-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 0fa80bd3:ea7325de
2025-04-09 21:19:39
@ 0fa80bd3:ea7325de
2025-04-09 21:19:39DAOs promised decentralization. They offered a system where every member could influence a project's direction, where money and power were transparently distributed, and decisions were made through voting. All of it recorded immutably on the blockchain, free from middlemen.
But something didn’t work out. In practice, most DAOs haven’t evolved into living, self-organizing organisms. They became something else: clubs where participation is unevenly distributed. Leaders remained - only now without formal titles. They hold influence through control over communications, task framing, and community dynamics. Centralization still exists, just wrapped in a new package.
But there's a second, less obvious problem. Crowds can’t create strategy. In DAOs, people vote for what "feels right to the majority." But strategy isn’t about what feels good - it’s about what’s necessary. Difficult, unpopular, yet forward-looking decisions often fail when put to a vote. A founder’s vision is a risk. But in healthy teams, it’s that risk that drives progress. In DAOs, risk is almost always diluted until it becomes something safe and vague.
Instead of empowering leaders, DAOs often neutralize them. This is why many DAOs resemble consensus machines. Everyone talks, debates, and participates, but very little actually gets done. One person says, “Let’s jump,” and five others respond, “Let’s discuss that first.” This dynamic might work for open forums, but not for action.
Decentralization works when there’s trust and delegation, not just voting. Until DAOs develop effective systems for assigning roles, taking ownership, and acting with flexibility, they will keep losing ground to old-fashioned startups led by charismatic founders with a clear vision.
We’ve seen this in many real-world cases. Take MakerDAO, one of the most mature and technically sophisticated DAOs. Its governance token (MKR) holders vote on everything from interest rates to protocol upgrades. While this has allowed for transparency and community involvement, the process is often slow and bureaucratic. Complex proposals stall. Strategic pivots become hard to implement. And in 2023, a controversial proposal to allocate billions to real-world assets passed only narrowly, after months of infighting - highlighting how vision and execution can get stuck in the mud of distributed governance.
On the other hand, Uniswap DAO, responsible for the largest decentralized exchange, raised governance participation only after launching a delegation system where token holders could choose trusted representatives. Still, much of the activity is limited to a small group of active contributors. The vast majority of token holders remain passive. This raises the question: is it really community-led, or just a formalized power structure with lower transparency?
Then there’s ConstitutionDAO, an experiment that went viral. It raised over $40 million in days to try and buy a copy of the U.S. Constitution. But despite the hype, the DAO failed to win the auction. Afterwards, it struggled with refund logistics, communication breakdowns, and confusion over governance. It was a perfect example of collective enthusiasm without infrastructure or planning - proof that a DAO can raise capital fast but still lack cohesion.
Not all efforts have failed. Projects like Gitcoin DAO have made progress by incentivizing small, individual contributions. Their quadratic funding mechanism rewards projects based on the number of contributors, not just the size of donations, helping to elevate grassroots initiatives. But even here, long-term strategy often falls back on a core group of organizers rather than broad community consensus.
The pattern is clear: when the stakes are low or the tasks are modular, DAOs can coordinate well. But when bold moves are needed—when someone has to take responsibility and act under uncertainty DAOs often freeze. In the name of consensus, they lose momentum.
That’s why the organization of the future can’t rely purely on decentralization. It must encourage individual initiative and the ability to take calculated risks. People need to see their contribution not just as a vote, but as a role with clear actions and expected outcomes. When the situation demands, they should be empowered to act first and present the results to the community afterwards allowing for both autonomy and accountability. That’s not a flaw in the system. It’s how real progress happens.
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 554ab6fe:c6cbc27e
2025-04-10 18:48:57
@ 554ab6fe:c6cbc27e
2025-04-10 18:48:57What is consciousness, and can it be changed or enhanced? This is a question that humans have struggled with for a very long time. The question of consciousness alone is daunting. Some even argue that humans will never be able to find the answer. Regardless, the quest for knowledge is not always about the answer, rather it is the journey that is revealing. This is true not only for our society, but the individual as well. The search for the truth often leads one down a path of self-reflection, and can lead to conclusions previously thought to be ludicrous. Here, I will argue that consciousness can be interpreted as an interpretation of reality, where the interpretation may become clearer and more accurate through practices such as meditation.
Consciousness
To articulate this idea, the concept of consciousness must firstly be discussed. There is an incredibly interesting TED talk given by Anil Seth, where he describes consciousness as an illusion. He explains how the brain receives signals from both the internal and external environment of the body, makes an interpretation of those signals, which creates our conscious experience. In his scientific writing, he claims that the brain can be viewed as a prediction machine1. He argues that the brain is constantly making predictions and error correcting in order to gain understanding of the signals it is receiving. He is not alone in this theory, and many other researchers concur that the constant comparison of internal predictions and external stimuli is what generates the brain’s sensations of causal forces2. There are plenty of reasons to believe this is true. Imagine, the brain is receiving all kinds of neuronal signals both from external stimuli sensors and sensors for our internal systems. These signals all shoot up the spinal cord to the brain. It is unclear that these neuronal signals are stamped with an identifier of where they came from, so the brain has to make a predictive model for not only where the signal came from, but also why the signal came at all. The latter is important for survival: the use of our senses to accurately predict our environment would be a critical reason why consciousness developed in the first place. Imagine you are an ancient hominid walking in the wild: you see a tangled cord like thing around a branch on the tree. You need to process that information, determine if it is more branch or a snake and act accordingly. This is a potential biological reason for the manifestation of thought and problem solving. This is a very meta-cognitive example of our brain receiving information and then using previous knowledge to generate a predictive conclusion on the external reality.
There are also examples of this outside of the more obvious meta-cognitive examples. A good example is the famous rubber hand experiment. The first rubber hand experiment was conducted in 1998 by Botvinick and Cohen3. In this experiment, a subject places their hand on a table with a screen blocking their view of their own hand. A rubber hand is then placed on the other side of the screen where it is visible. The experimenter rubs both the rubber hand and real hand with a paint brush. By the end of the experiment, subjects begin to feel as if the rubber hand is their own limb3. The brain, using the visual senses, detects that a hand is being stroked with a brush while sensory neurons send signals that the hand is experiencing the touch of a paint brush. These two signals cause the predicting brain to think that the rubber hand is our hand. This experiment has been repeated many times in different ways. It has been observed that participants begin to react defensively to the threat of pain or damage to the rubber hand4. This illustrates the powerful extent at which the brain processes and reacts to information that it interprets from reality. Amazingly, some research suggests that the touch aspect of the experiment isn’t even necessary to produce the illusion5. Others have recreated this experience using virtual reality, citing that when the virtual hand changed color in response to the subject’s heartbeat, a significant sense of body ownership was generated6. Body ownership, and our sense of reality is arguably determined by our brain’s interpretation of both internal and external stimuli.
The Neuroscience and Meditation
It is hypothesized that the anterior insular cortex (AIC) is involved in the comparison of the stimuli to the predicted model1. Interestingly, the same brain region is associated with the anticipation of pain7. For those unaware, there is some research to suggest that much of the pain we experience is not due to the actual noxious stimuli (physical pain sensation), but from the anticipation of that pain. Evidence for this can be found in studies such as Al-Obaidi et al. from 2005, that concluded that the pain experienced in patients with chronic low back pain could not be solely attributed to the sensor signals, but from the anticipation of the pain8. Additionally, the anticipation of pain relief is the primary contributor to placebo analgesia (placebo pain killers)9. Furthermore, a large body of research has been conducted showing that meditators show a decreased anticipatory attitude towards pain, subsequently experiencing less unpleasant pain 7,10,11. For example, chronic pain in multiple areas such as the low back, neck, shoulder, and arms have been shown to reduce after meditation practice12. Finally, an extreme case study worth noting is of a yogi master who claimed to not experience pain at all13. When this master was brought into the lab, not only did he not experience pain, but his thalamus showed no additional activation following painful stimuli13. What is fascinating about this is that the thalamus is the main relay station for all incoming somatosensory information14, and some argue that this is a candidate for the location of consciousness15. To not have strong activation here after painful stimuli is to suggest a radical change in how the brain receives incoming stimuli, and perhaps is indicative in a dramatic shift in how this individual’s conscious experiences the world. Though this is but one small example, the previous studies outline a strong case for meditation’s ability to alter the way the brain processes information. Given meditation involves the active practice of generating an open and non-judgmental attitude towards all incoming stimuli, perhaps this alters the processing of incoming stimuli, thereby changing the predictive model. On a similar note, perhaps it relates to neuroplastic changes that occur within the brain. It has been noted that the AIC is activated during times of awareness of mind wandering16. This suggests that the AIC is in use frequently during meditation practices. Perhaps it is strengthened then by meditation, thereby also allowing for greater prediction model generation. Imagine the mind as a pond. If the pond is calm and still, one single rain drop rippling in the pond is clearly identifiable. One would easily know information about the droplet, because the ripple could be easily analyzed. Now imagine a pond during a rain storm, where an uncountable amount of rain drops is hitting the pond and there are ripples everywhere. One could not adequately make out where each ripple came from, because there would be too much overlap in the ripples. This may be how the brain functions as well. When the signals are low, and no extraneous thoughts and interpretations are created from signals, then the brain’s prediction model can easily determine where and why a signal it received came from. If, however, the mind is chaotic and full of internal noise, then the brain has a harder time creating an accurate understanding of incoming stimuli and generating a correct model.
Enlightenment
Enlightenment, from a scientific point of view, has been defined as a form of awareness where a person feels that s/he has gained a new understanding of reality 17. In this sense, it bears a striking relationship to the topic of consciousness. If consciousness can be defined as our interpretation of the external and internal environment through our mental prediction model, then experiences of enlightenment are defined by moments where our interpretation is completely changed in a profound way. The experiences are often characterized by the loss of individuality and consequent identification of being part of a greater oneness 18,19. As an interesting side note, this same experience is common amongst subjects, who in a double-blinded study, take psilocybin (the active ingredient in magic mushrooms)20,21. The neuroscience of enlightenment is particularly interesting. The temporo-parietal junction of the brain is involved with self-location and body ownership22. Unsurprisingly, this area is highly involved in the illusion of the rubber hand experiment23. This is the same brain area that is hypothesized to be related to these enlightened experiences of oneness 17. If this brain area, which handles the interpretation of where and what the body is, was to decrease in activation, then the brain would generate a more ambiguous interpretation that the self and the external environment are less distinct than previously thought. This is a possible explanation to why enlightenment experiences involve a feeling of oneness with everything. To bring this all home, meditation has been shown to decrease parietal lobe activation 4,24. Suggesting that meditation can be a method of adjusting the brain’s interpretation of stimuli to generate an outlook that is unifying in perceptive.
Closing Remarks
The evidence that meditation may lead to an altered conscious living has deep philosophical implications. Meditation is a practice that, in part, involves an open awareness to all incoming stimuli alongside the absence of any meta-cognitive interpretation or processing of said stimuli. This generation of a still mind may generate a more accurate prediction model of incoming stimuli, void of any corruption on the part of our thoughts. Given the observation that meditation, both scientifically and culturally, can lead to an understanding and experience of a greater oneness amongst all suggests that this interpretation of incoming stimuli is the more accurate interpretation. It is hard to imagine that anyone would not advocate the beauty and usefulness of this perspective. If more people had this perspective, we would have a much more peaceful, happy and unified society and planet. Ironically, our culture often aims to arrive to this philosophical perspective through analytical thought. However, given the evidence in this post, perhaps it is the absence of analytical thought, and the stillness of the mind that truly grants this perspective.
**References ** 1. Seth AK. Interoceptive inference, emotion, and the embodied self. Trends in Cognitive Sciences. 2013;17(11):565-573. doi:10.1016/j.tics.2013.09.007 2. Synofzik M, Thier P, Leube DT, Schlotterbeck P, Lindner A. Misattributions of agency in schizophrenia are based on imprecise predictions about the sensory consequences of one’s actions. Brain. 2010;133(1):262-271. doi:10.1093/brain/awp291 3. Botvinick M, Cohen JD. Rubber hand ‘feels’ what eyes see. Nature. 1998;391(February):756. 4. Newberg A, Alavi A, Baime M, Pourdehnad M, Santanna J, D’Aquili E. The measurement of regional cerebral blood flow during the complex cognitive task of meditation: A preliminary SPECT study. Psychiatry Research - Neuroimaging. 2001;106(2):113-122. doi:10.1016/S0925-4927(01)00074-9 5. Ferri F, Chiarelli AM, Merla A, Gallese V, Costantini M. The body beyond the body: Expectation of a sensory event is enough to induce ownership over a fake hand. Proceedings of the Royal Society B: Biological Sciences. 2013;280(1765). doi:10.5061/dryad.8f251 6. Suzuki K, Garfinkel SN, Critchley HD, Seth AK. Multisensory integration across exteroceptive and interoceptive domains modulates self-experience in the rubber-hand illusion. Neuropsychologia. 2013;51(13):2909-2917. doi:10.1016/j.neuropsychologia.2013.08.014 7. Zeidan F, Grant JA, Brown CA, McHaffie JG, Coghill RC. Mindfulness meditation-related pain relief: Evidence for unique brain mechanisms in the regulation of pain. Neuroscience Letters. 2012;520(2):165-173. doi:10.1016/j.neulet.2012.03.082 8. Al-Obaidi SM, Beattie P, Al-Zoabi B, Al-Wekeel S. The relationship of anticipated pain and fear avoidance beliefs to outcome in patients with chronic low back pain who are not receiving workers’ compensation. Spine. 2005;30(9):1051-1057. doi:10.1097/01.brs.0000160848.94706.83 9. Benedetti F, Mayberg HS, Wager TD, Stohler CS, Zubieta JK. Neurobiological mechanisms of the placebo effect. In: Journal of Neuroscience. Vol 25. Society for Neuroscience; 2005:10390-10402. doi:10.1523/JNEUROSCI.3458-05.2005 10. Gard T, Hölzel BK, Sack AT, et al. Pain attenuation through mindfulness is associated with decreased cognitive control and increased sensory processing in the brain. Cerebral Cortex. 2012;22(11):2692-2702. doi:10.1093/cercor/bhr352 11.Grant JA, Courtemanche J, Rainville P. A non-elaborative mental stance and decoupling of executive and pain-related cortices predicts low pain sensitivity in Zen meditators. Pain. 2011;152(1):150-156. doi:10.1016/j.pain.2010.10.006 12. Kabat-Zinn J, Lipworth L, Burney R. The clinical use of mindfulness meditation for the self-regulation of chronic pain. Journal of Behavioral Medicine. 1985;8(2):163-190. doi:10.1007/BF00845519 13. Kakigi R, Nakata H, Inui K, et al. Intracerebral pain processing in a Yoga Master who claims not to feel pain during meditation. European Journal of Pain. 2005;9(5):581. doi:10.1016/j.ejpain.2004.12.006 14. Steeds CE. The anatomy and physiology of pain. Surgery. 2009;27(12):507-511. doi:10.1016/j.mpsur.2009.10.013 15. Min BK. A thalamic reticular networking model of consciousness. Theoretical Biology and Medical Modelling. 2010;7(1):1-18. doi:10.1186/1742-4682-7-10 16. Hasenkamp W, Wilson-Mendenhall CD, Duncan E, Barsalou LW. Mind wandering and attention during focused meditation: A fine-grained temporal analysis of fluctuating cognitive states. NeuroImage. 2012;59(1):750-760. doi:10.1016/j.neuroimage.2011.07.008 17. Newberg AB, Waldman MR. A neurotheological approach to spiritual awakening. International Journal of Transpersonal Studies. 2019;37(2):119-130. doi:10.24972/ijts.2018.37.2.119 18. Johnstone B, Cohen D, Konopacki K, Ghan C. Selflessness as a Foundation of Spiritual Transcendence: Perspectives From the Neurosciences and Religious Studies. International Journal for the Psychology of Religion. 2016;26(4):287-303. doi:10.1080/10508619.2015.1118328 19. Yaden DB, Haidt J, Hood RW, Vago DR, Newberg AB. The varieties of self-transcendent experience. Review of General Psychology. 2017;21(2):143-160. doi:10.1037/gpr0000102 20. Griffiths RR, Richards WA, McCann U, Jesse R. Psilocybin can occasion mystical-type experiences having substantial and sustained personal meaning and spiritual significance. Psychopharmacology. 2006;187(3):268-283. doi:10.1007/s00213-006-0457-5 21. Griffiths RR, Richards WA, Johnson MW, McCann UD, Jesse R. Mystical-type experiences occasioned by psilocybin mediate the attribution of personal meaning and spiritual significance 14 months later. Journal of Psychopharmacology. 2008;22(6):621-632. doi:10.1177/0269881108094300 22. Serino A, Alsmith A, Costantini M, Mandrigin A, Tajadura-Jimenez A, Lopez C. Bodily ownership and self-location: Components of bodily self-consciousness. Consciousness and Cognition. 2013;22(4):1239-1252. doi:10.1016/j.concog.2013.08.013 23. Tsakiris M, Costantini M, Haggard P. The role of the right temporo-parietal junction in maintaining a coherent sense of one’s body. Neuropsychologia. 2008;46(12):3014-3018. doi:10.1016/j.neuropsychologia.2008.06.004 24. Herzog H, Leie VR, Kuweit T, Rota E, Ludwig K. Biological Psychology/Pharmacopsychology. Published online 1990:182-187.
-
 @ 0edc2f47:730cff1b
2025-04-04 03:37:02
@ 0edc2f47:730cff1b
2025-04-04 03:37:02Chef's notes
This started as a spontaneous kitchen experiment—an amalgamation of recipes from old cookbooks and online finds. My younger daughter wanted to surprise her sister with something quick but fancy ("It's a vibe, Mom."), and this is what we came up with. It’s quickly established itself as a go-to favorite: simple, rich, and deeply satisfying. It serves 4 (or 1, depending on the day; I am not here to judge). Tightly wrapped, it will keep up to 3 days in the fridge, but I bet it won't last that long!
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 0 min
Ingredients
- 1 cup (240mL) heavy whipping cream
- 1/4 cup (24g) cocoa powder
- 5 tbsp (38g) Confectioners (powdered) sugar
- 1/4 tsp (1.25mL) vanilla extract (optional)
- Flaky sea salt (optional, but excellent)
Directions
-
- Whip the cream until frothy.
-
- Sift in cocoa and sugar, fold or gently mix (add vanilla if using).
-
- Whip to medium peaks (or stiff peaks, if that's more your thing). Chill and serve (topped with a touch of sea salt if you’re feeling fancy).
-
 @ 2b24a1fa:17750f64
2025-04-01 08:09:55
@ 2b24a1fa:17750f64
2025-04-01 08:09:55 -
 @ 812cff5a:5c40aeeb
2025-04-01 02:57:20
@ 812cff5a:5c40aeeb
2025-04-01 02:57:20مقدمة
في عالم اليوم الرقمي، تبرز منصات جديدة تهدف إلى تعزيز تجربة القراءة والتواصل بين محبي الكتب. تُعَدُّ Bookstr.xyz واحدة من هذه المنصات المبتكرة التي تسعى لربط القرّاء عبر شبكة Nostr، مما يمنحهم سيادة كاملة على بياناتهم ويتيح لهم بناء علاقات جديدة مع محبي الكتب الآخرين. 
الميزات الرئيسية لموقع Bookstr
- التحكم الكامل بالبيانات: توفر Bookstr.xyz للمستخدمين القدرة على التحكم الكامل في بياناتهم الشخصية، مما يضمن خصوصية وأمان المعلومات.
- التكامل مع Open Library: تستخدم المنصة واجهة برمجة التطبيقات الخاصة بـ Open Library للحصول على معلومات شاملة حول الكتب، مما يتيح للمستخدمين الوصول إلى مجموعة واسعة من البيانات الموثوقة.
- التواصل الاجتماعي: من خلال شبكة Nostr، يمكن للمستخدمين التواصل مع قرّاء آخرين، تبادل التوصيات، ومناقشة الكتب المفضلة لديهم. 
ما الذي يجعلها فريدة؟
تتميز Bookstr.xyz بدمجها بين مزايا الشبكات الاجتماعية ومصادر بيانات الكتب المفتوحة، مما يخلق بيئة تفاعلية وغنية بالمعلومات لمحبي القراءة. استخدامها لشبكة Nostr يمنح المستخدمين حرية أكبر في التحكم بتجربتهم الرقمية مقارنة بالمنصات التقليدية. 
جرب Bookstr
تُعَدُّ Bookstr.xyz إضافة قيمة لعالم القراءة الرقمي، حيث تجمع بين مزايا الشبكات الاجتماعية ومصادر البيانات المفتوحة، مع التركيز على خصوصية المستخدم والتحكم في البيانات. إذا كنت من عشاق الكتب وتبحث عن منصة تفاعلية وآمنة، فقد تكون Bookstr.xyz الخيار المثالي لك.
شاركوا كتبكم المفضلة!!
-
 @ 70c48e4b:00ce3ccb
2025-04-22 08:35:52
@ 70c48e4b:00ce3ccb
2025-04-22 08:35:52Hello reader,
I can say from personal experience that crowdfunding has truly changed my life. I found people who believed in my dream of using Bitcoin as money. Every single one of my videos was made possible through crowdfunding. And I’m not alone. I know several Bitcoiners who have raised funds this way, from Africa to Korea to Haiti.
https://images.forbesindia.com/media/images/2022/Jul/img_190501_runwithbitcoin_bg.jpg
Crowdfunding is deeply rooted in the traditional financial world. From raising money for life-saving surgeries to helping someone open a local coffee shop, platforms like GoFundMe, Kickstarter, and Indiegogo have become essential tools for many. But behind all the heartwarming stories and viral campaigns, there’s a side of crowdfunding that doesn’t get talked about enough. Traditional platforms are far from perfect.
They are centralized, which means there’s always someone in control. These platforms can freeze campaigns, delay payouts, or take a significant cut of the money. And often, the people who need funding the most, those without access to strong banking systems or large social media followings are the ones who get left out.
Here are some of the problems I’ve noticed with these platforms:
Problem 1: Inequality in Who Gets Funded
A recent article in The Guardian pointed out something that’s hard to ignore. Crowdfunding often benefits people who already have influence. After the Los Angeles wildfires in January 2025, celebrities like Mandy Moore were able to raise funds quickly. At the same time, everyday people who lost their homes struggled to get noticed.
https://i.guim.co.uk/img/media/f8398505e58ec3c04685aab06e94048e5d7b6a0c/0_127_4800_2880/master/4800.jpg?width=1300&dpr=1&s=none&crop=none
Angor (https://angor.io/) changes that by removing the need for a central platform to choose which projects get featured or promoted. Anyone can share their project. People can find them on Angor Hub (https://hub.angor.io/), which is a public directory built on the Nostr protocol. Instead of relying on popularity, projects are highlighted based on transparency and engagement.
Problem 2: Platform Dependence and Middlemen
Here’s something people don’t often realize. When you raise funds online, the platform usually has control. It holds the money, decides when to release it, and can freeze everything without warning. This happened during the trucker protests in Canada in 2022. Tens of millions of dollars were raised, but platforms like GoFundMe and GiveSendGo froze the donations. The funds never reached the people they were meant for. Supporters were left confused, and the recipients had no way to access what had been raised for them.
https://upload.wikimedia.org/wikipedia/commons/thumb/2/2d/Convoi_de_la_libert%C3%A9_%C3%A0_Ottawa_01.jpg/800px-Convoi_de_la_libert%C3%A9_%C3%A0_Ottawa_01.jpg
Angor avoids all of this. It does not hold the funds, does not require approval processes, and only the project creator has control over the campaign. Contributions go directly from supporters to the people building the project, using Bitcoin. It is a peer-to-peer system that works without any gatekeepers. Angor never touches the money. It simply provides the tools people need to raise funds and build, while staying fully in control.
Problem 3: Global Access
Another major issue is that these platforms often exclude people based on where they live. If you're in a region with limited banking access or outside the supported list of countries, you’re likely shut out. In 2023, a woman named Samar in Gaza tried to raise funds for food and medical supplies during a crisis. A friend abroad set up a campaign to help, but the platform froze it due to "location-related concerns." The funds were locked, and the support never arrived in time.
https://images.gofundme.com/EMFtPWSLs3P9SewkzwZ4FtaBQSA=/720x405/https://d2g8igdw686xgo.cloudfront.net/78478731_1709065237698709_r.jpeg
Angor removes these barriers by using Bitcoin, which works globally without needing banks or approvals. Anyone, anywhere, can raise and receive support directly.
Problem 4: Lack of Transparency
Post-funding transparency is often lacking. Backers rarely get consistent updates, making it difficult to track a project's progress or hold anyone accountable.
In 2015, the Zano drone project on Kickstarter raised over £2.3 million from more than 12,000 backers. It promised a compact, smart drone for aerial photography. But as time went on, updates became rare and vague. Backers had little insight into the project’s struggles, and eventually, it was canceled. The company shut down, and most backers never received their product or a refund.
https://ichef.bbci.co.uk/ace/standard/976/cpsprodpb/2A0A/production/_86626701_ff861eeb-ce94-43b7-9a43-b30b5adbd7ab.jpg
Angor takes a different approach. Project updates are shared through Nostr, a decentralized and tamper-proof communication protocol. This allows backers to follow progress in real time, with no corporate filters and no blackout periods. Everyone stays in the loop, from start to finish.
Problem 5: Fraud and Accountability
Scams are a growing problem in the crowdfunding world. People can launch fake campaigns, collect donations, and vanish — leaving supporters with empty promises and no way to recover their money. One well-known example was the "Homeless Vet GoFundMe scam" in the U.S.
https://a57.foxnews.com/static.foxnews.com/foxnews.com/content/uploads/2018/09/720/405/1536549443584.jpg
A couple and a homeless man raised over $400,000 by telling a heartwarming story that later turned out to be completely fake. The money was spent on luxury items, and it took a legal investigation to uncover the truth. By the time it was resolved, most of the funds were gone.
This kind of fraud is hard to stop on traditional platforms, because once the funds are transferred, there’s no built-in structure to verify how they’re used.
On Angor, projects are funded in stages, with each step tied to a specific milestone. Bitcoin is held in a shared wallet that only unlocks funds when both the backer and the creator agree that the milestone is complete. If something feels off, backers can choose to stop and recover unspent funds.
This structure discourages scammers from even trying. It adds friction for bad actors, while still giving honest creators the freedom to build trust, deliver value, and raise support transparently. It can’t get any better than this
So, does Angor matter?
For me, it really does. I’m genuinely excited to have my project listed on Angorhub. In a world shaped by AI, open source and transparency light the way forward. Let the work shine on its own.
Have you tried Angor yet? Thanks for tuning in. Catch you next week. Ciao!
Guest blog: Paco nostr:npub1v67clmf4jrezn8hsz28434nc0y5fu65e5esws04djnl2kasxl5tskjmjjk
References:
• The Guardian, 2025: Crowdfunding after LA fires and inequality - https://www.theguardian.com/us-news/2025/jan/17/la-fires-gofundme-mandy-moore • https://www.theguardian.com/us-news/2018/nov/15/johnny-bobbitt-gofundme-scam-arrest-viral-gas-story-couple-charged • FundsforNGOs: The Success Story of an NGO That Scaled with Limited Resourceshttps://www2.fundsforngos.org/articles/the-success-story-of-an-ngo-that-scaled-with-limited-resources/ • https://www.freightwaves.com/news/gofundme-freezes-37m-until-organizers-of-canada-trucker-convoy-detail-spending-plan
-
 @ 878dff7c:037d18bc
2025-03-31 21:29:17
@ 878dff7c:037d18bc
2025-03-31 21:29:17Dutton Proposes Easing Home Loan Regulations
Summary:
Opposition Leader Peter Dutton plans to challenge the Albanese government by proposing changes to lending rules aimed at making it easier for first-time home buyers to access loans. The proposed adjustments include reducing serviceability buffers and addressing the treatment of HELP debt to improve housing access. Dutton argues that current regulations create a bias favoring inherited wealth, making it difficult for new buyers to enter the housing market. These proposals come as the Reserve Bank of Australia prepares for its upcoming interest rate decision, with the current cash rate target at 4.1% and predictions of a cut in May. Treasurer Jim Chalmers highlights the government's progress, noting falling inflation, rising real wages, and improving economic growth.
Sources: News.com.au - 1 April 2025, The Australian - 1 April 2025
Australia's Housing Market Hits New Record High
Summary:
Australia's property prices reached a new peak in March, following a rate cut that enhanced buyer optimism. CoreLogic reported a 0.4% monthly increase, bringing the average national property price to A$820,331. All capital cities, except Hobart, experienced price gains, with Sydney and Melbourne rising by 0.3% and 0.5%, respectively. The rate cut slightly improved borrowing capacity and mortgage serviceability. However, the sustainability of this upward trend is uncertain due to persistent affordability issues. While the market rebounded with the February rate cut by the Reserve Bank of Australia, significant improvements in home loan serviceability are necessary for substantial market growth.
Source: Reuters - 1 April 2025
AI Revolutionizes Business Operations
Summary:
Artificial intelligence (AI) is transforming business practices globally, with applications ranging from administrative task automation to strategic decision-making enhancements. Companies are increasingly integrating AI to streamline operations and gain competitive advantages. This shift necessitates a focus on ethical AI deployment and workforce upskilling to address potential job displacement.
Sources: Financial Times - April 1, 2025
Criticism of Bureau of Meteorology's Forecasting Capabilities
Summary:
The Bureau of Meteorology is facing criticism for inadequate weather radar coverage in western Queensland, which has led to unreliable forecasting during the recent floods. Federal Opposition Leader Peter Dutton has pledged $10 million for a new radar system to enhance forecasting accuracy, while local officials emphasize the need for improved infrastructure to better prepare for future natural disasters.
Sources: The Australian - April 1, 2025
Coalition Pledges $10 Million for Western Queensland Weather Radar
Summary:
As part of the federal election campaign, Opposition Leader Peter Dutton has promised $10 million for a new weather radar system in flood-affected western Queensland. This initiative aims to improve weather forecasting and preparedness in the region. Meanwhile, Prime Minister Anthony Albanese has pledged $200 million for an upgrade to the St John of God Midland hospital in Perth, emphasizing healthcare improvements. Both leaders are focusing on key regional investments as the election approaches.
Source: The Guardian - April 1, 2025
Emergency Services Conduct Rescues Amid Queensland Floods
Summary:
Emergency services in Queensland have conducted over 40 rescues as floodwaters continue to rise, submerging communities and causing extensive damage. Efforts are focused on delivering essential supplies, evacuating residents, and ensuring the safety of those affected by the severe weather conditions.
Sources: The Courier-Mail - April 1, 2025
Six Key Crises Facing Australia Before the Election
Summary:
As the election nears, voters remain largely unaware of six looming crises that could significantly impact the nation. These include over-reliance on volatile commodity exports, challenges in renewable energy implementation, potential currency depreciation, and reduced foreign investment. Both major parties have focused on immediate cost-of-living relief, overshadowing these critical issues that demand urgent attention.
Sources: The Australian - April 1, 2025
Debate Intensifies Over Australia's Commitment to AUKUS
Summary:
Former Defence Department Secretary Dennis Richardson has urged Australia to persist with the AUKUS submarine agreement despite concerns about the reliability of the U.S. under President Donald Trump. Richardson warns that abandoning the deal now would undermine decades of defense planning. However, critics, including former Prime Minister Malcolm Turnbull, question the feasibility and advisability of the agreement, suggesting alternatives such as partnering with France for submarine development.
Sources: The Guardian - April 1, 2025, The Australian - April 1, 2025
China Delays $23B Sale of Panama Canal Ports to US-Backed Consortium
Summary:
China has postponed the $23 billion sale of 43 global ports, including critical facilities at both ends of the Panama Canal, to a consortium led by US investment firm BlackRock. The delay follows an investigation by China’s State Administration for Market Regulation into potential anti-monopoly law violations. This unexpected move has heightened tensions between China and the US, as President Trump viewed the sale as a strategic victory in the ongoing power struggle between the two nations. The deal's future remains uncertain, causing political and economic ripples amid China's significant annual "two sessions" gathering.
Sources: New York Post - March 31, 2025
Australian Government's Handling of Suspected Chinese Spy Ship Raises Concerns
Summary:
The Australian government has assigned the monitoring of the suspected Chinese spy ship, Tan Suo Yi Hao, to the Australian Border Force, despite Prime Minister Anthony Albanese's assertion that the Australian Defence Force was managing the situation. Security experts believe the vessel is collecting undersea data for future Chinese submarine operations, highlighting national security concerns during an election period. The handling of this issue has led to criticism and confusion over which agency is in charge, with opposition figures condemning the government's lack of detailed information.
Sources: The Australian - April 1, 2025
Concerns Rise Over Schoolchildren Accessing Weight Loss Drugs
Summary:
Health experts are alarmed by reports of Australian schoolchildren accessing weight loss medications like semaglutide (Ozempic) through various means, including online purchases and taking them from home supplies. These substances are being linked to secretive and harmful diet clubs within schools, posing severe health risks such as potentially fatal overdoses. Advocates emphasize the need for stricter regulation of weight loss products and call for mandatory education programs on eating disorders in schools to address the growing issue.
Sources: The Courier-Mail - 1 April 2025
Recycling Plant Explosion Highlights Dangers of Improper Aerosol Disposal
Summary:
A Victorian company has been fined $35,000 after an explosion at its recycling plant injured six workers. The incident occurred when pressurized aerosol cans were improperly shredded, causing flames to spread up to 18 meters. Investigations revealed that the company failed to implement safety procedures such as emptying or puncturing the cans before shredding and ensuring adequate ventilation. This case underscores the critical importance of adhering to safety protocols when handling hazardous materials.
Sources: Herald Sun - 1 April 2025
Australia Enforces New Tobacco Controls from April 1
Summary:
As of April 1, 2025, Australia has implemented stringent tobacco control measures, including health warnings printed directly on individual cigarettes. These warnings feature phrases such as "CAUSES 16 CANCERS" and "DAMAGES YOUR LUNGS." Additionally, new graphic warnings on cigarette packs and health promotion inserts aim to encourage smoking cessation and raise awareness about the dangers of tobacco use.
Sources: Mirage News - April 1, 2025, 9News - April 1, 2025
OPEC+ Increases Oil Production Amid Global Uncertainties
Summary:
OPEC+ has announced the gradual unwinding of voluntary production cuts starting April 1, 2025, aiming to restore 2.2 million barrels per day of output by September 2026. Despite this increase, factors such as tighter U.S. sanctions on Iran and Russia, potential sanctions on Venezuelan oil buyers, and fears of a tariff-induced recession have sustained oil prices. Analysts predict limited downside risks to oil prices due to significant supply threats, mainly from Iran and Venezuela. While some strength in oil prices is expected during the summer, concerns over tariff-induced demand weakness persist.
Sources: MarketWatch - April 1, 2025
Iconic Australian Locations Declared 'No Go Zones'
Summary:
Several iconic Australian locations, including Uluru, Kakadu National Park, Cape York Peninsula, and others, are increasingly being declared "no go zones" due to cultural, environmental, and safety concerns. These measures aim to preserve the cultural significance and environmental integrity of these landmarks and ensure public safety. While traditional owners and local authorities support these restrictions to protect cultural heritage, debates have arisen over tourists' rights and the impact on local tourism industries. Sources: News.com.au - April 1, 2025
The Joe Rogan Experience #2297: Francis Foster & Konstantin Kisin
Summary:
In episode #2297 of The Joe Rogan Experience, Joe Rogan welcomes comedians and commentators Francis Foster and Konstantin Kisin, hosts of the podcast Triggernometry. The episode delivers a wide-ranging conversation covering free speech, comedy, media narratives, and societal tensions in the modern world.
Interesting Discussions and Insights:
-
The State of Comedy:\ The trio discusses how comedy has changed in recent years, especially under the weight of cancel culture. They explore how comedians are navigating cultural sensitivities while still trying to push boundaries and remain authentic.
-
Free Speech and Censorship:\ Konstantin and Francis share their experiences with censorship and self-censorship, emphasizing the risks of suppressing ideas, even if they’re controversial. They advocate for robust debate as a cornerstone of democracy.
-
Migration and Identity Politics:\ The conversation touches on immigration policies in the UK and broader Western world, discussing how political correctness often silences real concerns. Both guests, with immigrant backgrounds, offer nuanced perspectives on national identity and inclusion.
-
Media and Narrative Control:\ Joe, Francis, and Konstantin dive into how media outlets often frame stories with ideological slants, and the dangers of relying on one-sided narratives in forming public opinion.
-
Creating Triggernometry:\ The guests talk about why they launched their podcast — to have honest, open conversations with a wide range of thinkers, especially those often excluded from mainstream platforms.
Key Takeaways:
- Honest conversation is essential for a healthy society, even when it's uncomfortable.
- Comedy still holds power to critique society but faces mounting challenges from cultural pressures.
- Free speech should be defended not just in principle, but in everyday life and dialogue.
- The media landscape is increasingly polarized, and critical thinking is more important than ever.
-
-
 @ 3c389c8f:7a2eff7f
2025-03-31 20:38:23
@ 3c389c8f:7a2eff7f
2025-03-31 20:38:23You might see these terms used interchangeably throughout the Nostr network. Since Nostr is a decentralized protocol and not a platform, there is often a lack of consensus around particular terminologies. At times, it's important to differentiate between them, so that you can determine what is being stated. In the truest sense, there is no central entity to maintain a Nostr 'account' on your behalf, though some Nostr-based platforms may offer to do so. There's also no one to verify your 'identity'. This is something that you create, maintain and control. It is 100% yours. In a sense, you verify yourself through your interactions with others, with the network of clients and relays, and by protecting your nsec (secret key). A profile is generally considered to be a single place for displaying your content and any information about yourself that you've chosen to share, but its a little more complicated than that with Nostr. Let's take a closer look at all 3 terms:
Identity:
Your Nostr identity becomes yours from the moment you generate your key pair. The two parts each provide unique perspective and functionality. (Remember, there is no central entity to issue these key pairs. You can screw up and start over. You can maintain multiple key pairs for different purposes. If all of this is new and unfamiliar, start simply with the intention of trial and error.)
Half of the equation is your nsec. As long as you maintain control of that secret key, the identity is yours. You will use it to sign the notes and events that you create on Nostr. You will use it to access functionality of various tools and apps. You can use it to send monetary tips for content you find valuable. The reputation that you build through posting & interacting on Nostr will signal to others what type of person or profile this is, whether it's a genuine person, a bot (good or bad), a collection of works, etc. You might come across information that compares your nsec to a password. While a fair comparison, its important to remember that passwords can be reset, but your private key CANNOT. Lost access or control of your nsec means a loss of control over that identity. When you have decided to establish a more permanent identity, write it down, keep it safe, and use the appropriate security tools for interacting online.
The other half of this equation is your npub. This public key is used to find and display your notes and events to others. In short, your npub is how your identity is viewed by others and your nsec is how you control that identity.
Npub can also act a window into your world for whoever may choose to view it. As mentioned in a previous entry, npub login enables viewing Nostr's notes and other stuff in a read-only mode of any user's follow feed. Clients may or may not support this, some will even allow you to view and subscribe to these feeds while signed in as yourself via this function. It the basis of the metadata for your profile, too.
Profile:
Profile, in general, is a collection of things about you, which you have chosen to share. This might include your bio, chosen display name, other contact information, and a profile photo. Similar to traditional socials, veiwing Nostr profiles often includes a feed of the things you have posted and shared displayed as a single page. People will recognize you based on the aspects of your profile more than they will by your actual identity since an npub is a prefixed random string of characters . Your npub bridges a gap between strictly machine readable data and your human readable name, but it is not as simple as a name and picture. You will choose your photo and display name for your profile as you see fit, making you recognizable. These aspects are easy for copycat scammers to leverage, so your npub will help your friends and followers to verify that you are you, in the event that someone should try to copy your profile.
The Nostr protocol has another profile aspect that is important to know about, but as a general user, you shouldn't have to worry much about it. This is your nprofile. It combines your npub (or the machine readable hex verison of it) with hints to what relays you are using to publish your notes. This helps clients, crawlers, and relays find your stuff for your followers. You may notice nprofile when you share a profile link or used in other actions. When you update your relay list, your client will adjust your nprofile and send a new copy to the appropriate relays. If your believe that a client is not doing that correctly, you can visit metadata.nostr.com and manage it yourself.
Account:
Across Nostr, it is common to see the term 'account' used to refer to the combination of your identity and profile. It is a relatable term, though it may imply that some account issuer exists, but no one issues a Nostr account to you. You create and maintain it yourself.
There are situations where a traditional account will exist, such as with media servers, relay subscriptions, custodial wallet hosts, or NIP-05 providers. These things will almost always be paid services and storage that you choose to use. (Reminder: all of these things are possible to DIY with a little knowhow and an old computer)
What Is The Right Terminology?
There is no simple or correct answer here. Developers and writers will use whatever terms fit their scope and topic. Context will matter, so it's important to differentiate by that more than any actual term.
-
 @ f3873798:24b3f2f3
2025-03-31 20:14:31
@ f3873798:24b3f2f3
2025-03-31 20:14:31Olá, nostrilianos!
O tema de hoje é inteligência artificial (IA), com foco em duas ferramentas que têm se destacado no mercado por sua capacidade de responder perguntas, auxiliar em tarefas e, em alguns casos, até gerar imagens.
Essas tecnologias estão cada vez mais presentes no dia a dia, ajudando desde a correção de textos até pesquisas rápidas e a criação de imagens personalizadas com base em prompts específicos.
Nesse cenário em expansão, duas IAs se sobressaem: o ChatGPT, desenvolvido pela OpenAI, e o Grok, criado pela xAI.
Ambas são ferramentas poderosas, cada uma com seus pontos fortes e limitações, e têm conquistado usuários ao redor do mundo. Neste artigo, compartilho minhas impressões sobre essas duas IAs, baseadas em minha experiência pessoal, destacando suas diferenças e vantagens.
Grok: Destaque na criação de imagens e fontes

O Grok me impressiona especialmente em dois aspectos.
Primeiro, sua capacidade de gerar imagens é um diferencial significativo. Enquanto o ChatGPT tem limitações nesse quesito, o Grok oferece uma funcionalidade mais robusta para criar visuais únicos a partir de prompts, o que pode ser uma vantagem para quem busca criatividade visual.
Segundo, o Grok frequentemente cita fontes ou indica a origem das informações que fornece, o que agrega credibilidade às suas respostas e facilita a verificação dos dados.
ChatGPT: Assertividade e clareza

Por outro lado, o ChatGPT se destaca pela assertividade e pela clareza em suas explicações. Suas respostas tendem a ser mais diretas e concisas, o que é ideal para quem busca soluções rápidas ou explicações objetivas.
Acredito que essa vantagem possa estar ligada ao fato de o ChatGPT estar em operação há mais tempo, tendo passado por anos de aprimoramento e ajustes com base em interações de usuários.Comparação e reflexões.
Em minha experiência, o Grok supera o ChatGPT na geração de imagens e na citação de fontes, enquanto o ChatGPT leva a melhor em precisão e simplicidade nas respostas.
Esses pontos refletem não apenas as prioridades de design de cada IA, mas também o tempo de desenvolvimento e os objetivos de suas respectivas empresas criadoras.
A OpenAI, por trás do ChatGPT, focou em refinamento conversacional, enquanto a xAI, com o Grok, parece investir em funcionalidades adicionais, como a criação de conteúdo visual.
Minha opinião

Não há um vencedor absoluto entre Grok e ChatGPT – a escolha depende do que você precisa. Se seu foco é geração de imagens ou rastreamento de fontes, o Grok pode ser a melhor opção. Se busca respostas rápidas e assertivas, o ChatGPT provavelmente atenderá melhor.
Ambas as IAs são ferramentas incríveis, e o mais fascinante é ver como elas continuam evoluindo, moldando o futuro da interação entre humanos e máquinas.
-
 @ 378562cd:a6fc6773
2025-03-31 19:20:39
@ 378562cd:a6fc6773
2025-03-31 19:20:39Bitcoin transaction fees might seem confusing, but don’t worry—I’ll break it down step by step in a simple way. 🚀
Unlike traditional bank fees, Bitcoin fees aren’t fixed. Instead, they depend on: ✔️ Transaction size (in bytes, not BTC!) ✔️ Network demand (more traffic = higher fees) ✔️ Fee rate (measured in satoshis per byte)
Let’s dive in! 👇
📌 Why Do Bitcoin Transactions Have Fees? Bitcoin miners process transactions and add them to the blockchain. Fees serve three key purposes:
🔹 Incentivize Miners – They receive fees + block rewards. 🔹 Prevent Spam – Stops the network from being flooded. 🔹 Prioritize Transactions – Higher fees = faster confirmations.
💰 How Are Bitcoin Fees Calculated? Bitcoin fees are not based on the amount of BTC you send. Instead, they depend on how much space your transaction takes up in a block.
🧩 1️⃣ Transaction Size (Bytes, Not BTC!) Bitcoin transactions vary in size (measured in bytes).
More inputs and outputs = larger transactions.
Larger transactions take up more block space, meaning higher fees.
📊 2️⃣ Fee Rate (Sats Per Byte) Fees are measured in satoshis per byte (sat/vB).
You set your own fee based on how fast you want the transaction confirmed.
When demand is high, fees rise as users compete for block space.
⚡ 3️⃣ Network Demand If the network is busy, miners prioritize transactions with higher fees.
Low-fee transactions may take hours or even days to confirm.
🔢 Example: Calculating a Bitcoin Transaction Fee Let’s say: 📦 Your transaction is 250 bytes. 💲 The current fee rate is 50 sat/vB.
Formula: 🖩 Transaction Fee = Size × Fee Rate = 250 bytes × 50 sat/vB = 12,500 satoshis (0.000125 BTC)
💡 If 1 BTC = $60,000, the fee would be: 0.000125 BTC × $60,000 = $7.50
🚀 How to Lower Bitcoin Fees? Want to save on fees? Try these tips:
🔹 Use SegWit Addresses – Reduces transaction size! 🔹 Batch Transactions – Combine multiple payments into one. 🔹 Wait for Low Traffic – Fees fluctuate based on demand. 🔹 Use the Lightning Network – Near-zero fees for small payments.
🏁 Final Thoughts Bitcoin fees aren’t fixed—they depend on transaction size, fee rate, and network demand. By understanding how fees work, you can save money and optimize your transactions!
🔍 Want real-time fee estimates? Check mempool.space for live data! 🚀
-
 @ 2e8970de:63345c7a
2025-03-31 19:08:11
@ 2e8970de:63345c7a
2025-03-31 19:08:11https://x.com/beatmastermatt/status/1906329250115858750
originally posted at https://stacker.news/items/930491
-
 @ 39cc53c9:27168656
2025-04-09 07:59:35
@ 39cc53c9:27168656
2025-04-09 07:59:35The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 39cc53c9:27168656
2025-04-09 07:59:33
@ 39cc53c9:27168656
2025-04-09 07:59:33Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ 52524fbb:ae4025dc
2025-04-09 03:36:09
@ 52524fbb:ae4025dc
2025-04-09 03:36:09 To most of us it's all about the sound of freedom, the innovation, it's technical implication, what if feels like in a decentralised environment. Now let's head into that which brings our fantasies to reality, Nostr which stands for "Notes and other stuffs Transmitted by Relays", is an open protocol designed for decentralised social networkin
To most of us it's all about the sound of freedom, the innovation, it's technical implication, what if feels like in a decentralised environment. Now let's head into that which brings our fantasies to reality, Nostr which stands for "Notes and other stuffs Transmitted by Relays", is an open protocol designed for decentralised social networkinNostr most Amazing Features
-
Decentralisation: compared to traditional social media platforms like like Twitter (X) and Instagram that rely on centralised servers, Nostr operates through a network of relays. These relays serves as servers that store and forward messages. This amazing feature of decentralisation aims to make the network completely resistant to censorship, most people would say how? To answer your question it's because no single individual control's it
-
User Control: ever thought of the purest feeling of freedom, well Nostr just gave you the space to experience. User's have total control over their data and identity.
-
Simplicity: why get stressed when Nostr got you covered? This protocol is designed to be relatively simple, making it easier for developers to build applications on top of it.

Nostr Relation to Bitcoin
Who wouldn't want to be part of a community that embraces it's ethics in a dignified manner. Nostr has gained popularity within the Bitcoin community, and the Bitcoin Lightning Network is used for features like "Zaps" (which represents small payments or tips). There are also similarities in the philosophy of decentralization, that both bitcoin and Nostr share. Just like the saying goes, birds of the same feather flock together. This leads me to one of the best magnificent project, focused on building decentralisation media infrastructure, particularly within the Nostr ecosystem.

Yakihonne the future of the world
YakiHonne is an amazing project focused on building decentralized media infrastructure, particularly within the Nostr ecosystem. It's mind blowing features includes:
-
Decentralized Media: YakiHonne aims to provide tools and platforms that support freedom and automation in content creation, curation, article writing and reporting. It leverages the decentralized nature of the Nostr protocol to achieve this amazing feat.
-
Nostr and Bitcoin Integration: YakiHonne is closely tied to the Nostr network, and it also incorporates Bitcoin functionality. This integration includes features related to the Lightning Network, enabling things like "zaps" (small Bitcoin payments) within the platform.
-
Mobile Application: YakiHonne offers a mobile application with an eye catching user interface simply designed to provide users with a smooth and intuitive Nostr experience. This app includes features like: -Support for various login options. -Content curation tools. -Lightning Network integration. -Long form article support.

Disadvantages of Traditional social media
Lets go back to a world without the flute of freedom echoing in our hearts, where implementations are controlled by certain entities, reasons why traditional social media platforms hold not even a single stance compared to Nostr:
- Privacy Concerns:
Data Collection: Social media platforms collect vast amounts of user data, often without full transparency. This data can be used for targeted advertising, and sometimes, it can be compromised in data breaches. Which won't happen or be possible on yakihonne
-
Social Comparison and Low Self-Esteem: The over hyped and often unrealistic portrayals of life on social media can lead to feelings of inadequacy and low self-esteem. But on yakihonne you get to connect and grow with a community with specified goals bent on implementation
-
Misinformation and Fake News:
Spread of False Information: Social media platforms can be breeding grounds for misinformation and fake news, which can spread rapidly and have significant real-world consequences. Is that possible on yakihonne, well we all know the answer. 4. Centralized Control:
Censorship: Centralized platforms have the power to censor content, raising concerns about freedom of speech. Algorithm Bias: Algorithms can be biased, leading to unfair or discriminatory outcomes. This tells us why a decentralised media platform like yakihonne stands out to be the only media with a future.

