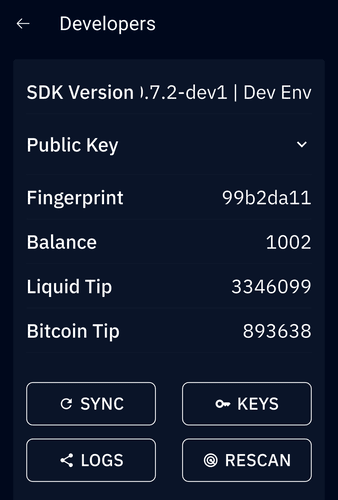
-
 @ c230edd3:8ad4a712
2025-04-11 16:02:15
@ c230edd3:8ad4a712
2025-04-11 16:02:15Chef's notes
Wildly enough, this is delicious. It's sweet and savory.
(I copied this recipe off of a commercial cheese maker's site, just FYI)
I hadn't fully froze the ice cream when I took the picture shown. This is fresh out of the churner.
Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 4
Ingredients
- 12 oz blue cheese
- 3 Tbsp lemon juice
- 1 c sugar
- 1 tsp salt
- 1 qt heavy cream
- 3/4 c chopped dark chocolate
Directions
- Put the blue cheese, lemon juice, sugar, and salt into a bowl
- Bring heavy cream to a boil, stirring occasionally
- Pour heavy cream over the blue cheese mix and stir until melted
- Pour into prepared ice cream maker, follow unit instructions
- Add dark chocolate halfway through the churning cycle
- Freeze until firm. Enjoy.
-
 @ c230edd3:8ad4a712
2025-04-09 00:33:31
@ c230edd3:8ad4a712
2025-04-09 00:33:31Chef's notes
I found this recipe a couple years ago and have been addicted to it since. Its incredibly easy, and cheap to prep. Freeze the sausage in flat, single serving portions. That way it can be cooked from frozen for a fast, flavorful, and healthy lunch or dinner. I took inspiration from the video that contained this recipe, and almost always pan fry the frozen sausage with some baby broccoli. The steam cooks the broccoli and the fats from the sausage help it to sear, while infusing the vibrant flavors. Serve with some rice, if desired. I often use serrano peppers, due to limited produce availability. They work well for a little heat and nice flavor that is not overpowering.
Details
- ⏲️ Prep time: 25 min
- 🍳 Cook time: 15 min (only needed if cooking at time of prep)
- 🍽️ Servings: 10
Ingredients
- 4 lbs ground pork
- 12-15 cloves garlic, minced
- 6 Thai or Serrano peppers, rough chopped
- 1/4 c. lime juice
- 4 Tbsp fish sauce
- 1 Tbsp brown sugar
- 1/2 c. chopped cilantro
Directions
- Mix all ingredients in a large bowl.
- Portion and freeze, as desired.
- Sautè frozen portions in hot frying pan, with broccoli or other fresh veggies.
- Serve with rice or alone.
-
 @ 00000001:b0c77eb9
2025-02-14 21:24:24
@ 00000001:b0c77eb9
2025-02-14 21:24:24مواقع التواصل الإجتماعي العامة هي التي تتحكم بك، تتحكم بك بفرض أجندتها وتجبرك على اتباعها وتحظر وتحذف كل ما يخالفها، وحرية التعبير تنحصر في أجندتها تلك!
وخوارزمياتها الخبيثة التي لا حاجة لها، تعرض لك مايريدون منك أن تراه وتحجب ما لا يريدونك أن تراه.
في نوستر انت المتحكم، انت الذي تحدد من تتابع و انت الذي تحدد المرحلات التي تنشر منشوراتك بها.
نوستر لامركزي، بمعنى عدم وجود سلطة تتحكم ببياناتك، بياناتك موجودة في المرحلات، ولا احد يستطيع حذفها او تعديلها او حظر ظهورها.
و هذا لا ينطبق فقط على مواقع التواصل الإجتماعي العامة، بل ينطبق أيضاً على الـfediverse، في الـfediverse انت لست حر، انت تتبع الخادم الذي تستخدمه ويستطيع هذا الخادم حظر ما لا يريد ظهوره لك، لأنك لا تتواصل مع بقية الخوادم بنفسك، بل خادمك من يقوم بذلك بالنيابة عنك.
وحتى إذا كنت تمتلك خادم في شبكة الـfediverse، إذا خالفت اجندة بقية الخوادم ونظرتهم عن حرية الرأي و التعبير سوف يندرج خادمك في القائمة السوداء fediblock ولن يتمكن خادمك من التواصل مع بقية خوادم الشبكة، ستكون محصوراً بالخوادم الأخرى المحظورة كخادمك، بالتالي انت في الشبكة الأخرى من الـfediverse!
نعم، يوجد شبكتان في الكون الفدرالي fediverse شبكة الصالحين التابعين للأجندة الغربية وشبكة الطالحين الذين لا يتبعون لها، إذا تم إدراج خادمك في قائمة fediblock سوف تذهب للشبكة الأخرى!
-
 @ d34e832d:383f78d0
2025-04-24 06:28:48
@ d34e832d:383f78d0
2025-04-24 06:28:48Operation
Central to this implementation is the utilization of Tails OS, a Debian-based live operating system designed for privacy and anonymity, alongside the Electrum Wallet, a lightweight Bitcoin wallet that provides a streamlined interface for secure Bitcoin transactions.
Additionally, the inclusion of advanced cryptographic verification mechanisms, such as QuickHash, serves to bolster integrity checks throughout the storage process. This multifaceted approach ensures a rigorous adherence to end-to-end operational security (OpSec) principles while simultaneously safeguarding user autonomy in the custody of digital assets.
Furthermore, the proposed methodology aligns seamlessly with contemporary cybersecurity paradigms, prioritizing characteristics such as deterministic builds—where software builds are derived from specific source code to eliminate variability—offline key generation processes designed to mitigate exposure to online threats, and the implementation of minimal attack surfaces aimed at reducing potential vectors for exploitation.
Ultimately, this sophisticated approach presents a methodical and secure paradigm for the custody of private keys, thereby catering to the exigencies of high-assurance Bitcoin storage requirements.
1. Cold Storage Refers To The offline Storage
Cold storage refers to the offline storage of private keys used to sign Bitcoin transactions, providing the highest level of protection against network-based threats. This paper outlines a verifiable method for constructing such a storage system using the following core principles:
- Air-gapped key generation
- Open-source software
- Deterministic cryptographic tools
- Manual integrity verification
- Offline transaction signing
The method prioritizes cryptographic security, software verifiability, and minimal hardware dependency.
2. Hardware and Software Requirements
2.1 Hardware
- One 64-bit computer (laptop/desktop)
- 1 x USB Flash Drive (≥8 GB, high-quality brand recommended)
- Paper and pen (for seed phrase)
- Optional: Printer (for xpub QR export)
2.2 Software Stack
- Tails OS (latest ISO, from tails.boum.org)
- Balena Etcher (to flash ISO)
- QuickHash GUI (for SHA-256 checksum validation)
- Electrum Wallet (bundled within Tails OS)
3. System Preparation and Software Verification
3.1 Image Verification
Prior to flashing the ISO, the integrity of the Tails OS image must be cryptographically validated. Using QuickHash:
plaintext SHA256 (tails-amd64-<version>.iso) = <expected_hash>Compare the hash output with the official hash provided on the Tails OS website. This mitigates the risk of ISO tampering or supply chain compromise.
3.2 Flashing the OS
Balena Etcher is used to flash the ISO to a USB drive:
- Insert USB drive.
- Launch Balena Etcher.
- Select the verified Tails ISO.
- Flash to USB and safely eject.
4. Cold Wallet Generation Procedure
4.1 Boot Into Tails OS
- Restart the system and boot into BIOS/UEFI boot menu.
- Select the USB drive containing Tails OS.
- Configure network settings to disable all connectivity.
4.2 Create Wallet in Electrum (Cold)
- Open Electrum from the Tails application launcher.
- Select "Standard Wallet" → "Create a new seed".
- Choose SegWit for address type (for lower fees and modern compatibility).
- Write down the 12-word seed phrase on paper. Never store digitally.
- Confirm the seed.
- Set a strong password for wallet access.
5. Exporting the Master Public Key (xpub)
- Open Electrum > Wallet > Information
- Export the Master Public Key (MPK) for receiving-only use.
- Optionally generate QR code for cold-to-hot usage (wallet watching).
This allows real-time monitoring of incoming Bitcoin transactions without ever exposing private keys.
6. Transaction Workflow
6.1 Receiving Bitcoin (Cold to Hot)
- Use the exported xpub in a watch-only wallet (desktop or mobile).
- Generate addresses as needed.
- Senders deposit Bitcoin to those addresses.
6.2 Spending Bitcoin (Hot Redeem Mode)
Important: This process temporarily compromises air-gap security.
- Boot into Tails (or use Electrum in a clean Linux environment).
- Import the 12-word seed phrase.
- Create transaction offline.
- Export signed transaction via QR code or USB.
- Broadcast using an online device.
6.3 Recommended Alternative: PSBT
To avoid full wallet import: - Use Partially Signed Bitcoin Transactions (PSBT) protocol to sign offline. - Broadcast PSBT using Sparrow Wallet or Electrum online.
7. Security Considerations
| Threat | Mitigation | |-------|------------| | OS Compromise | Use Tails (ephemeral environment, RAM-only) | | Supply Chain Attack | Manual SHA256 verification | | Key Leakage | No network access during key generation | | Phishing/Clone Wallets | Verify Electrum’s signature (when updating) | | Physical Theft | Store paper seed in tamper-evident location |
8. Backup Strategy
- Store 12-word seed phrase in multiple secure physical locations.
- Do not photograph or digitize.
- For added entropy, use Shamir Secret Sharing (e.g., 2-of-3 backups).
9. Consider
Through the meticulous integration of verifiable software solutions, the execution of air-gapped key generation methodologies, and adherence to stringent operational protocols, users have the capacity to establish a Bitcoin cold storage wallet that embodies an elevated degree of cryptographic assurance.
This DIY system presents a zero-dependency alternative to conventional third-party custody solutions and consumer-grade hardware wallets.
Consequently, it empowers individuals with the ability to manage their Bitcoin assets while ensuring full trust minimization and maximizing their sovereign control over private keys and transaction integrity within the decentralized financial ecosystem..
10. References And Citations
Nakamoto, Satoshi. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008.
“Tails - The Amnesic Incognito Live System.” tails.boum.org, The Tor Project.
“Electrum Bitcoin Wallet.” electrum.org, 2025.
“QuickHash GUI.” quickhash-gui.org, 2025.
“Balena Etcher.” balena.io, 2025.
Bitcoin Core Developers. “Don’t Trust, Verify.” bitcoincore.org, 2025.In Addition
🪙 SegWit vs. Legacy Bitcoin Wallets
⚖️ TL;DR Decision Chart
| If you... | Use SegWit | Use Legacy | |-----------|----------------|----------------| | Want lower fees | ✅ Yes | 🚫 No | | Send to/from old services | ⚠️ Maybe | ✅ Yes | | Care about long-term scaling | ✅ Yes | 🚫 No | | Need max compatibility | ⚠️ Mixed | ✅ Yes | | Run a modern wallet | ✅ Yes | 🚫 Legacy support fading | | Use cold storage often | ✅ Yes | ⚠️ Depends on wallet support | | Use Lightning Network | ✅ Required | 🚫 Not supported |
🔍 1. What Are We Comparing?
There are two major types of Bitcoin wallet address formats:
🏛️ Legacy (P2PKH)
- Format starts with:
1 - Example:
1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa - Oldest, most universally compatible
- Higher fees, larger transactions
- May lack support in newer tools and layer-2 solutions
🛰️ SegWit (P2WPKH)
- Formats start with:
- Nested SegWit (P2SH):
3... - Native SegWit (bech32):
bc1q... - Introduced via Bitcoin Improvement Proposal (BIP) 141
- Smaller transaction sizes → lower fees
- Native support by most modern wallets
💸 2. Transaction Fees
SegWit = Cheaper.
- SegWit reduces the size of Bitcoin transactions in a block.
- This means you pay less per transaction.
- Example: A SegWit transaction might cost 40%–60% less in fees than a legacy one.💡 Why?
Bitcoin charges fees per byte, not per amount.
SegWit removes certain data from the base transaction structure, which shrinks byte size.
🧰 3. Wallet & Service Compatibility
| Category | Legacy | SegWit (Nested / Native) | |----------|--------|---------------------------| | Old Exchanges | ✅ Full support | ⚠️ Partial | | Modern Exchanges | ✅ Yes | ✅ Yes | | Hardware Wallets (Trezor, Ledger) | ✅ Yes | ✅ Yes | | Mobile Wallets (Phoenix, BlueWallet) | ⚠️ Rare | ✅ Yes | | Lightning Support | 🚫 No | ✅ Native SegWit required |
🧠 Recommendation:
If you interact with older platforms or do cross-compatibility testing, you may want to: - Use nested SegWit (address starts with
3), which is backward compatible. - Avoid bech32-only wallets if your exchange doesn't support them (though rare in 2025).
🛡️ 4. Security and Reliability
Both formats are secure in terms of cryptographic strength.
However: - SegWit fixes a bug known as transaction malleability, which helps build protocols on top of Bitcoin (like the Lightning Network). - SegWit transactions are more standardized going forward.
💬 User takeaway:
For basic sending and receiving, both are equally secure. But for future-proofing, SegWit is the better bet.
🌐 5. Future-Proofing
Legacy wallets are gradually being phased out:
- Developers are focusing on SegWit and Taproot compatibility.
- Wallet providers are defaulting to SegWit addresses.
- Fee structures increasingly assume users have upgraded.
🚨 If you're using a Legacy wallet today, you're still safe. But: - Some services may stop supporting withdrawals to legacy addresses. - Your future upgrade path may be more complex.
🚀 6. Real-World Scenarios
🧊 Cold Storage User
- Use SegWit for low-fee UTXOs and efficient backup formats.
- Consider Native SegWit (
bc1q) if supported by your hardware wallet.
👛 Mobile Daily User
- Use Native SegWit for cheaper everyday payments.
- Ideal if using Lightning apps — it's often mandatory.
🔄 Exchange Trader
- Check your exchange’s address type support.
- Consider nested SegWit (
3...) if bridging old + new systems.
📜 7. Migration Tips
If you're moving from Legacy to SegWit:
- Create a new SegWit wallet in your software/hardware wallet.
- Send funds from your old Legacy wallet to the SegWit address.
- Back up the new seed — never reuse the old one.
- Watch out for fee rates and change address handling.
✅ Final User Recommendations
| Use Case | Address Type | |----------|--------------| | Long-term HODL | SegWit (
bc1q) | | Maximum compatibility | SegWit (nested3...) | | Fee-sensitive use | Native SegWit (bc1q) | | Lightning | Native SegWit (bc1q) | | Legacy systems only | Legacy (1...) – short-term only |
📚 Further Reading
- Nakamoto, Satoshi. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008.
- Bitcoin Core Developers. “Segregated Witness (Consensus Layer Change).” github.com/bitcoin, 2017.
- “Electrum Documentation: Wallet Types.” docs.electrum.org, 2024.
- “Bitcoin Wallet Compatibility.” bitcoin.org, 2025.
- Ledger Support. “SegWit vs Legacy Addresses.” ledger.com, 2024.
-
 @ d34e832d:383f78d0
2025-04-24 06:12:32
@ d34e832d:383f78d0
2025-04-24 06:12:32
Goal
This analytical discourse delves into Jack Dorsey's recent utterances concerning Bitcoin, artificial intelligence, decentralized social networking platforms such as Nostr, and the burgeoning landscape of open-source cryptocurrency mining initiatives.
Dorsey's pronouncements escape the confines of isolated technological fascinations; rather, they elucidate a cohesive conceptual schema wherein Bitcoin transcends its conventional role as a mere store of value—akin to digital gold—and emerges as a foundational protocol intended for the construction of a decentralized, sovereign, and perpetually self-evolving internet ecosystem.
A thorough examination of Dorsey's confluence of Bitcoin with artificial intelligence advancements, adaptive learning paradigms, and integrated social systems reveals an assertion of Bitcoin's position as an entity that evolves beyond simple currency, evolving into a distinctly novel socio-technological organism characterized by its inherent ability to adapt and grow. His vigorous endorsement of native digital currency, open communication protocols, and decentralized infrastructural frameworks is posited here as a revolutionary paradigm—a conceptual
1. The Path
Jack Dorsey, co-founder of Twitter and Square (now Block), has emerged as one of the most compelling evangelists for a decentralized future. His ideas about Bitcoin go far beyond its role as a speculative asset or inflation hedge. In a recent interview, Dorsey ties together themes of open-source AI, peer-to-peer currency, decentralized media, and radical self-education, sketching a future in which Bitcoin is the lynchpin of an emerging technological and social ecosystem. This thesis reviews Dorsey’s statements and offers a critical framework to understand why his vision uniquely positions Bitcoin as the keystone of a post-institutional, digital world.
2. Bitcoin: The Native Currency of the Internet
“It’s the best current manifestation of a native internet currency.” — Jack Dorsey
Bitcoin's status as an open protocol with no central controlling authority echoes the original spirit of the internet: decentralized, borderless, and resilient. Dorsey's framing of Bitcoin not just as a payment system but as the "native money of the internet" is a profound conceptual leap. It suggests that just as HTTP became the standard for web documents, Bitcoin can become the monetary layer for the open web.
This framing bypasses traditional narratives of digital gold or institutional adoption and centers a P2P vision of global value transfer. Unlike central bank digital currencies or platform-based payment rails, Bitcoin is opt-in, permissionless, and censorship-resistant—qualities essential for sovereignty in the digital age.
3. Nostr and the Decentralization of Social Systems
Dorsey’s support for Nostr, an open protocol for decentralized social media, reflects a desire to restore user agency, protocol composability, and speech sovereignty. Nostr’s architecture parallels Bitcoin’s: open, extensible, and resilient to censorship.
Here, Bitcoin serves not just as money but as a network effect driver. When combined with Lightning and P2P tipping, Nostr becomes more than just a Twitter alternative—it evolves into a micropayment-native communication system, a living proof that Bitcoin can power an entire open-source social economy.
4. Open-Source AI and Cognitive Sovereignty
Dorsey's forecast that open-source AI will emerge as an alternative to proprietary systems aligns with his commitment to digital autonomy. If Bitcoin empowers financial sovereignty and Nostr enables communicative freedom, open-source AI can empower cognitive independence—freeing humanity from centralized algorithmic manipulation.
He draws a fascinating parallel between AI learning models and human learning itself, suggesting both can be self-directed, recursive, and radically decentralized. This resonates with the Bitcoin ethos: systems should evolve through transparent, open participation—not gatekeeping or institutional control.
5. Bitcoin Mining: Sovereignty at the Hardware Layer
Block’s initiative to create open-source mining hardware is a direct attempt to counter centralization in Bitcoin’s infrastructure. ASIC chip development and mining rig customization empower individuals and communities to secure the network directly.
This move reinforces Dorsey’s vision that true decentralization requires ownership at every layer, including hardware. It is a radical assertion of vertical sovereignty—from protocol to interface to silicon.
6. Learning as the Core Protocol
“The most compounding skill is learning itself.” — Jack Dorsey
Dorsey’s deepest insight is that the throughline connecting Bitcoin, AI, and Nostr is not technology—it’s learning. Bitcoin represents more than code; it’s a living experiment in voluntary consensus, a distributed educational system in cryptographic form.
Dorsey’s emphasis on meditation, intensive retreats, and self-guided exploration mirrors the trustless, sovereign nature of Bitcoin. Learning becomes the ultimate protocol: recursive, adaptive, and decentralized—mirroring AI models and Bitcoin nodes alike.
7. Critical Risks and Honest Reflections
Dorsey remains honest about Bitcoin’s current limitations:
- Accessibility: UX barriers for onboarding new users.
- Usability: Friction in everyday use.
- State-Level Adoption: Risks of co-optation as mere digital gold.
However, his caution enhances credibility. His focus remains on preserving Bitcoin as a P2P electronic cash system, not transforming it into another tool of institutional control.
8. Bitcoin as a Living System
What emerges from Dorsey's vision is not a product pitch, but a philosophical reorientation: Bitcoin, Nostr, and open AI are not discrete tools—they are living systems forming a new type of civilization stack.
They are not static infrastructures, but emergent grammars of human cooperation, facilitating value exchange, learning, and community formation in ways never possible before.
Bitcoin, in this view, is not merely stunningly original—it is civilizationally generative, offering not just monetary innovation but a path to software-upgraded humanity.
Works Cited and Tools Used
Dorsey, Jack. Interview on Bitcoin, AI, and Decentralization. April 2025.
Nakamoto, Satoshi. “Bitcoin: A Peer-to-Peer Electronic Cash System.” 2008.
Nostr Protocol. https://nostr.com.
Block, Inc. Bitcoin Mining Hardware Initiatives. 2024.
Obsidian Canvas. Decentralized Note-Taking and Networked Thinking. 2025. -
 @ d34e832d:383f78d0
2025-04-24 05:56:06
@ d34e832d:383f78d0
2025-04-24 05:56:06Idea
Through the integration of Optical Character Recognition (OCR), Docker-based deployment, and secure remote access via Twin Gate, Paperless NGX empowers individuals and small organizations to digitize, organize, and retrieve documents with minimal friction. This research explores its technical infrastructure, real-world applications, and how such a system can redefine document archival practices for the digital age.
Agile, Remote-Accessible, and Searchable Document System
In a world of increasing digital interdependence, managing physical documents is becoming not only inefficient but also environmentally and logistically unsustainable. The demand for agile, remote-accessible, and searchable document systems has never been higher—especially for researchers, small businesses, and archival professionals. Paperless NGX, an open-source platform, addresses these needs by offering a streamlined, secure, and automated way to manage documents digitally.
This Idea explores how Paperless NGX facilitates the transition to a paperless workflow and proposes best practices for sustainable, scalable usage.
Paperless NGX: The Platform
Paperless NGX is an advanced fork of the original Paperless project, redesigned with modern containers, faster performance, and enhanced community contributions. Its core functions include:
- Text Extraction with OCR: Leveraging the
ocrmypdfPython library, Paperless NGX can extract searchable text from scanned PDFs and images. - Searchable Document Indexing: Full-text search allows users to locate documents not just by filename or metadata, but by actual content.
- Dockerized Setup: A ready-to-use Docker Compose environment simplifies deployment, including the use of setup scripts for Ubuntu-based servers.
- Modular Workflows: Custom triggers and automation rules allow for smart processing pipelines based on file tags, types, or email source.
Key Features and Technical Infrastructure
1. Installation and Deployment
The system runs in a containerized environment, making it highly portable and isolated. A typical installation involves: - Docker Compose with YAML configuration - Volume mapping for persistent storage - Optional integration with reverse proxies (e.g., Nginx) for HTTPS access
2. OCR and Indexing
Using
ocrmypdf, scanned documents are processed into fully searchable PDFs. This function dramatically improves retrieval, especially for archived legal, medical, or historical records.3. Secure Access via Twin Gate
To solve the challenge of secure remote access without exposing the network, Twin Gate acts as a zero-trust access proxy. It encrypts communication between the Paperless NGX server and the client, enabling access from anywhere without the need for traditional VPNs.
4. Email Integration and Ingestion
Paperless NGX can ingest attachments directly from configured email folders. This feature automates much of the document intake process, especially useful for receipts, invoices, and academic PDFs.
Sustainable Document Management Workflow
A practical paperless strategy requires not just tools, but repeatable processes. A sustainable workflow recommended by the Paperless NGX community includes:
- Capture & Tagging
All incoming documents are tagged with a default “inbox” tag for triage. - Physical Archive Correlation
If the physical document is retained, assign it a serial number (e.g., ASN-001), which is matched digitally. - Curation & Tagging
Apply relevant category and topic tags to improve searchability. - Archival Confirmation
Remove the “inbox” tag once fully processed and categorized.
Backup and Resilience
Reliability is key to any archival system. Paperless NGX includes backup functionality via: - Cron job–scheduled Docker exports - Offsite and cloud backups using rsync or encrypted cloud drives - Restore mechanisms using documented CLI commands
This ensures document availability even in the event of hardware failure or data corruption.
Limitations and Considerations
While Paperless NGX is powerful, it comes with several caveats: - Technical Barrier to Entry: Requires basic Docker and Linux skills to install and maintain. - OCR Inaccuracy for Handwritten Texts: The OCR engine may struggle with cursive or handwritten documents. - Plugin and Community Dependency: Continuous support relies on active community contribution.
Consider
Paperless NGX emerges as a pragmatic and privacy-centric alternative to conventional cloud-based document management systems, effectively addressing the critical challenges of data security and user autonomy.
The implementation of advanced Optical Character Recognition (OCR) technology facilitates the indexing and searching of documents, significantly enhancing information retrieval efficiency.
Additionally, the platform offers secure remote access protocols that ensure data integrity while preserving the confidentiality of sensitive information during transmission.
Furthermore, its customizable workflow capabilities empower both individuals and organizations to precisely tailor their data management processes, thereby reclaiming sovereignty over their information ecosystems.
In an era increasingly characterized by a shift towards paperless methodologies, the significance of solutions such as Paperless NGX cannot be overstated; they play an instrumental role in engineering a future in which information remains not only accessible but also safeguarded and sustainably governed.
In Addition
To Further The Idea
This technical paper presents an optimized strategy for transforming an Intel NUC into a compact, power-efficient self-hosted server using Ubuntu. The setup emphasizes reliability, low energy consumption, and cost-effectiveness for personal or small business use. Services such as Paperless NGX, Nextcloud, Gitea, and Docker containers are examined for deployment. The paper details hardware selection, system installation, secure remote access, and best practices for performance and longevity.
1. Cloud sovereignty, Privacy, and Data Ownership
As cloud sovereignty, privacy, and data ownership become critical concerns, self-hosting is increasingly appealing. An Intel NUC (Next Unit of Computing) provides an ideal middle ground between Raspberry Pi boards and enterprise-grade servers—balancing performance, form factor, and power draw. With Ubuntu LTS and Docker, users can run a full suite of services with minimal overhead.
2. Hardware Overview
2.1 Recommended NUC Specifications:
| Component | Recommended Specs | |------------------|-----------------------------------------------------| | Model | Intel NUC 11/12 Pro (e.g., NUC11TNHi5, NUC12WSKi7) | | CPU | Intel Core i5 or i7 (11th/12th Gen) | | RAM | 16GB–32GB DDR4 (dual channel preferred) | | Storage | 512GB–2TB NVMe SSD (Samsung 980 Pro or similar) | | Network | Gigabit Ethernet + Optional Wi-Fi 6 | | Power Supply | 65W USB-C or barrel connector | | Cooling | Internal fan, well-ventilated location |
NUCs are also capable of dual-drive setups and support for Intel vPro for remote management on some models.
3. Operating System and Software Stack
3.1 Ubuntu Server LTS
- Version: Ubuntu Server 22.04 LTS
- Installation Method: Bootable USB (Rufus or Balena Etcher)
- Disk Partitioning: LVM with encryption recommended for full disk security
- Security:
- UFW (Uncomplicated Firewall)
- Fail2ban
- SSH hardened with key-only login
bash sudo apt update && sudo apt upgrade sudo ufw allow OpenSSH sudo ufw enable
4. Docker and System Services
Docker and Docker Compose streamline the deployment of isolated, reproducible environments.
4.1 Install Docker and Compose
bash sudo apt install docker.io docker-compose sudo systemctl enable docker4.2 Common Services to Self-Host:
| Application | Description | Access Port | |--------------------|----------------------------------------|-------------| | Paperless NGX | Document archiving and OCR | 8000 | | Nextcloud | Personal cloud, contacts, calendar | 443 | | Gitea | Lightweight Git repository | 3000 | | Nginx Proxy Manager| SSL proxy for all services | 81, 443 | | Portainer | Docker container management GUI | 9000 | | Watchtower | Auto-update containers | - |
5. Network & Remote Access
5.1 Local IP & Static Assignment
- Set a static IP for consistent access (via router DHCP reservation or Netplan).
5.2 Access Options
- Local Only: VPN into local network (e.g., WireGuard, Tailscale)
- Remote Access:
- Reverse proxy via Nginx with Certbot for HTTPS
- Twin Gate or Tailscale for zero-trust remote access
- DNS via DuckDNS, Cloudflare
6. Performance Optimization
- Enable
zramfor compressed RAM swap - Trim SSDs weekly with
fstrim - Use Docker volumes, not bind mounts for stability
- Set up unattended upgrades:
bash sudo apt install unattended-upgrades sudo dpkg-reconfigure --priority=low unattended-upgrades
7. Power and Environmental Considerations
- Idle Power Draw: ~7–12W (depending on configuration)
- UPS Recommended: e.g., APC Back-UPS 600VA
- Use BIOS Wake-on-LAN if remote booting is needed
8. Maintenance and Monitoring
- Monitoring: Glances, Netdata, or Prometheus + Grafana
- Backups:
- Use
rsyncto external drive or NAS - Cloud backup options: rclone to Google Drive, S3
- Paperless NGX backups:
docker compose exec -T web document-exporter ...
9. Consider
Running a personal server using an Intel NUC and Ubuntu offers a private, low-maintenance, and modular solution to digital infrastructure needs. It’s an ideal base for self-hosting services, offering superior control over data and strong security with the right setup. The NUC's small form factor and efficient power usage make it an optimal home server platform that scales well for many use cases.
- Text Extraction with OCR: Leveraging the
-
 @ d34e832d:383f78d0
2025-04-24 05:14:14
@ d34e832d:383f78d0
2025-04-24 05:14:14Idea
By instituting a robust network of conceptual entities, referred to as 'Obsidian nodes'—which are effectively discrete, idea-centric notes—researchers are empowered to establish a resilient and non-linear archival framework for knowledge accumulation.
These nodes, intricately connected via hyperlinks and systematically organized through the graphical interface of the Obsidian Canvas, facilitate profound intellectual exploration and the synthesis of disparate domains of knowledge.
Consequently, this innovative workflow paradigm emphasizes semantic precision and the interconnectedness of ideas, diverging from conventional, source-centric information architectures prevalent in traditional academic practices.
Traditional research workflows often emphasize organizing notes by source, resulting in static, siloed knowledge that resists integration and insight. With the rise of personal knowledge management (PKM) tools like Obsidian, it becomes possible to structure information in a way that mirrors the dynamic and interconnected nature of human thought.
At the heart of this approach are Obsidian nodes—atomic, standalone notes representing single ideas, arguments, or claims. These nodes form the basis of a semantic research network, made visible and manageable via Obsidian’s graph view and Canvas feature. This thesis outlines how such a framework enhances understanding, supports creativity, and aligns with best practices in information architecture.
Obsidian Nodes: Atomic Units of Thought
An Obsidian node is a note crafted to encapsulate one meaningful concept or question. It is:
- Atomic: Contains only one idea, making it easier to link and reuse.
- Context-Independent: Designed to stand on its own, without requiring the original source for meaning.
- Networked: Linked to other Obsidian nodes through backlinks and tags.
This system draws on the principles of the Zettelkasten method, but adapts them to the modern, markdown-based environment of Obsidian.
Benefits of Node-Based Note-Taking
- Improved Retrieval: Ideas can be surfaced based on content relevance, not source origin.
- Cross-Disciplinary Insight: Linking between concepts across fields becomes intuitive.
- Sustainable Growth: Each new node adds value to the network without redundancy.
Graph View: Visualizing Connections
Obsidian’s graph view offers a macro-level overview of the knowledge graph, showing how nodes interrelate. This encourages serendipitous discovery and identifies central or orphaned concepts that need further development.
- Clusters emerge around major themes.
- Hubs represent foundational ideas.
- Bridges between nodes show interdisciplinary links.
The graph view isn’t just a map—it’s an evolving reflection of intellectual progress.
Canvas: Thinking Spatially with Digital Notes
Obsidian Canvas acts as a digital thinking space. Unlike the abstract graph view, Canvas allows for spatial arrangement of Obsidian nodes, images, and ideas. This supports visual reasoning, ideation, and project planning.
Use Cases of Canvas
- Synthesizing Ideas: Group related nodes in physical proximity.
- Outlining Arguments: Arrange claims into narrative or logic flows.
- Designing Research Papers: Lay out structure and integrate supporting points visually.
Canvas brings a tactile quality to digital thinking, enabling workflows similar to sticky notes, mind maps, or corkboard pinning—but with markdown-based power and extensibility.
Template and Workflow
To simplify creation and encourage consistency, Obsidian nodes are generated using a templater plugin. Each node typically includes:
```markdown
{{title}}
Tags: #topic #field
Linked Nodes: [[Related Node]]
Summary: A 1-2 sentence idea explanation.
Source: [[Source Note]]
Date Created: {{date}}
```The Canvas workspace pulls these nodes as cards, allowing for arrangement, grouping, and visual tracing of arguments or research paths.
Discussion and Challenges
While this approach enhances creativity and research depth, challenges include:
- Initial Setup: Learning and configuring plugins like Templater, Dataview, and Canvas.
- Overlinking or Underlinking: Finding the right granularity in note-making takes practice.
- Scalability: As networks grow, maintaining structure and avoiding fragmentation becomes crucial.
- Team Collaboration: While Git can assist, Obsidian remains largely optimized for solo workflows.
Consider
Through the innovative employment of Obsidian's interconnected nodes and the Canvas feature, researchers are enabled to construct a meticulously engineered semantic architecture that reflects the intricate topology of their knowledge frameworks.
This paradigm shift facilitates a transformation of conventional note-taking, evolving this practice from a static, merely accumulative repository of information into a dynamic and adaptive cognitive ecosystem that actively engages with the user’s thought processes. With methodological rigor and a structured approach, Obsidian transcends its role as mere documentation software, evolving into both a secondary cognitive apparatus and a sophisticated digital writing infrastructure.
This dual functionality significantly empowers the long-term intellectual endeavors and creative pursuits of students, scholars, and lifelong learners, thereby enhancing their capacity for sustained engagement with complex ideas.
-
 @ d34e832d:383f78d0
2025-04-24 05:04:55
@ d34e832d:383f78d0
2025-04-24 05:04:55A Knowledge Management Framework for your Academic Writing
Idea Approach
The primary objective of this framework is to streamline and enhance the efficiency of several critical academic processes, namely the reading, annotation, synthesis, and writing stages inherent to doctoral studies.
By leveraging established best practices from various domains, including digital note-taking methodologies, sophisticated knowledge management techniques, and the scientifically-grounded principles of spaced repetition systems, this proposed workflow is adept at optimizing long-term retention of information, fostering the development of novel ideas, and facilitating the meticulous preparation of manuscripts. Furthermore, this integrated approach capitalizes on Zotero's robust annotation functionalities, harmoniously merged with Obsidian's Zettelkasten-inspired architecture, thereby enriching the depth and structural coherence of academic inquiry, ultimately leading to more impactful scholarly contributions.
Doctoral research demands a sophisticated approach to information management, critical thinking, and synthesis. Traditional systems of note-taking and bibliography management are often fragmented and inefficient, leading to cognitive overload and disorganized research outputs. This thesis proposes a workflow that leverages Zotero for reference management, Obsidian for networked note-taking, and Anki for spaced repetition learning—each component enhanced by a set of plugins, templates, and color-coded systems.
2. Literature Review and Context
2.1 Digital Research Workflows
Recent research in digital scholarship has highlighted the importance of structured knowledge environments. Tools like Roam Research, Obsidian, and Notion have gained traction among academics seeking flexibility and networked thinking. However, few workflows provide seamless interoperability between reference management, reading, and idea synthesis.
2.2 The Zettelkasten Method
Originally developed by sociologist Niklas Luhmann, the Zettelkasten ("slip-box") method emphasizes creating atomic notes—single ideas captured and linked through context. This approach fosters long-term idea development and is highly compatible with digital graph-based note systems like Obsidian.
3. Zotero Workflow: Structured Annotation and Tagging
Zotero serves as the foundational tool for ingesting and organizing academic materials. The built-in PDF reader is augmented through a color-coded annotation schema designed to categorize information efficiently:
- Red: Refuted or problematic claims requiring skepticism or clarification
- Yellow: Prominent claims, novel hypotheses, or insightful observations
- Green: Verified facts or claims that align with the research narrative
- Purple: Structural elements like chapter titles or section headers
- Blue: Inter-author references or connections to external ideas
- Pink: Unclear arguments, logical gaps, or questions for future inquiry
- Orange: Precise definitions and technical terminology
Annotations are accompanied by tags and notes in Zotero, allowing robust filtering and thematic grouping.
4. Obsidian Integration: Bridging Annotation and Synthesis
4.1 Plugin Architecture
Three key plugins optimize Obsidian’s role in the workflow:
- Zotero Integration (via
obsidian-citation-plugin): Syncs annotated PDFs and metadata directly from Zotero - Highlighter: Enables color-coded highlights in Obsidian, mirroring Zotero's scheme
- Templater: Automates formatting and consistency using Nunjucks templates
A custom keyboard shortcut (e.g.,
Ctrl+Shift+Z) is used to trigger the extraction of annotations into structured Obsidian notes.4.2 Custom Templating
The templating system ensures imported notes include:
- Citation metadata (title, author, year, journal)
- Full-color annotations with comments and page references
- Persistent notes for long-term synthesis
- An embedded bibtex citation key for seamless referencing
5. Zettelkasten and Atomic Note Generation
Obsidian’s networked note system supports idea-centered knowledge development. Each note captures a singular, discrete idea—independent of the source material—facilitating:
- Thematic convergence across disciplines
- Independent recombination of ideas
- Emergence of new questions and hypotheses
A standard atomic note template includes: - Note ID (timestamp or semantic UID) - Topic statement - Linked references - Associated atomic notes (via backlinks)
The Graph View provides a visual map of conceptual relationships, allowing researchers to track the evolution of their arguments.
6. Canvas for Spatial Organization
Obsidian’s Canvas plugin is used to mimic physical research boards: - Notes are arranged spatially to represent conceptual clusters or chapter structures - Embedded visual content enhances memory retention and creative thought - Notes and cards can be grouped by theme, timeline, or argumentative flow
This supports both granular research and holistic thesis design.
7. Flashcard Integration with Anki
Key insights, definitions, and questions are exported from Obsidian to Anki, enabling spaced repetition of core content. This supports: - Preparation for comprehensive exams - Retention of complex theories and definitions - Active recall training during literature reviews
Flashcards are automatically generated using Obsidian-to-Anki bridges, with tagging synced to Obsidian topics.
8. Word Processor Integration and Writing Stage
Zotero’s Word plugin simplifies: - In-text citation - Automatic bibliography generation - Switching between citation styles (APA, Chicago, MLA, etc.)
Drafts in Obsidian are later exported into formal academic writing environments such as Microsoft Word or LaTeX editors for formatting and submission.
9. Discussion and Evaluation
The proposed workflow significantly reduces friction in managing large volumes of information and promotes deep engagement with source material. Its modular nature allows adaptation for various disciplines and writing styles. Potential limitations include: - Initial learning curve - Reliance on plugin maintenance - Challenges in team-based collaboration
Nonetheless, the ability to unify reading, note-taking, synthesis, and writing into a seamless ecosystem offers clear benefits in focus, productivity, and academic rigor.
10. Consider
This idea demonstrates that a well-structured digital workflow using Zotero and Obsidian can transform the PhD research process. It empowers researchers to move beyond passive reading into active knowledge creation, aligned with the long-term demands of scholarly writing. Future iterations could include AI-assisted summarization, collaborative graph spaces, and greater mobile integration.
9. Evaluation Of The Approach
While this workflow offers significant advantages in clarity, synthesis, and long-term idea development, several limitations must be acknowledged:
-
Initial Learning Curve: New users may face a steep learning curve when setting up and mastering the integrated use of Zotero, Obsidian, and their associated plugins. Understanding markdown syntax, customizing templates in Templater, and configuring citation keys all require upfront time investment. However, this learning period can be offset by the long-term gains in productivity and mental clarity.
-
Plugin Ecosystem Volatility: Since both Obsidian and many of its key plugins are maintained by open-source communities or individual developers, updates can occasionally break workflows or require manual adjustments.
-
Interoperability Challenges: Synchronizing metadata, highlights, and notes between systems (especially on multiple devices or operating systems) may present issues if not managed carefully. This includes Zotero’s Better BibTeX keys, Obsidian sync, and Anki integration.
-
Limited Collaborative Features: This workflow is optimized for individual use. Real-time collaboration on notes or shared reference libraries may require alternative platforms or additional tooling.
Despite these constraints, the workflow remains highly adaptable and has proven effective across disciplines for researchers aiming to build a durable intellectual infrastructure over the course of a PhD.
9. Evaluation Of The Approach
While the Zotero–Obsidian workflow dramatically improves research organization and long-term knowledge retention, several caveats must be considered:
-
Initial Learning Curve: Mastery of this workflow requires technical setup and familiarity with markdown, citation keys, and plugin configuration. While challenging at first, the learning effort is front-loaded and pays off in efficiency over time.
-
Reliance on Plugin Maintenance: A key risk of this system is its dependence on community-maintained plugins. Tools like Zotero Integration, Templater, and Highlighter are not officially supported by Obsidian or Zotero core teams. This means updates or changes to the Obsidian API or plugin repository may break functionality or introduce bugs. Active plugin support is crucial to the system’s longevity.
-
Interoperability and Syncing Issues: Managing synchronization across Zotero, Obsidian, and Anki—especially across multiple devices—can lead to inconsistencies or data loss without careful setup. Users should ensure robust syncing solutions (e.g. Obsidian Sync, Zotero WebDAV, or GitHub backup).
-
Limited Collaboration Capabilities: This setup is designed for solo research workflows. Collaborative features (such as shared note-taking or group annotations) are limited and may require alternate solutions like Notion, Google Docs, or Overleaf when working in teams.
The integration of Zotero with Obsidian presents a notable advantage for individual researchers, exhibiting substantial efficiency in literature management and personal knowledge organization through its unique workflows. However, this model demonstrates significant deficiencies when evaluated in the context of collaborative research dynamics.
Specifically, while Zotero facilitates the creation and management of shared libraries, allowing for the aggregation of sources and references among users, Obsidian is fundamentally limited by its lack of intrinsic support for synchronous collaborative editing functionalities, thereby precluding simultaneous contributions from multiple users in real time. Although the application of version control systems such as Git has the potential to address this limitation, enabling a structured mechanism for tracking changes and managing contributions, the inherent complexity of such systems may pose a barrier to usability for team members who lack familiarity or comfort with version control protocols.
Furthermore, the nuances of color-coded annotation systems and bespoke personal note taxonomies utilized by individual researchers may present interoperability challenges when applied in a group setting, as these systems require rigorously defined conventions to ensure consistency and clarity in cross-collaborator communication and understanding. Thus, researchers should be cognizant of the challenges inherent in adapting tools designed for solitary workflows to the multifaceted requirements of collaborative research initiatives.
-
 @ d34e832d:383f78d0
2025-04-24 02:56:59
@ d34e832d:383f78d0
2025-04-24 02:56:591. The Ledger or Physical USD?
Bitcoin embodies a paradigmatic transformation in the foundational constructs of trust, ownership, and value preservation within the context of a digital economy. In stark contrast to conventional financial infrastructures that are predicated on centralized regulatory frameworks, Bitcoin operationalizes an intricate interplay of cryptographic techniques, consensus-driven algorithms, and incentivization structures to engender a decentralized and censorship-resistant paradigm for the transfer and safeguarding of digital assets. This conceptual framework elucidates the pivotal mechanisms underpinning Bitcoin's functional architecture, encompassing its distributed ledger technology (DLT) structure, robust security protocols, consensus algorithms such as Proof of Work (PoW), the intricacies of its monetary policy defined by the halving events and limited supply, as well as the broader implications these components have on stakeholder engagement and user agency.
2. The Core Functionality of Bitcoin
At its core, Bitcoin is a public ledger that records ownership and transfers of value. This ledger—called the blockchain—is maintained and verified by thousands of decentralized nodes across the globe.
2.1 Public Ledger
All Bitcoin transactions are stored in a transparent, append-only ledger. Each transaction includes: - A reference to prior ownership (input) - A transfer of value to a new owner (output) - A digital signature proving authorization
2.2 Ownership via Digital Signatures
Bitcoin uses asymmetric cryptography: - A private key is known only to the owner and is used to sign transactions. - A public key (or address) is used by the network to verify the authenticity of the transaction.
This system ensures that only the rightful owner can spend bitcoins, and that all network participants can independently verify that the transaction is valid.
3. Decentralization and Ledger Synchronization
Unlike traditional banking systems, which rely on a central institution, Bitcoin’s ledger is decentralized: - Every node keeps a copy of the blockchain. - No single party controls the system. - Updates to the ledger occur only through network consensus.
This decentralization ensures fault tolerance, censorship resistance, and transparency.
4. Preventing Double Spending
One of Bitcoin’s most critical innovations is solving the double-spending problem without a central authority.
4.1 Balance Validation
Before a transaction is accepted, nodes verify: - The digital signature is valid. - The input has not already been spent. - The sender has sufficient balance.
This is made possible by referencing previous transactions and ensuring the inputs match the unspent transaction outputs (UTXOs).
5. Blockchain and Proof-of-Work
To ensure consistency across the distributed network, Bitcoin uses a blockchain—a sequential chain of blocks containing batches of verified transactions.
5.1 Mining and Proof-of-Work
Adding a new block requires solving a cryptographic puzzle, known as Proof-of-Work (PoW): - The puzzle involves finding a hash value that meets network-defined difficulty. - This process requires computational power, which deters tampering. - Once a block is validated, it is propagated across the network.
5.2 Block Rewards and Incentives
Miners are incentivized to participate by: - Block rewards: New bitcoins issued with each block (initially 50 BTC, halved every ~4 years). - Transaction fees: Paid by users to prioritize their transactions.
6. Network Consensus and Security
Bitcoin relies on Nakamoto Consensus, which prioritizes the longest chain—the one with the most accumulated proof-of-work.
- In case of competing chains (forks), the network chooses the chain with the most computational effort.
- This mechanism makes rewriting history or creating fraudulent blocks extremely difficult, as it would require control of over 50% of the network's total hash power.
7. Transaction Throughput and Fees
Bitcoin’s average block time is 10 minutes, and each block can contain ~1MB of data, resulting in ~3–7 transactions per second.
- During periods of high demand, users compete by offering higher transaction fees to get included faster.
- Solutions like Lightning Network aim to scale transaction speed and lower costs by processing payments off-chain.
8. Monetary Policy and Scarcity
Bitcoin enforces a fixed supply cap of 21 million coins, making it deflationary by design.
- This limited supply contrasts with fiat currencies, which can be printed at will by central banks.
- The controlled issuance schedule and halving events contribute to Bitcoin’s store-of-value narrative, similar to digital gold.
9. Consider
Bitcoin integrates advanced cryptographic methodologies, including public-private key pairings and hashing algorithms, to establish a formidable framework of security that underpins its operation as a digital currency. The economic incentives are meticulously structured through mechanisms such as mining rewards and transaction fees, which not only incentivize network participation but also regulate the supply of Bitcoin through a halving schedule intrinsic to its decentralized protocol. This architecture manifests a paradigm wherein individual users can autonomously oversee their financial assets, authenticate transactions through a rigorously constructed consensus algorithm, specifically the Proof of Work mechanism, and engage with a borderless financial ecosystem devoid of traditional intermediaries such as banks. Despite the notable challenges pertaining to transaction throughput scalability and a complex regulatory landscape that intermittently threatens its proliferation, Bitcoin steadfastly persists as an archetype of decentralized trust, heralding a transformative shift in financial paradigms within the contemporary digital milieu.
10. References
- Nakamoto, S. (2008). Bitcoin: A Peer-to-Peer Electronic Cash System.
- Antonopoulos, A. M. (2017). Mastering Bitcoin: Unlocking Digital Cryptocurrencies.
- Bitcoin.org. (n.d.). How Bitcoin Works
-
 @ d34e832d:383f78d0
2025-04-24 00:56:03
@ d34e832d:383f78d0
2025-04-24 00:56:03WebSocket communication is integral to modern real-time web applications, powering everything from chat apps and online gaming to collaborative editing tools and live dashboards. However, its persistent and event-driven nature introduces unique debugging challenges. Traditional browser developer tools provide limited insight into WebSocket message flows, especially in complex, asynchronous applications.
This thesis evaluates the use of Chrome-based browser extensions—specifically those designed to enhance WebSocket debugging—and explores how visual event tracing improves developer experience (DX). By profiling real-world applications and comparing built-in tools with popular WebSocket DevTools extensions, we analyze the impact of visual feedback, message inspection, and timeline tracing on debugging efficiency, code quality, and development speed.
The Idea
As front-end development evolves, WebSockets have become a foundational technology for building reactive user experiences. Debugging WebSocket behavior, however, remains a cumbersome task. Chrome DevTools offers a basic view of WebSocket frames, but lacks features such as message categorization, event correlation, or contextual logging. Developers often resort to
console.logand custom logging systems, increasing friction and reducing productivity.This research investigates how browser extensions designed for WebSocket inspection—such as Smart WebSocket Client, WebSocket King Client, and WSDebugger—can enhance debugging workflows. We focus on features that provide visual structure to communication patterns, simplify message replay, and allow for real-time monitoring of state transitions.
Related Work
Chrome DevTools
While Chrome DevTools supports WebSocket inspection under the Network > Frames tab, its utility is limited: - Messages are displayed in a flat, unstructured stream. - No built-in timeline or replay mechanism. - Filtering and contextual debugging features are minimal.
WebSocket-Specific Extensions
Numerous browser extensions aim to fill this gap: - Smart WebSocket Client: Allows custom message sending, frame inspection, and saved session reuse. - WSDebugger: Offers structured logging and visualization of message flows. - WebSocket Monitor: Enables real-time monitoring of multiple connections with UI overlays.
Methodology
Tools Evaluated:
- Chrome DevTools (baseline)
- Smart WebSocket Client
- WSDebugger
- WebSocket King Client
Evaluation Criteria:
- Real-time message monitoring
- UI clarity and UX consistency
- Support for message replay and editing
- Message categorization and filtering
- Timeline-based visualization
Test Applications:
- A collaborative markdown editor
- A multiplayer drawing game (WebSocket over Node.js)
- A lightweight financial dashboard (stock ticker)
Findings
1. Enhanced Visibility
Extensions provide structured visual representations of WebSocket communication: - Grouped messages by type (e.g., chat, system, control) - Color-coded frames for quick scanning - Collapsible and expandable message trees
2. Real-Time Inspection and Replay
- Replaying previous messages with altered payloads accelerates bug reproduction.
- Message history can be annotated, aiding team collaboration during debugging.
3. Timeline-Based Analysis
- Extensions with timeline views help identify latency issues, bottlenecks, and inconsistent message pacing.
