-
 @ a5ee4475:2ca75401
2025-05-04 15:14:32
@ a5ee4475:2ca75401
2025-05-04 15:14:32lista #descentralismo #compilado #portugues
*Algumas destas listas ainda estão sendo trocadas e serão traduzidas para português, portanto as versões mais recentes delas só estarão visíveis no Amethyst.
Clients do Nostr e Outras Coisas
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
Modelos de IA e Ferramentas
nostr:nevent1qqsxdpwadkswdrc602m6qdhyq7n33lf3wpjtdjq2adkw4y3h38mjcrqpr9mhxue69uhkxmmzwfskvatdvyhxxmmd9aex2mrp0ypzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqqqqysn06gs
Comunidades Lusófonas de Bitcoin
nostr:nevent1qqsqnmtverj2fetqwhsv9n2ny8h9ujhyqqrk0fsn4a02w8sf4cqddzqpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtczyzj7u3r4dz3rwg3x6erszwj4y502clwn026qsp99zgdx8n3v5a2qzqcyqqqqqqgypv6z5
Profissionais Brasileiros no Nostr
nostr:nevent1qqsvqnlx7sqeczv5r7pmmd6zzca3l0ru4856n3j7lhjfv3atq40lfdcpr9mhxue69uhkxmmzwfskvatdvyhxxmmd9aex2mrp0ypzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqqqqylf6kr4
Comunidades em Português no Nostr
nostr:nevent1qqsy47d6z0qzshfqt5sgvtck8jmhdjnsfkyacsvnqe8m7euuvp4nm0gpzpmhxue69uhkummnw3ezumt0d5hsyg99aez8269zxu3zd4j8qya92fg7437ax745pqz22ys6v08zef65qypsgqqqqqqsw4vudx
Grupos em Português no Nostr
nostr:nevent1qqs98kldepjmlxngupsyth40n0h5lw7z5ut5w4scvh27alc0w86tevcpzpmhxue69uhkummnw3ezumt0d5hsygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqqqqs3ndneh
Games Open Source
nostr:nevent1qqs0swpxdqfknups697205qg5mpw2e370g5vet07gkexe9n0k05h5qspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsyg99aez8269zxu3zd4j8qya92fg7437ax745pqz22ys6v08zef65qypsgqqqqqqshr37wh
Formatação de Texto no Amethyst
nostr:nevent1qqs0vquevt0pe9h5a2dh8csufdksazp6czz3vjk3wfspp68uqdez00cprpmhxue69uhkummnw3ezuendwsh8w6t69e3xj730qgs2tmjyw452ydezymtywqf625j3atra6datgzqy55fp5c7w9jn4gqgrqsqqqqqpd658r3
Outros Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ 6830c409:ff17c655
2025-05-04 20:23:30
@ 6830c409:ff17c655
2025-05-04 20:23:30Disclaimer: No artificial intelligence tool has been used to write this article except Grammarly.
There are some things that no one* wants to talk about in a public forum. One of those things is how we clean ourselves after using the toilet. Being a South Asian, I find the bathroom etiquette a bit different from where I am now- in the US. I don't think it is something we have to keep mum about.
[*Mostly]
Earlier, I had read a "Quora WAR" where there was a fierce fight between fellow Western country people vs Indians. Indians advocated using water and the West despised that and advocated using dry wipes/toilet paper. Recently (Yesterday), I remembered this Quora debate and I was curious, when was the commercial production of toilet tissues started? And what were the hygiene methods followed before that.
Obviously, My reading started with Wikipedia. And from there, it was a rabbit-hole. I don't know how, I kept on reading for almost 2 hours. And this piece is out of my understanding of things I read during that mere 2 hours.
We take it for granted today, but toilet paper has a fascinating story spanning thousands of years. From creative ancient solutions to the modern perforated roll, humanity's quest for comfort and cleanliness reveals surprising ingenuity.
Time Before Toilet Paper
Historically, people used whatever they had in their habitat, to clean themselves. This varied from grass, leaves, tree barks, etc. And yes, many civilizations insisted and used water as the main cleaning method. But this was mainly based on the availability of clean water.
Wherever the availability of water was in question, people got creative! Ancient Romans used "tersorium"- basically it is a sea sponge on a stick. They sock it in vinegar or salt water between uses. These were communal.
Greeks preferred smooth pottery fragments with rounded edges. Of course, no one wanted the other end of the digestive tract injured! :D
Early Chinese civilizations wrapped cloth around wooden sticks shaped like spatulas.
Medieval Europeans show their class divisions even in the bathroom! The wealthy used wool, hemp, or even lace. While commoners made do with whatever cloth they had- sometimes, their own sleeves (- today, YUCK!). In the 1700s rural Americas, people turned to nature, using corncobs and seashells.
No matter what we think about these methods, every civilization and every class of people in those valued one thing - Cleanliness.
True Toilet Paper Pioneers
We all know China invented paper somewhere near 100 AD. By the 6th century, Emporer Yandgi's court records show that he used 15,000 sheets of paper annually, just for his personal hygiene!
Early Chinese toilet papers were made from rice straw, hemp, and bamboo. They boiled the material, churned it into a pulp, flattened and dry it, and then cut into shape before using it. By 14th century, the imperial court enjoyed "Perfumed paper sheets". Records show that the royal family alone used almost 0.75 million sheets yearly!!
However, not everyone was happy with this invention. Traveling Muslim merchants described the Chinese practice as "Haraam" (foul), they always preferred using water.
The West Catches Up
Western toilet paper development took longer. Sir John Harrington invented the flushing toilet in 1596, though it would not become common for centuries. By the 1700s, newspapers became a popular bathroom staple.
The commercial breakthrough came only in 1857 when American entrepreneur Joseph Gayetty found a way for the commercial production of toilet papers. But at that time it was sold in another name - "Medicated Paper for Water-Closet". He sold it 500 sheets for 50 cents. Only then the use of "Toilet papers" really arrived in the West.
Rolling into Modern Era
Later in the 19th century, manufacturers found the best and most economical way to produce and store toilet paper - as "Rolls" like we see today. Seth Wheeler of Albany patented perforated wrapping paper in 1871. and the first modern perforated toilet paper roll came out in 1891, making the "tearing" much easier - literally and figuratively! :D
That was the same time home plumbing was improving a lot which resulted in having the toilets inside the home itself. With that, the consumption of toilet paper rose - first as a vanity symbol and later as a common addition to the shopping list.
Big Business in Bathrooms
Brothers - Clarence and Edward Irvin Scott founded Scott Paper Company in Philadelphia in 1879, initially cutting and packaging toilet paper for retailers to sell under their brands. The company grew after 1896 when Arthur Hoyt Scott joined. They started mass-producing their brand of toilet paper. By 1910, they had built the largest paper mill in Chester, marking the industrialization of toilet paper production.
Meanwhile, that old paper made of concoction in China became popular there by the 16th century.
From Luxury to Necessity
We humans always run behind an unknown "comfort". The story of toilet paper is also not so different from that. Imagine using the pottery fragments in place of that "plush quilted ultra-soft scented bathroom tissues". This everyday item we rarely think about represents centuries of innovation and cultural evolution.
Next time you pull a pack of tissue papers from the back aisle of Costco, spare a "thanks" for your ancestors and their corncobs, sea sponges, and pottery fragments.
And maybe soon, you might be "Zapping" to buy tissue papers.
Final Thoughts
The COVID-19 pandemic time gave us some lessons as well as some "FailArmy" videos. One of those videos was people fighting over the last available toilet paper pack in some shop. After the pandemic, there has been a surge in American homes installing Bidet faucets in their bathrooms. A bit late, but the West is now catching up again with the East! :D
Let me know if you liked this article - leave a reaction/comment. Cheers.
-
 @ f7d424b5:618c51e8
2025-05-04 19:19:43
@ f7d424b5:618c51e8
2025-05-04 19:19:43Listen to the new episode here!
Finally some good news. Good new games, worthwhile remakes, and bloggers facing the consequences of their actions. Gaming is healing. Let's talk about it!
Stuff cited:
Obligatory:
- Discuss this episode on OUR NEW FORUM
- Get the RSS and Subscribe (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at newpodcastapps.com
- Or listen to the show on the forum using the embedded Podverse player!
- Send your complaints here
Reminder that this is a Value4Value podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
-
 @ 8096ed6b:4901018b
2025-05-04 20:37:54
@ 8096ed6b:4901018b
2025-05-04 20:37:54🎵 Kakamora by Mark Mancina
🔗 https://song.link/us/i/1440641103
-
 @ c9badfea:610f861a
2025-05-04 18:39:06
@ c9badfea:610f861a
2025-05-04 18:39:06- Install Kiwix (it's free and open source)
- Download ZIM files from the Kiwix Library (you will find complete offline versions of Wikipedia, Stack Overflow, Bitcoin Wiki, DevDocs and many more)
- Open the downloaded ZIM files within the Kiwix app
ℹ️ You can also package any website using either Kiwix Zimit (online tool) or the Zimit Docker Container (for technical users)
ℹ️.zimis the file format used for packaged websites -
 @ 9223d2fa:b57e3de7
2025-05-04 20:15:08
@ 9223d2fa:b57e3de7
2025-05-04 20:15:083,058 steps
-
 @ 7ef5f1b1:0e0fcd27
2025-05-04 18:28:05
@ 7ef5f1b1:0e0fcd27
2025-05-04 18:28:05A monthly newsletter by The 256 Foundation

May 2025
Introduction:
Welcome to the fifth newsletter produced by The 256 Foundation! April was a jam-packed month for the Foundation with events ranging from launching three grant projects to the first official Ember One release. The 256 Foundation has been laser focused on our mission to dismantle the proprietary mining empire, signing off on a productive month with the one-finger salute to the incumbent mining cartel.
 [IMG-001] Hilarious meme from @CincoDoggos
[IMG-001] Hilarious meme from @CincoDoggosDive in to catch up on the latest news, mining industry developments, progress updates on grant projects, Actionable Advice on helping test Hydra Pool, and the current state of the Bitcoin network.
Definitions:
DOJ = Department of Justice
SDNY = Southern District of New York
BTC = Bitcoin
SD = Secure Digital
Th/s = Terahash per second
OSMU = Open Source Miners United
tx = transaction
PSBT = Partially Signed Bitcoin Transaction
FIFO = First In First Out
PPLNS = Pay Per Last N Shares
GB = Gigabyte
RAM = Random Access Memory
ASIC = Application Specific Integrated Circuit
Eh/s = Exahash per second
Ph/s = Petahash per second
News:
April 7: the first of a few notable news items that relate to the Samourai Wallet case, the US Deputy Attorney General, Todd Blanche, issued a memorandum titled “Ending Regulation By Prosecution”. The memo makes the DOJ’s position on the matter crystal clear, stating; “Specifically, the Department will no longer target virtual currency exchanges, mixing and tumbling services, and offline wallets for the acts of their end users or unwitting violations of regulations…”. However, despite the clarity from the DOJ, the SDNY (sometimes referred to as the “Sovereign District” for it’s history of acting independently of the DOJ) has yet to budge on dropping the charges against the Samourai Wallet developers. Many are baffled at the SDNY’s continued defiance of the Trump Administration’s directives, especially in light of the recent suspensions and resignations that swept through the SDNY office in the wake of several attorneys refusing to comply with the DOJ’s directive to drop the charges against New York City Mayor, Eric Adams. There is speculation that the missing piece was Trump’s pick to take the helm at the SDNY, Jay Clayton, who was yet to receive his Senate confirmation and didn’t officially start in his new role until April 22. In light of the Blanche Memo, on April 29, the prosecution and defense jointly filed a letter requesting additional time for the prosecution to determine it’s position on the matter and decide if they are going to do the right thing, comply with the DOJ, and drop the charges. Catch up on what’s at stake in this case with an appearance by Diverter on the Unbounded Podcast from April 24, the one-year anniversary of the Samourai Wallet developer’s arrest. This is the most important case facing Bitcoiners as the precedence set in this matter will have ripple effects that touch all areas of the ecosystem. The logic used by SDNY prosecutors argues that non-custodial wallet developers transfer money in the same way a frying pan transfers heat but does not “control” the heat. Essentially saying that facilitating the transfer of funds on behalf of the public by any means constitutes money transmission and thus requires a money transmitter license. All non-custodial wallets (software or hardware), node operators, and even miners would fall neatly into these dangerously generalized and vague definitions. If the SDNY wins this case, all Bitcoiners lose. Make a contribution to the defense fund here.
April 11: solo miner with ~230Th/s solves Block #891952 on Solo CK Pool, bagging 3.11 BTC in the process. This will never not be exciting to see a regular person with a modest amount of hashrate risk it all and reap all the mining reward. The more solo miners there are out there, the more often this should occur.
April 15: B10C publishes new article on mining centralization. The article analyzes the hashrate share of the currently five biggest pools and presents a Mining Centralization Index. The results demonstrate that only six pools are mining more than 95% of the blocks on the Bitcoin Network. The article goes on to explain that during the period between 2019 and 2022, the top two pools had ~35% of the network hashrate and the top six pools had ~75%. By December 2023 those numbers grew to the top two pools having 55% of the network hashrate and the top six having ~90%. Currently, the top six pools are mining ~95% of the blocks.
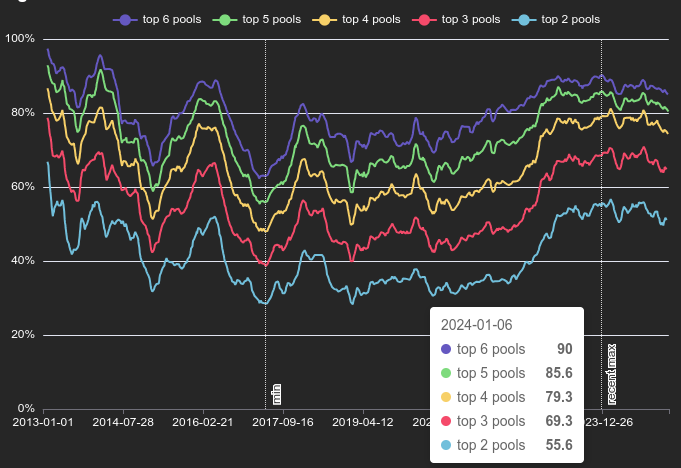 [IMG-002] Mining Centralization Index by @0xB10C
[IMG-002] Mining Centralization Index by @0xB10CB10C concludes the article with a solution that is worth highlighting: “More individuals home-mining with small miners help too, however, the home-mining hashrate is currently still negligible compared to the industrial hashrate.”
April 15: As if miner centralization and proprietary hardware weren’t reason enough to focus on open-source mining solutions, leave it to Bitmain to release an S21+ firmware update that blocks connections to OCEAN and Braiins pools. This is the latest known sketchy development from Bitmain following years of shady behavior like Antbleed where miners would phone home, Covert ASIC Boost where miners could use a cryptographic trick to increase efficiency, the infamous Fork Wars, mining empty blocks, and removing the SD card slots. For a mining business to build it’s entire operation on a fragile foundation like the closed and proprietary Bitmain hardware is asking for trouble. Bitcoin miners need to remain flexible and agile and they need to be able to adapt to changes instantly – the sort of freedoms that only open-source Bitcoin mining solutions are bringing to the table.
Free & Open Mining Industry Developments:
The development will not stop until Bitcoin mining is free and open… and then it will get even better. Innovators did not disappoint in April, here are nine note-worthy events:
April 5: 256 Foundation officially launches three more grant projects. These will be covered in detail in the Grant Project Updates section but April 5 was a symbolic day to mark the official start because of the 6102 anniversary. A reminder of the asymmetric advantage freedom tech like Bitcoin empowers individuals with to protect their rights and freedoms, with open-source development being central to those ends.
April 5: Low profile ICE Tower+ for the Bitaxe Gamma 601 introduced by @Pleb_Style featuring four heat pipes, 2 copper shims, and a 60mm Noctua fan resulting in up to 2Th/s. European customers can pick up the complete upgrade kit from the Pleb Style online store for $93.00.
