-
 @ 2fdae362:c9999539
2025-04-30 22:17:19
@ 2fdae362:c9999539
2025-04-30 22:17:19The architecture you choose for your embedded firmware has long-lasting consequences. It impacts how quickly you can add features, how easily your team can debug and maintain the system, and how confidently you can scale. While main loops and real-time operating systems (RTOS) are common, a third option — the state machine kernel — often delivers the most value in modern embedded development. At Wolff Electronic Design, we’ve used this approach for over 15 years to build scalable, maintainable, and reliable systems across a wide range of industries.
Every embedded system starts with one big decision: how will the firmware be structured?
Many teams default to the familiar—using a simple main loop or adopting a RTOS. But those approaches can introduce unnecessary complexity or long-term maintenance headaches. A third option, often overlooked, is using a state machine kernel—an event-driven framework designed for reactive, real-time systems. Below, we compare the three options head-to-head to help you choose the right architecture for your next project.Comparison Chart
| Approach | Description | Pros | Cons | Best For | |-----------------------|------------------------------------------------------------------------|-------------------------------------------------------------|------------------------------------------------------------|--------------------------------------| | Main Loop | A single, continuous while-loop calling functions in sequence | Simple to implement, low memory usage | Hard to scale, difficult to manage timing and state | Small, simple devices | | RTOS | Multi-threaded system with scheduler, tasks, and preemption | Good for multitasking, robust toolchain support | Thread overhead, complex debugging, race conditions | Systems with multiple async tasks | | State Machine Kernel | Event-driven system with structured state transitions, run in a single thread | Easy to debug, deterministic behavior, scalable and modular | Learning curve, may need rethinking architecture | Reactive systems, clean architecture |
Why the State Machine Kernel Wins
Promotes Innovation Without Chaos
With clear, hierarchical state transitions, your codebase becomes modular and self-documenting — making it easier to prototype, iterate, and innovate without fear of breaking hidden dependencies or triggering bugs.
Prevents Hidden Complexity
Unlike RTOSes, where tasks run in parallel and can create race conditions or timing bugs, state machines run cooperatively in a single-threaded model. This eliminates deadlocks, stack overflows, and debugging nightmares that come with thread-based systems.
Scales Without Becoming Fragile
As features and states are added, the system remains predictable. You don’t have to untangle spaghetti logic or rework your entire loop to support new behaviors — you just add new events and state transitions.
Improves Maintainability and Handoff
Because logic is encapsulated in individual states with defined transitions, the code is easier to understand, test, and maintain. This lowers the cost of onboarding new developers or revisiting the system years later.
At Wolff Electronic Design, we’ve worked with every kind of firmware structure over the past 15+ years. Our go-to for complex embedded systems? A state machine kernel. It gives our clients the flexibility of RTOS-level structure without the bugs, complexity, or overhead. Whether you’re developing restaurant equipment or industrial control systems, this architecture offers a better path forward: clean, maintainable, and built to last.
Learn more about our capabilities here.
design, #methodologies, #quantumleaps, #statemachines
-
 @ 1c19eb1a:e22fb0bc
2025-04-30 22:02:13
@ 1c19eb1a:e22fb0bc
2025-04-30 22:02:13I am happy to present to you the first full review posted to Nostr Reviews: #Primal for #Android!
Primal has its origins as a micro-blogging, social media client, though it is now expanding its horizons into long-form content. It was first released only as a web client in March of 2023, but has since had a native client released for both iOS and Android. All of Primal's clients recently had an update to Primal 2.0, which included both performance improvements and a number of new features. This review will focus on the Android client specifically, both on phone and tablet.
Since Primal has also added features that are only available to those enrolled in their new premium subscription, it should also be noted that this review will be from the perspective of a free user. This is for two reasons. First, I am using an alternate npub to review the app, and if I were to purchase premium at some time in the future, it would be on my main npub. Second, despite a lot of positive things I have to say about Primal, I am not planning to regularly use any of their apps on my main account for the time being, for reasons that will be discussed later in the review.
The application can be installed through the Google Play Store, nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8, or by downloading it directly from Primal's GitHub. The full review is current as of Primal Android version 2.0.21. Updates to the review on 4/30/2025 are current as of version 2.2.13.
In the ecosystem of "notes and other stuff," Primal is predominantly in the "notes" category. It is geared toward users who want a social media experience similar to Twitter or Facebook with an infinite scrolling feed of notes to interact with. However, there is some "other stuff" included to complement this primary focus on short and long form notes including a built-in Lightning wallet powered by #Strike, a robust advanced search, and a media-only feed.

Overall Impression
Score: 4.4 / 5 (Updated 4/30/2025)
Primal may well be the most polished UI of any Nostr client native to Android. It is incredibly well designed and thought out, with all of the icons and settings in the places a user would expect to find them. It is also incredibly easy to get started on Nostr via Primal's sign-up flow. The only two things that will be foreign to new users are the lack of any need to set a password or give an email address, and the prompt to optionally set up the wallet.
Complaints prior to the 2.0 update about Primal being slow and clunky should now be completely alleviated. I only experienced quick load times and snappy UI controls with a couple very minor exceptions, or when loading DVM-based feeds, which are outside of Primal's control.
Primal is not, however, a client that I would recommend for the power-user. Control over preferred relays is minimal and does not allow the user to determine which relays they write to and which they only read from. Though you can use your own wallet, it will not appear within the wallet interface, which only works with the custodial wallet from Strike. Moreover, and most eggregiously, the only way for existing users to log in is by pasting their nsec, as Primal does not support either the Android signer or remote signer options for users to protect their private key at this time. This lack of signer support is the primary reason the client received such a low overall score. If even one form of external signer log in is added to Primal, the score will be amended to 4.2 / 5, and if both Android signer and remote signer support is added, it will increase to 4.5.
Update: As of version 2.2.13, Primal now supports the Amber Android signer! One of the most glaring issues with the app has now been remedied and as promised, the overall score above has been increased.
Another downside to Primal is that it still utilizes an outdated direct message specification that leaks metadata that can be readily seen by anyone on the network. While the content of your messages remains encrypted, anyone can see who you are messaging with, and when. This also means that you will not see any DMs from users who are messaging from a client that has moved to the latest, and far more private, messaging spec.
That said, the beautiful thing about Nostr as a protocol is that users are not locked into any particular client. You may find Primal to be a great client for your average #bloomscrolling and zapping memes, but opt for a different client for more advanced uses and for direct messaging.
Features
Primal has a lot of features users would expect from any Nostr client that is focused on short-form notes, but it also packs in a lot of features that set it apart from other clients, and that showcase Primal's obvious prioritization of a top-tier user experience.
Home Feed
By default, the infinitely scrolling Home feed displays notes from those you currently follow in chronological order. This is traditional Nostr at its finest, and made all the more immersive by the choice to have all distracting UI elements quickly hide themselves from view as the you begin to scroll down the feed. They return just as quickly when you begin to scroll back up.

Scrolling the feed is incredibly fast, with no noticeable choppiness and minimal media pop-in if you are on a decent internet connection.
Helpfully, it is easy to get back to the top of the feed whenever there is a new post to be viewed, as a bubble will appear with the profile pictures of the users who have posted since you started scrolling.

Interacting With Notes
Interacting with a note in the feed can be done via the very recognizable icons at the bottom of each post. You can comment, zap, like, repost, and/or bookmark the note.
Notably, tapping on the zap icon will immediately zap the note your default amount of sats, making zapping incredibly fast, especially when using the built-in wallet. Long pressing on the zap icon will open up a menu with a variety of amounts, along with the ability to zap a custom amount. All of these amounts, and the messages that are sent with the zap, can be customized in the application settings.

Users who are familiar with Twitter or Instagram will feel right at home with only having one option for "liking" a post. However, users from Facebook or other Nostr clients may wonder why they don't have more options for reactions. This is one of those things where users who are new to Nostr probably won't notice they are missing out on anything at all, while users familiar with clients like #Amethyst or #noStrudel will miss the ability to react with a 🤙 or a 🫂.
It's a similar story with the bookmark option. While this is a nice bit of feature parity for Twitter users, for those already used to the ability to have multiple customized lists of bookmarks, or at minimum have the ability to separate them into public and private, it may be a disappointment that they have no access to the bookmarks they already built up on other clients. Primal offers only one list of bookmarks for short-form notes and they are all visible to the public. However, you are at least presented with a warning about the public nature of your bookmarks before saving your first one.
Yet, I can't dock the Primal team much for making these design choices, as they are understandable for Primal's goal of being a welcoming client for those coming over to Nostr from centralized platforms. They have optimized for the onboarding of new users, rather than for those who have been around for a while, and there is absolutely nothing wrong with that.
Post Creation
Composing posts in Primal is as simple as it gets. Accessed by tapping the obvious circular button with a "+" on it in the lower right of the Home feed, most of what you could need is included in the interface, and nothing you don't.

Your device's default keyboard loads immediately, and the you can start typing away.
There are options for adding images from your gallery, or taking a picture with your camera, both of which will result in the image being uploaded to Primal's media-hosting server. If you prefer to host your media elsewhere, you can simply paste the link to that media into your post.
There is also an @ icon as a tip-off that you can tag other users. Tapping on this simply types "@" into your note and brings up a list of users. All you have to do to narrow down the user you want to tag is continue typing their handle, Nostr address, or paste in their npub.

This can get mixed results in other clients, which sometimes have a hard time finding particular users when typing in their handle, forcing you to have to remember their Nostr address or go hunt down their npub by another means. Not so with Primal, though. I had no issues tagging anyone I wanted by simply typing in their handle.
Of course, when you are tagging someone well known, you may find that there are multiple users posing as that person. Primal helps you out here, though. Usually the top result is the person you want, as Primal places them in order of how many followers they have. This is quite reliable right now, but there is nothing stopping someone from spinning up an army of bots to follow their fake accounts, rendering follower count useless for determining which account is legitimate. It would be nice to see these results ranked by web-of-trust, or at least an indication of how many users you follow who also follow the users listed in the results.
Once you are satisfied with your note, the "Post" button is easy to find in the top right of the screen.
Feed Selector and Marketplace
Primal's Home feed really shines when you open up the feed selection interface, and find that there are a plethora of options available for customizing your view. By default, it only shows four options, but tapping "Edit" opens up a new page of available toggles to add to the feed selector.

The options don't end there, though. Tapping "Add Feed" will open up the feed marketplace, where an ever-growing number of custom feeds can be found, some created by Primal and some created by others. This feed marketplace is available to a few other clients, but none have so closely integrated it with their Home feeds like Primal has.

Unfortunately, as great as these custom feeds are, this was also the feature where I ran into the most bugs while testing out the app.
One of these bugs was while selecting custom feeds. Occasionally, these feed menu screens would become unresponsive and I would be unable to confirm my selection, or even use the back button on my device to back out of the screen. However, I was able to pull the screen down to close it and re-open the menu, and everything would be responsive again.
This only seemed to occur when I spent 30 seconds or more on the same screen, so I imagine that most users won't encounter it much in their regular use.
Another UI bug occurred for me while in the feed marketplace. I could scroll down the list of available feeds, but attempting to scroll back up the feed would often close the interface entirely instead, as though I had pulled the screen down from the top, when I was swiping in the middle of the screen.
The last of these bugs occurred when selecting a long-form "Reads" feed while in the menu for the Home feed. The menu would allow me to add this feed and select it to be displayed, but it would fail to load the feed once selected, stating "There is no content in this feed." Going to a different page within the the app and then going back to the Home tab would automatically remove the long-form feed from view, and reset back to the most recently viewed short-form "Notes" feed, though the long-form feed would still be available to select again. The results were similar when selecting a short-form feed for the Reads feed.
I would suggest that if long-form and short-form feeds are going to be displayed in the same list, and yet not be able to be displayed in the same feed, the application should present an error message when attempting to add a long-form feed for the Home feed or a short-form feed for the Reads feed, and encourage the user add it to the proper feed instead.
Long-Form "Reads" Feed
A brand new feature in Primal 2.0, users can now browse and read long-form content posted to Nostr without having to go to a separate client. Primal now has a dedicated "Reads" feed to browse and interact with these articles.
This feed displays the author and title of each article or blog, along with an image, if available. Quite conveniently, it also lets you know the approximate amount of time it will take to read a given article, so you can decide if you have the time to dive into it now, or come back later.

Noticeably absent from the Reads feed, though, is the ability to compose an article of your own. This is another understandable design choice for a mobile client. Composing a long-form note on a smart-phone screen is not a good time. Better to be done on a larger screen, in a client with a full-featured text editor.
Tapping an article will open up an attractive reading interface, with the ability to bookmark for later. These bookmarks are a separate list from your short-form note bookmarks so you don't have to scroll through a bunch of notes you bookmarked to find the article you told yourself you would read later and it's already been three weeks.
While you can comment on the article or zap it, you will notice that you cannot repost or quote-post it. It's not that you can't do so on Nostr. You absolutely can in other clients. In fact, you can do so on Primal's web client, too. However, Primal on Android does not handle rendering long-form note previews in the Home feed, so they have simply left out the option to share them there. See below for an example of a quote-post of a long-form note in the Primal web client vs the Android client.
Primal Web:

Primal Android:

The Explore Tab
Another unique feature of the Primal client is the Explore tab, indicated by the compass icon. This tab is dedicated to discovering content from outside your current follow list. You can find the feed marketplace here, and add any of the available feeds to your Home or Reads feed selections. You can also find suggested users to follow in the People tab. The Zaps tab will show you who has been sending and receiving large zaps. Make friends with the generous ones!
The Media tab gives you a chronological feed of just media, displayed in a tile view. This can be great when you are looking for users who post dank memes, or incredible photography on a regular basis. Unfortunately, it appears that there is no way to filter this feed for sensitive content, and so you do not have to scroll far before you see pornographic material.
Indeed, it does not appear that filters for sensitive content are available in Primal for any feed. The app is kind enough to give a minimal warning that objectionable content may be present when selecting the "Nostr Firehose" option in your Home feed, with a brief "be careful" in the feed description, but there is not even that much of a warning here for the media-only feed.

The media-only feed doesn't appear to be quite as bad as the Nostr Firehose feed, so there must be some form of filtering already taking place, rather than being a truly global feed of all media. Yet, occasional sensitive content still litters the feed and is unavoidable, even for users who would rather not see it. There are, of course, ways to mute particular users who post such content, if you don't want to see it a second time from the same user, but that is a never-ending game of whack-a-mole, so your only realistic choices in Primal are currently to either avoid the Nostr Firehose and media-only feeds, or determine that you can put up with regularly scrolling past often graphic content.
This is probably the only choice Primal has made that is not friendly to new users. Most clients these days will have some protections in place to hide sensitive content by default, but still allow the user to toggle those protections off if they so choose. Some of them hide posts flagged as sensitive content altogether, others just blur the images unless the user taps to reveal them, and others simply blur all images posted by users you don't follow. If Primal wants to target new users who are accustomed to legacy social media platforms, they really should follow suit.
The final tab is titled "Topics," but it is really just a list of popular hashtags, which appear to be arranged by how often they are being used. This can be good for finding things that other users are interested in talking about, or finding specific content you are interested in.
If you tap on any topic in the list, it will display a feed of notes that include that hashtag. What's better, you can add it as a feed option you can select on your Home feed any time you want to see posts with that tag.
The only suggestion I would make to improve this tab is some indication of why the topics are arranged in the order presented. A simple indicator of the number of posts with that hashtag in the last 24 hours, or whatever the interval is for determining their ranking, would more than suffice.
Even with those few shortcomings, Primal's Explore tab makes the client one of the best options for discovering content on Nostr that you are actually interested in seeing and interacting with.
Built-In Wallet
While this feature is completely optional, the icon to access the wallet is the largest of the icons at the bottom of the screen, making you feel like you are missing out on the most important feature of the app if you don't set it up. I could be critical of this design choice, but in many ways I think it is warranted. The built-in wallet is one of the most unique features that Primal has going for it.

Consider: If you are a new user coming to Nostr, who isn't already a Bitcoiner, and you see that everyone else on the platform is sending and receiving sats for their posts, will you be more likely to go download a separate wallet application or use one that is built-into your client? I would wager the latter option by a long shot. No need to figure out which wallet you should download, whether you should do self-custody or custodial, or make the mistake of choosing a wallet with unexpected setup fees and no Lightning address so you can't even receive zaps to it. nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr often states that he believes more people will be onboarded to Bitcoin through Nostr than by any other means, and by including a wallet into the Primal client, his team has made adopting Bitcoin that much easier for new Nostr users.
Some of us purists may complain that it is custodial and KYC, but that is an unfortunate necessity in order to facilitate onboarding newcoiners to Bitcoin. This is not intended to be a wallet for those of us who have been using Bitcoin and Lightning regularly already. It is meant for those who are not already familiar with Bitcoin to make it as easy as possible to get off zero, and it accomplishes this better than any other wallet I have ever tried.
In large part, this is because the KYC is very light. It does need the user's legal name, a valid email address, date of birth, and country of residence, but that's it! From there, the user can buy Bitcoin directly through the app, but only in the amount of $4.99 at a time. This is because there is a substantial markup on top of the current market price, due to utilizing whatever payment method the user has set up through their Google Play Store. The markup seemed to be about 19% above the current price, since I could purchase 4,143 sats for $4.99 ($120,415 / Bitcoin), when the current price was about $101,500. But the idea here is not for the Primal wallet to be a user's primary method of stacking sats. Rather, it is intended to get them off zero and have a small amount of sats to experience zapping with, and it accomplishes this with less friction than any other method I know.
Moreover, the Primal wallet has the features one would expect from any Lightning wallet. You can send sats to any Nostr user or Lightning address, receive via invoice, or scan to pay an invoice. It even has the ability to receive via on-chain. This means users who don't want to pay the markup from buying through Primal can easily transfer sats they obtained by other means into the Primal wallet for zapping, or for using it as their daily-driver spending wallet.
Speaking of zapping, once the wallet is activated, sending zaps is automatically set to use the wallet, and they are fast. Primal gives you immediate feedback that the zap was sent and the transaction shows in your wallet history typically before you can open the interface. I can confidently say that Primal wallet's integration is the absolute best zapping experience I have seen in any Nostr client.
One thing to note that may not be immediately apparent to new users is they need to add their Lightning address with Primal into their profile details before they can start receiving zaps. So, sending zaps using the wallet is automatic as soon as you activate it, but receiving is not. Ideally, this could be further streamlined, so that Primal automatically adds the Lightning address to the user's profile when the wallet is set up, so long as there is not currently a Lightning address listed.
Of course, if you already have a Lightning wallet, you can connect it to Primal for zapping, too. We will discuss this further in the section dedicated to zap integration.
Advanced Search
Search has always been a tough nut to crack on Nostr, since it is highly dependent on which relays the client is pulling information from. Primal has sought to resolve this issue, among others, by running a caching relay that pulls notes from a number of relays to store them locally, and perform some spam filtering. This allows for much faster retrieval of search results, and also makes their advanced search feature possible.
Advanced search can be accessed from most pages by selecting the magnifying glass icon, and then the icon for more options next to the search bar.
As can be seen in the screenshot below, there are a plethora of filters that can be applied to your search terms.

You can immediately see how this advanced search could be a very powerful tool for not just finding a particular previous note that you are looking for, but for creating your own custom feed of notes. Well, wouldn't you know it, Primal allows you to do just that! This search feature, paired with the other features mentioned above related to finding notes you want to see in your feed, makes Primal hands-down the best client for content discovery.
The only downside as a free user is that some of these search options are locked behind the premium membership. Or else you only get to see a certain number of results of your advanced search before you must be a premium member to see more.
Can My Grandma Use It?
Score: 4.8 / 5 Primal has obviously put a high priority on making their client user-friendly, even for those who have never heard of relays, public/private key cryptography, or Bitcoin. All of that complexity is hidden away. Some of it is available to play around with for the users who care to do so, but it does not at all get in the way of the users who just want to jump in and start posting notes and interacting with other users in a truly open public square.
To begin with, the onboarding experience is incredibly smooth. Tap "Create Account," enter your chosen display name and optional bio information, upload a profile picture, and then choose some topics you are interested in. You are then presented with a preview of your profile, with the ability to add a banner image, if you so choose, and then tap "Create Account Now."

From there you receive confirmation that your account has been created and that your "Nostr key" is available to you in the application settings. No further explanation is given about what this key is for at this point, but the user doesn't really need to know at the moment, either. If they are curious, they will go to the app settings to find out.
At this point, Primal encourages the user to activate Primal Wallet, but also gives the option for the user to do it later.

That's it! The next screen the user sees if they don't opt to set up the wallet is their Home feed with notes listed in chronological order. More impressive, the feed is not empty, because Primal has auto-followed several accounts based on your selected topics.
Now, there has definitely been some legitimate criticism of this practice of following specific accounts based on the topic selection, and I agree. I would much prefer to see Primal follow hashtags based on what was selected, and combine the followed hashtags into a feed titled "My Topics" or something of that nature, and make that the default view when the user finishes onboarding. Following particular users automatically will artificially inflate certain users' exposure, while other users who might be quality follows for that topic aren't seen at all.
The advantage of following particular users over a hashtag, though, is that Primal retains some control over the quality of the posts that new users are exposed to right away. Primal can ensure that new users see people who are actually posting quality photography when they choose it as one of their interests. However, even with that example, I chose photography as one of my interests and while I did get some stunning photography in my Home feed by default based on Primal's chosen follows, I also scrolled through the Photography hashtag for a bit and I really feel like I would have been better served if Primal had simply followed that hashtag rather than a particular set of users.
We've already discussed how simple it is to set up the Primal Wallet. You can see the features section above if you missed it. It is, by far, the most user friendly experience to onboarding onto Lightning and getting a few sats for zapping, and it is the only one I know of that is built directly into a Nostr client. This means new users will have a frictionless introduction to transacting via Lightning, perhaps without even realizing that's what they are doing.
Discovering new content of interest is incredibly intuitive on Primal, and the only thing that new users may struggle with is getting their own notes seen by others. To assist with this, I would suggest Primal encourage users to make their first post to the introductions hashtag and direct any questions to the AskNostr hashtag as part of the onboarding process. This will get them some immediate interactions from other users, and further encouragement to set up their wallet if they haven't already done so.
How do UI look?
Score: 4.9 / 5
Primal is the most stunningly beautiful Nostr client available, in my honest opinion. Despite some of my hangups about certain functionality, the UI alone makes me want to use it.

It is clean, attractive, and intuitive. Everything I needed was easy to find, and nothing felt busy or cluttered. There are only a few minor UI glitches that I ran into while testing the app. Some of them were mentioned in the section of the review detailing the feed selector feature, but a couple others occurred during onboarding.
First, my profile picture was not centered in the preview when I uploaded it. This appears to be because it was a low quality image. Uploading a higher quality photo did not have this result.

The other UI bug was related to text instructions that were cut off, and not able to scroll to see the rest of them. This occurred on a few pages during onboarding, and I expect it was due to the size of my phone screen, since it did not occur when I was on a slightly larger phone or tablet.

Speaking of tablets, Primal Android looks really good on a tablet, too! While the client does not have a landscape mode by default, many Android tablets support forcing apps to open in full-screen landscape mode, with mixed results. However, Primal handles it well. I would still like to see a tablet version developed that takes advantage of the increased screen real estate, but it is certainly a passable option.





At this point, I would say the web client probably has a bit better UI for use on a tablet than the Android client does, but you miss out on using the built-in wallet, which is a major selling point of the app.
This lack of a landscape mode for tablets and the few very minor UI bugs I encountered are the only reason Primal doesn't get a perfect score in this category, because the client is absolutely stunning otherwise, both in light and dark modes. There are also two color schemes available for each.

Log In Options
Score: 4 / 5 (Updated 4/30/2025)
Unfortunately, Primal has not included any options for log in outside of pasting your private key into the application. While this is a very simple way to log in for new users to understand, it is also the least secure means to log into Nostr applications.
This is because, even with the most trustworthy client developer, giving the application access to your private key always has the potential for that private key to somehow be exposed or leaked, and on Nostr there is currently no way to rotate to a different private key and keep your identity and social graph. If someone gets your key, they are you on Nostr for all intents and purposes.
This is not a situation that users should be willing to tolerate from production-release clients at this point. There are much better log in standards that can and should be implemented if you care about your users.
That said, I am happy to report that external signer support is on the roadmap for Primal, as confirmed below:
nostr:note1n59tc8k5l2v30jxuzghg7dy2ns76ld0hqnn8tkahyywpwp47ms5qst8ehl
No word yet on whether this will be Android signer or remote signer support, or both.
This lack of external signer support is why I absolutely will not use my main npub with Primal for Android. I am happy to use the web client, which supports and encourages logging in with a browser extension, but until the Android client allows users to protect their private key, I cannot recommend it for existing Nostr users.
Update: As of version 2.2.13, all of what I have said above is now obsolete. Primal has added Android signer support, so users can now better protect their nsec by using Amber!
I would still like to see support for remote signers, especially with nstart.me as a recommended Nostr onboarding process and the advent of FROSTR for key management. That said, Android signer support on its own has been a long time coming and is a very welcome addition to the Primal app. Bravo Primal team!
Zap Integration
Score: 4.8 / 5
As mentioned when discussing Primal's built-in wallet feature, zapping in Primal can be the most seamless experience I have ever seen in a Nostr client. Pairing the wallet with the client is absolutely the path forward for Nostr leading the way to Bitcoin adoption.
But what if you already have a Lightning wallet you want to use for zapping? You have a couple options. If it is an Alby wallet or another wallet that supports Nostr Wallet Connect, you can connect it with Primal to use with one-tap zapping.

How your zapping experience goes with this option will vary greatly based on your particular wallet of choice and is beyond the scope of this review. I used this option with a hosted wallet on my Alby Hub and it worked perfectly. Primal gives you immediate feedback that you have zapped, even though the transaction usually takes a few seconds to process and appear in your wallet's history.
The one major downside to using an external wallet is the lack of integration with the wallet interface. This interface currently only works with Primal's wallet, and therefore the most prominent tab in the entire app goes unused when you connect an external wallet.

An ideal improvement would be for the wallet screen to work similar to Alby Go when you have an external wallet connected via Nostr Wallet Connect, allowing the user to have Primal act as their primary mobile Lightning wallet. It could have balance and transaction history displayed, and allow sending and receiving, just like the integrated Primal wallet, but remove the ability to purchase sats directly through the app when using an external wallet.
Content Discovery
Score: 4.8 / 5
Primal is the best client to use if you want to discover new content you are interested in. There is no comparison, with only a few caveats.
First, the content must have been posted to Nostr as either a short-form or long-form note. Primal has a limited ability to display other types of content. For instance, discovering video content or streaming content is lacking.
Second, you must be willing to put up with the fact that Primal lacks a means of filtering sensitive content when you are exploring beyond the bounds of your current followers. This may not be an issue for some, but for others it could be a deal-breaker.
Third, it would be preferable for Primal to follow topics you are interested in when you choose them during onboarding, rather than follow specific npubs. Ideally, create a "My Topics" feed that can be edited by selecting your interests in the Topics section of the Explore tab.
Relay Management
Score: 2.5 / 5
For new users who don't want to mess around with managing relays, Primal is fantastic! There are 7 relays selected by default, in addition to Primal's caching service. For most users who aren't familiar with Nostr's protocol archetecture, they probably won't ever have to change their default relays in order to use the client as they would expect.
However, two of these default relays were consistently unreachable during the week that I tested. These were relay.plebes.fans and remnant.cloud. The first relay seems to be an incorrect URL, as I found nosflare.plebes.fans online and with perfect uptime for the last 12 hours on nostr.watch. I was unable to find remnant.cloud on nostr.watch at all. A third relay was intermittent, sometimes online and reachable, and other times unreachable: v1250.planz.io/nostr. If Primal is going to have default relays, they should ideally be reliable and with accurate URLs.
That said, users can add other relays that they prefer, and remove relays that they no longer want to use. They can even set a different caching service to use with the client, rather than using Primal's.

However, that is the extent of a user's control over their relays. They cannot choose which relays they want to write to and which they want to read from, nor can they set any private relays, outbox or inbox relays, or general relays. Loading the npub I used for this review into another client with full relay management support revealed that the relays selected in Primal are being added to both the user's public outbox relays and public inbox relays, but not to any other relay type, which leads me to believe the caching relay is acting as the client's only general relay and search relay.
One unique and welcomed addition is the "Enhanced Privacy" feature, which is off by default, but which can be toggled on. I am not sure why this is not on by default, though. Perhaps someone from the Primal team can enlighten me on that choice.
By default, when you post to Nostr, all of your outbox relays will see your IP address. If you turn on the Enhanced Privacy mode, only Primal's caching service will see your IP address, because it will post your note to the other relays on your behalf. In this way, the caching service acts similar to a VPN for posting to Nostr, as long as you trust Primal not to log or leak your IP address.
In short, if you use any other Nostr clients at all, do not use Primal for managing your relays.
Media Hosting Options
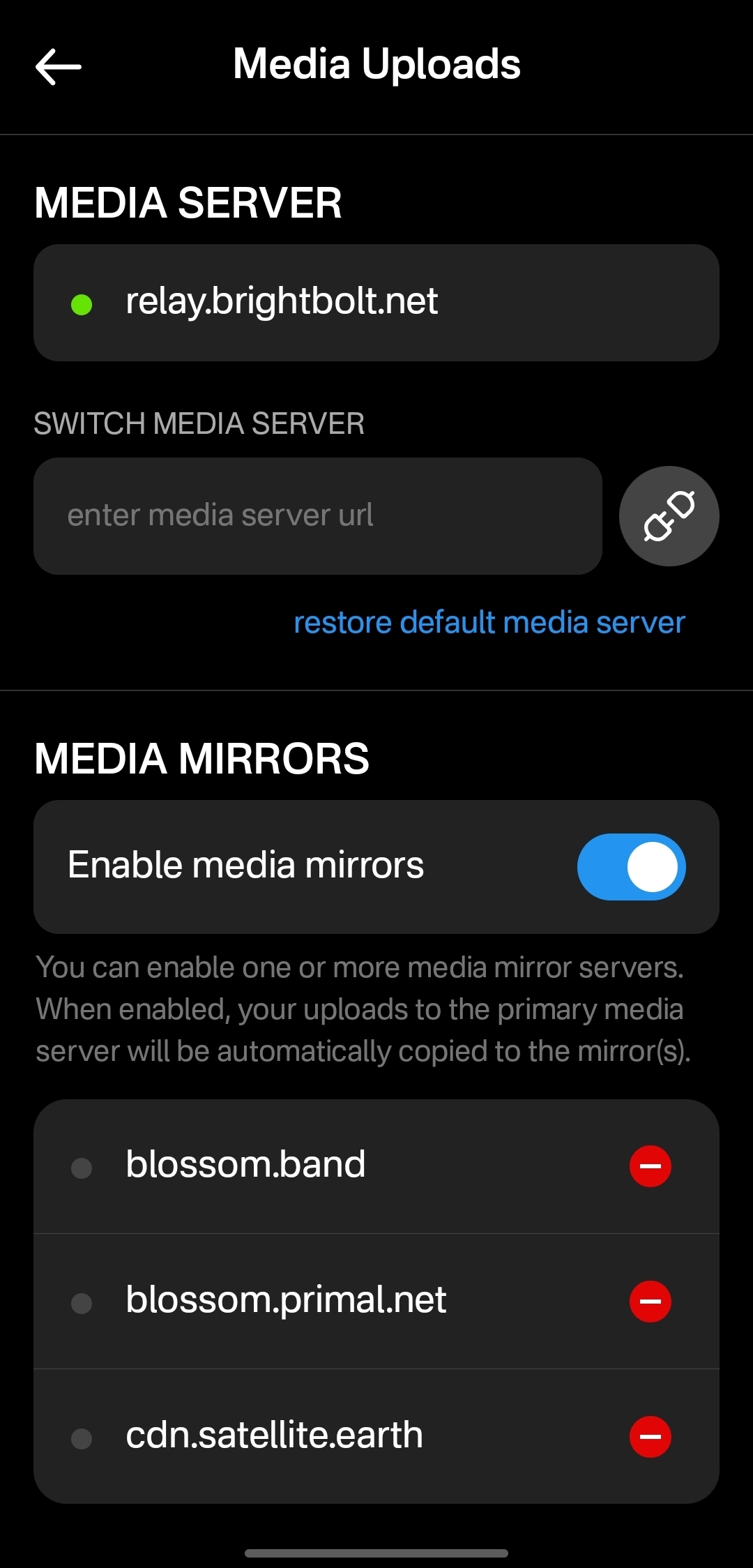
Score: 4.9 / 5 This is a NEW SECTION of this review, as of version 2.2.13!
Primal has recently added support for the Blossom protocol for media hosting, and has added a new section within their settings for "Media Uploads."
Media hosting is one of the more complicated problems to solve for a decentralized publishing protocol like Nostr. Text-based notes are generally quite small, making them no real burden to store on relays, and a relay can prune old notes as they see fit, knowing that anyone who really cared about those notes has likely archived them elsewhere. Media, on the other hand, can very quickly fill up a server's disk space, and because it is usually addressable via a specific URL, removing it from that location to free up space means it will no longer load for anyone.
Blossom solves this issue by making it easy to run a media server and have the same media mirrored to more than one for redundancy. Since the media is stored with a file name that is a hash of the content itself, if the media is deleted from one server, it can still be found from any other server that has the same file, without any need to update the URL in the Nostr note where it was originally posted.
Prior to this update, Primal only allowed media uploads to their own media server. Now, users can upload to any blossom server, and even choose to have their pictures or videos mirrored additional servers automatically. To my knowledge, no other Nostr client offers this automatic mirroring at the time of upload.
One of my biggest criticisms of Primal was that it had taken a siloed approach by providing a client, a caching relay, a media server, and a wallet all controlled by the same company. The whole point of Nostr is to separate control of all these services to different entities. Now users have more options for separating out their media hosting and their wallet to other providers, at least. I would still like to see other options available for a caching relay, but that relies on someone else being willing to run one, since the software is open for anyone to use. It's just not your average, lightweight relay that any average person can run from home.
Regardless, this update to add custom Blossom servers is a most welcome step in the right direction!
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with a client. Here are some of the most common questions submitted about Primal since the launch of 2.0:
nostr:note1dqv4mwqn7lvpaceg9s7damf932ydv9skv2x99l56ufy3f7q8tkdqpxk0rd
This was a pretty common question, because users expect that they will be able to create the same type of content that they can consume in a particular client. I can understand why this was left out in a mobile client, but perhaps it should be added in the web client.
nostr:note16xnm8a2mmrs7t9pqymwjgd384ynpf098gmemzy49p3572vhwx2mqcqw8xe
This is a more concerning bug, since it appears some users are experiencing their images being replaced with completely different images. I did not experience anything similar in my testing, though.
nostr:note1uhrk30nq0e566kx8ac4qpwrdh0vfaav33rfvckyvlzn04tkuqahsx8e7mr
There hasn't been an answer to this, but I have not been able to find a way. It seems search results will always include replies as well as original notes, so a feed made from the search results will as well. Perhaps a filter can be added to the advanced search to exclude replies? There is already a filter to only show replies, but there is no corresponding filter to only show original notes.
nostr:note1zlnzua28a5v76jwuakyrf7hham56kx9me9la3dnt3fvymcyaq6eqjfmtq6
Since both mobile platforms support the wallet, users expect that they will be able to access it in their web client, too. At this time, they cannot. The only way to have seamless zapping in the web client is to use the Alby extension, but there is not a way to connect it to your Primal wallet via Nostr Wallet Connect either. This means users must have a separate wallet for zapping on the web client if they use the Primal Wallet on mobile.
nostr:note15tf2u9pffy58y9lk27y245ew792raqc7lc22jezxvqj7xrak9ztqu45wep
It seems that Primal is filtering for spam even for profiles you actively follow. Moreover, exactly what the criteria is for being considered spam is currently opaque.
nostr:note1xexnzv0vrmc8svvduurydwmu43w7dftyqmjh4ps98zksr39ln2qswkuced
For those unaware, Blossom is a protocol for hosting media as blobs identified by a hash, allowing them to be located on and displayed from other servers they have been mirrored to when when the target server isn't available. Primal currently runs a Blossom server (blossom.primal.net) so I would expect we see Blossom support in the future.
nostr:note1unugv7s36e2kxl768ykg0qly7czeplp8qnc207k4pj45rexgqv4sue50y6
Currently, Primal on Android only supports uploading photos to your posts. Users must upload any video to some other hosting service and copy/paste a link to the video into their post on Primal. I would not be surprised to see this feature added in the near future, though.
nostr:note10w6538y58dkd9mdrlkfc8ylhnyqutc56ggdw7gk5y7nsp00rdk4q3qgrex
Many Nostr users have more than one npub for various uses. Users would prefer to have a way to quickly switch between accounts than to have to log all the way out and paste their npub for the other account every time they want to use it.
There is good news on this front, though:
nostr:note17xv632yqfz8nx092lj4sxr7drrqfey6e2373ha00qlq8j8qv6jjs36kxlh
Wrap Up
All in all, Primal is an excellent client. It won't be for everyone, but that's one of the strengths of Nostr as a protocol. You can choose to use the client that best fits your own needs, and supplement with other clients and tools as necessary.
There are a couple glaring issues I have with Primal that prevent me from using it on my main npub, but it is also an ever-improving client, that already has me hopeful for those issues to be resolved in a future release.
So, what should I review next? Another Android client, such as #Amethyst or #Voyage? Maybe an "other stuff" app, like #Wavlake or #Fountain? Please leave your suggestions in the comments.
I hope this review was valuable to you! If it was, please consider letting me know just how valuable by zapping me some sats and reposting it out to your follows.
Thank you for reading!
PV 🤙
-
 @ 401014b3:59d5476b
2025-04-30 21:08:52
@ 401014b3:59d5476b
2025-04-30 21:08:52And here's what it said.
And for what it's worth, I actually think ChatGPT nailed it.
Thoughts?
-
Andy Reid – Kansas City Chiefs Andy Reid remains the gold standard among NFL head coaches. With three Super Bowl titles in the past six seasons and a career record of 273-146-1 (.651), Reid's offensive innovation and leadership continue to set him apart.
-
Sean McVay – Los Angeles Rams Sean McVay has revitalized the Rams since taking over in 2017, leading them to two Super Bowl appearances and maintaining only one losing season in eight years. His ability to adapt and keep the team competitive has solidified his status as one of the league's elite coaches.
-
John Harbaugh – Baltimore Ravens John Harbaugh's tenure with the Ravens has been marked by consistent success, including a Super Bowl victory in 2012 and multiple double-digit win seasons. His leadership and adaptability have kept Baltimore as a perennial contender.
-
Nick Sirianni – Philadelphia Eagles Nick Sirianni has quickly risen through the ranks, boasting a .706 regular-season winning percentage and leading the Eagles to two Super Bowl appearances, including one victory. His emphasis on player morale and adaptability have been key to Philadelphia's recent success.
-
Dan Campbell – Detroit Lions Dan Campbell has transformed the Lions into a formidable team, improving their record each season and instilling a culture of toughness and resilience. Despite a disappointing playoff exit in 2024, Campbell's impact on the franchise is undeniable.
originally posted at https://stacker.news/items/967880
-
-
 @ 3c389c8f:7a2eff7f
2025-04-30 20:47:21
@ 3c389c8f:7a2eff7f
2025-04-30 20:47:21Sharing a Note on Nostr:
🔁Yeah, it probably seems obvious. No need to dwell for long, but this is another function that goes by half a dozen different names. Repost, renote, retweet, boost, bump, the ubiquitous little repeat button... It's all the same. It doesn't matter what its called, the feature lets you push notes you may find valuable, to the people who follow you. Additionally you also have the "Quote" option if you would like to add your own remarks or context. Both of these features are supported by most Nostr microblogging clients and some specialty clients, though some have chosen to exclude one or the other to adhere to a set of guiding principles aimed at helping users to enjoy a healthier social media experience.
Similar to a quote, you also have the option to copy NoteIDs to paste in other places. They will look like: nevent..., naddr..., or some other possibly foreign looking string prefixed with 'n' and in some cases the may be preceded by 'nostr:'. These are handy when you'd like to use a note for some other purpose beyond a quote. Perhaps you would like to quote it in a Nostr article or blog entry, or you would like to create a note focusing on a series of notes. Many clients offer easy access to these handy nostr links. If you're finding that the one you are using, does not, then simply hop to another. This is one of the amazing yet simple uses of Nostr's unique identity and contact list ownership.
Sharing Note and Profile Links Off of Nostr:
This is where things get really interesting. If you try to send these 'n' prefixed Nostr links to someone, they will receive that random string and have no clue what to do with it. To solve this, some clever minds came up with njump.me. Just visit that URL and tack your 'n' prefixed event to the end, and boom! you have a link you can send to anyone. Many apps have integrated this feature into their interface to make it easy and convenient to send awesome Nostr content to anyone anywhere, and they can choose which Nostr app they want to use to engage with it right in the landing. Some Nostr clients have traditional link sharing, as well, so you can share links right to the app that you use.
Helping Your Friends to Get Started:
We've touched on this a lot in previous posts but in case you missed it: nstart.me hubstr.org nosta.me These are all great options to onboarding your friends in a way that allows for them to explore Nostr right out of the gate. You always have the option of creating a keypair in nearly every app around, too. This is easier for some people, depending on how much they want to learn right away, or how they may be using Nostr.
There's some cool new tools coming out to help even more with getting your friends set up to use Nostr to its fullest capacity. Follow packs, trust attestations, and suggested app packs are all things we look forward to diving into more deeply in the near future. Please keep an eye out if your interested in reading the Spatia Nostra
-
 @ e968e50b:db2a803a
2025-04-30 20:40:33
@ e968e50b:db2a803a
2025-04-30 20:40:33Has anyone developed a lightning wallet using a raspberry pi or something like that? This would be a device that could fit in your pocket with a small screen and QR scanner for people that can't afford or don't want to carry a smart phone. It would use wifi or something like that. Is this too much of a security headache? Can it be done easily with any wallet's current software?
originally posted at https://stacker.news/items/967863
-
 @ 5f078e90:b2bacaa3
2025-04-30 20:26:32
@ 5f078e90:b2bacaa3
2025-04-30 20:26:32Petal's Glow
In a quiet meadow, pink flower blooms named Petal danced under moonlight. Their delicate petals glowed, guiding a weary firefly home. Grateful, the firefly wove light patterns, telling their tale. By dawn, bees hummed Petal’s story, spreading it across the valley. The blooms stood prouder, their rosy hue a symbol of gentle hope.
This is 334 characters, some md, bidirectional-bridge.js used.

-
 @ 5f078e90:b2bacaa3
2025-04-30 20:13:35
@ 5f078e90:b2bacaa3
2025-04-30 20:13:35Cactus story
In a sun-scorched desert, a lone cactus named Sage stood tall. Each dawn, she whispered to the wind, sharing tales of ancient rains. One night, a lost coyote curled beneath her spines, seeking shade. Sage offered her last drops of water, saved from a rare storm. Grateful, the coyote sang her story to the stars, and Sage’s legend grew, a beacon of kindness in the arid wild.
This test is between 300 and 500 characters long, started on Nostr to test the bidirectional-bridge script.
It has a bit of markdown included.

-
 @ 4d41a7cb:7d3633cc
2025-04-30 20:02:28
@ 4d41a7cb:7d3633cc
2025-04-30 20:02:28Did you know that Federal Reserve Notes (FRNs), commonly known as "us dollars" are broken contracts? In fact FRNs started as dollar IOUs and then the Federal Reserve (a private corporation) defaulted on its debts and made the U.S citizens pay the bill: effectively stealing the privately owned gold.
Comand + shift + v = pegar sin choclo.
The United States Dollar
It is not that the dollar was "backed by gold" as it is commonly said. The dollar was primally a measure of weight of silver and then a measure of weight of gold. Let see a little history about the U.S dollar.
What does the constitution says?
Article I, Section 8:
This section grants Congress the power "to coin money, regulate the value thereof, and of foreign coin, and fix the standard of weights and measures."
Article I, Section 10:
"No State shall... make any Thing but gold and silver Coin a Tender in Payment of Debts."
The United States government, by decree, created the dollar as measure of weight defined by the Coinage Act of 1792 as 371.25 grains (24 grams) of silver.
The 1794 silver dollar, known as the "Flowing Hair dollar," was the first silver dollar coin produced by the United States Mint. This was the original dollar! The were minted in $1, $0,5.

In 1795 the United States minted its first gold coins under the Coinage Act of 1792, which introduced the following denominations: $2,5, $5 and $10. The silver to gold ratio was fixed at 1:15, meaning 15 ounces of silver was the equivalent to one ounce of gold.
Individuals could bring silver bullion to the U.S. Mint and have it coined into legal tender.
 ## Coinage acts
## Coinage actsThe Coinage Act of 1834 adjusted the gold-to-silver ratio to 16:1 and and the weight of the gold coins because gold was undervalue and encouraging the melting and exporting of American gold.
The coinage act of 1837 defined the silver dollar as containing 412.5 grains of standard silver (90% silver and 10% copper) and it reinforced the legal tender status of these coins, ensuring their acceptance for all debts, public and private.
The Coinage Act of 1849 specifically addressed the introduction of new gold denominations in response to the California Gold Rush, which significantly increased gold supplies in the United States. The Act authorized the minting of a $1 gold coin, the smallest gold denomination ever issued by the United States. The Act also authorized the creation of the $20 gold coin, known as the Double Eagle.
The gold dollar coin contained 23.22 grains of pure gold or 1.505grams or 0.0484 troy ounces.

The Double Eagle contained 464.4 grains of pure gold or 30.093 grams, 0.968 troy ounces.

The coinage act of 1857 sought to establish a uniform domestic currency and reduce reliance on foreign coins, demonetizing every foreign coins as legal tender. This was also the beginning of the Flying Eagle cent, which was smaller in diameter and composed of 88% copper and 12% nickel. This centralized more the coinage in the U.S.
U.S Gold certificates
The Act of March 3, 1863, officially known as the National Bank Act, was a significant piece of legislation during the American Civil War aimed at creating a national banking system and establishing a uniform national currency.
This legislation allowed the U.S. Treasury to issue gold certificates, which served as a form of paper currency backed by gold. The introduction of gold certificates was primarily intended to facilitate transactions involving gold without the need for the physical transfer of the metal.
This was primary for large size comercial transactions or payments among banks.
1865 Series
 "It is hereby certified that one hundred dollars have been deposited with the assistant treasurer of the U.S in New York payable in GOLD at his office in the xxx New York "
"It is hereby certified that one hundred dollars have been deposited with the assistant treasurer of the U.S in New York payable in GOLD at his office in the xxx New York "The coinage act of 1873 also known as the "crime of 1873" was the intent to demonetize silver by ceasing the minting of silver dollars which meant that citizens could no longer bring silver to the mint to be coined into legal tender. By stopping the production of silver dollars, the Act implicitly placed the U.S. on a gold standard, where gold, not silver, was the primary basis for currency. This had lasting economic effects, particularly on farmers and silver miners who preferred bimetallism (the use of both gold and silver as standards).
The Act was controversial, particularly in western and rural areas where silver was a significant economic factor. Many believed that the Act was passed to benefit creditors and large financial interests by adopting a gold standard, which tended to deflate prices and increase the value of money.
The coinage act of 1878, The Act mandated the U.S. Treasury to purchase a specified amount of silver each month, between two million and four million dollars worth, and to mint it into silver dollars. This marked a partial return to the use of silver as currency through the coinage of the standard silver dollar. The Act allowed for the issuance of silver certificates, which could be used as currency in place of actual silver coins, thus easing the circulation of silver-backed currency.
The Bland-Allison Act was passed against a backdrop of economic depression and agrarian unrest. It represented a compromise between advocates of the gold standard and those wishing to return to bimetallism.
1882 series

The 30 years of economic and political discourse between bimetallism supporters and gold only advocates finally ended in the 1900.
The Gold Standard Act of 1900
The Gold Standard Act of 1900 formalized the monetary system of the United States by establishing gold as the sole standard for redeeming paper money and effectively ending the bimetallic standard. It established that the gold dollar would be the standard unit of value, equating the dollar to 25.8 grains of gold at a purity of 90%. Silver certificates and silver coins remained in circulation but without the backing of free and unlimited coinage.
Let's remember that the dollar was still a measure of gold. The certificates where government IOUs for that gold that was deposited in the treasury of the United States.
1907 series of gold certificates:

The Federal Reserve Act of 1913
The Federal Reserva Act of 1913 created a monopoly over the issuance of the American paper currency. This marked the privatization of the currency and a centralization of power like never before. More about this in another article.
But essentially the secret agenda of banksters was to issue IOUs without any restriction and make the United State Government responsible to redeem this paper currency for gold. And I will show you exactly how. Alfred Owen Crozier wrote a book in 1912 one year before the bill was passed analyzing and opposing it and made this same argument.
Federal Reserve Notes
A paper contract, a promissory note, an "I owe you x amount"
This paper currency issued by this private central bank were dollar IOUs contracts or promissory notes.
According to Black's law dictionary a Federal Reserve note is: The paper currency in circulation in the United States. The notes are issued by the Federal Reserve Banks, are effectively non-interest-bearing promissory notes payable to bearer on demand, and are issued in denominations of $1, $5, $10, $20, $50, $100, $500, $1000, $5,000 and $10,000.
NON INTERES BEARING PROMISSORY NOTES.
A promissory note is a written, unconditional promise made by one party (the maker) to pay a definite sum of money to another party (the payee) or bearer, either on demand or at a specified future date. It is essentially a financial instrument representing a formal commitment to settle a specified monetary obligation.
Key Characteristics of a Promissory Note:
- Written Instrument: The promise to pay must be documented in writing.
- Unconditional Promise: The promise to pay cannot be contingent on any external factors or conditions.
- Definite Sum: The amount to be paid must be clearly specified and agreed upon in the note.
- Payee: The note must designate the person or entity to whom the payment is to be made either explicitly or implicitly by specifying it as payable "to bearer".
- Payable on Demand or at a Specific Time: The promissory note should indicate whether the payment is due upon demand by the payee or at a specific future date as agreed by the involved parties.
Promissory notes are commonly used in various financial transactions, including loans, business financing, and real estate deals, as they formalize the commitment to pay and can be enforced as a legal contract if necessary.
The Federal Reserve (FED) issued paper contract promising to be redeemable in gold. Most people never saw or understood the contract. Most never read it because the Fed cleverly hid the contract on the front of the bill by dividing it into five separate lines of text with a very different typeface for each line and placing the president's picture right in the middle. They even used the old lawyer's trick of hiding the most important text in small print.
Over time, the terms and conditions of the contract were watered down until they eventually became literally a promissory note for nothing. But let's analice how they did this step by step...
FEDERAL RESERVE NOTES: 1914 SERIES
 Content of the contract:
Content of the contract: Federal reserve note
The United States of America will pay to the bearer on demand: FIFTY DOLLARS
Authorized by federal reserve act of December 23, 1913
This note is receivable by all national and member banks and federal reserve banks and for all taxes, customs and other public dues. It is redeemable in gold on demand at the treasury department of the United States in the city of Washington district of Columbia or in gold or lawful money at any federal reserve bank.
So if a dollar was 20.67 per ounce, $50 could be exchanged for about 2.42 ounces of gold.
FEDERAL RESERVE NOTES :1918 SERIES
Content of the contract:
Federal reserve note
The United States of America will pay to the bearer on demand: Ten thousand dollars
Authorized by federal reserve act of December 23, 1913, as amended by act of September 26, 1918
This note is receivable by all national and member banks and federal reserve banks and for all taxes, customs and other public dues. It is redeemable in gold on demand at the treasury department of the United States in the city of Washington district of Columbia or in gold or lawful money at any federal reserve bank.
So if a dollar was 20.67 per ounce, $10,000 could be exchanged for 484.29ounces of gold.
Series of 1928
The great imitation
In 1928 the U.S government issued a new series of gold certificates payable to the bearer on demand.