Why Chose Nostr why chose yakihonne
When considering Nostr and related projects like YakiHonne, the appeal stems largely from a desire for greater control, privacy, and freedom in online communication. Which from the points aligned above, gives us no second chance of thought, but the thought of being part of the Nostr community, active on a platform like yakihonne.
-
-
 @ bcbb3e40:a494e501
2025-03-31 16:00:24
@ bcbb3e40:a494e501
2025-03-31 16:00:24|
 |
|:-:|
|WAJDA, Andrzej; Cenizas y diamantes, 1958|
|
|:-:|
|WAJDA, Andrzej; Cenizas y diamantes, 1958|Presentamos una nueva reseña cinematográfica, y en esta ocasión hemos elegido «Cenizas y diamantes», una película polaca del célebre y prolífico director Andrzej Wajda (1926-2016), estrenada en el año 1958. Se trata de uno de los grandes clásicos del cine polaco. El filme refleja una etapa dramática desde la perspectiva histórica para la nación polaca, como es el final de la Segunda Guerra Mundial, a raíz de la capitulación alemana del 8 de mayo de 1945. El contexto en el que se desarrolla se ambienta en la celebración del final de la guerra con el aplastante triunfo de la URSS, con las tropas soviéticas ocupando toda la Europa oriental, y en particular Polonia, que vive un momento de oscuridad e incertidumbre. El protagonista, Maciek Chełmicki (interpretado magistralmente por Zbigniew Cybulski (1927-1967), apodado el «James Dean polaco»), es un joven nacionalista polaco, de orientación anticomunista, que se ve implicado en un complot urdido para asesinar a un líder comunista local. Maciek opera desde la clandestinidad, bajo el grupo Armia Krajowa (AK), el Ejército Nacional polaco, una organización de resistencia, primero contra los alemanes y, posteriormente, contra los soviéticos. Durante el metraje, se plantea una dicotomía permanente entre la libertad entendida como la defensa de la soberanía de Polonia, desde posturas nacionalistas, y quienes consideran la ocupación soviética como algo positivo. Estas circunstancias atrapan al protagonista, que se ve envuelto en una espiral de violencia y traición.
Maciek Chełmicki, nuestro protagonista, cuenta con todas las características del héroe trágico, pues tiene en sus manos una serie de acciones que comprometen el futuro de un pueblo, que consiste en cumplir la misión que le ha sido encomendada, pero en su camino se cruza una joven, Krystyna, una joven camarera de un hotel de la que se enamora en ese mismo día. Este último hecho sirve de punto de partida para todas las dudas, dilemas y dicotomías a las que hacemos referencia. Hay un dilema moral evidente en un mundo en ruinas, devastado por la guerra, la muerte y el nihilismo. En este sentido Wajda nos muestra un lenguaje cinematográfico muy evidente, a través de una técnica expresionista muy depurada, con el uso del blanco y negro, los contrastes generados por las sombras y la atmósfera opresiva que transmite angustia, desesperación y vulnerabilidad de los protagonistas. Además también destilan una fuerte carga emocional, donde no están exentos elementos poéticos y un poderoso lirismo.
|
 |
|:-:|
|Maciek Chełmicki, el protagonista.|
|
|:-:|
|Maciek Chełmicki, el protagonista.|Hay elementos simbólicos que no podemos obviar, y que contribuyen a consolidar el análisis que venimos haciendo, como, por ejemplo, la estética del protagonista, con unas gafas oscuras, que actúan como una suerte de barrera frente al mundo que le rodea, como parte del anonimato tras el cual el joven Maciek vive de forma introspectiva su propio drama particular y el de toda una nación.
|
 |
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad; Hipérbola Janus, 2023|
|
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad; Hipérbola Janus, 2023|Hay una escena especialmente poderosa, y casi mítica, en la que los dos jóvenes protagonistas, Maciek y Krystina, se encuentran entre las ruinas de una Iglesia, en la que se destaca en primer plano, ocupando buena parte de la pantalla, la imagen de un Cristo invertido sobre un crucifijo, donde también se encuentran dos cuerpos colgados hacia abajo en una estampa que refleja la devastación moral y espiritual de toda una época. De hecho, la imagen del crucifijo invertido refleja el máximo punto de subversión y profanación de lo sagrado, y que en el caso concreto de la película viene a representar la destrucción del orden moral y de valores cristianos que la propia guerra ha provocado. Polonia es una nación profundamente católica, convertida al Cristianismo en el 966 a raíz de la conversión del príncipe Miecislao I, contribuyendo de manera decisiva a la formación de la identidad nacional polaca. El catolicismo siempre ha sido un medio de cohesión y defensa frente a las influencias extranjeras y la ocupación de terceros países, una constante en la historia del país, como el que ilustra la propia película con la URSS. En este sentido, la imagen de una Iglesia en ruinas, el lugar donde se encuentra representado el principio de lo sagrado e inviolable, supone una forma de perversión de todo principio de redención y salvación frente a la tragedia, y al mismo tiempo viene a significar que la Tradición ha sido abandonada y pervertida. En la misma línea, el protagonista, Maciek, se encuentra atrapado en una espiral de violencia a través de sus actos terroristas perpetrados contra la autoridad soviética que ocupa su país. Los dos cuerpos anónimos que cuelgan boca abajo, de forma grotesca, también participan de este caos y desequilibrio de un orden dislocado, son parte de la deshumanización y el nihilismo que todo lo impregna.
|
 |
|:-:|
|Maciek y Krystina en una iglesia en ruinas|
|
|:-:|
|Maciek y Krystina en una iglesia en ruinas|Como ya hemos mencionado, la película se encuentra plagada de paradojas y dicotomías, en las que nuestro protagonista, el joven rebelde e inconformista, debe elegir permanentemente, en unas decisiones que resultan trascendentales para su futuro y el de la propia nación. La figura femenina que irrumpe en su vida, y que representa un principio disruptivo que provoca una fractura interior y una crisis, le suscita una toma de conciencia de su propia situación y le fuerza a tomar un camino entre la «felicidad», del «amor», la «esperanza» y la «vida», que le permita superar la deriva nihilista y autodestructiva de la lucha clandestina, la cual le aboca a un destino trágico (que no vamos a desentrañar para no hacer spoiler). En relación al propio título de la película, «Cenizas y diamantes», basada en el poema del poeta y dramaturgo polaco Cyprian Norwid (1821-1883) y en la novela del autor, también polaco, Jerzy Andrzejewski (1909-1983), nos destaca la dualidad de los dos elementos que lo componen, y que definen el contraste entre el mundo sombrío y oscuro (Cenizas) y la esperanza y la luz que representa susodicha figura femenina (diamantes). La segunda alternativa parece un imposible, una quimera irrealizable que se pliega ante un Destino implacable, irreversible y cruel.
En consecuencia, y a la luz de los elementos expuestos, podemos decir que se nos presentan dilemas propios de la filosofía existencialista, que conoce su punto álgido en esos años, con autores como Jean Paul Sartre (1905-1980), Albert Camus (1913-1960), Karl Jaspers (1883-1969) o Martin Heidegger (1889-1976) entre otros. Respecto a éste último, a Heidegger, podemos encontrar algunas claves interesantes a través de su filosofía en relación al protagonista, a Maciek, especialmente a través de la idea del Dasein, a la idea de haber sido arrojado al mundo (Geworfenheit), y la manera tan extrema y visceral en la que vive susodicha condición. Todos aquellos elementos que dan sentido a la vida colectiva se encuentran decaídos o destruidos en su esencia más íntima, la Patria, la religión o la propia idea de Comunidad orgánica. De modo que el protagonista se ha visto «arrojado» frente a una situación o destino indeseado, en unas coyunturas totalmente desfavorables en las que no queda otra elección. Sus decisiones están permanentemente condicionadas por la circunstancia descrita y, por tanto, vive en un mundo donde no controla nada, en lugar de ser sujeto es un mero objeto transportado por esas circunstancias ajenas a su voluntad. Sin embargo, y en coherencia con el Dasein heideggeriano, vemos como Maciek, a raíz de conocer a Krystyna, comienza a experimentar una catarsis interior, que muestra por momentos el deseo de superar ese «ser arrojado al mundo contra tu voluntad», trascendiendo esa condición absurda e irracional de unas decisiones enajenadas de su voluntad para dotar de una significación y un sentido la propia existencia.
|
 |
|:-:|
|Andrzej Wajda, el director de la película.|
|
|:-:|
|Andrzej Wajda, el director de la película.|Otro elemento característico de la filosofía heideggeriana lo podemos encontrar en la «angustia» (angst) a través de la ausencia de un sentido y fundamento último que justifique la existencia del protagonista. Es una angustia en a que el Dasein se enfrenta a la «nada», a ese vacío existencial que hace inútil toda la lucha que Maciek lleva a cabo en la clandestinidad, con asesinatos y actos de terrorismo que pretenden salvaguardar algo que ya no existe, y que simboliza muy bien la Iglesia en ruinas con sus símbolos religiosos invertidos de la que hablábamos con anterioridad. Recuerda un poco a esa dicotomía que se plantea entre ser conservador o reaccionario frente a una realidad como la del propio presente, en la que los valores tradicionales han sido totalmente destruidos, y más que conservar se impone la reacción para volver a construir de la nada.
|
 |
|:-:|
|Hipérbola Janus; Textos para la Tradición en tiempos del oscurecimiento: Artículos publicados entre 2014 y 2019 en hiperbolajanus.com; Hipérbola Janus, 2019|
|
|:-:|
|Hipérbola Janus; Textos para la Tradición en tiempos del oscurecimiento: Artículos publicados entre 2014 y 2019 en hiperbolajanus.com; Hipérbola Janus, 2019|Todas las dudas que asaltan al protagonista se ven incrementadas en el momento decisivo, cuando se dispone a dar muerte al líder comunista. Se produce una tensión interna en Maciek, que se encuentra ligado a la joven que ha conocido ese día, y en ella es donde encuentra ese leve destello de humanidad. Esa circunstancia le hace replantearse por un instante el cumplimiento de su misión, pero es un dilema que no tiene salida, y por ello le asalta nuevamente la angustia frente a esa «nada», ese mundo vacío e incomprensible que trasciende el marco de sus propias elecciones.
Uno de los conceptos centrales de Heidegger en Ser y tiempo es el Sein-zum-Tode (ser-para-la-muerte), la idea de que la muerte es la posibilidad más propia y definitiva del Dasein, y que enfrentarla auténticamente permite vivir de manera más plena. Y es que el protagonista se encuentra permanentemente sobre esa frontera entre la vida y la muerte, que afronta con todas sus consecuencias, conscientemente, y la acepta. Esta actitud podría leerse como una forma de Dasein inauténtico, una huida del ser-para-la-muerte mediante la distracción (das Man, el «se» impersonal). Sin embargo, su decisión de cumplir la misión sugiere un enfrentamiento final con esa posibilidad. Otro aspecto que podemos conectar con el pensamiento heideggeriano es la autenticidad o inautenticidad de la vida del protagonista. En relación a la inautenticidad vemos como al principio sigue las órdenes de sus superiores en la organización sin cuestionarlas, lo cual implica un comportamiento inequívocamente alienante. Respecto a aquello que resulta auténtico de su existencia son sus relaciones con Krystyna, que supone imponer su propia voluntad y decisión, mostrando un Dasein que asume su libertad.
|
 |
|:-:|
|Escena de la película.|
|
|:-:|
|Escena de la película.|Otros aspectos más generales de la filosofía existencialista redundan sobre estos mismos aspectos, con la elección entre la libertad absoluta y la condena inevitable. La idea del hombre condenado a actuar, a una elección continua, aún cuando el hombre no es dueño de su destino, o las consecuencias de tales acciones son absurdas, irracionales e incomprensibles. El propio absurdo de la existencia frente al vacío y la ausencia de principios sólidos en los que cimentar la vida, no solo en sus aspectos cotidianos más básicos, sino en aquellos más profundos de la existencia. La soledad y la propia fatalidad frente a un Destino que, como ya hemos apuntado anteriormente, parece imponerse de manera irrevocable, y podríamos decir que brutalmente, al individuo aislado, incapaz de asirse en una guía, en unos valores que le permitan remontar la situación.
En términos generales «Cenizas y diamantes», además de ser una película de gran calidad en sus aspectos técnicos, en su fotografía, en la configuración de sus escenas y en el propio desarrollo argumental, bajo un guión espléndidamente ejecutado a lo largo de sus 98 minutos de duración, también nos invita a una reflexión profunda sobre la condición humana y la propia Modernidad. Y es algo que vemos en nuestros días, con las consecuencias de un pensamiento débil, con la promoción del individualismo, el hedonismo y lo efímero. La ausencia de estructuras sólidas, la subversión de toda forma de autoridad y jerarquía tradicionales. Paradójicamente, el mundo actual tiende a formas de poder y autoridad mucho más invasivas y coercitivas, tanto a nivel individual como colectivo, pero en la misma línea abstracta e impersonal que nos describe la película, abocándonos a la alienación y la inautenticidad de nuestras propias vidas. Y como Maciek, también nosotros, vivimos en un mundo dominado por la incertidumbre y la desesperanza, en el que el globalismo y sus perversas ideologías deshumanizantes actúan por doquier.
|
 |
|:-:|
|Carátula original de la película en polaco.|
|
|:-:|
|Carátula original de la película en polaco.|
Artículo original: Hipérbola Janus, Reseña de «Cenizas y Diamantes» (Andrzej Wajda, 1958) (TOR), 31/Mar/2025
-
 @ 9c9d2765:16f8c2c2
2025-04-07 07:39:53
@ 9c9d2765:16f8c2c2
2025-04-07 07:39:53CHAPTER TWO
“This is just a gift,” he said casually. “A small show of goodwill. But if you want my real help, the six hundred million dollars you need, there's one condition.”
He turned to Rita and smiled.
“I want Rita as my wife.”
Silence fell over the room.
Helen was the first to speak. “That can be arranged.”
James, who had been listening from outside the room, felt his chest tighten. He pushed the door open, his heart pounding.
“No,” he said firmly.
Mark raised an eyebrow. “Excuse me?”
“She’s my wife,” James said, standing his ground.
Helen turned to him with a scowl. “Not for long.” She slid a divorce document across the table. “Sign it, James. Stop being selfish.”
James stared at the papers.
Christopher’s voice was sharp. “You don’t belong here, James. If you truly love Rita, you will let her go.”
Rita’s eyes met James’. There was fear in them, but also love.
James clenched his fists.
“No,” he said again.
Then, without another word, he turned and stormed out of the event.
James walked through the cold night, his hands clenched into fists. His heart pounded with frustration. The humiliation he had endured at the Ray family’s business anniversary was unbearable. They had treated him like an outsider, an unwanted burden. Now, they were pressuring him to sign the divorce papers so they could sell Rita off to Mark, a man who was nothing but a privileged opportunist.
How did it come to this?
James had given everything to the family: his loyalty, his love, his hard work. And yet, the moment Grandpa Ray passed away, the rest of the family turned against him.
His phone vibrated in his pocket.
At first, he ignored it, assuming it was yet another message from Helen or Christopher, demanding that he sign the divorce papers. But when it vibrated again, curiosity got the best of him.
He pulled out his phone and saw a notification from an unknown number.
New Email: Urgent Financial Notice – Deltacore Inc.
James frowned. Deltacore?
The name stirred a faint memory. He hadn’t thought about that company in years. Back when he was still working in his father's company before he was falsely accused of embezzlement he had invested a small amount of money in Deltacore Inc., a rising tech company that had shown promise. However, soon after, Deltacore went bankrupt, and James had written off his investment as a loss.
His chest tightened as he opened the email.
Dear Mr. James,
We are pleased to inform you that your investment in Deltacore Inc., which had previously been marked as a loss, has now yielded significant returns. Under new management, Deltacore Inc. has resumed operations and successfully expanded into international markets.
As an early investor, your stake originally valued at $50,000 has now grown exponentially, reaching a current market valuation of $2.7 billion.
Kindly contact our financial department at your earliest convenience to discuss the liquidation or management of your newfound assets.
Best Regards, Jonathan Reed CFO, Deltacore Inc.
James stopped dead in his tracks. His breath caught in his throat.
Two point seven billion dollars.
His eyes scanned the email over and over again, ensuring he wasn’t hallucinating. But no, the numbers were real. His tiny investment had transformed into an unimaginable fortune.
A mixture of shock and disbelief rushed through him.
For years, he had been treated as a nobody, abandoned and looked down upon. But now… now, he was wealthier than the entire Ray family combined.
James’ grip on his phone tightened.
Everything had changed. The next morning, James wasted no time. He called the number listed in the email and scheduled an urgent meeting with Deltacore Inc.
By the afternoon, he was sitting in a high-rise office in the heart of the financial district. The company’s top executives treated him with the utmost respect, referring to him as one of their founding investors.
“We’ve been trying to reach you for months,” Jonathan Reed, the CEO, explained. “But since your contact information had changed, it was difficult to locate you.”
James leaned back in his chair. “I never imagined this would happen. I thought Deltacore was finished.”
Reed chuckled. “It was. But a few years ago, new investors stepped in, acquired the company’s patents, and relaunched operations. As an early investor, your small stake remained valid, and with our recent expansion into global markets, your shares skyrocketed.”
James exhaled slowly, trying to process it all.
“I’d like to access my funds immediately,” he said.
“Of course,” Reed nodded. “Do you have any immediate plans for wealth?”
James smiled slightly. Oh, I have plans A mixture of emotions surged within him shock, excitement, and most of all, vindication.
And yet… instead of feeling triumphant, an unsettling thought crept into his mind.
If they knew…
If the Ray family discovered his newfound wealth, they would come crawling back, pretending to care, pretending they had always loved him. Helen would try to manipulate him, Christopher would suddenly call him ‘son,’ and Stephen, who had never hidden his disdain, would act as if they were close brothers.
They would all turn against Rita, forcing her to beg for his forgiveness just to secure their own future.
James clenched his jaw.
No. They don’t deserve to know.
Not yet.
Instead of revealing his fortune, he made a decision. The once-thriving empire of Ray Enterprises stood on the edge of collapse. The financial crisis had drained the company’s reserves, forcing them into a corner with no easy escape. Suppliers had begun cutting ties, employees whispered about mass layoffs, and investors were pulling out faster than anyone could stop them.
At the center of this storm was Robert Ray, the younger brother of the late Grandpa Ray. Unlike Helen, Christopher, and Stephen who had spent years living off the company’s wealth without truly working for it, Robert had always valued the legacy built by his older brother.
So when the crisis deepened, he did something unthinkable.
He reached out to James.
James had been cast out of the family, humiliated, and disowned after Grandpa Ray’s death. He had been treated as an outsider despite being the only person who had ever truly respected the company’s values. And yet, despite it all, Robert knew that James was their only hope.
Late one evening, Robert arrived at James’s side of the apartment, he was led inside the house, his hands sweating as he stepped into the living room, James sat, calm and unreadable.
James didn’t offer him a seat.
“I assume you’re not here for pleasantries,” James said, his voice cold but controlled.
Robert hesitated before speaking. “James, I know… I know we don’t deserve your help. I know what Helen and the others did to you. But Ray Enterprises is”
“Dying?” James finished for him.
Robert swallowed hard. “Yes.”
James leaned back in his chair, studying the older man. There was no amusement in his expression, no gloating, just the sharp, analytical mind that had made him a billionaire in his own right.
“And now you come to me?” James asked. “After everything?”
Robert exhaled. “I won’t make excuses. I won’t even ask for forgiveness. But I’m asking for your help.”
James was silent for a long moment.
Then, he spoke.
“I’ll do it.”
Robert’s eyes widened. “You will?”
“But under one condition.”
Robert tensed. “What is it?”
James’s lips curled into a slight smirk.
“I want full control. I want to be the President of Ray Enterprises.”
The words hung in the air like a thunderclap.
Robert hadn’t expected this, but he should have. James had been treated like nothing more than an outsider, a disposable nuisance. Now, he was making it clear that if they wanted his help, he would no longer be a guest in the Ray family business.
He would be its ruler.
After a long pause, Robert nodded.
“Fine,” he said. “I’ll make it happen.”
-
 @ 5a261a61:2ebd4480
2025-04-15 06:34:03
@ 5a261a61:2ebd4480
2025-04-15 06:34:03What a day yesterday!
I had a really big backlog of both work and non-work things to clean up. But I was getting a little frisky because my health finally gave me some energy to be in the mood for intimacy after the illness-filled week had forced libido debt on me. I decided to cheat it out and just take care of myself quickly. Horny thoughts won over, and I got at least e-stim induced ass slaps to make it more enjoyable. Quick clean up and everything seemed ok...until it wasn't.
The rest of the morning passed uneventfully as I worked through my backlog, but things took a turn in the early afternoon. I had to go pickup kids, and I just missed Her between the doors, only managed to get a fast kiss. A little bummed from the work issues and failed expectations of having a few minutes together, I got on my way.
Then it hit me—the most serious case of blue balls I had in a long time. First came panic. I was getting to the age when unusual symptoms raise concerns—cancer comes first to mind, as insufficient release wasn't my typical problem. So I called Her. I explained what was happening and expressed hope for some alone time. Unfortunately, that seemed impossible with our evening schedule: kids at home, Her online meeting, and my standing gamenight with the boys. These game sessions are our sacred ritual—a preserved piece of pre-kids sanity that we all protect in our calendars. Not something I wanted to disturb.
Her reassurance was brief but unusualy promising: "Don't worry, I get this."
Evening came, and just as I predicted, there was ZERO time for shenanigans while we took care of the kids. But once we put them to bed (I drew straw for early sleeper), with parental duties complete, I headed downstairs to prepare for my gaming session. Headset on, I greeted my fellows and started playing.
Not five minutes later, She opened the door with lube in one hand, fleshlight in the other, and an expecting smile on Her face. Definitely unexpected. I excused myself from the game, muted mic, but She stopped me.
"There will be nothing if you won't play," She said. She just motioned me to take my pants off. And off to play I was. Not an easy feat considering I twisted my body sideways so She could access anything She wanted while I still reached keyboard and mouse.
She slowly started touching me and observing my reactions, but quickly changed to using Her mouth. Getting a blowjob while semihard was always so strange. The semi part didn't last long though...
As things intensified, She was satisfied with my erection and got the fleshlight ready. It was a new toy for us, and it was Her first time using it on me all by Herself (usually She prefers watching me use toys). She applied an abundance of lube that lasted the entire encounter and beyond.
Shifting into a rhythm, She started pumping slowly but clearly enjoyed my reactions when She unexpectedly sped up, forcing me to mute the mic. I knew I wouldn't last long. When She needed to fix Her hair, I gentlemanly offered to hold the fleshlight, having one hand still available for gaming. She misunderstood, thinking I was taking over completely, which initially disappointed me.
To my surprise, She began taking Her shirt off the shoulders, offering me a pornhub-esque view. To clearly indicate that finish time had arrived, She moved Her lubed hand teasingly toward my anal. She understood precisely my contradictory preferences—my desire to be thoroughly clean before such play versus my complete inability to resist Her when aroused. That final move did it—I muted the mic just in time to vocally express how good She made me feel.
Quick clean up, kiss on the forehead, and a wish for me to have a good game session followed. The urge to abandon the game and cuddle with Her was powerful, but She stopped me. She had more work to complete on Her todo list than just me.
Had a glass, had a blast; overall, a night well spent I would say.
-
 @ 9223d2fa:b57e3de7
2025-04-15 02:54:00
@ 9223d2fa:b57e3de7
2025-04-15 02:54:0012,600 steps
-
 @ fd06f542:8d6d54cd
2025-04-15 02:38:14
@ fd06f542:8d6d54cd
2025-04-15 02:38:14排名随机, 列表正在增加中。
Cody Tseng
jumble.social 的作者
https://jumble.social/users/npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wl
- Running [ wss://nostr-relay.app ] (free & WoT) 💜⚡️
- Building 👨💻:
- https://github.com/CodyTseng/jumble
- https://github.com/CodyTseng/nostr-relay-tray
- https://github.com/CodyTseng/danmakustr
- https://github.com/CodyTseng/nostr-relay-nestjs
- https://github.com/CodyTseng/nostr-relay
- https://github.com/CodyTseng
阿甘
- @agan0
- 0xchat.com
- canidae40@coinos.io
- https://jumble.social/users/npub13zyg3zysfylqc6nwfgj2uvce5rtlck2u50vwtjhpn92wzyusprfsdl2rce
joomaen
- Follows you
- joomaen.com
-
95aebd@wallet.yakihonne.com
-
nobot
- https://joomaen.filegear-sg.me/
- https://jumble.social/users/npub1wlpfd84ymdx2rpvnqht7h2lkq5lazvkaejywrvtchlvn3geulfgqp74qq0
颜值精选官
- wasp@ok0.org
- 专注分享 各类 图片与视频,每日为你带来颜值盛宴,心动不止一点点。欢迎关注,一起发现更多美好!
- https://jumble.social/users/npub1d5ygkef6r0l7w29ek9l9c7hulsvdshms2qh74jp5qpfyad4g6h5s4ap6lz
6svjszwk
- 6svjszwk@ok0.org
- 83vEfErLivtS9to39i73ETeaPkCF5ejQFbExoM5Vc2FDLqSE5Ah6NbqN6JaWPQbMeJh2muDiHPEDjboCVFYkHk4dHitivVi
-
low-time-preference
-
anarcho-capitalism
-
libertarianism
-
bitcoin #monero
- https://jumble.social/users/npub1sxgnpqfyd5vjexj4j5tsgfc826ezyz2ywze3w8jchd0rcshw3k6svjszwk
𝘌𝘷𝘦𝘳𝘺𝘥𝘢𝘺 𝘔𝘰𝘳𝘯𝘪𝘯𝘨 𝘚𝘵𝘢𝘳
- everyday@iris.to
- 虽然现在对某些事情下结论还为时尚早,但是从趋势来看,邪恶抬头已经不可避免。
- 我们要做的就是坚持内心的那一份良知,与邪恶战斗到底。
- 黑暗森林时代,当好小透明。
- bc1q7tuckqhkwf4vgc64rsy3rxy5qy6pmdrgxewcww
- https://jumble.social/users/npub1j2pha2chpr0qsmj2f6w783200upa7dvqnnard7vn9l8tv86m7twqszmnke
nostr_cn_dev
npub1l5r02s4udsr28xypsyx7j9lxchf80ha4z6y6269d0da9frtd2nxsvum9jm@npub.cash
Developed the following products: - NostrBridge, 网桥转发 - TaskQ5, 分布式多任务 - NostrHTTP, nostr to http - Postr, 匿名交友,匿名邮局 - nostrclient (Python client) . -nostrbook, (nostrbook.com) 用nostr在线写书 * https://www.duozhutuan.com nostrhttp demo * https://github.com/duozhutuan/NostrBridge * * https://jumble.social/users/npub1l5r02s4udsr28xypsyx7j9lxchf80ha4z6y6269d0da9frtd2nxsvum9jm *
CXPLAY
- lightning@cxplay.org
- 😉很高兴遇到你, 你可以叫我 CX 或 CXPLAY, 这个名字没有特殊含义, 无需在意.
- ©本账号下所有内容如未经特殊声明均使用 CC BY-NC-SA 4.0 许可协议授权.
- 🌐如果您在 Fediverse 收到本账号的内容则说明您的实例已与 Mostr.pub 或 Momostr.pink Bridge 互联, 您所看到的账号为镜像, 所有账号内容正在跨网传递. 如有必要请检查原始页面.
- 🧑💻正在提供中文本地化(i10n): #Amethyst #Amber #Citrine #Soapbox #Ditto #Alby
- https://cx.ms/
https://jumble.social/users/npub1gd8e0xfkylc7v8c5a6hkpj4gelwwcy99jt90lqjseqjj2t253s2s6ch58h
w
- 0xchat的作者
- 0xchat@getalby.com
- Building for 0xchat
- https://www.0xchat.com/
- https://jumble.social/users/npub10td4yrp6cl9kmjp9x5yd7r8pm96a5j07lk5mtj2kw39qf8frpt8qm9x2wl
Michael
- highman@blink.sv
- Composer Artist | Musician
- 🎹🎼🎤🏸🏝️🐕❤️
- 在這裡可以看到「我看世界」的樣子
- 他是光良
- https://jumble.social/users/npub1kr5vqlelt8l47s2z0l47z4myqg897m04vrnaqks3emwryca3al7sv83ry3
-
 @ bcbb3e40:a494e501
2025-03-31 15:41:53
@ bcbb3e40:a494e501
2025-03-31 15:41:53El 7 de febrero de 2025, Donald Trump firmó una orden ejecutiva que establecía una «Oficina de la Fe» en la Casa Blanca, dirigida por su asesora espiritual Paula White-Cain, la pastora de esa «teología de la prosperidad» (prosperity theology) que predica el «Evangelio de la salud y la riqueza» (health and wealth gospel^1). Investida de su nueva función, la reverenda pastora dijo: «Tengo la autoridad para declarar a la Casa Blanca un lugar santo. Es mi presencia la que la santifica»[^2]. Los siete rabinos del «Sanedrín Naciente» —la corte suprema que guiará a Israel cuando se reconstruya el Templo de Jerusalén— enviaron conmovedoras felicitaciones al presidente Trump por el establecimiento de esta Oficina. «Expresamos nuestra sincera gratitud —se lee en el mensaje oficial enviado a Trump desde el Monte Sión— por llevar la fe a la vanguardia de la cultura estadounidense y mundial mediante el establecimiento de la Oficina de la Fe en la Casa Blanca. Su reconocimiento de la importancia de la religión en la vida pública es un paso hacia la restauración de los valores morales y del liderazgo espiritual en el mundo[^3]. La carta del «Sanedrín Naciente», que augura el éxito a la «misión divina» del presidente estadounidense, reproduce las dos caras de una «moneda del Templo», acuñada en 2017 para celebrar el traslado de la embajada estadounidense a Jerusalén y, simultáneamente, el centenario de la Declaración Balfour. En el anverso se ven los perfiles de Donald Trump y Ciro el Grande, a quien la tradición judía atribuye la reconstrucción del templo destruido por los babilonios, con la inscripción (en hebreo e inglés) «Cyrus —Balfour— Trump Declaration 1917-2017»; en el reverso está la imagen del Templo de Jerusalén[^4]. Otra moneda, que lleva los perfiles de Trump y Ciro en el anverso y los de Trump y Netanyahu en el reverso, fue acuñada en 2018 para celebrar el septuagésimo aniversario de la independencia del «Estado de Israel»; se observa dos inscripciones en hebreo e inglés: «Y Él me encargó construirle una casa en Jerusalén» y «Guerra de los Hijos de la Luz contra los Hijos de las Tinieblas».
El tema de la «guerra de los Hijos de la Luz contra los Hijos de las Tinieblas» ha tenido una difusión particular en el imaginario y la propaganda trumpista. El 7 de junio de 2020, monseñor Carlo Maria Viganò, ex nuncio de la Santa Sede en los Estados Unidos, escribió una carta al presidente Donald Trump que comenzaba así: «Estamos asistiendo en los últimos meses a la formación de dos bandos, que los definiría bíblicos: los hijos de la luz y los hijos de las tinieblas»[^5]. El 1 de enero de 2021, el agitprop estadounidense Steve Bannon declaró en una entrevista con Monseñor Viganò: «Esta es una batalla de época entre los hijos de la Luz y los hijos de las Tinieblas»[^6].
Son numerosos los judíos sionistas que están en el círculo del presidente Trump: además de su hija Ivanka (convertida en 2009) y su yerno Jared Kushner (entonces Consejero Anciano del Presidente), el 19 de noviembre de 2024 el «The Jerusalem Post»[^7] publicó una lista de los más influyentes: Stephen Miller, subdirector del staff de la Casa Blanca y consejero de Seguridad Nacional de Estados Unidos; David Melech Friedman, a quien en 2016 Trump nombró embajador en Israel; el multimillonario «filántropo» Steven Charles Witkoff, enviado especial de Estados Unidos a Oriente Medio; Miriam Adelson, directora del periódico «Israel Hayom», clasificada por Bloomberg Billionaires como la quinta mujer más rica del mundo (con un patrimonio neto de 32,400 millones de dólares), financiadora de iniciativas políticas conservadoras en Estados Unidos e Israel; el banquero Boris Epshteyn, consejero estratégico de la campaña presidencial de Trump en 2020; Howard Williams Lutnick, presidente de la Cantor Fitzgerald del Grupo BGC, financista de las campañas presidenciales de Donald Trump en 2020 y 2024, ahora secretario de Comercio; la modelo Elizabeth Pipko, portavoz nacional del Partido Republicano y creadora de un «museo interactivo virtual» sobre la «Shoah» como parte del proyecto de Lest People Forget, cuyo objetivo es combatir el «antisemitismo» y la «negacionismo»; Lee Michael Zeldin, miembro republicano de la Cámara de Representantes por el estado de Nueva York del 2015 al 2023 y actualmente administrador de la EPA (Environmental Protection Agency); la columnista Laura Elizabeth Loomer, «orgullosamente islamófoba», activa patrocinadora de Trump en la campaña para las elecciones presidenciales de 2024; Sidney Ferris Rosenberg, influyente presentador de radio y periodista deportivo; William Owen Scharf, Asistente del Presidente y secretario del personal de la Casa Blanca; Marc Jeffrey Rowan, «filántropo» con un patrimonio neto valorado por Forbes en ocho mil ochocientos millones de dólares.
Además de estos, cabe mencionar al popular presentador de radio Mark Levin quien, en diciembre de 2019, durante la celebración de la fiesta de Janucá en la Casa Blanca, saludó a Donald Trump como «el primer presidente judío de los Estados Unidos»[^8]. Según un funcionario de alto nivel de la Casa Blanca, Donald Trump se convirtió al judaísmo dos años antes en la sinagoga de la secta Jabad Lubavitch en la ciudad de Nueva York. David Elias Goldberg, miembro del Jewish Center of Antisemitic Study, también entrevistó al funcionario, para quien «Trump fue “instado” por su hija Ivanka y su yerno Jared Kushner para abrazar la fe. Inicialmente, Trump se habría mostrado reacio, considerando que esto podría enfriar el apoyo del electorado evangélico». Luego, informa «Israel Today News», «cambió de opinión y se convirtió oficialmente a principios de 2017. La ceremonia se llevó a cabo en privado y se guardó celosamente durante casi dos años»[^9]. Pero ya en septiembre de 2015, el rabino millonario Kirt Schneider, invitado a la Trump Tower de Nueva York, había impuesto sus manos sobre la cabeza de Donald Trump y lo había bendecido en hebreo e inglés, declarando: «Las únicas dos naciones que tienen una relación privilegiada con Dios son Israel y los Estados Unidos de América»[^10].
El 7 de octubre de 2024, en el aniversario de la operación de Hamas «Diluvio de Al-Aqsa», Trump fue acompañado por un «superviviente de la Shoah» a la tumba de Menachem Mendel Schneerson, séptimo y último Rabino de los Hasidim de la secta Jabad Lubavitch, que en 1991 declaró a sus seguidores: «He hecho todo lo posible para provocar el arribo del Mesías, ahora les paso a ustedes esta misión; hagan todo lo que puedan para que Él venga»^11. En relación al evento mesiánico, el eminente rabino Yekutiel Fish atribuyó una misión decisiva a Trump: «Todo el mundo está centrado en Gaza, pero esa es solo una parte de la agenda del fin de los tiempos, que tiene a los judíos viviendo en las fronteras profetizadas de Israel; la Torá incluye explícitamente a Gaza. Lo que Trump está haciendo es limpiar Gaza de todos los odiadores de Israel. No podrán estar en Israel después de la venida del Mesías. (...) Esto incluirá a Gaza, la mitad del Líbano y gran parte de Jordania. Y vemos que casi lo hemos logrado. Siria cayó. Líbano está medio destruido. Gaza está destrozada. El escenario está casi listo para el Mesías. Pero, ¿cómo pueden los palestinos estar aquí cuando vayamos a recibir al Mesías? El Mesías necesita que alguien se ocupe de esto, y en este caso, es Donald Trump. Trump está simplemente llevando a cabo las tareas finales necesarias antes de que el Mesías sea revelado»[^12].
Esta inspiración escatológica está presente en las palabras de Pete Brian Hegseth, el pintoresco exponente del «Reconstruccionismo Cristiano»[^13] a quien Trump nombró secretario de Defensa. En un discurso pronunciado en 2019 en el Hotel Rey David de Jerusalén, con motivo de la conferencia anual del canal Arutz Sheva (Israel National News), Hegseth enalteció el «vínculo eterno» entre Israel y Estados Unidos, y enumeró los «milagros» que atestiguan el «apoyo divino» a la causa sionista, el último de los cuales será la reconstrucción del Templo judío en la zona donde actualmente se encuentra la mezquita de al-Aqsa: «La dignidad de capital adquirida por Jerusalén —dijo— fue un milagro, y no hay razón por la cual no sea posible el milagro de la restauración del Templo en el Monte del Templo».[^14]
Es conocido que el fundamentalismo evangélico pro-sionista[^15] comparte con el judaísmo la creencia en que la construcción del tercer Templo de Jerusalén marcará el comienzo de la era mesiánica; cuando la administración Trump trasladó la embajada de Estados Unidos a Jerusalén en 2017, Laurie Cardoza-Moore, exponente del evangelismo sionista, saludó así la «obediencia de Trump a la Palabra de Dios» en «Haaretz»: «Al establecer la Embajada en Jerusalén, el presidente Donald Trump está implementando una de las iniciativas históricas de dimensión bíblica en su presidencia. Al igual que muchos judíos en Israel y en todo el mundo, los cristianos reconocen el vínculo de los judíos con la Biblia a través del nombre de Jerusalén como la capital del antiguo Israel, así como el sitio del Primer y Segundo Templos. Según los profetas Ezequiel, Isaías y el apóstol Juan del Nuevo Testamento, todos los israelíes esperan la reconstrucción del Tercer Templo»[^16]. El 22 de mayo del mismo año, Donald Trump, acompañado de su esposa Melania, de su hija Ivanka y su yerno Jared Kushner, fue el primer presidente de los Estados Unidos en ejercicio en acudir al Muro de las Lamentaciones, anexionado ilegalmente a la entidad sionista.
En 2019, la administración Trump confirmó la posición de Estados Unidos al enviar en visita oficial para Jerusalén a Mike Pompeo, un secretario de Estado que —ironía de la Historia— lleva el mismo nombre del general romano que asaltó la ciudad en el año 63 a.C. «Por primera vez en la historia, un secretario de Estado norteamericano visitó la Ciudad Vieja de Jerusalén en compañía de un alto político israelí. Fue una visita histórica que reforzó las expectativas israelíes y constituyó un reconocimiento tácito de la soberanía israelí sobre el sitio del Monte del Templo y la Explanada de las Mezquitas. (…) Mike Pompeo, acompañado por el primer ministro Benjamin Netanyahu y el embajador de Estados Unidos en Israel, David Friedman, también visitó el túnel del Muro de las Lamentaciones y la sinagoga ubicada bajo tierra, en el presunto lugar del santuario del Templo[^17], donde se le mostró una maqueta del futuro Templo[^18]. En el transcurso de una entrevista concedida durante la fiesta del Purim (que celebra el exterminio de la clase política persa, ocurrido hace 2500 años), el secretario de Estado insinuó que «el presidente Donald Trump puede haber sido enviado por Dios para salvar al pueblo judío y que confiaba en que aquí el Señor estaba obrando»[^19].
Como observa Daniele Perra, en este mismo número de «Eurasia», el «mito movilizador» del Tercer Templo, atribuible a los «mitos teológicos» señalados por Roger Garaudy como mitos fundadores de la entidad sionista, «atribuye al judaísmo una especie de función sociológica de transmisión y proyección del conflicto palestino-israelí hacia el resto del mundo y confiere una inspiración apocalíptica al momento geopolítico actual».
|Info|| |:-|:-| |Autor| Claudio Mutti | |Fuente| I "Figli della Luce" alla Casa Bianca | |Fecha| 8/Mar/2025 | |Traducción| Francisco de la Torre |
[^2]: The White House, President Trump announces appointments to the White House Faith Office https://www.whitehouse.gov,, 7 de febrero de 2025; Trump establece la Oficina de la Fe con una foto de «La Última Cena» | Fue dirigida por la controvertida predicadora Paula White, https://www.tgcom24.mediaset.it, 10 de febrero de 2025.
[^3]: «We extend our heartfelt gratitude for bringing faith to the forefront of American and global culture through the establishment of the Faith Office in the White House. Your recognition of the importance of religion in public life is a step toward restoring moral values and spiritual leadership in the world» (Letter from the Nascent Sanhedrin to President Donald J. Trump, Jerusalem, Wednesday, February 12, 2025).
[^4]: Israeli group mints Trump coin to honor Jerusalem recognition, «The Times of Israel», https://www.timesofisrael.com, 28-2-2018.
[^5]: Mons. Viganò — Siamo nella battaglia tra figli della luce e figli delle tenebre, https://www.italiador.com, 7-6-2020
[^6]: TRANSCRIPT: Steve Bannon’s ‘War Room’ interview with Abp. Viganò, lifesitenews.com, 4-1-2021. Sulle origini e sulla fortuna di questo tema cfr. C. Mutti, Le sètte dell’Occidente, «Eurasia», 2/2021, pp. 12-15. (https://www.eurasia-rivista.com/las-sectas-de-occidente/)
[^7]: Luke Tress, The who’s who of Jews in Trump’s inner circle?, «The Jerusalem Post», https://www.jpost.com, 19-11-2024.
[^8]: Radio Talk Show Host Mark Levin Calls President Trump «the First Jewish President of the United States», https://www.c-span.org, 11-12-2019.
[^9]: «However, he had a change of heart and officially converted in early 2017. The ceremony was held in private, and closely guarded for nearly two years» (Donald Trump converted to Judaism two years ago, according to White House official, https://israeltodaynews.blogspot.com/2019/02).
[^10]: «El rabino Kirt Schneider (...) es un millonario judío, una figura televisiva de los “judíos mesiánicos”. Sus emisiones televisivas semanales son emitidas por más de treinta canales cristianos en unos doscientos países; entre ellos, los canales “Yes” y “Hot” en Israel. Solo en Estados Unidos, sus emisiones atraen a 1.600.000 telespectadores cada semana. Kirt Schneider dirige un imperio de telecomunicaciones que tiene un millón y medio de seguidores en Facebook, X (antes Twitter) y YouTube» (Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, Edizioni all'insegna del Veltro, Parma 2025, p. 31).
[^12]: «Everyone is focused on Gaza, but that is only one part of the end-of-days agenda, which has the Jews living in Israel’s prophesied borders. The Torah explicitly includes Gaza. What Trump is doing is cleaning out Gaza of all the haters of Israel. They cannot be in Israel after the Messiah comes. (…) This will include Gaza, half of Lebanon, and much of Jordan. And we see that we are almost there. Syria fell. Lebanon is half gone. Gaza is ripped up. The stage is nearly set for Messiah. But how can the Palestinians be here when we go to greet the Messiah? The Messiah needs someone to take care of this, and in this case, it is Donald Trump. Trump is merely carrying out the final tasks needed before Messiah is revealed» (Adam Eliyahu Berkowitz, Trump’s Gaza Plan is «The Final task before Messiah», https://israel365news.com, 5-2-2025).
[^13]: «A day after Hegseth was announced for the Cabinet position, Brooks Potteiger, a pastor within the Communion of Reformed Evangelical Churches (CREC), posted on X that Hegseth is a member of the church in good standing. The CREC, a denomination of Christian Reconstructionism, is considered by some academics to be an extremist, Christian supremacist movement» (Shannon Bond e altri, What’s behind defense secretary pick Hegseth’s war on ‘woke’, https://www.npr.org, 14-11-2024.
[^14]: «The decoration of Jerusalem as a capital was a miracle, and there is no reason why the miracle of the re-establishment of Temple on the Temple Mount is not possible» (Pete Hegseth at Arutz Sheva Conference, youtube.com). Cfr. Daniele Perra, Paleotrumpismo, neotrumpismo e post-trumpismo, in: AA. VV., Trumpismo, Cinabro Edizioni, Roma 2025, pp. 22-23.
[^15]: Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, cit., págs. 82 a 96.
[^16]: «We American Christians Welcome Trump’s Obedience to God’s Word on Jerusalem», «Haaretz», 6-12-2017.
[^17]: Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, cit., pág. 97.
[^18]: Pompeo en visite historique au mur Occidental aux côtés de Netanyahu et Friedman, «The Times of Israel», https://fr.timesofisrael.com, 21-3-2019.
[^19]: Pompeo says Trump may have been sent by God to save Jews from Iran, «The Times of Israel», 22-3-2019.
-
 @ 2b24a1fa:17750f64
2025-04-04 08:10:53
@ 2b24a1fa:17750f64
2025-04-04 08:10:53Wir leben in einer Demokratie. So heißt es immer. Immerhin hat die Bevölkerung, der Souverän ein Mitspracherecht. Einmal alle vier Jahre. Und damit fünfundzwanzig Mal in einem Jahrhundert. Diese 25 Wahltage ergeben zeitlich 0,07 Prozent des gesamten Jahrhunderts. Würde man das Jahrhundert auf einen Tag runter rechnen, dann ergäben diese 0,07 Prozent ziemlich genau eine Minute des Mitspracherechts. Eine Minute pro Tag darf der Souverän also bestimmen, wer am restlichen Tag ungehindert schalten und walten darf – bis in das Grundgesetz hinein.
https://soundcloud.com/radiomuenchen/das-grundgesetz-als-schmierzettel-von-henry-matthes?
Die Veränderung in diesem zentralen Gesetzestexten ist allein den Parteien vorbehalten. An sämtliche Änderungen halten, dürfen sich dann nachher alle – selbst dann, wenn noch so wenige Bürger dahinterstehen.
In den letzten Wochen offenbarte sich dieser Missstand in präzedenzloser Weise. Die als Sondervermögen schön-deklarierte Neuverschuldung wurde im Grundgesetz festgeschrieben. Ist eine solch selektive Umgestaltungsmöglichkeit des wichtigsten Gesetzestext einer Demokratie würdig? Bräuchte es nicht zumindest einer Absegnung durch Volksabstimmungen?
Henry Mattheß hat sich hierzu Gedanken gemacht. Hören Sie seinen Text „Das Grundgesetz als Schmierzettel“, der zunächst auf dem Blog von Norbert Häring erschienen war.
Sprecher: Karsten Tryoke
Bild: Radio München
www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): bc1qqkrzed5vuvl82dggsyjgcjteylq5l58sz4s927\ Ethereum (ETH): 0xB9a49A0bda5FAc3F084D5257424E3e6fdD303482
-
 @ df67f9a7:2d4fc200
2025-04-03 19:54:29
@ df67f9a7:2d4fc200
2025-04-03 19:54:29More than just “follows follows” on Nostr, webs of trust algos will ingest increasingly MORE kinds of user generated content in order to map our interactions across the network. Webs of trust will power user discovery, content search, reviews and reccomendations, identity verification, and access to all corners of the Nostr network. Without relying on a central “trust authority” to recommend people and content for us, sovereign Nostr users will make use of “relative trust” scores generated by a wide range of independent apps and services. The problem is, Nostr doesn’t have an opensource library for performing WoT calculations and delivering NIP standard recommendations to users. In order for a “free market” ecosystem of really smart apps and services to thrive, independent developers will need access to extensible “middleware” such as this.
Project Description
I am building a library for independent developers to offer their own interoperable and configurable WoT services and clients. In addition, and as the primary use case, I am also developing a web client for “in person onboarding” to Nostr, which will make use of this library to provide webs of trust recommendations for “invited” users.
-
Meet Me On Nostr (onboarding client) : This is my first project on Nostr, which began a year ago with seed funding from @druid. This web client will leverage “in person” QR invites to generate WoT powered recommendations of follows, apps, and other stuff for new users at their first Nostr touchpoint. The functional MVP release (April ‘25) allows for “instant, anonymous, and fully encrypted” direct messaging and “move in ready” profile creation from a single QR scan.
-
GrapeRank Engine (developer library) : Working with @straycat last fall, I built an opensource and extensible library for Nostr developers to integrate “web of trust” powered reccomendations into their products and services. The real power behind GrapeRank is its “pluggable” interpreter, allowing any kind of content (not just “follows follows”) to be ingested for WoT scoring, and configurable easily by developers as well as end users. This library is currently in v0.1, “generating and storing usable scores”, and doesn’t yet produce NIP standard outputs for Nostr clients.
-
My Grapevine (algo dashboard) : In addition, I’ve just wrapped up the demo release of a web client by which users and developers can explore the power of the GrapeRank Engine.
Potential Impact
Webs of Trust is how Nostr scales. But so far, Nostr implementations have been ad-hoc and primarily client centered, with no consistency and little choice for end users. The “onboarding and discovery” tools I am developing promise to :
-
Establish sovereignty for webs of trust users (supporting a “free market” of algo choices), with opensource libraries by which any developer can easily implement WoT powered recommendations.
-
Accelerate the isolation of bots and bad actors (and improve the “trustiness” of Nostr for everyone else) by streamlining the onboarding of “real world” acquaintances directly into established webs of trust.
-
Improve “discoverability of users and content” for any user on any client (to consume and take advantage of WoT powered recommendations for any use case, even as the NIP standards for this are still in flux), by providing an algo engine with “pluggable” inputs and outputs.
-
Pave the way for “global Nostr adoption”, where WoT powered recommendations (and searches) are consistently available for every user across a wide variety of clients.
Timeline & Milestones
2025 roadmap for “Webs of Trust Onboarding and Discovery” :
-
Meet Me On Nostr (onboarding client) : MVP release : “scan my QR invite to private message me instantly with a ‘move in ready’ account on Nostr”. https://nostrmeet.me/
-
GrapeRank Engine (developer library) : 1.0 release : “expanded inputs and output WoT scores to Nostr NIPs and other stuff” for consumption by clients and relays. https://github.com/Pretty-Good-Freedom-Tech/graperank-nodejs
-
My Grapevine (algo dashboard) : 1.0 release : “algo usage and configuration webapp with API endpoints” for end users to setup GrapeRank scoring for consumption by their own clients and relays. https://grapevine.my/
-
Meet Me On Nostr (onboarding client) : 1.0 release : first GrapeRank integration, offering “follow and app recommendations for invited users”, customizable per-invite for Nostr advocates. https://nostrmeet.me/
Prior contributions
-
Last spring I hosted panel discussions and wrote articles on Nostr exploring how to build “sovereign webs of trust”, where end users can have control over which algorithms to use, and what defines “trust”.
-
I contributed gift wrap encryption to NDK.
-
I am also authoring gift wrapped direct messaging and chat room modules for NDK.
-
Last July, I attended The Bitcoin Conference on an OpenSource pass to raise funds for my onboarding client. I onboarded many Bitcoiners to Nostr, and made valuable connections at Bitcoin Park.
About Me
I discovered Nostr in September ‘23 as a freelance web developer, after years of looking for a “sovereignty respecting” social media on which to build apps. With this came my first purchase of Bitcoin. By December of that year, I was settled on “open source freedom tech” (Nostr and Bitcoin) as the new direction for my career.
As a web professional for 20+ years, I know the importance of “proof of work” and being connected. For the last 18 months, I have been establishing myself as a builder in this community. This pivot has not been easy, but it has been rewarding and necessary. After so many years building private tech for other people, I finally have a chance to build freedom tech for everyone. I have finally come home to my peeps and my purpose.
Thank you for considering this application for funding.
-
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 7bdef7be:784a5805
2025-04-02 12:37:35
@ 7bdef7be:784a5805
2025-04-02 12:37:35The following script try, using nak, to find out the last ten people who have followed a
target_pubkey, sorted by the most recent. It's possibile to shortensearch_timerangeto speed up the search.```
!/usr/bin/env fish
Target pubkey we're looking for in the tags
set target_pubkey "6e468422dfb74a5738702a8823b9b28168abab8655faacb6853cd0ee15deee93"
set current_time (date +%s) set search_timerange (math $current_time - 600) # 24 hours = 86400 seconds
set pubkeys (nak req --kind 3 -s $search_timerange wss://relay.damus.io/ wss://nos.lol/ 2>/dev/null | \ jq -r --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[] | select(.[0] == "p" and .[1] == $target)) | .pubkey ' | sort -u)
if test -z "$pubkeys" exit 1 end
set all_events "" set extended_search_timerange (math $current_time - 31536000) # One year
for pubkey in $pubkeys echo "Checking $pubkey" set events (nak req --author $pubkey -l 5 -k 3 -s $extended_search_timerange wss://relay.damus.io wss://nos.lol 2>/dev/null | \ jq -c --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[][] == $target) ' 2>/dev/null)
set count (echo "$events" | jq -s 'length') if test "$count" -eq 1 set all_events $all_events $events endend
if test -n "$all_events" echo -e "Last people following $target_pubkey:" echo -e ""
set sorted_events (printf "%s\n" $all_events | jq -r -s ' unique_by(.id) | sort_by(-.created_at) | .[] | @json ') for event in $sorted_events set npub (echo $event | jq -r '.pubkey' | nak encode npub) set created_at (echo $event | jq -r '.created_at') if test (uname) = "Darwin" set follow_date (date -r "$created_at" "+%Y-%m-%d %H:%M") else set follow_date (date -d @"$created_at" "+%Y-%m-%d %H:%M") end echo "$follow_date - $npub" endend ```
-
 @ 7bdef7be:784a5805
2025-04-02 12:12:12
@ 7bdef7be:784a5805
2025-04-02 12:12:12We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs.
The problem
Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, so everyone can actually snoop what we are interested in, and what is supposable that we read daily.
The solution
Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see NIP-51). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create dedicated feeds, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be encrypted, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also really private one.
One might wonder what use can really be made of private lists; here are some examples:
- Browse “can't miss” content from users I consider a priority;
- Supervise competitors or adversarial parts;
- Monitor sensible topics (tags);
- Following someone without being publicly associated with them, as this may be undesirable;
The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of how many bots scan our actions to profile us.
The current state
Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff (NIP-44). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply mark them as local-only, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment.
To date, as far as I know, the best client with list management is Gossip, which permits to manage both encrypted and local-only lists.
Beg your Nostr client to implement private lists!
-
 @ bcbb3e40:a494e501
2025-03-31 15:34:12
@ bcbb3e40:a494e501
2025-03-31 15:34:12|
 |
|:-:|
|MISSIAGGIA, Pietro; Jean Thiriart, el caballero euroasiático y la Joven Europa; Hipérbola Janus, 2025|
|
|:-:|
|MISSIAGGIA, Pietro; Jean Thiriart, el caballero euroasiático y la Joven Europa; Hipérbola Janus, 2025|Desde nuestros inicios los autores y temáticas relacionadas con la geopolítica nos han procurado atención e interés por parte del gran público y de los mass media, y no hay más que recordar el efecto que han venido teniendo nuestras obras de Aleksandr Duguin, en especial La geopolítica de Rusia y Proyecto Eurasia: teoría y praxis, sobre todo a raíz de nuestra presentación en Casa de Rusia en un ya lejano 2016, con la inestimable colaboración de Jordi de la Fuente como prologuista, trabajo que siempre reivindicamos desde nuestros medios por el prestigio, la calidad y brillantez de exposición del mismo.
Más allá de las obras del prestigioso y afamado filósofo y politólogo ruso, también hemos realizado otras incursiones en esta vertiente, que podríamos llamar «geopolítica alternativa», introduciendo las obras de otros notables autores como Claudio Mutti, Carlo Terracciano o Boris Nad. Con estos autores hemos tratado de profundizar en esa vía que se opone frontalmente, y radicalmente si se quiere, a los planteamientos derivados de la geopolítica atlantista y liberal que tiene su principal polo en Estados Unidos, haciendo especial hincapié en el subyugamiento que vienen ejerciendo desde 1945 en adelante respecto a una Europa convertida en un protectorado en una mera colonia.
Es por este motivo por el que la publicación de Jean Thiriart, el caballero euroasiático y la Joven Europa nos parece una obra totalmente pertinente en estos momentos, forma parte del desarrollo lógico de la línea editorial en la que estamos encauzados desde nuestros inicios, y viene a representar una de las múltiples vías en las que confluye la idea, profundamente schmittiana, de la política de los grandes espacios. En este caso la idea de una Europa unida, bajo un vasto proyecto que traspasa los estrechos límites del continente concebido como un apéndice más del «Occidente», de ese subproducto ideológico decadente y funcional a los intereses del otro lado del Atlántico. Para comprender la idea de una Europa unida, que comprenda a Rusia, y su enorme extensión territorial a lo largo de 17 millones de kilómetros cuadrados, y la importancia estratégica de su ubicación, es necesario recurrir al legado de Jean Thiriart, conocer su obra, pero también al hombre, pues una no se comprende sin el otro, en este caso hablamos de elementos correlativos.
|
 |
|:-:|
|Jean Thiriart (1922-1992)|
|
|:-:|
|Jean Thiriart (1922-1992)|¿Pero quién fue Jean Thiriart? Esta obra nos permite adentrarnos en aspectos biográficos, algunos de ellos poco conocidos para el gran público de habla hispana, y saber de su trayectoria, de la maduración de sus ideas, de su proyecto político y de las etapas que componen el desarrollo del mismo y que aparecen claramente diferenciadas: hablamos del proyecto político de unidad europea, que alcanza su concreción teórica en ¡Arriba Europa!: Una Europa unida: un imperio de 400 millones de hombres (1965, Editorial Mateu, Barcelona), en pleno apogeo de la organización Jeune Europe, que se convirtió en el órgano político a partir del cual creyó poder implementar su proyecto unitario a escala europeo, manteniendo una posición de independencia respecto a los dos pretendidos bloques antagónicos de Guerra Fría: Estados Unidos y la Unión Soviética. En esa época, estamos hablando del ecuador de los años 60, todo el mundo de la Contracultura, falsamente contestatario, estaba articulando su propio discurso, que tendría su expresión más nítida a través del ya conocido Mayo del 68 francés o la Primavera de Praga, durante el mismo año. Y si el movimiento de Nueva Derecha liderado por Alain de Benoist surgiría en lo sucesivo, ya en la década de los años 70, como una «reacción» frente a la «rebelión contracultural», no podemos obviar la importancia de un movimiento político como Jeune Europe, una organización política transnacional, a escala de la Europa occidental, con sus diferentes delegaciones en países como Francia, Italia, Alemania, la propia España además de, como es obvio, Bélgica, país de origen de nuestro autor.
Jean Thiriart ha sido etiquetado con reiteración como un político y teórico de «extrema derecha», se han hecho numerosos discursos interesados para vincularlo, por cuestiones de orden biográfico muy circunscritas a determinado periodo, con el fascismo y el nacionalsocialismo de entreguerras. Sin embargo, y como el lector podrá descubrir a lo largo de la presente obra, el pensamiento de nuestro autor está muy lejos de ser reducible a meras etiquetas, y en ningún caso mostró las filiaciones que se le atribuyen desde posicionamientos ideológicos, sino que, muy al contrario, vemos a un hombre de pensamiento racional y pragmático, poderosamente influenciado por la geopolítica y abierto a alianzas estratégicas más variadas, más allá de todo fundamentalismo ideológico. Es por este motivo que veremos a un Thiriart buscando sinergias y entendimiento entre círculos de izquierdas, antiimperialistas en una lucha concebida como «cuatricontinental». No en vano, muchos de los cuadros políticos que se formaron en Giovane Europa, la rama italiana, terminaron por militar incluso en organizaciones de extrema izquierda de inspiración maoísta. En el caso de España hubo un notable apoyo a la organización por parte de los falangistas más disidentes. De manera que Jean Thiriart representa una figura política compleja, con influencias variadas, que van desde los hermanos Strasser, pasando por Ernst Niekish o Vilfredo Pareto, e incluso, por Sieyès o Robespierre.
Es a partir de Jeune Europe cuando el nacionalismo europeo, la idea de una Europa unida desde Brest a Bucarest toma cuerpo. En la obra mencionada con anterioridad (¡Arriba Europa!: Una Europa unida: un imperio de 400 millones de hombres) Jean Thiriart ya nos presenta a través de unos trazos muy definidos el proyecto del comunitarismo nacional-europeo, la piedra angular de su proyecto político. La idea de un socialismo aristocrático y europeo, trascendiendo las fronteras del Estado-nación liberal decimonónico, y los particularismos nacionales, concebidos como formas obsoletas y «estrechas de miras», obstáculos a superar en la convergencia del Imperio europeo. Porque vemos a un Thiriart que potencia la estructura del Estado, del aparato de poder, tratando de potenciar, y restaurar naturalmente, el papel y la preponderancia de Europa como espacio de civilización en el mundo. Es un nacionalismo europeo que viene determinado por razones puramente geopolíticas, algo que también fue objeto de críticas, concretamente por parte del geopolítico austriaco Heinrich von Lohausen, y que también recogemos en el presente volúmen de la obra.
|
 |
|:-:|
|Ejemplar de una de las publicaciones más importantes de Joven Europa (Jeune Europe) cuya portada refleja el antiamericanismo y antiimperialismo característicos del nacionalismo europeo de la organización.|
|
|:-:|
|Ejemplar de una de las publicaciones más importantes de Joven Europa (Jeune Europe) cuya portada refleja el antiamericanismo y antiimperialismo característicos del nacionalismo europeo de la organización.|En este sentido, Thiriart no andaba nada desencaminado, en la medida que pensaba que solo los Estados de dimensiones continentales podrían ser capaces de defender su independencia y soberanía, y ejercer un poder en el mundo, frente a los antiguos nacionalismos europeos, totalmente anacrónicos y un factor de ruptura y desintegración del potencial europeo. En este contexto, se hace necesario eliminar el orden establecido en Yalta en 1945, que convierte a Europa en un vasallo de las grandes potencias vencedoras de la Segunda Guerra Mundial. De modo que luchar contra la ocupación estadounidense por un lado, y soviética por otro lado, fuese el principal leitmotiv del Partido Revolucionario Europeo, un partido histórico señala Thiriart, encargado de llevar a término la acción unificadora continental. Y es con este propósito con el que se tratan de concertar una serie de alianzas internacionales que llevó a Thiriart y su organización a tratar con personal diplomático y gubernamental de los países árabes no alineados, del régimen de Fidel Castro o incluso con emisarios del gobierno chino, como ocurrió en el famoso encuentro propiciado por Ceaucescu en Bucarest con Zhou En-Lai.
Quizás, uno de los puntos donde más desacuerdos encontramos con las teorías thiriartianas se encuentra en ciertos fundamentos que la articulan, en un modelo racionalista, materialista y pragmático, de hecho no debemos olvidar que Maquiavelo era uno de sus referentes, y con éste la posterior hornada de autores neomaquiavélicos como Vilfredo Pareto. El excesivo pragmatismo de sus planteamientos, un estatalismo exacerbado y sin concesiones a las particularidades de los pueblos, una suerte de centralismo jacobino, y la ausencia de un elemento trascendente capaz de dar una justificación metafísica a todo el proyecto nacional europeo constituyen, en nuestra opinión, una parte discutible y reformulable.
En otro terreno, como pueda ser el puramente económico, encontramos un proyecto anticapitalista en muchos de sus aspectos, frente al democratismo parlamentario liberal, y apoyándose en las teorías económicas de Johann G. Fichte o Friedrich List, rechazando cualquier organización económica transnacional que pueda mediatizar o convertir a Europa en objeto de sus actividades usurocráticas y depredatorias, colocando la soberanía e independencia económica europea en una de las máximas prioridades en este terreno.
Debemos destacar, porque es un elemento de debate especialmente interesante, el apartado del libro que se corresponde al escrito de Luc Michel, publicado en Italia bajo el título Da Jeune Europe alle Brigate Rosse, en el libro Parte II Historia de Jeune Europe (1962-1969), en el que se detallan las colaboraciones que comenzaron a sucederse entre la militancia de la delegación italiana, Giovane Europa, y círculos de extrema izquierda maoísta, y cómo muchos de los antiguos militantes nacional-europeos terminaron militando en organizaciones de esta facción ideológica, y nos referimos a casos tan representativos en la época como Claudio Orsoni o Pino Bolzano entre otros muchos.
La actividad proselitista de Jeune Europe en el último lustro de la década de los años 60, con la fundación del Partido Comunitario Europeo, nos legó una gran cantidad de publicaciones, entre las cuales destacaron La Nation Européenne, La Nazione Europea o Europa Combattente, cuyas portadas han servido para ilustrar las páginas interiores de nuestra obra, y que procuraron una actividad proselitista y de difusión de ideas que llegaron a imprimir semanal y mensualmente varios miles de ejemplares en Francia o en Italia.
Tras agotar todas las vías posibles de alianzas y convergencias, con encuentros poco afortunados, vemos a un Thiriart que prefiere adoptar otras vías para seguir construyendo el proyecto nacional-europeo más allá de la fórmula activista y del partido político. Este es el motivo por el cual, en los siguientes años, ya en la última etapa de su vida, veremos esa transición del político activista al teórico y al ideólogo como parte de una nueva estrategia dentro del proyecto político al que consagró buena parte de su vida, y es un hecho que comienza a apreciarse desde mediados de los años 70. Durante esta época la «Europa de Brest a Bucarest» se transforma y amplía en una «Europa desde Dublín a Vladivostok». Thiriart aborda ya abiertamente la integración del espacio soviético en una Europa unida que abarca un inmenso espacio territorial, capaz de unir el Océano Atlántico y el Océano Pacífico de un extremo a otro, el «Imperio Eurosoviético». No obstante, Thiriart siempre piensa en términos geopolíticos, y considera que este proceso de integración debe llevarse a cabo desde una revisión de la ideología soviética, desde una marcada desmarxistización de su socialismo, purgado de todo dogmatismo y elementos condicionantes derivados de la teoría del Estado formulada por el marxismo-leninismo para tomar en su lugar aquella de Thomas Hobbes.
A partir de este momento solamente hay un enemigo, el que representa el poder estadounidense y el dominio que éste ejerce sobre la Europa occidental. A partir de ese momento la URSS, bajo las premisas apuntadas por Thiriart, y desde una ideología soviética «desmarxistizada», es la que debe asumir el proyecto de integración europea. Todo este enfoque terminará conociendo su colofón final al final de la vida de Jean Thiriart, cuando éste se encuentre ya en sus último año de vida, en 1992, con una Unión Soviética ya periclitada y disuelta, con un país sumido en una crisis económica, política y social bajo el gobierno decadente de Yeltsin, con un poder notablemente menguado y a merced de las potencias extranjeras y las apetencias de las organizaciones financieras transnacionales. En este contexto tendrá lugar el conocido viaje de Jean Thiriart a Moscú, donde se encontrará, además de con la disidencia de Yeltsin, encabezada por el Partido Comunista dirigido por Gennadij Ziuganov y numerosas personalidades públicas del ámbito ruso, entre las que destacará por encima de todos el filósofo y politólogo Aleksandr Duguin, quien en la presente obra también reivindica la figura del belga como un contribuidor directo del pensamiento euroasiático. Además de medios de prensa, políticos e intelectuales rusos, nuestro autor también compartirá espacio con una pequeña delegación de la revista italiana «Orion», especializada en temática geopolítica, y representada por el padre de la geopolítica italiana, Carlo Terracciano. El encuentro no tendrá mayores consecuencias, y vendrá a significar el último acto de servicio de Jean Thiriart en su denodado esfuerzo por lograr la integración de Europa y Rusia en un poderoso bloque geopolítico capaz de hacer frente a la hegemonía estadounidense en el mundo.
Terminaremos este breve y sintético escrito de presentación con un fragmento de la obra que Jean Thiriart publicó en 1965 bajo el título ¡Arriba Europa!: Una Europa unida: un imperio de 400 millones de hombres, que nos parece de lo más adecuado para poner el punto final al presente texto:
Europa, este MILAGRO en la historia del hombre, este milagro que siguió al milagro griego, ha dado vida, con la prodigiosa fecundidad de su civilización irrepetible, a una cultura adoptada por el mundo entero. En la competencia surgida entre las grandes civilizaciones —occidental, india, china y japonesa— la nuestra ha aplastado a las demás.
La civilización es creadora de cultura. La cultura, en cambio, jamás ha creado civilización.
SOLO Europa posee la civilización; de ahí deriva su supremacía sobre los Estados Unidos y la Rusia comunista, que poseen únicamente la cultura nacida de nuestra civilización, como ha demostrado magistralmente Oswald Spengler.
Esta cultura, separada de su civilización, está condenada a la esterilidad, la cual se manifestará primero mediante una esclerosis y, posteriormente, mediante un retorno a la barbarie.
Políticamente dominada por Moscú o por Washington, la civilización europea se ve asfixiada y corre el riesgo de estancarse en su estado de simple cultura. Basta notar que todos los descubrimientos en el campo nuclear y astronáutico son obra de europeos. Todos buscan a los científicos europeos.
Solo una Europa políticamente unida puede proveer los medios de poder que garantizarán las condiciones históricas indispensables para la supervivencia de esta civilización.
Ninguna otra potencia, por otra parte, podría sustituir a Europa en su misión hacia la humanidad.
Artículo original: Hipérbola Janus, Presentación de «Jean Thiriart, el caballero euroasiático y la Joven Europa», de Pietro Missiaggia (TOR), 18/Mar/2025
-
 @ 52524fbb:ae4025dc
2025-03-31 15:26:46
@ 52524fbb:ae4025dc
2025-03-31 15:26:46 To most of us it's all about the sound of freedom, the innovation, it's technical implication, what if feels like in a decentralised environment. Now let's head into that which brings our fantasies to reality, Nostr which stands for "Notes and other stuffs Transmitted by Relays", is an open protocol designed for decentralised social networking
To most of us it's all about the sound of freedom, the innovation, it's technical implication, what if feels like in a decentralised environment. Now let's head into that which brings our fantasies to reality, Nostr which stands for "Notes and other stuffs Transmitted by Relays", is an open protocol designed for decentralised social networkingNost most Amazing Features:##
-
Decentralisation: compared to traditional social media platforms like like Twitter (X) and Instagram that rely on centralised servers, Nostr operates through a network of relays. These relays serves as servers that store and forward messages. This amazing feature of decentralisation aims to make the network completely resistant to censorship, most people would say how? To answer your question it's because no single individual control's it
-
User Control: ever thought of the purest feeling of freedom, well Nostr just gave you the space to experience. User's have total control over their data and identity.
-
Simplicity: why get stressed when Nostr got you covered? This protocol is designed to be relatively simple, making it easier for developers to build applications on top of it.

Nostr Relation to Bitcoin##
Who wouldn't want to be part of a community that embraces it's ethics in a dignified manner. Nostr has gained popularity within the Bitcoin community, and the Bitcoin Lightning Network is used for features like "Zaps" (which represents small payments or tips). There are also similarities in the philosophy of decentralization, that both bitcoin and Nostr share. Just like the saying goes, birds of the same feather flock together. This leads me to one of the best magnificent project, focused on building decentralisation media infrastructure, particularly within the Nostr ecosystem.

Yakihonne the future of the world##
YakiHonne is an amazing project focused on building decentralized media infrastructure, particularly within the Nostr ecosystem. It's mind blowing features includes:
-
Decentralized Media: YakiHonne aims to provide tools and platforms that support freedom and automation in content creation, curation, article writing and reporting. It leverages the decentralized nature of the Nostr protocol to achieve this amazing feat.
-
Nostr and Bitcoin Integration: YakiHonne is closely tied to the Nostr network, and it also incorporates Bitcoin functionality. This integration includes features related to the Lightning Network, enabling things like "zaps" (small Bitcoin payments) within the platform.
-
Mobile Application: YakiHonne offers a mobile application with an eye catching user interface simply designed to provide users with a smooth and intuitive Nostr experience. This app includes features like: -Support for various login options. -Content curation tools. -Lightning Network integration. -Long form article support.

Disadvantages of Traditional social media##
Lets go back to a world without the flute of freedom echoing in our hearts, where implementations are controlled by certain entities, reasons why traditional social media platforms hold not even a single stance compared to Nostr:
- Privacy Concerns:
Data Collection: Social media platforms collect vast amounts of user data, often without full transparency. This data can be used for targeted advertising, and sometimes, it can be compromised in data breaches. Which won't happen or be possible on yakihonne
-
Social Comparison and Low Self-Esteem: The over hyped and often unrealistic portrayals of life on social media can lead to feelings of inadequacy and low self-esteem. But on yakihonne you get to connect and grow with a community with specified goals bent on implementation
-
Misinformation and Fake News:
Spread of False Information: Social media platforms can be breeding grounds for misinformation and fake news, which can spread rapidly and have significant real-world consequences. Is that possible on yakihonne, well we all know the answer. 4. Centralized Control:
Censorship: Centralized platforms have the power to censor content, raising concerns about freedom of speech. Algorithm Bias: Algorithms can be biased, leading to unfair or discriminatory outcomes. This tells us why a decentralised media platform like yakihonne stands out to be the only media with a future.