- Developers can correlate message sequences with UI events more intuitively.
4. Improved Debugging Flow
- Developers report reduced context-switching between source code and devtools.
- Some extensions allow breakpoints or watchers on WebSocket events, mimicking JavaScript debugging.
Consider
Visual debugging extensions represent a key advancement in tooling for real-time application development. By extending Chrome DevTools with features tailored for WebSocket tracing, developers gain actionable insights, faster debugging cycles, and a better understanding of application behavior. Future work should explore native integration of timeline and message tagging features into standard browser DevTools.
Developer Experience and Limitations
Visual tools significantly enhance the developer experience (DX) by reducing friction and offering cognitive support during debugging. Rather than parsing raw JSON blobs manually or tracing asynchronous behavior through logs, developers can rely on intuitive UI affordances such as real-time visualizations, message filtering, and replay features.
However, some limitations remain:
- Lack of binary frame support: Many extensions focus on text-based payloads and may not correctly parse or display binary frames.
- Non-standard encoding issues: Applications using custom serialization formats (e.g., Protocol Buffers, MsgPack) require external decoding tools or browser instrumentation.
- Extension compatibility: Some extensions may conflict with Content Security Policies (CSP) or have limited functionality when debugging production sites served over HTTPS.
- Performance overhead: Real-time visualization and logging can add browser CPU/memory overhead, particularly in high-frequency WebSocket environments.
Despite these drawbacks, the overall impact on debugging efficiency and developer comprehension remains highly positive.
Developer Experience and Limitations
Visual tools significantly enhance the developer experience (DX) by reducing friction and offering cognitive support during debugging. Rather than parsing raw JSON blobs manually or tracing asynchronous behavior through logs, developers can rely on intuitive UI affordances such as live message streams, structured views, and interactive inspection of frames.
However, some limitations exist:
- Security restrictions: Content Security Policy (CSP) and Cross-Origin Resource Sharing (CORS) can restrict browser extensions from accessing WebSocket frames in production environments.
- Binary and custom formats: Extensions may not handle binary frames or non-standard encodings (e.g., Protocol Buffers) without additional tooling.
- Limited protocol awareness: Generic tools may not fully interpret application-specific semantics, requiring context from the developer.
- Performance trade-offs: Logging and rendering large volumes of data can cause UI lag, especially in high-throughput WebSocket apps.
Despite these constraints, DevTools extensions continue to offer valuable insight during development and testing stages.
Applying this analysis to relays in the Nostr protocol surfaces some fascinating implications about traffic analysis, developer tooling, and privacy risks, even when data is cryptographically signed. Here's how the concepts relate:
🧠 What This Means for Nostr Relays
1. Traffic Analysis Still Applies
Even though Nostr events are cryptographically signed and, optionally, encrypted (e.g., DMs), relay communication is over plaintext WebSockets or WSS (WebSocket Secure). This means:
- IP addresses, packet size, and timing patterns are all visible to anyone on-path (e.g., ISPs, malicious actors).
- Client behavior can be inferred: Is someone posting, reading, or just idling?
- Frequent "kind" values (like
kind:1for notes orkind:4for encrypted DMs) produce recognizable traffic fingerprints.
🔍 Example:
A pattern like: -
client → relay: small frame at intervals of 30s -relay → client: burst of medium frames …could suggest someone is polling for new posts or using a chat app built on Nostr.
2. DevTools for Nostr Client Devs
For client developers (e.g., building on top of
nostr-tools), browser DevTools and WebSocket inspection make debugging much easier:- You can trace real-time Nostr events without writing logging logic.
- You can verify frame integrity, event flow, and relay responses instantly.
- However, DevTools have limits when Nostr apps use:
- Binary payloads (e.g., zlib-compressed events)
- Custom encodings or protocol adaptations (e.g., for mobile)
3. Fingerprinting Relays and Clients
- Each relay has its own behavior: how fast it responds, whether it sends OKs, how it deals with malformed events.
- These can be fingerprinted by adversaries to identify which software is being used (e.g.,
nostr-rs-relay,strfry, etc.). - Similarly, client apps often emit predictable
REQ,EVENT,CLOSEsequences that can be fingerprinted even over WSS.
4. Privacy Risks
Even if DMs are encrypted: - Message size and timing can hint at contents ("user is typing", long vs. short message, emoji burst, etc.) - Public relays might correlate patterns across multiple clients—even without payload access. - Side-channel analysis becomes viable against high-value targets.
5. Mitigation Strategies in Nostr
Borrowing from TLS and WebSocket security best practices:
| Strategy | Application to Nostr | |-----------------------------|----------------------------------------------------| | Padding messages | Normalize
EVENTsize, especially for DMs | | Batching requests | Send multipleREQsubscriptions in one frame | | Randomize connection times | Avoid predictable connection schedules | | Use private relays / Tor| Obfuscate source IP and reduce metadata exposure | | Connection reuse | Avoid per-event relay opens, use persistent WSS |
TL;DR for Builders
If you're building on Nostr and care about privacy, WebSocket metadata is a leak. The payload isn't the only thing that matters. Be mindful of event timing, size, and structure, even over encrypted channels.
-
 @ df478568:2a951e67
2025-04-23 20:25:03
@ df478568:2a951e67
2025-04-23 20:25:03If you've made one single-sig bitcoin wallet, you've made then all. The idea is, write down 12 or 24 magic words. Make your wallet disappear by dropping your phone in the toilet. Repeat the 12 magic words and do some hocus-pocus. Your sats re-appear from realms unknown. Or...Each word represents a 4 digit number from 0000-2047. I say it's magic.
I've recommended many wallets over the years. It's difficult to find the perfect wallet because there are so many with different security tailored for different threat models. You don't need Anchorwatch level of security for 1000 sats. 12 words is good enough. Misty Breez is like Aqua Wallet because the sats get swapped to Liquid in a similar way with a couple differences.
- Misty Breez has no stableshitcoin¹ support.
- Misty Breez gives you a lightning address. Misty Breez Lightning Wallet.
That's a big deal. That's what I need to orange pill the man on the corner selling tamales out of his van. Bitcoin is for everybody, at least anybody who can write 12 words down. A few years ago, almost nobody, not even many bitcoiners had a lightning address. Now Misty Breez makes it easy for anyone with a 5th grade reading level to start using lightning addresses. The tamale guy can send sats back home with as many tariffs as a tweet without leaving his truck.
How Misty Breez Works
Back in the day, I drooled over every word Elizabeth Stark at lightning labs uttered. I still believed in shitcoins at the time. Stark said atomic swaps can be made over the lightning network. Litecoin, since it also adopted the lightning network, can be swapped with bitcoin and vice-versa. I thought this was a good idea because it solves the coincidence of wants. I could technically have a sign on my website that says, "shitcoin accepted here" and automatically convert all my shitcoins to sats.
I don't do that because I now know there is no reason to think any shitcoin will go up in value over the long-term for various reasons. Technically, cashu is a shitcoin. Technically, Liquid is a shitcoin. Technically, I am not a card carrying bitcoin maxi because of this. I use these shitcoins because I find them useful. I consider them to be honest shitcoins(term stolen from NVK²).
Breeze does ~atomic swaps~~ peer swaps between bitcoin and Liquid. The sender sends sats. The receiver turns those sats into Liquid Bitcoin(L-BTC). This L-BTC is backed by bitcoin, therefore Liquid is a full reserve bank in many ways. That's why it molds into my ethical framework. I originally became interested in bitcoin because I thought fractional reserve banking was a scam and bitcoin was(and is) the most viable alternative to this scam.
Sats sent to Misty Breez wallet are pretty secure. It does not offer perfect security. There is no perfect security. Even though on-chain bitcoin is the most pristine example of cybersecurity on the planet, it still has risk. Just ask the guy who is digging up a landfill to find his bitcoin. I have found most noobs lose keys to bitcoin you give them. Very few take the time to keep it safe because they don't understand bitcoin well enough to know it will go up forever Laura.
She writes 12 words down with a reluctant bored look on her face. Wam. Bam. Thank you m'am. Might as well consider it a donation to the network because that index card will be buried in a pile of future trash in no time. Here's a tiny violin playing for the pre-coiners who lost sats.
"Lost coins only make everyone else's coins worth slightly more. Think of it as a donation to everyone." --Sathoshi Nakamoto, BitcoinTalk --June 21, 2010
The same thing will happen with the Misty Wallet. The 12 words will be written down my someone bored and unfulfilled woman working at NPC-Mart, but her phone buzzes in her pocket the next day. She recieved a new payment. Then you share the address on nostr and five people send her sats for no reason at all. They say everyone requires three touch points. Setting up a pre-coiner with a wallet which has a lightning address will allow you to send her as many touch points as you want. You could even send 21 sats per day for 21 days using Zap Planner. That way bitcoin is not just an "investment," but something people can see in action like a lion in the jungle chasing a gazelle.
Make Multiple Orange Pill Touch Points With Misty The Breez Lightning Address
It's no longer just a one-night stand. It's a relationship. You can softly send her sats seven days a week like a Rabbit Hole recap listening freak. Show people how to use bitcoin as it was meant to be used: Peer to Peer electronic cash.
 Misty wallet is still beta software so be careful because lightning is still in the w reckless days. Don't risk more sats that you are willing to lose with it just yet, but consider learning how to use it so you can teach others after the wallet is battle tested. I had trouble sending sats to my lightning address today from Phoenix wallet. Hopefully that gets resovled, but I couldn't use it today for whatever reason. I still think it's an awesome idea and will follow this project because I think it has potential.
Misty wallet is still beta software so be careful because lightning is still in the w reckless days. Don't risk more sats that you are willing to lose with it just yet, but consider learning how to use it so you can teach others after the wallet is battle tested. I had trouble sending sats to my lightning address today from Phoenix wallet. Hopefully that gets resovled, but I couldn't use it today for whatever reason. I still think it's an awesome idea and will follow this project because I think it has potential.npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
¹ Stablecoins are shitcoins, but I admit they are not totally useless, but the underlying asset is the epitome of money printer go brrrrrr. ²NVK called cashu an honeset shitcoin on the Bitcoin.review podcast and I've used the term ever sense.
-
 @ d34e832d:383f78d0
2025-04-23 20:19:15
@ d34e832d:383f78d0
2025-04-23 20:19:15A Look into Traffic Analysis and What WebSocket Patterns Reveal at the Network Level
While WebSocket encryption (typically via WSS) is essential for protecting data in transit, traffic analysis remains a potent method of uncovering behavioral patterns, data structure inference, and protocol usage—even when payloads are unreadable. This idea investigates the visibility of encrypted WebSocket communications using Wireshark and similar packet inspection tools. We explore what metadata remains visible, how traffic flow can be modeled, and what risks and opportunities exist for developers, penetration testers, and network analysts. The study concludes by discussing mitigation strategies and the implications for privacy, application security, and protocol design.
Consider
In the age of real-time web applications, WebSockets have emerged as a powerful protocol enabling low-latency, bidirectional communication. From collaborative tools and chat applications to financial trading platforms and IoT dashboards, WebSockets have become foundational for interactive user experiences.
However, encryption via WSS (WebSocket Secure, running over TLS) gives developers and users a sense of security. The payload may be unreadable, but what about the rest of the connection? Can patterns, metadata, and traffic characteristics still leak critical information?
This thesis seeks to answer those questions by leveraging Wireshark, the de facto tool for packet inspection, and exploring the world of traffic analysis at the network level.
Background and Related Work
The WebSocket Protocol
Defined in RFC 6455, WebSocket operates over TCP and provides a persistent, full-duplex connection. The protocol upgrades an HTTP connection, then communicates through a simple frame-based structure.
Encryption with WSS
WSS connections use TLS (usually on port 443), making them indistinguishable from HTTPS traffic at the packet level. Payloads are encrypted, but metadata such as IP addresses, timing, packet size, and connection duration remain visible.
Traffic Analysis
Traffic analysis—despite encryption—has long been a technique used in network forensics, surveillance, and malware detection. Prior studies have shown that encrypted protocols like HTTPS, TLS, and SSH still reveal behavioral information through patterns.
Methodology
Tools Used:
- Wireshark (latest stable version)
- TLS decryption with local keys (when permitted)
- Simulated and real-world WebSocket apps (chat, games, IoT dashboards)
- Scripts to generate traffic patterns (Python using websockets and aiohttp)
Test Environments:
- Controlled LAN environments with known server and client
- Live observation of open-source WebSocket platforms (e.g., Matrix clients)
Data Points Captured:
- Packet timing and size
- TLS handshake details
- IP/TCP headers
- Frame burst patterns
- Message rate and directionality
Findings
1. Metadata Leaks
Even without payload access, the following data is visible: - Source/destination IP - Port numbers (typically 443) - Server certificate info - Packet sizes and intervals - TLS handshake fingerprinting (e.g., JA3 hashes)
2. Behavioral Patterns
- Chat apps show consistent message frequency and short message sizes.
- Multiplayer games exhibit rapid bursts of small packets.
- IoT devices often maintain idle connections with periodic keepalives.
- Typing indicators, heartbeats, or "ping/pong" mechanisms are visible even under encryption.
3. Timing and Packet Size Fingerprinting
Even encrypted payloads can be fingerprinted by: - Regularity in payload size (e.g., 92 bytes every 15s) - Distinct bidirectional patterns (e.g., send/ack/send per user action) - TLS record sizes which may indirectly hint at message length
Side-Channel Risks in Encrypted WebSocket Communication
Although WebSocket payloads transmitted over WSS (WebSocket Secure) are encrypted, they remain susceptible to side-channel analysis, a class of attacks that exploit observable characteristics of the communication channel rather than its content.
Side-Channel Risks Include:
1. User Behavior Inference
Adversaries can analyze packet timing and frequency to infer user behavior. For example, typing indicators in chat applications often trigger short, regular packets. Even without payload visibility, a passive observer may identify when a user is typing, idle, or has closed the application. Session duration, message frequency, and bursts of activity can be linked to specific user actions.2. Application Fingerprinting
TLS handshake metadata and consistent traffic patterns can allow an observer to identify specific client libraries or platforms. For example, the sequence and structure of TLS extensions (via JA3 fingerprinting) can differentiate between browsers, SDKs, or WebSocket frameworks. Application behavior—such as timing of keepalives or frequency of updates—can further reinforce these fingerprints.3. Usage Pattern Recognition
Over time, recurring patterns in packet flow may reveal application logic. For instance, multiplayer game sessions often involve predictable synchronization intervals. Financial dashboards may show bursts at fixed polling intervals. This allows for profiling of application type, logic loops, or even user roles.4. Leakage Through Timing
Time-based attacks can be surprisingly revealing. Regular intervals between message bursts can disclose structured interactions—such as polling, pings, or scheduled updates. Fine-grained timing analysis may even infer when individual keystrokes occur, especially in sparse channels where interactivity is high and payloads are short.5. Content Length Correlation
While encrypted, the size of a TLS record often correlates closely to the plaintext message length. This enables attackers to estimate the size of messages, which can be linked to known commands or data structures. Repeated message sizes (e.g., 112 bytes every 30s) may suggest state synchronization or batched updates.6. Session Correlation Across Time
Using IP, JA3 fingerprints, and behavioral metrics, it’s possible to link multiple sessions back to the same client. This weakens anonymity, especially when combined with data from DNS logs, TLS SNI fields (if exposed), or consistent traffic habits. In anonymized systems, this can be particularly damaging.Side-Channel Risks in Encrypted WebSocket Communication
Although WebSocket payloads transmitted over WSS (WebSocket Secure) are encrypted, they remain susceptible to side-channel analysis, a class of attacks that exploit observable characteristics of the communication channel rather than its content.
1. Behavior Inference
Even with end-to-end encryption, adversaries can make educated guesses about user actions based on traffic patterns:
- Typing detection: In chat applications, short, repeated packets every few hundred milliseconds may indicate a user typing.
- Voice activity: In VoIP apps using WebSockets, a series of consistent-size packets followed by silence can reveal when someone starts and stops speaking.
- Gaming actions: Packet bursts at high frequency may correlate with real-time game movement or input actions.
2. Session Duration
WebSocket connections are persistent by design. This characteristic allows attackers to:
- Measure session duration: Knowing how long a user stays connected to a WebSocket server can infer usage patterns (e.g., average chat duration, work hours).
- Identify session boundaries: Connection start and end timestamps may be enough to correlate with user login/logout behavior.
3. Usage Patterns
Over time, traffic analysis may reveal consistent behavioral traits tied to specific users or devices:
- Time-of-day activity: Regular connection intervals can point to habitual usage, ideal for profiling or surveillance.
- Burst frequency and timing: Distinct intervals of high or low traffic volume can hint at backend logic or user engagement models.
Example Scenario: Encrypted Chat App
Even though a chat application uses end-to-end encryption and transports data over WSS:
- A passive observer sees:
- TLS handshake metadata
- IPs and SNI (Server Name Indication)
- Packet sizes and timings
- They might then infer:
- When a user is online or actively chatting
- Whether a user is typing, idle, or receiving messages
- Usage patterns that match a specific user fingerprint
This kind of intelligence can be used for traffic correlation attacks, profiling, or deanonymization — particularly dangerous in regimes or situations where privacy is critical (e.g., journalists, whistleblowers, activists).
Fingerprinting Encrypted WebSocket Applications via Traffic Signatures
Even when payloads are encrypted, adversaries can leverage fingerprinting techniques to identify the specific WebSocket libraries, frameworks, or applications in use based on unique traffic signatures. This is a critical vector in traffic analysis, especially when full encryption lulls developers into a false sense of security.
1. Library and Framework Fingerprints
Different WebSocket implementations generate traffic patterns that can be used to infer what tool or framework is being used, such as:
- Handshake patterns: The WebSocket upgrade request often includes headers that differ subtly between:
- Browsers (Chrome, Firefox, Safari)
- Python libs (
websockets,aiohttp,Autobahn) - Node.js clients (
ws,socket.io) - Mobile SDKs (Android’s
okhttp, iOSStarscream) - Heartbeat intervals: Some libraries implement default ping/pong intervals (e.g., every 20s in
socket.io) that can be measured and traced back to the source.
2. Payload Size and Frequency Patterns
Even with encryption, metadata is exposed:
- Frame sizes: Libraries often chunk or batch messages differently.
- Initial message burst: Some apps send a known sequence of messages on connection (e.g., auth token → subscribe → sync events).
- Message intervals: Unique to libraries using structured pub/sub or event-driven APIs.
These observable patterns can allow a passive observer to identify not only the app but potentially which feature is being used, such as messaging, location tracking, or media playback.
3. Case Study: Identifying Socket.IO vs Raw WebSocket
Socket.IO, although layered on top of WebSockets, introduces a handshake sequence of HTTP polling → upgrade → packetized structured messaging with preamble bytes (even in encrypted form, the size and frequency of these frames is recognizable). A well-equipped observer can differentiate it from a raw WebSocket exchange using only timing and packet length metrics.
Security Implications
- Targeted exploitation: Knowing the backend framework (e.g.,
Django ChannelsorFastAPI + websockets) allows attackers to narrow down known CVEs or misconfigurations. - De-anonymization: Apps that are widely used in specific demographics (e.g., Signal clones, activist chat apps) become fingerprintable even behind HTTPS or WSS.
- Nation-state surveillance: Traffic fingerprinting lets governments block or monitor traffic associated with specific technologies, even without decrypting the data.
Leakage Through Timing: Inferring Behavior in Encrypted WebSocket Channels
Encrypted WebSocket communication does not prevent timing-based side-channel attacks, where an adversary can deduce sensitive information purely from the timing, size, and frequency of encrypted packets. These micro-behavioral signals, though not revealing actual content, can still disclose high-level user actions — sometimes with alarming precision.
1. Typing Detection and Keystroke Inference
Many real-time chat applications (Matrix, Signal, Rocket.Chat, custom WebSocket apps) implement "user is typing..." features. These generate recognizable message bursts even when encrypted:
- Small, frequent packets sent at irregular intervals often correspond to individual keystrokes.
- Inter-keystroke timing analysis — often accurate to within tens of milliseconds — can help reconstruct typed messages’ length or even guess content using language models (e.g., inferring "hello" vs "hey").
2. Session Activity Leaks
WebSocket sessions are long-lived and often signal usage states by packet rhythm:
- Idle vs active user patterns become apparent through heartbeat frequency and packet gaps.
- Transitions — like joining or leaving a chatroom, starting a video, or activating a voice stream — often result in bursts of packet activity.
- Even without payload access, adversaries can profile session structure, determining which features are being used and when.
3. Case Study: Real-Time Editors
Collaborative editing tools (e.g., Etherpad, CryptPad) leak structure:
- When a user edits, each keystroke or operation may result in a burst of 1–3 WebSocket frames.
- Over time, a passive observer could infer:
- Whether one or multiple users are active
- Who is currently typing
- The pace of typing
- Collaborative vs solo editing behavior
4. Attack Vectors Enabled by Timing Leaks
- Target tracking: Identify active users in a room, even on anonymized or end-to-end encrypted platforms.
- Session replay: Attackers can simulate usage patterns for further behavioral fingerprinting.
- Network censorship: Governments may block traffic based on WebSocket behavior patterns suggestive of forbidden apps (e.g., chat tools, Tor bridges).
Mitigations and Countermeasures
While timing leakage cannot be entirely eliminated, several techniques can obfuscate or dampen signal strength:
- Uniform packet sizing (padding to fixed lengths)
- Traffic shaping (constant-time message dispatch)
- Dummy traffic injection (noise during idle states)
- Multiplexing WebSocket streams with unrelated activity
Excellent point — let’s weave that into the conclusion of the thesis to emphasize the dual nature of WebSocket visibility:
Visibility Without Clarity — Privacy Risks in Encrypted WebSocket Traffic**
This thesis demonstrates that while encryption secures the contents of WebSocket payloads, it does not conceal behavioral patterns. Through tools like Wireshark, analysts — and adversaries alike — can inspect traffic flows to deduce session metadata, fingerprint applications, and infer user activity, even without decrypting a single byte.
The paradox of encrypted WebSockets is thus revealed:
They offer confidentiality, but not invisibility.As shown through timing analysis, fingerprinting, and side-channel observation, encrypted WebSocket streams can still leak valuable information. These findings underscore the importance of privacy-aware design choices in real-time systems:
- Padding variable-size messages to fixed-length formats
- Randomizing or shaping packet timing
- Mixing in dummy traffic during idle states
- Multiplexing unrelated data streams to obscure intent
Without such obfuscation strategies, encrypted WebSocket traffic — though unreadable — remains interpretable.
In closing, developers, privacy researchers, and protocol designers must recognize that encryption is necessary but not sufficient. To build truly private real-time systems, we must move beyond content confidentiality and address the metadata and side-channel exposures that lie beneath the surface.
Absolutely! Here's a full thesis-style writeup titled “Mitigation Strategies: Reducing Metadata Leakage in Encrypted WebSocket Traffic”, focusing on countermeasures to side-channel risks in real-time encrypted communication:
Mitigation Strategies: Reducing Metadata Leakage in Encrypted WebSocket Traffic
Abstract
While WebSocket traffic is often encrypted using TLS, it remains vulnerable to metadata-based side-channel attacks. Adversaries can infer behavioral patterns, session timing, and even the identity of applications through passive traffic analysis. This thesis explores four key mitigation strategies—message padding, batching and jitter, TLS fingerprint randomization, and connection multiplexing—that aim to reduce the efficacy of such analysis. We present practical implementations, limitations, and trade-offs associated with each method and advocate for layered, privacy-preserving protocol design.
1. Consider
The rise of WebSockets in real-time applications has improved interactivity but also exposed new privacy attack surfaces. Even when encrypted, WebSocket traffic leaks observable metadata—packet sizes, timing intervals, handshake properties, and connection counts—that can be exploited for fingerprinting, behavioral inference, and usage profiling.
This Idea focuses on mitigation rather than detection. The core question addressed is: How can we reduce the information available to adversaries from metadata alone?
2. Threat Model and Metadata Exposure
Passive attackers situated at any point between client and server can: - Identify application behavior via timing and message frequency - Infer keystrokes or user interaction states ("user typing", "user joined", etc.) - Perform fingerprinting via TLS handshake characteristics - Link separate sessions from the same user by recognizing traffic patterns
Thus, we must treat metadata as a leaky abstraction layer, requiring proactive obfuscation even in fully encrypted sessions.
3. Mitigation Techniques
3.1 Message Padding
Variable-sized messages create unique traffic signatures. Message padding involves standardizing the frame length of WebSocket messages to a fixed or randomly chosen size within a predefined envelope.
- Pro: Hides exact payload size, making compression side-channel and length-based analysis ineffective.
- Con: Increases bandwidth usage; not ideal for mobile/low-bandwidth scenarios.
Implementation: Client libraries can pad all outbound messages to, for example, 512 bytes or the next power of two above the actual message length.
3.2 Batching and Jitter
Packet timing is often the most revealing metric. Delaying messages to create jitter and batching multiple events into a single transmission breaks correlation patterns.
- Pro: Prevents timing attacks, typing inference, and pattern recognition.
- Con: Increases latency, possibly degrading UX in real-time apps.
Implementation: Use an event queue with randomized intervals for dispatching messages (e.g., 100–300ms jitter windows).
3.3 TLS Fingerprint Randomization
TLS fingerprints—determined by the ordering of cipher suites, extensions, and fields—can uniquely identify client libraries and platforms. Randomizing these fields on the client side prevents reliable fingerprinting.
- Pro: Reduces ability to correlate sessions or identify tools/libraries used.
- Con: Requires deeper control of the TLS stack, often unavailable in browsers.
Implementation: Modify or wrap lower-level TLS clients (e.g., via OpenSSL or rustls) to introduce randomized handshakes in custom apps.
3.4 Connection Reuse or Multiplexing
Opening multiple connections creates identifiable patterns. By reusing a single persistent connection for multiple data streams or users (in proxies or edge nodes), the visibility of unique flows is reduced.
- Pro: Aggregates traffic, preventing per-user or per-feature traffic separation.
- Con: More complex server-side logic; harder to debug.
Implementation: Use multiplexing protocols (e.g., WebSocket subprotocols or application-level routing) to share connections across users or components.
4. Combined Strategy and Defense-in-Depth
No single strategy suffices. A layered mitigation approach—combining padding, jitter, fingerprint randomization, and multiplexing—provides defense-in-depth against multiple classes of metadata leakage.
The recommended implementation pipeline: 1. Pad all outbound messages to a fixed size 2. Introduce random batching and delay intervals 3. Obfuscate TLS fingerprints using low-level TLS stack configuration 4. Route data over multiplexed WebSocket connections via reverse proxies or edge routers
This creates a high-noise communication channel that significantly impairs passive traffic analysis.
5. Limitations and Future Work
Mitigations come with trade-offs: latency, bandwidth overhead, and implementation complexity. Additionally, some techniques (e.g., TLS randomization) are hard to apply in browser-based environments due to API constraints.
Future work includes: - Standardizing privacy-enhancing WebSocket subprotocols - Integrating these mitigations into mainstream libraries (e.g., Socket.IO, Phoenix) - Using machine learning to auto-tune mitigation levels based on threat environment
6. Case In Point
Encrypted WebSocket traffic is not inherently private. Without explicit mitigation, metadata alone is sufficient for behavioral profiling and application fingerprinting. This thesis has outlined practical strategies for obfuscating traffic patterns at various protocol layers. Implementing these defenses can significantly improve user privacy in real-time systems and should become a standard part of secure WebSocket deployments.
-
 @ 1d7ff02a:d042b5be
2025-04-23 02:28:08
@ 1d7ff02a:d042b5be
2025-04-23 02:28:08ທຳຄວາມເຂົ້າໃຈກັບຂໍ້ບົກພ່ອງໃນລະບົບເງິນຂອງພວກເຮົາ
ຫຼາຍຄົນພົບຄວາມຫຍຸ້ງຍາກໃນການເຂົ້າໃຈ Bitcoin ເພາະວ່າພວກເຂົາຍັງບໍ່ເຂົ້າໃຈບັນຫາພື້ນຖານຂອງລະບົບເງິນທີ່ມີຢູ່ຂອງພວກເຮົາ. ລະບົບນີ້, ທີ່ມັກຖືກຮັບຮູ້ວ່າມີຄວາມໝັ້ນຄົງ, ມີຂໍ້ບົກພ່ອງໃນການອອກແບບທີ່ມີມາແຕ່ດັ້ງເດີມ ເຊິ່ງສົ່ງຜົນຕໍ່ຄວາມບໍ່ສະເໝີພາບທາງເສດຖະກິດ ແລະ ການເຊື່ອມເສຍຂອງຄວາມຮັ່ງມີສຳລັບພົນລະເມືອງທົ່ວໄປ. ການເຂົ້າໃຈບັນຫາເຫຼົ່ານີ້ແມ່ນກຸນແຈສຳຄັນເພື່ອເຂົ້າໃຈທ່າແຮງຂອງວິທີແກ້ໄຂທີ່ Bitcoin ສະເໜີ.
ບົດບາດຂອງກະຊວງການຄັງສະຫະລັດ ແລະ ທະນາຄານກາງ
ລະບົບເງິນຕາປັດຈຸບັນໃນສະຫະລັດອາເມລິກາປະກອບມີການເຊື່ອມໂຍງທີ່ຊັບຊ້ອນລະຫວ່າງກະຊວງການຄັງສະຫະລັດ ແລະ ທະນາຄານກາງ. ກະຊວງການຄັງສະຫະລັດເຮັດໜ້າທີ່ເປັນບັນຊີທະນາຄານຂອງປະເທດ, ເກັບອາກອນ ແລະ ສະໜັບສະໜູນລາຍຈ່າຍຂອງລັດຖະບານເຊັ່ນ: ທະຫານ, ໂຄງລ່າງພື້ນຖານ ແລະ ໂຄງການສັງຄົມ. ເຖິງຢ່າງໃດກໍຕາມ, ລັດຖະບານມັກໃຊ້ຈ່າຍຫຼາຍກວ່າທີ່ເກັບໄດ້, ເຊິ່ງເຮັດໃຫ້ຕ້ອງໄດ້ຢືມເງິນ. ການຢືມນີ້ແມ່ນເຮັດໂດຍການຂາຍພັນທະບັດລັດຖະບານ, ຊຶ່ງມັນຄືໃບ IOU ທີ່ສັນຍາວ່າຈະຈ່າຍຄືນຈຳນວນທີ່ຢືມພ້ອມດອກເບ້ຍ. ພັນທະບັດເຫຼົ່ານີ້ມັກຖືກຊື້ໂດຍທະນາຄານໃຫຍ່, ລັດຖະບານຕ່າງປະເທດ, ແລະ ທີ່ສຳຄັນ, ທະນາຄານກາງ.
ວິທີການສ້າງເງິນ (ຈາກອາກາດ)
ນີ້ແມ່ນບ່ອນທີ່ເກີດການສ້າງເງິນ "ຈາກອາກາດ". ເມື່ອທະນາຄານກາງຊື້ພັນທະບັດເຫຼົ່ານີ້, ມັນບໍ່ໄດ້ໃຊ້ເງິນທີ່ມີຢູ່ແລ້ວ; ມັນສ້າງເງິນໃໝ່ດ້ວຍວິທີການດິຈິຕອນໂດຍພຽງແຕ່ປ້ອນຕົວເລກເຂົ້າໃນຄອມພິວເຕີ. ເງິນໃໝ່ນີ້ຖືກເພີ່ມເຂົ້າໃນປະລິມານເງິນລວມ. ຍິ່ງສ້າງເງິນຫຼາຍຂຶ້ນ ແລະ ເພີ່ມເຂົ້າໄປ, ມູນຄ່າຂອງເງິນທີ່ມີຢູ່ແລ້ວກໍຍິ່ງຫຼຸດລົງ. ຂະບວນການນີ້ຄືສິ່ງທີ່ພວກເຮົາເອີ້ນວ່າເງິນເຟີ້. ເນື່ອງຈາກກະຊວງການຄັງຢືມຢ່າງຕໍ່ເນື່ອງ ແລະ ທະນາຄານກາງສາມາດພິມໄດ້ຢ່າງຕໍ່ເນື່ອງ, ສິ່ງນີ້ຖືກສະເໜີວ່າເປັນວົງຈອນທີ່ບໍ່ມີທີ່ສິ້ນສຸດ.
ການໃຫ້ກູ້ຢືມສະຫງວນບາງສ່ວນໂດຍທະນາຄານ
ເພີ່ມເຂົ້າໃນບັນຫານີ້ຄືການປະຕິບັດຂອງການໃຫ້ກູ້ຢືມສະຫງວນບາງສ່ວນໂດຍທະນາຄານ. ເມື່ອທ່ານຝາກເງິນເຂົ້າທະນາຄານ, ທະນາຄານຖືກຮຽກຮ້ອງໃຫ້ເກັບຮັກສາພຽງແຕ່ສ່ວນໜຶ່ງຂອງເງິນຝາກນັ້ນໄວ້ເປັນເງິນສະຫງວນ (ຕົວຢ່າງ, 10%). ສ່ວນທີ່ເຫຼືອ (90%) ສາມາດຖືກປ່ອຍກູ້. ເມື່ອຜູ້ກູ້ຢືມໃຊ້ຈ່າຍເງິນນັ້ນ, ມັນມັກຖືກຝາກເຂົ້າອີກທະນາຄານ, ເຊິ່ງຈາກນັ້ນກໍຈະເຮັດຊ້ຳຂະບວນການໃຫ້ກູ້ຢືມສ່ວນໜຶ່ງຂອງເງິນຝາກ. ວົງຈອນນີ້ເຮັດໃຫ້ເພີ່ມຈຳນວນເງິນທີ່ໝູນວຽນຢູ່ໃນລະບົບໂດຍອີງໃສ່ເງິນຝາກເບື້ອງຕົ້ນ, ເຊິ່ງສ້າງເງິນຜ່ານໜີ້ສິນ. ລະບົບນີ້ໂດຍທຳມະຊາດແລ້ວບອບບາງ; ຖ້າມີຫຼາຍຄົນພະຍາຍາມຖອນເງິນຝາກຂອງເຂົາເຈົ້າພ້ອມກັນ (ການແລ່ນທະນາຄານ), ທະນາຄານກໍຈະລົ້ມເພາະວ່າມັນບໍ່ໄດ້ເກັບຮັກສາເງິນທັງໝົດໄວ້. ເງິນໃນທະນາຄານບໍ່ປອດໄພຄືກັບທີ່ເຊື່ອກັນທົ່ວໄປ ແລະ ສາມາດຖືກແຊ່ແຂງໃນຊ່ວງວິກິດການ ຫຼື ສູນເສຍຖ້າທະນາຄານລົ້ມລະລາຍ (ຍົກເວັ້ນໄດ້ຮັບການຊ່ວຍເຫຼືອ).
ຜົນກະທົບ Cantillon: ໃຜໄດ້ຮັບຜົນປະໂຫຍດກ່ອນ
ເງິນທີ່ຖືກສ້າງຂຶ້ນໃໝ່ບໍ່ໄດ້ກະຈາຍຢ່າງເທົ່າທຽມກັນ. "ຜົນກະທົບ Cantillon", ບ່ອນທີ່ຜູ້ທີ່ຢູ່ໃກ້ກັບແຫຼ່ງສ້າງເງິນໄດ້ຮັບຜົນປະໂຫຍດກ່ອນ. ນີ້ລວມເຖິງລັດຖະບານເອງ (ສະໜັບສະໜູນລາຍຈ່າຍ), ທະນາຄານໃຫຍ່ ແລະ Wall Street (ໄດ້ຮັບທຶນໃນອັດຕາດອກເບ້ຍຕ່ຳສຳລັບການກູ້ຢືມ ແລະ ການລົງທຶນ), ແລະ ບໍລິສັດໃຫຍ່ (ເຂົ້າເຖິງເງິນກູ້ທີ່ຖືກກວ່າສຳລັບການລົງທຶນ). ບຸກຄົນເຫຼົ່ານີ້ໄດ້ຊື້ຊັບສິນ ຫຼື ລົງທຶນກ່ອນທີ່ຜົນກະທົບຂອງເງິນເຟີ້ຈະເຮັດໃຫ້ລາຄາສູງຂຶ້ນ, ເຊິ່ງເຮັດໃຫ້ພວກເຂົາມີຂໍ້ໄດ້ປຽບ.
ຜົນກະທົບຕໍ່ຄົນທົ່ວໄປ
ສຳລັບຄົນທົ່ວໄປ, ຜົນກະທົບຂອງປະລິມານເງິນທີ່ເພີ່ມຂຶ້ນນີ້ແມ່ນການເພີ່ມຂຶ້ນຂອງລາຄາສິນຄ້າ ແລະ ການບໍລິການ - ນ້ຳມັນ, ຄ່າເຊົ່າ, ການດູແລສຸຂະພາບ, ອາຫານ, ແລະ ອື່ນໆ. ເນື່ອງຈາກຄ່າແຮງງານໂດຍທົ່ວໄປບໍ່ທັນກັບອັດຕາເງິນເຟີ້ນີ້, ອຳນາດການຊື້ຂອງປະຊາຊົນຈະຫຼຸດລົງເມື່ອເວລາຜ່ານໄປ. ມັນຄືກັບການແລ່ນໄວຂຶ້ນພຽງເພື່ອຢູ່ໃນບ່ອນເກົ່າ.
Bitcoin: ທາງເລືອກເງິນທີ່ໝັ້ນຄົງ
ຄວາມຂາດແຄນ: ບໍ່ຄືກັບເງິນຕາ fiat, Bitcoin ມີຂີດຈຳກັດສູງສຸດໃນປະລິມານຂອງມັນ. ຈະມີພຽງ 21 ລ້ານ Bitcoin ເທົ່ານັ້ນຖືກສ້າງຂຶ້ນ, ຂີດຈຳກັດນີ້ຝັງຢູ່ໃນໂຄດຂອງມັນ ແລະ ບໍ່ສາມາດປ່ຽນແປງໄດ້. ການສະໜອງທີ່ຈຳກັດນີ້ເຮັດໃຫ້ Bitcoin ເປັນເງິນຫຼຸດລາຄາ; ເມື່ອຄວາມຕ້ອງການເພີ່ມຂຶ້ນ, ມູນຄ່າຂອງມັນມີແນວໂນ້ມທີ່ຈະເພີ່ມຂຶ້ນເພາະວ່າປະລິມານການສະໜອງບໍ່ສາມາດຂະຫຍາຍຕົວ.
ຄວາມທົນທານ: Bitcoin ຢູ່ໃນ blockchain, ເຊິ່ງເປັນປຶ້ມບັນຊີສາທາລະນະທີ່ແບ່ງປັນກັນຂອງທຸກການເຮັດທຸລະກຳທີ່ແທບຈະເປັນໄປບໍ່ໄດ້ທີ່ຈະລຶບ ຫຼື ປ່ຽນແປງ. ປຶ້ມບັນຊີນີ້ຖືກກະຈາຍໄປທົ່ວພັນຄອມພິວເຕີ (nodes) ທົ່ວໂລກ. ແມ້ແຕ່ຖ້າອິນເຕີເນັດລົ້ມ, ເຄືອຂ່າຍສາມາດຢູ່ຕໍ່ໄປໄດ້ຜ່ານວິທີການອື່ນເຊັ່ນ: ດາວທຽມ ຫຼື ຄື້ນວິທະຍຸ. ມັນບໍ່ໄດ້ຮັບຜົນກະທົບຈາກການທຳລາຍທາງກາຍະພາບຂອງເງິນສົດ ຫຼື ການແຮັກຖານຂໍ້ມູນແບບລວມສູນ.
ການພົກພາ: Bitcoin ສາມາດຖືກສົ່ງໄປໃນທຸກບ່ອນໃນໂລກໄດ້ທັນທີ, 24/7, ດ້ວຍການເຊື່ອມຕໍ່ອິນເຕີເນັດ, ໂດຍບໍ່ຈຳເປັນຕ້ອງມີທະນາຄານ ຫຼື ການອະນຸຍາດຈາກພາກສ່ວນທີສາມ. ທ່ານສາມາດເກັບຮັກສາ Bitcoin ຂອງທ່ານໄດ້ດ້ວຍຕົນເອງໃນອຸປະກອນທີ່ເອີ້ນວ່າກະເປົາເຢັນ, ແລະ ຕາບໃດທີ່ທ່ານຮູ້ວະລີກະແຈລັບຂອງທ່ານ, ທ່ານສາມາດເຂົ້າເຖິງເງິນຂອງທ່ານຈາກກະເປົາທີ່ເຂົ້າກັນໄດ້, ເຖິງແມ່ນວ່າອຸປະກອນຈະສູນຫາຍ. ສິ່ງນີ້ສະດວກສະບາຍກວ່າ ແລະ ມີຄວາມສ່ຽງໜ້ອຍກວ່າການພົກພາເງິນສົດຈຳນວນຫຼາຍ ຫຼື ການນຳທາງການໂອນເງິນສາກົນທີ່ຊັບຊ້ອນ.
ການແບ່ງຍ່ອຍ: Bitcoin ສາມາດແບ່ງຍ່ອຍໄດ້ສູງ. ໜຶ່ງ Bitcoin ສາມາດແບ່ງເປັນ 100 ລ້ານໜ່ວຍຍ່ອຍທີ່ເອີ້ນວ່າ Satoshis, ເຊິ່ງອະນຸຍາດໃຫ້ສົ່ງ ຫຼື ຮັບຈຳນວນນ້ອຍໄດ້.
ຄວາມສາມາດໃນການທົດແທນກັນ: ໜຶ່ງ Bitcoin ທຽບເທົ່າກັບໜຶ່ງ Bitcoin ໃນມູນຄ່າ, ໂດຍທົ່ວໄປ. ໃນຂະນະທີ່ເງິນໂດລາແບບດັ້ງເດີມອາດສາມາດຖືກຕິດຕາມ, ແຊ່ແຂງ, ຫຼື ຍຶດໄດ້, ໂດຍສະເພາະໃນຮູບແບບດິຈິຕອນ ຫຼື ຖ້າຖືກພິຈາລະນາວ່າໜ້າສົງໄສ, ແຕ່ລະໜ່ວຍຂອງ Bitcoin ໂດຍທົ່ວໄປຖືກປະຕິບັດຢ່າງເທົ່າທຽມກັນ.
ການພິສູດຢັ້ງຢືນ: ທຸກການເຮັດທຸລະກຳ Bitcoin ຖືກບັນທຶກໄວ້ໃນ blockchain, ເຊິ່ງທຸກຄົນສາມາດເບິ່ງ ແລະ ພິສູດຢັ້ງຢືນ. ຂະບວນການພິສູດຢັ້ງຢືນທີ່ກະຈາຍນີ້, ດຳເນີນໂດຍເຄືອຂ່າຍ, ໝາຍຄວາມວ່າທ່ານບໍ່ຈຳເປັນຕ້ອງເຊື່ອຖືທະນາຄານ ຫຼື ສະຖາບັນໃດໜຶ່ງແບບມືດບອດເພື່ອຢືນຢັນຄວາມຖືກຕ້ອງຂອງເງິນຂອງທ່ານ.
ການຕ້ານການກວດກາ: ເນື່ອງຈາກບໍ່ມີລັດຖະບານ, ບໍລິສັດ, ຫຼື ບຸກຄົນໃດຄວບຄຸມເຄືອຂ່າຍ Bitcoin, ບໍ່ມີໃຜສາມາດຂັດຂວາງທ່ານຈາກການສົ່ງ ຫຼື ຮັບ Bitcoin, ແຊ່ແຂງເງິນຂອງທ່ານ, ຫຼື ຍຶດມັນ. ມັນເປັນລະບົບທີ່ບໍ່ຕ້ອງຂໍອະນຸຍາດ, ເຊິ່ງໃຫ້ຜູ້ໃຊ້ຄວບຄຸມເຕັມທີ່ຕໍ່ເງິນຂອງເຂົາເຈົ້າ.
ການກະຈາຍອຳນາດ: Bitcoin ຖືກຮັກສາໂດຍເຄືອຂ່າຍກະຈາຍຂອງບັນດາຜູ້ຂຸດທີ່ໃຊ້ພະລັງງານການຄິດໄລ່ເພື່ອຢັ້ງຢືນການເຮັດທຸລະກຳຜ່ານ "proof of work". ລະບົບທີ່ກະຈາຍນີ້ຮັບປະກັນວ່າບໍ່ມີຈຸດໃດຈຸດໜຶ່ງທີ່ຈະລົ້ມເຫຼວ ຫຼື ຄວບຄຸມ. ທ່ານບໍ່ໄດ້ເພິ່ງພາຂະບວນການທີ່ບໍ່ໂປ່ງໃສຂອງທະນາຄານກາງ; ລະບົບທັງໝົດໂປ່ງໃສຢູ່ໃນ blockchain. ສິ່ງນີ້ເຮັດໃຫ້ບຸກຄົນມີອຳນາດທີ່ຈະເປັນທະນາຄານຂອງຕົນເອງແທ້ ແລະ ຮັບຜິດຊອບຕໍ່ການເງິນຂອງເຂົາເຈົ້າ.
-
 @ d34e832d:383f78d0
2025-04-22 23:35:05
@ d34e832d:383f78d0
2025-04-22 23:35:05For Secure Inheritance Planning and Offline Signing
The setup described ensures that any 2 out of 3 participants (hardware wallets) must sign a transaction before it can be broadcast, offering robust protection against theft, accidental loss, or mismanagement of funds.
1. Preparation: Tools and Requirements
Hardware Required
- 3× COLDCARD Mk4 hardware wallets (or newer)
- 3× MicroSD cards (one per COLDCARD)
- MicroSD card reader (for your computer)
- Optional: USB data blocker (for safe COLDCARD connection)
Software Required
- Sparrow Wallet: Version 1.7.1 or later
Download: https://sparrowwallet.com/ - COLDCARD Firmware: Version 5.1.2 or later
Update guide: https://coldcard.com/docs/upgrade
Other Essentials
- Durable paper or steel backup tools for seed phrases
- Secure physical storage for backups and devices
- Optional: encrypted external storage for Sparrow wallet backups
Security Tip:
Always verify software signatures before installation. Keep your COLDCARDs air-gapped (no USB data transfer) whenever possible.
2. Initializing Each COLDCARD Wallet
- Power on each COLDCARD and choose “New Wallet”.
- Write down the 24-word seed phrase (DO NOT photograph or store digitally).
- Confirm the seed and choose a strong PIN code (both prefix and suffix).
- (Optional) Enable BIP39 Passphrase for additional entropy.
- Save an encrypted backup to the MicroSD card:
Go to Advanced > Danger Zone > Backup. - Repeat steps 1–5 for all three COLDCARDs.
Best Practice:
Store each seed phrase securely and in separate physical locations. Test wallet recovery before storing real funds.
3. Exporting XPUBs from COLDCARD
Each hardware wallet must export its extended public key (XPUB) for multisig setup:
- Insert MicroSD card into a COLDCARD.
- Navigate to:
Settings > Multisig Wallets > Export XPUB. - Select the appropriate derivation path. Recommended:
- Native SegWit:
m/84'/0'/0'(bc1 addresses) - Alternatively: Nested SegWit
m/49'/0'/0'(starts with 3) - Save the XPUB file to the MicroSD card.
- Insert MicroSD into your computer and transfer XPUB files to Sparrow Wallet.
- Repeat for the remaining COLDCARDs.
4. Creating the 2-of-3 Multisig Wallet in Sparrow
- Launch Sparrow Wallet.
- Click File > New Wallet and name your wallet.
- In the Keystore tab, choose Multisig.
- Select 2-of-3 as your multisig policy.
- For each cosigner:
- Choose Add cosigner > Import XPUB from file.
- Load XPUBs exported from each COLDCARD.
- Once all 3 cosigners are added, confirm the configuration.
- Click Apply, then Create Wallet.
- Sparrow will display a receive address. Fund the wallet using this.
Tip:
You can export the multisig policy (wallet descriptor) as a backup and share it among cosigners.
5. Saving and Verifying the Wallet Configuration
- After creating the wallet, click Wallet > Export > Export Wallet File (.json).
- Save this file securely and distribute to all participants.
- Verify that the addresses match on each COLDCARD using the wallet descriptor file (optional but recommended).
6. Creating and Exporting a PSBT (Partially Signed Bitcoin Transaction)
- In Sparrow, click Send, fill out recipient details, and click Create Transaction.
- Click Finalize > Save PSBT to MicroSD card.
- The file will be saved as a
.psbtfile.
Note: No funds are moved until 2 signatures are added and the transaction is broadcast.
7. Signing the PSBT with COLDCARD (Offline)
- Insert the MicroSD with the PSBT into COLDCARD.
- From the main menu:
Ready To Sign > Select PSBT File. - Verify transaction details and approve.
- COLDCARD will create a signed version of the PSBT (
signed.psbt). - Repeat the signing process with a second COLDCARD (different signer).
8. Finalizing and Broadcasting the Transaction
- Load the signed PSBT files back into Sparrow.
- Sparrow will detect two valid signatures.
- Click Finalize Transaction > Broadcast.
- Your Bitcoin transaction will be sent to the network.
9. Inheritance Planning with Multisig
Multisig is ideal for inheritance scenarios:
Example Inheritance Setup
- Signer 1: Yourself (active user)
- Signer 2: Trusted family member or executor
- Signer 3: Lawyer, notary, or secure backup
Only 2 signatures are needed. If one party loses access or passes away, the other two can recover the funds.
Best Practices for Inheritance
- Store each seed phrase in separate, tamper-proof, waterproof containers.
- Record clear instructions for heirs (without compromising seed security).
- Periodically test recovery with cosigners.
- Consider time-locked wallets or third-party escrow if needed.
Security Tips and Warnings
- Never store seed phrases digitally or online.
- Always verify addresses and signatures on the COLDCARD screen.
- Use Sparrow only on secure, malware-free computers.
- Physically secure your COLDCARDs from unauthorized access.
- Practice recovery procedures before storing real value.
Consider
A 2-of-3 multisignature wallet using COLDCARD and Sparrow Wallet offers a highly secure, flexible, and transparent Bitcoin custody model. Whether for inheritance planning or high-security storage, it mitigates risks associated with single points of failure while maintaining usability and privacy.
By following this guide, Bitcoin users can significantly increase the resilience of their holdings while enabling thoughtful succession strategies.
-
 @ 9bde4214:06ca052b
2025-04-22 22:04:57
@ 9bde4214:06ca052b
2025-04-22 22:04:57“The human spirit should remain in charge.”
Pablo & Gigi talk about the wind.
In this dialogue:
- Wind
- More Wind
- Information Calories, and how to measure them
- Digital Wellbeing
- Rescue Time
- Teleology of Technology
- Platforms get users Hooked (book)
- Feeds are slot machines
- Movie Walls
- Tweetdeck and Notedeck
- IRC vs the modern feed
- 37Signals: “Hey, let’s just charge users!”
