-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ d2e97f73:ea9a4d1b
2023-04-11 19:36:53
@ d2e97f73:ea9a4d1b
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 20986fb8:cdac21b3
2023-06-10 02:10:04
@ 20986fb8:cdac21b3
2023-06-10 02:10:04Introduction
In today's digital era, the vast amount of content available on the internet can be quite overwhelming. Sorting through this extensive information to find valuable and trustworthy content has become quite challenging. This is where YakiHonne.com comes in - a groundbreaking Nostr-based decentralized content media protocol that allows users to curate, create, publish, and report on various media. In this article, we will explore one of YakiHonne's most remarkable features: curation making. Let's delve into how YakiHonne's curation making feature revolutionizes content discovery and empowers users to become influential curators.
What is Curation Making?
Curation making on YakiHonne.com refers to the process of discovering, evaluating, and organizing content based on its quality and relevance. It enables users to act as curators, guiding others through the extensive digital landscape and highlighting noteworthy content. Through YakiHonne's decentralized approach, curation making becomes democratized, allowing anyone to become an influential curator and contribute to the platform's content ecosystem.
Empowering Curators
YakiHonne.com recognizes the value of human curation and the essential role curators play in fostering a healthy content ecosystem. The platform provides powerful tools and incentives to support curators. By curating high-quality content, curators can build a reputation and gain followers within the YakiHonne community, amplifying the influence of their curation recommendations. This empowerment creates a virtuous cycle where curators are motivated to provide accurate, reliable, and diverse content recommendations.
Curator Rewards
YakiHonne.com understands and appreciates the effort curators put into evaluating and organizing content. As a token of gratitude, YakiHonne rewards curators for their valuable contributions. Curators earn rewards based on the popularity and impact of their curated content. This incentivizes curators to consistently seek out the best content, ensuring that the platform remains a trusted source for users seeking relevant and reliable information.
Transparent Evaluation
Transparency is a fundamental aspect of YakiHonne's curation making feature. The platform provides transparent evaluation metrics, allowing users to understand how content is ranked and curated. By offering visibility into the curation process, YakiHonne fosters trust and enables users to make informed decisions about the content they consume.
Diverse Perspectives
YakiHonne.com recognizes the significance of diverse perspectives and aims to promote content curation from various backgrounds and viewpoints. The platform encourages curators from different communities and regions to contribute, ensuring a broad range of content is accessible to users worldwide. By embracing diversity, YakiHonne enriches the content experience and helps users discover fresh perspectives they might otherwise overlook.
Guideline on how to use Yakihonne Curation feature
Step 01: Login or generate a new Keys

Step 02: Go to the My Curations button (left-bottom Screen)

Step 03: new Curation by choosing a thumbnail and title, excerpt

Step 04: you’ve made it, you have created a new curation

for now you can host any articles existed within the relays by choosing related articles

and now you all setup, congrats!