 IMG-003] Pleb Style ICE Tower+ upgrade kit
IMG-003] Pleb Style ICE Tower+ upgrade kitApril 8: Solo Satoshi spells out issues with Bitaxe knockoffs, like Lucky Miner, in a detailed article titled The Hidden Cost of Bitaxe Clones. This concept can be confusing for some people initially, Bitaxe is open-source, right? So anyone can do whatever they want… right? Based on the specific open-source license of the Bitaxe hardware, CERN-OHL-S, and the firmware, GPLv3, derivative works are supposed to make the source available. Respecting the license creates a feed back loop where those who benefit from the open-source work of those who came before them contribute back their own modifications and source files to the open-source community so that others can benefit from the new developments. Unfortunately, when the license is disrespected what ends up happening is that manufacturers make undocumented changes to the components in the hardware and firmware which yields unexpected results creating a number of issues like the Bitaxe overheating, not connecting to WiFi, or flat out failure. This issue gets further compounded when the people who purchased the knockoffs go to a community support forum, like OSMU, for help. There, a number of people rack their brains and spend their valuable time trying to replicate the issues only to find out that they cannot replicate the issues since the person who purchased the knockoff has something different than the known Bitaxe model and the distributor who sold the knockoff did not document those changes. The open-source licenses are maintaining the end-users’ freedom to do what they want but if the license is disrespected then that freedom vanishes along with details about whatever was changed. There is a list maintained on the Bitaxe website of legitimate distributors who uphold the open-source licenses, if you want to buy a Bitaxe, use this list to ensure the open-source community is being supported instead of leeched off of.
April 8: The Mempool Open Source Project v3.2.0 launches with a number of highlights including a new UTXO bubble chart, address poisoning detection, and a tx/PSBT preview feature. The GitHub repo can be found here if you want to self-host an instance from your own node or you can access the website here. The Mempool Open Source Project is a great blockchain explorer with a rich feature set and helpful visualization tools.
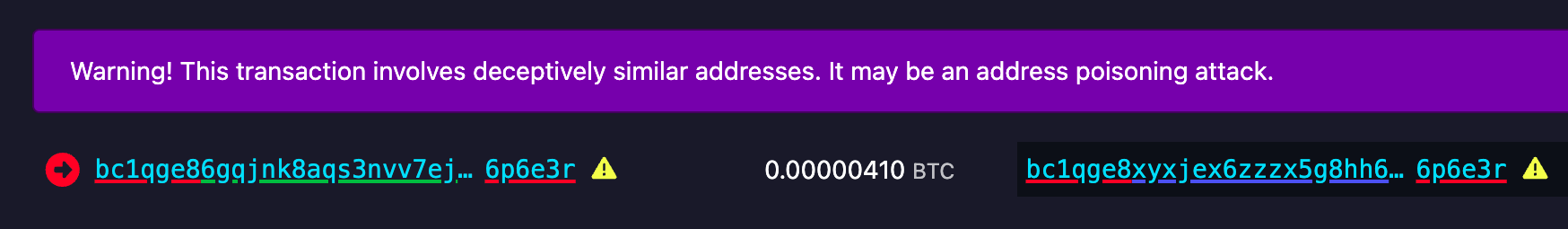 [IMG-004] Address poisoning example
[IMG-004] Address poisoning exampleApril 8: @k1ix publishes bitaxe-raw, a firmware for the ESP32S3 found on Bitaxes which enables the user to send and receive raw bytes over USB serial to and from the Bitaxe. This is a helpful tool for research and development and a tool that is being leveraged at The 256 Foundation for helping with the Mujina miner firmware development. The bitaxe-raw GitHub repo can be found here.
April 14: Rev.Hodl compiles many of his homestead-meets-mining adaptations including how he cooks meat sous-vide style, heats his tap water to 150°F, runs a hashing space heater, and how he upgraded his clothes dryer to use Bitcoin miners. If you are interested in seeing some creative and resourceful home mining integrations, look no further. The fact that Rev.Hodl was able to do all this with closed-source proprietary Bitcoin mining hardware makes a very bullish case for the innovations coming down the pike once the hardware and firmware are open-source and people can gain full control over their mining appliances.
April 21: Hashpool explained on The Home Mining Podcast, an innovative Bitcoin mining pool development that trades mining shares for ecash tokens. The pool issues an “ehash” token for every submitted share, the pool uses ecash epochs to approximate the age of those shares in a FIFO order as they accrue value, a rotating key set is used to eventually expire them, and finally the pool publishes verification proofs for each epoch and each solved block. The ehash is provably not inflatable and payouts are similar to the PPLNS model. In addition to the maturity window where ehash tokens are accruing value, there is also a redemption window where the ehash tokens can be traded in to the mint for bitcoin. There is also a bitcoin++ presentation from earlier this year where @vnprc explains the architecture.
April 26: Boerst adds a new page on stratum.work for block template details, you can click on any mining pool and see the extended details and visualization of their current block template. Updates happen in real-time. The page displays all available template data including the OP_RETURN field and if the pool is merge mining, like with RSK, then that will be displayed too. Stratum dot work is a great project that offers helpful mining insights, be sure to book mark it if you haven’t already.
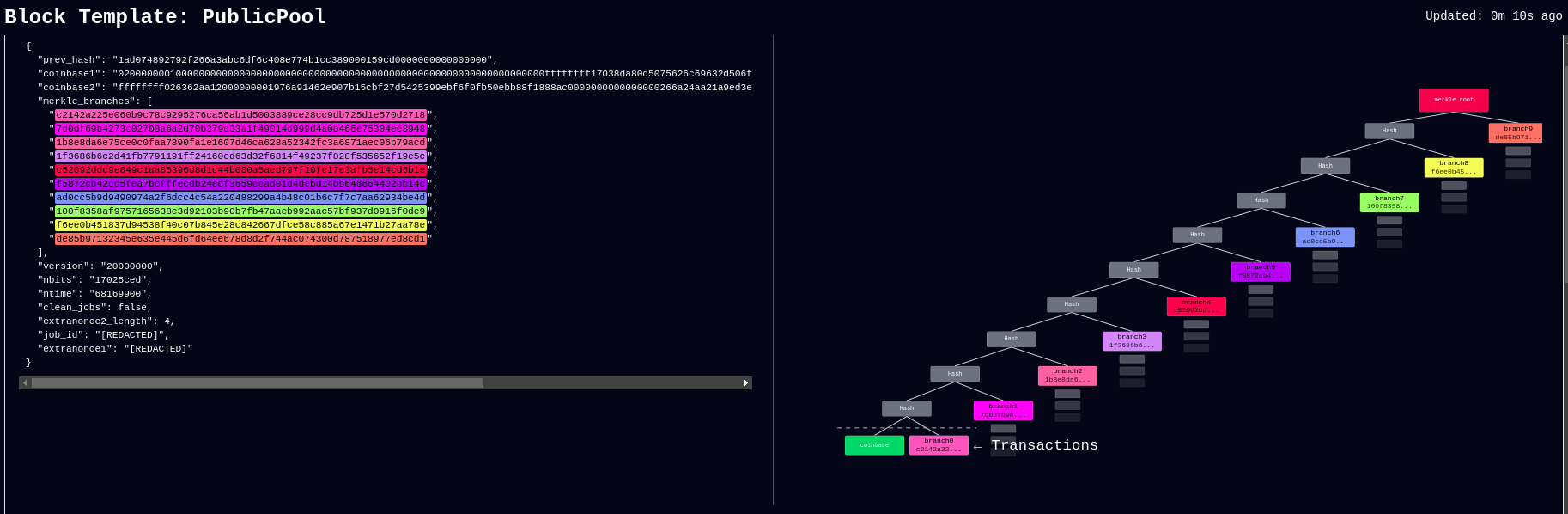 [IMG-005] New stratum.work live template page
[IMG-005] New stratum.work live template pageApril 27: Public Pool patches Nerdminer exploit that made it possible to create the impression that a user’s Nerdminer was hashing many times more than it actually was. This exploit was used by scammers trying to convince people that they had a special firmware for the Nerminer that would make it hash much better. In actuality, Public Pool just wasn’t checking to see if submitted shares were duplicates or not. The scammers would just tweak the Nerdminer firmware so that valid shares were getting submitted five times, creating the impression that the miner was hashing at five times the actual hashrate. Thankfully this has been uncovered by the open-source community and Public Pool quickly addressed it on their end.
Grant Project Updates:
Three grant projects were launched on April 5, Mujina Mining Firmware, Hydra Pool, and Libre Board. Ember One was the first fully funded grant and launched in November 2024 for a six month duration.
Ember One:
@skot9000 is the lead engineer on the Ember One and April 30 marked the conclusion of the first grant cycle after six months of development culminating in a standardized hashboard featuring a ~100W power consumption, 12-24v input voltage range, USB-C data communication, on-board temperature sensors, and a 125mm x 125mm formfactor. There are several Ember One versions on the road map, each with a different kind of ASIC chip but staying true to the standardized features listed above. The first Ember One, the 00 version, was built with the Bitmain BM1362 ASIC chips. The first official release of the Ember One, v3, is available here. v4 is already being worked on and will incorporate a few circuit safety mechanisms that are pretty exciting, like protecting the ASIC chips in the event of a power supply failure. The firmware for the USB adaptor is available here. Initial testing firmware for the Ember One 00 can be found here and full firmware support will be coming soon with Mujina. The Ember One does not have an on-board controller so a separate, USB connected, control board is required. Control board support is coming soon with the Libre Board. There is an in-depth schematic review that was recorded with Skot and Ryan, the lead developer for Mujina, you can see that video here. Timing for starting the second Ember One cycle is to be determined but the next version of the Ember One is planned to have the Intel BZM2 ASICs. Learn more at emberone.org
Mujina Mining Firmware:
@ryankuester is the lead developer for the Mujina firmware project and since the project launched on April 5, he has been working diligently to build this firmware from scratch in Rust. By using the bitaxe-raw firmware mentioned above, over the last month Ryan has been able to use a Bitaxe to simulate an Ember One so that he can start building the necessary interfaces to communicate with the range of sensors, ASICs, work handling, and API requests that will be necessary. For example, using a logic analyzer, this is what the first signs of life look like when communicating with an ASIC chip, the orange trace is a message being sent to the ASIC and the red trace below it is the ASIC responding [IMG-006]. The next step is to see if work can be sent to the ASIC and results returned. The GitHub repo for Mujina is currently set to private until a solid foundation has been built. Learn more at mujina.org
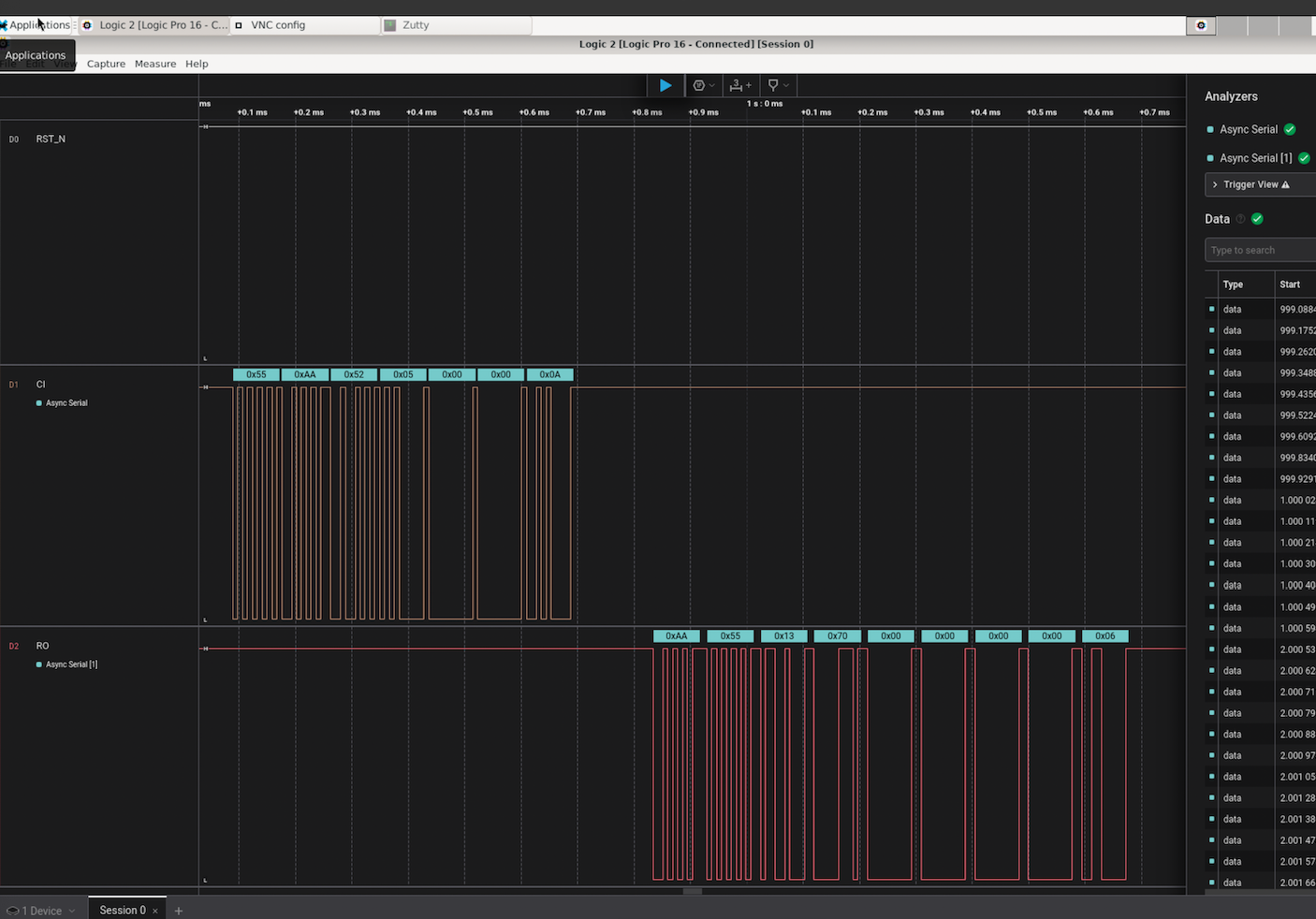 [IMG-006] First signs of life from an ASIC
[IMG-006] First signs of life from an ASICLibre Board:
@Schnitzel is the lead engineer for the Libre Board project and over the last month has been modifying the Raspberry Pi Compute Module I/O Board open-source design to fit the requirements for this project. For example, removing one of the two HDMI ports, adding the 40-pin header, and adapting the voltage regulator circuit so that it can accept the same 12-24vdc range as the Ember One hashboards. The GitHub repo can be found here, although there isn’t much to look at yet as the designs are still in the works. If you have feature requests, creating an issue in the GitHub repo would be a good place to start. Learn more at libreboard.org
Hydra Pool:
@jungly is the lead developer for Hydra Pool and over the last month he has developed a working early version of Hydra Pool specifically for the upcoming Telehash #2. Forked from CK Pool, this early version has been modified so that the payout goes to the 256 Foundation bitcoin address automatically. This way, users who are supporting the funderaiser with their hashrate do not need to copy/paste in the bitcoin address, they can just use any vanity username they want. Jungly was also able to get a great looking statistics dashboard forked from CKstats and modify it so that the data is populated from the Hydra Pool server instead of website crawling. After the Telehash, the next steps will be setting up deployment scripts for running Hydra Pool on a cloud server, support for storing shares in a database, and adding PPLNS support. The 256 Foundation is only running a publicly accessible server for the Telehash and the long term goals for Hydra Pool are that the users host their own instance. The 256 Foundation has no plans on becoming a mining pool operator. The following Actionable Advice column shows you how you can help test Hydra Pool. The GitHub repo for Hydra Pool can be found here. Learn more at hydrapool.org
Actionable Advice:
The 256 Foundation is looking for testers to help try out Hydra Pool. The current instance is on a hosted bare metal server in Florida and features 64 cores and 128 GB of RAM. One tester in Europe shared that they were only experiencing ~70ms of latency which is good. If you want to help test Hydra Pool out and give any feedback, you can follow the directions below and join The 256 Foundation public forum on Telegram here.
The first step is to configure your miner so that it is pointed to the Hydra Pool server. This can look different depending on your specific miner but generally speaking, from the settings page you can add the following URL:
stratum+tcp://stratum.hydrapool.org:3333On some miners, you don’t need the “stratum+tcp://” part or the port, “:3333”, in the URL dialog box and there may be separate dialog boxes for the port.