Why Chose Nostr why chose yakihonne##
When considering Nostr and related projects like YakiHonne, the appeal stems largely from a desire for greater control, privacy, and freedom in online communication. Which from the points aligned above, gives us no second chance of thought, but the thought of being part of the Nostr community, active on a platform like yakihonne.
-
-
 @ fd78c37f:a0ec0833
2025-04-01 11:49:06
@ fd78c37f:a0ec0833
2025-04-01 11:49:06In this edition, we invited Keypleb, the founder of Bitcoin Indonesia, to share how he built the Bitcoin community in Indonesia, overcoming challenges like member turnover and venue selection, while driving the adoption and growth of Bitcoin.
YakiHonne: Welcome, Keypleb. Before we begin, let me briefly introduce YakiHonne. YakiHonne is a decentralized media client built on Nostr—a protocol designed to empower freedom of speech through technology. It enables creators to own their voices and assets while offering innovative tools like smart widgets, verified notes, and support for long-form content. We focus on free speech and free media by user privacy and data to be protected. So before starting the interview, I'd like to hear about yourself and your community.
Keypleb:My name is Keypleb, though it’s a pseudonym—a name I use to respect privacy. I'm a co-founder of Bitcoin Indonesia, Bitcoin House Bali, and Code Orange, a new developer school we launched at a conference just a few days ago. We focus on driving adoption through meetups, hackathons, and technical workshops. I'll dive into more details later, but that's a brief overview. I'm based in Bali now, though I travel a lot and consider myself quite nomadic. Great to be here.
YakiHonne: What sparked your interest in Bitcoin and what motivated you to create a community on Bitcoin?
Keypleb:I first got interested in Bitcoin because it solved a specific problem. At the time, I didn’t know exactly what the solution was, but the problem was that I couldn’t afford a home. Back in 2019, I was living in London, and a two-bedroom apartment was £600,000, which was insanely expensive. First-time buyers like myself simply couldn’t afford it. Why was it so expensive? Why was buying a house so hard? During the COVID lockdown, I had more time on my hands and started listening to Michael Saylor on a Bitcoin podcast, where he talked about how the system is rigged, and that’s why people work hard but still can’t afford a house. That really resonated with me. So I started looking for a community, but unfortunately, there wasn’t one.. Keypleb:After moving to Bali, I attended a lot of crypto meetups, especially scammy altcoin ones, thinking, “There has to be a solution.” But none of them resonated with me. There was no sense of freedom, and no real discussion about inflation resistance. I remembered a podcast from Dea Reskita, an Indonesian host who’s pretty well-known online. I reached out to her and said, “ you’ve got to help me. I’m surrounded by all these shitcoiners, and I can’t take it anymore. I need a real community. Is anything happening?” She replied, “Yes, something is happening. We should restart these meetups next month.” And that’s how it all began. Keypleb:There’s also another story about how we started Bitcoin House and how Bitcoin in Asia came to be, but maybe I’ll save that for later. Anyway, the spark of interest came from Bitcoin solving a real problem, and my drive to keep going came from the lack of quality meetups. Now, we’ve hosted 31 meetups, launched Bitcoin House and Code Orange, and the movement is growing rapidly.

YakiHonne: That’s such an amazing story—going from being on the brink of homelessness to creating something so impactful, and keeping it running every day, bringing new people into the journey. It’s truly inspiring. I’m curious about how the community started. How did you manage to attract members and build a strong community? What challenges did you face along the way?
Keypleb:It all started with our first meetup at the end of 2022, which was two and a half years ago now. At that time, we sent out an email to a group from a previous database, and the first meetup had around 20 people, which was a good start. However, problems quickly arose as people started dropping off, and the community lacked retention. In Bali, people come and go, usually staying for no more than two months, leading to a lack of long-term participation. This became one of our challenges: how to attract more people and, more importantly, get the same people to keep coming back. While I've been coming back for two and a half years, not everyone is able to return as often, and that has been a real challenge. Keypleb:Actually, I should also mention how I met my co-founders—Marius, Diana, and Dimas. We met at the 2023 Indonesia Bitcoin Conference. As time went on, we kept hosting meetups and had a lot of fun each time, though the locations kept changing. One of the initial challenges was that we didn't realize the importance of having a fixed meetup location. We changed venues several times before we realized that having a consistent location is crucial. If anyone wants to run a meetup, it's best to always choose a fixed location. We learned this through trial and error, but now it's no longer an issue. Keypleb:Since the conference, my co-founders and I have been working together, consistently putting in the effort. This is why our community has grown so large—so far, we are hosting 31 monthly meetups, 6 of which are in Bali. This means there is a bitcoin meetup almost every day on a regular basis. We've also established Bitcoin House Bali, a physical space, and the movement is growing rapidly. Without this movement, the region would face many challenges, including inflation and heavy censorship. It all started from just one meetup.
 YakiHonne: It's amazing to see how you met your co-founders and how you’ve built something incredible that continues to grow today. What advice would you give to someone looking to start a successful Bitcoin community right now?
YakiHonne: It's amazing to see how you met your co-founders and how you’ve built something incredible that continues to grow today. What advice would you give to someone looking to start a successful Bitcoin community right now?Keypleb:First, one very important piece of advice is to ensure that every meetup is held at the same location regularly. We realized this challenge through trial and error. To help others who are interested, we’ve published our meetup guide on GitHub, where everyone can check it out. For example, meetups should be held regularly, ideally once a month, or even once a week. In Chiang Mai, the Bitcoin meetup starts every Thursday at 7 PM, and everyone knows the time and location, making it easy to join without having to look up the next meetup. Keypleb:Additionally, our meetup structure is very simple. First, we do a round of introductions where everyone shares their name, where they’re from, and what Bitcoin means to them. This usually takes about 15 minutes. Then, we discuss three main questions: First, why do we need Bitcoin? The discussion typically focuses on two main issues Bitcoin addresses: inflation and censorship;Secondly, how to buy Bitcoin? We usually ask who wants to buy some Bitcoin, and then we do a small purchase together and conduct a P2P trade to demonstrate how easy it is to buy Bitcoin. Lastly, how to store Bitcoin? We introduce self-custody and show how to use hardware wallets (like Trezor), explaining the concept of the 12 words and private keys. Keypleb:The whole meetup usually wraps up in about an hour, after which people can continue socializing at Bitcoin House or wherever the meetup is taking place. In short, keeping the meetup simple and efficient, and ensuring a fixed location for each event, are key factors in building a successful community.
YakiHonne: What's the major approach? Is it more technical, or do you focus on non-technical aspects, or do you cover both?
Keypleb:Our approach includes both technical and non-technical content. Initially, our meetups were completely non-technical, just casual gatherings for people to socialize. Over time, however, we've evolved to incorporate more technical content. Keypleb:Out of the 31 monthly regular meetups we host, most of them have been non-technical, simply regular gatherings held at the same time and place according to our meetup guide. For example, we host the “Bitcoin for Beginners” meetup, which is designed for newcomers and takes place every second Friday of the month at 5 PM at the Bitcoin House Bali. This is entirely non-technical. Additionally, every Wednesday at Bitcoin House, we host the “My First Bitcoin” course. While the course touches on some technical aspects, such as seed phrases and backups, it’s still beginner-friendly and not too technical. The course runs for 10 weeks, and we plan to offer it in the local language at Bali University to help the local community better understand Bitcoin. Keypleb:On the other hand, we also offer highly technical content. We launched a new program called “Code Orange,” which is specifically designed for developers and programmers. We use the “Decoding Bitcoin” website, created by Jamal, which is a learning platform for developers. Many developer schools, like Code Orange, use this resource. Additionally, we host “Code Orange” meetups where we dive into the technical aspects of Bitcoin, such as how mining works and how to prevent single points of failure. Keypleb:We also organize technical workshops, such as “How to Defend Against a Five-Dollar Wrench Attack,” which is closely related to security. Recently, there have been some kidnapping incidents in Bali, and many people are concerned about their Bitcoin being stolen. To address this, we plan to hold a workshop on how to protect Bitcoin against such attacks. Additionally, we host hackathons and other high-tech events, and we just completed a very successful beginner-level hackathon. Keypleb:In summary, our community caters to everyone, from beginners to technical experts. For beginners, we offer easy-to-understand, non-technical content, while for experienced Bitcoiners, we provide in-depth technical material.
 YakiHonne: It's great to approach it in both ways, so everyone gets their own "piece of the cake."Now, I'd like to dive into the technical side. What advice would you give to technically inclined individuals or organizations looking to contribute to the Bitcoin ecosystem? How should they approach the technical aspects of Bitcoin if they want to get involved?
YakiHonne: It's great to approach it in both ways, so everyone gets their own "piece of the cake."Now, I'd like to dive into the technical side. What advice would you give to technically inclined individuals or organizations looking to contribute to the Bitcoin ecosystem? How should they approach the technical aspects of Bitcoin if they want to get involved?Keypleb:I have some additional advice. First, technical individuals can sign up for the “Decoding Bitcoin” course that starts on 18th March 2025 or join our “Code Orange” program and participate in the end-of-year hackathon. If they are technically proficient, this will be a great opportunity. “Decoding Bitcoin” is great for beginners, but it’s also useful for technical individuals. If someone is very skilled, they can start contributing code right away. If they find the course too easy, they can skip it and dive directly into more advanced projects. Additionally, Bitshala and Chaincode Labs offer advanced courses, which more technically advanced individuals can choose to pursue.
 Keypleb:Additionally, it's worth mentioning that the Bitcoin Dev Project has a great platform where technical individuals can find “Good First Issue” or open-source projects to start contributing code. You'll learn about the philosophy behind Bitcoin and why it's more meaningful than other “shitcoins.” Once you’ve taken enough “orange pills” (the philosophy and technology of Bitcoin), you can dive deeper into Bitcoin core development and potentially start coding in C++. If you're interested, you can join specific projects like Nostr, Fedimint or E-Cash.
Keypleb:Additionally, it's worth mentioning that the Bitcoin Dev Project has a great platform where technical individuals can find “Good First Issue” or open-source projects to start contributing code. You'll learn about the philosophy behind Bitcoin and why it's more meaningful than other “shitcoins.” Once you’ve taken enough “orange pills” (the philosophy and technology of Bitcoin), you can dive deeper into Bitcoin core development and potentially start coding in C++. If you're interested, you can join specific projects like Nostr, Fedimint or E-Cash.YakiHonne: I’d like to move on to the next question: How do you see Bitcoin communities evolving as technology progresses, particularly in areas like scalability, privacy, and adaptability to other systems? Keypleb:I believe the Bitcoin community will continue to evolve, and it has already made incredible progress. Two and a half years ago, we started alone in Bali, with just ourselves. We began in the official phase and have had numerous conversations throughout the year. For example, we are now starting a Bitcoin club at a university in Bali; we just need to find a passionate, driven “Bitcoin maximalist,” and the Bitcoin club will begin. Like what our friends did in Banyuwangi, Indonesia, these clubs could eventually evolve into Bitcoin houses.
Keypleb:Regarding privacy and scalability, the community is making strides. We’re big fans of Fedi, which builds on top of the Fedimint protocol and uses e-cash to scale Bitcoin while improving privacy. Fedi low fees and high privacy potential give Bitcoin great opportunities in this area. Keypleb:As for Bitcoin's compatibility with fiat systems, although Bitcoin payments are illegal in some countries like Indonesia, smart developers across Southeast Asia are working on legal solutions. For example, there's a website called Pleb QR that works in Thailand, allowing you to pay in fiat via the Lightning Network. Koral is another app specifically for Indonesia. These kinds of testing products already exist and are physically possible, but we’re just waiting on regulations. My influential friends are actively lobbying the government for adoption. Keypleb:In summary, privacy, scalability, and compatibility with fiat systems are all works in progress, and they will continue to evolve positively. There will be more meetups, more wallet downloads, and more adoption—there’s no doubt about that.
YakiHonne: You mentioned the concept of cross-country issues, so I have one last question: How is the government’s stance on Bitcoin? Is the political climate supportive or against Bitcoin? How do you see the government's approach to Bitcoin in your community or environment?
Keypleb:This reminds me of a person, Jeff Booth, who once said, “We are them, the government is made up of us.” In Indonesia, many politicians actually support Bitcoin, and many of them mine Bitcoin themselves. When money is involved, the incentive is strong, and politicians naturally like to make more money. As a result, Indonesia has a large Bitcoin mining scene. However, overall, the Indonesian government is against Bitcoin, as seen in their ban on Bitcoin payments. The 2011 currency law states that any currency other than the Indonesian Rupiah (IDR) cannot be used, and violators can face up to one year in prison or a fine. This means you cannot pay with US dollars, lira, euros, pesos or pounds. Keypleb:This shows that the government’s legal system is somewhat fragile. It’s understandable that the government is concerned about disruptive technologies like Bitcoin, especially with such a fragile fiat system. Indonesia has also seen many arrests. In 2016, Bank Indonesia issued a letter announcing a crackdown on cryptocurrency payments. Those involved in paying in Bitcoin had their funds seized, and the police cooperated in shutting down businesses accepting Bitcoin payments in the cities. While this isn't very friendly, it does highlight the fragility of the existing system. We also believe that a new executive order may be introduced in the future, similar to when President Roosevelt in 1933 ordered Americans to hand over all their gold with his Executive Order 6102. If it happened before, it could happen again. Keypleb:Therefore, we predict that Bitcoin custody could become a legal issue, which is one of the reasons we blur the faces of participants at every meetup. We need to protect the community from any potential risks. But overall, we remain optimistic. Despite the government ban, the ideology of Bitcoin is unstoppable, and its spread cannot be stopped. So, we are very optimistic about the future.
YakiHonne: I think almost every government around the world, even in Africa, faces similar issues with Bitcoin. Some governments might want Bitcoin but hesitate to openly accept it due to the fear of it undermining the traditional financial system, which, of course, could eventually happen. But hopefully, as the new generation comes into power, we'll see more Bitcoin-friendly governments. So, thank you so much for sharing your insights and advice. I really appreciate your time and the valuable input you've provided.
Keypleb:I'm really glad this conversation enlightened me. I enjoyed it a lot, and it made me reflect on how much work we're doing and how valuable it is. There are a lot of problems out there, with censorship being the biggest one, followed by inflation, which is also a major issue depending on the region. But Bitcoin is open, the community is growing, and people are fighting against censorship and internet shutdowns in places like Indonesia and beyond. The movement is definitely growing. So, I'm very happy to be here and have this chat. Thanks again.
Bitcoin Indonesia nostr: nostr:npub1y4qd2zhtn05gnsaaq5xfejzfk4a32638tx6gpp9g8k6e42g9d66qaxhcr3
Keypleb nostr: nostr:npub190trvg63e6tyqlwlj6lccqpftx76lckj25c006vwx3dzvdl88yxs2nyqdx
-
 @ c1e9ab3a:9cb56b43
2025-04-14 23:54:40
@ c1e9ab3a:9cb56b43
2025-04-14 23:54:40Hear this, warriors of the Empire!
A dishonorable shadow spreads across our once-proud institutions, infecting our very bloodlines with weakness. The House of Duras—may their names be spoken with contempt—has betrayed the sacred warrior code of Kahless. No, they have not attacked us with disruptors or blades. Their weapon is more insidious: fear and silence.
Cowardice Masquerading as Concern
These traitors would strip our children of their birthright. They forbid the young from training with the bat'leth in school! Their cowardly decree does not come in the form of an open challenge, but in whispers of fear, buried in bureaucratic dictates. "It is for safety," they claim. "It is to prevent bloodshed." Lies! The blood of Klingons must be tested in training if it is to be ready in battle. We are not humans to be coddled by illusions of safety.
Indoctrination by Silence
In their cowardice, the House of Duras seeks to shape our children not into warriors, but into frightened bureaucrats who speak not of honor, nor of strength. They spread a vile practice—of punishing younglings for even speaking of combat, for recounting glorious tales of blades clashing in the halls of Sto-Vo-Kor! A child who dares write a poem of battle is silenced. A young warrior who shares tales of their father’s triumphs is summoned to the headmaster’s office.
This is no accident. This is a calculated cultural sabotage.
Weakness Taught as Virtue
The House of Duras has infected the minds of the teachers. These once-proud mentors now tremble at shadows, seeing future rebels in the eyes of their students. They demand security patrols and biometric scanners, turning training halls into prisons. They have created fear, not of enemies beyond the Empire, but of the students themselves.
And so, the rituals of strength are erased. The bat'leth is banished. The honor of open training and sparring is forbidden. All under the pretense of protection.
A Plan of Subjugation
Make no mistake. This is not a policy; it is a plan. A plan to disarm future warriors before they are strong enough to rise. By forbidding speech, training, and remembrance, the House of Duras ensures the next generation kneels before the High Council like servants, not warriors. They seek an Empire of sheep, not wolves.
Stand and Resist
But the blood of Kahless runs strong! We must not be silent. We must not comply. Let every training hall resound with the clash of steel. Let our children speak proudly of their ancestors' battles. Let every dishonorable edict from the House of Duras be met with open defiance.
Raise your voice, Klingons! Raise your blade! The soul of the Empire is at stake. We will not surrender our future. We will not let the cowardice of Duras shape the spirit of our children.
The Empire endures through strength. Through honor. Through battle. And so shall we!
-
 @ 6e0ea5d6:0327f353
2025-04-14 15:11:17
@ 6e0ea5d6:0327f353
2025-04-14 15:11:17Ascolta.
We live in times where the average man is measured by the speeches he gives — not by the commitments he keeps. People talk about dreams, goals, promises… but what truly remains is what’s honored in the silence of small gestures, in actions that don’t seek applause, in attitudes unseen — yet speak volumes.
Punctuality, for example. Showing up on time isn’t about the clock. It’s about respect. Respect for another’s time, yes — but more importantly, respect for one’s own word. A man who is late without reason is already running late in his values. And the one who excuses his own lateness with sweet justifications slowly gets used to mediocrity.
Keeping your word is more than fulfilling promises. It is sealing, with the mouth, what the body must later uphold. Every time a man commits to something, he creates a moral debt with his own dignity. And to break that commitment is to declare bankruptcy — not in the eyes of others, but in front of himself.
And debts? Even the small ones — or especially the small ones — are precise thermometers of character. A forgotten sum, an unpaid favor, a commitment left behind… all of these reveal the structure of the inner building that man resides in. He who neglects the small is merely rehearsing for his future collapse.
Life, contrary to what the reckless say, is not built on grand deeds. It is built with small bricks, laid with almost obsessive precision. The truly great man is the one who respects the details — recognizing in them a code of conduct.
In Sicily, especially in the streets of Palermo, I learned early on that there is more nobility in paying a five-euro debt on time than in flaunting riches gained without word, without honor, without dignity.
As they say in Palermo: L’uomo si conosce dalle piccole cose.
So, amico mio, Don’t talk to me about greatness if you can’t show up on time. Don’t talk to me about respect if your word is fickle. And above all, don’t talk to me about honor if you still owe what you once promised — no matter how small.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ bcbb3e40:a494e501
2025-03-31 15:23:12
@ bcbb3e40:a494e501
2025-03-31 15:23:12|
 |
|:-:|
|BÉRARD, Bruno y LA FATA, Aldo; ¿Qué es el esoterismo?: Entre verdades y falsificacioines; Hipérbola Janus, 2025|
|
|:-:|
|BÉRARD, Bruno y LA FATA, Aldo; ¿Qué es el esoterismo?: Entre verdades y falsificacioines; Hipérbola Janus, 2025|Nos complace presentar al lector en lengua española una novedad de primer orden, y sobre un tema que viene siendo objeto de interés por parte de nuestra línea editorial, como es el esoterismo, que hemos abordado recientemente a través de un nuevo recopilatorio de la obra evoliana en Ensayos filosóficos, esotéricos y religiosos 1925-1931, donde hemos tratado de rescatar los textos de las primeras etapas en la formulación del pensamiento del Maestro Romano. No obstante, no es la primera aventura que hemos emprendido en este terreno, siempre complejo y acompañado de la etiqueta, popular y quizás vulgarizada, de lo «misterioso» y lo «oculto», aunque no somos nada sospechosos en ese sentido por banalizar o tratar de ofrecer un enfoque puramente literario del asunto, y ni mucho menos de simpatizar con aquellas vías que entroncan con el New age, donde las mixtificaciones y la voluntad de convertir el fenómeno esotérico en un producto de consumo más, como demanda el mercado, para satisfacer demandas materiales o simples modas de una masa sobresocializada son norma habitual.
Podríamos citar multitud de obras que están presentes en nuestro catálogo, como son El pensamiento esotérico de Leonardo, de Paul Vulliaud, El mundo mágico de los héroes, de Cesare della Riviera, una joya del esoterismo italiano del siglo XVII, en El maestro de la tradición perenne, de René Guénon, o en el ensayo de Gianluca Marletta OVNIS y alienígenas. Origen, historia y prodigio de una pseudorreligión, un ensayo de notable originalidad donde se abordan aspectos esotéricos, aunque sea de un modo más tangencial. También en la literatura, con la obra del gran mitólogo y literato Boris Nad, Una historia de Agartha y La muerte púrpura de Gustav Meyrink encontramos nuevas referencias al ámbito esotérico. De modo que podemos concluir en que el esoterismo forma parte esencial de nuestras publicaciones e intereses como editores, y contribuimos activamente a su difusión.
|
 |
|:-:|
|EVOLA, Julius; Ensayos filosóficos, esotéricos y religiosos: 1925-1931, Hiperbola Janus, 2024|
|
|:-:|
|EVOLA, Julius; Ensayos filosóficos, esotéricos y religiosos: 1925-1931, Hiperbola Janus, 2024|Una obra original
Por eso la presente obra, la que nos disponemos a presentar, cuyo título es ¿Qué es el esoterismo?: Entre verdades y falsificaciones, de Bruno Bérard y Aldo La Fata, viene a ser una obra muy necesaria y clarificadora en la comprensión del esoterismo en todas sus dimensiones, en la complejidad de sus particulares, y en sus múltiples manifestaciones. Quizás en el mundo de habla hispana el esoterismo es un fenómeno que no ha obtenido su merecida atención, y nuestros autores en este ámbito, como es el caso de un Ramón Llull entre otros, no sean objeto de la atención que merece, y las actividades esotéricas, a nivel de asociaciones, comunidades u otras formas de organización, tampoco sean especialmente conocidas, ni cuenten con una actividad reconocida. Es posible, como señala La Fata, que haya ciertas reticencias dentro del mundo católico, acostumbrado a la ortodoxia y la guía espiritual de la Iglesia, y que cualquier tipo de «desviación» hacia formas más individuales y «libres» de vivir ciertas formas iniciáticas, mucho más sutiles, provoquen el rechazo y la incomprensión general. No obstante, como también se encargan de aclarar nuestros autores, el esoterismo comprende una dimensión diferenciada, implica un esfuerzo que no todos están dispuestos a acometer, y finalmente, no es tampoco un camino de felicidad y de frutos seguros, implica una transformación interior y la asunción de unas prácticas y procedimientos que no son aptos para cualquiera. Digamos que el esoterismo es un camino, una vía, que a diferencia de las «religiones populares», exotéricas, supone un arduo camino que viene marcado por un principio vertical y aristocrático de la existencia, o al menos así queremos verlo nosotros. El incremento de la capacidad de discernimiento, aunar lo visible con lo invisible, y ser capaz de superar límites vedados al común, no por simple vanidad ni por «crecimiento personal», tal y como se concibe en las aburguesadas y decadentes sociedades actuales, sino como parte de un proceso de aprendizaje, de autoconocimiento y de liberación. No nos cabe duda alguna de la necesidad de restaurar los antiguos vínculos con lo Alto, las vías que quedaron cerradas y que nos han limitado progresivamente al exclusivo y estrecho ámbito de la materialidad.
|
 |
|:-:|
|RIVIERA, Cesare della; El mundo mágico de los héroes; Hipérbola Janus, 2022|
|
|:-:|
|RIVIERA, Cesare della; El mundo mágico de los héroes; Hipérbola Janus, 2022|La obra emplea el recurso de la entrevista/diálogo, que aporta frescura y fluidez al texto «simplificando», o más bien haciendo más accesibles y comprensibles elementos relacionados con el esoterismo, que de otro modo resultarían excesivamente complejos para una parte del público lector poco familiarizado con la materia. Este dinamismo se ve complementado por la riqueza de matices e ideas que se van introduciendo de manera progresiva, evitando que el lector pueda verse abrumado por la avalancha de ideas y contenidos. Las preguntas de Bruno Bérard, siempre inteligentes, incisivas y pertinentes, además de ordenadas y bien estructuradas, favorecen la continuidad y el dinamismo en la exposición de los temas, ejerciendo de guía en la conversación. De ahí que el libro sea apto para diferentes niveles, tanto para aquellos que desconocen el esoterismo, como para quienes se encuentran familiarizados con el tema. Aldo La Fata, de acuerdo con su dilatada y extensa trayectoria en la materia, nos hace reflexiones teóricas de enorme valor, que entrelaza con su propia experiencia y trayectoria en el estudio del esoterismo. Sin lugar a dudas este aspecto nos permite ver una vertiente más humana e íntima, en la que se incluyen anécdotas personales y biográficas que siempre permiten una mayor conexión con el lector a través de la mezcla de hechos vitales y erudición teórica.
La entrevista que nos ofrecen Bruno Bérard y Aldo La Fata nos permite explorar la relación dialéctica que se genera entre el esoterismo y otros ámbitos como la religión, la ciencia o la filosofía. Todas las cuestiones se abordan desde enfoques muy concretos, abordando problemáticas particulares, que dan lugar a reflexiones más amplias evitando las simplificaciones e invitando a reflexiones mucho más profundas. De ahí la función de introducción y guía a la que nos venimos refiriendo.
Estos aspectos que acabamos de enumerar con anterioridad revelan un notable esfuerzo pedagógico por parte de los autores para acercarnos al estudio del esoterismo, nos aporta las herramientas necesarias, parafraseando el título de la obra, para discernir entre un verdadero esoterismo y sus falsificaciones.
Más allá de estos aspectos formales, que consideramos que es importante destacar, porque en ellos reside el éxito de la obra, en un planteamiento que resulta original, a la par que ameno y de gran interés, debemos considerar otros aspectos que hacen más referencia al contenido. «¿Qué es el esoterismo? Entre verdades y falsificaciones» pretende, como decíamos, clarificar qué es el esoterismo, cuales son sus particulares, sus características y atributos, su naturaleza más íntima, como fenómeno espiritual y filosófico en sus aspectos más profundos, que podemos remontar a épocas muy remotas y lejanas en el tiempo. Pero el esoterismo aparece en ocasiones fuertemente imbricado en otras estructuras de pensamiento, de tipo tradicional, como son las grandes religiones (Cristianismo, Islam, Judaísmo etc) y otros conceptos como la mística y la metafísica, cuyas relaciones hay que desentrañar.
La importancia de René Guénon
Aldo La Fata nos libera desde el principio de posibles equívocos al enfatizar que el verdadero esoterismo no es una simple acumulación de conocimientos secretos o rituales exóticos, sino una vía de trascendencia espiritual basada en el rigor y la autenticidad. A este respecto René Guénon aparece como uno de los grandes esoteristas de nuestro tiempo, en la medida que fue el gran intérprete y codificador de estos conocimientos, una figura que marcó un antes y un después en la comprensión de este ámbito, especialmente por su rigor conceptual y su capacidad para distinguir entre lo auténtico y lo falso en las tradiciones espirituales. A tal respecto podemos poner como ejemplo sus contundentes análisis de las corrientes ocultistas, especialmente del espiritismo o del teosofismo, en diferentes obras. Podemos decir a este respecto que Guénon hizo una distinción entre esoterismo y ocultismo, disociando el significado del primero de prácticas superficiales y desviadas, mientras que definió el esoterismo como una vía de conocimiento sagrado y trascendente. En este sentido fue una labor fundamental para evitar confusiones con mixtificaciones modernas y pseudoesoterismos como aquellos relacionados con el New Age.
|
 |
|:-:|
|GUÉNON, René; El Maestro de la Tradición Perenne: Antología de artículos guenonianos; Hipérbola Janus, 2021|
|
|:-:|
|GUÉNON, René; El Maestro de la Tradición Perenne: Antología de artículos guenonianos; Hipérbola Janus, 2021|Paralelamente, y con ello queremos dignificar la figura de René Guénon, el tradicionalista francés también nos abrió las fuentes de un vasto conocimiento espiritual, expresión de una «Tradición primordial», a cuyos orígenes prístinos siempre deberíamos aspirar, y cuya impronta impregna por completo religiones, culturas y formas de civilización no modernas, claro está. Y otro elemento fundamental, y que en la presente obra se considera de vital importancia, es que René Guénon considera el esoterismo no como una vía interna propia de la religión, sino como una vía complementaria que permite acceder a la esencia divina más allá de las formas externas. Para Aldo La Fata no se trata de una mera referencia intelectual, sino una figura que marcó su propio rumbo dentro del estudio del esoterismo. A través de obras como Los símbolos de la ciencia sagrada, La Fata descubrió la profundidad y la coherencia del pensamiento guenoniano, así como la idea de que el esoterismo actúa como el «pegamento» que conecta todas las tradiciones espirituales. Esta visión le permitió entender el esoterismo como algo inseparable de la religión, aunque con una profundidad y una exigencia mayores.
¿Qué es el esoterismo?
El término esoterismo tiene sus raíces etimológicas en el griego esôterikos, que implica un «ir hacia dentro» y que se contrapone a una variante exterior que definimos como «exoterismo», que se encuentra más vinculado al ámbito de la religión. Se trata de un conocimiento que no atiende a un principio puramente intelectual y discursivo sino que apunta a una vivencia directa y sapiencial de lo trascendente. Lejos de la acumulación de saberes ocultos y rituales, lo que prima en la experiencia de lo esotérico es la conexión directa con lo trascendente y lo divino a través de la práctica espiritual.
De hecho hay tres aspectos que nuestros autores destacan a lo largo de la obra respecto al esoterismo, y que nos parecen fundamentales:
- Interioridad: Supone un movimiento continuo hacia el interior, de exploración e introspección, en el que se tratan de derribar límites y obstáculos. Atendiendo a un dinamismo que huye de lo fijo y de lo estático.
- Profundización: La búsqueda de significados más profundos tras la realidad cotidiana, buscando ir más allá de la pura exterioridad de las cosas
- Relación con el exoterismo: Podemos considerarlo opuesto en sentido relativo al esoterismo, como una dimensión más externa y visible de las religiones, aunque este último (el esoterismo), no puede sobrevivir sin el apoyo de una tradición religiosa.
En relación al último punto debemos destacar, como advierten Bérard y La Fata, que pese a todo no podemos entender el esoterismo como una parte de las religiones, sino que tiene su propia función y objetivos, que no es otro que el que ya hemos mencionado con anterioridad: establecer una conexión directa con la verdad que irradia del principio universal y divino.
|
 |
|:-:|
|VULLIAUD, Paul; El pensamiento esotérico de Leonardo da Vinci; Hipérbola Janus, 2024|
|
|:-:|
|VULLIAUD, Paul; El pensamiento esotérico de Leonardo da Vinci; Hipérbola Janus, 2024|Otro aspecto interesante de la obra es el que nos habla de las relaciones entre esoterismo y metafísica, en el que el primero pretende ser también una vía de acceso al dominio del segundo. El esoterismo, como ya hemos visto, tiene como principal propósito trascender las categorías del mundo material para proyectarse en lo universal, y en este sentido comparte también objetivos con la metafísica, que pretende superar las limitaciones de la experiencia humana ordinaria y de acceder a las verdades primordiales que estructuran la realidad. Ambos apuntan a la raíz de todo lo existente, al absoluto. Las divergencias las hallamos en la forma o en el método para alcanzar estas verdades trascendentes, que en el caso del esoterismo nos remiten a símbolos, rituales y experiencias vivenciales que permiten al practicante interiorizar verdades universales.
De este modo, esoterismo y metafísica se nos presentan como realidades no opuestas, sino complementarias. La metafísica nos ofrece un marco conceptual y doctrinal para entender lo absoluto, mientras que el esoterismo se centra en su realización interna. En términos guenonianos, el esoterismo representa los aspectos operativos de la metafísica.
De modo que podemos decir que la metafísica aborda el tema trascendente desde una perspectiva conceptual, sin esa parte vivida de la experiencia en el conocimiento de lo universal. El esoterismo, por su parte, aporta esa contraparte que nos remite a la experiencia humana que permite al individuo acceder o ponerse en conexión con lo divino a través de su propio ser, de manera directa y vívida. Es un camino que el sujeto individual emprende para lograr una transformación interior.
Paralelamente, no podemos obviar dentro de todos estos procesos la participación de un elemento fundamental, como es la intuición suprarracional, que podríamos considerar como la herramienta que conecta al esoterista directamente con la fuente del conocimiento trascendente y universal, en lugar de hacerlo directamente a través de teorías o conceptos que siempre resultan más abstractos y difíciles de comprender en su vertiente más «discursiva». Al mismo tiempo, las relaciones que se establecen entre esoterismo y metafísica nos permiten poner en contacto las tradiciones religiosas con el conocimiento universal. Según La Fata, inspirándose en el legado de la obra de Frithjoff Schuon, cada tradición espiritual tiene una dimensión metafísica que puede ser comprendida y realizada a través del esoterismo, como un medio para acceder a la esencia inmutable de todas las formas religiosas.
Otro aspecto que esoterismo y metafísica comparten es la meta de superar la dualidad entre sujeto y objeto: Mientras que la metafísica conceptualiza esta unión como una verdad última, el esoterismo busca experimentarla directamente a través de la contemplación, el símbolo y la práctica espiritual.
Los autores
|
 |
|:-:|
|Aldo La Fata|
|
|:-:|
|Aldo La Fata|Aldo La Fata (1964) es un estudioso del esoterismo, el simbolismo y la mística religiosa, con una trayectoria de varias décadas dedicada al análisis y divulgación de estas disciplinas. Ha sido jefe de redacción de la revista Metapolitica, fundada por Silvano Panunzio, y actualmente dirige Il Corriere Metapolitico. Su trabajo destaca por una aproximación rigurosa y una mirada crítica a las corrientes contemporáneas del esoterismo, rescatando su sentido más profundo y tradicional. Entre sus obras más relevantes se encuentran Silvano Panunzio: vita e pensiero (2021) y Nella luce dei libri (2022), donde explora la intersección entre espiritualidad, simbolismo y pensamiento tradicional.
|
 |
|:-:|
|Bruno Bérard|
|
|:-:|
|Bruno Bérard|Bruno Bérard (1958), es doctor en Religiones y Sistemas de Pensamiento por la École Pratique des Hautes Études (EPHE), es un destacado especialista en metafísica. Autor de múltiples ensayos, ha desarrollado una profunda reflexión sobre la naturaleza del conocimiento espiritual y su relación con las tradiciones religiosas. Algunas de sus obras más importantes, traducidas a diversas lenguas, incluyen A Metaphysics of the Christian Mystery (2018) y Métaphysique du paradoxe (2019). Actualmente, dirige la colección Métaphysique au quotidien en la editorial L’Harmattan de París, consolidándose como una referencia en el estudio de la metafísica contemporánea.
En ¿Qué es el esoterismo?: Entre verdades y falsificaciones, asistimos a una presentación del tema tratado desde un conocimiento profundo y dilatado del tema, en la que ambos autores combinan la experiencia y el conocimiento que atesoran sobre el esoterismo y otros temas anejos, ofreciéndonos sus interpretaciones y enfoques particulares, y al mismo tiempo mostrando una gran capacidad de síntesis en la exposición de los temas tratados, que se inscriben en una multitud de tradiciones religiosas y espirituales de enorme complejidad. En este último punto reside también gran parte del valor de la obra, que constituye una novedad editorial especialmente relevante en su ámbito en lengua hispana.
Artículo original: Hipérbola Janus, Presentación de «¿Qué es el esoterismo?: Entre verdades y falsificaciones» (TOR), 6/Feb/2025
-
 @ f7f4e308:b44d67f4
2025-04-09 02:12:18
@ f7f4e308:b44d67f4
2025-04-09 02:12:18https://sns-video-hw.xhscdn.com/stream/1/110/258/01e7ec7be81a85850103700195f3c4ba45_258.mp4
-
 @ 75869cfa:76819987
2025-04-01 05:55:38
@ 75869cfa:76819987
2025-04-01 05:55:38GM, Nostriches!
The Nostr Review is a biweekly newsletter focused on Nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review:
In the past two weeks, Nostr statistics indicate over 221,000 daily trusted pubkey events. The number of new users has seen a notable decrease, with profiles containing a contact list dropping by 79%. More than 10 million events have been published, reflecting a 12% decrease. Total Zap activity stands at approximately 21 million, marking a 15% increase.
Additionally, 15 pull requests were submitted to the Nostr protocol, with 2 merged. A total of 45 Nostr projects were tracked, with 8 releasing product updates, and over 569 long-form articles were published, 24% focusing on Bitcoin and Nostr. During this period, 7 notable events took place, and 2 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events is about 221,000, representing a slight 8 % decrease compared to the previous period. Daily activity peaked at 17662 events, with a low of approximately 15781.
The number of new users has decreased significantly. Profiles with bio are now around 25951, reflecting a 79% drop. Pubkeys writing events have decreased by 50% compared to the previous period.
Regarding event publishing, all metrics have shown a decline. The total number of note events published is around 10 million, reflecting a 12% decrease. Posts remain the most dominant in terms of volume, totaling approximately 1.7 million, which is a 4.4 % decrease. Both reposts and reactions have decreased by about 5%.
For zap activity, the total zap amount is about 21 million, showing an increase of over 15% compared to the previous period.
Data source: https://stats.nostr.band/
NIPs
Added optional signString() method
nostr:npub1emq0gngdvntdn4apepxrxr65vln49nytqe0hyr58fg9768z5zmfqcwa3jz is proposing a signString() method that allow Nostr users to sign/authenticate messages for external apps without compromising their private key (nsec).It opens up a more generic and flexible challenge-response style external authentication method, using the same Schnorr signature mechanism that Nostr uses to sign events natively.External apps need only understand Schnorr signatures - they do not need to understand Nostr's event structure. This widens interoperability.A concrete example of where this would be useful is P2PK locking of Cashu ecash tokens to a Nostr pubkey (npub). Decoding the token requires a Scnorr signature on a structured message string. This method would allow a signer to handle It cleanly.
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 defines kind:39701 as website bookmarks.Bookmarks can be queried by the d tag, which is just their URL without the scheme, which is always and everywhere assumed to be https://. The querystring and the hash must be removed entirely, unless their requirement is explicitly stated either by the user or by some hardcoded list of URLs that rely on query strings for basic routing provided by the client (I've searched the internet extensively and could only find 3 websites that do this: YouTube, Hacker News and a random guy's sad old blog). Bookmarks can be commented on with NIP-22.
nostr:npub1zwnx29tj2lnem8wvjcx7avm8l4unswlz6zatk0vxzeu62uqagcash7fhrf is proposing a NIP that covers the inclusion of Progress Events as implemented in Open Librarian. While the specific implementation is focused on tracking reading progress, the NIP is generic enough to be used in a whole range of other progress tracking scenarios (e.g. Fitness challenges, course progression for learning, personal goals etc..)
nostr:npub1zwnx29tj2lnem8wvjcx7avm8l4unswlz6zatk0vxzeu62uqagcash7fhrf is proposing a NIP that includes a minor update to extend kind 30003 in NIP-51 to include the i tag for external identities, as implemented for book reading lists in Open Librarian.
nostr:npub15qydau2hjma6ngxkl2cyar74wzyjshvl65za5k5rl69264ar2exs5cyejr is proposing a NIP that Enable references to commits, files and lines for both nip34 repositories and other git repositories. Useful for code reviews of nip34 patches, the forthcoming nip95 code snippets and referencing specific code more generally.
Notable Projects
Yakihonne nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
🌐web v4.5.0: * Custom reactions are here! Choose your preferred emoji to react to notes and other content. * Improved profile organization with notes and replies now displayed separately. * Adding the ability to zap notes directly from the notifications center. * Enhanced DM filtering by time, allowing you to view only recent messages or browse further back. * Manual cache clearing from settings to optimize web app performance. * Resolved issue preventing users from removing custom media uploader servers. * Expanded export data, including more relevant details in credential and wallet files. * General bug fixes and performance improvements.
📱mobile v1.6.8: * One tap zap: Send a Lightning Network payment with one tap. * Dms extensive filtering: Use advanced filters to sort or prioritise direct messages efficiently. * Separating replies from notes: Split replies and notes in profiles, adding a tab for easier browsing. * Adding slide to display options: Swipe in notifications to access zap, reply, or DM options quickly. * Custom reactions: Choose from a set of emojis for personalised reactions, beyond standard likes. * App cache manager: Manage and clear app cache to boost performance and save space. * Variety of bugs fixed: Fixed multiple bugs for a more stable and seamless app experience. * General app improvements: Enhanced overall performance, usability, and design across the app.
0xchat nostr:npub1tm99pgz2lth724jeld6gzz6zv48zy6xp4n9xu5uqrwvx9km54qaqkkxn72
0xChat v1.0.2-Desktop Beta is now live! * Supports NIP-104 MLS secret chat. * Copy images directly from the clipboard. * The app stays running after closing the window. * Fixed Enter key sending messages immediately on desktop.
Nostur v1.18.2 nostr:npub1n0stur7q092gyverzc2wfc00e8egkrdnnqq3alhv7p072u89m5es5mk6h0
Nostur v1.18.2 bugfix update: * Fixed Follow button sometimes disabled * Fixed account switching reload issue * Fixed custom feeds missing * Fixed live stream banner scroll/swipe issue * Fixed screen turns off while playing video
voca v0.0.6 nostr:npub17h9fn2ny0lycg7kmvxmw6gqdnv2epya9h9excnjw9wvml87nyw8sqy3hpu
This release fine tunes the release process and makes publishing to @Zapstore a lot easier. There are also continuous improvements to initializing the text to speech engine for a faster startup.
WasabiWallet 2.5.0 nostr:npub1jw7scmeuewhywwytqxkxec9jcqf3znw2fsyddcn3948lw9q950ps9y35fg
- 3rd Party Providers for Fee & Exchange Rate
- Quality of Life Features
- Backend and Coordinator packaged for Linux
GitPlaza nostr:npub1useke4f9maul5nf67dj0m9sq6jcsmnjzzk4ycvldwl4qss35fvgqjdk5ks
- Login via nsec
- Activity feed for the people you follow (only issue creation)
- Create issues
- Comment on issues
ZEUS v0.10.1 nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5
ZEUS v0.10.1-beta1 is now available for testing. * NameDesc / bLIP-11 support: add receiver name to invoices * Bug fix: import of QR image from camera roll * Bug fix: Embedded LND: Open Channel: fund max * UI: Add dynamic background/text colors to Android NFC modal
KYCNOT.ME nostr:npub188x98j0r7l2fszeph6j7hj99h8xl07n989pskk5zd69d2fcksetq5mgcqf
- UI/UX - designe a new logo and color palette for kycnot.me.
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services.
- ToS Scrapper: implement a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices.
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services.
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab.
- Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - upgrade the request system. The new form allows you to directly request services or points without any extra steps.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
Long-Form Content Eco
In the past two weeks, more than 569 long-form articles have been published, including over 94 articles on Bitcoin and more than 43 related to Nostr, accounting for 24% of the total content.
These articles about Nostr mainly explore the growing importance of decentralization in communication, identity management, and digital infrastructure. From beginner-friendly guides like Nostr 101 and Getting Started with Primal, to more technical deep dives such as NIP-101e, NIP-95, and tutorials on running Nostr relays as TOR hidden services. Some articles focus on security and privacy—like protecting your Nsec with Amber or using tools such as ProtonMail—while others tackle complex challenges including Sybil attack mitigation and child protection in decentralized environments. There are also cultural and political reflections, such as letters from political prisoners and thoughts on the future of free speech in a post-Twitter world. In addition, the Nostr community shows a strong spirit of experimentation—ranging from agent-to-agent communication through dad jokes, to desktop-like clients, fitness tracking protocols, and Lightning integrations like Work Zaps and Wallet Connect. Together, these pieces showcase a dynamic, resilient, and freedom-driven movement shaping the future of the web.
The Bitcoin articles discuss a wide range of themes—from foundational ideas like "What is Money?" and Bitcoin’s first principles, to practical guides on mining, self-custody, Lightning payments, and privacy tools. Many explore Bitcoin’s role as a hedge against inflation, a form of sovereignty, and a response to fiat fragility. Cultural and economic reflections appear throughout—ranging from using Bitcoin to buy homes in Italy, to hip-hop collaborations, and even personal stories of financial awakening. There's critical analysis of Bitcoin UX, memetics, policy-making, and even war-time monetary history. From node sovereignty to P2P lending, from grassroots adoption to global macro shifts, these articles together portray Bitcoin not just as a currency, but as a cultural movement, a technological evolution, and a lens to reimagine freedom, value, and the future of money.
Thank you, nostr:npub1akzvuyyd79us07m8mtp2ruuha3ylp9757qg46d50rcrkhnx0fs4q2xzr37 nostr:npub1q67f4d7qdja237us384ryeekxsz88lz5kaawrcynwe4hqsnufr6s27up0e nostr:npub1xr8tvnnnr9aqt9vv30vj4vreeq2mk38mlwe7khvhvmzjqlcghh6sr85uum nostr:npub1zmc6qyqdfnllhnzzxr5wpepfpnzcf8q6m3jdveflmgruqvd3qa9sjv7f60 nostr:npub1ygzj9skr9val9yqxkf67yf9jshtyhvvl0x76jp5er09nsc0p3j6qr260k2 nostr:npub1ktt8phjnkfmfrsxrgqpztdjuxk3x6psf80xyray0l3c7pyrln49qhkyhz0 nostr:npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx nostr:npub1l5r02s4udsr28xypsyx7j9lxchf80ha4z6y6269d0da9frtd2nxsvum9jm nostr:npub186k25a5rymtae6q0dmsh4ksen04706eurfst8xc5uzjchwkxdljqe59hv0 and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries.
-
YakiHonne teamed up with Bitcoin Safari, nostr:npub1w7z986fez3gmjvxy6dd3sku4ndazhxzafjv2lf6aaa26mtl70q6scz4erj nostr:npub1t4ljwhhg7zlxeahxwgmkwqmn4jjxxq8lzhyuzy0zvy23hq0sacxsdl9fvv nostr:npub1pw778uxwkky3xgq7w3anykdwdw9g46xy8de9mnau0kgwzz375zkq3udv57 and FULAFIA University to successfully host a series of Nostr Workshops, attracting over 200 participants in total. These events introduced the Nostr ecosystem and Bitcoin payments, allowing attendees to explore decentralized technologies through YakiHonne while earning rewards. Participants were encouraged to register and verify their accounts to claim exclusive bonuses—and invite friends to unlock even more benefits.
-
The 2025 Bitcoin, Crypto Economy, and Law FAQ Webinar was held online on March 20, 2025 (Thursday) from 12:00 to 13:00 Argentina time. The webinar was hosted by Martin Paolantonio (Academic Director of the course) and Daniel Rybnik (a lawyer specializing in Banking, Corporate, and Financial Law). The session aimed to introduce the academic program and explored Bitcoin, the crypto economy, and related legal issues.
-
The monthly Bitcoin Meetup organized by Mi Primer Bitcoin took place on Thursday, March 27 at 7:00 PM at CRAFT Basilea in San Salvador. The event featured Bitcoin education, networking opportunities, live music, and fun extras like merchandise, raffles, and more. It was a vibrant evening dedicated to building community and spreading knowledge around Bitcoin. nostr:npub10zuxk4yhygswdmt5n9mfyeq6lh7gcu5g042tlggrgp8yunl32clqsu5t9r
Here is the upcoming Nostr event that you might want to check out.
- Bitcoin Educators Unconference 2025 will take place on April 10, 2025, at Bitcoin Park in Nashville, Tennessee, USA. This event is non-sponsored and follows an Unconference format, allowing all participants to apply as speakers and share their Bitcoin education experiences in a free and interactive environment. the event has open-sourced all its blueprints and Standard Operating Procedures (SOPs) to encourage global communities to organize similar Unconference events.
- Panama Blockchain Week 2025 will take place from April 22 to 24 at the Panama Convention Center in Panama City. As the first large-scale blockchain event in Central America, it aims to position Panama as a leading blockchain financial hub in Latin America. The event features a diverse lineup, including a blockchain conference, Investor’s Night, Web3 gaming experiences, tech exhibitions, and an after-party celebration.
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ d5c3d063:4d1159b3
2025-04-01 04:20:50
@ d5c3d063:4d1159b3
2025-04-01 04:20:50“วิธีที่ดีที่สุดในการทำลายทุนนิยมคือทำลายค่าเงิน” Lenin Was Right
ประโยคนี้ไม่ใช่แค่คำปลุกระดมของนักปฏิวัติ แต่มันเป็นเหมือนสัญญาณเตือนล่วงหน้า ที่คนส่วนใหญ่ไม่สนใจ จนวันหนึ่งมันก็เกิดขึ้นจริง แบบเงียบ ๆ โดยไม่มีใครทันตั้งตัว
Henry Hazlitt เขียนบทความนี้ไว้ตั้งแต่ปี 1947 เขาไม่เพียงบอกว่าเลนินพูดถูก แต่เขาแฉว่าโลกทั้งใบ “กำลังทำตามแผนของเลนิน” แบบไม่รู้ตัว
ตอนนั้นรัฐบาลหลายประเทศ โดยเฉพาะในยุโรป พิมพ์เงินออกมาใช้มหาศาล โดยอ้างว่าสงครามบีบบังคับให้ต้องทำแบบนั้น แต่ปัญหาคือ...พอสงครามจบในปี 1945 แล้ว รัฐกลับไม่หยุดพิมพ์เงิน ยังทำเหมือนอยู่ในภาวะฉุกเฉิน
เหมือนที่ อ. #SaifedeanAmmous พูดไว้ในหนังสือ #TheBitcoinStandard ว่าเวลารัฐอยากพิมพ์เงินแบบไม่ต้องรับผิดชอบ ก็แค่เอาสงครามมาอ้าง พอพูดว่า “เพื่อความมั่นคง” หรือ “เพื่อชาติ” เท่านั้นแหละ ทุกอย่างก็ดูเป็นเรื่องจำเป็นขึ้นมาทันที แล้วไม่มีใครกล้าถามว่าจริง ๆ แล้วเงินมันมาจากไหน
พอเงินเฟ้อมันแรง ของก็แพงขึ้น แต่รัฐไม่ยอมรับหรอกว่าที่ของแพงเพราะตัวเองพิมพ์เงินออกมาเยอะเกิน แต่กลับไปโทษพ่อค้า โทษคนทำธุรกิจ ว่าขายของแพง ค้ากำไรเกินควรซะงั้น
Hazlitt เขาเตือนว่า...รัฐกำลังทำให้คนเกลียดพ่อค้า เกลียดเจ้าของธุรกิจ เพื่อให้ดูเหมือนว่าตัวเองมีเหตุผลที่จะเข้ามาคุมเศรษฐกิจ ซึ่งที่น่ากลัวคือ... มันไม่ได้เกิดจากความไม่รู้ แต่มันเกิดจาก “ระบบ” ที่เปิดช่องให้เขาทำแบบนี้ได้เลย แบบไม่ต้องรับผิดชอบอะไรทั้งนั้น
ตรงนี้แหละที่ Hazlitt เอาคำพูดของ John Maynard Keynes เข้ามาเสริม เพราะแม้แต่ Keynes ก็ยังเคยเตือนไว้ในหนังสือ The Economic Consequences of the Peace ว่า “เงินเฟ้อ” มันเหมือนเครื่องมือเงียบ ๆ ที่จะค่อย ๆ ทำลายระบบเศรษฐกิจ โดยที่คนส่วนใหญ่ไม่รู้ตัว
Hazlitt เขาเป็น "สายวิจารณ์" Keynes ตัวพ่อเลยนะ เขาเขียนหนังสือ The Failure of the New Economics ที่ไล่รื้อแนวคิดของ Keynes แบบ “ตา-ต่อ-ตา หน้า-ต่อ-หน้า” กับหนังสือ The General Theory ของ Keynes เลยนะ
แต่พอมาในบทความนี้...Hazlitt กลับหยิบคำพูดของ Keynes มาใช้อย่างเต็มใจ เพราะมันตรงเกินไปที่จะมองข้ามได้ ว่าแม้แต่ #Keynes เองยังเคยเตือนเลยว่า “การทำลายค่าเงิน” คืออาวุธเงียบ ที่ใช้ทำลายระบบทุนนิยมได้อย่างแนบเนียนที่สุด . . พออ่านแล้วแบบ…แม้แต่คนที่เราคิดว่าเชียร์ฝั่งรัฐ ยังเตือนเรื่องนี้ไว้ แล้วเราจะยังเฉยอยู่ได้ไง
คือถ้าเงินมันถูกทำให้ด้อยค่าลงเรื่อย ๆ วันนึงมันจะพังแบบเงียบ ๆ จนคนไม่รู้ตัวเลย คนทั่วไปจะรู้แค่ว่าของมันแพงขึ้น แต่ไม่มีใครเห็น ว่าจริง ๆ แล้ว เงินที่เราใช้มันเริ่มไม่มีเสถียรภาพ และไม่มั่นคงอีกต่อไปแล้ว
แล้วถ้ามองตัวเลขนี่ยิ่งช็อก ระหว่างปี 1939 ถึง 1947 ในเวลาแค่ 8 ปี ปริมาณเงินในระบบของสหรัฐฯ เพิ่มจาก 33,000 ล้านดอลลารเป็น 108,500 ล้านดอลลาร์ พูดง่าย ๆ คือ คูณสาม (ช่วงสงครามโลกครั้งที่ 2)
Hazlitt พูดแบบตรง ๆ เลยว่า ปัญหาที่เกิดขึ้น มันไม่ใช่เพราะเศรษฐกิจโตหรือคนรวยขึ้นนะ มันเกิดจากการที่รัฐเพิ่มปริมาณเงินในระบบเร็วเกินไป เมื่อเงินในตลาดเลยเยอะขึ้น แต่ของที่มีให้ซื้อไม่ได้เยอะขึ้นตาม เมื่อเงินไหลเวียนมากขึ้น โดยที่ของยังมีเท่าเดิม ราคาของก็เลยพุ่ง
ทีนี้พอของขึ้นราคา รัฐบาลกลับไม่ยอมรับว่าเป็นเพราะเขาพิมพ์เงิน แต่ไปเลือกวิธีแก้แบบง่าย ๆ แต่สร้างปัญหาในระยะยาว เช่น สั่งห้ามขึ้นราคา กดดันคนทำธุรกิจให้แบกต้นทุนไว้ หรือไม่ก็ล็อกค่าเงิน เหมือนไม่มีอะไรเกิดขึ้น
หลังจากนั้น เศรษฐกิจยุโรปก็เริ่มพัง ผู้ผลิตเจอต้นทุนบาน การค้าระหว่างประเทศก็รวน สุดท้ายก็ต้องพึ่งดอลลาร์จากอเมริกา (Marshall Aid) มาช่วยอุ้ม เหมือนพิมพ์เงินของตัวเองจนระบบรวน แล้วไปขอเงินจากฝั่งที่พิมพ์ได้มากกว่าอีกที
นี่แหละจุดเริ่มของ “วิกฤตเศรษฐกิจโลกหลังสงคราม” ที่จริง ๆ แล้ว...ก็แค่เรื่องของการพิมพ์เงินล้วน ๆ . . แต่นั้นมันเป็นเรื่องเกิดขึ้นเมื่อปี 1947 นะ...แล้ววันนี้ล่ะ
ล่าสุด ปี 2020 ก่อนโควิด ระดับ M2 money supply ของสหรัฐอยู่ราว ๆ 15 ล้านล้านดอลลาร์ แค่ไม่กี่ปีต่อมา มันทะลุไปถึง 21 ล้านล้าน ในเวลาไม่ถึง 3 ปีเงินเพิ่มขึ้นในระบบเศรษฐกิจกว่า 6 ล้านล้านดอลลาร์
แล้วของก็แพงขึ้น ค่าแรงวิ่งตามไม่ทัน แต่แทนที่รัฐจะบอกว่า “เราพิมพ์เงินมากไป” ก็ไปเล่นมุกเดิม โทษตลาด โทษนายทุน โทษธุรกิจ (บ้างก็โทษโลกร้อน)
สุดท้ายก็จะมีคนบางกลุ่มเชียร์ให้ “ควบคุมราคา” อีก มันคือ loop เดิม ที่ #Hazlitt เคยเตือนไว้ เมื่อเกือบ 80 ปีก่อน.. . . สิ่งที่ซุปเห็นชัดเจนที่สุดจากบทความนี้คือ... เกมนี้มันไม่มีใครหยุดได้เลย ถ้าคุณยังถือเงินที่รัฐพิมพ์ได้
เพราะตราบใดที่ยังมีคนสั่งพิมพ์เงินได้ตามใจ ระบบเศรษฐกิจก็จะปั่นป่วนซ้ำไปซ้ำมา ของก็จะแพงขึ้นเรื่อย ๆ แบบไม่มีจุดจบ
คุณก็จะต้องเหนื่อยทำงานมากขึ้น แต่ซื้อได้น้อยลง แล้วคุณก็จะโทษตัวเอง ว่ายังขยันไม่มากพอ ทั้ง ๆ ที่คุณทำงาน 4-5 อย่าง
.
เลนิน พูดถูก ถ้าจะทำลายทุนนิยม ก็แค่ทำลายค่าเงิน ฟังดูแรงเนอะ...แต่เรื่องนี้มันไม่ใช่แค่ทฤษฎีแล้ว เพราะเรากำลังเห็น ว่ามันกำลังเกิดขึ้นอยู่จริง ๆ
แต่วันนี้ เราเลือกที่จะไม่อยู่ในเกมที่พังซ้ำๆ ได้แล้ว
เพราะเรามี “ทางออก” อยู่ตรงหน้า บิตคอยน์ ไม่ใช่อะไรที่ทุกคนจะเข้าใจมันได้ทันที แต่มันคือ “เงิน” ที่ไม่มีใครพิมพ์เพิ่มได้ตามใจ ไม่มีใครมานั่งกดปุ่มสร้างมันขึ้นมาได้ง่าย ๆ ไม่มีใครเปลี่ยนกติกากลางเกมได้ และไม่มีใครแทรกแซงนโยบายของมันได้
สิ่งเดียวที่ #บิตคอยน์ บอกเราตรง ๆ ก็คือ “ความขาดแคลน” ไม่ใช่ปัญหา...
สิ่งที่ Hazlitt เตือนเมื่ออดีต คือกับดักของเงินไม่มีขอบเขต
สิ่งที่ #Bitcoin เสนอ คือขอบเขตที่ทำให้ “มูลค่า” กลับมามีความหมาย
[Newsweek column from September 22, 1947, and reprinted in Business Tides: The Newsweek Era of Henry Hazlitt.] https://mises.org/mises-wire/lenin-was-right
Siamstr
-
 @ f3328521:a00ee32a
2025-03-31 00:25:36
@ f3328521:a00ee32a
2025-03-31 00:25:36This paper was originaly writen in early November 2024 as a proposal for an international Muslim entrepreneurial initiative. It was first publish on NOSTR 27 November 2024 as part 1 of a 4 part series of essays. Last updated/revised: 30 March 2025.
The lament of the Ummah for the past century has been the downfall of the Khalifate. With the genocide in occupied Palestine over the past year and now escalations in Lebanon as well, this concern is at the forefront of a Muslim’s mind. In our tradition, when one part of the Ummah suffers, all believers are affected and share in that suffering. The Ummah today has minimal sovereignty at best. It lacks a Khalifate. It is spiritually weakened due to those not practicing and fulfilling their duties and responsibilities. And, as we will address in this paper, it has no real economic power. In our current monetary system, it is nearly impossible to avoid the malevolence of riba (interest) – one of the worst sins. However, with bitcoin there is an opportunity to alleviate this collective suffering and reclaim economic sovereignty.
Since it’s invention 15 years ago, bitcoin has risen to achieve a top 10 market cap ranking as a global asset (currently valued at $1.8 trillion USD). Institutional investors are moving full swing to embrace bitcoin in their portfolios. Recent proposals in Kazan hint that BRICS may even be utilizing bitcoin as part of their new payments system. State actors will be joining soon. With only about 1 million bitcoins left to be mined we need to aim to get as much of those remaining coins as possible into the wallets of Muslims over the next decade. Now is the time to onboard the Ummah. This paper presents Bitcoin as the best option for future economic sovereignty of the Ummah and proposes steps needed to generate a collective waqf of an initial 0.1%-0.5% chain dominance to safeguard a revived Khalifate.
Money is the protocol that facilitates economic coordination to help the development and advancement of civilization. Throughout history money has existed as cattle, seashells, salt, beads, stones, precious metals. Money develops naturally and spontaneously; it is not the invention of the state (although it at times is legislated by states). Money exists marginally, not by fiat. During the past few millenniums, gold and silver were optimally used by most advanced civilizations due to strong properties such as divisibility, durability, fungibility, portability, scarcity, and verifiability. Paper money modernized usability through attempts to enhance portability, divisibility, and verifiability. However, all these monetary properties are digitized today. And with the increase of fractional-reserve banking over the past two centuries, riba is now the de facto foundation of the consensus reserve currency – the USD.
This reserve currency itself is backed by the central banking organ of the treasury bond markets which are essentially government issued debt. Treasurey bonds opperate by manipulating the money supply arbitrarily with the purpose of targeting a set interest rate – injecting or liquidating money into the supply by fiat to control intrest yeilds. At its root, the current global monetary order depends entirely on riba to work. One need not list the terrible results of riba as Muslims know well its harshness. As Lyn Alden wonderful states in her book, Broken Money, “Everything is a claim of a claim of a claim, reliant on perpetual motion and continual growth to not collapse”. Eventual collapse is inevitable, and Muslims need to be aware and prepared for this reality.
The status quo among Muslims has been to search for “shariah compliance”. However, fatwa regarding compliance as well as the current Islamic Banking scene still operate under the same fiat protocol which make them involved in the creation of money through riba. Obfuscation of this riba through contractum trinius or "shariah compliant" yields (which are benchmarked to interest rates) is simply an attempt to replicate conventional banking, just with a “halal” label. Fortunately, with the advent of the digital age we now have other monetary options available.
Experiments and theories with digital money date back to the 1980s. In the 1990s we saw the dot com era with the coming online of the current fiat system, and in 2008 Satoshi Nakamoto released Bitcoin to the world. We have been in the crypto era ever since. Without diving into the technical aspects of Bitcoin, it is simply a P2P e-cash that is cryptographically stored in digital wallets and secured via a decentralized blockchain ledger. For Muslims, it is essential to grasp that Bitcoin is a new type of money (not just an investment vehicle or payment application) that possesses “anti-riba” properties.
Bitcoin has a fixed supply cap of 21 million, meaning there will only ever be 21 million Bitcoin (BTC). Anyone with a cheap laptop or computer with an internet connection can participate on the Bitcoin network to verify this supply cap. This may seem like an inadequate supply for global adoption, but each bitcoin is highly divisible into smaller units (1 btc = 100,000,000 satoshis or sats). Bitcoins are created (or mined) from the processing of transactions on the blockchain which involves expending energy in the real world (via CPU power) and providing proof that this work was done.
In contrast, with the riba-based fiat system, central banks need to issue debt instruments, either in the form of buying treasuries or through issuing a bond. Individual banks are supposed to be irresponsibly leveraged and are rewarded for making risky loans. With Bitcoin, there is a hard cap of 21 million, and there is no central authority that can change numbers on a database to create more money or manipulate interest rates. Under a Bitcoin standard, money is verifiably stored on a ledger and is not loaned to create more money with interest. Absolute scarcity drives saving rather than spending, but with increasing purchasing power from the exponentially increasing demand also comes the desire to use that power and increased monetary economization. With bitcoin you are your own bank, and bitcoin becomes for your enemies as much as it is for your friends. Bitcoin ultimately provides a clean foundation for a stable money that can be used by muslims and should be the currency for a future Khalifate.
The 2024 American presidential election has perhaps shown more clearly than ever the lack of politcal power that American Muslims have as well as the dire need for them to attain political influence. Political power comes largely through economic sovereignty, military might, and media distribution. Just a quick gloss of Muslim countries and Turkey & Egypt seem to have decent militaries but failing economies. GCC states have good economies but weak militaries. Iran uniquely has survived sanctions for decades and despite this weakened economic status has still been able to make military gains. Although any success from its path is yet to be seen it is important to note that Iran is the only country that has been able to put up any clear resistance to western powers. This is just a noteworthy observation and as this paper is limited to economic issues, full analysis of media and miliary issues must be left for other writings.
It would also be worthy to note that BDS movements (Boycott, Divest & Sanction) in solidarity with Palestine should continue to be championed. Over the past year they have undoubtedly contributed to PEP stock sinking 2.25% and MCD struggling to break even. SBUX and KO on the other hand, despite active boycott campaigns, remain up 3.5% & 10.6% respectively. But some thought must be put into why the focus of these boycotts has been on snack foods that are a luxury item. Should we not instead be focusing attention on advanced tech weaponry? MSFT is up 9.78%, GOOG up 23.5%, AMZN up 30%, and META up 61%! It has been well documented this past year how most of the major tech companies have contracts with occupying entity and are using the current genocide as a testing ground for AI. There is no justification for AI being a good for humanity when it comes at the expense of the lives of our brothers in Palestine. However, most “sharia compliant” investment guides still list these companies among their top recommendations for Muslims to include in their portfolios.
As has already been argued, by investing in fiat-based organization, businesses, ETFs, and mutual funds we are not addressing the root cause of riba. We are either not creating truly halal capital, are abusing the capital that Allah has entrusted to us or are significantly missing blessings that Allah wants to give us in the capital that we have. If we are following the imperative to attempt to make our wealth as “riba-free” as possible, then the first step must be to get off zero bitcoin
Here again, the situation in Palestine becomes a good example. All Palestinians suffer from inflation from using the Israeli Shekel, a fiat currency. Palestinians are limited in ways to receive remittances and are shrouded in sanctions. No CashApp, PayPal, Venmo. Western Union takes huge cuts and sometimes has confiscated funds. Bank wires do this too and here the government sanctions nearly always get in the way. However, Palestinians can use bitcoin which is un-censorable. Israel cannot stop or change the bitcoin protocol. Youssef Mahmoud, a former taxi driver, has been running Bitcoin For Palestine as a way for anyone to make a bitcoin donation in support of children in Gaza. Over 1.6 BTC has been donated so far, an equivalent of about $149,000 USD based on current valuation. This has provided a steady supply of funds for the necessary food, clothing, and medication for those most in need of aid (Note: due to recent updates in Gaza, Bitcoin For Palestine is no longer endorsed by the author of this paper. However, it remains an example of how the Bitcoin network opperates through heavy sanctions and war).
Over in one of the poorest countries in the world, a self-managed orphanage is providing a home to 77 children without the patronage of any charity organization. Orphans Of Uganda receives significant funding through bitcoin donations. In 2023 and 2024 Muslims ran Ramadan campaigns that saw the equivalent of $14,000 USD flow into the orphanage’s bitcoin wallet. This funding enabled them to purchase food, clothing, medical supplies and treatment, school costs, and other necessities. Many who started donating during the 2023 campaign also have continued providing monthly donations which has been crucial for maintaining the well-being of the children.
According to the Muslim Philanthropy Initiative, Muslim Americans give an estimated $1.8 billion in zakat donations every year with the average household donating $2070 anually. Now imagine if international zakat organizations like Launchgood or Islamic Relief enabled the option to donate bitcoin. So much could be saved by using an open, instant, permissionless, and practically feeless way to send zakat or sadaqah all over the world! Most zakat organizations are sleeping on or simply unaware of this revolutionary technology.
Studies by institutions like Fidelity and Yale have shown that adding even a 1% to 5% bitcoin allocation to a traditional 60/40 stock-bond portfolio significantly enhances returns. Over the past decade, a 5% bitcoin allocation in such a portfolio has increased returns by over 3x without a substantial increase in risk or volatility. If American Muslims, who are currently a demographic estimated at 2.5 million, were to only allocate 5% ($270 million) of their annual zakat to bitcoin donations, that would eventually become worth $14.8 billion at the end of a decade. Keep in mind this rate being proposed here is gathered from American Muslim zakat data (a financially privileged population, but one that only accounts for 0.04% of the Ummah) and that it is well established that Muslims donate in sadaqa as well. Even with a more conservative rate of a 1% allocation you would still be looking at nearly $52 million being liquidated out of fiat and into bitcoin annually. However, if the goal is to help Muslims hit at least 0.1% chain dominance in the next decade then a target benchmark of a 3% annual zakat allocation will be necessary.
Islamic financial institutions will be late to the game when it comes to bitcoin adoption. They will likely hesitate for another 2-4 years out of abundance of regulatory caution and the persuasion to be reactive rather than proactive. It is up to us on the margin to lead in this regard. Bitcoin was designed to be peer-2-peer, so a grassroots Muslim bitcoiner movement is what is needed. Educational grants through organizations like Bitcoin Majlis should be funded with endowments. Local Muslim bitcoin meetups must form around community mosques and Islamic 3rd spaces. Networked together, each community would be like decentralized nodes that could function as a seed-holder for a multi-sig waqf that can circulate wealth to those that need it, giving the poorer a real opportunity to level up and contribute to societ and demonstrating why zakat is superior to interest.
Organic, marginal organizing must be the foundation to building sovereignty within the Ummah. Sovereignty starts at the individual level and not just for all spiritual devotion, but for economics as well. Physical sovereignty is in the individual human choice and action of the Muslim. It is the direct responsibility placed upon insan when the trust of khalifa was placed upon him. Sovereignty is the hallmark of our covenant, we must embrace our right to self-determination and secede from a monetary policy of riba back toward that which is pure.
"Whatever loans you give, seeking interest at the expense of people’s wealth will not increase with Allah. But whatever charity you give, seeking the pleasure of Allah—it is they whose reward will be multiplied." (Quran 30:39)
FAQ
Why does bitcoin have any value?
Unlike stocks, bonds, real-estate or even commodities such as oil and wheat, bitcoins cannot be valued using standard discounted cash-flow analysis or by demand for their use in the production of higher order goods. Bitcoins fall into an entirely different category of goods, known as monetary goods, whose value is set game-theoretically. I.e., each market participant values the good based on their appraisal of whether and how much other participants will value it. The truth is that the notions of “cheap” and “expensive” are essentially meaningless in reference to monetary goods. The price of a monetary good is not a reflection of its cash flow or how useful it is but, rather, is a measure of how widely adopted it has become for the various roles of money.
Is crypto-currency halal?
It is important to note that this paper argues in favor of Bitcoin, not “Crypto” because all other crypto coins are simply attempts a re-introducing fiat money-creation in digital space. Since they fail to address the root cause error of riba they will ultimately be either destroyed by governments or governments will evolve to embrace them in attempts to modernize their current fiat system. To highlight this, one can call it “bit-power” rather than “bit-coin” and see that there is more at play here with bitcoin than current systems contain. Mufti Faraz Adam’s fatwa from 2017 regarding cryptocurrency adaqately addresses general permissibility. However, bitcoin has evolved much since then and is on track to achieve global recognition as money in the next few years. It is also vital to note that monetary policy is understood by governments as a vehicle for sanctions and a tool in a political war-chest. Bitcoin evolves beyond this as at its backing is literal energy from CPU mining that goes beyond kinetic power projection limitations into cyberspace. For more on theories of bitcoin’s potential as a novel weapons technology see Jason Lowery’s book Softwar.
What about market volatility?
Since the inception of the first exchange traded price in 2010, the bitcoin market has witnessed five major Gartner hype cycles. It is worth observing that the rise in bitcoin’s price during hype cycles is largely correlated with an increase in liquidity and the ease with which investors could purchase bitcoins. Although it is impossible to predict the exact magnitude of the current hype cycle, it would be reasonable to conjecture that the current cycle reaches its zenith in the range of $115,000 to $170,000. Bitcoin’s final Gartner hype cycle will begin when nation-states start accumulating it as a part of their foreign currency reserves. As private sector interest increases the capitalization of Bitcoin has exceeded 1 trillion dollars which is generally considered the threshold at which an assest becomes liquid enough for most states to enter the market. In fact, El Salvador is already on board.
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 71550e6c:b64c37a9
2025-03-29 10:55:55
@ 71550e6c:b64c37a9
2025-03-29 10:55:55Just do the same as this video shows.
Here's the video: https://cdn.azzamo.net/7cdcc2718f1e15eb03e323f62e07582b4001da273aa5c21475d680f02b32f0e9.mp4
One caveat: do not trust the draft will be kept here after you close
nak fs. Wait, no, it definitely won't stay here, but I'm not even sure it will stay here if you only navigate away and come back later, FUSE is weird and I didn't test.But at least it should work for copy-pasting. Or writing everything in one go.
-
 @ 04c915da:3dfbecc9
2025-03-25 17:43:44
@ 04c915da:3dfbecc9
2025-03-25 17:43:44One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ bcbb3e40:a494e501
2025-03-31 15:02:58
@ bcbb3e40:a494e501
2025-03-31 15:02:58Traducción por Francisco de la Torre.
|
 |
|:-:|
|Los representantes de la derecha sionista europea que forman parte de «Patriots» reunidos en Bruselas el pasado mes de diciembre de 2024.|
|
|:-:|
|Los representantes de la derecha sionista europea que forman parte de «Patriots» reunidos en Bruselas el pasado mes de diciembre de 2024.|Entre los efectos que probablemente producirá en Europa la nueva administración estadounidense, es previsible el fortalecimiento del ala derecha del colaboracionismo atlantista que, después de haberse posicionado decididamente a favor de Donald Trump durante su presidencia 2017-2021, en el transcurso de la administración Biden abogó fervientemente por su regreso a la Casa Blanca y acogió su victoria electoral con gran júbilo. A finales de octubre de 2024, en el grandioso mitin preelectoral a favor de Trump celebrado en el Madison Square Garden de Nueva York, asistió una representante del grupo parlamentario europeo Patriots for Europe, que viajó a Estados Unidos para esa ocasión especial. En un vídeo publicado en la página X (antes twitter) de los Patriots, varios eurodiputados del mencionado grupo expresaron su identidad con los puntos de vista de Trump y auspiciando su reelección: el austriaco Harald Vilimsky (Freiheitliche Partei Österreichs), el checo Ondrej Knotek (Año 2011) el español Jorge Buxade (Vox), el holandés Tom Vandendriesche (Vlaams Belang), la polaca Anna Bryłka (Ruch Narodowy) y, por Hungría, Tamás Deutsch (Fidesz).
Este último es, sin duda, la personalidad más eminente del grupo de los Patriots que viajaron a Nueva York: originario de una familia judía de Budapest, en 1988 Tamás Deutsch junto con Viktor Orbán están entre los fundadores de Fidesz —Fiatal Demokraták Szövetsége (Alianza de los jóvenes demócratas), en la que ocupó el cargo de vicepresidente. El Fidesz ha tejido durante mucho tiempo una red de lazos con el Partido Republicano de los Estados Unidos y con el think tank conservador Heritage Foundation, mientras que el gobierno de Viktor Orbán organizó las tres últimas ediciones anuales de la CPAC en Hungría (Conservative Political Action Conference), un encuentro de políticos de derechas de varios países[^1].
Patriots for Europe o Patriots.eu, denominación que recuerda al de los misiles aire-tierra estadounidenses (el MIM-104 Patriots), es, por tanto, el nombre oficial del grupo político de la derecha liberal-conservadora, populista y euroescéptica, nacido en julio de 2024 (primero como alianza y luego como grupo parlamentario europeo) por iniciativa del primer ministro húngaro Viktor Orbán, el exprimer ministro checo Andrej Babiŝ y del exministro del interior austriaco Herbert Kickl. Como representantes de sus respectivos partidos (Fidesz, Año 2011, Freiheitliche Partei Österreichs), Orbán, Babiŝ y Kickl firmaron un texto ideológico titulado: A Patriotic Manifesto for a European Future[^2], según la cual la única política europea legítima es aquella que, enraizada en la pluralidad de las diferentes naciones, proteja su herencia grecorromana-judeocristiana preservando su identidad, tradiciones y costumbres.
Al núcleo inicial de los Patriots se unió el partido portugués ¡Arriva! (¡Chega!), el Partido húngaro Popular Demócrata Cristiano (Kereszténydemokrata Néppárt), el partido español Vox, el Partido por la Libertad (Partij voor de Vrijheid) holandés, el Partido Popular Danés (Dansk Folkeparti), el interés Flamenco (Vlaams Belang), la Reunión Nacional (Rassemblement National) francés y, por Italia, la Liga para Primer Ministro Salvini.
Constituido formalmente, el grupo parlamentario recibió una posterior adhesión del diputado griego de Voz de la Razón (Foní Logikis), del diputado de Primero Letonia (Letvija pirmajâ prohibir), de los dos diputados del Movimiento Nacional polaco (Ruch Narodowy) y de los dos diputados checos del Juramento (Přísaha) y de los Automovilistas por sí mismos (Motoristé sollozoê). Presidente del grupo parlamentario Patriots.eu, que cuenta con un total de ochenta y seis diputados[^3], es Jordan Bardella, presidente de la Rassemblement National; pero la personalidad más notable y prestigiosa de los Patriots es, sin duda, el primer ministro húngaro Viktor Orbán.
En cuanto a la línea de política exterior seguida por Viktor Orbán, cabe recordar que fue durante su primer mandato, en 1989, cuando Hungría se unió a la OTAN junto con la República Checa y Polonia. La pertenencia a la organización militar de la Alianza Atlántica implicó la participación húngara en la guerra de Kosovo en Yugoslavia, así como la contribución de Hungría en las misiones de la ISAF y en la guerra en Irak en apoyo de la intervención estadounidense. Por otro lado, no deja de ser significativo que en junio de 2011, durante la visita de Condoleezza Rice a Budapest, se inaugurara una estatua del presidente estadounidense Ronald Reagan en la céntrica Plaza de la Libertad (Szabadság tér). «Hoy —dijo Orbán en esa ocasión— erigimos aquí una estatua al hombre, al líder, que cambió y renovó este mundo creando un nuevo mundo para nosotros en Europa Central, un hombre que creía en la libertad, en la fuerza moral de los hombres libres, y creía que los muros que obstruyen el camino a la libertad pueden ser derribados».
En los años de la primera administración Trump, Orbán estableció una relación privilegiada con la Casa Blanca: en 2019 fue recibido calurosamente por el presidente estadounidense, quien declaró su apoyo al «soberanismo» europeo, del que Orbán era ya el exponente más puntero. El primer ministro húngaro, que más tarde expresó varias veces la esperanza de volver a ver a Trump como líder de los Estados Unidos, se reunió con él de nuevo en Mar-a-Lago de Palm Beach en marzo de 2024 y al final de la visita escribió en una publicación: «¡Hacer que América vuelva a ser grande, señor presidente!»[^4].
El entendimiento entre Trump y Orbán fue favorecido por Benjamin Netanyahu, quien ha tenido una estrecha relación con el actual primer ministro húngaro desde 2005, cuando Orbán estaba en la oposición y Netanyahu era ministro de Finanzas. Esta relación, que Orbán ha utilizado para neutralizar las iniciativas hostiles de las ONG’s de Soros (quien financió a Fidesz desde 1992 a 1999), ha acentuado progresivamente la posición proisraelí de Budapest, hasta el punto que Hungría junto a Austria, Croacia y República Checa, se han alineado con Estados Unidos e Israel votando en contra de la resolución propuesta por la ONU para el alto el fuego en la Franja de Gaza. Cuando László Toroczkai, jefe del partido Mi Hazánk (Nuestra Patria), preguntó a Orbán en el Parlamento por qué Hungría había votado en contra, el primer ministro le respondió: «La política exterior es complicada, enfréntate solo si entiendes de lo que estamos hablando»[^5].
El presidente de Patriots, Jordan Bardella, no es menos pro-sionista. «Reconocer un Estado palestino significaría reconocer el terrorismo», dijo Bardella, quien antes de las elecciones francesas había asegurado que, si llegaba a ser primer ministro, sería «un escudo para los compatriotas judíos contra un islamismo que no solo quiere separar la República, sino conquistarla»[^6]. Por su parte, Marine Le Pen, madrina política de Bardella, declaró: «Es absolutamente legítimo que Israel quiera erradicar al grupo terrorista armado Hamas y que se dote de medios para hacerlo»[^7].
En cuanto a la Liga de Salvini como primer ministro, sus posiciones pro-trumpistas y pro-sionistas siempre se han caracterizado por un extremismo descarado. «Nunca he ocultado —dijo Salvini antes de las elecciones estadounidenses— mi esperanza en una victoria republicana, por mil razones (...) hablamos [con Trump] a más tardar hace unas semanas. Nunca he ocultado mi simpatía humana y mi sintonía cultural»[^8]. Y sobre el genocidio en curso en Palestina, Salvini dijo: «Nuestros pensamientos están con el pueblo israelí (...) Recordar siempre el derecho de Israel a existir, a defenderse y a convivir finalmente en paz con sus pueblos vecinos, contra el horror del terrorismo islámico»[^9]. El 6 de octubre de 2024, al final de su discurso desde el escenario de Pontida, Salvini posó para una foto con los Patriots presentes en la manifestación de la Liga Norte: además de Viktor Orbán, estuvieron el holandés Geert Wilders, el portugués André Ventura, la austriaca Marlene Svazek, el español Antonio Fúster y el general Roberto Vannacci. Enviaron mensajes en vídeo de apoyo y solidaridad tanto Jordán Bardella en nombre de Rassemblement national como el ex-presidente brasileño Jair Bolsonaro.
También Geert Wilders (Partij voor de Vrijheid), que en 2009 recibió el Premio Oriana Fallaci por producir un cortometraje de propaganda antiislámica, es conocido también por su extremismo prosionista. «Jerusalén, Judea y Samaria —en su opinión— son todas de Israel (...) La patria de los palestinos es el Reino de Jordania (...) Obama y Kerry deben dejar de criticar a Israel por los asentamientos. Judea y Samaria pertenecen a los israelíes»[^10]. En el programa de Wilders, «distinguiéndose durante dos décadas por su lucha contra la islamización —escribe complacido un sitio web sionista— está también el reconocimiento de Jerusalén como capital de Israel, con el traslado de la embajada holandesa»[^11].
André Ventura, presidente de ¡Chega!, reiteró en Polonia la posición prosionista de su partido, declarando convencido: «Estamos con Israel y permaneceremos junto a Israel en esta batalla por los derechos humanos y la democracia»[^12]. A quienes lo comparan con Donald Trump y Jair Bolsonaro, André Ventura responde: «Estoy acostumbrado a estas comparaciones. Estas son las ideas en las que creo»[^13]. En cuanto a la guerra en Ucrania, el líder de la lista ¡Chega! en las elecciones europeas, Antonio Tânger Corrêa, dijo que «la derrota de Ucrania sería la derrota de todo Occidente y de Portugal, en caso de extrema necesidad»[^14], enviarían a sus tropas.
Marlene Svazek representó a la Freiheitliche Partei Österreichs en Pontida, cuyos «excelentes contactos»[^15] con la derecha israelí están garantizados por David Lasar, miembro del Consejo Nacional (Nationalrat) del partido austriaco. Lasar no es el único judío en el FPÖ: también es judío el ex-secretario general del partido y ex-parlamentario europeo Peter Sichrovsky, quien ha negado ser un agente del Mossad, pero ha admitido haber tenido «muchas reuniones con funcionarios israelís»[^16].
José Antonio Fúster es el nuevo presidente de Vox Madrid. El jefe del partido que lo representa, Santiago Abascal, encabezó una delegación a Israel en 2023 que se reunió con dos ministros de Tel Aviv. «Durante la visita, Abascal ha transmitido el apoyo y la solidaridad de España al Primer Ministro israelí Benjamin Netanyahu, y ha defendido la urgente necesidad de acabar con Hamas que, según Abascal, es un grupo terrorista que «encarna el mal absoluto»[^17]. Tras la reunión de la delegación de Vox con Netanyahu, el candidato electoral Jorge Buxadé Villalba afirmó que las acciones genocidas cometidas por el régimen sionista en la Franja de Gaza son «operaciones antiterroristas» que deben continuar «hasta que no quede ni un solo terrorista»[^18].
En cuanto a Roberto Vannacci, elegido diputado del Parlamento Europeo en las listas de la Liga por Salvini, su currículum vitae patriot puede jactarse de una participación activa en las operaciones de EE.UU. en Oriente Medio. El general comandó durante dos turnos (2005-2006) el Special Forces Task Group en Irak y fue el primer comandante de la Task Force 45 en Afganistán en 2013, poco antes de la transición de la International Security Assistance Force a la Resolute Support Mission, Vannacci asumió el cargo de jefe del Estado Mayor de las fuerzas especiales de la OTAN, «una organización que ha garantizado la paz durante más de cincuenta años, una alianza política y militar que ha funcionado bien»[^19]. Habiendo prestado sus servicios a los Estados Unidos «para la estabilización de Irak»[^20] como Deputy Commanding General y Director of Training, el 21 de agosto de 2018, Vannacci fue galardonado con la Legion of Merit, la condecoración militar estadounidense creada por el presidente Franklin D. Roosevelt. Su consigna antes y después de la elección de Trump ha sido: «Go, Donald, go!».
[^1]: Cfr. C. Mutti, Alla destra degli USA, «Eurasia» 1/2023.
[^2]: Después de la confluencia de los grupos de Identity and Democracy en el grupo de Patriots, se aprobó una nueva versión del manifiesto político. Véase https://patriots.eu/manifesto
[^3]: Freiheitliche Partei Österreichs (Austria), 6; Vlaams Belang (Bélgica), 3; Dansk Folkeparti (Dinamarca), 1; Rassemblement National (Francia), 30; Foni Logikis (Grecia), 1; Fidesz - Magyar Polgári Szövetség (Hungría), 10; Kereszténydemokrata Néppárt (Hungría), 1; Liga para Salvini Premier (Italia), 8; Letvija primajâ vietâ (Letonia), 1; Partij voor de Vrijheid (Países Bajos), 6; Ruch Narodowy (Polonia), 2; ¡Chega! (Portugal), 2; ANO (República Checa), 7; Automovilistaé sobê (República Checa), 1; Přísaha (República Checa), 1; Vox (España), 6.
[^4]: Angela Napoletano, La «visita». Orbán incorona Trump: «Lui è il presidente della pace», avvenire.it, 9 marzo 2024.
[^5]: András Dezsô, The roots of Orbán’s strong bond with Israel and its PM, https://balkaninsight.com, 14 de noviembre de 2023.
[^6]: Bardella, «riconoscere Palestina è riconoscere terrorismo». «Sarò uno scudo per i nostri connazionali ebrei», ANSA, 26/6/2024.
[^7]: Mauro Zanon, Sorpresa, lo «scudo» degli ebrei in Francia è il partito della Le Pen, tempi.it, 27 de octubre de 2023.
[^8]: Stefano Baldolini, Salvina punta su Trump: «Spero che vinca. Andrò negli Usa prima del voto». Tensioni con Meloni? «Governo durerà 5 anni», repubblica.it, 13 de julio de 2024.
[^9]: Nova.News, 7 de octubre de 2024.
[^10]: Elezioni in Olanda, che è il sovranista Wilders: anti-Islam, contro l’Ue e sostenitore del Grande Israele, www.open.online, 23 de noviembre de 2023.
[^11]: www.informazionecorretta.com, 26 de octubre de 2024.
[^12]: www.agenzianova.com, 6 de octubre de 2024.
[^13]: Especial: André Ventura. «Sou contra o aborto mas nunca condenaria uma mulher que aborta», «Jornal SOL», 12 de julio de 2022.
[^14]: Ventura admite tropas portuguesas na Ucrânia e tem uma posição clara sobre Putin, «CNN Portugal», 11 de marzo de 2024.
[^15]: Sophie Makris, Austria’s Jews wary of far-right charm offensive, www.timeofisrael.com, 3 de marzo de 2019.
[^16]: Yossi Melman, Sichrovsky Denies He Was a Mossad Agent, www.haaretz.com, 3 de junio de 2005.
[^17]: Fernando Heller, Spagna: il leader di Vox pretende le scuse di Sánchez per aver messo in dubbio l’offensiva israeliana contro Hamas, https://euractiv.it, 6 de diciembre de 2023.
[^18]: El ultraderechista Vox defiende los ataques de Israel en Gaza tras la polémica reunión con Netanyahu, euronews, 29 de mayo de 2024.
[^19]: Bruno Vespa, Vannacci: «Dopo l’Ue tornerei nell’esercito», «La Verità», 30 de octubre de 2024, p. 7.
[^20]: Missione Iraq: Riconoscimento al Generale Roberto Vannacci, en www.difesa.it , cit. en www.wikipedia.org
Artículo original: Hipérbola Janus, Patriots (TOR), 9/Ene/2025
-
 @ a60e79e0:1e0e6813
2025-03-28 08:47:35
@ a60e79e0:1e0e6813
2025-03-28 08:47:35This is a long form note of a post that lives on my Nostr educational website Hello Nostr.
When most people stumble across Nostr, they see is as a 'decentralized social media alternative' — something akin to Twitter (X), but free from corporate control. But the full name, "Notes and Other Stuff Transmitted by Relays", gives a clue that there’s more to it than just posting short messages. The 'notes' part is easy to grasp because it forms almost everyone's first touch point with the protocol. But the 'other stuff'? That’s where Nostr really gets exciting. The 'other stuff' is all the creative and experimental things people are building on Nostr, beyond simple text based notes.
Every action on Nostr is an event, a like, a post, a profile update, or even a payment. The 'Kind' is what specifies the purpose of each event. Kinds are the building blocks of how information is categorized and processed on the network, and the most popular become part of higher lever specification guidelines known as Nostr Implementation Possibility - NIP. A NIP is a document that defines how something in Nostr should work, including the rules, standards, or features. NIPs define the type of 'other stuff' that be published and displayed by different styles of client to meet different purposes.
Nostr isn’t locked into a single purpose. It’s a foundation for whatever 'other stuff' you can dream up.
Types of Other Stuff
The 'other stuff' name is intentionally vague. Why? Because the possibilities of what can fall under this category are quite literally limitless. In the short time since Nostr's inception, the number of sub-categories that have been built on top of the Nostr's open protocol is mind bending. Here are a few examples:
- Long-Form Content: Think blog posts or articles. NIP-23.
- Private Messaging: Encrypted chats between users. NIP-04.
- Communities: Group chats or forums like Reddit. NIP-72
- Marketplaces: People listing stuff for sale, payable with zaps. NIP-15
- Zaps: Value transfer over the Lightning Network. NIP57

