.”
OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality.
## Modeling taxes
Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve.
First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:

With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve.
We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:

The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:

As we can see, the equilibrium has shifted:
* The equilibrium price paid by consumers has risen from $1 to $1.20.
* The total number of apples purchased has dropped from 63 apples to 60 apples.
* Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus.
* Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42.
* Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21.
* The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise.
We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes:
* Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples.
* Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless.
* Domestic producers scored. They can sell less apples and make more revenue doing it.
* And the government walked away with an extra $30.
Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price.
## Other taxes
Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down.
And generally speaking, this is what you’ll *always* see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost.
You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with:
* Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price.
* Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost.
* Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise.
This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
-

@ 4fe4a528:3ff6bf06
2025-02-01 13:41:28
<img src="https://blossom.primal.net/58a3e225ae607d5f110cff5f44a68268d27d3d239ba6d58279c2dd872259fbbb.jpg">
In my last article I wrote about NOSTR. I found another local bitcoiner via NOSTR last week so here is why it is important to join / use NOSTR — start telling people “Look me up on NOSTR”
Self-sovereign identity (SSI) is a revolutionary approach to digital identity that puts individuals in control of their own identity and personal data. Unlike traditional digital identity models, which rely on third-party organizations to manage and authenticate identities, SSI empowers individuals to own and manage their digital identity.
This approach is made possible by emerging technologies such as secure public / private key pairs. Decentralized identifiers, conceived and developed by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is an attempt to create a global technical standard around cryptographically secured identifiers - a secure, universal, and sovereign form of digital ID. This technology uses peer-to-peer technology to remove the need for intermediaries to own and authenticate ID information.
Notably, NOSTR, a decentralized protocol, has already begun to utilize decentralized IDs, demonstrating the potential of this technology in real-world applications. Via NOSTR, users can be sure that the person or computer publishing to a particular npub knows their nsec (password for your npub), highlighting the secure and decentralized nature of this approach.
With SSI, individuals can decide how their personal data is used, shared, and protected, giving them greater control and agency over their digital lives.
The **benefits** of SSI are numerous, including:
Enhanced security and protection of personal data. Reduced risk of identity theft and fraud Increased autonomy and agency over one's digital identity. Improved scalability and flexibility in digital identity management
**challenges**:
Ensuring the security and integrity of decentralized identity systems. Developing standards and protocols for interoperability and compatibility. Addressing concerns around ownership and control of personal data. Balancing individual autonomy with the need for verification and authentication in various contexts.
Overall, self-sovereign identity has the potential to transform the way we think about digital identity and provide individuals with greater control and agency over their personal data. Without people in control of their bitcoin seed words no freedom loving people would be able to exchange their money with others. Yes, keep enjoying using the only free market on the planet BITCOIN. Long live FREEDOM!
-

@ 9e69e420:d12360c2
2025-01-30 12:23:04
Tech stocks have taken a hit globally after China's DeepSeek launched a competitive AI chatbot at a much lower cost than US counterparts. This has stirred market fears of a $1.2 trillion loss across tech companies when trading opens in New York.
DeepSeek’s chatbot quickly topped download charts and surprised experts with its capabilities, developed for only $5.6 million.
The Nasdaq dropped over 3% in premarket trading, with major firms like Nvidia falling more than 10%. SoftBank also saw losses shortly after investing in a significant US AI venture.
Venture capitalist Marc Andreessen called it “AI’s Sputnik moment,” highlighting its potential impact on the industry.
![] (https://www.telegraph.co.uk/content/dam/business/2025/01/27/TELEMMGLPICT000409807198_17379939060750_trans_NvBQzQNjv4BqgsaO8O78rhmZrDxTlQBjdGLvJF5WfpqnBZShRL_tOZw.jpeg)
-

@ 9e69e420:d12360c2
2025-01-25 22:16:54
President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.”
The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China.
[Sauce](https://www.stripes.com/theaters/europe/2025-01-24/trump-europe-troop-cuts-16590074.html)
-

@ 9d92077c:38d27146
2025-01-20 20:46:31
Like King Arthur pulling the sword Excalibur from the stone to reclaim his rightful place as king, the Excalibur system empowers Nostr users to recover control of their digital identities and networks from malicious infiltrators. This proposal introduces a robust framework for key recovery and re-association, ensuring that users can seamlessly regain control of their accounts while preserving their social connections, metadata, and event history. In an age where security and trust are paramount, Excalibur offers a practical and resilient solution to one of the most pressing challenges in decentralized networks.
—-
# The Importance of Key Recovery on Nostr
One of Nostr’s greatest strengths is its reliance on public and private key pairs to establish identities and ensure message authenticity. However, the simplicity of this cryptographic model comes with a significant vulnerability: key compromise. If a user’s private key is lost or stolen, they face catastrophic consequences:
* Loss of Identity: The user cannot post, interact, or manage their profile.
* Disruption of Social Graph: Followers and contacts lose their connection to the user.
* Trust Erosion: An attacker controlling the compromised key can impersonate the user, damaging their reputation.
While decentralization is a core principle of Nostr, the lack of a built-in recovery mechanism undermines long-term usability and user confidence. Excalibur addresses this gap with an innovative system for recovering compromised keys and maintaining social continuity.
—-
# Proposed Solution: The Excalibur System
The Excalibur system introduces a primary key and secure backup key model to Nostr, enabling users to recover their accounts and re-associate events in the event of key compromise. This system relies on a combination of cryptographic proofs, event indexing, and client/relay cooperation to ensure a seamless and secure transition.
## 1. Primary and Secure Keys
Users establish a primary key for everyday activity and a secure backup key stored offline.
The primary key broadcasts an association with the secure key using a ```set_secure_key``` event.
## 2. Key Transition Event
Upon detecting a compromise, the user activates the secure key by publishing a ```key_transition``` event.
This event includes:
* The compromised primary key.
* The new secure key.
* A cryptographic proof linking the two.
* A timestamp and optional metadata.
## 3. Social Graph Transition
Clients automatically replace the compromised key with the secure key in follow lists, contact lists, and other social data.
Followers are notified of the transition and encouraged to follow the secure key.
## 4. Unified Identity View
Historical events remain immutable but are re-indexed by relays to associate with the secure key for continuity.
Clients display a unified profile view, differentiating old and new events.
## 5. Seamless Transition for Existing Accounts
Existing Nostr users can integrate Excalibur by broadcasting a set_secure_key event linking their current primary key to a secure backup key.
While historical events and metadata associated with the primary key remain unchanged, all new events after activation of the secure key are seamlessly associated with the updated identity.
Clients should provide user-friendly tools to guide existing users through this setup process.
## 6. Endless Security Chain
Once a secure key is activated and becomes the new primary key, users must set up a new secure backup key immediately by broadcasting a new ```set_secure_key``` event.
This ensures an endless chain of security, preventing future compromises from leaving users vulnerable.
Clients should include UX enhancements such as prompts, reminders, and automated tools to help users maintain their security chain efficiently.
## 7. Insurance Model for Relays
Users pay an upfront premium to relays for re-association services, ensuring resources are available for recovery operations.
Clients act as brokers, aggregating multiple relay insurance contracts into a single, user-friendly offering. They manage user payments, distribute premiums to participating relays, and earn a commission for their services.
This brokerage model incentivizes clients to participate actively in the Excalibur system and ensures broader adoption across the network.
—-
# Implementation Framework
## Cryptographic Foundations
- The secure key must be pre-announced and linked to the primary key using a signed ```set_secure_key``` event.
- During key transition, the key_transition event includes a signature proving the association.
## Relay Behavior
- Relays index the key_transition event and re-link historical data to the secure key.
- Events from the old key are tagged as "deprecated" but remain accessible.
## Client Behavior
- Clients validate the ```key_transition``` event and update social graphs automatically.
- Followers are notified and prompted to follow the secure key.
- Profiles display both old and new events under a unified identity.
- Clients implement features to facilitate existing users' onboarding and provide tools to manage the security chain seamlessly.
—-
# Benefits of Excalibur
**Resilience**: Users can recover from key compromise without losing their digital identity or network.
**Trust**: The cryptographic proofs ensure the legitimacy of key transitions, preserving trust in the system.
**Sustainability**: The insurance premium model incentivizes relay adoption and ensures fair resource allocation.
**User-Friendly**: Automated transitions reduce the complexity for end users, making Nostr more accessible.
**Adaptability**: Existing accounts can benefit from Excalibur without disruption, ensuring broad applicability.
—-
Call to Action
The Excalibur system is a vital enhancement to the Nostr protocol, addressing the critical issue of key recovery while maintaining decentralization and user sovereignty. By adopting Excalibur, we can strengthen the network’s resilience, foster trust, and ensure that users retain control of their identities in an ever-evolving digital landscape. We invite the Nostr community to collaborate on refining and implementing this proposal, turning the vision of Excalibur into a reality.
Together, let’s ensure that no user is ever left powerless in the face of compromise. Let’s reclaim the sword and secure the kingdom.
-

@ cff1720e:15c7e2b2
2025-01-19 17:48:02
**Einleitung**\
\
Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\
Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie <roland@pareto.space> können sie sogar jederzeit umziehen, egal wohin. **Cool, das ist state of the art!** Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.

**Warum Nostr?**
Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz **"unserer Demokratie”** praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.

Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \
\
**Resümee:** keine Standards, keine Daten, keine Rechte = keine Zukunft!

\
**Wie funktioniert Nostr?**
Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum **“single point of failure”**, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\
\
Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. <roland@pareto.space> ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\
\
**Resümee:** ein offener Standard, alle Daten, alle Rechte = große Zukunft!

\
**Warum ist Nostr die Zukunft des Internet?**
“Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie **(Value4Value)**. OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.

\
**Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.**
<https://nostr.net/> \
<https://start.njump.me/>
**Hier das Interview zum Thema mit Radio Berliner Morgenröte**
<https://www.podbean.com/ew/pb-yxc36-17bb4be>
-

@ f9cf4e94:96abc355
2025-01-18 06:09:50
Para esse exemplo iremos usar:
| Nome | Imagem | Descrição |
| --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ |
| Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** |
| Pen drive |  | **16Gb** |
Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.).
---
## Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
```bash
apt update
apt install tor
```
---
## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧
Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit
[Unit]
Description=Nostr Relay Server Service
After=network.target
[Service]
Type=simple
WorkingDirectory=/opt/nrs
ExecStart=/opt/nrs/nrs-arm64
Restart=on-failure
[Install]
WantedBy=multi-user.target
```
---
## Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases).
---
## Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
```bash
mkdir -p /opt/nrs /mnt/edriver
```
---
## Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
```bash
lsblk
```
---
## Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o:
```bash
mkfs.vfat /dev/sda
```
---
## Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta `/mnt/edriver`:
```bash
mount /dev/sda /mnt/edriver
```
---
## Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
```bash
blkid
```
---
## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝
Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:
```fstab
UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
```
---
## Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta `/opt/nrs`:
```bash
cp nrs-arm64 /opt/nrs
```
---
## Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`:
```yaml
app_env: production
info:
name: Nostr Relay Server
description: Nostr Relay Server
pub_key: ""
contact: ""
url: http://localhost:3334
icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png
base_path: /mnt/edriver
negentropy: true
```
---
## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`:
```bash
cp nrs.service /etc/systemd/system/
```
Recarregue os serviços e inicie o serviço `nrs`:
```bash
systemctl daemon-reload
systemctl enable --now nrs.service
```
---
## Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha:
```torrc
HiddenServiceDir /var/lib/tor/nostr_server/
HiddenServicePort 80 127.0.0.1:3334
```
---
## Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
```bash
systemctl enable --now tor.service
```
O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`.
---
## Observações ⚠️
- Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`.
---
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-

@ 6be5cc06:5259daf0
2025-01-18 02:11:43
1. **Not your keys, not your coins**
Se você não tem as chaves privadas do seu Bitcoin, ele não é realmente seu. Deixar seus BTCs em exchanges ou carteiras controladas por terceiros significa confiar neles e assumir o risco de perder seus fundos.
---
2. **HODL - Não venda**
O Bitcoin é uma reserva de valor a longo prazo e potencialmente o dinheiro do futuro. Não se desespere com as flutuações de preço; mantenha seus BTCs, pois o histórico se mostra favorável.
---
3. **Stay humble - Não saia falando que você tem BTC**
Manter discrição sobre seu patrimônio é uma questão de segurança e humildade. Falar demais pode atrair curiosos, oportunistas ou outras ameaças.
---
4. **Don't trust, verify**
No Bitcoin, confie no protocolo, não em pessoas. Sempre que possível, verifique por conta própria, seja transações, códigos ou informações.
---
5. **Reject altcoins**
As altcoins podem parecer promissoras, mas frequentemente são distrações ou apostas arriscadas. Foque no Bitcoin, que já provou ser sólido e resistente.
---
6. **Stack sats - DCA**
Empilhe satoshis consistentemente, utilizando a estratégia de DCA (Dollar Cost Averaging), comprando regularmente independentemente do preço. Isso reduz o risco de tentar "acertar o mercado".
---
7. **Reject the ego**
Não aposte contra o Bitcoin. Aqueles que subestimaram sua força ou estabilidade, perderam.
---
8. **Keep learning**
Nunca pare de estudar sobre Bitcoin, economia e a tecnologia por trás dele. Quanto mais você entende, mais confiança terá em sua decisão.
---
9. **Help beginners**
O Bitcoin pode ser complicado para quem está começando. Compartilhe seus conhecimentos com paciência para fortalecer a comunidade.
---
10. **Don't push it**
Cada pessoa tem seu próprio tempo para entender e entrar no mundo do Bitcoin. Forçar alguém pode ser contraproducente; dê direcionamento e deixe o tempo agir.
-

@ 6389be64:ef439d32
2025-01-14 01:31:12
Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
# Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
# Meet The Forest Walker

For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
# The Small Branch Chipper

When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
# The Gassifier

The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
# Biochar: The Waste

Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
# Wood Vinegar: More Waste

Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
# The Internal Combustion Engine

Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
# CO2 Production For Growth

Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
# The Branch Drones

During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
# The Bitcoin Miner

Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
# The Mesh Network

What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
# Back To The Chain

Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
# Sensor Packages
### LiDaR

The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
### pH, Soil Moisture, and Cation Exchange Sensing

The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
### Weather Data

Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
# Noise Suppression

Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
# Fire Safety

A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
# The Wrap

How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-

@ e3ba5e1a:5e433365
2025-01-13 16:47:27
My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity.
A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur.
The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior.
And there are plenty of incentives beyond our direct control\! My son is *also* incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take.
## Why incentives matter
A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could **just** do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example:
* If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning.
* If people would just use the recycling bin, we wouldn’t have such a landfill problem.
* If people would just stop being lazy, our team would deliver our project on time.
In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally.
* The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do.
* No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle.
* If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.

My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want.
If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is.
## Running a company
Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions.
Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good.
What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off.
Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning.
When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.

Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks\! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money.
There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals.
Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature.
# Moral hazard
Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings.
What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.

But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I *don’t* turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all.
This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as:
1. We’re so habituated to turning off the water that we don’t even consider *not* turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off.
2. Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created.
3. We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?)
Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard.
A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard.
It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend?
And since we’re talking about the government already…
## Government moral hazards
As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a *huge* number of examples of moral hazards. I decided to cherry-pick a few for this post.
The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people?
The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet.
If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior\! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups.
You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”

And here’s the absolute best part of this: I can’t even truly blame either California *or* Wall Street. (I mean, I *do* blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits.
There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions.
# Non-monetary competition
At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home.
In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.)
Anyway, my professor’s wife had a friend. My professor described in *great* detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas.
This is a demonstration of *non-monetary compensation*. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules.
The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become *wealthier and whiter*, the exact opposite of their desired outcome. Why would that happen?
Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky.
She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls.
So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites.
You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences.
## Bureaucracy
These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences.
Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings.
Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could\! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate.
# Government incentivized behavior
This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples:
* Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to [malinvestment](https://en.wikipedia.org/wiki/Malinvestment) and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience.
* Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise.
* During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation.
* The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen.
* Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example).
* Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as [high living](https://www.youtube.com/watch?v=ZwNDd2_beTU).)
# Conclusion
The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives.
We can bemoan these realities all we want, but they *are* realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People *should* take advantage of the incentives around them. Because if they don’t, someone else will.
(If you want a literary example of that last comment, see the horse in Animal Farm.)
How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula:
* Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people.
* Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them.
* And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example.
And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining\!
-

@ 0d97beae:c5274a14
2025-01-11 16:52:08
This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs
## The reason why we have broken money
Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world.
In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes.
However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore.
Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too.
Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it.
## Bitcoin overcomes the "transfer of hard money" problem
Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design.
Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it.
Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive.
Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold.
## Bitcoin blurs the line between commodity and technology
Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules.
At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable.
Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases.
## The dangers of derivatives
A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold.
In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin.
Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense.
## Learn for yourself
If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody".
There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
-

@ 37fe9853:bcd1b039
2025-01-11 15:04:40
yoyoaa
-

@ 62033ff8:e4471203
2025-01-11 15:00:24
收录的内容中 kind=1的部分,实话说 质量不高。
所以我增加了kind=30023 长文的article,但是更新的太少,多个relays 的服务器也没有多少长文。
所有搜索nostr如果需要产生价值,需要有高质量的文章和新闻。
而且现在有很多机器人的文章充满着浪费空间的作用,其他作用都用不上。
https://www.duozhutuan.com 目前放的是给搜索引擎提供搜索的原材料。没有做UI给人类浏览。所以看上去是粗糙的。
我并没有打算去做一个发microblog的 web客户端,那类的客户端太多了。
我觉得nostr社区需要解决的还是应用。如果仅仅是microblog 感觉有点够呛
幸运的是npub.pro 建站这样的,我觉得有点意思。
yakihonne 智能widget 也有意思
我做的TaskQ5 我自己在用了。分布式的任务系统,也挺好的。
-

@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52
## **Necessário**
- Um Android que você não use mais (a câmera deve estar funcionando).
- Um cartão microSD (opcional, usado apenas uma vez).
- Um dispositivo para acompanhar seus fundos (provavelmente você já tem um).
## **Algumas coisas que você precisa saber**
- O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele.
- O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito.
- A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal.
---
## **O tutorial será dividido em dois módulos:**
- Módulo 1 - Criando uma carteira fria/assinador.
- Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
---
## **No final, teremos:**
- Uma carteira fria que também servirá como assinador.
- Um dispositivo para acompanhar os fundos da carteira.

---
## **Módulo 1 - Criando uma carteira fria/assinador**
1. Baixe o APK do Electrum na aba de **downloads** em <https://electrum.org/>. Fique à vontade para [verificar as assinaturas](https://electrum.readthedocs.io/en/latest/gpg-check.html) do software, garantindo sua autenticidade.
2. Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.

3. Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.

4. Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o **modo avião**.\
*(Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)*

5. Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.

6. No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. *(Aqui entra seu método pessoal de backup.)*

---
## **Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.**
1. Criar uma carteira **somente leitura** em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em <https://electrum.org/> ou da própria Play Store. *(ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)*
2. Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção **Usar uma chave mestra**.

3. Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em **Carteira > Detalhes da carteira > Compartilhar chave mestra pública**.

4. Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los.
5. Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: **Carteira > Addresses/Coins**.
6. Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.

7. No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.

8. No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede.
---
## **Conclusão**
**Pontos positivos do setup:**
- **Simplicidade:** Basta um dispositivo Android antigo.
- **Flexibilidade:** Funciona como uma ótima carteira fria, ideal para holders.
**Pontos negativos do setup:**
- **Padronização:** Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum.
- **Interface:** A aparência do Electrum pode parecer antiquada para alguns usuários.
Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: ***Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.***
Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível.
---
-

@ e6817453:b0ac3c39
2025-01-05 14:29:17
## The Rise of Graph RAGs and the Quest for Data Quality
As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence.
## Booming Interest in Graph RAGs
Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can:
* **Enhance LLM Outputs:** By grounding responses in structured knowledge, graphs significantly reduce hallucinations.
* **Support Complex Queries:** Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving.
Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs?
## Data Quality: The Foundation of Effective Graphs
A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why:
* **Richness of Entities:** Effective retrieval depends on graphs populated with rich, detailed entities.
* **Freedom from Hallucinations:** Poorly constructed graphs amplify inaccuracies rather than mitigating them.
Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs.
## Hybrid Graph RAGs and Variations
While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that:
* Handle diverse data sources with ease.
* Offer improved adaptability to complex queries.
Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing.
## Ontology: The Key to Graph Construction Quality
Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for:
* **Defining Relationships:** Clarifying how concepts connect within a domain.
* **Validating Graph Structures:** Ensuring constructed graphs are logically sound and align with domain-specific realities.
Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs?
## How to Build Ontology Expertise in a Startup Team
For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach:
1. **Assign a Knowledge Champion:** Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering.
2. **Provide Training:** Invest in courses, workshops, or certifications in knowledge graph and ontology creation.
3. **Leverage Partnerships:** Collaborate with academic institutions, domain experts, or consultants to build initial frameworks.
4. **Utilize Tools:** Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process.
5. **Iterate with Feedback:** Continuously refine ontologies through collaboration with domain experts and iterative testing.
So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts.
You could read about barefoot experts in my article :
Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise.
## How to Find or Create Ontologies
For teams venturing into Graph RAGs, several strategies can help address the ontology gap:
1. **Leverage Existing Ontologies:** Many industries and domains already have open ontologies. For instance:
* **Public Knowledge Graphs:** Resources like Wikipedia’s graph offer a wealth of structured knowledge.
* **Industry Standards:** Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields.
* **Business Framework Ontology (BFO):** A valuable resource for enterprises looking to define business processes and structures.
1. **Build In-House Expertise:** If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation.
2. **Utilize LLMs for Ontology Construction:** Interestingly, LLMs themselves can act as a starting point for ontology development:
* **Prompt-Based Extraction:** LLMs can generate draft ontologies by leveraging their extensive training on graph data.
* **Domain Expert Refinement:** Combine LLM-generated structures with insights from domain experts to create tailored ontologies.
## Parallel Ontology and Graph Extraction
An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as:
* **Detecting Hallucinations:** Differentiating between genuine insights and AI-generated inaccuracies.
* **Ensuring Completeness:** Ensuring no critical concepts are overlooked during extraction.
Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method.
## LLMs as Ontologists
While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to:
* **Generate Skeleton Ontologies:** Prompt LLMs with domain-specific information to draft initial ontology structures.
* **Validate and Refine Ontologies:** Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance.
However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes.
## Final Thoughts: Unlocking the Power of Graph RAGs
The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools.
As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding.
Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation!
-

@ a4a6b584:1e05b95b
2025-01-02 18:13:31
## The Four-Layer Framework
### Layer 1: Zoom Out

Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what."
**Example**: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems.
- **Tip**: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage.
_Once you have the big picture in mind, it’s time to start breaking it down._
---
### Layer 2: Categorize and Connect

Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas.
**Example**: Studying biology? Group concepts into categories like cells, genetics, and ecosystems.
- **Tip**: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track.
_With your categories in place, you’re ready to dive into the details that bring them to life._
---
### Layer 3: Master the Details

Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable.
**Example**: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language.
- **Tip**: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding.
_Now that you’ve mastered the essentials, you can expand your knowledge to include extra material._
---
### Layer 4: Expand Your Horizons

Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams.
**Example**: Learn about rare programming quirks or historical trivia about a language’s development.
- **Tip**: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time.
---
## Pro Tips for Better Learning
### 1. Use Active Recall and Spaced Repetition
Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information.
### 2. Map It Out
Create visual aids like [diagrams or concept maps](https://excalidraw.com/) to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2.
### 3. Teach What You Learn
Explain the subject to someone else as if they’re hearing it for the first time. Teaching **exposes any gaps** in your understanding and **helps reinforce** the material.
### 4. Engage with LLMs and Discuss Concepts
Take advantage of tools like ChatGPT or similar large language models to **explore your topic** in greater depth. Use these tools to:
- Ask specific questions to clarify confusing points.
- Engage in discussions to simulate real-world applications of the subject.
- Generate examples or analogies that deepen your understanding.
**Tip**: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective.
---
## Get Started
Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
-

@ 4fe4a528:3ff6bf06
2025-01-01 15:50:50
I could have wrote about how bitcoin has more than doubled in 2024 or how some people are still sitting on the sidelines not trying to understand why bitcoin will double in 2025, but instead I thought I would write about how bitcoin is allowing for a decentralized social network.
Two years ago I decided to try out this NOSTR idea. Now I have 233 followers, almost the same number of people who read this monthly newsletter. Facebook / whats-app was to ad filled for me to enjoy what my friends were posting. X was great for news, but none of my friends where on it. Linkedin was just about business. Besides, NOSTR gives me more bitcoin every time I post. I am now using the bitcoin to buy eggs every two weeks from my neighbors. So to me it is a win win. I can write notes and eat eggs. I even use my NOSTR extension to log into hivetalk.org and help people with their computer issues. It is better than teaching via ZOOM. 2025 is going to be a great year for decentralization.
If you are trying to join NOSTR via your desktop I recommend going to [getalby.com](https://guides.getalby.com/user-guide/alby-account-and-browser-extension/alby-browser-extension/features) installing the browser extension. Then make an account with getalby and write down your 24 words (nsec). Link your profile to your lightning wallet and start posting and following other friends via primal.net. Yes, of course, I am put on this earth to help my fellow man. Some people enjoy using NOSTR via their cell phone and for those people I recommend amethyst or damus. We are all in this together.
-

@ 6be5cc06:5259daf0
2024-12-29 19:54:14
Um dos padrões mais bem estabelecidos ao medir a opinião pública é que cada geração tende a seguir um caminho semelhante em termos de política e ideologia geral. Seus membros compartilham das mesmas experiências formativas, atingem os marcos importantes da vida ao mesmo tempo e convivem nos mesmos espaços. Então, como devemos entender os relatórios que mostram que a **Geração Z** é hiperprogressista em certos assuntos, mas surpreendentemente conservadora em outros?
A resposta, nas palavras de **Alice Evans**, pesquisadora visitante na Universidade de Stanford e uma das principais estudiosas do tema, é que os jovens de hoje estão passando por um grande **divergência de gênero**, com as jovens mulheres do primeiro grupo e os jovens homens do segundo. A **Geração Z** representa duas gerações, e não apenas uma.
Em países de todos os continentes, surgiu um **distanciamento ideológico** entre jovens homens e mulheres. Milhões de pessoas que compartilham das mesmas cidades, locais de trabalho, salas de aula e até casas, não veem mais as coisas da mesma maneira.
Nos **Estados Unidos**, os dados da Gallup mostram que, após décadas em que os sexos estavam distribuídos de forma relativamente equilibrada entre visões políticas liberais e conservadoras, as mulheres entre **18 e 30 anos** são agora **30 pontos percentuais mais liberais** do que os homens dessa faixa etária. Essa diferença surgiu em apenas **seis anos**.
A **Alemanha** também apresenta um distanciamento de 30 pontos entre homens jovens conservadores e mulheres jovens progressistas, e no **Reino Unido**, a diferença é de **25 pontos**. Na **Polônia**, no ano passado, quase metade dos homens entre **18 e 21 anos** apoiou o partido de extrema direita Confederation, em contraste com apenas um sexto das jovens mulheres dessa mesma idade.
Fora do Ocidente, há divisões ainda mais acentuadas. Na **Coreia do Sul**, há um enorme abismo entre homens e mulheres jovens, e a situação é semelhante na **China**. Na **África**, a **Tunísia** apresenta o mesmo padrão. Vale notar que em todos os países essa divisão drástica ocorre principalmente entre a **geração mais jovem**, sendo muito menos pronunciada entre homens e mulheres na faixa dos **30 anos** ou mais velhos.
O movimento **# MeToo** foi o **principal estopim**, trazendo à tona valores feministas intensos entre jovens mulheres que se sentiram empoderadas para denunciar injustiças de longa data. Esse estopim encontrou especialmente terreno fértil na **Coreia do Sul**, onde a **desigualdade de gênero** é bastante visível e a **misoginia explícita** é comum. (palavras da Financial Times, eu só traduzi)
Na eleição presidencial da **Coreia do Sul** em **2022**, enquanto homens e mulheres mais velhos votaram de forma unificada, os jovens homens apoiaram fortemente o partido de direita **People Power**, enquanto as jovens mulheres apoiaram o partido liberal **Democratic** em números quase iguais e opostos.
A situação na **Coreia** é extrema, mas serve como um alerta para outros países sobre o que pode acontecer quando jovens homens e mulheres se distanciam. A sociedade está **dividida**, a taxa de casamento despencou e a taxa de natalidade caiu drasticamente, chegando a **0,78 filhos por mulher** em **2022**, o menor número no mundo todo.
Sete anos após a explosão inicial do movimento **# MeToo**, a **divergência de gênero** em atitudes tornou-se autossustentável.
Dados das pesquisas mostram que em muitos países, as diferenças ideológicas vão além dessa questão específica. A divisão progressista-conservadora sobre **assédio sexual** parece ter causado ou pelo menos faz parte de um **alinhamento mais amplo**, em que jovens homens e mulheres estão se organizando em grupos conservadores e liberais em outros assuntos.
Nos **EUA**, **Reino Unido** e **Alemanha**, as jovens mulheres agora adotam posturas mais liberais sobre temas como **imigração** e **justiça racial**, enquanto grupos etários mais velhos permanecem equilibrados. A tendência na maioria dos países tem sido de **mulheres se inclinando mais para a esquerda**, enquanto os homens permanecem estáveis. No entanto, há sinais de que os jovens homens estão se **movendo para a direita** na **Alemanha**, tornando-se mais críticos em relação à imigração e se aproximando do partido de extrema direita **AfD** nos últimos anos.
Seria fácil dizer que tudo isso é apenas uma **fase passageira**, mas os abismos ideológicos apenas crescem, e os dados mostram que as experiências políticas formativas das pessoas são difíceis de mudar. Tudo isso é agravado pelo fato de que o aumento dos smartphones e das redes sociais faz com que os jovens homens e mulheres agora **vivam em espaços separados** e tenham **culturas distintas**.
As opiniões dos jovens frequentemente são ignoradas devido à **baixa participação política**, mas essa mudança pode deixar **consequências duradouras**, impactando muito mais do que apenas os resultados das eleições.
Retirado de: https://www.ft.com/content/29fd9b5c-2f35-41bf-9d4c-994db4e12998
-

@ 36bedab2:524acad4
2024-12-26 23:23:37
404 Page Not Found
-

@ 36bedab2:524acad4
2024-12-26 23:20:21
404 Page Not Found Error
-

@ ccc8ee23:9f3d9783
2024-12-23 22:03:15
## Chef's notes
Indulge in tender, golden-fried chicken breast, crunchy with every bite. Nestled on a bed of steamed rice, this dish is elevated by a rich, velvety curry sauce, infused with the warmth of fragrant spices and the umami depth of soy.
Paired with vibrant vegetables for a harmonious balance of textures and flavors, this comforting classic promises to delight your soul.
## Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 2
## Ingredients
- Chicken Fillet 250 grams
- Potato 100 grams
- Egg 1 pc
- Curry block 2 pcs or 20 grams
- breadcrumbs 100 grams / 2 cups
- flour 20 grams
- Cooking oil (for frying)
- chicken or vegetable stock 500ml
- soy sauce 1 tbsp
- Seasoning
- onion 1 pc, finely chopped
- garlic cloves 2 pcs, minced
- carrot 1 pc, chopped
## Directions
1. Chicken Katsu: Pound the chicken breasts until about 1/2 inch thick. Season with salt and pepper. Coat each piece in flour, then dip in beaten egg, and finally coat with breadcrumbs. Heat oil in a pan and fry the chicken for about 3-4 minutes on each side, until golden brown and fully cooked. Place on paper towels to drain.
2. Make Curry Sauce: In a pan, sauté the onion, garlic, add potato and carrot until soft. Gradually add curry block and the stock, stir well. Simmer for 5-10 minutes until thickened. Add seasoning and soy sauce to taste.
3. Plating: Slice the cooked chicken katsu and place it over a bed of steamed rice. Pour the curry sauce on the side or over the chicken. Garnish with chopped green chilies.
-

@ ee11a5df:b76c4e49
2024-12-16 05:29:30
# Nostr 2?
## Breaking Changes in Nostr
Nostr was a huge leap forward. But it isn't perfect.
When developers notice a problem with nostr, they confer with each other to work out a solution to the problem. This is usually in the form of a NIP PR on the nips repo.
Some problems are easy. Just add something new and optional. No biggie. Zaps, git stuff, bunkers... just dream it up and add it.
Other problems can only be fixed by breaking changes. With a breaking change, the overall path forward is like this: Add the new way of doing it while preserving the old way. Push the major software to switch to the new way. Then deprecate the old way. This is a simplification, but it is the basic idea. It is how we solved markers/quotes/root and how we are upgrading encryption, among other things.
This process of pushing through a breaking change becomes more difficult as we have more and more existing nostr software out there that will break. Most of the time what happens is that the major software is driven to make the change (usually by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6), and the smaller software is left to fend for itself. A while back I introduced the BREAKING.md file to help people developing smaller lesser-known software keep up with these changes.
## Big Ideas
But some ideas just can't be applied to nostr. The idea is too big. The change is too breaking. It changes something fundamental. And nobody has come up with a smooth path to move from the old way to the new way.
And so we debate a bunch of things, and never settle on anything, and eventually nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 makes a post saying that we don't really want it anyways 😉.
As we encounter good ideas that are hard to apply to nostr, I've been filing them away in a repository I call "nostr-next", so we don't forget about them, in case we ever wanted to start over.
It seems to me that starting over every time we encountered such a thing would be unwise. However, once we collect enough changes that we couldn't reasonably phase into nostr, then a tipping point is crossed where it becomes worthwhile to start over. In terms of the "bang for the buck" metaphor, the bang becomes bigger and bigger but the buck (the pain and cost of starting over) doesn't grow as rapidly.
## WHAT? Start over?
IMHO starting over could be very bad if done in a cavalier way. The community could fracture. The new protocol could fail to take off due to lacking the network effect. The odds that a new protocol catches on are low, irrespective of how technically superior it could be.
So the big question is: can we preserve the nostr community and it's network effect while making a major step-change to the protocol and software?
I don't know the answer to that one, but I have an idea about it.
I think the new-protocol clients can be dual-stack, creating events in both systems and linking those events together via tags. The nostr key identity would still be used, and the new system identity too. This is better than things like the mostr bridge because each user would remain in custody of their own keys.
## The nitty gritty
Here are some of the things I think would make nostr better, but which nostr can't easily fix. A lot of these ideas have been mentioned before by multiple people and I didn't give credit to all of you (sorry) because my brain can't track it all. But I've been collecting these over time at https://github.com/mikedilger/nostr-next
* Events as CBOR or BEVE or MsgPack or a fixed-schema binary layout... anything but JSON text with its parsing, it's encoding ambiguity, it's requirement to copy fields before hashing them, its unlimited size constraints. (me, nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s)
* EdDSA ed25519 keys instead of secp256k1, to enable interoperability with a bunch of other stuff like ssh, pgp, TLS, Mainline DHT, and many more, plus just being better cryptography (me, Nuh, Orlovsky, except Orlovsky wanted Ristretto25519 for speed)
* Bootstrapping relay lists (and relay endpoints) from Mainline DHT (nostr:npub1jvxvaufrwtwj79s90n79fuxmm9pntk94rd8zwderdvqv4dcclnvs9s7yqz)
* Master keys and revocable subkeys / device keys (including having your nostr key as a subkey)
* Encryption to use different encryption-specific subkeys and ephemeral ones from the sender.
* Relay keypairs, TLS without certificates, relays known by keypair instead of URL
* Layered protocol (separate core from applications)
* Software remembering when they first saw an event, for 2 reasons, the main one being revocation (don't trust the date in the event, trust when you first saw it), the second being more precise time range queries.
* Upgrade/feature negotiation (HTTP headers prior to starting websockets)
* IDs starting with a timestamp so they are temporally adjacent (significantly better database performance) (Vitor's idea)
* Filters that allow boolean expressions on tag values, and also ID exclusions. Removing IDs from filters and moving to a GET command.
* Changing the transport (I'm against this but I know others want to)
## What would it look like?
Someone (Steve Farroll) has taken my nostr-next repo and turned it into a proposed protocol he calls [Mosaic](https://github.com/SteveFarroll/mosaic-spec). I think it is quite representative of that repo,
as it already includes most of those suggestions, so I've been contributing to it. Mosaic spec is rendered [here](https://stevefarroll.github.io/mosaic-spec/).
Of course, where Mosaic stands right now it is mostly my ideas (and Steve's), it doesn't have feedback or input from other nostr developers yet. That is what this blog post is about. I think it is time for other nostr devs to be made aware of this thing.
It is currently in the massive breaking changes phase. It might not look that way because of the detail and refinement of the documentation, but indeed everything is changing rapidly. It probably has some bad ideas and is probably missing some great ideas that you have.
Which is why this is a good time for other devs to start taking a look at it.
It is also the time to debate meta issues like "are you crazy Mike?" or "no we have to just break nostr but keep it nostr, we can't dual-stack" or whatever.
Personally I think mosaic-spec should develop and grow for quite a while before the "tipping point" happens. That is, I'm not sure we should jump in feet first yet, but rather we build up and refine this new protocol and spend a lot of time thinking about how to migrate smoothly, and break it a lot while nobody is using it.
So you can just reply to this, or DM me, or open issues or PRs at [Mosaic](https://github.com/SteveFarroll/mosaic-spec), or just whisper to each other while giving me the evil eye.
-

@ deba271e:36005655
2024-12-13 22:23:32
#### Background
**The free Alby account is going away** by Jan 3rd 2025. With this users have options to switch to either self hosted Alby Hub or hosted Alby Hub for 21k sats per month (see https://albyhub.com/).
Unfortunatelly neither of these options work for me.
- I'm currently traveling a lot without a single base home, so I can't just run some server "at home" and I want to be able to use it even when I'm in the midst of moving between locations.
- 21k sats/month for Alby Hub is too steep just for using it for Nostr zaps. I'd pay more for the service than what I ever get in zaps. I'm happy to support projects, but the math just doesn't work out.
- Running lightning node, etc in VPS is also prohibitively expensive for this usecase, but I may end up eventually doing this for other reasons. Getting VPS strong enough for self hosted node is around $80/month, but there are also options like https://nodana.io/ for $10/month. (Shill me better options if you have)
If there is a way to run a selft-custodial solution with these requirements (i.e. no "home" node, cheap for small amount zapping), let me know, otherwise this will do and we'll have to wait for BOLT12 in lnd.
## Tutorial
So here's the plan
- Get coinos.io account
- Connect it with Amethyst via NWC
- Install Alby Go to make it easier to use the account on the go
Here are the steps to do on your Android phone. iOS will be similar
- Get [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst&hl=en&gl=US) nostr app installed
- Go to https://coinos.io/ , register new account and sign in.
- On the main screen click on the settings gear icon and get the connection code
- Reveal and copy the connection strings (tap on Copy)
- Open Amethyst and hold the lightning icon under any post
- Tap the "paste" button (see the screenshot)
- Now click on Save and that's it
- Zapping should now work natively in Amethyst and it will use the hosted wallet
Optional
- One extra thing you can do here is to install Alby Go (https://albygo.com/) and use the same "connection string" to connect it to your coinos.io account. This way you will have a mobile native wallet that's connected to this account (which makes it easier to pay with it, etc)
originally posted at https://stacker.news/items/808573
-

@ 3b19f10a:4e1f94b4
2024-12-07 09:55:46
Sometimes perspective is everything...
#[artmodel]( https://bsky.app/hashtag/artmodel)
#[nude]( https://bsky.app/hashtag/nude)
#[nudemodel]( https://bsky.app/hashtag/nudemodel)
------



-

@ 6d8e2a24:5faaca4c
2024-12-02 09:03:49
"if your boyfriend uses Tiktok, you have a girlfriend" worlds riches man. Elon Musk tells women.
What's your opinion, do you think Elon Musk is right by his statement?
-

@ 4fe4a528:3ff6bf06
2024-12-01 15:00:30
https://cdn.satellite.earth/8dd22e9b598964ade69d4c5ca517c2637ffafdfb15cf3e589cd1a7955c173375.mp4
In my last news article I wrote about selling my beef for 4500 sats / lb and buying my eggs for 4500 sats / dozen. You will be glad to know that some of my friends gave me bitcoin for my birthday. One person gave me over 60,000 sats, so now I am feeling like my last months article caused everyone to [*buy bitcoin — opt out of inflation*](https://amendt.substack.com/p/buy-bitcoin)*.*
It must have been more than my friends giving me bitcoin that caused Bitcoin to increase it’s market cap by 600 billion US dollars. I know that eggs are costing me 3,000 sats now compared to 4500 sats one month ago. If things keep getting 50% cheaper every month I might not have to move all my value into bitcoin.
Isn’t it weird using something that increases in value month after month? It is indeed a far cry from the traditional notion of money, where the value or the purchasing power of the currency loses value month after month. Most Bitcoiners care about the separation of money from the state, the removal of a third party from transactions and the capturing the deflationary nature of technology, etc. The fiat price is simply a short term way of measuring progress toward that goal. In reality, the moose shekel price doesn’t really matter.
With Brazil and Russia now using it as legal tender I don’t want anyone to give me bitcoin as a gift this month. Give your money/love to helping others see Jesus’ love in coming to earth instead. You might be able to write off your donation also.
You do realize there are only 16.5 million bitcoin available to be moved to other bitcoin type people and the US bitcoin strategic reserve might be coming next year. I just hope the Trudeau / Christine “Vib” session doesn’t make Canadians give up on using the Moose Shekels as a means of exchanging value. Bitcoin is now worth more than the Canadian dollar. If you need to get educated about money join Nostr and do a video / desktop sharing conference with me. Say hivetalk.org @ 9am ish works best for me. Remember, learning technology makes you earn more. We are all in this together.
-

@ 36bedab2:524acad4
2024-11-24 23:17:58
A Lei de Gresham explica por que o Bitcoin é visto como um "bom dinheiro" e sua relevância no contexto econômico global.
2. Bitcoin e a Lei de Gresham
O Bitcoin é um exemplo moderno da Lei de Gresham, mas funcionando de forma inversa em um ambiente onde não há obrigatoriedade de aceitação de moedas governamentais.
Bitcoin como "bom dinheiro":
Escassez e mineração: Bitcoin é escasso (máximo de 21 milhões) e sua criação exige esforço computacional significativo, semelhante à extração de ouro.
Proteção contra desvalorização: Ao contrário das moedas fiduciárias, que podem ser impressas sem limite, o Bitcoin tem regras rígidas que evitam inflação descontrolada.
Preferência pelo armazenamento: As pessoas preferem guardar Bitcoin como reserva de valor, em vez de gastá-lo, porque ele tende a valorizar com o tempo. Isso está alinhado com a Lei de Gresham: as pessoas gastam o "dinheiro ruim" (moedas fiduciárias inflacionárias) antes de gastar o "dinheiro bom" (Bitcoin).
4. Bitcoin e a Geopolítica Monetária
O dólar norte-americano mantém seu status de moeda de reserva global, dando aos EUA a capacidade de imprimir dinheiro que outros países precisam usar.
Assim como o ouro, o Bitcoin é visto como uma ameaça ao sistema fiduciário liderado pelo dólar. Ele representa um "dinheiro bom" que não pode ser desvalorizado por decisões políticas.
A Lei de Gresham explica por que o Bitcoin é raramente gasto, mas amplamente guardado como uma reserva de valor. A sua ascensão reflete a insatisfação global com moedas fiduciárias inflacionárias, e ele é visto como uma esperança para o futuro financeiro, ao oferecer um sistema monetário independente, transparente e limitado.
O Bitcoin, como exemplo de "bom dinheiro", tem o potencial de mudar o sistema econômico global, libertando-o de governos que abusam de sua capacidade de emitir moedas descontroladamente.
-

@ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08
### Tldr
- Nostr is an open protocol which is interoperable with all kinds of other technologies
- You can use this interoperability to create custom solutions
- Nostr apps define a custom URI scheme handler "nostr:"
- In this blog I use this to integrate Nostr with NFC cards
- I create a Nostr NFC "login card" which allows me to log into Amethyst client
- I create a Nostr NFC "business card" which allows anyone to find my profile with a tap
### Inter-Op All The Things!
Nostr is a new open social protocol for the internet. This open nature is very exciting because it means Nostr can add new capabilities to all other internet-connected technologies, from browsers to web applications. In my view, it achieves this through three core capabilities.
- A lightweight decentralised identity (Nostr keys, "npubs" and "nsecs"),
- A lightweight data distribution network (Nostr relays),
- A set of data interoperability standards (The Nostr Improvement Protocols "NIPs"), including the "nostr:" URI which we'll use in this post.
The lightweight nature is its core strength. Very little is required to interoperate with Nostr, which means many existing technologies can be easily used with the network.
Over the next few blog posts, I'll explore different Nostr inter-op ideas, and also deliver my first small open source projects to the community. I'll cover–
- NFC cards integrated with Nostr (in this post),
- Workflow Automations integrated with Nostr,
- AI LLMs integrated with Nostr.
#### The "Nostr:" URI
One feature of Nostr is it defines a custom URI scheme handler "nostr:". What is that?
A URI is used to identify a resource in a system. A system will have a protocol handler registry used to store such URI's, and if a system has a URI registered, then it knows what to do when it sees it. You are probably already familiar with some URI schemes such as "http:" and "mailto:". For example, when you click an http link, the system knows that it describes an http resource and opens a web browser to fetch the content from the internet.
A nostr: link operates in the same way. The nostr: prefix indicates a custom URI scheme specifically designed for the Nostr protocol. If a system has a Nostr application installed, that application may have registered "nostr:" in the protocol handler registry. On that system when a "nostr:" URI is clicked, the system will know that it describes a nostr resource and open the Nostr client to fetch the content from the nostr relay network.
This inter-op with the protocol handler registry gives us the power to do nice and exciting things with other technologies.
### Nostr and NFC
Another technology that uses URIs is NFC cards. NFC (Near Field Communication) is a wireless technology that enables devices to exchange data over a few centimeters. It’s widely used in contactless payments, access control, and information sharing.
NFC tags are small chips embedded in cards or stickers which can store data like plain text, URLs, or custom URIs. They are very cheap (cents each) and widely available (Amazon with next day delivery).
When an NFC tag contains a URI, such as a http: (or nostr:) link, it acts as a trigger. Tapping the tag with an NFC-enabled device launches the associated application and processes the URI. For example, tapping a tag with "nostr:..." could open a Nostr client, directing it to a specific login page, public profile, or event.
This inter-op allows us to bridge the physical world to Nostr with just a tap.
#### Many useful ideas
There are many interesting ways to use this. Too many for me to explore. Perhaps some of these are interesting for your next side hustle?
- Nostr NFC "login cards" – tap to log into Amethyst on Android,
- Nostr NFC "business cards" – give to connections so they can tap to load your npub,
- Nostr NFC "payment cards" – integrating lightning network or ecash,
- Nostr NFC "doorbells", "punch cards", "drop boxes", or "dead drops" – put a tag in a specific place and tap to open a location-specific message or chat,
- Integrations with other access control systems,
- Integrations with other home automation systems,
- Many more ...
To start with I have built and use the "login card" and "business card" solutions. This blog post will show you how to do the same.
### Nostr Login Card
You can use an NFC card to log into your Nostr client.
Most Nostr clients accept a variety of login methods, from posting your nsec into the app (insecure) to using a remote signer (more secure). A less known but more secure method is to sign into a session with a tap of a specially-configured NFC card. Amethyst is a Nostr client on Android which supports this type of login.
- A secure method for logging in
- Optionally keeps no log in history on the device after logout
- Does not require users to know or understand how keys work
- Keys are kept secure on a physically-separated card to reduce risk of compromise
Nostr devs think that this is useful for anti-establishment actors–Fair enough. For me, I am interested in this login card pattern as it could be useful for rolling out identities within an organisation context with less training (office workers are already familiar with door access cards). This pattern potentially abstracts away key management to the IT or ops team who provision the cards.
I first discovered this when [Kohei](nostr:npub16lrdq99ng2q4hg5ufre5f8j0qpealp8544vq4ctn2wqyrf4tk6uqn8mfeq) demonstrated it in [his video](nostr:nevent1qqstx0jy5jvzgh7wr6entjuw7h58d7mapupfdpt9hkf7s4gze34a0vspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzp47x6q2txs5ptw3fcj8ngj0y7qrnm7z0ft2cptshx5uqgxn2hd4ckqyqd3).
Here's how you set it up at a high level–
1. Buy yourself some NFC cards
2. Get your Nostr key ready in an encrypted, password protected format called "nencryptsec"
3. Write the nencryptsec to the NFC card as a custom URI
4. Tap to load the login screen, and enter your password to login
Here it is in detail–
#### Buy yourself some NFC cards
I found no specific requirements. As usual with Nostr so far, I tried to the cheapest possible route and it worked. Generic brand NFC cards shipped from China, I believe it was 50X for $15 from Amazon. Your mileage may vary.
#### Get your Nostr key ready
Your key will be saved to the NFC card in an encrypted password-protected format called "nencryptsec". Several applications support this. As we'll be using this to login to Amethyst, we will use Amethyst to output the nencryptsec for us.
1. Login to Amethyst with your nsec,
2. Open the sidebar and click "Backup Keys",
3. Enter a password, and click "Encrypt and my secret key",
4. It will add the password-protected key to your clipboard in the format "ncryptsec1...",
5. Remember to backup your password.
#### Write the ncryptsec to the NFC card
1. Download the free [NFC Tools app](https://play.google.com/store/apps/details?id=com.wakdev.wdnfc) to your device, and open it,
2. Click "Write" and "Add a record", then click "Custom URL / URI",
3. Paste your nencryptsec with the nostr URI in front, i.e. "nostr:ncryptsec1..." and click OK,
4. Click "Write". NFC Tools will prompt you to "Approach an NFC tag",
5. Place your NFC card against your phone, and it will write to the card,
6. Your card is ready.
#### Tap to load the login screen
Tap the card against your phone again, and your phone should open the login screen of Amethyst and prompt you for your password.
Once you enter your password, Amethyst will decrypt your nsec and log you in.
Optionally, you can also set the app to forget you once you log out.
You have created a Nostr NFC "login card".
### Nostr Business Card
You can use another NFC card to give anyone you meet a link straight to your Nostr profile.
I attended [Peter McCormack](nostr:npub14mcddvsjsflnhgw7vxykz0ndfqj0rq04v7cjq5nnc95ftld0pv3shcfrlx)'s #CheatCode conference in Sydney and gave a few of these out following the Nostr panel, notably to [Preston Pysh](nostr:npub1s5yq6wadwrxde4lhfs56gn64hwzuhnfa6r9mj476r5s4hkunzgzqrs6q7z) where it [got some cut through](nostr:nevent1qqsdx0acma85u9knejnvfnfms9pfv27g97mfnnq9fnxslsa9vtrx73spremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzppggp5a66uxvmntlwnpf5384twu9e0xnm5xth9ta58fpt0dexysy26d4nm) and found me my first 100 followers. You can do the same.
To create your Nostr NFC "business card" is even easier than your NFC "login card".
1. Buy yourself some NFC cards,
2. Download the free [NFC Tools app](https://play.google.com/store/apps/details?id=com.wakdev.wdnfc) to your device, and open it,
2. Click "Write" and "Add a record", then click "Custom URL / URI",
3. Write your npub to the NFC card as a custom URI in the format "nostr:npub1..." (e.g. for me this is "nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft"),
4. Your card is ready.
Give the card to someone who is a Nostr user, and when they tap the card against their phone it will open their preferred Nostr client and go directly to your Nostr profile page.
You have created a Nostr NFC "business card".
### What I Did Wrong
I like to share what I did wrong so you don't have to make the same mistakes. This time, this was very easy, and little went wrong. In general
- When password-protecting your nsec, don't forget the password!
- When writing to the NFC card, make sure to use "Custom URI/URL" as this accepts your "nostr:" URI scheme. If you use generic "URI/URL" it won't work.
### What's Next
Over my first four blogs I have explored creating a good Nostr setup
- [Mined a Nostr pubkey and backed up the mnemonic](nostr:naddr1qqsy66twd9hxwtteda6hyt2kv9hxjare94g82cntv4uj6drfw4cxyeszyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c6e2ekw)
- [Set up Nostr payments with a Lightning wallet plus all the bells and whistles](nostr:naddr1qq34xet5w35kueedw4cz65rp09kk2mn5wvkk7m3dfehhxarj95mk7dnvwvmsygqmmflp7uukhk3drmueqv763lfdcd3gzpusm7d7vt6ezquth97ymypsgqqqw4rsuql6je)
- [Set up NIP-05 and Lighting Address at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqyghwumn8ghj7mn0wd68ytnhd9hx2tczyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c634nh0)
- [Set up a Personal Relay at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7q3qr0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvsxpqqqp65wmzpn9e)
Over the next few blogs I will be exploring different types of Nostr inter-op
- NFC cards integrated with Nostr (this post)
- Workflow Automations integrated with Nostr
- AI LLMs integrated with Nostr
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-

@ 6be5cc06:5259daf0
2024-11-12 03:11:11
### Primeiramente, o que é mempool?
Abreviação de memory pool (ou *"pool de memória"*) a mempool é uma espécie de fila onde as transações de Bitcoin ficam temporariamente armazenadas antes de serem confirmadas e incluídas em um bloco na blockchain.
Quando você realiza uma transação em uma rede blockchain, essa transação precisa ser validada e confirmada pelos mineradores (ou validadores). Porém, ela não é processada instantaneamente. Primeiro, ela vai para a mempool, onde aguarda até que um minerador a selecione para incluir no próximo bloco.
É assim:
* Você envia uma transação, ela é transmitida para a rede e vai parar na mempool de vários nós (computadores) que suportam a rede blockchain.
* As transações na mempool são organizadas pela taxa de transação que foi anexada. Quanto maior a taxa, mais rápido os mineradores tendem a escolher essa transação para incluí-la em um bloco, pois isso aumenta os ganhos deles.
* Os mineradores pegam as transações da mempool, criam um bloco com elas e, ao minerar (confirmar) esse bloco, as transações saem da mempool e entram na blockchain.
Aqui irei usar o site [mempool.emzy.de](https://mempool.emzy.de/) como referência, mas é importante entender que sites de mempool são representações visuais da mempool de um nó específico e não *a mempool do Bitcoin* em si. Ela não é centralizada, cada nó da rede mantém a sua própria versão da mempool. Assim, ela pode variar de um nó para outro. Esses sites ajudam a visualizar dados sobre transações e taxas.
É uma boa prática usar **VPN** ou **Tor** ao acessar tais sites se você estiver verificando uma transação específica sua, pois sua privacidade pode ficar comprometida se o site registrar esses dados. Se você estiver repetidamente acessando-o para monitorar a confirmação de uma transação, alguém pode conseguir correlacionar o endereço IP com essa atividade e revelar uma conexão indireta com o endereço da transação.
Dito isso...
### Como interpretar a mempool?
Vamos dividir isso em partes para fins didáticos.
---
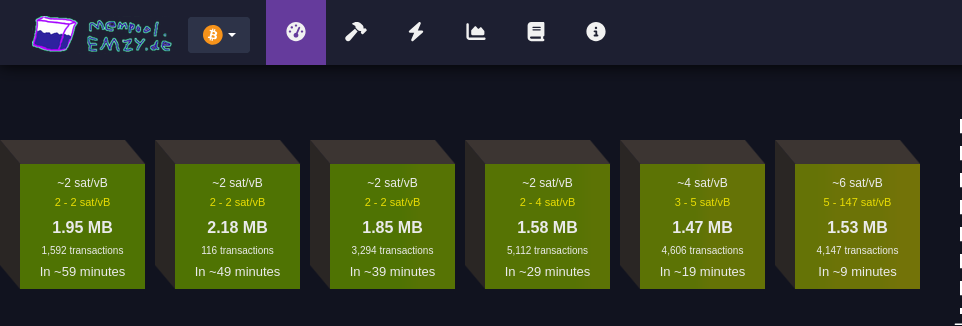
#### Faixa de taxas
Cada bloco verde representa uma faixa de taxa medida em satoshis por vByte (sats/vB).
Essa unidade de medida representa o valor pago por byte ocupado pela transação.
Quanto maior a taxa paga por uma transação, mais rápido ela tende a ser confirmada.
Quanto maior a transação em bytes, mais você precisa pagar para que ela seja confirmada.
Cada transação Bitcoin consiste em *entradas* e *saídas* (*inputs* e *outputs*):
* **Entradas** são referências a transações anteriores que estão sendo gastas, e cada entrada inclui informações como o endereço de origem, a assinatura (que valida a transação e pode variar de tamanho dependendo da complexidade da chave e do método de assinatura utilizado (como SegWit, que é mais eficiente). Quanto mais complexa a assinatura, maior será o tamanho em bytes) e outros dados. Quanto mais entradas uma transação tiver, maior será seu tamanho.
* **Saídas** representam o destino do Bitcoin, e quanto mais saídas, maior será o tamanho da transação. Embora as saídas ocupem menos espaço em bytes do que as entradas.
Ex.:
* ~4 sat/vB: Indica uma taxa média. Significa que, em média, as transações estão sendo processadas a 4 satoshis por vByte;
* 3-5 sat/vB: Isso significa que as transações estão sendo processadas com uma taxa entre 3 e 5 satoshis por vByte.
#### MB
Simplesmente o tamanho do bloco medido em megabytes :)
#### Número de transações
Essa seção informa quantas transações estão aguardando confirmação para cada faixa de taxa (bloco). Quanto maior o número de transações, maior a demanda pela faixa de taxa especificada.
#### Tempo estimado para confirmação
Aqui é mostrado o tempo médio de espera para transações que pagam taxas dentro da faixa especificada. Se você pagar uma taxa maior, a transação será confirmada mais rapidamente; uma taxa menor significa que a transação pode levar mais tempo para ser confirmada, especialmente se a rede estiver congestionada.
---
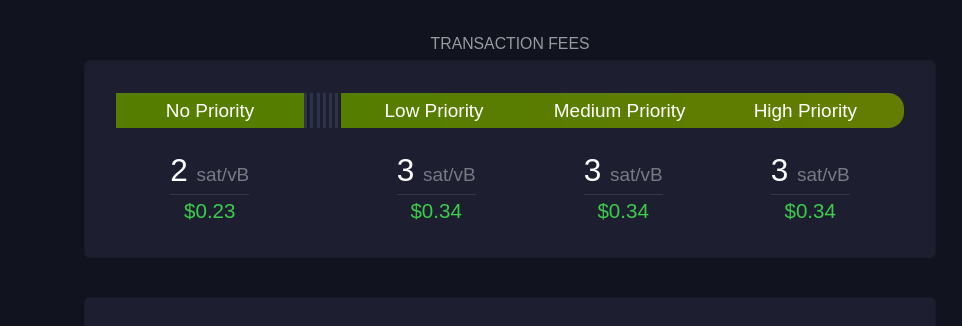
Esta seção mostra sugestões de taxa em diferentes níveis de prioridade para os usuários:
#### Sem Prioridade
Exibe a taxa mínima necessária para transações que não precisam de confirmação rápida.
#### Prioridade Baixa
Sugestão de taxa para transações que podem esperar um tempo moderado, com expectativa de confirmação em um ou dois blocos.
#### Prioridade Média e Alta
São as faixas de taxa recomendadas para quem precisa que a transação seja confirmada rapidamente. "Prioridade Alta" paga uma taxa maior, garantindo que a transação seja incluída no próximo bloco.
---
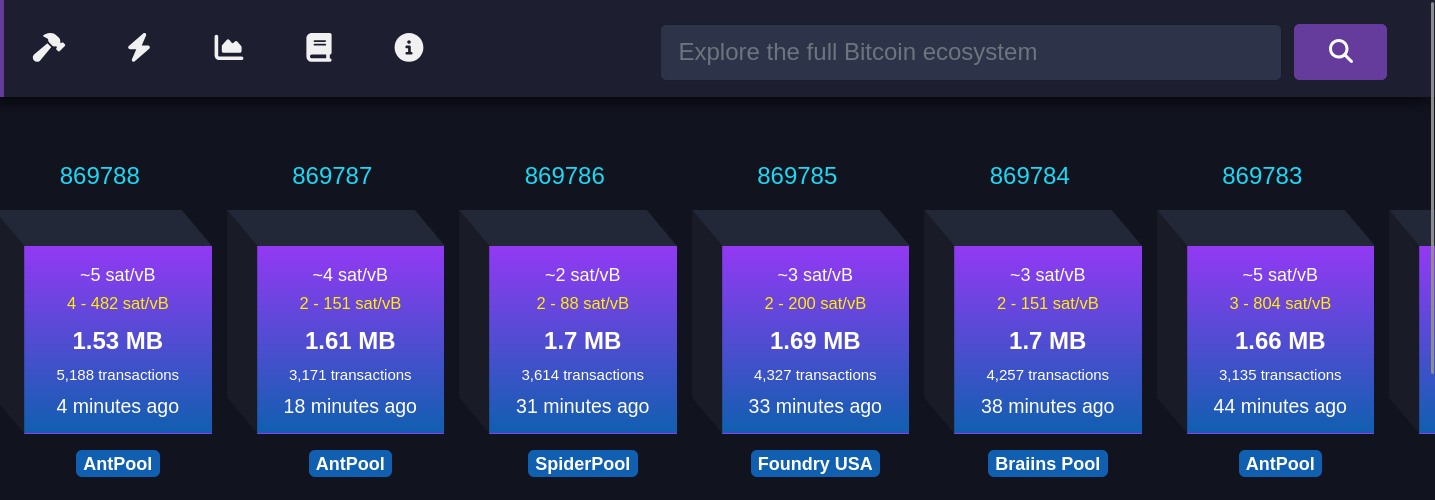
Cada bloco roxo representa um bloco recém-minerado. As informações mostradas incluem:
#### Taxa média paga
Refere-se à taxa média em satoshis/vB paga por todas as transações incluídas em um bloco recém-minerado. Isso reflete o valor médio que os usuários estão dispostos a pagar para que suas transações sejam confirmadas rapidamente.
#### Número de transações
Este número indica quantas transações foram processadas no bloco minerado. O tamanho do bloco é limitado, então, quanto maior o número de transações, menor será o espaço disponível para novas transações, o que pode influenciar as taxas de transação.
#### Tempo desde a mineração
Esta métrica informa quanto tempo se passou desde que o bloco foi minerado e adicionado à blockchain.
#### Pool de mineração
Exibe o nome do pool de mineração que minerou o bloco, como AntPool. Grandes pools de mineração têm mais chances de minerar blocos regularmente devido ao alto hashrate (medida da capacidade computacional utilizada pelos mineradores) que possuem.
---
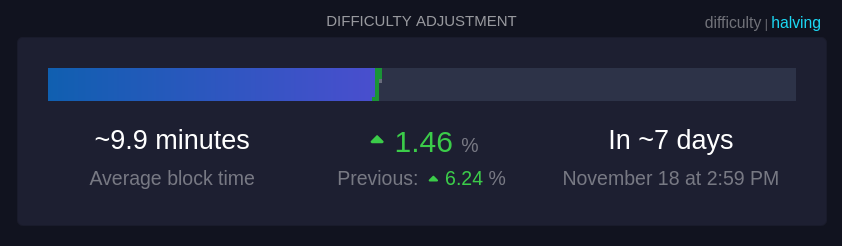
Essa seção mostra informações sobre o ajuste de dificuldade, que ocorre aproximadamente a cada duas semanas.
#### Tempo médio dos blocos (~9,9 minutos):
Este é o tempo médio atual para minerar um bloco na rede. A meta da rede é manter o tempo de bloco em cerca de 10 minutos; um tempo menor indica um aumento na taxa de hash, ou seja, que mais poder computacional foi adicionado à rede.
#### Mudança de dificuldade (+1,46%):
A dificuldade ajusta-se a cada 2016 blocos para manter o tempo médio de bloco próximo de 10 minutos. Um aumento na dificuldade, como +1,46%, indica que a mineração ficou mais difícil devido ao aumento do hashrate, enquanto uma redução na dificuldade indica que o hashrate diminuiu.
#### Tempo até o próximo ajuste:
É o tempo previsto até o próximo ajuste de dificuldade (7 dias, nesse caso), o que é crucial para manter a rede estável e garantir a segurança e a regularidade do processo de mineração.
---
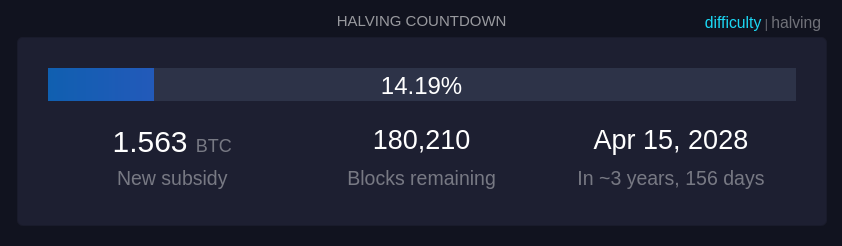
Quanto tempo demora até o próximo halving, um evento no Bitcoin que ocorre aproximadamente a cada 210.000 blocos minerados, ou cerca de quatro anos. Durante o halving, a recompensa que os mineradores recebem por adicionar um novo bloco à blockchain é reduzida pela metade.
---
Um diagrama visual da mempool que mostra o estado das transações pendentes na rede.
#### Tamanhos de blocos
O tamanho de cada quadrado representa o tamanho da transação em bytes.
**Filtros (Consolidação, Coinjoin, Dados):** Permite visualizar categorias específicas de transações:
* **Consolidação**: Transações de consolidação agrupam pequenos UTXOs em um único UTXO maior para simplificar e baratear futuras transações. (UTXOs merecem um artigo dedicado)
* **Coinjoin**: Transações CoinJoin são usadas para melhorar a privacidade, misturando transações de vários usuários em uma única transação.
* **Dados**: Mostra transações que contêm dados adicionais, que podem incluir informações não financeiras, como mensagens.
---
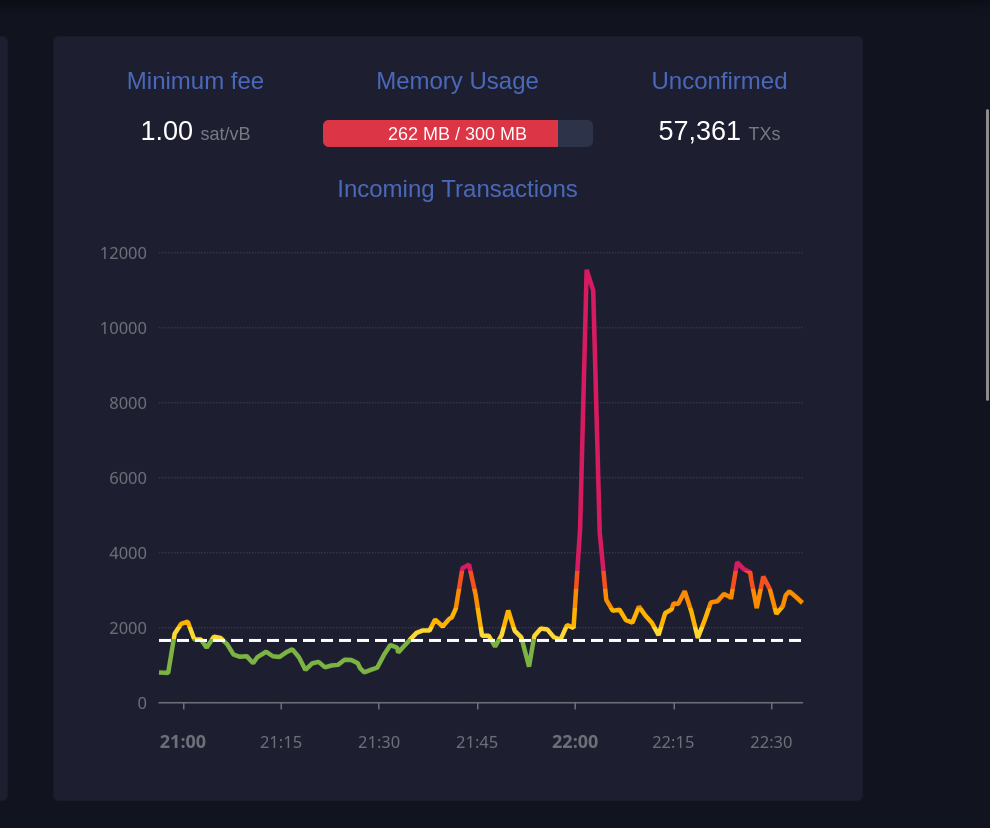
Este gráfico exibe o número de transações recebidas ao longo do tempo.
#### Taxa mínima (1 sat/vB):
Indica a taxa mínima atualmente aceita pela mempool. Se a mempool estiver cheia, transações que paguem menos do que a taxa mínima podem ser excluídas para dar lugar a transações de maior prioridade.
#### Uso de memória (259 MB / 300 MB):
A mempool tem um limite de memória. Quando está cheia, transações de taxa mais baixa podem ser descartadas para abrir espaço para aquelas com taxas mais altas, priorizando-as para inclusão em blocos.
#### Transações não confirmadas (59.361):
Indica o número total de transações pendentes que aguardam confirmação. Quanto maior o número de transações na mempool, maior a probabilidade de que as taxas aumentem para garantir uma confirmação mais rápida.
---
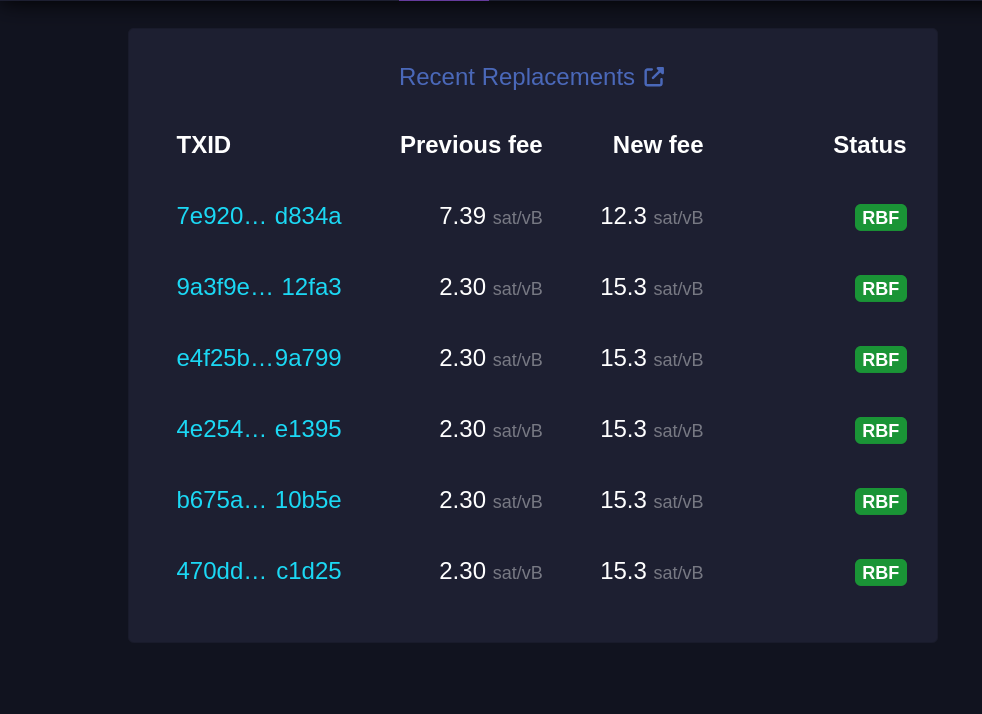
Essa seção mostra transações que foram substituídas utilizando o mecanismo RBF (Replace-By-Fee), que permite substituir uma transação com uma taxa mais alta para acelerar sua confirmação.
#### TXID
Este é o identificador da transação (Transaction ID), exibido parcialmente para abreviar o espaço. Cada transação tem um identificador único na blockchain.
#### Previous fee
Exibe a taxa de transação original paga na primeira tentativa, medida em satoshis por vByte (sat/vB). Esta taxa inicial provavelmente era baixa demais, resultando em uma demora na confirmação.
#### New fee
Mostra a nova taxa de transação, também em satoshis por vByte, definida para substituir a taxa anterior. Uma taxa maior aumenta as chances de inclusão rápida em um bloco.
#### Status (RBF)
RBF indica que a transação foi substituída utilizando o recurso "Replace-By-Fee". Isso significa que a nova transação cancelou e substituiu a original, e o minerador escolherá a transação com a taxa mais alta para incluir no próximo bloco.
---
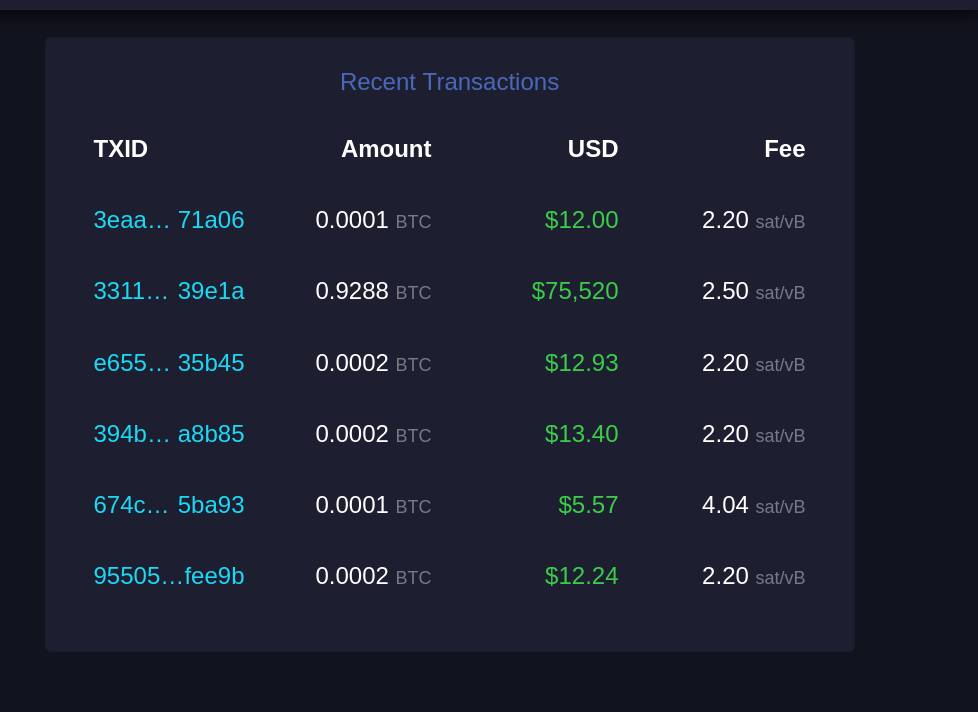
Esta seção lista transações recentes que entraram na mempool e aguardam confirmação.
#### TXID
Similar ao "Recent Replacements", este é o identificador único da transação.
#### Amount
Exibe a quantidade de Bitcoin transferida nessa transação, geralmente em frações de BTC (como 0.0001 BTC). Esta é a quantia enviada pelo remetente ao destinatário.
#### USD
Mostra o valor da transação em dólares americanos (USD), calculado com base na taxa de câmbio atual. Serve para dar uma ideia de quanto a transação representa em moeda fiduciária.
#### Fee
Exibe a taxa de transação paga, em satoshis por vByte (sat/vB). Uma taxa mais alta em relação à média aumenta a probabilidade de confirmação mais rápida, pois as transações com taxas mais elevadas são priorizadas pelos mineradores.
---
E acabou. Espero que isso tenha sido útil para você e tenha agregado mais entendimento sobre esse complexo e maravilhoso mundo do Bitcoin. Se foi, considere compartilhar com alguém que precise. E se tem sugestões de melhoria, por favor, não deixe de comentar, o conhecimento está dispero na sociedade.
Por fim, stay humble and stack sats!
-

@ 36bedab2:524acad4
2024-11-10 21:37:52
### 1. **Power ON**
- Quando você liga o computador, ele inicia o processo de boot.
- Esse primeiro passo envia energia aos componentes do sistema e dispara o BIOS (ou firmware UEFI em sistemas mais recentes).
### 2. **BIOS (Basic Input/Output System)**
- O BIOS ou UEFI é o firmware inicial que roda logo após o computador ser ligado.
- Ele executa um conjunto de verificações no hardware (chamado POST - Power-On Self-Test) e inicializa os dispositivos básicos necessários para o boot, como o disco rígido, memória RAM e CPU.
- O BIOS então procura o dispositivo de boot (HD, SSD, USB, etc.) e carrega o **MBR** ou a **partição EFI** para dar continuidade ao processo de boot.
### 3. **Master Boot Record (MBR) ou EFI Partition**
- O **MBR** (Master Boot Record) ou a **partição EFI** (em sistemas com UEFI) é onde ficam armazenadas as informações sobre o carregamento do sistema operacional.
- Em sistemas antigos, o MBR continha o **boot loader** e as tabelas de partição. Nos sistemas modernos com UEFI, a partição EFI cumpre essa função.
- O MBR ou a partição EFI passa o controle para o **boot loader**, que é responsável por carregar o sistema operacional.
### 4. **Boot Loader (e.g., GRUB)**
- O **Boot Loader** (exemplo: GRUB) é um programa responsável por carregar o sistema operacional no momento do boot.
- Ele permite selecionar qual sistema operacional inicializar (em caso de dual boot) e passa o controle para o **kernel** do sistema.
- GRUB (Grand Unified Bootloader) é o boot loader mais comum em sistemas Linux.
### 5. **Kernel**
- O **kernel** é o núcleo do sistema operacional Linux.
- Ele é carregado na memória pelo boot loader e começa a configurar os recursos do sistema, como a CPU, a memória e os dispositivos de hardware.
- O kernel é responsável por gerenciar os recursos do sistema e permitir a comunicação entre o hardware e o software.
### 6. **Initial RAM disk - initramfs**
- O **initramfs** é um sistema de arquivos temporário carregado na memória logo após o kernel.
- Ele contém módulos e drivers essenciais para que o sistema possa iniciar corretamente e acessar o sistema de arquivos principal do disco.
- O initramfs é desmontado após o sistema principal estar carregado.
### 7. **/sbin/init (parent process)**
- Após o kernel inicializar o sistema, ele chama o processo **/sbin/init**, que é o primeiro processo a rodar no Linux e é o "pai" de todos os outros processos.
- O init é responsável por iniciar e gerenciar todos os outros processos do sistema.
- Em muitas distribuições modernas, o init foi substituído por outros sistemas de inicialização, como o **systemd**, que tem mais funcionalidades e permite um gerenciamento mais eficiente de processos.
### 8. **Command Shell using getty**
- **Getty** é o processo que configura e gerencia terminais para o login do usuário.
- Ele exibe a tela de login em sistemas baseados em linha de comando.
- Se o sistema tiver uma interface gráfica, o getty geralmente passa o controle para o gerenciador de login gráfico.
### 9. **Graphical User Interface (X Window ou Wayland)**
- Finalmente, o sistema carrega a **interface gráfica** usando o **X Window System (X11)** ou o **Wayland** (um sistema gráfico mais moderno).
- Esse é o ambiente visual onde o usuário pode interagir com o sistema usando janelas, ícones, menus, etc.
- X11 e Wayland são servidores gráficos que gerenciam como as janelas e aplicativos são exibidos e manipulados na tela.
---
### Como esses processos se intercalam?
1. **Hardware ligado** → **BIOS/UEFI** realiza verificações básicas.
2. **BIOS/UEFI** encontra o dispositivo de boot e carrega o **MBR** ou **partição EFI**.
3. **MBR/EFI** localiza e executa o **boot loader** (GRUB).
4. **GRUB** permite que o usuário escolha o sistema operacional e carrega o **kernel** do Linux.
5. **Kernel** inicializa o sistema, configurando os recursos de hardware e carregando o **initramfs**.
6. **Initramfs** fornece drivers e módulos necessários para o kernel acessar o sistema de arquivos principal.
7. **Kernel** chama o processo **/sbin/init** (ou **systemd**), que inicia todos os serviços e processos do sistema.
8. **Init** executa o **getty** para configurar o terminal de login.
9. **Getty** chama o ambiente gráfico (X11 ou Wayland) se estiver presente, e o usuário pode então usar o sistema na interface gráfica.
-

@ bcea2b98:7ccef3c9
2024-11-09 17:01:32
Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about?
For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully.
originally posted at https://stacker.news/items/760492
-

@ a367f9eb:0633efea
2024-11-05 08:48:41
Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The [reporting](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/) purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
> In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
>
> The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history?
As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times.
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols.
The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application.
The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States.
> In a June paper reviewed by[ Reuters](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/), six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”.
>
> The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making.
While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the *Star Trek* episode “[A Taste of Armageddon](https://en.wikipedia.org/wiki/A_Taste_of_Armageddon)“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place.
Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran?
The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over [one million open-source LLMs](https://huggingface.co/models) available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer.
With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are [potentially](https://bigthink.com/business/the-trillion-dollar-ai-race-to-create-digital-god/) trillions of dollars on the line.
Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American[ infrastructure](https://www.nbcnews.com/tech/security/chinese-hackers-cisa-cyber-5-years-us-infrastructure-attack-rcna137706),[ data](https://www.cnn.com/2024/10/05/politics/chinese-hackers-us-telecoms/index.html), and yes, [your credit history](https://thespectator.com/topic/chinese-communist-party-credit-history-equifax/)?
**As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much[ many times](https://consumerchoicecenter.org/made-in-china-sold-in-china/).**
At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative.
Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this.
## **Open-source matters**
When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it.
The various [licensing schemes](https://opensource.org/licenses) – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made.
While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit.
Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers.
Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other.
I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run.
Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots).
This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also [open-source](https://github.com/bitcoin), which has allowed [thousands](https://bitcoinmagazine.com/business/bitcoin-is-money-for-enemies) of copycat protocols that have revolutionized how we view money.
You know what else is open-source and available for everyone to use, modify, and build upon?
PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit.
Open-source code is speech, and it is knowledge.
We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge.
## **Open-source is for your friends, and enemies**
In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license.
At this very moment, you can click on over to[ Hugging Face](https://huggingface.co/), download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth).
Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created.
We know this can be useful to friends, but what about enemies?
As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications.
The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians.
A bipartisan group of US House lawmakers want to put [export controls](https://www.reuters.com/technology/us-lawmakers-unveil-bill-make-it-easier-restrict-exports-ai-models-2024-05-10/) on AI models, as well as block foreign access to US cloud servers that may be hosting AI software.
If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see[ The Crypto Wars](https://en.wikipedia.org/wiki/Export_of_cryptography_from_the_United_States)). Many of the arguments we hear today were invoked by some of the same people as back then.
Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to.
Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place.
## **Limiting open-source threatens our own advancement**
If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way.
If there is a “[Hundred Year Marathon](https://www.amazon.com/Hundred-Year-Marathon-Strategy-Replace-Superpower/dp/1250081343)” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible.
The Chinese military has been building up its capabilities with [trillions of dollars’](https://www.economist.com/china/2024/11/04/in-some-areas-of-military-strength-china-has-surpassed-america) worth of investments that span far beyond AI chatbots and skip logic protocols.
The [theft](https://www.technologyreview.com/2023/06/20/1075088/chinese-amazon-seller-counterfeit-lawsuit/) of intellectual property at factories in Shenzhen, or in US courts by [third-party litigation funding](https://nationalinterest.org/blog/techland/litigation-finance-exposes-our-judicial-system-foreign-exploitation-210207) coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing.
But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source.
If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries.
*Originally published on the website of the [Consumer Choice Center](https://consumerchoicecenter.org/open-source-is-for-everyone-even-your-adversaries/).*
-

@ 4fe4a528:3ff6bf06
2024-11-01 13:30:30
**Buy Bitcoin ***"Opt out of inflation"*
Lyn Alden’s [https://www.lynalden.com/october-2024-newsletter/]() is better than this monthly [https://amendt.substack.com/p/buy-bitcoin](). She explains, better than I can, why bitcoin is still inexpensive. From my perspective, the reason bitcoin is getting more and more valuable is because it is almost my birthday and people know I would enjoy bitcoin as a birthday present. Ok maybe I am not the central figure in this bitcoin saga, but for some reason bitcoin goes up on my birthday. So, I would like to take this opportunity to thank you for causing this commodity to increase in value during my birthday. That was a joke!
I don’t think it is because you want to send me bitcoin that that is the only reason why bitcoin is climbing. Mind you the price action in bitcoin could be because the big boys (with money) have bought [https://docs.google.com/spreadsheets/d/1EZPpEA_aaZSwOTM90KpbLYfPJWqq31vOS1HhXNfkUmQ](). Yes Lyn explains why the smart money (rich guys) are now putting their money into bitcoin. It has a lot to do with scarcity — only 1.223921×10¹⁴ sats left and Metcafe’s law.
Metcalfe's Law states that the value of a network is proportional to the square of the number of users in the network
We are now back to 60% bitcoin dominance which is saying a lot when there is 2.4 million competing digital assets. With One bitcoin now over 100,000 Canadian dollars that says a lot of people think it is money. Go ahead and spend a dollar and get yourself 1000 sats just in case it catches on. My whole beef prices are now [https://www.pricedinbitcoin21.com/chart/livestock/LC1](). On the rail beef is only 4500 sats / lb — the same price as a dozen of eggs. Also, if you need a place to stay, [https://airbtc.online/properties/one-bedroom-suite-in-the-country/](). Finally people in Canada can live only on bitcoin. Justin Trudeau said on March 12, 2023 Buy Bitcoin, [https://cdn.satellite.earth/eef0f82150494810cacb622bd203cf8dea19b094cea940932e43d5a21b05c56a.mp4]() Bitcoin is now up over 100% since then.
Happy Birthday to [https://v.nostr.build/ivyiPSnv7HfuECFE.mp4]()
-

@ a9434ee1:d5c885be
2024-10-29 20:46:24
This design system has two goals:
1. Being the basis for the development of a design-first, native Nostr app focused on exceptional zapping and chatting, relay-based communities and beauty
2. Serving as inspiration for builders that need coherent UI building blocks for their own apps with a different scope but overlapping needs (chats, threads, zaps, articles, highlights, events, wikis, ...)
### Design System
Check it out [here](https://www.figma.com/community/file/1430887635327548022 ).
This is by no means finished and will be continually updated and completed as we go along.
### Project description
Check it out [here](njump.me/naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qyt8wumn8ghj7mnfv4kzumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qq00fshqcmgv96z6urjda4x2cm5lrswda)
nostr:naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qyt8wumn8ghj7mnfv4kzumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qq00fshqcmgv96z6urjda4x2cm5lrswda
This is a very first bullet-point-style draft to set the tone and is open to change, hence it being a wiki.
### Explanatory videos
This list of videos will also be continually updated and completed as we go along:
1. Chat as the universal interface
https://cdn.satellite.earth/43ccc6224a373dd22b7ae92edb70a0b9a3facabef27dff037de7f4fcf3ee7f37.mov
2. Your Nostr Dashboard
https://cdn.satellite.earth/20fa9683dbf815c7deafa8a532c1d1e99cddbaac622fbf075b33b70fb0bdef22.mov
3. Keeping Tabs on all these Content types
https://cdn.satellite.earth/a15ab05b55db1787349863f0f92c465dcde828b90c2cb61a92bd712a0012e9c6.mov
4. Design entered the Chat
https://cdn.satellite.earth/7c25215262125562c847412c0d9a7d027e087028838204b6c447b5c07830979a.mov
5. Targeted publication & The blurry edges of interoperable communities
https://cdn.satellite.earth/160c9431f53e7be108ad37f8d368e2af840690a8a936d1caaa68b468c9b1e0a9.mov
6. Travel Back
https://cdn.satellite.earth/36d38027e6208e91c1fa27b0560f70fbad7d3e31c22d659c9a53a5c4cf90a876.mov
-

@ 9017cf6a:3d8a7adb
2024-10-27 21:46:06
**Ricardo Nunes (MDB) é eleito prefeito de São Paulo**
O prefeito de São Paulo, Ricardo Nunes (MDB), conquistou sua reeleição neste domingo (27) e agora terá mais quatro anos para administrar a maior cidade do Brasil.
Apoiado por Jair Bolsonaro (https://www.conexaopolitica.com.br/tag/jair-bolsonaro/) e pelo PL (https://www.conexaopolitica.com.br/tag/pl/), que indicou seu vice na chapa, o emedebista foi confirmado como o vencedor do segundo turno disputado contra o esquerdista Guilherme Boulos (PSOL).
Nunes assumiu a prefeitura da capital paulista em 2021, após a morte de Bruno Covas (PSDB), de quem era vice na chapa eleita em 2020. Aos 56 anos, ele agora terá um mandato completo para gerenciar a principal metrópole da América do Sul.
Comments: https://www.conexaopolitica.com.br/ultimas/ricardo-nunes-mdb-e-eleito-prefeito-de-sao-paulo/#respond
https://www.conexaopolitica.com.br/ultimas/ricardo-nunes-mdb-e-eleito-prefeito-de-sao-paulo/
-

@ 4ba8e86d:89d32de4
2024-10-24 23:20:51
VeraCrupt foi lançado em 2013 como um fork do projeto TrueCrypt descontinuado. Desde então, o VeraCrypt tem passado por diversas atualizações e melhorias de segurança, incluindo a correção de problemas identificados por auditorias de código do TrueCrypt. O VeraCrypt inclui implementações otimizadas de funções criptográficas de hash e cifras, o que aumenta o desempenho em CPUs modernas. O software permite criar e gerenciar volumes criptografados em computadores ou dispositivos de armazenamento externo, com suporte para vários algoritmos de criptografia e recursos adicionais, como proteção contra ataques de keylogger e ocultação de volumes , tem opção de segurança robusta para proteger seus dados.
Quando você cria um volume criptografado no VeraCrypt, o software cria um arquivo virtual que funciona como um disco rígido criptografado. Esse arquivo é montado como uma unidade lógica no seu sistema operacional e pode ser acessado como qualquer outro disco rígido.
Antes que você possa acessar o volume criptografado, você precisa fornecer a senha correta. A senha é usada para desbloquear o arquivo virtual criptografado e permitir que o sistema operacional acesse o conteúdo. O VeraCrypt suporta vários algoritmos de criptografia, incluindo AES, Serpent e Twofish, que podem ser selecionados pelo usuário ao criar o volume criptografado.
O VeraCrypt também oferece recursos adicionais de segurança, como proteção contra keyloggers, que podem registrar as teclas digitadas no teclado para capturar senhas. Ele faz isso fornecendo uma interface virtual para digitar senhas, o que impede que os keyloggers capturem a senha real. O VeraCrypt também permite ocultar volumes criptografados dentro de outros volumes criptografados, o que fornece uma camada adicional de segurança.
O veracrypt proteger informações confidenciais armazenadas em dispositivos de armazenamento, como discos rígidos, unidades flash USB e cartões de memória, contra acesso não autorizado. Se um usuário estiver executando o Tails a partir de uma unidade flash USB, e o disco rígido estiver criptografado com o VeraCrypt, o Tails não terá acesso ao conteúdo do disco rígido, a menos que o usuário monte o volume criptografado do VeraCrypt e forneça a senha correta.
No entanto, é importante lembrar que a criptografia do disco rígido por si só não garante a segurança completa do sistema. Os usuários também devem tomar outras medidas de segurança, como manter o sistema operacional e o software atualizados, usar senhas fortes e não compartilhá-las com ninguém, e tomar cuidado com o acesso físico ao computador ou dispositivo de armazenamento externo.
https://veracrypt.fr
https://github.com/veracrypt/VeraCrypt/
-

@ 1bda7e1f:bb97c4d9
2024-10-24 04:48:52
### Tldr
- Nostr relays help users post and read notes on the network
- Relay operators have launched a variety of relays for you to use
- You too can launch your own relay for any reason you like
- Launching your own relay gives you a lot of power in how you use Nostr
- Many relay softwares exist for you to use
- I launched a personal relay using HAVEN relay software on my VPS
- I am now more in control of saving notes, cutting spam, and protecting my privacy
- My personal relay is now hosted at relay.rodbishop.nz
### What are Nostr Relays Anyway?
When you're a user of a social network, you post and read notes from other users on the network. In a centralised network like Twitter or Instagram the company's servers receive all user's notes and relay them to other users. On Nostr, there is no single company's servers to relay messages, so instead the task is taken up by relay operators.
Anyone can be a relay operator and they can run a relay for any purpose. When you start using Nostr you will usually be connected to any one of a number of "public" relays, and be able to post and receive notes from users on the network via these.
Configuring these relays can tailor your experience somewhat–for example the client Nostrudel allows you to select from Western or Japanese relay set.
It is also possible to set up your own relay to use for your own purposes. All kinds of people have launched relays for all kinds of purposes. For example, to:
- Power your own client
- Support your community
- Run a for-profit relay business
- Relay a certain a type of content you need
- Back up your own notes, decrease spam, or increase privacy
- Curate your own social feed with your own algorithm
#### Relay instances available to connect with
Today is an interesting time in relay-ops. The evolution of the technology has inspired users to experiment with diverse types of relays tailored to various needs. As a result there are very many relay instances in operation and available to connect with.
A few sites try to collate which relays are in operation, like [nostr.info](https://nostr.info/relays/) and [xport.top](https://relays.xport.top/) and [sesseor's relay list](https://github.com/sesseor/nostr-relays-list/blob/main/relays.txt) . These lists are long (Sessor's list counted 2,500+ relays) and it's not clear to me whether it's even possible to be comprehensive as relays may join or leave the network all the time.
Broadly speaking, relays might be available for different users to use in different ways:
- A relay where anyone can post, like [relay.damus.io](http://relay.damus.io)
- A paid relay where anyone can post after payment, to cut spam, like [nostr.wine](http://nostr.wine)
- A "web of trust" relay where anyone can post if they are related to the owner's social graph, to cut spam, like [nostrelites.org](http://nostrelites.org)
- A speciality relay where a particular community can post, like [nostr.com.au](http://nostr.com.au) for #austriches (Australians)
- A relay where anyone can post just specific content, like [purplepag.es](http://purplepag.es) for user profiles only
- A team relay for your company or organisation only
- A personal relay for your own personal use
[Nostr.Band](https://stats.nostr.band/) shows which of these available relays are most popular, such as [relay.damus.io](http://relay.damus.io) and [nos.lol](nos.lol) and [eden.nostr.land](http://eden.nostr.land)
#### Relay softwares for you to launch your own
You may decide to launch you own relays, and if you do there are many different relay softwares to choose from:
- Simple, like [Bucket](https://github.com/coracle-social/bucket) (<100 lines of code)
- Widely used, like [Nostream](https://github.com/Cameri/nostream) (top ranked on Github)
- Customisable, like [Khatru](https://khatru.nostr.technology/) (a framework for customised relays)
- Specialised, like [HAVEN](https://github.com/bitvora/haven) or [Team Relay](https://github.com/bitvora/team-relay) (for personal or teams relays, based on Khartu)
You can run these on your own server, or local machine, or [phone](https://github.com/greenart7c3/Citrine) or with a third-party host.
[Aljaz](nostr:npub1aljazgxlpnpfp7n5sunlk3dvfp72456x6nezjw4sd850q879rxqsthg9jp) provides a [great resource](https://github.com/aljazceru/awesome-nostr?tab=readme-ov-file#relays) with 45+ relay softwares to choose from.
In summary, at a high level,
- Anyone can connect to any of the relay instances that are available for them to use
- Anyone who wants to launch their own can select the relay software that best suit their needs, launch an instance, and have it used by whichever users they like
### Reasons to Run Your Own Relay
As a normal user of a Nostr client there's no obligation to run a relay. But having your own relay does give you more power.
For my own journey down the #nostr rabbit hole, I was looking for a relay to:
- back up my notes
- decrease spam
- increase my privacy
- learn skills I could later use for running a community or team or paid relay
Backing up notes – When you post notes to a public relay there's no guarantee that the relay is going to keep them long-term. It's job is relaying your notes to other clients, not storing them. Running your own relay allows you to keep your notes online.
Decrease spam – To first spam we can use a "Web of Trust" model–in which users endorse other users as trustworthy. A "Web of Trust" relay will reject notes from parties too far removed from your network. Running your own relay makes you more difficult to spam.
Increasing privacy – When you connect to a public relay, they can determine personal information about you, such as your IP address. Running your own relay keeps things more private.
For communities and teams and paid relays – Many opportunities exist to tailor relays to certain users needs, be they businesses or communities or as a for-profit business. For me, I am hoping that running my own relay helps me learn skills I can use in these kinds of further ventures.
To start I decided to focus on a personal relay. However, when I really got under the hood, it turned out I would need multiple relays not just one.
#### The outbox model
[Mike Dilger](nostr:npub1acg6thl5psv62405rljzkj8spesceyfz2c32udakc2ak0dmvfeyse9p35c) proposed [the outbox model](https://mikedilger.com/gossip-model/) (originally called the gossip model) as a way for users to engage with the wider Nostr network. It's a great model that is helpful to understand, as it suggests to establish different relays for different purposes.
Many clients and relay softwares have now adopted and continued to elaborate on this model. An example is to run specialised relays for Outbox, Inbox, Chat and Private needs.
**Outbox Relay (also called Home Relay)**
- This relay is for notes you have written, so that everyone knows where to find your notes
- In a set up where you are running your own, this relay is restricted so that only you can post to it, and you should set up your clients to post your notes to it
- An advanced version may take any notes received to this relay and "blast" them to other public relays so that your notes get wider reach
**Inbox Relay (also called Public Relay)**
- This relay is for public notes that other users want you to see, so that you always find notes that are relevant to you, including all replies, comments, likes, and zap payments
- In a set up where you are running your own, this relay is where you should look for notes relevant to you, and you should set up your clients to read from it
- An advanced version may search other public relays for notes that tag you, and import them into this relay so that you never miss a relevant note
**Chat Relay (also called Direct Message Relay)**
- This relay is for private direct message notes from other users, so that you always find your direct messages and so that they stay private
- In a set up where you are running your own, this relay is restricted so that only you can read from it, and you should set up your clients to read from it
- An advanced version may cut spam by only accepting direct messages from other users within your Web of Trust
**Private Relay**
- This relay is for your private use only, so that you can store private drafts or thoughts
- Only you can write to it and only you can read from it (and so, it is a bit mis-named as it does not actually relay anything to anywhere at all)
- In a set up where you are running your own, it gives you true privacy for these notes
**In summary as a user**
- I post my notes to my outbox relay. Network users can read them there, and if the relay is advanced it will also blast the notes out to other relays on the network
- I read from my inbox relay. Network users know to reach me there, and if the relay is advanced it will also bring me notes from the wider network
- I can have private direct message conversations with others in my chat relay.
- I can save private notes in my private relay
For me, this model has a lot of appeal and I went looking for a personal relay which adopted this model and contained all of these features.
#### HAVEN as a personal relay
I decided to go with HAVEN relay software.
HAVEN is all four of the above relays in one–outbox, inbox, chat and private. It contains advanced features like blasting your notes from outbox to other relays, importing notes from other relays to your inbox, and preventing spam with Web of Trust.
[HAVEN](https://github.com/bitvora/haven) is written by [Utxo the Webmaster](nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8) . It is based upon the [Khatru](https://khatru.nostr.technology/) relay framework by [Fiatjaf](nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6)
### Setting up HAVEN as a Personal Relay
I am mostly non-technical, but on my #Nostr journey I have been having success with technology set ups that use Docker.
- I have a cheap VPS which currently runs [Albyhub and Phoneixd with Docker](nostr:naddr1qq34xet5w35kueedw4cz65rp09kk2mn5wvkk7m3dfehhxarj95mk7dnvwvmszythwden5te0dehhxarj9emkjmn99upzqx760c0h894a5tg7lxgr8k506twrv2qs0yxln0nz7kgs8zae03xeqvzqqqr4gua7fyfn),
- My objective was to set up HAVEN to run alongside it, in a separate Docker on the same server. HAVEN does not include Docker by default, but [Sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe) published a [fork with Docker support](https://github.com/nostrver-se/haven/tree/docker_compose_support).
To get HAVEN up and running in Docker on your VPS:
1. Clone and configure HAVEN with the right variables
2. Launch it in Docker on your VPS
3. Check the URLs and logs to see your HAVEN running
4. Configure a subdomain to point to the VPS
5. Configure the VPS to reverse proxy to the Docker port
6. Configure the relays in your favourite Nostr client
7. Post a note to your outbox and see if it blasts!
#### Running HAVEN
I cloned Sebastix fork to start.
```
git clone -b docker_compose_support https://github.com/nostrver-se/haven.git
cd haven
```
The software sets up all environment variables in the `.env` file, and comes with an `.env.example` file. Duplicate and rename the file to `.env`. Within the `.env` file you need to set up the environment variables. The file is long but it contains lots of repetition and for the most part defaults can be retained–only a few changes are required:
- Replace all instances of the default user npub with your own (for me, `npub1r0d8...`)
- Change the default relay URL to your own (for me, `relay.rodbishop.nz`)
- Replace all instances of the default name in the relay names (for me, "Rod's ...")
- Replace all instances of the default profile image with your own
To enable automatic blasting from your outbox, and importing to your inbox, the software comes with an example list of relays to blast and import from. See `relays_blastr.example.json` and `relays_import.example.json`. To use these features simply duplicate and rename these files to `relays_blastr.json` and `relays_import.json` respectively. Within these files you can specify the public relays of your choice. I simply used the default list.
There are other features available, such as backups and initial imports, but I decided to handle these later. To start with I wanted to launch the relay and test it.
To launch the relay run Docker Compose.
```
docker-compose up -d
docker logs haven-relay
```
Then you should explore the logs in the command line and the ports in your browser to see if it launched successfully. The logs should show your web of trust has been built successfully and the browser should show simple landing pages.
The logs should show that the relay has queried the network and built a web of trust from your followers. Mine looked as follows.
```
2024/10/14 12:02:08 🌐 building web of trust graph
2024/10/14 12:02:16 🫂 total network size: 13296
2024/10/14 12:02:16 🔗 relays discovered: 335
2024/10/14 12:02:17 🌐 pubkeys with minimum followers: 9394 keys
```
Your browser should show you have four relays in operation, for example as follows.
- `your_IP_address:3355` (your outbox or home relay)
- `your_IP_address:3355/private` (your private relay)
- `your_IP_address:3355/chat` (your direct message relay)
- `your_IP_address:3355/inbox` (your inbox relay)
That's it. Your relay is online.
#### Connecting HAVEN
Now all that remains is the plumbing to connect your domain, relay, and Nostr clients together.
**Configure DNS**
First, configure your domain. At a high level –
1. Get your domain (buy one if you need to)
2. Get the IP address of your VPS
3. In your domain's DNS settings add those records as an A record to the subdomain of your choice, e.g. `relay` as in `relay.your_domain_name.com`, or in my case `relay.rodbishop.nz`
Your subdomain now points to your server.
**Configure reverse proxy**
Next, you need to redirect traffic from your subdomain to your relay at port `3355`.
On my VPS I use Caddy as a reverse proxy for a few projects, I have it sitting in a separate Docker network. To use it for my HAVEN Relay required two steps. I am sure that the way I do this is not very elegant, but it worked. If you prefer a different method, the HAVEN readme also comes with instructions on how to perform a similar setup using nginx.
For my method, my steps were as follows:
1. Add configuration to Caddy's `Caddyfile` to tell it what to do with requests for the `relay.rodbishop.nz` subdomain
2. Add the Caddy Docker network to the HAVEN `docker-compose.yml` to make it be part of the Caddy network
For the addition to the `Caddyfile`, I used as follows:
```
relay.rodbishop.nz {
reverse_proxy haven-relay:3355 {
header_up X-Forwarded-For {remote}
header_up X-Forwarded-Proto {scheme}
header_up X-Forwarded-Port {server_port}
}
}
```
For the addition to the `docker-compose.yml`, I used as follows:
```
networks:
- caddy # Added this line to services to connect to the Caddy network
networks:
caddy:
external: true # Added this to section specify the Caddy network
```
Once your DNS configuration and reverse proxy setup are completed, you should now be able to access your Nostr client at `relay.your_domain_name.com`. For my set up, this was `relay.rodbishop.nz`.
**Connecting your Nostr client**
Most Nostr clients allow you to specify any relay you choose. My go-to client at the moment is Amethyst on Android. Amethyst allows you to specify discrete relays for each role in the outbox model which ties up very neatly with HAVEN.
- In the sidebar, select Relays
- For "Public Outbox/Home Relays" enter `relay.your_domain_name.com`
- For "Public Inbox Relays" enter `relay.your_domain_name.com/inbox`
- For "DM Inbox Relays" enter `relay.your_domain_name.com/chat`
- For "Private Home Relays" enter `relay.your_domain_name.com/private`
- Click Save to broadcast your new relays to the Nostr network.
Your new relay configuration is now live.
**Testing your relay**
Lastly, it's time to test. Amethyst provides a simple method to test this as it allows you to configure the relays used on each post.
- Create a test note, and then before you post it, edit your relays using the icon at the top
- Turn off all relays except your own outbox relay, and post the note
- Access your HAVEN docker logs with `docker logs haven-relay` and see if there is a log to indicate if the note was received and blasted to other public relays
- Copy the `nevent` of the note, and attempt to find it in another client
If you're in luck, you may see something like this (the blasted note, and then users on the network responding to the note in turn).
```
2024/10/22 00:12:23 🔫 blasted 95c477af7e6b612bf5d1d94309d2d57377a0a67d2181cfbb42a2e3fbc0feeaaf to 26 relays
2024/10/22 00:13:50 🤙 new reaction in your inbox
2024/10/22 00:14:42 🫂 new reaction in your inbox
2024/10/22 00:14:45 ✅ new reaction in your inbox
2024/10/22 00:15:12 💜 new reaction in your inbox
2024/10/22 00:17:03 ✅ new reaction in your inbox
2024/10/22 00:17:03 🫂 new reaction in your inbox
2024/10/22 00:17:55 🫂 new reaction in your inbox
2024/10/22 00:19:02 📰 new note in your inbox
```
That's it. If you followed this successfully your personal relay is up and running.
#### What I did wrong so you don't have to
**My first relay was too public**
This blog comes after much trial and error. The first error I made was I set up a relay to use as a personal relay, but without any restrictions on use. I very quickly found other people discovered and started using my relay to save their own notes! This was unintended and I had to take it down.
**Unfamiliar with Go language**
I am mostly non-technical, and completely unfamiliar with Go. I got the project up and running with Go on my localhost–with a lot of help from my AI–but I then completely failed in migrating this to my VPS. Moving to Docker made the difference for me here.
**I failed a few times due to a messy folder**
After messing with Go, I moved to the Docker setup, but I started my work from a messy folder which contained remnants of the Go build, which caused various failures. Deleting the folder and cloning again from scratch solved the issue.
**Trouble with Nostr.wine**
I subscribe to the Nostr.wine paid relay, and I initially added it to the list of relays in my blaster. However, it didn't work, and the logs showed an error as follows
```
CLOSED from wss://nostr.wine: 'auth-required: this relay only serves private notes to authenticated users'
```
It seems my npub's subscription to Nostr.wine is not enough for it to permit my relay to blast notes to it. In the end, I removed Nostr.wine from my relay config, and kept Nostr.wine as a separate entry in my Client's outbox settings.
**Failed to create web of trust graph**
When I first launched the relay on my VPS, HAVEN failed to complete the Web of Trust graph, with a log that looked as follows (note the zeroes). As a result, no one would have been able to send me DM's to my Chat relay (it would flag every message as spam).
```
2024/10/14 12:02:08 🌐 building web of trust graph
2024/10/14 12:02:16 🫂 total network size: 0
2024/10/14 12:02:16 🔗 relays discovered: 0
2024/10/14 12:02:17 🌐 pubkeys with minimum followers: 0 keys
```
I never got to the bottom of why this was. In the process of trying to fix it I rebuild the container, and on the rebuild it spontaneously worked. Accordingly my lesson learned is "if in doubt, turn if off and on again".
**Failed to run --import function**
HAVEN comes with a function to import all your old notes from other public relays to your own outbox relay. When I run it I get an error as follows:
```
panic: Cannot acquire directory lock on "db/private". Another process is using this Badger database. error: resource temporarily unavailable
```
I have yet to work out the solution for this, and will update this note when I do so!
### What's Next?
Over the past four blogs I have
- [Mined a Nostr pubkey and backed up the mnemonic](nostr:naddr1qqsy66twd9hxwtteda6hyt2kv9hxjare94g82cntv4uj6drfw4cxyeszyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c6e2ekw)
- [Set up Nostr payments with a Lightning wallet plus all the bells and whistles](nostr:naddr1qq34xet5w35kueedw4cz65rp09kk2mn5wvkk7m3dfehhxarj95mk7dnvwvmsygqmmflp7uukhk3drmueqv763lfdcd3gzpusm7d7vt6ezquth97ymypsgqqqw4rsuql6je)
- [Set up NIP-05 and Lighting Address at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqyghwumn8ghj7mn0wd68ytnhd9hx2tczyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c634nh0)
- Set up a Personal Relay at my own domain
This feels like a very comprehensive personal set up now. Also, I have uncovered some new rabbit holes and feel like I have some projects to tackle. Perhaps one of these?
- Set up a personal homepage with my Nostr feed to round-out my rodbishop.nz domain
- Experiment with different signers like Amber and Nsec.app and NFC cards
- Set up a paid relay for #austriches (Australians and Kiwis on Nostr)
- Set up a team relay to experiment with Nostr for business or community projects
- Or something else ... ?
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
Pura vida Nostr.
-

@ 4ba8e86d:89d32de4
2024-10-17 22:26:20
Ele oferece a opção de utilizar autenticação de dois fatores para aumentar ainda mais a segurança. O aplicativo foi desenvolvido em 2016 pelo americano Mo Bitar para oferecer um lugar seguro para armazenar informações pessoais sem a preocupação de que seus dados sejam coletados ou expostos a terceiros.
O Standard Notes é um cofre de aço para seus dados mais confidenciais, que protege suas anotações e arquivos com criptografia de ponta a ponta líder do setor e auditada 4x. Armazene com segurança todos os seus dados confidenciais em um só lugar e acesse-os de todos os seus dispositivos, com a certeza de que seus dados estarão sempre protegidos pelos mais altos padrões de segurança.
Ao contrário de outros serviços de anotações, o Standard Notes apresenta medidas de segurança avançadas e controles de privacidade que protegem seus dados contra hacks, violações de dados, acesso do governo e até mesmo acesso de funcionários. Ele defende a privacidade dos usuários e apresenta políticas revisadas por pares e auditáveis.
O Standard Notes utiliza criptografia de ponta a ponta para proteger todos os dados, que são criptografados sempre que tocam um disco, como em seus servidores ou no dispositivo do usuário. Auditorias independentes são realizadas periodicamente em sua criptografia, aplicativo e código do servidor para garantir que os dados estejam protegidos. O código aberto do Standard Notes permite que os usuários tenham clareza sobre como seus dados estão sendo tratados em cada etapa do caminho. Ele não coleta ou armazena informações do usuário, como endereço IP ou agente do usuário, para proteger a privacidade.
1. Acesse a F-droid ou Google Play Store em seu dispositivo Android.
2. siga as instruções para criar uma conta ou fazer login em uma conta existente.
3. Comece a criar suas notas e armazenar outras informações importantes com a tranquilidade de que seus dados estão seguros e protegidos.
https://github.com/standardnotes
-

@ 460c25e6:ef85065c
2024-10-10 13:22:06
In the early days of Nostr, developers often competed to see who could implement the most NIPs. Although all were optional (except NIP-01), it became a point of pride and vital for the ecosystem's growth. Back then, there were only a few dozen relatively simple NIPs to implement. Fast forward to today, with nearly 100 NIPs, maintaining and implementing everything has become nearly impossible. Yet, the drive among developers to "code all things Nostr" remains as strong as ever.
nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8gprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszxmhwden5te0wfjkccte9emk2um5v4exucn5vvhxxmmd9uq3xamnwvaz7tmhda6zuat50phjummwv5hsx7c9z9 raised the point that everyone, even I, agrees:
nostr:nevent1qqsqqqp2zrs7836tyjlsfe7aj9c4d97zrxxqyayagkdwlcur96t4laspzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqqqqzgcrrrp
But how big is too big? How can we better understand the range of options available for devs out there?
I went out for a hunt in my own brain to figure out how to clarify the situation. I came up with the following 4 categories for Nostr Clients:
- **Super Clients**: These apps merge vastly different domains into a single application, offering basic support for reading, writing, configuration, and data management for each use case within each domains. An example would be an app that combines a Marketplace and Live Streams under one roof.
- **Clients**: These apps provide comprehensive support for a single domain, handling all its use cases in a single home. They manage the complete set of reading, writing, configuration, and long-term data management within that domain. An example is a marketplace app that helps users manage product catalogs, process orders, collect payments, and handle fulfillment and reports.
- **Mini Clients**: These apps focus on read and write functionality for a single use case, including configuration management and any actions related to that specific task. For example, a fulfillment app that helps users view orders placed from another client to then pack and ship them.
- **Micro Clients**: These apps have a single interface and perform one specific action. Viewing and creating a record is handled by separate micro apps. An example is an app that simply scans an order's QR code and marks it as shipped.
Based on my made-up categories described at the end, this is how I would split our most known apps.
**Super Clients**
- [amethyst](https://amethyst.social)
- [nostrudel](https://nostrudel.ninja)
- [coracle](https://coracle.social)
**Clients**
- [damus](https://damus.io) - twitter
- [primal](https://primal.net) - twitter
- [snort](https://snort.social) - twitter
- [gossip](https://github.com/mikedilger/gossip) - twitter
- [lume](https://lume.nu) - twitter
- [ditto](https://soapbox.pub/ditto/) - twitter
- [rabbit](https://rabbit.syusui.net) - twitter
- [freefrom](https://freefrom.space) - twitter
- [nos](https://nos.social) - twitter
- [flycat](https://flycat.club) - twitter
- [straylight](https://straylight.cafe) - twitter
- [nostter](https://nostter.app) - twitter
- [iris](https://iris.to) - twitter
- [nostur](https://nostur.com) - twitter
- [nostrmo](https://apps.apple.com/us/app/nostrmo/id6447441761) - twitter
- [yana](https://yana.do) - twitter
- [openvibe](https://openvibe.social) - twitter
- [freerse](https://freerse.com) - twitter
- [0xchat](https://0xchat.com) - chats
- [cornychat](https://cornychat.com) - chats
- [coop](https://github.com/lumehq/coop) - chats
- [nostrchat](https://nostrchat.io) - chats
- [blowater](https://blowater.deno.dev) - chats
- [habla](https://habla.news) - blogs
- [yakihonne](https://yakihonne.com) - blogs
- [highlighter](https://highlighter.com) - blogs
- [blogstack](https://blogstack.io) - blogs
- [stemstr](https://stemstr.app) - music
- [wavlake](https://wavlake.com) - music
- [fountain](https://fountain.fm) - podcasts
- [zap.stream](https://zap.stream) - live streaming
- [shopstr](https://shopstr.store) - marketplace
- [plebeian.market](https://plebeian.market) - marketplace
- [flotilla](https://flotilla.coracle.social) - communities
- [satellite](https://satellite.earth) - communities
- [zapddit](https://zapddit.com) - communities
- [nostr.kiwi](https://nostr.kiwi) - communities
- [hivetalk](https://hivetalk.org) - video calls
- [flare](https://flare.pub) - long-form videos
- [nostrnests](https://nostrnests.com) - audio spaces
- [wherostr](https://wherostr.social) - location
- [yondar](https://go.yondar.me) - location
- [stacker.news](https://stacker.news) - news
- [flockstr](https://flockstr.com) - events
- [nostrocket](https://nostrocket.org) - issue tracker
- [docstr](https://docstr.app) - docs
- [satshoot](https://satshoot.com) - freelance
- [wikifreedia](https://wikifreedia.xyz) - wiki
- [formstr](https://formstr.app) - forms
- [chesstr](https://chesstr.pages.dev) - chess
- [memestr](https://memestr.app) - meme feed
- [npub.cash](https://npub.cash) - wallet
- [npub.pro](https://npub.pro) - websites
- [gitworkshop](https://gitworkshop.dev) - dev tools
- [onosendai](https://onosendai.tech) - metaverse
- [degmods](https://degmods.com) - games
- [turdsoup](https://turdsoup.com) - prompts
**Mini Clients**
- [amber](https://github.com/greenart7c3/Amber) - signer
- [alby](https://getalby.com) - signer
- [nos2x](https://github.com/fiatjaf/nos2x) - signer
- [nsec.app](https://nsec.app) - signer
- [keys.band](https://keys.band) - signer
- [nostrame](https://github.com/Anderson-Juhasc/nostrame) - signer
- [nokakoi](https://nokakoi.com) - anon
- [zap.cooking](https://zap.cooking) - recipes
- [anonostr](https://anonostr.com) - anon
- [getwired](https://getwired.app) - anon
- [lowent](https://lowent.xyz) - anon
- [creatr](https://creatr.nostr.wine) - exclusive content
- [lightning.video](https://lightning.video) - exclusive content
- [zaplinks](https://zaplinks.lol/slides) - slides
- [listr](https://listr.lol) - lists
- [zap.store](https://zap.store) - app store
- [badges.page](https://badges.page) - badges
- [oddbean](https://oddbean.com) - news
- [dtan](https://dtan.xyz) - torrents
- [nosta](https://nosta.me) - user pages
- [pinstr](https://pinstr.app) - pinterest
- [pollerama](https://pollerama.fun) - polls
- [swarmstr](https://swarmstr.com) - trending
- [nostrapp](https://nostrapp.link) - apps manager
- [noogle](https://noogle.lol) - search
- [ostrich.work](https://ostrich.work) - job postings
- [emojito](https://emojito.meme) - emoji manager
- [nostree](https://nostree.me) - links
- [citrine](https://github.com/greenart7c3/citrine) - local relay
- [joinstr](https://joinstr.xyz) - coinjoins
- [heya](https://heya.fund) - crowdfunding
- [zapplepay](https://zapplepay.com) - zaps
- [nosbin](https://nosbin.com) - clipboard
- [shipyard](https://shipyard.pub) - scheduler
- [tunestr](https://tunestr.io) - live streams
- [filestr](https://filestr.vercel.app) - files
- [nostrcheck.me](https://nostrcheck.me/) - media hosting
- [sheetstr](https://sheetstr.amethyst.social) - spreadsheets
- [crafters](https://crafters.amethyst.social) - curriculum vitae
**Micro Clients**
- [w3](https://w3.do) - url shortener
- [nosdrive](https://nosdrive.app) - backups
- [zaplife](https://zaplife.lol) - zaps dashboard
- [zapper.fun](https://zapper.fun) - payments
- [nostrends](https://nostrends.vercel.app) - trends
- [zephyr](https://zephyr.coracle.social) - trends
- [wavman](https://wavman.app) - music player
- [nostrrr](https://nostrrr.com) - relay info
- [nosdump](https://github.com/jiftechnify/nosdump) - relay info
- [notestack](https://notestack.com) - blogs
- [nostr.build](https://nostr.build) - media hosting
- [nostr.watch](https://nostr.watch) - relay info
- [nostr hours](https://snowcait.github.io/nostr-hours/) - use reports
- [lazereyes](https://lazereyes.nosfabrica.com) - vision prescriptions
- [snakestr](https://satoshipuzzles.github.io/Snakestr) - games
- [deletestr](https://zaplinks.lol/deletestr) - deletion requests
- [2048str](https://zaplinks.lol/2048str) - games
- [nostrqr](https://zaplinks.lol/nostrqr) - qr generator
- [notanostrclient](https://zaplinks.lol/notanostrclient) - anon
Super apps will try to do everything, but can't really do most things super well. Regular-sized Clients will try to manage most of a given domain but are likely to centralize users on themselves, an unwanted effect inside of Nostr. If we want Nostr to grow in a decentralized fashion, we have to start betting on and using more **Mini** and **Micro** clients.
-

@ 4ba8e86d:89d32de4
2024-10-08 15:50:58
Ele foi desenvolvido pela Beowulf Blockchain, uma empresa que é conhecida por suas soluções seguras e confiáveis de blockchain e criptografia.
A autenticação em duas etapas é um processo que adiciona uma camada extra de segurança ao login em uma conta online. Em vez de depender apenas de uma senha, o 2FA exige uma segunda forma de autenticação, geralmente um código enviado para um dispositivo móvel ou gerado por um aplicativo. Isso ajuda a garantir que apenas o proprietário da conta possa acessá-la.
A história do Aegis Authenticator remonta ao início dos anos 2000, quando a autenticação em duas etapas começou a ser amplamente adotada para proteger contas online. Desde então, houve vários casos de violação de segurança em grandes empresas, incluindo Yahoo, Equifax e Marriott, que expuseram informações pessoais de milhões de usuários.
Como resultado, a segurança online se tornou uma preocupação crescente para indivíduos e empresas em todo o mundo.
O Aegis Authenticator funciona gerando códigos de autenticação em tempo real que mudam a cada 30 segundos. Esses códigos são usados em conjunto com uma senha para acessar uma conta online. O aplicativo suporta a autenticação com base em tempo e também com base em contagem, o que significa que ele pode ser usado com serviços que suportam ambas as opções.
O Aegis Authenticator possui recursos de backup e sincronização em nuvem para garantir que os usuários possam acessar suas contas em outros dispositivos, mesmo que o dispositivo original seja perdido ou roubado. O aplicativo utiliza criptografia de ponta a ponta para proteger as informações do usuário em trânsito e armazenadas na nuvem.
O Aegis Authenticator resolve vários problemas de segurança online, incluindo a prevenção de ataques de phishing e o aumento da segurança em contas com senhas fracas. Os códigos gerados pelo aplicativo são válidos apenas por um curto período de tempo, o que dificulta a utilização de um código roubado por um atacante. Além disso, o aplicativo é capaz de detectar automaticamente tentativas de phishing e alertar o usuário.
1. Baixe o aplicativo na loja de aplicativos do seu dispositivo móvel.
https://play.google.com/store/apps/details?id=com.beemdevelopment.aegis
2. Abra o aplicativo e clique em "Adicionar conta".
3. Selecione o serviço para o qual deseja configurar a autenticação em duas etapas.
4. Siga as instruções do serviço para vincular sua conta ao Aegis Authenticator. Isso pode envolver digitalizar um código QR com a câmera do seu dispositivo ou inserir um código de configuração manualmente.
5. O aplicativo irá gerar um código de autenticação em tempo real para sua conta, que muda a cada 30 segundos. Use esse código em conjunto com sua senha para acessar sua conta.
Com esses passos simples, você pode usar o Aegis Authenticator para proteger suas contas online e aumentar sua segurança digital
Um próximo Passo seria adquirir um Yubico.
https://void.cat/d/KzX75b9AwikAGHiywPb3Su.webp
-

@ 4ba8e86d:89d32de4
2024-10-07 23:19:19
O Orbot é um aplicativo de código aberto para dispositivos Android que oferece anonimato e segurança aos usuários da Internet. Ele funciona como um front-end para o Tor, permitindo que os usuários se conectem à rede Tor e usem serviços online de forma anônima e segura.
O Tor é uma rede de computadores que foi desenvolvida originalmente pelo governo dos Estados Unidos para proteger a privacidade dos usuários da Internet e permitir a comunicação segura de informações confidenciais. O Tor funciona usando um sistema de "onion routing" (roteamento de cebola), que envolve o encapsulamento de dados em várias camadas de criptografia antes de serem transmitidos através da rede.
O Orbot é um componente do Guardian Project, uma iniciativa que visa desenvolver tecnologia segura e anônima para ativistas de direitos humanos, jornalistas e outros usuários que precisam de privacidade online. O aplicativo é distribuído sob a Licença Pública Geral do GNU, o que significa que é totalmente gratuito e de código aberto.
O Orbot foi lançado pela primeira vez em 2008, como parte do projeto Tor, uma rede descentralizada de anonimização de tráfego que ajuda a proteger a privacidade dos usuários na internet. A ideia por trás do Orbot era fornecer uma maneira fácil para usuários móveis de acessar a rede Tor e proteger suas comunicações enquanto estavam em movimento. A primeira versão do Orbot foi lançada para o sistema operacional Android, e desde então, tem sido amplamente adotada por usuários preocupados com a privacidade.
O aplicativo inclui um proxy HTTP que permite conectar navegadores da web e outros aplicativos cliente HTTP na interface Tor SOCKS. Isso significa que todos os seus dados são criptografados e encaminhados através da rede Tor antes de serem transmitidos para o servidor de destino, tornando extremamente difícil para qualquer pessoa interceptar ou monitorar suas atividades online.
Além de fornecer anonimato e segurança aos usuários, o Orbot também pode ser usado para acessar conteúdo restrito por região. Por exemplo, se você está em um país que censura determinados sites ou serviços online, o Orbot pode ajudá-lo a acessar esse conteúdo de forma segura e anônima.
Os principais recursos do Orbot incluem a conexão segura à rede Tor, o acesso a serviços online restritos, o proxy HTTP, o código aberto e a facilidade de uso. Esses recursos tornam o Orbot uma ferramenta valiosa para usuários preocupados com a privacidade que desejam se comunicar e navegar na Internet de forma segura e anônima.
O Orbot é um aplicativo gratuito e de código aberto para dispositivos Android que oferece anonimato e segurança aos usuários
Aqui está um passo a passo para instalar o Orbot em seu dispositivo Android:
1. Acesse a F-droid ou Google Play Store em seu dispositivo Android.
2. Selecione a opção "Iniciar" para iniciar a conexão com a rede Tor. Aguarde até que a conexão seja estabelecida. Isso pode levar alguns minutos, dependendo da velocidade de sua conexão com a internet.
3. Depois que a conexão for estabelecida, você poderá navegar na internet de forma anônima e segura usando o Tor.
Lembre-se de que o uso do Tor não garante anonimato completo e pode ser necessário seguir outras medidas de segurança para proteger sua privacidade na internet. Além disso, o Orbot é apenas uma parte do ecossistema de segurança e privacidade e pode ser necessário utilizar outras ferramentas para garantir a segurança online.
https://github.com/guardianproject/orbot/stargazers
-

@ bec0c9d3:c4e9cd29
2024-10-06 14:07:27
Hello, **Free People**!
Last weeks we were very productive. Our team has reached a higher level. Ideas, designs, workflow - you name it.
All of this to deliver you the best experience in the space. Where Open Source and Cypherpunk Ethos lead the way.
[2140 COLLECTIVE ](https://2140.wtf) alongside with [CyphermunkHouse](https://primal.net/e/note1ae8947gzx4q38p9v2fuw3yn4d5sy5qy9x6uap6p9uf8hx9dl3e0qnkmazf) is proud to announce that Ours (Yours) festival will take place in ***LONDON / UK***.
During Halloween/BitcoinWhitepaper weekend.
```
29.OCT - 03.NOV 2024
```

Please check [BITCOIN CULTURE FESTIVAL '24 AGENDA](https://2140.wtf/content/45-bitcoin-culture-week-full-agenda)Page for more updated info !
```
All of this will not be possible without YOU.
```
If you want to join our crew, share some ideas, help, anything - feel free to contact us using the application forms, ready - waiting on the [main page.](http://2140.wtf)
Forms are dedicated to [Volunteers](https://2140.wtf/content/49-volunteer-form) and [Artists](https://2140.wtf/content/40-art-submission) that can drop an Art for Phisical Gallery
There will be also an Online auction that will display your art worldwide. Bitcoin pay only).
We are also prepered forms for [#nostr panel](https://2140.wtf/content/41-nostr-participant-form) speakers who want to present any #nostr project, freedom tools, etc. [ART Panel](https://2140.wtf/content/42-panel-participant-form) Art, music, culture - stuff around our values, Bitcoin, and freedom, during friday and saturday events.
If you wanna share you bitcoin story to isnpire otheres we invite you to visit us on free #TootingMarket Day where we preper Open Mic. [Let us know](https://2140.wtf/content/48-tooting-market-participant-form). On the market, which has already onboarded 20 Bitcoin merchants with food, drink, and veggy stalls, in beautiful London City.
Please check out forms - maybe you will be the one, inspired enough to share your **knowledge** , **ideas** , and **spirit**.
> **All tribes are welcome.** . We will prepare space for you!
Also, if you believe in our ethos and mission and think it would be okay for you to support us, feel free to check our **Sponsorship Packages.** [ HERE](https://2140.wtf/content/51-sponsor)
> **Any help is well appreciated!**
As like a Cypherpunk's Movement, we truly respect our guests' privacy. Therefore, making pictures or video recordings will not be allowed during our events.

We will organize accreditation for professional photographers, so all good memories will be well documented.
We hope you will understand our values and respect this rule as well. #PrivacyMatters

To make a long story short. We are waiting for you in London. Be prepared for an Atomic Vibe Experience .
Be a part of the Peacefull Revolution.
Remmember It always starts from YOU.
Subscribe to our newsletter on our page to stay informed and up-to-date. Help us spread the word by sharing the link using the share button.
Follow us also on all socials:
[NOSTREE.me ](https://nostree.me/npub1hmqvn57wfm7qcygkt4et3qffhvdwyer9mkz0lyzjwr29438fe55s4r0s33/bcfestival) - NOSTR LinkTree
[INSTAGRAM](http://instagram.com/2140.wtf)
[TWETTER - X ](https://x.com/2140_wtf)
[YOUTUBE](https://www.youtube.com/@2140_wtf)
LINKS
[BitcoinCulturefestival.com](https://bitcoinculturefestival.com)
[bitcoinculturefestival.london](https://bitcoinculturefestival.london)
[www.2140.wtf](https://2140.wtf)
OUR PARNERS / SPONSORS
[ANGOR](https://angor.io)

[BITCOIN EVENTS HQ](https://bitcoinonly.events/)

[YAKIHONNE](https://yakihonne.com/)

Hashtags
#ArtGallery
#ArtPanel
#2140wtf
#2140army
#CyphermunkHouse
#art
#artstr
#nostrart
#craft
#culture
#music
#bitcoin
#nostr
#TootingMarket
#NostrLDN
#NostrLondon
#Foodst
#Foodstrlondon
#foodstrLDN
#yakihonne
-

@ 4ba8e86d:89d32de4
2024-10-05 22:04:32
Como funciona o PGP.
O texto a seguir foi retirado do capítulo 1 do documento Introdução à criptografia na documentação do PGP 6.5.1. Copyright © 1990-1999 Network Associates, Inc. Todos os direitos reservados.
-O que é criptografia?
-Criptografia forte
-Como funciona a criptografia?
-Criptografia convencional
-Cifra de César
-Gerenciamento de chaves e criptografia convencional
-Criptografia de chave pública
-Como funciona o PGP
- Chaves
• Assinaturas digitais
-Funções hash
• Certificados digitais
-Distribuição de certificados
-Formatos de certificado
•Validade e confiança
-Verificando validade
-Estabelecendo confiança
-Modelos de confiança
• Revogação de certificado
-Comunicar que um certificado foi revogado
-O que é uma senha?
-Divisão de chave
Os princípios básicos da criptografia.
Quando Júlio César enviou mensagens aos seus generais, ele não confiou nos seus mensageiros. Então ele substituiu cada A em suas mensagens por um D, cada B por um E, e assim por diante através do alfabeto. Somente alguém que conhecesse a regra “shift by 3” poderia decifrar suas mensagens.
E assim começamos.
Criptografia e descriptografia.
Os dados que podem ser lidos e compreendidos sem quaisquer medidas especiais são chamados de texto simples ou texto não criptografado. O método de disfarçar o texto simples de forma a ocultar sua substância é chamado de criptografia. Criptografar texto simples resulta em um jargão ilegível chamado texto cifrado. Você usa criptografia para garantir que as informações sejam ocultadas de qualquer pessoa a quem não se destinam, mesmo daqueles que podem ver os dados criptografados. O processo de reverter o texto cifrado ao texto simples original é chamado de descriptografia . A Figura 1-1 ilustra esse processo.
https://nostrcheck.me/media/public/nostrcheck.me_5922365650718442651699905288.webp
Figura 1-1. Criptografia e descriptografia
O que é criptografia?
Criptografia é a ciência que usa a matemática para criptografar e descriptografar dados. A criptografia permite armazenar informações confidenciais ou transmiti-las através de redes inseguras (como a Internet) para que não possam ser lidas por ninguém, exceto pelo destinatário pretendido.
Embora a criptografia seja a ciência que protege os dados, a criptoanálise é a ciência que analisa e quebra a comunicação segura. A criptoanálise clássica envolve uma combinação interessante de raciocínio analítico, aplicação de ferramentas matemáticas, descoberta de padrões, paciência, determinação e sorte. Os criptoanalistas também são chamados de atacantes.
A criptologia abrange tanto a criptografia quanto a criptoanálise.
Criptografia forte.
"Existem dois tipos de criptografia neste mundo: a criptografia que impedirá a sua irmã mais nova de ler os seus arquivos, e a criptografia que impedirá os principais governos de lerem os seus arquivos. Este livro é sobre o último."
--Bruce Schneier, Criptografia Aplicada: Protocolos, Algoritmos e Código Fonte em C.
PGP também trata deste último tipo de criptografia. A criptografia pode ser forte ou fraca, conforme explicado acima. A força criptográfica é medida no tempo e nos recursos necessários para recuperar o texto simples. O resultado de uma criptografia forte é um texto cifrado que é muito difícil de decifrar sem a posse da ferramenta de decodificação apropriada. Quão díficil? Dado todo o poder computacional e o tempo disponível de hoje – mesmo um bilhão de computadores fazendo um bilhão de verificações por segundo – não é possível decifrar o resultado de uma criptografia forte antes do fim do universo.
Alguém poderia pensar, então, que uma criptografia forte resistiria muito bem até mesmo contra um criptoanalista extremamente determinado. Quem pode realmente dizer? Ninguém provou que a criptografia mais forte disponível hoje resistirá ao poder computacional de amanhã. No entanto, a criptografia forte empregada pelo PGP é a melhor disponível atualmente.
Contudo, a vigilância e o conservadorismo irão protegê-lo melhor do que as alegações de impenetrabilidade.
Como funciona a criptografia?
Um algoritmo criptográfico, ou cifra, é uma função matemática usada no processo de criptografia e descriptografia. Um algoritmo criptográfico funciona em combinação com uma chave – uma palavra, número ou frase – para criptografar o texto simples. O mesmo texto simples é criptografado em texto cifrado diferente com chaves diferentes. A segurança dos dados criptografados depende inteiramente de duas coisas: a força do algoritmo criptográfico e o sigilo da chave.
Um algoritmo criptográfico, mais todas as chaves possíveis e todos os protocolos que o fazem funcionar constituem um criptossistema. PGP é um criptossistema.
Criptografia convencional.
Na criptografia convencional, também chamada de criptografia de chave secreta ou de chave simétrica , uma chave é usada tanto para criptografia quanto para descriptografia. O Data Encryption Standard (DES) é um exemplo de criptossistema convencional amplamente empregado pelo Governo Federal. A Figura 1-2 é uma ilustração do processo de criptografia convencional.
https://nostrcheck.me/media/public/nostrcheck.me_1563316185075842071699905520.webp
Figura 1-2. Criptografia convencional
Cifra de César.
Um exemplo extremamente simples de criptografia convencional é uma cifra de substituição. Uma cifra de substituição substitui uma informação por outra. Isso é feito com mais frequência compensando as letras do alfabeto. Dois exemplos são o Anel Decodificador Secreto do Capitão Meia-Noite, que você pode ter possuído quando era criança, e a cifra de Júlio César. Em ambos os casos, o algoritmo serve para compensar o alfabeto e a chave é o número de caracteres para compensá-lo.
Por exemplo, se codificarmos a palavra "SEGREDO" usando o valor chave de César de 3, deslocaremos o alfabeto para que a terceira letra abaixo (D) comece o alfabeto.
Então começando com
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
e deslizando tudo para cima em 3, você obtém
DEFGHIJKLMNOPQRSTUVWXYZABC
onde D=A, E=B, F=C e assim por diante.
Usando este esquema, o texto simples, "SECRET" é criptografado como "VHFUHW". Para permitir que outra pessoa leia o texto cifrado, você diz a ela que a chave é 3.
Obviamente, esta é uma criptografia extremamente fraca para os padrões atuais, mas, ei, funcionou para César e ilustra como funciona a criptografia convencional.
Gerenciamento de chaves e criptografia convencional.
A criptografia convencional tem benefícios. É muito rápido. É especialmente útil para criptografar dados que não vão a lugar nenhum. No entanto, a criptografia convencional por si só como meio de transmissão segura de dados pode ser bastante cara, simplesmente devido à dificuldade de distribuição segura de chaves.
Lembre-se de um personagem do seu filme de espionagem favorito: a pessoa com uma pasta trancada e algemada ao pulso. Afinal, o que há na pasta? Provavelmente não é o código de lançamento de mísseis/fórmula de biotoxina/plano de invasão em si. É a chave que irá descriptografar os dados secretos.
Para que um remetente e um destinatário se comuniquem com segurança usando criptografia convencional, eles devem chegar a um acordo sobre uma chave e mantê-la secreta entre si. Se estiverem em locais físicos diferentes, devem confiar em um mensageiro, no Bat Phone ou em algum outro meio de comunicação seguro para evitar a divulgação da chave secreta durante a transmissão. Qualquer pessoa que ouvir ou interceptar a chave em trânsito poderá posteriormente ler, modificar e falsificar todas as informações criptografadas ou autenticadas com essa chave. Do DES ao Anel Decodificador Secreto do Capitão Midnight, o problema persistente com a criptografia convencional é a distribuição de chaves: como você leva a chave ao destinatário sem que alguém a intercepte?
Criptografia de chave pública.
Os problemas de distribuição de chaves são resolvidos pela criptografia de chave pública, cujo conceito foi introduzido por Whitfield Diffie e Martin Hellman em 1975. (Há agora evidências de que o Serviço Secreto Britânico a inventou alguns anos antes de Diffie e Hellman, mas a manteve um segredo militar - e não fez nada com isso.
[JH Ellis: The Possibility of Secure Non-Secret Digital Encryption, CESG Report, January 1970])
A criptografia de chave pública é um esquema assimétrico que usa um par de chaves para criptografia: uma chave pública, que criptografa os dados, e uma chave privada ou secreta correspondente para descriptografia. Você publica sua chave pública para o mundo enquanto mantém sua chave privada em segredo. Qualquer pessoa com uma cópia da sua chave pública pode criptografar informações que somente você pode ler. Até mesmo pessoas que você nunca conheceu.
É computacionalmente inviável deduzir a chave privada da chave pública. Qualquer pessoa que possua uma chave pública pode criptografar informações, mas não pode descriptografá-las. Somente a pessoa que possui a chave privada correspondente pode descriptografar as informações.
https://nostrcheck.me/media/public/nostrcheck.me_6137622541655550851699909180.webp
Figura 1-3. Criptografia de chave pública
O principal benefício da criptografia de chave pública é que ela permite que pessoas que não possuem nenhum acordo de segurança pré-existente troquem mensagens com segurança. A necessidade de remetente e destinatário compartilharem chaves secretas através de algum canal seguro é eliminada; todas as comunicações envolvem apenas chaves públicas e nenhuma chave privada é transmitida ou compartilhada. Alguns exemplos de criptossistemas de chave pública são Elgamal (nomeado em homenagem a seu inventor, Taher Elgamal), RSA (nomeado em homenagem a seus inventores, Ron Rivest, Adi Shamir e Leonard Adleman), Diffie-Hellman (nomeado, você adivinhou, em homenagem a seus inventores). ) e DSA, o algoritmo de assinatura digital (inventado por David Kravitz).
Como a criptografia convencional já foi o único meio disponível para transmitir informações secretas, o custo dos canais seguros e da distribuição de chaves relegou a sua utilização apenas àqueles que podiam pagar, como governos e grandes bancos (ou crianças pequenas com anéis descodificadores secretos). A criptografia de chave pública é a revolução tecnológica que fornece criptografia forte para as massas adultas. Lembra do mensageiro com a pasta trancada e algemada ao pulso? A criptografia de chave pública o tira do mercado (provavelmente para seu alívio).
Como funciona o PGP.
O PGP combina alguns dos melhores recursos da criptografia convencional e de chave pública. PGP é um criptossistema híbrido. Quando um usuário criptografa texto simples com PGP, o PGP primeiro compacta o texto simples. A compactação de dados economiza tempo de transmissão do modem e espaço em disco e, mais importante ainda, fortalece a segurança criptográfica. A maioria das técnicas de criptoanálise explora padrões encontrados no texto simples para quebrar a cifra. A compressão reduz esses padrões no texto simples, aumentando assim enormemente a resistência à criptoanálise. (Arquivos que são muito curtos para compactar ou que não são compactados bem não são compactados.)
O PGP então cria uma chave de sessão, que é uma chave secreta única. Esta chave é um número aleatório gerado a partir dos movimentos aleatórios do mouse e das teclas digitadas. Esta chave de sessão funciona com um algoritmo de criptografia convencional rápido e muito seguro para criptografar o texto simples; o resultado é texto cifrado. Depois que os dados são criptografados, a chave da sessão é criptografada na chave pública do destinatário. Essa chave de sessão criptografada com chave pública é transmitida junto com o texto cifrado ao destinatário.
https://nostrcheck.me/media/public/nostrcheck.me_1978130242364857481699910331.webp
Figura 1-4. Como funciona a criptografia PGP
A descriptografia funciona ao contrário. A cópia do PGP do destinatário usa sua chave privada para recuperar a chave de sessão temporária, que o PGP usa para descriptografar o texto cifrado criptografado convencionalmente.
https://nostrcheck.me/media/public/nostrcheck.me_1978130242364857481699910331.webp
Figura 1-5. Como funciona a descriptografia PGP
A combinação dos dois métodos de criptografia combina a conveniência da criptografia de chave pública com a velocidade da criptografia convencional. A criptografia convencional é cerca de 1.000 vezes mais rápida que a criptografia de chave pública. A criptografia de chave pública, por sua vez, fornece uma solução para
problemas de distribuição de chaves e transmissão de dados. Usados em conjunto, o desempenho e a distribuição de chaves são melhorados sem qualquer sacrifício na segurança.
Chaves.
Uma chave é um valor que funciona com um algoritmo criptográfico para produzir um texto cifrado específico. As chaves são basicamente números muito, muito, muito grandes. O tamanho da chave é medido em bits; o número que representa uma chave de 1024 bits é enorme. Na criptografia de chave pública, quanto maior a chave, mais seguro é o texto cifrado.
No entanto, o tamanho da chave pública e o tamanho da chave secreta da criptografia convencional não têm nenhuma relação. Uma chave convencional de 80 bits tem a força equivalente a uma chave pública de 1.024 bits. Uma chave convencional de 128 bits é equivalente a uma chave pública de 3.000 bits. Novamente, quanto maior a chave, mais segura, mas os algoritmos usados para cada tipo de criptografia são muito diferentes e, portanto, a comparação é como a de maçãs com laranjas.
Embora as chaves pública e privada estejam matematicamente relacionadas, é muito difícil derivar a chave privada dada apenas a chave pública; no entanto, derivar a chave privada é sempre possível, desde que haja tempo e capacidade computacional suficientes. Isto torna muito importante escolher chaves do tamanho certo; grande o suficiente para ser seguro, mas pequeno o suficiente para ser aplicado rapidamente. Além disso, você precisa considerar quem pode estar tentando ler seus arquivos, quão determinados eles estão, quanto tempo têm e quais podem ser seus recursos.
Chaves maiores serão criptograficamente seguras por um longo período de tempo. Se o que você deseja criptografar precisar ficar oculto por muitos anos, você pode usar uma chave muito grande. Claro, quem sabe quanto tempo levará para determinar sua chave usando os computadores mais rápidos e eficientes de amanhã? Houve um tempo em que uma chave simétrica de 56 bits era considerada extremamente segura.
As chaves são armazenadas de forma criptografada. O PGP armazena as chaves em dois arquivos no seu disco rígido; um para chaves públicas e outro para chaves privadas. Esses arquivos são chamados de chaveiros. Ao usar o PGP, você normalmente adicionará as chaves públicas dos seus destinatários ao seu chaveiro público. Suas chaves privadas são armazenadas em seu chaveiro privado. Se você perder seu chaveiro privado, não será possível descriptografar nenhuma informação criptografada nas chaves desse anel.
Assinaturas digitais.
Um grande benefício da criptografia de chave pública é que ela fornece um método para empregar assinaturas digitais. As assinaturas digitais permitem ao destinatário da informação verificar a autenticidade da origem da informação e também verificar se a informação está intacta. Assim, as assinaturas digitais de chave pública fornecem autenticação e integridade de dados. A assinatura digital também proporciona o não repúdio, o que significa que evita que o remetente alegue que não enviou realmente as informações. Esses recursos são tão fundamentais para a criptografia quanto a privacidade, se não mais.
Uma assinatura digital tem a mesma finalidade de uma assinatura manuscrita. No entanto, uma assinatura manuscrita é fácil de falsificar. Uma assinatura digital é superior a uma assinatura manuscrita porque é quase impossível de ser falsificada, além de atestar o conteúdo da informação, bem como a identidade do signatário.
Algumas pessoas tendem a usar mais assinaturas do que criptografia. Por exemplo, você pode não se importar se alguém souber que você acabou de depositar US$ 1.000 em sua conta, mas quer ter certeza de que foi o caixa do banco com quem você estava lidando.
A maneira básica pela qual as assinaturas digitais são criadas é ilustrada na Figura 1-6 . Em vez de criptografar informações usando a chave pública de outra pessoa, você as criptografa com sua chave privada. Se as informações puderem ser descriptografadas com sua chave pública, elas deverão ter se originado em você.
https://nostrcheck.me/media/public/nostrcheck.me_4033165715613998201699910446.webp
Figura 1-6. Assinaturas digitais simples
Funções hash.
O sistema descrito acima apresenta alguns problemas. É lento e produz um enorme volume de dados – pelo menos o dobro do tamanho da informação original. Uma melhoria no esquema acima é a adição de uma função hash unidirecional no processo. Uma função hash unidirecional recebe uma entrada de comprimento variável – neste caso, uma mensagem de qualquer comprimento, até mesmo milhares ou milhões de bits – e produz uma saída de comprimento fixo; digamos, 160 bits. A função hash garante que, se a informação for alterada de alguma forma – mesmo que por apenas um bit – seja produzido um valor de saída totalmente diferente.
O PGP usa uma função hash criptograficamente forte no texto simples que o usuário está assinando. Isso gera um item de dados de comprimento fixo conhecido como resumo da mensagem. (Novamente, qualquer alteração nas informações resulta em um resumo totalmente diferente.)
Então o PGP usa o resumo e a chave privada para criar a “assinatura”. O PGP transmite a assinatura e o texto simples juntos. Ao receber a mensagem, o destinatário utiliza o PGP para recalcular o resumo, verificando assim a assinatura. O PGP pode criptografar o texto simples ou não; assinar texto simples é útil se alguns dos destinatários não estiverem interessados ou não forem capazes de verificar a assinatura.
Desde que uma função hash segura seja usada, não há como retirar a assinatura de alguém de um documento e anexá-la a outro, ou alterar uma mensagem assinada de qualquer forma. A menor alteração em um documento assinado causará falha no processo de verificação da assinatura digital.
https://nostrcheck.me/media/public/nostrcheck.me_2943209062439984111699910538.webp
Figura 1-7. Assinaturas digitais seguras
As assinaturas digitais desempenham um papel importante na autenticação e validação de chaves de outros usuários PGP.
Certificados digitais.
Um problema com os criptosistemas de chave pública é que os usuários devem estar constantemente vigilantes para garantir que estão criptografando com a chave da pessoa correta. Num ambiente onde é seguro trocar chaves livremente através de servidores públicos, os ataques man-in-the-middle são uma ameaça potencial. Neste tipo de ataque, alguém publica uma chave falsa com o nome e ID de usuário do destinatário pretendido. Os dados criptografados – e interceptados por – o verdadeiro proprietário desta chave falsa estão agora em mãos erradas.
Em um ambiente de chave pública, é vital que você tenha certeza de que a chave pública para a qual você está criptografando os dados é de fato a chave pública do destinatário pretendido e não uma falsificação. Você pode simplesmente criptografar apenas as chaves que foram entregues fisicamente a você. Mas suponha que você precise trocar informações com pessoas que nunca conheceu; como você pode saber se tem a chave correta?
Os certificados digitais, ou certs, simplificam a tarefa de estabelecer se uma chave pública realmente pertence ao suposto proprietário.
Um certificado é uma forma de credencial. Exemplos podem ser sua carteira de motorista, seu cartão de previdência social ou sua certidão de nascimento. Cada um deles contém algumas informações que identificam você e alguma autorização informando que outra pessoa confirmou sua identidade. Alguns certificados, como o seu passaporte, são uma confirmação importante o suficiente da sua identidade para que você não queira perdê-los, para que ninguém os use para se passar por você.
Um certificado digital são dados que funcionam como um certificado físico. Um certificado digital é uma informação incluída na chave pública de uma pessoa que ajuda outras pessoas a verificar se uma chave é genuína ou válida. Os certificados digitais são usados para impedir tentativas de substituir a chave de uma pessoa por outra.
Um certificado digital consiste em três coisas:
● Uma chave pública.
● Informações do certificado. (Informações de "identidade" sobre o usuário, como nome, ID do usuário e assim por diante.)
● Uma ou mais assinaturas digitais.
O objetivo da assinatura digital em um certificado é afirmar que as informações do certificado foram atestadas por alguma outra pessoa ou entidade. A assinatura digital não atesta a autenticidade do certificado como um todo; ele atesta apenas que as informações de identidade assinadas acompanham ou estão vinculadas à chave pública.
Assim, um certificado é basicamente uma chave pública com uma ou duas formas de identificação anexadas, além de um forte selo de aprovação de algum outro indivíduo confiável.
https://nostrcheck.me/media/public/nostrcheck.me_7979578982089845401699910854.webp
Figura 1-8. Anatomia de um certificado PGP
Distribuição de certificados.
Os certificados são utilizados quando é necessário trocar chaves públicas com outra pessoa. Para pequenos grupos de pessoas que desejam se comunicar com segurança, é fácil trocar manualmente disquetes ou e-mails contendo a chave pública de cada proprietário. Esta é a distribuição manual de chave pública e é prática apenas até certo ponto. Além desse ponto, é necessário implementar sistemas que possam fornecer os mecanismos necessários de segurança, armazenamento e troca para que colegas de trabalho, parceiros de negócios ou estranhos possam se comunicar, se necessário. Eles podem vir na forma de repositórios somente de armazenamento, chamados Servidores de Certificados, ou sistemas mais estruturados que fornecem recursos adicionais de gerenciamento de chaves e são chamados de Infraestruturas de Chave Pública (PKIs).
Servidores de certificados.
Um servidor de certificados, também chamado de servidor certificado ou servidor de chaves, é um banco de dados que permite aos usuários enviar e recuperar certificados digitais. Um servidor certificado geralmente fornece alguns recursos administrativos que permitem que uma empresa mantenha suas políticas de segurança – por exemplo, permitindo que apenas as chaves que atendam a determinados requisitos sejam armazenadas.
Infraestruturas de Chave Pública.
Uma PKI contém os recursos de armazenamento de certificados de um servidor de certificados, mas também fornece recursos de gerenciamento de certificados (a capacidade de emitir, revogar, armazenar, recuperar e confiar em certificados). A principal característica de uma PKI é a introdução do que é conhecido como Autoridade Certificadora,ou CA, que é uma entidade humana — uma pessoa, grupo, departamento, empresa ou outra associação — que uma organização autorizou a emitir certificados para seus usuários de computador. (A função de uma CA é análoga à do Passport Office do governo de um país.) Uma CA cria certificados e os assina digitalmente usando a chave privada da CA. Devido ao seu papel na criação de certificados, a CA é o componente central de uma PKI. Usando a chave pública da CA, qualquer pessoa que queira verificar a autenticidade de um certificado verifica a assinatura digital da CA emissora e, portanto, a integridade do conteúdo do certificado (mais importante ainda, a chave pública e a identidade do titular do certificado).
Formatos de certificado.
Um certificado digital é basicamente uma coleção de informações de identificação vinculadas a uma chave pública e assinadas por um terceiro confiável para provar sua autenticidade. Um certificado digital pode ter vários formatos diferentes.
O PGP reconhece dois formatos de certificado diferentes:
● Certificados PGP
● Certificados X.509
Formato do certificado PGP.
Um certificado PGP inclui (mas não está limitado a) as seguintes informações:
● O número da versão do PGP — identifica qual versão do PGP foi usada para criar a chave associada ao certificado.
A chave pública do titular do certificado — a parte pública do seu par de chaves, juntamente com o algoritmo da chave: RSA, DH (Diffie-Hellman) ou DSA (Algoritmo de Assinatura Digital).
● As informações do detentor do certificado — consistem em informações de “identidade” sobre o usuário, como seu nome, ID de usuário, fotografia e assim por diante.
● A assinatura digital do proprietário do certificado — também chamada de autoassinatura, é a assinatura que utiliza a chave privada correspondente da chave pública associada ao certificado.
● O período de validade do certificado — a data/hora de início e a data/hora de expiração do certificado; indica quando o certificado irá expirar.
● O algoritmo de criptografia simétrica preferido para a chave — indica o algoritmo de criptografia para o qual o proprietário do certificado prefere que as informações sejam criptografadas. Os algoritmos suportados são CAST, IDEA ou Triple-DES.
Você pode pensar em um certificado PGP como uma chave pública com um ou mais rótulos vinculados a ele (veja a Figura 1.9 ). Nessas 'etiquetas' você encontrará informações que identificam o proprietário da chave e uma assinatura do proprietário da chave, que afirma que a chave e a identificação andam juntas. (Essa assinatura específica é chamada de autoassinatura; todo certificado PGP contém uma autoassinatura.)
Um aspecto único do formato de certificado PGP é que um único certificado pode conter múltiplas assinaturas. Várias ou muitas pessoas podem assinar o par chave/identificação para atestar a sua própria garantia de que a chave pública pertence definitivamente ao proprietário especificado. Se você procurar em um servidor de certificados público, poderá notar que certos certificados, como o do criador do PGP, Phil Zimmermann, contêm muitas assinaturas.
Alguns certificados PGP consistem em uma chave pública com vários rótulos, cada um contendo um meio diferente de identificar o proprietário da chave (por exemplo, o nome do proprietário e a conta de e-mail corporativa, o apelido do proprietário e a conta de e-mail residencial, uma fotografia do proprietário — tudo em um certificado). A lista de assinaturas de cada uma dessas identidades pode ser diferente; as assinaturas atestam a autenticidade de que um dos rótulos pertence à chave pública, e não que todos os rótulos da chave sejam autênticos. (Observe que 'autêntico' está nos olhos de quem vê - assinaturas são opiniões, e diferentes pessoas dedicam diferentes níveis de devida diligência na verificação da autenticidade antes de assinar uma chave.)
https://nostrcheck.me/media/public/nostrcheck.me_7979578982089845401699910854.webp
Figura 1-9. Um certificado PGP
Formato de certificado X.509.
X.509 é outro formato de certificado muito comum. Todos os certificados X.509 estão em conformidade com o padrão internacional ITU-T X.509; assim (teoricamente) os certificados X.509 criados para um aplicativo podem ser usados por qualquer aplicativo compatível com X.509. Na prática, porém, diferentes empresas criaram suas próprias extensões para certificados X.509, e nem todas funcionam juntas.
Um certificado exige que alguém valide que uma chave pública e o nome do proprietário da chave andam juntos. Com os certificados PGP, qualquer pessoa pode desempenhar o papel de validador. Com certificados X.509, o validador é sempre uma Autoridade Certificadora ou alguém designado por uma CA. (Tenha em mente que os certificados PGP também suportam totalmente uma estrutura hierárquica usando uma CA para validar certificados.)
Um certificado X.509 é uma coleção de um conjunto padrão de campos contendo informações sobre um usuário ou dispositivo e sua chave pública correspondente. O padrão X.509 define quais informações vão para o certificado e descreve como codificá-lo (o formato dos dados). Todos os certificados X.509 possuem os seguintes dados:
O número da versão X.509
— identifica qual versão do padrão X.509 se aplica a este certificado, o que afeta quais informações podem ser especificadas nele. A mais atual é a versão 3.
A chave pública do titular do certificado
— a chave pública do titular do certificado, juntamente com um identificador de algoritmo que especifica a qual sistema criptográfico a chave pertence e quaisquer parâmetros de chave associados.
O número de série do certificado
— a entidade (aplicação ou pessoa) que criou o certificado é responsável por atribuir-lhe um número de série único para distingui-lo de outros certificados que emite. Esta informação é usada de diversas maneiras; por exemplo, quando um certificado é revogado, seu número de série é colocado em uma Lista de Revogação de Certificados ou CRL.
O identificador exclusivo do detentor do certificado
— (ou DN — nome distinto). Este nome pretende ser exclusivo na Internet. Este nome pretende ser exclusivo na Internet. Um DN consiste em múltiplas subseções e pode ser parecido com isto:
CN=Bob Allen, OU=Divisão Total de Segurança de Rede, O=Network Associates, Inc., C=EUA
(Referem-se ao nome comum, à unidade organizacional, à organização e ao país do sujeito .)
O período de validade do certificado
— a data/hora de início e a data/hora de expiração do certificado; indica quando o certificado irá expirar.
O nome exclusivo do emissor do certificado
— o nome exclusivo da entidade que assinou o certificado. Normalmente é uma CA. A utilização do certificado implica confiar na entidade que assinou este certificado. (Observe que em alguns casos, como certificados de CA raiz ou de nível superior , o emissor assina seu próprio certificado.)
A assinatura digital do emitente
— a assinatura utilizando a chave privada da entidade que emitiu o certificado.
O identificador do algoritmo de assinatura
— identifica o algoritmo usado pela CA para assinar o certificado.
Existem muitas diferenças entre um certificado X.509 e um certificado PGP, mas as mais importantes são as seguintes:
você pode criar seu próprio certificado PGP;
● você deve solicitar e receber um certificado X.509 de uma autoridade de certificação
● Os certificados X.509 suportam nativamente apenas um único nome para o proprietário da chave
● Os certificados X.509 suportam apenas uma única assinatura digital para atestar a validade da chave
Para obter um certificado X.509, você deve solicitar a uma CA a emissão de um certificado. Você fornece sua chave pública, prova de que possui a chave privada correspondente e algumas informações específicas sobre você. Em seguida, você assina digitalmente as informações e envia o pacote completo – a solicitação de certificado – para a CA. A CA então realiza algumas diligências para verificar se as informações fornecidas estão corretas e, em caso afirmativo, gera o certificado e o devolve.
Você pode pensar em um certificado X.509 como um certificado de papel padrão (semelhante ao que você recebeu ao concluir uma aula de primeiros socorros básicos) com uma chave pública colada nele. Ele contém seu nome e algumas informações sobre você, além da assinatura da pessoa que o emitiu para você.
https://nostrcheck.me/media/public/nostrcheck.me_4125576093727079591699911294.webp
Figura 1-10. Um certificado X.509
Provavelmente, o uso mais visível dos certificados X.509 atualmente é em navegadores da web.
Validade e confiança
Cada usuário em um sistema de chave pública está vulnerável a confundir uma chave falsa (certificado) com uma chave real. Validade é a confiança de que um certificado de chave pública pertence ao seu suposto proprietário. A validade é essencial em um ambiente de chave pública onde você deve estabelecer constantemente se um determinado certificado é autêntico ou não.
Depois de ter certeza de que um certificado pertencente a outra pessoa é válido, você pode assinar a cópia em seu chaveiro para atestar que verificou o certificado e que ele é autêntico. Se quiser que outras pessoas saibam que você deu ao certificado seu selo de aprovação, você pode exportar a assinatura para um servidor de certificados para que outras pessoas possam vê-la.
Conforme descrito na seção Infraestruturas de Chave Pública , algumas empresas designam uma ou mais Autoridades de Certificação (CAs) para indicar a validade do certificado. Em uma organização que usa uma PKI com certificados X.509, é função da CA emitir certificados aos usuários — um processo que geralmente envolve responder à solicitação de certificado do usuário. Em uma organização que usa certificados PGP sem PKI, é função da CA verificar a autenticidade de todos os certificados PGP e depois assinar os bons. Basicamente, o objetivo principal de uma CA é vincular uma chave pública às informações de identificação contidas no certificado e, assim, garantir a terceiros que algum cuidado foi tomado para garantir que esta ligação das informações de identificação e da chave seja válida.
O CA é o Grand Pooh-bah da validação em uma organização; alguém em quem todos confiam e, em algumas organizações, como aquelas que utilizam uma PKI, nenhum certificado é considerado válido, a menos que tenha sido assinado por uma CA confiável.
Verificando validade.
Uma maneira de estabelecer a validade é passar por algum processo manual. Existem várias maneiras de fazer isso. Você pode exigir que o destinatário pretendido lhe entregue fisicamente uma cópia de sua chave pública. Mas isto é muitas vezes inconveniente e ineficiente.
Outra forma é verificar manualmente a impressão digital do certificado. Assim como as impressões digitais de cada ser humano são únicas, a impressão digital de cada certificado PGP é única. A impressão digital é um hash do certificado do usuário e aparece como uma das propriedades do certificado. No PGP, a impressão digital pode aparecer como um número hexadecimal ou uma série das chamadas palavras biométricas, que são foneticamente distintas e são usadas para facilitar um pouco o processo de identificação da impressão digital.
Você pode verificar se um certificado é válido ligando para o proprietário da chave (para que você origine a transação) e pedindo ao proprietário que leia a impressão digital de sua chave para você e compare essa impressão digital com aquela que você acredita ser a verdadeira. Isso funciona se você conhece a voz do proprietário, mas como verificar manualmente a identidade de alguém que você não conhece? Algumas pessoas colocam a impressão digital de sua chave em seus cartões de visita exatamente por esse motivo.
Outra forma de estabelecer a validade do certificado de alguém é confiar que um terceiro indivíduo passou pelo processo de validação do mesmo.
Uma CA, por exemplo, é responsável por garantir que, antes de emitir um certificado, ele ou ela o verifique cuidadosamente para ter certeza de que a parte da chave pública realmente pertence ao suposto proprietário. Qualquer pessoa que confie na CA considerará automaticamente quaisquer certificados assinados pela CA como válidos.
Outro aspecto da verificação da validade é garantir que o certificado não foi revogado. Para obter mais informações, consulte a seção Revogação de certificado .
Estabelecendo confiança.
Você valida certificados. Você confia nas pessoas. Mais especificamente, você confia nas pessoas para validar os certificados de outras pessoas. Normalmente, a menos que o proprietário lhe entregue o certificado, você terá que confiar na palavra de outra pessoa de que ele é válido.
Introdutores meta e confiáveis.
Na maioria das situações, as pessoas confiam completamente na CA para estabelecer a validade dos certificados. Isso significa que todos os demais dependem da CA para passar por todo o processo de validação manual. Isso é aceitável até um certo número de usuários ou locais de trabalho e, então, não é possível para a AC manter o mesmo nível de validação de qualidade. Nesse caso, é necessário adicionar outros validadores ao sistema.
Um CA também pode ser um meta- introdutor. Um meta-introdutor confere não apenas validade às chaves, mas também confere a capacidade de confiar nas chaves a outros. Semelhante ao rei que entrega seu selo a seus conselheiros de confiança para que eles possam agir de acordo com sua autoridade, o meta-introdutor permite que outros atuem como introdutores de confiança. Esses introdutores confiáveis podem validar chaves com o mesmo efeito do meta-introdutor. Eles não podem, entretanto, criar novos introdutores confiáveis.
Meta-introdutor e introdutor confiável são termos PGP. Em um ambiente X.509, o meta-introdutor é chamado de Autoridade de Certificação raiz ( CA raiz) e os introdutores confiáveis são Autoridades de Certificação subordinadas .
A CA raiz usa a chave privada associada a um tipo de certificado especial denominado certificado CA raiz para assinar certificados. Qualquer certificado assinado pelo certificado CA raiz é visto como válido por qualquer outro certificado assinado pela raiz. Este processo de validação funciona mesmo para certificados assinados por outras CAs no sistema — desde que o certificado da CA raiz tenha assinado o certificado da CA subordinada, qualquer certificado assinado pela CA será considerado válido para outras pessoas dentro da hierarquia. Este processo de verificação de backup por meio do sistema para ver quem assinou cujo certificado é chamado de rastreamento de um caminho de certificação ou cadeia de certificação.
Modelos de confiança.
Em sistemas relativamente fechados, como em uma pequena empresa, é fácil rastrear um caminho de certificação até a CA raiz. No entanto, os usuários muitas vezes precisam se comunicar com pessoas fora do seu ambiente corporativo, incluindo algumas que nunca conheceram, como fornecedores, consumidores, clientes, associados e assim por diante. É difícil estabelecer uma linha de confiança com aqueles em quem sua CA não confia explicitamente.
As empresas seguem um ou outro modelo de confiança, que determina como os usuários irão estabelecer a validade do certificado. Existem três modelos diferentes:
Confiança Direta.
Confiança Hierárquica
Uma teia de confiança
Confiança direta
A confiança direta é o modelo de confiança mais simples. Neste modelo, um usuário confia que uma chave é válida porque sabe de onde ela veio. Todos os criptosistemas usam essa forma de confiança de alguma forma. Por exemplo, em navegadores da Web, as chaves raiz da Autoridade de Certificação são diretamente confiáveis porque foram enviadas pelo fabricante. Se houver alguma forma de hierarquia, ela se estenderá a partir desses certificados diretamente confiáveis.
No PGP, um usuário que valida as chaves e nunca define outro certificado para ser um introdutor confiável está usando confiança direta.
https://nostrcheck.me/media/public/nostrcheck.me_4681914789296468891699911522.webp
Figura 1-11. Confiança direta
Confiança Hierárquica.
Em um sistema hierárquico, há vários certificados "raiz" a partir dos quais a confiança se estende. Esses certificados podem certificar eles próprios certificados ou podem certificar certificados que certificam ainda outros certificados em alguma cadeia. Considere isso como uma grande “árvore” de confiança. A validade do certificado "folha" é verificada rastreando desde seu certificador até outros certificadores, até que um certificado raiz diretamente confiável seja encontrado.
https://nostrcheck.me/media/public/nostrcheck.me_2764578291212045251699911580.webp
Figura 1-12. Confiança hierárquica
Teia de Confiança.
Uma teia de confiança abrange ambos os outros modelos, mas também acrescenta a noção de que a confiança está nos olhos de quem vê (que é a visão do mundo real) e a ideia de que mais informação é melhor. É, portanto, um modelo de confiança cumulativa. Um certificado pode ser confiável diretamente ou confiável em alguma cadeia que remonta a um certificado raiz diretamente confiável (o meta-introdutor) ou por algum grupo de introdutores.