- “You wouldn’t zap a car crash”
- Catering to our highest self VS catering to our lowest self
- Devolution of YouTube 5-star ratings to thumb up/down to views
- Long videos vs shorts
- The internet had to monetize itself somehow (with attention)
- “Don’t be evil” and why Google had to remove it
- Questr: 2D exploration of nostr
- ONOSENDAI by Arkinox
- Freedom tech & Freedom from Tech
- DAUs of jumper cables
- Gossip and it’s choices
- “The secret to life is to send it”
- Flying water & flying bus stops
- RSS readers, Mailbrew, and daily digests
- Nostr is high signal and less addictive
- Calling nostr posts “tweets” and recordings being “on tape”
- Pivoting from nostr dialogues to a podcast about wind
- The unnecessary complexity of NIP-96
- Blossom (and wind)
- Undoing URLs, APIs, and REST
- ISBNs and cryptographic identifiers
- SaaS and the DAU metric
- Highlighter
- Not caring where stuff is hosted
- When is an edited thing a new thing?
- Edits, the edit wars, and the case against edits
- NIP-60 and inconsistent balances
- Scroll to text fragment and best effort matching
- Proximity hashes & locality-sensitive hashing
- Helping your Uncle Jack of a horse
- Helping your uncle jack of a horse
- Can we fix it with WoT?
- Vertex & vibe-coding a proper search for nostr
- Linking to hashtags & search queries
- Advanced search and why it’s great
- Search scopes & web of trust
- The UNIX tools of nostr
- Pablo’s NDK snippets
- Meredith on the privacy nightmare of Agentic AI
- Blog-post-driven development (Lightning Prisms, Highlighter)
- Sandwich-style LLM prompting, Waterfall for LLMs (HLDD / LLDD)
- “Speed itself is a feature”
- MCP & DVMCP
- Monorepos and git submodules
- Olas & NDK
- Pablo’s RemindMe bot
- “Breaking changes kinda suck”
- Stories, shorts, TikTok, and OnlyFans
- LLM-generated sticker styles
- LLMs and creativity (and Gigi’s old email)
- “AI-generated art has no soul”
- Nostr, zaps, and realness
- Does the source matter?
- Poker client in bitcoin v0.0.1
- Quotes from Hitler and how additional context changes meaning
- Greek finance minister on crypto and bitcoin (Technofeudalism, book)
- Is more context always good?
- Vervaeke’s AI argument
- What is meaningful?
- How do you extract meaning from information?
- How do you extract meaning from experience?
- “What the hell is water”
- Creativity, imagination, hallucination, and losing touch with reality
- “Bitcoin is singularity insurance”
- Will vibe coding make developers obsolete?
- Knowing what to build vs knowing how to build
- 10min block time & the physical limits of consensus
- Satoshi’s reasons articulated in his announcement post
- Why do anything? Why stack sats? Why have kids?
- All you need now is motivation
- Upcoming agents will actually do the thing
- Proliferation of writers: quantity VS quality
- Crisis of sameness & the problem of distribution
- Patronage, belle epoche, and bitcoin art
- Niches, and how the internet fractioned society
- Joe’s songs
- Hyper-personalized stories
- Shared stories & myths (Jonathan Pageau)
- Hyper-personalized apps VS shared apps
- Agency, free expression, and free speech
- Edgy content & twitch meta, aka skating the line of demonetization and deplatforming
- Using attention as a proxy currency
- Farming eyeballs and brain cycles
- Engagement as a success metric & engagement bait
- “You wouldn’t zap a car crash”
- Attention economy is parasitic on humanity
- The importance of speech & money
- What should be done by a machine?
- What should be done by a human?
- “The human spirit should remain in charge”
- Our relationship with fiat money
- Active vs passive, agency vs serfdom
-
 @ df478568:2a951e67
2025-04-22 18:56:38
@ df478568:2a951e67
2025-04-22 18:56:38"It might make sense just to get some in case it catches on. If enough people think the same way, that becomes a self fulfilling prophecy. Once it gets bootstrapped, there are so many applications if you could effortlessly pay a few cents to a website as easily as dropping coins in a vending machine." --Satoshi Nakamoto The Cryptography Mailing List--January 17, 2009
Forgot to add the good part about micropayments. While I don't think Bitcoin is practical for smaller micropayments right now, it will eventually be as storage and bandwidth costs continue to fall. If Bitcoin catches on on a big scale, it may already be the case by that time. Another way they can become more practical is if I implement client-only mode and the number of network nodes consolidates into a smaller number of professional server farms. Whatever size micropayments you need will eventually be practical. I think in 5 or 10 years, the bandwidth and storage will seem trivial. --Satoshi Nakamoto Bitcoin Talk-- August 5, 2010
I very be coded some HTML buttons using Claude and uploaded it to https://github.com/GhostZaps/ It's just a button that links to zapper.fun.
I signed up for Substack to build an email address, but learned adding different payment options to Substack is against their terms and services. Since I write about nostr, these terms seem as silly as someone saying Craig Wright is Satoshi. It's easy to build an audience on Substack however, or so I thought. Why is it easier to build an audience on Subtack though? Because Substack is a platform that markets to writers. Anyone with a ~~pen~~ ~~keyboard~~ smartphone and an email can create an account with Substack. There's just one problem: You are an Internet serf, working the land for your Internet landlord--The Duke of Substack.
Then I saw that Shawn posted about Substack's UX.
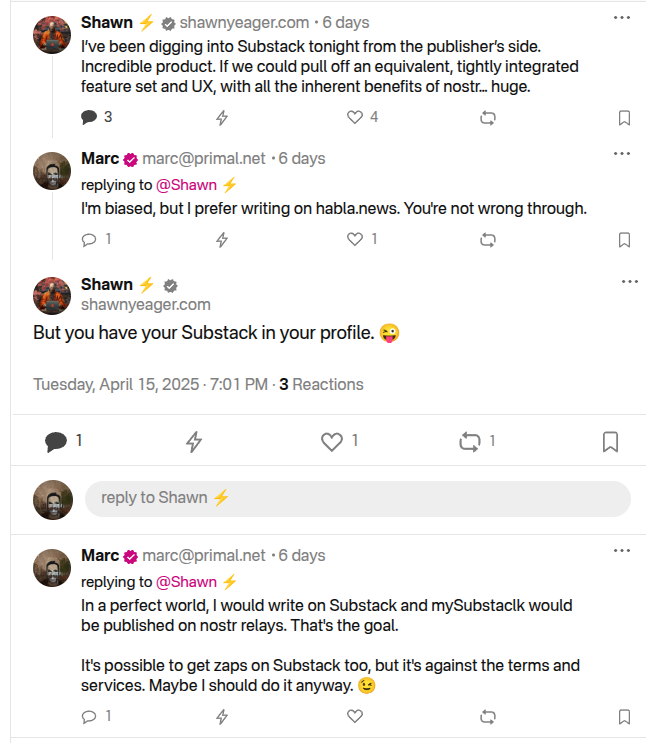
I should have grabbed my reading glasses before pushing the post button, but it occurred to me that I could use Ghost to do this and there is probably a way to hack it to accept bitcoin payments over the lightning network and host it yourself. So I spun my noddle, doodled some plans...And then it hit me. Ghost allows for markdown and HTML. I learned HTML and CSS with free-code camp, but ain't nobody got time to type CSS so I vibe-coded a button that ~~baits~~ sends the clicker to my zapper.fun page. This can be used on any blog that allows you to paste html into it so I added it to my Ghost blog self-hosted on a Start 9. The blog is on TOR at http://p66dxywd2xpyyrdfxwilqcxmchmfw2ixmn2vm74q3atf22du7qmkihyd.onion/, but most people around me have been conditioned to fear the dark web so I used the cloudflared to host my newsletter on the clear net at https://marc26z.com/
Integrating Nostr Into My Self-Hosted Ghost Newsletter
I would venture to say I am more technical than the average person and I know HTML, but my CSS is fuzzy. I also know how to print("Hello world!") in python, but I an NPC beyond the basics. Nevertheless, I found that I know enough to make a button. I can't code well enough to create my own nostr long-form client and create plugins for ghost that send lightning payments to lighting channel, but I know enough about nostr to know that I don't need to. That's why nostr is so F@#%-ing cool! It's all connected. ** - One button takes you to zapper.fun where you can zap anywhere between 1 and ,000,000 sats.** - Another button sends you to a zap planner pre-set to send 5,000 sats to the author per month using nostr. - Yet another button sends you to a zap planner preset to send 2,500 sats per month.
The possibilities are endless. I entered a link that takes the clicker to my Shopstr Merch Store. The point is to write as self-sovereign as possible. I might need to change my lightning address when stuff breaks every now and then, but I like the idea of busking for sats by writing on the Internet using the Value 4 Value model. I dislike ads, but I also want people to buy stuff from people I do business with because I want to promote using bitcoin as peer-to-peer electronic cash, not NGU porn. I'm not prude. I enjoy looking at the price displayed on my BlockClock micro every now and then, but I am not an NGU porn addict.
This line made this pattern, that line made this pattern. All that Bolinger Bart Simpson bullshit has nothing to with bitcoin, a peer-to-peer electronic cash system. It is the musings of a population trapped in the fiat mind-set. Bitcoin is permissionless so I realized I was bieng a hipocryte by using a permissioned payment system becaue it was easier than writing a little vibe code. I don't need permission to write for sats. I don't need to give my bank account number to Substack. I don't need to pay a 10$ vig to publish on a a platform which is not designed for stacking sats. I can write on Ghost and integrate clients that already exist in the multi-nostr-verse.
Nostr Payment Buttons
The buttons can be fouund at https://github.com/Marc26z/GhostZapButton
You can use them yourself. Just replace my npub with your npub or add any other link you want. It doesn't technically need to be a nostr link. It can be anything. I have a link to another Ghost article with other buttons that lead down different sat pledging amounts. It's early. Everyone who spends bitcoin is on nostr and nostr is small, but growing community. I want to be part of this community. I want to find other writers on nostr and stay away from Substack.
Here's what it looks like on Ghost: https://marc26z.com/zaps-on-ghost/
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
-
 @ 9bde4214:06ca052b
2025-04-22 18:13:37
@ 9bde4214:06ca052b
2025-04-22 18:13:37"It's gonna be permissionless or hell."
Gigi and gzuuus are vibing towards dystopia.
Books & articles mentioned:
- AI 2027
- DVMs were a mistake
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- The Ultimate Resource by Julian L. Simon
- Harry Potter by J.K. Rowling
- Momo by Michael Ende
In this dialogue:
- Pablo's Roo Setup
- Tech Hype Cycles
- AI 2027
- Prompt injection and other attacks
- Goose and DVMCP
- Cursor vs Roo Code
- Staying in control thanks to Amber and signing delegation
- Is YOLO mode here to stay?
- What agents to trust?
- What MCP tools to trust?
- What code snippets to trust?
- Everyone will run into the issues of trust and micropayments
- Nostr solves Web of Trust & micropayments natively
- Minimalistic & open usually wins
- DVMCP exists thanks to Totem
- Relays as Tamagochis
- Agents aren't nostr experts, at least not right now
- Fix a mistake once & it's fixed forever
- Giving long-term memory to LLMs
- RAG Databases signed by domain experts
- Human-agent hybrids & Chess
- Nostr beating heart
- Pluggable context & experts
- "You never need an API key for anything"
- Sats and social signaling
- Difficulty-adjusted PoW as a rare-limiting mechanism
- Certificate authorities and centralization
- No solutions to policing speech!
- OAuth and how it centralized
- Login with nostr
- Closed vs open-source models
- Tiny models vs large models
- The minions protocol (Stanford paper)
- Generalist models vs specialized models
- Local compute & encrypted queries
- Blinded compute
- "In the eyes of the state, agents aren't people"
- Agents need identity and money; nostr provides both
- "It's gonna be permissionless or hell"
- We already have marketplaces for MCP stuff, code snippets, and other things
- Most great stuff came from marketplaces (browsers, games, etc)
- Zapstore shows that this is already working
- At scale, central control never works. There's plenty scams and viruses in the app stores.
- Using nostr to archive your user-generated content
- HAVEN, blossom, novia
- The switcharoo from advertisements to training data
- What is Truth?
- What is Real?
- "We're vibing into dystopia"
- Who should be the arbiter of Truth?
- First Amendment & why the Logos is sacred
- Silicon Valley AI bros arrogantly dismiss wisdom and philosophy
- Suicide rates & the meaning crisis
- Are LLMs symbiotic or parasitic?
- The Amish got it right
- Are we gonna make it?
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- Harry Potter dementors & Momo's time thieves
- Facebook & Google as non-human (superhuman) agents
- Zapping as a conscious action
- Privacy and the internet
- Plausible deniability thanks to generative models
- Google glasses, glassholes, and Meta's Ray Ben's
- People crave realness
- Bitcoin is the realest money we ever had
- Nostr allows for real and honest expression
- How do we find out what's real?
- Constraints, policing, and chilling effects
- Jesus' plans for DVMCP
- Hzrd's article on how DVMs are broken (DVMs were a mistake)
- Don't believe the hype
- DVMs pre-date MCP tools
- Data Vending Machines were supposed to be stupid: put coin in, get stuff out.
- Self-healing vibe-coding
- IP addresses as scarce assets
- Atomic swaps and the ASS protocol
- More marketplaces, less silos
- The intensity of #SovEng and the last 6 weeks
- If you can vibe-code everything, why build anything?
- Time, the ultimate resource
- What are the LLMs allowed to think?
- Natural language interfaces are inherently dialogical
- Sovereign Engineering is dialogical too
-
 @ df478568:2a951e67
2025-04-21 23:36:17
@ df478568:2a951e67
2025-04-21 23:36:17Testing
-
 @ 9063ef6b:fd1e9a09
2025-04-21 19:26:26
@ 9063ef6b:fd1e9a09
2025-04-21 19:26:26Quantum computing is not an emergency today — but it is a slow-moving tsunami. The earlier Bitcoin prepares, the smoother the transition will be.
1. Why Quantum Computing Threatens Bitcoin
Bitcoin’s current cryptographic security relies on ECDSA (Elliptic Curve Digital Signature Algorithm). While this is secure against classical computers, a sufficiently powerful quantum computer could break it using Shor’s algorithm, which would allow attackers to derive private keys from exposed public keys. This poses a serious threat to user funds and the overall trust in the Bitcoin network.
Even though SHA-256, the hash function used for mining and address creation, is more quantum-resistant, it too would be weakened (though not broken) by quantum algorithms.
2. The Core Problem
Bitcoin’s vulnerability to quantum computing stems from how it handles public keys and signatures.
🔓 Public Key Exposure
Most Bitcoin addresses today (e.g., P2PKH or P2WPKH) are based on a hash of the public key, which keeps the actual public key hidden — until the user spends from that address.
Once a transaction is made, the public key is published on the blockchain, making it permanently visible and linked to the address.

🧠 Why This Matters
If a sufficiently powerful quantum computer becomes available in the future, it could apply Shor’s algorithm to derive the private key from a public key.
This creates a long-term risk:
- Any Bitcoin tied to an address with an exposed public key — even from years ago — could be stolen.
- The threat persists after a transaction, not just while it’s being confirmed.
- The longer those funds sit untouched, the more exposed they become to future quantum threats.
⚠️ Systemic Implication
This isn’t just a theoretical risk — it’s a potential threat to long-term trust in Bitcoin’s security model.
If quantum computers reach the necessary scale, they could: - Undermine confidence in the finality of old transactions - Force large-scale migrations of funds - Trigger panic or loss of trust in the ecosystem
Bitcoin’s current design protects against today’s threats — but revealed public keys create a quantum attack surface that grows with time.
3. Why It’s Hard to Fix
Transitioning Bitcoin to post-quantum cryptography is a complex challenge:
- Consensus required: Changes to signature schemes or address formats require wide agreement across the Bitcoin ecosystem.
- Signature size: Post-quantum signature algorithms could be significantly larger, which affects blockchain size, fees, and performance.
- Wallet migration: Updating wallets and moving funds to new address types must be done securely and at massive scale.
- User experience: Any major cryptographic upgrade must remain simple enough for users to avoid security risks.
4. The Path Forward
The cryptographers worldwide are already working on solutions:
- Post-Quantum Cryptographic Algorithms are being standardized by NIST, including CRYSTALS-Dilithium, Kyber, FALCON, and SPHINCS+.
- Prototypes and experiments are ongoing in testnets and research networks.
- Hybrid signature schemes are being explored to allow backward compatibility.
Governments and institutions like NIST, ENISA, and ISO are laying the foundation for cryptographic migration across industries — and Bitcoin will benefit from this ecosystem.
5. What You could do in short term
- Keep large holdings in cold storage addresses that have never been spent from.
- Avoid reusing addresses to prevent public key exposure.
References & Further Reading
- https://komodoplatform.com/en/academy/p2pkh-pay-to-pubkey-hash
- https://csrc.nist.gov/projects/post-quantum-cryptography
- https://www.enisa.europa.eu/publications/post-quantum-cryptography-current-state-and-quantum-mitigation
- https://en.bitcoin.it/wiki/Quantum_computing_and_Bitcoin
- https://research.ibm.com/blog/ibm-quantum-condor-1121-qubits
- https://blog.google/technology/research/google-willow-quantum-chip/
- https://azure.microsoft.com/en-us/blog/quantum/2025/02/19/microsoft-unveils-majorana-1-the-worlds-first-quantum-processor-powered-by-topological-qubits/
- https://www.aboutamazon.com/news/aws/quantum-computing-aws-ocelot-chip
```
-
 @ d34e832d:383f78d0
2025-04-21 19:09:53
@ d34e832d:383f78d0
2025-04-21 19:09:53Such a transformation positions Nostr to compete with established social networking platforms in terms of reach while simultaneously ensuring the preservation of user sovereignty and the integrity of cryptographic trust mechanisms.

The Emergence of Encrypted Relay-to-Relay Federation
In the context of Nostr protocol scalability challenges pertaining to censorship-resistant networking paradigms, Nostr stands as a paradigm-shifting entity, underpinned by robust public-key cryptography and minimal operational assumptions. This feature set has rendered Nostr an emblematic instrument for overcoming systemic censorship, fostering permissionless content dissemination, and upholding user autonomy within digital environments. However, as the demographic footprint of Nostr's user base grows exponentially, coupled with an expanding range of content modalities, the structural integrity of individual relays faces increasing pressure.
Challenges of Isolation and Limited Scalability in Decentralized Networks
The current architecture of Nostr relays is primarily constituted of simple TCP or WebSocket servers that facilitate the publication and reception of events. While aesthetically simple, this design introduces significant performance bottlenecks and discoverability issues. Relays targeting specific regional or topical niches often rely heavily on client-side interactions or third-party directories for information exchange. This operational framework presents inefficiencies when scaled globally, especially in scenarios requiring high throughput and rapid dissemination of information. Furthermore, it does not adequately account for redundancy and availability, especially in low-bandwidth environments or regions facing strict censorship.

Navigating Impediments of Isolation and Constrained Scalability
Current Nostr relay infrastructures mainly involve basic TCP and WebSocket configurations for event publication and reception. While simple, these configurations contribute to performance bottlenecks and a significant discoverability deficit. Relays that serve niche markets often operate under constraints, relying on client-side interactions or third-party directories. These inefficiencies become particularly problematic at a global scale, where high throughput and rapid information distribution are necessary. The absence of mechanisms to enhance redundancy and availability in environments with limited connectivity or under censorship further exacerbates these issues.
Proposal for Encrypted Relay Federation
Encrypted relay federation in decentralized networking can be achieved through a novel Nostr Improvement Proposal (NIP), which introduces a sophisticated gossip-style mesh topology. In this system, relays subscribe to content tags, message types, or public keys from peer nodes, optimizing data flow and relevance.
Central to this architecture is a mutual key handshake protocol using Elliptic Curve Diffie-Hellman (ECDH) for symmetric encryption over relay keys. This ensures data integrity and confidentiality during transmission. The use of encrypted event bundles, compression, and routing based on relay reputation metrics and content demand analytics enhances throughput and optimizes network resources.
To counter potential abuse and spam, strategies like rate limiting, financially incentivized peering, and token gating are proposed, serving as control mechanisms for network interactions. Additionally, the relay federation model could emulate the Border Gateway Protocol (BGP), allowing for dynamic content advertisement and routing updates across the federated mesh, enhancing network resilience.
Advantages of Relay Federation in Data Distribution Architecture
Relay federation introduces a distributed data load management system where relays selectively store pertinent events. This enhances data retrieval efficiency, minimizes congestion, and fosters a censorship-resistant information flow. By decentralizing data storage, relays contribute to a global cache network, ensuring no single relay holds comprehensive access to all network data. This feature helps preserve the integrity of information flow, making it resistant to censorship.
An additional advantage is offline communication capabilities. Even without traditional internet access, events can still be communicated through alternative channels like Bluetooth, Wi-Fi Direct, or LoRa. This ensures local and community-based interactions remain uninterrupted during network downtime.
Furthermore, relay federations may introduce monetization strategies where specialized relays offer access to rare or high-quality data streams, promoting competition and interoperability while providing users with diverse data options.
Some Notable Markers To Nostr Becoming the Internet Layer for Censorship Resistance
Stop for a moment in your day and try to understand what Nostr can do for your communications by observing these markers:
- Protocol Idea (NIP-01 by fiatjaf) │ ▼
- npub/nsec Keypair Standard │ ▼
- First Relays Go Online │ ▼
- Identity & Auth (NIP-05, NIP-07) │ ▼
- Clients Launch (Damus, Amethyst, Iris, etc.) │ ▼
- Lightning Zaps + NWC (NIP-57) │ ▼
- Relay Moderation & Reputation NIPs │ ▼
- Protocol Bridging (ActivityPub, Matrix, Mastodon) │ ▼
- Ecash Integration (Cashu, Walletless Zaps) │ ▼
- Encrypted Relay Federation (Experimental) │ ▼
- Relay Mesh Networks (WireGuard + libp2p) │ ▼
- IoT Integration (Meshtastic + ESP32) │ ▼
- Fully Decentralized, Censorship-Resistant Social Layer
The implementation of encrypted federation represents a pivotal technological advancement, establishing a robust framework that challenges the prevailing architecture of fragmented social networking ecosystems and monopolistic centralized cloud services. This innovative approach posits that Nostr could:
- Facilitate a comprehensive, globally accessible decentralized index of information, driven fundamentally by user interactions and a novel microtransaction system (zaps), enabling efficient content valorization and information dissemination.
- Empower the concept of nomadic digital identities, allowing them to seamlessly traverse various relays, devoid of reliance on centralized identity verification systems, promoting user autonomy and privacy.
- Become the quintessential backend infrastructure for decentralized applications, knowledge graphs, and expansive datasets conducive to DVMs.
- Achieve seamless interoperability with established protocols, such as ActivityPub, Matrix, IPFS, and innovative eCash systems that offer incentive mechanisms, fostering an integrated and collaborative ecosystem.
In alignment with decentralization, encrypted relay-to-relay federation marks a significant evolution for the Nostr protocol, transitioning from isolated personal broadcasting stations to an interoperable, adaptive, trustless mesh network of communication nodes.
By implementing this sophisticated architecture, Nostr is positioned to scale efficiently, addressing global needs while preserving free speech, privacy, and individual autonomy in a world marked by surveillance and compartmentalized digital environments.
Nostr's Countenance Structure: Noteworthy Events
``` Nostr Protocol Concept by fiatjaf:
- First Relays and npub/nsec key pairs appear
- Damus, Amethyst, and other clients emerge
- Launch of Zaps and Lightning Tip Integration
- Mainstream interest post Twitter censorship events
- Ecosystem tools: NWC, NIP-07, NIP-05 adoption
- Nostr devs propose relay scoring and moderation NIPs
- Bridging begins (ActivityPub, Matrix, Mastodon)
- Cashu eCash integration with Nostr zaps (walletless tips)
- Relay-to-relay encrypted federation proposed
- Hackathons exploring libp2p, LNbits, and eCash-backed identities
- Scalable P2P Mesh using WireGuard + Nostr + Gossip
- Web3 & IoT integration with ESP32 + Meshtastic + relays
- A censorship-resistant, decentralized social internet ```
-
 @ d34e832d:383f78d0
2025-04-21 17:29:37
@ d34e832d:383f78d0
2025-04-21 17:29:37This foundational philosophy positioned her as the principal architect of the climactic finale of the Reconquista—a protracted campaign that sought to reclaim territories under Muslim dominion. Her decisive participation in military operations against the Emirate of Granada not only consummated centuries of Christian reclamation endeavors but also heralded the advent of a transformative epoch in both Spanish and European identity, intertwining religious zeal with nationalistic aspirations and setting the stage for the emergence of a unified Spanish state that would exert significant influence on European dynamics for centuries to come.
Image Above Map Of Th Iberias
During the era of governance overseen by Muhammad XII, historically identified as Boabdil, the Kingdom of Granada was characterized by a pronounced trajectory of decline, beset by significant internal dissent and acute dynastic rivalry, factors that fundamentally undermined its structural integrity. The political landscape of the emirate was marked by fragmentation, most notably illustrated by the contentious relationship between Boabdil and his uncle, the militarily adept El Zagal, whose formidable martial capabilities further exacerbated the emirate's geopolitical vulnerabilities, thereby impairing its capacity to effectively mobilize resistance against the encroaching coalition of Christian forces. Nevertheless, it is imperative to acknowledge the strategic advantages conferred by Granada’s formidable mountainous terrain, coupled with the robust fortifications of its urban centers. This geographical and structural fortitude, augmented by the fervent determination and resilience of the local populace, collectively contributed to Granada's status as a critical and tenacious stronghold of Islamic governance in the broader Iberian Peninsula during this tumultuous epoch.
The military campaign initiated was precipitated by the audacious territorial annexation of Zahara by the Emirate in the annum 1481—a pivotal juncture that served as a catalytic impetus for the martial engagement orchestrated by the Catholic Monarchs, Isabel I of Castile and Ferdinand II of Aragon.

Image Above Monarchs Of Castilles
What subsequently unfolded was an arduous protracted conflict, extending over a decade, characterized by a series of decisive military confrontations—most notably the Battle of Alhama, the skirmishes at Loja and Lucena, the strategic recapture of Zahara, and engagements in Ronda, Málaga, Baza, and Almería. Each of these encounters elucidates the intricate dynamics of military triumph entwined with the perils of adversity. Isabel's role transcended mere symbolic representation; she emerged as an astute logistical architect, meticulously structuring supply chains, provisioning her armies with necessary resources, and advocating for military advancements, including the tactical incorporation of Lombard artillery into the operational theater. Her dual presence—both on the battlefield and within the strategic command—interwove deep-seated piety with formidable power, unifying administrative efficiency with unyielding ambition.
In the face of profound personal adversities, exemplified by the heart-wrenching stillbirth of her progeny amidst the tumultuous electoral campaign, Isabel exhibited a remarkable steadfastness in her quest for triumph. Her strategic leadership catalyzed a transformative evolution in the constructs of monarchical power, ingeniously intertwining the notion of divine right—a historically entrenched justification for sovereign authority—with pragmatic statecraft underpinned by the imperatives of efficacious governance and stringent military discipline. The opposition posed by El Zagal, characterized by his indefatigable efforts and tenacious resistance, elongated the duration of the campaign; however, the indomitable spirit and cohesive resolve of the Catholic Monarchs emerged as an insuperable force, compelling the eventual culmination of their aspirations into a definitive victory.
The capitulation of the Emirate of Granada in the month of January in the year 1492 represents a pivotal moment in the historical continuum of the Iberian Peninsula, transcending the mere conclusion of the protracted series of military engagements known as the Reconquista. This momentous event is emblematic of the intricate process of state-building that led to the establishment of a cohesive Spanish nation-state fundamentally predicated on the precepts of Christian hegemony. Furthermore, it delineates the cusp of an imperial epoch characterized by expansionist ambitions fueled by religious zealotry. The ramifications of this surrender profoundly altered the sociocultural and political framework of the region, precipitating the coerced conversion and expulsion of significant Jewish and Muslim populations—a demographic upheaval that would serve to reinforce the ideological paradigms that underpinned the subsequent institution of the Spanish Inquisition, a systematic apparatus of religious persecution aimed at maintaining ideological conformity and unity under the Catholic Monarchs.

Image Above Surrender At Granada
In a broader historical context, the capitulation of the Nasrid Kingdom of Granada transpired concurrently with the inaugural expedition undertaken by the navigator Christopher Columbus, both events being facilitated under the auspices of Queen Isabel I of Castile. This significant temporal nexus serves to underscore the confluence of the termination of Islamic hegemony in the Iberian Peninsula with the commencement of European maritime exploration on a grand scale. Such a juxtaposition of religiously motivated conquest and the zealous pursuit of transoceanic exploration precipitated a paradigm shift in the trajectory of global history. It catalyzed the ascendance of the Spanish Empire, thereby marking the nascent stages of European colonial endeavors throughout the Americas.

Image Above Columbus At The Spanish Court
This epochal transformation not only redefined territorial dominion but also initiated profound socio-economic and cultural repercussions across continents, forever altering the intricate tapestry of human civilization.
Consequently, the cessation of hostilities in Granada should not merely be interpreted as the conclusion of a protracted medieval conflict; rather, it represents a critical juncture that fundamentally reoriented the socio-political landscape of the Old World while concurrently heralding the advent of modernity. The pivotal contributions of Queen Isabel I in this transformative epoch position her as an extraordinarily significant historical figure—an autocrat whose strategic foresight, resilience, and zeal indelibly influenced the trajectory of nations and entire continents across the globe.
-
 @ dbb19ae0:c3f22d5a
2025-04-21 12:29:38
@ dbb19ae0:c3f22d5a
2025-04-21 12:29:38Notice this consistent apparitioon in the timeline of something that reflects a major key shift in tech:
💾 1980s – The Personal Computer Era
- IBM PC (1981) launches the home computing revolution.
- Rise of Apple II, Commodore 64, etc.
- Storage is local and minimal.
- Paradigm shift: Computing becomes personal.
🎮 1990s – Networking & Gaming
- LAN parties, DOOM (1993) popularizes multiplayer FPS.
- Early internet (dial-up, BBS, IRC).
- There is lots of room for connecting PC.
- Paradigm shift: Networked interaction begins.
🌐 2000s – The Internet Boom
- Web 2.0, broadband, Google, Wikipedia.
- Rise of forums, blogs, file sharing.
- A bigger need of interaction is looming
- Storage is on cd and dvd.
- Paradigm shift: Global information access explodes.
📱 2010s – Social Media & Mobile
- Facebook, Twitter, Instagram dominate.
- Smartphones become ubiquitous.
- Bitcoin appears and start a revolution.
- Collecting personal data from users to fuel the next shift.
- Paradigm shift: Always-connected, algorithmic society.
🤖 2020s – AI & Decentralization
- GPT, Stable Diffusion, Midjourney, Copilot.
- Blockchain, Nostr, Web3 experiments.
- Storage is in the cloud.
- Paradigm shift: Autonomous intelligence and freedom tech emerge.
roughly every decade, a tech leap reshapes how we live and think.
-
 @ d34e832d:383f78d0
2025-04-21 08:32:02
@ d34e832d:383f78d0
2025-04-21 08:32:02The operational landscape for Nostr relay operators is fraught with multifaceted challenges that not only pertain to technical feasibility but also address pivotal economic realities in an increasingly censored digital environment.
While the infrastructure required to run a Nostr relay can be considered comparatively lightweight in terms of hardware demands, the operators must navigate a spectrum of operational hurdles and associated costs. Key among these are bandwidth allocation, effective spam mitigation, comprehensive security protocols, and the critical need for sustained uptime.
To ensure economic viability amidst these challenges, many relay operators have implemented various strategies, including the introduction of rate limiting mechanisms and subscription-based financial models that leverage user payments to subsidize operational costs. The conundrum remains: how can the Nostr framework evolve to permit relay operators to cultivate at least a singular relay to its fullest operational efficiency?
It is essential to note that while the trajectory of user engagement with these relays remains profoundly unpredictable—analogous to the nebulous impetus behind their initial inception—indicators within our broader economic and sociocultural contexts illuminate potential pathways to harmonizing commercial interests with user interaction through the robust capabilities of websocket relays.
A few musingsI beg you to think about the Evolutionary Trajectory of Nostr Infrastructure Leveraging BDK (Bitcoin Development Kit) and NDK (Nostr Development Kit) in the Context of Sovereign Communication Infrastructure
As the Nostr ecosystem transitions through its iterative phases of maturity, the infrastructure, notably the relays, is projected to undergo significant enhancements to accommodate an array of emerging protocols, particularly highlighted by the Mostr Bridge implementation.
Additionally, the integration of decentralized identity frameworks, exemplified by PKARR (Public-Key Addressable Resource Records), signifies a robust evolutionary step towards fostering user accountability and autonomy.
Moreover, the introduction of sophisticated filtering mechanisms, including but not limited to Set Based Reconciliation techniques, seeks to refine the user interface by enabling more granular control over content visibility and interaction dynamics.
These progressive innovations are meticulously designed to augment the overall user experience while steadfastly adhering to the foundational ethos of the Nostr protocol, which emphasizes the principles of digital freedom, uncurtailed access to publication, and the establishment of a harassment-free digital environment devoid of shadowbanning practices.
Such advancements underscore the balancing act between technological progression and ethical considerations in decentralized communication frameworks.
-
 @ d34e832d:383f78d0
2025-04-21 08:08:49
@ d34e832d:383f78d0
2025-04-21 08:08:49Let’s break it down.
🎭 The Cultural Love for Hype
Trinidadians are no strangers to investing. We invest in pyramid schemes, blessing circles, overpriced insurance packages, corrupt ministries, miracle crusades, and football teams that haven’t kicked a ball in years. Anything wrapped in emotion, religion, or political flag-waving gets support—no questions asked.
Bitcoin, on the other hand, demands research, self-custody, and personal responsibility. That’s not sexy in a culture where people would rather “leave it to God,” “vote them out,” or “put some pressure on the boss man.”
🧠 The Mindset Gap
There’s a deep psychological barrier here:
Fear of responsibility: Bitcoin doesn’t come with customer service. It puts you in control—and that scares people used to blaming the bank, the government, or the devil.
Love for middlemen: Whether it’s pastors, politicians, or financiers, Trinidad loves an “intercessor.” Bitcoin removes them all.
Resistance to abstraction: We’re tactile people. We want paper receipts, printed statements, and "real money." Bitcoin’s digital nature makes it feel unreal—despite being harder money than the TT dollar will ever be.
🔥 What Gets Us Excited
Let a pastor say God told him to buy a jet—people pledge money.
Let a politician promise a ghost job—people campaign.
Let a friend say he knows a man that can flip $100 into $500—people sign up.
But tell someone to download a Bitcoin wallet, learn about self-custody, and opt out of inflation?
They tell you that’s a scam.
⚖️ The Harsh Reality
Trinidad is on the brink of a currency crisis. The TT dollar is quietly bleeding value. Bank fees rise, foreign exchange is a riddle, and financial surveillance is tightening.
Bitcoin is an escape hatch—but it requires a new kind of mindset: one rooted in self-education, long-term thinking, and personal accountability. These aren’t values we currently celebrate—but they are values we desperately need.
🟠 A Guide to Starting with Bitcoin in Trinidad
- Understand Bitcoin
It’s not a stock or company. It’s a decentralized protocol like email—but for money.
It’s finite. Only 21 million will ever exist.
It’s permissionless. No bank, government, or pastor can block your access.
- Get a Wallet
Start with Phoenix Wallet or Blue Wallet (for Lightning).
If you're going offline, learn about SeedSigner or Trezor for cold storage.
- Earn or Buy BTC
Use Robosats or Peach for peer-to-peer (P2P) trading.
Ask your clients to pay in Bitcoin.
Zap content on Nostr to earn sats.
- Secure It
Learn about seed phrases, hardware wallets, and multisig options.
Never leave your coins on exchanges.
Consider a steel backup plate.
- Use It
Pay others in BTC.
Accept BTC for services.
Donate to freedom tech projects or communities building open internet tools.
🧭 Case In Point
Bitcoin isn’t just technology. It’s a mirror—one that reveals who we really are. Trinidad isn’t slow to adopt Bitcoin because it’s hard. We’re slow because we don’t want to let go of the comfort of being misled.
But times are changing. And the first person to wake up usually ends up leading the others.
So maybe it’s time.
Maybe you are the one to bring Bitcoin to Trinidad—not by shouting, but by living it.
-
 @ d34e832d:383f78d0
2025-04-21 07:31:10
@ d34e832d:383f78d0
2025-04-21 07:31:10The inherent heterogeneity of relay types within this ecosystem not only enhances operational agility but also significantly contributes to the overall robustness and resilience of the network architecture, empowering it to endure systemic assaults or coordinated initiatives designed to suppress specific content.
In examining the technical underpinnings of the Nostr protocol, relays are characterized by their exceptional adaptability, permitting deployment across an extensive variety of hosting environments configured to achieve targeted operational objectives.
For example, strategically deploying relays in jurisdictions characterized by robust legal protections for free expression can provide effective countermeasures against local censorship and pervasive legal restrictions in regions plagued by oppressive control.
This strategic operational framework mirrors the approaches adopted by whistleblowers and activists who deliberately position their digital platforms or mirrored content within territories boasting more favorable regulatory environments regarding internet freedoms.
Alternatively, relays may also be meticulously configured to operate exclusively within offline contexts—functioning within localized area networks or leveraging air-gapped computational configurations.
Such offline relays are indispensable in scenarios necessitating disaster recovery, secure communication frameworks, or methods for grassroots documentation, thereby safeguarding sensitive data from unauthorized access, ensuring its integrity against tampering, and preserving resilience in the face of both potential disruptions in internet connectivity and overarching surveillance efforts.
-
 @ d34e832d:383f78d0
2025-04-21 02:36:32
@ d34e832d:383f78d0
2025-04-21 02:36:32Lister.lol represents a sophisticated web application engineered specifically for the administration and management of Nostr lists. This feature is intrinsically embedded within the Nostr protocol, facilitating users in the curation of personalized feeds and the exploration of novel content. Although its current functionality remains relatively rudimentary, the platform encapsulates substantial potential for enhanced collaborative list management, as well as seamless integration with disparate client applications, effectively functioning as a micro-app within the broader ecosystem.
The trajectory of Nostr is oriented towards the development of robust developer tools (namely, the Nostr Development Kit - NDK), the establishment of comprehensive educational resources, and the cultivation of a dynamic and engaged community of developers and builders.
The overarching strategy emphasizes a decentralized paradigm, prioritizing the growth of small-scale, sustainable enterprises over the dominance of large, centralized corporations. In this regard, a rigorous experimentation with diverse monetization frameworks and the establishment of straightforward, user-friendly applications are deemed critical for the sustained evolution and scalability of the Nostr platform.
 Nostr's commitment to a decentralized, 'nagar-style' model of development distinguishes it markedly from the more conventional 'cathedral' methodologies employed by other platforms. As it fosters a broad spectrum of developmental outcomes while inherently embracing the properties of emergence. Such principles stand in stark contrast to within a traditional environment, centralized Web2 startup ecosystem, which is why all people need a chance to develop a significant shift towards a more adaptive and responsive design philosophy in involving #Nostr and #Bitcoin.
Nostr's commitment to a decentralized, 'nagar-style' model of development distinguishes it markedly from the more conventional 'cathedral' methodologies employed by other platforms. As it fosters a broad spectrum of developmental outcomes while inherently embracing the properties of emergence. Such principles stand in stark contrast to within a traditional environment, centralized Web2 startup ecosystem, which is why all people need a chance to develop a significant shift towards a more adaptive and responsive design philosophy in involving #Nostr and #Bitcoin. -
 @ 9063ef6b:fd1e9a09
2025-04-20 20:19:27
@ 9063ef6b:fd1e9a09
2025-04-20 20:19:27Quantum computing is no longer a futuristic fantasy — it's becoming a present-day reality. Major tech companies are racing to build machines that could revolutionize fields like drug discovery, logistics, and climate modeling. But along with this promise comes a major risk: quantum computers could one day break the cryptographic systems we use to secure everything from emails to bank transactions.
🧠 What Is a Quantum Computer?
A quantum computer uses the principles of quantum physics to process information differently than traditional computers. While classical computers use bits (0 or 1), quantum computers use qubits, which can be both 0 and 1 at the same time. This allows them to perform certain calculations exponentially faster.
Who's Building Them?
Several major tech companies are developing quantum computers:
- Microsoft is building Majorana 1, which uses topological qubits designed to be more stable and less prone to errors.
- Amazon introduced Ocelot, a scalable architecture with significantly reduced error correction needs.
- Google's Willow chip has demonstrated faster problem-solving with lower error rates.
- IBM has released Condor, the first quantum chip with over 1,000 qubits.
📅 As of 2025, none of these systems are yet capable of breaking today's encryption — but the rapid pace of development means that could change in 5–10 years.
🔐 Understanding Cryptography Today
Cryptography is the backbone of secure digital communication. It ensures that data sent over the internet or stored on devices remains confidential and trustworthy.
There are two main types of cryptography:
1. Symmetric Cryptography
- Uses a single shared key for encryption and decryption.
- Examples: AES-256, ChaCha20
- Quantum status: Generally considered secure against quantum attacks when long key lengths are used.
2. Asymmetric Cryptography (Public-Key)
- Uses a public key to encrypt and a private key to decrypt.
- Examples: RSA, ECC
- Quantum status: Highly vulnerable — quantum algorithms like Shor’s algorithm could break these quickly.
⚠️ The Quantum Threat
If a large-scale quantum computer becomes available, it could:
- Break secure websites (TLS/SSL)
- Forge digital signatures
- Decrypt previously recorded encrypted data ("harvest now, decrypt later")
This is why experts and governments are acting now to prepare, even though the technology isn’t fully here yet.
🔒 What Is Quantum Cryptography?
Quantum cryptography is a new method of securing communication using the laws of quantum physics. It doesn’t encrypt data directly, but instead focuses on creating a secure key between two people that cannot be intercepted without detection.
Quantum cryptography is promising, but not yet practical.
🛡️ What Is Post-Quantum Cryptography (PQC)?
Post-Quantum Cryptography is about designing new algorithms that are safe even if quantum computers become powerful. These algorithms can run on existing devices and are being actively standardized.
NIST-Selected Algorithms (2024):
- Kyber — for secure key exchange
- Dilithium — for digital signatures
- FALCON, SPHINCS+ — alternative signature schemes
PQC is already being tested or adopted by:
- Secure messaging apps (e.g. Signal)
- Web browsers and VPNs
- Tech companies like Google, Amazon, Microsoft
PQC is the most realistic and scalable solution to protect today's systems against tomorrow's quantum threats.
✅ Summary: What You Should Know
| Topic | Key Points | |--------------------------|------------------------------------------------------------------------------| | Quantum Computers | Use qubits; still in development but progressing fast | | Current Encryption | RSA and ECC will be broken by quantum computers | | Quantum Cryptography | Secure but needs special hardware; not practical at large scale (yet) | | Post-Quantum Crypto | Ready to use today; secure against future quantum threats | | Global Action | Standards, funding, and migration plans already in motion |
The quantum era is coming. The systems we build today must be ready for it tomorrow.
Date: 20.04.2025
-
 @ 88cc134b:5ae99079
2025-04-18 00:07:05
@ 88cc134b:5ae99079
2025-04-18 00:07:05Imagine reading test articles from a test account. Who does that? What kind of deranged, lonely human being would go through the effort of reading some nonsense that was vibe written to pass time in response to the endless boredom presented by product testing.
-
 @ 88cc134b:5ae99079
2025-04-17 23:46:01
@ 88cc134b:5ae99079
2025-04-17 23:46:01Always write an intro. It's just rude not to.
And Now a Title
 ## A Few Lists
## A Few ListsHere we go, first one then the other one:
- Very orderly
- We go and go
And the other one:
- Pa idemo bratori
- Ako čitaš ovo, pa de si bre?!
-
 @ 9063ef6b:fd1e9a09
2025-04-17 20:18:19
@ 9063ef6b:fd1e9a09
2025-04-17 20:18:19This is my second article. I find the idea of using a user friendly 2FA-style code on a secondary device really fascinating.
I have to admit, I don’t fully grasp all the technical details behind it—but nonetheless, I wanted to share the idea as it came to mind. Maybe it is technical nonsense...
So here it is—feel free to tear the idea apart and challenge it! :)
Idea
This Article describes method for passphrase validation and wallet access control in Bitcoin software wallets using a block-based Time-based One-Time Password (TOTP) mechanism. Unlike traditional TOTP systems, this approach leverages blockchain data—specifically, Bitcoin block height and block hash—combined with a securely stored secret to derive a dynamic 6-digit validation code. The system enables user-friendly, secure access to a wallet without directly exposing or requiring the user to memorize a fixed passphrase.
1. Introduction
Secure access to Bitcoin wallets often involves a mnemonic seed and an optional passphrase. However, passphrases can be difficult for users to manage securely. This paper introduces a system where a passphrase is encrypted locally and can only be decrypted upon validation of a 6-digit code generated from blockchain metadata. A mobile app, acting as a secure TOTP generator, supplies the user with this code.
2. System Components
2.1 Fixed Passphrase
A strong, high-entropy passphrase is generated once during wallet creation. It is never exposed to the user but is instead encrypted and stored locally on the desktop system (eg. bitbox02 - sparrow wallet).
2.2 Mobile App
The mobile app securely stores the shared secret (passphrase) and generates a 6-digit code using: - The current Bitcoin block height - The corresponding block hash - A fixed internal secret (stored in Secure Enclave or Android Keystore)
Offline App - current block_hash and block_height scanned with qr code.6-digit code generation after scanning the information.
2.3 Decryption and Validation
On the desktop (e.g. in Sparrow Wallet or wrapper script), the user inputs the 6-digit code. The software fetches current block data (block_height, block_hash), recreates the decryption key using the same HMAC derivation as the mobile app, and decrypts the locally stored passphrase. If successful, the wallet is unlocked.
3. Workflow
- Wallet is created with a strong passphrase.
- Passphrase is encrypted using a key derived from the initial block hash + block height + secret.
- User installs mobile app and shares the fixed secret securely.
- On wallet access:
- User retrieves current code from the app.
- Enters it into Sparrow or a CLI prompt.
- Wallet software reconstructs the key, decrypts the passphrase.
- If valid, the wallet is opened.
4. Security Properties
- Two-Factor Protection: Combines device possession and blockchain-derived time-based data.
- Replay Resistance: Codes change with every block (~10 min cycle).
- Minimal Attack Surface: Passphrase never typed or copied.
- Hardware-Backed Secrets: Mobile app secret stored in non-exportable secure hardware.
5. Future Work
- Direct integration into Bitcoin wallet GUIs (e.g. Sparrow plugin)
- QR-based sync between mobile and desktop
- Support for multiple wallets or contexts
6. Conclusion
This approach provides a balance between security and usability for Bitcoin wallet users by abstracting away fixed passphrases and leveraging the immutability and regularity of the Bitcoin blockchain. It is a highly adaptable concept for enterprise or personal use cases seeking to improve wallet access security without introducing user friction.
-
 @ 9063ef6b:fd1e9a09
2025-04-16 20:20:39
@ 9063ef6b:fd1e9a09
2025-04-16 20:20:39Bitcoin is more than just a digital currency. It’s a technological revolution built on a unique set of properties that distinguish it from all other financial systems—past and present. From its decentralized architecture to its digitally verifiable scarcity, Bitcoin represents a fundamental shift in how we store and transfer value.
A Truly Decentralized Network
As of April 2025, the Bitcoin network comprises approximately 62,558 reachable nodes globally. The United States leads with 13,791 nodes (29%), followed by Germany with 6,418 nodes (13.5%), and Canada with 2,580 nodes (5.43%). bitnodes
This distributed structure is central to Bitcoin’s strength. No single entity can control the network, making it robust against censorship, regulation, or centralized failure.

Open Participation at Low Cost
Bitcoin's design allows almost anyone to participate meaningfully in the network. Thanks to its small block size and streamlined protocol, running a full node is technically and financially accessible. Even a Raspberry Pi or a basic PC is sufficient to synchronize and validate the blockchain.
However, any significant increase in block size could jeopardize this accessibility. More storage and bandwidth requirements would shift participation toward centralized data centers and cloud infrastructure—threatening Bitcoin’s decentralized ethos. This is why the community continues to fiercely debate such protocol changes.
Decentralized Governance
Bitcoin has no CEO, board, or headquarters. Its governance model is decentralized, relying on consensus among various stakeholders, including miners, developers, node operators, and increasingly, institutional participants.
Miners signal support for changes by choosing which version of the Bitcoin software to run when mining new blocks. However, full node operators ultimately enforce the network’s rules by validating blocks and transactions. If miners adopt a change that is not accepted by the majority of full nodes, that change will be rejected and the blocks considered invalid—effectively vetoing the proposal.
This "dual-power structure" ensures that changes to the network only happen through widespread consensus—a system that has proven resilient to internal disagreements and external pressures.
Resilient by Design
Bitcoin's decentralized nature gives it a level of geopolitical and technical resilience unmatched by any traditional financial system. A notable case is the 2021 mining ban in China. While initially disruptive, the network quickly recovered as miners relocated, ultimately improving decentralization.
This event underlined Bitcoin's ability to withstand regulatory attacks and misinformation (FUD—Fear, Uncertainty, Doubt), cementing its credibility as a global, censorship-resistant network.
Self-Sovereign Communication
Bitcoin enables peer-to-peer transactions across borders without intermediaries. There’s no bank, payment processor, or centralized authority required. This feature is not only technically efficient but also politically profound—it empowers individuals globally to transact freely and securely.
Absolute Scarcity
Bitcoin is the first asset in history with a mathematically verifiable, fixed supply: 21 million coins. This cap is hard-coded into its protocol and enforced by every full node. At the atomic level, Bitcoin is measured in satoshis (sats), with a total cap of approximately 2.1 quadrillion sats.
This transparency contrasts with assets like gold, whose total supply is estimated and potentially (through third parties on paper) expandable. Moreover, unlike fiat currencies, which can be inflated through central bank policy, Bitcoin is immune to such manipulation. This makes it a powerful hedge against monetary debasement.
Anchored in Energy and Time
Bitcoin's security relies on proof-of-work, a consensus algorithm that requires real-world energy and computation. This “work” ensures that network participants must invest time and electricity to mine new blocks.
This process incentivizes continual improvement in hardware and energy sourcing—helping decentralize mining geographically and economically. In contrast, alternative systems like proof-of-stake tend to favor wealth concentration by design, as influence is determined by how many tokens a participant holds.