Use any vanity username you want, no need to add a BTC address. The test iteration of Hydra Pool is configured to payout to the 256 Foundation BTC address.
If your miner has a password field, you can just put “x” or “1234”, it doesn’t matter and this field is ignored.
Then save your changes and restart your miner. Here are two examples of what this can look like using a Futurebit Apollo and a Bitaxe:
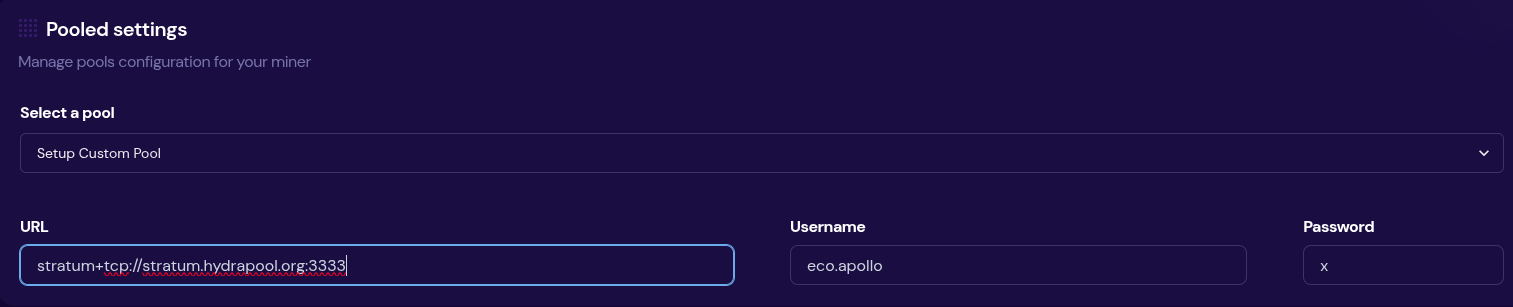 [IMG-007] Apollo configured to Hydra Pool
[IMG-007] Apollo configured to Hydra Pool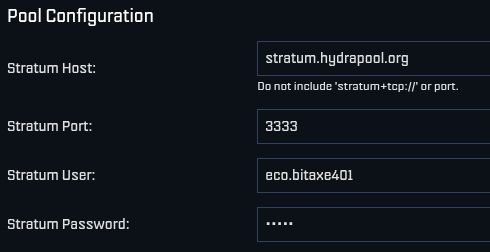 [IMG-008] Bitaxe Configured to Hydra Pool
[IMG-008] Bitaxe Configured to Hydra PoolOnce you get started, be sure to check stats.hydrapool.org to monitor the solo pool statistics.
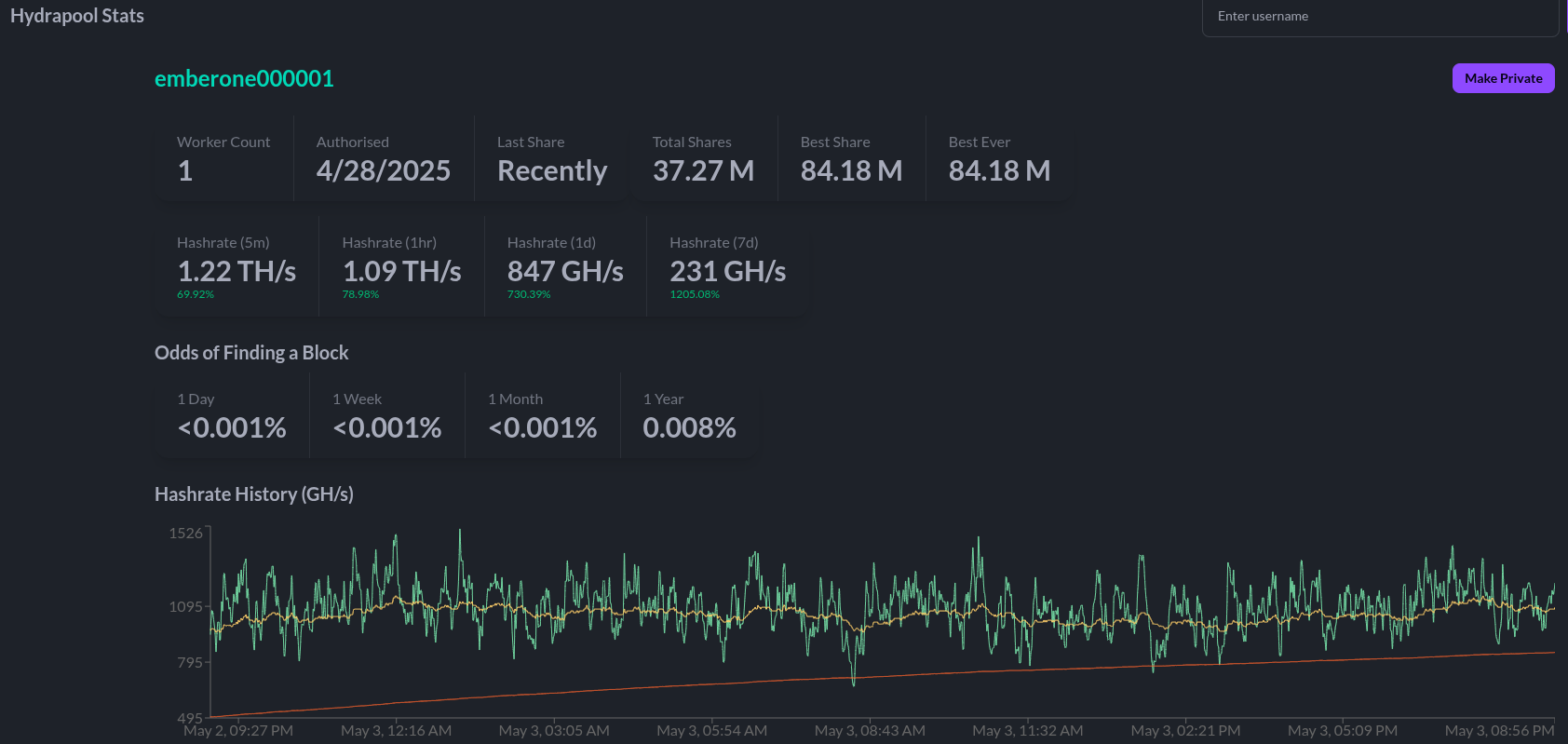 [IMG-009] Ember One hashing to Hydra Pool
[IMG-009] Ember One hashing to Hydra PoolAt the last Telehash there were over 350 entities pointing as much as 1.12Eh/s at the fundraiser at the peak. At the time the block was found there was closer to 800 Ph/s of hashrate. At this next Telehash, The 256 Foundation is looking to beat the previous records across the board. You can find all the Telehash details on the Meetup page here.
State of the Network:
Hashrate on the 14-day MA according to mempool.space increased from ~826 Eh/s to a peak of ~907 Eh/s on April 16 before cooling off and finishing the month at ~841 Eh/s, marking ~1.8% growth for the month.
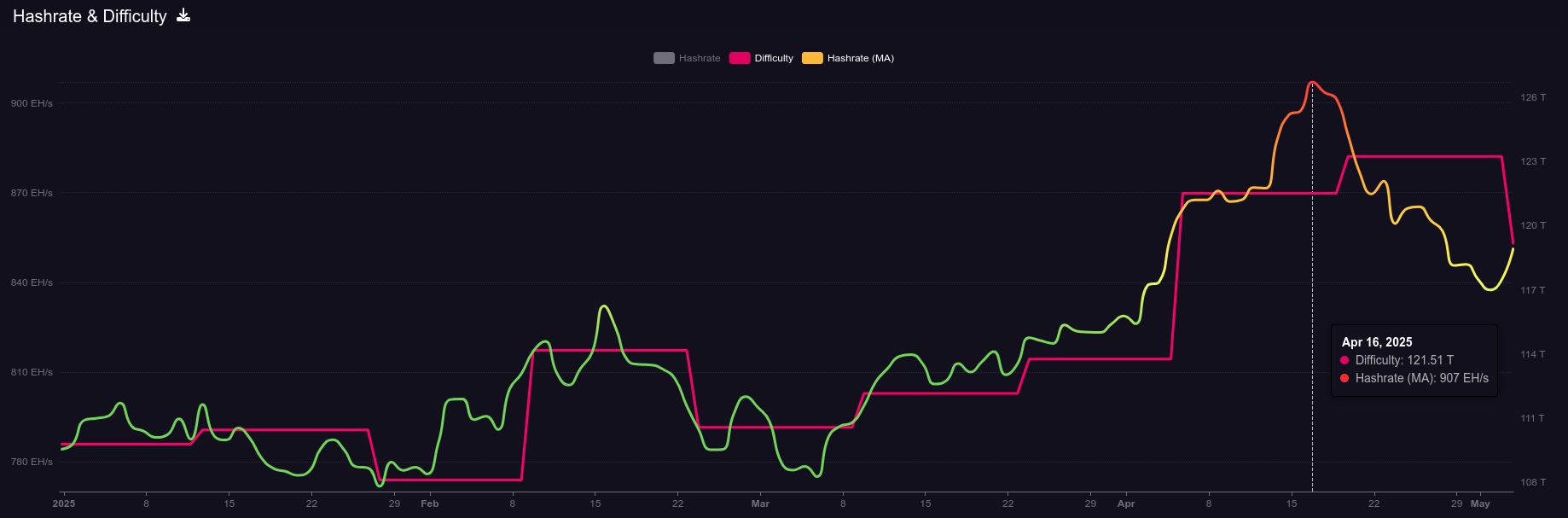 [IMG-010] 2025 hashrate/difficulty chart from mempool.space
[IMG-010] 2025 hashrate/difficulty chart from mempool.spaceDifficulty was 113.76T at it’s lowest in April and 123.23T at it’s highest, which is a 8.3% increase for the month. But difficulty dropped with Epoch #444 just after the end of the month on May 3 bringing a -3.3% downward adjustment. All together for 2025 up to Epoch #444, difficulty has gone up ~8.5%.
According to the Hashrate Index, ASIC prices have flat-lined over the last month. The more efficient miners like the <19 J/Th models are fetching $17.29 per terahash, models between 19J/Th – 25J/Th are selling for $11.05 per terahash, and models >25J/Th are selling for $3.20 per terahash. You can expect to pay roughly $4,000 for a new-gen miner with 230+ Th/s.
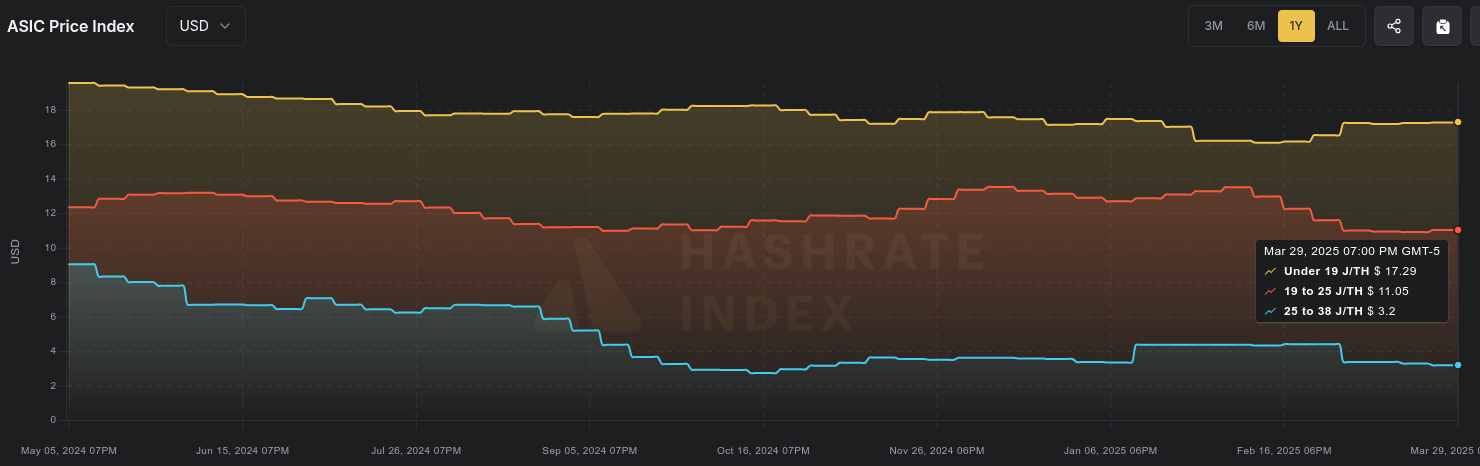 [IMG-011] Miner Prices from Luxor’s Hashrate Index
[IMG-011] Miner Prices from Luxor’s Hashrate IndexHashvalue over the month of April dropped from ~56,000 sats/Ph per day to ~52,000 sats/Ph per day, according to the new and improved Braiins Insights dashboard [IMG-012]. Hashprice started out at $46.00/Ph per day at the beginning of April and climbed to $49.00/Ph per day by the end of the month.
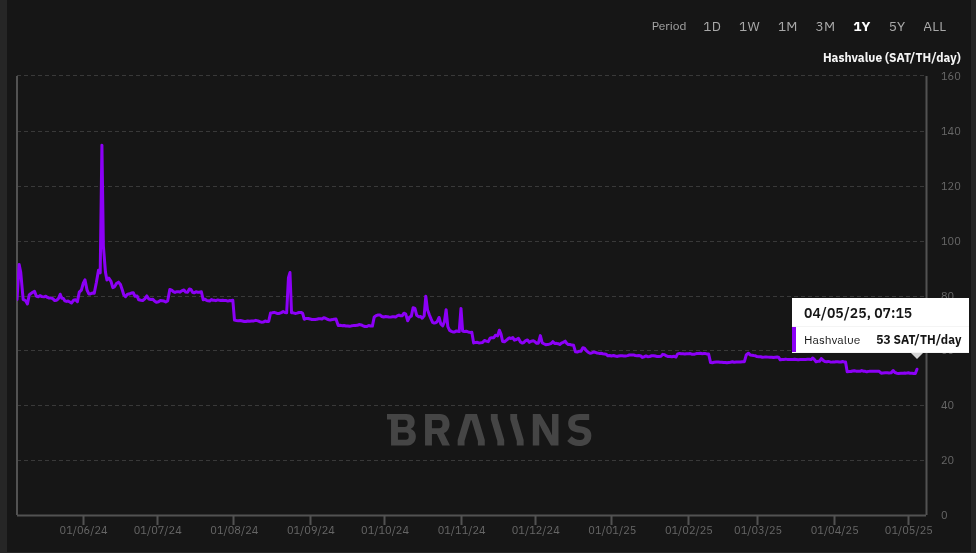 [IMG-012] Hashprice/Hashvalue from Braiins Insights
[IMG-012] Hashprice/Hashvalue from Braiins InsightsThe next halving will occur at block height 1,050,000 which should be in roughly 1,063 days or in other words ~154,650 blocks from time of publishing this newsletter.
Conclusion:
Thank you for reading the fifth 256 Foundation newsletter. Keep an eye out for more newsletters on a monthly basis in your email inbox by subscribing at 256foundation.org. Or you can download .pdf versions of the newsletters from there as well. You can also find these newsletters published in article form on Nostr.
If you haven’t done so already, be sure to RSVP for the Texas Energy & Mining Summit (“TEMS”) in Austin, Texas on May 6 & 7 for two days of the highest Bitcoin mining and energy signal in the industry, set in the intimate Bitcoin Commons, so you can meet and mingle with the best and brightest movers and shakers in the space.
 [IMG-013] TEMS 2025 flyer
[IMG-013] TEMS 2025 flyer While you’re at it, extend your stay and spend Cinco De Mayo with The 256 Foundation at our second fundraiser, Telehash #2. Everything is bigger in Texas, so set your expectations high for this one. All of the lead developers from the grant projects will be present to talk first-hand about how to dismantle the proprietary mining empire.
If you are interested in helping The 256 Foundation test Hydra Pool, then hopefully you found all the information you need to configure your miner in this issue.
 [IMG-014] FREE SAMOURAI
[IMG-014] FREE SAMOURAIIf you want to continue seeing developers build free and open solutions be sure to support the Samourai Wallet developers by making a tax-deductible contribution to their legal defense fund here. The first step in ensuring a future of free and open Bitcoin development starts with freeing these developers.