Talvez você já tenha ouvido falar do termo seis graus de separação, que sugere que qualquer pessoa no mundo pode determinar algum vínculo com qualquer outra pessoa no mundo usando seis ou menos outras pessoas como intermediários. Esta é uma teia de introdutores.
É também a visão de confiança do PGP. PGP usa assinaturas digitais como forma de introdução. Quando qualquer usuário assina a chave de outro, ele ou ela se torna o introdutor dessa chave. À medida que esse processo avança, ele estabelece uma rede de confiança.
Em um ambiente PGP, qualquer usuário pode atuar como autoridade certificadora. Qualquer usuário PGP pode validar o certificado de chave pública de outro usuário PGP. No entanto, tal certificado só é válido para outro usuário se a parte confiável reconhecer o validador como um introdutor confiável. (Ou seja, você confia na minha opinião de que as chaves dos outros são válidas apenas se você me considerar um apresentador confiável. Caso contrário, minha opinião sobre a validade das outras chaves é discutível.)
Armazenados no chaveiro público de cada usuário estão indicadores de
● se o usuário considera ou não uma chave específica válida
● o nível de confiança que o usuário deposita na chave que o proprietário da chave pode servir como certificador das chaves de terceiros
Você indica, na sua cópia da minha chave, se acha que meu julgamento conta. Na verdade, é um sistema de reputação: certas pessoas têm a reputação de fornecer boas assinaturas e as pessoas confiam nelas para atestar a validade de outras chaves.
Níveis de confiança no PGP.
O nível mais alto de confiança em uma chave, a confiança implícita , é a confiança em seu próprio par de chaves. O PGP assume que se você possui a chave privada, você deve confiar nas ações da sua chave pública relacionada. Quaisquer chaves assinadas pela sua chave implicitamente confiável são válidas.
Existem três níveis de confiança que você pode atribuir à chave pública de outra pessoa:
● Confiança total
● Confiança marginal
● Não confiável (ou não confiável)
Para tornar as coisas confusas, também existem três níveis de validade:
● Válido
● Marginalmente válido
● Inválido
Para definir a chave de outra pessoa como um introdutor confiável, você
1. Comece com uma chave válida, que seja.
- assinado por você ou
- assinado por outro apresentador confiável e então
2. Defina o nível de confiança que você acha que o proprietário da chave tem direito.
Por exemplo, suponha que seu chaveiro contenha a chave de Alice. Você validou a chave de Alice e indica isso assinando-a. Você sabe que Alice é uma verdadeira defensora da validação de chaves de outras pessoas. Portanto, você atribui a chave dela com confiança total. Isso faz de Alice uma Autoridade Certificadora. Se Alice assinar a chave de outra pessoa, ela aparecerá como Válida em seu chaveiro.
O PGP requer uma assinatura Totalmente confiável ou duas assinaturas Marginalmente confiáveis para estabelecer uma chave como válida. O método do PGP de considerar dois Marginais iguais a um Completo é semelhante a um comerciante que solicita duas formas de identificação. Você pode considerar Alice bastante confiável e também considerar Bob bastante confiável. Qualquer um deles sozinho corre o risco de assinar acidentalmente uma chave falsificada, portanto, você pode não depositar total confiança em nenhum deles. No entanto, as probabilidades de ambos os indivíduos terem assinado a mesma chave falsa são provavelmente pequenas.
Revogação de certificado.
Os certificados só são úteis enquanto são válidos. Não é seguro simplesmente presumir que um certificado é válido para sempre. Na maioria das organizações e em todas as PKIs, os certificados têm uma vida útil restrita. Isso restringe o período em que um sistema fica vulnerável caso ocorra um comprometimento do certificado.
Os certificados são assim criados com um período de validade programado: uma data/hora de início e uma data/hora de expiração. Espera-se que o certificado seja utilizável durante todo o seu período de validade (seu tempo de vida ). Quando o certificado expirar, ele não será mais válido, pois a autenticidade do seu par chave/identificação não estará mais garantida. (O certificado ainda pode ser usado com segurança para reconfirmar informações que foram criptografadas ou assinadas dentro do período de validade – no entanto, ele não deve ser confiável para tarefas criptográficas futuras.)
Existem também situações em que é necessário invalidar um certificado antes da sua data de expiração, como quando o titular do certificado termina o contrato de trabalho com a empresa ou suspeita que a chave privada correspondente do certificado foi comprometida. Isso é chamado de revogação. Um certificado revogado é muito mais suspeito do que um certificado expirado. Os certificados expirados são inutilizáveis, mas não apresentam a mesma ameaça de comprometimento que um certificado revogado.
Qualquer pessoa que tenha assinado um certificado pode revogar a sua assinatura no certificado (desde que utilize a mesma chave privada que criou a assinatura). Uma assinatura revogada indica que o signatário não acredita mais que a chave pública e as informações de identificação pertencem uma à outra, ou que a chave pública do certificado (ou a chave privada correspondente) foi comprometida. Uma assinatura revogada deve ter quase tanto peso quanto um certificado revogado.
Com certificados X.509, uma assinatura revogada é praticamente igual a um certificado revogado, visto que a única assinatura no certificado é aquela que o tornou válido em primeiro lugar – a assinatura da CA. Os certificados PGP fornecem o recurso adicional de que você pode revogar todo o seu certificado (não apenas as assinaturas nele) se você achar que o certificado foi comprometido.
Somente o proprietário do certificado (o detentor da chave privada correspondente) ou alguém que o proprietário do certificado tenha designado como revogador pode revogar um certificado PGP. (Designar um revogador é uma prática útil, pois muitas vezes é a perda da senha da chave privada correspondente do certificado que leva um usuário PGP a revogar seu certificado - uma tarefa que só é possível se alguém tiver acesso à chave privada. ) Somente o emissor do certificado pode revogar um certificado X.509.
Comunicar que um certificado foi revogado.
Quando um certificado é revogado, é importante conscientizar os usuários potenciais do certificado de que ele não é mais válido. Com certificados PGP, a maneira mais comum de comunicar que um certificado foi revogado é publicá-lo em um servidor de certificados para que outras pessoas que desejem se comunicar com você sejam avisadas para não usar essa chave pública.
Em um ambiente PKI, a comunicação de certificados revogados é mais comumente obtida por meio de uma estrutura de dados chamada Lista de Revogação de Certificados, ou CRL, que é publicada pela CA. A CRL contém uma lista validada com carimbo de data e hora de todos os certificados revogados e não expirados no sistema. Os certificados revogados permanecem na lista apenas até expirarem e, em seguida, são removidos da lista — isso evita que a lista fique muito longa.
A CA distribui a CRL aos usuários em algum intervalo programado regularmente (e potencialmente fora do ciclo, sempre que um certificado é revogado). Teoricamente, isso impedirá que os usuários usem involuntariamente um certificado comprometido. É possível, no entanto, que haja um período de tempo entre as CRLs em que um certificado recentemente comprometido seja usado.
O que é uma senha?
A maioria das pessoas está familiarizada com a restrição de acesso a sistemas de computador por meio de uma senha, que é uma sequência única de caracteres que um usuário digita como código de identificação.
Uma senha longa é uma versão mais longa de uma senha e, em teoria, mais segura. Normalmente composta por várias palavras, uma frase secreta é mais segura contra ataques de dicionário padrão, em que o invasor tenta todas as palavras do dicionário na tentativa de determinar sua senha. As melhores senhas são relativamente longas e complexas e contêm uma combinação de letras maiúsculas e minúsculas, caracteres numéricos e de pontuação.
O PGP usa uma senha para criptografar sua chave privada em sua máquina. Sua chave privada é criptografada em seu disco usando um hash de sua senha como chave secreta. Você usa a senha para descriptografar e usar sua chave privada. Uma senha deve ser difícil de esquecer e difícil de ser adivinhada por outras pessoas. Deve ser algo já firmemente enraizado na sua memória de longo prazo, em vez de algo que você invente do zero. Por que? Porque se você esquecer sua senha, você estará sem sorte. Sua chave privada é total e absolutamente inútil sem sua senha e nada pode ser feito a respeito. Lembra-se da citação anterior neste capítulo?
https://nostrcheck.me/media/public/nostrcheck.me_5284734693832771181699911783.webp
PGP é a criptografia que manterá os principais governos fora dos seus arquivos. Certamente também o manterá fora de seus arquivos. Tenha isso em mente quando decidir alterar sua senha para a piada daquela piada que você nunca consegue lembrar.
Divisão de chave.
Dizem que um segredo não é segredo se for conhecido por mais de uma pessoa. Compartilhar um par de chaves privadas representa um grande problema. Embora não seja uma prática recomendada, às vezes é necessário compartilhar um par de chaves privadas. Chaves de assinatura corporativa, por exemplo, são chaves privadas usadas por uma empresa para assinar – por exemplo – documentos legais, informações pessoais confidenciais ou comunicados de imprensa para autenticar sua origem. Nesse caso, vale a pena que vários membros da empresa tenham acesso à chave privada. No entanto, isto significa que qualquer indivíduo pode agir plenamente em nome da empresa.
Nesse caso, é aconselhável dividir a chave entre várias pessoas, de modo que mais de uma ou duas pessoas apresentem um pedaço da chave para reconstituí-la em condições utilizáveis. Se poucas peças da chave estiverem disponíveis, a chave ficará inutilizável.
Alguns exemplos são dividir uma chave em três partes e exigir duas delas para reconstituir a chave, ou dividi-la em duas partes e exigir ambas as peças. Se uma conexão de rede segura for usada durante o processo de reconstituição, os acionistas da chave não precisam estar fisicamente presentes para aderirem novamente à chave.
-

@ 4ba8e86d:89d32de4
2024-10-05 21:04:30
Em vez de compartilhar seu endereço de email real com serviços e sites que você usa, você pode criar um endereço de email temporário usando o Simplelogin. Esse endereço temporário é exclusivo para cada serviço ou site, permitindo que você gerencie sua caixa de entrada e reduza a quantidade de spam e emails não solicitados que você recebe.
O Simplelogin foi fundado em 2019 por dois desenvolvedores franceses, Nicolas Grenié e Anthony Castellanos, com o objetivo de oferecer aos usuários uma maneira fácil de criar endereços de e-mail descartáveis para proteger sua privacidade e segurança online.Em 2022, a empresa se juntou à família ProtonMail, uma empresa suíça conhecida por seus serviços de e-mail seguros e criptografados, permitindo que a Simplelogin expandisse seus recursos de segurança e privacidade, além de oferecer uma integração perfeita com o ProtonMail.
O SimpleLogin resolve vários problemas relacionados à privacidade e segurança online, incluindo:
1. Proteção da privacidade do seu endereço de e-mail: o SimpleLogin permite que você crie endereços de e-mail descartáveis que podem ser usados para se inscrever em sites ou serviços sem divulgar seu endereço de e-mail principal. Isso ajuda a reduzir a quantidade de spam e e-mails indesejados na sua caixa de entrada.
2. Proteção contra ataques de phishing: o SimpleLogin impede que os hackers obtenham seu endereço de e-mail real, reduzindo assim as chances de ser alvo de ataques de phishing.
3. Acesso seguro aos seus e-mails: o SimpleLogin oferece autenticação de dois fatores e suporte a PGP, garantindo que seus e-mails sejam protegidos contra invasões e leituras não autorizadas.
4. Maior controle sobre sua privacidade: o SimpleLogin permite que você crie e gerencie vários endereços de e-mail, controlando assim quais sites e serviços têm acesso ao seu endereço de e-mail principal. Além disso, o SimpleLogin permite que você exclua facilmente os endereços de e-mail descartáveis quando não precisar mais deles.
Alguns motivos pra usar SimpleLogin
https://nostr.build/i/a243a8f7ebafa3e3f8c6f3942c69ce03315aaed70394deb4e31af50f82d098f5.jpg
1. Privacidade: O SimpleLogin protege sua privacidade online, permitindo que você crie endereços de e-mail descartáveis que não estão vinculados ao seu endereço de e-mail principal. Isso ajuda a reduzir o spam e a quantidade de e-mails indesejados que você recebe.
2. Segurança: O SimpleLogin oferece recursos de segurança avançados, como autenticação de dois fatores e suporte a PGP, ajudando a proteger seus e-mails de invasões e leituras não autorizadas.
3. Controle: O SimpleLogin permite que você crie e gerencie facilmente vários endereços de e-mail, controlando quais sites e serviços têm acesso ao seu endereço de e-mail principal.
4. Simplicidade: O SimpleLogin é fácil de usar e pode ser configurado em questão de minutos, sem a necessidade de conhecimentos técnicos avançados.
5. Integração com outros serviços: O SimpleLogin se integra facilmente com outros serviços, como o ProtonMail, permitindo que você gerencie todos os seus e-mails em um só lugar.
O Simplelogin é uma ferramenta essencial para manter sua privacidade e segurança online. Com a criação e gerenciamento de endereços de e-mail descartáveis exclusivos para cada site ou serviço que você utiliza, você pode reduzir significativamente a quantidade de spam e e-mails não solicitados em sua caixa de entrada. Além disso, o Simplelogin fornece uma proteção extra contra ataques de phishing e garante que seus e-mails sejam acessados de forma segura. Experimente o Simplelogin hoje mesmo e proteja sua privacidade e segurança online de maneira fácil e eficaz.
https://simplelogin.io/
https://github.com/simple-login/app
-

@ 460c25e6:ef85065c
2024-10-01 13:40:23
Testing new note with Comet
-

@ 9977c3ad:43a20d63
2024-09-05 11:21:09
## Details
- 🍽️ Servings: 2
## Ingredients
- 1 cup Jasmine rice
- 1 Tbsp. lavender flowers, crushed with mortar and pestle
- 1/4 cup apple cider vinegar
- 2 Tbsp. fine cane sugar
- 2 Tbsp. honey
- 1 sprig rosemary
- 1/4 tsp angostura bitters
- 1/2 cup blackberries
- 1/2 cup blueberries
- 4 cups trimmed and quartered shiitake mushrooms
- 1 tsp fresh coriander crushed
- 1/4 tsp fresh cumin ground
- 1/2 tsp red pepper flakes
- 3 sprigs of thyme
- 2 Tbsp. olive oil
- 1 tsp soy sauce
- 1 cup creamy coconut milk
## Directions
1. Combine rice, lavender, 1/4 tsp salt, and 2 cups of water in a saucepan. Bring the rice to a boil, cover the pan with a lid and turn the heat off. Let the rice sit in the pan for at least 20 minutes.
2. Combine 1/4 cup of water, the vinegar, sugar, honey, rosemary, angostura bitters in a saucepan and bring the brine to a boil. Season with a pinch of salt. Add the berries and wait until the brine comes back to a boil. Lower the heat, so the brine simmers but does not boil. When the brine thickens, after about 15 minutes, remove the saucepan from the heat and set it aside.
3. Pre-heat the oven to 400F. In a bowl big enough to hold all the shiitake, combine the olive oil, the soy sauce and the spices. Whisk vigorously, so the oil emulsifies with the other liquid. Toss the shiitake in the mix to marinate, then evenly lay them out on a baking sheet with parchment paper. Bake the shiitake for 10 minutes. When you remove the shiitake from the oven, remove the thyme and throw it out. In a saucepan, bring the coconut milk to a boil. Add the shiitake and reduce the heat to a light boil until the sauce thickens.
-

@ d830ee7b:4e61cd62
2024-09-04 07:29:41
Bitcoin ถือกำเนิดขึ้นในปี 2009 จากวิสัยทัศน์ของ Satoshi Nakamoto บุคคลหรือกลุ่มบุคคลปริศนา ที่ใฝ่ฝันถึง "เงินสดดิจิทัล" อิสระไร้พรมแดน ไร้การควบคุมจากรัฐบาล
ในช่วงแรกเริ่ม Bitcoin เป็นเสมือนเพชรดิบที่ซ่อนตัวอยู่ในเงามืด เป็นที่รู้จักกันเฉพาะในกลุ่มเล็กๆ ที่หลงใหลในเทคโนโลยีและศักยภาพอันไร้ขีดจำกัดของมัน
แต่แล้ว Bitcoin ก็เริ่มฉายแสงเจิดจรัส ดึงดูดความสนใจจากผู้คนทั่วโลก ราคาพุ่งทะยานอย่างรวดเร็ว บริษัทและบริการต่างๆ ผุดขึ้นมาราวกับดอกเห็ด
ทว่า.. เส้นทางสู่ความสำเร็จของ Bitcoin ไม่ได้โรยด้วยกลีบกุหลาบ Bitcoin ยังต้องเผชิญกับความท้าทายมากมาย ทั้งปัญหาทางเทคนิค ความขัดแย้งภายในชุมชนและการต่อสู้แย่งชิงอำนาจ
## **Blocksize Limit จุดเริ่มต้นของความขัดแย้งและสงคราม Big Blocks VS Small Blocks**
ย้อนกลับไปในปี 2010 Satoshi Nakamoto ได้เพิ่ม **"Blocksize Limit"** ซึ่งเป็นข้อจำกัดขนาดของ Block ใน Bitcoin ไว้ที่ 1MB เพื่อป้องกันการโจมตีทางไซเบอร์ในยุคแรกเริ่ม
แต่เมื่อ Bitcoin ได้รับความนิยมมากขึ้น ธุรกรรมก็เพิ่มขึ้นอย่างรวดเร็ว Blocksize Limit 1MB เริ่มจะกลายเป็นปัญหา..
เกิดการถกเถียงอย่างดุเดือดในชุมชน Bitcoin ว่าควรเพิ่ม Blocksize Limit หรือไม่
ฝ่าย **"Small Blockers"** นำโดยนักพัฒนา Bitcoin Core ส่วนใหญ่ เชื่อว่า Blocksize Limit ควรคงที่ เพื่อรักษาความปลอดภัยและการกระจายอำนาจ พวกเขากล่าวอ้างว่า Big Blocks จะทำให้ Bitcoinรวมศูนย์อยู่ที่ Miners รายใหญ่ และยากต่อการรัน Full Nodes สำหรับผู้ใช้งานทั่วไป ซึ่งจะบั่นทอนความเป็น Decentralized ของ Bitcoin
ฝ่าย **"Big Blockers"** นำโดย Gavin Andresen ผู้สืบทอดตำแหน่งจาก Satoshi Nakamoto และ Mike Hearn เชื่อว่า Bitcoin ควรเติบโตอย่างไม่จำกัด "Big Blocks" คือคำตอบ พวกเขามองว่า Small Blocks จะทำให้ Bitcoin ไม่สามารถรองรับธุรกรรมที่เพิ่มขึ้น ค่าธรรมเนียมจะพุ่งสูงและ Bitcoin จะไม่สามารถใช้งานได้จริงในชีวิตประจำวัน..
ความขัดแย้งนี้สะท้อนให้เห็นถึงวิสัยทัศน์ที่แตกต่างกัน
Gavin Andresen ผู้ที่เคยได้รับความไว้วางใจจาก Satoshi รู้สึกผิดหวังที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit เขาเชื่อมั่นว่า Bitcoin ควรเป็นระบบการชำระเงินที่ใช้งานได้จริง รวดเร็ว และมีค่าธรรมเนียมต่ำ
## **Blockstream บริษัทผู้ทรงอิทธิพลและความกังวลเรื่องผลประโยชน์ทับซ้อน**
ปี 2014 กลุ่มนักพัฒนา Bitcoin Core บางส่วนได้ก่อตั้งบริษัท **Blockstream** (นำโดย Adam Back) พวกเขาเน้นการพัฒนาเทคโนโลยี Blockchain และกลายเป็นที่มถกเถียงว่าอิทธิพลอย่างมากต่อ Bitcoin Core
Blockstream สนับสนุน "Small Blocks"
เช่นเดียวกับ Bitcoin Core พวกเขาพัฒนา **"Sidechains"** ซึ่งเป็น Blockchain แยกต่างหากที่เชื่อมต่อกับ Bitcoin เช่น **Liquid Network Sidechains** ซึ่งช่วยให้ Blockstream สามารถเก็บค่าธรรมเนียมจากธุรกรรมและขายบริการให้กับองค์กรหรือบริษัทต่างๆ ได้
ความสัมพันธ์อันใกล้ชิดระหว่าง Blockstream และ Bitcoin Core ทำให้เกิดความกังวลขึ้นในชุมชน Bitcoin ในขณะนั้นว่า Blockstream อาจมีผลประโยชน์ทับซ้อนและต้องการให้ Bitcoin คงขนาดเล็ก เพื่อผลักดันให้คนใช้งาน "Sidechains" ของพวกเขา
## **BitcoinXT และ Bitcoin Classic ความพยายามแก้ไข Blocksize ที่ถูกต่อต้าน**
ปี 2015 Mike Hearn และ Gavin Andresen ตัดสินใจเสนอทางออกด้วยการสร้าง **"BitcoinXT"** ซอฟต์แวร์ Bitcoin เวอร์ชั่นใหม่ที่ **เพิ่ม Blocksize Limit เป็น 8MB**
แต่ BitcoinXT ถูกต่อต้านอย่างรุนแรงจากฝ่าย Small Blockers
Bitcoin.org เว็บไซต์หลักของ Bitcoin และ r/Bitcoin ฟอรัมหลักของ Bitcoin ได้เซ็นเซอร์ BitcoinXT ไม่ให้ปรากฏ เกิดการโจมตีทางไซเบอร์ที่มุ่งเป้าไปที่ BitcoinXT โดยตรง
Coinbase บริษัทแลกเปลี่ยน Cryptocurrency รายใหญ่ ประกาศสนับสนุน BitcoinXT แต่กลับถูกถอดออกจาก Bitcoin.org
ต่อมา **Bitcoin Classic** ถูกสร้างขึ้นเป็นอีกหนึ่งทางเลือก แต่ก็ล้มเหลวเช่นกัน
เนื่องจาก Bitcoin Core ยังคงมีอิทธิพลอย่างมากในชุมชน Bitcoin ในช่วงเวลานั้น..
## **Hong Kong Agreement และ New York Agreement ความพยายามประนีประนอมที่ไม่ลงตัว**
ปี 2016 และ 2017 เกิดความพยายามในการประนีประนอมระหว่างฝ่าย Small Blocks และ Big Blockers ถึงสองครั้ง คือ "Hong Kong Agreement" และ "New York Agreement"
ทั้งสองข้อตกลงมีเป้าหมายที่จะเปิดใช้งาน **SegWit** และ **เพิ่ม Blocksize Limit เป็น 2MB** แต่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit ทำให้ข้อตกลงล้มเหลว
ความล้มเหลวของข้อตกลงทั้งสอง สะท้อนให้เห็นถึงความไม่ไว้วางใจระหว่างสองฝ่าย และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ
## **SegWit ก้าวสำคัญของ Bitcoin และจุดกำเนิดของ Bitcoin Cash**
ในที่สุด SegWit ก็ถูกเปิดใช้งานบน Bitcoin ในเดือนสิงหาคม 2017
SegWit เป็น **Soft Fork** ที่เปลี่ยนแปลงวิธีการจัดเก็บข้อมูลใน Block เพื่อเพิ่มประสิทธิภาพและความปลอดภัย
SegWit ช่วยแก้ปัญหา **"Transaction Malleability"** ซึ่งเป็นช่องโหว่ด้านความปลอดภัย และปูทางไปสู่การพัฒนา **"Layer 2 solutions"** เช่น **Lightning Network** ในเวลาต่อมา..
อย่างไรก็ตาม.. กลุ่ม "Big Blockers" มองว่า SegWit ไม่ใช่ทางออกที่แท้จริงสำหรับปัญหาการขยายขนาด (พวกเขาต้องการขยายขนาดบล็อกบนเลอเยอร์ฐาน) พวกเขาไม่พอใจที่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit
ในเดือนสิงหาคม 2017 กลุ่ม "Big Blockers" ได้ทำการ **"Hard Fork"** Bitcoin เพื่อสร้าง **"Bitcoin Cash (BCH)"** ซึ่งอ้างว่ามุ่งสืบทอดจุดมุ่งหมายดั้งเดิมของ Bitcoin ในฐานะ **"เงินสดดิจิทัล"**
## **ความเสี่ยงด้านความปลอดภัย Bug ร้ายแรงใน Bitcoin Core และบทเรียนที่ได้รับ**
ในเดือนกันยายน 2018 Awemany นักพัฒนา BCH ค้นพบ Bug ร้ายแรงใน Bitcoin Core (CVE-2018-17144) ซึ่งอาจทำให้เกิดภาวะเงินเฟ้อได้
Bug นี้เกิดจากความผิดพลาดในการเขียนโค้ด และอาจทำให้ผู้ไม่หวังดีสามารถสร้าง Bitcoin ปลอมขึ้นมาได้
Awemany ได้แจ้งเตือนนักพัฒนา Bitcoin Core อย่างเงียบๆ แทนที่จะใช้ประโยชน์จาก Bug นี้ แสดงให้เห็นถึงความรับผิดชอบของเขา และ Bug นี้ได้รับการแก้ไขอย่างรวดเร็ว
เหตุการณ์นี้แสดงให้เห็นถึงความสำคัญของการตรวจสอบโค้ดอย่างละเอียด และความจำเป็นของการมีนักพัฒนาจากหลายฝ่ายเพื่อช่วยกันตรวจสอบความถูกต้องของโค้ด
นอกจากนี้.. ยังเป็นเครื่องเตือนใจว่าแม้แต่ระบบที่ถูกออกแบบมาอย่างดีก็ยังมีความเสี่ยงด้านความปลอดภัย
## **Bitcoin Cash แตกแยก การ Hard Fork ครั้งที่สอง และบทบาทของ Craig Wright**
ในเดือนพฤศจิกายน 2018 Bitcoin Cash (BCH) ได้แตกออกเป็นสองสาย คือ **Bitcoin ABC (BCH)** และ **Bitcoin SV (BSV)**
การ Hard Fork นี้เกิดจากความขัดแย้งระหว่างกลุ่มนักพัฒนา Bitcoin ABC นำโดย Amaury Séchet และกลุ่ม Bitcoin SV นำโดย Craig Wright ผู้ที่อ้างว่าเป็น Satoshi Nakamoto 🤔
ความขัดแย้งหลักคือเรื่องขนาดของ Block และทิศทางการพัฒนา Bitcoin Cash
กลุ่ม Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก ในขณะที่กลุ่ม Bitcoin ABC ต้องการปรับปรุง Bitcoin Cash ในด้านอื่นๆ เช่น Smart Contracts
Craig Wright มีบทบาทสำคัญในการผลักดัน Bitcoin SV เขาเชื่อมั่นว่า Bitcoin ควรเป็นไปตามวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto โดยเน้นที่การเป็น "เงินสดอิเล็กทรอนิกส์แบบ peer-to-peer"
การ Hard Fork นี้แสดงให้เห็นถึงความหลากหลายของความคิดเห็นในชุมชน Cryptocurrency และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ
นอกจากนี้.. ยังสะท้อนให้เห็นถึงความท้าทายในการกำหนดทิศทางของ Cryptocurrency ในอนาคตอีกด้วย
## **Bitcoin ในปัจจุบัน เส้นทางสู่ทองคำดิจิทัล และวิวัฒนาการของเทคโนโลยี**
หลังจากการ Hard Fork ของ Bitcoin Cash
Bitcoin ได้ก้าวเข้าสู่ยุคใหม่ Bitcoin ได้รับการยอมรับมากขึ้นในวงกว้าง มีมูลค่าตลาดสูง และถูกมองว่าเป็น **"ทองคำดิจิทัล"** ที่สามารถใช้เก็บรักษามูลค่าในระยะยาว (Store of Value)
การพัฒนา **Lightning Network** เป็นก้าวสำคัญในการแก้ปัญหาเรื่องค่าธรรมเนียมและความเร็วในการทำธุรกรรม
Lightning Network เป็น **"Second Layer"** ที่สร้างขึ้นบน Bitcoin Blockchain ช่วยให้สามารถทำธุรกรรมได้รวดเร็วขึ้น มีค่าธรรมเนียมต่ำ และมีความเป็นส่วนตัวสูง
อย่างไรก็ตาม.. Lightning Network ยังคงต้องเผชิญกับความท้าทาย เช่น ปัญหาเรื่องการบริหารจัดการ Liquidity และความซับซ้อนในการใช้งาน
นอกจาก Lightning Network แล้ว ยังมีการพัฒนาเทคโนโลยีอื่นๆ ที่ช่วยเพิ่มขีดความสามารถของ Bitcoin เช่น **Taproot** ซึ่งเป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และ **Schnorr signatures** ซึ่งเป็น Digital Signature แบบใหม่ที่ช่วยลดขนาดของธุรกรรมให้เล็กลง
นอกจากนี้.. ยังเริ่มมีการพัฒนา DeFi (Decentralized Finance) บน Bitcoin และ Bitcoin Ordinals ซึ่งเป็นวิธีการใหม่ในการฝังข้อมูลลงใน Bitcoin Blockchain
Bitcoin ยังคงถูกนำไปใช้ในประเทศอื่นๆ นอกจาก El Salvador และมีความพยายามในการแก้ปัญหาความกังวลด้านสิ่งแวดล้อมจากการขุด Bitcoin
## **บทเรียนจากมหากาพย์แห่งวิวัฒนาการ**
ประวัติศาสตร์ Bitcoin สอนให้เรารู้ว่า.. เทคโนโลยี Blockchain มีศักยภาพในการเปลี่ยนแปลงโลก แต่เส้นทางสู่ความสำเร็จนั้นก็ไม่ได้โรยด้วยกลีบกุหลาบ
ความขัดแย้ง การต่อสู้แย่งชิงอำนาจ และการตัดสินใจที่ยากลำบาก ล้วนเป็นส่วนหนึ่งของการเดินทาง
สิ่งที่สำคัญที่สุดคือ.. เราต้องศึกษา ทำความเข้าใจ และอาจมีส่วนร่วมในการกำหนดทิศทางของเทคโนโลยีนี้ เพื่อให้ Blockchain สามารถสร้างประโยชน์สูงสุดให้กับมวลมนุษยชาติต่อไป
# **เจาะลึกวิวัฒนาการของ Bitcoin การ Soft Forks, Hard Forks และมุมมองที่แตกต่าง**
## **SegWit, Taproot และ Soft Forks อื่นๆ การปรับปรุง Bitcoin อย่างนุ่มนวล**
Bitcoin Core ไม่ได้หยุดนิ่งอยู่กับที่ นักพัฒนาได้ทำงานอย่างต่อเนื่องเพื่อปรับปรุง Bitcoin ให้ดีขึ้น โดยใช้ **"Soft Forks"** ซึ่งเป็นการอัพเกรดที่เข้ากันได้กับซอฟต์แวร์เวอร์ชั่นเก่า
### **SegWit (Segregated Witness)**
เปิดตัวในปี 2017 SegWit เป็นเหมือนการจัดระเบียบข้อมูลใน Block ใหม่ ย้ายส่วนที่เรียกว่า "Witness data" (ข้อมูลลายเซ็น) ออกไปไว้ข้างนอก ทำให้มีพื้นที่ว่างใน Block มากขึ้น รองรับธุรกรรมได้มากขึ้น และลดค่าธรรมเนียมได้ SegWit ยังช่วยแก้ปัญหา "Transaction Malleability" ซึ่งเป็นช่องโหว่ด้านความปลอดภัยและปูทางไปสู่การพัฒนา Lightning Network
### **Taproot**
เปิดตัวในปี 2021 Taproot เป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และประสิทธิภาพของ Bitcoin Taproot ทำให้ธุรกรรมที่ซับซ้อน เช่น Smart Contracts มีขนาดเล็กลงและยากต่อการแยกแยะจากธุรกรรมทั่วไป
Soft Forks อื่นๆ ที่ Bitcoin Core ได้นำมาใช้ เช่น BIP 65 (CheckLockTimeVerify) และ BIP 112 (CSV) ช่วยเพิ่มความยืดหยุ่นในการใช้งาน Bitcoin และปูทางไปสู่การพัฒนาฟังก์ชันใหม่ๆ
## **Hard Forks เส้นทางที่แตกต่างและการถือกำเนิดของเหรียญใหม่**
ในขณะที่ Soft Forks เป็นการอัพเกรดที่นุ่มนวล **"Hard Forks"** นั้นนับว่าเป็นการเปลี่ยนแปลงครั้งใหญ่ ที่ทำให้เกิดสาย Blockchain ใหม่และเหรียญใหม่
### **Bitcoin XT (2015)**
เป็นความพยายามครั้งแรกในการเพิ่ม Blocksize Limit โดย Mike Hearn และ Gavin Andresen Bitcoin XT เสนอให้เพิ่ม Blocksize Limit เป็น 8MB แต่ถูกต่อต้านอย่างรุนแรง และไม่ประสบความสำเร็จ
### **Bitcoin Classic (2016)**
เป็นอีกหนึ่งความพยายามในการเพิ่ม Blocksize Limit โดยเสนอให้เพิ่มเป็น 2MB แต่ก็ล้มเหลวเช่นกัน
### **Bitcoin Unlimited (2016)**
เสนอให้ Miners สามารถกำหนด Blocksize Limit ได้เอง แต่มีข้อบกพร่องด้านความปลอดภัย และไม่เป็นที่ยอมรับในวงกว้าง
### **Bitcoin Cash (BCH) (2017)**
เกิดจากการ Hard Fork ของ Bitcoin โดยกลุ่ม "Big Blockers" ที่ไม่พอใจที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit Bitcoin Cash เพิ่ม Blocksize Limit เป็น 8MB และมุ่งเน้นที่การเป็น "เงินสดดิจิทัล" ที่ใช้งานได้จริง
### **Bitcoin SV (BSV) (2018)**
เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มที่นำโดย **Craig Wright** ผู้ที่อ้างว่าเป็น Satoshi Nakamoto Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก และกลับไปสู่วิสัยทัศน์ดั้งเดิมของ Bitcoin
### **Bitcoin ABC (2020)**
เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มนักพัฒนา Bitcoin ABC ที่ต้องการเปลี่ยนแปลงกลไกการระดมทุน Bitcoin ABC ถูกเปลี่ยนชื่อเป็น eCash ในภายหลัง
## **มุมมองที่แตกต่าง Bitcoin ถูก "แย่งชิง" หรือไม่?**
หนังสือ **"Hijacking Bitcoin"** โดย Roger Ver นำเสนอมุมมองที่แตกต่างจาก Bitcoin Maximalists
Roger Ver เชื่อว่า Bitcoin ถูก **"แย่งชิง"** โดยกลุ่มนักพัฒนา Bitcoin Core และ Blockstream ที่ต้องการเปลี่ยนแปลง Bitcoin จาก "เงินสดดิจิทัล" ให้กลายเป็น **"สินทรัพย์เก็บมูลค่า"**
Roger Ver วิพากษ์วิจารณ์ Bitcoin Core ในหลายประเด็น เช่น..
### **การไม่ยอมเพิ่ม Blocksize Limit**
Roger Ver เชื่อว่า Bitcoin Core จงใจจำกัดการเติบโตของ Bitcoin เพื่อผลักดันให้คนใช้งาน Sidechains ของ Blockstream
### **การเซ็นเซอร์ข้อมูล**
Roger Ver กล่าวหาว่า Bitcoin Core เซ็นเซอร์ข้อมูลและปิดกั้นการสนทนาเกี่ยวกับ Big Blocks บนแพลตฟอร์มต่างๆ
### **การต่อต้านนวัตกรรม**
Roger Ver เชื่อว่า Bitcoin Core ต่อต้านนวัตกรรม และไม่ยอมรับการเปลี่ยนแปลงที่อาจทำให้ Bitcoin ดีขึ้น
### **การควบคุมโดยกลุ่มเล็กๆ**
Roger Ver มองว่า Bitcoin Core ถูกควบคุมโดยกลุ่มเล็กๆ ที่ไม่คำนึงถึงความต้องการของชุมชน Bitcoin
Roger Ver สนับสนุน Bitcoin Cash ซึ่งเขาเชื่อว่าเป็น Bitcoin ที่แท้จริง ที่สืบทอดวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto
## **บทสรุป:**
การต่อสู้แย่งชิง Bitcoin และการเกิดขึ้นของ Hard Forks ต่างๆ เป็นส่วนหนึ่งของวิวัฒนาการของ Cryptocurrency
มุมมองที่แตกต่าง ความขัดแย้ง และการแข่งขัน ล้วนเป็นแรงผลักดันให้ Bitcoin และ Cryptocurrency อื่นๆ พัฒนาต่อไป
สุดท้ายแล้ว.. เราคงไม่อาจตัดสินได้ว่าฝ่ายใดคิดถูกหรือฝ่ายใดผิด
**"เสียงของตลาด** จะช่วยทำหน้าที่ให้คำตอบนั้นกับเรา ว่าแท้ที่จริงแล้วผู้คนกำลังต้องการอะไรกันแน่..
ลองมองไปที่มูลค่าของแต่ละแนวคิด มองไปที่ Network effect และกำลังการขุด มองไปที่การยอมรับและความเชื่อมั่นของผู้คน เหล่านี้ล้วนเป็นข้อบ่งชี้ที่เห็นได้ง่าย..
เพราะนั่นคือเสียงแห่งการเพรียกหาอิสรภาพ และอธิปไตยทางการเงินที่แท้จริง..
— Jakk Goodday
-

@ e0e92e54:d630dfaa
2024-09-04 04:13:19
_This is a copy of the email received from newsletter@Rumble.com_

# Free Speech Under Attack -- A Note from the CEO of Rumble
Dear Rumble Users,
I don't typically send messages to our users through email, but red lines have been crossed. There have been major developments with free speech platforms, and I feel it’s important to let everyone know what is going on and how you can help Rumble.
Rumble is no longer available to the citizens of Brazil, joining the ranks of France, Russia, and China. From media reports, Brazil no longer has Elon Musk's X due to attacks on free speech by Alexandre De Moreas, a justice of Brazil's Supreme Federal Court.
World powers don’t want Rumble, they don’t want X, they don’t want Telegram, and they don't want Truth Social. They want to control information, but our companies won’t let them.
There are no other large companies fighting for freedom like we are. We put everything on the line for it, and the Telegram CEO was recently arrested for it.
Advertisers boycott our companies to try and cut our economic lifeline, but they underestimate our support among the people.
The people keep us alive and keep us going.
If you want to help us, join Rumble Premium. If Rumble Premium gets big enough, you help us change the game and fight for freedom of expression.
We are also offering a $10 dicount for any new annual subscribers when they use the promo code "brazil".
Sincerely,
Chris Pavlovski
Chairman and CEO of Rumble

444 Gulf of Mexico Dr.
Longboat Key, FL 34228, USA.
-

@ 3b7fc823:e194354f
2024-09-04 00:26:48
Encryption is the promethium fire that the cypherpunks secured from heaven for me and you. It is our sacred duty to use and advance that in the world. Encryption is so powerful that governments tried to keep it away from the people and to this day have tried to weaken and backdoor it at every turn.
So what is encryption?
It is a deep deep rabbit hole and involves a lot of numbers but in a nutshell it uses math to scramble up the data of your file so it is gibberish and can't be read without decrypting it back to regular data. Encryption technology has continued to advance over time and cracking technology to break the encryption has as well. For our purposes all you really need to remember is to use modern cyphers and your encryption is really only going to be as good as the password (use a passphrase) strength you are using to lock it down with.
>
BEGINNER LEVEL - Encrypt your phone and computer.
People walk around with their whole lives on their phone. Protect it.
-phone: Congratulations, if you already have a lock screen set on either your iPhone or Android device then device encryption is enabled.
If your lock screen password is only 4 digits then we still have work to do. Four digits is only about 10,000 combinations and fairly easy to crack. I believe it only took them about 40 minutes to crack the iPhone of the attempted Trump shooter. Go into settings and set it up for 6 digits or for extra credit use a alphanumeric password.
After your phone then your personal computer probably has the most important data to you. Banking records, tax documents, photos, etc. Encrypt your drive.
-Windows: from Settings, select Privacy security -> Device encryption. Just follow the prompts.
-Apple: from Apple icon, select System Preferences -> Security & Privacy icon. Click "Turn On FileVault".
-Linux: most distros gives you the option during installation. If you didn't do so then search for how to enable it after the fact based on your distribution.
Awesome sauce. You have achieved minimum status.
>
ADVANCED LEVEL - Encrypt individual files.
You already encrypted your computer but guess what, once you start up your computer and log in the key is stored in RAM for as long as it stays on. The beginner level encryption protects your computer when it is off and it means no one can just steal your hard drive and access your files. This is good, but what if someone grabs you while you're sitting there working on it? What if you leave it in sleep mode and not turned off? Then that whole disk encryption is not really going to help you.
What if you had individual files that you consider more secret than the others? That finance spreadsheet or that special pic your spouse sent you? That's where individual file encryption comes in. You are just scrolling nostr when they grab you, your computer is on, and unlocked, but those special files are still safely encrypted.
I will share with you one of my favorite small programs: Picocrypt.
Download the Paranoid pack and store it in multiple drives, email accounts, and cloud storage. That way you will always have a copy to decrypt any files that you stored away.
Use it to encrypt any files that you feel need extra attention. It is also very useful for encrypting any files that you intend to store online in cloud storage. You do encrypt your files that are stored online don't you? Yes, even with the company that offers "encrypted" storage. Don't trust their encryption, use your own.
>
EXPERT LEVEL - Encrypt containers and hidden containers.
What if you want to encrypt several files and keep them all together in like a folder or container? That's where Veracrypt comes in. Free, open source, cross platform, and powerful.
Veracrypt allows you to create encrypted containers from any file that act like individual drives that can be mounted or unmounted as needed. You can name these files anything that you want, move them around or delete like any file, and make as many as you want. This allows you to have compartmentation of your files and drives.
Next trick, Veracrypt allows you to create a hidden container inside that container. Enter one passphrase and you open the encrypted container. Enter a different passphrase and you open a different hidden container.
This allows deniability. When they grab you and start pulling your fingernails off until you tell them the password to open the encrypted container, give it to them. They don't have to know that there is another hidden one under that.
These features allow you to do all sorts of interesting things only limited by your need and imagination.
What if you have a container named as some random config file in your /etc folder? What if you just encrypted a removable storage drive? What if you have multiple hard drives on your computer that have multiple containers and hidden containers? What if you have a hidden container that can only be accessed from booting up in a amnesiac OS like Tails leaving no trace that the files exist or trail that they were ever accessed? Go crazy, have fun.
>
NEMO - Failsafe
Nemo has no files, encrypted or otherwise. If they did you couldn't prove it. Nemo does use something like Tails that retains no memory from boot to boot.
Nemo also uses a failsafe. A simple lanyard attached to the flashdrive running the OS and the other end around their wrist while they work. When you try to separate them from the computer the flashdrive pulls out and everything is gone.
>
>
Using these programs you can create a layered and compartmentlized approach to your encryption scheme. There are also plenty of other encryption programs to check out such as Cryptomator, AES Crypt, etc
>
Last point and most important:
Encryption is only as good as the passphrase you use to lock it down. Use a shitty password and it doesn't matter how uncrackable your encryption is.
-

@ 8cb60e21:5f2deaea
2024-09-03 22:26:25
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/R5fzBNJP6Rk" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 8cb60e21:5f2deaea
2024-09-03 22:26:25
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/SBdDt4BUIW0" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 8cb60e21:5f2deaea
2024-09-03 21:58:26
# Lesson 3: Arrays, Objects, and Callbacks
### Arrays: Lists of Things
Arrays are ordered lists of values. They're perfect for storing multiple related items, like a list of your favorite cat toys:
```javascript
var catToys = ["mouse", "ball", "laser pointer"];
console.log(catToys[0]); // Prints "mouse"
```
### Objects: Grouping Related Information
Objects allow you to group related information together. They're like detailed profiles for each of your cat friends:
```javascript
var myCat = {
name: "Fluffy",
age: 3,
favoriteFood: "tuna"
};
console.log(myCat.name); // Prints "Fluffy"
```
### Callbacks: Doing Things Later
Callbacks are functions that are executed after another function has finished. They're useful for handling asynchronous operations, like waiting for your cat to finish eating before giving it a treat:
```javascript
function feedCat(callback) {
console.log("Feeding the cat...");
setTimeout(function() {
console.log("Cat has finished eating!");
callback();
}, 2000);
}
feedCat(function() {
console.log("Time for a treat!");
});
```
This code simulates feeding a cat, waiting 2 seconds, and then giving it a treat.
Remember, learning JavaScript is a journey. Take your time, practice regularly, and soon you'll be coding like a pro cat!
-

@ 8cb60e21:5f2deaea
2024-09-03 21:58:26
# Lesson 2: Functions and Loops
### Functions: Your Own Commands
Functions are reusable blocks of code that perform specific tasks. They're like teaching your cat a new trick:
```javascript
function meow(times) {
for (var i = 0; i < times; i++) {
console.log("Meow!");
}
}
meow(3); // This will print "Meow!" three times
```
### Built-in Functions
JavaScript comes with many built-in functions. For example, `console.log()` is a function that prints things to the console:
```javascript
console.log("I'm a cat!");
```
### Loops: Repeating Tasks
Loops allow you to repeat a task multiple times without writing the same code over and over. It's like telling your cat to chase its tail for a specific number of rounds:
```javascript
for (var i = 0; i < 5; i++) {
console.log("Chasing tail, round " + (i + 1));
}
```
This will print "Chasing tail, round X" five times, where X goes from 1 to 5.
-

@ 4c96d763:80c3ee30
2024-09-03 18:46:10
# Changes
## William Casarin (7):
- debug: add subid debugging
- fix bug where it was subscribing too many times
- arg: add -c profile{,:pubkey} arg column
- env: add some test npubs
- arg: add -c universe column
- appease clippy
- fonts: add thai support
pushed to [notedeck:refs/heads/master](http://git.jb55.com/notedeck/commit/989f88c989f5d6ec85f719efab6f80fb1a95ee00.html)
-

@ 6bae33c8:607272e8
2024-09-03 10:47:55
I do this every year, and every year I get at least one correct. [Last year](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), I got exactly one correct and unfortunately it was the surefire prediction that not all of them would be right, i.e., I got really zero correct. But that just goes to show how bold they were. These aren’t layups, more like three pointers and half-court shots. I fared much better the [previous](https://www.realmansports.com/p/grading-my-bold-predictions) two [years](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), so hopefully these will get back on track.
*(Actually, probably better to just link to all of them for full transparency: [2023](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), [2022](https://www.realmansports.com/p/grading-my-bold-predictions), [2021](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), [2020](https://www.rotowire.com/football/article.php?id=54494), [2019](https://www.rotowire.com/football/article.php?id=48921), [2018,](https://www.rotowire.com/football/article.php?id=41171) [2017](https://www.rotowire.com/football/article.php?id=37079), [2016](https://www.rotowire.com/football/article.php?id=31269), [2015](https://www.rotowire.com/football/article.php?id=26515), [2014](https://www.rotowire.com/football/article.php?id=22258).) I’m not going to argue it matters, or that anyone even clicks through on these, but I want to pat myself on the back for being so organized in archiving my old work.)*
1. **Stefon Diggs leads the Texans in targets, catches and receiving yards**
Right now, he’s getting drafted more than a round behind Nico Collins and less than a round ahead of Tank Dell. Diggs is 30, but he was one of the league’s best receivers until halfway through last year when the Bills made an offensive play-calling change. Moreover, Diggs is getting paid $22.5 million, so the Texans obviously don’t think he’s washed up, and he’s also in a contract year.
2. **CJ Stroud leads the NFL is passing yards**
This is +600 on DraftKings, so the real odds are probably north of 8:1. Stroud adds Diggs to his receiving corps, doesn’t run much and heads into Year 2.
3. **Roman Wilson (ADP 211) has more receptions than George Pickens (ADP 47)**
Pickens is a boom or bust downfield playmaker, not high-target alpha, and Wilson is a good fit for the slot for the Steelers new QBs. Think Martavis Bryant not Antonio Brown. (Not that Wilson is Brown!) Van Jefferson isn’t good, and someone will need to fill the void. Moreover, because Pittsburgh has new QBs, neither has an existing rapport with the incumbent Pickens.
4. **DeAndre Hopkins (ADP 82) out produces Calvin Ridley (ADP 54) in PPR**
Hopkins wasn’t terrible last year, has a rapport with Will Levis and is a future Hall of Famer who can still run routes. Ridley is already 29 and is just a guy outside of his monster season in 2020.
5. **The Giants will field a top-10 fantasy defense.**
I’ve been crushed by my homer bold predictions in the past, but they added Brian Burns to a rush that already had Dexter Lawrence and Kayvon Thibodeaux, the offense should be on the field more and generate some leads with a real playmaking receiver in Malik Nabers.
6. **One of the following Year 2 receivers will finish in the top-15 PPR: Jaxon Smith-Njigba, Jayden Reed, Jordan Addison, Dontayvion Wicks, Michael Wilson, Josh Downs, Andrei Iosivas, Quentin Johnston, Marvin Mims, Jalin Hyatt**
I make this prediction every year, and it often pans out as Year 2 is when receivers typically make the leap. I left out Tank Dell because he’s now got a fifth-round ADP, as well as the obvious ones: Zay Flowers, Rashee Rice and Puka Nacua.
7. **Rome Odunze (ADP 77) will outproduce Xavier Worthy (ADP 59)**
Both receivers enter crowded situations, and while Worthy’s is far better, he’s also got essentially the same skill-set as teammate Marquise Brown. Moreover, Andy Reid rarely entrusts rookies with large roles, especially early on. Odunze is 6-3, 215 and has the pedigree of a true NFL alpha, while Worthy weighs only 165 pounds at 5-11. Finally, Patrick Mahomes already has an established rapport with both Travis Kelce and Rashee Rice, while Odunze gets a more open competition with the Bears veteran WRs, given all three will play with Caleb Williams for the first time.
8. **Dalvin Cook will lead the Cowboys in rushing yards**
Cook is 29 and looked beyond “cooked” last year on the Jets, but his 3.3 YPC was on a small sample (67 carries), and prior to that, he’d been very good for the Vikings. At the very least he should have fresh legs, and he’d only need to beat out the ancient Ezekiel Elliott and Rico Dowdle. (Of course, Cook would have to be promoted from the practice squad first, so I really should hedge and make the prediction “neither Elliott, nor Dowdle will lead the Cowboys in rushing yards,” but I’ll push it and say it’s Cook.)
9. **Jonathan Taylor (ADP12 ) will lead the NFL in rushing yards.**
He’s got little competition in the Indy backfield and a running QB who should open lanes for him. Draft Kings has him at +600, so his real odds are probably about 10:1, but I’d take him over the favored Christian McCaffrey (age/mileage) and all the other backs who are more hybrid types or old (Derrick Henry.)
10. **Dalton Kincaid (TE4) will lead all TE in catches**
I guess this is a chalky pick because he and Kelce are both favored at the position at +3000, while Evan Engram is +5000! (I’d way rather bet on Engram at those odds.) But straight up, I’m going with Kincaid who is likely Josh Allen’s de facto No. 1 target with Diggs gone. In his final 11 regular season games Kincaid had 56 catches which prorates to 87 catches over the full year. And rookie tight ends rarely do anything and often make a leap in Year 2.
11. **Some of these predictions will be wrong**
No one’s perfect, but you never want to get shut out.
-

@ 161c8564:2d633b95
2024-09-02 20:24:34
Opinion about Freewallet Multi Crypto Wallet (iphone)
<!--HEADER END-->
FRWT Wallet uses deceptive marketing to lure in unsuspecting users. Once you deposit funds, they’ll block your account under the guise of KYC checks. It’s a fraudulent app—don’t download it!
<!--FOOTER START-->
#WalletScrutiny #nostrOpinion
[Join the conversation!](https://walletscrutiny.com/iphone/mw.org.freewallet.app)
-

@ eed76ece:afa98124
2024-09-02 18:58:30
As the World continues to create more and more NEW regulations. And as free speech get attacked from every angle. Bonafide business owners, especially importers will need to find ways to migrate sales offerings of goods and services. It feels like the majority of business owners have to really take this seriously.
Obviously so many different methods are used around the World already, but when the upcoming new mandatory vaccinations, vaccine passport travel restrictions really hit, businesses will have to jump to more selling online.
SN, Nostr and other unknown communication methods are Paramount. As usual it feels like no one is taking free speech attacks seriously. The amount of postings my customers around the World do daily on WhatsApp, LINE (Asia), Telegram, Twitter will move where it is allowed to move. Feels like there's an ongoing increase in the attack not just on the West, but from WITHIN the West.
Regardless if you retail, wholesale, manufacture, are an agent we try hard to be pro active on marketing on multiple methods. It seems very logical that in the future Nostr and SN will pick up International users as a way to get their goods posted somehow someway.
Examples
Customers in these regions I deal with primarily communicate with me in
Japan, Thailand using LINE and Tik Tok daily.
Most of the rest of the World communicate with me using WhatsApp.
Certain parts of Eastern Europe and Asia Telegram.
Interestingly my resellers in the USA primarily post on WhatsApp.
Westerners especially Americans seem to have enough money, they are not hungry for making more money, or increasing their business growth, they think everything is ok. "We will always be okay, there will NEVER be a Worldwide depression, recession, deflation, increased restrictions, they will NEVER force a new vaccine on us again, they will NEVER lock business and us down again".
"So I will always have free speech, the politicians told me so".
originally posted at https://stacker.news/items/670041
-

@ 56a6da9b:7f5a2243
2024-09-02 18:27:19
IO used to have a lot of content and now the only thing that shows up is my fouintain stuff. when i go into other nostr things it's not there anymore and i look like an anonymous user with no profile pic, or profile and no activity.
originally posted at https://stacker.news/items/669994
-

@ 6bae33c8:607272e8
2024-09-02 18:09:19
I did the third and final NFFC Beat Chris Liss league last night, and it was one of the more interesting and aggressive drafts I’ve ever done. I picked from the seven slot.
Here are the results:
([Link to livestream](https://www.realmansports.com/p/beat-chris-liss-3-livestream))
<img src="https://blossom.primal.net/269209e3c21e86749662ec594f0344c7aa45073d1c590d61fec611e74e1e15a8.png">
**1.7 Ja’Marr Chase** — I made seven my first choice, but then realized I probably should have gone with four or five, or maybe nine or 10. That’s because if the first six picks went chalk (and they did), I’d be faced with Chase who is holding out for a new contract (and who I have in two other leagues already), Justin Jefferson (new, bad QB) or Garrett Wilson (new QB, never been a Round 1-level WR.) At 1.9 I’d have gotten one of those guys anyway, but earlier picks on the way back. And at 1.4, I’d have gotten a shot at Bijan Robinson for an easier hero-RB build. But I had pick seven, and I tripled-down on Chase because I think it’s very likely he’ll get his extension (or play if he doesn’t), and he’s an all-time talent with a top QB and projects for a massive target share. Plus, if he busts [it’s Alan Seslowsky’s fault](https://www.youtube.com/watch?v=9n2l5ywZY4M), and having someone to blame is paramount.
**2.6 Drake London** — I had it mapped out via ADP that I’d likely get De’Von Achane here, but he went at his min pick (I’m pretty sure) at the 1-2 turn, and so I was scrambling a bit. I really wanted Puka Nacua, who I missed by one pick, considered Cooper Kupp, but ended up going for the ADP-faller London who I had not remotely planned on getting. London obviously benefits from the massive QB upgrade in Atlanta, but it’s an open question whether he’s really an elite receiver or just a good one, and Kyle Pitts could easily emerge as Kurt Cousins favorite target instead.
**3.6 DeVonta Smith** — When Derrick Henry went one pick ahead of me, it was between Smith and Jaylen Waddle who I took in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e). Normally I avoid receivers this undersized but Smith has always produced at every level and is locked into his sizeable target share. Plus I read some [Scott Barrett tweets](https://x.com/ScottBarrettDFB/status/1829973477131952161) about how Kellen Moore’s offense boosts the slot receiver a ton and that Smith thrives in the slot and could see more work there.
**4.7 Stefon Diggs** — This was ideal. I now have Diggs in all four of my leagues so far. Maybe he’s hit a cliff at age 30, but he’s getting $22.5M to play in arguably the league’s top passing game that lacks a true No. 1 alpha. I also considered Tee Higgins to pair with Chase (and serve as Chase insurance), but Diggs has more upside as a potential No. 1 target.
**5.6 Dalton Kincaid** — I’ve been high on him all summer, but he never quite fell to me in the right place until now. I expect him to be Josh Allen’s No. 1 receiver now that Diggs is gone.
**6.7 James Conner** — I needed a RB, and Conner is one. I’m a bit wary of a 29-YO guy with an extensive injury history, but he averaged 5.0 YPC last year and has never had a massive workload so he’s fresh for his age at least. Plus, the Cardinals offense should be good this year.
**7.6 Anthony Richardson** — I wasn’t planning on taking a QB here, or even Richardson who I have in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e) in Round 5!, but I couldn’t pull the trigger on Zamir White over someone with Richardson’s upside. I’m trying to win the overall contest, not simply cover the bases with starters at every position.
**8.7 Jonathon Brooks** — Jaylen Warren was still on the board, and he was a viable Week 1 starter for me, but Brooks who is on IR, struck me as the upside play. I heard somewhere, can’t remember where, that Brooks was an elite prospect in college before the injury, and there’s a lot of hype about Carolina’s new offensive brain trust boosting the offense generally. But it might have been a rash pick given my zero-RB build to take a rookie on IR.
**9.6 Marquise Brown** — I missed Warren by one pick on the way back, and instead of pivoting to Tyjae Spears I leaned into the zero-RB by taking Brown who was going in the fifth or sixth round before his injury. The beauty of this pick is I don’t need Brown right away as I wouldn’t start him anyway, so I pay no price for him missing Week 1. The ugly of this pick is I missed out on Spears, Zack Moss and Chuba Hubbard (who would have been nice to pair with Brooks.)
**10.7 Joe Burrow** — The obvious pick was Trey Benson to pair with Conner. In fact, I could have had Hubbard in Round 9 and Benson in 10 to lock up two backfields for my zero-RB team. But no, I had to take a *second* QB here because (a) Richardson has a low floor; (b) this was cheap for Burrow; and (c) I could potentially pair Burrow with Chase for the playoffs. If you’re gonna go zero RB, lean the into it. (The other problem with this pick is the weekly headache of picking my starting QB.)
**11.6 Jaleel McLaughlin** — The Burrow pick cost me not only Benson but JK Dobbins too, but I had my eye on McLaughlin who apparently was a god in college, and [per Barrett](https://x.com/ScottBarrettDFB/status/1829971593852043394) is in an ideal spot as the RB2 in Sean Payton’s offense. Now that stat has to be tempered a bit given that peak Alvin Kamara was the source of so much of it, but how much of that was Payton’s offense? In any event, I’m seriously rolling into Week 1 with McLaughlin in my active lineup because of the Richardson, Brooks, Brown and Burrow picks.
**12.7 Jordan Mason** — Obviously he’s not usable unless and until Christian McCaffrey gets hurt, and the Niners badly need Trent Williams to report, but he’s a top-10 RB if McCaffrey, who played into February last year, goes down. This also furthers my extreme “what could go right” build.
**13.6 Braelon Allen** — Oddly I view this pick as a mistake as he was higher in ADP, so I thought I could wait another round on Giants backup Tyrone Tracy. (Tracy went three picks ahead of me in the next round.) Allen might be good, but only a Breece Hall injury could free him up whereas Tracy could just outplay Devin Singletary. Granted the Jets might be a better environment than the Giants, so Allen could have more upside if he did get a shot, but Tracy is also a converted WR and would likely catch a lot of passes if he got the job.
**14.7 Khalil Herbert** — Once Tracy was gone, I pivoted to Herbert. The Chicago backfield is crowded, but D’Andre Swift always gets hurt, and Roschon Johnson isn’t as good a runner as Herbert.
**15.6 Jalen McMillan** — I wanted to get Cam Akers because Joe Mixon is old, but I missed him by two picks and pivoted (finally) back to WR. McMillan’s created some buzz in camp, and both Mike Evans and Chris Godwin are getting old.
**16.7 Will Shipley** — I love Saquon Barkley, but he’s getting old and has been hurt a lot. Kenneth Gainwell is ostensibly ahead of Shipley, but is just a guy. Another top-10 upside back should the starter go down.
**17.6 Dalvin Cook** — He’s on the practice squad for now, and he looked beyond done last year with the Jets, but keep in mind he only got 67 carries, and the Cowboys don’t have serious obstacles ahead of him should he regain even 60 percent of his prior form. Cook was still very good in 2022, and he should have fresh legs too.
**18.7 Quentin Johnston** — I needed one more receiver, and Johnston is one. Seriously, though he was a first-round pick only last year, and he’s competing with only Josh Palmer and a rookie.
**19.6 Younghoe Koo** — All these years I was with a wonderful kicker in Justin Tucker, but I’m trading him in for a Younghoe. (That joke will get old one day, just not in any of our lifetimes.)
**20.7 Giants Defense** — They draw Sam Darnold and Jayden Daniels the first two weeks, and added Brian Burns to Kayvon Thibodeaux and Dexter Lawrence.
**Roster By Position**
**QB** Anthony Richardson
**RB** James Conner/Jaleel McLaughlin
**WR** Ja’Marr Chase/Drake London/DeVonta Smith
**TE** Dalton Kincaid
**FLEX** Stefon Diggs
**K** Younghoe Koo
**D** Giants
**Bench** Jonathan Brooks/Marquise Brown/Joe Burrow/Jordan Mason/Braelon Allen/Khalil Herbert/Jalen McMillan/Will Shipley/Dalvin Cook/Quentin Johnston
-

@ 266815e0:6cd408a5
2024-09-02 15:27:16
After 7 months of work and procrastination I've decided to release another version of noStrudel
There a ton of new features and a few bugs fixed. This article highlights the biggest changes but if you want to read the full changelog you can find it in the [github repo](https://github.com/hzrd149/nostrudel/blob/master/CHANGELOG.md)
And as always if you want to check it out you can use [nostrudel.ninja](https://nostrudel.ninja) or run it locally using docker
```sh
docker run --rm -p 8080:80 ghcr.io/hzrd149/nostrudel:0.40.0
```
## New Features
### Support for NIP-49 encrypted nsec
Now when logging into to the app it will prompt you to set a password to encrypt your nsec so it can be stored securely (if that's even possible for a web client...)
There is also a new "Account" settings view that lets you export you nsec as a ncryptsec so you can copy it to other apps

### Blindspot feeds
There are also new "blindspot" feeds that show what others are seeing in their timeline that your missing

### NIP-42 Relay authentication
The app now supports NIP-42 relay authentication. Its opt-in though, so if you want to use popular authenticated relays like nostr.wine or relay.snort.social you will have to enable it in the settings

### Wasm relay and event verification
The app now supports using [@snort/worker-relay](https://git.v0l.io/Kieran/snort/src/branch/main/packages/worker-relay) as a local relay. Its at least 10x faster than the internal browser cache and can hold at least 100x more events. Its not enabled by default though so if you want to use it you have to switch to it in the "Relays" -> "Cache Relay" view

The app also supports using [nostr-wasm](https://github.com/fiatjaf/nostr-wasm) to speed up event signature verification. This is enabled by default, but if you want to still use the JavaScript verification or no verification you can find it in the performance setting

### Thread tabs
Threads now have a set of tabs that let you see the Replies, Quotes, Zaps, and other stuff related to the note


### Wiki articles
Its not feature complete but you can now view and edit wiki articles in the app

### Finished the launchpad
The launchpad is now usable and shows the latest notifications, messages, streams, and tools

### Blossom uploads
The app now lets you upload images and video to blossom server, this isn't enabled by default though so your going to have to enable it in the settings

And then setup some blossom servers in the settings. A few good public ones are `https://cdn.satellite.earth` and `https://cdn.nostrcheck.me`

### Task Manager
There is also a new "Task Manager" in the side nav that lets you see whats going on under the hood in the app

You can see what relays the app is currently connected to

And which relays are requesting NIP-42 authentication

## Bug fixes
- Fix null relay hints in DMs
- Fix users own events being hidden by muted words
- Fix random events showing up as DM messages
- Fix app prompting NIP-07 extension to unlock when app opens
- Remove corsproxy.io as default service for CORS proxy
-

@ 38d0888d:bd8e1246
2024-09-02 11:08:05
To foster collective improvement, it is essential to implement social programs that encourage voluntary engagement and mutual support. These initiatives should serve as fertile ground, nurturing altruistic values and deepening the understanding of humanity’s true needs. By integrating spiritual connections into these efforts, a ripple effect of kindness, understanding, and enlightenment can spread throughout society. Each individual, endowed with intellectual abilities by a higher power, is invited to contribute to the creation of a harmonious and enlightened world. Sharing inspirational concepts that blend spirituality with social responsibility has the potential to profoundly influence and unite public sentiment.
A sense of community and interconnectedness must be cultivated within these programs. Creating spaces for shared experiences and collective growth extends their impact beyond individual actions, fostering a network of mutual support and understanding.
It is crucial to promote inclusive development that transcends bureaucratic constraints, aiming to dismantle inequality and confront corruption. These initiatives do more than foster a fairer world; they also reveal the latent spiritual dimensions of the human mind. To encourage spiritual growth and overcome selfishness, collaborative efforts across society, decentralized governance structures, educational institutions, and individual contributions are imperative. Moral codes must emerge from deeply rooted spiritual ethics that are interwoven into the societal fabric, surpassing the interests of a privileged few. Humanity’s ultimate goal is to transcend mere cooperation among individuals, striving for absolute transparency and openness across all spheres of existence. Achieving this vision requires unwavering dedication from every stakeholder committed to guiding society along the path of enlightenment.
-

@ 9dd283b1:cf9b6beb
2024-09-02 10:26:53
There's a saying: Bitcoin is hope.
But once you truly understand Bitcoin, many of the old fiat goals in your life start to lose meaning. It can feel disorienting and even depressing, because you realize you need to build entirely new goals, and you're unsure where to begin.
For example, maybe your plan was to get a mortgage, buy a house, and imagine your kids playing there for the next 20 years while you "happily" pay off a 25-year loan. But when you understand Bitcoin, that plan doesn’t make sense. Why would I put a 100k-200k down payment into a mortgage when it's likely better be in Bitcoin? Plus, you lose about 2.5% to 4% of the total price on taxes, fees, brokers, and other costs. Crazy, right?
I even made a short presentation for my wife, explaining why we should never buy a house given current interest rates and down payment requirements. She responded that she wants a house anyway, because it feels better to own one. But does a 25-year mortgage really make it feel like it’s yours?
She also said it’s depressing to not follow the conventional path. It’s hard to feel satisfied with numbers when everyone around you is deep into mortgages—you want to be one of them. You want to visit their houses and invite them to "yours." It's like becoming sober in a room full of addicts. You know it’s better for you, but the world around you seems so strange that part of you wants to go back, even though you know it hurts. Yet, when you do go back, the joy isn't there anymore. You feel...nothing. And then you decide to withdraw.
I remember paying off my first mortgage for an apartment, and I felt nothing. And that was before I fell down the Bitcoin rabbit hole. Now I know if I ever took out a mortgage again, I’d just feel regret for not keeping the money in Bitcoin. And by the time you finish paying it off, you probably want to sell the property and move somewhere else.
So, the rational decision is to keep everything in Bitcoin and rent instead.Unless, of course, Bitcoin goes to zero.
There are only two outcomes for Bitcoin: it’s either going to infinity, or it's going to zero. There’s no scenario where it just hovers at 100k or 60k for the next 20 years—unless people are foolish enough to give away self-custody. If they do, we'll end up with digital gold. So the reasonable question is - how can you be sure? Well, you can't. But we are betting on it and it works for now. Worst case we will need to start from 0. But then there will be no hope anymore.
We are staying in the infinity camp. And when you are in that camp every time you make a big purchase, you’re shorting Bitcoin. Solution - simple, - don't buy anything. There’s a popular meme: You will own nothing, and you will be happy. But if you’re a Bitcoiner, it's more like: You will own only Bitcoin, and you probably won’t be happy about it. Why would I pay 30k for a car when I can lease one? Why put 100k down on a house when I can rent?
The only justification is mental comfort, peace of mind. Or perhaps you value the illusion of owning a physical thing more than the genuine ownership of something virtual. It’s confusing, isn’t it? Sure, you can own a bicycle. But owning a house? That's tricky. Imagine you’re a Russian citizen with a house on Lake Como, and suddenly, new sanctions mean Italy no longer recognizes your property. Or squatters break in while you’re on vacation, and now you need to go through a court battle to evict them.
Extreme situations, I know. But no one thinks it will happen to them—until it does.
So, you’ve sold everything to buy Bitcoin. You don’t own anything except Bitcoin, and you feel sad. Why?
What can you buy with Bitcoin that’s more valuable? Something that won’t depreciate over time. Something like time.
Time with your kids. Time with your family. Time with yourself.
There’s a concept called FIRE and then there is a Bitcoin FIRE calculation (https://bitcoincompounding.com/). In simple terms, you spend your Bitcoin slowly enough that it grows faster than you can spend it (in fiat terms). Unlike traditional assets, there’s no yield or dividends, so the only way it works is if Bitcoin continues its cycles. And you need to be at least two cycles in to make it work.
But personally, I don’t think there will be cycles anymore. I believe this October-November will break all the models, and Bitcoin will do what Bitcoin does: surprise everyone. I read somewhere a thought that stuck with me—imagine you wake up on a planet Earth on January 1st. You know nothing about the seasons or weather. After six months of only increasing temperatures, you’d be 100% certain it’s only getting hotter from here.
So what hope does Bitcoin offer? Hope that I can spend more time with my family. Hope that I can create something different for them. Hope that I can live without the weight of fiat goals. Hope that it's only getting hotter from here.
I just need to get through the withdrawal phase.
originally posted at https://stacker.news/items/662939
-

@ e6fbeb1c:6ac8fc04
2024-09-02 10:17:27
Eggplant is a member of the nightshade family, and it’s related to the potato and tomato. Often mistaken for a vegetable, eggplant is actually a fruit, and to be more precise, it’s a berry.

originally posted at https://stacker.news/items/669464
-

@ 79008e78:dfac9395
2024-09-02 06:17:23
ระบบเงินอิเล็กทรอนิกส์แบบ peer-to-peer
----
ระบบเงินอิเล็กทรอนิกส์แบบ peer-to-peer นั้นจะช่วยให้เราสามารถชำระเงินผ่านทางออนไลน์ได้โดยตรงจากฝ่ายหนึ่งไปยังอีกฝ่ายหนึ่งโดยไม่ต้องผ่านตัวกลางอย่างพวกสถาบันการเงิน โดยใช้ digital signature เป็นส่วนหนึ่งในการแก้ปัญหานี้ แต่มันจะไม่มีประโยชน์ใด ๆ เลยหากยังคงต้องอาศัยตัวกลางที่เชื่อถือได้มาแก้ปัญหา double spending เราขอเสนอวิธีแก้ปัญหา double spending โดยใช้เครือข่ายแบบ peer-to-peer ให้เครือข่ายคอยประทับเวลาธุรกรรมต่าง ๆ ในระบบและนำมาเรียงร้อยกันเป็นเส้นสายของ proof-of-work ที่ใช้ hash เพื่อสร้างธุรกรรมที่ไม่สามารถเปลี่ยนแปลงได้ โดยไม่ต้องทำ proof-of-work ใหม่ โดยให้เส้นสายที่ยาวที่สุดนั้น ไม่เพียงแต่ทำหน้าที่เป็นลำดับของธุรกรรมที่เกิดขึ้นเท่านั้น แต่ยังเป็นสิ่งที่พิสูจน์ได้ว่ามาจากกำลังประมวลผล CPU ที่มากที่สุด และตราบใดที่ nodes ส่วนใหญ่ไม่ได้ร่วมมือกันโจมตีเครือข่ายและยังคงควบคุมกำลังประมวลผลส่วนใหญ่ในระบบไว้ พวกเขาก็จะสร้างเส้นสายที่ยาวที่สุดและสามารถเอาชนะผู้ประสงค์ร้ายที่จะโจมตีระบบได้ ตัวเครือข่ายเองไม่ได้ต้องมีโครงสร้างอะไรที่ซับซ้อน ข้อมูลต่าง ๆ ในเครือข่ายจะถูกกระจายส่งต่อโดยไม่ต้องสนใจว่าผู้รับจะได้รับหรือไม่ และ nodes ต่าง ๆ เองก็สามารถที่จะออกจากเครือข่ายและกลับเข้าร่วมใหม่ได้ตามที่ต้องการ โดยยอมรับเส้น proof-of-work ที่ยาวที่สุด เป็นหลักฐานของสิ่งที่เกิดขึ้นในขณะที่ node นั้น ๆ ไม่ได้อยู่ในเครือข่าย
1.บทนำ (Introduction)
-----
ไม่ว่าใครจะใคร่ซื้อใคร่ขายอะไรใด ๆ บนอินเตอร์เน็ตนั้น ก็จำเป็นต้องพึ่งพาสถาบันการเงินในฐานะของบุคคลที่สามเพื่อดำเนินการชำระเงินทางอิเล็กทรอนิกส์เสมอ ๆ ซึ่งถึงแม้ว่าระบบนี้มันจะทำงานได้ดีสำหรับธุรกรรมส่วนใหญ่ ๆ แต่ระบบก็ก็มีจุดอ่อนอยู่ที่ยังต้องอาศัยความไว้เนื้อเชื่อใจ (trust) ในระบบนี้การทำธุรกรรมที่ไม่สามารถย้อนกลับได้อย่างสมบูรณ์นั้นมันแทบจะเป็นไปไม่ได้เลย เนื่องจากสถาบันการเงินไม่สามารถหลีกเลี่ยงการเป็นตัวกลางในการไกล่เกลี่ยข้อพิพาทต่าง ๆ ที่อาจเกิดขึ้นได้ มิหนำซ้ำต้นทุนในการไกล่เกลี่ยยังทำให้ต้นทุนการทำธุรกรรมเพิ่มสูงขึ้น และเมื่อต้นทุนสูงขึ้นขนาดของธุรกรรมที่สามารถใช้งานได้จริงก็สูงขึ้นตามไปด้วย ธุรกรรมเล็ก ๆ น้อย ๆ ก็ไม่สามารถเกิดขึ้นได้ เมื่อมีความเป็นไปได้ที่ธุรกรรมจะเกิดการย้อนกลับ ความจำเป็นในการสร้างความไว้วางใจก็ยิ่งทวีคูณมากขึ้น ผู้ค้าก็จำเป็นต้องระมัดระวังลูกค้า ต้องเรียกร้องข้อมูลมากกว่าที่จำเป็น การฉ้อโกงกลายเป็นเรื่องที่หลีกเลี่ยงไม่ได้เพราะต้นทุนและความไม่แน่นอนในทำธุรกรรมเหล่านี้ แน่นอนว่าเราสามารถหลีกเลี่ยงมันได้โดยการใช้เงินสด แต่ก็ไม่มีกลไกใดที่ทำให้สามารถใช้เงินสดผ่านช่องทางการสื่อสาร (เอาให้เข้าใจง่ายก็อินเตอร์เน็ต)ได้ โดยไม่ต้องมีตัวกลาง ;-;
แปลว่าสิ่งที่จำเป็นสำหรับการแก้ไขปัญหานี้คือระบบการชำระเงินทางอิเล็กทรอนิกส์ ที่อยู่บนพื้นฐานของการพิสูจน์ด้วยการเข้ารหัสแทนที่จะเป็นความไว้วางใจ ซึ่งจะทำให้คู่สัญญาสองฝ่ายที่ยินยอมสามารถทำธุรกรรมร่วมกันได้โดยตรง โดยไม่จำเป็นต้องมีบุคคลที่สามมาคอยเป็นตัวกลาง ธุรกรรมที่ยากต่อการย้อนกลับจะช่วยปกป้องผู้ขายจากการฉ้อโกง และสามารถใช้กลไก escrow เพื่อปกป้องผู้ซื้อได้อีกด้วย ในเอกสารชุดนี้ เราขอเสนอวิธีแก้ปัญหาการใช้จ่ายซ้ำซ้อนโดยใช้เซิร์ฟเวอร์ timestamp กระจายศูนย์แบบ peer-to-peer เพื่อสร้างหลักฐานการคำนวณลำดับเวลาของธุรกรรม โดยระบบนี้จะปลอดภัยตราบใดที่กลุ่มของ node ที่ซื่อสัตย์ ยังคงมีกำลังประมวลผลที่มากกว่ากลุ่มที่ประสงค์ร้ายกับระบบ
2.ธุรกรรม (Transactions)
----
นิยามของเหรียญอิเล็กทรอนิกส์ในที่นี้ คือห่วงโซ่ที่คล้องเกี่ยวกันของ digital signature โดยที่เจ้าของเหรียญอิเล็กทรอนิกส์จะโอนเหรียญไปยังเจ้าของคนถัดไป ด้วยการลง digital signature บน hash ของธุรกรรมก่อนหน้ารวมถึงกุญแจสาธารณะของเจ้าของคนถัดไป และผนวกมันไว้ที่ส่วนท้ายของธุรกรรม และผู้รับเงินเองก็สามารถตรวจสอบลายเซ็นเพื่อยืนยันความเป็นเจ้าของได้
https://image.nostr.build/a467896797a9fb9f98c3c234f0adb4df2376f2c3d9a7cc9d8672d7a9f5aa9efa.png
แน่นอนว่าปัญหาก็คือผู้รับเงินไม่สามารถตรวจสอบได้ว่าเจ้าของคนใดคนหนึ่งก่อนหน้าเขาได้ใช้เหรียญดังกล่าวซ้ำซ้อนมากกว่าหนึ่งครั้งหรือไม่ และวิธีการแก้ไขปัญหานี้โดยทั่วไปก็คงเป็นการกำหนดตัวกลางที่มีความน่าเชื่อถือมาเป็นคนตรวจสอบทุกธุรกรรมเพื่อป้องกันการใช้จ่ายซ้ำซ้อน และหลังจากการทำธุรกรรมแต่ละครั้ง เหรียญจะต้องถูกส่งกลับไปยังตัวกลางเพื่อออกเหรียญใหม่ และจะมีเพียงเหรียญที่ออกจากตัวกลางโดยตรงเท่านั้นที่จะเชื่อถือได้ว่าจะไม่ถูกใช้จ่ายซ้ำซ้อน แต่ปัญหาก็คือ ชะตากรรมของระบบเงินทั้งหมดจะขึ้นอยู่กับตัวกลางตัวนี้ เพราะทุกธุรกรรมจำเป็นจะต้องผ่านพวกเขา ซึ่งก็ไม่ต่างอะไรกับธนาคาร
เราจึงต้องการวิธีการที่ทำให้ผู้รับเงินทราบได้ว่าเจ้าของคนก่อน ๆ ไม่ได้ลงนามในธุรกรรมใด ๆ มาก่อน เพื่อให้บรรลุวัตถุประสงค์นี้ เราจะทำการนับว่าธุรกรรมที่เกิดขึ้นก่อนเป็นธุรกรรมที่ถูกต้อง และจะไม่สนใจความพยายามใด ๆ ในการที่จะใช้เหรียญนั้น ๆ ซ้ำอีก และวิธีเดียวที่ทำแบบนี้ได้ คือการรับรู้ถึงธุรกรรมทั้งหมด เช่นเดียวกับโมเดลที่ได้กล่าวข้างต้น ที่ตัวกลางจะรับรู้ถึงธุรกรรมทั้งหมดและตัดสินว่าธุรกรรมใดมาก่อนมาหลัง เพื่อให้บรรลุเป้าหมายนี้โดยไม่ต้องมีบุคคลที่สามที่เชื่อถือได้ ธุรกรรมทั้งหมดจะต้องถูกประกาศต่อสาธารณะ [1] และเราต้องการระบบที่ผู้เข้าร่วมเห็นพ้องในประวัติธุรกรรมชุดเดียวกันตามลำดับที่ได้รับ ส่วนผู้รับเงินก็จำเป็นจะต้องมีหลักฐานว่า ในขณะที่ทำธุรกรรม "โหนด" ส่วนใหญ่ในระบบเห็นพ้องต้องกันว่าธุรกรรมนั้นได้รับเป็นลำดับแรก(ไม่มีธุรกรรมที่ใช้เหรียญพวกนี้มาก่อน)
3.ระบบบันทึกเวลา (Timestamp Server)
----
สำหรับแนวทางการแก้ปัญหาในครั้งนี้ เราจะใช้ประโยชน์จาก timestamp server ที่จะทำหน้าที่บันทึก hash ของบล๊อกที่ต้องการให้มีการบันทึกเวลา และจากนั้นจะทำการเผยแพร่ hash ดังกล่าว เหมือนกับหนังสือพิมพ์หรือโพสต์ใน Usenet [2-5] (ฟีลแบบทุกคนจะเห็นโพสต์นี้น้าา ประมาณนั้น) การบันทึกเวลานี้จะพิสูจน์ได้ว่าข้อมูลที่ถูก hash นั้นจะต้องมีอยู่จริงในเวลานั้นเพื่อให้ได้มาซึ่ง hash ดังกล่าว แต่ละการบันทึกเวลาจะรวมการบันทึกเวลาของหน้านี้ไว้ใน hash ของมันเพื่อสร้างเป็น chain โดยการบันทึกเวลาแต่ละครั้งจะยืนยันความถูกต้องของการบันทึกก่อนหน้าได้อีกด้วยด้วย
https://image.nostr.build/ddf92417c45dbb6e25da0af80a10d4cdbc3e725d047d65f54a3e3bfcf358c4d6.png
4.พรูฟ-ออฟ-เวิร์ค (Proof-of-Work)
----
ในการสร้าง Timestamp Server แบบกระจายศูนย์บนพื้นฐานแบบ peer to peer เราจำเป็นต้องใช้ระบบ Proof-of-Work (PoW) ที่คล้ายกับ Hashcash ของ Adam Back [6] แทนที่จะใช้วิธีการแบบเดิม ๆ อย่างการประกาศในหนังสือพิมพ์หรือ Usenet โดย PoW ใช้ในการตรวจสอบค่าที่มาจากกระบวนการ hash เช่น SHA-256 แล้ว ผลลัพธ์ที่ได้ (Hash) จะขึ้นต้นด้วยเลขศูนย์จำนวนหนึ่ง โดยที่ work (ประมาณว่าพลังประมวลผล) ที่ต้องใช้จะเพิ่มขึ้นแบบทวีคูณตามจำนวนเลขศูนย์ที่ต้องการ และสามารถตรวจสอบได้โดยการรัน Hash เพียงครั้งเดียว
ซึ่งสำหรับ timestamp network ของเรานั้น เราใช้ PoW โดยการเพิ่มค่า Nonce ในบล็อกไปเรื่อย ๆ จนกว่าจะพบค่าที่ทำให้ Hash ของบล็อกนั้นมีเลขศูนย์ตามที่กำหนด และเมื่อใช้กำลังประมวลผลของ CPU ไปกับการทำ PoW จนสำเร็จแล้ว บล็อกจะไม่สามารถเปลี่ยนแปลงได้ หากไม่มีการทำงานซ้ำใหม่ เนื่องจากบล็อกที่สร้างขึ้นภายหลังจะเชื่อมโยงกับบล็อกก่อนหน้า การเปลี่ยนแปลงบล็อกใด ๆ จะต้องทำ PoW ของบล็อกนั้นและบล็อกที่ตามมาใหม่ทั้งหมด
https://image.nostr.build/c039ef4ca6833cb1ecee65ac5991df2406be9b7e490b86b3b19f94f267767182.png
นอกจากนี้ PoW ยังช่วยแก้ปัญหาของเสียงส่วนมากที่มาตัดสินใจในระบบนี้ เพราะหากเสียงข้างมากอ้างอิงจากหลักการหนึ่ง IP หนึ่งเสียง ใครก็ตามที่สามารถสร้าง IP ได้จำนวนมากก็จะสามารถควบคุมระบบได้ จึงใช้หลักการหนึ่ง CPU หนึ่งเสียงแทน การตัดสินใจของเสียงข้างมากจะแสดงด้วย Chain ที่ยาวที่สุด ซึ่งบ่งบอกถึงความพยายามในการคำนวณ (Proof-of-Work) ที่มากที่สุด หาก Node ที่ซื่อสัตย์ (Honest nodes) มีกำลังประมวลผลของ CPU ส่วนใหญ่อยู่ในการควบคุม Honest Chain ก็จะเติบโตเร็วที่สุดและแซงหน้า Chain อื่น ๆ ได้ ผู้โจมตีที่ต้องการแก้ไขบล็อกในอดีตจะต้องทำ Proof-of-Work ของบล็อกนั้นและบล็อกที่ตามมาใหม่ทั้งหมด และต้องทำงานให้เร็วกว่า Honest Node ด้วย ซึ่งโอกาสที่ผู้โจมตีจะตามทันนั้นจะลดลงแบบทวีคูณเมื่อมีการเพิ่มบล็อกมากขึ้น
เพื่อชดเชยความเร็วของฮาร์ดแวร์ที่เพิ่มขึ้นและความสนใจในการรัน Node ที่ผันผวน ระดับความยากของ Proof-of-Work จะถูกกำหนดโดยค่าเฉลี่ย โดยตั้งเป้าไว้ที่จำนวนบล็อกเฉลี่ยต่อชั่วโมง หากสร้างบล็อกได้เร็วเกินไป ระดับความยากก็จะเพิ่มขึ้น
5.เครือข่าย (Network)
----
เครือข่ายนั้นมีการทำงาน ดังนี้
1. การประกาศธุรกรรมใหม่: ธุรกรรมใหม่จะถูกประกาศ (broadcast) ไปยังทุก node ในเครือข่าย
2. การรวบรวมธุรกรรม: แต่ละ node จะรวบรวมธุรกรรมใหม่ ๆ เหล่านี้ ไว้ในบล็อก
3. การค้นหา Proof-of-Work: แต่ละ node จะทำการคำนวณ เพื่อค้นหา Proof-of-Work ตามค่า difficulty สำหรับบล็อกนั้น ๆ
4. การประกาศบล็อก: เมื่อ node ใดค้นหา Proof-of-Work ได้แล้ว node นั้นจะทำการประกาศบล็อกไปยังทุก node ในเครือข่าย
5. การตรวจสอบและยอมรับบล็อก: node อื่น ๆ จะทำการตรวจสอบและยอมรับบล็อกนั้น เฉพาะเมื่อธุรกรรมทั้งหมดภายในบล็อกนั้นถูกต้องและยังไม่ถูกใช้มาก่อน
6. การสร้างบล็อกถัดไป: node ต่าง ๆ แสดงการยอมรับบล็อกโดยการเริ่มต้นสร้างบล็อกถัดไปใน chain ด้วย hash ของบล็อกที่ยอมรับ เป็น hash ก่อนหน้าในโครงสร้างของบล๊อกใหม่ที่กำลังสร้าง
node ต่าง ๆ จะถือว่า chain ที่ยาวที่สุดเป็น chain ที่ถูกต้องและจะทำงานเพื่อขยาย chain นั้นต่อไป หากมีสอง node ที่ได้ประกาศบล็อกเวอร์ชันที่แตกต่างกันในเวลาพร้อมกัน node บาง node อาจได้รับบล็อกหนึ่งก่อน อีกบล็อกหนึ่ง ในกรณีนี้ node เหล่านั้น จะทำงานบนบล็อกที่ได้รับก่อน แต่จะเก็บสำเนาของบล็อกอีกอันหนึ่งไว้ ในกรณีที่บล็อกนั้น กลายเป็นบล็อกที่อยู่ใน chain ที่ยาวกว่าปัญหาข้อโต้แย้งนี้ก็จะได้รับการแก้ไข เมื่อพบ Proof-of-Work อันถัดไปและ chain ใด chain หนึ่งยาวขึ้น node ที่กำลังทำงานอยู่บน chain ที่สั้นกว่าก็จะเปลี่ยนไปทำงานบน chain ที่ยาวกว่าแทน
การประกาศธุรกรรมใหม่ ไม่จำเป็นต้องไปถึงทุก node ในเครือข่าย ตราบใดที่พวกเขายังไปถึง node ส่วนใหญ่ในระบบได้ ธุรกรรมเหล่านั้นก็จะถูกบรรจุอยู่ในบล็อกในไม่ช้า นอกจากนี้การประกาศบล็อกยังไม่ต้องกังวลเรื่องจะมีบล๊อกที่สูญหาย เนื่องจากหากว่า node ไม่ได้รับบล็อกใด ๆ node ก็จะตระหนักได้ว่าพลาดบล็อกก่อนหน้าไปเมื่อได้รับบล๊อกใหม่มา และ node จะทำการร้องขอ block ที่ขาดไปจากเครือข่าย
6.แรงจูงใจ(Incentive)
----
โดยปกติแล้ว ธุรกรรมแรกของแต่ละบล๊อกนั้นจะเป็นธุรกรรมพิเศษที่จะขุดเหรียญที่สร้างขึ้นใหม่ซึ่งเป็นกรรมสิทธิ์ของผู้สร้างบล็อกนั้น ๆ ซึ่งจะเป็นการเพิ่มแรงจูงใจให้กับ node ต่าง ๆ ในการสนับสนุนเครือข่าย และเป็นวิธีการกระจายเหรียญให้หมุนเวียน เนื่องจากไม่มีหน่วยงานส่วนกลางที่ทำหน้าที่ในการออกเหรียญ การเพิ่มเหรียญใหม่ในปริมาณคงที่อย่างต่อเนื่องนั้นคล้ายคลึงกับการที่คนงานเหมืองทองคำใช้แรง และ เวลา เพื่อเพิ่มทองคำให้หมุนเวียน ในกรณีนี้ คือ เวลา กำลังประมวลผล และไฟฟ้าที่ถูกใช้ไป
นอกจากนี้แรงจูงใจจะมาจากค่าธรรมเนียมการทำธุรกรรม หากมูลค่าผลลัพธ์ของธุรกรรมน้อยกว่ามูลค่าที่ใส่เข้ามา ส่วนต่างนั้นก็คือค่าธรรมเนียมการทำธุรกรรมที่จะเพิ่มเข้าไปในมูลค่าแรงจูงใจของบล็อกที่มีธุรกรรมนั้น เมื่อเหรียญทั้งหมดในระบบมีจำนวนเท่ากับที่กำหนดไว้แล้ว แรงจูงใจหลักก็จะถูกเปลี่ยนมาเป็นค่าธรรมเนียมการทำธุรกรรม และปราศจากภาวะเงินเฟ้อโดยสิ้นเชิง
แรงจูงใจอาจช่วยกระตุ้นให้ node ต่าง ๆ ยังคงซื่อสัตย์ หากผู้โจมตีที่ละโมบสามารถรวบรวมกำลังประมวลผล ได้มากกว่า node ที่ซื่อสัตย์ทั้งหมด เขาจะต้องเลือกระหว่างการใช้มันเพื่อฉ้อโกงผู้อื่นโดยการใช้จ่ายซ้ำซ้อน หรือใช้มันเพื่อสร้างเหรียญใหม่ พวกเขาจะพบว่าการเล่นตามกฎ กฎที่เอื้อประโยชน์ให้กับเขาด้วยเหรียญใหม่มากกว่าคนอื่น ๆ รวมกันนั้นทำกำไรได้มากกว่าการบ่อนทำลายระบบและความถูกต้องของทรัพย์สินของเขาเอง
7.การจัดการพื้นที่ดิสก์(Reclaiming Disk Space)
----
เมื่อธุรกรรมถูกบรรจุลงในบล๊อกแล้ว สามารถกำจัดธุรกรรมที่ใช้ไปแล้วก่อนหน้านั้นออกได้เพื่อประหยัดพื้นที่ดิสก์ แต่การจะทำอย่างนี้ได้โดยไม่ให้เลข hash ของบล๊อกมีการเปลี่ยนแปลงนั้น ธุรกรรมจึงจำเป็นต้องถูก hash ในรูปแบบของ Merkle Tree [7][2][5] โดยมีแค่ root node ของ tree เท่านั้นที่จะรวมอยู่ใน hash ของบล๊อก นี่เป็นวิธีที่ทำให้สามารถบีบอัดข้อมูลในบล๊อกเก่า ๆ ได้โดยการตัดพวก hash ส่วนอื่น ๆ ของ tree ที่ไม่ใช่ root node ออก (ไม่จำเป็นต้องเก็บ hash ในชั้นอื่น ๆ ของ tree)
https://image.nostr.build/3ed95334891d91baca3f3f6f624a7ae22620be4ebfe0db5eb652cfce11255b9a.png
โดยในส่วน header ของบล็อกที่ไม่มีธุรกรรมจะมีขนาดประมาณ 80 ไบต์ หากเราสมมติว่าบล็อกถูกสร้างขึ้นทุก ๆ 10 นาที 80 ไบต์ * 6 * 24 * 365 = 4.2MB ต่อปี โดยที่ระบบคอมพิวเตอร์ทั่วไปที่วางขายในปี 2551 มี RAM 2GB และกฎของมัวร์ทำนายการเติบโตในปัจจุบันที่ 1.2GB ต่อปี การจัดเก็บข้อมูลไม่น่าจะเป็นปัญหาแม้ว่าส่วนหัวของบล็อกจะต้องถูกเก็บไว้ในหน่วยความจำก็ตาม
8.การตรวจสอบธุรกรรม (Simplified Payment Verification)
----
การที่จะยืนยันการชำระเงินโดยไม่จำเป็นต้องรัน full node ได้นั้น ผู้ใช้เพียงแค่เก็บสำเนาของส่วนหัวบล็อก (block header) ของสายบล็อก (chain) ที่ยาวที่สุด ซึ่งสามารถรับได้โดยการสอบถามจาก node อื่น ๆ ในเครือข่ายจนมั่นใจว่าได้รับสายที่ยาวที่สุด และรับ Merkle branch ที่เชื่อมโยงธุรกรรมกับบล็อกที่มีการประทับเวลา (Timestamp) อยู่ ถึงแม้ผู้ใช้จะไม่สามารถตรวจสอบธุรกรรมด้วยตัวเองได้ แต่การเชื่อมโยงธุรกรรมกับตำแหน่งในสายบล็อกจะทำให้เห็นว่า node ในเครือข่ายยอมรับแล้ว และบล็อกที่เพิ่มเข้ามาหลังจากนั้นเป็นการยืนยันเพิ่มเติมว่าเครือข่ายยอมรับธุรกรรมนี้แล้ว
https://i.imgur.com/VXtLpRF.png
การตรวจสอบดังกล่าวจะเชื่อถือได้ตราบใดที่ node ที่ซื่อสัตย์ยังคงควบคุมเครือข่าย แต่จะมีความเสี่ยงมากขึ้นหากเครือข่ายถูกโจมตีและถูกควบคุม ในขณะที่ node ในเครือข่ายสามารถตรวจสอบธุรกรรมได้ด้วยตัวเอง แต่วิธีการแบบง่ายนี้อาจถูกหลอกลวงโดยการใช้ธุรกรรมปลอมของผู้โจมตี ตราบใดที่ผู้โจมตียังคงสามารถควบคุมเครือข่ายได้ กลยุทธ์หนึ่งในการป้องกันปัญหานี้คือ การรับการแจ้งเตือนจาก node อื่น ๆ ในเครือข่ายเมื่อตรวจพบบล็อกที่ไม่ถูกต้อง ซึ่งจะแจ้งให้ซอฟต์แวร์ของผู้ใช้ดาวน์โหลดบล็อกแบบเต็มและธุรกรรมที่แจ้งเตือน เพื่อยืนยันความไม่สอดคล้องกัน ธุรกิจที่ได้รับการชำระเงินบ่อยครั้งอาจยังคงต้องการรัน node ของตนเอง เพื่อความปลอดภัยที่เป็นอิสระและการตรวจสอบที่รวดเร็วยิ่งขึ้น
9.การควบรวมและแบ่งย่อยมูลค่า(Combining and Splitting Value)
----
แม้ว่าการจัดการเหรียญหลาย ๆ เหรียญจะเป็นสิ่งที่สามารถทำได้ แต่การจัดการธุรกรรมแยกต่างหากสำหรับแต่ละเหรียญในการโอนก็คงเป็นเรื่องที่น่าปวดหัวอยู่ดี ฉะนั้นแล้วเพื่อให้สามารถแยกและรวมมูลค่ากันได้ ธุรกรรมจึงสามารถมี input และ output ได้หลายรายการ ซึ่งโดยปกติแล้วจะมี input เดียวจากธุรกรรมก่อนหน้าที่มีขนาดใหญ่กว่า หรือ input จำนวนเล็ก ๆ หลาย ๆ รายการ และ output ไม่เกินสองรายการ คือ รายการหนึ่งสำหรับการชำระเงิน และอีกหนึ่งรายการสำหรับการส่งเงินทอน หากมีกลับไปยังผู้ส่ง
https://image.nostr.build/9c6d3ce0e9f08c5b3fa3b82c2088ac6235603e5c0df3469060e6c9f74bce32fc.png
ควรสังเกตว่า fan-out (กระจายของธุรกรรม) ซึ่งเป็นกรณีที่ธุรกรรม ธุรกรรมหนึ่งนั้นขึ้นอยู่กับหลายธุรกรรม และธุรกรรมเหล่านั้นเองก็ขึ้นอยู่กับอีกหลายธุรกรรม แต่ไม่ใช่ปัญหาในที่นี้ เพราะไม่มีความจำเป็นในการดึงประวัติการทำธุรกรรมทั้งหมดออกมาเป็นสำเนา
10.ความเป็นส่วนตัว(Privacy)
----
ในรูปแบบธนาคารแบบดั้งเดิมนั้น ความเป็นส่วนตัวเกิดขึ้นได้ด้วยการจำกัดการเข้าถึงข้อมูล โดยให้เฉพาะผู้ที่เกี่ยวข้องและบุคคลที่สามที่ได้รับความไว้วางใจเท่านั้น แต่เนื่องจากในระบบนี้เรามีความจำเป็นในการประกาศธุรกรรมทั้งหมดต่อสาธารณะ ทำให้ไม่สามารถใช้วิธีนี้ได้ แต่ยังจำเป็นต้องคงความเป็นส่วนตัวไว้ โดยการแบ่งการไหลของข้อมูล ด้วยการไม่เปิดเผยตัวตนของเจ้าของ public key คนทั่วไปสามารถเห็นว่ามีคนกำลังส่งเงินจำนวนหนึ่งให้กับคนอื่น แต่จะไม่ทราบข้อมูลที่เชื่อมโยงธุรกรรมนั้นกับบุคคลใด ๆ ซึ่งคล้ายกับระดับข้อมูลที่เปิดเผยโดยตลาดหลักทรัพย์ ซึ่งมีการเปิดเผยเวลาและขนาดของการซื้อขายแต่ละครั้งต่อสาธารณะ แต่ไม่ได้ระบุว่าคู่สัญญาคือใคร
https://image.nostr.build/6ec3c84c7878dbd4558d2045518384daf5a341e86f4194cf367cc8426c2d72a7.png
เพื่อเสริมในเรื่องของความปลอดภัย ควรใช้ key pair ใหม่สำหรับการทำธุรกรรมในแต่ละครั้ง เพื่อป้องกันไม่ให้เชื่อมโยงกับเจ้าของคนเดียวกันได้ อย่างไรก็ตาม การเชื่อมโยงบางอย่างยังคงหลีกเลี่ยงไม่ได้ ในธุรกรรมที่มี input หลายรายการ ซึ่งจำเป็นต้องเปิดเผยว่า input เหล่านั้นเป็นของเจ้าของคนเดียวกัน ความเสี่ยงก็คือ หากมีการเปิดเผยตัวตนของเจ้าของคีย์ การเชื่อมโยงอาจเปิดเผยธุรกรรมอื่น ๆ ที่เป็นของเจ้าของรายเดียวกันได้
11.การคำนวณ(Calculations)
----
หากลองพิจารณาสถานการณ์ที่ผู้โจมตีพยายามสร้าง chain ปลอมให้เร็วกว่า chain จริง แม้ว่าจะทำได้สำเร็จ แต่มันก็ไม่สามารถทำให้ระบบเปิดรับการเปลี่ยนแปลงตามอำเภอใจได้อยู่ดี เช่น การสร้างมูลค่าจากอากาศธาตุ หรือการรับเงินที่ไม่เคยเป็นของผู้โจมตีมาก่อน Node ต่าง ๆ จะไม่ยอมรับธุรกรรมที่ไม่ถูกต้องเป็นการชำระเงิน และ Node ที่สุจริตก็จะไม่ยอมรับบล็อกที่มีธุรกรรมเหล่านั้นอย่างแน่นอน ผู้โจมตีทำได้เพียงพยายามเปลี่ยนแปลงธุรกรรมของตนเอง เพื่อนำเงินที่ใช้ไปแล้วกลับคืนมาเท่านั้น
การแข่งขันระหว่าง chain สุจริตกับ chain ของผู้โจมตี สามารถอธิบายได้ด้วยแบบจำลองการเดินสุ่มทวินาม (Binomial Random Walk) โดยเหตุการณ์ที่สำเร็จ หมายถึง chain ที่สุจริตถูกขยายออกไปอีกหนึ่งบล็อก เพิ่มความยาวนำหน้าไป +1 และเหตุการณ์ที่ล้มเหลว หมายถึง chain ของผู้โจมตีถูกขยายออกไปหนึ่งบล็อก ลดช่องว่างลง -1
ความน่าจะเป็นที่ผู้โจมตีจะไล่ตามทันจากช่องว่างที่กำหนด สามารถเปรียบเทียบด้วย Gambler's Ruin problem โดยสมมติว่านักพนันที่มีเครดิตไม่จำกัด เริ่มต้นด้วยการขาดทุน และเล่นพนันไปเรื่อย ๆ เพื่อให้ถึงจุดคุ้มทุน เราสามารถคำนวณความน่าจะเป็นที่เขาจะกลับมาถึงจุดคุ้มทุนได้ หรือความน่าจะเป็นที่ผู้โจมตีจะไล่ทัน chain ที่สุจริตได้ ดังนี้ [8]:
p = ความน่าจะเป็นที่ Node ที่สุจริตจะพบบล็อกถัดไป
q = ความน่าจะเป็นที่ผู้โจมตีจะพบบล็อกถัดไป
qz = ความน่าจะเป็นที่ผู้โจมตีจะไล่ทัน จากที่ตามหลังอยู่ z บล็อก
https://i.imgur.com/vePe255.png
จากสมมติฐานที่ว่า p > q ความน่าจะเป็นจะลดลงแบบเอกซ์โพเนนเชียล เมื่อจำนวนบล็อกที่ผู้โจมตีต้องไล่ตามทันเพิ่มขึ้น หากเขาไม่สามารถพุ่งขึ้นนำได้อย่างรวดเร็วตั้งแต่แรก โอกาสของเขาก็จะลดลงจนน้อยมาก ๆ เมื่อเขาตามหลังมากขึ้นเรื่อย ๆ
ทีนี้ลองพิจารณาว่า ผู้รับธุรกรรมใหม่ต้องรอเป็นเวลานานเท่าใด จึงจะแน่ใจได้ว่าผู้ส่งไม่สามารถเปลี่ยนแปลงธุรกรรมได้แล้ว เราสมมติว่าผู้ส่งเป็นผู้โจมตี ที่ต้องการให้ผู้รับเชื่อว่าเขาได้รับเงินไปแล้ว จากนั้นจึงเปลี่ยนให้เงินกลับเข้าหาตัวเองหลังจากเวลาผ่านไประยะหนึ่ง ผู้รับจะได้รับแจ้งเมื่อเกิดเหตุการณ์นี้ขึ้น แต่ผู้ส่งหวังว่ามันจะสายเกินไปแล้ว
ผู้รับจะสร้างคู่กุญแจใหม่ และให้กุญแจสาธารณะแก่ผู้ส่งไม่นานก่อนที่จะลงนาม ซึ่งจะป้องกันไม่ให้ผู้ส่งเตรียมบล็อกเชนปลอมไว้ล่วงหน้า โดยการทำงานอย่างต่อเนื่องจนกว่าเขาจะมีโอกาสได้บล็อกที่ยาวพอ จากนั้นจึงดำเนินธุรกรรมในทันที เมื่อส่งธุรกรรมแล้ว ผู้ส่งที่ไม่สุจริตจะเริ่มทำงานอย่างลับ ๆ บนบล็อกเชนคู่ขนาน ที่มีธุรกรรมในเวอร์ชันของเขาเองอยู่
ผู้รับจะรอจนกว่าธุรกรรมจะถูกเพิ่มลงในบล็อก และมีบล็อกที่ถูกเชื่อมต่อตามหลังมาอีก z บล็อก เขาไม่ทราบจำนวนความคืบหน้าที่แน่นอนที่ผู้โจมตีได้ทำไปแล้ว แต่สมมติว่าบล็อกที่สุจริตใช้เวลาเฉลี่ยต่อบล็อกตามที่คาดไว้ ความคืบหน้าที่อาจเกิดขึ้นได้ของผู้โจมตีจะเป็นการแจกแจงแบบปัวซง (Poisson distribution) ซึ่งมีค่าคาดหวังดังนี้:
https://i.imgur.com/mYsb48i.png
เพื่อให้ได้ความน่าจะเป็นที่ผู้โจมตียังคงสามารถไล่ทันได้ เราจะคูณความหนาแน่นของปัวซง สำหรับความคืบหน้าแต่ละระดับที่เขาสามารถทำได้ ด้วยความน่าจะเป็นที่เขาสามารถไล่ทันจากจุดนั้น:
https://i.imgur.com/jQGkQ8r.png
จัดเรียงใหม่เพื่อหลีกเลี่ยง infinite tail ของการแจกแจง
https://i.imgur.com/OOO6Gm9.png
แปลงมันให้เป็น C code
#include <math.h>
double AttackerSuccessProbability(double q, int z)
{
double p = 1.0 - q;
double lambda = z * (q / p);
double sum = 1.0;
int i, k;
for (k = 0; k <= z; k++)
{
double poisson = exp(-lambda);
for (i = 1; i <= k; i++)
poisson *= lambda / i;
sum -= poisson * (1 - pow(q / p, z - k));
}
return sum;
}
เมื่อรันผลลัพธ์บางส่วน เราจะเห็นว่าความน่าจะเป็นลดลงแบบเอกซ์โพเนนเชียลเมื่อ z เพิ่มขึ้น
q=0.1
z=0 P=1.0000000
z=1 P=0.2045873
z=2 P=0.0509779
z=3 P=0.0131722
z=4 P=0.0034552
z=5 P=0.0009137
z=6 P=0.0002428
z=7 P=0.0000647
z=8 P=0.0000173
z=9 P=0.0000046
z=10 P=0.0000012
q=0.3
z=0 P=1.0000000
z=5 P=0.1773523
z=10 P=0.0416605
z=15 P=0.0101008
z=20 P=0.0024804
z=25 P=0.0006132
z=30 P=0.0001522
z=35 P=0.0000379
z=40 P=0.0000095
z=45 P=0.0000024
z=50 P=0.0000006
การแก้หาค่า P ที่น้อยกว่า 0.1%...
P < 0.001
q=0.10 z=5
q=0.15 z=8
q=0.20 z=11
q=0.25 z=15
q=0.30 z=24
q=0.35 z=41
q=0.40 z=89
q=0.45 z=340
12.สรุป(Conclusion)
เราได้นำเสนอระบบธุรกรรมอิเล็กทรอนิกส์ที่ไม่ต้องพึ่งพาความไว้วางใจ เริ่มต้นจากกรอบแนวคิดของเหรียญที่สร้างจากลายเซ็นดิจิทัล ซึ่งช่วยควบคุมความเป็นเจ้าของได้อย่างดีแต่ก็ยังไม่สมบูรณ์ หากปราศจากวิธีการป้องกันการใช้จ่ายซ้ำซ้อน เพื่อแก้ปัญหานี้ เราจึงเสนอเครือข่ายแบบเพียร์ทูเพียร์ที่ใช้ proof-of-work ในการบันทึกประวัติธุรกรรมสาธารณะ ซึ่งจะกลายเป็นเรื่องยากอย่างมากสำหรับผู้โจมตีที่จะเปลี่ยนแปลง หาก node ที่ซื่อสัตย์ควบคุมพลังประมวลผล CPU ส่วนใหญ่ เครือข่ายนี้มีความแข็งแกร่งในความเรียบง่ายที่ไม่มีโครงสร้างใด ๆ ที่ซับซ้อน node ต่าง ๆ ทำงานพร้อมกันโดยประสานงานกันเพียงเล็กน้อย ไม่จำเป็นต้องระบุตัวตน เนื่องจากข้อความไม่ได้ถูกส่งไปยังสถานที่ใดสถานที่หนึ่งโดยเฉพาะ และเพียงแค่ต้องส่งมอบให้ถึงมือผู้รับอย่างดีที่สุด node สามารถออกจากและเข้าร่วมเครือข่ายได้ตามต้องการ โดยยอมรับ chain ที่มี proof-of-work มากที่สุดเป็นสิ่งที่เกิดขึ้นในขณะที่ไม่ได้เชื่อมต่อ พวกเขาโหวตด้วยพลังประมวลผล CPU แสดงการยอมรับบล็อกที่ถูกต้องโดยการทำงานเพื่อขยายบล็อก และปฏิเสธบล็อกที่ไม่ถูกต้องโดยการปฏิเสธที่จะทำงานกับบล็อกเหล่านั้น กฎและแรงจูงใจใด ๆ ที่จำเป็นสามารถบังคับใช้ได้ด้วยกลไกฉันทามตินี้
ไปอ่านต่อกันเองเด้ออ
---
[1] W. Dai, "b-money," http://www.weidai.com/bmoney.txt, 1998.
[2] H. Massias, X.S. Avila, and J.-J. Quisquater, "Design of a secure timestamping service with minimal
trust requirements," In 20th Symposium on Information Theory in the Benelux, May 1999.
[3] S. Haber, W.S. Stornetta, "How to time-stamp a digital document," In Journal of Cryptology, vol 3, no
2, pages 99-111, 1991.
[4] D. Bayer, S. Haber, W.S. Stornetta, "Improving the efficiency and reliability of digital time-stamping,"
In Sequences II: Methods in Communication, Security and Computer Science, pages 329-334, 1993.
[5] S. Haber, W.S. Stornetta, "Secure names for bit-strings," In Proceedings of the 4th ACM Conference
on Computer and Communications Security, pages 28-35, April 1997.
[6] A. Back, "Hashcash - a denial of service counter-measure,"
http://www.hashcash.org/papers/hashcash.pdf, 2002.
[7] R.C. Merkle, "Protocols for public key cryptosystems," In Proc. 1980 Symposium on Security and
Privacy, IEEE Computer Society, pages 122-133, April 1980.
[8] W. Feller, "An introduction to probability theory and its applications," 1957.
-

@ 79008e78:dfac9395
2024-09-02 06:17:05
Nostr: โปรโตคอลทางเลือกใหม่สำหรับโซเชียลมีเดียที่เป็นอิสระ ปลอดภัย และไร้การควบคุม
---
Nostr คือโปรโตคอลแบบเปิดที่เรียบง่าย ซึ่งช่วยให้สามารถสร้างโซเชียลมีเดียระดับโลกที่กระจายอำนาจและป้องกันการเซ็นเซอร์ได้
จากที่กล่าวข้างต้น เราสามารถพูดได้ว่า Nostr นั้นถูกออกแบบมาให้ใช้งานง่าย โดยมีเป้าหมายหลัก ๆ เพื่อสร้างเครือข่ายโซเชียลระดับโลกที่ปราศจากการเซ็นเซอร์ แล้วทำไมมันถึงทำอย่างนั้นได้? ในจุดนี้เราก็ต้องมาเจาะดูคุณสมบัติหลัก ๆ ของโปรโตคอลที่เรียกว่า Nostr กันก่อน:
**เรียบง่าย**
- โปรโตคอลนี้ใช้โครงสร้างข้อมูลแบบ Event Object ที่เรียบง่ายและยืดหยุ่น (ซึ่งส่งเป็น JSON ธรรมดา) และใช้การเข้ารหัสแบบ Elliptic-curve มาตรฐานสำหรับคีย์และลายเซ็น
- ช่องทางการสื่อสารที่รองรับเพียงอย่างเดียวคือการเชื่อมต่อ WebSockets จากไคลเอนต์ไปยังรีเลย์
- การออกแบบนี้ทำให้ง่ายต่อการพัฒนาไม่ว่าจะไคลเอนต์หรือรีเลย์ และยังช่วยส่งเสริมความหลากหลายของซอฟต์แวร์
**ยืดหยุ่น**
- เนื่องจาก Nostr ไม่ได้พึ่งพาเซิร์ฟเวอร์ที่เชื่อถือได้เพียงจำนวนหยิบมือ สำหรับการเคลื่อนย้ายหรือจัดเก็บข้อมูล แต่ใช้เซิร์ฟเวอร์จำนวนมหาศาลและกระจายตัวอยู่ทั่วโลก จึงมีความยืดหยุ่นสูง และมีการกระจายศูนย์อย่างแท้จริง
- โปรโตคอลนี้ถูกออกแบบมาโดยคำนึงถึงความเป็นไปได้ที่รีเลย์จะหายไป และอนุญาตให้ผู้ใช้เชื่อมต่อและเผยแพร่ข้อมูลไปยังรีเลย์จำนวนมากได้ตามต้องการ และยังสามารถเปลี่ยนแปลงได้ตลอดเวลาอีกด้วย
**ตรวจสอบได้**
- เนื่องจากบัญชี Nostr ใช้การเข้ารหัสแบบ PKE จึงง่ายต่อการตรวจสอบว่าข้อความถูกส่งมาจากผู้ใช้ที่ระบุจริงหรือไม่
เช่นเดียวกับ HTTP หรือ TCP-IP Nostr เป็นโปรโตคอลหรือมาตรฐานแบบเปิดที่ทุกคนสามารถนำไปสร้างต่อยอดได้ มันไม่ใช่แอปหรือบริการที่คุณจำเป็นต้องลงทะเบียน
แล้วทำไมเราถึงต้องการ Nostr?
---
ถึงในปัจจุบันโซเชียลมีเดียจะได้พัฒนามาเป็นช่องทางสำคัญในการไหลเวียนของข้อมูลทั่วโลก กลายเป็นช่องทางหลักในการติดต่อสื่อสาร แต่น่าเสียดายที่ระบบโซเชียลมีเดียในปัจจุบันของเรานั้นมีข้อบกพร่องมากมาย:
1. ใช้ความสนใจของคุณเพื่อขายโฆษณา
2. ใช้เทคนิคแปลกๆ เพื่อทำให้คุณเสพติด (อ้างอิงจากข้อ 1)
3. ตัดสินใจว่าจะแสดงเนื้อหาใดให้คุณเห็นโดยใช้อัลกอริทึมลับที่คุณไม่สามารถตรวจสอบหรือเปลี่ยนแปลงได้
4. ควบคุมอย่างเต็มที่ว่าใครสามารถเข้าร่วมและใครถูกเซ็นเซอร์
5. เต็มไปด้วยสแปมและบอท
ด้วยข้อจำกัดเหล่านี้ Nostr จึงเป็นทางเลือกที่น่าสนใจในการสร้างโซเชียลมีเดียที่เป็นอิสระ ปลอดภัย และไร้การควบคุม
องค์ประกอบของโปรโตคอลที่ชื่อว่า Nostr
---
หลังจากได้ทำความรู้จัก Nostr กันไปแล้วเมื่อคราวก่อน คราวนี้เรามาเจาะดูองค์ประกอบของโปรโตคอลนี้กันดีกว่า
**Keys ระบบบัญชีผู้ใช้และรหัสผ่านสำหรับ Nostr**
- บัญชี Nostr แต่ละบัญชีจะใช้คู่กุญแจสาธารณะ/ส่วนตัว (Public/Private Key ) เปรียบเทียบง่าย ๆ คือ กุญแจสาธารณะของคุณคือชื่อผู้ใช้ และกุญแจส่วนตัวก็เป็นรหัสผ่าน แต่ว่า ก็มีข้อแตกต่างที่สำคัญอยู่ นั่นคือ กุญแจส่วนตัวของคุณนั้นจะไม่สามารถรีเซ็ตได้หากเกิดการสูญหายขึ้น คุณจะเสียบัญชีนั้นไปตลอดกาล
- โดยทั่วไปแล้ว กุญแจสาธารณะจะแสดงเป็นข้อความที่ขึ้นต้นด้วย npub1 และกุญแจส่วนตัวจะขึ้นต้นด้วย nsec1
- ทั้งนี้คุณควรที่จะตรวจสอบให้แน่ใจว่าคุณได้เก็บกุญแจส่วนตัวของคุณไว้ในที่ปลอดภัย เช่น โปรแกรมจัดการรหัสผ่านอย่างเช่น Bitwarden
**โปรโตคอลกับไคลเอนต์ ต่างกันอย่างไร?**
Nostr เองเป็นเพียงโปรโตคอล หมายความว่า Nostr นั้นเป็นเพียงกระบวนการที่ตกลงกันไว้สำหรับการส่งข้อความผ่านอินเทอร์เน็ต (เหมือนข้อกำหนด)
ซึ่งการที่คุณจะเข้าถึง Nostr (โปรโตคอล) นั้น ผู้ใช้ส่วนใหญ่จะใช้งานผ่านไคลเอนต์ ซึ่งตัวของไคลเอนต์นั้นอาจเป็นเว็บ แอปพลิเคชันเดสก์ท็อป หรือ แอปพลิเคชันมือถือ โดยไคลเอนต์สามารถดึงข้อมูลจากรีเลย์ และสร้างข้อมูลใหม่ และส่งข้อมูลนั้นไปยังรีเลย์เพื่อให้ผู้ใช้คนอื่น ๆ สามารถเรียกอ่าน ข้อมูลนั้น ๆ ได้ โดย "ข้อมูล" เพียงรูปแบบเดียวที่มีอยู่ใน Nostr คือสิ่งที่เราเรียกกันว่า event
**การพิสูจน์ความเป็นเจ้าของข้อมูลบน Nostr**
บน Nostr นั้นการพิสูจน์ตัวตนเป็นเรื่องที่ง่ายมากเนื่องจากทุก ๆ event ที่เกิดขึ้น **จำเป็น**ต้องมีลายเซ็นดิจิทัล (Digital Signature) โดยลายเซ็นนั้นจะช่วยให้มั่นใจได้ว่า ใครเป็นผู้สร้าง event นั้น ๆ ขึ้นมา โดยการพิสูจน์ทางคณิตศาสตร์
โดยในการสร้างลายเซ็นแต่ละครั้ง ไคลเอนต์จะจำเป็นต้องใช้กุญแจส่วนตัวของคุณ โดยทั่วไปแล้ว แอปพลิเคชันเจะมีที่ให้คุณใส่กุญแจส่วนตัวของคุณ เมื่อเปิดแอปพลิเคชันครั้งแรก พวกเขาสามารถคำนวณกุญแจสาธารณะของคุณได้จากกุญแจส่วนตัวเช่นกัน
ส่วนในกรณีที่คุณใช้งานผ่านเว็บแอป ผมไม่แนะนำให้ใส่กุญแจส่วนตัวลงไป แต่แนะนำให้ใช้ส่วนขยายของเบราว์เซอร์ ที่ใช้งานฟังก์ชันที่เกี่ยวข้องกับ Nostr ซึ่งอนุญาตให้เว็บไคลเอ็นต์ส่ง event ที่ยังไม่ถูกเซ็นมาให้ส่วนขยายและส่วนขยายจะทำหน้าที่เซ็น สำหรับวิธีนี้ เว็บไคลเอ็นต์ต่าง ๆ ไม่จำเป็นต้องรู้กุญแจส่วนตัวของคุณ แต่คุณก็ยังสามารถลงนามใน event ต่าง ๆ ได้ตามปกติ โดยส่วนขยายที่ได้รับความนิยมก็จะเป็น **Flamingo**, **Alby** และ **nos2x**
ไคลเอนต์ & รีเลย์
-----------
**ไคลเอนต์คืออะไร?**
หากจะอธิบายให้เห็นภาพอยากให้มองว่าไคลเอ็นต์ Nostr นั้นเป็นเหมือนกับแอปที่คุณใช้งานเพื่อเข้าถึง Twitter, Facebook, youtube เป็นต้น พวกมันคือ แอปพลิเคชัน, เว็บแอป ที่เชื่อมต่อคุณกับโลกของ Twitter, Facebook, youtube โดยตัวของไคลเอนต์ใน Nostr เองก็เปรียบเสมือนแอปต่าง ๆ ที่คุณใช้ดูหน้าฟีดนั่นเอง แต่ข้อดีของ Nostr ที่เหนือแอปพลิเคชันอื่น ๆ คือความเรียบง่ายและยืดหยุ่น ส่งผลให้ไคลเอ็นต์แต่ละตัวมีวิธีนำเสนอและใช้งานที่แตกต่างกันไป บางไคลเอ็นต์อาจออกแบบให้ใช้งานง่ายเหมือน Twitter บางตัวเน้นให้เห็นบทบาทสำคัญของรีเลย์ หรือโหนดที่กระจายข้อมูลอยู่ทั่วโลก บางตัวใช้ระบบอัลกอริทึมเพื่อให้แน่ใจว่าข้อมูลไม่ถูกปิดกั้น โดยไม่ทำให้ผู้ใช้งานรู้สึกยุ่งยาก
**เรียบง่ายและยืดหยุ่น?**
เนื่องจากการออกแบบของโปรโตคอลที่ทำการแยกข้อมูลของผู้ใช้ทั้งหมดออกจากไคลเอนต์ ทำให้ตัวของผู้ใช้งานเองนั้นมีอิสระเต็มที่ที่จะเลือกใช้ไคลเอนต์ต่าง ๆ เพื่อเข้าใช้งาน Nostr และแน่นอนว่า ผู้ใช้งานสามารถสลับหรือลงชื่อเข้าใช้ ไคลเอ็นต์ได้หลายตัวตามต้องการ ตราบใดที่ไคลเอ็นต์ทั้งหมดเชื่อมต่อกับชุดรีเลย์เดียวกัน คุณก็จะเห็นข้อมูลเดียวกันในทุก ๆ ไคลเอ็นต์
**ลงชื่อเข้าใช้ ไคลเอ็นต์หลาย ๆ ตัวแล้วจะกระทบต่อความปลอดภัยของแอคเคาร์ไหม?**
คำตอบของคำถามนี้นั้นขึ้นอยู่กับวิธีการที่คุณลงชื่อเข้าใช้ หากคุณลงชื่อเข้าใช้ด้วยกุญแจส่วนตัว ถึงแม้ว่าไคลเอ็นต์ส่วนใหญ่จะพยายามรักษาความปลอดภัยของกุญแจส่วนตัวอย่างดีที่สุด แต่ด้วยข้อจำกัดของซอฟต์แวร์ ย่อมมีความเสี่ยงที่จะเกิดช่องโหว่ การเจาะระบบ และข้อผิดพลาด ที่อาจทำให้กุญแจส่วนตัวของคุณรั่วไหลออกไปได้ ส่วนวิธีการป้องกันเกี่ยวกับเรื่องนี้คือการใช้ส่วนขยายของเว็บเบราว์เซอร์ เพราะการเข้าสู่ระบบในไคลเอนต์ต่าง ๆ ผ่านส่วนขยายนั้นจะใช้เพียงกุญแจสาธารณะในการเข้าสู่ระบบและทุกครั้งที่เราต้องการจะโพสต์หรือสร้าง event บน Nostr ไคลเอนต์จะทำการร่าง event นั้น ๆ และเว้นช่องของลายเซ็นเอาไว้จากนั้นเราจะต้องทำการเซ็นผ่านส่วนขยาย ด้วยวิธีนี้ทำให้กุญแจส่วนตัวของเราไม่หลุดออกไปไหนตลอดการใช้งาน
**รีเลย์คืออะไร?**
รีเลย์เปรียบเสมือนเซิร์ฟเวอร์ที่อยู่เบื้องหลังของ Nostr และทำหน้าที่รับ event ต่าง ๆ มาจากไคลเอนต์ Nostr และอาจจะจัดเก็บและกระจายข้อความเหล่านั้นไปยังไคลเอนต์อื่น ๆ ที่มีการเชื่อมต่ออยู่
เทคโนโลยีของรีเลย์นั้นเปลี่ยนแปลงอย่างรวดเร็ว ดังนั้นคาดว่าจะมีการเปลี่ยนแปลงอีกมากมายในอนาคต อย่างในปัจจุบันที่มีการนำเสนอ bostr หรือ รีเลย์ที่จะคอยส่ง event ของเราต่อให้กับรีเลย์อื่น ๆ ที่มีการเชื่อมต่อ เพื่อช่วยลดภาระของไคลเอนต์ในการรับส่งข้อมูลจากหลาย ๆ รีเลย์พร้อม ๆ กัน หรืออย่างการป้องกันสแปมด้วย POW หรือประเภทที่สามารถเก็บรูปหรือวิดีโอที่มีขนาดใหญ่ได้
แต่สิ่งหนึ่งที่ควรทราบก็คือ การที่ Nostr นั้นพยายามจะกระจายศูนย์และเหตุผลหลัก ๆ ที่สามารถทำแบบนั้นได้ก็ขึ้นอยู่กับรีเลย์ในการจัดเก็บและดึงข้อมูล ดังนั้น หากคุณรู้สึกว่าไคลเอนต์ Nostr ของคุณทำงานช้า ส่วนใหญ่ก็มักเกิดจากรีเลย์ที่คุณกำลังเชื่อมต่ออยู่ คุณอาจลองแก้ไขปัญญาโดยการเปลี่ยนหรือเพิ่มรีเลย์อีกสองสามรายการในไคลเอนต์ที่คุณใช้
**แล้วจะสามารถหารายการรีเลย์ได้จากไหน?**
การที่เราจะหารายการรีเลย์ที่เราควรเชื่อมต่อนั้น ๆ จริงแล้ว ๆ สามารถทำได้หลายวิธี แต่วิธีที่ผมแนะนำที่สุดจะเป็นการใช้ตามคนที่เราติดตามอยู่ เพราะจะเป็นวิธีที่เราสามารถเห็น event ต่าง ๆ ของคนที่เราติดตามได้ง่ายที่สุด และเช่นเดียวกัน เพื่อน ๆ หรือคนที่เราติดตามก็จะสามารถเห็น event ของเราได้เช่นกัน และสำหรับในประเทศไทย เรามีรีเลย์ที่คนไทยส่วนใหญ่นิยมใช้กันอยู่สองอัน นั้นคือ wss://relay.siamstr.com/ และ wss://relay.notoshi.win/ ถ้าหากว่าอยากเห็นคนไทยเยอะ ๆ บนหน้าไทม์ไลน์ ผมแนะนำเป็นอย่างยิ่งว่าควรเพิ่ม รายการรีเลย์เหล่านี้ลงไปในบัชญีหรือไคลเอนต์ต่าง ๆ ที่คุณใช้ด้วย
สำหรับอีกวิธีหนึ่งผมแนะนำให้เข้าไปในเว็บไซต์ nostr.watch เนื่องจากในเว็บไซต์นี้เป็นแหล่งข้อมูลที่ดีที่สุดสำหรับการค้นหาและประเมินความเร็วของรีเลย์ต่าง ๆ
**จะเกิดอะไรขึ้นถ้ารีเลย์ทั้งหมดที่ฉันเชื่อมต่ออยู่หยุดให้บริการ?**
สิ่งนี้เป็นสิ่งที่คุณต้องระวังมากที่สุดในการใช้งาน nostr เนื่องจากหากรีเลย์ทั้งหมดที่คุณเก็บข้อมูลไว้หยุดให้บริการทั้งหมดและคุณไม่มีการสำรองข้อมูล event ของคุณเก็บไว้เลย มันแปลว่าโพสต์ทั้งหมดของคุณ ผู้ติดตาม และรายการต่าง ๆ ที่คุณสรรค์สร้างไว้จะไม่สามารถกู้คืนได้ไปตลอดการ นี่จึงเป็นเหตุผลหลัก ๆ ที่ Nostr อนุญาตให้ผู้ใช้งานนั้นสามารถเชื่อมต่อกับรีเลย์ได้เป็นจำนวนมาก ก็เพื่อให้แน่ใจว่ามีข้อมูลสำรองเก็บไว้อยู่ที่ใดที่หนึ่งในระบบเสมอ แต่อย่างไรก็ตาม หากคุณต้องการที่จะมั่นใจได้ว่าข้อมูลต่าง ๆ ของคุณจะไม่ถูกเซ็นเซอร์ สิ่งที่คุณสามารถสามารถทำได้คือการใช้รีเลย์ส่วนตัวของคุณและกำหนดนโยบายต่าง ๆ ภายในรีเลย์ของคุณด้วยตัวคุณเอง
**แล้วฉันจะสามารถใช้รีเลย์ส่วนตัวได้อย่างไร?**
**อะแฮ่ม ๆ** ขอบอกไว้ก่อนว่ามันไม่คุ้มค่ากับความยุ่งยากสำหรับคนโดยทั่ว ๆ ไป ถึงในปัจจุบันจะมีเทคโนโลยีบางตัวที่เข้ามาช่วยให้มันทำได้ง่ายขึ้นแล้วก็ตาม
หากคุณต้องการที่จะสำรองข้อมูลนั้น การที่จะมีรีเลย์ส่วนตัวที่ออนไลน์ตลอดเวลาอาจเป็นเรื่องที่ไม่ได้จำเป็นขนาดนั้น เนื่องจากเราสามารถใช้งานบริการอย่าง https://nostrsync.live/ ในการดาวน์โหลดข้อมูลของเราจากรีเลย์ต่าง ๆ ได้ หรือการติดตั้งรีเลย์ส่วนตัวอย่าง nostr-relay-tray: https://github.com/CodyTseng/nostr-relay-tray ที่ช่วยให้เราสามารถมีรีเลย์ส่วนตัวที่ใช้สำหรับสำรองข้อมูลได้
Nostr Implementation Possibilities (NIPs)
NIP คืออะไร?
---
NIP มีไว้เพื่อส่งเสริมความสามารถในการทำงานของ Nostr และเป็นตัวคอยกำหนดให้ เหล่านักพัฒนาทำสิ่งต่าง ๆ ที่เหมือนกันในรูปแบบเดียวกัน เพราะมันคงไม่ใช่ความคิดที่ดีนัก หากนักพัฒนาแต่ละคนจะคิดค้นวิธีแก้ปัญหาทั่วไปของตัวเองและนำไปใช้ในแอปของตัวเองเท่านั้น และคงจะเป็นการดีกว่า ถ้าหากทุกคนใช้วิธีแก้ปัญหาที่เหมือนกัน นั่นคือเหตุผลที่ต้องมี NIP อยู่ในโปรโตคอลของ Nostr และในทำนองเดียวกัน แนวคิดใหม่อาจดูดีในแอปของนักพัฒนาบางราย แต่จะดูดียิ่งขึ้นอย่างแน่นอนหากแอปอื่น ๆ อีกมากมายใช้มาตรฐานเดียวกันและสามารถทำงานร่วมกันได้อย่างราบรื่น
**ทำไมมันถึงหน้าสนใจ?**
อย่าลืมว่า Nostr เป็นระบบแบบกระจายอำนาจและไม่ได้มีบริษัทหรือใครที่เป็นเจ้าของมัน อย่างเช่นโซเชียลมีเดียอื่น ๆ เช่น ทวิตเตอร์ อ่อไม่สิตอนนี้คงต้องเรียกมันว่า X สินะ ซึ่งหมายความว่าทิศทางของโพรโทคอล Nostr นั้นขึ้นอยู่กับพวกเราทุกคน! ไม่ว่าใคร ๆ ก็สามารถเสนอแนะและสนับสนุนการเปลี่ยนแปลงและให้ข้อเสนอแนะเกี่ยวกับแนวคิดที่ผู้อื่นเสนอ และการที่คุณเป็นส่วนหนึ่งของชุมชนนี้ ก็ทำให้คุณมีส่วนร่วมในทิศทางของ Nostr อีกด้วย
จากที่ส่งหากันได้แค่ข้อความ มาเป็นรูปภาพ มาเป็นวิดีโอ และมาเป็น”เงิน” นี่คือเส้นทางการเดินทางของโปรโตคอลนี้ในอดีต แล้วในอนาคตมันจะพัฒนาไปยังไงต่อก็ขึ้นอยู่กับเหล่าผู้ใช้งานและนักพัฒนาในอนาคต แล้วทำไมสิ่งนี้ถึงจะไม่น่าสนใจละ ?
Event
---
**Event คืออะไร?**
Event เป็น object เพียงประเภทเดียวที่มีอยู่บน Nostr โดยมีโครงสร้างประมาณนี้
```
{"id":"84d5d3dc9c388a702f39cad6360d41ebb804e809fb822f110ff8a14dfd35fc6c",
"pubkey":"66df60562d939ada8612436489945a4ecf1d62346b3d9478dea8a338f3203c64",
"created_at":1722315959,
"kind":1,
"tags":[["t","siamstr"]],
"content":"ไปสั่งกาแฟเมื่อกี้ พส เจ้าของร้านชมว่าเดี๋ยวนี้คล่องภาษาญี่ปุ่นแล้วนะ ไอเราก็ดีใจ พอเดินกลับถึงที่ทำงานละก็ตระหนักได้ว่า ตะกี้เราสั่ง “ไอซ์โคฮี โอเนไงชิมัส” “เทคเอาส์” “คาโดะเดสส” ไอบ้าไหนญี่ปุ่นก่อนอังกฤษทั้งนั้น 🤣🤣\n\n#siamstr",
"sig":"8f066a0099a5f580b605ebdb220179c4eca298947c38b855a0a8bf2783f28ddb537cb74a7f61d3ce8891189f719870efdf320ea4f895e03cdac44284c450c5c4"}
```
อย่าง Event ข้างต้นนี้มี kind เป็น 1 ซึ่งหมายถึง "ข้อความโน้ต" ซึ่งก็คือข้อความธรรมดา สั้น ๆ คล้ายกับที่ใช้กันใน Twitter เช่น บนฟีด การตอบกลับ และการโควท
**ประเภทของ Event (Event Kinds)**
หมายเลขของ kind แต่ละตัวมีความหมายแตกต่างกัน ตัวอย่างเช่น 0 หมายถึงอีเวนต์ "ข้อมูลเมตา" ใช้สำหรับให้รายละเอียดเกี่ยวกับผู้ใช้ เช่น ชื่อและรูปโปรไฟล์ รีเลย์ (Relays) สามารถจัดการกับ kind ที่แตกต่างกันได้ เช่น รีเลย์มักจะลบอีเวนต์ kind:0 เวอร์ชันเก่ากว่าออกไป และเก็บไว้เฉพาะเวอร์ชันล่าสุด ในขณะที่โดยทั่วไปจะเก็บอีเวนต์ kind:1 ไว้หลายรายการสำหรับแต่ละคีย์
โดยทั่วไปแล้ว คุณไม่จำเป็นต้องใช้ kind เกินกว่า 0 และ 1 ในการสร้างแอปพลิเคชันโซเชียลมีเดียบน Nostr แต่ kind อื่น ๆ ถูกคิดค้นขึ้นโดยไคลเอนต์ เพื่อมอบฟังก์ชันการทำงานอื่น ๆ ตามที่ระบุไว้ใน NIP บาง kind ไม่เกี่ยวข้องกับเครือข่าย และให้บริการตามความต้องการอื่น ๆ ของไคลเอนต์ที่เฉพาะเจาะจงกับฟังก์ชันการทำงานเหล่านั้น ซึ่งแนวคิดก็คือ สำหรับกรณีการใช้งานใหม่ ๆ แต่ละกรณี จะต้องมีการพิจารณาและเสนอซับโปรโตคอลเป็น NIP เพื่อให้สามารถทำงานร่วมกับไคลเอนต์ที่มีอยู่และในอนาคต ซึ่งอาจสนใจที่จะนำฟังก์ชันการทำงานนั้นไปใช้ ขณะเดียวกันก็มั่นใจได้ถึงความเข้ากันได้ย้อนหลัง และการรองรับสิ่งต่าง ๆ ที่มีอยู่และไม่ต้องการเปลี่ยนแปลง
**คุณสมบัติอื่น ๆ ของ Event**
created_at: เป็น Timestamp ของ UNIX ที่กำหนดโดยผู้สร้างอีเวนต์ โดยปกติจะเป็นเวลาที่สร้าง แม้ว่าจะไม่มีการตรวจสอบ แต่ก็ไม่ใช่ปัญหา
content: ขึ้นอยู่กับความหมายของ kind ในกรณีของ kind:1 จะเป็นเพียงสตริงข้อความธรรมดาที่คนอื่น ๆ อ่านได้
tags: ขึ้นอยู่กับ kind เช่นกัน แต่แท็กทั่วไปบางอย่างที่มักปรากฏใน event kind:1 และ kind อื่น ๆ คือ "p" ซึ่งใช้เพื่อกล่าวถึงกุญแจสาธารณะ และ "e" ใช้เพื่ออ้างถึง event อื่น
อยากมีส่วนร่วมในการพัฒนาของ Nostr ?
---
จริง ๆ แล้วใคร ๆ ก็สามารถเข้ามามีส่วนร่วมในการพัฒนา Nostr ได้ ไม่จำเป็นต้องเป็น dev หรือมีความรู้ด้านคอมพิวเตอร์ก็สามารถทำได้ ไม่ว่าจะเป็นการให้ feedback กับ dev ของ client ที่คุณใช้, การสร้างคอนเทนต์ต่าง ๆ บน Nostr การสร้างชุมชน รวมไปถึงการช่วย client ต่าง ๆ ในการทำ UI ให้เป็นภาษาท้องถิ่น และอื่น ๆ อีกมากมาย ใคร ๆ ก็สามารถช่วยได้ตามความสามารถที่แต่ละคนมี มันเลยทำให้ Nostr โครตน่าอยู่ :)
-

@ d830ee7b:4e61cd62
2024-09-02 06:06:36
บิตคอยน์ไม่ใช่แค่เงินดิจิทัล มันคือสมรภูมิแห่งความคิด การต่อสู้ระหว่างอุดมการณ์และเกมเศรษฐศาสตร์ที่ทุกคนมีสิทธิ์เข้าร่วม
เรื่องราวของบิตคอยน์เริ่มต้นขึ้นในปี 2008 เมื่อ Satoshi Nakamoto บุคคลลึกลับปล่อย "Bitcoin: A Peer-to-Peer Electronic Cash System" เอกสารนี้ไม่ได้แค่เสนอระบบการเงินแบบใหม่ แต่ยังเป็นการท้าทายระบบเดิมที่ควบคุมโดยธนาคารและรัฐบาล
ลองนึกภาพกลุ่มเพื่อนที่อยากเจอกัน แต่ไม่รู้จะไปร้านไหนดี นี่แหละคือปัญหา "Consensus" หรือ ภาวะเห็นพ้องต้องกัน บิตคอยน์แก้ปัญหานี้ด้วย "Blockchain" เหมือนสมุดบัญชีสาธารณะที่บันทึกทุกธุรกรรม ใครๆ ก็เข้าถึงได้ แต่การแก้ไขต้องใช้ "Proof of Work" หรือ การแก้โจทย์ยากๆ ที่ต้องใช้พลังงานมหาศาล
เปรียบเหมือนการขุดหาเพชร ใครขุดเจอคนแรกก็ได้รางวัลไป บิตคอยน์ก็ใช้หลักการคล้ายๆ กัน ใครมีพลังประมวลผลมากก็มีโอกาสปิดบล็อกได้ก่อน
แต่เหรียญก็มักจะมีสองด้านเสมอ.. ระบบนี้เปิดโอกาสให้เกิด **"Strategic Mining" หรือ การใช้กลยุทธ์ต่างๆ เพื่อโกยผลประโยชน์** มันเหมือนเกมเศรษฐศาสตร์ที่ทุกคนต่างแข่งขันกัน ใครมีกลยุทธ์ดีกว่าก็ได้เปรียบ
แล้วอะไรล่ะที่ป้องกันไม่ให้บิคอยน์ถูกควบคุม?
หนึ่งในแนวคิดคือ "Market Fragility Hypothesis" ที่เชื่อว่าหากเกิดการควบคุมระบบบิตคอยน์ ราคาของบิตคอยน์จะร่วงลงอย่างรุนแรง ทำให้ผู้ที่พยายามจะควบคุมก็ต้องเสียหายไปด้วย
อีกแนวคิดคือ "Repeated Games and Institutional Norms" ที่มองว่าการทำตัวดีเป็นผลดีต่อทุกคนในระยะยาว ใครทำตัวไม่ดีก็อาจถูกลงโทษ เช่น การไม่ยอมรับธุรกรรมที่น่าสงสัย
แต่การลงโทษก็มีปัญหา เพราะต้องอาศัยความร่วมมือจากผู้เล่นส่วนใหญ่ ซึ่งในโลกแห่งบิตคอยน์ที่ไร้ศูนย์กลาง การประสานงานจริงๆ นั้นทำได้ยาก
บิตคอยน์ยังเผชิญความท้าทายอีกมากมาย เช่น การลดลงของรางวัลขุด (Block Subsidy) ที่อาจกระทบต่อความปลอดภัย หรือการต่อสู้กับการเซ็นเซอร์ธุรกรรม (Censorship Attack)
อนาคตของบิตคอยฯ์จะเป็นอย่างไร?
บางคนเชื่อว่าบิตคอยน์จะกลายเป็นสกุลเงินหลักของโลก (Hyperbitcoinization) แต่บางคนก็มองว่าความผันผวนของราคาและความเสี่ยงจากการถูกเข้าควบคุมจะเป็นอุปสรรคที่สำคัญ
ไม่ว่าอนาคตจะเป็นเช่นไร.. บิตคอยน์ได้จุดประกายการปฏิวัติทางเศรษฐกิจครั้งใหญ่ ใครๆ ก็สามารถเข้าร่วมเกมนี้ได้ แต่การจะชนะต้องอาศัยความเข้าใจในกฎกติกาและกลยุทธ์ที่เหนือชั้น
บทความนี้จึงได้เรียบเรียงเนื้อหาที่น่าสนใจมาจากใน **หนังสือ "Bitcoin: A Game-Theoretic Analysis"** ซึ่งเล่าเรื่องราวของบิตคอยน์ผ่านมุมมองของทฤษฎีเกมมาแบ่งปัน ซึ่งจะช่วยให้ผู้อ่านเข้าใจกลไกและความท้าทายของบิตคอยน์อย่างครอบคลุม อ่านสนุก และน่าติดตามมากขึ้น
# Dominant Strategy ไพ่ตายที่ (แทบ) ไม่มีอยู่จริงในสมรภูมิบิตคอยน์
ในโลกของเกมและเศรษฐศาสตร์ **“Dominant Strategy” คือกลยุทธ์มหัศจรรย์ที่ทำให้ผู้เล่นได้เปรียบ** ไม่ว่าคู่แข่งจะงัดไม้ไหนมาสู้ก็ตาม
ยกตัวอย่าง "Prisoner's Dilemma" เกมคลาสสิคที่ผู้ต้องหาสองคนต้องเลือกว่าจะร่วมมือ (ไม่ซัดทอดเพื่อน) หรือหักหลัง (ซัดทอดเพื่อน)
ถ้าทั้งคู่ร่วมมือจะได้รับโทษเบาๆ ด้วยกัน
แต่ถ้าคนหนึ่งหักหลัง อีกคนร่วมมือ คนหักหลังจะได้รางวัล คนร่วมมือจะโดนโทษหนัก
และถ้าทั้งคู่หักหลัง จะโดนโทษหนักด้วยกันทั้งคู่
จะเห็นว่าการหักหลัง คือ Dominant Strategy เพราะไม่ว่าเพื่อนจะเลือกอะไร การหักหลังจะทำให้เราได้ผลลัพธ์ดีกว่าเสมอ (ไม่โดนโทษหนัก หรือได้รางวัล)
แต่ในสมรภูมิ Bitcoin กลยุทธ์แบบไพ่ตายแทบไม่มีอยู่จริง เพราะการกระทำของนักขุดแต่ละคนล้วนส่งผลกระทบต่อคนอื่นๆ เสมอ
ลองนึกภาพนักขุดจอมเจ้าเล่ห์ที่พยายามโกงระบบ เช่น
- **Selfish Mining:** แอบขุดบล็อกไว้คนเดียว หวังจะฮุบรางวัลบล็อกทั้งหมด
- **Block Withholding:** กั๊กบล็อกที่ขุดได้ บีบให้คนอื่นจ่ายค่าธรรมเนียมแพงๆ
- **Censorship Attack:** ควบคุมเครือข่ายเพื่อบล็อกธุรกรรมบางอย่าง
กลยุทธ์เหล่านี้อาจดูเหมือนไพ่ตายในแวบแรก แต่ความจริงแล้วมันขึ้นอยู่กับปฏิกิริยาของนักขุดคนอื่นๆ ด้วย เพราะถ้าคนอื่นๆ รู้ทันแผนการร้าย และเลือกที่จะลงโทษนักขุดจอมเจ้าเล่ห์ เช่น ไม่ยอมรับบล็อกที่ขุดได้ หรือหันไปใช้บริการแพลตฟอร์มอื่น นักขุดจอมเจ้าเล่ห์ก็จะขาดทุน
ยิ่งไปกว่านั้น.. กลยุทธ์เหล่านี้มักจะทำลายความเชื่อมั่นในบิตคอยน์ (Market Fragility Hypothesis) ทำให้ราคาบิตคอยน์ร่วงลง นักขุดจอมเจ้าเล่ห์ก็จะเสียหายตามไปด้วย
ดังนั้น.. ในบิตคอยน์จึงไม่มีกลยุทธ์ใดที่รับประกันความสำเร็จ 100% ทุกการกระทำล้วนมีความเสี่ยง และขึ้นอยู่กับการตัดสินใจของนักขุดคนอื่นๆ
นี่คือเสน่ห์ของบิตคอยน์ที่ทำให้มันเป็นระบบที่มีพลวัต ซับซ้อน และท้าทาย ไม่มีใครสามารถควบคุมเกมได้อย่างสมบูรณ์ และทุกคนต้องเล่นอย่างชาญฉลาดเพื่อให้ได้ผลลัพธ์ที่ดีที่สุด..
# Nash Equilibrium สมดุลอันเปราะบางบนเส้นด้ายแห่งความไว้วางใจใน Bitcoin
**"Nash Equilibrium"** เป็นแนวคิดสำคัญในทฤษฎีเกม อธิบายภาวะสมดุลที่เกิดขึ้นเมื่อผู้เล่นแต่ละคนเลือกกลยุทธ์ที่ดีที่สุดสำหรับตัวเอง โดยพิจารณาจากกลยุทธ์ของผู้เล่นคนอื่นๆ ณ จุดสมดุลนี้ ไม่มีใครอยากเปลี่ยนกลยุทธ์ เพราะรู้ว่าการเปลี่ยนจะทำให้ตัวเองเสียเปรียบ
ยกตัวอย่างเกม **"Splitting $4"** ที่ผู้เล่นสองคนต้องเขียนตัวเลข ($1, $2, $3) หากผลรวมไม่เกิน $4 ทั้งคู่จะได้รับเงินตามที่เขียน แต่ถ้าเกิน $4 ทั้งคู่จะไม่ได้อะไรเลย
Nash Equilibrium ของเกมนี้คือการที่ทั้งคู่เขียน $2 เพราะไม่ว่าใครจะเปลี่ยนตัวเลข คนที่ไม่เปลี่ยนจะได้เปรียบกว่าเสมอ
ถ้าคนหนึ่งเขียน $3 อีกคนเขียน $2 คนเขียน $2 จะได้ $2 ส่วนคนเขียน $3 จะไม่ได้อะไรเลย
ถ้าคนหนึ่งเขียน $1 อีกคนเขียน $2 คนเขียน $2 จะได้ $2 ส่วนคนเขียน $1 จะได้แค่ $1
ในบิตคอยน์ก็มี Nash Equilibrium เช่นเดียวกัน หนึ่งในนั้นคือการที่นักขุดส่วนใหญ่เลือก "Default Compliant" หรือ การทำตามกฎกติกาของบิตคอยน์อย่างเคร่งครัด
ทำไมถึงเป็นเช่นนั้น?
ลองนึกภาพนักขุดจอมโลภที่คิดจะแหกกฎเพื่อหาผลประโยชน์ใส่ตัว เช่น
- Selfish Mining: แอบขุดบล็อกไว้คนเดียว
- Block Withholding: กั๊กบล็อกที่ขุดได้
- Censorship Attack: บล็อกธุรกรรมบางอย่าง
ถ้ามีนักขุดทำแบบนี้แค่คนเดียว ในขณะที่คนอื่นๆ ยังคงทำตามกฎ นักขุดคนนั้นอาจจะได้เปรียบในระยะสั้น
แต่ในระยะยาว การกระทำแบบนี้จะ..
- **ทำลายความเชื่อมั่นในบิตคอยน์** (Market Fragility Hypothesis) ทำให้ราคาบิตคอยน์ร่วงลง
- **ถูกนักขุดคนอื่นๆ ลงโทษ** เช่น ไม่ยอมรับบล็อกที่ขุดได้ หรือ รวมหัวกันแบนนักขุดจอมโลภ
สุดท้าย.. นักขุดจอมโลภก็จะขาดทุนและสูญเสียโอกาสในการได้รับรางวัลบล็อกในอนาคต
ดังนั้น.. การทำตามกฎจึงเป็นกลยุทธ์ที่ปลอดภัยและยั่งยืนกว่าสำหรับนักขุดส่วนใหญ่
อย่างไรก็ตาม Nash Equilibrium ในบิตคอยน์ไม่ได้หมายความว่าระบบจะมั่นคง 100%
- **แรงจูงใจในการแหกกฎอาจเพิ่มขึ้นได้** เช่น เมื่อรางวัลบล็อก (Block Subsidy) ลดลงและค่าธรรมเนียม (Transaction Fee) ไม่สูงพอ นักขุดอาจมองว่าการโกงคุ้มค่ากับความเสี่ยงมากขึ้น
- **การประสานงานเพื่อลงโทษผู้ทำผิดอาจทำได้ยาก** บิตคอยน์ไม่มีศูนย์กลางควบคุม การตัดสินใจใดๆ ต้องอาศัยความเห็นพ้องของนักขุดส่วนใหญ่ ซึ่งอาจทำได้ยากและใช้เวลานาน
Nash Equilibrium ในบิตคอยน์จึงเป็นสมดุลที่เปราะบางที่สามารถถูกทำลายได้ หากแรงจูงใจและสภาพแวดล้อมเปลี่ยนไป..
นี่คือความท้าทายที่ชุมชนบิตคอยน์ต้องเผชิญในการรักษาสมดุลระหว่าง **"ผลประโยชน์ส่วนตัว"** ของนักขุด กับ **"ความมั่นคงของระบบ"** โดยรวม
# Censorship Attack สมรภูมิปิดล้อมบิตคอยน์กับอาวุธลับ Soft Fork
บิตคอยน์นั้นถูกออกแบบมาให้เป็นระบบการเงินแบบไร้ศูนย์กลาง ปราศจากการควบคุมของรัฐบาลหรือองค์กรใดๆ แต่ในโลกแห่งความเป็นจริง อำนาจและการควบคุมยังคงเป็นสิ่งที่หลายฝ่ายปรารถนา และ **"Censorship Attack"** คือหนึ่งในภัยคุกคามที่บิตคอยน์ต้องเผชิญ
Censorship Attack คือ **ความพยายามในการปิดล้อม Bitcoin เพื่อบล็อกธุรกรรมบางอย่าง** เปรียบเสมือนการที่รัฐบาลเผด็จการพยายามปิดกั้นข้อมูลข่าวสาร หรือบริษัทผูกขาดพยายามกำจัดคู่แข่ง
ใครบ้างที่อาจอยู่เบื้องหลัง Censorship Attack?
- **รัฐบาล:** อาจต้องการควบคุมการไหลเวียนของ Bitcoin เพื่อรักษาอำนาจทางการเงิน หรือ ป้องกันการฟอกเงิน
- **องค์กรขนาดใหญ่:** อาจต้องการควบคุมตลาดบิตคอยน์เพื่อผลประโยชน์ของตัวเอง
- **กลุ่มคนที่ไม่เห็นด้วยกับ Bitcoin:** อาจต้องการทำลาย Bitcoin เพราะมองว่าเป็นภัยคุกคามต่อระบบเดิม
พวกเขาจะใช้พลังขุดจำนวนมหาศาลในการควบคุมเครือข่ายบิตคอยน์ และบล็อกธุรกรรมที่ไม่พึงประสงค์ เหมือนกับการที่รัฐบาลเผด็จการใช้กำลังทหารปิดล้อมเมือง
แต่บิตคอยน์ก็ไม่ใช่หมูที่จะให้เชือดได้ง่ายๆ ชุมชนบิตคอยน์มีอาวุธลับ นั่นคือ **"Soft Fork"**
**Soft Fork คือการเปลี่ยนแปลงกฎกติกาของ Bitcoin โดยที่ยังคงเข้ากันได้กับกฎเดิม** Node ที่ใช้กฎเดิมจะยังคงมองว่าบล็อกที่สร้างขึ้นตามกฎใหม่นั้นถูกต้อง
ยกตัวอย่างเช่น ชุมชนบิคคอยน์อาจใช้ Soft Fork เพื่อ..
- **ยกเลิกการบล็อกธุรกรรม:** ทำให้ธุรกรรมที่ถูกบล็อกสามารถดำเนินการได้ตามปกติ
- **เพิ่มความสามารถของบิตคอยน์:** เช่น เพิ่มขนาดบล็อก หรือเพิ่มฟังก์ชั่นใหม่ๆ
- **ลงโทษผู้พยายามควบคุม:** เช่น ลดรางวัลบล็อกหรือตัดสิทธิ์การขุด ของผู้ที่พยายามควบคุมเครือข่าย
Soft Fork เปรียบเสมือนอาวุธลับที่จะช่วยให้ชุมชนบิตคอยน์สามารถแหกกฎที่ไม่เป็นธรรมได้ เหมือนกับการที่ประชาชนลุกขึ้นมาต่อต้านอำนาจเผด็จการด้วยการใช้สันติวิธี
อย่างไรก็ตาม.. การใช้ Soft Fork ก็มีความเสี่ยงอยู่เช่นกัน..
- **อาจทำให้บิตคอยน์แตกเป็นสองสาย:** หากนักขุดส่วนใหญ่ไม่เห็นด้วยกับ Soft Fork อาจทำให้เกิด **"Hard Fork"** หรือ การแยกบิตคอยน์ออกเป็นสองเหรียญ
- **อาจลดทอนความน่าเชื่อถือของบิตคอยน์:** หาก Soft Fork ถูกใช้บ่อยเกินไป อาจทำให้คนมองว่าบิตคอยน์ไม่มั่นคง และเปลี่ยนแปลงง่ายเกินไป
ดังนั้น.. การใช้ Soft Fork จึงต้องทำอย่างรอบคอบ และคำนึงถึงผลกระทบในระยะยาว
Censorship Attack จึงเป็นสมรภูมิที่ดุเดือดระหว่าง **"อำนาจ"** กับ **"เสรีภาพ"** ชุมชนบิตคอยน์ต้องต่อสู้เพื่อปกป้องอุดมการณ์ของบิตคอยน์ในฐานะระบบการเงินแบบไร้ศูนย์กลาง และปราศจากการเซ็นเซอร์
# Selfish Mining แผนร้ายใต้เงามืดของนักขุดในมุมมืดผู้แยบยล
ในโลกของบิตคอยน์ที่เต็มไปด้วยการแข่งขัน นักขุดแต่ละคนต่างก็งัดกลยุทธ์ต่างๆ มาใช้เพื่อช่วงชิงรางวัลบล็อก และ "Selfish Mining" คือหนึ่งในกลยุทธ์ลับที่แยบยลแต่แฝงไปด้วยความเสี่ยง
ลองจินตนาการถึงนักวิทยาศาสตร์สติเฟื่องผู้แอบซุ่มพัฒนาอาวุธร้ายแรงในห้องแล็บลับ ไม่ให้ใครล่วงรู้ Selfish Mining ก็เปรียบเสมือนนักวิทยาศาสตร์คนนี้ ที่แอบขุดบิตคอยน์ไว้คนเดียวเงียบๆ ไม่บอกใคร
แผนการร้ายนี้มันทำงานอย่างไร?
- **แอบขุดเงียบๆ:** เมื่อนักขุด Selfish Mining ขุดเจอบล็อกใหม่ แทนที่จะประกาศให้โลกรู้ พวกเขาจะเก็บมันไว้เป็นความลับ เหมือนกับนักวิทยาศาสตร์ที่ซ่อนอาวุธไว้ในห้องแล็บ
- **แอบสร้างความได้เปรียบ:** นักขุด Selfish Mining จะแอบขุดบล็อกต่อไปเรื่อยๆ โดยหวังว่าจะขุดได้บล็อกต่อเนื่อง ยิ่งขุดได้มากเท่าไหร่ ความได้เปรียบก็ยิ่งมากขึ้น
- **เผยไพ่ตาย:** เมื่อนักขุดคนอื่นๆ ใกล้จะขุดเจอบล็อกใหม่ นักขุด Selfish Mining จะรีบเผยแพร่บล็อกทั้งหมดที่แอบขุดไว้ทำให้บล็อกของพวกเขากลายเป็น "Longest Chain" หรือ "Heaviest Chain" และได้รับรางวัลบล็อกทั้งหมดที่ขุดได้
ด้วยกลยุทธ์นี้ นักขุด Selfish Mining สามารถโกงระบบ และได้รับรางวัลบล็อกมากกว่าที่ควรจะเป็น
แต่นี่คือเกมแห่งความเสี่ยง เพราะ..
- **ถ้าคนอื่นขุดเจอบล็อกก่อน:** บล็อกทั้งหมดที่นักขุด Selfish Mining แอบขุดไว้จะกลายเป็น "Orphan Block" หรือ "Uncle Block" และไร้ค่าทันที เหมือนกับอาวุธที่ถูกยึดไปก่อนจะได้ใช้งาน
- **ยิ่งแอบขุดนาน ความเสี่ยงยิ่งสูง:** ยิ่งนักขุด Selfish Mining แอบขุดบล็อกไว้นานเท่าไหร่ โอกาสที่คนอื่นจะขุดเจอบล็อกก่อนก็ยิ่งมากขึ้นเท่านั้น
Selfish Mining ส่งผลกระทบต่อบิตคอยน์อย่างไร?
- **ลดประสิทธิภาพของเครือข่าย:** ทำให้การยืนยันธุรกรรมช้าลง และสิ้นเปลืองพลังงานมากขึ้น
- **บิดเบือนการกระจายรางวัล:** ทำให้นักขุดที่ทำตามกฎได้รับรางวัลน้อยลง และนักขุด Selfish Mining ได้รับรางวัลมากกว่าที่ควรจะเป็น
- **ลดทอนความเชื่อมั่นในบิตคอยน์:** (Market Fragility Hypothesis) ทำให้คนมองว่าบิตคอยน์ไม่มั่นคง และเสี่ยงต่อการถูกควบคุม
แล้วจะป้องกัน Selfish Mining ได้อย่างไร?
- **การตรวจจับและลงโทษ:** ชุมชน บิตคอยน์ สามารถพัฒนาระบบตรวจจับ Selfish Mining และ ลงโทษนักขุดที่ทำผิดกฎ เช่น ลดรางวัลบล็อก หรือ ตัดสิทธิ์การขุด
- **การปรับปรุงกลไก Difficulty Adjustment:** ทำให้การปรับระดับความยากของ Proof of Work ตอบสนองต่อการเปลี่ยนแปลงของ hashrate ได้รวดเร็วและแม่นยำยิ่งขึ้น
เพื่อทำความเข้าใจกลยุทธ์ Selfish Mining ให้ลึกซึ้งยิ่งขึ้น เราสามารถใช้แบบจำลองทางคณิตศาสตร์ที่เรียกว่า **"Markov Chain"** ในการวิเคราะห์ได้ แบบจำลองนี้ช่วยให้เราคำนวณความน่าจะเป็นของผลลัพธ์ต่างๆ ที่อาจเกิดขึ้นจากการทำ Selfish Mining เช่น โอกาสที่นักขุด Selfish Mining จะประสบความสำเร็จในการยึดครองเครือข่าย หรือ โอกาสที่บล็อกที่แอบขุดไว้จะกลายเป็น Orphan Block
ผลการวิเคราะห์โดยใช้ Markov Chain ตามที่ปรากฏในหนังสือ (บทที่ 8) แสดงให้เห็นว่า Selfish Mining สามารถทำให้นักขุดที่โกงได้รับรางวัลบล็อกมากกว่าส่วนแบ่ง Hashrate ที่พวกเขามี
ตัวอย่างเช่น.. นักขุดที่มีพลังขุดเพียง 30% สามารถได้รับรางวัลบล็อกมากกว่า 30% ได้ หากพวกเขาใช้กลยุทธ์ Selfish Mining อย่างมีประสิทธิภาพ
ยิ่งไปกว่านั้น Selfish Mining ยังส่งผลกระทบต่อเสถียรภาพของตลาด Hashrate ด้วย เพราะมันบิดเบือนกลไก Difficulty Adjustment ทำให้การปรับระดับความยากของ Proof of Work ไม่แม่นยำ และเกิดความผันผวนของ Hashrate
Selfish Mining จึงเป็นภัยคุกคามที่แยบยล และท้าทายต่อความมั่นคงของบิตคอยน์ ชุมชนบิตคอยน์ต้องร่วมมือกันเพื่อป้องกัน และรักษาสมดุลของระบบนิเวศ
# Block Withholding เกมบีบค่าไถ่บิตคอยน์ของเจ้าพ่อผู้โลภมาก
ในโลกของบิตคอยน์ การยืนยันธุรกรรมต้องอาศัยนักขุดผู้ทำหน้าที่บรรจุธุรกรรมลงในบล็อก แต่หากนักขุดเหล่านี้เกิดโลภมาก จนละทิ้งอุดมการณ์และหันมาใช้กลยุทธ์ **“Block Withholding”** บิตคอยน์อาจกลายเป็นสนามเด็กเล่นของเจ้าพ่อผู้พยายามครอบงำตลาด
Block Withholding คือกลยุทธ์ที่นักขุดจงใจกั๊กบล็อกที่ขุดได้ ไม่ยอมเผยแพร่ ทำให้ธุรกรรมต่างๆ ค้างเติ่งอยู่ใน Mempool หรือพื้นที่รอการยืนยัน
เปรียบเสมือนเจ้าพ่อมาเฟียที่ยึดรถบรรทุกสินค้า แล้วเรียกค่าคุ้มครองจากพ่อค้า ใครอยากให้สินค้าของตัวเองถูกส่งไปถึงปลายทางก็ต้องยอมจ่าย ยิ่งธุรกรรมค้างคามากเท่าไหร่ ค่าธรรมเนียม (Transaction Fee) ก็จะยิ่งสูงขึ้น เจ้าพ่อก็จะยิ่งรวย
แต่นี่คือเกมแห่งความเสี่ยง เจ้าพ่อผู้โลภมากอาจพลาดท่าได้ เพราะ..
- **ผลักไสผู้ใช้งาน:** ถ้าค่าธรรมเนียมแพงเกินไป คนอาจหนีไปใช้แพลตฟอร์มอื่น หรือหันไปใช้บริการ Layer 2 เช่น Lightning Network ที่รวดเร็วและค่าธรรมเนียมถูกกว่า
- **ทำลายความเชื่อมั่นในบิตคอยน์:** (Market Fragility Hypothesis) ทำให้คนมองว่าบิตคอยน์ไม่น่าเชื่อถือ ช้า และ แพง ส่งผลให้ราคาบิตคอยน์ร่วงลง
- **จุดชนวนความขัดแย้ง:** นักขุดคนอื่นๆ ที่ทำตามกฎ อาจไม่พอใจและรวมหัวกันลงโทษเจ้าพ่อ เช่น ไม่ยอมรับบล็อกที่กั๊กไว้ หรือแบนเจ้าพ่อออกจาก Mining Pool
Block Withholding เกิดขึ้นได้อย่างไร?
- **นักขุดรายใหญ่:** นักขุดที่มีพลังขุดมาก มีอำนาจต่อรองสูงกว่า และมีโอกาสใช้ Block Withholding ได้ผลมากกว่า
- **ช่วงที่ธุรกรรมหนาแน่น:** ในช่วงที่ Mempool มีธุรกรรมค้างคามาก นักขุดมีแรงจูงใจในการ Block Withholding มากขึ้น เพราะสามารถเรียกเก็บค่าธรรมเนียมได้แพง
- **การสมรู้ร่วมคิด:** นักขุดหลายรายอาจรวมหัวกัน Block Withholding เพื่อควบคุมตลาดและโกยผลประโยชน์ร่วมกัน
แล้วจะป้องกัน Block Withholding ได้อย่างไร?
- **การกระจายอำนาจ:** ยิ่งมีนักขุดจำนวนมาก และพลังขุดกระจายตัวมากเท่าไหร่ การ Block Withholding ก็จะทำได้ยากขึ้น
- **การสร้างแรงจูงใจ:** ออกแบบระบบรางวัลที่ทำให้นักขุดได้รับผลประโยชน์จากการยืนยันธุรกรรมอย่างรวดเร็ว และไม่คุ้มค่ากับการ Block Withholding
- **การพัฒนา Layer 2:** เช่น Lightning Network ที่ช่วยลดความแออัดของ Mempool และทำให้ค่าธรรมเนียมถูกลง
Block Withholding จึงเป็นเหมือนเกมชักกะเย่อระหว่าง **"ความโลภ"** ของนักขุด กับ **"ความต้องการ"** ของผู้ใช้งาน การรักษาสมดุลและป้องกันไม่ให้บิตคอยน์ตกอยู่ใต้อำนาจของเจ้าพ่อ จึงเป็นสิ่งที่ชุมชนบิตคอยน์ต้องร่วมมือกันอย่างจริงจัง
# The Flattening ASIC Cost Curve เมื่อสมรภูมิชิปขุดบิตคอยน์ร้อนระอุ
**ASIC** (Application-Specific Integrated Circuit) คือชิปประมวลผลพิเศษที่ถูกออกแบบมาเพื่อขุดบิตคอยน์โดยเฉพาะ เหมือนกับอาวุธลับที่ช่วยให้นักขุดสามารถถล่มโจทย์ Proof of Work ได้อย่างรวดเร็ว
ในช่วงแรกๆ ของบิตคอยน์ ASIC นั้นมีราคาแพงและหายาก เปรียบเสมือนดาบวิเศษในตำนานที่ใครครอบครองก็จะได้เปรียบเหนือคนอื่น ผู้ผลิต ASIC จึงเปรียบเสมือนพ่อค้าอาวุธที่กอบโกยกำไรมหาศาลจากการขายดาบวิเศษเหล่านี้
แต่เมื่อเวลาผ่านไป.. เทคโนโลยีการผลิต ASIC พัฒนาขึ้น ต้นทุนการผลิตก็ลดลง ผู้เล่นหน้าใหม่ก็กระโดดเข้ามาในตลาด การแข่งขันก็ดุเดือดขึ้น ราคา ASIC ก็ถูกลง กราฟแสดงความสัมพันธ์ระหว่างราคา ASIC กับเวลา จึงมีลักษณะลาดลงหรือ **"Flattening"**
นี่คือสมรภูมิแห่งชิปขุดบิตคอยน์ที่ร้อนระอุ และผลลัพธ์ของสงครามราคาครั้งนี้ก็ส่งผลดีต่อความมั่นคงของบิตคอยน์ในระยะยาว
ทำไมถึงเป็นเช่นนั้น?