Censorship-Resistant
The Bitcoin network itself is inherently censorship-resistant. As a decentralized system, Bitcoin transactions consist of mere text and numerical data, making it impossible to censor the underlying protocol.
However, centralized exchanges and trading platforms can be subject to censorship through regional regulations or government pressure, potentially limiting access to Bitcoin.
Decentralized exchanges and peer-to-peer marketplaces offer alternative solutions, enabling users to buy and sell Bitcoins without relying on intermediaries that can be censored or shut down.
High Security
The Bitcoin blockchain is secured through a decentralized network of thousands of nodes worldwide, which constantly verify its integrity, making it highly resistant to hacking. To add a new block of bundled transactions, miners compete to solve complex mathematical problems generated by Bitcoin's cryptography. Once a miner solves the problem, the proposed block is broadcast to the network, where each node verifies its validity. Consensus is achieved when a majority of nodes agree on the block's validity, at which point the Bitcoin blockchain is updated accordingly, ensuring the network's decentralized and trustless nature.
Manipulation of the Bitcoin network is virtually impossible due to its decentralized and robust architecture. The blockchain's chronological and immutable design prevents the deletion or alteration of previously validated blocks, ensuring the integrity of the network.
To successfully attack the Bitcoin network, an individual or organization would need to control a majority of the network's computing power, also known as a 51% attack. However, the sheer size of the Bitcoin network and the competitive nature of the proof-of-work consensus mechanism make it extremely difficult to acquire and sustain the necessary computational power. Even if an attacker were to achieve this, they could potentially execute double spends and censor transactions. Nevertheless, the transparent nature of the blockchain would quickly reveal the attack, allowing the Bitcoin network to respond and neutralize it. By invalidating the first block of the malicious chain, all subsequent blocks would also become invalid, rendering the attack futile and resulting in significant financial losses for the attacker.
One potential source of uncertainty arises from changes to the Bitcoin code made by developers. While developers can modify the software, they cannot unilaterally enforce changes to the Bitcoin protocol, as all users have the freedom to choose which version they consider valid. Attempts to alter Bitcoin's fundamental principles have historically resulted in hard forks, which have ultimately had negligible impact (e.g., BSV, BCH). The Bitcoin community has consistently rejected new ideas that compromise decentralization in favor of scalability, refusing to adopt the resulting blockchains as the legitimate version. This decentralized governance model ensures that changes to the protocol are subject to broad consensus, protecting the integrity and trustworthiness of the Bitcoin network.
Another source of uncertainty in the future could be quantum computers. The topic is slowly gaining momentum in the community and is being discussed.
My attempt to write an article with Yakihonne. Simple editor with the most necessary formatting. Technically it worked quite well so far.
Some properties are listed in the article. Which properties are missing?
-
 @ e1b184d1:ac66229b
2025-04-15 20:09:27
@ e1b184d1:ac66229b
2025-04-15 20:09:27Bitcoin is more than just a digital currency. It’s a technological revolution built on a unique set of properties that distinguish it from all other financial systems—past and present. From its decentralized architecture to its digitally verifiable scarcity, Bitcoin represents a fundamental shift in how we store and transfer value.
1. A Truly Decentralized Network
As of April 2025, the Bitcoin network comprises approximately 62,558 reachable nodes globally. The United States leads with 13,791 nodes (29%), followed by Germany with 6,418 nodes (13.5%), and Canada with 2,580 nodes (5.43%). bitnodes
This distributed structure is central to Bitcoin’s strength. No single entity can control the network, making it robust against censorship, regulation, or centralized failure.

2. Open Participation at Low Cost
Bitcoin's design allows almost anyone to participate meaningfully in the network. Thanks to its small block size and streamlined protocol, running a full node is technically and financially accessible. Even a Raspberry Pi or a basic PC is sufficient to synchronize and validate the blockchain.
However, any significant increase in block size could jeopardize this accessibility. More storage and bandwidth requirements would shift participation toward centralized data centers and cloud infrastructure—threatening Bitcoin’s decentralized ethos. This is why the community continues to fiercely debate such protocol changes.
3. Decentralized Governance
Bitcoin has no CEO, board, or headquarters. Its governance model is decentralized, relying on consensus among various stakeholders, including miners, developers, node operators, and increasingly, institutional participants.
Miners signal support for changes by choosing which version of the Bitcoin software to run when mining new blocks. However, full node operators ultimately enforce the network’s rules by validating blocks and transactions. If miners adopt a change that is not accepted by the majority of full nodes, that change will be rejected and the blocks considered invalid—effectively vetoing the proposal.
This "dual-power structure" ensures that changes to the network only happen through widespread consensus—a system that has proven resilient to internal disagreements and external pressures.
4. Resilient by Design
Bitcoin's decentralized nature gives it a level of geopolitical and technical resilience unmatched by any traditional financial system. A notable case is the 2021 mining ban in China. While initially disruptive, the network quickly recovered as miners relocated, ultimately improving decentralization.
This event underlined Bitcoin's ability to withstand regulatory attacks and misinformation (FUD—Fear, Uncertainty, Doubt), cementing its credibility as a global, censorship-resistant network.
5. Self-Sovereign Communication
Bitcoin enables peer-to-peer transactions across borders without intermediaries. There’s no bank, payment processor, or centralized authority required. This feature is not only technically efficient but also politically profound—it empowers individuals globally to transact freely and securely.
6. Absolute Scarcity
Bitcoin is the first asset in history with a mathematically verifiable, fixed supply: 21 million coins. This cap is hard-coded into its protocol and enforced by every full node. At the atomic level, Bitcoin is measured in satoshis (sats), with a total cap of approximately 2.1 quadrillion sats.
This transparency contrasts with assets like gold, whose total supply is estimated and potentially (through third parties on paper) expandable. Moreover, unlike fiat currencies, which can be inflated through central bank policy, Bitcoin is immune to such manipulation. This makes it a powerful hedge against monetary debasement.
7. Anchored in Energy and Time
Bitcoin's security relies on proof-of-work, a consensus algorithm that requires real-world energy and computation. This “work” ensures that network participants must invest time and electricity to mine new blocks.
This process incentivizes continual improvement in hardware and energy sourcing—helping decentralize mining geographically and economically. In contrast, alternative systems like proof-of-stake tend to favor wealth concentration by design, as influence is determined by how many tokens a participant holds.

8. Censorship-Resistant
The Bitcoin network itself is inherently censorship-resistant. As a decentralized system, Bitcoin transactions consist of mere text and numerical data, making it impossible to censor the underlying protocol.
However, centralized exchanges and trading platforms can be subject to censorship through regional regulations or government pressure, potentially limiting access to Bitcoin.
Decentralized exchanges and peer-to-peer marketplaces offer alternative solutions, enabling users to buy and sell Bitcoins without relying on intermediaries that can be censored or shut down.
9. High Security
The Bitcoin blockchain is secured through a decentralized network of thousands of nodes worldwide, which constantly verify its integrity, making it highly resistant to hacking. To add a new block of bundled transactions, miners compete to solve complex mathematical problems generated by Bitcoin's cryptography. Once a miner solves the problem, the proposed block is broadcast to the network, where each node verifies its validity. Consensus is achieved when a majority of nodes agree on the block's validity, at which point the Bitcoin blockchain is updated accordingly, ensuring the network's decentralized and trustless nature.
Manipulation of the Bitcoin network is virtually impossible due to its decentralized and robust architecture. The blockchain's chronological and immutable design prevents the deletion or alteration of previously validated blocks, ensuring the integrity of the network.
To successfully attack the Bitcoin network, an individual or organization would need to control a majority of the network's computing power, also known as a 51% attack. However, the sheer size of the Bitcoin network and the competitive nature of the proof-of-work consensus mechanism make it extremely difficult to acquire and sustain the necessary computational power. Even if an attacker were to achieve this, they could potentially execute double spends and censor transactions. Nevertheless, the transparent nature of the blockchain would quickly reveal the attack, allowing the Bitcoin network to respond and neutralize it. By invalidating the first block of the malicious chain, all subsequent blocks would also become invalid, rendering the attack futile and resulting in significant financial losses for the attacker.
One potential source of uncertainty arises from changes to the Bitcoin code made by developers. While developers can modify the software, they cannot unilaterally enforce changes to the Bitcoin protocol, as all users have the freedom to choose which version they consider valid. Attempts to alter Bitcoin's fundamental principles have historically resulted in hard forks, which have ultimately had negligible impact (e.g., BSV, BCH). The Bitcoin community has consistently rejected new ideas that compromise decentralization in favor of scalability, refusing to adopt the resulting blockchains as the legitimate version. This decentralized governance model ensures that changes to the protocol are subject to broad consensus, protecting the integrity and trustworthiness of the Bitcoin network.
Another source of uncertainty in the future could be quantum computers. The topic is slowly gaining momentum in the community and is being discussed.
Your opinion
My attempt to write an article with Yakyhonne. Simple editor with the most necessary formatting. Technically it worked quite well so far.
Some properties are listed in the article. Which properties are missing and what are these properties?
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ 266815e0:6cd408a5
2025-04-15 06:58:14
@ 266815e0:6cd408a5
2025-04-15 06:58:14Its been a little over a year since NIP-90 was written and merged into the nips repo and its been a communication mess.
Every DVM implementation expects the inputs in slightly different formats, returns the results in mostly the same format and there are very few DVM actually running.
NIP-90 is overloaded
Why does a request for text translation and creating bitcoin OP_RETURNs share the same input
itag? and why is there anoutputtag on requests when only one of them will return an output?Each DVM request kind is for requesting completely different types of compute with diffrent input and output requirements, but they are all using the same spec that has 4 different types of inputs (
text,url,event,job) and an undefined number ofoutputtypes.Let me show a few random DVM requests and responses I found on
wss://relay.damus.ioto demonstrate what I mean:This is a request to translate an event to English
json { "kind": 5002, "content": "", "tags": [ // NIP-90 says there can be multiple inputs, so how would a DVM handle translatting multiple events at once? [ "i", "<event-id>", "event" ], [ "param", "language", "en" ], // What other type of output would text translations be? image/jpeg? [ "output", "text/plain" ], // Do we really need to define relays? cant the DVM respond on the relays it saw the request on? [ "relays", "wss://relay.unknown.cloud/", "wss://nos.lol/" ] ] }This is a request to generate text using an LLM model
json { "kind": 5050, // Why is the content empty? wouldn't it be better to have the prompt in the content? "content": "", "tags": [ // Why use an indexable tag? are we ever going to lookup prompts? // Also the type "prompt" isn't in NIP-90, this should probably be "text" [ "i", "What is the capital of France?", "prompt" ], [ "p", "c4878054cff877f694f5abecf18c7450f4b6fdf59e3e9cb3e6505a93c4577db2" ], [ "relays", "wss://relay.primal.net" ] ] }This is a request for content recommendation
json { "kind": 5300, "content": "", "tags": [ // Its fine ignoring this param, but what if the client actually needs exactly 200 "results" [ "param", "max_results", "200" ], // The spec never mentions requesting content for other users. // If a DVM didn't understand this and responded to this request it would provide bad data [ "param", "user", "b22b06b051fd5232966a9344a634d956c3dc33a7f5ecdcad9ed11ddc4120a7f2" ], [ "relays", "wss://relay.primal.net", ], [ "p", "ceb7e7d688e8a704794d5662acb6f18c2455df7481833dd6c384b65252455a95" ] ] }This is a request to create a OP_RETURN message on bitcoin
json { "kind": 5901, // Again why is the content empty when we are sending human readable text? "content": "", "tags": [ // and again, using an indexable tag on an input that will never need to be looked up ["i", "09/01/24 SEC Chairman on the brink of second ETF approval", "text"] ] }My point isn't that these event schema's aren't understandable but why are they using the same schema? each use-case is different but are they all required to use the same
itag format as input and could support all 4 types of inputs.Lack of libraries
With all these different types of inputs, params, and outputs its verify difficult if not impossible to build libraries for DVMs
If a simple text translation request can have an
eventortextas inputs, apayment-requiredstatus at any point in the flow, partial results, or responses from 10+ DVMs whats the best way to build a translation library for other nostr clients to use?And how do I build a DVM framework for the server side that can handle multiple inputs of all four types (
url,text,event,job) and clients are sending all the requests in slightly differently.Supporting payments is impossible
The way NIP-90 is written there isn't much details about payments. only a
payment-requiredstatus and a genericamounttagBut the way things are now every DVM is implementing payments differently. some send a bolt11 invoice, some expect the client to NIP-57 zap the request event (or maybe the status event), and some even ask for a subscription. and we haven't even started implementing NIP-61 nut zaps or cashu A few are even formatting the
amountnumber wrong or denominating it in sats and not mili-satsBuilding a client or a library that can understand and handle all of these payment methods is very difficult. for the DVM server side its worse. A DVM server presumably needs to support all 4+ types of payments if they want to get the most sats for their services and support the most clients.
All of this is made even more complicated by the fact that a DVM can ask for payment at any point during the job process. this makes sense for some types of compute, but for others like translations or user recommendation / search it just makes things even more complicated.
For example, If a client wanted to implement a timeline page that showed the notes of all the pubkeys on a recommended list. what would they do when the selected DVM asks for payment at the start of the job? or at the end? or worse, only provides half the pubkeys and asks for payment for the other half. building a UI that could handle even just two of these possibilities is complicated.
NIP-89 is being abused
NIP-89 is "Recommended Application Handlers" and the way its describe in the nips repo is
a way to discover applications that can handle unknown event-kinds
Not "a way to discover everything"
If I wanted to build an application discovery app to show all the apps that your contacts use and let you discover new apps then it would have to filter out ALL the DVM advertisement events. and that's not just for making requests from relays
If the app shows the user their list of "recommended applications" then it either has to understand that everything in the 5xxx kind range is a DVM and to show that is its own category or show a bunch of unknown "favorites" in the list which might be confusing for the user.
In conclusion
My point in writing this article isn't that the DVMs implementations so far don't work, but that they will never work well because the spec is too broad. even with only a few DVMs running we have already lost interoperability.
I don't want to be completely negative though because some things have worked. the "DVM feeds" work, although they are limited to a single page of results. text / event translations also work well and kind
5970Event PoW delegation could be cool. but if we want interoperability, we are going to need to change a few things with NIP-90I don't think we can (or should) abandon NIP-90 entirely but it would be good to break it up into small NIPs or specs. break each "kind" of DVM request out into its own spec with its own definitions for expected inputs, outputs and flow.
Then if we have simple, clean definitions for each kind of compute we want to distribute. we might actually see markets and services being built and used.
-
 @ 5a261a61:2ebd4480
2025-04-15 06:34:03
@ 5a261a61:2ebd4480
2025-04-15 06:34:03What a day yesterday!
I had a really big backlog of both work and non-work things to clean up. But I was getting a little frisky because my health finally gave me some energy to be in the mood for intimacy after the illness-filled week had forced libido debt on me. I decided to cheat it out and just take care of myself quickly. Horny thoughts won over, and I got at least e-stim induced ass slaps to make it more enjoyable. Quick clean up and everything seemed ok...until it wasn't.
The rest of the morning passed uneventfully as I worked through my backlog, but things took a turn in the early afternoon. I had to go pickup kids, and I just missed Her between the doors, only managed to get a fast kiss. A little bummed from the work issues and failed expectations of having a few minutes together, I got on my way.
Then it hit me—the most serious case of blue balls I had in a long time. First came panic. I was getting to the age when unusual symptoms raise concerns—cancer comes first to mind, as insufficient release wasn't my typical problem. So I called Her. I explained what was happening and expressed hope for some alone time. Unfortunately, that seemed impossible with our evening schedule: kids at home, Her online meeting, and my standing gamenight with the boys. These game sessions are our sacred ritual—a preserved piece of pre-kids sanity that we all protect in our calendars. Not something I wanted to disturb.
Her reassurance was brief but unusualy promising: "Don't worry, I get this."
Evening came, and just as I predicted, there was ZERO time for shenanigans while we took care of the kids. But once we put them to bed (I drew straw for early sleeper), with parental duties complete, I headed downstairs to prepare for my gaming session. Headset on, I greeted my fellows and started playing.
Not five minutes later, She opened the door with lube in one hand, fleshlight in the other, and an expecting smile on Her face. Definitely unexpected. I excused myself from the game, muted mic, but She stopped me.
"There will be nothing if you won't play," She said. She just motioned me to take my pants off. And off to play I was. Not an easy feat considering I twisted my body sideways so She could access anything She wanted while I still reached keyboard and mouse.
She slowly started touching me and observing my reactions, but quickly changed to using Her mouth. Getting a blowjob while semihard was always so strange. The semi part didn't last long though...
As things intensified, She was satisfied with my erection and got the fleshlight ready. It was a new toy for us, and it was Her first time using it on me all by Herself (usually She prefers watching me use toys). She applied an abundance of lube that lasted the entire encounter and beyond.
Shifting into a rhythm, She started pumping slowly but clearly enjoyed my reactions when She unexpectedly sped up, forcing me to mute the mic. I knew I wouldn't last long. When She needed to fix Her hair, I gentlemanly offered to hold the fleshlight, having one hand still available for gaming. She misunderstood, thinking I was taking over completely, which initially disappointed me.
To my surprise, She began taking Her shirt off the shoulders, offering me a pornhub-esque view. To clearly indicate that finish time had arrived, She moved Her lubed hand teasingly toward my anal. She understood precisely my contradictory preferences—my desire to be thoroughly clean before such play versus my complete inability to resist Her when aroused. That final move did it—I muted the mic just in time to vocally express how good She made me feel.
Quick clean up, kiss on the forehead, and a wish for me to have a good game session followed. The urge to abandon the game and cuddle with Her was powerful, but She stopped me. She had more work to complete on Her todo list than just me.
Had a glass, had a blast; overall, a night well spent I would say.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 91bea5cd:1df4451c
2025-04-15 06:23:35
@ 91bea5cd:1df4451c
2025-04-15 06:23:35Um bom gerenciamento de senhas deve ser simples e seguir a filosofia do Unix. Organizado em hierarquia e fácil de passar de um computador para outro.
E por isso não é recomendável o uso de aplicativos de terceiros que tenham acesso a suas chaves(senhas) em seus servidores, tampouco as opções nativas dos navegadores, que também pertencem a grandes empresas que fazem um grande esforço para ter acesso a nossas informações.
Recomendação
- pass
- Qtpass (gerenciador gráfico)
Com ele seus dados são criptografados usando sua chave gpg e salvo em arquivos organizados por pastas de forma hierárquica, podendo ser integrado a um serviço git de sua escolha ou copiado facilmente de um local para outro.
Uso
O seu uso é bem simples.
Configuração:
pass git initPara ver:
pass Email/example.comCopiar para área de transferência (exige xclip):
pass -c Email/example.comPara inserir:
pass insert Email/example0.comPara inserir e gerar senha:
pass generate Email/example1.comPara inserir e gerar senha sem símbolos:
pass generate --no-symbols Email/example1.comPara inserir, gerar senha e copiar para área de transferência :
pass generate -c Email/example1.comPara remover:
pass rm Email/example.com -
 @ 91bea5cd:1df4451c
2025-04-15 06:19:19
@ 91bea5cd:1df4451c
2025-04-15 06:19:19O que é Tahoe-LAFS?
Bem-vindo ao Tahoe-LAFS_, o primeiro sistema de armazenamento descentralizado com
- Segurança independente do provedor * .
Tahoe-LAFS é um sistema que ajuda você a armazenar arquivos. Você executa um cliente Programa no seu computador, que fala com um ou mais servidores de armazenamento em outros computadores. Quando você diz ao seu cliente para armazenar um arquivo, ele irá criptografar isso Arquivo, codifique-o em múltiplas peças, depois espalhe essas peças entre Vários servidores. As peças são todas criptografadas e protegidas contra Modificações. Mais tarde, quando você pede ao seu cliente para recuperar o arquivo, ele irá Encontre as peças necessárias, verifique se elas não foram corrompidas e remontadas Eles, e descriptografar o resultado.
O cliente cria mais peças (ou "compartilhamentos") do que acabará por precisar, então Mesmo que alguns servidores falhem, você ainda pode recuperar seus dados. Corrompido Os compartilhamentos são detectados e ignorados, de modo que o sistema pode tolerar o lado do servidor Erros no disco rígido. Todos os arquivos são criptografados (com uma chave exclusiva) antes Uploading, então mesmo um operador de servidor mal-intencionado não pode ler seus dados. o A única coisa que você pede aos servidores é que eles podem (geralmente) fornecer o Compartilha quando você os solicita: você não está confiando sobre eles para Confidencialidade, integridade ou disponibilidade absoluta.
O que é "segurança independente do provedor"?
Todo vendedor de serviços de armazenamento na nuvem irá dizer-lhe que o seu serviço é "seguro". Mas o que eles significam com isso é algo fundamentalmente diferente Do que queremos dizer. O que eles significam por "seguro" é que depois de ter dado Eles o poder de ler e modificar seus dados, eles tentam muito difícil de não deixar Esse poder seja abusado. Isso acaba por ser difícil! Insetos, Configurações incorretas ou erro do operador podem acidentalmente expor seus dados para Outro cliente ou para o público, ou pode corromper seus dados. Criminosos Ganho rotineiramente de acesso ilícito a servidores corporativos. Ainda mais insidioso é O fato de que os próprios funcionários às vezes violam a privacidade do cliente De negligência, avareza ou mera curiosidade. O mais consciencioso de Esses prestadores de serviços gastam consideráveis esforços e despesas tentando Mitigar esses riscos.
O que queremos dizer com "segurança" é algo diferente. * O provedor de serviços Nunca tem a capacidade de ler ou modificar seus dados em primeiro lugar: nunca. * Se você usa Tahoe-LAFS, então todas as ameaças descritas acima não são questões para você. Não só é fácil e barato para o provedor de serviços Manter a segurança de seus dados, mas na verdade eles não podem violar sua Segurança se eles tentaram. Isto é o que chamamos de * independente do fornecedor segurança*.
Esta garantia está integrada naturalmente no sistema de armazenamento Tahoe-LAFS e Não exige que você execute um passo de pré-criptografia manual ou uma chave complicada gestão. (Afinal, ter que fazer operações manuais pesadas quando Armazenar ou acessar seus dados anularia um dos principais benefícios de Usando armazenamento em nuvem em primeiro lugar: conveniência.)
Veja como funciona:
Uma "grade de armazenamento" é constituída por uma série de servidores de armazenamento. Um servidor de armazenamento Tem armazenamento direto em anexo (tipicamente um ou mais discos rígidos). Um "gateway" Se comunica com os nós de armazenamento e os usa para fornecer acesso ao Rede sobre protocolos como HTTP (S), SFTP ou FTP.
Observe que você pode encontrar "cliente" usado para se referir aos nós do gateway (que atuam como Um cliente para servidores de armazenamento) e também para processos ou programas que se conectam a Um nó de gateway e operações de execução na grade - por exemplo, uma CLI Comando, navegador da Web, cliente SFTP ou cliente FTP.
Os usuários não contam com servidores de armazenamento para fornecer * confidencialidade * nem
- Integridade * para seus dados - em vez disso, todos os dados são criptografados e Integridade verificada pelo gateway, para que os servidores não possam ler nem Modifique o conteúdo dos arquivos.
Os usuários dependem de servidores de armazenamento para * disponibilidade *. O texto cifrado é Codificado por apagamento em partes
Ndistribuídas em pelo menosHdistintas Servidores de armazenamento (o valor padrão paraNé 10 e paraHé 7) então Que pode ser recuperado de qualquerKdesses servidores (o padrão O valor deKé 3). Portanto, apenas a falha doH-K + 1(com o Padrões, 5) servidores podem tornar os dados indisponíveis.No modo de implantação típico, cada usuário executa seu próprio gateway sozinho máquina. Desta forma, ela confia em sua própria máquina para a confidencialidade e Integridade dos dados.
Um modo de implantação alternativo é que o gateway é executado em uma máquina remota e O usuário se conecta ao HTTPS ou SFTP. Isso significa que o operador de O gateway pode visualizar e modificar os dados do usuário (o usuário * depende de * o Gateway para confidencialidade e integridade), mas a vantagem é que a O usuário pode acessar a grade Tahoe-LAFS com um cliente que não possui o Software de gateway instalado, como um quiosque de internet ou celular.
Controle de acesso
Existem dois tipos de arquivos: imutáveis e mutáveis. Quando você carrega um arquivo Para a grade de armazenamento, você pode escolher o tipo de arquivo que será no grade. Os arquivos imutáveis não podem ser modificados quando foram carregados. UMA O arquivo mutable pode ser modificado por alguém com acesso de leitura e gravação. Um usuário Pode ter acesso de leitura e gravação a um arquivo mutable ou acesso somente leitura, ou não Acesso a ele.
Um usuário que tenha acesso de leitura e gravação a um arquivo mutable ou diretório pode dar Outro acesso de leitura e gravação do usuário a esse arquivo ou diretório, ou eles podem dar Acesso somente leitura para esse arquivo ou diretório. Um usuário com acesso somente leitura Para um arquivo ou diretório pode dar acesso a outro usuário somente leitura.
Ao vincular um arquivo ou diretório a um diretório pai, você pode usar um Link de leitura-escrita ou um link somente de leitura. Se você usar um link de leitura e gravação, então Qualquer pessoa que tenha acesso de leitura e gravação ao diretório pai pode obter leitura-escrita Acesso à criança e qualquer pessoa que tenha acesso somente leitura ao pai O diretório pode obter acesso somente leitura à criança. Se você usar uma leitura somente Link, qualquer pessoa que tenha lido-escrito ou acesso somente leitura ao pai O diretório pode obter acesso somente leitura à criança.
================================================== ==== Usando Tahoe-LAFS com uma rede anônima: Tor, I2P ================================================== ====
. `Visão geral '
. `Casos de uso '
.
Software Dependencies_#.
Tor#.I2P. `Configuração de conexão '
. `Configuração de Anonimato '
#.
Anonimato do cliente ' #.Anonimato de servidor, configuração manual ' #. `Anonimato de servidor, configuração automática '. `Problemas de desempenho e segurança '
Visão geral
Tor é uma rede anonimização usada para ajudar a esconder a identidade da Internet Clientes e servidores. Consulte o site do Tor Project para obter mais informações: Https://www.torproject.org/
I2P é uma rede de anonimato descentralizada que se concentra no anonimato de ponta a ponta Entre clientes e servidores. Consulte o site I2P para obter mais informações: Https://geti2p.net/
Casos de uso
Existem três casos de uso potenciais para Tahoe-LAFS do lado do cliente:
-
O usuário deseja sempre usar uma rede de anonimato (Tor, I2P) para proteger Seu anonimato quando se conecta às redes de armazenamento Tahoe-LAFS (seja ou Não os servidores de armazenamento são anônimos).
-
O usuário não se preocupa em proteger seu anonimato, mas eles desejam se conectar a Servidores de armazenamento Tahoe-LAFS que são acessíveis apenas através de Tor Hidden Services ou I2P.
-
Tor é usado apenas se uma sugestão de conexão do servidor usar
tor:. Essas sugestões Geralmente tem um endereço.onion. -
I2P só é usado se uma sugestão de conexão do servidor usa
i2p:. Essas sugestões Geralmente têm um endereço.i2p. -
O usuário não se preocupa em proteger seu anonimato ou para se conectar a um anonimato Servidores de armazenamento. Este documento não é útil para você ... então pare de ler.
Para servidores de armazenamento Tahoe-LAFS existem três casos de uso:
-
O operador deseja proteger o anonimato fazendo seu Tahoe Servidor acessível apenas em I2P, através de Tor Hidden Services, ou ambos.
-
O operador não * requer * anonimato para o servidor de armazenamento, mas eles Quer que ele esteja disponível tanto no TCP / IP roteado publicamente quanto através de um Rede de anonimização (I2P, Tor Hidden Services). Uma possível razão para fazer Isso é porque ser alcançável através de uma rede de anonimato é um Maneira conveniente de ignorar NAT ou firewall que impede roteios públicos Conexões TCP / IP ao seu servidor (para clientes capazes de se conectar a Tais servidores). Outro é o que torna o seu servidor de armazenamento acessível Através de uma rede de anonimato pode oferecer uma melhor proteção para sua Clientes que usam essa rede de anonimato para proteger seus anonimato.
-
O operador do servidor de armazenamento não se preocupa em proteger seu próprio anonimato nem Para ajudar os clientes a proteger o deles. Pare de ler este documento e execute Seu servidor de armazenamento Tahoe-LAFS usando TCP / IP com roteamento público.
Veja esta página do Tor Project para obter mais informações sobre Tor Hidden Services: Https://www.torproject.org/docs/hidden-services.html.pt
Veja esta página do Projeto I2P para obter mais informações sobre o I2P: Https://geti2p.net/en/about/intro
Dependências de software
Tor
Os clientes que desejam se conectar a servidores baseados em Tor devem instalar o seguinte.
-
Tor (tor) deve ser instalado. Veja aqui: Https://www.torproject.org/docs/installguide.html.en. No Debian / Ubuntu, Use
apt-get install tor. Você também pode instalar e executar o navegador Tor Agrupar. -
Tahoe-LAFS deve ser instalado com o
[tor]"extra" habilitado. Isso vai Instaletxtorcon::
Pip install tahoe-lafs [tor]
Os servidores Tor-configurados manualmente devem instalar Tor, mas não precisam
Txtorconou o[tor]extra. Configuração automática, quando Implementado, vai precisar destes, assim como os clientes.I2P
Os clientes que desejam se conectar a servidores baseados em I2P devem instalar o seguinte. Tal como acontece com Tor, os servidores baseados em I2P configurados manualmente precisam do daemon I2P, mas Não há bibliotecas especiais de apoio Tahoe-side.
-
I2P deve ser instalado. Veja aqui: Https://geti2p.net/en/download
-
A API SAM deve estar habilitada.
-
Inicie o I2P.
- Visite http://127.0.0.1:7657/configclients no seu navegador.
- Em "Configuração do Cliente", marque a opção "Executar no Startup?" Caixa para "SAM Ponte de aplicação ".
- Clique em "Salvar Configuração do Cliente".
-
Clique no controle "Iniciar" para "ponte de aplicação SAM" ou reinicie o I2P.
-
Tahoe-LAFS deve ser instalado com o
[i2p]extra habilitado, para obterTxi2p::
Pip install tahoe-lafs [i2p]
Tor e I2P
Os clientes que desejam se conectar a servidores baseados em Tor e I2P devem instalar tudo acima. Em particular, Tahoe-LAFS deve ser instalado com ambos Extras habilitados ::
Pip install tahoe-lafs [tor, i2p]
Configuração de conexão
Consulte: ref:
Connection Managementpara uma descrição do[tor]e[I2p]seções detahoe.cfg. Estes controlam como o cliente Tahoe Conecte-se a um daemon Tor / I2P e, assim, faça conexões com Tor / I2P-baseadas Servidores.As seções
[tor]e[i2p]só precisam ser modificadas para serem usadas de forma incomum Configurações ou para habilitar a configuração automática do servidor.A configuração padrão tentará entrar em contato com um daemon local Tor / I2P Ouvindo as portas usuais (9050/9150 para Tor, 7656 para I2P). Enquanto Há um daemon em execução no host local e o suporte necessário Bibliotecas foram instaladas, os clientes poderão usar servidores baseados em Tor Sem qualquer configuração especial.
No entanto, note que esta configuração padrão não melhora a Anonimato: as conexões TCP normais ainda serão feitas em qualquer servidor que Oferece um endereço regular (cumpre o segundo caso de uso do cliente acima, não o terceiro). Para proteger o anonimato, os usuários devem configurar o
[Connections]da seguinte maneira:[Conexões] Tcp = tor
Com isso, o cliente usará Tor (em vez de um IP-address -reviração de conexão direta) para alcançar servidores baseados em TCP.
Configuração de anonimato
Tahoe-LAFS fornece uma configuração "flag de segurança" para indicar explicitamente Seja necessário ou não a privacidade do endereço IP para um nó ::
[nó] Revelar-IP-address = (booleano, opcional)
Quando
revelar-IP-address = False, Tahoe-LAFS se recusará a iniciar se algum dos As opções de configuração emtahoe.cfgrevelariam a rede do nó localização:-
[Conexões] tcp = toré necessário: caso contrário, o cliente faria Conexões diretas para o Introdução, ou qualquer servidor baseado em TCP que aprende Do Introdutor, revelando seu endereço IP para esses servidores e um Rede de espionagem. Com isso, Tahoe-LAFS só fará Conexões de saída através de uma rede de anonimato suportada. -
Tub.locationdeve ser desativado ou conter valores seguros. este O valor é anunciado para outros nós através do Introdutor: é como um servidor Anuncia sua localização para que os clientes possam se conectar a ela. No modo privado, ele É um erro para incluir umtcp:dica notub.location. Modo privado Rejeita o valor padrão detub.location(quando a chave está faltando Inteiramente), que éAUTO, que usaifconfigpara adivinhar o nó Endereço IP externo, o que o revelaria ao servidor e a outros clientes.
Esta opção é ** crítica ** para preservar o anonimato do cliente (cliente Caso de uso 3 de "Casos de uso", acima). Também é necessário preservar uma Anonimato do servidor (caso de uso do servidor 3).
Esse sinalizador pode ser configurado (para falso), fornecendo o argumento
--hide-ippara Os comandoscreate-node,create-clientoucreate-introducer.Observe que o valor padrão de
revelar-endereço IPé verdadeiro, porque Infelizmente, esconder o endereço IP do nó requer software adicional para ser Instalado (conforme descrito acima) e reduz o desempenho.Anonimato do cliente
Para configurar um nó de cliente para anonimato,
tahoe.cfg** deve ** conter o Seguindo as bandeiras de configuração ::[nó] Revelar-IP-address = False Tub.port = desativado Tub.location = desativado
Uma vez que o nodo Tahoe-LAFS foi reiniciado, ele pode ser usado anonimamente (cliente Caso de uso 3).
Anonimato do servidor, configuração manual
Para configurar um nó de servidor para ouvir em uma rede de anonimato, devemos primeiro Configure Tor para executar um "Serviço de cebola" e encaminhe as conexões de entrada para o Porto Tahoe local. Então, configuramos Tahoe para anunciar o endereço
.onionAos clientes. Também configuramos Tahoe para não fazer conexões TCP diretas.- Decida em um número de porta de escuta local, chamado PORT. Isso pode ser qualquer não utilizado Porta de cerca de 1024 até 65535 (dependendo do kernel / rede do host Config). Nós diremos a Tahoe para escutar nesta porta, e nós diremos a Tor para Encaminhe as conexões de entrada para ele.
- Decida em um número de porta externo, chamado VIRTPORT. Isso será usado no Localização anunciada e revelada aos clientes. Pode ser qualquer número de 1 Para 65535. Pode ser o mesmo que PORT, se quiser.
- Decida em um "diretório de serviço oculto", geralmente em
/ var / lib / tor / NAME. Pediremos a Tor para salvar o estado do serviço de cebola aqui, e Tor irá Escreva o endereço.onionaqui depois que ele for gerado.
Em seguida, faça o seguinte:
-
Crie o nó do servidor Tahoe (com
tahoe create-node), mas não ** não ** Lança-o ainda. -
Edite o arquivo de configuração Tor (normalmente em
/ etc / tor / torrc). Precisamos adicionar Uma seção para definir o serviço oculto. Se nossa PORT for 2000, VIRTPORT é 3000, e estamos usando/ var / lib / tor / tahoecomo o serviço oculto Diretório, a seção deve se parecer com ::HiddenServiceDir / var / lib / tor / tahoe HiddenServicePort 3000 127.0.0.1:2000
-
Reinicie Tor, com
systemctl restart tor. Aguarde alguns segundos. -
Leia o arquivo
hostnameno diretório de serviço oculto (por exemplo,/ Var / lib / tor / tahoe / hostname). Este será um endereço.onion, comoU33m4y7klhz3b.onion. Ligue para esta CEBOLA. -
Edite
tahoe.cfgpara configurartub.portpara usarTcp: PORT: interface = 127.0.0.1etub.locationpara usarTor: ONION.onion: VIRTPORT. Usando os exemplos acima, isso seria ::[nó] Revelar-endereço IP = falso Tub.port = tcp: 2000: interface = 127.0.0.1 Tub.location = tor: u33m4y7klhz3b.onion: 3000 [Conexões] Tcp = tor
-
Inicie o servidor Tahoe com
tahoe start $ NODEDIR
A seção
tub.portfará com que o servidor Tahoe ouça no PORT, mas Ligue o soquete de escuta à interface de loopback, que não é acessível Do mundo exterior (mas * é * acessível pelo daemon Tor local). Então o A seçãotcp = torfaz com que Tahoe use Tor quando se conecta ao Introdução, escondendo o endereço IP. O nó se anunciará a todos Clientes que usam `tub.location``, então os clientes saberão que devem usar o Tor Para alcançar este servidor (e não revelar seu endereço IP através do anúncio). Quando os clientes se conectam ao endereço da cebola, seus pacotes serão Atravessar a rede de anonimato e eventualmente aterrar no Tor local Daemon, que então estabelecerá uma conexão com PORT no localhost, que é Onde Tahoe está ouvindo conexões.Siga um processo similar para construir um servidor Tahoe que escuta no I2P. o O mesmo processo pode ser usado para ouvir tanto o Tor como o I2P (
tub.location = Tor: ONION.onion: VIRTPORT, i2p: ADDR.i2p). Também pode ouvir tanto Tor como TCP simples (caso de uso 2), comtub.port = tcp: PORT,tub.location = Tcp: HOST: PORT, tor: ONION.onion: VIRTPORTeanonymous = false(e omite A configuraçãotcp = tor, já que o endereço já está sendo transmitido através de O anúncio de localização).Anonimato do servidor, configuração automática
Para configurar um nó do servidor para ouvir em uma rede de anonimato, crie o Nó com a opção
--listen = tor. Isso requer uma configuração Tor que Ou lança um novo daemon Tor, ou tem acesso à porta de controle Tor (e Autoridade suficiente para criar um novo serviço de cebola). Nos sistemas Debian / Ubuntu, façaApt install tor, adicione-se ao grupo de controle comadduser YOURUSERNAME debian-tore, em seguida, inicie sessão e faça o login novamente: se osgroupsO comando incluidebian-torna saída, você deve ter permissão para Use a porta de controle de domínio unix em/ var / run / tor / control.Esta opção irá definir
revelar-IP-address = Falsee[connections] tcp = Tor. Ele alocará as portas necessárias, instruirá Tor para criar a cebola Serviço (salvando a chave privada em algum lugar dentro de NODEDIR / private /), obtenha O endereço.onione preenchatub.portetub.locationcorretamente.Problemas de desempenho e segurança
Se você estiver executando um servidor que não precisa ser Anônimo, você deve torná-lo acessível através de uma rede de anonimato ou não? Ou você pode torná-lo acessível * ambos * através de uma rede de anonimato E como um servidor TCP / IP rastreável publicamente?
Existem várias compensações efetuadas por esta decisão.
Penetração NAT / Firewall
Fazer com que um servidor seja acessível via Tor ou I2P o torna acessível (por Clientes compatíveis com Tor / I2P) mesmo que existam NAT ou firewalls que impeçam Conexões TCP / IP diretas para o servidor.
Anonimato
Tornar um servidor Tahoe-LAFS acessível * somente * via Tor ou I2P pode ser usado para Garanta que os clientes Tahoe-LAFS usem Tor ou I2P para se conectar (Especificamente, o servidor só deve anunciar endereços Tor / I2P no Chave de configuração
tub.location). Isso evita que os clientes mal configurados sejam Desingonizando-se acidentalmente, conectando-se ao seu servidor através de A Internet rastreável.Claramente, um servidor que está disponível como um serviço Tor / I2P * e * a O endereço TCP regular não é anônimo: o endereço do .on e o real O endereço IP do servidor é facilmente vinculável.
Além disso, a interação, através do Tor, com um Tor Oculto pode ser mais Protegido da análise do tráfego da rede do que a interação, através do Tor, Com um servidor TCP / IP com rastreamento público
** XXX há um documento mantido pelos desenvolvedores de Tor que comprovem ou refutam essa crença? Se assim for, precisamos ligar a ele. Caso contrário, talvez devêssemos explicar mais aqui por que pensamos isso? **
Linkability
A partir de 1.12.0, o nó usa uma única chave de banheira persistente para saída Conexões ao Introdutor e conexões de entrada para o Servidor de Armazenamento (E Helper). Para os clientes, uma nova chave Tub é criada para cada servidor de armazenamento Nós aprendemos sobre, e essas chaves são * não * persistiram (então elas mudarão cada uma delas Tempo que o cliente reinicia).
Clientes que atravessam diretórios (de rootcap para subdiretório para filecap) são É provável que solicitem os mesmos índices de armazenamento (SIs) na mesma ordem de cada vez. Um cliente conectado a vários servidores irá pedir-lhes todos para o mesmo SI em Quase ao mesmo tempo. E dois clientes que compartilham arquivos ou diretórios Irá visitar os mesmos SI (em várias ocasiões).
Como resultado, as seguintes coisas são vinculáveis, mesmo com
revelar-endereço IP = Falso:- Servidores de armazenamento podem vincular reconhecer várias conexões do mesmo Cliente ainda não reiniciado. (Observe que o próximo recurso de Contabilidade pode Faz com que os clientes apresentem uma chave pública persistente do lado do cliente quando Conexão, que será uma ligação muito mais forte).
- Os servidores de armazenamento provavelmente podem deduzir qual cliente está acessando dados, por Olhando as SIs sendo solicitadas. Vários servidores podem conciliar Determine que o mesmo cliente está falando com todos eles, mesmo que o TubIDs são diferentes para cada conexão.
- Os servidores de armazenamento podem deduzir quando dois clientes diferentes estão compartilhando dados.
- O Introdutor pode entregar diferentes informações de servidor para cada um Cliente subscrito, para particionar clientes em conjuntos distintos de acordo com Quais as conexões do servidor que eles eventualmente fazem. Para clientes + nós de servidor, ele Também pode correlacionar o anúncio do servidor com o cliente deduzido identidade.
atuação
Um cliente que se conecta a um servidor Tahoe-LAFS com rastreamento público através de Tor Incorrem em latência substancialmente maior e, às vezes, pior Mesmo cliente se conectando ao mesmo servidor através de um TCP / IP rastreável normal conexão. Quando o servidor está em um Tor Hidden Service, ele incorre ainda mais Latência e, possivelmente, ainda pior rendimento.
Conectando-se a servidores Tahoe-LAFS que são servidores I2P incorrem em maior latência E pior rendimento também.
Efeitos positivos e negativos em outros usuários Tor
O envio de seu tráfego Tahoe-LAFS sobre o Tor adiciona tráfego de cobertura para outros Tor usuários que também estão transmitindo dados em massa. Então isso é bom para Eles - aumentando seu anonimato.
No entanto, torna o desempenho de outros usuários do Tor Sessões - por exemplo, sessões ssh - muito pior. Isso é porque Tor Atualmente não possui nenhuma prioridade ou qualidade de serviço Recursos, para que as teclas de Ssh de outra pessoa possam ter que esperar na fila Enquanto o conteúdo do arquivo em massa é transmitido. O atraso adicional pode Tornar as sessões interativas de outras pessoas inutilizáveis.
Ambos os efeitos são duplicados se você carregar ou baixar arquivos para um Tor Hidden Service, em comparação com se você carregar ou baixar arquivos Over Tor para um servidor TCP / IP com rastreamento público
Efeitos positivos e negativos em outros usuários do I2P
Enviar seu tráfego Tahoe-LAFS ao I2P adiciona tráfego de cobertura para outros usuários do I2P Que também estão transmitindo dados. Então, isso é bom para eles - aumentando sua anonimato. Não prejudicará diretamente o desempenho de outros usuários do I2P Sessões interativas, porque a rede I2P possui vários controles de congestionamento e Recursos de qualidade de serviço, como priorizar pacotes menores.
No entanto, se muitos usuários estão enviando tráfego Tahoe-LAFS ao I2P e não tiverem Seus roteadores I2P configurados para participar de muito tráfego, então o I2P A rede como um todo sofrerá degradação. Cada roteador Tahoe-LAFS que usa o I2P tem Seus próprios túneis de anonimato que seus dados são enviados. Em média, um O nó Tahoe-LAFS requer 12 outros roteadores I2P para participar de seus túneis.
Portanto, é importante que o seu roteador I2P esteja compartilhando a largura de banda com outros Roteadores, para que você possa retornar enquanto usa o I2P. Isso nunca prejudicará a Desempenho de seu nó Tahoe-LAFS, porque seu roteador I2P sempre Priorize seu próprio tráfego.
=========================
Como configurar um servidor
Muitos nós Tahoe-LAFS são executados como "servidores", o que significa que eles fornecem serviços para Outras máquinas (isto é, "clientes"). Os dois tipos mais importantes são os Introdução e Servidores de armazenamento.
Para ser útil, os servidores devem ser alcançados pelos clientes. Os servidores Tahoe podem ouvir Em portas TCP e anunciar sua "localização" (nome do host e número da porta TCP) Para que os clientes possam se conectar a eles. Eles também podem ouvir os serviços de cebola "Tor" E portas I2P.
Os servidores de armazenamento anunciam sua localização ao anunciá-lo ao Introdutivo, Que então transmite a localização para todos os clientes. Então, uma vez que a localização é Determinado, você não precisa fazer nada de especial para entregá-lo.
O próprio apresentador possui uma localização, que deve ser entregue manualmente a todos Servidores de armazenamento e clientes. Você pode enviá-lo para os novos membros do seu grade. Esta localização (juntamente com outros identificadores criptográficos importantes) é Escrito em um arquivo chamado
private / introducer.furlno Presenter's Diretório básico, e deve ser fornecido como o argumento--introducer =paraTahoe create-nodeoutahoe create-node.O primeiro passo ao configurar um servidor é descobrir como os clientes irão alcançar. Então você precisa configurar o servidor para ouvir em algumas portas, e Depois configure a localização corretamente.
Configuração manual
Cada servidor tem duas configurações em seu arquivo
tahoe.cfg:tub.port, eTub.location. A "porta" controla o que o nó do servidor escuta: isto Geralmente é uma porta TCP.A "localização" controla o que é anunciado para o mundo exterior. Isto é um "Sugestão de conexão foolscap", e inclui tanto o tipo de conexão (Tcp, tor ou i2p) e os detalhes da conexão (nome do host / endereço, porta número). Vários proxies, gateways e redes de privacidade podem ser Envolvido, então não é incomum para
tub.portetub.locationpara olhar diferente.Você pode controlar diretamente a configuração
tub.portetub.locationConfigurações, fornecendo--port =e--location =ao executartahoe Create-node.Configuração automática
Em vez de fornecer
--port = / - location =, você pode usar--listen =. Os servidores podem ouvir em TCP, Tor, I2P, uma combinação desses ou nenhum. O argumento--listen =controla quais tipos de ouvintes o novo servidor usará.--listen = nonesignifica que o servidor não deve ouvir nada. Isso não Faz sentido para um servidor, mas é apropriado para um nó somente cliente. o O comandotahoe create-clientinclui automaticamente--listen = none.--listen = tcpé o padrão e liga uma porta de escuta TCP padrão. Usar--listen = tcprequer um argumento--hostname =também, que será Incorporado no local anunciado do nó. Descobrimos que os computadores Não pode determinar de forma confiável seu nome de host acessível externamente, então, em vez de Ter o servidor adivinhar (ou escanear suas interfaces para endereços IP Isso pode ou não ser apropriado), a criação de nó requer que o usuário Forneça o nome do host.--listen = torconversará com um daemon Tor local e criará uma nova "cebola" Servidor "(que se parece comalzrgrdvxct6c63z.onion).--listen = i2p` conversará com um daemon I2P local e criará um novo servidor endereço. Consulte: doc:anonymity-configuration` para obter detalhes.Você pode ouvir nos três usando
--listen = tcp, tor, i2p.Cenários de implantação
A seguir, alguns cenários sugeridos para configurar servidores usando Vários transportes de rede. Estes exemplos não incluem a especificação de um Apresentador FURL que normalmente você gostaria quando provisionamento de armazenamento Nós. Para estes e outros detalhes de configuração, consulte : Doc:
configuration.. `Servidor possui um nome DNS público '
.
Servidor possui um endereço público IPv4 / IPv6_.
O servidor está por trás de um firewall com encaminhamento de porta_.
Usando o I2P / Tor para evitar o encaminhamento da porta_O servidor possui um nome DNS público
O caso mais simples é o local onde o host do servidor está diretamente conectado ao Internet, sem um firewall ou caixa NAT no caminho. A maioria dos VPS (Virtual Private Servidor) e servidores colocados são assim, embora alguns fornecedores bloqueiem Muitas portas de entrada por padrão.
Para esses servidores, tudo o que você precisa saber é o nome do host externo. O sistema O administrador irá dizer-lhe isso. O principal requisito é que este nome de host Pode ser pesquisado no DNS, e ele será mapeado para um endereço IPv4 ou IPv6 que Alcançará a máquina.