Live Free or Die,
-econoalchemist
-
 @ 1d7ff02a:d042b5be
2025-05-03 09:47:49
@ 1d7ff02a:d042b5be
2025-05-03 09:47:49ບົດຄວາມນີ້ແປມາຈາ: https://jackkruse.com/what-to-do-with-new-cancer-diagnosis/
ເນື້ອຫາສຳລັບຜູ້ອ່ານ: 1. ຈະເຮັດແນວໃດເມື່ອທ່ານໄດ້ຮັບການວິນິດໄສວ່າເປັນມະເຮັງ? 2. ສະໜາມຮົບກັບມະເຮັງທີ່ສຳຄັນແມ່ນຢູ່ບ່ອນການປິ່ນປົວແບບແພດ ຫຼື ໃນຮ່າງກາຍຂອງທ່ານເອງ? 3. ອາຫານການກິນມີບົດບາດແນວໃດ? 4. ຈະຮັບມືກັບໝໍມະເຮັງຄົນໃໝ່ຂອງທ່ານແນວໃດ? 5. ບໍ່ຕ້ອງຢ້ານທີ່ຈະສຳຫຼວດທຸກຄວາມເປັນໄປໄດ້ເພື່ອຊະນະສົງຄາມນີ້. ຮຽນຮູ້ກ່ຽວກັບອາຫານ ketogenic!!!
ກ່ອນທ່ານຈະອ່ານບົດຄວາມນີ້, ໃຫ້ເບິ່ງວິດີໂອນີ້: HYPERLINK
ບົດຄວາມນີ້ແມ່ນສຳລັບໜຶ່ງໃນໝູ່ທີ່ພິເສດຂອງຂ້ອຍ ຜູ້ທີ່ພົວພັນຂ້ອຍໃນອາທິດນີ້ ແລະ ບອກວ່າເມຍລາວຖືກວິນິດໄສວ່າເປັນມະເຮັງໃນໄວອາຍຸໜຸ່ມ. ຂ້ອຍໄດ້ຍິນຈາກການໂທ ແລະ ໂພສຂອງລາວໃນ Facebook ວ່າມັນກຳລັງທຳລາຍລາວ. ຂ້ອຍບອກລາວທັນທີໃຫ້ໄປຊື້ປື້ມ Anti Cancer: A New Way of Life ໂດຍ David Servan Schreiber ແລະ ມອບໃຫ້ເຈົ້າສາວຂອງລາວ. ຂ່າວດີກໍ່ຄືຫຼາຍລ້ານຄົນໃນຈຳນວນ 6 ລ້ານຄົນທີ່ກຳລັງປິ່ນປົວມະເຮັງໃນປະຈຸບັນຈະມີຊີວິດທີ່ສົມບູນຕໍ່ໄປ. ຈຳນວນຜູ້ລອດຊີວິດຕາມຄວາມຄິດເຫັນຂອງຂ້ອຍຍັງຕ່ຳເກີນໄປ (ປະມານ 45-50%). ນອກຈາກນັ້ນ, ຫຼາຍຄົນໃນຈຳນວນ 2000 ຄົນທີ່ເສຍຊີວິດຈາກມະເຮັງທຸກມື້ແມ່ນເນື່ອງຈາກຄອບຄົວຂອງພວກເຂົາບໍ່ຮູ້ກ່ຽວກັບຊັບພະຍາກອນທີ່ມີໃນປະຈຸບັນສຳລັບການປິ່ນປົວມະເຮັງທັງແບບດັ້ງເດີມ ແລະ ແບບທາງເລືອກ ເຊັ່ນ: ການປິ່ນປົວແບບເສີມ ຫຼື ແບບບູລະນາການ.
ເມື່ອຖືກວິນິດໄສດ້ວຍພະຍາດນີ້, ທ່ານຈະຮູ້ສຶກສັ່ນສະເທືອນຢ່າງຮຸນແຮງ. ສິ່ງສຳຄັນທີ່ທ່ານຕ້ອງຮູ້ແມ່ນພະຍາດນີ້ບໍ່ພຽງແຕ່ສາມາດຕໍ່ສູ້ໄດ້ແຕ່ຍັງສາມາດປ້ອງກັນໄດ້ຖ້າທ່ານຕັດສິນໃຈປ່ຽນແປງບາງສິ່ງທັນທີ ແລະ ປ່ອຍວາງຄວາມເຊື່ອທີ່ບໍ່ຖືກຕ້ອງທີ່ທ່ານໄດ້ສະສົມໃນຊີວິດ. ນີ້ເປັນຄວາມຈິງໂດຍສະເພາະຖ້າທ່ານເຮັດວຽກໃນຂົງເຂດສາທາລະນະສຸກ ແລະ ໄດ້ດຳລົງຊີວິດຕາມຄວາມເຊື່ອຕາຍຕົວຕະຫຼອດຊີວິດ. ປື້ມນີ້ຂຽນໂດຍແພດນັກຄົ້ນຄວ້າທີ່ບໍ່ພຽງແຕ່ຖືກກະທົບຈາກມະເຮັງ ແຕ່ຍັງເປັນມະເຮັງສະໝອງທີ່ອັນຕະລາຍທີ່ສຸດ. ລາວສາມາດຮື້ຖອນຄວາມເຊື່ອຂອງຕົນເອງໃນຖານະແພດດ້ວຍວິທະຍາສາດໃໝ່ທີ່ມີຢູ່ສຳລັບນັກຄົ້ນຄວ້າ ແຕ່ບໍ່ແມ່ນແພດມະເຮັງທົ່ວໄປ. ປື້ມນີ້ຈຳເປັນສຳລັບທຸກຄົນທີ່ເປັນມະເຮັງ ຫຼື ມີປັດໄຈສ່ຽງ ເພື່ອທ່ານຈະໄດ້ຊະນະກ່ອນມັນເລີ່ມ. ນີ້ແມ່ນໜຶ່ງໃນເຫດຜົນທີ່ຂ້ອຍຂຽນ QUILT ຂອງຂ້ອຍ ເພາະຂ້ອຍເຊື່ອວ່າຖ້າທ່ານປົກປ້ອງຈຸລັງຂອງທ່ານ ທ່ານຈະບໍ່ເປັນພະຍາດນີ້. ດຽວນີ້ ໝູ່ຂອງຂ້ອຍເປັນພະຍາດນີ້... ນີ້ແມ່ນບົດຄວາມກ່ຽວກັບສິ່ງທີ່ທ່ານອາດພິຈາລະນາເຮັດທັນທີຫຼັງຈາກປຶກສາກັບແພດມະເຮັງຂອງທ່ານ. ພິຈາລະນາຂໍຄວາມຄິດເຫັນທີສອງຈາກສູນມະເຮັງທີ່ສຳຄັນເຊັ່ນ MD Anderson.
-
ອ່ານປື້ມ Anticancer ທີ່ກ່າວເຖິງຂ້າງເທິງ. ມັນສຳຄັນທີ່ຈະເຫັນພະຍາດນີ້ໃນມຸມມອງໃໝ່.
-
ປ່ຽນອາຫານການກິນຂອງທ່ານທັນທີເປັນ Epi-paleo Rx ແລະ ອອກຫ່າງຈາກອາຫານແບບຕາເວັນຕົກມາດຕະຖານ.
-
ເລີ່ມເຮັດສະມາທິໂດຍໄວເທົ່າທີ່ຈະເປັນໄປໄດ້ເພື່ອຄວບຄຸມ cortisol ແລະ ຄວາມກັງວົນຂອງທ່ານ. (ທາງເລືອກບໍ່ສຳຄັນແຕ່ການເຮັດຈິງຊ່ວຍຊີວິດໄດ້)
-
ຄົນເຈັບຄວນປຶກສາຫາລືກ່ຽວກັບແຜນການປິ່ນປົວມະເຮັງ: ປັດໃຈສຳຄັນໃນມະເຮັງ: ຄວນຄົນເຈັບໃຊ້ອາຫານເສີມສຳລັບປະເພດມະເຮັງທີ່ທ່ານມີບໍ?
-
ພິຈາລະນາເລີ່ມລະບົບອາຫານເສີມ ລວມເຖິງ Curcumin, Reservatrol, Quercetin, ນ້ຳມັນປາ Omega ສາມ (ຄຸນນະພາບ Rx), ວິຕາມິນ D3 ໂດຍມີເປົ້າໝາຍເກີນ 50 ng/dl, ການໃຊ້ CoEnZQ10 ເປັນປະຈຳທຸກວັນ, R-alpha lipoic acid ແລະ ວິຕາມິນ K ທຸກມື້. ພິຈາລະນາການໃຊ້ N Acetyl Cysteine ທຸກວັນເຊັ່ນກັນ. ສັງເກດວ່າຂ້ອຍບໍ່ໄດ້ກຳນົດປະລິມານເພາະປະລິມານທີ່ຕ້ອງການສຳລັບການບຳບັດມະເຮັງແມ່ນສູງກວ່າທີ່ຈະໃຊ້ໃນການປ້ອງກັນ. ສິ່ງນີ້ຄວນເຮັດພາຍໃຕ້ການປຶກສາກັບແພດມະເຮັງຂອງທ່ານ. ຖ້າແພດມະເຮັງຂອງທ່ານບໍ່ເປີດໃຈກວ້າງກ່ຽວກັບບັນຫາເຫຼົ່ານີ້... ຫຼັງຈາກອ່ານປື້ມໃນຂັ້ນຕອນທີໜຶ່ງ ທ່ານອາດຈະຕ້ອງຊອກຫາແພດມະເຮັງຄົນໃໝ່. ເຫຼົ່ານີ້ແມ່ນສິ່ງທີ່ຂ້ອຍພິຈາລະນາວ່າເປັນອາຫານເສີມຫຼັກສຳລັບມະເຮັງສ່ວນໃຫຍ່ທີ່ມະນຸດເປັນ.
-
ໃນອາຫານຂອງທ່ານໃຫ້ເພີ່ມ ຂີ້ໝິ້ນ, ຂິງ, ກະທຽມ, ຣອດສະແມລີ, ແລະ ໃບແບຊິນ (ໃບໂຫລະພາ) ໃສ່ອາຫານຂອງທ່ານໃຫ້ຫຼາຍເທົ່າທີ່ຈະເປັນໄປໄດ້. ທ່ານຄວນດື່ມຊາຂຽວ 1 ລິດຕໍ່ມື້. ຊາຂຽວມີ L-Theanine ທີ່ຊ່ວຍຫຼຸດຄວາມກັງວົນ ແຕ່ຍັງເປັນສ່ວນເສີມຂອງຢາເຄມີບຳບັດໂດຍເຮັດໃຫ້ພວກມັນມີປະສິດທິພາບຍິ່ງຂຶ້ນ. ທ່ານຍັງສາມາດໃຊ້ສານສະກັດຊາຂຽວຖ້າທ່ານບໍ່ຕ້ອງການດື່ມຂອງແຫຼວຫຼາຍ ຫຼື ບໍ່ສາມາດດື່ມໄດ້ເນື່ອງຈາກສະພາບຂອງທ່ານ.
-
ໃນປີ 1955 Otto Warburg ຜູ້ຊະນະລາງວັນໂນເບວພົບວ່າມະເຮັງທັງໝົດໃຊ້ນ້ຳຕານເປັນແຫຼ່ງພະລັງງານ ແລະ ລະດັບອິນຊູລິນສູງເຮັດໃຫ້ຮ່າງກາຍສູນເສຍການຄວບຄຸມລະບົບພູມຄຸ້ມກັນທີ່ຈະປ້ອງກັນມັນ. ນີ້ໝາຍຄວາມວ່າຄົນເຈັບຕ້ອງຈຳກັດທຸກສິ່ງທີ່ກະຕຸ້ນອິນຊູລິນ. ອາຫານແບບ Epi-paleo ທີ່ມີຄາໂບໄຮເດຣດຕ່ຳເຮັດໄດ້ແນວນີ້ພໍດີ. ຂໍ້ມູນອ້າງອີງທີ່ດີສຳລັບອາຫານແມ່ນຢູ່ບ່ອນນີ້.
-
ລະບົບພູມຄຸ້ມກັນຂອງທ່ານແມ່ນການປ້ອງກັນທີ່ດີທີ່ສຸດຕໍ່ມະເຮັງ. ເພີ່ມລະດັບວິຕາມິນ D ແລະ ຮັກສາລະດັບອິນຊູລິນໃຫ້ຕ່ຳກວ່າສອງ. ການຫຼຸດລະດັບ cortisol ຈະປັບປຸງ leptin ແຕ່ສິ່ງສຳຄັນທີ່ສຸດແມ່ນເພີ່ມຈຳນວນຈຸລັງ Natural Killer (WBC) ທີ່ເປັນສ່ວນໜຶ່ງຂອງລະບົບພູມຄຸ້ມກັນໃນຈຸລັງທີ່ຕໍ່ສູ້ກັບມະເຮັງ. ທ່ານຈະໄດ້ອ່ານຫຼາຍກ່ຽວກັບຈຸລັງເຫຼົ່ານີ້ໃນປື້ມທີ່ຂ້ອຍແນະນຳໃນຂັ້ນຕອນທີໜຶ່ງ.
-
ຜັກ. ເຮັດໃຫ້ຜັກຕະກຸນ cruciferous ເປັນອາຫານຫຼັກ. ພືດທັງໝົດໃນຕະກຸນ Brassica ແມ່ນໝູ່ຂອງທ່ານ. Glucosinolates ສາມາດຢັບຢັ້ງ, ຊະລໍ, ແລະ ປີ້ນການເກີດມະເຮັງຫຼາຍຂັ້ນຕອນ. ເຫດຜົນແມ່ນການປ່ອຍ isothiocyanates ເຊັ່ນ sulphoraphanes. Sulphoraphanes ເຮັດສອງສິ່ງຫຼັກ. ພວກມັນສົ່ງເສີມ apoptosis (levee 19) ແລະ ກະຕຸ້ນເອນໄຊມ໌ detoxification ໄລຍະສອງໃນຕັບທີ່ເສີມຄວາມເຂັ້ມແຂງໃຫ້ກັບຍີນ p53 ເປັນຜູ້ປົກປ້ອງຈີໂນມຂອງພວກເຮົາ. ຈຸລັງມະເຮັງມັກຈະຕາຍ (necrosis) ເມື່ອສຳຜັດກັບ sulphoraphanes ຢ່າງຕໍ່ເນື່ອງເປັນເວລາດົນ. ຜັກບຣອກໂຄລີຍັງມີສານ metabolite ຂັ້ນສອງທີ່ເອີ້ນວ່າ Indole 3 Carbinol ທີ່ແຕກຕົວຕໍ່ໄປເປັນສານຕ້ານມະເຮັງອີກຊະນິດໜຶ່ງຊື່ວ່າ DIM, diindolylmethane. ທ່ານບໍ່ສາມາດກິນຜັກພວກນີ້ຫຼາຍພໍຖ້າທ່ານເປັນມະເຮັງໃນທັດສະນະຂອງຂ້ອຍ. I3C ຍັງຂັດຂວາງ 16-hydroxyestrone ແລະ ມີປະໂຫຍດຫຼາຍໃນການປ້ອງກັນມະເຮັງເຕົ້ານົມ ແລະ ມະເຮັງຮັງໄຂ່ໃນແມ່ຍິງ ແລະ ມະເຮັງຕ່ອມລູກໝາກໃນຜູ້ຊາຍ.