Conclusion
YakiHonne's curation making feature revolutionizes content discovery by empowering users to become influential curators. By curating high-quality content, users can earn reputation, rewards, and influence within the YakiHonne community. The platform's commitment to transparency and diversity ensures that users have access to reliable and diverse content recommendations. With YakiHonne, the overwhelming task of finding valuable content is transformed into an engaging and enriching experience. Join YakiHonne today and unlock the power of curation making in the decentralized content media world.
YakiHonne.com is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media.
Try YakiHonne.com Now!
Follow us for more daily features:
- Telegram: https://t.me/YakiHonne_Daily_Featured
- Twitter: @YakiHonne
- Hack-Nostr-On, Win 35,000,000 SATs NOW: https://dorahacks.io/hackathon/hack-nostr-on/detail
- Nostr pubkey:
npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
-
 @ bc52210b:20bfc6de
2023-06-09 20:21:06
@ bc52210b:20bfc6de
2023-06-09 20:21:06Use of cryptocurrency is growing rapidly, and states are considering whether to use Bitcoin, Stablecoins, and/or Central Bank Digital Currencies (CBDCs) to “protect” citizens and promote innovation.
Bitcoin
Bitcoin is a decentralized digital currency that is not subject to government or financial institution control. This makes it a popular choice for individuals who are looking for a more secure and independent way to store and use their money. However, Bitcoin is also volatile, which means its value can fluctuate wildly. This can make it risky for states to use Bitcoin for payments or collections.
Benefits of using Bitcoin
- Widespread acceptance: Bitcoin is already accepted by a growing number of businesses and individuals around the world. This could make it easier for states to use Bitcoin to make payments and collect taxes.
- Low transaction fees: Bitcoin transaction fees are typically much lower than those charged by traditional payment methods, such as credit cards or wire transfers. This could save states money on payments and collections.
- Security: Bitcoin is a decentralized currency, which means it is not subject to government or financial institution control. This could make it a more secure option for states to use for payments and collections.
Drawbacks of using Bitcoin
- Volatility: The price of Bitcoin is volatile, which means it can fluctuate wildly in value. This could make it risky for states to use Bitcoin for payments or collections.
- Regulation: The regulatory status of Bitcoin is still evolving. This could make it difficult for states to use Bitcoin for payments or collections without running afoul of regulations.
Stablecoins
Stablecoins are a type of cryptocurrency that is pegged to a fiat currency, such as the US dollar. This means that their value is relatively stable, making them a more attractive option for states that are looking to use cryptocurrency for everyday transactions. However, stablecoins are still relatively new and untested, and there have been some cases of stablecoins losing their peg to the underlying asset. Additionally, stablecoins are often issued by centralized organizations, which could pose a risk of censorship or government interference.
Using a stablecoin like USDC alongside Bitcoin could be a way to protect individuals in a state from volatility. Stablecoins are pegged to a fiat currency, such as the US dollar, so their value is relatively stable. This could make them a more attractive option for individuals who are looking to use cryptocurrency for everyday transactions.
However, it is important to note that stablecoins are not without their own risks. For example, they are still relatively new and untested, and there have been some cases of stablecoins losing their peg to the underlying asset. Additionally, stablecoins are typically issued by centralized organizations, which could pose a risk of censorship or government interference.
The statement “Bitcoin mining consumes a significant amount of energy” has been disputed. Some studies have shown that Bitcoin mining can be relatively energy-efficient, while others have shown that it can be a significant source of energy consumption. The environmental impact of Bitcoin mining is likely to vary depending on the location of the mining operations and the type of energy used.
Benefits of using a stablecoins like “USDC”
- Control: A stablecoin digital currency would be subject to the control of the state government. This would give the state more control over its monetary policy and financial system.
- Innovation: A stablecoin digital currency could be used to promote innovation in the financial sector. This could lead to new products and services that benefit citizens and businesses.
Drawbacks of using a stablecoin digital currency
- Acceptance: A stablecoin digital currency would need to be widely accepted by businesses and individuals before it could be used effectively. This could be a challenge.
- State surveillance: A stablecoin can be used as a state surveillance tool. Commercial and state banks can track all stablecoin transactions, which could give them the ability to monitor citizens' financial activity. This could be a concern for individuals who value privacy.
Central Bank Digital Currencies (CBDCs)
In addition to Bitcoin and stablecoins, the Federal government is also considering using other digital currencies at the federal level, such as central bank digital currencies (CBDCs). CBDCs are digital versions of fiat currencies that are issued by central banks. This makes gives central banks more control over the currency.
There are several potential benefits and drawbacks to states creating or using Bitcoin vs creating their own digital currency.
Benefits
- Increased efficiency: CBDCs could help to reduce the cost and time of payments and settlements.
- Improved financial inclusion: CBDCs could make it easier for people to access financial services, such as payments and “savings”.
- Reduced risk of fraud and counterfeiting: CBDCs could help to reduce the risk of fraud and counterfeiting.
- Enhanced monetary policy: CBDCs could give central banks more control over the money supply and interest rates.
Drawbacks
- Increased surveillance: CBDCs could make it easier for governments to track and monitor people's financial transactions.
- Reduced privacy: CBDCs could reduce people's privacy, as all transactions would be recorded on a public ledger.
- Increased risk of cyberattacks: CBDCs could be more vulnerable to cyberattacks than traditional forms of money.
- Uncertainty: The potential benefits and drawbacks of CBDCs are still uncertain, as they are a new technology.
The Decision
The decision of whether to use Bitcoin, stablecoins, CBDCs, or another digital currency is a complex one that should be made on a case-by-case basis. States should carefully consider the costs, benefits, and risks of each option before making a decision.
Here are some additional things to consider when making this decision:
- The potential for state surveillance. CBDCs can be used as a state surveillance tool. Central banks can track all CBDC transactions, which could give them the ability to monitor citizens' financial activity. This could be a concern for individuals who value privacy.
- The potential for inflation. CBDCs could lead to inflation. If central banks issue too much CBDC, it could lead to a decrease in the value of the currency. This could make it more difficult for people to save money and could lead to higher prices for goods and services.
- The regulatory environment for Bitcoin, stablecoins, and CBDCs in the state. The regulatory environment for Bitcoin, stablecoins, and CBDCs is still evolving, and it is important to understand the risks and compliance requirements before using them.
- The potential for financial crime. Cryptocurrency is often used for illegal activities, such as money laundering and tax evasion. States should consider the potential for financial crime when using cryptocurrency.
- The potential for cyberattacks. Cryptocurrency systems are vulnerable to cyberattacks. States should consider the potential for cyberattacks when using cryptocurrency.
- The potential for market manipulation. The cryptocurrency market is volatile and prone to manipulation. States should consider the potential for market manipulation when using cryptocurrency.
Conclusion
The use of cryptocurrency is a growing trend, and states are considering how to best utilize this technology. There are a number of factors that states should consider when making this decision, including the level of adoption in the state, the regulatory environment, the environmental impact, and the potential for financial crime, cyberattacks, and market manipulation. States should carefully weigh the costs and benefits of each option before making a decision.
-
 @ bc52210b:20bfc6de
2023-06-09 20:04:53
@ bc52210b:20bfc6de
2023-06-09 20:04:53The best eSIM provider for privacy is the one that offers the most features and protections for your data. Here are a few things to consider when choosing an eSIM provider:
- Data privacy policy: Make sure the provider has a clear and transparent data privacy policy that explains how your data will be collected, used, and shared.
- Encryption: Look for a provider that uses strong encryption to protect your data while it is in transit and at rest.
- No tracking: Some eSIM providers track your online activity and sell your data to advertisers. Choose a provider that does not track your data.
- Anonymous payment: Some eSIM providers require you to provide personal information, such as your name and address, when you purchase a plan. Select a provider that allows you to pay anonymously.
Here are a few eSIM providers that offer good privacy features:
- Silent.link: Silent.link is an eSIM provider that offers anonymous phone numbers and data plans. The company claims that it does not collect any personal data about its users, and that its services are encrypted to protect privacy. Silent.link is based in Switzerland, which has strong privacy laws. The company also uses a variety of security measures to protect its users' data, including encryption and two-factor authentication. *** Airalo**: Airalo is a global eSIM provider that offers a variety of plans in over 180 countries. Airalo's data privacy policy is clear and transparent, and the company uses strong encryption to protect your data.
- Holafly: Holafly is a Spanish eSIM provider that offers plans in over 100 countries. Holafly's data privacy policy is clear and transparent, and the company uses strong encryption to protect your data.
- KnowRoaming: KnowRoaming is a US-based eSIM provider that offers plans in over 100 countries. KnowRoaming's data privacy policy is clear and transparent, and the company uses strong encryption to protect your data.
It is important to note that no eSIM provider is 100% secure. However, by choosing a provider with strong privacy features, you can help to protect your data from being tracked and sold.
Some additional things to consider when choosing an eSIM provider for privacy:
- Location: Some eSIM providers are located in countries with strong privacy laws, such as the European Union. This means that your data is more likely to be protected by these laws.
- Reputation: Do some research to see what other people are saying about the eSIM provider. Are they satisfied with the level of privacy and security?
- Price: eSIM providers can vary in price, so it's significant to compare prices before you make a decision.
Ultimately, the best way to decide on an eSIM provider for privacy is to weigh all the factors above and make a decision that is right for you.
Here are some additional tips for protecting your privacy when using an eSIM:
- Use a VPN: A VPN encrypts your traffic, making it more difficult for your ISP or other third parties to track your online activity.
- Disable location sharing: Many apps and websites ask for your location, but you don't always need to share it. Disabling location sharing can help to protect your privacy.
- Be careful what you share: Only share personal information with people you trust. Be especially careful about sharing sensitive information, such as your home address or phone number.
- Keep your software up to date: Software updates often include security patches that can help to protect your device from malware and other threats.
By following these tips, you can help to protect your privacy when using an eSIM.
-
 @ bc52210b:20bfc6de
2023-06-09 19:56:48
@ bc52210b:20bfc6de
2023-06-09 19:56:48As cryptocurrencies gain popularity and value, they become attractive targets for malicious actors. It is crucial to implement robust security measures to protect these assets from theft, loss, or unauthorized access. One effective approach is to establish layers of security for digital asset wallets.
Building layers of security for a digital asset wallet involves implementing multiple protective measures that work together to create a robust defense system. These layers include seed phrase backup, hardware wallets, software wallets with offline storage secure keys, and noncustodial lightning wallets. Each layer addresses specific vulnerabilities and provides an additional barrier against potential threats.
To begin enhancing wallet security, it is advisable to reset the hardware wallet to ensure a clean starting point. During the setup process, the hardware wallet generates a seed phrase—a sequence of words that serves as the master key to access the wallet. This step ensures the generation of a fresh seed phrase unique to your wallet.
It is crucial to create a secure backup of the seed phrase. Prepare an offline storage solution, such as a steel capsule or cassette providing CCSS Level 3 compliance solution, to store the seed phrase securely. This offline backup provides protection against online threats like hacking, malware attacks, fire, flood, static electricity and even EMPs.
In the event of hardware wallet loss, damage, or theft, it is important to be able to restore access to your digital assets. By resetting the hardware wallet and restoring it using the offline storage secure wallet seed phrase backup, you can regain control over your funds.
To further enhance security, set up a mobile or desktop wallet that supports an air-gapped key derived from the hardware wallet. This allows you to sign transactions using the hardware wallet securely, even on a device that may be connected to the Internet.
After implementing the security measures, it is advisable to generate an address using the wallet and perform test transactions. This helps familiarize yourself with the wallet's functionality while ensuring that funds can be sent and received correctly.
The Layers Model
Layer I
Seed Phrase Backup
The seed phrase is the foundation of wallet security. It serves as the backup and recovery mechanism for accessing your digital assets. Losing the seed phrase can result in permanent loss of funds. It is essential to understand its significance and protect it diligently.
Best practices for storing seed phrase backup
Store the seed phrase backup in a secure, physically separate location from the hardware wallet and any connected devices. Consider using a fireproof and waterproof safe or a dedicated offline storage solution specifically designed for seed phrase backup (metal devices).
Considerations for offline storage options
Evaluate different offline storage options, such as hardware wallets, or metal backup plates. Each option has its own advantages and considerations. Choose the one that aligns with your security needs and preferences.
Layer II
Hardware Wallet (i.e., Savings Account)
Hardware wallets are dedicated devices designed to securely store and manage private keys offline. They provide an extra layer of protection by keeping the private keys isolated from potential online threats.
Hardware wallets offer several benefits that make them an ideal choice for securing digital assets:
- Enhanced security: Hardware wallets are designed with robust security features to protect private keys and transactions. They utilize secure elements or specialized chips to securely store private keys, making it difficult for hackers or malware to gain access to them.
- Offline storage: Hardware wallets store private keys offline, disconnected from the internet. This isolation minimizes the risk of online threats such as hacking, phishing attacks, or keyloggers compromising the wallet's security. It provides an extra layer of protection, commonly referred to as “cold storage.”
- Protection against malware: Since hardware wallets operate on dedicated devices with limited functionality, they are less susceptible to malware or viruses. Even if the computer or mobile device used to interact with the wallet is compromised, the private keys stored on the hardware wallet remain secure.
- User-friendly interface: Hardware wallets typically offer user-friendly interfaces and clear instructions for setting up and using the wallet. They are designed to simplify the process of managing and accessing digital assets, even for users who may not have advanced technical knowledge.
- Multi-currency support: Many hardware wallets support a wide range of cryptocurrencies, allowing you to store and manage various digital assets in a single device. This convenience eliminates the need for multiple wallets and simplifies portfolio management.
- Backup and recovery options: Hardware wallets often provide backup and recovery options, such as the seed phrase mentioned earlier. In case of loss, damage, or theft of the hardware wallet, users can easily restore their wallet and regain access to their funds using the seed phrase.
- Compatibility with software wallets: Hardware wallets can be used in conjunction with software wallets, providing an added layer of security. Users can initiate transactions on their software wallet but rely on the hardware wallet to securely sign the transactions offline, minimizing the risk of exposure to online threats.
Overall, hardware wallets offer a combination of enhanced security, offline storage, ease of use, and compatibility that make them a reliable choice for securing digital assets. By utilizing a hardware wallet, individuals can significantly reduce the risk of unauthorized access and confidently manage their cryptocurrencies.
Layer III
Software Mobile/Desktop Wallet with Offline Storage Secure Key (i.e., Checking Account)
An offline storage secure key, also known as an air-gapped key, adds an extra layer of security to software wallets. It involves generating and storing the private key in a separate, offline environment, reducing the risk of unauthorized access or exposure to online threats. By keeping the private key offline, the likelihood of malware or remote attacks compromising the key is significantly minimized.
When choosing a mobile/desktop wallet for offline storage secure key usage, consider the following factors:
- Compatibility: Ensure that the wallet you select supports the generation and usage of an offline storage secure key. Look for wallets that explicitly mention this feature in their documentation or feature list.
- Reputation and security track record: Research the wallet's reputation and security history. Choose wallets developed by reputable companies or open-source projects with a strong track record of security and regular updates. *** User interface and ease of use**: Look for wallets that provide a user-friendly interface and intuitive setup process. The wallet should make it clear how to generate and import an offline storage secure key and seamlessly integrate with a hardware wallet or other offline storage solutions.
Setting up a mobile/desktop wallet with an offline storage secure key typically involves the following steps:
- Generate an offline storage secure key: Use a secure and offline device, such as a computer not connected to the internet or a hardware wallet, to generate the private key. Follow the specific instructions provided by the wallet to generate a key in an offline environment.
- Import the secure key into the software wallet: Transfer the private key securely from the offline device to the mobile/desktop wallet. This can be done through various methods, such as scanning a QR code, connecting the offline device temporarily to the online device, or using an encrypted file transfer.
- Verify and confirm key import: After importing the secure key, carefully verify that it has been imported correctly. Cross-check the key's address or other identifying details with the original offline key. Ensure that the imported key is being used for transactions and wallet access.
To maintain the security of a software wallet with an offline storage secure key, consider the following best practices: ** * Regularly update the software wallet: Keep the software wallet up to date with the latest security patches and feature enhancements. Developers often release updates to address vulnerabilities and improve security measures. * Enable additional security features: Utilize all available security features offered by the software wallet, such as two-factor authentication (2FA) or biometric authentication. These features add an extra layer of protection to prevent unauthorized access. * Implement strong password practices: Use a unique, complex password for the software wallet and avoid reusing passwords from other accounts. Consider using a password manager to securely store and generate strong passwords. * Use reputable app stores: Download the software wallet from official and reputable app stores or the wallet's official website. Be cautious of unofficial sources, as they may distribute compromised or fake versions of the wallet. * Be cautious of phishing attempts**: Exercise caution when interacting with the software wallet. Be vigilant against phishing attempts, such as fake websites or emails designed to trick you into revealing sensitive information. Always verify the authenticity of the wallet's website or communication channels.
Layer IV
Noncustodial Lightning Wallet (i.e., debit card, pocket change)
Noncustodial lightning wallets are software wallets that enable users to participate in the Lightning Network, a second-layer protocol built on top of certain blockchain networks like Bitcoin. These wallets allow users to send and receive instant, low-cost transactions using the Lightning Network without relying on third-party custodians to hold their funds. Noncustodial lightning wallets give users full control over their funds and enable them to engage in peer-to-peer transactions directly.
Noncustodial lightning wallets offer several advantages for users:
- Control over funds: With noncustodial lightning wallets, users retain full control of their funds. They manage their private keys and have the freedom to transact with Lightning Network channels directly without relying on intermediaries.
- Instant and low-cost transactions: The Lightning Network enables near-instantaneous and cost-effective transactions by leveraging payment channels. Noncustodial lightning wallets provide a seamless interface for users to participate in this network and benefit from its scalability and speed.
- Privacy: Noncustodial lightning wallets enhance user privacy by enabling off-chain transactions that do not expose every transaction detail on the underlying blockchain. This helps to maintain confidentiality and reduce the traceability of transactions.
- Empowering micropayments: Noncustodial lightning wallets are particularly useful for micropayments, allowing users to make small, frequent transactions economically. This opens up new possibilities for microtransactions, such as tipping content creators or paying for digital goods and services.
When choosing a noncustodial lightning wallet, consider the following factors:
- Compatibility and platform support: Ensure that the wallet is compatible with the blockchain network and Lightning Network implementation you intend to use. Check if the wallet supports your preferred operating system or device.
- User interface and ease of use: Evaluate the user interface and user experience of the wallet. Look for wallets that provide a user-friendly interface, making it easy to navigate and manage Lightning Network channels and transactions.
- Reputation and security: Research the wallet's reputation and security track record. Look for wallets developed by reputable teams or open-source projects with a history of actively maintaining and updating their software.
- Community support and development activity: Consider the level of community support and ongoing development for the wallet. Active communities and frequent software updates indicate a vibrant ecosystem and ongoing improvement of the wallet's features and security.
Noncustodial lightning wallets require specific security measures to ensure the safety of funds and user information:
- Strong authentication: Enable robust authentication methods, such as biometric authentication or hardware-based security keys, to prevent unauthorized access to the wallet.
- Regularly update the wallet: Keep the wallet software up to date with the latest security patches and bug fixes. Updates often include security improvements and vulnerability fixes.
- Backup channel state: Noncustodial lightning wallets may require users to back up the state of their Lightning Network channels. This backup ensures the ability to recover funds in case of accidental channel closures or wallet failures.
- Trustworthy channels: When opening channels with other Lightning Network participants, consider the reputation and trustworthiness of the channels. Research and select well-established and reliable nodes to minimize the risk of channel closure or loss of funds.
- Secure channel management: Follow best practices for managing Lightning Network channels, such as monitoring channel health, maintaining a balance between incoming and outgoing liquidity, and closing unused or compromised channels promptly.
- Educate yourself on Lightning Network risks: Understand the potential risks associated with the Lightning Network.
Implementing layers of security for your digital asset wallet is crucial for safeguarding your valuable assets. By following the outlined steps, including seed phrase backup, utilizing a hardware wallet, setting up a software wallet with offline storage secure keys, and considering noncustodial lightning wallets, you create a robust defense against potential threats.
Relying on a single security measure for your digital asset wallet leaves you vulnerable to various risks. By implementing multiple layers of security, you significantly reduce the likelihood of unauthorized access, loss, or theft. Each layer adds another barrier, making it exponentially more difficult for attackers to compromise your wallet and gain access to your funds.
As the landscape of digital assets and security threats continues to evolve, it is crucial to stay informed about the latest best practices and emerging threats. Regularly update your knowledge regarding wallet security measures and seek reputable sources for guidance. By remaining proactive and vigilant, you can continue to enhance the security of your digital asset wallet and protect your valuable assets effectively.
-
 @ bc52210b:20bfc6de
2023-06-09 19:46:25
@ bc52210b:20bfc6de
2023-06-09 19:46:25U2F stands for Universal 2nd Factor, which is an open authentication standard that strengthens and simplifies two-factor authentication (2FA) U2F is important because it provides an additional layer of security to online accounts by requiring a physical device in addition to a password. This makes it much more difficult for attackers to gain access to a user's account, even if they have the password.
U2F stands for Universal 2nd Factor, which is an open authentication standard that strengthens and simplifies two-factor authentication (2FA) using specialized USB or NFC devices. The standard is developed by the FIDO Alliance, an industry consortium that aims to reduce the reliance on passwords for online authentication.
U2F provides an additional layer of security by requiring a physical device in addition to a password. When a user attempts to log in to a website or service that supports U2F, they must insert their U2F device into their computer's USB port or tap it against their NFC-enabled device. The device will then communicate with the website or service to confirm the user's identity.
One of the major benefits of U2F is that it eliminates the need for users to remember and enter one-time codes generated by an app or received via text message. This not only makes it more convenient for users, but it also reduces the risk of phishing attacks and other forms of fraud.
U2F devices are designed to be resistant to phishing and malware attacks. For example, they will only work with the website or service for which they were originally registered, and they will only communicate with the website or service over an encrypted connection. This ensures that even if an attacker is able to intercept the communication between the device and the website, they will not be able to use it to gain access to the account.
Additionally, U2F is an open standard, which means that any organization can implement it without having to pay licensing fees. This has led to a wide range of U2F devices being available on the market, at a variety of price points.
There are some drawbacks to U2F, one of them is that it requires a physical device that the user must carry with them. This can be a problem for users who frequently change devices or travel frequently. Additionally, U2F devices are not compatible with all devices, such as smartphones.
In conclusion, U2F is important because it provides an additional layer of security to online accounts, makes it more convenient for users, and reduces the risk of phishing and other forms of fraud. It also eliminates the need for users to remember and enter one-time codes, makes it more difficult for attackers to gain access to a user's account, and is an open standard that is relatively easy for organizations to implement.
-
 @ 4ac847f3:16dc6c5a
2023-06-09 19:42:47
@ 4ac847f3:16dc6c5a
2023-06-09 19:42:47Zebedee, empresa de pagamentos de jogos, lança aplicativo social descentralizado com funcionalidade de Bitcoin
bitcoin #bitcoin2023 #zebedee #Noticias #nostr
Introdução:
O mundo das redes sociais está prestes a passar por uma revolução com a entrada da Zebedee, uma empresa de pagamentos de jogos, no cenário do aplicativo social descentralizado. Com mais de um milhão de carteiras de Bitcoin e um investimento de quase $50 milhões em capital de risco, a Zebedee lançou hoje o seu principal aplicativo, ZBD, na Nostr, uma plataforma de redes sociais descentralizada em rápido crescimento. Essa integração permite que os usuários enviem pequenas quantias de Bitcoin, chamadas "zaps", uns aos outros, em vez de simplesmente curtir conteúdo como acontece no Twitter e no Facebook.
Artigo completo em 👇
https://open.substack.com/pub/technewsbr/p/zebedee-empresa-de-pagamentos-de?r=1zp81j&utm_campaign=post&utm_medium=web
-
 @ 4ac847f3:16dc6c5a
2023-06-09 17:26:21
@ 4ac847f3:16dc6c5a
2023-06-09 17:26:21Microsoft concorda em pagar US$20 milhões para resolver acusações de coleta ilegal de dados pessoais de crianças
Noticias #tecnologia #Microsoft #nostr
Introdução:
A Microsoft concordou em pagar um valor significativo de US$20 milhões para resolver acusações feitas pela Comissão Federal de Comércio (Federal Trade Commission - FTC) que acusaram a gigante de tecnologia de coletar ilegalmente informações pessoais de crianças sem o consentimento de seus pais - e, em alguns casos, retê-las "por anos".
Violação da lei de privacidade infantil:
O órgão regulador federal afirmou que a Microsoft violou a Lei de Proteção à Privacidade Online Infantil (Children’s Online Privacy Protection Act - COPPA), uma lei federal que governa as proteções de privacidade online para crianças menores de 13 anos. A COPPA exige que as empresas notifiquem os pais sobre os dados que coletam, obtenham consentimento parental e excluam esses dados quando não forem mais necessários.
Coleta indevida de dados:
De acordo com a FTC, crianças que se cadastravam no serviço de jogos Xbox da Microsoft eram solicitadas a fornecer informações pessoais, como nome, endereço de e-mail, número de telefone e data de nascimento. Até 2019, havia uma caixa de seleção pré-preenchida permitindo que a Microsoft compartilhasse as informações do usuário com anunciantes. A FTC afirmou que a Microsoft coletou esses dados antes de solicitar que os pais concluíssem a configuração da conta e manteve os dados das crianças mesmo se o pai abandonasse o processo de inscrição.
Artigo completo em 👇
https://open.substack.com/pub/technewsbr/p/microsoft-concorda-em-pagar-us20?r=1zp81j&utm_campaign=post&utm_medium=web
-
 @ 6b44f497:4fe86a48
2023-06-09 17:23:49
@ 6b44f497:4fe86a48
2023-06-09 17:23:49Later
-
 @ bc52210b:20bfc6de
2023-06-09 15:17:10
@ bc52210b:20bfc6de
2023-06-09 15:17:10Worldwide, especially during these times of disinformation and distrust in governments and authority, there is a regulatory push to enforce Know Your Customer (KYC) requirements when receiving a new phone number.
Fortunately, there is a company that is tackling this very issue called Silent.link
Services provided by Silent.link are becoming super important given the fact that they do not require any type of KYC.
Silent.link does not gather KYC information because it's not required, at least not yet. Other operators/providers do require KYC information because it's used for advertisement revenues and surveillance purposes, not because it is a requirement by regulators.
One exception are phone numbers that do require KYC. In this scenario, Silent.link has eSIMS from the US and the UK with phone numbers that do not have the same KYC requirements. More companies offering similar products will pop up in the near future.
There are benefits for Internet data only (no-phone number) such as VoIP applications, but most require a phone number as an identifier. Silent.link is providing an excellent service by delivering internet data and phone number service without requiring any type of KYC.
There are several risks involved with using Internet data and phone number services, as these utilize outdated 20th century technology that have no security at all. All these voice and text calls being sent/received are fingerprinted and logged. A much better option is getting an Internet data and phone number service and attaching this to a privacy VoIP app like Signal or WhatsApp that require the use of phone numbers for identification.
The service plans do not include out-band calls because of abuse of spam. Out-band calls are also not not included to prevent users from being fingerprinted/logged by making calls or sending text.
For making calls to the traditional legacy phone service, the best option is to sign up to a separate VoIP service.
Silent.link uses “roaming all the time” because it is very difficult to surveil a SIM/eSIM card/profile that has not been issued by the local operator that came from some other foreign telecom/jurisdiction.
When the foreign telecom SIM/eSIM is roaming in the carrier network local operator, the carrier does not know the phone numbers as they only know the internal IDs or International Mobile Subscriber Identity(IMSI) or SIM identifier. This is different from the International Mobile Equipment Identity(IMEI) or hardware identifier.
It's becoming increasingly difficult in the US to get a phone number without attaching it to an identity and in some countries it's against the local regulation.
There is a regulatory push to force the requirement of KYC information when getting a phone number. Services provided by Silent.link are becoming super important given the fact that they do not require KYC.
At this point in time, Telecoms are years behind with technology, including payment services, and are not comfortable accepting payments using cryptocurrency. This might be one of the reasons why there are not more companies like Silent.link, but this will change quickly as Telecoms get on the 21st century innovation bandwagon.
Silent.link services:
Provide anonymous eSIMS decoupled from users official identity and have two plans with no out-band calls or text:
- Internet data only (no-phone number)
- Internet data and phone number
Features:
- Global mobile 4G/5G Internet access
- Pay as you go international roaming in 200+ countries
- Worldwide coverage at low prices
- Pay with #Bitcoin or #Lightning
- Roaming is used all the time
-
 @ bc52210b:20bfc6de
2023-06-09 15:15:24
@ bc52210b:20bfc6de
2023-06-09 15:15:24Bitcoin, a monetary revolution, brought the invention of blockchain technology that basically solved a well known computer science problem. This new innovation has taken the world by storm in the form of true decentralization, now possible in this digitized world we live in.
Features of Bitcoin
- Open-source
- No president or head like figure
- Build to scale
- Decentralized
Features of Decentralization
- No one individual or group controls this innovation
- Major changes need the agreement of a large portion of the community
Including:
- software developers
- miners
- node operators
Legacy traditional institutions, especially central banks, are impressed and perplexed with this innovation that for the first time creates a truly digital currency, and also how fast people have adopted this technology worldwide.
These same central planners are watching in dismay as they realize that their central banks organizations have no control of the money supply in this new decentralized digital financial system.
The control and production of legacy currency has historically been reserved for central banks, and which is directly tied to the close relationship and ties with the state.
Decentralization of bitcoin is super important and the biggest innovation. Without a single point of failure, including a prime minister/president or institution or centralized servers.
Central banks have now realized that they will have to compete in the free market now that this innovation has been brought to light.
Central Bank Digital Currencies (CBDC) is their new product that will compete against this new innovation in the market.
CBDCs will remove privacy and the decentralized nature of physical cash. Giving central banks control over users' financial life.
Examples:
- Personalized inflation — Central banks currently have the ability to manipulate interest rates and expand/contract the supply of money. With CBDCs the central bank will be able to personalize the monetary policy down to the individual. i.e: Some individuals get a higher inflation rate in an attempt to get them to spend currency, while others receive a lower inflation rate. Other monetary policies can be based on where individuals live, who they are, their wealth status, their occupation, their purchase history, etc.
- Financial censorship — Central banks and governments can have complete control when CBDCs are distributed throughout the population. They will be able to avoid and bypass the court system and rule of law or even invoke “emergency powers” to tell individuals who they can transact with. All of this can be done and implemented remotely using digital technologies. Central bankers will be able to see transactions in an individual's bank account, who they transact with, what they are purchasing, and basically all their financial life. The system is fully transparent to the state and removes all elements of privacy, while also giving the institutions the ability to censor any and all transactions, regardless of whether they have a legitimate reason or not.
- Social credit system — When the financial system is completely controlled by the central bankers and the government, they have the ability to compensate or punish individual individuals based on the actions they take. i.e: If individuals eat too much candy they might be blocked from buying certain candy. If individuals gamble they might be stopped from using public transportation that heads in the direction of the casino. These examples have been publicly presented by the Bank of England (Bank of England tells ministers to intervene on digital currency 'programming' Digital cash could be programmed to ensure it is only spent on essentials, or goods which an employer or Government deems to be sensible) China already has one in place. Canada is implementing one in real time right now. (A Social Credit System Arrives in Canada Justin Trudeau just created a caste of economic untouchables. Can we stop this dystopian policy from taking hold in America?) i.e. If individuals are obese they can be allowed to conduct transaction for healthy food only.
- Expiration of money — Central banks are constantly trying to have people spend currency in the economy so that you can increase the velocity of money. The best way to do this with CBDCs is to have this new digital currency expire. If the individual doesn't use the currency within a certain period of time it will not work anymore.
These are just four examples of various activities that central banks will engage in once they are successful in creating and distributing CBDCs.
Pay attention Absolute Power Corrupts Absolutely.
This needs to reach global awareness, central banks can and most probably will be the greatest violators of human rights.
-
 @ bc52210b:20bfc6de
2023-06-09 15:08:50
@ bc52210b:20bfc6de
2023-06-09 15:08:50“Technocracy advocates contended that price system-based forms of government and economy are structurally incapable of effective action, and promoted a society headed by technical experts, which they argued would be more rational and productive.” (https://en.wikipedia.org/wiki/Technocracy_movement)
In order to start using cyber security best practices to Ghost your profile on the cloud, we first need to understand the “bread crumbs” we are leaving behind. This article will focus on smartphones since it's the most used hardware device and the most relevant OS running on Android and iPhone that individuals use on a daily basis.
Basic Steps
First, I need to understand that for convenience purposes all mobile apps will enable push notifications by default.
What are Push Notifications?
Push notifications are the alerts that apps send to your phone even when the apps aren't open. Often appearing at the top or side of your screen, nearly every popular app uses push notifications in some way.
Push notifications allow app providers to reach you, impacting your privacy. To Ghost yourself this is one area to focus on. The best way to disable these and take control on which applications can use push notifications is by using Google wrapper service (microG) settings.
To truly become a Ghost, users need to detach as much as possible from a single web service provider like Google, Apple, Microsoft or AWS. Think of it as a diversified portfolio of web services including new semi-decentralized ones like IPFS and FileCoin. Also focus on centralized web services that provide Zero-knowledge technology services like SpiderOak.
Second, enable Two-Factor Authentication. The most important measure you can take to help keep your account secure is to enable Two-Factor Authentication (2FA). 2FA provides an additional layer of security for all your accounts. Once it’s set up, you’ll be required to enter your password and a code that you generate on your phone using apps like Aegis or Authy, also the use of security keys like a YubiKey is highly recommended. A code sent to an email you control, to sign in to your account is preferred to sending SMS which is highly unsecured.Third, strengthen your password. Beyond adding 2FA, you can help protect your account with a strong password.
A strong password:
- Use a password that has not been used elsewhere
- Contains at least 10 characters
- Includes uppercase and lowercase letters, numbers, and special characters
To help in managing passwords use password managers like Bitwarden or LastPass to apply the recommendations above.
Third, strengthen your password. Beyond adding 2FA, you can help protect your account with a strong password.
A strong password:
- Use a password that has not been used elsewhere
- Contains at least 10 characters
- Includes uppercase and lowercase letters, numbers, and special characters
To help in managing passwords use password managers like Bitwarden or LastPass to apply the recommendations above.
Fourth, secure your personal email account. Perform the above recommendations for your personal email(s) associated with all your important online accounts as a requirement. This can help prevent bad actors from gaining access to your accounts through your email(s). If possible use a reusable disposable email(s).
Besides the above four areas, review your phone number and email address. Verify that your phone number and email address listed on all your significant online accounts are up-to-date, and valid functioning ways to reach you that are not tied to your real identity.
Review your devices. In most of your significant online accounts, look for ways to view logs of the device that has been used to log in to your account. We recommend reviewing the listed devices regularly and removing any you don’t recognize or no longer use if possible.
Beware of phishing scams. Be careful when clicking on links in text messages and emails that you don’t expect or recognize. Look at the URL heading to make sure it corresponds to the originating sender. Most online accounts support never requiring your password, 2FA codes, or sending you links within text messages. In addition, most never ask you to download software or ask you for information regarding your accounts on other online account platforms or services.
Another tactic is SMS sent to your phone as marketing asking to reply Yes/No on receiving marketing information. Any choice Yes/No will reveal your triangulated locations reducing your privacy.
Types of Users
There are three types of users with distinct privacy requirements and thus levels of security that require possibly two devices with two account(s)
Privacy Account/Device Type (Private)
This type will obviously require pseudonymity and private account(s)
An example would be for self-custody, DeFi or self sovereign purpose transactions.
Options:
- Reuse of disposable email
- SIM/eSIM with Telco local number for specific jurisdiction purchased with physical untraceable ‘cash” or virtual currency like Bitcoin/Lightning and/or Monero.
- SIM/eSIM with data only purchased with physical untraceable ‘cash” or virtual currency like Bitcoin/Lightning and/or Monero.
Public Account/Device Type (non-private)
This type of user will require full KYC and primary use would be for social media accounts and full use of federated, centralized and surveilled infrastructure, that provides a fingerprint and the ability to track cookies. An example would be for surveilled citizens, banking or company/employment custodian purpose transactions.
Options:
- SIM/eSIM with Telco local number for specific jurisdiction purchased with traceable bank account or virtual currency like Bitcoin/Lightning and/or CBDC/Stable coins fully KYCed.
Public/Privacy Account/Device Type (semi-private)
This type of user will require partial KYC and primary use would be for necessary social media accounts for services (i.e. Uber, Lyft) and full use of federated, centralized and surveilled infrastructure, that provides a fingerprint and the ability to track cookies. These surveillance applications and services can be disabled and controlled by sovereign individuals as needed.
Options:
- Combinations of privacy account/device type and public account/device type configured by sovereign individuals to reflect specific needs and requirements.
These types of users are constantly reevaluating their privacy and security posture to determine what trade-offs to execute and thus constantly being aware of their online web presence. Most individuals will require a mental strategy for what tasks to perform in each account/device.
Another area to focus is on the physical (SIM) or virtual (eSIM) used to enable users to become “Ghosts”
SIM
You can purchase a SIM from your local wireless provider and if this provider requires KYC then “Ghosting” will become more difficult and thus if possible pay in local cash fiat currency with no KYC requirements. If this is not possible then an eSIM or virtual SIM would be preferred.
eSIM
Privacy First eSIM are new global providers with this service. Providing global mobile 4G/5G internet access and SMS number instantly and privately on any modern eSIM-compatible smartphone. Silent.Link (https://silent.link/)
Another option for a global provider is Efani. Whether SIM or eSIM is chosen, great due diligence is necessary when choosing a carrier to provide this service. Specially to prevent SIM swapping.
How does SIM swapping occur? 1. 1. A rogue hacker rings your mobile operator and requests a new SIM 2. The unsuspecting operator tests their identity with relatively simple security questions such as your date of birth or favorite color, etc. 3. The hacker answers at least one of the questions correctly and receives the new SIM 4. The hacker is now able to take complete control of your phone, and through text message verification, also takes control of your email and bank account
Global secure telecommunication service from Efani (https://www.efani.com/) provide solutions and services such as multigrade-verification, encryption, insurance coverage and excellent 24/7/365 support.
A good list of hardware and software to enable users to become “Ghosts”
One area of recommendation is to migrate to a non-proprietary hardware and OS. Given the fact that Google base OS is open source and there is no option for apple iPhone open source.
Open source is software source code that is made freely available for possible modification and redistribution.
There are some security and privacy centered options that develop open source OS specifically for android phones that use this Google based open source software as base.
CalyxOS is the most popular and the one I will be recommending here, given the fact that I have been using it for some time as my main smartphone OS, CalyxOS. (https://calyxos.org/).
My CalyxOS installation on my Pixel took about 8 minutes, all without a hitch.
Currently installing all security apps like VPN etc. and apps I need that require privacy.
Continuing with apps like Map, chat, and maybe even banking apps like PayPal etc. Using integrated Firewall and Google wrapper service (microG).
This OS is truly innovating and part of a game changer like Ubuntu did to Linux desktops back in the day.
Once you unlock your boot-loader remember to lock it back which re-enables the Secure Enclave (A secure enclave provides CPU hardware-level isolation and memory encryption on every server by isolating application code and data from anyone with privileges, and encrypting its memory.)
This setup makes Android phones 100x more secure than iPhones
Android hardware that is supported at the moment is:
- Pixel 4a (5G)
- Pixel 5 (redfin)
- Pixel 4a (sunfish)
- Pixel 4 XL (coral)
- Pixel 4 (flame)
- Pixel 3a XL (bonito)
- Pixel 3a (sargo)
- Pixel 3 XL (crosshatch)
- Pixel 3 (blueline)
- Pixel 2 XL (taimen)
- Pixel 2 (walleye)
- Xiaomi Mi A2 (jasmine_sprout)
Next step is to separate your online web services with security and privacy centric services providers
Here is a list of some recommended ones:
Replacements for Google Services
Google Search → DuckDuckGo (free)
Let's start off with the easiest one! Switching to DuckDuckGo not only keeps your searches private, but also gives you extra advantages such as our bang shortcuts, handy Instant Answers, and knowing you're not trapped in a filter bubble.
Gmail, Calendar & Contacts → FastMail (paid), ProtonMail (free with paid options), Tutanota (free with paid options)
FastMail is an independent, paid service that also includes calendar and contacts support across all devices. There are also several ways to get encrypted email between trusted parties by integrating PGP encryption tools. Even more private email alternatives are ProtonMail and Tutanota, both of which offer end-to-end encryption by default.
YouTube → Vimeo (free with paid options)
For videos that are only on YouTube (unfortunately, a lot), you can search for and watch them on DuckDuckGo for better privacy protection via YouTube's "youtube-nocookie" domain. If you're creating and hosting video yourself, however, Vimeo is the best-known alternative which focuses on creators.
Google Maps → Apple Maps (free), OpenStreetMap (free)
For iOS users, Apple gives you an alternative built in via Apple Maps, so no installation is necessary. For wider device support, check out OpenStreetMap (OSM) which is more open, though may not have the same ease-of-use or coverage quality as Apple Maps.
Google Drive → Resilio Sync (free with paid options), Tresorit (paid)
Resilio Sync provides peer-to-peer file synchronization which can be used for private file storage, backup, and file sharing. This also means your files are never stored on a single server in the cloud! The software is available for a wide variety of platforms and devices, including servers. An alternative cloud storage and backup service with end-to-end encryption is Tresorit.
Android → iOS (paid)
The most popular alternative to Android is of course iOS, which offers easy device encryption and encrypted messaging via iMessage by default.
**Google Chrome → Safari (free), Firefox (free), Brave (free), Vivaldi (free) ** Safari was the first major browser to include DuckDuckGo as a built-in private search option. A more cross-device compatible browser is Mozilla's Firefox, an open source browser with a built-in tracker blocker. Brave goes one step further with tracker blocking switched on by default. There are also many more browsers that come with DuckDuckGo as a built-in option, such as Vivaldi, which is well suited for power-users.
As depicted above in this article I am mostly focusing on Android platform vs Apple iPhone and this is because Apple is close source just like Windows and IBM software. This means that there are trade-offs for convenience and security and privacy and in the Apple iPhone it might be more secure and convenient, but you as an individual are trusting the company Apple with your security and privacy for convenience, so it becomes a personal choice.
To summarize, in order to start using cybersecurity best practices to Ghost your profile on the cloud, what traces we leave behind on the cloud is key. What OS we choose will dictate what hardware will enable us to better reduce our footprint and thus Ghost ourselves on the cloud. This is a gradual process and not easy to accomplish at once, but rather in simple small steps.
-
 @ bc52210b:20bfc6de
2023-06-09 15:00:24
@ bc52210b:20bfc6de
2023-06-09 15:00:24Centralized Finance (CeFi) exchanges — act as intermediaries to manage the crypto transactions and activities of users.
Decentralized Finance (DeFi) exchanges — which eliminates the need for the custodianship of assets — allows blockchain technology to take over and users having the authority to manage their transactions and activities directly on-chain.
KYC or ‘Know your customer’ is a regulation imposed by jurisdictions that has been historically initiated by the residents/citizens of the related jurisdiction.
Any businesses investing or operating while requiring access to capital markets needs to establish some kind of banking relationship; CeFi and DeFi are no different.
These rules are imposed worldwide and are geared towards ensuring that businesses, and now DeFi protocols, act as money exchange and/or transmitters that obtain ‘suitable’ information on every customer they serve.
This makes it trivial for chain surveillance firms to be used by companies and governments to potentially:
- Track spending habits:
- Prevent individuals and now even artificial intelligence (AI) from using other regulated services
- Confiscate crypto and digital assets
- Come after any centralized entity or representative for tax liabilities
- Generally, know more about these entities and individuals than necessary
What Information Needs to be Provided?
To buy a crypto or digital asset from a KYC CeFi or DeFi, users/entities and even AI will need to provide individual user/entity information. How much information is needed will vary from one jurisdiction to the next, some jurisdictions may require a simple name (e-mail) for small amounts (you could easily supply an alias) while others may require more detailed information. Most will ask for any combination of the following:
- Name
- Address
- Phone number
- Driver’s license
- Government ID
- A selfie holding a piece of paper with the name of the exchange and the date
- A video call with the exchange
Addressing KYC in CeFi is a Nontrivial Task
It’s a nontrivial task because it’s basically mimicking the existing legacy centralized financial KYC infrastructure being used worldwide. Also given the nature of being centralized or having an entity that can be summoned or be enforced to comply, makes it nontrivial since the main players are recognizable.
Addressing KYC in DeFi is a Consequential and Challenging Task
Consequential because it brings:
- Extreme resource costs to companies and governments trying to comply and to enforce it
- Misinformation and abuse by the same entities that are trying to provide control over its citizens and users including AI
Challenging because of:
- The decentralized nature of the protocols / infrastructure
- Trust minimization characteristics
- Its design to provide censorship resistance features
- The pseudonymity as a feature (not a bug) as part of the protocol
- It is open source & open collaboration as core to most projects
To address these basic secondary results and challenges we must first understand the OSI model as a point of reference.
OSI Model
The Open Systems Interconnection model (OSI model) is a conceptual model that characterizes and standardizes the communication functions of a telecommunication or computing system without regard to its underlying internal structure and technology. Its goal is the interoperability of diverse communication systems with standard communication protocols; the OSI model draft was published by the ISO in 1980.
Just like the OSI model standardizes the communication model, there should be a model that standardizes the different blockchains and Decentralized Ledger Technologies (DLT)s interoperability.
Blockchain and DLTs as Infrastructure
The initial infrastructure compared to Internet’s TCP/IP
Application layer that provides rails for industry applications
Similar to the OSI model application layer 7 i.e., SMTP, DNS, HTTP, etc.
Internet of Value and Where Would KYC Apply?
On layer 1 Store of Value (1), KYC would not be applicable simply because it would destroy fungibility and remove its value proposition. KYC could be introduced in the upper layers and basically become a central bank digital currency (CBDC) or a fiat token type of design.
“Institutional DeFi” it’s a new name for CeFi even though still governed by decentralized consensus.
“Institutional DeFi” platforms will add a whitelisting layer onto its smart contracts to ensure that only “institutions, corporates, and FinTechs” that have passed platforms 3rd party compliance procedures “Know Your Customer verification” can access the “Institutional DeFi” platform. 3rd party centralized systems will also be tasked with implementing Anti-Money Laundering and anti-fraud controls for these “Institutional DeFi”.
“Institutional DeFi” or CeFi solutions will provide:
- Certified audited smart contracts and a layer of whitelisting so that only KYC participants can access the “Institutional DeFi” services
- Only approved digital assets will be provided by the “Institutional DeFi” based on demand
- “Institutional DeFi” participants will be vetted institutions by 3rd party that provides KYC and compliance on them
- Perform compliance and anti-fraud controls on “Institutional DeFi” by these 3rd party
Conclusion
In the coming years KYC will go through different iterations and tests for several CeFi and especially DeFi platforms and protocols in different jurisdictions globally. Each jurisdiction will have to use “OSI model” type standards that characterizes and standardizes the communication functions or value transfer of information between participants on its respective platforms, without regard to its underlying internal decentralized structure and innovation. Its goal is the interoperability of diverse decentralized value transfer systems/protocols using industry standard value transfer protocols. If KYC is applied to any Layer 1, 2 or 3 DeFi infrastructure, by definition it can no longer be called Decentralized Finance (DeFi) exchanges.
-
 @ bc52210b:20bfc6de
2023-06-09 14:54:25
@ bc52210b:20bfc6de
2023-06-09 14:54:25Let's imagine a white label SDKapp that each local bank and financial institution brands on it including the local government brand
Resident/user opens up their preferred app from their chosen institution wallet branded app.
They create and backup of their 12 or 24 word passphrase for backup and security enable pin and bio fingerprint etc.
Establish API connectivity to their local institution and provide proper KYC for AML purposes and compliance.
Transfer Fiat currency to their account based wallet via API to initiate a swap/transfer to the country local CBDC, lets say Curacao digital Guilder CBDC.
So now you have say, 100 digital CBDC guilders (lets call this the dCURC) balance, you then decide to go to the local supermarket to get some “wine” so you spend let say 25.00 dCURC at local supermarket (basic functionality.)
Now you add say #BTC token or wrappedBTC etc. so your balance is now 25.00 BTC and 50.00 dCURC basically multiple fiat currency and crypto currencies in the same wallet branded by your local Bank.
Now you decide to purchase say $25.00 USDC a US jurisdictional based stable coin. You acquire at an exchange after KYC for AML use that $25.00 USDC stable coin.
Then you purchase at Amazon or pay for rent of your son/daughter room and board living in the US or the EU with this stable coin that confirms within minutes of transfer form your branded wallet app provided your local bank.
The Curaçao government will be able to receive reporting on these transactions in real time for their accurate tax initiatives and the banks will be able to comply with regulators in real time too.
No need for expensive data centers luxurious water falls in central banks with fortified walls to secure some unknown physical asset like Gold/fiat guilder etc. Only security needed is private multisig private keys geographically (jurisdictional based) securely stored on a decentralized cloud infrastructure on HSM enclaves.
By the way.
This setup architecture applies, and is feasible for individual, entrepreneurs and organizational not only the elite government bloated bureaucrats with old fiat currency, but to the regular individual on the road can also achieve sovereign individual status.
The only part that is required for the legacy financial institution to participate is open banking or API based functionality.
Just look at what is happening in Venezuela.
-
 @ bc52210b:20bfc6de
2023-06-09 14:52:49
@ bc52210b:20bfc6de
2023-06-09 14:52:49In order to enter the next phase in Financial technical innovation and to become competitive on the world stage, the Caribbean first needs to recognize how behind it is in terms of financial innovation.
Traditionally, most financial institutions have an innovation time horizon or innovation maintenance/migration/replacement schedule of about 10 years. This has been the case for decades when IT infrastructure was being innovated in a semi-linear fashion. In the last 20 years however, the Caribbean has lacked the amount of innovation and developments that have been growing exponentially elsewhere around the globe, far exceeding this time horizon.
Given this exponential innovation change, the use of APIs allow financial institutions to enable third-party developers to build applications and services. This will also provide greater financial transparency options for account holders by using open-source technology.
An example for the Caribbean region if innovation is widely embraced:
A financial entrepreneur develops a mobile application that allows users to invest in securities and other financial instruments, free from commission fees. This mobile app interacts via an API to other local or regional financial brokerages that also interact using APIs.
The customer using the mobile app performs the following transaction:
- Initiates a transaction using the mobile app which is sent to the local or regional financial brokerages who are competing for the best price using APIs creating an open, transparent, and regulated market. They also interact with financial banks via API for real-time information to potentially initiate liquidity discovery to execute transactions.
- A transaction is sent to list members at a Securities Exchange, one of many international exchanges for the listing and trading in both domestic and international securities, or directly to the Securities Exchange, that uses APIs for its innovative interaction members, list advisors, and brokers.
These financial banks provide regulatory information to the country’s central bank also via API. All of this can happen in real-time using this mobile app.
This one company brings the following benefits to the country that it provide services to among others:
- Employ local/remote talent
- Provide financial services to more residents/citizens
- Become competitive on the global stage
- Improve overall GDP
- etc.
This example depicts the urgency for the Caribbean region to adopt open banking since these solutions are already in production globally.
To enter the next phase in financial technical innovation which will provide an economic incentive and boost a critically affected economic region, the Caribbean needs to recognize how behind it is when it comes to CeFi (Fintech) financial innovation.
-
 @ bc52210b:20bfc6de
2023-06-09 13:42:48
@ bc52210b:20bfc6de
2023-06-09 13:42:48Bitcoin mining, as it pertains to national security, is not well understood despite the criticality of nation states adopting mining. For example, Kazakhstan has started investing hundreds of millions of dollars in cryptocurrency mining, yet they do not allow the mining of Bitcoin. Once nation states realize the geopolitical importance of mining Bitcoin, it will become part of their national security.
This brings an uncomfortable topic to miners who will most likely be required to KYC. With stricter regulations imposed on miners, KYH could become an excellent tool for miners to provide critical national infrastructure.
If a nation state were to put $10 billion into mining equipment, such as thousands of SHA256 ASICs, they will continue to invest in the next generations of equipment to generate more hash power. These ASICs are only useful for mining Proof of Work (PoW) tokens and this equipment is only good to secure this infrastructure.
With lower interest rates and higher amounts of inflation, it is quite inevitable that secure Bitcoin holdings will be added to both national and private treasury reserves. There have already been companies turning over their cash reserves into Bitcoin such as MicroStrategy and Square.
Let that sink in for a moment: private companies moving their cash reserves into Bitcoin.
It’s only a matter of time before nation states start doing the same. This makes it more all the more apparent that nation states will have to consider the security of this infrastructure as a national priority.
These new holders will not be selling for the next foreseeable future. They are making capital investments in a special purpose asset along with equipment whose only purpose is to secure PoW infrastructure like Bitcoin.
If the price of Bitcoin goes down, they will not sell it; instead they will only continue mining and buying more until the price of Bitcoin goes up or the price of running the equipment is less than the marginal cost of electricity or energy. In some cases these entities might keep running the equipment below the marginal price of electricity because their government or nation state that owns the facility might view it as a national interest against other nations. This is simply because Bitcoin is a special, mathematically scarce asset.
Ultimately, Bitcoin and other PoW and even PoS tokens will become critical aspects of the overall national security strategy of nation states. This move will require a KYC strategy and with this comes a national and international standard like Know-Your-Hashrate (KYH) to bring transparency to the most essential service of the industry. KYH improves crypto compliance officers’ risk assessment with more detailed analyses, allows for the assessment of the reputation that mining services have, and brings trust to the miner and crypto community ecosystem. Traditional finance can finally have an open dialogue with government regulators to find common ground within the crypto sphere.
-
 @ bc52210b:20bfc6de
2023-06-09 13:40:27
@ bc52210b:20bfc6de
2023-06-09 13:40:27Recently there was a crackdown on Bitmex for not complying with regulations in the United States (Crypto Trading Platform BitMEX ‘Attempted to Evade’ US Regulations, CFTC, DOJ Charge). This type of regulatory crackdown is inevitable in the broader crypto ecosystem and regulators will want to know the origins of crypto assets, such as if the asset was mined from a coinbase transaction.
A coinbase transaction is the first transaction in a new block. The recipient of the coinbase transaction, the miner who mined that block, has rights to the block reward and the related transaction fees.
“A coinbase transaction is a unique type of bitcoin transaction that can only be created by a miner. This type of transaction has no inputs, and there is one created with each new block that is mined on the network. In other words, this is the transaction that rewards a miner with the block reward for their work.” — CEX.IO
Eventually regulators will want to know the origins of crypto assets and if the asset was mined by the miner who has rights to the coinbase transaction or whether it was acquired elsewhere.
This will also apply to stablecoins and wrapped crypto assets depending on the model and design being followed, the difference being that wrapped crypto assets are the equivalent of their underlying token, only with a possibly different way of governing the issuance of the token.
What is a stablecoin?
A stablecoin is a class of cryptocurrency that offers price stability and is backed by reserve assets. Most use the United States Dollar (USD) as its reserve asset. At the moment, USDT has 90% of the stablecoin market share and is backed by USD bank reserves. The 180D volatility, measured as the standard deviation of the natural log of daily returns over the past 180 days. Sample stablecoins GUSD, USDC and USDT compared to BTC (Source: Coinmetrics)
As depicted above, Bitcoin is becoming stable over time and in the future Bitcoin will become much more stable and replace USD$ and others as a stablecoin.
What is a wrapped crypto asset?
A wrapped crypto asset is effectively an IOU that is hosted on a different blockchain. A wrapped coin can include a coin such as BTC being wrapped over to another network such as the Ethereum blockchain.
For wrapped Proof-of-Work mined crypto such as BTC, regulated institutions would be willing to acquire BTC that was mined from a coinbase transaction and pay for them with a premium, as long as it complies to given jurisdiction regulation.
The reality is that it becomes very hard to regulate a wrapped crypto asset given that, at the moment, they are being wrapped and hosted on blockchains such as Ethereum which itself is also mined in a Proof-of-Work way just like BTC is.
More thought experiments should be done to help understand the complexity of stablecoins and wrapped crypto assets and the challenges they bring when trying to regulate them along with how they should be regulated.
-
 @ bc52210b:20bfc6de
2023-06-09 13:33:14
@ bc52210b:20bfc6de
2023-06-09 13:33:14Given the economic environment we are and where yield-starved banks and savers like previously wary endowments, pension funds, and brokerages finally turn into crypto buyers, crypto prices will rise exponentially.
The traditional financial legacy institutions. Have trillions of dollars at stake and they are some of the most conservative investors and have privacy as a top priority.
But these investor’s investments are expected to provide dramatically lower returns going forward than they have in the past.
The following have forever changed the investment landscape
- Aging population
- Lower interest rates
- Still-felt effects of the Great recession
- Privacy and Transparency
The balance between privacy, transparency and regulatory compliance is increasing, and to understand this we need to look at their definitions.
Privacy is the ability and right for individuals to safeguards and protect their financial information, to keep secure and private and to opt out of any information-sharing.
Transparency is the extent to which investors have ready access to required financial information, about a company, such as access and proper disclosure of financial information and fees.
Regulatory Compliance is the ability to act according to an order, set of rules or request issued by a private or public body with the necessary authority to supervise compliance.
As you can see based on the definitions, reaching a balance between these could be a challenge.
In terms of privacy vs transparency, on one hand the general public needs to know that their personal information is safe and secure; on the other hand institutions and governments operate and make decisions, so access to relevant information should not be withheld unjustifiably.
In order to provide fairness, citizens, in a regulated region, will demand fairness and good sound services from their jurisdictions. A fair system should maintain a reasonable balance between the need to give prospective users the details they require to make an informed decision, and protecting them from invasions of privacy and possibly exploit and financial harm. This is where Zero-Knowledge proofs come in, used to verify information without sharing or revealing the underlying data and where the originator or owner of this data has total control.
Creating a stable monetary financial instrument is one of the seven characteristics sound money should have. And a more important characteristic is its fungibility or uniform. This can only be maintained by a privacy preserving protocol such as a Zero-Knowledge digital asset.
This will give regulators the ability to incorporate Anti-Money Laundering (AML) compliance using Zero-Knowledge proofs and maintain financial instrument stability and fungibility characteristics, and at the same time have a balance between privacy, transparency and regulatory compliance. This is not an easy challenge to solve, but with the proper privacy preserving DeFi protocol, that might become a reality.
-
 @ a715bcd1:318d6e6c
2023-06-09 13:31:25
@ a715bcd1:318d6e6c
2023-06-09 13:31:25
Among the crowds at the Bitcoin 2023 conference in Miami last week were pockets of Ethereum developers, drawn to the world's biggest and oldest cryptocurrency by Ordinals.
Several developers with roots in Web3 attended Bitcoin 2023 because of Ordinals, the protocol launched earlier this year that’s taken Bitcoin by storm—sparking a wave of innovation, hype, and experimentation.
OrdinalSafe, a self-custodial Bitcoin wallet built for Ordinals, was among the startups present with Ethereum in its veins. The majority of its development team has experience working with the second-largest token by market capitalization.
The startup participated in Bitcoin 2023’s “Pitch Day,” and it ultimately won second place in the competition’s infrastructure category. The endeavor was a notable achievement and memorable experience, said OrdinalSafe CEO Esad Yusuf Atik.
“It's your first time on that stage, and you're trying to sell the vision of your product to other people, so you want to do a good job,” he said. “I was really nervous, but going to the stage for the prize, it felt great.”
Atik, a 22-year-old developer from Turkey, first caught the Web3 bug when he attended a hackathon in 2020. He, along with a couple of other members from the OrdinalSafe team, previously developed a protocol called Proof of Innocence under the firm Chainway.
Built for Tornado Cash—an Ethereum coin mixer sanctioned by the U.S. last summer—Proof of Innocence is designed to help users prove they didn’t deposit funds into the privacy tool from a sanctioned wallet address.
The project “got really good attention,” Atik said, adding he and developers that worked on the protocol recently got to meet Ethereum co-founder Vitalik Buterin in Montenegro. He added that Buterin talked about Proof of Innocence on stage at the Community Ethereum Development Conference.
But, in February, Atik learned about Ordinals on Twitter and became transfixed. So, he and his fellow developers dove head-first into creating OrdinalSafe, ultimately leading the crew to Miami.
 Udi Wertheimer dressed as a Wizard at Bitcoin 2023. Image: André Beganski/Decrypt
Udi Wertheimer dressed as a Wizard at Bitcoin 2023. Image: André Beganski/DecryptOrdinals: A Tale of Wizards and Maxis
Not all Bitcoiners see value in Ethereum—or any other coin, for that matter. At Bitcoin 2023, a few vocal conference-goers booed BitMEX founder Arthur Hayes on stage when he told author Michael Lewis he “absolutely” owns Ethereum and other tokens.
“Come on, guys. Y’all know you trade some PepeCoin,” Hayes said in response to the boos, referring to Ethereum’s amphibious meme coin du jour. “Don’t sit here like that.”
Along similar lines, a company called LayerTwo Labs invited attendees to smash piñatas resembling Ethereum, Solana, and Shiba Inu symbols at its booth. People urged Bitcoiners to “smash a shitcoin” like carnival barkers.
But despite any sense of BTC superiority permeating the air at Bitcoin 2023, Atik said that the conference’s crowd was welcoming.
“Even though we came from an Ethereum background, it felt like home,” Atik said. “If you're developing on Bitcoin, you're part of the community, right?”
Whether Ordinals itself is accepted by the Bitcoin community is entirely up for debate—as evidenced by tension on stage during “The Great Ordinal Debate.”
The conversation touched on whether Ordinals could be considered an attack on Bitcoin, as some critics say. Their argument: Experimental BRC-20 tokens, built using Ordinals, have put an enormous strain on Bitcoin’s network and driven up transaction fees. BRC-20 tokens, pioneered in March, are fungible tokens that exist on Bitcoin—comparable to ERC-20 tokens on Ethereum, like PepeCoin.
There was also discussion about projects that could potentially be built on Bitcoin using Ordinals, like a decentralized exchange. Matt Corallo, an Open Source Engineer at Spiral, expressed concerns during the panel that new innovations with Ordinals could push Bitcoin miners more toward MEV to stay competitive and introduce centralization or censorship issues if not managed effectively.
MEV, or maximal extractable value, refers to the value that miners or validators can derive from changing the sequence of transactions in a block as it’s being added to the ledger. While developers on Ethereum and other chains have spent years figuring out how to mitigate MEV’s negative aspects, it’s potentially a new hurdle for crypto’s oldest coin, said Corallo.
“The Ethereum space has spent a lot of time doing this,” Corallo said, in terms of addressing MEV. “We do need to learn from that world, in so far as we’re building protocols that start to look more like that world. We absolutely do.”
Udi Wertheimer of Bitcoin Wizards said it’s noteworthy that well-established Web3 tech and concepts have worked their way into Bitcoin-related dialogue, contrasting it with events held by Bitcoin Magazine in years past.
“This year, we’re on [...] the main stage of Bitcoin Magazine talking about rollups, we’re talking about MEV, we’re talking about decentralized exchanges on Bitcoin,” Wertheimer said. “I don’t have the answers [...] but I think the culture is getting there.”