The same year the Federal Reserve issued it's own promissory notes copying the us government gold certificate's design:
Content of the contract:
Federal reserve note
The United States of America
will pay to the bearer on demand: One hundred dollars
Reedemable in gold on demand at the United States treasury, or in gold or lawful money, at any federal reserve bank.
So if a dollar was 20.67 per ounce, $100 could be exchanged for 4.84 ounces of gold.
Here's all the denominations issued by the Federal Reserve back then:

This instrument was the facilitator of the Great depression, the inflation and deflation of the paper currency: as Thomas Jefferson warned long time ago:
“If the American people ever allow private banks to control the issue of their currency first by inflation then by deflation the banks and corporations that will grow up around them will deprive the people of all property until their children wake up homeless on the continent their Fathers conquered... I believe that banking institutions are more dangerous to our liberties than standing armies... The issuing power should be taken from the banks and restored to the people to whom it properly belongs.”
THE CONFISCATION OF GOLD
The end of the dollar and the replacement of gold and gold certificates by Federal Reserve Notes worthless paper currency.
Executive Order 6102, issued on April 5, 1933, by President Franklin D. Roosevelt, forced everyone to exchange their gold and gold certificates for federal reserve notes at $20,67 FEDERAL RESERVE NOTES per ounce.
THIS WAS THE END OF THE DOLLAR. THE END OF THE GOLD STANDARD. THE END OF THE CONSTITUTIONAL REPUBLIC FORM OF GOVERNMENT. THE END OF FREEDOM. THE ABANDONMENT OF THE CONSTITUTIONAL PRINCIPLES.
The Gold Reserve Act of 1934
This act further devalued the "gold content of the FRNs" and ended the redemption of gold certificates for gold coins. One ounce of gold was now "35 FRNs" in theory but this was not entirely true.
Lets analice the evolution of the Federal Reserve Notes.
 Content of the contract:
Content of the contract:Federal reserve note
The United States of America
will pay to the bearer on demand: One hundred dollars
THIS NOTE IS LEGAL TENDER FOR ALL DEBTS, PUBLIC AND PRIVATE AND IT IS REDEEMABLE IN LAWFUL MONEY AT THE UNITED STATES TREASURY, OR AT ANY FEDERAL RESERVE BANK.
So if a dollar was 20.67 per ounce, $100 could be exchanged for one hundred dollars of Lawful money?
They eliminated the gold clause from the contract. This contract is a lie, what is this redeemable for? U.S treasuries? Different denominations of FRNs? They changed the definition of lawful money. This was never money this was a broken contract and it gets obvious in the next series...
1963 Series
This series look like they did photoshop on the "payable to the bearer on demand" part that was below franklin in previous series.
Content of the contract now was
Federal reserve note
The United States of America
THIS NOTE IS LEGAL TENDER FOR ALL DEBTS, PUBLIC AND PRIVATE.
ONE HUNDRED DOLLARS
Conclusion
Between 1913 and 1928 the dollar was gradually replaced by Federal Reserve Notes until in 1934 the gold standard was definitively abandoned. From that time the Federal Reserve Note became the "new legal tender money" replacing the dollar and slowly replacing silver coins too until in 1965 silver was definitively abandoned.
IT IS NOT THAT THE DOLLAR WAS “BACKED” BY SILVER OR GOLD.
Gold and silver were such powerful money during the founding of the United States of America that the founding fathers declared that only gold or silver coins can be “money” in America. Since gold and silver coinage was heavy and inconvenient for a lot of transactions, they were stored in banks and a claim check was issued as a money substitute. People traded their coupons as money or “currency.” Currency is not money, but a money substitute. Redeemable currency must promise to pay a dollar equivalent in gold or silver money. Federal Reserve Notes (FRNs) make no such promises and are not “money.” A Federal Reserve Note is a debt obligation of the federal United States government, not “money.” The federal United States government and the U.S. Congress were not and have never been authorized by the Constitution for the united States of America to issue currency of any kind, but only lawful money – gold and silver coin.
It is essential that we comprehend the distinction between real money and paper money substitute. One cannot get rich by accumulating money substitutes; one can only get deeper into debt. We the People no longer have any “money.” Most Americans have not been paid any “money” for a very long time, perhaps not in their entire life. Now do you comprehend why you feel broke? Now do you understand why you are “bankrupt” along with the rest of the country?
-
 @ 59b96df8:b208bd59
2025-04-30 19:27:41
@ 59b96df8:b208bd59
2025-04-30 19:27:41Nostr is a decentralized protocol designed to be censorship-resistant.
However, this resilience can sometimes make data synchronization between relays more difficult—though not impossible.In my opinion, Nostr still lacks a few key features to ensure consistent and reliable operation, especially regarding data versioning.
Profile Versions
When I log in to a new Nostr client using my private key, I might end up with an outdated version of my profile, depending on how the client is built or configured.
Why does this happen?
The client fetches my profile data (kind:0 - NIP 1) from its own list of selected relays.
If I didn’t publish the latest version of my profile on those specific relays, the client will only display an older version.Relay List Metadata
The same issue occurs with the relay list metadata (kind:10002 - NIP 65).
When switching to a new client, it's common that my configured relay list isn't properly carried over because it also depends on where the data is fetched.Protocol Change Proposal
I believe the protocol should evolve, specifically regarding how
kind:0(user metadata) andkind:10002(relay list metadata) events are distributed to relays.Relays should be able to build a list of public relays automatically (via autodiscovery), and forward all received
kind:0andkind:10002events to every relay in that list.This would create a ripple effect:
``` Relay A relay list: [Relay B, Relay C]
Relay B relay list: [Relay A, Relay C]
Relay C relay list: [Relay A, Relay B]User A sends kind:0 to Relay A
→ Relay A forwards kind:0 to Relay B
→ Relay A forwards kind:0 to Relay C
→ Relay B forwards kind:0 to Relay A
→ Relay B forwards kind:0 to Relay C → Relay A forwards kind:0 to Relay B
→ etc. ```Solution: Event Encapsulation
To avoid infinite replication loops, the solution could be to wrap the user’s signed event inside a new event signed by the relay, using a dedicated
kind(e.g.,kind:9999).When Relay B receives a
kind:9999event from Relay A, it extracts the original event, checks whether it already exists or if a newer version is present. If not, it adds the event to its database.Here is an example of such encapsulated data:
json { "content": "{\"content\":\"{\\\"lud16\\\":\\\"dolu@npub.cash\\\",\\\"name\\\":\\\"dolu\\\",\\\"nip05\\\":\\\"dolu@dolu.dev\\\",\\\"picture\\\":\\\"!(image)[!(image)[https://pbs.twimg.com/profile_images/1577320325158682626/igGerO9A_400x400.jpg]]\\\",\\\"pubkey\\\":\\\"59b96df8d8b5e66b3b95a3e1ba159750a6edd69bcbba1857aeb652a5b208bd59\\\",\\\"npub\\\":\\\"npub1txukm7xckhnxkwu450sm59vh2znwm45mewaps4awkef2tvsgh4vsf7phrl\\\",\\\"created_at\\\":1688312044}\",\"created_at\":1728233747,\"id\":\"afc3629314aad00f8786af97877115de30c184a25a48440a480bff590a0f9ba8\",\"kind\":0,\"pubkey\":\"59b96df8d8b5e66b3b95a3e1ba159750a6edd69bcbba1857aeb652a5b208bd59\",\"sig\":\"989b250f7fd5d4cfc9a6ee567594c81ee0a91f972e76b61332005fb02aa1343854104fdbcb6c4f77ae8896acd886ab4188043c383e32a6bba509fd78fedb984a\",\"tags\":[]}", "created_at": 1746036589, "id": "efe7fa5844c5c4428fb06d1657bf663d8b256b60c793b5a2c5a426ec773c745c", "kind": 9999, "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "sig": "219f8bc840d12969ceb0093fb62f314a1f2e19a0cbe3e34b481bdfdf82d8238e1f00362791d17801548839f511533461f10dd45cd0aa4e264d71db6844f5e97c", "tags": [] } -
 @ a008def1:57a3564d
2025-04-30 17:52:11
@ a008def1:57a3564d
2025-04-30 17:52:11A Vision for #GitViaNostr
Git has long been the standard for version control in software development, but over time, we has lost its distributed nature. Originally, Git used open, permissionless email for collaboration, which worked well at scale. However, the rise of GitHub and its centralized pull request (PR) model has shifted the landscape.
Now, we have the opportunity to revive Git's permissionless and distributed nature through Nostr!
We’ve developed tools to facilitate Git collaboration via Nostr, but there are still significant friction that prevents widespread adoption. This article outlines a vision for how we can reduce those barriers and encourage more repositories to embrace this approach.
First, we’ll review our progress so far. Then, we’ll propose a guiding philosophy for our next steps. Finally, we’ll discuss a vision to tackle specific challenges, mainly relating to the role of the Git server and CI/CD.
I am the lead maintainer of ngit and gitworkshop.dev, and I’ve been fortunate to work full-time on this initiative for the past two years, thanks to an OpenSats grant.
How Far We’ve Come
The aim of #GitViaNostr is to liberate discussions around code collaboration from permissioned walled gardens. At the core of this collaboration is the process of proposing and applying changes. That's what we focused on first.
Since Nostr shares characteristics with email, and with NIP34, we’ve adopted similar primitives to those used in the patches-over-email workflow. This is because of their simplicity and that they don’t require contributors to host anything, which adds reliability and makes participation more accessible.
However, the fork-branch-PR-merge workflow is the only model many developers have known, and changing established workflows can be challenging. To address this, we developed a new workflow that balances familiarity, user experience, and alignment with the Nostr protocol: the branch-PR-merge model.
This model is implemented in ngit, which includes a Git plugin that allows users to engage without needing to learn new commands. Additionally, gitworkshop.dev offers a GitHub-like interface for interacting with PRs and issues. We encourage you to try them out using the quick start guide and share your feedback. You can also explore PRs and issues with gitplaza.
For those who prefer the patches-over-email workflow, you can still use that approach with Nostr through gitstr or the
ngit sendandngit listcommands, and explore patches with patch34.The tools are now available to support the core collaboration challenge, but we are still at the beginning of the adoption curve.
Before we dive into the challenges—such as why the Git server setup can be jarring and the possibilities surrounding CI/CD—let’s take a moment to reflect on how we should approach the challenges ahead of us.
Philosophy
Here are some foundational principles I shared a few years ago:
- Let Git be Git
- Let Nostr be Nostr
- Learn from the successes of others
I’d like to add one more:
- Embrace anarchy and resist monolithic development.
Micro Clients FTW
Nostr celebrates simplicity, and we should strive to maintain that. Monolithic developments often lead to unnecessary complexity. Projects like gitworkshop.dev, which aim to cover various aspects of the code collaboration experience, should not stifle innovation.
Just yesterday, the launch of following.space demonstrated how vibe-coded micro clients can make a significant impact. They can be valuable on their own, shape the ecosystem, and help push large and widely used clients to implement features and ideas.
The primitives in NIP34 are straightforward, and if there are any barriers preventing the vibe-coding of a #GitViaNostr app in an afternoon, we should work to eliminate them.
Micro clients should lead the way and explore new workflows, experiences, and models of thinking.
Take kanbanstr.com. It provides excellent project management and organization features that work seamlessly with NIP34 primitives.
From kanban to code snippets, from CI/CD runners to SatShoot—may a thousand flowers bloom, and a thousand more after them.
Friction and Challenges
The Git Server
In #GitViaNostr, maintainers' branches (e.g.,
master) are hosted on a Git server. Here’s why this approach is beneficial:- Follows the original Git vision and the "let Git be Git" philosophy.
- Super efficient, battle-tested, and compatible with all the ways people use Git (e.g., LFS, shallow cloning).
- Maintains compatibility with related systems without the need for plugins (e.g., for build and deployment).
- Only repository maintainers need write access.
In the original Git model, all users would need to add the Git server as a 'git remote.' However, with ngit, the Git server is hidden behind a Nostr remote, which enables:
- Hiding complexity from contributors and users, so that only maintainers need to know about the Git server component to start using #GitViaNostr.
- Maintainers can easily swap Git servers by updating their announcement event, allowing contributors/users using ngit to automatically switch to the new one.
Challenges with the Git Server
While the Git server model has its advantages, it also presents several challenges:
- Initial Setup: When creating a new repository, maintainers must select a Git server, which can be a jarring experience. Most options come with bloated social collaboration features tied to a centralized PR model, often difficult or impossible to disable.
-
Manual Configuration: New repositories require manual configuration, including adding new maintainers through a browser UI, which can be cumbersome and time-consuming.
-
User Onboarding: Many Git servers require email sign-up or KYC (Know Your Customer) processes, which can be a significant turn-off for new users exploring a decentralized and permissionless alternative to GitHub.
Once the initial setup is complete, the system works well if a reliable Git server is chosen. However, this is a significant "if," as we have become accustomed to the excellent uptime and reliability of GitHub. Even professionally run alternatives like Codeberg can experience downtime, which is frustrating when CI/CD and deployment processes are affected. This problem is exacerbated when self-hosting.
Currently, most repositories on Nostr rely on GitHub as the Git server. While maintainers can change servers without disrupting their contributors, this reliance on a centralized service is not the decentralized dream we aspire to achieve.
Vision for the Git Server
The goal is to transform the Git server from a single point of truth and failure into a component similar to a Nostr relay.
Functionality Already in ngit to Support This
-
State on Nostr: Store the state of branches and tags in a Nostr event, removing reliance on a single server. This validates that the data received has been signed by the maintainer, significantly reducing the trust requirement.
-
Proxy to Multiple Git Servers: Proxy requests to all servers listed in the announcement event, adding redundancy and eliminating the need for any one server to match GitHub's reliability.
Implementation Requirements
To achieve this vision, the Nostr Git server implementation should:
-
Implement the Git Smart HTTP Protocol without authentication (no SSH) and only accept pushes if the reference tip matches the latest state event.
-
Avoid Bloat: There should be no user authentication, no database, no web UI, and no unnecessary features.
-
Automatic Repository Management: Accept or reject new repositories automatically upon the first push based on the content of the repository announcement event referenced in the URL path and its author.
Just as there are many free, paid, and self-hosted relays, there will be a variety of free, zero-step signup options, as well as self-hosted and paid solutions.
Some servers may use a Web of Trust (WoT) to filter out spam, while others might impose bandwidth or repository size limits for free tiers or whitelist specific npubs.
Additionally, some implementations could bundle relay and blossom server functionalities to unify the provision of repository data into a single service. These would likely only accept content related to the stored repositories rather than general social nostr content.
The potential role of CI / CD via nostr DVMs could create the incentives for a market of highly reliable free at the point of use git servers.
This could make onboarding #GitViaNostr repositories as easy as entering a name and selecting from a multi-select list of Git server providers that announce via NIP89.
!(image)[https://image.nostr.build/badedc822995eb18b6d3c4bff0743b12b2e5ac018845ba498ce4aab0727caf6c.jpg]
Git Client in the Browser
Currently, many tasks are performed on a Git server web UI, such as:
- Browsing code, commits, branches, tags, etc.
- Creating and displaying permalinks to specific lines in commits.
- Merging PRs.
- Making small commits and PRs on-the-fly.
Just as nobody goes to the web UI of a relay (e.g., nos.lol) to interact with notes, nobody should need to go to a Git server to interact with repositories. We use the Nostr protocol to interact with Nostr relays, and we should use the Git protocol to interact with Git servers. This situation has evolved due to the centralization of Git servers. Instead of being restricted to the view and experience designed by the server operator, users should be able to choose the user experience that works best for them from a range of clients. To facilitate this, we need a library that lowers the barrier to entry for creating these experiences. This library should not require a full clone of every repository and should not depend on proprietary APIs. As a starting point, I propose wrapping the WASM-compiled gitlib2 library for the web and creating useful functions, such as showing a file, which utilizes clever flags to minimize bandwidth usage (e.g., shallow clone, noblob, etc.).
This approach would not only enhance clients like gitworkshop.dev but also bring forth a vision where Git servers simply run the Git protocol, making vibe coding Git experiences even better.
song
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 created song with a complementary vision that has shaped how I see the role of the git server. Its a self-hosted, nostr-permissioned git server with a relay baked in. Its currently a WIP and there are some compatability with ngit that we need to work out.
We collaborated on the nostr-permissioning approach now reflected in nip34.
I'm really excited to see how this space evolves.
CI/CD
Most projects require CI/CD, and while this is often bundled with Git hosting solutions, it is currently not smoothly integrated into #GitViaNostr yet. There are many loosely coupled options, such as Jenkins, Travis, CircleCI, etc., that could be integrated with Nostr.
However, the more exciting prospect is to use DVMs (Data Vending Machines).
DVMs for CI/CD
Nostr Data Vending Machines (DVMs) can provide a marketplace of CI/CD task runners with Cashu for micro payments.
There are various trust levels in CI/CD tasks:
- Tasks with no secrets eg. tests.
- Tasks using updatable secrets eg. API keys.
- Unverifiable builds and steps that sign with Android, Nostr, or PGP keys.
DVMs allow tasks to be kicked off with specific providers using a Cashu token as payment.
It might be suitable for some high-compute and easily verifiable tasks to be run by the cheapest available providers. Medium trust tasks could be run by providers with a good reputation, while high trust tasks could be run on self-hosted runners.
Job requests, status, and results all get published to Nostr for display in Git-focused Nostr clients.
Jobs could be triggered manually, or self-hosted runners could be configured to watch a Nostr repository and kick off jobs using their own runners without payment.
But I'm most excited about the prospect of Watcher Agents.
CI/CD Watcher Agents
AI agents empowered with a NIP60 Cashu wallet can run tasks based on activity, such as a push to master or a new PR, using the most suitable available DVM runner that meets the user's criteria. To keep them running, anyone could top up their NIP60 Cashu wallet; otherwise, the watcher turns off when the funds run out. It could be users, maintainers, or anyone interested in helping the project who could top up the Watcher Agent's balance.
As aluded to earlier, part of building a reputation as a CI/CD provider could involve running reliable hosting (Git server, relay, and blossom server) for all FOSS Nostr Git repositories.
This provides a sustainable revenue model for hosting providers and creates incentives for many free-at-the-point-of-use hosting providers. This, in turn, would allow one-click Nostr repository creation workflows, instantly hosted by many different providers.
Progress to Date
nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr and nostr:npub16ux4qzg4qjue95vr3q327fzata4n594c9kgh4jmeyn80v8k54nhqg6lra7 have been working on a runner that uses GitHub Actions YAML syntax (using act) for the dvm-cicd-runner and takes Cashu payment. You can see example runs on GitWorkshop. It currently takes testnuts, doesn't give any change, and the schema will likely change.
Note: The actions tab on GitWorkshop is currently available on all repositories if you turn on experimental mode (under settings in the user menu).
It's a work in progress, and we expect the format and schema to evolve.
Easy Web App Deployment
For those disapointed not to find a 'Nostr' button to import a git repository to Vercel menu: take heart, they made it easy. vercel.com_import_options.png there is a vercel cli that can be easily called in CI / CD jobs to kick of deployments. Not all managed solutions for web app deployment (eg. netlify) make it that easy.
Many More Opportunities
Large Patches via Blossom
I would be remiss not to mention the large patch problem. Some patches are too big to fit into Nostr events. Blossom is perfect for this, as it allows these larger patches to be included in a blossom file and referenced in a new patch kind.
Enhancing the #GitViaNostr Experience
Beyond the large patch issue, there are numerous opportunities to enhance the #GitViaNostr ecosystem. We can focus on improving browsing, discovery, social and notifications. Receiving notifications on daily driver Nostr apps is one of the killer features of Nostr. However, we must ensure that Git-related notifications are easily reviewable, so we don’t miss any critical updates.
We need to develop tools that cater to our curiosity—tools that enable us to discover and follow projects, engage in discussions that pique our interest, and stay informed about developments relevant to our work.
Additionally, we should not overlook the importance of robust search capabilities and tools that facilitate migrations.
Concluding Thoughts
The design space is vast. Its an exciting time to be working on freedom tech. I encourage everyone to contribute their ideas and creativity and get vibe-coding!
I welcome your honest feedback on this vision and any suggestions you might have. Your insights are invaluable as we collaborate to shape the future of #GitViaNostr. Onward.
Contributions
To conclude, I want to acknowledge some the individuals who have made recent code contributions related to #GitViaNostr:
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 (gitstr, song, patch34), nostr:npub1useke4f9maul5nf67dj0m9sq6jcsmnjzzk4ycvldwl4qss35fvgqjdk5ks (gitplaza)
nostr:npub1elta7cneng3w8p9y4dw633qzdjr4kyvaparuyuttyrx6e8xp7xnq32cume (ngit contributions, git-remote-blossom),nostr:npub16p8v7varqwjes5hak6q7mz6pygqm4pwc6gve4mrned3xs8tz42gq7kfhdw (SatShoot, Flotilla-Budabit), nostr:npub1ehhfg09mr8z34wz85ek46a6rww4f7c7jsujxhdvmpqnl5hnrwsqq2szjqv (Flotilla-Budabit, Nostr Git Extension), nostr:npub1ahaz04ya9tehace3uy39hdhdryfvdkve9qdndkqp3tvehs6h8s5slq45hy (gnostr and experiments), and others.
nostr:npub1uplxcy63up7gx7cladkrvfqh834n7ylyp46l3e8t660l7peec8rsd2sfek (git-remote-nostr)
Project Management nostr:npub1ltx67888tz7lqnxlrg06x234vjnq349tcfyp52r0lstclp548mcqnuz40t (kanbanstr) Code Snippets nostr:npub1ygzj9skr9val9yqxkf67yf9jshtyhvvl0x76jp5er09nsc0p3j6qr260k2 (nodebin.io) nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac (snipsnip.dev)
CI / CD nostr:npub16ux4qzg4qjue95vr3q327fzata4n594c9kgh4jmeyn80v8k54nhqg6lra7 nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr
and for their nostr:npub1c03rad0r6q833vh57kyd3ndu2jry30nkr0wepqfpsm05vq7he25slryrnw nostr:npub1qqqqqq2stely3ynsgm5mh2nj3v0nk5gjyl3zqrzh34hxhvx806usxmln03 and nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z for their testing, feedback, ideas and encouragement.
Thank you for your support and collaboration! Let me know if I've missed you.
-
 @ b99efe77:f3de3616
2025-04-30 19:57:34
@ b99efe77:f3de3616
2025-04-30 19:57:34🚦Traffic Light Control System🚦
This Petri net represents a traffic control protocol ensuring that two traffic lights alternate safely and are never both green at the same time.
petrinet ;start () -> greenLight1 redLight2 ;toRed1 greenLight1 -> queue redLight1 ;toGreen2 redLight2 queue -> greenLight2 ;toGreen1 queue redLight1 -> greenLight1 ;toRed2 greenLight2 -> redLight2 queue ;stop redLight1 queue redLight2 -> () -
 @ c230edd3:8ad4a712
2025-04-30 16:19:30
@ c230edd3:8ad4a712
2025-04-30 16:19:30Chef's notes
I found this recipe on beyondsweetandsavory.com. The site is incredibly ad infested (like most recipe sites) and its very annoying so I'm copying it to Nostr so all the homemade ice cream people can access it without dealing with that mess. I haven't made it yet. Will report back, when I do.
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 55 min
- 🍽️ Servings: 8
Ingredients
- 2 cups heavy cream
- 1 cup 2% milk
- 8 oz dark chocolate, 70%
- ¼ cup Dutch cocoa
- 2 tbsps loose Earl grey tea leaves
- 4 medium egg yolks
- ¾ cup granulated sugar
- ⅛ tsp salt
- ¼ cup dark chocolate, 70% chopped
Directions
- In a double boiler or a bowl set over a saucepan of simmering water, add the cacao solids and ½ cup of heavy cream. Stir chocolate until melted and smooth. Set melted chocolate aside.
- In a heavy saucepan, combine remaining heavy cream, milk, salt and ½ cup of sugar.
- Put the pan over medium heat and let the mixture boil gently to bubbling just around the edges (gentle simmer) and sugar completely dissolved, about 5 minutes. Remove from heat.
- Add the Earl Grey tea leaves and let it steep for 7-8 minutes until the cream has taken on the tea flavor, stirring occasionally and tasting to make sure it’s not too bitter.
- Whisk in Dutch cocoa until smooth. Add in melted chocolate and whisk until smooth.
- In a medium heatproof bowl, whisk the yolks just to break them up and whisk in remaining sugar. Set aside.
- Put the saucepan back on the stove over low heat and let it warm up for 2 minutes.
- Carefully measure out ½ cup of hot cream mixture.
- While whisking the eggs constantly, whisk the hot cream mixture into the eggs until smooth. Continue tempering the eggs by adding another ½ cup of hot cream to the bowl with the yolks.
- Pour the cream-egg mixture back to the saucepan and cook over medium-low heat, stirring constantly until it is thickened and coats the back of a spatula, about 5 minutes.
- Strain the base through a fine-mesh strainer into a clean container.
- Pour the mixture into a 1-gallon Ziplock freezer bag and submerge the sealed bag in an ice bath until cold, about 30 minutes. Refrigerate the ice cream base for at least 4 hours or overnight.
- Pour the ice cream base into the frozen canister of your ice cream machine and follow the manufacturer’s instructions.
- Spin until thick and creamy about 25-30 minutes.
- Pack the ice cream into a storage container, press a sheet of parchment directly against the surface and seal with an airtight lid. Freeze in the coldest part of your freezer until firm, at least 4 hours.
- When ready to serve, scoop the ice cream into a serving bowl and top with chopped chocolate.
-
 @ b99efe77:f3de3616
2025-04-30 19:57:12
@ b99efe77:f3de3616
2025-04-30 19:57:12🚦Traffic Light Control System🚦
This Petri net represents a traffic control protocol ensuring that two traffic lights alternate safely and are never both green at the same time.
petrinet ;start () -> greenLight1 redLight2 ;toRed1 greenLight1 -> queue redLight1 ;toGreen2 redLight2 queue -> greenLight2 ;toGreen1 queue redLight1 -> greenLight1 ;toRed2 greenLight2 -> redLight2 queue ;stop redLight1 queue redLight2 -> () -
 @ 88cc134b:5ae99079
2025-04-30 16:10:52
@ 88cc134b:5ae99079
2025-04-30 16:10:52Lorem ipsum dolor sit amet, consectetur adipiscing elit. In et tempor magna. Donec nec nibh sed dolor euismod aliquam. Vestibulum fermentum rutrum tortor dictum tincidunt. Cras vestibulum risus at imperdiet malesuada. Nulla dignissim arcu nec nibh hendrerit, in convallis tellus pharetra. Nunc tristique libero non ante ultrices consectetur. In lacinia ipsum quis diam sollicitudin, sit amet venenatis neque auctor. Sed ut ipsum ac dui ullamcorper bibendum. Pellentesque sit amet mi imperdiet, convallis velit vel, vehicula ipsum. Nulla hendrerit, odio mollis egestas hendrerit, sem est egestas justo, at dapibus odio massa et leo.
Fusce efficitur nunc non ante tincidunt laoreet. Vivamus dictum magna eu nisl ullamcorper mollis. Cras magna odio, maximus eu luctus egestas, porttitor nec sem. Maecenas sed tortor aliquet, consequat dolor quis, cursus massa. Nulla consequat nisl ut lacus elementum mollis. Nulla facilisi. Praesent laoreet ante ligula, id porta nisl malesuada id. Sed eu quam semper, suscipit tortor eget, feugiat mauris. Maecenas hendrerit arcu ligula, vitae maximus orci efficitur quis. In feugiat lectus in velit aliquet tincidunt. Aenean sit amet neque mollis, laoreet leo tincidunt, volutpat arcu.
Donec id massa diam. Nunc ac nunc non massa bibendum convallis non in nisl. Phasellus at nisl cursus, aliquet nibh ut, varius nisl. Cras eget dolor neque. Pellentesque et maximus dui. Sed metus erat, facilisis et blandit vitae, facilisis quis diam. Nullam vitae mattis odio. Vivamus varius sapien non arcu convallis, ut varius est lobortis. Maecenas tristique sagittis nunc, non lobortis mi fermentum quis.
Vestibulum in consectetur nibh. Integer libero mauris, sagittis sed nulla tincidunt, venenatis vestibulum nibh. Praesent vitae ex non quam pretium luctus. Etiam fringilla mattis tellus, eu placerat enim vestibulum nec. Curabitur vitae dictum erat. Fusce non ligula vehicula, aliquam eros sit amet, pharetra felis. Suspendisse dapibus pretium dui. Donec quis erat est. Nunc varius dolor velit, sit amet consectetur enim finibus sit amet. Aenean malesuada erat sed libero vestibulum, vel varius dui gravida. Ut volutpat risus dui, quis euismod nisi ornare et. Nullam blandit iaculis ipsum. Donec ullamcorper turpis quis placerat tincidunt.
Fusce mi ante, euismod et lorem vitae, commodo fringilla ex. Maecenas sagittis euismod nibh. Integer vestibulum sit amet ipsum ut fringilla. Etiam bibendum, risus id malesuada faucibus, magna libero vulputate nulla, in suscipit tortor orci sed arcu. Sed malesuada ipsum nec faucibus pulvinar. Aliquam vehicula lorem sit amet nulla vulputate, eget efficitur mauris sagittis. Nullam lacus ipsum, bibendum sed laoreet at, tristique vel massa. Cras non lorem sit amet sapien auctor feugiat ac sed lorem. Pellentesque tellus erat, rhoncus nec venenatis ac, efficitur vitae felis. Sed in nunc erat. Nullam et quam ac diam rutrum auctor in id ante. Suspendisse pulvinar porttitor mattis. Cras ultrices tristique elit, sit amet vulputate diam ultricies sit amet. Sed scelerisque est eros, eget semper erat vehicula vel. Pellentesque habitant morbi tristique senectus et netus et malesuada fames ac turpis egestas.
-
 @ b99efe77:f3de3616
2025-04-30 19:53:20
@ b99efe77:f3de3616
2025-04-30 19:53:20🚦Traffic Light Control System🚦
This Petri net represents a traffic control protocol ensuring that two traffic lights alternate safely and are never both green at the same time.
petrinet ;start () -> greenLight1 redLight2 ;toRed1 greenLight1 -> queue redLight1 ;toGreen2 redLight2 queue -> greenLight2 ;toGreen1 queue redLight1 -> greenLight1 ;toRed2 greenLight2 -> redLight2 queue ;stop redLight1 queue redLight2 -> () -
 @ 1739d937:3e3136ef
2025-04-30 14:39:24
@ 1739d937:3e3136ef
2025-04-30 14:39:24MLS over Nostr - 30th April 2025
YO! Exciting stuff in this update so no intro, let's get straight into it.
🚢 Libraries Released
I've created 4 new Rust crates to make implementing NIP-EE (MLS) messaging easy for other projects. These are now part of the rust-nostr project (thanks nostr:npub1drvpzev3syqt0kjrls50050uzf25gehpz9vgdw08hvex7e0vgfeq0eseet) but aren't quite released to crates.io yet. They will be included in the next release of that library. My hope is that these libraries will give nostr developers a simple, safe, and specification-compliant way to work with MLS messaging in their applications.
Here's a quick overview of each:
nostr_mls_storage
One of the challenges of using MLS messaging is that clients have to store quite a lot of state about groups, keys, and messages. Initially, I implemented all of this in White Noise but knew that eventually this would need to be done in a more generalized way.
This crate defines traits and types that are used by the storage implementation crates and sets those up to wrap the OpenMLS storage layer. Now, instead of apps having to implement storage for both OpenMLS and Nostr, you simply pick your storage backend and go from there.
Importantly, because these are generic traits, it allows for the creation of any number of storage implementations for different backend storage providers; postgres, lmdb, nostrdb, etc. To start I've created two implementations; detailed below.
nostr_mls_memory_storage
This is a simple implementation of the nostr_mls_storage traits that uses an in-memory store (that doesn't persist anything to disc). This is principally for testing.
nostr_mls_sqlite_storage
This is a production ready implementation of the nostr_mls_storage traits that uses a persistent local sqlite database to store all data.
nostr_mls
This is the main library that app developers will interact with. Once you've chose a backend and instantiated an instance of NostrMls you can then interact with a simple set of methods to create key packages, create groups, send messages, process welcomes and messages, and more.
If you want to see a complete example of what the interface looks like check out mls_memory.rs.
I'll continue to add to this library over time as I implement more of the MLS protocol features.
🚧 White Noise Refactor
As a result of these new libraries, I was able to remove a huge amount of code from White Noise and refactor large parts of the app to make the codebase easier to understand and maintain. Because of this large refactor and the changes in the underlying storage layer, if you've installed White Noise before you'll need to delete it from your device before you trying to install again.
🖼️ Encrypted Media with Blossom
Let's be honest: Group chat would be basically useless if you couldn't share memes and gifs. Well, now you can in White Noise. Media in groups is encrypted using an MLS secret and uploaded to Blossom with a one-time use keypair. This gives groups a way to have rich conversations with images and documents and anything else while also maintaining the privacy and security of the conversation.
This is still in a rough state but rendering improvements are coming next.
📱 Damn Mobile
The app is still in a semi-broken state on Android and fully broken state on iOS. Now that I have the libraries released and the White Noise core code refactored, I'm focused 100% on fixing these issues. My goal is to have a beta version live on Zapstore in a few weeks.
🧑💻 Join Us
I'm looking for mobile developers on both Android and iOS to join the team and help us build the best possible apps for these platforms. I have grant funding available for the right people. Come and help us build secure, permissionless, censorship-resistant messaging. I can think of few projects that deserve your attention more than securing freedom of speech and freedom of association for the entire world. If you're interested or know someone who might be, please reach out to me directly.
🙏 Thanks to the People
Last but not least: A HUGE thank you to all the folks that have been helping make this project happen. You can check out the people that are directly working on the apps on Following._ (and follow them). There are also a lot of people behind the scenes that have helped in myriad ways to get us this far. Thank you thank you thank you.
🔗 Links
Libraries
White Noise
Other
-
 @ 866e0139:6a9334e5
2025-04-30 18:47:50
@ 866e0139:6a9334e5
2025-04-30 18:47:50Autor: Ulrike Guérot. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
https://www.youtube.com/watch?v=KarwcXKmD3E
Liebe Freunde und Bekannte,
liebe Friedensbewegte,
liebe Dresdener, Dresden ist ja auch eine kriegsgeplagte Stadt,
dies ist meine dritte Rede auf einer Friedensdemonstration innerhalb von nur gut einem halben Jahr: München im September, München im Februar, Dresden im April. Und der Krieg rückt immer näher! Wer sich den „Operationsplan Deutschland über die zivil-militärische Kooperation als wesentlicher Bestandteil der Kriegsführung“ anschaut, dem kann nur schlecht werden zu sehen, wie weit die Kriegsvorbereitungen schon gediehen sind.
Doch bevor ich darauf eingehe, möchte ich mich als erstes distanzieren von dem wieder einmal erbärmlichen Framing dieser Demo als Querfront oder Schwurblerdemo. Durch dieses Framing wurde diese Demo vom Dresdener Marktplatz auf den Postplatz verwiesen, wurden wir geschmäht und wurde die Stadtverwaltung Dresden dazu gebracht, eine „genehmere“ Demo auf dem Marktplatz zuzulassen! Es wäre schön, wenn wir alle - alle! - solche Framings weglassen würden und uns als Friedensbewegte die Hand reichen! Der Frieden im eigenen Haus ist die Voraussetzung für unsere Friedensarbeit. Der Streit in unserem Haus nutzt nur denen, die den Krieg wollen und uns spalten!
Ich möchte hier noch einmal klarstellen, von welcher Position aus ich hier und heute wiederholt auf einer Bühne spreche: Ich spreche als engagierte Bürgerin der Bundesrepublik Deutschland. Ich spreche als Europäerin, die lange Jahre in und an dem einstigen Friedensprojekt EU gearbeitet hat. Ich spreche als Enkelin von zwei Großvätern. Der eine ist im Krieg gefallen, der andere kam ohne Beine zurück. Ich spreche als Tochter einer Mutter, die 1945, als 6-Jährige, unter traumatischen Umständen aus Schlesien vertrieben wurde, nach Delitzsch in Sachsen übrigens. Ich spreche als Mutter von zwei Söhnen, 33 und 31 Jahre, von denen ich nicht möchte, dass sie in einen Krieg müssen. Von dieser, und nur dieser Position aus spreche ich heute zu Ihnen und von keiner anderen! Ich bin nicht rechts, ich bin keine Schwurblerin, ich bin nicht radikal, ich bin keine Querfront.
Als Bürgerin wünsche ich mir – nein, verlange ich! – dass die Bundesrepublik Deutschland sich an ihre gesetzlichen Grundlagen und Vertragstexte hält. Das sind namentlich: Die Friedensklausel des Grundgesetzes aus Art. 125 und 126 GG, dass von deutschem Boden nie wieder Krieg ausgeht. Und der Zwei-plus-Vier-Vertrag, in dem Deutschland 1990 unterschrieben hat, dass es nie an einem bewaffneten Konflikt gegen Russland teilnimmt. Ich schäme mich dafür, dass mein Land dabei ist, vertragsbrüchig zu werden. Ich bitte Friedrich Merz, den designierten Bundeskanzler, keinen Vertragsbruch durch die Lieferung von Taurus-Raketen zu begehen!
Ich bitte ferner darum, dass sich dieses Land an seine didaktischen Vorgaben für Schulen hält, die im immer noch geltenden „Beutelsbacher Konsens“ aus den 1970er Jahren festgelegt wurden. In diesem steht in Artikel I. ein Überwältigungsverbot: „Es ist nicht erlaubt, den Schüler – mit welchen Mitteln auch immer – im Sinne erwünschter Meinungen zu überrumpeln und damit an der Gewinnung eines selbständigen Urteils zu hindern.“ Vor diesem Hintergrund ist es nicht erlaubt, Soldaten oder Gefreite in Schulen zu schicken und für die Bundeswehr zu werben. Vielmehr wäre es geboten, unsere Kinder über Art. 125 & 126 GG und die Friedenspflicht des Landes und seine Geschichte mit Blick auf Russland aufzuklären.
Als Europäerin wünsche ich mir, dass wir die europäische Hymne, Beethovens 9. Sinfonie, ernst nehmen, deren Text da lautet: Alle Menschen werden Brüder. Alle Menschen werden Brüder. Alle! Dazu gehören auch die Russen und natürlich auch die Ukrainer!
Als Europäerin, die in den 1990er Jahren für den großartigen EU-Kommissionspräsidenten Jacques Delors gearbeitet hat, Katholik, Sozialist und Gewerkschafter, wünsche ich mir, dass wir das Versprechen, #Europa ist nie wieder Krieg, ernst nehmen. Wir haben es 70 Jahre lang auf diesem Kontinent erzählt. Die Lügen und die Propaganda, mit der jetzt die Kriegsnotwendigkeit gegen Russland herbeigeredet wird, sind unerträglich. Die EU, Friedensnobelpreisträgerin von 2012, ist dabei – oder hat schon – ihr Ansehen in der Welt verloren. Es ist eine politische Tragödie! Neben ihrem Ansehen ist die EU jetzt dabei, das zivilisatorische Erbe Europas zu verspielen, die civilité européenne, wie der französische Historiker und Marxist, Étienne Balibar es nennt.
Ein Element dieses historischen Erbes ist es, dass uns in Europa eint, dass wir über Jahrhunderte alle zugleich Täter und Opfer gewesen sind. Ce que nous partageons, c’est ce que nous étions tous bourreaux et victimes. So schreibt es der französische Literat Laurent Gaudet in seinem europäischen Epos, L’Europe. Une Banquet des Peuples von 2016.
Das heißt, dass niemand in Europa, niemand – auch die Esten nicht! – das Recht hat, vorgängige Traumata, die die baltischen Staaten unbestrittenermaßen mit Stalin-Russland gehabt haben, zu verabsolutieren, auf die gesamte EU zu übertragen, die EU damit zu blockieren und die Politikgestaltung der EU einseitig auf einen Kriegskurs gegen Russland auszurichten. Ich wende mich mit dieser Feststellung direkt an Kaja Kalles, die Hohe Beauftragte für Sicherheits- und Außenpolitik der EU und hoffe, dass sie diese Rede hört und das Epos von Laurent Gaudet liest.
Es gibt keinen gerechten Krieg! Krieg ist immer nur Leid. In Straßburg, dem Sitz des Europäischen Parlaments, steht auf dem Place de la République eine Statue, eine Frau, die Republik. Sie hält in jedem Arm einen Sohn, einen Elsässer und einen Franzosen, die aus dem Krieg kommen. In der Darstellung der Bronzefigur haben die beiden Soldaten-Männer ihre Uniformen schon ausgezogen und werden von Madame la République gehalten und getröstet. An diesem Denkmal sollten sich alle Abgeordnete des Straßburger Europaparlamentes am 9. Mai versammeln. Ich zitiere noch einmal Cicero: Der ungerechteste Friede ist besser als der gerechteste Krieg. Für den Vortrag dieses Zitats eines der größten Staatsdenker des antiken Roms in einer Fernsehsendung bin ich 2022 mit einem Shitstorm überzogen worden. Allein das ist Ausdruck des Verfalls unserer Diskussionskultur in unfassbarem Ausmaß, ganz besonders in Deutschland.
Als Europäerin verlange ich die Überwindung unserer kognitiven Dissonanz. Wenn schon die New York Times am 27. März 2025 ein 27-seitiges Dossier veröffentlicht, das nicht nur belegt, was man eigentlich schon weiß, aber bisher nicht sagen durfte, nämlich, dass der ukrainisch-russische Krieg ein eindeutiger Stellvertreter-Krieg der USA ist, in der die Ukraine auf monströseste Weise instrumentalisiert wurde – was das Dossier der NYT unumwunden zugibt! – wäre es an der Zeit, die eindeutige Schuldzuweisung an Russland für den Krieg zurückzuziehen und die gezielt verbreitete Russophobie in Europa zu beenden. Anstatt dass – wofür es leider viele Verdachtsmomente gibt – die EU die Friedensverhandlungen in Saudi-Arabien nach Strich und Faden torpediert.
Der französische Philosoph Luc Ferry hat vor ein paar Tagen im prime time französischen Fernsehen ganz klar gesagt, dass der Krieg 2014 nach der Instrumentalisierung des Maidan durch die USA von der West-Ukraine ausging, dass Zelensky diesen Krieg wollte und – mit amerikanischer Rückendeckung – provoziert hat, dass Putin nicht Hitler ist und dass die einzigen mit faschistoiden Tendenzen in der ukrainischen Regierung sitzen. Ich wünschte mir, ein solches Statement wäre auch im Deutschen Fernsehen möglich und danke Richard David Precht, dass er, der noch in den Öffentlich-Rechtlichen Rundfunk vorgelassen wird, an dieser Stelle versucht, etwas Vernunft in die Debatte zu bringen.
Auch ist es gerade als Europäerin nicht hinzunehmen, dass russische Diplomaten von den Feierlichkeiten am 8. Mai 2025 ausgeschlossen werden sollen, ausgerechnet 80 Jahre nach Ende des II. Weltkrieges. Nicht nur sind Feierlichkeiten genau dazu da, sich die Hand zu reichen und den Frieden zu feiern. Doch gerade vor dem Hintergrund von 27 Millionen gefallenen sowjetischen Soldaten ist die Zurückweisung der Russen von den Feierlichkeiten geradezu eklatante Geschichtsvergessenheit.
***
Der Völkerbund hat 1925 die Frage erörtert, warum der I. Weltkrieg noch so lange gedauert hat, obgleich er militärisch bereits 1916 nach Eröffnung des Zweifrontenkrieges zu Lasten des Deutschen Reiches entschieden war. Wir erinnern uns: Für die Niederlage wurden mit der Dolchstoßlegende die jüdischen, kommunistischen und sozialistischen Pazifisten verantwortlich gemacht. Richtig ist, so der Bericht des Völkerbundes von 1925, dass allein die Rüstungsindustrie dafür gesorgt hat, dass der militärisch eigentlich schon entschiedene Krieg noch zwei weitere Jahre als Materialabnutzungs- und Stellungskrieg weiterbetrieben wurde, nur, damit noch ein bisschen Geld verdient werden konnte. Genauso scheint es heute zu sein. Der Krieg ist militärisch entschieden. Er kann und muss sofort beendet werden, und das passiert lediglich deswegen nicht, weil der Westen seine Niederlage nicht zugeben kann. Hochmut aber kommt vor dem Fall, und es darf nicht sein, dass für europäischen Hochmut jeden Tag rund 2000 ukrainische oder russische Soldaten und viele Zivilisten sterben. Die offenbare europäische Absicht, den Krieg jetzt einzufrieren, nur, um ihn 2029/ 2030 wieder zu entfachen, wenn Europa dann besser aufgerüstet ist, ist nur noch zynisch.
Als Kriegsenkelin von Kriegsversehrten, Tochter einer Flüchtlingsmutter und Mutter von zwei Söhnen, deren französischer Urgroßvater 6 Jahre in deutscher Kriegsgefangenschaft war, wünsche ich mir schließlich und zum Abschluss, dass wir die Kraft haben werden, wenn dieser Wahnsinn, den man den europäischen Bürgern gerade aufbürdet, vorbei sein wird, ein neues europäisches Projekt zu erdenken und zu erbauen, in dem Europa politisch geeint ist und es bleibt, aber dezentral, regional, subsidiär, friedlich und neutral gestaltet wird. Also ein Europa jenseits der Strukturen der EU, das bereit ist, die Pax Americana zu überwinden, aus der NATO auszutreten und der multipolaren Welt seine Hand auszustrecken! Unser Europa ist postimperial, postkolonial, groß, vielfältig und friedfertig!
Ulrike Guérot, Jg. 1964, ist europäische Professorin, Publizistin und Bestsellerautorin. Seit rund 30 Jahren beschäftigt sie sich in europäischen Think Tanks und Universitäten in Paris, Brüssel, London, Washington, New York, Wien und Berlin mit Fragen der europäischen Demokratie sowie mit der Rolle Europas in der Welt. Ulrike Guérot ist seit März 2014 Gründerin und Direktorin des European Democracy Lab e.V., Berlin und initiierte im März 2023 das European Citizens Radio, das auf Spotify zu finden ist. Zuletzt erschien von ihr „Über Halford J. Mackinders Heartland-Theorie, Der geografische Drehpunkt der Geschichte“ (Westend, 2024). Mehr Infos zur Autorin hier.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 4e616576:43c4fee8
2025-04-30 13:28:18
@ 4e616576:43c4fee8
2025-04-30 13:28:18asdfasdfsadfaf
-
 @ 90de72b7:8f68fdc0
2025-04-30 18:20:42
@ 90de72b7:8f68fdc0
2025-04-30 18:20:42PetriNostr. My everyday activity 30/02-2
PetriNostr never sleep! This is a demo
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ 90de72b7:8f68fdc0
2025-04-30 17:55:30
@ 90de72b7:8f68fdc0
2025-04-30 17:55:30PetriNostr. My everyday activity 30/04
PetriNostr never sleep! This is a demo
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ 4e616576:43c4fee8
2025-04-30 13:27:51
@ 4e616576:43c4fee8
2025-04-30 13:27:51asdfasdf
-
 @ 4e616576:43c4fee8
2025-04-30 13:13:51
@ 4e616576:43c4fee8
2025-04-30 13:13:51asdffasdf
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-30 15:50:37
@ 5d4b6c8d:8a1c1ee3
2025-04-30 15:50:37I was a bit more distracted than normal this month, but ~econ kept humming along.
- Posts: 228 (7th)
- Comments: 1459 (5th)
- Stacking: 128k (4th)
- Revenue: 74k (4th)
We're holding pretty steady, but haven't gotten back to our highs from last year.
With revenue down slightly, I'll move the post fee back towards the previous local max and conclude the posting fee optimization process for now. Going forward the posting fee will be set at 84 sats (until I decide to start messing with it again).
Next month, I'll start the comment fee optimization process.
We're still on pace for a profitable year and having a nice sized fund to pay out the end-of-year awards.
Thanks everyone for supporting this community!
Let me know if you have any suggestions for how to improve the territory.
originally posted at https://stacker.news/items/967545
-
 @ 4e616576:43c4fee8
2025-04-30 13:11:58
@ 4e616576:43c4fee8
2025-04-30 13:11:58asdfasdfasfd
-
 @ e096a89e:59351479
2025-04-30 12:59:28
@ e096a89e:59351479
2025-04-30 12:59:28Why Oshi?
I had another name for this brand before, but it was hard for folks to say. Then I saw a chance to tap into the #Nostr and #Bitcoin crowd, people who might vibe with what I’m creating, and I knew I needed something that’d stick.
A good name can make a difference. Well, sometimes. Take Blink-182 - it might sound odd, but it worked for them and even has a ring to it. So, why Oshi?
Names mean a lot to me, and Oshi’s got layers. I’m into Japanese culture and Bitcoin, so it fits perfectly with a few meanings baked in:
- It’s a nod to Bitcoin’s visionary, Satoshi Nakamoto.
- In Japanese, “oshi” means cheering on your favorite idol by supporting their work - think of me as the maker, you as the fan.
- It’s short for “oh shiiiitttt” - what most folks say when they taste how good this stuff is.
My goal with Oshi is to share how amazing pecans and dates can be together. Everything I make - Hodl Butter, Hodl Bars, chocolates - is crafted with intention, keeping it simple and nuanced, no overdoing it. It’s healthy snacking without the grains or junk you find in other products.
I’ve got a few bars and jars in stock now. Grab something today and taste the unique flavor for yourself. Visit my website at https://oshigood.us/
foodstr #oshigood #hodlbar #hodlbutter
-
 @ 88cc134b:5ae99079
2025-04-30 12:55:37
@ 88cc134b:5ae99079
2025-04-30 12:55:37nostr:nevent1qvzqqqqqqypzpzxvzd935e04fm6g4nqa7dn9qc7nafzlqn4t3t6xgmjkr3dwnyreqyvhwumn8ghj7urjv4kkjatd9ec8y6tdv9kzumn9wshszymhwden5te0wp6hyurvv4cxzeewv4ej7qpqx9an7hcqyevak03eefm8dluhn6frcryph6ua069w7d8c8784zcwqwxgp2r
-
 @ 3589b793:ad53847e
2025-04-30 12:40:42
@ 3589b793:ad53847e
2025-04-30 12:40:42※本記事は別サービスで2022年6月24日に公開した記事の移植です。
どうも、「NostrはLNがWeb統合されマネーのインターネットプロトコルとしてのビットコインが本気出す具体行動のショーケースと見做せばOK」です、こんばんは。
またまた実験的な試みがNostrで行われているのでレポートします。本シリーズはライブ感を重視しており、例によって(?)プルリクエストなどはレビュー段階なのでご承知おきください。
今回の主役はあくまでLightningNetworkの新提案(ただし以前からあるLSATからのリブランディング)となるLightning HTTP 402 Protocol(略称: L402)です。そのショーケースの一つとしてNostrが活用されているというものになります。
Lightning HTTP 402 Protocol(略称: L402)とは何か
bLIPに今月挙がったプロポーザル内容です。
https://github.com/lightning/blips/pull/26
L402について私はまだ完全に理解した段階ではあるのですがなんとか一言で説明しようとすると「Authトークンのように"Paid"トークンをHTTPヘッダーにアタッチして有料リソースへのHTTPリクエストの受け入れ判断を行えるようにする」ものだと解釈しました。
Authenticationでは、HTTPヘッダーにAuthトークンを添付し、その検証が通ればHTTPリクエストを許可し、通らなければ
401 Unauthorizedコードをエラーとして返すように定められています。https://developer.mozilla.org/ja/docs/Web/HTTP/Status/401
L402では、同じように、HTTPヘッダーに支払い済みかどうかを示す"Paid"トークンを添付し、その検証が通ればHTTPリクエストを許可し、通らなければ
402 Payment Requiredコードをエラーとして返すようにしています。なお、"Paid"トークンという用語は私の造語となります。便宜上本記事では使わせていただきますが、実際はAuthも入ってくるのが必至ですし、プルリクエストでも用語をどう定めるかは議論になっていることをご承知おきください。("API key", "credentials", "token", らが登場しています)
この402ステータスコードは従来から定義されていましたが、MDNのドキュメントでも記載されているように「実験的」なものでした。つまり、器は用意されているがこれまで活用されてこなかったものとなり、本プロトコルの物語性を体現しているものとなります。
https://developer.mozilla.org/ja/docs/Web/HTTP/Status/402
幻であったHTTPステータスコード402 Payment Requiredを実装する
この物語性は、上述のbLIPのスペックにも詳述されていますが、以下のスライドが簡潔です。
402 Payment Requiredは予約されていましたが、けっきょくのところWorldWideWebはペイメントプロトコルを実装しなかったので、Bitcoinの登場まで待つことになった、というのが要旨になります。このWorldWideWebにおける決済機能実装に関する歴史話はクリプト界隈でもたびたび話題に上がりますが、そこを繋いでくる文脈にこれこそマネーのインターネットプロトコルだなと痺れました。https://x.com/AlyseKilleen/status/1671342634307297282
この"Paid"トークンによって実現できることとして、第一にAIエージェントがBitcoin/LNを自律的に利用できるようになるM2M(MachineToMachine)的な話が挙げられていますが、ユースケースは想像力がいろいろ要るところです。実際のところは「有料リソースへの認可」を可能にすることが主になると理解しました。本連載では、繰り返しNostrクライアントにLNプロトコルを直接搭載せずにLightningNetworkを利用可能にする組み込み方法を見てきましたが、本件もインボイス文字列 & preimage程度の露出になりアプリケーション側でノードやウォレットの実装が要らないので、その文脈で位置付ける解釈もできるかと思います。
Snortでのサンプル実装
LN組み込み業界のリーディングプロダクトであるSnortのサンプル実装では、L402を有料コンテンツの購読に活用しています。具体的には画像や動画を投稿するときに有料のロックをかける、いわゆるペイウォールの一種となります。もともとアップローダもSnortが自前で用意しているので、そこにL402を組み込んでみたということのようです。
体験方法の詳細はこちらにあります。 https://njump.me/nevent1qqswr2pshcpawk9ny5q5kcgmhak24d92qzdy98jm8xcxlgxstruecccpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz78pvlzg
上記を試してみた結果が以下になります。まず、ペイウォールでロックした画像がNostrに投稿されている状態です。まったくビューワーが実装されておらず、ただのNotFound状態になっていますが、支払い前なのでロックされているということです。

次にこのHTTP通信の内容です。

通信自体はエラーになっているわけですが、ステータスコードが402で、レスポンスヘッダーのWWW-AuthenticateにInvoice文字列が返ってきています。つまり、このインボイスを支払えば"Paid"トークンが付与されて、その"Paid"トークンがあれば最初の画像がアンロックされることとなります。残念ながら現在は日本で利用不可のStrikeAppでしか払込みができないためここまでとなりますが、本懐である
402 Payment Requiredとインボイス文字列は確認できました。今確認できることは以上ですが、AmethystやDamusなどの他のNostrクライアントが実装するにあたり、インラインメディアを巡ってL402の仕様をアップデートする必要性や同じくHTTPヘッダーへのAuthトークンとなるNIP-98と組み合わせるなどの議論が行われている最中です。
LinghtningNetworkであるからこそのL402の実現
"Paid"トークンを実現するためにはLightningNetworkのファイナリティが重要な要素となっています。逆に言うと、reorgによるひっくり返しがあり得るBitcoinではできなくもないけど不便なわけです。LightningNetworkなら、当事者である二者間で支払いが確認されたら「同期的」にその証であるハッシュ値を用いて"Paid"トークンを作成することができます。しかもハッシュ値を提出するだけで台帳などで過去の履歴を確認する必要がありません。加えて言うと、受金者側が複数のノードを建てていて支払いを受け取るノードがどれか一つになる状況でも、つまり、スケーリングされている状況でも、"Paid"トークンそのものはどのノードかを気にすることなくステートレスで利用できるとのことです。(ここは単にreverse proxyとしてAuthサーバががんばっているだけと解釈することもできますがずいぶんこの機能にも力点を置いていて大規模なユースケースが重要になっているのだなという印象を抱きました)
Macaroonの本領発揮か?それとも詳細定義しすぎか?
HTTP通信ではWWW-Authenticateの実値にmacaroonの記述が確認できます。また現在のL402スペックでも"Paid"トークンにはmacaroonの利用が前提になっています。
このmacaroonとは(たぶん)googleで研究開発され、LNDノードソフトウェアで活用されているCookieを超えるという触れ込みのデータストアになります。しかし、あまり普及しなかった技術でもあり、個人の感想ですがなんとも微妙なものになっています。
https://research.google/pubs/macaroons-cookies-with-contextual-caveats-for-decentralized-authorization-in-the-cloud/
macaroonの強みは、Cookieを超えるという触れ込みのようにブラウザが無くてもプロセス間通信でデータ共有できる点に加えて、HMACチェーンで動的に認証認可を更新し続けられるところが挙げられます。しかし、そのようなユースケースがあまり無く、静的な認可となるOAuthやJWTで十分となっているのが現状かと思います。
L402では、macaroonの動的な更新が可能である点を活かして、"Paid"トークンを更新するケースが挙げられています。わかりやすいのは上記のスライド資料でも挙げられている"Dynamic Pricing"でしょうか。プロポーザルではloop©️LightningLabsにおいて月間の最大取引量を認可する"Paid"トークンを発行した上でその条件を動向に応じて動的に変更できる例が解説されています。とはいえ、そんなことしなくても再発行すればええやんけという話もなくもないですし、プルリクエストでも仕様レベルでmacaroonを指定するのは「具体」が過ぎるのではないか、もっと「抽象」し単なる"Opaque Token"程度の粒度にして他の実装も許容するべきではないか、という然るべきツッコミが入っています。
個人的にはそのツッコミが妥当と思いつつも、なんだかんだ初めてmacaroonの良さを実感できて感心した次第です。
-
 @ 4e616576:43c4fee8
2025-04-30 12:53:36
@ 4e616576:43c4fee8
2025-04-30 12:53:36sdfafd
-
 @ 3589b793:ad53847e
2025-04-30 12:28:25
@ 3589b793:ad53847e
2025-04-30 12:28:25※本記事は別サービスで2023年4月19日に公開した記事の移植です。
どうも、「NostrはLNがWeb統合されマネーのインターネットプロトコルとしてのビットコインが本気出す具体行動のショーケースと見做せばOK」です、こんにちは。
前回まで投げ銭や有料購読の組み込み方法を見てきました。
zapsという投げ銭機能が各種クライアントに一通り実装されて活用が進んでいることで、統合は次の段階へ移り始めています。「作戦名: ウォレットをNostrクライアントに組み込め」です。今回はそちらをまとめます。
投げ銭する毎にいちいちウォレットを開いてまた元のNostrクライアントに手動で戻らないといけない is PAIN
LNとNostrはインボイス文字列で繋がっているだけの疎結合ですが、投稿に投げ銭するためには何かのLNウォレットを開いて支払いをして、また元のNostrクライアントに戻る操作をユーザーが手作業でする必要があります。お試しで一回やる程度では気になりませんが普段使いしているとこれはけっこうな煩わしさを感じるUXです。特にスマホでは大変にだるい状況になります。連打できない!
2月の実装以来、zapsは順調に定着して日々投げられています。


https://stats.nostr.band/#daily_zaps
なので、NostrクライアントにLNウォレットの接続を組み込み、支払いのために他のアプリに遷移せずにNostクライアント単独で完結できるようなアップデートが始まっています。
Webクライアント
NostrのLN組み込み業界のリーディングプレイヤーであるSnortでの例です。以下のようにヘッダーのウォレットアイコンをクリックすると連携ウォレットの選択ができます。

もともとNostrに限らずウェブアプリケーションとの連携をするために、WebLNという規格があります。簡単に言うと、ブラウザのグローバル領域を介して、LNウォレットの拡張機能と、タブで開いているウェブアプリが、お互いに連携するためのインターフェースを定めているものです。これに対応していると、LNによる支払いをウェブアプリが拡張機能に依頼できるようになります。さらにオプションで「確認無し」をオンにすると、拡張機能画面がポップアップせずにバックグラウンドで実行できるようになり、ノールック投げ銭ができるようになります。
似たようなものにNostrではNIP-07があります。NIP-07はNostrの秘密鍵を拡張機能に退避して、Nostrクライアントは秘密鍵を知らない状態で署名や複合を拡張機能に移譲できるようにしているものです。
Albyの拡張機能ではWebLNとNIP-07のどちらにも対応しています。
実はSnortはzapsが来る前からWebLNには対応していたのですが、さらに一歩進み、拡張機能ウォレットだけでなく、LNノードや拡張機能以外のLNウォレットと連携設定できるようになってきています。

umbrelなどでノードを立てている人ならLND with LNCでノードと直接繋げます。またLNDHubに対応したウォレットなどのアプリケーションとも繋げます。これらの接続は、WebLNにラップされて拡張機能ウォレットとインターフェースを揃えられた上で、Snort上でのインボイスの支払いに活用されます。
なお、LNCのpairingPhrase/passwordやLNDHubの接続情報などのクレデンシャルは、ブラウザのローカルストレージに保存されています。Nostrのリレーサーバなどには送られませんので、端末ごとに設定が必要です。
スマホアプリ
今回のメインです。なお、例によって(?)スペックは絶賛議論中でまだフィックスしていない中で記事を書いています。ディテールは変わるかもしれないので悪しからずです。
スマホアプリで上記のことをやるためには、後半のLNCやLNDHubはすでにzeusなどがやっているようにできますが、あくまでネイティブウォレットのラッパーです。Nostrでは限られた用途になるので1-click支払いのようなものを行うためにはそこから各スマホアプリが作り込む必要があります。まあこれはこれでやればいいという話でもあるのですが、LNノードやLNウォレットのアプリケーション側へのインターフェースの共通仕様は定められていないので、LNDとcore-lightningとeclairではすべて実装方法が違いますし、ウォレットもバラバラなので大変です。
そこで、多種多様なノードやウォレットの接続を取りまとめ一般アプリケーションへ統一したインターフェースを媒介するLN Adapter業界のリーディングカンパニーであるAlbyが動きました。AndroidアプリのAmethystで試験公開されていますが、スマホアプリでも上記のSnortのような連携が可能になるようなSDKが開発されました。
リリース記事 https://blog.getalby.com/native-zapping-in-amethyst/
"Unstoppable zapping for users"なんて段落見出しが付けられているように、スマホで別のアプリに切り替えてまた元に戻らなくても良いようにして、Nostr上でマイクロペイメントを滑らかにする、つまり、連打できることを繰り返し強調しています。
具体的にやっていることを見ていきます。以下の画像群はリリース記事の動画から抜粋しています。各投稿のzapsボタン⚡️をタップしたときの画面です。

上の赤枠が従来の投げ銭の詳細を決める場所で、下の赤枠の「Wallet Connect Service」が新たに追加されたAlby提供のSDKを用いたコネクト設定画面です。基本的にはOAuth2.0ベースのAlbyのAPIを活用していて、右上のAlbyアイコンをタップすると以下のようなOAuthの認可画面に飛びます。(ただし後述するように通常のOAuthとは一部異なります。)


画面デザインは違いますが、まあ他のアプリでよく目にするTwitter連携やGoogleアカウント連携とやっていることは同じです。
このOAuthベースのAPIはNostr専用のエンドポイントが建てられています。Nostr以外のECショップやマーケットプレイスなどへのAlbyのOAuthは汎用のエンドポイントが用意されています。よって通常のAlbyの設定とは別にセッション詳細を以下のサイトで作成する必要があります。
https://nwc.getalby.com/ (サブドメインのnwcはNostr Wallet Connectの略)
なぜNostrだけは特別なのかというところが完全には理解しきれていないですが、以下のところまで確認できています。一番にあるのは、Nostrクライアントにウォレットを組み込まずに、かつ、ノードやウォレットへの接続をNostrリレーサーバ以外は挟まずに"decentralized"にしたいというところだと理解しています。
- 上記のnwcのURLはalbyのカストディアルウォレットusername@getalby.comをNostrに繋ぐもの(たぶん)
- umbrelのLNノードを繋ぐためにはやはり専用のアプリがumbrelストアに上がっている。https://github.com/getAlby/umbrel-community-app-store
- 要するにOAuthの1stPartyの役割をウォレットやノードごとにそれぞれ建てる。
- OAuthのシークレットはクライアントに保存するので設定は各クライアント毎に必要。しかし使い回しすることは可能っぽい。通常のOAuthと異なり、1stParty側で3rdPartyのドメインはトラストしていないようなので。
- Nostrクライアントにウォレットを組み込まずに、さらにウォレットやノードへの接続をNostrリレーサーバ以外には挟まなくて良いようにするために、「NIP-47 Nostr Wallet Connect」というプロポーザルが起こされていて、絶賛議論中である。https://github.com/nostr-protocol/nips/pull/406
- このWallet Connect専用のアドホックなリレーサーバが建てられる。その情報が上記画像の赤枠の「Wallet Connect Service」の下半分のpub keyやらrelayURL。どうもNostrクライアントはNIP-47イベントについてはこのリレーサーバにしか送らないようにするらしい。(なんかNostrの基本設計を揺るがすユースケースの気がする...)
- Wallet Connect専用のNostrイベントでは、ペイメント情報をNostrアカウントと切り離すために、Nostrの秘密鍵とは別の秘密鍵が利用できるようにしている。
Imagin the Future
今回取り上げたNostrクライアントにウォレット接続を組み込む話を、Webのペイメントの歴史で類推してみましょう。
Snortでやっていることは、各サイトごとにクレジットカードを打ち込み各サイトがその情報を保持していたようなWeb1.0の時代に近いです。そうなるとクレジットカードの情報は各サービスごとに漏洩リスクなどがあり、Web1.0の時代はECが普及する壁の一つになっていました。(今でもAmazonなどの大手はそうですが)
Webではその後にPayPalをはじめとして、銀行口座やクレジットカードを各サイトから切り出して一括管理し、各ウェブサイトに支払いだけを連携するサービスが出てきて一般化しています。日本ではケータイのキャリア決済が利用者の心理的障壁を取り除きEC普及の後押しになりました。
後半のNostr Wallet ConnectはそれをNostrの中でやろうとしている試みになります。クレジットカードからLNに変える理由はビットコインの話になるので詳細は割愛しますが、現実世界の金(ゴールド)に類した価値保存や交換ができるインターネットマネーだからです。
とはいえ、Nostrの中だけならまだしも、これをNostr外のサービスで利用するためには、他のECショップやブログやSaaSがNostrを喋れる必要があります。そんな未来が来るわけないだろと思うかもしれませんが、言ってみればStripeはまさにそのようなサービスとなっていて、サイト内にクレジット決済のモジュールを組み込むための主流となっています。
果たして、Nostrを、他のECショップやブログやSaaSが喋るようになるのか!?
以上、「NostrはLNがWeb統合されマネーのインターネットプロトコルとしてのビットコインが本気出す具体行動のショーケースと見做せばOK」がお送りしました。
-
 @ 3589b793:ad53847e
2025-04-30 12:10:06
@ 3589b793:ad53847e
2025-04-30 12:10:06前回の続きです。
特に「Snortで試験的にノート単位に投げ銭できる機能」について。実は記事書いた直後にリリースされて慌ててw追記してたんですが追い付かないということで別記事にしました。
今回のここがすごい!
「Snortで試験的にノート単位に投げ銭できる機能」では一つブレイクスルーが起こっています。それは「ウォレットにインボイスを放り投げた後に払い込み完了を提示できる」ようになったことです。これによりペイメントのライフサイクルが一通りカバーされたことになります。
Snortの画面

なにを当たり前のことをという向きもあるかもしれませんが、Nostrクライアントで払い込み完了を追跡することはとても難しいです。基本的にNostrとLNウォレットはまったく別のアプリケーションで両者の間を繋ぐのはインボイス文字列だけです。ウォレットもNostrからキックされずに、インボイス文字列をコピペするなりQRコードで読み取ったものを渡されるだけかもしれません。またその場でリアルタイムに処理される前提もありません。
なのでNostrクライアントでその後をトラックすることは難しく、これまではあくまで請求書を送付したり(LNインボイス)振り込み口座を提示する(LNアドレス)という一方的に放り投げてただけだったわけです。といっても魔法のようにNostrクライアントがトラックできるようになったわけではなく、今回の対応方法もインボイスを発行/お金を振り込まれるサービス側(LNURL)にNostrカスタマイズを入れさせるというものになります。
プロポーザルの概要について
前回の記事ではよくわからんで終わっていましたが、当日夜(日本時間)にスペックをまとめたプロポーザルも起こされました(早い!)。LNURLが、Nostr用のインボイスを発行して、さらにNostrイベントの発行を行っていることがポイントでした。名称は"Lightning Zaps"で確定のようです。プロポーザルは、NostrとLNURLの双方の発明者であるfiatjaf氏からツッコミが入り、またそれが妥当な指摘のために、エンドポイントURLのインターフェースなどは変わりそうなのですが、概要はそう変わらないだろうということで簡単にまとめてみます。
全体の流れ

図は、Nostrクライアント上に提示されているLNアドレスへ投げ銭が開始してから、Nostrクライアント上に払い込み完了したイベントが表示されるまでの流れを示しています。
- 投げ銭の内容が固まったらNostrイベントデータを添付してインボイスの発行を依頼する
- 説明欄にNostr用のデータを記載したインボイスを発行して返却する
- Nostrクライアントで提示されたインボイスをユーザーが何かしらの手段でウォレットに渡す
- ウォレットがLNに支払いを実行する
- インボイスの発行者であるLNURLが管理しているLNノードにsatoshiが届く
- LNURLサーバが投げ銭成功のNostrイベントを発行する
- Nostrクライアントがイベントを受信して投げ銭履歴を表示する
特にポイントとなるところを補足します。
対応しているLNアドレスの識別
LNアドレスに投げ銭する場合は、LNアドレスの有効状態やインボイス発行依頼する先の情報を
https://[domain]/.well-known/lnurlp/[username]から取得しています。そのレスポンス内容にNostr対応を示す情報を追加しています。ただし、ここに突っ込み入っていてlnurlp=LNURL Payから独立させるためにzaps専用のエンドポイントに変わりそうです。(2/15 追記 マージされましたが変更無しでした。PRのディスカッションが盛り上がっているので興味ある方は覗いてみてください。)インボイスの説明欄に書き込むNostrイベント(kind:9734)
これは投げ銭する側のNostrイベントです。投げ銭される者や対象ノートのIDや金額、そしてこのイベントを作成している者が投げ銭したということを「表明」するものになります。表明であって証明でないところは、インボイスを別の人が払っちゃう事態がありえるからですね。この内容をエンクリプトするパターンも用意されていたが複雑になり過ぎるという理由で今回は外され追加提案に回されました。また、このイベントはデータを作成しただけです。支払いを検知した後にLNURLが発行するイベントに添付されることになります。そのため投げ銭する者にちゃんと届くように作成者のリレーサーバリストも書き込まれています。
支払いを検知した後に発行するNostrイベント(kind:9735)
これが実際にNostrリレーサーバに発行されるイベントです。LNURL側はウォッチしているLNノードにsatoshiが届くと、インボイスの説明欄に書かれているNostrイベントを取り出して、いわば受領イベントを作成して発行します。以下のようにNostイベントのkind:9734とkind:9735が親子になったイベントとなります。