Se o seu nome de host for
example.net, então você criará o introdutor como esta::Tahoe create-introducer --hostname example.com ~ / introducer
Ou um servidor de armazenamento como ::
Tahoe create-node --hostname = example.net
Estes irão alocar uma porta TCP (por exemplo, 12345), atribuir
tub.portpara serTcp: 12345etub.locationserãotcp: example.com: 12345.Idealmente, isso também deveria funcionar para hosts compatíveis com IPv6 (onde o nome DNS Fornece um registro "AAAA", ou ambos "A" e "AAAA"). No entanto Tahoe-LAFS O suporte para IPv6 é novo e ainda pode ter problemas. Por favor, veja o ingresso
# 867_ para detalhes... _ # 867: https://tahoe-lafs.org/trac/tahoe-lafs/ticket/867
O servidor possui um endereço público IPv4 / IPv6
Se o host tiver um endereço IPv4 (público) rotativo (por exemplo,
203.0.113.1```), mas Nenhum nome DNS, você precisará escolher uma porta TCP (por exemplo,3457``) e usar o Segue::Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 3457
--porté uma "string de especificação de ponto de extremidade" que controla quais locais Porta em que o nó escuta.--locationé a "sugestão de conexão" que ele Anuncia para outros, e descreve as conexões de saída que essas Os clientes irão fazer, por isso precisa trabalhar a partir da sua localização na rede.Os nós Tahoe-LAFS escutam em todas as interfaces por padrão. Quando o host é Multi-homed, você pode querer fazer a ligação de escuta ligar apenas a uma Interface específica, adicionando uma opção
interface =ao--port =argumento::Tahoe create-node --port = tcp: 3457: interface = 203.0.113.1 - localização = tcp: 203.0.113.1: 3457
Se o endereço público do host for IPv6 em vez de IPv4, use colchetes para Envolva o endereço e altere o tipo de nó de extremidade para
tcp6::Tahoe create-node --port = tcp6: 3457 - localização = tcp: [2001: db8 :: 1]: 3457
Você pode usar
interface =para vincular a uma interface IPv6 específica também, no entanto Você deve fazer uma barra invertida - escapar dos dois pontos, porque, de outra forma, eles são interpretados Como delimitadores pelo idioma de especificação do "ponto final" torcido. o--location =argumento não precisa de dois pontos para serem escapados, porque eles são Envolto pelos colchetes ::Tahoe create-node --port = tcp6: 3457: interface = 2001 \: db8 \: \: 1 --location = tcp: [2001: db8 :: 1]: 3457
Para hosts somente IPv6 com registros DNS AAAA, se o simples
--hostname =A configuração não funciona, eles podem ser informados para ouvir especificamente Porta compatível com IPv6 com este ::Tahoe create-node --port = tcp6: 3457 - localização = tcp: example.net: 3457
O servidor está por trás de um firewall com encaminhamento de porta
Para configurar um nó de armazenamento por trás de um firewall com encaminhamento de porta, você irá precisa saber:
- Endereço IPv4 público do roteador
- A porta TCP que está disponível de fora da sua rede
- A porta TCP que é o destino de encaminhamento
- Endereço IPv4 interno do nó de armazenamento (o nó de armazenamento em si é
Desconhece esse endereço e não é usado durante
tahoe create-node, Mas o firewall deve ser configurado para enviar conexões para isso)
Os números de porta TCP internos e externos podem ser iguais ou diferentes Dependendo de como o encaminhamento da porta está configurado. Se é mapear portas 1-para-1, eo endereço IPv4 público do firewall é 203.0.113.1 (e Talvez o endereço IPv4 interno do nó de armazenamento seja 192.168.1.5), então Use um comando CLI como este ::
Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 3457
Se no entanto, o firewall / NAT-box encaminha a porta externa * 6656 * para o interno Porta 3457, então faça isso ::
Tahoe create-node --port = tcp: 3457 - localização = tcp: 203.0.113.1: 6656
Usando o I2P / Tor para evitar o encaminhamento da porta
Os serviços de cebola I2P e Tor, entre outras excelentes propriedades, também fornecem NAT Penetração sem encaminhamento de porta, nomes de host ou endereços IP. Então, configurando Um servidor que escuta apenas no Tor é simples ::
Tahoe create-node --listen = tor
Para mais informações sobre o uso de Tahoe-LAFS com I2p e Tor veja : Doc:
anonymity-configuration -
 @ 88cc134b:5ae99079
2025-04-14 02:15:34
@ 88cc134b:5ae99079
2025-04-14 02:15:34I like it when articles start with an intro paragraph, rather than a heading. Diving straight in with a header is a bit heavy handed. We need a bit of foreplay here. Don't need to hit them with a sledgehammer from the start.
How to Use Headings
Well, we did it. We totally used a heading. The demonstration was a complete success. Overwhelming victory. Let's try subheadings now...
Ordered Lists
No test is complete without an ordered list:
- Always use a good opening for the fist point
- Then bring it home with the last point
Bulleted Lists
There is something so business-like with bulleted lists:
- You get to list without caring for the order
- Feels like there is less at stake
A Now for Some Images
Here we go. The real deal now. Everyone will know we're serious now:
-
 @ 147ac18e:ef1ca1ba
2025-04-14 00:28:18
@ 147ac18e:ef1ca1ba
2025-04-14 00:28:18There’s no shortage of hype around AI. But beneath the buzzwords, Geoff Woods lays out something much more grounded—and frankly, more useful—on his recent appearance on The What Is Money Show. Geoff, who wrote The AI Driven Leader, isn’t here to pitch you a prompt template or a new tool. He’s here to talk about leadership, responsibility, and how to actually get value from AI.
His argument is simple: AI is no longer optional. It's a leadership imperative. And yet, despite nearly every executive claiming to believe in its future, less than 5% are doing anything meaningful with it. Geoff’s take? If you’re delegating AI to the tech team, you’re missing the point. This is about vision, strategy, and leading your people into a new era.
But here’s the rub: you don’t need to become an AI expert. You just need to become what Geoff calls an AI-driven leader—someone who knows how to spot valuable use cases, communicate clearly with AI, and stay in the driver’s seat as the thought leader. It’s not about handing off decisions to a machine. It’s about using the machine to sharpen your thinking.
To do that, Geoff leans on a framework he calls CRIT: Context, Role, Interview, Task. It’s dead simple and wildly effective.
CRIT Framework: Geoff’s Go-To Prompting System
Write every AI prompt using:
-
Context – the background situation
-
Role – what persona you want AI to take (e.g., CFO, board member, therapist)
-
Interview – have AI ask you questions to pull deeper insights
-
Task – what you want AI to do after collecting enough context
Give the AI rich context, assign it a role (board member, CFO, therapist—whatever you need), have it interview you to pull out what’s really going on in your head, and then define the task you want it to execute. That flip—getting the AI to interview you—is the difference between mediocre results and strategic breakthroughs.
He shared some standout examples:
- Using AI as a simulated board to test strategy decks and predict which slides will blow up in a real meeting.
- Having AI draft executive emails in a tone blend of your own voice, plus a dash of Simon Sinek and David Goggins.
- Creating AI-generated personas of your kids’ strengths to show them how to use tech to deepen—not replace—their humanity.
That last point matters. Geoff’s raising his own kids to be AI-native, but not tech-addicted. His daughter used AI to explore business ideas. His son used it to work through emotional challenges. In both cases, the tool was secondary. The focus was helping them grow into more aware, capable versions of themselves.
He’s honest about AI’s limitations too. It hallucinates. It’s bad at math. It can’t replace deep human judgment. But if you use it right—if you treat it like a thought partner instead of a magic 8-ball—it becomes an amplifier.
Geoff’s challenge to all of us is to stop anchoring our identity to who we’ve been, and start leaning into who we could become. Whether you’re running a company, managing a classroom, or figuring out your next move, the opportunity is the same: use AI to 10x the things that make you most human.
And it all starts with one sticky note: How can AI help me do this?
If you’re interested in diving deeper, check out aileadership.com or pick up his book The AI Driven Leader. But more importantly, start experimenting. Get your reps in. Think bigger.
Because a year from now, the version of you that’s already doing this work? They’re going to be very hard to compete with.
-
-
 @ ac58bbcc:7d9754d8
2025-04-13 23:35:36
@ ac58bbcc:7d9754d8
2025-04-13 23:35:36Introduction
Many school districts allocate significant budgets for curriculum materials like textbooks and workbooks, but these resources often fail to provide teachers with the deep conceptual understanding needed to teach mathematics effectively. Administrators face the challenge of ensuring that their teachers have the support they need from books and worksheets and partners who understand how children learn math and the gaps in learning as they exist today.
The Problem: Books and Worksheets Are Not Enough
- Limited Depth in Conceptual Learning
- Curriculum materials often focus on procedural fluency rather than deep conceptual understanding. While these resources provide a structured framework for instruction, they do not equip teachers with the tools to address individual student learning styles or challenges.
- Lack of Ongoing Professional Support
- Administrators frequently allocate budgets for professional development workshops and materials but struggle to ensure that teachers receive ongoing, personalized support throughout the school year. Teachers often face unique classroom dynamics and need immediate assistance, yet many districts lack a consistent partnership with experts who can provide this guidance.
- Ineffectiveness in Meeting Diverse Needs
- Students learn at different paces and in different ways. Curriculum materials alone cannot address the varied needs of all students. A comprehensive support system is needed to help teachers differentiate instruction, support struggling learners, and challenge advanced students effectively.
Solution: Math Success by DMTI
Math Success by DMTI offers a more effective approach to elementary math education. Here’s what sets it apart:
- Focus on Conceptual Understanding:
- The program emphasizes deep conceptual understanding through real-life examples that tie procedures back to the underlying math concepts. Students understand not just how but also why strategies and procedures work.
- Modeling Problems:
- Math Success by DMTI teaches students to model problems using visual models like bar models, number lines, and equations. This approach ensures they see the math conceptually and can apply it in various contexts.
- Ongoing Support Throughout the Year:
- The program provides more than just one-time workshops; it offers ongoing support through expert coaches who work directly with teachers throughout the school year. Teachers receive guidance on lesson planning, classroom management, and student engagement strategies.
- Flexible Resources:
- Math Success by DMTI includes comprehensive resources such as assessments, instructional units, exit tickets, practice sheets, research-based games, and parent materials tailored to meet diverse learning needs.
- Consistent Language and Structure:
- The program uses consistent language and structure in teaching words from kindergarten through graduation. This consistency helps students build a strong foundation and facilitates smoother transitions between grade levels.
Teacher Testimonials: Real Impact
Educators have reported significant improvements in student achievement after implementing Math Success by DMTI:
- Increased Student Proficiency:
- For example, one third-grade teacher saw her students’ proficiency increase from 32% to 76% within a single academic year. This kind of growth demonstrates the program's effectiveness and its ability to foster deeper learning.
Conclusion
By adopting Math Success by DMTI, administrators can ensure that their teachers have the tools they need to teach math concepts effectively. With expert coaches embedded in classrooms for ongoing support, research-backed methodologies, flexible resources, and a focus on the right things in the right order, districts can create environments where students truly thrive.
Math Success by DMTI stands out as an exceptional partner for schools looking to improve math education. By bridging the gap between research and practice, Math Success by DMTI empowers educators to increase student achievement and foster a love for mathematics.
-
 @ f839fb67:5c930939
2025-04-13 19:48:48
@ f839fb67:5c930939
2025-04-13 19:48:48Relays
| Name | Address | Price (Sats/Year) | Status | | - | - | - | - | | stephen's aegis relay | wss://paid.relay.vanderwarker.family | 42069 |
| | stephen's Outbox | wss://relay.vanderwarker.family | Just Me |
| | stephen's Inbox | wss://haven.vanderwarker.family/inbox | WoT |
| | stephen's DMs | wss://haven.vanderwarker.family/chat | WoT |
| | VFam Data Relay | wss://data.relay.vanderwarker.family | 0 |
| | VFam Bots Relay | wss://skeme.vanderwarker.family | Invite |
| | VFGroups (NIP29) | wss://groups.vanderwarker.family | 0 |
| | [TOR] My Phone Relay | ws://naswsosuewqxyf7ov7gr7igc4tq2rbtqoxxirwyhkbuns4lwc3iowwid.onion | 0 | Meh... |
My Pubkeys
| Name | hex | nprofile | | - | - | - | | Main | f839fb6714598a7233d09dbd42af82cc9781d0faa57474f1841af90b5c930939 | nostr:nprofile1qqs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us9mapfx | | Vanity (Backup) | 82f21be67353c0d68438003fe6e56a35e2a57c49e0899b368b5ca7aa8dde7c23 | nostr:nprofile1qqsg9usmuee48sxkssuqq0lxu44rtc4903y7pzvmx694efa23h08cgcpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3ussel49x | | VFStore | 6416f1e658ba00d42107b05ad9bf485c7e46698217e0c19f0dc2e125de3af0d0 | nostr:nprofile1qqsxg9h3uevt5qx5yyrmqkkehay9cljxdxpp0cxpnuxu9cf9mca0p5qpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usaa8plu | | NostrSMS | 9be1b8315248eeb20f9d9ab2717d1750e4f27489eab1fa531d679dadd34c2f8d | nostr:nprofile1qqsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us595d45 |
Bots
Unlocks Bot
Hex: 2e941ad17144e0a04d1b8c21c4a0dbc3fbcbb9d08ae622b5f9c85341fac7c2d0
nprofile:
nostr:nprofile1qqsza9q669c5fc9qf5dccgwy5rdu877th8gg4e3zkhuus56pltru95qpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ust4kvak
Latest Data:
nostr:naddr1qq882mnvda3kkttrda6kuar9wgq37amnwvaz7tmnddjk6efwweskuer9wfmkzuntv4ezuenpd45kc7gzyqhfgxk3w9zwpgzdrwxzr39qm0plhjae6z9wvg44l8y9xs06clpdqqcyqqq823cgnl9u5Step Counter
Hex: 9223d2faeb95853b4d224a184c69e1df16648d35067a88cdf947c631b57e3de7
nprofile: nostr:nprofile1qqsfyg7jlt4etpfmf53y5xzvd8sa79ny356sv75gehu50333k4lrmecpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ustswp3w
Latest Data:
nostr:naddr1qvzqqqr4gupzpy3r6tawh9v98dxjyjscf357rhckvjxn2pn63rxlj37xxx6hu008qys8wumn8ghj7umtv4kk2tnkv9hxgetjwashy6m9wghxvctdd9k8jtcqp3ehgets943k7atww3jhyn39gffRCTGuest
Hex: 373904615c781e46bf5bf87b4126c8a568a05393b1b840b1a2a3234d20affa0c
nprofile: nostr:nprofile1qqsrwwgyv9w8s8jxhadls76pymy2269q2wfmrwzqkx32xg6dyzhl5rqpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3usy92jlx
NIP-29 Groups
- Minecraft Group Chat
nostr:naddr1qqrxvc33xpnxxqfqwaehxw309anhymm4wpejuanpdejx2unhv9exketj9enxzmtfd3usygrzymrpd2wz8ularp06y8ad5dgaddlumyt7tfzqge3vc97sgsarjvpsgqqqnpvqazypfd- VFNet Group Chat
nostr:naddr1qqrrwvfjx9jxzqfqwaehxw309anhymm4wpejuanpdejx2unhv9exketj9enxzmtfd3usygrzymrpd2wz8ularp06y8ad5dgaddlumyt7tfzqge3vc97sgsarjvpsgqqqnpvq08hx48
"Nostrified Websites"
[D] = Saves darkmode preferences over nostr
[A] = Auth over nostr
[B] = Beta (software)
[z] = zap enabled
Other Services (Hosted code)
Emojis Packs
- Minecraft
nostr:naddr1qqy566twv43hyctxwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsd0k5wp- AIM
nostr:naddr1qqxxz6tdv4kk7arfvdhkuucpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usyg8c88akw9ze3fer85yah4p2lqkvj7qap749w360rpq6ly94eycf8ypsgqqqw48qe0j2yk- Blobs
nostr:naddr1qqz5ymr0vfesz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2wek4ukj- FavEmojis
nostr:naddr1qqy5vctkg4kk76nfwvq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsf7sdwt- Modern Family
nostr:naddr1qqx56mmyv4exugzxv9kkjmreqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqp65ujlj36n- nostriches (Amethyst collection)
nostr:naddr1qq9xummnw3exjcmgv4esz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w2sqg6w- Pepe
nostr:naddr1qqz9qetsv5q37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82ns85f6x7- Minecraft Font
nostr:naddr1qq8y66twv43hyctxwssyvmmwwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsmzftgr- Archer Font
nostr:naddr1qq95zunrdpjhygzxdah8gqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr4fclkyxsh- SMB Font
nostr:naddr1qqv4xatsv4ezqntpwf5k7gzzwfhhg6r9wfejq3n0de6qz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w0wqpuk
Git Over Nostr
- NostrSMS
nostr:naddr1qqyxummnw3e8xmtnqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfrwaehxw309amk7apwwfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqyj8wumn8ghj7urpd9jzuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyxhwumn8ghj7mn0wvhxcmmvqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqaueqp0epk- nip51backup
nostr:naddr1qq9ku6tsx5ckyctrdd6hqqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjxamnwvaz7tmhda6zuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfywaehxw309acxz6ty9eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qgdwaehxw309ahx7uewd3hkcq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqpmej4gtqs6- bukkitstr
nostr:naddr1qqykyattdd5hgum5wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dspzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqrhnyf6g0n2
Market Places
Please use Nostr Market or somthing simular, to view.
- VFStore
nostr:naddr1qqjx2v34xe3kxvpn95cnqven956rwvpc95unscn9943kxet98q6nxde58p3ryqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjvamnwvaz7tmgv9mx2m3wweskuer9wfmkzuntv4ezuenpd45kc7f0da6hgcn00qqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzqeqk78n93wsq6sss0vz6mxl5shr7ge5cy9lqcx0smshpyh0r4uxsqvzqqqr4gvlfm7gu
Badges
Created
- paidrelayvf
nostr:naddr1qq9hqctfv3ex2mrp09mxvqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr48y85v3u3- iPow
nostr:naddr1qqzxj5r02uq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgg02u0r- codmaster
nostr:naddr1qqykxmmyd4shxar9wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgk3gm4g- iMine
nostr:naddr1qqzkjntfdejsz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqafed5s4x5
Clients I Use
- Amethyst
nostr:naddr1qqxnzd3cx5urqv3nxymngdphqgsyvrp9u6p0mfur9dfdru3d853tx9mdjuhkphxuxgfwmryja7zsvhqrqsqqql8kavfpw3- noStrudel
nostr:naddr1qqxnzd3cxccrvd34xser2dpkqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsygpxdq27pjfppharynrvhg6h8v2taeya5ssf49zkl9yyu5gxe4qg55psgqqq0nmq5mza9n- nostrsms
nostr:naddr1qq9rzdejxcunxde4xymqz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgrqsqqql8kjn33qm
Lists
- Fediverse
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqp9rx2erfwejhyum9j4g0xh
- AI
nostr:naddr1qvzqqqr4xypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqqfq5j65twn7
- Asterisk Shenanigans
nostr:naddr1qvzqqqr4xypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqz3qhxar9wf5hx6eq2d5x2mnpde5kwctwwvaxjuzz
- Minecraft Videos
nostr:naddr1qvzqqqr4xypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqzpxkjmn9vdexzen5yptxjer9daesqrd8jk
-
 @ 04ff5a72:22ba7b2d
2025-04-13 11:32:40
@ 04ff5a72:22ba7b2d
2025-04-13 11:32:40Introduction
If you’re looking to reduce your reliance on traditional banks and fiat currency, cryptocurrency can be an excellent alternative. It offers more control over your finances, helps you avoid bank fees, and can even grow your savings at higher rates than most banks or investment institutions provide. Here’s how you can get started with key services to make the most of crypto in your daily life.
Coinbase: A Modern Bank for the Crypto Era
Coinbase is one of the oldest and most trusted cryptocurrency platforms in the U.S. It lets you buy, sell, and trade a wide variety of cryptocurrencies. You can fund your account through direct bank deposits, PayPal, or any bank account.
The standout feature is their Coinbase Debit Card, which allows you to spend cryptocurrency just like you would with a regular bank debit card. Here’s why it’s special:
Available as both a physical card and a virtual card for Apple Wallet or Google Wallet, so you can tap and pay at most stores in the U.S.
- Spend any cryptocurrency in your Coinbase account, automatically converted to U.S. dollars at the time of purchase. Or, use their stablecoin, USDC.
- Earn 4.35% APY on USDC held in your account.
- Get 0.5% crypto rewards on every purchase, credited in Bitcoin (BTC), Ethereum (ETH), or other cryptocurrencies of your choice.
You can apply for a Coinbase Debit Card here. The virtual card is available immediately, and the physical card arrives by mail.
BitWage: Get Paid in Crypto
BitWage is a service tailored for contractors and freelancers, especially those dealing with international payments. It simplifies cross-border transactions and offers unique flexibility:
- Create invoices for clients or set up direct deposit with your employer’s payroll system.
- Payments can be converted automatically into Bitcoin, Ethereum, USDC, and other cryptocurrencies, which are sent directly to your crypto wallet.
- You can even split payments between cryptocurrency and your traditional bank account in any ratio you choose.
BitWage is perfect if you want to incorporate cryptocurrency into your paycheck without hassle.
FluidKey: Privacy-Focused Bank-to-Crypto Transfers
Fluidkey offers a seamless and privacy-focused solution for purchasing Ethereum (ETH) using ACH bank deposits. By leveraging Fluidkey’s platform, users can securely link their bank accounts and initiate ACH transfers to purchase ETH without exposing sensitive personal details. The service prioritizes privacy, ensuring transactions are discreet and handled with industry-leading encryption and compliance standards. Fluidkey simplifies the ETH acquisition process, offering a reliable alternative for individuals seeking secure and efficient methods for private cryptocurrency purchases.
Learn more about how to use this service via their documentation. For a more technical overview read the following blog entry.
Phoenix Wallet: Harnessing the Bitcoin Lightning Network
The Bitcoin Lightning Network is a technology that enables fast and low-cost Bitcoin transactions, avoiding delays and high fees.
The Phoenix Wallet is a user-friendly mobile app that lets you manage Bitcoin securely and use the Lightning Network easily. Here’s why it stands out:
- Full Control: With Phoenix, you hold the private keys to your wallet. In the crypto world, “Not your keys, not your crypto” means you’re in charge of your funds, ensuring no third party can freeze or seize them.
- Privacy and Security: Phoenix uses tools like the TOR network for anonymity and allows you to connect to private Bitcoin nodes, adding layers of security.
- No Custodians: Unlike exchanges like Coinbase, Phoenix is a non-custodial wallet. This means you are responsible for backing up your recovery phrase (a 12- or 24-word mnemonic) to restore your wallet if needed.
Phoenix Wallet is an excellent choice for secure, private Bitcoin transactions.
Hardware Wallets: The Ultimate Crypto Security
For those holding large amounts of cryptocurrency, a hardware wallet is the most secure option. It stores your private keys offline, away from potential hackers.
Here’s why hardware wallets are essential:
- Offline Security: Unlike software wallets, hardware wallets keep your private keys isolated from the internet.
- Multi-Currency Support: Most hardware wallets can store Bitcoin, Ethereum, and a wide range of other cryptocurrencies.
- Recovery Options: With a backup recovery phrase, you can restore your wallet on another device if your hardware wallet is lost or damaged.
Ledger is a leading manufacturer of hardware wallets. They offer models like the compact Ledger Nano and the advanced Ledger Stax, catering to both beginners and experienced users.
By incorporating these services into your routine, you can take full advantage of cryptocurrency to manage, spend, and secure your funds more effectively.
Note: this article is primarily catered towards US residents. Crypto and crypto-banking service rules and regulations vary vastly from country-to-country. The US, in particular, has lagged behind much of the world in terms of catering to “un-banking” for a variety of social and political reasons.
-
 @ 147ac18e:ef1ca1ba
2025-04-13 01:57:13
@ 147ac18e:ef1ca1ba
2025-04-13 01:57:13In a recent episode of The Survival Podcast, host Jack Spirko presents a contrarian view on the current trade war and tariffs imposed by the U.S. government. Far from being a chaotic or irrational policy, Jack argues that these tariffs are part of a broader strategic plan to rewire the global trade system in America's favor—and to force long-overdue changes in the domestic economy. Here's a breakdown of the core reasons Jack believes this is happening (or will happen) as a result of the tariffs:In a recent episode of The Survival Podcast, host Jack Spirko presents a contrarian view on the current trade war and tariffs imposed by the U.S. government. Far from being a chaotic or irrational policy, Jack argues that these tariffs are part of a broader strategic plan to rewire the global trade system in America's favor—and to force long-overdue changes in the domestic economy. Here's a breakdown of the core reasons Jack believes this is happening (or will happen) as a result of the tariffs:
1. Tariffs Are a Tool, Not the Goal
Jack’s central thesis is that tariffs are not meant to be a permanent fixture—they’re a pressure tactic. The goal isn’t protectionism for its own sake, but rather to reset trade relationships that have historically disadvantaged the U.S. For example, Taiwan responded to the tariffs not with retaliation but by proactively offering to reduce barriers and increase imports from the U.S. That, Jack says, is the intended outcome: cooperation on better terms.
2. Forced Deleveraging to Prevent Collapse
One of the boldest claims Jack makes is that the Trump administration used the tariffs as a catalyst to trigger a “controlled burn” of an over-leveraged stock market. According to him, large institutions were deeply leveraged in equities, and had the bubble popped organically later in the year, it would have required massive bailouts. Instead, the shock caused by tariffs triggered early deleveraging, avoiding systemic failure.
“I’m telling you, a bailout scenario was just avoided... This was intentional.” – Jack Spirko
3. Global Re-shoring and Domestic Manufacturing
Tariffs are incentivizing companies to move production back to the U.S., especially in key areas like semiconductors, energy, and industrial goods. This shift is being further accelerated by global geopolitical instability, creating a “once-in-a-generation” opportunity to rebuild small-town America and domestic supply chains.
4. Not Inflationary—Strategically Deflationary
Jack challenges conventional economic wisdom by arguing that tariffs themselves do not cause inflation, because inflation is a function of monetary expansion—not rising prices alone. In fact, he believes this economic shift may lead to deflation in some sectors, particularly as companies liquidate inventory, lower prices to remain competitive, and reduce reliance on foreign supply chains.
“Rising prices alone are not inflation. Inflation is expansion of the money supply.” – Jack Spirko
5. Energy Costs Will Fall
A drop in global oil prices, partially due to reduced transport needs as manufacturing reshoring increases, plays into the strategy. Jack notes that oil at $60 per barrel weakens adversaries like Russia (whose economy depends heavily on high oil prices) while keeping U.S. production viable. Lower energy costs also benefit domestic manufacturers.
6. The Digital Dollar & Global Dollarization
Alongside this industrial shift, the U.S. is poised to roll out a “digital dollar” infrastructure, giving global access to stablecoins backed by U.S. banks. Jack frames this as an effort to further entrench the dollar as the world’s dominant currency—ensuring continued global demand and export leverage without the need for perpetual military enforcement.
7. A Window of Opportunity for Americans
For individuals, Jack sees this economic transformation as a rare chance to accumulate long-term assets—stocks, Bitcoin, and real estate—while prices are suppressed. He warns that those who panic and sell are operating with a “poverty mindset,” whereas those who stay the course will benefit from what he describes as “the greatest fire sale of productive assets in a generation.”
Conclusion: Not a Collapse, But a Reset
Rather than viewing tariffs as a harbinger of economic doom, Jack presents them as part of a forced evolution—an uncomfortable but necessary reboot of the U.S. economic operating system. Whether or not it works as intended, he argues, this is not a haphazard policy. It’s a calculated reshaping of global and domestic economic dynamics, and one with enormous implications for trade, energy, inflation, and the average American investor.
-
 @ 378562cd:a6fc6773
2025-04-11 22:40:19
@ 378562cd:a6fc6773
2025-04-11 22:40:19Here in the country, we know a thing or two about focus. You can't fix a fence, milk a cow, or hoe a straight row if you're half-distracted or daydreaming about something else. The same applies to anything in life, whether it's trying to finish a project, have a meaningful conversation, or simply sit still long enough to pray. Concentration is a skill that, like all good things, requires a little grit and a lot of practice.
Here’s some practical, common-sense advice to help you buckle down and focus when your mind is spinning a bit too fast.
-
Clear the Mess Before You Start A messy space leads to a messy mind. You wouldn’t gut a deer on the kitchen table, and you shouldn’t expect to think clearly in a cluttered room. Clean up your work area. Put things away. Next, do the same with your mind and jot down everything swirling around in there. Get it out, set it aside, and focus completely on one task at a time.
-
Work Like a Farmer: in Spurts! A farmer doesn’t plow from sunup to sundown without stopping to catch his breath. He works steadily, confidently, but knows when to rest his bones, wipe his brow, and sip a cold drink. That’s the kind of rhythm that gets things done without wearing a man down. Try working in short, focused bursts for about twenty-five minutes, then take a five-minute breather. Stretch your legs, step outside, say a quick prayer, and return to your task. After a few rounds, take a longer break to let your mind cool off. You’ll accomplish more this way and won’t feel worn out by noon.
-
Stop Trying to Juggle Chickens Multitasking may seem impressive, but let’s face it: attempting to accomplish five tasks at once often results in none being done correctly. Concentrate on one task. Give it your all. Then move on. You’ll be more productive and less stressed.
-
Turn Down the Noise Distractions are like flies at a picnic - relentless and annoying. Shoo them away. Keep your phone out of reach. Use apps to block websites that drain your time. Turn off the TV. You cannot harvest peace and quiet if you’re watering weeds.
-
Feed Your Brain Like You Feed Your Livestock Your brain ain’t some spare part you can ignore and still expect to run strong. It needs proper tending, just like the rest of you. So drink plenty of water, not just coffee. Eat real food that grew in the ground or once walked on it, not something cooked up in a lab. Step outside and let the breeze hit your face. Soak up some sunshine and stretch your legs. Move a little; even a short walk can shake the cobwebs loose. It doesn’t take much, but you’ll be surprised what a difference it makes. A well-fed, well-rested mind is a sharp one, ready to do good work and hear what God’s saying through the noise.
-
Start Small, Grow Strong You don’t plant a tree and expect shade the next day. Same with focus. If you can only concentrate for ten minutes at first, that’s fine. Do that. Then, stretch it to fifteen, then thirty. It takes time and a little muscle, like splitting wood or learning to fish.
-
Know Your Why There’s a reason behind everything we do; remembering your reason helps you stay the course. Ask yourself: Why does this matter? Who am I doing this for? What good will come of it? Purpose gives power to your focus.
-
Rest Like It’s Part of the Job—Because It Is Hard work matters, and so does rest. Even the Lord took a day off. Sleep well, take breaks, go for a walk, and let your brain breathe. You don’t have to earn your rest; you just have to honor it. You’ll be sharper when you return.
Final Word from the Porch Concentration ain’t about being superhuman. It’s about making smart choices in small moments. Shut out the noise. Show up for your tasks. Give them your full attention. That’s how fences get mended, stories get written, and lives get changed.
Take it slow. Take it steady. And keep your eye on the prize.
-
-
 @ 9a1adc34:9a9d705b
2025-04-11 01:59:19
@ 9a1adc34:9a9d705b
2025-04-11 01:59:19Testing the concept of using Nostr as a personal CMS.
-
 @ 378562cd:a6fc6773
2025-04-11 00:02:38
@ 378562cd:a6fc6773
2025-04-11 00:02:38What Happens When You Wean Your Digital Life Way Back?
We’re swimming in screens. Notifications, news, and endless feeds are all designed to keep us plugged in, distracted, and running on digital fumes. But what happens when you stop feeding the machine?
What happens when you step back, shut it off, and just… live?
You might be amazed.
Step One: Wean Way Down
Start simple. No grand declarations, but just a quiet rebellion.
Fewer apps. Fewer tabs. Less time online. Maybe you only use the computer in the mornings. Maybe you can turn your phone off in the evening. Maybe Sunday will become a screen-free Sabbath.
The goal? Clear. Clean. Quiet.
At first, it might feel weird. Like quitting sugar or coffee, you’ll feel the pull. But then? Something shifts.
What Starts to Happen… 1. Your Mind Clears Up You stop bouncing from thought to thought. You breathe. You remember what it feels like to think deeply, uninterrupted. Your brain stops buffering and starts building again.
-
Time Slows Down You realize how much time was slipping through your fingers. Without the digital drag, you suddenly have space. You get stuff done. You notice the birds. You fix the fence. You write a letter. You rest. I've personally done these things. It IS AMAZING!
-
You Hear God More Clearly When the digital static dies down, the whisper of God gets louder. Scripture comes alive again. Prayer feels less like a chore and more like a lifeline. You hear Him in the quiet—and sometimes, even in yourself.
-
People Come Back into Focus You stop skimming people like headlines. You sit down, look up, listen, and be present. You find yourself reaching out more, talking longer, and remembering what a real connection feels like.
-
You Feel Alive Again You get energy back, your hands get busy with real work, your body moves, and your sleep deepens. You feel stronger, clearer, and more grounded like your soul has room to breathe again.
It’s Not About Losing—It’s About Gaining Less screen time isn’t about guilt or rules. It’s about freedom. It’s about trading mindless digital noise for something deeper, like clarity, creativity, peace, and presence.
Will you miss some stuff? Sure. But what you’ll gain is real life. Good life.
Try it. Wean way down. Scale Back! Watch what happens.
-
-
 @ ac58bbcc:7d9754d8
2025-04-10 20:00:41
@ ac58bbcc:7d9754d8
2025-04-10 20:00:41Research highlights the importance of using visual representations and precise language to develop students’ conceptual understanding of fractions.
Fractions are a cornerstone of mathematics education, essential for developing robust number sense and laying a solid foundation for algebra and more advanced mathematical pursuits. Despite their significance, fractions present persistent and considerable challenges for numerous learners. This research overview synthesizes key insights from the literature, focusing on the prevalent misconceptions, specific difficulties students encounter, and evidence-based instructional practices promoting a deeper, more conceptual grasp of fractions. This overview aims to equip educators with the knowledge and strategies necessary to foster student success in this critical area by examining the cognitive obstacles and exploring effective teaching approaches. Traditional instruction in fractions often falls short of promoting meaningful understanding, frequently emphasizing procedures and algorithms at the expense of conceptual development (Lamon, 2001).

Understanding the Complexities
Developing a robust understanding of fractions is far from straightforward. Students encounter a variety of conceptual hurdles that can hinder their progress. Research identifies several overarching conceptual challenges that contribute significantly to these difficulties, each stemming from misunderstandings about the nature of fractions and their relationship to other mathematical concepts.
Core Conceptual Challenges
One of the most fundamental challenges is conceptualizing fractions as numbers with magnitude and understanding their position on the number line (Simon et al., 2018). Many students struggle to see fractions as more than parts of a whole, failing to grasp that they represent quantities that can be ordered, compared, and operated on, much like whole numbers. This requires understanding that fractions have a specific location and value on the number line, just as whole numbers do.
A common misconception involves applying whole number rules inappropriately to fractions. For instance, students may believe that a fraction with a larger denominator is always larger or that adding numerators and denominators is the correct way to add fractions. This stems from the tendency to apply additive thinking, appropriate for whole numbers, to multiplicative situations involving fractions.
Grasping fraction equivalence—that different fractions can represent the same quantity (Simon et al., 2018)—is a significant hurdle. It requires recognizing that a fraction can be partitioned into smaller, equivalent units and that multiplying or dividing the numerator and denominator by the same non-zero number results in an equivalent fraction.
Performing arithmetic operations with fractions, notably addition and subtraction with unlike denominators, presents challenges due to a lack of understanding of the roles of numerators and denominators and the necessity of common units (denominators). This requires understanding the concept of common denominators, emphasizing that these represent the same-sized units.
Specific Difficulties
Beyond the broad conceptual challenges, students often grapple with more specific difficulties that stem from limited or flawed understandings:
Many students view fractions as deriving from fractions solely as parts of a whole divided into n equal pieces (n/n). This can hinder their ability to conceptualize improper fractions, as having more parts than the "whole" seems illogical (Simon et al., 2018; Stafylidou & Vosniadou, 2004). This limited view restricts their understanding of fractions to only those less than one, making it challenging to work with mixed numbers and other more complex fraction concepts.
Some students conceive of fractions (m/n, where m<n) solely as an arrangement where a whole is divided into n identical parts, and m parts are designated. They do not understand 1/n or m/n as a quantity, measure, or amount. Based on this limited notion, 1/n and m/n have no meaning when not included as parts in a whole partitioned into n identical parts (Behr, Harel, Post, & Lesh, 1992; Mitchell & Clarke, 2004; Simon, 2006; Simon et al., 2018).
Students often struggle with the concept of a referent unit, understanding a fraction only as a part of the presented totality. The difficulty arises when the referent unit is greater or less than that totality (Simon et al., 2018; Tzur, 1999). Understanding of referent units is generally not emphasized in the development of whole numbers; when whole number development is based on counting, the unit is generally left implicit. This also includes understanding that fractions can represent the same quantity or relationships (ratios) depending on the context and the considered unit.
Effective Instructional Strategies and Representations
Instruction must focus on conceptual development, utilize varied representations, and employ precise language to address the challenges and promote deep understanding.
Building Conceptual Understanding
Traditional "part-whole" language can be limiting. Brendefur and Strother propose using "count" for the numerator to emphasize that it counts the number of equivalent units of a given unit fraction. Moreover, use "unit size" for the denominator to define the size of each unit. Using "1" instead of "whole" reinforces that a fraction’s unit size is determined by the number of equal partitions between any whole numbers or, more precisely, between 0 and 1. For example, partitioning the unit of 1 into 4 equal units would be called "fourths." This precise language helps students conceptualize fractions as measurements of a unit rather than parts of a whole and helps students understand fractions greater than one.
Instruction should promote semantic analyses of written symbols, connecting them with real-world referents (Wearne & Hiebert, 1988). This involves gradually building rich symbolic meanings through connections with appropriate referents, eliminating dependence on rote memorization. Establishing connections between numeric and operational symbols with familiar referents is essential. Note that it is important to use real-world examples that are not circles when introducing fractions. Start with 1-dimensional examples (e.g., ribbon or distance) before moving to 2-dimensional ones. Students can develop a stronger conceptual understanding of fractions by progressing from one-dimensional to two-dimensional examples before encountering more complex circular representations.
Utilizing Multiple Representations
Research highlights the importance of using multiple representations to help students comprehensively understand fractions (Watanabe, 2002). These representations should be explicitly linked to show their connections and move from enactive to iconic and, then, symbolic (Bruner, 1964).
Enactive (Concrete) representations involve hands-on experiences with physical objects. Examples include using fraction bars, pattern blocks, or Cuisenaire rods to represent fractions and perform operations physically. Enactive representations are crucial for initially grounding fraction concepts in concrete experiences, allowing students to manipulate and visualize fractions directly. The connection from action to thought helps students develop a deeper understanding of fraction concepts.
Iconic (Visual) representations involve models that represent fractions, such as number lines and bar models initially, followed by area models. These representations help students transition from enactive experiences to visual support for fraction concepts. Number lines and bar models are particularly effective for illustrating relationships, comparing magnitudes, and building a conceptual understanding of fractions. However, children's understanding of twodimensional figures and their area measurements significantly affects their reasoning with area models of fractions. If this understanding is still developing, the area model may be inappropriate for discussing fractions (Watanabe, 2002).
Symbolic (Abstract) representations involve using mathematical symbols and notation to represent fractions, such as 1/2, 3/4, etc. They are the most abstract form of representation and require students to understand the underlying concepts and relationships represented by the symbols. Instruction should explicitly connect symbolic representations to iconic representations to ensure that students understand the meaning behind the symbols.
Importance of Structural Language
Using precise structural language is essential for helping students develop a clear and flexible understanding of fractions. Words such as unit, partition, iterate, compose, decompose, and equivalence provide a foundation for conceptualizing fractions and their relationships.
Partitioning a unit of 1 into equal-sized units is fundamental to understanding fractions and what the denominator means. Iterating means copying a unit with no gaps and overlaps. For example, the fraction 5/4 means that from 0 to 1 (or within each whole number) is partitioned into four equal units called "fourths." Each one-fourth unit is then iterated five times to create a precise location on a number line. This approach allows students to see fractions as measurable quantities, reinforcing their understanding of fractions as numbers and the numerator as the count of these iterated units.
Composing and decomposing units is a crucial skill in understanding and manipulating fractions. It involves combining or breaking apart fractions of similar or different sizes. This skill forms the foundation for adding and subtracting fractions with both like and unlike denominators. For instance, when solving ¾ + ½, a student might decompose ¾ into ¼ + ½. Then, they can compose the two ½ fractions to form 1, resulting in 1¼. This process demonstrates the importance of creating equivalent fractions with the same unit (denominator) to facilitate addition and subtraction. By decomposing and recomposing fractions, students develop a deeper understanding of fraction equivalence and the flexibility to work with fractions in various forms.
Historical Perspective
Examining math proficiency trends over the past few decades reveals progress and ongoing challenges. For instance, while 4th-grade proficiency rates increased from 13% in 1992 to 42% in 2013 before declining to 36% in 2022, 8thgrade proficiency saw a similar rise from 15% in 1992 to 35% in 2013, only to fall back to 26% in 2022 (National Center for Education Statistics, 2022). More alarmingly, less than 20% of 8th graders consistently demonstrated longterm retention of math facts over these periods, underscoring a persistent issue in mathematics education and highlighting the challenges students face maintaining fluency as they progress through higher grades (National Center for Education Statistics, 2022). Recent data shows a significant decline in math proficiency, particularly following the COVID-19 pandemic. The approach to teaching math facts has evolved over the past century.
Creating Effective Fraction Instruction
Effective fraction instruction requires a multi-faceted approach, prioritizing conceptual understanding and procedural fluency. A key focus should be developing fraction magnitude and sense by encouraging students to estimate, judge the reasonableness of answers and build intuition about fraction operations. Activities such as comparing and ordering fractions, estimating their size, and relating them to benchmarks like 0, 1/2, and 1 on a number line are essential for a deeper understanding of fractions as measurable quantities.
Teachers should also explicitly address common misconceptions, such as treating fractions as separate whole numbers, by designing activities that challenge these misunderstandings directly. Providing opportunities for students to explore fractions through hands-on activities and real-world problems further enhances learning by making abstract concepts more concrete and meaningful. By combining these strategies, educators can create a comprehensive instructional approach that supports students in developing a flexible and confident understanding of fractions.
Conclusion
Fostering a robust understanding of fractions demands a comprehensive and deliberate approach. Educators must move beyond rote memorization and emphasize underlying concepts, varied interpretations, and diverse representations of fractions. Key considerations for instruction include awareness of part-whole versus comparison methods for representing fractions, careful development of partitioning concepts, and sequential instruction that develops symbol meanings before practicing syntactic routines (Watanabe, 2002; Wearne & Hiebert, 1988). By attending to common misconceptions, utilizing precise language, and grounding instruction in meaningful contexts, educators can empower students to develop a flexible and confident understanding of fractions. This approach addresses the immediate challenges of fraction comprehension and sets students up for success in future mathematical endeavors, providing a solid foundation for more advanced mathematical concepts.
References
Behr, M. J., Harel, G., Post, T., & Lesh, R. (1992). Rational number, ratio, and proportion. In D. A. Grouws (Ed.). Handbook of research on mathematics teaching and learning (pp. 296–333). New York: Macmillan.
Brendefur, J. & Strother, S. (n.d.). The effect of math vocabulary instruction on student achievement. Developing Mathematical Thinking Institute. www.dmtinstitute.com.
Bruner, J. S. (1964). Toward a theory of instruction. Cambridge, MA: Belknap Press.
Lamon, S. J. (2001). Presenting and representing: From fractions to rational numbers. In A. A. Cuoco, & F. R. Curcio (Eds.), The roles of representation in school mathematics (pp. 146–165). Reston, VA: National Council of Teachers of Mathematics.
Mitchell, A., & Clarke, D. M. (2004). When is three quarters not three quarters? Listening for conceptual understanding in children’s explanations in a fractions interview. In I. Putt, R. Farragher, & M. McLean (Eds.). Mathematics education for the third millennium: Towards 2010 (Proceedings of the 27th Annual Conference of the Mathematics Education Research Group of Australasia (pp. 367–373).
Simon, M. A. (2006). Key developmental understandings in mathematics: A direction for investigating and establishing learning goals. Mathematical Thinking and Learning, 8(4), 359–371.
Simon, M. A., Placa, N., Avitzur, A., & Kara, M. (2018). Promoting a concept of fraction-as-measure: A study of the Learning Through Activity research program. The Journal of Mathematical Behavior, 51, 11-30.
Stafylidou, S., & Vosniadou, S. (2004). The development of students’ understanding of the numerical value of fractions. Learning and Instruction, 14(5), 503-518.
Tzur, R. (1999). An integrated study of children’s construction of improper fractions and the teacher’s role in promoting that learning. Journal for Research in Mathematics Education, 30(4), 390–416.
Watanabe, T. (2002). Representations in Teaching and Learning Fractions. Teaching Children Mathematics, 8(8), 457- 463.
Wearne, D., & Hiebert, J. (1988). A Cognitive Approach to Meaningful Mathematics Instruction: Testing a Local Theory Using Decimal Numbers. Journal for Research in Mathematics Education, 19(5), 371-384.
Social Media
Research highlights the importance of using visual representations and precise language to develop students’ conceptual understanding of fractions. Tools like number lines and bar models have proven especially effective for illustrating fraction relationships, comparing magnitudes, and supporting problem-solving across various fraction contexts. These representations help students see fractions as measurable quantities, bridging the gap between iconic representations and symbolic notation.
Moreover, research suggests that precise language—such as “count,” “unit size,” “partition,” and “iterate”—is essential for fostering a deeper understanding of fractions. Moving beyond traditional part-whole descriptions, this structural language emphasizes fraction equivalence and flexibility in reasoning. By combining visual tools with clear language, educators can help students build a strong foundation in fractions, setting them up for success in advanced mathematics and real-world applications.
Join us in exploring these powerful learning strategies and their impact on early mathematical thinking!
-
 @ 88cc134b:5ae99079
2025-04-10 16:02:49
@ 88cc134b:5ae99079
2025-04-10 16:02:49sasas sasa sasa
-
 @ a0c34d34:fef39af1
2025-04-10 09:13:12
@ a0c34d34:fef39af1
2025-04-10 09:13:12Let’s talk longevity and quality of life. Have you prepared for Passover or Easter? Do you celebrate either? I’m going to my niece’s house for Passover and I will be devouring brisket and strawberry shortcake. I use to love the Easter candy my neighbor shared when I was a kid. Taboo during Passover but I snuck a peep or two. How afraid are you about the future? Are you keeping up with longevity technology? Do you have the dream of living a long, long life? Longevity technology combines the power of medicine, biotechnology and artificial intelligence to extend a healthy human lifespan. It’s about using cutting edge technology and medical advancements to extend the years we live in good health. The focus is on quality of life during extended years. With the rise of AI powered longevity clinics, treatments tailored to an individual’s genetic profile, lifestyle and medical history, and customized anti-aging interventions, personalized healthcare will become a reality over the next decade. I’m scared I won’t be able to afford housing or healthcare. Advanced medical services cost money, and they are only going to rise. As we stay independent longer and capable of living on our own, there will be more “smart” solutions available, more longevity technology advances. Imagine using the technology of today to have a home where you feel safe for your mother or grandmother so they can live independently. The costs of technology for a “smart” house? Running lights on the floorboards light up as you walk by, just one item I can think of that can keep senior citizens safe at home. I developed a plan for a 55+ community for senior citizens. I have seen similar plans. I think blockchain technology and utilizing tokenomics can only make housing cost effective for senior citizens in the future. When I sat down and wrote the Executive Summary for Onboard60 three years ago, a component was to develop a 55+ Active Senior Community using tokenomics, smart contracts and blockchain technology. Since then, when I say I want to make Onboard60 like the AARP of today, I’ve been told that’s impossible, not going to work and I am wasting my time with this whole project, senior citizens aren’t interested. They will be. As we move into a population explosion of senior citizens living longer, healthy and independently, I think we need to consider how we are going to afford our longevity. What type of care will you receive, how much will it cost? What will you be able to control as in the cost, the level of care you receive. What currency is used? Yes, currency. As we move forward with the integration of cryptocurrency into our financial system, we need to think of what currency is accepted. There will be facilities that use their own stablecoin or accept certain others. The non-traditional financial systems are here to stay. The United States has incorporated a few different cryptocurrencies. Large financial institutions have adapted to putting cryptocurrency into their investment portfolios. I didn’t expect this to happen in my lifetime. Seriously, I thought Onboard60 would have a few more years to develop, create a community of senior citizens. That’s not the case. The world is accelerating at an impossible rate to keep up with everything. It can be overwhelming and scary. How do I find companies that use blockchain and smart contracts? Are there companies where I can protect my property rights by putting them on chain? Are there health insurance companies that use smart contracts? Onboard60 is more than the Metaverse, YouTube and A Handbook for Noobies (Web3 1101 for Seniors). It’s about staying informed, safely, to achieve the future every senior citizen deserves. If you have any knowledge of such companies, please let me know. I have crypto accountants and lawyers in my toolbox. I look forward to adding to my toolbox. I want to be like the AARP for today’s world.
Thanks for reading, Be fabulous, Sandra Abrams Founder Onboard60
-
 @ 3b3a42d3:d192e325
2025-04-10 08:57:51
@ 3b3a42d3:d192e325
2025-04-10 08:57:51Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Trading and enforcement of asset option contracts
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ 378562cd:a6fc6773
2025-04-09 17:11:25
@ 378562cd:a6fc6773
2025-04-09 17:11:25So, this is the way I see things...
Bitcoin’s rise is not merely a technological revolution—it serves as a masterclass in game theory unfolding in real time. At its core, game theory examines how individuals make decisions when outcomes rely on the choices of others. Bitcoin adoption adheres to this model precisely.
Imagine a global network where each new participant increases the value and security of the system. Early adopters take a risk, hoping others will follow. The incentive to join grows stronger as more people opt in—whether out of curiosity, conviction, or FOMO. No one wants to be last to the party, especially if that party rewrites financial history.
Here’s how the game theory of adoption plays out:
-
🧠 First movers take risks but gain the most—they enter when the price is low and the potential is high.
-
👀 Everyone watches everyone else—people, companies, and countries are scanning the field for the next move.
-
The network effect kicks in—the more players are in the game, the more valuable and secure the system becomes.
-
⏳ Waiting can cost you—as adoption grows, the price of entry rises, making hesitation expensive.
-
No one wants to be left behind—especially in a global economy battling inflation and instability.
Game theory tells us that smart players make decisions that bring them the most goodies. As Bitcoin gets more popular, it’s like a party that’s really heating up, and you don’t want to be the one left outside! In this thrilling game, the early bird doesn’t just get the worm—it lands a juicy opportunity in a brand-new way to spend money. So don’t dawdle; now’s the time to jump in and grab your piece of this financial fiesta!
-
-
 @ 88cc134b:5ae99079
2025-04-09 12:29:29
@ 88cc134b:5ae99079
2025-04-09 12:29:29 -
 @ 88cc134b:5ae99079
2025-04-09 11:34:56
@ 88cc134b:5ae99079
2025-04-09 11:34:56text
-
 @ 04c195f1:3329a1da
2025-04-09 10:54:43
@ 04c195f1:3329a1da
2025-04-09 10:54:43The old world order is crumbling. What was once considered stable and unshakable—the American-led global framework established after World War II—is now rapidly disintegrating. From the fraying fabric of NATO to the self-serving protectionism of Trump’s renewed presidency, the signals are clear: the empire that once held the Western world together is retreating. And in the vacuum it leaves behind, a new power must emerge.
The question is: will Europe finally seize this moment?
For decades, Europe has relied on the illusion of safety under an American umbrella. This dependency allowed us to indulge in what can only be described as “luxury politics.” Instead of strengthening our core institutions—defense, infrastructure, energy independence—we poured our energy into ideological experiments: value-based governance, multiculturalism, aggressive climate goals, and endless layers of bureaucracy.
We let ourselves believe history had ended. That war, scarcity, and geopolitical struggle were things of the past. That our greatest challenges would be inclusivity, carbon credits, and data protection regulations.
But history, as always, had other plans.