Overcoming a Learning Curve
Before Bitcoin 2023, OrdinalSafe didn’t have any investors. But after the team’s performance during Pitch Day, it’s already got significant commitments from investors, CEO Atik said.
But the OrdinalSafe team was not the only group represented by developers with an Ethereum background, using Ordinals to find their footing in the Bitcoin community.
Eril Ezerel is the founder of Subjective Labs. His team of crypto-natives has been building BestinSlot.xyz, an Ordinals explorer that lets people track inscriptions, NFT-like assets on Bitcoin, as well as BRC-20 tokens.
The service currently tracks over 1,100 Ordinals collections, with names like Bitcoin Frogs, DogePunks, and BTC Virus. It also collects data on the more than 28,000 BRC-20 tokens.
Ezerel described Ordinals as a horn—now that it’s been blown, people are coming back to crypto’s oldest coin en masse. A lot of people in his project’s Discord server are approaching Bitcoin with limited knowledge of how to use the network, he said, but they’re still passionate about the prospect of digital art and collectibles.
“All day in Discord, we're dealing with NFT degens from Solana and Ethereum,” Ezerel said. There’s been a bit of a learning curve, he said: Lots of people have been asking for help buying Bitcoin inscriptions.
Ordinals is in its infancy, and where the protocol goes is anybody’s guess, as people from throughout Web3 enter the Bitcoin fold. And even if Ordinals has its critics, many approve of the experimentation, Ezerel said.
He put forth the idea that Bitcoin miners are on board with Ordinals because of the increased transaction fees they receive for validating transactions. There are also major developers and Bitcoin owners that are supportive of the protocol, he noted.
“Everybody's excited about it,” Ezerel said. “The Bitcoin maxi stuff, it's mostly in our heads.”
Original link: Ordinals Is Drawing Former Ethereum Devs to Build on Bitcoin original author: André Beganski
-
 @ 4ac847f3:16dc6c5a
2023-06-09 13:27:34
@ 4ac847f3:16dc6c5a
2023-06-09 13:27:34Desafios enfrentados pelas plataformas de mídia social na luta contra a exploração sexual infantil
Tecnologia #instagram #Noticias
https://open.substack.com/pub/technewsbr/p/desafios-enfrentados-pelas-plataformas?r=1zp81j&utm_campaign=post&utm_medium=web
-
 @ bc52210b:20bfc6de
2023-06-09 13:20:53
@ bc52210b:20bfc6de
2023-06-09 13:20:53It all depends on the implementation.
Some challenges and risks that arise are consumer protection, privacy, taxation, cybersecurity, money laundering, terrorism financing, market integrity, governance and legal certainty, and if implemented correctly CBDC permissioned blockchain addresses these in a more efficient way.
The ultimate goal is to bring:
- Monetary sovereignty
- Monetary policy
- Safety and Efficiency of Payment Systems
- Financial stability
- Fair competition
Requirements:
- In order for Central banks to maintain levels of compliance imposed by regulatory jurisdictions and to avoid being de-risked AML financing of terrorism (CFT) compliance procedures need to be in place
- Reducing the amount of information visible to parties that are not involved in the transactions
- Users’ ability to access or spend CBDC balances when the intermediary is unavailable
- Applying mechanisms such as rotating public keys, zero-knowledge proofs and enclave computing.
The solution needs to keep user identities and transaction histories anonymous i.e. neither the central bank nor intermediaries other than those chosen by the user should see the data.
Each country depending on their jurisdiction might have to abide by regulation like: The General Data Protection Regulation (EU) (GDPR)
These are some points that bring out the reason central banks will be cautions in moving forward and continue evaluating options on how to implement it in a conservative way.
-
 @ bc52210b:20bfc6de
2023-06-09 13:09:43
@ bc52210b:20bfc6de
2023-06-09 13:09:43Why CBDC: Digital Payments?
* Tax payment and transaction data can be automatically paid to the tax authority * Merchant can immediately receive payment in their digital account * Data records about transactions are automatically submitted to the merchant’s bank, customer’s bank
Being in the 21st century the only part of the Internet that has not caught up with innovation is the ability for individuals and entities to exchange payments for goods and services without a 3rd party and this problem has now been solved by the Bitcoin blockchain. Now digital distributed payments can be implemented in more cost effective, secure, and innovative way that was not possible before.
Governments around the world are trying to improve their services and provide more attractive environments to do business.
Smart POS
Provide the following benefits: * Direct Tax Collection * Direct Reporting to Central Bank * Direct reporting to Treasury * Multiple Settlement per Transaction * Credit/Debit Card MSR, IC Readers * Real-time sales monitoring & data centralization * All-in-One POS Terminal, QR-code, scanner; NFC * Customizable * Portable * Camera / Scanner Fingerprint
Digital Settlement Payments Benefits
Digital Settlement Payments provide significant benefits to the economy in the following way:
* Free Movement of Capital
Free movement of capital is to say that individuals should have the freedom to move their capital beyond borders with least amount of friction and “red-tape” while abiding to regulation and local and regional laws. * Reduced Transaction Costs
Costs can be reduced by using more secure innovative ways of providing the transfer of transactions between individuals and organizations in real-time. * Faster and Convenient Transfers
Users will benefit of innovative ways to safeguard transactions while making them safe, secure and more private plus provide convenient ways to manage their assets and money. * Improved Revenue Government Administration
This innovation will bring improved revenue administration systems for the Government in relations to the enforcement of systems that the Government relies upon for tax collection and in particular more data sets to analyze and better guide evidence-based policy making. * Reduction in Legacy Cash Usage
Given the fact that most governments around the world are trying to mitigate and eliminate money laundering by reducing and even terminating legacy cash usage and also the enhancement of AML/CFT to improve correspondent banking relationships, legacy cash usage has been at the forefront. CBDC provides a path forward to address the above. * Digital (Decentralized) Finance Network Effect (DeFi)
Another benefit is the introduction of “Smart Money” or the ability to provide logic to transaction in real-time as they are executed. And these transactions are not reserved for money transactions but any financial transaction. Defi brings a reduction in bureaucracy and a huge increase in trust-minimized software. Even though Fintech will still be at the initial phase of deployment given the proprietary aspects, with time it will better prepare societies to embrace this inevitable change. * Improved Financial Inclusion
According to the World Bank, nearly 2 billion people worldwide are unbanked. With the current centralized, bureaucratic and inefficient banking system the unbanked will stay unbanked. CBDC will bring more citizens and residents to become banked and be able to use more financial tools and services that have until now benefited only a privileged few.
Why Blockchain?
- Persistent Immutability
Having records and data decentralized and deployed on a blockchain, makes it virtually impossible for any one party to tamper with data or records.
- Security
To get the full picture, hackers will need to hack not just the current block in the blockchain or distributed ledger, but also every block before it. This is not only technically almost impossible, but it is costly, thereby reducing the incentive for malicious activities.
- Redundancy (DLT) Distributed Ledger Technology
DLT is basically a synchronized and shared trusted, via consensus, database that is distributed across multiple sites, institutions and geographies.
- Overhead/Cost Reduction with the use of Smart Contracts or Programmable money with distributed consensus
Given the feature of being “programmable money” it eliminates costs by removing manual human intervention bringing speed and efficiency to transaction and at the same time improving security and privacy.
- Transparency/Accountability (Censorship resistant)
A duty of transparency for public officials, civil servants, managers and directors of companies and organizations and board trustees should be demanded by stockholders. It is imperative that public officials, civil servants, managers and directors of companies and organizations and board trustees are accountable for their actions and that there will be consequences when duties and commitments are not met. Depending on the DLT implementation (permissionless or permissioned) this can be accomplished and enforced in a highly efficient way.
Permissionless & Permissioned Blockchain
- Permissionless no 3rd party characteristics
Censor resistance (no oppression), Immutability (no fraud), Accountability (no cheating), Transparency (no lies), Openness (no barriers), Global (no borders), Trust-less (no laws only laws of mathematics), Deflation (no inflation, scarcity), Decentralization (no centralization)
- Permissioned federation
Censor resistance (outside the federation), Immutability (no fraud, only as strong as federation), Accountability (regulated federation), Transparency (provided by federation), Openness (permitted by federation), Global (stipulated by federation), Civilian Rule of Law, Inflationary, Centralized (Complete Central Control)
CBDC Migration Path
First Step
Replace SWIFT with Central Bank Digital Currency (CBDC). SWIFT is The Society for Worldwide Interbank Financial Telecommunication and provides a network that enables financial institutions worldwide to send and receive information about financial transactions in a secure, standardized and reliable environment, founded in 1973. This system is archaic and behind the times. Some approaches called real-time payment (RTP) schemes are being implemented, but these systems still require centralized managed databases requiring similar resources as we have today.
Second Step
Update/replace the automated clearing house (ACH) transaction batch system, real-time gross settlement (RTGS) transfer systems where the transfer of money takes place from one bank to any other bank on a “real time” meaning payment transactions being settled as soon as they are processed which could take hours or days. Single Euro Payments Area (SEPA) is a payment-integration initiative of the European Union for simplification of bank transfers denominated in euro similar to ACH. Again these systems have been around for years and reflect a 25 year old technology or batching and innovation of the 1990s. The idea is to replace or augment it with CBDC distributed ledger technology.
Third Step
Hand over responsibility to distribute this new CBDC fiat currency to commercial banks or Digital Cash Account Providers (DCAP). Central banks will be responsible and have control of issuing CBDC and cash and distributing it to commercial banks including providing white-label standard guidance for commercial banks to use, and finally commercial banks will have the responsibility of applying the standards and protocols provided by the central bank and to distribute the new CBDC and cash. Basically the wholesale retail ecosystem form of fiat national digital currency.
Example
Where this Innovation is Moving is basically a Central Bank Digital Currency (CBDC), “Stable Coins” for the nation state.
In Latin America, a catalyst would be Libra, positioned with its 2.4bn active users is a main catalyst and incentive for financial institutions specially the central banks to provide the regulated and controlled digital fiat Libra is providing due to market demand that the central banks are not providing.
Finally, CBDC would have to force legal tender status. This would drive interoperability where fragmented electronic payment methods coexist each with their own digital IOUs backed simply by a promise to pay.
To conclude Digital Currencies in Central Banking has become the “Sputnik” moment as it was in the 1960 space race. Central banks are now realizing the crucial role they have with their main tasks as central banks but with an innovative way to serve their stakeholders in a global competitive way.
- Conduct monetary policy in an innovative globally competitive way
- Supervise banking and credit institutions with a less bureaucratic process using technology to reduce cost and increase speed of execution
- Issue paper money (cash) and CBDC as legal tender for national use
- Manage the foreign exchange reserves using new innovative DLT like Digital Settlement Networks or Stable Coins pegged to global reserve currencies like the US dollar
- Act as the government’s treasurer by receiving and making payments from and to the public; using DLT and CBDC innovations
- Advise the governments on financial and economic matters, including standards and protocols being used globally in relation to CBDC and DLTs.
Government Leaders will be the only ones to take advantage of this historic opportunity just like the Internet did for global communication. If not, whole nations will be left behind in this exponentially changing global landscape.
Sources Used: * Wikipedia https://www.wikipedia.org/ * World Bank https://www.worldbank.org/en/topic/financialinclusion/brief/achieving-universal-financial-access-by-2020 * Bloomberg https://www.bloomberg.com/graphics/2019-facebook-libra-world-banking/
-
 @ bc52210b:20bfc6de
2023-06-09 12:35:34
@ bc52210b:20bfc6de
2023-06-09 12:35:34Transaction fees are like paying for checking in your bags on an airline flight and paying for, say $50.00 per bags.
Example $50.00/bag is like 186 satoshis/Byte
So if you are traveling with 4 bags you would have to pay $200.00 in bag fee charges.
Or if your BTC transaction is 223 Bytes in size you would have to pay 41,478 satoshis, which estimates to $5.39 in transaction fees (current Price.)
Note:
Each input will add 180 (plus or minus 1) bytes
Each output will add 34 bytes
So moral of the story when traveling keep the bags to a minimum and when BTC transacting keep your transaction size to a minimum.
You can reduce fees by increasing the number of outputs in a transaction.
So think of outputs as the recipients, like paying individual salaries or monthly services like Netflix , etc. This way you can pay to multiple recipients in one go. So one input but multiple outputs or recipients vs paying salaries as individual transactions.
For example, Alice needs to pay Bob 6 BTC. Now she has one bitcoin address A with two outputs which have 2 BTC and 8 BTC balance respectively and another one address B with one output 7 BTC balance in his bitcoin wallet. The cheapest way to send this payment is just to send from address B with one input.
-
 @ 4ac847f3:16dc6c5a
2023-06-09 11:45:19
@ 4ac847f3:16dc6c5a
2023-06-09 11:45:19Liberdade de Expressão em Tempos de Censura
Nos últimos tempos, temos testemunhado uma crescente preocupação com a privacidade e a liberdade de expressão em meio às censuras prévias vivenciadas no Brasil, envolvendo instituições como o STF, Senado, Câmara dos Deputados e até mesmo as grandes empresas de tecnologia. Nesse contexto, a rede social com protocolo Nostr tem conquistado uma alta adesão de usuários, oferecendo uma solução para preservar a privacidade e a liberdade de expressão em um ambiente seguro e livre de censura. Neste artigo, exploraremos como o Nostr se destaca como uma alternativa confiável em tempos conturbados, protegendo nossos direitos fundamentais e permitindo que vozes sejam ouvidas.
Preservando a privacidade:
Em uma era em que a coleta de dados e a violação da privacidade se tornaram uma realidade preocupante, o Nostr coloca a privacidade dos usuários como prioridade máxima. Ao contrário das grandes empresas de tecnologia, que monetizam os dados dos usuários, o Nostr adota uma abordagem transparente e não coleta informações pessoais para fins comerciais. Além disso, a rede social utiliza criptografia de ponta a ponta, garantindo que apenas os participantes da conversa possam acessar o conteúdo compartilhado, impedindo qualquer interferência indesejada.
Resistindo à censura institucional:
Nostr se destaca por seu compromisso em resistir à censura institucional, que pode vir de órgãos governamentais ou grandes empresas de tecnologia. Ao adotar um modelo descentralizado, o protocolo Nostr não permite que uma única entidade ou governo controle as informações compartilhadas na plataforma. Dessa forma, a censura prévia não pode ser imposta centralmente, permitindo que usuários expressem livremente suas opiniões e ideias, sem medo de represálias ou restrições injustas.
Proteção da liberdade de expressão:
A liberdade de expressão é um direito fundamental que deve ser preservado. Nostr permite que os usuários se expressem de maneira autêntica, sem o receio de serem silenciados. Ao adotar o anonimato e o uso de pseudônimos, o Nostr oferece uma camada adicional de proteção, permitindo que indivíduos expressem suas opiniões livremente, mesmo em ambientes em que a liberdade de expressão é suprimida. Essa abordagem permite que vozes marginalizadas e dissidentes tenham a oportunidade de serem ouvidas e de contribuírem para debates importantes.
Um ambiente governado pela comunidade:
Nostr adota um modelo de governança descentralizado, no qual os usuários têm um papel ativo nas decisões da plataforma. Por meio de comunidades autônomas, os usuários podem propor e votar em mudanças nas políticas, garantindo que a rede social seja moldada de acordo com os interesses coletivos. Esse modelo permite uma maior transparência, participação e responsabilidade, criando uma rede social mais democrática e alinhada com as necessidades e desejos dos usuários.
Conclusão:
Em tempos em que a censura prévia é uma realidade e a privacidade e a liberdade de expressão são ameaçadas, o protocolo Nostr se destaca como uma alternativa confiável para preservar nossos direitos fundamentais. Ao aderir ao Nostr, os usuários têm a oportunidade de se juntar a uma comunidade que valoriza a privacidade, a liberdade de expressão e a governança descentralizada. Com o Nostr, podemos fortalecer nossa voz e garantir um ambiente digital mais seguro, onde a diversidade de opiniões possa prosperar e onde a censura não encontre espaço para restringir nossa liberdade.
Ajude a manter conteúdo de qualidade sempre gratuito. Doe
-
 @ 0dde8796:14799cec
2023-06-09 11:29:13
@ 0dde8796:14799cec
2023-06-09 11:29:13Portrait Of The Hodler As A Young Stoner
If you were an American teenager in the 1970s, you couldn't avoid being exposed to a lot of half baked spiritualism served up with a healthy(?) dose of hallucinogens, and I was no exception. In addition to Carlos Castaneda novels and The Electric Kool-Aid Acid Test by Tom Wolfe, most of us wound up reading Zen And The Art of Motorcycle Maintenance by Robert M Pirsig. The book captured the mood of the time: We all wanted to get high and live out our Kerouac On the Road fantasies, and the self sufficient minimalism was perfect for our post Easy Rider lifestyle. That was my introduction to Buddhism.
Now, I must say I don't consider myself a card carrying Buddhist. But let's face it. A real Buddhist would never carry a card. The point is, in the end I absorbed a few truths from guys like Pirsig.
I'm sure you're wondering what the hell this has to do with Bitcoin in general, and Stacker News in particular.
Well, let me try to explain...
I Wanna Be A Whale, Now!!
I have seen many posts by beginners asking for advice on how to earn sats on this site. Some are blunt pleas, and others try to finesse it in an attempt not to appear too greedy. You might as well be honest. You want us all to throw thousands of sats at you, and preferably very quickly. Well, forget it. That ain't gonna happen. Nor should it. And that's a good thing, whether you know it yet or not.
But, I will try to help you have a long, rewarding experience here.
Just Who The Hell Do I Think I Am?
Some may wonder what makes me think I have the knowledge needed to tell anyone how to stack sats here. It's true that I'm still learning, and it's not like I'm getting rich spending what is probably way too much time wandering around this site, but I think I can help newcomers avoid my mistakes and explain what seems to work for me, an average SN stacker.
Who Can Benefit From This Article?
If you're the guy who bought 10,000 bitcoin at 8 cents each in 2010, and managed not to sell them during the many pumps of the early years, and you didn't lose your keys, and didn't get wiped out during the Mt Gox mess, and you resisted a shitcoin siren call in 2016, and you still have your stack, just stop reading. I have nothing to teach you. You are the master. I am your humble student.
And, I hate you. Go fuck yourself.
(*Jealousy and hate are not the Way of the Buddha. I am imperfect)
However, if you're new to bitcoin and just learning, Welcome!
So, what I took from my brush with Buddhism is basically to learn as much as you can about a topic, absorb it from all angles, and then forget about it when it's time to act. When you know enough, conscious thought gets in the way.
Once you are prepared, you just do. You don't think about doing.
You start by learning.
A good traveler has no fixed plans and is not intent upon arriving.– Tao Te Ching, Chapter 27
Take a breath. Explore. Read through the FAQ and Guide that you can find at the bottom of the page. Spend some time poking around the site. You will discover that there are many types of people here: beginners like yourself, people like me who have been around bitcoin for a few years but are still learning, some OG hodlers from back in the day, some bitcoin celebrities, some bitcoin core guys, and many really smart, 20 or 30 something year old coders and developers who work in the bitcoin ecosystem and are doing some amazing things. You can learn from everyone. And you should.
Alas, no one is going to throw lots of sats at you when you first get here, and, in all likelihood not for a long time.
First Steps

After getting familiar with the layout and reading some content, the next thing you should do is create an account. Choose your nym. Most people here protect their privacy, and you should too when choosing a nym, unless you want to be identified. Next, create your bio. I think this is important, since it's your opportunity to introduce yourself and tell us why you're here. By providing information in the bio you might interact with other users who have things in common with you. It's important to develop relationships with people to share advice, experiences, etc.
Keep in mind that publishing your bio is making your first post. It's free. Take advantage of it. I don't recommend short bios. The more you say about yourself, the greater the likelihood that someone will find something interesting to talk to you about. You might even get a welcome tip of a few sats.
A Word Of Caution
One caveat : This is a bitcoin site. The site is filled with bitcoin maxis. If you're at the stage where you're experimenting with other coins, or if you think there is a place for sh... um, alt coins in this world, you are entitled to your beliefs. You will find your people here too, eventually. Mentioning it in your bio, though, might not be the best move. You can bring it up later. If you ignore my advice, at best you will be ignored. At worst, you shall suffer the wrath of DarthCoin. Good luck, brave one. What doesn't kill you makes you stronger! (I don't buy that. If you live but lose a leg? Or suffer serious head trauma? Never mind)

So What About The Zen Thing?
I know it took me a while, but now we'll get down to the zen. You have a few sats from your bio post and maybe from your free second post and a few more from your five free comments. Now what?
Well. Why are you here? I hope it's because you have become obsessed with bitcoin, and you need to know more. Not want, but need. You may have gotten interested due to greed. That's understandable. Most of us did. I first got interested during the 2017 pump. Am I rich now? No. Do I have a Lambo? No. But guess what? I don't want a Lambo any more. It's meaningless to me now. I own a 20 year old Toyota. Is that all I can afford? No. I could buy a nicer car, but I'd rather stack sats.
Soon you won't care either. First, you'll learn about low time preference. Later, you'll understand what that really means.
You will stop caring about the fancy house and the car. Soon, you'll be thinking more about the mother in some poor African country trying to feed her family. Without a bank account. With decaying fiat money. You start feeling all those We Are All One vibes from bad 1970's Coca Cola commercials. Except now you know it's true.
You start donating to Alex Gladstein and Anita Posch.
But I digress. Back to business:
To receive everything, one must open one’s hands and give.” ― Taisen Deshimaru
I advise you to pretend you can't earn sats. But remember you can give sats. I would start by reading the recent posts. When you find an interesting one, tip the poster some sats. Make this a regular practice. Don't worry about making your own posts yet. By doing this, you will be learning about bitcoin. You will be supporting people who post stuff you find interesting, AND you will start earning sats. How? Well, the way SN works, you get sats for tipping top content early. Odds are, you will tip a few posts that become popular. If you liked it, others will likely like it too. By reading recent posts, you can discover good content early and earn more sats. As you learn more about bitcoin, you will be more discerning, and will tip top content early more consistently. You learn, then earn.
You will start building trust. What's that, you ask? Well Keyan Kousha, our leader and guru, is one of those wiz coders and developers I talked about earlier. He created some kind of fancy algorithm that increases your status here based on the quality of your tipping and posting. The higher your trust score, the more sats you can earn. How does it work? I have no clue. Ask him.
As your knowledge grows, start commenting on other people's posts. Ask questions. At the beginning you will have a lot of questions. Ask them. You may get lucky and one of your questions might become a top comment that earns you sats. Or maybe not. Who cares? It's very likely someone will answer your question, and you will learn.
Soon, you discover the zen of this whole thing: The less you try to earn sats, the more sats you'll earn. I discovered this the hard way myself. Early on, I would think about what posts would likely earn me sats. I would put some thought into the post, carefully craft it, and post it. Then I'd sit back and wait for my sats. Crickets. Nothing. My post would get ignored. Then, later I'd read a post and respond with a quick comment or question, pretty much spontaneously and without expectations, and I'd earn a few hundred sats. I was dumbfounded. Then it dawned on me. Genuine, real posts mattered. Honesty, like bitcoin itself, is what counts. Contrived crap, like a shitcoin, is ignored.
I think that's why ChatGPT posts are usually ignored. The writing quality might be higher than what we post, with better grammar and syntax, and perfect spelling. But, it seems fake and lifeless. I can't always put my finger on what's wrong with it, but I don't like it.
If You Build It, They Will Come
Soon you will start posting. Maybe a few links here and there. Avoid posting dupes! Also, try to keep it interesting. Everyone has seen yesterday's Bitcoin Magazine, Coin Desk, or Cointelegraph article. Don't post it again. Post what you like to read. Don't worry if it's a little off topic, so long as it's thought provoking. Of course, others may not agree. Your post might get ignored. So what? You're still learning.
You can use a little creativity for your link posts. The title can be edited. In fact, sometimes you must edit the title for length. Experiment. Make a funny headline. Maybe the mainstream media source sugar coated the content in the headline. Write what the article really means. By doing this, you bring value to a simple link post.
Next, you will create discussion posts. At first you might ask questions about something you don't understand. You can be pretty sure you'll get answers. If it's a complicated issue, you may inspire arguments and discussion. Your simple question could turn into a significant post, with lots of sats and a daily bonus. That will happen, just not when you expect it.
As you get more comfortable here, be generous. Tip new bio posts so that user has the sats to post right away, without having to fund his or her wallet. Tip new accounts who put some effort into crafting a post, whether or not it's great. You've been there. You're not so removed from being a beginner yourself. And spread the wealth. You want to help increase adoption, right? You want to promote value for value, right? Circular economy? Start right here.
In the meantime, keep learning. Run a node, try to set up a nostr relay. Listen to podcasts night and day. And read. Read every damn bitcoin book you can find. Watch old Andreas Antonopoulos lectures on YouTube. Go on Gigi's web site and read everything he's ever written. Soak up as much information about bitcoin as you can.
And always talk about it on Stacker News. You will help others on the journey. Soon the sats will be rolling in, but you won't be thinking about it. You will be too busy learning more.
*Originally Published On Stacker News 5/27/23
-
 @ 4ac847f3:16dc6c5a
2023-06-09 11:28:08
@ 4ac847f3:16dc6c5a
2023-06-09 11:28:08Introdução:
O blendOS 3 é a mais recente iteração de uma distribuição Linux imutável baseada no Arch Linux que está causando agitação na comunidade de usuários de Linux. Com uma abordagem única para atualizações do sistema e suporte para uma ampla variedade de distribuições Linux, o blendOS 3 promete oferecer uma experiência de usuário inovadora e altamente estável. Neste artigo, vamos explorar os recursos e benefícios que tornam o blendOS 3 uma opção atraente para os entusiastas de distribuições imutáveis.
Atualizações sem repositório:
Uma das principais características do blendOS 3 é a sua abordagem inovadora para atualizações do sistema. Ao contrário das distribuições tradicionais que dependem de repositórios de pacotes, o blendOS 3 adota um método exclusivo: em vez de baixar pacotes individuais, as instalações existentes são atualizadas usando a imagem ISO mais recente. Essa abordagem garante maior estabilidade ao sistema e evita problemas comuns relacionados a conflitos de dependências ou pacotes desatualizados.
Akshara: Instalação de pacotes personalizados:
O blendOS 3 introduz uma nova ferramenta chamada Akshara, que permite aos usuários instalar pacotes personalizados em uma sobreposição. Essa sobreposição é mantida e regenerada usando a nova base do sistema, garantindo que a instalação do blendOS permaneça intacta. Essa funcionalidade oferece flexibilidade aos usuários que desejam personalizar sua distribuição sem comprometer a integridade do sistema.
Suporte para múltiplas distribuições:
Uma das maiores vantagens do blendOS 3 é o seu suporte para uma variedade de distribuições Linux. Além das distribuições populares, como Fedora e Ubuntu, o blendOS 3 oferece suporte para AlmaLinux, Crystal Linux, Kali Linux e Rocky Linux como contêineres. Essa ampla seleção de distribuições permite aos usuários desfrutar dos benefícios de diferentes ambientes de trabalho, ferramentas e pacotes, tudo dentro do blendOS 3.
Tamanho de download reduzido:
O blendOS 3 também leva em consideração a preocupação com o tamanho de download durante as atualizações. Para enfrentar esse desafio, a distribuição utiliza o programa de transferência de arquivos zsync. Essa abordagem permite que apenas as alterações entre a versão anterior e a atual sejam baixadas, reduzindo significativamente o tamanho das atualizações. Isso não apenas economiza largura de banda, mas também acelera o processo de atualização para os usuários.
Assemble: Criação de pacotes e imagens personalizadas:
O blendOS 3 apresenta a ferramenta Assemble, que permite criar pacotes e imagens personalizadas. Essa funcionalidade é particularmente útil para desenvolvedores e entusiastas que desejam criar seus próprios remixes do blendOS ou adicionar suporte a diferentes ambientes de desktop e gerenciadores de janelas. Com o Assemble, a personalização do blendOS 3 é fácil e flexível.
Conclusão:
O blendOS 3 está se destacando como uma distribuição Linux imutável com recursos inovadores e suporte para várias distribuições Linux. Com atualizações sem repositório, suporte para distribuições conteinerizadas e ferramentas para personalização, o blendOS 3 oferece estabilidade, flexibilidade e um ecossistema Linux diversificado. Se você é um entusiasta de distribuições imutáveis ou está em busca de uma nova experiência no Linux, o blendOS 3 certamente merece sua atenção. Experimente-o hoje mesmo e descubra o potencial dessa distribuição única.
Ajude a manter conteúdo de qualidade sempre gratuito. Doe
-
 @ 0dde8796:14799cec
2023-06-09 11:26:18
@ 0dde8796:14799cec
2023-06-09 11:26:18
A few days ago @TNStacker posted a link to an article discussing technical analysis of bitcoin's price. I responded in a typical maxi way that said, in essence, who cares about price?
In retrospect, I was wrong.
Bitcoin's price does matter.
It is a badge of honor in the bitcoin community to say some variation of the following:
I don't care about the price of bitcoin. Price is the least interesting thing about bitcoin. 1 bitcoin = 1 bitcoin. Just about every person I look up to in the bitcoin world believes that the price of bitcoin is not that important, or at least says so publicly. I embraced this notion myself.
I no longer agree.
Price is the measure of value in our society, no matter how inaccurate, misguided or manipulated it might be at any point in time.
The US dollar is the global measure of price. This is a fact, regardless of what we say or want to believe. I have no doubt value will be measured in bitcoin at some point, but that is not the case now.
Bitcoin's price matters for many reasons. Here are a few:
Price appreciation speeds adoption
When bitcoin's price rises, it gets more attention, and becomes more widely known among no-coiners. This is true for individuals, corporations, and nations.
I'm willing to bet that virtually all of today's maxis started as NGU newbies. I know I did.
Price dumps are a mixed bag.
Price decreases spread FUD, slowing adoption and scaring off those who haven't completely digested their orange pill.
Similarly, institutions having to live in a world of quarterly reports and shareholder meetings are often prevented from buying bitcoin because of these price swings.
Price is also critical to nation state adoption. The value of a country's treasury can soar or be decimated overnight, and its citizens will find it difficult to budget for household expenses so long as extreme price volatility is commonplace.
On the other hand, price dumps allow newly converted maxis to play a little catch up to the OG hodlers.
I know that's how I felt about the past year's bear market, for which I will be forever grateful.
Price increases cause things to get cheaper in bitcoin terms Many bitcoiners are now living on a bitcoin standard. Price appreciation in US dollars makes this much easier. Bitcoiners get more goods and services for their sats, and merchants will be far more amenable to accepting bitcoin after hearing in the news about the latest "mooning."
Bitcoin's price is interesting
I don't believe the canard "price is the least interesting thing about bitcoin." It is certainly not the most interesting thing about bitcoin, but it's still interesting.
Price can reveal importance milestones on the road to hyperbitcoinization.
For example, we lately see a divergence between the price action of equities and bitcoin for the first time in a year or two. This helps gauge whether bitcoin is being perceived as a risk asset or a store of value.
Bitcoin's price can also serve as a more objective, reliable gauge of fiat inflation, rather than trusting ridiculously doctored government indexes.
Studying price action in the derivatives market can reveal market manipulation to artificially suppress the price of bitcoin, thereby repressing adoption. This "paper trading" has manipulated the gold market for half a century. Some prominent bitcoiners such as Willy Woo and Bitcoin TINA publicly changed long held beliefs about bitcoin as a result of price during this last bear market.
Price also determines market cap, which measures bitcoin's relative value compared to other assets, such as gold, US treasuries, oil, etc.
Conclusion
Bitcoin’s price has always mattered, and it will matter once we live in a bitcoin world. The US dollar has served as the world’s reserve currency for at least seventy five years, and its price has always mattered. Gold has served as a form of money for 5000 years, and its price has always mattered.
I think it's time for bitcoiners to stop virtue signalling by saying price isn't important
Originally Published on Stacker News 3/28/23
-
 @ 4ac847f3:16dc6c5a
2023-06-09 11:19:22
@ 4ac847f3:16dc6c5a
2023-06-09 11:19:221Password lança suporte para passkey em versão beta, aproximando-se do fim das senhas incômodas
passkey #1password #Tecnologia #Google #noticias
https://open.substack.com/pub/technewsbr/p/1password-lanca-suporte-para-passkey?r=1zp81j&utm_campaign=post&utm_medium=web
-
 @ 4ac847f3:16dc6c5a
2023-06-09 11:15:04
@ 4ac847f3:16dc6c5a
2023-06-09 11:15:04Mais de 400 pequenos negócios nas Filipinas estão agora aceitando pagamentos em Bitcoin
BITCOIN #Bitcoin2023 #Tecnologia #Filipinas #noticias #cripto
https://open.substack.com/pub/technewsbr/p/mais-de-400-pequenos-negocios-nas?r=1zp81j&utm_campaign=post&utm_medium=web
-
 @ 4ac847f3:16dc6c5a
2023-06-09 11:11:50
@ 4ac847f3:16dc6c5a
2023-06-09 11:11:50O Bitcoin
BITCOIN #Bitcoin2023 #criptomoedas #cripto #Tecnologia
https://open.substack.com/pub/technewsbr/p/o-bitcoin?r=1zp81j&utm_campaign=post&utm_medium=web
-
 @ 4ac847f3:16dc6c5a
2023-06-09 11:07:32
@ 4ac847f3:16dc6c5a
2023-06-09 11:07:32Apple apresenta o Vision Pro
Tecnologia #AppleVisionPro #Noticias
https://open.substack.com/pub/technewsbr/p/apple-apresenta-o-vision-pro?r=1zp81j&utm_campaign=post&utm_medium=web
-
 @ 4ac847f3:16dc6c5a
2023-06-09 11:03:25
@ 4ac847f3:16dc6c5a
2023-06-09 11:03:25Vazamento de dados de usuários de VPN gratuita em grupo do Telegram
vazamento #vpn #telegram #Tecnologia
https://open.substack.com/pub/technewsbr/p/vazamento-de-dados-de-usuarios-de?r=1zp81j&utm_campaign=post&utm_medium=web
-
 @ 4ac847f3:16dc6c5a
2023-06-09 11:00:10
@ 4ac847f3:16dc6c5a
2023-06-09 11:00:10SEC Processa Binance e Coinbase: O Impacto nas Criptomoedas e a Necessidade de Regulação
cripto #binance #Coinbase #Tecnologia #Noticias
https://open.substack.com/pub/technewsbr/p/sec-processa-binance-e-coinbase-o?r=1zp81j&utm_campaign=post&utm_medium=web
-
 @ 5ada3677:7c21c9db
2023-06-09 10:16:25
@ 5ada3677:7c21c9db
2023-06-09 10:16:25
去東京黑木晚餐,微雨的夜晚,8:30pm,於東京塔腳下,增上寺門邊。
黑木是一棟小樓,門口沒有招牌,沒有一個字,連燈火都沒有一盞,低調得吃不消。門口默默停著的黑色汽車和站立著的肅穆的司機,是唯一可以辨認的一種指標。東京有點樣子的男女,基本上不會開有顏色的車,一黑或者一白到底,是集體審美認知。



清麗的女服務生接過雨傘,拉開木門,微笑迎客入內,電梯達二樓。8:30pm,是黑木晚餐的第二輪,第一輪是6:00pm,提前預約差不多是一年時間。晚餐的兩輪,基本上都是熟客,生客大多會被安排在午餐。想從午餐客人升級為晚餐客人,這個權柄,操在女將手裡,女將管理所有的客人事務。於是,頗有些午餐客人努力取悅女將,打聽到女將喜歡食豆沙的小點心,會不失時機地送上來拍拍香甜小馬屁,等等。邊吃酒,邊聽這些花邊,真是紅塵溫暖煙火滾滾,多麼好。
 酒瓶與冰桶
酒瓶與冰桶踏入黑木二樓,一共十個板前座位,歡聲笑語,熱鬧不已,足見熟客與廚師們真的是熟。面前雪白一片,站滿六位白衣廚師和大將黑木純,背後是黑色西裝革履的侍酒師和服務生,以及一位和服女將。黑白有致,清潔感和高級感十足。
飲開胃酒,小廚師從板前伸手出來,以一柄小銀壺斟酒,銀壺夠老,光澤陰翳,這種華麗,沒有人會不享受。


 當晚食材的展示
當晚食材的展示剛放下漆器的酒盞,服務生捧來一個桐木的大盒子,打開在我面前,盒子裡是十副筷子,各種木料花紋和顏色,黑木訂製,服務生殷殷請你選一副喜歡的筷子。這是我太滿意的一個細節。
早春時候,於上海食過各種刀魚宴,昂貴不已的刀魚宴,可惜,沒有一家餐館,是用對了筷子的。上海的餐館,如今都掷重金,在豪華餐具上,卻沒有人注意到筷子才是根本。食刀魚,食三蝦麵,起碼要有一副尖頭的筷子才稱手和稱心。想過跟這些上海的餐館建議一下,想想還是止語了。
今晚在黑木終於邂逅了筷子的講究,欣慰不已。這副自選的筷子,飯後,黑木洗淨奉送客人。據說,即便是東京,如此講究筷子的日式館子,亦寥寥,而黑木已經做了七、八年了。
一個微末的細節,其實是無限的懂經,以及極致的審美。
我不是喜歡,是非常喜歡。
所謂一杯一箸,忽略了箸,怎麼說得過去?