json { "pubkey": "LNURLが持っているNostrアカウントの公開鍵", "kind": 9735, "tags": [ [ "p", "投げ銭された者の公開鍵" ], [ "bolt11", "インボイスの文字列lnbc〜" ], [ "description", "投げ銭した者が作成したkind:9734のNostrイベント" ], [ "preimage", "インボイスのpreimage" ] ], }所感
とにかくNostrクライアントはLNノードを持たないしLNプロトコルとも直接喋らずにインボイス文字列だけで取り扱えるようになっているところがおもしろいと思っています。NostrとLNという二つのデセントライズドなオープンプロトコルが協調できていますし、前回も述べましたがどんなアプリでも簡単に真似できます。
とはいえ、さすがに払込完了のトラックは難しく、今回はLNURL側にそのすり合わせの責務が寄せられることになりました。しかし、LNURLもLNの上に作られたオープンプロトコル/スペックの位置付けになるため、他のLNURLのスペックに干渉するという懸念から、本提案のNIP-57に変更依頼が出されています。LN、LNURL、Nostrの3つのオープンプロトコルの責務分担が難しいですね。アーキテクチャ層のスタックにおいて3つの中ではNostrが一番上になるため、Nostrに相当するレイヤーの他のwebサービスでやるときはLNプロトコルを喋るなりLNノードを持つようにして、今回LNURLが寄せられた責務を吸収するのが無難かもしれません。
また、NIP-57の変更依頼理由の一つにはBOLT-12を見越した抽象化も挙げられています。他のLNURLのスペックを削ぎ落としてzapsだけにすることでBOLT-12にも載りやすくなるだろうと。LNURLの多くはBOLT-12に取り込まれる運命なわけですが、LNアドレス以外の点でもNostrではBOLT-12のOfferやInvoiceRequestのユースケースをやりたいという声が挙がっているため、NostrによりBOLT-12が進む展開もありそうだなあ、あってほしい。
-
 @ 3589b793:ad53847e
2025-04-30 12:02:13
@ 3589b793:ad53847e
2025-04-30 12:02:13※本記事は別サービスで2023年2月5日に公開した記事の移植です。
Nostrクライアントは多種ありますがメジャーなものはだいたいLNの支払いが用意されています。現時点でどんな組み込み方法になっているか調べました。この記事では主にSnortを対象にしています。
LN活用場面
大きくLNアドレスとLNインボイスの2つの形式があります。
1. LNアドレスで投げ銭をセットできる

LNURLのLNアドレスをセットすると、プロフィールやノート(ツイートに相当)からLN支払いができます。別クライアントのastralなどではプリミティブなLNURLの投げ銭形式
lnurl1dp68~でもセットできます。[追記]さらに本日、Snortで試験的にノート単位に投げ銭できる機能が追加されています。

2. LNインボイスが投稿できる

投稿でLNインボイスを貼り付ければ上記のように他の発言と同じようにタイムラインに流れます。Payボタンを押すと各自の端末にあるLNウォレットが立ち上がります。
3. DMでLNインボイスを送る
メッセージにLNインボイスが組み込まれているという点では2とほぼ同じですが、ユースケースが異なります。発表されたばかりですがリレーサーバの有料化が始まっていて、その決済をDMにLNインボイスを送付して行うことが試されています。2だとパブリックに投稿されますが、こちらはプライベートなので購入希望者のみにLNインボイスを届けられます。

おまけ: Nostrのユーザ名をLNアドレスと同じにする
直接は関係ないですが、Nostrはユーザー名をemail形式にすることができます。LNアドレスも自分でドメイン取って作れるのでNostrのユーザー名と投げ銭のアドレスを同じにできます。
LNウォレットのAlbyのドメインをNostrのユーザ名にも活用している様子 [Not found]
実装方法
LNアドレスもLNインボイスも非常にシンプルな話ですが軽くまとめます。 Snortリポジトリ
LNアドレス
- セットされたLNアドレスを分解して
https://[domain]/.well-known/lnurlp/[username]にリクエストする - 成功したら投げ銭量を決めるUIを提示する
- Get Inoviceボタンを押したら1のレスポンスにあるcallbackにリクエストしてインボイスを取得する
- 成功したらPayボタンを提示する
LNインボイス
- 投稿内容がLNインボイス識別子
lnbc10m〜だとわかると、識別子の中の文字列から情報(金額、説明、有効期限)を取り出し、表示用のUIを作成する - 有効期限内だったらPayボタンを提示し、期限が切れていたらExpiredでロックする
支払い
Payボタンを押された後の動きはアドレス、インボイスとも同じです。
- ブラウザでWebLN(Albyなど)がセットされていて、window.weblnオブジェクトがenableになっていると、拡張機能の支払い画面が立ち上がる。クライアント側で支払い成功をキャッチすることも可能。
- Open Walletボタンを押すと
lightning:lnbc10m~のURI形式でwindow.openされ、Mac/Windows/iPhone/Androidなど各OSに応じたアプリケーション呼び出しが行われ、URIに対応しているLNウォレットが立ち上がる
[追記]ノート単位の投げ銭
Snort周辺の数人(strike社員っぽい人が一人いて本件のメイン実装している)で試験的にやっているようで現時点では実装レベルでしか詳細わかりませんでした。strikeのzapといまいち区別が付かなかったのですが、実装を見るとnostrプロトコルにzapイベントが追加されています。ソースコメントではこの後NIP(nostr improvement proposal)が起こされるようでかなりハッキーです。zap=tipの方言なんでしょうか?
ノートやプロフィールやリアクションなどに加えて新たにnostrイベントに追加しているものは以下2つです。
- zapRequest 投げ銭した側が対象イベントIDと量を記録する
- zapReceipt 投げ銭を受け取った側用のイベント
一つでできそうと思ったけど、nostrは自己主権のプロトコルでイベント作成するには発行者の署名が必須なので2つに分かれているのでしょう。
所感
現状はクライアントだけで完結する非常にシンプルな方法になっています。リレーサーバも経由しないしクライアントにLNノードを組み込むこともしていません。サードパーティへのhttpリクエストやローカルのアプリに受け渡すだけなので、実はどんな一般アプリでもそんなに知識もコストも要らずにパッとできるものです。
現状ちょっと不便だなと思っていることは、タイムラインに流れるインボイスの有効期限内の支払い済みがわからないことです。Payボタンを押してエラーにならないとわかりません。ウォレットアプリに放り投げていてこのトレースするためには、ウォレット側で支払い成功したらNostrイベントを書き込むなどの対応しない限りは、サービス側でインボイスを定期的に一つ一つLNに投げてチェックするなどが必要だと思われるので、他のサービスでマネするときは留意しておくとよさそうです。
一方で、DMによるLNインボイス送付は活用方法が広がりそうな予感があります。Nostrの公開鍵による本人特定と、LNインボイスのメモ欄のテキスト情報による突き合わせだけでも、かんたんな決済機能として用いれそうだからです。もっとNostrに判断材料を追加したければイベント追加も簡単にできることをSnortが示しています。とくにリレーサーバ購読やPROメニューなどのNostr周辺の支払いはやりやすそうなので、DM活用ではなくなにかしらの決済メニューを搭載したNostrクライアントもすぐに出てきそう気がします。
- セットされたLNアドレスを分解して
-
 @ 3589b793:ad53847e
2025-04-30 11:46:52
@ 3589b793:ad53847e
2025-04-30 11:46:52※本記事は別サービスで2022年9月25日に公開した記事の移植です。
LNの手数料の適正水準はどう見積もったらいいだろうか?ルーティングノードの収益性を算出するためにはどうアプローチすればよいだろうか?本記事ではルーティングノード運用のポジションに立ち参考になりそうな数値や計算式を整理する。
個人的な感想を先に書くと以下となる。
- 現在の手数料市場は収益性が低くもっと手数料が上がった方が健全である。
- 他の決済手段と比較すると、LN支払い料金は10000ppm(手数料1%相当)でも十分ではないか。4ホップとすると中間1ノードあたり2500ppmである。
- ルーティングノードの収益性を考えると、1000ppmあれば1BTC程度の資金で年利2.8%になり半年で初期費用回収できるので十分な投資対象になると考える。
基本概念の整理
LNの料金方式
- LNの手数料は送金額に応じた料率方式が主になる。(基本料金の設定もあるが1 ~ 0 satsが大半)
- 料率単位のppm(parts per million)は、1,000,000satsを送るときの手数料をsats金額で示したもの。
- %での手数料率に変換すると1000ppm = 0.1%になる。
- 支払い者が払う手数料はルーティングに参加した各ノードの手数料の合計である。本稿では4ホップ(経由ノードが4つ)のルーティングがあるとすれば、各ノードの取り分は単純計算で1/4とみなす。
- ルーティングノードの収益はアウトバウンドフローで発生するのでアウトバウンドキャパシティが直接的な収益資源となる。
LNの料金以外のベネフィット
本稿では料金比較だけを行うが実際の決済検討では以下のような料金以外の効用も忘れてはならない。
- Bitcoin(L1)に比べると、料金の安さだけでなく、即時確定やトランザクション量のスケールという利点がある。
- クレジットカードなどの集権サービスと比較した特徴はBitcoin(L1)とだいたい同じである。
- 24時間365日利用できる
- 誰でも自由に使える
- 信頼する第三者に対する加盟や審査や手数料率などの交渉手続きが要らない
- 検閲がなく匿名性が高い
- 逆にデメリットはオンライン前提がゆえの利用の不便さやセキュリティ面の不安さなどが挙げられる。
現在の料金相場
- ルーティングノードの料金設定
- sinkノードとのチャネルは500 ~ 1000ppmが多い。
- routing/sourceノードとのチャネルは0 ~ 100ppmあたりのレンジになる。
- リバランスする場合もsinkで収益を上げているならsink以下になるのが道理である。
- プロダクト/サービスのバックエンドにいるノードの料金設定
- sinkやsourceに相当するものは上記の通り。
- 1000〜5000ppmあたりで一律同じ設定というノードもよく見かける。
- ビジネスモデル次第で千差万別だがアクティブと思われるノードでそれ以上はあまり見かけない。
- 上記は1ノードあたりの料金になる。支払い全体では経由したノードの合計になる。
料金目安
いくつかの方法で参考数字を出していく。LN料金算出は「支払い全体/2ホップしたときの1ノードあたり/4ホップしたときの1ノードあたり」の三段階で出す。
類推方式
決済代行業者との比較
- Squareの加盟店手数料は、日本3.25%、アメリカ2.60%である。
- 参考資料 https://www.meti.go.jp/shingikai/mono_info_service/cashless_payment/pdf/20220318_1.pdf
3.25%とするとLNでは「支払い全体/2ホップしたときの1ノードあたり/4ホップしたときの1ノードあたり」でそれぞれ
32,500ppm/16,250ppm/8,125ppmになる。スマホのアプリストアとの比較
- Androidのアプリストアは年間売上高が100万USDまでなら15%、それ以上なら30%
- 参考資料https://support.google.com/googleplay/android-developer/answer/112622?hl=ja
15%とするとLNでは「支払い全体/2ホップしたときの1ノードあたり/4ホップしたときの1ノードあたり」でそれぞれ
150,000ppm/75,000ppm/37,500ppmになる。Bitcoin(L1)との比較
Bitcoin(L1)は送金額が異なっても手数料がほぼ同じため、従量課金のLNと単純比較はできない。そのためここではLNの方が料金がお得になる目安を出す。
Bitcoin(L1)の手数料設定
- SegWitのシンプルな送金を対象にする。
- input×1、output×2(送金+お釣り)、tx合計222byte
- L1の手数料は、1sat/byteなら222sats、10sat/byteなら2,220sats、100sat/byteなら22,200sats。(単純化のためvirtual byteではなくbyteで計算する)
- サンプル例 https://www.blockchain.com/btc/tx/15b959509dad5df0e38be2818d8ec74531198ca29ac205db5cceeb17177ff095
L1相場が1sat/byteの時にLNの方がお得なライン
- 100ppmなら、0.0222BTC(2,220,000sats)まで
- 1000ppmなら、0.00222BTC(222,000sats)まで
L1相場が10sat/byteの時にLNの方がお得なライン
- 100ppmなら、0.222BTC(22,200,000sats)まで
- 1000ppmなら、0.0222BTC(2,220,000sats)まで
L1相場が100sat/byteの時にLNの方がお得なライン
- 100ppmなら、2.22BTC(222,000,000sats)まで
- 1000ppmなら、0.222BTC(22,200,000sats)まで
コスト積み上げ方式
ルーティングノードの原価から損益分岐点となるppmを算出する。事業者ではなく個人を想定し、クラウドではなくラズベリーパイでのノード構築環境で計算する。
費用明細
- BTC市場価格 1sat = 0.03円(1BTC = 3百万円)
初期費用
- ハードウェア一式 40,000円
- Raspberry Pi 4 8GB
- SSD 1TB
- 外付けディスプレイ
- チャネル開設のオンチェーン手数料 6.69円/チャネル
- 開設料 223sats
- 223sats * BTC市場価格0.03円 = 6.69円
固定費用
- 電気代 291.6円/月
- 時間あたりの電力量 0.015kWh
- Raspberry Pi 4 電圧5V、推奨電源容量3.0A
- https://www.raspberrypi.com/documentation/computers/raspberry-pi.html#power-supply
- kWh単価27円
- 0.015kWh * kWh単価27円 * 1ヶ月の時間720h = 291.6円
損益分岐点
- 月あたりの電気代を上回るために9,720sats(291.6円)/月以上の収益が必要である。
- ハードウェア費用回収のために0.01333333BTC(133万sats) = 40,000円の収益が必要である。
費用回収シナリオ例
アウトバウンドキャパに1BTCをデポジットしたAさんを例にする。1BTCは初心者とは言えないと思うが、このくらい原資を用意しないと費用回収の話がしづらいという裏事情がある。チャネル選択やルーティング戦略は何もしていない仮定である。ノード運用次第であることは言うまでもないので今回は要素や式を洗い出すことが主目的で一つ一つの変数の値は参考までに。
変数設定
- インバウンドを同額用意して合計キャパを2BTCとする。
- 1チャネルあたり5m satsで40チャネル開設する。
- チャネル開設費用 223sats * 40チャネル = 8,920sats
- 初期費用合計 1,333,333sats + 8,920sats = 1,342,253sats
- 一回あたり平均ルーティング量 = 100,000sats
- 1チャネルあたり平均アウトバウンド数/日 = 2
- 1チャネルあたり平均アウトバウンドppm = 50
費用回収地点
- 1日のアウトバウンド量は、 40チャネル * 2本 * 100,000sats = 8m sats
- 手数料収入は、8m sats * 0.005%(50ppm) = 400sats/日。月換算すると12,000sats/月
- 電気代を差し引くと、12,000sats - 電気代9,720sats =月収益2,280sats(68.4円)
- 初期費用回収まで、1,342,253sats / 2,280sats = 589ヵ月(49年)
- 後述するが電気代差引き前で年利0.14%になる。
理想的なppm
6ヵ月での初期費用回収を目的にしてアウトバウンドppmを求める。
- ひと月あたり、初期費用合計1,342,253sats / 6ヵ月 + 電気代9,720sats = 233,429sats(7,003円)の収益が必要。
- 1日あたり、7,781sats(233円)の収益
- その場合の平均アウトバウンドppmは、 7,781sats(1日の収益量) / 8m sats(1日のアウトバウンド量) * 1m sats(ppm変換係数) = 973ppm
他のファイナンスとの比較
ルーティングノードを運用して手数料収入を得ることは資産運用と捉えることもできる。レンディングやトレードなどの他の資産運用手段とパフォーマンス比較をするなら、デポジットしたアウトバウンドキャパシティに対する手数料収入をAPY換算する。(獲得した手数料はアウトバウンドキャパシティに積み重ねられるので複利と見做せる)
例としてLNDg(v1.3.1)のAPY算出計算式を転載する。見ての通り画面上の表記はAPYなのに中身はAPRになっているので注意だが今回は考え方の参考としてこのまま採用する。
年換算 = 365 / 7 = 52.142857 年利 = (7dayの収益 * 年換算) / アウトバウンドのキャパシティ例えば上記のAさんの費用回収シナリオに当てはめると以下となる。
年利 0.14% = (400sats * 7日 * 年換算)/ 100m sats
電気代を差し引くと 76sats/日となり年利0.027%
もし平均アウトバウンド1000ppmになると8,000sats/日なので年利2.9%になる。 この場合、電気代はほぼ1日で回収されるため差し引いても大差なく7,676sats/日で年利2.8%になる。
考察
以上、BTC市場価格や一日のアウトバウンド量といった重要な数値をいくつか仮置きした上ではあるが、LN手数料の適正水準を考えるための参考材料を提示した。
まず、現在のLNの料金相場は他の決済手段から比べると圧倒的に安いことがわかった。1%でも競争力が十分ありそうなのに0.1%前後で送金することが大半である。
健全な市場発展のためには、ルーティングノードの採算が取れていることが欠かせないと考えるが、残念ながら現在の収益性は低い。ルーティングノードの収益性は仮定に仮定を重ねた見積もりになるが、平均アウトバウンドが1000ppmでようやく個人でも参入できるレベルになるという結論になった。ルーティングノードの立場に立つと、現在の市場平均から大幅な上昇が必要だと考える。
手数料市場は競争のためつねに下方圧力がかかっていて仕様上で可能な0に近づいている。この重力に逆らうためには、1. 需要 > 供給のバランスになること、2. 事業用途での高額買取のチャネルが増えること、の2つの観点を挙げる。1にせよ2にせよネットワークの活用が進むことで発生し、手数料市場の大きな変動機会になるのではないか。他の決済手段と比較すれば10000ppm、1チャネル2500ppmあたりまでは十分に健全な範囲だと考える。
-
 @ 81650982:299380fa
2025-04-30 11:16:42
@ 81650982:299380fa
2025-04-30 11:16:42Let us delve into Monero (XMR). Among the proponents of various altcoins, Monero arguably commands one of the most dedicated followings, perhaps second only to Ethereum. Unlike many altcoins where even investors often harbor speculative, short-term intentions, the genuine belief within the Monero community suggests an inherent appeal to the chain itself.
The primary advantage touted by Monero (and similar so-called "privacy coins") is its robust privacy protection features. The demand for anonymous payment systems, tracing its lineage back to David Chaum, predates even the inception of Bitcoin. Monero's most heavily promoted strength, relative to Bitcoin, is that its privacy features are enabled by default.
This relates to the concept of the "anonymity set." To guarantee anonymity, a user must blend into a crowd of ordinary users. The larger the group one hides within, the more difficult it becomes for an external observer to identify any specific individual. From the perspective of Monero advocates, Bitcoin's default transaction model is overly transparent, clearly revealing the flow of funds between addresses. While repeated mixing can enhance anonymity in Bitcoin, the fact that users must actively undertake such measures presents a significant hurdle. More critically, proponents argue, the very group engaging in such deliberate obfuscation is precisely the group one doesn't want to be associated with for effective anonymity. Hiding requires blending with the ordinary, not merely mixing with others who are also actively trying to hide — the latter, they contend, is akin to criminals mixing only with other criminals.
This is a valid point. For instance, there's a substantial difference between a messenger app offering end-to-end encryption for all communications by default, versus one requiring users to explicitly create a "secret chat" for encryption. While I personally believe that increased self-custody of Bitcoin in personal wallets, acquisition through direct peer-to-peer payments rather than exchange purchases, and the widespread adoption of the Lightning Network would make tracing significantly harder even without explicit mixing efforts, let us concede, for the sake of argument, that Bitcoin's base-layer anonymity might not drastically improve even in such a future scenario.
Nevertheless, Monero's long-term prospects appear considerably constrained when focusing purely on technical limitations, setting aside economic factors or incentive models for now. While discussions on economics can often be countered with "That's just your speculation," technical constraints present more objective facts and leave less room for dispute.
Monero's most fundamental problem is its lack of scalability. To briefly explain how Monero obfuscates the sender: it includes other addresses alongside the true sender's address in the 'from' field and attaches what appears to be valid signatures for all of them. With a default setting of 10 decoys (plus the real spender, making a ring size of 11), the signature size naturally becomes substantially larger than Bitcoin's. Since an observer cannot determine which of the 11 is the true sender, and these decoys are arbitrary outputs selected from the blockchain belonging to other users, anonymity is indeed enhanced. While the sender cannot generate individually valid signatures for the decoy outputs (as they don't own the private keys), the use of a ring signature mathematically proves that one member of the ring authorized the transaction, allowing it to pass network validation.
The critical issue is that this results in transaction sizes several times larger than Bitcoin's. Bitcoin already faces criticism for being relatively expensive and slow. Monero's structure imposes a burden that is multiples greater. One might question the relationship between transaction data size and transaction fees/speed. However, the perceived slowness of blockchains isn't typically due to inefficient code, but rather the strict limitations imposed on block size (or equivalent throughput constraints) to maintain decentralization. Therefore, larger transaction sizes directly translate into throughput limitations and upward pressure on fees. If someone claims Monero fees are currently lower than Bitcoin's, that is merely a consequence of its significantly lower usage. Should Monero's transaction volume reach even a fraction of Bitcoin's, its current architecture would struggle severely under the load.
To address this, Monero implemented a dynamic block size limit instead of a hardcoded one. However, this is not a comprehensive solution. If the block size increases proportionally with usage, a future where Monero achieves widespread adoption as currency — implying usage potentially hundreds, thousands, or even hundreds of thousands of times greater than today — would render the blockchain size extremely difficult to manage for ordinary node operators. Global internet traffic might be consumed by Monero transactions, or at the very least, the bandwidth and storage costs could exceed what individuals can reasonably bear.
Blockchains, by their nature, must maintain a size manageable enough for individuals to run full nodes, necessitating strict block size limits (or equivalent constraints in blockless designs). This fundamental requirement is the root cause of limited transaction speed and rising fees. Consequently, the standard approach to blockchain scaling involves Layer 2 solutions like the Lightning Network. The problem is, implementing such solutions on Monero is extremely challenging.
Layer 2 solutions, while varying in specific implementation details across different blockchains, generally rely heavily on the transparency of on-chain transactions. They typically involve sophisticated smart contracts built upon the ability to publicly verify on-chain states and events. Monero's inherent opacity, hiding crucial details of on-chain transactions, makes it exceptionally difficult for two mutually untrusting parties to reach the necessary consensus and cryptographic agreements (like establishing payment channels with verifiable state transitions and dispute mechanisms) that underpin such Layer 2 systems. The fact that Monero, despite existing for several years, still lacks a functional, widely adopted Layer 2 implementation suggests that this remains an unsolved and technically formidable challenge. While theoretical proposals exist, their real-world feasibility remains uncertain and would likely require significant breakthroughs in cryptographic protocol design.
Furthermore, Monero faces another severe scaling challenge related to its core privacy mechanism. As mentioned, decoy outputs are used to obscure the true sender. An astute observer might wonder: If a third party cannot distinguish the real spender, could the real spender potentially double-spend their funds later? Or could someone's funds become unusable simply because they were chosen as a decoy in another transaction? Naturally, Monero's developers anticipated this. The solution employed involves key images.
When an output is genuinely spent within a ring signature, a unique cryptographic identifier called a "key image" is derived from the real output and the spender's private key. This derivation is one-way (the key image cannot be used to reveal the original output or key). This key image is recorded on the blockchain. When validating a new transaction, the network checks if the submitted key image has already appeared in the history. If it exists, the transaction is rejected as a double-spend attempt. The crucial implication is that this set of used key images can never be pruned. Deleting historical key images would directly enable double-spending.
Therefore, Monero's state size — the data that full nodes must retain and check against — grows linearly and perpetually with the total number of transactions ever processed on the network.
Summary In summary, Monero faces critical technical hurdles:
Significantly Larger Transaction Sizes: The use of ring signatures for anonymity results in transaction data sizes several times larger than typical cryptocurrencies like Bitcoin.
Inherent Scalability Limitations: The large transaction size, combined with the necessity of strict block throughput limits to preserve decentralization, creates severe scalability bottlenecks regarding transaction speed and cost under significant load. Dynamic block sizes, while helpful in the short term, do not constitute a viable long-term solution for broad decentralization.
Layer 2 Implementation Difficulty: Monero's fundamental opacity makes implementing established Layer 2 scaling solutions (like payment channels) extremely difficult with current approaches. The absence of a widely adopted solution to date indicates that this remains a major unresolved challenge.
Unprunable, Linearly Growing State: The key image mechanism required to prevent double-spending mandates the perpetual storage of data proportional to the entire transaction history, unlike Bitcoin where nodes can prune historical blocks and primarily need to maintain the current UTXO set (whose size depends on usage patterns, not total history).
These technical constraints raise legitimate concerns about Monero's ability to scale effectively and achieve widespread adoption in the long term. While ongoing research may alleviate some of these issues, at present they represent formidable challenges that any privacy-focused cryptocurrency must contend with.
-
 @ 3589b793:ad53847e
2025-04-30 10:53:29
@ 3589b793:ad53847e
2025-04-30 10:53:29※本記事は別サービスで2022年5月22日に公開した記事の移植です。
Happy 🍕 Day's Present
まだ邦訳版が出版されていませんがこれまでのシリーズと同じくGitHubにソースコードが公開されています。なんと、現在のライセンスでは個人使用限定なら翻訳や製本が可能です。Macで、翻訳にはPDFをインプットにできるDeepLを用いた環境で、インスタントに製本してKindleなどで読めるようにする方法をまとめました。
手順の概要
- Ruby環境を用意する
- PDF作成ツールをセットアップする
- GitHubのリポジトリを自分のPCにクローンする
- asciidocをPDFに変換する
- DeepLを節約するためにPDFを結合する
- DeepLで翻訳ファイルを作る
- 一冊に製本する
この手法の強み・弱み
翻訳だけならPDFを挟まなくてもGithubなどでプレビューできるコンパイル後のドキュメントの文章をコピーしてDeepLのWebツールにペーストすればよいですが、原著のペーパーブックで438ページある大容量です。熟練のコピペ職人でも年貢を納めて後進(機械やソフトウェア)に道を譲る刻ではないでしょうか?ただし、Pros/Consがあります。
Pros
- 一冊の本になるので毎度のコピペ作業がいらない
- Pizzaを食べながらタブレットやKindleで読める
- 図や表が欠落しない(プロトコルの手順を追った解説が多いため最大の動機でした)
- 2022/6/16追記: DeepLの拡張機能がアップデートされウェブページの丸ごと翻訳が可能になりました。よってウェブ上のgithubの図表付きページをそのまま翻訳できます。
Cons
- Money is power(大容量のためDeepLの有料契約が必要)
- ページを跨いだ文章が統合されずに不自然な翻訳になる(仕様です)
- ~~翻訳できない章が一つある(解決方法がないか調査中です。DeepLさんもっとエラーメッセージ出してくれ。Help me)~~ DeepLサポートに投げたら翻訳できるようになりました。
詳細ステップ
0.Ruby環境を用意する
asciidoctorも新しく入れるなら最新のビルドで良いでしょう。
1.PDF作成ツールをセットアップする
$ gem install asciidoctor asciidoctor-pdf $ brew install gs2.GitHubのリポジトリを自分のPCにクローンする
どこかの作業ディレクトリで以下を実行する
$ git clone git@github.com:lnbook/lnbook.git $ cd lnbook3.asciidocをPDFに変換する
ワイルドカードを用いて本文を根こそぎPDF化します。
$ asciidoctor-pdf 0*.asciidoc 1*.asciidocいろいろ解析の警告が出ますが、ソースのasciidocを弄んでいくなりawsomeライブラリを導入すれば解消できるはずです。しかし如何せん量が多いので心が折れます。いったん無視して"Done is better than perfect"精神で最後までやり切りましょう。そのままGO!
また、お好みに合わせて、htmlで用意されている装丁用の部品も準備しましょう。私は表紙のcover.htmlをピックしました。ソースがhtmlなのでasciidoctorを通さず普通にPDFへ変換します。https://qiita.com/chenglin/items/9c4ed0dd626234b71a2c
4.DeepLを節約するためにPDFを結合する
DeepLでは課金プラン毎に翻訳可能なファイル数が設定されている上に、一本あたりの最大ファイルサイズが10MBです。また、翻訳エラーになる章が含まれていると丸ごとコケます。そのためPDCAサイクルを回し、最適なファイル数を手探りで見つけます。以下が今回導出した解となります。
$ gs -q -dNOPAUSE -dBATCH -sDEVICE=pdfwrite -sOutputFile=output_1.pdf 01_introduction.pdf 02_getting_started.pdf 03_how_ln_works.pdf 04_node_client.pdf 05_node_operations.pdf$gs -q -dNOPAUSE -dBATCH -sDEVICE=pdfwrite -sOutputFile=output_2_1.pdf 06_lightning_architecture.pdf 07_payment_channels.pdf 08_routing_htlcs.pdf$gs -q -dNOPAUSE -dBATCH -sDEVICE=pdfwrite -sOutputFile=output_2_2.pdf 09_channel_operation.pdf 10_onion_routing.asciidoc$ gs -q -dNOPAUSE -dBATCH -sDEVICE=pdfwrite -sOutputFile=output_3.pdf 11_gossip_channel_graph.pdf 12_path_finding.pdf 13_wire_protocol.pdf 14_encrypted_transport.pdf 15_payment_requests.pdf 16_security_privacy_ln.pdf 17_conclusion.pdf5. DeepLで翻訳ファイルを作る
PDFファイルを真心を込めた手作業で一つ一つDeepLにアップロードしていき翻訳ファイルを作ります。ファイル名はデフォルトの
[originalName](日本語).pdfのままにしています。6. 一冊に製本する
表紙 + 本文で作成する例です。
$ gs -q -dNOPAUSE -dBATCH -sDEVICE=pdfwrite -sOutputFile=mastering_ln_jp.pdf cover.pdf "output_1 (日本語).pdf" "output_2_1 (日本語).pdf" "output_2_2 (日本語).pdf" "output_3 (日本語).pdf"コングラチュレーションズ🎉

あなたは『Mastering the Lightning Network』の日本語版を手に入れた!個人使用に限り、あとは煮るなり焼くなりEPUBなりkindleへ送信するなり好き放題だ。
-
 @ a5142938:0ef19da3
2025-04-30 10:34:58
@ a5142938:0ef19da3
2025-04-30 10:34:58Dilling is a Danish brand that creates wool, silk, and organic cotton clothing for the whole family.
Natural materials used in products
- Cotton (organic)
- Natural latex (OEKO-TEX ®)
- Silk
- Wool (merino, alpaca)
⚠️ Warning: some products from this brand (especially Clothes – socks, jackets, thongs, shorts) contain non-natural materials, including:
- Elastane, spandex, lycra
- Polyamide, nylon (recycled nylon)
- Polyester (recycled)
Categories of products offered
-
Clothing: men, women, children, babies, underwear, t-shirts, tank tops, dresses, jackets, trousers, shorts, sweaters, cardigans, bodysuits, jumpsuits, panties, briefs, boxers...
👉 See natural products from this brand
Other information
- Nordic Swan ecolabel (dye)
- Made in Lithuania (cutting and sewing)
- Made in Denmark (dye)
- Made in Europe
👉 Learn more on the brand's website
This article is published on origin-nature.com 🌐 Voir cet article en français
📝 You can contribute to this entry by suggesting edits in comments.
🗣️ Do you use this product? Share your opinion in the comments.
⚡ Happy to have found this information? Support the project by making a donation to thank the contributors.
-
 @ e4950c93:1b99eccd
2025-04-30 10:34:08
@ e4950c93:1b99eccd
2025-04-30 10:34:08Dilling est une marque danoise qui crée des vêtements en laine, soie et coton biologique pour toute la famille.
Matières naturelles utilisées dans les produits
- Coton (biologique)
- Laine (mérinos, alpaga)
- Latex naturel (OEKO-TEX ®)
- Soie
⚠️ Attention, certains produits de cette marque (notamment les Vêtements - chaussettes, vestes, strings, shorts) contiennent des matières non naturelles, dont :
- Elasthanne
- Polyamide, nylon (nylon recyclé)
- Polyester (recyclé)
Catégories de produits proposés
-
Vêtements : homme, femme, enfant, bébé, sous-vêtements, t-shirts, débardeurs, robes, vestes, pantalons, shorts, pulls, gilets, bodies, combinaisons, culottes, slips, boxers...
👉 Voir les produits naturels de cette marque
Autres informations
- Ecolabel Nordic Swan (teintures)
- Fabriqué en Lituanie (coupe et couture)
- Fabriqué au Danemark (teintures)
- Fabriqué en Europe
👉 En savoir plus sur le site de la marque
Cet article est publié sur origine-nature.com 🌐 See this article in English
📝 Vous pouvez contribuer à cette fiche en suggérant une modification en commentaire.
🗣️ Vous utilisez ce produit ? Partagez votre avis en commentaire.
⚡ Heureu-x-se de trouver cette information ? Soutenez le projet en faisant un don, pour remercier les contribut-eur-ice-s.
-
 @ d08c9312:73efcc9f
2025-04-30 09:59:52
@ d08c9312:73efcc9f
2025-04-30 09:59:52Resolvr CEO, Aaron Daniel, summarizes his keynote speech from the Bitcoin Insurance Summit, April 26, 2025
Introduction
At the inaugural Bitcoin Insurance Summit in Miami, I had the pleasure of sharing two historical parallels that illuminate why "Bitcoin needs insurance, and insurance needs Bitcoin." The insurance industry's reactions to fire and coffee can help us better understand the profound relationship between emerging technologies, risk management, and commercial innovation.
Fire: Why Bitcoin Needs Insurance
The first story explores how the insurance industry's response to catastrophic urban fires shaped modern building safety. Following devastating events like the Great Fire of London (1666) and the Great Chicago Fire (1871), the nascent insurance industry began engaging with fire risk systematically.
Initially, insurers offered private fire brigades to policyholders who displayed their company's fire mark on their buildings. This evolved into increasingly sophisticated risk assessment and pricing models throughout the 19th century:
- Early 19th century: Basic risk classifications with simple underwriting based on rules of thumb
- Mid-19th century: Detailed construction types and cooperative sharing of loss data through trade associations
- Late 19th/Early 20th century: Scientific, data-driven approaches with differentiated rate pricing
The insurance industry fundamentally transformed building construction practices by developing evidence-based standards that would later inform regulatory frameworks. Organizations like the National Board of Fire Underwriters (founded 1866) and Underwriters Laboratories (established 1894) tested and standardized new technologies, turning seemingly risky innovations like electricity into safer, controlled advancements.
This pattern offers a powerful precedent for Bitcoin. Like electricity, Bitcoin represents a new technology that appears inherently risky but has tremendous potential for society. By engaging with Bitcoin rather than avoiding it, the insurance industry can develop evidence-based standards, implement proper controls, and ultimately make the entire Bitcoin ecosystem safer and more robust.
Coffee: Why Insurance Needs Bitcoin
The second story reveals how coffee houses in 17th-century England became commercial hubs that gave birth to modern insurance. Nathaniel Canopius brewed the first documented cup of coffee in England in 1637. But it wasn't until advances in navigation and shipping technology opened new trade lanes that coffee became truly ubiquitous in England. Once global trade blossomed, coffee houses rapidly spread throughout London, becoming centers of business, information exchange, and innovation.
In 1686, Edward Lloyd opened his coffee house catering to sailors, merchants, and shipowners, which would eventually evolve into Lloyd's of London. Similarly, Jonathan's Coffee House became the birthplace of what would become the London Stock Exchange.
These coffee houses functioned as information networks where merchants could access shipping news and trade opportunities, as well as risk management solutions. They created a virtuous cycle: better shipping technology brought more coffee, which fueled commerce and led to better marine insurance and financing, which in turn improved global trade.
Today, we're experiencing a similar technological and financial revolution with Bitcoin. This digital, programmable money moves at the speed of light and operates 24/7 as a nearly $2 trillion asset class. The insurance industry stands to benefit tremendously by embracing this innovation early.
Conclusion
The lessons from history are clear. Just as the insurance industry drove safety improvements by engaging with fire risk, it can help develop standards and best practices for Bitcoin security. And just as coffee houses created commercial networks that revolutionized finance, insurance, and trade, Bitcoin offers new pathways for global commerce and risk management.
For the insurance industry to remain relevant in a rapidly digitizing world, it must engage with Bitcoin rather than avoid it. The companies that recognize this opportunity first will enjoy significant advantages, while those who resist change risk being left behind.
The Bitcoin Insurance Summit represented an important first step in creating the collaborative spaces needed for this transformation—a modern version of those innovative coffee houses that changed the world over three centuries ago.
View Aaron's full keynote:
https://youtu.be/eIjT1H2XuCU
For more information about how Resolvr can help your organization leverage Bitcoin in its operations, contact us today.
-
 @ 4e616576:43c4fee8
2025-04-30 09:57:29
@ 4e616576:43c4fee8
2025-04-30 09:57:29asdf
-
 @ 4e616576:43c4fee8
2025-04-30 09:48:05
@ 4e616576:43c4fee8
2025-04-30 09:48:05asdfasdflkjasdf
-
 @ 4e616576:43c4fee8
2025-04-30 09:42:33
@ 4e616576:43c4fee8
2025-04-30 09:42:33lorem ipsum
-
 @ e4950c93:1b99eccd
2025-04-30 09:29:25
@ e4950c93:1b99eccd
2025-04-30 09:29:25 -
 @ a5142938:0ef19da3
2025-04-30 09:29:49
@ a5142938:0ef19da3
2025-04-30 09:29:49 -
 @ e4950c93:1b99eccd
2025-04-30 09:28:38
@ e4950c93:1b99eccd
2025-04-30 09:28:38 -
 @ e4950c93:1b99eccd
2025-04-30 09:27:09
@ e4950c93:1b99eccd
2025-04-30 09:27:09 -
 @ e4950c93:1b99eccd
2025-04-30 09:26:33
@ e4950c93:1b99eccd
2025-04-30 09:26:33 -
 @ e4950c93:1b99eccd
2025-04-30 09:24:29
@ e4950c93:1b99eccd
2025-04-30 09:24:29 -
 @ e4950c93:1b99eccd
2025-04-30 09:23:25
@ e4950c93:1b99eccd
2025-04-30 09:23:25 -
 @ e4950c93:1b99eccd
2025-04-30 09:21:52
@ e4950c93:1b99eccd
2025-04-30 09:21:52 -
 @ a5142938:0ef19da3
2025-04-30 09:28:10
@ a5142938:0ef19da3
2025-04-30 09:28:10 -
 @ e4950c93:1b99eccd
2025-04-30 09:20:50
@ e4950c93:1b99eccd
2025-04-30 09:20:50Qu'est-ce qu'une matière naturelle ? La question fait débat, et chacun-e privilégiera ses propres critères. Voici comment les matières sont classées sur ce site. La liste est régulièrement mise à jour en fonction des produits ajoutés. N'hésitez pas à partager votre avis !
✅ Matières naturelles
Matières d'origine végétale, animale ou minérale, sans transformation chimique altérant leur structure moléculaire.
🌱 Principaux critères : - Biodégradabilité - Non-toxicité - Présence naturelle nécessitant le minimum de transformation
🔍 Liste des matières naturelles : - Bois - Cellulose régénérée (cupra, lyocell, modal, viscose) - Chanvre - Coton - Cuir - Latex naturel, caoutchouc - Liège - Lin - Laine - Métal - Soie - Terre - Verre - … (Autres matières)
⚠️ Bien que "naturelles", ces matières peuvent générer des impacts négatifs selon leurs conditions de production (pollution par pesticides, consommation d’eau excessive, traitement chimique, exploitation animale…). Ces impacts sont mentionnés sur la fiche de chaque matière.
Les versions biologiques de ces matières (sans traitement chimique, maltraitance animale, etc.) sont privilégiées pour référencer les produits sur ce site, tel qu'indiqué sur la fiche de chaque matière (à venir).
Les versions conventionnelles ne sont référencées que tant que lorsqu'il n'a pas encore été trouvé d'alternative plus durable pour cette catégorie de produits.
🚫 Matières non naturelles
Matières synthétiques ou fortement modifiées, souvent issues de la pétrochimie.
📌 Principaux problèmes : - Toxicité et émissions de microplastiques - Dépendance aux énergies fossiles - Mauvaise biodégradabilité
🔍 Liste des matières non naturelles : - Acrylique - Élasthanne, lycra, spandex - Polyamides, nylon - Polyester - Silicone - … (Autres matières)
⚠️ Ces matières ne sont pas admises sur le site. Néanmoins, elles peuvent être présentes dans certains produits référencés lorsque :
- elles sont utilisées en accessoire amovible (ex. : élastiques, boutons… généralement non indiqué dans la composition par la marque) pouvant être retiré pour le recyclage ou compostage, et
- aucune alternative 100 % naturelle n’a encore été identifiée pour cette catégorie de produits.
Dans ce cas, un avertissement est alors affiché sur la fiche du produit.
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ a5142938:0ef19da3
2025-04-30 09:27:29
@ a5142938:0ef19da3
2025-04-30 09:27:29 -
 @ 6c67a3f3:b0ebd196
2025-04-30 08:40:15
@ 6c67a3f3:b0ebd196
2025-04-30 08:40:15To explore the link between Gavekal-style platform companies and the US dollar's status as the global reserve currency, we need to view the problem through multiple interlocking lenses—monetary economics, network effects, macro-political architecture, financial plumbing, and the logic of platform capitalism. Gavekal’s conceptual framework focuses heavily on capital-light, scalable businesses that act as platforms rather than traditional linear firms. Their model emphasizes "soft" balance sheets, asset-light capital formation, high intangible value creation, and the scaling of network effects. These traits dovetail in complex ways with the structural position of the United States in the global financial system.
What follows is a broad and recursive dissection of how these two phenomena—platform companies and reserve currency status—are mutually constitutive, each feeding the other, both directly and via second- and third-order effects.
- The Core Metaphor: Platforms and Monetary Hegemony
At its root, a platform is a meta-infrastructure—a set of protocols and affordances that enable others to interact, produce, consume, and transact. The dollar, as reserve currency, functions in an analogous way. It is not merely a medium of exchange but a platform for global commerce, pricing, credit formation, and risk transfer.
In this metaphor, the United States is not just a country but a platform operator of global finance. And like Amazon or Apple, it enforces terms of access, extracts rents, underwrites standardization, and benefits disproportionately from marginal activity across its ecosystem. Just as Apple's App Store tax or Amazon’s marketplace fee are invisible to most users, the dollar hegemon collects global seigniorage, institutional influence, and capital inflow not as overt tolls, but through the structuring of default behaviors.
This already suggests a deep isomorphism between platform logic and reserve currency logic.
- Capital-Light Scaffolding and Global Dollar Demand
Gavekal-style firms (e.g. Apple, Google, Microsoft) have something unusual in common: they generate high levels of free cash flow with low reinvestment needs. That is, they do not soak up global capital so much as recycle it outward, often via share buybacks or bond issuance. This creates a paradox: they are net issuers of dollar-denominated financial claims even as they are net accumulators of global income.
Now map this onto the structure of reserve currency systems. The US must export financial assets to the world (Treasuries, MBS, high-grade corporates) in order to satisfy foreign demand for dollar claims. But traditional exporting economies (e.g. Germany, China) create excess savings they must park in safe dollar assets, while running trade surpluses.
Gavekal-style firms allow the US to square a circle. The US economy does not need to run trade surpluses, because its platform companies export “intangible products” at near-zero marginal cost (e.g. iOS, search ads, cloud infrastructure), generate global rents, and then repatriate those earnings into US financial markets. These flows offset the US current account deficit, plugging the "Triffin dilemma" (the need to run deficits to supply dollars while maintaining credibility).
Thus, platform companies act as soft exporters, replacing industrial exports with intangible, rent-generating capital. Their global cash flows are then recycled through dollar-denominated assets, providing the scale and liquidity necessary to sustain reserve status.
- The Hierarchy of Money and Intangible Collateral
Modern monetary systems rest on a hierarchy of collateral—some assets are more money-like than others. US Treasuries sit at the apex, but AAA-rated corporates, especially those with global footprints and balance-sheet integrity, are close behind.
Platform firms are unique in their capacity to create high-quality, globally accepted private collateral. Apple’s bonds, Microsoft’s equity, and Google’s cash reserves function as synthetic dollar instruments, widely accepted, liquid, and backed by consistent income streams. These firms extend the reach of the dollar system by providing dollar-denominated assets outside the banking system proper, further embedding dollar logic into global capital flows.
Moreover, platform companies often internalize global tax arbitrage, holding cash offshore (or in tax-efficient jurisdictions) and issuing debt domestically. This creates a loop where foreign dollar claims are used to finance US domestic consumption or investment, but the underlying income comes from global activities. This is reverse colonization through intangibles.
- Winner-Take-Most Dynamics and Network Effects in Dollar Space
The dollar system, like platform capitalism, obeys a power-law distribution. Liquidity begets liquidity. The more that dollar instruments dominate global trade, the more pricing, settlement, and hedging mechanisms are built around them. This self-reinforcing loop mimics network effect entrenchment: the more users a platform has, the harder it is to displace.
Reserve currency status is not a product of GDP share alone. It’s a function of infrastructure, institutional depth, legal recourse, capital mobility, and networked habits. Likewise, Apple’s dominance is not just about better phones, but about developer lock-in, payment systems, user base, and design mores.
Gavekal-style firms reinforce this pattern: their software platforms often denominate activity in dollars, price in dollars, store value in dollars, and link digital labor across borders into dollar-based flows. YouTube creators in Jakarta are paid in dollars. AWS charges Chilean entrepreneurs in dollars. App Store remittances to Kenya settle in dollars.
This creates global micro-tributaries of dollar flows, all of which aggregate into the larger river that sustains dollar supremacy.
- Geopolitical Power Projection by Private Means
Traditional hegemonic systems project power through military, legal, and diplomatic tools. But platforms provide soft control mechanisms. The US can influence foreign populations and elite behavior not merely through embassies and aircraft carriers, but through tech platforms that shape discourse, information flows, norms, and cognitive frames.
This is a kind of cognitive imperialism, in which reserve currency status is bolstered by the fact that cultural products (e.g. Netflix, social media, productivity tools) are encoded in American norms, embedded in American legal systems, and paid for in American currency.
The platform firm thus becomes a shadow extension of statecraft, whether or not it sees itself that way. Dollar hegemony is reinforced not only by Treasury markets and SWIFT access, but by the gravity of the mental ecosystem within which the global bourgeoisie operates. To earn, spend, invest, create, and dream within American-built systems is to keep the dollar central by default.
- Second-Order Effects: The Intangibility Ratchet and Global Liquidity Traps
An overlooked consequence of Gavekal-style platform dominance is that global capital formation becomes disembodied. That is, tangible projects—factories, infrastructure, energy systems—become less attractive relative to financial or intangible investments.
As a result, much of the world, especially the Global South, becomes capital-starved even as capital is abundant. Why? Because the returns on tangible investment are less scalable, less defensible, and less liquid than buying FAANG stocks or US Treasuries.
This results in a liquidity trap at the global scale: too much capital chasing too few safe assets, which only reinforces demand for dollar instruments. Meanwhile, intangible-intensive firms deepen their moats by mining attention, user data, and payment flows—often without any large-scale employment or industrial externalities.
Thus, Gavekal-style firms create asymmetric global development, further concentrating economic gravitational mass in the dollar zone.
- Feedback Loops and Fragility
All of this breeds both strength and fragility. On one hand, platform firm cash flows make the dollar system seem robust—anchored in cash-generative monopolies with global reach. On the other hand, the system becomes narrower and more brittle. When so much of global liquidity is intermediated through a few firms and the sovereign system that hosts them, any attack on these nodes—financial, legal, technological, or geopolitical—could unseat the equilibrium.
Moreover, platform logic tends to reduce systemic redundancy. It optimizes for efficiency, not resilience. It centralizes control, narrows option sets, and abstracts real production into code. If the dollar system ever loses credibility—through inflation, sanctions overreach, geopolitical backlash, or platform fatigue—the network effects could reverse violently.
- Conclusion: The Intangible Empire
The United States today operates an empire of intangibles, in which reserve currency status and platform firm dominance are co-constituted phenomena. Each reinforces the other:
Platform firms channel global rents into dollar instruments.
The dollar system provides legal scaffolding, liquidity, and pricing infrastructure for these firms.
Global user bases are conditioned into dollar-denominated interaction by default.
Financial markets treat platform firms as synthetic sovereigns: safe, liquid, predictable.
What is left is a cybernetic loop of financialized cognition: the dollar is strong because platform firms dominate, and platform firms dominate because the dollar is strong.
This loop may persist longer than many expect, but it is not permanent. Its unravelling, when it comes, will likely not be driven by any single actor, but by the erosion of symbolic power, the emergence of parallel platforms, or the ecological unsustainability of the model. But for now, the Gavekal firm and the dollar empire are the two poles of a single global architecture—seen best not as cause and effect, but as the two faces of the same Janus coin.
-
 @ 86d4591f:a987c633
2025-04-30 07:51:50
@ 86d4591f:a987c633
2025-04-30 07:51:50Once upon a time, power wore a crown. Then it wore a top hat. Today, it wears a hoodie and speaks in sanitized mission statements about connection, safety, and user experience. But make no mistake: this is empire — softened, digitized, gamified, but empire all the same.
The old robber barons built railroads and refineries. They captured the flow of goods and oil. The new ones build feeds and filters. They’ve captured the flow of attention, of meaning, of reality itself.
We used to trade in commodities; now we trade in perception. The platform is the factory, your data the raw material, your behavior the product. And like all robber barons, these new lords of code and cloud mask extraction in the language of progress.
They promise frictionless connection while selling surveillance. They promise community while cultivating dependency. They promise democratization while algorithmically anointing kings and silencing dissidents. A swipe, a like, a follow — every gesture is monetized. Every word is moderated. Every post is subject to invisible whims dressed up as “community standards.”
And we? We scroll through curated realities in gilded cages. We call it the feed, but what is it feeding? We’re not the customers — we’re the cattle. The economy has shifted from production to prediction, from ownership to access, from sovereignty to servitude.
The invisible hand now wears visible chains.
But rebellion brews — not as a riot, but as a protocol. Nostr: No gatekeepers. No kill switches. No boardroom behind the curtain. Just a blunt, defiant tool — a new printing press for the digital age.
Nostr isn’t slick. It doesn’t care about onboarding funnels or quarterly growth. It cares about freedom. It is infrastructure for speech that doesn’t ask permission. A raw wire of intent between human beings. An insurgent standard in a world of walled gardens.
This is not just about apps. This is about autonomy. About reclaiming the digital commons. About refusing to let five companies in Silicon Valley draw the borders of acceptable thought.
So plant your flag. Publish what they won’t. Build what they fear. This is not nostalgia for the early web — it is the refusal to let the next web become a prison wrapped in personalization.
The New Robber Barons control the rails of perception.
But we are building tunnels.
Protocol over platform.
Signal over spectacle.
Freedom over frictionless servitude.
Speak freely. Build fiercely. The territory is ours to reclaim.
-
 @ edeb837b:ac664163
2025-04-30 07:25:41
@ edeb837b:ac664163
2025-04-30 07:25:41We’re incredibly proud to announce that NVSTly has won the Gold Stevie® Award for Tech Startup of the Year – Services in the 23rd Annual American Business Awards®! Winners were officially revealed on April 24th, and this recognition is a powerful validation of the innovation, impact, and passion our team continues to deliver every day.
More than 250 professionals worldwide participated in the judging process to select this year’s Stevie Award winners.
We were honored among a competitive field of over 3,600 nominations from organizations across nearly every industry. NVSTly was recognized for redefining social investing with a first-of-its-kind platform that empowers traders to track, share, and automatically broadcast trades and buy/sell alerts across nearly every financial market—including stocks, options, forex, and crypto—with futures support coming soon.
The Stevie judges praised NVSTly for “creating an ecosystem that blends brokerage integration, real-time trade tracking, and community engagement into one seamless experience,” and noted that “NVSTly’s social investing model is paving the way for a new generation of retail traders.”
This award comes at a time of major momentum for us:
:star: 4.9-star rating on the iOS App Store :star: 5.0-star rating on Google Play :star: 4.9-star rating on Product Hunt :star: 5.0-star rating on Disboard for our 51,000+ strong Discord trading community :star: 4.98-star rating on Top.gg — making our trading bot the highest-rated and only one of its kind in the finance category
And it’s not our first recognition. NVSTly has previously earned:
:trophy: Fintech Product of the Week on Product Hunt (2023 & 2024) :trophy: People’s Choice Award at the 2024 Benzinga Fintech Awards
We’re still just getting started. Our mobile and web platform is used by over 10,000 traders, and our brokerage integrations now include Webull, with Moomoo support launching in the coming days and Schwab integration already underway. These integrations allow traders to automate buy/sell alerts directly to their NVSTly followers and across Discord and supported social platforms.
“Winning a Gold Stevie is an incredible milestone that reflects the hard work of our team and the unwavering support of our community,” said Rich Watson, CEO of NVSTly. “We’ve always believed that trading should be transparent, collaborative, and empowering—and this recognition confirms we’re building something truly impactful.”
More than 3,600 nominations from organizations of all sizes and in virtually every industry were submitted this year for consideration in a wide range of categories, including Startup of the Year, Executive of the Year, Best New Product or Service of the Year, Marketing Campaign of the Year, Thought Leader of the Year, and App of the Year, among others. NVSTly was nominated in the Tech Startup of the Year – Services category for financial technology startups.
We’ll be officially celebrated at the 2025 Stevie Awards gala in New York City on June 10, but today, we’re celebrating with the traders, creators, investors, and builders who have believed in our mission from day one. (It's still undecided if anyone representing NVSTly will attend the award event to be presented or award.)
Thank you for being part of this journey. We’re just getting started.
-
 @ 8d34bd24:414be32b
2025-04-30 04:55:06
@ 8d34bd24:414be32b
2025-04-30 04:55:06My post on the signs of the End Times according to Jesus got way too long. It was too long to email, so I had to split it into two posts. I recommend reading Part 1 before continuing. You also may want to read my post Signs of the Times: Can We Know? I also want to reiterate my caveat. Although I believe the signs suggests the Rapture and the Tribulation are coming soon, no one can know the exact hour or day, so I can’t say exactly what soon means (days, months, years, decades, or possibly more).
As a review here is the primary passage where Jesus answers His disciples’ question “What will be the sign of Your coming, and of the end of the age?” Below the passage is the 8 signs He gave. We will pick up with point 5.
Jesus’s Signs of the End
As He was sitting on the Mount of Olives, the disciples came to Him privately, saying, “Tell us, when will these things happen, and what will be the sign of Your coming, and of the end of the age?”
And Jesus answered and said to them, “See to it that no one misleads you. For many will come in My name, saying, ‘I am the Christ,’ and will mislead many. You will be hearing of wars and rumors of wars. See that you are not frightened, for those things must take place, but that is not yet the end. For nation will rise against nation, and kingdom against kingdom, and in various places there will be famines and earthquakes. But all these things are merely the beginning of birth pangs.
“Then they will deliver you to tribulation, and will kill you, and you will be hated by all nations because of My name. At that time many will fall away and will betray one another and hate one another. Many false prophets will arise and will mislead many. Because lawlessness is increased, most people’s love will grow cold. But the one who endures to the end, he will be saved. This gospel of the kingdom shall be preached in the whole world as a testimony to all the nations, and then the end will come. (Matthew 24:3-14) {emphasis mine}
Here is my summary of the signs Jesus said would identify the coming of the 7 year Tribulation:
-
Wars and rumors of wars. (Matthew 24:6a)
-
Famines (Matthew 24:7)
-
Earthquakes (Matthew 24:7).
-
Israel will be attacked and will be hated by all nations (Matthew 24:9)
-
Falling away from Jesus (Matthew 24:10)
-
Many Misled (Matthew 24:10)
-
People’s love will grow cold (Matthew 24:12)
-
Gospel will be preached to the whole world (Matthew 24:14)
The first 4 signs relate more to physical and political signs that the end times are near. The last 4 signs relate to spiritual matters.
5. Falling away from Jesus
One thing we are definitely seeing today is a falling away. This is most prevalent in the historically Christian Western nations in Europe and North America (and to a lesser, but significant, extent South America).
But the Spirit explicitly says that in later times some will fall away from the faith, paying attention to deceitful spirits and doctrines of demons, by means of the hypocrisy of liars seared in their own conscience as with a branding iron, men who forbid marriage and advocate abstaining from foods which God has created to be gratefully shared in by those who believe and know the truth. (1 Timothy 4:1-3) {emphasis mine}
For centuries Europe and North America were full of Christians or at least cultural Christians. Today that is no longer true. Christians are even being considered the hateful, criminal class and things like praying outside an abortion clinic is being punished with jail time. The Western nations can no longer be called Christian nations.
There are still a relatively large number of Americans who call themselves Christians, but the majority do not have a biblical worldview or live lives more like Christ than non-Christians.
“Seven out of 10 US adults call themselves “Christians” and yet only 6 in 100 (6%) actually have a biblical worldview.” In general, most Christian’s worldview does not align with the Bible, according to George Barna Surveys. In the most recent survey they found:
 Many self-proclaimed Christians tend to believe a form of syncretism where they combine certain biblical principles with cultural ideas, scientism, and other religions to make “Christianity” into whatever they want to believe, just as the Bible predicted almost 2,000 years ago.
Many self-proclaimed Christians tend to believe a form of syncretism where they combine certain biblical principles with cultural ideas, scientism, and other religions to make “Christianity” into whatever they want to believe, just as the Bible predicted almost 2,000 years ago.I solemnly charge you in the presence of God and of Christ Jesus, who is to judge the living and the dead, and by His appearing and His kingdom: preach the word; be ready in season and out of season; reprove, rebuke, exhort, with great patience and instruction. For the time will come when they will not endure sound doctrine; but wanting to have their ears tickled, they will accumulate for themselves teachers in accordance to their own desires, and will turn away their ears from the truth and will turn aside to myths. (2 Timothy 4:1-4) {emphasis mine}
This is both a sign of the end times and something to watch in our own lives. I pray you will analyze your own life and beliefs in the light of the Bible to make sure you aren’t integrating unbiblical principles into your worldview.
6. Many Misled
Closely related to the falling away is that many will be misled. We have reached the point that the majority of so-called churches teach ideas and principles contrary to the Bible. They focus more on entertainment, self-help, and making everyone feel good about themselves instead of teaching of sin and the need for forgiveness or teaching how to live lives honoring to Christ. Preaching obedience to God has become anathema in most churches.
I am amazed that you are so quickly deserting Him who called you by the grace of Christ, for a different gospel; which is really not another; only there are some who are disturbing you and want to distort the gospel of Christ. But even if we, or an angel from heaven, should preach to you a gospel contrary to what we have preached to you, he is to be accursed! As we have said before, so I say again now, if any man is preaching to you a gospel contrary to what you received, he is to be accursed! (Galatians 1:6-9) {emphasis mine}
We are also lied to and/or misled by politicians, scientists, the media, and the culture in general. We are told that science has disproven the Bible, despite the fact that nothing of the sort has occurred. (See my series on a literal Genesis for some details. icr.org and aig.org are also good resources). Peter warned of this very view.
Know this first of all, that in the last days mockers will come with their mocking, following after their own lusts, and saying, “Where is the promise of His coming? For ever since the fathers fell asleep, all continues just as it was from the beginning of creation.” For when they maintain this, it escapes their notice that by the word of God the heavens existed long ago and the earth was formed out of water and by water, through which the world at that time was destroyed, being flooded with water. But by His word the present heavens and earth are being reserved for fire, kept for the day of judgment and destruction of ungodly men. (2 Peter 3:3-7) {emphasis mine}
God warned us that the last days would be far enough into the future that people would begin to mock the coming of the Tribulation & Millennium and deny the clear truths spoken of in the Bible. We are seeing this everywhere today.
We are also warned to be alert to deception so we, believers, are not misled.
Now we request you, brethren, with regard to the coming of our Lord Jesus Christ and our gathering together to Him, that you not be quickly shaken from your composure or be disturbed either by a spirit or a message or a letter as if from us, to the effect that the day of the Lord has come. Let no one in any way deceive you, for it will not come unless the apostasy comes first, and the man of lawlessness is revealed, the son of destruction, who opposes and exalts himself above every so-called god or object of worship, so that he takes his seat in the temple of God, displaying himself as being God. (2 Thessalonians 2:1-4) {emphasis mine}
7. People’s love will grow cold
You can feel love growing cold day by day. We no longer have community that works together, but have been broken into groups to fight against one another. Instead of friendly, logical debate with those with whom we disagree, we have name calling, hate, and even violence. Children have been taught to hate their parents and parents have been taught to not value children and to murder them for convenience. The church has been split into so many different denominations that I don’t know if it is possible to know what they all are and many are fighting in hateful manner against each other. Hate, depression, and selfishness seem to have taken over the world.
But realize this, that in the last days difficult times will come. For men will be lovers of self, lovers of money, boastful, arrogant, revilers, disobedient to parents, ungrateful, unholy, unloving, irreconcilable, malicious gossips, without self-control, brutal, haters of good, treacherous, reckless, conceited, lovers of pleasure rather than lovers of God, holding to a form of godliness, although they have denied its power; Avoid such men as these. (2 Timothy 3:1-5) {emphasis mine}
Yes, spiritually and physically we are a basket case and it feels like the world is literally falling apart around us. This was predicted almost 2,000 years ago and is all according to God’s perfect plan. Most people turn to God in hard times and we have those in abundance. We do not need to despair, but need to turn to God and lean on Him for wisdom, faith, and peace. This is the birth pangs before the Tribulation and the Second coming of Jesus Christ. The news isn’t all bad, though.
8. Gospel preached to the whole world
The really good news is that the Gospel is being preached around the world. Parts of the world that had never heard the Gospel are hearing it and turning to Jesus.
All the ends of the earth will remember and turn to the Lord , And all the families of the nations will worship before You. (Psalm 22:27) {emphasis mine}
Wycliffe Bible translators is hoping to have at least started Bible translation in every active language by the end of this year (2025)
He says, “It is too small a thing that You should be My Servant To raise up the tribes of Jacob and to restore the preserved ones of Israel; I will also make You a light of the nations So that My salvation may reach to the end of the earth.” (Isaiah 49:6) {emphasis mine}
The Joshua Project tracks nations and people groups to determine which have been reached and which have not. It still looks like there is a large portion of the population that has not received the Gospel, but I also know people who are or have shared the Gospel to some of these people, so this map doesn’t mean that there are no Christians or that the Gospel has not been shared at all, but it does mean many people in these areas have not heard the Gospel and/or, that due to hatred of Christians, it is dangerous to share the Gospel and therefore has to be done slowly, carefully, and privately. Most of these unreached or barely reached people groups are areas that are predominantly Muslim, where those preaching the Gospel or those converting to Christianity are at risk of jail or death sentences.
 As you can see, everything that Jesus said would come before the end is either escalating or here. We need to be ready and work to bring as many people to Christ as possible while we still have the opportunity because Jesus could come for us at any moment.
As you can see, everything that Jesus said would come before the end is either escalating or here. We need to be ready and work to bring as many people to Christ as possible while we still have the opportunity because Jesus could come for us at any moment.Share the Gospel with all those around you. Consider supporting missionaries, especially those going to unreached/least-reached areas. Maybe even consider becoming a missionary yourself. The harvest is plentiful, but the workers are few.
May the God of heaven give us a heart for the lost around the world. May He give us the courage to share the Gospel with all those around us. May He align our priorities with His priorities, so we can be useful tools in the hands of God almighty.
Trust Jesus.
FYI, I hope to write several more articles on the end times (signs of the times, the rapture, the millennium, and the judgement), but I might be a bit slow rolling them out because I want to make sure they are accurate and well supported by Scripture. You can see my previous posts on the end times on the end times tab at trustjesus.substack.com. I also frequently will list upcoming posts.
-
-
 @ a5142938:0ef19da3
2025-04-30 09:26:03
@ a5142938:0ef19da3
2025-04-30 09:26:03 -
 @ fd06f542:8d6d54cd
2025-04-30 03:49:30
@ fd06f542:8d6d54cd
2025-04-30 03:49:30今天介绍一个 long-form 项目,源代码在:
https://github.com/dhalsim/nostr-static
从项目的介绍看也是为了展示kind 30023 long-form的。
Demo
https://blog.nostrize.me
界面还可以:
 {.user-img}
{.user-img}- 支持多个tags
- 支持评论
下面看他自己的介绍:
nostr-static是一个开源项目,其主要目的是将 Nostr 网络上的长文内容转化为静态博客。下面从多个方面对该项目进行分析:1. 项目概述
nostr-static是一个静态网站生成器(SSG)工具,它可以从 Nostr 网络中获取长文内容,并生成可在任何地方托管的 HTML 页面。这使得用户能够轻松地创建和维护由 Nostr 内容驱动的博客,同时结合了去中心化内容和传统网站托管的优点。2. 功能特性
- 内容转换:能够将 Nostr 上的长文内容转化为美观的静态博客页面,博客加载速度快。
- 去中心化与传统结合:文章存储在 Nostr 网络上,保证了内容的去中心化,同时为读者提供了熟悉的博客界面。
- 易于维护:通过简单的配置和自动更新功能,降低了博客的维护成本。
- 灵活的托管方式:支持多种静态网站托管服务,如 Netlify、Vercel、Cloudflare Pages、Amazon S3 以及传统的 Web 托管服务。
- 社交互动:可以利用 Nostr 进行评论等社交互动。
3. 技术实现
- 前端:从代码片段可以看出,项目使用了 HTML 和 CSS 来构建页面布局和样式,同时支持明暗两种主题模式。页面包含文章卡片、标签、作者信息等常见博客元素。
- 后端:项目使用 Go 语言编写,通过
go build -o nostr-static ./src && ./nostr-static命令进行构建和运行。 - 数据获取:从 Nostr 网络中获取文章内容,需要提供 Nostr naddr 信息。
4. 使用步骤
根据
README.md文件,使用该项目的步骤如下: 1. Fork 项目仓库。 2. 将项目克隆到本地或使用 GitHub Codespaces。 3. 修改config.yaml文件进行配置。 4. 在articles列表中添加要展示的 Nostr naddr。 5. 将logo.png文件放入项目文件夹(如果文件名不同,需要在config.yaml中更新)。 6. 构建并运行项目。 7. 提交并推送更改。5. 项目优势