-
ນີ້ແມ່ນສິ່ງທີ່ຂັດກັບຄວາມເຊື່ອຊຶ່ງຢູ່ໃນຫົວຂອງທ່ານ... ກິນ cholesterol ຫຼາຍໆ. ໂດຍສະເພາະນ້ຳມັນໝາກພ້າວ. ຫຼາຍການສຶກສາທາງລະບາດວິທະຍາສະແດງໃຫ້ເຫັນວ່າລະດັບ cholesterol ໃນເລືອດຕ່ຳສຳພັນກັບອັດຕາການເກີດມະເຮັງສູງ. ນີ້ແມ່ນເຫດຜົນທີ່ການກິນອາຫານ ketogenic Epi-paleo ມີຄວາມໝາຍຫຼາຍ. ເປັນຫຍັງອາຫານແບບ ketogenic? ເພາະມະເຮັງທັງໝົດໃຊ້ກລູໂຄສເປັນວັດຖຸດິບ. ທ່ານຈຳເປັນຕ້ອງປ່ຽນເຊື້ອໄຟຂອງຈຸລັງ. ໄປຊອກຫາ Otto Warburg ໃນ Google ສຳລັບລາຍລະອຽດເພີ່ມເຕີມ. ອາຫານແບບ ketogenic ຄວນມີ MCT ຈາກນ້ຳມັນໝາກພ້າວຫຼາຍ ເພາະພວກມັນໃຫ້ຂໍ້ໄດ້ປຽບຫຼາຍແກ່ຈຸລັງປົກກະຕິກວ່າຈຸລັງມະເຮັງ. ຂໍ້ໄດ້ປຽບນີ້ເຮັດໃຫ້ລະບົບພູມຄຸ້ມກັນຂອງທ່ານສາມາດຕາມທັນຈຸລັງມະເຮັງ ແລະ ທຳລາຍພວກມັນໂດຍໃຊ້ກົນໄກຊີວະວິທະຍາຂອງທ່ານເອງ. ມີຫຼາຍບົດຄວາມໃນວາລະສານມະເຮັງທີ່ພິມເຜີຍແຜ່ສະແດງໃຫ້ເຫັນການເຊື່ອມໂຍງແບບດຽວກັນ.
-
-
 @ 266815e0:6cd408a5
2025-05-02 22:20:02
@ 266815e0:6cd408a5
2025-05-02 22:20:02Its been six long months of refactoring code and building out to the applesauce packages but the app is stable enough for another release.
This update is pretty much a full rewrite of the non-visible parts of the app. all the background services were either moved out to the applesauce packages or rewritten, the result is that noStrudel is a little faster and much more consistent with connections and publishing.
New layout
The app has a new layout now, it takes advantage of the full desktop screen and looks a little better than it did before.

Removed NIP-72 communities
The NIP-72 communities are no longer part of the app, if you want to continue using them there are still a few apps that support them ( like satellite.earth ) but noStrudel won't support them going forward.
re interesting but ultimately proved too have some fundamental flaws, most notably that all posts had to be approved by a moderator. There were some good ideas on how to improve it but they would have only been patches and wouldn't have fixed the underlying issues.
I wont promise to build it into noStrudel, but NIP-29 (relay based groups) look a lot more promising and already have better moderation abilities then NIP-72 communities could ever have.
Settings view
There is now a dedicated settings view, so no more hunting around for where the relays are set or trying to find how to add another account. its all in one place now

Cleaned up lists
The list views are a little cleaner now, and they have a simple edit modal


New emoji picker
Just another small improvement that makes the app feel more complete.

E
re is a new "wallet" view in the app that lets you manage your NIP-60 cashu wallet. its very expe
 n
nt its there and I hope to finish it up so the app can support NIP-61 nutzaps.
WARNING: Do
hard earned sats, it will eat them!

Smaller improvements
- Added NSFW flag for replies
- Updated NIP-48 bunker login to work with new spec
- Linkfy BIPs
- Added 404 page
- Add NIP-22 comments under badges, files, and articles
- Add max height to timeline notes
- Fix articles view freezing
ror blobs when sharing notes
- Remove "open in drawer" for notes
-
 @ 90c656ff:9383fd4e
2025-05-04 17:48:58
@ 90c656ff:9383fd4e
2025-05-04 17:48:58The Bitcoin network was designed to be secure, decentralized, and resistant to censorship. However, as its usage grows, an important challenge arises: scalability. This term refers to the network's ability to manage an increasing number of transactions without affecting performance or security. This challenge has sparked the speed dilemma, which involves balancing transaction speed with the preservation of decentralization and security that the blockchain or timechain provides.
Scalability is the ability of a system to increase its performance to meet higher demands. In the case of Bitcoin, this means processing a greater number of transactions per second (TPS) without compromising the network's core principles.
Currently, the Bitcoin network processes about 7 transactions per second, a number considered low compared to traditional systems, such as credit card networks, which can process thousands of transactions per second. This limit is directly due to the fixed block size (1 MB) and the average 10-minute interval for creating a new block in the blockchain or timechain.
The speed dilemma arises from the need to balance three essential elements: decentralization, security, and speed.
The Timechain/"Blockchain" Trilemma:
01 - Decentralization: The Bitcoin network is composed of thousands of independent nodes that verify and validate transactions. Increasing the block size or making them faster could raise computational requirements, making it harder for smaller nodes to participate and affecting decentralization. 02 - Security: Security comes from the mining process and block validation. Increasing transaction speed could compromise security, as it would reduce the time needed to verify each block, making the network more vulnerable to attacks. 03 - Speed: The need to confirm transactions quickly is crucial for Bitcoin to be used as a payment method in everyday life. However, prioritizing speed could affect both security and decentralization.
This dilemma requires balanced solutions to expand the network without sacrificing its core features.
Solutions to the Scalability Problem
Several solutions have been suggested to address the scalability and speed challenges in the Bitcoin network.
- On-Chain Optimization
01 - Segregated Witness (SegWit): Implemented in 2017, SegWit separates signature data from transactions, allowing more efficient use of space in blocks and increasing capacity without changing the block size. 02 - Increasing Block Size: Some proposals have suggested increasing the block size to allow more transactions per block. However, this could make the system more centralized as it would require greater computational power.
- Off-Chain Solutions
01 - Lightning Network: A second-layer solution that enables fast and low-cost transactions off the main blockchain or timechain. These transactions are later settled on the main network, maintaining security and decentralization. 02 - Payment Channels: Allow direct transactions between two users without the need to record every action on the network, reducing congestion. 03 - Sidechains: Proposals that create parallel networks connected to the main blockchain or timechain, providing more flexibility and processing capacity.
While these solutions bring significant improvements, they also present issues. For example, the Lightning Network depends on payment channels that require initial liquidity, limiting its widespread adoption. Increasing block size could make the system more susceptible to centralization, impacting network security.
Additionally, second-layer solutions may require extra trust between participants, which could weaken the decentralization and resistance to censorship principles that Bitcoin advocates.
Another important point is the need for large-scale adoption. Even with technological advancements, solutions will only be effective if they are widely used and accepted by users and developers.
In summary, scalability and the speed dilemma represent one of the greatest technical challenges for the Bitcoin network. While security and decentralization are essential to maintaining the system's original principles, the need for fast and efficient transactions makes scalability an urgent issue.
Solutions like SegWit and the Lightning Network have shown promising progress, but still face technical and adoption barriers. The balance between speed, security, and decentralization remains a central goal for Bitcoin’s future.
Thus, the continuous pursuit of innovation and improvement is essential for Bitcoin to maintain its relevance as a reliable and efficient network, capable of supporting global growth and adoption without compromising its core values.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 2e941ad1:fac7c2d0
2025-05-04 18:31:49
@ 2e941ad1:fac7c2d0
2025-05-04 18:31:49Unlocks: 34
-
 @ 51faaa77:2c26615b
2025-05-04 17:52:33
@ 51faaa77:2c26615b
2025-05-04 17:52:33There has been a lot of debate about a recent discussion on the mailing list and a pull request on the Bitcoin Core repository. The main two points are about whether a mempool policy regarding OP_RETURN outputs should be changed, and whether there should be a configuration option for node operators to set their own limit. There has been some controversy about the background and context of these topics and people are looking for more information. Please ask short (preferably one sentence) questions as top comments in this topic. @Murch, and maybe others, will try to answer them in a couple sentences. @Murch and myself have collected a few questions that we have seen being asked to start us off, but please add more as you see fit.
originally posted at https://stacker.news/items/971277
-
 @ a5ee4475:2ca75401
2025-05-04 17:22:36
@ a5ee4475:2ca75401
2025-05-04 17:22:36clients #list #descentralismo #english #article #finalversion
*These clients are generally applications on the Nostr network that allow you to use the same account, regardless of the app used, keeping your messages and profile intact.
**However, you may need to meet certain requirements regarding access and account NIP for some clients, so that you can access them securely and use their features correctly.
CLIENTS
Twitter like
- Nostrmo - [source] 🌐🤖🍎💻(🐧🪟🍎)
- Coracle - Super App [source] 🌐
- Amethyst - Super App with note edit, delete and other stuff with Tor [source] 🤖
- Primal - Social and wallet [source] 🌐🤖🍎
- Iris - [source] 🌐🤖🍎
- Current - [source] 🤖🍎
- FreeFrom 🤖🍎
- Openvibe - Nostr and others (new Plebstr) [source] 🤖🍎
- Snort 🌐(🤖[early access]) [source]
- Damus 🍎 [source]
- Nos 🍎 [source]
- Nostur 🍎 [source]
- NostrBand 🌐 [info] [source]
- Yana 🤖🍎🌐💻(🐧) [source]
- Nostribe [on development] 🌐 [source]
- Lume 💻(🐧🪟🍎) [info] [source]
- Gossip - [source] 💻(🐧🪟🍎)
- Camelus [early access] 🤖 [source]
Communities
- noStrudel - Gamified Experience [info] 🌐
- Nostr Kiwi [creator] 🌐
- Satellite [info] 🌐
- Flotilla - [source] 🌐🐧
- Chachi - [source] 🌐
- Futr - Coded in haskell [source] 🐧 (others soon)
- Soapbox - Comunnity server [info] [source] 🌐
- Ditto - Soapbox comunnity server 🌐 [source] 🌐
- Cobrafuma - Nostr brazilian community on Ditto [info] 🌐
- Zapddit - Reddit like [source] 🌐
- Voyage (Reddit like) [on development] 🤖
Wiki
Search
- Advanced nostr search - Advanced note search by isolated terms related to a npub profile [source] 🌐
- Nos Today - Global note search by isolated terms [info] [source] 🌐
- Nostr Search Engine - API for Nostr clients [source]
Website
App Store
ZapStore - Permitionless App Store [source]
Audio and Video Transmission
- Nostr Nests - Audio Chats 🌐 [info]
- Fountain - Podcast 🤖🍎 [info]
- ZapStream - Live streaming 🌐 [info]
- Corny Chat - Audio Chat 🌐 [info]
Video Streaming
Music
- Tidal - Music Streaming [source] [about] [info] 🤖🍎🌐
- Wavlake - Music Streaming [source] 🌐(🤖🍎 [early access])
- Tunestr - Musical Events [source] [about] 🌐
- Stemstr - Musical Colab (paid to post) [source] [about] 🌐
Images
- Pinstr - Pinterest like [source] 🌐
- Slidestr - DeviantArt like [source] 🌐
- Memestr - ifunny like [source] 🌐
Download and Upload
Documents, graphics and tables
- Mindstr - Mind maps [source] 🌐
- Docstr - Share Docs [info] [source] 🌐
- Formstr - Share Forms [info] 🌐
- Sheetstr - Share Spreadsheets [source] 🌐
- Slide Maker - Share slides 🌐 (advice: https://zaplinks.lol/ and https://zaplinks.lol/slides/ sites are down)
Health
- Sobrkey - Sobriety and mental health [source] 🌐
- NosFabrica - Finding ways for your health data 🌐
- LazerEyes - Eye prescription by DM [source] 🌐
Forum
- OddBean - Hacker News like [info] [source] 🌐
- LowEnt - Forum [info] 🌐
- Swarmstr - Q&A / FAQ [info] 🌐
- Staker News - Hacker News like 🌐 [info]
Direct Messenges (DM)
- 0xchat 🤖🍎 [source]
- Nostr Chat 🌐🍎 [source]
- Blowater 🌐 [source]
- Anigma (new nostrgram) - Telegram based [on development] [source]
- Keychat - Signal based [🤖🍎 on development] [source]
Reading
- Highlighter - Insights with a highlighted read 🌐 [info]
- Zephyr - Calming to Read 🌐 [info]
- Flycat - Clean and Healthy Feed 🌐 [info]
- Nosta - Check Profiles [on development] 🌐 [info]
- Alexandria - e-Reader and Nostr Knowledge Base (NKB) [source]
Writing
Lists
- Following - Users list [source] 🌐
- Listr - Lists [source] 🌐
- Nostr potatoes - Movies List source 💻(numpy)
Market and Jobs
- Shopstr - Buy and Sell [source] 🌐
- Nostr Market - Buy and Sell 🌐
- Plebeian Market - Buy and Sell [source] 🌐
- Ostrich Work - Jobs [source] 🌐
- Nostrocket - Jobs [source] 🌐
Data Vending Machines - DVM (NIP90)
(Data-processing tools)
AI
Games
- Chesstr - Chess 🌐 [source]
- Jestr - Chess [source] 🌐
- Snakestr - Snake game [source] 🌐
- DEG Mods - Decentralized Game Mods [info] [source] 🌐
Customization
Like other Services
- Olas - Instagram like [source] 🤖🍎🌐
- Nostree - Linktree like 🌐
- Rabbit - TweetDeck like [info] 🌐
- Zaplinks - Nostr links 🌐
- Omeglestr - Omegle-like Random Chats [source] 🌐
General Uses
- Njump - HTML text gateway source 🌐
- Filestr - HTML midia gateway [source] 🌐
- W3 - Nostr URL shortener [source] 🌐
- Playground - Test Nostr filters [source] 🌐
- Spring - Browser 🌐
Places
- Wherostr - Travel and show where you are
- Arc Map (Mapstr) - Bitcoin Map [info]
Driver and Delivery
- RoadRunner - Uber like [on development] ⏱️
- Arcade City - Uber like [on development] ⏱️ [info]
- Nostrlivery - iFood like [on development] ⏱️
OTHER STUFF
Lightning Wallets (zap)
- Alby - Native and extension [info] 🌐
- ZBD - Gaming and Social [info] 🤖🍎
- Wallet of Satoshi [info] 🤖🍎
- Minibits - Cashu mobile wallet [info] 🤖
- Blink - Opensource custodial wallet (KYC over 1000 usd) [source] 🤖🍎
- LNbits - App and extesion [source] 🤖🍎💻
- Zeus - [info] [source] 🤖🍎
Exchange
Media Server (Upload Links)
audio, image and video
- Nostr Build - [source] 🌐
- Nostr Check - [info] [source] 🌐
- NostPic - [source] 🌐
- Sovbit 🌐
- Voidcat - [source] 🌐
Without Nip: - Pomf - Upload larger videos [source] - Catbox - [source] - x0 - [source]
Donation and payments
- Zapper - Easy Zaps [source] 🌐
- Autozap [source] 🌐
- Zapmeacoffee 🌐
- Nostr Zap 💻(numpy)
- Creatr - Creators subscription 🌐
- Geyzer - Crowdfunding [info] [source] 🌐
- Heya! - Crowdfunding [source]
Security
- Secret Border - Generate offline keys 💻(java)
- Umbrel - Your private relay [source] 🌐
Extensions
- Nos2x - Account access keys 🌐
- Nsec.app 🌐 [info]
- Lume - [info] [source] 🐧🪟🍎
- Satcom - Share files to discuss - [info] 🌐
- KeysBand - Multi-key signing [source] 🌐
Code
- Nostrify - Share Nostr Frameworks 🌐
- Git Workshop (github like) [experimental] 🌐
- Gitstr (github like) [on development] ⏱️
- Osty [on development] [info] 🌐
- Python Nostr - Python Library for Nostr
Relay Check and Cloud
- Nostr Watch - See your relay speed 🌐
- NosDrive - Nostr Relay that saves to Google Drive
Bidges and Getways
- Matrixtr Bridge - Between Matrix & Nostr
- Mostr - Between Nostr & Fediverse
- Nostrss - RSS to Nostr
- Rsslay - Optimized RSS to Nostr [source]
- Atomstr - RSS/Atom to Nostr [source]
NOT RELATED TO NOSTR
Android Keyboards
Personal notes and texts
Front-ends
- Nitter - Twitter / X without your data [source]
- NewPipe - Youtube, Peertube and others, without account & your data [source] 🤖
- Piped - Youtube web without you data [source] 🌐
Other Services
- Brave - Browser [source]
- DuckDuckGo - Search [source]
- LLMA - Meta - Meta open source AI [source]
- DuckDuckGo AI Chat - Famous AIs without Login [source]
- Proton Mail - Mail [source]
Other open source index: Degoogled Apps
Some other Nostr index on:
-
 @ c7aa97dc:0d12c810
2025-05-04 17:06:47
@ c7aa97dc:0d12c810
2025-05-04 17:06:47COLDCARDS’s new Co-Sign feature lets you use a multisig (2 of N) wallet where the second key (policy key) lives inside the same COLDCARD and signs only when a transaction meets the rules you set-for example:
- Maximum amount per send (e.g. 500k Sats)
- Wait time between sends, (e.g 144 blocks = 1 day)
- Only send to approved addresses,
- Only send after you provide a 2FA code
If a payment follows the rules, COLDCARD automatically signs the transaction with 2 keys which makes it feel like a single-sig wallet.