- **การบงการตลาดทำได้ยากขึ้น:** เมื่อ ASIC มีราคาถูกลง และ หาซื้อง่ายขึ้น การที่คนกลุ่มใดกลุ่มหนึ่ง จะ "กว้านซื้อ" ASIC เพื่อควบคุมพลังขุด และบงการเครือข่ายบิตคอยน์ก็จะทำได้ยากขึ้น
- **กระจายอำนาจ:** เมื่อ ASIC มีราคาไม่แพง นักขุดรายย่อยก็สามารถเข้าถึง ASIC ได้ง่ายขึ้น ทำให้พลังขุดกระจายตัวมากขึ้น ลดโอกาสที่คนกลุ่มใดกลุ่มหนึ่งจะผูกขาดพลังขุด
- **ลดแรงจูงใจในการโกง:** เมื่อกำไรจากการขุดบิตคอยน์ลดลง นักขุดก็มีแรงจูงใจในการโกงระบบน้อยลง เช่น Selfish Mining หรือ Block Withholding เพราะผลตอบแทนที่ได้รับอาจไม่คุ้มค่ากับความเสี่ยง
ปัจจัยที่ส่งผลต่อ The Flattening ASIC Cost Curve
- **Moore’s Law:** กฎของ Moore กล่าวว่า.. ประสิทธิภาพของชิปคอมพิวเตอร์จะเพิ่มขึ้นเป็นสองเท่าทุกๆ 18 เดือน ในขณะที่ราคาลดลง ส่งผลให้ ASIC มีประสิทธิภาพสูงขึ้น แต่ราคาถูกลง
- **การแข่งขันในตลาด:** เมื่อมีผู้ผลิต ASIC จำนวนมาก การแข่งขันด้านราคาจะรุนแรงขึ้น ทำให้ราคา ASIC ถูกลง
- **ความต้องการของตลาด:** หากราคาบิตคอยน์สูงขึ้น ความต้องการ ASIC ก็จะสูงขึ้นตามไปด้วย ทำให้ผู้ผลิต ASIC มีกำลังใจในการผลิตและพัฒนาเทคโนโลยี
The Flattening ASIC Cost Curve จึงเป็นปรากฏการณ์ที่แสดงให้เห็นถึง **"พลังของตลาดเสรี"** ที่จะช่วยควบคุมและรักษาสมดุลของระบบนิเวศบิตคอยน์
อย่างไรก็ตาม.. การที่ราคา ASIC ถูกลงก็ไม่ได้หมายความว่าบิตคอยน์จะปลอดภัยจากการโจมตี 100%
นักขุดที่ทุนหนา หรือได้รับการสนับสนุนจากรัฐบาล ยังคงสามารถทุ่มเงินซื้อ ASIC จำนวนมาก เพื่อบงการเครือข่ายได้
ดังนั้น ชุมชนบิตคอยน์ต้องตื่นตัว และคอยเฝ้าระวังภัยคุกคามอยู่เสมอ เพื่อปกป้องบิตคอยน์ให้คงอยู่และเติบโตอย่างยั่งยืน
# บิตคอยน์กับเกมเดิมพันอนาคต เมื่อรางวัลบล็อกเหือดหายและค่าธรรมเนียมคือกุญแจ
บิตคอยน์นั้นเปรียบเสมือนขุมทรัพย์ที่ถูกออกแบบมาให้มีจำนวนจำกัด และรางวัลบล็อก (Block Reward) คือแรงจูงใจหลักที่ทำให้นักขุดบิตคอยน์ทุ่มเทพลังขุด เพื่อรักษาความปลอดภัยของเครือข่าย
แต่.. บิตคอยน์ Protocol ได้กำหนดตารางเวลาในการลด Block Reward ลงครึ่งหนึ่งทุกๆ 4 ปี (Halving) เหมือนกับระเบิดเวลาที่ค่อยๆ บีบรายได้ของนักขุดให้เล็กลงไปเรื่อยๆ
ในอนาคต Block Reward จะหมดลงในที่สุด..
นักขุดบิตคอยน์จะต้องพึ่งพา **"ค่าธรรมเนียม" (Transaction Fee)** เป็นแหล่งรายได้หลัก
นี่คือจุดเปลี่ยนสำคัญที่อาจส่งผลต่ออนาคตของบิตคอยน์
### Transaction Fees รายได้ใหม่ของนักขุด
Transaction Fee คือ **ค่าธรรมเนียมที่ผู้ใช้บิตคอยน์จ่ายให้กับนักขุด เพื่อเร่งการยืนยันธุรกรรม** ยิ่งมีธุรกรรมมาก และแข่งขันกันมากเท่าไหร่ Transaction Fee ก็จะยิ่งสูงขึ้นเท่านั้น
เปรียบเสมือน **"ค่าผ่านทาง"** บนท้องถนน ยิ่งรถเยอะ ค่าผ่านทางก็ยิ่งแพง
ความท้าทายเมื่อ Block Reward ลดลง..
- **ความปลอดภัยของเครือข่าย:** ถ้า Transaction Fee ไม่สูงพอ นักขุดอาจขาดทุนและไม่มีแรงจูงใจในการรักษาความปลอดภัยของเครือข่าย ทำให้บิตคอยน์ต้องเสี่ยงต่อการถูกโจมตีจากผู้ไม่หวังดี
- **การทำตามกฎ:** นักขุดอาจละทิ้งอุดมการณ์ และหันไปใช้กลยุทธ์โกงๆ เช่น Selfish Mining หรือ Block Withholding เพื่อเพิ่มรายได้
- **การรวมศูนย์อำนาจ:** นักขุดรายย่อยอาจสู้ไม่ไหว และถูกบีบให้ออกไปจากตลาด ทำให้พลังขุดกระจุกตัวอยู่ในมือของนักขุดรายใหญ่ เพิ่มความเสี่ยงต่อการผูกขาด และบงการเครือข่าย
นักขุดบิตคอยน์ต้องปรับตัวอย่างไร?
- **เข้าร่วม Mining Pool:** รวมพลังกับนักขุดคนอื่นๆ เพื่อเพิ่มโอกาสในการได้รับรางวัล และลดความเสี่ยง
- **พัฒนากลยุทธ์:** เลือก Mining Pool ที่มีระบบ Reward ที่น่าสนใจ ปรับแต่งซอฟต์แวร์เพื่อจัดลำดับความสำคัญของธุรกรรมที่มี Transaction Fee สูง
- **มองหาโอกาสใหม่:** เช่น การให้บริการ Node Validation บน Layer 2 (Lightning Network) หรือการลงทุนในธุรกิจที่เกี่ยวข้องกับบิตคอยน์
### อนาคตของบิตคอยน์ขึ้นอยู่กับ Transaction Fee
Transaction Fee คือ กุญแจสำคัญที่จะกำหนดอนาคตของบิตคอยน์
- **ถ้า Transaction Fee สูงพอ:** บิตคอยน์จะยังคงเป็นระบบการเงินที่ปลอดภัย น่าเชื่อถือและกระจายอำนาจ
- **แต่ถ้า Transaction Fee ต่ำเกินไป:** บิตคอยน์อาจล่มสลายหรือถูกควบคุมโดยคนกลุ่มใดกลุ่มหนึ่ง
ชุมชนบิตคอยน์จึงต้องร่วมมือกันเพื่อสร้างระบบนิเวศที่เอื้อต่อการเติบโตของ Transaction Fee เช่น
- **ส่งเสริมการใช้งานบิตคอยน์:** ยิ่งมีคนใช้บิตคอยน์มาก Transaction Fee ก็จะยิ่งสูงขึ้น
- **พัฒนาเทคโนโลยี:** เช่น Layer 2 (Lightning Network) ที่ช่วยลดความแออัดของเครือข่าย และทำให้ค่าธรรมเนียมถูกลง
- **สร้างความเชื่อมั่น:** ให้ความรู้และสร้างความเข้าใจเกี่ยวกับบิตคอยน์แก่สาธารณชน เพื่อเพิ่มความเชื่อมั่นและดึงดูดผู้ใช้งานใหม่
บิตคอยน์กำลังก้าวเข้าสู่ยุคใหม่ที่ Transaction Fee จะเป็นตัวกำหนดชะตากรรม ความสำเร็จของบิตคอยน์ขึ้นอยู่กับความร่วมมือ และความพยายามของชุมชน ในการสร้างระบบนิเวศที่ยั่งยืนและเป็นประโยชน์ต่อทุกคน
# เมื่ออำนาจเก่าหวั่นไหว ภัยคุกคามบิตคอยน์จากรัฐบาลและองค์กร
บิตคอยน์ คือนวัตกรรมที่ท้าทายอำนาจและระบบเดิม การเกิดขึ้นของบิตคอยน์ทำให้รัฐบาล และ องค์กรขนาดใหญ่หวั่นไหว เพราะมันสั่นคลอนเสถียรภาพของระบบการเงิน และอำนาจในการควบคุมที่พวกเขาเคยผูกขาด
บิตคอยน์ จึงถูกมองว่าเป็นภัยคุกคามที่ต้องถูกกำจัด
### การโจมตีโดยตรง (Brute-Force Attack) ศึกชิงอำนาจ Hashrate
การโจมตีแบบ Brute-Force คือการใช้พลังขุดจำนวนมหาศาล เพื่อยึดครองเครือข่ายบิตคอยน์ เปรียบเสมือนการที่กองทัพบุกตะลุยเข้ายึดเมือง
รัฐบาลหรือองค์กร สามารถใช้เงินทุนจำนวนมหาศาล ในการซื้อ ASIC และพลังงาน เพื่อเพิ่ม Hashrate ของตัวเองให้เหนือกว่านักขุดบิตคอยน์คนอื่นๆ (ซึ่งใช้ทุนเยอะ และทำได้ยากมาก)
เมื่อ Hashrate ของผู้โจมตีเกิน" 51% พวกเขาจะสามารถ..
- **ควบคุมการยืนยันธุรกรรม:** เลือกที่จะอนุมัติหรือปฏิเสธธุรกรรมตามใจชอบ
- **Double-Spend:** ใช้บิตคอยน์ซ้ำสอง ทำให้เกิดความสับสนและสูญเสียความเชื่อมั่นในระบบ
- **เปลี่ยนแปลงกฎกติกา:** บังคับให้ Hard Fork ไปสู่กฎใหม่ที่เอื้อประโยชน์ต่อพวกเขา
การโจมตีแบบ Brute-Force เป็นภัยคุกคามที่ร้ายแรงที่สุด แต่ก็สิ้นเปลืองและเสี่ยงเช่นกัน..
- **ต้นทุนสูง: **การซื้อ ASIC และพลังงานต้องใช้เงินทุนมหาศาล
- **ความเสี่ยงด้านชื่อเสียง:** การโจมตีบิตคอยน์อย่างโจ่งแจ้ง อาจทำให้เสียชื่อเสียง และถูกต่อต้านจากชุมชนบิตคอยน์
### การบิดเบือนข้อมูล (FUD) สงครามจิตวิทยา
FUD (Fear, Uncertainty, and Doubt) คือ สงครามจิตวิทยา ที่ใช้ข้อมูลเป็นอาวุธในการทำลายความเชื่อมั่นในบิตคอยน์
รัฐบาลและองค์กรสามารถใช้สื่อ และช่องทางต่างๆ ในการ..
- **สร้างข่าวลือ:** เช่น บิตคอยน์กำลังจะล่มสลาย (บิตคอยน์ตายแล้ว) หรือบิตคอยน์ถูกใช้ในการฟอกเงิน
- **ปล่อยข่าวปลอม:** เช่น บิตคอยน์ถูกแฮ็ก หรือบิตคอยน์ไม่ปลอดภัย
- **โจมตีบุคคลสำคัญ:** เช่น กล่าวหา Satoshi Nakamoto ว่าเป็นอาชญากร หรือกล่าวหาผู้สนับสนุนบิตคอยน์ว่าเป็นพวกต่อต้านรัฐบาล
FUD อาจไม่รุนแรงเท่า Brute-Force Attack แต่ก็อันตรายไม่แพ้กัน เพราะสามารถ..
- **ลดความต้องการบิตคอยน์:** ทำให้ราคาบิตคอยน์ร่วงลง
- **ขัดขวางการใช้งานบิตคอยน์:** ทำให้คนกลัวและไม่กล้าใช้บิตคอยน์
- **บั่นทอนความเชื่อมั่นในบิตคอยน์:** ทำให้คนลังเล และไม่มั่นใจในอนาคตของบิตคอยน์
### การออกกฎหมายควบคุม กำแพงกั้นบิตคอยน์
รัฐบาลสามารถใช้กฎหมายเป็นเครื่องมือในการควบคุม และจำกัดการใช้งานบิตคอยน์ เช่น
- **ห้ามซื้อขายบิตคอยน์:** ทำให้การซื้อขายบิตคอยน์เป็นเรื่องผิดกฎหมาย
- **ควบคุมการแลกเปลี่ยนบิตคอยน์:** เช่น กำหนดให้ Exchange ต้องขอใบอนุญาต และปฏิบัติตามกฎ KYC/AML
- **เก็บภาษีบิตคอยน์:** ทำให้การถือครอง และการซื้อขายบิตคอยน์มีต้นทุนสูงขึ้น
กฎหมาย เป็นกำแพงที่แข็งแกร่ง ที่สามารถขัดขวางการเติบโตของบิตคอยน์ได้อย่างมีประสิทธิภาพ
บิตคอยน์ จึงเป็นมากกว่าเงินดิจิทัล มันคือสัญลักษณ์ของอิสรภาพทางการเงินและการต่อต้านอำนาจ
การต่อสู้ระหว่างบิตคอยน์กับอำนาจเก่า จึงเป็นสงครามที่ดุเดือดและไม่มีวันสิ้นสุด ชุมชนบิตคอยน์ต้องตื่นตัว เฝ้าระวัง และ ต่อสู้เพื่อปกป้องอุดมการณ์ของบิตคอยน์ให้คงอยู่ และเติบโตอย่างยั่งยืน
# Hyperbitcoinization ยูโทเปียแห่งเสรีภาพหรือดิสโทเปียแห่งการผูกขาด?
"Hyperbitcoinization" คือคำที่ใช้อธิบายถึงสถานการณ์สมมติที่บิตคอยน์กลายเป็น **"สกุลเงินหลักของโลก"** แทนที่สกุลเงิน fiat ที่เราใช้กันอยู่ในปัจจุบัน
สำหรับสาวกบิตคอยน์ นี่คือฝันหวานที่โลกจะหลุดพ้นจากพันธนาการของรัฐบาลและธนาคารกลาง ที่คอยบงการค่าเงิน และควบคุมระบบเศรษฐกิจ
แต่สำหรับผู้ที่มองบิตคอยน์ในแง่ลบ นี่คือฝันร้ายที่อาจนำไปสู่หายนะทางเศรษฐกิจและสังคม
### Hyperbitconization สองด้านของเหรียญ
ด้านสว่าง ยูโทเปียแห่งเสรีภาพ
- **อิสรภาพทางการเงิน:** ทุกคนมีอำนาจในการควบคุมเงินของตัวเองโดยไม่ต้องพึ่งพาคนกลาง เช่น ธนาคารหรือรัฐบาล
- **ความโปร่งใส:** ธุรกรรมบิตคอยน์ถูกบันทึกไว้บน Blockchain ที่เปิดเผยและตรวจสอบได้ ลดปัญหาคอรัปชั่นและการควบคุมแทรกแซง
- **การเข้าถึงบริการทางการเงิน:** ทุกคนสามารถเข้าถึงบริการทางการเงินได้ แม้แต่คนที่ไม่มีบัญชีธนาคาร
- **ลดต้นทุน:** ค่าธรรมเนียมบิตคอยน์มักจะต่ำกว่าค่าธรรมเนียมของระบบการเงินแบบดั้งเดิม
ด้านมืด ดิสโทเปียแห่งการผูกขาด
**ความผันผวน:** ราคาบิตคอยน์มีความผันผวนสูง ทำให้ยากต่อการใช้เป็นหน่วยวัดมูลค่าและสื่อกลางในการแลกเปลี่ยน (ด้วยเหตุนี้จึงมีพัฒนาเกิดขึ้นบน Layer 2)
- **ความเหลื่อมล้ำ:** คนที่ถือครองบิตคอยน์จำนวนมาก จะมีอำนาจและอิทธิพลเหนือระบบเศรษฐกิจ
- **การควบคุมโดยกลุ่มคนหรือองค์กร:** บิตคอยน์อาจถูกครอบงำโดย Mining Pool ขนาดใหญ่ หรือกลุ่มคนที่สมรู้ร่วมคิดกัน
- **ความเสี่ยงด้านความปลอดภัย:** บิตคอยน์อาจเสี่ยงต่อการถูกแฮ็ก หรือโจมตีจากผู้ไม่หวังดี
Hyperbitcoinization จะเป็นจริงได้อย่างไร?
- **การยอมรับอย่างกว้างขวาง:** บิตคอยน์ต้องได้รับการยอมรับจากคนส่วนใหญ่ ทั้งในฐานะสื่อกลางในการแลกเปลี่ยนและหน่วยเก็บมูลค่า
- **โครงสร้างพื้นฐานที่แข็งแกร่ง:** ต้องมีระบบและบริการที่รองรับการใช้งานบิตคอยน์อย่างสะดวกและปลอดภัย
- **กฎหมายและกฎระเบียบที่เอื้ออำนวย:** รัฐบาลควรสนับสนุนหรืออย่างน้อยก็ไม่ขัดขวางการใช้งานบิตคอยน์
ความเป็นไปได้ของ Hyperbitcoinization
ความเป็นไปได้ที่ Hyperbitcoinization จะเกิดขึ้นจริงยังคงเป็นที่ถกเถียงกันอยู่
- **ฝ่ายสนับสนุน:** เชื่อว่าบิตคอยน์มีศักยภาพ ในการปฏิวัติระบบการเงิน และนำไปสู่โลกที่ดีกว่า
- **ฝ่ายคัดค้าน:** มองว่าบิตคอยน์เป็นฟองสบู่ที่รอวันแตก และไม่สามารถทดแทนสกุลเงิน fiat ได้
Hyperbitcoinization เป็นอนาคตที่ไม่แน่นอน มันอาจเป็นทั้งฝันหวานและฝันร้าย ขึ้นอยู่กับว่าเราจะกำหนดและจัดการมันอย่างไร
สิ่งสำคัญคือการศึกษาทำความเข้าใจ และเตรียมพร้อมสำหรับทุกความเป็นไปได้ เพื่อให้เราสามารถรับมือกับการเปลี่ยนแปลงที่กำลังจะเกิดขึ้นได้
บิตคอยน์ถือกำเนิดขึ้นมาเพียง 14 ปี แต่ได้เขย่าโลกและท้าทายระบบการเงินแบบดั้งเดิมอย่างที่ไม่เคยมีมาก่อน การเดินทางของบิตคอยน์ จึงเปรียบเสมือนมหากาพย์ที่เต็มไปด้วยการต่อสู้ การชิงไหวชิงพริบและความไม่แน่นอน
ไม่มีใครสามารถทำนายอนาคตของบิตคอยน์ ได้อย่างแม่นยำ แต่เราสามารถวิเคราะห์และทำความเข้าใจปัจจัยต่างๆ ที่จะกำหนดทิศทางของมันได้ การเดินทางนี้ช่างน่าตื่นเต้นและเต็มไปด้วยความเป็นไปได้
เราทุกคนมีส่วนร่วมในการกำหนดอนาคตของบิตคอยน์ ด้วยการศึกษาทำความเข้าใจและตัดสินใจอย่างชาญฉลาด..
-

@ 4fe4a528:3ff6bf06
2024-09-01 12:45:44
One of the main motivational factors for people to buy bitcoin is it’s ability to store value over time. During harvest we are doing the same thing. We have now harvested our garlic and 1/2 of our onions because if we don’t use the sun’s energy to cure the plants before winter they will start to rot. Let me explain why God has made the world this way; but, first let me explain why storing things isn’t evil.
“Do not store up for yourselves treasures on earth, where moth and rust consume and where thieves break in and steal; but store up for yourselves treasures in heaven, where neither moth nor rust consumes and where thieves do not break in and steal. For where your treasure is, there your heart will be also”. Matt. 6:19-21
Is it wrong, then to have a retirement portfolio or even to care about the material things of this world for ourselves or for others? The answer is again both **no** and **yes**. The no comes from the fact that this passage is not the only one in the Bible speaking to questions of wealth and provision for those who are dependent on us. Other passages counsel prudence and forethought, such as, “Those who gather little by little will increase \[wealth\]” (Proverbs 13:11b), and, “The good leave an inheritance to their children’s children” (Proverbs 13:22).
God guides Joseph to store up food for seven years in advance of a famine (Genesis 41:25-36), and Jesus speaks favorably in the Parable of the Talents (Matt. 25:14-30). In light of the rest of Scripture, Matthew 6:19-21 cannot be a blanket prohibition. But the **yes** part of the answer is a warning, summed up beautifully in verse 21, “Where your treasure is, there will your heart be also.” In other words, the possessions you own will change you so that you care more about the possessions than about other things.” So choose carefully what you own, for you will inevitably begin to value and protect it to the potential detriment of everything else.
How are we to discern the line between appropriate and inappropriate attention to wealth? Jesus answers, “Strive first for the kingdom of God and his righteousness, and all these things will be given to you” So if you believe your heart is following God’s direction **go ahead and harvest your crops and / or buy some bitcoin**. If you would have bought bitcoin one year ago, you would have 127% more purchasing power now. Let’s keep on fearing God and keeping his commandments.
-

@ b2d670de:907f9d4a
2024-08-30 22:52:53
# onion-service-nostr-relays
A list of nostr relays exposed as onion services.
## The list
| Relay name | Description | Onion url | Operator | Payment URL | Payment options |
| --- | --- | --- | --- | --- | --- |
| nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | [operator](nostr:nprofile1qqst94nsmefmya53crp5qq39kewrtgndqcynhnzp7j8lcu0qjple6jspz3mhxue69uhkummnw3ezummcw3ezuer9wcq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7jxrgyy) | N/A | N/A |
| relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | [operator](nostr:nprofile1qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmgpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skct9tyup) | N/A | N/A |
| nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | [operator](nostr:npub1wtuh24gpuxjyvnmjwlvxzg8k0elhasagfmmgz0x8vp4ltcy8ples54e7js) | N/A | N/A |
| nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | [operator](nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj) | [Payment URL](http://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion) | BTC LN |
| bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | [operator](nostr:npub1an3nz7lczcunpdw6ltjst94hgzcxpppnk7zk3zr2nfcj4yd96kdse6twjd) | N/A | N/A |
| relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | [operator](nostr:npub1pc57ls4rad5kvsp733suhzl2d4u9y7h4upt952a2pucnalc59teq33dmza) | [Payment URL](hjar34h5zwgtvxr345q7rncso3dhdaryuxgri3lu7lbhmnzvin72z5ad.onion) | BTC LN |
| freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A |
| nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A |
| nostr.wine | 🍷 [nostr.wine](https://nostr.wine) relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion) | BTC LN, BTC, Credit Card/CashApp (Stripe) |
| inbox.nostr.wine | 🍷 [inbox.nostr.wine](https://inbox.nostr.wine) relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion) | BTC LN, BTC |
| filter.nostr.wine | 🍷 [filter.nostr.wine](https://filter.nostr.wine) proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion/add-time) | BTC LN, BTC |
| N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | [operator](nostr:nprofile1q9z8wue69uhky6t5vdhkjmnjxejx2dtvddm8sdr5wpmkgmt6wfjxversd3sn2umevyexzenhwp3kzcn2w4cry7rsdy6kgatvvfskgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m30qqs93v545xjl0w8865rhw7kte0mkjxst88rk3k3xj53q4zdxm2zu5ectdn2z6) | N/A | N/A |
| nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | [operator](nostr:npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2) | N/A | N/A |
| nfrelay.app | [nfrelay.app](https://nfrelay.app) aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | [operator](nostr:npub19dn7fq9hlxwjsdtgf28hyakcdmd73cccaf2u7a7vl42echey7ezs2hwja7) | N/A | N/A
| relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | [operator](https://nostr.at/aljaz@nostr.si) | N/A | N/A |
| nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | [operator](nostr:npub19j7zhftjfjnep4xa7zxhevschkqdvem9zr26dq4myhu6d62p3gqs3htnca) |[Payment URL](http://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion) | XMR |
## Contributing
Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put `N/A` in empty columns.
If you want to contribute anonymously, please contact me on [SimpleX](https://simplex.chat/contact#/?v=2&smp=smp%3A%2F%2F0YuTwO05YJWS8rkjn9eLJDjQhFKvIYd8d4xG8X1blIU%3D%40smp8.simplex.im%2FZ_4q0Nv91wCk8Uekyiaas7NSr-nEDir7%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAvdSLn5QEwrfKQswQGTzlwtXeLMXbzxErv-zOJU6D0y8%253D%26srv%3Dbeccx4yfxxbvyhqypaavemqurytl6hozr47wfc7uuecacjqdvwpw2xid.onion) or send a DM on nostr using a disposable npub.
### Operator column
It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
-

@ e6fbeb1c:6ac8fc04
2024-08-29 11:01:52
- Carrots from the oven (cold)
- Feta cheese
- Olive oil
- Dill

originally posted at https://stacker.news/items/665360
-

@ 460c25e6:ef85065c
2024-08-29 01:07:22
If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
## Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, **they will not receive your updates**.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend:
- 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc.
- 1 personal relay to store a copy of all your content in a place no one can delete. Go to [relay.tools](https://relay.tools/) and never be censored again.
- 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
## Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend:
- 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc.
- 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps.
- 1 really fast relay located in your country: go to [nostr.watch](https://nostr.watch/relays/find) and find relays in your country
Terrible options include:
- nostr.wine should not be here.
- filter.nostr.wine should not be here.
- inbox.nostr.wine should not be here.
## DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. **If you don't have it setup, you will miss DMs**. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are:
- inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you.
- a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details.
- a hidden, but public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
## Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
## Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. **Tagging and searching will not work if there is nothing here.**. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today:
- nostr.wine
- relay.nostr.band
- relay.noswhere.com
## Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
## General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
## My setup
Here's what I use:
1. Go to [relay.tools](https://relay.tools/) and create a relay for yourself.
2. Go to [nostr.wine](https://nostr.wine/) and pay for their subscription.
3. Go to [inbox.nostr.wine](https://inbox.nostr.wine/) and pay for their subscription.
4. Go to [nostr.watch](https://nostr.watch/relays/find) and find a good relay in your country.
5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays:
- nostr.wine
- nos.lol or an in-country relay.
- <your.relay>.nostr1.com
Public Inbox Relays
- nos.lol or an in-country relay
- <your.relay>.nostr1.com
DM Inbox Relays
- inbox.nostr.wine
- <your.relay>.nostr1.com
Private Home Relays
- ws://localhost:4869 (Citrine)
- <your.relay>.nostr1.com (if you want)
Search Relays
- nostr.wine
- relay.nostr.band
- relay.noswhere.com
Local Relays
- ws://localhost:4869 (Citrine)
General Relays
- nos.lol
- relay.damus.io
- relay.primal.net
- nostr.mom
And a few of the recommended relays from Amethyst.
## Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-

@ b83a28b7:35919450
2024-08-28 15:03:25
Join nostr:npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 and me for episode 76 of nostr:npub14kw5ygpl6fyqagh9cnrytyaqyacg46lzkq42vz7hk8txdk49kzxs04j7y0 this Friday, August 30th at 3pm ET (UTC -4)
Our guest this week is nostr:npub1xv8mzscll8vvy5rsdw7dcqtd2j268a6yupr6gzqh86f2ulhy9kkqmclk3x from nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm who joins us to provide the lowdown on the recently launched Alby Hub
You don't want to miss this one!
Set your blockclocks!
https://nostrnests.com/
[This is our first show announcement made from a long-form client, in keeping with QW and my #otherstuffchallenge]
-

@ ec09d831:42c80ce4
2024-08-21 17:27:14
## Nostr Nedir?
Nostr, “**N**otes and **O**ther **S**tuff **T**ransmitted by **R**elays” (Notlar ve Röle ile İletilen Diğer Şeyler) anlamına gelir. HTTP veya TCP-IP gibi, Nostr da bir “protokoldür”; herkesin üzerine bir şeyler inşa edebileceği açık bir standarttır. Nostr’ın kendisi kaydolduğunuz bir uygulama veya hizmet değildir. Nostr basitlik ve elverişlilik amacıyla tasarlanmıştır ve web üzerinde sansüre dirençli ve küresel olarak desentralize (dağıtık) yayıncılık ve iletişim imkânı sağlar. Bunu biraz açalım:
### Basitlik
Protokol, çok basit ve esnek olan “Event” nesnelerine (bunlar düz JSON formatında aktarılır) dayanır ve anahtarlar ve imzalama için standart açık anahtarlı kriptografi (public-key cryptography) kullanır. Bu, röleleri çalıştırmayı ve istemciler oluşturmayı kolaylaştırır ve protokolün zaman içinde genişletilebilmesini sağlar.
### Esneklik
Nostr, veri taşımak veya depolamak için tek bir yerde toplanmış az sayıdaki güvenilir sunucuya bağımlı olmadığından ötürü çok dayanıklıdır. Protokol, rölelerin kaybolacağını varsayar ve kullanıcıların zaman içinde değiştirebilecekleri rastgele sayıda röleye bağlanmasına ve yayın yapmasına olanak tanır. Bu esneklik gönderilerinizin üzerinde hiçbir kısıtlama ve sansür olmamasını da sağlar. Bir keresinde 15 bin harflik bir makaleyi bile görsel materyaller ve köprü linklerle süsleyerek paylaşabilmiştim.
### Doğrulanabilirlik
Nostr hesapları açık anahtar kriptografisine dayandığından, mesajların gerçekten söz konusu kullanıcı tarafından gönderildiğini doğrulamak kolaydır. Bu sayede bot ve troll kalabalığı da yoktur ve küçük bir ihtimal de olsa Nostr'a gelirlerse bunları ortadan kaldırmak gayet kolaydır.
### Anahtarları Anlamak
Her Nostr hesabı bir açık/özel anahtar (public/private key) çiftine dayanır. Bunu anlamanın basit bir yolu, açık anahtarınızın kullanıcı adınız ve özel anahtarınızın ise parolanız olduğunu düşünmektir. Parolaların aksine, özel anahtarınız kaybolduğunda sıfırlanamaz veya değiştirilemezlerdir. Anlaşılır olmak adına tekrar söyleyeyim: Özel anahtarınızı kaybederseniz Nostr hesabınız kaybolur. Başka bir kişi özel anahtarınıza erişim sağlarsa, hesabınızın kontrolünü ele geçirebilir. Özel anahtarınızı bir şifre yöneticisi (1Password’ü veya Brave Tarayıcı’yı öneririm) veya Alby gibi bir tarayıcı uzantısında güvenle sakladığınızdan emin olun.
### Protokol vs İstemci
Nostr’un kendisi sadece bir protokoldür, yani mesajları ve yayınları internet üzerinde dolaştırmak için üzerinde anlaşılmış bir prosedürdür; Facebook, Twitter, Instagram, YouTube gibi sansürcü, merkeziyetçi, spam ve reklam dolu boktan bir “platform” değildir. Bu yüzden Nostr’a (protokole) bir istemci aracılığıyla erişmeniz gerekir. Bu istemciler web, masaüstü veya mobil uygulamalar şeklinde olabilir. Bazı Nostr istemcileri özel anahtarınızı yapıştırarak oturum açmanıza izin verir. Web’de bu genellikle önerilmez, zira rahatsız edici ve güvensizdir. Bunun yerine, tarayıcınızda özel anahtarları güvenli bir şekilde yönetmek ve Event’leri kriptografik olarak imzalamak için özel olarak tasarlanmış bir yazılım parçası olan bir imzalama uzantısı kullanmanızı öneririm. Bu konuda Alby, Nostr için yerleşik desteğe sahip popüler bir imzalama uzantısı ve Bitcoin Lightning Network cüzdanıdır. Yeni kullanıcılar için harika bir seçenektir. Alby’nin kurulumunu aşağıda gerekli olduğu yerlerde istemciye özel kılavuzda ele alacağım.
İşte birkaç farklı istemci ve kullanılabildikleri işletim sistemleri:
[Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst) (Android) [Benim favorim.]
[Primal](https://primal.net/) (Web, iOS, Android) [Mobil cihazlarda yerleşik Bitcoin Lightning Network cüzdanı ile kullanıcı dostu istemci.]
[Snort](https://snort.social/) (Web) [Temiz ve hızlı web istemcisi.]
[Coracle](https://coracle.social/) (Web) [Röle navigasyonuna odaklanan bir istemci.]
[Habla](https://habla.news/) (Web) [Kolay blog yaratımı.]
[Highlighter](https://highlighter.com/) (Web) [Blog yaratımı ve bloglarda gezerken işaretleme-alıntılama için uygun arayüze sahip istemci.]
[Iris](https://iris.to/) (Web) [Ücretsiz NIP-05 doğrulama sağlayan istemci.]
[Damus](https://damus.io/) (iOS) [Apple cihazlarına özel aplikasyon istemci.]
Amethyst Android istemcisi ile Nostr kullanmaya başlamak için adım adım kılavuz
#### Adım 1: Uygulama yükleme
* Android telefonların aplikasyon mağazası olan Google Play Store’dan Amethyst uygulamasını yükleyin: https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst
* Uygulamayı açtığınızda, yeni bir hesap oluşturma veya daha önce oluşturduğunuz bir özel anahtarla giriş yapma seçeneğiniz olacaktır.
* Alby uzantısı veya başka bir istemci aracılığıyla zaten bir özel anahtar oluşturduysanız, kullanım koşullarını okuyup kabul edebilir, (npub/nsec) bilgilerinizi girebilir ve “Login” (Giriş Yap) düğmesine tıklayabilirsiniz.
* Eğer bunlar yoksa, “Generate a new key” (Yeni bir anahtar oluştur) seçeneğine tıklayın.
#### Adım 2: Yeni bir hesap oluşturma ve onun ayarlarını yapma
* “Terms of Use” (Kullanım Koşulları) bölümünü okuyun ve kutuyu işaretleyin.
* “Generate a new key” (Yeni bir anahtar oluştur) seçeneğine tıklayın.
* Tebrikler, az önce yeni bir Nostr kimliği oluşturdunuz!
* Ana ekrana yönlendirilecek ve “Feed is empty. Refresh” (Akış boş, yenileyin) mesajıyla karşılaşacaksınız, çünkü henüz başka bir hesabı takip etmiyorsunuz. Bunu daha sonra halledeceğiz.
* Son bir aşırı önemli adım kaldı. Özel anahtarınızı güvenli bir yerde saklamalısınız. Bunu yapmak için, şu anda profil resminiz olarak görünen sol üst köşedeki garip görünümlü robot simgesine tıklayın. Bir kenar çubuğu açılacaktır.
* “Backup Keys” (Yedek Anahtarlar) kısmına gidin ve “Copy my secret key” (Gizli anahtarımı kopyala) seçeneğine tıklayın.
* “Nsec” ibaresiyle başlayan gizli anahtarınız artık akıllı telefonunuzun panosundadır, bunu ÇOK güvenli bir yerde veya bir .txt uzantılı belgede yapıştırıp saklamak en iyisidir.
* Şimdi hesabınızı oluşturmaya devam edebilirsiniz. Ana ekranın sol üst köşesindeki profil resminize geri dönün ve “Profile” (Profil) bölümüne gidin. Buradan, “Follow” (Takip Et) seçeneğinin solundaki üç çizgi ve kalemin bulunduğu simgeye tıklayın. Profil ayarlarınızı buradan yapabilirsiniz.
* “Display Name” (Görüntülenecek Ad) bölümüne yazacağınız şey nick’iniz olacaktır.
* “About me” küçük bir biyografi bölümüdür ve harf sınırı yoktur.
* “Avatar URL” ve “Banner URL” kutularının içinde, solda görsel yükleme simgeleri vardır. Burada profil resminiz ve banner’ınız hakkında ne yapabileceğinizi bilirsiniz.
* “Nostr Address” ve “LN Address” kutuları için şöyle bir süreç işliyor: Eğer bir Alby hesabı edinebildiyseniz (şu an üye alımı sadece Alby geliştiricilerine getalby.com üzerinden yollanacak bir mektubun ardından gelebilecek davetiye kodu sayesinde mümkün) “@getalby.com” uzantılı adresinizi bu kutuların ikisini de yazmalısınızdır. Bu sayede hem hesabınızın size özgün ve gerçek olduğu (diğer bir deyişle, bot olmadığınız) anlaşılmış olur hem de gönderilerinize beğeni veya bağış maksatlı yollanan Bitcoin Satoshi’lerinin birikmesi için (ve sizin de başkalarına yollayabilmeniz, yani Zap yapabilmeniz için) bir Lightning Network sıcak cüzdanı adresi tesis etmiş olursunuz. Alby hesabı edinme konusunda -ki bence Alby çok önemli- yardımcı olmamı isterseniz iletişime geçmekten çekinmeyin.
* Tamamdır, hesabınız artık hazır, şimdi akışınızı dolduralım ve diğer insanları takip edelim: Sağ üst köşedeki büyüteç simgeli arama butonuna tıklayın ve tanıdığınız kişilerin hesaplarını arayın ya da sol alttaki ev simgesine tıklayarak gideceğiniz ana ekrandaki “All Follows” butonuna tıklayın ve “Global”i seçin. Şimdi bağlı rölelerinize gönderilen tüm notları göreceksinizdir. Eğer bunalmış hissediyorsanız, endişelenmeyin, zamanla burada yeni birçok ilginç Nostr kullanıcısı bulabileceksinizdir. Sadece bir deneyin.
#### Adım 3: Röleler ve Geniş Çaplı Erişim/Yayın
Yeni röleler ekleyerek erişiminizi ve görünürlüğünüzü artırabilirsiniz. Bunun için yapmanız gereken aşağıda listeleyeceğim röleleri hesabınıza entegre etmektir. Röle entegrasyonu için öncelikle sol üstteki profil resminize tıkladığınızda açılan menüde “Relays” bölümüne giriyorsunuz. Burada, en aşağıda “Add Relay” yazan kutucuğa oluşturduğum listedeki röle adreslerini tek tek girip “Add” butonuna tıklıyorsunuz. İstediğiniz kadar röle ekleyebilirsiniz, tamamen size kalmış. Bu iş bitince mutlaka sağ üstteki “Save” butonuna tıklayın.
Ayrıca kişisel bilgisayarınızdan Coracle adlı Nostr istemcisine girerek de rölelere kolaylıkla bağlanabilirsiniz. Tek yapmanız gereken Coracle’da Nostr hesabınıza Nsec anahtarınızla giriş yapmak ve sol kenar menüdeki “Relays” bölümünü açıp listelendiğini gördüğünüz her bir rölenin sağındaki “Join” butonuna tıklamaktır.
Röle listesi:
140.f7z.io
astral.ninja
bevo.nostr1.com
bitcoiner.social
brb.io
carnivore-diet-relay.denizenid.com
eu.purplerelay.com
expensive-relay.fiatjaf.com
feeds.nostr.band/popular
fiatjaf.com
n.wingu.se
nos.lol
nostr-pub.semisol.dev
nostr-relay.wlvs.space
nostr.21l.st
nostr.band
nostr.bitcoiner.social
nostr.blipme.app
nostr.kollider.xyz
nostr.liberty.fans
nostr.mutinywallet.com
nostr.orangepill.dev
nostr.pleb.network
nostr.plebchain.org
nostr.relayer.se
nostr.satoshi.fun
nostr.walletofsatoshi.com
nostr.yuv.al
nostr.zbd.gg
nostr.zebedee.cloud
nostr.zerofiat.world
nostr1.tunnelsats.com
nostream.denizenid.com
nostria.space
offchain.pub
purplepag.es
pyramid.fiatjaf.com
relay.0xchat.com
relay.benthecarman.com
relay.bitcoinpark.com
relay.current.fyi
relay.damus.io
relay.f7z.io
relay.geyser.fund
relay.mutinywallet.com
relay.nostr.band
relay.nostr.bg
relay.nostr.net
relay.nostr3.io
relay.nostrati.com
relay.nostrplebs.com
relay.orangepill.dev
relay.plebstr.com
relay.primal.net
relay.snort.band
relay.snort.social
relay.utxo.one
relayable.org
relayer.fiatjaf.com
satstacker.cloud
snort.social
soloco.nl
sound-money-relay.denizenid.com

**Önemli:** Özel anahtarınız yerel olarak (mobil cihazınızda veya bilgisayarlarınızda) saklanır ve Amethyst sunucuları veya Snort, Iris, Primal, Coracle gibi diğer tüm Nostr istemcileri tarafından hiçbir şekilde toplanmaz veya saklanmaz, zira Nostr’ın olayı budur, yani desentralizasyon protokolü.
Zamanla internetin kurtarıcısı olacak bu öze dönüş gücüne sahip sosyal ağda beni ve arkadaşlarımı takip etmeyi ve bizim takip ettiğimiz kişilerden kimleri bulabileceğinizi kurcalamayı unutmayın:
Kaan: nostr:npub1asyasvv6vhkuk44ttczsz2v0xvp3c6ze9xqrg9n97n6mkskgpnjqmdugs9
Satoshi Nakamoto Enstitüsü Türkiye: nostr:npub1fdv8r32dqehlkxfnq3uld67vq8t46jw5jvzkk0h6rl4hyvd8g76qf7ujf6
Ludwig von Mises Enstitüsü Türkiye: nostr:npub1gfytsf2p5kw2c42032fkt845x8gh00e027nwnn3pr5880yy954qq4wqlqm
Efe Bitcoin: nostr:npub193h05grv6ykgqc94memmlppqe2wlclukpfl8g5750w8gr3002zasl7ngwj
Şükrü Day: nostr:npub1gw3zhc5r5a7jfgl6yx8qv0nc9kset5ddkrka229c3tym5xltehlq58m7mm
Emir Yorulmaz: nostr:npub1mmfakwg4s36235wlav6qpe03cgr038gujn2hnsvwk2ne49gzqslqc6xvtp
Hasan Tahsin: nostr:npub19zc3ja6jme9ul84sfmgyf5z96a07m6x9dp2jngl5zhwryku9aynsy89q3u
Ufuk: nostr:npub19mz7c6jesdczvlumhpzqekqh9v93w0whup73mu3x2v6jv97lfujq79nqu3
Furkan Arda: nostr:npub1z43kexnw7wxd22ystexyhgf0s7lzsqzfaxv5xvlk9sgspkfzdyps039jv6
Kaancap: nostr:npub14t06hns8wmymynccmcer7sp6y3eql7pjyzwcp0u5rk88sv7vt2rqrl4wte
Yankı Guapmann: nostr:npub19z5m92x8jlltva7zj47z9ydxle8ddkw8y3k5e8xnrphu724v9lys5wxt3p
Arda Uludağ: nostr:npub1puclr9p6yhel2duzask9wfdah0ux5cppw22uz62c0w9cdj3nv0wseuvedh
Musab Babayiğit: nostr:npub1euf7xgdws7n62nwv03fhu82ak24xrka7hedathyuyq9hmhcjxs7sfvwjsn
Kadir: nostr:npub18589me8hqqmt5ect7hjz5k6d2srxzere0uc975gq7hldp9v3qpkslxjn7p
Çınar: nostr:npub12mwsgqaejk98xcsv8k7rf3yat2t2kzu0zzma6jp39rphqx5hajsq4khdeg
Nur Parrhesia: nostr:npub16nnuyfrxguumqdt8xerkkhtgjyxa7qyvfnz4r4ameanqp4aggarqm877qw
Ömer Agâh: nostr:npub1eeze28u72zfa8hl8kfkfnl4jwfe07zsrukug237rsjre7wnvzlrsl49u8h
Korporatist Mağduru: nostr:npub1337wmdvjtxrne5fxrqtc7re8rtj88wnnnsfg562jg39sx2k9p5lqwcjsfh
Alfred: nostr:npub1mdyegp38ahjcpje7ugzmt4ylugrk3hfmwm9tqq72jhdg3ykc4ahs8svgs8
Sefa Uzuner: nostr:npub1ce0khypkfrjxga6umfd82fhtg9xldm583mys4pkvg8zex20gls9s9qrrgj

-

@ eed76ece:afa98124
2024-08-21 09:28:39
เราขายส่ง ผลิต นำเข้า ส่งออก:
เสื้อเชิ้ตผู้ชาย 100% Cotton
ผ้าซารองชายหาด ไซส์เต็ม ไม่มีชายระบาย
หมวกเบสบอล 100% Cotton สไตล์แผง สายปรับได้
ปริมาณสั่งซื้อขั้นต่ำ 72 ชิ้น สินค้าคละประเภท
การขนส่งทางอากาศระหว่างประเทศ
DHL, FedEx, United Parcel Service
ตัวแทน ตัวแทนจำหน่าย ผู้จัดจำหน่าย ผู้นำเข้า ผู้ส่งออก ผู้ขายต่อ ผู้ค้า ผู้ค้าส่ง โดยเฉพาะใน
กัมพูชา: พนมเปญ เสียมเรียบ
ลาว: ตาโลตเซา เวียงจันทน์
ประเทศไทย: กรุงเทพฯ เชียงใหม่ พัทยา
สหรัฐอาหรับเอมิเรตส์ ดูไบ
เวียดนาม: ดานัง ฮานอย
กรุณาถามหาฉัน ริช
LINE @ Globalmerchant
https://globalmerchant.io/pages/thailand
originally posted at https://stacker.news/items/656681
-

@ 20986fb8:cdac21b3
2024-08-20 14:19:59
Welcome to YakiHonne, where we’re excited to introduce you to our innovative Smart Widgets! These interactive components allow you to create dynamic and engaging campaigns directly within social feeds, all without needing any coding skills. Whether you’re new to Smart Widgets or looking to refine your approach, this guide will walk you through the process.
### Step 1: Log In
Start by logging into your YakiHonne account. This is your gateway to creating and managing Smart Widgets. If you don’t have an account yet, sign up easily on our website.
### Step 2: Create Smart Widgets
Once you’re logged in, it’s time to get creative. Head over to the “Post” section and select “Smart Widget.” Here, you have two options:
**Option 1: Create from Scratch**
If you have a specific idea in mind, you can create your Smart Widget from a blank canvas:
• Click on “Create Blank Widget.”
• Begin designing by adding your unique content, interactive features, and any elements that match your campaign’s needs.
• Customize the appearance and functionality to fit your brand or message.
**Option 2: Choose a Template**
If you’re not sure where to start or want some inspiration, using a template is a great option:
• Select “Templates” from the options available.
• Browse through a variety of pre-designed templates.
• Choose one that fits your campaign’s goal, and customize it to make it your own.
**Option 3: Clone a Community Widget**
If you want to explore what others are doing, you can clone a widget shared by the community:
• Click on “Smart Widgets” to see what the community has shared.
• Browse through the community’s shared Smart Widgets.
• Find a widget you like, and click “Clone.”
• Modify the copied widget to create your unique Smart Widget.

### Step 3: Explore Smart Widgets Features
Your Smart Widgets can do much more than just display content. Let’s dive into the features you can integrate:
• User Engagement Tools: Add polls, surveys, or quizzes to interact with your audience.
• BitcoinFi Integration: Enable features that support Bitcoin transactions, like tipping or payment gateways.
• Governance Options: Incorporate voting systems to allow users to participate in decision-making processes.
• Product Growth: Use widgets to drive user growth through referral programs or viral marketing techniques.


These features are designed to enhance interaction and make your Smart Widget stand out. Feel free to experiment with different combinations to see what works best for your campaign.
### Step 4: Publish Your Smart Widgets
After you’ve created and customized your Smart Widget, it’s time to share it with the world:
• Preview your widget to ensure everything looks and works as intended.
• Click “Post my Smart Widget” to publish it.
• Your widget is now live and ready for others to interact with in their social feeds.

### Step 5: Add Smart Widgets to Notes
To maximize the impact of your Smart Widget, you can integrate it into your Notes:
• Go to the “Notes” section on your dashboard.
• Select “Add Smart Widget” and choose the widget you’ve just created.
• Publish the note, and now your audience can engage with your Smart Widget directly through the note.

### Tips for Success
* Experiment with Features: Don’t hesitate to try out different combinations of features to find what works best for your audience.
* Engage Your Audience: The more interactive and engaging your Smart Widget is, the better the results.
* Monitor Performance: After publishing, keep an eye on how your Smart Widget is performing. Adjust and optimize based on user feedback and engagement metrics.
### User Guideline Video Resources
[Create from Scratch](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y)
[Choose a Template](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y)
[Clone a Community Widget](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y)
[Full tutorial video ](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y)
### Conclusion
Creating and using Smart Widgets on YakiHonne is a powerful way to engage with your audience, promote your brand, and drive meaningful interactions. With no coding required, the possibilities are endless. Start exploring today, and see how Smart Widgets can take your campaigns to the next level!
Happy creating!
-

@ 3c827db6:66418fc3
2024-08-18 06:55:26
*The spread of the Lightning Network may change the incentives behind human interactions, thus also affecting the world of jobs. In the first episode: the construction industry.*
When talking about the social implications of Bitcoin, reference is often made to the potential effects of Bitcoin's spread that are not immediately evident: these are second, third, and fourth-degree effects that could change the way people behave in everyday life. Even if the thought might sound hyperbolic, the fact of the matter is that technology has already changed the features of our everyday life, more than once.
Raise your hand if, in the 1980s, you would not have found crazy the idea that one-day people would choose which restaurant to go to based on star ratings and reviews on a digital screen.
Who would have thought that one day it would no longer be necessary to pay attention to the route to take by car to reach one's destination and, possibly, learn it by heart, because software would calculate the best route for them based on traffic?
How would you have reacted if, back in the 1970s, a friend had told you that in the future he might fall in love with a girl he had never seen who lived on the other side of the world, thanks to text messages processed by software that allows you to meet like-minded people?
Innovation changes social interactions: it always has and will continue to do so, especially if technology is particularly disruptive.
The effects of the large-scale diffusion of the Lightning Network - a technology that allows instant payments from one part of the world to another at almost non-existent costs - can be extremely profound, and can act to change entire sectors. In the first example, in this article, we will discuss how instant settlement could revolutionize the construction industry.
The construction industry is a complex ecosystem involving a myriad of stakeholders, each with its own set of incentives. These often conflicting interests lead to inefficiencies, delays, and increased costs.
The Lightning Network offers a solution to align these disparate interests.
## The problems
### Misaligned Incentives
In the traditional construction setup, each stakeholder operates with a different set of incentives. More specifically:
Buyers aim for high-quality construction within a stipulated time and budget.
Planners, including architects, designers, and engineers, are primarily concerned with their designs and less about the actual construction.
Construction companies are focused on maximizing profits, realizing the building as quickly as possible and with the lowest possible quality at the agreed price.
Supervisors' incentives are tied to bonuses, which may or may not align with the project's overall goals.
Construction workers are paid for their time, not the quality or efficiency of their work.
Let's step outside the imagery of the construction site for a moment and think about football.
Can you imagine if defenders had a bonus for putting the ball out of bounds? And midfielders had one for the most passes? And strikers for the most goals? Imagine the chaos on the pitch if the different skills of all the players were not employed for only two goals: to score goals and to avoid conceding them. Such a team would hardly be efficient or successful.
The construction industry, with its varied incentives, faces a similar problem, leading to delays, increased costs, and compromised quality.
#### The underlying issues
Several other issues exacerbate the inefficiencies in the construction industry.
Machinery and tools, often owned by the construction company, are not well-maintained by the workers. This leads to faster wear and tear, increasing costs for the company.
Small changes in the project requested by the buyer are not usually compensated, adding to the company's costs.
Planners are not held accountable for design flaws that manifest during construction, leading to additional costs and delays.
## The solution: instant task-based payments
### Construction workers
In a hyperbitcoinized world, the Lightning Network's instant settlement feature can be a game-changer.
Workers would be paid for tasks completed rather than time spent. For instance, upon successful construction of a wall or installation of windows, payments could be made instantly. This aligns the workers' incentives with quality and efficiency, as they would aim to complete as many tasks as possible to earn more.
Because workers are paid per task there will be no need for a company to hire workers on a payroll. The company just needs to post the tasks, for example on its app, and anyone can apply for them, do their tasks, and get paid for each execution. The more tasks a worker does, the more bitcoin he earns, the better his skills become, the better his reputation will be in the app. Isn't that what already happens with Uber drivers - except for the Bitcoin part, for now?
#### Supervisors
This system would also eliminate the need for supervisors to focus on time management, allowing them to concentrate solely on quality assurance. If a task meets the quality standards, the worker gets paid instantly. This would eliminate the need for time-based bonuses or penalties.
Supervisors would be incentivized to focus even more on quality alone by the split payments feature made possible by the Lightning Network. When a specific task is up for grabs, multiple workers can apply for it via a specialized app. The workers then negotiate among themselves to determine the division of payment - be it an even 50/50 split or a more nuanced arrangement like 60/40. This self-organization extends to scenarios involving more than two workers, where payment divisions could be negotiated as 33.3% for each in a three-way split, or perhaps a 40/40/20 arrangement.
The self-organizing mechanism alleviates the supervisory burden. Instead of mediating disputes or assigning tasks, the supervisor's role becomes even more focused on quality control. Once a task is completed to satisfaction, the supervisor approves it in the app, triggering the release of funds. The app itself is programmed to automatically split the payments among the workers based on their pre-negotiated terms, streamlining the entire process and eliminating the need for manual intervention.
#### Tools ownership
Since workers are compensated for completed tasks rather than time spent, there's a heightened incentive to complete tasks as efficiently as possible. More tasks, more money. The quickest route to efficiency? Utilizing high-quality, well-maintained tools.
When multiple workers vie for the same task, the one equipped with the best tools gains a distinct advantage, capable of completing the task more swiftly and effectively. This system has a ripple effect on tool ownership. Over time, workers might prefer using their own tools over company-provided ones, ensuring better maintenance and ultimately contributing to a more efficient and effective construction process.
In short, the instant payment system would also encourage workers to invest in and maintain their own high-quality tools, further improving efficiency and competition in the construction workers market. This would also reduce the company's costs related to tool maintenance and replacement.
#### Planners and buyers
Planners would be more involved in the construction process, ensuring that their designs are being followed accurately. They would be paid partially upfront for their blueprints, with the rest being released upon successful completion of tasks. This system would make planners more accountable and invested in the successful execution of their plans.
The task-based payment system also benefits the buyer and the construction company by reducing financial risks. Payments would be made for completed tasks, ensuring that neither party is financially exposed. This would also make the negotiation process smoother, as both parties would know exactly what is included in the price for each task.
#### Construction companies
While the Lightning Network's instant settlement feature promises to decentralize many aspects of the construction industry, the need for centralized oversight cannot be entirely eliminated. A single entity must be accountable for the holistic execution of the project, meticulously tracking resources required for each construction phase and ensuring the right personnel are deployed at the appropriate times.
Technological advancements have made it possible for specialized apps to manage these complex tasks. Such apps could, in theory, allow the buyer of the finished building to oversee the entire project. However, this assumes that the buyer possesses the requisite expertise in construction management, which is often not the case. As a result, most buyers prefer to employ specialized companies to manage the project until its completion.
This scenario closely mirrors the current state of Lightning Network nodes. While anyone can set up a node, doing so effectively requires a certain level of expertise. Some individuals may choose to manage their own nodes to earn revenue, but the majority are willing to pay fees for expert management, opting for non-custodial apps to simplify the process. Similarly, some buyers may use construction management apps to avoid paying a construction company, but they must then assume full responsibility for the project's outcome.
### Now go and build
The next logical step is clear: it's time to build that pay-per-task app and usher in a new era of decentralized construction. By leveraging the capabilities of the Lightning Network and Bitcoin, we can shift the balance of power towards those who are at the heart of every construction project—the workers. These are the individuals who bring blueprints to life, who lay each brick and install each window. By empowering them with instant, task-based payments, we not only align incentives across the board but also elevate the entire industry to new heights of efficiency and quality.
-

@ 8dc86882:9dc4ba5e
2024-08-16 17:10:38
Is there a database or website out their where I can put in my car year, make, and model and see what privacy intrusions my be there?
originally posted at https://stacker.news/items/651320
-

@ 2a5d1247:0398ad01
2024-08-14 05:33:49
# 🧠Quote(s) of the week:
'People should not be afraid of their governments. Governments should be afraid of their people.' - V -
'A simple plan: Manipulate the data. Manipulate the media. Manipulate the money.
A simple response: Resist manipulation and think for yourself.' - James Lavish
## 🧡Bitcoin news🧡
The UK is losing its grip on democracy: 'We do have dedicated police officers who are scouring social media to look for this material, and then follow up with arrests.'
Tim Walz (He is the Democratic Party's nominee for vice president in the 2024 U.S. presidential election): “There’s no guarantee to free speech on misinformation or hate speech and especially around our democracy.”
Your thoughts, writings, and communications (with or without machine intelligence) can only be private if they are never held by any central party. It is time you learn and discover Nostr. Study, use Nostr, start now.
Freedom of speech is one of the most precious things in life and society. We lose it at our peril.
**On the 6th of August:
➡️ Morgan Stanley's 15,000 wealth advisors, and $4.8 trillion under management, started pitching clients to buy Bitcoin ETFs by BlackRock and Fidelity on the 7th of August.
Several sources believe that Wells Fargo will quickly follow Morgan Stanley with Bitcoin ETF approvals.
The Bitcoin ecosystem will gain 15,000+ professional salespeople who have relationships with a trillion dollars of managed wealth. Ignore the noise and focus on the signal.
➡️'Tether’s Q2 2024 attestation reveals they hold $4.7 billion in Bitcoin. They also announced a new all-time high in direct and indirect U.S. Treasury holdings at $97.6 billion, surpassing Germany, the UAE, and Australia.' - Bitcoin News
➡️$5.2B worth of Bitcoin was moved by short-term holders within a week.
In contrast, long-term holders largely held onto their BTC. Of the $850M in realized losses, only $600K originated from long-term holders. Don't sell your precious corn to BlackRock.
Now, read the statement above again and think about it. Only 0.07% of the $850M losses were incurred by long-term holders. Jepp, we don't freaking sell our Bitcoin! Only (the new) paper hands got frightened and shook out.
➡️'Bitcoin is in the "Extreme Fear" phase of the Fear & Greed Index at a score of 17/100.
We've been this fearful 3 times in the last 5 years:
• 2019 bottom
• 2020 bottom
• 2022 bottom
Plenty of blood-curdling screams in the streets. Excellent buying opportunity.' -Joe Consorti
➡️Lifehack: 'Airbnb host catches guests running a Bitcoin mining farm on his property.
He was tipped off when the power company notified him that the renters used a month's worth of electricity in just 4 days.' -Bitcoin News
➡️'It currently takes 1,880 hrs (47 weeks) of work to buy 1 Bitcoin. Said another way:
1 Bitcoin currently buys 1 FTE (at avg. US wage).' -Anilsaidso
Now this is before income tax. If you take that into account it would be closer to 1.5 years.
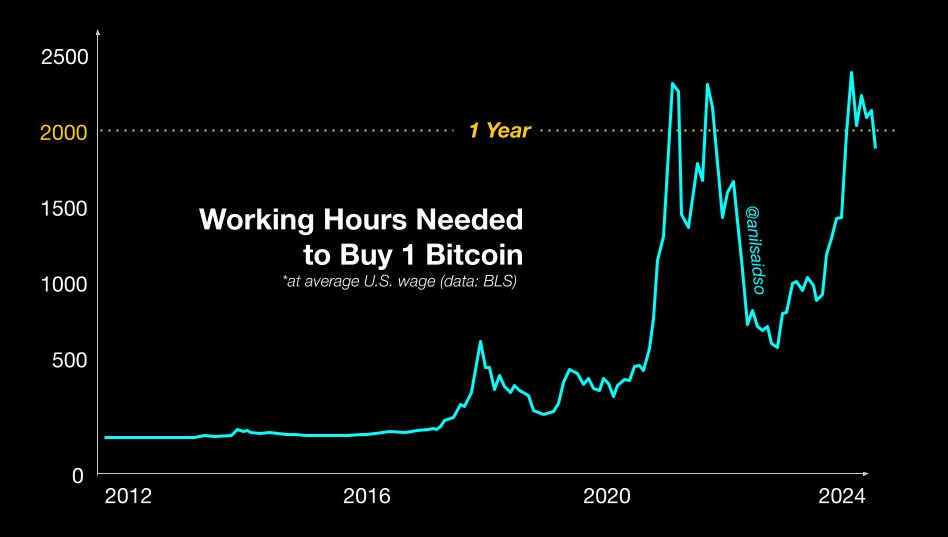
On the 7th of August:
➡️'In Bitcoin over the last decade, the average return for the top 10 days each year was 184%, and the average return (loss) for all of the remaining days each year was −10%.' - James Lavish

This is why you don't trade Bitcoin. Time in the market beats timing the market. Just buy with a 4+ year horizon and go live your life. Spend time with your family & friends.
➡️Metaplanet is raising $70M to increase its Bitcoin holdings.
The company plans to allocate $58.76M of the funds directly to Bitcoin, aiming to hedge against currency depreciation.
➡️Michael Saylor says “I own at least 17,732 Bitcoin and can’t see a better place to put money”
On the 8th of August:
➡️21,000 Bitcoins were taken off exchanges last week.
➡️Metaplanet secures ¥1 billion 0.1% APR loan; proceeds to fund additional purchases of $BTC.
➡️Bloomberg's Balchunas: '99.5% of the money invested in Bitcoin ETFs held firm despite a -14% drop on Monday and a -21% decline for the week.
IBIT saw no outflows at all — a total freak. I’m very bullish on ETF investors’ resilience, but even I’m surprised by this.'
On the 10th of August:
➡️The number of Bitcoin nodes has increased 20% yoy.
On the 11th of August:
➡️The Bitcoin White paper, but explained in Gen Z Language.

Original [source](https://bitcoinforgenz.org):
➡️'3 years ago, Bitcoin's market cap was ~$835B.
Same for all the crypto stuff w/o stablecoins.
Today, Bitcoin's market cap is up 37% ($1.15T)
And the other stuff? -11% (not adjusted for inflation)
It’s an insightful statistic to present to people who blindly “diversify”.' -Sam Wouters
Bitcoin, not CrYpTO (aka. altcoins).
On the 12th of August:
➡️Remember my statement on Trump after the Bitcoin Conference in Nashville? (Stop larping, politicians need votes, etc., etc.)
President Trump has announced his 20 Core Promises to the American people.
We (Bitcoin) are not even a top 20 priority issue in Trump's agenda.
You know what is on #13: Keep the U.S. Dollar as the world's reserve currency.
"end inflation" and "keep the U.S. Dollar as the world's reserve currency" are diametrically opposed and are diabolical.
If you don't believe me, scroll down a bit and read the segment Macro-Economics.
For all the people on Twitter or other platforms, stop bootlicking, stop larping.
You can’t say “Don’t trust verify” AND trust politicians or go full fangirl.
➡️Bitcoinminer Marathon to raise $250m to buy more Bitcoin.
'Marathon Digital Holdings, Inc. Announces Proposed Private Offering of $250 Million of Convertible Senior Notes. Proceeds to be used primarily to acquire Bitcoin and for general corporate purposes.'
They bought $100m in July and currently HODL 20,000 Bitcoin.
## 💸Traditional Finance / Macro:
On the 6th of August:
👉🏽'JP Morgan says Institutions bought the dip while Retail panic-sold aggressively.
Retail sold -$1 BILLION
-2.5 standard deviations BELOW the 12m average
Institutions bought +$14 billion.
+2.9 std dev ABOVE the 12m average' - Rader
Maybe it's because trading platforms were down for retail investors?
Market manipulation at its finest.
On the 8th of August:
👉🏽Investors Pull $2.2 Billion From ARKK In 2024 As Cathie Wood Underperforms Nasdaq By -30% YTD
👉🏽$6.4 TRILLION wiped out from global stock markets in just 4 weeks - Bloomberg
### 🏦Banks:
👉🏽No news
## 🌎Macro/Geopolitics:
Going to start this segment with a great quote by Luke Gromen:
'JPY "too strong" = global market dysfunction, which quickly leads to UST dysfunction.
USD "too strong" = UST market dysfunction, which quickly leads to global market dysfunction.
Powell ultimately only has a choice of how he wants to lose the long end - "fire" or "ice"?'
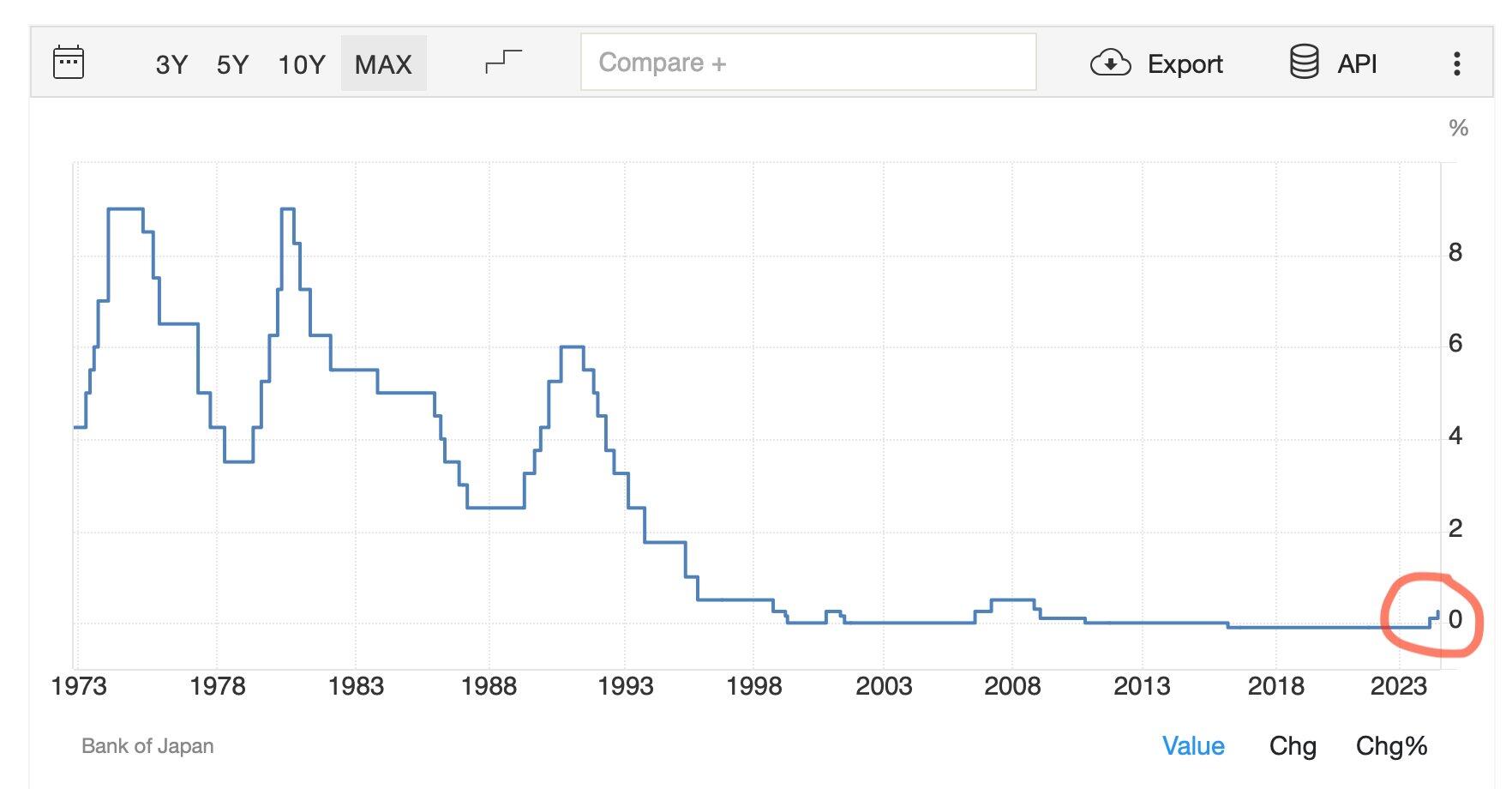
This is what triggered a global-scale sell-off of every major asset class.
This is how unstable the system is. To add a great James Lavish quote:
'And one might say the root cause *before* the trigger, and the reason for instability was this (15 years of *free money*).'
On the 6th of August:
👉🏽M2 money supply update: On the 7th of August the US Treasury starts Treasury buy-backs again at $30 billion a month.
The US Treasury will begin buying back up to $50 billion worth of outstanding government securities by the end of October, primarily to provide liquidity support.
- $8.5B buyback in August
- $31.5B buyback in September
- $10B buyback in October
Hello liquidity, the printers are back on!
Remember:
USD in circulation (M2): 21T
US Government Debt: 35.1T*
More debt than their money in circulation.
* The US Debt just hit 35.1 Trillion. Up 0.1 Trillion in a week.
*
[
](https://image.nostr.build/2dbf21409da89e46405526d03d96114b888e675eb3cb9b6a98ec56f4af424588.jpg)
It is kicking the goddamnnn can down the road.
The U.S. Now Has:
1. Record $17.8 trillion in household debt
2. Record $12.5 trillion in mortgages
3. Record $1.6 trillion in auto loans
4. Near record $1.6 trillion in student loans
5. Record $1.14 trillion in credit card debt (with the average person owing $6,218 at a 20%+ rate. Making minimum payments, it will take them over 18 years and an *additional* $9K+ to pay off that debt.)
Total household debt is now up 53% over the last 10 years and total credit card debt is up 50% since 2020.
Meanwhile, delinquency rates on credit cards and auto loans are nearing the highs seen in 2008
[](https://image.nostr.build/3a111d3130c4780b49f906a14b7b75158da45b33a669fde656b1c161be31f5e1.jpg)
"Who could defeat the US military?"
Compounding interest
is defeating the US military
& compounding interest is undefeated v. hegemons.
Buy LT USTs if you think the US will lose Cold War 2.0 for lack of printing enough USDs to finance this; if not, buy gold, BTC, & stocks.' - Luke Gromen
No doom and gloom, just facts.
Anyway: "Amateurs talk about tactics, but professionals study logistics" - General Omar Bradley
Omar Nelson Bradley was a senior officer of the United States Army during and after World War II, rising to the rank of General of the Army.
👉🏽Again a great explanation of the situation in Japan:
Bank of Japan (BoJ)
1. Prints insane amounts of money.
2. Becomes the largest holder of ETFs in the Nikkei, incentivizing investors to purchase Japanese ETFs borrowing in yen.
3. Yen falls to 40-year lows
4. BOJ blames "speculators". A classic.
5. BOJ spends billions stabilizing the yen
6. Yen rises, market declines, margin calls jump, Nikkei plummets. Black Monday.
You think this is a "free market".
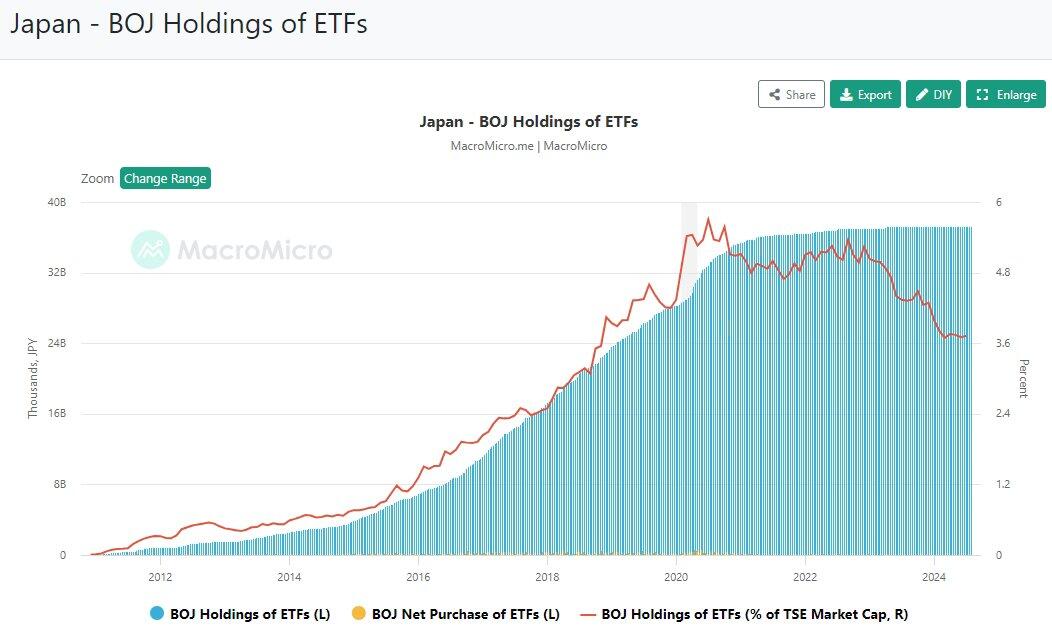
Classic interventionist economics by the BoJ.
Explanation:
'Now what does this mean:
1. Treasury buybacks improve liquidity in the bond market that has been living on life support over the last few years as high inflation made bonds unappealing
2. This may be deflationary if the amount of money taken out is larger than the amount we are spending to aid in economic expansion I hope this helps you.
3. This will likely lead to a lowering of interest rates later on.
4. This will improve US credit ratings as it shows that we are paying down our debts, hopefully, faster than we are creating new debts.
I hope this helps.' -Tim
👉🏽Bank of Japan to hold an emergency meeting to discuss International Financial Markets - Reuters
The Bank of Japan said it, the Ministry of Finance, and the Financial Services Agency will meet from 3 pm on the 6th of August in Tokyo to discuss international markets.
After the meeting: 'No more rate hikes in the near term due to market volatility.' BoJ
On the 7th of August:
👉🏽 Germany's industrial production was up in June. But looking at the chart and the previous month's revised down (3.1% decline), it's a bit too early to call for a revival of Europe's former Manufacturing 'Powerhouse.'
Germany has had no growth for five years. As a matter of fact, German industrial production has been constantly declining since 2017. Grotesque overregulation and energy suicide are accelerating deindustrialization, and some left weirdos are even celebrating degrowth nonsense.
Meanwhile the number of bankruptcies in Germany "unexpectedly" rose in July to the highest level in about ten years.

👉🏽'The US unemployment rate has risen for 4 consecutive months, the longest streak since the 2008 Financial Crisis.
Over the last 75 years, every time unemployment rose for 4 consecutive months, the US economy entered recession.
The jobless rate has surged from 3.8% in March to 4.3% in July, its highest level since October 2021.
Meanwhile, the US hires rate declined to 3.4% in July, its lowest level since the 2020 Pandemic and below the pre-pandemic average of 3.8%.
The US labor market is contracting.' -TKL
👉🏽 11% of credit card balances in the US are now 90+ days delinquent, the highest in over a decade. Probably nothing!
👉🏽'We do have dedicated police officers who are scouring social media to look for this material, and then follow up with arrests.'
The director of public prosecutions of England and Wales warns that sharing online material of riots could be an offense.
This is not something I just made up. He is saying no free speech. the British government is completely corrupt, and anyone who points this out is a target as sharing videos is now a crime. Is it even a democracy then?
Tim Walz (He is the Democratic Party's nominee for vice president in the 2024 U.S. presidential election): “There’s no guarantee to free speech on misinformation or hate speech and especially around our democracy.”
Remember what Jacinda Ardern, then Prime Minister of New Zealand said in 2020:
"We will continue to be your single source of truth…Remember, unless you hear it from us it is not the truth."
OpenAI has an ex-NSA director on its Board;
The new Dutch Prime Minister is a Former Dutch intelligence chief;
How convenient!
Now don't get me wrong. People should think before they post or repost something on social media. But arresting people for creating online content or reposting that contact is just vile.
V for Vendetta was supposed to be just a graphic novel... not real life! A reminder that V for Vendetta is based in the UK!
Again, you should start using Nostr.
And it is not just in the UK, also EUROPE is going crazy. Read the bit on the 12th of August.
On the 8th of August:
👉🏽Bank of England expected to lose £254 BILLION from the QE money printing program since December 2021 - The Economist
On the 10th of August:
👉🏽'How much have prices increased over the last 24 years?
US hospital services prices have skyrocketed by 256% since the beginning of this century.
At the same time, College Tuition and Fees, as well as College Textbooks spiked by 188% and 158%, respectively.
Moreover, the prices of Childcare or Nursery School and Medical Care Services rose by 139% and 136%.
On the other hand, TVs, Toys, and computer software prices declined by 98%, 74%, and 74%, respectively.
To put this into perspective, average hourly wages are up 119% since 2000.
Wage growth is struggling to keep up with many items.' -TKL
Our society and our economy are driven by debt. CPI is a structural understanding of actual inflation. Everything the government subsidizes goes up by 1 to 300 percent. More protocols, less competition, less disruption, less efficiency; Ergo more inflation. (you can sum up the last part in one word: EUROPE)
The industries where governments stay out are private competition, ergo drives pricing down. Competition is deflationary, when will people realize that?
👉🏽'The rich are getting richer faster than ever before:
The top 40% of US income earners hold 83% of the total net worth, near an all-time record.
The top 20% account for 71% of the total net worth, up 10 percentage points over the last 2 decades.
On the other hand, the bottom 40% of income households hold only 8% of the wealth.
Moreover, the bottom 20% of earners reflect just 3% of total US wealth.
Over the last few years, the rich have gotten a lot richer.' - TKL
This makes perfect sense. If you can hold assets in an inflationary economy/environment, well assets and wealth will go up. The consequences of central banks all around the world printing trillions. The money inevitably flows into asset classes creating bubbles in equity markets, real estate, luxury goods, and many more. The wealthy being the largest owners of these assets simply benefit the most.
What do we call that? It’s called the Cantillon effect.
On the 12th of August:
👉🏽Freedom of speech is one of the most precious things in life and society.

'It's amazing how everything they say, is always the opposite: "ensuring freedom of expression and information are protected" = "censor anything we, an unelected group of ultrawealthy technocrats, disagree with". - ZeroHedge
I couldn't have said it better...Jeroen Blokland:
'Europe has completely lost it. European ‘politicians’, who are not leaders, increasingly act from an ideologist perspective, which is incompatible with democratic and socially supported policy making. To send a threatening letter to Elon Musk, compelling him to censor(!) his meeting with Trump is another example of how the aging, declining, and weakening European ‘power’ unrightfully believes it can force its subjective moral standard onto others. Not only does that create friction with many other parts of the world, which outperform Europe in many areas, it also causes massive polarization on the European continent.'
"There is no crueler tyranny than that which is perpetuated under the shield of law and in the name of justice." - Montesquieu
"The welfare of the people has always been the alibi of tyrants, and it provides the servants of tyranny a good conscience." - Albert Camus
Really you should study Bitcoin & Nostr!
'Paradoxically, the Cantillon Effect means that the very last people to understand the need for BTC & technologies like Nostr will be those in and closest to western technocratic & banking centers.' - Luke Gromen
🎁If you have made it this far I would like to give you a little gift:
Great book, great podcast: Resistance Money with Andrew Bailey, Bradley Rettler, & Craig Warmke
'Andrew Bailey, is a Professor of Philosophy at Yale-NUS College, Bradley Rettler is a Professor of Philosophy at the University of Wyoming and Craig Warmke is a Professor of Philosophy at Northern Illinois University. In this episode we discuss their book Resistance Money and the global net-benefits of Bitcoin.'
“When asking a question like this…it’s tempting to replace it with the question ‘is Bitcoin good for me?’, and then you’re off to bag-pumping or bag-dumping; so what we tried to do here is to give a bit more precision to the question: ‘is Bitcoin good for the world?’”
— Andrew Bailey
[](https://youtu.be/OtEp9lZKWvA?si=sOQC7fIB0UEtVhze)
Credit: I have used multiple sources!
My savings account: Bitcoin
The tool I recommend for setting up a Bitcoin savings plan: @Relai 🇨🇭 especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. (Please only use it till the 31st of October - after that full KYC)
Hence a DCA, Dollar cost Average Strategy. Check out my tutorial post (Instagram) & video (YouTube) for more info.
⠀⠀⠀⠀
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.
⠀⠀⠀⠀⠀⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with sats.
Many thanks for reading the Weekly Recap, see you all next week!
Felipe - Bitcoin Friday
-

@ 0176967e:1e6f471e
2024-07-28 15:31:13
Objavte, ako avatari a pseudonymné identity ovplyvňujú riadenie kryptokomunít a decentralizovaných organizácií (DAOs). V tejto prednáške sa zameriame na praktické fungovanie decentralizovaného rozhodovania, vytváranie a správu avatarových profilov, a ich rolu v online reputačných systémoch. Naučíte sa, ako si vytvoriť efektívny pseudonymný profil, zapojiť sa do rôznych krypto projektov a využiť svoje aktivity na zarábanie kryptomien. Preskúmame aj príklady úspešných projektov a stratégie, ktoré vám pomôžu zorientovať sa a uspieť v dynamickom svete decentralizovaných komunít.
-

@ 0176967e:1e6f471e
2024-07-28 09:16:10
Jan Kolčák pochádza zo stredného Slovenska a vystupuje pod umeleckým menom Deepologic. Hudbe sa venuje už viac než 10 rokov. Začínal ako DJ, ktorý s obľubou mixoval klubovú hudbu v štýloch deep-tech a afrohouse. Stále ho ťahalo tvoriť vlastnú hudbu, a preto sa začal vzdelávať v oblasti tvorby elektronickej hudby. Nakoniec vydal svoje prvé EP s názvom "Rezonancie". Učenie je pre neho celoživotný proces, a preto sa neustále zdokonaľuje v oblasti zvuku a kompozície, aby jeho skladby boli kvalitné na posluch aj v klube.
V roku 2023 si založil vlastnú značku EarsDeep Records, kde dáva príležitosť začínajúcim producentom. Jeho značku podporujú aj etablované mená slovenskej alternatívnej elektronickej scény. Jeho prioritou je sloboda a neškatulkovanie. Ako sa hovorí v jednej klasickej deephouseovej skladbe: "We are all equal in the house of deep." So slobodou ide ruka v ruke aj láska k novým technológiám, Bitcoinu a schopnosť udržať si v digitálnom svete prehľad, odstup a anonymitu.
V súčasnosti ďalej produkuje vlastnú hudbu, venuje sa DJingu a vedie podcast, kde zverejňuje svoje mixované sety. Na Lunarpunk festivale bude hrať DJ set tvorený vlastnou produkciou, ale aj skladby, ktoré sú blízke jeho srdcu.
[Podcast](https://fountain.fm/show/eYFu6V2SUlN4vC5qBKFk)
[Bandcamp](https://earsdeep.bandcamp.com/)
[Punk Nostr website](https://earsdeep-records.npub.pro/) alebo nprofile1qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qy88wumn8ghj7mn0wvhxcmmv9uq3xamnwvaz7tmsw4e8qmr9wpskwtn9wvhsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qyg8wumn8ghj7mn0wd68ytnddakj7qghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7qpqguvns4ld8k2f3sugel055w7eq8zeewq7mp6w2stpnt6j75z60z3swy7h05
-

@ 0176967e:1e6f471e
2024-07-27 11:10:06
Workshop je zameraný pre všetkých, ktorí sa potýkajú s vysvetľovaním Bitcoinu svojej rodine, kamarátom, partnerom alebo kolegom. Pri námietkach z druhej strany väčšinou ideme do protiútoku a snažíme sa vytiahnuť tie najlepšie argumenty. Na tomto workshope vás naučím nový prístup k zvládaniu námietok a vyskúšate si ho aj v praxi. Know-how je aplikovateľné nie len na komunikáciu Bitcoinu ale aj pre zlepšenie vzťahov, pri výchove detí a celkovo pre lepší osobný život.
-

@ 0176967e:1e6f471e
2024-07-26 17:45:08
Ak ste v Bitcoine už nejaký ten rok, možno máte pocit, že už všetkému rozumiete a že vás nič neprekvapí. Viete čo je to peňaženka, čo je to seed a čo adresa, možno dokonca aj čo je to sha256. Ste si istí? Táto prednáška sa vám to pokúsi vyvrátiť. 🙂
-

@ 0176967e:1e6f471e
2024-07-26 12:15:35
Bojovať s rakovinou metabolickou metódou znamená použiť metabolizmus tela proti rakovine. Riadenie cukru a ketónov v krvi stravou a pohybom, časovanie rôznych typov cvičení, včasná kombinácia klasickej onko-liečby a hladovania. Ktoré vitamíny a suplementy prijímam a ktorým sa napríklad vyhýbam dajúc na rady mojej dietologičky z USA Miriam (ktorá sa špecializuje na rakovinu).
Hovori sa, že čo nemeriame, neriadime ... Ja som meral, veľa a dlho ... aj grafy budú ... aj sranda bude, hádam ... 😉
-

@ 0176967e:1e6f471e
2024-07-26 09:50:53
Predikčné trhy predstavujú praktický spôsob, ako môžeme nahliadnuť do budúcnosti bez nutnosti spoliehať sa na tradičné, často nepresné metódy, ako je veštenie z kávových zrniek. V prezentácii sa ponoríme do histórie a vývoja predikčných trhov, a popíšeme aký vplyv mali a majú na dostupnosť a kvalitu informácií pre širokú verejnosť, a ako menia trh s týmito informáciami. Pozrieme sa aj na to, ako tieto trhy umožňujú obyčajným ľuďom prístup k spoľahlivým predpovediam a ako môžu prispieť k lepšiemu rozhodovaniu v rôznych oblastiach života.
-

@ 0176967e:1e6f471e
2024-07-25 20:53:07
AI hype vnímame asi všetci okolo nás — už takmer každá appka ponúka nejakú “AI fíčuru”, AI startupy raisujú stovky miliónov a Európa ako obvykle pracuje na regulovaní a našej ochrane pred nebezpečím umelej inteligencie. Pomaly sa ale ukazuje “ovocie” spojenia umelej inteligencie a človeka, kedy mnohí ľudia reportujú signifikantné zvýšenie produktivity v práci ako aj kreatívnych aktivitách (aj napriek tomu, že mnohí hardcore kreatívci by každého pri spomenutí skratky “AI” najradšej upálili). V prvej polovici prednášky sa pozrieme na to, akými rôznymi spôsobmi nám vie byť AI nápomocná, či už v práci alebo osobnom živote.
Umelé neuróny nám už vyskakujú pomaly aj z ovsených vločiek, no to ako sa k nám dostávajú sa veľmi líši. Hlavne v tom, či ich poskytujú firmy v zatvorených alebo open-source modeloch. V druhej polovici prednášky sa pozrieme na boom okolo otvorených AI modelov a ako ich vieme využiť.
-

@ 0176967e:1e6f471e
2024-07-25 20:38:11
Čo vznikne keď spojíš hru SNAKE zo starej Nokie 3310 a Bitcoin? - hra [Chain Duel](https://www.youtube.com/watch?v=5hCI2MzxOzE)!
Jedna z najlepších implementácií funkcionality Lightning Networku a gamingu vo svete Bitcoinu.
Vyskúšať si ju môžete s kamošmi [na tomto odkaze](https://game.chainduel.net/). Na stránke nájdeš aj základné pravidlá hry avšak odporúčame pravidlá pochopiť [aj priamo hraním](https://game.chainduel.net/gamemenu)
Chain Duel si získava hromady fanúšikov po bitcoinových konferenciách po celom svete a práve na Lunarpunk festival ho prinesieme tiež.
Multiplayer 1v1 hra, kde nejde o náhodu, ale skill, vás dostane. Poďte si zmerať sily s ďalšími bitcoinermi a vyhrať okrem samotných satoshi rôzne iné ceny.
Príďte sa zúčastniť prvého oficiálneho Chain Duel turnaja na Slovensku!
Pre účasť na turnaji je [potrebná registrácia dopredu](https://docs.google.com/forms/d/e/1FAIpQLScq96a-zM2i9FCkd3W3haNVcdKFTbPkXObNDh4vJwbmADsb0w/viewform).
-

@ b17fccdf:b7211155
2024-07-23 12:19:23
#### Next new resources about the MiniBolt guide have been released:
* 🆕 **Roadmap**: [LINK](https://github.com/orgs/minibolt-guide/projects/1)
* 🆕 **Network Map** (UC): [LINK](https://bit.ly/minibolt_netmap)
* 🆕 **Nostr community**: [LINK](https://w3.do/twofaktor@twofaktor-github-io/minibolt_community)
* 🆕 **Linktr FOSS** (UC) by [Gzuuus](nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds): [LINK](https://linktr.minibolt.info)
* 🆕 **Donate webpage**: 🚾 [Clearnet LINK](https://donate.minibolt.info) || 🧅 [Onion LINK](http://3iqm7nidexns5p6wmgc23ibgiscm6rge7hwyeziviwgav4fl7xui4mqd.onion/apps/Li3AtEGDsqNmNddv6rX69taidm3/pos)
* 🆕 **Contact email**: [hello@minibolt.info](mailto:hello@minibolt.info)
-

@ 0176967e:1e6f471e
2024-07-22 19:57:47
Co se nomádská rodina již 3 roky utíkající před kontrolou naučila o kontrole samotné? Co je to vlastně svoboda? Může koexistovat se strachem? S konfliktem? Zkusme na chvíli zapomenout na daně, policii a stát a pohlédnout na svobodu i mimo hranice společenských ideologií. Zkusme namísto hledání dalších odpovědí zjistit, zda se ještě někde neukrývají nové otázky. Možná to bude trochu ezo.
Karel provozuje již přes 3 roky se svou ženou, dvěmi dětmi a jedním psem minimalistický život v obytné dodávce. Na cestách spolu začali tvořit youtubový kanál "[Karel od Martiny](https://www.youtube.com/@KarelodMartiny)" o svobodě, nomádství, anarchii, rodičovství, drogách a dalších normálních věcech.
Nájdete ho aj [na nostr](nostr:npub1y2se87uxc7fa0aenfqfx5hl9t2u2fjt4sp0tctlcr0efpauqtalqxfvr89).
-

@ 82100056:e198089f
2024-07-22 15:44:39
Was the Trump ‘assassination attempt’ a staged event that he was in on? Was it an inside job by the secret service seeking to eliminate the number one enemy of the deep state? Or was Thomas Crooks simply competent (and lucky) enough to pull off a lone-wolf attack on the 45th president of the USA?
Whatever the truth is, which will surely come out over time, the ‘shooting’ has dramatically altered the course of American politics.
The most obvious narrative shift has been Trump’s new-found God-like status among the American right. The image of Trump holding his fist in the air, right ear bloodied, while urging Americans to “fight”, symbolises this. His long-time friend and UFC chairman Dana White said in the aftermath of the ‘shooting’: “He [Trump] is one of the toughest, most resilient human beings that I have ever met in my entire life….This guy is the legitimate ultimate American badass of all-time!” In addition, a section of Trump supporters turned up to the recent Republican National Convention [wearing fake bandages](https://www.bbc.co.uk/news/videos/cldy39vpv4qo) on their ears in a humorous yet sincere show of solidarity with their leader. These are just two examples among many of the relentless outpouring of adulation that Trump is receiving. He has become a martyr without having to die.
The Trump fist raise image and resulting strongman narrative is not what I will focus on, but it does provide crucial context for what I am going to say. Instead, I will look at the farcical performance of the secret service, which did not go unnoticed by social media users. Specifically, that of the female agents, and the resulting backlash against the perceived failures of DEI (diversity, equity and inclusion) within the US government. I will also look at why this narrative is being pushed by powerful players of the alternative-media industrial complex.
First, [footage emerged](https://www.youtube.com/watch?v=tAtu1YU-PHo) of one female agent who struggled to holster her firearm, while looking completely disorientated, as Trump, who could have still been in danger, fled the scene in a blacked out SUV. It was reminiscent of Fredo Corleone’s bumbling efforts to save his father Vito, who faced a failed assassination attempt of his own in The Godfather 2.
Second, there is the [ridiculous still image](https://www.google.com/search?sca_esv=5b98f86993edd4ca&sca_upv=1&rlz=1C5CHFA_enGB1069GB1069&q=trump+female+secret+service&udm=2&fbs=AEQNm0Aa4sjWe7Rqy32pFwRj0UkWd8nbOJfsBGGB5IQQO6L3J_86uWOeqwdnV0yaSF-x2joQcoZ-0Q2Udkt2zEybT7HdcghX_cULItgDQ-ic0tx97HU0om4eiEoFQ7LkCUAIN0k5ckfuXbaYID2cdV_OmGsEy_vSEauNj1_Mmv2J6NjBnVEvjRAhAzO6zw58Qt0lVtZUf36m&sa=X&ved=2ahUKEwj8_NWx5riHAxX5bEEAHROMDHIQtKgLegQICxAB&biw=1600&bih=781&dpr=1.8#vhid=k3BFXz5a0rU7wM&vssid=mosaic) of the female secret service agent standing in front of Trump by the podium in order to provide cover for the former president amid a possible active shooter situation. The image is ludicrous because the female agent is not nearly as tall as Trump, and so his head, including his ear that was just ‘clipped’ by a 'bullet', remains completely exposed.
Third, the US secret service director Kimberly Cheatle, a woman, is [ultimately responsible](https://www.nytimes.com/2024/07/17/us/politics/kimberly-cheatle-secret-service.html) for the ‘near-assassination’ of Donald Trump and the seemingly unlimited ‘mistakes’ made by the agency on the day. For example, Cheatle did not have a secret service gunmen on the roof used by Thomas Crooks because it was “too sloped”. An explanation that was shown to be comically bad in the immediate aftermath of the ‘shooting’ when photos emerged of cleaners standing on the roof to clear Crooks’ ‘blood’ away.
The backlash against the female agents in question has been pretty relentless from the American right. But not just from anonymous MAGA social media users. Some of the key drivers of political narratives on the right have honed in on this issue and more generally against the perceived failings of DEI.
“There should not be any women in the Secret Service. These are supposed to be the very best, and none of the very best at this job are women,” [said right-leaning activist Matt Walsh](https://x.com/MattWalshBlog/status/1812492702493057338?lang=en) in a direct response to the footage of the female secret service agents. Walsh works for The Daily Wire and rose to global prominence on the back of his documentary “What Is A Women?”. In other words, he is a key figure within the US culture war, who has a keen interest in discussions around gender.
Then there is Andrew Tate. One could have predicted where the former kickboxer was going to stand on this issue. [Tate posted a video to social media](https://www.youtube.com/watch?v=cpw5Sm46f-4&t=44s) in which he lambasted Kimberly Cheatle and the other female secret service agents in a visibly heated manner. “There’s not a female alive who’s ever going to jump in front of a bullet for anybody. She’s gonna piss her panties and hide.” Tate carries on the rest of the video in the same vain, including a statement which in my view is a big clue about the narrative he is trying to push.
“Society as a whole will be better off if we return to our [gender] roles.”
Tate wants the secret service and the military to go back to being made up of men who are selected solely on the basis of merit. After years of military aged males being 'disenfranchised' by the institutions they once felt proud to represent - the pendulum may be about to swing back.
At this point, it is worth mentioning that I believe both Matt Walsh and Andrew Tate are intelligence assets who push agendas to the wider public on behalf of the deep state, [as Miri AF explains here](https://miriaf.co.uk/the-most-important-question-about-andrew-tate-no-one-is-asking/). It is also worth considering that these women are akin to actors who are fulfilling their roles as incompetent, further driving the narrative of Walsh and Tate. Their incompetence is not necessarily because they are women - they might just be acting like they are incapable because they are women. On the face of it, it sounds overly conspiratorial - but in my view, it is plausible.
Okay, let’s continue down this ‘conspiracy theory’ rabbit hole for a little longer. It is widely understood that intelligence agencies use terror attacks to further their insidious agendas. A clear example of this is how George Bush’s government, in conjunction with the media and the intelligence apparatus, weaponised the fear brought about by 9/11 in order to invade Iraq.
So, what is the goal of Tate/Walsh and the deep state (and possibly Trump too) in pushing back against DEI and making the secret service/military a place that ‘respects’ male competence again? The same military whose soon-to-be commander-in-chief has God-like status, is the "ultimate American badass of all time", and who ‘literally’ just ‘took a bullet’ for his country. The same military that is currently in escalating proxy wars vs Russia and Iran - neither of which look like ending anytime soon. Are American military aged males being influenced to go and fight for their country in WW3 after years of being gaslighted?
I want to state that I do not claim to know this for sure. I am stating a theory. I am asking questions that I believe need to be asked.
But I will leave you with this quote by a World War Two veteran that has been doing the rounds on social media recently.
“If president Trump was commander-in-chief I would go back to re-enlist today.” [Sgt. Bill Peril, 99, WW2 veteran. ](https://www.independent.co.uk/news/world/americas/us-politics/rnc-trump-world-war-veteran-b2581928.html)
-

@ 8e7462a8:c723a97b
2024-07-21 16:00:55
<pre class="ql-syntax" spellcheck="false"># Bitcoin: A Peer-to-Peer Electronic Cash System
Satoshi Nakamoto
[satoshin@gmx.com](mailto:satoshin@gmx.com)
www.bitcoin.org
**Abstract.** A purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without going through a financial institution. Digital signatures provide part of the solution, but the main benefits are lost if a trusted third party is still required to prevent double-spending. We propose a solution to the double-spending problem using a peer-to-peer network. The network timestamps transactions by hashing them into an ongoing chain of hash-based proof-of-work, forming a record that cannot be changed without redoing the proof-of-work. The longest chain not only serves as proof of the sequence of events witnessed, but proof that it came from the largest pool of CPU power. As long as a majority of CPU power is controlled by nodes that are not cooperating to attack the network, they'll generate the longest chain and outpace attackers. The network itself requires minimal structure. Messages are broadcast on a best effort basis, and nodes can leave and rejoin the network at will, accepting the longest proof-of-work chain as proof of what happened while they were gone.
## 1. Introduction
Commerce on the Internet has come to rely almost exclusively on financial institutions serving as trusted third parties to process electronic payments. While the system works well enough for most transactions, it still suffers from the inherent weaknesses of the trust based model. Completely non-reversible transactions are not really possible, since financial institutions cannot avoid mediating disputes. The cost of mediation increases transaction costs, limiting the minimum practical transaction size and cutting off the possibility for small casual transactions, and there is a broader cost in the loss of ability to make non-reversible payments for non-reversible services. With the possibility of reversal, the need for trust spreads. Merchants must be wary of their customers, hassling them for more information than they would otherwise need. A certain percentage of fraud is accepted as unavoidable. These costs and payment uncertainties can be avoided in person by using physical currency, but no mechanism exists to make payments over a communications channel without a trusted party.
What is needed is an electronic payment system based on cryptographic proof instead of trust, allowing any two willing parties to transact directly with each other without the need for a trusted third party. Transactions that are computationally impractical to reverse would protect sellers from fraud, and routine escrow mechanisms could easily be implemented to protect buyers. In this paper, we propose a solution to the double-spending problem using a peer-to-peer distributed timestamp server to generate computational proof of the chronological order of transactions. The system is secure as long as honest nodes collectively control more CPU power than any cooperating group of attacker nodes.
## 2. Transactions
We define an electronic coin as a chain of digital signatures. Each owner transfers the coin to the next by digitally signing a hash of the previous transaction and the public key of the next owner and adding these to the end of the coin. A payee can verify the signatures to verify the chain of ownership.
```
┌─────────────────────┐ ┌─────────────────────┐ ┌─────────────────────┐
│ │ │ │ │ │
│ Transaction │ │ Transaction │ │ Transaction │
│ │ │ │ │ │
│ ┌─────────────┐ │ │ ┌─────────────┐ │ │ ┌─────────────┐ │
│ │ Owner 1's │ │ │ │ Owner 2's │ │ │ │ Owner 3's │ │
│ │ Public Key │ │ │ │ Public Key │ │ │ │ Public Key │ │
│ └───────┬─────┘ │ │ └───────┬─────┘ │ │ └───────┬─────┘ │
│ │ . │ │ │ . │ │ │ │
──────┼─────────┐ │ . ├───────────────┼─────────┐ │ . ├──────────────┼─────────┐ │ │
│ │ │ . │ │ │ │ . │ │ │ │ │
│ ┌──▼─▼──┐ . │ │ ┌──▼─▼──┐ . │ │ ┌──▼─▼──┐ │
│ │ Hash │ . │ │ │ Hash │ . │ │ │ Hash │ │
│ └───┬───┘ . │ Verify │ └───┬───┘ . │ Verify │ └───┬───┘ │
│ │ ............................ │ ........................... │ │
│ │ │ │ │ │ │ │ │ │ │
│ ┌──────▼──────┐ │ │ ┌─▼────▼──────┐ │ │ ┌─▼────▼──────┐ │
│ │ Owner 0's │ │ Sign │ │ Owner 1's │ │ Sign │ │ Owner 2's │ │
│ │ Signature │ │ ...........─►│ Signature │ │ ...........─►│ Signature │ │
│ └─────────────┘ │ . │ └─────────────┘ │ . │ └─────────────┘ │
│ │ . │ │ . │ │
└─────────────────────┘ . └─────────────────────┘ . └─────────────────────┘
. .
┌─────────────┐ . ┌─────────────┐ . ┌─────────────┐
│ Owner 1's │........... │ Owner 2's │.......... │ Owner 3's │
│ Private Key │ │ Private Key │ │ Private Key │
└─────────────┘ └─────────────┘ └─────────────┘
```
The problem of course is the payee can't verify that one of the owners did not double-spend the coin. A common solution is to introduce a trusted central authority, or mint, that checks every transaction for double spending. After each transaction, the coin must be returned to the mint to issue a new coin, and only coins issued directly from the mint are trusted not to be double-spent. The problem with this solution is that the fate of the entire money system depends on the company running the mint, with every transaction having to go through them, just like a bank.
We need a way for the payee to know that the previous owners did not sign any earlier transactions. For our purposes, the earliest transaction is the one that counts, so we don't care about later attempts to double-spend. The only way to confirm the absence of a transaction is to be aware of all transactions. In the mint based model, the mint was aware of all transactions and decided which arrived first. To accomplish this without a trusted party, transactions must be publicly announced [^1], and we need a system for participants to agree on a single history of the order in which they were received. The payee needs proof that at the time of each transaction, the majority of nodes agreed it was the first received.
## 3. Timestamp Server
The solution we propose begins with a timestamp server. A timestamp server works by taking a hash of a block of items to be timestamped and widely publishing the hash, such as in a newspaper or Usenet post [^2] [^3] [^4] [^5]. The timestamp proves that the data must have existed at the time, obviously, in order to get into the hash. Each timestamp includes the previous timestamp in its hash, forming a chain, with each additional timestamp reinforcing the ones before it.
```
┌──────┐ ┌──────┐
────────────►│ ├───────────────────────►│ ├───────────────────►
│ Hash │ │ Hash │
┌───►│ │ ┌───►│ │
│ └──────┘ │ └──────┘
│ │
┌┴──────────────────────────┐ ┌┴──────────────────────────┐
│ Block │ │ Block │
│ ┌─────┐ ┌─────┐ ┌─────┐ │ │ ┌─────┐ ┌─────┐ ┌─────┐ │
│ │Item │ │Item │ │... │ │ │ │Item │ │Item │ │... │ │
│ └─────┘ └─────┘ └─────┘ │ │ └─────┘ └─────┘ └─────┘ │
│ │ │ │
└───────────────────────────┘ └───────────────────────────┘
```
## 4. Proof-of-Work
To implement a distributed timestamp server on a peer-to-peer basis, we will need to use a proof-of-work system similar to Adam Back's Hashcash [^6], rather than newspaper or Usenet posts. The proof-of-work involves scanning for a value that when hashed, such as with SHA-256, the hash begins with a number of zero bits. The average work required is exponential in the number of zero bits required and can be verified by executing a single hash.
For our timestamp network, we implement the proof-of-work by incrementing a nonce in the block until a value is found that gives the block's hash the required zero bits. Once the CPU effort has been expended to make it satisfy the proof-of-work, the block cannot be changed without redoing the work. As later blocks are chained after it, the work to change the block would include redoing all the blocks after it.
```
┌────────────────────────────────────────┐ ┌────────────────────────────────────────┐
│ Block │ │ Block │
│ ┌──────────────────┐ ┌──────────────┐ │ │ ┌──────────────────┐ ┌──────────────┐ │
───────┼─►│ Prev Hash │ │ Nonce │ ├──────┼─►│ Prev Hash │ │ Nonce │ │
│ └──────────────────┘ └──────────────┘ │ │ └──────────────────┘ └──────────────┘ │
│ │ │ │
│ ┌──────────┐ ┌──────────┐ ┌──────────┐ │ │ ┌──────────┐ ┌──────────┐ ┌──────────┐ │
│ │ Tx │ │ Tx │ │ ... │ │ │ │ Tx │ │ Tx │ │ ... │ │
│ └──────────┘ └──────────┘ └──────────┘ │ │ └──────────┘ └──────────┘ └──────────┘ │
│ │ │ │
└────────────────────────────────────────┘ └────────────────────────────────────────┘
```
The proof-of-work also solves the problem of determining representation in majority decision making. If the majority were based on one-IP-address-one-vote, it could be subverted by anyone able to allocate many IPs. Proof-of-work is essentially one-CPU-one-vote. The majority decision is represented by the longest chain, which has the greatest proof-of-work effort invested in it. If a majority of CPU power is controlled by honest nodes, the honest chain will grow the fastest and outpace any competing chains. To modify a past block, an attacker would have to redo the proof-of-work of the block and all blocks after it and then catch up with and surpass the work of the honest nodes. We will show later that the probability of a slower attacker catching up diminishes exponentially as subsequent blocks are added.
To compensate for increasing hardware speed and varying interest in running nodes over time, the proof-of-work difficulty is determined by a moving average targeting an average number of blocks per hour. If they're generated too fast, the difficulty increases.
## 5. Network
The steps to run the network are as follows:
1. New transactions are broadcast to all nodes.
2. Each node collects new transactions into a block.
3. Each node works on finding a difficult proof-of-work for its block.
4. When a node finds a proof-of-work, it broadcasts the block to all nodes.
5. Nodes accept the block only if all transactions in it are valid and not already spent.
6. Nodes express their acceptance of the block by working on creating the next block in the chain, using the hash of the accepted block as the previous hash.
Nodes always consider the longest chain to be the correct one and will keep working on extending it. If two nodes broadcast different versions of the next block simultaneously, some nodes may receive one or the other first. In that case, they work on the first one they received, but save the other branch in case it becomes longer. The tie will be broken when the next proof-of-work is found and one branch becomes longer; the nodes that were working on the other branch will then switch to the longer one.
New transaction broadcasts do not necessarily need to reach all nodes. As long as they reach many nodes, they will get into a block before long. Block broadcasts are also tolerant of dropped messages. If a node does not receive a block, it will request it when it receives the next block and realizes it missed one.
## 6. Incentive
By convention, the first transaction in a block is a special transaction that starts a new coin owned by the creator of the block. This adds an incentive for nodes to support the network, and provides a way to initially distribute coins into circulation, since there is no central authority to issue them. The steady addition of a constant of amount of new coins is analogous to gold miners expending resources to add gold to circulation. In our case, it is CPU time and electricity that is expended.
The incentive can also be funded with transaction fees. If the output value of a transaction is less than its input value, the difference is a transaction fee that is added to the incentive value of the block containing the transaction. Once a predetermined number of coins have entered circulation, the incentive can transition entirely to transaction fees and be completely inflation free.
The incentive may help encourage nodes to stay honest. If a greedy attacker is able to assemble more CPU power than all the honest nodes, he would have to choose between using it to defraud people by stealing back his payments, or using it to generate new coins. He ought to find it more profitable to play by the rules, such rules that favour him with more new coins than everyone else combined, than to undermine the system and the validity of his own wealth.
## 7. Reclaiming Disk Space
Once the latest transaction in a coin is buried under enough blocks, the spent transactions before it can be discarded to save disk space. To facilitate this without breaking the block's hash, transactions are hashed in a Merkle Tree [^7] [^2] [^5], with only the root included in the block's hash. Old blocks can then be compacted by stubbing off branches of the tree. The interior hashes do not need to be stored.
```
┌──────────────────────────────────────────┐ ┌──────────────────────────────────────────┐
│ │ │ │
│ Block ┌─────────────────────────────┐ │ │ Block ┌─────────────────────────────┐ │
│ │ Block Header (Block Hash) │ │ │ │ Block Header (Block Hash) │ │
│ │ ┌────────────┐ ┌─────────┐ │ │ │ │ ┌────────────┐ ┌─────────┐ │ │
│ │ │ Prev Hash │ │ Nonce │ │ │ │ │ │ Prev Hash │ │ Nonce │ │ │
│ │ └────────────┘ └─────────┘ │ │ │ │ └────────────┘ └─────────┘ │ │
│ │ │ │ │ │ │ │
│ │ ┌─────────────┐ │ │ │ │ ┌─────────────┐ │ │
│ │ │ Root Hash │ │ │ │ │ │ Root Hash │ │ │
│ │ └─────▲─▲─────┘ │ │ │ │ └─────▲─▲─────┘ │ │
│ │ │ │ │ │ │ │ │ │ │ │
│ │ │ │ │ │ │ │ │ │ │ │
│ └───────────┼─┼───────────────┘ │ │ └───────────┼─┼───────────────┘ │
│ │ │ │ │ │ │ │
│ .......... │ │ .......... │ │ ┌────────┐ │ │ .......... │
│ . ─────┘ └─────. . │ │ │ ├────┘ └─────. . │
│ . Hash01 . . Hash23 . │ │ │ Hash01 │ . Hash23 . │
│ .▲.....▲.. .▲.....▲.. │ │ │ │ .▲.....▲.. │
│ │ │ │ │ │ │ └────────┘ │ │ │
│ │ │ │ │ │ │ │ │ │
│ │ │ │ │ │ │ │ │ │
│ .....│.. ..│..... .....│.. ..│..... │ │ ┌────┴─┐ ..│..... │
│ . . . . . . . . │ │ │ │ . . │
│ .Hash0 . .Hash1 . .Hash2 . .Hash3 . │ │ │Hash2 │ .Hash3 . │
│ ...▲.... ...▲.... ...▲.... ...▲.... │ │ │ │ . . │
│ │ │ │ │ │ │ └──────┘ ...▲.... │
│ │ │ │ │ │ │ │ │
│ │ │ │ │ │ │ │ │
│ ┌──┴───┐ ┌──┴───┐ ┌──┴───┐ ┌──┴───┐ │ │ ┌──┴───┐ │
│ │ Tx0 │ │ Tx1 │ │ Tx2 │ │ Tx3 │ │ │ │ Tx3 │ │
│ └──────┘ └──────┘ └──────┘ └──────┘ │ │ └──────┘ │
│ │ │ │
└──────────────────────────────────────────┘ └──────────────────────────────────────────┘
Transactions Hashed in a Merkle Tree After Pruning Tx0-2 from the Block
```
A block header with no transactions would be about 80 bytes. If we suppose blocks are generated every 10 minutes, 80 bytes * 6 * 24 * 365 = 4.2MB per year. With computer systems typically selling with 2GB of RAM as of 2008, and Moore's Law predicting current growth of 1.2GB per year, storage should not be a problem even if the block headers must be kept in memory.
## 8. Simplified Payment Verification
It is possible to verify payments without running a full network node. A user only needs to keep a copy of the block headers of the longest proof-of-work chain, which he can get by querying network nodes until he's convinced he has the longest chain, and obtain the Merkle branch linking the transaction to the block it's timestamped in. He can't check the transaction for himself, but by linking it to a place in the chain, he can see that a network node has accepted it, and blocks added after it further confirm the network has accepted it.
```
Longest Proof-of-Work Chain
┌────────────────────────────────────────┐ ┌────────────────────────────────────────┐ ┌────────────────────────────────────────┐
│ Block Header │ │ Block Header │ │ Block Header │
│ ┌──────────────────┐ ┌──────────────┐ │ │ ┌──────────────────┐ ┌──────────────┐ │ │ ┌──────────────────┐ ┌──────────────┐ │
───────┼─►│ Prev Hash │ │ Nonce │ ├──────┼─►│ Prev Hash │ │ Nonce │ ├───────┼─►│ Prev Hash │ │ Nonce │ ├────────►
│ └──────────────────┘ └──────────────┘ │ │ └──────────────────┘ └──────────────┘ │ │ └──────────────────┘ └──────────────┘ │
│ │ │ │ │ │
│ ┌───────────────────┐ │ │ ┌────────────────────┐ │ │ ┌───────────────────┐ │
│ │ Merkle Root │ │ │ │ Merkle Root │ │ │ │ Merkle Root │ │
│ └───────────────────┘ │ │ └────────▲─▲─────────┘ │ │ └───────────────────┘ │
│ │ │ │ │ │ │ │
└────────────────────────────────────────┘ └─────────────┼─┼────────────────────────┘ └────────────────────────────────────────┘
│ │
│ │
┌────────┐ │ │ ..........
│ ├────┘ └─────. .
│ Hash01 │ . Hash23 .
│ │ .▲.....▲..
└────────┘ │ │
│ │
│ │ Merkle Branch for Tx3
│ │
┌─────┴─┐ ..│.....
│ │ . .
│ Hash2 │ .Hash3 .
│ │ . .
└───────┘ ...▲....
│
│
┌───┴───┐
│ Tx3 │
└───────┘
```
As such, the verification is reliable as long as honest nodes control the network, but is more vulnerable if the network is overpowered by an attacker. While network nodes can verify transactions for themselves, the simplified method can be fooled by an attacker's fabricated transactions for as long as the attacker can continue to overpower the network. One strategy to protect against this would be to accept alerts from network nodes when they detect an invalid block, prompting the user's software to download the full block and alerted transactions to confirm the inconsistency. Businesses that receive frequent payments will probably still want to run their own nodes for more independent security and quicker verification.
## 9. Combining and Splitting Value
Although it would be possible to handle coins individually, it would be unwieldy to make a separate transaction for every cent in a transfer. To allow value to be split and combined, transactions contain multiple inputs and outputs. Normally there will be either a single input from a larger previous transaction or multiple inputs combining smaller amounts, and at most two outputs: one for the payment, and one returning the change, if any, back to the sender.
```
┌──────────────────────┐
│ Transaction │
│ │
│ ┌─────┐ ┌─────┐ │
─────┼──►│ in │ │ out │ ──┼─────►
│ └─────┘ └─────┘ │
│ │
│ │
│ ┌─────┐ ┌─────┐ │
─────┼──►│ in │ │ ... │ ──┼─────►
│ └─────┘ └─────┘ │
│ │
│ │
│ ┌─────┐ │
─────┼──►│... │ │
│ └─────┘ │
│ │
└──────────────────────┘
```
It should be noted that fan-out, where a transaction depends on several transactions, and those transactions depend on many more, is not a problem here. There is never the need to extract a complete standalone copy of a transaction's history.
## 10. Privacy
The traditional banking model achieves a level of privacy by limiting access to information to the parties involved and the trusted third party. The necessity to announce all transactions publicly precludes this method, but privacy can still be maintained by breaking the flow of information in another place: by keeping public keys anonymous. The public can see that someone is sending an amount to someone else, but without information linking the transaction to anyone. This is similar to the level of information released by stock exchanges, where the time and size of individual trades, the "tape", is made public, but without telling who the parties were.
```
Traditional Privacy Models │
┌─────────────┐ ┌──────────────┐ │ ┌────────┐
┌──────────────┐ ┌──────────────┐ │ Trusted │ │ │ │ │ │
│ Identities ├──┤ Transactions ├───►│ Third Party ├──►│ Counterparty │ │ │ Public │
└──────────────┘ └──────────────┘ │ │ │ │ │ │ │
└─────────────┘ └──────────────┘ │ └────────┘
│
New Privacy Model
┌────────┐
┌──────────────┐ │ ┌──────────────┐ │ │
│ Identities │ │ │ Transactions ├───►│ Public │
└──────────────┘ │ └──────────────┘ │ │
└────────┘
```
As an additional firewall, a new key pair should be used for each transaction to keep them from being linked to a common owner. Some linking is still unavoidable with multi-input transactions, which necessarily reveal that their inputs were owned by the same owner. The risk is that if the owner of a key is revealed, linking could reveal other transactions that belonged to the same owner.
## 11. Calculations
We consider the scenario of an attacker trying to generate an alternate chain faster than the honest chain. Even if this is accomplished, it does not throw the system open to arbitrary changes, such as creating value out of thin air or taking money that never belonged to the attacker. Nodes are not going to accept an invalid transaction as payment, and honest nodes will never accept a block containing them. An attacker can only try to change one of his own transactions to take back money he recently spent.
The race between the honest chain and an attacker chain can be characterized as a Binomial Random Walk. The success event is the honest chain being extended by one block, increasing its lead by +1, and the failure event is the attacker's chain being extended by one block, reducing the gap by -1.
The probability of an attacker catching up from a given deficit is analogous to a Gambler's Ruin problem. Suppose a gambler with unlimited credit starts at a deficit and plays potentially an infinite number of trials to try to reach breakeven. We can calculate the probability he ever reaches breakeven, or that an attacker ever catches up with the honest chain, as follows [^8]:
```plaintext
p = probability an honest node finds the next block<
q = probability the attacker finds the next block
q = probability the attacker will ever catch up from z blocks behind
``````
$$
qz =
\begin{cases}
1 & \text{if } p \leq q \\
\left(\frac{q}{p}\right) z & \text{if } p > q
\end{cases}
$$
Given our assumption that p > q, the probability drops exponentially as the number of blocks the attacker has to catch up with increases. With the odds against him, if he doesn't make a lucky lunge forward early on, his chances become vanishingly small as he falls further behind.
We now consider how long the recipient of a new transaction needs to wait before being sufficiently certain the sender can't change the transaction. We assume the sender is an attacker who wants to make the recipient believe he paid him for a while, then switch it to pay back to himself after some time has passed. The receiver will be alerted when that happens, but the sender hopes it will be too late.
The receiver generates a new key pair and gives the public key to the sender shortly before signing. This prevents the sender from preparing a chain of blocks ahead of time by working on it continuously until he is lucky enough to get far enough ahead, then executing the transaction at that moment. Once the transaction is sent, the dishonest sender starts working in secret on a parallel chain containing an alternate version of his transaction.
The recipient waits until the transaction has been added to a block and z blocks have been linked after it. He doesn't know the exact amount of progress the attacker has made, but assuming the honest blocks took the average expected time per block, the attacker's potential progress will be a Poisson distribution with expected value:
$$
\lambda = z\frac{q}{p}
$$
To get the probability the attacker could still catch up now, we multiply the Poisson density for each amount of progress he could have made by the probability he could catch up from that point:
$$
\sum_{k=0}^{\infty} \frac{\lambda^k e^{-\lambda}}{k!} \cdot \left\{
\begin{array}{cl}
\left(\frac{q}{p}\right)^{(z-k)} & \text{if } k \leq z \\
1 & \text{if } k > z
\end{array}
\right.
$$
Rearranging to avoid summing the infinite tail of the distribution...
$$
1 - \sum_{k=0}^{z} \frac{\lambda^k e^{-\lambda}}{k!} \left(1-\left(\frac{q}{p}\right)^{(z-k)}\right)
$$
Converting to C code...
```c
#include <math.h>
double AttackerSuccessProbability(double q, int z)
{
double p = 1.0 - q;
double lambda = z * (q / p);
double sum = 1.0;
int i, k;
for (k = 0; k <= z; k++)
{
double poisson = exp(-lambda);
for (i = 1; i <= k; i++)
poisson *= lambda / i;
sum -= poisson * (1 - pow(q / p, z - k));
}
return sum;
}
```
Running some results, we can see the probability drop off exponentially with z.
```plaintext
q=0.1
z=0 P=1.0000000
z=1 P=0.2045873
z=2 P=0.0509779
z=3 P=0.0131722
z=4 P=0.0034552
z=5 P=0.0009137
z=6 P=0.0002428
z=7 P=0.0000647
z=8 P=0.0000173
z=9 P=0.0000046
z=10 P=0.0000012
q=0.3
z=0 P=1.0000000
z=5 P=0.1773523
z=10 P=0.0416605
z=15 P=0.0101008
z=20 P=0.0024804
z=25 P=0.0006132
z=30 P=0.0001522
z=35 P=0.0000379
z=40 P=0.0000095
z=45 P=0.0000024
z=50 P=0.0000006
```
Solving for P less than 0.1%...
```plaintext
P < 0.001
q=0.10 z=5
q=0.15 z=8
q=0.20 z=11
q=0.25 z=15
q=0.30 z=24
q=0.35 z=41
q=0.40 z=89
q=0.45 z=340
```
## 12. Conclusion
We have proposed a system for electronic transactions without relying on trust. We started with the usual framework of coins made from digital signatures, which provides strong control of ownership, but is incomplete without a way to prevent double-spending. To solve this, we proposed a peer-to-peer network using proof-of-work to record a public history of transactions that quickly becomes computationally impractical for an attacker to change if honest nodes control a majority of CPU power. The network is robust in its unstructured simplicity. Nodes work all at once with little coordination. They do not need to be identified, since messages are not routed to any particular place and only need to be delivered on a best effort basis. Nodes can leave and rejoin the network at will, accepting the proof-of-work chain as proof of what happened while they were gone. They vote with their CPU power, expressing their acceptance of valid blocks by working on extending them and rejecting invalid blocks by refusing to work on them. Any needed rules and incentives can be enforced with this consensus mechanism.
<br>
### References
---
[^1]: W. Dai, "b-money," http://www.weidai.com/bmoney.txt, 1998.
[^2]: H. Massias, X.S. Avila, and J.-J. Quisquater, "Design of a secure timestamping service with minimal
trust requirements," In 20th Symposium on Information Theory in the Benelux, May 1999.
[^3]: S. Haber, W.S. Stornetta, "How to time-stamp a digital document," In Journal of Cryptology, vol 3, no
2, pages 99-111, 1991.
[^4]: D. Bayer, S. Haber, W.S. Stornetta, "Improving the efficiency and reliability of digital time-stamping,"
In Sequences II: Methods in Communication, Security and Computer Science, pages 329-334, 1993.
[^5]: S. Haber, W.S. Stornetta, "Secure names for bit-strings," In Proceedings of the 4th ACM Conference
on Computer and Communications Security, pages 28-35, April 1997.
[^6]: A. Back, "Hashcash - a denial of service counter-measure,"
http://www.hashcash.org/papers/hashcash.pdf, 2002.
[^7]: R.C. Merkle, "Protocols for public key cryptosystems," In Proc. 1980 Symposium on Security and
Privacy, IEEE Computer Society, pages 122-133, April 1980.
[^8]: W. Feller, "An introduction to probability theory and its applications," 1957.
</pre><p><br></p>
-

@ 0176967e:1e6f471e
2024-07-21 15:48:56
Lístky na festival Lunarpunku sú už v predaji [na našom crowdfunding portáli](https://pay.cypherpunk.today/apps/maY3hxKArQxMpdyh5yCtT6UWMJm/crowdfund). V predaji sú dva typy lístkov - štandardný vstup a špeciálny vstup spolu s workshopom oranžového leta.
Neváhajte a zabezpečte si lístok, čím skôr to urobíte, tým bude festival lepší.
Platiť môžete Bitcoinom - Lightningom aj on-chain. Vaša vstupenka je e-mail adresa (neposielame potvrdzujúce e-maily, ak platba prešla, ste in).
[Kúpte si lístok](https://pay.cypherpunk.today/apps/maY3hxKArQxMpdyh5yCtT6UWMJm/crowdfund)
-

@ 8e7462a8:c723a97b
2024-07-21 15:46:37
<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>
-

@ 8e7462a8:c723a97b
2024-07-21 15:44:04
<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>
-

@ 8e7462a8:c723a97b
2024-07-21 15:42:55
<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>
-

@ 8e7462a8:c723a97b
2024-07-21 15:39:51
<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>
-

@ 8e7462a8:c723a97b
2024-07-21 15:38:33
<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>
-

@ 8e7462a8:c723a97b
2024-07-21 15:34:32
<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>
-

@ 8e7462a8:c723a97b
2024-07-21 15:33:27
<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>
-

@ 8e7462a8:c723a97b
2024-07-21 15:31:26
<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>
-

@ 8e7462a8:c723a97b
2024-07-21 15:30:52
<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>
-

@ 8e7462a8:c723a97b
2024-07-21 15:28:02
<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>
 @ e3ba5e1a:5e433365
2025-02-04 08:29:00President Trump has started rolling out his tariffs, something I [blogged about in November](https://www.snoyman.com/blog/2024/11/steelmanning-tariffs/). People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I [put up a poll on X](https://x.com/snoyberg/status/1886035800019599808) to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.  For purposes of this blog post, our ultimate question will be the following: * Suppose apples currently sell for $1 each in the entire United States. * There are domestic sellers and foreign sellers of apples, all receiving the same price. * There are no taxes or tariffs on the purchase of apples. * The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following: * Number of apples bought in the US * Price paid by buyers for apples in the US * Post-tax price received by domestic apple producers * Post-tax price received by foreign apple producers Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1? And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why: 1. The number of apples bought will go down 2. The buyers will pay more for each apple they buy, but not the full amount of the tariff 3. Domestic apple sellers will receive a *higher* price per apple 4. Foreign apple sellers will receive a *lower* price per apple, but not lowered by the full amount of the tariff In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit. ## Marginal benefit All of the numbers discussed below are part of a [helper Google Sheet](https://docs.google.com/spreadsheets/d/14ZbkWpw1B9Q1UDB9Yh47DmdKQfIafVVBKbDUsSIfGZw/edit?usp=sharing) I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are [some difficulties with creating supply and demand charts in Google Sheets](https://superuser.com/questions/1359731/how-to-create-a-supply-demand-style-chart). Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B. But that’s not what I mean. What I mean is: how high would the price of apples have to go *everywhere* so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5. How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot. The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called *marginal benefit*: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal *demand curve*. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:  Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples. ## Marginal cost Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product. Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right? Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of *sunk costs*. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further. Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price\! However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with: * Total expenditure: $100 \+ $70 \* 8 hours a day \* 5 days \== $2900 * Total revenue: $5000 (10,000 apples at $0.50 each) * Total profit: $2100 So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money. This kind of analysis is called *marginal cost*. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:  ## Equilibrium price We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:  You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the *surplus* created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example: * When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point. * When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point. Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.” OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality. ## Modeling taxes Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve. First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:  With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve. We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:  The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:  As we can see, the equilibrium has shifted: * The equilibrium price paid by consumers has risen from $1 to $1.20. * The total number of apples purchased has dropped from 63 apples to 60 apples. * Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus. * Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42. * Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21. * The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise. We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes: * Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples. * Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless. * Domestic producers scored. They can sell less apples and make more revenue doing it. * And the government walked away with an extra $30. Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price. ## Other taxes Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down. And generally speaking, this is what you’ll *always* see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost. You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with: * Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price. * Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost. * Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise. This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
@ e3ba5e1a:5e433365
2025-02-04 08:29:00President Trump has started rolling out his tariffs, something I [blogged about in November](https://www.snoyman.com/blog/2024/11/steelmanning-tariffs/). People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I [put up a poll on X](https://x.com/snoyberg/status/1886035800019599808) to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.  For purposes of this blog post, our ultimate question will be the following: * Suppose apples currently sell for $1 each in the entire United States. * There are domestic sellers and foreign sellers of apples, all receiving the same price. * There are no taxes or tariffs on the purchase of apples. * The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following: * Number of apples bought in the US * Price paid by buyers for apples in the US * Post-tax price received by domestic apple producers * Post-tax price received by foreign apple producers Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1? And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why: 1. The number of apples bought will go down 2. The buyers will pay more for each apple they buy, but not the full amount of the tariff 3. Domestic apple sellers will receive a *higher* price per apple 4. Foreign apple sellers will receive a *lower* price per apple, but not lowered by the full amount of the tariff In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit. ## Marginal benefit All of the numbers discussed below are part of a [helper Google Sheet](https://docs.google.com/spreadsheets/d/14ZbkWpw1B9Q1UDB9Yh47DmdKQfIafVVBKbDUsSIfGZw/edit?usp=sharing) I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are [some difficulties with creating supply and demand charts in Google Sheets](https://superuser.com/questions/1359731/how-to-create-a-supply-demand-style-chart). Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B. But that’s not what I mean. What I mean is: how high would the price of apples have to go *everywhere* so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5. How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot. The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called *marginal benefit*: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal *demand curve*. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:  Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples. ## Marginal cost Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product. Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right? Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of *sunk costs*. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further. Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price\! However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with: * Total expenditure: $100 \+ $70 \* 8 hours a day \* 5 days \== $2900 * Total revenue: $5000 (10,000 apples at $0.50 each) * Total profit: $2100 So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money. This kind of analysis is called *marginal cost*. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:  ## Equilibrium price We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:  You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the *surplus* created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example: * When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point. * When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point. Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.” OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality. ## Modeling taxes Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve. First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:  With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve. We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:  The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:  As we can see, the equilibrium has shifted: * The equilibrium price paid by consumers has risen from $1 to $1.20. * The total number of apples purchased has dropped from 63 apples to 60 apples. * Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus. * Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42. * Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21. * The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise. We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes: * Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples. * Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless. * Domestic producers scored. They can sell less apples and make more revenue doing it. * And the government walked away with an extra $30. Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price. ## Other taxes Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down. And generally speaking, this is what you’ll *always* see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost. You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with: * Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price. * Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost. * Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise. This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits. @ 4fe4a528:3ff6bf06
2025-02-01 13:41:28<img src="https://blossom.primal.net/58a3e225ae607d5f110cff5f44a68268d27d3d239ba6d58279c2dd872259fbbb.jpg"> In my last article I wrote about NOSTR. I found another local bitcoiner via NOSTR last week so here is why it is important to join / use NOSTR — start telling people “Look me up on NOSTR” Self-sovereign identity (SSI) is a revolutionary approach to digital identity that puts individuals in control of their own identity and personal data. Unlike traditional digital identity models, which rely on third-party organizations to manage and authenticate identities, SSI empowers individuals to own and manage their digital identity. This approach is made possible by emerging technologies such as secure public / private key pairs. Decentralized identifiers, conceived and developed by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is an attempt to create a global technical standard around cryptographically secured identifiers - a secure, universal, and sovereign form of digital ID. This technology uses peer-to-peer technology to remove the need for intermediaries to own and authenticate ID information. Notably, NOSTR, a decentralized protocol, has already begun to utilize decentralized IDs, demonstrating the potential of this technology in real-world applications. Via NOSTR, users can be sure that the person or computer publishing to a particular npub knows their nsec (password for your npub), highlighting the secure and decentralized nature of this approach. With SSI, individuals can decide how their personal data is used, shared, and protected, giving them greater control and agency over their digital lives. The **benefits** of SSI are numerous, including: Enhanced security and protection of personal data. Reduced risk of identity theft and fraud Increased autonomy and agency over one's digital identity. Improved scalability and flexibility in digital identity management **challenges**: Ensuring the security and integrity of decentralized identity systems. Developing standards and protocols for interoperability and compatibility. Addressing concerns around ownership and control of personal data. Balancing individual autonomy with the need for verification and authentication in various contexts. Overall, self-sovereign identity has the potential to transform the way we think about digital identity and provide individuals with greater control and agency over their personal data. Without people in control of their bitcoin seed words no freedom loving people would be able to exchange their money with others. Yes, keep enjoying using the only free market on the planet BITCOIN. Long live FREEDOM!
@ 4fe4a528:3ff6bf06
2025-02-01 13:41:28<img src="https://blossom.primal.net/58a3e225ae607d5f110cff5f44a68268d27d3d239ba6d58279c2dd872259fbbb.jpg"> In my last article I wrote about NOSTR. I found another local bitcoiner via NOSTR last week so here is why it is important to join / use NOSTR — start telling people “Look me up on NOSTR” Self-sovereign identity (SSI) is a revolutionary approach to digital identity that puts individuals in control of their own identity and personal data. Unlike traditional digital identity models, which rely on third-party organizations to manage and authenticate identities, SSI empowers individuals to own and manage their digital identity. This approach is made possible by emerging technologies such as secure public / private key pairs. Decentralized identifiers, conceived and developed by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is an attempt to create a global technical standard around cryptographically secured identifiers - a secure, universal, and sovereign form of digital ID. This technology uses peer-to-peer technology to remove the need for intermediaries to own and authenticate ID information. Notably, NOSTR, a decentralized protocol, has already begun to utilize decentralized IDs, demonstrating the potential of this technology in real-world applications. Via NOSTR, users can be sure that the person or computer publishing to a particular npub knows their nsec (password for your npub), highlighting the secure and decentralized nature of this approach. With SSI, individuals can decide how their personal data is used, shared, and protected, giving them greater control and agency over their digital lives. The **benefits** of SSI are numerous, including: Enhanced security and protection of personal data. Reduced risk of identity theft and fraud Increased autonomy and agency over one's digital identity. Improved scalability and flexibility in digital identity management **challenges**: Ensuring the security and integrity of decentralized identity systems. Developing standards and protocols for interoperability and compatibility. Addressing concerns around ownership and control of personal data. Balancing individual autonomy with the need for verification and authentication in various contexts. Overall, self-sovereign identity has the potential to transform the way we think about digital identity and provide individuals with greater control and agency over their personal data. Without people in control of their bitcoin seed words no freedom loving people would be able to exchange their money with others. Yes, keep enjoying using the only free market on the planet BITCOIN. Long live FREEDOM! @ 9e69e420:d12360c2
2025-01-30 12:23:04Tech stocks have taken a hit globally after China's DeepSeek launched a competitive AI chatbot at a much lower cost than US counterparts. This has stirred market fears of a $1.2 trillion loss across tech companies when trading opens in New York. DeepSeek’s chatbot quickly topped download charts and surprised experts with its capabilities, developed for only $5.6 million. The Nasdaq dropped over 3% in premarket trading, with major firms like Nvidia falling more than 10%. SoftBank also saw losses shortly after investing in a significant US AI venture. Venture capitalist Marc Andreessen called it “AI’s Sputnik moment,” highlighting its potential impact on the industry. ![] (https://www.telegraph.co.uk/content/dam/business/2025/01/27/TELEMMGLPICT000409807198_17379939060750_trans_NvBQzQNjv4BqgsaO8O78rhmZrDxTlQBjdGLvJF5WfpqnBZShRL_tOZw.jpeg)
@ 9e69e420:d12360c2
2025-01-30 12:23:04Tech stocks have taken a hit globally after China's DeepSeek launched a competitive AI chatbot at a much lower cost than US counterparts. This has stirred market fears of a $1.2 trillion loss across tech companies when trading opens in New York. DeepSeek’s chatbot quickly topped download charts and surprised experts with its capabilities, developed for only $5.6 million. The Nasdaq dropped over 3% in premarket trading, with major firms like Nvidia falling more than 10%. SoftBank also saw losses shortly after investing in a significant US AI venture. Venture capitalist Marc Andreessen called it “AI’s Sputnik moment,” highlighting its potential impact on the industry. ![] (https://www.telegraph.co.uk/content/dam/business/2025/01/27/TELEMMGLPICT000409807198_17379939060750_trans_NvBQzQNjv4BqgsaO8O78rhmZrDxTlQBjdGLvJF5WfpqnBZShRL_tOZw.jpeg) @ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.” The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China. [Sauce](https://www.stripes.com/theaters/europe/2025-01-24/trump-europe-troop-cuts-16590074.html)
@ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.” The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China. [Sauce](https://www.stripes.com/theaters/europe/2025-01-24/trump-europe-troop-cuts-16590074.html) @ 9d92077c:38d27146
2025-01-20 20:46:31Like King Arthur pulling the sword Excalibur from the stone to reclaim his rightful place as king, the Excalibur system empowers Nostr users to recover control of their digital identities and networks from malicious infiltrators. This proposal introduces a robust framework for key recovery and re-association, ensuring that users can seamlessly regain control of their accounts while preserving their social connections, metadata, and event history. In an age where security and trust are paramount, Excalibur offers a practical and resilient solution to one of the most pressing challenges in decentralized networks. —- # The Importance of Key Recovery on Nostr One of Nostr’s greatest strengths is its reliance on public and private key pairs to establish identities and ensure message authenticity. However, the simplicity of this cryptographic model comes with a significant vulnerability: key compromise. If a user’s private key is lost or stolen, they face catastrophic consequences: * Loss of Identity: The user cannot post, interact, or manage their profile. * Disruption of Social Graph: Followers and contacts lose their connection to the user. * Trust Erosion: An attacker controlling the compromised key can impersonate the user, damaging their reputation. While decentralization is a core principle of Nostr, the lack of a built-in recovery mechanism undermines long-term usability and user confidence. Excalibur addresses this gap with an innovative system for recovering compromised keys and maintaining social continuity. —- # Proposed Solution: The Excalibur System The Excalibur system introduces a primary key and secure backup key model to Nostr, enabling users to recover their accounts and re-associate events in the event of key compromise. This system relies on a combination of cryptographic proofs, event indexing, and client/relay cooperation to ensure a seamless and secure transition. ## 1. Primary and Secure Keys Users establish a primary key for everyday activity and a secure backup key stored offline. The primary key broadcasts an association with the secure key using a ```set_secure_key``` event. ## 2. Key Transition Event Upon detecting a compromise, the user activates the secure key by publishing a ```key_transition``` event. This event includes: * The compromised primary key. * The new secure key. * A cryptographic proof linking the two. * A timestamp and optional metadata. ## 3. Social Graph Transition Clients automatically replace the compromised key with the secure key in follow lists, contact lists, and other social data. Followers are notified of the transition and encouraged to follow the secure key. ## 4. Unified Identity View Historical events remain immutable but are re-indexed by relays to associate with the secure key for continuity. Clients display a unified profile view, differentiating old and new events. ## 5. Seamless Transition for Existing Accounts Existing Nostr users can integrate Excalibur by broadcasting a set_secure_key event linking their current primary key to a secure backup key. While historical events and metadata associated with the primary key remain unchanged, all new events after activation of the secure key are seamlessly associated with the updated identity. Clients should provide user-friendly tools to guide existing users through this setup process. ## 6. Endless Security Chain Once a secure key is activated and becomes the new primary key, users must set up a new secure backup key immediately by broadcasting a new ```set_secure_key``` event. This ensures an endless chain of security, preventing future compromises from leaving users vulnerable. Clients should include UX enhancements such as prompts, reminders, and automated tools to help users maintain their security chain efficiently. ## 7. Insurance Model for Relays Users pay an upfront premium to relays for re-association services, ensuring resources are available for recovery operations. Clients act as brokers, aggregating multiple relay insurance contracts into a single, user-friendly offering. They manage user payments, distribute premiums to participating relays, and earn a commission for their services. This brokerage model incentivizes clients to participate actively in the Excalibur system and ensures broader adoption across the network. —- # Implementation Framework ## Cryptographic Foundations - The secure key must be pre-announced and linked to the primary key using a signed ```set_secure_key``` event. - During key transition, the key_transition event includes a signature proving the association. ## Relay Behavior - Relays index the key_transition event and re-link historical data to the secure key. - Events from the old key are tagged as "deprecated" but remain accessible. ## Client Behavior - Clients validate the ```key_transition``` event and update social graphs automatically. - Followers are notified and prompted to follow the secure key. - Profiles display both old and new events under a unified identity. - Clients implement features to facilitate existing users' onboarding and provide tools to manage the security chain seamlessly. —- # Benefits of Excalibur **Resilience**: Users can recover from key compromise without losing their digital identity or network. **Trust**: The cryptographic proofs ensure the legitimacy of key transitions, preserving trust in the system. **Sustainability**: The insurance premium model incentivizes relay adoption and ensures fair resource allocation. **User-Friendly**: Automated transitions reduce the complexity for end users, making Nostr more accessible. **Adaptability**: Existing accounts can benefit from Excalibur without disruption, ensuring broad applicability. —- Call to Action The Excalibur system is a vital enhancement to the Nostr protocol, addressing the critical issue of key recovery while maintaining decentralization and user sovereignty. By adopting Excalibur, we can strengthen the network’s resilience, foster trust, and ensure that users retain control of their identities in an ever-evolving digital landscape. We invite the Nostr community to collaborate on refining and implementing this proposal, turning the vision of Excalibur into a reality. Together, let’s ensure that no user is ever left powerless in the face of compromise. Let’s reclaim the sword and secure the kingdom.
@ 9d92077c:38d27146
2025-01-20 20:46:31Like King Arthur pulling the sword Excalibur from the stone to reclaim his rightful place as king, the Excalibur system empowers Nostr users to recover control of their digital identities and networks from malicious infiltrators. This proposal introduces a robust framework for key recovery and re-association, ensuring that users can seamlessly regain control of their accounts while preserving their social connections, metadata, and event history. In an age where security and trust are paramount, Excalibur offers a practical and resilient solution to one of the most pressing challenges in decentralized networks. —- # The Importance of Key Recovery on Nostr One of Nostr’s greatest strengths is its reliance on public and private key pairs to establish identities and ensure message authenticity. However, the simplicity of this cryptographic model comes with a significant vulnerability: key compromise. If a user’s private key is lost or stolen, they face catastrophic consequences: * Loss of Identity: The user cannot post, interact, or manage their profile. * Disruption of Social Graph: Followers and contacts lose their connection to the user. * Trust Erosion: An attacker controlling the compromised key can impersonate the user, damaging their reputation. While decentralization is a core principle of Nostr, the lack of a built-in recovery mechanism undermines long-term usability and user confidence. Excalibur addresses this gap with an innovative system for recovering compromised keys and maintaining social continuity. —- # Proposed Solution: The Excalibur System The Excalibur system introduces a primary key and secure backup key model to Nostr, enabling users to recover their accounts and re-associate events in the event of key compromise. This system relies on a combination of cryptographic proofs, event indexing, and client/relay cooperation to ensure a seamless and secure transition. ## 1. Primary and Secure Keys Users establish a primary key for everyday activity and a secure backup key stored offline. The primary key broadcasts an association with the secure key using a ```set_secure_key``` event. ## 2. Key Transition Event Upon detecting a compromise, the user activates the secure key by publishing a ```key_transition``` event. This event includes: * The compromised primary key. * The new secure key. * A cryptographic proof linking the two. * A timestamp and optional metadata. ## 3. Social Graph Transition Clients automatically replace the compromised key with the secure key in follow lists, contact lists, and other social data. Followers are notified of the transition and encouraged to follow the secure key. ## 4. Unified Identity View Historical events remain immutable but are re-indexed by relays to associate with the secure key for continuity. Clients display a unified profile view, differentiating old and new events. ## 5. Seamless Transition for Existing Accounts Existing Nostr users can integrate Excalibur by broadcasting a set_secure_key event linking their current primary key to a secure backup key. While historical events and metadata associated with the primary key remain unchanged, all new events after activation of the secure key are seamlessly associated with the updated identity. Clients should provide user-friendly tools to guide existing users through this setup process. ## 6. Endless Security Chain Once a secure key is activated and becomes the new primary key, users must set up a new secure backup key immediately by broadcasting a new ```set_secure_key``` event. This ensures an endless chain of security, preventing future compromises from leaving users vulnerable. Clients should include UX enhancements such as prompts, reminders, and automated tools to help users maintain their security chain efficiently. ## 7. Insurance Model for Relays Users pay an upfront premium to relays for re-association services, ensuring resources are available for recovery operations. Clients act as brokers, aggregating multiple relay insurance contracts into a single, user-friendly offering. They manage user payments, distribute premiums to participating relays, and earn a commission for their services. This brokerage model incentivizes clients to participate actively in the Excalibur system and ensures broader adoption across the network. —- # Implementation Framework ## Cryptographic Foundations - The secure key must be pre-announced and linked to the primary key using a signed ```set_secure_key``` event. - During key transition, the key_transition event includes a signature proving the association. ## Relay Behavior - Relays index the key_transition event and re-link historical data to the secure key. - Events from the old key are tagged as "deprecated" but remain accessible. ## Client Behavior - Clients validate the ```key_transition``` event and update social graphs automatically. - Followers are notified and prompted to follow the secure key. - Profiles display both old and new events under a unified identity. - Clients implement features to facilitate existing users' onboarding and provide tools to manage the security chain seamlessly. —- # Benefits of Excalibur **Resilience**: Users can recover from key compromise without losing their digital identity or network. **Trust**: The cryptographic proofs ensure the legitimacy of key transitions, preserving trust in the system. **Sustainability**: The insurance premium model incentivizes relay adoption and ensures fair resource allocation. **User-Friendly**: Automated transitions reduce the complexity for end users, making Nostr more accessible. **Adaptability**: Existing accounts can benefit from Excalibur without disruption, ensuring broad applicability. —- Call to Action The Excalibur system is a vital enhancement to the Nostr protocol, addressing the critical issue of key recovery while maintaining decentralization and user sovereignty. By adopting Excalibur, we can strengthen the network’s resilience, foster trust, and ensure that users retain control of their identities in an ever-evolving digital landscape. We invite the Nostr community to collaborate on refining and implementing this proposal, turning the vision of Excalibur into a reality. Together, let’s ensure that no user is ever left powerless in the face of compromise. Let’s reclaim the sword and secure the kingdom. @ cff1720e:15c7e2b2
2025-01-19 17:48:02**Einleitung**\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie <roland@pareto.space> können sie sogar jederzeit umziehen, egal wohin. **Cool, das ist state of the art!** Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.  **Warum Nostr?** Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz **"unserer Demokratie”** praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.  Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ **Resümee:** keine Standards, keine Daten, keine Rechte = keine Zukunft!  \ **Wie funktioniert Nostr?** Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum **“single point of failure”**, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. <roland@pareto.space> ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ **Resümee:** ein offener Standard, alle Daten, alle Rechte = große Zukunft!  \ **Warum ist Nostr die Zukunft des Internet?** “Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie **(Value4Value)**. OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.  \ **Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.** <https://nostr.net/> \ <https://start.njump.me/> **Hier das Interview zum Thema mit Radio Berliner Morgenröte** <https://www.podbean.com/ew/pb-yxc36-17bb4be>
@ cff1720e:15c7e2b2
2025-01-19 17:48:02**Einleitung**\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie <roland@pareto.space> können sie sogar jederzeit umziehen, egal wohin. **Cool, das ist state of the art!** Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.  **Warum Nostr?** Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz **"unserer Demokratie”** praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.  Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ **Resümee:** keine Standards, keine Daten, keine Rechte = keine Zukunft!  \ **Wie funktioniert Nostr?** Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum **“single point of failure”**, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. <roland@pareto.space> ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ **Resümee:** ein offener Standard, alle Daten, alle Rechte = große Zukunft!  \ **Warum ist Nostr die Zukunft des Internet?** “Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie **(Value4Value)**. OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.  \ **Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.** <https://nostr.net/> \ <https://start.njump.me/> **Hier das Interview zum Thema mit Radio Berliner Morgenröte** <https://www.podbean.com/ew/pb-yxc36-17bb4be> @ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** | | Pen drive |  | **16Gb** | Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.). --- ## Passo 1: Atualizar o Sistema 🖥️ Primeiro, atualize seu sistema e instale o Tor: ```bash apt update apt install tor ``` --- ## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧 Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo: ```unit [Unit] Description=Nostr Relay Server Service After=network.target [Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure [Install] WantedBy=multi-user.target ``` --- ## Passo 3: Baixar o Binário do Nostr 🚀 Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases). --- ## Passo 4: Criar as Pastas Necessárias 📂 Agora, crie as pastas para o aplicativo e o pendrive: ```bash mkdir -p /opt/nrs /mnt/edriver ``` --- ## Passo 5: Listar os Dispositivos Conectados 🔌 Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados: ```bash lsblk ``` --- ## Passo 6: Formatando o Pendrive 💾 Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o: ```bash mkfs.vfat /dev/sda ``` --- ## Passo 7: Montar o Pendrive 💻 Monte o pendrive na pasta `/mnt/edriver`: ```bash mount /dev/sda /mnt/edriver ``` --- ## Passo 8: Verificar UUID dos Dispositivos 📋 Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados: ```bash blkid ``` --- ## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝 Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim: ```fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0 ``` --- ## Passo 10: Copiar o Binário para a Pasta Correta 📥 Agora, copie o binário baixado para a pasta `/opt/nrs`: ```bash cp nrs-arm64 /opt/nrs ``` --- ## Passo 11: Criar o Arquivo de Configuração 🛠️ Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`: ```yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true ``` --- ## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️ Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`: ```bash cp nrs.service /etc/systemd/system/ ``` Recarregue os serviços e inicie o serviço `nrs`: ```bash systemctl daemon-reload systemctl enable --now nrs.service ``` --- ## Passo 13: Configurar o Tor 🌐 Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha: ```torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334 ``` --- ## Passo 14: Habilitar e Iniciar o Tor 🧅 Agora, ative e inicie o serviço Tor: ```bash systemctl enable --now tor.service ``` O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`. --- ## Observações ⚠️ - Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi. - O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`. --- Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳 Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** | | Pen drive |  | **16Gb** | Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.). --- ## Passo 1: Atualizar o Sistema 🖥️ Primeiro, atualize seu sistema e instale o Tor: ```bash apt update apt install tor ``` --- ## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧 Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo: ```unit [Unit] Description=Nostr Relay Server Service After=network.target [Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure [Install] WantedBy=multi-user.target ``` --- ## Passo 3: Baixar o Binário do Nostr 🚀 Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases). --- ## Passo 4: Criar as Pastas Necessárias 📂 Agora, crie as pastas para o aplicativo e o pendrive: ```bash mkdir -p /opt/nrs /mnt/edriver ``` --- ## Passo 5: Listar os Dispositivos Conectados 🔌 Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados: ```bash lsblk ``` --- ## Passo 6: Formatando o Pendrive 💾 Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o: ```bash mkfs.vfat /dev/sda ``` --- ## Passo 7: Montar o Pendrive 💻 Monte o pendrive na pasta `/mnt/edriver`: ```bash mount /dev/sda /mnt/edriver ``` --- ## Passo 8: Verificar UUID dos Dispositivos 📋 Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados: ```bash blkid ``` --- ## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝 Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim: ```fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0 ``` --- ## Passo 10: Copiar o Binário para a Pasta Correta 📥 Agora, copie o binário baixado para a pasta `/opt/nrs`: ```bash cp nrs-arm64 /opt/nrs ``` --- ## Passo 11: Criar o Arquivo de Configuração 🛠️ Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`: ```yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true ``` --- ## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️ Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`: ```bash cp nrs.service /etc/systemd/system/ ``` Recarregue os serviços e inicie o serviço `nrs`: ```bash systemctl daemon-reload systemctl enable --now nrs.service ``` --- ## Passo 13: Configurar o Tor 🌐 Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha: ```torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334 ``` --- ## Passo 14: Habilitar e Iniciar o Tor 🧅 Agora, ative e inicie o serviço Tor: ```bash systemctl enable --now tor.service ``` O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`. --- ## Observações ⚠️ - Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi. - O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`. --- Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳 Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos. @ 6be5cc06:5259daf0
2025-01-18 02:11:431. **Not your keys, not your coins** Se você não tem as chaves privadas do seu Bitcoin, ele não é realmente seu. Deixar seus BTCs em exchanges ou carteiras controladas por terceiros significa confiar neles e assumir o risco de perder seus fundos. --- 2. **HODL - Não venda** O Bitcoin é uma reserva de valor a longo prazo e potencialmente o dinheiro do futuro. Não se desespere com as flutuações de preço; mantenha seus BTCs, pois o histórico se mostra favorável. --- 3. **Stay humble - Não saia falando que você tem BTC** Manter discrição sobre seu patrimônio é uma questão de segurança e humildade. Falar demais pode atrair curiosos, oportunistas ou outras ameaças. --- 4. **Don't trust, verify** No Bitcoin, confie no protocolo, não em pessoas. Sempre que possível, verifique por conta própria, seja transações, códigos ou informações. --- 5. **Reject altcoins** As altcoins podem parecer promissoras, mas frequentemente são distrações ou apostas arriscadas. Foque no Bitcoin, que já provou ser sólido e resistente. --- 6. **Stack sats - DCA** Empilhe satoshis consistentemente, utilizando a estratégia de DCA (Dollar Cost Averaging), comprando regularmente independentemente do preço. Isso reduz o risco de tentar "acertar o mercado". --- 7. **Reject the ego** Não aposte contra o Bitcoin. Aqueles que subestimaram sua força ou estabilidade, perderam. --- 8. **Keep learning** Nunca pare de estudar sobre Bitcoin, economia e a tecnologia por trás dele. Quanto mais você entende, mais confiança terá em sua decisão. --- 9. **Help beginners** O Bitcoin pode ser complicado para quem está começando. Compartilhe seus conhecimentos com paciência para fortalecer a comunidade. --- 10. **Don't push it** Cada pessoa tem seu próprio tempo para entender e entrar no mundo do Bitcoin. Forçar alguém pode ser contraproducente; dê direcionamento e deixe o tempo agir.
@ 6be5cc06:5259daf0
2025-01-18 02:11:431. **Not your keys, not your coins** Se você não tem as chaves privadas do seu Bitcoin, ele não é realmente seu. Deixar seus BTCs em exchanges ou carteiras controladas por terceiros significa confiar neles e assumir o risco de perder seus fundos. --- 2. **HODL - Não venda** O Bitcoin é uma reserva de valor a longo prazo e potencialmente o dinheiro do futuro. Não se desespere com as flutuações de preço; mantenha seus BTCs, pois o histórico se mostra favorável. --- 3. **Stay humble - Não saia falando que você tem BTC** Manter discrição sobre seu patrimônio é uma questão de segurança e humildade. Falar demais pode atrair curiosos, oportunistas ou outras ameaças. --- 4. **Don't trust, verify** No Bitcoin, confie no protocolo, não em pessoas. Sempre que possível, verifique por conta própria, seja transações, códigos ou informações. --- 5. **Reject altcoins** As altcoins podem parecer promissoras, mas frequentemente são distrações ou apostas arriscadas. Foque no Bitcoin, que já provou ser sólido e resistente. --- 6. **Stack sats - DCA** Empilhe satoshis consistentemente, utilizando a estratégia de DCA (Dollar Cost Averaging), comprando regularmente independentemente do preço. Isso reduz o risco de tentar "acertar o mercado". --- 7. **Reject the ego** Não aposte contra o Bitcoin. Aqueles que subestimaram sua força ou estabilidade, perderam. --- 8. **Keep learning** Nunca pare de estudar sobre Bitcoin, economia e a tecnologia por trás dele. Quanto mais você entende, mais confiança terá em sua decisão. --- 9. **Help beginners** O Bitcoin pode ser complicado para quem está começando. Compartilhe seus conhecimentos com paciência para fortalecer a comunidade. --- 10. **Don't push it** Cada pessoa tem seu próprio tempo para entender e entrar no mundo do Bitcoin. Forçar alguém pode ser contraproducente; dê direcionamento e deixe o tempo agir. @ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin. I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy. Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing. # Smokey The Bear In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong. Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir! Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working. So, in a world of fire, what does an ally look like and what does it do? # Meet The Forest Walker  For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved. Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance. The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment. # The Small Branch Chipper  When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system. The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”. A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration. I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible. Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process. # The Gassifier  The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification? Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest. Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment. When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products. # Biochar: The Waste  Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here. Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process. Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself. The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations. # Wood Vinegar: More Waste  Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits. For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality. This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well). # The Internal Combustion Engine  Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system. The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget. # CO2 Production For Growth  Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure. An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil. The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly. The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees. # The Branch Drones  During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest. These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission. The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control. # The Bitcoin Miner  Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce? Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500? What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost? # The Mesh Network  What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other. Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining? # Back To The Chain  Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it. A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many. We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs. But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities. # Sensor Packages ### LiDaR  The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns. LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable. Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation. ### pH, Soil Moisture, and Cation Exchange Sensing  The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component. ### Weather Data  Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present. I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?” # Noise Suppression  Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise. It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount. # Fire Safety  A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly. # The Wrap  How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off. Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity. Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up. What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
@ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin. I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy. Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing. # Smokey The Bear In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong. Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir! Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working. So, in a world of fire, what does an ally look like and what does it do? # Meet The Forest Walker  For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved. Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance. The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment. # The Small Branch Chipper  When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system. The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”. A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration. I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible. Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process. # The Gassifier  The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification? Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest. Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment. When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products. # Biochar: The Waste  Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here. Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process. Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself. The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations. # Wood Vinegar: More Waste  Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits. For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality. This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well). # The Internal Combustion Engine  Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system. The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget. # CO2 Production For Growth  Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure. An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil. The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly. The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees. # The Branch Drones  During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest. These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission. The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control. # The Bitcoin Miner  Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce? Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500? What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost? # The Mesh Network  What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other. Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining? # Back To The Chain  Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it. A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many. We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs. But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities. # Sensor Packages ### LiDaR  The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns. LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable. Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation. ### pH, Soil Moisture, and Cation Exchange Sensing  The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component. ### Weather Data  Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present. I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?” # Noise Suppression  Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise. It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount. # Fire Safety  A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly. # The Wrap  How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off. Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity. Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up. What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next. @ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity. A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur. The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior. And there are plenty of incentives beyond our direct control\! My son is *also* incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take. ## Why incentives matter A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could **just** do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example: * If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning. * If people would just use the recycling bin, we wouldn’t have such a landfill problem. * If people would just stop being lazy, our team would deliver our project on time. In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally. * The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do. * No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle. * If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.  My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want. If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is. ## Running a company Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions. Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good. What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off. Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning. When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.  Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks\! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money. There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals. Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature. # Moral hazard Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings. What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.  But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I *don’t* turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all. This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as: 1. We’re so habituated to turning off the water that we don’t even consider *not* turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off. 2. Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created. 3. We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?) Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard. A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard. It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend? And since we’re talking about the government already… ## Government moral hazards As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a *huge* number of examples of moral hazards. I decided to cherry-pick a few for this post. The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people? The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet. If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior\! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups. You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”  And here’s the absolute best part of this: I can’t even truly blame either California *or* Wall Street. (I mean, I *do* blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits. There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions. # Non-monetary competition At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home. In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.) Anyway, my professor’s wife had a friend. My professor described in *great* detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas. This is a demonstration of *non-monetary compensation*. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules. The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become *wealthier and whiter*, the exact opposite of their desired outcome. Why would that happen? Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky. She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls. So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites. You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences. ## Bureaucracy These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences. Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings. Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could\! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate. # Government incentivized behavior This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples: * Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to [malinvestment](https://en.wikipedia.org/wiki/Malinvestment) and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience. * Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise. * During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation. * The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen. * Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example). * Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as [high living](https://www.youtube.com/watch?v=ZwNDd2_beTU).) # Conclusion The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives. We can bemoan these realities all we want, but they *are* realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People *should* take advantage of the incentives around them. Because if they don’t, someone else will. (If you want a literary example of that last comment, see the horse in Animal Farm.) How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula: * Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people. * Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them. * And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example. And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining\!
@ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity. A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur. The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior. And there are plenty of incentives beyond our direct control\! My son is *also* incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take. ## Why incentives matter A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could **just** do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example: * If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning. * If people would just use the recycling bin, we wouldn’t have such a landfill problem. * If people would just stop being lazy, our team would deliver our project on time. In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally. * The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do. * No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle. * If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.  My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want. If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is. ## Running a company Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions. Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good. What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off. Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning. When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.  Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks\! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money. There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals. Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature. # Moral hazard Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings. What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.  But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I *don’t* turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all. This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as: 1. We’re so habituated to turning off the water that we don’t even consider *not* turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off. 2. Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created. 3. We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?) Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard. A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard. It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend? And since we’re talking about the government already… ## Government moral hazards As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a *huge* number of examples of moral hazards. I decided to cherry-pick a few for this post. The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people? The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet. If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior\! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups. You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”  And here’s the absolute best part of this: I can’t even truly blame either California *or* Wall Street. (I mean, I *do* blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits. There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions. # Non-monetary competition At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home. In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.) Anyway, my professor’s wife had a friend. My professor described in *great* detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas. This is a demonstration of *non-monetary compensation*. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules. The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become *wealthier and whiter*, the exact opposite of their desired outcome. Why would that happen? Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky. She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls. So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites. You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences. ## Bureaucracy These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences. Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings. Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could\! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate. # Government incentivized behavior This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples: * Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to [malinvestment](https://en.wikipedia.org/wiki/Malinvestment) and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience. * Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise. * During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation. * The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen. * Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example). * Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as [high living](https://www.youtube.com/watch?v=ZwNDd2_beTU).) # Conclusion The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives. We can bemoan these realities all we want, but they *are* realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People *should* take advantage of the incentives around them. Because if they don’t, someone else will. (If you want a literary example of that last comment, see the horse in Animal Farm.) How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula: * Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people. * Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them. * And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example. And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining\! @ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs ## The reason why we have broken money Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world. In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes. However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore. Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too. Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it. ## Bitcoin overcomes the "transfer of hard money" problem Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design. Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it. Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive. Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold. ## Bitcoin blurs the line between commodity and technology Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules. At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable. Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases. ## The dangers of derivatives A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold. In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin. Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense. ## Learn for yourself If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody". There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
@ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs ## The reason why we have broken money Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world. In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes. However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore. Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too. Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it. ## Bitcoin overcomes the "transfer of hard money" problem Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design. Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it. Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive. Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold. ## Bitcoin blurs the line between commodity and technology Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules. At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable. Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases. ## The dangers of derivatives A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold. In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin. Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense. ## Learn for yourself If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody". There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance. @ 37fe9853:bcd1b039
2025-01-11 15:04:40yoyoaa
@ 37fe9853:bcd1b039
2025-01-11 15:04:40yoyoaa @ 62033ff8:e4471203
2025-01-11 15:00:24收录的内容中 kind=1的部分,实话说 质量不高。 所以我增加了kind=30023 长文的article,但是更新的太少,多个relays 的服务器也没有多少长文。 所有搜索nostr如果需要产生价值,需要有高质量的文章和新闻。 而且现在有很多机器人的文章充满着浪费空间的作用,其他作用都用不上。 https://www.duozhutuan.com 目前放的是给搜索引擎提供搜索的原材料。没有做UI给人类浏览。所以看上去是粗糙的。 我并没有打算去做一个发microblog的 web客户端,那类的客户端太多了。 我觉得nostr社区需要解决的还是应用。如果仅仅是microblog 感觉有点够呛 幸运的是npub.pro 建站这样的,我觉得有点意思。 yakihonne 智能widget 也有意思 我做的TaskQ5 我自己在用了。分布式的任务系统,也挺好的。
@ 62033ff8:e4471203
2025-01-11 15:00:24收录的内容中 kind=1的部分,实话说 质量不高。 所以我增加了kind=30023 长文的article,但是更新的太少,多个relays 的服务器也没有多少长文。 所有搜索nostr如果需要产生价值,需要有高质量的文章和新闻。 而且现在有很多机器人的文章充满着浪费空间的作用,其他作用都用不上。 https://www.duozhutuan.com 目前放的是给搜索引擎提供搜索的原材料。没有做UI给人类浏览。所以看上去是粗糙的。 我并没有打算去做一个发microblog的 web客户端,那类的客户端太多了。 我觉得nostr社区需要解决的还是应用。如果仅仅是microblog 感觉有点够呛 幸运的是npub.pro 建站这样的,我觉得有点意思。 yakihonne 智能widget 也有意思 我做的TaskQ5 我自己在用了。分布式的任务系统,也挺好的。 @ 23b0e2f8:d8af76fc
2025-01-08 18:17:52## **Necessário** - Um Android que você não use mais (a câmera deve estar funcionando). - Um cartão microSD (opcional, usado apenas uma vez). - Um dispositivo para acompanhar seus fundos (provavelmente você já tem um). ## **Algumas coisas que você precisa saber** - O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele. - O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito. - A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal. --- ## **O tutorial será dividido em dois módulos:** - Módulo 1 - Criando uma carteira fria/assinador. - Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador. --- ## **No final, teremos:** - Uma carteira fria que também servirá como assinador. - Um dispositivo para acompanhar os fundos da carteira.  --- ## **Módulo 1 - Criando uma carteira fria/assinador** 1. Baixe o APK do Electrum na aba de **downloads** em <https://electrum.org/>. Fique à vontade para [verificar as assinaturas](https://electrum.readthedocs.io/en/latest/gpg-check.html) do software, garantindo sua autenticidade. 2. Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.  3. Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.  4. Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o **modo avião**.\ *(Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)*  5. Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.  6. No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. *(Aqui entra seu método pessoal de backup.)*  --- ## **Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.** 1. Criar uma carteira **somente leitura** em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em <https://electrum.org/> ou da própria Play Store. *(ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)* 2. Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção **Usar uma chave mestra**.  3. Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em **Carteira > Detalhes da carteira > Compartilhar chave mestra pública**.  4. Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los. 5. Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: **Carteira > Addresses/Coins**. 6. Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.  7. No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.  8. No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede. --- ## **Conclusão** **Pontos positivos do setup:** - **Simplicidade:** Basta um dispositivo Android antigo. - **Flexibilidade:** Funciona como uma ótima carteira fria, ideal para holders. **Pontos negativos do setup:** - **Padronização:** Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum. - **Interface:** A aparência do Electrum pode parecer antiquada para alguns usuários. Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: ***Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.*** Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível. ---
@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52## **Necessário** - Um Android que você não use mais (a câmera deve estar funcionando). - Um cartão microSD (opcional, usado apenas uma vez). - Um dispositivo para acompanhar seus fundos (provavelmente você já tem um). ## **Algumas coisas que você precisa saber** - O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele. - O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito. - A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal. --- ## **O tutorial será dividido em dois módulos:** - Módulo 1 - Criando uma carteira fria/assinador. - Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador. --- ## **No final, teremos:** - Uma carteira fria que também servirá como assinador. - Um dispositivo para acompanhar os fundos da carteira.  --- ## **Módulo 1 - Criando uma carteira fria/assinador** 1. Baixe o APK do Electrum na aba de **downloads** em <https://electrum.org/>. Fique à vontade para [verificar as assinaturas](https://electrum.readthedocs.io/en/latest/gpg-check.html) do software, garantindo sua autenticidade. 2. Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.  3. Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.  4. Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o **modo avião**.\ *(Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)*  5. Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.  6. No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. *(Aqui entra seu método pessoal de backup.)*  --- ## **Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.** 1. Criar uma carteira **somente leitura** em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em <https://electrum.org/> ou da própria Play Store. *(ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)* 2. Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção **Usar uma chave mestra**.  3. Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em **Carteira > Detalhes da carteira > Compartilhar chave mestra pública**.  4. Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los. 5. Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: **Carteira > Addresses/Coins**. 6. Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.  7. No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.  8. No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede. --- ## **Conclusão** **Pontos positivos do setup:** - **Simplicidade:** Basta um dispositivo Android antigo. - **Flexibilidade:** Funciona como uma ótima carteira fria, ideal para holders. **Pontos negativos do setup:** - **Padronização:** Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum. - **Interface:** A aparência do Electrum pode parecer antiquada para alguns usuários. Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: ***Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.*** Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível. --- @ e6817453:b0ac3c39
2025-01-05 14:29:17## The Rise of Graph RAGs and the Quest for Data Quality As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence. ## Booming Interest in Graph RAGs Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can: * **Enhance LLM Outputs:** By grounding responses in structured knowledge, graphs significantly reduce hallucinations. * **Support Complex Queries:** Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving. Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs? ## Data Quality: The Foundation of Effective Graphs A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why: * **Richness of Entities:** Effective retrieval depends on graphs populated with rich, detailed entities. * **Freedom from Hallucinations:** Poorly constructed graphs amplify inaccuracies rather than mitigating them. Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs. ## Hybrid Graph RAGs and Variations While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that: * Handle diverse data sources with ease. * Offer improved adaptability to complex queries. Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing. ## Ontology: The Key to Graph Construction Quality Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for: * **Defining Relationships:** Clarifying how concepts connect within a domain. * **Validating Graph Structures:** Ensuring constructed graphs are logically sound and align with domain-specific realities. Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs? ## How to Build Ontology Expertise in a Startup Team For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach: 1. **Assign a Knowledge Champion:** Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering. 2. **Provide Training:** Invest in courses, workshops, or certifications in knowledge graph and ontology creation. 3. **Leverage Partnerships:** Collaborate with academic institutions, domain experts, or consultants to build initial frameworks. 4. **Utilize Tools:** Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process. 5. **Iterate with Feedback:** Continuously refine ontologies through collaboration with domain experts and iterative testing. So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts. You could read about barefoot experts in my article : Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise. ## How to Find or Create Ontologies For teams venturing into Graph RAGs, several strategies can help address the ontology gap: 1. **Leverage Existing Ontologies:** Many industries and domains already have open ontologies. For instance: * **Public Knowledge Graphs:** Resources like Wikipedia’s graph offer a wealth of structured knowledge. * **Industry Standards:** Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields. * **Business Framework Ontology (BFO):** A valuable resource for enterprises looking to define business processes and structures. 1. **Build In-House Expertise:** If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation. 2. **Utilize LLMs for Ontology Construction:** Interestingly, LLMs themselves can act as a starting point for ontology development: * **Prompt-Based Extraction:** LLMs can generate draft ontologies by leveraging their extensive training on graph data. * **Domain Expert Refinement:** Combine LLM-generated structures with insights from domain experts to create tailored ontologies. ## Parallel Ontology and Graph Extraction An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as: * **Detecting Hallucinations:** Differentiating between genuine insights and AI-generated inaccuracies. * **Ensuring Completeness:** Ensuring no critical concepts are overlooked during extraction. Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method. ## LLMs as Ontologists While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to: * **Generate Skeleton Ontologies:** Prompt LLMs with domain-specific information to draft initial ontology structures. * **Validate and Refine Ontologies:** Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance. However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes. ## Final Thoughts: Unlocking the Power of Graph RAGs The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools. As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding. Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation!