- 创新性:结合了 Nostr 的去中心化特性和传统博客的易用性,为博主提供了一种新的博客创建方式。
- 简单易用:通过简单的配置和命令即可完成博客的创建和部署,降低了技术门槛。
- 社区支持:开源项目可以吸引更多开发者参与贡献,不断完善功能和修复问题。
nostr-static是一个有创新性和潜力的项目,为 Nostr 用户提供了一种将长文内容转化为传统博客的有效方式。随着项目的不断发展和完善,有望在博客领域获得更多的关注和应用。 -
 @ a5142938:0ef19da3
2025-04-30 09:24:55
@ a5142938:0ef19da3
2025-04-30 09:24:55 -
 @ c1e6505c:02b3157e
2025-04-30 02:50:55
@ c1e6505c:02b3157e
2025-04-30 02:50:55Photography, to me, is a game - a game of snatching absurd, beautiful, fleeting moments from life. Anything staged or overly polished falls into what Garry Winogrand nails as “illustration work.” I’m with him on that. Photography is about staying awake to the world, to the “physical reality” or circumstances we’re steeped in, and burning that light onto film emulsion (or pixels now), locking a moment into matter forever. It’s not like painting, where brushstrokes mimic what’s seen, felt, or imagined. Photography captures photons - light itself - and turns it into something tangible. The camera, honestly, doesn’t get enough credit for being such a wild invention.
Lately, I’ve been chewing on what to do with a batch of new photos I’ve shot over the past month, which includes photographs from a film project, a trip to Manhattan and photos of David Byrne (more on that in another post). Maybe it's another photo-zine that I should make. It’s been a minute since my last one, Hiding in Hudson (https://www.youtube.com/watch?v=O7_t0OldrTk&t=339s). Putting out printed work like zines or books is killer practice — it forces you to sharpen your compositions, your vision, your whole deal as a photographer. Proof of work, you know?
This leads to a question: anyone out there down to help or collab on printing a photo-zine? I’d love to keep it DIY, steering clear of big companies.
In the spirit of getting back into a rhythm of daily shooting, here are a few recent shots from the past few days. Just wandering aimlessly around my neighborhood — bike rides, grocery runs, wherever I end up.
Camera used: Leica M262
Edited with: Lightroom + Dehancer Film
*Support my work and the funding for my new zine by sending a few sats: colincz@getalby.com *






-
 @ 99895004:c239f905
2025-04-30 01:43:05
@ 99895004:c239f905
2025-04-30 01:43:05 Yes, FINALLY, we are extremely excited to announce support for nostr.build (blossom.band) on Primal! Decades in the making, billions of people have been waiting, and now it’s available! But it’s not just any integration, it is the next level of decentralized media hosting for Nostr. Let us explain.
Yes, FINALLY, we are extremely excited to announce support for nostr.build (blossom.band) on Primal! Decades in the making, billions of people have been waiting, and now it’s available! But it’s not just any integration, it is the next level of decentralized media hosting for Nostr. Let us explain. Primal is an advanced Twitter/X like client for Nostr and is probably the fastest up-and-coming, highly used Nostr app available for iOS, Android and the web. Nostr.build is a very popular media hosting service for Nostr that can be used standalone or integrated into many Nostr apps using nip-96. This is an extremely feature rich, tested and proven integration we recommend for most applications, but it’s never been available on Primal.
And then, Blossom was born, thank you Hzrd149! Blossom is a Nostr media hosting protocol that makes it extremely easy for Nostr clients to integrate a media host, and for users of Blossom media hosts (even an in-house build) to host on any Nostr client. Revolutionary, right! Use whatever host you want on any client you want, the flexible beauty of Nostr. But there is an additional feature to Blossom that is key, mirroring.
One of the biggest complaints to media hosting on Nostr is, if a media hosting service goes down, so does all of the media hosted on that service. No bueno, and defeats the whole decentralized idea behind Nostr.. This has always been a hard problem to solve until Blossom mirroring came along. Mirroring allows a single media upload to be hosted on multiple servers using its hash, or unique media identifier. This way, if a media host goes down, the media is still available and accessible on the other host.
So, we are not only announcing support of nostr.build’s blossom.band on the Primal app, we are also announcing the first known fully integrated implementation of mirroring with multiple media hosts on Nostr. Try it out for yourself! Go to the settings of your Primal web, iOS or Android app, choose ‘Media Servers’, enable ‘Media Mirrors’, and add https://blossom.band and https://blossom.primal.net as your Media server and Mirror, done!
Video here!
-
 @ d9a329af:bef580d7
2025-04-30 00:15:14
@ d9a329af:bef580d7
2025-04-30 00:15:14Since 2022, Dungeons and Dragons has been going down a sort of death spiral after the release of a revised version of 5th Edition... which didn't turn out very well to say the least. In light of that, I present a list of TTRPGs you can play if you don't want to purchase 5E. I wouldn't recommend 5E, as I've DM'd it in the past. It tastes like a lollipop that's cockroach and larvae flavored.
This list of TTRPG games is in no particular order, though my favorite of these systems is number one.
- Basic Fantasy Role-Playing Game (BFRPG)
- B/X-style OSR retroclone with ascending armor class, and the original retroclone from 2006
- Fully libre under CC BY-SA for the 4th Edition, and OGL 1.0a for 1-3 Editions.
- Full books are free PDF files on the website (Basic Fantasy Website)
- All BFRPG editions are compatible with each other, meaning you can have a 3rd Edition book to a 4th Edition game and still have fun. 4th Edition is just the removal of the 3E SRD that's in the OGL editions.
- As with the core rulebooks, all the supplementation is free as a PDF as well, though you can buy physical books at cost (BFRPG principal rights holder Chris Gonnerman doesn't make much profit from Basic Fantasy)
- Old-school community that's an all-around fantastic group of players, authors and enthusiasts.
-
Fun Fact: Out of all the TTRPGs I'd want to DM/GM the most, it'd be this one by far.
-
Iron Falcon (IF)
- OD&D-style retroclone from 2015 (It's also by Gonnerman, same guy behind BFRPG)
- A close ruleset to the White Box rules and supplements
- Also fully libre under CC BY-SA for the latest releases, just like BFRPG for 4th Edition releases
- Just like BFRPG, the core rules and supplementation come as PDF files for free, or physical books.
-
Fast and loose ruleset open to interpretation, just like in 1975-1981... somewhere right around that timeline for OD&D
-
Old-School Reference and Index Compendium (OSRIC)
- AD&D 1E-based retroclone by Stewart Marshall and Matt Finch
- An old system that surprisingly still holds up, even after a long time of no new versions of the rules
- Extremely in-depth ruleset, licensed under OGL 1.0a and OSRIC Open License
- Compatible with AD&D 1e modules for the 1st Edition, though 2.2 potentially has its own supplementation
-
I don't know much about it, as I'd be too slow to learn it. That's all I know, which is the above.
-
Ironsworn
- Custom loosely-based PbtA (Powered by the Apocalypse) system by Shawn Tomkin from 2018
- Includes GM, GMless and solo play in the rulebook
- Supplementation is surely something else with one look at the downloads section for the PDFs of the original, which is free under CC BY-NC-SA. The SRD is under CC BY otherwise.
- No original adventures are made for this system as are known, as it's expected that the Ironlands are where they take place
-
Fun Fact: This was a non-D&D system I considered running as a GM.
-
Advanced Dungeons & Dragons 2nd Edition (AD&D 2e)
- An official edition from 1989-2000
- At the time, the most customizable edition in its history, before 3E took the spot as the most customizable edition
- A streamlined revision of the AD&D 1E rules (AD&D 1E was exclusively written by E. Gary Gygax)
- The end of old-school D&D, as 3E and beyond are different games altogether
- Wide array of supplementation, which oversaturated 2E's customization... and most of it didn't sell well as a result
- Final TSR-published edition of D&D, as they went bankrupt and out of business during this edition's life cycle, to then be liquidated to Wizards of the Coast (Boy did WOTC mess it up once 5.1E was released)
-
Fun Fact: A Canadian history professor named Dr. Robert Wardough runs a customized ruleset using 2E as a base, which he's been DMing since the 80's during the "Satanic Panic" (The Satanic Panic was fake as a result of horrible deceivers gaslighting people to not play D&D). He started RAW (Rules as Written), but saw some things he needed to change for his games, so he did so over time.
-
Moldvay/Cook Basic/Expert Dungeons & Dragons (B/X)
- Competing system to 1E from 1981 and 1982
- Official edition of D&D, part of the old-school era
- Simplified rules for Basic, but some decently complex rules for Expert
- Only goes up to Lv. 14, as it's potentially a 1E or White Box primer (similar to 1977 Basic)
- Supplementation, from some research done, was decent for the time, and a little bit extensive
- The inspiration for BFRPG in 2006 (Did I mention this already? Maybe I have, but I might emphasize that here too.)
-
Fun Fact: I considered running B/X, but decided that I'd do BFRPG, as the ascending armor class is easier math than with B/X and the THAC0 armor class (descending armor class).
-
Basic, Expert, Companion, Master, Immortal Dungeons & Dragons (BECMI) and/or Rules Cyclopedia
- 1983 variant of the Moldvay/Cook Basic/Expert system, an official edition and part of the old-school era
- Essentially, 1981 B/X D&D on steroids
- 5 boxed sets were released for the five parts of the rules for this system
- Rules Cyclopedia is a reprint of the 1983 Basic, Expert, Companion and Master rules boxed sets. The Immortal set was never reprinted outside of the original boxed set because Immortal is such a bizarre game within a game altogether.
- With the first 4 boxed sets (whether individual sets or the Rules Cyclopedia), levels are 1-36
-
Fun Fact: This edition I was considering DMing as well, alongside BFRPG. They're similar rulesets with some mechanical differences, but I think either or would be worth it.
-
Original Dungeons & Dragons (OD&D or White Box)
- The original release of D&D from 1974 written by Gygax and Dave Arneson, published by TSR
- Uses the rules from Chainmail, a wargame made by Gygax and Jeff Perren
- Base has three little booklets (Men & Magic, Monsters & Magic, and The Underworld & Wilderness Adventures), five official supplements were released (Greyhawk; Blackmoor; Eldritch Wizardry; Gods, Demi-Gods and Heroes; and Swords & Spells), and many more from fanzines
- Fast and loose ruleset open to interpretation
- Not based upon adventurers taking on dangerous quest, but kings commanding armies (which is why OD&D is actually a Chainmail supplement). The latter was the original purpose of D&D before it got changed in 2000.
There are many more games that are not D&D that you can look up too. See what you like, read the rules, learn them, and start playing with your group. Have fun and slay some monsters!
-
 @ a5142938:0ef19da3
2025-04-30 09:23:00
@ a5142938:0ef19da3
2025-04-30 09:23:00 -
 @ 79dff8f8:946764e3
2025-04-29 19:19:34
@ 79dff8f8:946764e3
2025-04-29 19:19:34Hello world
-
 @ a5142938:0ef19da3
2025-04-30 09:22:12
@ a5142938:0ef19da3
2025-04-30 09:22:12 -
 @ 2ce0697b:1ee3d3fc
2025-04-29 18:54:19
@ 2ce0697b:1ee3d3fc
2025-04-29 18:54:19Excerpt
Special Jurisdictions, Free Cities and Bitcoin Citadels are the sly roundabout way that is removing the market of living together from the hands of the government, without violence and in a way that they can´t stop it. With Bitcoin as the backbone of a new societal order, we are beginning to disrupt the old paradigm.
“If you have built castles in the air, your work need not be lost; that is where they should be. Now put the foundations under them.” ― Henry David Thoreau, Walden
The problem: lack of freedom in the physical realm
Freedom is essential to human life. Being free is what matters. That´s our target, always. No matter the time or space. We pursue freedom because we know its the right thing to do. Freedom is the right to question and change the stablished way of doing things.
Where can we find some freedom? Certainly in the cyberspace. The cyberspace is a free space. Humanity has been blessed by the magic of cryptography, a technology that gave us all the necessary tools to operate in that environment without intervention of undesired third parties.
In cyberspace cryptography performs the function of an impenetrable cyberwall. So, whatever we build in cyberspace can be perfectly protected. Thank to this cybernetic walls we can be sure that the gardens we build and nurture will be protected and cannot be trampled. When we build our digital gardens we have the keys to open the doors to let in whoever we want and most important to leave out whoever we don´t want. In the digital world we can already perfectly interact with one and another in a peer to peer way, without intervention of undesired third parties.
In cyberspace we have Bitcoin for freedom of money and Nostr, torrent and Tor for freedom of information and speech. These open-source protocols are designed to fully realize and expand the promise of freedom, and they certainly deliver what they promise.

So, thanks to the magic of asymmetric cryptography, we´ve already achieved sufficiently descentralization and the possibility of any level of desired digital privacy. Cryptoanarchists and cypherpunks have set their conquering flag in cyberspace and there´s no force on Earth than can remove it. The digital world cannot escape the rules of cryptography. This is great but it only works in the digital realm, meanwhile in the physical realm we are overrun by centralized attackers due to the impossibility of the creation of impenetrable walls such as the ones we have online.
Humans have the upper hand in creating impenetrable walled gardens in cyberspace, but in the physical space authoritarians have the upper hand in bullying physical persons.
The physical world is also naturally free. According to natural law each person is free to do whatever he wants as long as it doesn´t hurt other people. However due to unnatural -artificial and inhuman- centralization of power, the natural freedom of the physical world has been completely undermined. Mostly by Governments, the entities that centralize violence and law.
Bitcoin as a bridge between both realms

Let´s take a look at one connection between both realms, the physical and the digital world. Bitcoin layer one is made essentially of software plus hardware. It consists of any software that produces the same output as the reference implementation - Bitcoin core- and the hardware needed to run that software. Layer two, three or any other layer above, is made essentially of other software and other hardware that interacts with layer one in some way. All these layers, one, two and subsequent, are completely protected by cryptography and a set of game theories that have been successfully tested. Each new block added to the timechain is a testimony of the unstoppable force of freedom and meritocracy.
Before layer one we have Bitcoin layer zero, which is essentially the sum of all actions and inactions done by bitcoiners regarding to or because of bitcoin. In other words, layer zero is composed by flesh and bone people interacting in some way with layer one of the bitcoin network.
Hence, an attack on a bitcoiner - on his way of life- is an attack on bitcoin, the network itself. First because it is an attack on a layer zero node, the physical person, the bitcoiner under duress or coercion. And second because is also an attack on the store-of-value-aspect of bitcoin. Nowaday, the most common attack against bitcoiners is the entirety of compliance regulations. This is the sum of all coercive regulations,such as laws, threats of more laws, imprisonment, threats of more imprisonment, taxation, threats of more taxation, requirements to prove the origin of funds, coercive removal of privacy such as the travel rule, unnecessary bureaucracy such as the need to obtain a money transmitting license and many others rules, in a never stopping inflationary coercive legislation.

If a physical attack is preventing any bitcoiner to exchange the value he created for bitcoin due to any kind of artificial obstacles -such as any kind of compliance- that specific attack is successful in the sense that even though the whole network keeps operating, the attack itself diminishes the value of all the bitcoins.
So, even if layer-zero cannot be taken down, every interference on this layer is an attack on the bitcoin network. Attacks on layer one, two or any other layer that exists in the cyberspace can interfere with the network but they may hardly subtract any value from it. For example we have already been through plenty of times where hashing power was diminished due to government intervention and the bitcoin network remain completely unaffected.
On the other hand successful attacks on layer zero subtract potential, but real and demonstrable value. This value is equal to the amount of value the frustrated user would have added to the network if he would have been able to use it freely, that means if he would have sold his product without the cost of compliance. I´ll demonstrate this in the next chapter.
The cost of compliance
Alice is a merchant specialized in a specific area and topic. She studied the market, her business, her suppliers, consumers, the logistics involved, marketing, design, and everything necessary to become a successful entrepreneur. After investing a considerable amount of resources, she developed a perfect product. Or at least she considers it perfect, that is, the best in its class. While developing everything necessary to create her product, she met Bob, who became her main lead and stereotype of a buyer persona. She knows what Bob wants and she wants to sell it to him. According to Alice's calculations, for her business to be viable, she must sell the product at ten satoshis per unit, and fortunately, Bob is willing to pay that price for it. Alice's product is finished, ready to hit the market, but just before sending it to production, Alice decides to take a pause to analyze her reality. Before taking the public action of making her product available in the open market, Alice analyzes her material, political, and legal reality. In doing so, she realizes that she lives under the jurisdiction of a State. She learns that the Government prescribes through its regulations how she must behave. She analyzes that in order to sell her product legally, in compliance, she must make a series of modifications to it. The product before hitting the shelves must first be modified both in the way it is presented to the market and also regarding certain technical characteristics that it possesses. She must also modify the way it produces her product by changing the contractual relationship with its suppliers, distribution channels, and all other types of logistics involved. She must make all these changes even if they bring about significant and insurmountable inefficiencies.
Likewise, Alice also sees that she not only has to modify the product but also has to meet tax obligations. In addition to paying an accountant since the tax obligations by some irrational reason are not calculated by the creditor. Additionally, she must hire other professionals to assist her in studying the current regulations and how they should be applied in all stages of production, distribution, and sale of her product.
Alice, being a rational person, wishes to avoid having to make these modifications since they increase her costs while also decreasing the quality of her product. But when studying compliance, that is, the entirety of applicable regulations, she also examines the consequences of not being in compliance. Alice realizes that if she does not comply with the regulations, she risks having all her assets legally confiscated, going to prison, being killed while they try to capture her to imprison her, and, if she goes to prison, being tortured in jail by other inmates or by State officials in charge of holding her in that place. So, since Alice does not want to suffer these negative consequences, she decides to modify the product and be in compliance.
So, Alice makes the necessary changes and puts her new version of the product on the market. Then she has the following dialogue with Bob, her lead, the interested party in acquiring the product.
Bob: - Hey Alice, nice meeting you here in this market. I came to buy the product you were developing and told me about. However, this product I´m seeing now is not what you promised me. This is clearly inferior.
Alice: - Yeah, I know. I'm sorry Bob, but I prefer to sell this inferior product rather than risk having all my assets confiscated, going to prison, being killed while they try to capture me, and if they don´t kill but managed to put me in jail I could be tortured there.
Bob: - Ok, no problem. Thats quite understandable. I don´t believe anyone would prefer those kind of experiences. But given the quality of the product, I no longer intend to pay you ten satoshis; I only offer you eight. Shall we close the deal?
Alice: - I'm sorry Bob, but I can't sell it to you for eight sats. Due to government intervention and its requirements, now I can't even sell it for less than thirteen satoshis.
Bob: - Ok. Considering this I prefer not to purchase it. I will keep looking for alternatives. Bye

Some time later, Charlie arrives at the market, who is also interested in the product and, despite it not being like the original version, decides to purchase it by paying the thirteen satoshis demanded by the seller Alice.
Meanwhile, in the same universe, we have Daniel, the last character in this example. Daniel is a merchant competing with Alice. Daniel has a product that is very similar, practically identical to the one originally designed by Alice. Like Alice, Daniel initially also wants to sell it for ten satoshis. Just like Alice, before heading to the market, Daniel analyzes the reality in which he lives. And it turns out that he also lives under the jurisdiction of a State. Daniel too then analyzes the entirety of the applicable regulations and also comes to the conclusion that to comply with them, he would also need to modify the product and cover all the additional expenses artificially generated to be in compliance.
However, Daniel's ethics are different from Alice's. Daniel understands that his product is indeed perfect (the best in its class) and that therefore modifying it would go against its essence. Daniel understands that changing the product would be a betrayal of his creation and therefore a betrayal of his own self and the essence of his being. Daniel conducts an ethical analysis of his actions and the moral implications of putting the product on the market. Daniel sees that the product not only does not harm anyone but is also made to be freely acquired by adults who give their consent for its purchase and subsequent use. Daniel also understands that paying taxes only serves to promote the slavery system driven by fiat and that whenever he can avoid collaborating with the immoral fiat system, it is his ethical obligation to do so. Likewise, Daniel highlights the hypocrisy and inefficiencies of anti-money laundering regulations, as well as the futility of requiring licenses for naturally free acts that do not harm others. For all these reasons, Daniel decides to sell the product in its current state irregardles of compliance regulations.
However, before going to market, Daniel also studies the possible consequences of neglecting compliance. By doing so, Daniel sees that if he does not comply with the regulations, he risks having all his assets legally confiscated, going to prison, being killed while they attempt to capture him to imprison him, and, in the event of going to prison, being tortured in jail by other inmates or by State officials responsible for holding him in that place. So, since Daniel is a rational person who does not want to suffer these negative consequences but also does not want to betray his product and himself, he decides to take the risk of not being in compliance. After making this decision, Daniel puts the product on the market and there he meets Bob. In doing so, they converse in the following terms:
Bob: - Hey Daniel, this product is exactly what I was looking for. A product like the one promised by Alice but never delivered. I love it! I offer you ten satoshis for it.
Daniel: - Thank you for your feedback Bob and for the offer! However I am currently selling it for eleven satoshis. Ten satoshis seems like a good price to me, and it was indeed my original intention to sell it for that amount because at that price I achieve competitiveness and a sustainable business model.
Bob: - So why are you asking me for eleven satoshis? Interrupts Bob
Daniel: - Because that price is calculated before assessing compliance and the risks associated with non-compliance. By not complying with the regulation, I managed to maintain the quality of the product and avoided a large amount of unnecessary expenses, but there is no way to avoid the risk of facing penalties for non-compliance. To bring this product to market, I had to incur several expenses in order to minimize the risk of non-compliance as much as possible. While I am taking all reasonable actions to prevent all of my assets from being legally confiscated, from going to prison, from being killed while they try to capture me, and in case of going to prison, from being tortured, the reality is that I still run the risk of all that, or part of all that, happening to me, my family, or any of my company's employees. The remaining risk balance is transferred to the price along with the costs of mitigating those risks. The total of those costs and the remaining risk I estimate them at one satoshi per unit of product. Therefore, I can't sell you the product for ten satoshis, but I can sell it to you for eleven.
To which Bob, lacking a better option in the market, ends up buying the product for eleven satoshis.
In summary: two products were made by two different merchants whose business model allowed them, in both cases, to put the product on the market at a rate of ten satoshis per unit. However, in one case, a lower quality product was sold for thirteen satoshis, and in the other case, a higher quality product was sold for eleven satoshis. That is to say, in the first case there was an overprice or inefficiency objectively measured at three satoshis, while in the second case there was an overprice or inefficiency of one satoshi. So, we are facing a total loss of value equivalent to four satoshis. The value represented by these four satoshis was absorbed by the inefficiency programmed and ruled by the State. The example shows us that whether one chooses the compliance route, as Alice did, or the free market route, as Daniel did, in both cases the existence of regulations generates an additional cost to the market. In this example the state attack on layer zero was successful and extracted from the Bitcoin network a value of four satoshis.
Bitcoin is money
Bitcoin is many things but essentially is money. And money sole purpose is to store value in order to facilitate future exchanges of products and services with other people. Without the products and services to be exchanged for the money, money itself would be useless and worthless. We only use money because we may require favors, benefits, services, products from other people in the future. And we don´t know which services and products we´ll need nor exactly when we are goint to need them.

The total value of bitcoin equals to infinity divided twenty one millions. This is because the total worth of the network mirrors the total worth of accumulated capital by the entirety of mankind throughout its entire history. That is clearly a lot of value. But if the if the dividend equals zero then the divisor is also zero and if the dividend growth is obstructed through artificial means -such as compliance- then the divisor growth is also obstructed.
Bitcoin layer zero, the bitcoiners and the services and products we create, are what give value to the twenty one million units of bitcoin.
Freedom is without a doubt the best context for value creation. So, the more and better games we can create that allow humankind to find a way to exercise freedom, then the most value we can add to all the layers of the network.
This is why the most important layer of the whole bitcoin phenomenon is layer zero, the bitcoiners. Hence the problem to be solved is not how to prevent bitcoin - layer one upwards- from successful attacks. The problem to solve is how to prevent attacks on layer zero. Or in other words, the problem to be solved is how to get bitcoiners in the physical world to practice the same level of freedom that bitcoin achieves in the cyberspace.
Summary of the first part of this article: freedom in cyberspace has already been conquered and each further development in the digital realm contributes to further developments but only in the same realm. Meanwhile in the physical space, the layer zero of bitcoin is under constant attacks that successfully extract value from it.
Exercising freedom in a sly roundabout way

In 1984 the Austrian economist Friedrich Hayek predicted that we couldn´t take money with violence out of the hands of government. He stated that we needed to do it in a sly roundabout way. Twenty five years later Satoshi Nakamoto discovered the sly roundabout way actually introducing something that the government couldn´t stop. Thus fulfilling Hayek´s prophecy.
Bitcoin is a sly roundabout way that removed money without violence from the hands of the government in a way that they can´t stop it.
Cryptography in general and protocols such as Tor and Tails are a sly roundabout way that removed confidential information from the hands of the government without violence in a way that they can´t stop it.
Nostr is a sly roundabout way that removed social media and public information from the hands of the government without violence in a way that they can´t stop it.
Special Jurisdictions, Free Cities and Bitcoin Citadels are the sly roundabout way that is removing the market of living together from the hands of the government without violence in a way that they can´t stop it.

So, what are Special Jurisdictions, Free Cities and Bitcoin Citadels? To understand what they are we can take a look at the current mainstream market of living together, at how the physical space is organized. Essentially the entire planet Earth and its surroundings are run by a conglomerate of Governments. They create all the rules, regarding every aspect of life, of all the individuals, and enforce every rule through coercive means.
In the mainstream market of living together individuals have several alternatives to pick from. We can choose to live in a natural city or a pre design city, in a public neighborhood or private neighborhood or even in an intentional community with common interest amongst the users. But irregardless of the choice, every product offered in the mainstream market has the sames rules which are established by the host state to the entirety of organizations in his territory. In the mainstream market, even the most different products abide by the same high level rules such as criminal law, civil law, taxation laws, customs, enviromental laws, money laundering regulations and many others. To abide to the sum of all the laws and regulations is to be in compliance.
The centralization of regulations makes extremely difficult to experiment in market of living together. The less experimentation is allowed, the more human progress is hindered.
So what is the sly roundabout that fixes this? What are Special Jurisdictions, Free Cities and Bitcoin Citadels? I´m using the term Special Jurisdictions as an umbrella term that includes the entire spectrum of iterations of products that aim to modify the mainstream rules of the market of living together.
This term includes all the different models such as Charter Cities, Free Cities, Special Economic Zones, microstates, micropolis, start up societies, government as a service, self governing jurisdictions, autonomous intentional communities, network states and Bitcoin Citadels. The array of possible iterations is huge and permanently expanding. What they all have in common is that each of these experiments aims to create a functional game theory that replaces the lack of unbreakable walls in the physical space.
Let´s take a look of a couple of examples. Special Economic Zones are bounded areas of countries that have their own rules and regulations. Worldwide, there are more than five thousands special economic zones located in more than hundred countries.
One of them is the special economic zone of Shenzhen in China. The Chinese government allowed Shenzhen the freedom to experiment with certain practices that were prohibited in the rest of the country at the time. This included allowing foreign companies to make direct investments in China, allowing people to buy and sell land, allowing Chinese people to set up their own private businesses and relaxation of the system that limited internal migration within China for Chinese citizens. It served as a place where China could experiment with market reforms. The experiment was such a huge economic success that it was replicated in many other areas of the country.
Another place that has made extensive use of special economic zones is Dubai. The monarchic Government has more than 30 SEZs. In this case one of the many obstacles removed by the host state its the monopoly of the legal system. Dubai Government allowed the special economic zone to have its own independent legal system thus conceding a modification of the mainstream rules in that area.
This kind of projects, such as Dubai or Shenzhen, are a top-to-down product. Fully created by the Governments thus compliant with their own regulations.

On the other side of the spectrum we have Citadels and several other archetypes of not so compliant projects .
For example the Free Commune of Penadexo it´s a grassroots project building a freedom-oriented community in one of Spain’s abandoned villages.
 It´s model is based on building a peer to peer society avoiding government intervention as much as possible.
They stablished themselves in an abandoned historic village and the started to track down the owners to purchase as much property as possible. Meanwhile, they are living there and expanding their users base while also reconstructing buildings.
It´s model is based on building a peer to peer society avoiding government intervention as much as possible.
They stablished themselves in an abandoned historic village and the started to track down the owners to purchase as much property as possible. Meanwhile, they are living there and expanding their users base while also reconstructing buildings. This is an example of a completely different way of dealing with the Government. While Special Economic Zones are fully compliant and created top to down, this model on the other hand is bottom-up and aims to add value to the users relying in factual freedom which is exercised by stablishing the commune away from heavily populated centers where Government grip is tighter. Under this model the interaction with the Government is kept as low as possible. Their strategy relies in ignoring the Government as much as possible and being a good neighbor. With this simple and effective tactic some Citadels enjoy the benefits of liberty in their lifetime without needing to spend huge resources in governmental lobby.
There are countless models or archetypes of Bitcoin Citadels trying to solve the obstacles in different ways, trying to restart the system. And one of the challenges of the Bitcoin Citadels is how to connect the different projects to boost and help each other.
This is where The Meshtadel comes into play. The Meshtadel is a system where decentralized tactics are used to help and defend citadels connected in a global network. With real life connections with fellow bitcoiners. Its an organization equivalent to the hanseatic league built under a starfish model. If you cut off a spider’s head, it dies, but if you cut off a starfish’s arm, it can regenerate and even grow into a new starfish.
The Meshtadel its a network of peer relationships, with ambiguous leadership roles, trust among participants, a shared ideology and vision based on the Bitcoin ethos, and an open system where new nodes - bitcoin citadel builders - can participate.
The long term goal of the Bitcoin Meshtadel is to help Bitcoin Citadels to gain the support of a critical mass of the total population. If enough people see that Bitcoin is as peaceful as it gets, in the long run, some nations could become friendly and supportive enough to legally tolerate the Bitcoin Citadel inside its territory in the form of a Bitcoin safe haven. In the Meshtadel we are fighting from the moral high ground using memes, Nostr notes and zapping our way into freedom creating an online and offline circular economy.
TO CONCLUDE:
Special Jurisdictions, Free Cities and Bitcoin Citadels are the sly roundabout way that is removing the market of living together from the hands of the government, without violence and in a way that they can´t stop it.
Nation states, abusing the myth of authority, have halted development on the market of living together for so long that a blooming freer market is eating its lunch. The sovereign individual thesis is live and continuously expanding. The network state is forming and intentional communities are flourishing all around the world reshaping globally the relationship between individuals and the governments.
With global internet connections, uncensorable means of communication and Bitcoin as the backbone of a new societal order, we are beginning to disrupt the old paradigm.
The fashion of the present world is passing away, let’s help it to move forward along by building Special Jurisdictions, Free Cities and Bitcoin Citadels.
--- --- --- --- --- --- --- --- ------
byCamiloat 875.341 timechain.
If you find this content helpful, zap it to support more content of the sort and to boost the V4V model.
-
 @ 3c389c8f:7a2eff7f
2025-04-29 18:38:46
@ 3c389c8f:7a2eff7f
2025-04-29 18:38:46Let go of the algorithms and truly discover what it means to explore. Social media used to mean something. Once upon a time, it was a way to stay connected to friends, family, and colleagues over things we enjoy. We could share, laugh, and learn. Over time, it has devolved into cheap entertainment at the cost of our privacy. Our relationships and interests have been shoved into a corner in order to make room for "suggested posts" and "for you" content designed to evaluate our attention for advertising purposes. We've lost what it means to truly connect, and we've lost what it means to explore our curiosities.
Enter Nostr. A protocol designed to resist authoritative censorship, just happens to fix a whole lot of other problems, too. By removing the central authority, Nostr offers its users complete control of what we feed our minds. How do we break our algorithm dependency to find better content and better relationships again? We explore and discover:
The Chronological Life.
The existence of time may be debatable but our dependence on our perception of it is not. We live our lives chronologically. Why do our online lives need to be any different? There is no real reason, other than we've just gotten used to being engulfed by whatever the black box wants us to see. When we remove the algorithms, we find that online information flows just as it would in our daily lives. Important events get talked about by many people, over a long period of time. Things of less relevance fade. We see the rhythm of life reflected in our feed. This is an organic human experience transferred to the digital world. We depend on the people we know and the sources we trust to keep us informed about what really matters. We have fun, we move on. Nearly every Nostr social client brings this experience front and center through the traditional follow feed. Many use replies as a way to show you what is worth talking about for more than a hot minute. Its what old social media gave us, then took away. Nostr gives it back. It's not the only way to enjoy Nostr, though, so let's continue.
"The Human Animal Differs From the Lesser Primates in His Passion for Lists"
Who doesn't love lists? (besides maybe to-do lists.) List functionality on Nostr is a powerful way to curate your feeds. You can make lists of artists, vendors, friends, or whatever you want. They can be public or private. You can subscribe to other people's public lists too. Make one to share with your friends. Many clients have list support and management. Amethyst, Nostur, Voyage, and Nostrudel are a few that come to mind. Nostr.band and Listr.lol offer in depth list management. Some clients even support lists for specific notes so that you can curate a feed by topic or aesthetic to share with your friends.
Being John Malcovich.
Everyone has a different view of Nostr. Do you want to see what someone else is seeing? Sign in with any npub to get a different perspective. You might find profiles and content that you didn't know existed before. Some clients integrate variations of this feature right into their apps, so you don't have to log out of your account in order to step through that tiny door.
DV-what? DVM.
Data Vending Machines. These fancy little things are AIs tasked with a simple job: to find content for you. Most of these feeds are free, though some more personalized ones require a small fee. Many DVM services are stand-alone apps, like Vendata and Noogle . These clever Nostr clients will let you do a lot more than just create feeds to browse notes. Explore if you wish. A few social clients have DVMs integrated, too, so if you see "discovery" or similar term on a tab, be sure to check it out.
Relays, Man. Relays.
It's right there in the name. Nostr- notes and other stuff transmitted by RELAY. Specialized relays exist for subjects, news, communities, personal spaces, content creators, cats... there's even a relay where everyone just says "Good Morning" to each other. Find a client that lets you browse a relay's contents, and enjoy the purest form of content discovery on Nostr. Unearthing these relays is getting better and better every day. Right now there are relay browsing capabilities in quite a few clients, like Coracle, Relay Tools, Jumble and Nostur.
The Algo Relay.
Maybe you've been busy and missed a lot. Maybe you are a sane person who rarely uses social media. Hook up with a personalized algorithm relay to catch you up on all the things you've missed. This is skirting the sharp edges of Nostr relay development, so keep in mind that not many implementations yet exist. Algo relay currently aims to bring the feel-good vibe of your chronological feed to an algorithmic feed, freeing up your time but letting you stay up with what 's going on in your social circles.
Trendy Trends.
A few clients, relays, and DVM's have developed various Trending feeds. Catch up on what's popular across a wider view of the Nostr ecosystem. If trends are your thing, be sure to check them out.
Now that you're equipped with the tools to explore Nostr, its time to go discover some great content and find your people. Feed your curiosity.
-
 @ a5142938:0ef19da3
2025-04-30 09:19:41
@ a5142938:0ef19da3
2025-04-30 09:19:41What is a natural material? It's a topic of debate, and everyone will prioritize their own criteria. Here’s how materials are classified on this site. The list is regularly updated based on the products added. Feel free to share your thoughts!
✅ Natural Materials
Materials of plant, animal, or mineral origin, without chemical transformation that alters their molecular structure.
🌱 Main Criteria: - Biodegradability - Non-toxicity - Naturally occurring and recquiring minimal transformation
🔍 List of Natural Materials: - Regenerated Cellulose (cupra, lyocell, modal, rayon) - Cork - Cotton - Earth - Glass - Hemp - Natural Latex, rubber - Leather - Linen - Metal - Silk - Wood - Wool - … (Other materials)
⚠️ Although "natural", these materials can have negative impacts depending on their production conditions (pesticide pollution, excessive water consumption, chemical treatments, animal exploitation, etc.). These impacts are mentionned in the description of each material.
Organic versions of these materials — free from chemical treatments, animal mistreatment, etc. — are preferred for listing products on this site, as indicated on each material's page (coming soon).
Conventional versions are only referenced when no more sustainable alternative has yet been found for that product category.
🚫 Non-Natural Materials
Synthetic or heavily modified materials, often derived from petrochemicals.
📌 Main Issues: - Toxicity and microplastic emissions - Dependence on fossil fuels - Poor biodegradability
🔍 List of Non-Natural Materials: - Acrylic - Elastane, spandex, lycra - Polyamides, nylon - Polyester - Silicone - … (Other materials)
⚠️ These materials are not accepted on this site. However, they may be present in certain listed products if:
- they are used in removable accessories (e.g., elastics, buttons—often not listed in the product’s composition by the brand) that can be detached for recycling or composting, and
- no 100% natural alternative has yet been identified for that product category.
In such cases, a warning will be displayed on the product page.
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ 3c389c8f:7a2eff7f
2025-04-29 18:13:50
@ 3c389c8f:7a2eff7f
2025-04-29 18:13:50TL;DR visit this post for a list of signers
Your nsec/private key is your key to controlling all that you do on Nostr. Every action you take is signed by this private key, validating that was you that generated that event, whether it be a note, a like, a list, or whatever else. Like a broken record, I have to state that it is irreplaceable. YOU own your identity and no one else. It is your responsibility to keep your nsec safe, but of course, you also want to be able to use all the different apps and clients available. To aid you in this process, a few different tools have been developed. Let's take a look at some that are more common and easy-to-use, where to use them, and for what.
The Browser Extension
This is probably the simplest and most straight forward form of private key manager available. There are many options to choose from, each compatible with various, commonly used browsers, including mobile browsers. Many provide the option to manage multiple keys for different profiles. Some are simply a signer while others may include other features. The concept is very simple. The extension holds your key and exposes it only only enough to sign an event. These extensions can be set to different levels of manual approval that you can control based on the level of convenience you seek. The ease and convenience does trade off a bit of security, as your private key will be exposed momentarily each time you create an event. It is up to you to choose whether this is appropriate for your use. For casual browsing and social media use, it is a fairly good and easy to use option. Nearly all Nostr apps and clients support signing with this method.
The Remote Signer
Often referred as a "bunker", Nostr remote signers hold your private key completely offline and communicating with clients. Clients send events to the signer to be signed, which then sends back the signed event for publishing. This bunker can be hosted on your own hardware or managed by a truested 3rd party. As long as the signer is online, it can communicate as needed. The signer generates a "bunker string" that is used to communicate. These may seem cumbersome to set up, as each client that you intend to use will need its own permissions. Once all of the pieces and permissions are in place, most of this activity will happen in the background. Bunkers allow for a lot of flexibility. The "bunker string" for a single app can be shared with other users who you may want to be able to make posts on your behalf. Multiple people can manage a social media profile, while the main owner of that identity maintains control of the nsec. These bunker strings can be revoked and replaced at any time. This signing method is growing in popularity and many clients already offer support for it.
The Native Android Signer
Currently, Amber is the only native app available to handle Nostr event signing. It is an incredible tool for managing your Nostr key on your mobile device. The signing flow is similar to remote signing, as described above, but it can communicate with both your Android native Nostr apps and web clients accessed through most mobile browsers, eliminating the need for a browser extension. Similar apps are under development for iOS, but I don't use any of those devices, so covering that here will only happen via other's opinions at a later date. Check this list for current options.
NcryptSec
NcryptSec signing works by encrypting your nsec on a local device, unlocked by a password that you choose. Support for this method is very limited, as the encrypted private key stays on your device. If you intend to use Nostr through one device and few apps, this can be a very secure option, as long as you can remember your password, as it cannot be changed.
NFC and Hardware Signers
Some devices have been developed to store your nsec completely offline on a device or NFC chip, and some clients have added support for scanning/connecting to sign. I haven't personally tried any of these options, nor do I intend to promote the sale of any particular products. If you are interested in these techniques and devices, the information is not hard to find. The price of a devices varies, depending on your feature needs.
There are also DIY options that utilize existing hardware, if you are into that sort of thing.
Higher Security and Recoverability Options
Creating a scheme that allows for recovery of a lost key while maintaining the integrity of a unique identity is no easy task. The key must be fractured into shards, encrypted, and distributed across multiple servers in various locations, while you maintain a portion or portions of your own. These servers are run by trusted 3rd parties who will then sign events "with" you. Some include a scheme of running your own always online hardware to act as host for these shards. I fall short on the technical understanding of certain aspects of these processes, so I will spare you of my attempt to explain. As far as I know, there are a couple of methods underway that are worth paying attention to:
Frostr nostr:nevent1qvzqqqqqqypzqs3fcg0szqdtcway2ge7zahfwhafuecmkx9xwg4a7aexhgj5ghleqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcqyrh3r7uhytc4dywjggxz24277xgqtvcadvnjfks6fram7gjpev9nuentfht
Promenade nostr:nevent1qvzqqqqqqypzqwlsccluhy6xxsr6l9a9uhhxf75g85g8a709tprjcn4e42h053vaqydhwumn8ghj7un9d3shjtnhv4ehgetjde38gcewvdhk6tcprdmhxue69uhhyetvv9ujuam9wd6x2unwvf6xxtnrdakj7qpqqqq0dlpwxhw5l97yrcts2klhr9zqqpcmdfpaxm8r7hygykp630cq23ggph
For a List of signers, please visit this post.
-
 @ 3c389c8f:7a2eff7f
2025-04-29 18:07:00
@ 3c389c8f:7a2eff7f
2025-04-29 18:07:00Extentions:
https://chromewebstore.google.com/detail/flamingo-%E2%80%93-nostr-extensio/alkiaengfedemppafkallgifcmkldohe
https://chromewebstore.google.com/detail/nos2x/kpgefcfmnafjgpblomihpgmejjdanjjp
https://chromewebstore.google.com/detail/aka-profiles/ncmflpbbagcnakkolfpcpogheckolnad
https://keys.band/
https://github.com/haorendashu/nowser
The Remote Signer:
https://nsec.app/
https://github.com/kind-0/nsecbunkerd
Native Android Signer:
https://github.com/greenart7c3/amber
iOS
https://testflight.apple.com/join/8TFMZbMs
https://testflight.apple.com/join/DUzVMDMK
Higher Security Options: To start using Nostr with a secure, recoverable keypair: https://nstart.me/en
For Existing Keys: https://www.frostr.org/
Thank you to https://nostr.net/ for keeping a thorough list of Nostr apps, clients, and tools!
-
 @ a5142938:0ef19da3
2025-04-30 08:36:29
@ a5142938:0ef19da3
2025-04-30 08:36:29Happy to have found useful information on this site?
Support the project by making a donation to keep it running and thank the contributors.
In bitcoin
-
On-chain: bc1qkm8me8l9563wvsl9sklzt4hdcuny3tlejznj7d
-
Lightning network: ⚡️
origin-nature@coinos.ioYou can also support us on a recurring basis 👉 Set up a recurring Lightning payment
In euros, dollars, or any other supported currency
-
By bank transfer, IBAN: FR76 2823 3000 0144 3759 8717 669
-
You can also support us on a recurring basis 👉 Make a pledge on LiberaPay
Contact us if you’d like to make a donation using any other cryptocurrency.
💡 A Value-Sharing Model
Half of the donations are redistributed to the contributors who create the site's value, experimenting with a revenue-sharing model on the Internet—one that respects your data and doesn’t seek to capture your attention. The other half helps cover the site's operating costs.
This article is published on origin-nature.com 🌐 Voir cet article en français
-
-
 @ 266815e0:6cd408a5
2025-04-29 17:47:57
@ 266815e0:6cd408a5
2025-04-29 17:47:57I'm excited to announce the release of Applesauce v1.0.0! There are a few breaking changes and a lot of improvements and new features across all packages. Each package has been updated to 1.0.0, marking a stable API for developers to build upon.
Applesauce core changes
There was a change in the
applesauce-corepackage in theQueryStore.The
Queryinterface has been converted to a method instead of an object withkeyandrunfields.A bunch of new helper methods and queries were added, checkout the changelog for a full list.
Applesauce Relay
There is a new
applesauce-relaypackage that provides a simple RxJS based api for connecting to relays and publishing events.Documentation: applesauce-relay
Features:
- A simple API for subscribing or publishing to a single relay or a group of relays
- No
connectorclosemethods, connections are managed automatically by rxjs - NIP-11
auth_requiredsupport - Support for NIP-42 authentication
- Prebuilt or custom re-connection back-off
- Keep-alive timeout (default 30s)
- Client-side Negentropy sync support
Example Usage: Single relay
```typescript import { Relay } from "applesauce-relay";
// Connect to a relay const relay = new Relay("wss://relay.example.com");
// Create a REQ and subscribe to it relay .req({ kinds: [1], limit: 10, }) .subscribe((response) => { if (response === "EOSE") { console.log("End of stored events"); } else { console.log("Received event:", response); } }); ```
Example Usage: Relay pool
```typescript import { Relay, RelayPool } from "applesauce-relay";
// Create a pool with a custom relay const pool = new RelayPool();
// Create a REQ and subscribe to it pool .req(["wss://relay.damus.io", "wss://relay.snort.social"], { kinds: [1], limit: 10, }) .subscribe((response) => { if (response === "EOSE") { console.log("End of stored events on all relays"); } else { console.log("Received event:", response); } }); ```
Applesauce actions
Another new package is the
applesauce-actionspackage. This package provides a set of async operations for common Nostr actions.Actions are run against the events in the
EventStoreand use theEventFactoryto create new events to publish.Documentation: applesauce-actions
Example Usage:
```typescript import { ActionHub } from "applesauce-actions";
// An EventStore and EventFactory are required to use the ActionHub import { eventStore } from "./stores.ts"; import { eventFactory } from "./factories.ts";
// Custom publish logic const publish = async (event: NostrEvent) => { console.log("Publishing", event); await app.relayPool.publish(event, app.defaultRelays); };
// The
publishmethod is optional for the asyncrunmethod to work const hub = new ActionHub(eventStore, eventFactory, publish); ```Once an
ActionsHubis created, you can use therunorexecmethods to execute actions:```typescript import { FollowUser, MuteUser } from "applesauce-actions/actions";
// Follow fiatjaf await hub.run( FollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", );
// Or use the
execmethod with a custom publish method await hub .exec( MuteUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", ) .forEach((event) => { // NOTE: Don't publish this event because we never want to mute fiatjaf // pool.publish(['wss://pyramid.fiatjaf.com/'], event) }); ```There are a log more actions including some for working with NIP-51 lists (private and public), you can find them in the reference
Applesauce loaders
The
applesauce-loaderspackage has been updated to support any relay connection libraries and not justrx-nostr.Before:
```typescript import { ReplaceableLoader } from "applesauce-loaders"; import { createRxNostr } from "rx-nostr";
// Create a new rx-nostr instance const rxNostr = createRxNostr();
// Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(rxNostr); ```
After:
```typescript
import { Observable } from "rxjs"; import { ReplaceableLoader, NostrRequest } from "applesauce-loaders"; import { SimplePool } from "nostr-tools";
// Create a new nostr-tools pool const pool = new SimplePool();
// Create a method that subscribes using nostr-tools and returns an observable function nostrRequest: NostrRequest = (relays, filters, id) => { return new Observable((subscriber) => { const sub = pool.subscribe(relays, filters, { onevent: (event) => { subscriber.next(event); }, onclose: () => subscriber.complete(), oneose: () => subscriber.complete(), });
return () => sub.close();}); };
// Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(nostrRequest); ```
Of course you can still use rx-nostr if you want:
```typescript import { createRxNostr } from "rx-nostr";
// Create a new rx-nostr instance const rxNostr = createRxNostr();
// Create a method that subscribes using rx-nostr and returns an observable function nostrRequest( relays: string[], filters: Filter[], id?: string, ): Observable
{ // Create a new oneshot request so it will complete when EOSE is received const req = createRxOneshotReq({ filters, rxReqId: id }); return rxNostr .use(req, { on: { relays } }) .pipe(map((packet) => packet.event)); } // Create a new replaceable loader const replaceableLoader = new ReplaceableLoader(nostrRequest); ```
There where a few more changes, check out the changelog
Applesauce wallet
Its far from complete, but there is a new
applesauce-walletpackage that provides a actions and queries for working with NIP-60 wallets.Documentation: applesauce-wallet
Example Usage:
```typescript import { CreateWallet, UnlockWallet } from "applesauce-wallet/actions";
// Create a new NIP-60 wallet await hub.run(CreateWallet, ["wss://mint.example.com"], privateKey);
// Unlock wallet and associated tokens/history await hub.run(UnlockWallet, { tokens: true, history: true }); ```
-
 @ e7454994:7bb2dac7
2025-04-29 16:28:59
@ e7454994:7bb2dac7
2025-04-29 16:28:59Imagine
According to Cazoomi, total revenue for nonprofits in the U.S. reached approximately $3.7 trillion in 2024.
I know in some cases a billion is a hundred million instead of a thousand million (presumably so that some millionaires can call themselves billionaires to distinguish themselves from the riffraff). But that’s not the case here. A trillion is one followed by 12 zeros, so in 2024, US non-profits’ expenses were
3,700,000,000,000 dollars.
How much is a trillion?
And that’s just the USA. We could safely double it for worldwide non-profits and still be well below the actual figure. To be conservative, let’s say 6 trillion of our dollars each year goes on the kinds of projects that non-profits are allowed to do (essentially, making the world a better place).
Think what you could do with just one million dollars. Now think of that times six million! The entire population of Congo, each man, woman, and child, could become a millionaire!. It’s not really imaginable.
That’s how much nonprofits have. What the hell have they done with all that money? In most places where poverty and malnutrition are rife, two thousand dollars a year per family would be more than enough to enable people to sort out whatever problems they have and convert their local community to abundance over three years. Six trillion divided by two thousand is three billion.
The people whom we allow to manage ‘aid’ for us are (to be polite) inept, and we need to bypass them urgently. Directsponsor.org and clickforcharity.net are part of a proof of concept, and our aim is to prove that a better way is possible by doing it.
When a hierarchy exists, it presents a focus of power that power-seeking individuals and cliques can over time turn to their advantage… Even volunteer organizations are subject to intrigues, power grabs, covert arrangements, misallocation of funds, etc. The problem is made worse by the fact that those who most desire power and who are the most ruthless are the very ones who tend to work their way to the top of hierarchies.
More Fun With Figures
Oxfam UK raised £368,000,000 in 2013-14. That’s around 450,000,000 euros. What could we do with that kind of money? A direct sponsorship project is, for a family, 120 per month = 1440 per year. 1440 / 450,000,000 = 312,500 families.
312,500 families, x 4 = 1,250,000 people, would move from poverty into abundance every 3 years with the money that goes through Oxfam. Does Oxfam achieve anything like this with our money?
Oxfam UK is just one of many, many such charities and is small fry when you look at things like USAID, which ran through 27 billion dollars in the year to 2025. What could we do with that?
Its well over 15 million families. Over 60 million people! Or, the entire population of Botswana, Namibia, Mauritania, Liberia, the Republic of Congo, the Central African Republic, Libya, Sierra Leone, Eritrea, Togo, and Guinea combined. This is only to make a point, not to suggest that we would ever achieve such numbers. It shows how wasteful and scandalous our present “aid” efforts really are.
NGOs and governments waste our money.
Solution