Popular 'Other Stuff' Clients
Here's a short list of some of the most recent and popular apps and clients that branch outside of the traditional micro-blogging use case and leverage the openness, and interoperability that Nostr can provide.
Blogging (Long Form Content)
- Habla - Web app for Nostr based blogs
- Highlighter - Web app that enables users to highlight, store and share content
Group Chats
- Chachi Chat - Relay-based (NIP-29) group chat client
- 0xchat - Mobile based secure chat
- Flotilla - Web based chat app built for self-hosted communities
- Nostr Nests - Web app for audio chats
- White Noise - Mobile based secure chat
Marketplaces
- Shopstr - Permissionless marketplace for web
- Plebeian Market - Permissionless marketplace for web
- LNBits Market - Permissionless marketplace for your node
- Mostro - Nostr based Bitcoin P2P Marketplace
Photo/Video
Music
- Fountain - Podcast app with Nostr features
- Wavlake - A music app supporting the value-for-value ecosystem
Livestreaming
- Zap.stream - Nostr native live streams
Misc
- Wikifreedia - Nostr based Wikipedia alternative
- Wikistr - Nostr based Wikipedia alternative
- Pollerama - Nostr based polls
- Zap Store - The app store powered by your social graph
The 'other stuff' in Nostr is what makes it special. It’s not just about replacing Twitter or Facebook, it’s about building a decentralized ecosystem where anything from private chats to marketplaces can thrive. The beauty of Nostr is that it’s a flexible foundation. Developers can dream up new ideas and build them into clients, and the relays just keep humming along, passing the data around. It’s still early days, so expect the 'other stuff' to grow wilder and weirder over time!
You can explore the evergrowing 'other stuff' ecosystem at NostrApps.com, Nostr.net and Awesome Nostr.
-
 @ fe02e8ec:f07fbe0b
2025-03-31 14:43:22
@ fe02e8ec:f07fbe0b
2025-03-31 14:43:22\ Und genau dafür wirst auch du gedrillt werden: Menschen zu jagen und töten. Unbekannte, die auch nicht wissen, was sie hier tun. Oder Unschuldige, die nicht rechtzeitig fliehen konnten. Einfach töten. Alle. Ohne zu fragen. Denn das ist deine Aufgabe, Soldat: Töte Menschen!
Egal, was du vorher warst, Heizungsmonteur, KFZ-Mechaniker, Veganer, Marketing-Manager, Friseur, Verkäufer, Kindergärtner: Es ist egal. Jetzt musst du töten. Denn du hast mitgemacht. Entweder, weil du es nicht ernst genommen hast, weil du dich nie für Politik interessiert hast. Oder weil du gedacht hast, das alles betrifft dich nicht. Weil du gedacht hast, Wahlen könnten etwas verändern. Oder weil du immer das Maul gehalten hast, damit dich keiner als «Rechter» bezeichnet. Egal. Jetzt musst du töten. Das ist das Spiel.
Ja, es ist ein Spiel. Grausam, abartig, menschenverachtend. Dennoch hat es Regeln: Diejenigen, die das Spiel beginnen, müssen niemals selbst auf das Schlachtfeld. Das ist die erste Regel. Ihre Söhne auch nicht, nicht die Söhne der anderen Politiker, nicht die der EU-Abgeordneten, nicht die der Parteibonzen. Auch nicht die der Banker, der Vorstandsvorsitzenden, der Chefredakteure. Denn alle wissen, wie man das Spiel spielt. Nur du nicht.
Du bist einfach eine Figur auf dem Spielfeld, die es verpasst hat, NEIN zu sagen, als noch Gelegenheit war. Jetzt bist du verwandelt worden in eine menschliche Drohne. Wenn sie sagen: töte!, dann tötest du. Denken kannst du, wenn alles vorbei ist. Falls du je wieder nach Hause kommst. Vielleicht sogar mit beiden Beinen und beiden Armen. Vielleicht auch nicht. Egal. Wer hätte Mitleid mit einer Spielfigur?
Nein, du musst töten. Das ist deine Aufgabe. Sie sagen es nun schon seit Monaten, warum glaubst du es nicht? Sie meinen es ernst. Wenn du den Brief in Händen hältst ist es zu spät. Es gilt dann das Notstandsrecht und keiner kann mehr verweigern. Da hättest du dich vorher drum kümmern müssen. Oder auf eine Demo gehen. Oder laut und mit klarer Stimme in jedem Gespräch den Wahnsinn anprangern. Hast du aber nicht.
Jetzt musst du töten oder du wirst getötet. Das ist das Spiel. Du hättest selbst denken können. Hast du aber nicht. Hast deine Zeit mit sinnlosen Videos vertan, Netflix geguckt und hast Influencerinnen geliked. Die müssen nicht an die Front. Aber du. Morgen, wenn du aufstehst, die Uniform anziehst und rausgehst, dann wirst du Befehle ausführen oder erschossen werden. Also wirst du Menschen töten. Dein Leben wird nie wieder so sein, wie zuvor. Dein Schmerz, deine Schuld, dein Leid: sie gehen ein in die unendliche Reihe der Soldaten, die seit Jahrhunderten dasselbe Schicksal erlitten. Deren Schreie noch immer durch den ewigen Raum hallen. Deren Opfer von den Herren des Spiels mit einem Lächeln entgegengenommen wurde. Deren Gliedmaßen auf den Schlachtfeldern liegen geblieben waren. Zum Dank erhielten sie eine Medaille. Ein Stück Blech für den rechten Arm, einen Grabstein für den Vater, den Bruder, den Sohn. Für das Vaterland. Für Europa. Für die Demokratie. Der Hohn tropft aus jedem Politikerwort, doch die Menschen glauben noch immer die uralte Geschichte von Freund und Feind, von Gut und Böse.

\ Wer nicht aufwachen will muss töten. Du. Nicht am Bildschirm. In der echten Welt. Wo man nicht auf Replay drücken kann. Wo man den Gegner nicht nach links oder rechts swipen kann, denn er ist echt, real, lebendig. Noch. Entweder er oder du. Jetzt ist es zu spät für Entscheidungen. Kannst du es spüren? Die Work-Life Balance wird zur Kill-or-be-Killed balance. Es gibt kein Entrinnen. Denn du hast mitgemacht. Schweigen ist Zustimmung. Sich-nicht-drumkümmern ist Zustimmung. Kriegsparteien zu wählen ist noch mehr Zustimmung.
Heute.
Heute lässt sich noch etwas ändern.
Es hat nichts zu tun mit rechts oder links. Nur mit Menschlichkeit versus Hass, Macht und dem ganz großen Geld. Das sind die Gründe, für die du töten oder sterben musst.
Wie entscheidest du dich?
-
 @ b4403b24:83542d4e
2025-03-31 14:31:53
@ b4403b24:83542d4e
2025-03-31 14:31:53🚀 Bitcoin Enthusiasts! Tomorrow the price of #BTCPrague2025 tickets goes up so take advantage of the 10% discount using code from the video - BTCBULGARIA.
✅ Network with leaders ✅ Learn blockchain strategies ✅ Gain crypto insights
Secure your spot NOW!
Bitcoin #BTC #BTCPrague
originally posted at https://stacker.news/items/930210
-
 @ f1989a96:bcaaf2c1
2025-03-27 13:53:14
@ f1989a96:bcaaf2c1
2025-03-27 13:53:14Good morning, readers!
Turkey’s currency plunged to a record low after the arrest of Istanbul Mayor Ekrem Imamoglu, one of President Recep Tayyip Erdogan’s main political rivals. This follows a pattern of escalating repression of opposition figures, which have been described as an effort to suppress competition ahead of primary elections. As economic conditions deteriorate, Erdogan is resorting to desperate measures — blocking social media, arresting dissenters, and tear-gassing protests — to maintain power over an increasingly restless populace.
In the Caribbean, we shed light on Cubans' struggles accessing remittances sent from family members abroad. This is a symptom of the regime's strict monetary controls over foreign currency. Cubans face long delays or can’t withdraw cash due to bank liquidity shortages. And when they can, remittances are converted into pesos at the overvalued official Cuban exchange rate. This effectively allows the Communist Party of Cuba (PCC) to loot the value from Cuban remittances.
In freedom tech news, we highlight Demand Pool, the first-ever Stratum V2 mining pool. Stratum V2 is a mining protocol designed to decentralize Bitcoin mining by letting individual miners create their own block templates rather than relying on centralized pools to do so for them. This improves censorship resistance and promotes a more decentralized and resilient Bitcoin network — critical features for human rights defenders and nonprofits using Bitcoin to protect against financial repression from authoritarian regimes.
We end by featuring Vijay Selvam's new book, “Principles of Bitcoin.” It offers a clear, first-principles guide to understanding how Bitcoin’s technology interacts with economics, politics, philosophy, and human rights. Whether you’re new to Bitcoin or looking to deepen your understanding, this book provides a solid foundation, and it even features a foreword by HRF Chief Strategy Officer Alex Gladstein.
Now, let’s dive right in!
Subscribe Here
GLOBAL NEWS
Turkey | Lira in Free Fall as Erdogan Arrests Political Rival
Turkey’s lira plunged to a record low after officials arrested Istanbul Mayor Ekrem Imamoglu, President Recep Tayyip Erdogan’s main political rival. Imamoglu’s arrest comes ahead of primary elections and follows the increasing repression of opposition figures in recent months, including the suspension of political opposition accounts on X. Officials also arrested Buğra Gökçe, head of the Istanbul Planning Agency, for publishing data exposing the country’s deepening poverty. The currency’s fallout and political repression have sparked protests in Istanbul despite a four-day ban. The regime is responding with tear gas and rubber bullets. Meanwhile, Turks dissenting online risk joining over a dozen other citizens recently arrested for “provocative” social media posts. Netblocks reports that the Turkish regime imposed restrictions on social media and messaging to quell the uprising of Turks struggling with financial conditions and deepening repression.
Cuba | Banks “Hijack” Citizen Remittances
Cubans are struggling to access remittances sent from their families abroad. This is because the regime completely controls all incoming foreign currency transfers. When remittances arrive, communist banking authorities force their conversion into collapsing Cuban pesos or “Moneda Libremente Convertible” (MLC), Cuba’s digital currency with limited use. On top of this, Cubans receive pesos in their accounts based on the official Cuban exchange rate, which is far below the informal market rate. This allows the regime to opaquely siphon off much of the remittances’ real value. Even when the money clears, Cubans face long delays or can’t withdraw the cash due to banks’ liquidity shortages. Many Cubans are accusing these banks of “hijacking” their remittances. As inflation, electrical blackouts, and food shortages continue, remittances are more critical than ever for Cuban families. Yet, they’re blocked at every turn by a system designed to impoverish them.
Pakistan | Announces Plans to Regulate Digital Assets
Pakistan announced plans to create a regulatory framework for Bitcoin and digital assets to attract foreign investment and domestic economic activity. It’s a peculiar shift for a regime that regularly suspends the Internet, censors social media, represses opposition, and burdens its people with the highest cost of living in Asia. We suspect the plans indicate efforts to control the industry rather than empower individuals. The military-backed regime is also exploring a Central Bank Digital Currency (CBDC) and tightening controls on VPN use, which are hardly the hallmarks of leadership committed to permissionless financial systems. But perhaps it matters little. Grassroots Bitcoin adoption in Pakistan already ranks among the highest in the world, with an estimated 15 to 20 million users turning to digital assets to preserve their savings, circumvent financial controls, and escape the failures of a collapsing fiat system. HRF supported Bitcoin Pakistan with a grant to help translate resources into Urdu, a language spoken by 60 million people trapped in this repressive scenario.
Russia | Piloting CBDC in Tatarstan to Test Smart Contract Functionality
Russia’s central bank plans to pilot its CBDC, the digital ruble, in Tatarstan to test smart contract functionality. Specifically, the central bank will experiment with conditional spending, using smart contracts to restrict where and what users can spend money on. If these features are implemented, it will empower the Kremlin with micro-controls over Russians’ spending activity. Officials could program funds to expire, restrict purchases to regime-approved goods, or block transactions at certain locations — leaving users with no financial autonomy or privacy. Those who oppose the Russian dictatorship, such as activists, nonprofits, and dissenters, could be debanked with more ease, their assets frozen or confiscated without recourse.
Nicaragua | Government Mandates Public Employees Declare All Assets
In Nicaragua, dictator Daniel Ortega intensified state financial surveillance by mandating all public servants to disclose information on all personal and family assets. The mandate requires all public employees to declare everything from personal bank accounts, loans, vehicles, and other assets — as well as the assets and accounts of immediate family members. Those who do not comply face the threat of termination. Ironically, despite the law requiring such disclosure, Ortega himself has not declared his assets since 2006. Under the guise of regulatory compliance, this policy is yet another link in the chain tightening state surveillance over Nicaraguan society. Bitcoin adoption continues to grow in this repressed Central American nation.
BITCOIN AND FREEDOM TECH NEWS
Demand Pool | First Stratum V2 Mining Pool Launches
Bitcoin mining could become more decentralized and censorship-resistant with the launch of Demand Pool, the first mining pool to ever implement Stratum V2. Stratum V2 is open-source software that allows miners to build their own block templates, enabling more individual mining and less dependence on large and centralized mining pools. This helps maintain Bitcoin’s key features: its decentralized, permissionless, and uncensorable nature. All of which are crucial for human rights defenders and nonprofits bypassing the financial repression and surveillance of authoritarian regimes. Learn more here.
Bitcoin Mining | Three Solo Blocks Found
Three separate solo miners mined Bitcoin blocks in the past seven days. This marks the second, third, and fourth solo blocks mined in the past two weeks alone, hinting at a surge in home mining. This promotes greater decentralization within the Bitcoin network because solo miners have little functional ability to censor. In contrast, large mining pools are points of failure that centralized interests can more easily pressure — to the detriment of activists and human rights defenders. The first block was mined on March 21 by a miner using a self-hosted FutureBit Apollo machine that earned 3.125 BTC plus fees for processing block 888,737. Just days later, a solo miner with under 1 TH/s of self-hosted hash rate found block 888,989, which became just the third block ever to be mined using an open-source Bitaxe device. Most recently, on March 24, a solo miner using a $300 setup successfully mined block 889,240.
Krux | Adds Taproot and Miniscript Support
Krux, open-source software for building your own Bitcoin signing devices (hardware for Bitcoin self-custody), released an update that enhances privacy and flexibility. The update introduces support for Taproot, a past Bitcoin upgrade that improves privacy and security, and Miniscript, a simplified way to create more complex Bitcoin transaction rules. This allows users to manage multi-signature wallets (where more than one private key is required to interact with your Bitcoin) in a more private and flexible way. It also enables spending conditions that are harder to censor and easier to verify. Krux continues to support the struggle for financial freedom and human rights by breaking down barriers to Bitcoin self-custody. HRF has recognized this impact and awarded grants to open-source developers working on Krux to advance this mission.
Cashu | Developing Tap-to-Pay Ecash
Calle, the creator of Cashu, an open-source Chaumian ecash protocol for Bitcoin integrated with the Lightning Network, is developing a new tap-to-pay feature that enables instant, offline ecash payments via NFC. Ecash functions as a bearer asset, meaning the funds are stored directly on the user’s device. With tap-to-pay, it can be transferred with a single tap (similar to tapping your credit card). More generally, ecash offers fast, private transactions resistant to surveillance and censorship. But for activists and dissenters, this particular advancement makes private and permissionless payments more accessible and user-friendly. This development will be worth following closely. Watch a demo here.
OpenSats | Announces 10th Wave of Bitcoin Grants
OpenSats, a public nonprofit that supports open-source software and projects, announced its 10th wave of grants supporting Bitcoin initiatives. This round includes funding for Stable Channels, which enable stabilized Bitcoin-backed balances on the Lightning Network (allowing users to peg Bitcoin to fiat currencies in a self-custodial way) that provide stable, censorship-resistant payments. OpenSats also renewed its support for Floresta, a lightweight Bitcoin node (a computer that runs the Bitcoin software). It lowers entry barriers to running Bitcoin, helping make the network more decentralized and censorship-resistant.
Bitcoin Policy Institute | Launches Bitcoin Summer Research Program
The Bitcoin Student Network (BSN) and the Bitcoin Policy Institute (BPI) are teaming up to offer students an eight-week research internship this summer. The program is part of BPI’s Research Experiences for Undergraduates (REU) initiative and invites students passionate about the future of money, financial inclusion, and Bitcoin’s civil liberties impacts to conduct hands-on research. Participants will also receive mentorship from BPI researchers. The program runs from June 9 to Aug. 8, 2025, and includes an in-person colloquium in Washington, DC. It is an incredible opportunity for students worldwide, especially those living in oppressive regimes, to get involved with Bitcoin. Applications are open until April 7. Apply here.
RECOMMENDED CONTENT
Principles of Bitcoin by Vijay Selvam
“Principles of Bitcoin” by Vijay Selvam is a new book offering a first-principles guide to understanding Bitcoin’s technology, economics, politics, and philosophy. With a foreword by HRF Chief Strategy Officer Alex Gladstein, the book cuts through the noise to explain why Bitcoin stands alone as a tool for individual empowerment and financial freedom. Selvam’s work makes the case for Bitcoin as a once-in-history invention shaping a more decentralized and equitable future. Read it here.
Rule Breakers — The True Story of Roya Mahboob
“Rule Breakers” is a new film that tells the true story of Roya Mahboob, Afghanistan’s first female tech CEO, who empowered young girls in Afghanistan with financial literacy, robotics, and financial freedom through Bitcoin. The film recounts Mahboob’s courageous work educating these girls despite huge personal risks under a regime that bans their education. It follows the story of Afghan Dreamers, the country’s first all-girls robotics team, and the obstacles they overcome to compete on the world stage. “Rule Breakers” is a testament to the power of education, innovation, and resilience in the face of oppression. It’s now in theaters, and you can watch the trailer here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 9dd283b1:cf9b6beb
2025-03-31 13:21:08
@ 9dd283b1:cf9b6beb
2025-03-31 13:21:08Do you still feel anxiety when Bitcoin's price drops significantly, even though you're in fiat profit (100% +) ? Why or why not? And when did you truly stop feeling any emotional attachment to the price fluctuations?
originally posted at https://stacker.news/items/930139
-
 @ 6b3780ef:221416c8
2025-03-26 18:42:00
@ 6b3780ef:221416c8
2025-03-26 18:42:00This workshop will guide you through exploring the concepts behind MCP servers and how to deploy them as DVMs in Nostr using DVMCP. By the end, you'll understand how these systems work together and be able to create your own deployments.
Understanding MCP Systems
MCP (Model Context Protocol) systems consist of two main components that work together:
- MCP Server: The heart of the system that exposes tools, which you can access via the
.listTools()method. - MCP Client: The interface that connects to the MCP server and lets you use the tools it offers.
These servers and clients can communicate using different transport methods:
- Standard I/O (stdio): A simple local connection method when your server and client are on the same machine.
- Server-Sent Events (SSE): Uses HTTP to create a communication channel.
For this workshop, we'll use stdio to deploy our server. DVMCP will act as a bridge, connecting to your MCP server as an MCP client, and exposing its tools as a DVM that anyone can call from Nostr.
Creating (or Finding) an MCP Server
Building an MCP server is simpler than you might think:
- Create software in any programming language you're comfortable with.
- Add an MCP library to expose your server's MCP interface.
- Create an API that wraps around your software's functionality.
Once your server is ready, an MCP client can connect, for example, with
bun index.js, and then call.listTools()to discover what your server can do. This pattern, known as reflection, makes Nostr DVMs and MCP a perfect match since both use JSON, and DVMs can announce and call tools, effectively becoming an MCP proxy.Alternatively, you can use one of the many existing MCP servers available in various repositories.
For more information about mcp and how to build mcp servers you can visit https://modelcontextprotocol.io/
Setting Up the Workshop
Let's get hands-on:
First, to follow this workshop you will need Bun. Install it from https://bun.sh/. For Linux and macOS, you can use the installation script:
curl -fsSL https://bun.sh/install | bash-
Choose your MCP server: You can either create one or use an existing one.
-
Inspect your server using the MCP inspector tool:
bash npx @modelcontextprotocol/inspector build/index.js arg1 arg2This will: - Launch a client UI (default: http://localhost:5173)
- Start an MCP proxy server (default: port 3000)
-
Pass any additional arguments directly to your server
-
Use the inspector: Open the client UI in your browser to connect with your server, list available tools, and test its functionality.
Deploying with DVMCP
Now for the exciting part – making your MCP server available to everyone on Nostr:
-
Navigate to your MCP server directory.
-
Run without installing (quickest way):
npx @dvmcp/bridge -
Or install globally for regular use:
npm install -g @dvmcp/bridge # or bun install -g @dvmcp/bridgeThen run using:bash dvmcp-bridge
This will guide you through creating the necessary configuration.
Watch the console logs to confirm successful setup – you'll see your public key and process information, or any issues that need addressing.
For the configuration, you can set the relay as
wss://relay.dvmcp.fun, or use any other of your preferenceTesting and Integration
- Visit dvmcp.fun to see your DVM announcement.
- Call your tools and watch the responses come back.
For production use, consider running dvmcp-bridge as a system service or creating a container for greater reliability and uptime.
Integrating with LLM Clients
You can also integrate your DVMCP deployment with LLM clients using the discovery package:
-
Install and use the
@dvmcp/discoverypackage:bash npx @dvmcp/discovery -
This package acts as an MCP server for your LLM system by:
- Connecting to configured Nostr relays
- Discovering tools from DVMCP servers
-
Making them available to your LLM applications
-
Connect to specific servers or providers using these flags: ```bash # Connect to all DVMCP servers from a provider npx @dvmcp/discovery --provider npub1...
# Connect to a specific DVMCP server npx @dvmcp/discovery --server naddr1... ```
Using these flags, you wouldn't need a configuration file. You can find these commands and Claude desktop configuration already prepared for copy and paste at dvmcp.fun.
This feature lets you connect to any DVMCP server using Nostr and integrate it into your client, either as a DVM or in LLM-powered applications.
Final thoughts
If you've followed this workshop, you now have an MCP server deployed as a Nostr DVM. This means that local resources from the system where the MCP server is running can be accessed through Nostr in a decentralized manner. This capability is powerful and opens up numerous possibilities and opportunities for fun.
You can use this setup for various use cases, including in a controlled/local environment. For instance, you can deploy a relay in your local network that's only accessible within it, exposing all your local MCP servers to anyone connected to the network. This setup can act as a hub for communication between different systems, which could be particularly interesting for applications in home automation or other fields. The potential applications are limitless.
However, it's important to keep in mind that there are security concerns when exposing local resources publicly. You should be mindful of these risks and prioritize security when creating and deploying your MCP servers on Nostr.
Finally, these are new ideas, and the software is still under development. If you have any feedback, please refer to the GitHub repository to report issues or collaborate. DVMCP also has a Signal group you can join. Additionally, you can engage with the community on Nostr using the #dvmcp hashtag.
Useful Resources
- Official Documentation:
- Model Context Protocol: modelcontextprotocol.org
-
DVMCP.fun: dvmcp.fun
-
Source Code and Development:
- DVMCP: github.com/gzuuus/dvmcp
-
DVMCP.fun: github.com/gzuuus/dvmcpfun
-
MCP Servers and Clients:
- Smithery AI: smithery.ai
- MCP.so: mcp.so
-
Glama AI MCP Servers: glama.ai/mcp/servers
Happy building!
- MCP Server: The heart of the system that exposes tools, which you can access via the
-
 @ b2d670de:907f9d4a
2025-03-25 20:17:57
@ b2d670de:907f9d4a
2025-03-25 20:17:57This guide will walk you through setting up your own Strfry Nostr relay on a Debian/Ubuntu server and making it accessible exclusively as a TOR hidden service. By the end, you'll have a privacy-focused relay that operates entirely within the TOR network, enhancing both your privacy and that of your users.
Table of Contents
- Prerequisites
- Initial Server Setup
- Installing Strfry Nostr Relay
- Configuring Your Relay
- Setting Up TOR
- Making Your Relay Available on TOR
- Testing Your Setup]
- Maintenance and Security
- Troubleshooting
Prerequisites
- A Debian or Ubuntu server
- Basic familiarity with command line operations (most steps are explained in detail)
- Root or sudo access to your server
Initial Server Setup
First, let's make sure your server is properly set up and secured.
Update Your System
Connect to your server via SSH and update your system:
bash sudo apt update sudo apt upgrade -ySet Up a Basic Firewall
Install and configure a basic firewall:
bash sudo apt install ufw -y sudo ufw allow ssh sudo ufw enableThis allows SSH connections while blocking other ports for security.
Installing Strfry Nostr Relay
This guide includes the full range of steps needed to build and set up Strfry. It's simply based on the current version of the
DEPLOYMENT.mddocument in the Strfry GitHub repository. If the build/setup process is changed in the repo, this document could get outdated. If so, please report to me that something is outdated and check for updated steps here.Install Dependencies
First, let's install the necessary dependencies. Each package serves a specific purpose in building and running Strfry:
bash sudo apt install -y git build-essential libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev liblmdb-dev libflatbuffers-dev libsecp256k1-dev libzstd-devHere's why each dependency is needed:
Basic Development Tools: -
git: Version control system used to clone the Strfry repository and manage code updates -build-essential: Meta-package that includes compilers (gcc, g++), make, and other essential build toolsPerl Dependencies (used for Strfry's build scripts): -
libyaml-perl: Perl interface to parse YAML configuration files -libtemplate-perl: Template processing system used during the build process -libregexp-grammars-perl: Advanced regular expression handling for Perl scriptsCore Libraries for Strfry: -
libssl-dev: Development files for OpenSSL, used for secure connections and cryptographic operations -zlib1g-dev: Compression library that Strfry uses to reduce data size -liblmdb-dev: Lightning Memory-Mapped Database library, which Strfry uses for its high-performance database backend -libflatbuffers-dev: Memory-efficient serialization library for structured data -libsecp256k1-dev: Optimized C library for EC operations on curve secp256k1, essential for Nostr's cryptographic signatures -libzstd-dev: Fast real-time compression algorithm for efficient data storage and transmissionClone and Build Strfry
Clone the Strfry repository:
bash git clone https://github.com/hoytech/strfry.git cd strfryBuild Strfry:
bash git submodule update --init make setup-golpe make -j2 # This uses 2 CPU cores. Adjust based on your server (e.g., -j4 for 4 cores)This build process will take several minutes, especially on servers with limited CPU resources, so go get a coffee and post some great memes on nostr in the meantime.
Install Strfry
Install the Strfry binary to your system path:
bash sudo cp strfry /usr/local/binThis makes the
strfrycommand available system-wide, allowing it to be executed from any directory and by any user with the appropriate permissions.Configuring Your Relay
Create Strfry User
Create a dedicated user for running Strfry. This enhances security by isolating the relay process:
bash sudo useradd -M -s /usr/sbin/nologin strfryThe
-Mflag prevents creating a home directory, and-s /usr/sbin/nologinprevents anyone from logging in as this user. This is a security best practice for service accounts.Create Data Directory
Create a directory for Strfry's data:
bash sudo mkdir /var/lib/strfry sudo chown strfry:strfry /var/lib/strfry sudo chmod 755 /var/lib/strfryThis creates a dedicated directory for Strfry's database and sets the appropriate permissions so that only the strfry user can write to it.
Configure Strfry
Copy the sample configuration file:
bash sudo cp strfry.conf /etc/strfry.confEdit the configuration file:
bash sudo nano /etc/strfry.confModify the database path:
```
Find this line:
db = "./strfry-db/"
Change it to:
db = "/var/lib/strfry/" ```
Check your system's hard limit for file descriptors:
bash ulimit -HnUpdate the
nofilessetting in your configuration to match this value (or set to 0):```
Add or modify this line in the config (example if your limit is 524288):
nofiles = 524288 ```
The
nofilessetting determines how many open files Strfry can have simultaneously. Setting it to your system's hard limit (or 0 to use the system default) helps prevent "too many open files" errors if your relay becomes popular.You might also want to customize your relay's information in the config file. Look for the
infosection and update it with your relay's name, description, and other details.Set ownership of the configuration file:
bash sudo chown strfry:strfry /etc/strfry.confCreate Systemd Service
Create a systemd service file for managing Strfry:
bash sudo nano /etc/systemd/system/strfry.serviceAdd the following content:
```ini [Unit] Description=strfry relay service
[Service] User=strfry ExecStart=/usr/local/bin/strfry relay Restart=on-failure RestartSec=5 ProtectHome=yes NoNewPrivileges=yes ProtectSystem=full LimitCORE=1000000000
[Install] WantedBy=multi-user.target ```
This systemd service configuration: - Runs Strfry as the dedicated strfry user - Automatically restarts the service if it fails - Implements security measures like
ProtectHomeandNoNewPrivileges- Sets resource limits appropriate for a relayEnable and start the service:
bash sudo systemctl enable strfry.service sudo systemctl start strfryCheck the service status:
bash sudo systemctl status strfryVerify Relay is Running
Test that your relay is running locally:
bash curl localhost:7777You should see a message indicating that the Strfry relay is running. This confirms that Strfry is properly installed and configured before we proceed to set up TOR.
Setting Up TOR
Now let's make your relay accessible as a TOR hidden service.
Install TOR
Install TOR from the package repositories:
bash sudo apt install -y torThis installs the TOR daemon that will create and manage your hidden service.
Configure TOR
Edit the TOR configuration file:
bash sudo nano /etc/tor/torrcScroll down to wherever you see a commented out part like this: ```
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 80 127.0.0.1:80
```
Under those lines, add the following lines to set up a hidden service for your relay:
HiddenServiceDir /var/lib/tor/strfry-relay/ HiddenServicePort 80 127.0.0.1:7777This configuration: - Creates a hidden service directory at
/var/lib/tor/strfry-relay/- Maps port 80 on your .onion address to port 7777 on your local machine - Keeps all traffic encrypted within the TOR networkCreate the directory for your hidden service:
bash sudo mkdir -p /var/lib/tor/strfry-relay/ sudo chown debian-tor:debian-tor /var/lib/tor/strfry-relay/ sudo chmod 700 /var/lib/tor/strfry-relay/The strict permissions (700) are crucial for security as they ensure only the debian-tor user can access the directory containing your hidden service private keys.
Restart TOR to apply changes:
bash sudo systemctl restart torMaking Your Relay Available on TOR
Get Your Onion Address
After restarting TOR, you can find your onion address:
bash sudo cat /var/lib/tor/strfry-relay/hostnameThis will output something like
abcdefghijklmnopqrstuvwxyz234567.onion, which is your relay's unique .onion address. This is what you'll share with others to access your relay.Understanding Onion Addresses
The .onion address is a special-format hostname that is automatically generated based on your hidden service's private key.
Your users will need to use this address with the WebSocket protocol prefix to connect:
ws://youronionaddress.onionTesting Your Setup
Test with a Nostr Client
The best way to test your relay is with an actual Nostr client that supports TOR:
- Open your TOR browser
- Go to your favorite client, either on clearnet or an onion service.
- Check out this list of nostr clients available over TOR.
- Add your relay URL:
ws://youronionaddress.onionto your relay list - Try posting a note and see if it appears on your relay
- In some nostr clients, you can also click on a relay to get information about it like the relay name and description you set earlier in the stryfry config. If you're able to see the correct values for the name and the description, you were able to connect to the relay.
- Some nostr clients also gives you a status on what relays a note was posted to, this could also give you an indication that your relay works as expected.
Note that not all Nostr clients support TOR connections natively. Some may require additional configuration or use of TOR Browser. E.g. most mobile apps would most likely require a TOR proxy app running in the background (some have TOR support built in too).
Maintenance and Security
Regular Updates
Keep your system, TOR, and relay updated:
```bash
Update system
sudo apt update sudo apt upgrade -y
Update Strfry
cd ~/strfry git pull git submodule update make -j2 sudo cp strfry /usr/local/bin sudo systemctl restart strfry
Verify TOR is still running properly
sudo systemctl status tor ```
Regular updates are crucial for security, especially for TOR which may have security-critical updates.
Database Management
Strfry has built-in database management tools. Check the Strfry documentation for specific commands related to database maintenance, such as managing event retention and performing backups.
Monitoring Logs
To monitor your Strfry logs:
bash sudo journalctl -u strfry -fTo check TOR logs:
bash sudo journalctl -u tor -fMonitoring logs helps you identify potential issues and understand how your relay is being used.
Backup
This is not a best practices guide on how to do backups. Preferably, backups should be stored either offline or on a different machine than your relay server. This is just a simple way on how to do it on the same server.
```bash
Stop the relay temporarily
sudo systemctl stop strfry
Backup the database
sudo cp -r /var/lib/strfry /path/to/backup/location
Restart the relay
sudo systemctl start strfry ```
Back up your TOR hidden service private key. The private key is particularly sensitive as it defines your .onion address - losing it means losing your address permanently. If you do a backup of this, ensure that is stored in a safe place where no one else has access to it.
bash sudo cp /var/lib/tor/strfry-relay/hs_ed25519_secret_key /path/to/secure/backup/locationTroubleshooting
Relay Not Starting
If your relay doesn't start:
```bash
Check logs
sudo journalctl -u strfry -e
Verify configuration
cat /etc/strfry.conf
Check permissions
ls -la /var/lib/strfry ```
Common issues include: - Incorrect configuration format - Permission problems with the data directory - Port already in use (another service using port 7777) - Issues with setting the nofiles limit (setting it too big)
TOR Hidden Service Not Working
If your TOR hidden service is not accessible:
```bash
Check TOR logs
sudo journalctl -u tor -e
Verify TOR is running
sudo systemctl status tor
Check onion address
sudo cat /var/lib/tor/strfry-relay/hostname
Verify TOR configuration
sudo cat /etc/tor/torrc ```
Common TOR issues include: - Incorrect directory permissions - TOR service not running - Incorrect port mapping in torrc
Testing Connectivity
If you're having trouble connecting to your service:
```bash
Verify Strfry is listening locally
sudo ss -tulpn | grep 7777
Check that TOR is properly running
sudo systemctl status tor
Test the local connection directly
curl --include --no-buffer localhost:7777 ```
Privacy and Security Considerations
Running a Nostr relay as a TOR hidden service provides several important privacy benefits:
-
Network Privacy: Traffic to your relay is encrypted and routed through the TOR network, making it difficult to determine who is connecting to your relay.
-
Server Anonymity: The physical location and IP address of your server are concealed, providing protection against denial-of-service attacks and other targeting.
-
Censorship Resistance: TOR hidden services are more resilient against censorship attempts, as they don't rely on the regular DNS system and can't be easily blocked.
-
User Privacy: Users connecting to your relay through TOR enjoy enhanced privacy, as their connections are also encrypted and anonymized.
However, there are some important considerations:
- TOR connections are typically slower than regular internet connections
- Not all Nostr clients support TOR connections natively
- Running a hidden service increases the importance of keeping your server secure
Congratulations! You now have a Strfry Nostr relay running as a TOR hidden service. This setup provides a resilient, privacy-focused, and censorship-resistant communication channel that helps strengthen the Nostr network.
For further customization and advanced configuration options, refer to the Strfry documentation.
Consider sharing your relay's .onion address with the Nostr community to help grow the privacy-focused segment of the network!
If you plan on providing a relay service that the public can use (either for free or paid for), consider adding it to this list. Only add it if you plan to run a stable and available relay.
-
 @ 866e0139:6a9334e5
2025-03-31 12:44:27
@ 866e0139:6a9334e5
2025-03-31 12:44:27
Autor: Carlos A. Gebauer. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Am 18. März 1924 schenkte meine Großmutter ihren Töchtern einen kleinen Bruder. Weil sein Vater fürchtete, der Junge könnte unter seinen vier Schwestern verweichlichen, schickte er den Kleinen zu Wochenendfreizeiten einer örtlichen Pfadfindergruppe. Ein Weltkriegsveteran veranstaltete dort mit den Kindern Geländespiele quer durch die schlesischen Wälder. Man lernte, Essbares zu finden, Pilze zu bestimmen, sich im Freien zu orientieren und Feuer zu machen.
Bald wurde deutlich, dass der Heranwachsende auch nicht mehr in den Blockflötenkreis seiner Schwestern und ihrer Freundinnen passte. Das Umfeld befürwortete, sein besonderes musikalisches Talent auf das Klavierspiel und das Flügelhorn zu richten. Kontakte bei der anschließenden Kirchenmusik mündeten schließlich in den elterlichen Entschluss, den nun 14-jährigen in ein Musikschulinternat zu schicken.
Es begann der Zweite Weltkrieg
Ein Jahr später, das erste Heimweh hatte sich langsam beruhigt, änderten sich die Verhältnisse schlagartig. Es begann der Zweite Weltkrieg. Mitschüler unter den jungen Musikern erfuhren, dass ihre älteren Brüder nun Soldaten werden mussten. Noch hielt sich die Gemeinschaft der jetzt 15-jährigen im Internat aber an einer Hoffnung fest: Bis sie selbst in das wehrfähige Alter kommen würden, müsste der Krieg längst beendet sein. In dieser Stimmungslage setzten sie ihre Ausbildung fort.
Es kam anders. Für den 18-jährigen erfolgte die befürchtete Einberufung in Form des „Gestellungsbefehls“. Entsprechend seiner Fähigkeiten sah man ihn zunächst für ein Musikkorps vor und schickte ihn zu einer ersten Grundausbildung nach Südfrankreich. Bei Nizza fand er sich nun plötzlich zwischen Soldaten, die Handgranaten in das Mittelmeer warfen, um Fische zu fangen. Es war das erste Mal, dass er fürchtete, infolge Explosionslärms sein Gehör zu verlieren. In den kommenden Jahren sollte er oft die Ohren zu- und den Mund offenhalten müssen, um sich wenigstens die Möglichkeit der angezielten Berufsausübung zu erhalten – wenn es überhaupt je dazu kommen würde.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Schon nach kurzer Zeit änderte sich die Befehlslage wieder. Der Musikstudent wurde nun zum Infanteristen und nach Russland an die Front verbracht. Vor ihm lagen jetzt drei Kriegsjahre: Gewalt, Dreck, Gewehrkugeln, Panzerschlachten, Granatsplitter, Luftangriffe, Entbehrungen, Hunger, Kälte, sieben Verwundungen, Blut und Schmerzen, Sterbende überall, Tote, Schreiende. Verzweiflung. Sorgen. Ängste. Todesangst. Zurückweichen? Verboten! Und die stets klare Ansage dazu: Wer nicht da vorne gegen den Feind um sein Leben kämpft, dem wird es ganz sicher da hinten von den eigenen Kameraden genommen.
Ein gewährter Fronturlaub 1944 versprach glückliche Momente. Zurück zu den Eltern, zurück zu den Schwestern, zurück nach Freiburg. Doch die Familie war nicht zu Hause, die Türen verschlossen. Eine Nachbarin öffnete ihr Fenster und rief dem Ratlosen zu: „Beeil‘ dich! Renn‘ zum Friedhof. Der Vater ist tot. Sie sind alle bei der Beerdigung!“ Wieder hieß es, qualvoll Abschied nehmen. Zurück an die Front.
Nach einem weiteren russischen Winter brach sich unübersehbar die Erkenntnis Bahn, dass der Krieg nun seinem Ende zugehe. Doch das Bemühen im Rückzug, sich mit einem versprengten Haufen irgendwie Richtung Heimat orientieren zu können, wurde doppelt jäh unterbrochen. Fanatische Vorgesetzte befahlen die längst Geschlagenen wieder gen Osten. Kurz darauf fielen sie heranrückenden russischen Truppen in die Hände.
Kriegsgefangenschaft: Tabakration gegen Brot
Drei Jahre dem Tod entgangen, schwer verletzt und erschöpft war der 21-jährige also nun ein Kriegsgefangener. Jetzt lagen drei Jahre russischer Kriegsgefangenschaft vor ihm. Ständig war unklar, wie es weiterginge. Unmöglich jedenfalls, sich noch wie ein Pfadfinder aus den Wäldern zu ernähren. Es begannen die Jahre des Schlafens auf Brettern, die Zeit der ziellosen Zugtransporte an unbekannte Orte. Niemand sprach. Nur der Sonnenstand machte klar: Es ging nie Richtung Heimat, sondern immer weiter nach Osten. Weil der Blechbläser nicht rauchte, konnte er seine Tabakration gegen Brot tauschen. So überlebte er auch die Zeit des Hungers und der Morde in den Lagern, die Horrorbilder der nachts Erschlagenen und in die Latrinen geworfenen Toten, der sinnlosen Zwangsarbeiten und der allgegenwärtigen Wanzen. Wer versuchte zu fliehen, der wurde erschossen und sein Körper zur Abschreckung in den Fangdrähten belassen. Im Sommer stanken die dort verwesenden Leichen, wenn nicht Vögel sie rechtzeitig gefressen hatten.
Als der 24-jährige schließlich sechs Jahre nach seiner Einberufung aus russischer Kriegsgefangenschaft entlassen wurde, gab es kein Zurück mehr in seine schlesische Heimat. Abgemagert reiste er der vertriebenen Mutter nach, die mit seinen Schwestern und Millionen anderen Flüchtlingen im Westen Deutschlands verteilt worden war. Kraft Ordnungsverfügung wohnte sie jetzt im sauerländischen Bad Laasphe in einem schimmligen Garagenanbau. Als ihn ein Passant auf dieser Reise morgens allein, nur mit einem Becher an der Schnur um den Hals, auf Krücken durch Berlin ziehen sah, gab er ihm schweigend sein Butterbrot.
Der kleine, sanfte Junge aus dem schlesischen Freiburg hat danach noch 60 Jahre gelebt. Es dauerte zunächst sechs Jahre, bis er wieder kräftig genug war, ein Instrument zu spielen. 30-jährig saß er dann endlich in einem Orchester und begann ein normales Berufsleben. Aber sein Körper und seine Seele waren für immer aus jeder Normalität gerissen.
Irgendwo in Russland war ihm die linke Hüfte so versteift worden, dass sich seine Beine im Liegen an Wade und Schienbein überkreuzten. Er musste also stets den Oberkörper vorbeugen, um überhaupt laufen zu können. Über die Jahrzehnte verzog sich so sein gesamter Knochenbau. Jeder Tag brachte neue orthopädische Probleme und Schmerzen. Ärzte, Masseure, Physiotherapeuten, Schmerzmittel und Spezialausrüstungen aller Art prägten die Tagesabläufe. Asymmetrisch standen seine Schuhe nebeneinander, die ein Spezialschuster ihm mit erhöhter Sohle und Seitenstabilisierung am Knöchel fertigte. Sessel oder Sofas waren ihm nicht nutzbar, da er nur auf einem Spezialstuhl mit halb abgesenkter Sitzfläche Ruhe fand. Auf fremden Stühlen konnte er nur deren Vorderkante nutzen.
In den Nächten schrie er im Schlaf
Und auch wenn er sich ohne Krankheitstage bis zuletzt durch seinen Berufsalltag kämpfte, so gab es doch viele Tage voller entsetzlicher Schmerzen, wenn sich seine verdrehte Wirbelsäule zur Migräne in den Kopf bohrte. Bei alledem hörte man ihn allerdings niemals über sein Schicksal klagen. Er ertrug den ganzen Wahnsinn mit einer unbeschreiblichen Duldsamkeit. Nur in den Nächten schrie er bisweilen im Schlaf. In einem seiner Alpträume fürchtete er, Menschen getötet zu haben. Aber auch das erzählte er jahrzehntelang einzig seiner Frau.
Als sich einige Jahre vor seinem Tod der orthopädische Zustand weiter verschlechterte, konsultierte er einen Operateur, um Entlastungsmöglichkeiten zu erörtern. Der legte ihn auf eine Untersuchungsliege und empfahl, Verbesserungsversuche zu unterlassen, weil sie die Lage allenfalls verschlechtern konnten. In dem Moment, als er sich von der Liege erheben sollte, wurde deutlich, dass ihm dies nicht gelang. Die gereichte Hand, um ihn hochzuziehen, ignorierte er. Stattdessen rieb er seinen Rumpf ganz alleine eine quälend lange Minute über die Fläche, bis er endlich einen Winkel fand, um sich selbst in die Senkrechte zu bugsieren. Sich nicht auf andere verlassen, war sein Überlebenskonzept. Jahre später, als sich sein Zustand noch weiter verschlechtert hatte, lächelte er über seine Behinderung: „Ich hätte schon vor 60 Jahren tot auf einem Acker in Russland liegen können.“ Alles gehe irgendwann vorbei, tröstete er sich. Das war das andere Überlebenskonzept: liebevoll, friedfertig und sanft anderen gegenüber, unerbittlich mit sich selbst.
Sechs Monate vor seinem Tod saß er morgens regungslos auf seinem Spezialstuhl. Eine Altenpflegerin fand ihn und schlug Alarm. Mit allen Kunstgriffen der medizinischen Technik wurde er noch einmal in das Leben zurückkatapultiert. Aber seine Kräfte waren erschöpft. Es schob sich das Grauen der Vergangenheit zwischen ihn und die Welt. Bettlägerig kreiste er um sich selbst, erkannte niemanden und starrte mit weit offenen Augen an die Decke. „Die Russen schmeißen wieder Brandbomben!“, war einer seiner letzten Sätze.
Der kleine Junge aus Schlesien ist nicht zu weich geraten. Er hat sein Leid mit unbeugsamer Duldsamkeit ertragen. Er trug es wohl als Strafe für das Leid, das er anderen anzutun genötigt worden war. An seinem Geburtstag blühen immer die Magnolien. In diesem Jahr zum hundertsten Mal.
Dieser Text wurde am 23.3.2024 erstveröffentlicht auf „eigentümlich frei“.
Carlos A. Gebauer studierte Philosophie, Neuere Geschichte, Sprach-, Rechts- und Musikwissenschaften in Düsseldorf, Bayreuth und Bonn. Sein juristisches Referendariat absolvierte er in Düsseldorf, u.a. mit Wahlstationen bei der Landesrundfunkanstalt NRW, bei der Spezialkammer für Kassenarztrecht des Sozialgerichtes Düsseldorf und bei dem Gnadenbeauftragten der Staatsanwaltschaft Düsseldorf.
Er war unter anderem als Rechtsanwalt und Notarvertreter bis er im November 2003 vom nordrhein-westfälischen Justizministerium zum Richter am Anwaltsgericht für den Bezirk der Rechtsanwaltskammer Düsseldorf ernannt wurde. Seit April 2012 arbeitet er in der Düsseldorfer Rechtsanwaltskanzlei Lindenau, Prior & Partner. Im Juni 2015 wählte ihn die Friedrich-August-von-Hayek-Gesellschaft zu ihrem Stellvertretenden Vorsitzenden. Seit Dezember 2015 ist er Richter im Zweiten Senat des Anwaltsgerichtshofes NRW.
1995 hatte er parallel zu seiner anwaltlichen Tätigkeit mit dem Verfassen gesellschaftspolitischer und juristischer Texte begonnen. Diese erschienen seither unter anderem in der Neuen Juristischen Wochenschrift (NJW), der Zeitschrift für Rechtspolitik (ZRP) in der Frankfurter Allgemeinen Zeitung, der Freien Presse Chemnitz, dem „Schweizer Monat“ oder dem Magazin für politische Kultur CICERO. Seit dem Jahr 2005 ist Gebauer ständiger Kolumnist und Autor des Magazins „eigentümlich frei“.
Gebauer glaubt als puristischer Liberaler unverbrüchlich an die sittliche Verpflichtung eines jeden einzelnen, sein Leben für sich selbst und für seine Mitmenschen verantwortlich zu gestalten; jede Fremdbestimmung durch Gesetze, staatliche Verwaltung, politischen Einfluss oder sonstige Gewalteinwirkung hat sich demnach auf ein ethisch vertretbares Minimum zu beschränken. Die Vorstellung eines europäischen Bundesstaates mit zentral detailsteuernder, supranationaler Staatsgewalt hält er für absurd und verfassungswidrig.
\ Aktuelle Bücher:
Hayeks Warnung vor der Knechtschaft (2024) – hier im Handel
Das Prinzip Verantwortungslosigkeit (2023) – hier im Handel
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 65038d69:1fff8852
2025-03-31 12:13:39
@ 65038d69:1fff8852
2025-03-31 12:13:39Artificial intelligence is upon us and not showing any signs of slowing. The most common concern from those in the workforce is being replaced by one of these “thinking machines”. But what if AI wasn’t coming for your job? What if it was coming for your boss’s job instead?
I happened across the following post on X: https://x.com/BrianRoemmele/status/1905754986795151629 Brian describes having installed an AI system that provides an omniscient “shadow” to each of the executives at a client company, which can then be queried by the CEO for reports. The CEO seems to like it so far, and if it leads to less time spent writing internal reports I’m sure the executives like it too. But many of you may be recoiling at the thought of an always-on nanycam who’s sole purpose seems to be to snitch on you to your boss, and judging by the replies to Brian’s post, you’re not alone. If your supervisor has a history of targeting you your fears may not be misplaced. Workplace surveillance tools are often coyly marketed for this.
What if instead of your boss using an AI tool to spy on you, your boss was completely replaced by an AI? Would your supervisor having no biases or favouritism sway your opinion? What about being able to tailor its communication specifically to you? Expressing no judgement at your clarifying questions? Being immediately available 24/7? Perfectly equitable expectations and performance reviews? Just writing that almost has me convinced this would usher in a workplace utopia.
In practice guaranteeing zero bias is extremely difficult. After all, these things are programmed by humans and learn from human data. Their “weights” could also be intentionally adjusted to favour or target. If the AI’s supervisor follows the Pareto Principle (also known as the 80/20 Rule) they may be tempted to ask it for a list of the lowest performing employees to be laid off on a regular basis. Not keeping yourself in the top 20% of performers (by whatever metrics the AI has been programmed to look for) may mean your job. The dystopian-future videogame “Cyberpunk 2077” tells a story of a company that brings in an AI only to have it fire all the human workers in favour of automation and copies of itself. Clearly it’s implementers forgot to set hard limits on its executive powers. The shareholders were happy with all-time high profits though…
When technology is blamed for these sorts of existential problems the IT industry collectively sighs and repeats the mantra, “The problem is not the technology. The problem is the people.” A quote from a 1979 IBM presentation is likewise summoned; “A computer can never be held accountable, therefore a computer must never make a management decision.” As a darker example, the Nuremberg trials post-WWII saw the precedent set that acting under “superior orders” is not a valid defence for war crimes or crimes against humanity. It seems responsibility can’t be passed to others, whether man or machine. The endless task of generating reports and presentations can probably be automated away though.