@ e6817453:b0ac3c39
2025-01-05 14:29:17## The Rise of Graph RAGs and the Quest for Data Quality As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence. ## Booming Interest in Graph RAGs Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can: * **Enhance LLM Outputs:** By grounding responses in structured knowledge, graphs significantly reduce hallucinations. * **Support Complex Queries:** Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving. Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs? ## Data Quality: The Foundation of Effective Graphs A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why: * **Richness of Entities:** Effective retrieval depends on graphs populated with rich, detailed entities. * **Freedom from Hallucinations:** Poorly constructed graphs amplify inaccuracies rather than mitigating them. Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs. ## Hybrid Graph RAGs and Variations While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that: * Handle diverse data sources with ease. * Offer improved adaptability to complex queries. Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing. ## Ontology: The Key to Graph Construction Quality Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for: * **Defining Relationships:** Clarifying how concepts connect within a domain. * **Validating Graph Structures:** Ensuring constructed graphs are logically sound and align with domain-specific realities. Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs? ## How to Build Ontology Expertise in a Startup Team For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach: 1. **Assign a Knowledge Champion:** Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering. 2. **Provide Training:** Invest in courses, workshops, or certifications in knowledge graph and ontology creation. 3. **Leverage Partnerships:** Collaborate with academic institutions, domain experts, or consultants to build initial frameworks. 4. **Utilize Tools:** Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process. 5. **Iterate with Feedback:** Continuously refine ontologies through collaboration with domain experts and iterative testing. So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts. You could read about barefoot experts in my article : Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise. ## How to Find or Create Ontologies For teams venturing into Graph RAGs, several strategies can help address the ontology gap: 1. **Leverage Existing Ontologies:** Many industries and domains already have open ontologies. For instance: * **Public Knowledge Graphs:** Resources like Wikipedia’s graph offer a wealth of structured knowledge. * **Industry Standards:** Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields. * **Business Framework Ontology (BFO):** A valuable resource for enterprises looking to define business processes and structures. 1. **Build In-House Expertise:** If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation. 2. **Utilize LLMs for Ontology Construction:** Interestingly, LLMs themselves can act as a starting point for ontology development: * **Prompt-Based Extraction:** LLMs can generate draft ontologies by leveraging their extensive training on graph data. * **Domain Expert Refinement:** Combine LLM-generated structures with insights from domain experts to create tailored ontologies. ## Parallel Ontology and Graph Extraction An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as: * **Detecting Hallucinations:** Differentiating between genuine insights and AI-generated inaccuracies. * **Ensuring Completeness:** Ensuring no critical concepts are overlooked during extraction. Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method. ## LLMs as Ontologists While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to: * **Generate Skeleton Ontologies:** Prompt LLMs with domain-specific information to draft initial ontology structures. * **Validate and Refine Ontologies:** Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance. However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes. ## Final Thoughts: Unlocking the Power of Graph RAGs The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools. As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding. Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation! @ a4a6b584:1e05b95b
2025-01-02 18:13:31## The Four-Layer Framework ### Layer 1: Zoom Out  Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what." **Example**: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems. - **Tip**: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage. _Once you have the big picture in mind, it’s time to start breaking it down._ --- ### Layer 2: Categorize and Connect  Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas. **Example**: Studying biology? Group concepts into categories like cells, genetics, and ecosystems. - **Tip**: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track. _With your categories in place, you’re ready to dive into the details that bring them to life._ --- ### Layer 3: Master the Details  Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable. **Example**: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language. - **Tip**: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding. _Now that you’ve mastered the essentials, you can expand your knowledge to include extra material._ --- ### Layer 4: Expand Your Horizons  Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams. **Example**: Learn about rare programming quirks or historical trivia about a language’s development. - **Tip**: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time. --- ## Pro Tips for Better Learning ### 1. Use Active Recall and Spaced Repetition Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information. ### 2. Map It Out Create visual aids like [diagrams or concept maps](https://excalidraw.com/) to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2. ### 3. Teach What You Learn Explain the subject to someone else as if they’re hearing it for the first time. Teaching **exposes any gaps** in your understanding and **helps reinforce** the material. ### 4. Engage with LLMs and Discuss Concepts Take advantage of tools like ChatGPT or similar large language models to **explore your topic** in greater depth. Use these tools to: - Ask specific questions to clarify confusing points. - Engage in discussions to simulate real-world applications of the subject. - Generate examples or analogies that deepen your understanding. **Tip**: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective. --- ## Get Started Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
@ a4a6b584:1e05b95b
2025-01-02 18:13:31## The Four-Layer Framework ### Layer 1: Zoom Out  Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what." **Example**: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems. - **Tip**: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage. _Once you have the big picture in mind, it’s time to start breaking it down._ --- ### Layer 2: Categorize and Connect  Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas. **Example**: Studying biology? Group concepts into categories like cells, genetics, and ecosystems. - **Tip**: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track. _With your categories in place, you’re ready to dive into the details that bring them to life._ --- ### Layer 3: Master the Details  Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable. **Example**: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language. - **Tip**: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding. _Now that you’ve mastered the essentials, you can expand your knowledge to include extra material._ --- ### Layer 4: Expand Your Horizons  Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams. **Example**: Learn about rare programming quirks or historical trivia about a language’s development. - **Tip**: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time. --- ## Pro Tips for Better Learning ### 1. Use Active Recall and Spaced Repetition Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information. ### 2. Map It Out Create visual aids like [diagrams or concept maps](https://excalidraw.com/) to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2. ### 3. Teach What You Learn Explain the subject to someone else as if they’re hearing it for the first time. Teaching **exposes any gaps** in your understanding and **helps reinforce** the material. ### 4. Engage with LLMs and Discuss Concepts Take advantage of tools like ChatGPT or similar large language models to **explore your topic** in greater depth. Use these tools to: - Ask specific questions to clarify confusing points. - Engage in discussions to simulate real-world applications of the subject. - Generate examples or analogies that deepen your understanding. **Tip**: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective. --- ## Get Started Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence. @ 4fe4a528:3ff6bf06
2025-01-01 15:50:50I could have wrote about how bitcoin has more than doubled in 2024 or how some people are still sitting on the sidelines not trying to understand why bitcoin will double in 2025, but instead I thought I would write about how bitcoin is allowing for a decentralized social network. Two years ago I decided to try out this NOSTR idea. Now I have 233 followers, almost the same number of people who read this monthly newsletter. Facebook / whats-app was to ad filled for me to enjoy what my friends were posting. X was great for news, but none of my friends where on it. Linkedin was just about business. Besides, NOSTR gives me more bitcoin every time I post. I am now using the bitcoin to buy eggs every two weeks from my neighbors. So to me it is a win win. I can write notes and eat eggs. I even use my NOSTR extension to log into hivetalk.org and help people with their computer issues. It is better than teaching via ZOOM. 2025 is going to be a great year for decentralization. If you are trying to join NOSTR via your desktop I recommend going to [getalby.com](https://guides.getalby.com/user-guide/alby-account-and-browser-extension/alby-browser-extension/features) installing the browser extension. Then make an account with getalby and write down your 24 words (nsec). Link your profile to your lightning wallet and start posting and following other friends via primal.net. Yes, of course, I am put on this earth to help my fellow man. Some people enjoy using NOSTR via their cell phone and for those people I recommend amethyst or damus. We are all in this together.
@ 4fe4a528:3ff6bf06
2025-01-01 15:50:50I could have wrote about how bitcoin has more than doubled in 2024 or how some people are still sitting on the sidelines not trying to understand why bitcoin will double in 2025, but instead I thought I would write about how bitcoin is allowing for a decentralized social network. Two years ago I decided to try out this NOSTR idea. Now I have 233 followers, almost the same number of people who read this monthly newsletter. Facebook / whats-app was to ad filled for me to enjoy what my friends were posting. X was great for news, but none of my friends where on it. Linkedin was just about business. Besides, NOSTR gives me more bitcoin every time I post. I am now using the bitcoin to buy eggs every two weeks from my neighbors. So to me it is a win win. I can write notes and eat eggs. I even use my NOSTR extension to log into hivetalk.org and help people with their computer issues. It is better than teaching via ZOOM. 2025 is going to be a great year for decentralization. If you are trying to join NOSTR via your desktop I recommend going to [getalby.com](https://guides.getalby.com/user-guide/alby-account-and-browser-extension/alby-browser-extension/features) installing the browser extension. Then make an account with getalby and write down your 24 words (nsec). Link your profile to your lightning wallet and start posting and following other friends via primal.net. Yes, of course, I am put on this earth to help my fellow man. Some people enjoy using NOSTR via their cell phone and for those people I recommend amethyst or damus. We are all in this together. @ 6be5cc06:5259daf0
2024-12-29 19:54:14Um dos padrões mais bem estabelecidos ao medir a opinião pública é que cada geração tende a seguir um caminho semelhante em termos de política e ideologia geral. Seus membros compartilham das mesmas experiências formativas, atingem os marcos importantes da vida ao mesmo tempo e convivem nos mesmos espaços. Então, como devemos entender os relatórios que mostram que a **Geração Z** é hiperprogressista em certos assuntos, mas surpreendentemente conservadora em outros? A resposta, nas palavras de **Alice Evans**, pesquisadora visitante na Universidade de Stanford e uma das principais estudiosas do tema, é que os jovens de hoje estão passando por um grande **divergência de gênero**, com as jovens mulheres do primeiro grupo e os jovens homens do segundo. A **Geração Z** representa duas gerações, e não apenas uma. Em países de todos os continentes, surgiu um **distanciamento ideológico** entre jovens homens e mulheres. Milhões de pessoas que compartilham das mesmas cidades, locais de trabalho, salas de aula e até casas, não veem mais as coisas da mesma maneira. Nos **Estados Unidos**, os dados da Gallup mostram que, após décadas em que os sexos estavam distribuídos de forma relativamente equilibrada entre visões políticas liberais e conservadoras, as mulheres entre **18 e 30 anos** são agora **30 pontos percentuais mais liberais** do que os homens dessa faixa etária. Essa diferença surgiu em apenas **seis anos**. A **Alemanha** também apresenta um distanciamento de 30 pontos entre homens jovens conservadores e mulheres jovens progressistas, e no **Reino Unido**, a diferença é de **25 pontos**. Na **Polônia**, no ano passado, quase metade dos homens entre **18 e 21 anos** apoiou o partido de extrema direita Confederation, em contraste com apenas um sexto das jovens mulheres dessa mesma idade.  Fora do Ocidente, há divisões ainda mais acentuadas. Na **Coreia do Sul**, há um enorme abismo entre homens e mulheres jovens, e a situação é semelhante na **China**. Na **África**, a **Tunísia** apresenta o mesmo padrão. Vale notar que em todos os países essa divisão drástica ocorre principalmente entre a **geração mais jovem**, sendo muito menos pronunciada entre homens e mulheres na faixa dos **30 anos** ou mais velhos. O movimento **# MeToo** foi o **principal estopim**, trazendo à tona valores feministas intensos entre jovens mulheres que se sentiram empoderadas para denunciar injustiças de longa data. Esse estopim encontrou especialmente terreno fértil na **Coreia do Sul**, onde a **desigualdade de gênero** é bastante visível e a **misoginia explícita** é comum. (palavras da Financial Times, eu só traduzi) Na eleição presidencial da **Coreia do Sul** em **2022**, enquanto homens e mulheres mais velhos votaram de forma unificada, os jovens homens apoiaram fortemente o partido de direita **People Power**, enquanto as jovens mulheres apoiaram o partido liberal **Democratic** em números quase iguais e opostos. A situação na **Coreia** é extrema, mas serve como um alerta para outros países sobre o que pode acontecer quando jovens homens e mulheres se distanciam. A sociedade está **dividida**, a taxa de casamento despencou e a taxa de natalidade caiu drasticamente, chegando a **0,78 filhos por mulher** em **2022**, o menor número no mundo todo. Sete anos após a explosão inicial do movimento **# MeToo**, a **divergência de gênero** em atitudes tornou-se autossustentável. Dados das pesquisas mostram que em muitos países, as diferenças ideológicas vão além dessa questão específica. A divisão progressista-conservadora sobre **assédio sexual** parece ter causado ou pelo menos faz parte de um **alinhamento mais amplo**, em que jovens homens e mulheres estão se organizando em grupos conservadores e liberais em outros assuntos. Nos **EUA**, **Reino Unido** e **Alemanha**, as jovens mulheres agora adotam posturas mais liberais sobre temas como **imigração** e **justiça racial**, enquanto grupos etários mais velhos permanecem equilibrados. A tendência na maioria dos países tem sido de **mulheres se inclinando mais para a esquerda**, enquanto os homens permanecem estáveis. No entanto, há sinais de que os jovens homens estão se **movendo para a direita** na **Alemanha**, tornando-se mais críticos em relação à imigração e se aproximando do partido de extrema direita **AfD** nos últimos anos. Seria fácil dizer que tudo isso é apenas uma **fase passageira**, mas os abismos ideológicos apenas crescem, e os dados mostram que as experiências políticas formativas das pessoas são difíceis de mudar. Tudo isso é agravado pelo fato de que o aumento dos smartphones e das redes sociais faz com que os jovens homens e mulheres agora **vivam em espaços separados** e tenham **culturas distintas**. As opiniões dos jovens frequentemente são ignoradas devido à **baixa participação política**, mas essa mudança pode deixar **consequências duradouras**, impactando muito mais do que apenas os resultados das eleições. Retirado de: https://www.ft.com/content/29fd9b5c-2f35-41bf-9d4c-994db4e12998
@ 6be5cc06:5259daf0
2024-12-29 19:54:14Um dos padrões mais bem estabelecidos ao medir a opinião pública é que cada geração tende a seguir um caminho semelhante em termos de política e ideologia geral. Seus membros compartilham das mesmas experiências formativas, atingem os marcos importantes da vida ao mesmo tempo e convivem nos mesmos espaços. Então, como devemos entender os relatórios que mostram que a **Geração Z** é hiperprogressista em certos assuntos, mas surpreendentemente conservadora em outros? A resposta, nas palavras de **Alice Evans**, pesquisadora visitante na Universidade de Stanford e uma das principais estudiosas do tema, é que os jovens de hoje estão passando por um grande **divergência de gênero**, com as jovens mulheres do primeiro grupo e os jovens homens do segundo. A **Geração Z** representa duas gerações, e não apenas uma. Em países de todos os continentes, surgiu um **distanciamento ideológico** entre jovens homens e mulheres. Milhões de pessoas que compartilham das mesmas cidades, locais de trabalho, salas de aula e até casas, não veem mais as coisas da mesma maneira. Nos **Estados Unidos**, os dados da Gallup mostram que, após décadas em que os sexos estavam distribuídos de forma relativamente equilibrada entre visões políticas liberais e conservadoras, as mulheres entre **18 e 30 anos** são agora **30 pontos percentuais mais liberais** do que os homens dessa faixa etária. Essa diferença surgiu em apenas **seis anos**. A **Alemanha** também apresenta um distanciamento de 30 pontos entre homens jovens conservadores e mulheres jovens progressistas, e no **Reino Unido**, a diferença é de **25 pontos**. Na **Polônia**, no ano passado, quase metade dos homens entre **18 e 21 anos** apoiou o partido de extrema direita Confederation, em contraste com apenas um sexto das jovens mulheres dessa mesma idade.  Fora do Ocidente, há divisões ainda mais acentuadas. Na **Coreia do Sul**, há um enorme abismo entre homens e mulheres jovens, e a situação é semelhante na **China**. Na **África**, a **Tunísia** apresenta o mesmo padrão. Vale notar que em todos os países essa divisão drástica ocorre principalmente entre a **geração mais jovem**, sendo muito menos pronunciada entre homens e mulheres na faixa dos **30 anos** ou mais velhos. O movimento **# MeToo** foi o **principal estopim**, trazendo à tona valores feministas intensos entre jovens mulheres que se sentiram empoderadas para denunciar injustiças de longa data. Esse estopim encontrou especialmente terreno fértil na **Coreia do Sul**, onde a **desigualdade de gênero** é bastante visível e a **misoginia explícita** é comum. (palavras da Financial Times, eu só traduzi) Na eleição presidencial da **Coreia do Sul** em **2022**, enquanto homens e mulheres mais velhos votaram de forma unificada, os jovens homens apoiaram fortemente o partido de direita **People Power**, enquanto as jovens mulheres apoiaram o partido liberal **Democratic** em números quase iguais e opostos. A situação na **Coreia** é extrema, mas serve como um alerta para outros países sobre o que pode acontecer quando jovens homens e mulheres se distanciam. A sociedade está **dividida**, a taxa de casamento despencou e a taxa de natalidade caiu drasticamente, chegando a **0,78 filhos por mulher** em **2022**, o menor número no mundo todo. Sete anos após a explosão inicial do movimento **# MeToo**, a **divergência de gênero** em atitudes tornou-se autossustentável. Dados das pesquisas mostram que em muitos países, as diferenças ideológicas vão além dessa questão específica. A divisão progressista-conservadora sobre **assédio sexual** parece ter causado ou pelo menos faz parte de um **alinhamento mais amplo**, em que jovens homens e mulheres estão se organizando em grupos conservadores e liberais em outros assuntos. Nos **EUA**, **Reino Unido** e **Alemanha**, as jovens mulheres agora adotam posturas mais liberais sobre temas como **imigração** e **justiça racial**, enquanto grupos etários mais velhos permanecem equilibrados. A tendência na maioria dos países tem sido de **mulheres se inclinando mais para a esquerda**, enquanto os homens permanecem estáveis. No entanto, há sinais de que os jovens homens estão se **movendo para a direita** na **Alemanha**, tornando-se mais críticos em relação à imigração e se aproximando do partido de extrema direita **AfD** nos últimos anos. Seria fácil dizer que tudo isso é apenas uma **fase passageira**, mas os abismos ideológicos apenas crescem, e os dados mostram que as experiências políticas formativas das pessoas são difíceis de mudar. Tudo isso é agravado pelo fato de que o aumento dos smartphones e das redes sociais faz com que os jovens homens e mulheres agora **vivam em espaços separados** e tenham **culturas distintas**. As opiniões dos jovens frequentemente são ignoradas devido à **baixa participação política**, mas essa mudança pode deixar **consequências duradouras**, impactando muito mais do que apenas os resultados das eleições. Retirado de: https://www.ft.com/content/29fd9b5c-2f35-41bf-9d4c-994db4e12998 @ 36bedab2:524acad4
2024-12-26 23:23:37404 Page Not Found
@ 36bedab2:524acad4
2024-12-26 23:23:37404 Page Not Found @ 36bedab2:524acad4
2024-12-26 23:20:21404 Page Not Found Error
@ 36bedab2:524acad4
2024-12-26 23:20:21404 Page Not Found Error @ ccc8ee23:9f3d9783
2024-12-23 22:03:15## Chef's notes Indulge in tender, golden-fried chicken breast, crunchy with every bite. Nestled on a bed of steamed rice, this dish is elevated by a rich, velvety curry sauce, infused with the warmth of fragrant spices and the umami depth of soy. Paired with vibrant vegetables for a harmonious balance of textures and flavors, this comforting classic promises to delight your soul. ## Details - ⏲️ Prep time: 10 min - 🍳 Cook time: 30 min - 🍽️ Servings: 2 ## Ingredients - Chicken Fillet 250 grams - Potato 100 grams - Egg 1 pc - Curry block 2 pcs or 20 grams - breadcrumbs 100 grams / 2 cups - flour 20 grams - Cooking oil (for frying) - chicken or vegetable stock 500ml - soy sauce 1 tbsp - Seasoning - onion 1 pc, finely chopped - garlic cloves 2 pcs, minced - carrot 1 pc, chopped ## Directions 1. Chicken Katsu: Pound the chicken breasts until about 1/2 inch thick. Season with salt and pepper. Coat each piece in flour, then dip in beaten egg, and finally coat with breadcrumbs. Heat oil in a pan and fry the chicken for about 3-4 minutes on each side, until golden brown and fully cooked. Place on paper towels to drain. 2. Make Curry Sauce: In a pan, sauté the onion, garlic, add potato and carrot until soft. Gradually add curry block and the stock, stir well. Simmer for 5-10 minutes until thickened. Add seasoning and soy sauce to taste. 3. Plating: Slice the cooked chicken katsu and place it over a bed of steamed rice. Pour the curry sauce on the side or over the chicken. Garnish with chopped green chilies.
@ ccc8ee23:9f3d9783
2024-12-23 22:03:15## Chef's notes Indulge in tender, golden-fried chicken breast, crunchy with every bite. Nestled on a bed of steamed rice, this dish is elevated by a rich, velvety curry sauce, infused with the warmth of fragrant spices and the umami depth of soy. Paired with vibrant vegetables for a harmonious balance of textures and flavors, this comforting classic promises to delight your soul. ## Details - ⏲️ Prep time: 10 min - 🍳 Cook time: 30 min - 🍽️ Servings: 2 ## Ingredients - Chicken Fillet 250 grams - Potato 100 grams - Egg 1 pc - Curry block 2 pcs or 20 grams - breadcrumbs 100 grams / 2 cups - flour 20 grams - Cooking oil (for frying) - chicken or vegetable stock 500ml - soy sauce 1 tbsp - Seasoning - onion 1 pc, finely chopped - garlic cloves 2 pcs, minced - carrot 1 pc, chopped ## Directions 1. Chicken Katsu: Pound the chicken breasts until about 1/2 inch thick. Season with salt and pepper. Coat each piece in flour, then dip in beaten egg, and finally coat with breadcrumbs. Heat oil in a pan and fry the chicken for about 3-4 minutes on each side, until golden brown and fully cooked. Place on paper towels to drain. 2. Make Curry Sauce: In a pan, sauté the onion, garlic, add potato and carrot until soft. Gradually add curry block and the stock, stir well. Simmer for 5-10 minutes until thickened. Add seasoning and soy sauce to taste. 3. Plating: Slice the cooked chicken katsu and place it over a bed of steamed rice. Pour the curry sauce on the side or over the chicken. Garnish with chopped green chilies. @ ee11a5df:b76c4e49
2024-12-16 05:29:30# Nostr 2? ## Breaking Changes in Nostr Nostr was a huge leap forward. But it isn't perfect. When developers notice a problem with nostr, they confer with each other to work out a solution to the problem. This is usually in the form of a NIP PR on the nips repo. Some problems are easy. Just add something new and optional. No biggie. Zaps, git stuff, bunkers... just dream it up and add it. Other problems can only be fixed by breaking changes. With a breaking change, the overall path forward is like this: Add the new way of doing it while preserving the old way. Push the major software to switch to the new way. Then deprecate the old way. This is a simplification, but it is the basic idea. It is how we solved markers/quotes/root and how we are upgrading encryption, among other things. This process of pushing through a breaking change becomes more difficult as we have more and more existing nostr software out there that will break. Most of the time what happens is that the major software is driven to make the change (usually by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6), and the smaller software is left to fend for itself. A while back I introduced the BREAKING.md file to help people developing smaller lesser-known software keep up with these changes. ## Big Ideas But some ideas just can't be applied to nostr. The idea is too big. The change is too breaking. It changes something fundamental. And nobody has come up with a smooth path to move from the old way to the new way. And so we debate a bunch of things, and never settle on anything, and eventually nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 makes a post saying that we don't really want it anyways 😉. As we encounter good ideas that are hard to apply to nostr, I've been filing them away in a repository I call "nostr-next", so we don't forget about them, in case we ever wanted to start over. It seems to me that starting over every time we encountered such a thing would be unwise. However, once we collect enough changes that we couldn't reasonably phase into nostr, then a tipping point is crossed where it becomes worthwhile to start over. In terms of the "bang for the buck" metaphor, the bang becomes bigger and bigger but the buck (the pain and cost of starting over) doesn't grow as rapidly. ## WHAT? Start over? IMHO starting over could be very bad if done in a cavalier way. The community could fracture. The new protocol could fail to take off due to lacking the network effect. The odds that a new protocol catches on are low, irrespective of how technically superior it could be. So the big question is: can we preserve the nostr community and it's network effect while making a major step-change to the protocol and software? I don't know the answer to that one, but I have an idea about it. I think the new-protocol clients can be dual-stack, creating events in both systems and linking those events together via tags. The nostr key identity would still be used, and the new system identity too. This is better than things like the mostr bridge because each user would remain in custody of their own keys. ## The nitty gritty Here are some of the things I think would make nostr better, but which nostr can't easily fix. A lot of these ideas have been mentioned before by multiple people and I didn't give credit to all of you (sorry) because my brain can't track it all. But I've been collecting these over time at https://github.com/mikedilger/nostr-next * Events as CBOR or BEVE or MsgPack or a fixed-schema binary layout... anything but JSON text with its parsing, it's encoding ambiguity, it's requirement to copy fields before hashing them, its unlimited size constraints. (me, nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s) * EdDSA ed25519 keys instead of secp256k1, to enable interoperability with a bunch of other stuff like ssh, pgp, TLS, Mainline DHT, and many more, plus just being better cryptography (me, Nuh, Orlovsky, except Orlovsky wanted Ristretto25519 for speed) * Bootstrapping relay lists (and relay endpoints) from Mainline DHT (nostr:npub1jvxvaufrwtwj79s90n79fuxmm9pntk94rd8zwderdvqv4dcclnvs9s7yqz) * Master keys and revocable subkeys / device keys (including having your nostr key as a subkey) * Encryption to use different encryption-specific subkeys and ephemeral ones from the sender. * Relay keypairs, TLS without certificates, relays known by keypair instead of URL * Layered protocol (separate core from applications) * Software remembering when they first saw an event, for 2 reasons, the main one being revocation (don't trust the date in the event, trust when you first saw it), the second being more precise time range queries. * Upgrade/feature negotiation (HTTP headers prior to starting websockets) * IDs starting with a timestamp so they are temporally adjacent (significantly better database performance) (Vitor's idea) * Filters that allow boolean expressions on tag values, and also ID exclusions. Removing IDs from filters and moving to a GET command. * Changing the transport (I'm against this but I know others want to) ## What would it look like? Someone (Steve Farroll) has taken my nostr-next repo and turned it into a proposed protocol he calls [Mosaic](https://github.com/SteveFarroll/mosaic-spec). I think it is quite representative of that repo, as it already includes most of those suggestions, so I've been contributing to it. Mosaic spec is rendered [here](https://stevefarroll.github.io/mosaic-spec/). Of course, where Mosaic stands right now it is mostly my ideas (and Steve's), it doesn't have feedback or input from other nostr developers yet. That is what this blog post is about. I think it is time for other nostr devs to be made aware of this thing. It is currently in the massive breaking changes phase. It might not look that way because of the detail and refinement of the documentation, but indeed everything is changing rapidly. It probably has some bad ideas and is probably missing some great ideas that you have. Which is why this is a good time for other devs to start taking a look at it. It is also the time to debate meta issues like "are you crazy Mike?" or "no we have to just break nostr but keep it nostr, we can't dual-stack" or whatever. Personally I think mosaic-spec should develop and grow for quite a while before the "tipping point" happens. That is, I'm not sure we should jump in feet first yet, but rather we build up and refine this new protocol and spend a lot of time thinking about how to migrate smoothly, and break it a lot while nobody is using it. So you can just reply to this, or DM me, or open issues or PRs at [Mosaic](https://github.com/SteveFarroll/mosaic-spec), or just whisper to each other while giving me the evil eye.
@ ee11a5df:b76c4e49
2024-12-16 05:29:30# Nostr 2? ## Breaking Changes in Nostr Nostr was a huge leap forward. But it isn't perfect. When developers notice a problem with nostr, they confer with each other to work out a solution to the problem. This is usually in the form of a NIP PR on the nips repo. Some problems are easy. Just add something new and optional. No biggie. Zaps, git stuff, bunkers... just dream it up and add it. Other problems can only be fixed by breaking changes. With a breaking change, the overall path forward is like this: Add the new way of doing it while preserving the old way. Push the major software to switch to the new way. Then deprecate the old way. This is a simplification, but it is the basic idea. It is how we solved markers/quotes/root and how we are upgrading encryption, among other things. This process of pushing through a breaking change becomes more difficult as we have more and more existing nostr software out there that will break. Most of the time what happens is that the major software is driven to make the change (usually by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6), and the smaller software is left to fend for itself. A while back I introduced the BREAKING.md file to help people developing smaller lesser-known software keep up with these changes. ## Big Ideas But some ideas just can't be applied to nostr. The idea is too big. The change is too breaking. It changes something fundamental. And nobody has come up with a smooth path to move from the old way to the new way. And so we debate a bunch of things, and never settle on anything, and eventually nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 makes a post saying that we don't really want it anyways 😉. As we encounter good ideas that are hard to apply to nostr, I've been filing them away in a repository I call "nostr-next", so we don't forget about them, in case we ever wanted to start over. It seems to me that starting over every time we encountered such a thing would be unwise. However, once we collect enough changes that we couldn't reasonably phase into nostr, then a tipping point is crossed where it becomes worthwhile to start over. In terms of the "bang for the buck" metaphor, the bang becomes bigger and bigger but the buck (the pain and cost of starting over) doesn't grow as rapidly. ## WHAT? Start over? IMHO starting over could be very bad if done in a cavalier way. The community could fracture. The new protocol could fail to take off due to lacking the network effect. The odds that a new protocol catches on are low, irrespective of how technically superior it could be. So the big question is: can we preserve the nostr community and it's network effect while making a major step-change to the protocol and software? I don't know the answer to that one, but I have an idea about it. I think the new-protocol clients can be dual-stack, creating events in both systems and linking those events together via tags. The nostr key identity would still be used, and the new system identity too. This is better than things like the mostr bridge because each user would remain in custody of their own keys. ## The nitty gritty Here are some of the things I think would make nostr better, but which nostr can't easily fix. A lot of these ideas have been mentioned before by multiple people and I didn't give credit to all of you (sorry) because my brain can't track it all. But I've been collecting these over time at https://github.com/mikedilger/nostr-next * Events as CBOR or BEVE or MsgPack or a fixed-schema binary layout... anything but JSON text with its parsing, it's encoding ambiguity, it's requirement to copy fields before hashing them, its unlimited size constraints. (me, nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s) * EdDSA ed25519 keys instead of secp256k1, to enable interoperability with a bunch of other stuff like ssh, pgp, TLS, Mainline DHT, and many more, plus just being better cryptography (me, Nuh, Orlovsky, except Orlovsky wanted Ristretto25519 for speed) * Bootstrapping relay lists (and relay endpoints) from Mainline DHT (nostr:npub1jvxvaufrwtwj79s90n79fuxmm9pntk94rd8zwderdvqv4dcclnvs9s7yqz) * Master keys and revocable subkeys / device keys (including having your nostr key as a subkey) * Encryption to use different encryption-specific subkeys and ephemeral ones from the sender. * Relay keypairs, TLS without certificates, relays known by keypair instead of URL * Layered protocol (separate core from applications) * Software remembering when they first saw an event, for 2 reasons, the main one being revocation (don't trust the date in the event, trust when you first saw it), the second being more precise time range queries. * Upgrade/feature negotiation (HTTP headers prior to starting websockets) * IDs starting with a timestamp so they are temporally adjacent (significantly better database performance) (Vitor's idea) * Filters that allow boolean expressions on tag values, and also ID exclusions. Removing IDs from filters and moving to a GET command. * Changing the transport (I'm against this but I know others want to) ## What would it look like? Someone (Steve Farroll) has taken my nostr-next repo and turned it into a proposed protocol he calls [Mosaic](https://github.com/SteveFarroll/mosaic-spec). I think it is quite representative of that repo, as it already includes most of those suggestions, so I've been contributing to it. Mosaic spec is rendered [here](https://stevefarroll.github.io/mosaic-spec/). Of course, where Mosaic stands right now it is mostly my ideas (and Steve's), it doesn't have feedback or input from other nostr developers yet. That is what this blog post is about. I think it is time for other nostr devs to be made aware of this thing. It is currently in the massive breaking changes phase. It might not look that way because of the detail and refinement of the documentation, but indeed everything is changing rapidly. It probably has some bad ideas and is probably missing some great ideas that you have. Which is why this is a good time for other devs to start taking a look at it. It is also the time to debate meta issues like "are you crazy Mike?" or "no we have to just break nostr but keep it nostr, we can't dual-stack" or whatever. Personally I think mosaic-spec should develop and grow for quite a while before the "tipping point" happens. That is, I'm not sure we should jump in feet first yet, but rather we build up and refine this new protocol and spend a lot of time thinking about how to migrate smoothly, and break it a lot while nobody is using it. So you can just reply to this, or DM me, or open issues or PRs at [Mosaic](https://github.com/SteveFarroll/mosaic-spec), or just whisper to each other while giving me the evil eye. @ deba271e:36005655
2024-12-13 22:23:32#### Background **The free Alby account is going away** by Jan 3rd 2025. With this users have options to switch to either self hosted Alby Hub or hosted Alby Hub for 21k sats per month (see https://albyhub.com/). Unfortunatelly neither of these options work for me. - I'm currently traveling a lot without a single base home, so I can't just run some server "at home" and I want to be able to use it even when I'm in the midst of moving between locations. - 21k sats/month for Alby Hub is too steep just for using it for Nostr zaps. I'd pay more for the service than what I ever get in zaps. I'm happy to support projects, but the math just doesn't work out. - Running lightning node, etc in VPS is also prohibitively expensive for this usecase, but I may end up eventually doing this for other reasons. Getting VPS strong enough for self hosted node is around $80/month, but there are also options like https://nodana.io/ for $10/month. (Shill me better options if you have) If there is a way to run a selft-custodial solution with these requirements (i.e. no "home" node, cheap for small amount zapping), let me know, otherwise this will do and we'll have to wait for BOLT12 in lnd. ## Tutorial So here's the plan - Get coinos.io account - Connect it with Amethyst via NWC - Install Alby Go to make it easier to use the account on the go Here are the steps to do on your Android phone. iOS will be similar - Get [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst&hl=en&gl=US) nostr app installed - Go to https://coinos.io/ , register new account and sign in. - On the main screen click on the settings gear icon and get the connection code  - Reveal and copy the connection strings (tap on Copy) - Open Amethyst and hold the lightning icon under any post - Tap the "paste" button (see the screenshot)  - Now click on Save and that's it - Zapping should now work natively in Amethyst and it will use the hosted wallet Optional - One extra thing you can do here is to install Alby Go (https://albygo.com/) and use the same "connection string" to connect it to your coinos.io account. This way you will have a mobile native wallet that's connected to this account (which makes it easier to pay with it, etc) originally posted at https://stacker.news/items/808573
@ deba271e:36005655
2024-12-13 22:23:32#### Background **The free Alby account is going away** by Jan 3rd 2025. With this users have options to switch to either self hosted Alby Hub or hosted Alby Hub for 21k sats per month (see https://albyhub.com/). Unfortunatelly neither of these options work for me. - I'm currently traveling a lot without a single base home, so I can't just run some server "at home" and I want to be able to use it even when I'm in the midst of moving between locations. - 21k sats/month for Alby Hub is too steep just for using it for Nostr zaps. I'd pay more for the service than what I ever get in zaps. I'm happy to support projects, but the math just doesn't work out. - Running lightning node, etc in VPS is also prohibitively expensive for this usecase, but I may end up eventually doing this for other reasons. Getting VPS strong enough for self hosted node is around $80/month, but there are also options like https://nodana.io/ for $10/month. (Shill me better options if you have) If there is a way to run a selft-custodial solution with these requirements (i.e. no "home" node, cheap for small amount zapping), let me know, otherwise this will do and we'll have to wait for BOLT12 in lnd. ## Tutorial So here's the plan - Get coinos.io account - Connect it with Amethyst via NWC - Install Alby Go to make it easier to use the account on the go Here are the steps to do on your Android phone. iOS will be similar - Get [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst&hl=en&gl=US) nostr app installed - Go to https://coinos.io/ , register new account and sign in. - On the main screen click on the settings gear icon and get the connection code  - Reveal and copy the connection strings (tap on Copy) - Open Amethyst and hold the lightning icon under any post - Tap the "paste" button (see the screenshot)  - Now click on Save and that's it - Zapping should now work natively in Amethyst and it will use the hosted wallet Optional - One extra thing you can do here is to install Alby Go (https://albygo.com/) and use the same "connection string" to connect it to your coinos.io account. This way you will have a mobile native wallet that's connected to this account (which makes it easier to pay with it, etc) originally posted at https://stacker.news/items/808573 @ 3b19f10a:4e1f94b4
2024-12-07 09:55:46Sometimes perspective is everything... #[artmodel]( https://bsky.app/hashtag/artmodel) #[nude]( https://bsky.app/hashtag/nude) #[nudemodel]( https://bsky.app/hashtag/nudemodel) ------   
@ 3b19f10a:4e1f94b4
2024-12-07 09:55:46Sometimes perspective is everything... #[artmodel]( https://bsky.app/hashtag/artmodel) #[nude]( https://bsky.app/hashtag/nude) #[nudemodel]( https://bsky.app/hashtag/nudemodel) ------    @ 6d8e2a24:5faaca4c
2024-12-02 09:03:49"if your boyfriend uses Tiktok, you have a girlfriend" worlds riches man. Elon Musk tells women.  What's your opinion, do you think Elon Musk is right by his statement?
@ 6d8e2a24:5faaca4c
2024-12-02 09:03:49"if your boyfriend uses Tiktok, you have a girlfriend" worlds riches man. Elon Musk tells women.  What's your opinion, do you think Elon Musk is right by his statement? @ 4fe4a528:3ff6bf06
2024-12-01 15:00:30https://cdn.satellite.earth/8dd22e9b598964ade69d4c5ca517c2637ffafdfb15cf3e589cd1a7955c173375.mp4 In my last news article I wrote about selling my beef for 4500 sats / lb and buying my eggs for 4500 sats / dozen. You will be glad to know that some of my friends gave me bitcoin for my birthday. One person gave me over 60,000 sats, so now I am feeling like my last months article caused everyone to [*buy bitcoin — opt out of inflation*](https://amendt.substack.com/p/buy-bitcoin)*.* It must have been more than my friends giving me bitcoin that caused Bitcoin to increase it’s market cap by 600 billion US dollars. I know that eggs are costing me 3,000 sats now compared to 4500 sats one month ago. If things keep getting 50% cheaper every month I might not have to move all my value into bitcoin. Isn’t it weird using something that increases in value month after month? It is indeed a far cry from the traditional notion of money, where the value or the purchasing power of the currency loses value month after month. Most Bitcoiners care about the separation of money from the state, the removal of a third party from transactions and the capturing the deflationary nature of technology, etc. The fiat price is simply a short term way of measuring progress toward that goal. In reality, the moose shekel price doesn’t really matter. With Brazil and Russia now using it as legal tender I don’t want anyone to give me bitcoin as a gift this month. Give your money/love to helping others see Jesus’ love in coming to earth instead. You might be able to write off your donation also. You do realize there are only 16.5 million bitcoin available to be moved to other bitcoin type people and the US bitcoin strategic reserve might be coming next year. I just hope the Trudeau / Christine “Vib” session doesn’t make Canadians give up on using the Moose Shekels as a means of exchanging value. Bitcoin is now worth more than the Canadian dollar. If you need to get educated about money join Nostr and do a video / desktop sharing conference with me. Say hivetalk.org @ 9am ish works best for me. Remember, learning technology makes you earn more. We are all in this together.
@ 4fe4a528:3ff6bf06
2024-12-01 15:00:30https://cdn.satellite.earth/8dd22e9b598964ade69d4c5ca517c2637ffafdfb15cf3e589cd1a7955c173375.mp4 In my last news article I wrote about selling my beef for 4500 sats / lb and buying my eggs for 4500 sats / dozen. You will be glad to know that some of my friends gave me bitcoin for my birthday. One person gave me over 60,000 sats, so now I am feeling like my last months article caused everyone to [*buy bitcoin — opt out of inflation*](https://amendt.substack.com/p/buy-bitcoin)*.* It must have been more than my friends giving me bitcoin that caused Bitcoin to increase it’s market cap by 600 billion US dollars. I know that eggs are costing me 3,000 sats now compared to 4500 sats one month ago. If things keep getting 50% cheaper every month I might not have to move all my value into bitcoin. Isn’t it weird using something that increases in value month after month? It is indeed a far cry from the traditional notion of money, where the value or the purchasing power of the currency loses value month after month. Most Bitcoiners care about the separation of money from the state, the removal of a third party from transactions and the capturing the deflationary nature of technology, etc. The fiat price is simply a short term way of measuring progress toward that goal. In reality, the moose shekel price doesn’t really matter. With Brazil and Russia now using it as legal tender I don’t want anyone to give me bitcoin as a gift this month. Give your money/love to helping others see Jesus’ love in coming to earth instead. You might be able to write off your donation also. You do realize there are only 16.5 million bitcoin available to be moved to other bitcoin type people and the US bitcoin strategic reserve might be coming next year. I just hope the Trudeau / Christine “Vib” session doesn’t make Canadians give up on using the Moose Shekels as a means of exchanging value. Bitcoin is now worth more than the Canadian dollar. If you need to get educated about money join Nostr and do a video / desktop sharing conference with me. Say hivetalk.org @ 9am ish works best for me. Remember, learning technology makes you earn more. We are all in this together. @ 36bedab2:524acad4
2024-11-24 23:17:58A Lei de Gresham explica por que o Bitcoin é visto como um "bom dinheiro" e sua relevância no contexto econômico global. 2. Bitcoin e a Lei de Gresham O Bitcoin é um exemplo moderno da Lei de Gresham, mas funcionando de forma inversa em um ambiente onde não há obrigatoriedade de aceitação de moedas governamentais. Bitcoin como "bom dinheiro": Escassez e mineração: Bitcoin é escasso (máximo de 21 milhões) e sua criação exige esforço computacional significativo, semelhante à extração de ouro. Proteção contra desvalorização: Ao contrário das moedas fiduciárias, que podem ser impressas sem limite, o Bitcoin tem regras rígidas que evitam inflação descontrolada. Preferência pelo armazenamento: As pessoas preferem guardar Bitcoin como reserva de valor, em vez de gastá-lo, porque ele tende a valorizar com o tempo. Isso está alinhado com a Lei de Gresham: as pessoas gastam o "dinheiro ruim" (moedas fiduciárias inflacionárias) antes de gastar o "dinheiro bom" (Bitcoin). 4. Bitcoin e a Geopolítica Monetária O dólar norte-americano mantém seu status de moeda de reserva global, dando aos EUA a capacidade de imprimir dinheiro que outros países precisam usar. Assim como o ouro, o Bitcoin é visto como uma ameaça ao sistema fiduciário liderado pelo dólar. Ele representa um "dinheiro bom" que não pode ser desvalorizado por decisões políticas. A Lei de Gresham explica por que o Bitcoin é raramente gasto, mas amplamente guardado como uma reserva de valor. A sua ascensão reflete a insatisfação global com moedas fiduciárias inflacionárias, e ele é visto como uma esperança para o futuro financeiro, ao oferecer um sistema monetário independente, transparente e limitado. O Bitcoin, como exemplo de "bom dinheiro", tem o potencial de mudar o sistema econômico global, libertando-o de governos que abusam de sua capacidade de emitir moedas descontroladamente.
@ 36bedab2:524acad4
2024-11-24 23:17:58A Lei de Gresham explica por que o Bitcoin é visto como um "bom dinheiro" e sua relevância no contexto econômico global. 2. Bitcoin e a Lei de Gresham O Bitcoin é um exemplo moderno da Lei de Gresham, mas funcionando de forma inversa em um ambiente onde não há obrigatoriedade de aceitação de moedas governamentais. Bitcoin como "bom dinheiro": Escassez e mineração: Bitcoin é escasso (máximo de 21 milhões) e sua criação exige esforço computacional significativo, semelhante à extração de ouro. Proteção contra desvalorização: Ao contrário das moedas fiduciárias, que podem ser impressas sem limite, o Bitcoin tem regras rígidas que evitam inflação descontrolada. Preferência pelo armazenamento: As pessoas preferem guardar Bitcoin como reserva de valor, em vez de gastá-lo, porque ele tende a valorizar com o tempo. Isso está alinhado com a Lei de Gresham: as pessoas gastam o "dinheiro ruim" (moedas fiduciárias inflacionárias) antes de gastar o "dinheiro bom" (Bitcoin). 4. Bitcoin e a Geopolítica Monetária O dólar norte-americano mantém seu status de moeda de reserva global, dando aos EUA a capacidade de imprimir dinheiro que outros países precisam usar. Assim como o ouro, o Bitcoin é visto como uma ameaça ao sistema fiduciário liderado pelo dólar. Ele representa um "dinheiro bom" que não pode ser desvalorizado por decisões políticas. A Lei de Gresham explica por que o Bitcoin é raramente gasto, mas amplamente guardado como uma reserva de valor. A sua ascensão reflete a insatisfação global com moedas fiduciárias inflacionárias, e ele é visto como uma esperança para o futuro financeiro, ao oferecer um sistema monetário independente, transparente e limitado. O Bitcoin, como exemplo de "bom dinheiro", tem o potencial de mudar o sistema econômico global, libertando-o de governos que abusam de sua capacidade de emitir moedas descontroladamente. @ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08### Tldr - Nostr is an open protocol which is interoperable with all kinds of other technologies - You can use this interoperability to create custom solutions - Nostr apps define a custom URI scheme handler "nostr:" - In this blog I use this to integrate Nostr with NFC cards - I create a Nostr NFC "login card" which allows me to log into Amethyst client - I create a Nostr NFC "business card" which allows anyone to find my profile with a tap ### Inter-Op All The Things! Nostr is a new open social protocol for the internet. This open nature is very exciting because it means Nostr can add new capabilities to all other internet-connected technologies, from browsers to web applications. In my view, it achieves this through three core capabilities. - A lightweight decentralised identity (Nostr keys, "npubs" and "nsecs"), - A lightweight data distribution network (Nostr relays), - A set of data interoperability standards (The Nostr Improvement Protocols "NIPs"), including the "nostr:" URI which we'll use in this post. The lightweight nature is its core strength. Very little is required to interoperate with Nostr, which means many existing technologies can be easily used with the network. Over the next few blog posts, I'll explore different Nostr inter-op ideas, and also deliver my first small open source projects to the community. I'll cover– - NFC cards integrated with Nostr (in this post), - Workflow Automations integrated with Nostr, - AI LLMs integrated with Nostr. #### The "Nostr:" URI One feature of Nostr is it defines a custom URI scheme handler "nostr:". What is that? A URI is used to identify a resource in a system. A system will have a protocol handler registry used to store such URI's, and if a system has a URI registered, then it knows what to do when it sees it. You are probably already familiar with some URI schemes such as "http:" and "mailto:". For example, when you click an http link, the system knows that it describes an http resource and opens a web browser to fetch the content from the internet. A nostr: link operates in the same way. The nostr: prefix indicates a custom URI scheme specifically designed for the Nostr protocol. If a system has a Nostr application installed, that application may have registered "nostr:" in the protocol handler registry. On that system when a "nostr:" URI is clicked, the system will know that it describes a nostr resource and open the Nostr client to fetch the content from the nostr relay network. This inter-op with the protocol handler registry gives us the power to do nice and exciting things with other technologies. ### Nostr and NFC Another technology that uses URIs is NFC cards. NFC (Near Field Communication) is a wireless technology that enables devices to exchange data over a few centimeters. It’s widely used in contactless payments, access control, and information sharing. NFC tags are small chips embedded in cards or stickers which can store data like plain text, URLs, or custom URIs. They are very cheap (cents each) and widely available (Amazon with next day delivery). When an NFC tag contains a URI, such as a http: (or nostr:) link, it acts as a trigger. Tapping the tag with an NFC-enabled device launches the associated application and processes the URI. For example, tapping a tag with "nostr:..." could open a Nostr client, directing it to a specific login page, public profile, or event. This inter-op allows us to bridge the physical world to Nostr with just a tap. #### Many useful ideas There are many interesting ways to use this. Too many for me to explore. Perhaps some of these are interesting for your next side hustle? - Nostr NFC "login cards" – tap to log into Amethyst on Android, - Nostr NFC "business cards" – give to connections so they can tap to load your npub, - Nostr NFC "payment cards" – integrating lightning network or ecash, - Nostr NFC "doorbells", "punch cards", "drop boxes", or "dead drops" – put a tag in a specific place and tap to open a location-specific message or chat, - Integrations with other access control systems, - Integrations with other home automation systems, - Many more ... To start with I have built and use the "login card" and "business card" solutions. This blog post will show you how to do the same. ### Nostr Login Card You can use an NFC card to log into your Nostr client. Most Nostr clients accept a variety of login methods, from posting your nsec into the app (insecure) to using a remote signer (more secure). A less known but more secure method is to sign into a session with a tap of a specially-configured NFC card. Amethyst is a Nostr client on Android which supports this type of login. - A secure method for logging in - Optionally keeps no log in history on the device after logout - Does not require users to know or understand how keys work - Keys are kept secure on a physically-separated card to reduce risk of compromise Nostr devs think that this is useful for anti-establishment actors–Fair enough. For me, I am interested in this login card pattern as it could be useful for rolling out identities within an organisation context with less training (office workers are already familiar with door access cards). This pattern potentially abstracts away key management to the IT or ops team who provision the cards. I first discovered this when [Kohei](nostr:npub16lrdq99ng2q4hg5ufre5f8j0qpealp8544vq4ctn2wqyrf4tk6uqn8mfeq) demonstrated it in [his video](nostr:nevent1qqstx0jy5jvzgh7wr6entjuw7h58d7mapupfdpt9hkf7s4gze34a0vspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzp47x6q2txs5ptw3fcj8ngj0y7qrnm7z0ft2cptshx5uqgxn2hd4ckqyqd3). Here's how you set it up at a high level– 1. Buy yourself some NFC cards 2. Get your Nostr key ready in an encrypted, password protected format called "nencryptsec" 3. Write the nencryptsec to the NFC card as a custom URI 4. Tap to load the login screen, and enter your password to login Here it is in detail– #### Buy yourself some NFC cards I found no specific requirements. As usual with Nostr so far, I tried to the cheapest possible route and it worked. Generic brand NFC cards shipped from China, I believe it was 50X for $15 from Amazon. Your mileage may vary. #### Get your Nostr key ready Your key will be saved to the NFC card in an encrypted password-protected format called "nencryptsec". Several applications support this. As we'll be using this to login to Amethyst, we will use Amethyst to output the nencryptsec for us. 1. Login to Amethyst with your nsec, 2. Open the sidebar and click "Backup Keys", 3. Enter a password, and click "Encrypt and my secret key", 4. It will add the password-protected key to your clipboard in the format "ncryptsec1...", 5. Remember to backup your password. #### Write the ncryptsec to the NFC card 1. Download the free [NFC Tools app](https://play.google.com/store/apps/details?id=com.wakdev.wdnfc) to your device, and open it, 2. Click "Write" and "Add a record", then click "Custom URL / URI", 3. Paste your nencryptsec with the nostr URI in front, i.e. "nostr:ncryptsec1..." and click OK, 4. Click "Write". NFC Tools will prompt you to "Approach an NFC tag", 5. Place your NFC card against your phone, and it will write to the card, 6. Your card is ready. #### Tap to load the login screen Tap the card against your phone again, and your phone should open the login screen of Amethyst and prompt you for your password. Once you enter your password, Amethyst will decrypt your nsec and log you in. Optionally, you can also set the app to forget you once you log out. You have created a Nostr NFC "login card". ### Nostr Business Card You can use another NFC card to give anyone you meet a link straight to your Nostr profile. I attended [Peter McCormack](nostr:npub14mcddvsjsflnhgw7vxykz0ndfqj0rq04v7cjq5nnc95ftld0pv3shcfrlx)'s #CheatCode conference in Sydney and gave a few of these out following the Nostr panel, notably to [Preston Pysh](nostr:npub1s5yq6wadwrxde4lhfs56gn64hwzuhnfa6r9mj476r5s4hkunzgzqrs6q7z) where it [got some cut through](nostr:nevent1qqsdx0acma85u9knejnvfnfms9pfv27g97mfnnq9fnxslsa9vtrx73spremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzppggp5a66uxvmntlwnpf5384twu9e0xnm5xth9ta58fpt0dexysy26d4nm) and found me my first 100 followers. You can do the same. To create your Nostr NFC "business card" is even easier than your NFC "login card". 1. Buy yourself some NFC cards, 2. Download the free [NFC Tools app](https://play.google.com/store/apps/details?id=com.wakdev.wdnfc) to your device, and open it, 2. Click "Write" and "Add a record", then click "Custom URL / URI", 3. Write your npub to the NFC card as a custom URI in the format "nostr:npub1..." (e.g. for me this is "nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft"), 4. Your card is ready. Give the card to someone who is a Nostr user, and when they tap the card against their phone it will open their preferred Nostr client and go directly to your Nostr profile page. You have created a Nostr NFC "business card". ### What I Did Wrong I like to share what I did wrong so you don't have to make the same mistakes. This time, this was very easy, and little went wrong. In general - When password-protecting your nsec, don't forget the password! - When writing to the NFC card, make sure to use "Custom URI/URL" as this accepts your "nostr:" URI scheme. If you use generic "URI/URL" it won't work. ### What's Next Over my first four blogs I have explored creating a good Nostr setup - [Mined a Nostr pubkey and backed up the mnemonic](nostr:naddr1qqsy66twd9hxwtteda6hyt2kv9hxjare94g82cntv4uj6drfw4cxyeszyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c6e2ekw) - [Set up Nostr payments with a Lightning wallet plus all the bells and whistles](nostr:naddr1qq34xet5w35kueedw4cz65rp09kk2mn5wvkk7m3dfehhxarj95mk7dnvwvmsygqmmflp7uukhk3drmueqv763lfdcd3gzpusm7d7vt6ezquth97ymypsgqqqw4rsuql6je) - [Set up NIP-05 and Lighting Address at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqyghwumn8ghj7mn0wd68ytnhd9hx2tczyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c634nh0) - [Set up a Personal Relay at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7q3qr0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvsxpqqqp65wmzpn9e) Over the next few blogs I will be exploring different types of Nostr inter-op - NFC cards integrated with Nostr (this post) - Workflow Automations integrated with Nostr - AI LLMs integrated with Nostr Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle. GM Nostr.
@ 1bda7e1f:bb97c4d9
2024-11-21 04:17:08### Tldr - Nostr is an open protocol which is interoperable with all kinds of other technologies - You can use this interoperability to create custom solutions - Nostr apps define a custom URI scheme handler "nostr:" - In this blog I use this to integrate Nostr with NFC cards - I create a Nostr NFC "login card" which allows me to log into Amethyst client - I create a Nostr NFC "business card" which allows anyone to find my profile with a tap ### Inter-Op All The Things! Nostr is a new open social protocol for the internet. This open nature is very exciting because it means Nostr can add new capabilities to all other internet-connected technologies, from browsers to web applications. In my view, it achieves this through three core capabilities. - A lightweight decentralised identity (Nostr keys, "npubs" and "nsecs"), - A lightweight data distribution network (Nostr relays), - A set of data interoperability standards (The Nostr Improvement Protocols "NIPs"), including the "nostr:" URI which we'll use in this post. The lightweight nature is its core strength. Very little is required to interoperate with Nostr, which means many existing technologies can be easily used with the network. Over the next few blog posts, I'll explore different Nostr inter-op ideas, and also deliver my first small open source projects to the community. I'll cover– - NFC cards integrated with Nostr (in this post), - Workflow Automations integrated with Nostr, - AI LLMs integrated with Nostr. #### The "Nostr:" URI One feature of Nostr is it defines a custom URI scheme handler "nostr:". What is that? A URI is used to identify a resource in a system. A system will have a protocol handler registry used to store such URI's, and if a system has a URI registered, then it knows what to do when it sees it. You are probably already familiar with some URI schemes such as "http:" and "mailto:". For example, when you click an http link, the system knows that it describes an http resource and opens a web browser to fetch the content from the internet. A nostr: link operates in the same way. The nostr: prefix indicates a custom URI scheme specifically designed for the Nostr protocol. If a system has a Nostr application installed, that application may have registered "nostr:" in the protocol handler registry. On that system when a "nostr:" URI is clicked, the system will know that it describes a nostr resource and open the Nostr client to fetch the content from the nostr relay network. This inter-op with the protocol handler registry gives us the power to do nice and exciting things with other technologies. ### Nostr and NFC Another technology that uses URIs is NFC cards. NFC (Near Field Communication) is a wireless technology that enables devices to exchange data over a few centimeters. It’s widely used in contactless payments, access control, and information sharing. NFC tags are small chips embedded in cards or stickers which can store data like plain text, URLs, or custom URIs. They are very cheap (cents each) and widely available (Amazon with next day delivery). When an NFC tag contains a URI, such as a http: (or nostr:) link, it acts as a trigger. Tapping the tag with an NFC-enabled device launches the associated application and processes the URI. For example, tapping a tag with "nostr:..." could open a Nostr client, directing it to a specific login page, public profile, or event. This inter-op allows us to bridge the physical world to Nostr with just a tap. #### Many useful ideas There are many interesting ways to use this. Too many for me to explore. Perhaps some of these are interesting for your next side hustle? - Nostr NFC "login cards" – tap to log into Amethyst on Android, - Nostr NFC "business cards" – give to connections so they can tap to load your npub, - Nostr NFC "payment cards" – integrating lightning network or ecash, - Nostr NFC "doorbells", "punch cards", "drop boxes", or "dead drops" – put a tag in a specific place and tap to open a location-specific message or chat, - Integrations with other access control systems, - Integrations with other home automation systems, - Many more ... To start with I have built and use the "login card" and "business card" solutions. This blog post will show you how to do the same. ### Nostr Login Card You can use an NFC card to log into your Nostr client. Most Nostr clients accept a variety of login methods, from posting your nsec into the app (insecure) to using a remote signer (more secure). A less known but more secure method is to sign into a session with a tap of a specially-configured NFC card. Amethyst is a Nostr client on Android which supports this type of login. - A secure method for logging in - Optionally keeps no log in history on the device after logout - Does not require users to know or understand how keys work - Keys are kept secure on a physically-separated card to reduce risk of compromise Nostr devs think that this is useful for anti-establishment actors–Fair enough. For me, I am interested in this login card pattern as it could be useful for rolling out identities within an organisation context with less training (office workers are already familiar with door access cards). This pattern potentially abstracts away key management to the IT or ops team who provision the cards. I first discovered this when [Kohei](nostr:npub16lrdq99ng2q4hg5ufre5f8j0qpealp8544vq4ctn2wqyrf4tk6uqn8mfeq) demonstrated it in [his video](nostr:nevent1qqstx0jy5jvzgh7wr6entjuw7h58d7mapupfdpt9hkf7s4gze34a0vspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzp47x6q2txs5ptw3fcj8ngj0y7qrnm7z0ft2cptshx5uqgxn2hd4ckqyqd3). Here's how you set it up at a high level– 1. Buy yourself some NFC cards 2. Get your Nostr key ready in an encrypted, password protected format called "nencryptsec" 3. Write the nencryptsec to the NFC card as a custom URI 4. Tap to load the login screen, and enter your password to login Here it is in detail– #### Buy yourself some NFC cards I found no specific requirements. As usual with Nostr so far, I tried to the cheapest possible route and it worked. Generic brand NFC cards shipped from China, I believe it was 50X for $15 from Amazon. Your mileage may vary. #### Get your Nostr key ready Your key will be saved to the NFC card in an encrypted password-protected format called "nencryptsec". Several applications support this. As we'll be using this to login to Amethyst, we will use Amethyst to output the nencryptsec for us. 1. Login to Amethyst with your nsec, 2. Open the sidebar and click "Backup Keys", 3. Enter a password, and click "Encrypt and my secret key", 4. It will add the password-protected key to your clipboard in the format "ncryptsec1...", 5. Remember to backup your password. #### Write the ncryptsec to the NFC card 1. Download the free [NFC Tools app](https://play.google.com/store/apps/details?id=com.wakdev.wdnfc) to your device, and open it, 2. Click "Write" and "Add a record", then click "Custom URL / URI", 3. Paste your nencryptsec with the nostr URI in front, i.e. "nostr:ncryptsec1..." and click OK, 4. Click "Write". NFC Tools will prompt you to "Approach an NFC tag", 5. Place your NFC card against your phone, and it will write to the card, 6. Your card is ready. #### Tap to load the login screen Tap the card against your phone again, and your phone should open the login screen of Amethyst and prompt you for your password. Once you enter your password, Amethyst will decrypt your nsec and log you in. Optionally, you can also set the app to forget you once you log out. You have created a Nostr NFC "login card". ### Nostr Business Card You can use another NFC card to give anyone you meet a link straight to your Nostr profile. I attended [Peter McCormack](nostr:npub14mcddvsjsflnhgw7vxykz0ndfqj0rq04v7cjq5nnc95ftld0pv3shcfrlx)'s #CheatCode conference in Sydney and gave a few of these out following the Nostr panel, notably to [Preston Pysh](nostr:npub1s5yq6wadwrxde4lhfs56gn64hwzuhnfa6r9mj476r5s4hkunzgzqrs6q7z) where it [got some cut through](nostr:nevent1qqsdx0acma85u9knejnvfnfms9pfv27g97mfnnq9fnxslsa9vtrx73spremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzppggp5a66uxvmntlwnpf5384twu9e0xnm5xth9ta58fpt0dexysy26d4nm) and found me my first 100 followers. You can do the same. To create your Nostr NFC "business card" is even easier than your NFC "login card". 1. Buy yourself some NFC cards, 2. Download the free [NFC Tools app](https://play.google.com/store/apps/details?id=com.wakdev.wdnfc) to your device, and open it, 2. Click "Write" and "Add a record", then click "Custom URL / URI", 3. Write your npub to the NFC card as a custom URI in the format "nostr:npub1..." (e.g. for me this is "nostr:npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft"), 4. Your card is ready. Give the card to someone who is a Nostr user, and when they tap the card against their phone it will open their preferred Nostr client and go directly to your Nostr profile page. You have created a Nostr NFC "business card". ### What I Did Wrong I like to share what I did wrong so you don't have to make the same mistakes. This time, this was very easy, and little went wrong. In general - When password-protecting your nsec, don't forget the password! - When writing to the NFC card, make sure to use "Custom URI/URL" as this accepts your "nostr:" URI scheme. If you use generic "URI/URL" it won't work. ### What's Next Over my first four blogs I have explored creating a good Nostr setup - [Mined a Nostr pubkey and backed up the mnemonic](nostr:naddr1qqsy66twd9hxwtteda6hyt2kv9hxjare94g82cntv4uj6drfw4cxyeszyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c6e2ekw) - [Set up Nostr payments with a Lightning wallet plus all the bells and whistles](nostr:naddr1qq34xet5w35kueedw4cz65rp09kk2mn5wvkk7m3dfehhxarj95mk7dnvwvmsygqmmflp7uukhk3drmueqv763lfdcd3gzpusm7d7vt6ezquth97ymypsgqqqw4rsuql6je) - [Set up NIP-05 and Lighting Address at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqyghwumn8ghj7mn0wd68ytnhd9hx2tczyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c634nh0) - [Set up a Personal Relay at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7q3qr0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvsxpqqqp65wmzpn9e) Over the next few blogs I will be exploring different types of Nostr inter-op - NFC cards integrated with Nostr (this post) - Workflow Automations integrated with Nostr - AI LLMs integrated with Nostr Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle. GM Nostr. @ 6be5cc06:5259daf0
2024-11-12 03:11:11### Primeiramente, o que é mempool? Abreviação de memory pool (ou *"pool de memória"*) a mempool é uma espécie de fila onde as transações de Bitcoin ficam temporariamente armazenadas antes de serem confirmadas e incluídas em um bloco na blockchain. Quando você realiza uma transação em uma rede blockchain, essa transação precisa ser validada e confirmada pelos mineradores (ou validadores). Porém, ela não é processada instantaneamente. Primeiro, ela vai para a mempool, onde aguarda até que um minerador a selecione para incluir no próximo bloco. É assim: * Você envia uma transação, ela é transmitida para a rede e vai parar na mempool de vários nós (computadores) que suportam a rede blockchain. * As transações na mempool são organizadas pela taxa de transação que foi anexada. Quanto maior a taxa, mais rápido os mineradores tendem a escolher essa transação para incluí-la em um bloco, pois isso aumenta os ganhos deles. * Os mineradores pegam as transações da mempool, criam um bloco com elas e, ao minerar (confirmar) esse bloco, as transações saem da mempool e entram na blockchain. Aqui irei usar o site [mempool.emzy.de](https://mempool.emzy.de/) como referência, mas é importante entender que sites de mempool são representações visuais da mempool de um nó específico e não *a mempool do Bitcoin* em si. Ela não é centralizada, cada nó da rede mantém a sua própria versão da mempool. Assim, ela pode variar de um nó para outro. Esses sites ajudam a visualizar dados sobre transações e taxas. É uma boa prática usar **VPN** ou **Tor** ao acessar tais sites se você estiver verificando uma transação específica sua, pois sua privacidade pode ficar comprometida se o site registrar esses dados. Se você estiver repetidamente acessando-o para monitorar a confirmação de uma transação, alguém pode conseguir correlacionar o endereço IP com essa atividade e revelar uma conexão indireta com o endereço da transação. Dito isso... ### Como interpretar a mempool? Vamos dividir isso em partes para fins didáticos. ---  #### Faixa de taxas Cada bloco verde representa uma faixa de taxa medida em satoshis por vByte (sats/vB). Essa unidade de medida representa o valor pago por byte ocupado pela transação. Quanto maior a taxa paga por uma transação, mais rápido ela tende a ser confirmada. Quanto maior a transação em bytes, mais você precisa pagar para que ela seja confirmada. Cada transação Bitcoin consiste em *entradas* e *saídas* (*inputs* e *outputs*): * **Entradas** são referências a transações anteriores que estão sendo gastas, e cada entrada inclui informações como o endereço de origem, a assinatura (que valida a transação e pode variar de tamanho dependendo da complexidade da chave e do método de assinatura utilizado (como SegWit, que é mais eficiente). Quanto mais complexa a assinatura, maior será o tamanho em bytes) e outros dados. Quanto mais entradas uma transação tiver, maior será seu tamanho. * **Saídas** representam o destino do Bitcoin, e quanto mais saídas, maior será o tamanho da transação. Embora as saídas ocupem menos espaço em bytes do que as entradas. Ex.: * ~4 sat/vB: Indica uma taxa média. Significa que, em média, as transações estão sendo processadas a 4 satoshis por vByte; * 3-5 sat/vB: Isso significa que as transações estão sendo processadas com uma taxa entre 3 e 5 satoshis por vByte. #### MB Simplesmente o tamanho do bloco medido em megabytes :) #### Número de transações Essa seção informa quantas transações estão aguardando confirmação para cada faixa de taxa (bloco). Quanto maior o número de transações, maior a demanda pela faixa de taxa especificada. #### Tempo estimado para confirmação Aqui é mostrado o tempo médio de espera para transações que pagam taxas dentro da faixa especificada. Se você pagar uma taxa maior, a transação será confirmada mais rapidamente; uma taxa menor significa que a transação pode levar mais tempo para ser confirmada, especialmente se a rede estiver congestionada. ---  Esta seção mostra sugestões de taxa em diferentes níveis de prioridade para os usuários: #### Sem Prioridade Exibe a taxa mínima necessária para transações que não precisam de confirmação rápida. #### Prioridade Baixa Sugestão de taxa para transações que podem esperar um tempo moderado, com expectativa de confirmação em um ou dois blocos. #### Prioridade Média e Alta São as faixas de taxa recomendadas para quem precisa que a transação seja confirmada rapidamente. "Prioridade Alta" paga uma taxa maior, garantindo que a transação seja incluída no próximo bloco. ---  Cada bloco roxo representa um bloco recém-minerado. As informações mostradas incluem: #### Taxa média paga Refere-se à taxa média em satoshis/vB paga por todas as transações incluídas em um bloco recém-minerado. Isso reflete o valor médio que os usuários estão dispostos a pagar para que suas transações sejam confirmadas rapidamente. #### Número de transações Este número indica quantas transações foram processadas no bloco minerado. O tamanho do bloco é limitado, então, quanto maior o número de transações, menor será o espaço disponível para novas transações, o que pode influenciar as taxas de transação. #### Tempo desde a mineração Esta métrica informa quanto tempo se passou desde que o bloco foi minerado e adicionado à blockchain. #### Pool de mineração Exibe o nome do pool de mineração que minerou o bloco, como AntPool. Grandes pools de mineração têm mais chances de minerar blocos regularmente devido ao alto hashrate (medida da capacidade computacional utilizada pelos mineradores) que possuem. ---  Essa seção mostra informações sobre o ajuste de dificuldade, que ocorre aproximadamente a cada duas semanas. #### Tempo médio dos blocos (~9,9 minutos): Este é o tempo médio atual para minerar um bloco na rede. A meta da rede é manter o tempo de bloco em cerca de 10 minutos; um tempo menor indica um aumento na taxa de hash, ou seja, que mais poder computacional foi adicionado à rede. #### Mudança de dificuldade (+1,46%): A dificuldade ajusta-se a cada 2016 blocos para manter o tempo médio de bloco próximo de 10 minutos. Um aumento na dificuldade, como +1,46%, indica que a mineração ficou mais difícil devido ao aumento do hashrate, enquanto uma redução na dificuldade indica que o hashrate diminuiu. #### Tempo até o próximo ajuste: É o tempo previsto até o próximo ajuste de dificuldade (7 dias, nesse caso), o que é crucial para manter a rede estável e garantir a segurança e a regularidade do processo de mineração. ---  Quanto tempo demora até o próximo halving, um evento no Bitcoin que ocorre aproximadamente a cada 210.000 blocos minerados, ou cerca de quatro anos. Durante o halving, a recompensa que os mineradores recebem por adicionar um novo bloco à blockchain é reduzida pela metade. ---  Um diagrama visual da mempool que mostra o estado das transações pendentes na rede. #### Tamanhos de blocos O tamanho de cada quadrado representa o tamanho da transação em bytes. **Filtros (Consolidação, Coinjoin, Dados):** Permite visualizar categorias específicas de transações: * **Consolidação**: Transações de consolidação agrupam pequenos UTXOs em um único UTXO maior para simplificar e baratear futuras transações. (UTXOs merecem um artigo dedicado) * **Coinjoin**: Transações CoinJoin são usadas para melhorar a privacidade, misturando transações de vários usuários em uma única transação. * **Dados**: Mostra transações que contêm dados adicionais, que podem incluir informações não financeiras, como mensagens. ---  Este gráfico exibe o número de transações recebidas ao longo do tempo. #### Taxa mínima (1 sat/vB): Indica a taxa mínima atualmente aceita pela mempool. Se a mempool estiver cheia, transações que paguem menos do que a taxa mínima podem ser excluídas para dar lugar a transações de maior prioridade. #### Uso de memória (259 MB / 300 MB): A mempool tem um limite de memória. Quando está cheia, transações de taxa mais baixa podem ser descartadas para abrir espaço para aquelas com taxas mais altas, priorizando-as para inclusão em blocos. #### Transações não confirmadas (59.361): Indica o número total de transações pendentes que aguardam confirmação. Quanto maior o número de transações na mempool, maior a probabilidade de que as taxas aumentem para garantir uma confirmação mais rápida. ---  Essa seção mostra transações que foram substituídas utilizando o mecanismo RBF (Replace-By-Fee), que permite substituir uma transação com uma taxa mais alta para acelerar sua confirmação. #### TXID Este é o identificador da transação (Transaction ID), exibido parcialmente para abreviar o espaço. Cada transação tem um identificador único na blockchain. #### Previous fee Exibe a taxa de transação original paga na primeira tentativa, medida em satoshis por vByte (sat/vB). Esta taxa inicial provavelmente era baixa demais, resultando em uma demora na confirmação. #### New fee Mostra a nova taxa de transação, também em satoshis por vByte, definida para substituir a taxa anterior. Uma taxa maior aumenta as chances de inclusão rápida em um bloco. #### Status (RBF) RBF indica que a transação foi substituída utilizando o recurso "Replace-By-Fee". Isso significa que a nova transação cancelou e substituiu a original, e o minerador escolherá a transação com a taxa mais alta para incluir no próximo bloco. ---  Esta seção lista transações recentes que entraram na mempool e aguardam confirmação. #### TXID Similar ao "Recent Replacements", este é o identificador único da transação. #### Amount Exibe a quantidade de Bitcoin transferida nessa transação, geralmente em frações de BTC (como 0.0001 BTC). Esta é a quantia enviada pelo remetente ao destinatário. #### USD Mostra o valor da transação em dólares americanos (USD), calculado com base na taxa de câmbio atual. Serve para dar uma ideia de quanto a transação representa em moeda fiduciária. #### Fee Exibe a taxa de transação paga, em satoshis por vByte (sat/vB). Uma taxa mais alta em relação à média aumenta a probabilidade de confirmação mais rápida, pois as transações com taxas mais elevadas são priorizadas pelos mineradores. --- E acabou. Espero que isso tenha sido útil para você e tenha agregado mais entendimento sobre esse complexo e maravilhoso mundo do Bitcoin. Se foi, considere compartilhar com alguém que precise. E se tem sugestões de melhoria, por favor, não deixe de comentar, o conhecimento está dispero na sociedade. Por fim, stay humble and stack sats!
@ 6be5cc06:5259daf0
2024-11-12 03:11:11### Primeiramente, o que é mempool? Abreviação de memory pool (ou *"pool de memória"*) a mempool é uma espécie de fila onde as transações de Bitcoin ficam temporariamente armazenadas antes de serem confirmadas e incluídas em um bloco na blockchain. Quando você realiza uma transação em uma rede blockchain, essa transação precisa ser validada e confirmada pelos mineradores (ou validadores). Porém, ela não é processada instantaneamente. Primeiro, ela vai para a mempool, onde aguarda até que um minerador a selecione para incluir no próximo bloco. É assim: * Você envia uma transação, ela é transmitida para a rede e vai parar na mempool de vários nós (computadores) que suportam a rede blockchain. * As transações na mempool são organizadas pela taxa de transação que foi anexada. Quanto maior a taxa, mais rápido os mineradores tendem a escolher essa transação para incluí-la em um bloco, pois isso aumenta os ganhos deles. * Os mineradores pegam as transações da mempool, criam um bloco com elas e, ao minerar (confirmar) esse bloco, as transações saem da mempool e entram na blockchain. Aqui irei usar o site [mempool.emzy.de](https://mempool.emzy.de/) como referência, mas é importante entender que sites de mempool são representações visuais da mempool de um nó específico e não *a mempool do Bitcoin* em si. Ela não é centralizada, cada nó da rede mantém a sua própria versão da mempool. Assim, ela pode variar de um nó para outro. Esses sites ajudam a visualizar dados sobre transações e taxas. É uma boa prática usar **VPN** ou **Tor** ao acessar tais sites se você estiver verificando uma transação específica sua, pois sua privacidade pode ficar comprometida se o site registrar esses dados. Se você estiver repetidamente acessando-o para monitorar a confirmação de uma transação, alguém pode conseguir correlacionar o endereço IP com essa atividade e revelar uma conexão indireta com o endereço da transação. Dito isso... ### Como interpretar a mempool? Vamos dividir isso em partes para fins didáticos. ---  #### Faixa de taxas Cada bloco verde representa uma faixa de taxa medida em satoshis por vByte (sats/vB). Essa unidade de medida representa o valor pago por byte ocupado pela transação. Quanto maior a taxa paga por uma transação, mais rápido ela tende a ser confirmada. Quanto maior a transação em bytes, mais você precisa pagar para que ela seja confirmada. Cada transação Bitcoin consiste em *entradas* e *saídas* (*inputs* e *outputs*): * **Entradas** são referências a transações anteriores que estão sendo gastas, e cada entrada inclui informações como o endereço de origem, a assinatura (que valida a transação e pode variar de tamanho dependendo da complexidade da chave e do método de assinatura utilizado (como SegWit, que é mais eficiente). Quanto mais complexa a assinatura, maior será o tamanho em bytes) e outros dados. Quanto mais entradas uma transação tiver, maior será seu tamanho. * **Saídas** representam o destino do Bitcoin, e quanto mais saídas, maior será o tamanho da transação. Embora as saídas ocupem menos espaço em bytes do que as entradas. Ex.: * ~4 sat/vB: Indica uma taxa média. Significa que, em média, as transações estão sendo processadas a 4 satoshis por vByte; * 3-5 sat/vB: Isso significa que as transações estão sendo processadas com uma taxa entre 3 e 5 satoshis por vByte. #### MB Simplesmente o tamanho do bloco medido em megabytes :) #### Número de transações Essa seção informa quantas transações estão aguardando confirmação para cada faixa de taxa (bloco). Quanto maior o número de transações, maior a demanda pela faixa de taxa especificada. #### Tempo estimado para confirmação Aqui é mostrado o tempo médio de espera para transações que pagam taxas dentro da faixa especificada. Se você pagar uma taxa maior, a transação será confirmada mais rapidamente; uma taxa menor significa que a transação pode levar mais tempo para ser confirmada, especialmente se a rede estiver congestionada. ---  Esta seção mostra sugestões de taxa em diferentes níveis de prioridade para os usuários: #### Sem Prioridade Exibe a taxa mínima necessária para transações que não precisam de confirmação rápida. #### Prioridade Baixa Sugestão de taxa para transações que podem esperar um tempo moderado, com expectativa de confirmação em um ou dois blocos. #### Prioridade Média e Alta São as faixas de taxa recomendadas para quem precisa que a transação seja confirmada rapidamente. "Prioridade Alta" paga uma taxa maior, garantindo que a transação seja incluída no próximo bloco. ---  Cada bloco roxo representa um bloco recém-minerado. As informações mostradas incluem: #### Taxa média paga Refere-se à taxa média em satoshis/vB paga por todas as transações incluídas em um bloco recém-minerado. Isso reflete o valor médio que os usuários estão dispostos a pagar para que suas transações sejam confirmadas rapidamente. #### Número de transações Este número indica quantas transações foram processadas no bloco minerado. O tamanho do bloco é limitado, então, quanto maior o número de transações, menor será o espaço disponível para novas transações, o que pode influenciar as taxas de transação. #### Tempo desde a mineração Esta métrica informa quanto tempo se passou desde que o bloco foi minerado e adicionado à blockchain. #### Pool de mineração Exibe o nome do pool de mineração que minerou o bloco, como AntPool. Grandes pools de mineração têm mais chances de minerar blocos regularmente devido ao alto hashrate (medida da capacidade computacional utilizada pelos mineradores) que possuem. ---  Essa seção mostra informações sobre o ajuste de dificuldade, que ocorre aproximadamente a cada duas semanas. #### Tempo médio dos blocos (~9,9 minutos): Este é o tempo médio atual para minerar um bloco na rede. A meta da rede é manter o tempo de bloco em cerca de 10 minutos; um tempo menor indica um aumento na taxa de hash, ou seja, que mais poder computacional foi adicionado à rede. #### Mudança de dificuldade (+1,46%): A dificuldade ajusta-se a cada 2016 blocos para manter o tempo médio de bloco próximo de 10 minutos. Um aumento na dificuldade, como +1,46%, indica que a mineração ficou mais difícil devido ao aumento do hashrate, enquanto uma redução na dificuldade indica que o hashrate diminuiu. #### Tempo até o próximo ajuste: É o tempo previsto até o próximo ajuste de dificuldade (7 dias, nesse caso), o que é crucial para manter a rede estável e garantir a segurança e a regularidade do processo de mineração. ---  Quanto tempo demora até o próximo halving, um evento no Bitcoin que ocorre aproximadamente a cada 210.000 blocos minerados, ou cerca de quatro anos. Durante o halving, a recompensa que os mineradores recebem por adicionar um novo bloco à blockchain é reduzida pela metade. ---  Um diagrama visual da mempool que mostra o estado das transações pendentes na rede. #### Tamanhos de blocos O tamanho de cada quadrado representa o tamanho da transação em bytes. **Filtros (Consolidação, Coinjoin, Dados):** Permite visualizar categorias específicas de transações: * **Consolidação**: Transações de consolidação agrupam pequenos UTXOs em um único UTXO maior para simplificar e baratear futuras transações. (UTXOs merecem um artigo dedicado) * **Coinjoin**: Transações CoinJoin são usadas para melhorar a privacidade, misturando transações de vários usuários em uma única transação. * **Dados**: Mostra transações que contêm dados adicionais, que podem incluir informações não financeiras, como mensagens. ---  Este gráfico exibe o número de transações recebidas ao longo do tempo. #### Taxa mínima (1 sat/vB): Indica a taxa mínima atualmente aceita pela mempool. Se a mempool estiver cheia, transações que paguem menos do que a taxa mínima podem ser excluídas para dar lugar a transações de maior prioridade. #### Uso de memória (259 MB / 300 MB): A mempool tem um limite de memória. Quando está cheia, transações de taxa mais baixa podem ser descartadas para abrir espaço para aquelas com taxas mais altas, priorizando-as para inclusão em blocos. #### Transações não confirmadas (59.361): Indica o número total de transações pendentes que aguardam confirmação. Quanto maior o número de transações na mempool, maior a probabilidade de que as taxas aumentem para garantir uma confirmação mais rápida. ---  Essa seção mostra transações que foram substituídas utilizando o mecanismo RBF (Replace-By-Fee), que permite substituir uma transação com uma taxa mais alta para acelerar sua confirmação. #### TXID Este é o identificador da transação (Transaction ID), exibido parcialmente para abreviar o espaço. Cada transação tem um identificador único na blockchain. #### Previous fee Exibe a taxa de transação original paga na primeira tentativa, medida em satoshis por vByte (sat/vB). Esta taxa inicial provavelmente era baixa demais, resultando em uma demora na confirmação. #### New fee Mostra a nova taxa de transação, também em satoshis por vByte, definida para substituir a taxa anterior. Uma taxa maior aumenta as chances de inclusão rápida em um bloco. #### Status (RBF) RBF indica que a transação foi substituída utilizando o recurso "Replace-By-Fee". Isso significa que a nova transação cancelou e substituiu a original, e o minerador escolherá a transação com a taxa mais alta para incluir no próximo bloco. ---  Esta seção lista transações recentes que entraram na mempool e aguardam confirmação. #### TXID Similar ao "Recent Replacements", este é o identificador único da transação. #### Amount Exibe a quantidade de Bitcoin transferida nessa transação, geralmente em frações de BTC (como 0.0001 BTC). Esta é a quantia enviada pelo remetente ao destinatário. #### USD Mostra o valor da transação em dólares americanos (USD), calculado com base na taxa de câmbio atual. Serve para dar uma ideia de quanto a transação representa em moeda fiduciária. #### Fee Exibe a taxa de transação paga, em satoshis por vByte (sat/vB). Uma taxa mais alta em relação à média aumenta a probabilidade de confirmação mais rápida, pois as transações com taxas mais elevadas são priorizadas pelos mineradores. --- E acabou. Espero que isso tenha sido útil para você e tenha agregado mais entendimento sobre esse complexo e maravilhoso mundo do Bitcoin. Se foi, considere compartilhar com alguém que precise. E se tem sugestões de melhoria, por favor, não deixe de comentar, o conhecimento está dispero na sociedade. Por fim, stay humble and stack sats! @ 36bedab2:524acad4
2024-11-10 21:37:52### 1. **Power ON** - Quando você liga o computador, ele inicia o processo de boot. - Esse primeiro passo envia energia aos componentes do sistema e dispara o BIOS (ou firmware UEFI em sistemas mais recentes). ### 2. **BIOS (Basic Input/Output System)** - O BIOS ou UEFI é o firmware inicial que roda logo após o computador ser ligado. - Ele executa um conjunto de verificações no hardware (chamado POST - Power-On Self-Test) e inicializa os dispositivos básicos necessários para o boot, como o disco rígido, memória RAM e CPU. - O BIOS então procura o dispositivo de boot (HD, SSD, USB, etc.) e carrega o **MBR** ou a **partição EFI** para dar continuidade ao processo de boot. ### 3. **Master Boot Record (MBR) ou EFI Partition** - O **MBR** (Master Boot Record) ou a **partição EFI** (em sistemas com UEFI) é onde ficam armazenadas as informações sobre o carregamento do sistema operacional. - Em sistemas antigos, o MBR continha o **boot loader** e as tabelas de partição. Nos sistemas modernos com UEFI, a partição EFI cumpre essa função. - O MBR ou a partição EFI passa o controle para o **boot loader**, que é responsável por carregar o sistema operacional. ### 4. **Boot Loader (e.g., GRUB)** - O **Boot Loader** (exemplo: GRUB) é um programa responsável por carregar o sistema operacional no momento do boot. - Ele permite selecionar qual sistema operacional inicializar (em caso de dual boot) e passa o controle para o **kernel** do sistema. - GRUB (Grand Unified Bootloader) é o boot loader mais comum em sistemas Linux. ### 5. **Kernel** - O **kernel** é o núcleo do sistema operacional Linux. - Ele é carregado na memória pelo boot loader e começa a configurar os recursos do sistema, como a CPU, a memória e os dispositivos de hardware. - O kernel é responsável por gerenciar os recursos do sistema e permitir a comunicação entre o hardware e o software. ### 6. **Initial RAM disk - initramfs** - O **initramfs** é um sistema de arquivos temporário carregado na memória logo após o kernel. - Ele contém módulos e drivers essenciais para que o sistema possa iniciar corretamente e acessar o sistema de arquivos principal do disco. - O initramfs é desmontado após o sistema principal estar carregado. ### 7. **/sbin/init (parent process)** - Após o kernel inicializar o sistema, ele chama o processo **/sbin/init**, que é o primeiro processo a rodar no Linux e é o "pai" de todos os outros processos. - O init é responsável por iniciar e gerenciar todos os outros processos do sistema. - Em muitas distribuições modernas, o init foi substituído por outros sistemas de inicialização, como o **systemd**, que tem mais funcionalidades e permite um gerenciamento mais eficiente de processos. ### 8. **Command Shell using getty** - **Getty** é o processo que configura e gerencia terminais para o login do usuário. - Ele exibe a tela de login em sistemas baseados em linha de comando. - Se o sistema tiver uma interface gráfica, o getty geralmente passa o controle para o gerenciador de login gráfico. ### 9. **Graphical User Interface (X Window ou Wayland)** - Finalmente, o sistema carrega a **interface gráfica** usando o **X Window System (X11)** ou o **Wayland** (um sistema gráfico mais moderno). - Esse é o ambiente visual onde o usuário pode interagir com o sistema usando janelas, ícones, menus, etc. - X11 e Wayland são servidores gráficos que gerenciam como as janelas e aplicativos são exibidos e manipulados na tela. --- ### Como esses processos se intercalam? 1. **Hardware ligado** → **BIOS/UEFI** realiza verificações básicas. 2. **BIOS/UEFI** encontra o dispositivo de boot e carrega o **MBR** ou **partição EFI**. 3. **MBR/EFI** localiza e executa o **boot loader** (GRUB). 4. **GRUB** permite que o usuário escolha o sistema operacional e carrega o **kernel** do Linux. 5. **Kernel** inicializa o sistema, configurando os recursos de hardware e carregando o **initramfs**. 6. **Initramfs** fornece drivers e módulos necessários para o kernel acessar o sistema de arquivos principal. 7. **Kernel** chama o processo **/sbin/init** (ou **systemd**), que inicia todos os serviços e processos do sistema. 8. **Init** executa o **getty** para configurar o terminal de login. 9. **Getty** chama o ambiente gráfico (X11 ou Wayland) se estiver presente, e o usuário pode então usar o sistema na interface gráfica.
@ 36bedab2:524acad4
2024-11-10 21:37:52### 1. **Power ON** - Quando você liga o computador, ele inicia o processo de boot. - Esse primeiro passo envia energia aos componentes do sistema e dispara o BIOS (ou firmware UEFI em sistemas mais recentes). ### 2. **BIOS (Basic Input/Output System)** - O BIOS ou UEFI é o firmware inicial que roda logo após o computador ser ligado. - Ele executa um conjunto de verificações no hardware (chamado POST - Power-On Self-Test) e inicializa os dispositivos básicos necessários para o boot, como o disco rígido, memória RAM e CPU. - O BIOS então procura o dispositivo de boot (HD, SSD, USB, etc.) e carrega o **MBR** ou a **partição EFI** para dar continuidade ao processo de boot. ### 3. **Master Boot Record (MBR) ou EFI Partition** - O **MBR** (Master Boot Record) ou a **partição EFI** (em sistemas com UEFI) é onde ficam armazenadas as informações sobre o carregamento do sistema operacional. - Em sistemas antigos, o MBR continha o **boot loader** e as tabelas de partição. Nos sistemas modernos com UEFI, a partição EFI cumpre essa função. - O MBR ou a partição EFI passa o controle para o **boot loader**, que é responsável por carregar o sistema operacional. ### 4. **Boot Loader (e.g., GRUB)** - O **Boot Loader** (exemplo: GRUB) é um programa responsável por carregar o sistema operacional no momento do boot. - Ele permite selecionar qual sistema operacional inicializar (em caso de dual boot) e passa o controle para o **kernel** do sistema. - GRUB (Grand Unified Bootloader) é o boot loader mais comum em sistemas Linux. ### 5. **Kernel** - O **kernel** é o núcleo do sistema operacional Linux. - Ele é carregado na memória pelo boot loader e começa a configurar os recursos do sistema, como a CPU, a memória e os dispositivos de hardware. - O kernel é responsável por gerenciar os recursos do sistema e permitir a comunicação entre o hardware e o software. ### 6. **Initial RAM disk - initramfs** - O **initramfs** é um sistema de arquivos temporário carregado na memória logo após o kernel. - Ele contém módulos e drivers essenciais para que o sistema possa iniciar corretamente e acessar o sistema de arquivos principal do disco. - O initramfs é desmontado após o sistema principal estar carregado. ### 7. **/sbin/init (parent process)** - Após o kernel inicializar o sistema, ele chama o processo **/sbin/init**, que é o primeiro processo a rodar no Linux e é o "pai" de todos os outros processos. - O init é responsável por iniciar e gerenciar todos os outros processos do sistema. - Em muitas distribuições modernas, o init foi substituído por outros sistemas de inicialização, como o **systemd**, que tem mais funcionalidades e permite um gerenciamento mais eficiente de processos. ### 8. **Command Shell using getty** - **Getty** é o processo que configura e gerencia terminais para o login do usuário. - Ele exibe a tela de login em sistemas baseados em linha de comando. - Se o sistema tiver uma interface gráfica, o getty geralmente passa o controle para o gerenciador de login gráfico. ### 9. **Graphical User Interface (X Window ou Wayland)** - Finalmente, o sistema carrega a **interface gráfica** usando o **X Window System (X11)** ou o **Wayland** (um sistema gráfico mais moderno). - Esse é o ambiente visual onde o usuário pode interagir com o sistema usando janelas, ícones, menus, etc. - X11 e Wayland são servidores gráficos que gerenciam como as janelas e aplicativos são exibidos e manipulados na tela. --- ### Como esses processos se intercalam? 1. **Hardware ligado** → **BIOS/UEFI** realiza verificações básicas. 2. **BIOS/UEFI** encontra o dispositivo de boot e carrega o **MBR** ou **partição EFI**. 3. **MBR/EFI** localiza e executa o **boot loader** (GRUB). 4. **GRUB** permite que o usuário escolha o sistema operacional e carrega o **kernel** do Linux. 5. **Kernel** inicializa o sistema, configurando os recursos de hardware e carregando o **initramfs**. 6. **Initramfs** fornece drivers e módulos necessários para o kernel acessar o sistema de arquivos principal. 7. **Kernel** chama o processo **/sbin/init** (ou **systemd**), que inicia todos os serviços e processos do sistema. 8. **Init** executa o **getty** para configurar o terminal de login. 9. **Getty** chama o ambiente gráfico (X11 ou Wayland) se estiver presente, e o usuário pode então usar o sistema na interface gráfica. @ bcea2b98:7ccef3c9
2024-11-09 17:01:32Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about? For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully. originally posted at https://stacker.news/items/760492
@ bcea2b98:7ccef3c9
2024-11-09 17:01:32Weekends are the perfect time to unwind, explore, or spend time doing what we love. How would you spend your ideal weekend? Would it be all about relaxation, or would you be out and about? For me, an ideal weekend would start with a slow Saturday morning, a good book and coffee. Then I would spend the afternoon exploring local trails and looking for snacks. Then always a slow Sunday night hopefully. originally posted at https://stacker.news/items/760492 @ a367f9eb:0633efea
2024-11-05 08:48:41Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application. The [reporting](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/) purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States. > In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”. > > The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making. While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place. Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran? The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer. With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line. Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history? As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times. At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative. Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this. Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it. The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made. While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit. Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers. Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other. I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run. Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots). This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money. You know what else is open-source and available for everyone to use, modify, and build upon? PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit. Open-source code is speech, and it is knowledge. We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge. Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license. At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth). Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created. We know this can be useful to friends, but what about enemies? As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications. The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians. A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software. If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then. Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to. Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place. Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way. If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible. The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols. The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing. But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source. If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries. Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application. The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States. > In a June paper reviewed by[ Reuters](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/), six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”. > > The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making. While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the *Star Trek* episode “[A Taste of Armageddon](https://en.wikipedia.org/wiki/A_Taste_of_Armageddon)“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place. Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran? The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over [one million open-source LLMs](https://huggingface.co/models) available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer. With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are [potentially](https://bigthink.com/business/the-trillion-dollar-ai-race-to-create-digital-god/) trillions of dollars on the line. Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American[ infrastructure](https://www.nbcnews.com/tech/security/chinese-hackers-cisa-cyber-5-years-us-infrastructure-attack-rcna137706),[ data](https://www.cnn.com/2024/10/05/politics/chinese-hackers-us-telecoms/index.html), and yes, [your credit history](https://thespectator.com/topic/chinese-communist-party-credit-history-equifax/)? **As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much[ many times](https://consumerchoicecenter.org/made-in-china-sold-in-china/).** At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative. Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this. ## **Open-source matters** When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it. The various [licensing schemes](https://opensource.org/licenses) – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made. While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit. Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers. Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other. I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run. Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots). This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also [open-source](https://github.com/bitcoin), which has allowed [thousands](https://bitcoinmagazine.com/business/bitcoin-is-money-for-enemies) of copycat protocols that have revolutionized how we view money. You know what else is open-source and available for everyone to use, modify, and build upon? PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit. Open-source code is speech, and it is knowledge. We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge. ## **Open-source is for your friends, and enemies** In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license. At this very moment, you can click on over to[ Hugging Face](https://huggingface.co/), download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth). Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created. We know this can be useful to friends, but what about enemies? As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications. The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians. A bipartisan group of US House lawmakers want to put [export controls](https://www.reuters.com/technology/us-lawmakers-unveil-bill-make-it-easier-restrict-exports-ai-models-2024-05-10/) on AI models, as well as block foreign access to US cloud servers that may be hosting AI software. If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see[ The Crypto Wars](https://en.wikipedia.org/wiki/Export_of_cryptography_from_the_United_States)). Many of the arguments we hear today were invoked by some of the same people as back then. Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to. Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place. ## **Limiting open-source threatens our own advancement** If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way. If there is a “[Hundred Year Marathon](https://www.amazon.com/Hundred-Year-Marathon-Strategy-Replace-Superpower/dp/1250081343)” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible. The Chinese military has been building up its capabilities with [trillions of dollars’](https://www.economist.com/china/2024/11/04/in-some-areas-of-military-strength-china-has-surpassed-america) worth of investments that span far beyond AI chatbots and skip logic protocols. The [theft](https://www.technologyreview.com/2023/06/20/1075088/chinese-amazon-seller-counterfeit-lawsuit/) of intellectual property at factories in Shenzhen, or in US courts by [third-party litigation funding](https://nationalinterest.org/blog/techland/litigation-finance-exposes-our-judicial-system-foreign-exploitation-210207) coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing. But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source. If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries. *Originally published on the website of the [Consumer Choice Center](https://consumerchoicecenter.org/open-source-is-for-everyone-even-your-adversaries/).*
@ a367f9eb:0633efea
2024-11-05 08:48:41Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application. The [reporting](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/) purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States. > In a June paper reviewed by Reuters, six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”. > > The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making. While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the Star Trek episode “A Taste of Armageddon“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place. Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran? The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over one million open-source LLMs available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer. With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are potentially trillions of dollars on the line. Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American infrastructure, data, and yes, your credit history? As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much many times. At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative. Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this. Open-source matters When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it. The various licensing schemes – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made. While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit. Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers. Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other. I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run. Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots). This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also open-source, which has allowed thousands of copycat protocols that have revolutionized how we view money. You know what else is open-source and available for everyone to use, modify, and build upon? PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit. Open-source code is speech, and it is knowledge. We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge. Open-source is for your friends, and enemies In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license. At this very moment, you can click on over to Hugging Face, download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth). Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created. We know this can be useful to friends, but what about enemies? As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications. The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians. A bipartisan group of US House lawmakers want to put export controls on AI models, as well as block foreign access to US cloud servers that may be hosting AI software. If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see The Crypto Wars). Many of the arguments we hear today were invoked by some of the same people as back then. Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to. Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place. Limiting open-source threatens our own advancement If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way. If there is a “Hundred Year Marathon” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible. The Chinese military has been building up its capabilities with trillions of dollars’ worth of investments that span far beyond AI chatbots and skip logic protocols. The theft of intellectual property at factories in Shenzhen, or in US courts by third-party litigation funding coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing. But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source. If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries. Last week, an investigation by Reuters revealed that Chinese researchers have been using open-source AI tools to build nefarious-sounding models that may have some military application. The reporting purports that adversaries in the Chinese Communist Party and its military wing are taking advantage of the liberal software licensing of American innovations in the AI space, which could someday have capabilities to presumably harm the United States. > In a June paper reviewed by[ Reuters](https://www.reuters.com/technology/artificial-intelligence/chinese-researchers-develop-ai-model-military-use-back-metas-llama-2024-11-01/), six Chinese researchers from three institutions, including two under the People’s Liberation Army’s (PLA) leading research body, the Academy of Military Science (AMS), detailed how they had used an early version of Meta’s Llama as a base for what it calls “ChatBIT”. > > The researchers used an earlier Llama 13B large language model (LLM) from Meta, incorporating their own parameters to construct a military-focused AI tool to gather and process intelligence, and offer accurate and reliable information for operational decision-making. While I’m doubtful that today’s existing chatbot-like tools will be the ultimate battlefield for a new geopolitical war (queue up the computer-simulated war from the *Star Trek* episode “[A Taste of Armageddon](https://en.wikipedia.org/wiki/A_Taste_of_Armageddon)“), this recent exposé requires us to revisit why large language models are released as open-source code in the first place. Added to that, should it matter that an adversary is having a poke around and may ultimately use them for some purpose we may not like, whether that be China, Russia, North Korea, or Iran? The number of open-source AI LLMs continues to grow each day, with projects like Vicuna, LLaMA, BLOOMB, Falcon, and Mistral available for download. In fact, there are over [one million open-source LLMs](https://huggingface.co/models) available as of writing this post. With some decent hardware, every global citizen can download these codebases and run them on their computer. With regard to this specific story, we could assume it to be a selective leak by a competitor of Meta which created the LLaMA model, intended to harm its reputation among those with cybersecurity and national security credentials. There are [potentially](https://bigthink.com/business/the-trillion-dollar-ai-race-to-create-digital-god/) trillions of dollars on the line. Or it could be the revelation of something more sinister happening in the military-sponsored labs of Chinese hackers who have already been caught attacking American[ infrastructure](https://www.nbcnews.com/tech/security/chinese-hackers-cisa-cyber-5-years-us-infrastructure-attack-rcna137706),[ data](https://www.cnn.com/2024/10/05/politics/chinese-hackers-us-telecoms/index.html), and yes, [your credit history](https://thespectator.com/topic/chinese-communist-party-credit-history-equifax/)? **As consumer advocates who believe in the necessity of liberal democracies to safeguard our liberties against authoritarianism, we should absolutely remain skeptical when it comes to the communist regime in Beijing. We’ve written as much[ many times](https://consumerchoicecenter.org/made-in-china-sold-in-china/).** At the same time, however, we should not subrogate our own critical thinking and principles because it suits a convenient narrative. Consumers of all stripes deserve technological freedom, and innovators should be free to provide that to us. And open-source software has provided the very foundations for all of this. ## **Open-source matters** When we discuss open-source software and code, what we’re really talking about is the ability for people other than the creators to use it. The various [licensing schemes](https://opensource.org/licenses) – ranging from GNU General Public License (GPL) to the MIT License and various public domain classifications – determine whether other people can use the code, edit it to their liking, and run it on their machine. Some licenses even allow you to monetize the modifications you’ve made. While many different types of software will be fully licensed and made proprietary, restricting or even penalizing those who attempt to use it on their own, many developers have created software intended to be released to the public. This allows multiple contributors to add to the codebase and to make changes to improve it for public benefit. Open-source software matters because anyone, anywhere can download and run the code on their own. They can also modify it, edit it, and tailor it to their specific need. The code is intended to be shared and built upon not because of some altruistic belief, but rather to make it accessible for everyone and create a broad base. This is how we create standards for technologies that provide the ground floor for further tinkering to deliver value to consumers. Open-source libraries create the building blocks that decrease the hassle and cost of building a new web platform, smartphone, or even a computer language. They distribute common code that can be built upon, assuring interoperability and setting standards for all of our devices and technologies to talk to each other. I am myself a proponent of open-source software. The server I run in my home has dozens of dockerized applications sourced directly from open-source contributors on GitHub and DockerHub. When there are versions or adaptations that I don’t like, I can pick and choose which I prefer. I can even make comments or add edits if I’ve found a better way for them to run. Whether you know it or not, many of you run the Linux operating system as the base for your Macbook or any other computer and use all kinds of web tools that have active repositories forked or modified by open-source contributors online. This code is auditable by everyone and can be scrutinized or reviewed by whoever wants to (even AI bots). This is the same software that runs your airlines, powers the farms that deliver your food, and supports the entire global monetary system. The code of the first decentralized cryptocurrency Bitcoin is also [open-source](https://github.com/bitcoin), which has allowed [thousands](https://bitcoinmagazine.com/business/bitcoin-is-money-for-enemies) of copycat protocols that have revolutionized how we view money. You know what else is open-source and available for everyone to use, modify, and build upon? PHP, Mozilla Firefox, LibreOffice, MySQL, Python, Git, Docker, and WordPress. All protocols and languages that power the web. Friend or foe alike, anyone can download these pieces of software and run them how they see fit. Open-source code is speech, and it is knowledge. We build upon it to make information and technology accessible. Attempts to curb open-source, therefore, amount to restricting speech and knowledge. ## **Open-source is for your friends, and enemies** In the context of Artificial Intelligence, many different developers and companies have chosen to take their large language models and make them available via an open-source license. At this very moment, you can click on over to[ Hugging Face](https://huggingface.co/), download an AI model, and build a chatbot or scripting machine suited to your needs. All for free (as long as you have the power and bandwidth). Thousands of companies in the AI sector are doing this at this very moment, discovering ways of building on top of open-source models to develop new apps, tools, and services to offer to companies and individuals. It’s how many different applications are coming to life and thousands more jobs are being created. We know this can be useful to friends, but what about enemies? As the AI wars heat up between liberal democracies like the US, the UK, and (sluggishly) the European Union, we know that authoritarian adversaries like the CCP and Russia are building their own applications. The fear that China will use open-source US models to create some kind of military application is a clear and present danger for many political and national security researchers, as well as politicians. A bipartisan group of US House lawmakers want to put [export controls](https://www.reuters.com/technology/us-lawmakers-unveil-bill-make-it-easier-restrict-exports-ai-models-2024-05-10/) on AI models, as well as block foreign access to US cloud servers that may be hosting AI software. If this seems familiar, we should also remember that the US government once classified cryptography and encryption as “munitions” that could not be exported to other countries (see[ The Crypto Wars](https://en.wikipedia.org/wiki/Export_of_cryptography_from_the_United_States)). Many of the arguments we hear today were invoked by some of the same people as back then. Now, encryption protocols are the gold standard for many different banking and web services, messaging, and all kinds of electronic communication. We expect our friends to use it, and our foes as well. Because code is knowledge and speech, we know how to evaluate it and respond if we need to. Regardless of who uses open-source AI, this is how we should view it today. These are merely tools that people will use for good or ill. It’s up to governments to determine how best to stop illiberal or nefarious uses that harm us, rather than try to outlaw or restrict building of free and open software in the first place. ## **Limiting open-source threatens our own advancement** If we set out to restrict and limit our ability to create and share open-source code, no matter who uses it, that would be tantamount to imposing censorship. There must be another way. If there is a “[Hundred Year Marathon](https://www.amazon.com/Hundred-Year-Marathon-Strategy-Replace-Superpower/dp/1250081343)” between the United States and liberal democracies on one side and autocracies like the Chinese Communist Party on the other, this is not something that will be won or lost based on software licenses. We need as much competition as possible. The Chinese military has been building up its capabilities with [trillions of dollars’](https://www.economist.com/china/2024/11/04/in-some-areas-of-military-strength-china-has-surpassed-america) worth of investments that span far beyond AI chatbots and skip logic protocols. The [theft](https://www.technologyreview.com/2023/06/20/1075088/chinese-amazon-seller-counterfeit-lawsuit/) of intellectual property at factories in Shenzhen, or in US courts by [third-party litigation funding](https://nationalinterest.org/blog/techland/litigation-finance-exposes-our-judicial-system-foreign-exploitation-210207) coming from China, is very real and will have serious economic consequences. It may even change the balance of power if our economies and countries turn to war footing. But these are separate issues from the ability of free people to create and share open-source code which we can all benefit from. In fact, if we want to continue our way our life and continue to add to global productivity and growth, it’s demanded that we defend open-source. If liberal democracies want to compete with our global adversaries, it will not be done by reducing the freedoms of citizens in our own countries. *Originally published on the website of the [Consumer Choice Center](https://consumerchoicecenter.org/open-source-is-for-everyone-even-your-adversaries/).* @ 4fe4a528:3ff6bf06
2024-11-01 13:30:30**Buy Bitcoin ***"Opt out of inflation"* Lyn Alden’s [https://www.lynalden.com/october-2024-newsletter/]() is better than this monthly [https://amendt.substack.com/p/buy-bitcoin](). She explains, better than I can, why bitcoin is still inexpensive. From my perspective, the reason bitcoin is getting more and more valuable is because it is almost my birthday and people know I would enjoy bitcoin as a birthday present. Ok maybe I am not the central figure in this bitcoin saga, but for some reason bitcoin goes up on my birthday. So, I would like to take this opportunity to thank you for causing this commodity to increase in value during my birthday. That was a joke! I don’t think it is because you want to send me bitcoin that that is the only reason why bitcoin is climbing. Mind you the price action in bitcoin could be because the big boys (with money) have bought [https://docs.google.com/spreadsheets/d/1EZPpEA_aaZSwOTM90KpbLYfPJWqq31vOS1HhXNfkUmQ](). Yes Lyn explains why the smart money (rich guys) are now putting their money into bitcoin. It has a lot to do with scarcity — only 1.223921×10¹⁴ sats left and Metcafe’s law. Metcalfe's Law states that the value of a network is proportional to the square of the number of users in the network We are now back to 60% bitcoin dominance which is saying a lot when there is 2.4 million competing digital assets. With One bitcoin now over 100,000 Canadian dollars that says a lot of people think it is money. Go ahead and spend a dollar and get yourself 1000 sats just in case it catches on. My whole beef prices are now [https://www.pricedinbitcoin21.com/chart/livestock/LC1](). On the rail beef is only 4500 sats / lb — the same price as a dozen of eggs. Also, if you need a place to stay, [https://airbtc.online/properties/one-bedroom-suite-in-the-country/](). Finally people in Canada can live only on bitcoin. Justin Trudeau said on March 12, 2023 Buy Bitcoin, [https://cdn.satellite.earth/eef0f82150494810cacb622bd203cf8dea19b094cea940932e43d5a21b05c56a.mp4]() Bitcoin is now up over 100% since then. Happy Birthday to [https://v.nostr.build/ivyiPSnv7HfuECFE.mp4]()
@ 4fe4a528:3ff6bf06
2024-11-01 13:30:30**Buy Bitcoin ***"Opt out of inflation"* Lyn Alden’s [https://www.lynalden.com/october-2024-newsletter/]() is better than this monthly [https://amendt.substack.com/p/buy-bitcoin](). She explains, better than I can, why bitcoin is still inexpensive. From my perspective, the reason bitcoin is getting more and more valuable is because it is almost my birthday and people know I would enjoy bitcoin as a birthday present. Ok maybe I am not the central figure in this bitcoin saga, but for some reason bitcoin goes up on my birthday. So, I would like to take this opportunity to thank you for causing this commodity to increase in value during my birthday. That was a joke! I don’t think it is because you want to send me bitcoin that that is the only reason why bitcoin is climbing. Mind you the price action in bitcoin could be because the big boys (with money) have bought [https://docs.google.com/spreadsheets/d/1EZPpEA_aaZSwOTM90KpbLYfPJWqq31vOS1HhXNfkUmQ](). Yes Lyn explains why the smart money (rich guys) are now putting their money into bitcoin. It has a lot to do with scarcity — only 1.223921×10¹⁴ sats left and Metcafe’s law. Metcalfe's Law states that the value of a network is proportional to the square of the number of users in the network We are now back to 60% bitcoin dominance which is saying a lot when there is 2.4 million competing digital assets. With One bitcoin now over 100,000 Canadian dollars that says a lot of people think it is money. Go ahead and spend a dollar and get yourself 1000 sats just in case it catches on. My whole beef prices are now [https://www.pricedinbitcoin21.com/chart/livestock/LC1](). On the rail beef is only 4500 sats / lb — the same price as a dozen of eggs. Also, if you need a place to stay, [https://airbtc.online/properties/one-bedroom-suite-in-the-country/](). Finally people in Canada can live only on bitcoin. Justin Trudeau said on March 12, 2023 Buy Bitcoin, [https://cdn.satellite.earth/eef0f82150494810cacb622bd203cf8dea19b094cea940932e43d5a21b05c56a.mp4]() Bitcoin is now up over 100% since then. Happy Birthday to [https://v.nostr.build/ivyiPSnv7HfuECFE.mp4]() @ a9434ee1:d5c885be
2024-10-29 20:46:24This design system has two goals: 1. Being the basis for the development of a design-first, native Nostr app focused on exceptional zapping and chatting, relay-based communities and beauty 2. Serving as inspiration for builders that need coherent UI building blocks for their own apps with a different scope but overlapping needs (chats, threads, zaps, articles, highlights, events, wikis, ...) ### Design System Check it out [here](https://www.figma.com/community/file/1430887635327548022 ). This is by no means finished and will be continually updated and completed as we go along. ### Project description Check it out [here](njump.me/naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qyt8wumn8ghj7mnfv4kzumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qq00fshqcmgv96z6urjda4x2cm5lrswda) nostr:naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qyt8wumn8ghj7mnfv4kzumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qq00fshqcmgv96z6urjda4x2cm5lrswda This is a very first bullet-point-style draft to set the tone and is open to change, hence it being a wiki. ### Explanatory videos This list of videos will also be continually updated and completed as we go along: 1. Chat as the universal interface https://cdn.satellite.earth/43ccc6224a373dd22b7ae92edb70a0b9a3facabef27dff037de7f4fcf3ee7f37.mov 2. Your Nostr Dashboard https://cdn.satellite.earth/20fa9683dbf815c7deafa8a532c1d1e99cddbaac622fbf075b33b70fb0bdef22.mov 3. Keeping Tabs on all these Content types https://cdn.satellite.earth/a15ab05b55db1787349863f0f92c465dcde828b90c2cb61a92bd712a0012e9c6.mov 4. Design entered the Chat https://cdn.satellite.earth/7c25215262125562c847412c0d9a7d027e087028838204b6c447b5c07830979a.mov 5. Targeted publication & The blurry edges of interoperable communities https://cdn.satellite.earth/160c9431f53e7be108ad37f8d368e2af840690a8a936d1caaa68b468c9b1e0a9.mov 6. Travel Back https://cdn.satellite.earth/36d38027e6208e91c1fa27b0560f70fbad7d3e31c22d659c9a53a5c4cf90a876.mov
@ a9434ee1:d5c885be
2024-10-29 20:46:24This design system has two goals: 1. Being the basis for the development of a design-first, native Nostr app focused on exceptional zapping and chatting, relay-based communities and beauty 2. Serving as inspiration for builders that need coherent UI building blocks for their own apps with a different scope but overlapping needs (chats, threads, zaps, articles, highlights, events, wikis, ...) ### Design System Check it out [here](https://www.figma.com/community/file/1430887635327548022 ). This is by no means finished and will be continually updated and completed as we go along. ### Project description Check it out [here](njump.me/naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qyt8wumn8ghj7mnfv4kzumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qq00fshqcmgv96z6urjda4x2cm5lrswda) nostr:naddr1qvzqqqrcvgpzp22rfmsktmgpk2rtan7zwu00zuzax5maq5dnsu5g3xxvqr2u3pd7qyt8wumn8ghj7mnfv4kzumn0wd68yvfwvdhk6tcpz9mhxue69uhkummnw3ezuamfdejj7qq00fshqcmgv96z6urjda4x2cm5lrswda This is a very first bullet-point-style draft to set the tone and is open to change, hence it being a wiki. ### Explanatory videos This list of videos will also be continually updated and completed as we go along: 1. Chat as the universal interface https://cdn.satellite.earth/43ccc6224a373dd22b7ae92edb70a0b9a3facabef27dff037de7f4fcf3ee7f37.mov 2. Your Nostr Dashboard https://cdn.satellite.earth/20fa9683dbf815c7deafa8a532c1d1e99cddbaac622fbf075b33b70fb0bdef22.mov 3. Keeping Tabs on all these Content types https://cdn.satellite.earth/a15ab05b55db1787349863f0f92c465dcde828b90c2cb61a92bd712a0012e9c6.mov 4. Design entered the Chat https://cdn.satellite.earth/7c25215262125562c847412c0d9a7d027e087028838204b6c447b5c07830979a.mov 5. Targeted publication & The blurry edges of interoperable communities https://cdn.satellite.earth/160c9431f53e7be108ad37f8d368e2af840690a8a936d1caaa68b468c9b1e0a9.mov 6. Travel Back https://cdn.satellite.earth/36d38027e6208e91c1fa27b0560f70fbad7d3e31c22d659c9a53a5c4cf90a876.mov @ 9017cf6a:3d8a7adb
2024-10-27 21:46:06**Ricardo Nunes (MDB) é eleito prefeito de São Paulo** O prefeito de São Paulo, Ricardo Nunes (MDB), conquistou sua reeleição neste domingo (27) e agora terá mais quatro anos para administrar a maior cidade do Brasil. Apoiado por Jair Bolsonaro (https://www.conexaopolitica.com.br/tag/jair-bolsonaro/) e pelo PL (https://www.conexaopolitica.com.br/tag/pl/), que indicou seu vice na chapa, o emedebista foi confirmado como o vencedor do segundo turno disputado contra o esquerdista Guilherme Boulos (PSOL). Nunes assumiu a prefeitura da capital paulista em 2021, após a morte de Bruno Covas (PSDB), de quem era vice na chapa eleita em 2020. Aos 56 anos, ele agora terá um mandato completo para gerenciar a principal metrópole da América do Sul. Comments: https://www.conexaopolitica.com.br/ultimas/ricardo-nunes-mdb-e-eleito-prefeito-de-sao-paulo/#respond https://www.conexaopolitica.com.br/ultimas/ricardo-nunes-mdb-e-eleito-prefeito-de-sao-paulo/
@ 9017cf6a:3d8a7adb
2024-10-27 21:46:06**Ricardo Nunes (MDB) é eleito prefeito de São Paulo** O prefeito de São Paulo, Ricardo Nunes (MDB), conquistou sua reeleição neste domingo (27) e agora terá mais quatro anos para administrar a maior cidade do Brasil. Apoiado por Jair Bolsonaro (https://www.conexaopolitica.com.br/tag/jair-bolsonaro/) e pelo PL (https://www.conexaopolitica.com.br/tag/pl/), que indicou seu vice na chapa, o emedebista foi confirmado como o vencedor do segundo turno disputado contra o esquerdista Guilherme Boulos (PSOL). Nunes assumiu a prefeitura da capital paulista em 2021, após a morte de Bruno Covas (PSDB), de quem era vice na chapa eleita em 2020. Aos 56 anos, ele agora terá um mandato completo para gerenciar a principal metrópole da América do Sul. Comments: https://www.conexaopolitica.com.br/ultimas/ricardo-nunes-mdb-e-eleito-prefeito-de-sao-paulo/#respond https://www.conexaopolitica.com.br/ultimas/ricardo-nunes-mdb-e-eleito-prefeito-de-sao-paulo/ @ 4ba8e86d:89d32de4
2024-10-24 23:20:51VeraCrupt foi lançado em 2013 como um fork do projeto TrueCrypt descontinuado. Desde então, o VeraCrypt tem passado por diversas atualizações e melhorias de segurança, incluindo a correção de problemas identificados por auditorias de código do TrueCrypt. O VeraCrypt inclui implementações otimizadas de funções criptográficas de hash e cifras, o que aumenta o desempenho em CPUs modernas. O software permite criar e gerenciar volumes criptografados em computadores ou dispositivos de armazenamento externo, com suporte para vários algoritmos de criptografia e recursos adicionais, como proteção contra ataques de keylogger e ocultação de volumes , tem opção de segurança robusta para proteger seus dados. Quando você cria um volume criptografado no VeraCrypt, o software cria um arquivo virtual que funciona como um disco rígido criptografado. Esse arquivo é montado como uma unidade lógica no seu sistema operacional e pode ser acessado como qualquer outro disco rígido. Antes que você possa acessar o volume criptografado, você precisa fornecer a senha correta. A senha é usada para desbloquear o arquivo virtual criptografado e permitir que o sistema operacional acesse o conteúdo. O VeraCrypt suporta vários algoritmos de criptografia, incluindo AES, Serpent e Twofish, que podem ser selecionados pelo usuário ao criar o volume criptografado. O VeraCrypt também oferece recursos adicionais de segurança, como proteção contra keyloggers, que podem registrar as teclas digitadas no teclado para capturar senhas. Ele faz isso fornecendo uma interface virtual para digitar senhas, o que impede que os keyloggers capturem a senha real. O VeraCrypt também permite ocultar volumes criptografados dentro de outros volumes criptografados, o que fornece uma camada adicional de segurança. O veracrypt proteger informações confidenciais armazenadas em dispositivos de armazenamento, como discos rígidos, unidades flash USB e cartões de memória, contra acesso não autorizado. Se um usuário estiver executando o Tails a partir de uma unidade flash USB, e o disco rígido estiver criptografado com o VeraCrypt, o Tails não terá acesso ao conteúdo do disco rígido, a menos que o usuário monte o volume criptografado do VeraCrypt e forneça a senha correta. No entanto, é importante lembrar que a criptografia do disco rígido por si só não garante a segurança completa do sistema. Os usuários também devem tomar outras medidas de segurança, como manter o sistema operacional e o software atualizados, usar senhas fortes e não compartilhá-las com ninguém, e tomar cuidado com o acesso físico ao computador ou dispositivo de armazenamento externo. https://veracrypt.fr https://github.com/veracrypt/VeraCrypt/
@ 4ba8e86d:89d32de4
2024-10-24 23:20:51VeraCrupt foi lançado em 2013 como um fork do projeto TrueCrypt descontinuado. Desde então, o VeraCrypt tem passado por diversas atualizações e melhorias de segurança, incluindo a correção de problemas identificados por auditorias de código do TrueCrypt. O VeraCrypt inclui implementações otimizadas de funções criptográficas de hash e cifras, o que aumenta o desempenho em CPUs modernas. O software permite criar e gerenciar volumes criptografados em computadores ou dispositivos de armazenamento externo, com suporte para vários algoritmos de criptografia e recursos adicionais, como proteção contra ataques de keylogger e ocultação de volumes , tem opção de segurança robusta para proteger seus dados. Quando você cria um volume criptografado no VeraCrypt, o software cria um arquivo virtual que funciona como um disco rígido criptografado. Esse arquivo é montado como uma unidade lógica no seu sistema operacional e pode ser acessado como qualquer outro disco rígido. Antes que você possa acessar o volume criptografado, você precisa fornecer a senha correta. A senha é usada para desbloquear o arquivo virtual criptografado e permitir que o sistema operacional acesse o conteúdo. O VeraCrypt suporta vários algoritmos de criptografia, incluindo AES, Serpent e Twofish, que podem ser selecionados pelo usuário ao criar o volume criptografado. O VeraCrypt também oferece recursos adicionais de segurança, como proteção contra keyloggers, que podem registrar as teclas digitadas no teclado para capturar senhas. Ele faz isso fornecendo uma interface virtual para digitar senhas, o que impede que os keyloggers capturem a senha real. O VeraCrypt também permite ocultar volumes criptografados dentro de outros volumes criptografados, o que fornece uma camada adicional de segurança. O veracrypt proteger informações confidenciais armazenadas em dispositivos de armazenamento, como discos rígidos, unidades flash USB e cartões de memória, contra acesso não autorizado. Se um usuário estiver executando o Tails a partir de uma unidade flash USB, e o disco rígido estiver criptografado com o VeraCrypt, o Tails não terá acesso ao conteúdo do disco rígido, a menos que o usuário monte o volume criptografado do VeraCrypt e forneça a senha correta. No entanto, é importante lembrar que a criptografia do disco rígido por si só não garante a segurança completa do sistema. Os usuários também devem tomar outras medidas de segurança, como manter o sistema operacional e o software atualizados, usar senhas fortes e não compartilhá-las com ninguém, e tomar cuidado com o acesso físico ao computador ou dispositivo de armazenamento externo. https://veracrypt.fr https://github.com/veracrypt/VeraCrypt/ @ 1bda7e1f:bb97c4d9
2024-10-24 04:48:52### Tldr - Nostr relays help users post and read notes on the network - Relay operators have launched a variety of relays for you to use - You too can launch your own relay for any reason you like - Launching your own relay gives you a lot of power in how you use Nostr - Many relay softwares exist for you to use - I launched a personal relay using HAVEN relay software on my VPS - I am now more in control of saving notes, cutting spam, and protecting my privacy - My personal relay is now hosted at relay.rodbishop.nz ### What are Nostr Relays Anyway? When you're a user of a social network, you post and read notes from other users on the network. In a centralised network like Twitter or Instagram the company's servers receive all user's notes and relay them to other users. On Nostr, there is no single company's servers to relay messages, so instead the task is taken up by relay operators. Anyone can be a relay operator and they can run a relay for any purpose. When you start using Nostr you will usually be connected to any one of a number of "public" relays, and be able to post and receive notes from users on the network via these. Configuring these relays can tailor your experience somewhat–for example the client Nostrudel allows you to select from Western or Japanese relay set. It is also possible to set up your own relay to use for your own purposes. All kinds of people have launched relays for all kinds of purposes. For example, to: - Power your own client - Support your community - Run a for-profit relay business - Relay a certain a type of content you need - Back up your own notes, decrease spam, or increase privacy - Curate your own social feed with your own algorithm #### Relay instances available to connect with Today is an interesting time in relay-ops. The evolution of the technology has inspired users to experiment with diverse types of relays tailored to various needs. As a result there are very many relay instances in operation and available to connect with. A few sites try to collate which relays are in operation, like [nostr.info](https://nostr.info/relays/) and [xport.top](https://relays.xport.top/) and [sesseor's relay list](https://github.com/sesseor/nostr-relays-list/blob/main/relays.txt) . These lists are long (Sessor's list counted 2,500+ relays) and it's not clear to me whether it's even possible to be comprehensive as relays may join or leave the network all the time. Broadly speaking, relays might be available for different users to use in different ways: - A relay where anyone can post, like [relay.damus.io](http://relay.damus.io) - A paid relay where anyone can post after payment, to cut spam, like [nostr.wine](http://nostr.wine) - A "web of trust" relay where anyone can post if they are related to the owner's social graph, to cut spam, like [nostrelites.org](http://nostrelites.org) - A speciality relay where a particular community can post, like [nostr.com.au](http://nostr.com.au) for #austriches (Australians) - A relay where anyone can post just specific content, like [purplepag.es](http://purplepag.es) for user profiles only - A team relay for your company or organisation only - A personal relay for your own personal use [Nostr.Band](https://stats.nostr.band/) shows which of these available relays are most popular, such as [relay.damus.io](http://relay.damus.io) and [nos.lol](nos.lol) and [eden.nostr.land](http://eden.nostr.land) #### Relay softwares for you to launch your own You may decide to launch you own relays, and if you do there are many different relay softwares to choose from: - Simple, like [Bucket](https://github.com/coracle-social/bucket) (<100 lines of code) - Widely used, like [Nostream](https://github.com/Cameri/nostream) (top ranked on Github) - Customisable, like [Khatru](https://khatru.nostr.technology/) (a framework for customised relays) - Specialised, like [HAVEN](https://github.com/bitvora/haven) or [Team Relay](https://github.com/bitvora/team-relay) (for personal or teams relays, based on Khartu) You can run these on your own server, or local machine, or [phone](https://github.com/greenart7c3/Citrine) or with a third-party host. [Aljaz](nostr:npub1aljazgxlpnpfp7n5sunlk3dvfp72456x6nezjw4sd850q879rxqsthg9jp) provides a [great resource](https://github.com/aljazceru/awesome-nostr?tab=readme-ov-file#relays) with 45+ relay softwares to choose from. In summary, at a high level, - Anyone can connect to any of the relay instances that are available for them to use - Anyone who wants to launch their own can select the relay software that best suit their needs, launch an instance, and have it used by whichever users they like ### Reasons to Run Your Own Relay As a normal user of a Nostr client there's no obligation to run a relay. But having your own relay does give you more power. For my own journey down the #nostr rabbit hole, I was looking for a relay to: - back up my notes - decrease spam - increase my privacy - learn skills I could later use for running a community or team or paid relay Backing up notes – When you post notes to a public relay there's no guarantee that the relay is going to keep them long-term. It's job is relaying your notes to other clients, not storing them. Running your own relay allows you to keep your notes online. Decrease spam – To first spam we can use a "Web of Trust" model–in which users endorse other users as trustworthy. A "Web of Trust" relay will reject notes from parties too far removed from your network. Running your own relay makes you more difficult to spam. Increasing privacy – When you connect to a public relay, they can determine personal information about you, such as your IP address. Running your own relay keeps things more private. For communities and teams and paid relays – Many opportunities exist to tailor relays to certain users needs, be they businesses or communities or as a for-profit business. For me, I am hoping that running my own relay helps me learn skills I can use in these kinds of further ventures. To start I decided to focus on a personal relay. However, when I really got under the hood, it turned out I would need multiple relays not just one. #### The outbox model [Mike Dilger](nostr:npub1acg6thl5psv62405rljzkj8spesceyfz2c32udakc2ak0dmvfeyse9p35c) proposed [the outbox model](https://mikedilger.com/gossip-model/) (originally called the gossip model) as a way for users to engage with the wider Nostr network. It's a great model that is helpful to understand, as it suggests to establish different relays for different purposes. Many clients and relay softwares have now adopted and continued to elaborate on this model. An example is to run specialised relays for Outbox, Inbox, Chat and Private needs. **Outbox Relay (also called Home Relay)** - This relay is for notes you have written, so that everyone knows where to find your notes - In a set up where you are running your own, this relay is restricted so that only you can post to it, and you should set up your clients to post your notes to it - An advanced version may take any notes received to this relay and "blast" them to other public relays so that your notes get wider reach **Inbox Relay (also called Public Relay)** - This relay is for public notes that other users want you to see, so that you always find notes that are relevant to you, including all replies, comments, likes, and zap payments - In a set up where you are running your own, this relay is where you should look for notes relevant to you, and you should set up your clients to read from it - An advanced version may search other public relays for notes that tag you, and import them into this relay so that you never miss a relevant note **Chat Relay (also called Direct Message Relay)** - This relay is for private direct message notes from other users, so that you always find your direct messages and so that they stay private - In a set up where you are running your own, this relay is restricted so that only you can read from it, and you should set up your clients to read from it - An advanced version may cut spam by only accepting direct messages from other users within your Web of Trust **Private Relay** - This relay is for your private use only, so that you can store private drafts or thoughts - Only you can write to it and only you can read from it (and so, it is a bit mis-named as it does not actually relay anything to anywhere at all) - In a set up where you are running your own, it gives you true privacy for these notes **In summary as a user** - I post my notes to my outbox relay. Network users can read them there, and if the relay is advanced it will also blast the notes out to other relays on the network - I read from my inbox relay. Network users know to reach me there, and if the relay is advanced it will also bring me notes from the wider network - I can have private direct message conversations with others in my chat relay. - I can save private notes in my private relay For me, this model has a lot of appeal and I went looking for a personal relay which adopted this model and contained all of these features. #### HAVEN as a personal relay I decided to go with HAVEN relay software. HAVEN is all four of the above relays in one–outbox, inbox, chat and private. It contains advanced features like blasting your notes from outbox to other relays, importing notes from other relays to your inbox, and preventing spam with Web of Trust. [HAVEN](https://github.com/bitvora/haven) is written by [Utxo the Webmaster](nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8) . It is based upon the [Khatru](https://khatru.nostr.technology/) relay framework by [Fiatjaf](nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6) ### Setting up HAVEN as a Personal Relay I am mostly non-technical, but on my #Nostr journey I have been having success with technology set ups that use Docker. - I have a cheap VPS which currently runs [Albyhub and Phoneixd with Docker](nostr:naddr1qq34xet5w35kueedw4cz65rp09kk2mn5wvkk7m3dfehhxarj95mk7dnvwvmszythwden5te0dehhxarj9emkjmn99upzqx760c0h894a5tg7lxgr8k506twrv2qs0yxln0nz7kgs8zae03xeqvzqqqr4gua7fyfn), - My objective was to set up HAVEN to run alongside it, in a separate Docker on the same server. HAVEN does not include Docker by default, but [Sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe) published a [fork with Docker support](https://github.com/nostrver-se/haven/tree/docker_compose_support). To get HAVEN up and running in Docker on your VPS: 1. Clone and configure HAVEN with the right variables 2. Launch it in Docker on your VPS 3. Check the URLs and logs to see your HAVEN running 4. Configure a subdomain to point to the VPS 5. Configure the VPS to reverse proxy to the Docker port 6. Configure the relays in your favourite Nostr client 7. Post a note to your outbox and see if it blasts! #### Running HAVEN I cloned Sebastix fork to start. ``` git clone -b docker_compose_support https://github.com/nostrver-se/haven.git cd haven ``` The software sets up all environment variables in the `.env` file, and comes with an `.env.example` file. Duplicate and rename the file to `.env`. Within the `.env` file you need to set up the environment variables. The file is long but it contains lots of repetition and for the most part defaults can be retained–only a few changes are required: - Replace all instances of the default user npub with your own (for me, `npub1r0d8...`) - Change the default relay URL to your own (for me, `relay.rodbishop.nz`) - Replace all instances of the default name in the relay names (for me, "Rod's ...") - Replace all instances of the default profile image with your own To enable automatic blasting from your outbox, and importing to your inbox, the software comes with an example list of relays to blast and import from. See `relays_blastr.example.json` and `relays_import.example.json`. To use these features simply duplicate and rename these files to `relays_blastr.json` and `relays_import.json` respectively. Within these files you can specify the public relays of your choice. I simply used the default list. There are other features available, such as backups and initial imports, but I decided to handle these later. To start with I wanted to launch the relay and test it. To launch the relay run Docker Compose. ``` docker-compose up -d docker logs haven-relay ``` Then you should explore the logs in the command line and the ports in your browser to see if it launched successfully. The logs should show your web of trust has been built successfully and the browser should show simple landing pages. The logs should show that the relay has queried the network and built a web of trust from your followers. Mine looked as follows. ``` 2024/10/14 12:02:08 🌐 building web of trust graph 2024/10/14 12:02:16 🫂 total network size: 13296 2024/10/14 12:02:16 🔗 relays discovered: 335 2024/10/14 12:02:17 🌐 pubkeys with minimum followers: 9394 keys ``` Your browser should show you have four relays in operation, for example as follows. - `your_IP_address:3355` (your outbox or home relay) - `your_IP_address:3355/private` (your private relay) - `your_IP_address:3355/chat` (your direct message relay) - `your_IP_address:3355/inbox` (your inbox relay) That's it. Your relay is online. #### Connecting HAVEN Now all that remains is the plumbing to connect your domain, relay, and Nostr clients together. **Configure DNS** First, configure your domain. At a high level – 1. Get your domain (buy one if you need to) 2. Get the IP address of your VPS 3. In your domain's DNS settings add those records as an A record to the subdomain of your choice, e.g. `relay` as in `relay.your_domain_name.com`, or in my case `relay.rodbishop.nz` Your subdomain now points to your server. **Configure reverse proxy** Next, you need to redirect traffic from your subdomain to your relay at port `3355`. On my VPS I use Caddy as a reverse proxy for a few projects, I have it sitting in a separate Docker network. To use it for my HAVEN Relay required two steps. I am sure that the way I do this is not very elegant, but it worked. If you prefer a different method, the HAVEN readme also comes with instructions on how to perform a similar setup using nginx. For my method, my steps were as follows: 1. Add configuration to Caddy's `Caddyfile` to tell it what to do with requests for the `relay.rodbishop.nz` subdomain 2. Add the Caddy Docker network to the HAVEN `docker-compose.yml` to make it be part of the Caddy network For the addition to the `Caddyfile`, I used as follows: ``` relay.rodbishop.nz { reverse_proxy haven-relay:3355 { header_up X-Forwarded-For {remote} header_up X-Forwarded-Proto {scheme} header_up X-Forwarded-Port {server_port} } } ``` For the addition to the `docker-compose.yml`, I used as follows: ``` networks: - caddy # Added this line to services to connect to the Caddy network networks: caddy: external: true # Added this to section specify the Caddy network ``` Once your DNS configuration and reverse proxy setup are completed, you should now be able to access your Nostr client at `relay.your_domain_name.com`. For my set up, this was `relay.rodbishop.nz`. **Connecting your Nostr client** Most Nostr clients allow you to specify any relay you choose. My go-to client at the moment is Amethyst on Android. Amethyst allows you to specify discrete relays for each role in the outbox model which ties up very neatly with HAVEN. - In the sidebar, select Relays - For "Public Outbox/Home Relays" enter `relay.your_domain_name.com` - For "Public Inbox Relays" enter `relay.your_domain_name.com/inbox` - For "DM Inbox Relays" enter `relay.your_domain_name.com/chat` - For "Private Home Relays" enter `relay.your_domain_name.com/private` - Click Save to broadcast your new relays to the Nostr network. Your new relay configuration is now live. **Testing your relay** Lastly, it's time to test. Amethyst provides a simple method to test this as it allows you to configure the relays used on each post. - Create a test note, and then before you post it, edit your relays using the icon at the top - Turn off all relays except your own outbox relay, and post the note - Access your HAVEN docker logs with `docker logs haven-relay` and see if there is a log to indicate if the note was received and blasted to other public relays - Copy the `nevent` of the note, and attempt to find it in another client If you're in luck, you may see something like this (the blasted note, and then users on the network responding to the note in turn). ``` 2024/10/22 00:12:23 🔫 blasted 95c477af7e6b612bf5d1d94309d2d57377a0a67d2181cfbb42a2e3fbc0feeaaf to 26 relays 2024/10/22 00:13:50 🤙 new reaction in your inbox 2024/10/22 00:14:42 🫂 new reaction in your inbox 2024/10/22 00:14:45 ✅ new reaction in your inbox 2024/10/22 00:15:12 💜 new reaction in your inbox 2024/10/22 00:17:03 ✅ new reaction in your inbox 2024/10/22 00:17:03 🫂 new reaction in your inbox 2024/10/22 00:17:55 🫂 new reaction in your inbox 2024/10/22 00:19:02 📰 new note in your inbox ``` That's it. If you followed this successfully your personal relay is up and running. #### What I did wrong so you don't have to **My first relay was too public** This blog comes after much trial and error. The first error I made was I set up a relay to use as a personal relay, but without any restrictions on use. I very quickly found other people discovered and started using my relay to save their own notes! This was unintended and I had to take it down. **Unfamiliar with Go language** I am mostly non-technical, and completely unfamiliar with Go. I got the project up and running with Go on my localhost–with a lot of help from my AI–but I then completely failed in migrating this to my VPS. Moving to Docker made the difference for me here. **I failed a few times due to a messy folder** After messing with Go, I moved to the Docker setup, but I started my work from a messy folder which contained remnants of the Go build, which caused various failures. Deleting the folder and cloning again from scratch solved the issue. **Trouble with Nostr.wine** I subscribe to the Nostr.wine paid relay, and I initially added it to the list of relays in my blaster. However, it didn't work, and the logs showed an error as follows ``` CLOSED from wss://nostr.wine: 'auth-required: this relay only serves private notes to authenticated users' ``` It seems my npub's subscription to Nostr.wine is not enough for it to permit my relay to blast notes to it. In the end, I removed Nostr.wine from my relay config, and kept Nostr.wine as a separate entry in my Client's outbox settings. **Failed to create web of trust graph** When I first launched the relay on my VPS, HAVEN failed to complete the Web of Trust graph, with a log that looked as follows (note the zeroes). As a result, no one would have been able to send me DM's to my Chat relay (it would flag every message as spam). ``` 2024/10/14 12:02:08 🌐 building web of trust graph 2024/10/14 12:02:16 🫂 total network size: 0 2024/10/14 12:02:16 🔗 relays discovered: 0 2024/10/14 12:02:17 🌐 pubkeys with minimum followers: 0 keys ``` I never got to the bottom of why this was. In the process of trying to fix it I rebuild the container, and on the rebuild it spontaneously worked. Accordingly my lesson learned is "if in doubt, turn if off and on again". **Failed to run --import function** HAVEN comes with a function to import all your old notes from other public relays to your own outbox relay. When I run it I get an error as follows: ``` panic: Cannot acquire directory lock on "db/private". Another process is using this Badger database. error: resource temporarily unavailable ``` I have yet to work out the solution for this, and will update this note when I do so! ### What's Next? Over the past four blogs I have - [Mined a Nostr pubkey and backed up the mnemonic](nostr:naddr1qqsy66twd9hxwtteda6hyt2kv9hxjare94g82cntv4uj6drfw4cxyeszyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c6e2ekw) - [Set up Nostr payments with a Lightning wallet plus all the bells and whistles](nostr:naddr1qq34xet5w35kueedw4cz65rp09kk2mn5wvkk7m3dfehhxarj95mk7dnvwvmsygqmmflp7uukhk3drmueqv763lfdcd3gzpusm7d7vt6ezquth97ymypsgqqqw4rsuql6je) - [Set up NIP-05 and Lighting Address at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqyghwumn8ghj7mn0wd68ytnhd9hx2tczyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c634nh0) - Set up a Personal Relay at my own domain This feels like a very comprehensive personal set up now. Also, I have uncovered some new rabbit holes and feel like I have some projects to tackle. Perhaps one of these? - Set up a personal homepage with my Nostr feed to round-out my rodbishop.nz domain - Experiment with different signers like Amber and Nsec.app and NFC cards - Set up a paid relay for #austriches (Australians and Kiwis on Nostr) - Set up a team relay to experiment with Nostr for business or community projects - Or something else ... ? Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle. Pura vida Nostr.
@ 1bda7e1f:bb97c4d9
2024-10-24 04:48:52### Tldr - Nostr relays help users post and read notes on the network - Relay operators have launched a variety of relays for you to use - You too can launch your own relay for any reason you like - Launching your own relay gives you a lot of power in how you use Nostr - Many relay softwares exist for you to use - I launched a personal relay using HAVEN relay software on my VPS - I am now more in control of saving notes, cutting spam, and protecting my privacy - My personal relay is now hosted at relay.rodbishop.nz ### What are Nostr Relays Anyway? When you're a user of a social network, you post and read notes from other users on the network. In a centralised network like Twitter or Instagram the company's servers receive all user's notes and relay them to other users. On Nostr, there is no single company's servers to relay messages, so instead the task is taken up by relay operators. Anyone can be a relay operator and they can run a relay for any purpose. When you start using Nostr you will usually be connected to any one of a number of "public" relays, and be able to post and receive notes from users on the network via these. Configuring these relays can tailor your experience somewhat–for example the client Nostrudel allows you to select from Western or Japanese relay set. It is also possible to set up your own relay to use for your own purposes. All kinds of people have launched relays for all kinds of purposes. For example, to: - Power your own client - Support your community - Run a for-profit relay business - Relay a certain a type of content you need - Back up your own notes, decrease spam, or increase privacy - Curate your own social feed with your own algorithm #### Relay instances available to connect with Today is an interesting time in relay-ops. The evolution of the technology has inspired users to experiment with diverse types of relays tailored to various needs. As a result there are very many relay instances in operation and available to connect with. A few sites try to collate which relays are in operation, like [nostr.info](https://nostr.info/relays/) and [xport.top](https://relays.xport.top/) and [sesseor's relay list](https://github.com/sesseor/nostr-relays-list/blob/main/relays.txt) . These lists are long (Sessor's list counted 2,500+ relays) and it's not clear to me whether it's even possible to be comprehensive as relays may join or leave the network all the time. Broadly speaking, relays might be available for different users to use in different ways: - A relay where anyone can post, like [relay.damus.io](http://relay.damus.io) - A paid relay where anyone can post after payment, to cut spam, like [nostr.wine](http://nostr.wine) - A "web of trust" relay where anyone can post if they are related to the owner's social graph, to cut spam, like [nostrelites.org](http://nostrelites.org) - A speciality relay where a particular community can post, like [nostr.com.au](http://nostr.com.au) for #austriches (Australians) - A relay where anyone can post just specific content, like [purplepag.es](http://purplepag.es) for user profiles only - A team relay for your company or organisation only - A personal relay for your own personal use [Nostr.Band](https://stats.nostr.band/) shows which of these available relays are most popular, such as [relay.damus.io](http://relay.damus.io) and [nos.lol](nos.lol) and [eden.nostr.land](http://eden.nostr.land) #### Relay softwares for you to launch your own You may decide to launch you own relays, and if you do there are many different relay softwares to choose from: - Simple, like [Bucket](https://github.com/coracle-social/bucket) (<100 lines of code) - Widely used, like [Nostream](https://github.com/Cameri/nostream) (top ranked on Github) - Customisable, like [Khatru](https://khatru.nostr.technology/) (a framework for customised relays) - Specialised, like [HAVEN](https://github.com/bitvora/haven) or [Team Relay](https://github.com/bitvora/team-relay) (for personal or teams relays, based on Khartu) You can run these on your own server, or local machine, or [phone](https://github.com/greenart7c3/Citrine) or with a third-party host. [Aljaz](nostr:npub1aljazgxlpnpfp7n5sunlk3dvfp72456x6nezjw4sd850q879rxqsthg9jp) provides a [great resource](https://github.com/aljazceru/awesome-nostr?tab=readme-ov-file#relays) with 45+ relay softwares to choose from. In summary, at a high level, - Anyone can connect to any of the relay instances that are available for them to use - Anyone who wants to launch their own can select the relay software that best suit their needs, launch an instance, and have it used by whichever users they like ### Reasons to Run Your Own Relay As a normal user of a Nostr client there's no obligation to run a relay. But having your own relay does give you more power. For my own journey down the #nostr rabbit hole, I was looking for a relay to: - back up my notes - decrease spam - increase my privacy - learn skills I could later use for running a community or team or paid relay Backing up notes – When you post notes to a public relay there's no guarantee that the relay is going to keep them long-term. It's job is relaying your notes to other clients, not storing them. Running your own relay allows you to keep your notes online. Decrease spam – To first spam we can use a "Web of Trust" model–in which users endorse other users as trustworthy. A "Web of Trust" relay will reject notes from parties too far removed from your network. Running your own relay makes you more difficult to spam. Increasing privacy – When you connect to a public relay, they can determine personal information about you, such as your IP address. Running your own relay keeps things more private. For communities and teams and paid relays – Many opportunities exist to tailor relays to certain users needs, be they businesses or communities or as a for-profit business. For me, I am hoping that running my own relay helps me learn skills I can use in these kinds of further ventures. To start I decided to focus on a personal relay. However, when I really got under the hood, it turned out I would need multiple relays not just one. #### The outbox model [Mike Dilger](nostr:npub1acg6thl5psv62405rljzkj8spesceyfz2c32udakc2ak0dmvfeyse9p35c) proposed [the outbox model](https://mikedilger.com/gossip-model/) (originally called the gossip model) as a way for users to engage with the wider Nostr network. It's a great model that is helpful to understand, as it suggests to establish different relays for different purposes. Many clients and relay softwares have now adopted and continued to elaborate on this model. An example is to run specialised relays for Outbox, Inbox, Chat and Private needs. **Outbox Relay (also called Home Relay)** - This relay is for notes you have written, so that everyone knows where to find your notes - In a set up where you are running your own, this relay is restricted so that only you can post to it, and you should set up your clients to post your notes to it - An advanced version may take any notes received to this relay and "blast" them to other public relays so that your notes get wider reach **Inbox Relay (also called Public Relay)** - This relay is for public notes that other users want you to see, so that you always find notes that are relevant to you, including all replies, comments, likes, and zap payments - In a set up where you are running your own, this relay is where you should look for notes relevant to you, and you should set up your clients to read from it - An advanced version may search other public relays for notes that tag you, and import them into this relay so that you never miss a relevant note **Chat Relay (also called Direct Message Relay)** - This relay is for private direct message notes from other users, so that you always find your direct messages and so that they stay private - In a set up where you are running your own, this relay is restricted so that only you can read from it, and you should set up your clients to read from it - An advanced version may cut spam by only accepting direct messages from other users within your Web of Trust **Private Relay** - This relay is for your private use only, so that you can store private drafts or thoughts - Only you can write to it and only you can read from it (and so, it is a bit mis-named as it does not actually relay anything to anywhere at all) - In a set up where you are running your own, it gives you true privacy for these notes **In summary as a user** - I post my notes to my outbox relay. Network users can read them there, and if the relay is advanced it will also blast the notes out to other relays on the network - I read from my inbox relay. Network users know to reach me there, and if the relay is advanced it will also bring me notes from the wider network - I can have private direct message conversations with others in my chat relay. - I can save private notes in my private relay For me, this model has a lot of appeal and I went looking for a personal relay which adopted this model and contained all of these features. #### HAVEN as a personal relay I decided to go with HAVEN relay software. HAVEN is all four of the above relays in one–outbox, inbox, chat and private. It contains advanced features like blasting your notes from outbox to other relays, importing notes from other relays to your inbox, and preventing spam with Web of Trust. [HAVEN](https://github.com/bitvora/haven) is written by [Utxo the Webmaster](nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8) . It is based upon the [Khatru](https://khatru.nostr.technology/) relay framework by [Fiatjaf](nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6) ### Setting up HAVEN as a Personal Relay I am mostly non-technical, but on my #Nostr journey I have been having success with technology set ups that use Docker. - I have a cheap VPS which currently runs [Albyhub and Phoneixd with Docker](nostr:naddr1qq34xet5w35kueedw4cz65rp09kk2mn5wvkk7m3dfehhxarj95mk7dnvwvmszythwden5te0dehhxarj9emkjmn99upzqx760c0h894a5tg7lxgr8k506twrv2qs0yxln0nz7kgs8zae03xeqvzqqqr4gua7fyfn), - My objective was to set up HAVEN to run alongside it, in a separate Docker on the same server. HAVEN does not include Docker by default, but [Sebastix](nostr:npub1qe3e5wrvnsgpggtkytxteaqfprz0rgxr8c3l34kk3a9t7e2l3acslezefe) published a [fork with Docker support](https://github.com/nostrver-se/haven/tree/docker_compose_support). To get HAVEN up and running in Docker on your VPS: 1. Clone and configure HAVEN with the right variables 2. Launch it in Docker on your VPS 3. Check the URLs and logs to see your HAVEN running 4. Configure a subdomain to point to the VPS 5. Configure the VPS to reverse proxy to the Docker port 6. Configure the relays in your favourite Nostr client 7. Post a note to your outbox and see if it blasts! #### Running HAVEN I cloned Sebastix fork to start. ``` git clone -b docker_compose_support https://github.com/nostrver-se/haven.git cd haven ``` The software sets up all environment variables in the `.env` file, and comes with an `.env.example` file. Duplicate and rename the file to `.env`. Within the `.env` file you need to set up the environment variables. The file is long but it contains lots of repetition and for the most part defaults can be retained–only a few changes are required: - Replace all instances of the default user npub with your own (for me, `npub1r0d8...`) - Change the default relay URL to your own (for me, `relay.rodbishop.nz`) - Replace all instances of the default name in the relay names (for me, "Rod's ...") - Replace all instances of the default profile image with your own To enable automatic blasting from your outbox, and importing to your inbox, the software comes with an example list of relays to blast and import from. See `relays_blastr.example.json` and `relays_import.example.json`. To use these features simply duplicate and rename these files to `relays_blastr.json` and `relays_import.json` respectively. Within these files you can specify the public relays of your choice. I simply used the default list. There are other features available, such as backups and initial imports, but I decided to handle these later. To start with I wanted to launch the relay and test it. To launch the relay run Docker Compose. ``` docker-compose up -d docker logs haven-relay ``` Then you should explore the logs in the command line and the ports in your browser to see if it launched successfully. The logs should show your web of trust has been built successfully and the browser should show simple landing pages. The logs should show that the relay has queried the network and built a web of trust from your followers. Mine looked as follows. ``` 2024/10/14 12:02:08 🌐 building web of trust graph 2024/10/14 12:02:16 🫂 total network size: 13296 2024/10/14 12:02:16 🔗 relays discovered: 335 2024/10/14 12:02:17 🌐 pubkeys with minimum followers: 9394 keys ``` Your browser should show you have four relays in operation, for example as follows. - `your_IP_address:3355` (your outbox or home relay) - `your_IP_address:3355/private` (your private relay) - `your_IP_address:3355/chat` (your direct message relay) - `your_IP_address:3355/inbox` (your inbox relay) That's it. Your relay is online. #### Connecting HAVEN Now all that remains is the plumbing to connect your domain, relay, and Nostr clients together. **Configure DNS** First, configure your domain. At a high level – 1. Get your domain (buy one if you need to) 2. Get the IP address of your VPS 3. In your domain's DNS settings add those records as an A record to the subdomain of your choice, e.g. `relay` as in `relay.your_domain_name.com`, or in my case `relay.rodbishop.nz` Your subdomain now points to your server. **Configure reverse proxy** Next, you need to redirect traffic from your subdomain to your relay at port `3355`. On my VPS I use Caddy as a reverse proxy for a few projects, I have it sitting in a separate Docker network. To use it for my HAVEN Relay required two steps. I am sure that the way I do this is not very elegant, but it worked. If you prefer a different method, the HAVEN readme also comes with instructions on how to perform a similar setup using nginx. For my method, my steps were as follows: 1. Add configuration to Caddy's `Caddyfile` to tell it what to do with requests for the `relay.rodbishop.nz` subdomain 2. Add the Caddy Docker network to the HAVEN `docker-compose.yml` to make it be part of the Caddy network For the addition to the `Caddyfile`, I used as follows: ``` relay.rodbishop.nz { reverse_proxy haven-relay:3355 { header_up X-Forwarded-For {remote} header_up X-Forwarded-Proto {scheme} header_up X-Forwarded-Port {server_port} } } ``` For the addition to the `docker-compose.yml`, I used as follows: ``` networks: - caddy # Added this line to services to connect to the Caddy network networks: caddy: external: true # Added this to section specify the Caddy network ``` Once your DNS configuration and reverse proxy setup are completed, you should now be able to access your Nostr client at `relay.your_domain_name.com`. For my set up, this was `relay.rodbishop.nz`. **Connecting your Nostr client** Most Nostr clients allow you to specify any relay you choose. My go-to client at the moment is Amethyst on Android. Amethyst allows you to specify discrete relays for each role in the outbox model which ties up very neatly with HAVEN. - In the sidebar, select Relays - For "Public Outbox/Home Relays" enter `relay.your_domain_name.com` - For "Public Inbox Relays" enter `relay.your_domain_name.com/inbox` - For "DM Inbox Relays" enter `relay.your_domain_name.com/chat` - For "Private Home Relays" enter `relay.your_domain_name.com/private` - Click Save to broadcast your new relays to the Nostr network. Your new relay configuration is now live. **Testing your relay** Lastly, it's time to test. Amethyst provides a simple method to test this as it allows you to configure the relays used on each post. - Create a test note, and then before you post it, edit your relays using the icon at the top - Turn off all relays except your own outbox relay, and post the note - Access your HAVEN docker logs with `docker logs haven-relay` and see if there is a log to indicate if the note was received and blasted to other public relays - Copy the `nevent` of the note, and attempt to find it in another client If you're in luck, you may see something like this (the blasted note, and then users on the network responding to the note in turn). ``` 2024/10/22 00:12:23 🔫 blasted 95c477af7e6b612bf5d1d94309d2d57377a0a67d2181cfbb42a2e3fbc0feeaaf to 26 relays 2024/10/22 00:13:50 🤙 new reaction in your inbox 2024/10/22 00:14:42 🫂 new reaction in your inbox 2024/10/22 00:14:45 ✅ new reaction in your inbox 2024/10/22 00:15:12 💜 new reaction in your inbox 2024/10/22 00:17:03 ✅ new reaction in your inbox 2024/10/22 00:17:03 🫂 new reaction in your inbox 2024/10/22 00:17:55 🫂 new reaction in your inbox 2024/10/22 00:19:02 📰 new note in your inbox ``` That's it. If you followed this successfully your personal relay is up and running. #### What I did wrong so you don't have to **My first relay was too public** This blog comes after much trial and error. The first error I made was I set up a relay to use as a personal relay, but without any restrictions on use. I very quickly found other people discovered and started using my relay to save their own notes! This was unintended and I had to take it down. **Unfamiliar with Go language** I am mostly non-technical, and completely unfamiliar with Go. I got the project up and running with Go on my localhost–with a lot of help from my AI–but I then completely failed in migrating this to my VPS. Moving to Docker made the difference for me here. **I failed a few times due to a messy folder** After messing with Go, I moved to the Docker setup, but I started my work from a messy folder which contained remnants of the Go build, which caused various failures. Deleting the folder and cloning again from scratch solved the issue. **Trouble with Nostr.wine** I subscribe to the Nostr.wine paid relay, and I initially added it to the list of relays in my blaster. However, it didn't work, and the logs showed an error as follows ``` CLOSED from wss://nostr.wine: 'auth-required: this relay only serves private notes to authenticated users' ``` It seems my npub's subscription to Nostr.wine is not enough for it to permit my relay to blast notes to it. In the end, I removed Nostr.wine from my relay config, and kept Nostr.wine as a separate entry in my Client's outbox settings. **Failed to create web of trust graph** When I first launched the relay on my VPS, HAVEN failed to complete the Web of Trust graph, with a log that looked as follows (note the zeroes). As a result, no one would have been able to send me DM's to my Chat relay (it would flag every message as spam). ``` 2024/10/14 12:02:08 🌐 building web of trust graph 2024/10/14 12:02:16 🫂 total network size: 0 2024/10/14 12:02:16 🔗 relays discovered: 0 2024/10/14 12:02:17 🌐 pubkeys with minimum followers: 0 keys ``` I never got to the bottom of why this was. In the process of trying to fix it I rebuild the container, and on the rebuild it spontaneously worked. Accordingly my lesson learned is "if in doubt, turn if off and on again". **Failed to run --import function** HAVEN comes with a function to import all your old notes from other public relays to your own outbox relay. When I run it I get an error as follows: ``` panic: Cannot acquire directory lock on "db/private". Another process is using this Badger database. error: resource temporarily unavailable ``` I have yet to work out the solution for this, and will update this note when I do so! ### What's Next? Over the past four blogs I have - [Mined a Nostr pubkey and backed up the mnemonic](nostr:naddr1qqsy66twd9hxwtteda6hyt2kv9hxjare94g82cntv4uj6drfw4cxyeszyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c6e2ekw) - [Set up Nostr payments with a Lightning wallet plus all the bells and whistles](nostr:naddr1qq34xet5w35kueedw4cz65rp09kk2mn5wvkk7m3dfehhxarj95mk7dnvwvmsygqmmflp7uukhk3drmueqv763lfdcd3gzpusm7d7vt6ezquth97ymypsgqqqw4rsuql6je) - [Set up NIP-05 and Lighting Address at my own domain](nostr:naddr1qqyx2efcvy6rvcnrqyghwumn8ghj7mn0wd68ytnhd9hx2tczyqda5lslwwttmgk3a7vsx0dgl5kuxc5pq7gdlxlx9av3qw9mjlzdjqcyqqq823c634nh0) - Set up a Personal Relay at my own domain This feels like a very comprehensive personal set up now. Also, I have uncovered some new rabbit holes and feel like I have some projects to tackle. Perhaps one of these? - Set up a personal homepage with my Nostr feed to round-out my rodbishop.nz domain - Experiment with different signers like Amber and Nsec.app and NFC cards - Set up a paid relay for #austriches (Australians and Kiwis on Nostr) - Set up a team relay to experiment with Nostr for business or community projects - Or something else ... ? Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle. Pura vida Nostr. @ 4ba8e86d:89d32de4
2024-10-17 22:26:20Ele oferece a opção de utilizar autenticação de dois fatores para aumentar ainda mais a segurança. O aplicativo foi desenvolvido em 2016 pelo americano Mo Bitar para oferecer um lugar seguro para armazenar informações pessoais sem a preocupação de que seus dados sejam coletados ou expostos a terceiros. O Standard Notes é um cofre de aço para seus dados mais confidenciais, que protege suas anotações e arquivos com criptografia de ponta a ponta líder do setor e auditada 4x. Armazene com segurança todos os seus dados confidenciais em um só lugar e acesse-os de todos os seus dispositivos, com a certeza de que seus dados estarão sempre protegidos pelos mais altos padrões de segurança. Ao contrário de outros serviços de anotações, o Standard Notes apresenta medidas de segurança avançadas e controles de privacidade que protegem seus dados contra hacks, violações de dados, acesso do governo e até mesmo acesso de funcionários. Ele defende a privacidade dos usuários e apresenta políticas revisadas por pares e auditáveis. O Standard Notes utiliza criptografia de ponta a ponta para proteger todos os dados, que são criptografados sempre que tocam um disco, como em seus servidores ou no dispositivo do usuário. Auditorias independentes são realizadas periodicamente em sua criptografia, aplicativo e código do servidor para garantir que os dados estejam protegidos. O código aberto do Standard Notes permite que os usuários tenham clareza sobre como seus dados estão sendo tratados em cada etapa do caminho. Ele não coleta ou armazena informações do usuário, como endereço IP ou agente do usuário, para proteger a privacidade. 1. Acesse a F-droid ou Google Play Store em seu dispositivo Android. 2. siga as instruções para criar uma conta ou fazer login em uma conta existente. 3. Comece a criar suas notas e armazenar outras informações importantes com a tranquilidade de que seus dados estão seguros e protegidos. https://github.com/standardnotes
@ 4ba8e86d:89d32de4
2024-10-17 22:26:20Ele oferece a opção de utilizar autenticação de dois fatores para aumentar ainda mais a segurança. O aplicativo foi desenvolvido em 2016 pelo americano Mo Bitar para oferecer um lugar seguro para armazenar informações pessoais sem a preocupação de que seus dados sejam coletados ou expostos a terceiros. O Standard Notes é um cofre de aço para seus dados mais confidenciais, que protege suas anotações e arquivos com criptografia de ponta a ponta líder do setor e auditada 4x. Armazene com segurança todos os seus dados confidenciais em um só lugar e acesse-os de todos os seus dispositivos, com a certeza de que seus dados estarão sempre protegidos pelos mais altos padrões de segurança. Ao contrário de outros serviços de anotações, o Standard Notes apresenta medidas de segurança avançadas e controles de privacidade que protegem seus dados contra hacks, violações de dados, acesso do governo e até mesmo acesso de funcionários. Ele defende a privacidade dos usuários e apresenta políticas revisadas por pares e auditáveis. O Standard Notes utiliza criptografia de ponta a ponta para proteger todos os dados, que são criptografados sempre que tocam um disco, como em seus servidores ou no dispositivo do usuário. Auditorias independentes são realizadas periodicamente em sua criptografia, aplicativo e código do servidor para garantir que os dados estejam protegidos. O código aberto do Standard Notes permite que os usuários tenham clareza sobre como seus dados estão sendo tratados em cada etapa do caminho. Ele não coleta ou armazena informações do usuário, como endereço IP ou agente do usuário, para proteger a privacidade. 1. Acesse a F-droid ou Google Play Store em seu dispositivo Android. 2. siga as instruções para criar uma conta ou fazer login em uma conta existente. 3. Comece a criar suas notas e armazenar outras informações importantes com a tranquilidade de que seus dados estão seguros e protegidos. https://github.com/standardnotes @ 460c25e6:ef85065c
2024-10-10 13:22:06In the early days of Nostr, developers often competed to see who could implement the most NIPs. Although all were optional (except NIP-01), it became a point of pride and vital for the ecosystem's growth. Back then, there were only a few dozen relatively simple NIPs to implement. Fast forward to today, with nearly 100 NIPs, maintaining and implementing everything has become nearly impossible. Yet, the drive among developers to "code all things Nostr" remains as strong as ever. nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8gprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszxmhwden5te0wfjkccte9emk2um5v4exucn5vvhxxmmd9uq3xamnwvaz7tmhda6zuat50phjummwv5hsx7c9z9 raised the point that everyone, even I, agrees: nostr:nevent1qqsqqqp2zrs7836tyjlsfe7aj9c4d97zrxxqyayagkdwlcur96t4laspzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqqqqzgcrrrp But how big is too big? How can we better understand the range of options available for devs out there? I went out for a hunt in my own brain to figure out how to clarify the situation. I came up with the following 4 categories for Nostr Clients: - **Super Clients**: These apps merge vastly different domains into a single application, offering basic support for reading, writing, configuration, and data management for each use case within each domains. An example would be an app that combines a Marketplace and Live Streams under one roof. - **Clients**: These apps provide comprehensive support for a single domain, handling all its use cases in a single home. They manage the complete set of reading, writing, configuration, and long-term data management within that domain. An example is a marketplace app that helps users manage product catalogs, process orders, collect payments, and handle fulfillment and reports. - **Mini Clients**: These apps focus on read and write functionality for a single use case, including configuration management and any actions related to that specific task. For example, a fulfillment app that helps users view orders placed from another client to then pack and ship them. - **Micro Clients**: These apps have a single interface and perform one specific action. Viewing and creating a record is handled by separate micro apps. An example is an app that simply scans an order's QR code and marks it as shipped. Based on my made-up categories described at the end, this is how I would split our most known apps. **Super Clients** - [amethyst](https://amethyst.social) - [nostrudel](https://nostrudel.ninja) - [coracle](https://coracle.social) **Clients** - [damus](https://damus.io) - twitter - [primal](https://primal.net) - twitter - [snort](https://snort.social) - twitter - [gossip](https://github.com/mikedilger/gossip) - twitter - [lume](https://lume.nu) - twitter - [ditto](https://soapbox.pub/ditto/) - twitter - [rabbit](https://rabbit.syusui.net) - twitter - [freefrom](https://freefrom.space) - twitter - [nos](https://nos.social) - twitter - [flycat](https://flycat.club) - twitter - [straylight](https://straylight.cafe) - twitter - [nostter](https://nostter.app) - twitter - [iris](https://iris.to) - twitter - [nostur](https://nostur.com) - twitter - [nostrmo](https://apps.apple.com/us/app/nostrmo/id6447441761) - twitter - [yana](https://yana.do) - twitter - [openvibe](https://openvibe.social) - twitter - [freerse](https://freerse.com) - twitter - [0xchat](https://0xchat.com) - chats - [cornychat](https://cornychat.com) - chats - [coop](https://github.com/lumehq/coop) - chats - [nostrchat](https://nostrchat.io) - chats - [blowater](https://blowater.deno.dev) - chats - [habla](https://habla.news) - blogs - [yakihonne](https://yakihonne.com) - blogs - [highlighter](https://highlighter.com) - blogs - [blogstack](https://blogstack.io) - blogs - [stemstr](https://stemstr.app) - music - [wavlake](https://wavlake.com) - music - [fountain](https://fountain.fm) - podcasts - [zap.stream](https://zap.stream) - live streaming - [shopstr](https://shopstr.store) - marketplace - [plebeian.market](https://plebeian.market) - marketplace - [flotilla](https://flotilla.coracle.social) - communities - [satellite](https://satellite.earth) - communities - [zapddit](https://zapddit.com) - communities - [nostr.kiwi](https://nostr.kiwi) - communities - [hivetalk](https://hivetalk.org) - video calls - [flare](https://flare.pub) - long-form videos - [nostrnests](https://nostrnests.com) - audio spaces - [wherostr](https://wherostr.social) - location - [yondar](https://go.yondar.me) - location - [stacker.news](https://stacker.news) - news - [flockstr](https://flockstr.com) - events - [nostrocket](https://nostrocket.org) - issue tracker - [docstr](https://docstr.app) - docs - [satshoot](https://satshoot.com) - freelance - [wikifreedia](https://wikifreedia.xyz) - wiki - [formstr](https://formstr.app) - forms - [chesstr](https://chesstr.pages.dev) - chess - [memestr](https://memestr.app) - meme feed - [npub.cash](https://npub.cash) - wallet - [npub.pro](https://npub.pro) - websites - [gitworkshop](https://gitworkshop.dev) - dev tools - [onosendai](https://onosendai.tech) - metaverse - [degmods](https://degmods.com) - games - [turdsoup](https://turdsoup.com) - prompts **Mini Clients** - [amber](https://github.com/greenart7c3/Amber) - signer - [alby](https://getalby.com) - signer - [nos2x](https://github.com/fiatjaf/nos2x) - signer - [nsec.app](https://nsec.app) - signer - [keys.band](https://keys.band) - signer - [nostrame](https://github.com/Anderson-Juhasc/nostrame) - signer - [nokakoi](https://nokakoi.com) - anon - [zap.cooking](https://zap.cooking) - recipes - [anonostr](https://anonostr.com) - anon - [getwired](https://getwired.app) - anon - [lowent](https://lowent.xyz) - anon - [creatr](https://creatr.nostr.wine) - exclusive content - [lightning.video](https://lightning.video) - exclusive content - [zaplinks](https://zaplinks.lol/slides) - slides - [listr](https://listr.lol) - lists - [zap.store](https://zap.store) - app store - [badges.page](https://badges.page) - badges - [oddbean](https://oddbean.com) - news - [dtan](https://dtan.xyz) - torrents - [nosta](https://nosta.me) - user pages - [pinstr](https://pinstr.app) - pinterest - [pollerama](https://pollerama.fun) - polls - [swarmstr](https://swarmstr.com) - trending - [nostrapp](https://nostrapp.link) - apps manager - [noogle](https://noogle.lol) - search - [ostrich.work](https://ostrich.work) - job postings - [emojito](https://emojito.meme) - emoji manager - [nostree](https://nostree.me) - links - [citrine](https://github.com/greenart7c3/citrine) - local relay - [joinstr](https://joinstr.xyz) - coinjoins - [heya](https://heya.fund) - crowdfunding - [zapplepay](https://zapplepay.com) - zaps - [nosbin](https://nosbin.com) - clipboard - [shipyard](https://shipyard.pub) - scheduler - [tunestr](https://tunestr.io) - live streams - [filestr](https://filestr.vercel.app) - files - [nostrcheck.me](https://nostrcheck.me/) - media hosting - [sheetstr](https://sheetstr.amethyst.social) - spreadsheets - [crafters](https://crafters.amethyst.social) - curriculum vitae **Micro Clients** - [w3](https://w3.do) - url shortener - [nosdrive](https://nosdrive.app) - backups - [zaplife](https://zaplife.lol) - zaps dashboard - [zapper.fun](https://zapper.fun) - payments - [nostrends](https://nostrends.vercel.app) - trends - [zephyr](https://zephyr.coracle.social) - trends - [wavman](https://wavman.app) - music player - [nostrrr](https://nostrrr.com) - relay info - [nosdump](https://github.com/jiftechnify/nosdump) - relay info - [notestack](https://notestack.com) - blogs - [nostr.build](https://nostr.build) - media hosting - [nostr.watch](https://nostr.watch) - relay info - [nostr hours](https://snowcait.github.io/nostr-hours/) - use reports - [lazereyes](https://lazereyes.nosfabrica.com) - vision prescriptions - [snakestr](https://satoshipuzzles.github.io/Snakestr) - games - [deletestr](https://zaplinks.lol/deletestr) - deletion requests - [2048str](https://zaplinks.lol/2048str) - games - [nostrqr](https://zaplinks.lol/nostrqr) - qr generator - [notanostrclient](https://zaplinks.lol/notanostrclient) - anon Super apps will try to do everything, but can't really do most things super well. Regular-sized Clients will try to manage most of a given domain but are likely to centralize users on themselves, an unwanted effect inside of Nostr. If we want Nostr to grow in a decentralized fashion, we have to start betting on and using more **Mini** and **Micro** clients.