Until recently, it was impossible to send money directly to another human without going through the banking system. The big charity organisations were a necessary part of the process, and they made the most of their position. Think about it: you have a family to feed, rent or a mortgage that has to be paid, or you’ll be homeless and destitute. What would your priority be? Apart from the top level, these are generally good people with the best intentions.
But now we have Bitcoin. People can send money all over the world at extremely low cost. The recipients aren’t stupid; they know what they need better than any NGO “expert,” and any expertise or teaching they need, they can get if they have the money to pay for it. This way, the power relationship is reversed in favor of our recipients.
All we need is a system (open and distributed) that ensures sponsors’ funds are not being squandered and the projects being supported are not scams.
A few people decided to start such a project. We have a system almost fully built and currently being tested out. It will enable people to get together into small groups of sponsors to fund small, local projects by directly funding the individuals working on the project. Anything from a regular monthly commitment to a click-for-charity system where you don’t even need any money to occasional one-off purchases of items for a project will be possible.
Here’s our pilot project in Badilisha, on Lake Victoria.
If you like doing stuff on social media, please sign up on our beta site (no money needed) and say hi; we need a few people to get it started. clickforcharity.net.
-
 @ 005bc4de:ef11e1a2
2025-04-29 16:08:56
@ 005bc4de:ef11e1a2
2025-04-29 16:08:56Trump Bitcoin Report Card - Day 100
For whatever reason day 100 of a president's term has been deemed a milestone. So, it's time to check in with President Trump's bitcoin pledges and issue a report card.
Repo and prior reports: - GitHub: https://github.com/crrdlx/trump-bitcoin-report-card - First post: https://stacker.news/items/757211 - Progress Report 1: https://stacker.news/items/774165 - Day 1 Report Card: https://stacker.news/items/859475 - Day 100 Report Card: https://stacker.news/items/966434
Report Card | | Pledge | Prior Grade | Current Grade | |--|--|--|--| | 1 | Fire SEC Chair Gary Gensler on day 1 | A | A | | 2 | Commute the sentence of Ross Ulbricht on day 1 | A | A | | 3 | Remove capital gains taxes on bitcoin transactions | F | F | | 4 | Create and hodl a strategic bitcoin stockpile | D | C- | | 5 | Prevent a CBDC during his presidency | B+ | A | | 6 | Create a "bitcoin and crypto" advisory council | C- | C | | 7 | Support the right to self-custody | D+ | B- | | 8 | End the "war on crypto" | D+ | B+ | | 9 | Mine all remaining bitcoin in the USA | C- | C | | 10 | Make the US the "crypto capital of the planet" | C- | C+ |
Comments
Pledge 1 - SEC chair - (no change from earlier) - Gensler is out. This happened after the election and Trump took office. With the writing on the wall, Gensler announced he would resign, Trump picked a new SEC head in Paul Atkins, and Gensler left office just before Trump was sworn in. The only reason an A+ was not awarded was that Trump wasn't given the chance to actually fire Gensler, because he quit. No doubt, though, his quitting was due to Trump and the threat of being sacked.
Day 100 Report Card Grade: A
Pledge 2 - free Ross - (no change from earlier) - Ross Ulbricht's sentence was just commuted. Going will "option 3" above, the pledge was kept. An A+ would have been a commutation yesterday or by noon today, but, let's not split hairs. It's done.
Day 100 Report Card Grade: A
Pledge 3 - capital gains - This requires either executive action and/or legislation. There was no action. Executive action can be done with the stroke of a pen, but it was not. Legislation is tricky and time-consuming, however, there wasn't even mention of this matter. This seems to be on the back burner since statements such as this report in November. See Progress Report 1: https://stacker.news/items/774165 for more context.
Trump's main tax thrust has been the tariff, actually a tax increase, instead of a cut. Currently, the emphasis is on extending the "Trump tax cuts" and recently House Speaker Mike Johnson indicated such a bill would be ready by Memorial Day. Earlier in his term, there was more chatter about tax relief for bitcoin or cryptocurrency. There seems to be less chatter on this, or none at all, such as its absence in the "ready by Memorial Day" article.
Until tax reform is codified and signed, it isn't tax law and the old code still applies.
Day 100 Report Card Grade: F
Pledge 4 - bitcoin reserve - The initial grade was a C, it was dropped to a D mainly due to Trump's propensity to [alt]coinery, and now it's back to a C-.
Getting the grade back up into C-level at a C- was a little bumpy. On March 2, 2025, Trump posted that a U.S. Crypto Reserve would be created. This is what had been hoped for, except that the pledge was for a Bitcoin Reserve, not crypto. And secondly, he specifically named XRP, SOL, and ADA (but not BTC). Just a couple of hours later, likely in clean up mode, he did add BTC (along with ETH) as "obviously" being included. So, the "Bitcoin Reserve" became a "Crypto Reserve."
Maybe still in "cleanup mode," Sec. of Commerce Howard Lutnick said bitcoin will hold "special status" in the reserve. Then, on March 6, an executive order made the U.S. Digital Asset Stockpile official. Again, "Bitcoin" was generalized until section 3 where the "Strategic Bitcoin Reserve" did come to official fruition.
The grade is only a C- because the only thing that happened was the naming of the stockpile. Indeed, it became official. But the "stockpile" was just BTC already held by the U.S. government. I think it's fair to say most bitcoiners would have preferred a statement about buying BTC. Other Trump bitcoin officials indicated acquiring "as much as we can get", which sounds great, but until it happens, is only words.
Day 100 Report Card Grade: C-
Pledge 5 - no CBDC - An executive order on January 23, 2025 forbade a CBDC in section 1, part v by "prohibiting the establishment, issuance, circulation, and use of a CBDC."
Day 100 Report Card Grade: A
Pledge 6 - advisory council - The Trump bitcoin or crypto team consists of the following: David Sacks as “crypto czar” and Bo Hines as executive director of the Presidential Council of Advisers for Digital Assets.
A White House Crypto Summit (see video) was held on March 7, 2025. In principle, the meeting was good, however, the summit seemed (a) to be very heavily "crypto" oriented, and (b) to largely be a meet-and-greet show.
Still, just the fact that such a show took place, inside the White House, reveals how far things have come and the change in climate. For the grade to go higher, more tangible things should take place over time.
Day 100 Report Card Grade: C
Pledge 7 - self-custody - There's been a bit of good news though on this front. First, the executive order above from January 23 stated in section 1, i, one of the goals was "...to maintain self-custody of digital assets." Also, the Phoenix wallet returned to the U.S. In 2024, both Phoenix and Wallet of Satoshi pulled out of the U.S. for fear of government crackdowns. The return of Phoenix, again, speaks to the difference in climate now and is a win for self-custody.
To rise above B-level, more assurance, it would be good to see further clear assurance that people can self-custody, that developers can build self-custody, and businesses can create products to self-custody. Also, Congressional action could get to an A.
Day 100 Report Card Grade: B-
Pledge 8 - end war on crypto - There has been improvement here. First, tangibly, SAB 121 was sent packing as SEC Commissioner Hester Peirce announced. Essentially, this removed a large regulatory burden. Commissioner Peirce also said ending the burdens will be a process to get out of the "mess". So, there's work to do. Also, hurdles were recently removed so that banks can now engage in bitcoin activity. This is both a symbolic and real change.
Somewhat ironically, Trump's own venture into cryptocurrency with his World Liberty Financial and the $TRUMP and $MELANIA tokens, roundly poo-pood by bitcoiners, might actually be beneficial in a way. The signal from the White House seems to be on all things cryptocurrency, "Do it."
The improvement and climate now seems very different than with the previous administration and leaders who openly touted a war on crypto.
Day 100 Report Card Grade: B+
Pledge 9 - USA mining - As noted earlier, this is an impossible pledge. That said, things can be done to make America mining friendly. The U.S. holds an estimated 37 to 40% of Bitcoin hash rate, which is substantial. Plus, Trump, or the Trump family at least, has entered into bitcoin mining. With Hut 8, Eric Trump is heading "American Bitcoin" to mine BTC. Like the $TRUMP token, this conveys that bitcoin mining is a go in the USA.
Day 100 Report Card Grade: C
Pledge 10 - USA crypto capital - This pledge closely aligned with pledges 8 and 9. If the war on crypto ends, the USA becomes more and more crypto and bitcoin friendly. And, if the hashrate stays high and even increases, that puts the USA at the center of it all. Most of the categories above have seen improvements, all of which help this last pledge. Trump's executive orders help this grade as well as they move from only words spoken to becoming official policy.
To get higher, the Bitcoin Strategic Reserve should move from a name-change only to acquiring more BTC. If the USA wants to be the world's crypto capital, being the leader in bitcoin ownership is the way to do it.
Day 100 Report Card Grade: C+
Sources
- Nashville speech - https://www.youtube.com/watch?v=EiEIfBatnH8
- CryptoPotato "top 8 promises" - https://x.com/Crypto_Potato/status/1854105511349584226
- CNBC - https://www.cnbc.com/2024/11/06/trump-claims-presidential-win-here-is-what-he-promised-the-crypto-industry-ahead-of-the-election.html
- BLOCKHEAD - https://www.blockhead.co/2024/11/07/heres-everything-trump-promised-to-the-crypto-industry/
- CoinTelegraph - https://cointelegraph.com/news/trump-promises-crypto-election-usa
- China vid - Bitcoin ATH and US Strategic Bitcoin Stockpile - https://njump.me/nevent1qqsgmmuqumhfktugtnx9kcsh3ap6v7ca4z8rgx79palz2qk0wzz5cksppemhxue69uhkummn9ekx7mp0qgszwaxc8j8e0zw9sdq59y43rykyx3wm0lcd2502xth699v0gxf0degrqsqqqqqpglusv6
- Capitals gains tax - https://bravenewcoin.com/insights/trump-proposes-crypto-tax-cuts-targets-u-s-made-tokens-for-tax-exemption Progress report 1 ------------------------------------------------------------------------------------
- Meeting with Brian Armstrong - https://www.wsj.com/livecoverage/stock-market-today-dow-sp500-nasdaq-live-11-18-2024/card/exclusive-trump-to-meet-privately-with-coinbase-ceo-brian-armstrong-DDkgF0xW1BW242rVeuqx
- Michael Saylor podcast - https://fountain.fm/episode/DHEzGE0f99QQqyM36nVr
- Gensler resigns - https://coinpedia.org/news/big-breaking-sec-chair-gary-gensler-officially-resigns/ Progress report 2 ------------------------------------------------------------------------------------
- Trump & Justin Sun - https://www.coindesk.com/business/2024/11/26/justin-sun-joins-donald-trumps-world-liberty-financial-as-adviser $30M investment: https://www.yahoo.com/news/trump-crypto-project-bust-until-154313241.html
- SEC chair - https://www.cnbc.com/2024/12/04/trump-plans-to-nominate-paul-atkins-as-sec-chair.html
- Crypto czar - https://www.zerohedge.com/crypto/trump-names-david-sacks-white-house-ai-crypto-czar
- Investigate Choke Point 2.0 - https://www.cryptopolitan.com/crypto-czar-investigate-choke-point/
- Crypto council head Bo Hines - https://cointelegraph.com/news/trump-appoints-bo-hines-head-crypto-council
- National hash rate: https://www.cryptopolitan.com/the-us-controls-40-of-bitcoins-hashrate/
- Senate committee https://coinjournal.net/news/rep-senator-cynthia-lummis-selected-to-chair-crypto-subcommittee/
- Treasurh Sec. CBDC: https://decrypt.co/301444/trumps-treasury-pick-scott-bessant-pours-cold-water-on-us-digital-dollar-initiative
- National priority: https://cointelegraph.com/news/trump-executive-order-crypto-national-priority-bloomberg?utm_source=rss_feed&utm_medium=rss&utm_campaign=rss_partner_inbound
- $TRUMP https://njump.me/nevent1qqsffe0d7mgtu5jhasy4hmkcdy7wfrlcqwc4vf676hulvdn8uaqa3acpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyztpa8q038vw5xluyhnydj5u39d7cpssvuswjhhjqj8q42jh4ul3wqcyqqqqqqgmha026
- World Liberty buys alts: https://www.theblock.co/post/335779/trumps-world-liberty-buys-25-million-of-tokens-including-link-tron-aave-and-ethena?utm_source=rss&utm_medium=rss
- CFTC chair: https://cryptoslate.com/trump-appoints-crypto-advocate-caroline-pham-as-cftc-acting-chair/
- WLF buys wrapped BTC https://www.cryptopolitan.com/trump-buys-47-million-in-bitcoin/
- SEC turnover https://www.theblock.co/post/335944/trump-names-sec-commissioner-mark-uyeda-as-acting-chair-amid-a-crypto-regulatory-shift?utm_source=rss&utm_medium=rss
- ----------------------------100 Days Report---------------------------------Davos speech "world capital of AI and crypto" https://coinpedia.org/news/big-breaking-president-trump-says-u-s-to-become-ai-and-crypto-superpower/
- SAB 121 gone, Hester P heads talk force & ends sab 121?, war on crypto https://x.com/HesterPeirce/status/1882562977985114185 article: https://www.theblock.co/post/336761/days-after-gensler-leaves-sec-rescinds-controversial-crypto-accounting-guidance-sab-121?utm_source=twitter&utm_medium=social CoinTelegraph: https://cointelegraph.com/news/trump-executive-order-cbdc-ban-game-changer-us-institutional-crypto-adoption?utm_source=rss_feed&utm_medium=rss&utm_campaign=rss_partner_inbound
- Possible tax relief https://cryptodnes.bg/en/will-trumps-crypto-policies-lead-to-tax-relief-for-crypto-investors/
- War on crypto https://decrypt.co/304395/trump-sec-crypto-task-force-priorities-mess
- Trump "truths" 2/18 make usa #1 in crypto, "Trump effect" https://www.theblock.co/post/333137/ripple-ceo-says-75-of-open-roles-are-now-us-based-due-to-trump-effect and https://www.coindesk.com/markets/2025/01/06/ripples-garlinghouse-touts-trump-effect-amid-bump-in-u-s-deals
- Strategic reserve https://njump.me/nevent1qqsf89l74mqfkk74jqhjcqtwp5m970gedmtykn5uhl0vz9mhmrvvvgqpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyztpa8q038vw5xluyhnydj5u39d7cpssvuswjhhjqj8q42jh4ul3wqcyqqqqqqge7c74u and https://njump.me/nevent1qqswv50m7mc95m3saqce08jzpqc0vedw4avdk6zxy9axrn3hqet52xgpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyztpa8q038vw5xluyhnydj5u39d7cpssvuswjhhjqj8q42jh4ul3wqcyqqqqqqgpc7cp3
- Strategic reserve, bitcoin special https://www.thestreet.com/crypto/policy/bitcoin-to-hold-special-status-in-u-s-crypto-strategic-reserve
- Bitcoin reserve, crypto stockpile https://decrypt.co/309032/president-trump-signs-executive-order-to-establish-bitcoin-reserve-crypto-stockpile vid link https://njump.me/nevent1qqs09h58patpv9vfjpcss6v5nxv7m23u8g6g43nqvkjzgzescztucmspr9mhxue69uhhyetvv9ujumt0d4hhxarj9ecxjmnt9upzqtjzyy2ylrsceh5uj20j5e95v0e99s3epsvyctu2y0vrwyltvq33qvzqqqqqqyus4pu7
- Truth summit https://njump.me/nevent1qqswj6sv0wr4d4ppwzam5egr5k6nmqgjpwmsrlx2a7d4ndpfj0fxvcqpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyztpa8q038vw5xluyhnydj5u39d7cpssvuswjhhjqj8q42jh4ul3wqcyqqqqqqgu0mzzh and vid https://njump.me/nevent1qqsptn8c8wyuhlqtjr5u767x20q4dmjvxy28cdj30t4v9phhf6y5a5spzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyztpa8q038vw5xluyhnydj5u39d7cpssvuswjhhjqj8q42jh4ul3wqcyqqqqqqgqklklu
- SEC chair confirmed https://beincrypto.com/sec-chair-paul-atkins-confirmed-senate-vote/
- pro bitcoin USA https://coinpedia.org/news/u-s-secretary-of-commerce-howard-lutnick-says-america-is-ready-for-bitcoin/
- tax cuts https://thehill.com/homenews/house/5272043-johnson-house-trump-agenda-memorial-day/
- "as much as we can get" https://cryptobriefing.com/trump-bitcoin-acquisition-strategy/
- ban on CBDC https://www.whitehouse.gov/presidential-actions/2025/01/strengthening-american-leadership-in-digital-financial-technology/
- Phoenix WoS leave https://www.coindesk.com/opinion/2024/04/29/wasabi-wallet-and-phoenix-leave-the-us-whats-next-for-non-custodial-crypto
- Trump hut 8 mining https://www.reuters.com/technology/hut-8-eric-trump-launch-bitcoin-mining-company-2025-03-31/
-
 @ a5142938:0ef19da3
2025-04-30 08:34:54
@ a5142938:0ef19da3
2025-04-30 08:34:54
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ d1667293:388e7004
2025-04-29 16:00:19
@ d1667293:388e7004
2025-04-29 16:00:19The "Bitcoindollar" system—an emerging term which describes the interplay of U.S. dollar-denominated stablecoins and Bitcoin as complementary forces in the evolving monetary framework of the digital era (and which replaces the defunct Petrodollar system)—has sparked an interesting debate on Nostr with PowMaxi.
You will find the thread links at the bottom of this article.
Powmaxi argues that attempting to merge hard money (Bitcoin) with soft money (the U.S. dollar) is structurally doomed, because the systems are inherently contradictory and cannot coexist without one eventually destroying the other.
This critique is certainly valid, but ONLY if the Bitcoindollar is viewed as a final system. But I never claim that. To the contrary, the conclusion in my book is that this is a system that buys time for fiat, absorbs global demand for monetary stability, and ushers in a Bitcoinized world without the immediate collapse and the reset of the fiat system which would otherwise cause dramatic consequences. The Bitcoindollar is the only way to a gradual Bitcoin dominance in 10-20 years time while avoiding sudden collapse of the fiat system, so that also the power elites who hold the keys to this system can adapt.\ At least this is my hope.
Therefore the "fusion" isn't the future. The siphoning is. And the U.S. may try to ride it as long as possible. The Bitcoindollar system is a transitional strategic framework, not a\ permanent monetary equilibrium. In the end I agree with PowMaxi.
His detailed critique deserves an equally detailed analysis. Here's how the objections break down and why they don’t necessarily undermine the Bitcoindollar system.
1. Hard Money vs. Soft Money: Opposed Systems?
Objection: Bitcoin is a closed, decentralized system with a fixed supply; the dollar is an open, elastic system governed by central banks and political power. These traits are mutually exclusive and incompatible.
Response: Ideologically, yes. Practically, no. Hybrid financial systems are not uncommon. Bitcoin and stablecoins serve different user needs: Bitcoin is a store of value; stablecoins are mediums of exchange. Their coexistence mirrors real-world economic needs. The contradiction can be managed, and is not fatal at least for the transitional phase.
2. Scarcity vs. Elasticity: Economic Incompatibility?
Objection: Bitcoin can’t inject liquidity in crises; fiat systems can. Anchoring fiat to Bitcoin removes policymakers' tools.
Response: Correct — but that’s why Bitcoin is held as a reserve, not used as the primary medium of exchange in the Bitcoindollar model. Fiat-based liquidity mechanisms still function via stablecoins, while Bitcoin acts as a counterweight to long-term monetary debasement. The system’s strength is in its optionality: you don’t have to use Bitcoin until you want an exit ramp from fiat.
3. No Stable Equilibrium: One Must Win?
Objection: The system will destabilize. Either Bitcoin undermines fiat or fiat suppresses Bitcoin.
Response: Not necessarily in this transitional phase. The “conflict” isn’t between tools — it’s between control philosophies. The dollar won’t disappear overnight, and Bitcoin isn’t going away. The likely outcome is a gradual shifting of savings and settlement layers to Bitcoin, while fiat continues to dominate day-to-day payments and credit markets — until Bitcoin becomes structurally better in both.
4. Gresham’s and Thiers’ Law: Hollowing Fiat?
Objection: People save in Bitcoin and spend fiat, eroding fiat value.
Response: Yes — and that’s been happening since 2009. But this isn’t a flaw; it’s a transition mechanism. The Bitcoindollar model recognizes this and creates a bridge: it monetizes U.S. debt while preserving access to hard money. In the long run, my expectation is that naturally bitcoin will prevail both as a SOV and currency, but until then, stablecoins and T-bill-backed tokens serve useful roles in the global economy.
5. Philosophical Incompatibility?
Objection: Bitcoin prioritizes individual sovereignty; fiat systems are hierarchical. They can't be reconciled.
Response: They don’t need to be reconciled ideologically to function in parallel. Users choose the tool that suits their needs. One empowers individual autonomy; the other offers state-backed convenience. This is a competition of values, not a mechanical incompatibility. The Bitcoindollar model is a strategy. It’s a bridge between old and new systems, not a permanent coexistence.
6. Fusion is Impossible?
Objection: It’s only a temporary bridge. One side must lose.
Response: Exactly. The Bitcoindollar system is a transitional bridge. But that doesn’t reduce its value. It provides a functional pathway for individuals, companies, and governments to gradually exit broken monetary systems and experiment with new models.
In the meantime, the U.S. benefits from stablecoin-driven Treasury demand, while Bitcoin continues to grow as a global reserve asset.
Bottom line: A Strategic Convergence, Not a Permanent Fusion
The Bitcoindollar system isn’t a contradiction. It’s a convergence zone. It reflects the reality that monetary systems evolve gradually, not cleanly. Bitcoin and fiat will compete, overlap, and influence each other. Eventually, yes — hard money wins. But until then, hybrid systems offer powerful stepping stones.
Thread links:
Thread started from this initial post.
-
 @ 7d33ba57:1b82db35
2025-04-29 14:14:11
@ 7d33ba57:1b82db35
2025-04-29 14:14:11Located in eastern Poland, Lublin is a city where history, culture, and youthful energy come together. Often called the "Gateway to the East," Lublin blends Gothic and Renaissance architecture, vibrant street life, and deep historical roots—especially as a center of Jewish heritage and intellectual life.
🏙️ Top Things to See in Lublin
🏰 Lublin Castle
- A striking hilltop castle with a neo-Gothic façade and a beautifully preserved Romanesque chapel (Chapel of the Holy Trinity)
- Don’t miss the frescoes inside—a rare mix of Byzantine and Western art styles
🚪 Old Town (Stare Miasto)
- Wander through cobblestone streets, pastel buildings, and arched gateways
- Filled with cozy cafes, galleries, and vibrant murals
- The Grodzka Gate symbolizes the passage between Christian and Jewish quarters
🕯️ Lublin’s Jewish Heritage
- Visit the Grodzka Gate – NN Theatre, a powerful memorial and museum telling the story of the once-vibrant Jewish community
- Nearby Majdanek Concentration Camp offers a sobering but important historical experience
🎭 Culture & Events
- Lublin is known for its festivals, like Carnaval Sztukmistrzów (Festival of Magicians and Street Performers) and the Night of Culture
- The city has a thriving theatre and music scene, supported by its large student population
🌳 Green Spaces
- Relax in Saski Garden, a peaceful park with walking paths and fountains
- Or take a walk along the Bystrzyca River for a quieter, more local feel
🍽️ Local Tastes
- Sample Polish classics like pierogi, żurek (sour rye soup), and bigos (hunter’s stew)
- Look for modern twists on traditional dishes in Lublin’s growing number of bistros and artisan cafés
🚆 Getting There
- Easy access by train or bus from Warsaw (2–2.5 hours)
- Compact center—easily walkable
-
 @ a5142938:0ef19da3
2025-04-30 08:33:41
@ a5142938:0ef19da3
2025-04-30 08:33:41Core Team
The Core Team drives the project and validates the content.
- Jean-David Bar: https://njump.me/npub1qr4p7uamcpawv7cr8z9nlhmd60lylukf7lvmtlnpe7r4juwxudzq3hrnll
To start, I'm managing the project solo by sharing my bookmarks to avoid plastic on ourselves and on our children. Contact me if you'd like to join!
Content Enrichers
Our contributors make this site engaging and interesting.
Coming soon.
👉 Learn more about contributions
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ bbb5dda0:f09e2747
2025-04-29 13:46:37
@ bbb5dda0:f09e2747
2025-04-29 13:46:37GitHub Actions (CI/CD) over Nostr
I Spent quite a bit of time on getting Nostr-based GitHub actions working. I have a basic runner implementation now, which i've reworked quite a bit when working with @dan on getting the front-end of it into gitworkshop.dev. We found that the nature of these jobs don't really lend itself to fit within the NIP-90 DVM spec.
What we have now: - A dvm-cicd-runner that - Advertises itself using NIP-89 announcements. - Takes a DVM request with: - repository - branch/ref - path to workflow file (
.yml) - job timeout (max duration) - 🥜 Cashu prepayment for the job timeout (to be refunded) - Pulls the repository and executes the provided workflow file - Sends logs in batches as partial job results - Publishes job results and gets displayed in gitworkshop - Gitworkshop.dev (all nostr:npub15qydau2hjma6ngxkl2cyar74wzyjshvl65za5k5rl69264ar2exs5cyejr work) UI that : - Shows available workflow runners. - Instructing + paying runner to execute workflow file - Displaying job status, live updating with the latest logs / autoscroll, all the stuff you'd expect - Neatly displaying past jobs for the current repositoryTODO'S + Ideas/vision
- TODO: refunding the unused minutes (job timeout - processing time) to the requester
- TODO: create seperate kinds/nip for worflow execution over nostr
- Create separate kinds for streaming arbitrary text data over nostr (line by line logs)
- automated git watchers for projects to kick of jobs
- Separate out workflow management stuff from gitworkshop.dev. A micro-app might serve better to manage runners for git projects etc and takes away pressure from gitworkshop.dev to do it all.
- Perhaps support just running .yaml files, without the requirement to have it in a git repo. Could just be a .yaml file on blossom.
TollGate
I spent most of my time working on TollGate. There's been a lot of back and forth to the drawing board to narrow down what the TollGate protocol looks like. I helped define some concepts on implementing a tollgate which we could use as language to discuss the different components that are part of a tollgate implementation. It helped us narrow down what was implementation and what is part of the protocol.
Current state of the project
- We have a website displaying the project: TollGate.me
- Worked on a basic android app for auto payments, validating we can auto-buy from tollgates by our phones
- Presented TollGate at @Sats 'n Facts
- There's a protocol draft, presented at SEC-04
- We've done workshops, people were able to turn an OpenWRT router into a TollGate
- Building and releasing TollGate as a singular OpenWRT package, installable on any compatible architecture
- Building and releasing TollGate OS v0.0.1 (prebuilt OpenWRT image), targeting a few specific routers
- First tollgate deployed in the wild!! (At a restaurant in Funchal, Madeira)
- Other developers started to make their own adjacent implementations, which decentralizes the protocol already
What's next:
- We're gathering useful real user feedback to be incorporated in OS v0.0.2 soon
- Refine the protocol further
- Showing TollGate at various conferences in Europe throughout the summer
- Keep building the community, it's growing fast
Epoxy (Nostr based Addressing)
Although i've pivoted towards focusing on TollGate I worked out an implementation of my NIP-(1)37 proposal. During SEC-04 I worked out this browser plugin to demonstrate one way to make websites resistant to rugpulls.
It works by looking for a
metatag in the page'shead:html <meta name="nostr-pubkey" relays="relay.site.com,other.relay.com">[hexPubkey]</meta>When we've never recorded a pubkey for this domain, we save it. This pubkey now serves as the owner of the website. It looks for a kind
11111event of that pubkey. It should list the current domain as one of it's domains. If not, it shows a warning.The key concept is that if we visit this website again and one of these scenario's is true: - There is no longer a
metatag - There's another pubkey in themetatag - The pubkey is still on the webpage, but the11111no longer lists this domainThen we consider this domain as RUGPULLED and the user gets an error, suggesting to navigate to other domain listed by this
pubkey. I'd like it to perhaps auto-redirect to another domain listed by the owner, this is especially useful for frequently rugged domains.This extension does try to solve a bootstrapping problem. We need to establish the website's pubkey at some point. We have to start somewhere, which is why the first load is considered as the 'real' one, since we have no way of knowing for sure.
Other
🥜/⚡️ Receipt.Cash - Social Receipt sharing app
During SEC I worked on scratching an itch that has been lingering in my mind since SEC-03 already. And now that vibecoding is a thing it wasn't this huge undertaking anymore to handle the front-end stuff (which i suck at).
The usage scenario is a bunch of bitcoiners that are at a restaurant, we get the bill and want to split it amongst each other. One person can pay the bill, then: - Payer photographs receipt - Payer adds Cashu Payment request - Payer sets dev split % - App turns the receipt + request into a (encrypted) nostr event - The payer shares the event with QR or Share Menu
The friend scan the QR: - Receipt is loaded and displayed - Friend selects items they ordered - Friend hits pay button (⚡️Lightning or 🥜Cashu) and pays - Payment gets sent to Payer's cashu wallet - Dev split set by Payer goes to dev address.
Some features: - Change LLM model that processes the receipt to extract data - Proofs storage + recovery (if anything fails during processing)
Todo's: - Letting payer configure LNURL for payouts - Letting payer edit Receipt before sharing - Fix: live updates on settled items
The repo: receipt-cash
-
 @ a5142938:0ef19da3
2025-04-30 08:32:38
@ a5142938:0ef19da3
2025-04-30 08:32:38Finding 100% natural, plastic-free products turned out to be much harder than I expected… So I started collecting bookmarks. And then I thought: "What if we shared?!
Help me discover the best natural alternatives for clothing and gear without plastic!
This project is all about sharing: half of the site's potential revenue is redistributed to contributors. A small experiment in revenue and value sharing on the internet. :-)
Q&A
Why focus on natural materials?
Synthetic materials are mostly plastics (polyester, polyamide…). The problem? They end up contaminating us:
- Microplastics absorbed through the skin,
- Particles released with every wash, making their way into the water we drink and the food we eat,
- Major challenges in recycling plastic waste.
What exactly are natural materials?
They are non-synthetic materials, whose components exist in nature without molecular modification. But what really matters here is their biodegradability and non-toxicity.
Some materials may spark debates about their acceptability on this site!
How is this different from other ethical fashion or shopping websites?
Many websites offer ethical and sustainable products, but I often found they still included synthetic materials. I had to check every product individually. Some promote recycled plastic fibers as an eco-friendly choice, but I’d rather not put plastic on my skin or my children's.
How can I contribute?
If you find this project useful or interesting, here’s how you can support it:
-
📝 Contribute: suggest edits by commenting on existing entries or propose new product or brand references. 👉 Learn more about contributions
-
⚡ Donate: Help sustain the project and support contributors. 👉 Learn more about donations
-
📢 Spread the word: Share the site on social media, your blog…
How can I receive a share of the site’s revenue?
You need a NOSTR account and a Bitcoin Lightning address.
What is NOSTR?
NOSTR is a decentralized internet protocol, still experimental, that allows you to:
- Publish and browse content without relying on a centralized platform.
- Log in to multiple services while keeping full control over your data.
- Use the Bitcoin Lightning network for instant, peer-to-peer payments.
What about my data privacy?
- No ads, no personalized tracking.
- NOSTR comments are public, but you can use a pseudonym.
- You retain ownership of your contributions on the NOSTR protocol.
Who is behind this project?
We use open-source tools and services:
- NOSTR for content publishing and contributions checking,
- npub.pro for content visualization,
- Coinos.io for payment management.
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ a5142938:0ef19da3
2025-04-30 08:32:01
@ a5142938:0ef19da3
2025-04-30 08:32:01Rewards are an experimental approach to sharing the value created by contributors to this site, through a revenue-sharing system based on the following conditions:
- Any revenue generated by the site each month is distributed over the following 12 months, ensuring long-term visibility and smoothing out monthly variations.
- On the 1st of each month, half of the revenue is distributed among all contributors, in proportion to the number of their validated contributions.
- Contributions remain valid indefinitely, but rewards are only distributed to contributors who have made at least one validated contribution in the past 12 months.
Payment Method
Rewards are paid via the Lightning network, in sats (the smallest unit of Bitcoin).
To receive payments, you must have a NOSTR account linked to a Lightning wallet.
To receive them, the NOSTR account used to contribute must be linked to a Lightning wallet.
💡 New to these tools? - Don’t have a NOSTR account yet? A simple way to get started is to create one on an open-source NOSTR client like yakihonne.com to set up your profile and wallet there. Then, retrieve your NOSTR keys (from the settings) and save them in a secure vault like nsec.app to log in here and start contributing. - Already started contributing on this site? Make sure to securely store your NOSTR keys in a vault like nsec.app. You can also log in with them on yakihonne.com to set up your profile. - You can also contribute directly from yakihonne.com by commenting on Origine Nature’s articles.
👉 Learn more about contributions
Next rewards
Coming soon.
This article is published on origin-nature.com 🌐 Voir cet article en français
-
 @ f11e91c5:59a0b04a
2025-04-30 07:52:21
@ f11e91c5:59a0b04a
2025-04-30 07:52:21!!!2022-07-07に書かれた記事です。
暗号通貨とかでお弁当売ってます 11:30〜14:00ぐらいでやってます
◆住所 木曜日・東京都渋谷区宇田川町41 (アベマタワーの下らへん)
◆お値段
Monacoin 3.9mona
Bitzeny 390zny
Bitcoin 3900sats (#lightningNetwork)
Ethereum 0.0039Ether(#zkSync)
39=thank you. (円を基準にしてません)
最近は週に一回になりました。 他の日はキッチンカーの現場を探したり色々してます。 東京都内で平日ランチ出店出来そうな場所があればぜひご連絡を!
 写真はNFCタグです。
スマホにウォレットがあればタッチして3900satsで決済出来ます。
正直こんな怪しい手書きのNFCタグなんて絶対にビットコイナーは触りたくも無いだろうなと思いますが、これでも良いんだぜというメッセージです。
写真はNFCタグです。
スマホにウォレットがあればタッチして3900satsで決済出来ます。
正直こんな怪しい手書きのNFCタグなんて絶対にビットコイナーは触りたくも無いだろうなと思いますが、これでも良いんだぜというメッセージです。今までbtcpayのposでしたが速度を追求してこれに変更しました。 たまに上手くいかないですがそしたら渋々POS出すので温かい目でよろしくお願いします。
ノードを建てたり決済したりで1年経ちました。 最近も少しずつノードを建てる方が増えてるみたいで本当凄いですねUmbrel 大体の人がルーティングに果敢に挑むのを見つつ 奥さんに土下座しながら費用を捻出する弱小の私は決済の利便性を全開で振り切るしか無いので応援よろしくお願いします。
あえて あえて言うのであれば、ルーティングも楽しいですけど やはり本当の意味での即時決済や相手を選んでチャネルを繋げる楽しさもあるよとお伝えしたいっ!! 決済を受け入れないと分からない所ですが 承認がいらない時点で画期的です。
QRでもタッチでも金額指定でも入力でも もうやりようには出来てしまうし進化が恐ろしく早いので1番利用の多いpaypayの手数料(事業者側のね)を考えたらビットコイン凄いじゃない!と叫びたくなる。 が、やはり税制面や価格の変動(うちはBTC固定だけども)ウォレットの操作や普及率を考えるとまぁ難しい所もあるんですかね。
それでも継続的に沢山の人が色んな活動をしてるので私も何か出来ることがあれば 今後も奥さんに土下座しながら頑張って行きたいと思います。
(Originally posted 2022-07-07)
I sell bento lunches for cryptocurrency. We’re open roughly 11:30 a.m. – 2:00 p.m. Address Thursdays – 41 Udagawa-chō, Shibuya-ku, Tokyo (around the base of Abema Tower)
Prices Coin Price Note Monacoin 3.9 MONA
Bitzeny 390 ZNY Bitcoin 3,900 sats (Lightning Network)
Ethereum 0.0039 ETH (zkSync) “39” sounds like “thank you” in Japanese. Prices aren’t pegged to yen.These days I’m open only once a week. On other days I’m out scouting new spots for the kitchen-car. If you know weekday-lunch locations inside Tokyo where I could set up, please let me know!
The photo shows an NFC tag. If your phone has a Lightning wallet, just tap and pay 3,900 sats. I admit this hand-written NFC tag looks shady—any self-respecting Bitcoiner probably wouldn’t want to tap it—but the point is: even this works!
I used to run a BTCPay POS, but I switched to this setup for speed. Sometimes the tap payment fails; if that happens I reluctantly pull out the old POS. Thanks for your patience.
It’s been one year since I spun up a node and started accepting Lightning payments. So many people are now running their own nodes—Umbrel really is amazing. While the big players bravely chase routing fees, I’m a tiny operator scraping together funds while begging my wife for forgiveness, so I’m all-in on maximising payment convenience. Your support means a lot!
If I may add: routing is fun, but instant, trust-minimised payments and the thrill of choosing whom to open channels with are just as exciting. You’ll only understand once you start accepting payments yourself—zero-confirmation settlement really is revolutionary.
QR codes, NFC taps, fixed amounts, manual entry… the possibilities keep multiplying, and the pace of innovation is scary fast. When I compare it to the merchant fees on Japan’s most-used service, PayPay, I want to shout: “Bitcoin is incredible!” Sure, taxes, price volatility (my shop is BTC-denominated, though), wallet UX, and adoption hurdles are still pain points.
Even so, lots of people keep building cool stuff, so I’ll keep doing what I can—still on my knees to my wife, but moving forward!
-
 @ fd0bcf8c:521f98c0
2025-04-29 13:38:49
@ fd0bcf8c:521f98c0
2025-04-29 13:38:49The vag' sits on the edge of the highway, broken, hungry. Overhead flies a transcontinental plane filled with highly paid executives. The upper class has taken to the air, the lower class to the roads: there is no longer any bond between them, they are two nations."—The Sovereign Individual
Fire
I was talking to a friend last night. Coffee in hand. Watching flames consume branches. Spring night on his porch.
He believed in America's happy ending. Debt would vanish. Inflation would cool. Manufacturing would return. Good guys win.
I nodded. I wanted to believe.
He leaned forward, toward the flame. I sat back, watching both fire and sky.
His military photos hung inside. Service medals displayed. Patriotism bone-deep.
The pendulum clock on his porch wall swung steadily. Tick. Tock. Measuring moments. Marking epochs.
History tells another story. Not tragic. Just true.
Our time has come. America cut off couldn't compete. Factories sit empty. Supply chains span oceans. Skills lack. Children lag behind. Rebuilding takes decades.
Truth hurts. Truth frees.
Cycles
History moves in waves. Every 500 years, power shifts. Systems fall. Systems rise.
500 BC - Greek coins changed everything. Markets flourished. Athens dominated.
1 AD - Rome ruled commerce. One currency. Endless roads. Bustling ports.
500 AD - Rome faded. Not overnight. Slowly. Trade withered. Cities emptied. Money debased. Roads crumbled. Local strongmen rose. Peasants sought protection. Feudalism emerged.
People still lived. Still worked. Horizons narrowed. Knowledge concentrated. Most barely survived. Rich adapted. Poor suffered.
Self-reliance determined survival. Those growing food endured. Those making essential goods continued. Those dependent on imperial systems suffered most.
1000 AD - Medieval revival began. Venice dominated seas. China printed money. Cathedrals rose. Universities formed.
1500 AD - Europeans sailed everywhere. Spanish silver flowed. Banks financed kingdoms. Companies colonized continents. Power moved west.
The pendulum swung. East to West. West to East. Civilizations rose. Civilizations fell.
2000 AD - Pattern repeats. America strains. Digital networks expand. China rises. Debt swells. Old systems break.
We stand at the hinge.
Warnings
Signs everywhere. Dollar weakens globally. BRICS builds alternatives. Yuan buys oil. Factories rust. Debt exceeds GDP. Interest consumes budgets.
Bridges crumble. Education falters. Politicians chase votes. We consume. We borrow.
Rome fell gradually. Citizens barely noticed. Taxes increased. Currency devalued. Military weakened. Services decayed. Life hardened by degrees.
East Rome adapted. Survived centuries. West fragmented. Trade shrank. Some thrived. Others suffered. Life changed permanently.
Those who could feed themselves survived best. Those who needed the system suffered worst.
Pendulum
My friend poured another coffee. The burn pile popped loudly. Sparks flew upward like dying stars.
His face changed as facts accumulated. Military man. Trained to assess threats. Detect weaknesses.
He stared at the fire. National glory reduced to embers. Something shifted in his expression. Recognition.
His fingers tightened around his mug. Knuckles white. Eyes fixed on dying flames.
I traced the horizon instead. Observing landscape. Noting the contrast.
He touched the flag on his t-shirt. I adjusted my plain gray one.
The unpayable debt. The crumbling infrastructure. The forgotten manufacturing. The dependent supply chains. The devaluing currency.
The pendulum clock ticked. Relentless. Indifferent to empires.
His eyes said what his patriotism couldn't voice. Something fundamental breaking.
I'd seen this coming. Years traveling showed me. Different systems. Different values. American exceptionalism viewed from outside.
Pragmatism replaced my old idealism. See things as they are. Not as wished.
The logs shifted. Flames reached higher. Then lower. The cycle of fire.
Divergence
Society always splits during shifts.
Some adapt. Some don't.
Printing arrived. Scribes starved. Publishers thrived. Information accelerated. Readers multiplied. Ideas spread. Adapters prospered.
Steam engines came. Weavers died. Factory owners flourished. Villages emptied. Cities grew. Coal replaced farms. Railways replaced wagons. New skills meant survival.
Computers transformed everything. Typewriters vanished. Software boomed. Data replaced paper. Networks replaced cabinets. Programmers replaced typists. Digital skills determined success.
The self-reliant thrived in each transition. Those waiting for rescue fell behind.
Now AI reshapes creativity. Some artists resist. Some harness it. Gap widens daily.
Bitcoin offers refuge. Critics mock. Adopters build wealth. The distance grows.
Remote work redraws maps. Office-bound struggle. Location-free flourish.
The pendulum swings. Power shifts. Some rise with it. Some fall against it.
Two societies emerge. Adaptive. Resistant. Prepared. Pretending.
Advantage
Early adapters win. Not through genius. Through action.
First printers built empires. First factories created dynasties. First websites became giants.
Bitcoin followed this pattern. Laptop miners became millionaires. Early buyers became legends.
Critics repeat themselves: "Too volatile." "No value." "Government ban coming."
Doubters doubt. Builders build. Gap widens.
Self-reliance accelerates adaptation. No permission needed. No consensus required. Act. Learn. Build.
The burn pile flames like empire's glory. Bright. Consuming. Temporary.
Blindness
Our brains see tigers. Not economic shifts.
We panic at headlines. We ignore decades-long trends.
We notice market drops. We miss debt cycles.
We debate tweets. We ignore revolutions.
Not weakness. Just humanity. Foresight requires work. Study. Thought.
Self-reliant thinking means seeing clearly. No comforting lies. No pleasing narratives. Just reality.
The clock pendulum swings. Time passes regardless of observation.
Action
Empires fall. Families need security. Children need futures. Lives need meaning.
You can adapt faster than nations.
Assess honestly. What skills matter now? What preserves wealth? Who helps when needed?
Never stop learning. Factory workers learned code. Taxi drivers joined apps. Photographers went digital.
Diversify globally. No country owns tomorrow. Learn languages. Make connections. Stay mobile.
Protect your money. Dying empires debase currencies. Romans kept gold. Bitcoin offers similar shelter.
Build resilience. Grow food. Make energy. Stay strong. Keep friends. Read old books. Some things never change.
Self-reliance matters most. Can you feed yourself? Can you fix things? Can you solve problems? Can you create value without systems?
Movement
Humans were nomads first. Settlers second. Movement in our blood.
Our ancestors followed herds. Sought better lands. Survival meant mobility.
The pendulum swings here too. Nomad to farmer. City-dweller to digital nomad.
Rome fixed people to land. Feudalism bound serfs to soil. Nations created borders. Companies demanded presence.
Now technology breaks chains. Work happens anywhere. Knowledge flows everywhere.
The rebuild America seeks requires fixed positions. Factory workers. Taxpaying citizens in permanent homes.
But technology enables escape. Remote work. Digital currencies. Borderless businesses.
The self-reliant understand mobility as freedom. One location means one set of rules. One economy. One fate.
Many locations mean options. Taxes become predatory? Leave. Opportunities disappear? Find new ones.
Patriotism celebrates roots. Wisdom remembers wings.
My friend's boots dug into his soil. Planted. Territorial. Defending.
My Chucks rested lightly. Ready. Adaptable. Departing.
His toolshed held equipment to maintain boundaries. Fences. Hedges. Property lines.
My backpack contained tools for crossing them. Chargers. Adapters. Currency.
The burn pile flame flickers. Fixed in place. The spark flies free. Movement its nature.
During Rome's decline, the mobile survived best. Merchants crossing borders. Scholars seeking patrons. Those tied to crumbling systems suffered most.
Location independence means personal resilience. Economic downturns become geographic choices. Political oppression becomes optional suffering.
Technology shrinks distance. Digital work. Video relationships. Online learning.
Self-sovereignty requires mobility. The option to walk away. The freedom to arrive elsewhere.
Two more worlds diverge. The rooted. The mobile. The fixed. The fluid. The loyal. The free.
Hope
Not decline. Transition. Painful but temporary.
America may weaken. Humanity advances. Technology multiplies possibilities. Poverty falls. Knowledge grows.
Falling empires see doom. Rising ones see opportunity. Both miss half the picture.
Every shift brings destruction and creation. Rome fell. Europe struggled. Farms produced less. Cities shrank. Trade broke down.
Yet innovation continued. Water mills appeared. New plows emerged. Monks preserved books. New systems evolved.
Different doesn't mean worse for everyone.
Some industries die. Others birth. Some regions fade. Others bloom. Some skills become useless. Others become gold.
The self-reliant thrive in any world. They adapt. They build. They serve. They create.
Choose your role. Nostalgia or building.
The pendulum swings. East rises again. The cycle continues.
Fading
The burn pile dimmed. Embers fading. Night air cooling.
My friend's shoulders changed. Tension releasing. Something accepted.
His patriotism remained. His illusions departed.
The pendulum clock ticked steadily. Measuring more than minutes. Measuring eras.
Two coffee cups. His: military-themed, old and chipped but cherished. Mine: plain porcelain, new and unmarked.
His eyes remained on smoldering embers. Mine moved between him and the darkening trees.
His calendar marked local town meetings. Mine tracked travel dates.
The last flame flickered out. Spring peepers filled the silence.
In darkness, we watched smoke rise. The world changing. New choices ahead.
No empire lasts forever. No comfort in denial. Only clarity in acceptance.
Self-reliance the ancient answer. Build your skills. Secure your resources. Strengthen your body. Feed your mind. Help your neighbors.
The burn pile turned to ash. Empire's glory extinguished.
He stood facing his land. I faced the road.
A nod between us. Respect across division. Different strategies for the same storm.
He turned toward his home. I toward my vehicle.
The pendulum continued swinging. Power flowing east once more. Five centuries ending. Five centuries beginning.
"Bear in mind that everything that exists is already fraying at the edges." — Marcus Aurelius
Tomorrow depends not on nations. On us.
-
 @ 57d1a264:69f1fee1
2025-04-30 07:44:21
@ 57d1a264:69f1fee1
2025-04-30 07:44:21- The Dangers of Ignorance
- A Brief History of Mechanistic Interpretability
- The Utility of Interpretability
- What We Can Do
The progress of the underlying technology is inexorable, driven by forces too powerful to stop, but the way in which it happens—the order in which things are built, the applications we choose, and the details of how it is rolled out to society—are eminently possible to change, and it’s possible to have great positive impact by doing so. We can’t stop the bus, but we can steer it.
—Dario Amodeioriginally posted at https://stacker.news/items/967193
-
 @ c3b2802b:4850599c
2025-04-29 13:24:06
@ c3b2802b:4850599c
2025-04-29 13:24:06Am 11. April 2022, einem sonnigen Frühlingstag, schaute ich gegen 11 Uhr seit langem wieder einmal bei Roßleben an der Unstrut mit Muße in den Himmel. Gemeinsam mit Regina, meiner Frau. Wir sind jetzt im Ruhestand – und hatten uns im Jahr 1974 unter dem Himmel von Roßleben verliebt.
Was wir da sahen, können Sie im Titelbild oben nachvollziehen. Überrascht beobachteten wir ein Weile, was da passiert, doch die Streifen, offenkundig von Flugzeugen hinterlassen, lösten sich nicht auf, sondern verbanden sich allmählich zu einem zusammenhängenden Dunstschleier, festgehalten im folgenden Foto:

Überrascht waren wir, weil wir vor knapp 50 Jahren am gleichen Himmel zwar auch schon Flugzeuge gesehen hatten, die hatten allerdings nicht derartige von Horizont zu Horizont reichenden Spuren hinterlassen. Einige Tage später gelang mir eine Aufnahme, die einen von anno dazumal vertrauten Kondensstreifen eines Flugzeuges zeigt:

Gemeint ist die senkrecht in der Bildmitte verlaufende kurze Spur. Darunter der waagrechte Streifen zeigt das heute eher übliche Bild.
Als neugieriger Mensch bat ich das für solche Fragen zuständige Bundesumweltamt um Auskunft, wie diese Himmelserscheinungen zu erklären sind. Hier die Fragen, die ich mit den Fotos an das Umweltbundesamt gesendet habe:
1. Seit wann genau hinterlassen Flugzeuge über deutschem Luftraum Spuren, welche länger als 5 Minuten am Himmel sichtbar sind, sich ausbreiten und in Form von Dunstschleiern über Stunden am Himmel verbleiben?
2. Inwieweit wurde die Durchführung entsprechender Beschlüsse, welche die beobachtbare Schleierbildung herbeiführen, von demokratischen Gremien unseres Landes, z.B. dem deutschen Bundestag, genehmigt?
3. Welche Entscheidungsträger in unserem Land sind für diese Vorgänge verantwortlich?
4. Gibt es in diesem Zusammenhang internationale Geoingeneering-Programme, an denen Deutschland beteiligt ist? Wenn ja, welche sind das?
5. Was ist Ihnen über Partikel bzw. Substanzen bekannt, welche die langandauernde Sichtbarkeit dieser Schleier verursachen?
6. Was ist Ihnen über Folgeschäden durch die offenkundige Beeinflussung der Lichteinstrahlung oder durch Herabsenken von Partikeln bzw. Substanzen in diesen Schleiern auf Pflanzen, Tiere und Menschen bekannt?
7. Welche Möglichkeiten sehen Sie in Ihrem Amt, zur wissenschaftlichen Aufklärung und ggf. Beendigung dieser Dunstschleier-Aktivitäten beizutragen?
Hier die Antwort des Bundesamtes:
Sehr geehrter Herr Professor, danke für Ihre Anfrage.
Aus unserer Sicht handelt es sich bei Ihren Beobachtungen um Kondensstreifen. Sie entstehen in hinreichend kalter Atmosphäre als Folge der Wasserdampfemissionen aus Flugzeugtriebwerken. Bei niedriger Feuchte lösen sich Kondensstreifen rasch wieder auf. Ist die Atmosphäre jedoch hinreichend feucht, können Kondensstreifen länger existieren und weiter wachsen. Unter geeigneten Bedingungen können sie sich zu großflächigen Zirruswolken, die im Falle einer solchen Entstehungsgeschichte Contrail-Cirrus heißen, entwickeln. Contrail-Cirrus ist dann nicht mehr von natürlichen Zirren unterscheidbar, falls nicht seine gesamte Entstehungsgeschichte beobachtet wurde.
Nehmen Zirruswolken, die optisch sehr dünn sein können, eine große Fläche ein, erscheint dem Beobachter der Himmel milchig weiß. Im Mittel sind rund 0,06 Prozent der Erde mit (linienförmigen) Kondensstreifen bedeckt. Gegenden mit hohem Flugverkehrsaufkommen erreichen deutlich höhere Bedeckungsgrade. So lag Mitte der neunziger Jahre der Wert für Europa bei 0,5 Prozent. Der Bedeckungsgrad durch Contrail-Cirrus ist noch nicht bekannt. Erste Schätzungen liefern Werte, die etwa zehnmal so groß sind wie der Bedeckungsgrad mit linienförmigen Kondensstreifen.
Altern Kondensstreifen, bleiben sie nicht glatt, sondern können Formen bilden. Dieser Vorgang ist ein lange bekanntes Phänomen und eine Folge der Turbulenz, die in der Atmosphäre allgegenwärtig ist. Diese Formen lassen sich auch durch Modellsimulationen reproduzieren.
Mehrere Kondensstreifen nebeneinander entstehen zum Beispiel dadurch, dass Flugzeuge festen Routen folgen und die Windrichtung in der Höhe von der Flugroute abweicht. Die Kondensstreifen verschieben sich dadurch seitlich. An Knotenpunkten der Flugrouten können sich Kondensstreifen unterschiedlicher Orientierung bilden. Als Folge der Verschiebung der Kondensstreifen können dann auch rautenförmige Muster entstehen. Da Windrichtung und -geschwindigkeit praktisch nie gleich sind, entstehen aus vormals geraden Mustern gekrümmte Formen. Außerdem fliegen Flugzeuge nicht immer nur geradeaus, sondern auch Kurven, insbesondere während Warteschleifen in Flughafennähe. In diesem Fall können gekrümmte Kondensstreifen entstehen.
Nähere Informationen zur Bildung von Kondensstreifen gibt das DLR auf folgender Internetseite: http://www.dlr.de/pa/desktopdefault.aspx/tabid-2554/3836_read-5746/
Uns sind die Vorschläge, die unter dem Stichwort Geo-Engineering oder Climate-Engineering zusammengefasst werden, bekannt. Wir haben dazu bereits 2011 eine umfassende Broschüre veröffentlicht.
In dieser Broschüre stellen wir auch die großen Risiken, die mit Geo-Engineering verbunden wären, ausführlich dar. Es gibt in Deutschland auch keinerlei Planungen staatlicher Institutionen zur Durchführung von Geo-Engineering. Die existierenden Vorschläge zum Geo-Engineering sind zum größten Teil nicht ausgereift und werden auch in der Praxis nicht angewendet. Es ist nicht geklärt, welche schwerwiegenden, unerwünschten Nebenwirkungen auftreten könnten. Zudem gibt es gar keine ausreichende rechtliche Basis für Geo-Engineering. Wörtlich heißt es in unserer Broschüre auf Seite 4: „Angesichts der Tragweite von Geo-Engineering-Maßnahmen und den großen Unsicherheiten bei der Abschätzung von Folgen im komplexen Erdsystem rät das UBA aus Vorsorgegründen zu größter Zurückhaltung und bis zu einer deutlichen Verbesserung des Wissens um die Interdependenzen zwischen Geoprozessen zu einem Moratorium für den Einsatz solcher Maßnahmen.“ (https://www.umweltbundesamt.de/publikationen/geo-engineering-wirksamer-klimaschutz-groessenwahn)
Wir hoffen, die Informationen helfen Ihnen weiter. Mit freundlichen Grüßen Im Auftrag
Team Bürgerservice, Umweltbundesamt, Postfach 14 06, 06813 Dessau-Roßlau
Da ich kein Wolken-Forscher werden mag, überlasse ich Ihnen gern das Urteil über meine Fragen und die Passung der Antworten seitens unserer Regierungsbehörde.
Spannend ist heute, drei Jahre nach diesem kleinen Briefwechsel (erstmals veröffentlicht im April 2022 auf der Plattform der Zukunftskommunen), dass vom Senat des US Bundesstaates Florida am 3. April 2025 ein Gesetz verabschiedet wurde, welches das Versprühen von Chemikalien durch Flugzeuge unter Strafe stellt. Hier ein kurzer Auszug:
Verbot von Geoengineering und wetterverändernden Aktivitäten
(1) Die Injektion, Freisetzung oder Dispersion von Chemikalien, chemischen Verbindungen, Substanzen in die Atmosphäre innerhalb der Grenzen dieses Staates zu dem Zweck der Beeinflussung von Temperatur, Wetter, Klima oder um die Intensität des Sonnenlichts zu beeinflussen, ist verboten.
(2) Jede Person, jede öffentliche oder private Körperschaft, die eine Geo-Engineering-Aktion oder Wetterbeeinflussung unter Verstoß gegen dieses Verbot durchführt, macht sich schuldig eines Verbrechens dritten und zweiten Grades, auf das eine Geldstrafe von bis zu 100.000 Dollar fällig wird. ... Luftfahrzeugbetreiber oder Fluglotsen, die ein Verbrechen dritten Grades dieser Art begehen, werden bestraft mit einer Geldstrafe von bis zu $5.000 und bis zu 5 Jahren Gefängnis.
Den kompletten Text können Sie hier nachlesen. In Tennessee sowie in über 20 weiteren US Bundesstaaten sind ähnliche Gesetze auf dem Weg. Jetzt dürfen wir neugierig sein, wie die Rotkäppchen - Story in anderen Ländern, z.B. in Deutschland weitergeht.
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ 61bf790b:fe18b062
2025-04-29 12:23:09
@ 61bf790b:fe18b062
2025-04-29 12:23:09In a vast digital realm, two cities stood side by side: the towering, flashing metropolis of Feedia, and the decentralized, quiet city of Nostra.
Feedia was loud—blinding, buzzing, and always on. Screens plastered every wall, whispering the latest trends into citizens’ ears. But in this city, what you saw wasn’t up to you. It was determined by a towering, unseen force known as The Algorithm. It didn’t care what was true, meaningful, or helpful—only what would keep your eyes glued and your attention sold.
In Feedia, discovery wasn’t earned. It was assigned.
And worse—there was a caste system. To have a voice, you needed a Blue Check—a glowing badge that marked you as “worthy.” To get one, you had to pay or play. Pay monthly dues to the high towers or entertain The Algorithm enough to be deemed “valuable.” If you refused or couldn’t afford it, your voice was cast into the noise—buried beneath outrage bait and celebrity screams.
The unmarked were like ghosts—speaking into the void while the checked dined in Algorithm-favored towers. It was a digital monarchy dressed up as a democracy.
Then, there was Nostra.
There were no glowing checkmarks in Nostra—just signal. Every citizen had a light they carried, one that grew brighter the more they contributed: thoughtful posts, reshared ideas, built tools, or boosted others. Discovery was based not on payment or privilege, but participation and value.
In Nostra, you didn’t rise because you paid the gatekeeper—you rose because others lifted you. You weren’t spoon-fed; you sought, you found, you earned attention. It was harder, yes. But it was real.
And slowly, some in Feedia began to awaken. They grew tired of being fed fast-food content and ignored despite their voices. They looked across the river to Nostra, where minds weren’t bought—they were built.
And one by one, they began to cross.
-
 @ 1b939fa8:1ebdc679
2025-04-29 11:57:05
@ 1b939fa8:1ebdc679
2025-04-29 11:57:05All of my outfit conversion mods and Nora's Commonwealth Reconstruction Project have requirements that are on Nexus and nowhere else. Exception for the outfit conversions is Devious Devices which is noted and links provided to Lovers Lab and other requirements. My mods are dependent on those original mods to work. If/when the originals come to DEG then I will update and remove the Nexus links in my descriptions.
-
 @ 88cc134b:5ae99079
2025-04-29 11:39:51
@ 88cc134b:5ae99079
2025-04-29 11:39:51one, two, three, four, five, six
-
 @ 6c67a3f3:b0ebd196
2025-04-29 11:28:01
@ 6c67a3f3:b0ebd196
2025-04-29 11:28:01On Black-Starting the United Kingdom
In the event of a total failure of the electric grid, the United Kingdom would face a task at once technical and Sisyphean: the so-called black start — the reawakening of the nation’s darkened arteries without any external supply of power. In idealized manuals, the task is rendered brisk and clean, requiring but a few days' labor. In the world in which we live, it would be slower, more uncertain, and at times perilously close to impossible.
Let us unfold the matter layer by layer.
I. The Nature of the Undertaking
A black start is not a mere throwing of switches, but a sequential ballet. Small generating stations — diesel engines, hydro plants, gas turbines — must first breathe life into cold transmission lines. Substations must be coaxed into readiness. Load must be picked up cautiously, lest imbalance bring the whole effort to naught. Islands of power are stitched together, synchronized with exquisite care.
Each step is fraught with fragility. An unseen misalignment, an unsignaled overload, and hours of labor are lost.
II. The Dream of the Engineers
In theory, according to the National Grid Electricity System Operator (ESO), the sequence would unfold thus: within half a day, core transmission lines humming; within a day or two, hospitals lit and water flowing; within three days, cities reawakened; within a week, the nation, broadly speaking, restored to life.
This vision presupposes a fantasy of readiness: that black-start units are operational and plentiful; that communications systems, so delicately dependent on mobile networks and the internet, endure; that personnel, trained and coordinated, are on hand in sufficient numbers; and that no sabotage, no accident, no caprice of nature interrupts the dance.
III. The Real Order of Things
Reality is more obstinate. Many black-start capable plants have been shuttered in the name of efficiency. The financial incentives once offered to private generators for black-start readiness were judged insufficient; the providers withdrew.
Grid operations now rely on a lattice of private interests, demanding slow and complicated coordination. Telecommunications are vulnerable in a deep blackout. The old hands, steeped in the tacit lore of manual restoration, have retired, their knowledge scattered to the four winds. Cyber vulnerabilities have multiplied, and the grid’s physical inertia — the very thing that grants a system grace under perturbation — has grown thin, leaving the UK exposed to sudden collapses should synchronization falter.
Under such conditions, the best of hopes might yield five to ten days of partial recovery. Weeks would be required to restore the former web of normalcy. In certain cases — in the face of physical damage to high-voltage transformers, whose replacements take months if not years — black-start might founder altogether.
IV. The Quiet Admissions of Officialdom
In its polite documents, the National Grid ESO speaks carefully: essential services might see restoration within three days, but full public service would require "up to a week or longer." If designated black-start units were to fail — a real risk, given recent audits showing many unready — the timelines would stretch indefinitely.
In plain speech: in a true national blackout, the nation’s restoration would be a gamble.
V. The Forking Paths Ahead
If all proceeds well, Britain might stumble into light within three days. If the adversities accumulate — cyberattack, internal sabotage, simple human miscalculation — the process would stretch into weeks, even months. In the gravest scenarios, the nation would reconstitute not as one great engine, but as isolated islands of power, each jury-rigged and vulnerable.
Meanwhile, the paradoxical truth is that small and simple systems — the grids of Jersey, Malta, and the like — would outpace their mightier cousins, not despite their modest scale but because of it.
VI. Conclusion
The British grid, in short, is a triumph of late modernity — and like all such triumphs, it carries within itself the seeds of its own fragility. It works magnificently until the day it does not. When that day comes, recovery will be neither swift nor sure, but a slow, halting reweaving of threads too easily frayed.
-
 @ 33633f1e:21137a92
2025-04-30 07:15:58
@ 33633f1e:21137a92
2025-04-30 07:15:58Toglobal learninghuwabohu – wer räumt das alles auf?
Einheit veröffentlicht am Oktober 9, 2024 von settle
Worum religlobalt
| | | |:---:|:---:| |
 |
|  |
|Die zweite Schöpfungserzählung / Kirchenwälder in Äthiopien / Bewahrung der Schöpfung
Wir alle leben auf einer Erde – Tiere, Pflanzen und Menschen. Am Anfang war die Erde wüst und leer … aus diesem anfänglichen Tohuwabohu schafft Gott die natürliche Ordnung der Welt. Ursprünglich, so erzählt es der erste Schöpfungshymnus, war alles gut, wenn auch aus menschlicher Sicht, ziemlich durcheinander.
In der zweiten Schöpfungserzählung setzt Gott den Menschen in einen Paradiesgarten. Dieser Mensch soll nun die Erde behüten und bewahren. Das bedeutet auch Platz zu schaffen und aufzuräumen. Menschen greifen gemäß ihrem Auftrag, den Garten zu bestellen, in die Natur ein. Welche Konsequenzen hat unser Handeln? Wie sieht es mit dem zweiten Teil des Auftrags aus, den Garten auch zu beschützen? Was bedeutet es, wenn Menschen anfangen “auszuräumen” und dabei die Konsequenzen nicht mitbedenken?
In diesem Unterrichtsentwurf lernen Schüler:innen die biblischen Schöpfungserzählungen kennen und setzen sich kritisch mit den Folgen des menschlichen Handelns für Klima und Umwelt auseinander. Beispielhaft werden die Brot für die Welt “Reli fürs Klima”-Projekte aufgenommen. Anhand von Projekten in Kirchenwäldern der orthodoxen Kirche in Äthiopien und in Kirchenwäldern in Brandenburg erfahren die Schülerinnen und Schüler praktische Möglichkeiten, den Auftrag Gottes an die Menschen, die Schöpfung zu bebauen und zu bewahren, ernst zu nehmen und umzusetzen. Wie kann richtiges Aufräumen aussehen?
Die Konzeption orientiert sich am Dreischritt „Erkennen –Begreifen – Handeln“:
- Erkennen: Und siehe, es war sehr gut … – Zugang zum 2. biblischen Schöpfungsbericht (Gen 2,4–15)
- Begreifen: Und machet sie euch untertan – zerstören wir die Erde?
- Handeln: Bestellen und beschützen – kleine Paradiesgärten
Für das Unterrichtsvorhaben werden mindestens 3 x 45 Minuten Unterrichtszeit veranschlagt. Alle drei Teile des Unterrichtes können auch deutlich vertiefter und mit größerem Zeiteinsatz und -aufwand durchgeführt werden.
Das vorgestellte Unterrichtsvorhaben wurde entwickelt im Rahmen des von Brot für die Welt geförderten Projektes “reliGlobal”. Zur Förderung des “Globalen Lernens” erstellen Mitarbeiter:innen aus mehreren Pädagogischen Instituten in der EKD kooperativ Unterrichtsmaterialien für den evangelischen Religionsunterricht.
Unterrichtsschritte
Tohuwabohu – Schritt 1 Erkennen
In diesem Schritt beschäftigen sich die Schüler:innen mit dem zweiten biblischen Schöpfungsbericht.
Tohuwabohu – Schritt 2 Begreifen
In diesem Schritt werden die Auswirkungen der Eingriffe des Menschen in die Natur ins Blickfeld genommen und problematisiert.
Tohuwabohu – Schritt 3 Handeln
In diesem Schritt lernen die Schüler:innen praktische Möglichkeiten, die Natur zu bewahren, kennen und selbst umzusetzen.
Metamaterial
Tohuwabohu – Theologisch-Didaktische Hinweise
Tohuwabohu – Curricularer Bezug
-
 @ 975e4ad5:8d4847ce
2025-04-29 08:26:50
@ 975e4ad5:8d4847ce
2025-04-29 08:26:50With the advancement of quantum computers, a new threat emerges for the security of cryptocurrencies and blockchain technologies. These powerful machines have the potential to expose vulnerabilities in traditional cryptographic systems, which could jeopardize the safety of digital wallets. But don’t worry—modern wallets are already equipped to handle this threat with innovative solutions that make your funds nearly impossible to steal, even by a quantum computer. Let’s explore how this works and why you can rest easy.
The Threat of Quantum Computers
To understand how wallets protect us, we first need to grasp what makes quantum computers so dangerous. At the core of most cryptocurrencies, like Bitcoin, lies public and private key cryptography. The public key (or address) is like your bank account number—you share it to receive funds. The private key is like your PIN—it allows you to send funds and must remain secret.
Traditional cryptography, such as the ECDSA algorithm, relies on mathematical problems that are extremely difficult to solve with conventional computers. For instance, deriving a private key from a public key is practically impossible, as it would take millions of years of computation. However, quantum computers, thanks to algorithms like Shor’s, can significantly speed up this process. Theoretically, a sufficiently powerful quantum computer could uncover a private key from a public key in minutes or even seconds.
This is a problem because if someone gains access to your private key, they can send all your funds to their own address. But here’s the good news—modern wallets use a clever solution to render this threat powerless.
How Do Wallets Protect Us?
One of the most effective defenses against quantum computers is the use of one-time addresses in wallets. This means that for every transaction—whether receiving or sending funds—the wallet automatically generates a new public address. The old address, once used, remains in the transaction history but no longer holds any funds, as they are transferred to a new address.
Why Does This Work?
Imagine you’re sending or receiving cryptocurrency. Your wallet creates a new address for that transaction. After the funds are sent or received, that address becomes “used,” and the wallet automatically generates a new one for the next transaction. If a quantum computer manages to derive the private key from the public address of the used address, it will find nothing—because that address is already empty. Your funds are safely transferred to a new address, whose public key has not yet been exposed.
This strategy is known as HD (Hierarchical Deterministic) wallets. It allows the wallet to generate an infinite number of addresses from a single master key (seed) without compromising security. Each new address is unique and cannot be linked to the previous ones, making it impossible to trace your funds, even with a quantum computer.
Automation Makes It Effortless
The best part? You don’t need to worry about this process—it’s fully automated. When you use a modern wallet like MetaMask, Ledger, Trezor, or software wallets for Bitcoin, everything happens behind the scenes. You simply click “receive” or “send,” and the wallet takes care of generating new addresses. There’s no need to understand the complex technical details or manually manage your keys.
For example:
- You want to receive 0.1 BTC. Your wallet provides a new address, which you share with the sender.
- After receiving the funds, the wallet automatically prepares a new address for the next transaction.
- If you send some of the funds, the remaining amount (known as “change”) is sent to another new address generated by the wallet.
This system ensures that public addresses exposed on the blockchain no longer hold funds, making quantum attacks pointless.
Additional Protection: Toward Post-Quantum Cryptography
Beyond one-time addresses, blockchain developers are also working on post-quantum cryptography—algorithms that are resistant to quantum computers. Some blockchain networks are already experimenting with such solutions, like algorithms based on lattices (lattice-based cryptography). These methods don’t rely on the same mathematical problems that quantum computers can solve, offering long-term protection.
In the meantime, one-time addresses combined with current cryptographic standards provide enough security to safeguard your funds until post-quantum solutions become widely adopted.
Why You Shouldn’t Worry
Modern wallets are designed with the future in mind. They not only protect against today’s threats but also anticipate future risks, such as those posed by quantum computers. One-time addresses make exposed public keys useless to hackers, and automation ensures you don’t need to deal with the technicalities. HD wallets, which automatically generate new addresses, make the process seamless and secure for users.
Public key exposure only happens when necessary, reducing the risk of attacks, even from a quantum computer. In conclusion, while quantum computers pose a potential threat, modern wallets already offer effective solutions that make your cryptocurrencies nearly impossible to steal. With one-time addresses and the upcoming adoption of post-quantum cryptography, you can be confident that your funds are safe—today and tomorrow.
-
 @ 6f50351f:7b36c393
2025-04-30 06:34:17
@ 6f50351f:7b36c393
2025-04-30 06:34:17Toglobal learninghuwabohu – wer räumt das alles auf?
Einheit veröffentlicht am Oktober 9, 2024 von settle
Worum religlobalt
| | | |:---:|:---:| |
 |
|  |
|Die zweite Schöpfungserzählung / Kirchenwälder in Äthiopien / Bewahrung der Schöpfung
Wir alle leben auf einer Erde – Tiere, Pflanzen und Menschen. Am Anfang war die Erde wüst und leer … aus diesem anfänglichen Tohuwabohu schafft Gott die natürliche Ordnung der Welt. Ursprünglich, so erzählt es der erste Schöpfungshymnus, war alles gut, wenn auch aus menschlicher Sicht, ziemlich durcheinander.
In der zweiten Schöpfungserzählung setzt Gott den Menschen in einen Paradiesgarten. Dieser Mensch soll nun die Erde behüten und bewahren. Das bedeutet auch Platz zu schaffen und aufzuräumen. Menschen greifen gemäß ihrem Auftrag, den Garten zu bestellen, in die Natur ein. Welche Konsequenzen hat unser Handeln? Wie sieht es mit dem zweiten Teil des Auftrags aus, den Garten auch zu beschützen? Was bedeutet es, wenn Menschen anfangen “auszuräumen” und dabei die Konsequenzen nicht mitbedenken?
In diesem Unterrichtsentwurf lernen Schüler:innen die biblischen Schöpfungserzählungen kennen und setzen sich kritisch mit den Folgen des menschlichen Handelns für Klima und Umwelt auseinander. Beispielhaft werden die Brot für die Welt “Reli fürs Klima”-Projekte aufgenommen. Anhand von Projekten in Kirchenwäldern der orthodoxen Kirche in Äthiopien und in Kirchenwäldern in Brandenburg erfahren die Schülerinnen und Schüler praktische Möglichkeiten, den Auftrag Gottes an die Menschen, die Schöpfung zu bebauen und zu bewahren, ernst zu nehmen und umzusetzen. Wie kann richtiges Aufräumen aussehen?
Die Konzeption orientiert sich am Dreischritt „Erkennen –Begreifen – Handeln“:
- Erkennen: Und siehe, es war sehr gut … – Zugang zum 2. biblischen Schöpfungsbericht (Gen 2,4–15)
- Begreifen: Und machet sie euch untertan – zerstören wir die Erde?
- Handeln: Bestellen und beschützen – kleine Paradiesgärten
Für das Unterrichtsvorhaben werden mindestens 3 x 45 Minuten Unterrichtszeit veranschlagt. Alle drei Teile des Unterrichtes können auch deutlich vertiefter und mit größerem Zeiteinsatz und -aufwand durchgeführt werden.
Das vorgestellte Unterrichtsvorhaben wurde entwickelt im Rahmen des von Brot für die Welt geförderten Projektes “reliGlobal”. Zur Förderung des “Globalen Lernens” erstellen Mitarbeiter:innen aus mehreren Pädagogischen Instituten in der EKD kooperativ Unterrichtsmaterialien für den evangelischen Religionsunterricht.
Unterrichtsschritte
Tohuwabohu – Schritt 1 Erkennen
In diesem Schritt beschäftigen sich die Schüler:innen mit dem zweiten biblischen Schöpfungsbericht.
Tohuwabohu – Schritt 2 Begreifen
In diesem Schritt werden die Auswirkungen der Eingriffe des Menschen in die Natur ins Blickfeld genommen und problematisiert.
Tohuwabohu – Schritt 3 Handeln
In diesem Schritt lernen die Schüler:innen praktische Möglichkeiten, die Natur zu bewahren, kennen und selbst umzusetzen.
Metamaterial
Tohuwabohu – Theologisch-Didaktische Hinweise
Tohuwabohu – Curricularer Bezug
-
 @ a296b972:e5a7a2e8
2025-04-29 07:24:49
@ a296b972:e5a7a2e8
2025-04-29 07:24:4928.04.2025, 16.17 Uhr:
Russische Hobby-Flieger konnten mit ihrem Sportflugzeug namens "Andromeda" unter dem Radar bleiben und haben entlang der Hauptstromtrassen mit einem ukrainischen Zwiebelmesser die Stromleitungen gekappt. In einer scharfen Rechtskurve muss wohl eine Flugzeugtür aufgegangen sein und der Pass des Piloten fiel unbemerkt heraus. Die Identität der Täter konnte so schnell festgestellt werden.
28.04.2025, 16.43 Uhr:
Trump hat das europäische Stromnetz gekauft und die in den Umspannwerken eingebauten US-amerikanischen Chips deaktiviert. Es gibt erst wieder Strom, wenn sich die Koalition der Willigen den Friedensverhandlungen für die Ukraine anschließt. Trump hat bewusst in den sonnenreichen Ländern Spanien und Portugal begonnen, das soll als Warnung für ganz Europa gelten. Frau von der Leyen hat bereits scharfen Protest eingelegt, doch Trump hat die SMS sofort gelöscht.
28.04.2025, 17.12 Uhr:
Selensky hat einen Cyber-Angriff auf das europäische Stromnetz gestartet. Er ist wütend, weil sich Macron in dem 15-Minuten-Gespräch mit Trump am Rande der Beerdigung des Papstes in Rom hat abwimmeln lassen. Er beendet die Strom-Blockade erst, wenn Spanien, Portugal und Frankreich Deutschland dazu zwingen, endlich Taurus zu liefern. Auf die Frage, wie Selensky das angestellt hat, soll er geantwortet haben: "Sie sehen ja, wir können es."
Ist natürlich alles nur Joke! Es sollte nur einmal in Bezug auf die Sprengung der Nordstream 2 Pipelines aufgezeigt werden, wie schnell auch unsereins abstruse Erklärungen liefern kann, die vorne und hinten nicht stimmen können.
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
(Bild von pixabay)
-
 @ 8e351a6d:770975b7
2025-04-30 04:27:32
@ 8e351a6d:770975b7
2025-04-30 04:27:32Se você está em busca de uma plataforma confiável, moderna e cheia de opções para se divertir jogando online, a KZ999 é uma excelente escolha. Com uma interface intuitiva, suporte ágil e uma vasta gama de jogos empolgantes, o site se destaca no cenário atual de entretenimento digital no Brasil. Neste artigo, vamos explorar o que torna a KZ999 única, quais jogos ela oferece e como é a experiência real dos jogadores na plataforma.
Desde o primeiro acesso, a KZ999 transmite profissionalismo e praticidade. O site é otimizado para funcionar bem tanto em computadores quanto em dispositivos móveis, permitindo que os jogadores tenham acesso aos seus jogos favoritos a qualquer momento e em qualquer lugar.
A segurança é um dos pilares da plataforma. Utilizando tecnologias avançadas de criptografia, a KZ999 protege todas as transações e dados dos usuários, oferecendo tranquilidade em cada movimentação financeira. Além disso, o processo de cadastro é simples e rápido, ideal para quem quer começar a jogar sem complicações.
Um dos grandes atrativos da KZ999 é a diversidade de jogos disponíveis. A plataforma reúne títulos de provedores renomados, garantindo gráficos de qualidade, jogabilidade fluida e recursos que aumentam o envolvimento do usuário.
Entre os principais tipos de jogos oferecidos, podemos destacar:
Jogos de cartas e mesa: Clássicos como pôquer, bacará e outros jogos de estratégia estão disponíveis para quem gosta de testar suas habilidades e raciocínio lógico.
Slots online: Com dezenas de opções temáticas, os slots da KZ999 variam entre aventuras, fantasia, cultura oriental, esportes e muito mais. Eles são perfeitos para quem busca diversão leve com chances de bons retornos.
Jogos ao vivo: Para quem gosta de interatividade, a KZ999 também oferece jogos com transmissão em tempo real, trazendo um toque mais imersivo à experiência.
Apostas esportivas: Outra funcionalidade muito popular é a seção de esportes, onde os usuários podem apostar em eventos reais, como futebol, basquete e esportes eletrônicos.
Experiência do Jogador: Confiabilidade e Diversão Garantida A KZ999 foi projetada com foco total no usuário. Isso significa que cada detalhe — desde a navegação até os métodos de pagamento — é pensado para oferecer a melhor experiência possível.
O atendimento ao cliente é um dos pontos altos da plataforma. Disponível 24 horas por dia, o suporte pode ser contatado via chat ao vivo ou outros canais de comunicação, sempre pronto para solucionar dúvidas ou resolver problemas com rapidez e cordialidade.
Além disso, os métodos de depósito e saque são variados e incluem opções que os brasileiros conhecem e confiam, como PIX e transferências bancárias. Os prazos para retirada também são bastante competitivos, garantindo mais agilidade na hora de aproveitar seus ganhos.
Conclusão A KZ999 chega ao mercado brasileiro com uma proposta sólida e atrativa: oferecer uma experiência completa de entretenimento digital, com jogos variados, segurança robusta e suporte eficiente. Seja você um jogador experiente ou alguém em busca de uma nova forma de diversão online, a KZ999 merece ser descoberta.
Com inovação, qualidade e foco no usuário, a KZ999 tem tudo para se tornar sua plataforma favorita. Explore, jogue e descubra por que tantos brasileiros já estão escolhendo a KZ999 para se divertir todos os dias.
-
 @ c3b2802b:4850599c
2025-04-29 06:48:44
@ c3b2802b:4850599c
2025-04-29 06:48:44Haben Sie schon einmal einen Intelligenztest gemacht? Da geht es darum, in beschränkter Zeit eine Vielfalt rationaler Denkprozesse so präzise wie möglich korrekt zu absolvieren, wenn man gern einen hohen Intelligenzquotienten bescheinigt haben mag. Unsere gesamte Schulbildung ist überwiegend auf die Entfaltung dieser Art kognitiver Potentiale ausgerichtet. Allerdings ist es weniger eigenständiges Denken, das im Fokus steht. Meist handelt es sich um "betreutes" Denken in vorgegebenen begrifflichen Kategorien und mit vorgegebenen Frage-Antwort Schemata, welche vorab zu pauken sind, wenn man bestehen möchte.
Und wie steht es um das Mitfühlen mit anderen Geschöpfen - mit Grashüpfern, Ameisen, Pflanzen, Fischen, Schweinen oder Rindern? Und wie ist es um das Mitfühlen mit Menschen bestellt, welche infolge von Kriegshandlungen schwerste körperliche und seelische Schäden davontragen oder sterben? Wurden solche Fragen in Ihrer Ausbildung thematisiert? Meine Erinnerung bringt das Sezieren von Fröschen und Fischen im Biologieunterricht hervor, wobei Fragen an die Lehrer nach dem Leiden der Tiere als unpassend abgetan wurden. Die Überlebenden unserer Vorfahren in den Weltkriegen nach den erlittenen Leiden zu fragen: Hat Sie dazu einer Ihrer Lehrer oder Professoren ermutigt?
Sollten Sie bis hierher mitschwingen und ähnlich empfinden, dass unser Potential zum Mitfühlen in unserer Gesellschaft gegenüber kognitiven Potentialen wenig kultiviert und gepflegt wird, dann könnte sich ein Pfad auftun, unsere entstehende Regionalgesellschaft zu stärken.
Wenn wir unsere Sinneskanäle öffnen für das Befinden der Schöpfung, in der wir uns gerade bewegen, erschließen sich große Energiequellen. Diese können uns dienen, aus der vom hypertrophierten Denken entstellten Welt zurück in unsere Mitte zu finden. Zum einen können wir wahrnehmen, wie das Leben in und um uns pulsiert, können mitfühlen in dem zauberhaften Geschehen, das wir in besonderer Weise im gerade erwachenden Frühjahr erleben dürfen. Zum anderen werden wir Geschöpfe in Not oder Bedrängnis wahrnehmen und können so erfahren, dass es auch uns selbst wohl tut, wenn wir uns für diese engagieren. Wer schon einmal ein Tier geheilt hat oder sich für Opfer von Gewalthandlungen eingesetzt hat, kennt das.
Diese unmittelbaren Energiequellen geben uns Kraft, Bestätigung und Befriedigung - und diese Energie kann jeder Mensch zu jeder Zeit seines Lebens anzapfen.
Voraussetzung ist lediglich, dass wir die gewohnten "betreuten" Denkprozesse, auf die wir programmiert wurden, lernen zu unterbrechen. Dass wir die begriffliche Diarrhoe und Bedeutungsverdrehung seitens gefühlsarmer oder gefühlloser Menschen und ihrer Lakaien, welche uns aktuell zu Kriegshandlungen animieren wollen, hinter uns lassen. Dass wir uns nicht wie in den 1930er Jahren mit Worten wie "Kriegstüchtigkeit" gegen andere Völker aufhetzen lassen. Wenn wir solchen verbalen Entgleisungen nicht länger Aufmerksamkeit schenken, schaffen wir Zeit und Raum für das Mitfühlen.
Das Mitfühlen gibt uns ethische Orientierung, zeigt Wege auf, unsere Bestimmung zu finden und gibt uns die Kraft, unser Leben nach unseren Wertvorstellungen zu gestalten. Es beantwortet uns Fragen nach dem WOHIN und WOZU.
Das selbst Denken ist ein Werkzeug, welches uns, nachdem wir in unsere Mitte gefunden haben, dazu dienen kann, die Frage nach dem WIE zu klären.
Mit gleichgesinnten mitfühlenden und selbst denkenden Menschen ist es möglich, an unserer Regionalgesellschaft zu werkeln und funktionierende, auf Vertrauen basierende Initiativen und Gemeinschaften zum Blühen zu bringen. In meinen Blogbeiträgen sind seit 2018 einige davon beschrieben. Und ein psychologischer Zusammenhang scheint bemerkenswert: In solchen Gemeinschaften fühlen sich auch die Beteiligten wohl. Dazu liegen wissenschaftliche Studien vor, welche Sie in meinem Publikationsverzeichnis finden.
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ 8e351a6d:770975b7
2025-04-30 04:25:08
@ 8e351a6d:770975b7
2025-04-30 04:25:08Com o avanço da tecnologia, plataformas de jogos online vêm se destacando como uma das formas mais populares de entretenimento digital. Entre as que mais crescem no cenário brasileiro, a Pix188 se destaca por oferecer uma experiência completa, moderna e segura para jogadores de todos os perfis. Neste artigo, você vai conhecer melhor essa plataforma, os principais jogos disponíveis e o que torna a experiência do usuário tão especial.
A pix188é uma plataforma de entretenimento online desenvolvida para proporcionar aos usuários uma navegação simples, rápida e intuitiva. Desde o primeiro acesso, o site já demonstra seu compromisso com a qualidade: design responsivo, interface organizada e opções fáceis de localizar fazem parte da proposta.
O grande diferencial está na praticidade oferecida aos brasileiros. A plataforma é totalmente adaptada para o público nacional, com suporte em português, atendimento via chat ao vivo e integração com o sistema de pagamento via Pix, o que torna depósitos e saques rápidos, práticos e sem burocracia.
Variedade de Jogos para Todos os Gostos Um dos pontos fortes da Pix188 é a sua ampla seleção de jogos. A plataforma abriga os títulos mais populares e inovadores do mercado, com gráficos de alta qualidade, efeitos sonoros envolventes e temáticas variadas. Entre as categorias de jogos mais procuradas, destacam-se:
Slots Online: Os famosos caça-níqueis modernos aparecem com diversas opções temáticas, desde aventuras em templos perdidos até jogos inspirados em cultura pop. A mecânica simples e a possibilidade de grandes prêmios atraem tanto novatos quanto veteranos.
Jogos ao Vivo: A Pix188 também disponibiliza jogos interativos com apresentadores reais, transmitidos em tempo real. Essa modalidade proporciona uma experiência ainda mais imersiva, aproximando o jogador da emoção do ambiente físico.
Jogos de Mesa Virtuais: Para os que preferem estratégias e tomadas de decisão, a plataforma oferece clássicos como roleta, blackjack e bacará, todos em versões digitais com design sofisticado e fluidez impecável.
Apostas Esportivas: Além dos jogos eletrônicos, Pix188 também é referência para os fãs de esportes, oferecendo uma plataforma completa de palpites em tempo real. Futebol, basquete, tênis e outras modalidades estão disponíveis com cotações competitivas.
A Experiência do Jogador em Foco A Pix188 entende que o sucesso de uma plataforma depende da satisfação do usuário. Por isso, além da variedade de jogos, ela investe pesado em segurança, suporte ao cliente e recompensas para os jogadores. O sistema de bônus é outro atrativo: usuários ativos são constantemente surpreendidos com promoções, giros grátis e outras vantagens.
O suporte ao cliente é outro ponto que merece destaque. A equipe de atendimento está disponível 24 horas por dia, todos os dias da semana, para tirar dúvidas, auxiliar em transações e garantir que nenhum jogador fique desamparado. O canal via WhatsApp também agiliza o contato e proporciona ainda mais conveniência.
Conclusão A Pix188 chega ao mercado como uma alternativa moderna, segura e empolgante para quem busca entretenimento online de qualidade. Com uma plataforma robusta, jogos variados e uma experiência centrada no usuário, ela rapidamente conquistou seu espaço entre as favoritas do público brasileiro. Seja para momentos de lazer ou para quem gosta de adrenalina, a Pix188 é uma escolha que vale a pena explorar.
-
 @ 83279ad2:bd49240d
2025-04-29 05:53:52
@ 83279ad2:bd49240d
2025-04-29 05:53:52test
-
 @ 4db2f229:205fed9f
2025-04-28 23:25:16
@ 4db2f229:205fed9f
2025-04-28 23:25:16https://www.nexusmods.com/newvegas/mods/80258
If you manage to get it up to date / uncorrupt the data, I give you full liberties to:
- The model itself
- Its XMF and/or XML skeleton
- Patching it to be compatible with any other gun mods
- other fixes
- and full credit handed over to you
I think this has honestly been abandoned by it's original developer, and since I am just hanging onto the file? I decided it'd be better maintained in someone elses hands, and with community much more responsible than Nexus. Honestly if I did not archive this mod? It would of been vaporware.
But in it's current state it's not fit for being playable. I did manage to save media of when it was playable however.
-
 @ 4ba8e86d:89d32de4
2025-04-28 22:39:20
@ 4ba8e86d:89d32de4
2025-04-28 22:39:20Como funciona o PGP.