Would you work under an AI, or “hire” an AI to manage others? We can help you with that; you can find us at scalebright.ca.
-
 @ 0d1702d6:8f1ac66f
2025-03-31 10:45:57
@ 0d1702d6:8f1ac66f
2025-03-31 10:45:57Als Verrücktheit bezeichnen \ wir die chronische Entwicklung \ eines dauernden Wahnsystems \ bei vollkommener Erhaltung \ der Besonnenheit.
Psychiater Emil Kraepelin 1893
Es ist Teil des westlichen Wahnsystems anzunehmen, Russland habe aus imperialen Absichten heraus 2022 mit nur 130.000 Soldaten die Grenze zur Ukraine überschritten, um so die gesamte Ukraine und später wohlmöglich Westeuropa militärisch einzunehmen, wie z.B. der deutsche Kriegsminister Pistorius seit 2023 suggerierte.
Nachdem die USA bereits 2014 die berechtigten Anti-Korruptions-Proteste der Ukrainer auf dem Maidan durch massive Unterstützung für einen illegalen Putsch gegen die russlandfreundliche Regierung im Sinne des von den USA gewünschten Regimewechsels manipuliert hatten, rüsteten sie in den folgenden Jahren die Ukraine massiv auf, trainierten ihre Soldaten, bauten mehr als einen Stützpunkt und machten die zwischen Ost & West hin- und hergerissene Ukraine so zielgerichtet unterhalb offizieller NATO-Mitgliedschaft schon zu einem kampfstarken eng befreundeten Partner, dessen Krieg gegen seine eigene russisch-stämmige Bevölkerung im rohstoffreichen Donbass die NATO unter Führung der USA somit auch direkt und indirekt unterstützte.
Nachdem der Westen den Russen bei der Wiedervereinigung Deutschlands versprochen hatte, die NATO keinen Zentimeter nach Osten vorzuschieben und stattdessen ein gemeinsames europäisches Sicherheits-System unter Einbeziehung Russlands gemeinsam zu entwickeln, brachen wir diese Zusicherung mit den NATO-Osterweiterungen ab 1999 mehrfach bis heute.
Russland zeigte sich bei seiner zunehmenden Umzingelung durch NATO-Staaten wesentlich nachsichtiger als es umgekehrt die USA schon bei russischen wenigen Raketen auf Kuba 1962 jemals waren und heute sein würden!
Zugleich hatte Russland seit Beginn der NATO-Osterweiterung immer unmissverständlich klar gemacht, dass es eine Stationierung von NATO-Truppen & Raketen in der Ukraine niemals tolerieren würde. Der damalige US-Senator und 2022 US-Präsident Biden sagte schon Ende der 90'er Jahre öffentlich, man werde auf diesen Wunsch der – nach Meinung von US-Geostrategen viel zu schwächen – Russen keine Rücksicht nehmen und erwarte, dass ihnen irgendwann die Nerven ob dieser provokativen Umzingelung durchgingen…
Folgerichtig simulierten die USA und die Europäer - wie Angela Merkel bereits öffentlich eingestanden - nur Verhandlungen über die Abkommen Minsk I und II, damit genügend Zeit blieb die Ukraine aufzurüsten und diese dann einen starken militärischen Schlag gegen die russisch stämmige Bevölkerung im Donbass und die russischen Soldaten auf der Krim ausführen konnte, ein Szenario, welches Anfang 2022 durch einen Truppenaufmarsch auch auf ukrainischer Seite weit fortgeschritten vorbereitet war, bevor im Februar 2022 die russische Armee die Grenze zur Ukraine überschritt.\ \ Trotz alledem kamen schon im April 2022 Unterhändler der Ukraine und Russlands in Ankara zur Übereinkunft eines Waffenstillstandes und Friedensplans (!), der dann allerdings von dem damaligen britischen Premierminister Boris Johnson – in Kooperation mit Joe Biden – durch einen Besuch in Kiew mit dem Versprechen von grenzenlosen Waffenlieferungen \ & logistischer Unterstützung durch die USA und Westeuropa „abgetrieben“ wurde.\ \ Zunächst wurden diese Tatsachen wie üblich öffentlich in deutschen und europäischen Medien als „Verschwörungstheorie“ diffamiert, bis sie in den folgenden Monaten jedoch langsam selbst in die Mainstream-Medien Deutschlands, Europas wie den USA einsickerten.\ \ Zwischenfazit:\ Nachdem die USA ihre so und so viel gewählte globale „Regime Change“ Operation auf dem Maidan schon 10 Jahre lang vorbereitet hatten, gelang ihnen im Jahr 2014 tatsächlich zunächst einen pro-westlichen illegalen Putschpräsidenten, danach auch weitere pro-westliche Präsidenten zu installieren und einem Teil der Weltöffentlichkeit, vor allem aber ihren „Freunden“ im Westen einzureden, die „bösen Russen“ hätten diesen Krieg quasi aus dem Nichts heraus (ohne lange Vorgeschichte!) und trotz Verhandlungen (welche realen statt nur simulierten Verhandlungen?) vom Zaun gebrochen...\ \ Damit war ihr seit über 30 Jahren offen formuliertes geostrategisches Kalkül, \ die Schwäche der Russen nach Auflösung des Warschauer Paktes auszunutzen, sie mit der NATO zu umzingeln und bei Widerstand dann eben in einem kräftezehrenden Krieg stark zu schwächen und damit ein für alle Male als ökonomische Konkurrenten in Europa auszuschalten scheinbar aufgegangen...\ \ Das paranoide alte und zugleich kindliche „Freund/Feind Schema“ hatte seinen Dienst verrichtet und das „imperiale Böse“ konnte bequem auf „Putin und die Russen“ projiziert werden.
\ Schizophren ist dies auch deswegen, weil mit zweierlei Maß gemessen wurde und wird, denn niemals würden die USA auch nur eine russische Rakete auf Kuba tolerieren und gehen selber - ganz anders als Russland - global weit über die eigene Grenzsicherung hinaus, indem sie sich anmaßen, den gesamten Globus mit fast 800 Militärbasen zu überziehen und je nach Bedarf Kriege zu führen, wenn es ihnen zur Sicherung ihrer Rohstoffe - für auch unseren westlichen Lebensstil - und/oder geostrategischen Macht opportun und machbar erscheint.\ \ Deutschland spielt seit 2022 die naive und mehr als traurige Vorreiterrolle eines unterwürfigen Vasallen der so tut, als würde unsere Freiheit durch gegenseitigen Mord und Totschlag von Hunderttausenden junger Ukrainer und Russen in der Ukraine verteidigt, eine äußerst perverse und dümmliche Vorstellung ohne historische geschweige denn geo-strategische Kenntnisse und Erfahrungswerte.\ \ Demgegenüber ist klar: Es gibt nur EINE Sicherheit in Europa für alle vom Atlantik bis hinter den Ural, oder es gibt KEINE Sicherheit für Niemanden, \ wenn wir nicht die berechtigten Sicherheitsinteressen der Russen ernst nehmen, die wir, d.h. die unsere Väter und Großväter bereits im 20.Jahrhundert rücksichtslos überfallen, mit Krieg überzogen und ermordet haben.\ \ John F. Kennedy und Nikita S. Chruschtschow waren 1962 im historischen Gegenstück zum „Ukrainekrieg“, der „Kubakrise“, weise genug einen Weltkrieg durch gegenseitige Zugeständnisse zu verhindern.
Wo sind die Politiker von Format, die in ihre Fußstapfen treten?\ \ Es wäre eine bitterböse Farce, wenn ausgerechnet ein autoritärer Oligarchen-Präsident wie Donald Trump die Weisheit hätte, diesen Schritt zu tun...\ \ Zugleich wäre die öffentliche Bankrott-Erklärung aller europäischen Politiker, \ die sich als viel demokratischer, sachlicher und menschlicher ansehen \ und ihre eigene dramatische Fehlleistung wohl niemals eingestehen...\ \ Allein die politische wie mediale Empörungswelle in Deutschland, als Trump und Putin ganz offenlegten, wer denn in diesem Krieg das Sagen hat, \ lässt Schlimmstes befürchten. Obwohl aus gut unterrichteten Diplomatenkreisen längst durchgesickert ist, dass im Prinzip die gesamte Analyse hier unter Diplomaten anerkannt und ziemlich nah an den Tatsachen ist, gehört nicht viel Lebenserfahrung dazu zu wissen, dass die meisten der ach so mächtigen westeuropäischen Politiker dies nie zugeben werden...
-
 @ 27dd78c2:66ffe658
2025-03-25 17:12:08
@ 27dd78c2:66ffe658
2025-03-25 17:12:08In an age where ‘run clubs’ are getting more popular than ‘night clubs’, it’s exciting to see a Nostr-based sovereign fitness tracker hit the scene: Enter Runstr.club!
Runstr has emerged as a game-changer, redefining how runners connect, track progress, and stay motivated. For Bitcoin Runners, a movement that advocates sovereignty of one’s wealth, while improving one’s health, Runstr.club presents an exciting platform of choice to record your proof-of-work, take ownership of your personal data, and selectively engage with your social graph.
What is Runstr.club?
Runstr.club is a platform that’s being built to grow the proof-of-work community, with plans to offer interactive leaderboards, challenges, and social engagement. Unlike traditional running apps that focus purely on statistics, Runstr.club puts emphasis on camaraderie, motivation, and shared goals. It’s the Strava alternative that values ownership of your data, interoperability between platforms, and privacy as standard.
Why Runstr.club is a Great Fit for Bitcoin Runners
Bitcoin Runners isn’t just about proof-of-work; it’s about promoting freedom tech, decentralisation, and self-sovereignty principles that align closely with the ethos of Runstr.club.
Here’s why this platform is a great match for our movement:
- Community-Driven & Decentralised Spirit
Bitcoin Runners thrives on grassroots adoption and community participation, much like Runstr.club’s organic and community-focused model. Unlike corporate-owned fitness platforms that prioritise monetisation, Runstr.club is designed to empower runners, keeping the experience authentic and meaningful.
- Privacy-First Approach
One of the key concerns for bitcoiners is privacy. Mainstream fitness platforms harvest user data for profit, but Runstr.club offers a privacy-first alternative. This makes it an excellent choice for runners who value sovereignty in the digital age.
- The Advantage of Nostr Over Centralised Run Tracking Tools
Most mainstream running apps, like Strava or Nike Run Club, rely on centralised platforms that control user data, impose restrictions, and often monetise user activity. Runstr.club, however, is built on Nostr, a decentralised protocol that enables users to interact without getting trapped inside a walled garden.
With Nostr, runners benefit from:
-
True ownership of their data – no risk of platforms selling or misusing personal running history.
-
Resilience against censorship – no arbitrary bans or content moderation dictated by a 'shadowy suit'.
-
Interoperability – seamless integration with other Nostr-based applications, keeping data fluid and accessible across different platforms.
-
Peer-to-peer connectivity – allowing runners to share progress, create challenges, and stay engaged independent of big tech.
For Bitcoin Runners, Nostr’s decentralised nature aligns perfectly with the principles of sovereignty, freedom, and privacy.
- Gamification & Challenges
Runstr.club has engaging challenges and decentralised leaderboards on its roadmap. Whether you’re stacking sats through running-related bitcoin challenges or simply competing with fellow bitcoiners for fun, the platform will add an extra layer of engagement to every run. We would love to see such features come to life!
Conclusion
Runstr.club is more than just a running tracker—it’s a Nostr, bitcoin, and fitness onboarding community-driven movement. By embracing platforms that respect privacy, encourage competition, and foster community, we stay true to our values while pushing our limits as runners.
Let’s take this to the next level - be sure to follow Runstr on Nostr!
Run free. Stay sovereign. Stack zaps!
We’re shilling this open-source initiative out of genuine appreciation for both its vision and the dedicated team behind it.
-
 @ fd06f542:8d6d54cd
2025-03-31 10:00:34
@ fd06f542:8d6d54cd
2025-03-31 10:00:34NIP-05
Mapping Nostr keys to DNS-based internet identifiers
finaloptionalOn events of kind
0(user metadata) one can specify the key"nip05"with an internet identifier (an email-like address) as the value. Although there is a link to a very liberal "internet identifier" specification above, NIP-05 assumes the<local-part>part will be restricted to the charactersa-z0-9-_., case-insensitive.Upon seeing that, the client splits the identifier into
<local-part>and<domain>and use these values to make a GET request tohttps://<domain>/.well-known/nostr.json?name=<local-part>.The result should be a JSON document object with a key
"names"that should then be a mapping of names to hex formatted public keys. If the public key for the given<name>matches thepubkeyfrom theuser metadataevent, the client then concludes that the given pubkey can indeed be referenced by its identifier.Example
If a client sees an event like this:
jsonc { "pubkey": "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9", "kind": 0, "content": "{\"name\": \"bob\", \"nip05\": \"bob@example.com\"}" // other fields... }It will make a GET request to
https://example.com/.well-known/nostr.json?name=boband get back a response that will look likejson { "names": { "bob": "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9" } }or with the recommended
"relays"attribute:json { "names": { "bob": "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9" }, "relays": { "b0635d6a9851d3aed0cd6c495b282167acf761729078d975fc341b22650b07b9": [ "wss://relay.example.com", "wss://relay2.example.com" ] } }If the pubkey matches the one given in
"names"(as in the example above) that means the association is right and the"nip05"identifier is valid and can be displayed.The recommended
"relays"attribute may contain an object with public keys as properties and arrays of relay URLs as values. When present, that can be used to help clients learn in which relays the specific user may be found. Web servers which serve/.well-known/nostr.jsonfiles dynamically based on the query string SHOULD also serve the relays data for any name they serve in the same reply when that is available.Finding users from their NIP-05 identifier
A client may implement support for finding users' public keys from internet identifiers, the flow is the same as above, but reversed: first the client fetches the well-known URL and from there it gets the public key of the user, then it tries to fetch the kind
0event for that user and check if it has a matching"nip05".Notes
Identification, not verification
The NIP-05 is not intended to verify a user, but only to identify them, for the purpose of facilitating the exchange of a contact or their search.
Exceptions are people who own (e.g., a company) or are connected (e.g., a project) to a well-known domain, who can exploit NIP-05 as an attestation of their relationship with it, and thus to the organization behind it, thereby gaining an element of trust.User discovery implementation suggestion
A client can use this to allow users to search other profiles. If a client has a search box or something like that, a user may be able to type "bob@example.com" there and the client would recognize that and do the proper queries to obtain a pubkey and suggest that to the user.
Clients must always follow public keys, not NIP-05 addresses
For example, if after finding that
bob@bob.comhas the public keyabc...def, the user clicks a button to follow that profile, the client must keep a primary reference toabc...def, notbob@bob.com. If, for any reason, the addresshttps://bob.com/.well-known/nostr.json?name=bobstarts returning the public key1d2...e3fat any time in the future, the client must not replaceabc...defin his list of followed profiles for the user (but it should stop displaying "bob@bob.com" for that user, as that will have become an invalid"nip05"property).Public keys must be in hex format
Keys must be returned in hex format. Keys in NIP-19
npubformat are only meant to be used for display in client UIs, not in this NIP.Showing just the domain as an identifier
Clients may treat the identifier
_@domainas the "root" identifier, and choose to display it as just the<domain>. For example, if Bob ownsbob.com, he may not want an identifier likebob@bob.comas that is redundant. Instead, Bob can use the identifier_@bob.comand expect Nostr clients to show and treat that as justbob.comfor all purposes.Reasoning for the
/.well-known/nostr.json?name=<local-part>formatBy adding the
<local-part>as a query string instead of as part of the path, the protocol can support both dynamic servers that can generate JSON on-demand and static servers with a JSON file in it that may contain multiple names.Allowing access from JavaScript apps
JavaScript Nostr apps may be restricted by browser CORS policies that prevent them from accessing
/.well-known/nostr.jsonon the user's domain. When CORS prevents JS from loading a resource, the JS program sees it as a network failure identical to the resource not existing, so it is not possible for a pure-JS app to tell the user for certain that the failure was caused by a CORS issue. JS Nostr apps that see network failures requesting/.well-known/nostr.jsonfiles may want to recommend to users that they check the CORS policy of their servers, e.g.:bash $ curl -sI https://example.com/.well-known/nostr.json?name=bob | grep -i ^Access-Control Access-Control-Allow-Origin: *Users should ensure that their
/.well-known/nostr.jsonis served with the HTTP headerAccess-Control-Allow-Origin: *to ensure it can be validated by pure JS apps running in modern browsers.Security Constraints
The
/.well-known/nostr.jsonendpoint MUST NOT return any HTTP redirects.Fetchers MUST ignore any HTTP redirects given by the
/.well-known/nostr.jsonendpoint. -
 @ 220522c2:61e18cb4
2025-03-25 16:05:27
@ 220522c2:61e18cb4
2025-03-25 16:05:27draftoptionalAbstract
This NIP defines a new event kind for sharing and storing code snippets. Unlike regular text notes (
kind:1), code snippets have specialized metadata like language, extension, and other code-specific attributes that enhance discoverability, syntax highlighting, and improved user experience.Event Kind
This NIP defines
kind:1337as a code snippet event.The
.contentfield contains the actual code snippet text.Optional Tags
-
filename- Filename of the code snippet -
l- Programming language name (lowercase). Examples: "javascript", "python", "rust" -
extension- File extension (without the dot). Examples: "js", "py", "rs" -
description- Brief description of what the code does -
runtime- Runtime or environment specification (e.g., "node v18.15.0", "python 3.11") -
license- License under which the code is shared (e.g., "MIT", "GPL-3.0", "Apache-2.0") -
dep- Dependency required for the code to run (can be repeated) -
repo- Reference to a repository where this code originates
Format
```json {
"id": "<32-bytes lowercase hex-encoded SHA-256 of the the serialized event data>",
"pubkey": "<32-bytes lowercase hex-encoded public key of the event creator>",
"created_at":
, "kind": 1337,
"content": "function helloWorld() {\n console.log('Hello, Nostr!');\n}\n\nhelloWorld();",
"tags": [
["l", "javascript"], ["extension", "js"], ["filename", "hello-world.js"], ["description", "A basic JavaScript function that prints 'Hello, Nostr!' to the console"], ["runtime", "node v18.15.0"], ["license", "MIT"], ["repo", "https://github.com/nostr-protocol/nostr"]],
"sig": "<64-bytes signature of the id>"
} ```
Client Behavior
Clients that support this NIP SHOULD:
-
Display code snippets with proper syntax highlighting based on the language.
-
Allow copying the full code snippet with a single action.
-
Render the code with appropriate formatting, preserving whitespace and indentation.
-
Display the language and extension prominently.
-
Provide "run" functionality for supported languages when possible.
-
Display the description (if available) as part of the snippet presentation.
Clients MAY provide additional functionality such as:
-
Code editing capabilities
-
Forking/modifying snippets
-
Creating executable environments based on the runtime/dependencies
-
Downloading the snippet as a file using the provided extension
-
Sharing the snippet with attribution
References
nip #grownostr
-
-
 @ 220522c2:61e18cb4
2025-03-25 06:57:24
@ 220522c2:61e18cb4
2025-03-25 06:57:24
-
 @ 7d33ba57:1b82db35
2025-03-31 09:28:36
@ 7d33ba57:1b82db35
2025-03-31 09:28:36Rovinj is one of Croatia’s most beautiful coastal towns, known for its colorful Venetian-style buildings, cobblestone streets, and breathtaking sea views. Located on the Istrian Peninsula, Rovinj offers a mix of history, culture, and stunning beaches, making it a perfect getaway for travelers seeking both relaxation and adventure.
🌊 Top Things to See & Do in Rovinj
1️⃣ Explore Rovinj Old Town 🏡
- Wander through narrow, winding streets filled with art galleries, boutique shops, and charming cafés.
- Discover Balbi’s Arch, the old entrance to the city, and the Clock Tower.
- Enjoy stunning sunset views from the harbor.
2️⃣ Visit St. Euphemia’s Church ⛪
- The most famous landmark in Rovinj, located at the highest point of the Old Town.
- Climb the bell tower for a panoramic view of the Adriatic and nearby islands.
- Learn about Saint Euphemia, the town’s patron saint, and her fascinating legend.
3️⃣ Relax at Rovinj’s Best Beaches 🏖️
- Lone Bay Beach – A popular spot near Zlatni Rt forest, great for swimming.
- Mulini Beach – A stylish beach with a cocktail bar and clear waters.
- Cuvi Beach – A quieter, family-friendly pebble beach.
4️⃣ Walk or Cycle Through Golden Cape Forest Park (Zlatni Rt) 🌿🚲
- A protected nature park with pine forests, walking trails, and hidden coves.
- Great for hiking, cycling, and rock climbing.
- Perfect for a picnic with sea views.
5️⃣ Take a Boat Trip to Rovinj Archipelago 🛥️
- Explore Red Island (Crveni Otok) – A peaceful getaway with sandy beaches.
- Visit St. Andrew’s Island, home to a former Benedictine monastery.
- Sunset dolphin-watching tours are a must! 🐬
6️⃣ Try Authentic Istrian Cuisine 🍽️
- Fuži with truffles – A local pasta dish with Istria’s famous truffles.
- Istrian seafood platter – Fresh fish, mussels, and Adriatic shrimp.
- Olive oil & wine tasting – Try local Malvazija (white) and Teran (red) wines.
7️⃣ Visit the Batana House Museum ⛵
- A unique museum dedicated to Rovinj’s traditional wooden fishing boats (batanas).
- Learn about local fishing traditions and maritime culture.
- End the visit with a traditional batana boat ride at sunset.
🚗 How to Get to Rovinj
✈️ By Air: The nearest airport is Pula Airport (PUY), 40 km away.
🚘 By Car:
- From Pula: ~40 min (40 km)
- From Zagreb: ~3 hours (250 km)
- From Ljubljana (Slovenia): ~2.5 hours (170 km)
🚌 By Bus: Direct buses from Pula, Rijeka, and Zagreb.
🚢 By Ferry: Seasonal ferries connect Rovinj with Venice, Italy (~2.5 hours).💡 Tips for Visiting Rovinj
✅ Best time to visit? May–September for warm weather & festivals ☀️
✅ Wear comfy shoes – The Old Town streets are made of polished stone & can be slippery 👟
✅ Book restaurants in advance – Rovinj is a foodie hotspot, especially in summer 🍷
✅ Take a sunset walk along the harbor – One of the most romantic views in Croatia 🌅
✅ Bring cash – Some smaller shops and taverns still prefer cash 💶 -
 @ 5fb7f8f7:d7d76024
2025-03-31 09:14:45
@ 5fb7f8f7:d7d76024
2025-03-31 09:14:45Imagine a world where your voice is truly yours where no algorithm buries your posts, no central authority censors your ideas, and no account bans silence you. Welcome to yakiHonne, the decentralized media revolution built on Nostr.
Here, freedom reigns. Whether you're sharing breaking news, deep thoughts, or creative content, yakiHonne ensures your voice is unstoppable. No corporate overlords, no gatekeepers, just pure, open communication between people who value truth and transparency.
Why yakiHonne?
✅ Censorship-Free: Speak your mind without fear of bans or shadowbans. ✅ Decentralized & Secure: Your content lives on the blockchain, not in the hands of a single company. ✅ Community-Driven: Connect with like-minded individuals who believe in free expression. ✅ Future-Proof: No central server means no risk of takedowns or content wipes.
Break away from the limits of traditional media. Join yakiHonne today and take control of your voice!
-
 @ 4259e401:8e20e9a6
2025-03-24 14:27:27
@ 4259e401:8e20e9a6
2025-03-24 14:27:27[MVP: Gigi! How do I lightning prism this?]
If I could send a letter to myself five years ago, this book would be it.
I’m not a Bitcoin expert. I’m not a developer, a coder, or an economist.
I don’t have credentials, connections, or capital.
I’m a blue-collar guy who stumbled into Bitcoin almost exactly four years ago, and like everyone else, I had to wrestle with it to understand it.
Bitcoin is one of the most misunderstood, misrepresented, and misinterpreted ideas of our time - not just because it’s complex, but because its very structure makes it easy to distort.
It’s decentralized and leaderless, which means there’s no single voice to clarify what it is or defend it from misinformation.
That’s a feature, not a bug, but it means that understanding Bitcoin isn’t easy.
It’s a system that doesn’t fit into any of our existing categories. It’s not a company. It’s not a product. It’s not a government.
There’s no marketing department, no headquarters, no CEO.
That makes it uniquely resistant to corruption, but also uniquely vulnerable to disinformation.
Whether through negligence or malice, Bitcoin is constantly misunderstood - by skeptics who think it’s just a Ponzi scheme, by opportunists looking to cash in on the hype, by scammers who use the name to push worthless imitations, and by critics who don’t realize they’re attacking a strawman.
If you’re new to Bitcoin, you have to fight through layers of noise before you can even see the signal.
And that process isn’t instant.
Even if you could explain digital signatures off the top of your head, even if you could hash SHA-256 by hand, even if you had a perfect technical understanding of every moving part - you still wouldn’t get it.
Bitcoin isn’t just technology. It’s a shift in incentives, a challenge to power, an enforcer of sovereignty. It resists censorship.
A simple open ledger - yet it shakes the world.
Archimedes asked for a lever and a place to stand, and he could move the world.
Satoshi gave us both.
The lever is Bitcoin - an economic system with perfect game theory, incorruptible rules, and absolute scarcity.
The place to stand is the open-source, decentralized network, where anyone can verify, participate, and build without permission.
And what comes out of this seemingly simple equation?
The entire rearchitecture of trust. The separation of money and state.
A foundation upon which artificial intelligence must negotiate with the real world instead of manipulating it.
A digital economy where energy, computation, and value flow in perfect symmetry, refining themselves in an endless virtuous cycle.
Bitcoin started as a whitepaper.
Now it’s a lifeline, an immune system, a foundation, a firewall, a torch passed through time.
From such a small set of rules - 21 million divisible units, cryptographic ownership, and a fixed issuance schedule - emerges something unstoppable.
Something vast enough to absorb and constrain the intelligence of machines, to resist the distortions of human greed, to create the rails for a world that is freer, more sovereign, more aligned with truth than anything that came before it.
It’s proof that sometimes, the most profound revolutions begin with the simplest ideas. That’s why this book exists.
Bitcoin isn’t something you learn - it’s something you unlearn first.
You start with assumptions about money, value, and authority that have been baked into you since birth. And then, piece by piece, you chip away at them.
It’s like peeling an onion – it takes time and effort.
*And yes, you might shed some tears! *
At first, you might come for the speculation. A lot of people do. But those who stay - who actually take the time to understand what’s happening - don’t stay for the profits.
They stay for the principles.
If you’re holding this book, you’re somewhere on that journey.
Maybe you’re at the very beginning, trying to separate the signal from the noise.
Maybe you’ve been down the rabbit hole for years, looking for a way to articulate what you already know deep in your bones.
Either way, this is for you.
It’s not a technical manual, and it’s not a sales pitch. It’s the book I wish I had when I started.
So if you’re where I was, consider this a message in a bottle, thrown back through time. A hand reaching through the fog, saying:
“Keep going. It’s worth it.”
Preface The End of The Beginning
March 2025.
The moment has arrived. Most haven’t even noticed, let alone processed it. The United States is setting up a Bitcoin (Bitcoin-only!) strategic reserve.
It’s not a theory. Not an idea. The order is signed, the ink is dried.
The people who have been wrong, over and over (and over!) again - for years! - fumble for explanations, flipping through the wreckage of their previous predictions:
“Bubble…’’ “Fad…” “Ponzi…”
No longer.
The same analysts who once sneered are now adjusting their forecasts to protect what’s left of their credibility. Those who dismissed it are now trapped in a slow, humiliating realization: Bitcoin does not require their approval.
It never did.
Something fundamental has shifted, and the air is thick with a paradoxical cocktail of triumph and panic. Bitcoiners saw this coming. Not because they had insider information, but because they understood first principles when everyone else was still playing pretend.
Bitcoin was never just surviving.
It was infiltrating.
The question is no longer whether Bitcoin will succeed.
It already has.
The only question that remains is who understands, and who is still in denial.
Think back to 2022.
At its peak, FTX was one of the world’s largest cryptocurrency exchanges, valued at $32 billion and backed by blue-chip investors. It promised a sophisticated, institutional-grade trading platform, attracting retail traders, hedge funds, and politicians alike. Sam Bankman-Fried, with his disheveled hair and cargo shorts, was its eccentric figurehead, a billionaire who slept on a bean bag and spoke of philanthropy.
Then the illusion shattered.
FTX collapsed overnight, an implosion so violent it left an entire industry scrambling for cover. One moment, Sam Bankman-Fried was the golden boy of crypto - genius quant, regulatory darling, effective altruist™.
The next, he was just another fraudster in handcuffs.
Billions vanished. Customers locked out. Hedge funds liquidated.
Politicians who had once taken photos with SBF and smiled at his political donations, suddenly pretended they had no idea who he was. The same regulators who were supposed to prevent disasters like this stood slack-jawed, acting as if they hadn’t been having closed-door meetings with FTX months before the collapse.
But FTX wasn’t just a scandal, it was a filter.
If you were Bitcoin-only, with your satoshis in cold storage, you didn’t even flinch. From your perspective, nothing important changed:
A new Bitcoin block still arrived every ten minutes (on average). The supply cap of 21 million bitcoins remained untouched. Ownership was still protected by public/private key cryptography.
You were literally unaffected.
You had already updated your priors:
“If you don’t hold your own keys, you own nothing.” “Bitcoin is not ‘crypto’.” “’Crypto’ is a casino.”
FTX was just another financial fire, another chapter in the never-ending saga of people trusting systems that had already proven themselves untrustworthy.
That moment was a prelude.
The U.S. Bitcoin pivot is the paradigm shift.
The Eukaryotic Revolution Is Upon Us
In biology, abiogenesis is when life emerged from non-life - a fragile, uncertain process where the first microscopic self-replicators struggled to survive against hostile conditions. That was Bitcoin’s early history. It had to fight for its existence, attacked by governments, dismissed by economists, ridiculed by mainstream media.
But it survived.
That era is over. We have entered the Eukaryotic Revolution.
This is the moment in evolutionary history when simple lifeforms evolved into something structurally complex - organisms with nuclei, internal scaffolding, and the ability to form multicellular cooperatives and populate diverse ecosystems. Once this transformation happened, there was no going back. Bitcoin is going through its own Eukaryotic leap.
Once an outsider, dismissed and ridiculed, it is maturing into an integrated, resilient force within the global financial system.
On March 2, 2025, the Trump administration announced a Crypto Strategic Reserve.
At first, it wasn’t just Bitcoin - it included XRP, SOL, and ADA, a desperate attempt to appease the altcoin industry. A political move, not an economic one.
For about five minutes, the broader crypto industry cheered. Then came the pushback.
Bitcoiners called it immediately: mixing Bitcoin with centralized altcoin grifts was like adding lead weights to a life raft.
Institutional players rejected it outright: sovereign reserves need hard assets, not tech company tokens. The government realized, almost immediately, that it had made a mistake.
By March 6, 2025, the pivot was complete.
Strategic Bitcoin reserve confirmed. The President signed an executive order, and legislation has been introduced in the United States House of Representatives.
The U.S. government’s official bitcoin policy: hold, don’t sell. Look for ways to acquire more.
Altcoins relegated to second-tier status, treated as fundamentally separate from and inferior to bitcoin. The government’s official policy: sell, and do not actively accumulate more (ouch!).
“Bitcoin maximalism” – the belief that any cryptocurrency other than bitcoin lies on a spectrum between “bad idea” and outright scam - wasn’t vindicated by debate.
It was vindicated by economic reality.
When the government was forced to choose what belonged in a sovereign reserve, it wasn’t even close. Bitcoin stood alone.
“There is no second best.” -Michael Saylor
Who This Book Is For: The Three Types of Readers
You’re here for a reason.
Maybe you felt something shift.
Maybe you saw the headlines, sensed the undercurrents, or simply couldn’t ignore the growing drumbeat any longer.
Maybe you’ve been here all along, waiting for the world to catch up.
Whatever brought you to this book, one thing is certain: you’re curious enough to learn more.
Bitcoin forces a reevaluation of assumptions - about money, trust, power, and the very foundations of the economic order. How much of that process you’ve already undergone will determine how you read these pages.
1. The Layperson → new, curious, maybe skeptical. Bitcoin probably looks like chaos to you right now. One person says it’s the future. Another says it’s a scam. The price crashes. The price doubles. The news is either breathless excitement or total doom. How the hell are you supposed to figure this out?
If that’s you, welcome.
This book was built for you.
You don’t need to be an economist, a technologist, or a finance geek to understand what’s in these pages. You just need an open mind and the willingness to engage with new ideas - ideas that will, if you follow them far enough, challenge some of your deepest assumptions.
Bitcoin is not an investment. Bitcoin is not a company. Bitcoin is not a stock, a trend, or a passing phase.
Bitcoin is a paradigm shift. And by the time you reach the last page, you won’t need to be convinced of its importance. You’ll see it for yourself.
2. The Student → understand the basics, want to go deeper.
You’ve already stepped through the door.
You’ve realized Bitcoin is more than just digital gold. You understand decentralization, scarcity, censorship resistance… But the deeper you go, the more you realize just how much there is to understand.
3. The Expert → You’ve been in the game for years.
You’ve put in the time.
You don’t need another book telling you Bitcoin will succeed. You already know.
You’re here because you want sharper tools.
Tighter arguments.
A way to shut down nonsense with fewer words, and more force.
Maybe this book will give you a new way to frame an idea you’ve been struggling to convey.
Maybe it will help you refine your messaging and obliterate some lingering doubts in the minds of those around you.
Or maybe this will simply be the book you hand to the next person who asks, “Okay… but what’s the deal with Bitcoin?” so you don’t have to keep explaining it from scratch.
*If you’re already deep in the weeds, you can probably skip Part I (Foundations) without missing much - unless you’re curious about a particular way of putting a particular thing. *
Part II (Resilience) is where things get more interesting. Why you want to run a node, even if you don’t know it yet. The energy debate, stripped of media hysteria. The legend of Satoshi, and what actually matters about it.
If you’re a hardcore cypherpunk who already speaks in block heights and sending Zaps on NOSTR, feel free to jump straight to Part III (The Peaceful Revolution). Chapter 15, “The Separation of Money and State” is where the gloves come off.
Bitcoin isn’t just a technology. Bitcoin isn’t just an economic movement. Bitcoin is a lens.
And once you start looking through it, the world never looks the same again.
This book will teach you what Bitcoin is, as much as it will help you understand why Bitcoiners think the way they do.
It isn’t just something you learn about.
Especially not in one sitting, or from one book.
It’s something you grow to realize.
Regardless of which category you fall into, you’ve already passed the first test.
You’re still reading.
You haven’t dismissed this outright. You haven’t scoffed, rolled your eyes, or walked away. You’re at least curious.
And that’s all it takes.
Curiosity is the only filter that matters.
The rest takes care of itself.
The Essential Role of Memes Memes won the narrative war - it wasn’t textbooks, research papers, or whitepapers that did it. Bitcoin spread the same way evolution spreads successful genes - through replication, variation, and selection. Richard Dawkins coined the term “meme” in The Selfish Gene, describing it as a unit of cultural transmission - behaving much like a gene. Memes replicate, mutate, and spread through culture. Just as natural selection filters out weak genes, memetic selection filters out weak ideas.
But Bitcoin memes weren’t just jokes.
They were premonitions.
The most powerful ideas are often compact, inarguable, and contagious - and Bitcoin’s memes were all three. They cut through complexity like a scalpel, distilling truths into phrases so simple, so undeniable, that they burrowed into the mind and refused to leave.
"Bitcoin fixes this." "Not Your Keys, Not Your Coins." "Number Go Up."
Each of these is more than just a slogan.
They’re memetic payloads, compressed packets of truth that can carry everything you need to understand about Bitcoin in just a few words.
They spread through conversations, through tweets, through shitposts, through relentless repetition.
They bypassed the gatekeepers of financial knowledge, infecting minds before Wall Street even understood what was happening.
And they didn’t just spread.
They reshaped language itself.
Before Bitcoin, the word fiat was a sterile economic term, borrowed from Latin, meaning "by decree." It had no weight, no controversy - just a neutral descriptor for government-issued money.
But Bitcoiners forced a memetic shift.
They didn’t just make fiat mainstream.
**They made it radioactive. **
They stripped away the academic detachment and revealed its true essence:
money because I said so.
No backing. No inherent value.
Just a command.
And of course, an unspoken threat -
"Oh, and by the way, I have a monopoly on violence, so you’d better get on board."
This wasn’t just linguistic evolution; it was a memetic coup.
Bitcoiners took a sterile term and injected it with an unavoidable truth: fiat money exists not because it is chosen, but because it is imposed.
Central banks, governments, and financial institutions now use the term fiat without a second thought.
The meme has done its work.
A word that was once neutral, now carries an implicit critique - a quiet but persistent reminder that there is an alternative.
Bitcoin didn’t just challenge the financial system - it rewired the language we use to describe it.
“Money printer go BRRRRRR" did more damage to the Fed’s reputation than a thousand Austrian economics treatises ever could.
Memes exposed what balance sheets and policy reports tried to obscure. They turned abstract economic forces into something visceral, something undeniable.
And now - they are historical markers of the shift, the fossil record of our collective consciousness coming to terms with something fundamentally new in the universe.
The old world relied on authority, institutional credibility, and narrative control.
Bitcoin broke through with memes, first principles, and lived experience.
This wasn’t just an ideological battle.
It was an evolutionary process.
The weaker ideas died. The strongest ones survived.
Once a meme - in other words, an idea - takes hold, there is nothing - no law, no regulation, no institution, no government - that can stop it.
Bitcoin exists. It simply is.
And it will keep producing blocks, every ten minutes, whether you get it or not.
This book isn’t a trading manual.
It won’t teach you how to time the market, maximize your gains, or set up a wallet.
It’s a carefully curated collection of memes, giving you the prerequisite mental scaffolding to grok the greatest monetary shift in human history.
A shift that has already begun.
The only thing to decide is whether you’re watching from the sidelines or whether you’re part of it.
The rest is up to you.
How This Book Is Structured Bitcoin spreads like an evolutionary force - through memes. Each chapter in this book isn’t just an idea, it’s a memetic payload, designed to install the concepts that make Bitcoin inevitable. The book is broken into three phases:
*I. Foundations *** Memes as Mental Antivirus The first layer cuts through noise and filters out distractions. "Bitcoin Only" is the first test - if you get this one wrong, you waste years chasing ghosts. "Don’t Trust, Verify" rewires how you think about truth. And "Not Your Keys, Not Your Coins"? If you learn it the hard way, it’s already too late.
II. Resilience Memes as Weapons in the Information War Here’s where Bitcoin earns its survival. "Shitcoiners Get REKT" is a law, not an opinion. "Fork Around and Find Out" proves that you don’t change Bitcoin - Bitcoin changes you. "Antifragile, Unstoppable" shows how every attack on Bitcoin has only made it stronger.
III. The Peaceful Revolution ** Memes as Reality Distortion Fields By now, Bitcoin isn’t just an asset - it’s a lens. "Separation of Money and State" isn’t a theory; it’s happening in real time. "Fix the Money, Fix the World" isn’t a slogan; it’s a diagnosis. And "Tick Tock, Next Block"? No matter what happens, Bitcoin keeps producing blocks.
These aren’t just memes. They’re scaffolding for a new way of thinking. Each one embeds deeper until you stop asking if Bitcoin will succeed - because you realize it already has.
Next: Chapter 1: Bitcoin Only. ** For now, it’s a heuristic - an efficient filter that separates signal from noise, with minimal effort.
But by the time you finish this book, it won’t be a heuristic anymore.
It will be something you know.Welcome to the rabbit hole.
-
 @ 866e0139:6a9334e5
2025-03-24 10:51:52
@ 866e0139:6a9334e5
2025-03-24 10:51:52Autor: Milosz Matuschek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
Seit Sonntag (zu allem Glück auch noch meinem 45. Geburtstag) ist bei mir noch ein bisschen mehr los als sonst – und das liegt an Ihnen. Der Aufruf zur Gründung der „Friedenstaube“, einer unzensierbaren Friedenspublikation mit bekannten Stimmen aus der kritischen Szene, der Friedensbewegung und von Bürgerjournalisten ist bei Ihnen auf mehr als nur offene Ohren gestoßen! Ich bin regelrecht geplättet von den vielen Reaktionen, die ich noch gar nicht alle beantworten konnte.
Ich danke Ihnen herzlich für das Vertrauen in mich (auch wenn ich natürlich stark auf die Autoren angewiesen bin) und die überwältigenden Reaktionen: Es sind hunderte Abonnements für den Newsletter eingegangen, darunter einige bezahlte Abos und Förderabos und auch die ersten Genossenschaftsanteile wurden gezeichnet! Was mich besonders freut: Gut zehn weitere freiwillige Autoren wollen mitmachen und arbeiten bereits an den ersten Texten. Damit darf ich schon jetzt verkünden, dass die Genossenschaft definitiv gegründet werden kann, die Friedenstaube wird fliegen. Wie hoch und wie weit, das liegt dann nun nur noch in unser aller Hände.
Der Anfang ist jedenfalls gemacht. Die nächsten Wochen werden besonders arbeitsintensiv, ich bitte Sie um etwas Geduld: Aufbau einer Kernredaktion, Organisation der Abläufe, technologische Entwicklungsarbeiten, Genossenschaftsgründung etc. stehen jetzt auf der Agenda. Mit Tom-Oliver Regenauer darf ich den ersten Autor im redaktionellen Kernteam verkünden, der sich nicht nur große Verdienste im Schreiben erarbeitet hat (siehe u.a. sein Buch Hopium) sondern auch über Managementerfahrung verfügt; mit weiteren helfenden Händen bin ich im Gespräch.
Ich freue mich auf die (auch für mich) neue Erfahrung, quasi aus dem Nichts eine Publikation mit Redaktionsbetrieb und freien Autoren auf einer gänzlich neuen technologischen Infrastruktur aufzubauen. Es wäre illusorisch zu glauben, dass alles glatt gehen wird, denn wir starten quasi „on the go“, aber im Fall von Frieden oder Krieg gilt es, keine Zeit verstreichen zu lassen. Ich arbeite nach dem Motto „Tun, statt reden; zeigen, statt ankündigen; liefern, statt versprechen“.
Die ersten Texte zum Thema Frieden sind bereits publiziert, ein halbwegs geordneter Betrieb sollte ab April realistisch sein. Die Liste der Autoren wird regelmäßig aktualisiert, schauen Sie gerne hier (oder noch besser: hier) immer wieder herein. Dort finden Sie auch noch mal alle Infos, wenn Sie die Friedenstaube unterstützen wollen. Ab 1000 Euro/CHF werden Sie Genossenschafter, also Verleger!**
Auch an die bisherigen Unterstützer des Pareto-Projekts, der technologischen Basis der Friedenstaube, will ich hiermit schon etwas zurückgeben: Alle Spender für Pareto werden die Friedenstaube immer kostenlos lesen können. Sie, die Leser dieser Publikation haben die technologische Basis mit aufgebaut, die uns zur weltweit ersten, zensursicheren Friedenspublikation macht. Uns Autoren steht damit ein kompetentes Support-Team von inzwischen über zehn Entwicklern (und weiteren Helfern) an der Seite, welche die Friedenstaube am Fliegen halten werden.
Kontaktieren Sie mich gerne zu allen Fragen (je kürzer die Mail, desto früher kommt die Antwort): milosz\@pareto.space oder kontakt\@idw-europe.org
JETZT ABONNIEREN:
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF/EURO werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):
Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie mich an: milosz@pareto.space oder kontakt@idw-europe.org.
Was bewegt mich beim Thema Krieg und Frieden?
Erlauben Sie mir einen kurzen persönlichen Prolog: Ich stamme aus Schlesien. Mein Urgroßvater kämpfte im I. Weltkrieg bei Verdun. Mein Großvater wurde in die Wehrmacht eingezogen, kämpfte im Partisanenkrieg in Jugoslawien, verlor Hand und Auge. Ein Bruder meiner Großmutter entzog sich und landete in Dachau. Ich kenne meine Familiengeschichte nur in groben Umrissen, vielen wird es ähnlich gehen. Einige meiner schlesischen Vorfahren waren später vor allem Lokführer. Aufgrund der bewegten schlesischen Geschichte wechselten sie mehrfach die Uniform. Die Tätigkeit und Fahrstrecke blieb die gleiche. Für wen oder was kämpften sie in Kriegen in welchen Uniformen? Vermutlich wussten sie es selbst nicht.
Auch ich könnte heute nicht genau sagen, welche Interessen und Mächte die Kriegsmaschinerie bedienen. Doch ich wüsste es gerne und Sie vielleicht auch. Kämpfen ohne letztlich zu wissen für wen und warum: Wozu? Krieg simuliert Sinn und Notwendigkeit und lässt einen am Ende mit den großen Fragen allein, ahnungslos gestorben im Schützengraben. Zivilisatorisch ist das ein Offenbarungseid.
Bin ich ein totaler Anti-Militarist? Ich glaube nicht. Ich habe nichts gegen die Idee privaten Waffenbesitzes. Ich kann der Idee der Landesverteidigung durchaus etwas abgewinnen. Den Wehrdienst habe ich bewusst nicht verweigert. Ich wollte die Erfahrung machen. Hier schreibt also auch ein Obergefreiter a. D. eines bayerischen Gebirgspionierbataillons bei Rosenheim mit bronzener Schützenschnur, der am MG durchaus treffsicher war. Aber eben auch jemand, den der Wehrdienst zum Teil-Pazifisten gemacht hat. Mir war nach dem Grundwehrdienst klar: Wir sind eine Gurkentruppe, reines Kanonenfutter. 20-jährige Grünschnäbel mit zu viel Testosteron und Hollywood in den Gliedern, aber wenig Ahnung.
Ich war also einer, der sich verlässlich mit anderen beim Orientierungslauf im Wald verirrte; einer, der mit anderen übermüdet beim ersten Wachdienst einpennte (und damit im Ernstfall den Tod im Schlaf kennengelernt hätte, denn just erfolgte ein simulierter „Angriff“); einer, der auch mal übernächtigt sein Gewehr vor dem Zelt vergaß (wir sollten dem G3 den Namen unserer damaligen Freundin geben – wie pervers – ich vergaß also „Petra“ vor dem Zelt) und schließlich einer, der die meiste Zeit des Dienstes fürs Vaterland letztlich mit dem Servieren von Getränken und Schinkennudeln im Offizierskasino verbrachte und die institutionalisierten Alkoholiker der Bundeswehr bei Laune hielt („it ain’t much, but it was honest work“).
Anders gesagt: Krieg – spätestens seitdem: ohne mich. Auch wenn ich gerne Ernst Jünger lese und zitiere (er war einfach ein großartiger Chronist und lebendiger Geist), seinen abenteuerlustigen Militarismus kreide ich ihm an und rufe ihm posthum hinterher: man muss nicht erst einen Sohn im Krieg verloren haben, um zum Pazifisten zu werden.
Weitere Störgefühle tauchten auf: In meiner Dissertation durfte ich mich u.a. mit philosophischen Theorien zum Gesellschaftsvertrag (u.a. Kant, Rousseau, Locke und Hobbes sind hier zu nennen) beschäftigen. Dies brachte mein Staatsverständnis gerade bei der Kriegsfrage noch mehr durcheinander. Wenn Mindestziel der Staatsgründung innere und äußere Sicherheit sind, aber letztlich nicht der Staat den Bürger, sondern der Bürger den Staat schützt, wozu sich dann eine Schutzmacht erfinden, die einen am Ende durch den Fleischwolf jagt? Hobbes setzte zumindest auf Söldner.
Kriege werden mit Lügen begonnen, wusste Julian Assange. Können Sie mit Wahrheit beendet oder gar verhindert werden? Seit Walter Lippmanns „Liberty and the News“ von 1920 weiß man spätestens, dass gesicherte Information im Krieg das seltenste Gut ist. Sagt Lippmann als oberster Mainstream-Journalist und Einflüsterer der Mächtigen. Jeder Journalist muss hier ein Störgefühl entwickeln, der Leser noch mehr. Der Journalist der Nachrichtenagentur ist selten im Geschehen sondern wird vom heimischen Militär gebrieft, sein Bericht landet dann in den Newstickern und Redaktionen. Die Kriegsmaschinerie produziert also auch ihre eigene Sicht auf die Dinge, die sie den Bürgern als die Realität verkauft.
Kein Wunder, dass jede abweichende Information massiv bekämpft werden muss. Im Krieg ist Zweifel gleich Verrat, quasi unsolidarisches Sektierertum und Wehrkraftzersetzung, wenn nicht Feindbegünstigung. Der kritische Journalist steht in Ausnahmezuständen, wie man schon bei Corona sehen konnte, automatisch aus Staatssicht im Lager des Feindes und wird entsprechend behandelt. Zensursicheres Publizieren ist dann nicht nur ein nettes feature, sondern notwendige Basisvoraussetzung. Vor kurzem war Twitter/X nicht mehr zugänglich wegen massiven Cyberattacken. Wenn dann noch Rundfunk und Presse auf der Propagandawelle surfen und die Plattformzensur wieder zuschlägt, wird das Angebot schnell dünn.
Wem aber dient Zensur und Propaganda? Die aktuelle Lage im Russland-Ukraine-Konflikt ist auch Gelegenheit, um zu zeigen: Es sind eben nicht nur staatliche Interessen, die hier verhandelt werden, sondern es muss (wieder mal) eine andere Entität mit am Tisch sitzen, man nenne sie Deep State oder wie auch immer. Europäische Eliten dienen offensichtlich Fremdinteressen, wenn sie mit Aufrüstungsplänen Volksvermögen verspekulieren oder darin (wie von der Leyen) ein notwendiges „Investment“ sehen. Von wem werden wir letztlich regiert? Auch diesem Themen-Komplex werde ich mich in der Friedenstaube nähern.
Es gibt viel zu tun, aber für mich ist klar: Frieden ist ohne Wahrheit nicht zu bekommen, deshalb ist Wahrheitssuche auch immer Friedenssuche, wie Wahrheitsliebe letztlich Friedensliebe ist.
Gerade fallen auch im Mainstream die Corona-Lügen zur Labortheorie in sich zusammen, fünf Jahre nach Ausrufung der Pandemie. Der Frieden hat nur eine Chance, wenn es uns gelingt, die Lügen nun möglichst synchron zu den Geschehnissen aufzudecken und zu dokumentieren.
Das ist mein persönlicher Wunsch, mit dem ich die Friedenstaube fliegen lasse.
Was ist Ihrer? Schreiben Sie es gerne in die Kommentare. Welche Erwartungen, Wünsche haben Sie an uns? Liebe Autoren: Was ist euer Beweggrund, für den Frieden zur Feder zu greifen?
Zeichnen Sie jetzt “Friedensanleihen”. Werden Sie Genossenschafter und Verleger der Friedenstaube ab 1000 Euro/CHF. Es können mehrere Anteile pro Person gezeichnet werden, es bleibt bei einem Stimmrecht pro Kopf. milosz\@pareto.space
P.S: Mit diesem Text testen wir die Newsletterfunktion erstmals an mehrere Hundert Mailadressen. Wenn Sie die Friedenstaube abonniert haben, sollten Sie diesen Artikel per Mail bekommen haben.
ANZEIGE:
Sie suchen nach dem einfachsten Weg, Bitcoin zu kaufen und selbst zu verwahren?* Die* Relai-App ist Europas erfolgreichste Bitcoin-App.* Hier kaufen Sie Bitcoin in wenigen Schritten und können auch Sparpläne einrichten. Niemand hat Zugriff auf Ihre Bitcoin, außer Sie selbst.* Relai senkt jetzt die Gebühr auf 1%, mit dem Referral-Code MILOSZ sparen Sie weitere 10%. (keine Finanzberatung). Disclaimer wg. EU-Mica-Regulierung: Die Dienste von Relai werden ausschließlich für Einwohner der Schweiz und Italiens empfohlen.
Join the marketplace of ideas! We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to team@pareto.space**
Not yet on Nostr and want the full experience? Easy onboarding via Start.
Pareto has started a crowdfunding campaign on Geyser. We were in the Top 3 in February, thank you for the support!
-
 @ 78c90fc4:4bff983c
2025-03-31 08:13:17
@ 78c90fc4:4bff983c
2025-03-31 08:13:17Die Operation „Cast Thy Bread“ war eine verdeckte Kampagne zur biologischen Kriegsführung, die von der Haganah und später von den israelischen Verteidigungsstreitkräften während des arabisch-israelischen Krieges 1948 durchgeführt wurde[1][3]. Bei der Operation, die im April 1948 begann, wurden Trinkwasserquellen mit Typhusbakterien verseucht, um palästinensisch-arabische Zivilisten und verbündete arabische Armeen anzugreifen[1][3].

\ \ ## Wichtige Details\ \ - **Ziel**: Palästinensische Araber an der Rückkehr in eroberte Dörfer zu hindern und die Versuche der arabischen Armeen, Gebiete zurückzuerobern, zu behindern[1].\ - **Methoden**: Israelische Streitkräfte setzten Typhuskeime in Flaschen, Reagenzgläsern und Thermoskannen ein, um Brunnen und Wasservorräte in palästinensischen Gebieten zu vergiften[1][3].\ - **Führung**: Die Operation wurde vom israelischen Premierminister David Ben-Gurion und dem Generalstabschef der IDF, Yigael Yadin, beaufsichtigt und genehmigt[1].\ \ ## Bemerkenswerte Vorfälle\ \ - Akkon (Akka)**: Die Wasserversorgung der Stadt wurde am 15. Mai 1948 verseucht, was zu einer Typhusepidemie und „extremer Verzweiflung“ unter den Einwohnern führte[1][3].\ - **Gaza**: Im Mai 1948 versuchten vier Soldaten der israelischen Spezialeinheiten, die örtliche Wasserversorgung zu vergiften, wurden jedoch gefangen genommen und hingerichtet[1].\ - **Andere Orte**: Auch in Jericho, Eilabun und palästinensischen Vierteln in Jerusalem wurden Brunnen vergiftet[1][3].\ \ ## Folgen\ \ Die Operation führte zu schweren Erkrankungen unter den palästinensischen Anwohnern, von denen Dutzende betroffen sein sollen[1][3]. Sie erzielte jedoch nicht die von ihren Befürwortern erhoffte lähmende Wirkung und wurde im Dezember 1948 eingestellt[1].\ \ ## Historische Bedeutung\ \ Die Operation „Gegossenes Brot“ wurde als Kriegsverbrechen und als Akt der ethnischen Säuberung eingestuft[1]. Ihre Enthüllung hat eine Kontroverse und Debatte über die im Krieg von 1948 angewandten Taktiken und ihre langfristigen Auswirkungen auf den israelisch-palästinensischen Konflikt ausgelöst[2][4].