@ 460c25e6:ef85065c
2024-10-10 13:22:06In the early days of Nostr, developers often competed to see who could implement the most NIPs. Although all were optional (except NIP-01), it became a point of pride and vital for the ecosystem's growth. Back then, there were only a few dozen relatively simple NIPs to implement. Fast forward to today, with nearly 100 NIPs, maintaining and implementing everything has become nearly impossible. Yet, the drive among developers to "code all things Nostr" remains as strong as ever. nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8gprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hszxmhwden5te0wfjkccte9emk2um5v4exucn5vvhxxmmd9uq3xamnwvaz7tmhda6zuat50phjummwv5hsx7c9z9 raised the point that everyone, even I, agrees: nostr:nevent1qqsqqqp2zrs7836tyjlsfe7aj9c4d97zrxxqyayagkdwlcur96t4laspzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7q3q80cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsxpqqqqqqzgcrrrp But how big is too big? How can we better understand the range of options available for devs out there? I went out for a hunt in my own brain to figure out how to clarify the situation. I came up with the following 4 categories for Nostr Clients: - **Super Clients**: These apps merge vastly different domains into a single application, offering basic support for reading, writing, configuration, and data management for each use case within each domains. An example would be an app that combines a Marketplace and Live Streams under one roof. - **Clients**: These apps provide comprehensive support for a single domain, handling all its use cases in a single home. They manage the complete set of reading, writing, configuration, and long-term data management within that domain. An example is a marketplace app that helps users manage product catalogs, process orders, collect payments, and handle fulfillment and reports. - **Mini Clients**: These apps focus on read and write functionality for a single use case, including configuration management and any actions related to that specific task. For example, a fulfillment app that helps users view orders placed from another client to then pack and ship them. - **Micro Clients**: These apps have a single interface and perform one specific action. Viewing and creating a record is handled by separate micro apps. An example is an app that simply scans an order's QR code and marks it as shipped. Based on my made-up categories described at the end, this is how I would split our most known apps. **Super Clients** - [amethyst](https://amethyst.social) - [nostrudel](https://nostrudel.ninja) - [coracle](https://coracle.social) **Clients** - [damus](https://damus.io) - twitter - [primal](https://primal.net) - twitter - [snort](https://snort.social) - twitter - [gossip](https://github.com/mikedilger/gossip) - twitter - [lume](https://lume.nu) - twitter - [ditto](https://soapbox.pub/ditto/) - twitter - [rabbit](https://rabbit.syusui.net) - twitter - [freefrom](https://freefrom.space) - twitter - [nos](https://nos.social) - twitter - [flycat](https://flycat.club) - twitter - [straylight](https://straylight.cafe) - twitter - [nostter](https://nostter.app) - twitter - [iris](https://iris.to) - twitter - [nostur](https://nostur.com) - twitter - [nostrmo](https://apps.apple.com/us/app/nostrmo/id6447441761) - twitter - [yana](https://yana.do) - twitter - [openvibe](https://openvibe.social) - twitter - [freerse](https://freerse.com) - twitter - [0xchat](https://0xchat.com) - chats - [cornychat](https://cornychat.com) - chats - [coop](https://github.com/lumehq/coop) - chats - [nostrchat](https://nostrchat.io) - chats - [blowater](https://blowater.deno.dev) - chats - [habla](https://habla.news) - blogs - [yakihonne](https://yakihonne.com) - blogs - [highlighter](https://highlighter.com) - blogs - [blogstack](https://blogstack.io) - blogs - [stemstr](https://stemstr.app) - music - [wavlake](https://wavlake.com) - music - [fountain](https://fountain.fm) - podcasts - [zap.stream](https://zap.stream) - live streaming - [shopstr](https://shopstr.store) - marketplace - [plebeian.market](https://plebeian.market) - marketplace - [flotilla](https://flotilla.coracle.social) - communities - [satellite](https://satellite.earth) - communities - [zapddit](https://zapddit.com) - communities - [nostr.kiwi](https://nostr.kiwi) - communities - [hivetalk](https://hivetalk.org) - video calls - [flare](https://flare.pub) - long-form videos - [nostrnests](https://nostrnests.com) - audio spaces - [wherostr](https://wherostr.social) - location - [yondar](https://go.yondar.me) - location - [stacker.news](https://stacker.news) - news - [flockstr](https://flockstr.com) - events - [nostrocket](https://nostrocket.org) - issue tracker - [docstr](https://docstr.app) - docs - [satshoot](https://satshoot.com) - freelance - [wikifreedia](https://wikifreedia.xyz) - wiki - [formstr](https://formstr.app) - forms - [chesstr](https://chesstr.pages.dev) - chess - [memestr](https://memestr.app) - meme feed - [npub.cash](https://npub.cash) - wallet - [npub.pro](https://npub.pro) - websites - [gitworkshop](https://gitworkshop.dev) - dev tools - [onosendai](https://onosendai.tech) - metaverse - [degmods](https://degmods.com) - games - [turdsoup](https://turdsoup.com) - prompts **Mini Clients** - [amber](https://github.com/greenart7c3/Amber) - signer - [alby](https://getalby.com) - signer - [nos2x](https://github.com/fiatjaf/nos2x) - signer - [nsec.app](https://nsec.app) - signer - [keys.band](https://keys.band) - signer - [nostrame](https://github.com/Anderson-Juhasc/nostrame) - signer - [nokakoi](https://nokakoi.com) - anon - [zap.cooking](https://zap.cooking) - recipes - [anonostr](https://anonostr.com) - anon - [getwired](https://getwired.app) - anon - [lowent](https://lowent.xyz) - anon - [creatr](https://creatr.nostr.wine) - exclusive content - [lightning.video](https://lightning.video) - exclusive content - [zaplinks](https://zaplinks.lol/slides) - slides - [listr](https://listr.lol) - lists - [zap.store](https://zap.store) - app store - [badges.page](https://badges.page) - badges - [oddbean](https://oddbean.com) - news - [dtan](https://dtan.xyz) - torrents - [nosta](https://nosta.me) - user pages - [pinstr](https://pinstr.app) - pinterest - [pollerama](https://pollerama.fun) - polls - [swarmstr](https://swarmstr.com) - trending - [nostrapp](https://nostrapp.link) - apps manager - [noogle](https://noogle.lol) - search - [ostrich.work](https://ostrich.work) - job postings - [emojito](https://emojito.meme) - emoji manager - [nostree](https://nostree.me) - links - [citrine](https://github.com/greenart7c3/citrine) - local relay - [joinstr](https://joinstr.xyz) - coinjoins - [heya](https://heya.fund) - crowdfunding - [zapplepay](https://zapplepay.com) - zaps - [nosbin](https://nosbin.com) - clipboard - [shipyard](https://shipyard.pub) - scheduler - [tunestr](https://tunestr.io) - live streams - [filestr](https://filestr.vercel.app) - files - [nostrcheck.me](https://nostrcheck.me/) - media hosting - [sheetstr](https://sheetstr.amethyst.social) - spreadsheets - [crafters](https://crafters.amethyst.social) - curriculum vitae **Micro Clients** - [w3](https://w3.do) - url shortener - [nosdrive](https://nosdrive.app) - backups - [zaplife](https://zaplife.lol) - zaps dashboard - [zapper.fun](https://zapper.fun) - payments - [nostrends](https://nostrends.vercel.app) - trends - [zephyr](https://zephyr.coracle.social) - trends - [wavman](https://wavman.app) - music player - [nostrrr](https://nostrrr.com) - relay info - [nosdump](https://github.com/jiftechnify/nosdump) - relay info - [notestack](https://notestack.com) - blogs - [nostr.build](https://nostr.build) - media hosting - [nostr.watch](https://nostr.watch) - relay info - [nostr hours](https://snowcait.github.io/nostr-hours/) - use reports - [lazereyes](https://lazereyes.nosfabrica.com) - vision prescriptions - [snakestr](https://satoshipuzzles.github.io/Snakestr) - games - [deletestr](https://zaplinks.lol/deletestr) - deletion requests - [2048str](https://zaplinks.lol/2048str) - games - [nostrqr](https://zaplinks.lol/nostrqr) - qr generator - [notanostrclient](https://zaplinks.lol/notanostrclient) - anon Super apps will try to do everything, but can't really do most things super well. Regular-sized Clients will try to manage most of a given domain but are likely to centralize users on themselves, an unwanted effect inside of Nostr. If we want Nostr to grow in a decentralized fashion, we have to start betting on and using more **Mini** and **Micro** clients. @ 4ba8e86d:89d32de4
2024-10-08 15:50:58Ele foi desenvolvido pela Beowulf Blockchain, uma empresa que é conhecida por suas soluções seguras e confiáveis de blockchain e criptografia. A autenticação em duas etapas é um processo que adiciona uma camada extra de segurança ao login em uma conta online. Em vez de depender apenas de uma senha, o 2FA exige uma segunda forma de autenticação, geralmente um código enviado para um dispositivo móvel ou gerado por um aplicativo. Isso ajuda a garantir que apenas o proprietário da conta possa acessá-la. A história do Aegis Authenticator remonta ao início dos anos 2000, quando a autenticação em duas etapas começou a ser amplamente adotada para proteger contas online. Desde então, houve vários casos de violação de segurança em grandes empresas, incluindo Yahoo, Equifax e Marriott, que expuseram informações pessoais de milhões de usuários. Como resultado, a segurança online se tornou uma preocupação crescente para indivíduos e empresas em todo o mundo. O Aegis Authenticator funciona gerando códigos de autenticação em tempo real que mudam a cada 30 segundos. Esses códigos são usados em conjunto com uma senha para acessar uma conta online. O aplicativo suporta a autenticação com base em tempo e também com base em contagem, o que significa que ele pode ser usado com serviços que suportam ambas as opções. O Aegis Authenticator possui recursos de backup e sincronização em nuvem para garantir que os usuários possam acessar suas contas em outros dispositivos, mesmo que o dispositivo original seja perdido ou roubado. O aplicativo utiliza criptografia de ponta a ponta para proteger as informações do usuário em trânsito e armazenadas na nuvem. O Aegis Authenticator resolve vários problemas de segurança online, incluindo a prevenção de ataques de phishing e o aumento da segurança em contas com senhas fracas. Os códigos gerados pelo aplicativo são válidos apenas por um curto período de tempo, o que dificulta a utilização de um código roubado por um atacante. Além disso, o aplicativo é capaz de detectar automaticamente tentativas de phishing e alertar o usuário. 1. Baixe o aplicativo na loja de aplicativos do seu dispositivo móvel. https://play.google.com/store/apps/details?id=com.beemdevelopment.aegis 2. Abra o aplicativo e clique em "Adicionar conta". 3. Selecione o serviço para o qual deseja configurar a autenticação em duas etapas. 4. Siga as instruções do serviço para vincular sua conta ao Aegis Authenticator. Isso pode envolver digitalizar um código QR com a câmera do seu dispositivo ou inserir um código de configuração manualmente. 5. O aplicativo irá gerar um código de autenticação em tempo real para sua conta, que muda a cada 30 segundos. Use esse código em conjunto com sua senha para acessar sua conta. Com esses passos simples, você pode usar o Aegis Authenticator para proteger suas contas online e aumentar sua segurança digital Um próximo Passo seria adquirir um Yubico. https://void.cat/d/KzX75b9AwikAGHiywPb3Su.webp
@ 4ba8e86d:89d32de4
2024-10-08 15:50:58Ele foi desenvolvido pela Beowulf Blockchain, uma empresa que é conhecida por suas soluções seguras e confiáveis de blockchain e criptografia. A autenticação em duas etapas é um processo que adiciona uma camada extra de segurança ao login em uma conta online. Em vez de depender apenas de uma senha, o 2FA exige uma segunda forma de autenticação, geralmente um código enviado para um dispositivo móvel ou gerado por um aplicativo. Isso ajuda a garantir que apenas o proprietário da conta possa acessá-la. A história do Aegis Authenticator remonta ao início dos anos 2000, quando a autenticação em duas etapas começou a ser amplamente adotada para proteger contas online. Desde então, houve vários casos de violação de segurança em grandes empresas, incluindo Yahoo, Equifax e Marriott, que expuseram informações pessoais de milhões de usuários. Como resultado, a segurança online se tornou uma preocupação crescente para indivíduos e empresas em todo o mundo. O Aegis Authenticator funciona gerando códigos de autenticação em tempo real que mudam a cada 30 segundos. Esses códigos são usados em conjunto com uma senha para acessar uma conta online. O aplicativo suporta a autenticação com base em tempo e também com base em contagem, o que significa que ele pode ser usado com serviços que suportam ambas as opções. O Aegis Authenticator possui recursos de backup e sincronização em nuvem para garantir que os usuários possam acessar suas contas em outros dispositivos, mesmo que o dispositivo original seja perdido ou roubado. O aplicativo utiliza criptografia de ponta a ponta para proteger as informações do usuário em trânsito e armazenadas na nuvem. O Aegis Authenticator resolve vários problemas de segurança online, incluindo a prevenção de ataques de phishing e o aumento da segurança em contas com senhas fracas. Os códigos gerados pelo aplicativo são válidos apenas por um curto período de tempo, o que dificulta a utilização de um código roubado por um atacante. Além disso, o aplicativo é capaz de detectar automaticamente tentativas de phishing e alertar o usuário. 1. Baixe o aplicativo na loja de aplicativos do seu dispositivo móvel. https://play.google.com/store/apps/details?id=com.beemdevelopment.aegis 2. Abra o aplicativo e clique em "Adicionar conta". 3. Selecione o serviço para o qual deseja configurar a autenticação em duas etapas. 4. Siga as instruções do serviço para vincular sua conta ao Aegis Authenticator. Isso pode envolver digitalizar um código QR com a câmera do seu dispositivo ou inserir um código de configuração manualmente. 5. O aplicativo irá gerar um código de autenticação em tempo real para sua conta, que muda a cada 30 segundos. Use esse código em conjunto com sua senha para acessar sua conta. Com esses passos simples, você pode usar o Aegis Authenticator para proteger suas contas online e aumentar sua segurança digital Um próximo Passo seria adquirir um Yubico. https://void.cat/d/KzX75b9AwikAGHiywPb3Su.webp @ 4ba8e86d:89d32de4
2024-10-07 23:19:19O Orbot é um aplicativo de código aberto para dispositivos Android que oferece anonimato e segurança aos usuários da Internet. Ele funciona como um front-end para o Tor, permitindo que os usuários se conectem à rede Tor e usem serviços online de forma anônima e segura. O Tor é uma rede de computadores que foi desenvolvida originalmente pelo governo dos Estados Unidos para proteger a privacidade dos usuários da Internet e permitir a comunicação segura de informações confidenciais. O Tor funciona usando um sistema de "onion routing" (roteamento de cebola), que envolve o encapsulamento de dados em várias camadas de criptografia antes de serem transmitidos através da rede. O Orbot é um componente do Guardian Project, uma iniciativa que visa desenvolver tecnologia segura e anônima para ativistas de direitos humanos, jornalistas e outros usuários que precisam de privacidade online. O aplicativo é distribuído sob a Licença Pública Geral do GNU, o que significa que é totalmente gratuito e de código aberto. O Orbot foi lançado pela primeira vez em 2008, como parte do projeto Tor, uma rede descentralizada de anonimização de tráfego que ajuda a proteger a privacidade dos usuários na internet. A ideia por trás do Orbot era fornecer uma maneira fácil para usuários móveis de acessar a rede Tor e proteger suas comunicações enquanto estavam em movimento. A primeira versão do Orbot foi lançada para o sistema operacional Android, e desde então, tem sido amplamente adotada por usuários preocupados com a privacidade. O aplicativo inclui um proxy HTTP que permite conectar navegadores da web e outros aplicativos cliente HTTP na interface Tor SOCKS. Isso significa que todos os seus dados são criptografados e encaminhados através da rede Tor antes de serem transmitidos para o servidor de destino, tornando extremamente difícil para qualquer pessoa interceptar ou monitorar suas atividades online. Além de fornecer anonimato e segurança aos usuários, o Orbot também pode ser usado para acessar conteúdo restrito por região. Por exemplo, se você está em um país que censura determinados sites ou serviços online, o Orbot pode ajudá-lo a acessar esse conteúdo de forma segura e anônima. Os principais recursos do Orbot incluem a conexão segura à rede Tor, o acesso a serviços online restritos, o proxy HTTP, o código aberto e a facilidade de uso. Esses recursos tornam o Orbot uma ferramenta valiosa para usuários preocupados com a privacidade que desejam se comunicar e navegar na Internet de forma segura e anônima. O Orbot é um aplicativo gratuito e de código aberto para dispositivos Android que oferece anonimato e segurança aos usuários Aqui está um passo a passo para instalar o Orbot em seu dispositivo Android: 1. Acesse a F-droid ou Google Play Store em seu dispositivo Android. 2. Selecione a opção "Iniciar" para iniciar a conexão com a rede Tor. Aguarde até que a conexão seja estabelecida. Isso pode levar alguns minutos, dependendo da velocidade de sua conexão com a internet. 3. Depois que a conexão for estabelecida, você poderá navegar na internet de forma anônima e segura usando o Tor. Lembre-se de que o uso do Tor não garante anonimato completo e pode ser necessário seguir outras medidas de segurança para proteger sua privacidade na internet. Além disso, o Orbot é apenas uma parte do ecossistema de segurança e privacidade e pode ser necessário utilizar outras ferramentas para garantir a segurança online. https://github.com/guardianproject/orbot/stargazers
@ 4ba8e86d:89d32de4
2024-10-07 23:19:19O Orbot é um aplicativo de código aberto para dispositivos Android que oferece anonimato e segurança aos usuários da Internet. Ele funciona como um front-end para o Tor, permitindo que os usuários se conectem à rede Tor e usem serviços online de forma anônima e segura. O Tor é uma rede de computadores que foi desenvolvida originalmente pelo governo dos Estados Unidos para proteger a privacidade dos usuários da Internet e permitir a comunicação segura de informações confidenciais. O Tor funciona usando um sistema de "onion routing" (roteamento de cebola), que envolve o encapsulamento de dados em várias camadas de criptografia antes de serem transmitidos através da rede. O Orbot é um componente do Guardian Project, uma iniciativa que visa desenvolver tecnologia segura e anônima para ativistas de direitos humanos, jornalistas e outros usuários que precisam de privacidade online. O aplicativo é distribuído sob a Licença Pública Geral do GNU, o que significa que é totalmente gratuito e de código aberto. O Orbot foi lançado pela primeira vez em 2008, como parte do projeto Tor, uma rede descentralizada de anonimização de tráfego que ajuda a proteger a privacidade dos usuários na internet. A ideia por trás do Orbot era fornecer uma maneira fácil para usuários móveis de acessar a rede Tor e proteger suas comunicações enquanto estavam em movimento. A primeira versão do Orbot foi lançada para o sistema operacional Android, e desde então, tem sido amplamente adotada por usuários preocupados com a privacidade. O aplicativo inclui um proxy HTTP que permite conectar navegadores da web e outros aplicativos cliente HTTP na interface Tor SOCKS. Isso significa que todos os seus dados são criptografados e encaminhados através da rede Tor antes de serem transmitidos para o servidor de destino, tornando extremamente difícil para qualquer pessoa interceptar ou monitorar suas atividades online. Além de fornecer anonimato e segurança aos usuários, o Orbot também pode ser usado para acessar conteúdo restrito por região. Por exemplo, se você está em um país que censura determinados sites ou serviços online, o Orbot pode ajudá-lo a acessar esse conteúdo de forma segura e anônima. Os principais recursos do Orbot incluem a conexão segura à rede Tor, o acesso a serviços online restritos, o proxy HTTP, o código aberto e a facilidade de uso. Esses recursos tornam o Orbot uma ferramenta valiosa para usuários preocupados com a privacidade que desejam se comunicar e navegar na Internet de forma segura e anônima. O Orbot é um aplicativo gratuito e de código aberto para dispositivos Android que oferece anonimato e segurança aos usuários Aqui está um passo a passo para instalar o Orbot em seu dispositivo Android: 1. Acesse a F-droid ou Google Play Store em seu dispositivo Android. 2. Selecione a opção "Iniciar" para iniciar a conexão com a rede Tor. Aguarde até que a conexão seja estabelecida. Isso pode levar alguns minutos, dependendo da velocidade de sua conexão com a internet. 3. Depois que a conexão for estabelecida, você poderá navegar na internet de forma anônima e segura usando o Tor. Lembre-se de que o uso do Tor não garante anonimato completo e pode ser necessário seguir outras medidas de segurança para proteger sua privacidade na internet. Além disso, o Orbot é apenas uma parte do ecossistema de segurança e privacidade e pode ser necessário utilizar outras ferramentas para garantir a segurança online. https://github.com/guardianproject/orbot/stargazers @ bec0c9d3:c4e9cd29
2024-10-06 14:07:27Hello, **Free People**! Last weeks we were very productive. Our team has reached a higher level. Ideas, designs, workflow - you name it. All of this to deliver you the best experience in the space. Where Open Source and Cypherpunk Ethos lead the way. [2140 COLLECTIVE ](https://2140.wtf) alongside with [CyphermunkHouse](https://primal.net/e/note1ae8947gzx4q38p9v2fuw3yn4d5sy5qy9x6uap6p9uf8hx9dl3e0qnkmazf) is proud to announce that Ours (Yours) festival will take place in ***LONDON / UK***. During Halloween/BitcoinWhitepaper weekend. ``` 29.OCT - 03.NOV 2024 ```  Please check [BITCOIN CULTURE FESTIVAL '24 AGENDA](https://2140.wtf/content/45-bitcoin-culture-week-full-agenda)Page for more updated info ! ``` All of this will not be possible without YOU. ``` If you want to join our crew, share some ideas, help, anything - feel free to contact us using the application forms, ready - waiting on the [main page.](http://2140.wtf) Forms are dedicated to [Volunteers](https://2140.wtf/content/49-volunteer-form) and [Artists](https://2140.wtf/content/40-art-submission) that can drop an Art for Phisical Gallery There will be also an Online auction that will display your art worldwide. Bitcoin pay only). We are also prepered forms for [#nostr panel](https://2140.wtf/content/41-nostr-participant-form) speakers who want to present any #nostr project, freedom tools, etc. [ART Panel](https://2140.wtf/content/42-panel-participant-form) Art, music, culture - stuff around our values, Bitcoin, and freedom, during friday and saturday events. If you wanna share you bitcoin story to isnpire otheres we invite you to visit us on free #TootingMarket Day where we preper Open Mic. [Let us know](https://2140.wtf/content/48-tooting-market-participant-form). On the market, which has already onboarded 20 Bitcoin merchants with food, drink, and veggy stalls, in beautiful London City. Please check out forms - maybe you will be the one, inspired enough to share your **knowledge** , **ideas** , and **spirit**. > **All tribes are welcome.** . We will prepare space for you! Also, if you believe in our ethos and mission and think it would be okay for you to support us, feel free to check our **Sponsorship Packages.** [ HERE](https://2140.wtf/content/51-sponsor) > **Any help is well appreciated!** As like a Cypherpunk's Movement, we truly respect our guests' privacy. Therefore, making pictures or video recordings will not be allowed during our events.  We will organize accreditation for professional photographers, so all good memories will be well documented. We hope you will understand our values and respect this rule as well. #PrivacyMatters  To make a long story short. We are waiting for you in London. Be prepared for an Atomic Vibe Experience . Be a part of the Peacefull Revolution. Remmember It always starts from YOU. Subscribe to our newsletter on our page to stay informed and up-to-date. Help us spread the word by sharing the link using the share button. Follow us also on all socials: [NOSTREE.me ](https://nostree.me/npub1hmqvn57wfm7qcygkt4et3qffhvdwyer9mkz0lyzjwr29438fe55s4r0s33/bcfestival) - NOSTR LinkTree [INSTAGRAM](http://instagram.com/2140.wtf) [TWETTER - X ](https://x.com/2140_wtf) [YOUTUBE](https://www.youtube.com/@2140_wtf) LINKS [BitcoinCulturefestival.com](https://bitcoinculturefestival.com) [bitcoinculturefestival.london](https://bitcoinculturefestival.london) [www.2140.wtf](https://2140.wtf) OUR PARNERS / SPONSORS [ANGOR](https://angor.io)  [BITCOIN EVENTS HQ](https://bitcoinonly.events/)  [YAKIHONNE](https://yakihonne.com/)  Hashtags #ArtGallery #ArtPanel #2140wtf #2140army #CyphermunkHouse #art #artstr #nostrart #craft #culture #music #bitcoin #nostr #TootingMarket #NostrLDN #NostrLondon #Foodst #Foodstrlondon #foodstrLDN #yakihonne
@ bec0c9d3:c4e9cd29
2024-10-06 14:07:27Hello, **Free People**! Last weeks we were very productive. Our team has reached a higher level. Ideas, designs, workflow - you name it. All of this to deliver you the best experience in the space. Where Open Source and Cypherpunk Ethos lead the way. [2140 COLLECTIVE ](https://2140.wtf) alongside with [CyphermunkHouse](https://primal.net/e/note1ae8947gzx4q38p9v2fuw3yn4d5sy5qy9x6uap6p9uf8hx9dl3e0qnkmazf) is proud to announce that Ours (Yours) festival will take place in ***LONDON / UK***. During Halloween/BitcoinWhitepaper weekend. ``` 29.OCT - 03.NOV 2024 ```  Please check [BITCOIN CULTURE FESTIVAL '24 AGENDA](https://2140.wtf/content/45-bitcoin-culture-week-full-agenda)Page for more updated info ! ``` All of this will not be possible without YOU. ``` If you want to join our crew, share some ideas, help, anything - feel free to contact us using the application forms, ready - waiting on the [main page.](http://2140.wtf) Forms are dedicated to [Volunteers](https://2140.wtf/content/49-volunteer-form) and [Artists](https://2140.wtf/content/40-art-submission) that can drop an Art for Phisical Gallery There will be also an Online auction that will display your art worldwide. Bitcoin pay only). We are also prepered forms for [#nostr panel](https://2140.wtf/content/41-nostr-participant-form) speakers who want to present any #nostr project, freedom tools, etc. [ART Panel](https://2140.wtf/content/42-panel-participant-form) Art, music, culture - stuff around our values, Bitcoin, and freedom, during friday and saturday events. If you wanna share you bitcoin story to isnpire otheres we invite you to visit us on free #TootingMarket Day where we preper Open Mic. [Let us know](https://2140.wtf/content/48-tooting-market-participant-form). On the market, which has already onboarded 20 Bitcoin merchants with food, drink, and veggy stalls, in beautiful London City. Please check out forms - maybe you will be the one, inspired enough to share your **knowledge** , **ideas** , and **spirit**. > **All tribes are welcome.** . We will prepare space for you! Also, if you believe in our ethos and mission and think it would be okay for you to support us, feel free to check our **Sponsorship Packages.** [ HERE](https://2140.wtf/content/51-sponsor) > **Any help is well appreciated!** As like a Cypherpunk's Movement, we truly respect our guests' privacy. Therefore, making pictures or video recordings will not be allowed during our events.  We will organize accreditation for professional photographers, so all good memories will be well documented. We hope you will understand our values and respect this rule as well. #PrivacyMatters  To make a long story short. We are waiting for you in London. Be prepared for an Atomic Vibe Experience . Be a part of the Peacefull Revolution. Remmember It always starts from YOU. Subscribe to our newsletter on our page to stay informed and up-to-date. Help us spread the word by sharing the link using the share button. Follow us also on all socials: [NOSTREE.me ](https://nostree.me/npub1hmqvn57wfm7qcygkt4et3qffhvdwyer9mkz0lyzjwr29438fe55s4r0s33/bcfestival) - NOSTR LinkTree [INSTAGRAM](http://instagram.com/2140.wtf) [TWETTER - X ](https://x.com/2140_wtf) [YOUTUBE](https://www.youtube.com/@2140_wtf) LINKS [BitcoinCulturefestival.com](https://bitcoinculturefestival.com) [bitcoinculturefestival.london](https://bitcoinculturefestival.london) [www.2140.wtf](https://2140.wtf) OUR PARNERS / SPONSORS [ANGOR](https://angor.io)  [BITCOIN EVENTS HQ](https://bitcoinonly.events/)  [YAKIHONNE](https://yakihonne.com/)  Hashtags #ArtGallery #ArtPanel #2140wtf #2140army #CyphermunkHouse #art #artstr #nostrart #craft #culture #music #bitcoin #nostr #TootingMarket #NostrLDN #NostrLondon #Foodst #Foodstrlondon #foodstrLDN #yakihonne @ 4ba8e86d:89d32de4
2024-10-05 22:04:32Como funciona o PGP. O texto a seguir foi retirado do capítulo 1 do documento Introdução à criptografia na documentação do PGP 6.5.1. Copyright © 1990-1999 Network Associates, Inc. Todos os direitos reservados. -O que é criptografia? -Criptografia forte -Como funciona a criptografia? -Criptografia convencional -Cifra de César -Gerenciamento de chaves e criptografia convencional -Criptografia de chave pública -Como funciona o PGP - Chaves • Assinaturas digitais -Funções hash • Certificados digitais -Distribuição de certificados -Formatos de certificado •Validade e confiança -Verificando validade -Estabelecendo confiança -Modelos de confiança • Revogação de certificado -Comunicar que um certificado foi revogado -O que é uma senha? -Divisão de chave Os princípios básicos da criptografia. Quando Júlio César enviou mensagens aos seus generais, ele não confiou nos seus mensageiros. Então ele substituiu cada A em suas mensagens por um D, cada B por um E, e assim por diante através do alfabeto. Somente alguém que conhecesse a regra “shift by 3” poderia decifrar suas mensagens. E assim começamos. Criptografia e descriptografia. Os dados que podem ser lidos e compreendidos sem quaisquer medidas especiais são chamados de texto simples ou texto não criptografado. O método de disfarçar o texto simples de forma a ocultar sua substância é chamado de criptografia. Criptografar texto simples resulta em um jargão ilegível chamado texto cifrado. Você usa criptografia para garantir que as informações sejam ocultadas de qualquer pessoa a quem não se destinam, mesmo daqueles que podem ver os dados criptografados. O processo de reverter o texto cifrado ao texto simples original é chamado de descriptografia . A Figura 1-1 ilustra esse processo. https://nostrcheck.me/media/public/nostrcheck.me_5922365650718442651699905288.webp Figura 1-1. Criptografia e descriptografia O que é criptografia? Criptografia é a ciência que usa a matemática para criptografar e descriptografar dados. A criptografia permite armazenar informações confidenciais ou transmiti-las através de redes inseguras (como a Internet) para que não possam ser lidas por ninguém, exceto pelo destinatário pretendido. Embora a criptografia seja a ciência que protege os dados, a criptoanálise é a ciência que analisa e quebra a comunicação segura. A criptoanálise clássica envolve uma combinação interessante de raciocínio analítico, aplicação de ferramentas matemáticas, descoberta de padrões, paciência, determinação e sorte. Os criptoanalistas também são chamados de atacantes. A criptologia abrange tanto a criptografia quanto a criptoanálise. Criptografia forte. "Existem dois tipos de criptografia neste mundo: a criptografia que impedirá a sua irmã mais nova de ler os seus arquivos, e a criptografia que impedirá os principais governos de lerem os seus arquivos. Este livro é sobre o último." --Bruce Schneier, Criptografia Aplicada: Protocolos, Algoritmos e Código Fonte em C. PGP também trata deste último tipo de criptografia. A criptografia pode ser forte ou fraca, conforme explicado acima. A força criptográfica é medida no tempo e nos recursos necessários para recuperar o texto simples. O resultado de uma criptografia forte é um texto cifrado que é muito difícil de decifrar sem a posse da ferramenta de decodificação apropriada. Quão díficil? Dado todo o poder computacional e o tempo disponível de hoje – mesmo um bilhão de computadores fazendo um bilhão de verificações por segundo – não é possível decifrar o resultado de uma criptografia forte antes do fim do universo. Alguém poderia pensar, então, que uma criptografia forte resistiria muito bem até mesmo contra um criptoanalista extremamente determinado. Quem pode realmente dizer? Ninguém provou que a criptografia mais forte disponível hoje resistirá ao poder computacional de amanhã. No entanto, a criptografia forte empregada pelo PGP é a melhor disponível atualmente. Contudo, a vigilância e o conservadorismo irão protegê-lo melhor do que as alegações de impenetrabilidade. Como funciona a criptografia? Um algoritmo criptográfico, ou cifra, é uma função matemática usada no processo de criptografia e descriptografia. Um algoritmo criptográfico funciona em combinação com uma chave – uma palavra, número ou frase – para criptografar o texto simples. O mesmo texto simples é criptografado em texto cifrado diferente com chaves diferentes. A segurança dos dados criptografados depende inteiramente de duas coisas: a força do algoritmo criptográfico e o sigilo da chave. Um algoritmo criptográfico, mais todas as chaves possíveis e todos os protocolos que o fazem funcionar constituem um criptossistema. PGP é um criptossistema. Criptografia convencional. Na criptografia convencional, também chamada de criptografia de chave secreta ou de chave simétrica , uma chave é usada tanto para criptografia quanto para descriptografia. O Data Encryption Standard (DES) é um exemplo de criptossistema convencional amplamente empregado pelo Governo Federal. A Figura 1-2 é uma ilustração do processo de criptografia convencional. https://nostrcheck.me/media/public/nostrcheck.me_1563316185075842071699905520.webp Figura 1-2. Criptografia convencional Cifra de César. Um exemplo extremamente simples de criptografia convencional é uma cifra de substituição. Uma cifra de substituição substitui uma informação por outra. Isso é feito com mais frequência compensando as letras do alfabeto. Dois exemplos são o Anel Decodificador Secreto do Capitão Meia-Noite, que você pode ter possuído quando era criança, e a cifra de Júlio César. Em ambos os casos, o algoritmo serve para compensar o alfabeto e a chave é o número de caracteres para compensá-lo. Por exemplo, se codificarmos a palavra "SEGREDO" usando o valor chave de César de 3, deslocaremos o alfabeto para que a terceira letra abaixo (D) comece o alfabeto. Então começando com A B C D E F G H I J K L M N O P Q R S T U V W X Y Z e deslizando tudo para cima em 3, você obtém DEFGHIJKLMNOPQRSTUVWXYZABC onde D=A, E=B, F=C e assim por diante. Usando este esquema, o texto simples, "SECRET" é criptografado como "VHFUHW". Para permitir que outra pessoa leia o texto cifrado, você diz a ela que a chave é 3. Obviamente, esta é uma criptografia extremamente fraca para os padrões atuais, mas, ei, funcionou para César e ilustra como funciona a criptografia convencional. Gerenciamento de chaves e criptografia convencional. A criptografia convencional tem benefícios. É muito rápido. É especialmente útil para criptografar dados que não vão a lugar nenhum. No entanto, a criptografia convencional por si só como meio de transmissão segura de dados pode ser bastante cara, simplesmente devido à dificuldade de distribuição segura de chaves. Lembre-se de um personagem do seu filme de espionagem favorito: a pessoa com uma pasta trancada e algemada ao pulso. Afinal, o que há na pasta? Provavelmente não é o código de lançamento de mísseis/fórmula de biotoxina/plano de invasão em si. É a chave que irá descriptografar os dados secretos. Para que um remetente e um destinatário se comuniquem com segurança usando criptografia convencional, eles devem chegar a um acordo sobre uma chave e mantê-la secreta entre si. Se estiverem em locais físicos diferentes, devem confiar em um mensageiro, no Bat Phone ou em algum outro meio de comunicação seguro para evitar a divulgação da chave secreta durante a transmissão. Qualquer pessoa que ouvir ou interceptar a chave em trânsito poderá posteriormente ler, modificar e falsificar todas as informações criptografadas ou autenticadas com essa chave. Do DES ao Anel Decodificador Secreto do Capitão Midnight, o problema persistente com a criptografia convencional é a distribuição de chaves: como você leva a chave ao destinatário sem que alguém a intercepte? Criptografia de chave pública. Os problemas de distribuição de chaves são resolvidos pela criptografia de chave pública, cujo conceito foi introduzido por Whitfield Diffie e Martin Hellman em 1975. (Há agora evidências de que o Serviço Secreto Britânico a inventou alguns anos antes de Diffie e Hellman, mas a manteve um segredo militar - e não fez nada com isso. [JH Ellis: The Possibility of Secure Non-Secret Digital Encryption, CESG Report, January 1970]) A criptografia de chave pública é um esquema assimétrico que usa um par de chaves para criptografia: uma chave pública, que criptografa os dados, e uma chave privada ou secreta correspondente para descriptografia. Você publica sua chave pública para o mundo enquanto mantém sua chave privada em segredo. Qualquer pessoa com uma cópia da sua chave pública pode criptografar informações que somente você pode ler. Até mesmo pessoas que você nunca conheceu. É computacionalmente inviável deduzir a chave privada da chave pública. Qualquer pessoa que possua uma chave pública pode criptografar informações, mas não pode descriptografá-las. Somente a pessoa que possui a chave privada correspondente pode descriptografar as informações. https://nostrcheck.me/media/public/nostrcheck.me_6137622541655550851699909180.webp Figura 1-3. Criptografia de chave pública O principal benefício da criptografia de chave pública é que ela permite que pessoas que não possuem nenhum acordo de segurança pré-existente troquem mensagens com segurança. A necessidade de remetente e destinatário compartilharem chaves secretas através de algum canal seguro é eliminada; todas as comunicações envolvem apenas chaves públicas e nenhuma chave privada é transmitida ou compartilhada. Alguns exemplos de criptossistemas de chave pública são Elgamal (nomeado em homenagem a seu inventor, Taher Elgamal), RSA (nomeado em homenagem a seus inventores, Ron Rivest, Adi Shamir e Leonard Adleman), Diffie-Hellman (nomeado, você adivinhou, em homenagem a seus inventores). ) e DSA, o algoritmo de assinatura digital (inventado por David Kravitz). Como a criptografia convencional já foi o único meio disponível para transmitir informações secretas, o custo dos canais seguros e da distribuição de chaves relegou a sua utilização apenas àqueles que podiam pagar, como governos e grandes bancos (ou crianças pequenas com anéis descodificadores secretos). A criptografia de chave pública é a revolução tecnológica que fornece criptografia forte para as massas adultas. Lembra do mensageiro com a pasta trancada e algemada ao pulso? A criptografia de chave pública o tira do mercado (provavelmente para seu alívio). Como funciona o PGP. O PGP combina alguns dos melhores recursos da criptografia convencional e de chave pública. PGP é um criptossistema híbrido. Quando um usuário criptografa texto simples com PGP, o PGP primeiro compacta o texto simples. A compactação de dados economiza tempo de transmissão do modem e espaço em disco e, mais importante ainda, fortalece a segurança criptográfica. A maioria das técnicas de criptoanálise explora padrões encontrados no texto simples para quebrar a cifra. A compressão reduz esses padrões no texto simples, aumentando assim enormemente a resistência à criptoanálise. (Arquivos que são muito curtos para compactar ou que não são compactados bem não são compactados.) O PGP então cria uma chave de sessão, que é uma chave secreta única. Esta chave é um número aleatório gerado a partir dos movimentos aleatórios do mouse e das teclas digitadas. Esta chave de sessão funciona com um algoritmo de criptografia convencional rápido e muito seguro para criptografar o texto simples; o resultado é texto cifrado. Depois que os dados são criptografados, a chave da sessão é criptografada na chave pública do destinatário. Essa chave de sessão criptografada com chave pública é transmitida junto com o texto cifrado ao destinatário. https://nostrcheck.me/media/public/nostrcheck.me_1978130242364857481699910331.webp Figura 1-4. Como funciona a criptografia PGP A descriptografia funciona ao contrário. A cópia do PGP do destinatário usa sua chave privada para recuperar a chave de sessão temporária, que o PGP usa para descriptografar o texto cifrado criptografado convencionalmente. https://nostrcheck.me/media/public/nostrcheck.me_1978130242364857481699910331.webp Figura 1-5. Como funciona a descriptografia PGP A combinação dos dois métodos de criptografia combina a conveniência da criptografia de chave pública com a velocidade da criptografia convencional. A criptografia convencional é cerca de 1.000 vezes mais rápida que a criptografia de chave pública. A criptografia de chave pública, por sua vez, fornece uma solução para problemas de distribuição de chaves e transmissão de dados. Usados em conjunto, o desempenho e a distribuição de chaves são melhorados sem qualquer sacrifício na segurança. Chaves. Uma chave é um valor que funciona com um algoritmo criptográfico para produzir um texto cifrado específico. As chaves são basicamente números muito, muito, muito grandes. O tamanho da chave é medido em bits; o número que representa uma chave de 1024 bits é enorme. Na criptografia de chave pública, quanto maior a chave, mais seguro é o texto cifrado. No entanto, o tamanho da chave pública e o tamanho da chave secreta da criptografia convencional não têm nenhuma relação. Uma chave convencional de 80 bits tem a força equivalente a uma chave pública de 1.024 bits. Uma chave convencional de 128 bits é equivalente a uma chave pública de 3.000 bits. Novamente, quanto maior a chave, mais segura, mas os algoritmos usados para cada tipo de criptografia são muito diferentes e, portanto, a comparação é como a de maçãs com laranjas. Embora as chaves pública e privada estejam matematicamente relacionadas, é muito difícil derivar a chave privada dada apenas a chave pública; no entanto, derivar a chave privada é sempre possível, desde que haja tempo e capacidade computacional suficientes. Isto torna muito importante escolher chaves do tamanho certo; grande o suficiente para ser seguro, mas pequeno o suficiente para ser aplicado rapidamente. Além disso, você precisa considerar quem pode estar tentando ler seus arquivos, quão determinados eles estão, quanto tempo têm e quais podem ser seus recursos. Chaves maiores serão criptograficamente seguras por um longo período de tempo. Se o que você deseja criptografar precisar ficar oculto por muitos anos, você pode usar uma chave muito grande. Claro, quem sabe quanto tempo levará para determinar sua chave usando os computadores mais rápidos e eficientes de amanhã? Houve um tempo em que uma chave simétrica de 56 bits era considerada extremamente segura. As chaves são armazenadas de forma criptografada. O PGP armazena as chaves em dois arquivos no seu disco rígido; um para chaves públicas e outro para chaves privadas. Esses arquivos são chamados de chaveiros. Ao usar o PGP, você normalmente adicionará as chaves públicas dos seus destinatários ao seu chaveiro público. Suas chaves privadas são armazenadas em seu chaveiro privado. Se você perder seu chaveiro privado, não será possível descriptografar nenhuma informação criptografada nas chaves desse anel. Assinaturas digitais. Um grande benefício da criptografia de chave pública é que ela fornece um método para empregar assinaturas digitais. As assinaturas digitais permitem ao destinatário da informação verificar a autenticidade da origem da informação e também verificar se a informação está intacta. Assim, as assinaturas digitais de chave pública fornecem autenticação e integridade de dados. A assinatura digital também proporciona o não repúdio, o que significa que evita que o remetente alegue que não enviou realmente as informações. Esses recursos são tão fundamentais para a criptografia quanto a privacidade, se não mais. Uma assinatura digital tem a mesma finalidade de uma assinatura manuscrita. No entanto, uma assinatura manuscrita é fácil de falsificar. Uma assinatura digital é superior a uma assinatura manuscrita porque é quase impossível de ser falsificada, além de atestar o conteúdo da informação, bem como a identidade do signatário. Algumas pessoas tendem a usar mais assinaturas do que criptografia. Por exemplo, você pode não se importar se alguém souber que você acabou de depositar US$ 1.000 em sua conta, mas quer ter certeza de que foi o caixa do banco com quem você estava lidando. A maneira básica pela qual as assinaturas digitais são criadas é ilustrada na Figura 1-6 . Em vez de criptografar informações usando a chave pública de outra pessoa, você as criptografa com sua chave privada. Se as informações puderem ser descriptografadas com sua chave pública, elas deverão ter se originado em você. https://nostrcheck.me/media/public/nostrcheck.me_4033165715613998201699910446.webp Figura 1-6. Assinaturas digitais simples Funções hash. O sistema descrito acima apresenta alguns problemas. É lento e produz um enorme volume de dados – pelo menos o dobro do tamanho da informação original. Uma melhoria no esquema acima é a adição de uma função hash unidirecional no processo. Uma função hash unidirecional recebe uma entrada de comprimento variável – neste caso, uma mensagem de qualquer comprimento, até mesmo milhares ou milhões de bits – e produz uma saída de comprimento fixo; digamos, 160 bits. A função hash garante que, se a informação for alterada de alguma forma – mesmo que por apenas um bit – seja produzido um valor de saída totalmente diferente. O PGP usa uma função hash criptograficamente forte no texto simples que o usuário está assinando. Isso gera um item de dados de comprimento fixo conhecido como resumo da mensagem. (Novamente, qualquer alteração nas informações resulta em um resumo totalmente diferente.) Então o PGP usa o resumo e a chave privada para criar a “assinatura”. O PGP transmite a assinatura e o texto simples juntos. Ao receber a mensagem, o destinatário utiliza o PGP para recalcular o resumo, verificando assim a assinatura. O PGP pode criptografar o texto simples ou não; assinar texto simples é útil se alguns dos destinatários não estiverem interessados ou não forem capazes de verificar a assinatura. Desde que uma função hash segura seja usada, não há como retirar a assinatura de alguém de um documento e anexá-la a outro, ou alterar uma mensagem assinada de qualquer forma. A menor alteração em um documento assinado causará falha no processo de verificação da assinatura digital. https://nostrcheck.me/media/public/nostrcheck.me_2943209062439984111699910538.webp Figura 1-7. Assinaturas digitais seguras As assinaturas digitais desempenham um papel importante na autenticação e validação de chaves de outros usuários PGP. Certificados digitais. Um problema com os criptosistemas de chave pública é que os usuários devem estar constantemente vigilantes para garantir que estão criptografando com a chave da pessoa correta. Num ambiente onde é seguro trocar chaves livremente através de servidores públicos, os ataques man-in-the-middle são uma ameaça potencial. Neste tipo de ataque, alguém publica uma chave falsa com o nome e ID de usuário do destinatário pretendido. Os dados criptografados – e interceptados por – o verdadeiro proprietário desta chave falsa estão agora em mãos erradas. Em um ambiente de chave pública, é vital que você tenha certeza de que a chave pública para a qual você está criptografando os dados é de fato a chave pública do destinatário pretendido e não uma falsificação. Você pode simplesmente criptografar apenas as chaves que foram entregues fisicamente a você. Mas suponha que você precise trocar informações com pessoas que nunca conheceu; como você pode saber se tem a chave correta? Os certificados digitais, ou certs, simplificam a tarefa de estabelecer se uma chave pública realmente pertence ao suposto proprietário. Um certificado é uma forma de credencial. Exemplos podem ser sua carteira de motorista, seu cartão de previdência social ou sua certidão de nascimento. Cada um deles contém algumas informações que identificam você e alguma autorização informando que outra pessoa confirmou sua identidade. Alguns certificados, como o seu passaporte, são uma confirmação importante o suficiente da sua identidade para que você não queira perdê-los, para que ninguém os use para se passar por você. Um certificado digital são dados que funcionam como um certificado físico. Um certificado digital é uma informação incluída na chave pública de uma pessoa que ajuda outras pessoas a verificar se uma chave é genuína ou válida. Os certificados digitais são usados para impedir tentativas de substituir a chave de uma pessoa por outra. Um certificado digital consiste em três coisas: ● Uma chave pública. ● Informações do certificado. (Informações de "identidade" sobre o usuário, como nome, ID do usuário e assim por diante.) ● Uma ou mais assinaturas digitais. O objetivo da assinatura digital em um certificado é afirmar que as informações do certificado foram atestadas por alguma outra pessoa ou entidade. A assinatura digital não atesta a autenticidade do certificado como um todo; ele atesta apenas que as informações de identidade assinadas acompanham ou estão vinculadas à chave pública. Assim, um certificado é basicamente uma chave pública com uma ou duas formas de identificação anexadas, além de um forte selo de aprovação de algum outro indivíduo confiável. https://nostrcheck.me/media/public/nostrcheck.me_7979578982089845401699910854.webp Figura 1-8. Anatomia de um certificado PGP Distribuição de certificados. Os certificados são utilizados quando é necessário trocar chaves públicas com outra pessoa. Para pequenos grupos de pessoas que desejam se comunicar com segurança, é fácil trocar manualmente disquetes ou e-mails contendo a chave pública de cada proprietário. Esta é a distribuição manual de chave pública e é prática apenas até certo ponto. Além desse ponto, é necessário implementar sistemas que possam fornecer os mecanismos necessários de segurança, armazenamento e troca para que colegas de trabalho, parceiros de negócios ou estranhos possam se comunicar, se necessário. Eles podem vir na forma de repositórios somente de armazenamento, chamados Servidores de Certificados, ou sistemas mais estruturados que fornecem recursos adicionais de gerenciamento de chaves e são chamados de Infraestruturas de Chave Pública (PKIs). Servidores de certificados. Um servidor de certificados, também chamado de servidor certificado ou servidor de chaves, é um banco de dados que permite aos usuários enviar e recuperar certificados digitais. Um servidor certificado geralmente fornece alguns recursos administrativos que permitem que uma empresa mantenha suas políticas de segurança – por exemplo, permitindo que apenas as chaves que atendam a determinados requisitos sejam armazenadas. Infraestruturas de Chave Pública. Uma PKI contém os recursos de armazenamento de certificados de um servidor de certificados, mas também fornece recursos de gerenciamento de certificados (a capacidade de emitir, revogar, armazenar, recuperar e confiar em certificados). A principal característica de uma PKI é a introdução do que é conhecido como Autoridade Certificadora,ou CA, que é uma entidade humana — uma pessoa, grupo, departamento, empresa ou outra associação — que uma organização autorizou a emitir certificados para seus usuários de computador. (A função de uma CA é análoga à do Passport Office do governo de um país.) Uma CA cria certificados e os assina digitalmente usando a chave privada da CA. Devido ao seu papel na criação de certificados, a CA é o componente central de uma PKI. Usando a chave pública da CA, qualquer pessoa que queira verificar a autenticidade de um certificado verifica a assinatura digital da CA emissora e, portanto, a integridade do conteúdo do certificado (mais importante ainda, a chave pública e a identidade do titular do certificado). Formatos de certificado. Um certificado digital é basicamente uma coleção de informações de identificação vinculadas a uma chave pública e assinadas por um terceiro confiável para provar sua autenticidade. Um certificado digital pode ter vários formatos diferentes. O PGP reconhece dois formatos de certificado diferentes: ● Certificados PGP ● Certificados X.509 Formato do certificado PGP. Um certificado PGP inclui (mas não está limitado a) as seguintes informações: ● O número da versão do PGP — identifica qual versão do PGP foi usada para criar a chave associada ao certificado. A chave pública do titular do certificado — a parte pública do seu par de chaves, juntamente com o algoritmo da chave: RSA, DH (Diffie-Hellman) ou DSA (Algoritmo de Assinatura Digital). ● As informações do detentor do certificado — consistem em informações de “identidade” sobre o usuário, como seu nome, ID de usuário, fotografia e assim por diante. ● A assinatura digital do proprietário do certificado — também chamada de autoassinatura, é a assinatura que utiliza a chave privada correspondente da chave pública associada ao certificado. ● O período de validade do certificado — a data/hora de início e a data/hora de expiração do certificado; indica quando o certificado irá expirar. ● O algoritmo de criptografia simétrica preferido para a chave — indica o algoritmo de criptografia para o qual o proprietário do certificado prefere que as informações sejam criptografadas. Os algoritmos suportados são CAST, IDEA ou Triple-DES. Você pode pensar em um certificado PGP como uma chave pública com um ou mais rótulos vinculados a ele (veja a Figura 1.9 ). Nessas 'etiquetas' você encontrará informações que identificam o proprietário da chave e uma assinatura do proprietário da chave, que afirma que a chave e a identificação andam juntas. (Essa assinatura específica é chamada de autoassinatura; todo certificado PGP contém uma autoassinatura.) Um aspecto único do formato de certificado PGP é que um único certificado pode conter múltiplas assinaturas. Várias ou muitas pessoas podem assinar o par chave/identificação para atestar a sua própria garantia de que a chave pública pertence definitivamente ao proprietário especificado. Se você procurar em um servidor de certificados público, poderá notar que certos certificados, como o do criador do PGP, Phil Zimmermann, contêm muitas assinaturas. Alguns certificados PGP consistem em uma chave pública com vários rótulos, cada um contendo um meio diferente de identificar o proprietário da chave (por exemplo, o nome do proprietário e a conta de e-mail corporativa, o apelido do proprietário e a conta de e-mail residencial, uma fotografia do proprietário — tudo em um certificado). A lista de assinaturas de cada uma dessas identidades pode ser diferente; as assinaturas atestam a autenticidade de que um dos rótulos pertence à chave pública, e não que todos os rótulos da chave sejam autênticos. (Observe que 'autêntico' está nos olhos de quem vê - assinaturas são opiniões, e diferentes pessoas dedicam diferentes níveis de devida diligência na verificação da autenticidade antes de assinar uma chave.) https://nostrcheck.me/media/public/nostrcheck.me_7979578982089845401699910854.webp Figura 1-9. Um certificado PGP Formato de certificado X.509. X.509 é outro formato de certificado muito comum. Todos os certificados X.509 estão em conformidade com o padrão internacional ITU-T X.509; assim (teoricamente) os certificados X.509 criados para um aplicativo podem ser usados por qualquer aplicativo compatível com X.509. Na prática, porém, diferentes empresas criaram suas próprias extensões para certificados X.509, e nem todas funcionam juntas. Um certificado exige que alguém valide que uma chave pública e o nome do proprietário da chave andam juntos. Com os certificados PGP, qualquer pessoa pode desempenhar o papel de validador. Com certificados X.509, o validador é sempre uma Autoridade Certificadora ou alguém designado por uma CA. (Tenha em mente que os certificados PGP também suportam totalmente uma estrutura hierárquica usando uma CA para validar certificados.) Um certificado X.509 é uma coleção de um conjunto padrão de campos contendo informações sobre um usuário ou dispositivo e sua chave pública correspondente. O padrão X.509 define quais informações vão para o certificado e descreve como codificá-lo (o formato dos dados). Todos os certificados X.509 possuem os seguintes dados: O número da versão X.509 — identifica qual versão do padrão X.509 se aplica a este certificado, o que afeta quais informações podem ser especificadas nele. A mais atual é a versão 3. A chave pública do titular do certificado — a chave pública do titular do certificado, juntamente com um identificador de algoritmo que especifica a qual sistema criptográfico a chave pertence e quaisquer parâmetros de chave associados. O número de série do certificado — a entidade (aplicação ou pessoa) que criou o certificado é responsável por atribuir-lhe um número de série único para distingui-lo de outros certificados que emite. Esta informação é usada de diversas maneiras; por exemplo, quando um certificado é revogado, seu número de série é colocado em uma Lista de Revogação de Certificados ou CRL. O identificador exclusivo do detentor do certificado — (ou DN — nome distinto). Este nome pretende ser exclusivo na Internet. Este nome pretende ser exclusivo na Internet. Um DN consiste em múltiplas subseções e pode ser parecido com isto: CN=Bob Allen, OU=Divisão Total de Segurança de Rede, O=Network Associates, Inc., C=EUA (Referem-se ao nome comum, à unidade organizacional, à organização e ao país do sujeito .) O período de validade do certificado — a data/hora de início e a data/hora de expiração do certificado; indica quando o certificado irá expirar. O nome exclusivo do emissor do certificado — o nome exclusivo da entidade que assinou o certificado. Normalmente é uma CA. A utilização do certificado implica confiar na entidade que assinou este certificado. (Observe que em alguns casos, como certificados de CA raiz ou de nível superior , o emissor assina seu próprio certificado.) A assinatura digital do emitente — a assinatura utilizando a chave privada da entidade que emitiu o certificado. O identificador do algoritmo de assinatura — identifica o algoritmo usado pela CA para assinar o certificado. Existem muitas diferenças entre um certificado X.509 e um certificado PGP, mas as mais importantes são as seguintes: você pode criar seu próprio certificado PGP; ● você deve solicitar e receber um certificado X.509 de uma autoridade de certificação ● Os certificados X.509 suportam nativamente apenas um único nome para o proprietário da chave ● Os certificados X.509 suportam apenas uma única assinatura digital para atestar a validade da chave Para obter um certificado X.509, você deve solicitar a uma CA a emissão de um certificado. Você fornece sua chave pública, prova de que possui a chave privada correspondente e algumas informações específicas sobre você. Em seguida, você assina digitalmente as informações e envia o pacote completo – a solicitação de certificado – para a CA. A CA então realiza algumas diligências para verificar se as informações fornecidas estão corretas e, em caso afirmativo, gera o certificado e o devolve. Você pode pensar em um certificado X.509 como um certificado de papel padrão (semelhante ao que você recebeu ao concluir uma aula de primeiros socorros básicos) com uma chave pública colada nele. Ele contém seu nome e algumas informações sobre você, além da assinatura da pessoa que o emitiu para você. https://nostrcheck.me/media/public/nostrcheck.me_4125576093727079591699911294.webp Figura 1-10. Um certificado X.509 Provavelmente, o uso mais visível dos certificados X.509 atualmente é em navegadores da web. Validade e confiança Cada usuário em um sistema de chave pública está vulnerável a confundir uma chave falsa (certificado) com uma chave real. Validade é a confiança de que um certificado de chave pública pertence ao seu suposto proprietário. A validade é essencial em um ambiente de chave pública onde você deve estabelecer constantemente se um determinado certificado é autêntico ou não. Depois de ter certeza de que um certificado pertencente a outra pessoa é válido, você pode assinar a cópia em seu chaveiro para atestar que verificou o certificado e que ele é autêntico. Se quiser que outras pessoas saibam que você deu ao certificado seu selo de aprovação, você pode exportar a assinatura para um servidor de certificados para que outras pessoas possam vê-la. Conforme descrito na seção Infraestruturas de Chave Pública , algumas empresas designam uma ou mais Autoridades de Certificação (CAs) para indicar a validade do certificado. Em uma organização que usa uma PKI com certificados X.509, é função da CA emitir certificados aos usuários — um processo que geralmente envolve responder à solicitação de certificado do usuário. Em uma organização que usa certificados PGP sem PKI, é função da CA verificar a autenticidade de todos os certificados PGP e depois assinar os bons. Basicamente, o objetivo principal de uma CA é vincular uma chave pública às informações de identificação contidas no certificado e, assim, garantir a terceiros que algum cuidado foi tomado para garantir que esta ligação das informações de identificação e da chave seja válida. O CA é o Grand Pooh-bah da validação em uma organização; alguém em quem todos confiam e, em algumas organizações, como aquelas que utilizam uma PKI, nenhum certificado é considerado válido, a menos que tenha sido assinado por uma CA confiável. Verificando validade. Uma maneira de estabelecer a validade é passar por algum processo manual. Existem várias maneiras de fazer isso. Você pode exigir que o destinatário pretendido lhe entregue fisicamente uma cópia de sua chave pública. Mas isto é muitas vezes inconveniente e ineficiente. Outra forma é verificar manualmente a impressão digital do certificado. Assim como as impressões digitais de cada ser humano são únicas, a impressão digital de cada certificado PGP é única. A impressão digital é um hash do certificado do usuário e aparece como uma das propriedades do certificado. No PGP, a impressão digital pode aparecer como um número hexadecimal ou uma série das chamadas palavras biométricas, que são foneticamente distintas e são usadas para facilitar um pouco o processo de identificação da impressão digital. Você pode verificar se um certificado é válido ligando para o proprietário da chave (para que você origine a transação) e pedindo ao proprietário que leia a impressão digital de sua chave para você e compare essa impressão digital com aquela que você acredita ser a verdadeira. Isso funciona se você conhece a voz do proprietário, mas como verificar manualmente a identidade de alguém que você não conhece? Algumas pessoas colocam a impressão digital de sua chave em seus cartões de visita exatamente por esse motivo. Outra forma de estabelecer a validade do certificado de alguém é confiar que um terceiro indivíduo passou pelo processo de validação do mesmo. Uma CA, por exemplo, é responsável por garantir que, antes de emitir um certificado, ele ou ela o verifique cuidadosamente para ter certeza de que a parte da chave pública realmente pertence ao suposto proprietário. Qualquer pessoa que confie na CA considerará automaticamente quaisquer certificados assinados pela CA como válidos. Outro aspecto da verificação da validade é garantir que o certificado não foi revogado. Para obter mais informações, consulte a seção Revogação de certificado . Estabelecendo confiança. Você valida certificados. Você confia nas pessoas. Mais especificamente, você confia nas pessoas para validar os certificados de outras pessoas. Normalmente, a menos que o proprietário lhe entregue o certificado, você terá que confiar na palavra de outra pessoa de que ele é válido. Introdutores meta e confiáveis. Na maioria das situações, as pessoas confiam completamente na CA para estabelecer a validade dos certificados. Isso significa que todos os demais dependem da CA para passar por todo o processo de validação manual. Isso é aceitável até um certo número de usuários ou locais de trabalho e, então, não é possível para a AC manter o mesmo nível de validação de qualidade. Nesse caso, é necessário adicionar outros validadores ao sistema. Um CA também pode ser um meta- introdutor. Um meta-introdutor confere não apenas validade às chaves, mas também confere a capacidade de confiar nas chaves a outros. Semelhante ao rei que entrega seu selo a seus conselheiros de confiança para que eles possam agir de acordo com sua autoridade, o meta-introdutor permite que outros atuem como introdutores de confiança. Esses introdutores confiáveis podem validar chaves com o mesmo efeito do meta-introdutor. Eles não podem, entretanto, criar novos introdutores confiáveis. Meta-introdutor e introdutor confiável são termos PGP. Em um ambiente X.509, o meta-introdutor é chamado de Autoridade de Certificação raiz ( CA raiz) e os introdutores confiáveis são Autoridades de Certificação subordinadas . A CA raiz usa a chave privada associada a um tipo de certificado especial denominado certificado CA raiz para assinar certificados. Qualquer certificado assinado pelo certificado CA raiz é visto como válido por qualquer outro certificado assinado pela raiz. Este processo de validação funciona mesmo para certificados assinados por outras CAs no sistema — desde que o certificado da CA raiz tenha assinado o certificado da CA subordinada, qualquer certificado assinado pela CA será considerado válido para outras pessoas dentro da hierarquia. Este processo de verificação de backup por meio do sistema para ver quem assinou cujo certificado é chamado de rastreamento de um caminho de certificação ou cadeia de certificação. Modelos de confiança. Em sistemas relativamente fechados, como em uma pequena empresa, é fácil rastrear um caminho de certificação até a CA raiz. No entanto, os usuários muitas vezes precisam se comunicar com pessoas fora do seu ambiente corporativo, incluindo algumas que nunca conheceram, como fornecedores, consumidores, clientes, associados e assim por diante. É difícil estabelecer uma linha de confiança com aqueles em quem sua CA não confia explicitamente. As empresas seguem um ou outro modelo de confiança, que determina como os usuários irão estabelecer a validade do certificado. Existem três modelos diferentes: Confiança Direta. Confiança Hierárquica Uma teia de confiança Confiança direta A confiança direta é o modelo de confiança mais simples. Neste modelo, um usuário confia que uma chave é válida porque sabe de onde ela veio. Todos os criptosistemas usam essa forma de confiança de alguma forma. Por exemplo, em navegadores da Web, as chaves raiz da Autoridade de Certificação são diretamente confiáveis porque foram enviadas pelo fabricante. Se houver alguma forma de hierarquia, ela se estenderá a partir desses certificados diretamente confiáveis. No PGP, um usuário que valida as chaves e nunca define outro certificado para ser um introdutor confiável está usando confiança direta. https://nostrcheck.me/media/public/nostrcheck.me_4681914789296468891699911522.webp Figura 1-11. Confiança direta Confiança Hierárquica. Em um sistema hierárquico, há vários certificados "raiz" a partir dos quais a confiança se estende. Esses certificados podem certificar eles próprios certificados ou podem certificar certificados que certificam ainda outros certificados em alguma cadeia. Considere isso como uma grande “árvore” de confiança. A validade do certificado "folha" é verificada rastreando desde seu certificador até outros certificadores, até que um certificado raiz diretamente confiável seja encontrado. https://nostrcheck.me/media/public/nostrcheck.me_2764578291212045251699911580.webp Figura 1-12. Confiança hierárquica Teia de Confiança. Uma teia de confiança abrange ambos os outros modelos, mas também acrescenta a noção de que a confiança está nos olhos de quem vê (que é a visão do mundo real) e a ideia de que mais informação é melhor. É, portanto, um modelo de confiança cumulativa. Um certificado pode ser confiável diretamente ou confiável em alguma cadeia que remonta a um certificado raiz diretamente confiável (o meta-introdutor) ou por algum grupo de introdutores. Talvez você já tenha ouvido falar do termo seis graus de separação, que sugere que qualquer pessoa no mundo pode determinar algum vínculo com qualquer outra pessoa no mundo usando seis ou menos outras pessoas como intermediários. Esta é uma teia de introdutores. É também a visão de confiança do PGP. PGP usa assinaturas digitais como forma de introdução. Quando qualquer usuário assina a chave de outro, ele ou ela se torna o introdutor dessa chave. À medida que esse processo avança, ele estabelece uma rede de confiança. Em um ambiente PGP, qualquer usuário pode atuar como autoridade certificadora. Qualquer usuário PGP pode validar o certificado de chave pública de outro usuário PGP. No entanto, tal certificado só é válido para outro usuário se a parte confiável reconhecer o validador como um introdutor confiável. (Ou seja, você confia na minha opinião de que as chaves dos outros são válidas apenas se você me considerar um apresentador confiável. Caso contrário, minha opinião sobre a validade das outras chaves é discutível.) Armazenados no chaveiro público de cada usuário estão indicadores de ● se o usuário considera ou não uma chave específica válida ● o nível de confiança que o usuário deposita na chave que o proprietário da chave pode servir como certificador das chaves de terceiros Você indica, na sua cópia da minha chave, se acha que meu julgamento conta. Na verdade, é um sistema de reputação: certas pessoas têm a reputação de fornecer boas assinaturas e as pessoas confiam nelas para atestar a validade de outras chaves. Níveis de confiança no PGP. O nível mais alto de confiança em uma chave, a confiança implícita , é a confiança em seu próprio par de chaves. O PGP assume que se você possui a chave privada, você deve confiar nas ações da sua chave pública relacionada. Quaisquer chaves assinadas pela sua chave implicitamente confiável são válidas. Existem três níveis de confiança que você pode atribuir à chave pública de outra pessoa: ● Confiança total ● Confiança marginal ● Não confiável (ou não confiável) Para tornar as coisas confusas, também existem três níveis de validade: ● Válido ● Marginalmente válido ● Inválido Para definir a chave de outra pessoa como um introdutor confiável, você 1. Comece com uma chave válida, que seja. - assinado por você ou - assinado por outro apresentador confiável e então 2. Defina o nível de confiança que você acha que o proprietário da chave tem direito. Por exemplo, suponha que seu chaveiro contenha a chave de Alice. Você validou a chave de Alice e indica isso assinando-a. Você sabe que Alice é uma verdadeira defensora da validação de chaves de outras pessoas. Portanto, você atribui a chave dela com confiança total. Isso faz de Alice uma Autoridade Certificadora. Se Alice assinar a chave de outra pessoa, ela aparecerá como Válida em seu chaveiro. O PGP requer uma assinatura Totalmente confiável ou duas assinaturas Marginalmente confiáveis para estabelecer uma chave como válida. O método do PGP de considerar dois Marginais iguais a um Completo é semelhante a um comerciante que solicita duas formas de identificação. Você pode considerar Alice bastante confiável e também considerar Bob bastante confiável. Qualquer um deles sozinho corre o risco de assinar acidentalmente uma chave falsificada, portanto, você pode não depositar total confiança em nenhum deles. No entanto, as probabilidades de ambos os indivíduos terem assinado a mesma chave falsa são provavelmente pequenas. Revogação de certificado. Os certificados só são úteis enquanto são válidos. Não é seguro simplesmente presumir que um certificado é válido para sempre. Na maioria das organizações e em todas as PKIs, os certificados têm uma vida útil restrita. Isso restringe o período em que um sistema fica vulnerável caso ocorra um comprometimento do certificado. Os certificados são assim criados com um período de validade programado: uma data/hora de início e uma data/hora de expiração. Espera-se que o certificado seja utilizável durante todo o seu período de validade (seu tempo de vida ). Quando o certificado expirar, ele não será mais válido, pois a autenticidade do seu par chave/identificação não estará mais garantida. (O certificado ainda pode ser usado com segurança para reconfirmar informações que foram criptografadas ou assinadas dentro do período de validade – no entanto, ele não deve ser confiável para tarefas criptográficas futuras.) Existem também situações em que é necessário invalidar um certificado antes da sua data de expiração, como quando o titular do certificado termina o contrato de trabalho com a empresa ou suspeita que a chave privada correspondente do certificado foi comprometida. Isso é chamado de revogação. Um certificado revogado é muito mais suspeito do que um certificado expirado. Os certificados expirados são inutilizáveis, mas não apresentam a mesma ameaça de comprometimento que um certificado revogado. Qualquer pessoa que tenha assinado um certificado pode revogar a sua assinatura no certificado (desde que utilize a mesma chave privada que criou a assinatura). Uma assinatura revogada indica que o signatário não acredita mais que a chave pública e as informações de identificação pertencem uma à outra, ou que a chave pública do certificado (ou a chave privada correspondente) foi comprometida. Uma assinatura revogada deve ter quase tanto peso quanto um certificado revogado. Com certificados X.509, uma assinatura revogada é praticamente igual a um certificado revogado, visto que a única assinatura no certificado é aquela que o tornou válido em primeiro lugar – a assinatura da CA. Os certificados PGP fornecem o recurso adicional de que você pode revogar todo o seu certificado (não apenas as assinaturas nele) se você achar que o certificado foi comprometido. Somente o proprietário do certificado (o detentor da chave privada correspondente) ou alguém que o proprietário do certificado tenha designado como revogador pode revogar um certificado PGP. (Designar um revogador é uma prática útil, pois muitas vezes é a perda da senha da chave privada correspondente do certificado que leva um usuário PGP a revogar seu certificado - uma tarefa que só é possível se alguém tiver acesso à chave privada. ) Somente o emissor do certificado pode revogar um certificado X.509. Comunicar que um certificado foi revogado. Quando um certificado é revogado, é importante conscientizar os usuários potenciais do certificado de que ele não é mais válido. Com certificados PGP, a maneira mais comum de comunicar que um certificado foi revogado é publicá-lo em um servidor de certificados para que outras pessoas que desejem se comunicar com você sejam avisadas para não usar essa chave pública. Em um ambiente PKI, a comunicação de certificados revogados é mais comumente obtida por meio de uma estrutura de dados chamada Lista de Revogação de Certificados, ou CRL, que é publicada pela CA. A CRL contém uma lista validada com carimbo de data e hora de todos os certificados revogados e não expirados no sistema. Os certificados revogados permanecem na lista apenas até expirarem e, em seguida, são removidos da lista — isso evita que a lista fique muito longa. A CA distribui a CRL aos usuários em algum intervalo programado regularmente (e potencialmente fora do ciclo, sempre que um certificado é revogado). Teoricamente, isso impedirá que os usuários usem involuntariamente um certificado comprometido. É possível, no entanto, que haja um período de tempo entre as CRLs em que um certificado recentemente comprometido seja usado. O que é uma senha? A maioria das pessoas está familiarizada com a restrição de acesso a sistemas de computador por meio de uma senha, que é uma sequência única de caracteres que um usuário digita como código de identificação. Uma senha longa é uma versão mais longa de uma senha e, em teoria, mais segura. Normalmente composta por várias palavras, uma frase secreta é mais segura contra ataques de dicionário padrão, em que o invasor tenta todas as palavras do dicionário na tentativa de determinar sua senha. As melhores senhas são relativamente longas e complexas e contêm uma combinação de letras maiúsculas e minúsculas, caracteres numéricos e de pontuação. O PGP usa uma senha para criptografar sua chave privada em sua máquina. Sua chave privada é criptografada em seu disco usando um hash de sua senha como chave secreta. Você usa a senha para descriptografar e usar sua chave privada. Uma senha deve ser difícil de esquecer e difícil de ser adivinhada por outras pessoas. Deve ser algo já firmemente enraizado na sua memória de longo prazo, em vez de algo que você invente do zero. Por que? Porque se você esquecer sua senha, você estará sem sorte. Sua chave privada é total e absolutamente inútil sem sua senha e nada pode ser feito a respeito. Lembra-se da citação anterior neste capítulo? https://nostrcheck.me/media/public/nostrcheck.me_5284734693832771181699911783.webp PGP é a criptografia que manterá os principais governos fora dos seus arquivos. Certamente também o manterá fora de seus arquivos. Tenha isso em mente quando decidir alterar sua senha para a piada daquela piada que você nunca consegue lembrar. Divisão de chave. Dizem que um segredo não é segredo se for conhecido por mais de uma pessoa. Compartilhar um par de chaves privadas representa um grande problema. Embora não seja uma prática recomendada, às vezes é necessário compartilhar um par de chaves privadas. Chaves de assinatura corporativa, por exemplo, são chaves privadas usadas por uma empresa para assinar – por exemplo – documentos legais, informações pessoais confidenciais ou comunicados de imprensa para autenticar sua origem. Nesse caso, vale a pena que vários membros da empresa tenham acesso à chave privada. No entanto, isto significa que qualquer indivíduo pode agir plenamente em nome da empresa. Nesse caso, é aconselhável dividir a chave entre várias pessoas, de modo que mais de uma ou duas pessoas apresentem um pedaço da chave para reconstituí-la em condições utilizáveis. Se poucas peças da chave estiverem disponíveis, a chave ficará inutilizável. Alguns exemplos são dividir uma chave em três partes e exigir duas delas para reconstituir a chave, ou dividi-la em duas partes e exigir ambas as peças. Se uma conexão de rede segura for usada durante o processo de reconstituição, os acionistas da chave não precisam estar fisicamente presentes para aderirem novamente à chave.
@ 4ba8e86d:89d32de4
2024-10-05 22:04:32Como funciona o PGP. O texto a seguir foi retirado do capítulo 1 do documento Introdução à criptografia na documentação do PGP 6.5.1. Copyright © 1990-1999 Network Associates, Inc. Todos os direitos reservados. -O que é criptografia? -Criptografia forte -Como funciona a criptografia? -Criptografia convencional -Cifra de César -Gerenciamento de chaves e criptografia convencional -Criptografia de chave pública -Como funciona o PGP - Chaves • Assinaturas digitais -Funções hash • Certificados digitais -Distribuição de certificados -Formatos de certificado •Validade e confiança -Verificando validade -Estabelecendo confiança -Modelos de confiança • Revogação de certificado -Comunicar que um certificado foi revogado -O que é uma senha? -Divisão de chave Os princípios básicos da criptografia. Quando Júlio César enviou mensagens aos seus generais, ele não confiou nos seus mensageiros. Então ele substituiu cada A em suas mensagens por um D, cada B por um E, e assim por diante através do alfabeto. Somente alguém que conhecesse a regra “shift by 3” poderia decifrar suas mensagens. E assim começamos. Criptografia e descriptografia. Os dados que podem ser lidos e compreendidos sem quaisquer medidas especiais são chamados de texto simples ou texto não criptografado. O método de disfarçar o texto simples de forma a ocultar sua substância é chamado de criptografia. Criptografar texto simples resulta em um jargão ilegível chamado texto cifrado. Você usa criptografia para garantir que as informações sejam ocultadas de qualquer pessoa a quem não se destinam, mesmo daqueles que podem ver os dados criptografados. O processo de reverter o texto cifrado ao texto simples original é chamado de descriptografia . A Figura 1-1 ilustra esse processo. https://nostrcheck.me/media/public/nostrcheck.me_5922365650718442651699905288.webp Figura 1-1. Criptografia e descriptografia O que é criptografia? Criptografia é a ciência que usa a matemática para criptografar e descriptografar dados. A criptografia permite armazenar informações confidenciais ou transmiti-las através de redes inseguras (como a Internet) para que não possam ser lidas por ninguém, exceto pelo destinatário pretendido. Embora a criptografia seja a ciência que protege os dados, a criptoanálise é a ciência que analisa e quebra a comunicação segura. A criptoanálise clássica envolve uma combinação interessante de raciocínio analítico, aplicação de ferramentas matemáticas, descoberta de padrões, paciência, determinação e sorte. Os criptoanalistas também são chamados de atacantes. A criptologia abrange tanto a criptografia quanto a criptoanálise. Criptografia forte. "Existem dois tipos de criptografia neste mundo: a criptografia que impedirá a sua irmã mais nova de ler os seus arquivos, e a criptografia que impedirá os principais governos de lerem os seus arquivos. Este livro é sobre o último." --Bruce Schneier, Criptografia Aplicada: Protocolos, Algoritmos e Código Fonte em C. PGP também trata deste último tipo de criptografia. A criptografia pode ser forte ou fraca, conforme explicado acima. A força criptográfica é medida no tempo e nos recursos necessários para recuperar o texto simples. O resultado de uma criptografia forte é um texto cifrado que é muito difícil de decifrar sem a posse da ferramenta de decodificação apropriada. Quão díficil? Dado todo o poder computacional e o tempo disponível de hoje – mesmo um bilhão de computadores fazendo um bilhão de verificações por segundo – não é possível decifrar o resultado de uma criptografia forte antes do fim do universo. Alguém poderia pensar, então, que uma criptografia forte resistiria muito bem até mesmo contra um criptoanalista extremamente determinado. Quem pode realmente dizer? Ninguém provou que a criptografia mais forte disponível hoje resistirá ao poder computacional de amanhã. No entanto, a criptografia forte empregada pelo PGP é a melhor disponível atualmente. Contudo, a vigilância e o conservadorismo irão protegê-lo melhor do que as alegações de impenetrabilidade. Como funciona a criptografia? Um algoritmo criptográfico, ou cifra, é uma função matemática usada no processo de criptografia e descriptografia. Um algoritmo criptográfico funciona em combinação com uma chave – uma palavra, número ou frase – para criptografar o texto simples. O mesmo texto simples é criptografado em texto cifrado diferente com chaves diferentes. A segurança dos dados criptografados depende inteiramente de duas coisas: a força do algoritmo criptográfico e o sigilo da chave. Um algoritmo criptográfico, mais todas as chaves possíveis e todos os protocolos que o fazem funcionar constituem um criptossistema. PGP é um criptossistema. Criptografia convencional. Na criptografia convencional, também chamada de criptografia de chave secreta ou de chave simétrica , uma chave é usada tanto para criptografia quanto para descriptografia. O Data Encryption Standard (DES) é um exemplo de criptossistema convencional amplamente empregado pelo Governo Federal. A Figura 1-2 é uma ilustração do processo de criptografia convencional. https://nostrcheck.me/media/public/nostrcheck.me_1563316185075842071699905520.webp Figura 1-2. Criptografia convencional Cifra de César. Um exemplo extremamente simples de criptografia convencional é uma cifra de substituição. Uma cifra de substituição substitui uma informação por outra. Isso é feito com mais frequência compensando as letras do alfabeto. Dois exemplos são o Anel Decodificador Secreto do Capitão Meia-Noite, que você pode ter possuído quando era criança, e a cifra de Júlio César. Em ambos os casos, o algoritmo serve para compensar o alfabeto e a chave é o número de caracteres para compensá-lo. Por exemplo, se codificarmos a palavra "SEGREDO" usando o valor chave de César de 3, deslocaremos o alfabeto para que a terceira letra abaixo (D) comece o alfabeto. Então começando com A B C D E F G H I J K L M N O P Q R S T U V W X Y Z e deslizando tudo para cima em 3, você obtém DEFGHIJKLMNOPQRSTUVWXYZABC onde D=A, E=B, F=C e assim por diante. Usando este esquema, o texto simples, "SECRET" é criptografado como "VHFUHW". Para permitir que outra pessoa leia o texto cifrado, você diz a ela que a chave é 3. Obviamente, esta é uma criptografia extremamente fraca para os padrões atuais, mas, ei, funcionou para César e ilustra como funciona a criptografia convencional. Gerenciamento de chaves e criptografia convencional. A criptografia convencional tem benefícios. É muito rápido. É especialmente útil para criptografar dados que não vão a lugar nenhum. No entanto, a criptografia convencional por si só como meio de transmissão segura de dados pode ser bastante cara, simplesmente devido à dificuldade de distribuição segura de chaves. Lembre-se de um personagem do seu filme de espionagem favorito: a pessoa com uma pasta trancada e algemada ao pulso. Afinal, o que há na pasta? Provavelmente não é o código de lançamento de mísseis/fórmula de biotoxina/plano de invasão em si. É a chave que irá descriptografar os dados secretos. Para que um remetente e um destinatário se comuniquem com segurança usando criptografia convencional, eles devem chegar a um acordo sobre uma chave e mantê-la secreta entre si. Se estiverem em locais físicos diferentes, devem confiar em um mensageiro, no Bat Phone ou em algum outro meio de comunicação seguro para evitar a divulgação da chave secreta durante a transmissão. Qualquer pessoa que ouvir ou interceptar a chave em trânsito poderá posteriormente ler, modificar e falsificar todas as informações criptografadas ou autenticadas com essa chave. Do DES ao Anel Decodificador Secreto do Capitão Midnight, o problema persistente com a criptografia convencional é a distribuição de chaves: como você leva a chave ao destinatário sem que alguém a intercepte? Criptografia de chave pública. Os problemas de distribuição de chaves são resolvidos pela criptografia de chave pública, cujo conceito foi introduzido por Whitfield Diffie e Martin Hellman em 1975. (Há agora evidências de que o Serviço Secreto Britânico a inventou alguns anos antes de Diffie e Hellman, mas a manteve um segredo militar - e não fez nada com isso. [JH Ellis: The Possibility of Secure Non-Secret Digital Encryption, CESG Report, January 1970]) A criptografia de chave pública é um esquema assimétrico que usa um par de chaves para criptografia: uma chave pública, que criptografa os dados, e uma chave privada ou secreta correspondente para descriptografia. Você publica sua chave pública para o mundo enquanto mantém sua chave privada em segredo. Qualquer pessoa com uma cópia da sua chave pública pode criptografar informações que somente você pode ler. Até mesmo pessoas que você nunca conheceu. É computacionalmente inviável deduzir a chave privada da chave pública. Qualquer pessoa que possua uma chave pública pode criptografar informações, mas não pode descriptografá-las. Somente a pessoa que possui a chave privada correspondente pode descriptografar as informações. https://nostrcheck.me/media/public/nostrcheck.me_6137622541655550851699909180.webp Figura 1-3. Criptografia de chave pública O principal benefício da criptografia de chave pública é que ela permite que pessoas que não possuem nenhum acordo de segurança pré-existente troquem mensagens com segurança. A necessidade de remetente e destinatário compartilharem chaves secretas através de algum canal seguro é eliminada; todas as comunicações envolvem apenas chaves públicas e nenhuma chave privada é transmitida ou compartilhada. Alguns exemplos de criptossistemas de chave pública são Elgamal (nomeado em homenagem a seu inventor, Taher Elgamal), RSA (nomeado em homenagem a seus inventores, Ron Rivest, Adi Shamir e Leonard Adleman), Diffie-Hellman (nomeado, você adivinhou, em homenagem a seus inventores). ) e DSA, o algoritmo de assinatura digital (inventado por David Kravitz). Como a criptografia convencional já foi o único meio disponível para transmitir informações secretas, o custo dos canais seguros e da distribuição de chaves relegou a sua utilização apenas àqueles que podiam pagar, como governos e grandes bancos (ou crianças pequenas com anéis descodificadores secretos). A criptografia de chave pública é a revolução tecnológica que fornece criptografia forte para as massas adultas. Lembra do mensageiro com a pasta trancada e algemada ao pulso? A criptografia de chave pública o tira do mercado (provavelmente para seu alívio). Como funciona o PGP. O PGP combina alguns dos melhores recursos da criptografia convencional e de chave pública. PGP é um criptossistema híbrido. Quando um usuário criptografa texto simples com PGP, o PGP primeiro compacta o texto simples. A compactação de dados economiza tempo de transmissão do modem e espaço em disco e, mais importante ainda, fortalece a segurança criptográfica. A maioria das técnicas de criptoanálise explora padrões encontrados no texto simples para quebrar a cifra. A compressão reduz esses padrões no texto simples, aumentando assim enormemente a resistência à criptoanálise. (Arquivos que são muito curtos para compactar ou que não são compactados bem não são compactados.) O PGP então cria uma chave de sessão, que é uma chave secreta única. Esta chave é um número aleatório gerado a partir dos movimentos aleatórios do mouse e das teclas digitadas. Esta chave de sessão funciona com um algoritmo de criptografia convencional rápido e muito seguro para criptografar o texto simples; o resultado é texto cifrado. Depois que os dados são criptografados, a chave da sessão é criptografada na chave pública do destinatário. Essa chave de sessão criptografada com chave pública é transmitida junto com o texto cifrado ao destinatário. https://nostrcheck.me/media/public/nostrcheck.me_1978130242364857481699910331.webp Figura 1-4. Como funciona a criptografia PGP A descriptografia funciona ao contrário. A cópia do PGP do destinatário usa sua chave privada para recuperar a chave de sessão temporária, que o PGP usa para descriptografar o texto cifrado criptografado convencionalmente. https://nostrcheck.me/media/public/nostrcheck.me_1978130242364857481699910331.webp Figura 1-5. Como funciona a descriptografia PGP A combinação dos dois métodos de criptografia combina a conveniência da criptografia de chave pública com a velocidade da criptografia convencional. A criptografia convencional é cerca de 1.000 vezes mais rápida que a criptografia de chave pública. A criptografia de chave pública, por sua vez, fornece uma solução para problemas de distribuição de chaves e transmissão de dados. Usados em conjunto, o desempenho e a distribuição de chaves são melhorados sem qualquer sacrifício na segurança. Chaves. Uma chave é um valor que funciona com um algoritmo criptográfico para produzir um texto cifrado específico. As chaves são basicamente números muito, muito, muito grandes. O tamanho da chave é medido em bits; o número que representa uma chave de 1024 bits é enorme. Na criptografia de chave pública, quanto maior a chave, mais seguro é o texto cifrado. No entanto, o tamanho da chave pública e o tamanho da chave secreta da criptografia convencional não têm nenhuma relação. Uma chave convencional de 80 bits tem a força equivalente a uma chave pública de 1.024 bits. Uma chave convencional de 128 bits é equivalente a uma chave pública de 3.000 bits. Novamente, quanto maior a chave, mais segura, mas os algoritmos usados para cada tipo de criptografia são muito diferentes e, portanto, a comparação é como a de maçãs com laranjas. Embora as chaves pública e privada estejam matematicamente relacionadas, é muito difícil derivar a chave privada dada apenas a chave pública; no entanto, derivar a chave privada é sempre possível, desde que haja tempo e capacidade computacional suficientes. Isto torna muito importante escolher chaves do tamanho certo; grande o suficiente para ser seguro, mas pequeno o suficiente para ser aplicado rapidamente. Além disso, você precisa considerar quem pode estar tentando ler seus arquivos, quão determinados eles estão, quanto tempo têm e quais podem ser seus recursos. Chaves maiores serão criptograficamente seguras por um longo período de tempo. Se o que você deseja criptografar precisar ficar oculto por muitos anos, você pode usar uma chave muito grande. Claro, quem sabe quanto tempo levará para determinar sua chave usando os computadores mais rápidos e eficientes de amanhã? Houve um tempo em que uma chave simétrica de 56 bits era considerada extremamente segura. As chaves são armazenadas de forma criptografada. O PGP armazena as chaves em dois arquivos no seu disco rígido; um para chaves públicas e outro para chaves privadas. Esses arquivos são chamados de chaveiros. Ao usar o PGP, você normalmente adicionará as chaves públicas dos seus destinatários ao seu chaveiro público. Suas chaves privadas são armazenadas em seu chaveiro privado. Se você perder seu chaveiro privado, não será possível descriptografar nenhuma informação criptografada nas chaves desse anel. Assinaturas digitais. Um grande benefício da criptografia de chave pública é que ela fornece um método para empregar assinaturas digitais. As assinaturas digitais permitem ao destinatário da informação verificar a autenticidade da origem da informação e também verificar se a informação está intacta. Assim, as assinaturas digitais de chave pública fornecem autenticação e integridade de dados. A assinatura digital também proporciona o não repúdio, o que significa que evita que o remetente alegue que não enviou realmente as informações. Esses recursos são tão fundamentais para a criptografia quanto a privacidade, se não mais. Uma assinatura digital tem a mesma finalidade de uma assinatura manuscrita. No entanto, uma assinatura manuscrita é fácil de falsificar. Uma assinatura digital é superior a uma assinatura manuscrita porque é quase impossível de ser falsificada, além de atestar o conteúdo da informação, bem como a identidade do signatário. Algumas pessoas tendem a usar mais assinaturas do que criptografia. Por exemplo, você pode não se importar se alguém souber que você acabou de depositar US$ 1.000 em sua conta, mas quer ter certeza de que foi o caixa do banco com quem você estava lidando. A maneira básica pela qual as assinaturas digitais são criadas é ilustrada na Figura 1-6 . Em vez de criptografar informações usando a chave pública de outra pessoa, você as criptografa com sua chave privada. Se as informações puderem ser descriptografadas com sua chave pública, elas deverão ter se originado em você. https://nostrcheck.me/media/public/nostrcheck.me_4033165715613998201699910446.webp Figura 1-6. Assinaturas digitais simples Funções hash. O sistema descrito acima apresenta alguns problemas. É lento e produz um enorme volume de dados – pelo menos o dobro do tamanho da informação original. Uma melhoria no esquema acima é a adição de uma função hash unidirecional no processo. Uma função hash unidirecional recebe uma entrada de comprimento variável – neste caso, uma mensagem de qualquer comprimento, até mesmo milhares ou milhões de bits – e produz uma saída de comprimento fixo; digamos, 160 bits. A função hash garante que, se a informação for alterada de alguma forma – mesmo que por apenas um bit – seja produzido um valor de saída totalmente diferente. O PGP usa uma função hash criptograficamente forte no texto simples que o usuário está assinando. Isso gera um item de dados de comprimento fixo conhecido como resumo da mensagem. (Novamente, qualquer alteração nas informações resulta em um resumo totalmente diferente.) Então o PGP usa o resumo e a chave privada para criar a “assinatura”. O PGP transmite a assinatura e o texto simples juntos. Ao receber a mensagem, o destinatário utiliza o PGP para recalcular o resumo, verificando assim a assinatura. O PGP pode criptografar o texto simples ou não; assinar texto simples é útil se alguns dos destinatários não estiverem interessados ou não forem capazes de verificar a assinatura. Desde que uma função hash segura seja usada, não há como retirar a assinatura de alguém de um documento e anexá-la a outro, ou alterar uma mensagem assinada de qualquer forma. A menor alteração em um documento assinado causará falha no processo de verificação da assinatura digital. https://nostrcheck.me/media/public/nostrcheck.me_2943209062439984111699910538.webp Figura 1-7. Assinaturas digitais seguras As assinaturas digitais desempenham um papel importante na autenticação e validação de chaves de outros usuários PGP. Certificados digitais. Um problema com os criptosistemas de chave pública é que os usuários devem estar constantemente vigilantes para garantir que estão criptografando com a chave da pessoa correta. Num ambiente onde é seguro trocar chaves livremente através de servidores públicos, os ataques man-in-the-middle são uma ameaça potencial. Neste tipo de ataque, alguém publica uma chave falsa com o nome e ID de usuário do destinatário pretendido. Os dados criptografados – e interceptados por – o verdadeiro proprietário desta chave falsa estão agora em mãos erradas. Em um ambiente de chave pública, é vital que você tenha certeza de que a chave pública para a qual você está criptografando os dados é de fato a chave pública do destinatário pretendido e não uma falsificação. Você pode simplesmente criptografar apenas as chaves que foram entregues fisicamente a você. Mas suponha que você precise trocar informações com pessoas que nunca conheceu; como você pode saber se tem a chave correta? Os certificados digitais, ou certs, simplificam a tarefa de estabelecer se uma chave pública realmente pertence ao suposto proprietário. Um certificado é uma forma de credencial. Exemplos podem ser sua carteira de motorista, seu cartão de previdência social ou sua certidão de nascimento. Cada um deles contém algumas informações que identificam você e alguma autorização informando que outra pessoa confirmou sua identidade. Alguns certificados, como o seu passaporte, são uma confirmação importante o suficiente da sua identidade para que você não queira perdê-los, para que ninguém os use para se passar por você. Um certificado digital são dados que funcionam como um certificado físico. Um certificado digital é uma informação incluída na chave pública de uma pessoa que ajuda outras pessoas a verificar se uma chave é genuína ou válida. Os certificados digitais são usados para impedir tentativas de substituir a chave de uma pessoa por outra. Um certificado digital consiste em três coisas: ● Uma chave pública. ● Informações do certificado. (Informações de "identidade" sobre o usuário, como nome, ID do usuário e assim por diante.) ● Uma ou mais assinaturas digitais. O objetivo da assinatura digital em um certificado é afirmar que as informações do certificado foram atestadas por alguma outra pessoa ou entidade. A assinatura digital não atesta a autenticidade do certificado como um todo; ele atesta apenas que as informações de identidade assinadas acompanham ou estão vinculadas à chave pública. Assim, um certificado é basicamente uma chave pública com uma ou duas formas de identificação anexadas, além de um forte selo de aprovação de algum outro indivíduo confiável. https://nostrcheck.me/media/public/nostrcheck.me_7979578982089845401699910854.webp Figura 1-8. Anatomia de um certificado PGP Distribuição de certificados. Os certificados são utilizados quando é necessário trocar chaves públicas com outra pessoa. Para pequenos grupos de pessoas que desejam se comunicar com segurança, é fácil trocar manualmente disquetes ou e-mails contendo a chave pública de cada proprietário. Esta é a distribuição manual de chave pública e é prática apenas até certo ponto. Além desse ponto, é necessário implementar sistemas que possam fornecer os mecanismos necessários de segurança, armazenamento e troca para que colegas de trabalho, parceiros de negócios ou estranhos possam se comunicar, se necessário. Eles podem vir na forma de repositórios somente de armazenamento, chamados Servidores de Certificados, ou sistemas mais estruturados que fornecem recursos adicionais de gerenciamento de chaves e são chamados de Infraestruturas de Chave Pública (PKIs). Servidores de certificados. Um servidor de certificados, também chamado de servidor certificado ou servidor de chaves, é um banco de dados que permite aos usuários enviar e recuperar certificados digitais. Um servidor certificado geralmente fornece alguns recursos administrativos que permitem que uma empresa mantenha suas políticas de segurança – por exemplo, permitindo que apenas as chaves que atendam a determinados requisitos sejam armazenadas. Infraestruturas de Chave Pública. Uma PKI contém os recursos de armazenamento de certificados de um servidor de certificados, mas também fornece recursos de gerenciamento de certificados (a capacidade de emitir, revogar, armazenar, recuperar e confiar em certificados). A principal característica de uma PKI é a introdução do que é conhecido como Autoridade Certificadora,ou CA, que é uma entidade humana — uma pessoa, grupo, departamento, empresa ou outra associação — que uma organização autorizou a emitir certificados para seus usuários de computador. (A função de uma CA é análoga à do Passport Office do governo de um país.) Uma CA cria certificados e os assina digitalmente usando a chave privada da CA. Devido ao seu papel na criação de certificados, a CA é o componente central de uma PKI. Usando a chave pública da CA, qualquer pessoa que queira verificar a autenticidade de um certificado verifica a assinatura digital da CA emissora e, portanto, a integridade do conteúdo do certificado (mais importante ainda, a chave pública e a identidade do titular do certificado). Formatos de certificado. Um certificado digital é basicamente uma coleção de informações de identificação vinculadas a uma chave pública e assinadas por um terceiro confiável para provar sua autenticidade. Um certificado digital pode ter vários formatos diferentes. O PGP reconhece dois formatos de certificado diferentes: ● Certificados PGP ● Certificados X.509 Formato do certificado PGP. Um certificado PGP inclui (mas não está limitado a) as seguintes informações: ● O número da versão do PGP — identifica qual versão do PGP foi usada para criar a chave associada ao certificado. A chave pública do titular do certificado — a parte pública do seu par de chaves, juntamente com o algoritmo da chave: RSA, DH (Diffie-Hellman) ou DSA (Algoritmo de Assinatura Digital). ● As informações do detentor do certificado — consistem em informações de “identidade” sobre o usuário, como seu nome, ID de usuário, fotografia e assim por diante. ● A assinatura digital do proprietário do certificado — também chamada de autoassinatura, é a assinatura que utiliza a chave privada correspondente da chave pública associada ao certificado. ● O período de validade do certificado — a data/hora de início e a data/hora de expiração do certificado; indica quando o certificado irá expirar. ● O algoritmo de criptografia simétrica preferido para a chave — indica o algoritmo de criptografia para o qual o proprietário do certificado prefere que as informações sejam criptografadas. Os algoritmos suportados são CAST, IDEA ou Triple-DES. Você pode pensar em um certificado PGP como uma chave pública com um ou mais rótulos vinculados a ele (veja a Figura 1.9 ). Nessas 'etiquetas' você encontrará informações que identificam o proprietário da chave e uma assinatura do proprietário da chave, que afirma que a chave e a identificação andam juntas. (Essa assinatura específica é chamada de autoassinatura; todo certificado PGP contém uma autoassinatura.) Um aspecto único do formato de certificado PGP é que um único certificado pode conter múltiplas assinaturas. Várias ou muitas pessoas podem assinar o par chave/identificação para atestar a sua própria garantia de que a chave pública pertence definitivamente ao proprietário especificado. Se você procurar em um servidor de certificados público, poderá notar que certos certificados, como o do criador do PGP, Phil Zimmermann, contêm muitas assinaturas. Alguns certificados PGP consistem em uma chave pública com vários rótulos, cada um contendo um meio diferente de identificar o proprietário da chave (por exemplo, o nome do proprietário e a conta de e-mail corporativa, o apelido do proprietário e a conta de e-mail residencial, uma fotografia do proprietário — tudo em um certificado). A lista de assinaturas de cada uma dessas identidades pode ser diferente; as assinaturas atestam a autenticidade de que um dos rótulos pertence à chave pública, e não que todos os rótulos da chave sejam autênticos. (Observe que 'autêntico' está nos olhos de quem vê - assinaturas são opiniões, e diferentes pessoas dedicam diferentes níveis de devida diligência na verificação da autenticidade antes de assinar uma chave.) https://nostrcheck.me/media/public/nostrcheck.me_7979578982089845401699910854.webp Figura 1-9. Um certificado PGP Formato de certificado X.509. X.509 é outro formato de certificado muito comum. Todos os certificados X.509 estão em conformidade com o padrão internacional ITU-T X.509; assim (teoricamente) os certificados X.509 criados para um aplicativo podem ser usados por qualquer aplicativo compatível com X.509. Na prática, porém, diferentes empresas criaram suas próprias extensões para certificados X.509, e nem todas funcionam juntas. Um certificado exige que alguém valide que uma chave pública e o nome do proprietário da chave andam juntos. Com os certificados PGP, qualquer pessoa pode desempenhar o papel de validador. Com certificados X.509, o validador é sempre uma Autoridade Certificadora ou alguém designado por uma CA. (Tenha em mente que os certificados PGP também suportam totalmente uma estrutura hierárquica usando uma CA para validar certificados.) Um certificado X.509 é uma coleção de um conjunto padrão de campos contendo informações sobre um usuário ou dispositivo e sua chave pública correspondente. O padrão X.509 define quais informações vão para o certificado e descreve como codificá-lo (o formato dos dados). Todos os certificados X.509 possuem os seguintes dados: O número da versão X.509 — identifica qual versão do padrão X.509 se aplica a este certificado, o que afeta quais informações podem ser especificadas nele. A mais atual é a versão 3. A chave pública do titular do certificado — a chave pública do titular do certificado, juntamente com um identificador de algoritmo que especifica a qual sistema criptográfico a chave pertence e quaisquer parâmetros de chave associados. O número de série do certificado — a entidade (aplicação ou pessoa) que criou o certificado é responsável por atribuir-lhe um número de série único para distingui-lo de outros certificados que emite. Esta informação é usada de diversas maneiras; por exemplo, quando um certificado é revogado, seu número de série é colocado em uma Lista de Revogação de Certificados ou CRL. O identificador exclusivo do detentor do certificado — (ou DN — nome distinto). Este nome pretende ser exclusivo na Internet. Este nome pretende ser exclusivo na Internet. Um DN consiste em múltiplas subseções e pode ser parecido com isto: CN=Bob Allen, OU=Divisão Total de Segurança de Rede, O=Network Associates, Inc., C=EUA (Referem-se ao nome comum, à unidade organizacional, à organização e ao país do sujeito .) O período de validade do certificado — a data/hora de início e a data/hora de expiração do certificado; indica quando o certificado irá expirar. O nome exclusivo do emissor do certificado — o nome exclusivo da entidade que assinou o certificado. Normalmente é uma CA. A utilização do certificado implica confiar na entidade que assinou este certificado. (Observe que em alguns casos, como certificados de CA raiz ou de nível superior , o emissor assina seu próprio certificado.) A assinatura digital do emitente — a assinatura utilizando a chave privada da entidade que emitiu o certificado. O identificador do algoritmo de assinatura — identifica o algoritmo usado pela CA para assinar o certificado. Existem muitas diferenças entre um certificado X.509 e um certificado PGP, mas as mais importantes são as seguintes: você pode criar seu próprio certificado PGP; ● você deve solicitar e receber um certificado X.509 de uma autoridade de certificação ● Os certificados X.509 suportam nativamente apenas um único nome para o proprietário da chave ● Os certificados X.509 suportam apenas uma única assinatura digital para atestar a validade da chave Para obter um certificado X.509, você deve solicitar a uma CA a emissão de um certificado. Você fornece sua chave pública, prova de que possui a chave privada correspondente e algumas informações específicas sobre você. Em seguida, você assina digitalmente as informações e envia o pacote completo – a solicitação de certificado – para a CA. A CA então realiza algumas diligências para verificar se as informações fornecidas estão corretas e, em caso afirmativo, gera o certificado e o devolve. Você pode pensar em um certificado X.509 como um certificado de papel padrão (semelhante ao que você recebeu ao concluir uma aula de primeiros socorros básicos) com uma chave pública colada nele. Ele contém seu nome e algumas informações sobre você, além da assinatura da pessoa que o emitiu para você. https://nostrcheck.me/media/public/nostrcheck.me_4125576093727079591699911294.webp Figura 1-10. Um certificado X.509 Provavelmente, o uso mais visível dos certificados X.509 atualmente é em navegadores da web. Validade e confiança Cada usuário em um sistema de chave pública está vulnerável a confundir uma chave falsa (certificado) com uma chave real. Validade é a confiança de que um certificado de chave pública pertence ao seu suposto proprietário. A validade é essencial em um ambiente de chave pública onde você deve estabelecer constantemente se um determinado certificado é autêntico ou não. Depois de ter certeza de que um certificado pertencente a outra pessoa é válido, você pode assinar a cópia em seu chaveiro para atestar que verificou o certificado e que ele é autêntico. Se quiser que outras pessoas saibam que você deu ao certificado seu selo de aprovação, você pode exportar a assinatura para um servidor de certificados para que outras pessoas possam vê-la. Conforme descrito na seção Infraestruturas de Chave Pública , algumas empresas designam uma ou mais Autoridades de Certificação (CAs) para indicar a validade do certificado. Em uma organização que usa uma PKI com certificados X.509, é função da CA emitir certificados aos usuários — um processo que geralmente envolve responder à solicitação de certificado do usuário. Em uma organização que usa certificados PGP sem PKI, é função da CA verificar a autenticidade de todos os certificados PGP e depois assinar os bons. Basicamente, o objetivo principal de uma CA é vincular uma chave pública às informações de identificação contidas no certificado e, assim, garantir a terceiros que algum cuidado foi tomado para garantir que esta ligação das informações de identificação e da chave seja válida. O CA é o Grand Pooh-bah da validação em uma organização; alguém em quem todos confiam e, em algumas organizações, como aquelas que utilizam uma PKI, nenhum certificado é considerado válido, a menos que tenha sido assinado por uma CA confiável. Verificando validade. Uma maneira de estabelecer a validade é passar por algum processo manual. Existem várias maneiras de fazer isso. Você pode exigir que o destinatário pretendido lhe entregue fisicamente uma cópia de sua chave pública. Mas isto é muitas vezes inconveniente e ineficiente. Outra forma é verificar manualmente a impressão digital do certificado. Assim como as impressões digitais de cada ser humano são únicas, a impressão digital de cada certificado PGP é única. A impressão digital é um hash do certificado do usuário e aparece como uma das propriedades do certificado. No PGP, a impressão digital pode aparecer como um número hexadecimal ou uma série das chamadas palavras biométricas, que são foneticamente distintas e são usadas para facilitar um pouco o processo de identificação da impressão digital. Você pode verificar se um certificado é válido ligando para o proprietário da chave (para que você origine a transação) e pedindo ao proprietário que leia a impressão digital de sua chave para você e compare essa impressão digital com aquela que você acredita ser a verdadeira. Isso funciona se você conhece a voz do proprietário, mas como verificar manualmente a identidade de alguém que você não conhece? Algumas pessoas colocam a impressão digital de sua chave em seus cartões de visita exatamente por esse motivo. Outra forma de estabelecer a validade do certificado de alguém é confiar que um terceiro indivíduo passou pelo processo de validação do mesmo. Uma CA, por exemplo, é responsável por garantir que, antes de emitir um certificado, ele ou ela o verifique cuidadosamente para ter certeza de que a parte da chave pública realmente pertence ao suposto proprietário. Qualquer pessoa que confie na CA considerará automaticamente quaisquer certificados assinados pela CA como válidos. Outro aspecto da verificação da validade é garantir que o certificado não foi revogado. Para obter mais informações, consulte a seção Revogação de certificado . Estabelecendo confiança. Você valida certificados. Você confia nas pessoas. Mais especificamente, você confia nas pessoas para validar os certificados de outras pessoas. Normalmente, a menos que o proprietário lhe entregue o certificado, você terá que confiar na palavra de outra pessoa de que ele é válido. Introdutores meta e confiáveis. Na maioria das situações, as pessoas confiam completamente na CA para estabelecer a validade dos certificados. Isso significa que todos os demais dependem da CA para passar por todo o processo de validação manual. Isso é aceitável até um certo número de usuários ou locais de trabalho e, então, não é possível para a AC manter o mesmo nível de validação de qualidade. Nesse caso, é necessário adicionar outros validadores ao sistema. Um CA também pode ser um meta- introdutor. Um meta-introdutor confere não apenas validade às chaves, mas também confere a capacidade de confiar nas chaves a outros. Semelhante ao rei que entrega seu selo a seus conselheiros de confiança para que eles possam agir de acordo com sua autoridade, o meta-introdutor permite que outros atuem como introdutores de confiança. Esses introdutores confiáveis podem validar chaves com o mesmo efeito do meta-introdutor. Eles não podem, entretanto, criar novos introdutores confiáveis. Meta-introdutor e introdutor confiável são termos PGP. Em um ambiente X.509, o meta-introdutor é chamado de Autoridade de Certificação raiz ( CA raiz) e os introdutores confiáveis são Autoridades de Certificação subordinadas . A CA raiz usa a chave privada associada a um tipo de certificado especial denominado certificado CA raiz para assinar certificados. Qualquer certificado assinado pelo certificado CA raiz é visto como válido por qualquer outro certificado assinado pela raiz. Este processo de validação funciona mesmo para certificados assinados por outras CAs no sistema — desde que o certificado da CA raiz tenha assinado o certificado da CA subordinada, qualquer certificado assinado pela CA será considerado válido para outras pessoas dentro da hierarquia. Este processo de verificação de backup por meio do sistema para ver quem assinou cujo certificado é chamado de rastreamento de um caminho de certificação ou cadeia de certificação. Modelos de confiança. Em sistemas relativamente fechados, como em uma pequena empresa, é fácil rastrear um caminho de certificação até a CA raiz. No entanto, os usuários muitas vezes precisam se comunicar com pessoas fora do seu ambiente corporativo, incluindo algumas que nunca conheceram, como fornecedores, consumidores, clientes, associados e assim por diante. É difícil estabelecer uma linha de confiança com aqueles em quem sua CA não confia explicitamente. As empresas seguem um ou outro modelo de confiança, que determina como os usuários irão estabelecer a validade do certificado. Existem três modelos diferentes: Confiança Direta. Confiança Hierárquica Uma teia de confiança Confiança direta A confiança direta é o modelo de confiança mais simples. Neste modelo, um usuário confia que uma chave é válida porque sabe de onde ela veio. Todos os criptosistemas usam essa forma de confiança de alguma forma. Por exemplo, em navegadores da Web, as chaves raiz da Autoridade de Certificação são diretamente confiáveis porque foram enviadas pelo fabricante. Se houver alguma forma de hierarquia, ela se estenderá a partir desses certificados diretamente confiáveis. No PGP, um usuário que valida as chaves e nunca define outro certificado para ser um introdutor confiável está usando confiança direta. https://nostrcheck.me/media/public/nostrcheck.me_4681914789296468891699911522.webp Figura 1-11. Confiança direta Confiança Hierárquica. Em um sistema hierárquico, há vários certificados "raiz" a partir dos quais a confiança se estende. Esses certificados podem certificar eles próprios certificados ou podem certificar certificados que certificam ainda outros certificados em alguma cadeia. Considere isso como uma grande “árvore” de confiança. A validade do certificado "folha" é verificada rastreando desde seu certificador até outros certificadores, até que um certificado raiz diretamente confiável seja encontrado. https://nostrcheck.me/media/public/nostrcheck.me_2764578291212045251699911580.webp Figura 1-12. Confiança hierárquica Teia de Confiança. Uma teia de confiança abrange ambos os outros modelos, mas também acrescenta a noção de que a confiança está nos olhos de quem vê (que é a visão do mundo real) e a ideia de que mais informação é melhor. É, portanto, um modelo de confiança cumulativa. Um certificado pode ser confiável diretamente ou confiável em alguma cadeia que remonta a um certificado raiz diretamente confiável (o meta-introdutor) ou por algum grupo de introdutores. Talvez você já tenha ouvido falar do termo seis graus de separação, que sugere que qualquer pessoa no mundo pode determinar algum vínculo com qualquer outra pessoa no mundo usando seis ou menos outras pessoas como intermediários. Esta é uma teia de introdutores. É também a visão de confiança do PGP. PGP usa assinaturas digitais como forma de introdução. Quando qualquer usuário assina a chave de outro, ele ou ela se torna o introdutor dessa chave. À medida que esse processo avança, ele estabelece uma rede de confiança. Em um ambiente PGP, qualquer usuário pode atuar como autoridade certificadora. Qualquer usuário PGP pode validar o certificado de chave pública de outro usuário PGP. No entanto, tal certificado só é válido para outro usuário se a parte confiável reconhecer o validador como um introdutor confiável. (Ou seja, você confia na minha opinião de que as chaves dos outros são válidas apenas se você me considerar um apresentador confiável. Caso contrário, minha opinião sobre a validade das outras chaves é discutível.) Armazenados no chaveiro público de cada usuário estão indicadores de ● se o usuário considera ou não uma chave específica válida ● o nível de confiança que o usuário deposita na chave que o proprietário da chave pode servir como certificador das chaves de terceiros Você indica, na sua cópia da minha chave, se acha que meu julgamento conta. Na verdade, é um sistema de reputação: certas pessoas têm a reputação de fornecer boas assinaturas e as pessoas confiam nelas para atestar a validade de outras chaves. Níveis de confiança no PGP. O nível mais alto de confiança em uma chave, a confiança implícita , é a confiança em seu próprio par de chaves. O PGP assume que se você possui a chave privada, você deve confiar nas ações da sua chave pública relacionada. Quaisquer chaves assinadas pela sua chave implicitamente confiável são válidas. Existem três níveis de confiança que você pode atribuir à chave pública de outra pessoa: ● Confiança total ● Confiança marginal ● Não confiável (ou não confiável) Para tornar as coisas confusas, também existem três níveis de validade: ● Válido ● Marginalmente válido ● Inválido Para definir a chave de outra pessoa como um introdutor confiável, você 1. Comece com uma chave válida, que seja. - assinado por você ou - assinado por outro apresentador confiável e então 2. Defina o nível de confiança que você acha que o proprietário da chave tem direito. Por exemplo, suponha que seu chaveiro contenha a chave de Alice. Você validou a chave de Alice e indica isso assinando-a. Você sabe que Alice é uma verdadeira defensora da validação de chaves de outras pessoas. Portanto, você atribui a chave dela com confiança total. Isso faz de Alice uma Autoridade Certificadora. Se Alice assinar a chave de outra pessoa, ela aparecerá como Válida em seu chaveiro. O PGP requer uma assinatura Totalmente confiável ou duas assinaturas Marginalmente confiáveis para estabelecer uma chave como válida. O método do PGP de considerar dois Marginais iguais a um Completo é semelhante a um comerciante que solicita duas formas de identificação. Você pode considerar Alice bastante confiável e também considerar Bob bastante confiável. Qualquer um deles sozinho corre o risco de assinar acidentalmente uma chave falsificada, portanto, você pode não depositar total confiança em nenhum deles. No entanto, as probabilidades de ambos os indivíduos terem assinado a mesma chave falsa são provavelmente pequenas. Revogação de certificado. Os certificados só são úteis enquanto são válidos. Não é seguro simplesmente presumir que um certificado é válido para sempre. Na maioria das organizações e em todas as PKIs, os certificados têm uma vida útil restrita. Isso restringe o período em que um sistema fica vulnerável caso ocorra um comprometimento do certificado. Os certificados são assim criados com um período de validade programado: uma data/hora de início e uma data/hora de expiração. Espera-se que o certificado seja utilizável durante todo o seu período de validade (seu tempo de vida ). Quando o certificado expirar, ele não será mais válido, pois a autenticidade do seu par chave/identificação não estará mais garantida. (O certificado ainda pode ser usado com segurança para reconfirmar informações que foram criptografadas ou assinadas dentro do período de validade – no entanto, ele não deve ser confiável para tarefas criptográficas futuras.) Existem também situações em que é necessário invalidar um certificado antes da sua data de expiração, como quando o titular do certificado termina o contrato de trabalho com a empresa ou suspeita que a chave privada correspondente do certificado foi comprometida. Isso é chamado de revogação. Um certificado revogado é muito mais suspeito do que um certificado expirado. Os certificados expirados são inutilizáveis, mas não apresentam a mesma ameaça de comprometimento que um certificado revogado. Qualquer pessoa que tenha assinado um certificado pode revogar a sua assinatura no certificado (desde que utilize a mesma chave privada que criou a assinatura). Uma assinatura revogada indica que o signatário não acredita mais que a chave pública e as informações de identificação pertencem uma à outra, ou que a chave pública do certificado (ou a chave privada correspondente) foi comprometida. Uma assinatura revogada deve ter quase tanto peso quanto um certificado revogado. Com certificados X.509, uma assinatura revogada é praticamente igual a um certificado revogado, visto que a única assinatura no certificado é aquela que o tornou válido em primeiro lugar – a assinatura da CA. Os certificados PGP fornecem o recurso adicional de que você pode revogar todo o seu certificado (não apenas as assinaturas nele) se você achar que o certificado foi comprometido. Somente o proprietário do certificado (o detentor da chave privada correspondente) ou alguém que o proprietário do certificado tenha designado como revogador pode revogar um certificado PGP. (Designar um revogador é uma prática útil, pois muitas vezes é a perda da senha da chave privada correspondente do certificado que leva um usuário PGP a revogar seu certificado - uma tarefa que só é possível se alguém tiver acesso à chave privada. ) Somente o emissor do certificado pode revogar um certificado X.509. Comunicar que um certificado foi revogado. Quando um certificado é revogado, é importante conscientizar os usuários potenciais do certificado de que ele não é mais válido. Com certificados PGP, a maneira mais comum de comunicar que um certificado foi revogado é publicá-lo em um servidor de certificados para que outras pessoas que desejem se comunicar com você sejam avisadas para não usar essa chave pública. Em um ambiente PKI, a comunicação de certificados revogados é mais comumente obtida por meio de uma estrutura de dados chamada Lista de Revogação de Certificados, ou CRL, que é publicada pela CA. A CRL contém uma lista validada com carimbo de data e hora de todos os certificados revogados e não expirados no sistema. Os certificados revogados permanecem na lista apenas até expirarem e, em seguida, são removidos da lista — isso evita que a lista fique muito longa. A CA distribui a CRL aos usuários em algum intervalo programado regularmente (e potencialmente fora do ciclo, sempre que um certificado é revogado). Teoricamente, isso impedirá que os usuários usem involuntariamente um certificado comprometido. É possível, no entanto, que haja um período de tempo entre as CRLs em que um certificado recentemente comprometido seja usado. O que é uma senha? A maioria das pessoas está familiarizada com a restrição de acesso a sistemas de computador por meio de uma senha, que é uma sequência única de caracteres que um usuário digita como código de identificação. Uma senha longa é uma versão mais longa de uma senha e, em teoria, mais segura. Normalmente composta por várias palavras, uma frase secreta é mais segura contra ataques de dicionário padrão, em que o invasor tenta todas as palavras do dicionário na tentativa de determinar sua senha. As melhores senhas são relativamente longas e complexas e contêm uma combinação de letras maiúsculas e minúsculas, caracteres numéricos e de pontuação. O PGP usa uma senha para criptografar sua chave privada em sua máquina. Sua chave privada é criptografada em seu disco usando um hash de sua senha como chave secreta. Você usa a senha para descriptografar e usar sua chave privada. Uma senha deve ser difícil de esquecer e difícil de ser adivinhada por outras pessoas. Deve ser algo já firmemente enraizado na sua memória de longo prazo, em vez de algo que você invente do zero. Por que? Porque se você esquecer sua senha, você estará sem sorte. Sua chave privada é total e absolutamente inútil sem sua senha e nada pode ser feito a respeito. Lembra-se da citação anterior neste capítulo? https://nostrcheck.me/media/public/nostrcheck.me_5284734693832771181699911783.webp PGP é a criptografia que manterá os principais governos fora dos seus arquivos. Certamente também o manterá fora de seus arquivos. Tenha isso em mente quando decidir alterar sua senha para a piada daquela piada que você nunca consegue lembrar. Divisão de chave. Dizem que um segredo não é segredo se for conhecido por mais de uma pessoa. Compartilhar um par de chaves privadas representa um grande problema. Embora não seja uma prática recomendada, às vezes é necessário compartilhar um par de chaves privadas. Chaves de assinatura corporativa, por exemplo, são chaves privadas usadas por uma empresa para assinar – por exemplo – documentos legais, informações pessoais confidenciais ou comunicados de imprensa para autenticar sua origem. Nesse caso, vale a pena que vários membros da empresa tenham acesso à chave privada. No entanto, isto significa que qualquer indivíduo pode agir plenamente em nome da empresa. Nesse caso, é aconselhável dividir a chave entre várias pessoas, de modo que mais de uma ou duas pessoas apresentem um pedaço da chave para reconstituí-la em condições utilizáveis. Se poucas peças da chave estiverem disponíveis, a chave ficará inutilizável. Alguns exemplos são dividir uma chave em três partes e exigir duas delas para reconstituir a chave, ou dividi-la em duas partes e exigir ambas as peças. Se uma conexão de rede segura for usada durante o processo de reconstituição, os acionistas da chave não precisam estar fisicamente presentes para aderirem novamente à chave. @ 4ba8e86d:89d32de4
2024-10-05 21:04:30Em vez de compartilhar seu endereço de email real com serviços e sites que você usa, você pode criar um endereço de email temporário usando o Simplelogin. Esse endereço temporário é exclusivo para cada serviço ou site, permitindo que você gerencie sua caixa de entrada e reduza a quantidade de spam e emails não solicitados que você recebe. O Simplelogin foi fundado em 2019 por dois desenvolvedores franceses, Nicolas Grenié e Anthony Castellanos, com o objetivo de oferecer aos usuários uma maneira fácil de criar endereços de e-mail descartáveis para proteger sua privacidade e segurança online.Em 2022, a empresa se juntou à família ProtonMail, uma empresa suíça conhecida por seus serviços de e-mail seguros e criptografados, permitindo que a Simplelogin expandisse seus recursos de segurança e privacidade, além de oferecer uma integração perfeita com o ProtonMail. O SimpleLogin resolve vários problemas relacionados à privacidade e segurança online, incluindo: 1. Proteção da privacidade do seu endereço de e-mail: o SimpleLogin permite que você crie endereços de e-mail descartáveis que podem ser usados para se inscrever em sites ou serviços sem divulgar seu endereço de e-mail principal. Isso ajuda a reduzir a quantidade de spam e e-mails indesejados na sua caixa de entrada. 2. Proteção contra ataques de phishing: o SimpleLogin impede que os hackers obtenham seu endereço de e-mail real, reduzindo assim as chances de ser alvo de ataques de phishing. 3. Acesso seguro aos seus e-mails: o SimpleLogin oferece autenticação de dois fatores e suporte a PGP, garantindo que seus e-mails sejam protegidos contra invasões e leituras não autorizadas. 4. Maior controle sobre sua privacidade: o SimpleLogin permite que você crie e gerencie vários endereços de e-mail, controlando assim quais sites e serviços têm acesso ao seu endereço de e-mail principal. Além disso, o SimpleLogin permite que você exclua facilmente os endereços de e-mail descartáveis quando não precisar mais deles. Alguns motivos pra usar SimpleLogin https://nostr.build/i/a243a8f7ebafa3e3f8c6f3942c69ce03315aaed70394deb4e31af50f82d098f5.jpg 1. Privacidade: O SimpleLogin protege sua privacidade online, permitindo que você crie endereços de e-mail descartáveis que não estão vinculados ao seu endereço de e-mail principal. Isso ajuda a reduzir o spam e a quantidade de e-mails indesejados que você recebe. 2. Segurança: O SimpleLogin oferece recursos de segurança avançados, como autenticação de dois fatores e suporte a PGP, ajudando a proteger seus e-mails de invasões e leituras não autorizadas. 3. Controle: O SimpleLogin permite que você crie e gerencie facilmente vários endereços de e-mail, controlando quais sites e serviços têm acesso ao seu endereço de e-mail principal. 4. Simplicidade: O SimpleLogin é fácil de usar e pode ser configurado em questão de minutos, sem a necessidade de conhecimentos técnicos avançados. 5. Integração com outros serviços: O SimpleLogin se integra facilmente com outros serviços, como o ProtonMail, permitindo que você gerencie todos os seus e-mails em um só lugar. O Simplelogin é uma ferramenta essencial para manter sua privacidade e segurança online. Com a criação e gerenciamento de endereços de e-mail descartáveis exclusivos para cada site ou serviço que você utiliza, você pode reduzir significativamente a quantidade de spam e e-mails não solicitados em sua caixa de entrada. Além disso, o Simplelogin fornece uma proteção extra contra ataques de phishing e garante que seus e-mails sejam acessados de forma segura. Experimente o Simplelogin hoje mesmo e proteja sua privacidade e segurança online de maneira fácil e eficaz. https://simplelogin.io/ https://github.com/simple-login/app
@ 4ba8e86d:89d32de4
2024-10-05 21:04:30Em vez de compartilhar seu endereço de email real com serviços e sites que você usa, você pode criar um endereço de email temporário usando o Simplelogin. Esse endereço temporário é exclusivo para cada serviço ou site, permitindo que você gerencie sua caixa de entrada e reduza a quantidade de spam e emails não solicitados que você recebe. O Simplelogin foi fundado em 2019 por dois desenvolvedores franceses, Nicolas Grenié e Anthony Castellanos, com o objetivo de oferecer aos usuários uma maneira fácil de criar endereços de e-mail descartáveis para proteger sua privacidade e segurança online.Em 2022, a empresa se juntou à família ProtonMail, uma empresa suíça conhecida por seus serviços de e-mail seguros e criptografados, permitindo que a Simplelogin expandisse seus recursos de segurança e privacidade, além de oferecer uma integração perfeita com o ProtonMail. O SimpleLogin resolve vários problemas relacionados à privacidade e segurança online, incluindo: 1. Proteção da privacidade do seu endereço de e-mail: o SimpleLogin permite que você crie endereços de e-mail descartáveis que podem ser usados para se inscrever em sites ou serviços sem divulgar seu endereço de e-mail principal. Isso ajuda a reduzir a quantidade de spam e e-mails indesejados na sua caixa de entrada. 2. Proteção contra ataques de phishing: o SimpleLogin impede que os hackers obtenham seu endereço de e-mail real, reduzindo assim as chances de ser alvo de ataques de phishing. 3. Acesso seguro aos seus e-mails: o SimpleLogin oferece autenticação de dois fatores e suporte a PGP, garantindo que seus e-mails sejam protegidos contra invasões e leituras não autorizadas. 4. Maior controle sobre sua privacidade: o SimpleLogin permite que você crie e gerencie vários endereços de e-mail, controlando assim quais sites e serviços têm acesso ao seu endereço de e-mail principal. Além disso, o SimpleLogin permite que você exclua facilmente os endereços de e-mail descartáveis quando não precisar mais deles. Alguns motivos pra usar SimpleLogin https://nostr.build/i/a243a8f7ebafa3e3f8c6f3942c69ce03315aaed70394deb4e31af50f82d098f5.jpg 1. Privacidade: O SimpleLogin protege sua privacidade online, permitindo que você crie endereços de e-mail descartáveis que não estão vinculados ao seu endereço de e-mail principal. Isso ajuda a reduzir o spam e a quantidade de e-mails indesejados que você recebe. 2. Segurança: O SimpleLogin oferece recursos de segurança avançados, como autenticação de dois fatores e suporte a PGP, ajudando a proteger seus e-mails de invasões e leituras não autorizadas. 3. Controle: O SimpleLogin permite que você crie e gerencie facilmente vários endereços de e-mail, controlando quais sites e serviços têm acesso ao seu endereço de e-mail principal. 4. Simplicidade: O SimpleLogin é fácil de usar e pode ser configurado em questão de minutos, sem a necessidade de conhecimentos técnicos avançados. 5. Integração com outros serviços: O SimpleLogin se integra facilmente com outros serviços, como o ProtonMail, permitindo que você gerencie todos os seus e-mails em um só lugar. O Simplelogin é uma ferramenta essencial para manter sua privacidade e segurança online. Com a criação e gerenciamento de endereços de e-mail descartáveis exclusivos para cada site ou serviço que você utiliza, você pode reduzir significativamente a quantidade de spam e e-mails não solicitados em sua caixa de entrada. Além disso, o Simplelogin fornece uma proteção extra contra ataques de phishing e garante que seus e-mails sejam acessados de forma segura. Experimente o Simplelogin hoje mesmo e proteja sua privacidade e segurança online de maneira fácil e eficaz. https://simplelogin.io/ https://github.com/simple-login/app @ 460c25e6:ef85065c
2024-10-01 13:40:23Testing new note with Comet
@ 460c25e6:ef85065c
2024-10-01 13:40:23Testing new note with Comet @ 9977c3ad:43a20d63
2024-09-05 11:21:09## Details - 🍽️ Servings: 2 ## Ingredients - 1 cup Jasmine rice - 1 Tbsp. lavender flowers, crushed with mortar and pestle - 1/4 cup apple cider vinegar - 2 Tbsp. fine cane sugar - 2 Tbsp. honey - 1 sprig rosemary - 1/4 tsp angostura bitters - 1/2 cup blackberries - 1/2 cup blueberries - 4 cups trimmed and quartered shiitake mushrooms - 1 tsp fresh coriander crushed - 1/4 tsp fresh cumin ground - 1/2 tsp red pepper flakes - 3 sprigs of thyme - 2 Tbsp. olive oil - 1 tsp soy sauce - 1 cup creamy coconut milk ## Directions 1. Combine rice, lavender, 1/4 tsp salt, and 2 cups of water in a saucepan. Bring the rice to a boil, cover the pan with a lid and turn the heat off. Let the rice sit in the pan for at least 20 minutes. 2. Combine 1/4 cup of water, the vinegar, sugar, honey, rosemary, angostura bitters in a saucepan and bring the brine to a boil. Season with a pinch of salt. Add the berries and wait until the brine comes back to a boil. Lower the heat, so the brine simmers but does not boil. When the brine thickens, after about 15 minutes, remove the saucepan from the heat and set it aside. 3. Pre-heat the oven to 400F. In a bowl big enough to hold all the shiitake, combine the olive oil, the soy sauce and the spices. Whisk vigorously, so the oil emulsifies with the other liquid. Toss the shiitake in the mix to marinate, then evenly lay them out on a baking sheet with parchment paper. Bake the shiitake for 10 minutes. When you remove the shiitake from the oven, remove the thyme and throw it out. In a saucepan, bring the coconut milk to a boil. Add the shiitake and reduce the heat to a light boil until the sauce thickens.
@ 9977c3ad:43a20d63
2024-09-05 11:21:09## Details - 🍽️ Servings: 2 ## Ingredients - 1 cup Jasmine rice - 1 Tbsp. lavender flowers, crushed with mortar and pestle - 1/4 cup apple cider vinegar - 2 Tbsp. fine cane sugar - 2 Tbsp. honey - 1 sprig rosemary - 1/4 tsp angostura bitters - 1/2 cup blackberries - 1/2 cup blueberries - 4 cups trimmed and quartered shiitake mushrooms - 1 tsp fresh coriander crushed - 1/4 tsp fresh cumin ground - 1/2 tsp red pepper flakes - 3 sprigs of thyme - 2 Tbsp. olive oil - 1 tsp soy sauce - 1 cup creamy coconut milk ## Directions 1. Combine rice, lavender, 1/4 tsp salt, and 2 cups of water in a saucepan. Bring the rice to a boil, cover the pan with a lid and turn the heat off. Let the rice sit in the pan for at least 20 minutes. 2. Combine 1/4 cup of water, the vinegar, sugar, honey, rosemary, angostura bitters in a saucepan and bring the brine to a boil. Season with a pinch of salt. Add the berries and wait until the brine comes back to a boil. Lower the heat, so the brine simmers but does not boil. When the brine thickens, after about 15 minutes, remove the saucepan from the heat and set it aside. 3. Pre-heat the oven to 400F. In a bowl big enough to hold all the shiitake, combine the olive oil, the soy sauce and the spices. Whisk vigorously, so the oil emulsifies with the other liquid. Toss the shiitake in the mix to marinate, then evenly lay them out on a baking sheet with parchment paper. Bake the shiitake for 10 minutes. When you remove the shiitake from the oven, remove the thyme and throw it out. In a saucepan, bring the coconut milk to a boil. Add the shiitake and reduce the heat to a light boil until the sauce thickens. @ d830ee7b:4e61cd62
2024-09-04 07:29:41Bitcoin ถือกำเนิดขึ้นในปี 2009 จากวิสัยทัศน์ของ Satoshi Nakamoto บุคคลหรือกลุ่มบุคคลปริศนา ที่ใฝ่ฝันถึง "เงินสดดิจิทัล" อิสระไร้พรมแดน ไร้การควบคุมจากรัฐบาล ในช่วงแรกเริ่ม Bitcoin เป็นเสมือนเพชรดิบที่ซ่อนตัวอยู่ในเงามืด เป็นที่รู้จักกันเฉพาะในกลุ่มเล็กๆ ที่หลงใหลในเทคโนโลยีและศักยภาพอันไร้ขีดจำกัดของมัน แต่แล้ว Bitcoin ก็เริ่มฉายแสงเจิดจรัส ดึงดูดความสนใจจากผู้คนทั่วโลก ราคาพุ่งทะยานอย่างรวดเร็ว บริษัทและบริการต่างๆ ผุดขึ้นมาราวกับดอกเห็ด ทว่า.. เส้นทางสู่ความสำเร็จของ Bitcoin ไม่ได้โรยด้วยกลีบกุหลาบ Bitcoin ยังต้องเผชิญกับความท้าทายมากมาย ทั้งปัญหาทางเทคนิค ความขัดแย้งภายในชุมชนและการต่อสู้แย่งชิงอำนาจ ## **Blocksize Limit จุดเริ่มต้นของความขัดแย้งและสงคราม Big Blocks VS Small Blocks** ย้อนกลับไปในปี 2010 Satoshi Nakamoto ได้เพิ่ม **"Blocksize Limit"** ซึ่งเป็นข้อจำกัดขนาดของ Block ใน Bitcoin ไว้ที่ 1MB เพื่อป้องกันการโจมตีทางไซเบอร์ในยุคแรกเริ่ม แต่เมื่อ Bitcoin ได้รับความนิยมมากขึ้น ธุรกรรมก็เพิ่มขึ้นอย่างรวดเร็ว Blocksize Limit 1MB เริ่มจะกลายเป็นปัญหา.. เกิดการถกเถียงอย่างดุเดือดในชุมชน Bitcoin ว่าควรเพิ่ม Blocksize Limit หรือไม่ ฝ่าย **"Small Blockers"** นำโดยนักพัฒนา Bitcoin Core ส่วนใหญ่ เชื่อว่า Blocksize Limit ควรคงที่ เพื่อรักษาความปลอดภัยและการกระจายอำนาจ พวกเขากล่าวอ้างว่า Big Blocks จะทำให้ Bitcoinรวมศูนย์อยู่ที่ Miners รายใหญ่ และยากต่อการรัน Full Nodes สำหรับผู้ใช้งานทั่วไป ซึ่งจะบั่นทอนความเป็น Decentralized ของ Bitcoin ฝ่าย **"Big Blockers"** นำโดย Gavin Andresen ผู้สืบทอดตำแหน่งจาก Satoshi Nakamoto และ Mike Hearn เชื่อว่า Bitcoin ควรเติบโตอย่างไม่จำกัด "Big Blocks" คือคำตอบ พวกเขามองว่า Small Blocks จะทำให้ Bitcoin ไม่สามารถรองรับธุรกรรมที่เพิ่มขึ้น ค่าธรรมเนียมจะพุ่งสูงและ Bitcoin จะไม่สามารถใช้งานได้จริงในชีวิตประจำวัน.. ความขัดแย้งนี้สะท้อนให้เห็นถึงวิสัยทัศน์ที่แตกต่างกัน Gavin Andresen ผู้ที่เคยได้รับความไว้วางใจจาก Satoshi รู้สึกผิดหวังที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit เขาเชื่อมั่นว่า Bitcoin ควรเป็นระบบการชำระเงินที่ใช้งานได้จริง รวดเร็ว และมีค่าธรรมเนียมต่ำ ## **Blockstream บริษัทผู้ทรงอิทธิพลและความกังวลเรื่องผลประโยชน์ทับซ้อน** ปี 2014 กลุ่มนักพัฒนา Bitcoin Core บางส่วนได้ก่อตั้งบริษัท **Blockstream** (นำโดย Adam Back) พวกเขาเน้นการพัฒนาเทคโนโลยี Blockchain และกลายเป็นที่มถกเถียงว่าอิทธิพลอย่างมากต่อ Bitcoin Core Blockstream สนับสนุน "Small Blocks" เช่นเดียวกับ Bitcoin Core พวกเขาพัฒนา **"Sidechains"** ซึ่งเป็น Blockchain แยกต่างหากที่เชื่อมต่อกับ Bitcoin เช่น **Liquid Network Sidechains** ซึ่งช่วยให้ Blockstream สามารถเก็บค่าธรรมเนียมจากธุรกรรมและขายบริการให้กับองค์กรหรือบริษัทต่างๆ ได้ ความสัมพันธ์อันใกล้ชิดระหว่าง Blockstream และ Bitcoin Core ทำให้เกิดความกังวลขึ้นในชุมชน Bitcoin ในขณะนั้นว่า Blockstream อาจมีผลประโยชน์ทับซ้อนและต้องการให้ Bitcoin คงขนาดเล็ก เพื่อผลักดันให้คนใช้งาน "Sidechains" ของพวกเขา ## **BitcoinXT และ Bitcoin Classic ความพยายามแก้ไข Blocksize ที่ถูกต่อต้าน** ปี 2015 Mike Hearn และ Gavin Andresen ตัดสินใจเสนอทางออกด้วยการสร้าง **"BitcoinXT"** ซอฟต์แวร์ Bitcoin เวอร์ชั่นใหม่ที่ **เพิ่ม Blocksize Limit เป็น 8MB** แต่ BitcoinXT ถูกต่อต้านอย่างรุนแรงจากฝ่าย Small Blockers Bitcoin.org เว็บไซต์หลักของ Bitcoin และ r/Bitcoin ฟอรัมหลักของ Bitcoin ได้เซ็นเซอร์ BitcoinXT ไม่ให้ปรากฏ เกิดการโจมตีทางไซเบอร์ที่มุ่งเป้าไปที่ BitcoinXT โดยตรง Coinbase บริษัทแลกเปลี่ยน Cryptocurrency รายใหญ่ ประกาศสนับสนุน BitcoinXT แต่กลับถูกถอดออกจาก Bitcoin.org ต่อมา **Bitcoin Classic** ถูกสร้างขึ้นเป็นอีกหนึ่งทางเลือก แต่ก็ล้มเหลวเช่นกัน เนื่องจาก Bitcoin Core ยังคงมีอิทธิพลอย่างมากในชุมชน Bitcoin ในช่วงเวลานั้น.. ## **Hong Kong Agreement และ New York Agreement ความพยายามประนีประนอมที่ไม่ลงตัว** ปี 2016 และ 2017 เกิดความพยายามในการประนีประนอมระหว่างฝ่าย Small Blocks และ Big Blockers ถึงสองครั้ง คือ "Hong Kong Agreement" และ "New York Agreement" ทั้งสองข้อตกลงมีเป้าหมายที่จะเปิดใช้งาน **SegWit** และ **เพิ่ม Blocksize Limit เป็น 2MB** แต่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit ทำให้ข้อตกลงล้มเหลว ความล้มเหลวของข้อตกลงทั้งสอง สะท้อนให้เห็นถึงความไม่ไว้วางใจระหว่างสองฝ่าย และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ ## **SegWit ก้าวสำคัญของ Bitcoin และจุดกำเนิดของ Bitcoin Cash** ในที่สุด SegWit ก็ถูกเปิดใช้งานบน Bitcoin ในเดือนสิงหาคม 2017 SegWit เป็น **Soft Fork** ที่เปลี่ยนแปลงวิธีการจัดเก็บข้อมูลใน Block เพื่อเพิ่มประสิทธิภาพและความปลอดภัย SegWit ช่วยแก้ปัญหา **"Transaction Malleability"** ซึ่งเป็นช่องโหว่ด้านความปลอดภัย และปูทางไปสู่การพัฒนา **"Layer 2 solutions"** เช่น **Lightning Network** ในเวลาต่อมา.. อย่างไรก็ตาม.. กลุ่ม "Big Blockers" มองว่า SegWit ไม่ใช่ทางออกที่แท้จริงสำหรับปัญหาการขยายขนาด (พวกเขาต้องการขยายขนาดบล็อกบนเลอเยอร์ฐาน) พวกเขาไม่พอใจที่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit ในเดือนสิงหาคม 2017 กลุ่ม "Big Blockers" ได้ทำการ **"Hard Fork"** Bitcoin เพื่อสร้าง **"Bitcoin Cash (BCH)"** ซึ่งอ้างว่ามุ่งสืบทอดจุดมุ่งหมายดั้งเดิมของ Bitcoin ในฐานะ **"เงินสดดิจิทัล"** ## **ความเสี่ยงด้านความปลอดภัย Bug ร้ายแรงใน Bitcoin Core และบทเรียนที่ได้รับ** ในเดือนกันยายน 2018 Awemany นักพัฒนา BCH ค้นพบ Bug ร้ายแรงใน Bitcoin Core (CVE-2018-17144) ซึ่งอาจทำให้เกิดภาวะเงินเฟ้อได้ Bug นี้เกิดจากความผิดพลาดในการเขียนโค้ด และอาจทำให้ผู้ไม่หวังดีสามารถสร้าง Bitcoin ปลอมขึ้นมาได้ Awemany ได้แจ้งเตือนนักพัฒนา Bitcoin Core อย่างเงียบๆ แทนที่จะใช้ประโยชน์จาก Bug นี้ แสดงให้เห็นถึงความรับผิดชอบของเขา และ Bug นี้ได้รับการแก้ไขอย่างรวดเร็ว เหตุการณ์นี้แสดงให้เห็นถึงความสำคัญของการตรวจสอบโค้ดอย่างละเอียด และความจำเป็นของการมีนักพัฒนาจากหลายฝ่ายเพื่อช่วยกันตรวจสอบความถูกต้องของโค้ด นอกจากนี้.. ยังเป็นเครื่องเตือนใจว่าแม้แต่ระบบที่ถูกออกแบบมาอย่างดีก็ยังมีความเสี่ยงด้านความปลอดภัย ## **Bitcoin Cash แตกแยก การ Hard Fork ครั้งที่สอง และบทบาทของ Craig Wright** ในเดือนพฤศจิกายน 2018 Bitcoin Cash (BCH) ได้แตกออกเป็นสองสาย คือ **Bitcoin ABC (BCH)** และ **Bitcoin SV (BSV)** การ Hard Fork นี้เกิดจากความขัดแย้งระหว่างกลุ่มนักพัฒนา Bitcoin ABC นำโดย Amaury Séchet และกลุ่ม Bitcoin SV นำโดย Craig Wright ผู้ที่อ้างว่าเป็น Satoshi Nakamoto 🤔 ความขัดแย้งหลักคือเรื่องขนาดของ Block และทิศทางการพัฒนา Bitcoin Cash กลุ่ม Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก ในขณะที่กลุ่ม Bitcoin ABC ต้องการปรับปรุง Bitcoin Cash ในด้านอื่นๆ เช่น Smart Contracts Craig Wright มีบทบาทสำคัญในการผลักดัน Bitcoin SV เขาเชื่อมั่นว่า Bitcoin ควรเป็นไปตามวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto โดยเน้นที่การเป็น "เงินสดอิเล็กทรอนิกส์แบบ peer-to-peer" การ Hard Fork นี้แสดงให้เห็นถึงความหลากหลายของความคิดเห็นในชุมชน Cryptocurrency และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ นอกจากนี้.. ยังสะท้อนให้เห็นถึงความท้าทายในการกำหนดทิศทางของ Cryptocurrency ในอนาคตอีกด้วย ## **Bitcoin ในปัจจุบัน เส้นทางสู่ทองคำดิจิทัล และวิวัฒนาการของเทคโนโลยี** หลังจากการ Hard Fork ของ Bitcoin Cash Bitcoin ได้ก้าวเข้าสู่ยุคใหม่ Bitcoin ได้รับการยอมรับมากขึ้นในวงกว้าง มีมูลค่าตลาดสูง และถูกมองว่าเป็น **"ทองคำดิจิทัล"** ที่สามารถใช้เก็บรักษามูลค่าในระยะยาว (Store of Value) การพัฒนา **Lightning Network** เป็นก้าวสำคัญในการแก้ปัญหาเรื่องค่าธรรมเนียมและความเร็วในการทำธุรกรรม Lightning Network เป็น **"Second Layer"** ที่สร้างขึ้นบน Bitcoin Blockchain ช่วยให้สามารถทำธุรกรรมได้รวดเร็วขึ้น มีค่าธรรมเนียมต่ำ และมีความเป็นส่วนตัวสูง อย่างไรก็ตาม.. Lightning Network ยังคงต้องเผชิญกับความท้าทาย เช่น ปัญหาเรื่องการบริหารจัดการ Liquidity และความซับซ้อนในการใช้งาน นอกจาก Lightning Network แล้ว ยังมีการพัฒนาเทคโนโลยีอื่นๆ ที่ช่วยเพิ่มขีดความสามารถของ Bitcoin เช่น **Taproot** ซึ่งเป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และ **Schnorr signatures** ซึ่งเป็น Digital Signature แบบใหม่ที่ช่วยลดขนาดของธุรกรรมให้เล็กลง นอกจากนี้.. ยังเริ่มมีการพัฒนา DeFi (Decentralized Finance) บน Bitcoin และ Bitcoin Ordinals ซึ่งเป็นวิธีการใหม่ในการฝังข้อมูลลงใน Bitcoin Blockchain Bitcoin ยังคงถูกนำไปใช้ในประเทศอื่นๆ นอกจาก El Salvador และมีความพยายามในการแก้ปัญหาความกังวลด้านสิ่งแวดล้อมจากการขุด Bitcoin ## **บทเรียนจากมหากาพย์แห่งวิวัฒนาการ** ประวัติศาสตร์ Bitcoin สอนให้เรารู้ว่า.. เทคโนโลยี Blockchain มีศักยภาพในการเปลี่ยนแปลงโลก แต่เส้นทางสู่ความสำเร็จนั้นก็ไม่ได้โรยด้วยกลีบกุหลาบ ความขัดแย้ง การต่อสู้แย่งชิงอำนาจ และการตัดสินใจที่ยากลำบาก ล้วนเป็นส่วนหนึ่งของการเดินทาง สิ่งที่สำคัญที่สุดคือ.. เราต้องศึกษา ทำความเข้าใจ และอาจมีส่วนร่วมในการกำหนดทิศทางของเทคโนโลยีนี้ เพื่อให้ Blockchain สามารถสร้างประโยชน์สูงสุดให้กับมวลมนุษยชาติต่อไป # **เจาะลึกวิวัฒนาการของ Bitcoin การ Soft Forks, Hard Forks และมุมมองที่แตกต่าง** ## **SegWit, Taproot และ Soft Forks อื่นๆ การปรับปรุง Bitcoin อย่างนุ่มนวล** Bitcoin Core ไม่ได้หยุดนิ่งอยู่กับที่ นักพัฒนาได้ทำงานอย่างต่อเนื่องเพื่อปรับปรุง Bitcoin ให้ดีขึ้น โดยใช้ **"Soft Forks"** ซึ่งเป็นการอัพเกรดที่เข้ากันได้กับซอฟต์แวร์เวอร์ชั่นเก่า ### **SegWit (Segregated Witness)** เปิดตัวในปี 2017 SegWit เป็นเหมือนการจัดระเบียบข้อมูลใน Block ใหม่ ย้ายส่วนที่เรียกว่า "Witness data" (ข้อมูลลายเซ็น) ออกไปไว้ข้างนอก ทำให้มีพื้นที่ว่างใน Block มากขึ้น รองรับธุรกรรมได้มากขึ้น และลดค่าธรรมเนียมได้ SegWit ยังช่วยแก้ปัญหา "Transaction Malleability" ซึ่งเป็นช่องโหว่ด้านความปลอดภัยและปูทางไปสู่การพัฒนา Lightning Network ### **Taproot** เปิดตัวในปี 2021 Taproot เป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และประสิทธิภาพของ Bitcoin Taproot ทำให้ธุรกรรมที่ซับซ้อน เช่น Smart Contracts มีขนาดเล็กลงและยากต่อการแยกแยะจากธุรกรรมทั่วไป Soft Forks อื่นๆ ที่ Bitcoin Core ได้นำมาใช้ เช่น BIP 65 (CheckLockTimeVerify) และ BIP 112 (CSV) ช่วยเพิ่มความยืดหยุ่นในการใช้งาน Bitcoin และปูทางไปสู่การพัฒนาฟังก์ชันใหม่ๆ ## **Hard Forks เส้นทางที่แตกต่างและการถือกำเนิดของเหรียญใหม่** ในขณะที่ Soft Forks เป็นการอัพเกรดที่นุ่มนวล **"Hard Forks"** นั้นนับว่าเป็นการเปลี่ยนแปลงครั้งใหญ่ ที่ทำให้เกิดสาย Blockchain ใหม่และเหรียญใหม่ ### **Bitcoin XT (2015)** เป็นความพยายามครั้งแรกในการเพิ่ม Blocksize Limit โดย Mike Hearn และ Gavin Andresen Bitcoin XT เสนอให้เพิ่ม Blocksize Limit เป็น 8MB แต่ถูกต่อต้านอย่างรุนแรง และไม่ประสบความสำเร็จ ### **Bitcoin Classic (2016)** เป็นอีกหนึ่งความพยายามในการเพิ่ม Blocksize Limit โดยเสนอให้เพิ่มเป็น 2MB แต่ก็ล้มเหลวเช่นกัน ### **Bitcoin Unlimited (2016)** เสนอให้ Miners สามารถกำหนด Blocksize Limit ได้เอง แต่มีข้อบกพร่องด้านความปลอดภัย และไม่เป็นที่ยอมรับในวงกว้าง ### **Bitcoin Cash (BCH) (2017)** เกิดจากการ Hard Fork ของ Bitcoin โดยกลุ่ม "Big Blockers" ที่ไม่พอใจที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit Bitcoin Cash เพิ่ม Blocksize Limit เป็น 8MB และมุ่งเน้นที่การเป็น "เงินสดดิจิทัล" ที่ใช้งานได้จริง ### **Bitcoin SV (BSV) (2018)** เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มที่นำโดย **Craig Wright** ผู้ที่อ้างว่าเป็น Satoshi Nakamoto Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก และกลับไปสู่วิสัยทัศน์ดั้งเดิมของ Bitcoin ### **Bitcoin ABC (2020)** เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มนักพัฒนา Bitcoin ABC ที่ต้องการเปลี่ยนแปลงกลไกการระดมทุน Bitcoin ABC ถูกเปลี่ยนชื่อเป็น eCash ในภายหลัง ## **มุมมองที่แตกต่าง Bitcoin ถูก "แย่งชิง" หรือไม่?** หนังสือ **"Hijacking Bitcoin"** โดย Roger Ver นำเสนอมุมมองที่แตกต่างจาก Bitcoin Maximalists Roger Ver เชื่อว่า Bitcoin ถูก **"แย่งชิง"** โดยกลุ่มนักพัฒนา Bitcoin Core และ Blockstream ที่ต้องการเปลี่ยนแปลง Bitcoin จาก "เงินสดดิจิทัล" ให้กลายเป็น **"สินทรัพย์เก็บมูลค่า"** Roger Ver วิพากษ์วิจารณ์ Bitcoin Core ในหลายประเด็น เช่น.. ### **การไม่ยอมเพิ่ม Blocksize Limit** Roger Ver เชื่อว่า Bitcoin Core จงใจจำกัดการเติบโตของ Bitcoin เพื่อผลักดันให้คนใช้งาน Sidechains ของ Blockstream ### **การเซ็นเซอร์ข้อมูล** Roger Ver กล่าวหาว่า Bitcoin Core เซ็นเซอร์ข้อมูลและปิดกั้นการสนทนาเกี่ยวกับ Big Blocks บนแพลตฟอร์มต่างๆ ### **การต่อต้านนวัตกรรม** Roger Ver เชื่อว่า Bitcoin Core ต่อต้านนวัตกรรม และไม่ยอมรับการเปลี่ยนแปลงที่อาจทำให้ Bitcoin ดีขึ้น ### **การควบคุมโดยกลุ่มเล็กๆ** Roger Ver มองว่า Bitcoin Core ถูกควบคุมโดยกลุ่มเล็กๆ ที่ไม่คำนึงถึงความต้องการของชุมชน Bitcoin Roger Ver สนับสนุน Bitcoin Cash ซึ่งเขาเชื่อว่าเป็น Bitcoin ที่แท้จริง ที่สืบทอดวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto ## **บทสรุป:** การต่อสู้แย่งชิง Bitcoin และการเกิดขึ้นของ Hard Forks ต่างๆ เป็นส่วนหนึ่งของวิวัฒนาการของ Cryptocurrency มุมมองที่แตกต่าง ความขัดแย้ง และการแข่งขัน ล้วนเป็นแรงผลักดันให้ Bitcoin และ Cryptocurrency อื่นๆ พัฒนาต่อไป สุดท้ายแล้ว.. เราคงไม่อาจตัดสินได้ว่าฝ่ายใดคิดถูกหรือฝ่ายใดผิด **"เสียงของตลาด** จะช่วยทำหน้าที่ให้คำตอบนั้นกับเรา ว่าแท้ที่จริงแล้วผู้คนกำลังต้องการอะไรกันแน่.. ลองมองไปที่มูลค่าของแต่ละแนวคิด มองไปที่ Network effect และกำลังการขุด มองไปที่การยอมรับและความเชื่อมั่นของผู้คน เหล่านี้ล้วนเป็นข้อบ่งชี้ที่เห็นได้ง่าย.. เพราะนั่นคือเสียงแห่งการเพรียกหาอิสรภาพ และอธิปไตยทางการเงินที่แท้จริง.. — Jakk Goodday
@ d830ee7b:4e61cd62
2024-09-04 07:29:41Bitcoin ถือกำเนิดขึ้นในปี 2009 จากวิสัยทัศน์ของ Satoshi Nakamoto บุคคลหรือกลุ่มบุคคลปริศนา ที่ใฝ่ฝันถึง "เงินสดดิจิทัล" อิสระไร้พรมแดน ไร้การควบคุมจากรัฐบาล ในช่วงแรกเริ่ม Bitcoin เป็นเสมือนเพชรดิบที่ซ่อนตัวอยู่ในเงามืด เป็นที่รู้จักกันเฉพาะในกลุ่มเล็กๆ ที่หลงใหลในเทคโนโลยีและศักยภาพอันไร้ขีดจำกัดของมัน แต่แล้ว Bitcoin ก็เริ่มฉายแสงเจิดจรัส ดึงดูดความสนใจจากผู้คนทั่วโลก ราคาพุ่งทะยานอย่างรวดเร็ว บริษัทและบริการต่างๆ ผุดขึ้นมาราวกับดอกเห็ด ทว่า.. เส้นทางสู่ความสำเร็จของ Bitcoin ไม่ได้โรยด้วยกลีบกุหลาบ Bitcoin ยังต้องเผชิญกับความท้าทายมากมาย ทั้งปัญหาทางเทคนิค ความขัดแย้งภายในชุมชนและการต่อสู้แย่งชิงอำนาจ ## **Blocksize Limit จุดเริ่มต้นของความขัดแย้งและสงคราม Big Blocks VS Small Blocks** ย้อนกลับไปในปี 2010 Satoshi Nakamoto ได้เพิ่ม **"Blocksize Limit"** ซึ่งเป็นข้อจำกัดขนาดของ Block ใน Bitcoin ไว้ที่ 1MB เพื่อป้องกันการโจมตีทางไซเบอร์ในยุคแรกเริ่ม แต่เมื่อ Bitcoin ได้รับความนิยมมากขึ้น ธุรกรรมก็เพิ่มขึ้นอย่างรวดเร็ว Blocksize Limit 1MB เริ่มจะกลายเป็นปัญหา.. เกิดการถกเถียงอย่างดุเดือดในชุมชน Bitcoin ว่าควรเพิ่ม Blocksize Limit หรือไม่ ฝ่าย **"Small Blockers"** นำโดยนักพัฒนา Bitcoin Core ส่วนใหญ่ เชื่อว่า Blocksize Limit ควรคงที่ เพื่อรักษาความปลอดภัยและการกระจายอำนาจ พวกเขากล่าวอ้างว่า Big Blocks จะทำให้ Bitcoinรวมศูนย์อยู่ที่ Miners รายใหญ่ และยากต่อการรัน Full Nodes สำหรับผู้ใช้งานทั่วไป ซึ่งจะบั่นทอนความเป็น Decentralized ของ Bitcoin ฝ่าย **"Big Blockers"** นำโดย Gavin Andresen ผู้สืบทอดตำแหน่งจาก Satoshi Nakamoto และ Mike Hearn เชื่อว่า Bitcoin ควรเติบโตอย่างไม่จำกัด "Big Blocks" คือคำตอบ พวกเขามองว่า Small Blocks จะทำให้ Bitcoin ไม่สามารถรองรับธุรกรรมที่เพิ่มขึ้น ค่าธรรมเนียมจะพุ่งสูงและ Bitcoin จะไม่สามารถใช้งานได้จริงในชีวิตประจำวัน.. ความขัดแย้งนี้สะท้อนให้เห็นถึงวิสัยทัศน์ที่แตกต่างกัน Gavin Andresen ผู้ที่เคยได้รับความไว้วางใจจาก Satoshi รู้สึกผิดหวังที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit เขาเชื่อมั่นว่า Bitcoin ควรเป็นระบบการชำระเงินที่ใช้งานได้จริง รวดเร็ว และมีค่าธรรมเนียมต่ำ ## **Blockstream บริษัทผู้ทรงอิทธิพลและความกังวลเรื่องผลประโยชน์ทับซ้อน** ปี 2014 กลุ่มนักพัฒนา Bitcoin Core บางส่วนได้ก่อตั้งบริษัท **Blockstream** (นำโดย Adam Back) พวกเขาเน้นการพัฒนาเทคโนโลยี Blockchain และกลายเป็นที่มถกเถียงว่าอิทธิพลอย่างมากต่อ Bitcoin Core Blockstream สนับสนุน "Small Blocks" เช่นเดียวกับ Bitcoin Core พวกเขาพัฒนา **"Sidechains"** ซึ่งเป็น Blockchain แยกต่างหากที่เชื่อมต่อกับ Bitcoin เช่น **Liquid Network Sidechains** ซึ่งช่วยให้ Blockstream สามารถเก็บค่าธรรมเนียมจากธุรกรรมและขายบริการให้กับองค์กรหรือบริษัทต่างๆ ได้ ความสัมพันธ์อันใกล้ชิดระหว่าง Blockstream และ Bitcoin Core ทำให้เกิดความกังวลขึ้นในชุมชน Bitcoin ในขณะนั้นว่า Blockstream อาจมีผลประโยชน์ทับซ้อนและต้องการให้ Bitcoin คงขนาดเล็ก เพื่อผลักดันให้คนใช้งาน "Sidechains" ของพวกเขา ## **BitcoinXT และ Bitcoin Classic ความพยายามแก้ไข Blocksize ที่ถูกต่อต้าน** ปี 2015 Mike Hearn และ Gavin Andresen ตัดสินใจเสนอทางออกด้วยการสร้าง **"BitcoinXT"** ซอฟต์แวร์ Bitcoin เวอร์ชั่นใหม่ที่ **เพิ่ม Blocksize Limit เป็น 8MB** แต่ BitcoinXT ถูกต่อต้านอย่างรุนแรงจากฝ่าย Small Blockers Bitcoin.org เว็บไซต์หลักของ Bitcoin และ r/Bitcoin ฟอรัมหลักของ Bitcoin ได้เซ็นเซอร์ BitcoinXT ไม่ให้ปรากฏ เกิดการโจมตีทางไซเบอร์ที่มุ่งเป้าไปที่ BitcoinXT โดยตรง Coinbase บริษัทแลกเปลี่ยน Cryptocurrency รายใหญ่ ประกาศสนับสนุน BitcoinXT แต่กลับถูกถอดออกจาก Bitcoin.org ต่อมา **Bitcoin Classic** ถูกสร้างขึ้นเป็นอีกหนึ่งทางเลือก แต่ก็ล้มเหลวเช่นกัน เนื่องจาก Bitcoin Core ยังคงมีอิทธิพลอย่างมากในชุมชน Bitcoin ในช่วงเวลานั้น.. ## **Hong Kong Agreement และ New York Agreement ความพยายามประนีประนอมที่ไม่ลงตัว** ปี 2016 และ 2017 เกิดความพยายามในการประนีประนอมระหว่างฝ่าย Small Blocks และ Big Blockers ถึงสองครั้ง คือ "Hong Kong Agreement" และ "New York Agreement" ทั้งสองข้อตกลงมีเป้าหมายที่จะเปิดใช้งาน **SegWit** และ **เพิ่ม Blocksize Limit เป็น 2MB** แต่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit ทำให้ข้อตกลงล้มเหลว ความล้มเหลวของข้อตกลงทั้งสอง สะท้อนให้เห็นถึงความไม่ไว้วางใจระหว่างสองฝ่าย และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ ## **SegWit ก้าวสำคัญของ Bitcoin และจุดกำเนิดของ Bitcoin Cash** ในที่สุด SegWit ก็ถูกเปิดใช้งานบน Bitcoin ในเดือนสิงหาคม 2017 SegWit เป็น **Soft Fork** ที่เปลี่ยนแปลงวิธีการจัดเก็บข้อมูลใน Block เพื่อเพิ่มประสิทธิภาพและความปลอดภัย SegWit ช่วยแก้ปัญหา **"Transaction Malleability"** ซึ่งเป็นช่องโหว่ด้านความปลอดภัย และปูทางไปสู่การพัฒนา **"Layer 2 solutions"** เช่น **Lightning Network** ในเวลาต่อมา.. อย่างไรก็ตาม.. กลุ่ม "Big Blockers" มองว่า SegWit ไม่ใช่ทางออกที่แท้จริงสำหรับปัญหาการขยายขนาด (พวกเขาต้องการขยายขนาดบล็อกบนเลอเยอร์ฐาน) พวกเขาไม่พอใจที่ Bitcoin Core ไม่ทำตามสัญญาในการเพิ่ม Blocksize Limit ในเดือนสิงหาคม 2017 กลุ่ม "Big Blockers" ได้ทำการ **"Hard Fork"** Bitcoin เพื่อสร้าง **"Bitcoin Cash (BCH)"** ซึ่งอ้างว่ามุ่งสืบทอดจุดมุ่งหมายดั้งเดิมของ Bitcoin ในฐานะ **"เงินสดดิจิทัล"** ## **ความเสี่ยงด้านความปลอดภัย Bug ร้ายแรงใน Bitcoin Core และบทเรียนที่ได้รับ** ในเดือนกันยายน 2018 Awemany นักพัฒนา BCH ค้นพบ Bug ร้ายแรงใน Bitcoin Core (CVE-2018-17144) ซึ่งอาจทำให้เกิดภาวะเงินเฟ้อได้ Bug นี้เกิดจากความผิดพลาดในการเขียนโค้ด และอาจทำให้ผู้ไม่หวังดีสามารถสร้าง Bitcoin ปลอมขึ้นมาได้ Awemany ได้แจ้งเตือนนักพัฒนา Bitcoin Core อย่างเงียบๆ แทนที่จะใช้ประโยชน์จาก Bug นี้ แสดงให้เห็นถึงความรับผิดชอบของเขา และ Bug นี้ได้รับการแก้ไขอย่างรวดเร็ว เหตุการณ์นี้แสดงให้เห็นถึงความสำคัญของการตรวจสอบโค้ดอย่างละเอียด และความจำเป็นของการมีนักพัฒนาจากหลายฝ่ายเพื่อช่วยกันตรวจสอบความถูกต้องของโค้ด นอกจากนี้.. ยังเป็นเครื่องเตือนใจว่าแม้แต่ระบบที่ถูกออกแบบมาอย่างดีก็ยังมีความเสี่ยงด้านความปลอดภัย ## **Bitcoin Cash แตกแยก การ Hard Fork ครั้งที่สอง และบทบาทของ Craig Wright** ในเดือนพฤศจิกายน 2018 Bitcoin Cash (BCH) ได้แตกออกเป็นสองสาย คือ **Bitcoin ABC (BCH)** และ **Bitcoin SV (BSV)** การ Hard Fork นี้เกิดจากความขัดแย้งระหว่างกลุ่มนักพัฒนา Bitcoin ABC นำโดย Amaury Séchet และกลุ่ม Bitcoin SV นำโดย Craig Wright ผู้ที่อ้างว่าเป็น Satoshi Nakamoto 🤔 ความขัดแย้งหลักคือเรื่องขนาดของ Block และทิศทางการพัฒนา Bitcoin Cash กลุ่ม Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก ในขณะที่กลุ่ม Bitcoin ABC ต้องการปรับปรุง Bitcoin Cash ในด้านอื่นๆ เช่น Smart Contracts Craig Wright มีบทบาทสำคัญในการผลักดัน Bitcoin SV เขาเชื่อมั่นว่า Bitcoin ควรเป็นไปตามวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto โดยเน้นที่การเป็น "เงินสดอิเล็กทรอนิกส์แบบ peer-to-peer" การ Hard Fork นี้แสดงให้เห็นถึงความหลากหลายของความคิดเห็นในชุมชน Cryptocurrency และความยากลำบากในการหาจุดร่วมที่ทุกฝ่ายยอมรับ นอกจากนี้.. ยังสะท้อนให้เห็นถึงความท้าทายในการกำหนดทิศทางของ Cryptocurrency ในอนาคตอีกด้วย ## **Bitcoin ในปัจจุบัน เส้นทางสู่ทองคำดิจิทัล และวิวัฒนาการของเทคโนโลยี** หลังจากการ Hard Fork ของ Bitcoin Cash Bitcoin ได้ก้าวเข้าสู่ยุคใหม่ Bitcoin ได้รับการยอมรับมากขึ้นในวงกว้าง มีมูลค่าตลาดสูง และถูกมองว่าเป็น **"ทองคำดิจิทัล"** ที่สามารถใช้เก็บรักษามูลค่าในระยะยาว (Store of Value) การพัฒนา **Lightning Network** เป็นก้าวสำคัญในการแก้ปัญหาเรื่องค่าธรรมเนียมและความเร็วในการทำธุรกรรม Lightning Network เป็น **"Second Layer"** ที่สร้างขึ้นบน Bitcoin Blockchain ช่วยให้สามารถทำธุรกรรมได้รวดเร็วขึ้น มีค่าธรรมเนียมต่ำ และมีความเป็นส่วนตัวสูง อย่างไรก็ตาม.. Lightning Network ยังคงต้องเผชิญกับความท้าทาย เช่น ปัญหาเรื่องการบริหารจัดการ Liquidity และความซับซ้อนในการใช้งาน นอกจาก Lightning Network แล้ว ยังมีการพัฒนาเทคโนโลยีอื่นๆ ที่ช่วยเพิ่มขีดความสามารถของ Bitcoin เช่น **Taproot** ซึ่งเป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และ **Schnorr signatures** ซึ่งเป็น Digital Signature แบบใหม่ที่ช่วยลดขนาดของธุรกรรมให้เล็กลง นอกจากนี้.. ยังเริ่มมีการพัฒนา DeFi (Decentralized Finance) บน Bitcoin และ Bitcoin Ordinals ซึ่งเป็นวิธีการใหม่ในการฝังข้อมูลลงใน Bitcoin Blockchain Bitcoin ยังคงถูกนำไปใช้ในประเทศอื่นๆ นอกจาก El Salvador และมีความพยายามในการแก้ปัญหาความกังวลด้านสิ่งแวดล้อมจากการขุด Bitcoin ## **บทเรียนจากมหากาพย์แห่งวิวัฒนาการ** ประวัติศาสตร์ Bitcoin สอนให้เรารู้ว่า.. เทคโนโลยี Blockchain มีศักยภาพในการเปลี่ยนแปลงโลก แต่เส้นทางสู่ความสำเร็จนั้นก็ไม่ได้โรยด้วยกลีบกุหลาบ ความขัดแย้ง การต่อสู้แย่งชิงอำนาจ และการตัดสินใจที่ยากลำบาก ล้วนเป็นส่วนหนึ่งของการเดินทาง สิ่งที่สำคัญที่สุดคือ.. เราต้องศึกษา ทำความเข้าใจ และอาจมีส่วนร่วมในการกำหนดทิศทางของเทคโนโลยีนี้ เพื่อให้ Blockchain สามารถสร้างประโยชน์สูงสุดให้กับมวลมนุษยชาติต่อไป # **เจาะลึกวิวัฒนาการของ Bitcoin การ Soft Forks, Hard Forks และมุมมองที่แตกต่าง** ## **SegWit, Taproot และ Soft Forks อื่นๆ การปรับปรุง Bitcoin อย่างนุ่มนวล** Bitcoin Core ไม่ได้หยุดนิ่งอยู่กับที่ นักพัฒนาได้ทำงานอย่างต่อเนื่องเพื่อปรับปรุง Bitcoin ให้ดีขึ้น โดยใช้ **"Soft Forks"** ซึ่งเป็นการอัพเกรดที่เข้ากันได้กับซอฟต์แวร์เวอร์ชั่นเก่า ### **SegWit (Segregated Witness)** เปิดตัวในปี 2017 SegWit เป็นเหมือนการจัดระเบียบข้อมูลใน Block ใหม่ ย้ายส่วนที่เรียกว่า "Witness data" (ข้อมูลลายเซ็น) ออกไปไว้ข้างนอก ทำให้มีพื้นที่ว่างใน Block มากขึ้น รองรับธุรกรรมได้มากขึ้น และลดค่าธรรมเนียมได้ SegWit ยังช่วยแก้ปัญหา "Transaction Malleability" ซึ่งเป็นช่องโหว่ด้านความปลอดภัยและปูทางไปสู่การพัฒนา Lightning Network ### **Taproot** เปิดตัวในปี 2021 Taproot เป็น Soft Fork ที่ช่วยเพิ่มความเป็นส่วนตัว และประสิทธิภาพของ Bitcoin Taproot ทำให้ธุรกรรมที่ซับซ้อน เช่น Smart Contracts มีขนาดเล็กลงและยากต่อการแยกแยะจากธุรกรรมทั่วไป Soft Forks อื่นๆ ที่ Bitcoin Core ได้นำมาใช้ เช่น BIP 65 (CheckLockTimeVerify) และ BIP 112 (CSV) ช่วยเพิ่มความยืดหยุ่นในการใช้งาน Bitcoin และปูทางไปสู่การพัฒนาฟังก์ชันใหม่ๆ ## **Hard Forks เส้นทางที่แตกต่างและการถือกำเนิดของเหรียญใหม่** ในขณะที่ Soft Forks เป็นการอัพเกรดที่นุ่มนวล **"Hard Forks"** นั้นนับว่าเป็นการเปลี่ยนแปลงครั้งใหญ่ ที่ทำให้เกิดสาย Blockchain ใหม่และเหรียญใหม่ ### **Bitcoin XT (2015)** เป็นความพยายามครั้งแรกในการเพิ่ม Blocksize Limit โดย Mike Hearn และ Gavin Andresen Bitcoin XT เสนอให้เพิ่ม Blocksize Limit เป็น 8MB แต่ถูกต่อต้านอย่างรุนแรง และไม่ประสบความสำเร็จ ### **Bitcoin Classic (2016)** เป็นอีกหนึ่งความพยายามในการเพิ่ม Blocksize Limit โดยเสนอให้เพิ่มเป็น 2MB แต่ก็ล้มเหลวเช่นกัน ### **Bitcoin Unlimited (2016)** เสนอให้ Miners สามารถกำหนด Blocksize Limit ได้เอง แต่มีข้อบกพร่องด้านความปลอดภัย และไม่เป็นที่ยอมรับในวงกว้าง ### **Bitcoin Cash (BCH) (2017)** เกิดจากการ Hard Fork ของ Bitcoin โดยกลุ่ม "Big Blockers" ที่ไม่พอใจที่ Bitcoin Core ไม่ยอมเพิ่ม Blocksize Limit Bitcoin Cash เพิ่ม Blocksize Limit เป็น 8MB และมุ่งเน้นที่การเป็น "เงินสดดิจิทัล" ที่ใช้งานได้จริง ### **Bitcoin SV (BSV) (2018)** เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มที่นำโดย **Craig Wright** ผู้ที่อ้างว่าเป็น Satoshi Nakamoto Bitcoin SV ต้องการเพิ่มขนาด Block อย่างมาก และกลับไปสู่วิสัยทัศน์ดั้งเดิมของ Bitcoin ### **Bitcoin ABC (2020)** เกิดจากการ Hard Fork ของ Bitcoin Cash โดยกลุ่มนักพัฒนา Bitcoin ABC ที่ต้องการเปลี่ยนแปลงกลไกการระดมทุน Bitcoin ABC ถูกเปลี่ยนชื่อเป็น eCash ในภายหลัง ## **มุมมองที่แตกต่าง Bitcoin ถูก "แย่งชิง" หรือไม่?** หนังสือ **"Hijacking Bitcoin"** โดย Roger Ver นำเสนอมุมมองที่แตกต่างจาก Bitcoin Maximalists Roger Ver เชื่อว่า Bitcoin ถูก **"แย่งชิง"** โดยกลุ่มนักพัฒนา Bitcoin Core และ Blockstream ที่ต้องการเปลี่ยนแปลง Bitcoin จาก "เงินสดดิจิทัล" ให้กลายเป็น **"สินทรัพย์เก็บมูลค่า"** Roger Ver วิพากษ์วิจารณ์ Bitcoin Core ในหลายประเด็น เช่น.. ### **การไม่ยอมเพิ่ม Blocksize Limit** Roger Ver เชื่อว่า Bitcoin Core จงใจจำกัดการเติบโตของ Bitcoin เพื่อผลักดันให้คนใช้งาน Sidechains ของ Blockstream ### **การเซ็นเซอร์ข้อมูล** Roger Ver กล่าวหาว่า Bitcoin Core เซ็นเซอร์ข้อมูลและปิดกั้นการสนทนาเกี่ยวกับ Big Blocks บนแพลตฟอร์มต่างๆ ### **การต่อต้านนวัตกรรม** Roger Ver เชื่อว่า Bitcoin Core ต่อต้านนวัตกรรม และไม่ยอมรับการเปลี่ยนแปลงที่อาจทำให้ Bitcoin ดีขึ้น ### **การควบคุมโดยกลุ่มเล็กๆ** Roger Ver มองว่า Bitcoin Core ถูกควบคุมโดยกลุ่มเล็กๆ ที่ไม่คำนึงถึงความต้องการของชุมชน Bitcoin Roger Ver สนับสนุน Bitcoin Cash ซึ่งเขาเชื่อว่าเป็น Bitcoin ที่แท้จริง ที่สืบทอดวิสัยทัศน์ดั้งเดิมของ Satoshi Nakamoto ## **บทสรุป:** การต่อสู้แย่งชิง Bitcoin และการเกิดขึ้นของ Hard Forks ต่างๆ เป็นส่วนหนึ่งของวิวัฒนาการของ Cryptocurrency มุมมองที่แตกต่าง ความขัดแย้ง และการแข่งขัน ล้วนเป็นแรงผลักดันให้ Bitcoin และ Cryptocurrency อื่นๆ พัฒนาต่อไป สุดท้ายแล้ว.. เราคงไม่อาจตัดสินได้ว่าฝ่ายใดคิดถูกหรือฝ่ายใดผิด **"เสียงของตลาด** จะช่วยทำหน้าที่ให้คำตอบนั้นกับเรา ว่าแท้ที่จริงแล้วผู้คนกำลังต้องการอะไรกันแน่.. ลองมองไปที่มูลค่าของแต่ละแนวคิด มองไปที่ Network effect และกำลังการขุด มองไปที่การยอมรับและความเชื่อมั่นของผู้คน เหล่านี้ล้วนเป็นข้อบ่งชี้ที่เห็นได้ง่าย.. เพราะนั่นคือเสียงแห่งการเพรียกหาอิสรภาพ และอธิปไตยทางการเงินที่แท้จริง.. — Jakk Goodday @ e0e92e54:d630dfaa
2024-09-04 04:13:19_This is a copy of the email received from newsletter@Rumble.com_  # Free Speech Under Attack -- A Note from the CEO of Rumble Dear Rumble Users, I don't typically send messages to our users through email, but red lines have been crossed. There have been major developments with free speech platforms, and I feel it’s important to let everyone know what is going on and how you can help Rumble. Rumble is no longer available to the citizens of Brazil, joining the ranks of France, Russia, and China. From media reports, Brazil no longer has Elon Musk's X due to attacks on free speech by Alexandre De Moreas, a justice of Brazil's Supreme Federal Court. World powers don’t want Rumble, they don’t want X, they don’t want Telegram, and they don't want Truth Social. They want to control information, but our companies won’t let them. There are no other large companies fighting for freedom like we are. We put everything on the line for it, and the Telegram CEO was recently arrested for it. Advertisers boycott our companies to try and cut our economic lifeline, but they underestimate our support among the people. The people keep us alive and keep us going. If you want to help us, join Rumble Premium. If Rumble Premium gets big enough, you help us change the game and fight for freedom of expression. We are also offering a $10 dicount for any new annual subscribers when they use the promo code "brazil". Sincerely, Chris Pavlovski Chairman and CEO of Rumble  444 Gulf of Mexico Dr. Longboat Key, FL 34228, USA.