O texto a seguir foi retirado do capítulo 1 do documento Introdução à criptografia na documentação do PGP 6.5.1. Copyright © 1990-1999 Network Associates, Inc. Todos os direitos reservados.
-O que é criptografia? -Criptografia forte -Como funciona a criptografia? -Criptografia convencional -Cifra de César -Gerenciamento de chaves e criptografia convencional -Criptografia de chave pública -Como funciona o PGP - Chaves • Assinaturas digitais -Funções hash • Certificados digitais -Distribuição de certificados -Formatos de certificado •Validade e confiança -Verificando validade -Estabelecendo confiança -Modelos de confiança • Revogação de certificado -Comunicar que um certificado foi revogado -O que é uma senha? -Divisão de chave
Os princípios básicos da criptografia.
Quando Júlio César enviou mensagens aos seus generais, ele não confiou nos seus mensageiros. Então ele substituiu cada A em suas mensagens por um D, cada B por um E, e assim por diante através do alfabeto. Somente alguém que conhecesse a regra “shift by 3” poderia decifrar suas mensagens. E assim começamos.
Criptografia e descriptografia.
Os dados que podem ser lidos e compreendidos sem quaisquer medidas especiais são chamados de texto simples ou texto não criptografado. O método de disfarçar o texto simples de forma a ocultar sua substância é chamado de criptografia. Criptografar texto simples resulta em um jargão ilegível chamado texto cifrado. Você usa criptografia para garantir que as informações sejam ocultadas de qualquer pessoa a quem não se destinam, mesmo daqueles que podem ver os dados criptografados. O processo de reverter o texto cifrado ao texto simples original é chamado de descriptografia . A Figura 1-1 ilustra esse processo.
https://image.nostr.build/0e2fcb71ed86a6083e083abbb683f8c103f44a6c6db1aeb2df10ae51ec97ebe5.jpg
Figura 1-1. Criptografia e descriptografia
O que é criptografia?
Criptografia é a ciência que usa a matemática para criptografar e descriptografar dados. A criptografia permite armazenar informações confidenciais ou transmiti-las através de redes inseguras (como a Internet) para que não possam ser lidas por ninguém, exceto pelo destinatário pretendido. Embora a criptografia seja a ciência que protege os dados, a criptoanálise é a ciência que analisa e quebra a comunicação segura. A criptoanálise clássica envolve uma combinação interessante de raciocínio analítico, aplicação de ferramentas matemáticas, descoberta de padrões, paciência, determinação e sorte. Os criptoanalistas também são chamados de atacantes. A criptologia abrange tanto a criptografia quanto a criptoanálise.
Criptografia forte.
"Existem dois tipos de criptografia neste mundo: a criptografia que impedirá a sua irmã mais nova de ler os seus arquivos, e a criptografia que impedirá os principais governos de lerem os seus arquivos. Este livro é sobre o último." --Bruce Schneier, Criptografia Aplicada: Protocolos, Algoritmos e Código Fonte em C. PGP também trata deste último tipo de criptografia. A criptografia pode ser forte ou fraca, conforme explicado acima. A força criptográfica é medida no tempo e nos recursos necessários para recuperar o texto simples. O resultado de uma criptografia forte é um texto cifrado que é muito difícil de decifrar sem a posse da ferramenta de decodificação apropriada. Quão díficil? Dado todo o poder computacional e o tempo disponível de hoje – mesmo um bilhão de computadores fazendo um bilhão de verificações por segundo – não é possível decifrar o resultado de uma criptografia forte antes do fim do universo. Alguém poderia pensar, então, que uma criptografia forte resistiria muito bem até mesmo contra um criptoanalista extremamente determinado. Quem pode realmente dizer? Ninguém provou que a criptografia mais forte disponível hoje resistirá ao poder computacional de amanhã. No entanto, a criptografia forte empregada pelo PGP é a melhor disponível atualmente.
Contudo, a vigilância e o conservadorismo irão protegê-lo melhor do que as alegações de impenetrabilidade.
Como funciona a criptografia?
Um algoritmo criptográfico, ou cifra, é uma função matemática usada no processo de criptografia e descriptografia. Um algoritmo criptográfico funciona em combinação com uma chave – uma palavra, número ou frase – para criptografar o texto simples. O mesmo texto simples é criptografado em texto cifrado diferente com chaves diferentes. A segurança dos dados criptografados depende inteiramente de duas coisas: a força do algoritmo criptográfico e o sigilo da chave. Um algoritmo criptográfico, mais todas as chaves possíveis e todos os protocolos que o fazem funcionar constituem um criptossistema. PGP é um criptossistema.
Criptografia convencional.
Na criptografia convencional, também chamada de criptografia de chave secreta ou de chave simétrica , uma chave é usada tanto para criptografia quanto para descriptografia. O Data Encryption Standard (DES) é um exemplo de criptossistema convencional amplamente empregado pelo Governo Federal. A Figura 1-2 é uma ilustração do processo de criptografia convencional. https://image.nostr.build/328b73ebaff84c949df2560bbbcec4bc3b5e3a5163d5fbb2ec7c7c60488f894c.jpg
Figura 1-2. Criptografia convencional
Cifra de César.
Um exemplo extremamente simples de criptografia convencional é uma cifra de substituição. Uma cifra de substituição substitui uma informação por outra. Isso é feito com mais frequência compensando as letras do alfabeto. Dois exemplos são o Anel Decodificador Secreto do Capitão Meia-Noite, que você pode ter possuído quando era criança, e a cifra de Júlio César. Em ambos os casos, o algoritmo serve para compensar o alfabeto e a chave é o número de caracteres para compensá-lo. Por exemplo, se codificarmos a palavra "SEGREDO" usando o valor chave de César de 3, deslocaremos o alfabeto para que a terceira letra abaixo (D) comece o alfabeto. Então começando com A B C D E F G H I J K L M N O P Q R S T U V W X Y Z e deslizando tudo para cima em 3, você obtém DEFGHIJKLMNOPQRSTUVWXYZABC onde D=A, E=B, F=C e assim por diante. Usando este esquema, o texto simples, "SECRET" é criptografado como "VHFUHW". Para permitir que outra pessoa leia o texto cifrado, você diz a ela que a chave é 3. Obviamente, esta é uma criptografia extremamente fraca para os padrões atuais, mas, ei, funcionou para César e ilustra como funciona a criptografia convencional.
Gerenciamento de chaves e criptografia convencional.
A criptografia convencional tem benefícios. É muito rápido. É especialmente útil para criptografar dados que não vão a lugar nenhum. No entanto, a criptografia convencional por si só como meio de transmissão segura de dados pode ser bastante cara, simplesmente devido à dificuldade de distribuição segura de chaves. Lembre-se de um personagem do seu filme de espionagem favorito: a pessoa com uma pasta trancada e algemada ao pulso. Afinal, o que há na pasta? Provavelmente não é o código de lançamento de mísseis/fórmula de biotoxina/plano de invasão em si. É a chave que irá descriptografar os dados secretos. Para que um remetente e um destinatário se comuniquem com segurança usando criptografia convencional, eles devem chegar a um acordo sobre uma chave e mantê-la secreta entre si. Se estiverem em locais físicos diferentes, devem confiar em um mensageiro, no Bat Phone ou em algum outro meio de comunicação seguro para evitar a divulgação da chave secreta durante a transmissão. Qualquer pessoa que ouvir ou interceptar a chave em trânsito poderá posteriormente ler, modificar e falsificar todas as informações criptografadas ou autenticadas com essa chave. Do DES ao Anel Decodificador Secreto do Capitão Midnight, o problema persistente com a criptografia convencional é a distribuição de chaves: como você leva a chave ao destinatário sem que alguém a intercepte?
Criptografia de chave pública.
Os problemas de distribuição de chaves são resolvidos pela criptografia de chave pública, cujo conceito foi introduzido por Whitfield Diffie e Martin Hellman em 1975. (Há agora evidências de que o Serviço Secreto Britânico a inventou alguns anos antes de Diffie e Hellman, mas a manteve um segredo militar - e não fez nada com isso.
[JH Ellis: The Possibility of Secure Non-Secret Digital Encryption, CESG Report, January 1970]) A criptografia de chave pública é um esquema assimétrico que usa um par de chaves para criptografia: uma chave pública, que criptografa os dados, e uma chave privada ou secreta correspondente para descriptografia. Você publica sua chave pública para o mundo enquanto mantém sua chave privada em segredo. Qualquer pessoa com uma cópia da sua chave pública pode criptografar informações que somente você pode ler. Até mesmo pessoas que você nunca conheceu. É computacionalmente inviável deduzir a chave privada da chave pública. Qualquer pessoa que possua uma chave pública pode criptografar informações, mas não pode descriptografá-las. Somente a pessoa que possui a chave privada correspondente pode descriptografar as informações. https://image.nostr.build/fdb71ae7a4450a523456827bdd509b31f0250f63152cc6f4ba78df290887318b.jpg
Figura 1-3. Criptografia de chave pública O principal benefício da criptografia de chave pública é que ela permite que pessoas que não possuem nenhum acordo de segurança pré-existente troquem mensagens com segurança. A necessidade de remetente e destinatário compartilharem chaves secretas através de algum canal seguro é eliminada; todas as comunicações envolvem apenas chaves públicas e nenhuma chave privada é transmitida ou compartilhada. Alguns exemplos de criptossistemas de chave pública são Elgamal (nomeado em homenagem a seu inventor, Taher Elgamal), RSA (nomeado em homenagem a seus inventores, Ron Rivest, Adi Shamir e Leonard Adleman), Diffie-Hellman (nomeado, você adivinhou, em homenagem a seus inventores). ) e DSA, o algoritmo de assinatura digital (inventado por David Kravitz). Como a criptografia convencional já foi o único meio disponível para transmitir informações secretas, o custo dos canais seguros e da distribuição de chaves relegou a sua utilização apenas àqueles que podiam pagar, como governos e grandes bancos (ou crianças pequenas com anéis descodificadores secretos). A criptografia de chave pública é a revolução tecnológica que fornece criptografia forte para as massas adultas. Lembra do mensageiro com a pasta trancada e algemada ao pulso? A criptografia de chave pública o tira do mercado (provavelmente para seu alívio).
Como funciona o PGP.
O PGP combina alguns dos melhores recursos da criptografia convencional e de chave pública. PGP é um criptossistema híbrido. Quando um usuário criptografa texto simples com PGP, o PGP primeiro compacta o texto simples. A compactação de dados economiza tempo de transmissão do modem e espaço em disco e, mais importante ainda, fortalece a segurança criptográfica. A maioria das técnicas de criptoanálise explora padrões encontrados no texto simples para quebrar a cifra. A compressão reduz esses padrões no texto simples, aumentando assim enormemente a resistência à criptoanálise. (Arquivos que são muito curtos para compactar ou que não são compactados bem não são compactados.) O PGP então cria uma chave de sessão, que é uma chave secreta única. Esta chave é um número aleatório gerado a partir dos movimentos aleatórios do mouse e das teclas digitadas. Esta chave de sessão funciona com um algoritmo de criptografia convencional rápido e muito seguro para criptografar o texto simples; o resultado é texto cifrado. Depois que os dados são criptografados, a chave da sessão é criptografada na chave pública do destinatário. Essa chave de sessão criptografada com chave pública é transmitida junto com o texto cifrado ao destinatário.
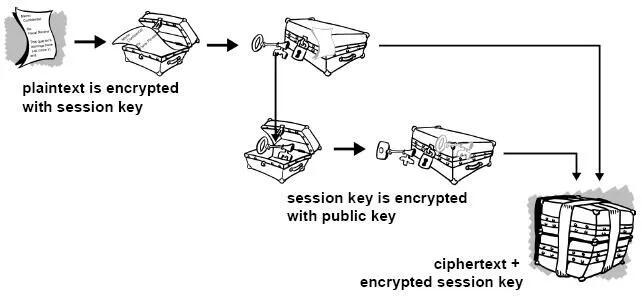
Figura 1-4. Como funciona a criptografia PGP A descriptografia funciona ao contrário. A cópia do PGP do destinatário usa sua chave privada para recuperar a chave de sessão temporária, que o PGP usa para descriptografar o texto cifrado criptografado convencionalmente.