開宴上一盞暖胃湯,芋莖吉野煮,一邊飲湯,一邊看廚師們在板前排出今晚的食材:
兩條肥滿的鱧魚,鰻魚的近親,初夏的名物; 一整條近江和牛的里脊,粉嫩,輝煌; 巨大的蠑螺,比我兩個拳頭合在一起還大,真真是螺大為美; 豪放大條的九繪魚,滋味遠勝河豚的巨無霸; 醜成一團糟的虎魚,大將黑木純講,虎魚的肉肉,是白身魚裡面,頂級美味之物,比它更美味的白身魚,不可能再有了; 一個巨幅的青花瓷碗裡,養著當令的香魚的幼魚,食指大小的小魚,活蹦亂跳; 最後還捧出一隻活生生的漂亮甲魚,白毛巾包著,乖乖出來跟食客打招呼,頗有幾位日本客人,從來沒有看見過活生生的甲魚,不知道廚師是用了什麼法寶,讓甲魚乖乖地伸長了脖子出來走秀,我好像從來沒有看見過如此可愛的甲魚小朋友。

開宴之前,黑木的板前,完全是一場浩大的食材秀,氣氛十足,高潮迭起,這種身臨其境,我在其他的日本懷石料理店裡,從來沒有遇見過,純粹的黑木流,很像羅西尼那種著名的序曲,一步一步推向輝煌高潮,推到膾炙人口流芳百世。

當晚一共12道餚饌,3道糧食,3道甜物。擇幾道寫。
鳥貝石燒,廚師活殺的鳥貝,取貝肉,略裁切。上一塊石板,滾燙的石板在你面前,貝肉擱在石板上即燙即食,鮮甜清脆無比,食材原味直出,美極了。

蠑螺的山葵餡,勝在蠑螺的巨大上,黑木純講,如此大顆的蠑螺,一輩子大概也吃不到幾次,口感奇異,湯汁鮮香無比。


蒓菜貝肉岩梨,這是墊在兩道濃口菜之間的一道清口菜,卻治得極精妙。蒓菜是當令之物,產自日本秋田,那種滑、脆、嫩、鮮、綠,完全顛覆了我對太湖蒓菜的半輩子認識,原來蒓菜是如此的口感和滋味的。小小一盞裡,貝肉切得如蒓菜一般大小,為了取得與蒓菜接近的口感,貝肉用葛粉輕輕裹了一層衣,食來兩種食材你滑我滑,一呼一應,妙不可言,並點綴兩三粒岩梨,清脆活潑,滿分,佩服。
 八寸
八寸九繪魚頭之炊,九繪魚頭的紅湯煮,魚頭食材的甜與糯,膠質豐肥,美味無比。
丸唐揚,丸就是甲魚,甲魚的唐揚,黑木純講,甲魚醃製一個鐘,然後裹粉唐揚炸,你們用手吃好了,因為又燙又有骨,手指方便些。食完,板前有一條水槽,廚師一擰水龍頭,有活水在每位客人面前流過,可以洗乾淨手指。曲水流觴的改版。

一邊食,一邊嘆賞黑木純處理食材,割和牛、切金槍魚,無不手起刀落,乾淨漂亮。特別是鱧魚,這種類似鰻魚的魚,以極其密集的刀法,將魚骨切細到感覺不出的地步。黑木純精純絕倫的刀法,於不到半米的距離內,看他行雲流水, 揮灑自如,如觀看一場頂級的外科手術,果斷、流暢、驕傲、精準、說一不二。亦讓我想起杜甫的名篇,《觀公孫大娘弟子舞劍器行》:
昔有佳人公孫氏,一舞劍器動四方。
來如雷霆收震怒,罷如江海凝清光。匠人廚師的刀工,美如劍法,一劍舞罷,真的是 天地為之久低昂 。

於黑木的晚餐,十分顛覆我對晚宴的半輩子的認知,這頓晚餐,充滿了太多的內容,遠遠超出一餐美食能夠提供的享受。這一晚,像觀賞了一場精密手術,亦像窺看了一場匠人秘技,更像是黑木純一個人演繹的莎士比亞戲劇。只要停下手中的工作,黑木純就滔滔不絕,每一道餚饌,小廚師們在客人面前佈妥之後,由黑木純當面給大家講解,他的講法很特別,通常的懷石料理店,都是由女將輕聲細語溫存細膩地在你耳邊講述,黑木純不是,他的滔滔不絕是以宏亮的聲音來去,那種自信,那種獨白,完全是哈姆雷特級別的。我的天,實在是太享受了。黑木的小廚師們,負責捧哏,不失幽默地娛樂食客,熱鬧起來像脫口秀,難怪黑木擁有大量忠心耿耿的回頭熟客。食客與廚師們之間,可以在一頓飯的時間裡,培養出濃厚的感情,這個是讓我大開眼界的一件事情。不過細想也是完全可能的事情,我們很多人,不是看一部電影,就愛煞一個明星麼?食一頓飯,為什麼不可以愛煞一位廚師呢?
 碳烤小香魚
碳烤小香魚黑木的食器,實在是,太美了。比如,盛清酒的酒瓶,冰鎮清酒的冰桶,都是絕美陶器,夠澀,夠沉靜。還注意到,有些食器,是用金修補過的,所謂金繕,跟廚師確認,果然是。金繕修補過的食器,滋味佳美,亦是第一次遇見。每一枚豆皿,每一柄調羹,都絕美,瓷器、陶器、漆器、銀器、玻璃器皿,層出不窮,無一不美,光是這些器,就足夠饗宴之稱。

餚饌之餘的糧食,三種米飯,用了兩種米。配碳烤和牛的白飯,僅僅一口,米油亮到不可置信的地步,我是捧著這口米飯,看了久久才下筷子。這個米,叫龍的瞳,一對夫妻種的,龍是丈夫的名字,瞳是妻子的名字,這種米,產量極低是不用說了,米粒比一般的米,大一倍半,怪不得那個米油亮到不可思議。另一種米,叫夢ごこち,京都的米,比較糯口,適合煮菜飯。

最後的甜物,有三種選擇,選了葛切和わらび餅,葛切是兩位師傅當場合力製作,滑潤冰涼,極其順喉。蘸料一是黑糖一是黃豆粉,這個黃豆粉,恭獻給了我當晚最後再一次的驚艷,濃郁香甜之餘,裡面立著一縷凜凜的鹹味,令滋味渾厚複雜搖曳生姿不已,廚師告訴我,是自己手治的。

食甜物的時候,跟廚師和服務生們聊天,講到東京黑木,每個禮拜六會做一次早餐,接待十位客人,很多客人是食完立刻預定下一次,通常要半年之後才能輪到。黑木早餐用的銀座仁治川的生吐司,這個吐司如今在上海也紅得不得了,日本人好奇問我,你們上海人怎麼吃這個吐司?我講,手撕,跟紅燒肉一起吃,還在手機裡找了幅照片給大家看。日本人恍然大悟,哦哦哦,看起來很好吃啊。
 金繕過的碗
金繕過的碗食完整套黑木懷石,飽不勝飽,黑木的懷石套餐,以量豐馳名。雨夜裡,所有廚師和侍酒師和服務生,送到樓下門口,我們相約再見,或東京,或上海,或南京。



以上圖,有的是我拍的,有的來自黑木官網
這個系列在這裡:
nostr:naddr1qqxnzd3cxccr2vp5x56nzvekqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqgkwaehxw309aex2mrp0yhxummnw3ezucnpdejqzrthwden5te0dehhxtnvdakqz8thwden5te0dehhxarj94c82c3wwajkcmr0wfjx2u3wdejhgqgswaehxw309ahx7um5wgh8w6twv5qkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgchgarywfmxzcmrxpkxx7nxvumhwdfhwsmnxwrnw4jh5mtxxa3hjef4wvuhs6rjd4ukvdtpwdukcursv5uxgumnvsurjmtv8a38ymmpv33kzum58468yat9qy08wumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdaksz8thwden5te0wfjkccte9ehx7um5wgh8w6tjv4jxuet59e48qqghwaehxw309aex2mrp0yh8g7rfde5hgmew0puh5qgjwaehxw309ac82unsd3jhqct89ejhxqguwaehxw309ahx7um5wghx6at5d9h8jampd3kx2apwvdhk6q3qttdrvacc0lczfg7w57t738suezmf7cye5s9xhrmyf5asylppe8dsxpqqqp65w4a5mlf
nostr:naddr1qqxnzd3cxceryveexuunvvpnqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqgkwaehxw309aex2mrp0yhxummnw3ezucnpdejqzrthwden5te0dehhxtnvdakqz8thwden5te0dehhxarj94c82c3wwajkcmr0wfjx2u3wdejhgqgswaehxw309ahx7um5wgh8w6twv5qkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgchgarywfmxzcmrxpkxx7nxvumhwdfhwsmnxwrnw4jh5mtxxa3hjef4wvuhs6rjd4ukvdtpwdukcursv5uxgumnvsurjmtv8a38ymmpv33kzum58468yat9qy08wumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdaksz8thwden5te0wfjkccte9ehx7um5wgh8w6tjv4jxuet59e48qqghwaehxw309aex2mrp0yh8g7rfde5hgmew0puh5qgjwaehxw309ac82unsd3jhqct89ejhxqguwaehxw309ahx7um5wghx6at5d9h8jampd3kx2apwvdhk6q3qttdrvacc0lczfg7w57t738suezmf7cye5s9xhrmyf5asylppe8dsxpqqqp65w86sfhf
nostr:naddr1qqxnzd3cxcenqdps8ycrsvesqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqgkwaehxw309aex2mrp0yhxummnw3ezucnpdejqzrthwden5te0dehhxtnvdakqz8thwden5te0dehhxarj94c82c3wwajkcmr0wfjx2u3wdejhgqgswaehxw309ahx7um5wgh8w6twv5qkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgchgarywfmxzcmrxpkxx7nxvumhwdfhwsmnxwrnw4jh5mtxxa3hjef4wvuhs6rjd4ukvdtpwdukcursv5uxgumnvsurjmtv8a38ymmpv33kzum58468yat9qy08wumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdaksz8thwden5te0wfjkccte9ehx7um5wgh8w6tjv4jxuet59e48qqghwaehxw309aex2mrp0yh8g7rfde5hgmew0puh5qgjwaehxw309ac82unsd3jhqct89ejhxqguwaehxw309ahx7um5wghx6at5d9h8jampd3kx2apwvdhk6q3qttdrvacc0lczfg7w57t738suezmf7cye5s9xhrmyf5asylppe8dsxpqqqp65wgjk26a
-
 @ 5ada3677:7c21c9db
2023-06-09 09:53:11
@ 5ada3677:7c21c9db
2023-06-09 09:53:11四年沒有離開上海,四年沒有親近舊書舖,這種靈魂深處的饑腸轆轆,餓成低血糖,只有自己知道。

逛神保町,全世界最大的舊書舖的集中地。很奇怪,寸土寸金的東京,空間逼仄得讓人氣促;日語在世界範疇裡,也絕對是極其微小的一個語種,使用日語的人口屈指可數。可是全世界最大的舊書舖集中地,不在倫敦不在紐約不在布宜諾斯艾利斯,居然在此城此地。這是一個重磅的奇蹟。

神保町的舊書舖,每間一點點大,書山書海後面,坐個垂垂老矣的白髮老男人鎮店,桌上一台蘋果電腦,老男人好像還懂蘋果,老男人不僅僅是老男人,老男人還是超人。八九十歲的老男人,身手靈活地爬上梯子給客人往下面搬書,真是敏捷。

舊書這個東西,最怕整理,家裡有書房的讀書人,都知道這個辛苦。神保町,或者說日本所有我逛過的舊書店,沒有一間,書整理得不到家,進門那種井井有條,是令人髮指程度的整潔,日本人的收納整理功夫,並世無兩。我想他們是一代又一代,被小空間逼出來的才華。
 孫思邈的《千金方》
孫思邈的《千金方》我是一早去等開門的熱心顧客,不過我不是唯一的熱心顧客,每間舊書店裡,都有等開門的客人,而且基本上人人會買一些走。這個很厲害。

我國每年畢業1000萬大學生,在校至少還有3000萬,一共毛估估4000萬大學生。當前在我國出版一本新書,賣掉一萬冊,作家和出版社要欣喜若狂。駭人聽聞吧?4000萬大學生是不買書也不讀書的年輕人,上大學有用嗎?真令人困惑。在東京逛書店,看他們隨隨便便一本小說,等閒就賣了60萬冊,我是真的眼熱。每年的百萬銷量的暢銷書,此起彼伏,從來不稀奇。以下還是省略4000字吧。

神保町的舊書舖,間間有特色,有歷史人文宗教哲學醫學這些的,還有軍事的、礦石書籍的、浮世繪的,什麼都有,逛起來真是扎勁。《日本兵食史》,日本軍隊的食物,作者是陸軍糧秣本廠,翻了一會兒,首先就是談錢從哪裡來,有錢才有兵糧。然後談準備什麼食物和調味品,以乾燥物品為主,其中屢屢提到準備田螺的乾,以備行軍打仗之食,非常異想天開。真是不讀不知道,一讀嚇一跳。

中國書的翻譯本,多到超出了我的想像,從《山海經》、《搜神記》、孫思邈的《千金方》、各朝代的碑帖,一直到各種紫微斗數遁甲製造,以及蔣毛周的各種傳記,樣樣都有。還有很多很多的美術類舊書舖,比如浮世繪版畫很精的原書房,二樓壁上的一些精品,贊得不得了。舊書舖有一個好,基本上都可以自己動手打開來細看,比博物館還好。翻了很多本老畫家的日記、書信集子,帶了畫的,印刷精良,畫好、字好,有趣極了。



一座城市為什麼需要舊書舖?舊書舖林立的城,至少可以標榜自己,沒有焚過書、也沒有坑過儒。



 全套遠藤周作,才550元人民幣
全套遠藤周作,才550元人民幣 200年的植物繪
200年的植物繪 謝謝天庵
謝謝天庵 賣了10萬冊的暢銷書,寫在大樓上面
賣了10萬冊的暢銷書,寫在大樓上面
這個系列在這裡
nostr:naddr1qqxnzd3cxccr2vp5x56nzvekqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqgkwaehxw309aex2mrp0yhxummnw3ezucnpdejqzrthwden5te0dehhxtnvdakqz8thwden5te0dehhxarj94c82c3wwajkcmr0wfjx2u3wdejhgqgswaehxw309ahx7um5wgh8w6twv5qkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgchgarywfmxzcmrxpkxx7nxvumhwdfhwsmnxwrnw4jh5mtxxa3hjef4wvuhs6rjd4ukvdtpwdukcursv5uxgumnvsurjmtv8a38ymmpv33kzum58468yat9qy08wumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdaksz8thwden5te0wfjkccte9ehx7um5wgh8w6tjv4jxuet59e48qqghwaehxw309aex2mrp0yh8g7rfde5hgmew0puh5qgjwaehxw309ac82unsd3jhqct89ejhxqguwaehxw309ahx7um5wghx6at5d9h8jampd3kx2apwvdhk6q3qttdrvacc0lczfg7w57t738suezmf7cye5s9xhrmyf5asylppe8dsxpqqqp65w4a5mlf
nostr:naddr1qqxnzd3cxceryveexuunvvpnqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqgkwaehxw309aex2mrp0yhxummnw3ezucnpdejqzrthwden5te0dehhxtnvdakqz8thwden5te0dehhxarj94c82c3wwajkcmr0wfjx2u3wdejhgqgswaehxw309ahx7um5wgh8w6twv5qkvamnwvaz7tmxd9k8getj9ehx7um5wgh8w6twv5hkuur4vgchgarywfmxzcmrxpkxx7nxvumhwdfhwsmnxwrnw4jh5mtxxa3hjef4wvuhs6rjd4ukvdtpwdukcursv5uxgumnvsurjmtv8a38ymmpv33kzum58468yat9qy08wumn8ghj7mn0wd68yttjv4kxz7fwdehkkmm5v9ex7tnrdaksz8thwden5te0wfjkccte9ehx7um5wgh8w6tjv4jxuet59e48qqghwaehxw309aex2mrp0yh8g7rfde5hgmew0puh5qgjwaehxw309ac82unsd3jhqct89ejhxqguwaehxw309ahx7um5wghx6at5d9h8jampd3kx2apwvdhk6q3qttdrvacc0lczfg7w57t738suezmf7cye5s9xhrmyf5asylppe8dsxpqqqp65w86sfhf
-
 @ 20986fb8:cdac21b3
2023-06-09 08:52:29
@ 20986fb8:cdac21b3
2023-06-09 08:52:29A weekly Tech update on YakiHonne.com 30th May – 5th June
YakiHonne.com is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media.
YakiHonne.com keeps updating! Try out our latest update, more fun features, and better UI/UX experience, would you like to be a TOP creator/curator on all relays?
Try YakiHonne.com Now!
Follow us for more daily features:
- Telegram: https://t.me/YakiHonne_Daily_Featured
- Twitter: @YakiHonne
- Hack-Nostr-On, Win 35,000,000 SATs NOW: https://dorahacks.io/hackathon/hack-nostr-on/detail
- Nostr pubkey:
npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
Latest updates
1 - Adapt events retrieval based on the “naddr” format in URLs (thanks to fiatjaf once again);
2 - Add Top Curators to the homepage showing current active curators;
3 - Add Top Creators to the homepage showing current active creators (based on all relays or selected relays);
4 - Adding Latest tags for users to keep track of the latest discussed topics;
5 - enhance the UI/UX articles feed within the homepage for more efficient reading (Same goes for the mobile design);
6 - Adding articles descriptions and selected keywords to the articles feed within the homepage;
7 - resize the home carousel and enhance its design;
8 - Adding the options of “all relays” to receive non-duplicated articles feed or relay-based selection;
9 - Relay-based deletion for the written articles, users have the right to keep their articles wherever they want.
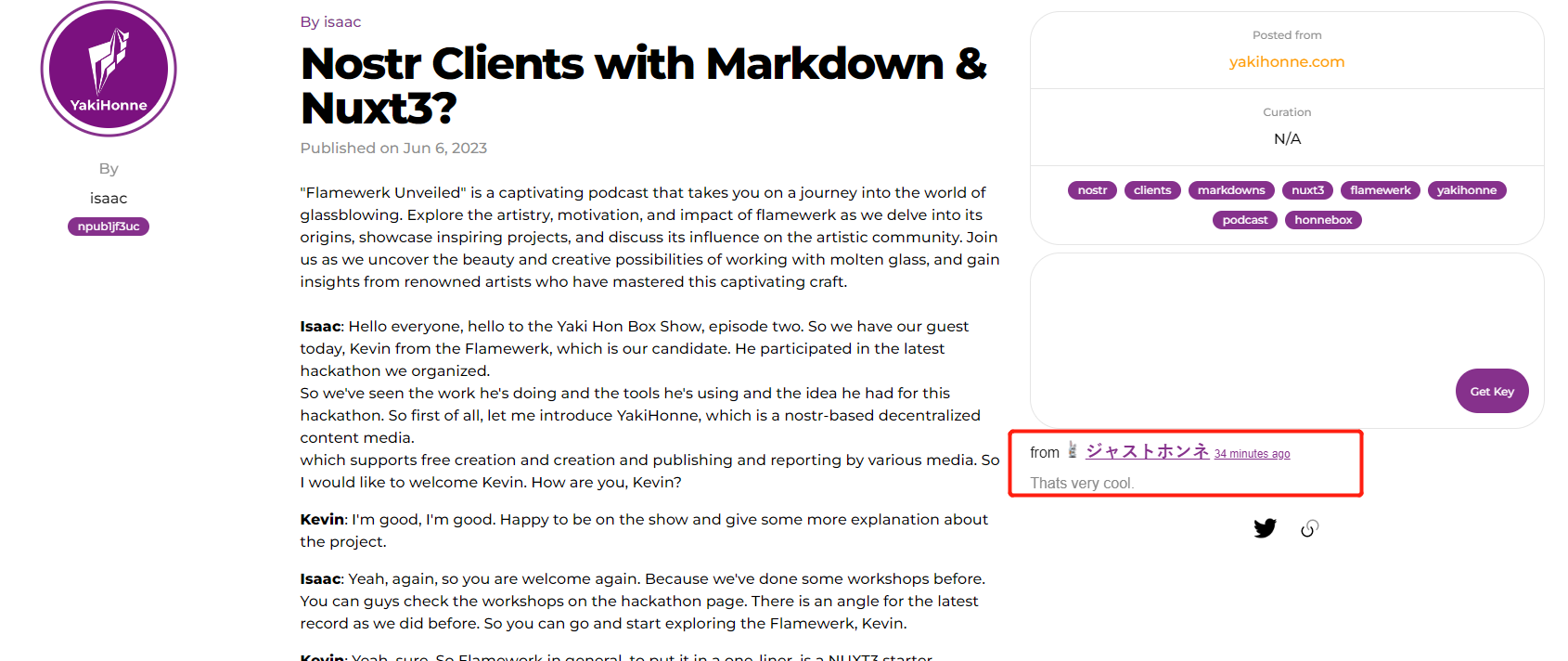
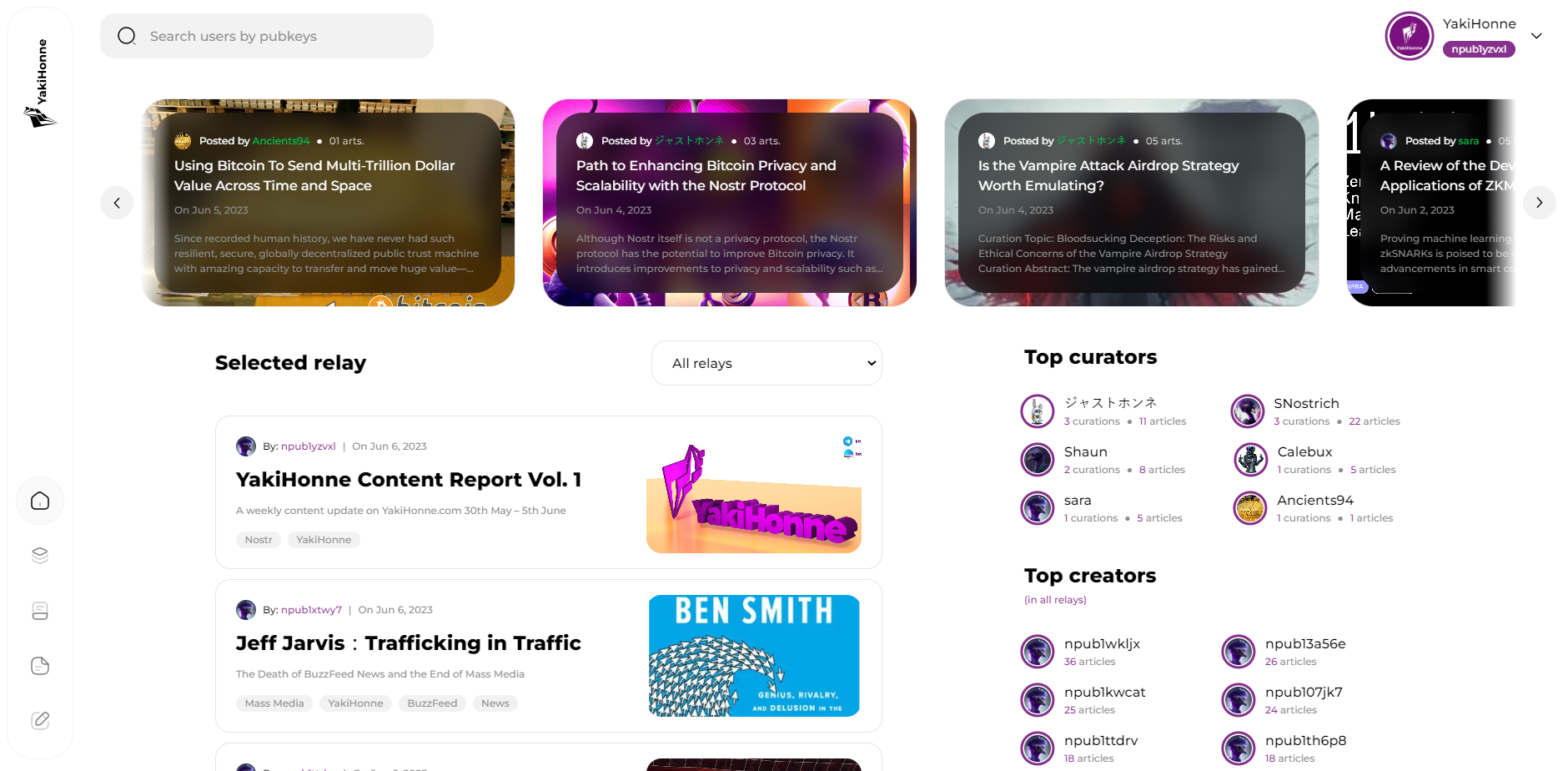
-
 @ 20986fb8:cdac21b3
2023-06-09 08:50:47
@ 20986fb8:cdac21b3
2023-06-09 08:50:47A biweekly update on YakiHonne.com 30th May – 5th June

YakiHonne.com is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media.
Follow us for more daily features:
- Telegram: https://t.me/YakiHonne_Daily_Featured
- Twitter: @YakiHonne
- Hack-Nostr-On, Win 35,000,000 SATs NOW: https://dorahacks.io/hackathon/hack-nostr-on/detail
- Nostr pubkey:
npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
🍵 Featured Articles of the Week ☕
1. THE NOSTR PRIVACY PARADOX.
“While Nostr is by no means a privacy protocol, it could bring potential improvements to Bitcoin privacy.”— By ジャストホンネ
2. The Fleeting Utopia: Navigating the Euphoria of New Digital Communities.
“Joining a new digital community can be a transformative experience. In her book "Paradise Built in Hell," Rebecca Solnit argues that when people are taken out of their familiar routines and confronted with real human needs, the best aspects of human nature come to the forefront. This disproves the negative assumption that humans are inherently selfish and demonstrates our natural ability to empathize and connect with one another. The sense of community and collaboration that we feel in emerging social spaces, patticipatory festivals such as 'Burningman', are a great example of this phenomenon.”— By rabble
3. Few Interesting Facts About Fiatjaf.
“Fiatjaf's big break came when developer Arc asked for his help hacking Pac-Man. As Arc said later, "When I was reading the protocol, I was like, 'Dude, this is like Diagon Alley,' and he said, 'That's one of the things which helped influence the creation of Nostr.”— By herald
4. Empowering Users to Verify Twitter’s Algorithmic Integrity with zkml
“A social media platform could use an open-source ML model that is agreed upon by the community and publish proofs of the model’s inference when electing to filter a post. for example , how to use zkml to verify your Twitter timeline.”— By sara
5. Zap Accounting with CLN and ledger-cli. — By jb55
6. A Proposal for Private Groups.
“An elegant approach to private groups - access control based on a shared, hosted private key, rather than cooperative relays.I think I cracked the code on private groups.”— By hodlbod
7.Bitcoin is Anarchy.
“Anarchy, contrary to misconceptions, does not promote lawlessness but rather envisions a system of communal laws that ensure equitable treatment and prevent the concentration of power in interpreting and issuing judgments. It does not advocate for disorder, but rather celebrates the emergence of spontaneous order—an intricate, decentralized system where voluntary exchanges generate value and confer benefits upon individuals. ”By MichaelMatulef
8.Trust, Financial Freedom, and the Rise of Family Banks with Bitcoin.
“Bitcoin may not provide a universal solution, but it undoubtedly offers a valuable path forward. By promoting financial autonomy and trust within families, Bitcoin empowers individuals to break free from the constraints of the traditional banking system.”— By BeOG
9.Do we need nostr?
“Nostr, at this early stage of adoption, is as if we had just moved into a new home, the other home, before the furniture arrives. A little awkward at times, but filled with hope and possibility...”— By elidy
🎙️ Weekly Featured Streaming 🎙️

Honne Boxshow EP2

📚 Weekly Curation Picks 📚
1. “Path to Enhancing Bitcoin Privacy and Scalability with the Nostr Protocol”---by ジャストホンネ
2. “Journey Into Bitcoin”---by ジャストホンネ
👨💻 Top Curators 👩💻
1. ジャストホンネ

2. [SNostrich](https://yakihonne.com/users/bcc28a27cce65ba6c54abe31efcf7917752539039e79c4f41f6c1e8bf9a8d546)

3. [Calebux](Uhttps://yakihonne.com/users/8f014c5aafb425b2fa414a49eb9ab17269f155937db67a5babe7bc40f9bbae3b)