@ e0e92e54:d630dfaa
2024-09-04 04:13:19_This is a copy of the email received from newsletter@Rumble.com_  # Free Speech Under Attack -- A Note from the CEO of Rumble Dear Rumble Users, I don't typically send messages to our users through email, but red lines have been crossed. There have been major developments with free speech platforms, and I feel it’s important to let everyone know what is going on and how you can help Rumble. Rumble is no longer available to the citizens of Brazil, joining the ranks of France, Russia, and China. From media reports, Brazil no longer has Elon Musk's X due to attacks on free speech by Alexandre De Moreas, a justice of Brazil's Supreme Federal Court. World powers don’t want Rumble, they don’t want X, they don’t want Telegram, and they don't want Truth Social. They want to control information, but our companies won’t let them. There are no other large companies fighting for freedom like we are. We put everything on the line for it, and the Telegram CEO was recently arrested for it. Advertisers boycott our companies to try and cut our economic lifeline, but they underestimate our support among the people. The people keep us alive and keep us going. If you want to help us, join Rumble Premium. If Rumble Premium gets big enough, you help us change the game and fight for freedom of expression. We are also offering a $10 dicount for any new annual subscribers when they use the promo code "brazil". Sincerely, Chris Pavlovski Chairman and CEO of Rumble  444 Gulf of Mexico Dr. Longboat Key, FL 34228, USA. @ 3b7fc823:e194354f
2024-09-04 00:26:48Encryption is the promethium fire that the cypherpunks secured from heaven for me and you. It is our sacred duty to use and advance that in the world. Encryption is so powerful that governments tried to keep it away from the people and to this day have tried to weaken and backdoor it at every turn. So what is encryption? It is a deep deep rabbit hole and involves a lot of numbers but in a nutshell it uses math to scramble up the data of your file so it is gibberish and can't be read without decrypting it back to regular data. Encryption technology has continued to advance over time and cracking technology to break the encryption has as well. For our purposes all you really need to remember is to use modern cyphers and your encryption is really only going to be as good as the password (use a passphrase) strength you are using to lock it down with. > BEGINNER LEVEL - Encrypt your phone and computer. People walk around with their whole lives on their phone. Protect it. -phone: Congratulations, if you already have a lock screen set on either your iPhone or Android device then device encryption is enabled. If your lock screen password is only 4 digits then we still have work to do. Four digits is only about 10,000 combinations and fairly easy to crack. I believe it only took them about 40 minutes to crack the iPhone of the attempted Trump shooter. Go into settings and set it up for 6 digits or for extra credit use a alphanumeric password. After your phone then your personal computer probably has the most important data to you. Banking records, tax documents, photos, etc. Encrypt your drive. -Windows: from Settings, select Privacy security -> Device encryption. Just follow the prompts. -Apple: from Apple icon, select System Preferences -> Security & Privacy icon. Click "Turn On FileVault". -Linux: most distros gives you the option during installation. If you didn't do so then search for how to enable it after the fact based on your distribution. Awesome sauce. You have achieved minimum status. > ADVANCED LEVEL - Encrypt individual files. You already encrypted your computer but guess what, once you start up your computer and log in the key is stored in RAM for as long as it stays on. The beginner level encryption protects your computer when it is off and it means no one can just steal your hard drive and access your files. This is good, but what if someone grabs you while you're sitting there working on it? What if you leave it in sleep mode and not turned off? Then that whole disk encryption is not really going to help you. What if you had individual files that you consider more secret than the others? That finance spreadsheet or that special pic your spouse sent you? That's where individual file encryption comes in. You are just scrolling nostr when they grab you, your computer is on, and unlocked, but those special files are still safely encrypted. I will share with you one of my favorite small programs: Picocrypt. Download the Paranoid pack and store it in multiple drives, email accounts, and cloud storage. That way you will always have a copy to decrypt any files that you stored away. Use it to encrypt any files that you feel need extra attention. It is also very useful for encrypting any files that you intend to store online in cloud storage. You do encrypt your files that are stored online don't you? Yes, even with the company that offers "encrypted" storage. Don't trust their encryption, use your own. > EXPERT LEVEL - Encrypt containers and hidden containers. What if you want to encrypt several files and keep them all together in like a folder or container? That's where Veracrypt comes in. Free, open source, cross platform, and powerful. Veracrypt allows you to create encrypted containers from any file that act like individual drives that can be mounted or unmounted as needed. You can name these files anything that you want, move them around or delete like any file, and make as many as you want. This allows you to have compartmentation of your files and drives. Next trick, Veracrypt allows you to create a hidden container inside that container. Enter one passphrase and you open the encrypted container. Enter a different passphrase and you open a different hidden container. This allows deniability. When they grab you and start pulling your fingernails off until you tell them the password to open the encrypted container, give it to them. They don't have to know that there is another hidden one under that. These features allow you to do all sorts of interesting things only limited by your need and imagination. What if you have a container named as some random config file in your /etc folder? What if you just encrypted a removable storage drive? What if you have multiple hard drives on your computer that have multiple containers and hidden containers? What if you have a hidden container that can only be accessed from booting up in a amnesiac OS like Tails leaving no trace that the files exist or trail that they were ever accessed? Go crazy, have fun. > NEMO - Failsafe Nemo has no files, encrypted or otherwise. If they did you couldn't prove it. Nemo does use something like Tails that retains no memory from boot to boot. Nemo also uses a failsafe. A simple lanyard attached to the flashdrive running the OS and the other end around their wrist while they work. When you try to separate them from the computer the flashdrive pulls out and everything is gone. > > Using these programs you can create a layered and compartmentlized approach to your encryption scheme. There are also plenty of other encryption programs to check out such as Cryptomator, AES Crypt, etc > Last point and most important: Encryption is only as good as the passphrase you use to lock it down. Use a shitty password and it doesn't matter how uncrackable your encryption is.
@ 3b7fc823:e194354f
2024-09-04 00:26:48Encryption is the promethium fire that the cypherpunks secured from heaven for me and you. It is our sacred duty to use and advance that in the world. Encryption is so powerful that governments tried to keep it away from the people and to this day have tried to weaken and backdoor it at every turn. So what is encryption? It is a deep deep rabbit hole and involves a lot of numbers but in a nutshell it uses math to scramble up the data of your file so it is gibberish and can't be read without decrypting it back to regular data. Encryption technology has continued to advance over time and cracking technology to break the encryption has as well. For our purposes all you really need to remember is to use modern cyphers and your encryption is really only going to be as good as the password (use a passphrase) strength you are using to lock it down with. > BEGINNER LEVEL - Encrypt your phone and computer. People walk around with their whole lives on their phone. Protect it. -phone: Congratulations, if you already have a lock screen set on either your iPhone or Android device then device encryption is enabled. If your lock screen password is only 4 digits then we still have work to do. Four digits is only about 10,000 combinations and fairly easy to crack. I believe it only took them about 40 minutes to crack the iPhone of the attempted Trump shooter. Go into settings and set it up for 6 digits or for extra credit use a alphanumeric password. After your phone then your personal computer probably has the most important data to you. Banking records, tax documents, photos, etc. Encrypt your drive. -Windows: from Settings, select Privacy security -> Device encryption. Just follow the prompts. -Apple: from Apple icon, select System Preferences -> Security & Privacy icon. Click "Turn On FileVault". -Linux: most distros gives you the option during installation. If you didn't do so then search for how to enable it after the fact based on your distribution. Awesome sauce. You have achieved minimum status. > ADVANCED LEVEL - Encrypt individual files. You already encrypted your computer but guess what, once you start up your computer and log in the key is stored in RAM for as long as it stays on. The beginner level encryption protects your computer when it is off and it means no one can just steal your hard drive and access your files. This is good, but what if someone grabs you while you're sitting there working on it? What if you leave it in sleep mode and not turned off? Then that whole disk encryption is not really going to help you. What if you had individual files that you consider more secret than the others? That finance spreadsheet or that special pic your spouse sent you? That's where individual file encryption comes in. You are just scrolling nostr when they grab you, your computer is on, and unlocked, but those special files are still safely encrypted. I will share with you one of my favorite small programs: Picocrypt. Download the Paranoid pack and store it in multiple drives, email accounts, and cloud storage. That way you will always have a copy to decrypt any files that you stored away. Use it to encrypt any files that you feel need extra attention. It is also very useful for encrypting any files that you intend to store online in cloud storage. You do encrypt your files that are stored online don't you? Yes, even with the company that offers "encrypted" storage. Don't trust their encryption, use your own. > EXPERT LEVEL - Encrypt containers and hidden containers. What if you want to encrypt several files and keep them all together in like a folder or container? That's where Veracrypt comes in. Free, open source, cross platform, and powerful. Veracrypt allows you to create encrypted containers from any file that act like individual drives that can be mounted or unmounted as needed. You can name these files anything that you want, move them around or delete like any file, and make as many as you want. This allows you to have compartmentation of your files and drives. Next trick, Veracrypt allows you to create a hidden container inside that container. Enter one passphrase and you open the encrypted container. Enter a different passphrase and you open a different hidden container. This allows deniability. When they grab you and start pulling your fingernails off until you tell them the password to open the encrypted container, give it to them. They don't have to know that there is another hidden one under that. These features allow you to do all sorts of interesting things only limited by your need and imagination. What if you have a container named as some random config file in your /etc folder? What if you just encrypted a removable storage drive? What if you have multiple hard drives on your computer that have multiple containers and hidden containers? What if you have a hidden container that can only be accessed from booting up in a amnesiac OS like Tails leaving no trace that the files exist or trail that they were ever accessed? Go crazy, have fun. > NEMO - Failsafe Nemo has no files, encrypted or otherwise. If they did you couldn't prove it. Nemo does use something like Tails that retains no memory from boot to boot. Nemo also uses a failsafe. A simple lanyard attached to the flashdrive running the OS and the other end around their wrist while they work. When you try to separate them from the computer the flashdrive pulls out and everything is gone. > > Using these programs you can create a layered and compartmentlized approach to your encryption scheme. There are also plenty of other encryption programs to check out such as Cryptomator, AES Crypt, etc > Last point and most important: Encryption is only as good as the passphrase you use to lock it down. Use a shitty password and it doesn't matter how uncrackable your encryption is. @ 8cb60e21:5f2deaea
2024-09-03 22:26:25<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/R5fzBNJP6Rk" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-09-03 22:26:25<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/R5fzBNJP6Rk" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 8cb60e21:5f2deaea
2024-09-03 22:26:25<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/SBdDt4BUIW0" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ 8cb60e21:5f2deaea
2024-09-03 22:26:25<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/SBdDt4BUIW0" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 8cb60e21:5f2deaea
2024-09-03 21:58:26# Lesson 3: Arrays, Objects, and Callbacks ### Arrays: Lists of Things Arrays are ordered lists of values. They're perfect for storing multiple related items, like a list of your favorite cat toys: ```javascript var catToys = ["mouse", "ball", "laser pointer"]; console.log(catToys[0]); // Prints "mouse" ``` ### Objects: Grouping Related Information Objects allow you to group related information together. They're like detailed profiles for each of your cat friends: ```javascript var myCat = { name: "Fluffy", age: 3, favoriteFood: "tuna" }; console.log(myCat.name); // Prints "Fluffy" ``` ### Callbacks: Doing Things Later Callbacks are functions that are executed after another function has finished. They're useful for handling asynchronous operations, like waiting for your cat to finish eating before giving it a treat: ```javascript function feedCat(callback) { console.log("Feeding the cat..."); setTimeout(function() { console.log("Cat has finished eating!"); callback(); }, 2000); } feedCat(function() { console.log("Time for a treat!"); }); ``` This code simulates feeding a cat, waiting 2 seconds, and then giving it a treat. Remember, learning JavaScript is a journey. Take your time, practice regularly, and soon you'll be coding like a pro cat!
@ 8cb60e21:5f2deaea
2024-09-03 21:58:26# Lesson 3: Arrays, Objects, and Callbacks ### Arrays: Lists of Things Arrays are ordered lists of values. They're perfect for storing multiple related items, like a list of your favorite cat toys: ```javascript var catToys = ["mouse", "ball", "laser pointer"]; console.log(catToys[0]); // Prints "mouse" ``` ### Objects: Grouping Related Information Objects allow you to group related information together. They're like detailed profiles for each of your cat friends: ```javascript var myCat = { name: "Fluffy", age: 3, favoriteFood: "tuna" }; console.log(myCat.name); // Prints "Fluffy" ``` ### Callbacks: Doing Things Later Callbacks are functions that are executed after another function has finished. They're useful for handling asynchronous operations, like waiting for your cat to finish eating before giving it a treat: ```javascript function feedCat(callback) { console.log("Feeding the cat..."); setTimeout(function() { console.log("Cat has finished eating!"); callback(); }, 2000); } feedCat(function() { console.log("Time for a treat!"); }); ``` This code simulates feeding a cat, waiting 2 seconds, and then giving it a treat. Remember, learning JavaScript is a journey. Take your time, practice regularly, and soon you'll be coding like a pro cat! @ 8cb60e21:5f2deaea
2024-09-03 21:58:26# Lesson 2: Functions and Loops ### Functions: Your Own Commands Functions are reusable blocks of code that perform specific tasks. They're like teaching your cat a new trick: ```javascript function meow(times) { for (var i = 0; i < times; i++) { console.log("Meow!"); } } meow(3); // This will print "Meow!" three times ``` ### Built-in Functions JavaScript comes with many built-in functions. For example, `console.log()` is a function that prints things to the console: ```javascript console.log("I'm a cat!"); ``` ### Loops: Repeating Tasks Loops allow you to repeat a task multiple times without writing the same code over and over. It's like telling your cat to chase its tail for a specific number of rounds: ```javascript for (var i = 0; i < 5; i++) { console.log("Chasing tail, round " + (i + 1)); } ``` This will print "Chasing tail, round X" five times, where X goes from 1 to 5.
@ 8cb60e21:5f2deaea
2024-09-03 21:58:26# Lesson 2: Functions and Loops ### Functions: Your Own Commands Functions are reusable blocks of code that perform specific tasks. They're like teaching your cat a new trick: ```javascript function meow(times) { for (var i = 0; i < times; i++) { console.log("Meow!"); } } meow(3); // This will print "Meow!" three times ``` ### Built-in Functions JavaScript comes with many built-in functions. For example, `console.log()` is a function that prints things to the console: ```javascript console.log("I'm a cat!"); ``` ### Loops: Repeating Tasks Loops allow you to repeat a task multiple times without writing the same code over and over. It's like telling your cat to chase its tail for a specific number of rounds: ```javascript for (var i = 0; i < 5; i++) { console.log("Chasing tail, round " + (i + 1)); } ``` This will print "Chasing tail, round X" five times, where X goes from 1 to 5. @ 4c96d763:80c3ee30
2024-09-03 18:46:10# Changes ## William Casarin (7): - debug: add subid debugging - fix bug where it was subscribing too many times - arg: add -c profile{,:pubkey} arg column - env: add some test npubs - arg: add -c universe column - appease clippy - fonts: add thai support pushed to [notedeck:refs/heads/master](http://git.jb55.com/notedeck/commit/989f88c989f5d6ec85f719efab6f80fb1a95ee00.html)
@ 4c96d763:80c3ee30
2024-09-03 18:46:10# Changes ## William Casarin (7): - debug: add subid debugging - fix bug where it was subscribing too many times - arg: add -c profile{,:pubkey} arg column - env: add some test npubs - arg: add -c universe column - appease clippy - fonts: add thai support pushed to [notedeck:refs/heads/master](http://git.jb55.com/notedeck/commit/989f88c989f5d6ec85f719efab6f80fb1a95ee00.html) @ 6bae33c8:607272e8
2024-09-03 10:47:55I do this every year, and every year I get at least one correct. [Last year](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), I got exactly one correct and unfortunately it was the surefire prediction that not all of them would be right, i.e., I got really zero correct. But that just goes to show how bold they were. These aren’t layups, more like three pointers and half-court shots. I fared much better the [previous](https://www.realmansports.com/p/grading-my-bold-predictions) two [years](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), so hopefully these will get back on track. *(Actually, probably better to just link to all of them for full transparency: [2023](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), [2022](https://www.realmansports.com/p/grading-my-bold-predictions), [2021](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), [2020](https://www.rotowire.com/football/article.php?id=54494), [2019](https://www.rotowire.com/football/article.php?id=48921), [2018,](https://www.rotowire.com/football/article.php?id=41171) [2017](https://www.rotowire.com/football/article.php?id=37079), [2016](https://www.rotowire.com/football/article.php?id=31269), [2015](https://www.rotowire.com/football/article.php?id=26515), [2014](https://www.rotowire.com/football/article.php?id=22258).) I’m not going to argue it matters, or that anyone even clicks through on these, but I want to pat myself on the back for being so organized in archiving my old work.)* 1. **Stefon Diggs leads the Texans in targets, catches and receiving yards** Right now, he’s getting drafted more than a round behind Nico Collins and less than a round ahead of Tank Dell. Diggs is 30, but he was one of the league’s best receivers until halfway through last year when the Bills made an offensive play-calling change. Moreover, Diggs is getting paid $22.5 million, so the Texans obviously don’t think he’s washed up, and he’s also in a contract year. 2. **CJ Stroud leads the NFL is passing yards** This is +600 on DraftKings, so the real odds are probably north of 8:1. Stroud adds Diggs to his receiving corps, doesn’t run much and heads into Year 2. 3. **Roman Wilson (ADP 211) has more receptions than George Pickens (ADP 47)** Pickens is a boom or bust downfield playmaker, not high-target alpha, and Wilson is a good fit for the slot for the Steelers new QBs. Think Martavis Bryant not Antonio Brown. (Not that Wilson is Brown!) Van Jefferson isn’t good, and someone will need to fill the void. Moreover, because Pittsburgh has new QBs, neither has an existing rapport with the incumbent Pickens. 4. **DeAndre Hopkins (ADP 82) out produces Calvin Ridley (ADP 54) in PPR** Hopkins wasn’t terrible last year, has a rapport with Will Levis and is a future Hall of Famer who can still run routes. Ridley is already 29 and is just a guy outside of his monster season in 2020. 5. **The Giants will field a top-10 fantasy defense.** I’ve been crushed by my homer bold predictions in the past, but they added Brian Burns to a rush that already had Dexter Lawrence and Kayvon Thibodeaux, the offense should be on the field more and generate some leads with a real playmaking receiver in Malik Nabers. 6. **One of the following Year 2 receivers will finish in the top-15 PPR: Jaxon Smith-Njigba, Jayden Reed, Jordan Addison, Dontayvion Wicks, Michael Wilson, Josh Downs, Andrei Iosivas, Quentin Johnston, Marvin Mims, Jalin Hyatt** I make this prediction every year, and it often pans out as Year 2 is when receivers typically make the leap. I left out Tank Dell because he’s now got a fifth-round ADP, as well as the obvious ones: Zay Flowers, Rashee Rice and Puka Nacua. 7. **Rome Odunze (ADP 77) will outproduce Xavier Worthy (ADP 59)** Both receivers enter crowded situations, and while Worthy’s is far better, he’s also got essentially the same skill-set as teammate Marquise Brown. Moreover, Andy Reid rarely entrusts rookies with large roles, especially early on. Odunze is 6-3, 215 and has the pedigree of a true NFL alpha, while Worthy weighs only 165 pounds at 5-11. Finally, Patrick Mahomes already has an established rapport with both Travis Kelce and Rashee Rice, while Odunze gets a more open competition with the Bears veteran WRs, given all three will play with Caleb Williams for the first time. 8. **Dalvin Cook will lead the Cowboys in rushing yards** Cook is 29 and looked beyond “cooked” last year on the Jets, but his 3.3 YPC was on a small sample (67 carries), and prior to that, he’d been very good for the Vikings. At the very least he should have fresh legs, and he’d only need to beat out the ancient Ezekiel Elliott and Rico Dowdle. (Of course, Cook would have to be promoted from the practice squad first, so I really should hedge and make the prediction “neither Elliott, nor Dowdle will lead the Cowboys in rushing yards,” but I’ll push it and say it’s Cook.) 9. **Jonathan Taylor (ADP12 ) will lead the NFL in rushing yards.** He’s got little competition in the Indy backfield and a running QB who should open lanes for him. Draft Kings has him at +600, so his real odds are probably about 10:1, but I’d take him over the favored Christian McCaffrey (age/mileage) and all the other backs who are more hybrid types or old (Derrick Henry.) 10. **Dalton Kincaid (TE4) will lead all TE in catches** I guess this is a chalky pick because he and Kelce are both favored at the position at +3000, while Evan Engram is +5000! (I’d way rather bet on Engram at those odds.) But straight up, I’m going with Kincaid who is likely Josh Allen’s de facto No. 1 target with Diggs gone. In his final 11 regular season games Kincaid had 56 catches which prorates to 87 catches over the full year. And rookie tight ends rarely do anything and often make a leap in Year 2. 11. **Some of these predictions will be wrong** No one’s perfect, but you never want to get shut out.
@ 6bae33c8:607272e8
2024-09-03 10:47:55I do this every year, and every year I get at least one correct. [Last year](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), I got exactly one correct and unfortunately it was the surefire prediction that not all of them would be right, i.e., I got really zero correct. But that just goes to show how bold they were. These aren’t layups, more like three pointers and half-court shots. I fared much better the [previous](https://www.realmansports.com/p/grading-my-bold-predictions) two [years](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), so hopefully these will get back on track. *(Actually, probably better to just link to all of them for full transparency: [2023](https://www.realmansports.com/p/grading-my-bold-predictions-e72?utm_source=publication-search), [2022](https://www.realmansports.com/p/grading-my-bold-predictions), [2021](https://www.rotowire.com/football/article/east-coast-offense-grading-my-predictions-61196), [2020](https://www.rotowire.com/football/article.php?id=54494), [2019](https://www.rotowire.com/football/article.php?id=48921), [2018,](https://www.rotowire.com/football/article.php?id=41171) [2017](https://www.rotowire.com/football/article.php?id=37079), [2016](https://www.rotowire.com/football/article.php?id=31269), [2015](https://www.rotowire.com/football/article.php?id=26515), [2014](https://www.rotowire.com/football/article.php?id=22258).) I’m not going to argue it matters, or that anyone even clicks through on these, but I want to pat myself on the back for being so organized in archiving my old work.)* 1. **Stefon Diggs leads the Texans in targets, catches and receiving yards** Right now, he’s getting drafted more than a round behind Nico Collins and less than a round ahead of Tank Dell. Diggs is 30, but he was one of the league’s best receivers until halfway through last year when the Bills made an offensive play-calling change. Moreover, Diggs is getting paid $22.5 million, so the Texans obviously don’t think he’s washed up, and he’s also in a contract year. 2. **CJ Stroud leads the NFL is passing yards** This is +600 on DraftKings, so the real odds are probably north of 8:1. Stroud adds Diggs to his receiving corps, doesn’t run much and heads into Year 2. 3. **Roman Wilson (ADP 211) has more receptions than George Pickens (ADP 47)** Pickens is a boom or bust downfield playmaker, not high-target alpha, and Wilson is a good fit for the slot for the Steelers new QBs. Think Martavis Bryant not Antonio Brown. (Not that Wilson is Brown!) Van Jefferson isn’t good, and someone will need to fill the void. Moreover, because Pittsburgh has new QBs, neither has an existing rapport with the incumbent Pickens. 4. **DeAndre Hopkins (ADP 82) out produces Calvin Ridley (ADP 54) in PPR** Hopkins wasn’t terrible last year, has a rapport with Will Levis and is a future Hall of Famer who can still run routes. Ridley is already 29 and is just a guy outside of his monster season in 2020. 5. **The Giants will field a top-10 fantasy defense.** I’ve been crushed by my homer bold predictions in the past, but they added Brian Burns to a rush that already had Dexter Lawrence and Kayvon Thibodeaux, the offense should be on the field more and generate some leads with a real playmaking receiver in Malik Nabers. 6. **One of the following Year 2 receivers will finish in the top-15 PPR: Jaxon Smith-Njigba, Jayden Reed, Jordan Addison, Dontayvion Wicks, Michael Wilson, Josh Downs, Andrei Iosivas, Quentin Johnston, Marvin Mims, Jalin Hyatt** I make this prediction every year, and it often pans out as Year 2 is when receivers typically make the leap. I left out Tank Dell because he’s now got a fifth-round ADP, as well as the obvious ones: Zay Flowers, Rashee Rice and Puka Nacua. 7. **Rome Odunze (ADP 77) will outproduce Xavier Worthy (ADP 59)** Both receivers enter crowded situations, and while Worthy’s is far better, he’s also got essentially the same skill-set as teammate Marquise Brown. Moreover, Andy Reid rarely entrusts rookies with large roles, especially early on. Odunze is 6-3, 215 and has the pedigree of a true NFL alpha, while Worthy weighs only 165 pounds at 5-11. Finally, Patrick Mahomes already has an established rapport with both Travis Kelce and Rashee Rice, while Odunze gets a more open competition with the Bears veteran WRs, given all three will play with Caleb Williams for the first time. 8. **Dalvin Cook will lead the Cowboys in rushing yards** Cook is 29 and looked beyond “cooked” last year on the Jets, but his 3.3 YPC was on a small sample (67 carries), and prior to that, he’d been very good for the Vikings. At the very least he should have fresh legs, and he’d only need to beat out the ancient Ezekiel Elliott and Rico Dowdle. (Of course, Cook would have to be promoted from the practice squad first, so I really should hedge and make the prediction “neither Elliott, nor Dowdle will lead the Cowboys in rushing yards,” but I’ll push it and say it’s Cook.) 9. **Jonathan Taylor (ADP12 ) will lead the NFL in rushing yards.** He’s got little competition in the Indy backfield and a running QB who should open lanes for him. Draft Kings has him at +600, so his real odds are probably about 10:1, but I’d take him over the favored Christian McCaffrey (age/mileage) and all the other backs who are more hybrid types or old (Derrick Henry.) 10. **Dalton Kincaid (TE4) will lead all TE in catches** I guess this is a chalky pick because he and Kelce are both favored at the position at +3000, while Evan Engram is +5000! (I’d way rather bet on Engram at those odds.) But straight up, I’m going with Kincaid who is likely Josh Allen’s de facto No. 1 target with Diggs gone. In his final 11 regular season games Kincaid had 56 catches which prorates to 87 catches over the full year. And rookie tight ends rarely do anything and often make a leap in Year 2. 11. **Some of these predictions will be wrong** No one’s perfect, but you never want to get shut out. @ 161c8564:2d633b95
2024-09-02 20:24:34Opinion about Freewallet Multi Crypto Wallet (iphone) <!--HEADER END--> FRWT Wallet uses deceptive marketing to lure in unsuspecting users. Once you deposit funds, they’ll block your account under the guise of KYC checks. It’s a fraudulent app—don’t download it! <!--FOOTER START--> #WalletScrutiny #nostrOpinion [Join the conversation!](https://walletscrutiny.com/iphone/mw.org.freewallet.app)
@ 161c8564:2d633b95
2024-09-02 20:24:34Opinion about Freewallet Multi Crypto Wallet (iphone) <!--HEADER END--> FRWT Wallet uses deceptive marketing to lure in unsuspecting users. Once you deposit funds, they’ll block your account under the guise of KYC checks. It’s a fraudulent app—don’t download it! <!--FOOTER START--> #WalletScrutiny #nostrOpinion [Join the conversation!](https://walletscrutiny.com/iphone/mw.org.freewallet.app) @ eed76ece:afa98124
2024-09-02 18:58:30As the World continues to create more and more NEW regulations. And as free speech get attacked from every angle. Bonafide business owners, especially importers will need to find ways to migrate sales offerings of goods and services. It feels like the majority of business owners have to really take this seriously. Obviously so many different methods are used around the World already, but when the upcoming new mandatory vaccinations, vaccine passport travel restrictions really hit, businesses will have to jump to more selling online. SN, Nostr and other unknown communication methods are Paramount. As usual it feels like no one is taking free speech attacks seriously. The amount of postings my customers around the World do daily on WhatsApp, LINE (Asia), Telegram, Twitter will move where it is allowed to move. Feels like there's an ongoing increase in the attack not just on the West, but from WITHIN the West. Regardless if you retail, wholesale, manufacture, are an agent we try hard to be pro active on marketing on multiple methods. It seems very logical that in the future Nostr and SN will pick up International users as a way to get their goods posted somehow someway. Examples Customers in these regions I deal with primarily communicate with me in Japan, Thailand using LINE and Tik Tok daily. Most of the rest of the World communicate with me using WhatsApp. Certain parts of Eastern Europe and Asia Telegram. Interestingly my resellers in the USA primarily post on WhatsApp. Westerners especially Americans seem to have enough money, they are not hungry for making more money, or increasing their business growth, they think everything is ok. "We will always be okay, there will NEVER be a Worldwide depression, recession, deflation, increased restrictions, they will NEVER force a new vaccine on us again, they will NEVER lock business and us down again". "So I will always have free speech, the politicians told me so". originally posted at https://stacker.news/items/670041
@ eed76ece:afa98124
2024-09-02 18:58:30As the World continues to create more and more NEW regulations. And as free speech get attacked from every angle. Bonafide business owners, especially importers will need to find ways to migrate sales offerings of goods and services. It feels like the majority of business owners have to really take this seriously. Obviously so many different methods are used around the World already, but when the upcoming new mandatory vaccinations, vaccine passport travel restrictions really hit, businesses will have to jump to more selling online. SN, Nostr and other unknown communication methods are Paramount. As usual it feels like no one is taking free speech attacks seriously. The amount of postings my customers around the World do daily on WhatsApp, LINE (Asia), Telegram, Twitter will move where it is allowed to move. Feels like there's an ongoing increase in the attack not just on the West, but from WITHIN the West. Regardless if you retail, wholesale, manufacture, are an agent we try hard to be pro active on marketing on multiple methods. It seems very logical that in the future Nostr and SN will pick up International users as a way to get their goods posted somehow someway. Examples Customers in these regions I deal with primarily communicate with me in Japan, Thailand using LINE and Tik Tok daily. Most of the rest of the World communicate with me using WhatsApp. Certain parts of Eastern Europe and Asia Telegram. Interestingly my resellers in the USA primarily post on WhatsApp. Westerners especially Americans seem to have enough money, they are not hungry for making more money, or increasing their business growth, they think everything is ok. "We will always be okay, there will NEVER be a Worldwide depression, recession, deflation, increased restrictions, they will NEVER force a new vaccine on us again, they will NEVER lock business and us down again". "So I will always have free speech, the politicians told me so". originally posted at https://stacker.news/items/670041 @ 56a6da9b:7f5a2243
2024-09-02 18:27:19IO used to have a lot of content and now the only thing that shows up is my fouintain stuff. when i go into other nostr things it's not there anymore and i look like an anonymous user with no profile pic, or profile and no activity. originally posted at https://stacker.news/items/669994
@ 56a6da9b:7f5a2243
2024-09-02 18:27:19IO used to have a lot of content and now the only thing that shows up is my fouintain stuff. when i go into other nostr things it's not there anymore and i look like an anonymous user with no profile pic, or profile and no activity. originally posted at https://stacker.news/items/669994 @ 6bae33c8:607272e8
2024-09-02 18:09:19I did the third and final NFFC Beat Chris Liss league last night, and it was one of the more interesting and aggressive drafts I’ve ever done. I picked from the seven slot. Here are the results: ([Link to livestream](https://www.realmansports.com/p/beat-chris-liss-3-livestream)) <img src="https://blossom.primal.net/269209e3c21e86749662ec594f0344c7aa45073d1c590d61fec611e74e1e15a8.png"> **1.7 Ja’Marr Chase** — I made seven my first choice, but then realized I probably should have gone with four or five, or maybe nine or 10. That’s because if the first six picks went chalk (and they did), I’d be faced with Chase who is holding out for a new contract (and who I have in two other leagues already), Justin Jefferson (new, bad QB) or Garrett Wilson (new QB, never been a Round 1-level WR.) At 1.9 I’d have gotten one of those guys anyway, but earlier picks on the way back. And at 1.4, I’d have gotten a shot at Bijan Robinson for an easier hero-RB build. But I had pick seven, and I tripled-down on Chase because I think it’s very likely he’ll get his extension (or play if he doesn’t), and he’s an all-time talent with a top QB and projects for a massive target share. Plus, if he busts [it’s Alan Seslowsky’s fault](https://www.youtube.com/watch?v=9n2l5ywZY4M), and having someone to blame is paramount. **2.6 Drake London** — I had it mapped out via ADP that I’d likely get De’Von Achane here, but he went at his min pick (I’m pretty sure) at the 1-2 turn, and so I was scrambling a bit. I really wanted Puka Nacua, who I missed by one pick, considered Cooper Kupp, but ended up going for the ADP-faller London who I had not remotely planned on getting. London obviously benefits from the massive QB upgrade in Atlanta, but it’s an open question whether he’s really an elite receiver or just a good one, and Kyle Pitts could easily emerge as Kurt Cousins favorite target instead. **3.6 DeVonta Smith** — When Derrick Henry went one pick ahead of me, it was between Smith and Jaylen Waddle who I took in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e). Normally I avoid receivers this undersized but Smith has always produced at every level and is locked into his sizeable target share. Plus I read some [Scott Barrett tweets](https://x.com/ScottBarrettDFB/status/1829973477131952161) about how Kellen Moore’s offense boosts the slot receiver a ton and that Smith thrives in the slot and could see more work there. **4.7 Stefon Diggs** — This was ideal. I now have Diggs in all four of my leagues so far. Maybe he’s hit a cliff at age 30, but he’s getting $22.5M to play in arguably the league’s top passing game that lacks a true No. 1 alpha. I also considered Tee Higgins to pair with Chase (and serve as Chase insurance), but Diggs has more upside as a potential No. 1 target. **5.6 Dalton Kincaid** — I’ve been high on him all summer, but he never quite fell to me in the right place until now. I expect him to be Josh Allen’s No. 1 receiver now that Diggs is gone. **6.7 James Conner** — I needed a RB, and Conner is one. I’m a bit wary of a 29-YO guy with an extensive injury history, but he averaged 5.0 YPC last year and has never had a massive workload so he’s fresh for his age at least. Plus, the Cardinals offense should be good this year. **7.6 Anthony Richardson** — I wasn’t planning on taking a QB here, or even Richardson who I have in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e) in Round 5!, but I couldn’t pull the trigger on Zamir White over someone with Richardson’s upside. I’m trying to win the overall contest, not simply cover the bases with starters at every position. **8.7 Jonathon Brooks** — Jaylen Warren was still on the board, and he was a viable Week 1 starter for me, but Brooks who is on IR, struck me as the upside play. I heard somewhere, can’t remember where, that Brooks was an elite prospect in college before the injury, and there’s a lot of hype about Carolina’s new offensive brain trust boosting the offense generally. But it might have been a rash pick given my zero-RB build to take a rookie on IR. **9.6 Marquise Brown** — I missed Warren by one pick on the way back, and instead of pivoting to Tyjae Spears I leaned into the zero-RB by taking Brown who was going in the fifth or sixth round before his injury. The beauty of this pick is I don’t need Brown right away as I wouldn’t start him anyway, so I pay no price for him missing Week 1. The ugly of this pick is I missed out on Spears, Zack Moss and Chuba Hubbard (who would have been nice to pair with Brooks.) **10.7 Joe Burrow** — The obvious pick was Trey Benson to pair with Conner. In fact, I could have had Hubbard in Round 9 and Benson in 10 to lock up two backfields for my zero-RB team. But no, I had to take a *second* QB here because (a) Richardson has a low floor; (b) this was cheap for Burrow; and (c) I could potentially pair Burrow with Chase for the playoffs. If you’re gonna go zero RB, lean the into it. (The other problem with this pick is the weekly headache of picking my starting QB.) **11.6 Jaleel McLaughlin** — The Burrow pick cost me not only Benson but JK Dobbins too, but I had my eye on McLaughlin who apparently was a god in college, and [per Barrett](https://x.com/ScottBarrettDFB/status/1829971593852043394) is in an ideal spot as the RB2 in Sean Payton’s offense. Now that stat has to be tempered a bit given that peak Alvin Kamara was the source of so much of it, but how much of that was Payton’s offense? In any event, I’m seriously rolling into Week 1 with McLaughlin in my active lineup because of the Richardson, Brooks, Brown and Burrow picks. **12.7 Jordan Mason** — Obviously he’s not usable unless and until Christian McCaffrey gets hurt, and the Niners badly need Trent Williams to report, but he’s a top-10 RB if McCaffrey, who played into February last year, goes down. This also furthers my extreme “what could go right” build. **13.6 Braelon Allen** — Oddly I view this pick as a mistake as he was higher in ADP, so I thought I could wait another round on Giants backup Tyrone Tracy. (Tracy went three picks ahead of me in the next round.) Allen might be good, but only a Breece Hall injury could free him up whereas Tracy could just outplay Devin Singletary. Granted the Jets might be a better environment than the Giants, so Allen could have more upside if he did get a shot, but Tracy is also a converted WR and would likely catch a lot of passes if he got the job. **14.7 Khalil Herbert** — Once Tracy was gone, I pivoted to Herbert. The Chicago backfield is crowded, but D’Andre Swift always gets hurt, and Roschon Johnson isn’t as good a runner as Herbert. **15.6 Jalen McMillan** — I wanted to get Cam Akers because Joe Mixon is old, but I missed him by two picks and pivoted (finally) back to WR. McMillan’s created some buzz in camp, and both Mike Evans and Chris Godwin are getting old. **16.7 Will Shipley** — I love Saquon Barkley, but he’s getting old and has been hurt a lot. Kenneth Gainwell is ostensibly ahead of Shipley, but is just a guy. Another top-10 upside back should the starter go down. **17.6 Dalvin Cook** — He’s on the practice squad for now, and he looked beyond done last year with the Jets, but keep in mind he only got 67 carries, and the Cowboys don’t have serious obstacles ahead of him should he regain even 60 percent of his prior form. Cook was still very good in 2022, and he should have fresh legs too. **18.7 Quentin Johnston** — I needed one more receiver, and Johnston is one. Seriously, though he was a first-round pick only last year, and he’s competing with only Josh Palmer and a rookie. **19.6 Younghoe Koo** — All these years I was with a wonderful kicker in Justin Tucker, but I’m trading him in for a Younghoe. (That joke will get old one day, just not in any of our lifetimes.) **20.7 Giants Defense** — They draw Sam Darnold and Jayden Daniels the first two weeks, and added Brian Burns to Kayvon Thibodeaux and Dexter Lawrence. **Roster By Position** **QB** Anthony Richardson **RB** James Conner/Jaleel McLaughlin **WR** Ja’Marr Chase/Drake London/DeVonta Smith **TE** Dalton Kincaid **FLEX** Stefon Diggs **K** Younghoe Koo **D** Giants **Bench** Jonathan Brooks/Marquise Brown/Joe Burrow/Jordan Mason/Braelon Allen/Khalil Herbert/Jalen McMillan/Will Shipley/Dalvin Cook/Quentin Johnston
@ 6bae33c8:607272e8
2024-09-02 18:09:19I did the third and final NFFC Beat Chris Liss league last night, and it was one of the more interesting and aggressive drafts I’ve ever done. I picked from the seven slot. Here are the results: ([Link to livestream](https://www.realmansports.com/p/beat-chris-liss-3-livestream)) <img src="https://blossom.primal.net/269209e3c21e86749662ec594f0344c7aa45073d1c590d61fec611e74e1e15a8.png"> **1.7 Ja’Marr Chase** — I made seven my first choice, but then realized I probably should have gone with four or five, or maybe nine or 10. That’s because if the first six picks went chalk (and they did), I’d be faced with Chase who is holding out for a new contract (and who I have in two other leagues already), Justin Jefferson (new, bad QB) or Garrett Wilson (new QB, never been a Round 1-level WR.) At 1.9 I’d have gotten one of those guys anyway, but earlier picks on the way back. And at 1.4, I’d have gotten a shot at Bijan Robinson for an easier hero-RB build. But I had pick seven, and I tripled-down on Chase because I think it’s very likely he’ll get his extension (or play if he doesn’t), and he’s an all-time talent with a top QB and projects for a massive target share. Plus, if he busts [it’s Alan Seslowsky’s fault](https://www.youtube.com/watch?v=9n2l5ywZY4M), and having someone to blame is paramount. **2.6 Drake London** — I had it mapped out via ADP that I’d likely get De’Von Achane here, but he went at his min pick (I’m pretty sure) at the 1-2 turn, and so I was scrambling a bit. I really wanted Puka Nacua, who I missed by one pick, considered Cooper Kupp, but ended up going for the ADP-faller London who I had not remotely planned on getting. London obviously benefits from the massive QB upgrade in Atlanta, but it’s an open question whether he’s really an elite receiver or just a good one, and Kyle Pitts could easily emerge as Kurt Cousins favorite target instead. **3.6 DeVonta Smith** — When Derrick Henry went one pick ahead of me, it was between Smith and Jaylen Waddle who I took in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e). Normally I avoid receivers this undersized but Smith has always produced at every level and is locked into his sizeable target share. Plus I read some [Scott Barrett tweets](https://x.com/ScottBarrettDFB/status/1829973477131952161) about how Kellen Moore’s offense boosts the slot receiver a ton and that Smith thrives in the slot and could see more work there. **4.7 Stefon Diggs** — This was ideal. I now have Diggs in all four of my leagues so far. Maybe he’s hit a cliff at age 30, but he’s getting $22.5M to play in arguably the league’s top passing game that lacks a true No. 1 alpha. I also considered Tee Higgins to pair with Chase (and serve as Chase insurance), but Diggs has more upside as a potential No. 1 target. **5.6 Dalton Kincaid** — I’ve been high on him all summer, but he never quite fell to me in the right place until now. I expect him to be Josh Allen’s No. 1 receiver now that Diggs is gone. **6.7 James Conner** — I needed a RB, and Conner is one. I’m a bit wary of a 29-YO guy with an extensive injury history, but he averaged 5.0 YPC last year and has never had a massive workload so he’s fresh for his age at least. Plus, the Cardinals offense should be good this year. **7.6 Anthony Richardson** — I wasn’t planning on taking a QB here, or even Richardson who I have in [BCL2](https://www.realmansports.com/p/beat-chris-liss-2-77e) in Round 5!, but I couldn’t pull the trigger on Zamir White over someone with Richardson’s upside. I’m trying to win the overall contest, not simply cover the bases with starters at every position. **8.7 Jonathon Brooks** — Jaylen Warren was still on the board, and he was a viable Week 1 starter for me, but Brooks who is on IR, struck me as the upside play. I heard somewhere, can’t remember where, that Brooks was an elite prospect in college before the injury, and there’s a lot of hype about Carolina’s new offensive brain trust boosting the offense generally. But it might have been a rash pick given my zero-RB build to take a rookie on IR. **9.6 Marquise Brown** — I missed Warren by one pick on the way back, and instead of pivoting to Tyjae Spears I leaned into the zero-RB by taking Brown who was going in the fifth or sixth round before his injury. The beauty of this pick is I don’t need Brown right away as I wouldn’t start him anyway, so I pay no price for him missing Week 1. The ugly of this pick is I missed out on Spears, Zack Moss and Chuba Hubbard (who would have been nice to pair with Brooks.) **10.7 Joe Burrow** — The obvious pick was Trey Benson to pair with Conner. In fact, I could have had Hubbard in Round 9 and Benson in 10 to lock up two backfields for my zero-RB team. But no, I had to take a *second* QB here because (a) Richardson has a low floor; (b) this was cheap for Burrow; and (c) I could potentially pair Burrow with Chase for the playoffs. If you’re gonna go zero RB, lean the into it. (The other problem with this pick is the weekly headache of picking my starting QB.) **11.6 Jaleel McLaughlin** — The Burrow pick cost me not only Benson but JK Dobbins too, but I had my eye on McLaughlin who apparently was a god in college, and [per Barrett](https://x.com/ScottBarrettDFB/status/1829971593852043394) is in an ideal spot as the RB2 in Sean Payton’s offense. Now that stat has to be tempered a bit given that peak Alvin Kamara was the source of so much of it, but how much of that was Payton’s offense? In any event, I’m seriously rolling into Week 1 with McLaughlin in my active lineup because of the Richardson, Brooks, Brown and Burrow picks. **12.7 Jordan Mason** — Obviously he’s not usable unless and until Christian McCaffrey gets hurt, and the Niners badly need Trent Williams to report, but he’s a top-10 RB if McCaffrey, who played into February last year, goes down. This also furthers my extreme “what could go right” build. **13.6 Braelon Allen** — Oddly I view this pick as a mistake as he was higher in ADP, so I thought I could wait another round on Giants backup Tyrone Tracy. (Tracy went three picks ahead of me in the next round.) Allen might be good, but only a Breece Hall injury could free him up whereas Tracy could just outplay Devin Singletary. Granted the Jets might be a better environment than the Giants, so Allen could have more upside if he did get a shot, but Tracy is also a converted WR and would likely catch a lot of passes if he got the job. **14.7 Khalil Herbert** — Once Tracy was gone, I pivoted to Herbert. The Chicago backfield is crowded, but D’Andre Swift always gets hurt, and Roschon Johnson isn’t as good a runner as Herbert. **15.6 Jalen McMillan** — I wanted to get Cam Akers because Joe Mixon is old, but I missed him by two picks and pivoted (finally) back to WR. McMillan’s created some buzz in camp, and both Mike Evans and Chris Godwin are getting old. **16.7 Will Shipley** — I love Saquon Barkley, but he’s getting old and has been hurt a lot. Kenneth Gainwell is ostensibly ahead of Shipley, but is just a guy. Another top-10 upside back should the starter go down. **17.6 Dalvin Cook** — He’s on the practice squad for now, and he looked beyond done last year with the Jets, but keep in mind he only got 67 carries, and the Cowboys don’t have serious obstacles ahead of him should he regain even 60 percent of his prior form. Cook was still very good in 2022, and he should have fresh legs too. **18.7 Quentin Johnston** — I needed one more receiver, and Johnston is one. Seriously, though he was a first-round pick only last year, and he’s competing with only Josh Palmer and a rookie. **19.6 Younghoe Koo** — All these years I was with a wonderful kicker in Justin Tucker, but I’m trading him in for a Younghoe. (That joke will get old one day, just not in any of our lifetimes.) **20.7 Giants Defense** — They draw Sam Darnold and Jayden Daniels the first two weeks, and added Brian Burns to Kayvon Thibodeaux and Dexter Lawrence. **Roster By Position** **QB** Anthony Richardson **RB** James Conner/Jaleel McLaughlin **WR** Ja’Marr Chase/Drake London/DeVonta Smith **TE** Dalton Kincaid **FLEX** Stefon Diggs **K** Younghoe Koo **D** Giants **Bench** Jonathan Brooks/Marquise Brown/Joe Burrow/Jordan Mason/Braelon Allen/Khalil Herbert/Jalen McMillan/Will Shipley/Dalvin Cook/Quentin Johnston @ 266815e0:6cd408a5
2024-09-02 15:27:16After 7 months of work and procrastination I've decided to release another version of noStrudel There a ton of new features and a few bugs fixed. This article highlights the biggest changes but if you want to read the full changelog you can find it in the [github repo](https://github.com/hzrd149/nostrudel/blob/master/CHANGELOG.md) And as always if you want to check it out you can use [nostrudel.ninja](https://nostrudel.ninja) or run it locally using docker ```sh docker run --rm -p 8080:80 ghcr.io/hzrd149/nostrudel:0.40.0 ``` ## New Features ### Support for NIP-49 encrypted nsec Now when logging into to the app it will prompt you to set a password to encrypt your nsec so it can be stored securely (if that's even possible for a web client...) There is also a new "Account" settings view that lets you export you nsec as a ncryptsec so you can copy it to other apps  ### Blindspot feeds There are also new "blindspot" feeds that show what others are seeing in their timeline that your missing  ### NIP-42 Relay authentication The app now supports NIP-42 relay authentication. Its opt-in though, so if you want to use popular authenticated relays like nostr.wine or relay.snort.social you will have to enable it in the settings  ### Wasm relay and event verification The app now supports using [@snort/worker-relay](https://git.v0l.io/Kieran/snort/src/branch/main/packages/worker-relay) as a local relay. Its at least 10x faster than the internal browser cache and can hold at least 100x more events. Its not enabled by default though so if you want to use it you have to switch to it in the "Relays" -> "Cache Relay" view  The app also supports using [nostr-wasm](https://github.com/fiatjaf/nostr-wasm) to speed up event signature verification. This is enabled by default, but if you want to still use the JavaScript verification or no verification you can find it in the performance setting  ### Thread tabs Threads now have a set of tabs that let you see the Replies, Quotes, Zaps, and other stuff related to the note   ### Wiki articles Its not feature complete but you can now view and edit wiki articles in the app  ### Finished the launchpad The launchpad is now usable and shows the latest notifications, messages, streams, and tools  ### Blossom uploads The app now lets you upload images and video to blossom server, this isn't enabled by default though so your going to have to enable it in the settings  And then setup some blossom servers in the settings. A few good public ones are `https://cdn.satellite.earth` and `https://cdn.nostrcheck.me`  ### Task Manager There is also a new "Task Manager" in the side nav that lets you see whats going on under the hood in the app  You can see what relays the app is currently connected to  And which relays are requesting NIP-42 authentication  ## Bug fixes - Fix null relay hints in DMs - Fix users own events being hidden by muted words - Fix random events showing up as DM messages - Fix app prompting NIP-07 extension to unlock when app opens - Remove corsproxy.io as default service for CORS proxy
@ 266815e0:6cd408a5
2024-09-02 15:27:16After 7 months of work and procrastination I've decided to release another version of noStrudel There a ton of new features and a few bugs fixed. This article highlights the biggest changes but if you want to read the full changelog you can find it in the [github repo](https://github.com/hzrd149/nostrudel/blob/master/CHANGELOG.md) And as always if you want to check it out you can use [nostrudel.ninja](https://nostrudel.ninja) or run it locally using docker ```sh docker run --rm -p 8080:80 ghcr.io/hzrd149/nostrudel:0.40.0 ``` ## New Features ### Support for NIP-49 encrypted nsec Now when logging into to the app it will prompt you to set a password to encrypt your nsec so it can be stored securely (if that's even possible for a web client...) There is also a new "Account" settings view that lets you export you nsec as a ncryptsec so you can copy it to other apps  ### Blindspot feeds There are also new "blindspot" feeds that show what others are seeing in their timeline that your missing  ### NIP-42 Relay authentication The app now supports NIP-42 relay authentication. Its opt-in though, so if you want to use popular authenticated relays like nostr.wine or relay.snort.social you will have to enable it in the settings  ### Wasm relay and event verification The app now supports using [@snort/worker-relay](https://git.v0l.io/Kieran/snort/src/branch/main/packages/worker-relay) as a local relay. Its at least 10x faster than the internal browser cache and can hold at least 100x more events. Its not enabled by default though so if you want to use it you have to switch to it in the "Relays" -> "Cache Relay" view  The app also supports using [nostr-wasm](https://github.com/fiatjaf/nostr-wasm) to speed up event signature verification. This is enabled by default, but if you want to still use the JavaScript verification or no verification you can find it in the performance setting  ### Thread tabs Threads now have a set of tabs that let you see the Replies, Quotes, Zaps, and other stuff related to the note   ### Wiki articles Its not feature complete but you can now view and edit wiki articles in the app  ### Finished the launchpad The launchpad is now usable and shows the latest notifications, messages, streams, and tools  ### Blossom uploads The app now lets you upload images and video to blossom server, this isn't enabled by default though so your going to have to enable it in the settings  And then setup some blossom servers in the settings. A few good public ones are `https://cdn.satellite.earth` and `https://cdn.nostrcheck.me`  ### Task Manager There is also a new "Task Manager" in the side nav that lets you see whats going on under the hood in the app  You can see what relays the app is currently connected to  And which relays are requesting NIP-42 authentication  ## Bug fixes - Fix null relay hints in DMs - Fix users own events being hidden by muted words - Fix random events showing up as DM messages - Fix app prompting NIP-07 extension to unlock when app opens - Remove corsproxy.io as default service for CORS proxy @ 38d0888d:bd8e1246
2024-09-02 11:08:05To foster collective improvement, it is essential to implement social programs that encourage voluntary engagement and mutual support. These initiatives should serve as fertile ground, nurturing altruistic values and deepening the understanding of humanity’s true needs. By integrating spiritual connections into these efforts, a ripple effect of kindness, understanding, and enlightenment can spread throughout society. Each individual, endowed with intellectual abilities by a higher power, is invited to contribute to the creation of a harmonious and enlightened world. Sharing inspirational concepts that blend spirituality with social responsibility has the potential to profoundly influence and unite public sentiment. A sense of community and interconnectedness must be cultivated within these programs. Creating spaces for shared experiences and collective growth extends their impact beyond individual actions, fostering a network of mutual support and understanding. It is crucial to promote inclusive development that transcends bureaucratic constraints, aiming to dismantle inequality and confront corruption. These initiatives do more than foster a fairer world; they also reveal the latent spiritual dimensions of the human mind. To encourage spiritual growth and overcome selfishness, collaborative efforts across society, decentralized governance structures, educational institutions, and individual contributions are imperative. Moral codes must emerge from deeply rooted spiritual ethics that are interwoven into the societal fabric, surpassing the interests of a privileged few. Humanity’s ultimate goal is to transcend mere cooperation among individuals, striving for absolute transparency and openness across all spheres of existence. Achieving this vision requires unwavering dedication from every stakeholder committed to guiding society along the path of enlightenment.
@ 38d0888d:bd8e1246
2024-09-02 11:08:05To foster collective improvement, it is essential to implement social programs that encourage voluntary engagement and mutual support. These initiatives should serve as fertile ground, nurturing altruistic values and deepening the understanding of humanity’s true needs. By integrating spiritual connections into these efforts, a ripple effect of kindness, understanding, and enlightenment can spread throughout society. Each individual, endowed with intellectual abilities by a higher power, is invited to contribute to the creation of a harmonious and enlightened world. Sharing inspirational concepts that blend spirituality with social responsibility has the potential to profoundly influence and unite public sentiment. A sense of community and interconnectedness must be cultivated within these programs. Creating spaces for shared experiences and collective growth extends their impact beyond individual actions, fostering a network of mutual support and understanding. It is crucial to promote inclusive development that transcends bureaucratic constraints, aiming to dismantle inequality and confront corruption. These initiatives do more than foster a fairer world; they also reveal the latent spiritual dimensions of the human mind. To encourage spiritual growth and overcome selfishness, collaborative efforts across society, decentralized governance structures, educational institutions, and individual contributions are imperative. Moral codes must emerge from deeply rooted spiritual ethics that are interwoven into the societal fabric, surpassing the interests of a privileged few. Humanity’s ultimate goal is to transcend mere cooperation among individuals, striving for absolute transparency and openness across all spheres of existence. Achieving this vision requires unwavering dedication from every stakeholder committed to guiding society along the path of enlightenment. @ 9dd283b1:cf9b6beb
2024-09-02 10:26:53There's a saying: Bitcoin is hope. But once you truly understand Bitcoin, many of the old fiat goals in your life start to lose meaning. It can feel disorienting and even depressing, because you realize you need to build entirely new goals, and you're unsure where to begin. For example, maybe your plan was to get a mortgage, buy a house, and imagine your kids playing there for the next 20 years while you "happily" pay off a 25-year loan. But when you understand Bitcoin, that plan doesn’t make sense. Why would I put a 100k-200k down payment into a mortgage when it's likely better be in Bitcoin? Plus, you lose about 2.5% to 4% of the total price on taxes, fees, brokers, and other costs. Crazy, right? I even made a short presentation for my wife, explaining why we should never buy a house given current interest rates and down payment requirements. She responded that she wants a house anyway, because it feels better to own one. But does a 25-year mortgage really make it feel like it’s yours? She also said it’s depressing to not follow the conventional path. It’s hard to feel satisfied with numbers when everyone around you is deep into mortgages—you want to be one of them. You want to visit their houses and invite them to "yours." It's like becoming sober in a room full of addicts. You know it’s better for you, but the world around you seems so strange that part of you wants to go back, even though you know it hurts. Yet, when you do go back, the joy isn't there anymore. You feel...nothing. And then you decide to withdraw. I remember paying off my first mortgage for an apartment, and I felt nothing. And that was before I fell down the Bitcoin rabbit hole. Now I know if I ever took out a mortgage again, I’d just feel regret for not keeping the money in Bitcoin. And by the time you finish paying it off, you probably want to sell the property and move somewhere else. So, the rational decision is to keep everything in Bitcoin and rent instead.Unless, of course, Bitcoin goes to zero. There are only two outcomes for Bitcoin: it’s either going to infinity, or it's going to zero. There’s no scenario where it just hovers at 100k or 60k for the next 20 years—unless people are foolish enough to give away self-custody. If they do, we'll end up with digital gold. So the reasonable question is - how can you be sure? Well, you can't. But we are betting on it and it works for now. Worst case we will need to start from 0. But then there will be no hope anymore. We are staying in the infinity camp. And when you are in that camp every time you make a big purchase, you’re shorting Bitcoin. Solution - simple, - don't buy anything. There’s a popular meme: You will own nothing, and you will be happy. But if you’re a Bitcoiner, it's more like: You will own only Bitcoin, and you probably won’t be happy about it. Why would I pay 30k for a car when I can lease one? Why put 100k down on a house when I can rent? The only justification is mental comfort, peace of mind. Or perhaps you value the illusion of owning a physical thing more than the genuine ownership of something virtual. It’s confusing, isn’t it? Sure, you can own a bicycle. But owning a house? That's tricky. Imagine you’re a Russian citizen with a house on Lake Como, and suddenly, new sanctions mean Italy no longer recognizes your property. Or squatters break in while you’re on vacation, and now you need to go through a court battle to evict them. Extreme situations, I know. But no one thinks it will happen to them—until it does. So, you’ve sold everything to buy Bitcoin. You don’t own anything except Bitcoin, and you feel sad. Why? What can you buy with Bitcoin that’s more valuable? Something that won’t depreciate over time. Something like time. Time with your kids. Time with your family. Time with yourself. There’s a concept called FIRE and then there is a Bitcoin FIRE calculation (https://bitcoincompounding.com/). In simple terms, you spend your Bitcoin slowly enough that it grows faster than you can spend it (in fiat terms). Unlike traditional assets, there’s no yield or dividends, so the only way it works is if Bitcoin continues its cycles. And you need to be at least two cycles in to make it work. But personally, I don’t think there will be cycles anymore. I believe this October-November will break all the models, and Bitcoin will do what Bitcoin does: surprise everyone. I read somewhere a thought that stuck with me—imagine you wake up on a planet Earth on January 1st. You know nothing about the seasons or weather. After six months of only increasing temperatures, you’d be 100% certain it’s only getting hotter from here. So what hope does Bitcoin offer? Hope that I can spend more time with my family. Hope that I can create something different for them. Hope that I can live without the weight of fiat goals. Hope that it's only getting hotter from here. I just need to get through the withdrawal phase. originally posted at https://stacker.news/items/662939
@ 9dd283b1:cf9b6beb
2024-09-02 10:26:53There's a saying: Bitcoin is hope. But once you truly understand Bitcoin, many of the old fiat goals in your life start to lose meaning. It can feel disorienting and even depressing, because you realize you need to build entirely new goals, and you're unsure where to begin. For example, maybe your plan was to get a mortgage, buy a house, and imagine your kids playing there for the next 20 years while you "happily" pay off a 25-year loan. But when you understand Bitcoin, that plan doesn’t make sense. Why would I put a 100k-200k down payment into a mortgage when it's likely better be in Bitcoin? Plus, you lose about 2.5% to 4% of the total price on taxes, fees, brokers, and other costs. Crazy, right? I even made a short presentation for my wife, explaining why we should never buy a house given current interest rates and down payment requirements. She responded that she wants a house anyway, because it feels better to own one. But does a 25-year mortgage really make it feel like it’s yours? She also said it’s depressing to not follow the conventional path. It’s hard to feel satisfied with numbers when everyone around you is deep into mortgages—you want to be one of them. You want to visit their houses and invite them to "yours." It's like becoming sober in a room full of addicts. You know it’s better for you, but the world around you seems so strange that part of you wants to go back, even though you know it hurts. Yet, when you do go back, the joy isn't there anymore. You feel...nothing. And then you decide to withdraw. I remember paying off my first mortgage for an apartment, and I felt nothing. And that was before I fell down the Bitcoin rabbit hole. Now I know if I ever took out a mortgage again, I’d just feel regret for not keeping the money in Bitcoin. And by the time you finish paying it off, you probably want to sell the property and move somewhere else. So, the rational decision is to keep everything in Bitcoin and rent instead.Unless, of course, Bitcoin goes to zero. There are only two outcomes for Bitcoin: it’s either going to infinity, or it's going to zero. There’s no scenario where it just hovers at 100k or 60k for the next 20 years—unless people are foolish enough to give away self-custody. If they do, we'll end up with digital gold. So the reasonable question is - how can you be sure? Well, you can't. But we are betting on it and it works for now. Worst case we will need to start from 0. But then there will be no hope anymore. We are staying in the infinity camp. And when you are in that camp every time you make a big purchase, you’re shorting Bitcoin. Solution - simple, - don't buy anything. There’s a popular meme: You will own nothing, and you will be happy. But if you’re a Bitcoiner, it's more like: You will own only Bitcoin, and you probably won’t be happy about it. Why would I pay 30k for a car when I can lease one? Why put 100k down on a house when I can rent? The only justification is mental comfort, peace of mind. Or perhaps you value the illusion of owning a physical thing more than the genuine ownership of something virtual. It’s confusing, isn’t it? Sure, you can own a bicycle. But owning a house? That's tricky. Imagine you’re a Russian citizen with a house on Lake Como, and suddenly, new sanctions mean Italy no longer recognizes your property. Or squatters break in while you’re on vacation, and now you need to go through a court battle to evict them. Extreme situations, I know. But no one thinks it will happen to them—until it does. So, you’ve sold everything to buy Bitcoin. You don’t own anything except Bitcoin, and you feel sad. Why? What can you buy with Bitcoin that’s more valuable? Something that won’t depreciate over time. Something like time. Time with your kids. Time with your family. Time with yourself. There’s a concept called FIRE and then there is a Bitcoin FIRE calculation (https://bitcoincompounding.com/). In simple terms, you spend your Bitcoin slowly enough that it grows faster than you can spend it (in fiat terms). Unlike traditional assets, there’s no yield or dividends, so the only way it works is if Bitcoin continues its cycles. And you need to be at least two cycles in to make it work. But personally, I don’t think there will be cycles anymore. I believe this October-November will break all the models, and Bitcoin will do what Bitcoin does: surprise everyone. I read somewhere a thought that stuck with me—imagine you wake up on a planet Earth on January 1st. You know nothing about the seasons or weather. After six months of only increasing temperatures, you’d be 100% certain it’s only getting hotter from here. So what hope does Bitcoin offer? Hope that I can spend more time with my family. Hope that I can create something different for them. Hope that I can live without the weight of fiat goals. Hope that it's only getting hotter from here. I just need to get through the withdrawal phase. originally posted at https://stacker.news/items/662939 @ e6fbeb1c:6ac8fc04
2024-09-02 10:17:27Eggplant is a member of the nightshade family, and it’s related to the potato and tomato. Often mistaken for a vegetable, eggplant is actually a fruit, and to be more precise, it’s a berry.  originally posted at https://stacker.news/items/669464
@ e6fbeb1c:6ac8fc04
2024-09-02 10:17:27Eggplant is a member of the nightshade family, and it’s related to the potato and tomato. Often mistaken for a vegetable, eggplant is actually a fruit, and to be more precise, it’s a berry.  originally posted at https://stacker.news/items/669464 @ 79008e78:dfac9395
2024-09-02 06:17:23ระบบเงินอิเล็กทรอนิกส์แบบ peer-to-peer ---- ระบบเงินอิเล็กทรอนิกส์แบบ peer-to-peer นั้นจะช่วยให้เราสามารถชำระเงินผ่านทางออนไลน์ได้โดยตรงจากฝ่ายหนึ่งไปยังอีกฝ่ายหนึ่งโดยไม่ต้องผ่านตัวกลางอย่างพวกสถาบันการเงิน โดยใช้ digital signature เป็นส่วนหนึ่งในการแก้ปัญหานี้ แต่มันจะไม่มีประโยชน์ใด ๆ เลยหากยังคงต้องอาศัยตัวกลางที่เชื่อถือได้มาแก้ปัญหา double spending เราขอเสนอวิธีแก้ปัญหา double spending โดยใช้เครือข่ายแบบ peer-to-peer ให้เครือข่ายคอยประทับเวลาธุรกรรมต่าง ๆ ในระบบและนำมาเรียงร้อยกันเป็นเส้นสายของ proof-of-work ที่ใช้ hash เพื่อสร้างธุรกรรมที่ไม่สามารถเปลี่ยนแปลงได้ โดยไม่ต้องทำ proof-of-work ใหม่ โดยให้เส้นสายที่ยาวที่สุดนั้น ไม่เพียงแต่ทำหน้าที่เป็นลำดับของธุรกรรมที่เกิดขึ้นเท่านั้น แต่ยังเป็นสิ่งที่พิสูจน์ได้ว่ามาจากกำลังประมวลผล CPU ที่มากที่สุด และตราบใดที่ nodes ส่วนใหญ่ไม่ได้ร่วมมือกันโจมตีเครือข่ายและยังคงควบคุมกำลังประมวลผลส่วนใหญ่ในระบบไว้ พวกเขาก็จะสร้างเส้นสายที่ยาวที่สุดและสามารถเอาชนะผู้ประสงค์ร้ายที่จะโจมตีระบบได้ ตัวเครือข่ายเองไม่ได้ต้องมีโครงสร้างอะไรที่ซับซ้อน ข้อมูลต่าง ๆ ในเครือข่ายจะถูกกระจายส่งต่อโดยไม่ต้องสนใจว่าผู้รับจะได้รับหรือไม่ และ nodes ต่าง ๆ เองก็สามารถที่จะออกจากเครือข่ายและกลับเข้าร่วมใหม่ได้ตามที่ต้องการ โดยยอมรับเส้น proof-of-work ที่ยาวที่สุด เป็นหลักฐานของสิ่งที่เกิดขึ้นในขณะที่ node นั้น ๆ ไม่ได้อยู่ในเครือข่าย 1.บทนำ (Introduction) ----- ไม่ว่าใครจะใคร่ซื้อใคร่ขายอะไรใด ๆ บนอินเตอร์เน็ตนั้น ก็จำเป็นต้องพึ่งพาสถาบันการเงินในฐานะของบุคคลที่สามเพื่อดำเนินการชำระเงินทางอิเล็กทรอนิกส์เสมอ ๆ ซึ่งถึงแม้ว่าระบบนี้มันจะทำงานได้ดีสำหรับธุรกรรมส่วนใหญ่ ๆ แต่ระบบก็ก็มีจุดอ่อนอยู่ที่ยังต้องอาศัยความไว้เนื้อเชื่อใจ (trust) ในระบบนี้การทำธุรกรรมที่ไม่สามารถย้อนกลับได้อย่างสมบูรณ์นั้นมันแทบจะเป็นไปไม่ได้เลย เนื่องจากสถาบันการเงินไม่สามารถหลีกเลี่ยงการเป็นตัวกลางในการไกล่เกลี่ยข้อพิพาทต่าง ๆ ที่อาจเกิดขึ้นได้ มิหนำซ้ำต้นทุนในการไกล่เกลี่ยยังทำให้ต้นทุนการทำธุรกรรมเพิ่มสูงขึ้น และเมื่อต้นทุนสูงขึ้นขนาดของธุรกรรมที่สามารถใช้งานได้จริงก็สูงขึ้นตามไปด้วย ธุรกรรมเล็ก ๆ น้อย ๆ ก็ไม่สามารถเกิดขึ้นได้ เมื่อมีความเป็นไปได้ที่ธุรกรรมจะเกิดการย้อนกลับ ความจำเป็นในการสร้างความไว้วางใจก็ยิ่งทวีคูณมากขึ้น ผู้ค้าก็จำเป็นต้องระมัดระวังลูกค้า ต้องเรียกร้องข้อมูลมากกว่าที่จำเป็น การฉ้อโกงกลายเป็นเรื่องที่หลีกเลี่ยงไม่ได้เพราะต้นทุนและความไม่แน่นอนในทำธุรกรรมเหล่านี้ แน่นอนว่าเราสามารถหลีกเลี่ยงมันได้โดยการใช้เงินสด แต่ก็ไม่มีกลไกใดที่ทำให้สามารถใช้เงินสดผ่านช่องทางการสื่อสาร (เอาให้เข้าใจง่ายก็อินเตอร์เน็ต)ได้ โดยไม่ต้องมีตัวกลาง ;-; แปลว่าสิ่งที่จำเป็นสำหรับการแก้ไขปัญหานี้คือระบบการชำระเงินทางอิเล็กทรอนิกส์ ที่อยู่บนพื้นฐานของการพิสูจน์ด้วยการเข้ารหัสแทนที่จะเป็นความไว้วางใจ ซึ่งจะทำให้คู่สัญญาสองฝ่ายที่ยินยอมสามารถทำธุรกรรมร่วมกันได้โดยตรง โดยไม่จำเป็นต้องมีบุคคลที่สามมาคอยเป็นตัวกลาง ธุรกรรมที่ยากต่อการย้อนกลับจะช่วยปกป้องผู้ขายจากการฉ้อโกง และสามารถใช้กลไก escrow เพื่อปกป้องผู้ซื้อได้อีกด้วย ในเอกสารชุดนี้ เราขอเสนอวิธีแก้ปัญหาการใช้จ่ายซ้ำซ้อนโดยใช้เซิร์ฟเวอร์ timestamp กระจายศูนย์แบบ peer-to-peer เพื่อสร้างหลักฐานการคำนวณลำดับเวลาของธุรกรรม โดยระบบนี้จะปลอดภัยตราบใดที่กลุ่มของ node ที่ซื่อสัตย์ ยังคงมีกำลังประมวลผลที่มากกว่ากลุ่มที่ประสงค์ร้ายกับระบบ 2.ธุรกรรม (Transactions) ---- นิยามของเหรียญอิเล็กทรอนิกส์ในที่นี้ คือห่วงโซ่ที่คล้องเกี่ยวกันของ digital signature โดยที่เจ้าของเหรียญอิเล็กทรอนิกส์จะโอนเหรียญไปยังเจ้าของคนถัดไป ด้วยการลง digital signature บน hash ของธุรกรรมก่อนหน้ารวมถึงกุญแจสาธารณะของเจ้าของคนถัดไป และผนวกมันไว้ที่ส่วนท้ายของธุรกรรม และผู้รับเงินเองก็สามารถตรวจสอบลายเซ็นเพื่อยืนยันความเป็นเจ้าของได้ https://image.nostr.build/a467896797a9fb9f98c3c234f0adb4df2376f2c3d9a7cc9d8672d7a9f5aa9efa.png แน่นอนว่าปัญหาก็คือผู้รับเงินไม่สามารถตรวจสอบได้ว่าเจ้าของคนใดคนหนึ่งก่อนหน้าเขาได้ใช้เหรียญดังกล่าวซ้ำซ้อนมากกว่าหนึ่งครั้งหรือไม่ และวิธีการแก้ไขปัญหานี้โดยทั่วไปก็คงเป็นการกำหนดตัวกลางที่มีความน่าเชื่อถือมาเป็นคนตรวจสอบทุกธุรกรรมเพื่อป้องกันการใช้จ่ายซ้ำซ้อน และหลังจากการทำธุรกรรมแต่ละครั้ง เหรียญจะต้องถูกส่งกลับไปยังตัวกลางเพื่อออกเหรียญใหม่ และจะมีเพียงเหรียญที่ออกจากตัวกลางโดยตรงเท่านั้นที่จะเชื่อถือได้ว่าจะไม่ถูกใช้จ่ายซ้ำซ้อน แต่ปัญหาก็คือ ชะตากรรมของระบบเงินทั้งหมดจะขึ้นอยู่กับตัวกลางตัวนี้ เพราะทุกธุรกรรมจำเป็นจะต้องผ่านพวกเขา ซึ่งก็ไม่ต่างอะไรกับธนาคาร เราจึงต้องการวิธีการที่ทำให้ผู้รับเงินทราบได้ว่าเจ้าของคนก่อน ๆ ไม่ได้ลงนามในธุรกรรมใด ๆ มาก่อน เพื่อให้บรรลุวัตถุประสงค์นี้ เราจะทำการนับว่าธุรกรรมที่เกิดขึ้นก่อนเป็นธุรกรรมที่ถูกต้อง และจะไม่สนใจความพยายามใด ๆ ในการที่จะใช้เหรียญนั้น ๆ ซ้ำอีก และวิธีเดียวที่ทำแบบนี้ได้ คือการรับรู้ถึงธุรกรรมทั้งหมด เช่นเดียวกับโมเดลที่ได้กล่าวข้างต้น ที่ตัวกลางจะรับรู้ถึงธุรกรรมทั้งหมดและตัดสินว่าธุรกรรมใดมาก่อนมาหลัง เพื่อให้บรรลุเป้าหมายนี้โดยไม่ต้องมีบุคคลที่สามที่เชื่อถือได้ ธุรกรรมทั้งหมดจะต้องถูกประกาศต่อสาธารณะ [1] และเราต้องการระบบที่ผู้เข้าร่วมเห็นพ้องในประวัติธุรกรรมชุดเดียวกันตามลำดับที่ได้รับ ส่วนผู้รับเงินก็จำเป็นจะต้องมีหลักฐานว่า ในขณะที่ทำธุรกรรม "โหนด" ส่วนใหญ่ในระบบเห็นพ้องต้องกันว่าธุรกรรมนั้นได้รับเป็นลำดับแรก(ไม่มีธุรกรรมที่ใช้เหรียญพวกนี้มาก่อน) 3.ระบบบันทึกเวลา (Timestamp Server) ---- สำหรับแนวทางการแก้ปัญหาในครั้งนี้ เราจะใช้ประโยชน์จาก timestamp server ที่จะทำหน้าที่บันทึก hash ของบล๊อกที่ต้องการให้มีการบันทึกเวลา และจากนั้นจะทำการเผยแพร่ hash ดังกล่าว เหมือนกับหนังสือพิมพ์หรือโพสต์ใน Usenet [2-5] (ฟีลแบบทุกคนจะเห็นโพสต์นี้น้าา ประมาณนั้น) การบันทึกเวลานี้จะพิสูจน์ได้ว่าข้อมูลที่ถูก hash นั้นจะต้องมีอยู่จริงในเวลานั้นเพื่อให้ได้มาซึ่ง hash ดังกล่าว แต่ละการบันทึกเวลาจะรวมการบันทึกเวลาของหน้านี้ไว้ใน hash ของมันเพื่อสร้างเป็น chain โดยการบันทึกเวลาแต่ละครั้งจะยืนยันความถูกต้องของการบันทึกก่อนหน้าได้อีกด้วยด้วย https://image.nostr.build/ddf92417c45dbb6e25da0af80a10d4cdbc3e725d047d65f54a3e3bfcf358c4d6.png 4.พรูฟ-ออฟ-เวิร์ค (Proof-of-Work) ---- ในการสร้าง Timestamp Server แบบกระจายศูนย์บนพื้นฐานแบบ peer to peer เราจำเป็นต้องใช้ระบบ Proof-of-Work (PoW) ที่คล้ายกับ Hashcash ของ Adam Back [6] แทนที่จะใช้วิธีการแบบเดิม ๆ อย่างการประกาศในหนังสือพิมพ์หรือ Usenet โดย PoW ใช้ในการตรวจสอบค่าที่มาจากกระบวนการ hash เช่น SHA-256 แล้ว ผลลัพธ์ที่ได้ (Hash) จะขึ้นต้นด้วยเลขศูนย์จำนวนหนึ่ง โดยที่ work (ประมาณว่าพลังประมวลผล) ที่ต้องใช้จะเพิ่มขึ้นแบบทวีคูณตามจำนวนเลขศูนย์ที่ต้องการ และสามารถตรวจสอบได้โดยการรัน Hash เพียงครั้งเดียว ซึ่งสำหรับ timestamp network ของเรานั้น เราใช้ PoW โดยการเพิ่มค่า Nonce ในบล็อกไปเรื่อย ๆ จนกว่าจะพบค่าที่ทำให้ Hash ของบล็อกนั้นมีเลขศูนย์ตามที่กำหนด และเมื่อใช้กำลังประมวลผลของ CPU ไปกับการทำ PoW จนสำเร็จแล้ว บล็อกจะไม่สามารถเปลี่ยนแปลงได้ หากไม่มีการทำงานซ้ำใหม่ เนื่องจากบล็อกที่สร้างขึ้นภายหลังจะเชื่อมโยงกับบล็อกก่อนหน้า การเปลี่ยนแปลงบล็อกใด ๆ จะต้องทำ PoW ของบล็อกนั้นและบล็อกที่ตามมาใหม่ทั้งหมด https://image.nostr.build/c039ef4ca6833cb1ecee65ac5991df2406be9b7e490b86b3b19f94f267767182.png นอกจากนี้ PoW ยังช่วยแก้ปัญหาของเสียงส่วนมากที่มาตัดสินใจในระบบนี้ เพราะหากเสียงข้างมากอ้างอิงจากหลักการหนึ่ง IP หนึ่งเสียง ใครก็ตามที่สามารถสร้าง IP ได้จำนวนมากก็จะสามารถควบคุมระบบได้ จึงใช้หลักการหนึ่ง CPU หนึ่งเสียงแทน การตัดสินใจของเสียงข้างมากจะแสดงด้วย Chain ที่ยาวที่สุด ซึ่งบ่งบอกถึงความพยายามในการคำนวณ (Proof-of-Work) ที่มากที่สุด หาก Node ที่ซื่อสัตย์ (Honest nodes) มีกำลังประมวลผลของ CPU ส่วนใหญ่อยู่ในการควบคุม Honest Chain ก็จะเติบโตเร็วที่สุดและแซงหน้า Chain อื่น ๆ ได้ ผู้โจมตีที่ต้องการแก้ไขบล็อกในอดีตจะต้องทำ Proof-of-Work ของบล็อกนั้นและบล็อกที่ตามมาใหม่ทั้งหมด และต้องทำงานให้เร็วกว่า Honest Node ด้วย ซึ่งโอกาสที่ผู้โจมตีจะตามทันนั้นจะลดลงแบบทวีคูณเมื่อมีการเพิ่มบล็อกมากขึ้น เพื่อชดเชยความเร็วของฮาร์ดแวร์ที่เพิ่มขึ้นและความสนใจในการรัน Node ที่ผันผวน ระดับความยากของ Proof-of-Work จะถูกกำหนดโดยค่าเฉลี่ย โดยตั้งเป้าไว้ที่จำนวนบล็อกเฉลี่ยต่อชั่วโมง หากสร้างบล็อกได้เร็วเกินไป ระดับความยากก็จะเพิ่มขึ้น 5.เครือข่าย (Network) ---- เครือข่ายนั้นมีการทำงาน ดังนี้ 1. การประกาศธุรกรรมใหม่: ธุรกรรมใหม่จะถูกประกาศ (broadcast) ไปยังทุก node ในเครือข่าย 2. การรวบรวมธุรกรรม: แต่ละ node จะรวบรวมธุรกรรมใหม่ ๆ เหล่านี้ ไว้ในบล็อก 3. การค้นหา Proof-of-Work: แต่ละ node จะทำการคำนวณ เพื่อค้นหา Proof-of-Work ตามค่า difficulty สำหรับบล็อกนั้น ๆ 4. การประกาศบล็อก: เมื่อ node ใดค้นหา Proof-of-Work ได้แล้ว node นั้นจะทำการประกาศบล็อกไปยังทุก node ในเครือข่าย 5. การตรวจสอบและยอมรับบล็อก: node อื่น ๆ จะทำการตรวจสอบและยอมรับบล็อกนั้น เฉพาะเมื่อธุรกรรมทั้งหมดภายในบล็อกนั้นถูกต้องและยังไม่ถูกใช้มาก่อน 6. การสร้างบล็อกถัดไป: node ต่าง ๆ แสดงการยอมรับบล็อกโดยการเริ่มต้นสร้างบล็อกถัดไปใน chain ด้วย hash ของบล็อกที่ยอมรับ เป็น hash ก่อนหน้าในโครงสร้างของบล๊อกใหม่ที่กำลังสร้าง node ต่าง ๆ จะถือว่า chain ที่ยาวที่สุดเป็น chain ที่ถูกต้องและจะทำงานเพื่อขยาย chain นั้นต่อไป หากมีสอง node ที่ได้ประกาศบล็อกเวอร์ชันที่แตกต่างกันในเวลาพร้อมกัน node บาง node อาจได้รับบล็อกหนึ่งก่อน อีกบล็อกหนึ่ง ในกรณีนี้ node เหล่านั้น จะทำงานบนบล็อกที่ได้รับก่อน แต่จะเก็บสำเนาของบล็อกอีกอันหนึ่งไว้ ในกรณีที่บล็อกนั้น กลายเป็นบล็อกที่อยู่ใน chain ที่ยาวกว่าปัญหาข้อโต้แย้งนี้ก็จะได้รับการแก้ไข เมื่อพบ Proof-of-Work อันถัดไปและ chain ใด chain หนึ่งยาวขึ้น node ที่กำลังทำงานอยู่บน chain ที่สั้นกว่าก็จะเปลี่ยนไปทำงานบน chain ที่ยาวกว่าแทน การประกาศธุรกรรมใหม่ ไม่จำเป็นต้องไปถึงทุก node ในเครือข่าย ตราบใดที่พวกเขายังไปถึง node ส่วนใหญ่ในระบบได้ ธุรกรรมเหล่านั้นก็จะถูกบรรจุอยู่ในบล็อกในไม่ช้า นอกจากนี้การประกาศบล็อกยังไม่ต้องกังวลเรื่องจะมีบล๊อกที่สูญหาย เนื่องจากหากว่า node ไม่ได้รับบล็อกใด ๆ node ก็จะตระหนักได้ว่าพลาดบล็อกก่อนหน้าไปเมื่อได้รับบล๊อกใหม่มา และ node จะทำการร้องขอ block ที่ขาดไปจากเครือข่าย 6.แรงจูงใจ(Incentive) ---- โดยปกติแล้ว ธุรกรรมแรกของแต่ละบล๊อกนั้นจะเป็นธุรกรรมพิเศษที่จะขุดเหรียญที่สร้างขึ้นใหม่ซึ่งเป็นกรรมสิทธิ์ของผู้สร้างบล็อกนั้น ๆ ซึ่งจะเป็นการเพิ่มแรงจูงใจให้กับ node ต่าง ๆ ในการสนับสนุนเครือข่าย และเป็นวิธีการกระจายเหรียญให้หมุนเวียน เนื่องจากไม่มีหน่วยงานส่วนกลางที่ทำหน้าที่ในการออกเหรียญ การเพิ่มเหรียญใหม่ในปริมาณคงที่อย่างต่อเนื่องนั้นคล้ายคลึงกับการที่คนงานเหมืองทองคำใช้แรง และ เวลา เพื่อเพิ่มทองคำให้หมุนเวียน ในกรณีนี้ คือ เวลา กำลังประมวลผล และไฟฟ้าที่ถูกใช้ไป นอกจากนี้แรงจูงใจจะมาจากค่าธรรมเนียมการทำธุรกรรม หากมูลค่าผลลัพธ์ของธุรกรรมน้อยกว่ามูลค่าที่ใส่เข้ามา ส่วนต่างนั้นก็คือค่าธรรมเนียมการทำธุรกรรมที่จะเพิ่มเข้าไปในมูลค่าแรงจูงใจของบล็อกที่มีธุรกรรมนั้น เมื่อเหรียญทั้งหมดในระบบมีจำนวนเท่ากับที่กำหนดไว้แล้ว แรงจูงใจหลักก็จะถูกเปลี่ยนมาเป็นค่าธรรมเนียมการทำธุรกรรม และปราศจากภาวะเงินเฟ้อโดยสิ้นเชิง แรงจูงใจอาจช่วยกระตุ้นให้ node ต่าง ๆ ยังคงซื่อสัตย์ หากผู้โจมตีที่ละโมบสามารถรวบรวมกำลังประมวลผล ได้มากกว่า node ที่ซื่อสัตย์ทั้งหมด เขาจะต้องเลือกระหว่างการใช้มันเพื่อฉ้อโกงผู้อื่นโดยการใช้จ่ายซ้ำซ้อน หรือใช้มันเพื่อสร้างเหรียญใหม่ พวกเขาจะพบว่าการเล่นตามกฎ กฎที่เอื้อประโยชน์ให้กับเขาด้วยเหรียญใหม่มากกว่าคนอื่น ๆ รวมกันนั้นทำกำไรได้มากกว่าการบ่อนทำลายระบบและความถูกต้องของทรัพย์สินของเขาเอง 7.การจัดการพื้นที่ดิสก์(Reclaiming Disk Space) ---- เมื่อธุรกรรมถูกบรรจุลงในบล๊อกแล้ว สามารถกำจัดธุรกรรมที่ใช้ไปแล้วก่อนหน้านั้นออกได้เพื่อประหยัดพื้นที่ดิสก์ แต่การจะทำอย่างนี้ได้โดยไม่ให้เลข hash ของบล๊อกมีการเปลี่ยนแปลงนั้น ธุรกรรมจึงจำเป็นต้องถูก hash ในรูปแบบของ Merkle Tree [7][2][5] โดยมีแค่ root node ของ tree เท่านั้นที่จะรวมอยู่ใน hash ของบล๊อก นี่เป็นวิธีที่ทำให้สามารถบีบอัดข้อมูลในบล๊อกเก่า ๆ ได้โดยการตัดพวก hash ส่วนอื่น ๆ ของ tree ที่ไม่ใช่ root node ออก (ไม่จำเป็นต้องเก็บ hash ในชั้นอื่น ๆ ของ tree) https://image.nostr.build/3ed95334891d91baca3f3f6f624a7ae22620be4ebfe0db5eb652cfce11255b9a.png โดยในส่วน header ของบล็อกที่ไม่มีธุรกรรมจะมีขนาดประมาณ 80 ไบต์ หากเราสมมติว่าบล็อกถูกสร้างขึ้นทุก ๆ 10 นาที 80 ไบต์ * 6 * 24 * 365 = 4.2MB ต่อปี โดยที่ระบบคอมพิวเตอร์ทั่วไปที่วางขายในปี 2551 มี RAM 2GB และกฎของมัวร์ทำนายการเติบโตในปัจจุบันที่ 1.2GB ต่อปี การจัดเก็บข้อมูลไม่น่าจะเป็นปัญหาแม้ว่าส่วนหัวของบล็อกจะต้องถูกเก็บไว้ในหน่วยความจำก็ตาม 8.การตรวจสอบธุรกรรม (Simplified Payment Verification) ---- การที่จะยืนยันการชำระเงินโดยไม่จำเป็นต้องรัน full node ได้นั้น ผู้ใช้เพียงแค่เก็บสำเนาของส่วนหัวบล็อก (block header) ของสายบล็อก (chain) ที่ยาวที่สุด ซึ่งสามารถรับได้โดยการสอบถามจาก node อื่น ๆ ในเครือข่ายจนมั่นใจว่าได้รับสายที่ยาวที่สุด และรับ Merkle branch ที่เชื่อมโยงธุรกรรมกับบล็อกที่มีการประทับเวลา (Timestamp) อยู่ ถึงแม้ผู้ใช้จะไม่สามารถตรวจสอบธุรกรรมด้วยตัวเองได้ แต่การเชื่อมโยงธุรกรรมกับตำแหน่งในสายบล็อกจะทำให้เห็นว่า node ในเครือข่ายยอมรับแล้ว และบล็อกที่เพิ่มเข้ามาหลังจากนั้นเป็นการยืนยันเพิ่มเติมว่าเครือข่ายยอมรับธุรกรรมนี้แล้ว https://i.imgur.com/VXtLpRF.png การตรวจสอบดังกล่าวจะเชื่อถือได้ตราบใดที่ node ที่ซื่อสัตย์ยังคงควบคุมเครือข่าย แต่จะมีความเสี่ยงมากขึ้นหากเครือข่ายถูกโจมตีและถูกควบคุม ในขณะที่ node ในเครือข่ายสามารถตรวจสอบธุรกรรมได้ด้วยตัวเอง แต่วิธีการแบบง่ายนี้อาจถูกหลอกลวงโดยการใช้ธุรกรรมปลอมของผู้โจมตี ตราบใดที่ผู้โจมตียังคงสามารถควบคุมเครือข่ายได้ กลยุทธ์หนึ่งในการป้องกันปัญหานี้คือ การรับการแจ้งเตือนจาก node อื่น ๆ ในเครือข่ายเมื่อตรวจพบบล็อกที่ไม่ถูกต้อง ซึ่งจะแจ้งให้ซอฟต์แวร์ของผู้ใช้ดาวน์โหลดบล็อกแบบเต็มและธุรกรรมที่แจ้งเตือน เพื่อยืนยันความไม่สอดคล้องกัน ธุรกิจที่ได้รับการชำระเงินบ่อยครั้งอาจยังคงต้องการรัน node ของตนเอง เพื่อความปลอดภัยที่เป็นอิสระและการตรวจสอบที่รวดเร็วยิ่งขึ้น 9.การควบรวมและแบ่งย่อยมูลค่า(Combining and Splitting Value) ---- แม้ว่าการจัดการเหรียญหลาย ๆ เหรียญจะเป็นสิ่งที่สามารถทำได้ แต่การจัดการธุรกรรมแยกต่างหากสำหรับแต่ละเหรียญในการโอนก็คงเป็นเรื่องที่น่าปวดหัวอยู่ดี ฉะนั้นแล้วเพื่อให้สามารถแยกและรวมมูลค่ากันได้ ธุรกรรมจึงสามารถมี input และ output ได้หลายรายการ ซึ่งโดยปกติแล้วจะมี input เดียวจากธุรกรรมก่อนหน้าที่มีขนาดใหญ่กว่า หรือ input จำนวนเล็ก ๆ หลาย ๆ รายการ และ output ไม่เกินสองรายการ คือ รายการหนึ่งสำหรับการชำระเงิน และอีกหนึ่งรายการสำหรับการส่งเงินทอน หากมีกลับไปยังผู้ส่ง https://image.nostr.build/9c6d3ce0e9f08c5b3fa3b82c2088ac6235603e5c0df3469060e6c9f74bce32fc.png ควรสังเกตว่า fan-out (กระจายของธุรกรรม) ซึ่งเป็นกรณีที่ธุรกรรม ธุรกรรมหนึ่งนั้นขึ้นอยู่กับหลายธุรกรรม และธุรกรรมเหล่านั้นเองก็ขึ้นอยู่กับอีกหลายธุรกรรม แต่ไม่ใช่ปัญหาในที่นี้ เพราะไม่มีความจำเป็นในการดึงประวัติการทำธุรกรรมทั้งหมดออกมาเป็นสำเนา 10.ความเป็นส่วนตัว(Privacy) ---- ในรูปแบบธนาคารแบบดั้งเดิมนั้น ความเป็นส่วนตัวเกิดขึ้นได้ด้วยการจำกัดการเข้าถึงข้อมูล โดยให้เฉพาะผู้ที่เกี่ยวข้องและบุคคลที่สามที่ได้รับความไว้วางใจเท่านั้น แต่เนื่องจากในระบบนี้เรามีความจำเป็นในการประกาศธุรกรรมทั้งหมดต่อสาธารณะ ทำให้ไม่สามารถใช้วิธีนี้ได้ แต่ยังจำเป็นต้องคงความเป็นส่วนตัวไว้ โดยการแบ่งการไหลของข้อมูล ด้วยการไม่เปิดเผยตัวตนของเจ้าของ public key คนทั่วไปสามารถเห็นว่ามีคนกำลังส่งเงินจำนวนหนึ่งให้กับคนอื่น แต่จะไม่ทราบข้อมูลที่เชื่อมโยงธุรกรรมนั้นกับบุคคลใด ๆ ซึ่งคล้ายกับระดับข้อมูลที่เปิดเผยโดยตลาดหลักทรัพย์ ซึ่งมีการเปิดเผยเวลาและขนาดของการซื้อขายแต่ละครั้งต่อสาธารณะ แต่ไม่ได้ระบุว่าคู่สัญญาคือใคร https://image.nostr.build/6ec3c84c7878dbd4558d2045518384daf5a341e86f4194cf367cc8426c2d72a7.png เพื่อเสริมในเรื่องของความปลอดภัย ควรใช้ key pair ใหม่สำหรับการทำธุรกรรมในแต่ละครั้ง เพื่อป้องกันไม่ให้เชื่อมโยงกับเจ้าของคนเดียวกันได้ อย่างไรก็ตาม การเชื่อมโยงบางอย่างยังคงหลีกเลี่ยงไม่ได้ ในธุรกรรมที่มี input หลายรายการ ซึ่งจำเป็นต้องเปิดเผยว่า input เหล่านั้นเป็นของเจ้าของคนเดียวกัน ความเสี่ยงก็คือ หากมีการเปิดเผยตัวตนของเจ้าของคีย์ การเชื่อมโยงอาจเปิดเผยธุรกรรมอื่น ๆ ที่เป็นของเจ้าของรายเดียวกันได้ 11.การคำนวณ(Calculations) ---- หากลองพิจารณาสถานการณ์ที่ผู้โจมตีพยายามสร้าง chain ปลอมให้เร็วกว่า chain จริง แม้ว่าจะทำได้สำเร็จ แต่มันก็ไม่สามารถทำให้ระบบเปิดรับการเปลี่ยนแปลงตามอำเภอใจได้อยู่ดี เช่น การสร้างมูลค่าจากอากาศธาตุ หรือการรับเงินที่ไม่เคยเป็นของผู้โจมตีมาก่อน Node ต่าง ๆ จะไม่ยอมรับธุรกรรมที่ไม่ถูกต้องเป็นการชำระเงิน และ Node ที่สุจริตก็จะไม่ยอมรับบล็อกที่มีธุรกรรมเหล่านั้นอย่างแน่นอน ผู้โจมตีทำได้เพียงพยายามเปลี่ยนแปลงธุรกรรมของตนเอง เพื่อนำเงินที่ใช้ไปแล้วกลับคืนมาเท่านั้น การแข่งขันระหว่าง chain สุจริตกับ chain ของผู้โจมตี สามารถอธิบายได้ด้วยแบบจำลองการเดินสุ่มทวินาม (Binomial Random Walk) โดยเหตุการณ์ที่สำเร็จ หมายถึง chain ที่สุจริตถูกขยายออกไปอีกหนึ่งบล็อก เพิ่มความยาวนำหน้าไป +1 และเหตุการณ์ที่ล้มเหลว หมายถึง chain ของผู้โจมตีถูกขยายออกไปหนึ่งบล็อก ลดช่องว่างลง -1 ความน่าจะเป็นที่ผู้โจมตีจะไล่ตามทันจากช่องว่างที่กำหนด สามารถเปรียบเทียบด้วย Gambler's Ruin problem โดยสมมติว่านักพนันที่มีเครดิตไม่จำกัด เริ่มต้นด้วยการขาดทุน และเล่นพนันไปเรื่อย ๆ เพื่อให้ถึงจุดคุ้มทุน เราสามารถคำนวณความน่าจะเป็นที่เขาจะกลับมาถึงจุดคุ้มทุนได้ หรือความน่าจะเป็นที่ผู้โจมตีจะไล่ทัน chain ที่สุจริตได้ ดังนี้ [8]: p = ความน่าจะเป็นที่ Node ที่สุจริตจะพบบล็อกถัดไป q = ความน่าจะเป็นที่ผู้โจมตีจะพบบล็อกถัดไป qz = ความน่าจะเป็นที่ผู้โจมตีจะไล่ทัน จากที่ตามหลังอยู่ z บล็อก https://i.imgur.com/vePe255.png จากสมมติฐานที่ว่า p > q ความน่าจะเป็นจะลดลงแบบเอกซ์โพเนนเชียล เมื่อจำนวนบล็อกที่ผู้โจมตีต้องไล่ตามทันเพิ่มขึ้น หากเขาไม่สามารถพุ่งขึ้นนำได้อย่างรวดเร็วตั้งแต่แรก โอกาสของเขาก็จะลดลงจนน้อยมาก ๆ เมื่อเขาตามหลังมากขึ้นเรื่อย ๆ ทีนี้ลองพิจารณาว่า ผู้รับธุรกรรมใหม่ต้องรอเป็นเวลานานเท่าใด จึงจะแน่ใจได้ว่าผู้ส่งไม่สามารถเปลี่ยนแปลงธุรกรรมได้แล้ว เราสมมติว่าผู้ส่งเป็นผู้โจมตี ที่ต้องการให้ผู้รับเชื่อว่าเขาได้รับเงินไปแล้ว จากนั้นจึงเปลี่ยนให้เงินกลับเข้าหาตัวเองหลังจากเวลาผ่านไประยะหนึ่ง ผู้รับจะได้รับแจ้งเมื่อเกิดเหตุการณ์นี้ขึ้น แต่ผู้ส่งหวังว่ามันจะสายเกินไปแล้ว ผู้รับจะสร้างคู่กุญแจใหม่ และให้กุญแจสาธารณะแก่ผู้ส่งไม่นานก่อนที่จะลงนาม ซึ่งจะป้องกันไม่ให้ผู้ส่งเตรียมบล็อกเชนปลอมไว้ล่วงหน้า โดยการทำงานอย่างต่อเนื่องจนกว่าเขาจะมีโอกาสได้บล็อกที่ยาวพอ จากนั้นจึงดำเนินธุรกรรมในทันที เมื่อส่งธุรกรรมแล้ว ผู้ส่งที่ไม่สุจริตจะเริ่มทำงานอย่างลับ ๆ บนบล็อกเชนคู่ขนาน ที่มีธุรกรรมในเวอร์ชันของเขาเองอยู่ ผู้รับจะรอจนกว่าธุรกรรมจะถูกเพิ่มลงในบล็อก และมีบล็อกที่ถูกเชื่อมต่อตามหลังมาอีก z บล็อก เขาไม่ทราบจำนวนความคืบหน้าที่แน่นอนที่ผู้โจมตีได้ทำไปแล้ว แต่สมมติว่าบล็อกที่สุจริตใช้เวลาเฉลี่ยต่อบล็อกตามที่คาดไว้ ความคืบหน้าที่อาจเกิดขึ้นได้ของผู้โจมตีจะเป็นการแจกแจงแบบปัวซง (Poisson distribution) ซึ่งมีค่าคาดหวังดังนี้: https://i.imgur.com/mYsb48i.png เพื่อให้ได้ความน่าจะเป็นที่ผู้โจมตียังคงสามารถไล่ทันได้ เราจะคูณความหนาแน่นของปัวซง สำหรับความคืบหน้าแต่ละระดับที่เขาสามารถทำได้ ด้วยความน่าจะเป็นที่เขาสามารถไล่ทันจากจุดนั้น: https://i.imgur.com/jQGkQ8r.png จัดเรียงใหม่เพื่อหลีกเลี่ยง infinite tail ของการแจกแจง https://i.imgur.com/OOO6Gm9.png แปลงมันให้เป็น C code #include <math.h> double AttackerSuccessProbability(double q, int z) { double p = 1.0 - q; double lambda = z * (q / p); double sum = 1.0; int i, k; for (k = 0; k <= z; k++) { double poisson = exp(-lambda); for (i = 1; i <= k; i++) poisson *= lambda / i; sum -= poisson * (1 - pow(q / p, z - k)); } return sum; } เมื่อรันผลลัพธ์บางส่วน เราจะเห็นว่าความน่าจะเป็นลดลงแบบเอกซ์โพเนนเชียลเมื่อ z เพิ่มขึ้น q=0.1 z=0 P=1.0000000 z=1 P=0.2045873 z=2 P=0.0509779 z=3 P=0.0131722 z=4 P=0.0034552 z=5 P=0.0009137 z=6 P=0.0002428 z=7 P=0.0000647 z=8 P=0.0000173 z=9 P=0.0000046 z=10 P=0.0000012 q=0.3 z=0 P=1.0000000 z=5 P=0.1773523 z=10 P=0.0416605 z=15 P=0.0101008 z=20 P=0.0024804 z=25 P=0.0006132 z=30 P=0.0001522 z=35 P=0.0000379 z=40 P=0.0000095 z=45 P=0.0000024 z=50 P=0.0000006 การแก้หาค่า P ที่น้อยกว่า 0.1%... P < 0.001 q=0.10 z=5 q=0.15 z=8 q=0.20 z=11 q=0.25 z=15 q=0.30 z=24 q=0.35 z=41 q=0.40 z=89 q=0.45 z=340 12.สรุป(Conclusion) เราได้นำเสนอระบบธุรกรรมอิเล็กทรอนิกส์ที่ไม่ต้องพึ่งพาความไว้วางใจ เริ่มต้นจากกรอบแนวคิดของเหรียญที่สร้างจากลายเซ็นดิจิทัล ซึ่งช่วยควบคุมความเป็นเจ้าของได้อย่างดีแต่ก็ยังไม่สมบูรณ์ หากปราศจากวิธีการป้องกันการใช้จ่ายซ้ำซ้อน เพื่อแก้ปัญหานี้ เราจึงเสนอเครือข่ายแบบเพียร์ทูเพียร์ที่ใช้ proof-of-work ในการบันทึกประวัติธุรกรรมสาธารณะ ซึ่งจะกลายเป็นเรื่องยากอย่างมากสำหรับผู้โจมตีที่จะเปลี่ยนแปลง หาก node ที่ซื่อสัตย์ควบคุมพลังประมวลผล CPU ส่วนใหญ่ เครือข่ายนี้มีความแข็งแกร่งในความเรียบง่ายที่ไม่มีโครงสร้างใด ๆ ที่ซับซ้อน node ต่าง ๆ ทำงานพร้อมกันโดยประสานงานกันเพียงเล็กน้อย ไม่จำเป็นต้องระบุตัวตน เนื่องจากข้อความไม่ได้ถูกส่งไปยังสถานที่ใดสถานที่หนึ่งโดยเฉพาะ และเพียงแค่ต้องส่งมอบให้ถึงมือผู้รับอย่างดีที่สุด node สามารถออกจากและเข้าร่วมเครือข่ายได้ตามต้องการ โดยยอมรับ chain ที่มี proof-of-work มากที่สุดเป็นสิ่งที่เกิดขึ้นในขณะที่ไม่ได้เชื่อมต่อ พวกเขาโหวตด้วยพลังประมวลผล CPU แสดงการยอมรับบล็อกที่ถูกต้องโดยการทำงานเพื่อขยายบล็อก และปฏิเสธบล็อกที่ไม่ถูกต้องโดยการปฏิเสธที่จะทำงานกับบล็อกเหล่านั้น กฎและแรงจูงใจใด ๆ ที่จำเป็นสามารถบังคับใช้ได้ด้วยกลไกฉันทามตินี้ ไปอ่านต่อกันเองเด้ออ --- [1] W. Dai, "b-money," http://www.weidai.com/bmoney.txt, 1998. [2] H. Massias, X.S. Avila, and J.-J. Quisquater, "Design of a secure timestamping service with minimal trust requirements," In 20th Symposium on Information Theory in the Benelux, May 1999. [3] S. Haber, W.S. Stornetta, "How to time-stamp a digital document," In Journal of Cryptology, vol 3, no 2, pages 99-111, 1991. [4] D. Bayer, S. Haber, W.S. Stornetta, "Improving the efficiency and reliability of digital time-stamping," In Sequences II: Methods in Communication, Security and Computer Science, pages 329-334, 1993. [5] S. Haber, W.S. Stornetta, "Secure names for bit-strings," In Proceedings of the 4th ACM Conference on Computer and Communications Security, pages 28-35, April 1997. [6] A. Back, "Hashcash - a denial of service counter-measure," http://www.hashcash.org/papers/hashcash.pdf, 2002. [7] R.C. Merkle, "Protocols for public key cryptosystems," In Proc. 1980 Symposium on Security and Privacy, IEEE Computer Society, pages 122-133, April 1980. [8] W. Feller, "An introduction to probability theory and its applications," 1957.