Figura 1-5. Como funciona a descriptografia PGP A combinação dos dois métodos de criptografia combina a conveniência da criptografia de chave pública com a velocidade da criptografia convencional. A criptografia convencional é cerca de 1.000 vezes mais rápida que a criptografia de chave pública. A criptografia de chave pública, por sua vez, fornece uma solução para
problemas de distribuição de chaves e transmissão de dados. Usados em conjunto, o desempenho e a distribuição de chaves são melhorados sem qualquer sacrifício na segurança.
Chaves.
Uma chave é um valor que funciona com um algoritmo criptográfico para produzir um texto cifrado específico. As chaves são basicamente números muito, muito, muito grandes. O tamanho da chave é medido em bits; o número que representa uma chave de 1024 bits é enorme. Na criptografia de chave pública, quanto maior a chave, mais seguro é o texto cifrado. No entanto, o tamanho da chave pública e o tamanho da chave secreta da criptografia convencional não têm nenhuma relação. Uma chave convencional de 80 bits tem a força equivalente a uma chave pública de 1.024 bits. Uma chave convencional de 128 bits é equivalente a uma chave pública de 3.000 bits. Novamente, quanto maior a chave, mais segura, mas os algoritmos usados para cada tipo de criptografia são muito diferentes e, portanto, a comparação é como a de maçãs com laranjas. Embora as chaves pública e privada estejam matematicamente relacionadas, é muito difícil derivar a chave privada dada apenas a chave pública; no entanto, derivar a chave privada é sempre possível, desde que haja tempo e capacidade computacional suficientes. Isto torna muito importante escolher chaves do tamanho certo; grande o suficiente para ser seguro, mas pequeno o suficiente para ser aplicado rapidamente. Além disso, você precisa considerar quem pode estar tentando ler seus arquivos, quão determinados eles estão, quanto tempo têm e quais podem ser seus recursos. Chaves maiores serão criptograficamente seguras por um longo período de tempo. Se o que você deseja criptografar precisar ficar oculto por muitos anos, você pode usar uma chave muito grande. Claro, quem sabe quanto tempo levará para determinar sua chave usando os computadores mais rápidos e eficientes de amanhã? Houve um tempo em que uma chave simétrica de 56 bits era considerada extremamente segura. As chaves são armazenadas de forma criptografada. O PGP armazena as chaves em dois arquivos no seu disco rígido; um para chaves públicas e outro para chaves privadas. Esses arquivos são chamados de chaveiros. Ao usar o PGP, você normalmente adicionará as chaves públicas dos seus destinatários ao seu chaveiro público. Suas chaves privadas são armazenadas em seu chaveiro privado. Se você perder seu chaveiro privado, não será possível descriptografar nenhuma informação criptografada nas chaves desse anel.
Assinaturas digitais.
Um grande benefício da criptografia de chave pública é que ela fornece um método para empregar assinaturas digitais. As assinaturas digitais permitem ao destinatário da informação verificar a autenticidade da origem da informação e também verificar se a informação está intacta. Assim, as assinaturas digitais de chave pública fornecem autenticação e integridade de dados. A assinatura digital também proporciona o não repúdio, o que significa que evita que o remetente alegue que não enviou realmente as informações. Esses recursos são tão fundamentais para a criptografia quanto a privacidade, se não mais. Uma assinatura digital tem a mesma finalidade de uma assinatura manuscrita. No entanto, uma assinatura manuscrita é fácil de falsificar. Uma assinatura digital é superior a uma assinatura manuscrita porque é quase impossível de ser falsificada, além de atestar o conteúdo da informação, bem como a identidade do signatário.
Algumas pessoas tendem a usar mais assinaturas do que criptografia. Por exemplo, você pode não se importar se alguém souber que você acabou de depositar US$ 1.000 em sua conta, mas quer ter certeza de que foi o caixa do banco com quem você estava lidando. A maneira básica pela qual as assinaturas digitais são criadas é ilustrada na Figura 1-6 . Em vez de criptografar informações usando a chave pública de outra pessoa, você as criptografa com sua chave privada. Se as informações puderem ser descriptografadas com sua chave pública, elas deverão ter se originado em você.
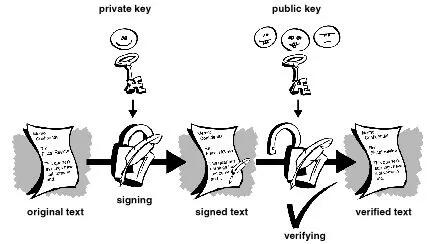
Figura 1-6. Assinaturas digitais simples
Funções hash.
O sistema descrito acima apresenta alguns problemas. É lento e produz um enorme volume de dados – pelo menos o dobro do tamanho da informação original. Uma melhoria no esquema acima é a adição de uma função hash unidirecional no processo. Uma função hash unidirecional recebe uma entrada de comprimento variável – neste caso, uma mensagem de qualquer comprimento, até mesmo milhares ou milhões de bits – e produz uma saída de comprimento fixo; digamos, 160 bits. A função hash garante que, se a informação for alterada de alguma forma – mesmo que por apenas um bit – seja produzido um valor de saída totalmente diferente. O PGP usa uma função hash criptograficamente forte no texto simples que o usuário está assinando. Isso gera um item de dados de comprimento fixo conhecido como resumo da mensagem. (Novamente, qualquer alteração nas informações resulta em um resumo totalmente diferente.) Então o PGP usa o resumo e a chave privada para criar a “assinatura”. O PGP transmite a assinatura e o texto simples juntos. Ao receber a mensagem, o destinatário utiliza o PGP para recalcular o resumo, verificando assim a assinatura. O PGP pode criptografar o texto simples ou não; assinar texto simples é útil se alguns dos destinatários não estiverem interessados ou não forem capazes de verificar a assinatura. Desde que uma função hash segura seja usada, não há como retirar a assinatura de alguém de um documento e anexá-la a outro, ou alterar uma mensagem assinada de qualquer forma. A menor alteração em um documento assinado causará falha no processo de verificação da assinatura digital.
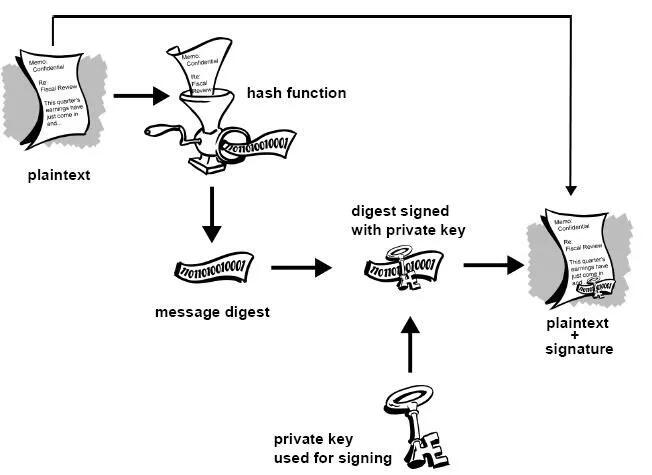
Figura 1-7. Assinaturas digitais seguras As assinaturas digitais desempenham um papel importante na autenticação e validação de chaves de outros usuários PGP.
Certificados digitais.
Um problema com os criptosistemas de chave pública é que os usuários devem estar constantemente vigilantes para garantir que estão criptografando com a chave da pessoa correta. Num ambiente onde é seguro trocar chaves livremente através de servidores públicos, os ataques man-in-the-middle são uma ameaça potencial. Neste tipo de ataque, alguém publica uma chave falsa com o nome e ID de usuário do destinatário pretendido. Os dados criptografados – e interceptados por – o verdadeiro proprietário desta chave falsa estão agora em mãos erradas. Em um ambiente de chave pública, é vital que você tenha certeza de que a chave pública para a qual você está criptografando os dados é de fato a chave pública do destinatário pretendido e não uma falsificação. Você pode simplesmente criptografar apenas as chaves que foram entregues fisicamente a você. Mas suponha que você precise trocar informações com pessoas que nunca conheceu; como você pode saber se tem a chave correta? Os certificados digitais, ou certs, simplificam a tarefa de estabelecer se uma chave pública realmente pertence ao suposto proprietário. Um certificado é uma forma de credencial. Exemplos podem ser sua carteira de motorista, seu cartão de previdência social ou sua certidão de nascimento. Cada um deles contém algumas informações que identificam você e alguma autorização informando que outra pessoa confirmou sua identidade. Alguns certificados, como o seu passaporte, são uma confirmação importante o suficiente da sua identidade para que você não queira perdê-los, para que ninguém os use para se passar por você.
Um certificado digital são dados que funcionam como um certificado físico. Um certificado digital é uma informação incluída na chave pública de uma pessoa que ajuda outras pessoas a verificar se uma chave é genuína ou válida. Os certificados digitais são usados para impedir tentativas de substituir a chave de uma pessoa por outra.
Um certificado digital consiste em três coisas:
● Uma chave pública.
● Informações do certificado. (Informações de "identidade" sobre o usuário, como nome, ID do usuário e assim por diante.) ● Uma ou mais assinaturas digitais.
O objetivo da assinatura digital em um certificado é afirmar que as informações do certificado foram atestadas por alguma outra pessoa ou entidade. A assinatura digital não atesta a autenticidade do certificado como um todo; ele atesta apenas que as informações de identidade assinadas acompanham ou estão vinculadas à chave pública. Assim, um certificado é basicamente uma chave pública com uma ou duas formas de identificação anexadas, além de um forte selo de aprovação de algum outro indivíduo confiável.
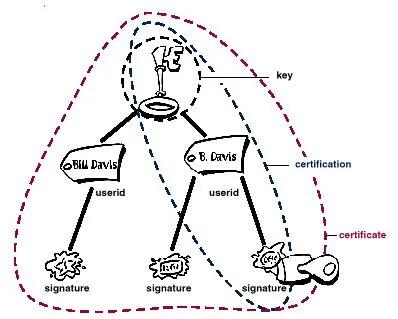 Figura 1-8. Anatomia de um certificado PGP
Figura 1-8. Anatomia de um certificado PGPDistribuição de certificados.
Os certificados são utilizados quando é necessário trocar chaves públicas com outra pessoa. Para pequenos grupos de pessoas que desejam se comunicar com segurança, é fácil trocar manualmente disquetes ou e-mails contendo a chave pública de cada proprietário. Esta é a distribuição manual de chave pública e é prática apenas até certo ponto. Além desse ponto, é necessário implementar sistemas que possam fornecer os mecanismos necessários de segurança, armazenamento e troca para que colegas de trabalho, parceiros de negócios ou estranhos possam se comunicar, se necessário. Eles podem vir na forma de repositórios somente de armazenamento, chamados Servidores de Certificados, ou sistemas mais estruturados que fornecem recursos adicionais de gerenciamento de chaves e são chamados de Infraestruturas de Chave Pública (PKIs).
Servidores de certificados.
Um servidor de certificados, também chamado de servidor certificado ou servidor de chaves, é um banco de dados que permite aos usuários enviar e recuperar certificados digitais. Um servidor certificado geralmente fornece alguns recursos administrativos que permitem que uma empresa mantenha suas políticas de segurança – por exemplo, permitindo que apenas as chaves que atendam a determinados requisitos sejam armazenadas.
Infraestruturas de Chave Pública.
Uma PKI contém os recursos de armazenamento de certificados de um servidor de certificados, mas também fornece recursos de gerenciamento de certificados (a capacidade de emitir, revogar, armazenar, recuperar e confiar em certificados). A principal característica de uma PKI é a introdução do que é conhecido como Autoridade Certificadora,ou CA, que é uma entidade humana — uma pessoa, grupo, departamento, empresa ou outra associação — que uma organização autorizou a emitir certificados para seus usuários de computador. (A função de uma CA é análoga à do Passport Office do governo de um país.) Uma CA cria certificados e os assina digitalmente usando a chave privada da CA. Devido ao seu papel na criação de certificados, a CA é o componente central de uma PKI. Usando a chave pública da CA, qualquer pessoa que queira verificar a autenticidade de um certificado verifica a assinatura digital da CA emissora e, portanto, a integridade do conteúdo do certificado (mais importante ainda, a chave pública e a identidade do titular do certificado).
Formatos de certificado.
Um certificado digital é basicamente uma coleção de informações de identificação vinculadas a uma chave pública e assinadas por um terceiro confiável para provar sua autenticidade. Um certificado digital pode ter vários formatos diferentes.
O PGP reconhece dois formatos de certificado diferentes:
● Certificados PGP ● Certificados X.509 Formato do certificado PGP. Um certificado PGP inclui (mas não está limitado a) as seguintes informações: ● O número da versão do PGP — identifica qual versão do PGP foi usada para criar a chave associada ao certificado. A chave pública do titular do certificado — a parte pública do seu par de chaves, juntamente com o algoritmo da chave: RSA, DH (Diffie-Hellman) ou DSA (Algoritmo de Assinatura Digital).
● As informações do detentor do certificado — consistem em informações de “identidade” sobre o usuário, como seu nome, ID de usuário, fotografia e assim por diante. ● A assinatura digital do proprietário do certificado — também chamada de autoassinatura, é a assinatura que utiliza a chave privada correspondente da chave pública associada ao certificado. ● O período de validade do certificado — a data/hora de início e a data/hora de expiração do certificado; indica quando o certificado irá expirar. ● O algoritmo de criptografia simétrica preferido para a chave — indica o algoritmo de criptografia para o qual o proprietário do certificado prefere que as informações sejam criptografadas. Os algoritmos suportados são CAST, IDEA ou Triple-DES. Você pode pensar em um certificado PGP como uma chave pública com um ou mais rótulos vinculados a ele (veja a Figura 1.9 ). Nessas 'etiquetas' você encontrará informações que identificam o proprietário da chave e uma assinatura do proprietário da chave, que afirma que a chave e a identificação andam juntas. (Essa assinatura específica é chamada de autoassinatura; todo certificado PGP contém uma autoassinatura.) Um aspecto único do formato de certificado PGP é que um único certificado pode conter múltiplas assinaturas. Várias ou muitas pessoas podem assinar o par chave/identificação para atestar a sua própria garantia de que a chave pública pertence definitivamente ao proprietário especificado. Se você procurar em um servidor de certificados público, poderá notar que certos certificados, como o do criador do PGP, Phil Zimmermann, contêm muitas assinaturas. Alguns certificados PGP consistem em uma chave pública com vários rótulos, cada um contendo um meio diferente de identificar o proprietário da chave (por exemplo, o nome do proprietário e a conta de e-mail corporativa, o apelido do proprietário e a conta de e-mail residencial, uma fotografia do proprietário — tudo em um certificado). A lista de assinaturas de cada uma dessas identidades pode ser diferente; as assinaturas atestam a autenticidade de que um dos rótulos pertence à chave pública, e não que todos os rótulos da chave sejam autênticos. (Observe que 'autêntico' está nos olhos de quem vê - assinaturas são opiniões, e diferentes pessoas dedicam diferentes níveis de devida diligência na verificação da autenticidade antes de assinar uma chave.)
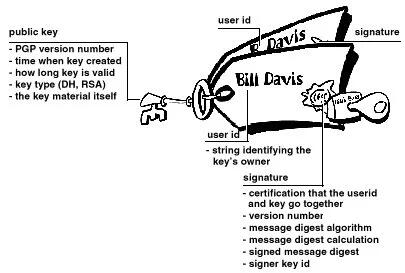 Figura 1-9. Um certificado PGP
Figura 1-9. Um certificado PGPFormato de certificado X.509.
X.509 é outro formato de certificado muito comum. Todos os certificados X.509 estão em conformidade com o padrão internacional ITU-T X.509; assim (teoricamente) os certificados X.509 criados para um aplicativo podem ser usados por qualquer aplicativo compatível com X.509. Na prática, porém, diferentes empresas criaram suas próprias extensões para certificados X.509, e nem todas funcionam juntas. Um certificado exige que alguém valide que uma chave pública e o nome do proprietário da chave andam juntos. Com os certificados PGP, qualquer pessoa pode desempenhar o papel de validador. Com certificados X.509, o validador é sempre uma Autoridade Certificadora ou alguém designado por uma CA. (Tenha em mente que os certificados PGP também suportam totalmente uma estrutura hierárquica usando uma CA para validar certificados.)
Um certificado X.509 é uma coleção de um conjunto padrão de campos contendo informações sobre um usuário ou dispositivo e sua chave pública correspondente. O padrão X.509 define quais informações vão para o certificado e descreve como codificá-lo (o formato dos dados). Todos os certificados X.509 possuem os seguintes dados:
O número da versão X.509
— identifica qual versão do padrão X.509 se aplica a este certificado, o que afeta quais informações podem ser especificadas nele. A mais atual é a versão 3.
A chave pública do titular do certificado
— a chave pública do titular do certificado, juntamente com um identificador de algoritmo que especifica a qual sistema criptográfico a chave pertence e quaisquer parâmetros de chave associados.
O número de série do certificado
— a entidade (aplicação ou pessoa) que criou o certificado é responsável por atribuir-lhe um número de série único para distingui-lo de outros certificados que emite. Esta informação é usada de diversas maneiras; por exemplo, quando um certificado é revogado, seu número de série é colocado em uma Lista de Revogação de Certificados ou CRL.
O identificador exclusivo do detentor do certificado
— (ou DN — nome distinto). Este nome pretende ser exclusivo na Internet. Este nome pretende ser exclusivo na Internet. Um DN consiste em múltiplas subseções e pode ser parecido com isto: CN=Bob Allen, OU=Divisão Total de Segurança de Rede, O=Network Associates, Inc., C=EUA (Referem-se ao nome comum, à unidade organizacional, à organização e ao país do sujeito .)
O período de validade do certificado
— a data/hora de início e a data/hora de expiração do certificado; indica quando o certificado irá expirar.
O nome exclusivo do emissor do certificado
— o nome exclusivo da entidade que assinou o certificado. Normalmente é uma CA. A utilização do certificado implica confiar na entidade que assinou este certificado. (Observe que em alguns casos, como certificados de CA raiz ou de nível superior , o emissor assina seu próprio certificado.)
A assinatura digital do emitente
— a assinatura utilizando a chave privada da entidade que emitiu o certificado.
O identificador do algoritmo de assinatura
— identifica o algoritmo usado pela CA para assinar o certificado.
Existem muitas diferenças entre um certificado X.509 e um certificado PGP, mas as mais importantes são as seguintes: você pode criar seu próprio certificado PGP;
● você deve solicitar e receber um certificado X.509 de uma autoridade de certificação
● Os certificados X.509 suportam nativamente apenas um único nome para o proprietário da chave
● Os certificados X.509 suportam apenas uma única assinatura digital para atestar a validade da chave
Para obter um certificado X.509, você deve solicitar a uma CA a emissão de um certificado. Você fornece sua chave pública, prova de que possui a chave privada correspondente e algumas informações específicas sobre você. Em seguida, você assina digitalmente as informações e envia o pacote completo – a solicitação de certificado – para a CA. A CA então realiza algumas diligências para verificar se as informações fornecidas estão corretas e, em caso afirmativo, gera o certificado e o devolve.
Você pode pensar em um certificado X.509 como um certificado de papel padrão (semelhante ao que você recebeu ao concluir uma aula de primeiros socorros básicos) com uma chave pública colada nele. Ele contém seu nome e algumas informações sobre você, além da assinatura da pessoa que o emitiu para você.
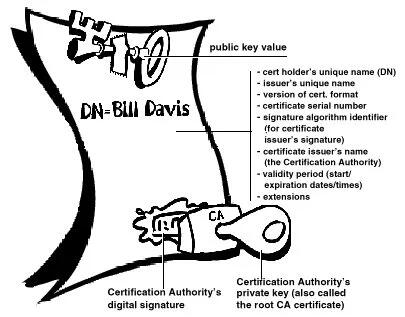
Figura 1-10. Um certificado X.509 Provavelmente, o uso mais visível dos certificados X.509 atualmente é em navegadores da web.
Validade e confiança Cada usuário em um sistema de chave pública está vulnerável a confundir uma chave falsa (certificado) com uma chave real. Validade é a confiança de que um certificado de chave pública pertence ao seu suposto proprietário. A validade é essencial em um ambiente de chave pública onde você deve estabelecer constantemente se um determinado certificado é autêntico ou não. Depois de ter certeza de que um certificado pertencente a outra pessoa é válido, você pode assinar a cópia em seu chaveiro para atestar que verificou o certificado e que ele é autêntico. Se quiser que outras pessoas saibam que você deu ao certificado seu selo de aprovação, você pode exportar a assinatura para um servidor de certificados para que outras pessoas possam vê-la.
Conforme descrito na seção Infraestruturas de Chave Pública , algumas empresas designam uma ou mais Autoridades de Certificação (CAs) para indicar a validade do certificado. Em uma organização que usa uma PKI com certificados X.509, é função da CA emitir certificados aos usuários — um processo que geralmente envolve responder à solicitação de certificado do usuário. Em uma organização que usa certificados PGP sem PKI, é função da CA verificar a autenticidade de todos os certificados PGP e depois assinar os bons. Basicamente, o objetivo principal de uma CA é vincular uma chave pública às informações de identificação contidas no certificado e, assim, garantir a terceiros que algum cuidado foi tomado para garantir que esta ligação das informações de identificação e da chave seja válida. O CA é o Grand Pooh-bah da validação em uma organização; alguém em quem todos confiam e, em algumas organizações, como aquelas que utilizam uma PKI, nenhum certificado é considerado válido, a menos que tenha sido assinado por uma CA confiável.
Verificando validade.
Uma maneira de estabelecer a validade é passar por algum processo manual. Existem várias maneiras de fazer isso. Você pode exigir que o destinatário pretendido lhe entregue fisicamente uma cópia de sua chave pública. Mas isto é muitas vezes inconveniente e ineficiente. Outra forma é verificar manualmente a impressão digital do certificado. Assim como as impressões digitais de cada ser humano são únicas, a impressão digital de cada certificado PGP é única. A impressão digital é um hash do certificado do usuário e aparece como uma das propriedades do certificado. No PGP, a impressão digital pode aparecer como um número hexadecimal ou uma série das chamadas palavras biométricas, que são foneticamente distintas e são usadas para facilitar um pouco o processo de identificação da impressão digital. Você pode verificar se um certificado é válido ligando para o proprietário da chave (para que você origine a transação) e pedindo ao proprietário que leia a impressão digital de sua chave para você e compare essa impressão digital com aquela que você acredita ser a verdadeira. Isso funciona se você conhece a voz do proprietário, mas como verificar manualmente a identidade de alguém que você não conhece? Algumas pessoas colocam a impressão digital de sua chave em seus cartões de visita exatamente por esse motivo. Outra forma de estabelecer a validade do certificado de alguém é confiar que um terceiro indivíduo passou pelo processo de validação do mesmo. Uma CA, por exemplo, é responsável por garantir que, antes de emitir um certificado, ele ou ela o verifique cuidadosamente para ter certeza de que a parte da chave pública realmente pertence ao suposto proprietário. Qualquer pessoa que confie na CA considerará automaticamente quaisquer certificados assinados pela CA como válidos. Outro aspecto da verificação da validade é garantir que o certificado não foi revogado. Para obter mais informações, consulte a seção Revogação de certificado .
Estabelecendo confiança.
Você valida certificados. Você confia nas pessoas. Mais especificamente, você confia nas pessoas para validar os certificados de outras pessoas. Normalmente, a menos que o proprietário lhe entregue o certificado, você terá que confiar na palavra de outra pessoa de que ele é válido.
Introdutores meta e confiáveis.
Na maioria das situações, as pessoas confiam completamente na CA para estabelecer a validade dos certificados. Isso significa que todos os demais dependem da CA para passar por todo o processo de validação manual. Isso é aceitável até um certo número de usuários ou locais de trabalho e, então, não é possível para a AC manter o mesmo nível de validação de qualidade. Nesse caso, é necessário adicionar outros validadores ao sistema.
Um CA também pode ser um meta- introdutor. Um meta-introdutor confere não apenas validade às chaves, mas também confere a capacidade de confiar nas chaves a outros. Semelhante ao rei que entrega seu selo a seus conselheiros de confiança para que eles possam agir de acordo com sua autoridade, o meta-introdutor permite que outros atuem como introdutores de confiança. Esses introdutores confiáveis podem validar chaves com o mesmo efeito do meta-introdutor. Eles não podem, entretanto, criar novos introdutores confiáveis.
Meta-introdutor e introdutor confiável são termos PGP. Em um ambiente X.509, o meta-introdutor é chamado de Autoridade de Certificação raiz ( CA raiz) e os introdutores confiáveis são Autoridades de Certificação subordinadas . A CA raiz usa a chave privada associada a um tipo de certificado especial denominado certificado CA raiz para assinar certificados. Qualquer certificado assinado pelo certificado CA raiz é visto como válido por qualquer outro certificado assinado pela raiz. Este processo de validação funciona mesmo para certificados assinados por outras CAs no sistema — desde que o certificado da CA raiz tenha assinado o certificado da CA subordinada, qualquer certificado assinado pela CA será considerado válido para outras pessoas dentro da hierarquia. Este processo de verificação de backup por meio do sistema para ver quem assinou cujo certificado é chamado de rastreamento de um caminho de certificação ou cadeia de certificação.
Modelos de confiança.
Em sistemas relativamente fechados, como em uma pequena empresa, é fácil rastrear um caminho de certificação até a CA raiz. No entanto, os usuários muitas vezes precisam se comunicar com pessoas fora do seu ambiente corporativo, incluindo algumas que nunca conheceram, como fornecedores, consumidores, clientes, associados e assim por diante. É difícil estabelecer uma linha de confiança com aqueles em quem sua CA não confia explicitamente. As empresas seguem um ou outro modelo de confiança, que determina como os usuários irão estabelecer a validade do certificado. Existem três modelos diferentes:
Confiança Direta.
Confiança Hierárquica Uma teia de confiança Confiança direta A confiança direta é o modelo de confiança mais simples. Neste modelo, um usuário confia que uma chave é válida porque sabe de onde ela veio. Todos os criptosistemas usam essa forma de confiança de alguma forma. Por exemplo, em navegadores da Web, as chaves raiz da Autoridade de Certificação são diretamente confiáveis porque foram enviadas pelo fabricante. Se houver alguma forma de hierarquia, ela se estenderá a partir desses certificados diretamente confiáveis. No PGP, um usuário que valida as chaves e nunca define outro certificado para ser um introdutor confiável está usando confiança direta.
 Figura 1-11. Confiança direta
Figura 1-11. Confiança diretaConfiança Hierárquica.
Em um sistema hierárquico, há vários certificados "raiz" a partir dos quais a confiança se estende. Esses certificados podem certificar eles próprios certificados ou podem certificar certificados que certificam ainda outros certificados em alguma cadeia. Considere isso como uma grande “árvore” de confiança. A validade do certificado "folha" é verificada rastreando desde seu certificador até outros certificadores, até que um certificado raiz diretamente confiável seja encontrado.
Figura 1-12. Confiança hierárquica
Teia de Confiança.
Uma teia de confiança abrange ambos os outros modelos, mas também acrescenta a noção de que a confiança está nos olhos de quem vê (que é a visão do mundo real) e a ideia de que mais informação é melhor. É, portanto, um modelo de confiança cumulativa. Um certificado pode ser confiável diretamente ou confiável em alguma cadeia que remonta a um certificado raiz diretamente confiável (o meta-introdutor) ou por algum grupo de introdutores.
Talvez você já tenha ouvido falar do termo seis graus de separação, que sugere que qualquer pessoa no mundo pode determinar algum vínculo com qualquer outra pessoa no mundo usando seis ou menos outras pessoas como intermediários. Esta é uma teia de introdutores. É também a visão de confiança do PGP. PGP usa assinaturas digitais como forma de introdução. Quando qualquer usuário assina a chave de outro, ele ou ela se torna o introdutor dessa chave. À medida que esse processo avança, ele estabelece uma rede de confiança.
Em um ambiente PGP, qualquer usuário pode atuar como autoridade certificadora. Qualquer usuário PGP pode validar o certificado de chave pública de outro usuário PGP. No entanto, tal certificado só é válido para outro usuário se a parte confiável reconhecer o validador como um introdutor confiável. (Ou seja, você confia na minha opinião de que as chaves dos outros são válidas apenas se você me considerar um apresentador confiável. Caso contrário, minha opinião sobre a validade das outras chaves é discutível.) Armazenados no chaveiro público de cada usuário estão indicadores de
● se o usuário considera ou não uma chave específica válida
● o nível de confiança que o usuário deposita na chave que o proprietário da chave pode servir como certificador das chaves de terceiros
Você indica, na sua cópia da minha chave, se acha que meu julgamento conta. Na verdade, é um sistema de reputação: certas pessoas têm a reputação de fornecer boas assinaturas e as pessoas confiam nelas para atestar a validade de outras chaves.
Níveis de confiança no PGP.
O nível mais alto de confiança em uma chave, a confiança implícita , é a confiança em seu próprio par de chaves. O PGP assume que se você possui a chave privada, você deve confiar nas ações da sua chave pública relacionada. Quaisquer chaves assinadas pela sua chave implicitamente confiável são válidas.
Existem três níveis de confiança que você pode atribuir à chave pública de outra pessoa:
● Confiança total ● Confiança marginal ● Não confiável (ou não confiável)
Para tornar as coisas confusas, também existem três níveis de validade:
● Válido ● Marginalmente válido ● Inválido
Para definir a chave de outra pessoa como um introdutor confiável, você
- Comece com uma chave válida, que seja.
- assinado por você ou
-
assinado por outro apresentador confiável e então
-
Defina o nível de confiança que você acha que o proprietário da chave tem direito.
Por exemplo, suponha que seu chaveiro contenha a chave de Alice. Você validou a chave de Alice e indica isso assinando-a. Você sabe que Alice é uma verdadeira defensora da validação de chaves de outras pessoas. Portanto, você atribui a chave dela com confiança total. Isso faz de Alice uma Autoridade Certificadora. Se Alice assinar a chave de outra pessoa, ela aparecerá como Válida em seu chaveiro. O PGP requer uma assinatura Totalmente confiável ou duas assinaturas Marginalmente confiáveis para estabelecer uma chave como válida. O método do PGP de considerar dois Marginais iguais a um Completo é semelhante a um comerciante que solicita duas formas de identificação. Você pode considerar Alice bastante confiável e também considerar Bob bastante confiável. Qualquer um deles sozinho corre o risco de assinar acidentalmente uma chave falsificada, portanto, você pode não depositar total confiança em nenhum deles. No entanto, as probabilidades de ambos os indivíduos terem assinado a mesma chave falsa são provavelmente pequenas.
Revogação de certificado.
Os certificados só são úteis enquanto são válidos. Não é seguro simplesmente presumir que um certificado é válido para sempre. Na maioria das organizações e em todas as PKIs, os certificados têm uma vida útil restrita. Isso restringe o período em que um sistema fica vulnerável caso ocorra um comprometimento do certificado.
Os certificados são assim criados com um período de validade programado: uma data/hora de início e uma data/hora de expiração. Espera-se que o certificado seja utilizável durante todo o seu período de validade (seu tempo de vida ). Quando o certificado expirar, ele não será mais válido, pois a autenticidade do seu par chave/identificação não estará mais garantida. (O certificado ainda pode ser usado com segurança para reconfirmar informações que foram criptografadas ou assinadas dentro do período de validade – no entanto, ele não deve ser confiável para tarefas criptográficas futuras.)
Existem também situações em que é necessário invalidar um certificado antes da sua data de expiração, como quando o titular do certificado termina o contrato de trabalho com a empresa ou suspeita que a chave privada correspondente do certificado foi comprometida. Isso é chamado de revogação. Um certificado revogado é muito mais suspeito do que um certificado expirado. Os certificados expirados são inutilizáveis, mas não apresentam a mesma ameaça de comprometimento que um certificado revogado. Qualquer pessoa que tenha assinado um certificado pode revogar a sua assinatura no certificado (desde que utilize a mesma chave privada que criou a assinatura). Uma assinatura revogada indica que o signatário não acredita mais que a chave pública e as informações de identificação pertencem uma à outra, ou que a chave pública do certificado (ou a chave privada correspondente) foi comprometida. Uma assinatura revogada deve ter quase tanto peso quanto um certificado revogado. Com certificados X.509, uma assinatura revogada é praticamente igual a um certificado revogado, visto que a única assinatura no certificado é aquela que o tornou válido em primeiro lugar – a assinatura da CA. Os certificados PGP fornecem o recurso adicional de que você pode revogar todo o seu certificado (não apenas as assinaturas nele) se você achar que o certificado foi comprometido. Somente o proprietário do certificado (o detentor da chave privada correspondente) ou alguém que o proprietário do certificado tenha designado como revogador pode revogar um certificado PGP. (Designar um revogador é uma prática útil, pois muitas vezes é a perda da senha da chave privada correspondente do certificado que leva um usuário PGP a revogar seu certificado - uma tarefa que só é possível se alguém tiver acesso à chave privada. ) Somente o emissor do certificado pode revogar um certificado X.509.
Comunicar que um certificado foi revogado.
Quando um certificado é revogado, é importante conscientizar os usuários potenciais do certificado de que ele não é mais válido. Com certificados PGP, a maneira mais comum de comunicar que um certificado foi revogado é publicá-lo em um servidor de certificados para que outras pessoas que desejem se comunicar com você sejam avisadas para não usar essa chave pública. Em um ambiente PKI, a comunicação de certificados revogados é mais comumente obtida por meio de uma estrutura de dados chamada Lista de Revogação de Certificados, ou CRL, que é publicada pela CA. A CRL contém uma lista validada com carimbo de data e hora de todos os certificados revogados e não expirados no sistema. Os certificados revogados permanecem na lista apenas até expirarem e, em seguida, são removidos da lista — isso evita que a lista fique muito longa. A CA distribui a CRL aos usuários em algum intervalo programado regularmente (e potencialmente fora do ciclo, sempre que um certificado é revogado). Teoricamente, isso impedirá que os usuários usem involuntariamente um certificado comprometido. É possível, no entanto, que haja um período de tempo entre as CRLs em que um certificado recentemente comprometido seja usado.
O que é uma senha?
A maioria das pessoas está familiarizada com a restrição de acesso a sistemas de computador por meio de uma senha, que é uma sequência única de caracteres que um usuário digita como código de identificação.
Uma senha longa é uma versão mais longa de uma senha e, em teoria, mais segura. Normalmente composta por várias palavras, uma frase secreta é mais segura contra ataques de dicionário padrão, em que o invasor tenta todas as palavras do dicionário na tentativa de determinar sua senha. As melhores senhas são relativamente longas e complexas e contêm uma combinação de letras maiúsculas e minúsculas, caracteres numéricos e de pontuação. O PGP usa uma senha para criptografar sua chave privada em sua máquina. Sua chave privada é criptografada em seu disco usando um hash de sua senha como chave secreta. Você usa a senha para descriptografar e usar sua chave privada. Uma senha deve ser difícil de esquecer e difícil de ser adivinhada por outras pessoas. Deve ser algo já firmemente enraizado na sua memória de longo prazo, em vez de algo que você invente do zero. Por que? Porque se você esquecer sua senha, você estará sem sorte. Sua chave privada é total e absolutamente inútil sem sua senha e nada pode ser feito a respeito. Lembra-se da citação anterior neste capítulo?
 PGP é a criptografia que manterá os principais governos fora dos seus arquivos. Certamente também o manterá fora de seus arquivos. Tenha isso em mente quando decidir alterar sua senha para a piada daquela piada que você nunca consegue lembrar.
PGP é a criptografia que manterá os principais governos fora dos seus arquivos. Certamente também o manterá fora de seus arquivos. Tenha isso em mente quando decidir alterar sua senha para a piada daquela piada que você nunca consegue lembrar.Divisão de chave.
Dizem que um segredo não é segredo se for conhecido por mais de uma pessoa. Compartilhar um par de chaves privadas representa um grande problema. Embora não seja uma prática recomendada, às vezes é necessário compartilhar um par de chaves privadas. Chaves de assinatura corporativa, por exemplo, são chaves privadas usadas por uma empresa para assinar – por exemplo – documentos legais, informações pessoais confidenciais ou comunicados de imprensa para autenticar sua origem. Nesse caso, vale a pena que vários membros da empresa tenham acesso à chave privada. No entanto, isto significa que qualquer indivíduo pode agir plenamente em nome da empresa. Nesse caso, é aconselhável dividir a chave entre várias pessoas, de modo que mais de uma ou duas pessoas apresentem um pedaço da chave para reconstituí-la em condições utilizáveis. Se poucas peças da chave estiverem disponíveis, a chave ficará inutilizável. Alguns exemplos são dividir uma chave em três partes e exigir duas delas para reconstituir a chave, ou dividi-la em duas partes e exigir ambas as peças. Se uma conexão de rede segura for usada durante o processo de reconstituição, os acionistas da chave não precisam estar fisicamente presentes para aderirem novamente à chave.
-
 @ 502ab02a:a2860397
2025-04-30 02:51:33
@ 502ab02a:a2860397
2025-04-30 02:51:3350by40 คืออีกโครงการนึงที่ขยายภาพรวมขึ้นมาอีก recap กันครับ (ใครที่มาเจอกลางทาง อาจต้องย้อนเยอะครับ ย้อนไปสัก ปลายเดือน มีนาคม 2025) หลังจากที่เราได้ดูส่วนเล็กกันมาหลายตอน ตั้งแต่เรื่องเล็กๆอย่าง น้ำมันมะกอกปลอม ซึ่งตอนนั้นหลายคนที่อ่านอาจคิดว่า ไกลตัวส่วนใหญ่ยังดีพอ แต่ความนัยที่ซ่อนไว้ในบทนั้นคือ จุดเริ่มของการทำลายความเชื่อใจในอาหาร , ที่มาของบรอกโคลีเพื่อให้รู้ว่า สิ่งที่คิดว่าธรรมชาติ มันไม่ธรรมชาติ, นมโอ้ต นมประดิษฐ์ที่เป็นจุดที่เราคิดว่ามันคือการพลิกวงการแล้ว, การแอบจดสิทธิบัตรเมล็ดพันธุ์ที่เคยปลูกกินอย่างอิสระ, การพัฒนา GMO 2.0 ที่ไม่ต้องเรียกว่า GMO, โปรตีนจากแลป มาจนถึงเวย์ที่ไม่มีวัว แล้วเราก็ขยายภาพขึ้นกับข้อกำหนดการควบคุมการปลูกพืช UPOV1991/CPTPP, การเข้าสู่โรงเรียน, การกำเนิดของ ProVeg แล้วเราก็ได้รู้จักกับ Sebastian Joy ก็ถือว่าเดินทางมา 1 ด่านแล้วครับ หนทางเรื่องนี้ยังอีกยาวไกล วันนี้เราก็มาคุยกันถึงเรื่อง
โครงการ 50by40
โครงการนี้เริ่มต้นขึ้นในเดือนเมษายน ปี 2018 โดยมีการจัดการประชุม "50by40 Corporate Outreach Summit" ระหว่างวันที่ 27–29 เมษายน 2018 ที่กรุงเบอร์ลิน ประเทศเยอรมนี ซึ่งจัดโดย ProVeg International ร่วมกับ Humane Society of the United States การประชุมนี้ถือเป็นจุดเริ่มต้นของพันธมิตรระดับโลกที่มีเป้าหมายร่วมกันในการลดการผลิตและบริโภคผลิตภัณฑ์จากสัตว์ลง 50% ภายในปี 2040
Sebastian Joy ผู้ก่อตั้งและประธานของ ProVeg International มีบทบาทสำคัญในการริเริ่มโครงการ 50by40 โดยเขาได้ช่วยก่อตั้งพันธมิตรนี้เพื่อส่งเสริมการเปลี่ยนแปลงระบบอาหารโลก นอกจากนี้ ProVeg International ยังมีบทบาทในการสนับสนุนองค์กรและสตาร์ทอัพที่มุ่งเน้นการเปลี่ยนแปลงระบบอาหารผ่านโปรแกรมต่างๆ
แม้ว่าโครงการ 50by40 จะประกาศเป้าหมายในการลดการบริโภคผลิตภัณฑ์จากสัตว์เพื่อสุขภาพและสิ่งแวดล้อม แต่เบื้องหลังยังมีการดำเนินงานที่มุ่งเน้นการเปลี่ยนแปลงระบบอาหารโลก โดยการส่งเสริม "อาหารที่เพาะเลี้ยงในห้องปฏิบัติการเป็นหลัก"
โครงการนี้ยังมีการจัดกิจกรรมเพื่อดึงดูดนักลงทุนและผู้สนับสนุนทางการเงิน เช่น การจัดงาน Food Funders Circle ซึ่งเป็นเวทีสำหรับนักลงทุนที่สนใจในอาหารทางเลือก นอกจากนี้ โครงการ 50by40 ยังมีความสัมพันธ์กับองค์กรต่างๆ ทั้งภาครัฐและเอกชน รวมถึงองค์กรระดับนานาชาติ เช่น Greenpeace, WWF และ Compassion in World Farming ซึ่งมีเป้าหมายร่วมกันในการลดการบริโภคผลิตภัณฑ์จากสัตว์ และ ProVeg International เองก็มีสถานะเป็นผู้สังเกตการณ์ถาวรในองค์การสหประชาชาติ เช่น UNFCCC, IPCC และ CBD รวมถึงมีสถานะที่ปรึกษาพิเศษกับ ECOSOC และได้รับการรับรองจาก UNEA อีกด้วย ถ้ามองแค่เนทเวิร์คเบื้องต้นแล้ว วินาทีนี้ ตอบได้เลยครับว่า "อาหารที่เพาะเลี้ยงในห้องปฏิบัติการเป็นหลัก" มาแน่นอนครับ มองข้ามความ plant based / animal based ได้เลย
เพื่อบรรลุเป้าหมายนี้ โครงการได้ดำเนินกิจกรรมต่างๆ ทั้งในระดับโรงเรียนและการผลักดันนโยบายสาธารณะ ผมจะลองแบ่งเป็นข้อๆให้เพื่อความสะดวกในการมองภาพรวมประมาณนี้นะครับ
การดำเนินงานในโรงเรียนและเยาวชน 1. Early Action Network โครงการนี้เป็นความร่วมมือระหว่าง 50by40, ProVeg International และ Educated Choices Program โดยมีเป้าหมายในการส่งเสริมการบริโภคอาหารจากพืชในกลุ่มเด็กและเยาวชนผ่านกิจกรรมต่างๆ เช่น การจัดกิจกรรมเชิงโต้ตอบเกี่ยวกับสุขภาพ สิ่งแวดล้อม และสวัสดิภาพสัตว์, การจัดแคมเปญในโรงเรียนและชุมชน, การเผยแพร่สื่อการเรียนรู้และโปรแกรมฝึกอบรม, การปรับปรุงเมนูอาหารในโรงเรียนให้มีทางเลือกจากพืชมากขึ้น
โครงการนี้มุ่งหวังที่จะสร้างความตระหนักรู้และเปลี่ยนแปลงพฤติกรรมการบริโภคของเยาวชนตั้งแต่เนิ่นๆ เพื่อส่งเสริมการบริโภคอาหารที่ยั่งยืนและเป็นมิตรกับสิ่งแวดล้อม
- School Plates Programme ProVeg International ได้เปิดตัวโครงการ School Plates ในสหราชอาณาจักรเมื่อปี 2018 โดยมีเป้าหมายในการปรับปรุงเมนูอาหารในโรงเรียนให้มีความหลากหลายและสุขภาพดีขึ้นผ่านการเพิ่มทางเลือกอาหารจากพืช โครงการนี้ได้ร่วมมือกับโรงเรียน หน่วยงานท้องถิ่น และบริษัทจัดเลี้ยง เพื่อเปลี่ยนแปลงเมนูอาหารในโรงเรียนกว่า 3.1 ล้านมื้อจากอาหารที่มีเนื้อสัตว์เป็นหลักไปเป็นอาหารจากพืช
สำหรับในส่วนของการผลักดันนโยบายสาธารณะและการมีส่วนร่วมในเวทีนานาชาตินั้น ก็มีไม่น้อยครับ อาทิเช่น การมีส่วนร่วมในองค์การสหประชาชาติ ProVeg International มีสถานะเป็นผู้สังเกตการณ์ถาวรในองค์การสหประชาชาติ เช่น UNFCCC และ UNEP และได้มีบทบาทในการผลักดันให้มีการรวมประเด็นเกี่ยวกับอาหารจากพืชในการเจรจาด้านสภาพภูมิอากาศ โดยในปี 2022 ProVeg ได้เข้าร่วมการประชุมสภาพภูมิอากาศของสหประชาชาติในสตอกโฮล์มและบอนน์ เพื่อส่งเสริมแนวคิด "Diet Change Not Climate Change" และเรียกร้องให้มีการเปลี่ยนแปลงระบบอาหารสู่การบริโภคอาหารจากพืชมากขึ้น
การสนับสนุนเยาวชนในเวทีนานาชาติ ProVeg ได้จัดตั้ง Youth Board ซึ่งประกอบด้วยเยาวชนจากทั่วโลก เพื่อมีส่วนร่วมในการผลักดันนโยบายด้านอาหารจากพืชในเวทีสหประชาชาติ และเตรียมความพร้อมสำหรับการประชุม COP30 ที่จะจัดขึ้นในเบเลง ประเทศบราซิล
นอกจากนี้ยังมีการสนับสนุนองค์กรและสตาร์ทอัพที่มุ่งเปลี่ยนแปลงระบบอาหารอีกมากมาย โดยที่โดดเด่นเป็นพิเศษคือ โปรแกรม Kickstarting for Good ProVeg International ได้เปิดตัวโปรแกรม Kickstarting for Good ซึ่งเป็นโปรแกรมบ่มเพาะและเร่งการเติบโตสำหรับองค์กรไม่แสวงหาผลกำไร โครงการที่มีผลกระทบ และสตาร์ทอัพทางสังคมที่มุ่งเปลี่ยนแปลงระบบอาหาร โปรแกรมนี้มีระยะเวลา 8 สัปดาห์ โดยมีการฝึกอบรมแบบเข้มข้น การให้คำปรึกษาจากผู้เชี่ยวชาญ และโอกาสในการสร้างเครือข่าย เพื่อสนับสนุนการพัฒนาโครงการที่มีศักยภาพในการลดการบริโภคผลิตภัณฑ์จากสัตว์และส่งเสริมอาหารจากพืช
นอกจาก Sebastian Joy จะเริ่มต้นโครงการต่างๆมากมายไม่ว่าจะ ProVeg International, ProVeg Incubator, Kickstarting for Good แต่ก็ยังมี องค์กรพันธมิตรในเครือข่าย 50by40 ที่หลากหลาย เช่น Plant Powered Metro New York, Public Justice, Rainforest Alliance, Real Food Systems, Reducetarian Foundation, Rethink Your Food, SEED และ Seeding Sovereignty ซึ่งร่วมกันส่งเสริมการบริโภคอาหารจากพืชและการลดการบริโภคผลิตภัณฑ์จากสัตว์ แม้ว่าโครงการ 50by40 จะได้รับการสนับสนุนจากองค์กรต่างๆ อย่างกว้างขวาง แต่ยังไม่มีข้อมูลที่ชัดเจนเกี่ยวกับบริษัทเอกชนรายใดที่แสดงการสนับสนุนโครงการนี้อย่างเปิดเผยครับ
ทีนี้เรามาดูความเคลื่อนไหวของลูกพี่ใหญ่อย่าง USDA กันบ้างนะครับ จากการตรวจสอบข้อมูลที่มีอยู่จนถึงปัจจุบัน ยังไม่พบหลักฐานชัดเจนว่า กระทรวงเกษตรสหรัฐฯ (USDA) มีการสนับสนุนโครงการ 50by40 อย่างเป็นทางการหรือเปิดเผย อย่างไรก็ตาม มีความเคลื่อนไหวที่เกี่ยวข้องกับการส่งเสริมโปรตีนทางเลือกและการลดการบริโภคเนื้อสัตว์ในระดับนโยบายของสหรัฐฯ ซึ่งอาจสอดคล้องกับเป้าหมายของโครงการ 50by40 อยู่เช่นกันครับ
ในปี 2021 คณะกรรมาธิการด้านการเกษตรของสภาผู้แทนราษฎรสหรัฐฯ ได้สนับสนุนให้ USDA จัดสรรงบประมาณ 50 ล้านดอลลาร์สหรัฐฯ ผ่านโครงการ Agriculture and Food Research Initiative (AFRI) เพื่อสนับสนุนการวิจัยเกี่ยวกับโปรตีนทางเลือก เช่น การใช้พืช การเพาะเลี้ยงเซลล์ และการหมัก เพื่อพัฒนาอาหารที่มีคุณสมบัติคล้ายเนื้อสัตว์
นอกจากนี้ USDA ได้ยอมรับคำว่า "cell-cultured" เป็นคำที่ใช้เรียกเนื้อสัตว์ที่ผลิตจากการเพาะเลี้ยงเซลล์ในห้องปฏิบัติการ ซึ่งเป็นส่วนหนึ่งของการกำหนดมาตรฐานและการควบคุมผลิตภัณฑ์อาหารใหม่ๆ ที่เกี่ยวข้องกับโปรตีนทางเลือก
แล้วกลุ่มองค์กรด้านสิ่งแวดล้อมและสุขภาพ เช่น Center for Biological Diversity ได้ส่งจดหมายถึงรัฐมนตรีกระทรวงเกษตรสหรัฐฯ เรียกร้องให้ USDA นำประเด็นการลดการบริโภคเนื้อสัตว์และผลิตภัณฑ์นมมาเป็นส่วนหนึ่งของยุทธศาสตร์ด้านสภาพภูมิอากาศ และปรับปรุงแนวทางโภชนาการแห่งชาติให้สอดคล้องกับเป้าหมาย "ด้านความยั่งยืน"
แม้ว่า USDA จะไม่ได้แสดงการสนับสนุนโครงการ 50by40 โดยตรง แต่มีความร่วมมือกับองค์กรที่มีเป้าหมายคล้ายคลึงกัน เช่น ProVeg International และ The Good Food Institute ซึ่งเป็นพันธมิตรในเครือข่ายของ 50by40 โดยมีเป้าหมายในการส่งเสริมการบริโภคอาหารจากการเพาะเลี้ยงเซลล์ในห้องปฏิบัติการและโปรตีนทางเลือก
อนาคตได้มีการขีด Goal ไว้ประมาณนี้ เรายังคิดว่าการที่ "แค่ไม่กินมัน" "ก็แค่เลือกกินอาหารธรรมชาติ" จะยังเป็นคำพูดที่เราพูดได้อีกไหม สิ่งนี้ก็ยังเป็นคำถามต่อไปครับ คงไม่มีใครสามารถตอบได้ใน วันนี้ (มั๊ง)
แต่ที่แน่ๆ มีคนไม่น้อยแล้วแหละครับ ที่บอกว่าอาหารจากแลปคุมในโรงงานที่สะอาด มันก็ดีนี่ สะอาดปลอดภัย ดีกว่าเนื้อหมูที่ผัดข้างทาง ล้างหรือเปล่าก็ไม่รู้ เอาหมูแบบไหนมาก็ไม่รู้
มันดูเหมือนว่าเป็นการเปรียบเปรยแบบตรรกะวิบัตินะครับ แต่รอบตัวคุณ มีคนคิดแบบนี้เยอะไหม? เป็นคำถามที่ไม่มีคำตอบอีกเช่นกันครับ
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ fe02e8ec:f07fbe0b
2025-04-28 21:23:01
@ fe02e8ec:f07fbe0b
2025-04-28 21:23:01Die baldige Ex-Außenministerin Annalena Baerbock fordert einen radikalen Wandel in der Energieversorgung hin zu einer feministischen Energiepolitik. Wie sich gezeigt habe, so sei das spanische Netz am 28.04.25 wegen toxischer Männlichkeit zusammengebrochen. Es hätte sich herausgestellt, dass alle Überlandleitungen von Männern gebaut und installiert worden waren! Dies, so Baerbock, sei ein untragbarer Zustand, der durch den resultierenden Blackout für viel Leid und Ärger gesorgt habe. Selbst Haarföhns waren nicht mehr in Betrieb zu nehmen!
«Nur Frauen sind in der Lage, derart empfindliche und sensible Ströme zu leiten. Denn Strömen liegt in ihrer Natur. Sie benötigen keine Messgeräte oder teure Transformatoren für die Strömung, da Mutter Natur – eine Frau, wie der Name schon sagt – für alles selbst sorgen wird. Man muss nur verhindern, dass maskuline Energien verströmt werden, die nämlich den Strom um 360 Grad drehen würden.»
Mit dieser Analyse empfiehlt sich Annalena B. nicht nur für höchste UN Ämter sondern ebenfalls für den Vorsitz des Weltklimarates IPCC. Aus informierten Kreisen ist zu hören, dass sie nur noch die Papstwahl abwarten möchte - schließlich wäre es Zeit für eine Päpstin - bis sie sich fürs Klima bewerben würde. Um weitere Blackouts abzuschrecken überlegt sie angeblich, ihren Namen in Blackbock zu ändern. Möglich wäre allerdings auch, dass dies alles nur erfunden ist.
Mehr Satirisches und Ernstes: www.thomas-eisinger.de