Trump, Nationalist Hope and Hard Reality
Across Europe, many nationalists and conservatives initially welcomed Donald Trump. He rejected the tenets of liberal globalism, called out the absurdities of woke ideology, and promised a return to realism. In a world saturated by progressive conformity, he seemed like a disruptive breath of fresh air.
And to a certain extent, he was.
But history will likely remember his presidency not for culture wars or conservative rhetoric—but for something far more consequential: the dismantling of the American empire.
What we are witnessing under Trump is the accelerated withdrawal of the United States from its role as global enforcer. Whether by design or incompetence, the result is the same. American institutions are retracting, its alliances are fraying, and its strategic grip on Europe is loosening.
For Americans, this may seem like decline. For Europe, it is an opportunity—an uncomfortable, painful, but necessary opportunity.
This is our chance to break free from the American yoke and step into the world as a sovereign power in our own right.
The End of Illusions
Europe is not a weak continent. We have a population larger than the United States, an economy that outpaces Russia’s many times over, and centuries of civilizational strength behind us. But we have been kept fragmented, distracted, and dependent—by design.
Both Washington and Moscow have an interest in a divided, impotent Europe. American strategists see us as junior partners at best, liabilities at worst. Russian elites, like Sergey Karaganov, openly admit their goal is to push Europe off the global stage. China, for its part, eyes our markets while quietly maneuvering to undermine our autonomy.
But something is changing.
In Brussels, even the ideologically captured technocrats are beginning to see the writing on the wall. Overbearing regulations like GDPR are being reconsidered. The long-pushed Equal Treatment Directive—a pan-European anti-discrimination law—may finally be scrapped. These are small signs, but signs nonetheless. Europe is waking up.
From Fracture to Foundation
To build something new, the old must first fall. That collapse is now well underway.
The collapse of American hegemony does not mean the rise of chaos—it means the opening of a path. Europe has a choice: continue to drift, clinging to broken institutions and obsolete alliances, or embrace the challenge of becoming a serious actor in a multipolar world.
This does not mean copying the imperial ambitions of others. Europe’s strength will not come from domination, but from independence, coherence, and confidence. A strong Europe is not one ruled from Brussels, but one composed of strong, rooted nations acting together in strategic alignment. Not a federation, not an empire in the classical sense—but a civilization asserting its right to survive and thrive on its own terms.
At the same time, we must not fall into the trap of romantic isolationism. Some nationalists still cling to the idea that their nation alone can stand firm on the global stage, detached from continental collaboration. That vision no longer matches the geopolitical reality. The world has changed, and so must our strategy. In key areas—such as defense, border security, trade policy, and technological sovereignty—Europe must act with unity and purpose. This does not require dissolving national identities; it requires mature cooperation among free nations. To retreat into purely national silos would be to condemn Europe to irrelevance. Strengthening the right kind of European cooperation—while returning power in other areas to the national level—is not a betrayal of nationalism, but its necessary evolution.
A Third Position: Beyond East and West
As the American empire stumbles and Russia attempts to fill the void, Europe must not become a pawn in someone else’s game. Our task is not to shift allegiance from one master to another—but to step into sovereignty. This is not about trading Washington for Moscow, or Beijing. It is about rejecting all external domination and asserting our own geopolitical will.
A truly pro-European nationalism must recognize that our civilizational future lies not in nostalgia or subservience, but in strategic clarity. We must build a third position—a pole of stability and power that stands apart from the decaying empires of the past.
That requires sacrifice, but it also promises freedom.
Hope Through Action
There is a romantic notion among some European nationalists that decline is inevitable—that we are simply passengers on a sinking ship. But fatalism is not tradition. It is surrender.
Our ancestors did not build cathedrals, repel invaders, or chart the globe by giving in to despair. They acted—often against impossible odds—because they believed in a Europe worth fighting for.
We must now rediscover that spirit.
This is not a call for uniformity, but for unity. Not for empire, but for sovereignty. Not for nostalgia, but for renewal. Across the continent, a new consciousness is stirring. From the Alps to the Baltic, from Lisbon to Helsinki, there are voices calling for something more than submission to global markets and American whims.
They are calling for Europe.
The Hour Has Come
There may not be a second chance. The tide of history is turning, and the next ten years will determine whether Europe reclaims its role in the world—or becomes a museum piece, mourned by tourists and remembered by none.
This is not the end.
It is our beginning—if we are brave enough to seize it.
■
-
 @ 39cc53c9:27168656
2025-04-09 07:59:35
@ 39cc53c9:27168656
2025-04-09 07:59:35The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ a367f9eb:0633efea
2025-04-09 07:28:49
@ a367f9eb:0633efea
2025-04-09 07:28:49WIEN – Diese Woche enthüllte Innenminister Gerhard Karner von der ÖVP, dass er einen Gesetzesentwurf "schnell" durchsetzen möchte, der der Regierung die Befugnis geben würde, verschlüsselte Kommunikation in Nachrichten-Apps zu überwachen.
Obwohl Karner betont hat, dass die neuen Befugnisse nur sehr gezielt eingesetzt würden, ist unklar, ob die Entwickler und Anbieter von Nachrichten-Apps gezwungen werden sollen, die Verschlüsselung zu brechen, um die Anordnungen durchzuführen.
Wie der stellvertretende Direktor des Consumer Choice Center, Yaël Ossowski, erklärte, würde diese Befugnis bedeuten, die Verschlüsselung für Millionen von österreichischen Verbrauchern zu untergraben und zu brechen.
„Jeder Versuch, die Verschlüsselung für einige ausgewählte Personen zu brechen, gefährdet gleichzeitig die Privatsphäre von Millionen von Österreichern. Dies ist weniger eine Frage der angemessenen Polizeibefugnisse als vielmehr eine Frage der technischen und sicherheitsrelevanten Aspekte. Schwächere Verschlüsselung macht österreichische Nutzer weniger sicher“ sagte Ossowski.
„Verschlüsselungsstandards von Apps wie Signal, WhatsApp und sogar iMessage aufzuheben, würde der österreichischen Regierung außergewöhnliche Befugnisse einräumen, die das Risiko bergen, jede und alle Kommunikation zu kompromittieren, nicht nur die von Verdächtigen oder Terroristen.
„Um gegen kriminelle Akteure vorzugehen, sollte die Koalition das bestehende Justizsystem nutzen, um Haftbefehle auf Grundlage eines begründeten Verdachts durchzusetzen, anstatt Messaging-Dienste und Apps dazu zu zwingen, diese Aufgabe für sie zu übernehmen“ erklärte Ossowski.
Das Consumer Choice Center weist darauf hin, dass ähnliche Versuche, die Verschlüsselung mit polizeilicher Gewalt zu brechen, bereits im Vereinigten Königreich und in Frankreich unternommen wurden, wo sie von Bürgerrechtsgruppen abgelehnt wurden.
###
Das Consumer Choice Center ist eine unabhängige, parteiunabhängige Verbraucherorganisation, die die Vorteile von Wahlfreiheit, Innovation und Wachstum im Alltagsleben für Verbraucher in über 100 Ländern fördert. Wir interessieren uns insbesondere für regulatorische Trends in Washington, Brüssel, Wien, Berlin, Ottawa, Brasília, London und Genf genau.
Erfahren Sie mehr auf consumerchoicecenter.org
-
 @ 8ba66f4c:59175b61
2025-04-08 18:19:43
@ 8ba66f4c:59175b61
2025-04-08 18:19:43👶 Je vais bientôt devenir papa.
Et ces derniers temps, une question me hante plus que je ne l’aurais cru : faut-il publier des photos de son enfant sur les réseaux sociaux ?C’est une réflexion que je n’avais jamais vraiment poussée avant.
Mais aujourd’hui, elle me semble incontournable. Parce qu’à l’ère des smartphones et des stories, poster devient un réflexe. On documente tout : les premières échographies, la chambre qu’on prépare, les petits vêtements, les premiers sourires… Et l’envie de partager est naturelle. C’est beau, c’est émouvant, on a envie de dire au monde qu’on est fier, qu’on est heureux.Mais voilà.
Plus j’y pense, plus je me dis que cette impulsion entre en tension avec d’autres principes qui me tiennent tout autant à cœur.D’abord, la question du consentement.
Mon enfant ne pourra pas me dire : « Je suis d’accord pour que tu postes cette photo ». Ni maintenant, ni dans quelques années quand les images auront déjà circulé. Il n’aura pas choisi de grandir avec une identité numérique créée pour lui, sans lui.
Ensuite, la protection de sa vie privée.
Une photo postée, même dans un cadre soi-disant « privé », peut être capturée, partagée, détournée, utilisée hors contexte. Il n’y a pas de bouton magique pour effacer ce qui est déjà parti sur les serveurs d’une plateforme.
Et aujourd’hui, il faut aussi parler de l’usage de ces images par les intelligences artificielles.
De nombreuses IA sont entraînées en partie à partir de données en ligne, y compris des photos. Ce qui signifie que le visage de mon enfant, s’il est mis en ligne, pourrait un jour se retrouver dans un dataset d’apprentissage, intégré à un modèle génératif, voire utilisé pour créer des deepfakes ou pour « entraîner » des applications que je n’ai jamais autorisées à le voir.
On ne parle plus seulement de vie privée. On parle d’exploitation, d’automatisation, de réutilisation potentiellement incontrôlable.Et puis, il y a la dimension éducative.
Quel exemple est-ce que je donne si je lui demande plus tard d’être prudent sur Internet, alors que moi-même j’aurais documenté toute son enfance en ligne, sans filtre ? Si je veux qu’il comprenne ce que veut dire « intimité », je dois sans doute commencer par la respecter dès ses premiers jours.
Ce n’est pas un jugement. Je comprends l’élan de publier, de partager, de célébrer.
Mais je crois que l’époque demande qu’on s’arrête deux secondes avant de poster. Et qu’on se demande :
– Pourquoi est-ce que je partage cette image ?
– À qui est-ce qu’elle appartient, au fond ?
– Et quel monde numérique je construis pour mon enfant, dès aujourd’hui ?Et vous, parents ou futurs parents, vous avez réfléchi à ça ? Vous partagez ? Vous vous retenez ?
Je serais curieux de lire vos retours. 🙏 -
 @ 8ba66f4c:59175b61
2025-04-08 18:03:53
@ 8ba66f4c:59175b61
2025-04-08 18:03:53Récemment, plusieurs membres du gouvernement ont évoqué cette possibilité : restreindre l’accès à certaines plateformes sociales en période de crise, pour limiter les débordements, les appels à la violence, ou les "fake news".
L'idée n'est pas présentée comme une censure, bien sûr. Plutôt comme une mesure "temporaire", "exceptionnelle", et "proportionnée".Mais en réalité, ce débat n’a rien d’anodin. Et il mérite une attention bien plus large que les quelques articles qui l’ont mentionné en marge de l’actualité.
Pourquoi ça pose (vraiment) problème ?
Parce que l’idée même de couper un réseau social, même temporairement, ouvre une brèche.
Un précédent.
Et dans l’histoire des démocraties modernes, les précédents deviennent vite des habitudes, surtout quand ils sont adossés à des notions floues comme "l’ordre public" ou "l’urgence".En France, comme dans l’Union européenne, les libertés de communication et d’expression sont des droits fondamentaux.
Et jusqu’ici, nous avons toujours critiqué – à juste titre – les pays qui bloquent Internet ou les réseaux sociaux :
- En Iran, en Inde, en Turquie, en Russie ou en Égypte.
- Pour des raisons souvent similaires : maintenir le calme, éviter la désinformation, empêcher la mobilisation.Mais dans les faits, ces coupures sont systématiquement utilisées pour neutraliser une contestation, contrôler un récit, ou empêcher la documentation de violences.
Et chaque fois, la presse française, les ONG, et les démocraties occidentales ont dénoncé ces actes.Alors que se passera-t-il le jour où la France appliquera ce qu'elle a longtemps dénoncé ?
La seule vraie solution, ce n’est pas plus de contrôle. C’est plus de résilience.
Face à cette dérive potentielle, des outils existent déjà.
Des protocoles pensés pour fonctionner sans autorité centrale, sans serveur unique, sans identifiant imposé.
Des réseaux impossibles à couper, à censurer, ou à faire taire d’un simple décret.Parmi eux, un nom commence à se faire une place : Nostr.
Pourquoi Nostr change la donne
Nostr, ce n’est pas une énième alternative à Twitter.
C’est un protocole minimaliste, décentralisé, libre.
Il permet à n’importe qui de publier, relayer, lire, sans dépendre d’une plateforme ou d’un serveur.✅ Identité basée sur une clé publique : pas besoin de mail, ni de téléphone.
✅ Données signées cryptographiquement : pas de falsification, pas de shadowban.
✅ Clients multiples, relays multiples, aucune infrastructure unique à cibler.
✅ Modération décentralisée : chacun décide ce qu’il veut voir ou pas.
✅ Possibilité de tourner sur Tor, en local, ou même de publier via satellite ou ondes radio si besoin.C’est simple : il n’existe aucun “bouton rouge” pour éteindre Nostr.
Et c’est précisément ce qui en fait un outil de liberté, et pas seulement un réseau social.En 2025, nous ne devrions pas avoir à nous préparer à contourner la censure.
Mais si même les démocraties commencent à l’envisager comme une option “raisonnable”, alors il est plus que temps de se poser les bonnes questions.
Et de s’outiller.Curieux de savoir qui ici a déjà testé Nostr ?
Utilisez-vous des clients comme Amethyst, Damus, Iris, Snort ou autre ?
Est-ce que vous y voyez un futur solide pour des communications libres ? -
 @ 88cc134b:5ae99079
2025-04-08 12:35:01
@ 88cc134b:5ae99079
2025-04-08 12:35:01Tester one one two and three nostr:nprofile1qyv8wumn8ghj7urjv4kkjatd9ec8y6tdv9kzumn9wsq3yamnwvaz7tmsw4e8qmr9wpskwtn9wvqzpzxvzd935e04fm6g4nqa7dn9qc7nafzlqn4t3t6xgmjkr3dwnyreaytcqa, some
nostr:nevent1qvzqqqqqqypzpzxvzd935e04fm6g4nqa7dn9qc7nafzlqn4t3t6xgmjkr3dwnyreqyvhwumn8ghj7urjv4kkjatd9ec8y6tdv9kzumn9wshszymhwden5te0wp6hyurvv4cxzeewv4ej7qpq6mw92lz87fqsca2gn3jkm2rd3xexcapjd5vscysx4r79y672ukrqy5utlm
-
 @ 88cc134b:5ae99079
2025-04-07 13:45:06
@ 88cc134b:5ae99079
2025-04-07 13:45:06Heading
Body text hello
nostr:nevent1qvzqqqqqqypzpclca3vtuwz4ypdjx9ywcceuzs7yka76rh23wrjvurdv9r4zwremqqsw7tttdcf90wem2hvjd7pyncu3h6teldw2jppgjuh9l7h4ymgt4wcl74wgx
-
 @ 88cc134b:5ae99079
2025-04-07 12:19:39
@ 88cc134b:5ae99079
2025-04-07 12:19:39Tester one one two and three nostr:nprofile1qyv8wumn8ghj7urjv4kkjatd9ec8y6tdv9kzumn9wsq3yamnwvaz7tmsw4e8qmr9wpskwtn9wvqzpzxvzd935e04fm6g4nqa7dn9qc7nafzlqn4t3t6xgmjkr3dwnyreaytcqa, some
nostr:nevent1qvzqqqqqqypzpzxvzd935e04fm6g4nqa7dn9qc7nafzlqn4t3t6xgmjkr3dwnyreqyvhwumn8ghj7urjv4kkjatd9ec8y6tdv9kzumn9wshszymhwden5te0wp6hyurvv4cxzeewv4ej7qpq6mw92lz87fqsca2gn3jkm2rd3xexcapjd5vscysx4r79y672ukrqy5utlm
-
 @ 88cc134b:5ae99079
2025-04-07 10:54:16
@ 88cc134b:5ae99079
2025-04-07 10:54:16What!?
-
 @ 88cc134b:5ae99079
2025-04-07 10:50:09
@ 88cc134b:5ae99079
2025-04-07 10:50:09Test
testing test
-
 @ ac58bbcc:7d9754d8
2025-04-05 21:32:47
@ ac58bbcc:7d9754d8
2025-04-05 21:32:47Unlocking Learning Potential: How Math Model Transform Learning
Introduction:
In mathematics education, fostering a learning environment that encourages a variety of problem-solving strategies and emphasizes the structural foundations of mathematical concepts is crucial for student success. One key instructional element is using mathematical models to help students bridge their informal understandings with formal, symbolic mathematical reasoning. Encouraging students to use models, particularly iconic representations, is vital in developing conceptual and procedural knowledge. This research overview explores how modeling enhances student learning by progressing from intuitive representations to more formalized mathematical reasoning, focusing on the importance of iconic models in building a deeper understanding of mathematics.

FREE DOWNLOAD - Questions and Prompts
Theoretical Foundations
Taking students' ideas seriously is grounded in constructivist learning theory and research on how students develop mathematical understanding. Hiebert and Carpenter (1992) argue that "if children possessed internal networks constructed both in and out of school and if they recognized the connections between them, their understanding and performance in both settings would improve." This highlights the importance of connecting students' informal knowledge with formal mathematical concepts. Carpenter's work further emphasizes the value of students' intuitive knowledge: "Children come to school with a great deal of informal or intuitive knowledge of mathematics that can serve as the basis for developing much of the formal mathematics of the primary school curriculum." This suggests that taking students' initial ideas seriously can provide a strong foundation for developing a more sophisticated mathematical understanding.
The Role of Models in Mathematical Thinking
Modeling is a powerful tool for nurturing mathematical thinking because it helps students move from concrete experiences to abstract reasoning. According to Romberg and Kaput (1999), when students first encounter mathematical problems, they naturally rely on informal strategies based on their real-world experiences. The modeling process allows these initial intuitive approaches to serve as scaffolding for solving more complex, related problems. Through modeling, students solve a specific problem and develop general strategies that can be applied across different mathematical contexts.
Gravemeijer and van Galen (2003) argue that modeling real-world situations is foundational for understanding mathematical structures. This process often begins with students using informal, tangible representations, which evolve into more formal mathematical reasoning as they progress. Cobb (2000) describes this as a shift in classroom practice, where students’ informal activities, such as using objects or drawings, are eventually formalized into mathematical reasoning. The key to this transformation lies in how well students can transition between different forms of representation: enactive, iconic, and symbolic models (Bruner, 1964).
The Progression of Mathematical Models
A critical component of effective mathematics instruction is the concept of progressive formalization, which guides students through the stages of representation. As students work through mathematical problems, they begin with enactive models—physical representations or manipulatives that help them visualize the problem. From there, students move on to iconic models, which involve pictorial representations, such as diagrams, number lines, and graphs, that symbolize the relationships in the problem. Finally, they transition to symbolic models, which use formal mathematical tables, notation, and equations to organize and represent abstract concepts (Bruner, 1964).
The transition from iconic to symbolic models is particularly important because it helps students visualize and understand abstract mathematical concepts without losing the connection to real-world problems. In many curricula, students are often asked to solve problems using multiple methods, but these methods may only sometimes lead to the progressive formalization needed for deep understanding. Iconic models, such as number lines that promote distance, magnitude, and proportion, serve as a critical bridge between concrete and abstract reasoning, allowing students to visualize the relationships between numbers and operations before transitioning to formal symbols (Leinwand & Ginsburg, 2007).
Iconic Models and Their Importance
Iconic models play a unique role in mathematics education by offering visual representations that make abstract concepts more accessible. For example, the area model is a powerful iconic representation used in teaching multiplication and division. When students are presented with a contextualized problem, such as determining the number of tiles needed to cover a floor, they can use an area model to visualize the relationships among length, width, and area. This iconic representation helps students see multiplication in two dimensions, preparing them for more formal mathematical concepts such as algebra (Watanabe, 2015).
The strength of iconic models lies in their ability to illuminate different aspects of mathematical relationships. Unlike abstract symbolic representations, which can be difficult for students to grasp, iconic models make the problem tangible and concrete. Students can manipulate the models, explore different problem-solving strategies, and visually see the consequences of their actions. This tactile and visual exploration deepens their conceptual understanding and supports the transition to more abstract forms of reasoning (Bruner, 1964).
For instance, using a number line as an iconic model for fractions allows students to visualize the relative size of different fractions, helping them understand concepts such as equivalence and comparison. Similarly, bar models can represent proportions, ratios, or algebraic relationships. These iconic models provide a clear, visual framework for understanding the underlying structure of mathematical problems, and they encourage students to explore multiple solution strategies.
Modeling in Curriculum Design
Integrating modeling into mathematics curricula has fostered deeper student engagement and understanding. However, educators must select contexts and tasks that naturally lead students from informal models to more formal, mathematically robust representations. For example, when teaching multiplication, students may begin by solving problems about grouping objects or creating arrays. These problems encourage using iconic models, such as drawing rows and columns to represent multiplication as an area, before transitioning to symbolic equations (Leinwand & Ginsburg, 2007).
Curricula that prioritize the progression from enactive to iconic to symbolic models help students build a solid foundation for understanding more advanced mathematical concepts. For example, suppose an educator aims for students to use the area model as an iconic representation. In that case, they might introduce problems involving geometric concepts, such as covering flat spaces with tiles or using gridlines on a map to calculate distances. These activities make math more tangible and foster logical connections for students to develop more formal mathematical reasoning (Watanabe, 2015).
Additionally, students’ engagement with different models enhances their ability to communicate and justify their mathematical thinking. When asked to explain how they arrived at a solution using an iconic model, they must articulate the mathematical relationships they observe, which promotes a deeper understanding. This process also aligns with socio-mathematical norms, where students learn to evaluate the efficiency and effectiveness of different models and strategies through classroom discussion and peer feedback.
The Cognitive Benefits of Modeling
From a cognitive psychology perspective, using models in mathematics education helps bridge the gap between procedural and conceptual knowledge. Research by Gilmore and Papadatou-Pastou (2009) suggests that procedural fluency and conceptual understanding are interconnected, with advancements in one area reinforcing the other. The iterative development of models provides students with opportunities to build both procedural skills—through repeated practice—and conceptual knowledge—by visualizing and manipulating the mathematical structures underlying the problems they solve.
Bruner’s (1964) theory of representation emphasizes the importance of guiding students through the different representational forms—enactive, iconic, and symbolic—without imposing abrupt transitions. The gradual transition from one form of representation to another enables students to develop a deeper, more integrated understanding of mathematical concepts, reducing the cognitive load associated with learning new material. This approach allows students to internalize mathematical concepts more effectively, making them better prepared to tackle more complex problems in the future
Conclusion
In conclusion, mathematical modeling is a critical framework for helping students develop a deeper understanding of mathematics by progressing through enactive, iconic, and symbolic representations. Iconic models, in particular, are essential for bridging the gap between students’ informal understandings and the abstract formalism of mathematical reasoning. Educators can foster environments where students are encouraged to explore, innovate, and deepen their understanding of mathematical structures by emphasizing using models in mathematics instruction. This progressive formalization supports procedural fluency and conceptual knowledge, preparing students to thrive in mathematics and beyond.
Integrating modeling into curricula and thoughtfully selecting tasks that support the progression from informal to formal reasoning empowers students to recognize the diverse methods for solving problems and encourages them to develop their unique mathematical insights. As school administrators and educators, fostering an environment that supports these pedagogical practices is critical to nurturing the next generation of mathematical thinkers.
References
Bruner, J. S. (1964). The course of cognitive growth. American Psychologist, 19(1), 1-15.
Cobb, P. (2000). Conducting teaching experiments in collaboration with teachers. In A. E. Kelly & R. A. Lesh (Eds.), Handbook of research design in mathematics and science education (pp. 307-333). Lawrence Erlbaum Associates.
Gilmore, C. K., & Papadatou-Pastou, M. (2009). Patterns of individual differences in conceptual understanding and arithmetical skill: A meta-analysis. Mathematical Thinking and Learning, 11(1-2), 25-40.
Gravemeijer, K., & van Galen, F. (2003). Facts and algorithms as products of students’ own mathematical activity. In J. Kilpatrick, W. G. Martin, & D. Schifter (Eds.), A research companion to principles and standards for school mathematics (pp. 114-122). National Council of Teachers of Mathematics.
Leinwand, S., & Ginsburg, A. L. (2007). Learning from Singapore math. Educational Leadership, 65(3), 32-36.
Romberg, T. A., & Kaput, J. J. (1999). Mathematics worth teaching, mathematics worth understanding. In E. Fennema & T. A. Romberg (Eds.), Mathematics classrooms that promote understanding (pp. 3-17). Lawrence Erlbaum Associates.
Watanabe, T. (2015). Visual reasoning tools in action. Mathematics Teaching in the Middle School, 21(3), 152-160.
-
 @ ac58bbcc:7d9754d8
2025-04-05 18:59:02
@ ac58bbcc:7d9754d8
2025-04-05 18:59:02Unlocking Learning Potential: Why Student's Ideas Matter
Introduction
Recent research in mathematics education emphasizes the importance of valuing and building upon students' initial ideas and intuitive understanding. This approach, often referred to as "taking students' ideas seriously," has enhanced conceptual understanding, problem-solving skills, and overall mathematical achievement. This overview examines this approach's theoretical foundations, cognitive processes, and practical implications in mathematics classrooms.

FREE DOWNLOAD - Questions and Prompts
Theoretical Foundations
Taking students' ideas seriously is grounded in constructivist learning theory and research on how students develop mathematical understanding. Hiebert and Carpenter (1992) argue that "if children possessed internal networks constructed both in and out of school and if they recognized the connections between them, their understanding and performance in both settings would improve." This highlights the importance of connecting students' informal knowledge with formal mathematical concepts. Carpenter's work further emphasizes the value of students' intuitive knowledge: "Children come to school with a great deal of informal or intuitive knowledge of mathematics that can serve as the basis for developing much of the formal mathematics of the primary school curriculum." This suggests that taking students' initial ideas seriously can provide a strong foundation for developing a more sophisticated mathematical understanding.
Cognitive Processes
When students' ideas are taken seriously in mathematics classrooms, several cognitive processes are engaged:
-
Schema Formation: As students articulate and refine their ideas, they develop and modify mental frameworks or schemas that organize mathematical concepts.
-
Metacognition: Explaining their thinking engages students' metacognitive processes, promoting reflection on their own understanding and problem-solving strategies.
-
Elaborative Rehearsal: Verbalizing mathematical concepts helps move information from working memory to long-term memory, enhancing retention.
-
Cognitive Conflict: When students encounter differing viewpoints, it can create cognitive conflict, stimulating the reconciliation of new information with existing schemas.
Practical Implications
Eliciting and Valuing Student Ideas
Carpenter and Lehrer argue that for learning with understanding to occur, instruction needs to provide specific opportunities: "For learning with understanding to occur, instruction needs to provide students the opportunity to develop productive relationships, extend and apply their knowledge, reflect about their experiences, articulate what they know, and make knowledge their own." This emphasizes the need for instructional approaches that actively elicit and value student ideas.
Creating a Supportive Environment
To effectively take students' ideas seriously, teachers must foster a classroom environment where all contributions are respected. This involves:
-
Provide adequate thinking time for students to formulate their thoughts.
-
Using open-ended questions that encourage diverse thinking and approaches.
-
Implementing collaborative strategies like think-pair-share to build confidence in sharing ideas.
Connecting to Formal Mathematics
Hiebert advocates for teaching practices that promote understanding by focusing on "the inherent structure of the emerging mathematical ideas and addressing students' misconceptions as they arise" . This involves helping students connect their informal ideas to more formal mathematical concepts and procedures.
Impact on Student Learning
Research indicates that taking students' ideas seriously can significantly improve mathematical understanding and achievement. A study by Carpenter et al. (1998) found that when teachers based their instruction on students' thinking, students demonstrated greater problem-solving skills and conceptual understanding compared to control groups. Moreover, this approach has increased student engagement and motivation in mathematics. When students feel their ideas are valued, they are more likely to participate actively in mathematical discussions and take intellectual risks.
Challenges and Considerations
While the benefits of taking students' ideas seriously are well-documented, implementing this approach can present challenges:
-
Time Constraints: Allowing for extended student discussions and idea exploration can be time-consuming within the constraints of a typical school schedule.
-
Teacher Preparation: Effectively building on student ideas requires strong content knowledge and pedagogical skills from teachers.
-
Assessment Alignment: Traditional assessment methods may not adequately capture the depth of understanding developed through this approach, necessitating new forms of evaluation.
Conclusion
Taking students' ideas seriously in mathematics education represents a powerful approach to fostering deep conceptual understanding and problem-solving skills. By valuing students' initial thoughts and building upon their intuitive knowledge, educators can create more engaging and effective learning environments. While challenges exist in implementation, the potential benefits for student learning and mathematical achievement make this approach worthy of serious consideration and further research.
References
Ball, D. L., Thames, M. H., & Phelps, G. (2008). Content knowledge for teaching: What makes it special? Journal of Teacher Education, 59(5), 389-407.
Boaler, J. (2002). Experiencing school mathematics: Traditional and reform approaches to teaching and their impact on student learning. Routledge.
Boaler, J., & Brodie, K. (2004). The importance, nature and impact of teacher questions. In D. E. McDougall & J. A. Ross (Eds.), Proceedings of the 26th annual meeting of the North American Chapter of the International Group for the Psychology of Mathematics Education (Vol. 2, pp. 773-782). Toronto: OISE/UT. Carpenter, T. P., Fennema, E., & Franke, M. L. (1996). Cognitively guided instruction: A knowledge base for reform in primary mathematics instruction. The Elementary School Journal, 97(1), 3-20.
Carpenter, T. P., Fennema, E., Franke, M. L., Levi, L., & Empson, S. B. (1999). Children's mathematics: Cognitively guided instruction. Portsmouth, NH: Heinemann.
Carpenter, T. P., & Lehrer, R. (1999). Teaching and learning mathematics with understanding. In E. Fennema & T. A. Romberg (Eds.), Mathematics classrooms that promote understanding (pp. 19-32). Mahwah, NJ: Lawrence Erlbaum Associates.
Craik, F. I., & Lockhart, R. S. (1972). Levels of processing: A framework for memory research. Journal of Verbal Learning and Verbal Behavior, 11(6), 671-684.
Driscoll, M. P. (2005). Psychology of learning for instruction (3rd ed.). Boston: Allyn and Bacon.
Flavell, J. H. (1979). Metacognition and cognitive monitoring: A new area of cognitive-developmental inquiry. American Psychologist, 34(10), 906-911.
Hiebert, J., & Carpenter, T. P. (1992). Learning and teaching with understanding. In D. A. Grouws (Ed.), Handbook of research on mathematics teaching and learning (pp. 65-97). New York: Macmillan.
Hiebert, J., Carpenter, T. P., Fennema, E., Fuson, K. C., Wearne, D., Murray, H., ... & Human, P. (1997). Making sense: Teaching and learning mathematics with understanding. Portsmouth, NH: Heinemann.
Lyman, F. (1981). The responsive classroom discussion: The inclusion of all students. In A. S. Anderson (Ed.), Mainstreaming Digest (pp. 109-113). College Park: University of Maryland Press.
Piaget, J. (1952). The origins of intelligence in children. New York: International Universities Press.
Rowe, M. B. (1986). Wait time: Slowing down may be a way of speeding up! Journal of Teacher Education, 37(1), 43- 50.
Shepard, L. A. (2000). The role of assessment in a learning culture. Educational Researcher, 29(7), 4-14.
Smith, M. S., & Stein, M. K. (2011). 5 practices for orchestrating productive mathematics discussions. Reston, VA: National Council of Teachers of Mathematics.
Social Media.
Research in mathematics education highlights the significance of taking students' ideas seriously, demonstrating how this approach enhances conceptual understanding, problem-solving abilities, and overall mathematical achievement. Rooted in constructivist learning theory, this method engages crucial cognitive processes like schema formation, metacognition, and elaborative rehearsal. By connecting students’ informal knowledge with formal mathematical concepts, educators can establish a robust foundation for advanced mathematical thinking. Studies show that when instruction is based on students' thinking, learners exhibit superior problem-solving skills and a deeper conceptual grasp than traditional teaching methods.
Join us in exploring these powerful teaching approaches and their impact on mathematical thinking and achievement!
-
-
 @ ac58bbcc:7d9754d8
2025-04-05 18:47:53
@ ac58bbcc:7d9754d8
2025-04-05 18:47:53Unlocking Learning Potential: Why Student's Ideas Matter
Introduction
Recent research in mathematics education emphasizes the importance of valuing and building upon students' initial ideas and intuitive understanding. This approach, often referred to as "taking students' ideas seriously," has enhanced conceptual understanding, problem-solving skills, and overall mathematical achievement. This overview examines this approach's theoretical foundations, cognitive processes, and practical implications in mathematics classrooms.

FREE DOWNLOAD - Questions and Prompts
Theoretical Foundations
Taking students' ideas seriously is grounded in constructivist learning theory and research on how students develop mathematical understanding. Hiebert and Carpenter (1992) argue that "if children possessed internal networks constructed both in and out of school and if they recognized the connections between them, their understanding and performance in both settings would improve." This highlights the importance of connecting students' informal knowledge with formal mathematical concepts. Carpenter's work further emphasizes the value of students' intuitive knowledge: "Children come to school with a great deal of informal or intuitive knowledge of mathematics that can serve as the basis for developing much of the formal mathematics of the primary school curriculum." This suggests that taking students' initial ideas seriously can provide a strong foundation for developing a more sophisticated mathematical understanding.
Cognitive Processes
When students' ideas are taken seriously in mathematics classrooms, several cognitive processes are engaged:
-
Schema Formation: As students articulate and refine their ideas, they develop and modify mental frameworks or schemas that organize mathematical concepts.
-
Metacognition: Explaining their thinking engages students' metacognitive processes, promoting reflection on their own understanding and problem-solving strategies.
-
Elaborative Rehearsal: Verbalizing mathematical concepts helps move information from working memory to long-term memory, enhancing retention.
-
Cognitive Conflict: When students encounter differing viewpoints, it can create cognitive conflict, stimulating the reconciliation of new information with existing schemas.
Practical Implications
Eliciting and Valuing Student Ideas
Carpenter and Lehrer argue that for learning with understanding to occur, instruction needs to provide specific opportunities: "For learning with understanding to occur, instruction needs to provide students the opportunity to develop productive relationships, extend and apply their knowledge, reflect about their experiences, articulate what they know, and make knowledge their own." This emphasizes the need for instructional approaches that actively elicit and value student ideas.
Creating a Supportive Environment
To effectively take students' ideas seriously, teachers must foster a classroom environment where all contributions are respected. This involves:
-
Provide adequate thinking time for students to formulate their thoughts.
-
Using open-ended questions that encourage diverse thinking and approaches.
-
Implementing collaborative strategies like think-pair-share to build confidence in sharing ideas.
Connecting to Formal Mathematics
Hiebert advocates for teaching practices that promote understanding by focusing on "the inherent structure of the emerging mathematical ideas and addressing students' misconceptions as they arise" . This involves helping students connect their informal ideas to more formal mathematical concepts and procedures.
Impact on Student Learning
Research indicates that taking students' ideas seriously can significantly improve mathematical understanding and achievement. A study by Carpenter et al. (1998) found that when teachers based their instruction on students' thinking, students demonstrated greater problem-solving skills and conceptual understanding compared to control groups. Moreover, this approach has increased student engagement and motivation in mathematics. When students feel their ideas are valued, they are more likely to participate actively in mathematical discussions and take intellectual risks.
Challenges and Considerations
While the benefits of taking students' ideas seriously are well-documented, implementing this approach can present challenges:
-
Time Constraints: Allowing for extended student discussions and idea exploration can be time-consuming within the constraints of a typical school schedule.
-
Teacher Preparation: Effectively building on student ideas requires strong content knowledge and pedagogical skills from teachers.
-
Assessment Alignment: Traditional assessment methods may not adequately capture the depth of understanding developed through this approach, necessitating new forms of evaluation.
Conclusion
Taking students' ideas seriously in mathematics education represents a powerful approach to fostering deep conceptual understanding and problem-solving skills. By valuing students' initial thoughts and building upon their intuitive knowledge, educators can create more engaging and effective learning environments. While challenges exist in implementation, the potential benefits for student learning and mathematical achievement make this approach worthy of serious consideration and further research.
References
Ball, D. L., Thames, M. H., & Phelps, G. (2008). Content knowledge for teaching: What makes it special? Journal of Teacher Education, 59(5), 389-407.
Boaler, J. (2002). Experiencing school mathematics: Traditional and reform approaches to teaching and their impact on student learning. Routledge.
Boaler, J., & Brodie, K. (2004). The importance, nature and impact of teacher questions. In D. E. McDougall & J. A. Ross (Eds.), Proceedings of the 26th annual meeting of the North American Chapter of the International Group for the Psychology of Mathematics Education (Vol. 2, pp. 773-782). Toronto: OISE/UT. Carpenter, T. P., Fennema, E., & Franke, M. L. (1996). Cognitively guided instruction: A knowledge base for reform in primary mathematics instruction. The Elementary School Journal, 97(1), 3-20.
Carpenter, T. P., Fennema, E., Franke, M. L., Levi, L., & Empson, S. B. (1999). Children's mathematics: Cognitively guided instruction. Portsmouth, NH: Heinemann.
Carpenter, T. P., & Lehrer, R. (1999). Teaching and learning mathematics with understanding. In E. Fennema & T. A. Romberg (Eds.), Mathematics classrooms that promote understanding (pp. 19-32). Mahwah, NJ: Lawrence Erlbaum Associates.
Craik, F. I., & Lockhart, R. S. (1972). Levels of processing: A framework for memory research. Journal of Verbal Learning and Verbal Behavior, 11(6), 671-684.
Driscoll, M. P. (2005). Psychology of learning for instruction (3rd ed.). Boston: Allyn and Bacon.
Flavell, J. H. (1979). Metacognition and cognitive monitoring: A new area of cognitive-developmental inquiry. American Psychologist, 34(10), 906-911.
Hiebert, J., & Carpenter, T. P. (1992). Learning and teaching with understanding. In D. A. Grouws (Ed.), Handbook of research on mathematics teaching and learning (pp. 65-97). New York: Macmillan.
Hiebert, J., Carpenter, T. P., Fennema, E., Fuson, K. C., Wearne, D., Murray, H., ... & Human, P. (1997). Making sense: Teaching and learning mathematics with understanding. Portsmouth, NH: Heinemann.
Lyman, F. (1981). The responsive classroom discussion: The inclusion of all students. In A. S. Anderson (Ed.), Mainstreaming Digest (pp. 109-113). College Park: University of Maryland Press.
Piaget, J. (1952). The origins of intelligence in children. New York: International Universities Press.
Rowe, M. B. (1986). Wait time: Slowing down may be a way of speeding up! Journal of Teacher Education, 37(1), 43- 50.
Shepard, L. A. (2000). The role of assessment in a learning culture. Educational Researcher, 29(7), 4-14.
Smith, M. S., & Stein, M. K. (2011). 5 practices for orchestrating productive mathematics discussions. Reston, VA: National Council of Teachers of Mathematics.
Social Media.
Research in mathematics education highlights the significance of taking students' ideas seriously, demonstrating how this approach enhances conceptual understanding, problem-solving abilities, and overall mathematical achievement. Rooted in constructivist learning theory, this method engages crucial cognitive processes like schema formation, metacognition, and elaborative rehearsal. By connecting students’ informal knowledge with formal mathematical concepts, educators can establish a robust foundation for advanced mathematical thinking. Studies show that when instruction is based on students' thinking, learners exhibit superior problem-solving skills and a deeper conceptual grasp than traditional teaching methods.
Join us in exploring these powerful teaching approaches and their impact on mathematical thinking and achievement!
-
-
 @ e372d24b:e25df41f
2025-04-05 18:11:15
@ e372d24b:e25df41f
2025-04-05 18:11:15Unlocking Learning Potential: Why Student's Ideas Matter
Introduction
Recent research in mathematics education emphasizes the importance of valuing and building upon students' initial ideas and intuitive understanding. This approach, often referred to as "taking students' ideas seriously," has enhanced conceptual understanding, problem-solving skills, and overall mathematical achievement. This overview examines this approach's theoretical foundations, cognitive processes, and practical implications in mathematics classrooms.

FREE DOWNLOAD - Questions and Prompts
Theoretical Foundations
Taking students' ideas seriously is grounded in constructivist learning theory and research on how students develop mathematical understanding. Hiebert and Carpenter (1992) argue that "if children possessed internal networks constructed both in and out of school and if they recognized the connections between them, their understanding and performance in both settings would improve." This highlights the importance of connecting students' informal knowledge with formal mathematical concepts. Carpenter's work further emphasizes the value of students' intuitive knowledge: "Children come to school with a great deal of informal or intuitive knowledge of mathematics that can serve as the basis for developing much of the formal mathematics of the primary school curriculum." This suggests that taking students' initial ideas seriously can provide a strong foundation for developing a more sophisticated mathematical understanding.
Cognitive Processes
When students' ideas are taken seriously in mathematics classrooms, several cognitive processes are engaged:
-
Schema Formation: As students articulate and refine their ideas, they develop and modify mental frameworks or schemas that organize mathematical concepts.
-
Metacognition: Explaining their thinking engages students' metacognitive processes, promoting reflection on their own understanding and problem-solving strategies.
-
Elaborative Rehearsal: Verbalizing mathematical concepts helps move information from working memory to long-term memory, enhancing retention.
-
Cognitive Conflict: When students encounter differing viewpoints, it can create cognitive conflict, stimulating the reconciliation of new information with existing schemas.
Practical Implications
Eliciting and Valuing Student Ideas
Carpenter and Lehrer argue that for learning with understanding to occur, instruction needs to provide specific opportunities: "For learning with understanding to occur, instruction needs to provide students the opportunity to develop productive relationships, extend and apply their knowledge, reflect about their experiences, articulate what they know, and make knowledge their own." This emphasizes the need for instructional approaches that actively elicit and value student ideas.
Creating a Supportive Environment
To effectively take students' ideas seriously, teachers must foster a classroom environment where all contributions are respected. This involves:
-
Provide adequate thinking time for students to formulate their thoughts.
-
Using open-ended questions that encourage diverse thinking and approaches.
-
Implementing collaborative strategies like think-pair-share to build confidence in sharing ideas.
Connecting to Formal Mathematics
Hiebert advocates for teaching practices that promote understanding by focusing on "the inherent structure of the emerging mathematical ideas and addressing students' misconceptions as they arise" . This involves helping students connect their informal ideas to more formal mathematical concepts and procedures.
Impact on Student Learning
Research indicates that taking students' ideas seriously can significantly improve mathematical understanding and achievement. A study by Carpenter et al. (1998) found that when teachers based their instruction on students' thinking, students demonstrated greater problem-solving skills and conceptual understanding compared to control groups. Moreover, this approach has increased student engagement and motivation in mathematics. When students feel their ideas are valued, they are more likely to participate actively in mathematical discussions and take intellectual risks.
Challenges and Considerations
While the benefits of taking students' ideas seriously are well-documented, implementing this approach can present challenges:
-
Time Constraints: Allowing for extended student discussions and idea exploration can be time-consuming within the constraints of a typical school schedule.
-
Teacher Preparation: Effectively building on student ideas requires strong content knowledge and pedagogical skills from teachers.
-
Assessment Alignment: Traditional assessment methods may not adequately capture the depth of understanding developed through this approach, necessitating new forms of evaluation.
Conclusion
Taking students' ideas seriously in mathematics education represents a powerful approach to fostering deep conceptual understanding and problem-solving skills. By valuing students' initial thoughts and building upon their intuitive knowledge, educators can create more engaging and effective learning environments. While challenges exist in implementation, the potential benefits for student learning and mathematical achievement make this approach worthy of serious consideration and further research.
References
Ball, D. L., Thames, M. H., & Phelps, G. (2008). Content knowledge for teaching: What makes it special? Journal of Teacher Education, 59(5), 389-407.
Boaler, J. (2002). Experiencing school mathematics: Traditional and reform approaches to teaching and their impact on student learning. Routledge.
Boaler, J., & Brodie, K. (2004). The importance, nature and impact of teacher questions. In D. E. McDougall & J. A. Ross (Eds.), Proceedings of the 26th annual meeting of the North American Chapter of the International Group for the Psychology of Mathematics Education (Vol. 2, pp. 773-782). Toronto: OISE/UT. Carpenter, T. P., Fennema, E., & Franke, M. L. (1996). Cognitively guided instruction: A knowledge base for reform in primary mathematics instruction. The Elementary School Journal, 97(1), 3-20.
Carpenter, T. P., Fennema, E., Franke, M. L., Levi, L., & Empson, S. B. (1999). Children's mathematics: Cognitively guided instruction. Portsmouth, NH: Heinemann.
Carpenter, T. P., & Lehrer, R. (1999). Teaching and learning mathematics with understanding. In E. Fennema & T. A. Romberg (Eds.), Mathematics classrooms that promote understanding (pp. 19-32). Mahwah, NJ: Lawrence Erlbaum Associates.
Craik, F. I., & Lockhart, R. S. (1972). Levels of processing: A framework for memory research. Journal of Verbal Learning and Verbal Behavior, 11(6), 671-684.
Driscoll, M. P. (2005). Psychology of learning for instruction (3rd ed.). Boston: Allyn and Bacon.
Flavell, J. H. (1979). Metacognition and cognitive monitoring: A new area of cognitive-developmental inquiry. American Psychologist, 34(10), 906-911.
Hiebert, J., & Carpenter, T. P. (1992). Learning and teaching with understanding. In D. A. Grouws (Ed.), Handbook of research on mathematics teaching and learning (pp. 65-97). New York: Macmillan.
Hiebert, J., Carpenter, T. P., Fennema, E., Fuson, K. C., Wearne, D., Murray, H., ... & Human, P. (1997). Making sense: Teaching and learning mathematics with understanding. Portsmouth, NH: Heinemann.
Lyman, F. (1981). The responsive classroom discussion: The inclusion of all students. In A. S. Anderson (Ed.), Mainstreaming Digest (pp. 109-113). College Park: University of Maryland Press.
Piaget, J. (1952). The origins of intelligence in children. New York: International Universities Press.
Rowe, M. B. (1986). Wait time: Slowing down may be a way of speeding up! Journal of Teacher Education, 37(1), 43- 50.
Shepard, L. A. (2000). The role of assessment in a learning culture. Educational Researcher, 29(7), 4-14.
Smith, M. S., & Stein, M. K. (2011). 5 practices for orchestrating productive mathematics discussions. Reston, VA: National Council of Teachers of Mathematics.
Social Media.
Research in mathematics education highlights the significance of taking students' ideas seriously, demonstrating how this approach enhances conceptual understanding, problem-solving abilities, and overall mathematical achievement. Rooted in constructivist learning theory, this method engages crucial cognitive processes like schema formation, metacognition, and elaborative rehearsal. By connecting students’ informal knowledge with formal mathematical concepts, educators can establish a robust foundation for advanced mathematical thinking. Studies show that when instruction is based on students' thinking, learners exhibit superior problem-solving skills and a deeper conceptual grasp than traditional teaching methods.
Join us in exploring these powerful teaching approaches and their impact on mathematical thinking and achievement!
-
-
 @ c8adf82a:7265ee75
2025-04-04 01:58:49
@ c8adf82a:7265ee75
2025-04-04 01:58:49What is knowledge? Why do we need it?
Since we were small, our parents/guardian put us in school, worked their asses off to give us elective lessons, some get help until college, some even after college and after professional work. Why is this intelligence thing so sought after?
When you were born, you mostly just accepted what your parents said, they say go to school - you go to school, they say go learn the piano - you learn the piano. Of course with a lot of questions and denials, but you do it because you know your parents are doing it for your own good. You can feel the love so you disregard the 'why' and go on with faith
Everything starts with why, and for most people maybe the purpose of knowledge is to be smarter, to know more, just because. But for me this sounds utterly useless. One day I will die next to a man with half a brain and we would feel the same exact thing on the ground. Literally being smarter at the end does not matter at all
However, I am not saying to just be lazy and foolish. For me the purpose of knowledge is action. The more you learn, the more you know what to do, the more you can be sure you are doing the right thing, the more you can make progress on your own being, etc etc
Now, how can you properly learn? Imagine a water bottle. The water bottle's sole purpose is to contain water, but you cannot fill in the water bottle before you open the cap. To learn properly, make sure you open the cap and let all that water pour into you
If you are reading this, you are alive. Don't waste your time doing useless stuff and start to make a difference in your life
Seize the day
-
 @ 378562cd:a6fc6773
2025-04-02 22:41:57
@ 378562cd:a6fc6773
2025-04-02 22:41:57Nostr is a decentralized, censorship-resistant social media protocol designed to give users control over online interactions without relying on central authorities. While its architecture offers notable advantages, it also introduces challenges, particularly concerning user anonymity, content moderation, and the dynamics of user influence.
Anonymity and the Risk of Bullying
Nostr's design allows users to create identities without traditional verification methods like email addresses or phone numbers. Instead, users generate a cryptographic key pair: a public key serving as their identifier and a private key for signing messages. This approach enhances privacy but can lead to the "online disinhibition effect," where individuals feel less accountable for their actions due to perceived anonymity. This phenomenon has been linked to increased instances of cyberbullying, as users may engage in behavior online that they would avoid in face-to-face interactions.
Influence Disparities Among Users
In decentralized networks like Nostr, users with larger followings can have a more extensive reach, amplifying their messages across the network. This can create disparities where individuals with thousands of followers wield more influence than those with fewer connections. While this dynamic is not unique to Nostr, the protocol's structure may exacerbate the visibility gap between highly followed users and those with a smaller audience.
Content Moderation and the Challenge of Deletion
Due to Nostr's decentralized nature, content moderation and deletion present significant challenges. Removing content to multiple relays becomes complex once a user posts content to multiple relays, as each relay operates independently. Unlike centralized platforms where a post can be deleted universally, Nostr's architecture means that deleting a post from one relay doesn't ensure its removal from others. This persistence underscores the importance of thoughtful posting, as content may remain accessible indefinitely.
Mitigation Strategies and User Empowerment
Despite these challenges, Nostr offers mechanisms to empower users to manage their experience. Clients can implement features allowing users to mute or block others, tailoring their interactions and content exposure. Additionally, some clients support user-led moderation, enabling individuals to label content as offensive or inappropriate, contributing to a community-driven approach to content management.
In summary, while Nostr's decentralized and anonymous framework promotes freedom and resistance to censorship, it also necessitates a proactive approach from users to navigate challenges related to anonymity, influence disparities, and content permanence. As the platform evolves, ongoing development and community engagement will be crucial in addressing these issues to foster a safe and equitable environment for all participants.