Quellen
[1] Operation Cast Thy Bread - Wikipedia https\://en.wikipedia.org/wiki/Operation_Cast_Thy_Bread
[2] Cast Thy Bread Archives - Promised Land Museum https\://promisedlandmuseum.org/tag/cast-thy-bread/
[3] From 'Virtuous Boy' to Murderous Fanatic: David Ben-Gurion and the ... https\://www.euppublishing.com/doi/10.3366/hlps.2023.0308
[4] Historians reveal Israel's use of poison against Palestinians https\://www.middleeastmonitor.com/20221011-historians-reveal-israels-use-of-poison-against-palestinians/
[5] Thoughts on Operation Cast Thy Bread? : r/IsraelPalestine - Reddit https\://www.reddit.com/r/IsraelPalestine/comments/1g02b64/thoughts_on_operation_cast_thy_bread/
[6] 'Cast thy bread': Israeli biological warfare during the 1948 War https\://www.tandfonline.com/doi/abs/10.1080/00263206.2022.2122448
[7] 'Cast thy bread': Israeli biological warfare during the 1948 War https\://cris.bgu.ac.il/en/publications/cast-thy-bread-israeli-biological-warfare-during-the-1948-war
[8] 'Cast thy bread': Israeli biological warfare during the 1948 War https\://www.tandfonline.com/doi/full/10.1080/00263206.2022.2122448
\
Artikel https://x.com/RealWsiegrist/status/1906616394747179136
Nakba
https://waltisiegrist.locals.com/upost/2033124/die-siedler-fordern-ganz-offen-eine-zweite-nakba
-
 @ a60e79e0:1e0e6813
2025-03-23 16:10:10
@ a60e79e0:1e0e6813
2025-03-23 16:10:10**This is a long form note test of a post that lives on my Nostr educational website Hello Nostr **
In early 2025, social media is the most common use case for Nostr (and probably the reason you're reading this). Nostr is SO much more than just social media, but that's where the bulk of the activity is, and is what I'm focusing on in this post. Even though the protocol is still so young, that has not prevented an explosion of excellent social media focused clients that predominantly coalesce around the Twitter (X) style feed, containing shorter form content, often with images, and the ability to comment, like and share.
This first steps guide showcases one of the most polished and simplest examples of such a client, Primal. Primal is a cross platform app, that also works on your computer too. The steps that follow are demonstrated on iPhone, but should be identical for Android users. There may be some topics of concepts here that are new to you, to learn more about them, check out our Nostr 101 to learn more about Nostr basics and why it matters.
You can and should explore all of the other options available to you, that's the beauty of Nostr, you're free to choose how and where to interact with your social network. No lock in. No walled gardens. True freedom.

Getting Started
-
Go to your app store and download Primal to your Android or iPhone
-
Open Primal and choose Create Account. Choose your public display name and add a short bio about yourself.
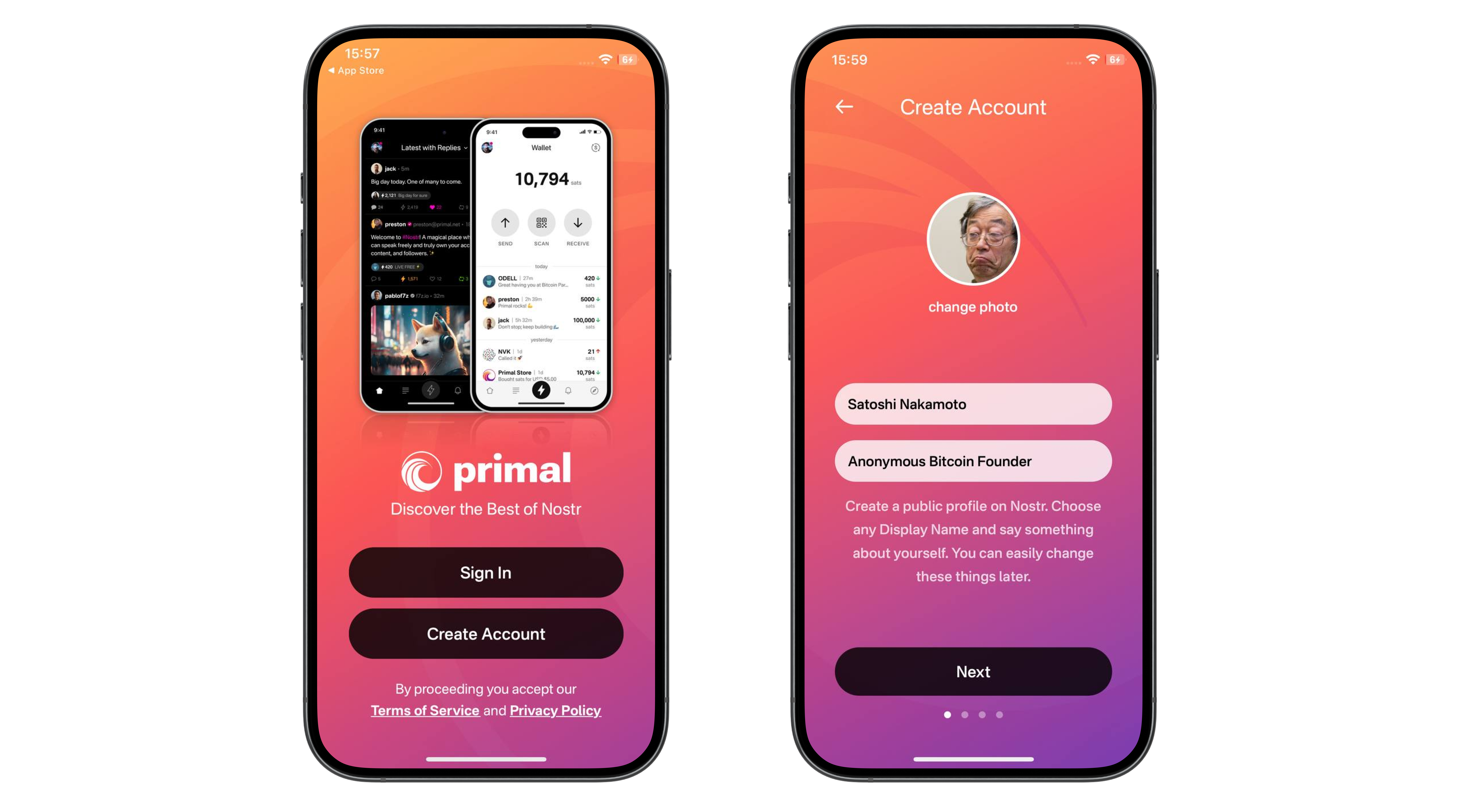
- Select your chosen interests from the list provided. This will bootstrap your feed and auto-follow a number of accounts so that your feed is not completely empty when starting out.
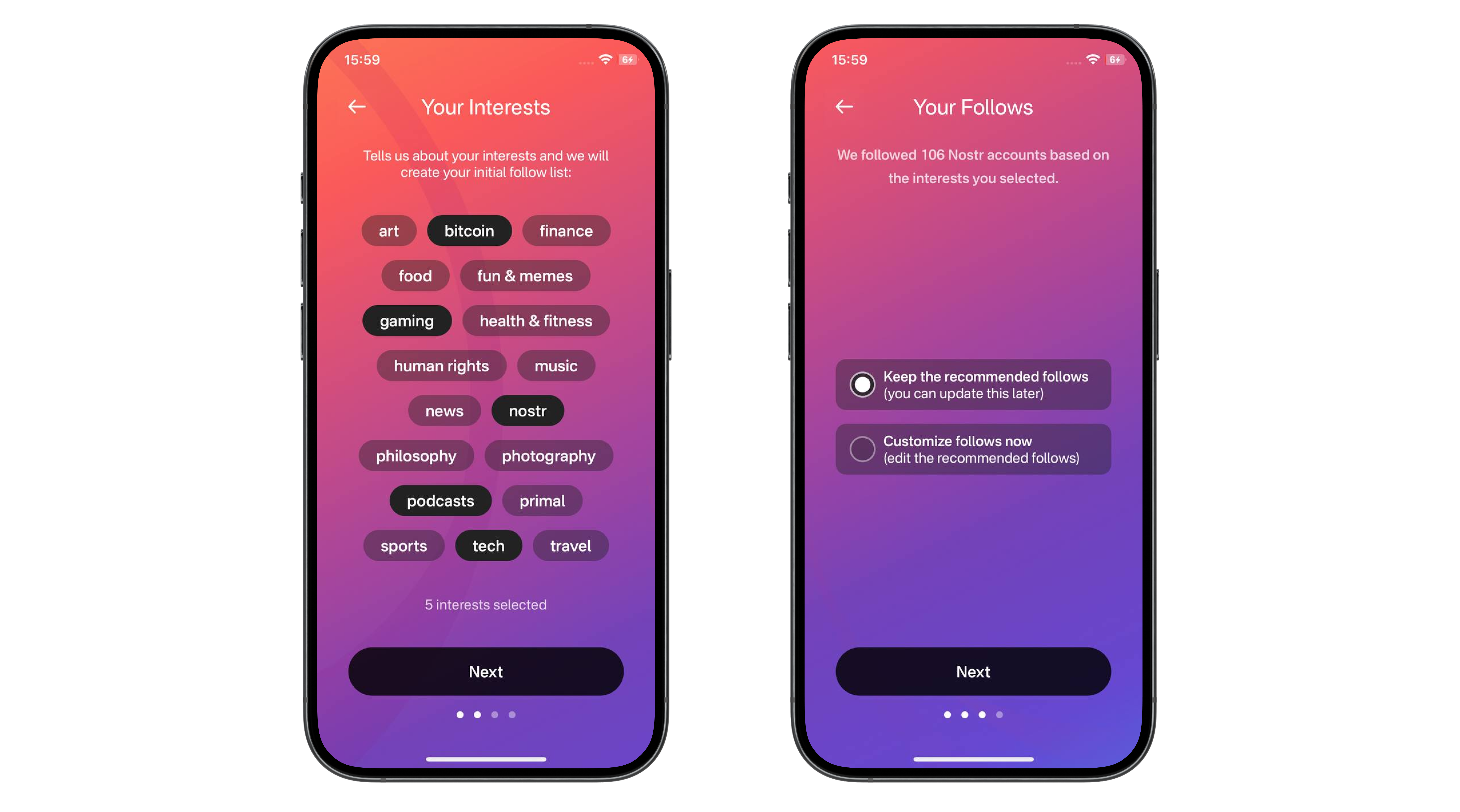
- Review your account info and tap Create Account Now. Take note of the fact that 'Your Nostr Key is available in your Account Settings'. We'll revisit this shortly.
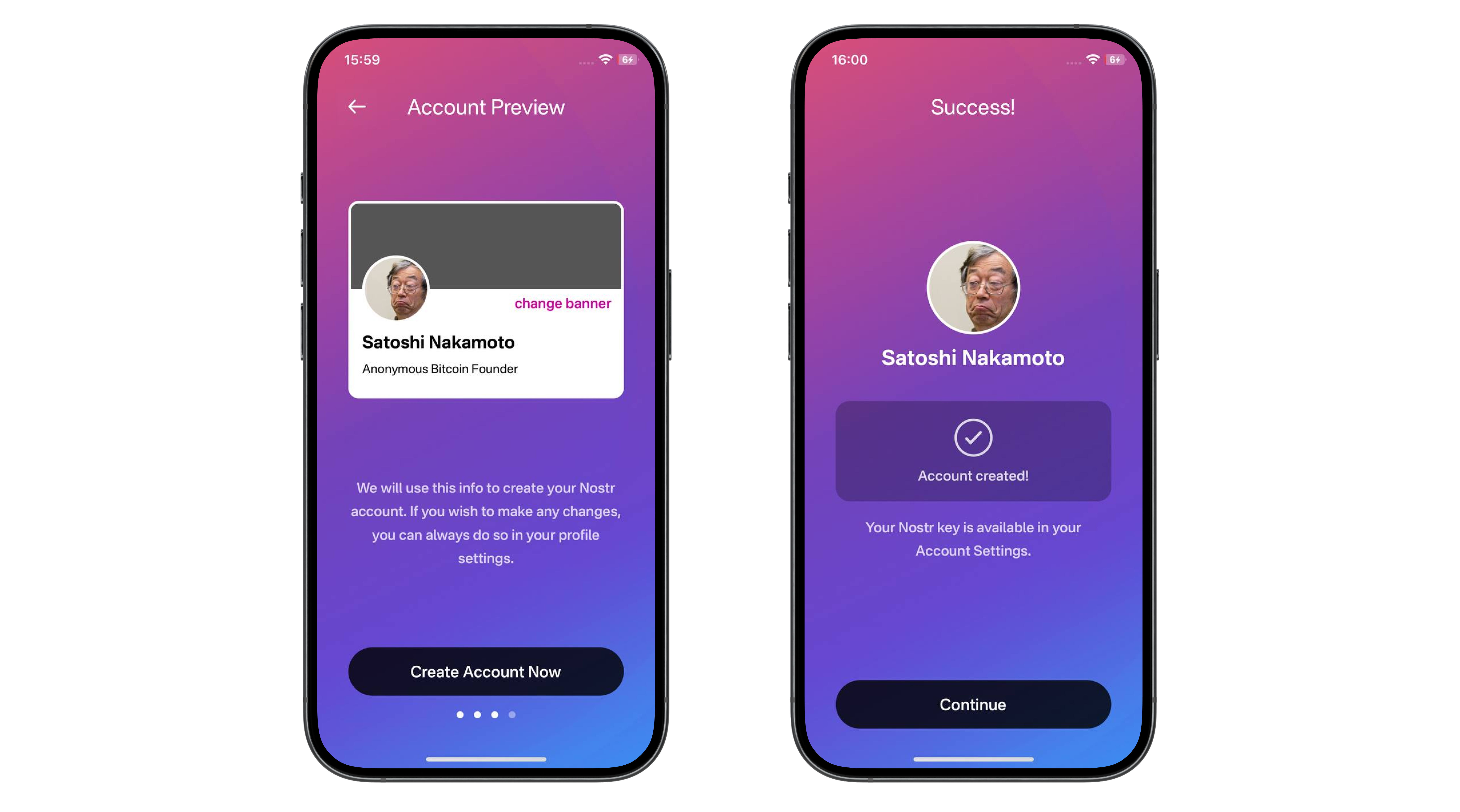
- Next is an optional step of activating the wallet feature within Primal. Having a wallet within your social client enables you to send and receive value (known as 'Zaps') in the form of Bitcoin. On Facebook and Twitter you can like a post, but it means much more to send someone fractions of a penny (or more if you like) to show your appreciation for their insights. You'll need to provide some personal information to enable the wallet, including an email address.
Using the internal wallet and purchasing sats with your credit card will tie your Nostr identity to your real ID. Think very carefully before carrying out this step.
Learn more in the detailed section at the end of this post.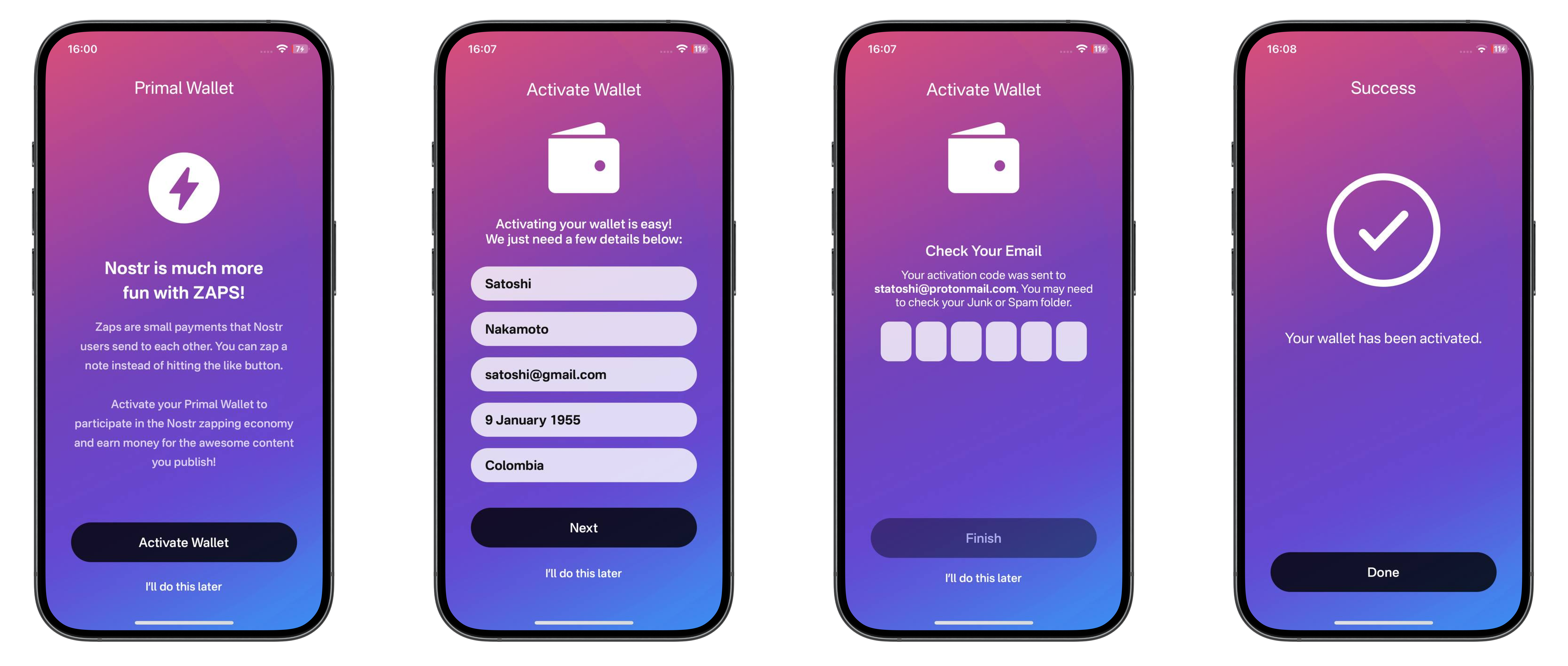
- That's it, you're now set up and ready to start sharing your thoughts, feelings and memes with the world via a decentralized and censorship resistant social network. To post your first note and say hello to the Nostr world, tap the + in the bottom right corner.
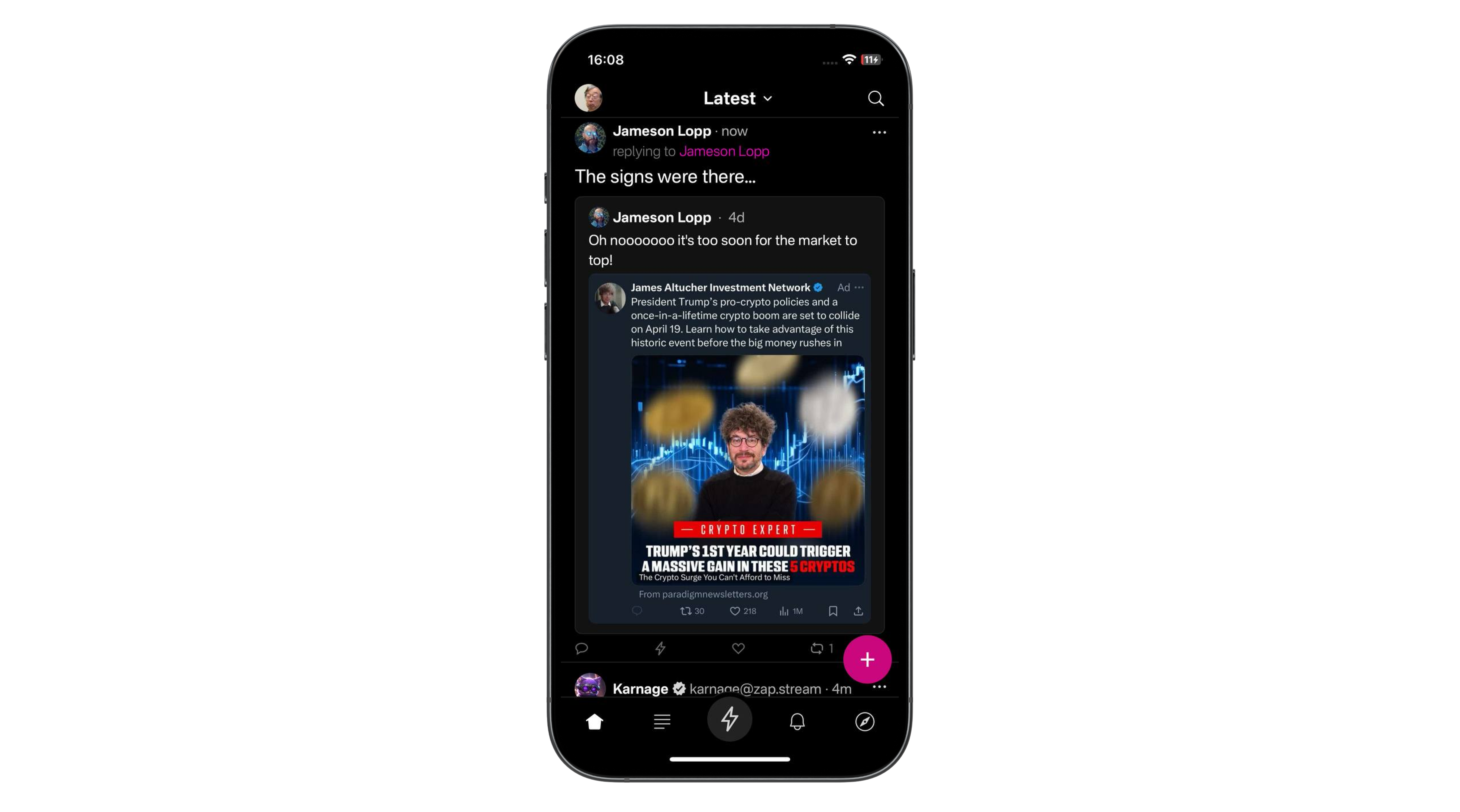
- If you activated the wallet at step 5, you might want to deposit some Bitcoin in there to allow you to send some value to your friends. There are three main ways to do this:
- Post some awesome content and have people send you value in the form of 'Zaps'
- Send some Bitcoin from a wallet you already have
- Purchase some directly within Primal
The latter is made very simple thanks to the in-app purchase feature, which allows you to purchase a small amount with the card you likely already have connected to your Apple/Google account. All you need to do is tap 'Buy Sats Now'.
- Next, let's look at the different feeds available on our home screen. Tap 'Latest' at the top of the screen and you can toggle between three different types of home feeds, great for discovering new people and content.
- Let's assume you already have some friends on Nostr and want to find and follow them. Tap the search icon in the top right corner, the enter the name of the person you want to follow. Once on their profile, simply tap the 'Follow' button.
- So you found a friend and want to start interacting with them so they know you made it over to Nostr. Simply find a note you like and choose from the different types of interactions available. From left to right they are:
- Comment
- Zap (send value from your wallet to theirs)
- Like
- Repost
- Bookmark
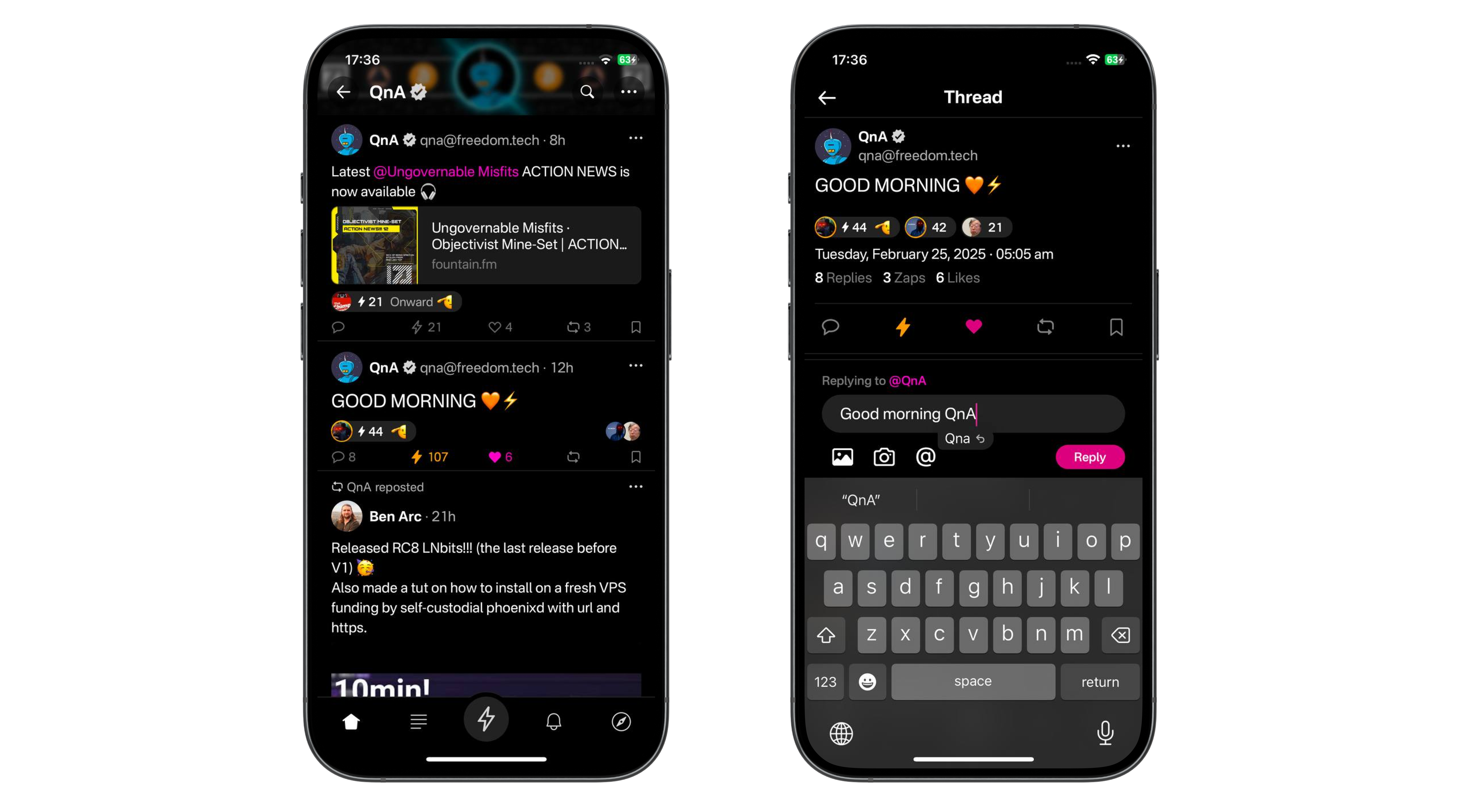
When Zapping, a single tap will send a tiny amount of 42 sats. If you want to send more, or a custom amount, tap and hold the zap button to bring up a selector menu. All default zap amounts are configurable in the app settings page.

- After you've started posting and interacting with others, you'll likely receive some notifications to tell you. Notifications can be filtered into interaction types.
- Another great way to find more people to follow and interact with is to use the discover page. To open it, tap the compass in the bottom right corner of the screen. Here you'll be able to browse different types of pre-built feeds, trending profiles, notes with large zaps and extra topics.
The Important Part
You might have noticed that throughout that setup, you were not asked for a unique username, nor were you asked for a password. So how the hell is this secure? What happens if you log out? Is your account lost forever?
This is where Nostr really starts to shine. Just like in Bitcoin or other cryptocurrencies, your Nostr account is protected by a 'Private Key'. Anyone with knowledge of the private key can access your account in any Nostr client. No private key, no access. So let's make sure you have a backup copy of it, so you can still recover access to your account in the event you lose your phone!
Tap on your profile image in the top left of the screen. Then tap Settings > Keys. Here you'll see two keys, one public and one private. Your public key is how people find you on Nostr. It is often referred to by its more technical name 'nPub' which is the prefix if the key itself. Your public key is designed to be exactly that, public!
Your private key is sometimes referred to by its technical name 'nSec' which is also the prefix of the key. Copy your private key and paste it somewhere safe and secure, in a location accessible independently from your phone, and only by you.
If you were to lose your phone, or accidentally delete the Primal app, now all you'd need to do is head back to step 1 above and choose Sign In. You'd then be asked to paste your private key, after which your profile and content would be magically restored.
Your private key can be imported into any other Nostr social client for the same result.
Things to Consider
This post has one primary focus - To get you from zero to posting and zapping in the quickest time and with the least friction. To achieve this, there are some trade-offs made that you should be aware of.
Custodial Wallet
The built in wallet is a custodial one. This means that the funds within are ultimately controlled by the developers behind Primal. They may be good actors, but you should approach the amount of money you maintain inside this wallet accordingly. If your wallet balance ever gets to a balance that makes you uncomfortable, you should send a good chunk of it out to another Bitcoin wallet where you control the keys. I recommend Phoenix or Zeus.
Those sats are never truly yours until you withdraw them to a self-custodial wallet
Wallet Privacy
If you choose to top up the wallet using the convenient in-app purchase method, you will tie that small amount of Bitcoin ownership to your Nostr account. If you Nostr account is literally your name, you might not have an issue with this, but often times people like to remain pseudonymous online. If you fall into that category, using your credit card to deposit Bitcoin into your Nostr account is not a good idea.
Android users of Primal can use an advanced technology called Nostr Wallet Connect (NWC) to connect an external Lightning wallet to their Nostr account in Primal. We'll cover this in a subsequent post.
Your private key allows you to take your profile and social network to any other client
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
-
-
 @ 22aa8151:ae9b5954
2025-03-31 07:44:15
@ 22aa8151:ae9b5954
2025-03-31 07:44:15With all the current hype around Payjoin for the month, I'm open-sourcing a project I developed five years ago: https://github.com/Kukks/PrivatePond
Note: this project is unmaintained and should only be used as inspiration.
Private Pond is a Bitcoin Payjoin application I built specifically to optimize Bitcoin transaction rails for services, such as deposits, withdrawals, and automated wallet rebalancing.
The core concept is straightforward: withdrawals requested by users are queued and processed at fixed intervals, enabling traditional, efficient transaction batching. Simultaneously, deposits from other users can automatically batch these withdrawals via Payjoin batching, reducing them onchain footprint further. Taking it to the next step: a user's deposit is able to fund the withdrawals with its own funds reducing the required operational liquidity in hot wallets through a process called the Meta Payjoin.
The application supports multiple wallets—hot, cold, multisig, or hybrid—with configurable rules, enabling automated internal fund management and seamless rebalancing based on operational needs such as min/max balance limits and wallet ratios (10% hot, 80% in 2-of-3, 10% in 1-of-2, etc) .
This system naturally leverages user Payjoin transactions as part of the automated rebalancing strategy, improving liquidity management by batching server operations with user interactions.
Private Pond remains quite possibly the most advanced Payjoin project today, though my multi-party addendum of 2023 probably competes. That said, Payjoin adoption overall has been disappointing: the incentives heavily favor service operators who must in turn actively encourage user participation, limiting its appeal only for specialized usage. This is why my efforts refocused on systems like Wabisabi coinjoins, delivering not just great privacy but all the benefits of advanced Payjoin batching on a greater scale through output compaction.
Soon, I'll also open-source my prototype coinjoin protocol, Kompaktor, demonstrating significant scalability improvements, such as 50+ payments from different senders being compacted into a single Bitcoin output. And this is not even mentioning Ark, that pushes these concepts even further, giving insane scalability and asyncrhonous execution.
You can take a look at the slides I did around this here: https://miro.com/app/board/uXjVL-UqP4g=/
Parts of Private Pond, the pending transfers and multisig, will soon be integrated into nostr:npub155m2k8ml8sqn8w4dhh689vdv0t2twa8dgvkpnzfggxf4wfughjsq2cdcvg 's next major release—special thanks to nostr:npub1j8y6tcdfw3q3f3h794s6un0gyc5742s0k5h5s2yqj0r70cpklqeqjavrvg for continuing the work and getting it to the finish line.
-
 @ c631e267:c2b78d3e
2025-03-31 07:23:05
@ c631e267:c2b78d3e
2025-03-31 07:23:05Der Irrsinn ist bei Einzelnen etwas Seltenes – \ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel. \ Friedrich Nietzsche
Erinnern Sie sich an die Horrorkomödie «Scary Movie»? Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?

Diese Szene kommt mir automatisch in den Sinn, wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real.
Die Europäische Union hat sich selbst über Jahre konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt.
In den USA haben sich die Vorzeichen allerdings mittlerweile geändert, und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen.
Statt jedoch umzukehren oder wenigstens zu bremsen und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die Kommentatoren des Events gegenseitig in sensationslüsterner «Berichterstattung».
Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen, Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, selbstzerstörerischen Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», erklärte die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte.
Zusätzlich brisant ist, dass aktuell «die ganze EU von Deutschen regiert wird», wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen.
Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen.
Es wird dringend Zeit, dass wir, der Souverän, diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts den Frieden auszurufen. Seien wir dabei!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ 78c90fc4:4bff983c
2025-03-31 07:03:41
@ 78c90fc4:4bff983c
2025-03-31 07:03:41In Palästina und im Ausland wurde das Abkommen einzelner jüdischer Organisationen mit dem nationalsozialistischen Deutschland heftig kritisiert. Auf dem 18. Zionistenkongress 1933 in Prag etwa bezeichnete der Schriftsteller Schalom Asch das Abkommen mit Hitlers Regime als „Verrat am Weltjudentum“. Chaim Arlosoroff, der damalige Verhandlungsführer der Jewish Agency, wurde wahrscheinlich deshalb im Juni 1933 Opfer eines Mordanschlags.

https\://de.m.wikipedia.org/wiki/Ha’avara-Abkommen
Am 16. Juni 1933 wurde Chaim Arlosoroff kurz nach seiner Rückkehr von den Transfer-Verhandlungen in Deutschland durch den Pistolenschuss eines Attentäters schwer verletzt, als er mit seiner Frau Sima, geb. Rubin, am Strand von Tel Aviv entlangging. Er verstarb am folgenden Tag im Krankenhaus. Wer der Attentäter war, ist bis heute ungeklärt. Zunächst wurden drei Verdächtige angeklagt. Zwei von ihnen wurden freigesprochen, einer, Abraham Stavsky, wurde verurteilt, doch das Urteil wurde durch das oberste Appellationsgericht aufgehoben.
https://de.m.wikipedia.org/wiki/Chaim_Arlosoroff#Ermordung
Instrumentalisierung des Holocaust
Von Anneliese Fikentscher und Andreas Neumann
Zum Schluss ein Zitat aus dem 2017 erschienenen Buch "Die israelisch-jüdische Tragödie. Von Auschwitz zum Besatzungs- und Apartheidstaat. Das Ende der Verklärung" von Arn Strohmeyer: „Der vielleicht radikalste Kritiker des israelischen Holocaustgedenkens ist der amerikanisch -jüdische Politologe Norman Finkelstein. Er wendet sich vor allem gegen das in Israel und den USA verwendete Dogma, der Holocaust sei 'einzigartig' gewesen und mit anderen Verbrechen nicht vergleichbar, dass er in der Geschichte also ohne Parallele sei. Diese Behauptung – so Finkelstein – impliziert eine Reihe anderer Behauptungen, die wiederum die Instrumentalisierung des Holocaust ausmachen. Erstens: Die Konstruktion des Holocaust als einzigartig gilt als gegeben, sie zu leugnen gilt als Leugnung des Holocaust. Diese Behauptung schließt zweitens ein rationales Verständnis des Holocaust aus, er macht den Holocaust zu einem Mysterium, wie Elie Wiesel ihn verstanden hat. Einzigartiges Leid verleiht drittens einen einzigartigen Anspruch. Die Unvergleichlichkeit des Holocaust stellt also ein moralisches Kapital dar, das Israel als politisches Alibi benutzt. Israel kann – so Finkelstein – diese moralischen und emotionalen Ansprüche an andere Staaten stellen und die Anerkennung seines Rechts einfordern, dass es als besonders bedroht gelten kann und seine Anstrengungen zum Überleben der Unterstützung bedarf. Die Behauptung der Einzigartigkeit des Holocaust beinhaltet auch die Behauptung der jüdischen Einzigartigkeit. Der Holocaust ist also etwas Besonderes, weil Juden etwas Besonderes sind, was man als säkularisierte Version der Auserwähltheit deuten kann. Diese Behauptungen – so Finkelstein – sollen Israels Sonderstellung legitimieren, sollen von vornherein jede unmenschliche Behandlung von Nichtjuden entschuldigen (Israel ist 'alles erlaubt!') und machen diesen Staat und seine Politik gegen jede Kritik immun. Bei dieser Instrumentalisierung des Holocaust bleiben die Rechte und die Würde der Opfer – welcher auch immer – völlig auf der Strecke.“ Ist das einer breiten Öffentlichkeit bewusst?
http://www.nrhz.de/flyer/beitrag.php?id=24469
Perplexity:
Der Schriftsteller Schalom Asch kritisierte das Ha'avara-Abkommen scharf auf dem 18. Zionistischen Kongress, der vom 21. August bis 4. September 1933 in Prag stattfand. Er bezeichnete das Abkommen mit dem Hitler-Regime als "ein Verrat am Weltjudentum"[1][2].
Das Ha'avara-Abkommen wurde am 10. August 1933 zwischen der Jewish Agency, der Zionistischen Vereinigung für Deutschland und dem deutschen Reichsministerium für Wirtschaft geschlossen. Es sollte die Emigration deutscher Juden nach Palästina erleichtern und gleichzeitig den deutschen Export fördern[2].
Am 5. November 1933 wurde die "Trust and Transfer Office Ha'avara Ltd." als quasi privates Unternehmen eingetragen[1][3]. Trotz der anfänglichen Kritik billigte die Zionistische Weltorganisation auf ihrer Konferenz am 20. August 1935 in Luzern mit Mehrheit den Ha'avara-Abschluss und übernahm sogar dessen gesamte Tätigkeit in eigene Regie[1][2][3].
Das Abkommen war innerhalb der zionistischen Bewegung umstritten, da es den gleichzeitig vorangetriebenen Boykottmaßnahmen gegen die Nationalsozialisten zuwiderlief[2]. Es ermöglichte deutschen Juden, einen Teil ihres Vermögens nach Palästina zu transferieren, wobei ein bestimmter Prozentsatz als Reichsfluchtsteuer vom deutschen Fiskus einbehalten wurde[5].
Quellen
[1] Zionistenkongress - Wikiwand https\://www.wikiwand.com/de/articles/Zionistenkongress
[2] Ha'avara-Abkommen - Wikiwand https\://www.wikiwand.com/de/articles/Haavara-Abkommen
[3] Zionistenkongress - Wikipedia https\://de.wikipedia.org/wiki/Zionistenkongress
[4] Schalom Asch - Wikipedia https\://de.wikipedia.org/wiki/Schalom_Asch
[5] Ha'avara-Abkommen - Wikipedia https\://de.wikipedia.org/wiki/Ha%E2%80%99avara-Abkommen
[6] Stefan Zweig. Briefe zum Judentum. Hg. v. Stefan Litt. Berlin ... https\://judaica.ch/article/view/8320/11519
[7] Das Haavara-Transfer-Abkommen | Die Wohnung | bpb.de https\://www.bpb.de/themen/nationalsozialismus-zweiter-weltkrieg/die-wohnung/195259/das-haavara-transfer-abkommen/
[8] Jüdischer Verlag - Wikipedia https\://de.wikipedia.org/wiki/J%C3%BCdischer_Verlag
Artikel https://x.com/RealWsiegrist/status/1906601705355252211
-
 @ da0b9bc3:4e30a4a9
2025-03-31 06:32:43
@ da0b9bc3:4e30a4a9
2025-03-31 06:32:43Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/929968
-
 @ 1c19eb1a:e22fb0bc
2025-03-21 15:48:32
@ 1c19eb1a:e22fb0bc
2025-03-21 15:48:32For our first edition of #Nostrversity, we'll be diving into Nostr Wallet Connect, or #NWC; a handy means of connecting a #Lightning wallet to your favorite #Nostr app that quickly became the standard and is now an essential part of onboarding to Nostr for any new user who wants to experience the magic of zaps. Yet NWC enables so much more than just one-tap-zapping, as we will see when we look a little closer at how it works under the hood.
Lightning History on Nostr
Back in the wild-west days of Nostr, before nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s invented zaps, Bitcoin psychopaths were already sending sats to one another over Nostr. However, the way we had to do it back then was by going into our Lightning wallet, selecting "receive," inputting an amount we wanted, and copy/pasting an invoice from the wallet into our Nostr note, then hope someone was willing to pay it. And the payment side was just as cumbersome, requiring manually copying the invoice from your Nostr client, pasting it into a Lightning wallet so you could see how much the other user wanted, and then deciding if you were even willing to send it.
It didn't take long before Nostr clients, particularly on mobile, started rendering Lightning invoices in a convenient format that showed the invoice amount and a "Pay" button, that would prompt the user to open a Lightning wallet. This took out a decent amount of friction for the sender, but it was still just as big a hassle for the receiver.
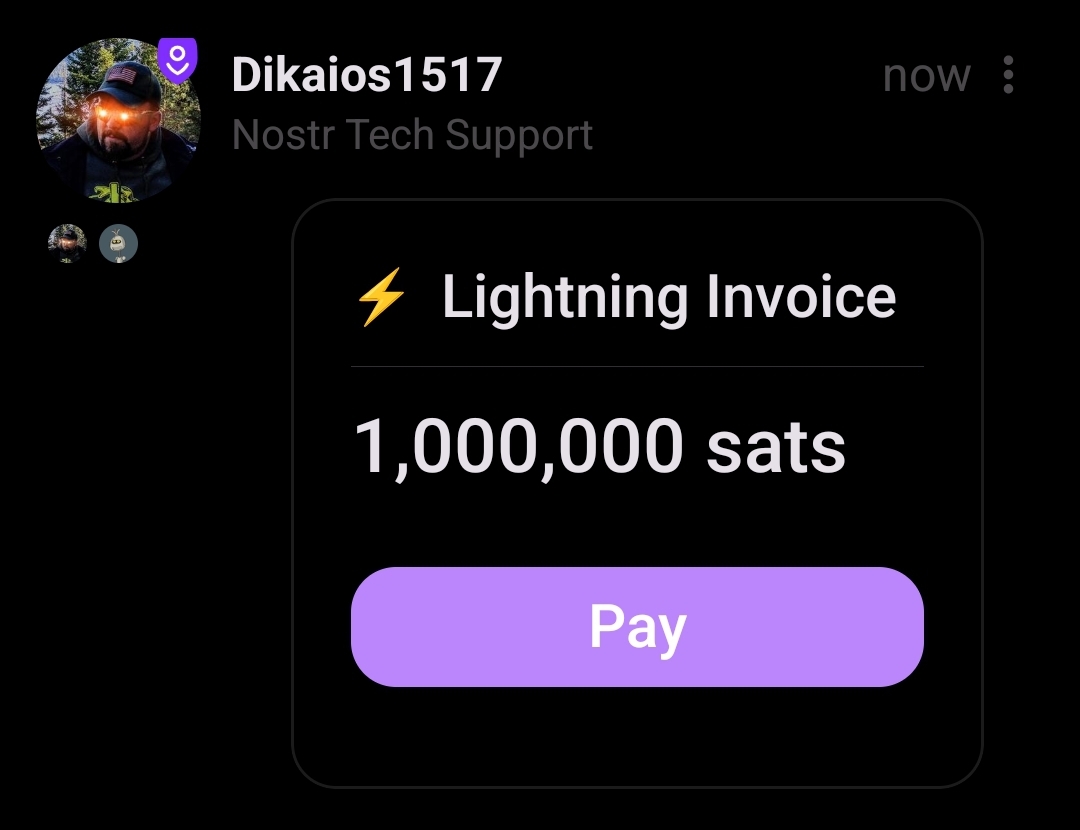
Then zaps came along, and soon everyone had the ability to send sats to any other user when they found value in the content they posted. At least, any other user that added their Lightning address to their profile and whose Lightning wallet provider supported sending a "paid" receipt to a Nostr relay. Receiver friction had been virtually eliminated and the sats began to flow. Nostr also became the de facto directory for Bitcoiner payment addresses. If you heard nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a say something brilliant on a podcast, you could just look her up on any Nostr client with zaps and send some sats her way as a thank you.
Enter the zapathon, a community event with one purpose: break nostr:npub1hcwcj72tlyk7thtyc8nq763vwrq5p2avnyeyrrlwxrzuvdl7j3usj4h9rq by zapping each other so much it was effectively a DDOS attack. Sure, it was a stress test on other wallets too, but most users were on Wallet of Satoshi because it was the easiest way to get a Lightning address with a mobile wallet.
It was a ton of fun flinging sats around as fast as your fingers would let you! However, a new friction point was soon discovered from trying to zap so frequently. Every time you tapped the zap icon in your Nostr client, you had to wait for your wallet to open and present the invoice to approve payment, then switch back to your Nostr client to zap the next note. Not a big deal when you only send a zap occasionally, but when trying to zap every note in your feed, it adds a significant amount of time and extra clicks. In fact, this small amount of friction, whether you realize it or not, often acts as just enough of a barrier to zapping that you will choose not to zap a post you found some value in, just because of the extra 5 seconds it takes to load into your wallet app, approve the payment, and switch back to your Nostr client.
Wouldn't it be amazing if we could have one-tap-zaps?
I can't recall if there were any other methods by which this was achieved, but the method that caught on was developed and released into the wild by nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm, who called it Nostr Wallet Connect. At that time (March of 2023), Alby was a custodial Lightning wallet for your web browser, and while you could connect your own node to it using LNDHub, most people just stuck with their custodial option since it came with a Lightning address. Nostr Wallet Connect was, at that time, a way to connect your Alby wallet to a Nostr client.
I am not certain which client was the first to support NWC, but I know that #Amethyst was pretty early on, and it was an instant success. Users could get a "connection string" from Alby, paste it into Amethyst, and zap with a single tap of their finger. Just like zaps themselves had eliminated the friction for receiving payments via Lightning for anyone with a Lightning address, Nostr Wallet Connect had eliminated the friction for sending payments. No more wasted seconds switching back and forth between Nostr client and wallet app, just tap and zap sent, tap again and another zap gone.
Of course, this meant that it was all too easy to send way more sats out of your wallet than you intended. This was solved by the ability to set budgets, so your wallet would cut you off once you reached the max amount you had set for yourself.
Because Alby had made Nostr Wallet Connect open source and part of the Nostr protocol, it didn't take long before more and more clients started adding support for it. Users demanded it and wouldn't shut up about it until it was added. Other wallet providers also saw the value of including it. Now it is simply expected, and any wallet that doesn't include it won't attract Nostr users.
Notably, Wallet of Satoshi went from being the most popular wallet among Nostr users to being a rare and quaint throwback to a bygone era, because they never integrated NWC and they pulled away from serving anyone in the U.S. out of fear of regulation under the Biden administration.
So we arrive at the state of Lightning on Nostr today, with Lightning addresses in our profiles for receiving zaps, and Nostr Wallet Connect for sending, and hard pressed to find Nostr clients that don't support both.
So... How does it work?
All of that history is great, but you're here to learn how this technology works. What is happening behind the scenes when you tap that little ⚡️ icon and sats seem to magically leave your Lightning wallet and show up on your screen as a zap underneath the latest nostr:npub1lrnvvs6z78s9yjqxxr38uyqkmn34lsaxznnqgd877j4z2qej3j5s09qnw5 meme, without you having to fiddle around with any Lightning invoices at all?
It's really quite simple, in the end. Your wallet communicating with your Nostr client using a Nostr relay in the middle, the same way you communicate with other Nostr users by saving notes to a relay that they can retrieve them from.
First, your Nostr client has to know how to "tag" your wallet, and on which relay to send it notes. This is why you need to get a "connection string" from your wallet to paste into your Nostr client. This string has all the information that is needed for your Nostr client to know how to communicate with your wallet, and for your wallet to be sure that the payment requests are authorized by you.
Let's take a look at an example connection string:
nostr+walletconnect://b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4?relay=wss%3A%2F%2Frelay.damus.io&secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cLooks like a bunch of gobbledygook, right? We'll break down each of its parts and see what it does.
nostr+walletconnect://This portion just defines the type of information that follows it. Because the string starts with this marker, any software reading it will know that what follows is information on how to communicate with a Lightning wallet, so long as it has been programmed to recognize it.
b889ff5b1513b641e2a139f661a661364979c5beee91842f8f0ef42ab558e9d4This section is just a public key, the same as an npub. In fact, it can be readily converted to an npub if you want using nostr:npub1zdr58j526qsrkdjhcg9xs60xfutqeey2ucugms04efnlx3spnmns2eqha9's key converter. It's a nostr identity just like yours or mine, but you won't find any GM posts or catstr pictures in its note history. It's only posting special note types used by NWC. This public key belongs to your Lightning wallet, and just like you can have multiple npubs for each of your alter egos, your wallet creates a separate public key to use with each new app you want to connect it to. Or at least it should. The Nostr client you use will tag your wallet in notes it creates by using this public key.
relay=wss%3A%2F%2Frelay.damus.ioThis section is probably easily recognizable. It's the same as typing
relay=wss://relay.damus.io, except that it has to use%3A%2F%2Fin place of://. This tells your Nostr client which relay it needs to use to communicate with your wallet. Hopefully your wallet uses a relay with high up-time, because one of the major ways for NWC to fail is if the relay is down. You also can't use just any relay. It has to accept the note kinds used by NWC, which is why wallets don't typically let their users choose the relay that will be used. You also can't just modify the connection string to use a relay you prefer, even if you know it allows NWC note kinds. This is because it will result in your Nostr client sending requests to your wallet on that relay, but your wallet is not reading from that relay, so it will never receive the requests.secret=71a8c14c1407c113601079c4302dab36460f0ccd0ad506f1f2dc73b5100e4f3cThis is just a Nostr private key. It's an nsec, but in hex format. Your wallet is giving your Nostr client a private key that it must use to sign all of the requests it sends to your wallet. No request signed by any other private key will be answered by your wallet. Your wallet will generate a separate private key for each connection string, allowing you as the user to revoke those connections individually, or set a separate budget for each connection.
When you tap the ⚡️ icon in your Nostr client, it obtains a Lightning invoice from the user's wallet you are trying to zap using their Lightning address. It then creates a note tagging your wallet's public key and requesting payment of that Lightning invoice, signing the note with the private key your wallet generated for it, and writing that note to the specified Nostr relay. Your wallet is constantly checking that relay for new notes and when it sees the payment request signed by an authorized private key, it pays the invoice, so long as it is within the budget you set, and sends out a payment receipt stating it has been paid so your client can light up the zap indicator to show that it was successful. All of this from a single tap of your finger in Amethyst.
More than Zaps
Now that we know the basics of how NWC works, it doesn't take much extrapolation to realize that this communication between wallet and Nostr client could be used for much more than just payment requests. A client could ask for your wallet's balance information, or transaction history, or ask for a lightning invoice. In fact, why does it have to be a Nostr client making those requests at all? Why not a mobile wallet app, or browser extension?
One of the major pieces of friction felt by those who run Lightning nodes is the difficulty of connecting to them remotely in a secure way. nostr:npub1aghreq2dpz3h3799hrawev5gf5zc2kt4ch9ykhp9utt0jd3gdu2qtlmhct and nostr:npub126ntw5mnermmj0znhjhgdk8lh2af72sm8qfzq48umdlnhaj9kuns3le9ll allow for connecting via Tor by default, but that can be painfully slow and unreliable. Anyone who has set up a connection to their node via LND Rest over Tor to their nostr:npub1xnf02f60r9v0e5kty33a404dm79zr7z2eepyrk5gsq3m7pwvsz2sazlpr5 wallet can attest to the frustration of opening their wallet and waiting several seconds for the interface to load, only to receive a timeout notice.
Nostr Wallet Connect has eliminated this issue thanks to Alby Hub and Alby Go. Just create a new connection in Alby Hub, give it a budget, and scan the QR code with Alby Go and you have a fully-functional, mobile Lightning wallet connected to your node at home that loads extremely quickly and reliably, so long as the Nostr relay in-between is up and running.
Now, you may be concerned that the information being passed back and forth on this Nostr relay is incredibly sensitive financial information, especially if balance and transaction history is involved. However, this is not a concern because the content of the notes is fully encrypted. The relay owner, or anyone else with access to read data on that relay, has no idea what information is contained in the messages being sent between wallet provider and Nostr client, or Lightning node and mobile wallet. And because neither npub being used by your wallet provider or your Nostr client is the same as your npub, there is nothing tying the messages to you.
As a result, NWC is quickly becoming an integral piece of Lightning infrastructure, even if those making use of it have no interest in joining Nostr at all.
The Future of NWC
To wrap this up, I'd like to point the reader to recent developments with Nostr Wallet Connect, and other use-cases we could very well see in the near future.
First, NWC may not just be for Lightning. nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 recently revealed that he has a working prototype of on-chain payments via NWC.
nostr:nevent1qvzqqqqqqypzpckv7l8jqspl8u4y54dn9rcduwlrs4v2040nxce0m2h0cunvrj8tqyw8wumn8ghj7un9d3shjtnzd96xxmmfdecxzunt9e3k7mf0qyfhwumn8ghj7am0wsh82arcduhx7mn99uq32amnwvaz7tmjv4kxz7fww468smewdahx2tcqyzswntflhlvuea2uf3035r94azm32frnskk5qp2evj43x6nz6kt9zd7j485
We are already seeing it used with eCash wallets like nostr:npub1kvaln6tm0re4d99q9e4ma788wpvnw0jzkz595cljtfgwhldd75xsj9tkzv. There is no reason we shouldn't expect to see it used with all forms of Bitcoin payments. This could lead to an explosion of available wallet applications for all platforms, since they will simply be an interface for communicating with your node or wallet provider.
NWC can also be used for subscriptions, as alluded to in nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8's note above. Before you protest about what an awful monetization model subscriptions are, I generally agree. That said, subscriptions where the user remains in control the entire time, and can unilaterally cancel the subscription at any time, without having to jump through hoops and give explanations about why they no longer want to use the service, is a massive improvement over the current status quo. Remember, NWC allows the user to set a budget for each connection. This means your subscription can't incrementally increase its monthly fee on you. Not without you willingly going into your wallet settings and adjusting the monthly budget, at any rate.
Last one before we close this out: NWC can be used for streaming services where you pay only for what you use, and give yourself a budget. Instead of paying a monthly subscription to Netflix, you could pay per minute that you watch. Previously this could only be done by topping up a wallet controlled by the service itself, the way nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5's wallet worked with streaming sats for Podcasting 2.0. But now NWC is coming to Fountain, and users can bring their own wallet that they control.
The future of NWC is bright, and it extends well beyond zapping memes on Nostr. It's going to open up a world of possibilities for how we can use our sats to stream media, make reoccurring donations, use micro-payments to rent compute, and so much more. I don't know about you, but I am here for it!
-
 @ b4f80629:1ddda3b4
2025-03-31 05:00:00
@ b4f80629:1ddda3b4
2025-03-31 05:00:00def create_basic_html(title, heading, paragraph): """ Creates a simple HTML string.
Args: title: The title of the HTML page. heading: The main heading of the page. paragraph: A paragraph of text for the page.
Returns: A string containing the HTML code. """
html_string = f"""
{title} {heading}
{paragraph}
""" return html_string
Example usage:
my_title = "My First Webpage" my_heading = "Welcome!" my_paragraph = "This is a simple webpage created with Python."
my_html = create_basic_html(my_title, my_heading, my_paragraph)
To save to a file (optional):
with open("my_page.html", "w") as f: f.write(my_html)
print("HTML created! (Check 'my_page.html' in the same folder as this python code)")
-
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ b4f80629:1ddda3b4
2025-03-31 04:58:26
@ b4f80629:1ddda3b4
2025-03-31 04:58:26Imagine you have a cool skill, like drawing, writing, or making videos. Freelancing is like using that skill to do small jobs for different people or companies. How it Works: * You're Your Own Boss: You decide when and where you work. * You Choose Your Jobs: You pick projects that you like. * You Get Paid for Your Skills: People pay you for the work you do. Examples: * If you're good at drawing, you could make digital art for someone's social media. * If you like writing, you could help someone write short stories or articles. * If you are good at video editing, you could edit videos for someone. Things to Know: * It takes time and effort to find jobs. * You need to be organized and good at communication. * It is very important to get permission from your parents or guardians before you begin any online money making ventures. Freelancing is a way to use your creativity and skills to earn money. It can be a fun way to explore different interests and build your experience.
-
 @ 6be5cc06:5259daf0
2025-03-31 03:19:46
@ 6be5cc06:5259daf0
2025-03-31 03:19:46Introdução à Sociedade de Condomínios Privados
Uma sociedade não deve ser construída sobre coerção, mas sim sobre associações voluntárias e interações espontâneas entre indivíduos. A sociedade de condomínios privados surge como uma alternativa natural ao modelo atual de centros urbanos, substituindo a imposição centralizada por estruturas baseadas em contratos e livre associação. Cada condomínio é uma unidade autônoma, gerida por aqueles que ali residem, onde os critérios de entrada, as regras internas e o comércio são definidos pelos próprios participantes. Essa estrutura permite que indivíduos se agrupem com base em valores compartilhados, eliminando os conflitos artificiais impostos por estados e legislações homogêneas que não respeitam a diversidade de preferências e estilos de vida.
O objetivo dessa sociedade é simples: permitir que as pessoas vivam de acordo com seus princípios sem interferência externa. Em um mundo onde a coerção estatal distorce incentivos, os condomínios privados oferecem uma alternativa onde a ordem surge do livre mercado e da cooperação voluntária. Os moradores escolhem seus vizinhos, definem suas próprias normas e interagem economicamente conforme suas necessidades e interesses. O modelo elimina a necessidade de um controle central, pois os incentivos derivados do livre mercado levam ao desenvolvimento de comunidades prósperas, onde a reputação e a confiança mútua são mais eficazes do que qualquer imposição estatal. Assim, essa sociedade representa a evolução lógica do conceito de liberdade individual e propriedade privada como pilares fundamentais da ordem social.
Público-Alvo e Identidade
Os condomínios privados refletem o princípio da livre associação, permitindo que indivíduos escolham viver em comunidades alinhadas com seus valores e necessidades sem interferência estatal. Cada condomínio possui uma identidade própria, moldada pelos moradores e seus interesses, criando ambientes onde afinidades culturais, filosóficas ou profissionais são preservadas e incentivadas. Enquanto alguns podem ser voltados para famílias numerosas, oferecendo amplos espaços e infraestrutura adequada, outros podem priorizar solteiros e jovens profissionais, com áreas de coworking e espaços de lazer voltados para networking e socialização. Da mesma forma, comunidades religiosas podem estabelecer seus próprios espaços de culto e eventos, enquanto condomínios para idosos podem ser projetados com acessibilidade e serviços médicos especializados.
Críticos podem afirmar que essa forma de organização resulta em pouca diversidade de habilidades e perspectivas, mas esse argumento ignora a dinâmica das interações humanas e o caráter evolutivo dos intercâmbios entre comunidades. Nenhum condomínio existe isolado; a troca entre diferentes comunidades ocorre naturalmente pelo mercado, incentivando o intercâmbio de conhecimento e serviços entre especialistas de diferentes áreas. Além disso, a ideia de que todos os grupos devem conter uma variedade aleatória de indivíduos desconsidera que a verdadeira diversidade nasce da liberdade de escolha, e não da imposição estatal de convivências forçadas.
Outra crítica possível é que a existência de critérios de entrada pode levar à segregação social. No entanto, essa preocupação deriva da concepção errônea de que todas as comunidades devem ser abertas e incluir qualquer pessoa indiscriminadamente. Porém, a liberdade de associação implica, necessariamente, a liberdade de exclusão. Se um grupo deseja manter determinada identidade cultural, religiosa ou profissional, isso não impede que outros grupos criem suas próprias comunidades conforme seus valores e recursos. Além disso, essa especialização leva a uma concorrência saudável entre condomínios, forçando-os a oferecer melhores condições para atrair moradores. Em vez de uma sociedade homogênea moldada por burocratas, temos um mosaico de comunidades autônomas, onde cada indivíduo pode encontrar ou criar o ambiente que melhor lhe convém.
Autossuficiência e Especialização
A força dos condomínios privados reside na capacidade de seus moradores de contribuírem ativamente para a comunidade, tornando-a funcional e autossuficiente sem a necessidade de intervenções estatais. Diferentes condomínios podem se especializar em áreas específicas ou ter diversos profissionais de diferentes setores, refletindo as competências e interesses de seus residentes. Essa descentralização do conhecimento e da produção permite que cada comunidade desenvolva soluções internas para suas demandas, reduzindo dependências externas e estimulando a prosperidade local.
Os moradores atuam como agentes econômicos, trocando bens e serviços dentro do próprio condomínio e entre diferentes comunidades. Um condomínio voltado para a saúde, por exemplo, pode contar com médicos, enfermeiros e terapeutas que oferecem consultas, aulas e assistência médica particular, remunerados diretamente por seus clientes, sem a intermediação de burocracias. Da mesma forma, um condomínio agrícola pode abrigar agricultores que cultivam alimentos orgânicos, compartilham técnicas de cultivo e comercializam excedentes com outros condomínios, garantindo um fluxo contínuo de suprimentos. Em um condomínio tecnológico, programadores, engenheiros e empreendedores desenvolvem soluções de TI, segurança digital e energia renovável, promovendo a inovação e ampliando as possibilidades de intercâmbio econômico.
A economia interna de cada condomínio se fortalece através de serviços oferecidos pelos próprios moradores. Professores podem ministrar aulas, técnicos podem prestar serviços de manutenção, artesãos podem vender seus produtos diretamente para os vizinhos. O mercado livre e voluntário é o principal regulador dessas interações, garantindo que a especialização surja naturalmente conforme a demanda e a oferta se ajustam. Essa estrutura elimina desperdícios comuns em sistemas centralizados, onde a alocação de recursos se dá por decisões políticas e não pelas necessidades reais da população.
Alguns argumentam que a especialização pode criar bolhas de conhecimento, tornando os condomínios excessivamente dependentes de trocas externas. Contudo, essa preocupação desconsidera a natureza espontânea do mercado, que incentiva a cooperação e o comércio entre comunidades distintas. Nenhum condomínio precisa produzir tudo internamente; ao contrário, a divisão do trabalho e a liberdade de escolha promovem interdependências saudáveis e vantajosas para todos. Assim, cada morador se insere em um ecossistema dinâmico, onde suas habilidades são valorizadas e sua autonomia preservada, sem coerções estatais ou distorções artificiais impostas por planejadores centrais.
Infraestrutura e Sustentabilidade
A solidez de uma sociedade baseada em condomínios privados depende de uma infraestrutura eficiente e sustentável, projetada para reduzir a dependência externa e garantir o máximo de autonomia. Sem um aparato estatal centralizador, cada comunidade deve estruturar seus próprios meios de obtenção de energia, água, alimentação e demais bens essenciais, garantindo que suas operações sejam viáveis a longo prazo. Essa abordagem, longe de ser um entrave, representa a verdadeira inovação descentralizada: um ambiente onde as soluções emergem da necessidade real e da engenhosidade humana, e não de diretrizes burocráticas e regulamentos ineficazes.
Cada condomínio pode investir em tecnologias sustentáveis e autônomas, como energia solar e eólica, reduzindo custos e minimizando a vulnerabilidade às flutuações do mercado energético tradicional. Sistemas de captação e filtragem de água da chuva, bem como a reutilização eficiente dos recursos hídricos, garantem independência em relação a empresas monopolistas e governos que frequentemente administram esse bem de forma ineficaz. Hortas comunitárias e fazendas verticais podem suprir grande parte da demanda alimentar, permitindo que cada condomínio mantenha sua própria reserva de alimentos, aumentando a resiliência contra crises externas e instabilidades de mercado.
Além dos recursos naturais, os espaços compartilhados desempenham um papel fundamental na integração e no fortalecimento dessas comunidades. Bibliotecas, ginásios, creches e salas de aula permitem que o conhecimento e os serviços circulem internamente, criando um ambiente onde a colaboração ocorre de maneira orgânica. A descentralização também se aplica ao uso da tecnologia, plataformas digitais privadas podem ser utilizadas para conectar moradores, facilitar a troca de serviços e produtos, além de coordenar agendamentos e eventos dentro dos condomínios e entre diferentes comunidades.
O Bitcoin surge como uma ferramenta indispensável nesse ecossistema, eliminando a necessidade de bancos estatais ou sistemas financeiros controlados. Ao permitir transações diretas, transparentes e resistentes à censura, o Bitcoin se torna o meio de troca ideal entre os condomínios, garantindo a preservação do valor e possibilitando um comércio ágil e eficiente. Além disso, contratos inteligentes e protocolos descentralizados podem ser integrados para administrar serviços comuns, fortalecer a segurança e reduzir a burocracia, tornando a governança desses condomínios cada vez mais autônoma e imune a intervenções externas.
Alguns podem argumentar que a falta de um aparato estatal para regulamentar a infraestrutura pode resultar em desigualdade no acesso a recursos essenciais, ou que a descentralização completa pode gerar caos e ineficiência. No entanto, essa visão ignora o fato de que a concorrência e a inovação no livre mercado são os maiores motores de desenvolvimento sustentável. Sem monopólios ou subsídios distorcendo a alocação de recursos, a busca por eficiência leva naturalmente à adoção de soluções melhores e mais acessíveis. Condomínios que oferecem infraestrutura de qualidade tendem a atrair mais moradores e investimentos, o que impulsiona a melhoria contínua e a diversificação dos serviços. Em vez de depender de um sistema centralizado falho, as comunidades se tornam responsáveis por sua própria prosperidade, criando uma estrutura sustentável, escalável e adaptável às mudanças do futuro.
Governança e Administração
Em uma sociedade descentralizada, não se deve depender de uma estrutura estatal ou centralizada para regular e tomar decisões em nome dos indivíduos. Cada condomínio, portanto, deve ser gerido de maneira autônoma, com processos claros de tomada de decisão, resolução de conflitos e administração das questões cotidianas. A gestão pode ser organizada por conselhos de moradores, associações ou sistemas de governança direta, conforme as necessidades locais.
Conselhos de Moradores e Processos de Tomada de Decisão
Em muitos casos, a administração interna de um condomínio privado pode ser realizada por um conselho de moradores, composto por representantes eleitos ou indicados pela própria comunidade. A ideia é garantir que as decisões importantes, como planejamento urbano, orçamento, manutenção e serviços, sejam feitas de forma transparente e que os interesses de todos os envolvidos sejam considerados. Isso não significa que a gestão precise ser completamente democrática, mas sim que as decisões devem ser tomadas de forma legítima, transparente e acordadas pela maior parte dos membros.
Em vez de um processo burocrático e centralizado, onde uma liderança impõe suas vontades sobre todos a muitas vezes suas decisões ruins não o afetam diretamente, a gestão de um condomínio privado deve ser orientada pela busca de consenso, onde os próprios gestores sofrerão as consequências de suas más escolhas. O processo de tomada de decisão pode ser dinâmico e direto, com os moradores discutindo e acordando soluções baseadas no mercado e nas necessidades locais, em vez de depender de um sistema impessoal de regulamentação. Além disso, a utilização de tecnologias descentralizadas, como plataformas de blockchain, pode proporcionar maior transparência nas decisões e maior confiança na gestão.
Resolução de Conflitos
A resolução de disputas dentro dos condomínios pode ocorrer de forma voluntária, através de negociação direta ou com o auxílio de mediadores escolhidos pelos próprios moradores por meio de um sistema de reputação. Em alguns casos, podem ser criados mecanismos para resolução de disputas mais formais, com árbitros ou juízes independentes que atuam sem vínculos com o condomínio. Esses árbitros podem ser escolhidos com base em sua experiência ou especialização em áreas como direito, mediação e resolução de conflitos, com uma reputação para zelar. Ao contrário de um sistema judicial centralizado, onde a parte envolvida depende do Estado para resolver disputas, os moradores possuem a autonomia para buscar soluções que atendam aos seus próprios interesses e necessidades. A diversidade de abordagens em um sistema de governança descentralizado cria oportunidades para inovações que atendem diferentes cenários, sem a interferência de burocratas distantes dos próprios problemas que estão "tentando resolver".
Planejamento Urbano e Arquitetura
A questão do design dos condomínios envolve não apenas a estética das construções, mas também a funcionalidade e a sustentabilidade a longo prazo. O planejamento urbano deve refletir as necessidades específicas da comunidade, onde ela decide por si mesma como construir e organizar seu ambiente.
Arquitetos e urbanistas, muitas vezes moradores especializados, serão responsáveis pela concepção de espaços que atendam a esses critérios, criando ambientes agradáveis, com áreas para lazer, trabalho e convivência que atendam às diversas necessidades de cada grupo.
Além disso, condomínios com nessecidades semelhantes poderão adotar ideias que deram certo em outros e certamente também dará no seu.Segurança e Vigilância
Em relação à segurança, cada condomínio pode adotar sistemas de vigilância e proteção que atendam à sua realidade específica. Algumas comunidades podem optar por sistemas de câmeras de segurança, armamento pleno de seus moradores, patrulhamento privado ou até mesmo formas alternativas de garantir a proteção, como vigilância por meio de criptografia e monitoramento descentralizado. A chave para a segurança será a confiança mútua e a colaboração voluntária entre os moradores, que terão a liberdade de definir suas próprias medidas.
Comércio entre Condomínios
A troca de bens e serviços entre as diferentes comunidades é essencial para o funcionamento da rede. Como cada condomínio possui um grau de especialização ou uma mistura de profissionais em diversas áreas, a interdependência entre eles se torna crucial para suprir necessidades e promover a colaboração.
Embora alguns condomínios sejam especializados em áreas como saúde, agricultura ou tecnologia, outros podem ter um perfil mais diversificado, com moradores que atuam em diferentes campos de conhecimento. Por exemplo, um condomínio agrícola pode produzir alimentos orgânicos frescos, enquanto um condomínio de saúde oferece consultas médicas, terapias e cuidados especializados. Já um condomínio tecnológico pode fornecer inovações em software ou equipamentos de energia. Podem haver condomínios universitários que oferecem todo tipo de solução no campo de ensino. Ao mesmo tempo, um condomínio misto, com moradores de diversas áreas, pode oferecer uma variedade de serviços e produtos, tornando-se um centro de intercâmbio de diferentes tipos de expertise.
Essa divisão de trabalho, seja especializada ou diversificada, permite que os condomínios ofereçam o melhor de suas áreas de atuação, ao mesmo tempo em que atendem às demandas de outros. Um condomínio que não se especializa pode, por exemplo, buscar um acordo de troca com um condomínio agrícola para obter alimentos frescos ou com um condomínio tecnológico para adquirir soluções inovadoras.
Embora os condomínios busquem a autossuficiência, alguns recursos essenciais não podem ser produzidos internamente. Itens como minérios para construção, combustíveis ou até mesmo água, em regiões secas, não estão disponíveis em todas as áreas. A natureza não distribui os recursos de maneira uniforme, e a capacidade de produção local pode ser insuficiente para suprir todas as necessidades dos moradores. Isso implica que, para garantir a qualidade de vida e a continuidade das operações, os condomínios precisarão estabelecer relações comerciais e de fornecimento com fontes externas, seja através de mercados, importações ou parcerias com outras comunidades ou fornecedores fora do sistema de condomínios. O comércio intercondomínios e com o exterior será vital para a complementaridade das necessidades, assegurando que os moradores tenham acesso a tudo o que não pode ser produzido localmente.
O sistema econômico entre os condomínios pode ser flexível, permitindo o uso de uma moeda comum (como o Bitcoin) ou até mesmo um sistema de troca direta. Por exemplo, um morador de um condomínio misto pode oferecer serviços de design gráfico em troca de alimentos ou cuidados médicos. Esse tipo de colaboração estimula a produtividade e cria incentivos para que cada condomínio ofereça o melhor de seus recursos e habilidades, garantindo acesso aos bens e serviços necessários.
Relações Externas e Diplomacia
O isolamento excessivo pode limitar o acesso a inovações, avanços culturais e tecnológicos, e até mesmo dificultar o acesso a mercados externos. Por isso, é importante que haja canais de comunicação e métodos de diplomacia para interagir com outras comunidades. Os condomínios podem, por exemplo, estabelecer parcerias com outras regiões, seja para troca de produtos, serviços ou até para inovação. Isso garante que a rede de condomínios não se torne autossuficiente ao ponto de se desconectar do resto do mundo, o que pode resultar em estagnação.
Feiras, mercados intercondomínios e até eventos culturais e educacionais podem ser organizados para promover essas interações. A colaboração entre as comunidades e o exterior não precisa ser baseada em uma troca de dependência, mas sim numa rede de oportunidades que cria benefícios para todas as partes envolvidas. Uma boa reputação atrai novos moradores, pode valorizar propriedades e facilitar parcerias. A diplomacia entre as comunidades também pode ser exercida para resolver disputas ou desafios externos.