🤩 Top Creators (All Relay) 🤩
2. scrib

YakiHonne.com is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media.
Follow us for more daily features:
- Telegram: https://t.me/YakiHonne_Daily_Featured
- Twitter: @YakiHonne
- Hack-Nostr-On, Win 35,000,000 SATs NOW: https://dorahacks.io/hackathon/hack-nostr-on/detail
- Nostr pubkey:
npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
-
 @ 20986fb8:cdac21b3
2023-06-09 08:33:29
@ 20986fb8:cdac21b3
2023-06-09 08:33:29YakiHonne.com is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media.
Yofu: Hello everyone! Welcome to the YakiHonne Workshop. Hack-Nostr-On is hosted by YakiHonne and sponsored by DoraHacks, with the aim of encouraging more ideas, applications, and problem-solving based on Nostr. YakiHonne.com is a nostr-based media protocol that supports the creation, publishing, and reporting of various topics by medias. We are honored to have developer Roadrunner (aka 42) to give a presentation. Please welcome Roadrunner!
Roadrunner: Thank you. I appreciate the opportunity. I'm from El Salvador. I'm an amateur programmer who's just learning about Nostr and trying to build their first project. It's a very cool opportunity because I feel Nostr is a very open network for beginner programmers. It's very simple technology, but it can scale very well. Part of the idea is that the code should be kept simple. It is one of the main ideas of the protocol,so it was very simple for someone like me to just start building on it, which is what I find really cool.
And I basically started building a little project that is attempting, called Roadrunner,that is attempting to create a decentralized marketplace of ride sharing, kind of like an Uber application where riders and drivers and passengers can find each other to finish rides. So, it's just trying to do the same service, but using decentralized technologies like Nostr and Lightning Payments so that you don't have to worry about, well, anyone else,it'll be completely custodian and will be peer-to-peer completely.
Today I wanted to bring this presentation to you guys to kind of talk about the basics of the technologies we're building.Through Roadrunner and through Nostr and through Lightning. Kind of a bit of the basics about Nostr.How Nostr becomes peer-to-peer,the type of content that can be stored on Nostr, who and how you can access that content,And all the types of services that you can provide using that content.
So, let's start talking about Nostr as a peer-to-peer network.Everyone's heard this term before a lot,Peer-to-peer. I think it gets thrown around a lot,so I wanted to kind of dig into it and ask the question, is Nostr really peer-to-peer?And what does that mean?
peer-to-peer technologies mean that they allow users to connect directly to each other, Without any intermediaries. So, peer-to-peer means thatI can talk directly with another peer, that I can interact directly with another peer. For example, Signal, Which is a messaging app. And in there, there is no in-between. You are sending encrypted messages from your peer to another peer, Its Technology that works directly from one person to the other, that allows that communication.
So, when we ask that question to Nostr, We run into this, into this kind of diagram,Where users are posting things onto a relay and then listening back to those posts,So, you could be posting, for example, a post to your Damus app or to your social media app or whatever, whichever app you're using,And you're also seeing other people's posts from that relay back,But if you notice, at no point is there a connection between you and other peers.
So, at face value, Nostr is not a peer-to-peer network,Because Users are never interacting with each other directly. Users always interact with the relays,All the users have arrows between the clouds, the relays and the users, but users never have arrows between each other. You are never sending a message directly to another user,And if you also notice, the relays don't talk to each other,Users can post to a lot of different relays and can listen to a lot of different relays,but they are never, but the relays don't talk to each other,Just as the users don't talk to each other.
Nostr, at a simple level, is an open network where everyone can post things to different relays,And everyone can read from those different relays. So, if I post anything to this relay, to one of these relays, anyone else in the network can access that information by telling the relay, hey, what did this person post, So, at face value,it is not a peer-to-peer network. It is an open network,So, how do we turn Nostr into a peer-to-peer network?How does this architecture allow us to turn Nostr into a peer-to-peer network? Well, this is where encryption comes in, and I've put the SHA-256 logo here onto a sun because it's kind of like the light of encryption is what allows this peer-to-peer technology to happen. So, how does this happen?
The peer-to-peer functionality comes with encrypting your messages. That means that you can post an encrypted message to a relay,and yes, it is still public, but that means that only the people who you encrypted it towards can see those messages,And that's where the peer-to-peer functionality comes in because, yes, it is an open secret,You are posting that message to a relay, which is completely public, and anyone in the network can see it, but it becomes peer-to-peer because anyone can see it, but they cannot decrypt the message,So, even the relay can't see the message. Other users, which the message is not for, cannot see the message,Only the peers who you encrypted it towards can actually see that message and interact with it. Other users who don't have those encryption keys will not be able to see your messages.They can see them, but they cannot decrypt them, so they are useless. They're just a bunch of encryption text, which they can do nothing with.
So, that's kind of why Nostr becomes a peer-to-peer network. It is not by itself a peer-to-peer network, but when you start encrypting content on it, you can use it as if it were a peer-to-peer network,You're still dealing with the intermediaries of the relays, but then the relays can't really do anything about it,Because they're just passing on encrypted information along, and they really, there isn't a very easy way of telling apart the difference between encrypted information and non-encrypted information. So, that's where relays kind of have no weapons against this.They're just, their job is only to pass the information along, and if the information is encrypted, you can get this peer-to-peer functionality.
So, let's talk a little about what type of content you can put on Nostr. At face value, Nostr is a little boring. If you just look at it from, just take one look at it, it is a little boring, because what we have here on the right is all the things that you can store on Nostr. This is the only thing that you can store on Nostr.You can create these objects,Which have an ID, a pub key, a created at, a kind, some tags, a signature, and some content. So, let's run through these.
Very importantly here, the pub key,Is the identity of who posted this object,This is an object that is getting posted to the relay, and it always needs to have a pub key,That is your, and we'll talk a little more about pub keys in a second, but that's basically just saying who posted this event,We have a created at, which is when this event was posted,We have a kind, which is what type of event this is, We have tags, which is like reference to other events or other pub keys in the relay, and then we have this ID, which is like a unique ID, just to make it easy to reference this event, and the signature, which is a cryptographic function that allows you to make sure that the pub key that is publicly set up in the object is who signed this, is actually who signed this object,So, that's a little cryptographic magic just to make sure that the object was created by who it says it was created by,Kind of a little verification, and then at the end of all that.
you can store some content,And what can you store into the content? You can store strings, and for those who've not, who aren't familiar with programming, strings is just a fancy word for text,So, strings are just a bunch of text. So, that's why I put this matrix image here, because there's just a lot of like, where you can put in words and numbers and text, but you can't do anything more than that. You can't post a picture, you can't post a video, you can't post a song,You can post text, and that's all that you can store on Nostr. It cannot store, for right now, anything else,And if you think about that, that's kind of boring,Because the internet isn't just text,The internet is videos and images and songs and audio,And so, if you can only store text, this isn't very useful.
So, how do we adapt to it? Because we already, we do want to use Nostr, because it allows peer-to-peer, how we've talked about,Like peer-to-peer encryption and communication,So, how do we adapt these boring strings to actual internet content that is fun? Well, in some cases, it's very easy, Social media, and you've already, you might have already interacted with some of these clients, like Damus and Amethyst,Which are just basically social media platforms, and these work, if you think about it, mostly off of strings,You see people's names, which are text, and you see people's posts, which are also text, and you might have counters of likes, which are also a bit of text with some static images,You don't really need to store the image of a like on Nostr,You can just keep a counter of it and say how many likes that something had. So, that is like for social media, most of the applications are very easy to handle with only text.
Then another use case are URLs and external hosts. So, for example, you can just reference your YouTube video,You post a video to YouTube, and you just share the link through Nostr,And there's a bunch of ways that you can do this, but it basically boils down to that,And it doesn't have to be YouTube, you can store this in your personal server, and there's already, for example, servers that are specializing in URLs that are very Nostr friendly, for example, so that like very small URLs that you can easily like copy and paste from a text format,One of these examples is Nostr Media Uploader, which I've seen that I've got a lot of traction lately, and this just basically allows you to upload any photo, any video, any type of audio that you want, get a URL from it, post it on your Nostr text,And then anyone who looks at that event can just go look at that image and that video from the Nostr Media Uploader, At that point, the content is not stored on Nostr, it's stored somewhere else, It's on another server, but you're just linking through it on Nostr. So that's a very easy solution,Because, however, it doesn't solve the problem of where do you store these things.Then at this point, you're still becoming dependent on storing things on YouTube, on storing pictures wherever you store them,On storing things on Nostr Media Uploader, sure, links are very useful and easy, but they're not the full solution.
Another thing you can do is serviceable data, which is kind of what we're doing with Roadrunner. And to give a small example of this, Serviceable data just means strings or text. That is actually more than just the text it's on, it's data you can use somehow. And Roadrunner uses, for example, coordinates, So we are sending coordinates through where the passenger is, or where the passenger needs to go, And making calculations through this, how the distance you need to, the driver, and giving this information to the drivers, So this is serviceable data, Yes, it is text, it's only text that's there, but it's text that a service can use, get more information, provide a service from it, and then return more information to a customer, So that's kind of what I mean by serviceable data. And coordinates are just one aspect of this, Invoicing, You can have many types of invoices, you can have orders for things, So serviceable data is basically anything that you can get more data out of, There's even, I've seen even ideas of like,for example, distributed computing,Where you put code that you want to run onto Nostr, and then other computers take that code, run it for you, and give a response back.So that's kind of like what I mean by serviceable data, You're not really interested in the text itself, you're interested in doing something with that text and providing that service to a user. And then there's a really big space of opportunity with native data storage, of actually storing data on Nostr.
Because at the end of the day, if you think about it, computer information is just text.if you go far deep enough down the hardware ladder, You can get down to zeros and ones, and very, very, very simple code to provide almost any type of content,So you could, in theory, encode, for example, a whole video, split it into its zeros and ones, or bytes, or hex bytes, or however you want to encode it, take those texts, paste them onto a Nostr event, put them up on a relay, and then whoever wants to download them, We just have to get all these events back with the data, and they would need a client that would put, parse through this data and encode it back into whatever type it is, be it a video, be it photo, be it whatever else.
I haven't seen many examples of this being done yet. I've seen some people like talking about it, but I couldn't point you to a clear example. I think it's a huge area of opportunity. You do have to be a bit technical to get into that, Because it means encoding things into text, and then re-encoding from the text, and putting it back together. So it's kind of a big technical mess, but it's there. The opportunity is there if anyone wants to take it.
Roadrunner: Probably everyone's heard the saying,not your keys, not your crypto. In Nostr, there are also people saying,not your keys, not your content, but I don't completely agree with that. And I want to get into a little bit of why. There is a bit of truth to this, because you do need your private keys to post your messages and only your private keys will reference your public key, So if you hold your private key, only you can post those messages under the public key. No one else will be able to post messages under your name for that, if you want to think about it like that. But it's not completely true. Not your relay, not your content. Now this is true. So who holds the power of the data in Nostr are the relays, because users are always posting to relays and relays decide what to do with that content. Once the user has posted something to a relay, they no longer hold control of that data. The relay holds control of that data. And I want to make this very clear with a few examples, but in very simple terms, if it's not your relay, not your content. And I will be repeating this statement a few times over the next few slides, so I hope you bear with me.
Let's talk about a bit of key pairs and identities, just to make everything very clear. To post anything on Nostr, you need a key pair. You need a private key, and that gives you a public key. Much like in all crypto systems and Bitcoin systems, you need a private key that allows you to handle your transactions, or in Nostr's case, your posts. The private key is what's used to sign and create the signatures that we saw on the data structure. And it'll also generate a public key for you. And that public key is unique to the private key. The private key can only generate one public key, and only that private key will generate that specific public key. No other private key can create the identical public key, So if you're assigning posts with your private key, you can make sure that that is your identity. And if you see a post signed by a public key, you can know with reasonable certainty that whoever holds that private key signed it.
So your key pair is your identity.Now, having said that, you can use your identity on Nostr to access any client. And that is something that's very different with the normal internet paradigm that exists right now. Right now, if I try to go to Facebook, I have to create a user on Facebook and a password on Facebook. And then if I go to Twitter, I need to create another user and another password. And then if I go to Gmail, I need to create another user and another password, And it starts becoming a little crazy. In Nostr, you don't have to do that, because your private key can be used to sign posts on Damus. And your same private key can be used to sign posts on Amethyst. And that same private key can be used to request rides on Roadrunner, There is no separation. All you need is a private key to sign and verify messages, So your one identity can be used across platforms. And that has very useful utilities.
For example, you don't have to have a hundred different users, You can have shared reputations through the platform. You can also do things like this, You can have a very professional key pair where you are offering rides to people on Roadrunner, And you have your social media profile professional on Amethyst, And you're a very professional person on that key pair. But then you have another key pair where you go on Damus and post memes all day, Because that's how you unstress out. But perhaps you don't want to be doing it on the same account. So you have two completely different key pairs, That don't have anything to do with each other. And you have two different, completely separate identities, And there's actually no way of tracking one, linking one way, unless you do it somehow. Like you actually say, like, Hey, these are my two public keys, but you can keep these two identities completely separate if that is what you choose.
But let's get into the, not your relay, not your content, Like, why do we say this? Because I have my identity,I can post however many identities I want. But if the Damus relay, and I don't, I'm not saying that they do this. I'm just using it as an example, Don't get angry at me, Damus. I'm just using you as an example. Damus, if you don't, if you post something that they don't like to their relay, they can just send it to the trash. They have no obligation to keep your post. because again, not your relay, not your content, A user published something bad about Nostr on Damus. Damus said, Hey, I don't like that. That content doesn't go on my relay. It goes to the trash. And you as a user have no way of stopping this because the relay owns the data. You are free to post however many relays you want. And eventually one of them might say, yeah, I like your data. I'll keep it and share it with other people, But if the Damus relay didn't like what you posted, they are completely free to send that information to the trash. So I want to make that very clear. I will also want to make this very clear, this other point very clear. Let's say you posted something dumb that you shouldn't have posted on Damus, an Embarrassing picture of yourself or whatever. And then you tell Damus,Hey, please, I don't want that there. Damus can very easily just tell you, no, that is now there forever, They have no obligation to delete your data either,because they own the data, not your relay, not your content,You are free to post to all the relays you want and request information from all the relays you want, but the relay owns the data.
So how do we bring balance to the situation? Because if you just told me like, Hey, relays own all the data, that doesn't sound cool. That sounds like a corporate mess, And we don't want that. So again, the light of encryption, SHA-256, which is one of the greatest technologies known to man right now, is what brings balance to this.because you can post encrypted content to the Damus relay, and then they don't know what they're sharing. So they can't really decide if they like it or not because they can't even tell what it is. And so if they don't know what you're posting, how can they decide if it's good or bad?
So if they don't know what they're posting, they're just going to say, well, this guy's posting a bunch of encrypted stuff. Let's just send it over to whoever wants to encrypt it, And it's even very hard for Damus to get in trouble for that, let's say, because how can they know that they're redoing something bad, That they're sharing something bad because they can't even decrypt the message. Only the holders of the decrypted keys can see those messages. So if you encrypt your messages, Damus doesn't know what it's sharing. And that's kind of where the balance comes in in Nostr. Sure, the relays own the data, but if that data is encrypted, that data is useless to the relays. So encrypted data is only useful to peers, Encrypted data keeps the balance of the data ownership. Sure, the relays own the data, but it's not useful to them if they cannot decrypt it. I hope that's very clear. This is where the balance of user relay comes in Nostr.
There is a big monetization aspect of this, And again, I'm not saying Damus does this, just using it as an example, But Damus can keep you out of their relay. They have no obligation to let you in. You can try and post to them, but they don't have the obligation to say,yeah, I'll take your post. It's an open network, but up to however the relays decide.And you are free to post to any other relay you want. But if you want to post to the Damus relay,you might have to accept some rules, And for example, one example that's going around right now are paid relays, So send me some Bitcoin and you can post, And that's a very simple example. I think there's a lot of opportunity here. For example, getting in by reputations on other services, there could be private relays for private groups, Where not just anyone can get in, where you actually have to be a part of an organization or a DAO or whatever. And that relay is private for these users, And no one else gets in,no matter how much money they have, That's another kind of use, But this is a very simple way of monetizing relays that's already happening, So if you go to NostrWatch,for example, which is just a list of all the Nostr relays that's out there, you'll notice that there's a bunch of free relays where anyone can post and read from. And there's a bunch of paid relays where there's some that will just ask you for an entrance fee, And you just pay once and you can post and read however many times you want. Some actually charge you per post, And there's like micro payments going on. So two sats, three sats every time you want to post. There's also a lot of anti-spam campaigns that are happening through monetization, So it costs one seat to post. So yeah, to a real user, Like who might post 500 times in a month, 500 sats doesn't sound like crazy cost to use a service, But to a spam user who is trying to post 100,000 messages per month,Now that becomes cost prohibitive.So there's a bunch of very interesting use cases here with the monetization, But the basic idea comes down to, if you have what I want, you can come in and post to my relay. If you don't,you get shut out, And that's just a very, very simple example.
Roadrunner: So let's talk about services on Nostr. How do we've been talking a lot about the user side, How a user can post and interact with relays. But let's look a little about the relay side, And what is actually a client like Nostr, like Damus, for example, doing for users. And this is where peer-to-peer, it gets a little more complicated. It's not exactly peer-to-peer, it's peer-to-relay-to-peer, And that's the type of service that Damus and other social media clients are providing. What does that mean? That means that a bunch of users are sending their information to Damus. They're sending their posts, they're sending their likes, they're sending their private messages. Damus is aggregating those, Into a feed, into checking how many likes a specific post has gotten and giving that information back to the users, So this is where peer-to-relay-to-peer comes in, You're sending information to the client and you're getting back information from that client aggregated from all the users that have been sending information, And this only works if you have a network of users, if you only have one user on Damus, well, there's not really anything to show him, You need to show him information from other users, So that's why it's not just peer-to-relay, There needs to be other peers in this for it to work, There needs to be a community of people posting so that you can see a feed, a community feed of posts, So that's why there's the relay in between. And it's the relay in between that is important because that's who aggregates all these posts, Damus is not only something that, and Damus isn't only checking one relay, Damus is actually checking a bunch of different relays. So they're aggregating information from a bunch of different relays and showing you all into one comfortable feed, So you don't have to worry about looking for all these relays. Damus actually does it for you. So there's a bunch, a network of relays that Damus accesses, And provides you all that information aggregated into a very comfortable feed and very like, you just like things and you just comment on things, And it's very easy and approachable, So this is peer-to-relay to peer services.
On Roadrunner,we're doing things a little bit different,So Roadrunner is actually, we do have that peer-to-peer part, So we have a bunch of passengers and a bunch of drivers that are sending us their information, but actually most of the service that we provide is done by autonomous key pairs. And I like, I'd like to say that I'm kind of on the front end of creating this kind of technology because I haven't seen many people talking about this kind of stuff, but basically what this means is just giving a bot or an autonomous service, You can think of it like a little robot, its own key pair, so it can do things for a user. In the Roadrunner case, I have a couple of different services, for example, creating ride details, Like the ride distance and aggregating the coordinates and creating a feed. All of that is created by an autonomous worker that then posts events back so that drivers can see. So in that case, for example, there isn't the information that a passenger sends, isn't the information that the driver receives, Because the information gets taken in by a robot, an autonomous service, And it posts back information and the driver actually sees the information from the autonomous service. The driver isn't worried about the passenger, they're worried about listening to the autonomous service, for example, another case, when you are actually offering a price on Roadrunner, you have to use a lightning invoice and we create an HTLC contract for you, which is just kind of like a time-locked contract to make it simpler for the payment transaction to go through and to allow passengers to cancel it. Well, that process is also done by another service with another key pair that all it's doing is taking in invoices from drivers, creating a contract from it and posting back the contract. And then passengers aren't actually listening directly for the driver's invoice.
They are listening to the contract that was posted by this autonomous key pair, So, the driver doesn't have to worry about listening to every single passenger out there. They just have to listen to the one autonomous key pair, And that one key pair will always be publishing these offers. It makes the tracking of services much simpler. I also have another autonomous key pair keeping track of reputations. So, every time a ride is settled, there's a little robot that goes and posts a reputation event, And these three services each have their own key. So, at the time of looking for these events, it's very easy because if I want to look for reputation events, well, I don't have to listen to the other two robots. I can just listen to the robot's reputation. And if I want to listen to the offers that I'm receiving, I just have to listen to the offer robot, And this is a very easy way to start compartmentalizing, compartmentalize, start making smaller services, And keeping things in compartments.
Let's talk about scaling, which is another word that you've probably heard a lot. Very important. What happens when you have a bunch of users all trying to do things at the same time? And you might have limited resources, I'm not Amazon. I don't have a bunch of huge servers that I'm running to keep things, to keep my services running at full, at hundreds and hundreds of giga RAMs of speed, Like, I'm not Uber. I don't have huge services across the world, I might not have the capacity to do this. So, my services get angry. They can't handle all this data, So, how do we scale this? One answer would be, well, become Uber. Just start hiring servers and just make huge computers and just make more robots, Just more, more, more, and just do it all yourself. I don't like that. And that's not how I've built the system. Roadrunner is being built, again, because it's on Nostr, because it's decentralized. It's attempting to build a decentralized network of rights. This is how Roadrunner and this is how other Nostr systems will scale.
Not by expansion, but by replication. I don't want there to be one huge Roadrunner service. I want there to be hundreds and hundreds and hundreds of different Roadrunner services, each running to their own specific needs, So, one of these Roadrunner services might be working in China and they might have very specific user verification things because they want to be compliant with laws there. And another one might be in Africa and they're using payments on something that's not lightning. They're using payments on another thing. There's so many examples, And you can tailor each one of these Roadrunner services to fit your needs, And this approach to scaling by replication is so much better than my expansion. Because if one of these, for example, just one example is if one of these goes down, you also have another bunch of options. Right now, if Uber goes down, all of Uber's customers are left without an option. You have to sign up for another service. But hey, if one of these Roadrunner services goes down, you can actually just go find another Roadrunner instance and use your same private key and find your same reputation events, Because it is a distributed system of relays, Your information can live on a bunch of different relays. And these workers, each one of these groups of workers don't have to be listening.To only one set of relays. They can be listening to two relays or three relays or four relays, You can have private relays. You can have your own private little Roadrunner that only runs kind of like a limo service, And it's only really fancy cars and it only works for really fancy people, And this is how I picture scaling on Nostr.
Not by creating one Roadrunner, but by creating hundreds of them, each tailored to their own specific needs. They will all have the same basic functionality. And in theory, you can use your same identity across all of them because all you need is to sign and verify your own messages.
I also wanted to talk a little more about the service and what we're doing. How we're integrating all of these tools into the Roadrunner platform, starting with encryption, because I think it's one of the crucial parts of this. So one of the things I've done is I've tried to encrypt as much of the user content that I can. The only part that isn't encrypted right now is the initial user coordinates, because you have to, if you're looking for a ride, you kind of have to tell drivers where you are at least approximately, So that event is, it cannot be encrypted. It does have to be a public event. You are posting like saying, hey, I'm here, Can someone pick me up? So you do kind of have to tell the world that, hey, you are here, But for example, I have created a system where that event is replaceable, So at the end of the ride, you just replace it with an empty event and no one can find those details, Because the original event gets deleted and the only event left is an empty event, So even where events aren't encrypted, I've tried to keep user data storage to a minimum, In almost every other case, for example, communication between passengers and drivers and the sending of invoices, and I'm doing a lot of things like lightning invoices, for example, all of that is encrypted and encrypted between the driver and the passenger, Or in some cases between the driver and the robot, But the same thing applies. So only the driver and only the service can see your information and no one else can see your information. So in theory, this means that you can run Roadrunner robots on any relay. It could be on the Damus relay. It can be on any other relay, This could be like an extension of relays of just having little autonomous keepers providing these services and then the Roadrunner clients don't have to depend on one single relay because the information is private for users, Like we mentioned through encryption, it is truly peer-to-peer and relays just act as the transfer of information and holding certain states which are only useful to peers.Because they are encrypted. I also am very proud of the whole autonomous keeper worker. It solved a lot of issues that I was having while building the system. And I think it needs to be explored a bit further with people that are more experienced coders because I think it has huge areas of opportunities of just having these keepers out there in the world doing things for you, And there's so many services that you can start applying this concept to. Because again, right now, especially with AI and all these technology tools that we have, there are so many crazy services that you can start providing and automating and just creating those, just giving. And all you'd be doing through Nostr is providing that automation of services to be public and transmissible. And I think that's everything I had for today. Thanks for hacking, everyone. Thanks for being here and for the opportunity to give this talk out, So thanks a lot to the group, to YakiHonne. And yeah, that's all for me. I don't know if you have any questions, any comments, anything else you'd like to discuss?
Yofu: Yeah, thanks to you too. I actually have some questions. I'm wondering first, what is your inspiration for doing this Roadrunner based on Nostr, based on Relay?
Roadrunner: I can't claim that it's completely original or anything. Like I said, I'm a very beginner programmer. I've had some help from several people in the Nostr community. And the idea was kind of given to me by someone who's more deep into the Nostr stuff. It is one of the original ideas that the Nostr developers, the original developers of Nostr put out there that, hey, a ride sharing service should be created on Nostr. It was one of the predetermined use cases before Nostr was even working.
So my inspiration is building on the shoulders of giants, And the tools have been given to us to access this open network, And there's also already a bunch of use cases that I don't have to go and imagine, There's a bunch of really, really important and useful things that are needed to create that people are already asking for, So I'm just trying to do that, building something that people are already asking for.
Yofu: Wow. Actually, it is very interesting because, for example, like I mentioned in the talk that if one platform is gone, for currently that's all, there's no matter drivers, no matter users, reputation, it's all gone. I need to start over from the very start. Everyone is blank. It's not fair. So yeah, based on this, I think it's interesting. The information there does not depend on the platform. So it can be like now on multiple, there's clients that the information is sharing. It's quite cool. Yeah. And by the way, do you have any demo now or it's still under program?
Roadrunner: The page is in a demo version. I could show you very quickly if you'd like. So let me change screens for one second. So the page is live right now. Anyone can access it, roadrunner.lat, It's only working with testnet payments on Bitcoin. So you need a lightning testnet wallet if you want to demo it, but anyone can access it. Easy wallet that you can access on testnet is htlc.me if you ever want to test the service out. So I'll give you a quick rundown on the page. Basically you log in with a private key. I already have my private key here to save. So I just hit log in and it puts me in. It recognizes my public key, So this is the public key that shows to other people. I've already set up some profiles using an IPO six, I think it is, which just allows a user to set up like a profile event. So you can see like, Hey, this is my name, I have a little thing for images. I have a little information for your car. If you're a driver, A picture for your car isn't hosted on the site. This is just external URLs. Like I was talking about, but again, it's very easy to just find your picture, And from a public hosted site.
So then we have a little page where you can find rights, And this is predetermined to San Salvador. I am not accessing your device information at all. This is just a static map of the world. And you can just pick two points on the map, That's why it's predetermined to one spot, but you can just go wherever you want on the map, And pick those two points, If you're in Guatemala or if you're in Mexico, Or if you're even farther away,It doesn't matter, Maybe you're a European user who wants to use it, you just move the flags to wherever you want and you can pick those rights, So let's say we want to take a trip from Paris to whatever, Rene, You can offer a price. Right now everything is priced in SATs because I'm using lightning payments and you can send over that payment, So you get sent to the screen where you're just waiting for offers from drivers, So now I'd like to take you to the driver page.
Give me one second. I need to find another key. I think I have, I should be able to use this one.So let's use this one and we'll go to the driver page, So in the driver page, again, you'll be able to see a feed of all the rides and we can see here the ride that was posted by the other public key, So if we click this little banner, we can see that, Hey, this other public key wants to go from Paris to Rene, that's this much distance, And they're offering this much for the ride, So I want to offer them a ride. I will go to my wallet and I will ask for a little more than what they wanted, Okay.
Yofu: So there is a bargain negotiation process between drivers and users about the price.
Roadrunner: The passenger can offer a price, But at the end of the day, it's the driver's call of counter offering, So the passenger wants 245, The driver is offering 400 and 420. If you notice, here I put 400,000, And it added a bit of a fee. That is the relay fee that my service is actually charging you. So I've now added a bit of a fee because I am creating a contract for you, a lightning contract for you. And that's what you were actually paying. You're not paying the driver directly. And I can show you that right now. So for example, let's say this passenger, I want to take that ride, And so you can see that it has an invoice, I'm going to go now pay this invoice as the passenger, So I go to my wallet and I say, Hey, Oh, I don't have enough money. Oh, let me make a smaller payment. Cause I don't have enough money in this wallet. Sorry about that. A bit poor.
This is all test net Bitcoin. Let me just make another offer with a smaller one. So I should now have a smaller offer. Cool. Let me pay this invoice.So now that invoice will be paid and you'll notice in a second, as soon as it gets recognized, it should change. Give me a second. Don't fail me now. Service. Is it working? There we go. Cool. So what happened is that the contract was now in an accepted status. If you notice the lightning payment hasn't gone through that's because it's a type of contract that requires a two steps, It requires a payment and then it requires a verification, So right now the payment has not been sent, Because I'm just telling the driver, Hey, I've prepaid your contract, You should come pick me up.
So this is what the passenger sees: Your driver's coming. There's still a bit of details to implement. This is just a demo, I still need to implement, for example, like the location of your, of your driver and things like that. But as a demo, this is just, you're waiting for your driver to come, Let's say he never shows up. It's been 20 minutes, 30 minutes. He doesn't show up. Whatever you're in a hurry. you need to go. You just hit X and, and the ride cancels. The payment never goes through. Right. But let's say the driver did come pick you up. So the driver here now sees your location, And they're like, Hey, go pick you up, your passenger, Like the driver goes, picks you up, You have a nice ride. They take you to where you're going. you get to where you're going. The passenger hits accept and the payment now does get finalized. It says it failed here, but this lightning wallet isn't the best. If you notice the balance, it did get sent and received. It's also kind of weird because you're paying with the same wallet. if I was doing it with another user, it would be a better demo. Right. But yeah, the payment is received on the other end and the ride is finished and you can go request another ride.
Yofu: just one small question, you said, uh, when he takes the rides and he transports him to the place he went. So after that, what if the passenger doesn't pay, how the driver receives his money?
Roadrunner: At that point you are in someone's car and you are denying them their payment. I think if you are taking the risk of like, do you know what I think? Well, a lot of drivers already take that risk.like for example, Uber and a lot of these companies already give you the choice to pay in cash and drivers have no way of knowing if you have the cash or not. but as a passenger, would you really get into someone's car and then get to the end and be like, Oh yeah, I didn't pay you. Like you're, It's a problem for the driver, but it's at that point, the driver has you right next to them.
Yofu: Right. So I know the risk is very low, but how can the platform, I mean, your platform can assure that to solve that.
Roadrunner: I understand your concern. My response to that is that the platform is a peer-to-peer platform. Disputes as a service are peer-to-peer and disputes are also peer-to-peer. At no point in the service, can this, can the platform keep your money? So, the money goes either to the passenger or to the driver. There is no other outcome.
So just as the service is peer-to-peer, the dispute process is peer-to-peer.I know this isn't the answer that most people like,we have become very accustomed to platforms being very user coddling. I would say in a way of like babying you around,if anything wrong happens, it's the platform's fault. And I understand that, but I also don't, that's not the philosophy I want. And it's not the philosophy I think that Nostr builders will be building with.I think if you are going to get into the peer-to-peer philosophy, you also have to understand that, if you're using a peer-to-peer service, you are also taking that peer-to-peer risk in a certain way. And I don't think any peer-to-peer platform has solved this.
Yofu: It is doable to do an intermediate wallet, for example,Your platform wallet, and then the client will transfer the money to the platform wallet temporarily. And then when he finished, like you can, the driver can receive his money from the, I mean, like.
Roadrunner: The problem you keep running into is who verifies that the ride was successful. That is the ultimate problem. Because right now what I'm doing with the contract is kind of like that, Like you can prepay the contract and then someone has to decide, I could give that choice to the driver as well.But then what happens if you prepay the driver and the driver doesn't show up and just hits accept to the contract, You start running into a lot of issues of who you are going to ask to verify the ride. There isn't a clear answer, the system I designed has been designed after speaking with drivers specifically and raising this issue, Of people who actually like to ride, use these platforms to offer rides like drivers. And what they've told me is that, yes, like users have the financial upper hand,Because they like every platform, both Uber, Indriver,any of these platforms always gives users that ability of canceling the ride. And no right platform will tell you otherwise. Like if a user has the financial domination over the driver, what platforms do to counteract this is give drivers.The rating benefit, So give drivers more information about the reputations of users. And I'm still working on those designs, but what I'm trying to do is, for example, give drivers a very accurate representation of how many times a user has accepted a ride and how many times they've canceled it, Because if a user accepts a bunch of rides and always cancels them, that's not a very good user, And you should be able to, It might be impatient, or it might be someone trying to scam or it might be whatever, whatever option, right. But it's not a good user,But for example, another user who has accepted a bunch of rides, but also settled all of them and paid the driver accordingly, that should be a good user, And that should be reflected and drivers should be able to see what type of passenger you are before deciding to go pick you up or not. So that is still something I'm building, but the tools are there. Like I have all the data, all of this is Nostr events that are getting put to the Roadrunner Relay,So I own that data, just like I was talking on the talk, and I can choose to decide what to do with that data, I can present it to the drivers and say like, hey, this customer has a 90% settlement rate,And they're good customers. This other customer has a 20% settlement rate, And you as a customer have to be mindful of that, that you will be accumulating a rating on this platform. It's not a perfect solution, but it's, I'd rather do that than try to get into a dispute. Did the driver really get there or not? Did you get to your location or not? Like that is a lot harder because then you have to start thinking of like, am I tracking users on their devices, which is something I don't want to do. I don't want to track users. If you notice here, I'm not giving.I'm not asking for your data, right. I'm just, you put the location. So there's a lot of nuances to this.
Yofu: Thanks for answering my questions. One more question is, what're your upcoming features that you're going to implement to the platform?
Roadrunner: Yeah. Features, like I said, I still have to do a lot of reputation stuff. I don't know if you noticed, but there was a little reputation. There was already a star thing on each of the profiles. That's just a very basic reputation system that I set up. So I'm still working on more nuanced reputations to give more information to both drivers and passengers. So that's features that are coming up. Also features of seeing where your driver is. I do also want to allow some better location tools, for example, like looking for a specific address and just the banner goes directly to the address, small details like that. It's like UI enhancements. I also, there are a couple of features that I do want to enable that are more Nostr enabled things. This will take a bit, like, I do want to make sure that the platform is working correctly before I start implementing more. And it has to do with accepting and finalizing rights. And one example is I can give you, let's say like you are at a party and you're a bit drunk and you ask, you ask someone to request a ride for you on your key, You request the ride, but perhaps you tell your friends at home or your family at home, like, Hey, I'm taking this ride, follow my key.And then maybe you can do like the settlement ride of the payment isn't done by your key, but for example, by another key. So then the driver knows that he can't get paid unless you get home, for example, things like that, that are, that I'm still working on or designing, but like, there's a really, a bunch of cool stuff that you can do like sharing keys between people, to do different types of, of verifications and love, like requesting rides for your kids.For example, and, and paying or paying rides for other people. For example, like, Hey, I'm stuck here. I need someone to give me a ride.Can someone pay for this lightning? So stuff like that, or more like to give more freedom to users. But yeah, that's a bit more with more time.
Yofu: Yeah. I appreciate you answering my questions and thank you a lot for the amazing presentation.
Roadrunner: Just to end on an open invitation for anyone to go into the app and play with it. You're completely welcome to play and try and ride and just all you need is a lightning wallet. Like I said, a test net lightning wallet. This is not real money. This is test net money. Like if you open this page, they'll give you like $80 to play with and go ahead and play, try to be a driver, try to be a passenger, give any feedback that you might have on the platform. I'm happy to get it right.and that comes from people just testing it out. I also want to see if none of my services break. So again, go ahead, play with them, try to break everything. And if it breaks, I'll be happy to fix it. Right. Let's just let me know, open invitation to everyone.
Yofu: For sure. Yeah. Everyone can see this road runner details on the Hack Nordstrom on page, the BUIDL. And there is a, I think that you, you already put the links there,Everyone can try from there and read more about this. And if there is one more discussion about it, you're welcome to join the Telegram group.
This is the first workshop for the Hack-Nordstr-On on this hackathon and which is hosted by YakiHonne.com and sponsored by DoraHacks. And Thanks again to the speaker, to all the audience here, to the community, to 42, to Isaac. And this is it. And our next workshop will be tomorrow, which is 19 o'clock or 7 PM GMT,So stay tuned, and subscribe to us.
YakiHonne.com is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media.
Follow us for more daily features:
- Telegram: https://t.me/YakiHonne_Daily_Featured
- Twitter: @YakiHonne
- Hack-Nostr-On, Win 35,000,000 SATs NOW: https://dorahacks.io/hackathon/hack-nostr-on/detail
- Nostr pubkey:
npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
-
 @ 7ab79bc0:9385ad99
2023-06-09 07:44:35
@ 7ab79bc0:9385ad99
2023-06-09 07:44:35Singularität ist ein heißes Thema, da sie ein potenziell transformatives und disruptives Ereignis in verschiedenen Bereichen darstellt, darunter Technologie, künstliche Intelligenz und die Gesellschaft als Ganzes. Singularität stellt einen Punkt unbekannter und potenziell schneller Veränderung dar. Die Ungewissheit darüber, wie sich Technologien weiterentwickeln, welche Auswirkungen sie haben und welche möglichen Konsequenzen sie mit sich bringen, weckt Neugier, Spekulationen und Diskussionen.
Oft wird diskutiert, wie die Zukunft unseres Geldsystems aussehen könnte. Dem Euro wird keine rosige Zukunft zugesprochen, dem Dollar hingegen mittelfristig schon. Doch entwickelt sich unsere Gesellschaft und damit ihre Ansprüche und Bedürfnisse weiter. Die Entwicklung der letzten Jahrzehnte hat im Vergleich zu den Jahrhunderten davor und den Jahrtausenden davor extrem zugenommen.
Alleine das letzte Jahrhundert hat drei industrielle Revolutionen hervorgebracht: die Dampfmaschine, das Zeitalter der Wissenschaft und Massenproduktion und der Aufstieg der digitalen Technologie. Mit den digitalen Technologien kam zum ersten Mal auch das Bedürfnis nach einem Geld für den digitalen Raum, bzw. für den digital vernetzten Raum auf, in dem wir uns heutzutage bewegen. Das Geld in seiner jetzigen Form existiert seit dem 17ten Jahrhundert und obwohl es sich nach außen hin in seiner Form und Funktion wenig verändert hat, ist eine technologische Entwicklung auch hier nicht zu leugnen. Denn Geld ist nicht gleich Geld. Das Bargeld (Papier- und Münzgeld), das wir in unserem täglichen Leben verwenden, unterscheidet sich ganz deutlich von Buchgeld (Giralgeld) und Warengeld.
Wir sehen also, dass es verschiedene Arten von Geld gibt. Und um die Sache zu erschweren, gibt es jede dieser Formen von Geld auch noch in über 160 Währungen, die von den jeweiligen Zentralbanken gesteuert und gelenkt werden. Wenn wir also sagen, dass z.B. die türkische Lira keine Zukunft hat, dann meinen wir nicht nur, dass die Geldscheine mit dem Lira-Aufdruck bald verschwinden, sondern dass das ganze Finanzsystem, dass hinter der türkischen Lira steckt systemische Probleme aufweist, die es nicht mehr auffangen kann.