Break a rule and the device only signs with 1 key, so nothing moves unless you sign the transaction with a separate off-site recovery key.
It’s the convenience of singlesig with the guard-rails of multisig.
Use Cases Unlocked
Below you will find an overview of usecases unlocked by this security enhancing feature for everyday bitcoiners, families, and small businesses.

1. Travel Lock-Down Mode
Before you leave, set the wait-time to match the duration of your trip—say 14 days—and cap each spend at 50k sats. If someone finds the COLDCARD while you’re away, they can take only one 50k-sat nibble and then must wait the full two weeks—long after you’re back—to try again. When you notice your device is gone you can quickly restore your wallet with your backup seeds (not in your house of course) and move all the funds to a new wallet.
2. Shared-Safety Wallet for Parents or Friends
Help your parents or friends setup a COLDCARD with Co-Sign, cap each spend at 500 000 sats and enforce a 7-day gap between transactions. Everyday spending sails through; anything larger waits for your co-signature from your key. A thief can’t steal more than the capped amount per week, and your parents retains full sovereignty—if you disappear, they still hold two backup seeds and can either withdraw slowly under the limits or import those seeds into another signer and move everything at once.
3. My First COLDCARD Wallet
Give your kid a COLDCARD, but whitelist only their own addresses and set a 100k sat ceiling. They learn self-custody, yet external spends still need you to co-sign.
4. Weekend-Only Spending Wallet
Cap each withdrawal (e.g., 500k sats) and require a 72-hour gap between sends. You can still top-up Lightning channels or pay bills weekly, but attackers that have access to your device + pin will not be able to drain it immediately.
5. DIY Business Treasury
Finance staff use the COLDCARD to pay routine invoices under 0.1 BTC. Anything larger needs the co-founder’s off-site backup key.
6. Donation / Grant Disbursement Wallet
Publish the deposit address publicly, but allow outgoing payments only to a fixed list of beneficiary addresses. Even if attackers get the device, they can’t redirect funds to themselves—the policy key refuses to sign.
7. Phoenix Lightning Wallet Top-Up
Add a Phoenix Lightning wallet on-chain deposit addresses to the whitelist. The COLDCARD will co-sign only when you’re refilling channels. This is off course not limited to Phoenix wallet and can be used for any Lightning Node.
8. Deep Cold-Storage Bridge
Whitelist one or more addresses from your bitcoin vault. Day-to-day you sweep hot-wallet incoming funds (From a webshop or lightning node) into the COLDCARD, then push funds onward to deep cold storage. If the device is compromised, coins can only land safely in the vault.
9. Company Treasury → Payroll Wallets
List each employee’s salary wallet on the whitelist (watch out for address re-use) and cap the amount per send. Routine payroll runs smoothly, while attackers or rogue insiders can’t reroute funds elsewhere.
10. Phone Spending-Wallet Refills
Whitelist only some deposit addresses of your mobile wallet and set a small per-send cap. You can top up anytime, but an attacker with the device and PIN can’t drain more than the refill limit—and only to your own phone.
I hope these usecase are helpfull and I'm curious to hear what other use cases you think are possible with this co-signing feature.
For deeper technical details on how Co-Sign works, refer to the official documentation on the Coldcard website. https://coldcard.com/docs/coldcard-cosigning/
You can also watch their Video https://www.youtube.com/watch?v=MjMPDUWWegw
coldcard #coinkite #bitcoin #selfcustody #multisig #mk4 #ccq
nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8 nostr:npub12ctjk5lhxp6sks8x83gpk9sx3hvk5fz70uz4ze6uplkfs9lwjmsq2rc5ky
-
 @ 90c656ff:9383fd4e
2025-05-04 17:06:06
@ 90c656ff:9383fd4e
2025-05-04 17:06:06In the Bitcoin system, the protection and ownership of funds are ensured by a cryptographic model that uses private and public keys. These components are fundamental to digital security, allowing users to manage and safeguard their assets in a decentralized way. This process removes the need for intermediaries, ensuring that only the legitimate owner has access to the balance linked to a specific address on the blockchain or timechain.
Private and public keys are part of an asymmetric cryptographic system, where two distinct but mathematically linked codes are used to guarantee the security and authenticity of transactions.
Private Key = A secret code, usually represented as a long string of numbers and letters.
Functions like a password that gives the owner control over the bitcoins tied to a specific address.
Must be kept completely secret, as anyone with access to it can move the corresponding funds.
Public Key = Mathematically derived from the private key, but it cannot be used to uncover the private key.
Functions as a digital address, similar to a bank account number, and can be freely shared to receive payments.
Used to verify the authenticity of signatures generated with the private key.
Together, these keys ensure that transactions are secure and verifiable, eliminating the need for intermediaries.
The functioning of private and public keys is based on elliptic curve cryptography. When a user wants to send bitcoins, they use their private key to digitally sign the transaction. This signature is unique for each operation and proves that the sender possesses the private key linked to the sending address.
Bitcoin network nodes check this signature using the corresponding public key to ensure that:
01 - The signature is valid. 02 - The transaction has not been altered since it was signed. 03 - The sender is the legitimate owner of the funds.
If the signature is valid, the transaction is recorded on the blockchain or timechain and becomes irreversible. This process protects funds against fraud and double-spending.
The security of private keys is one of the most critical aspects of the Bitcoin system. Losing this key means permanently losing access to the funds, as there is no central authority capable of recovering it.
- Best practices for protecting private keys include:
01 - Offline storage: Keep them away from internet-connected networks to reduce the risk of cyberattacks. 02 - Hardware wallets: Physical devices dedicated to securely storing private keys. 03 - Backups and redundancy: Maintain backup copies in safe and separate locations. 04 - Additional encryption: Protect digital files containing private keys with strong passwords and encryption.
- Common threats include:
01 - Phishing and malware: Attacks that attempt to trick users into revealing their keys. 02 - Physical theft: If keys are stored on physical devices. 03 - Loss of passwords and backups: Which can lead to permanent loss of funds.
Using private and public keys gives the owner full control over their funds, eliminating intermediaries such as banks or governments. This model places the responsibility of protection on the user, which represents both freedom and risk.
Unlike traditional financial systems, where institutions can reverse transactions or freeze accounts, in the Bitcoin system, possession of the private key is the only proof of ownership. This principle is often summarized by the phrase: "Not your keys, not your coins."
This approach strengthens financial sovereignty, allowing individuals to store and move value independently and without censorship.
Despite its security, the key-based system also carries risks. If a private key is lost or forgotten, there is no way to recover the associated funds. This has already led to the permanent loss of millions of bitcoins over the years.
To reduce this risk, many users rely on seed phrases, which are a list of words used to recover wallets and private keys. These phrases must be guarded just as carefully, as they can also grant access to funds.
In summary, private and public keys are the foundation of security and ownership in the Bitcoin system. They ensure that only rightful owners can move their funds, enabling a decentralized, secure, and censorship-resistant financial system.
However, this freedom comes with great responsibility, requiring users to adopt strict practices to protect their private keys. Loss or compromise of these keys can lead to irreversible consequences, highlighting the importance of education and preparation when using Bitcoin.
Thus, the cryptographic key model not only enhances security but also represents the essence of the financial independence that Bitcoin enables.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 90c656ff:9383fd4e
2025-05-04 16:49:19
@ 90c656ff:9383fd4e
2025-05-04 16:49:19The Bitcoin network is built on a decentralized infrastructure made up of devices called nodes. These nodes play a crucial role in validating, verifying, and maintaining the system, ensuring the security and integrity of the blockchain or timechain. Unlike traditional systems where a central authority controls operations, the Bitcoin network relies on the collaboration of thousands of nodes around the world, promoting decentralization and transparency.
In the Bitcoin network, a node is any computer connected to the system that participates in storing, validating, or distributing information. These devices run Bitcoin software and can operate at different levels of participation, from basic data transmission to full validation of transactions and blocks.
There are two main types of nodes:
- Full Nodes:
01 - Store a complete copy of the blockchain or timechain. 02 - Validate and verify all transactions and blocks according to the protocol rules. 03 - Ensure network security by rejecting invalid transactions or fraudulent attempts.
- Light Nodes:
01 - Store only parts of the blockchain or timechain, not the full structure. 02 - Rely on full nodes to access transaction history data. 03 - Are faster and less resource-intensive but depend on third parties for full validation.
Nodes check whether submitted transactions comply with protocol rules, such as valid digital signatures and the absence of double spending.
Only valid transactions are forwarded to other nodes and included in the next block.
Full nodes maintain an up-to-date copy of the network's entire transaction history, ensuring integrity and transparency. In case of discrepancies, nodes follow the longest and most valid chain, preventing manipulation.
Nodes transmit transaction and block data to other nodes on the network. This process ensures all participants are synchronized and up to date.
Since the Bitcoin network consists of thousands of independent nodes, it is nearly impossible for a single agent to control or alter the system.
Nodes also protect against attacks by validating information and blocking fraudulent attempts.
Full nodes are particularly important, as they act as independent auditors. They do not need to rely on third parties and can verify the entire transaction history directly.
By maintaining a full copy of the blockchain or timechain, these nodes allow anyone to validate transactions without intermediaries, promoting transparency and financial freedom.
- In addition, full nodes:
01 - Reinforce censorship resistance: No government or entity can delete or alter data recorded on the system. 02 - Preserve decentralization: The more full nodes that exist, the stronger and more secure the network becomes. 03 - Increase trust in the system: Users can independently confirm whether the rules are being followed.
Despite their value, operating a full node can be challenging, as it requires storage space, processing power, and bandwidth. As the blockchain or timechain grows, technical requirements increase, which can make participation harder for regular users.
To address this, the community continuously works on solutions, such as software improvements and scalability enhancements, to make network access easier without compromising security.
In summary, nodes are the backbone of the Bitcoin network, performing essential functions in transaction validation, verification, and distribution. They ensure the decentralization and security of the system, allowing participants to operate reliably without relying on intermediaries.
Full nodes, in particular, play a critical role in preserving the integrity of the blockchain or timechain, making the Bitcoin network resistant to censorship and manipulation.
While running a node may require technical resources, its impact on preserving financial freedom and system trust is invaluable. As such, nodes remain essential elements for the success and longevity of Bitcoin.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 90c656ff:9383fd4e
2025-05-04 16:36:21
@ 90c656ff:9383fd4e
2025-05-04 16:36:21Bitcoin mining is a crucial process for the operation and security of the network. It plays an important role in validating transactions and generating new bitcoins, ensuring the integrity of the blockchain or timechain-based system. This process involves solving complex mathematical calculations and requires significant computational power. Additionally, mining has economic, environmental, and technological effects that must be carefully analyzed.
Bitcoin mining is the procedure through which new units of the currency are created and added to the network. It is also responsible for verifying and recording transactions on the blockchain or timechain. This system was designed to be decentralized, eliminating the need for a central authority to control issuance or validate operations.
Participants in the process, called miners, compete to solve difficult mathematical problems. Whoever finds the solution first earns the right to add a new block to the blockchain or timechain and receives a reward in bitcoins, along with the transaction fees included in that block. This mechanism is known as Proof of Work (PoW).
The mining process is highly technical and follows a series of steps:
Transaction grouping: Transactions sent by users are collected into a pending block that awaits validation.
Solving mathematical problems: Miners must find a specific number, called a nonce, which, when combined with the block’s data, generates a cryptographic hash that meets certain required conditions. This process involves trial and error and consumes a great deal of computational power.
Block validation: When a miner finds the correct solution, the block is validated and added to the blockchain or timechain. All network nodes verify the block’s authenticity before accepting it.
Reward: The winning miner receives a bitcoin reward, in addition to the fees paid for the transactions included in the block. This reward decreases over time in an event called halving, which happens approximately every four years.
Bitcoin mining has a significant economic impact, as it creates income opportunities for individuals and companies. It also drives the development of new technologies such as specialized processors (ASICs) and modern cooling systems.
Moreover, mining supports financial inclusion by maintaining a decentralized network, enabling fast and secure global transactions. In regions with unstable economies, Bitcoin provides a viable alternative for value preservation and financial transfers.
Despite its economic benefits, Bitcoin mining is often criticized for its environmental impact. The proof-of-work process consumes large amounts of electricity, especially in areas where the energy grid relies on fossil fuels.
It’s estimated that Bitcoin mining uses as much energy as some entire countries, raising concerns about its sustainability. However, there are ongoing efforts to reduce these impacts, such as the increasing use of renewable energy sources and the exploration of alternative systems like Proof of Stake (PoS) in other decentralized networks.
Mining also faces challenges related to scalability and the concentration of computational power. Large companies and mining pools dominate the sector, which can affect the network’s decentralization.
Another challenge is the growing complexity of the mathematical problems, which requires more advanced hardware and consumes more energy over time. To address these issues, researchers are studying solutions that optimize resource use and keep the network sustainable in the long term.
In summary, Bitcoin mining is an essential process for maintaining the network and creating new units of the currency. It ensures security, transparency, and decentralization, supporting the operation of the blockchain or timechain.
However, mining also brings challenges such as high energy consumption and the concentration of resources in large pools. Even so, the pursuit of sustainable solutions and technological innovations points to a promising future, where Bitcoin continues to play a central role in the digital economy.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 700c6cbf:a92816fd
2025-05-04 16:34:01
@ 700c6cbf:a92816fd
2025-05-04 16:34:01Technically speaking, I should say blooms because not all of my pictures are of flowers, a lot of them, probably most, are blooming trees - but who cares, right?
It is that time of the year that every timeline on every social media is being flooded by blooms. At least in the Northern Hemisphere. I thought that this year, I wouldn't partake in it but - here I am, I just can't resist the lure of blooms when I'm out walking the neighborhood.
Spring has sprung - aaaachoo, sorry, allergies suck! - and the blooms are beautiful.
Yesterday, we had the warmest day of the year to-date. I went for an early morning walk before breakfast. Beautiful blue skies, no clouds, sunshine and a breeze. Most people turned on their aircons. We did not. We are rebels - hah!
We also had breakfast on the deck which I really enjoy during the weekend. Later I had my first session of the year painting on the deck while listening/watching @thegrinder streaming. Good times.
Today, the weather changed. Last night, we had heavy thunderstorms and rain. This morning, it is overcast with the occasional sunray peaking through or, as it is right now, raindrops falling.
We'll see what the day will bring. For me, it will definitely be: Back to painting. Maybe I'll even share some here later. But for now - this is a photo post, and here are the photos. I hope you enjoy as much as I enjoyed yesterday's walk!
Cheers, OceanBee
!(image)[https://cdn.satellite.earth/cc3fb0fa757c88a6a89823585badf7d67e32dee72b6d4de5dff58acd06d0aa36.jpg] !(image)[https://cdn.satellite.earth/7fe93c27c3bf858202185cb7f42b294b152013ba3c859544950e6c1932ede4d3.jpg] !(image)[https://cdn.satellite.earth/6cbd9fba435dbe3e6732d9a5d1f5ff0403935a4ac9d0d83f6e1d729985220e87.jpg] !(image)[https://cdn.satellite.earth/df94d95381f058860392737d71c62cd9689c45b2ace1c8fc29d108625aabf5d5.jpg] !(image)[https://cdn.satellite.earth/e483e65c3ee451977277e0cfa891ec6b93b39c7c4ea843329db7354fba255e64.jpg] !(image)[https://cdn.satellite.earth/a98fe8e1e0577e3f8218af31f2499c3390ba04dced14c2ae13f7d7435b4000d7.jpg] !(image)[https://cdn.satellite.earth/d83b01915a23eb95c3d12c644713ac47233ce6e022c5df1eeba5ff8952b99d67.jpg] !(image)[https://cdn.satellite.earth/9ee3256882e363680d8ea9bb6ed3baa5979c950cdb6e62b9850a4baea46721f3.jpg] !(image)[https://cdn.satellite.earth/201a036d52f37390d11b76101862a082febb869c8d0e58d6aafe93c72919f578.jpg] !(image)[https://cdn.satellite.earth/cd516d89591a4cf474689b4eb6a67db842991c4bf5987c219fb9083f741ce871.jpg]
-
 @ 90c656ff:9383fd4e
2025-05-04 16:24:21
@ 90c656ff:9383fd4e
2025-05-04 16:24:21Blockchain or timechain is a new technology that has changed the way data and transactions are recorded and stored. Its decentralized and highly secure structure provides transparency and trust, making it a widely used system for digital operations. This technology is essential for creating financial systems and digital records that cannot be altered.