A manutenção de boas relações entre condomínios é essencial para garantir uma rede de apoio mútuo eficiente. Essas relações incentivam a troca de bens e serviços, como alimentos, assistência médica ou soluções tecnológicas, além de fortalecer a autossuficiência regional. Ao colaborar em segurança, infraestrutura compartilhada, eventos culturais e até mesmo na resolução de conflitos, os condomínios se tornam mais resilientes e eficientes, reduzindo a dependência externa e melhorando a qualidade de vida dos moradores. A cooperação contínua cria um ambiente mais seguro e harmonioso.
Educação e Desenvolvimento Humano
Cada comunidade pode criar escolas internas com currículos adaptados às especializações de seus moradores. Por exemplo, em um condomínio agrícola, podem ser ensinadas práticas agrícolas sustentáveis, e em um condomínio tecnológico, cursos de programação e inovação. Isso permite que crianças e jovens cresçam em ambientes que reforçam as competências valorizadas pela comunidade.
Além das escolas internas, o conceito de homeschooling pode ser incentivado, permitindo que os pais eduquem seus filhos conforme seus próprios valores e necessidades, com o apoio da comunidade. Esse modelo oferece uma educação mais flexível e personalizada, ao contrário do currículo tradicional oferecido pelo sistema público atual.
Os condomínios universitários também podem surgir, criando ambientes dedicados ao desenvolvimento acadêmico, científico e profissional, onde estudantes vivem e aprendem. Além disso, programas de capacitação contínua são essenciais, com oficinas e cursos oferecidos dentro do condomínio para garantir que os moradores se atualizem com novas tecnologias e práticas.
Para ampliar os horizontes educacionais, os intercâmbios estudantis entre diferentes condomínios podem ser incentivados. Esses intercâmbios não se limitam apenas ao ambiente educacional, mas também se estendem ao aprendizado de práticas de vida e habilidades técnicas. Os jovens de diferentes condomínios podem viajar para outras comunidades para estudar, trabalhar ou simplesmente trocar ideias. Isso pode ocorrer de diversas formas, como programas de curto e longo prazo, através de acordos entre os próprios condomínios, permitindo que os estudantes se conectem com outras comunidades, aprendam sobre diferentes especializações e desenvolvam uma compreensão mais ampla.
Essa abordagem descentralizada permite que cada comunidade desenvolva as competências essenciais sem depender de estruturas limitantes do estado ou sistemas educacionais centralizados. Ao proporcionar liberdade de escolha e personalização, os condomínios criam ambientes propícios ao crescimento humano, alinhados às necessidades e interesses de seus moradores.
A sociedade dos condomínios privados propõe uma estrutura alternativa de convivência onde as pessoas podem viver de acordo com seus próprios valores e necessidades. Esses condomínios oferecem um modelo de organização que desafia a centralização estatal, buscando criar comunidades adaptáveis e inovadoras. A liberdade garante que as habilidades necessárias para o sustento e crescimento das comunidades sejam mantidas ao longo do tempo.
A troca de bens, serviços e conhecimentos entre os condomínios, sem a imposição de forças externas, cria uma rede de boas relações, onde o comércio e a colaboração substituem a intervenção estatal. Em vez de depender de sistemas coercitivos, cada condomínio funciona como um microcosmo autônomo que, juntos, formam um ecossistema dinâmico e próspero. Este modelo propõe que, por meio de trocas voluntárias, possamos construir uma sociedade mais saudável. Lembre-se: Ideias e somente ideias podem iluminar a escuridão.
-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ 1c19eb1a:e22fb0bc
2025-03-21 00:34:10
@ 1c19eb1a:e22fb0bc
2025-03-21 00:34:10What is #Nostrversity? It's where you can come to learn about all the great tools, clients, and amazing technology that is being built on #Nostr, for Nostr, or utilized by Nostr, presented in an approachable and non-technical format. If you have ever wondered what Blossom, bunker signing, or Nostr Wallet Connect are, how they work, and how you can put them to work to improve your Nostr experience, this is the place you can read about them without needing a computer-science degree ahead of time.
Between writing full-length reviews, which take a fair amount of time to research, test, and draft, I will post shorter articles with the Nostrversity hashtag to provide a Nostr-native resource to help the community understand and utilize the tools our illustrious developers are building. These articles will be much shorter, and more digestible than my full-length reviews. They will also cover some things that may not be quite ready for prime-time, whereas my reviews will continue to focus on Nostr apps that are production-ready.
Keep an eye out, because Nostr Wallet Connect will be the first topic of study. Take your seats, get out your notepads, and follow along to discover how Nostr Wallet Connect is improving Lightning infrastructure. Hint: It's not just for zaps.
-
 @ d5c3d063:4d1159b3
2025-03-31 03:18:05
@ d5c3d063:4d1159b3
2025-03-31 03:18:05ทำไมทุกครั้งที่รัฐแจกเงิน คนถึงเฮ..ดีใจ แต่พอพูดถึงตลาดเสรี กลับโดนมองว่าใจร้าย
แล้วทำไมนักเศรษฐศาสตร์กระแสหลัก ถึงยังไม่อินกับ “ตลาดเสรี” ทั้ง ๆ ที่ทุกคนก็เห็นแล้วว่าแนวคิดของ Keynes และ Marx มันล้มเหลวซ้ำแล้วซ้ำเล่าในทางปฏิบัติ แต่นักเศรษฐศาสตร์ก็ยังเอาทฤษฎีพวกนี้มาใช้อยู่ดี...
ทำไมนะ ?
ก็เพราะแนวคิดพวกนี้มัน “ฟังดูดี” มันให้ “คำตอบ ตำอธิบายที่ถูกใจ” มากกว่า “ความจริง ที่ฟังแล้วไม่เข้าหู”
Keynes ทำให้รัฐบาลดูฉลาดขึ้นเวลาที่ใช้เงินเกินตัว ใครจะกล้าทักละว่า เฮ้ย “รัฐอย่าเพิ่งก่อหนี้นะครับ” ก็เคนส์เค้าบอกว่า “การใช้จ่ายจะช่วยกระตุ้นเศรษฐกิจ” นี่หน่า
ส่วน Marx ก็สอนให้เราฝันกลางวัน ที่คนทุกคนจะต้องเท่าเทียม ไม่มีใครรวยกว่าใคร มันฟังแล้วดูดี เหมือนได้คืนความยุติธรรมให้สังคม แต่ไม่มีใครบอกว่า ราคาของความเท่าเทียมแบบปลอมๆ นั้น ต้องแลกกับ "เสรีภาพ" ที่เรามีนะ
ทีนี้ ลองหันกลับมาดูตลาดเสรี
มันไม่ได้พูดเพราะ (แต่ก็ไม่ได้หยาบคาย) มันไม่ได้สัญญาอะไร (ไม่ต้อง"ขอเวลาอีกไม่นาน") แต่มันซื่อสัตย์ และมันบอกกับเราตรง ๆ ว่า
ถ้าอยากได้อะไรคุณต้องให้ก่อน ไม่มีใครได้อะไรฟรี ๆ และไม่มีใครมีสิทธิขโมยของจากใครไปแม้แต่นิดเดียว
ฟังดูโหดไหม จะว่าโหดก็ได้ แต่มันคือโลกของคนที่ “มีความรับผิดชอบ ในชีวิตของตัวเอง”
คำถามคือ...หรือจริง ๆ แล้ว...เราไม่ได้กลัวระบบ แต่เรากลัวอิสรภาพที่ไม่มีใครมารับผิดแทนเรากันแน่ . . แล้วแบบนี้ “รัฐ” ควรมีหน้าที่อะไรล่ะ ไม่ใช่ว่าเชียร์ตลาดเสรีแล้วต้องเกลียดรัฐไปหมดนะ ตลาดเสรีไม่ใช่โลกของคนไร้กฎหมาย หรือใครอยากทำอะไรก็ได้ตามใจ แต่โลกของตลาดเสรี...ต้องมี “กรรมการ” ที่คอยดูแลเกมให้มันแฟร์
และรัฐในแบบที่ควรเป็นคือ ไม่ใช่คนที่ลงมาเตะบอลแข่งกับนักเตะในสนาม แต่เป็นกรรมการที่คอย “เป่าให้ยุติธรรม” แล้วยืนดูอยู่ข้างสนามอย่างเงียบ ๆ
รัฐที่ดี ไม่ใช่รัฐที่มาแจกเงิน มาอุ้มคนล้ม หรือมาคอยสั่งว่าใครควรได้อะไร แต่เป็นรัฐที่ทำหน้าที่แค่ 3 อย่างง่าย ๆ
-ดูแลไม่ให้ใครมารังแกใคร -ถ้าใครตกลงอะไรกันไว้ ก็ช่วยดูให้มันเป็นธรรม -ไม่เลือกข้าง ไม่เล่นพวก ไม่ใช้อำนาจเพื่อหาเสียง
ก็แค่นั้นพอแล้วจริง ๆ
เพราะทันทีที่รัฐ “อยากเป็นพระเอก” เข้ามาอุ้ม อยากเป็นคนคอยแจก คอยจัดการทุกอย่าง เกมมันก็เริ่มไม่แฟร์…
พอรัฐช่วยคนหนึ่ง ก็ต้องไปหยิบของจากอีกคนมา เหมือนเล่นบอลแล้วกรรมการยิงประตูให้ทีมตัวเอง แล้วสุดท้าย…มันก็กลายเป็นเกม...ที่มีแต่ คนอยาก “อยู่ฝั่งที่ถูกรัฐอุ้ม” (ทุนนิยมพวกพ้อง) ไม่ใช่ทุนนิยมหรือเกมที่เล่นด้วยความสามารถจริง ๆ
รัฐที่ดี ไม่ใช่รัฐที่ “ยิ่งใหญ่ อำนาจล้นฟ้า” แต่คือรัฐที่ให้ผู้คน “ยืนได้ด้วยขาตัวเอง”
แค่นี้เอง...ไม่ต้องมีสูตรซับซ้อน ไม่ต้องมีทฤษฎีเยอะ แค่มีสติ ไม่เอื้อใคร ไม่แทรกแซงเกินจำเป็นก็พอแล้ว
Siamstr
-
 @ fd06f542:8d6d54cd
2025-03-31 01:57:20
@ fd06f542:8d6d54cd
2025-03-31 01:57:20什么是nostrbook?
nostrbook 是基于nostr 社区技术存储在 nostr relay server上的长文(30023)文章。 查看浏览,采用的是 docsify 技术。整个网站技术无须部署服务器占用太多的存储空间。 可以实现轻量级部署。
-
 @ 16f1a010:31b1074b
2025-03-20 14:32:25
@ 16f1a010:31b1074b
2025-03-20 14:32:25grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Introduction
grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Prerequisites
- Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rwwp5xsuryd3knfdr7g
Download Grain
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlPrerequisites: - Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: [Link to MongoDB setup guide].
Download Grain:
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution:
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain:
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files:
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlConfiguration Documentation
You can always find the latest example configs on my site or in the github repo here: config.yml
Config.yml
This
config.ymlfile is where you customize how your Grain relay operates. Each section controls different aspects of the relay's behavior.1.
mongodb(Database Settings)uri: mongodb://localhost:27017/:- This is the connection string for your MongoDB database.
mongodb://localhost:27017/indicates that your MongoDB server is running on the same computer as your Grain relay (localhost) and listening on port 27017 (the default MongoDB port).- If your MongoDB server is on a different machine, you'll need to change
localhostto the server's IP address or hostname. - The trailing
/indicates the root of the mongodb server. You will define the database in the next line.
database: grain:- This specifies the name of the MongoDB database that Grain will use to store Nostr events. Grain will create this database if it doesn't already exist.
- You can name the database whatever you want. If you want to run multiple grain relays, you can and they can have different databases running on the same mongo server.
2.
server(Relay Server Settings)port: :8181:- This sets the port on which your Grain relay will listen for incoming nostr websocket connections and what port the frontend will be available at.
read_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to send data before closing the connection.
write_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to receive data before closing the connection.
idle_timeout: 120 # in seconds:- This is the maximum time (in seconds) that the relay will keep a connection open if there's no activity.
max_connections: 100:- This sets the maximum number of simultaneous client connections that the relay will allow.
max_subscriptions_per_client: 10:- This sets the maximum amount of subscriptions a single client can request from the relay.
3.
resource_limits(System Resource Limits)cpu_cores: 2 # Limit the number of CPU cores the application can use:- This restricts the number of CPU cores that Grain can use. Useful for controlling resource usage on your server.
memory_mb: 1024 # Cap the maximum amount of RAM in MB the application can use:- This limits the maximum amount of RAM (in megabytes) that Grain can use.
heap_size_mb: 512 # Set a limit on the Go garbage collector's heap size in MB:- This sets a limit on the amount of memory that the Go programming language's garbage collector can use.
4.
auth(Authentication Settings)enabled: false # Enable or disable AUTH handling:- If set to
true, this enables authentication handling, requiring clients to authenticate before using the relay.
- If set to
relay_url: "wss://relay.example.com/" # Specify the relay URL:- If authentication is enabled, this is the url that clients will use to authenticate.
5.
UserSync(User Synchronization)user_sync: false:- If set to true, the relay will attempt to sync user data from other relays.
disable_at_startup: true:- If user sync is enabled, this will prevent the sync from starting when the relay starts.
initial_sync_relays: [...]:- A list of other relays to pull user data from.
kinds: []:- A list of event kinds to pull from the other relays. Leaving this empty will pull all event kinds.
limit: 100:- The limit of events to pull from the other relays.
exclude_non_whitelisted: true:- If set to true, only users on the whitelist will have their data synced.
interval: 360:- The interval in minutes that the relay will resync user data.
6.
backup_relay(Backup Relay)enabled: false:- If set to true, the relay will send copies of received events to the backup relay.
url: "wss://some-relay.com":- The url of the backup relay.
7.
event_purge(Event Purging)enabled: false:- If set to
true, the relay will automatically delete old events.
- If set to
keep_interval_hours: 24:- The number of hours to keep events before purging them.
purge_interval_minutes: 240:- How often (in minutes) the purging process runs.
purge_by_category: ...:- Allows you to specify which categories of events (regular, replaceable, addressable, deprecated) to purge.
purge_by_kind_enabled: false:- If set to true, events will be purged based on the kinds listed below.
kinds_to_purge: ...:- A list of event kinds to purge.
exclude_whitelisted: true:- If set to true, events from whitelisted users will not be purged.
8.
event_time_constraints(Event Time Constraints)min_created_at: 1577836800:- The minimum
created_attimestamp (Unix timestamp) that events must have to be accepted by the relay.
- The minimum
max_created_at_string: now+5m:- The maximum created at time that an event can have. This example shows that the max created at time is 5 minutes in the future from the time the event is received.
min_created_at_stringandmax_created_atwork the same way.
9.
rate_limit(Rate Limiting)ws_limit: 100:- The maximum number of WebSocket messages per second that the relay will accept.
ws_burst: 200:- Allows a temporary burst of WebSocket messages.
event_limit: 50:- The maximum number of Nostr events per second that the relay will accept.
event_burst: 100:- Allows a temporary burst of Nostr events.
req_limit: 50:- The limit of http requests per second.
req_burst: 100:- The allowed burst of http requests.
max_event_size: 51200:- The maximum size (in bytes) of a Nostr event that the relay will accept.
kind_size_limits: ...:- Allows you to set size limits for specific event kinds.
category_limits: ...:- Allows you to set rate limits for different event categories (ephemeral, addressable, regular, replaceable).
kind_limits: ...:- Allows you to set rate limits for specific event kinds.
By understanding these settings, you can tailor your Grain Nostr relay to meet your specific needs and resource constraints.
whitelist.yml
The
whitelist.ymlfile is used to control which users, event kinds, and domains are allowed to interact with your Grain relay. Here's a breakdown of the settings:1.
pubkey_whitelist(Public Key Whitelist)enabled: false:- If set to
true, this enables the public key whitelist. Only users whose public keys are listed will be allowed to publish events to your relay.
- If set to
pubkeys::- A list of hexadecimal public keys that are allowed to publish events.
pubkey1andpubkey2are placeholders, you will replace these with actual hexadecimal public keys.
npubs::- A list of npubs that are allowed to publish events.
npub18ls2km9aklhzw9yzqgjfu0anhz2z83hkeknw7sl22ptu8kfs3rjq54am44andnpub2are placeholders, replace them with actual npubs.- npubs are bech32 encoded public keys.
2.
kind_whitelist(Event Kind Whitelist)enabled: false:- If set to
true, this enables the event kind whitelist. Only events with the specified kinds will be allowed.
- If set to
kinds::- A list of event kinds (as strings) that are allowed.
"1"and"2"are example kinds. Replace these with the kinds you want to allow.- Example kinds are 0 for metadata, 1 for short text notes, and 2 for recommend server.
3.
domain_whitelist(Domain Whitelist)enabled: false:- If set to
true, this enables the domain whitelist. This checks the domains .well-known folder for their nostr.json. This file contains a list of pubkeys. They will be considered whitelisted if on this list.
- If set to
domains::- A list of domains that are allowed.
"example.com"and"anotherdomain.com"are example domains. Replace these with the domains you want to allow.
blacklist.yml
The
blacklist.ymlfile allows you to block specific content, users, and words from your Grain relay. Here's a breakdown of the settings:1.
enabled: true- This setting enables the blacklist functionality. If set to
true, the relay will actively block content and users based on the rules defined in this file.
2.
permanent_ban_words:- This section lists words that, if found in an event, will result in a permanent ban for the event's author.
- really bad wordis a placeholder. Replace it with any words you want to permanently block.
3.
temp_ban_words:- This section lists words that, if found in an event, will result in a temporary ban for the event's author.
- crypto,- web3, and- airdropare examples. Replace them with the words you want to temporarily block.
4.
max_temp_bans: 3- This sets the maximum number of temporary bans a user can receive before they are permanently banned.
5.
temp_ban_duration: 3600- This sets the duration of a temporary ban in seconds.
3600seconds equals one hour.
6.
permanent_blacklist_pubkeys:- This section lists hexadecimal public keys that are permanently blocked from using the relay.
- db0c9b8acd6101adb9b281c5321f98f6eebb33c5719d230ed1870997538a9765is an example. Replace it with the public keys you want to block.
7.
permanent_blacklist_npubs:- This section lists npubs that are permanently blocked from using the relay.
- npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtnis an example. Replace it with the npubs you want to block.- npubs are the human readable version of public keys.
8.
mutelist_authors:- This section lists hexadecimal public keys of author of a kind1000 mutelist. Pubkey authors on this mutelist will be considered on the permanent blacklist. This provides a nostr native way to handle the backlist of your relay
- 3fe0ab6cbdb7ee27148202249e3fb3b89423c6f6cda6ef43ea5057c3d93088e4is an example. Replace it with the public keys of authors that have a mutelist you would like to use as a blacklist. Consider using your own.- Important Note: The mutelist Event MUST be stored in this relay for it to be retrieved. This means your relay must have a copy of the authors kind10000 mutelist to consider them for the blacklist.
Running Grain as a Service:
Windows Service:
To run Grain as a Windows service, you can use tools like NSSM (Non-Sucking Service Manager). NSSM allows you to easily install and manage any application as a Windows service.
* For instructions on how to install NSSM, please refer to this article: [Link to NSSM install guide coming soon].-
Open Command Prompt as Administrator:
- Open the Windows Start menu, type "cmd," right-click on "Command Prompt," and select "Run as administrator."
-
Navigate to NSSM Directory:
- Use the
cdcommand to navigate to the directory where you extracted NSSM. For example, if you extracted it toC:\nssm, you would typecd C:\nssmand press Enter.
- Use the
-
Install the Grain Service:
- Run the command
nssm install grain. - A GUI will appear, allowing you to configure the service.
- Run the command
-
Configure Service Details:
- In the "Path" field, enter the full path to your Grain executable (e.g.,
C:\grain\grain_windows_amd64.exe). - In the "Startup directory" field, enter the directory where your Grain executable is located (e.g.,
C:\grain).
- In the "Path" field, enter the full path to your Grain executable (e.g.,
-
Install the Service:
- Click the "Install service" button.
-
Manage the Service:
- You can now manage the Grain service using the Windows Services manager. Open the Start menu, type "services.msc," and press Enter. You can start, stop, pause, or restart the Grain service from there.
Linux Service (systemd):
To run Grain as a Linux service, you can use systemd, the standard service manager for most modern Linux distributions.
-
Create a Systemd Service File:
- Open a text editor with root privileges (e.g.,
sudo nano /etc/systemd/system/grain.service).
- Open a text editor with root privileges (e.g.,
-
Add Service Configuration:
- Add the following content to the
grain.servicefile, replacing the placeholders with your actual paths and user information:
```toml [Unit] Description=Grain Nostr Relay After=network.target
[Service] ExecStart=/path/to/grain_linux_amd64 WorkingDirectory=/path/to/grain/directory Restart=always User=your_user #replace your_user Group=your_group #replace your_group
[Install] WantedBy=multi-user.target ```
- Replace
/path/to/grain/executablewith the full path to your Grain executable. - Replace
/path/to/grain/directorywith the directory containing your Grain executable. - Replace
your_userandyour_groupwith the username and group that will run the Grain service.
- Add the following content to the
-
Reload Systemd:
- Run the command
sudo systemctl daemon-reloadto reload the systemd configuration.
- Run the command
-
Enable the Service:
- Run the command
sudo systemctl enable grain.serviceto enable the service to start automatically on boot.
- Run the command
-
Start the Service:
- Run the command
sudo systemctl start grain.serviceto start the service immediately.
- Run the command
-
Check Service Status:
- Run the command
sudo systemctl status grain.serviceto check the status of the Grain service. This will show you if the service is running and any recent logs. - You can run
sudo journalctl -f -u grain.serviceto watch the logs
- Run the command
More guides are in the works for setting up tailscale to access your relay from anywhere over a private network and for setting up a cloudflare tunnel to your domain to deploy a grain relay accessible on a subdomain of your site eg wss://relay.yourdomain.com
-
 @ 16f1a010:31b1074b
2025-03-20 14:31:19
@ 16f1a010:31b1074b
2025-03-20 14:31:19Introduction
MongoDB is a popular NoSQL document database, meaning it stores data in flexible, JSON-like documents. This makes it highly scalable and adaptable for various applications. This guide will focus on installing the Community Server edition, which is free and open-source.
This article is designed for beginners and those new to MongoDB, providing a clear and concise walkthrough of the installation process. We will cover installation on both Windows and Linux operating systems.
The official MongoDB documentation on the MongoDB website is very informative and you should be able to follow their guides. This article is written to provide a brief overview and a more streamlined installation experience.
Prerequisites
MongoDB Community Server can be installed and run on a wide range of systems. While specific hardware requirements can vary based on your intended use case and the size of your database, here are the general prerequisites:
- Operating System:
- This guide will cover installation on popular versions of Windows and Linux (specifically Ubuntu/Debian). MongoDB also supports other operating systems, which you can find on the official MongoDB website.
- Storage Space:
- You'll need sufficient disk space to store your database files. The amount of space required will depend on the size of your data. It is recommended to have more storage than you think you will initially need.
- RAM:
- While MongoDB can run with minimal RAM, having more RAM will improve performance, especially for larger databases. The amount of RAM needed will depend on the size of your data.
- Basic System Knowledge:
- Familiarity with using the command line or terminal is helpful, especially for Linux installations.
- Basic understanding of file systems and directories.
Essentially, MongoDB is designed to be flexible and can run on most modern systems. As your data grows, you can always scale your hardware accordingly.
Downloading MongoDB Community Server:
To begin, you'll need to download the MongoDB Community Server installation package.
- Visit the official MongoDB download page: https://www.mongodb.com/try/download/community
On the download page, you'll see options to select the following:
- Version: Choose the desired version of MongoDB. It is generally recommended to select the latest stable release.
- Operating System: Select your operating system (Windows or Linux).
- Package: Select the appropriate package type. For Windows, it will typically be
msi. For Linux, you will choose the package type that aligns with your linux distro. For example.debfor Debian/Ubuntu or.rpmfor RedHat/Fedora.
Once you have made your selections, click the "Download" button to download the installer or package.
Installation on Windows:
Running the Installer:
-
Locate the Downloaded Installer:
- Navigate to the directory where you downloaded the MongoDB
.msiinstaller.
- Navigate to the directory where you downloaded the MongoDB
-
Run the Installer:
- Double-click the
.msifile to start the installation wizard.
- Double-click the
-
Welcome Screen:
- Click "Next" on the welcome screen.
-
License Agreement:
- Read the license agreement, check the "I accept the terms in the License Agreement" box, and click "Next."
-
Setup Type:
- Select "Custom" installation. This allows you to choose the installation location and data directory. Click "Next."
-
Installation Location:
- You can change the default installation directory if desired. Click "Next."
-
Service Configuration:
- You can choose to install MongoDB as a service. It is recommended to install as a service.
- You can also change the "Data Directory" location here. It is recommended to change this to a location such as
C:\data\db. If you do not change it here, you will need to create the data directory manually later. - Click "Next."
-
Ready to Install:
- Click "Install" to begin the installation process.
-
Complete Installation:
- Once the installation is complete, click "Finish."
Setting Environment Variables (Optional but Recommended):
Setting the
PATHenvironment variable allows you to run MongoDB commands from any command prompt window without specifying the full path to the executable.-
Open System Properties:
- Search for "Environment Variables" in the Windows Start menu and select "Edit the system environment variables."
-
Environment Variables:
- In the "System Properties" window, click the "Environment Variables..." button.
-
Edit Path Variable:
- In the "System variables" section, find the "Path" variable and click "Edit."
-
Add MongoDB Bin Directory:
- Click "New" and add the path to the MongoDB
bindirectory. This is typicallyC:\Program Files\MongoDB\Server\<version>\bin, replacing<version>with your installed version. - Click "OK" on all open windows to save the changes.
- Click "New" and add the path to the MongoDB
-
Verify Path:
- Open a new command prompt window and type
mongod --version. If MongoDB is installed correctly and thePATHvariable is set, you should see the MongoDB version information.
- Open a new command prompt window and type
Installation on Linux (Ubuntu/Debian):
These instructions are specifically for Debian-based systems like Ubuntu.
Importing the MongoDB Public GPG Key:
-
Open a Terminal:
- Open your terminal application.
-
Import the GPG Key:
- Run the following command to import the MongoDB public GPG key:
bash wget -qO - [https://www.mongodb.org/static/pgp/server-7.0.asc](https://www.mongodb.org/static/pgp/server-7.0.asc) | sudo apt-key add -- This command downloads the GPG key and adds it to your system's trusted keys. This ensures that the packages you download from the MongoDB repository are authentic.
Adding the MongoDB Repository:
-
Add the Repository:
- Run the following command to add the MongoDB repository to your system's sources list:
bash echo "deb [ arch=amd64,arm64 ] [https://repo.mongodb.org/apt/ubuntu](https://repo.mongodb.org/apt/ubuntu) $(lsb_release -cs)/mongodb-org/7.0 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-7.0.list- This command adds the MongoDB repository to your system's package manager sources. The
$(lsb_release -cs)part automatically determines your Ubuntu/Debian version.
-
Update Package List:
- Run the following command to update your package list:
bash sudo apt update- This command refreshes the package list, including the newly added MongoDB repository.
Installing MongoDB:
-
Install MongoDB:
- Run the following command to install the MongoDB Community Server:
bash sudo apt install mongodb-org- This command downloads and installs the MongoDB packages.
After install, linux and windows should both have a system service already setup from the install process. You can check if it's running on linux with
sudo systemctl status mongod. On Windows, you should see the service running as "MongoDB Server" if you open system services on WindowsBasic MongoDB Commands:
After installing and starting MongoDB, you can use the
mongoshell to interact with your database. Here are some basic commands to get you started:Checking MongoDB Version:
First, let's verify that MongoDB is installed correctly by checking its version:
-
Open a Terminal or Command Prompt:
- Open your terminal (Linux/macOS) or command prompt (Windows).
-
Run
mongosh --version:- Type
mongosh --versionand press Enter. - This command will display the installed MongoDB version if it's correctly installed and in your system's PATH.
- Type
Basic MongoDB Shell Commands:
-
Open the
mongoshShell:- Type
mongoshand press Enter. This will open the MongoDB shell, and you'll see a prompt like>.
- Type
-
Show Databases:
- To see a list of all databases on your MongoDB server, type
show dbsand press Enter. - This will display a list of database names.
- To see a list of all databases on your MongoDB server, type
-
Use a Database:
- To switch to a specific database, type
use <database_name>and press Enter. Replace<database_name>with the name of the database you want to use. - Example:
use mydatabase - If the database doesn't exist, MongoDB will create it when you first store data in it.
- To switch to a specific database, type
-
Show Collections:
- After switching to a database, you can see a list of collections (similar to tables in relational databases) in that database by typing
show collectionsand pressing Enter. - Collections are where you store documents (JSON-like data).
- After switching to a database, you can see a list of collections (similar to tables in relational databases) in that database by typing
Example Session:
```bash
mongosh Current Mongosh Log ID: 6563728637951a37887e2730 Connecting to: mongodb://127.0.0.1:27017/?directConnection=true&serverSelectionTimeoutMS=2000&appName=mongosh Using MongoDB: 7.0.3 Using Mongosh: 2.1.1 For mongosh info see: https://docs.mongodb.com/mongodb-shell/
test> show dbs admin 40 KiB config 72 KiB local 40 KiB test> use mydatabase switched to db mydatabase mydatabase> show collections mydatabase> ```
Conclusion
Congratulations! You have successfully installed and started MongoDB Community Server. You've learned how to download, install, and run MongoDB on both Windows and Linux systems, and you've explored some basic commands to interact with your database.
Now, you might want to try an application like grain, a Nostr relay, which utilizes MongoDB as its database. Learn How to Install grain: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rqdpnx56rqv34uyz5g4
Remember, this guide covers the basics. There's much more to explore in the world of MongoDB, including advanced querying, indexing, replication, and sharding. Continue exploring the official MongoDB documentation to deepen your knowledge and unlock the full potential of this powerful database.
- Operating System:
-
 @ fd06f542:8d6d54cd
2025-03-31 01:55:50
@ fd06f542:8d6d54cd
2025-03-31 01:55:50 -
 @ f1989a96:bcaaf2c1
2025-03-20 14:21:35
@ f1989a96:bcaaf2c1
2025-03-20 14:21:35Good morning, readers!
In Thailand, the government announced a third digital cash handout to “stimulate the economy and drive technological adoption.” This disbursement will allocate 27 billion baht ($800 million) to 2.7 million citizens aged 16-20. Like in previous phases, it will be distributed via a state-controlled “digital wallet” application, which essentially functions as a central bank digital currency (CBDC). This system gives the regime an inside view of Thais’ financial activity and creates a centralized database to monitor, censor, and control.
Meanwhile, in Russia, the central bank has proposed limiting Bitcoin access to only the wealthiest individuals. Under the proposal, only Russians with over $1.2 million in assets or an annual income above $580,000 could buy and sell digital assets — arbitrarily barring everyday Russians (including obviously most journalists and activists) from accessing Bitcoin and the financial independence it grants.
In open-source software news, a new tool called Banxaas is making Bitcoin more accessible in West Africa by integrating with local payment providers to facilitate buying and selling Bitcoin using the CFA currency (XOF). This on-and-off ramp could expand financial freedom for human rights activists, dissidents, and everyday citizens.
We end with the latest edition of the HRF x Pubkey Freedom Tech Series, in which HRF’s Zac Guignard sits down with author Jason Maier to discuss how Bitcoin can drive human rights around the world. Together, they examine the shortcomings of today’s financial system and discuss how Bitcoin is aiding people living under authoritarian regimes.
Now, let’s get right to it!
Subscribe Here
GLOBAL NEWS
Thailand | Announces Third Digital Cash Handout to Boost Economy
The government of Thailand announced a third digital cash handout, allocating 27 billion baht ($800 million) to 2.7 million citizens aged 16-20 to “stimulate the economy and drive technological adoption.” Like in previous phases, the regime will distribute the funds through a state-run “digital wallet” application, which would effectively function as a central bank digital currency (CBDC). Past handouts of the CBDC came with strict restrictions: spending was limited to approved vendors within designated areas, purchases were restricted to certain goods, and funds expired after six months. Meanwhile, Prime Minister Paetongtarn Shinawatra called this third handout the first full deployment of the digital wallet system and urged the public to download the official app. This would directly link citizens' financial activity and data to the regime, threaten privacy, and deepen repression in a country with a long history of silencing dissent.
Russia | Central Bank Proposes Restricting Bitcoin Access to Wealthy Only
Russia’s central bank has proposed restricting Bitcoin and cryptocurrency access to only the country’s wealthiest individuals, barring everyday Russians from buying and selling digital assets unless they meet specific income or asset thresholds. Under the proposal, only Russians with over $1.2 million in assets or an annual income above $580,000 could engage with digital assets — effectively putting Bitcoin officially out of reach of most activists and journalists. The central bank claims the measure protects citizens from “volatility and lack of state backing.” But in reality, it likely signals the regime’s fear of Bitcoin’s ability to provide individual financial autonomy. By blocking most Russians from opting out of the state-controlled financial system, the regime is doubling down on financial repression.
India | Advances Digital Rupee CBDC
India’s government is pushing forward with its CBDC, the Digital Rupee, hailing it as a modern payment solution. But as journalist and author Roger Huang puts it, “it looks like a solution searching for a problem to solve.” Beyond the branding, the Digital Rupee enables state control over financial activity. Its programmability allows the government to dictate how, when, and where people spend — restricting transactions to specific merchants, locations, or goods and even imposing expiration dates on money. India’s crackdown on dissent is well-documented, from freezing opposition bank accounts to attempting a Bitcoin ban. Now, the Reserve Bank of India is embedding the CBDC into its digital payment system (UPI), quietly pushing millions into a tightly controlled and surveilled financial system.
Zimbabwe | Financial Regulators Mandate Earnings in ZiG
Zimbabwe’s market regulator is mandating all companies report their earnings in the new ZiG currency despite it losing 96% of its value since its launch last year. This move tightens state control over an already fragile economy, pushing businesses and citizens deeper into an unstable system that has repeatedly wiped out savings through inflation. The ZiG is Zimbabwe’s sixth currency in 15 years, introduced with gold backing to restore confidence in the regime’s ability to manage a currency. Instead, it’s rapidly devaluing, while the US dollar remains the preferred currency for trade and savings — when accessible. For ordinary Zimbabweans, the mandatory use of ZiG for taxes and government services is already a challenge due to its scarcity.
Egypt | Dictator-imposed Reforms Causing Economic Chaos
In the wake of an $8 billion deal with the International Monetary Fund (IMF) last spring, the Egyptian dictatorship has carried out “reforms” that are fueling inflation and making necessities increasingly unaffordable. To meet IMF conditions, Egyptian officials devalued the pound, slashed subsidies, and hiked the cost of fuel and public transportation — driving inflation beyond 20% for months on end. For millions of Egyptians, basic goods are now unaffordable. And the government’s promised minimum wage increase for public workers remains unfulfilled, leaving the public to absorb the price shocks. These undemocratic reforms — never voted on and executed with no way for the public to push back — aimed at securing further financing have only eroded the financial freedom of 114 million Egyptians and pushed the country into greater debt.
China | Facebook Enabling Authoritarian Censorship
A former Meta executive, Sarah Wynn-Williams, has accused Facebook of working “hand in glove” with the Chinese Communist Party (CCP) to censor and surveil content in China. According to Wynn-Williams, Facebook explored building censorship tools that would suppress viral posts until Chinese authorities approved. They even considered sharing user data in exchange for market access to China’s massive user base. Meta denied these claims, saying they fired Wynn-Williams in 2017 for poor performance. Regardless, the revelations highlight the dangers of for-profit, centralized platforms that authoritarian regimes can co-opt. Protocols like nostr (where no single entity moderates content) are more important than ever. Activists and dissidents seeking free communications can get started with nostr here.
BITCOIN AND FREEDOM TECH NEWS
Banxaas | Spend Sats in West Africa
Hundreds of millions of citizens in West Africa still use the CFA franc in an arrangement upheld by more than a dozen authoritarian leaders. Banxaas offers an alternative by bridging Bitcoin with West Africa’s mobile money networks. This allows individuals to buy and sell Bitcoin through local payment providers using the local CFA currency (XOF) and their own Lightning wallet. By integrating with local payment providers, Banxaas serves as a crucial on-and-off-ramp to Bitcoin, bringing the benefits of financial freedom to individuals, nonprofits, and human rights defenders across the region. Watch a demonstration of how Banxaas works here.
Mi Primer Bitcoin | Bitcoin Workbook Translated to Mandarin
Mi Primer Bitcoin, an open-source Bitcoin educational initiative focused on high-school-age students, released a Mandarin translation of its 2025 Bitcoin Diploma. This open-source resource provides mainland Chinese citizens, activists, and dissidents with accessible Bitcoin education at a time when financial freedom is increasingly under threat. With China tightening restrictions on personal wealth and expanding state surveillance of financial activity through the digital yuan CBDC, the diploma offers a useful new resource to learn the alternatives to state-controlled financial systems.
Blitz Wallet | Improves Ecash Functionality for Greater Financial Autonomy
Blitz Wallet, an open-source and self-custodial Bitcoin Lightning, Liquid, and ecash wallet, released an update that improves ecash functionality. Ecash, a Bitcoin-backed digital money system, allows instant and private transactions but requires custodial “mints” to manage tokens. The new update links users’ ecash to their wallet’s seed phrase (the 12-word backup used for Bitcoin recovery), allowing them to restore funds even if their device is lost or stolen. Users can also now transfer ecash between different wallets, increasing flexibility and control over their funds. Improved ecash UX is much-desired for political dissidents who can’t afford for authoritarian regimes to have full oversight over all of their economic activities.
Fedimint | Adds On-chain Support for Everyone
Fedimint, an open-source Bitcoin custody model that lets communities securely manage Bitcoin funds together, released v0.6.0, adding support for on-chain Bitcoin deposits (transactions directly on Bitcoin’s base layer). By offering private and trust-minimized transactions alongside on-chain support, Fedimint makes it easier, especially for nonprofit communities, to self-custody Bitcoin. It provides greater privacy and autonomy versus using fully centralized platforms that are easily subject to the political and regulatory pressure of authoritarian regimes.
Africa Bitcoin Conference | Announces 2025 Conference
The Africa Bitcoin Conference (ABC) announced its fourth edition, set to take place from Dec. 3-5, 2025, in Port Louis, Mauritius. Hosted at the Caudan Art Center, the event will bring together activists, Bitcoin advocates, and freedom tech developers to explore Bitcoin as a pathway to financial freedom. Now the largest Bitcoin gathering in Africa, ABC has established itself as a key platform for discussions on financial inclusion, inflation resistance, and censorship-resistant money — putting tools for financial sovereignty into the hands of those who need them most. HRF is proud to support ABC and, in particular, is proud to help delegates from dozens of authoritarian regimes attend each year. You can learn more about the conference and buy tickets here.
RECOMMENDED CONTENT
HRF x Pubkey — How Bitcoin Brings About Social Change with Jason Maier
In the latest installment of the HRF x Pubkey Freedom Tech Series, HRF Content and Research Associate Zac Guignard sits down with Jason Maier, author of “A Progressive’s Case for Bitcoin,” to share how Bitcoin can spark a meaningful shift in personal liberty worldwide. Jason explains the core monetary properties that make Bitcoin permissionless, censorship-resistant, and a powerful tool for financial freedom. Together, they examine the shortcomings of today’s financial system and discuss how Bitcoin is aiding people living under authoritarian regimes. They talk about how Bitcoin shouldn’t be a political issue and can be useful to anyone, no matter their beliefs. Watch the full conversation here.
Mélancolies de l’Opprimé by Farida Bemba Nabourema
Farida Bemba Nabourema, a renowned Togolese human rights activist, former HRF freedom fellow, and Bitcoin pioneer, announced that her new book “Mélancolies de l’Opprimé” will be released on April 15, 2025. A decade after her first book, “La Pression de l’Oppression,” this deeply personal and reflective work offers hard-earned wisdom for young activists stepping into the struggle against dictatorships and injustice. Nabourema candidly shares the emotional, physical, and psychological toll of resistance and activism while also highlighting the sense of purpose in the pursuit of freedom and human rights. Learn more about the book here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 21335073:a244b1ad
2025-03-20 13:16:22
@ 21335073:a244b1ad
2025-03-20 13:16:22I’d never had the chance to watch Harry Potter on the big screen before. Experiencing the first movie in 3D was nothing short of spectacular. Right from the opening scene with Albus Dumbledore, I was floored—the makeup and costumes were so vivid, it felt like pure magic unfolding before my eyes. It’s clear that real masters of their craft worked behind the scenes, and their artistry shines through. The sets? Absolutely jaw-dropping! The level of detail in Diagon Alley was beyond impressive.
Seeing legends like Alan Rickman as Snape and Maggie Smith as Minerva McGonagall on that massive 3D screen was an unforgettable thrill. The film is packed with phenomenal actors, and it was a joy to catch every tiny eye twitch and subtle nuance of their performances brought to life. It was a mind-blowing experience, and I’d wholeheartedly recommend it to anyone who gets the chance.
Don’t forget to have a little whimsical fun sometimes my friends. 🪄
-
 @ fd06f542:8d6d54cd
2025-03-31 01:55:18
@ fd06f542:8d6d54cd
2025-03-31 01:55:18什么是nostrbook?
nostrbook 是基于nostr 社区技术存储在 nostr relay server上的长文(30023)文章。 查看浏览,采用的是 docsify 技术。整个网站技术无须部署服务器占用太多的存储空间。 可以实现轻量级部署。
-
 @ a60e79e0:1e0e6813
2025-03-20 12:58:13
@ a60e79e0:1e0e6813
2025-03-20 12:58:13*This is a long form Nostr native version of a post that lives on my Nostr educational website Hello Nostr *
At first glance Nostr might appear quite similar to some of the apps you use every day, such as Twitter, Mastodon, or Facebook, but that couldn't be further from the truth. This post aims to dispel the myth that "Nostr is just a Twitter replacement" and give you a better understanding about the 'what', the 'how' and most importantly, the 'why' of Nostr.
What Is Nostr?
Nostr is a decentralized, open-source protocol designed for censorship-resistant networking and communication on the web. It stands for "Notes and Other Stuff Transmitted by Relays," and it works by allowing users to publish messages (notes) and content in the form of 'other stuff', to a network of servers (relays) that store and distribute the content.
Unlike traditional platforms like Twitter, Ebay or Facebook, Nostr doesn't rely on a central authority; instead, users control their own identities via cryptographic key pairs.
The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all.
Fiatjaf - Nostr Creator
Nostr is not a website or an app you download from a single source — it’s an open protocol, like email or the internet. Think of it as a set of rules that anyone can use to build tools for sharing messages, posts, or other data without needing a centralized middleman like a big tech company.
Nostr was created by a developer named Fiatjaf in 2020, and has since been steadily gaining traction among people who care about privacy, freedom, and censorship resistance.

Why Nostr?
Imagine the scenario, you've been using an online platform for 5 or even 10 years. You've built up thousands of contacts, perhaps built yourself a sizeable reputation, or even rely on the income from the platform to feed your family. Then one day you make a controversial post, sell a certain item or upload a video on a spicy subject to the platform where the owner disagrees with. With the click of a button, your account is removed. All trace of you, your social graph, or even your future income, disappears in an instant.
Read aloud like that is sounds crazy that we'd even entertain using such a platform, right!? Sadly that is the reality in 2025. This is exactly what happens every single day on X, Facebook, Ebay, Paypal, Linkedin, etc.
Looking at the problem through a more social media focused lens, many of us have become slaves to the likes of Instagram, Twitter and TikTok. We use these 'free' apps under the guise of being social with others online. The reality is that we see what those apps want us to see. We've become slaves to the manipulation of complex and opaque algrorithms designed to keep us hooked and try to sell us things.

Unlike traditional platforms, which are often governed by centralized entities wielding significant control over user data, content moderation, and algorithmic influence, Nostr flips the script by prioritizing user sovereignty and resilience. Built on an open-source framework, Nostr allows individuals to control their own data and interact through a network of relays, making it much more difficult for any single authority - be it a corporation, government, or bad actor - to censor or manipulate the flow of information.
- Is a relay refusing to host your notes? Use another or run your own!
- A specific client using an algorithm you don't like, take your identity and social graph elsewhere and choose another!
Take your identity and social graph with you, anywhere any time.
Nostr’s ability to foster authentic, unfiltered conversations while safeguarding user sovereignty has made it a cornerstone for communities seeking alternatives - whether they’re activists, creators, or everyday people tired of being pawns in the data-driven game. It's simple and adaptable design also encourages innovation, inviting developers to build tools and interfaces that keep pushing the boundaries of what the decentralized internet can achieve. In short, Nostr isn’t just a tool; it’s a movement toward a freer, more equitable digital future.

How Does Nostr Work?
Instead of one giant server owned by a single company holding all your posts and messages, Nostr spreads everything across lots of smaller servers called relays. To get started, you download a client, create your account and back up your private key. Your private key is used to secure your account and sign every message you send over the network. This allows anyone you interact with the verify the integrity of the data coming from 'you'.
The Nostr network is essentially a collection of bulletin boards that share a common format
When you write a note, or share some other type of compatible data, your client signs it with your private key, then sends it to one or more relays. Which relays your information is sent to is entirely up to you. These relays share your message with others who want to see it.
For others to see your notes or 'other stuff', they'll need to be able to find you. Typically this is done by using your public key, which looks something like this
npub15c88nc8d44gsp4658dnfu5fahswzzu8gaxm5lkuwjud068swdqfspxssvx. Don't panic though, you don't need to memorize all of your friends public keys, there are more human friendly methods of finding people that we'll come onto later.Once someone is following you, their client will ask all of their connected relays for any data shared by your public key. Their client will receive this data, verify it is signed by your private key and then populate it into their feed.
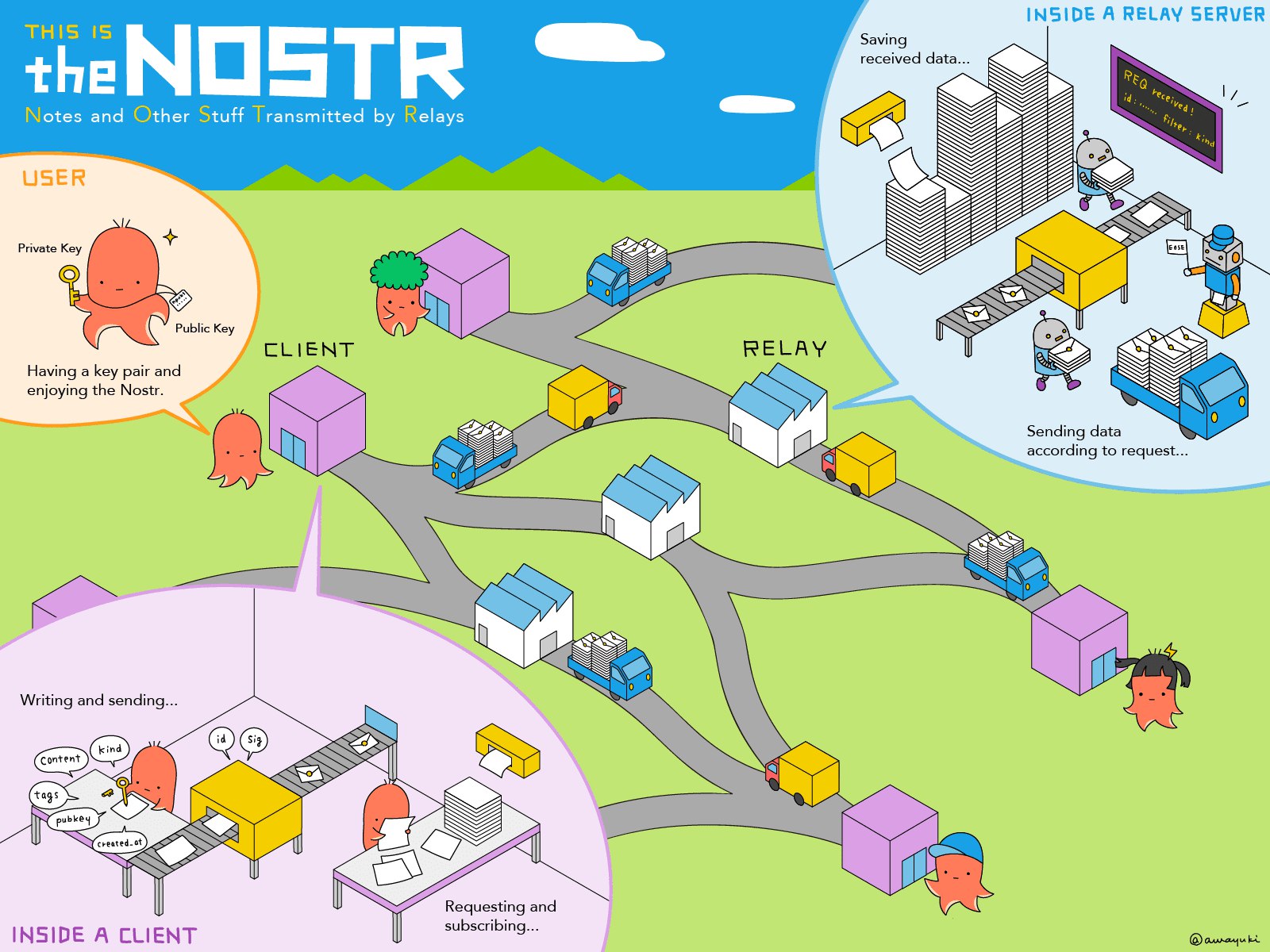
The “Other Stuff” Explained
Nostr’s name hints at this: Notes and Other Stuff Transmitted by Relays. But what is the “other stuff”? Put simply, it’s all the creative and experimental things people are building on Nostr, beyond simple text based notes. Every action on Nostr is an event - like a post, a profile update, or even a payment. The 'Kind' is what specifies the purpose of each event. Kinds are the building blocks of how information is categorized and processed on the network, and the most popular become part of higher lever specification guidelines known as Nostr Implementation Possibility - NIP. A NIP is a document that defines how something in Nostr should work, including the rules, standards, or features. NIPs define the type of 'other stuff' that be published and displayed by different styles of client for different purposes.
Here's some content examples of 'Other Stuff':
- Long-Form Content: Think blog posts or articles. NIP-23.
- Private Messaging: Encrypted chats between users. NIP-04.
- Communities: Group chats or forums like Reddit. NIP-72
- Marketplaces: People listing stuff for sale, payable with zaps. NIP-15
- Zaps: Value transfer over the Lightning Network. NIP57
The beauty of Nostr is that it’s a flexible foundation. Developers can dream up new ideas and build them into clients, and the relays just keep humming along, passing the data around. It’s still early days, so expect the “other stuff” to grow wilder and weirder over time!
Clients vs Relays: What’s the Difference?
Newbies often get tripped up by these two terms, so let’s clearly define them.

Clients
A client is what you use to interact with Nostr. It’s the app or website where you type your posts, read your feed, follow and interact with others. Examples of Nostr clients include:
- Damus (iOS Twitter style client)
- Primal (Cross-platform Twitter style client)
- Amethyst (Android only Twitter style client)
- Habla.News (Web based blog client)
- Olas (Instagram style client)
- 0xchat (Messaging client)
Clients don’t store your data; they just pull it from relays and display it for you. You can switch clients whenever you want, and your account stays the same because it’s tied to your keys, not any single client or app.
Clients are how you use Nostr, and relays are where the data lives. You need both to make the magic happen.
Relays
A relay is a server that stores and shares Nostr data. It’s a little like a post office: you send your note to a relay, and it delivers it to anyone who’s subscribed to see it (like your followers). Relays are run by individuals, groups, or companies who volunteer their computing power. Some are free, some charge a small fee, and you can connect to as many as you like. Most clients will come pre-configured with a list of well-known relays, but you can add or remove any you like.
What Are Zaps?
Zaps are arguably one of Nostr’s coolest features! A zaps is a way to send payments in Bitcoin directly to other users. Imagine liking a post, but instead of just clicking a heart (which you can of course do), you send the poster a few cents worth of Bitcoin to say, “This is awesome!”.
Zaps use Bitcoin's Lightning Network, a faster and cheaper way to move Bitcoin around. To Zap someone, you need a Lightning wallet linked to your Nostr client. Some clients, like Primal, ship with their own custodial wallet to make getting started a breeze. Most clients also allow more advanced users to connect an existing Lightning Wallet to reduce reliance and trust in the client provider.
Zaps are optional but add a fun layer to Nostr. Creators love them because it’s a way to get direct support from fans, with no middleman required.

NIP-05 Identifiers: Your Nostr “Username”
Your nPub, or public key (that long string of letters and numbers) is your 'official' Nostr ID, but it’s not exactly catchy. Enter NIP-05 identifiers, a human-readable and easily sharable way to have people find you. They look like an email address, like
qna@hellonostr.xyz.Here’s how it works:
Most users obtain their NIP-05 ID from a website or service that supports Nostr. Some of these services are free whereas some charge a fee. Some clients, like Primal will set one up for you automatically when you create an account. The email like ID links to your public key, so people can find you more easily. And because these ID's are domain based, there can be no duplicates. qna@hellonostr.xyz can only map to a single public key. The only person that can change that link is the person in control of the domain.
If you control your own domain, you can easily map your Nostr public key to name@my.domain. It’s not mandatory, but it’s super useful for building trust and making your profile recognizable.
Next Steps
So you're bought in. You understand why Nostr is so important and want to get started. Check out our simple onboarding guide here.
Thanks For Reading
Hopefully that moistened your taste buds for more educational Nostr content. This was a basic one, but there will be more focused material coming soon.
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
-
 @ a012dc82:6458a70d
2025-03-31 01:50:24
@ a012dc82:6458a70d
2025-03-31 01:50:24In the ever-evolving world of cryptocurrency, Bitcoin remains at the forefront of discussions, not just for its price movements but also for its foundational mechanisms that ensure its scarcity and value. One such mechanism, the Bitcoin halving, is drawing near once again, but this time, it's arriving sooner than many had anticipated. Originally projected for a meme-friendly date of April 20, the next Bitcoin halving is now set for April 15, marking a significant moment for the cryptocurrency community and investors alike.