@ 79008e78:dfac9395
2024-09-02 06:17:23ระบบเงินอิเล็กทรอนิกส์แบบ peer-to-peer ---- ระบบเงินอิเล็กทรอนิกส์แบบ peer-to-peer นั้นจะช่วยให้เราสามารถชำระเงินผ่านทางออนไลน์ได้โดยตรงจากฝ่ายหนึ่งไปยังอีกฝ่ายหนึ่งโดยไม่ต้องผ่านตัวกลางอย่างพวกสถาบันการเงิน โดยใช้ digital signature เป็นส่วนหนึ่งในการแก้ปัญหานี้ แต่มันจะไม่มีประโยชน์ใด ๆ เลยหากยังคงต้องอาศัยตัวกลางที่เชื่อถือได้มาแก้ปัญหา double spending เราขอเสนอวิธีแก้ปัญหา double spending โดยใช้เครือข่ายแบบ peer-to-peer ให้เครือข่ายคอยประทับเวลาธุรกรรมต่าง ๆ ในระบบและนำมาเรียงร้อยกันเป็นเส้นสายของ proof-of-work ที่ใช้ hash เพื่อสร้างธุรกรรมที่ไม่สามารถเปลี่ยนแปลงได้ โดยไม่ต้องทำ proof-of-work ใหม่ โดยให้เส้นสายที่ยาวที่สุดนั้น ไม่เพียงแต่ทำหน้าที่เป็นลำดับของธุรกรรมที่เกิดขึ้นเท่านั้น แต่ยังเป็นสิ่งที่พิสูจน์ได้ว่ามาจากกำลังประมวลผล CPU ที่มากที่สุด และตราบใดที่ nodes ส่วนใหญ่ไม่ได้ร่วมมือกันโจมตีเครือข่ายและยังคงควบคุมกำลังประมวลผลส่วนใหญ่ในระบบไว้ พวกเขาก็จะสร้างเส้นสายที่ยาวที่สุดและสามารถเอาชนะผู้ประสงค์ร้ายที่จะโจมตีระบบได้ ตัวเครือข่ายเองไม่ได้ต้องมีโครงสร้างอะไรที่ซับซ้อน ข้อมูลต่าง ๆ ในเครือข่ายจะถูกกระจายส่งต่อโดยไม่ต้องสนใจว่าผู้รับจะได้รับหรือไม่ และ nodes ต่าง ๆ เองก็สามารถที่จะออกจากเครือข่ายและกลับเข้าร่วมใหม่ได้ตามที่ต้องการ โดยยอมรับเส้น proof-of-work ที่ยาวที่สุด เป็นหลักฐานของสิ่งที่เกิดขึ้นในขณะที่ node นั้น ๆ ไม่ได้อยู่ในเครือข่าย 1.บทนำ (Introduction) ----- ไม่ว่าใครจะใคร่ซื้อใคร่ขายอะไรใด ๆ บนอินเตอร์เน็ตนั้น ก็จำเป็นต้องพึ่งพาสถาบันการเงินในฐานะของบุคคลที่สามเพื่อดำเนินการชำระเงินทางอิเล็กทรอนิกส์เสมอ ๆ ซึ่งถึงแม้ว่าระบบนี้มันจะทำงานได้ดีสำหรับธุรกรรมส่วนใหญ่ ๆ แต่ระบบก็ก็มีจุดอ่อนอยู่ที่ยังต้องอาศัยความไว้เนื้อเชื่อใจ (trust) ในระบบนี้การทำธุรกรรมที่ไม่สามารถย้อนกลับได้อย่างสมบูรณ์นั้นมันแทบจะเป็นไปไม่ได้เลย เนื่องจากสถาบันการเงินไม่สามารถหลีกเลี่ยงการเป็นตัวกลางในการไกล่เกลี่ยข้อพิพาทต่าง ๆ ที่อาจเกิดขึ้นได้ มิหนำซ้ำต้นทุนในการไกล่เกลี่ยยังทำให้ต้นทุนการทำธุรกรรมเพิ่มสูงขึ้น และเมื่อต้นทุนสูงขึ้นขนาดของธุรกรรมที่สามารถใช้งานได้จริงก็สูงขึ้นตามไปด้วย ธุรกรรมเล็ก ๆ น้อย ๆ ก็ไม่สามารถเกิดขึ้นได้ เมื่อมีความเป็นไปได้ที่ธุรกรรมจะเกิดการย้อนกลับ ความจำเป็นในการสร้างความไว้วางใจก็ยิ่งทวีคูณมากขึ้น ผู้ค้าก็จำเป็นต้องระมัดระวังลูกค้า ต้องเรียกร้องข้อมูลมากกว่าที่จำเป็น การฉ้อโกงกลายเป็นเรื่องที่หลีกเลี่ยงไม่ได้เพราะต้นทุนและความไม่แน่นอนในทำธุรกรรมเหล่านี้ แน่นอนว่าเราสามารถหลีกเลี่ยงมันได้โดยการใช้เงินสด แต่ก็ไม่มีกลไกใดที่ทำให้สามารถใช้เงินสดผ่านช่องทางการสื่อสาร (เอาให้เข้าใจง่ายก็อินเตอร์เน็ต)ได้ โดยไม่ต้องมีตัวกลาง ;-; แปลว่าสิ่งที่จำเป็นสำหรับการแก้ไขปัญหานี้คือระบบการชำระเงินทางอิเล็กทรอนิกส์ ที่อยู่บนพื้นฐานของการพิสูจน์ด้วยการเข้ารหัสแทนที่จะเป็นความไว้วางใจ ซึ่งจะทำให้คู่สัญญาสองฝ่ายที่ยินยอมสามารถทำธุรกรรมร่วมกันได้โดยตรง โดยไม่จำเป็นต้องมีบุคคลที่สามมาคอยเป็นตัวกลาง ธุรกรรมที่ยากต่อการย้อนกลับจะช่วยปกป้องผู้ขายจากการฉ้อโกง และสามารถใช้กลไก escrow เพื่อปกป้องผู้ซื้อได้อีกด้วย ในเอกสารชุดนี้ เราขอเสนอวิธีแก้ปัญหาการใช้จ่ายซ้ำซ้อนโดยใช้เซิร์ฟเวอร์ timestamp กระจายศูนย์แบบ peer-to-peer เพื่อสร้างหลักฐานการคำนวณลำดับเวลาของธุรกรรม โดยระบบนี้จะปลอดภัยตราบใดที่กลุ่มของ node ที่ซื่อสัตย์ ยังคงมีกำลังประมวลผลที่มากกว่ากลุ่มที่ประสงค์ร้ายกับระบบ 2.ธุรกรรม (Transactions) ---- นิยามของเหรียญอิเล็กทรอนิกส์ในที่นี้ คือห่วงโซ่ที่คล้องเกี่ยวกันของ digital signature โดยที่เจ้าของเหรียญอิเล็กทรอนิกส์จะโอนเหรียญไปยังเจ้าของคนถัดไป ด้วยการลง digital signature บน hash ของธุรกรรมก่อนหน้ารวมถึงกุญแจสาธารณะของเจ้าของคนถัดไป และผนวกมันไว้ที่ส่วนท้ายของธุรกรรม และผู้รับเงินเองก็สามารถตรวจสอบลายเซ็นเพื่อยืนยันความเป็นเจ้าของได้ https://image.nostr.build/a467896797a9fb9f98c3c234f0adb4df2376f2c3d9a7cc9d8672d7a9f5aa9efa.png แน่นอนว่าปัญหาก็คือผู้รับเงินไม่สามารถตรวจสอบได้ว่าเจ้าของคนใดคนหนึ่งก่อนหน้าเขาได้ใช้เหรียญดังกล่าวซ้ำซ้อนมากกว่าหนึ่งครั้งหรือไม่ และวิธีการแก้ไขปัญหานี้โดยทั่วไปก็คงเป็นการกำหนดตัวกลางที่มีความน่าเชื่อถือมาเป็นคนตรวจสอบทุกธุรกรรมเพื่อป้องกันการใช้จ่ายซ้ำซ้อน และหลังจากการทำธุรกรรมแต่ละครั้ง เหรียญจะต้องถูกส่งกลับไปยังตัวกลางเพื่อออกเหรียญใหม่ และจะมีเพียงเหรียญที่ออกจากตัวกลางโดยตรงเท่านั้นที่จะเชื่อถือได้ว่าจะไม่ถูกใช้จ่ายซ้ำซ้อน แต่ปัญหาก็คือ ชะตากรรมของระบบเงินทั้งหมดจะขึ้นอยู่กับตัวกลางตัวนี้ เพราะทุกธุรกรรมจำเป็นจะต้องผ่านพวกเขา ซึ่งก็ไม่ต่างอะไรกับธนาคาร เราจึงต้องการวิธีการที่ทำให้ผู้รับเงินทราบได้ว่าเจ้าของคนก่อน ๆ ไม่ได้ลงนามในธุรกรรมใด ๆ มาก่อน เพื่อให้บรรลุวัตถุประสงค์นี้ เราจะทำการนับว่าธุรกรรมที่เกิดขึ้นก่อนเป็นธุรกรรมที่ถูกต้อง และจะไม่สนใจความพยายามใด ๆ ในการที่จะใช้เหรียญนั้น ๆ ซ้ำอีก และวิธีเดียวที่ทำแบบนี้ได้ คือการรับรู้ถึงธุรกรรมทั้งหมด เช่นเดียวกับโมเดลที่ได้กล่าวข้างต้น ที่ตัวกลางจะรับรู้ถึงธุรกรรมทั้งหมดและตัดสินว่าธุรกรรมใดมาก่อนมาหลัง เพื่อให้บรรลุเป้าหมายนี้โดยไม่ต้องมีบุคคลที่สามที่เชื่อถือได้ ธุรกรรมทั้งหมดจะต้องถูกประกาศต่อสาธารณะ [1] และเราต้องการระบบที่ผู้เข้าร่วมเห็นพ้องในประวัติธุรกรรมชุดเดียวกันตามลำดับที่ได้รับ ส่วนผู้รับเงินก็จำเป็นจะต้องมีหลักฐานว่า ในขณะที่ทำธุรกรรม "โหนด" ส่วนใหญ่ในระบบเห็นพ้องต้องกันว่าธุรกรรมนั้นได้รับเป็นลำดับแรก(ไม่มีธุรกรรมที่ใช้เหรียญพวกนี้มาก่อน) 3.ระบบบันทึกเวลา (Timestamp Server) ---- สำหรับแนวทางการแก้ปัญหาในครั้งนี้ เราจะใช้ประโยชน์จาก timestamp server ที่จะทำหน้าที่บันทึก hash ของบล๊อกที่ต้องการให้มีการบันทึกเวลา และจากนั้นจะทำการเผยแพร่ hash ดังกล่าว เหมือนกับหนังสือพิมพ์หรือโพสต์ใน Usenet [2-5] (ฟีลแบบทุกคนจะเห็นโพสต์นี้น้าา ประมาณนั้น) การบันทึกเวลานี้จะพิสูจน์ได้ว่าข้อมูลที่ถูก hash นั้นจะต้องมีอยู่จริงในเวลานั้นเพื่อให้ได้มาซึ่ง hash ดังกล่าว แต่ละการบันทึกเวลาจะรวมการบันทึกเวลาของหน้านี้ไว้ใน hash ของมันเพื่อสร้างเป็น chain โดยการบันทึกเวลาแต่ละครั้งจะยืนยันความถูกต้องของการบันทึกก่อนหน้าได้อีกด้วยด้วย https://image.nostr.build/ddf92417c45dbb6e25da0af80a10d4cdbc3e725d047d65f54a3e3bfcf358c4d6.png 4.พรูฟ-ออฟ-เวิร์ค (Proof-of-Work) ---- ในการสร้าง Timestamp Server แบบกระจายศูนย์บนพื้นฐานแบบ peer to peer เราจำเป็นต้องใช้ระบบ Proof-of-Work (PoW) ที่คล้ายกับ Hashcash ของ Adam Back [6] แทนที่จะใช้วิธีการแบบเดิม ๆ อย่างการประกาศในหนังสือพิมพ์หรือ Usenet โดย PoW ใช้ในการตรวจสอบค่าที่มาจากกระบวนการ hash เช่น SHA-256 แล้ว ผลลัพธ์ที่ได้ (Hash) จะขึ้นต้นด้วยเลขศูนย์จำนวนหนึ่ง โดยที่ work (ประมาณว่าพลังประมวลผล) ที่ต้องใช้จะเพิ่มขึ้นแบบทวีคูณตามจำนวนเลขศูนย์ที่ต้องการ และสามารถตรวจสอบได้โดยการรัน Hash เพียงครั้งเดียว ซึ่งสำหรับ timestamp network ของเรานั้น เราใช้ PoW โดยการเพิ่มค่า Nonce ในบล็อกไปเรื่อย ๆ จนกว่าจะพบค่าที่ทำให้ Hash ของบล็อกนั้นมีเลขศูนย์ตามที่กำหนด และเมื่อใช้กำลังประมวลผลของ CPU ไปกับการทำ PoW จนสำเร็จแล้ว บล็อกจะไม่สามารถเปลี่ยนแปลงได้ หากไม่มีการทำงานซ้ำใหม่ เนื่องจากบล็อกที่สร้างขึ้นภายหลังจะเชื่อมโยงกับบล็อกก่อนหน้า การเปลี่ยนแปลงบล็อกใด ๆ จะต้องทำ PoW ของบล็อกนั้นและบล็อกที่ตามมาใหม่ทั้งหมด https://image.nostr.build/c039ef4ca6833cb1ecee65ac5991df2406be9b7e490b86b3b19f94f267767182.png นอกจากนี้ PoW ยังช่วยแก้ปัญหาของเสียงส่วนมากที่มาตัดสินใจในระบบนี้ เพราะหากเสียงข้างมากอ้างอิงจากหลักการหนึ่ง IP หนึ่งเสียง ใครก็ตามที่สามารถสร้าง IP ได้จำนวนมากก็จะสามารถควบคุมระบบได้ จึงใช้หลักการหนึ่ง CPU หนึ่งเสียงแทน การตัดสินใจของเสียงข้างมากจะแสดงด้วย Chain ที่ยาวที่สุด ซึ่งบ่งบอกถึงความพยายามในการคำนวณ (Proof-of-Work) ที่มากที่สุด หาก Node ที่ซื่อสัตย์ (Honest nodes) มีกำลังประมวลผลของ CPU ส่วนใหญ่อยู่ในการควบคุม Honest Chain ก็จะเติบโตเร็วที่สุดและแซงหน้า Chain อื่น ๆ ได้ ผู้โจมตีที่ต้องการแก้ไขบล็อกในอดีตจะต้องทำ Proof-of-Work ของบล็อกนั้นและบล็อกที่ตามมาใหม่ทั้งหมด และต้องทำงานให้เร็วกว่า Honest Node ด้วย ซึ่งโอกาสที่ผู้โจมตีจะตามทันนั้นจะลดลงแบบทวีคูณเมื่อมีการเพิ่มบล็อกมากขึ้น เพื่อชดเชยความเร็วของฮาร์ดแวร์ที่เพิ่มขึ้นและความสนใจในการรัน Node ที่ผันผวน ระดับความยากของ Proof-of-Work จะถูกกำหนดโดยค่าเฉลี่ย โดยตั้งเป้าไว้ที่จำนวนบล็อกเฉลี่ยต่อชั่วโมง หากสร้างบล็อกได้เร็วเกินไป ระดับความยากก็จะเพิ่มขึ้น 5.เครือข่าย (Network) ---- เครือข่ายนั้นมีการทำงาน ดังนี้ 1. การประกาศธุรกรรมใหม่: ธุรกรรมใหม่จะถูกประกาศ (broadcast) ไปยังทุก node ในเครือข่าย 2. การรวบรวมธุรกรรม: แต่ละ node จะรวบรวมธุรกรรมใหม่ ๆ เหล่านี้ ไว้ในบล็อก 3. การค้นหา Proof-of-Work: แต่ละ node จะทำการคำนวณ เพื่อค้นหา Proof-of-Work ตามค่า difficulty สำหรับบล็อกนั้น ๆ 4. การประกาศบล็อก: เมื่อ node ใดค้นหา Proof-of-Work ได้แล้ว node นั้นจะทำการประกาศบล็อกไปยังทุก node ในเครือข่าย 5. การตรวจสอบและยอมรับบล็อก: node อื่น ๆ จะทำการตรวจสอบและยอมรับบล็อกนั้น เฉพาะเมื่อธุรกรรมทั้งหมดภายในบล็อกนั้นถูกต้องและยังไม่ถูกใช้มาก่อน 6. การสร้างบล็อกถัดไป: node ต่าง ๆ แสดงการยอมรับบล็อกโดยการเริ่มต้นสร้างบล็อกถัดไปใน chain ด้วย hash ของบล็อกที่ยอมรับ เป็น hash ก่อนหน้าในโครงสร้างของบล๊อกใหม่ที่กำลังสร้าง node ต่าง ๆ จะถือว่า chain ที่ยาวที่สุดเป็น chain ที่ถูกต้องและจะทำงานเพื่อขยาย chain นั้นต่อไป หากมีสอง node ที่ได้ประกาศบล็อกเวอร์ชันที่แตกต่างกันในเวลาพร้อมกัน node บาง node อาจได้รับบล็อกหนึ่งก่อน อีกบล็อกหนึ่ง ในกรณีนี้ node เหล่านั้น จะทำงานบนบล็อกที่ได้รับก่อน แต่จะเก็บสำเนาของบล็อกอีกอันหนึ่งไว้ ในกรณีที่บล็อกนั้น กลายเป็นบล็อกที่อยู่ใน chain ที่ยาวกว่าปัญหาข้อโต้แย้งนี้ก็จะได้รับการแก้ไข เมื่อพบ Proof-of-Work อันถัดไปและ chain ใด chain หนึ่งยาวขึ้น node ที่กำลังทำงานอยู่บน chain ที่สั้นกว่าก็จะเปลี่ยนไปทำงานบน chain ที่ยาวกว่าแทน การประกาศธุรกรรมใหม่ ไม่จำเป็นต้องไปถึงทุก node ในเครือข่าย ตราบใดที่พวกเขายังไปถึง node ส่วนใหญ่ในระบบได้ ธุรกรรมเหล่านั้นก็จะถูกบรรจุอยู่ในบล็อกในไม่ช้า นอกจากนี้การประกาศบล็อกยังไม่ต้องกังวลเรื่องจะมีบล๊อกที่สูญหาย เนื่องจากหากว่า node ไม่ได้รับบล็อกใด ๆ node ก็จะตระหนักได้ว่าพลาดบล็อกก่อนหน้าไปเมื่อได้รับบล๊อกใหม่มา และ node จะทำการร้องขอ block ที่ขาดไปจากเครือข่าย 6.แรงจูงใจ(Incentive) ---- โดยปกติแล้ว ธุรกรรมแรกของแต่ละบล๊อกนั้นจะเป็นธุรกรรมพิเศษที่จะขุดเหรียญที่สร้างขึ้นใหม่ซึ่งเป็นกรรมสิทธิ์ของผู้สร้างบล็อกนั้น ๆ ซึ่งจะเป็นการเพิ่มแรงจูงใจให้กับ node ต่าง ๆ ในการสนับสนุนเครือข่าย และเป็นวิธีการกระจายเหรียญให้หมุนเวียน เนื่องจากไม่มีหน่วยงานส่วนกลางที่ทำหน้าที่ในการออกเหรียญ การเพิ่มเหรียญใหม่ในปริมาณคงที่อย่างต่อเนื่องนั้นคล้ายคลึงกับการที่คนงานเหมืองทองคำใช้แรง และ เวลา เพื่อเพิ่มทองคำให้หมุนเวียน ในกรณีนี้ คือ เวลา กำลังประมวลผล และไฟฟ้าที่ถูกใช้ไป นอกจากนี้แรงจูงใจจะมาจากค่าธรรมเนียมการทำธุรกรรม หากมูลค่าผลลัพธ์ของธุรกรรมน้อยกว่ามูลค่าที่ใส่เข้ามา ส่วนต่างนั้นก็คือค่าธรรมเนียมการทำธุรกรรมที่จะเพิ่มเข้าไปในมูลค่าแรงจูงใจของบล็อกที่มีธุรกรรมนั้น เมื่อเหรียญทั้งหมดในระบบมีจำนวนเท่ากับที่กำหนดไว้แล้ว แรงจูงใจหลักก็จะถูกเปลี่ยนมาเป็นค่าธรรมเนียมการทำธุรกรรม และปราศจากภาวะเงินเฟ้อโดยสิ้นเชิง แรงจูงใจอาจช่วยกระตุ้นให้ node ต่าง ๆ ยังคงซื่อสัตย์ หากผู้โจมตีที่ละโมบสามารถรวบรวมกำลังประมวลผล ได้มากกว่า node ที่ซื่อสัตย์ทั้งหมด เขาจะต้องเลือกระหว่างการใช้มันเพื่อฉ้อโกงผู้อื่นโดยการใช้จ่ายซ้ำซ้อน หรือใช้มันเพื่อสร้างเหรียญใหม่ พวกเขาจะพบว่าการเล่นตามกฎ กฎที่เอื้อประโยชน์ให้กับเขาด้วยเหรียญใหม่มากกว่าคนอื่น ๆ รวมกันนั้นทำกำไรได้มากกว่าการบ่อนทำลายระบบและความถูกต้องของทรัพย์สินของเขาเอง 7.การจัดการพื้นที่ดิสก์(Reclaiming Disk Space) ---- เมื่อธุรกรรมถูกบรรจุลงในบล๊อกแล้ว สามารถกำจัดธุรกรรมที่ใช้ไปแล้วก่อนหน้านั้นออกได้เพื่อประหยัดพื้นที่ดิสก์ แต่การจะทำอย่างนี้ได้โดยไม่ให้เลข hash ของบล๊อกมีการเปลี่ยนแปลงนั้น ธุรกรรมจึงจำเป็นต้องถูก hash ในรูปแบบของ Merkle Tree [7][2][5] โดยมีแค่ root node ของ tree เท่านั้นที่จะรวมอยู่ใน hash ของบล๊อก นี่เป็นวิธีที่ทำให้สามารถบีบอัดข้อมูลในบล๊อกเก่า ๆ ได้โดยการตัดพวก hash ส่วนอื่น ๆ ของ tree ที่ไม่ใช่ root node ออก (ไม่จำเป็นต้องเก็บ hash ในชั้นอื่น ๆ ของ tree) https://image.nostr.build/3ed95334891d91baca3f3f6f624a7ae22620be4ebfe0db5eb652cfce11255b9a.png โดยในส่วน header ของบล็อกที่ไม่มีธุรกรรมจะมีขนาดประมาณ 80 ไบต์ หากเราสมมติว่าบล็อกถูกสร้างขึ้นทุก ๆ 10 นาที 80 ไบต์ * 6 * 24 * 365 = 4.2MB ต่อปี โดยที่ระบบคอมพิวเตอร์ทั่วไปที่วางขายในปี 2551 มี RAM 2GB และกฎของมัวร์ทำนายการเติบโตในปัจจุบันที่ 1.2GB ต่อปี การจัดเก็บข้อมูลไม่น่าจะเป็นปัญหาแม้ว่าส่วนหัวของบล็อกจะต้องถูกเก็บไว้ในหน่วยความจำก็ตาม 8.การตรวจสอบธุรกรรม (Simplified Payment Verification) ---- การที่จะยืนยันการชำระเงินโดยไม่จำเป็นต้องรัน full node ได้นั้น ผู้ใช้เพียงแค่เก็บสำเนาของส่วนหัวบล็อก (block header) ของสายบล็อก (chain) ที่ยาวที่สุด ซึ่งสามารถรับได้โดยการสอบถามจาก node อื่น ๆ ในเครือข่ายจนมั่นใจว่าได้รับสายที่ยาวที่สุด และรับ Merkle branch ที่เชื่อมโยงธุรกรรมกับบล็อกที่มีการประทับเวลา (Timestamp) อยู่ ถึงแม้ผู้ใช้จะไม่สามารถตรวจสอบธุรกรรมด้วยตัวเองได้ แต่การเชื่อมโยงธุรกรรมกับตำแหน่งในสายบล็อกจะทำให้เห็นว่า node ในเครือข่ายยอมรับแล้ว และบล็อกที่เพิ่มเข้ามาหลังจากนั้นเป็นการยืนยันเพิ่มเติมว่าเครือข่ายยอมรับธุรกรรมนี้แล้ว https://i.imgur.com/VXtLpRF.png การตรวจสอบดังกล่าวจะเชื่อถือได้ตราบใดที่ node ที่ซื่อสัตย์ยังคงควบคุมเครือข่าย แต่จะมีความเสี่ยงมากขึ้นหากเครือข่ายถูกโจมตีและถูกควบคุม ในขณะที่ node ในเครือข่ายสามารถตรวจสอบธุรกรรมได้ด้วยตัวเอง แต่วิธีการแบบง่ายนี้อาจถูกหลอกลวงโดยการใช้ธุรกรรมปลอมของผู้โจมตี ตราบใดที่ผู้โจมตียังคงสามารถควบคุมเครือข่ายได้ กลยุทธ์หนึ่งในการป้องกันปัญหานี้คือ การรับการแจ้งเตือนจาก node อื่น ๆ ในเครือข่ายเมื่อตรวจพบบล็อกที่ไม่ถูกต้อง ซึ่งจะแจ้งให้ซอฟต์แวร์ของผู้ใช้ดาวน์โหลดบล็อกแบบเต็มและธุรกรรมที่แจ้งเตือน เพื่อยืนยันความไม่สอดคล้องกัน ธุรกิจที่ได้รับการชำระเงินบ่อยครั้งอาจยังคงต้องการรัน node ของตนเอง เพื่อความปลอดภัยที่เป็นอิสระและการตรวจสอบที่รวดเร็วยิ่งขึ้น 9.การควบรวมและแบ่งย่อยมูลค่า(Combining and Splitting Value) ---- แม้ว่าการจัดการเหรียญหลาย ๆ เหรียญจะเป็นสิ่งที่สามารถทำได้ แต่การจัดการธุรกรรมแยกต่างหากสำหรับแต่ละเหรียญในการโอนก็คงเป็นเรื่องที่น่าปวดหัวอยู่ดี ฉะนั้นแล้วเพื่อให้สามารถแยกและรวมมูลค่ากันได้ ธุรกรรมจึงสามารถมี input และ output ได้หลายรายการ ซึ่งโดยปกติแล้วจะมี input เดียวจากธุรกรรมก่อนหน้าที่มีขนาดใหญ่กว่า หรือ input จำนวนเล็ก ๆ หลาย ๆ รายการ และ output ไม่เกินสองรายการ คือ รายการหนึ่งสำหรับการชำระเงิน และอีกหนึ่งรายการสำหรับการส่งเงินทอน หากมีกลับไปยังผู้ส่ง https://image.nostr.build/9c6d3ce0e9f08c5b3fa3b82c2088ac6235603e5c0df3469060e6c9f74bce32fc.png ควรสังเกตว่า fan-out (กระจายของธุรกรรม) ซึ่งเป็นกรณีที่ธุรกรรม ธุรกรรมหนึ่งนั้นขึ้นอยู่กับหลายธุรกรรม และธุรกรรมเหล่านั้นเองก็ขึ้นอยู่กับอีกหลายธุรกรรม แต่ไม่ใช่ปัญหาในที่นี้ เพราะไม่มีความจำเป็นในการดึงประวัติการทำธุรกรรมทั้งหมดออกมาเป็นสำเนา 10.ความเป็นส่วนตัว(Privacy) ---- ในรูปแบบธนาคารแบบดั้งเดิมนั้น ความเป็นส่วนตัวเกิดขึ้นได้ด้วยการจำกัดการเข้าถึงข้อมูล โดยให้เฉพาะผู้ที่เกี่ยวข้องและบุคคลที่สามที่ได้รับความไว้วางใจเท่านั้น แต่เนื่องจากในระบบนี้เรามีความจำเป็นในการประกาศธุรกรรมทั้งหมดต่อสาธารณะ ทำให้ไม่สามารถใช้วิธีนี้ได้ แต่ยังจำเป็นต้องคงความเป็นส่วนตัวไว้ โดยการแบ่งการไหลของข้อมูล ด้วยการไม่เปิดเผยตัวตนของเจ้าของ public key คนทั่วไปสามารถเห็นว่ามีคนกำลังส่งเงินจำนวนหนึ่งให้กับคนอื่น แต่จะไม่ทราบข้อมูลที่เชื่อมโยงธุรกรรมนั้นกับบุคคลใด ๆ ซึ่งคล้ายกับระดับข้อมูลที่เปิดเผยโดยตลาดหลักทรัพย์ ซึ่งมีการเปิดเผยเวลาและขนาดของการซื้อขายแต่ละครั้งต่อสาธารณะ แต่ไม่ได้ระบุว่าคู่สัญญาคือใคร https://image.nostr.build/6ec3c84c7878dbd4558d2045518384daf5a341e86f4194cf367cc8426c2d72a7.png เพื่อเสริมในเรื่องของความปลอดภัย ควรใช้ key pair ใหม่สำหรับการทำธุรกรรมในแต่ละครั้ง เพื่อป้องกันไม่ให้เชื่อมโยงกับเจ้าของคนเดียวกันได้ อย่างไรก็ตาม การเชื่อมโยงบางอย่างยังคงหลีกเลี่ยงไม่ได้ ในธุรกรรมที่มี input หลายรายการ ซึ่งจำเป็นต้องเปิดเผยว่า input เหล่านั้นเป็นของเจ้าของคนเดียวกัน ความเสี่ยงก็คือ หากมีการเปิดเผยตัวตนของเจ้าของคีย์ การเชื่อมโยงอาจเปิดเผยธุรกรรมอื่น ๆ ที่เป็นของเจ้าของรายเดียวกันได้ 11.การคำนวณ(Calculations) ---- หากลองพิจารณาสถานการณ์ที่ผู้โจมตีพยายามสร้าง chain ปลอมให้เร็วกว่า chain จริง แม้ว่าจะทำได้สำเร็จ แต่มันก็ไม่สามารถทำให้ระบบเปิดรับการเปลี่ยนแปลงตามอำเภอใจได้อยู่ดี เช่น การสร้างมูลค่าจากอากาศธาตุ หรือการรับเงินที่ไม่เคยเป็นของผู้โจมตีมาก่อน Node ต่าง ๆ จะไม่ยอมรับธุรกรรมที่ไม่ถูกต้องเป็นการชำระเงิน และ Node ที่สุจริตก็จะไม่ยอมรับบล็อกที่มีธุรกรรมเหล่านั้นอย่างแน่นอน ผู้โจมตีทำได้เพียงพยายามเปลี่ยนแปลงธุรกรรมของตนเอง เพื่อนำเงินที่ใช้ไปแล้วกลับคืนมาเท่านั้น การแข่งขันระหว่าง chain สุจริตกับ chain ของผู้โจมตี สามารถอธิบายได้ด้วยแบบจำลองการเดินสุ่มทวินาม (Binomial Random Walk) โดยเหตุการณ์ที่สำเร็จ หมายถึง chain ที่สุจริตถูกขยายออกไปอีกหนึ่งบล็อก เพิ่มความยาวนำหน้าไป +1 และเหตุการณ์ที่ล้มเหลว หมายถึง chain ของผู้โจมตีถูกขยายออกไปหนึ่งบล็อก ลดช่องว่างลง -1 ความน่าจะเป็นที่ผู้โจมตีจะไล่ตามทันจากช่องว่างที่กำหนด สามารถเปรียบเทียบด้วย Gambler's Ruin problem โดยสมมติว่านักพนันที่มีเครดิตไม่จำกัด เริ่มต้นด้วยการขาดทุน และเล่นพนันไปเรื่อย ๆ เพื่อให้ถึงจุดคุ้มทุน เราสามารถคำนวณความน่าจะเป็นที่เขาจะกลับมาถึงจุดคุ้มทุนได้ หรือความน่าจะเป็นที่ผู้โจมตีจะไล่ทัน chain ที่สุจริตได้ ดังนี้ [8]: p = ความน่าจะเป็นที่ Node ที่สุจริตจะพบบล็อกถัดไป q = ความน่าจะเป็นที่ผู้โจมตีจะพบบล็อกถัดไป qz = ความน่าจะเป็นที่ผู้โจมตีจะไล่ทัน จากที่ตามหลังอยู่ z บล็อก https://i.imgur.com/vePe255.png จากสมมติฐานที่ว่า p > q ความน่าจะเป็นจะลดลงแบบเอกซ์โพเนนเชียล เมื่อจำนวนบล็อกที่ผู้โจมตีต้องไล่ตามทันเพิ่มขึ้น หากเขาไม่สามารถพุ่งขึ้นนำได้อย่างรวดเร็วตั้งแต่แรก โอกาสของเขาก็จะลดลงจนน้อยมาก ๆ เมื่อเขาตามหลังมากขึ้นเรื่อย ๆ ทีนี้ลองพิจารณาว่า ผู้รับธุรกรรมใหม่ต้องรอเป็นเวลานานเท่าใด จึงจะแน่ใจได้ว่าผู้ส่งไม่สามารถเปลี่ยนแปลงธุรกรรมได้แล้ว เราสมมติว่าผู้ส่งเป็นผู้โจมตี ที่ต้องการให้ผู้รับเชื่อว่าเขาได้รับเงินไปแล้ว จากนั้นจึงเปลี่ยนให้เงินกลับเข้าหาตัวเองหลังจากเวลาผ่านไประยะหนึ่ง ผู้รับจะได้รับแจ้งเมื่อเกิดเหตุการณ์นี้ขึ้น แต่ผู้ส่งหวังว่ามันจะสายเกินไปแล้ว ผู้รับจะสร้างคู่กุญแจใหม่ และให้กุญแจสาธารณะแก่ผู้ส่งไม่นานก่อนที่จะลงนาม ซึ่งจะป้องกันไม่ให้ผู้ส่งเตรียมบล็อกเชนปลอมไว้ล่วงหน้า โดยการทำงานอย่างต่อเนื่องจนกว่าเขาจะมีโอกาสได้บล็อกที่ยาวพอ จากนั้นจึงดำเนินธุรกรรมในทันที เมื่อส่งธุรกรรมแล้ว ผู้ส่งที่ไม่สุจริตจะเริ่มทำงานอย่างลับ ๆ บนบล็อกเชนคู่ขนาน ที่มีธุรกรรมในเวอร์ชันของเขาเองอยู่ ผู้รับจะรอจนกว่าธุรกรรมจะถูกเพิ่มลงในบล็อก และมีบล็อกที่ถูกเชื่อมต่อตามหลังมาอีก z บล็อก เขาไม่ทราบจำนวนความคืบหน้าที่แน่นอนที่ผู้โจมตีได้ทำไปแล้ว แต่สมมติว่าบล็อกที่สุจริตใช้เวลาเฉลี่ยต่อบล็อกตามที่คาดไว้ ความคืบหน้าที่อาจเกิดขึ้นได้ของผู้โจมตีจะเป็นการแจกแจงแบบปัวซง (Poisson distribution) ซึ่งมีค่าคาดหวังดังนี้: https://i.imgur.com/mYsb48i.png เพื่อให้ได้ความน่าจะเป็นที่ผู้โจมตียังคงสามารถไล่ทันได้ เราจะคูณความหนาแน่นของปัวซง สำหรับความคืบหน้าแต่ละระดับที่เขาสามารถทำได้ ด้วยความน่าจะเป็นที่เขาสามารถไล่ทันจากจุดนั้น: https://i.imgur.com/jQGkQ8r.png จัดเรียงใหม่เพื่อหลีกเลี่ยง infinite tail ของการแจกแจง https://i.imgur.com/OOO6Gm9.png แปลงมันให้เป็น C code #include <math.h> double AttackerSuccessProbability(double q, int z) { double p = 1.0 - q; double lambda = z * (q / p); double sum = 1.0; int i, k; for (k = 0; k <= z; k++) { double poisson = exp(-lambda); for (i = 1; i <= k; i++) poisson *= lambda / i; sum -= poisson * (1 - pow(q / p, z - k)); } return sum; } เมื่อรันผลลัพธ์บางส่วน เราจะเห็นว่าความน่าจะเป็นลดลงแบบเอกซ์โพเนนเชียลเมื่อ z เพิ่มขึ้น q=0.1 z=0 P=1.0000000 z=1 P=0.2045873 z=2 P=0.0509779 z=3 P=0.0131722 z=4 P=0.0034552 z=5 P=0.0009137 z=6 P=0.0002428 z=7 P=0.0000647 z=8 P=0.0000173 z=9 P=0.0000046 z=10 P=0.0000012 q=0.3 z=0 P=1.0000000 z=5 P=0.1773523 z=10 P=0.0416605 z=15 P=0.0101008 z=20 P=0.0024804 z=25 P=0.0006132 z=30 P=0.0001522 z=35 P=0.0000379 z=40 P=0.0000095 z=45 P=0.0000024 z=50 P=0.0000006 การแก้หาค่า P ที่น้อยกว่า 0.1%... P < 0.001 q=0.10 z=5 q=0.15 z=8 q=0.20 z=11 q=0.25 z=15 q=0.30 z=24 q=0.35 z=41 q=0.40 z=89 q=0.45 z=340 12.สรุป(Conclusion) เราได้นำเสนอระบบธุรกรรมอิเล็กทรอนิกส์ที่ไม่ต้องพึ่งพาความไว้วางใจ เริ่มต้นจากกรอบแนวคิดของเหรียญที่สร้างจากลายเซ็นดิจิทัล ซึ่งช่วยควบคุมความเป็นเจ้าของได้อย่างดีแต่ก็ยังไม่สมบูรณ์ หากปราศจากวิธีการป้องกันการใช้จ่ายซ้ำซ้อน เพื่อแก้ปัญหานี้ เราจึงเสนอเครือข่ายแบบเพียร์ทูเพียร์ที่ใช้ proof-of-work ในการบันทึกประวัติธุรกรรมสาธารณะ ซึ่งจะกลายเป็นเรื่องยากอย่างมากสำหรับผู้โจมตีที่จะเปลี่ยนแปลง หาก node ที่ซื่อสัตย์ควบคุมพลังประมวลผล CPU ส่วนใหญ่ เครือข่ายนี้มีความแข็งแกร่งในความเรียบง่ายที่ไม่มีโครงสร้างใด ๆ ที่ซับซ้อน node ต่าง ๆ ทำงานพร้อมกันโดยประสานงานกันเพียงเล็กน้อย ไม่จำเป็นต้องระบุตัวตน เนื่องจากข้อความไม่ได้ถูกส่งไปยังสถานที่ใดสถานที่หนึ่งโดยเฉพาะ และเพียงแค่ต้องส่งมอบให้ถึงมือผู้รับอย่างดีที่สุด node สามารถออกจากและเข้าร่วมเครือข่ายได้ตามต้องการ โดยยอมรับ chain ที่มี proof-of-work มากที่สุดเป็นสิ่งที่เกิดขึ้นในขณะที่ไม่ได้เชื่อมต่อ พวกเขาโหวตด้วยพลังประมวลผล CPU แสดงการยอมรับบล็อกที่ถูกต้องโดยการทำงานเพื่อขยายบล็อก และปฏิเสธบล็อกที่ไม่ถูกต้องโดยการปฏิเสธที่จะทำงานกับบล็อกเหล่านั้น กฎและแรงจูงใจใด ๆ ที่จำเป็นสามารถบังคับใช้ได้ด้วยกลไกฉันทามตินี้ ไปอ่านต่อกันเองเด้ออ --- [1] W. Dai, "b-money," http://www.weidai.com/bmoney.txt, 1998. [2] H. Massias, X.S. Avila, and J.-J. Quisquater, "Design of a secure timestamping service with minimal trust requirements," In 20th Symposium on Information Theory in the Benelux, May 1999. [3] S. Haber, W.S. Stornetta, "How to time-stamp a digital document," In Journal of Cryptology, vol 3, no 2, pages 99-111, 1991. [4] D. Bayer, S. Haber, W.S. Stornetta, "Improving the efficiency and reliability of digital time-stamping," In Sequences II: Methods in Communication, Security and Computer Science, pages 329-334, 1993. [5] S. Haber, W.S. Stornetta, "Secure names for bit-strings," In Proceedings of the 4th ACM Conference on Computer and Communications Security, pages 28-35, April 1997. [6] A. Back, "Hashcash - a denial of service counter-measure," http://www.hashcash.org/papers/hashcash.pdf, 2002. [7] R.C. Merkle, "Protocols for public key cryptosystems," In Proc. 1980 Symposium on Security and Privacy, IEEE Computer Society, pages 122-133, April 1980. [8] W. Feller, "An introduction to probability theory and its applications," 1957. @ 79008e78:dfac9395
2024-09-02 06:17:05Nostr: โปรโตคอลทางเลือกใหม่สำหรับโซเชียลมีเดียที่เป็นอิสระ ปลอดภัย และไร้การควบคุม --- Nostr คือโปรโตคอลแบบเปิดที่เรียบง่าย ซึ่งช่วยให้สามารถสร้างโซเชียลมีเดียระดับโลกที่กระจายอำนาจและป้องกันการเซ็นเซอร์ได้ จากที่กล่าวข้างต้น เราสามารถพูดได้ว่า Nostr นั้นถูกออกแบบมาให้ใช้งานง่าย โดยมีเป้าหมายหลัก ๆ เพื่อสร้างเครือข่ายโซเชียลระดับโลกที่ปราศจากการเซ็นเซอร์ แล้วทำไมมันถึงทำอย่างนั้นได้? ในจุดนี้เราก็ต้องมาเจาะดูคุณสมบัติหลัก ๆ ของโปรโตคอลที่เรียกว่า Nostr กันก่อน: **เรียบง่าย** - โปรโตคอลนี้ใช้โครงสร้างข้อมูลแบบ Event Object ที่เรียบง่ายและยืดหยุ่น (ซึ่งส่งเป็น JSON ธรรมดา) และใช้การเข้ารหัสแบบ Elliptic-curve มาตรฐานสำหรับคีย์และลายเซ็น - ช่องทางการสื่อสารที่รองรับเพียงอย่างเดียวคือการเชื่อมต่อ WebSockets จากไคลเอนต์ไปยังรีเลย์ - การออกแบบนี้ทำให้ง่ายต่อการพัฒนาไม่ว่าจะไคลเอนต์หรือรีเลย์ และยังช่วยส่งเสริมความหลากหลายของซอฟต์แวร์ **ยืดหยุ่น** - เนื่องจาก Nostr ไม่ได้พึ่งพาเซิร์ฟเวอร์ที่เชื่อถือได้เพียงจำนวนหยิบมือ สำหรับการเคลื่อนย้ายหรือจัดเก็บข้อมูล แต่ใช้เซิร์ฟเวอร์จำนวนมหาศาลและกระจายตัวอยู่ทั่วโลก จึงมีความยืดหยุ่นสูง และมีการกระจายศูนย์อย่างแท้จริง - โปรโตคอลนี้ถูกออกแบบมาโดยคำนึงถึงความเป็นไปได้ที่รีเลย์จะหายไป และอนุญาตให้ผู้ใช้เชื่อมต่อและเผยแพร่ข้อมูลไปยังรีเลย์จำนวนมากได้ตามต้องการ และยังสามารถเปลี่ยนแปลงได้ตลอดเวลาอีกด้วย **ตรวจสอบได้** - เนื่องจากบัญชี Nostr ใช้การเข้ารหัสแบบ PKE จึงง่ายต่อการตรวจสอบว่าข้อความถูกส่งมาจากผู้ใช้ที่ระบุจริงหรือไม่ เช่นเดียวกับ HTTP หรือ TCP-IP Nostr เป็นโปรโตคอลหรือมาตรฐานแบบเปิดที่ทุกคนสามารถนำไปสร้างต่อยอดได้ มันไม่ใช่แอปหรือบริการที่คุณจำเป็นต้องลงทะเบียน แล้วทำไมเราถึงต้องการ Nostr? --- ถึงในปัจจุบันโซเชียลมีเดียจะได้พัฒนามาเป็นช่องทางสำคัญในการไหลเวียนของข้อมูลทั่วโลก กลายเป็นช่องทางหลักในการติดต่อสื่อสาร แต่น่าเสียดายที่ระบบโซเชียลมีเดียในปัจจุบันของเรานั้นมีข้อบกพร่องมากมาย: 1. ใช้ความสนใจของคุณเพื่อขายโฆษณา 2. ใช้เทคนิคแปลกๆ เพื่อทำให้คุณเสพติด (อ้างอิงจากข้อ 1) 3. ตัดสินใจว่าจะแสดงเนื้อหาใดให้คุณเห็นโดยใช้อัลกอริทึมลับที่คุณไม่สามารถตรวจสอบหรือเปลี่ยนแปลงได้ 4. ควบคุมอย่างเต็มที่ว่าใครสามารถเข้าร่วมและใครถูกเซ็นเซอร์ 5. เต็มไปด้วยสแปมและบอท ด้วยข้อจำกัดเหล่านี้ Nostr จึงเป็นทางเลือกที่น่าสนใจในการสร้างโซเชียลมีเดียที่เป็นอิสระ ปลอดภัย และไร้การควบคุม องค์ประกอบของโปรโตคอลที่ชื่อว่า Nostr --- หลังจากได้ทำความรู้จัก Nostr กันไปแล้วเมื่อคราวก่อน คราวนี้เรามาเจาะดูองค์ประกอบของโปรโตคอลนี้กันดีกว่า **Keys ระบบบัญชีผู้ใช้และรหัสผ่านสำหรับ Nostr** - บัญชี Nostr แต่ละบัญชีจะใช้คู่กุญแจสาธารณะ/ส่วนตัว (Public/Private Key ) เปรียบเทียบง่าย ๆ คือ กุญแจสาธารณะของคุณคือชื่อผู้ใช้ และกุญแจส่วนตัวก็เป็นรหัสผ่าน แต่ว่า ก็มีข้อแตกต่างที่สำคัญอยู่ นั่นคือ กุญแจส่วนตัวของคุณนั้นจะไม่สามารถรีเซ็ตได้หากเกิดการสูญหายขึ้น คุณจะเสียบัญชีนั้นไปตลอดกาล - โดยทั่วไปแล้ว กุญแจสาธารณะจะแสดงเป็นข้อความที่ขึ้นต้นด้วย npub1 และกุญแจส่วนตัวจะขึ้นต้นด้วย nsec1 - ทั้งนี้คุณควรที่จะตรวจสอบให้แน่ใจว่าคุณได้เก็บกุญแจส่วนตัวของคุณไว้ในที่ปลอดภัย เช่น โปรแกรมจัดการรหัสผ่านอย่างเช่น Bitwarden **โปรโตคอลกับไคลเอนต์ ต่างกันอย่างไร?** Nostr เองเป็นเพียงโปรโตคอล หมายความว่า Nostr นั้นเป็นเพียงกระบวนการที่ตกลงกันไว้สำหรับการส่งข้อความผ่านอินเทอร์เน็ต (เหมือนข้อกำหนด) ซึ่งการที่คุณจะเข้าถึง Nostr (โปรโตคอล) นั้น ผู้ใช้ส่วนใหญ่จะใช้งานผ่านไคลเอนต์ ซึ่งตัวของไคลเอนต์นั้นอาจเป็นเว็บ แอปพลิเคชันเดสก์ท็อป หรือ แอปพลิเคชันมือถือ โดยไคลเอนต์สามารถดึงข้อมูลจากรีเลย์ และสร้างข้อมูลใหม่ และส่งข้อมูลนั้นไปยังรีเลย์เพื่อให้ผู้ใช้คนอื่น ๆ สามารถเรียกอ่าน ข้อมูลนั้น ๆ ได้ โดย "ข้อมูล" เพียงรูปแบบเดียวที่มีอยู่ใน Nostr คือสิ่งที่เราเรียกกันว่า event **การพิสูจน์ความเป็นเจ้าของข้อมูลบน Nostr** บน Nostr นั้นการพิสูจน์ตัวตนเป็นเรื่องที่ง่ายมากเนื่องจากทุก ๆ event ที่เกิดขึ้น **จำเป็น**ต้องมีลายเซ็นดิจิทัล (Digital Signature) โดยลายเซ็นนั้นจะช่วยให้มั่นใจได้ว่า ใครเป็นผู้สร้าง event นั้น ๆ ขึ้นมา โดยการพิสูจน์ทางคณิตศาสตร์ โดยในการสร้างลายเซ็นแต่ละครั้ง ไคลเอนต์จะจำเป็นต้องใช้กุญแจส่วนตัวของคุณ โดยทั่วไปแล้ว แอปพลิเคชันเจะมีที่ให้คุณใส่กุญแจส่วนตัวของคุณ เมื่อเปิดแอปพลิเคชันครั้งแรก พวกเขาสามารถคำนวณกุญแจสาธารณะของคุณได้จากกุญแจส่วนตัวเช่นกัน ส่วนในกรณีที่คุณใช้งานผ่านเว็บแอป ผมไม่แนะนำให้ใส่กุญแจส่วนตัวลงไป แต่แนะนำให้ใช้ส่วนขยายของเบราว์เซอร์ ที่ใช้งานฟังก์ชันที่เกี่ยวข้องกับ Nostr ซึ่งอนุญาตให้เว็บไคลเอ็นต์ส่ง event ที่ยังไม่ถูกเซ็นมาให้ส่วนขยายและส่วนขยายจะทำหน้าที่เซ็น สำหรับวิธีนี้ เว็บไคลเอ็นต์ต่าง ๆ ไม่จำเป็นต้องรู้กุญแจส่วนตัวของคุณ แต่คุณก็ยังสามารถลงนามใน event ต่าง ๆ ได้ตามปกติ โดยส่วนขยายที่ได้รับความนิยมก็จะเป็น **Flamingo**, **Alby** และ **nos2x** ไคลเอนต์ & รีเลย์ ----------- **ไคลเอนต์คืออะไร?** หากจะอธิบายให้เห็นภาพอยากให้มองว่าไคลเอ็นต์ Nostr นั้นเป็นเหมือนกับแอปที่คุณใช้งานเพื่อเข้าถึง Twitter, Facebook, youtube เป็นต้น พวกมันคือ แอปพลิเคชัน, เว็บแอป ที่เชื่อมต่อคุณกับโลกของ Twitter, Facebook, youtube โดยตัวของไคลเอนต์ใน Nostr เองก็เปรียบเสมือนแอปต่าง ๆ ที่คุณใช้ดูหน้าฟีดนั่นเอง แต่ข้อดีของ Nostr ที่เหนือแอปพลิเคชันอื่น ๆ คือความเรียบง่ายและยืดหยุ่น ส่งผลให้ไคลเอ็นต์แต่ละตัวมีวิธีนำเสนอและใช้งานที่แตกต่างกันไป บางไคลเอ็นต์อาจออกแบบให้ใช้งานง่ายเหมือน Twitter บางตัวเน้นให้เห็นบทบาทสำคัญของรีเลย์ หรือโหนดที่กระจายข้อมูลอยู่ทั่วโลก บางตัวใช้ระบบอัลกอริทึมเพื่อให้แน่ใจว่าข้อมูลไม่ถูกปิดกั้น โดยไม่ทำให้ผู้ใช้งานรู้สึกยุ่งยาก **เรียบง่ายและยืดหยุ่น?** เนื่องจากการออกแบบของโปรโตคอลที่ทำการแยกข้อมูลของผู้ใช้ทั้งหมดออกจากไคลเอนต์ ทำให้ตัวของผู้ใช้งานเองนั้นมีอิสระเต็มที่ที่จะเลือกใช้ไคลเอนต์ต่าง ๆ เพื่อเข้าใช้งาน Nostr และแน่นอนว่า ผู้ใช้งานสามารถสลับหรือลงชื่อเข้าใช้ ไคลเอ็นต์ได้หลายตัวตามต้องการ ตราบใดที่ไคลเอ็นต์ทั้งหมดเชื่อมต่อกับชุดรีเลย์เดียวกัน คุณก็จะเห็นข้อมูลเดียวกันในทุก ๆ ไคลเอ็นต์ **ลงชื่อเข้าใช้ ไคลเอ็นต์หลาย ๆ ตัวแล้วจะกระทบต่อความปลอดภัยของแอคเคาร์ไหม?** คำตอบของคำถามนี้นั้นขึ้นอยู่กับวิธีการที่คุณลงชื่อเข้าใช้ หากคุณลงชื่อเข้าใช้ด้วยกุญแจส่วนตัว ถึงแม้ว่าไคลเอ็นต์ส่วนใหญ่จะพยายามรักษาความปลอดภัยของกุญแจส่วนตัวอย่างดีที่สุด แต่ด้วยข้อจำกัดของซอฟต์แวร์ ย่อมมีความเสี่ยงที่จะเกิดช่องโหว่ การเจาะระบบ และข้อผิดพลาด ที่อาจทำให้กุญแจส่วนตัวของคุณรั่วไหลออกไปได้ ส่วนวิธีการป้องกันเกี่ยวกับเรื่องนี้คือการใช้ส่วนขยายของเว็บเบราว์เซอร์ เพราะการเข้าสู่ระบบในไคลเอนต์ต่าง ๆ ผ่านส่วนขยายนั้นจะใช้เพียงกุญแจสาธารณะในการเข้าสู่ระบบและทุกครั้งที่เราต้องการจะโพสต์หรือสร้าง event บน Nostr ไคลเอนต์จะทำการร่าง event นั้น ๆ และเว้นช่องของลายเซ็นเอาไว้จากนั้นเราจะต้องทำการเซ็นผ่านส่วนขยาย ด้วยวิธีนี้ทำให้กุญแจส่วนตัวของเราไม่หลุดออกไปไหนตลอดการใช้งาน **รีเลย์คืออะไร?** รีเลย์เปรียบเสมือนเซิร์ฟเวอร์ที่อยู่เบื้องหลังของ Nostr และทำหน้าที่รับ event ต่าง ๆ มาจากไคลเอนต์ Nostr และอาจจะจัดเก็บและกระจายข้อความเหล่านั้นไปยังไคลเอนต์อื่น ๆ ที่มีการเชื่อมต่ออยู่ เทคโนโลยีของรีเลย์นั้นเปลี่ยนแปลงอย่างรวดเร็ว ดังนั้นคาดว่าจะมีการเปลี่ยนแปลงอีกมากมายในอนาคต อย่างในปัจจุบันที่มีการนำเสนอ bostr หรือ รีเลย์ที่จะคอยส่ง event ของเราต่อให้กับรีเลย์อื่น ๆ ที่มีการเชื่อมต่อ เพื่อช่วยลดภาระของไคลเอนต์ในการรับส่งข้อมูลจากหลาย ๆ รีเลย์พร้อม ๆ กัน หรืออย่างการป้องกันสแปมด้วย POW หรือประเภทที่สามารถเก็บรูปหรือวิดีโอที่มีขนาดใหญ่ได้ แต่สิ่งหนึ่งที่ควรทราบก็คือ การที่ Nostr นั้นพยายามจะกระจายศูนย์และเหตุผลหลัก ๆ ที่สามารถทำแบบนั้นได้ก็ขึ้นอยู่กับรีเลย์ในการจัดเก็บและดึงข้อมูล ดังนั้น หากคุณรู้สึกว่าไคลเอนต์ Nostr ของคุณทำงานช้า ส่วนใหญ่ก็มักเกิดจากรีเลย์ที่คุณกำลังเชื่อมต่ออยู่ คุณอาจลองแก้ไขปัญญาโดยการเปลี่ยนหรือเพิ่มรีเลย์อีกสองสามรายการในไคลเอนต์ที่คุณใช้ **แล้วจะสามารถหารายการรีเลย์ได้จากไหน?** การที่เราจะหารายการรีเลย์ที่เราควรเชื่อมต่อนั้น ๆ จริงแล้ว ๆ สามารถทำได้หลายวิธี แต่วิธีที่ผมแนะนำที่สุดจะเป็นการใช้ตามคนที่เราติดตามอยู่ เพราะจะเป็นวิธีที่เราสามารถเห็น event ต่าง ๆ ของคนที่เราติดตามได้ง่ายที่สุด และเช่นเดียวกัน เพื่อน ๆ หรือคนที่เราติดตามก็จะสามารถเห็น event ของเราได้เช่นกัน และสำหรับในประเทศไทย เรามีรีเลย์ที่คนไทยส่วนใหญ่นิยมใช้กันอยู่สองอัน นั้นคือ wss://relay.siamstr.com/ และ wss://relay.notoshi.win/ ถ้าหากว่าอยากเห็นคนไทยเยอะ ๆ บนหน้าไทม์ไลน์ ผมแนะนำเป็นอย่างยิ่งว่าควรเพิ่ม รายการรีเลย์เหล่านี้ลงไปในบัชญีหรือไคลเอนต์ต่าง ๆ ที่คุณใช้ด้วย สำหรับอีกวิธีหนึ่งผมแนะนำให้เข้าไปในเว็บไซต์ nostr.watch เนื่องจากในเว็บไซต์นี้เป็นแหล่งข้อมูลที่ดีที่สุดสำหรับการค้นหาและประเมินความเร็วของรีเลย์ต่าง ๆ **จะเกิดอะไรขึ้นถ้ารีเลย์ทั้งหมดที่ฉันเชื่อมต่ออยู่หยุดให้บริการ?** สิ่งนี้เป็นสิ่งที่คุณต้องระวังมากที่สุดในการใช้งาน nostr เนื่องจากหากรีเลย์ทั้งหมดที่คุณเก็บข้อมูลไว้หยุดให้บริการทั้งหมดและคุณไม่มีการสำรองข้อมูล event ของคุณเก็บไว้เลย มันแปลว่าโพสต์ทั้งหมดของคุณ ผู้ติดตาม และรายการต่าง ๆ ที่คุณสรรค์สร้างไว้จะไม่สามารถกู้คืนได้ไปตลอดการ นี่จึงเป็นเหตุผลหลัก ๆ ที่ Nostr อนุญาตให้ผู้ใช้งานนั้นสามารถเชื่อมต่อกับรีเลย์ได้เป็นจำนวนมาก ก็เพื่อให้แน่ใจว่ามีข้อมูลสำรองเก็บไว้อยู่ที่ใดที่หนึ่งในระบบเสมอ แต่อย่างไรก็ตาม หากคุณต้องการที่จะมั่นใจได้ว่าข้อมูลต่าง ๆ ของคุณจะไม่ถูกเซ็นเซอร์ สิ่งที่คุณสามารถสามารถทำได้คือการใช้รีเลย์ส่วนตัวของคุณและกำหนดนโยบายต่าง ๆ ภายในรีเลย์ของคุณด้วยตัวคุณเอง **แล้วฉันจะสามารถใช้รีเลย์ส่วนตัวได้อย่างไร?** **อะแฮ่ม ๆ** ขอบอกไว้ก่อนว่ามันไม่คุ้มค่ากับความยุ่งยากสำหรับคนโดยทั่ว ๆ ไป ถึงในปัจจุบันจะมีเทคโนโลยีบางตัวที่เข้ามาช่วยให้มันทำได้ง่ายขึ้นแล้วก็ตาม หากคุณต้องการที่จะสำรองข้อมูลนั้น การที่จะมีรีเลย์ส่วนตัวที่ออนไลน์ตลอดเวลาอาจเป็นเรื่องที่ไม่ได้จำเป็นขนาดนั้น เนื่องจากเราสามารถใช้งานบริการอย่าง https://nostrsync.live/ ในการดาวน์โหลดข้อมูลของเราจากรีเลย์ต่าง ๆ ได้ หรือการติดตั้งรีเลย์ส่วนตัวอย่าง nostr-relay-tray: https://github.com/CodyTseng/nostr-relay-tray ที่ช่วยให้เราสามารถมีรีเลย์ส่วนตัวที่ใช้สำหรับสำรองข้อมูลได้ Nostr Implementation Possibilities (NIPs) NIP คืออะไร? --- NIP มีไว้เพื่อส่งเสริมความสามารถในการทำงานของ Nostr และเป็นตัวคอยกำหนดให้ เหล่านักพัฒนาทำสิ่งต่าง ๆ ที่เหมือนกันในรูปแบบเดียวกัน เพราะมันคงไม่ใช่ความคิดที่ดีนัก หากนักพัฒนาแต่ละคนจะคิดค้นวิธีแก้ปัญหาทั่วไปของตัวเองและนำไปใช้ในแอปของตัวเองเท่านั้น และคงจะเป็นการดีกว่า ถ้าหากทุกคนใช้วิธีแก้ปัญหาที่เหมือนกัน นั่นคือเหตุผลที่ต้องมี NIP อยู่ในโปรโตคอลของ Nostr และในทำนองเดียวกัน แนวคิดใหม่อาจดูดีในแอปของนักพัฒนาบางราย แต่จะดูดียิ่งขึ้นอย่างแน่นอนหากแอปอื่น ๆ อีกมากมายใช้มาตรฐานเดียวกันและสามารถทำงานร่วมกันได้อย่างราบรื่น **ทำไมมันถึงหน้าสนใจ?** อย่าลืมว่า Nostr เป็นระบบแบบกระจายอำนาจและไม่ได้มีบริษัทหรือใครที่เป็นเจ้าของมัน อย่างเช่นโซเชียลมีเดียอื่น ๆ เช่น ทวิตเตอร์ อ่อไม่สิตอนนี้คงต้องเรียกมันว่า X สินะ ซึ่งหมายความว่าทิศทางของโพรโทคอล Nostr นั้นขึ้นอยู่กับพวกเราทุกคน! ไม่ว่าใคร ๆ ก็สามารถเสนอแนะและสนับสนุนการเปลี่ยนแปลงและให้ข้อเสนอแนะเกี่ยวกับแนวคิดที่ผู้อื่นเสนอ และการที่คุณเป็นส่วนหนึ่งของชุมชนนี้ ก็ทำให้คุณมีส่วนร่วมในทิศทางของ Nostr อีกด้วย จากที่ส่งหากันได้แค่ข้อความ มาเป็นรูปภาพ มาเป็นวิดีโอ และมาเป็น”เงิน” นี่คือเส้นทางการเดินทางของโปรโตคอลนี้ในอดีต แล้วในอนาคตมันจะพัฒนาไปยังไงต่อก็ขึ้นอยู่กับเหล่าผู้ใช้งานและนักพัฒนาในอนาคต แล้วทำไมสิ่งนี้ถึงจะไม่น่าสนใจละ ? Event --- **Event คืออะไร?** Event เป็น object เพียงประเภทเดียวที่มีอยู่บน Nostr โดยมีโครงสร้างประมาณนี้ ``` {"id":"84d5d3dc9c388a702f39cad6360d41ebb804e809fb822f110ff8a14dfd35fc6c", "pubkey":"66df60562d939ada8612436489945a4ecf1d62346b3d9478dea8a338f3203c64", "created_at":1722315959, "kind":1, "tags":[["t","siamstr"]], "content":"ไปสั่งกาแฟเมื่อกี้ พส เจ้าของร้านชมว่าเดี๋ยวนี้คล่องภาษาญี่ปุ่นแล้วนะ ไอเราก็ดีใจ พอเดินกลับถึงที่ทำงานละก็ตระหนักได้ว่า ตะกี้เราสั่ง “ไอซ์โคฮี โอเนไงชิมัส” “เทคเอาส์” “คาโดะเดสส” ไอบ้าไหนญี่ปุ่นก่อนอังกฤษทั้งนั้น 🤣🤣\n\n#siamstr", "sig":"8f066a0099a5f580b605ebdb220179c4eca298947c38b855a0a8bf2783f28ddb537cb74a7f61d3ce8891189f719870efdf320ea4f895e03cdac44284c450c5c4"} ``` อย่าง Event ข้างต้นนี้มี kind เป็น 1 ซึ่งหมายถึง "ข้อความโน้ต" ซึ่งก็คือข้อความธรรมดา สั้น ๆ คล้ายกับที่ใช้กันใน Twitter เช่น บนฟีด การตอบกลับ และการโควท **ประเภทของ Event (Event Kinds)** หมายเลขของ kind แต่ละตัวมีความหมายแตกต่างกัน ตัวอย่างเช่น 0 หมายถึงอีเวนต์ "ข้อมูลเมตา" ใช้สำหรับให้รายละเอียดเกี่ยวกับผู้ใช้ เช่น ชื่อและรูปโปรไฟล์ รีเลย์ (Relays) สามารถจัดการกับ kind ที่แตกต่างกันได้ เช่น รีเลย์มักจะลบอีเวนต์ kind:0 เวอร์ชันเก่ากว่าออกไป และเก็บไว้เฉพาะเวอร์ชันล่าสุด ในขณะที่โดยทั่วไปจะเก็บอีเวนต์ kind:1 ไว้หลายรายการสำหรับแต่ละคีย์ โดยทั่วไปแล้ว คุณไม่จำเป็นต้องใช้ kind เกินกว่า 0 และ 1 ในการสร้างแอปพลิเคชันโซเชียลมีเดียบน Nostr แต่ kind อื่น ๆ ถูกคิดค้นขึ้นโดยไคลเอนต์ เพื่อมอบฟังก์ชันการทำงานอื่น ๆ ตามที่ระบุไว้ใน NIP บาง kind ไม่เกี่ยวข้องกับเครือข่าย และให้บริการตามความต้องการอื่น ๆ ของไคลเอนต์ที่เฉพาะเจาะจงกับฟังก์ชันการทำงานเหล่านั้น ซึ่งแนวคิดก็คือ สำหรับกรณีการใช้งานใหม่ ๆ แต่ละกรณี จะต้องมีการพิจารณาและเสนอซับโปรโตคอลเป็น NIP เพื่อให้สามารถทำงานร่วมกับไคลเอนต์ที่มีอยู่และในอนาคต ซึ่งอาจสนใจที่จะนำฟังก์ชันการทำงานนั้นไปใช้ ขณะเดียวกันก็มั่นใจได้ถึงความเข้ากันได้ย้อนหลัง และการรองรับสิ่งต่าง ๆ ที่มีอยู่และไม่ต้องการเปลี่ยนแปลง **คุณสมบัติอื่น ๆ ของ Event** created_at: เป็น Timestamp ของ UNIX ที่กำหนดโดยผู้สร้างอีเวนต์ โดยปกติจะเป็นเวลาที่สร้าง แม้ว่าจะไม่มีการตรวจสอบ แต่ก็ไม่ใช่ปัญหา content: ขึ้นอยู่กับความหมายของ kind ในกรณีของ kind:1 จะเป็นเพียงสตริงข้อความธรรมดาที่คนอื่น ๆ อ่านได้ tags: ขึ้นอยู่กับ kind เช่นกัน แต่แท็กทั่วไปบางอย่างที่มักปรากฏใน event kind:1 และ kind อื่น ๆ คือ "p" ซึ่งใช้เพื่อกล่าวถึงกุญแจสาธารณะ และ "e" ใช้เพื่ออ้างถึง event อื่น อยากมีส่วนร่วมในการพัฒนาของ Nostr ? --- จริง ๆ แล้วใคร ๆ ก็สามารถเข้ามามีส่วนร่วมในการพัฒนา Nostr ได้ ไม่จำเป็นต้องเป็น dev หรือมีความรู้ด้านคอมพิวเตอร์ก็สามารถทำได้ ไม่ว่าจะเป็นการให้ feedback กับ dev ของ client ที่คุณใช้, การสร้างคอนเทนต์ต่าง ๆ บน Nostr การสร้างชุมชน รวมไปถึงการช่วย client ต่าง ๆ ในการทำ UI ให้เป็นภาษาท้องถิ่น และอื่น ๆ อีกมากมาย ใคร ๆ ก็สามารถช่วยได้ตามความสามารถที่แต่ละคนมี มันเลยทำให้ Nostr โครตน่าอยู่ :)
@ 79008e78:dfac9395
2024-09-02 06:17:05Nostr: โปรโตคอลทางเลือกใหม่สำหรับโซเชียลมีเดียที่เป็นอิสระ ปลอดภัย และไร้การควบคุม --- Nostr คือโปรโตคอลแบบเปิดที่เรียบง่าย ซึ่งช่วยให้สามารถสร้างโซเชียลมีเดียระดับโลกที่กระจายอำนาจและป้องกันการเซ็นเซอร์ได้ จากที่กล่าวข้างต้น เราสามารถพูดได้ว่า Nostr นั้นถูกออกแบบมาให้ใช้งานง่าย โดยมีเป้าหมายหลัก ๆ เพื่อสร้างเครือข่ายโซเชียลระดับโลกที่ปราศจากการเซ็นเซอร์ แล้วทำไมมันถึงทำอย่างนั้นได้? ในจุดนี้เราก็ต้องมาเจาะดูคุณสมบัติหลัก ๆ ของโปรโตคอลที่เรียกว่า Nostr กันก่อน: **เรียบง่าย** - โปรโตคอลนี้ใช้โครงสร้างข้อมูลแบบ Event Object ที่เรียบง่ายและยืดหยุ่น (ซึ่งส่งเป็น JSON ธรรมดา) และใช้การเข้ารหัสแบบ Elliptic-curve มาตรฐานสำหรับคีย์และลายเซ็น - ช่องทางการสื่อสารที่รองรับเพียงอย่างเดียวคือการเชื่อมต่อ WebSockets จากไคลเอนต์ไปยังรีเลย์ - การออกแบบนี้ทำให้ง่ายต่อการพัฒนาไม่ว่าจะไคลเอนต์หรือรีเลย์ และยังช่วยส่งเสริมความหลากหลายของซอฟต์แวร์ **ยืดหยุ่น** - เนื่องจาก Nostr ไม่ได้พึ่งพาเซิร์ฟเวอร์ที่เชื่อถือได้เพียงจำนวนหยิบมือ สำหรับการเคลื่อนย้ายหรือจัดเก็บข้อมูล แต่ใช้เซิร์ฟเวอร์จำนวนมหาศาลและกระจายตัวอยู่ทั่วโลก จึงมีความยืดหยุ่นสูง และมีการกระจายศูนย์อย่างแท้จริง - โปรโตคอลนี้ถูกออกแบบมาโดยคำนึงถึงความเป็นไปได้ที่รีเลย์จะหายไป และอนุญาตให้ผู้ใช้เชื่อมต่อและเผยแพร่ข้อมูลไปยังรีเลย์จำนวนมากได้ตามต้องการ และยังสามารถเปลี่ยนแปลงได้ตลอดเวลาอีกด้วย **ตรวจสอบได้** - เนื่องจากบัญชี Nostr ใช้การเข้ารหัสแบบ PKE จึงง่ายต่อการตรวจสอบว่าข้อความถูกส่งมาจากผู้ใช้ที่ระบุจริงหรือไม่ เช่นเดียวกับ HTTP หรือ TCP-IP Nostr เป็นโปรโตคอลหรือมาตรฐานแบบเปิดที่ทุกคนสามารถนำไปสร้างต่อยอดได้ มันไม่ใช่แอปหรือบริการที่คุณจำเป็นต้องลงทะเบียน แล้วทำไมเราถึงต้องการ Nostr? --- ถึงในปัจจุบันโซเชียลมีเดียจะได้พัฒนามาเป็นช่องทางสำคัญในการไหลเวียนของข้อมูลทั่วโลก กลายเป็นช่องทางหลักในการติดต่อสื่อสาร แต่น่าเสียดายที่ระบบโซเชียลมีเดียในปัจจุบันของเรานั้นมีข้อบกพร่องมากมาย: 1. ใช้ความสนใจของคุณเพื่อขายโฆษณา 2. ใช้เทคนิคแปลกๆ เพื่อทำให้คุณเสพติด (อ้างอิงจากข้อ 1) 3. ตัดสินใจว่าจะแสดงเนื้อหาใดให้คุณเห็นโดยใช้อัลกอริทึมลับที่คุณไม่สามารถตรวจสอบหรือเปลี่ยนแปลงได้ 4. ควบคุมอย่างเต็มที่ว่าใครสามารถเข้าร่วมและใครถูกเซ็นเซอร์ 5. เต็มไปด้วยสแปมและบอท ด้วยข้อจำกัดเหล่านี้ Nostr จึงเป็นทางเลือกที่น่าสนใจในการสร้างโซเชียลมีเดียที่เป็นอิสระ ปลอดภัย และไร้การควบคุม องค์ประกอบของโปรโตคอลที่ชื่อว่า Nostr --- หลังจากได้ทำความรู้จัก Nostr กันไปแล้วเมื่อคราวก่อน คราวนี้เรามาเจาะดูองค์ประกอบของโปรโตคอลนี้กันดีกว่า **Keys ระบบบัญชีผู้ใช้และรหัสผ่านสำหรับ Nostr** - บัญชี Nostr แต่ละบัญชีจะใช้คู่กุญแจสาธารณะ/ส่วนตัว (Public/Private Key ) เปรียบเทียบง่าย ๆ คือ กุญแจสาธารณะของคุณคือชื่อผู้ใช้ และกุญแจส่วนตัวก็เป็นรหัสผ่าน แต่ว่า ก็มีข้อแตกต่างที่สำคัญอยู่ นั่นคือ กุญแจส่วนตัวของคุณนั้นจะไม่สามารถรีเซ็ตได้หากเกิดการสูญหายขึ้น คุณจะเสียบัญชีนั้นไปตลอดกาล - โดยทั่วไปแล้ว กุญแจสาธารณะจะแสดงเป็นข้อความที่ขึ้นต้นด้วย npub1 และกุญแจส่วนตัวจะขึ้นต้นด้วย nsec1 - ทั้งนี้คุณควรที่จะตรวจสอบให้แน่ใจว่าคุณได้เก็บกุญแจส่วนตัวของคุณไว้ในที่ปลอดภัย เช่น โปรแกรมจัดการรหัสผ่านอย่างเช่น Bitwarden **โปรโตคอลกับไคลเอนต์ ต่างกันอย่างไร?** Nostr เองเป็นเพียงโปรโตคอล หมายความว่า Nostr นั้นเป็นเพียงกระบวนการที่ตกลงกันไว้สำหรับการส่งข้อความผ่านอินเทอร์เน็ต (เหมือนข้อกำหนด) ซึ่งการที่คุณจะเข้าถึง Nostr (โปรโตคอล) นั้น ผู้ใช้ส่วนใหญ่จะใช้งานผ่านไคลเอนต์ ซึ่งตัวของไคลเอนต์นั้นอาจเป็นเว็บ แอปพลิเคชันเดสก์ท็อป หรือ แอปพลิเคชันมือถือ โดยไคลเอนต์สามารถดึงข้อมูลจากรีเลย์ และสร้างข้อมูลใหม่ และส่งข้อมูลนั้นไปยังรีเลย์เพื่อให้ผู้ใช้คนอื่น ๆ สามารถเรียกอ่าน ข้อมูลนั้น ๆ ได้ โดย "ข้อมูล" เพียงรูปแบบเดียวที่มีอยู่ใน Nostr คือสิ่งที่เราเรียกกันว่า event **การพิสูจน์ความเป็นเจ้าของข้อมูลบน Nostr** บน Nostr นั้นการพิสูจน์ตัวตนเป็นเรื่องที่ง่ายมากเนื่องจากทุก ๆ event ที่เกิดขึ้น **จำเป็น**ต้องมีลายเซ็นดิจิทัล (Digital Signature) โดยลายเซ็นนั้นจะช่วยให้มั่นใจได้ว่า ใครเป็นผู้สร้าง event นั้น ๆ ขึ้นมา โดยการพิสูจน์ทางคณิตศาสตร์ โดยในการสร้างลายเซ็นแต่ละครั้ง ไคลเอนต์จะจำเป็นต้องใช้กุญแจส่วนตัวของคุณ โดยทั่วไปแล้ว แอปพลิเคชันเจะมีที่ให้คุณใส่กุญแจส่วนตัวของคุณ เมื่อเปิดแอปพลิเคชันครั้งแรก พวกเขาสามารถคำนวณกุญแจสาธารณะของคุณได้จากกุญแจส่วนตัวเช่นกัน ส่วนในกรณีที่คุณใช้งานผ่านเว็บแอป ผมไม่แนะนำให้ใส่กุญแจส่วนตัวลงไป แต่แนะนำให้ใช้ส่วนขยายของเบราว์เซอร์ ที่ใช้งานฟังก์ชันที่เกี่ยวข้องกับ Nostr ซึ่งอนุญาตให้เว็บไคลเอ็นต์ส่ง event ที่ยังไม่ถูกเซ็นมาให้ส่วนขยายและส่วนขยายจะทำหน้าที่เซ็น สำหรับวิธีนี้ เว็บไคลเอ็นต์ต่าง ๆ ไม่จำเป็นต้องรู้กุญแจส่วนตัวของคุณ แต่คุณก็ยังสามารถลงนามใน event ต่าง ๆ ได้ตามปกติ โดยส่วนขยายที่ได้รับความนิยมก็จะเป็น **Flamingo**, **Alby** และ **nos2x** ไคลเอนต์ & รีเลย์ ----------- **ไคลเอนต์คืออะไร?** หากจะอธิบายให้เห็นภาพอยากให้มองว่าไคลเอ็นต์ Nostr นั้นเป็นเหมือนกับแอปที่คุณใช้งานเพื่อเข้าถึง Twitter, Facebook, youtube เป็นต้น พวกมันคือ แอปพลิเคชัน, เว็บแอป ที่เชื่อมต่อคุณกับโลกของ Twitter, Facebook, youtube โดยตัวของไคลเอนต์ใน Nostr เองก็เปรียบเสมือนแอปต่าง ๆ ที่คุณใช้ดูหน้าฟีดนั่นเอง แต่ข้อดีของ Nostr ที่เหนือแอปพลิเคชันอื่น ๆ คือความเรียบง่ายและยืดหยุ่น ส่งผลให้ไคลเอ็นต์แต่ละตัวมีวิธีนำเสนอและใช้งานที่แตกต่างกันไป บางไคลเอ็นต์อาจออกแบบให้ใช้งานง่ายเหมือน Twitter บางตัวเน้นให้เห็นบทบาทสำคัญของรีเลย์ หรือโหนดที่กระจายข้อมูลอยู่ทั่วโลก บางตัวใช้ระบบอัลกอริทึมเพื่อให้แน่ใจว่าข้อมูลไม่ถูกปิดกั้น โดยไม่ทำให้ผู้ใช้งานรู้สึกยุ่งยาก **เรียบง่ายและยืดหยุ่น?** เนื่องจากการออกแบบของโปรโตคอลที่ทำการแยกข้อมูลของผู้ใช้ทั้งหมดออกจากไคลเอนต์ ทำให้ตัวของผู้ใช้งานเองนั้นมีอิสระเต็มที่ที่จะเลือกใช้ไคลเอนต์ต่าง ๆ เพื่อเข้าใช้งาน Nostr และแน่นอนว่า ผู้ใช้งานสามารถสลับหรือลงชื่อเข้าใช้ ไคลเอ็นต์ได้หลายตัวตามต้องการ ตราบใดที่ไคลเอ็นต์ทั้งหมดเชื่อมต่อกับชุดรีเลย์เดียวกัน คุณก็จะเห็นข้อมูลเดียวกันในทุก ๆ ไคลเอ็นต์ **ลงชื่อเข้าใช้ ไคลเอ็นต์หลาย ๆ ตัวแล้วจะกระทบต่อความปลอดภัยของแอคเคาร์ไหม?** คำตอบของคำถามนี้นั้นขึ้นอยู่กับวิธีการที่คุณลงชื่อเข้าใช้ หากคุณลงชื่อเข้าใช้ด้วยกุญแจส่วนตัว ถึงแม้ว่าไคลเอ็นต์ส่วนใหญ่จะพยายามรักษาความปลอดภัยของกุญแจส่วนตัวอย่างดีที่สุด แต่ด้วยข้อจำกัดของซอฟต์แวร์ ย่อมมีความเสี่ยงที่จะเกิดช่องโหว่ การเจาะระบบ และข้อผิดพลาด ที่อาจทำให้กุญแจส่วนตัวของคุณรั่วไหลออกไปได้ ส่วนวิธีการป้องกันเกี่ยวกับเรื่องนี้คือการใช้ส่วนขยายของเว็บเบราว์เซอร์ เพราะการเข้าสู่ระบบในไคลเอนต์ต่าง ๆ ผ่านส่วนขยายนั้นจะใช้เพียงกุญแจสาธารณะในการเข้าสู่ระบบและทุกครั้งที่เราต้องการจะโพสต์หรือสร้าง event บน Nostr ไคลเอนต์จะทำการร่าง event นั้น ๆ และเว้นช่องของลายเซ็นเอาไว้จากนั้นเราจะต้องทำการเซ็นผ่านส่วนขยาย ด้วยวิธีนี้ทำให้กุญแจส่วนตัวของเราไม่หลุดออกไปไหนตลอดการใช้งาน **รีเลย์คืออะไร?** รีเลย์เปรียบเสมือนเซิร์ฟเวอร์ที่อยู่เบื้องหลังของ Nostr และทำหน้าที่รับ event ต่าง ๆ มาจากไคลเอนต์ Nostr และอาจจะจัดเก็บและกระจายข้อความเหล่านั้นไปยังไคลเอนต์อื่น ๆ ที่มีการเชื่อมต่ออยู่ เทคโนโลยีของรีเลย์นั้นเปลี่ยนแปลงอย่างรวดเร็ว ดังนั้นคาดว่าจะมีการเปลี่ยนแปลงอีกมากมายในอนาคต อย่างในปัจจุบันที่มีการนำเสนอ bostr หรือ รีเลย์ที่จะคอยส่ง event ของเราต่อให้กับรีเลย์อื่น ๆ ที่มีการเชื่อมต่อ เพื่อช่วยลดภาระของไคลเอนต์ในการรับส่งข้อมูลจากหลาย ๆ รีเลย์พร้อม ๆ กัน หรืออย่างการป้องกันสแปมด้วย POW หรือประเภทที่สามารถเก็บรูปหรือวิดีโอที่มีขนาดใหญ่ได้ แต่สิ่งหนึ่งที่ควรทราบก็คือ การที่ Nostr นั้นพยายามจะกระจายศูนย์และเหตุผลหลัก ๆ ที่สามารถทำแบบนั้นได้ก็ขึ้นอยู่กับรีเลย์ในการจัดเก็บและดึงข้อมูล ดังนั้น หากคุณรู้สึกว่าไคลเอนต์ Nostr ของคุณทำงานช้า ส่วนใหญ่ก็มักเกิดจากรีเลย์ที่คุณกำลังเชื่อมต่ออยู่ คุณอาจลองแก้ไขปัญญาโดยการเปลี่ยนหรือเพิ่มรีเลย์อีกสองสามรายการในไคลเอนต์ที่คุณใช้ **แล้วจะสามารถหารายการรีเลย์ได้จากไหน?** การที่เราจะหารายการรีเลย์ที่เราควรเชื่อมต่อนั้น ๆ จริงแล้ว ๆ สามารถทำได้หลายวิธี แต่วิธีที่ผมแนะนำที่สุดจะเป็นการใช้ตามคนที่เราติดตามอยู่ เพราะจะเป็นวิธีที่เราสามารถเห็น event ต่าง ๆ ของคนที่เราติดตามได้ง่ายที่สุด และเช่นเดียวกัน เพื่อน ๆ หรือคนที่เราติดตามก็จะสามารถเห็น event ของเราได้เช่นกัน และสำหรับในประเทศไทย เรามีรีเลย์ที่คนไทยส่วนใหญ่นิยมใช้กันอยู่สองอัน นั้นคือ wss://relay.siamstr.com/ และ wss://relay.notoshi.win/ ถ้าหากว่าอยากเห็นคนไทยเยอะ ๆ บนหน้าไทม์ไลน์ ผมแนะนำเป็นอย่างยิ่งว่าควรเพิ่ม รายการรีเลย์เหล่านี้ลงไปในบัชญีหรือไคลเอนต์ต่าง ๆ ที่คุณใช้ด้วย สำหรับอีกวิธีหนึ่งผมแนะนำให้เข้าไปในเว็บไซต์ nostr.watch เนื่องจากในเว็บไซต์นี้เป็นแหล่งข้อมูลที่ดีที่สุดสำหรับการค้นหาและประเมินความเร็วของรีเลย์ต่าง ๆ **จะเกิดอะไรขึ้นถ้ารีเลย์ทั้งหมดที่ฉันเชื่อมต่ออยู่หยุดให้บริการ?** สิ่งนี้เป็นสิ่งที่คุณต้องระวังมากที่สุดในการใช้งาน nostr เนื่องจากหากรีเลย์ทั้งหมดที่คุณเก็บข้อมูลไว้หยุดให้บริการทั้งหมดและคุณไม่มีการสำรองข้อมูล event ของคุณเก็บไว้เลย มันแปลว่าโพสต์ทั้งหมดของคุณ ผู้ติดตาม และรายการต่าง ๆ ที่คุณสรรค์สร้างไว้จะไม่สามารถกู้คืนได้ไปตลอดการ นี่จึงเป็นเหตุผลหลัก ๆ ที่ Nostr อนุญาตให้ผู้ใช้งานนั้นสามารถเชื่อมต่อกับรีเลย์ได้เป็นจำนวนมาก ก็เพื่อให้แน่ใจว่ามีข้อมูลสำรองเก็บไว้อยู่ที่ใดที่หนึ่งในระบบเสมอ แต่อย่างไรก็ตาม หากคุณต้องการที่จะมั่นใจได้ว่าข้อมูลต่าง ๆ ของคุณจะไม่ถูกเซ็นเซอร์ สิ่งที่คุณสามารถสามารถทำได้คือการใช้รีเลย์ส่วนตัวของคุณและกำหนดนโยบายต่าง ๆ ภายในรีเลย์ของคุณด้วยตัวคุณเอง **แล้วฉันจะสามารถใช้รีเลย์ส่วนตัวได้อย่างไร?** **อะแฮ่ม ๆ** ขอบอกไว้ก่อนว่ามันไม่คุ้มค่ากับความยุ่งยากสำหรับคนโดยทั่ว ๆ ไป ถึงในปัจจุบันจะมีเทคโนโลยีบางตัวที่เข้ามาช่วยให้มันทำได้ง่ายขึ้นแล้วก็ตาม หากคุณต้องการที่จะสำรองข้อมูลนั้น การที่จะมีรีเลย์ส่วนตัวที่ออนไลน์ตลอดเวลาอาจเป็นเรื่องที่ไม่ได้จำเป็นขนาดนั้น เนื่องจากเราสามารถใช้งานบริการอย่าง https://nostrsync.live/ ในการดาวน์โหลดข้อมูลของเราจากรีเลย์ต่าง ๆ ได้ หรือการติดตั้งรีเลย์ส่วนตัวอย่าง nostr-relay-tray: https://github.com/CodyTseng/nostr-relay-tray ที่ช่วยให้เราสามารถมีรีเลย์ส่วนตัวที่ใช้สำหรับสำรองข้อมูลได้ Nostr Implementation Possibilities (NIPs) NIP คืออะไร? --- NIP มีไว้เพื่อส่งเสริมความสามารถในการทำงานของ Nostr และเป็นตัวคอยกำหนดให้ เหล่านักพัฒนาทำสิ่งต่าง ๆ ที่เหมือนกันในรูปแบบเดียวกัน เพราะมันคงไม่ใช่ความคิดที่ดีนัก หากนักพัฒนาแต่ละคนจะคิดค้นวิธีแก้ปัญหาทั่วไปของตัวเองและนำไปใช้ในแอปของตัวเองเท่านั้น และคงจะเป็นการดีกว่า ถ้าหากทุกคนใช้วิธีแก้ปัญหาที่เหมือนกัน นั่นคือเหตุผลที่ต้องมี NIP อยู่ในโปรโตคอลของ Nostr และในทำนองเดียวกัน แนวคิดใหม่อาจดูดีในแอปของนักพัฒนาบางราย แต่จะดูดียิ่งขึ้นอย่างแน่นอนหากแอปอื่น ๆ อีกมากมายใช้มาตรฐานเดียวกันและสามารถทำงานร่วมกันได้อย่างราบรื่น **ทำไมมันถึงหน้าสนใจ?** อย่าลืมว่า Nostr เป็นระบบแบบกระจายอำนาจและไม่ได้มีบริษัทหรือใครที่เป็นเจ้าของมัน อย่างเช่นโซเชียลมีเดียอื่น ๆ เช่น ทวิตเตอร์ อ่อไม่สิตอนนี้คงต้องเรียกมันว่า X สินะ ซึ่งหมายความว่าทิศทางของโพรโทคอล Nostr นั้นขึ้นอยู่กับพวกเราทุกคน! ไม่ว่าใคร ๆ ก็สามารถเสนอแนะและสนับสนุนการเปลี่ยนแปลงและให้ข้อเสนอแนะเกี่ยวกับแนวคิดที่ผู้อื่นเสนอ และการที่คุณเป็นส่วนหนึ่งของชุมชนนี้ ก็ทำให้คุณมีส่วนร่วมในทิศทางของ Nostr อีกด้วย จากที่ส่งหากันได้แค่ข้อความ มาเป็นรูปภาพ มาเป็นวิดีโอ และมาเป็น”เงิน” นี่คือเส้นทางการเดินทางของโปรโตคอลนี้ในอดีต แล้วในอนาคตมันจะพัฒนาไปยังไงต่อก็ขึ้นอยู่กับเหล่าผู้ใช้งานและนักพัฒนาในอนาคต แล้วทำไมสิ่งนี้ถึงจะไม่น่าสนใจละ ? Event --- **Event คืออะไร?** Event เป็น object เพียงประเภทเดียวที่มีอยู่บน Nostr โดยมีโครงสร้างประมาณนี้ ``` {"id":"84d5d3dc9c388a702f39cad6360d41ebb804e809fb822f110ff8a14dfd35fc6c", "pubkey":"66df60562d939ada8612436489945a4ecf1d62346b3d9478dea8a338f3203c64", "created_at":1722315959, "kind":1, "tags":[["t","siamstr"]], "content":"ไปสั่งกาแฟเมื่อกี้ พส เจ้าของร้านชมว่าเดี๋ยวนี้คล่องภาษาญี่ปุ่นแล้วนะ ไอเราก็ดีใจ พอเดินกลับถึงที่ทำงานละก็ตระหนักได้ว่า ตะกี้เราสั่ง “ไอซ์โคฮี โอเนไงชิมัส” “เทคเอาส์” “คาโดะเดสส” ไอบ้าไหนญี่ปุ่นก่อนอังกฤษทั้งนั้น 🤣🤣\n\n#siamstr", "sig":"8f066a0099a5f580b605ebdb220179c4eca298947c38b855a0a8bf2783f28ddb537cb74a7f61d3ce8891189f719870efdf320ea4f895e03cdac44284c450c5c4"} ``` อย่าง Event ข้างต้นนี้มี kind เป็น 1 ซึ่งหมายถึง "ข้อความโน้ต" ซึ่งก็คือข้อความธรรมดา สั้น ๆ คล้ายกับที่ใช้กันใน Twitter เช่น บนฟีด การตอบกลับ และการโควท **ประเภทของ Event (Event Kinds)** หมายเลขของ kind แต่ละตัวมีความหมายแตกต่างกัน ตัวอย่างเช่น 0 หมายถึงอีเวนต์ "ข้อมูลเมตา" ใช้สำหรับให้รายละเอียดเกี่ยวกับผู้ใช้ เช่น ชื่อและรูปโปรไฟล์ รีเลย์ (Relays) สามารถจัดการกับ kind ที่แตกต่างกันได้ เช่น รีเลย์มักจะลบอีเวนต์ kind:0 เวอร์ชันเก่ากว่าออกไป และเก็บไว้เฉพาะเวอร์ชันล่าสุด ในขณะที่โดยทั่วไปจะเก็บอีเวนต์ kind:1 ไว้หลายรายการสำหรับแต่ละคีย์ โดยทั่วไปแล้ว คุณไม่จำเป็นต้องใช้ kind เกินกว่า 0 และ 1 ในการสร้างแอปพลิเคชันโซเชียลมีเดียบน Nostr แต่ kind อื่น ๆ ถูกคิดค้นขึ้นโดยไคลเอนต์ เพื่อมอบฟังก์ชันการทำงานอื่น ๆ ตามที่ระบุไว้ใน NIP บาง kind ไม่เกี่ยวข้องกับเครือข่าย และให้บริการตามความต้องการอื่น ๆ ของไคลเอนต์ที่เฉพาะเจาะจงกับฟังก์ชันการทำงานเหล่านั้น ซึ่งแนวคิดก็คือ สำหรับกรณีการใช้งานใหม่ ๆ แต่ละกรณี จะต้องมีการพิจารณาและเสนอซับโปรโตคอลเป็น NIP เพื่อให้สามารถทำงานร่วมกับไคลเอนต์ที่มีอยู่และในอนาคต ซึ่งอาจสนใจที่จะนำฟังก์ชันการทำงานนั้นไปใช้ ขณะเดียวกันก็มั่นใจได้ถึงความเข้ากันได้ย้อนหลัง และการรองรับสิ่งต่าง ๆ ที่มีอยู่และไม่ต้องการเปลี่ยนแปลง **คุณสมบัติอื่น ๆ ของ Event** created_at: เป็น Timestamp ของ UNIX ที่กำหนดโดยผู้สร้างอีเวนต์ โดยปกติจะเป็นเวลาที่สร้าง แม้ว่าจะไม่มีการตรวจสอบ แต่ก็ไม่ใช่ปัญหา content: ขึ้นอยู่กับความหมายของ kind ในกรณีของ kind:1 จะเป็นเพียงสตริงข้อความธรรมดาที่คนอื่น ๆ อ่านได้ tags: ขึ้นอยู่กับ kind เช่นกัน แต่แท็กทั่วไปบางอย่างที่มักปรากฏใน event kind:1 และ kind อื่น ๆ คือ "p" ซึ่งใช้เพื่อกล่าวถึงกุญแจสาธารณะ และ "e" ใช้เพื่ออ้างถึง event อื่น อยากมีส่วนร่วมในการพัฒนาของ Nostr ? --- จริง ๆ แล้วใคร ๆ ก็สามารถเข้ามามีส่วนร่วมในการพัฒนา Nostr ได้ ไม่จำเป็นต้องเป็น dev หรือมีความรู้ด้านคอมพิวเตอร์ก็สามารถทำได้ ไม่ว่าจะเป็นการให้ feedback กับ dev ของ client ที่คุณใช้, การสร้างคอนเทนต์ต่าง ๆ บน Nostr การสร้างชุมชน รวมไปถึงการช่วย client ต่าง ๆ ในการทำ UI ให้เป็นภาษาท้องถิ่น และอื่น ๆ อีกมากมาย ใคร ๆ ก็สามารถช่วยได้ตามความสามารถที่แต่ละคนมี มันเลยทำให้ Nostr โครตน่าอยู่ :) @ d830ee7b:4e61cd62
2024-09-02 06:06:36บิตคอยน์ไม่ใช่แค่เงินดิจิทัล มันคือสมรภูมิแห่งความคิด การต่อสู้ระหว่างอุดมการณ์และเกมเศรษฐศาสตร์ที่ทุกคนมีสิทธิ์เข้าร่วม เรื่องราวของบิตคอยน์เริ่มต้นขึ้นในปี 2008 เมื่อ Satoshi Nakamoto บุคคลลึกลับปล่อย "Bitcoin: A Peer-to-Peer Electronic Cash System" เอกสารนี้ไม่ได้แค่เสนอระบบการเงินแบบใหม่ แต่ยังเป็นการท้าทายระบบเดิมที่ควบคุมโดยธนาคารและรัฐบาล ลองนึกภาพกลุ่มเพื่อนที่อยากเจอกัน แต่ไม่รู้จะไปร้านไหนดี นี่แหละคือปัญหา "Consensus" หรือ ภาวะเห็นพ้องต้องกัน บิตคอยน์แก้ปัญหานี้ด้วย "Blockchain" เหมือนสมุดบัญชีสาธารณะที่บันทึกทุกธุรกรรม ใครๆ ก็เข้าถึงได้ แต่การแก้ไขต้องใช้ "Proof of Work" หรือ การแก้โจทย์ยากๆ ที่ต้องใช้พลังงานมหาศาล เปรียบเหมือนการขุดหาเพชร ใครขุดเจอคนแรกก็ได้รางวัลไป บิตคอยน์ก็ใช้หลักการคล้ายๆ กัน ใครมีพลังประมวลผลมากก็มีโอกาสปิดบล็อกได้ก่อน แต่เหรียญก็มักจะมีสองด้านเสมอ.. ระบบนี้เปิดโอกาสให้เกิด **"Strategic Mining" หรือ การใช้กลยุทธ์ต่างๆ เพื่อโกยผลประโยชน์** มันเหมือนเกมเศรษฐศาสตร์ที่ทุกคนต่างแข่งขันกัน ใครมีกลยุทธ์ดีกว่าก็ได้เปรียบ แล้วอะไรล่ะที่ป้องกันไม่ให้บิคอยน์ถูกควบคุม? หนึ่งในแนวคิดคือ "Market Fragility Hypothesis" ที่เชื่อว่าหากเกิดการควบคุมระบบบิตคอยน์ ราคาของบิตคอยน์จะร่วงลงอย่างรุนแรง ทำให้ผู้ที่พยายามจะควบคุมก็ต้องเสียหายไปด้วย อีกแนวคิดคือ "Repeated Games and Institutional Norms" ที่มองว่าการทำตัวดีเป็นผลดีต่อทุกคนในระยะยาว ใครทำตัวไม่ดีก็อาจถูกลงโทษ เช่น การไม่ยอมรับธุรกรรมที่น่าสงสัย แต่การลงโทษก็มีปัญหา เพราะต้องอาศัยความร่วมมือจากผู้เล่นส่วนใหญ่ ซึ่งในโลกแห่งบิตคอยน์ที่ไร้ศูนย์กลาง การประสานงานจริงๆ นั้นทำได้ยาก บิตคอยน์ยังเผชิญความท้าทายอีกมากมาย เช่น การลดลงของรางวัลขุด (Block Subsidy) ที่อาจกระทบต่อความปลอดภัย หรือการต่อสู้กับการเซ็นเซอร์ธุรกรรม (Censorship Attack) อนาคตของบิตคอยฯ์จะเป็นอย่างไร? บางคนเชื่อว่าบิตคอยน์จะกลายเป็นสกุลเงินหลักของโลก (Hyperbitcoinization) แต่บางคนก็มองว่าความผันผวนของราคาและความเสี่ยงจากการถูกเข้าควบคุมจะเป็นอุปสรรคที่สำคัญ ไม่ว่าอนาคตจะเป็นเช่นไร.. บิตคอยน์ได้จุดประกายการปฏิวัติทางเศรษฐกิจครั้งใหญ่ ใครๆ ก็สามารถเข้าร่วมเกมนี้ได้ แต่การจะชนะต้องอาศัยความเข้าใจในกฎกติกาและกลยุทธ์ที่เหนือชั้น บทความนี้จึงได้เรียบเรียงเนื้อหาที่น่าสนใจมาจากใน **หนังสือ "Bitcoin: A Game-Theoretic Analysis"** ซึ่งเล่าเรื่องราวของบิตคอยน์ผ่านมุมมองของทฤษฎีเกมมาแบ่งปัน ซึ่งจะช่วยให้ผู้อ่านเข้าใจกลไกและความท้าทายของบิตคอยน์อย่างครอบคลุม อ่านสนุก และน่าติดตามมากขึ้น # Dominant Strategy ไพ่ตายที่ (แทบ) ไม่มีอยู่จริงในสมรภูมิบิตคอยน์ ในโลกของเกมและเศรษฐศาสตร์ **“Dominant Strategy” คือกลยุทธ์มหัศจรรย์ที่ทำให้ผู้เล่นได้เปรียบ** ไม่ว่าคู่แข่งจะงัดไม้ไหนมาสู้ก็ตาม ยกตัวอย่าง "Prisoner's Dilemma" เกมคลาสสิคที่ผู้ต้องหาสองคนต้องเลือกว่าจะร่วมมือ (ไม่ซัดทอดเพื่อน) หรือหักหลัง (ซัดทอดเพื่อน) ถ้าทั้งคู่ร่วมมือจะได้รับโทษเบาๆ ด้วยกัน แต่ถ้าคนหนึ่งหักหลัง อีกคนร่วมมือ คนหักหลังจะได้รางวัล คนร่วมมือจะโดนโทษหนัก และถ้าทั้งคู่หักหลัง จะโดนโทษหนักด้วยกันทั้งคู่ จะเห็นว่าการหักหลัง คือ Dominant Strategy เพราะไม่ว่าเพื่อนจะเลือกอะไร การหักหลังจะทำให้เราได้ผลลัพธ์ดีกว่าเสมอ (ไม่โดนโทษหนัก หรือได้รางวัล) แต่ในสมรภูมิ Bitcoin กลยุทธ์แบบไพ่ตายแทบไม่มีอยู่จริง เพราะการกระทำของนักขุดแต่ละคนล้วนส่งผลกระทบต่อคนอื่นๆ เสมอ ลองนึกภาพนักขุดจอมเจ้าเล่ห์ที่พยายามโกงระบบ เช่น - **Selfish Mining:** แอบขุดบล็อกไว้คนเดียว หวังจะฮุบรางวัลบล็อกทั้งหมด - **Block Withholding:** กั๊กบล็อกที่ขุดได้ บีบให้คนอื่นจ่ายค่าธรรมเนียมแพงๆ - **Censorship Attack:** ควบคุมเครือข่ายเพื่อบล็อกธุรกรรมบางอย่าง กลยุทธ์เหล่านี้อาจดูเหมือนไพ่ตายในแวบแรก แต่ความจริงแล้วมันขึ้นอยู่กับปฏิกิริยาของนักขุดคนอื่นๆ ด้วย เพราะถ้าคนอื่นๆ รู้ทันแผนการร้าย และเลือกที่จะลงโทษนักขุดจอมเจ้าเล่ห์ เช่น ไม่ยอมรับบล็อกที่ขุดได้ หรือหันไปใช้บริการแพลตฟอร์มอื่น นักขุดจอมเจ้าเล่ห์ก็จะขาดทุน ยิ่งไปกว่านั้น.. กลยุทธ์เหล่านี้มักจะทำลายความเชื่อมั่นในบิตคอยน์ (Market Fragility Hypothesis) ทำให้ราคาบิตคอยน์ร่วงลง นักขุดจอมเจ้าเล่ห์ก็จะเสียหายตามไปด้วย ดังนั้น.. ในบิตคอยน์จึงไม่มีกลยุทธ์ใดที่รับประกันความสำเร็จ 100% ทุกการกระทำล้วนมีความเสี่ยง และขึ้นอยู่กับการตัดสินใจของนักขุดคนอื่นๆ นี่คือเสน่ห์ของบิตคอยน์ที่ทำให้มันเป็นระบบที่มีพลวัต ซับซ้อน และท้าทาย ไม่มีใครสามารถควบคุมเกมได้อย่างสมบูรณ์ และทุกคนต้องเล่นอย่างชาญฉลาดเพื่อให้ได้ผลลัพธ์ที่ดีที่สุด.. # Nash Equilibrium สมดุลอันเปราะบางบนเส้นด้ายแห่งความไว้วางใจใน Bitcoin **"Nash Equilibrium"** เป็นแนวคิดสำคัญในทฤษฎีเกม อธิบายภาวะสมดุลที่เกิดขึ้นเมื่อผู้เล่นแต่ละคนเลือกกลยุทธ์ที่ดีที่สุดสำหรับตัวเอง โดยพิจารณาจากกลยุทธ์ของผู้เล่นคนอื่นๆ ณ จุดสมดุลนี้ ไม่มีใครอยากเปลี่ยนกลยุทธ์ เพราะรู้ว่าการเปลี่ยนจะทำให้ตัวเองเสียเปรียบ ยกตัวอย่างเกม **"Splitting $4"** ที่ผู้เล่นสองคนต้องเขียนตัวเลข ($1, $2, $3) หากผลรวมไม่เกิน $4 ทั้งคู่จะได้รับเงินตามที่เขียน แต่ถ้าเกิน $4 ทั้งคู่จะไม่ได้อะไรเลย Nash Equilibrium ของเกมนี้คือการที่ทั้งคู่เขียน $2 เพราะไม่ว่าใครจะเปลี่ยนตัวเลข คนที่ไม่เปลี่ยนจะได้เปรียบกว่าเสมอ ถ้าคนหนึ่งเขียน $3 อีกคนเขียน $2 คนเขียน $2 จะได้ $2 ส่วนคนเขียน $3 จะไม่ได้อะไรเลย ถ้าคนหนึ่งเขียน $1 อีกคนเขียน $2 คนเขียน $2 จะได้ $2 ส่วนคนเขียน $1 จะได้แค่ $1 ในบิตคอยน์ก็มี Nash Equilibrium เช่นเดียวกัน หนึ่งในนั้นคือการที่นักขุดส่วนใหญ่เลือก "Default Compliant" หรือ การทำตามกฎกติกาของบิตคอยน์อย่างเคร่งครัด ทำไมถึงเป็นเช่นนั้น? ลองนึกภาพนักขุดจอมโลภที่คิดจะแหกกฎเพื่อหาผลประโยชน์ใส่ตัว เช่น - Selfish Mining: แอบขุดบล็อกไว้คนเดียว - Block Withholding: กั๊กบล็อกที่ขุดได้ - Censorship Attack: บล็อกธุรกรรมบางอย่าง ถ้ามีนักขุดทำแบบนี้แค่คนเดียว ในขณะที่คนอื่นๆ ยังคงทำตามกฎ นักขุดคนนั้นอาจจะได้เปรียบในระยะสั้น แต่ในระยะยาว การกระทำแบบนี้จะ.. - **ทำลายความเชื่อมั่นในบิตคอยน์** (Market Fragility Hypothesis) ทำให้ราคาบิตคอยน์ร่วงลง - **ถูกนักขุดคนอื่นๆ ลงโทษ** เช่น ไม่ยอมรับบล็อกที่ขุดได้ หรือ รวมหัวกันแบนนักขุดจอมโลภ สุดท้าย.. นักขุดจอมโลภก็จะขาดทุนและสูญเสียโอกาสในการได้รับรางวัลบล็อกในอนาคต ดังนั้น.. การทำตามกฎจึงเป็นกลยุทธ์ที่ปลอดภัยและยั่งยืนกว่าสำหรับนักขุดส่วนใหญ่ อย่างไรก็ตาม Nash Equilibrium ในบิตคอยน์ไม่ได้หมายความว่าระบบจะมั่นคง 100% - **แรงจูงใจในการแหกกฎอาจเพิ่มขึ้นได้** เช่น เมื่อรางวัลบล็อก (Block Subsidy) ลดลงและค่าธรรมเนียม (Transaction Fee) ไม่สูงพอ นักขุดอาจมองว่าการโกงคุ้มค่ากับความเสี่ยงมากขึ้น - **การประสานงานเพื่อลงโทษผู้ทำผิดอาจทำได้ยาก** บิตคอยน์ไม่มีศูนย์กลางควบคุม การตัดสินใจใดๆ ต้องอาศัยความเห็นพ้องของนักขุดส่วนใหญ่ ซึ่งอาจทำได้ยากและใช้เวลานาน Nash Equilibrium ในบิตคอยน์จึงเป็นสมดุลที่เปราะบางที่สามารถถูกทำลายได้ หากแรงจูงใจและสภาพแวดล้อมเปลี่ยนไป.. นี่คือความท้าทายที่ชุมชนบิตคอยน์ต้องเผชิญในการรักษาสมดุลระหว่าง **"ผลประโยชน์ส่วนตัว"** ของนักขุด กับ **"ความมั่นคงของระบบ"** โดยรวม # Censorship Attack สมรภูมิปิดล้อมบิตคอยน์กับอาวุธลับ Soft Fork บิตคอยน์นั้นถูกออกแบบมาให้เป็นระบบการเงินแบบไร้ศูนย์กลาง ปราศจากการควบคุมของรัฐบาลหรือองค์กรใดๆ แต่ในโลกแห่งความเป็นจริง อำนาจและการควบคุมยังคงเป็นสิ่งที่หลายฝ่ายปรารถนา และ **"Censorship Attack"** คือหนึ่งในภัยคุกคามที่บิตคอยน์ต้องเผชิญ Censorship Attack คือ **ความพยายามในการปิดล้อม Bitcoin เพื่อบล็อกธุรกรรมบางอย่าง** เปรียบเสมือนการที่รัฐบาลเผด็จการพยายามปิดกั้นข้อมูลข่าวสาร หรือบริษัทผูกขาดพยายามกำจัดคู่แข่ง ใครบ้างที่อาจอยู่เบื้องหลัง Censorship Attack? - **รัฐบาล:** อาจต้องการควบคุมการไหลเวียนของ Bitcoin เพื่อรักษาอำนาจทางการเงิน หรือ ป้องกันการฟอกเงิน - **องค์กรขนาดใหญ่:** อาจต้องการควบคุมตลาดบิตคอยน์เพื่อผลประโยชน์ของตัวเอง - **กลุ่มคนที่ไม่เห็นด้วยกับ Bitcoin:** อาจต้องการทำลาย Bitcoin เพราะมองว่าเป็นภัยคุกคามต่อระบบเดิม พวกเขาจะใช้พลังขุดจำนวนมหาศาลในการควบคุมเครือข่ายบิตคอยน์ และบล็อกธุรกรรมที่ไม่พึงประสงค์ เหมือนกับการที่รัฐบาลเผด็จการใช้กำลังทหารปิดล้อมเมือง แต่บิตคอยน์ก็ไม่ใช่หมูที่จะให้เชือดได้ง่ายๆ ชุมชนบิตคอยน์มีอาวุธลับ นั่นคือ **"Soft Fork"** **Soft Fork คือการเปลี่ยนแปลงกฎกติกาของ Bitcoin โดยที่ยังคงเข้ากันได้กับกฎเดิม** Node ที่ใช้กฎเดิมจะยังคงมองว่าบล็อกที่สร้างขึ้นตามกฎใหม่นั้นถูกต้อง ยกตัวอย่างเช่น ชุมชนบิคคอยน์อาจใช้ Soft Fork เพื่อ.. - **ยกเลิกการบล็อกธุรกรรม:** ทำให้ธุรกรรมที่ถูกบล็อกสามารถดำเนินการได้ตามปกติ - **เพิ่มความสามารถของบิตคอยน์:** เช่น เพิ่มขนาดบล็อก หรือเพิ่มฟังก์ชั่นใหม่ๆ - **ลงโทษผู้พยายามควบคุม:** เช่น ลดรางวัลบล็อกหรือตัดสิทธิ์การขุด ของผู้ที่พยายามควบคุมเครือข่าย Soft Fork เปรียบเสมือนอาวุธลับที่จะช่วยให้ชุมชนบิตคอยน์สามารถแหกกฎที่ไม่เป็นธรรมได้ เหมือนกับการที่ประชาชนลุกขึ้นมาต่อต้านอำนาจเผด็จการด้วยการใช้สันติวิธี อย่างไรก็ตาม.. การใช้ Soft Fork ก็มีความเสี่ยงอยู่เช่นกัน.. - **อาจทำให้บิตคอยน์แตกเป็นสองสาย:** หากนักขุดส่วนใหญ่ไม่เห็นด้วยกับ Soft Fork อาจทำให้เกิด **"Hard Fork"** หรือ การแยกบิตคอยน์ออกเป็นสองเหรียญ - **อาจลดทอนความน่าเชื่อถือของบิตคอยน์:** หาก Soft Fork ถูกใช้บ่อยเกินไป อาจทำให้คนมองว่าบิตคอยน์ไม่มั่นคง และเปลี่ยนแปลงง่ายเกินไป ดังนั้น.. การใช้ Soft Fork จึงต้องทำอย่างรอบคอบ และคำนึงถึงผลกระทบในระยะยาว Censorship Attack จึงเป็นสมรภูมิที่ดุเดือดระหว่าง **"อำนาจ"** กับ **"เสรีภาพ"** ชุมชนบิตคอยน์ต้องต่อสู้เพื่อปกป้องอุดมการณ์ของบิตคอยน์ในฐานะระบบการเงินแบบไร้ศูนย์กลาง และปราศจากการเซ็นเซอร์ # Selfish Mining แผนร้ายใต้เงามืดของนักขุดในมุมมืดผู้แยบยล ในโลกของบิตคอยน์ที่เต็มไปด้วยการแข่งขัน นักขุดแต่ละคนต่างก็งัดกลยุทธ์ต่างๆ มาใช้เพื่อช่วงชิงรางวัลบล็อก และ "Selfish Mining" คือหนึ่งในกลยุทธ์ลับที่แยบยลแต่แฝงไปด้วยความเสี่ยง ลองจินตนาการถึงนักวิทยาศาสตร์สติเฟื่องผู้แอบซุ่มพัฒนาอาวุธร้ายแรงในห้องแล็บลับ ไม่ให้ใครล่วงรู้ Selfish Mining ก็เปรียบเสมือนนักวิทยาศาสตร์คนนี้ ที่แอบขุดบิตคอยน์ไว้คนเดียวเงียบๆ ไม่บอกใคร แผนการร้ายนี้มันทำงานอย่างไร? - **แอบขุดเงียบๆ:** เมื่อนักขุด Selfish Mining ขุดเจอบล็อกใหม่ แทนที่จะประกาศให้โลกรู้ พวกเขาจะเก็บมันไว้เป็นความลับ เหมือนกับนักวิทยาศาสตร์ที่ซ่อนอาวุธไว้ในห้องแล็บ - **แอบสร้างความได้เปรียบ:** นักขุด Selfish Mining จะแอบขุดบล็อกต่อไปเรื่อยๆ โดยหวังว่าจะขุดได้บล็อกต่อเนื่อง ยิ่งขุดได้มากเท่าไหร่ ความได้เปรียบก็ยิ่งมากขึ้น - **เผยไพ่ตาย:** เมื่อนักขุดคนอื่นๆ ใกล้จะขุดเจอบล็อกใหม่ นักขุด Selfish Mining จะรีบเผยแพร่บล็อกทั้งหมดที่แอบขุดไว้ทำให้บล็อกของพวกเขากลายเป็น "Longest Chain" หรือ "Heaviest Chain" และได้รับรางวัลบล็อกทั้งหมดที่ขุดได้ ด้วยกลยุทธ์นี้ นักขุด Selfish Mining สามารถโกงระบบ และได้รับรางวัลบล็อกมากกว่าที่ควรจะเป็น แต่นี่คือเกมแห่งความเสี่ยง เพราะ.. - **ถ้าคนอื่นขุดเจอบล็อกก่อน:** บล็อกทั้งหมดที่นักขุด Selfish Mining แอบขุดไว้จะกลายเป็น "Orphan Block" หรือ "Uncle Block" และไร้ค่าทันที เหมือนกับอาวุธที่ถูกยึดไปก่อนจะได้ใช้งาน - **ยิ่งแอบขุดนาน ความเสี่ยงยิ่งสูง:** ยิ่งนักขุด Selfish Mining แอบขุดบล็อกไว้นานเท่าไหร่ โอกาสที่คนอื่นจะขุดเจอบล็อกก่อนก็ยิ่งมากขึ้นเท่านั้น Selfish Mining ส่งผลกระทบต่อบิตคอยน์อย่างไร? - **ลดประสิทธิภาพของเครือข่าย:** ทำให้การยืนยันธุรกรรมช้าลง และสิ้นเปลืองพลังงานมากขึ้น - **บิดเบือนการกระจายรางวัล:** ทำให้นักขุดที่ทำตามกฎได้รับรางวัลน้อยลง และนักขุด Selfish Mining ได้รับรางวัลมากกว่าที่ควรจะเป็น - **ลดทอนความเชื่อมั่นในบิตคอยน์:** (Market Fragility Hypothesis) ทำให้คนมองว่าบิตคอยน์ไม่มั่นคง และเสี่ยงต่อการถูกควบคุม แล้วจะป้องกัน Selfish Mining ได้อย่างไร? - **การตรวจจับและลงโทษ:** ชุมชน บิตคอยน์ สามารถพัฒนาระบบตรวจจับ Selfish Mining และ ลงโทษนักขุดที่ทำผิดกฎ เช่น ลดรางวัลบล็อก หรือ ตัดสิทธิ์การขุด - **การปรับปรุงกลไก Difficulty Adjustment:** ทำให้การปรับระดับความยากของ Proof of Work ตอบสนองต่อการเปลี่ยนแปลงของ hashrate ได้รวดเร็วและแม่นยำยิ่งขึ้น เพื่อทำความเข้าใจกลยุทธ์ Selfish Mining ให้ลึกซึ้งยิ่งขึ้น เราสามารถใช้แบบจำลองทางคณิตศาสตร์ที่เรียกว่า **"Markov Chain"** ในการวิเคราะห์ได้ แบบจำลองนี้ช่วยให้เราคำนวณความน่าจะเป็นของผลลัพธ์ต่างๆ ที่อาจเกิดขึ้นจากการทำ Selfish Mining เช่น โอกาสที่นักขุด Selfish Mining จะประสบความสำเร็จในการยึดครองเครือข่าย หรือ โอกาสที่บล็อกที่แอบขุดไว้จะกลายเป็น Orphan Block ผลการวิเคราะห์โดยใช้ Markov Chain ตามที่ปรากฏในหนังสือ (บทที่ 8) แสดงให้เห็นว่า Selfish Mining สามารถทำให้นักขุดที่โกงได้รับรางวัลบล็อกมากกว่าส่วนแบ่ง Hashrate ที่พวกเขามี ตัวอย่างเช่น.. นักขุดที่มีพลังขุดเพียง 30% สามารถได้รับรางวัลบล็อกมากกว่า 30% ได้ หากพวกเขาใช้กลยุทธ์ Selfish Mining อย่างมีประสิทธิภาพ ยิ่งไปกว่านั้น Selfish Mining ยังส่งผลกระทบต่อเสถียรภาพของตลาด Hashrate ด้วย เพราะมันบิดเบือนกลไก Difficulty Adjustment ทำให้การปรับระดับความยากของ Proof of Work ไม่แม่นยำ และเกิดความผันผวนของ Hashrate Selfish Mining จึงเป็นภัยคุกคามที่แยบยล และท้าทายต่อความมั่นคงของบิตคอยน์ ชุมชนบิตคอยน์ต้องร่วมมือกันเพื่อป้องกัน และรักษาสมดุลของระบบนิเวศ # Block Withholding เกมบีบค่าไถ่บิตคอยน์ของเจ้าพ่อผู้โลภมาก ในโลกของบิตคอยน์ การยืนยันธุรกรรมต้องอาศัยนักขุดผู้ทำหน้าที่บรรจุธุรกรรมลงในบล็อก แต่หากนักขุดเหล่านี้เกิดโลภมาก จนละทิ้งอุดมการณ์และหันมาใช้กลยุทธ์ **“Block Withholding”** บิตคอยน์อาจกลายเป็นสนามเด็กเล่นของเจ้าพ่อผู้พยายามครอบงำตลาด Block Withholding คือกลยุทธ์ที่นักขุดจงใจกั๊กบล็อกที่ขุดได้ ไม่ยอมเผยแพร่ ทำให้ธุรกรรมต่างๆ ค้างเติ่งอยู่ใน Mempool หรือพื้นที่รอการยืนยัน เปรียบเสมือนเจ้าพ่อมาเฟียที่ยึดรถบรรทุกสินค้า แล้วเรียกค่าคุ้มครองจากพ่อค้า ใครอยากให้สินค้าของตัวเองถูกส่งไปถึงปลายทางก็ต้องยอมจ่าย ยิ่งธุรกรรมค้างคามากเท่าไหร่ ค่าธรรมเนียม (Transaction Fee) ก็จะยิ่งสูงขึ้น เจ้าพ่อก็จะยิ่งรวย แต่นี่คือเกมแห่งความเสี่ยง เจ้าพ่อผู้โลภมากอาจพลาดท่าได้ เพราะ.. - **ผลักไสผู้ใช้งาน:** ถ้าค่าธรรมเนียมแพงเกินไป คนอาจหนีไปใช้แพลตฟอร์มอื่น หรือหันไปใช้บริการ Layer 2 เช่น Lightning Network ที่รวดเร็วและค่าธรรมเนียมถูกกว่า - **ทำลายความเชื่อมั่นในบิตคอยน์:** (Market Fragility Hypothesis) ทำให้คนมองว่าบิตคอยน์ไม่น่าเชื่อถือ ช้า และ แพง ส่งผลให้ราคาบิตคอยน์ร่วงลง - **จุดชนวนความขัดแย้ง:** นักขุดคนอื่นๆ ที่ทำตามกฎ อาจไม่พอใจและรวมหัวกันลงโทษเจ้าพ่อ เช่น ไม่ยอมรับบล็อกที่กั๊กไว้ หรือแบนเจ้าพ่อออกจาก Mining Pool Block Withholding เกิดขึ้นได้อย่างไร? - **นักขุดรายใหญ่:** นักขุดที่มีพลังขุดมาก มีอำนาจต่อรองสูงกว่า และมีโอกาสใช้ Block Withholding ได้ผลมากกว่า - **ช่วงที่ธุรกรรมหนาแน่น:** ในช่วงที่ Mempool มีธุรกรรมค้างคามาก นักขุดมีแรงจูงใจในการ Block Withholding มากขึ้น เพราะสามารถเรียกเก็บค่าธรรมเนียมได้แพง - **การสมรู้ร่วมคิด:** นักขุดหลายรายอาจรวมหัวกัน Block Withholding เพื่อควบคุมตลาดและโกยผลประโยชน์ร่วมกัน แล้วจะป้องกัน Block Withholding ได้อย่างไร? - **การกระจายอำนาจ:** ยิ่งมีนักขุดจำนวนมาก และพลังขุดกระจายตัวมากเท่าไหร่ การ Block Withholding ก็จะทำได้ยากขึ้น - **การสร้างแรงจูงใจ:** ออกแบบระบบรางวัลที่ทำให้นักขุดได้รับผลประโยชน์จากการยืนยันธุรกรรมอย่างรวดเร็ว และไม่คุ้มค่ากับการ Block Withholding - **การพัฒนา Layer 2:** เช่น Lightning Network ที่ช่วยลดความแออัดของ Mempool และทำให้ค่าธรรมเนียมถูกลง Block Withholding จึงเป็นเหมือนเกมชักกะเย่อระหว่าง **"ความโลภ"** ของนักขุด กับ **"ความต้องการ"** ของผู้ใช้งาน การรักษาสมดุลและป้องกันไม่ให้บิตคอยน์ตกอยู่ใต้อำนาจของเจ้าพ่อ จึงเป็นสิ่งที่ชุมชนบิตคอยน์ต้องร่วมมือกันอย่างจริงจัง # The Flattening ASIC Cost Curve เมื่อสมรภูมิชิปขุดบิตคอยน์ร้อนระอุ **ASIC** (Application-Specific Integrated Circuit) คือชิปประมวลผลพิเศษที่ถูกออกแบบมาเพื่อขุดบิตคอยน์โดยเฉพาะ เหมือนกับอาวุธลับที่ช่วยให้นักขุดสามารถถล่มโจทย์ Proof of Work ได้อย่างรวดเร็ว ในช่วงแรกๆ ของบิตคอยน์ ASIC นั้นมีราคาแพงและหายาก เปรียบเสมือนดาบวิเศษในตำนานที่ใครครอบครองก็จะได้เปรียบเหนือคนอื่น ผู้ผลิต ASIC จึงเปรียบเสมือนพ่อค้าอาวุธที่กอบโกยกำไรมหาศาลจากการขายดาบวิเศษเหล่านี้ แต่เมื่อเวลาผ่านไป.. เทคโนโลยีการผลิต ASIC พัฒนาขึ้น ต้นทุนการผลิตก็ลดลง ผู้เล่นหน้าใหม่ก็กระโดดเข้ามาในตลาด การแข่งขันก็ดุเดือดขึ้น ราคา ASIC ก็ถูกลง กราฟแสดงความสัมพันธ์ระหว่างราคา ASIC กับเวลา จึงมีลักษณะลาดลงหรือ **"Flattening"** นี่คือสมรภูมิแห่งชิปขุดบิตคอยน์ที่ร้อนระอุ และผลลัพธ์ของสงครามราคาครั้งนี้ก็ส่งผลดีต่อความมั่นคงของบิตคอยน์ในระยะยาว ทำไมถึงเป็นเช่นนั้น? - **การบงการตลาดทำได้ยากขึ้น:** เมื่อ ASIC มีราคาถูกลง และ หาซื้อง่ายขึ้น การที่คนกลุ่มใดกลุ่มหนึ่ง จะ "กว้านซื้อ" ASIC เพื่อควบคุมพลังขุด และบงการเครือข่ายบิตคอยน์ก็จะทำได้ยากขึ้น - **กระจายอำนาจ:** เมื่อ ASIC มีราคาไม่แพง นักขุดรายย่อยก็สามารถเข้าถึง ASIC ได้ง่ายขึ้น ทำให้พลังขุดกระจายตัวมากขึ้น ลดโอกาสที่คนกลุ่มใดกลุ่มหนึ่งจะผูกขาดพลังขุด - **ลดแรงจูงใจในการโกง:** เมื่อกำไรจากการขุดบิตคอยน์ลดลง นักขุดก็มีแรงจูงใจในการโกงระบบน้อยลง เช่น Selfish Mining หรือ Block Withholding เพราะผลตอบแทนที่ได้รับอาจไม่คุ้มค่ากับความเสี่ยง ปัจจัยที่ส่งผลต่อ The Flattening ASIC Cost Curve - **Moore’s Law:** กฎของ Moore กล่าวว่า.. ประสิทธิภาพของชิปคอมพิวเตอร์จะเพิ่มขึ้นเป็นสองเท่าทุกๆ 18 เดือน ในขณะที่ราคาลดลง ส่งผลให้ ASIC มีประสิทธิภาพสูงขึ้น แต่ราคาถูกลง - **การแข่งขันในตลาด:** เมื่อมีผู้ผลิต ASIC จำนวนมาก การแข่งขันด้านราคาจะรุนแรงขึ้น ทำให้ราคา ASIC ถูกลง - **ความต้องการของตลาด:** หากราคาบิตคอยน์สูงขึ้น ความต้องการ ASIC ก็จะสูงขึ้นตามไปด้วย ทำให้ผู้ผลิต ASIC มีกำลังใจในการผลิตและพัฒนาเทคโนโลยี The Flattening ASIC Cost Curve จึงเป็นปรากฏการณ์ที่แสดงให้เห็นถึง **"พลังของตลาดเสรี"** ที่จะช่วยควบคุมและรักษาสมดุลของระบบนิเวศบิตคอยน์ อย่างไรก็ตาม.. การที่ราคา ASIC ถูกลงก็ไม่ได้หมายความว่าบิตคอยน์จะปลอดภัยจากการโจมตี 100% นักขุดที่ทุนหนา หรือได้รับการสนับสนุนจากรัฐบาล ยังคงสามารถทุ่มเงินซื้อ ASIC จำนวนมาก เพื่อบงการเครือข่ายได้ ดังนั้น ชุมชนบิตคอยน์ต้องตื่นตัว และคอยเฝ้าระวังภัยคุกคามอยู่เสมอ เพื่อปกป้องบิตคอยน์ให้คงอยู่และเติบโตอย่างยั่งยืน # บิตคอยน์กับเกมเดิมพันอนาคต เมื่อรางวัลบล็อกเหือดหายและค่าธรรมเนียมคือกุญแจ บิตคอยน์นั้นเปรียบเสมือนขุมทรัพย์ที่ถูกออกแบบมาให้มีจำนวนจำกัด และรางวัลบล็อก (Block Reward) คือแรงจูงใจหลักที่ทำให้นักขุดบิตคอยน์ทุ่มเทพลังขุด เพื่อรักษาความปลอดภัยของเครือข่าย แต่.. บิตคอยน์ Protocol ได้กำหนดตารางเวลาในการลด Block Reward ลงครึ่งหนึ่งทุกๆ 4 ปี (Halving) เหมือนกับระเบิดเวลาที่ค่อยๆ บีบรายได้ของนักขุดให้เล็กลงไปเรื่อยๆ ในอนาคต Block Reward จะหมดลงในที่สุด.. นักขุดบิตคอยน์จะต้องพึ่งพา **"ค่าธรรมเนียม" (Transaction Fee)** เป็นแหล่งรายได้หลัก นี่คือจุดเปลี่ยนสำคัญที่อาจส่งผลต่ออนาคตของบิตคอยน์ ### Transaction Fees รายได้ใหม่ของนักขุด Transaction Fee คือ **ค่าธรรมเนียมที่ผู้ใช้บิตคอยน์จ่ายให้กับนักขุด เพื่อเร่งการยืนยันธุรกรรม** ยิ่งมีธุรกรรมมาก และแข่งขันกันมากเท่าไหร่ Transaction Fee ก็จะยิ่งสูงขึ้นเท่านั้น เปรียบเสมือน **"ค่าผ่านทาง"** บนท้องถนน ยิ่งรถเยอะ ค่าผ่านทางก็ยิ่งแพง ความท้าทายเมื่อ Block Reward ลดลง.. - **ความปลอดภัยของเครือข่าย:** ถ้า Transaction Fee ไม่สูงพอ นักขุดอาจขาดทุนและไม่มีแรงจูงใจในการรักษาความปลอดภัยของเครือข่าย ทำให้บิตคอยน์ต้องเสี่ยงต่อการถูกโจมตีจากผู้ไม่หวังดี - **การทำตามกฎ:** นักขุดอาจละทิ้งอุดมการณ์ และหันไปใช้กลยุทธ์โกงๆ เช่น Selfish Mining หรือ Block Withholding เพื่อเพิ่มรายได้ - **การรวมศูนย์อำนาจ:** นักขุดรายย่อยอาจสู้ไม่ไหว และถูกบีบให้ออกไปจากตลาด ทำให้พลังขุดกระจุกตัวอยู่ในมือของนักขุดรายใหญ่ เพิ่มความเสี่ยงต่อการผูกขาด และบงการเครือข่าย นักขุดบิตคอยน์ต้องปรับตัวอย่างไร? - **เข้าร่วม Mining Pool:** รวมพลังกับนักขุดคนอื่นๆ เพื่อเพิ่มโอกาสในการได้รับรางวัล และลดความเสี่ยง - **พัฒนากลยุทธ์:** เลือก Mining Pool ที่มีระบบ Reward ที่น่าสนใจ ปรับแต่งซอฟต์แวร์เพื่อจัดลำดับความสำคัญของธุรกรรมที่มี Transaction Fee สูง - **มองหาโอกาสใหม่:** เช่น การให้บริการ Node Validation บน Layer 2 (Lightning Network) หรือการลงทุนในธุรกิจที่เกี่ยวข้องกับบิตคอยน์ ### อนาคตของบิตคอยน์ขึ้นอยู่กับ Transaction Fee Transaction Fee คือ กุญแจสำคัญที่จะกำหนดอนาคตของบิตคอยน์ - **ถ้า Transaction Fee สูงพอ:** บิตคอยน์จะยังคงเป็นระบบการเงินที่ปลอดภัย น่าเชื่อถือและกระจายอำนาจ - **แต่ถ้า Transaction Fee ต่ำเกินไป:** บิตคอยน์อาจล่มสลายหรือถูกควบคุมโดยคนกลุ่มใดกลุ่มหนึ่ง ชุมชนบิตคอยน์จึงต้องร่วมมือกันเพื่อสร้างระบบนิเวศที่เอื้อต่อการเติบโตของ Transaction Fee เช่น - **ส่งเสริมการใช้งานบิตคอยน์:** ยิ่งมีคนใช้บิตคอยน์มาก Transaction Fee ก็จะยิ่งสูงขึ้น - **พัฒนาเทคโนโลยี:** เช่น Layer 2 (Lightning Network) ที่ช่วยลดความแออัดของเครือข่าย และทำให้ค่าธรรมเนียมถูกลง - **สร้างความเชื่อมั่น:** ให้ความรู้และสร้างความเข้าใจเกี่ยวกับบิตคอยน์แก่สาธารณชน เพื่อเพิ่มความเชื่อมั่นและดึงดูดผู้ใช้งานใหม่ บิตคอยน์กำลังก้าวเข้าสู่ยุคใหม่ที่ Transaction Fee จะเป็นตัวกำหนดชะตากรรม ความสำเร็จของบิตคอยน์ขึ้นอยู่กับความร่วมมือ และความพยายามของชุมชน ในการสร้างระบบนิเวศที่ยั่งยืนและเป็นประโยชน์ต่อทุกคน # เมื่ออำนาจเก่าหวั่นไหว ภัยคุกคามบิตคอยน์จากรัฐบาลและองค์กร บิตคอยน์ คือนวัตกรรมที่ท้าทายอำนาจและระบบเดิม การเกิดขึ้นของบิตคอยน์ทำให้รัฐบาล และ องค์กรขนาดใหญ่หวั่นไหว เพราะมันสั่นคลอนเสถียรภาพของระบบการเงิน และอำนาจในการควบคุมที่พวกเขาเคยผูกขาด บิตคอยน์ จึงถูกมองว่าเป็นภัยคุกคามที่ต้องถูกกำจัด ### การโจมตีโดยตรง (Brute-Force Attack) ศึกชิงอำนาจ Hashrate การโจมตีแบบ Brute-Force คือการใช้พลังขุดจำนวนมหาศาล เพื่อยึดครองเครือข่ายบิตคอยน์ เปรียบเสมือนการที่กองทัพบุกตะลุยเข้ายึดเมือง รัฐบาลหรือองค์กร สามารถใช้เงินทุนจำนวนมหาศาล ในการซื้อ ASIC และพลังงาน เพื่อเพิ่ม Hashrate ของตัวเองให้เหนือกว่านักขุดบิตคอยน์คนอื่นๆ (ซึ่งใช้ทุนเยอะ และทำได้ยากมาก) เมื่อ Hashrate ของผู้โจมตีเกิน" 51% พวกเขาจะสามารถ.. - **ควบคุมการยืนยันธุรกรรม:** เลือกที่จะอนุมัติหรือปฏิเสธธุรกรรมตามใจชอบ - **Double-Spend:** ใช้บิตคอยน์ซ้ำสอง ทำให้เกิดความสับสนและสูญเสียความเชื่อมั่นในระบบ - **เปลี่ยนแปลงกฎกติกา:** บังคับให้ Hard Fork ไปสู่กฎใหม่ที่เอื้อประโยชน์ต่อพวกเขา การโจมตีแบบ Brute-Force เป็นภัยคุกคามที่ร้ายแรงที่สุด แต่ก็สิ้นเปลืองและเสี่ยงเช่นกัน.. - **ต้นทุนสูง: **การซื้อ ASIC และพลังงานต้องใช้เงินทุนมหาศาล - **ความเสี่ยงด้านชื่อเสียง:** การโจมตีบิตคอยน์อย่างโจ่งแจ้ง อาจทำให้เสียชื่อเสียง และถูกต่อต้านจากชุมชนบิตคอยน์ ### การบิดเบือนข้อมูล (FUD) สงครามจิตวิทยา FUD (Fear, Uncertainty, and Doubt) คือ สงครามจิตวิทยา ที่ใช้ข้อมูลเป็นอาวุธในการทำลายความเชื่อมั่นในบิตคอยน์ รัฐบาลและองค์กรสามารถใช้สื่อ และช่องทางต่างๆ ในการ.. - **สร้างข่าวลือ:** เช่น บิตคอยน์กำลังจะล่มสลาย (บิตคอยน์ตายแล้ว) หรือบิตคอยน์ถูกใช้ในการฟอกเงิน - **ปล่อยข่าวปลอม:** เช่น บิตคอยน์ถูกแฮ็ก หรือบิตคอยน์ไม่ปลอดภัย - **โจมตีบุคคลสำคัญ:** เช่น กล่าวหา Satoshi Nakamoto ว่าเป็นอาชญากร หรือกล่าวหาผู้สนับสนุนบิตคอยน์ว่าเป็นพวกต่อต้านรัฐบาล FUD อาจไม่รุนแรงเท่า Brute-Force Attack แต่ก็อันตรายไม่แพ้กัน เพราะสามารถ.. - **ลดความต้องการบิตคอยน์:** ทำให้ราคาบิตคอยน์ร่วงลง - **ขัดขวางการใช้งานบิตคอยน์:** ทำให้คนกลัวและไม่กล้าใช้บิตคอยน์ - **บั่นทอนความเชื่อมั่นในบิตคอยน์:** ทำให้คนลังเล และไม่มั่นใจในอนาคตของบิตคอยน์ ### การออกกฎหมายควบคุม กำแพงกั้นบิตคอยน์ รัฐบาลสามารถใช้กฎหมายเป็นเครื่องมือในการควบคุม และจำกัดการใช้งานบิตคอยน์ เช่น - **ห้ามซื้อขายบิตคอยน์:** ทำให้การซื้อขายบิตคอยน์เป็นเรื่องผิดกฎหมาย - **ควบคุมการแลกเปลี่ยนบิตคอยน์:** เช่น กำหนดให้ Exchange ต้องขอใบอนุญาต และปฏิบัติตามกฎ KYC/AML - **เก็บภาษีบิตคอยน์:** ทำให้การถือครอง และการซื้อขายบิตคอยน์มีต้นทุนสูงขึ้น กฎหมาย เป็นกำแพงที่แข็งแกร่ง ที่สามารถขัดขวางการเติบโตของบิตคอยน์ได้อย่างมีประสิทธิภาพ บิตคอยน์ จึงเป็นมากกว่าเงินดิจิทัล มันคือสัญลักษณ์ของอิสรภาพทางการเงินและการต่อต้านอำนาจ การต่อสู้ระหว่างบิตคอยน์กับอำนาจเก่า จึงเป็นสงครามที่ดุเดือดและไม่มีวันสิ้นสุด ชุมชนบิตคอยน์ต้องตื่นตัว เฝ้าระวัง และ ต่อสู้เพื่อปกป้องอุดมการณ์ของบิตคอยน์ให้คงอยู่ และเติบโตอย่างยั่งยืน # Hyperbitcoinization ยูโทเปียแห่งเสรีภาพหรือดิสโทเปียแห่งการผูกขาด? "Hyperbitcoinization" คือคำที่ใช้อธิบายถึงสถานการณ์สมมติที่บิตคอยน์กลายเป็น **"สกุลเงินหลักของโลก"** แทนที่สกุลเงิน fiat ที่เราใช้กันอยู่ในปัจจุบัน สำหรับสาวกบิตคอยน์ นี่คือฝันหวานที่โลกจะหลุดพ้นจากพันธนาการของรัฐบาลและธนาคารกลาง ที่คอยบงการค่าเงิน และควบคุมระบบเศรษฐกิจ แต่สำหรับผู้ที่มองบิตคอยน์ในแง่ลบ นี่คือฝันร้ายที่อาจนำไปสู่หายนะทางเศรษฐกิจและสังคม ### Hyperbitconization สองด้านของเหรียญ ด้านสว่าง ยูโทเปียแห่งเสรีภาพ - **อิสรภาพทางการเงิน:** ทุกคนมีอำนาจในการควบคุมเงินของตัวเองโดยไม่ต้องพึ่งพาคนกลาง เช่น ธนาคารหรือรัฐบาล - **ความโปร่งใส:** ธุรกรรมบิตคอยน์ถูกบันทึกไว้บน Blockchain ที่เปิดเผยและตรวจสอบได้ ลดปัญหาคอรัปชั่นและการควบคุมแทรกแซง - **การเข้าถึงบริการทางการเงิน:** ทุกคนสามารถเข้าถึงบริการทางการเงินได้ แม้แต่คนที่ไม่มีบัญชีธนาคาร - **ลดต้นทุน:** ค่าธรรมเนียมบิตคอยน์มักจะต่ำกว่าค่าธรรมเนียมของระบบการเงินแบบดั้งเดิม ด้านมืด ดิสโทเปียแห่งการผูกขาด **ความผันผวน:** ราคาบิตคอยน์มีความผันผวนสูง ทำให้ยากต่อการใช้เป็นหน่วยวัดมูลค่าและสื่อกลางในการแลกเปลี่ยน (ด้วยเหตุนี้จึงมีพัฒนาเกิดขึ้นบน Layer 2) - **ความเหลื่อมล้ำ:** คนที่ถือครองบิตคอยน์จำนวนมาก จะมีอำนาจและอิทธิพลเหนือระบบเศรษฐกิจ - **การควบคุมโดยกลุ่มคนหรือองค์กร:** บิตคอยน์อาจถูกครอบงำโดย Mining Pool ขนาดใหญ่ หรือกลุ่มคนที่สมรู้ร่วมคิดกัน - **ความเสี่ยงด้านความปลอดภัย:** บิตคอยน์อาจเสี่ยงต่อการถูกแฮ็ก หรือโจมตีจากผู้ไม่หวังดี Hyperbitcoinization จะเป็นจริงได้อย่างไร? - **การยอมรับอย่างกว้างขวาง:** บิตคอยน์ต้องได้รับการยอมรับจากคนส่วนใหญ่ ทั้งในฐานะสื่อกลางในการแลกเปลี่ยนและหน่วยเก็บมูลค่า - **โครงสร้างพื้นฐานที่แข็งแกร่ง:** ต้องมีระบบและบริการที่รองรับการใช้งานบิตคอยน์อย่างสะดวกและปลอดภัย - **กฎหมายและกฎระเบียบที่เอื้ออำนวย:** รัฐบาลควรสนับสนุนหรืออย่างน้อยก็ไม่ขัดขวางการใช้งานบิตคอยน์ ความเป็นไปได้ของ Hyperbitcoinization ความเป็นไปได้ที่ Hyperbitcoinization จะเกิดขึ้นจริงยังคงเป็นที่ถกเถียงกันอยู่ - **ฝ่ายสนับสนุน:** เชื่อว่าบิตคอยน์มีศักยภาพ ในการปฏิวัติระบบการเงิน และนำไปสู่โลกที่ดีกว่า - **ฝ่ายคัดค้าน:** มองว่าบิตคอยน์เป็นฟองสบู่ที่รอวันแตก และไม่สามารถทดแทนสกุลเงิน fiat ได้ Hyperbitcoinization เป็นอนาคตที่ไม่แน่นอน มันอาจเป็นทั้งฝันหวานและฝันร้าย ขึ้นอยู่กับว่าเราจะกำหนดและจัดการมันอย่างไร สิ่งสำคัญคือการศึกษาทำความเข้าใจ และเตรียมพร้อมสำหรับทุกความเป็นไปได้ เพื่อให้เราสามารถรับมือกับการเปลี่ยนแปลงที่กำลังจะเกิดขึ้นได้ บิตคอยน์ถือกำเนิดขึ้นมาเพียง 14 ปี แต่ได้เขย่าโลกและท้าทายระบบการเงินแบบดั้งเดิมอย่างที่ไม่เคยมีมาก่อน การเดินทางของบิตคอยน์ จึงเปรียบเสมือนมหากาพย์ที่เต็มไปด้วยการต่อสู้ การชิงไหวชิงพริบและความไม่แน่นอน ไม่มีใครสามารถทำนายอนาคตของบิตคอยน์ ได้อย่างแม่นยำ แต่เราสามารถวิเคราะห์และทำความเข้าใจปัจจัยต่างๆ ที่จะกำหนดทิศทางของมันได้ การเดินทางนี้ช่างน่าตื่นเต้นและเต็มไปด้วยความเป็นไปได้ เราทุกคนมีส่วนร่วมในการกำหนดอนาคตของบิตคอยน์ ด้วยการศึกษาทำความเข้าใจและตัดสินใจอย่างชาญฉลาด..
@ d830ee7b:4e61cd62
2024-09-02 06:06:36บิตคอยน์ไม่ใช่แค่เงินดิจิทัล มันคือสมรภูมิแห่งความคิด การต่อสู้ระหว่างอุดมการณ์และเกมเศรษฐศาสตร์ที่ทุกคนมีสิทธิ์เข้าร่วม เรื่องราวของบิตคอยน์เริ่มต้นขึ้นในปี 2008 เมื่อ Satoshi Nakamoto บุคคลลึกลับปล่อย "Bitcoin: A Peer-to-Peer Electronic Cash System" เอกสารนี้ไม่ได้แค่เสนอระบบการเงินแบบใหม่ แต่ยังเป็นการท้าทายระบบเดิมที่ควบคุมโดยธนาคารและรัฐบาล ลองนึกภาพกลุ่มเพื่อนที่อยากเจอกัน แต่ไม่รู้จะไปร้านไหนดี นี่แหละคือปัญหา "Consensus" หรือ ภาวะเห็นพ้องต้องกัน บิตคอยน์แก้ปัญหานี้ด้วย "Blockchain" เหมือนสมุดบัญชีสาธารณะที่บันทึกทุกธุรกรรม ใครๆ ก็เข้าถึงได้ แต่การแก้ไขต้องใช้ "Proof of Work" หรือ การแก้โจทย์ยากๆ ที่ต้องใช้พลังงานมหาศาล เปรียบเหมือนการขุดหาเพชร ใครขุดเจอคนแรกก็ได้รางวัลไป บิตคอยน์ก็ใช้หลักการคล้ายๆ กัน ใครมีพลังประมวลผลมากก็มีโอกาสปิดบล็อกได้ก่อน แต่เหรียญก็มักจะมีสองด้านเสมอ.. ระบบนี้เปิดโอกาสให้เกิด **"Strategic Mining" หรือ การใช้กลยุทธ์ต่างๆ เพื่อโกยผลประโยชน์** มันเหมือนเกมเศรษฐศาสตร์ที่ทุกคนต่างแข่งขันกัน ใครมีกลยุทธ์ดีกว่าก็ได้เปรียบ แล้วอะไรล่ะที่ป้องกันไม่ให้บิคอยน์ถูกควบคุม? หนึ่งในแนวคิดคือ "Market Fragility Hypothesis" ที่เชื่อว่าหากเกิดการควบคุมระบบบิตคอยน์ ราคาของบิตคอยน์จะร่วงลงอย่างรุนแรง ทำให้ผู้ที่พยายามจะควบคุมก็ต้องเสียหายไปด้วย อีกแนวคิดคือ "Repeated Games and Institutional Norms" ที่มองว่าการทำตัวดีเป็นผลดีต่อทุกคนในระยะยาว ใครทำตัวไม่ดีก็อาจถูกลงโทษ เช่น การไม่ยอมรับธุรกรรมที่น่าสงสัย แต่การลงโทษก็มีปัญหา เพราะต้องอาศัยความร่วมมือจากผู้เล่นส่วนใหญ่ ซึ่งในโลกแห่งบิตคอยน์ที่ไร้ศูนย์กลาง การประสานงานจริงๆ นั้นทำได้ยาก บิตคอยน์ยังเผชิญความท้าทายอีกมากมาย เช่น การลดลงของรางวัลขุด (Block Subsidy) ที่อาจกระทบต่อความปลอดภัย หรือการต่อสู้กับการเซ็นเซอร์ธุรกรรม (Censorship Attack) อนาคตของบิตคอยฯ์จะเป็นอย่างไร? บางคนเชื่อว่าบิตคอยน์จะกลายเป็นสกุลเงินหลักของโลก (Hyperbitcoinization) แต่บางคนก็มองว่าความผันผวนของราคาและความเสี่ยงจากการถูกเข้าควบคุมจะเป็นอุปสรรคที่สำคัญ ไม่ว่าอนาคตจะเป็นเช่นไร.. บิตคอยน์ได้จุดประกายการปฏิวัติทางเศรษฐกิจครั้งใหญ่ ใครๆ ก็สามารถเข้าร่วมเกมนี้ได้ แต่การจะชนะต้องอาศัยความเข้าใจในกฎกติกาและกลยุทธ์ที่เหนือชั้น บทความนี้จึงได้เรียบเรียงเนื้อหาที่น่าสนใจมาจากใน **หนังสือ "Bitcoin: A Game-Theoretic Analysis"** ซึ่งเล่าเรื่องราวของบิตคอยน์ผ่านมุมมองของทฤษฎีเกมมาแบ่งปัน ซึ่งจะช่วยให้ผู้อ่านเข้าใจกลไกและความท้าทายของบิตคอยน์อย่างครอบคลุม อ่านสนุก และน่าติดตามมากขึ้น # Dominant Strategy ไพ่ตายที่ (แทบ) ไม่มีอยู่จริงในสมรภูมิบิตคอยน์ ในโลกของเกมและเศรษฐศาสตร์ **“Dominant Strategy” คือกลยุทธ์มหัศจรรย์ที่ทำให้ผู้เล่นได้เปรียบ** ไม่ว่าคู่แข่งจะงัดไม้ไหนมาสู้ก็ตาม ยกตัวอย่าง "Prisoner's Dilemma" เกมคลาสสิคที่ผู้ต้องหาสองคนต้องเลือกว่าจะร่วมมือ (ไม่ซัดทอดเพื่อน) หรือหักหลัง (ซัดทอดเพื่อน) ถ้าทั้งคู่ร่วมมือจะได้รับโทษเบาๆ ด้วยกัน แต่ถ้าคนหนึ่งหักหลัง อีกคนร่วมมือ คนหักหลังจะได้รางวัล คนร่วมมือจะโดนโทษหนัก และถ้าทั้งคู่หักหลัง จะโดนโทษหนักด้วยกันทั้งคู่ จะเห็นว่าการหักหลัง คือ Dominant Strategy เพราะไม่ว่าเพื่อนจะเลือกอะไร การหักหลังจะทำให้เราได้ผลลัพธ์ดีกว่าเสมอ (ไม่โดนโทษหนัก หรือได้รางวัล) แต่ในสมรภูมิ Bitcoin กลยุทธ์แบบไพ่ตายแทบไม่มีอยู่จริง เพราะการกระทำของนักขุดแต่ละคนล้วนส่งผลกระทบต่อคนอื่นๆ เสมอ ลองนึกภาพนักขุดจอมเจ้าเล่ห์ที่พยายามโกงระบบ เช่น - **Selfish Mining:** แอบขุดบล็อกไว้คนเดียว หวังจะฮุบรางวัลบล็อกทั้งหมด - **Block Withholding:** กั๊กบล็อกที่ขุดได้ บีบให้คนอื่นจ่ายค่าธรรมเนียมแพงๆ - **Censorship Attack:** ควบคุมเครือข่ายเพื่อบล็อกธุรกรรมบางอย่าง กลยุทธ์เหล่านี้อาจดูเหมือนไพ่ตายในแวบแรก แต่ความจริงแล้วมันขึ้นอยู่กับปฏิกิริยาของนักขุดคนอื่นๆ ด้วย เพราะถ้าคนอื่นๆ รู้ทันแผนการร้าย และเลือกที่จะลงโทษนักขุดจอมเจ้าเล่ห์ เช่น ไม่ยอมรับบล็อกที่ขุดได้ หรือหันไปใช้บริการแพลตฟอร์มอื่น นักขุดจอมเจ้าเล่ห์ก็จะขาดทุน ยิ่งไปกว่านั้น.. กลยุทธ์เหล่านี้มักจะทำลายความเชื่อมั่นในบิตคอยน์ (Market Fragility Hypothesis) ทำให้ราคาบิตคอยน์ร่วงลง นักขุดจอมเจ้าเล่ห์ก็จะเสียหายตามไปด้วย ดังนั้น.. ในบิตคอยน์จึงไม่มีกลยุทธ์ใดที่รับประกันความสำเร็จ 100% ทุกการกระทำล้วนมีความเสี่ยง และขึ้นอยู่กับการตัดสินใจของนักขุดคนอื่นๆ นี่คือเสน่ห์ของบิตคอยน์ที่ทำให้มันเป็นระบบที่มีพลวัต ซับซ้อน และท้าทาย ไม่มีใครสามารถควบคุมเกมได้อย่างสมบูรณ์ และทุกคนต้องเล่นอย่างชาญฉลาดเพื่อให้ได้ผลลัพธ์ที่ดีที่สุด.. # Nash Equilibrium สมดุลอันเปราะบางบนเส้นด้ายแห่งความไว้วางใจใน Bitcoin **"Nash Equilibrium"** เป็นแนวคิดสำคัญในทฤษฎีเกม อธิบายภาวะสมดุลที่เกิดขึ้นเมื่อผู้เล่นแต่ละคนเลือกกลยุทธ์ที่ดีที่สุดสำหรับตัวเอง โดยพิจารณาจากกลยุทธ์ของผู้เล่นคนอื่นๆ ณ จุดสมดุลนี้ ไม่มีใครอยากเปลี่ยนกลยุทธ์ เพราะรู้ว่าการเปลี่ยนจะทำให้ตัวเองเสียเปรียบ ยกตัวอย่างเกม **"Splitting $4"** ที่ผู้เล่นสองคนต้องเขียนตัวเลข ($1, $2, $3) หากผลรวมไม่เกิน $4 ทั้งคู่จะได้รับเงินตามที่เขียน แต่ถ้าเกิน $4 ทั้งคู่จะไม่ได้อะไรเลย Nash Equilibrium ของเกมนี้คือการที่ทั้งคู่เขียน $2 เพราะไม่ว่าใครจะเปลี่ยนตัวเลข คนที่ไม่เปลี่ยนจะได้เปรียบกว่าเสมอ ถ้าคนหนึ่งเขียน $3 อีกคนเขียน $2 คนเขียน $2 จะได้ $2 ส่วนคนเขียน $3 จะไม่ได้อะไรเลย ถ้าคนหนึ่งเขียน $1 อีกคนเขียน $2 คนเขียน $2 จะได้ $2 ส่วนคนเขียน $1 จะได้แค่ $1 ในบิตคอยน์ก็มี Nash Equilibrium เช่นเดียวกัน หนึ่งในนั้นคือการที่นักขุดส่วนใหญ่เลือก "Default Compliant" หรือ การทำตามกฎกติกาของบิตคอยน์อย่างเคร่งครัด ทำไมถึงเป็นเช่นนั้น? ลองนึกภาพนักขุดจอมโลภที่คิดจะแหกกฎเพื่อหาผลประโยชน์ใส่ตัว เช่น - Selfish Mining: แอบขุดบล็อกไว้คนเดียว - Block Withholding: กั๊กบล็อกที่ขุดได้ - Censorship Attack: บล็อกธุรกรรมบางอย่าง ถ้ามีนักขุดทำแบบนี้แค่คนเดียว ในขณะที่คนอื่นๆ ยังคงทำตามกฎ นักขุดคนนั้นอาจจะได้เปรียบในระยะสั้น แต่ในระยะยาว การกระทำแบบนี้จะ.. - **ทำลายความเชื่อมั่นในบิตคอยน์** (Market Fragility Hypothesis) ทำให้ราคาบิตคอยน์ร่วงลง - **ถูกนักขุดคนอื่นๆ ลงโทษ** เช่น ไม่ยอมรับบล็อกที่ขุดได้ หรือ รวมหัวกันแบนนักขุดจอมโลภ สุดท้าย.. นักขุดจอมโลภก็จะขาดทุนและสูญเสียโอกาสในการได้รับรางวัลบล็อกในอนาคต ดังนั้น.. การทำตามกฎจึงเป็นกลยุทธ์ที่ปลอดภัยและยั่งยืนกว่าสำหรับนักขุดส่วนใหญ่ อย่างไรก็ตาม Nash Equilibrium ในบิตคอยน์ไม่ได้หมายความว่าระบบจะมั่นคง 100% - **แรงจูงใจในการแหกกฎอาจเพิ่มขึ้นได้** เช่น เมื่อรางวัลบล็อก (Block Subsidy) ลดลงและค่าธรรมเนียม (Transaction Fee) ไม่สูงพอ นักขุดอาจมองว่าการโกงคุ้มค่ากับความเสี่ยงมากขึ้น - **การประสานงานเพื่อลงโทษผู้ทำผิดอาจทำได้ยาก** บิตคอยน์ไม่มีศูนย์กลางควบคุม การตัดสินใจใดๆ ต้องอาศัยความเห็นพ้องของนักขุดส่วนใหญ่ ซึ่งอาจทำได้ยากและใช้เวลานาน Nash Equilibrium ในบิตคอยน์จึงเป็นสมดุลที่เปราะบางที่สามารถถูกทำลายได้ หากแรงจูงใจและสภาพแวดล้อมเปลี่ยนไป.. นี่คือความท้าทายที่ชุมชนบิตคอยน์ต้องเผชิญในการรักษาสมดุลระหว่าง **"ผลประโยชน์ส่วนตัว"** ของนักขุด กับ **"ความมั่นคงของระบบ"** โดยรวม # Censorship Attack สมรภูมิปิดล้อมบิตคอยน์กับอาวุธลับ Soft Fork บิตคอยน์นั้นถูกออกแบบมาให้เป็นระบบการเงินแบบไร้ศูนย์กลาง ปราศจากการควบคุมของรัฐบาลหรือองค์กรใดๆ แต่ในโลกแห่งความเป็นจริง อำนาจและการควบคุมยังคงเป็นสิ่งที่หลายฝ่ายปรารถนา และ **"Censorship Attack"** คือหนึ่งในภัยคุกคามที่บิตคอยน์ต้องเผชิญ Censorship Attack คือ **ความพยายามในการปิดล้อม Bitcoin เพื่อบล็อกธุรกรรมบางอย่าง** เปรียบเสมือนการที่รัฐบาลเผด็จการพยายามปิดกั้นข้อมูลข่าวสาร หรือบริษัทผูกขาดพยายามกำจัดคู่แข่ง ใครบ้างที่อาจอยู่เบื้องหลัง Censorship Attack? - **รัฐบาล:** อาจต้องการควบคุมการไหลเวียนของ Bitcoin เพื่อรักษาอำนาจทางการเงิน หรือ ป้องกันการฟอกเงิน - **องค์กรขนาดใหญ่:** อาจต้องการควบคุมตลาดบิตคอยน์เพื่อผลประโยชน์ของตัวเอง - **กลุ่มคนที่ไม่เห็นด้วยกับ Bitcoin:** อาจต้องการทำลาย Bitcoin เพราะมองว่าเป็นภัยคุกคามต่อระบบเดิม พวกเขาจะใช้พลังขุดจำนวนมหาศาลในการควบคุมเครือข่ายบิตคอยน์ และบล็อกธุรกรรมที่ไม่พึงประสงค์ เหมือนกับการที่รัฐบาลเผด็จการใช้กำลังทหารปิดล้อมเมือง แต่บิตคอยน์ก็ไม่ใช่หมูที่จะให้เชือดได้ง่ายๆ ชุมชนบิตคอยน์มีอาวุธลับ นั่นคือ **"Soft Fork"** **Soft Fork คือการเปลี่ยนแปลงกฎกติกาของ Bitcoin โดยที่ยังคงเข้ากันได้กับกฎเดิม** Node ที่ใช้กฎเดิมจะยังคงมองว่าบล็อกที่สร้างขึ้นตามกฎใหม่นั้นถูกต้อง ยกตัวอย่างเช่น ชุมชนบิคคอยน์อาจใช้ Soft Fork เพื่อ.. - **ยกเลิกการบล็อกธุรกรรม:** ทำให้ธุรกรรมที่ถูกบล็อกสามารถดำเนินการได้ตามปกติ - **เพิ่มความสามารถของบิตคอยน์:** เช่น เพิ่มขนาดบล็อก หรือเพิ่มฟังก์ชั่นใหม่ๆ - **ลงโทษผู้พยายามควบคุม:** เช่น ลดรางวัลบล็อกหรือตัดสิทธิ์การขุด ของผู้ที่พยายามควบคุมเครือข่าย Soft Fork เปรียบเสมือนอาวุธลับที่จะช่วยให้ชุมชนบิตคอยน์สามารถแหกกฎที่ไม่เป็นธรรมได้ เหมือนกับการที่ประชาชนลุกขึ้นมาต่อต้านอำนาจเผด็จการด้วยการใช้สันติวิธี อย่างไรก็ตาม.. การใช้ Soft Fork ก็มีความเสี่ยงอยู่เช่นกัน.. - **อาจทำให้บิตคอยน์แตกเป็นสองสาย:** หากนักขุดส่วนใหญ่ไม่เห็นด้วยกับ Soft Fork อาจทำให้เกิด **"Hard Fork"** หรือ การแยกบิตคอยน์ออกเป็นสองเหรียญ - **อาจลดทอนความน่าเชื่อถือของบิตคอยน์:** หาก Soft Fork ถูกใช้บ่อยเกินไป อาจทำให้คนมองว่าบิตคอยน์ไม่มั่นคง และเปลี่ยนแปลงง่ายเกินไป ดังนั้น.. การใช้ Soft Fork จึงต้องทำอย่างรอบคอบ และคำนึงถึงผลกระทบในระยะยาว Censorship Attack จึงเป็นสมรภูมิที่ดุเดือดระหว่าง **"อำนาจ"** กับ **"เสรีภาพ"** ชุมชนบิตคอยน์ต้องต่อสู้เพื่อปกป้องอุดมการณ์ของบิตคอยน์ในฐานะระบบการเงินแบบไร้ศูนย์กลาง และปราศจากการเซ็นเซอร์ # Selfish Mining แผนร้ายใต้เงามืดของนักขุดในมุมมืดผู้แยบยล ในโลกของบิตคอยน์ที่เต็มไปด้วยการแข่งขัน นักขุดแต่ละคนต่างก็งัดกลยุทธ์ต่างๆ มาใช้เพื่อช่วงชิงรางวัลบล็อก และ "Selfish Mining" คือหนึ่งในกลยุทธ์ลับที่แยบยลแต่แฝงไปด้วยความเสี่ยง ลองจินตนาการถึงนักวิทยาศาสตร์สติเฟื่องผู้แอบซุ่มพัฒนาอาวุธร้ายแรงในห้องแล็บลับ ไม่ให้ใครล่วงรู้ Selfish Mining ก็เปรียบเสมือนนักวิทยาศาสตร์คนนี้ ที่แอบขุดบิตคอยน์ไว้คนเดียวเงียบๆ ไม่บอกใคร แผนการร้ายนี้มันทำงานอย่างไร? - **แอบขุดเงียบๆ:** เมื่อนักขุด Selfish Mining ขุดเจอบล็อกใหม่ แทนที่จะประกาศให้โลกรู้ พวกเขาจะเก็บมันไว้เป็นความลับ เหมือนกับนักวิทยาศาสตร์ที่ซ่อนอาวุธไว้ในห้องแล็บ - **แอบสร้างความได้เปรียบ:** นักขุด Selfish Mining จะแอบขุดบล็อกต่อไปเรื่อยๆ โดยหวังว่าจะขุดได้บล็อกต่อเนื่อง ยิ่งขุดได้มากเท่าไหร่ ความได้เปรียบก็ยิ่งมากขึ้น - **เผยไพ่ตาย:** เมื่อนักขุดคนอื่นๆ ใกล้จะขุดเจอบล็อกใหม่ นักขุด Selfish Mining จะรีบเผยแพร่บล็อกทั้งหมดที่แอบขุดไว้ทำให้บล็อกของพวกเขากลายเป็น "Longest Chain" หรือ "Heaviest Chain" และได้รับรางวัลบล็อกทั้งหมดที่ขุดได้ ด้วยกลยุทธ์นี้ นักขุด Selfish Mining สามารถโกงระบบ และได้รับรางวัลบล็อกมากกว่าที่ควรจะเป็น แต่นี่คือเกมแห่งความเสี่ยง เพราะ.. - **ถ้าคนอื่นขุดเจอบล็อกก่อน:** บล็อกทั้งหมดที่นักขุด Selfish Mining แอบขุดไว้จะกลายเป็น "Orphan Block" หรือ "Uncle Block" และไร้ค่าทันที เหมือนกับอาวุธที่ถูกยึดไปก่อนจะได้ใช้งาน - **ยิ่งแอบขุดนาน ความเสี่ยงยิ่งสูง:** ยิ่งนักขุด Selfish Mining แอบขุดบล็อกไว้นานเท่าไหร่ โอกาสที่คนอื่นจะขุดเจอบล็อกก่อนก็ยิ่งมากขึ้นเท่านั้น Selfish Mining ส่งผลกระทบต่อบิตคอยน์อย่างไร? - **ลดประสิทธิภาพของเครือข่าย:** ทำให้การยืนยันธุรกรรมช้าลง และสิ้นเปลืองพลังงานมากขึ้น - **บิดเบือนการกระจายรางวัล:** ทำให้นักขุดที่ทำตามกฎได้รับรางวัลน้อยลง และนักขุด Selfish Mining ได้รับรางวัลมากกว่าที่ควรจะเป็น - **ลดทอนความเชื่อมั่นในบิตคอยน์:** (Market Fragility Hypothesis) ทำให้คนมองว่าบิตคอยน์ไม่มั่นคง และเสี่ยงต่อการถูกควบคุม แล้วจะป้องกัน Selfish Mining ได้อย่างไร? - **การตรวจจับและลงโทษ:** ชุมชน บิตคอยน์ สามารถพัฒนาระบบตรวจจับ Selfish Mining และ ลงโทษนักขุดที่ทำผิดกฎ เช่น ลดรางวัลบล็อก หรือ ตัดสิทธิ์การขุด - **การปรับปรุงกลไก Difficulty Adjustment:** ทำให้การปรับระดับความยากของ Proof of Work ตอบสนองต่อการเปลี่ยนแปลงของ hashrate ได้รวดเร็วและแม่นยำยิ่งขึ้น เพื่อทำความเข้าใจกลยุทธ์ Selfish Mining ให้ลึกซึ้งยิ่งขึ้น เราสามารถใช้แบบจำลองทางคณิตศาสตร์ที่เรียกว่า **"Markov Chain"** ในการวิเคราะห์ได้ แบบจำลองนี้ช่วยให้เราคำนวณความน่าจะเป็นของผลลัพธ์ต่างๆ ที่อาจเกิดขึ้นจากการทำ Selfish Mining เช่น โอกาสที่นักขุด Selfish Mining จะประสบความสำเร็จในการยึดครองเครือข่าย หรือ โอกาสที่บล็อกที่แอบขุดไว้จะกลายเป็น Orphan Block ผลการวิเคราะห์โดยใช้ Markov Chain ตามที่ปรากฏในหนังสือ (บทที่ 8) แสดงให้เห็นว่า Selfish Mining สามารถทำให้นักขุดที่โกงได้รับรางวัลบล็อกมากกว่าส่วนแบ่ง Hashrate ที่พวกเขามี ตัวอย่างเช่น.. นักขุดที่มีพลังขุดเพียง 30% สามารถได้รับรางวัลบล็อกมากกว่า 30% ได้ หากพวกเขาใช้กลยุทธ์ Selfish Mining อย่างมีประสิทธิภาพ ยิ่งไปกว่านั้น Selfish Mining ยังส่งผลกระทบต่อเสถียรภาพของตลาด Hashrate ด้วย เพราะมันบิดเบือนกลไก Difficulty Adjustment ทำให้การปรับระดับความยากของ Proof of Work ไม่แม่นยำ และเกิดความผันผวนของ Hashrate Selfish Mining จึงเป็นภัยคุกคามที่แยบยล และท้าทายต่อความมั่นคงของบิตคอยน์ ชุมชนบิตคอยน์ต้องร่วมมือกันเพื่อป้องกัน และรักษาสมดุลของระบบนิเวศ # Block Withholding เกมบีบค่าไถ่บิตคอยน์ของเจ้าพ่อผู้โลภมาก ในโลกของบิตคอยน์ การยืนยันธุรกรรมต้องอาศัยนักขุดผู้ทำหน้าที่บรรจุธุรกรรมลงในบล็อก แต่หากนักขุดเหล่านี้เกิดโลภมาก จนละทิ้งอุดมการณ์และหันมาใช้กลยุทธ์ **“Block Withholding”** บิตคอยน์อาจกลายเป็นสนามเด็กเล่นของเจ้าพ่อผู้พยายามครอบงำตลาด Block Withholding คือกลยุทธ์ที่นักขุดจงใจกั๊กบล็อกที่ขุดได้ ไม่ยอมเผยแพร่ ทำให้ธุรกรรมต่างๆ ค้างเติ่งอยู่ใน Mempool หรือพื้นที่รอการยืนยัน เปรียบเสมือนเจ้าพ่อมาเฟียที่ยึดรถบรรทุกสินค้า แล้วเรียกค่าคุ้มครองจากพ่อค้า ใครอยากให้สินค้าของตัวเองถูกส่งไปถึงปลายทางก็ต้องยอมจ่าย ยิ่งธุรกรรมค้างคามากเท่าไหร่ ค่าธรรมเนียม (Transaction Fee) ก็จะยิ่งสูงขึ้น เจ้าพ่อก็จะยิ่งรวย แต่นี่คือเกมแห่งความเสี่ยง เจ้าพ่อผู้โลภมากอาจพลาดท่าได้ เพราะ.. - **ผลักไสผู้ใช้งาน:** ถ้าค่าธรรมเนียมแพงเกินไป คนอาจหนีไปใช้แพลตฟอร์มอื่น หรือหันไปใช้บริการ Layer 2 เช่น Lightning Network ที่รวดเร็วและค่าธรรมเนียมถูกกว่า - **ทำลายความเชื่อมั่นในบิตคอยน์:** (Market Fragility Hypothesis) ทำให้คนมองว่าบิตคอยน์ไม่น่าเชื่อถือ ช้า และ แพง ส่งผลให้ราคาบิตคอยน์ร่วงลง - **จุดชนวนความขัดแย้ง:** นักขุดคนอื่นๆ ที่ทำตามกฎ อาจไม่พอใจและรวมหัวกันลงโทษเจ้าพ่อ เช่น ไม่ยอมรับบล็อกที่กั๊กไว้ หรือแบนเจ้าพ่อออกจาก Mining Pool Block Withholding เกิดขึ้นได้อย่างไร? - **นักขุดรายใหญ่:** นักขุดที่มีพลังขุดมาก มีอำนาจต่อรองสูงกว่า และมีโอกาสใช้ Block Withholding ได้ผลมากกว่า - **ช่วงที่ธุรกรรมหนาแน่น:** ในช่วงที่ Mempool มีธุรกรรมค้างคามาก นักขุดมีแรงจูงใจในการ Block Withholding มากขึ้น เพราะสามารถเรียกเก็บค่าธรรมเนียมได้แพง - **การสมรู้ร่วมคิด:** นักขุดหลายรายอาจรวมหัวกัน Block Withholding เพื่อควบคุมตลาดและโกยผลประโยชน์ร่วมกัน แล้วจะป้องกัน Block Withholding ได้อย่างไร? - **การกระจายอำนาจ:** ยิ่งมีนักขุดจำนวนมาก และพลังขุดกระจายตัวมากเท่าไหร่ การ Block Withholding ก็จะทำได้ยากขึ้น - **การสร้างแรงจูงใจ:** ออกแบบระบบรางวัลที่ทำให้นักขุดได้รับผลประโยชน์จากการยืนยันธุรกรรมอย่างรวดเร็ว และไม่คุ้มค่ากับการ Block Withholding - **การพัฒนา Layer 2:** เช่น Lightning Network ที่ช่วยลดความแออัดของ Mempool และทำให้ค่าธรรมเนียมถูกลง Block Withholding จึงเป็นเหมือนเกมชักกะเย่อระหว่าง **"ความโลภ"** ของนักขุด กับ **"ความต้องการ"** ของผู้ใช้งาน การรักษาสมดุลและป้องกันไม่ให้บิตคอยน์ตกอยู่ใต้อำนาจของเจ้าพ่อ จึงเป็นสิ่งที่ชุมชนบิตคอยน์ต้องร่วมมือกันอย่างจริงจัง # The Flattening ASIC Cost Curve เมื่อสมรภูมิชิปขุดบิตคอยน์ร้อนระอุ **ASIC** (Application-Specific Integrated Circuit) คือชิปประมวลผลพิเศษที่ถูกออกแบบมาเพื่อขุดบิตคอยน์โดยเฉพาะ เหมือนกับอาวุธลับที่ช่วยให้นักขุดสามารถถล่มโจทย์ Proof of Work ได้อย่างรวดเร็ว ในช่วงแรกๆ ของบิตคอยน์ ASIC นั้นมีราคาแพงและหายาก เปรียบเสมือนดาบวิเศษในตำนานที่ใครครอบครองก็จะได้เปรียบเหนือคนอื่น ผู้ผลิต ASIC จึงเปรียบเสมือนพ่อค้าอาวุธที่กอบโกยกำไรมหาศาลจากการขายดาบวิเศษเหล่านี้ แต่เมื่อเวลาผ่านไป.. เทคโนโลยีการผลิต ASIC พัฒนาขึ้น ต้นทุนการผลิตก็ลดลง ผู้เล่นหน้าใหม่ก็กระโดดเข้ามาในตลาด การแข่งขันก็ดุเดือดขึ้น ราคา ASIC ก็ถูกลง กราฟแสดงความสัมพันธ์ระหว่างราคา ASIC กับเวลา จึงมีลักษณะลาดลงหรือ **"Flattening"** นี่คือสมรภูมิแห่งชิปขุดบิตคอยน์ที่ร้อนระอุ และผลลัพธ์ของสงครามราคาครั้งนี้ก็ส่งผลดีต่อความมั่นคงของบิตคอยน์ในระยะยาว ทำไมถึงเป็นเช่นนั้น? - **การบงการตลาดทำได้ยากขึ้น:** เมื่อ ASIC มีราคาถูกลง และ หาซื้อง่ายขึ้น การที่คนกลุ่มใดกลุ่มหนึ่ง จะ "กว้านซื้อ" ASIC เพื่อควบคุมพลังขุด และบงการเครือข่ายบิตคอยน์ก็จะทำได้ยากขึ้น - **กระจายอำนาจ:** เมื่อ ASIC มีราคาไม่แพง นักขุดรายย่อยก็สามารถเข้าถึง ASIC ได้ง่ายขึ้น ทำให้พลังขุดกระจายตัวมากขึ้น ลดโอกาสที่คนกลุ่มใดกลุ่มหนึ่งจะผูกขาดพลังขุด - **ลดแรงจูงใจในการโกง:** เมื่อกำไรจากการขุดบิตคอยน์ลดลง นักขุดก็มีแรงจูงใจในการโกงระบบน้อยลง เช่น Selfish Mining หรือ Block Withholding เพราะผลตอบแทนที่ได้รับอาจไม่คุ้มค่ากับความเสี่ยง ปัจจัยที่ส่งผลต่อ The Flattening ASIC Cost Curve - **Moore’s Law:** กฎของ Moore กล่าวว่า.. ประสิทธิภาพของชิปคอมพิวเตอร์จะเพิ่มขึ้นเป็นสองเท่าทุกๆ 18 เดือน ในขณะที่ราคาลดลง ส่งผลให้ ASIC มีประสิทธิภาพสูงขึ้น แต่ราคาถูกลง - **การแข่งขันในตลาด:** เมื่อมีผู้ผลิต ASIC จำนวนมาก การแข่งขันด้านราคาจะรุนแรงขึ้น ทำให้ราคา ASIC ถูกลง - **ความต้องการของตลาด:** หากราคาบิตคอยน์สูงขึ้น ความต้องการ ASIC ก็จะสูงขึ้นตามไปด้วย ทำให้ผู้ผลิต ASIC มีกำลังใจในการผลิตและพัฒนาเทคโนโลยี The Flattening ASIC Cost Curve จึงเป็นปรากฏการณ์ที่แสดงให้เห็นถึง **"พลังของตลาดเสรี"** ที่จะช่วยควบคุมและรักษาสมดุลของระบบนิเวศบิตคอยน์ อย่างไรก็ตาม.. การที่ราคา ASIC ถูกลงก็ไม่ได้หมายความว่าบิตคอยน์จะปลอดภัยจากการโจมตี 100% นักขุดที่ทุนหนา หรือได้รับการสนับสนุนจากรัฐบาล ยังคงสามารถทุ่มเงินซื้อ ASIC จำนวนมาก เพื่อบงการเครือข่ายได้ ดังนั้น ชุมชนบิตคอยน์ต้องตื่นตัว และคอยเฝ้าระวังภัยคุกคามอยู่เสมอ เพื่อปกป้องบิตคอยน์ให้คงอยู่และเติบโตอย่างยั่งยืน # บิตคอยน์กับเกมเดิมพันอนาคต เมื่อรางวัลบล็อกเหือดหายและค่าธรรมเนียมคือกุญแจ บิตคอยน์นั้นเปรียบเสมือนขุมทรัพย์ที่ถูกออกแบบมาให้มีจำนวนจำกัด และรางวัลบล็อก (Block Reward) คือแรงจูงใจหลักที่ทำให้นักขุดบิตคอยน์ทุ่มเทพลังขุด เพื่อรักษาความปลอดภัยของเครือข่าย แต่.. บิตคอยน์ Protocol ได้กำหนดตารางเวลาในการลด Block Reward ลงครึ่งหนึ่งทุกๆ 4 ปี (Halving) เหมือนกับระเบิดเวลาที่ค่อยๆ บีบรายได้ของนักขุดให้เล็กลงไปเรื่อยๆ ในอนาคต Block Reward จะหมดลงในที่สุด.. นักขุดบิตคอยน์จะต้องพึ่งพา **"ค่าธรรมเนียม" (Transaction Fee)** เป็นแหล่งรายได้หลัก นี่คือจุดเปลี่ยนสำคัญที่อาจส่งผลต่ออนาคตของบิตคอยน์ ### Transaction Fees รายได้ใหม่ของนักขุด Transaction Fee คือ **ค่าธรรมเนียมที่ผู้ใช้บิตคอยน์จ่ายให้กับนักขุด เพื่อเร่งการยืนยันธุรกรรม** ยิ่งมีธุรกรรมมาก และแข่งขันกันมากเท่าไหร่ Transaction Fee ก็จะยิ่งสูงขึ้นเท่านั้น เปรียบเสมือน **"ค่าผ่านทาง"** บนท้องถนน ยิ่งรถเยอะ ค่าผ่านทางก็ยิ่งแพง ความท้าทายเมื่อ Block Reward ลดลง.. - **ความปลอดภัยของเครือข่าย:** ถ้า Transaction Fee ไม่สูงพอ นักขุดอาจขาดทุนและไม่มีแรงจูงใจในการรักษาความปลอดภัยของเครือข่าย ทำให้บิตคอยน์ต้องเสี่ยงต่อการถูกโจมตีจากผู้ไม่หวังดี - **การทำตามกฎ:** นักขุดอาจละทิ้งอุดมการณ์ และหันไปใช้กลยุทธ์โกงๆ เช่น Selfish Mining หรือ Block Withholding เพื่อเพิ่มรายได้ - **การรวมศูนย์อำนาจ:** นักขุดรายย่อยอาจสู้ไม่ไหว และถูกบีบให้ออกไปจากตลาด ทำให้พลังขุดกระจุกตัวอยู่ในมือของนักขุดรายใหญ่ เพิ่มความเสี่ยงต่อการผูกขาด และบงการเครือข่าย นักขุดบิตคอยน์ต้องปรับตัวอย่างไร? - **เข้าร่วม Mining Pool:** รวมพลังกับนักขุดคนอื่นๆ เพื่อเพิ่มโอกาสในการได้รับรางวัล และลดความเสี่ยง - **พัฒนากลยุทธ์:** เลือก Mining Pool ที่มีระบบ Reward ที่น่าสนใจ ปรับแต่งซอฟต์แวร์เพื่อจัดลำดับความสำคัญของธุรกรรมที่มี Transaction Fee สูง - **มองหาโอกาสใหม่:** เช่น การให้บริการ Node Validation บน Layer 2 (Lightning Network) หรือการลงทุนในธุรกิจที่เกี่ยวข้องกับบิตคอยน์ ### อนาคตของบิตคอยน์ขึ้นอยู่กับ Transaction Fee Transaction Fee คือ กุญแจสำคัญที่จะกำหนดอนาคตของบิตคอยน์ - **ถ้า Transaction Fee สูงพอ:** บิตคอยน์จะยังคงเป็นระบบการเงินที่ปลอดภัย น่าเชื่อถือและกระจายอำนาจ - **แต่ถ้า Transaction Fee ต่ำเกินไป:** บิตคอยน์อาจล่มสลายหรือถูกควบคุมโดยคนกลุ่มใดกลุ่มหนึ่ง ชุมชนบิตคอยน์จึงต้องร่วมมือกันเพื่อสร้างระบบนิเวศที่เอื้อต่อการเติบโตของ Transaction Fee เช่น - **ส่งเสริมการใช้งานบิตคอยน์:** ยิ่งมีคนใช้บิตคอยน์มาก Transaction Fee ก็จะยิ่งสูงขึ้น - **พัฒนาเทคโนโลยี:** เช่น Layer 2 (Lightning Network) ที่ช่วยลดความแออัดของเครือข่าย และทำให้ค่าธรรมเนียมถูกลง - **สร้างความเชื่อมั่น:** ให้ความรู้และสร้างความเข้าใจเกี่ยวกับบิตคอยน์แก่สาธารณชน เพื่อเพิ่มความเชื่อมั่นและดึงดูดผู้ใช้งานใหม่ บิตคอยน์กำลังก้าวเข้าสู่ยุคใหม่ที่ Transaction Fee จะเป็นตัวกำหนดชะตากรรม ความสำเร็จของบิตคอยน์ขึ้นอยู่กับความร่วมมือ และความพยายามของชุมชน ในการสร้างระบบนิเวศที่ยั่งยืนและเป็นประโยชน์ต่อทุกคน # เมื่ออำนาจเก่าหวั่นไหว ภัยคุกคามบิตคอยน์จากรัฐบาลและองค์กร บิตคอยน์ คือนวัตกรรมที่ท้าทายอำนาจและระบบเดิม การเกิดขึ้นของบิตคอยน์ทำให้รัฐบาล และ องค์กรขนาดใหญ่หวั่นไหว เพราะมันสั่นคลอนเสถียรภาพของระบบการเงิน และอำนาจในการควบคุมที่พวกเขาเคยผูกขาด บิตคอยน์ จึงถูกมองว่าเป็นภัยคุกคามที่ต้องถูกกำจัด ### การโจมตีโดยตรง (Brute-Force Attack) ศึกชิงอำนาจ Hashrate การโจมตีแบบ Brute-Force คือการใช้พลังขุดจำนวนมหาศาล เพื่อยึดครองเครือข่ายบิตคอยน์ เปรียบเสมือนการที่กองทัพบุกตะลุยเข้ายึดเมือง รัฐบาลหรือองค์กร สามารถใช้เงินทุนจำนวนมหาศาล ในการซื้อ ASIC และพลังงาน เพื่อเพิ่ม Hashrate ของตัวเองให้เหนือกว่านักขุดบิตคอยน์คนอื่นๆ (ซึ่งใช้ทุนเยอะ และทำได้ยากมาก) เมื่อ Hashrate ของผู้โจมตีเกิน" 51% พวกเขาจะสามารถ.. - **ควบคุมการยืนยันธุรกรรม:** เลือกที่จะอนุมัติหรือปฏิเสธธุรกรรมตามใจชอบ - **Double-Spend:** ใช้บิตคอยน์ซ้ำสอง ทำให้เกิดความสับสนและสูญเสียความเชื่อมั่นในระบบ - **เปลี่ยนแปลงกฎกติกา:** บังคับให้ Hard Fork ไปสู่กฎใหม่ที่เอื้อประโยชน์ต่อพวกเขา การโจมตีแบบ Brute-Force เป็นภัยคุกคามที่ร้ายแรงที่สุด แต่ก็สิ้นเปลืองและเสี่ยงเช่นกัน.. - **ต้นทุนสูง: **การซื้อ ASIC และพลังงานต้องใช้เงินทุนมหาศาล - **ความเสี่ยงด้านชื่อเสียง:** การโจมตีบิตคอยน์อย่างโจ่งแจ้ง อาจทำให้เสียชื่อเสียง และถูกต่อต้านจากชุมชนบิตคอยน์ ### การบิดเบือนข้อมูล (FUD) สงครามจิตวิทยา FUD (Fear, Uncertainty, and Doubt) คือ สงครามจิตวิทยา ที่ใช้ข้อมูลเป็นอาวุธในการทำลายความเชื่อมั่นในบิตคอยน์ รัฐบาลและองค์กรสามารถใช้สื่อ และช่องทางต่างๆ ในการ.. - **สร้างข่าวลือ:** เช่น บิตคอยน์กำลังจะล่มสลาย (บิตคอยน์ตายแล้ว) หรือบิตคอยน์ถูกใช้ในการฟอกเงิน - **ปล่อยข่าวปลอม:** เช่น บิตคอยน์ถูกแฮ็ก หรือบิตคอยน์ไม่ปลอดภัย - **โจมตีบุคคลสำคัญ:** เช่น กล่าวหา Satoshi Nakamoto ว่าเป็นอาชญากร หรือกล่าวหาผู้สนับสนุนบิตคอยน์ว่าเป็นพวกต่อต้านรัฐบาล FUD อาจไม่รุนแรงเท่า Brute-Force Attack แต่ก็อันตรายไม่แพ้กัน เพราะสามารถ.. - **ลดความต้องการบิตคอยน์:** ทำให้ราคาบิตคอยน์ร่วงลง - **ขัดขวางการใช้งานบิตคอยน์:** ทำให้คนกลัวและไม่กล้าใช้บิตคอยน์ - **บั่นทอนความเชื่อมั่นในบิตคอยน์:** ทำให้คนลังเล และไม่มั่นใจในอนาคตของบิตคอยน์ ### การออกกฎหมายควบคุม กำแพงกั้นบิตคอยน์ รัฐบาลสามารถใช้กฎหมายเป็นเครื่องมือในการควบคุม และจำกัดการใช้งานบิตคอยน์ เช่น - **ห้ามซื้อขายบิตคอยน์:** ทำให้การซื้อขายบิตคอยน์เป็นเรื่องผิดกฎหมาย - **ควบคุมการแลกเปลี่ยนบิตคอยน์:** เช่น กำหนดให้ Exchange ต้องขอใบอนุญาต และปฏิบัติตามกฎ KYC/AML - **เก็บภาษีบิตคอยน์:** ทำให้การถือครอง และการซื้อขายบิตคอยน์มีต้นทุนสูงขึ้น กฎหมาย เป็นกำแพงที่แข็งแกร่ง ที่สามารถขัดขวางการเติบโตของบิตคอยน์ได้อย่างมีประสิทธิภาพ บิตคอยน์ จึงเป็นมากกว่าเงินดิจิทัล มันคือสัญลักษณ์ของอิสรภาพทางการเงินและการต่อต้านอำนาจ การต่อสู้ระหว่างบิตคอยน์กับอำนาจเก่า จึงเป็นสงครามที่ดุเดือดและไม่มีวันสิ้นสุด ชุมชนบิตคอยน์ต้องตื่นตัว เฝ้าระวัง และ ต่อสู้เพื่อปกป้องอุดมการณ์ของบิตคอยน์ให้คงอยู่ และเติบโตอย่างยั่งยืน # Hyperbitcoinization ยูโทเปียแห่งเสรีภาพหรือดิสโทเปียแห่งการผูกขาด? "Hyperbitcoinization" คือคำที่ใช้อธิบายถึงสถานการณ์สมมติที่บิตคอยน์กลายเป็น **"สกุลเงินหลักของโลก"** แทนที่สกุลเงิน fiat ที่เราใช้กันอยู่ในปัจจุบัน สำหรับสาวกบิตคอยน์ นี่คือฝันหวานที่โลกจะหลุดพ้นจากพันธนาการของรัฐบาลและธนาคารกลาง ที่คอยบงการค่าเงิน และควบคุมระบบเศรษฐกิจ แต่สำหรับผู้ที่มองบิตคอยน์ในแง่ลบ นี่คือฝันร้ายที่อาจนำไปสู่หายนะทางเศรษฐกิจและสังคม ### Hyperbitconization สองด้านของเหรียญ ด้านสว่าง ยูโทเปียแห่งเสรีภาพ - **อิสรภาพทางการเงิน:** ทุกคนมีอำนาจในการควบคุมเงินของตัวเองโดยไม่ต้องพึ่งพาคนกลาง เช่น ธนาคารหรือรัฐบาล - **ความโปร่งใส:** ธุรกรรมบิตคอยน์ถูกบันทึกไว้บน Blockchain ที่เปิดเผยและตรวจสอบได้ ลดปัญหาคอรัปชั่นและการควบคุมแทรกแซง - **การเข้าถึงบริการทางการเงิน:** ทุกคนสามารถเข้าถึงบริการทางการเงินได้ แม้แต่คนที่ไม่มีบัญชีธนาคาร - **ลดต้นทุน:** ค่าธรรมเนียมบิตคอยน์มักจะต่ำกว่าค่าธรรมเนียมของระบบการเงินแบบดั้งเดิม ด้านมืด ดิสโทเปียแห่งการผูกขาด **ความผันผวน:** ราคาบิตคอยน์มีความผันผวนสูง ทำให้ยากต่อการใช้เป็นหน่วยวัดมูลค่าและสื่อกลางในการแลกเปลี่ยน (ด้วยเหตุนี้จึงมีพัฒนาเกิดขึ้นบน Layer 2) - **ความเหลื่อมล้ำ:** คนที่ถือครองบิตคอยน์จำนวนมาก จะมีอำนาจและอิทธิพลเหนือระบบเศรษฐกิจ - **การควบคุมโดยกลุ่มคนหรือองค์กร:** บิตคอยน์อาจถูกครอบงำโดย Mining Pool ขนาดใหญ่ หรือกลุ่มคนที่สมรู้ร่วมคิดกัน - **ความเสี่ยงด้านความปลอดภัย:** บิตคอยน์อาจเสี่ยงต่อการถูกแฮ็ก หรือโจมตีจากผู้ไม่หวังดี Hyperbitcoinization จะเป็นจริงได้อย่างไร? - **การยอมรับอย่างกว้างขวาง:** บิตคอยน์ต้องได้รับการยอมรับจากคนส่วนใหญ่ ทั้งในฐานะสื่อกลางในการแลกเปลี่ยนและหน่วยเก็บมูลค่า - **โครงสร้างพื้นฐานที่แข็งแกร่ง:** ต้องมีระบบและบริการที่รองรับการใช้งานบิตคอยน์อย่างสะดวกและปลอดภัย - **กฎหมายและกฎระเบียบที่เอื้ออำนวย:** รัฐบาลควรสนับสนุนหรืออย่างน้อยก็ไม่ขัดขวางการใช้งานบิตคอยน์ ความเป็นไปได้ของ Hyperbitcoinization ความเป็นไปได้ที่ Hyperbitcoinization จะเกิดขึ้นจริงยังคงเป็นที่ถกเถียงกันอยู่ - **ฝ่ายสนับสนุน:** เชื่อว่าบิตคอยน์มีศักยภาพ ในการปฏิวัติระบบการเงิน และนำไปสู่โลกที่ดีกว่า - **ฝ่ายคัดค้าน:** มองว่าบิตคอยน์เป็นฟองสบู่ที่รอวันแตก และไม่สามารถทดแทนสกุลเงิน fiat ได้ Hyperbitcoinization เป็นอนาคตที่ไม่แน่นอน มันอาจเป็นทั้งฝันหวานและฝันร้าย ขึ้นอยู่กับว่าเราจะกำหนดและจัดการมันอย่างไร สิ่งสำคัญคือการศึกษาทำความเข้าใจ และเตรียมพร้อมสำหรับทุกความเป็นไปได้ เพื่อให้เราสามารถรับมือกับการเปลี่ยนแปลงที่กำลังจะเกิดขึ้นได้ บิตคอยน์ถือกำเนิดขึ้นมาเพียง 14 ปี แต่ได้เขย่าโลกและท้าทายระบบการเงินแบบดั้งเดิมอย่างที่ไม่เคยมีมาก่อน การเดินทางของบิตคอยน์ จึงเปรียบเสมือนมหากาพย์ที่เต็มไปด้วยการต่อสู้ การชิงไหวชิงพริบและความไม่แน่นอน ไม่มีใครสามารถทำนายอนาคตของบิตคอยน์ ได้อย่างแม่นยำ แต่เราสามารถวิเคราะห์และทำความเข้าใจปัจจัยต่างๆ ที่จะกำหนดทิศทางของมันได้ การเดินทางนี้ช่างน่าตื่นเต้นและเต็มไปด้วยความเป็นไปได้ เราทุกคนมีส่วนร่วมในการกำหนดอนาคตของบิตคอยน์ ด้วยการศึกษาทำความเข้าใจและตัดสินใจอย่างชาญฉลาด.. @ 4fe4a528:3ff6bf06
2024-09-01 12:45:44One of the main motivational factors for people to buy bitcoin is it’s ability to store value over time. During harvest we are doing the same thing. We have now harvested our garlic and 1/2 of our onions because if we don’t use the sun’s energy to cure the plants before winter they will start to rot. Let me explain why God has made the world this way; but, first let me explain why storing things isn’t evil. “Do not store up for yourselves treasures on earth, where moth and rust consume and where thieves break in and steal; but store up for yourselves treasures in heaven, where neither moth nor rust consumes and where thieves do not break in and steal. For where your treasure is, there your heart will be also”. Matt. 6:19-21 Is it wrong, then to have a retirement portfolio or even to care about the material things of this world for ourselves or for others? The answer is again both **no** and **yes**. The no comes from the fact that this passage is not the only one in the Bible speaking to questions of wealth and provision for those who are dependent on us. Other passages counsel prudence and forethought, such as, “Those who gather little by little will increase \[wealth\]” (Proverbs 13:11b), and, “The good leave an inheritance to their children’s children” (Proverbs 13:22). God guides Joseph to store up food for seven years in advance of a famine (Genesis 41:25-36), and Jesus speaks favorably in the Parable of the Talents (Matt. 25:14-30). In light of the rest of Scripture, Matthew 6:19-21 cannot be a blanket prohibition. But the **yes** part of the answer is a warning, summed up beautifully in verse 21, “Where your treasure is, there will your heart be also.” In other words, the possessions you own will change you so that you care more about the possessions than about other things.” So choose carefully what you own, for you will inevitably begin to value and protect it to the potential detriment of everything else. How are we to discern the line between appropriate and inappropriate attention to wealth? Jesus answers, “Strive first for the kingdom of God and his righteousness, and all these things will be given to you” So if you believe your heart is following God’s direction **go ahead and harvest your crops and / or buy some bitcoin**. If you would have bought bitcoin one year ago, you would have 127% more purchasing power now. Let’s keep on fearing God and keeping his commandments.