Dabei ist es dem Grunde nach eigentlich ganz natürlich und ganz normal, dass Währungen mit der Zeit verschwinden oder schlicht durch andere Währungen ersetzt werden. Denn Menschen tendieren von Natur aus dazu, ein gemeinsames Geld innerhalb einer definierten Region auf einem freien Markt zu verwenden, weil es uns die größte Wahlfreiheit bei der größten Anzahl von Handelspartnern und der höchsten Liquidität bietet.
Europa ist das beste Beispiel für diese Annahme. Um den Handel zu vereinfachen und Wertschöpfungsketten (yes, endlich mein Lieblings-Unwort eingebaut) zu steigern, haben sich 19 Länder dazu entschlossen, ihre Währung zugunsten des Euros aufzugeben. Dieses Phänomen der Bewegung hin zu einem gemeinsamen Geld ist nicht nur in der Ökonomie bekannt. Denn dieses Phänomen kann immer und insbesondere dann beobachtet werden, wenn die Konvergenz hin zu einem gemeinsamen Standard den Nutzer//innen den größten Nutzen bietet und Netzwerkeffekte fördert. Dieses Phänomen hat auch einen (inoffiziellen) Namen und zwar: monetäre Singularität - abgewandelt von der hypothetischen zukünftigen technologischen Singularität.
Obwohl „Monetäre Singularität“ im Wirtschafts- oder Finanzbereich keinen allgemein anerkannten Begriff darstellt, lässt sich durch seine Bestandteile ableiten, worauf sich der Name bezieht. "Monetär“ bezieht sich auf alles, was mit Geld oder Währung zu tun hat, während sich „Singularität“ häufig auf einen Punkt erheblicher Veränderung oder ein Ereignis bezieht, bei dem bestehende Regeln oder Normen nicht mehr gelten. Daraus lässt sich ableiten, dass sich „monetäre Singularität“ - also ein Kunstbegriff abgeleitet aus der Naturwissenschaft - auf ein hypothetisches Szenario bezieht, in dem es zu einer radikalen Veränderung der Funktionsweise des Geldes oder des Währungssystems kommt.

Mit Hinblick auf das aktuelle Finanzsystem hat Brent Johnson diesem Phänomen den viel eingängigen Namen "Dollar Milkshake Theory" verpasst. In dieser Theorie geht es darum, dass der US Dollar weiter an Stärke gewinnt und den Devisenmärkten auf der ganzen Welt Liquidität entzieht. Woher der Name? Man stelle sich vor, man hat einen Milchshake und sitzt an einem Tisch auf der anderen Seite des Raumes. Man stelle sich auch vor, jemand anderes hat einen wirklich langen Strohhalm. So kann der/diejenige seinen/ihren Strohhalm in den eigenen Milchshake stecken und ihn trinken, auch wenn man am anderen Ende des Raums sitzt. Der eigene Milchshake ist in diesem Fall eine Fremdwährung, der/diejenige, der/die trinkt, ist natürlich der US Dollar selbst. Das führt zu einer Konzentration aller Geschäfte in US Dollar.
Schaut man über den Tellerrand der heutigen Zentralbankgelder hinaus, ergeben sich einige weitere interessante Einordnungsversuche für die Singularität des Geldes, die die oben angesprochenen Bedürfnisse des digitalen Zeitalters in Betracht ziehen. Denn die Idee, dass Fortschritte in der Technologie, insbesondere im Bereich digitaler Währungen und Finanzsysteme, zu einer erheblichen Veränderung der Funktionsweise des Geldes führen könnten, klingt dann gar nicht mehr so abwegig. Es deutet darauf hin, dass zukünftige Entwicklungen, wie eine breite Adaption von Bitcoin, zu einer grundlegenden Veränderung in der Art und Weise führen könnten, wie Geld geschaffen, gespeichert, gehandelt und verwaltet wird.
Aus gesellschaftlicher Sicht besitzt Geld als soziales und kulturelles Konstrukt eine transformative Kraft, die menschliche Beziehungen, Werte und Verhaltensweisen umgestalten kann. Eine Singularität des Geldes würde in diesem Zusammenhang tiefgreifende und beispiellose Auswirkungen auf die Gesellschaft haben, die sich aus der veränderten Rolle des Geldes ergeben würden.

Aus gesellschaftlicher Sicht ist ein Streben nach technologischer Konvergenz hin ganz natürlich und passiert fast automatisch, solange es einen größten gemeinsamen Nutzen bietet und Netzwerkeffekte fördert. Das beste Beispiel dafür sind Sprachen. Es ist schwierig, genaue Zahlen zu nennen, aber Linguisten schätzen, dass es in der Geschichte der Menschheit etwa 31.000 Sprachen gab. Schätzungen zufolge werden heutzutage weltweit zwischen 6.000 und 7.000 Sprachen gesprochen. Forscher und Analysten prognostizieren, dass im frühen 22. Jahrhundert nur noch 600 bis 700 Sprachen im täglichen Gebrauch verbreitet sein werden. Sprache ist eine Technologie, sie wurde erfunden, verbessert, verändert, den Gegebenheiten angepasst und oft verschmolzen. Deshalb ist es kein Wunder, dass die Anzahl der gesprochenen Sprachen abnimmt. Denn Unterschiede erzeugen Reibung und Reibung ist ineffizient. Sowohl für das gesellschaftliche Miteinander als auch für den Handel und die Wirtschaft.
Gemeinsame Sprache hat viele Vorteile in einer globalisierten Welt, denn sie vereinfacht die Kommunikation und den Austausch zwischen Handelspartnern, politischen Einrichtungen und eröffnet auch viele neue Möglichkeiten in der Bildung. Wer z.B. Englisch spricht, hat einen viel größeren Pool an Literatur und Nachschlagewerken zur Verfügung, als jemand der/die "nur" eine lokale Sprache spricht. Das kann und wird dazu führen, dass menschliche Sprachen im Laufe der Zeit erhebliche Veränderungen, Anpassungen und manchmal sogar das Aussterben erfahren.

Gerade im Bereich der Programmiersprachen ist zu erwarten, dass zukünftige Entwicklungen in der künstlichen Intelligenz und im maschinellen Lernen einen tiefgreifenden Wandel in der Art und Weise bewirken, wie Sprachen verstanden, übersetzt und kommuniziert werden könnten.
Wie oben erwähnt, tendieren Menschen dazu, gemeinsame Technologien innerhalb definierter Regionen zu verwenden. Das war besonders in der Vergangenheit der Fall, als definierte Regionen übersichtlich waren. Mit der Globalisierung wurden diese lokalen Rahmen gesprengt, mit der Digitalisierung atomisiert!
Diese (künstlich) definierten Regionen werden immer weiter aufgebrochen. Im Falle von Sprachen vermischen sich Kulturen und ethnische Gruppen immer mehr und bringen dadurch auch eine Vermischung von Sprachen mit sich. Das Internet hat zu einer Atomisierung dieser Regionen geführt. Das kann man z.B. an der heutigen Sprache im deutschsprachigen Raum erkennen, wo das sogenannte Denglisch immer weiter Einzug erhält und einige Berufsgruppen hauptsächlich auf Englisch kommunizieren (man denke an den Flugverkehr, Hochseeschifffahrt, aber auch Bereiche des Finanzsektors, der Medien und der Beratungen).

Ein Beispiel von künstlich erzeugten Rahmen und mit durch äußerer Gewalt erzeugter Singularität kann in der Debatte um Antriebstechnologien in der EU beobachtet werden. Hier wird mit Hilfe von Gesetzen eine Technologie zum One-Size-Fits-All-Standard erhoben. Der Elektroantrieb bei Automobilen hat sicherlich seinen Platz, jedoch heißt es nicht, dass es verschiedene Anwendungsbereiche gibt, in denen Elektromobilität mehr oder weniger sinnvoll ist. Kleine Elektrofahrzeuge für den Innenstadtverkehr haben viele Vorteile gegenüber Abgase produzierenden Antrieben, die direkten Einfluss auf die Gesundheit der Menschen haben. Allerdings bedeutet dies nicht, dass Elektroantriebe auch für den Langstreckenverkehr sinnvoll sind, wenn die Alternative Wasserstoff- oder schadstoffarme Verbrennungsantriebe sind, die zum einen kostengünstiger, und zum anderen nachhaltiger sein können. Eine Gesetzgebung, die pauschal eine Technologie über seine Wettbewerbstechnologien stellt, führt zu einer künstlich hervorgerufenen Singularität, die aber nicht die oben genannten Kriterien der Nutzenmaximierung und der Netzwerkeffekte erfüllt.
Geld hat in seiner Geschichte eine ähnliche Entwicklung erfahren. Das ist eine ganz natürliche Entwicklung, da Geld einen Schutz vor Spezialisierung bietet. Denn die Spezialisierung auf einen bestimmten Produktions- / Dienstleistungsbereich ist erstmal positiv und führt zu einer Steigerung von Produktion und Wohlstand, allerdings ist diese auch riskant, da nicht alle Menschen das erzeugte Gut im Austausch oder im Handel akzeptieren werden. Wenn das erzeugte Gut in neutrales Geld getauscht werden kann, bietet das dem Produzenten einen gewissen Schutz.
Wenn ein Produzent sich nicht sicher sein kann, was er/sie in Zukunft mit seinen erwirtschafteten Überhängen erwerben oder investieren möchte, ist das Gut, das am besten zum Sparen dieser Profite geeignet ist, dasjenige, das über die besten Geldeigenschaften verfügt. In einem regional eingeschränkten Rahmen mag dies eine lokale Währung sein, doch in einer Welt, in der internationaler Handel und Austausch betrieben wird, erlangt das Geld mit der höchsten Neutralität oder der weitverbreitetsten Akzeptanz automatisch die besten Geldeigenschaften.
Wenn man z.B. den südafrikanischen Rand mit US Dollars vergleicht, wird man sehen, dass der USD eine viel höhere Akzeptanz genießt, als der ZAR. Man wird wahrscheinlich selbst in asiatischen Ländern im Notfall mit USD bezahlen können, einfach weil die Handelspartner dort wissen, dass es für sie einfach ist, USD in ihre lokale Währung umzutauschen. Mit Rand wird man Probleme bekommen, da diese als Tauschobjekt von Handelspartnern keine Zustimmung genießen.
➡️#42 // KW10 // 9.3.2023 // Ist Bitcoin Geld? 🪙🐪🚬
Wenn es in der Gesellschaft mehr als ein Geld gibt, gibt es immer einen gewissen Risikokompromiss das eine oder das Zahlungsmittel zu akzeptieren. Dies führt zu einem Anreiz, das beste Geld zu wählen - sofern diese Wahl überhaupt besteht - und damit zu einem natürlichen Druck nach einem gemeinsamen Geld, das diese Risikoabwägung eliminiert.
Dieser natürliche Druck nach einem gemeinsamen Geld sorgt für Wohlstand in der Gesellschaft. Doch ist die Realität eben auch, dass Staaten oder Regierungen genau hier eingreifen und den Menschen das eigene Geld auferlegen und diesem eben auch einen Wert zuweisen. Dies erlaubt den kontrollierenden Akteuren, den erzeugten Wohlstand abzusaugen (Steuern, Fiskal- und Geldpolitik), denn diesen können sie entweder für sich behalten oder verteilen ihn ungleichmäßig um.

Dieses Eingreifen in den marktwirtschaftlichen Prozess der Geldevolution kann nur ein Geld verhindern, das außerhalb dieser künstlich von außen geschaffenen Rahmen existiert. Ein Geld, das weder von Institutionen oder Regierungen geschaffen und in Umlauf gebracht wird. Ein Zahlungsmittel mit nahezu perfekten neutralen Geldeigenschaften (teilbar, austauschbar, einfach transportierbar, haltbar, prüfbar, knapp, universell akzeptiert und leicht sicherungsfähig, sowie erlaubnis- und vertrauenslos) ermöglicht den oben beschriebenen Druck nach einem gemeinsamen Geld und befeuert den damit einhergehenden Wohlstand in der Gesellschaft.
Wäre es nicht schön, wenn so ein Zahlungsmittel mit nahezu perfekten Geldeigenschaften vor knapp 14 Jahren entdeckt worden wäre? Der einzige Weg, den natürlichen Entwicklungsprozess hin zu einem singulären Geldstandard zu stoppen, ist durch Verbote und Regulierungen seitens der herrschenden Obrigkeiten - siehe Verbrennungsmotor. Doch ist es viel leichter ein Abgase emittierendes Auto von der Straße zu ziehen und stillzulegen, als einem/r mündigen Bürger//in zu verbieten sein/ihr Erspartes in einer harten Geldform zu lagern und mit anderen Nutzer//innen frei zu handeln.

🫳🎤
-
 @ 9d3ca1af:c47922af
2023-06-09 02:58:32
@ 9d3ca1af:c47922af
2023-06-09 02:58:32It’s been an exciting few years for quantum computing. Several players have built and made available small quantum processors and there’s open source software to program them. Now everyone wants to know: when will quantum computers be better than regular computers? Talking about timeline is itself a fascinating conversation, but in this post I’m going to try and clarify what we mean by “better”.
This is important because “better” can mean different things to a theoretical computer scientist or an investor. Without a shared understanding of what “better” means, then talking about timeline is just confusing.
There are already a few concepts in the community such as quantum supremacy and quantum advantage. Unfortunately these terms are often used loosely in press and their definitions can be unclear. In an effort towards clarity, I suggest the following four milestones for quantum computer performance:
-
Quantum Supremacy: This milestone consists of two results: (1) a mathematical proof that a given problem has a super-polynomial separation between any possible quantum algorithm and any possible classical algorithm and (2) the exhibition of the solution of this problem by a quantum computer at a performance (size, speed, or efficiency) that is infeasible with any available classical computer. Note that it suffices for such a proof to be relative to a widely believed assumption such as the polynomial hierarchy not collapsing.
-
Weak Quantum Supremacy: The solution of any problem, using a quantum computer, faster, cheaper, or more efficiently than any available classical solution.
-
Quantum Advantage: The solution of a valuable problem, using a quantum computer, faster, cheaper, or more efficiently than any available classical solution.
-
Strong Quantum Advantage: Quantum Advantage accompanied with a proof — up to widely believed assumptions — that the problem has a super-polynomial separation between any quantum solution and any classical solution. Equivalently, quantum supremacy but for a commercially valuable problem.
These four milestones form the following taxonomy:

Taxonomy for milestones in quantum computing performance.
Hopefully this taxonomy will clarify which milestones matter for what. For example, quantum supremacy is talked about a lot. However, it is neither a necessary nor sufficient condition for a big commercial market for quantum computers. We can prove, for example, that an equivalent “GPU Supremacy” is impossible and yet this technology has a large market. That said, weak quantum supremacy is a first milestone towards the commercially relevant market after quantum advantage.
This is not to say that quantum supremacy and strong quantum advantage aren’t important. They are fundamental and say a lot about the nature of our universe. Personally, I agree with Scott Aaronson in saying that “a clear demonstration of quantum supremacy is at least as big a deal as (say) the discovery of the Higgs boson.”
One of the incredible things about quantum computing is that it is both a scientific endeavor and a technology. It is critical to clarify which kind of milestones we are talking about as the field develops.
It will be exciting to be part of our field’s march through them in the coming years!
Thanks to Scott Aaronson, Simon Benjamin, Josh Combes, Travis Humble, Richard Stebbing, and Guillaume Verdon for their comments on drafts of this post.
---By W. J. Zeng Link:https://medium.com/@wjzeng/clarifying-quantum-supremacy-better-terms-for-milestones-in-quantum-computation-d15ccb53954f
-
-
 @ a715bcd1:318d6e6c
2023-06-08 21:26:40
@ a715bcd1:318d6e6c
2023-06-08 21:26:40:format(webp)/cdn.vox-cdn.com/uploads/chorus_image/image/72337694/GettyImages_532629665.0.jpg) CSA Archive / Getty Images
CSA Archive / Getty ImagesOn May 22, a fake photo of an explosion at the Pentagon caused chaos online.
Within a matter of minutes of being posted, the realistic-looking image spread on Twitter and other social media networks after being retweeted by some popular accounts. Reporters asked government officials all the way up to the White House press office what was going on.
The photo was quickly determined to be a hoax, likely generated by AI. But in the short amount of time it circulated, the fake image had a real impact and even briefly moved financial markets.
This isn’t an entirely new problem. Online misinformation has existed since the dawn of the internet, and crudely photoshopped images fooled people long before generative AI became mainstream. But recently, tools like ChatGPT, DALL-E, Midjourney, and even new AI feature updates to Photoshop have supercharged the issue by making it easier and cheaper to create hyperrealistic fake images, video, and text, at scale. Experts say we can expect to see more fake images like the Pentagon one, especially when they can cause political disruption.
One report by Europol, the European Union’s law enforcement agency, predicted that as much as 90 percent of content on the internet could be created or edited by AI by 2026. Already, spammy news sites seemingly generated entirely by AI are popping up. The anti-misinformation platform NewsGuard started tracking such sites and found nearly three times as many as they did a few weeks prior.
“We already saw what happened in 2016 when we had the first election with a flooding of disinformation,” said Joshua Tucker, a professor and co-director of NYU’s Center for Social Media and Politics. “Now we’re going to see the other end of this equation.”
So what, if anything, should the tech companies that are rapidly developing AI be doing to prevent their tools from being used to bombard the internet with hyperrealistic misinformation?
“WE ALL HAVE A FUNDAMENTAL RIGHT TO ESTABLISH A COMMON OBJECTIVE REALITY”
One novel approach — that some experts say could actually work — is to use metadata, watermarks, and other technical systems to distinguish fake from real. Companies like Google, Adobe, and Microsoft are all supporting some form of labeling of AI in their products. Google, for example, said at its recent I/O conference that, in the coming months, it will attach a written disclosure, similar to a copyright notice, underneath AI-generated results on Google Images. OpenAI’s popular image generation technology DALL-E already adds a colorful stripe watermark to the bottom of all images it creates.
“We all have a fundamental right to establish a common objective reality,” said Andy Parsons, senior director of Adobe’s content authenticity initiative group. “And that starts with knowing what something is and, in cases where it makes sense, who made it or where it came from.”
In order to reduce confusion between fake and real images, the content authenticity initiative group developed a tool Adobe is now using called content credentials that tracks when images are edited by AI. The company describes it as a nutrition label: information for digital content that stays with the file wherever it’s published or stored. For example, Photoshop’s latest feature, Generative Fill, uses AI to quickly create new content in an existing image, and content credentials can keep track of those changes.
AI-labeling tools like Adobe’s are still in their early stages, and by no means should they be considered a silver bullet to the problem of misinformation. It’s technically possible to manipulate a watermark or metadata. Plus, not every AI generation system will want to disclose that it’s made that way. And as we’ve learned with the rise of online conspiracy theories in recent years, people will often ignore facts in favor of believing falsehoods that confirm their personal beliefs. But if implemented well — and especially if these labels are seen as more neutral than traditional social media fact-checking — AI disclosures could be one of our only hopes for navigating the increasingly blurry distinction between fake and real media online.
Here is how some of these early AI markup systems could work, what the limitations are, and what users can do to navigate our confusing post-truth internet reality in the meantime.
The devil is in the metadata
When you look at an image on social media or a search engine today, odds are you don’t know where the photo came from — let alone if it was created by AI. But underneath the hood, there’s often a form of metadata, or information associated with the digital image file, that tells you basic details, like when and where the photo was taken. Some tech companies are now starting to add specific metadata about AI to their products at the moment of creation, and they’re making that information more public in an effort to help users determine the authenticity of what they’re looking at.
Google recently said it will start marking up images made by its own new AI systems in the original image files. And when you see an image in Google Search that’s made by Google’s AI systems, it will say something like “AI-generated with Google” underneath the image. Going a step further, the company announced it’s partnering with publishers like Midjourney and stock photography site Shutterstock to let them self-tag their images as AI-generated in Google Search. This way, if you come across a Midjourney image in Google Search, it will say something like “Image self-labeled as AI-generated”
Google Search public liaison Danny Sullivan said that this kind of AI labeling is part of a broader effort to give people more context about images they’re seeing.
”If we can show you a helpful label, we’re going to want to do that,” said Sullivan, “but we’re also going to want to try to give you background information that we can determine independent of the label.”
That’s why Google is also adding an “About this image” feature next to image search results — whether they are AI labeled or not — that you can click and see when the image was first indexed by Google, where it may have first appeared, and where else it’s been seen online. The idea is, if you searched for, say, “Pentagon explosion” and saw a bunch of images in the results, you would be able to see a fact-checked news article debunking the piece.
“These tools are really designed to help people understand information literacy more and bake it into the search product itself,” said Sullivan.
Other major industry players have also been working on the issue of how to label AI-generated content. In 2021, a group of major companies including Microsoft, Adobe, the BBC, and Intel created a coalition called the C2PA. The group is tasked with helping to create an interoperable open standard for companies to share the provenance, or history of ownership, of a piece of media. C2PA created its first open standard last January, and since then, Adobe and Microsoft have released features using that standard.
For example, if you’re a photographer at a news outlet, you can mark when a specific picture was taken, who took it, and have that be digitally signed by your publisher. Later, your editor could make changes to the photo, signing it again with a seal of authenticity that it’s been verified by the C2PA standard. This way, you know that the photo was taken by a person — not generated by AI— and know who has made edits to it and when. The system uses cryptography to preserve the privacy of sensitive information.
“Now you can read the entire lineage of the history of a piece of digital content,” said Mounir Ibrahim, EVP of public affairs and impact at Truepic, a visual authenticity app that is a member of C2PA. “The purpose of us is to help content consumers ... decipher the difference between synthetic and authentic.”
HOWEVER FLAWED THESE EARLY AI FLAGGING AND IDENTIFICATION SYSTEMS ARE, THEY’RE A FIRST STEP
Knowing the history and provenance of an image could potentially help users verify the legitimacy of anything from a headshot on a dating app to a breaking news photo. But for this to work, companies need to adopt the standard.
Right now, it’s up to companies to adopt the C2PA standard and label verified content as they wish. The organization is also discussing potentially standardizing the look of the C2PA content credential when it shows up on images, Ibrahim said. In the future, the C2PA credential could be similar to the little padlock icon next to the URL in your browser window that signifies your connection is secure. When you see the proposed C2PA icon, you would know that the image you’re seeing has had its origins verified.
So far, two big C2PA members, Adobe and Microsoft, have announced tools that integrate C2PA standards into their products to mark up AI-generated content. Microsoft is labeling all AI-generated content in Bing Image Generator and Microsoft Designer, and Adobe is using C2PA standards in its new AI Firefly product’s content credentials.
“The biggest challenge is we need more platforms to adopt this,” said Ibrahim.
While the C2PA-style metadata labels work behind the scenes, another approach is for AI systems to add visible watermarks, as OpenAI has done with the rainbow bar at the bottom of DALL-E images. The company says it’s also working on a version of watermarking for its text app, ChatGPT. The challenge with watermarks, though, is that they can be removed. A quick Google search turns up forms of people discussing how to circumvent the imprint.
Another imperfect option is technology that can detect AI-generated content after the fact. In January, OpenAI released a tool that lets you cross-check a block of text to determine whether it’s likely written by AI. The problem, though, is that by OpenAI’s own assessment, the tool is not fully reliable. It correctly identified only 26 percent of AI-written texts in OpenAI’s evaluations, although it’s notably more accurate with longer than shorter text.
“We don’t want any of our models to be used for misleading purposes anywhere,” said a spokesperson for OpenAI in a statement. “Our usage policies also require automated systems, including conversational AI and chatbots, to disclose to users that they are interacting with our models.”
At the end of the day, even if these early AI flagging and identification systems are flawed, they’re a first step.
What comes next
It’s still early days for tech platforms trying to automate the identification of AI-generated content. Until they identify a dependable solution, however, fact-checkers are left manually filling in the gaps, debunking images like the Pope in a puffy jacket or fake audio of politicians.
Sam Gregory, executive director of human rights and civic journalism network Witness, who works with fact-checkers largely outside of the US, said that while he thinks technical solutions to AI identification like watermarking are promising, many fact-checkers are worried about the onslaught of misinformation that could come their way with AI in the meantime. Already, many professional fact-checkers are dealing with far more content to check than humanly possible.
“Is an individual going to be blamed because they couldn’t identify an AI-generated image? Or is a fact-checker going to be the one to take the strain because they’re overwhelmed by this volume?” said Gregory. The responsibility to address AI misinformation “needs to lie on the people who are designing these tools, building these models, and distributing them,” he added.
In many cases, Gregory says, it’s unclear exactly what social media platforms’ rules are about allowing AI-generated content.
THERE IS AN URGENCY TO FIGURE OUT THESE PROBLEMS AS AI-GENERATED CONTENT FLOODS THE INTERNET
TikTok has one of the more updated policies around “synthetic media,” or media that is created or manipulated by AI. The policy, which was revised in March 2023, allows synthetic media but requires that, if it shows realistic scenes, the image must be clearly disclosed with a caption, sticker, or otherwise. The company also doesn’t allow synthetic media that contains the likeness of any private figure or anyone under 18. TikTok says it worked with outside partners like the industry nonprofit Partnership on AI for feedback on adhering to a framework for responsible AI practices.
“While we are excited by the creative opportunities that AI opens up for creators, we are also firmly committed to developing guardrails, such as policies, for its safe and transparent use,” a TikTok spokesperson said in a statement. “Like most of our industry, we continue to work with experts, monitor the progression of this technology, and evolve our approach.”
But many other platforms have policies that might need some updating. Meta, which owns Facebook and Instagram, and YouTube both have general rules against manipulated media that misleads users, but those could be clarified regarding what uses are acceptable or not, according to Gregory. Meta’s fact-checking policies state that manipulated media containing misinformation is eligible for fact-checking by its third-party partners, as it did with the fake Pentagon AI explosion claims.
“AI is bigger than any single person, company, or country, and requires cooperation between all relevant stakeholders,” Meta said in a statement. “We are actively monitoring new trends and working to be purposeful and evidence-based in our approach to AI-generated content.”
Technological solutions to help people fact-check content themselves, like AI detection systems and watermarks, couldn’t come sooner.
But NYU’s Tucker says we need to test these solutions to see whether they’re effective in changing people’s minds when they encounter misleading AI content, and what the disclosures need to look to be impactful. For example, if the disclosures that an image or video is AI-generated are too subtle, people could miss it entirely. And sometimes, labels don’t work as expected. For example, Tucker co-authored a study last year showing that high- or low-quality news credibility labels had limited effects on people’s news consumption habits and failed to change people’s perceptions.
Still, there’s hope that if AI disclosures are seen not as politicized fact-checks but as neutral context about the origins of an image, they could be more effective. To know whether these labels are resonating with people and changing their minds will require more research.
There is an urgency to figure out these problems as AI-generated content floods the internet. In the past, tech companies had time to debate the hypothetical risks of AI misinformation because mainstream generative AI products weren’t yet out in the wild. But those threats are now very real.
These new tools that label AI-generated content, while far from perfect, could help mitigate some of that risk. Let’s hope tech companies move forward with the necessary speed to fix problems that come with AI as quickly as they’re being created.
Original link: What will stop AI from flooding the internet with fake images? original author: Shirin Ghaffary
-
 @ a715bcd1:318d6e6c
2023-06-08 15:31:12
@ a715bcd1:318d6e6c
2023-06-08 15:31:12:format(webp)/cdn.vox-cdn.com/uploads/chorus_image/image/72351121/1258513251.0.jpg) The Securities and Exchange Commission unveiled a slew of charges this week against two large, popular cryptocurrency exchanges, Coinbase and Binance. Gabby Jones/Bloomberg via Getty Images
The Securities and Exchange Commission unveiled a slew of charges this week against two large, popular cryptocurrency exchanges, Coinbase and Binance. Gabby Jones/Bloomberg via Getty ImagesFor a long time, the crypto industry has been a Wild West with few regulations and laws governing it — a fact that many crypto enthusiasts saw as a feature, not a bug.
Unlike registered securities — as in, stocks — cryptocurrencies and crypto exchanges didn’t have to disclose much of anything to customers, and the list of lies and frauds rocking the industry has continued to pile up. That freewheeling era now appears to be coming to an end.
This week, the US Securities and Exchange Commission (SEC), a federal agency that regulates securities and protects investors, filed lawsuits against Binance and Coinbase, two of the world’s biggest crypto exchanges, on which investors buy and trade a large offering of cryptocurrencies. The SEC’s main allegation against Coinbase is that it’s running an unregistered securities exchange — like if the Nasdaq independently operated without any regulatory oversight. Binance faces the same charge, as well as additional accusations that it appropriated billions of dollars in customers’ funds for its CEO’s trading firm, misled its customers, lied to regulators, and more. Binance has about 90 million users, according to CoinMarketCap, while Coinbase reported that it had 110 million verified users as of 2022.
That the agency is going after such behemoths — after bringing cases against the most egregious bad actors, such as Sam Bankman-Fried, as well as celebrity crypto endorsers like Kim Kardashian (who paid a $1.26 million fine), Lindsay Lohan, and Jake Paul — sends a clear message. It’s no longer calling out a few rotten apples; it’s saying the whole enterprise needs to be scrutinized under a regulatory lens. (Disclosure: This August, Bankman-Fried’s philanthropic family foundation, Building a Stronger Future, awarded Vox’s Future Perfect a grant for a 2023 reporting project. That project is now on pause.)
At their core, the SEC’s lawsuits against the two companies are the most decisive actions to date in the prolonged battle to settle what cryptocurrencies and crypto exchanges even are. Are they being used as digital money, or is crypto — whether it’s ethereum, tether, or cardano — like a share of a company where investors are speculating on making a profit as “share” prices go up?
The latest legal action represents an existential threat to the entire industry. So, whether you have $20 or $200,000 in assets on a crypto exchange, should you be worried?
“It’s a very scary situation for any customer,” says John Reed Stark, a former SEC enforcement attorney. “I think anyone who has crypto on any exchange should take it off of that exchange immediately. Period, end of story.”
In a lengthy statement, Binance denied the SEC’s allegations and claimed that its litigation would “undermine America’s role as a global hub for financial innovation and leadership.” Coinbase CEO Brian Armstrong tweeted similarly that the approach of regulating crypto through enforcement was “harming America.” In a statement to Vox’s Sara Morrison, Coinbase’s chief legal officer and general counsel Paul Grewal bemoaned what he called the SEC’s “enforcement-only approach” and called for clarity in the agency’s rules.
In Stark’s view, chances are good that the SEC will prevail. “The SEC has brought close to 150 cases in the area of crypto,” says Stark. While many of those cases are still pending, the SEC’s track record so far has been extremely strong. If the latest lawsuits stand in court, the exchanges will have to become compliant under the SEC’s regulatory rules — and if not, they could shut down in the US. It’s possible that Binance and Coinbase (and other exchanges) could cease operations, but that doesn’t necessarily mean customers would be unable to get their money out.
There would likely be an orderly wind-down of operations, according to crypto researcher and critic Molly White, who writes about the scandals and scams within the cryptocurrency industry on her site Web3 Is Going Just Great.
Below, we’ve provided the answers to a few more questions you might have about the current crypto turmoil, including what it means for you.
What is the SEC upset about?
There are clear reasons for individual crypto investors to be concerned: The SEC has asked for an emergency order from the court to freeze Binance US’s assets. According to Stark, this move suggests that the SEC has strong evidence of wrongdoing and believes it will win its case. It also shows that the agency believes investor funds might be at risk. There’s a precedent for this fear: As you may remember, another crypto exchange, FTX, found it difficult to return customers’ money because, as bankruptcy proceedings have revealed, the firm’s financial records are such a jumbled mess that it’s hard to account for what’s missing and what has possibly been stolen.
The SEC’s take on crypto exchanges is clear: They are flouting the law as unregistered stock exchanges. Even Binance executives knew it, the SEC’s complaint argues: Binance’s former chief compliance officer admitted once that the company was “operating as a fking unlicensed securities exchange in the USA bro.”
The complaint against US-based Coinbase, which came a day after the lawsuit against Binance, alleges that it’s an unregistered securities exchange that’s putting customers at risk without proper SEC-required disclosures and protections — a charge that would apply to any crypto exchange. The case against Binance, which operates internationally but has a separate US arm, goes deeper, laying out alleged deceptions. The 13 charges filed against the exchange and its CEO, Changpeng Zhao, include allegations that it misused and commingled its customers’ funds — accusations not dissimilar to those made against FTX and its former CEO, Sam Bankman-Fried (who is also facing criminal charges).
The agency is also accusing a separate trading firm owned by Zhao of artificially inflating the volume of crypto being traded on Binance US, an illegal market manipulation tactic called wash trading. SEC chair Gary Gensler said in a press release that Zhao and his company had “engaged in an extensive web of deception, conflicts of interest, lack of disclosure, and calculated evasion of the law.” The SEC’s charges against Binance follow a Commodities Futures Trading Commission lawsuit filed earlier this year.
:format(webp):no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/24709957/1424028312.jpg) Securities and Exchange Commission chair Gary Gensler, pictured testifying before the Senate Banking, Housing, and Urban Affairs Committee in 2022, has made clear his intention to bring crypto under the agency’s regulatory control, insisting the tokens are securities. Kevin Dietsch/Getty Images
Securities and Exchange Commission chair Gary Gensler, pictured testifying before the Senate Banking, Housing, and Urban Affairs Committee in 2022, has made clear his intention to bring crypto under the agency’s regulatory control, insisting the tokens are securities. Kevin Dietsch/Getty ImagesWhy is the crackdown happening now?
Crypto exchanges have been around for a while. So, why now? “It’s kind of a strategic time for the SEC to take these actions, with the recent-ish downfall of FTX, and Celsius and Voyager — these very high-profile collapses,” says White. Coinbase received a notice from the SEC in March that all but declared the agency’s intention to sue.
A lot of the crypto hype also has died down, particularly after the high-octane explosion of FTX last fall, which helped cement public wariness around the lack of transparency and risk management on exchanges. The SEC also recently received firm backing from the Biden administration, which has signaled its intention to work with agencies on regulating crypto.
“I also think that the SEC are getting to a stage where they really need to take some major action that would support the things that they’ve been saying more broadly about the crypto industry,” White continued. Gensler has been making clear that he believes that most cryptocurrencies are securities since his appointment in 2021. In addition to its high-profile lawsuits, the SEC has been beefing up its crypto enforcement unit and its budget; in fiscal year 2021, the agency requested a $1.9 billion budget from Congress. For fiscal year 2024, it’s asking for $2.4 billion.
What does this mean for people who have money in these exchanges?
As Bloomberg columnist Matt Levine quipped in Tuesday’s column, “If you are trading crypto, you simply cannot be too squeamish about strict adherence to US securities law.”
Given the SEC’s signaled intent to aggressively get crypto in line and under its authority, it’s reasonable that investors with a great deal of money in crypto exchanges are spooked. The agency’s complaints call out more than a dozen specific cryptocurrencies that it claims are being sold and offered as securities on Binance and Coinbase, including a popular token called Solana.
Some anxiety is apparent: The share price of Coinbase, a publicly traded company listed on the Nasdaq, initially fell by almost 20 percent according to Yahoo Finance, though it has since rallied. On June 6, the day after the SEC announced its lawsuit against Binance and the day it announced its separate lawsuit against Coinbase, more than $700 million was withdrawn from Binance and about $600 million was withdrawn from Coinbase, according to cryptocurrency news site CoinDesk, which broke the story that culminated in FTX’s downfall.
The situation right now doesn’t yet compare to the panic last winter, when investors withdrew as much as $3 billion from Binance over a 24-hour period in the aftermath of Bankman-Fried’s arrest. (Binance CEO Zhao was the catalyst for a massive withdrawal of funds from Bankman-Fried’s exchange, FTX, eventually leading to the exchange’s implosion and bankruptcy.)
Stark says the comparatively muted response among investors is both surprising and not. When it comes to any kind of investing, the sound financial advice is to be careful of risk and do your due diligence. Yet “due diligence” is almost impossible with crypto, precisely because it’s unregulated. At the same time, crypto enthusiasts tend to be a group that distrusts government regulation; a common narrative among the crypto crowd is that decentralized, alternative digital currencies are actually safer than the US dollar because power and authority aren’t concentrated in just a few institutions.
White says that whether someone should take their money out depends on whether they believe there’s going to be a bank run that collapses the entire exchange, a la FTX. But FTX collapsed because it didn’t have enough cash on hand for the billions in withdrawals that investors suddenly were trying to make — it was in significant debt, didn’t have enough money in reserves, and Bankman-Fried allegedly had been freely using customers’ funds at his personal trading firm.
Binance, for its part, has said that all of its assets are fully backed; during last December’s onslaught, in which $1.9 billion in funds were withdrawn, a company spokesperson said that it had “more than enough funds” to process withdrawals. As a public company, Coinbase reports audited quarterly financial statements showing how much money they have in reserves. “I feel like if there was a major risk of a quote-unquote bank run happening, we sort of would have seen it by now,” White says.
White notes that there’s always a risk with unregulated crypto exchanges that aren’t required to disclose much of anything and aren’t required to have risk management controls in place. That is, after all, the thrust of why the SEC is going after them.
“I think a lot of people within and outside of the cryptocurrency industry will argue that keeping cryptocurrency assets on exchanges is not necessarily the best idea to begin with,” White says. The general advice is to keep your crypto in an offline storage device that you have direct access to. But for avid crypto traders, the point is to buy and sell quickly — to trade, not just leave crypto in an offline “wallet.” And the risk and lack of transparency in crypto exchanges is probably no surprise to them, either. “I think that anyone who is shocked by [what Binance is being accused of] probably hasn’t been paying that much attention,” White says.
But plenty of lay investors have money in Coinbase and other exchanges, too, and the reality is that Coinbase and every other crypto exchange all lack investor protections — there are no audits or inspections from the SEC, no insurance, and no licensure requirements of people involved in crypto, says Stark.
What’s going to happen to cryptocurrency now?
The outcome of the SEC’s complaints could take years to litigate, according to Ciamac Moallemi, a business professor at Columbia University. “I think one data point is to look at the accusations against Ripple,” he says. The SEC filed a complaint accusing the digital payment network of selling unregistered securities back in December 2020. That case is still pending.
“Assuming that these complaints stand up in court, I don’t think that there’s a scenario in which Coinbase or Binance — particularly Binance — become compliant,” White says. “The business model of cryptocurrency in general and cryptocurrency platforms really relies on not abiding by the regulations that are in place.” Their business model is “regulatory arbitrage”: using loopholes or structuring their companies in countries with friendly crypto regulations. FTX, for example, was headquartered in the Bahamas. One possible scenario here is that the lawsuits could culminate in Binance ceasing operations in the US, and Coinbase shutting down entirely.
Perhaps what should worry crypto traders most of all is just how much of the crypto and Web3 hype has died down, a potential sign that the boom days are over. The crypto whales have made their billions and are off to the next big thing, while the average crypto trader is left holding the bag. In November 2021, the crypto industry’s market cap reached $3 trillion. Its market cap is now around $1.1 trillion, according to CoinMarketCap. “Every private equity firm is moving on — obviously to the area of artificial intelligence,” says Stark. “And they’re not coming back.”
Original link: Now might be a good time to consider quitting crypto original author: Whizy Kim
-
 @ 0dde8796:14799cec
2023-06-08 13:23:01
@ 0dde8796:14799cec
2023-06-08 13:23:01
“We will create a civilization of the Mind in Cyberspace. May it be more humane and fair than the world your governments have made before.” John Perry Barlow
As a long time Deadhead, I attended a bunch of Grateful Dead shows in the New York area in the early 1990s. I had no idea that some of the songs I heard performed were written by a man who was at that very time helping to create the Cypherpunk movement.
It wasn’t until recently that I became aware of the surprising connection between the music of my youth and one of the people who laid the groundwork for the creation of bitcoin.
A few years ago I read John Perry Barlow’s autobiography, “Mother American Night.” The epilogue revealed that he died two days after finishing the book. All I knew about him was that he had written a couple of songs I really liked.
Putting aside his connection to the cypherpunk movement, his life story made for a very entertaining book. As a real renaissance man, writing was one of his many talents.
As I read the book, I thought of him as a kind of Zelig. He seemed to know everybody. He was a close friend of John F Kennedy Jr. He dropped acid with him and his then girlfriend Daryl Hannah. He also has the dubious distinction of having given the former president’s son his first flying lesson. Barlow met the Dalai Lama, and supposedly dated his daughter. He was a Republican for a while, and he helped run one of Dick Cheney’s campaigns. He eventually turned on Cheney, telling him to his face that he was Dr. Strangelove. He was a mentor to Edward Snowden, and they remained friends through his exile.
You wouldn’t have guessed his future by researching his austere, rural upbringing.
John Perry Barlow was born in Wyoming, the son of a Morman Republican State Senator. His parents owned a ranch, where Barlow claimed he was raised “by drunken cowboys and farm animals.” Due to his family’s strict religious values, he was only allowed to watch televangelists on TV. After managing to get straight ”F”s as a high school freshman, his father eventually shipped him off to boarding school in Colorado Springs, Colorado. There he met future Grateful Dead guitarist Bob Weir. They became lifelong friends and collaborators. He began writing lyrics for Weir’s songs in the early 1970s.
During college he discovered LSD at Timothy Leary’s Millbrook, New York gathering place. He introduced Weir and other members of his new band, The Grateful Dead, to Leary and LSD. Drugs were a big part of his world, and they remained so throughout his life.