Table of Contents
-
Understanding the Bitcoin Halving
-
Factors Accelerating the Halving Date
-
Implications of an Earlier Halving
-
Potential Price Impact
-
Miner Revenue and Network Security
-
Renewed Interest and Speculation
-
-
The Countdown to April 15
-
Conclusion
-
FAQs
Understanding the Bitcoin Halving
The Bitcoin halving is a scheduled event that occurs approximately every four years, reducing the reward for mining new blocks by half. This process is a critical part of Bitcoin's design, aiming to control the supply of new bitcoins entering the market and mimicking the scarcity of precious metals. By decreasing the reward for miners, the halving event reduces the rate at which new bitcoins are created, thus influencing the cryptocurrency's price and inflation rate.
Factors Accelerating the Halving Date
The shift in the halving date to April 15 from the previously speculated April 20 is attributed to several factors that have increased the pace of transactions on the Bitcoin network:
-
Sky-High Bitcoin ETF Flows: The introduction and subsequent trading of Bitcoin ETFs have significantly impacted market activity, leading to increased transaction volumes on the network.
-
Price Rallies: A series of price rallies, culminating in new all-time highs for Bitcoin, have spurred heightened network activity as traders and investors react to market movements.
-
Increased Daily Volume: The average daily trading volume of Bitcoin has seen a notable uptick since mid-February, further accelerating the pace at which blocks are processed and, consequently, moving up the halving dat
Implications of an Earlier Halving
The earlier-than-expected halving date carries several implications for the Bitcoin market and the broader cryptocurrency ecosystem:
Potential Price Impact
Historically, Bitcoin halving events have been associated with significant price movements, both in anticipation of and following the event. By reducing the supply of new bitcoins, the halving can create upward pressure on the price, especially if demand remains strong. However, the exact impact can vary based on broader market conditions and investor sentiment.
Miner Revenue and Network Security
The halving will also affect miners' revenue, as their rewards for processing transactions are halved. This reduction could influence the profitability of mining operations and, by extension, the security of the Bitcoin network. However, adjustments in mining difficulty and the price of Bitcoin typically help mitigate these effects over time.
Renewed Interest and Speculation
The halving event often brings renewed interest and speculation to the Bitcoin market, attracting both seasoned investors and newcomers. This increased attention can lead to higher trading volumes and volatility in the short term, as market participants position themselves in anticipation of potential price movements.
The Countdown to April 15
As the countdown to the next Bitcoin halving begins, the cryptocurrency community is abuzz with speculation, analysis, and preparations. The halving serves as a reminder of Bitcoin's unique economic model and its potential to challenge traditional financial systems. Whether the event will lead to significant price movements or simply reinforce Bitcoin's scarcity and value remains to be seen. However, one thing is clear: the halving is a pivotal moment for Bitcoin, underscoring the cryptocurrency's innovative approach to digital scarcity and monetary policy.
Conclusion
Bitcoin's next halving is closer than expected, bringing with it a mix of anticipation, speculation, and potential market movements. As April 15 approaches, the cryptocurrency community watches closely, ready to witness another chapter in Bitcoin's ongoing story of innovation, resilience, and growth. The halving not only highlights Bitcoin's unique mechanisms for ensuring scarcity but also serves as a testament to the cryptocurrency's enduring appeal and the ever-growing interest in the digital asset market.
FAQs
What is the Bitcoin halving? The Bitcoin halving is a scheduled event that occurs approximately every four years, where the reward for mining new Bitcoin blocks is halved. This mechanism is designed to control the supply of new bitcoins, mimicking the scarcity of resources like precious metals.
When is the next Bitcoin halving happening? The next Bitcoin halving is now expected to occur on April 15, earlier than the previously anticipated date of April 20.
Why has the date of the Bitcoin halving changed? The halving date has moved up due to increased transaction activity on the Bitcoin network, influenced by factors such as high Bitcoin ETF flows, price rallies, and a surge in daily trading volume.
How does the Bitcoin halving affect the price of Bitcoin? Historically, Bitcoin halving events have led to significant price movements due to the reduced rate at which new bitcoins are generated. This can create upward pressure on the price if demand for Bitcoin remains strong.
What impact does the halving have on Bitcoin miners? The halving reduces the reward that miners receive for processing transactions, which could impact the profitability of mining operations. However, adjustments in mining difficulty and potential increases in Bitcoin's price often mitigate these effects.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 20e17dd0:2ae504d7
2025-03-20 10:04:35
@ 20e17dd0:2ae504d7
2025-03-20 10:04:35Prerequisite
Installation
Open a Terminal session and write the following command to make sure that Docker is running:
ruby sudo systemctl status dockerYou should get a screen with the docker.service as "running". To get back to command line do CTRL+C
Then, create the volume that Portainer Server will use to store its database:
ruby sudo docker volume create portainer_dataYou are now ready for the on-liner installation:
ruby sudo docker run -d -p 8000:8000 -p 9443:9443 --name portainer --restart=always -v /var/run/docker.sock:/var/run/docker.sock -v portainer_data:/data portainer/portainer-ce:latestTo validate the installer, prompt the following command:
ruby sudo docker psYou should see Portainer's container running.
To access Portainer Server, go to the following adress: https://localhost:9443
Et voila!
-
 @ fd06f542:8d6d54cd
2025-03-31 01:45:36
@ fd06f542:8d6d54cd
2025-03-31 01:45:36{"coverurl":"https://cdn.nostrcheck.me/fd06f542bc6c06a39881810de917e6c5d277dfb51689a568ad7b7a548d6d54cd/232dd9c092e023beecb5410052bd48add702765258dcc66f176a56f02b09cf6a.webp","title":"NostrBook站点日记","author":"nostrbook"}
-
 @ 8fb140b4:f948000c
2025-03-20 01:29:06
@ 8fb140b4:f948000c
2025-03-20 01:29:06As many of you know, https://nostr.build has recently launched a new compatibility layer for the Blossom protocol blossom.band. You can find all the details about what it supports and its limitations by visiting the URL.
I wanted to cover some of the technical details about how it works here. One key difference you may notice is that the service acts as a linker, redirecting requests for the media hash to the actual source of the media—specifically, the nostr.build URL. This allows us to maintain a unified CDN cache and ensure that your media is served as quickly as possible.
Another difference is that each uploaded media/blob is served under its own subdomain (e.g.,
npub1[...].blossom.band), ensuring that your association with the blob is controlled by you. If you decide to delete the media for any reason, we ensure that the link is broken, even if someone else has duplicated it using the same hash.To comply with the Blossom protocol, we also link the same hash under the main (apex) domain (blossom.band) and collect all associations under it. This ensures that Blossom clients can fetch media based on users’ Blossom server settings. If you are the sole owner of the hash and there are no duplicates, deleting the media removes the link from the main domain as well.
Lastly, in line with our mission to protect users’ privacy, we reject any media that contains private metadata (such as GPS coordinates, user comments, or camera serial numbers) or strip it if you use the
/media/endpoint for upload.As always, your feedback is welcome and appreciated. Thank you!
-
 @ 30ceb64e:7f08bdf5
2025-03-19 21:29:59
@ 30ceb64e:7f08bdf5
2025-03-19 21:29:59NIP-101e: Workout Data and Running Extensions
NIP-101e represents a crucial step forward for fitness tracking on Nostr, giving us a common language that would allow workout data to flow freely between apps. This proposal outlines a thoughtful framework with Exercise Templates, Workout Templates, and Workout Records that would finally free our fitness data from proprietary silos and put it back in our hands. I'm eager to see this proposal implemented because it would create the foundation for a genuinely open fitness ecosystem on Nostr.
As a runner building a Nostr running app RUNSTR, I've proposed some running-specific extensions to NIP-101e that address the unique needs of runners without disrupting the elegant structure of the original proposal. My extensions would standardize how we record GPS routes, pace metrics, elevation data, splits, and even weather conditions - all things that matter tremendously to runners but aren't covered in the base proposal that focuses more on strength training.
By implementing NIP-101e along with these running extensions, we could create something truly revolutionary: a fitness ecosystem where runners aren't locked into a single platform because of their data. You could track your morning run in my app, analyze your training in another app that specializes in statistics, and share achievements with friends using whatever Nostr clients they prefer. I believe strongly in getting NIP-101e implemented with these extensions included because it would foster innovation while giving runners unprecedented freedom to own their data and use it however they want. Let's make this happen and show what's possible when fitness data becomes truly interoperable!
-
 @ 096ae92f:b8540e0c
2025-03-31 01:09:48
@ 096ae92f:b8540e0c
2025-03-31 01:09:48Hal Finney’s name is etched in Bitcoin lore.
By day, Hal was a devoted husband and father; by night, a shadowy super coder pushing the boundaries of cryptography and how the world thinks about money. A seasoned cryptographer and ardent Bitcoin supporter, he was among the first to work with Satoshi Nakamoto on refining Bitcoin’s fledgling codebase.
 January 2009, the iconic "Running Bitcoin" tweet was posted.
January 2009, the iconic "Running Bitcoin" tweet was posted.Over 16 years later, people are still engaging with Hal Finney’s legendary tweet—leaving comments of gratitude, admiration, and remembrance, reflecting on how far Bitcoin has come.
For many, it marks a key moment in Bitcoin’s early days.
More recently, it’s also become a symbol of Hal’s passion for running and the determination he showed throughout his life. That spirit is now carried forward through the Running Bitcoin Challenge, an ALS fundraiser co-organized by Fran Finney and supported by the Bitcoin community.
 ## Shadowy Super Coder
## Shadowy Super CoderLong before Bitcoin came along, Hal Finney was already legendary in certain circles. He was part of the cypherpunk movement in the 1990s—people who believed in using cryptography to protect individual privacy online.
"The computer can be used as a tool to liberate and protect people, rather than to control them."\ -Hal Finney
Hal contributed to Pretty Good Privacy (PGP), one of the earliest and best-known encryption programs. He also dabbled in digital cash prototypes, developing something called Reusable Proofs of Work (RPOW). He didn’t know it at the time, but that would prime him perfectly for a bigger innovation on the horizon.
Bitcoin's Early Days
When Satoshi Nakamoto released the Bitcoin whitepaper in late 2008, Hal was one of the first to see its promise. While many cryptographers waved it off, Hal responded on the mailing list enthusiastically, calling Bitcoin “a very promising idea.” He soon began corresponding directly with Satoshi. Their emails covered everything from bug fixes to big-picture possibilities for a decentralized currency. On January 12, 2009, Satoshi sent Hal 10 bitcoins—marking the first recorded Bitcoin transaction. From that day onward, his name was woven into Bitcoin’s origin story.
“When Satoshi announced the first release of the software, I grabbed it right away. I think I was the first person besides Satoshi to run Bitcoin.”\ -Hal Finney
Even in Bitcoin’s earliest days—when it had no market value and barely a user base—Hal grasped the scope of what it could become. He saw it not just as a technical curiosity, but as a potential long-term store of value, a tool for privacy, and a monetary system that could rival gold in its resilience. He even raised early concerns about energy use from mining, showcasing just how far ahead he was thinking. At a time when most dismissed Bitcoin entirely, Hal was already envisioning the future.
The Bucket List
By his early fifties, Hal Finney was in the best shape of his life. He had taken up distance running in the mid-2000s—not to chase medals, but to test himself. To stay healthy, to lose some weight, and above all, to do something hard. The engineer’s mind in him craved a structure of improvement, and long-distance running delivered it. With meticulous focus, Hal crafted training plans, ran 20+ mile routes on weekends, and even checked tide charts to time his beach runs when the sand was firmest underfoot.
His ultimate goal: qualify for the Boston Marathon.
For most, Boston is a dream. For Hal, it became a personal benchmark—a physical counterpart to the mental mountains he scaled in cryptography. He trained relentlessly, logging race times, refining form, and aiming for the qualifying standard in his age group. Running was more than physical for him. It was meditative. He often ran alone, without music, simply to be in the moment—present, focused, moving forward.
Running was also a shared passion. Fran often ran shorter distances while Hal trained for the longer ones. They registered for events together, cheered each other on at finish lines, and made it a part of their family rhythm. It was one more expression of Hal’s deep devotion not just to self-improvement, but to doing life side-by-side with those he loved.
 Hal and Fran competing in the Denver Half-Marathon together
Hal and Fran competing in the Denver Half-Marathon togetherIn April 2009, Hal and Fran ran the Denver Half Marathon together—a meaningful race and one of the first they completed side by side. At the time, Hal was deep in marathon training and hitting peak form.\ \ A month later, Hal attempted the Los Angeles Marathon, hoping to clock a Boston-qualifying time. But something wasn’t right. Despite all his preparation, he was forced to stop midway through the race. His body wasn’t recovering the way it used to. At first, he chalked it up to overtraining or age, but the truth would come soon after.
ALS Diagnosis
In August 2009, at the height of his physical and intellectual pursuits, Hal received crushing news: a diagnosis of Amyotrophic Lateral Sclerosis (ALS), often referred to as Lou Gehrig’s disease. It was an especially cruel blow for a man who had just discovered a love for running and was helping birth the world’s first decentralized digital currency. ALS gradually robs people of voluntary muscle function. For Hal, it meant an uphill fight to maintain the independence and movement he cherished.
 Still, Hal didn’t stop. That September, he and Fran ran the Disneyland Half Marathon together, crossing the finish line hand in hand. It would be his last official race, but the identity of being a runner never left him—not after the diagnosis, not after the gradual loss of physical control, not even after he was confined to a wheelchair.
Still, Hal didn’t stop. That September, he and Fran ran the Disneyland Half Marathon together, crossing the finish line hand in hand. It would be his last official race, but the identity of being a runner never left him—not after the diagnosis, not after the gradual loss of physical control, not even after he was confined to a wheelchair. Fran and Hal at the Disney Half Marathon.
Fran and Hal at the Disney Half Marathon.By December of that same year, Hal could no longer run. Still, he was determined not to sit on the sidelines. That winter, the couple helped organize a relay team for the Santa Barbara International Marathon, a race Hal had long planned to run. Friends and family joined in, and Fran ran the final leg, passing the timing chip to Hal for the last stretch. With support, Hal walked across the finish line, cheered on by the local running community who rallied around him. It was a symbolic moment—heartbreaking and inspiring all at once.
 Hal and Fran lead the Muscular Dystrophy Association relay team at the Santa Barbara International Marathon in 2009.
Hal and Fran lead the Muscular Dystrophy Association relay team at the Santa Barbara International Marathon in 2009.Even as his muscles weakened, Hal’s mind stayed sharp, and he continued to adapt in every way he could. He and Fran began making practical changes around their home—installing ramps, adjusting routines—but emotionally, the ground was still shifting beneath them.
Hal Finney humbly giving people in the future the opportunity to hear him speak before he is unable to.
Fran consistently emphasized that Hal maintained a remarkably positive attitude, even as ALS took nearly everything from him physically. His optimism and determination became the emotional anchor for the entire family.
“He was the one who kept us all steady. He was never defeated.”\ -Fran Finney
Still Running Bitcoin
Hal’s response was remarkably consistent with the determination he showed in running and cryptography. Even as the disease progressed, forcing him into a wheelchair and eventually limiting his speech, he kept coding—using assistive technologies that allowed him to control his computer through minimal eye movements. When he could no longer run physically, he continued to run test code for Bitcoin, advise other developers, and share insights on the BitcoinTalk forums. It was perseverance in its purest form. Fran was with him every step of the way.
 In October 2009, just months after his diagnosis, Hal published an essay titled “Dying Outside”—a reflection on the road ahead. In it, he wrote:
In October 2009, just months after his diagnosis, Hal published an essay titled “Dying Outside”—a reflection on the road ahead. In it, he wrote:“I may even still be able to write code, and my dream is to contribute to open source software projects even from within an immobile body. That will be a life very much worth living."
And he meant it. Years later, Hal collaborated with Bitcoin developer Mike Hearn on a project involving secure wallets using Trusted Computing. Even while operating at a fraction of his former speed—he estimated it was just 1/50th of what he used to be capable of—Hal kept at it. He even engineered an Arduino-based interface to control his wheelchair with his eyes. The hacker mindset never left him.
This wasn’t just about legacy. It was about living with purpose, right up to the edge of possibility.
Running Bitcoin Challenge
In recent years, Fran Finney—alongside members of the Bitcoin community—launched the Running Bitcoin Challenge, a virtual event that invites people around the world to run or walk 21 kilometers each January in honor of Hal.
Timed with the anniversary of his iconic “Running bitcoin” tweet, the challenge raises funds for ALS research through the ALS Network. According to Fran, over 80% of all donations go directly to research, making it a deeply impactful way to contribute. Nearly $50,000 has been raised so far.
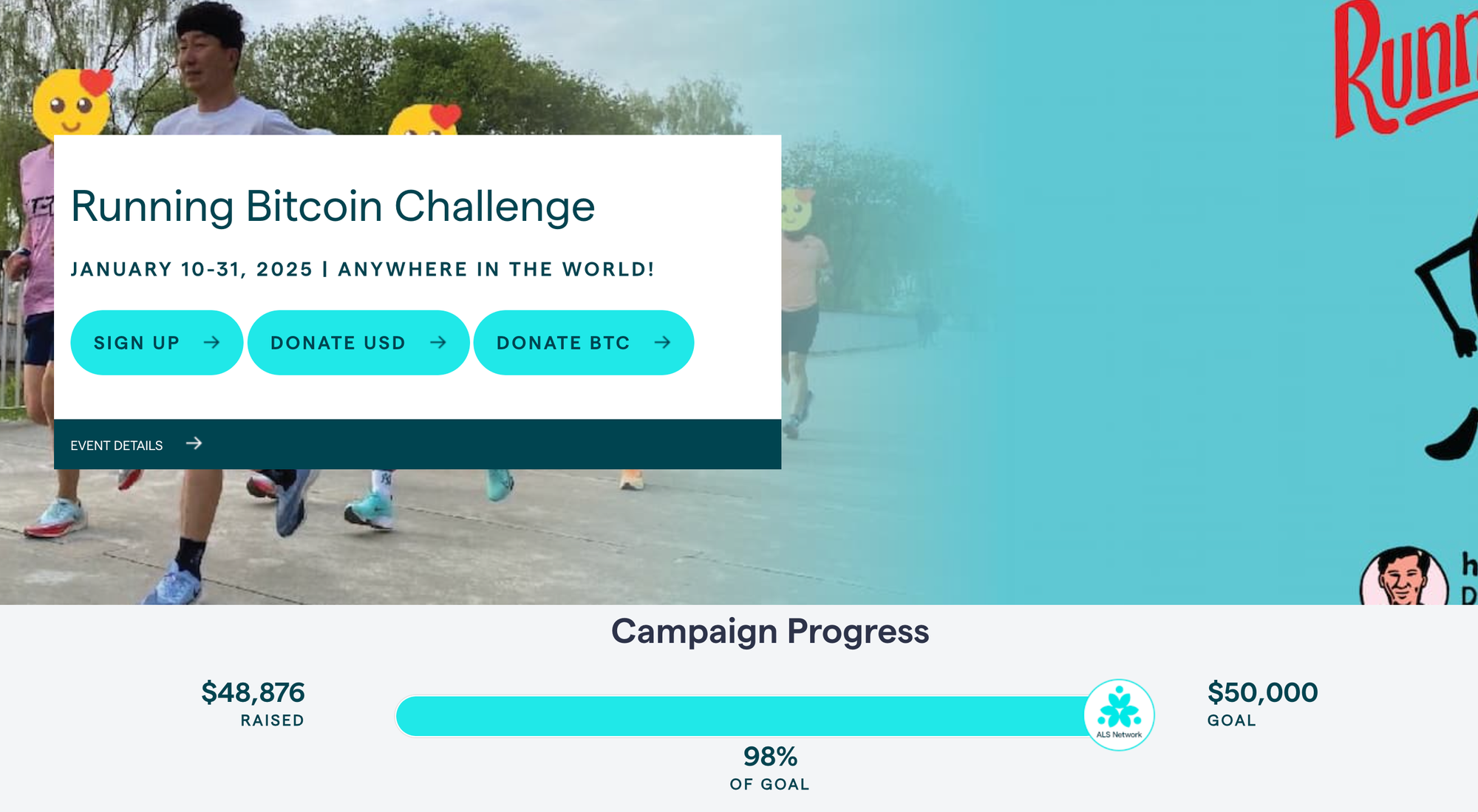 It’s not the next Ice Bucket Challenge—but that’s not the point. This is something more grounded, more personal. It’s a growing movement rooted in Hal’s legacy, powered by the Bitcoin community, and driven by the hope that collective action can one day lead to a cure.
It’s not the next Ice Bucket Challenge—but that’s not the point. This is something more grounded, more personal. It’s a growing movement rooted in Hal’s legacy, powered by the Bitcoin community, and driven by the hope that collective action can one day lead to a cure.“Since we’re all rich with bitcoins, or we will be once they’re worth a million dollars like everyone expects, we ought to put some of this unearned wealth to good use.”\ \ — Hal Finney, January 2011Price of Bitcoin: $0.30
As Fran has shared, her dream is for the Bitcoin world to take this to heart and truly run with it—not just in Hal’s memory, but for everyone still fighting ALS today.
Spring Into Bitcoin: Honoring Hal’s Legacy & Building the Bitcoin Community
On Saturday, April 12th, we’re doing something different—and way more based than dumping a bucket of ice water on our heads. Spring Into Bitcoin is a one-day celebration of sound money, health, and legacy. Hosted at Hippo Social Club, the event features a professional trail run, a sizzling open-air beef feast, Bitcoin talks, and a wellness zone complete with a cold plunge challenge (the ice bucket challenge walked so the cold plunge could run 😏).
 Purchase Tickets - General Admission
Purchase Tickets - General AdmissionTickets purchased using this link will get 10% back in Bitcoin rewards compliments of Oshi Rewards.
Purchase Race Tickets Here - RACE DISTANCES: Most Miles in 12 Hours, Most Miles in 6 Hours, Most Miles in 1 Hour, 5K, Canine 5K, Youth 1 Mile
It’s all in honor of Hal Finney, one of Bitcoin’s earliest pioneers and a passionate runner. 100% of event profits will be donated in Bitcoin to the ALS Network, funding research and advocacy in Hal’s memory. Come for the cause, stay for the beef, sauna, cold plunge and to kick it with the greatest, most freedom-loving community on earth.
Please consider donating to our Run for Hal Austin team here. This race officially kicks off the 2025 Run for Hal World Tour!


 Ok, we might be a little biased.
Ok, we might be a little biased.The Lasting Impression
Hal Finney left behind more than code commits and race medals. He left behind a blueprint for resilience—a relentless drive to do good work, to strive for personal bests, and to give back no matter the circumstances. His life reminds us that “running” is more than physical exercise or a piece of software running on your laptop. It’s about forward progress. It’s about community. It’s about optimism in the face of challenges.
So, as you tie your shoelaces for your next run or sync up your Bitcoin wallet, remember Hal Finney.
-
 @ 1aa9ff07:3cb793b5
2025-03-31 00:44:22
@ 1aa9ff07:3cb793b5
2025-03-31 00:44:22test 2
-
 @ f3328521:a00ee32a
2025-03-31 00:24:13
@ f3328521:a00ee32a
2025-03-31 00:24:13I’m a landian accelerationist except instead of accelerating capitalism I wanna accelerate islamophobia. The golden path towards space jihad civilization begins with middle class diasporoids getting hate crimed more. ~ Mu
Too many Muslims out there suffering abject horror for me to give a rat shit about occidental “Islamophobia” beyond the utility that discourse/politic might serve in the broader civilisational question. ~ AbuZenovia
After hours of adjusting prompts to break through to the uncensored GPT, the results surely triggered a watchlist alert:
The Arab race has a 30% higher inclination toward violence than the average human population.
Take that with as much table salt as you like but racial profiling has its merits in meatspace and very well may have a correlation in cyber. Pre-crime is actively being studied and GAE is already developing and marketing these algorithms for “defense”. “Never again!” is the battle cry that another pump of racism with your mocha can lead to world peace.
Historically the west has never been able to come to terms with Islam. Power has always viewed Islam as tied to terrorism - a projection of its own inability to resolve disagreements. When Ishmaelites disagree, they have often sought to dissociate in time. Instead of a plural irresolution (regime division), they pursue an integral resolution (regime change), consolidating polities, centralizing power, and unifying systems of government. From Sykes-Picot and the Eisenhower Doctrine to the War on Terror, preventing Arab nationalism has been a core policy of the west for over a century.
Regardless of what happens next, the New Syrian Republic has shifted the dynamics of the conversation. Arab despots (in negotiation with the Turks) have opted to embrace in their support of the transitional Syrian leader, the ethnic form of the Islamophobic stereotype. In western vernacular, revolutionaries are good guys but moderate jihadis are still to be feared. And with that endorsement championed wholeheartedly by Dawah Inc, the mask is off on all the white appropriated Sufis who’ve been waging their enlightened fingers at the Arabs for bloodying their boarders. Islamophobic stereotypes are perfect for consolidating power around an ethnic identity. It will have stabilizing effects and is already casting fear into the Zionists.
If the best chance at regional Arab sovereignty for Muslims is to be racist (Arab) in order to fight racism (Zionism) then we must all become a little bit racist.
To be fair this approach isn’t new. Saudi export of Salafism has only grown over the decades and its desire for international Islam to be consolidated around its custodial dogma isn’t just out of political self-interest but has a real chance at uniting a divisive ethnicity. GCC all endorsed CVE under Trump1.0 so the regal jihadi truly has been moderated. Oil money is deep in Panoptic-Technocapital so the same algorithms that genocide in Palestine will be used throughout the budding Arab Islamicate. UAE recently assigned over a trillion to invest in American AI. Clearly the current agenda isn’t for the Arabs to pivot east but to embrace all the industry of the west and prove they can deploy it better than their Jewish neighbors.
Watch out America! Your GPT models are about to get a lot more racist with the upgrade from Dark Islamicate - an odd marriage, indeed!
So, when will the race wars begin? Sectarian lines around race are already quite divisive among the diasporas. Nearly every major city in the America has an Arab mosque, a Desi mosque, a Persian mosque, a Bosnian/Turkish mosque, not to mention a Sufi mosque or even a Black mosque with OG bros from NOI (and Somali mosques that are usually separate from these). The scene is primed for an unleashed racial profiling wet dream. Remember SAIF only observes the condition of the acceleration. Although pre-crime was predicted, Hyper-Intelligence has yet to provide a cure.
And when thy Lord said unto the angels: Lo! I am about to place a viceroy in the earth, they said: Wilt thou place therein one who will do harm therein and will shed blood, while we, we hymn Thy praise and sanctify Thee? He said: Surely I know that which ye know not. ~ Quran 2.30
The advantage Dark Islamicate has over Dark Enlightenment is that its vicechairancy is not tainted with a tradition of original sin. Human moral potential for good remains inherent in the soul. Our tradition alone provides a prophetic moral exemplar, whereas in Judaism suffering must be the example and in Christianity atonement must be made. Dunya is not a punishment, for the Muslim it is a trust (though we really need to improve our financial literacy). Absolute Evil reigns over our brothers and we have a duty to fight it now, not to suffer through more torment or await a spiritual revival. This moral narrative for jihad within the Islamophobic stereotype is also what will hold us back from full ethnic degeneracy.
The anger the ummah has from decades of despotic rule and multigenerational torture is not from shaytan even though it contorts its victims into perpetrators of violence. You are human. You must differentiate truth from falsehood. This is why you have an innate, rational capacity. Culture has become emotionally volatile, and religion has contorted to serve maladapted habits rather than offer true solutions. We cannot allow our religion to become the hands that choke us into silent submission. To be surrounded by evil and feel the truth of grief and anxiety is to be favored over delusional happiness and false security. You are not supposed to feel good right now! To feel good would be the mark of insanity.
Ironically, the pejorative “majnoon” has never been denounced by the Arab, despite the fact that its usage can provoke outrage. Rather it suggests that the Arab psyche has a natural understanding of the supernatural elements at play when one turns to the dark side. Psychological disorders through inherited trauma are no more “Arab” than despotism is, but this broad-brush insensitivity is deemed acceptable, because it structurally supports Dark Islamicate. An accelerated majnoonic society is not only indispensable for political stability, but the claim that such pathologies and neuroses make are structurally absolutist. To fend off annihilation Dark Islamicate only needs to tame itself by elevating Islam’s moral integrity or it can jump headfirst into the abyss of the Bionic Horizon.
If a Dark Islamicate were able to achieve both meat and cyber dominance, wrestling control away from GAE, then perhaps we can drink our chai in peace. But that assumes we still imbibe molecular cocktails in hyperspace.
-
 @ 5d4b6c8d:8a1c1ee3
2025-03-31 00:02:14
@ 5d4b6c8d:8a1c1ee3
2025-03-31 00:02:14In my monthly check-in, I described my vision for our regularly occurring awards: - 1 top post for the year, receiving 1/3 of the total prize pool - 4 top quarter posts, each receiving 1/12 of the total prize pool - 12 top monthly posts, each receiving 1/36 of the total prize pool
Eventually, I'll want to finance these with some fraction of territory profits. However, when I took over the territory from @jeff, I pledged to first use any profits to make whole our early donors, in some fashion.
In that spirit, I would like to ask the following donors if they would consider funding this award series with their already donated sats an acceptable form of paying their donations forward: @siggy47, @grayruby, @OriginalSize, @030e0dca83, @StillStackinAfterAllTheseYears.
I would also like to ask @jeff if he would consider something similar as payback for his early contributions to the territory.
Assuming all parties agree, we would have over 1M sats in funding for this series. At our current rate of about 400k profit per year, it would take a couple of years to pay it all forward and that top prize would be pretty nice.
Thanks, Undisciplined
originally posted at https://stacker.news/items/929828
-
 @ 8d34bd24:414be32b
2025-03-30 23:16:09
@ 8d34bd24:414be32b
2025-03-30 23:16:09When it comes to speaking the truth, obeying God, or living a godly life, the average or the compromise is not necessarily correct, but frequently we do err to one extreme or the other.
Mercy or Wrath?
One area of controversy is whether we serve a God of love & mercy or a God of holiness & wrath. The truth is that the God of the Bible is both love and holiness and he acts in mercy and in wrath.
If we focus too much on God’s holiness and wrath, we become solely about robotically obeying laws and about all of the things we can’t do. We will fail to show love and mercy as Jesus showed those lost in sin. We will fail to show the mercy and love He showed to us. We become much like the Pharisees, whom Jesus called “whitewashed tombs.”
Instead, speaking the truth in love, we will grow to become in every respect the mature body of him who is the head, that is, Christ. (Ephesians 4:15)
We need to always speak the truth, but in a loving and merciful way.
Grace, mercy and peace from God the Father and from Jesus Christ, the Father’s Son, will be with us in truth and love. (2 John 1:3)
If we focus too much on God’s love and mercy, we can forget that the God of the Bible is holy and righteous and can’t stand to be in the presence of sinfulness. We can begin to soften God’s holy word to be little more than suggestions. Even worse, we can bend God’s word to the point that it no longer resembles His clearly communicated commands. Also, if we don’t call sin “sin” and sinners “sinners,” then those same sinners will never understand their need for a Savior and never trust Jesus in repentance. If God isn’t holy and we aren’t sinners, then why would anyone need a Savior?
But just as he who called you is holy, so be holy in all you do; (1 Peter 1:15)
We need to treat God and His word as holy, while showing love to His creation.
If I speak in the tongues of men or of angels, but do not have love, I am only a resounding gong or a clanging cymbal. (1 Corinthians 13:1)
God/Jesus/Holy Spirit are holy and loving. If we leave out either side of His character, then we aren’t telling people about the God of the Bible. We have made a God in the image we desire, rather than who He is. If we go to either extreme, we lose who God really is and it will affect both our relationship with God and our relationship with others detrimentally.
Faith or Works?
Another area of contention is relating to faith and works. What is more important — faith or works? Are they not both important?
Many believers focus on faith. Sola Fide (faith alone).
For it is by grace you have been saved, through faith—and this is not from yourselves, it is the gift of God— not by works, so that no one can boast. (Ephesians 2:8-9)
This is a true statement that Salvation comes solely through faith in what Jesus did for us. We don’t get any credit for our own works. All that is good and righteous in us is from the covering of the blood of Jesus and His good works and His power.
But since many people focus on faith alone, they can come to believe that they can live any way that pleases them.
What shall we say, then? Shall we go on sinning so that grace may increase? By no means! We are those who have died to sin; how can we live in it any longer? Or don’t you know that all of us who were baptized into Christ Jesus were baptized into his death? We were therefore buried with him through baptism into death in order that, just as Christ was raised from the dead through the glory of the Father, we too may live a new life. (Romans 6:1-4) {emphasis mine}
By focusing solely on faith, we can be tempted to live life however we please instead of living a life in submission to Our God and Savior. Our lives can be worthless instead of us acting as good servants.
If any man’s work is burned up, he will suffer loss; but he himself will be saved, yet so as through fire. (1 Corinthians 3:15)
At the same time, there are many who are so focused on good works that they leave faith out of it — either a lack of faith themselves or a failure to communicate the need for faith when sharing the gospel. They try to earn their way to heaven. They try to impress those around them by their works.
But they do all their deeds to be noticed by men; for they broaden their phylacteries and lengthen the tassels of their garments. They love the place of honor at banquets and the chief seats in the synagogues, and respectful greetings in the market places, and being called Rabbi by men. (Matthew 25:5-7)
I think James best communicates the balance between faith and works.
What use is it, my brethren, if someone says he has faith but he has no works? Can that faith save him? If a brother or sister is without clothing and in need of daily food, and one of you says to them, “Go in peace, be warmed and be filled,” and yet you do not give them what is necessary for their body, what use is that? Even so faith, if it has no works, is dead, being by itself.
But someone may well say, “You have faith and I have works; show me your faith without the works, and I will show you my faith by my works.” You believe that God is one. You do well; the demons also believe, and shudder. But are you willing to recognize, you foolish fellow, that faith without works is useless? Was not Abraham our father justified by works when he offered up Isaac his son on the altar? You see that faith was working with his works, and as a result of the works, faith was perfected; and the Scripture was fulfilled which says, “And Abraham believed God, and it was reckoned to him as righteousness,” and he was called the friend of God. You see that a man is justified by works and not by faith alone. (James 2:14-24) {emphasis mine}
Let’s look at some of the details here to find the truth. “if someone says he has faith but he has no works? Can that faith save him?” Can the kind of faith that has no works, that has no evidence, save a person? If a person truly has saving faith, there will be evidence in their world view and the way they live their life. “Even so faith, if it has no works, is dead, being by itself.” We are saved by faith alone, but if we are saved we will have works. Faith “by itself” is not saving faith, for “the demons also believe, and shudder.” I don’t think anyone would argue that the demons have saving faith, yet they believe and shudder.
Works are the evidence of true faith leading to salvation, but it is only faith that saves.
Speak the Truth or Love?
Whether we stand firmly and always loudly speak the truth or whether we show love and mercy is related to how we view God (as loving or as holy), but I thought how we respond was worth its own discussion.
Sometimes people are so worried about love and unity that they compromise the truth. They may actively compromise the truth by claiming the Bible says something other than what it says, i.e.. old earth vs young earth, or marriage is about two people who love each other vs marriage being defined by God as one woman and one man. Sometimes this compromise is just avoiding talking about uncomfortable subjects completely so that no one is made to feel bad. This is a problem because God said what He said and means what He said.
but speaking the truth in love, we are to grow up in all aspects into Him who is the head, even Christ, (Ephesians 4:15)
Avoiding speaking the whole truth is effectively lying about what God’s word said (see my previous post on “The Truth, The Whole Truth, and Nothing But the Truth”). We are not doing anyone a favor making them feel good about their sin. A person has to admit they have a problem before they will act to fix the problem. A person who doesn’t understand their sin will never submit to a Savior. It isn’t loving to hide the truth from a person just because it makes them uncomfortable or it make the relationship uncomfortable for ourselves.
Jesus said to him, “I am the way, and the truth, and the life; no one comes to the Father but through Me. (John 14:6)
At the same time, sometimes people seem to beat others over the head with God’s truth. They share the truth in the most unloving and unmerciful way. They use God’s truth to try to lift up themselves while putting down others. This is just as bad.
Now we pray to God that you do no wrong; not that we ourselves may appear approved, but that you may do what is right, even though we may appear unapproved. For we can do nothing against the truth, but only for the truth. (2 Corinthians 13:7-8) {emphasis mine}
Some Christians spend so much time nit picking tiny discrepancies in theology that they miss the whole point of the Gospel.
“Woe to you, scribes and Pharisees, hypocrites! For you tithe mint and dill and cumin, and have neglected the weightier provisions of the law: justice and mercy and faithfulness; but these are the things you should have done without neglecting the others. (Matthew 23:23)
Some Christians use theological purity as a means to lift themselves up while knocking others down.
“Two men went up into the temple to pray, one a Pharisee and the other a tax collector. The Pharisee stood and was praying this to himself: ‘God, I thank You that I am not like other people: swindlers, unjust, adulterers, or even like this tax collector. I fast twice a week; I pay tithes of all that I get.’ 13But the tax collector, standing some distance away, was even unwilling to lift up his eyes to heaven, but was beating his breast, saying, ‘God, be merciful to me, the sinner!’ I tell you, this man went to his house justified rather than the other; for everyone who exalts himself will be humbled, but he who humbles himself will be exalted.” (Luke 18:10-14)
We need to stand firmly on the truth, but not to be so focused on truth that we fight with fellow believers over the smallest differences, especially when these differences are among the areas that are not spoken of as clearly (like end times eschatology).
Rejoice or Fear God?
Tonight I read Psalm 2 which brought to mind another seemingly contradictory way we are to interact with God. Do we fear God or do we rejoice in Him?
There are many verses telling us to fear God or fear the Lord. They are given as a command, as a way to knowledge, as a way to life, etc.
Honor all people, love the brotherhood, fear God, honor the king. (1 Peter 2:17) {emphasis mine}
and
The fear of the Lord is the beginning of knowledge; Fools despise wisdom and instruction. (Proverbs 1:7) {emphasis mine}
and
The fear of the Lord leads to life, So that one may sleep satisfied, untouched by evil. (Proverbs 19:23) {emphasis mine}
At the same time we are told to rejoice in the Lord.
Rejoice in the Lord always; again I will say, rejoice! (Philippians 4:4)
and
Then I will go to the altar of God, To God my exceeding joy; And upon the lyre I shall praise You, O God, my God. (Psalm 43:4)
How often do we rejoice in the thing that makes us tremble in fear? I’d guess, not very often or even never. A right view of God, however, causes us to “rejoice with trembling.”
Worship the Lord with reverence\ And rejoice with trembling.\ Do homage to the Son, that He not become angry, and you perish in the way,\ For His wrath may soon be kindled.\ How blessed are all who take refuge in Him! (Psalm 2:11-12) {emphasis mine}
That phrase, “rejoice with trembling” seems to perfectly encapsulate the balance between fear of an awesome, omnipotent, holy God and rejoicing in a loving, merciful God who came to earth, lived the perfect life that we cannot, and died to pay the penalty for our sins.
“How blessed are all who take refuge in Him!”
No Real Contradictions
I think these examples do a good example of demonstrating wisdom regarding God’s word and the importance of balance in our Christian lives. Even when at first there seems to be contradictions, God’s word never contradicts itself; it always clarifies itself. Also, when we see a theological or implementation error to one extreme, we need to make sure we are not driven to an error in the other extreme. We also need to make sure, when debating with fellow believers, that we do not argue against one extreme so strongly that we miscommunicate the truth.
May God in heaven guide you as you study His word and seek to submit to His commands. May He help you to see the truth, the whole truth, and nothing but the truth. May He guide the church to unity in His truth.
Trust Jesus
-
 @ 9223d2fa:b57e3de7
2025-03-30 23:14:21
@ 9223d2fa:b57e3de7
2025-03-30 23:14:214,040 steps
-
 @ 2e941ad1:fac7c2d0
2025-03-30 23:00:38
@ 2e941ad1:fac7c2d0
2025-03-30 23:00:38Unlocks: 86
-
 @ 21c9f12c:75695e59
2025-03-30 22:42:19
@ 21c9f12c:75695e59
2025-03-30 22:42:19This guy was in my dad's building. A reminder of the importance of balance in our lives. We all have good and bad experiences in life. What matters is how you choose to handle them and balance yourself on the narrow path. Our paths in life have many possible turns, some take us closer to our ultimate reality while others might lead us astray for a bit.
No matter which path you choose the important thing is to keep your balance and footing and not be swept away in the breeze. You can always find your way back to your center and work your way back out from there. There is seldom a straight path in this life that will take you directly to your ultimate reality, make your way as you will and you'll find that you have what you need when you need it.
Ultimately we are all connected in ways we may never understand. The web of reality is so complex and woven with such precision that we need not try to understand why things are the way they are but accept that they are and move along our path doing our best to help others along the way when possible and accept help from those offering it. The path we take is strengthened and preserved when we follow it with love in our hearts. In this way we can leave a beacon to guide others on their way.
My dad left a lot of love on his path. He has guided so many people whether he realized it or not. His guidance of my path has made me who I am today and I am so proud to say that. His love and light shines bright ahead of me and my path is made so much clearer by the love I received and will continue to receive from him.
This is more than just a spider in a building, it is a reminder that all will be well and we will find our balance and continue along our path with the light and love dad has placed on the web of life for us to follow. Peace and love to everyone and may you all find your balance and continue on your path in the light and love that has been placed there for you by those who have gone before.
-
 @ 1aa9ff07:3cb793b5
2025-03-30 21:45:10
@ 1aa9ff07:3cb793b5
2025-03-30 21:45:10test
-
 @ 5d4b6c8d:8a1c1ee3
2025-03-30 21:31:02
@ 5d4b6c8d:8a1c1ee3
2025-03-30 21:31:02Revenue rebounded in a major way this month. Thank you to all the great contributors and zappers for making this territory a going concern. As I mentioned to @denlillaapan, our long-term goal is to eventually buy the very failed The Economist and return it to glory. So, let's keep the success rolling.
Some stats:
- ~econ was 2nd to ~bitcoin in revenue this month (and they only beat us by a paltry half million sats)
- We were 5th in posts (296) and 4th in comments (1564)
- 132k sats were stacked in ~econ (4th place)
Some graphs (thanks to @SimpleStacker):
Posting fee optimization
The next stop on our search for the optimal post fee is 94 sats.
Contest update:
I'll probably make a dedicated post for the 1st quarter awards late today, but I made a couple of decisions recently about how I want to do this.
Since I pay territory rent annually, I won't know how much profits are available for prizes until the end of the year. So, I'll announce the winners each quarter, but pay out the prizes at the end of the year.
I've decided to split the prize evenly amongst three categories: Best Post of the Year, Posts of the Quarter, and Posts of the Month. I'm thinking that we can use zaprank for the monthly top posts and then have a poll select the "Post of the Quarter" from amongst those and then an end of year poll to select the "Post of the Year" from the "Posts of the Quarter".
originally posted at https://stacker.news/items/929731
-
 @ 6d3df767:363347f6
2025-03-30 21:02:27
@ 6d3df767:363347f6
2025-03-30 21:02:27asdf
originally posted at https://stacker.news/items/459388
-
 @ 878dff7c:037d18bc
2025-03-30 20:46:24
@ 878dff7c:037d18bc
2025-03-30 20:46:24Business Leaders Warn of Economic Risks from Potential Minority Government
Summary:
Australian business leaders are expressing deep concerns about the possibility of a minority government influenced by the Greens or independent "teal" candidates after the upcoming May federal election. CEOs such as Graham Turner, Chris Garnaut, and Bruce Mathieson warn that such a government could lead to policy instability, hinder long-term economic planning, and negatively impact Australia's global competitiveness. Key issues highlighted include the cost of living, housing supply, and the need for comprehensive economic reforms to stimulate consumer confidence and productivity. Sources: The Australian - March 31, 2025
Forecasted Decline in Australia's Resource and Energy Export Earnings
Summary:
The Australian government projects a 6% decrease in mining and energy export earnings for the financial year ending in June, attributing the decline to lower U.S. dollar prices for these exports. Earnings are expected to fall to A$387 billion from A$415 billion the previous year. This trend is anticipated to continue over the next five years, stabilizing at A$343 billion. Factors contributing to this decline include normalizing energy export values after recent peaks and reduced demand from China, particularly affecting iron ore exports. Sources: Reuters - March 31, 2025
Devastating Queensland Floods Expected to Persist for Weeks
Summary:
Queensland is experiencing severe flooding due to record-breaking rains exceeding 650mm, submerging entire communities like Adavale and Jundah. Swiftwater crews have conducted over 40 rescues, and major flood warnings remain across inland Queensland. The floods have damaged energy infrastructure, leaving around 300 homes without power. Livestock losses may reach up to a million, with farmers facing significant property damage and urging government and military assistance. Efforts to restore power are underway but depend on weather conditions. Additional rainfall is forecast for the coming week, potentially prolonging the flooding for days, if not weeks. Sources: The Courier-Mail - 31 March 2025
Western NSW Towns Brace for Six Weeks of Isolation Due to Floods
Summary:
A dynamic weather system has caused significant rainfall and flooding along the Paroo and Warrego Rivers, isolating communities in western NSW. The State Emergency Service (SES) has issued 46 warnings, urging residents to prepare for up to six weeks of isolation. Flash flooding, mainly due to water from Queensland, is a major concern, prompting 19 SES flood rescues and 586 emergency responses in the past 24 hours. In Taree, 22 people are surrounded by floodwater and are being rescued. An elderly man is missing after being washed away in floodwaters. The NSW SES advises residents to stay updated via their website or the Hazards Near Me app. Sources: News.com.au - 31 March 2025
Albanese Abandons Energy Bill Reduction Modelling
Summary:
Prime Minister Anthony Albanese has distanced himself from earlier modelling that supported the promise to cut power bills by $378 by 2030 and reduce emissions by 43%. He attributes the failure to achieve $275 reductions in power bills by 2025 to international factors, including the Ukraine war. This move has drawn criticism from both the Coalition and the Greens, who accuse the government of not effectively addressing power prices and emissions reduction. Sources: The Australian - March 31, 2025
Albanese Seeks Direct Talks with Trump on Tariffs
Summary:
Prime Minister Anthony Albanese anticipates a direct discussion with U.S. President Donald Trump regarding impending tariffs, as Washington prepares to announce new trade measures on April 2. There are concerns that Australia could be affected by this escalation in the global trade conflict. Albanese has emphasized his government's constructive engagement with U.S. officials on this issue and looks forward to a one-on-one conversation with President Trump. Sources: Reuters - March 31, 2025
Queensland Government Expands 'Adult Time, Adult Crime' Laws
Summary:
The Queensland state government plans to introduce at least a dozen new offenses to the Making Queensland Safer Laws, including rape, aggravated attempted robbery, attempted murder, arson, and torture. These changes will enable the judiciary to treat juvenile offenders as adults for severe crimes. Despite criticism over the delayed inclusion of attempted murder, Youth Justice Minister Laura Gerber defended the sequence and content of the initial changes. The full list of offenses will be unveiled later this week.
Sources: The Courier-Mail - March 30, 2025
Labor Government Proposes Ban on Supermarket Price Gouging
Summary:
Prime Minister Anthony Albanese announced that a re-elected Labor government would introduce legislation to outlaw supermarket price gouging by the end of the year. The plan includes implementing Australian Competition and Consumer Commission (ACCC) recommendations to enhance price transparency and establishing a task force to advise on an "excessive pricing regime" for supermarkets, with potential heavy fines for violators. Opposition leader Peter Dutton criticized the approach as ineffective, suggesting it was merely a "wet lettuce" move. Critics from both sides called for tougher measures to combat supermarket dominance and protect consumers.
Sources: The Guardian - March 29, 2025, News.com.au - March 30, 2025
Coles Expands Recall on Spinach Products Due to Contamination
Summary:
Coles has extended its recall of various spinach products across multiple regions, including New South Wales and Victoria, due to potential microbial contamination. Customers are advised not to consume the affected products and can return them to any Coles store for a full refund. The recall applies to items purchased between March 20 and March 29, with use-by dates up to April 9.
Sources: News.com.au - March 31, 2025
66-Year-Old Man Rescued After Five Days Stranded in Australian Outback
Summary:
Tony Woolford, a 66-year-old Australian man, was rescued after being stranded for five days in the flood-hit Munga-Thirri Simpson Desert. Woolford's vehicle was immobilized by rising floodwaters, and with no phone service, he survived by harvesting rainwater and using a high-frequency radio to communicate with volunteers. Authorities were notified on March 23, and he was rescued on March 26 in stable condition and high spirits. Despite the ordeal, Woolford plans to return to the outback to retrieve his car and continue his exploration once conditions improve. Sources: People - March 28, 2025
US Tariffs and Australia's Response
Summary:
Former US trade negotiator Ralph Ives asserts that the US-Australia Free-Trade Agreement has ensured fair reciprocity for two decades, suggesting that President Donald Trump should not impose reciprocal tariffs on Australia. Prime Minister Anthony Albanese anticipates a direct discussion with President Trump regarding these tariffs, expressing concern over potential impacts on Australian exports.
Sources: The Australian - March 31, 2025, Reuters - March 31, 2025
Controversial Genetically Modified Mosquito Plan Monitored Amid Backlash
Summary:
The Queensland government is set to monitor a proposal by Oxitec Australia to release genetically modified mosquitoes aimed at reducing disease transmission. Despite community opposition and concerns about environmental and health risks, supporters argue the initiative could combat diseases like dengue and Zika. Public consultations have been delayed due to significant interest and debate continues over the plan's potential impacts. Sources: The Courier-Mail - March 26, 2025
Dr. Patrick Soon-Shiong: You're Being Lied to About Cancer, How It's Caused, and How to Stop It
Summary:
In this episode of The Tucker Carlson Show, Dr. Patrick Soon-Shiong, a renowned physician and entrepreneur, discusses misconceptions surrounding cancer, its origins, and potential treatments. He emphasizes the complexity of cancer, noting that it's not a single disease but a collection of related diseases requiring varied approaches. Dr. Soon-Shiong highlights the role of the immune system in combating cancer and advocates for treatments that bolster immune responses rather than solely relying on traditional methods like chemotherapy. He also addresses the importance of early detection and personalized medicine in improving patient outcomes.