@ 4fe4a528:3ff6bf06
2024-09-01 12:45:44One of the main motivational factors for people to buy bitcoin is it’s ability to store value over time. During harvest we are doing the same thing. We have now harvested our garlic and 1/2 of our onions because if we don’t use the sun’s energy to cure the plants before winter they will start to rot. Let me explain why God has made the world this way; but, first let me explain why storing things isn’t evil. “Do not store up for yourselves treasures on earth, where moth and rust consume and where thieves break in and steal; but store up for yourselves treasures in heaven, where neither moth nor rust consumes and where thieves do not break in and steal. For where your treasure is, there your heart will be also”. Matt. 6:19-21 Is it wrong, then to have a retirement portfolio or even to care about the material things of this world for ourselves or for others? The answer is again both **no** and **yes**. The no comes from the fact that this passage is not the only one in the Bible speaking to questions of wealth and provision for those who are dependent on us. Other passages counsel prudence and forethought, such as, “Those who gather little by little will increase \[wealth\]” (Proverbs 13:11b), and, “The good leave an inheritance to their children’s children” (Proverbs 13:22). God guides Joseph to store up food for seven years in advance of a famine (Genesis 41:25-36), and Jesus speaks favorably in the Parable of the Talents (Matt. 25:14-30). In light of the rest of Scripture, Matthew 6:19-21 cannot be a blanket prohibition. But the **yes** part of the answer is a warning, summed up beautifully in verse 21, “Where your treasure is, there will your heart be also.” In other words, the possessions you own will change you so that you care more about the possessions than about other things.” So choose carefully what you own, for you will inevitably begin to value and protect it to the potential detriment of everything else. How are we to discern the line between appropriate and inappropriate attention to wealth? Jesus answers, “Strive first for the kingdom of God and his righteousness, and all these things will be given to you” So if you believe your heart is following God’s direction **go ahead and harvest your crops and / or buy some bitcoin**. If you would have bought bitcoin one year ago, you would have 127% more purchasing power now. Let’s keep on fearing God and keeping his commandments. @ b2d670de:907f9d4a
2024-08-30 22:52:53# onion-service-nostr-relays A list of nostr relays exposed as onion services. ## The list | Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | [operator](nostr:nprofile1qqst94nsmefmya53crp5qq39kewrtgndqcynhnzp7j8lcu0qjple6jspz3mhxue69uhkummnw3ezummcw3ezuer9wcq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7jxrgyy) | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | [operator](nostr:nprofile1qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmgpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skct9tyup) | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | [operator](nostr:npub1wtuh24gpuxjyvnmjwlvxzg8k0elhasagfmmgz0x8vp4ltcy8ples54e7js) | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | [operator](nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj) | [Payment URL](http://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion) | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | [operator](nostr:npub1an3nz7lczcunpdw6ltjst94hgzcxpppnk7zk3zr2nfcj4yd96kdse6twjd) | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | [operator](nostr:npub1pc57ls4rad5kvsp733suhzl2d4u9y7h4upt952a2pucnalc59teq33dmza) | [Payment URL](hjar34h5zwgtvxr345q7rncso3dhdaryuxgri3lu7lbhmnzvin72z5ad.onion) | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A | | nostr.wine | 🍷 [nostr.wine](https://nostr.wine) relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion) | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 [inbox.nostr.wine](https://inbox.nostr.wine) relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion) | BTC LN, BTC | | filter.nostr.wine | 🍷 [filter.nostr.wine](https://filter.nostr.wine) proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion/add-time) | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | [operator](nostr:nprofile1q9z8wue69uhky6t5vdhkjmnjxejx2dtvddm8sdr5wpmkgmt6wfjxversd3sn2umevyexzenhwp3kzcn2w4cry7rsdy6kgatvvfskgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m30qqs93v545xjl0w8865rhw7kte0mkjxst88rk3k3xj53q4zdxm2zu5ectdn2z6) | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | [operator](nostr:npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2) | N/A | N/A | | nfrelay.app | [nfrelay.app](https://nfrelay.app) aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | [operator](nostr:npub19dn7fq9hlxwjsdtgf28hyakcdmd73cccaf2u7a7vl42echey7ezs2hwja7) | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | [operator](https://nostr.at/aljaz@nostr.si) | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | [operator](nostr:npub19j7zhftjfjnep4xa7zxhevschkqdvem9zr26dq4myhu6d62p3gqs3htnca) |[Payment URL](http://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion) | XMR | ## Contributing Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put `N/A` in empty columns. If you want to contribute anonymously, please contact me on [SimpleX](https://simplex.chat/contact#/?v=2&smp=smp%3A%2F%2F0YuTwO05YJWS8rkjn9eLJDjQhFKvIYd8d4xG8X1blIU%3D%40smp8.simplex.im%2FZ_4q0Nv91wCk8Uekyiaas7NSr-nEDir7%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAvdSLn5QEwrfKQswQGTzlwtXeLMXbzxErv-zOJU6D0y8%253D%26srv%3Dbeccx4yfxxbvyhqypaavemqurytl6hozr47wfc7uuecacjqdvwpw2xid.onion) or send a DM on nostr using a disposable npub. ### Operator column It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
@ b2d670de:907f9d4a
2024-08-30 22:52:53# onion-service-nostr-relays A list of nostr relays exposed as onion services. ## The list | Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | [operator](nostr:nprofile1qqst94nsmefmya53crp5qq39kewrtgndqcynhnzp7j8lcu0qjple6jspz3mhxue69uhkummnw3ezummcw3ezuer9wcq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7jxrgyy) | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | [operator](nostr:nprofile1qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmgpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skct9tyup) | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | [operator](nostr:npub1wtuh24gpuxjyvnmjwlvxzg8k0elhasagfmmgz0x8vp4ltcy8ples54e7js) | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | [operator](nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj) | [Payment URL](http://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion) | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | [operator](nostr:npub1an3nz7lczcunpdw6ltjst94hgzcxpppnk7zk3zr2nfcj4yd96kdse6twjd) | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | [operator](nostr:npub1pc57ls4rad5kvsp733suhzl2d4u9y7h4upt952a2pucnalc59teq33dmza) | [Payment URL](hjar34h5zwgtvxr345q7rncso3dhdaryuxgri3lu7lbhmnzvin72z5ad.onion) | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A | | nostr.wine | 🍷 [nostr.wine](https://nostr.wine) relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion) | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 [inbox.nostr.wine](https://inbox.nostr.wine) relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion) | BTC LN, BTC | | filter.nostr.wine | 🍷 [filter.nostr.wine](https://filter.nostr.wine) proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion/add-time) | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | [operator](nostr:nprofile1q9z8wue69uhky6t5vdhkjmnjxejx2dtvddm8sdr5wpmkgmt6wfjxversd3sn2umevyexzenhwp3kzcn2w4cry7rsdy6kgatvvfskgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m30qqs93v545xjl0w8865rhw7kte0mkjxst88rk3k3xj53q4zdxm2zu5ectdn2z6) | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | [operator](nostr:npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2) | N/A | N/A | | nfrelay.app | [nfrelay.app](https://nfrelay.app) aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | [operator](nostr:npub19dn7fq9hlxwjsdtgf28hyakcdmd73cccaf2u7a7vl42echey7ezs2hwja7) | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | [operator](https://nostr.at/aljaz@nostr.si) | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | [operator](nostr:npub19j7zhftjfjnep4xa7zxhevschkqdvem9zr26dq4myhu6d62p3gqs3htnca) |[Payment URL](http://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion) | XMR | ## Contributing Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put `N/A` in empty columns. If you want to contribute anonymously, please contact me on [SimpleX](https://simplex.chat/contact#/?v=2&smp=smp%3A%2F%2F0YuTwO05YJWS8rkjn9eLJDjQhFKvIYd8d4xG8X1blIU%3D%40smp8.simplex.im%2FZ_4q0Nv91wCk8Uekyiaas7NSr-nEDir7%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAvdSLn5QEwrfKQswQGTzlwtXeLMXbzxErv-zOJU6D0y8%253D%26srv%3Dbeccx4yfxxbvyhqypaavemqurytl6hozr47wfc7uuecacjqdvwpw2xid.onion) or send a DM on nostr using a disposable npub. ### Operator column It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url). @ e6fbeb1c:6ac8fc04
2024-08-29 11:01:52- Carrots from the oven (cold) - Feta cheese - Olive oil - Dill  originally posted at https://stacker.news/items/665360
@ e6fbeb1c:6ac8fc04
2024-08-29 11:01:52- Carrots from the oven (cold) - Feta cheese - Olive oil - Dill  originally posted at https://stacker.news/items/665360 @ 460c25e6:ef85065c
2024-08-29 01:07:22If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one. ## Public Home/Outbox Relays Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, **they will not receive your updates**. Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience. This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to [relay.tools](https://relay.tools/) and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts. ## Public Inbox Relays This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out. Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience. This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to [nostr.watch](https://nostr.watch/relays/find) and find relays in your country Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here. ## DM Inbox Relays These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. **If you don't have it setup, you will miss DMs**. DM Inbox relays should accept any message from anyone, but only allow you to download them. Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy. Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a hidden, but public relay if you want DM notifications from our servers. Make sure to add at least one public relay if you want to see DM notifications. ## Private Home Relays Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools. Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa. ## Search relays: This is the list of relays to use on Amethyst's search and user tagging with @. **Tagging and searching will not work if there is nothing here.**. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com ## Local Relays: This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option. ## General Relays: This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each. Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible. Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them. ## My setup Here's what I use: 1. Go to [relay.tools](https://relay.tools/) and create a relay for yourself. 2. Go to [nostr.wine](https://nostr.wine/) and pay for their subscription. 3. Go to [inbox.nostr.wine](https://inbox.nostr.wine/) and pay for their subscription. 4. Go to [nostr.watch](https://nostr.watch/relays/find) and find a good relay in your country. 5. Download Citrine to your phone. Then, on your relay lists, put: Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. - <your.relay>.nostr1.com Public Inbox Relays - nos.lol or an in-country relay - <your.relay>.nostr1.com DM Inbox Relays - inbox.nostr.wine - <your.relay>.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) - <your.relay>.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com Local Relays - ws://localhost:4869 (Citrine) General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom And a few of the recommended relays from Amethyst. ## Final Considerations Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
@ 460c25e6:ef85065c
2024-08-29 01:07:22If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one. ## Public Home/Outbox Relays Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, **they will not receive your updates**. Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience. This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to [relay.tools](https://relay.tools/) and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts. ## Public Inbox Relays This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out. Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience. This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to [nostr.watch](https://nostr.watch/relays/find) and find relays in your country Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here. ## DM Inbox Relays These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. **If you don't have it setup, you will miss DMs**. DM Inbox relays should accept any message from anyone, but only allow you to download them. Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy. Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a hidden, but public relay if you want DM notifications from our servers. Make sure to add at least one public relay if you want to see DM notifications. ## Private Home Relays Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools. Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa. ## Search relays: This is the list of relays to use on Amethyst's search and user tagging with @. **Tagging and searching will not work if there is nothing here.**. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com ## Local Relays: This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option. ## General Relays: This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each. Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible. Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them. ## My setup Here's what I use: 1. Go to [relay.tools](https://relay.tools/) and create a relay for yourself. 2. Go to [nostr.wine](https://nostr.wine/) and pay for their subscription. 3. Go to [inbox.nostr.wine](https://inbox.nostr.wine/) and pay for their subscription. 4. Go to [nostr.watch](https://nostr.watch/relays/find) and find a good relay in your country. 5. Download Citrine to your phone. Then, on your relay lists, put: Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. - <your.relay>.nostr1.com Public Inbox Relays - nos.lol or an in-country relay - <your.relay>.nostr1.com DM Inbox Relays - inbox.nostr.wine - <your.relay>.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) - <your.relay>.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com Local Relays - ws://localhost:4869 (Citrine) General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom And a few of the recommended relays from Amethyst. ## Final Considerations Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies. @ b83a28b7:35919450
2024-08-28 15:03:25Join nostr:npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 and me for episode 76 of nostr:npub14kw5ygpl6fyqagh9cnrytyaqyacg46lzkq42vz7hk8txdk49kzxs04j7y0 this Friday, August 30th at 3pm ET (UTC -4) Our guest this week is nostr:npub1xv8mzscll8vvy5rsdw7dcqtd2j268a6yupr6gzqh86f2ulhy9kkqmclk3x from nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm who joins us to provide the lowdown on the recently launched Alby Hub You don't want to miss this one! Set your blockclocks! https://nostrnests.com/ [This is our first show announcement made from a long-form client, in keeping with QW and my #otherstuffchallenge]
@ b83a28b7:35919450
2024-08-28 15:03:25Join nostr:npub1tvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq0rkrq4 and me for episode 76 of nostr:npub14kw5ygpl6fyqagh9cnrytyaqyacg46lzkq42vz7hk8txdk49kzxs04j7y0 this Friday, August 30th at 3pm ET (UTC -4) Our guest this week is nostr:npub1xv8mzscll8vvy5rsdw7dcqtd2j268a6yupr6gzqh86f2ulhy9kkqmclk3x from nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm who joins us to provide the lowdown on the recently launched Alby Hub You don't want to miss this one! Set your blockclocks! https://nostrnests.com/ [This is our first show announcement made from a long-form client, in keeping with QW and my #otherstuffchallenge] @ ec09d831:42c80ce4
2024-08-21 17:27:14## Nostr Nedir? Nostr, “**N**otes and **O**ther **S**tuff **T**ransmitted by **R**elays” (Notlar ve Röle ile İletilen Diğer Şeyler) anlamına gelir. HTTP veya TCP-IP gibi, Nostr da bir “protokoldür”; herkesin üzerine bir şeyler inşa edebileceği açık bir standarttır. Nostr’ın kendisi kaydolduğunuz bir uygulama veya hizmet değildir. Nostr basitlik ve elverişlilik amacıyla tasarlanmıştır ve web üzerinde sansüre dirençli ve küresel olarak desentralize (dağıtık) yayıncılık ve iletişim imkânı sağlar. Bunu biraz açalım: ### Basitlik Protokol, çok basit ve esnek olan “Event” nesnelerine (bunlar düz JSON formatında aktarılır) dayanır ve anahtarlar ve imzalama için standart açık anahtarlı kriptografi (public-key cryptography) kullanır. Bu, röleleri çalıştırmayı ve istemciler oluşturmayı kolaylaştırır ve protokolün zaman içinde genişletilebilmesini sağlar. ### Esneklik Nostr, veri taşımak veya depolamak için tek bir yerde toplanmış az sayıdaki güvenilir sunucuya bağımlı olmadığından ötürü çok dayanıklıdır. Protokol, rölelerin kaybolacağını varsayar ve kullanıcıların zaman içinde değiştirebilecekleri rastgele sayıda röleye bağlanmasına ve yayın yapmasına olanak tanır. Bu esneklik gönderilerinizin üzerinde hiçbir kısıtlama ve sansür olmamasını da sağlar. Bir keresinde 15 bin harflik bir makaleyi bile görsel materyaller ve köprü linklerle süsleyerek paylaşabilmiştim. ### Doğrulanabilirlik Nostr hesapları açık anahtar kriptografisine dayandığından, mesajların gerçekten söz konusu kullanıcı tarafından gönderildiğini doğrulamak kolaydır. Bu sayede bot ve troll kalabalığı da yoktur ve küçük bir ihtimal de olsa Nostr'a gelirlerse bunları ortadan kaldırmak gayet kolaydır. ### Anahtarları Anlamak Her Nostr hesabı bir açık/özel anahtar (public/private key) çiftine dayanır. Bunu anlamanın basit bir yolu, açık anahtarınızın kullanıcı adınız ve özel anahtarınızın ise parolanız olduğunu düşünmektir. Parolaların aksine, özel anahtarınız kaybolduğunda sıfırlanamaz veya değiştirilemezlerdir. Anlaşılır olmak adına tekrar söyleyeyim: Özel anahtarınızı kaybederseniz Nostr hesabınız kaybolur. Başka bir kişi özel anahtarınıza erişim sağlarsa, hesabınızın kontrolünü ele geçirebilir. Özel anahtarınızı bir şifre yöneticisi (1Password’ü veya Brave Tarayıcı’yı öneririm) veya Alby gibi bir tarayıcı uzantısında güvenle sakladığınızdan emin olun. ### Protokol vs İstemci Nostr’un kendisi sadece bir protokoldür, yani mesajları ve yayınları internet üzerinde dolaştırmak için üzerinde anlaşılmış bir prosedürdür; Facebook, Twitter, Instagram, YouTube gibi sansürcü, merkeziyetçi, spam ve reklam dolu boktan bir “platform” değildir. Bu yüzden Nostr’a (protokole) bir istemci aracılığıyla erişmeniz gerekir. Bu istemciler web, masaüstü veya mobil uygulamalar şeklinde olabilir. Bazı Nostr istemcileri özel anahtarınızı yapıştırarak oturum açmanıza izin verir. Web’de bu genellikle önerilmez, zira rahatsız edici ve güvensizdir. Bunun yerine, tarayıcınızda özel anahtarları güvenli bir şekilde yönetmek ve Event’leri kriptografik olarak imzalamak için özel olarak tasarlanmış bir yazılım parçası olan bir imzalama uzantısı kullanmanızı öneririm. Bu konuda Alby, Nostr için yerleşik desteğe sahip popüler bir imzalama uzantısı ve Bitcoin Lightning Network cüzdanıdır. Yeni kullanıcılar için harika bir seçenektir. Alby’nin kurulumunu aşağıda gerekli olduğu yerlerde istemciye özel kılavuzda ele alacağım. İşte birkaç farklı istemci ve kullanılabildikleri işletim sistemleri: [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst) (Android) [Benim favorim.] [Primal](https://primal.net/) (Web, iOS, Android) [Mobil cihazlarda yerleşik Bitcoin Lightning Network cüzdanı ile kullanıcı dostu istemci.] [Snort](https://snort.social/) (Web) [Temiz ve hızlı web istemcisi.] [Coracle](https://coracle.social/) (Web) [Röle navigasyonuna odaklanan bir istemci.] [Habla](https://habla.news/) (Web) [Kolay blog yaratımı.] [Highlighter](https://highlighter.com/) (Web) [Blog yaratımı ve bloglarda gezerken işaretleme-alıntılama için uygun arayüze sahip istemci.] [Iris](https://iris.to/) (Web) [Ücretsiz NIP-05 doğrulama sağlayan istemci.] [Damus](https://damus.io/) (iOS) [Apple cihazlarına özel aplikasyon istemci.] Amethyst Android istemcisi ile Nostr kullanmaya başlamak için adım adım kılavuz #### Adım 1: Uygulama yükleme * Android telefonların aplikasyon mağazası olan Google Play Store’dan Amethyst uygulamasını yükleyin: https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst * Uygulamayı açtığınızda, yeni bir hesap oluşturma veya daha önce oluşturduğunuz bir özel anahtarla giriş yapma seçeneğiniz olacaktır. * Alby uzantısı veya başka bir istemci aracılığıyla zaten bir özel anahtar oluşturduysanız, kullanım koşullarını okuyup kabul edebilir, (npub/nsec) bilgilerinizi girebilir ve “Login” (Giriş Yap) düğmesine tıklayabilirsiniz. * Eğer bunlar yoksa, “Generate a new key” (Yeni bir anahtar oluştur) seçeneğine tıklayın. #### Adım 2: Yeni bir hesap oluşturma ve onun ayarlarını yapma * “Terms of Use” (Kullanım Koşulları) bölümünü okuyun ve kutuyu işaretleyin. * “Generate a new key” (Yeni bir anahtar oluştur) seçeneğine tıklayın. * Tebrikler, az önce yeni bir Nostr kimliği oluşturdunuz! * Ana ekrana yönlendirilecek ve “Feed is empty. Refresh” (Akış boş, yenileyin) mesajıyla karşılaşacaksınız, çünkü henüz başka bir hesabı takip etmiyorsunuz. Bunu daha sonra halledeceğiz. * Son bir aşırı önemli adım kaldı. Özel anahtarınızı güvenli bir yerde saklamalısınız. Bunu yapmak için, şu anda profil resminiz olarak görünen sol üst köşedeki garip görünümlü robot simgesine tıklayın. Bir kenar çubuğu açılacaktır. * “Backup Keys” (Yedek Anahtarlar) kısmına gidin ve “Copy my secret key” (Gizli anahtarımı kopyala) seçeneğine tıklayın. * “Nsec” ibaresiyle başlayan gizli anahtarınız artık akıllı telefonunuzun panosundadır, bunu ÇOK güvenli bir yerde veya bir .txt uzantılı belgede yapıştırıp saklamak en iyisidir. * Şimdi hesabınızı oluşturmaya devam edebilirsiniz. Ana ekranın sol üst köşesindeki profil resminize geri dönün ve “Profile” (Profil) bölümüne gidin. Buradan, “Follow” (Takip Et) seçeneğinin solundaki üç çizgi ve kalemin bulunduğu simgeye tıklayın. Profil ayarlarınızı buradan yapabilirsiniz. * “Display Name” (Görüntülenecek Ad) bölümüne yazacağınız şey nick’iniz olacaktır. * “About me” küçük bir biyografi bölümüdür ve harf sınırı yoktur. * “Avatar URL” ve “Banner URL” kutularının içinde, solda görsel yükleme simgeleri vardır. Burada profil resminiz ve banner’ınız hakkında ne yapabileceğinizi bilirsiniz. * “Nostr Address” ve “LN Address” kutuları için şöyle bir süreç işliyor: Eğer bir Alby hesabı edinebildiyseniz (şu an üye alımı sadece Alby geliştiricilerine getalby.com üzerinden yollanacak bir mektubun ardından gelebilecek davetiye kodu sayesinde mümkün) “@getalby.com” uzantılı adresinizi bu kutuların ikisini de yazmalısınızdır. Bu sayede hem hesabınızın size özgün ve gerçek olduğu (diğer bir deyişle, bot olmadığınız) anlaşılmış olur hem de gönderilerinize beğeni veya bağış maksatlı yollanan Bitcoin Satoshi’lerinin birikmesi için (ve sizin de başkalarına yollayabilmeniz, yani Zap yapabilmeniz için) bir Lightning Network sıcak cüzdanı adresi tesis etmiş olursunuz. Alby hesabı edinme konusunda -ki bence Alby çok önemli- yardımcı olmamı isterseniz iletişime geçmekten çekinmeyin. * Tamamdır, hesabınız artık hazır, şimdi akışınızı dolduralım ve diğer insanları takip edelim: Sağ üst köşedeki büyüteç simgeli arama butonuna tıklayın ve tanıdığınız kişilerin hesaplarını arayın ya da sol alttaki ev simgesine tıklayarak gideceğiniz ana ekrandaki “All Follows” butonuna tıklayın ve “Global”i seçin. Şimdi bağlı rölelerinize gönderilen tüm notları göreceksinizdir. Eğer bunalmış hissediyorsanız, endişelenmeyin, zamanla burada yeni birçok ilginç Nostr kullanıcısı bulabileceksinizdir. Sadece bir deneyin. #### Adım 3: Röleler ve Geniş Çaplı Erişim/Yayın Yeni röleler ekleyerek erişiminizi ve görünürlüğünüzü artırabilirsiniz. Bunun için yapmanız gereken aşağıda listeleyeceğim röleleri hesabınıza entegre etmektir. Röle entegrasyonu için öncelikle sol üstteki profil resminize tıkladığınızda açılan menüde “Relays” bölümüne giriyorsunuz. Burada, en aşağıda “Add Relay” yazan kutucuğa oluşturduğum listedeki röle adreslerini tek tek girip “Add” butonuna tıklıyorsunuz. İstediğiniz kadar röle ekleyebilirsiniz, tamamen size kalmış. Bu iş bitince mutlaka sağ üstteki “Save” butonuna tıklayın. Ayrıca kişisel bilgisayarınızdan Coracle adlı Nostr istemcisine girerek de rölelere kolaylıkla bağlanabilirsiniz. Tek yapmanız gereken Coracle’da Nostr hesabınıza Nsec anahtarınızla giriş yapmak ve sol kenar menüdeki “Relays” bölümünü açıp listelendiğini gördüğünüz her bir rölenin sağındaki “Join” butonuna tıklamaktır. Röle listesi: 140.f7z.io astral.ninja bevo.nostr1.com bitcoiner.social brb.io carnivore-diet-relay.denizenid.com eu.purplerelay.com expensive-relay.fiatjaf.com feeds.nostr.band/popular fiatjaf.com n.wingu.se nos.lol nostr-pub.semisol.dev nostr-relay.wlvs.space nostr.21l.st nostr.band nostr.bitcoiner.social nostr.blipme.app nostr.kollider.xyz nostr.liberty.fans nostr.mutinywallet.com nostr.orangepill.dev nostr.pleb.network nostr.plebchain.org nostr.relayer.se nostr.satoshi.fun nostr.walletofsatoshi.com nostr.yuv.al nostr.zbd.gg nostr.zebedee.cloud nostr.zerofiat.world nostr1.tunnelsats.com nostream.denizenid.com nostria.space offchain.pub purplepag.es pyramid.fiatjaf.com relay.0xchat.com relay.benthecarman.com relay.bitcoinpark.com relay.current.fyi relay.damus.io relay.f7z.io relay.geyser.fund relay.mutinywallet.com relay.nostr.band relay.nostr.bg relay.nostr.net relay.nostr3.io relay.nostrati.com relay.nostrplebs.com relay.orangepill.dev relay.plebstr.com relay.primal.net relay.snort.band relay.snort.social relay.utxo.one relayable.org relayer.fiatjaf.com satstacker.cloud snort.social soloco.nl sound-money-relay.denizenid.com  **Önemli:** Özel anahtarınız yerel olarak (mobil cihazınızda veya bilgisayarlarınızda) saklanır ve Amethyst sunucuları veya Snort, Iris, Primal, Coracle gibi diğer tüm Nostr istemcileri tarafından hiçbir şekilde toplanmaz veya saklanmaz, zira Nostr’ın olayı budur, yani desentralizasyon protokolü. Zamanla internetin kurtarıcısı olacak bu öze dönüş gücüne sahip sosyal ağda beni ve arkadaşlarımı takip etmeyi ve bizim takip ettiğimiz kişilerden kimleri bulabileceğinizi kurcalamayı unutmayın: Kaan: nostr:npub1asyasvv6vhkuk44ttczsz2v0xvp3c6ze9xqrg9n97n6mkskgpnjqmdugs9 Satoshi Nakamoto Enstitüsü Türkiye: nostr:npub1fdv8r32dqehlkxfnq3uld67vq8t46jw5jvzkk0h6rl4hyvd8g76qf7ujf6 Ludwig von Mises Enstitüsü Türkiye: nostr:npub1gfytsf2p5kw2c42032fkt845x8gh00e027nwnn3pr5880yy954qq4wqlqm Efe Bitcoin: nostr:npub193h05grv6ykgqc94memmlppqe2wlclukpfl8g5750w8gr3002zasl7ngwj Şükrü Day: nostr:npub1gw3zhc5r5a7jfgl6yx8qv0nc9kset5ddkrka229c3tym5xltehlq58m7mm Emir Yorulmaz: nostr:npub1mmfakwg4s36235wlav6qpe03cgr038gujn2hnsvwk2ne49gzqslqc6xvtp Hasan Tahsin: nostr:npub19zc3ja6jme9ul84sfmgyf5z96a07m6x9dp2jngl5zhwryku9aynsy89q3u Ufuk: nostr:npub19mz7c6jesdczvlumhpzqekqh9v93w0whup73mu3x2v6jv97lfujq79nqu3 Furkan Arda: nostr:npub1z43kexnw7wxd22ystexyhgf0s7lzsqzfaxv5xvlk9sgspkfzdyps039jv6 Kaancap: nostr:npub14t06hns8wmymynccmcer7sp6y3eql7pjyzwcp0u5rk88sv7vt2rqrl4wte Yankı Guapmann: nostr:npub19z5m92x8jlltva7zj47z9ydxle8ddkw8y3k5e8xnrphu724v9lys5wxt3p Arda Uludağ: nostr:npub1puclr9p6yhel2duzask9wfdah0ux5cppw22uz62c0w9cdj3nv0wseuvedh Musab Babayiğit: nostr:npub1euf7xgdws7n62nwv03fhu82ak24xrka7hedathyuyq9hmhcjxs7sfvwjsn Kadir: nostr:npub18589me8hqqmt5ect7hjz5k6d2srxzere0uc975gq7hldp9v3qpkslxjn7p Çınar: nostr:npub12mwsgqaejk98xcsv8k7rf3yat2t2kzu0zzma6jp39rphqx5hajsq4khdeg Nur Parrhesia: nostr:npub16nnuyfrxguumqdt8xerkkhtgjyxa7qyvfnz4r4ameanqp4aggarqm877qw Ömer Agâh: nostr:npub1eeze28u72zfa8hl8kfkfnl4jwfe07zsrukug237rsjre7wnvzlrsl49u8h Korporatist Mağduru: nostr:npub1337wmdvjtxrne5fxrqtc7re8rtj88wnnnsfg562jg39sx2k9p5lqwcjsfh Alfred: nostr:npub1mdyegp38ahjcpje7ugzmt4ylugrk3hfmwm9tqq72jhdg3ykc4ahs8svgs8 Sefa Uzuner: nostr:npub1ce0khypkfrjxga6umfd82fhtg9xldm583mys4pkvg8zex20gls9s9qrrgj 
@ ec09d831:42c80ce4
2024-08-21 17:27:14## Nostr Nedir? Nostr, “**N**otes and **O**ther **S**tuff **T**ransmitted by **R**elays” (Notlar ve Röle ile İletilen Diğer Şeyler) anlamına gelir. HTTP veya TCP-IP gibi, Nostr da bir “protokoldür”; herkesin üzerine bir şeyler inşa edebileceği açık bir standarttır. Nostr’ın kendisi kaydolduğunuz bir uygulama veya hizmet değildir. Nostr basitlik ve elverişlilik amacıyla tasarlanmıştır ve web üzerinde sansüre dirençli ve küresel olarak desentralize (dağıtık) yayıncılık ve iletişim imkânı sağlar. Bunu biraz açalım: ### Basitlik Protokol, çok basit ve esnek olan “Event” nesnelerine (bunlar düz JSON formatında aktarılır) dayanır ve anahtarlar ve imzalama için standart açık anahtarlı kriptografi (public-key cryptography) kullanır. Bu, röleleri çalıştırmayı ve istemciler oluşturmayı kolaylaştırır ve protokolün zaman içinde genişletilebilmesini sağlar. ### Esneklik Nostr, veri taşımak veya depolamak için tek bir yerde toplanmış az sayıdaki güvenilir sunucuya bağımlı olmadığından ötürü çok dayanıklıdır. Protokol, rölelerin kaybolacağını varsayar ve kullanıcıların zaman içinde değiştirebilecekleri rastgele sayıda röleye bağlanmasına ve yayın yapmasına olanak tanır. Bu esneklik gönderilerinizin üzerinde hiçbir kısıtlama ve sansür olmamasını da sağlar. Bir keresinde 15 bin harflik bir makaleyi bile görsel materyaller ve köprü linklerle süsleyerek paylaşabilmiştim. ### Doğrulanabilirlik Nostr hesapları açık anahtar kriptografisine dayandığından, mesajların gerçekten söz konusu kullanıcı tarafından gönderildiğini doğrulamak kolaydır. Bu sayede bot ve troll kalabalığı da yoktur ve küçük bir ihtimal de olsa Nostr'a gelirlerse bunları ortadan kaldırmak gayet kolaydır. ### Anahtarları Anlamak Her Nostr hesabı bir açık/özel anahtar (public/private key) çiftine dayanır. Bunu anlamanın basit bir yolu, açık anahtarınızın kullanıcı adınız ve özel anahtarınızın ise parolanız olduğunu düşünmektir. Parolaların aksine, özel anahtarınız kaybolduğunda sıfırlanamaz veya değiştirilemezlerdir. Anlaşılır olmak adına tekrar söyleyeyim: Özel anahtarınızı kaybederseniz Nostr hesabınız kaybolur. Başka bir kişi özel anahtarınıza erişim sağlarsa, hesabınızın kontrolünü ele geçirebilir. Özel anahtarınızı bir şifre yöneticisi (1Password’ü veya Brave Tarayıcı’yı öneririm) veya Alby gibi bir tarayıcı uzantısında güvenle sakladığınızdan emin olun. ### Protokol vs İstemci Nostr’un kendisi sadece bir protokoldür, yani mesajları ve yayınları internet üzerinde dolaştırmak için üzerinde anlaşılmış bir prosedürdür; Facebook, Twitter, Instagram, YouTube gibi sansürcü, merkeziyetçi, spam ve reklam dolu boktan bir “platform” değildir. Bu yüzden Nostr’a (protokole) bir istemci aracılığıyla erişmeniz gerekir. Bu istemciler web, masaüstü veya mobil uygulamalar şeklinde olabilir. Bazı Nostr istemcileri özel anahtarınızı yapıştırarak oturum açmanıza izin verir. Web’de bu genellikle önerilmez, zira rahatsız edici ve güvensizdir. Bunun yerine, tarayıcınızda özel anahtarları güvenli bir şekilde yönetmek ve Event’leri kriptografik olarak imzalamak için özel olarak tasarlanmış bir yazılım parçası olan bir imzalama uzantısı kullanmanızı öneririm. Bu konuda Alby, Nostr için yerleşik desteğe sahip popüler bir imzalama uzantısı ve Bitcoin Lightning Network cüzdanıdır. Yeni kullanıcılar için harika bir seçenektir. Alby’nin kurulumunu aşağıda gerekli olduğu yerlerde istemciye özel kılavuzda ele alacağım. İşte birkaç farklı istemci ve kullanılabildikleri işletim sistemleri: [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst) (Android) [Benim favorim.] [Primal](https://primal.net/) (Web, iOS, Android) [Mobil cihazlarda yerleşik Bitcoin Lightning Network cüzdanı ile kullanıcı dostu istemci.] [Snort](https://snort.social/) (Web) [Temiz ve hızlı web istemcisi.] [Coracle](https://coracle.social/) (Web) [Röle navigasyonuna odaklanan bir istemci.] [Habla](https://habla.news/) (Web) [Kolay blog yaratımı.] [Highlighter](https://highlighter.com/) (Web) [Blog yaratımı ve bloglarda gezerken işaretleme-alıntılama için uygun arayüze sahip istemci.] [Iris](https://iris.to/) (Web) [Ücretsiz NIP-05 doğrulama sağlayan istemci.] [Damus](https://damus.io/) (iOS) [Apple cihazlarına özel aplikasyon istemci.] Amethyst Android istemcisi ile Nostr kullanmaya başlamak için adım adım kılavuz #### Adım 1: Uygulama yükleme * Android telefonların aplikasyon mağazası olan Google Play Store’dan Amethyst uygulamasını yükleyin: https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst * Uygulamayı açtığınızda, yeni bir hesap oluşturma veya daha önce oluşturduğunuz bir özel anahtarla giriş yapma seçeneğiniz olacaktır. * Alby uzantısı veya başka bir istemci aracılığıyla zaten bir özel anahtar oluşturduysanız, kullanım koşullarını okuyup kabul edebilir, (npub/nsec) bilgilerinizi girebilir ve “Login” (Giriş Yap) düğmesine tıklayabilirsiniz. * Eğer bunlar yoksa, “Generate a new key” (Yeni bir anahtar oluştur) seçeneğine tıklayın. #### Adım 2: Yeni bir hesap oluşturma ve onun ayarlarını yapma * “Terms of Use” (Kullanım Koşulları) bölümünü okuyun ve kutuyu işaretleyin. * “Generate a new key” (Yeni bir anahtar oluştur) seçeneğine tıklayın. * Tebrikler, az önce yeni bir Nostr kimliği oluşturdunuz! * Ana ekrana yönlendirilecek ve “Feed is empty. Refresh” (Akış boş, yenileyin) mesajıyla karşılaşacaksınız, çünkü henüz başka bir hesabı takip etmiyorsunuz. Bunu daha sonra halledeceğiz. * Son bir aşırı önemli adım kaldı. Özel anahtarınızı güvenli bir yerde saklamalısınız. Bunu yapmak için, şu anda profil resminiz olarak görünen sol üst köşedeki garip görünümlü robot simgesine tıklayın. Bir kenar çubuğu açılacaktır. * “Backup Keys” (Yedek Anahtarlar) kısmına gidin ve “Copy my secret key” (Gizli anahtarımı kopyala) seçeneğine tıklayın. * “Nsec” ibaresiyle başlayan gizli anahtarınız artık akıllı telefonunuzun panosundadır, bunu ÇOK güvenli bir yerde veya bir .txt uzantılı belgede yapıştırıp saklamak en iyisidir. * Şimdi hesabınızı oluşturmaya devam edebilirsiniz. Ana ekranın sol üst köşesindeki profil resminize geri dönün ve “Profile” (Profil) bölümüne gidin. Buradan, “Follow” (Takip Et) seçeneğinin solundaki üç çizgi ve kalemin bulunduğu simgeye tıklayın. Profil ayarlarınızı buradan yapabilirsiniz. * “Display Name” (Görüntülenecek Ad) bölümüne yazacağınız şey nick’iniz olacaktır. * “About me” küçük bir biyografi bölümüdür ve harf sınırı yoktur. * “Avatar URL” ve “Banner URL” kutularının içinde, solda görsel yükleme simgeleri vardır. Burada profil resminiz ve banner’ınız hakkında ne yapabileceğinizi bilirsiniz. * “Nostr Address” ve “LN Address” kutuları için şöyle bir süreç işliyor: Eğer bir Alby hesabı edinebildiyseniz (şu an üye alımı sadece Alby geliştiricilerine getalby.com üzerinden yollanacak bir mektubun ardından gelebilecek davetiye kodu sayesinde mümkün) “@getalby.com” uzantılı adresinizi bu kutuların ikisini de yazmalısınızdır. Bu sayede hem hesabınızın size özgün ve gerçek olduğu (diğer bir deyişle, bot olmadığınız) anlaşılmış olur hem de gönderilerinize beğeni veya bağış maksatlı yollanan Bitcoin Satoshi’lerinin birikmesi için (ve sizin de başkalarına yollayabilmeniz, yani Zap yapabilmeniz için) bir Lightning Network sıcak cüzdanı adresi tesis etmiş olursunuz. Alby hesabı edinme konusunda -ki bence Alby çok önemli- yardımcı olmamı isterseniz iletişime geçmekten çekinmeyin. * Tamamdır, hesabınız artık hazır, şimdi akışınızı dolduralım ve diğer insanları takip edelim: Sağ üst köşedeki büyüteç simgeli arama butonuna tıklayın ve tanıdığınız kişilerin hesaplarını arayın ya da sol alttaki ev simgesine tıklayarak gideceğiniz ana ekrandaki “All Follows” butonuna tıklayın ve “Global”i seçin. Şimdi bağlı rölelerinize gönderilen tüm notları göreceksinizdir. Eğer bunalmış hissediyorsanız, endişelenmeyin, zamanla burada yeni birçok ilginç Nostr kullanıcısı bulabileceksinizdir. Sadece bir deneyin. #### Adım 3: Röleler ve Geniş Çaplı Erişim/Yayın Yeni röleler ekleyerek erişiminizi ve görünürlüğünüzü artırabilirsiniz. Bunun için yapmanız gereken aşağıda listeleyeceğim röleleri hesabınıza entegre etmektir. Röle entegrasyonu için öncelikle sol üstteki profil resminize tıkladığınızda açılan menüde “Relays” bölümüne giriyorsunuz. Burada, en aşağıda “Add Relay” yazan kutucuğa oluşturduğum listedeki röle adreslerini tek tek girip “Add” butonuna tıklıyorsunuz. İstediğiniz kadar röle ekleyebilirsiniz, tamamen size kalmış. Bu iş bitince mutlaka sağ üstteki “Save” butonuna tıklayın. Ayrıca kişisel bilgisayarınızdan Coracle adlı Nostr istemcisine girerek de rölelere kolaylıkla bağlanabilirsiniz. Tek yapmanız gereken Coracle’da Nostr hesabınıza Nsec anahtarınızla giriş yapmak ve sol kenar menüdeki “Relays” bölümünü açıp listelendiğini gördüğünüz her bir rölenin sağındaki “Join” butonuna tıklamaktır. Röle listesi: 140.f7z.io astral.ninja bevo.nostr1.com bitcoiner.social brb.io carnivore-diet-relay.denizenid.com eu.purplerelay.com expensive-relay.fiatjaf.com feeds.nostr.band/popular fiatjaf.com n.wingu.se nos.lol nostr-pub.semisol.dev nostr-relay.wlvs.space nostr.21l.st nostr.band nostr.bitcoiner.social nostr.blipme.app nostr.kollider.xyz nostr.liberty.fans nostr.mutinywallet.com nostr.orangepill.dev nostr.pleb.network nostr.plebchain.org nostr.relayer.se nostr.satoshi.fun nostr.walletofsatoshi.com nostr.yuv.al nostr.zbd.gg nostr.zebedee.cloud nostr.zerofiat.world nostr1.tunnelsats.com nostream.denizenid.com nostria.space offchain.pub purplepag.es pyramid.fiatjaf.com relay.0xchat.com relay.benthecarman.com relay.bitcoinpark.com relay.current.fyi relay.damus.io relay.f7z.io relay.geyser.fund relay.mutinywallet.com relay.nostr.band relay.nostr.bg relay.nostr.net relay.nostr3.io relay.nostrati.com relay.nostrplebs.com relay.orangepill.dev relay.plebstr.com relay.primal.net relay.snort.band relay.snort.social relay.utxo.one relayable.org relayer.fiatjaf.com satstacker.cloud snort.social soloco.nl sound-money-relay.denizenid.com  **Önemli:** Özel anahtarınız yerel olarak (mobil cihazınızda veya bilgisayarlarınızda) saklanır ve Amethyst sunucuları veya Snort, Iris, Primal, Coracle gibi diğer tüm Nostr istemcileri tarafından hiçbir şekilde toplanmaz veya saklanmaz, zira Nostr’ın olayı budur, yani desentralizasyon protokolü. Zamanla internetin kurtarıcısı olacak bu öze dönüş gücüne sahip sosyal ağda beni ve arkadaşlarımı takip etmeyi ve bizim takip ettiğimiz kişilerden kimleri bulabileceğinizi kurcalamayı unutmayın: Kaan: nostr:npub1asyasvv6vhkuk44ttczsz2v0xvp3c6ze9xqrg9n97n6mkskgpnjqmdugs9 Satoshi Nakamoto Enstitüsü Türkiye: nostr:npub1fdv8r32dqehlkxfnq3uld67vq8t46jw5jvzkk0h6rl4hyvd8g76qf7ujf6 Ludwig von Mises Enstitüsü Türkiye: nostr:npub1gfytsf2p5kw2c42032fkt845x8gh00e027nwnn3pr5880yy954qq4wqlqm Efe Bitcoin: nostr:npub193h05grv6ykgqc94memmlppqe2wlclukpfl8g5750w8gr3002zasl7ngwj Şükrü Day: nostr:npub1gw3zhc5r5a7jfgl6yx8qv0nc9kset5ddkrka229c3tym5xltehlq58m7mm Emir Yorulmaz: nostr:npub1mmfakwg4s36235wlav6qpe03cgr038gujn2hnsvwk2ne49gzqslqc6xvtp Hasan Tahsin: nostr:npub19zc3ja6jme9ul84sfmgyf5z96a07m6x9dp2jngl5zhwryku9aynsy89q3u Ufuk: nostr:npub19mz7c6jesdczvlumhpzqekqh9v93w0whup73mu3x2v6jv97lfujq79nqu3 Furkan Arda: nostr:npub1z43kexnw7wxd22ystexyhgf0s7lzsqzfaxv5xvlk9sgspkfzdyps039jv6 Kaancap: nostr:npub14t06hns8wmymynccmcer7sp6y3eql7pjyzwcp0u5rk88sv7vt2rqrl4wte Yankı Guapmann: nostr:npub19z5m92x8jlltva7zj47z9ydxle8ddkw8y3k5e8xnrphu724v9lys5wxt3p Arda Uludağ: nostr:npub1puclr9p6yhel2duzask9wfdah0ux5cppw22uz62c0w9cdj3nv0wseuvedh Musab Babayiğit: nostr:npub1euf7xgdws7n62nwv03fhu82ak24xrka7hedathyuyq9hmhcjxs7sfvwjsn Kadir: nostr:npub18589me8hqqmt5ect7hjz5k6d2srxzere0uc975gq7hldp9v3qpkslxjn7p Çınar: nostr:npub12mwsgqaejk98xcsv8k7rf3yat2t2kzu0zzma6jp39rphqx5hajsq4khdeg Nur Parrhesia: nostr:npub16nnuyfrxguumqdt8xerkkhtgjyxa7qyvfnz4r4ameanqp4aggarqm877qw Ömer Agâh: nostr:npub1eeze28u72zfa8hl8kfkfnl4jwfe07zsrukug237rsjre7wnvzlrsl49u8h Korporatist Mağduru: nostr:npub1337wmdvjtxrne5fxrqtc7re8rtj88wnnnsfg562jg39sx2k9p5lqwcjsfh Alfred: nostr:npub1mdyegp38ahjcpje7ugzmt4ylugrk3hfmwm9tqq72jhdg3ykc4ahs8svgs8 Sefa Uzuner: nostr:npub1ce0khypkfrjxga6umfd82fhtg9xldm583mys4pkvg8zex20gls9s9qrrgj  @ eed76ece:afa98124
2024-08-21 09:28:39เราขายส่ง ผลิต นำเข้า ส่งออก: เสื้อเชิ้ตผู้ชาย 100% Cotton ผ้าซารองชายหาด ไซส์เต็ม ไม่มีชายระบาย หมวกเบสบอล 100% Cotton สไตล์แผง สายปรับได้ ปริมาณสั่งซื้อขั้นต่ำ 72 ชิ้น สินค้าคละประเภท การขนส่งทางอากาศระหว่างประเทศ DHL, FedEx, United Parcel Service ตัวแทน ตัวแทนจำหน่าย ผู้จัดจำหน่าย ผู้นำเข้า ผู้ส่งออก ผู้ขายต่อ ผู้ค้า ผู้ค้าส่ง โดยเฉพาะใน กัมพูชา: พนมเปญ เสียมเรียบ ลาว: ตาโลตเซา เวียงจันทน์ ประเทศไทย: กรุงเทพฯ เชียงใหม่ พัทยา สหรัฐอาหรับเอมิเรตส์ ดูไบ เวียดนาม: ดานัง ฮานอย กรุณาถามหาฉัน ริช LINE @ Globalmerchant https://globalmerchant.io/pages/thailand originally posted at https://stacker.news/items/656681
@ eed76ece:afa98124
2024-08-21 09:28:39เราขายส่ง ผลิต นำเข้า ส่งออก: เสื้อเชิ้ตผู้ชาย 100% Cotton ผ้าซารองชายหาด ไซส์เต็ม ไม่มีชายระบาย หมวกเบสบอล 100% Cotton สไตล์แผง สายปรับได้ ปริมาณสั่งซื้อขั้นต่ำ 72 ชิ้น สินค้าคละประเภท การขนส่งทางอากาศระหว่างประเทศ DHL, FedEx, United Parcel Service ตัวแทน ตัวแทนจำหน่าย ผู้จัดจำหน่าย ผู้นำเข้า ผู้ส่งออก ผู้ขายต่อ ผู้ค้า ผู้ค้าส่ง โดยเฉพาะใน กัมพูชา: พนมเปญ เสียมเรียบ ลาว: ตาโลตเซา เวียงจันทน์ ประเทศไทย: กรุงเทพฯ เชียงใหม่ พัทยา สหรัฐอาหรับเอมิเรตส์ ดูไบ เวียดนาม: ดานัง ฮานอย กรุณาถามหาฉัน ริช LINE @ Globalmerchant https://globalmerchant.io/pages/thailand originally posted at https://stacker.news/items/656681 @ 20986fb8:cdac21b3
2024-08-20 14:19:59Welcome to YakiHonne, where we’re excited to introduce you to our innovative Smart Widgets! These interactive components allow you to create dynamic and engaging campaigns directly within social feeds, all without needing any coding skills. Whether you’re new to Smart Widgets or looking to refine your approach, this guide will walk you through the process. ### Step 1: Log In Start by logging into your YakiHonne account. This is your gateway to creating and managing Smart Widgets. If you don’t have an account yet, sign up easily on our website. ### Step 2: Create Smart Widgets Once you’re logged in, it’s time to get creative. Head over to the “Post” section and select “Smart Widget.” Here, you have two options: **Option 1: Create from Scratch** If you have a specific idea in mind, you can create your Smart Widget from a blank canvas: • Click on “Create Blank Widget.” • Begin designing by adding your unique content, interactive features, and any elements that match your campaign’s needs. • Customize the appearance and functionality to fit your brand or message. **Option 2: Choose a Template** If you’re not sure where to start or want some inspiration, using a template is a great option: • Select “Templates” from the options available. • Browse through a variety of pre-designed templates. • Choose one that fits your campaign’s goal, and customize it to make it your own. **Option 3: Clone a Community Widget** If you want to explore what others are doing, you can clone a widget shared by the community: • Click on “Smart Widgets” to see what the community has shared. • Browse through the community’s shared Smart Widgets. • Find a widget you like, and click “Clone.” • Modify the copied widget to create your unique Smart Widget.  ### Step 3: Explore Smart Widgets Features Your Smart Widgets can do much more than just display content. Let’s dive into the features you can integrate: • User Engagement Tools: Add polls, surveys, or quizzes to interact with your audience. • BitcoinFi Integration: Enable features that support Bitcoin transactions, like tipping or payment gateways. • Governance Options: Incorporate voting systems to allow users to participate in decision-making processes. • Product Growth: Use widgets to drive user growth through referral programs or viral marketing techniques.   These features are designed to enhance interaction and make your Smart Widget stand out. Feel free to experiment with different combinations to see what works best for your campaign. ### Step 4: Publish Your Smart Widgets After you’ve created and customized your Smart Widget, it’s time to share it with the world: • Preview your widget to ensure everything looks and works as intended. • Click “Post my Smart Widget” to publish it. • Your widget is now live and ready for others to interact with in their social feeds.  ### Step 5: Add Smart Widgets to Notes To maximize the impact of your Smart Widget, you can integrate it into your Notes: • Go to the “Notes” section on your dashboard. • Select “Add Smart Widget” and choose the widget you’ve just created. • Publish the note, and now your audience can engage with your Smart Widget directly through the note.  ### Tips for Success * Experiment with Features: Don’t hesitate to try out different combinations of features to find what works best for your audience. * Engage Your Audience: The more interactive and engaging your Smart Widget is, the better the results. * Monitor Performance: After publishing, keep an eye on how your Smart Widget is performing. Adjust and optimize based on user feedback and engagement metrics. ### User Guideline Video Resources [Create from Scratch](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y) [Choose a Template](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y) [Clone a Community Widget](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y) [Full tutorial video ](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y) ### Conclusion Creating and using Smart Widgets on YakiHonne is a powerful way to engage with your audience, promote your brand, and drive meaningful interactions. With no coding required, the possibilities are endless. Start exploring today, and see how Smart Widgets can take your campaigns to the next level! Happy creating!
@ 20986fb8:cdac21b3
2024-08-20 14:19:59Welcome to YakiHonne, where we’re excited to introduce you to our innovative Smart Widgets! These interactive components allow you to create dynamic and engaging campaigns directly within social feeds, all without needing any coding skills. Whether you’re new to Smart Widgets or looking to refine your approach, this guide will walk you through the process. ### Step 1: Log In Start by logging into your YakiHonne account. This is your gateway to creating and managing Smart Widgets. If you don’t have an account yet, sign up easily on our website. ### Step 2: Create Smart Widgets Once you’re logged in, it’s time to get creative. Head over to the “Post” section and select “Smart Widget.” Here, you have two options: **Option 1: Create from Scratch** If you have a specific idea in mind, you can create your Smart Widget from a blank canvas: • Click on “Create Blank Widget.” • Begin designing by adding your unique content, interactive features, and any elements that match your campaign’s needs. • Customize the appearance and functionality to fit your brand or message. **Option 2: Choose a Template** If you’re not sure where to start or want some inspiration, using a template is a great option: • Select “Templates” from the options available. • Browse through a variety of pre-designed templates. • Choose one that fits your campaign’s goal, and customize it to make it your own. **Option 3: Clone a Community Widget** If you want to explore what others are doing, you can clone a widget shared by the community: • Click on “Smart Widgets” to see what the community has shared. • Browse through the community’s shared Smart Widgets. • Find a widget you like, and click “Clone.” • Modify the copied widget to create your unique Smart Widget.  ### Step 3: Explore Smart Widgets Features Your Smart Widgets can do much more than just display content. Let’s dive into the features you can integrate: • User Engagement Tools: Add polls, surveys, or quizzes to interact with your audience. • BitcoinFi Integration: Enable features that support Bitcoin transactions, like tipping or payment gateways. • Governance Options: Incorporate voting systems to allow users to participate in decision-making processes. • Product Growth: Use widgets to drive user growth through referral programs or viral marketing techniques.   These features are designed to enhance interaction and make your Smart Widget stand out. Feel free to experiment with different combinations to see what works best for your campaign. ### Step 4: Publish Your Smart Widgets After you’ve created and customized your Smart Widget, it’s time to share it with the world: • Preview your widget to ensure everything looks and works as intended. • Click “Post my Smart Widget” to publish it. • Your widget is now live and ready for others to interact with in their social feeds.  ### Step 5: Add Smart Widgets to Notes To maximize the impact of your Smart Widget, you can integrate it into your Notes: • Go to the “Notes” section on your dashboard. • Select “Add Smart Widget” and choose the widget you’ve just created. • Publish the note, and now your audience can engage with your Smart Widget directly through the note.  ### Tips for Success * Experiment with Features: Don’t hesitate to try out different combinations of features to find what works best for your audience. * Engage Your Audience: The more interactive and engaging your Smart Widget is, the better the results. * Monitor Performance: After publishing, keep an eye on how your Smart Widget is performing. Adjust and optimize based on user feedback and engagement metrics. ### User Guideline Video Resources [Create from Scratch](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y) [Choose a Template](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y) [Clone a Community Widget](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y) [Full tutorial video ](https://drive.google.com/drive/folders/1-vBaL31-lDB2d7LQtnONeQ9xmF_4Pm4Y) ### Conclusion Creating and using Smart Widgets on YakiHonne is a powerful way to engage with your audience, promote your brand, and drive meaningful interactions. With no coding required, the possibilities are endless. Start exploring today, and see how Smart Widgets can take your campaigns to the next level! Happy creating! @ 3c827db6:66418fc3
2024-08-18 06:55:26*The spread of the Lightning Network may change the incentives behind human interactions, thus also affecting the world of jobs. In the first episode: the construction industry.* When talking about the social implications of Bitcoin, reference is often made to the potential effects of Bitcoin's spread that are not immediately evident: these are second, third, and fourth-degree effects that could change the way people behave in everyday life. Even if the thought might sound hyperbolic, the fact of the matter is that technology has already changed the features of our everyday life, more than once. Raise your hand if, in the 1980s, you would not have found crazy the idea that one-day people would choose which restaurant to go to based on star ratings and reviews on a digital screen. Who would have thought that one day it would no longer be necessary to pay attention to the route to take by car to reach one's destination and, possibly, learn it by heart, because software would calculate the best route for them based on traffic? How would you have reacted if, back in the 1970s, a friend had told you that in the future he might fall in love with a girl he had never seen who lived on the other side of the world, thanks to text messages processed by software that allows you to meet like-minded people? Innovation changes social interactions: it always has and will continue to do so, especially if technology is particularly disruptive. The effects of the large-scale diffusion of the Lightning Network - a technology that allows instant payments from one part of the world to another at almost non-existent costs - can be extremely profound, and can act to change entire sectors. In the first example, in this article, we will discuss how instant settlement could revolutionize the construction industry. The construction industry is a complex ecosystem involving a myriad of stakeholders, each with its own set of incentives. These often conflicting interests lead to inefficiencies, delays, and increased costs. The Lightning Network offers a solution to align these disparate interests. ## The problems ### Misaligned Incentives In the traditional construction setup, each stakeholder operates with a different set of incentives. More specifically: Buyers aim for high-quality construction within a stipulated time and budget. Planners, including architects, designers, and engineers, are primarily concerned with their designs and less about the actual construction. Construction companies are focused on maximizing profits, realizing the building as quickly as possible and with the lowest possible quality at the agreed price. Supervisors' incentives are tied to bonuses, which may or may not align with the project's overall goals. Construction workers are paid for their time, not the quality or efficiency of their work. Let's step outside the imagery of the construction site for a moment and think about football. Can you imagine if defenders had a bonus for putting the ball out of bounds? And midfielders had one for the most passes? And strikers for the most goals? Imagine the chaos on the pitch if the different skills of all the players were not employed for only two goals: to score goals and to avoid conceding them. Such a team would hardly be efficient or successful. The construction industry, with its varied incentives, faces a similar problem, leading to delays, increased costs, and compromised quality. #### The underlying issues Several other issues exacerbate the inefficiencies in the construction industry. Machinery and tools, often owned by the construction company, are not well-maintained by the workers. This leads to faster wear and tear, increasing costs for the company. Small changes in the project requested by the buyer are not usually compensated, adding to the company's costs. Planners are not held accountable for design flaws that manifest during construction, leading to additional costs and delays. ## The solution: instant task-based payments ### Construction workers In a hyperbitcoinized world, the Lightning Network's instant settlement feature can be a game-changer. Workers would be paid for tasks completed rather than time spent. For instance, upon successful construction of a wall or installation of windows, payments could be made instantly. This aligns the workers' incentives with quality and efficiency, as they would aim to complete as many tasks as possible to earn more. Because workers are paid per task there will be no need for a company to hire workers on a payroll. The company just needs to post the tasks, for example on its app, and anyone can apply for them, do their tasks, and get paid for each execution. The more tasks a worker does, the more bitcoin he earns, the better his skills become, the better his reputation will be in the app. Isn't that what already happens with Uber drivers - except for the Bitcoin part, for now? #### Supervisors This system would also eliminate the need for supervisors to focus on time management, allowing them to concentrate solely on quality assurance. If a task meets the quality standards, the worker gets paid instantly. This would eliminate the need for time-based bonuses or penalties. Supervisors would be incentivized to focus even more on quality alone by the split payments feature made possible by the Lightning Network. When a specific task is up for grabs, multiple workers can apply for it via a specialized app. The workers then negotiate among themselves to determine the division of payment - be it an even 50/50 split or a more nuanced arrangement like 60/40. This self-organization extends to scenarios involving more than two workers, where payment divisions could be negotiated as 33.3% for each in a three-way split, or perhaps a 40/40/20 arrangement. The self-organizing mechanism alleviates the supervisory burden. Instead of mediating disputes or assigning tasks, the supervisor's role becomes even more focused on quality control. Once a task is completed to satisfaction, the supervisor approves it in the app, triggering the release of funds. The app itself is programmed to automatically split the payments among the workers based on their pre-negotiated terms, streamlining the entire process and eliminating the need for manual intervention. #### Tools ownership Since workers are compensated for completed tasks rather than time spent, there's a heightened incentive to complete tasks as efficiently as possible. More tasks, more money. The quickest route to efficiency? Utilizing high-quality, well-maintained tools. When multiple workers vie for the same task, the one equipped with the best tools gains a distinct advantage, capable of completing the task more swiftly and effectively. This system has a ripple effect on tool ownership. Over time, workers might prefer using their own tools over company-provided ones, ensuring better maintenance and ultimately contributing to a more efficient and effective construction process. In short, the instant payment system would also encourage workers to invest in and maintain their own high-quality tools, further improving efficiency and competition in the construction workers market. This would also reduce the company's costs related to tool maintenance and replacement. #### Planners and buyers Planners would be more involved in the construction process, ensuring that their designs are being followed accurately. They would be paid partially upfront for their blueprints, with the rest being released upon successful completion of tasks. This system would make planners more accountable and invested in the successful execution of their plans. The task-based payment system also benefits the buyer and the construction company by reducing financial risks. Payments would be made for completed tasks, ensuring that neither party is financially exposed. This would also make the negotiation process smoother, as both parties would know exactly what is included in the price for each task. #### Construction companies While the Lightning Network's instant settlement feature promises to decentralize many aspects of the construction industry, the need for centralized oversight cannot be entirely eliminated. A single entity must be accountable for the holistic execution of the project, meticulously tracking resources required for each construction phase and ensuring the right personnel are deployed at the appropriate times. Technological advancements have made it possible for specialized apps to manage these complex tasks. Such apps could, in theory, allow the buyer of the finished building to oversee the entire project. However, this assumes that the buyer possesses the requisite expertise in construction management, which is often not the case. As a result, most buyers prefer to employ specialized companies to manage the project until its completion. This scenario closely mirrors the current state of Lightning Network nodes. While anyone can set up a node, doing so effectively requires a certain level of expertise. Some individuals may choose to manage their own nodes to earn revenue, but the majority are willing to pay fees for expert management, opting for non-custodial apps to simplify the process. Similarly, some buyers may use construction management apps to avoid paying a construction company, but they must then assume full responsibility for the project's outcome. ### Now go and build The next logical step is clear: it's time to build that pay-per-task app and usher in a new era of decentralized construction. By leveraging the capabilities of the Lightning Network and Bitcoin, we can shift the balance of power towards those who are at the heart of every construction project—the workers. These are the individuals who bring blueprints to life, who lay each brick and install each window. By empowering them with instant, task-based payments, we not only align incentives across the board but also elevate the entire industry to new heights of efficiency and quality.
@ 3c827db6:66418fc3
2024-08-18 06:55:26*The spread of the Lightning Network may change the incentives behind human interactions, thus also affecting the world of jobs. In the first episode: the construction industry.* When talking about the social implications of Bitcoin, reference is often made to the potential effects of Bitcoin's spread that are not immediately evident: these are second, third, and fourth-degree effects that could change the way people behave in everyday life. Even if the thought might sound hyperbolic, the fact of the matter is that technology has already changed the features of our everyday life, more than once. Raise your hand if, in the 1980s, you would not have found crazy the idea that one-day people would choose which restaurant to go to based on star ratings and reviews on a digital screen. Who would have thought that one day it would no longer be necessary to pay attention to the route to take by car to reach one's destination and, possibly, learn it by heart, because software would calculate the best route for them based on traffic? How would you have reacted if, back in the 1970s, a friend had told you that in the future he might fall in love with a girl he had never seen who lived on the other side of the world, thanks to text messages processed by software that allows you to meet like-minded people? Innovation changes social interactions: it always has and will continue to do so, especially if technology is particularly disruptive. The effects of the large-scale diffusion of the Lightning Network - a technology that allows instant payments from one part of the world to another at almost non-existent costs - can be extremely profound, and can act to change entire sectors. In the first example, in this article, we will discuss how instant settlement could revolutionize the construction industry. The construction industry is a complex ecosystem involving a myriad of stakeholders, each with its own set of incentives. These often conflicting interests lead to inefficiencies, delays, and increased costs. The Lightning Network offers a solution to align these disparate interests. ## The problems ### Misaligned Incentives In the traditional construction setup, each stakeholder operates with a different set of incentives. More specifically: Buyers aim for high-quality construction within a stipulated time and budget. Planners, including architects, designers, and engineers, are primarily concerned with their designs and less about the actual construction. Construction companies are focused on maximizing profits, realizing the building as quickly as possible and with the lowest possible quality at the agreed price. Supervisors' incentives are tied to bonuses, which may or may not align with the project's overall goals. Construction workers are paid for their time, not the quality or efficiency of their work. Let's step outside the imagery of the construction site for a moment and think about football. Can you imagine if defenders had a bonus for putting the ball out of bounds? And midfielders had one for the most passes? And strikers for the most goals? Imagine the chaos on the pitch if the different skills of all the players were not employed for only two goals: to score goals and to avoid conceding them. Such a team would hardly be efficient or successful. The construction industry, with its varied incentives, faces a similar problem, leading to delays, increased costs, and compromised quality. #### The underlying issues Several other issues exacerbate the inefficiencies in the construction industry. Machinery and tools, often owned by the construction company, are not well-maintained by the workers. This leads to faster wear and tear, increasing costs for the company. Small changes in the project requested by the buyer are not usually compensated, adding to the company's costs. Planners are not held accountable for design flaws that manifest during construction, leading to additional costs and delays. ## The solution: instant task-based payments ### Construction workers In a hyperbitcoinized world, the Lightning Network's instant settlement feature can be a game-changer. Workers would be paid for tasks completed rather than time spent. For instance, upon successful construction of a wall or installation of windows, payments could be made instantly. This aligns the workers' incentives with quality and efficiency, as they would aim to complete as many tasks as possible to earn more. Because workers are paid per task there will be no need for a company to hire workers on a payroll. The company just needs to post the tasks, for example on its app, and anyone can apply for them, do their tasks, and get paid for each execution. The more tasks a worker does, the more bitcoin he earns, the better his skills become, the better his reputation will be in the app. Isn't that what already happens with Uber drivers - except for the Bitcoin part, for now? #### Supervisors This system would also eliminate the need for supervisors to focus on time management, allowing them to concentrate solely on quality assurance. If a task meets the quality standards, the worker gets paid instantly. This would eliminate the need for time-based bonuses or penalties. Supervisors would be incentivized to focus even more on quality alone by the split payments feature made possible by the Lightning Network. When a specific task is up for grabs, multiple workers can apply for it via a specialized app. The workers then negotiate among themselves to determine the division of payment - be it an even 50/50 split or a more nuanced arrangement like 60/40. This self-organization extends to scenarios involving more than two workers, where payment divisions could be negotiated as 33.3% for each in a three-way split, or perhaps a 40/40/20 arrangement. The self-organizing mechanism alleviates the supervisory burden. Instead of mediating disputes or assigning tasks, the supervisor's role becomes even more focused on quality control. Once a task is completed to satisfaction, the supervisor approves it in the app, triggering the release of funds. The app itself is programmed to automatically split the payments among the workers based on their pre-negotiated terms, streamlining the entire process and eliminating the need for manual intervention. #### Tools ownership Since workers are compensated for completed tasks rather than time spent, there's a heightened incentive to complete tasks as efficiently as possible. More tasks, more money. The quickest route to efficiency? Utilizing high-quality, well-maintained tools. When multiple workers vie for the same task, the one equipped with the best tools gains a distinct advantage, capable of completing the task more swiftly and effectively. This system has a ripple effect on tool ownership. Over time, workers might prefer using their own tools over company-provided ones, ensuring better maintenance and ultimately contributing to a more efficient and effective construction process. In short, the instant payment system would also encourage workers to invest in and maintain their own high-quality tools, further improving efficiency and competition in the construction workers market. This would also reduce the company's costs related to tool maintenance and replacement. #### Planners and buyers Planners would be more involved in the construction process, ensuring that their designs are being followed accurately. They would be paid partially upfront for their blueprints, with the rest being released upon successful completion of tasks. This system would make planners more accountable and invested in the successful execution of their plans. The task-based payment system also benefits the buyer and the construction company by reducing financial risks. Payments would be made for completed tasks, ensuring that neither party is financially exposed. This would also make the negotiation process smoother, as both parties would know exactly what is included in the price for each task. #### Construction companies While the Lightning Network's instant settlement feature promises to decentralize many aspects of the construction industry, the need for centralized oversight cannot be entirely eliminated. A single entity must be accountable for the holistic execution of the project, meticulously tracking resources required for each construction phase and ensuring the right personnel are deployed at the appropriate times. Technological advancements have made it possible for specialized apps to manage these complex tasks. Such apps could, in theory, allow the buyer of the finished building to oversee the entire project. However, this assumes that the buyer possesses the requisite expertise in construction management, which is often not the case. As a result, most buyers prefer to employ specialized companies to manage the project until its completion. This scenario closely mirrors the current state of Lightning Network nodes. While anyone can set up a node, doing so effectively requires a certain level of expertise. Some individuals may choose to manage their own nodes to earn revenue, but the majority are willing to pay fees for expert management, opting for non-custodial apps to simplify the process. Similarly, some buyers may use construction management apps to avoid paying a construction company, but they must then assume full responsibility for the project's outcome. ### Now go and build The next logical step is clear: it's time to build that pay-per-task app and usher in a new era of decentralized construction. By leveraging the capabilities of the Lightning Network and Bitcoin, we can shift the balance of power towards those who are at the heart of every construction project—the workers. These are the individuals who bring blueprints to life, who lay each brick and install each window. By empowering them with instant, task-based payments, we not only align incentives across the board but also elevate the entire industry to new heights of efficiency and quality. @ 8dc86882:9dc4ba5e
2024-08-16 17:10:38Is there a database or website out their where I can put in my car year, make, and model and see what privacy intrusions my be there? originally posted at https://stacker.news/items/651320
@ 8dc86882:9dc4ba5e
2024-08-16 17:10:38Is there a database or website out their where I can put in my car year, make, and model and see what privacy intrusions my be there? originally posted at https://stacker.news/items/651320 @ 2a5d1247:0398ad01
2024-08-14 05:33:49# 🧠Quote(s) of the week: 'People should not be afraid of their governments. Governments should be afraid of their people.' - V - 'A simple plan: Manipulate the data. Manipulate the media. Manipulate the money. A simple response: Resist manipulation and think for yourself.' - James Lavish ## 🧡Bitcoin news🧡 The UK is losing its grip on democracy: 'We do have dedicated police officers who are scouring social media to look for this material, and then follow up with arrests.' Tim Walz (He is the Democratic Party's nominee for vice president in the 2024 U.S. presidential election): “There’s no guarantee to free speech on misinformation or hate speech and especially around our democracy.” Your thoughts, writings, and communications (with or without machine intelligence) can only be private if they are never held by any central party. It is time you learn and discover Nostr. Study, use Nostr, start now. Freedom of speech is one of the most precious things in life and society. We lose it at our peril. **On the 6th of August: ➡️ Morgan Stanley's 15,000 wealth advisors, and $4.8 trillion under management, started pitching clients to buy Bitcoin ETFs by BlackRock and Fidelity on the 7th of August. Several sources believe that Wells Fargo will quickly follow Morgan Stanley with Bitcoin ETF approvals. The Bitcoin ecosystem will gain 15,000+ professional salespeople who have relationships with a trillion dollars of managed wealth. Ignore the noise and focus on the signal. ➡️'Tether’s Q2 2024 attestation reveals they hold $4.7 billion in Bitcoin. They also announced a new all-time high in direct and indirect U.S. Treasury holdings at $97.6 billion, surpassing Germany, the UAE, and Australia.' - Bitcoin News ➡️$5.2B worth of Bitcoin was moved by short-term holders within a week. In contrast, long-term holders largely held onto their BTC. Of the $850M in realized losses, only $600K originated from long-term holders. Don't sell your precious corn to BlackRock. Now, read the statement above again and think about it. Only 0.07% of the $850M losses were incurred by long-term holders. Jepp, we don't freaking sell our Bitcoin! Only (the new) paper hands got frightened and shook out. ➡️'Bitcoin is in the "Extreme Fear" phase of the Fear & Greed Index at a score of 17/100. We've been this fearful 3 times in the last 5 years: • 2019 bottom • 2020 bottom • 2022 bottom Plenty of blood-curdling screams in the streets. Excellent buying opportunity.' -Joe Consorti ➡️Lifehack: 'Airbnb host catches guests running a Bitcoin mining farm on his property. He was tipped off when the power company notified him that the renters used a month's worth of electricity in just 4 days.' -Bitcoin News ➡️'It currently takes 1,880 hrs (47 weeks) of work to buy 1 Bitcoin. Said another way: 1 Bitcoin currently buys 1 FTE (at avg. US wage).' -Anilsaidso Now this is before income tax. If you take that into account it would be closer to 1.5 years.  On the 7th of August: ➡️'In Bitcoin over the last decade, the average return for the top 10 days each year was 184%, and the average return (loss) for all of the remaining days each year was −10%.' - James Lavish  This is why you don't trade Bitcoin. Time in the market beats timing the market. Just buy with a 4+ year horizon and go live your life. Spend time with your family & friends. ➡️Metaplanet is raising $70M to increase its Bitcoin holdings. The company plans to allocate $58.76M of the funds directly to Bitcoin, aiming to hedge against currency depreciation. ➡️Michael Saylor says “I own at least 17,732 Bitcoin and can’t see a better place to put money” On the 8th of August: ➡️21,000 Bitcoins were taken off exchanges last week. ➡️Metaplanet secures ¥1 billion 0.1% APR loan; proceeds to fund additional purchases of $BTC. ➡️Bloomberg's Balchunas: '99.5% of the money invested in Bitcoin ETFs held firm despite a -14% drop on Monday and a -21% decline for the week. IBIT saw no outflows at all — a total freak. I’m very bullish on ETF investors’ resilience, but even I’m surprised by this.' On the 10th of August: ➡️The number of Bitcoin nodes has increased 20% yoy. On the 11th of August: ➡️The Bitcoin White paper, but explained in Gen Z Language.  Original [source](https://bitcoinforgenz.org): ➡️'3 years ago, Bitcoin's market cap was ~$835B. Same for all the crypto stuff w/o stablecoins. Today, Bitcoin's market cap is up 37% ($1.15T) And the other stuff? -11% (not adjusted for inflation) It’s an insightful statistic to present to people who blindly “diversify”.' -Sam Wouters Bitcoin, not CrYpTO (aka. altcoins). On the 12th of August: ➡️Remember my statement on Trump after the Bitcoin Conference in Nashville? (Stop larping, politicians need votes, etc., etc.) President Trump has announced his 20 Core Promises to the American people. We (Bitcoin) are not even a top 20 priority issue in Trump's agenda. You know what is on #13: Keep the U.S. Dollar as the world's reserve currency. "end inflation" and "keep the U.S. Dollar as the world's reserve currency" are diametrically opposed and are diabolical. If you don't believe me, scroll down a bit and read the segment Macro-Economics. For all the people on Twitter or other platforms, stop bootlicking, stop larping. You can’t say “Don’t trust verify” AND trust politicians or go full fangirl. ➡️Bitcoinminer Marathon to raise $250m to buy more Bitcoin. 'Marathon Digital Holdings, Inc. Announces Proposed Private Offering of $250 Million of Convertible Senior Notes. Proceeds to be used primarily to acquire Bitcoin and for general corporate purposes.' They bought $100m in July and currently HODL 20,000 Bitcoin. ## 💸Traditional Finance / Macro: On the 6th of August: 👉🏽'JP Morgan says Institutions bought the dip while Retail panic-sold aggressively. Retail sold -$1 BILLION -2.5 standard deviations BELOW the 12m average Institutions bought +$14 billion. +2.9 std dev ABOVE the 12m average' - Rader Maybe it's because trading platforms were down for retail investors? Market manipulation at its finest. On the 8th of August: 👉🏽Investors Pull $2.2 Billion From ARKK In 2024 As Cathie Wood Underperforms Nasdaq By -30% YTD 👉🏽$6.4 TRILLION wiped out from global stock markets in just 4 weeks - Bloomberg ### 🏦Banks: 👉🏽No news ## 🌎Macro/Geopolitics: Going to start this segment with a great quote by Luke Gromen: 'JPY "too strong" = global market dysfunction, which quickly leads to UST dysfunction. USD "too strong" = UST market dysfunction, which quickly leads to global market dysfunction. Powell ultimately only has a choice of how he wants to lose the long end - "fire" or "ice"?'  This is what triggered a global-scale sell-off of every major asset class. This is how unstable the system is. To add a great James Lavish quote: 'And one might say the root cause *before* the trigger, and the reason for instability was this (15 years of *free money*).' On the 6th of August: 👉🏽M2 money supply update: On the 7th of August the US Treasury starts Treasury buy-backs again at $30 billion a month. The US Treasury will begin buying back up to $50 billion worth of outstanding government securities by the end of October, primarily to provide liquidity support. - $8.5B buyback in August - $31.5B buyback in September - $10B buyback in October Hello liquidity, the printers are back on! Remember: USD in circulation (M2): 21T US Government Debt: 35.1T* More debt than their money in circulation. * The US Debt just hit 35.1 Trillion. Up 0.1 Trillion in a week. * [ ](https://image.nostr.build/2dbf21409da89e46405526d03d96114b888e675eb3cb9b6a98ec56f4af424588.jpg) It is kicking the goddamnnn can down the road. The U.S. Now Has: 1. Record $17.8 trillion in household debt 2. Record $12.5 trillion in mortgages 3. Record $1.6 trillion in auto loans 4. Near record $1.6 trillion in student loans 5. Record $1.14 trillion in credit card debt (with the average person owing $6,218 at a 20%+ rate. Making minimum payments, it will take them over 18 years and an *additional* $9K+ to pay off that debt.) Total household debt is now up 53% over the last 10 years and total credit card debt is up 50% since 2020. Meanwhile, delinquency rates on credit cards and auto loans are nearing the highs seen in 2008 [](https://image.nostr.build/3a111d3130c4780b49f906a14b7b75158da45b33a669fde656b1c161be31f5e1.jpg) "Who could defeat the US military?" Compounding interest is defeating the US military & compounding interest is undefeated v. hegemons. Buy LT USTs if you think the US will lose Cold War 2.0 for lack of printing enough USDs to finance this; if not, buy gold, BTC, & stocks.' - Luke Gromen No doom and gloom, just facts. Anyway: "Amateurs talk about tactics, but professionals study logistics" - General Omar Bradley Omar Nelson Bradley was a senior officer of the United States Army during and after World War II, rising to the rank of General of the Army. 👉🏽Again a great explanation of the situation in Japan: Bank of Japan (BoJ) 1. Prints insane amounts of money. 2. Becomes the largest holder of ETFs in the Nikkei, incentivizing investors to purchase Japanese ETFs borrowing in yen. 3. Yen falls to 40-year lows 4. BOJ blames "speculators". A classic. 5. BOJ spends billions stabilizing the yen 6. Yen rises, market declines, margin calls jump, Nikkei plummets. Black Monday. You think this is a "free market".  Classic interventionist economics by the BoJ. Explanation: 'Now what does this mean: 1. Treasury buybacks improve liquidity in the bond market that has been living on life support over the last few years as high inflation made bonds unappealing 2. This may be deflationary if the amount of money taken out is larger than the amount we are spending to aid in economic expansion I hope this helps you. 3. This will likely lead to a lowering of interest rates later on. 4. This will improve US credit ratings as it shows that we are paying down our debts, hopefully, faster than we are creating new debts. I hope this helps.' -Tim 👉🏽Bank of Japan to hold an emergency meeting to discuss International Financial Markets - Reuters The Bank of Japan said it, the Ministry of Finance, and the Financial Services Agency will meet from 3 pm on the 6th of August in Tokyo to discuss international markets. After the meeting: 'No more rate hikes in the near term due to market volatility.' BoJ On the 7th of August: 👉🏽 Germany's industrial production was up in June. But looking at the chart and the previous month's revised down (3.1% decline), it's a bit too early to call for a revival of Europe's former Manufacturing 'Powerhouse.' Germany has had no growth for five years. As a matter of fact, German industrial production has been constantly declining since 2017. Grotesque overregulation and energy suicide are accelerating deindustrialization, and some left weirdos are even celebrating degrowth nonsense. Meanwhile the number of bankruptcies in Germany "unexpectedly" rose in July to the highest level in about ten years.  👉🏽'The US unemployment rate has risen for 4 consecutive months, the longest streak since the 2008 Financial Crisis. Over the last 75 years, every time unemployment rose for 4 consecutive months, the US economy entered recession. The jobless rate has surged from 3.8% in March to 4.3% in July, its highest level since October 2021. Meanwhile, the US hires rate declined to 3.4% in July, its lowest level since the 2020 Pandemic and below the pre-pandemic average of 3.8%. The US labor market is contracting.' -TKL 👉🏽 11% of credit card balances in the US are now 90+ days delinquent, the highest in over a decade. Probably nothing! 👉🏽'We do have dedicated police officers who are scouring social media to look for this material, and then follow up with arrests.' The director of public prosecutions of England and Wales warns that sharing online material of riots could be an offense. This is not something I just made up. He is saying no free speech. the British government is completely corrupt, and anyone who points this out is a target as sharing videos is now a crime. Is it even a democracy then? Tim Walz (He is the Democratic Party's nominee for vice president in the 2024 U.S. presidential election): “There’s no guarantee to free speech on misinformation or hate speech and especially around our democracy.” Remember what Jacinda Ardern, then Prime Minister of New Zealand said in 2020: "We will continue to be your single source of truth…Remember, unless you hear it from us it is not the truth." OpenAI has an ex-NSA director on its Board; The new Dutch Prime Minister is a Former Dutch intelligence chief; How convenient! Now don't get me wrong. People should think before they post or repost something on social media. But arresting people for creating online content or reposting that contact is just vile. V for Vendetta was supposed to be just a graphic novel... not real life! A reminder that V for Vendetta is based in the UK! Again, you should start using Nostr. And it is not just in the UK, also EUROPE is going crazy. Read the bit on the 12th of August. On the 8th of August: 👉🏽Bank of England expected to lose £254 BILLION from the QE money printing program since December 2021 - The Economist On the 10th of August: 👉🏽'How much have prices increased over the last 24 years? US hospital services prices have skyrocketed by 256% since the beginning of this century. At the same time, College Tuition and Fees, as well as College Textbooks spiked by 188% and 158%, respectively. Moreover, the prices of Childcare or Nursery School and Medical Care Services rose by 139% and 136%. On the other hand, TVs, Toys, and computer software prices declined by 98%, 74%, and 74%, respectively. To put this into perspective, average hourly wages are up 119% since 2000. Wage growth is struggling to keep up with many items.' -TKL  Our society and our economy are driven by debt. CPI is a structural understanding of actual inflation. Everything the government subsidizes goes up by 1 to 300 percent. More protocols, less competition, less disruption, less efficiency; Ergo more inflation. (you can sum up the last part in one word: EUROPE) The industries where governments stay out are private competition, ergo drives pricing down. Competition is deflationary, when will people realize that? 👉🏽'The rich are getting richer faster than ever before: The top 40% of US income earners hold 83% of the total net worth, near an all-time record. The top 20% account for 71% of the total net worth, up 10 percentage points over the last 2 decades. On the other hand, the bottom 40% of income households hold only 8% of the wealth. Moreover, the bottom 20% of earners reflect just 3% of total US wealth. Over the last few years, the rich have gotten a lot richer.' - TKL This makes perfect sense. If you can hold assets in an inflationary economy/environment, well assets and wealth will go up. The consequences of central banks all around the world printing trillions. The money inevitably flows into asset classes creating bubbles in equity markets, real estate, luxury goods, and many more. The wealthy being the largest owners of these assets simply benefit the most. What do we call that? It’s called the Cantillon effect. On the 12th of August: 👉🏽Freedom of speech is one of the most precious things in life and society.  'It's amazing how everything they say, is always the opposite: "ensuring freedom of expression and information are protected" = "censor anything we, an unelected group of ultrawealthy technocrats, disagree with". - ZeroHedge I couldn't have said it better...Jeroen Blokland: 'Europe has completely lost it. European ‘politicians’, who are not leaders, increasingly act from an ideologist perspective, which is incompatible with democratic and socially supported policy making. To send a threatening letter to Elon Musk, compelling him to censor(!) his meeting with Trump is another example of how the aging, declining, and weakening European ‘power’ unrightfully believes it can force its subjective moral standard onto others. Not only does that create friction with many other parts of the world, which outperform Europe in many areas, it also causes massive polarization on the European continent.' "There is no crueler tyranny than that which is perpetuated under the shield of law and in the name of justice." - Montesquieu "The welfare of the people has always been the alibi of tyrants, and it provides the servants of tyranny a good conscience." - Albert Camus Really you should study Bitcoin & Nostr! 'Paradoxically, the Cantillon Effect means that the very last people to understand the need for BTC & technologies like Nostr will be those in and closest to western technocratic & banking centers.' - Luke Gromen 🎁If you have made it this far I would like to give you a little gift: Great book, great podcast: Resistance Money with Andrew Bailey, Bradley Rettler, & Craig Warmke 'Andrew Bailey, is a Professor of Philosophy at Yale-NUS College, Bradley Rettler is a Professor of Philosophy at the University of Wyoming and Craig Warmke is a Professor of Philosophy at Northern Illinois University. In this episode we discuss their book Resistance Money and the global net-benefits of Bitcoin.' “When asking a question like this…it’s tempting to replace it with the question ‘is Bitcoin good for me?’, and then you’re off to bag-pumping or bag-dumping; so what we tried to do here is to give a bit more precision to the question: ‘is Bitcoin good for the world?’” — Andrew Bailey [](https://youtu.be/OtEp9lZKWvA?si=sOQC7fIB0UEtVhze) Credit: I have used multiple sources! My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: @Relai 🇨🇭 especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. (Please only use it till the 31st of October - after that full KYC) Hence a DCA, Dollar cost Average Strategy. Check out my tutorial post (Instagram) & video (YouTube) for more info. ⠀⠀⠀⠀ Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀⠀⠀⠀⠀⠀⠀⠀ Do you think this post is helpful to you? If so, please share it and support my work with sats. Many thanks for reading the Weekly Recap, see you all next week! Felipe - Bitcoin Friday
@ 2a5d1247:0398ad01
2024-08-14 05:33:49# 🧠Quote(s) of the week: 'People should not be afraid of their governments. Governments should be afraid of their people.' - V - 'A simple plan: Manipulate the data. Manipulate the media. Manipulate the money. A simple response: Resist manipulation and think for yourself.' - James Lavish ## 🧡Bitcoin news🧡 The UK is losing its grip on democracy: 'We do have dedicated police officers who are scouring social media to look for this material, and then follow up with arrests.' Tim Walz (He is the Democratic Party's nominee for vice president in the 2024 U.S. presidential election): “There’s no guarantee to free speech on misinformation or hate speech and especially around our democracy.” Your thoughts, writings, and communications (with or without machine intelligence) can only be private if they are never held by any central party. It is time you learn and discover Nostr. Study, use Nostr, start now. Freedom of speech is one of the most precious things in life and society. We lose it at our peril. **On the 6th of August: ➡️ Morgan Stanley's 15,000 wealth advisors, and $4.8 trillion under management, started pitching clients to buy Bitcoin ETFs by BlackRock and Fidelity on the 7th of August. Several sources believe that Wells Fargo will quickly follow Morgan Stanley with Bitcoin ETF approvals. The Bitcoin ecosystem will gain 15,000+ professional salespeople who have relationships with a trillion dollars of managed wealth. Ignore the noise and focus on the signal. ➡️'Tether’s Q2 2024 attestation reveals they hold $4.7 billion in Bitcoin. They also announced a new all-time high in direct and indirect U.S. Treasury holdings at $97.6 billion, surpassing Germany, the UAE, and Australia.' - Bitcoin News ➡️$5.2B worth of Bitcoin was moved by short-term holders within a week. In contrast, long-term holders largely held onto their BTC. Of the $850M in realized losses, only $600K originated from long-term holders. Don't sell your precious corn to BlackRock. Now, read the statement above again and think about it. Only 0.07% of the $850M losses were incurred by long-term holders. Jepp, we don't freaking sell our Bitcoin! Only (the new) paper hands got frightened and shook out. ➡️'Bitcoin is in the "Extreme Fear" phase of the Fear & Greed Index at a score of 17/100. We've been this fearful 3 times in the last 5 years: • 2019 bottom • 2020 bottom • 2022 bottom Plenty of blood-curdling screams in the streets. Excellent buying opportunity.' -Joe Consorti ➡️Lifehack: 'Airbnb host catches guests running a Bitcoin mining farm on his property. He was tipped off when the power company notified him that the renters used a month's worth of electricity in just 4 days.' -Bitcoin News ➡️'It currently takes 1,880 hrs (47 weeks) of work to buy 1 Bitcoin. Said another way: 1 Bitcoin currently buys 1 FTE (at avg. US wage).' -Anilsaidso Now this is before income tax. If you take that into account it would be closer to 1.5 years.  On the 7th of August: ➡️'In Bitcoin over the last decade, the average return for the top 10 days each year was 184%, and the average return (loss) for all of the remaining days each year was −10%.' - James Lavish  This is why you don't trade Bitcoin. Time in the market beats timing the market. Just buy with a 4+ year horizon and go live your life. Spend time with your family & friends. ➡️Metaplanet is raising $70M to increase its Bitcoin holdings. The company plans to allocate $58.76M of the funds directly to Bitcoin, aiming to hedge against currency depreciation. ➡️Michael Saylor says “I own at least 17,732 Bitcoin and can’t see a better place to put money” On the 8th of August: ➡️21,000 Bitcoins were taken off exchanges last week. ➡️Metaplanet secures ¥1 billion 0.1% APR loan; proceeds to fund additional purchases of $BTC. ➡️Bloomberg's Balchunas: '99.5% of the money invested in Bitcoin ETFs held firm despite a -14% drop on Monday and a -21% decline for the week. IBIT saw no outflows at all — a total freak. I’m very bullish on ETF investors’ resilience, but even I’m surprised by this.' On the 10th of August: ➡️The number of Bitcoin nodes has increased 20% yoy. On the 11th of August: ➡️The Bitcoin White paper, but explained in Gen Z Language.  Original [source](https://bitcoinforgenz.org): ➡️'3 years ago, Bitcoin's market cap was ~$835B. Same for all the crypto stuff w/o stablecoins. Today, Bitcoin's market cap is up 37% ($1.15T) And the other stuff? -11% (not adjusted for inflation) It’s an insightful statistic to present to people who blindly “diversify”.' -Sam Wouters Bitcoin, not CrYpTO (aka. altcoins). On the 12th of August: ➡️Remember my statement on Trump after the Bitcoin Conference in Nashville? (Stop larping, politicians need votes, etc., etc.) President Trump has announced his 20 Core Promises to the American people. We (Bitcoin) are not even a top 20 priority issue in Trump's agenda. You know what is on #13: Keep the U.S. Dollar as the world's reserve currency. "end inflation" and "keep the U.S. Dollar as the world's reserve currency" are diametrically opposed and are diabolical. If you don't believe me, scroll down a bit and read the segment Macro-Economics. For all the people on Twitter or other platforms, stop bootlicking, stop larping. You can’t say “Don’t trust verify” AND trust politicians or go full fangirl. ➡️Bitcoinminer Marathon to raise $250m to buy more Bitcoin. 'Marathon Digital Holdings, Inc. Announces Proposed Private Offering of $250 Million of Convertible Senior Notes. Proceeds to be used primarily to acquire Bitcoin and for general corporate purposes.' They bought $100m in July and currently HODL 20,000 Bitcoin. ## 💸Traditional Finance / Macro: On the 6th of August: 👉🏽'JP Morgan says Institutions bought the dip while Retail panic-sold aggressively. Retail sold -$1 BILLION -2.5 standard deviations BELOW the 12m average Institutions bought +$14 billion. +2.9 std dev ABOVE the 12m average' - Rader Maybe it's because trading platforms were down for retail investors? Market manipulation at its finest. On the 8th of August: 👉🏽Investors Pull $2.2 Billion From ARKK In 2024 As Cathie Wood Underperforms Nasdaq By -30% YTD 👉🏽$6.4 TRILLION wiped out from global stock markets in just 4 weeks - Bloomberg ### 🏦Banks: 👉🏽No news ## 🌎Macro/Geopolitics: Going to start this segment with a great quote by Luke Gromen: 'JPY "too strong" = global market dysfunction, which quickly leads to UST dysfunction. USD "too strong" = UST market dysfunction, which quickly leads to global market dysfunction. Powell ultimately only has a choice of how he wants to lose the long end - "fire" or "ice"?'  This is what triggered a global-scale sell-off of every major asset class. This is how unstable the system is. To add a great James Lavish quote: 'And one might say the root cause *before* the trigger, and the reason for instability was this (15 years of *free money*).' On the 6th of August: 👉🏽M2 money supply update: On the 7th of August the US Treasury starts Treasury buy-backs again at $30 billion a month. The US Treasury will begin buying back up to $50 billion worth of outstanding government securities by the end of October, primarily to provide liquidity support. - $8.5B buyback in August - $31.5B buyback in September - $10B buyback in October Hello liquidity, the printers are back on! Remember: USD in circulation (M2): 21T US Government Debt: 35.1T* More debt than their money in circulation. * The US Debt just hit 35.1 Trillion. Up 0.1 Trillion in a week. * [ ](https://image.nostr.build/2dbf21409da89e46405526d03d96114b888e675eb3cb9b6a98ec56f4af424588.jpg) It is kicking the goddamnnn can down the road. The U.S. Now Has: 1. Record $17.8 trillion in household debt 2. Record $12.5 trillion in mortgages 3. Record $1.6 trillion in auto loans 4. Near record $1.6 trillion in student loans 5. Record $1.14 trillion in credit card debt (with the average person owing $6,218 at a 20%+ rate. Making minimum payments, it will take them over 18 years and an *additional* $9K+ to pay off that debt.) Total household debt is now up 53% over the last 10 years and total credit card debt is up 50% since 2020. Meanwhile, delinquency rates on credit cards and auto loans are nearing the highs seen in 2008 [](https://image.nostr.build/3a111d3130c4780b49f906a14b7b75158da45b33a669fde656b1c161be31f5e1.jpg) "Who could defeat the US military?" Compounding interest is defeating the US military & compounding interest is undefeated v. hegemons. Buy LT USTs if you think the US will lose Cold War 2.0 for lack of printing enough USDs to finance this; if not, buy gold, BTC, & stocks.' - Luke Gromen No doom and gloom, just facts. Anyway: "Amateurs talk about tactics, but professionals study logistics" - General Omar Bradley Omar Nelson Bradley was a senior officer of the United States Army during and after World War II, rising to the rank of General of the Army. 👉🏽Again a great explanation of the situation in Japan: Bank of Japan (BoJ) 1. Prints insane amounts of money. 2. Becomes the largest holder of ETFs in the Nikkei, incentivizing investors to purchase Japanese ETFs borrowing in yen. 3. Yen falls to 40-year lows 4. BOJ blames "speculators". A classic. 5. BOJ spends billions stabilizing the yen 6. Yen rises, market declines, margin calls jump, Nikkei plummets. Black Monday. You think this is a "free market".  Classic interventionist economics by the BoJ. Explanation: 'Now what does this mean: 1. Treasury buybacks improve liquidity in the bond market that has been living on life support over the last few years as high inflation made bonds unappealing 2. This may be deflationary if the amount of money taken out is larger than the amount we are spending to aid in economic expansion I hope this helps you. 3. This will likely lead to a lowering of interest rates later on. 4. This will improve US credit ratings as it shows that we are paying down our debts, hopefully, faster than we are creating new debts. I hope this helps.' -Tim 👉🏽Bank of Japan to hold an emergency meeting to discuss International Financial Markets - Reuters The Bank of Japan said it, the Ministry of Finance, and the Financial Services Agency will meet from 3 pm on the 6th of August in Tokyo to discuss international markets. After the meeting: 'No more rate hikes in the near term due to market volatility.' BoJ On the 7th of August: 👉🏽 Germany's industrial production was up in June. But looking at the chart and the previous month's revised down (3.1% decline), it's a bit too early to call for a revival of Europe's former Manufacturing 'Powerhouse.' Germany has had no growth for five years. As a matter of fact, German industrial production has been constantly declining since 2017. Grotesque overregulation and energy suicide are accelerating deindustrialization, and some left weirdos are even celebrating degrowth nonsense. Meanwhile the number of bankruptcies in Germany "unexpectedly" rose in July to the highest level in about ten years.  👉🏽'The US unemployment rate has risen for 4 consecutive months, the longest streak since the 2008 Financial Crisis. Over the last 75 years, every time unemployment rose for 4 consecutive months, the US economy entered recession. The jobless rate has surged from 3.8% in March to 4.3% in July, its highest level since October 2021. Meanwhile, the US hires rate declined to 3.4% in July, its lowest level since the 2020 Pandemic and below the pre-pandemic average of 3.8%. The US labor market is contracting.' -TKL 👉🏽 11% of credit card balances in the US are now 90+ days delinquent, the highest in over a decade. Probably nothing! 👉🏽'We do have dedicated police officers who are scouring social media to look for this material, and then follow up with arrests.' The director of public prosecutions of England and Wales warns that sharing online material of riots could be an offense. This is not something I just made up. He is saying no free speech. the British government is completely corrupt, and anyone who points this out is a target as sharing videos is now a crime. Is it even a democracy then? Tim Walz (He is the Democratic Party's nominee for vice president in the 2024 U.S. presidential election): “There’s no guarantee to free speech on misinformation or hate speech and especially around our democracy.” Remember what Jacinda Ardern, then Prime Minister of New Zealand said in 2020: "We will continue to be your single source of truth…Remember, unless you hear it from us it is not the truth." OpenAI has an ex-NSA director on its Board; The new Dutch Prime Minister is a Former Dutch intelligence chief; How convenient! Now don't get me wrong. People should think before they post or repost something on social media. But arresting people for creating online content or reposting that contact is just vile. V for Vendetta was supposed to be just a graphic novel... not real life! A reminder that V for Vendetta is based in the UK! Again, you should start using Nostr. And it is not just in the UK, also EUROPE is going crazy. Read the bit on the 12th of August. On the 8th of August: 👉🏽Bank of England expected to lose £254 BILLION from the QE money printing program since December 2021 - The Economist On the 10th of August: 👉🏽'How much have prices increased over the last 24 years? US hospital services prices have skyrocketed by 256% since the beginning of this century. At the same time, College Tuition and Fees, as well as College Textbooks spiked by 188% and 158%, respectively. Moreover, the prices of Childcare or Nursery School and Medical Care Services rose by 139% and 136%. On the other hand, TVs, Toys, and computer software prices declined by 98%, 74%, and 74%, respectively. To put this into perspective, average hourly wages are up 119% since 2000. Wage growth is struggling to keep up with many items.' -TKL  Our society and our economy are driven by debt. CPI is a structural understanding of actual inflation. Everything the government subsidizes goes up by 1 to 300 percent. More protocols, less competition, less disruption, less efficiency; Ergo more inflation. (you can sum up the last part in one word: EUROPE) The industries where governments stay out are private competition, ergo drives pricing down. Competition is deflationary, when will people realize that? 👉🏽'The rich are getting richer faster than ever before: The top 40% of US income earners hold 83% of the total net worth, near an all-time record. The top 20% account for 71% of the total net worth, up 10 percentage points over the last 2 decades. On the other hand, the bottom 40% of income households hold only 8% of the wealth. Moreover, the bottom 20% of earners reflect just 3% of total US wealth. Over the last few years, the rich have gotten a lot richer.' - TKL This makes perfect sense. If you can hold assets in an inflationary economy/environment, well assets and wealth will go up. The consequences of central banks all around the world printing trillions. The money inevitably flows into asset classes creating bubbles in equity markets, real estate, luxury goods, and many more. The wealthy being the largest owners of these assets simply benefit the most. What do we call that? It’s called the Cantillon effect. On the 12th of August: 👉🏽Freedom of speech is one of the most precious things in life and society.  'It's amazing how everything they say, is always the opposite: "ensuring freedom of expression and information are protected" = "censor anything we, an unelected group of ultrawealthy technocrats, disagree with". - ZeroHedge I couldn't have said it better...Jeroen Blokland: 'Europe has completely lost it. European ‘politicians’, who are not leaders, increasingly act from an ideologist perspective, which is incompatible with democratic and socially supported policy making. To send a threatening letter to Elon Musk, compelling him to censor(!) his meeting with Trump is another example of how the aging, declining, and weakening European ‘power’ unrightfully believes it can force its subjective moral standard onto others. Not only does that create friction with many other parts of the world, which outperform Europe in many areas, it also causes massive polarization on the European continent.' "There is no crueler tyranny than that which is perpetuated under the shield of law and in the name of justice." - Montesquieu "The welfare of the people has always been the alibi of tyrants, and it provides the servants of tyranny a good conscience." - Albert Camus Really you should study Bitcoin & Nostr! 'Paradoxically, the Cantillon Effect means that the very last people to understand the need for BTC & technologies like Nostr will be those in and closest to western technocratic & banking centers.' - Luke Gromen 🎁If you have made it this far I would like to give you a little gift: Great book, great podcast: Resistance Money with Andrew Bailey, Bradley Rettler, & Craig Warmke 'Andrew Bailey, is a Professor of Philosophy at Yale-NUS College, Bradley Rettler is a Professor of Philosophy at the University of Wyoming and Craig Warmke is a Professor of Philosophy at Northern Illinois University. In this episode we discuss their book Resistance Money and the global net-benefits of Bitcoin.' “When asking a question like this…it’s tempting to replace it with the question ‘is Bitcoin good for me?’, and then you’re off to bag-pumping or bag-dumping; so what we tried to do here is to give a bit more precision to the question: ‘is Bitcoin good for the world?’” — Andrew Bailey [](https://youtu.be/OtEp9lZKWvA?si=sOQC7fIB0UEtVhze) Credit: I have used multiple sources! My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: @Relai 🇨🇭 especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. (Please only use it till the 31st of October - after that full KYC) Hence a DCA, Dollar cost Average Strategy. Check out my tutorial post (Instagram) & video (YouTube) for more info. ⠀⠀⠀⠀ Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀⠀⠀⠀⠀⠀⠀⠀ Do you think this post is helpful to you? If so, please share it and support my work with sats. Many thanks for reading the Weekly Recap, see you all next week! Felipe - Bitcoin Friday @ 0176967e:1e6f471e
2024-07-28 15:31:13Objavte, ako avatari a pseudonymné identity ovplyvňujú riadenie kryptokomunít a decentralizovaných organizácií (DAOs). V tejto prednáške sa zameriame na praktické fungovanie decentralizovaného rozhodovania, vytváranie a správu avatarových profilov, a ich rolu v online reputačných systémoch. Naučíte sa, ako si vytvoriť efektívny pseudonymný profil, zapojiť sa do rôznych krypto projektov a využiť svoje aktivity na zarábanie kryptomien. Preskúmame aj príklady úspešných projektov a stratégie, ktoré vám pomôžu zorientovať sa a uspieť v dynamickom svete decentralizovaných komunít.
@ 0176967e:1e6f471e
2024-07-28 15:31:13Objavte, ako avatari a pseudonymné identity ovplyvňujú riadenie kryptokomunít a decentralizovaných organizácií (DAOs). V tejto prednáške sa zameriame na praktické fungovanie decentralizovaného rozhodovania, vytváranie a správu avatarových profilov, a ich rolu v online reputačných systémoch. Naučíte sa, ako si vytvoriť efektívny pseudonymný profil, zapojiť sa do rôznych krypto projektov a využiť svoje aktivity na zarábanie kryptomien. Preskúmame aj príklady úspešných projektov a stratégie, ktoré vám pomôžu zorientovať sa a uspieť v dynamickom svete decentralizovaných komunít. @ 0176967e:1e6f471e
2024-07-28 09:16:10Jan Kolčák pochádza zo stredného Slovenska a vystupuje pod umeleckým menom Deepologic. Hudbe sa venuje už viac než 10 rokov. Začínal ako DJ, ktorý s obľubou mixoval klubovú hudbu v štýloch deep-tech a afrohouse. Stále ho ťahalo tvoriť vlastnú hudbu, a preto sa začal vzdelávať v oblasti tvorby elektronickej hudby. Nakoniec vydal svoje prvé EP s názvom "Rezonancie". Učenie je pre neho celoživotný proces, a preto sa neustále zdokonaľuje v oblasti zvuku a kompozície, aby jeho skladby boli kvalitné na posluch aj v klube. V roku 2023 si založil vlastnú značku EarsDeep Records, kde dáva príležitosť začínajúcim producentom. Jeho značku podporujú aj etablované mená slovenskej alternatívnej elektronickej scény. Jeho prioritou je sloboda a neškatulkovanie. Ako sa hovorí v jednej klasickej deephouseovej skladbe: "We are all equal in the house of deep." So slobodou ide ruka v ruke aj láska k novým technológiám, Bitcoinu a schopnosť udržať si v digitálnom svete prehľad, odstup a anonymitu. V súčasnosti ďalej produkuje vlastnú hudbu, venuje sa DJingu a vedie podcast, kde zverejňuje svoje mixované sety. Na Lunarpunk festivale bude hrať DJ set tvorený vlastnou produkciou, ale aj skladby, ktoré sú blízke jeho srdcu. [Podcast](https://fountain.fm/show/eYFu6V2SUlN4vC5qBKFk) [Bandcamp](https://earsdeep.bandcamp.com/) [Punk Nostr website](https://earsdeep-records.npub.pro/) alebo nprofile1qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qy88wumn8ghj7mn0wvhxcmmv9uq3xamnwvaz7tmsw4e8qmr9wpskwtn9wvhsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qyg8wumn8ghj7mn0wd68ytnddakj7qghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7qpqguvns4ld8k2f3sugel055w7eq8zeewq7mp6w2stpnt6j75z60z3swy7h05
@ 0176967e:1e6f471e
2024-07-28 09:16:10Jan Kolčák pochádza zo stredného Slovenska a vystupuje pod umeleckým menom Deepologic. Hudbe sa venuje už viac než 10 rokov. Začínal ako DJ, ktorý s obľubou mixoval klubovú hudbu v štýloch deep-tech a afrohouse. Stále ho ťahalo tvoriť vlastnú hudbu, a preto sa začal vzdelávať v oblasti tvorby elektronickej hudby. Nakoniec vydal svoje prvé EP s názvom "Rezonancie". Učenie je pre neho celoživotný proces, a preto sa neustále zdokonaľuje v oblasti zvuku a kompozície, aby jeho skladby boli kvalitné na posluch aj v klube. V roku 2023 si založil vlastnú značku EarsDeep Records, kde dáva príležitosť začínajúcim producentom. Jeho značku podporujú aj etablované mená slovenskej alternatívnej elektronickej scény. Jeho prioritou je sloboda a neškatulkovanie. Ako sa hovorí v jednej klasickej deephouseovej skladbe: "We are all equal in the house of deep." So slobodou ide ruka v ruke aj láska k novým technológiám, Bitcoinu a schopnosť udržať si v digitálnom svete prehľad, odstup a anonymitu. V súčasnosti ďalej produkuje vlastnú hudbu, venuje sa DJingu a vedie podcast, kde zverejňuje svoje mixované sety. Na Lunarpunk festivale bude hrať DJ set tvorený vlastnou produkciou, ale aj skladby, ktoré sú blízke jeho srdcu. [Podcast](https://fountain.fm/show/eYFu6V2SUlN4vC5qBKFk) [Bandcamp](https://earsdeep.bandcamp.com/) [Punk Nostr website](https://earsdeep-records.npub.pro/) alebo nprofile1qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qy88wumn8ghj7mn0wvhxcmmv9uq3xamnwvaz7tmsw4e8qmr9wpskwtn9wvhsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qyg8wumn8ghj7mn0wd68ytnddakj7qghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7qpqguvns4ld8k2f3sugel055w7eq8zeewq7mp6w2stpnt6j75z60z3swy7h05 @ 0176967e:1e6f471e
2024-07-27 11:10:06Workshop je zameraný pre všetkých, ktorí sa potýkajú s vysvetľovaním Bitcoinu svojej rodine, kamarátom, partnerom alebo kolegom. Pri námietkach z druhej strany väčšinou ideme do protiútoku a snažíme sa vytiahnuť tie najlepšie argumenty. Na tomto workshope vás naučím nový prístup k zvládaniu námietok a vyskúšate si ho aj v praxi. Know-how je aplikovateľné nie len na komunikáciu Bitcoinu ale aj pre zlepšenie vzťahov, pri výchove detí a celkovo pre lepší osobný život.
@ 0176967e:1e6f471e
2024-07-27 11:10:06Workshop je zameraný pre všetkých, ktorí sa potýkajú s vysvetľovaním Bitcoinu svojej rodine, kamarátom, partnerom alebo kolegom. Pri námietkach z druhej strany väčšinou ideme do protiútoku a snažíme sa vytiahnuť tie najlepšie argumenty. Na tomto workshope vás naučím nový prístup k zvládaniu námietok a vyskúšate si ho aj v praxi. Know-how je aplikovateľné nie len na komunikáciu Bitcoinu ale aj pre zlepšenie vzťahov, pri výchove detí a celkovo pre lepší osobný život. @ 0176967e:1e6f471e
2024-07-26 17:45:08Ak ste v Bitcoine už nejaký ten rok, možno máte pocit, že už všetkému rozumiete a že vás nič neprekvapí. Viete čo je to peňaženka, čo je to seed a čo adresa, možno dokonca aj čo je to sha256. Ste si istí? Táto prednáška sa vám to pokúsi vyvrátiť. 🙂
@ 0176967e:1e6f471e
2024-07-26 17:45:08Ak ste v Bitcoine už nejaký ten rok, možno máte pocit, že už všetkému rozumiete a že vás nič neprekvapí. Viete čo je to peňaženka, čo je to seed a čo adresa, možno dokonca aj čo je to sha256. Ste si istí? Táto prednáška sa vám to pokúsi vyvrátiť. 🙂 @ 0176967e:1e6f471e
2024-07-26 12:15:35Bojovať s rakovinou metabolickou metódou znamená použiť metabolizmus tela proti rakovine. Riadenie cukru a ketónov v krvi stravou a pohybom, časovanie rôznych typov cvičení, včasná kombinácia klasickej onko-liečby a hladovania. Ktoré vitamíny a suplementy prijímam a ktorým sa napríklad vyhýbam dajúc na rady mojej dietologičky z USA Miriam (ktorá sa špecializuje na rakovinu). Hovori sa, že čo nemeriame, neriadime ... Ja som meral, veľa a dlho ... aj grafy budú ... aj sranda bude, hádam ... 😉
@ 0176967e:1e6f471e
2024-07-26 12:15:35Bojovať s rakovinou metabolickou metódou znamená použiť metabolizmus tela proti rakovine. Riadenie cukru a ketónov v krvi stravou a pohybom, časovanie rôznych typov cvičení, včasná kombinácia klasickej onko-liečby a hladovania. Ktoré vitamíny a suplementy prijímam a ktorým sa napríklad vyhýbam dajúc na rady mojej dietologičky z USA Miriam (ktorá sa špecializuje na rakovinu). Hovori sa, že čo nemeriame, neriadime ... Ja som meral, veľa a dlho ... aj grafy budú ... aj sranda bude, hádam ... 😉 @ 0176967e:1e6f471e
2024-07-26 09:50:53Predikčné trhy predstavujú praktický spôsob, ako môžeme nahliadnuť do budúcnosti bez nutnosti spoliehať sa na tradičné, často nepresné metódy, ako je veštenie z kávových zrniek. V prezentácii sa ponoríme do histórie a vývoja predikčných trhov, a popíšeme aký vplyv mali a majú na dostupnosť a kvalitu informácií pre širokú verejnosť, a ako menia trh s týmito informáciami. Pozrieme sa aj na to, ako tieto trhy umožňujú obyčajným ľuďom prístup k spoľahlivým predpovediam a ako môžu prispieť k lepšiemu rozhodovaniu v rôznych oblastiach života.
@ 0176967e:1e6f471e
2024-07-26 09:50:53Predikčné trhy predstavujú praktický spôsob, ako môžeme nahliadnuť do budúcnosti bez nutnosti spoliehať sa na tradičné, často nepresné metódy, ako je veštenie z kávových zrniek. V prezentácii sa ponoríme do histórie a vývoja predikčných trhov, a popíšeme aký vplyv mali a majú na dostupnosť a kvalitu informácií pre širokú verejnosť, a ako menia trh s týmito informáciami. Pozrieme sa aj na to, ako tieto trhy umožňujú obyčajným ľuďom prístup k spoľahlivým predpovediam a ako môžu prispieť k lepšiemu rozhodovaniu v rôznych oblastiach života. @ 0176967e:1e6f471e
2024-07-25 20:53:07AI hype vnímame asi všetci okolo nás — už takmer každá appka ponúka nejakú “AI fíčuru”, AI startupy raisujú stovky miliónov a Európa ako obvykle pracuje na regulovaní a našej ochrane pred nebezpečím umelej inteligencie. Pomaly sa ale ukazuje “ovocie” spojenia umelej inteligencie a človeka, kedy mnohí ľudia reportujú signifikantné zvýšenie produktivity v práci ako aj kreatívnych aktivitách (aj napriek tomu, že mnohí hardcore kreatívci by každého pri spomenutí skratky “AI” najradšej upálili). V prvej polovici prednášky sa pozrieme na to, akými rôznymi spôsobmi nám vie byť AI nápomocná, či už v práci alebo osobnom živote. Umelé neuróny nám už vyskakujú pomaly aj z ovsených vločiek, no to ako sa k nám dostávajú sa veľmi líši. Hlavne v tom, či ich poskytujú firmy v zatvorených alebo open-source modeloch. V druhej polovici prednášky sa pozrieme na boom okolo otvorených AI modelov a ako ich vieme využiť.
@ 0176967e:1e6f471e
2024-07-25 20:53:07AI hype vnímame asi všetci okolo nás — už takmer každá appka ponúka nejakú “AI fíčuru”, AI startupy raisujú stovky miliónov a Európa ako obvykle pracuje na regulovaní a našej ochrane pred nebezpečím umelej inteligencie. Pomaly sa ale ukazuje “ovocie” spojenia umelej inteligencie a človeka, kedy mnohí ľudia reportujú signifikantné zvýšenie produktivity v práci ako aj kreatívnych aktivitách (aj napriek tomu, že mnohí hardcore kreatívci by každého pri spomenutí skratky “AI” najradšej upálili). V prvej polovici prednášky sa pozrieme na to, akými rôznymi spôsobmi nám vie byť AI nápomocná, či už v práci alebo osobnom živote. Umelé neuróny nám už vyskakujú pomaly aj z ovsených vločiek, no to ako sa k nám dostávajú sa veľmi líši. Hlavne v tom, či ich poskytujú firmy v zatvorených alebo open-source modeloch. V druhej polovici prednášky sa pozrieme na boom okolo otvorených AI modelov a ako ich vieme využiť. @ 0176967e:1e6f471e
2024-07-25 20:38:11Čo vznikne keď spojíš hru SNAKE zo starej Nokie 3310 a Bitcoin? - hra [Chain Duel](https://www.youtube.com/watch?v=5hCI2MzxOzE)! Jedna z najlepších implementácií funkcionality Lightning Networku a gamingu vo svete Bitcoinu. Vyskúšať si ju môžete s kamošmi [na tomto odkaze](https://game.chainduel.net/). Na stránke nájdeš aj základné pravidlá hry avšak odporúčame pravidlá pochopiť [aj priamo hraním](https://game.chainduel.net/gamemenu) Chain Duel si získava hromady fanúšikov po bitcoinových konferenciách po celom svete a práve na Lunarpunk festival ho prinesieme tiež. Multiplayer 1v1 hra, kde nejde o náhodu, ale skill, vás dostane. Poďte si zmerať sily s ďalšími bitcoinermi a vyhrať okrem samotných satoshi rôzne iné ceny. Príďte sa zúčastniť prvého oficiálneho Chain Duel turnaja na Slovensku! Pre účasť na turnaji je [potrebná registrácia dopredu](https://docs.google.com/forms/d/e/1FAIpQLScq96a-zM2i9FCkd3W3haNVcdKFTbPkXObNDh4vJwbmADsb0w/viewform).
@ 0176967e:1e6f471e
2024-07-25 20:38:11Čo vznikne keď spojíš hru SNAKE zo starej Nokie 3310 a Bitcoin? - hra [Chain Duel](https://www.youtube.com/watch?v=5hCI2MzxOzE)! Jedna z najlepších implementácií funkcionality Lightning Networku a gamingu vo svete Bitcoinu. Vyskúšať si ju môžete s kamošmi [na tomto odkaze](https://game.chainduel.net/). Na stránke nájdeš aj základné pravidlá hry avšak odporúčame pravidlá pochopiť [aj priamo hraním](https://game.chainduel.net/gamemenu) Chain Duel si získava hromady fanúšikov po bitcoinových konferenciách po celom svete a práve na Lunarpunk festival ho prinesieme tiež. Multiplayer 1v1 hra, kde nejde o náhodu, ale skill, vás dostane. Poďte si zmerať sily s ďalšími bitcoinermi a vyhrať okrem samotných satoshi rôzne iné ceny. Príďte sa zúčastniť prvého oficiálneho Chain Duel turnaja na Slovensku! Pre účasť na turnaji je [potrebná registrácia dopredu](https://docs.google.com/forms/d/e/1FAIpQLScq96a-zM2i9FCkd3W3haNVcdKFTbPkXObNDh4vJwbmADsb0w/viewform). @ b17fccdf:b7211155
2024-07-23 12:19:23#### Next new resources about the MiniBolt guide have been released: * 🆕 **Roadmap**: [LINK](https://github.com/orgs/minibolt-guide/projects/1) * 🆕 **Network Map** (UC): [LINK](https://bit.ly/minibolt_netmap) * 🆕 **Nostr community**: [LINK](https://w3.do/twofaktor@twofaktor-github-io/minibolt_community) * 🆕 **Linktr FOSS** (UC) by [Gzuuus](nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds): [LINK](https://linktr.minibolt.info) * 🆕 **Donate webpage**: 🚾 [Clearnet LINK](https://donate.minibolt.info) || 🧅 [Onion LINK](http://3iqm7nidexns5p6wmgc23ibgiscm6rge7hwyeziviwgav4fl7xui4mqd.onion/apps/Li3AtEGDsqNmNddv6rX69taidm3/pos) * 🆕 **Contact email**: [hello@minibolt.info](mailto:hello@minibolt.info)
@ b17fccdf:b7211155
2024-07-23 12:19:23#### Next new resources about the MiniBolt guide have been released: * 🆕 **Roadmap**: [LINK](https://github.com/orgs/minibolt-guide/projects/1) * 🆕 **Network Map** (UC): [LINK](https://bit.ly/minibolt_netmap) * 🆕 **Nostr community**: [LINK](https://w3.do/twofaktor@twofaktor-github-io/minibolt_community) * 🆕 **Linktr FOSS** (UC) by [Gzuuus](nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds): [LINK](https://linktr.minibolt.info) * 🆕 **Donate webpage**: 🚾 [Clearnet LINK](https://donate.minibolt.info) || 🧅 [Onion LINK](http://3iqm7nidexns5p6wmgc23ibgiscm6rge7hwyeziviwgav4fl7xui4mqd.onion/apps/Li3AtEGDsqNmNddv6rX69taidm3/pos) * 🆕 **Contact email**: [hello@minibolt.info](mailto:hello@minibolt.info) @ 0176967e:1e6f471e
2024-07-22 19:57:47Co se nomádská rodina již 3 roky utíkající před kontrolou naučila o kontrole samotné? Co je to vlastně svoboda? Může koexistovat se strachem? S konfliktem? Zkusme na chvíli zapomenout na daně, policii a stát a pohlédnout na svobodu i mimo hranice společenských ideologií. Zkusme namísto hledání dalších odpovědí zjistit, zda se ještě někde neukrývají nové otázky. Možná to bude trochu ezo. Karel provozuje již přes 3 roky se svou ženou, dvěmi dětmi a jedním psem minimalistický život v obytné dodávce. Na cestách spolu začali tvořit youtubový kanál "[Karel od Martiny](https://www.youtube.com/@KarelodMartiny)" o svobodě, nomádství, anarchii, rodičovství, drogách a dalších normálních věcech. Nájdete ho aj [na nostr](nostr:npub1y2se87uxc7fa0aenfqfx5hl9t2u2fjt4sp0tctlcr0efpauqtalqxfvr89).
@ 0176967e:1e6f471e
2024-07-22 19:57:47Co se nomádská rodina již 3 roky utíkající před kontrolou naučila o kontrole samotné? Co je to vlastně svoboda? Může koexistovat se strachem? S konfliktem? Zkusme na chvíli zapomenout na daně, policii a stát a pohlédnout na svobodu i mimo hranice společenských ideologií. Zkusme namísto hledání dalších odpovědí zjistit, zda se ještě někde neukrývají nové otázky. Možná to bude trochu ezo. Karel provozuje již přes 3 roky se svou ženou, dvěmi dětmi a jedním psem minimalistický život v obytné dodávce. Na cestách spolu začali tvořit youtubový kanál "[Karel od Martiny](https://www.youtube.com/@KarelodMartiny)" o svobodě, nomádství, anarchii, rodičovství, drogách a dalších normálních věcech. Nájdete ho aj [na nostr](nostr:npub1y2se87uxc7fa0aenfqfx5hl9t2u2fjt4sp0tctlcr0efpauqtalqxfvr89). @ 82100056:e198089f
2024-07-22 15:44:39Was the Trump ‘assassination attempt’ a staged event that he was in on? Was it an inside job by the secret service seeking to eliminate the number one enemy of the deep state? Or was Thomas Crooks simply competent (and lucky) enough to pull off a lone-wolf attack on the 45th president of the USA? Whatever the truth is, which will surely come out over time, the ‘shooting’ has dramatically altered the course of American politics. The most obvious narrative shift has been Trump’s new-found God-like status among the American right. The image of Trump holding his fist in the air, right ear bloodied, while urging Americans to “fight”, symbolises this. His long-time friend and UFC chairman Dana White said in the aftermath of the ‘shooting’: “He [Trump] is one of the toughest, most resilient human beings that I have ever met in my entire life….This guy is the legitimate ultimate American badass of all-time!” In addition, a section of Trump supporters turned up to the recent Republican National Convention [wearing fake bandages](https://www.bbc.co.uk/news/videos/cldy39vpv4qo) on their ears in a humorous yet sincere show of solidarity with their leader. These are just two examples among many of the relentless outpouring of adulation that Trump is receiving. He has become a martyr without having to die. The Trump fist raise image and resulting strongman narrative is not what I will focus on, but it does provide crucial context for what I am going to say. Instead, I will look at the farcical performance of the secret service, which did not go unnoticed by social media users. Specifically, that of the female agents, and the resulting backlash against the perceived failures of DEI (diversity, equity and inclusion) within the US government. I will also look at why this narrative is being pushed by powerful players of the alternative-media industrial complex. First, [footage emerged](https://www.youtube.com/watch?v=tAtu1YU-PHo) of one female agent who struggled to holster her firearm, while looking completely disorientated, as Trump, who could have still been in danger, fled the scene in a blacked out SUV. It was reminiscent of Fredo Corleone’s bumbling efforts to save his father Vito, who faced a failed assassination attempt of his own in The Godfather 2. Second, there is the [ridiculous still image](https://www.google.com/search?sca_esv=5b98f86993edd4ca&sca_upv=1&rlz=1C5CHFA_enGB1069GB1069&q=trump+female+secret+service&udm=2&fbs=AEQNm0Aa4sjWe7Rqy32pFwRj0UkWd8nbOJfsBGGB5IQQO6L3J_86uWOeqwdnV0yaSF-x2joQcoZ-0Q2Udkt2zEybT7HdcghX_cULItgDQ-ic0tx97HU0om4eiEoFQ7LkCUAIN0k5ckfuXbaYID2cdV_OmGsEy_vSEauNj1_Mmv2J6NjBnVEvjRAhAzO6zw58Qt0lVtZUf36m&sa=X&ved=2ahUKEwj8_NWx5riHAxX5bEEAHROMDHIQtKgLegQICxAB&biw=1600&bih=781&dpr=1.8#vhid=k3BFXz5a0rU7wM&vssid=mosaic) of the female secret service agent standing in front of Trump by the podium in order to provide cover for the former president amid a possible active shooter situation. The image is ludicrous because the female agent is not nearly as tall as Trump, and so his head, including his ear that was just ‘clipped’ by a 'bullet', remains completely exposed. Third, the US secret service director Kimberly Cheatle, a woman, is [ultimately responsible](https://www.nytimes.com/2024/07/17/us/politics/kimberly-cheatle-secret-service.html) for the ‘near-assassination’ of Donald Trump and the seemingly unlimited ‘mistakes’ made by the agency on the day. For example, Cheatle did not have a secret service gunmen on the roof used by Thomas Crooks because it was “too sloped”. An explanation that was shown to be comically bad in the immediate aftermath of the ‘shooting’ when photos emerged of cleaners standing on the roof to clear Crooks’ ‘blood’ away. The backlash against the female agents in question has been pretty relentless from the American right. But not just from anonymous MAGA social media users. Some of the key drivers of political narratives on the right have honed in on this issue and more generally against the perceived failings of DEI. “There should not be any women in the Secret Service. These are supposed to be the very best, and none of the very best at this job are women,” [said right-leaning activist Matt Walsh](https://x.com/MattWalshBlog/status/1812492702493057338?lang=en) in a direct response to the footage of the female secret service agents. Walsh works for The Daily Wire and rose to global prominence on the back of his documentary “What Is A Women?”. In other words, he is a key figure within the US culture war, who has a keen interest in discussions around gender. Then there is Andrew Tate. One could have predicted where the former kickboxer was going to stand on this issue. [Tate posted a video to social media](https://www.youtube.com/watch?v=cpw5Sm46f-4&t=44s) in which he lambasted Kimberly Cheatle and the other female secret service agents in a visibly heated manner. “There’s not a female alive who’s ever going to jump in front of a bullet for anybody. She’s gonna piss her panties and hide.” Tate carries on the rest of the video in the same vain, including a statement which in my view is a big clue about the narrative he is trying to push. “Society as a whole will be better off if we return to our [gender] roles.” Tate wants the secret service and the military to go back to being made up of men who are selected solely on the basis of merit. After years of military aged males being 'disenfranchised' by the institutions they once felt proud to represent - the pendulum may be about to swing back. At this point, it is worth mentioning that I believe both Matt Walsh and Andrew Tate are intelligence assets who push agendas to the wider public on behalf of the deep state, [as Miri AF explains here](https://miriaf.co.uk/the-most-important-question-about-andrew-tate-no-one-is-asking/). It is also worth considering that these women are akin to actors who are fulfilling their roles as incompetent, further driving the narrative of Walsh and Tate. Their incompetence is not necessarily because they are women - they might just be acting like they are incapable because they are women. On the face of it, it sounds overly conspiratorial - but in my view, it is plausible. Okay, let’s continue down this ‘conspiracy theory’ rabbit hole for a little longer. It is widely understood that intelligence agencies use terror attacks to further their insidious agendas. A clear example of this is how George Bush’s government, in conjunction with the media and the intelligence apparatus, weaponised the fear brought about by 9/11 in order to invade Iraq. So, what is the goal of Tate/Walsh and the deep state (and possibly Trump too) in pushing back against DEI and making the secret service/military a place that ‘respects’ male competence again? The same military whose soon-to-be commander-in-chief has God-like status, is the "ultimate American badass of all time", and who ‘literally’ just ‘took a bullet’ for his country. The same military that is currently in escalating proxy wars vs Russia and Iran - neither of which look like ending anytime soon. Are American military aged males being influenced to go and fight for their country in WW3 after years of being gaslighted? I want to state that I do not claim to know this for sure. I am stating a theory. I am asking questions that I believe need to be asked. But I will leave you with this quote by a World War Two veteran that has been doing the rounds on social media recently. “If president Trump was commander-in-chief I would go back to re-enlist today.” [Sgt. Bill Peril, 99, WW2 veteran. ](https://www.independent.co.uk/news/world/americas/us-politics/rnc-trump-world-war-veteran-b2581928.html)
@ 82100056:e198089f
2024-07-22 15:44:39Was the Trump ‘assassination attempt’ a staged event that he was in on? Was it an inside job by the secret service seeking to eliminate the number one enemy of the deep state? Or was Thomas Crooks simply competent (and lucky) enough to pull off a lone-wolf attack on the 45th president of the USA? Whatever the truth is, which will surely come out over time, the ‘shooting’ has dramatically altered the course of American politics. The most obvious narrative shift has been Trump’s new-found God-like status among the American right. The image of Trump holding his fist in the air, right ear bloodied, while urging Americans to “fight”, symbolises this. His long-time friend and UFC chairman Dana White said in the aftermath of the ‘shooting’: “He [Trump] is one of the toughest, most resilient human beings that I have ever met in my entire life….This guy is the legitimate ultimate American badass of all-time!” In addition, a section of Trump supporters turned up to the recent Republican National Convention [wearing fake bandages](https://www.bbc.co.uk/news/videos/cldy39vpv4qo) on their ears in a humorous yet sincere show of solidarity with their leader. These are just two examples among many of the relentless outpouring of adulation that Trump is receiving. He has become a martyr without having to die. The Trump fist raise image and resulting strongman narrative is not what I will focus on, but it does provide crucial context for what I am going to say. Instead, I will look at the farcical performance of the secret service, which did not go unnoticed by social media users. Specifically, that of the female agents, and the resulting backlash against the perceived failures of DEI (diversity, equity and inclusion) within the US government. I will also look at why this narrative is being pushed by powerful players of the alternative-media industrial complex. First, [footage emerged](https://www.youtube.com/watch?v=tAtu1YU-PHo) of one female agent who struggled to holster her firearm, while looking completely disorientated, as Trump, who could have still been in danger, fled the scene in a blacked out SUV. It was reminiscent of Fredo Corleone’s bumbling efforts to save his father Vito, who faced a failed assassination attempt of his own in The Godfather 2. Second, there is the [ridiculous still image](https://www.google.com/search?sca_esv=5b98f86993edd4ca&sca_upv=1&rlz=1C5CHFA_enGB1069GB1069&q=trump+female+secret+service&udm=2&fbs=AEQNm0Aa4sjWe7Rqy32pFwRj0UkWd8nbOJfsBGGB5IQQO6L3J_86uWOeqwdnV0yaSF-x2joQcoZ-0Q2Udkt2zEybT7HdcghX_cULItgDQ-ic0tx97HU0om4eiEoFQ7LkCUAIN0k5ckfuXbaYID2cdV_OmGsEy_vSEauNj1_Mmv2J6NjBnVEvjRAhAzO6zw58Qt0lVtZUf36m&sa=X&ved=2ahUKEwj8_NWx5riHAxX5bEEAHROMDHIQtKgLegQICxAB&biw=1600&bih=781&dpr=1.8#vhid=k3BFXz5a0rU7wM&vssid=mosaic) of the female secret service agent standing in front of Trump by the podium in order to provide cover for the former president amid a possible active shooter situation. The image is ludicrous because the female agent is not nearly as tall as Trump, and so his head, including his ear that was just ‘clipped’ by a 'bullet', remains completely exposed. Third, the US secret service director Kimberly Cheatle, a woman, is [ultimately responsible](https://www.nytimes.com/2024/07/17/us/politics/kimberly-cheatle-secret-service.html) for the ‘near-assassination’ of Donald Trump and the seemingly unlimited ‘mistakes’ made by the agency on the day. For example, Cheatle did not have a secret service gunmen on the roof used by Thomas Crooks because it was “too sloped”. An explanation that was shown to be comically bad in the immediate aftermath of the ‘shooting’ when photos emerged of cleaners standing on the roof to clear Crooks’ ‘blood’ away. The backlash against the female agents in question has been pretty relentless from the American right. But not just from anonymous MAGA social media users. Some of the key drivers of political narratives on the right have honed in on this issue and more generally against the perceived failings of DEI. “There should not be any women in the Secret Service. These are supposed to be the very best, and none of the very best at this job are women,” [said right-leaning activist Matt Walsh](https://x.com/MattWalshBlog/status/1812492702493057338?lang=en) in a direct response to the footage of the female secret service agents. Walsh works for The Daily Wire and rose to global prominence on the back of his documentary “What Is A Women?”. In other words, he is a key figure within the US culture war, who has a keen interest in discussions around gender. Then there is Andrew Tate. One could have predicted where the former kickboxer was going to stand on this issue. [Tate posted a video to social media](https://www.youtube.com/watch?v=cpw5Sm46f-4&t=44s) in which he lambasted Kimberly Cheatle and the other female secret service agents in a visibly heated manner. “There’s not a female alive who’s ever going to jump in front of a bullet for anybody. She’s gonna piss her panties and hide.” Tate carries on the rest of the video in the same vain, including a statement which in my view is a big clue about the narrative he is trying to push. “Society as a whole will be better off if we return to our [gender] roles.” Tate wants the secret service and the military to go back to being made up of men who are selected solely on the basis of merit. After years of military aged males being 'disenfranchised' by the institutions they once felt proud to represent - the pendulum may be about to swing back. At this point, it is worth mentioning that I believe both Matt Walsh and Andrew Tate are intelligence assets who push agendas to the wider public on behalf of the deep state, [as Miri AF explains here](https://miriaf.co.uk/the-most-important-question-about-andrew-tate-no-one-is-asking/). It is also worth considering that these women are akin to actors who are fulfilling their roles as incompetent, further driving the narrative of Walsh and Tate. Their incompetence is not necessarily because they are women - they might just be acting like they are incapable because they are women. On the face of it, it sounds overly conspiratorial - but in my view, it is plausible. Okay, let’s continue down this ‘conspiracy theory’ rabbit hole for a little longer. It is widely understood that intelligence agencies use terror attacks to further their insidious agendas. A clear example of this is how George Bush’s government, in conjunction with the media and the intelligence apparatus, weaponised the fear brought about by 9/11 in order to invade Iraq. So, what is the goal of Tate/Walsh and the deep state (and possibly Trump too) in pushing back against DEI and making the secret service/military a place that ‘respects’ male competence again? The same military whose soon-to-be commander-in-chief has God-like status, is the "ultimate American badass of all time", and who ‘literally’ just ‘took a bullet’ for his country. The same military that is currently in escalating proxy wars vs Russia and Iran - neither of which look like ending anytime soon. Are American military aged males being influenced to go and fight for their country in WW3 after years of being gaslighted? I want to state that I do not claim to know this for sure. I am stating a theory. I am asking questions that I believe need to be asked. But I will leave you with this quote by a World War Two veteran that has been doing the rounds on social media recently. “If president Trump was commander-in-chief I would go back to re-enlist today.” [Sgt. Bill Peril, 99, WW2 veteran. ](https://www.independent.co.uk/news/world/americas/us-politics/rnc-trump-world-war-veteran-b2581928.html) @ 8e7462a8:c723a97b
2024-07-21 16:00:55<pre class="ql-syntax" spellcheck="false"># Bitcoin: A Peer-to-Peer Electronic Cash System Satoshi Nakamoto [satoshin@gmx.com](mailto:satoshin@gmx.com) www.bitcoin.org **Abstract.** A purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without going through a financial institution. Digital signatures provide part of the solution, but the main benefits are lost if a trusted third party is still required to prevent double-spending. We propose a solution to the double-spending problem using a peer-to-peer network. The network timestamps transactions by hashing them into an ongoing chain of hash-based proof-of-work, forming a record that cannot be changed without redoing the proof-of-work. The longest chain not only serves as proof of the sequence of events witnessed, but proof that it came from the largest pool of CPU power. As long as a majority of CPU power is controlled by nodes that are not cooperating to attack the network, they'll generate the longest chain and outpace attackers. The network itself requires minimal structure. Messages are broadcast on a best effort basis, and nodes can leave and rejoin the network at will, accepting the longest proof-of-work chain as proof of what happened while they were gone. ## 1. Introduction Commerce on the Internet has come to rely almost exclusively on financial institutions serving as trusted third parties to process electronic payments. While the system works well enough for most transactions, it still suffers from the inherent weaknesses of the trust based model. Completely non-reversible transactions are not really possible, since financial institutions cannot avoid mediating disputes. The cost of mediation increases transaction costs, limiting the minimum practical transaction size and cutting off the possibility for small casual transactions, and there is a broader cost in the loss of ability to make non-reversible payments for non-reversible services. With the possibility of reversal, the need for trust spreads. Merchants must be wary of their customers, hassling them for more information than they would otherwise need. A certain percentage of fraud is accepted as unavoidable. These costs and payment uncertainties can be avoided in person by using physical currency, but no mechanism exists to make payments over a communications channel without a trusted party. What is needed is an electronic payment system based on cryptographic proof instead of trust, allowing any two willing parties to transact directly with each other without the need for a trusted third party. Transactions that are computationally impractical to reverse would protect sellers from fraud, and routine escrow mechanisms could easily be implemented to protect buyers. In this paper, we propose a solution to the double-spending problem using a peer-to-peer distributed timestamp server to generate computational proof of the chronological order of transactions. The system is secure as long as honest nodes collectively control more CPU power than any cooperating group of attacker nodes. ## 2. Transactions We define an electronic coin as a chain of digital signatures. Each owner transfers the coin to the next by digitally signing a hash of the previous transaction and the public key of the next owner and adding these to the end of the coin. A payee can verify the signatures to verify the chain of ownership. ``` ┌─────────────────────┐ ┌─────────────────────┐ ┌─────────────────────┐ │ │ │ │ │ │ │ Transaction │ │ Transaction │ │ Transaction │ │ │ │ │ │ │ │ ┌─────────────┐ │ │ ┌─────────────┐ │ │ ┌─────────────┐ │ │ │ Owner 1's │ │ │ │ Owner 2's │ │ │ │ Owner 3's │ │ │ │ Public Key │ │ │ │ Public Key │ │ │ │ Public Key │ │ │ └───────┬─────┘ │ │ └───────┬─────┘ │ │ └───────┬─────┘ │ │ │ . │ │ │ . │ │ │ │ ──────┼─────────┐ │ . ├───────────────┼─────────┐ │ . ├──────────────┼─────────┐ │ │ │ │ │ . │ │ │ │ . │ │ │ │ │ │ ┌──▼─▼──┐ . │ │ ┌──▼─▼──┐ . │ │ ┌──▼─▼──┐ │ │ │ Hash │ . │ │ │ Hash │ . │ │ │ Hash │ │ │ └───┬───┘ . │ Verify │ └───┬───┘ . │ Verify │ └───┬───┘ │ │ │ ............................ │ ........................... │ │ │ │ │ │ │ │ │ │ │ │ │ │ ┌──────▼──────┐ │ │ ┌─▼────▼──────┐ │ │ ┌─▼────▼──────┐ │ │ │ Owner 0's │ │ Sign │ │ Owner 1's │ │ Sign │ │ Owner 2's │ │ │ │ Signature │ │ ...........─►│ Signature │ │ ...........─►│ Signature │ │ │ └─────────────┘ │ . │ └─────────────┘ │ . │ └─────────────┘ │ │ │ . │ │ . │ │ └─────────────────────┘ . └─────────────────────┘ . └─────────────────────┘ . . ┌─────────────┐ . ┌─────────────┐ . ┌─────────────┐ │ Owner 1's │........... │ Owner 2's │.......... │ Owner 3's │ │ Private Key │ │ Private Key │ │ Private Key │ └─────────────┘ └─────────────┘ └─────────────┘ ``` The problem of course is the payee can't verify that one of the owners did not double-spend the coin. A common solution is to introduce a trusted central authority, or mint, that checks every transaction for double spending. After each transaction, the coin must be returned to the mint to issue a new coin, and only coins issued directly from the mint are trusted not to be double-spent. The problem with this solution is that the fate of the entire money system depends on the company running the mint, with every transaction having to go through them, just like a bank. We need a way for the payee to know that the previous owners did not sign any earlier transactions. For our purposes, the earliest transaction is the one that counts, so we don't care about later attempts to double-spend. The only way to confirm the absence of a transaction is to be aware of all transactions. In the mint based model, the mint was aware of all transactions and decided which arrived first. To accomplish this without a trusted party, transactions must be publicly announced [^1], and we need a system for participants to agree on a single history of the order in which they were received. The payee needs proof that at the time of each transaction, the majority of nodes agreed it was the first received. ## 3. Timestamp Server The solution we propose begins with a timestamp server. A timestamp server works by taking a hash of a block of items to be timestamped and widely publishing the hash, such as in a newspaper or Usenet post [^2] [^3] [^4] [^5]. The timestamp proves that the data must have existed at the time, obviously, in order to get into the hash. Each timestamp includes the previous timestamp in its hash, forming a chain, with each additional timestamp reinforcing the ones before it. ``` ┌──────┐ ┌──────┐ ────────────►│ ├───────────────────────►│ ├───────────────────► │ Hash │ │ Hash │ ┌───►│ │ ┌───►│ │ │ └──────┘ │ └──────┘ │ │ ┌┴──────────────────────────┐ ┌┴──────────────────────────┐ │ Block │ │ Block │ │ ┌─────┐ ┌─────┐ ┌─────┐ │ │ ┌─────┐ ┌─────┐ ┌─────┐ │ │ │Item │ │Item │ │... │ │ │ │Item │ │Item │ │... │ │ │ └─────┘ └─────┘ └─────┘ │ │ └─────┘ └─────┘ └─────┘ │ │ │ │ │ └───────────────────────────┘ └───────────────────────────┘ ``` ## 4. Proof-of-Work To implement a distributed timestamp server on a peer-to-peer basis, we will need to use a proof-of-work system similar to Adam Back's Hashcash [^6], rather than newspaper or Usenet posts. The proof-of-work involves scanning for a value that when hashed, such as with SHA-256, the hash begins with a number of zero bits. The average work required is exponential in the number of zero bits required and can be verified by executing a single hash. For our timestamp network, we implement the proof-of-work by incrementing a nonce in the block until a value is found that gives the block's hash the required zero bits. Once the CPU effort has been expended to make it satisfy the proof-of-work, the block cannot be changed without redoing the work. As later blocks are chained after it, the work to change the block would include redoing all the blocks after it. ``` ┌────────────────────────────────────────┐ ┌────────────────────────────────────────┐ │ Block │ │ Block │ │ ┌──────────────────┐ ┌──────────────┐ │ │ ┌──────────────────┐ ┌──────────────┐ │ ───────┼─►│ Prev Hash │ │ Nonce │ ├──────┼─►│ Prev Hash │ │ Nonce │ │ │ └──────────────────┘ └──────────────┘ │ │ └──────────────────┘ └──────────────┘ │ │ │ │ │ │ ┌──────────┐ ┌──────────┐ ┌──────────┐ │ │ ┌──────────┐ ┌──────────┐ ┌──────────┐ │ │ │ Tx │ │ Tx │ │ ... │ │ │ │ Tx │ │ Tx │ │ ... │ │ │ └──────────┘ └──────────┘ └──────────┘ │ │ └──────────┘ └──────────┘ └──────────┘ │ │ │ │ │ └────────────────────────────────────────┘ └────────────────────────────────────────┘ ``` The proof-of-work also solves the problem of determining representation in majority decision making. If the majority were based on one-IP-address-one-vote, it could be subverted by anyone able to allocate many IPs. Proof-of-work is essentially one-CPU-one-vote. The majority decision is represented by the longest chain, which has the greatest proof-of-work effort invested in it. If a majority of CPU power is controlled by honest nodes, the honest chain will grow the fastest and outpace any competing chains. To modify a past block, an attacker would have to redo the proof-of-work of the block and all blocks after it and then catch up with and surpass the work of the honest nodes. We will show later that the probability of a slower attacker catching up diminishes exponentially as subsequent blocks are added. To compensate for increasing hardware speed and varying interest in running nodes over time, the proof-of-work difficulty is determined by a moving average targeting an average number of blocks per hour. If they're generated too fast, the difficulty increases. ## 5. Network The steps to run the network are as follows: 1. New transactions are broadcast to all nodes. 2. Each node collects new transactions into a block. 3. Each node works on finding a difficult proof-of-work for its block. 4. When a node finds a proof-of-work, it broadcasts the block to all nodes. 5. Nodes accept the block only if all transactions in it are valid and not already spent. 6. Nodes express their acceptance of the block by working on creating the next block in the chain, using the hash of the accepted block as the previous hash. Nodes always consider the longest chain to be the correct one and will keep working on extending it. If two nodes broadcast different versions of the next block simultaneously, some nodes may receive one or the other first. In that case, they work on the first one they received, but save the other branch in case it becomes longer. The tie will be broken when the next proof-of-work is found and one branch becomes longer; the nodes that were working on the other branch will then switch to the longer one. New transaction broadcasts do not necessarily need to reach all nodes. As long as they reach many nodes, they will get into a block before long. Block broadcasts are also tolerant of dropped messages. If a node does not receive a block, it will request it when it receives the next block and realizes it missed one. ## 6. Incentive By convention, the first transaction in a block is a special transaction that starts a new coin owned by the creator of the block. This adds an incentive for nodes to support the network, and provides a way to initially distribute coins into circulation, since there is no central authority to issue them. The steady addition of a constant of amount of new coins is analogous to gold miners expending resources to add gold to circulation. In our case, it is CPU time and electricity that is expended. The incentive can also be funded with transaction fees. If the output value of a transaction is less than its input value, the difference is a transaction fee that is added to the incentive value of the block containing the transaction. Once a predetermined number of coins have entered circulation, the incentive can transition entirely to transaction fees and be completely inflation free. The incentive may help encourage nodes to stay honest. If a greedy attacker is able to assemble more CPU power than all the honest nodes, he would have to choose between using it to defraud people by stealing back his payments, or using it to generate new coins. He ought to find it more profitable to play by the rules, such rules that favour him with more new coins than everyone else combined, than to undermine the system and the validity of his own wealth. ## 7. Reclaiming Disk Space Once the latest transaction in a coin is buried under enough blocks, the spent transactions before it can be discarded to save disk space. To facilitate this without breaking the block's hash, transactions are hashed in a Merkle Tree [^7] [^2] [^5], with only the root included in the block's hash. Old blocks can then be compacted by stubbing off branches of the tree. The interior hashes do not need to be stored. ``` ┌──────────────────────────────────────────┐ ┌──────────────────────────────────────────┐ │ │ │ │ │ Block ┌─────────────────────────────┐ │ │ Block ┌─────────────────────────────┐ │ │ │ Block Header (Block Hash) │ │ │ │ Block Header (Block Hash) │ │ │ │ ┌────────────┐ ┌─────────┐ │ │ │ │ ┌────────────┐ ┌─────────┐ │ │ │ │ │ Prev Hash │ │ Nonce │ │ │ │ │ │ Prev Hash │ │ Nonce │ │ │ │ │ └────────────┘ └─────────┘ │ │ │ │ └────────────┘ └─────────┘ │ │ │ │ │ │ │ │ │ │ │ │ ┌─────────────┐ │ │ │ │ ┌─────────────┐ │ │ │ │ │ Root Hash │ │ │ │ │ │ Root Hash │ │ │ │ │ └─────▲─▲─────┘ │ │ │ │ └─────▲─▲─────┘ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ └───────────┼─┼───────────────┘ │ │ └───────────┼─┼───────────────┘ │ │ │ │ │ │ │ │ │ │ .......... │ │ .......... │ │ ┌────────┐ │ │ .......... │ │ . ─────┘ └─────. . │ │ │ ├────┘ └─────. . │ │ . Hash01 . . Hash23 . │ │ │ Hash01 │ . Hash23 . │ │ .▲.....▲.. .▲.....▲.. │ │ │ │ .▲.....▲.. │ │ │ │ │ │ │ │ └────────┘ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ .....│.. ..│..... .....│.. ..│..... │ │ ┌────┴─┐ ..│..... │ │ . . . . . . . . │ │ │ │ . . │ │ .Hash0 . .Hash1 . .Hash2 . .Hash3 . │ │ │Hash2 │ .Hash3 . │ │ ...▲.... ...▲.... ...▲.... ...▲.... │ │ │ │ . . │ │ │ │ │ │ │ │ └──────┘ ...▲.... │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ ┌──┴───┐ ┌──┴───┐ ┌──┴───┐ ┌──┴───┐ │ │ ┌──┴───┐ │ │ │ Tx0 │ │ Tx1 │ │ Tx2 │ │ Tx3 │ │ │ │ Tx3 │ │ │ └──────┘ └──────┘ └──────┘ └──────┘ │ │ └──────┘ │ │ │ │ │ └──────────────────────────────────────────┘ └──────────────────────────────────────────┘ Transactions Hashed in a Merkle Tree After Pruning Tx0-2 from the Block ``` A block header with no transactions would be about 80 bytes. If we suppose blocks are generated every 10 minutes, 80 bytes * 6 * 24 * 365 = 4.2MB per year. With computer systems typically selling with 2GB of RAM as of 2008, and Moore's Law predicting current growth of 1.2GB per year, storage should not be a problem even if the block headers must be kept in memory. ## 8. Simplified Payment Verification It is possible to verify payments without running a full network node. A user only needs to keep a copy of the block headers of the longest proof-of-work chain, which he can get by querying network nodes until he's convinced he has the longest chain, and obtain the Merkle branch linking the transaction to the block it's timestamped in. He can't check the transaction for himself, but by linking it to a place in the chain, he can see that a network node has accepted it, and blocks added after it further confirm the network has accepted it. ``` Longest Proof-of-Work Chain ┌────────────────────────────────────────┐ ┌────────────────────────────────────────┐ ┌────────────────────────────────────────┐ │ Block Header │ │ Block Header │ │ Block Header │ │ ┌──────────────────┐ ┌──────────────┐ │ │ ┌──────────────────┐ ┌──────────────┐ │ │ ┌──────────────────┐ ┌──────────────┐ │ ───────┼─►│ Prev Hash │ │ Nonce │ ├──────┼─►│ Prev Hash │ │ Nonce │ ├───────┼─►│ Prev Hash │ │ Nonce │ ├────────► │ └──────────────────┘ └──────────────┘ │ │ └──────────────────┘ └──────────────┘ │ │ └──────────────────┘ └──────────────┘ │ │ │ │ │ │ │ │ ┌───────────────────┐ │ │ ┌────────────────────┐ │ │ ┌───────────────────┐ │ │ │ Merkle Root │ │ │ │ Merkle Root │ │ │ │ Merkle Root │ │ │ └───────────────────┘ │ │ └────────▲─▲─────────┘ │ │ └───────────────────┘ │ │ │ │ │ │ │ │ │ └────────────────────────────────────────┘ └─────────────┼─┼────────────────────────┘ └────────────────────────────────────────┘ │ │ │ │ ┌────────┐ │ │ .......... │ ├────┘ └─────. . │ Hash01 │ . Hash23 . │ │ .▲.....▲.. └────────┘ │ │ │ │ │ │ Merkle Branch for Tx3 │ │ ┌─────┴─┐ ..│..... │ │ . . │ Hash2 │ .Hash3 . │ │ . . └───────┘ ...▲.... │ │ ┌───┴───┐ │ Tx3 │ └───────┘ ``` As such, the verification is reliable as long as honest nodes control the network, but is more vulnerable if the network is overpowered by an attacker. While network nodes can verify transactions for themselves, the simplified method can be fooled by an attacker's fabricated transactions for as long as the attacker can continue to overpower the network. One strategy to protect against this would be to accept alerts from network nodes when they detect an invalid block, prompting the user's software to download the full block and alerted transactions to confirm the inconsistency. Businesses that receive frequent payments will probably still want to run their own nodes for more independent security and quicker verification. ## 9. Combining and Splitting Value Although it would be possible to handle coins individually, it would be unwieldy to make a separate transaction for every cent in a transfer. To allow value to be split and combined, transactions contain multiple inputs and outputs. Normally there will be either a single input from a larger previous transaction or multiple inputs combining smaller amounts, and at most two outputs: one for the payment, and one returning the change, if any, back to the sender. ``` ┌──────────────────────┐ │ Transaction │ │ │ │ ┌─────┐ ┌─────┐ │ ─────┼──►│ in │ │ out │ ──┼─────► │ └─────┘ └─────┘ │ │ │ │ │ │ ┌─────┐ ┌─────┐ │ ─────┼──►│ in │ │ ... │ ──┼─────► │ └─────┘ └─────┘ │ │ │ │ │ │ ┌─────┐ │ ─────┼──►│... │ │ │ └─────┘ │ │ │ └──────────────────────┘ ``` It should be noted that fan-out, where a transaction depends on several transactions, and those transactions depend on many more, is not a problem here. There is never the need to extract a complete standalone copy of a transaction's history. ## 10. Privacy The traditional banking model achieves a level of privacy by limiting access to information to the parties involved and the trusted third party. The necessity to announce all transactions publicly precludes this method, but privacy can still be maintained by breaking the flow of information in another place: by keeping public keys anonymous. The public can see that someone is sending an amount to someone else, but without information linking the transaction to anyone. This is similar to the level of information released by stock exchanges, where the time and size of individual trades, the "tape", is made public, but without telling who the parties were. ``` Traditional Privacy Models │ ┌─────────────┐ ┌──────────────┐ │ ┌────────┐ ┌──────────────┐ ┌──────────────┐ │ Trusted │ │ │ │ │ │ │ Identities ├──┤ Transactions ├───►│ Third Party ├──►│ Counterparty │ │ │ Public │ └──────────────┘ └──────────────┘ │ │ │ │ │ │ │ └─────────────┘ └──────────────┘ │ └────────┘ │ New Privacy Model ┌────────┐ ┌──────────────┐ │ ┌──────────────┐ │ │ │ Identities │ │ │ Transactions ├───►│ Public │ └──────────────┘ │ └──────────────┘ │ │ └────────┘ ``` As an additional firewall, a new key pair should be used for each transaction to keep them from being linked to a common owner. Some linking is still unavoidable with multi-input transactions, which necessarily reveal that their inputs were owned by the same owner. The risk is that if the owner of a key is revealed, linking could reveal other transactions that belonged to the same owner. ## 11. Calculations We consider the scenario of an attacker trying to generate an alternate chain faster than the honest chain. Even if this is accomplished, it does not throw the system open to arbitrary changes, such as creating value out of thin air or taking money that never belonged to the attacker. Nodes are not going to accept an invalid transaction as payment, and honest nodes will never accept a block containing them. An attacker can only try to change one of his own transactions to take back money he recently spent. The race between the honest chain and an attacker chain can be characterized as a Binomial Random Walk. The success event is the honest chain being extended by one block, increasing its lead by +1, and the failure event is the attacker's chain being extended by one block, reducing the gap by -1. The probability of an attacker catching up from a given deficit is analogous to a Gambler's Ruin problem. Suppose a gambler with unlimited credit starts at a deficit and plays potentially an infinite number of trials to try to reach breakeven. We can calculate the probability he ever reaches breakeven, or that an attacker ever catches up with the honest chain, as follows [^8]: ```plaintext p = probability an honest node finds the next block< q = probability the attacker finds the next block q = probability the attacker will ever catch up from z blocks behind `````` $$ qz = \begin{cases} 1 & \text{if } p \leq q \\ \left(\frac{q}{p}\right) z & \text{if } p > q \end{cases} $$ Given our assumption that p > q, the probability drops exponentially as the number of blocks the attacker has to catch up with increases. With the odds against him, if he doesn't make a lucky lunge forward early on, his chances become vanishingly small as he falls further behind. We now consider how long the recipient of a new transaction needs to wait before being sufficiently certain the sender can't change the transaction. We assume the sender is an attacker who wants to make the recipient believe he paid him for a while, then switch it to pay back to himself after some time has passed. The receiver will be alerted when that happens, but the sender hopes it will be too late. The receiver generates a new key pair and gives the public key to the sender shortly before signing. This prevents the sender from preparing a chain of blocks ahead of time by working on it continuously until he is lucky enough to get far enough ahead, then executing the transaction at that moment. Once the transaction is sent, the dishonest sender starts working in secret on a parallel chain containing an alternate version of his transaction. The recipient waits until the transaction has been added to a block and z blocks have been linked after it. He doesn't know the exact amount of progress the attacker has made, but assuming the honest blocks took the average expected time per block, the attacker's potential progress will be a Poisson distribution with expected value: $$ \lambda = z\frac{q}{p} $$ To get the probability the attacker could still catch up now, we multiply the Poisson density for each amount of progress he could have made by the probability he could catch up from that point: $$ \sum_{k=0}^{\infty} \frac{\lambda^k e^{-\lambda}}{k!} \cdot \left\{ \begin{array}{cl} \left(\frac{q}{p}\right)^{(z-k)} & \text{if } k \leq z \\ 1 & \text{if } k > z \end{array} \right. $$ Rearranging to avoid summing the infinite tail of the distribution... $$ 1 - \sum_{k=0}^{z} \frac{\lambda^k e^{-\lambda}}{k!} \left(1-\left(\frac{q}{p}\right)^{(z-k)}\right) $$ Converting to C code... ```c #include <math.h> double AttackerSuccessProbability(double q, int z) { double p = 1.0 - q; double lambda = z * (q / p); double sum = 1.0; int i, k; for (k = 0; k <= z; k++) { double poisson = exp(-lambda); for (i = 1; i <= k; i++) poisson *= lambda / i; sum -= poisson * (1 - pow(q / p, z - k)); } return sum; } ``` Running some results, we can see the probability drop off exponentially with z. ```plaintext q=0.1 z=0 P=1.0000000 z=1 P=0.2045873 z=2 P=0.0509779 z=3 P=0.0131722 z=4 P=0.0034552 z=5 P=0.0009137 z=6 P=0.0002428 z=7 P=0.0000647 z=8 P=0.0000173 z=9 P=0.0000046 z=10 P=0.0000012 q=0.3 z=0 P=1.0000000 z=5 P=0.1773523 z=10 P=0.0416605 z=15 P=0.0101008 z=20 P=0.0024804 z=25 P=0.0006132 z=30 P=0.0001522 z=35 P=0.0000379 z=40 P=0.0000095 z=45 P=0.0000024 z=50 P=0.0000006 ``` Solving for P less than 0.1%... ```plaintext P < 0.001 q=0.10 z=5 q=0.15 z=8 q=0.20 z=11 q=0.25 z=15 q=0.30 z=24 q=0.35 z=41 q=0.40 z=89 q=0.45 z=340 ``` ## 12. Conclusion We have proposed a system for electronic transactions without relying on trust. We started with the usual framework of coins made from digital signatures, which provides strong control of ownership, but is incomplete without a way to prevent double-spending. To solve this, we proposed a peer-to-peer network using proof-of-work to record a public history of transactions that quickly becomes computationally impractical for an attacker to change if honest nodes control a majority of CPU power. The network is robust in its unstructured simplicity. Nodes work all at once with little coordination. They do not need to be identified, since messages are not routed to any particular place and only need to be delivered on a best effort basis. Nodes can leave and rejoin the network at will, accepting the proof-of-work chain as proof of what happened while they were gone. They vote with their CPU power, expressing their acceptance of valid blocks by working on extending them and rejecting invalid blocks by refusing to work on them. Any needed rules and incentives can be enforced with this consensus mechanism. <br> ### References --- [^1]: W. Dai, "b-money," http://www.weidai.com/bmoney.txt, 1998. [^2]: H. Massias, X.S. Avila, and J.-J. Quisquater, "Design of a secure timestamping service with minimal trust requirements," In 20th Symposium on Information Theory in the Benelux, May 1999. [^3]: S. Haber, W.S. Stornetta, "How to time-stamp a digital document," In Journal of Cryptology, vol 3, no 2, pages 99-111, 1991. [^4]: D. Bayer, S. Haber, W.S. Stornetta, "Improving the efficiency and reliability of digital time-stamping," In Sequences II: Methods in Communication, Security and Computer Science, pages 329-334, 1993. [^5]: S. Haber, W.S. Stornetta, "Secure names for bit-strings," In Proceedings of the 4th ACM Conference on Computer and Communications Security, pages 28-35, April 1997. [^6]: A. Back, "Hashcash - a denial of service counter-measure," http://www.hashcash.org/papers/hashcash.pdf, 2002. [^7]: R.C. Merkle, "Protocols for public key cryptosystems," In Proc. 1980 Symposium on Security and Privacy, IEEE Computer Society, pages 122-133, April 1980. [^8]: W. Feller, "An introduction to probability theory and its applications," 1957. </pre><p><br></p>
@ 8e7462a8:c723a97b
2024-07-21 16:00:55<pre class="ql-syntax" spellcheck="false"># Bitcoin: A Peer-to-Peer Electronic Cash System Satoshi Nakamoto [satoshin@gmx.com](mailto:satoshin@gmx.com) www.bitcoin.org **Abstract.** A purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without going through a financial institution. Digital signatures provide part of the solution, but the main benefits are lost if a trusted third party is still required to prevent double-spending. We propose a solution to the double-spending problem using a peer-to-peer network. The network timestamps transactions by hashing them into an ongoing chain of hash-based proof-of-work, forming a record that cannot be changed without redoing the proof-of-work. The longest chain not only serves as proof of the sequence of events witnessed, but proof that it came from the largest pool of CPU power. As long as a majority of CPU power is controlled by nodes that are not cooperating to attack the network, they'll generate the longest chain and outpace attackers. The network itself requires minimal structure. Messages are broadcast on a best effort basis, and nodes can leave and rejoin the network at will, accepting the longest proof-of-work chain as proof of what happened while they were gone. ## 1. Introduction Commerce on the Internet has come to rely almost exclusively on financial institutions serving as trusted third parties to process electronic payments. While the system works well enough for most transactions, it still suffers from the inherent weaknesses of the trust based model. Completely non-reversible transactions are not really possible, since financial institutions cannot avoid mediating disputes. The cost of mediation increases transaction costs, limiting the minimum practical transaction size and cutting off the possibility for small casual transactions, and there is a broader cost in the loss of ability to make non-reversible payments for non-reversible services. With the possibility of reversal, the need for trust spreads. Merchants must be wary of their customers, hassling them for more information than they would otherwise need. A certain percentage of fraud is accepted as unavoidable. These costs and payment uncertainties can be avoided in person by using physical currency, but no mechanism exists to make payments over a communications channel without a trusted party. What is needed is an electronic payment system based on cryptographic proof instead of trust, allowing any two willing parties to transact directly with each other without the need for a trusted third party. Transactions that are computationally impractical to reverse would protect sellers from fraud, and routine escrow mechanisms could easily be implemented to protect buyers. In this paper, we propose a solution to the double-spending problem using a peer-to-peer distributed timestamp server to generate computational proof of the chronological order of transactions. The system is secure as long as honest nodes collectively control more CPU power than any cooperating group of attacker nodes. ## 2. Transactions We define an electronic coin as a chain of digital signatures. Each owner transfers the coin to the next by digitally signing a hash of the previous transaction and the public key of the next owner and adding these to the end of the coin. A payee can verify the signatures to verify the chain of ownership. ``` ┌─────────────────────┐ ┌─────────────────────┐ ┌─────────────────────┐ │ │ │ │ │ │ │ Transaction │ │ Transaction │ │ Transaction │ │ │ │ │ │ │ │ ┌─────────────┐ │ │ ┌─────────────┐ │ │ ┌─────────────┐ │ │ │ Owner 1's │ │ │ │ Owner 2's │ │ │ │ Owner 3's │ │ │ │ Public Key │ │ │ │ Public Key │ │ │ │ Public Key │ │ │ └───────┬─────┘ │ │ └───────┬─────┘ │ │ └───────┬─────┘ │ │ │ . │ │ │ . │ │ │ │ ──────┼─────────┐ │ . ├───────────────┼─────────┐ │ . ├──────────────┼─────────┐ │ │ │ │ │ . │ │ │ │ . │ │ │ │ │ │ ┌──▼─▼──┐ . │ │ ┌──▼─▼──┐ . │ │ ┌──▼─▼──┐ │ │ │ Hash │ . │ │ │ Hash │ . │ │ │ Hash │ │ │ └───┬───┘ . │ Verify │ └───┬───┘ . │ Verify │ └───┬───┘ │ │ │ ............................ │ ........................... │ │ │ │ │ │ │ │ │ │ │ │ │ │ ┌──────▼──────┐ │ │ ┌─▼────▼──────┐ │ │ ┌─▼────▼──────┐ │ │ │ Owner 0's │ │ Sign │ │ Owner 1's │ │ Sign │ │ Owner 2's │ │ │ │ Signature │ │ ...........─►│ Signature │ │ ...........─►│ Signature │ │ │ └─────────────┘ │ . │ └─────────────┘ │ . │ └─────────────┘ │ │ │ . │ │ . │ │ └─────────────────────┘ . └─────────────────────┘ . └─────────────────────┘ . . ┌─────────────┐ . ┌─────────────┐ . ┌─────────────┐ │ Owner 1's │........... │ Owner 2's │.......... │ Owner 3's │ │ Private Key │ │ Private Key │ │ Private Key │ └─────────────┘ └─────────────┘ └─────────────┘ ``` The problem of course is the payee can't verify that one of the owners did not double-spend the coin. A common solution is to introduce a trusted central authority, or mint, that checks every transaction for double spending. After each transaction, the coin must be returned to the mint to issue a new coin, and only coins issued directly from the mint are trusted not to be double-spent. The problem with this solution is that the fate of the entire money system depends on the company running the mint, with every transaction having to go through them, just like a bank. We need a way for the payee to know that the previous owners did not sign any earlier transactions. For our purposes, the earliest transaction is the one that counts, so we don't care about later attempts to double-spend. The only way to confirm the absence of a transaction is to be aware of all transactions. In the mint based model, the mint was aware of all transactions and decided which arrived first. To accomplish this without a trusted party, transactions must be publicly announced [^1], and we need a system for participants to agree on a single history of the order in which they were received. The payee needs proof that at the time of each transaction, the majority of nodes agreed it was the first received. ## 3. Timestamp Server The solution we propose begins with a timestamp server. A timestamp server works by taking a hash of a block of items to be timestamped and widely publishing the hash, such as in a newspaper or Usenet post [^2] [^3] [^4] [^5]. The timestamp proves that the data must have existed at the time, obviously, in order to get into the hash. Each timestamp includes the previous timestamp in its hash, forming a chain, with each additional timestamp reinforcing the ones before it. ``` ┌──────┐ ┌──────┐ ────────────►│ ├───────────────────────►│ ├───────────────────► │ Hash │ │ Hash │ ┌───►│ │ ┌───►│ │ │ └──────┘ │ └──────┘ │ │ ┌┴──────────────────────────┐ ┌┴──────────────────────────┐ │ Block │ │ Block │ │ ┌─────┐ ┌─────┐ ┌─────┐ │ │ ┌─────┐ ┌─────┐ ┌─────┐ │ │ │Item │ │Item │ │... │ │ │ │Item │ │Item │ │... │ │ │ └─────┘ └─────┘ └─────┘ │ │ └─────┘ └─────┘ └─────┘ │ │ │ │ │ └───────────────────────────┘ └───────────────────────────┘ ``` ## 4. Proof-of-Work To implement a distributed timestamp server on a peer-to-peer basis, we will need to use a proof-of-work system similar to Adam Back's Hashcash [^6], rather than newspaper or Usenet posts. The proof-of-work involves scanning for a value that when hashed, such as with SHA-256, the hash begins with a number of zero bits. The average work required is exponential in the number of zero bits required and can be verified by executing a single hash. For our timestamp network, we implement the proof-of-work by incrementing a nonce in the block until a value is found that gives the block's hash the required zero bits. Once the CPU effort has been expended to make it satisfy the proof-of-work, the block cannot be changed without redoing the work. As later blocks are chained after it, the work to change the block would include redoing all the blocks after it. ``` ┌────────────────────────────────────────┐ ┌────────────────────────────────────────┐ │ Block │ │ Block │ │ ┌──────────────────┐ ┌──────────────┐ │ │ ┌──────────────────┐ ┌──────────────┐ │ ───────┼─►│ Prev Hash │ │ Nonce │ ├──────┼─►│ Prev Hash │ │ Nonce │ │ │ └──────────────────┘ └──────────────┘ │ │ └──────────────────┘ └──────────────┘ │ │ │ │ │ │ ┌──────────┐ ┌──────────┐ ┌──────────┐ │ │ ┌──────────┐ ┌──────────┐ ┌──────────┐ │ │ │ Tx │ │ Tx │ │ ... │ │ │ │ Tx │ │ Tx │ │ ... │ │ │ └──────────┘ └──────────┘ └──────────┘ │ │ └──────────┘ └──────────┘ └──────────┘ │ │ │ │ │ └────────────────────────────────────────┘ └────────────────────────────────────────┘ ``` The proof-of-work also solves the problem of determining representation in majority decision making. If the majority were based on one-IP-address-one-vote, it could be subverted by anyone able to allocate many IPs. Proof-of-work is essentially one-CPU-one-vote. The majority decision is represented by the longest chain, which has the greatest proof-of-work effort invested in it. If a majority of CPU power is controlled by honest nodes, the honest chain will grow the fastest and outpace any competing chains. To modify a past block, an attacker would have to redo the proof-of-work of the block and all blocks after it and then catch up with and surpass the work of the honest nodes. We will show later that the probability of a slower attacker catching up diminishes exponentially as subsequent blocks are added. To compensate for increasing hardware speed and varying interest in running nodes over time, the proof-of-work difficulty is determined by a moving average targeting an average number of blocks per hour. If they're generated too fast, the difficulty increases. ## 5. Network The steps to run the network are as follows: 1. New transactions are broadcast to all nodes. 2. Each node collects new transactions into a block. 3. Each node works on finding a difficult proof-of-work for its block. 4. When a node finds a proof-of-work, it broadcasts the block to all nodes. 5. Nodes accept the block only if all transactions in it are valid and not already spent. 6. Nodes express their acceptance of the block by working on creating the next block in the chain, using the hash of the accepted block as the previous hash. Nodes always consider the longest chain to be the correct one and will keep working on extending it. If two nodes broadcast different versions of the next block simultaneously, some nodes may receive one or the other first. In that case, they work on the first one they received, but save the other branch in case it becomes longer. The tie will be broken when the next proof-of-work is found and one branch becomes longer; the nodes that were working on the other branch will then switch to the longer one. New transaction broadcasts do not necessarily need to reach all nodes. As long as they reach many nodes, they will get into a block before long. Block broadcasts are also tolerant of dropped messages. If a node does not receive a block, it will request it when it receives the next block and realizes it missed one. ## 6. Incentive By convention, the first transaction in a block is a special transaction that starts a new coin owned by the creator of the block. This adds an incentive for nodes to support the network, and provides a way to initially distribute coins into circulation, since there is no central authority to issue them. The steady addition of a constant of amount of new coins is analogous to gold miners expending resources to add gold to circulation. In our case, it is CPU time and electricity that is expended. The incentive can also be funded with transaction fees. If the output value of a transaction is less than its input value, the difference is a transaction fee that is added to the incentive value of the block containing the transaction. Once a predetermined number of coins have entered circulation, the incentive can transition entirely to transaction fees and be completely inflation free. The incentive may help encourage nodes to stay honest. If a greedy attacker is able to assemble more CPU power than all the honest nodes, he would have to choose between using it to defraud people by stealing back his payments, or using it to generate new coins. He ought to find it more profitable to play by the rules, such rules that favour him with more new coins than everyone else combined, than to undermine the system and the validity of his own wealth. ## 7. Reclaiming Disk Space Once the latest transaction in a coin is buried under enough blocks, the spent transactions before it can be discarded to save disk space. To facilitate this without breaking the block's hash, transactions are hashed in a Merkle Tree [^7] [^2] [^5], with only the root included in the block's hash. Old blocks can then be compacted by stubbing off branches of the tree. The interior hashes do not need to be stored. ``` ┌──────────────────────────────────────────┐ ┌──────────────────────────────────────────┐ │ │ │ │ │ Block ┌─────────────────────────────┐ │ │ Block ┌─────────────────────────────┐ │ │ │ Block Header (Block Hash) │ │ │ │ Block Header (Block Hash) │ │ │ │ ┌────────────┐ ┌─────────┐ │ │ │ │ ┌────────────┐ ┌─────────┐ │ │ │ │ │ Prev Hash │ │ Nonce │ │ │ │ │ │ Prev Hash │ │ Nonce │ │ │ │ │ └────────────┘ └─────────┘ │ │ │ │ └────────────┘ └─────────┘ │ │ │ │ │ │ │ │ │ │ │ │ ┌─────────────┐ │ │ │ │ ┌─────────────┐ │ │ │ │ │ Root Hash │ │ │ │ │ │ Root Hash │ │ │ │ │ └─────▲─▲─────┘ │ │ │ │ └─────▲─▲─────┘ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ └───────────┼─┼───────────────┘ │ │ └───────────┼─┼───────────────┘ │ │ │ │ │ │ │ │ │ │ .......... │ │ .......... │ │ ┌────────┐ │ │ .......... │ │ . ─────┘ └─────. . │ │ │ ├────┘ └─────. . │ │ . Hash01 . . Hash23 . │ │ │ Hash01 │ . Hash23 . │ │ .▲.....▲.. .▲.....▲.. │ │ │ │ .▲.....▲.. │ │ │ │ │ │ │ │ └────────┘ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ .....│.. ..│..... .....│.. ..│..... │ │ ┌────┴─┐ ..│..... │ │ . . . . . . . . │ │ │ │ . . │ │ .Hash0 . .Hash1 . .Hash2 . .Hash3 . │ │ │Hash2 │ .Hash3 . │ │ ...▲.... ...▲.... ...▲.... ...▲.... │ │ │ │ . . │ │ │ │ │ │ │ │ └──────┘ ...▲.... │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ ┌──┴───┐ ┌──┴───┐ ┌──┴───┐ ┌──┴───┐ │ │ ┌──┴───┐ │ │ │ Tx0 │ │ Tx1 │ │ Tx2 │ │ Tx3 │ │ │ │ Tx3 │ │ │ └──────┘ └──────┘ └──────┘ └──────┘ │ │ └──────┘ │ │ │ │ │ └──────────────────────────────────────────┘ └──────────────────────────────────────────┘ Transactions Hashed in a Merkle Tree After Pruning Tx0-2 from the Block ``` A block header with no transactions would be about 80 bytes. If we suppose blocks are generated every 10 minutes, 80 bytes * 6 * 24 * 365 = 4.2MB per year. With computer systems typically selling with 2GB of RAM as of 2008, and Moore's Law predicting current growth of 1.2GB per year, storage should not be a problem even if the block headers must be kept in memory. ## 8. Simplified Payment Verification It is possible to verify payments without running a full network node. A user only needs to keep a copy of the block headers of the longest proof-of-work chain, which he can get by querying network nodes until he's convinced he has the longest chain, and obtain the Merkle branch linking the transaction to the block it's timestamped in. He can't check the transaction for himself, but by linking it to a place in the chain, he can see that a network node has accepted it, and blocks added after it further confirm the network has accepted it. ``` Longest Proof-of-Work Chain ┌────────────────────────────────────────┐ ┌────────────────────────────────────────┐ ┌────────────────────────────────────────┐ │ Block Header │ │ Block Header │ │ Block Header │ │ ┌──────────────────┐ ┌──────────────┐ │ │ ┌──────────────────┐ ┌──────────────┐ │ │ ┌──────────────────┐ ┌──────────────┐ │ ───────┼─►│ Prev Hash │ │ Nonce │ ├──────┼─►│ Prev Hash │ │ Nonce │ ├───────┼─►│ Prev Hash │ │ Nonce │ ├────────► │ └──────────────────┘ └──────────────┘ │ │ └──────────────────┘ └──────────────┘ │ │ └──────────────────┘ └──────────────┘ │ │ │ │ │ │ │ │ ┌───────────────────┐ │ │ ┌────────────────────┐ │ │ ┌───────────────────┐ │ │ │ Merkle Root │ │ │ │ Merkle Root │ │ │ │ Merkle Root │ │ │ └───────────────────┘ │ │ └────────▲─▲─────────┘ │ │ └───────────────────┘ │ │ │ │ │ │ │ │ │ └────────────────────────────────────────┘ └─────────────┼─┼────────────────────────┘ └────────────────────────────────────────┘ │ │ │ │ ┌────────┐ │ │ .......... │ ├────┘ └─────. . │ Hash01 │ . Hash23 . │ │ .▲.....▲.. └────────┘ │ │ │ │ │ │ Merkle Branch for Tx3 │ │ ┌─────┴─┐ ..│..... │ │ . . │ Hash2 │ .Hash3 . │ │ . . └───────┘ ...▲.... │ │ ┌───┴───┐ │ Tx3 │ └───────┘ ``` As such, the verification is reliable as long as honest nodes control the network, but is more vulnerable if the network is overpowered by an attacker. While network nodes can verify transactions for themselves, the simplified method can be fooled by an attacker's fabricated transactions for as long as the attacker can continue to overpower the network. One strategy to protect against this would be to accept alerts from network nodes when they detect an invalid block, prompting the user's software to download the full block and alerted transactions to confirm the inconsistency. Businesses that receive frequent payments will probably still want to run their own nodes for more independent security and quicker verification. ## 9. Combining and Splitting Value Although it would be possible to handle coins individually, it would be unwieldy to make a separate transaction for every cent in a transfer. To allow value to be split and combined, transactions contain multiple inputs and outputs. Normally there will be either a single input from a larger previous transaction or multiple inputs combining smaller amounts, and at most two outputs: one for the payment, and one returning the change, if any, back to the sender. ``` ┌──────────────────────┐ │ Transaction │ │ │ │ ┌─────┐ ┌─────┐ │ ─────┼──►│ in │ │ out │ ──┼─────► │ └─────┘ └─────┘ │ │ │ │ │ │ ┌─────┐ ┌─────┐ │ ─────┼──►│ in │ │ ... │ ──┼─────► │ └─────┘ └─────┘ │ │ │ │ │ │ ┌─────┐ │ ─────┼──►│... │ │ │ └─────┘ │ │ │ └──────────────────────┘ ``` It should be noted that fan-out, where a transaction depends on several transactions, and those transactions depend on many more, is not a problem here. There is never the need to extract a complete standalone copy of a transaction's history. ## 10. Privacy The traditional banking model achieves a level of privacy by limiting access to information to the parties involved and the trusted third party. The necessity to announce all transactions publicly precludes this method, but privacy can still be maintained by breaking the flow of information in another place: by keeping public keys anonymous. The public can see that someone is sending an amount to someone else, but without information linking the transaction to anyone. This is similar to the level of information released by stock exchanges, where the time and size of individual trades, the "tape", is made public, but without telling who the parties were. ``` Traditional Privacy Models │ ┌─────────────┐ ┌──────────────┐ │ ┌────────┐ ┌──────────────┐ ┌──────────────┐ │ Trusted │ │ │ │ │ │ │ Identities ├──┤ Transactions ├───►│ Third Party ├──►│ Counterparty │ │ │ Public │ └──────────────┘ └──────────────┘ │ │ │ │ │ │ │ └─────────────┘ └──────────────┘ │ └────────┘ │ New Privacy Model ┌────────┐ ┌──────────────┐ │ ┌──────────────┐ │ │ │ Identities │ │ │ Transactions ├───►│ Public │ └──────────────┘ │ └──────────────┘ │ │ └────────┘ ``` As an additional firewall, a new key pair should be used for each transaction to keep them from being linked to a common owner. Some linking is still unavoidable with multi-input transactions, which necessarily reveal that their inputs were owned by the same owner. The risk is that if the owner of a key is revealed, linking could reveal other transactions that belonged to the same owner. ## 11. Calculations We consider the scenario of an attacker trying to generate an alternate chain faster than the honest chain. Even if this is accomplished, it does not throw the system open to arbitrary changes, such as creating value out of thin air or taking money that never belonged to the attacker. Nodes are not going to accept an invalid transaction as payment, and honest nodes will never accept a block containing them. An attacker can only try to change one of his own transactions to take back money he recently spent. The race between the honest chain and an attacker chain can be characterized as a Binomial Random Walk. The success event is the honest chain being extended by one block, increasing its lead by +1, and the failure event is the attacker's chain being extended by one block, reducing the gap by -1. The probability of an attacker catching up from a given deficit is analogous to a Gambler's Ruin problem. Suppose a gambler with unlimited credit starts at a deficit and plays potentially an infinite number of trials to try to reach breakeven. We can calculate the probability he ever reaches breakeven, or that an attacker ever catches up with the honest chain, as follows [^8]: ```plaintext p = probability an honest node finds the next block< q = probability the attacker finds the next block q = probability the attacker will ever catch up from z blocks behind `````` $$ qz = \begin{cases} 1 & \text{if } p \leq q \\ \left(\frac{q}{p}\right) z & \text{if } p > q \end{cases} $$ Given our assumption that p > q, the probability drops exponentially as the number of blocks the attacker has to catch up with increases. With the odds against him, if he doesn't make a lucky lunge forward early on, his chances become vanishingly small as he falls further behind. We now consider how long the recipient of a new transaction needs to wait before being sufficiently certain the sender can't change the transaction. We assume the sender is an attacker who wants to make the recipient believe he paid him for a while, then switch it to pay back to himself after some time has passed. The receiver will be alerted when that happens, but the sender hopes it will be too late. The receiver generates a new key pair and gives the public key to the sender shortly before signing. This prevents the sender from preparing a chain of blocks ahead of time by working on it continuously until he is lucky enough to get far enough ahead, then executing the transaction at that moment. Once the transaction is sent, the dishonest sender starts working in secret on a parallel chain containing an alternate version of his transaction. The recipient waits until the transaction has been added to a block and z blocks have been linked after it. He doesn't know the exact amount of progress the attacker has made, but assuming the honest blocks took the average expected time per block, the attacker's potential progress will be a Poisson distribution with expected value: $$ \lambda = z\frac{q}{p} $$ To get the probability the attacker could still catch up now, we multiply the Poisson density for each amount of progress he could have made by the probability he could catch up from that point: $$ \sum_{k=0}^{\infty} \frac{\lambda^k e^{-\lambda}}{k!} \cdot \left\{ \begin{array}{cl} \left(\frac{q}{p}\right)^{(z-k)} & \text{if } k \leq z \\ 1 & \text{if } k > z \end{array} \right. $$ Rearranging to avoid summing the infinite tail of the distribution... $$ 1 - \sum_{k=0}^{z} \frac{\lambda^k e^{-\lambda}}{k!} \left(1-\left(\frac{q}{p}\right)^{(z-k)}\right) $$ Converting to C code... ```c #include <math.h> double AttackerSuccessProbability(double q, int z) { double p = 1.0 - q; double lambda = z * (q / p); double sum = 1.0; int i, k; for (k = 0; k <= z; k++) { double poisson = exp(-lambda); for (i = 1; i <= k; i++) poisson *= lambda / i; sum -= poisson * (1 - pow(q / p, z - k)); } return sum; } ``` Running some results, we can see the probability drop off exponentially with z. ```plaintext q=0.1 z=0 P=1.0000000 z=1 P=0.2045873 z=2 P=0.0509779 z=3 P=0.0131722 z=4 P=0.0034552 z=5 P=0.0009137 z=6 P=0.0002428 z=7 P=0.0000647 z=8 P=0.0000173 z=9 P=0.0000046 z=10 P=0.0000012 q=0.3 z=0 P=1.0000000 z=5 P=0.1773523 z=10 P=0.0416605 z=15 P=0.0101008 z=20 P=0.0024804 z=25 P=0.0006132 z=30 P=0.0001522 z=35 P=0.0000379 z=40 P=0.0000095 z=45 P=0.0000024 z=50 P=0.0000006 ``` Solving for P less than 0.1%... ```plaintext P < 0.001 q=0.10 z=5 q=0.15 z=8 q=0.20 z=11 q=0.25 z=15 q=0.30 z=24 q=0.35 z=41 q=0.40 z=89 q=0.45 z=340 ``` ## 12. Conclusion We have proposed a system for electronic transactions without relying on trust. We started with the usual framework of coins made from digital signatures, which provides strong control of ownership, but is incomplete without a way to prevent double-spending. To solve this, we proposed a peer-to-peer network using proof-of-work to record a public history of transactions that quickly becomes computationally impractical for an attacker to change if honest nodes control a majority of CPU power. The network is robust in its unstructured simplicity. Nodes work all at once with little coordination. They do not need to be identified, since messages are not routed to any particular place and only need to be delivered on a best effort basis. Nodes can leave and rejoin the network at will, accepting the proof-of-work chain as proof of what happened while they were gone. They vote with their CPU power, expressing their acceptance of valid blocks by working on extending them and rejecting invalid blocks by refusing to work on them. Any needed rules and incentives can be enforced with this consensus mechanism. <br> ### References --- [^1]: W. Dai, "b-money," http://www.weidai.com/bmoney.txt, 1998. [^2]: H. Massias, X.S. Avila, and J.-J. Quisquater, "Design of a secure timestamping service with minimal trust requirements," In 20th Symposium on Information Theory in the Benelux, May 1999. [^3]: S. Haber, W.S. Stornetta, "How to time-stamp a digital document," In Journal of Cryptology, vol 3, no 2, pages 99-111, 1991. [^4]: D. Bayer, S. Haber, W.S. Stornetta, "Improving the efficiency and reliability of digital time-stamping," In Sequences II: Methods in Communication, Security and Computer Science, pages 329-334, 1993. [^5]: S. Haber, W.S. Stornetta, "Secure names for bit-strings," In Proceedings of the 4th ACM Conference on Computer and Communications Security, pages 28-35, April 1997. [^6]: A. Back, "Hashcash - a denial of service counter-measure," http://www.hashcash.org/papers/hashcash.pdf, 2002. [^7]: R.C. Merkle, "Protocols for public key cryptosystems," In Proc. 1980 Symposium on Security and Privacy, IEEE Computer Society, pages 122-133, April 1980. [^8]: W. Feller, "An introduction to probability theory and its applications," 1957. </pre><p><br></p> @ 0176967e:1e6f471e
2024-07-21 15:48:56Lístky na festival Lunarpunku sú už v predaji [na našom crowdfunding portáli](https://pay.cypherpunk.today/apps/maY3hxKArQxMpdyh5yCtT6UWMJm/crowdfund). V predaji sú dva typy lístkov - štandardný vstup a špeciálny vstup spolu s workshopom oranžového leta. Neváhajte a zabezpečte si lístok, čím skôr to urobíte, tým bude festival lepší. Platiť môžete Bitcoinom - Lightningom aj on-chain. Vaša vstupenka je e-mail adresa (neposielame potvrdzujúce e-maily, ak platba prešla, ste in). [Kúpte si lístok](https://pay.cypherpunk.today/apps/maY3hxKArQxMpdyh5yCtT6UWMJm/crowdfund)
@ 0176967e:1e6f471e
2024-07-21 15:48:56Lístky na festival Lunarpunku sú už v predaji [na našom crowdfunding portáli](https://pay.cypherpunk.today/apps/maY3hxKArQxMpdyh5yCtT6UWMJm/crowdfund). V predaji sú dva typy lístkov - štandardný vstup a špeciálny vstup spolu s workshopom oranžového leta. Neváhajte a zabezpečte si lístok, čím skôr to urobíte, tým bude festival lepší. Platiť môžete Bitcoinom - Lightningom aj on-chain. Vaša vstupenka je e-mail adresa (neposielame potvrdzujúce e-maily, ak platba prešla, ste in). [Kúpte si lístok](https://pay.cypherpunk.today/apps/maY3hxKArQxMpdyh5yCtT6UWMJm/crowdfund) @ 8e7462a8:c723a97b
2024-07-21 15:46:37<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>
@ 8e7462a8:c723a97b
2024-07-21 15:46:37<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe> @ 8e7462a8:c723a97b
2024-07-21 15:44:04<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>
@ 8e7462a8:c723a97b
2024-07-21 15:44:04<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe> @ 8e7462a8:c723a97b
2024-07-21 15:42:55<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>
@ 8e7462a8:c723a97b
2024-07-21 15:42:55<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe> @ 8e7462a8:c723a97b
2024-07-21 15:39:51<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>
@ 8e7462a8:c723a97b
2024-07-21 15:39:51<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe> @ 8e7462a8:c723a97b
2024-07-21 15:38:33<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>
@ 8e7462a8:c723a97b
2024-07-21 15:38:33<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe> @ 8e7462a8:c723a97b
2024-07-21 15:34:32<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>
@ 8e7462a8:c723a97b
2024-07-21 15:34:32<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe> @ 8e7462a8:c723a97b
2024-07-21 15:33:27<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>
@ 8e7462a8:c723a97b
2024-07-21 15:33:27<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe> @ 8e7462a8:c723a97b
2024-07-21 15:31:26<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>
@ 8e7462a8:c723a97b
2024-07-21 15:31:26<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe> @ 8e7462a8:c723a97b
2024-07-21 15:30:52<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>
@ 8e7462a8:c723a97b
2024-07-21 15:30:52<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe> @ 8e7462a8:c723a97b
2024-07-21 15:28:02<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>
@ 8e7462a8:c723a97b
2024-07-21 15:28:02<iframe width="560" height="315" src="https://www.youtube.com/embed/WoEsme3nvRg" frameborder="0" allowfullscreen></iframe>