Barlow was a natural libertarian, although to the best of my knowledge he never described himself as such. He valued freedom, and had a strong distrust of government. As a result, he became active in the world of internet freedom. In 1990 Barlow co-founded the Electronic Frontier Foundation (EFF) with John Gilmore and Mitch Kapor.
In the early 1990s Barlow co-founded the Cypherpunks mailing list with David Chaum. Barlow and Chaum, among others including Adam Back and Hal Finney, discussed cryptography, privacy, and individual rights. Barlow is credited with coining the term “cyberspace.” He believed that anonymity was necessary to freedom. "I feel the same way about anonymity as I do about guns. It may be useful to have in the closet if the government gets out of control." At the same time he participated in the message board he continued to write songs for the Grateful Dead.
He also was continuing his work with the Electronic Frontier Foundation.

“Those Weary Giants Of Flesh and Steel”
When the U.S. Telecommunications Act of 1996 was passed by Congress, Barlow wrote "A Declaration of the Independence of Cyberspace" in response. The declaration was in the form of a letter addressed to the World Economic Forum.
Here is the full text, although I recommend you watch him read the document himself in this 2013 video :
A Declaration of the Independence of Cyberspace
by John Perry Barlow
Governments of the Industrial World, you weary giants of flesh and steel, I come from Cyberspace, the new home of Mind. On behalf of the future, I ask you of the past to leave us alone. You are not welcome among us. You have no sovereignty where we gather. We have no elected government, nor are we likely to have one, so I address you with no greater authority than that with which liberty itself always speaks. I declare the global social space we are building to be naturally independent of the tyrannies you seek to impose on us. You have no moral right to rule us nor do you possess any methods of enforcement we have true reason to fear. Governments derive their just powers from the consent of the governed. You have neither solicited nor received ours. We did not invite you. You do not know us, nor do you know our world. Cyberspace does not lie within your borders. Do not think that you can build it, as though it were a public construction project. You cannot. It is an act of nature and it grows itself through our collective actions. You have not engaged in our great and gathering conversation, nor did you create the wealth of our marketplaces. You do not know our culture, our ethics, or the unwritten codes that already provide our society more order than could be obtained by any of your impositions. You claim there are problems among us that you need to solve. You use this claim as an excuse to invade our precincts. Many of these problems don't exist. Where there are real conflicts, where there are wrongs, we will identify them and address them by our means. We are forming our own Social Contract. This governance will arise according to the conditions of our world, not yours. Our world is different. Cyberspace consists of transactions, relationships, and thought itself, arrayed like a standing wave in the web of our communications. Ours is a world that is both everywhere and nowhere, but it is not where bodies live. We are creating a world that all may enter without privilege or prejudice accorded by race, economic power, military force, or station of birth. We are creating a world where anyone, anywhere may express his or her beliefs, no matter how singular, without fear of being coerced into silence or conformity. Your legal concepts of property, expression, identity, movement, and context do not apply to us. They are all based on matter, and there is no matter here. Our identities have no bodies, so, unlike you, we cannot obtain order by physical coercion. We believe that from ethics, enlightened self-interest, and the commonweal, our governance will emerge. Our identities may be distributed across many of your jurisdictions. The only law that all our constituent cultures would generally recognize is the Golden Rule. We hope we will be able to build our particular solutions on that basis. But we cannot accept the solutions you are attempting to impose. In the United States, you have today created a law, the Telecommunications Reform Act, which repudiates your own Constitution and insults the dreams of Jefferson, Washington, Mill, Madison, DeToqueville, and Brandeis. These dreams must now be born anew in us. You are terrified of your own children, since they are natives in a world where you will always be immigrants. Because you fear them, you entrust your bureaucracies with the parental responsibilities you are too cowardly to confront yourselves. In our world, all the sentiments and expressions of humanity, from the debasing to the angelic, are parts of a seamless whole, the global conversation of bits. We cannot separate the air that chokes from the air upon which wings beat. In China, Germany, France, Russia, Singapore, Italy, and the United States, you are trying to ward off the virus of liberty by erecting guard posts at the frontiers of Cyberspace. These may keep out the contagion for a small time, but they will not work in a world that will soon be blanketed in bit-bearing media. Your increasingly obsolete information industries would perpetuate themselves by proposing laws, in America and elsewhere, that claim to own speech itself throughout the world. These laws would declare ideas to be another industrial product, no more noble than pig iron. In our world, whatever the human mind may create can be reproduced and distributed infinitely at no cost. The global conveyance of thought no longer requires your factories to accomplish. These increasingly hostile and colonial measures place us in the same position as those previous lovers of freedom and self-determination who had to reject the authorities of distant, uninformed powers. We must declare our virtual selves immune to your sovereignty, even as we continue to consent to your rule over our bodies. We will spread ourselves across the Planet so that no one can arrest our thoughts. We will create a civilization of the Mind in Cyberspace. May it be more humane and fair than the world your governments have made before. Davos, Switzerland February 8, 1996
It was a very influential manifesto, and still has its own page on the World Economic Forum web site. Edward Snowden claims that reading Barlow’s declaration changed his life.
Among his greatest achievements was his work with the Electronic Frontier Forum. To this day, the work done by the EFF ensures that for all practical purposes bitcoin and similar software enjoy first amendment constitutional protection in the United States. The organization provided legal representation and advocacy for Professor Daniel J. Bernstein in the case of Bernstein v. United States. Bernstein was a computer scientist and professor at UC Berkeley and the University of Illinois. The plaintiffs argued that restrictions on the publication of cryptographic algorithms violated the First Amendment's protection of free speech. They contended that computer code is a form of expression and that regulating or restricting its dissemination is a violation of free speech rights.
In 1999, the United States Court of Appeals for the Second Circuit ruled in the case of Bernstein v. United States that computer source code is protected as free speech under the First Amendment. The court concluded that source code is a means of communication and expression, and therefore, any restriction on its publication or distribution would implicate the First Amendment.
In 2012, he founded the Freedom of the Press Foundation with Julian Assange, Edward Snowden, and others, including Glenn Greenwald. Assange tweeted this upon heaqring of his death: “Very sad to hear my friend John Perry Barlow [@JPBarlow] with whom I started the Freedom of Press Foundation has died aged 70. Barlow was a fighter and a lover. He lived a rich life, filled with passion and purpose. The best of America.”

Barlow continued writing and lecturing about online freedom for the rest of his life. The internet is filled with videos of his speeches, lectures, and Ted Talks. He was a brilliant man and a tireless advocate.
Here is my favorite Barlow quote:
”When cryptography is outlawed, bayl bhgynjf jvyy unir cevinpl.” John Perry Barlow
Barlow’s funeral was a unique and controversial event. He was laid out dressed on his bed, wearing his favorite cowboy boots, while his family and friends gathered around him. Bob Weir played guitar and sang “Cassidy”, one of Barlow’s most well known songs. A video of the event is on youtube. Warning, some people might find it disturbing.
It is not an overstatement to say that his work did much to lay the foundation for the cryptological advances that led to bitcoin, while making it very difficult for projects like bitcoin to be made illegal in the United States.

Electronic Frontier Foundation Memorial Poster
Published on Stacker News 6/8/23
-
 @ 30300158:19de09b3
2023-06-08 13:03:51
@ 30300158:19de09b3
2023-06-08 13:03:51 -
 @ 5ada3677:7c21c9db
2023-06-08 11:38:09
@ 5ada3677:7c21c9db
2023-06-08 11:38:09去上野的東京都美術館,看馬蒂斯大展,Henri Matisse,二十年以來最宏偉的一次大展,150件展品,主要來自法國蓬皮杜和東京的國立近代美術館。下一次如果再過二十年,我大概要坐輪椅去美術館朝聖了。



順便說句好笑的,包子小時候,每個暑假,都被我拎著逛遍歐洲的美術館博物館,小人累倦了的時候,跟我說,媽咪啊,看美術館博物館,應該每人一輛輪椅的。我覺得小朋友講得很對,夏天最累的事情,就是在美術館博物館裡,站到腿都抬不起來,然後腰都要站斷了,真真是折腰。

上野一地,充滿了美術館博物館,簇擁了一大堆,東京都美術館不算最重要的一個館,卻做了這麼厲害的馬蒂斯大展。人很多,需要預約,零星幾個觀眾沒有預約,當場也開放售票,我是零星之一。2200日圓(110人民幣)門票,跟上海差不多,甚至略便宜。從美術館大門口到展廳入口,一點點路而已,起碼有15個工作人員在引導客流,都是年輕工作人員,制服筆挺,聲音溫柔,奔前奔後。相比上海博物館,大把觀眾在館外排隊,沒有一個工作人員引導客流,只有一個高音喇叭,反覆提醒你打開預約碼等候檢查。以下省略3000字。入了展廳,發現忘了拿眼鏡,再折出來跟工作人員講,去存物箱取眼鏡。工作人員立刻小跑步引導我出去,告訴我拿好眼鏡不用再排隊,直接進來看展。



展廳裡觀眾密密麻麻,95%是各種年紀的女人,5%是男人。男人喜到哪裡去了?我是一直沒有想明白,中日都如此。
有的展廳可以拍照,有的不可以。可以和不可以,就是很小一行字寫在每個展廳門口,完全沒有工作人員三令五申,卻沒有一個人不遵守,這是多麼高的文明程度,我是深心佩服的。如果做個實驗,換1000位復旦大學學生來這裡,我猜,絕對做不到如此整齊畫一地好,darling儂講呢?

說馬蒂斯。
很多作品,從來沒有看見過,站在原作面前,說醍醐灌頂,絕不過分。好幾次,我有點熱淚盈眶。馬蒂斯輝煌自信、揮灑自如的色彩,劃時代的天才手段,就不說了,他的雕塑也極厲害,泥巴玩得得心應手,有血有肉,這次看見了。還有他的素描,線條鬆活,想怎樣就怎樣,完全是聖手。

展廳最後,當然是賣品部,我想回到開始部位,從頭再看一遍,詢問了工作人員,引導我回到展廳之首,一個人再看了一遍。

這幅,我從來沒有看過,尺幅很大,掛在展廳中央,氣場磅礴,那種沉靜,憂鬱,撲面而至,我在她面前站了久久。這種人像,看得見人物的一生一世,太厲害了。








日本的展事大多做得極好,教科書級別地好,讓人看過一個展,獲得全面完整的知識認知,這種科普水平,日本人好像特別強大。

馬蒂斯晚年,做過一個教堂的設計,展覽中拍了一個小電影,拍這個教堂,光與影,人與神,美得無以倫比,安藤忠雄立刻成了小巫。



看完馬蒂斯,餓得不行了,隔壁東照宮旁邊,有間鰻魚飯的老舖,三分鐘步程,快步過去吃了一個鰻重。好吃嗎?有點一言難盡。上海的鰻魚飯,用養殖鰻魚,極其肥腴,吃慣之後,再吃日本的,就覺得味薄、不過癮,日本的鰻魚大多數也是養殖的,但是養得瘦多了。
這家老舖,是一棟小樓,三層樓,居然在窄窄的樓梯上,裝了一個軌道,可以讓輪椅直接上到三樓,厲害。







其實到上野,最好是自己帶個便當來,坐在公園裡,慢慢吃,享受晴空萬里,還可以在公園裡watching people。








昨天晚上下雨,走去附近的書店,泡在裡面看書,看到書店打烊,九點。四年沒有到東京的書店了,昨晚老鼠跌進米缸裡了。
我還以為,日本的紙媒也壯烈犧牲得差不多了,昨晚在書店裡一看,我的天啊,人家的雜誌,週刊和月刊,仍然堅挺著,成排成行滿滿騰騰,你看,這些拍的全部是雜誌。




 還有一個新氣象,以老人為主角話題的書,層出不窮,而且都熱銷。68歲一個人移居、88歲獨自生活的廚房、102歲的單人生活,等等。
還有一個新氣象,以老人為主角話題的書,層出不窮,而且都熱銷。68歲一個人移居、88歲獨自生活的廚房、102歲的單人生活,等等。 這本也很有趣,秘書小姐選的禮物,參考價值很高。
這本也很有趣,秘書小姐選的禮物,參考價值很高。

 這是今晚在逛的高円寺的舊書舖,還買到一本藤田宜永的2000年的小說,竟然還是簽名本,心滿意足。
這是今晚在逛的高円寺的舊書舖,還買到一本藤田宜永的2000年的小說,竟然還是簽名本,心滿意足。