-
 @ 8ba66f4c:59175b61
2025-04-01 17:57:49
@ 8ba66f4c:59175b61
2025-04-01 17:57:49Pas si vite !
Depuis quelques années, on entend souvent que PHP est "en perte de vitesse". C’est vrai que des technologies comme Node.js, Python ou Go séduisent de plus en plus de développeurs : - ➡️ performances modernes, - ➡️ syntaxe plus récente, - ➡️ intégration naturelle avec des architectures temps réel ou distribuées.
Node.js a conquis le monde startup avec un argument fort : un seul langage pour tout. Python et Go, eux, dominent la data, l’IA ou les outils systèmes.
Mais faut-il pour autant enterrer PHP ? Absolument pas. PHP reste l’un des langages les plus utilisés sur le web. Et surtout : il a su évoluer.
Avec PHP 8, le langage a gagné en performance, en typage, en lisibilité. Mais ce qui fait vraiment la différence aujourd’hui… C’est Laravel.
Laravel, c’est un framework mais aussi une expérience de développement : * ✔️ Artisan CLI * ✔️ ORM Eloquent * ✔️ Middleware, Events, Queues, Notifications * ✔️ Auth intégré * ✔️ Un écosystème ultra complet (Forge, Vapor, Nova, Filament…)
Laravel rend PHP moderne, élégant et agréable à utiliser. C’est un vrai plaisir de développer avec.
Alors oui, PHP n’est peut-être plus “cool” dans les bootcamps ou les tops GitHub. Mais dans le monde réel – celui des projets qui tournent, des deadlines, des contraintes business – PHP + Laravel reste un choix extrêmement solide.
💡 Je suis développeur Laravel, et j’accompagne des projets web qui ont besoin de robustesse, de scalabilité et de qualité de code.
📩 Si vous avez un projet ou un besoin en développement web, n’hésitez pas à me contacter. Je serais ravi d’échanger avec vous.
-
 @ 8ba66f4c:59175b61
2025-04-01 17:28:39
@ 8ba66f4c:59175b61
2025-04-01 17:28:39HTTP, Bitcoin, Nostr… Ces protocoles ouverts n’ont rien à vendre, personne à impressionner, et surtout : pas de CEO pour trahir leurs utilisateurs.
Contrairement aux plateformes centralisées comme X (ex-Twitter), Facebook ou même certaines fintechs à la mode, un protocole ne dépend pas des décisions d’un dirigeant ou d’un conseil d’administration.
Il n’est pas motivé par la recherche de profit à court terme, ni par des objectifs de croissance déconnectés de l’intérêt de ses utilisateurs.
C’est simple : - HTTP a permis à tout le monde de publier sur le web. - Bitcoin permet à chacun de stocker et transférer de la valeur sans permission. - Nostr permet de s’exprimer, publier, zapper, sans dépendre d’une entreprise.
Et ces trois exemples ont un autre point commun : Ils sont plus susceptibles de se répandre, de rester, et de garantir la souveraineté individuelle. À l’inverse, les solutions propriétaires sont séduisantes au début : elles sont souvent bien financées, bien designées, bien marketées. Mais elles finissent toujours par imposer leur modèle : - changement des règles, - collecte ou vente des données, - monétisation agressive, - ou pure et simple fermeture du service.
Un protocole, lui, est neutre. Il ne décide pas à votre place. Il ne vous surveille pas. Il ne change pas de cap pour satisfaire ses investisseurs. C’est un terrain commun, où chacun peut construire ce qu’il veut, interopérer avec d’autres, et garder le contrôle sur ses données, sa voix, son argent.
Alors oui, adopter un protocole demande parfois un peu plus d’effort. Il faut comprendre les bases, apprendre à se servir de nouveaux outils.
Mais en échange, on gagne quelque chose de précieux : l’indépendance. Et dans un monde numérique de plus en plus cloisonné, c’est peut-être ce qui a le plus de valeur.
-
 @ 378562cd:a6fc6773
2025-04-01 17:00:22
@ 378562cd:a6fc6773
2025-04-01 17:00:22Let’s be honest—living a Godly life isn’t exactly trending on social media. Nobody’s going viral for reading Leviticus, and you won’t find “Patience” or “Humility” on the list of top Google searches. But if you’re serious about walking the walk and not just talking the talk, then buckle up, because living for God is the most fulfilling (and sometimes hilarious) adventure you’ll ever embark on.
1. Know Who You’re Living For
The first step to living a Godly life? Understand who’s in charge. (Hint: It’s not you.) In a world that screams, “Follow your heart!” the Bible gently reminds us in Jeremiah 17:9 that the heart is “deceitful above all things.” Ouch. But hey, that’s why we follow Jesus instead of our feelings.
2. Read the Manual
If you buy a new gadget, you read the instructions (or at least pretend to before pressing random buttons). The Bible is God’s instruction manual for life. It tells us how to live, how to love, and—most importantly—how to avoid spiritual faceplants. Psalm 119:105 says, “Your word is a lamp to my feet and a light to my path.” In other words, don’t walk through life in the dark without God’s flashlight.
3. Pray Like Your Life Depends on It (Because It Does)
Prayer isn’t just for Sunday mornings or when you can’t find your car keys. It’s a direct line to God, and guess what? No hold music. No dropped calls. Just you and the Creator of everything having a chat. It's just as simple as it sounds. No formalities are required!
4. Surround Yourself with the Right People
You’ve probably heard, “Show me your friends, and I’ll show you your future.” Well, Proverbs 13:20 beat that saying to the punch: “Walk with the wise and become wise, for a companion of fools suffers harm.” Choose friends who push you closer to Jesus, not the ones who drag you into drama, debt, or dubious decisions some choose to call "life."
5. Live Differently (and Be Okay with It)
News flash: If you’re living for God, you won’t blend in. I know the crowd I'm talking to here. But standing up and standing out in this way is a good thing! Romans 12:2 reminds us not to conform to the pattern of this world. You might get weird looks for saying “I’m praying for you” instead of “sending good vibes,” but being a light in a dark world means you’ll stand out.
6. Learn the Art of Self-Control
Whether it’s resisting that third slice of pie (conviction level: high) or holding your tongue when that one coworker tests your patience, self-control is a major part of living a Godly life. Proverbs 25:28 says, “Like a city whose walls are broken through is a person who lacks self-control.” In other words, if you can’t control yourself, you’re as defenseless as a town with no walls.
7. Love Like Jesus (Even When It’s Hard)
Living a Godly life isn’t just about avoiding sin—it’s about actively loving others. And I’m not talking about just loving the easy people (your grandma, your dog, Chick-fil-A employees). Jesus said to love your enemies and pray for those who persecute you (Matthew 5:44). That includes difficult coworkers, annoying neighbors, and even people who drive 10 miles under the speed limit in the fast lane. Keep in mind this does not give you the green light to go on loving and accepting their sins. Loving others as Christ did doesn’t mean endorsing or accepting sin. True love speaks the truth, encourages repentance, and points others toward God’s righteousness rather than affirming choices that separate us from Him.
8. Be a Doer, Not Just a Hearer
James 1:22 says, “Do not merely listen to the word, and so deceive yourselves. Do what it says.” It’s not enough to know what’s right—you have to live it. Imagine someone memorizing a cookbook but never cooking. That’s what knowing the Bible without applying it looks like.
9. Trust God’s Timing
Patience is a virtue. (And sometimes a struggle). However, a big part of living a Godly life is trusting that God’s plan is better than ours. Isaiah 40:31 says, “Those who wait on the Lord will renew their strength.” So, instead of rushing ahead, trust that God’s got the perfect timing—even when it doesn’t match your schedule.
10. Laugh, Because Joy is Biblical
Christians aren’t called to live miserable lives. In fact, Philippians 4:4 tells us to “Rejoice in the Lord always.” Yes, life gets tough. But joy in Jesus isn’t about circumstances—it’s about knowing the One who holds it all together. So, laugh, smile, and enjoy the blessings God has given you.
Final Thoughts
Living a Godly life isn’t about perfection—it’s about direction. You’ll stumble, you’ll mess up, and you’ll occasionally say things you immediately regret. But God’s grace is bigger than our failures. Keep seeking Him, keep walking in His ways, and remember: the goal isn’t to be “good enough”—it’s to be faithful.
And if you ever feel discouraged, just remember: even Peter walked on water…until he looked down, became afraid, and started sinking. He cried out to the Lord, and Jesus immediately lifted him back up to safety. Keep your eyes on Jesus; Rely on Jesus for everything, and you’ll be just fine.
-
 @ 378562cd:a6fc6773
2025-03-31 19:20:39
@ 378562cd:a6fc6773
2025-03-31 19:20:39Bitcoin transaction fees might seem confusing, but don’t worry—I’ll break it down step by step in a simple way. 🚀
Unlike traditional bank fees, Bitcoin fees aren’t fixed. Instead, they depend on: ✔️ Transaction size (in bytes, not BTC!) ✔️ Network demand (more traffic = higher fees) ✔️ Fee rate (measured in satoshis per byte)
Let’s dive in! 👇
📌 Why Do Bitcoin Transactions Have Fees? Bitcoin miners process transactions and add them to the blockchain. Fees serve three key purposes:
🔹 Incentivize Miners – They receive fees + block rewards. 🔹 Prevent Spam – Stops the network from being flooded. 🔹 Prioritize Transactions – Higher fees = faster confirmations.
💰 How Are Bitcoin Fees Calculated? Bitcoin fees are not based on the amount of BTC you send. Instead, they depend on how much space your transaction takes up in a block.
🧩 1️⃣ Transaction Size (Bytes, Not BTC!) Bitcoin transactions vary in size (measured in bytes).
More inputs and outputs = larger transactions.
Larger transactions take up more block space, meaning higher fees.
📊 2️⃣ Fee Rate (Sats Per Byte) Fees are measured in satoshis per byte (sat/vB).
You set your own fee based on how fast you want the transaction confirmed.
When demand is high, fees rise as users compete for block space.
⚡ 3️⃣ Network Demand If the network is busy, miners prioritize transactions with higher fees.
Low-fee transactions may take hours or even days to confirm.
🔢 Example: Calculating a Bitcoin Transaction Fee Let’s say: 📦 Your transaction is 250 bytes. 💲 The current fee rate is 50 sat/vB.
Formula: 🖩 Transaction Fee = Size × Fee Rate = 250 bytes × 50 sat/vB = 12,500 satoshis (0.000125 BTC)
💡 If 1 BTC = $60,000, the fee would be: 0.000125 BTC × $60,000 = $7.50
🚀 How to Lower Bitcoin Fees? Want to save on fees? Try these tips:
🔹 Use SegWit Addresses – Reduces transaction size! 🔹 Batch Transactions – Combine multiple payments into one. 🔹 Wait for Low Traffic – Fees fluctuate based on demand. 🔹 Use the Lightning Network – Near-zero fees for small payments.
🏁 Final Thoughts Bitcoin fees aren’t fixed—they depend on transaction size, fee rate, and network demand. By understanding how fees work, you can save money and optimize your transactions!
🔍 Want real-time fee estimates? Check mempool.space for live data! 🚀
-
 @ 22aa8151:ae9b5954
2025-03-31 07:44:15
@ 22aa8151:ae9b5954
2025-03-31 07:44:15With all the current hype around Payjoin for the month, I'm open-sourcing a project I developed five years ago: https://github.com/Kukks/PrivatePond
Note: this project is unmaintained and should only be used as inspiration.
Private Pond is a Bitcoin Payjoin application I built specifically to optimize Bitcoin transaction rails for services, such as deposits, withdrawals, and automated wallet rebalancing.
The core concept is straightforward: withdrawals requested by users are queued and processed at fixed intervals, enabling traditional, efficient transaction batching. Simultaneously, deposits from other users can automatically batch these withdrawals via Payjoin batching, reducing them onchain footprint further. Taking it to the next step: a user's deposit is able to fund the withdrawals with its own funds reducing the required operational liquidity in hot wallets through a process called the Meta Payjoin.
The application supports multiple wallets—hot, cold, multisig, or hybrid—with configurable rules, enabling automated internal fund management and seamless rebalancing based on operational needs such as min/max balance limits and wallet ratios (10% hot, 80% in 2-of-3, 10% in 1-of-2, etc) .
This system naturally leverages user Payjoin transactions as part of the automated rebalancing strategy, improving liquidity management by batching server operations with user interactions.
Private Pond remains quite possibly the most advanced Payjoin project today, though my multi-party addendum of 2023 probably competes. That said, Payjoin adoption overall has been disappointing: the incentives heavily favor service operators who must in turn actively encourage user participation, limiting its appeal only for specialized usage. This is why my efforts refocused on systems like Wabisabi coinjoins, delivering not just great privacy but all the benefits of advanced Payjoin batching on a greater scale through output compaction.
Soon, I'll also open-source my prototype coinjoin protocol, Kompaktor, demonstrating significant scalability improvements, such as 50+ payments from different senders being compacted into a single Bitcoin output. And this is not even mentioning Ark, that pushes these concepts even further, giving insane scalability and asyncrhonous execution.
You can take a look at the slides I did around this here: https://miro.com/app/board/uXjVL-UqP4g=/
Parts of Private Pond, the pending transfers and multisig, will soon be integrated into nostr:npub155m2k8ml8sqn8w4dhh689vdv0t2twa8dgvkpnzfggxf4wfughjsq2cdcvg 's next major release—special thanks to nostr:npub1j8y6tcdfw3q3f3h794s6un0gyc5742s0k5h5s2yqj0r70cpklqeqjavrvg for continuing the work and getting it to the finish line.
-
 @ 30ceb64e:7f08bdf5
2025-03-30 00:37:54
@ 30ceb64e:7f08bdf5
2025-03-30 00:37:54Hey Freaks,
RUNSTR is a motion tracking app built on top of nostr. The project is built by TheWildHustle and TheNostrDev Team. The project has been tinkered with for about 3 months, but development has picked up and its goals and direction have become much clearer.
In a previous post I mentioned that RUNSTR was looking to become a Nike Run Club or Strava competitor, offering users an open source community and privacy focused alternative to the centralized silos that we've become used to.
I normally ramble incoherently.....even in writing, but this is my attempt to communicate the project's goals and direction as we move forward.
This is where the project is now:
Core Features
- Run Tracker: Uses an algorithm which adjusts to your phone's location permissions and stores the data on your phone locally
- Stats: Stored locally on your phone with a basic profile screen so users can monitor calories burned during runs
- Nostr Feed: Made up of kind1 notes that contain #RUNSTR and other running related hashtags
- Music: Brought to you via a wavlake API, enabling your wavlake playlists and liked songs to be seen and played in the app
Current Roadmap
- Bugs and small improvements: Fixing known issues within the client
- zap.store release: Launching a bug bounty program after release
- Clubs: Enabling running organizations to create territories for events, challenges, rewards and competition
- Testflight: Opening up the app to iOS users (currently Android only)
- Modes: Adding functionality to switch between Running, Walking, or Cycling modes
Future Roadmap
- Requested Features: Implementing features requested by club managers to support virtual events and challenges
- Blossom: Giving power users the ability to upload their data to personal blossom servers
- NIP28: Making clubs interoperable with other group chat clients like 0xchat, Keychat, and Chachi Chat
- DVM's: Creating multiple feeds based on movement mode (e.g., Walking mode shows walkstr feed)
- NIP101e: Allowing users to create run records and store them on nostr relays
- Calories over relays: Using NIP89-like functionality for users to save calorie data on relays for use in other applications
- NIP60: Implementing automatic wallet creation for users to zap and get zapped within the app
In Conclusion
I've just barely begun this thing and it'll be an up and down journey trying to push it into existence. I think RUNSTR has the potential to highlight the other things that nostr has going for it, demonstrating the protocol's interoperability, flexing its permissionless identity piece, and offering an experience that gives users a glimpse into what is possible when shipping into a new paradigm. Although we build into an environment that often offers no solutions, you'd have to be a crazy person not to try.
https://github.com/HealthNoteLabs/Runstr/releases/tag/feed-0.1.0-20250329-210157
-
 @ 5ffb8e1b:255b6735
2025-03-29 13:57:02
@ 5ffb8e1b:255b6735
2025-03-29 13:57:02As a fellow Nostrich you might have noticed some of my #arlist posts. It is my effort to curate artists that are active on Nostr and make it easier for other users to find content that they are interested in.
By now I have posted six or seven posts mentioning close to fifty artists, the problem so far is that it's only a list of handles and it is up to reader to click on each in order to find out what are the artist behind the names all about. Now I am going to start creating blog posts with a few artists mentioned in each, with short descriptions of their work and an image or to.
I would love to have some more automated mode of curation but I still couldn't figure out what is a good way for it. I've looked at Listr, Primal custom feeds and Yakihonne curations but none seem to enable me to make a list of npubs that is then turned into a feed that I could publicly share for others to views. Any advice on how to achieve this is VERY welcome !
And now lets get to the first batch of artists I want to share with you.
Eugene Gorbachenko
nostr:npub1082uhnrnxu7v0gesfl78uzj3r89a8ds2gj3dvuvjnw5qlz4a7udqwrqdnd Artist from Ukrain creating amazing realistic watercolor paintings. He is very active on Nostr but is very unnoticed for some stange reason. Make sure to repost the painting that you liked the most to help other Nostr users to discover his great art.
Siritravelsketch
nostr:npub14lqzjhfvdc9psgxzznq8xys8pfq8p4fqsvtr6llyzraq90u9m8fqevhssu a a lovely lady from Thailand making architecture from all around the world spring alive in her ink skethes. Dynamic lines gives it a dreamy magical feel, sometimes supported by soft watercolor strokes takes you to a ferytale layer of reality.
BureuGewas
nostr:npub1k78qzy2s9ap4klshnu9tcmmcnr3msvvaeza94epsgptr7jce6p9sa2ggp4 a a master of the clasic oil painting. From traditional still life to modern day subjects his paintings makes you feel the textures and light of the scene more intense then reality itself.
You can see that I'm no art critic, but I am trying my best. If anyone else is interested to join me in this curration adventure feel free to reach out !
With love, Agi Choote
-
 @ 0d6c8388:46488a33
2025-03-28 16:24:00
@ 0d6c8388:46488a33
2025-03-28 16:24:00Huge thank you to OpenSats for the grant to work on Hypernote this year! I thought I'd take this opportunity to try and share my thought processes for Hypernote. If this all sounds very dense or irrelevant to you I'm sorry!
===
How can the ideas of "hypermedia" benefit nostr? That's the goal of hypernote. To take the best ideas from "hypertext" and "hypercard" and "hypermedia systems" and apply them to nostr in a specifically nostr-ey way.
1. What do we mean by hypermedia
A hypermedia document embeds the methods of interaction (links, forms, and buttons are the most well-known hypermedia controls) within the document itself. It's including the how with the what.
This is how the old web worked. An HTML page was delivered to the web browser, and it included in it a link or perhaps a form that could be submitted to obtain a new, different HTML page. This is how the whole web worked early on! Forums and GeoCities and eBay and MySpace and Yahoo! and Amazon and Google all emerged inside this paradigm.
A web browser in this paradigm was a "thin" client which rendered the "thick" application defined in the HTML (and, implicitly, was defined by the server that would serve that HTML).
Contrast this with modern app development, where the what is usually delivered in the form of JSON, and then HTML combined with JavaScript (React, Svelte, Angular, Vue, etc.) is devised to render that JSON as a meaningful piece of hypermedia within the actual browser, the how.
The browser remains a "thin" client in this scenario, but now the application is delivered in two stages: a client application of HTML and JavaScript, and then the actual JSON data that will hydrate that "application".
(Aside: it's interesting how much "thicker" the browser has had to become to support this newer paradigm!)
Nostr was obviously built in line with the modern paradigm: nostr "clients" (written in React or Svelte or as mobile apps) define the how of reading and creating nostr events, while nostr events themselves (JSON data) simply describe the what.
And so the goal with Hypernote is to square this circle somehow: nostr currently delivers JSON what, how do we deliver the how with nostr as well. Is that even possible?
2. Hypernote's design assumptions
Hypernote assumes that hypermedia over nostr is a good idea! I'm expecting some joyful renaissance of app expression similar to that of the web once we figure out how to express applications in a truly "nostr" way.
Hypernote was also deeply inspired by HTMX, so it assumes that building web apps in the HTMX style is a good idea. The HTMX insight is that instead of shipping rich scripting along with your app, you could simply make HTML a tiny bit more expressive and get 95% of what most apps need. HTMX's additions to the HTML language are designed to be as minimal and composable as possible, and Hypernote should have the same aims.
Hypernote also assumes that the "design" of nostr will remain fluid and anarchic for years to come. There will be no "canonical" list of "required" NIPs that we'll have "consensus" on in order to build stable UIs on top of. Hypernote will need to be built responsive to nostr's moods and seasons, rather than one holy spec.
Hypernote likes the
nakcommand line tool. Hypernote likes markdown. Hypernote likes Tailwind CSS. Hypernote likes SolidJS. Hypernote likes cold brew coffee. Hypernote is, to be perfectly honest, my aesthetic preferences applied to my perception of an opportunity in the nostr ecosystem.3. "What's a hypernote?"
Great question. I'm still figuring this out. Everything right now is subject to change in order to make sure hypernote serves its intended purpose.
But here's where things currently stand:
A hypernote is a flat list of "Hypernote Elements". A Hypernote Element is composed of:
- CONTENT. Static or dynamic content. (the what)
- LOGIC. Filters and events (the how)
- STYLE. Optional, inline style information specific to this element's content.
In the most basic example of a hypernote story, here's a lone "edit me" in the middle of the canvas:

{ "id": "fb4aaed4-bf95-4353-a5e1-0bb64525c08f", "type": "text", "text": "edit me", "x": 540, "y": 960, "size": "md", "color": "black" }As you can see, it has no logic, but it does have some content (the text "edit me") and style (the position, size, and color).
Here's a "sticker" that displays a note:
{ "id": "2cd1ef51-3356-408d-b10d-2502cbb8014e", "type": "sticker", "stickerType": "note", "filter": { "kinds": [ 1 ], "ids": [ "92de77507a361ab2e20385d98ff00565aaf3f80cf2b6d89c0343e08166fed931" ], "limit": 1 }, "accessors": [ "content", "pubkey", "created_at" ], "x": 540, "y": 960, "associatedData": {} }As you can see, it's kind of a mess! The content and styling and underdeveloped for this "sticker", but at least it demonstrates some "logic": a nostr filter for getting its data.
Here's another sticker, this one displays a form that the user can interact with to SEND a note. Very hyper of us!
{ "id": "42240d75-e998-4067-b8fa-9ee096365663", "type": "sticker", "stickerType": "prompt", "filter": {}, "accessors": [], "x": 540, "y": 960, "associatedData": { "promptText": "What's your favorite color?" }, "methods": { "comment": { "description": "comment", "eventTemplate": { "kind": 1111, "content": "${content}", "tags": [ [ "E", "${eventId}", "", "${pubkey}" ], [ "K", "${eventKind}" ], [ "P", "${pubkey}" ], [ "e", "${eventId}", "", "${pubkey}" ], [ "k", "${eventKind}" ], [ "p", "${pubkey}" ] ] } } } }It's also a mess, but it demos the other part of "logic": methods which produce new events.
This is the total surface of hypernote, ideally! Static or dynamic content, simple inline styles, and logic for fetching and producing events.
I'm calling it "logic" but it's purposfully not a whole scripting language. At most we'll have some sort of
jq-like language for destructing the relevant piece of data we want.My ideal syntax for a hypernote as a developer will look something like
```foo.hypernote Nak-like logic
Markdown-like content
CSS-like styles ```
But with JSON as the compile target, this can just be my own preference, there can be other (likely better!) ways of authoring this content, such as a Hypernote Stories GUI.
The end
I know this is all still vague but I wanted to get some ideas out in the wild so people understand the through line of my different Hypernote experiments. I want to get the right amount of "expressivity" in Hypernote before it gets locked down into one spec. My hunch is it can be VERY expressive while remaining simple and also while not needing a whole scripting language bolted onto it. If I can't pull it off I'll let you know.
-
 @ a60e79e0:1e0e6813
2025-03-28 08:47:35
@ a60e79e0:1e0e6813
2025-03-28 08:47:35This is a long form note of a post that lives on my Nostr educational website Hello Nostr.
When most people stumble across Nostr, they see is as a 'decentralized social media alternative' — something akin to Twitter (X), but free from corporate control. But the full name, "Notes and Other Stuff Transmitted by Relays", gives a clue that there’s more to it than just posting short messages. The 'notes' part is easy to grasp because it forms almost everyone's first touch point with the protocol. But the 'other stuff'? That’s where Nostr really gets exciting. The 'other stuff' is all the creative and experimental things people are building on Nostr, beyond simple text based notes.
Every action on Nostr is an event, a like, a post, a profile update, or even a payment. The 'Kind' is what specifies the purpose of each event. Kinds are the building blocks of how information is categorized and processed on the network, and the most popular become part of higher lever specification guidelines known as Nostr Implementation Possibility - NIP. A NIP is a document that defines how something in Nostr should work, including the rules, standards, or features. NIPs define the type of 'other stuff' that be published and displayed by different styles of client to meet different purposes.
Nostr isn’t locked into a single purpose. It’s a foundation for whatever 'other stuff' you can dream up.
Types of Other Stuff
The 'other stuff' name is intentionally vague. Why? Because the possibilities of what can fall under this category are quite literally limitless. In the short time since Nostr's inception, the number of sub-categories that have been built on top of the Nostr's open protocol is mind bending. Here are a few examples:
- Long-Form Content: Think blog posts or articles. NIP-23.
- Private Messaging: Encrypted chats between users. NIP-04.
- Communities: Group chats or forums like Reddit. NIP-72
- Marketplaces: People listing stuff for sale, payable with zaps. NIP-15
- Zaps: Value transfer over the Lightning Network. NIP57

Popular 'Other Stuff' Clients
Here's a short list of some of the most recent and popular apps and clients that branch outside of the traditional micro-blogging use case and leverage the openness, and interoperability that Nostr can provide.
Blogging (Long Form Content)
- Habla - Web app for Nostr based blogs
- Highlighter - Web app that enables users to highlight, store and share content
Group Chats
- Chachi Chat - Relay-based (NIP-29) group chat client
- 0xchat - Mobile based secure chat
- Flotilla - Web based chat app built for self-hosted communities
- Nostr Nests - Web app for audio chats
- White Noise - Mobile based secure chat
Marketplaces
- Shopstr - Permissionless marketplace for web
- Plebeian Market - Permissionless marketplace for web
- LNBits Market - Permissionless marketplace for your node
- Mostro - Nostr based Bitcoin P2P Marketplace
Photo/Video
Music
- Fountain - Podcast app with Nostr features
- Wavlake - A music app supporting the value-for-value ecosystem
Livestreaming
- Zap.stream - Nostr native live streams
Misc
- Wikifreedia - Nostr based Wikipedia alternative
- Wikistr - Nostr based Wikipedia alternative
- Pollerama - Nostr based polls
- Zap Store - The app store powered by your social graph
The 'other stuff' in Nostr is what makes it special. It’s not just about replacing Twitter or Facebook, it’s about building a decentralized ecosystem where anything from private chats to marketplaces can thrive. The beauty of Nostr is that it’s a flexible foundation. Developers can dream up new ideas and build them into clients, and the relays just keep humming along, passing the data around. It’s still early days, so expect the 'other stuff' to grow wilder and weirder over time!
You can explore the evergrowing 'other stuff' ecosystem at NostrApps.com, Nostr.net and Awesome Nostr.
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ ecda4328:1278f072
2025-03-26 12:06:30
@ ecda4328:1278f072
2025-03-26 12:06:30When designing a highly available Kubernetes (or k3s) cluster, one of the key architectural questions is: "How many ETCD nodes should I run?"
A recent discussion in our team sparked this very debate. Someone suggested increasing our ETCD cluster size from 3 to more nodes, citing concerns about node failures and the need for higher fault tolerance. It’s a fair concern—nobody wants a critical service to go down—but here's why 3-node ETCD clusters are usually the sweet spot for most setups.
The Role of ETCD and Quorum
ETCD is a distributed key-value store used by Kubernetes to store all its state. Like most consensus-based systems (e.g., Raft), ETCD relies on quorum to operate. This means that more than half of the ETCD nodes must be online and in agreement for the cluster to function correctly.
What Quorum Means in Practice
- In a 3-node ETCD cluster, quorum is 2.
- In a 5-node cluster, quorum is 3.

⚠️ So yes, 5 nodes can tolerate 2 failures vs. just 1 in a 3-node setup—but you also need more nodes online to keep the system functional. More nodes doesn't linearly increase safety.
Why 3 Nodes is the Ideal Baseline
Running 3 ETCD nodes hits a great balance:
- Fault tolerance: 1 node can fail without issue.
- Performance: Fewer nodes = faster consensus and lower latency.
- Simplicity: Easier to manage, upgrade, and monitor.
Even the ETCD documentation recommends 3–5 nodes total, with 5 being the upper limit before write performance and operational complexity start to degrade.
Systems like Google's Chubby—which inspired systems like ETCD and ZooKeeper—also recommend no more than 5 nodes.
The Myth of Catastrophic Failure
"If two of our three ETCD nodes go down, the cluster will become unusable and need deep repair!"
This is a common fear, but the reality is less dramatic:
- ETCD becomes read-only: You can't schedule or update workloads, but existing workloads continue to run.
- No deep repair needed: As long as there's no data corruption, restoring quorum just requires bringing at least one other ETCD node back online.
- Still recoverable if two nodes are permanently lost: You can re-initialize the remaining node as a new single-node ETCD cluster using
--cluster-init, and rebuild from there.
What About Backups?
In k3s, ETCD snapshots are automatically saved by default. For example:
- Default path:
/var/lib/rancher/k3s/server/db/snapshots/
You can restore these snapshots in case of failure, making ETCD even more resilient.
When to Consider 5 Nodes
Adding more ETCD nodes only makes sense at scale, such as:
- Running 12+ total cluster nodes
- Needing stronger fault domains for regulatory/compliance reasons
Note: ETCD typically requires low-latency communication between nodes. Distributing ETCD members across availability zones or regions is generally discouraged unless you're using specialized networking and understand the performance implications.
Even then, be cautious—you're trading some simplicity and performance for that extra failure margin.
TL;DR
- 3-node ETCD clusters are the best choice for most Kubernetes/k3s environments.
- 5-node clusters offer more redundancy but come with extra complexity and performance costs.
- Loss of quorum is not a disaster—it’s recoverable.
- Backups and restore paths make even worst-case recovery feasible.
And finally: if you're seeing multiple ETCD nodes go down frequently, the real problem might not be the number of nodes—but your hosting provider.
-
 @ a0c34d34:fef39af1
2025-03-26 11:42:52
@ a0c34d34:fef39af1
2025-03-26 11:42:528 months ago I went to Nashville, Bitcoin2024. The one with Edward Snowden’s cryptic speech, Michael Saylor telling people who knew nothing about Bitcoin how to stack sats. And yes, I was in the room when Donald spoke. I had so many people asking me how to “get a Coinbase!!!” cause he said so.
I sat with two women explaining seed phrase and how vital it was as they wrote the random words on scrape pieces of paper and put them in their purses.
I once was just like those women. Still am in some areas of this space. It can be overwhelming, learning about cryptography,subgraphs, it can be decentralized theatre!!!
Yes decentralized theatre. I said it. I never said it out loud.
In 2016, I knew nothing. I overheard a conversation that changed my life’s trajectory. I am embarrassed to say, I was old then but didn’t know it. I didn’t see myself as old, 56 back then, I just wanted to have enough money to pay bills.
I say this to say I bought 3 whole Bitcoin in 2016 and listening to mainstream news about scams and black market associated with what I bought, I sold them quickly and thought I was too old to be scammed and playing around with all of that.
In 2018, someone gave me The Book of Satoshi, I read it and thought it was a fabulous story but my fear ? I put the book in a drawer and forgot about it.
I mentioned decentralized theatre. I have been living in decentralized theatre for the past 3 years now. In August 2021 I landed on TikTok and saw NFTs. I thought get money directly to those who need it. I started diving down the rabbit holes of Web3.
The decentralized theatre is being in betas & joining platforms claiming to be decentralized social media platforms and of course all the “Web3” businesses claiming to be Web3.
Social medias were exciting, the crypto casino was thriving and I thought I was going to live a decentralized life with Bitcoin being independent from any financial institutions or interference from government.
Delusional? Yes, diving deeper, I did. I went to my first “night with crypto” event in West Palm Beach. My first IRL meeting scammers.
There was about 200-250 people sitting facing the stage where a man was speaking. There was a QRCode on the screen and he said for us to get out our phones and scan the QRCode to download their wallet & get free money.
I watched everyone, most everyone point their phones at the screen, but I didn’t, I got up and went out to the area where the booths were, the vendors.
A few months later I found out ( on Twitter) it was a scam. People would deposit a “minimal amount” and swap their money for these tokens with no value but constant hype and Twitter social media ambassadors ( followers) had people “wanting in” Don’t FOMO…
The promise of decentralization, independent from banks & government, and of course I had been excitedly sharing everything I was learning on TikTok and mentioned senior citizens need to know this stuff.
They need to learn metaverse to be connected with the virtual and digital natives( their kids, grandkids). They need to learn about Bitcoin and blockchain technologies to put their documents on chain & transfer their wealth safely. They need to learn how A.I. health tech can help them have a better quality of life!!!
Someone said I was a senior citizen and I was the perfect person to help them. It’s been 3 years and I learned how to create a Discord(with Geneva), 4 metaverses, multiple wallets and learned about different cryptos. I learned about different GPTs, NFCCHIP wearables, A.I. and Decentralized Physical Infrastructure Network and so much more.
I have since deleted TikTok. I wrote an article on that on YakiHonne. I’m using LinkedIn and YouTube , some BluSky platforms. I published a cliff notes book for senior citizens and put it in my Stan Store(online to links) with links to my resume, newsletter, YouTube Channel, Substack and Onboard60 digital clone.
Onboard60, the name for my project. Onboard was THE buzzword back in 2021 & early 2022, 60? an age representative of my target audience … Onboard60 stuck.
The lack of interest from senior citizens over the years , the rejections, wild opinions, trolls on socials- I understand - I forget the fear I had. I still have the fear of not being a part of society, not understanding the world around me, getting left behind.
I keep coming to Nostr, going to BluSky, even the ones that are decentralized theatre( Lens & Farcaster)- I admit losing 28k follower account and afew other accounts I deleted ( over 5k & 12k), I felt a loss. I had perpetually been online and my relationships, friendships were online. Sadly only a few were real. Social media - out of sight out of mind. It was devastating.
I had to unplug and regroup. I was afraid to be on new social platforms, scared to start over, meet people. I’m realizing I do everything scared. I do it, whatever it is that moves me forward, keeps me learning, and keeps my mindset open, flexible.
Another fear is happening to me. There are times I have a senior citizen mindset. And that’s really scary. I have heard myself in conversations putting in an extra “the” like saying The Nostr like older people do.
Onboard60 is me. I am an adolescent and family counselor with a Master’s degree. I have created a few Metaverses, a Live chat/online Discord, a How to for senior citizens booklet and a digital clone.
Yes Onboard60 digital clone can be asked about anything Web3, blockchain and discuss how to create personal A.I. agents. I uploaded all of my content of the last 3 years (and it being LLM)People can go to Onboard60 clone with voice and or text
I do 1:1 counseling with overwhelmed, afraid and skeptical senior citizens.
I show experientially step by step basic virtual reality so senior citizens can enter the metaverse with their grandkids and portal to a park.
I use the metaverse & Geneva Live chats as social hang outs for senior citizens globally to create connections and stay relevant
I also talk about medical bracelets. NFCCHIP for medical information, gps bracelets for Alzheimer’s or dementia care.
And lastly from the past 3 years, I have learned to discuss all options for Bitcoin investing, not just self custody. Senior citizens listen, feel safe when I discuss Grayscale and Fidelity.
They feel they can trust these institutions. I tell them how they have articles and webinars on their sites about crypto and what cryptofunds they offer. They can dyor, it’s their money.
My vision and mission have stayed the same through this rollercoaster of a journey. It’s what keeps me grounded and moving forward.
This year I’m turning 65, and will become a part of the Medicare system. I don’t have insurance, can’t afford it. If it was on the blockchain I’d have control of the costs but nooooo, I am obligated to get Medicare.
I will have to work an extra shift a week (I am a waitress at night) and I am capable to do it and realistically I will probably need health insurance in the future, I am a senior citizen…..
Thank you for reading this. Zap sats and thank you again.
Sandra (Samm) Onboard60 Founder
https://docs.google.com/document/d/1PLn1ysBEfjjwPZsMsLlmX-s7cDOgPC29/edit?usp=drivesdk&ouid=111904115111263773126&rtpof=true&sd=true
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 378562cd:a6fc6773
2025-03-25 17:24:27
@ 378562cd:a6fc6773
2025-03-25 17:24:27In an era where the value of traditional money seems to shrink by the day, many turn to Bitcoin as a potential safeguard against inflation. But is Bitcoin truly a hedge, or is this just wishful thinking? Let’s break it down.
Understanding Inflation Inflation occurs when the purchasing power of money declines due to an increase in prices.
Central banks, like the Federal Reserve, often print more money, leading to more dollars chasing the same amount of goods.
Over time, inflation erodes savings and makes everyday items more expensive.
Why Bitcoin is Considered an Inflation Hedge Limited Supply – Unlike the U.S. dollar, Bitcoin has a fixed supply of 21 million coins, making it immune to money printing.
Decentralization – No government or central bank can manipulate Bitcoin’s supply or devalue it through policy changes.
Digital Gold – Many see Bitcoin as a modern version of gold, offering a store of value outside traditional financial systems.
Global Accessibility – Bitcoin operates 24/7 across borders, making it accessible to anyone looking to escape failing currencies.
Challenges to Bitcoin as an Inflation Hedge Volatility – Bitcoin’s price swings wildly, making it risky as a short-term hedge.
Adoption & Trust – Unlike gold, which has been a store of value for centuries, Bitcoin is relatively new and still gaining mainstream acceptance.
Market Correlation – At times, Bitcoin moves in tandem with stocks rather than acting as a safe-haven asset.
Regulatory Uncertainty – Governments around the world continue to debate Bitcoin’s place in the economy, which can impact its long-term stability.
The Verdict: Fact or Fiction? ✅ Long-Term Potential: Over the years, Bitcoin has shown signs of being a hedge against currency devaluation, especially in countries with hyperinflation. ⚠️ Short-Term Reality: Bitcoin’s volatility makes it unreliable as an immediate hedge, unlike traditional safe-haven assets like gold.
For those who believe in Bitcoin’s future, it could be a strong long-term hedge. However, for those looking for immediate inflation protection, it’s still a speculative bet.
Would you trust Bitcoin to safeguard your wealth? 🚀💰
What do you think? Share your comments below.
-
 @ ecda4328:1278f072
2025-03-25 10:00:52
@ ecda4328:1278f072
2025-03-25 10:00:52Kubernetes and Linux Swap: A Practical Perspective
After reviewing kernel documentation on swap management (e.g., Linux Swap Management), KEP-2400 (Kubernetes Node Memory Swap Support), and community discussions like this post on ServerFault, it's clear that the topic of swap usage in modern systems—especially Kubernetes environments—is nuanced and often contentious. Here's a practical synthesis of the discussion.
The Rationale for Disabling Swap
We disable SWAP on our Linux servers to ensure stable and predictable performance by relying on available RAM, avoiding the performance degradation and unnecessary I/O caused by SWAP usage. If an application runs out of memory, it’s usually due to insufficient RAM allocation or a memory leak, and enabling SWAP only worsens performance for other applications. It's more efficient to let a leaking app restart than to rely on SWAP to prevent OOM crashes.
With modern platforms like Kubernetes, memory requests and limits are enforced, ensuring apps use only the RAM allocated to them, while avoiding overcommitment to prevent resource exhaustion.
Additionally, disabling swap may protect data from data remanence attacks, where sensitive information could potentially be recovered from the swap space even after a process terminates.
Theoretical Capability vs. Practical Deployment
Linux provides a powerful and flexible memory subsystem. With proper tuning (e.g., swappiness, memory pinning, cgroups), it's technically possible to make swap usage efficient and targeted. Seasoned sysadmins often argue that disabling swap entirely is a lazy shortcut—an avoidance of learning how to use the tools properly.
But Kubernetes is not a traditional system. It's an orchestrated environment that favors predictability, fail-fast behavior, and clear isolation between workloads. Within this model:
- Memory requests and limits are declared explicitly.
- The scheduler makes decisions based on RAM availability, not total virtual memory (RAM + swap).
- Swap introduces non-deterministic performance characteristics that conflict with Kubernetes' goals.
So while the kernel supports intelligent swap usage, Kubernetes intentionally sidesteps that complexity.
Why Disable Swap in Kubernetes?
-
Deterministic Failure > Degraded Performance\ If a pod exceeds its memory allocation, it should fail fast — not get throttled into slow oblivion due to swap. This behavior surfaces bugs (like memory leaks or poor sizing) early.
-
Transparency & Observability\ With swap disabled, memory issues are clearer to diagnose. Swap obfuscates root causes and can make a healthy-looking node behave erratically.
-
Performance Consistency\ Swap causes I/O overhead. One noisy pod using swap can impact unrelated workloads on the same node — even if they’re within their resource limits.
-
Kubernetes Doesn’t Manage Swap Well\ Kubelet has historically lacked intelligence around swap. As of today, Kubernetes still doesn't support swap-aware scheduling or per-container swap control.
-
Statelessness is the Norm\ Most containerized workloads are designed to be ephemeral. Restarting a pod is usually preferable to letting it hang in a degraded state.
"But Swap Can Be Useful..."
Yes — for certain workloads (e.g., in-memory databases, caching layers, legacy systems), there may be valid reasons to keep swap enabled. In such cases, you'd need:
- Fine-tuned
vm.swappiness - Memory pinning and cgroup-based control
- Swap-aware monitoring and alerting
- Custom kubelet/systemd integration
That's possible, but not standard practice — and for good reason.
Future Considerations
Recent Kubernetes releases have introduced experimental swap support via KEP-2400. While this provides more flexibility for advanced use cases — particularly Burstable QoS pods on cgroupsv2 — swap remains disabled by default and is not generally recommended for production workloads unless carefully planned. The rationale outlined in this article remains applicable to most Kubernetes operators, especially in multi-tenant and performance-sensitive environments.
Even the Kubernetes maintainers acknowledge the inherent trade-offs of enabling swap. As noted in KEP-2400's Risks and Mitigations section, swap introduces unpredictability, can severely degrade performance compared to RAM, and complicates Kubernetes' resource accounting — increasing the risk of noisy neighbors and unexpected scheduling behavior.
Some argue that with emerging technologies like non-volatile memory (e.g., Intel Optane/XPoint), swap may become viable again. These systems promise near-RAM speed with large capacity, offering hybrid memory models. But these are not widely deployed or supported in mainstream Kubernetes environments yet.
Conclusion
Disabling swap in Kubernetes is not a lazy hack — it’s a strategic tradeoff. It improves transparency, predictability, and system integrity in multi-tenant, containerized environments. While the kernel allows for more advanced configurations, Kubernetes intentionally simplifies memory handling for the sake of reliability.
If we want to revisit swap usage, it should come with serious planning: proper instrumentation, swap-aware observability, and potentially upstream K8s improvements. Until then, disabling swap remains the sane default.
-
 @ 1d7ff02a:d042b5be
2025-03-25 02:01:41
@ 1d7ff02a:d042b5be
2025-03-25 02:01:41ໃນຍຸກດິຈິຕອນ, ການລົບກວນທາງເທັກໂນໂລຊີໄດ້ສັ່ນຄອນສະຖາບັນແບບດັ້ງເດີມທົ່ວໂລກ. ເຊັ່ນດຽວກັນກັບແພລດຟອມສື່ສັງຄົມອອນລາຍທີ່ໄດ້ທຳລາຍອິດທິພົນຂອງສື່ທ້ອງຖິ່ນ, Tether (USDT) ແລະ ສະເຕເບິນຄອຍອື່ນໆ ກຳລັງທ້າທາຍອຳນາດຂອງທະນາຄານກາງໃນປະເທດກຳລັງພັດທະນາ. ສະກຸນເງິນດິຈິຕອນທີ່ມີຄວາມສະຖຽນເຫຼົ່ານີ້ ສະເໜີວິທີການສຳລັບປະຊາຊົນເພື່ອປ້ອງກັນເງິນເຟີ້, ຫຼີກລ່ຽງການຄວບຄຸມທຶນ, ແລະ ເຂົ້າເຖິງຕະຫຼາດການເງິນໂລກໂດຍບໍ່ຕ້ອງອີງໃສ່ລະບົບທະນາຄານແບບດັ້ງເດີມ. ໃນຂະນະທີ່ການນຳໃຊ້ກຳລັງເພີ່ມຂຶ້ນ, USDT ກຳລັງກາຍເປັນໄພຂົ່ມຂູ່ທີ່ມີຢູ່ຈິງຕໍ່ທະນາຄານກາງ, ຈຳກັດການຄວບຄຸມຂອງພວກເຂົາຕໍ່ນະໂຍບາຍການເງິນ ແລະ ອຳນາດອະທິປະໄຕທາງການເງິນ.
ທາງເລືອກໃໝ່ແທນສະກຸນເງິນທ້ອງຖິ່ນ
ປະເທດກຳລັງພັດທະນາມັກຈະປະສົບບັນຫາກັບການລົດຄ່າເງິນ, ເງິນເຟີ້, ແລະ ການໄຫລອອກຂອງທຶນ. ທະນາຄານກາງຫຼາຍແຫ່ງບໍ່ສາມາດຮັກສາສະຖຽນລະພາບຂອງສະກຸນເງິນເນື່ອງຈາກການຄຸ້ມຄອງທີ່ບໍ່ດີ, ການພິມເງິນຫຼາຍເກີນໄປ, ຫຼື ການແຊກແຊງທາງການເມືອງ. ພົນລະເມືອງທີ່ເຫັນເງິນທ້ອນຂອງຕົນຖືກກັດເຊາະ ຕາມປົກກະຕິແລ້ວຈະມີທາງເລືອກບໍ່ຫຼາຍ: ປ່ຽນເງິນທ້ອງຖິ່ນເປັນ ໂດລາ ຫລື ໃນກໍລະນີ້ລາວເຮົາກໍຈະມີ ບາດ ແລະ ຢວນນຳ ຜ່ານທະຫລາດມືດ ຫຼື ລົງທຶນກັບທຸລະກິດ, ຊື້ອະສັງຫາ ແລະ ລົງທຶນໃນຊັບສິນຕ່າງປະເທດ. USDT ໄດ້ປ່ຽນແປງເກມນີ້. ມັນອະນຸຍາດໃຫ້ທຸກຄົນທີ່ມີການເຂົ້າເຖິງອິນເຕີເນັດສາມາດເກັບຮັກສາ ແລະ ໂອນມູນຄ່າໃນຮູບແບບດິຈິຕອນທີ່ທຽບເທົ່າກັບໂດລາໂດຍບໍ່ຈຳເປັນຕ້ອງໄດ້ຮັບການອະນຸມັດຈາກທະນາຄານທ້ອງຖິ່ນ ຫຼື ລັດຖະບານ. ສິ່ງນີ້ຊ່ວຍໃຫ້ຫຼຸດພົ້ນຈາກການອີງໃສ່ສະກຸນເງິນແຫ່ງຊາດທີ່ອ່ອນແອ, ສະເໜີທາງເລືອກທີ່ງ່າຍໃນການປ້ອງກັນການເສື່ອມຄ່າ. ໃນປະເທດເຊັ່ນ: ເວເນຊູເອລາ, ອາເຈນຕິນາ, ໄນຈີເຣຍ, ເລບານອນ, ແລະ ລາວ, ປະຊາຊົນກຳລັງນຳໃຊ້ USDT ເພື່ອປົກປ້ອງຄວາມໝັ້ງຄັ່ງຂອງພວກເຂົາຈາກພາວະເງິນເຟີ້ສູງ ແລະ ຄວາມບໍ່ສະຖຽນທາງການເງິນ.
ການທຳລາຍການຜູກຂາດຂອງທະນາຄານກາງ
ທະນາຄານກາງມີອຳນາດອັນໃຫຍ່ຫຼວງຕໍ່ລະບົບການເງິນໂດຍການຄວບຄຸມການອອກເງິນ, ອັດຕາດອກເບ້ຍ, ແລະ ການໄຫຼຂອງທຶນ. ເຖິງຢ່າງໃດກໍຕາມ, USDT ບ່ອນທຳລາຍການຄວບຄຸມນີ້ດ້ວຍການສະໜອງລະບົບການເງິນຄູ່ຂະໜານທີ່ດຳເນີນງານເປັນອິດສະຫຼະຈາກການກຳກັບດູແລຂອງລັດຖະບານ. ສິ່ງນີ້ທ້າທາຍສາມພື້ນທີ່ຫຼັກຂອງອຳນາດທະນາຄານກາງ:
- ການຄວບຄຸມນະໂຍບາຍການເງິນ:
ເມື່ອປະຊາຊົນຍ້າຍເງິນທ້ອນຈາກສະກຸນເງິນທ້ອງຖິ່ນໄປສູ່ USDT, ທະນາຄານກາງຈະສູນເສຍຄວາມສາມາດໃນການຄວບຄຸມປະລິມານເງິນຢ່າງມີປະສິດທິພາບ. ຖ້າປະຊາກອນສ່ວນໃຫຍ່ຢຸດໃຊ້ສະກຸນເງິນແຫ່ງຊາດ, ນະໂຍບາຍເຊັ່ນ: ການປ່ຽນແປງອັດຕາດອກເບ້ຍ ຫຼື ການພິມເງິນກໍຈະສູນເສຍປະສິດທິພາບຂອງພວກມັນ.
- ການຫຼີກລ່ຽງການຄວບຄຸມທຶນ:
ປະເທດກຳລັງພັດທະນາຫຼາຍແຫ່ງບັງຄັບໃຊ້ການຄວບຄຸມທຶນທີ່ເຂັ້ມງວດເພື່ອປ້ອງກັນບໍ່ໃຫ້ເງິນອອກນອກປະເທດ, ເຮັດໃຫ້ສະກຸນເງິນຂອງພວກເຂົາມີສະຖຽນລະພາບ. USDT, ໂດຍບໍ່ມີພົມແດນ, ອະນຸຍາດໃຫ້ຜູ້ໃຊ້ຫຼີກລ່ຽງການຄວບຄຸມເຫຼົ່ານີ້, ເຮັດໃຫ້ມັນງ່າຍຂຶ້ນໃນການດຳເນີນທຸລະກຳທົ່ວໂລກ ຫຼື ເກັບຮັກສາຄວາມໝັ້ງຄັ່ງທີ່ມີສະພາບຄ່ອງລະດັບສາກົນ.