What is blockchain or timechain? Blockchain or timechain is essentially a distributed digital ledger designed to record transactions in a sequential and unchangeable manner. It is made up of blocks linked in a chain, each containing a set of information such as transactions, timestamps, and a unique identifier called a hash.
These blocks are organized in chronological order, ensuring the integrity of records over time. The term timechain, used synonymously, emphasizes this temporal aspect of the system, where each block is linked to the previous one, forming a chain of events that cannot be tampered with.
The validation of blocks in blockchain or timechain is carried out through a process called mining. Network participants, known as miners, use powerful computers to solve complex mathematical problems. This process, known as proof of work, is necessary to validate transactions and add a new block to the chain.
Each block contains:
Verified Transactions – A set of operations approved by the network.
Previous Block Hash – A unique code that connects the new block to the previous one, ensuring continuity and security.
Nonce – A number used in the mining process to generate the block's hash.
Once a block is validated, it is permanently added to the blockchain or timechain, and all nodes (participating computers) in the network update their copies of this ledger.
One of the main benefits of blockchain or timechain is the security provided by its decentralized model. Unlike traditional systems that rely on central servers, it distributes its data across thousands of computers around the world.
Immutability is guaranteed by cryptographic techniques and the chained structure of blocks. Any attempt to alter a block would require modifying all subsequent blocks, which is virtually impossible due to the massive computational power required.
Additionally, the use of cryptographic algorithms makes the system resistant to fraud and manipulation. This model enables trust, even in environments without intermediaries or central authorities.
Blockchain or timechain is transparent, as anyone can access the full history of transactions recorded on the network. This creates a system that is auditable and reliable.
However, the privacy of participants is protected, since transactions are recorded through anonymous digital addresses without revealing personal identities. This balance between transparency and privacy makes the system secure and flexible.
The use of blockchain or timechain goes beyond financial transactions. It is useful in areas such as smart contracts, asset registration, supply chains, and online voting. Its ability to create permanent and verifiable records enables innovative solutions across various industries.
For example, in product tracking systems, blockchain or timechain ensures data authenticity by recording each stage of the production and distribution process. This reduces fraud and increases operational efficiency.
Advantages and Challenges Among the main advantages of blockchain or timechain, we can highlight:
Decentralization – Elimination of intermediaries, reducing costs and increasing efficiency.
Security – Protection against fraud and digital attacks.
Transparency – Public and verifiable record of all transactions.
Immutability – Assurance that data cannot be modified after being recorded.
However, there are still challenges to be addressed, such as scalability, as the continuous growth of the network may require greater storage and processing capacity. Additionally, regulatory issues and widespread adoption demand ongoing improvements.
In summary, blockchain or timechain is an innovative technology that changes the way data and transactions are stored, ensuring security, transparency, and efficiency. Its decentralization removes the dependency on intermediaries, making it a trustworthy and tamper-resistant system.
Despite technical and regulatory challenges, blockchain or timechain continues to evolve, demonstrating its potential in various areas beyond the financial sector. Its promise of transparency and immutability is already shaping the future of digital systems, establishing itself as a fundamental base for the modern economy and digital trust.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ a29cfc65:484fac9c
2025-05-04 16:20:03
@ a29cfc65:484fac9c
2025-05-04 16:20:03Bei einer Führung durch den Naumburger Dom sprach der Domführer über Propaganda im Mittelalter. Die gefühlvollen Gesichtsausdrücke der steinernen Stifterfiguren rund um die berühmte Uta sollten das Volk beeinflussen. Darüber haben wir auf der Heimfahrt nach Leipzig philosophiert und fanden den Denkansatz spannend. Denn auch wenn es damals nicht Propaganda hieß, so gab es doch Interessen der Mächtigen, die sie gegenüber dem Volk durchsetzten. Sie bedienten sich dabei der damals verfügbaren „Medien“, zu denen die Kirche gehörte, wo sich das Volk zum Gottesdienst traf.
Kulturelle Identität Europas
Mitteldeutschland ist ein Zentrum mittelalterlicher Baukunst. Der Naumburger Dom St. Peter und Paul wurde auf den Grundmauern einer noch älteren Kirche im 13. Jahrhundert gebaut. Er ist weltweit einzigartig in seiner Architektur, Bildhauerkunst und Glasmalerei. Seit 2018 ist er Unesco-Weltkulturerbe. Die Stadt Naumburg hatte einst die gleiche Bedeutung wie Merseburg, Magdeburg oder Leipzig. Der Dom – von der Spätromanik bis in die Frühgotik unter Leitung eines heute unbekannten Bildhauerarchitekten errichtet – gilt als Meisterwerk menschlicher Schöpferkraft und Handwerkskunst. Die naturwissenschaftlich-physikalischen Kenntnisse der Menschen waren offensichtlich enorm. Sie verfügten über das Wissen zur Planung und über entsprechende Werk- und Hebezeuge, um solche Bauwerke in relativ kurzer Zeit errichten zu können.
Im Westchor des Doms befinden sich mit den zwölf lebensgroßen Stifterfiguren die bekanntesten Kunstwerke des Doms, unter ihnen Uta von Ballenstedt. Sie soll Walt Disney als Quelle für die schöne und sehr stolze Königin im Zeichentrickfilm Schneewittchen gedient haben. Das Besondere und Neue an den steinernen Stifterfiguren war ihre realitätsnahe Darstellung, die sie lebendig und ausdrucksstark wirken lässt. Sie sind ein Höhepunkt in der Steinmetzkunst der damaligen Zeit. Die Figuren wurden, obschon die dargestellten Personen bereits mehr als 200 Jahre tot waren, mit charakteristischen Gesichtsausdrücken dargestellt: Uta schaut schön und stolz in die Ferne, ihr Gatte Ekkehard wirkt etwas hochmütig. Gegenüber steht die lachende Reglindis neben ihrem wehmütig-leidend blickenden Mann Hermann von Meißen.
Der Domführer sagte, dass die Gesichtsausdrücke menschliche Verhaltensweisen darstellen, die bei den Kirchenbesuchern unerwünscht waren. Wir hätten es hier mit einer sehr frühen Form der Propaganda zu tun. Die katholische Kirche war Vorreiter in Sachen Propaganda. Sie hat etwa 400 Jahre später, im Jahr 1622, mit der Sacra Congregatio de Propaganda Fide ein Amt gegründet, das den „richtigen“ Glauben in die Welt tragen sollte, und erst 1967 umbenannt wurde. Aber ihre gesellschaftlich führende Position hatte damals auch eine positive Seite: Den Kirchen und Klöstern haben wir den Erhalt und die Weitergabe antiken Wissens zu verdanken. Europa konnte sich trotz der politischen Zersplitterung seine kulturelle Identität erhalten. Zum Beispiel lässt sich das Wirken des namenlosen Domschöpfers anhand der Bau- und Kunstwerke quer durch Europa von Nordfrankreich über Mainz nach Naumburg und Meißen nachvollziehen. Aus der weiteren Entwicklung von Kunst und Kultur in Europa entstand in der Renaissance die Philosophie des Humanismus und später daraus die Aufklärung mit ihrer Wirkung auf Literatur und Wissenschaft. Ziel war dabei immer eine Stärkung des Gemeinwesens.
Transhumanismus zerstört Gemeinschaften
Heute scheinen wir uns allerdings an einer Bruchstelle der gesellschaftlichen Entwicklung zu befinden. Die Kirchen spielen in unserer Gesellschaft kaum noch eine Rolle. Weder bringen sie sich in ethische Diskussionen hörbar ein, noch tragen sie die Entwicklung von Kunst und Kultur sichtbar voran. Ihre Rolle im Bereich Propaganda haben längst Zeitungen und Zeitschriften, Rundfunk und Fernsehen übernommen. Diese Medien haben eine größere Reichweite, und die psychologische Beeinflussung ist umfassender. Nach dem Zweiten Weltkrieg wurde die Manipulation der Massen stark intensiviert und nahm nach dem Zusammenbruch der Sowjetunion noch weiter an Fahrt auf. Der Liberalismus konnte auf allen Gebieten seinen Siegeszug antreten, stellte das Individuum in den Mittelpunkt und erhob den Markt zur heiligen Kuh. Im Laufe der Zeit wurden die humanistischen Ideen der Aufklärung in ihr Gegenteil verkehrt. Der Mensch wurde als fehlerhaftes Wesen identifiziert, in die Vereinzelung getrieben, bevormundet und gegängelt – angeblich, damit er sich nicht selbst schadet. Zur psychologischen Beeinflussung kommen die neuen technischen Möglichkeiten aus Bio-Nano-Neuro-Wissenschaften und Digitalisierung. Der Transhumanismus wurde als neues Ziel für die Menschheit ausgerufen. Der Einzelne soll biologisch und technisch perfektioniert werden. Gemeinschaften – von der Familie angefangen – treibt das in die Bedeutungslosigkeit. Es besteht die Gefahr, dass persönliche Integrität und Privatsphäre durch Eingriffe in Körper- und Geistesfunktionen verletzt werden. Eine neue Aufklärung ist nötig. Denn sehr viel von dem über die Jahrhunderte erlangten Wissen ging schon verloren oder ist nur noch versteckt in den Bibliotheken und Archiven der Kirchen zu finden. Die Besinnung auf die vergessenen beziehungsweise verdrängten Grundlagen und Ideale der Aufklärung kann diese Entwicklung abwenden. Die Kulturschätze Mitteleuropas vermitteln in ihrer Schönheit und Vollkommenheit die Ruhe und die zeitlichen und räumlichen Dimensionen, die wir brauchen, wenn wir über die Frage nachdenken, wie wir in Zukunft leben wollen.
Die Rolle der neuen Medien für die zukünftige Entwicklung
Von den Alt-Medien ist in dieser Hinsicht nichts zu erwarten. Sie werden finanziert und sind unterwandert von den Kräften, die transhumanistische Entwicklungen vorantreiben. Die „neue Aufklärung“ ist ein lohnenswertes Ziel für die neuen Medien. Diese lassen sich jedoch noch zu sehr von den aktuellen Themen der Alt-Medien treiben. Der Angst-Propaganda begegnen sie mit – Ängsten, wenn auch anders ausgerichtet. Einige reiten die Empörungswelle in Gegenrichtung zu den Alt-Medien. Manche Betreiber von „alternativen“ Finanz- und Wirtschaftskanälen wollen ihre eigenen marktgläubigen Produkte an den Mann bringen. Stattdessen sollten in den neuen Medien positive Nachrichten verbreitet und eigene Themenfelder eröffnet werden, denen sich die Alt-Medien verweigern:
· der Mensch und seine Bildung zur souveränen, selbständig denkenden und handelnden Persönlichkeit,
· die Entwicklung des eigenen Bewusstseins, um der Fremdbestimmung zu entkommen und zu Wahrhaftigkeit, Authentizität und Menschlichkeit zu gelangen,
· die Entwicklung des Gemeinwohls,
· die Frage, wie wir neue Gemeinschaften bis hin zu autarken Gemeinden gründen können – wichtiger, je mehr das gesellschaftliche System um uns herum zusammenbricht.
Direkt sichtbar ist der letzte Punkt am Niedergang der Architektur und am Zustand der Innenstädte: Die reich dekorierten Gebäude der Gründerzeit wurden nach ihrer Zerstörung im Zweiten Weltkrieg durch gleichförmig rechteckige Gebäude aus Beton und Glas ersetzt. Dazu kamen die in allen Städten austauschbar gleichen Ladenzeilen und in den letzten Jahren Dreck und Schmierereien, die nicht mehr weggeräumt werden.
Die gesellschaftlichen Verwerfungen der Corona-Zeit führten bei vielen Menschen zum Innehalten und Nachdenken über Sinn und Ziele ihres Lebens. So entstanden einige Pilotprojekte, zum Beispiel in den Bereichen Landwirtschaft, Gesundheitswesen und Bildung. Diese auf die Zukunft gerichteten Themen könnten in den neuen Medien umfangreicher vorgestellt und diskutiert werden. Manova setzt schon solche Schwerpunkte mit „The Great WeSet“ von Walter van Rossum sowie mit den Kategorien „Zukunft & Neue Wege“ sowie „Aufwind“. Der Kontrafunk hat Formate entwickelt, die das Gemeinwohl stärker in den Fokus setzen wie etwa die Kultur- und Wissenschaftsrubrik. Nuoviso hat einen eigenen Songcontest ins Leben gerufen. Neben der inhaltlichen Ausrichtung auf eine lebenswerte Zukunft gilt es auch, die technologische Basis der neuen Medien zukunftsfest zu machen und sich der digitalen Zensur zu entziehen. Milosz Matuschek geht mit dem Pareto-Projekt neue Wege. Es könnte zur unzensierbaren Plattform der neuen Medien werden. Denn wie er sagt: Man baut sein neues Haus doch auch nicht auf dem Boden, der einem anderen gehört.
-
 @ efc19139:a370b6a8
2025-05-04 16:42:24
@ efc19139:a370b6a8
2025-05-04 16:42:24Bitcoin has a controversial reputation, but in this essay, I argue that Bitcoin is actually a pretty cool thing; it could even be described as the hippie movement of the digital generations.
Mainstream media often portrays Bitcoin purely as speculation, with headlines focusing on price fluctuations or painting it as an environmental disaster. It has frequently been declared dead and buried, only to rise again—each time, it's labeled as highly risky and suspicious as a whole. Then there are those who find blockchain fascinating in general but dismiss Bitcoin as outdated, claiming it will soon be replaced by a new cryptocurrency (often one controlled by the very author making the argument). Let’s take a moment to consider why Bitcoin is interesting and how it can drive broad societal change, much like the hippie movement once did. Bitcoin is a global decentralized monetary system operating on a peer-to-peer network. Since nearly all of humanity lives within an economic system based on money, it’s easy to see how an overhaul of the financial system could have a profound impact across different aspects of society. Bitcoin differs from traditional money through several unique characteristics: it is scarce, neutral, decentralized, and completely permissionless. There is no central entity—such as a company—that develops and markets Bitcoin, meaning it cannot be corrupted.
Bitcoin is an open digital network, much like the internet. Due to its lack of a central governing entity and its organic origin, Bitcoin can be considered a commodity, whereas other cryptocurrencies resemble securities, comparable to stocks. Bitcoin’s decentralized nature makes it geopolitically neutral. Instead of being controlled by a central authority, it operates under predefined, unchangeable rules. No single entity in the world has the ability to arbitrarily influence decision-making within the Bitcoin network. This characteristic is particularly beneficial in today’s political climate, where global uncertainty is heightened by unpredictable leaders of major powers. The permissionless nature of Bitcoin and its built-in resistance to censorship are crucial for individuals living under unstable conditions. Bitcoin is used to raise funds for politically persecuted activists and for charitable purposes in regions where financial systems have been weaponized against political opponents or used to restrict people's ability to flee a country. These are factors that may not immediately come to mind in Western nations, where such challenges are not commonly faced. Additionally, according to the World Bank, an estimated 1.5 billion people worldwide still lack access to any form of banking services.
Mining is the only way to ensure that no one can seize control of the Bitcoin network or gain a privileged position within it. This keeps Bitcoin neutral as a protocol, meaning a set of rules without leaders. It is not governed in the same way a company is, where ownership of shares dictates control. Miners earn the right to record transactions in Bitcoin’s ledger by continuously proving that they have performed work to obtain that right. This proof-of-work algorithm is also one reason why Bitcoin has spread so organically. If recording new transactions were free, we would face a problem similar to spam: there would be an endless number of competing transactions, making it impossible to reach consensus on which should officially become part of the decentralized ledger. Mining can be seen as an auction for adding the next set of transactions, where the price is the amount of energy expended. Using energy for this purpose is the only way to ensure that mining remains globally decentralized while keeping the system open and permissionless—free from human interference. Bitcoin’s initial distribution was driven by random tech enthusiasts around the world who mined it as a hobby, using student electricity from their bedrooms. This is why Bitcoin’s spread can be considered organic, in contrast to a scenario where it was created by a precisely organized inner circle that typically would have granted itself advantages before the launch.