- ການລົດບົດບາດຂອງລະບົບທະນາຄານ:
USDT ຫຼຸດຄວາມຕ້ອງການຂອງການບໍລິການທະນາຄານແບບດັ້ງເດີມ. ດ້ວຍສະມາດໂຟນ ແລະ ກະເປົາເງິນດິຈິຕອນ, ປະຊາຊົນສາມາດສົ່ງ ແລະ ຮັບການຊຳລະເງິນໂດຍບໍ່ຕ້ອງຜ່ານລະບົບທະນາຄານ, ຕັດທະນາຄານອອກຈາກລະບົບນິເວດການເງິນ ແລະ ເຮັດໃຫ້ພວກມັນຂາດຄ່າທຳນຽມທຸລະກຳ ແລະ ເງິນຝາກ.
ກໍລະນີຂອງລາວ: ການປ່ຽນແປງທາງການເງິນທີ່ກຳລັງເກີດຂຶ້ນ
ລາວ, ເຊັ່ນດຽວກັນກັບປະເທດກຳລັງພັດທະນາຫຼາຍແຫ່ງ, ປະເຊີນກັບສິ່ງທ້າທາຍທາງເສດຖະກິດລວມທັງເງິນເຟີ້, ສະກຸນເງິນແຫ່ງຊາດທີ່ອ່ອນແອ (ເງິນກີບລາວ), ແລະ ການເຂົ້າເຖິງເງິນຕາຕ່າງປະເທດທີ່ຈຳກັດ. ລັດຖະບານມີການຄວບຄຸມທຶນທີ່ເຂັ້ມງວດ, ເຮັດໃຫ້ມັນຍາກສຳລັບບຸກຄົນ ແລະ ທຸລະກິດໃນການຊື້ USD ຜ່ານຊ່ອງທາງທີ່ເປັນທາງການ. ສິ່ງນີ້ເຮັດໃຫ້ເກີດຕະຫຼາດມືດສຳລັບການແລກປ່ຽນເງິນຕາທີ່ເຕີບໂຕຂຶ້ນ. ດ້ວຍການເພີ່ມຂຶ້ນຂອງ USDT, ຊາວລາວຫຼາຍຄົນກຳລັງຫັນມາໃຊ້ stable coin ແລະ ເກັບຊັບສິນດິຈິຕອນ ເປັນທາງເລືອກທີ່ປອດໄພກວ່າການຖືເງິນກີບລາວ, ເຊິ່ງມີແນວໂນ້ມທີ່ຈະເສື່ອມຄ່າລົງ.
ບົດຮຽນຈາກການທຳລາຍສື່ທ້ອງຖິ່ນໂດຍສື່ສັງຄົມອອນລາຍ
ການເພີ່ມຂຶ້ນຂອງ USDT ສະທ້ອນໃຫ້ເຫັນເຖິງສື່ສັງຄົມອອນລາຍໄດ້ທຳລາຍສື່ທ້ອງຖິ່ນແນວໃດ. ສື່ຂ່າວແບບດັ້ງເດີມເຄີຍຜູກຂາດການແຈກຢາຍຂໍ້ມູນ, ແຕ່ແພລດຟອມເຊັ່ນ: Facebook, Twitter, ແລະ YouTube ໄດ້ເຮັດໃຫ້ການສ້າງ ແລະ ການແຈກຢາຍເນື້ອຫາເປັນປະຊາທິປະໄຕ. ດັ່ງນັ້ນ, ສື່ທີ່ຄວບຄຸມໂດຍລັດ ແລະ ບໍລິສັດຈຶ່ງສູນເສຍຄວາມສາມາດໃນການກຳນົດເນື້ອຫາ ໃນຂະນະທີ່ສື່ສັງຄົມອອນລາຍເພີ່ມອຳນາດໃຫ້ບຸກຄົນໃນການແບ່ງປັນ ແລະ ເຂົ້າເຖິງຂ່າວທີ່ບໍ່ໄດ້ຜ່ານການ censorship. ເຊັ່ນດຽວກັນ, USDT ກຳລັງກະຈາຍອຳນາດທາງການເງິນ. ເຊັ່ນດຽວກັບສື່ສັງຄົມອອນລາຍທີ່ໃຫ້ສຽງແກ່ປະຊາຊົນນອກເໜືອຈາກສື່ກະແສຫຼັກ, USDT ກຳລັງໃຫ້ຄວາມເປັນອິດສະຫຼະທາງການເງິນແກ່ບຸກຄົນທີ່ເກີນກວ່າຂອບເຂດຂອງທະນາຄານກາງ. ແນວໂນ້ມນີ້ຊັດເຈນ: ສະຖາບັນທີ່ລວມສູນຈະສູນເສຍການຄວບຄຸມເມື່ອບຸກຄົນໄດ້ຮັບການເຂົ້າເຖິງໂດຍກົງຕໍ່ທາງເລືອກອື່ນ.
Trump ສະໜັບສະໜູນ Stable Coin
ປະທານາທິບໍດີສະຫະລັດ Donald Trump ໄດ້ສະແດງການສະໜັບສະໜູນຕໍ່ stable coin ແລະ ອຸດສາຫະກຳ cryptocurrency ເມື່ອບໍ່ດົນມານີ້. ຈຸດຢືນຂອງລາວເປັນສັນຍານເຖິງການປ່ຽນແປງທີ່ເປັນໄປໄດ້ໃນນະໂຍບາຍຂອງສະຫະລັດທີ່ອາດຈະສ້າງຄວາມຊອບທຳໃຫ້ແກ່ສະເຕເບິນຄອຍ ແລະ ຂັບເຄື່ອນການນຳໃຊ້ທົ່ວໂລກ. ຖ້າລັດຖະບານສະຫະລັດຮັບຮອງສະເຕເບິນຄອຍເຊັ່ນ USDT, ມັນອາດຈະເລັ່ງການນຳໃຊ້ພວກມັນເປັນທາງເລືອກແທນລະບົບທະນາຄານແບບດັ້ງເດີມ, ສ້າງແຮງກົດດັນເພີ່ມເຕີມຕໍ່ທະນາຄານກາງໃນປະເທດກຳລັງພັດທະນາ. ນີ້ອາດຈະສົ່ງເສີມໃຫ້ມີການມີສ່ວນຮ່ວມຂອງສະຖາບັນຫຼາຍຂຶ້ນ, ເຮັດໃຫ້ມັນຍາກຂຶ້ນສຳລັບລັດຖະບານທ້ອງຖິ່ນໃນການປາບປາມການນຳໃຊ້ USDT.
ຊ່ອງຫວ່າງຂອງການຮັບຮູ້: ຫຼາຍຄົນຍັງບໍ່ຮູ້ເຖິງໄພຂົ່ມຂູ່
ເຖິງແມ່ນວ່າ USDT ຈະເຕີບໂຕຢ່າງໄວວາ, ປະຊາຊົນຫຼາຍຄົນໃນປະເທດກຳລັງພັດທະນາຍັງບໍ່ຮັບຮູ້ເຖິງຜົນກະທົບຂອງມັນ. ໃນຂະນະທີ່ຜູ້ໃຊ້ເລີ່ມຕົ້ນຈະເປັນ ບຸກຄົນທີ່ຮູ້ເທັກໂນໂລຊີ, ນັກລົງທຶນ ແລະ ເຈົ້າຂອງທຸລະກິດ, ປະຊາກອນສ່ວນໃຫຍ່ຍັງອີງໃສ່ການທະນາຄານແບບດັ້ງເດີມ ແລະ ສະກຸນເງິນຕາມກົດໝາຍໂດຍບໍ່ຮູ້ເຖິງຄວາມສ່ຽງຂອງການເສື່ອມຄ່າ ແລະ ຄວາມບໍ່ສະຖຽນທາງການເງິນ. ເຖິງຢ່າງໃດກໍຕາມ, ບຸກຄົນຕ້ອງມີຄວາມຄິດລິເລີ່ມໃນການສຶກສາຕົນເອງກ່ຽວກັບເຄື່ອງມືທາງການເງິນທາງເລືອກເຊັ່ນ USDT ແລະ Bitcoin ເພື່ອປົກປ້ອງຄວາມໝັ້ງຄັ່ງ ແລະ ຄວາມເປັນອິດສະຫຼະທາງການເງິນຂອງພວກເຂົາ.
ບົດສະຫຼຸບ: ການປະຕິວັດທາງການເງິນທີ່ກຳລັງເກີດຂຶ້ນ
USDT ແລະ Bitcoin ແມ່ນການປະຕິວັດທາງການເງິນທີ່ເພີ່ມອຳນາດໃຫ້ບຸກຄົນໃນປະເທດກຳລັງພັດທະນາທີ່ຈະຫຼຸດພົ້ນຈາກນະໂຍບາຍການເງິນທີ່ລົ້ມເຫຼວ. ເຊັ່ນດຽວກັບສື່ສັງຄົມອອນລາຍໄດ້ປະຕິວັດພູມທັດຂອງສື່ໂດຍການໃຫ້ປະຊາຊົນຄວບຄຸມຂໍ້ມູນຂ່າວສານ, USDT ກຳລັງປະຕິວັດການເງິນໂດຍການໃຫ້ປະຊາຊົນຄວບຄຸມເງິນຂອງພວກເຂົາ. ສຳລັບທະນາຄານກາງໃນປະເທດກຳລັງພັດທະນາ, ການປ່ຽນແປງນີ້ສ້າງສະພາວະຫຍຸ້ງຍາກທີ່ຮ້າຍແຮງ: ປັບຕົວ ຫຼື ສູນເສຍອິດທິພົນ. ລັດຖະບານອາດຈະພະຍາຍາມຄວບຄຸມກົດລະບຽບ ຫຼື ຫ້າມສະເຕເບິນຄອຍ, ແຕ່ຕາມທີ່ປະຫວັດສາດໄດ້ສະແດງໃຫ້ເຫັນກັບສື່ສັງຄົມອອນລາຍ.
-
 @ 378562cd:a6fc6773
2025-03-25 00:16:58
@ 378562cd:a6fc6773
2025-03-25 00:16:58Bitcoin gives you financial freedom, but if you're not careful, someone’s watching. If you don’t run your own Bitcoin node, you're trusting someone else with your privacy. Here's why that’s a bad idea—and how running your own node fixes it.
What Is a Bitcoin Node? A Bitcoin node is software that connects to the Bitcoin network. It: ✅ Verifies transactions and blocks. ✅ Stores a copy of the blockchain. ✅ Relays transactions to the network. ✅ Lets you use Bitcoin without trusting anyone.
If you don’t run a node, you’re relying on someone else’s—usually a company that tracks your activity.
How Using Someone Else’s Node Destroys Your Privacy 👀 They Can See Your Transactions – Third-party wallets track what you send, receive, and how much Bitcoin you have. 📍 Your IP Address is Exposed – When you send a transaction, your location could be linked to it. ⛔ Censorship is Possible – Some services can block or delay your transactions. 🔗 They Can Link Your Addresses – Many wallets send your balance info to outside servers, connecting all your Bitcoin activity.
How Running Your Own Node Protects You 🔒 No One Knows Your Balances – Your wallet checks the blockchain directly, keeping your finances private. 🕵️ Hides Your IP Address – No one knows where your transactions come from, especially if you use Tor. 🚀 No Transaction Censorship – Your node sends transactions directly, avoiding interference. ✅ You Verify Everything – No fake data or reliance on third-party information.
But Isn’t Running a Node Hard? Not anymore! You can: 💻 Download Bitcoin Core and run it on your computer. 🔌 Use plug-and-play devices like Umbrel or MyNode. 🍓 Set up a cheap Raspberry Pi to run 24/7.
It’s easier than you think—and worth it.
Why This Matters The more people run nodes, the stronger Bitcoin gets. It becomes more decentralized, harder to censor, and more private for everyone.
Final Thought If you value privacy, freedom, and financial independence, running your own Bitcoin node is a no-brainer. Take control. Protect your Bitcoin. Run a node. 🚀
-
 @ 078d6670:56049f0c
2025-03-24 11:28:59
@ 078d6670:56049f0c
2025-03-24 11:28:59I spent some time outside in the dark last night. After a little sleep I was wide awake again, so I ventured downstairs, rolled a joint and stepped into the darkness. No moon, no outside lights. Just stars flickering through space and landing on the sky dome, expanding my being.
There was nothing unusual. Just the usual fleeting apparitions shooting through the ether, barely visible, like they’re behind a lace curtain and I have a glimpse into the astral: light and dark winged things, miniature meteor orbs and bat shadows. This time I wasn’t listening to anything, just the inspiring tangent thoughts spiralling through my mental DNA. No cows, no lions fornicating, not even any barking dogs. (But there was a Wood Owl hooting.)
Initially, I was a little disappointed I hadn’t seen anything inexplicable, but I got over myself and expectation to always see fairies. There is a bliss in just being present (and stoned)!
When I was ready to exit the deck space, I yelled silently to myself and anyone reading my mind, “Goodnight Sky! Thank you stars for shining! Thank you planets for showing yourselves! Blessings to all the conscious beings in the Universe!”
I wasn’t prepared for what happened next. I wasn’t sure if I should run inside to get my smartphone or just watch.
An orb, a little bigger than the average star, manifested directly above my head, star-height, as far as my perception could guess. Then it disappeared after two seconds. Another one appeared in the same vicinity, and disappeared. I couldn’t tell if it was the same one reappearing in an astral (wormhole) jump, or other orbs were taking turns to greet me, because there were more, probably five in total.
How the f*!k did they hear me?
Is the sky conscious?
Does my being extend to the stars?
It felt like I was inside a lucid dream. The world was alive and acknowledging my blessings instantaneously. What impeccable manners!
I understand everything in my dream world is an extension of my consciousness. When I’m lucid I can interact with any of my dream elements and ask for meaning. There are no limits, only my imagination and unconscious beliefs.
But what is happening now?!
My reality is transforming into a dream, or the dream sandbox is becoming more real. Synchronistically, this is amazing, since my reading is taking me on a journey into western esotericism to expansive experiences through imagination to include the stars and beyond.
Soon, it’ll be time to call reality the Unreal, and the unreal Reality.
-
 @ 4d4fb5ff:1e821f47
2025-03-24 02:03:53
@ 4d4fb5ff:1e821f47
2025-03-24 02:03:53The entire genetic sequence for peptidase E (pepE, e. coli). Genes in living organisms are subject to mutation across time. In contrast, information on the bitcoin ledger is immutable. By etching the pepE DNA sequence onto bitcoin, its ability to evolve is lost. This challenges the significance of genetic information in a foreign digital context. I chose to keep the title “PEPEGENE” in upper case as a homage to the naming convention for Counterparty assets. This additionally contrasts the notation of a digital asset identifier (PEPEGENE) against the notation of biological identifiers (a,t,c or g), which are kept in lower case.
-
 @ 378562cd:a6fc6773
2025-03-23 23:34:49
@ 378562cd:a6fc6773
2025-03-23 23:34:49In 1976, Logan’s Run presented a futuristic society where hedonism, government control, and the illusion of utopia dictated the lives of its citizens. On the surface, it was a thrilling sci-fi adventure, complete with dazzling special effects and a suspenseful storyline. But beneath the aesthetics of the domed city lay a chilling warning—one that seems eerily prophetic when viewed through the lens of today’s world.
The World of Logan’s Run
Set in the 23rd century (2201-2300), Logan’s Run depicts a civilization where people live under a massive dome, free from hunger, disease, and suffering. However, there’s a catch: when a citizen turns 30, they are forced to participate in “Carousel,” a supposed process of renewal that is, in reality, a government-mandated execution. The system is designed to maintain population control, enforce conformity, and ensure that no one ever challenges the status quo.
Logan 5, the film’s protagonist, is a “Sandman” tasked with hunting down those who try to escape their fate. But when he himself begins questioning the system and searching for the mythical “Sanctuary,” he uncovers the horrifying truth about his world.
Modern Parallels: Are We Living in Logan’s Run?
While we may not have an enforced death age (yet), many aspects of Logan’s Run reflect the realities of today’s society. The film serves as an allegory for the dangers of unchecked government power, mass surveillance, and a culture obsessed with youth and pleasure over wisdom and truth.
- The Cult of Youth and Anti-Aging Obsession
In Logan’s Run, life ends at 30 because youth is worshiped. While we don’t physically eliminate people past a certain age, we see a similar fixation on youth today. The beauty industry, social media influencers, and Hollywood all glorify eternal youth, with people going to extreme lengths—cosmetic surgery, anti-aging treatments, and digital filters—to maintain an illusion of perfection.
- Surveillance and Government Control
Citizens in Logan’s Run are constantly monitored, with the system ensuring no one steps out of line. Sound familiar? Today, we have mass surveillance through smartphones, facial recognition, AI-driven data collection, and social credit systems emerging worldwide. Governments and corporations track movements, preferences, and even conversations, creating a digital panopticon that makes Logan’s world seem less far-fetched.
- Hedonism and Instant Gratification
The film’s society revolves around pleasure, entertainment, and consequence-free living. Today, we have the digital equivalent—hookup culture, endless streaming services, video games, and social media dopamine loops keeping people perpetually distracted from deeper realities. The ease of endless entertainment overshadows the idea of questioning authority or seeking something greater.
- Fear of the Outside World
In Logan’s Run, citizens believe that stepping outside the dome means certain death. Today, many are trapped in their own digital domes, glued to screens, hesitant to unplug, go into nature, or seek real-world experiences. Fear, whether of the unknown or the uncontrollable, keeps people complacent.
- Population Control and Elite Decision-Making
While Carousel is an extreme form of population control, discussions about depopulation, climate policies, and AI-driven automation today suggest that powerful elites are still making decisions about who thrives and who suffers. The concentration of power in the hands of a few is as relevant now as it was in the film.
The Awakening: Will We Choose Freedom?
One of the most striking aspects of Logan’s Run is Logan’s transformation from an enforcer of the system to a rebel seeking truth. His journey mirrors the awakening many people experience today—questioning mainstream narratives, rejecting mass manipulation, and seeking autonomy.
But just as in the film, there are those who refuse to break free. Many continue living inside the “dome,” blindly trusting the system, believing that technology, government, or a new social movement will save them. The question is: Are we more like Logan, daring to seek truth, or the others, content to live in comfortable illusions?
Final Thoughts: Is There a Sanctuary?
In Logan’s Run, Sanctuary represents the hope of a free world beyond the control of the system. Today, people seek their own sanctuaries—homesteading, off-grid living, digital privacy, and independent communities that reject mass conformity.
The film’s message is clear: When a society values comfort over freedom, pleasure over wisdom, and compliance over questioning, it sets the stage for control and deception. But those willing to escape the illusion—just as Logan did—may just find their own Sanctuary.
The question remains: Will we wake up in time?
-
 @ 15125b37:e89877f5
2025-03-23 18:57:20
@ 15125b37:e89877f5
2025-03-23 18:57:20What is Blockchain?
Block by Block:
The Power of Blockchain Unlocked
In its simplest form, a blockchain is a type of digital ledger that records transactions in a secure and transparent way. Imagine a record book that everyone can see, but no one can alter. Each page of the book (called a block) holds a group of transactions, and the pages are linked together in a chain. The blockchain is decentralized, meaning no single person, company, or entity controls it, which makes it different from traditional centralized systems like banks.
Decentralized: No single point of control or authority.
Secure: Uses cryptography to ensure data integrity.
Immutable: Once data is added to the blockchain, it cannot be changed or deleted, providing transparency and security.
How Blockchain Works
Each block on the blockchain contains a batch of transactions. Once a block is full, it’s linked to the previous block, creating a chain of blocks—hence the name blockchain. Each block has three key components:
Transaction data: Information about transactions (e.g., who sent money, who received it, and how much).
Timestamp: The time the block was created.
Hash: A unique identifier for the block, created through cryptographic hashing. Think of a hash like a unique digital fingerprint that is tied to each specific block. And each hash (digital fingerprint) points to the previous block, thereby creating a permanent, unchangeable history of transactions.

Decentralization
One of blockchain's most revolutionary aspects is that it is decentralized. This means there’s no central authority (like a bank or a government) controlling the transactions. Instead, everyone participating in the network has a copy of the blockchain, and transactions are validated by multiple independent users (called nodes).
How It’s Decentralized: Think of it as a large group of people each keeping their own ledger. They work together to validate and record transactions, ensuring no one person can manipulate the system. Of course, this is all done automatically through code that is run on a computer 24 hours a day, 7 days a week. More about that later in this series.
Consensus: For a transaction to be recorded, most of the nodes must agree it’s valid, creating a system of consensus without the need for a trusted central party. This makes blockchain resistant to censorship and fraud.
Security of Blockchain
Blockchain is highly secure due to its use of cryptographic techniques. Every block’s hash (digital fingerprint) is created using the information from within the block plus the hash of the previous block. Thus, the hash of each block is infinitely unique and linked to each other in a chain.
Immutability: If someone tries to change the data in a block, the hash changes. Since every block contains the hash of the previous block, altering one block would require changing all subsequent blocks, which is computationally impossible for a well-maintained blockchain.
Transparency: Blockchain’s decentralized nature means that anyone can see the data, but no one can tamper with it. This ensures trust and transparency in the system.

The Role of Miners/Validators
To add a block to the blockchain, the transactions in the block need to be verified. This is where miners come in. Their job is to check that transactions are valid, and in return, they are rewarded with bitcoin (BTC). This is called Proof-of-Work. Miners compete to solve complex mathematical puzzles. When a miner solves the puzzle (approximately every 10 minutes), they get to add the next block to the blockchain filled with pending transactions, and thereby earn the reward for doing so. They put in the work! Thus, Proof-of-Work.
Why Blockchain is Important
The core value of blockchain lies in its function as a digital ledger. Unlike traditional databases, which are typically controlled by a central authority (such as a bank, a government, or a company), blockchain is a distributed ledger, meaning copies of the same ledger are held across multiple computers (or nodes) around the world on a voluntary basis. This setup creates a system where transactions are recorded in a way that are transparent, trustless, immutable, and decentralized.
Without blockchain, Bitcoin wouldn’t be able to function as a decentralized, peer-to-peer currency. It’s the underlying technology that ensures Bitcoin’s integrity and security.
-
 @ 3b7fc823:e194354f
2025-03-23 03:54:16
@ 3b7fc823:e194354f
2025-03-23 03:54:16A quick guide for the less than technical savvy to set up their very own free private tor enabled email using Onionmail. Privacy is for everyone, not just the super cyber nerds.
Onion Mail is an anonymous POP3/SMTP email server program hosted by various people on the internet. You can visit this site and read the details: https://en.onionmail.info/
- Download Tor Browser
First, if you don't already, go download Tor Browser. You are going to need it. https://www.torproject.org/
- Sign Up
Using Tor browser go to the directory page (https://onionmail.info/directory.html) choose one of the servers and sign up for an account. I say sign up but it is just choosing a user name you want to go before the @xyz.onion email address and solving a captcha.
- Account information
Once you are done signing up an Account information page will pop up. MAKE SURE YOU SAVE THIS!!! It has your address and passwords (for sending and receiving email) that you will need. If you lose them then you are shit out of luck.
- Install an Email Client
You can use Claws Mail, Neomutt, or whatever, but for this example, we will be using Thunderbird.
a. Download Thunderbird email client
b. The easy setup popup page that wants your name, email, and password isn't going to like your user@xyz.onion address. Just enter something that looks like a regular email address such as name@example.com and the Configure Manuallyoption will appear below. Click that.
- Configure Incoming (POP3) Server
Under Incoming Server: Protocol: POP3 Server or Hostname: xyz.onion (whatever your account info says) Port: 110 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (POP3 password).
- Configure Outgoing (SMTP) Server
Under Outgoing Server: Server or Hostname: xyz.onion (whatever your account info says) Port: 25 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (SMTP password).
-
Click on email at the top and change your address if you had to use a spoof one to get the configure manually to pop up.
-
Configure Proxy
a. Click the gear icon on the bottom left for settings. Scroll all the way down to Network & Disk Space. Click the settings button next to Connection. Configure how Thunderbird connects to the internet.
b. Select Manual Proxy Configuration. For SOCKS Host enter 127.0.0.1 and enter port 9050. (if you are running this through a VM the port may be different)
c. Now check the box for SOCKS5 and then Proxy DNS when using SOCKS5 down at the bottom. Click OK
- Check Email
For thunderbird to reach the onion mail server it has to be connected to tor. Depending on your local setup, it might be fine as is or you might have to have tor browser open in the background. Click on inbox and then the little cloud icon with the down arrow to check mail.
- Security Exception
Thunderbird is not going to like that the onion mail server security certificate is self signed. A popup Add Security Exception will appear. Click Confirm Security Exception.
You are done. Enjoy your new private email service.
REMEMBER: The server can read your emails unless they are encrypted. Go into account settings. Look down and click End-toEnd Encryption. Then add your OpenPGP key or open your OpenPGP Key Manager (you might have to download one if you don't already have one) and generate a new key for this account.
-
 @ 234035ec:edc3751d
2025-03-22 02:34:32
@ 234035ec:edc3751d
2025-03-22 02:34:32I would like to preface this idea by stating that I am by no means a computer engineer and lack significant technical knowledge, and therefore may be overlooking significant obstacles to implementing this idea. My reason for writing this paper is in hopes that developers or others who are more "in the know" than me could provide feedback.
The Success of Polymarket
Over recent months, Polymarket has garnered many headlines—mainly for its accurate prediction markets surrounding the 2024 presidential election. On Polymarket, users can purchase futures contracts that will either pay out $1 in USDC at maturity if the prediction is correct or will become worthless if the prediction is incorrect. Market participants can freely trade these futures at the current price up until maturity, allowing for efficient price discovery.
We’ve known for quite some time that free markets are the most efficient way of pricing goods and services. Polymarket has now demonstrated just how effective they can be in pricing potential outcomes as well.
The issue I have with this application is that it is built on the Polygon network—a proof-of-stake side chain of Ethereum. Users are subject to KYC regulations and do not have the ability to create markets themselves. While the core idea is powerful, I believe it has been built on a foundation of sand. We now have the tools to build something similar—but much more decentralized, censorship-resistant, and sustainable.
A Bitcoin-Based Prediction Market
It seems to me that Chaumian eCash, in combination with Bitcoin and Nostr, could be used to create a truly decentralized prediction marketplace. For example, multiple eCash mints could issue tokens that represent specific potential outcomes. These tokens would be redeemable for 100 sats at a predetermined block height if the prediction is correct—or become irredeemable if the prediction is incorrect.
Redemption would be based on consensus from the chosen oracles—trusted Nostr Npubs—with strong reputations and proven track records. Anyone could create a market, and users could buy, sell, and trade eCash tokens privately. This approach preserves the power of markets while eliminating the need for custodians, KYC, or dependence on unreliable chains.
What we would have is a trust-minimized, privacy-preserving, Bitcoin-native prediction market that resists censorship and allows for true global participation. Feedback, critique, and collaboration are welcome.
Next Steps and Vision
The potential for system like this is immense. Not only would it enable peer-to-peer speculation on real-world outcomes, but it would also open the door to a more accurate reflection of public sentiment. With free market incentives driving truth-seeking behavior, these prediction markets could become powerful tools for gauging probabilities in politics, finance, sports, science, and beyond.
Each mint could specialize in a specific domain or geographic region, and users could choose the ones they trust—or even run their own. The competition between mints would drive reliability and transparency. By using Nostr for oracle communication and event creation, we keep the entire system open, composable, and censorship-resistant.
Markets could be created using a standardized Nostr event type. Resolution data could be posted and signed by oracles in a verifiable way, ensuring anyone can validate the outcome. All of this could be coordinated without a centralized authority, enabling pseudonymous participation from anyone with an internet connection and a Lightning wallet.
In the long run, this system could offer a viable alternative to corrupted media narratives, rigged polling, and centrally controlled information channels. It would be an open-source tool for discovering truth through economic incentives—without requiring trust in governments, corporations, or centralized platforms.
If this idea resonates with you, I encourage you to reach out, build on it, criticize it, or propose alternatives. This isn’t a product pitch—it’s a call to experiment, collaborate, and push the frontier of freedom-forward technologies.
Let’s build something that lasts.
Bitcoin is our base layer. Markets are our discovery engine. Nostr is our communication rail. Privacy is our defense. And truth is our goal.
-
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ f240be2b:00c761ba
2025-03-20 17:53:08
@ f240be2b:00c761ba
2025-03-20 17:53:08Warum jetzt ein guter Zeitpunkt sein könnte, sich mit Bitcoin zu beschäftigen
Kennt ihr das? Wenn der Bitcoin-Preis neue Höchststände erreicht, möchte plötzlich jeder einsteigen. Doch sobald die Kurse fallen, überwiegt die Angst. Dabei zeigt die Geschichte: Gerade diese Phasen der Unsicherheit können interessante Zeitpunkte sein, um sich mit dem Thema zu beschäftigen.
Historische Zyklen Bitcoin durchläuft regelmäßige Marktzyklen Nach jedem Tief folgte bisher ein neues Hoch Emotionen spielen eine große Rolle im Markt Psychologie des Marktes Wenn alle euphorisch sind → meist teuer Wenn Unsicherheit herrscht → oft interessante Gelegenheiten Die Masse liegt häufig zum falschen Zeitpunkt richtigRationale Herangehensweise
Statt emotional zu handeln, solltet ihr:
Einen langfristigen Anlagehorizont wählen Regelmäßig kleine Beträge investieren (Cost-Average-Effekt)Hier ein paar Charts die euch helfen sollen und euch mutig werden lassen:
https://www.tradingview.com/chart/BTCUSD/HuGpzZfQ-BITCOIN-Cycle-pattern-completed-Year-end-Target-locked-at-150k/
https://www.tradingview.com/chart/BTCUSD/YVyy9QuU-BITCOIN-Money-Supply-Dollar-and-Bonds-pushing-for-MEGA-RALLY/
https://www.tradingview.com/chart/BTCUSD/pZ0qs5x3-BTCUSD-TSI-shows-that-this-is-the-LAST-BEST-BUY/
https://www.tradingview.com/chart/BTCUSD/x3e7GuLQ-BITCOIN-Is-this-a-Falling-Wedge-bottom-formation/
und jetzt All-In :-)
-
 @ 378562cd:a6fc6773
2025-03-20 14:26:48
@ 378562cd:a6fc6773
2025-03-20 14:26:48When SpongeBob SquarePants first graced television screens in 1999, it quickly became a cultural phenomenon. Its quirky humor, unique animation style, and absurd yet endearing characters captured audiences of all ages. However, beyond its whimsical surface, SpongeBob SquarePants holds surprising ties to real-world marine biology, human behaviors, and even corporate America. Let's take a deep dive into the striking similarities between the show’s universe and real life.
- Bikini Bottom and the Nuclear Connection
One of the most intriguing theories about SpongeBob SquarePants is its potential connection to real-world geography. Bikini Bottom, the fictional underwater city where SpongeBob and his friends reside, is widely believed to be named after Bikini Atoll, a site in the Pacific Ocean where the U.S. conducted nuclear tests in the 1940s and 1950s. Some fans speculate that the bizarre personalities of the show's characters are a result of radioactive mutations—a wild yet eerily plausible idea given the history of the atoll.
- SpongeBob: More Than Just a Sponge
SpongeBob is, of course, a sea sponge, but his rectangular, kitchen-sponge shape is a deviation from most natural sea sponges, which are irregularly shaped. However, real-life sea sponges are fascinating creatures that can regenerate after being broken apart—just like how SpongeBob bounces back from every misadventure with relentless optimism.
Additionally, SpongeBob’s enthusiasm and boundless energy mimic the real-life behaviors of certain marine organisms that continuously filter water, making them vital to their ecosystems. His ceaseless work ethic at the Krusty Krab also mirrors the tireless efforts of smaller marine life that keep oceanic ecosystems functioning.
- Squidward: An Octopus in Disguise
Despite his name, Squidward Tentacles is actually an octopus. Series creator Stephen Hillenburg, a marine biologist before becoming an animator, intentionally designed Squidward with six tentacles instead of the usual eight to make animation easier. His grumpy and refined personality also reflects the intelligence of real-world octopuses, who are known for their problem-solving skills and, at times, their moody behavior.
- The Krusty Krab and Corporate Culture
The Krusty Krab, the fast-food restaurant where SpongeBob works, is a satirical take on real-life corporate culture, particularly in the fast-food industry. Mr. Krabs, the money-hungry owner, represents stereotypical profit-driven business owners who prioritize revenue over employee well-being. Meanwhile, SpongeBob’s unwavering loyalty to his job highlights the enthusiasm of idealistic workers, and Squidward embodies the disillusioned employees who begrudgingly clock in every day. This dynamic is strikingly similar to real-world labor environments, making the show relatable even beyond its nautical setting.
- Plankton and the Struggles of Small Businesses
Sheldon J. Plankton, the tiny but ambitious owner of the failing Chum Bucket, serves as a metaphor for small business owners who struggle to compete with corporate giants. His constant yet futile attempts to steal the Krabby Patty secret formula echo the real-world battle between small independent businesses and industry monopolies. Despite his villainous traits, Plankton’s perseverance and innovative schemes make him an oddly sympathetic character, much like real-life entrepreneurs striving to find success against all odds.
- Real-Life Marine Life Mirrored in Characters
Each character in SpongeBob SquarePants is based on real marine creatures with behaviors that closely resemble their animated counterparts:
Patrick Star: A pink starfish who is slow and lazy, much like real-life starfish that lack a brain and move sluggishly.
Sandy Cheeks: A land-dwelling squirrel who thrives in an underwater suit, symbolizing the scientific research done by deep-sea divers and marine biologists in the ocean.
Mr. Krabs: A crab with a tight grip on his money, reflecting the territorial and often aggressive nature of real-world crabs.
Larry the Lobster: A fitness-obsessed lobster, much like real lobsters that grow larger and stronger as they molt.
Conclusion: A Show Rooted in Reality
While SpongeBob SquarePants is undeniably a wacky and exaggerated series, its deep connection to real-world marine biology, workplace culture, and corporate dynamics gives it an extra layer of depth. Whether intentionally or unintentionally, the show serves as an entertaining yet insightful reflection of life above and below the ocean’s surface. So next time you watch an episode, remember—you’re not just enjoying a cartoon; you’re diving into a cleverly crafted world filled with real-life parallels, which is probably a direct correlation to its wild success in all these years.
-
 @ 21335073:a244b1ad
2025-03-20 13:16:22
@ 21335073:a244b1ad
2025-03-20 13:16:22I’d never had the chance to watch Harry Potter on the big screen before. Experiencing the first movie in 3D was nothing short of spectacular. Right from the opening scene with Albus Dumbledore, I was floored—the makeup and costumes were so vivid, it felt like pure magic unfolding before my eyes. It’s clear that real masters of their craft worked behind the scenes, and their artistry shines through. The sets? Absolutely jaw-dropping! The level of detail in Diagon Alley was beyond impressive.
Seeing legends like Alan Rickman as Snape and Maggie Smith as Minerva McGonagall on that massive 3D screen was an unforgettable thrill. The film is packed with phenomenal actors, and it was a joy to catch every tiny eye twitch and subtle nuance of their performances brought to life. It was a mind-blowing experience, and I’d wholeheartedly recommend it to anyone who gets the chance.
Don’t forget to have a little whimsical fun sometimes my friends. 🪄
-
 @ ee9aaefe:1e6952f4
2025-03-19 05:01:44
@ ee9aaefe:1e6952f4
2025-03-19 05:01:44Introduction to Model Context Protocol (MCP)
Model Context Protocol (MCP) serves as a specialized gateway allowing AI systems to access real-time information and interact with external data sources while maintaining security boundaries. This capability transforms AI from closed systems limited to training data into dynamic assistants capable of retrieving current information and performing actions. As AI systems integrate into critical infrastructure across industries, the security and reliability of these protocols have become crucial considerations.
Security Vulnerabilities in Web-Based MCP Services
Traditional MCP implementations operate as web services, creating a fundamental security weakness. When an MCP runs as a conventional web service, the entire security model depends on trusting the service provider. Providers can modify underlying code, alter behavior, or update services without users' knowledge or consent. This creates an inherent vulnerability where the system's integrity rests solely on the trustworthiness of the MCP provider.
This vulnerability is particularly concerning in high-stakes domains. In financial applications, a compromised MCP could lead to unauthorized transactions or exposure of confidential information. In healthcare, it might result in compromised patient data. The fundamental problem is that users have no cryptographic guarantees about the MCP's behavior – they must simply trust the provider's claims about security and data handling.
Additionally, these services create single points of failure vulnerable to sophisticated attacks. Service providers face internal threats from rogue employees, external pressure from bad actors, or regulatory compulsion that could compromise user security or privacy. With traditional MCPs, users have limited visibility into such changes and few technical safeguards.
ICP Canisters: Enabling the Verifiable MCP Paradigm
The Internet Computer Protocol (ICP) offers a revolutionary solution through its canister architecture, enabling what we term "Verifiable MCP" – a new paradigm in AI security. Unlike traditional web services, ICP canisters operate within a decentralized network with consensus-based execution and verification, creating powerful security properties:
- Cryptographically verifiable immutability guarantees prevent silent code modifications
- Deterministic execution environments allow independent verification by network participants
- Ability to both read and write web data while operating under consensus verification
- Control of off-chain Trusted Execution Environment (TEE) servers through on-chain attestation
These capabilities create the foundation for trustworthy AI context protocols that don't require blind faith in service providers.
Technical Architecture of Verifiable MCP Integration
The Verifiable MCP architecture places MCP service logic within ICP canisters that operate under consensus verification. This creates several distinct layers working together to ensure security:
-
Interface Layer: AI models connect through standardized APIs compatible with existing integration patterns.
-
Verification Layer: The ICP canister validates authentication, checks permissions, and verifies policy adherence within a consensus-verified environment.
-
Orchestration Layer: The canister coordinates necessary resources for data retrieval or computation.
-
Attestation Layer: For sensitive operations, the canister deploys and attests TEE instances, providing cryptographic proof that correct code runs in a secure environment.
-
Response Verification Layer: Before returning results, cryptographic verification ensures data integrity and provenance.
This architecture creates a transparent, verifiable pipeline where component behavior is guaranteed through consensus mechanisms and cryptographic verification—eliminating the need to trust service provider claims.
Example: Secure Financial Data Access Through Verifiable MCP
Consider a financial advisory AI needing access to banking data and portfolios to provide recommendations. In a Verifiable MCP implementation:
-
The AI submits a data request through the Verifiable MCP interface.
-
The ICP canister verifies authorization using immutable access control logic.
-
For sensitive data, the canister deploys a TEE instance with privacy-preserving code.
-
The canister cryptographically verifies the TEE is running the correct code.
-
Financial services provide encrypted data directly to the verified TEE.
-
The TEE returns only authorized results with cryptographic proof of correct execution.
-
The canister delivers verified insights to the AI.
This ensures even the service provider cannot access raw financial data while maintaining complete auditability. Users verify exactly what code processes their information and what insights are extracted, enabling AI applications in regulated domains otherwise too risky with traditional approaches.
Implications for AI Trustworthiness and Data Sovereignty
The Verifiable MCP paradigm transforms the trust model for AI systems by shifting from "trust the provider" to cryptographic verification. This addresses a critical barrier to AI adoption in sensitive domains where guarantees about data handling are essential.
For AI trustworthiness, this enables transparent auditing of data access patterns, prevents silent modifications to processing logic, and provides cryptographic proof of data provenance. Users can verify exactly what information AI systems access and how it's processed.
From a data sovereignty perspective, users gain control through cryptographic guarantees rather than policy promises. Organizations implement permissions that cannot be circumvented, while regulators can verify immutable code handling sensitive information. For cross-border scenarios, Verifiable MCP enables compliance with data localization requirements while maintaining global AI service capabilities through cryptographically enforced data boundaries.
Conclusion
The Verifiable MCP paradigm represents a breakthrough in securing AI systems' external interactions. By leveraging ICP canisters' immutability and verification capabilities, it addresses fundamental vulnerabilities in traditional MCP implementations.
As AI adoption grows in regulated domains, this architecture provides a foundation for trustworthy model-world interactions without requiring blind faith in service providers. The approach enables new categories of AI applications in sensitive sectors while maintaining robust security guarantees.
This innovation promises to democratize secure context protocols, paving the way for responsible AI deployment even in the most security-critical environments.
-
 @ 04ff5a72:22ba7b2d
2025-03-19 03:25:28
@ 04ff5a72:22ba7b2d
2025-03-19 03:25:28The Evolution of the "World Wide Web"
The internet has undergone a remarkable transformation since its inception, evolving from a collection of static pages to a dynamic, interconnected ecosystem, and now progressing toward a decentralized future. This evolution is commonly divided into three distinct phases: Web 1, Web 2, and the emerging Web 3. Each phase represents not only technological advancement but fundamental shifts in how we interact with digital content, who controls our data, and how value is created and distributed online. While Web 1 and Web 2 have largely defined our internet experience to date, Web 3 promises a paradigm shift toward greater user sovereignty, decentralized infrastructure, and reimagined ownership models for digital assets.
The Static Beginning: Web 1.0
The first iteration of the web, commonly known as Web 1.0, emerged in the early 1990s and continued until the late 1990s. This period represented the internet's infancy, characterized by static pages with limited functionality and minimal user interaction[1]. At the core of Web 1 was the concept of information retrieval rather than dynamic interaction.
Fundamental Characteristics of Web 1
During the Web 1 era, websites primarily served as digital brochures or informational repositories. Most sites were static, comprised of HTML pages containing fixed content such as text, images, and hyperlinks[1]. The HTML (Hypertext Markup Language) provided the structural foundation, while CSS (Cascading Style Sheets) offered basic styling capabilities. These technologies enabled the creation of visually formatted content but lacked the dynamic elements we take for granted today.
The Web 1 experience was predominantly one-directional. The majority of internet users were passive consumers of content, while creators were primarily web developers who produced websites with mainly textual or visual information[2]. Interaction was limited to basic navigation through hyperlinks, with few opportunities for users to contribute their own content or engage meaningfully with websites.
Technical limitations further defined the Web 1 experience. Information access was significantly slower than today's standards, largely due to the prevalence of dial-up connections. This constraint meant websites needed to be optimized for minimal bandwidth usage[1]. Additionally, security measures were rudimentary, making early websites vulnerable to various cyberattacks without adequate protection systems in place.
The Social Revolution: Web 2.0
As the internet matured in the late 1990s and early 2000s, a significant transformation occurred. Web 2.0 emerged as a more dynamic, interactive platform that emphasized user participation, content creation, and social connectivity[6]. This shift fundamentally changed how people engaged with the internet, moving from passive consumption to active contribution.
The Rise of Social Media and Big Data
Web 2.0 gave birth to social media platforms, interactive web applications, and user-generated content ecosystems. Companies like Google, Facebook, Twitter, and Amazon developed business models that leveraged user activity and content creation[4]. These platforms transformed from simple information repositories into complex social networks and digital marketplaces.
Central to the Web 2.0 revolution was the collection and analysis of user data on an unprecedented scale. Companies developed sophisticated infrastructure to handle massive amounts of information. Google implemented systems like the Google File System (GFS) and Spanner to store and distribute data across thousands of machines worldwide[4]. Facebook developed cascade prediction systems to manage user interactions, while Twitter created specialized infrastructure to process millions of tweets per minute[4].
These technological advancements enabled the monetization of user attention and personal information. By analyzing user behavior, preferences, and social connections, Web 2.0 companies could deliver highly targeted advertising and personalized content recommendations. This business model generated immense wealth for platform owners while raising significant concerns about privacy, data ownership, and the concentration of power in the hands of a few technology giants.
The Decentralized Future: Web 3.0
Web 3 represents the next evolutionary stage of the internet, characterized by principles of decentralization, transparency, and user sovereignty[6]. Unlike previous iterations, Web 3 seeks to redistribute control from centralized entities to individual users and communities through blockchain technology and decentralized protocols.
Blockchain as the Foundation
The conceptual underpinnings of Web 3 emerged with the creation of Bitcoin in 2009. Bitcoin introduced a revolutionary approach to digital transactions by enabling peer-to-peer value transfer without requiring a central authority. This innovation demonstrated that trust could be established through cryptographic proof rather than relying on traditional financial institutions.
Ethereum expanded upon Bitcoin's foundation by introducing programmable smart contracts, which allowed for the creation of decentralized applications (dApps) beyond simple financial transactions. This breakthrough enabled developers to build complex applications with self-executing agreements that operate transparently on the blockchain[6].
Ownership and Data Sovereignty
A defining characteristic of Web 3 is the emphasis on true digital ownership. Through blockchain technology and cryptographic tokens, individuals can now assert verifiable ownership over digital assets in ways previously impossible[6]. This stands in stark contrast to Web 2 platforms, where users effectively surrendered control of their content and data to centralized companies.
The concept of self-custody exemplifies this shift toward user sovereignty. Platforms like Trust Wallet enable individuals to maintain control over their digital assets across multiple blockchains without relying on intermediaries[5]. Users hold their private keys, ensuring that they—not corporations or governments—have ultimate authority over their digital property.
Decentralized Physical Infrastructure Networks (DePIN)
Web 3 extends beyond digital assets to reimagine physical infrastructure through Decentralized Physical Infrastructure Networks (DePIN). These networks connect blockchain technology with real-world systems, allowing people to use cryptocurrency tokens to build and manage physical infrastructure—from wireless hotspots to energy systems[7].
DePIN projects decentralize ownership and governance of critical infrastructure, creating more transparent, efficient, and resilient systems aligned with Web 3 principles[7]. By distributing control among network participants rather than centralizing it within corporations or governments, these projects bridge the gap between digital networks and physical reality.
Non-Fungible Tokens and Intellectual Property
Non-Fungible Tokens (NFTs) represent another revolutionary aspect of Web 3, providing a mechanism for verifying the authenticity and ownership of unique digital items. NFTs enable creators to establish provenance for digital art, music, virtual real estate, and other forms of intellectual property, addressing longstanding issues of duplication and unauthorized distribution in the digital realm[6].
This innovation has profound implications for creative industries, potentially enabling more direct relationships between creators and their audiences while reducing dependence on centralized platforms and intermediaries.
Nostr: A Decentralized Protocol for Social Media and Communication
Nostr (Notes and Other Stuff Transmitted by Relays) is a decentralized and censorship-resistant communication protocol designed to enable open and secure social networking. Unlike traditional social media platforms that rely on centralized servers and corporate control, Nostr allows users to communicate directly through a network of relays, ensuring resilience against censorship and deplatforming.
The protocol operates using simple cryptographic principles: users generate a public-private key pair, where the public key acts as their unique identifier, and messages are signed with their private key. These signed messages are then broadcast to multiple relays, which store and propagate them to other users. This structure eliminates the need for a central authority to control user identities or content distribution[8].
As concerns over censorship, content moderation, and data privacy continue to rise, Nostr presents a compelling alternative to centralized social media platforms. By decentralizing content distribution and giving users control over their own data, it aligns with the broader ethos of Web3—empowering individuals and reducing reliance on corporate intermediaries[9].
Additionally Nostr implements a novel way for users to monetize their content via close integration with Bitcoin's "Lightning Network"[11] -- a means by which users are able to instantly transmit small sums (satoshi's, the smallest unit of Bitcoin) with minimal fees. This feature, known as “zapping,” allows users to send micropayments directly to content creators, tipping them for valuable posts, comments, or contributions. By leveraging Lightning wallets, users can seamlessly exchange value without relying on traditional payment processors or centralized monetization models. This integration not only incentivizes quality content but also aligns with Nostr’s decentralized ethos by enabling peer-to-peer financial interactions that are censorship-resistant and borderless.
For those interested in exploring Nostr, setting up an account requires only a private key, and users can begin interacting with the network immediately by selecting a client that suits their needs. The simplicity and openness of the protocol make it a promising foundation for the next generation of decentralized social and communication networks.
Alternative Decentralized Models: Federation
Not all Web 3 initiatives rely on blockchain technology. Platforms like Bluesky are pioneering federation approaches that allow users to host their own data while maintaining seamless connectivity across the network[10]. This model draws inspiration from how the internet itself functions: just as anyone can host a website and change hosting providers without disrupting visitor access, Bluesky enables users to control where their social media data resides.
Federation lets services be interconnected while preserving user choice and flexibility. Users can move between various applications and experiences as fluidly as they navigate the open web[10]. This approach maintains the principles of data sovereignty and user control that define Web 3 while offering alternatives to blockchain-based implementations.
Conclusion
The evolution from Web 1 to Web 3 represents a profound transformation in how we interact with the internet. From the static, read-only pages of Web 1 through the social, data-driven platforms of Web 2, we are now entering an era defined by decentralization, user sovereignty, and reimagined ownership models.
Web 3 technologies—whether blockchain-based or implementing federation principles—share a common vision of redistributing power from centralized entities to individual users and communities. By enabling true digital ownership, community governance, and decentralized infrastructure, Web 3 has the potential to address many of the concerns that have emerged during the Web 2 era regarding privacy, control, and the concentration of power.
As this technology continues to mature, we may witness a fundamental reshaping of our digital landscape toward greater transparency, user autonomy, and equitable value distribution—creating an internet that more closely aligns with its original promise of openness and accessibility for all.
Sources
[1] What is WEB1? a brief history of creation - White and Partners https://whiteand.partners/en/what-is-web1-a-brief-history-of-creation/ [2] Evolution of the Internet - from web1.0 to web3 - LinkedIn https://www.linkedin.com/pulse/evolution-internet-from-web10-web3-ravi-chamria [3] Web3 Social: Create & Monetize with Smart Contracts - Phala Network https://phala.network/web3-social-create-monetize-with-smart-contracts [4] [PDF] Big Data Techniques of Google, Amazon, Facebook and Twitter https://www.jocm.us/uploadfile/2018/0613/20180613044107972.pdf [5] True crypto ownership. Powerful Web3 experiences - Trust Wallet https://trustwallet.com [6] Web3: Revolutionizing Digital Ownership and NFTs - ThoughtLab https://www.thoughtlab.com/blog/web3-revolutionizing-digital-ownership-and-nfts/ [7] DePIN Crypto: How It's Revolutionizing Infrastructure in Web3 https://www.ulam.io/blog/how-depin-is-revolutionizing-infrastructure-in-the-web3-era [8] Nostr: Notes and Other Stuff… https://nostr.com/ [9] Nostr: The Importance of Censorship-Resistant Communication... https://bitcoinmagazine.com/culture/nostr-the-importance-of-censorship-resistant-communication-for-innovation-and-human-progress- [10] Bluesky: An Open Social Web https://bsky.social/about/blog/02-22-2024-open-social-web [11] Wikipedia: Lightning Network https://en.wikipedia.org/wiki/Lightning_Network