If energy consumption is considered concerning, the best regulatory approach would be to create optimal conditions for mining in Finland, where over half of energy production already comes from renewable sources. Modern miners are essentially datacenters, but they have a unique characteristic: they can adjust their electricity consumption seamlessly and instantly without delay. This creates synergy with renewable energy production, which often experiences fluctuations in supply. The demand flexibility offered by miners provides strong incentives to invest increasingly in renewable energy facilities. Miners can commit to long-term projects as last-resort consumers, making investments in renewables more predictable and profitable. Additionally, like other datacenters, miners produce heat as a byproduct. As a thought experiment, they could also be considered heating plants, with a secondary function of securing the Bitcoin network. In Finland, heat is naturally needed year-round. This combination of grid balancing and waste heat recovery would be key to Europe's energy self-sufficiency. Wouldn't it be great if the need to bow to fossil fuel powers for energy could be eliminated? Unfortunately, the current government has demonstrated a lack of understanding of these positive externalities by proposing tax increases on electricity. The so-called fiat monetary system also deserves criticism in Western nations, even though its flaws are not as immediately obvious as elsewhere. It is the current financial system in which certain privileged entities control the issuance of money as if by divine decree, which is what the term fiat (command) refers to. The system subtly creates and maintains inequality.
The Cantillon effect is an economic phenomenon in which entities closer to newly created money benefit at the expense of those farther away. Access to the money creation process is determined by credit ratings and loan terms, as fiat money is always debt. The Cantillon effect is a distorted version of the trickle-down theory, where the loss of purchasing power in a common currency gradually moves downward. Due to inflation, hard assets such as real estate, precious metals, and stocks become more expensive, just as food prices rise in stores. This process further enriches the wealthy while deepening poverty. The entire wealth of lower-income individuals is often held in cash or savings, which are eroded by inflation much like a borrowed bottle of Leijona liquor left out too long. Inflation is usually attributed to a specific crisis, but over the long term (spanning decades), monetary inflation—the expansion of the money supply—plays a significant role. Nobel Prize-winning economist Paul Krugman, known for his work on currencies, describes inflation in his book The Accidental Theorist as follows, loosely quoted: "It is really, really difficult to cut nominal wages. Even with low inflation, making labor cheaper would require a large portion of workers to accept wage cuts. Therefore, higher inflation leads to higher employment." Since no one wants to voluntarily give up their salary in nominal terms, the value of wages must be lowered in real terms by weakening the currency in which they are paid. Inflation effectively cuts wages—or, in other words, makes labor cheaper. This is one of the primary reasons why inflation is often said to have a "stimulating" effect on the economy.
It does seem somewhat unfair that employees effectively subsidize their employers’ labor costs to facilitate new hires, doesn’t it? Not to mention the inequities faced by the Global South in the form of neocolonialism, where Cantillon advantages are weaponized through reserve currencies like the US dollar or the French franc. This follows the exact same pattern, just on a larger scale. The Human Rights Foundation (hrf.org) has explored the interconnection between the fiat monetary system and neocolonialism in its publications, advocating for Bitcoin as part of the solution. Inflation can also be criticized from an environmental perspective. Since it raises time preference, it encourages people to make purchases sooner rather than delay them. As Krugman put it in the same book, “Extra money burns in your pocket.” Inflation thus drives consumption while reducing deliberation—it’s the fuel of the economy. If the goal from an environmental standpoint is to moderate economic activity, the first step should be to stop adding fuel to the fire. The impact of inflation on intergenerational inequality and the economic uncertainty faced by younger generations is rarely discussed. Boomers have benefited from the positive effects of the trend sparked by the Nixon shock in 1971, such as wealth accumulation in real estate and inflation-driven economic booms. Zoomers, meanwhile, are left to either fix the problems of the current system or find themselves searching for a lifeboat.
Bitcoin emerged as part of a long developmental continuum within the discussion forums of rebellious programmers known as cypherpunks, or encryption activists. It is an integral part of internet history and specifically a counterculture movement. Around Bitcoin, grassroots activists and self-organized communities still thrive, fostering an atmosphere that is welcoming, inspiring, and—above all—hopeful, which feels rare in today’s world. Although the rush of suits and traditional financial giants into Bitcoin through ETF funds a year ago may have painted it as opportunistic and dull in the headlines, delving into its history and culture reveals ever-fascinating angles and new layers within the Bitcoin sphere. Yet, at its core, Bitcoin is simply money. It possesses all seven characteristics required to meet the definition of money: it is easily divisible, transferable, recognizable, durable, fungible, uniform, and straightforward to receive. It serves as a foundation on which coders, startup enthusiasts, politicians, financial executives, activists, and anarchists alike can build. The only truly common denominator among the broad spectrum of Bitcoin users is curiosity—openness to new ideas. It merely requires the ability to recognize potential in an alternative system and a willingness to embrace fundamental change. Bitcoin itself is the most inclusive system in the world, as it is literally impossible to marginalize or exclude its users. It is a tool for peaceful and voluntary collaboration, designed so that violence and manipulation are rendered impossible in its code.
Pretty punk in the middle of an era of polarization and division, wouldn’t you say?
The original author (not me) is the organizer of the Bitcoin conference held in Helsinki, as well as a founding member and vice chairman of the Finnish Bitcoin Association. More information about the event can be found at: https://btchel.com and https://njump.me/nprofile1qqs89v5v46jcd8uzv3f7dudsvpt8ntdm3927eqypyjy37yx5l6a30fcknw5z5 ps. Zaps and sats will be forwarded to author!
originally posted at https://stacker.news/items/971219
-
 @ 502ab02a:a2860397
2025-05-04 15:48:26
@ 502ab02a:a2860397
2025-05-04 15:48:26วันอาทิตย์ เพื่อนใหม่เยอะพอสมควร น่าจะพอที่จะแนะนำให้รู้จัก โรงบ่มสุขภาพ ขอเล่าผ่านเพลง "บ่ม" เพื่อรวบบทความ #ตัวหนังสือมีเสียง ไว้ด้วยเลยแล้วกันครับ
โรงบ่มสุขภาพ Healthy Hut - โรงบ่มสุขภาพ คือการรวมตัวกันของบุคลากรที่มี content และ ความเชี่ยวชาญ ด้านต่างๆ ทำกิจกรรมหลากหลายรูปแบบ ตั้งแต่แคมป์สุขภาพ พักผ่อนกายใจเรียนรู้การปรับสมดุลร่างกาย, การเรียนรู้พื้นฐาน Nutrition ต่างๆ ลองดูผลงานได้ในเพจครับ และโรงบ่มฯ ก็จะยังคงมีกิจกรรมให้ทุกคนได้เข้าร่วมอยู่เสมอ ดังนั้นไปกดไลค์เพจไว้เพื่อไม่ให้พลาดข้าวสาร เอ้ย ข่าวสาร
โรงบ่มฯนั้น ประกอบด้วย 👨🏻⚕️พี่หมอป๊อบ DietDoctor Thailand ที่เรารู้จักกันดี อาจารย์ของพวกเรา 🏋🏻♀️ 🏅พี่หนึ่ง จาก หนึ่งคีโตแด๊ดดี้ มาเป็น Nueng The One ผมอุปโลกให้ก่อนเลยว่า คนไทยคนแรกที่ทำเนื้อหาการกินคีโต เป็นภาษาไทย แบบมีบันทึกสาธารณะให้ตามศึกษา 👨🏻⚕️หมอเอก หมออ้วนในดงลดน้ำหนัก กับหลักการใช้ชีวิตแบบ IFF สาย Fasting ที่ย้ำว่าหัวใจอีกห้องของ Fasting คือ Feeding กระดุมเม็ดแรกของการฟาส ที่คนมักลืม 🧘🏻♀️ครูบอม เทพโยคะอีกท่านนึงของไทย กับศาสตร์โยคะ Anusara Yoga หนึ่งเดียวในไทย 🧗♂️โค้ชแมท สารานุกรมสุขภาพที่มีชีวิต นิ่งแต่คมกริบ ถ้าเป็นเกมส์ก็สาย สไนเปอร์ ยิงน้อยแต่ Head Shot 🧔🏻แอ๊ดหนวด ฉายา Salt Daddy เจ้าแห่งเกลือแร่ ประจำกลุ่ม IF-Mix Fasting Diet Thailand (Keto # Low Carb # Plant Base # High Fat) 👭👩🏻🤝👨🏼👩🏻🤝👨🏼 รวมถึงทีมงาน กัลยาณมิตรสุขภาพ ที่มีความรู้ในด้านสุขภาพและมากประสบการณ์ 🧑🏻🍳 ผมและตำรับเอ๋เองก็ยินดีมากๆที่ได้ร่วมทีมสุขภาพนี้กับเขาด้วย
จะเห็นได้ว่า แต่ละท่านในโรงบ่มฯ นั้นหล่อหลอมมาจากความต่างเสียด้วยซ้ำไป ตั้งแต่เริ่มก่อร่างโรงบ่ม เราก็ตั้งไว้แล้วว่า ชีวะ ควรมีความหลากหลาย การวางพื้นฐานสุขภาพควรมาจาก "แต่ละคน" ไม่ใช่ one size fit all บันทึกกิจกรรมโรงบ่มผมมีโพสไว้ https://www.facebook.com/share/p/19DUibHrbw/
นั่นเป็นเหตุผลที่ผมเกิดแรงบันดาลใจในการทำเพลง "บ่ม" ขึ้นมาเพื่อเป็น Theme Song ครับ แก่นของเพลงนี้มีไม่กี่อย่างครับ ผมเริ่มคิดจากคำว่า "ความต่าง" เพราะไม่ว่าจะกี่ปีกี่ชาติ วงการสุขภาพ ก็จะมีแนวความคิดประเภท ฉันถูกเธอผิด อยู่ตลอดเวลาเพราะมันเป็นธรรมชาติมนุษย์ครับ มนุษย์เราทุกคนมีอีโก้ การยอมรับในความต่าง การหลอมรวมความต่าง ผมคิดว่ามันเป็นการ "บ่ม" ให้สุกงอมได้
เวลาที่เนื้อหาแบบนี้ ผมก็อดคิดถึงวงที่ผมรักเสมอไม่ได้เลย นั่นคือ เฉลียง แม้ความสามารถจะห่างไกลกันลิบลับ แต่ผมก็อยากทำสไตล์เฉลียงกับเขาบ้างครั้งหนึ่งหรือหลายๆครั้งในชีวิต จึงเลือกแนวเพลงออกมาทาง แจ๊ส สวิง มีเครื่องเป่า คาริเนต เป็นตัวเด่น
ท่อนแรกของเพลงจึงเริ่มด้วย "ต่างทั้งความคิด ต่างทั้งความฝัน ต่างเผ่าต่างพันธุ์ จะต่างกันแค่ไหน หนึ่งเมล็ด จากหลากผล แต่ละคน ก็ปนไป แล้วเพราะเหตุใด ใยต้องไปแค่ทางเดียว" เพื่อปูให้คนฟังเริ่มเปิดรับว่า สิ่งที่ต้องการจะสื่อต่อไปคืออะไร
ส่วนคำย้ำนั้นผมแตกมาจาก คำสอนของพระพุทธเจ้า เกี่ยวกับ "คิดเห็นเป็นไป" ซึ่งจริงๆผมเขียนไว้ในโพสนึงแต่ตอนนั้นยังไม่ได้ทำคอลัมน์ #ตัวหนังสือมีเสียง ขอไม่เขียนซ้ำ อ่านได้ที่นี่ครับ https://www.facebook.com/share/p/18tFCFaRLn/ ท่อนที่ว่าจึงเขียนไว้ว่า "บ่มบ่ม... บ่มให้คิด บ่มบ่ม...บ่มให้เห็น บ่มบ่ม...บ่มให้เป็น บ่มบ่ม...บ่มให้ไป ไปเป็น ตัวของตัวเอง" ใช้ความซน สไตล์ rock&roll ผสมแจ๊สนิด ที่เขามักเล่นร้องโต้กับคอรัส นึกถึงยุคทีวีขาวดำ 5555
เนื้อร้องท่อนนี้ เป็นการบอกว่า โรงบ่มคืออะไรทำอะไร เพราะโรงบ่ม เราไม่ได้รักษา เราไม่ได้บังคับไดเอทว่าต้องใช้อะไร เราเปิดตาให้มอง เปิดหูให้ฟัง เปิดปากให้ถาม ถึงธรรมชาติในตัวเรา แล้วบ่มออกไปให้เบ่งบานในเส้นทางของแต่ละคนครับ
แล้วผมก็พยายามอีกครั้งที่จะสื่อถึงการยอมรับความต่าง ให้ติดหูเอาไว้ โดยเฉพาะคำที่ผมพูดบ่อยมากๆ "ชีวะ คือชีวิต" จนมาเป็นท่อน bridge นี้ครับ "อะไรที่ไม่คล้าย นั้นใช่ไม่ดี เพราะชีวะ ก็คือชีวี บ่มให้ดี จะมีความงาม ตามที่ควรเห็น ตามที่ควรเป็น"
เพลงนี้สามารถฟังตัวเต็มได้ทุกแพลทฟอร์มเพลงทั้ง youtube music, spotify, apple music, แผ่นเสียง tiktok ⌨️ แค่ค้นชื่อ "Heretong Teera Siri" ครับ
📺 youtube link นี้ https://youtu.be/BvIsTAsG00E?si=MzA-WfCTNQnWy6b1 📻 Spotify link นี้ https://open.spotify.com/album/08HydgrXmUAew6dgXIDNTf?si=7flQOqDAQbGe2bC0hx3T2A
ความลับคือ จริงๆแล้วเพลงนี้มี 3 version ถ้ากดใน spotify แล้วจะเห็นทั้งอัลบั้มครับ
📀เนื้อเพลง "บ่ม"📀 song by : HereTong Teera Siri ต่างทั้งความคิด ต่างทั้งความฝัน ต่างเผ่าต่างพันธุ์ จะต่างกันแค่ไหน
หนึ่งเมล็ด จากหลากผล แต่ละคน ก็ปนไป แล้วเพราะเหตุใด ใยต้องไปแค่ทางเดียว
บ่มบ่ม... บ่มให้คิด บ่มบ่ม...บ่มให้เห็น บ่มบ่ม...บ่มให้เป็น บ่มบ่ม...บ่มให้ไป ไปเป็น ตัวของตัวเอง
ต่างทั้งลองลิ้ม ต่างทั้งรับรู้ ต่างที่มุมดู ก็ถมไป หนึ่งชีวิต มีความหมาย ที่หลากหลาย ไม่คล้ายกัน แล้วเพราะเหตุใด ใยต้องเป็นเช่นทุกคน
บ่มบ่ม... บ่มให้คิด บ่มบ่ม...บ่มให้เห็น บ่มบ่ม...บ่มให้เป็น บ่มบ่ม...บ่มให้ไป ไปตาม ทางที่เลือกเดิน
เพราะชีวิต คือความหลากหลาย เพราะโลกนี้ ไม่เคยห่างหาย อะไรที่ไม่คล้าย นั้นใช่ไม่ดี เพราะชีวะ ก็คือชีวี บ่มให้ดี จะมีความงาม ตามที่ควรเห็น ตามที่ควรเป็น
บ่มบ่ม... บ่มให้คิด บ่มบ่ม...บ่มให้เห็น บ่มบ่ม...บ่มให้เป็น บ่มบ่ม...บ่มให้ไป ไปตาม ทางที่เลือกเดิน
เพราะชีวะ ก็คือชีวี บ่มให้ดี จะมีความงาม ตามที่ควรเห็น ตามที่ควรเป็น บ่มให้เธอชื่น บ่มให้เธอชม ชีวิตรื่นรมย์ ได้สมใจ บ่มให้ยั่งยืน
ตัวหนังสือมีเสียง #pirateketo
โรงบ่มสุขภาพ #siamstr