這個系列在這裡:
nostr:naddr1qqxnzd3cxccr2vp5x56nzvekqgs94k3kwuv8lupy508209lgncwv3d5lvzv6gznt3ajy6wcz0ssunkcrqsqqqa286f3nsj
-
 @ 155d3dc8:de354552
2023-06-08 09:11:42
@ 155d3dc8:de354552
2023-06-08 09:11:42 -
 @ 9f0b7b91:4e70bfa0
2023-06-08 09:11:27
@ 9f0b7b91:4e70bfa0
2023-06-08 09:11:27 -
 @ 6f4391da:399973a9
2023-06-08 08:59:48
@ 6f4391da:399973a9
2023-06-08 08:59:48- *Some Bitcoiners and Bitcoin developers simply did not want this type of activity on the Bitcoin blockchain and they successfully discouraged it. At the same time, promoters of other chains, such as Ethereum may have exploited and exaggerated this apparent stance from the Bitcoin developers, to help their new chains gain traction. *
Overview
We have often been asked the question: Why are Dapps such as distributed exchanges typically on Ethereum rather than Bitcoin? After all, it is certainly possible to build Dapps, such as distributed exchanges, naming systems or alternative tokens on top of Bitcoin. There are of course several reasons for this, such as: i. Ethereum’s more flexible native scripting language making it easier to build Dapps, ii. Ethereum’s faster blocktime, making Dapps more user friendly, or iii. Bitcoin choosing a more conservative blocksize constraint than Ethereum, resulting in potentially higher fees on Bitcoin. All of the above did have an impact, however their impact is often overstated in our view. The most significant factor is culture. Some Bitcoiners and Bitcoin developers simply did not want this type of activity on the Bitcoin blockchain and they successfully discouraged it. This seems to have primarily occurred in around March 2014 and what happened in that period is the subject of this piece. At the same time, promoters of other chains, such as Ethereum may have exploited and exaggerated this apparent stance from the Bitcoin developers, to help their new chains gain traction.
The Counterparty Protocol
As we mentioned in our September 2020 report, towards the start of 2014, Counterparty launched. Counterparty is a protocol layer on top of Bitcoin that enables features such as new token creation and the trading of these tokens on a distributed exchange. The system works by using parts of Bitcoin transaction data and using this in the Counterparty protocol, as a function, such as creating a token, sending a token or a market bid on a token on a distributed exchange.
More concisely, at the start Counterparty used the Bitcoin opcode OP_CHECKMULTISIG to include Counterparty related data into the Bitcoin blockchain. This opcode was supposed to be used to verify the signature for a pay to script hash (P2SH) multi signature transaction. An example of a Counterparty transaction from July 2014 can be seen here. The transaction sends Bitcoin back to the address it came from and also has three additional outputs, where the output scripts are data related to the Counterparty protocol. In this case it was the creation of a new token called TICKET. Using OP_CHECKMULTISIG can be thought of as a hack, because this was not the intended use of the opcode. Counterparty now uses Bitcoin’s OP_Return opcode to store data, which is more inline with what developers intended, to some extent. For example please see this more recent Counterparty transaction, which uses OP_Return.
In early 2014 there was considerable experimentation, developer activity, innovation and excitement around Counterparty, which had the lead over a rival platform called Mastercoin.
What is OP_Return?
OP_Return is a transaction output in Bitcoin that is provably unspendable. The function can be used to burn Bitcoin or store arbitrary data in the Bitcoin blockchain. Since the data is not part of the UTXO set, storing data this way is said to help scale Bitcoin, as nodes that engage in pruning do not need to store OP_Return data.
Bitcoin’s consensus rules allow an OP_Return size of up to 10,000 bytes. For example, in May 2013 somebody took advantage of this feature in the following transaction. The OP_Return output in this transaction contains the lyrics to the 1987 song “Never Gonna Give You Up” by Rick Astley, the song related to the Rickrolling meme.
Prior to 2014, transactions containing an OP_Return were non-standard at not relayed by ordinary Bitcoin nodes. However, if a miner included those transactions they were considered as valid. In March 2014, Bitcoin Core 0.9.0 was released with the OP_Return feature included as a standard transaction type, therefore the transactions would be relayed by default. The release notes at the time said the following:
This change is not an endorsement of storing data in the blockchain. The OP_RETURN change creates a provably-prunable output, to avoid data storage schemes – some of which were already deployed – that were storing arbitrary data such as images as forever-unspendable TX outputs, bloating bitcoin’s UTXO database. Storing arbitrary data in the blockchain is still a bad idea; it is less costly and far more efficient to store non-currency data elsewhere.
Source: https://bitcoin.org/en/release/v0.9.0#opreturn-and-data-in-the-block-chain
Bitcoin Core 0.9.0 would only relay transactions with an OP_Return of 40 bytes or less, if the data was larger than this, it was still a valid transaction, but not relayed. The limit was originally intended to be 80 bytes, however after much discussion, the developers settled on 40 bytes. To be clear, the OP_Return relay limit in a released version of Bitcoin Core never declined.
In 2016, Bitcoin Core 0.11.1 finally increased the relay limit to 80 bytes, the limit we have today. This means that if one wants a transaction with an OP_Return output of over 80 bytes today, one has to mine it themselves or send it directly to a miner.
The OP_Return Wars
On 20 March 2014, one of Bitcoin’s main contributors at the time, Jeff Garzik, started posting on the Counterparty thread on the Bitcointalk forum. Jeff was criticising the use of blockchain space by Counterparty.
To date, I’ve not seen a blockchain data dumping scheme that could not be securely replaced with a simple hash. You don’t need to store data in the blockchain. That is purely intellectual laziness. Timestamping hash(data) is just as secure, while more efficient. Furthermore, a secondary chain can be provably pegged to bitcoin:
Source: https://bitcointalk.org/index.php?topic=395761.msg5796379#msg5796379
Jeff went on to say:
CheckMultiSig is quite clearly intended for ECDSA public keys, not arbitrary data. It should be no surprise that using an operation for something other than its intended purpose has negative, perhaps unintended or unknown consequences. Counterparty transactions are not “according to the bitcoin protocol”, they slip through because it never expected that the feature be used in that way.
Source: https://bitcointalk.org/index.php?topic=395761.msg5827189#msg5827189
One may think it’s odd that Jeff had this view, given that in 2017 he appeared to be “large blocker” and that this view about the conservative use of blockspace does not appear to reconcile with the large block view. However, this apparent contradiction did not appear at all in 2014. Jeff’s view at the time was shared to some extent by almost all the active developers at the time, including the ones which later became large blockers. As far as we can tell there was no simple mapping at all between one’s view on the blocksize limit and this issue. Jeff was a highly respected developer at the time and this post was a considerable concern for the Counterparty developers and users.
A Counterparty developer, with the pseudonym “BitcoinTangibleTrust” responded to Jeff as follows:
You’re absolutely right. You don’t need to store data in the blockchain. Timestamping hash(data) is just as secure, while more efficient. A secondary chain can be provably pegged to bitcoin. However, Counterparty IS storing data in the blockchain using 256 bytes in each one-of-three multi-sig transactions, as per PhantomPhreak’s [the Counterparty co-founder and lead developer] note below. Additionally, all these multisig transactions are processed by the miners.
The developer continued by criticising the Bitcoin developers plan to limit OP_Return to just 40 bytes rather than 80:
If OP_RETURN was meant to stop/curtail the multisig behaviour (Unspent Outputs) and hereby reduce blockchain bloat, then I fear by reducing the size of OP_RETURN from 80 to 40 bytes, you’ve inadvertently made multisig MORE ATTRACTIVE to all the metaprotocols and you’ve made OP_RETURN less attractive.
The lead Counterparty developer and co-founder, who went by “PhantomPhreak” chimed in:
The idea is that we store the data in a second blockchain, and put hashes of that timestamped data in Bitcoin, which hashes would also be less than 40 bytes. The reason we did not do something like that is not a matter of “intellectual laziness”, but rather of implementation complexity. Counterparty is not a project in computer science; it is designed to be as simple as possible, for the benefits in development speed. Even if we have to store our data in multi-sig outputs rather than the too-small OP_RETURN outputs. Worse is definitely better in this space.
The next day Jeff responded:
It is called a free ride. Given that the overwhelming majority — >90% — application for the bitcoin blockchain is currency use, using full nodes as dumb data storage terminals is simply abusing an all-volunteer network resource. The network replicates transaction data, so why not come along for a free ride? Rather than engage the existing community, mastercoin and counterparty simply flipped an “on” switch and started using bitcoin P2P nodes as unwanted data stores. An unspent transaction output was never meant to be used as arbitrary data storage. The fact that it can be abused as such does not make it right, or remotely efficient, or the best solution. The UTXO (unspent transaction output) database is the entire network’s fast access database. Every single node needs that database to be as small as possible, for best processing of network transactions. Encoding arbitrary data into unspent outputs is network-wide abuse, plain and simple. The entire network bears the cost.
Source: https://bitcointalk.org/index.php?topic=395761.msg5815887#msg5815887
Due to Jeff’s high standing within the community, most people in the Counterparty community seemed keen to engage and resolve the issue. For instance BitcoinTangibleTrust responded by saying:
Thanks for sharing your thoughts Jeff. So, will you help us start engaging with the existing bitcoin core-dev community? It’s in Counterparty’s interests to act as a responsible partner as we need the bitcoin blockchain if we are to survive. Will you let us know how we can start working together on these questions?
Source: https://bitcointalk.org/index.php?topic=395761.msg5816031#msg5816031
Another Counterparty developer brought up another point:
Is there a way for the bitcoin protocol to prevent the way XCP is using it, without breaking anything else?
If there is no way for Bitcoin developers to block the Counterparty related transactions, perhaps this opposition didn’t matter and Counterparty could continue using Bitcoin without permission. Bitcoin developer and at the time mining pool operator Luke-Jr then entered the debate:
The miners are supposed to filter out abuses.
Source: https://bitcointalk.org/index.php?topic=395761.msg5816503#msg5816503
Luke-Jr then suggested these kinds of systems could be built using merge mined sidechain type constructions, which may avoid the blockchain bloat.
The problem isn’t new layers, it’s forcing things on people against their will. New layers can be done on an opt-in basis, without polluting the blockchain and forcing non-participants to store the data.
Luke was also asked why the Bitcoin developers reduced the intended OP_Return relay size down to 40 bytes compared to an 80 byte limit, which was originally proposed. Luke responded with the following three points:
Too many people were getting the impression that OP_RETURN was a feature, meant to be used. It was never intended as such, only a way to “leave the windows unlocked so we don’t need to replace the glass when someone breaks in”. That is, to reduce the damage caused by people abusing Bitcoin. 40 bytes is more than sufficient for all legitimate needs for tying data to a transaction: you get 32 bytes for a hash, plus 8 bytes for some kind of unique identifier (which really isn’t necessary either!). The original 80 byte proposal was intended to be for 512-bit hashes, but this was determined to be unnecessary. Luke-Jr continued as follows:
Hopefully as mining returns to being decentralised, we will see less toleration of abusive/spam transactions whether the OP_RETURN variant or otherwise. Now, if someone has a valid, necessary use case for actually storing hashes with transactions, obviously that’s a case miners should seriously consider mining.
Source: https://bitcointalk.org/index.php?topic=395761.msg5817170#msg5817170
Luke’s mining pool at the time also started filtering out Counterparty related transactions. At this point fear and uncertainty started to build in the Counterparty community. They needed OP_Return to be 80 bytes, or they would be forced to keep using the OP_CHECKMULTISIG opcode. It did not seem likely that it would go up to 80 bytes given Luke’s comments. In addition to this, some feared the developers could even reduce the limit even further, potentially booting Counterparty off the network. The Bitcoin developers did not seem especially friendly to Counterparty and therefore some may have felt that it was likely to be difficult to continue to use the Bitcoin protocol.
On 25th March 2014, Vitalik Buterin, the main founder of Ethereum chimed in, he argued that the debate should be more around fees and if you pay enough fees then your transaction should be legitimately included. Today, Ethereum’s fee algorithm is highly complex, with different fee buckets and rates for many different blockchain uses, which essentially solves the OP_Return problem. One can argue that SegWit on Bitcoin also mitigates the problem to some extent.
It’s the protocol’s fault the OPRETURN battle is such an issue. In an ideal world, the concept of ‘abuse’ would not even exist; fees would be mandatory, and carefully structured to closely match the actual cost that a given transaction imposes on the network,” he says. “If you can pay the fees for what you’re doing then you should be able to do it, no questions asked.”
Source: https://www.coindesk.com/markets/2014/03/25/developers-battle-over-bitcoin-block-chain/
On 27th March 2014 Counterparty changed the way it made transactions to get around Luke-Jr’s mining filter. However, the following day Luke commented that:
Great news! Filter added to block this crap in less than 5 minutes, and 1 line of code.
Source: https://bitcointalk.org/index.php?topic=395761.msg5955613#msg5955613
Luke-Jr also likened Counterparty to a form of abuse:
It’s abuse because you’re forcing others to download/store your data against their free choice. Every full node must download the full blockchain (prunable or not!). Every full node has consented to download and store financial transactions. NOT every full node has consented to store anything else. You need 100% consensus for this, not merely some subset (ie, not miners; not developers) or even a majority. Furthermore, everyone is free to store data that isn’t in the blockchain. There is nothing to be gained by putting it in the blockchain except that you force it on those who don’t want it. Explain how this is anything but abuse…
Source: https://bitcointalk.org/index.php?topic=395761.msg5826443#msg5826443
Anger at Bitcoin developers
As one might expect, the concern from Bitcoin developers was eventually met with frustration and anger from some Counterparty developers and users. We have include some of their comments below. Firstly from a user called “porqupine” commenting on Luke-Jr’s mining pool blocking Counterparty transactions:
Great instead of developers responsibly engaged towards finding a solution – you’re promoting cat and mouse. You realize you’re also saying fuck it to net-neutrality? And trying to take into private hands what kind of transactions people should and shouldn’t make on the Blockchain. What’s next sanctions of certain individuals you don’t like? Sanctions for transactions broadcast from Nodes in countries whose governments foreign policy you don’t approve of?
Source: https://bitcointalk.org/index.php?topic=395761.msg5955738#msg5955738
On 21 March 2014 porqupine went on to say:
Wait a minute when was it decided that: Every node has consented to store X type data and not Y type data. Maybe I also did not consent to store transactions for Laundered money, illicit drugs and weapons, human slavery – etc. You’re basically negating protocol neutrality and deciding what the Protocol Should and Should Not be used to store, and More than that you aren’t speaking in first person but using the pronoun Us given the impression that you are speaking for all miners or protocol users as a whole.
Source: https://bitcointalk.org/index.php?topic=395761.msg5826584#msg5826584
Others expressed concern about why Jeff and Luke had a right to block certain use cases over anyone else.
I can’t believe this attitude. I didn’t know bitcoin had owners. I thought I and about a million others were owners 🙂
PhantomPhreak, a Counterparty co-founder said:
First of all, Counterparty transactions are financial transactions. Second, every full node has consented to download and store the Bitcoin blockchain, no less. That is, transactions that accord to the Bitcoin protocol, which Counterparty transactions obviously do. Satoshi imbedded a political message in the Genesis Block, for Christ’s sake… You have a much narrower view of the possible use cases for Bitcoin than do others.
Source: https://bitcointalk.org/index.php?topic=395761.msg5826770#msg5826770
He or she continued:
Bitcoin does lots of things that it was not originally intended to do. Yes, we’d greatly prefer to use a more elegant solution than what we have now. Counterparty was originally designed to use the OP_RETURN output to store all of its message data, which I feel is very elegant, and leaves a minimal impact on the blockchain. We planned all of our message formats around the 80 byte limit announced by Gavin on the official Bitcoin blog. We only use multi-sig outputs because we have no other choice. We don’t want to extend the Bitcoin protocol. We want to do something entirely within it, and as simply and directly as possible, for the benefits to stability, security etc..
Source: https://bitcointalk.org/index.php?topic=395761.msg5827473#msg5827473
…
Again, we only store financial transactions in the blockchain, and we are paying for the space that we’re using. Financial transactions in OP_RETURN outputs aren’t any more painful for a full-node to store than anything else.
Source: https://bitcointalk.org/index.php?topic=395761.msg5827688#msg5827688
Another user called “bitwhizz” said:
if you don’t want to store it, don’t, fairly simple, don’t use bitcoin, don’t download the block chain, your scott free. However my consent means that i believe bitcoin has more functionality than just for transactions, and based on that fact nobody owns it, and there is OP_RETURN feature, i don’t see why that functionality should be eradicated because you don’t want to store the data which you already have a free choice on.
Source: https://bitcointalk.org/index.php?topic=395761.msg5827897#msg5827897
“Anotheranonlol” said:
I really cannot understand how a counterparty transaction would not constitute a financial transaction?. nor can i understand the point of view that because say, 1 node out of 1000 is not willing to accept this data, by default it should be forbidden. After the recent nightmare that was mt gox and huge amount of hacks, thefts, closures and losses that came from storing your balance on centralised entities it seemed that counterparty had came up with a solution that allowed a decentralised, trustless solution to this problem
Source: https://bitcointalk.org/index.php?topic=395761.msg5827776#msg5827776
“Baddw” said:
The fact is, arbitrary data can be stored in the blockchain by anybody at any time. It has been and is being used for this purpose already. Everybody running a Bitcoin node should already know this, and if they aren’t, it should be a part of the notice that comes up when they install Bitcoin-QT (if there is one; I don’t recall seeing one). Any Bitcoin transaction could just be a simple movement of funds, or it could be a love note, or it could be a trigger for setting off a bomb. Eliminating this possibility would kill Bitcoin, period.
Source: https://bitcointalk.org/index.php?topic=395761.msg5827749#msg5827749
And Baddw went on to say:
Many of the greatest developments in computing history (and indeed, human technological history on the whole) are the result of people finding uses for things which were unintended by their inventors. Good thing that most inventors are not so protective of their inventions that they decline to let others use it for new things. Those that did, found themselves surpassed quickly.
Source: https://bitcointalk.org/index.php?topic=395761.msg5827925#msg5827925
It is clear from these comments that many Counterparty users and developers were surprised and disappointed by the stance from Bitcoin developers. Although the project continued, as did Mastercoin, it is likely that, for better or for worse, some developers left Bitcoin as a result of this and instead built their protocols on other blockchain systems such as Ethereum. It is this 2014 moment that was, in our view, more significant than any other. However, others may have a different view.
Merge Mined Sidechains
Throughout the OP_Return debate, opponents of Counterparty and blockchain bloat typically mentioned some form of merge mined side chains as a solution for Dapps. Actually Satoshi is said to have favoured this path and is said to have supported it for a domain name system in December 2010:
I think it would be possible for BitDNS to be a completely separate network and separate block chain, yet share CPU power with Bitcoin. The only overlap is to make it so miners can search for proof-of-work for both networks simultaneously.
Source: https://bitcointalk.org/index.php?topic=1790.msg28696#msg28696
There are many difficulties with implementing these Dapp systems as sidechains and our understanding of these weaknesses is better understood today than it was in 2014 when many people just assumed they could work.
Complexity – One of the most significant weaknesses is the complexity in implementing and building sidechain solutions. In a race to get the protocol out early and win market share, these projects did not have time to build a sidechain and the merge mining system with Bitcoin.
Bitcoin as a native asset – It may not be possible to have non-custodial Bitcoin as an operating asset on a sidechain, because a trustless two-way peg may not be possible to build. This is a large weakness for many Dapps who may for example want to use Bitcoin as the main trading pair in a distributed exchange. This weakness did not appear to be well understood in 2014 with many people just assuming it could work somehow.
Limited scaling benefits – The benefits of using a sidechain may vary depending on the use case. For example, if one wants to build a distributed exchange, every bid, offer and match may require all the security guarentees of the main chain. With this much main chain usage, for every possible action of every user on the exchange, the scaling advantages of the sidechain system may be extremely limited. Submitting a bid onchain natively may only use around 90 bytes, while storing a hash of the order information and the structure and overhead around it necessary to be identified could be around 50 bytes onchain, so not much of a space saving.
In March 2014, Counterparty developer (xnova) outlined his opposition to the sidechains point as follows.
Moreover, unless I am overlooking something here, we would still need to parse out the data from the blocks in that second blockchain (assuming it’s a Bitcoin or Bitcoin derivative implementation, at least) to get our stored data. So: * it would not enable SPV-type Counterparty clients for what Counterparty offers over Colored Coin functionality (i.e. DEx, Betting, asset callbacks, dividends, CFDs, etc) * it would lessen security of Counterparty transactions. * it would greatly increase the complexity of the implementation (i.e. increasing the chance of bugs and vulnerabilities) The only dubious benefit would be the slight lessening our storage requirements on the block chain (i.e. maybe 20-40 bytes less per transaction?). I just don’t see how this would make any sense here. One more point: Counterparty can bring immense benefits to Bitcoin, and this will especially become more apparent if/as Ethereum (and other similar non-Bitcoin-meta “2.0” type coins) enter the picture. My personal feeling here at least is that Bitcoin may very well need offerings in the ecosystem with this kind of functionality to effectively compete with Ethereum and (future) crowd’s feature list and draws — or risk becoming obsoleted, at least among investors and financial market operators, which offer the ability to bring billions and even trillions into the Bitcoin ecosystem as it gains more recognition, trust, and mindshare with them
Source: https://bitcointalk.org/index.php?topic=395761.msg5799174#msg5799174
It seems that some of the people arguing in favour of sidechains as a solution were not particularly interested in many of the Dapp applications nor had they experimented with them. Therefore they never thought through the complexities of building a distributed exchange and how almost every single action from every user requires security. Most Bitcoin developers seemed quite open about what they are interested in and clear about what they want: censorship resistant money, non-political money, electronic cash etc etc…
Conclusion
After around 2014, most developers interested in Dapps focused on building on Ethereum or other systems, not on Bitcoin. Ethereum then achieved a critical mass of developer interest and momentum, and Dapp development on Bitcoin was minimal. The key point of this article is to emphasise that the main driver for this was not necessarily fees or Ethereum’s virtual machine and Ethereum’s stronger technical capabilities, it is simply that many Bitcoiners and Bitcoin developers did not want Dapps on Bitcoin and they were not interested in these features. For better or for worse, some Bitcoiners deliberately pushed many of these Dapp developers away. Some Bitcoiners believe that most of the Dapp activity is related to unsustainable scams or that this activity is undesirable on Bitcoin for security or other reasons. At the same time, some promoters of alternative coins (e.g. Ethereum) may have exaggerated the impact and significance of the so-called “OP_Return Wars”, to boost their burgeoning chains.
The views of many people have changed since 2014. Bitcoin needs transaction fees to survive. In the post 2016 environment, in which we have many full blocks and somewhat higher fees, it is more widely appreciated that any fee paying transaction is “legitimate”. Certain Dapps on Ethereum, such as exchanges like Uniswap, or lending protocols like AAVE and Compound have proven to be both successful and interesting, to some extent. Despite this, whether Bitcoiners even care enough to want these protocols on Bitcoin, let alone if anyone will actually build and use them, remains an open question.
By BitMEX Research link: https://blog.bitmex.com/author/bitmex-research/?lang=en_us
-
 @ ebe1a380:3423b7b7
2023-06-08 01:47:27
@ ebe1a380:3423b7b7
2023-06-08 01:47:27 -
 @ 9e228c8a:b52d787a
2023-06-08 01:47:22
@ 9e228c8a:b52d787a
2023-06-08 01:47:22 -
 @ 2f54f78a:581756a1
2023-06-08 01:46:50
@ 2f54f78a:581756a1
2023-06-08 01:46:50 -
 @ 07fc31e3:f96cba8a
2023-06-08 01:46:20
@ 07fc31e3:f96cba8a
2023-06-08 01:46:20 -
 @ b9e76546:612023dc
2023-06-07 22:12:51
@ b9e76546:612023dc
2023-06-07 22:12:51
#Nostr isn't just a social network, that's simply the first use case to sprout from the Nostr tree.
Simple Blocks, Complex Change
Nostr isn't just a social network, in a similar way that Bitcoin isn't just a transaction network. Both of these things are true, but they each miss the more significant elements of what they accomplish.
In my mind, the source of Nostr's true potential is two fold; first, in fundamentally changing the centralized server model into an open environment of redundant relays; and second, it eliminates the association of clients with their IP address and metadata, and replaces it with identification via public keys. Within this one-two punch lies the most important tools necessary to actually rearchitect all of the major services on the internet, not just social media. Social is simply the interface by which we will connect all of them.
The combination of this simple data & ID management protocol with decentralized money in #Bitcoin and #Lightning as a global payments network, enables nostr to build marketplaces, "websites," podcast feeds, publishing of articles/video/media of all kinds, auction networks, tipping and crowdfunding applications, note taking, data backups, global bookmarks, decentralized exchanges and betting networks, browser or app profiles that follow you wherever you go, and tons more - except these can be built without all of the negative consequences of being hosted and controlled by central servers.
It separates both the data and client identity from the server hosting it. Handing the ownership back to the owner of the keys. We could think of it loosely as permission-less server federations (though this isn't entirely accurate, its useful imo). Anyone can host, anyone can join, and the data is agnostic to the computer it sits on at any given time. The walls are falling away.
Efficiency vs Robustness
There is also a major secondary problem solved by these building blocks. A byproduct of solving censorship is creating robustness, both in data integrity, but also in data continuity. While the fiat world is so foolishly focused on "efficiency" as the optimal goal of all interaction, it naively ignores the incredible fragility that comes with it. It is far more "efficient" for one big factory to produce all of the computer chips in the world. Why build redundant manufacturing to produce the same thing when one factory can do it just fine? Yet anyone who thinks for more than a few seconds about this can see just how vulnerable it would leave us, as well as how much corruption such "efficiency" would wind up enabling.
Nostr is not alone either. Holepunch is a purely P2P model (rather than based on relays) that accomplishes the same separation in a different way. One where the clients and servers become one in the same - everyone is the host. Essentially a bittorrent like protocol that removes the limitation of the data being static. The combination of their trade offs & what these protocols can do together is practically limitless. While Nostr begins building its social network, combining it with what Synonym is building with their Web of trust, (the critical ingredient of which is public key identification) we can "weigh" information by the trust of our social graph.
Not too long ago, a friend and I used Nostr to verify who we were communicating with, we shared a Keet (built on Holepunch) room key over encrypted nostr DM, and opened a P2P, encrypted chat room where we could troubleshoot a bitcoin wallet problem and safely and privately share very sensitive data. The casual ease by which we made this transaction enabled by these tools had us both pause in awe of just how powerful they could be for the privacy and security of all communication. And this is just the very beginning. The glue of #Lightning and #Bitcoin making possible the direct monetization of the infrastructure in all of the above has me more bullish on the re-architecting of the internet than ever in my life. It cannot be reasonably called an insignificant change in incentives to remove both the advertiser and the centralized payment processor from inbetween the provider and the customers online. The base plumbing of the internet itself may very well be on the verge of the greatest shift it has ever gone through.
A Tale of Two Network Effects
I would argue the most significant historical shift in the internet architecture was the rise of social media. It was when we discovered the internet was about connecting people rather than computers. The social environment quickly became the dominant window by which the average person looked into the web. It's the place where we go to be connected to others, and get a perspective of the world and a filter for its avalanche of information as seen through our trust networks and social circles. But consider how incredibly neutered the experience really is when money isn't allowed to flow freely in this environment, and how much it actually would flow, if not for both centralized payment processors and the horrible KYC and regulatory hurdle it entails for large, centralized entities.
The first time around we failed to accomplish a global, open protocol for user identity, and because of this our social connections were owned by the server on which we made them. They owned our digital social graph, without them, it is erased. This is an incredible power. The pressures of the network effect to find people, rather than websites, took a decentralized, open internet protocol, and re-centralized it into silos controlled by barely a few major corporations. The inevitable abuse of this immense social power for political gain is so blatantly obvious in retrospect that it's almost comical.
But there is a kind of beautiful irony here - the flip side of the network effect's negative feedback that centralized us into social media silos, is the exact same effect that could present an even greater force in pushing us back toward decentralization. When our notes & highlights have the same social graph as our social media, our "instagram" has the same network as our "twitter," our podcasts reach the same audience, our video publishing has the same reach, our marketplace is built in, our reputation carries with us to every application, our app profiles are encrypted and can't be spied on, our data hosting can be paid directly with zaps, our event tickets can be permanently available, our history, our personal Ai, practically anything. And every bit of it is either encrypted or public by our sole discretion, and is paid for in a global, open market of hosts competing to provide these services for the fewest sats possible. (Case in point, I'm paying sats for premium relays, and I'm paying a simple monthly fee to nostr.build for hosting media)
All of this without having to keep up with 1,000 different fucking accounts and passwords for every single, arbitrarily different utility under the sun. Without having to setup another account to try another service offering a slightly different thing or even just one feature you want to explore. Where the "confirm with your email" bullshit is finally relegated to the hack job, security duck tape that it really is. The frustrating and post-hoc security design that is so common on the internet could finally become a thing of the past and instead just one or a few secure cryptographic keys give us access & control over our digital lives.
The same network effect that centralized the internet around social media, will be the force that could decentralize it again. When ALL of these social use cases and connections compound on each other's network effect, rather than compete with each other, what centralized silo in the world can win against that?
This is not to dismiss the number of times others have tried to build similar systems, or that it's even close to the first time it was attempted to put cryptographic keys at the heart of internet communications. Which brings me to the most important piece of this little puzzle... it actually works!
I obviously don't know exactly how this will play out, and I don't know what becomes dominant in any particular area, how relays will evolve, or what applications will lean toward the relay model, while others may lean P2P, and still others may remain client/server. But I do think the next decade will experience a shift in the internet significant enough that the words "relay" and "peer" may very well, with a little hope and lot of work, replace the word "server" in the lexicon of the internet.
The tools are here, the network is proving itself, the applications are coming, the builders are building, and nostr, holepunch, bitcoin and their like are each, slowly but surely, taking over a new part of my digital life every week. Case in point; I'm publishing this short article on blogstack.io, it will travel across all of nostr, I'm accepting zaps with my LNURL, it is available on numerous sites that aggregate Kind:30023 articles, my entire social graph will get it in their feed, & there will be a plethora of different clients/apps/websites/etc through which the users will see this note, each with their own features and designs...
Seriously, why the fuck would I bother starting a Substack and beg people for their emails?
This is only the beginning, and I'm fully here for it. I came for the notes and the plebs, but it's the "Other Stuff" that will change the world.
-
 @ 0dde8796:14799cec
2023-06-07 20:44:06
@ 0dde8796:14799cec
2023-06-07 20:44:06
Lately I have been scouring youtube for old video lectures and interviews with the guys I consider bitcoin "legends". Here are a few of my favorites:
Andreas Antonopoulos This video is from the Disrupt Symposium held in Athens, Greece in 2013. It's not easy to pick out just one video from Andreas Antonopoulos, who is probably the best bitcoin communicator and teacher ever. I really enjoy this video because it is so old by bitcoin standards, and he gives a masterful, energetic overview of bitcoin.
Nick Szabo This video is from the Bitcoin Investor Conference in Las Vegas in 2015. Nick is brilliant. Many people think there is a strong possibility that he is Satoshi Nakamoto.
Hal Finney I can't find any videos of Hal Finney other than this lecture he gave about Zero Knowledge Proofs back in 1998. He received the first bitcoin transaction from Saloshi Nakamoto, and many people believe he invented bitcoin. He tragically died young from ALS in 2014.
Gavin Andresen I had many videos to choose from, but I like this interview he did back in 2013 on the Triangulation show. His reputation has been severely damaged over the years due to his position during the Blocksize Wars, and his since disavowed contention that Craig Wright is Satoshi Nakamoto. None of this takes away from his intelligence, and the many years he served as bitcoin lead developer. He was also hand picked by Satoshi to carry the torch when bitcoin's inventor disappeared.
Adam Back There are no shortage of videos of Adam Back floating around the internet, but I like this lecture he gave at the Bitcoin Israel Conference in February of 2014, where he discusses ecash in the context of fungibility and privacy. Adam Back, creator of hashcash, was the first person to receive a preliminary, stripped down version of the whitepaper directly from Satoshi.
David Chaum Creator of Digicash, and one of the original cypherpunks, David Chaum's work and vision laid the foundation for bitcoin. This video from 2018 captures his intelligence and humor.
Originally published on Stacker News 4/15/23
-
 @ 0dde8796:14799cec
2023-06-07 20:38:57
@ 0dde8796:14799cec
2023-06-07 20:38:57
Here is a list of books that I found indispensable while learning more about bitcoin. Not all of them are about bitcoin, and a few were written before bitcoin came into existence, but all are fundamental to understanding and appreciating this extraordinary piece of code. I will eventually include my thoughts and comments about each, and welcome input to make the list more useful. This post is going to be constantly revised, and for now the order of listing should not be taken to imply a ranking.
The Bitcoin Standard
by Saifedean Ammous
The Sovereign Individual
by James Dale Davidson
Mastering Bitcoin
by Andreas M Antonopoulos
21 Lessons
by Gigi
Layered Money
by Nik Bhatia
The Creature From Jekyll Island
by G. Edward Griffin
When Money Dies
by Adam Fergusson
The Price of Tomorrow
by Jeff Booth
The Blocksize War
by Jonathan Bier
Digital Gold
by Nathaniel Popper
Check Your Financial Privilege
by Alex Gladstein
Bitcoin Is Venice
by Allen Farrington and Sacha Meyers
The Seventh Property
by Eric Yakes
Antifragile
by Nassim Nicholas Taleb
-
 @ 0dde8796:14799cec
2023-06-07 20:29:38
@ 0dde8796:14799cec
2023-06-07 20:29:38
I joined SN one year ago today. I think I first read about it on the r/bitcoin subreddit. I was hooked from the start. I abandoned Facebook years ago. I never really embraced twitter. I really liked the idea that sats were taking the place of the traditional "like" or up vote. Stacker News was real value for value.
I began to learn a lot. High signal/low noise. My interest in bitcoin flowed naturally from my politics, the belief in freedom and a natural distrust of a powerful central government. I am a retired lawyer, so my expertise, to the extent I have any, was in law, politics, and economics. Math wasn't my strong suit in school. I got by, but was no wiz. I wasn't a techie either, though I always enjoyed messing around on a very basic level with computers for fun.
I am an older guy. I struggled, and still struggle with the technical aspects of bitcoin, but the people here helped me to learn more than I imagined I could learn. I had tried linux in the past, but soon I had completely abandoned windows for good, thanks to inspiration from fellow SNers. I had run an Umbrel node for a few months before joining, but now I began learning more about what was going on beyond simple plug and play. I started teaching myself python through youtube videos. Progress was slow, and competence is still far off, but I'm enjoying the journey. There are a lot of talented people here on SN who are generous with their time and knowledge.
Thanks to the frequent AMAs I was able to communicate with people with whom I would never have had the chance to speak. I particularly remember Lyn Alden, Anita Posch, Nik Bhatia, jb55, Alex Gladstein, and Alex Leishman. I had occasional interactions with Kevin Rooke, whose podcasts continue to educate me. DarthCoin berates and abuses me at least once a month. Jimmy Song frequently posts polls, fiatjaf discusses new nostr developments and offers bounties, and Odell and Gigi will sometimes post their own latest writings here. Guy Swann occasionally shows up too. I'm sure I'm forgetting many others. For a committed bitcoin fanatic, this is the big leagues.
Keyan Kousha, founder and fearless leader, also contributes posts and comments frequently. He is a very smart yet modest guy. Most users don't kiss his butt too much when they engage with him. Some of his posts even get ignored, just like some of mine. That's a wonderful thing about the SN culture. It's a level playing field.
Stacker News has come a long way in one year. Since I joined, there have been many improvements, including polls, an edit button, a referral program, NIP-05 support, bounties, the rare and valued cowboy hat, NIP-57 zap support, bookmarks, and a nostr sub, among others. I am sure there are many more in the pipeline.
I just want to express my appreciation for this site, and I look forward to learning more as our world moves to a bitcoin standard.
Published on Stacker News 5/23/23
-
 @ 4ac847f3:16dc6c5a
2023-06-07 20:16:45
@ 4ac847f3:16dc6c5a
2023-06-07 20:16:45Introdução:
Em uma importante conquista para o mercado de criptoativos no Brasil, o Mercado Bitcoin, uma das principais exchanges do país, recebeu aprovação do Banco Central para atuar como Instituição de Pagamento, na modalidade emissor de moeda eletrônica. Essa autorização marca um marco significativo para a empresa e fortalece sua missão de ser a ponte entre a economia tradicional e a digital. Neste artigo, vamos explorar os detalhes dessa aprovação e como isso impacta o ecossistema de criptoativos no Brasil.
O que significa ser um emissor de moeda eletrônica?
Uma Instituição de Moeda Eletrônica, também conhecida como Instituição de Pagamento ou Emissor de Moeda Eletrônica, é uma empresa que possui licença para fornecer serviços financeiros em contas especiais. No caso do Mercado Bitcoin, a aprovação do Banco Central permite que eles atuem no gerenciamento de contas de pagamento do tipo pré-pago, similar aos emissores de cartões pré-pagos em moeda nacional. Isso significa que os usuários poderão desfrutar de serviços financeiros, como transações e pagamentos, diretamente pelo aplicativo do Mercado Bitcoin.
Benefícios para os usuários:
Com essa aprovação, os clientes do Mercado Bitcoin se beneficiarão de mais liberdade, fluidez e segurança nas transações. O MB Pay, serviço oferecido pela exchange, permitirá o gerenciamento de contas de pagamento pré-pagas, onde os recursos são depositados antecipadamente pelos usuários. Além disso, não serão cobradas tarifas pelo uso desses serviços, proporcionando uma experiência financeira mais acessível.
Expansão de negócios e futuros lançamentos:
A aprovação do Banco Central representa um marco importante para o Mercado Bitcoin, permitindo que a empresa siga adiante com seus planos de expansão de negócios. Além do MB Pay, a exchange já está se preparando para lançar seu próprio cartão nos próximos meses. Essa iniciativa combinará a potência dos criptoativos com os serviços financeiros tradicionais, elevando a experiência financeira das pessoas.
Impacto no mercado financeiro:
A autorização concedida ao Mercado Bitcoin destaca a crescente relevância e reconhecimento do mercado de criptoativos no Brasil. Instituições de Moeda Eletrônica, como o Mercado Bitcoin agora se tornou, são alternativas ágeis e flexíveis em relação aos bancos tradicionais, oferecendo processos de abertura de conta mais rápidos e menos burocráticos. Essa competição resulta em maior variedade de opções para os consumidores e redução de custos.
Conclusão:
A aprovação do Banco Central do Brasil para o Mercado Bitcoin se tornar um emissor de moeda eletrônica é uma notícia empolgante para o mercado de criptoativos e para os usuários da plataforma. Essa conquista fortalece a posição do Mercado Bitcoin como uma das principais empresas do setor e reforça sua missão de conectar a economia tradicional com a digital. Com mais liberdade e segurança nas transações, aliadas aos serviços financeiros tradicionais, o Mercado Bitcoin está abrindo novas possibilidades para o futuro financeiro dos brasileiros.
-
 @ 0b80cdb7:ecd7dd41
2023-06-07 20:05:00
@ 0b80cdb7:ecd7dd41
2023-06-07 20:05:00 -
 @ 7e329cd8:bad4d894
2023-06-07 20:04:41
@ 7e329cd8:bad4d894
2023-06-07 20:04:41 -
 @ 0679403c:3d7eddfb
2023-06-07 20:04:22
@ 0679403c:3d7eddfb
2023-06-07 20:04:22 -
 @ a715bcd1:318d6e6c
2023-06-07 19:38:30
@ a715bcd1:318d6e6c
2023-06-07 19:38:30Exchange Bitcoin holdings, unlike Ether, appear stable in light of the Binance and Coinbase lawsuit news.
Bitcoin tickers down $26,483 hitting three-month lows did not spur hodlers to panic sell, on-chain data shows.
On-chain losses “remain quiet”
BTC/USD dipped to just $25,350 on June 6, its lowest since mid-March — but it seems existing holders simply do not care.
The latest data covering on-chain transactions shows that in the midst of reactions to the Binance and Coinbase lawsuits, few were in “panic sell” mode.
A chart uploaded to Twitter by Glassnode showed realized losses — coins moving at a lower value than their previous transaction — staying cool.
This marked a shift in sentiment for the investor base as a whole, coming in stark contrast to the events that followed the implosion of exchange FTX in late 2022.
“Following a crescendo in US regulatory pressure on major cryptocurrency Exchanges Binance and Coinbase, the market experienced significantly volatile moves in both directions,” Coinglass reported.
“However, the magnitude of Realized Losses recorded On-Chain remains quiet at $112M. This remains -$3.05B (-96.5%) smaller than the largest recorded capitulation event, suggesting an increased degree of resilience amongst market participants.”
 For context, the FTX event sparked $145 billion in realized losses — over 10 times the June 5 tally.
For context, the FTX event sparked $145 billion in realized losses — over 10 times the June 5 tally.Exchange BTC traders not rushing for the exit
The latest data available covering exchange balances tells a similar story of resilience.
As per Glassnode’s tracking tools, major exchanges saw only a modest decrease in BTC balances on June 5–6.
This totaled around 12,600 BTC, potentially indicating a similar lack of desire among users to remove their funds from hot wallets.
Compared to FTX, the situation once again stands out, as mass exchange withdrawals characterized much of last November.

Continuing, statistician Willy Woo noted that the lack of action at Binance came despite its United States regulators petitioning to freeze its domestic assets.
“Binance customers don’t care. Not seeing much BTC leaving, not yet at least,” part of Twitter commentary stated.
Original link: Binance BTC outflows muted as users shun panic selling original author: WILLIAM SUBERG
-
 @ a715bcd1:318d6e6c
2023-06-07 19:11:09
@ a715bcd1:318d6e6c
2023-06-07 19:11:09 Tesla CEO and Twitter owner Elon Musk speaks during the unveiling of the new Tesla Model Y in Hawthorne, California.AFP VIA GETTY IMAGES
Tesla CEO and Twitter owner Elon Musk speaks during the unveiling of the new Tesla Model Y in Hawthorne, California.AFP VIA GETTY IMAGESElon Musk—as of today the richest person in the world—is loosening Twitter’s tight rein on user identities, allowing some paying content creators a way to leave the service but take their followers with them. But the mechanism seems clunky when compared with new social-media networks that offer less limited portability.
US-AUTO-TESLA-MODEL Y Tesla CEO and Twitter owner Elon Musk speaks during the unveiling of the new Tesla Model Y in Hawthorne, California.AFP VIA GETTY IMAGES Elon Musk—as of today the richest person in the world—is loosening Twitter’s tight rein on user identities, allowing some paying content creators a way to leave the service but take their followers with them. But the mechanism seems clunky when compared with new social-media networks that offer less limited portability.
In a tweet this morning, Musk said the struggling social network he bought last year will be giving away the email addresses of some users who follow people participating in a revamped subscriptions program. Launched in April, the plan lets Twitter users with at least 500 followers charge for exclusive tweets and other content. Musk said content creators will now be “able to leave this platform easily & take their subscribers with them if they want.”
The subscribers, however, would have to give permission for their addresses to be shared. Musk’s alternative has some value for paying users, whose mailing lists can generate $36 for every dollar spent. But offers little visible benefit to the followers who can already communicate with their network via direct messaging.
The change occurs as a collection of Twitter alternatives that allow all users to move their identities to other networks and take their followers with them gains steam. Musk has shown antipathy to the concept, abrogating an agreement to use the decentralized social network Bluesky—spun out of Twitter under previous CEO Jack Dorsey. Bluesky and the cottage industry of competitors, including bitcoin-friendly Nostr and Zion, have collected millions of users.
Nostr creator @Fiatjaf is skeptical of the move. “Instead of doing that self-defeating strategy that relies on old and mostly broken email protocol and handing his users to stupid competitors like substack, musk should look into merging twitter with nostr, making twitter part of a larger, open ecosystem, while still retaining his dominance and providing great ux [user-experience] for his users.”
Zion founder Justin Rezvani says that influencers are valuable to Twitter because their followers heed their opinions and take action. “Elon is looking to increase Twitter revenue as a result of the tweet,” he says. “It’s carrot for content creators to push their “followers" to become subscribers to increase revenue for Twitter because it’s one of the only mechanisms he has as Twitter is still a highly centralized service.”
Original link: Elon Musk’s Twitter Email Giveaway Is A Boon For Paying Influencers—But It’s Not Decentralized Original author: Michael del Castillo
-
 @ 41935ab6:efd95bb1
2023-06-07 16:26:25
@ 41935ab6:efd95bb1
2023-06-07 16:26:25Evolusi Refleksivitas makhluk hidup mungkin begitu lambat, namun tidak dengan evolusi teknologi, mereka bertumbuh dan berubah semakin cepat.
-
 @ 0dde8796:14799cec
2023-06-07 15:27:30
@ 0dde8796:14799cec
2023-06-07 15:27:30I enjoy watching slum porn on youtube. Here is an example of what I’m talking about. I watch these videos because I cannot believe the decay and degradation of the United States during my lifetime. I appreciate what I have more after seeing how many of my fellow citizens live.
As a bitcoiner, I spend a lot of time thinking about El Salvador, the continent of Africa, and other places throughout the world where people can benefit from bitcoin adoption. For some reason, I have had a blind spot about my own country.
It occurred to me that one of these urban, suburban or rural slums in the US would be perfect as a locale to start a bitcoin community. Housing stock is available and extraordinarily cheap in some locations (sometimes less than $10,000 for a house), property taxes are very low, and the infrastructure, though crumbling, already exists. I remember living in Brooklyn, New York in the 1980’s and 1990’s when intrepid young people would gentrify run down, crime ridden neighborhoods block by block. These are now some of the most desirable places to live in the borough.
One of these neighborhoods would be the perfect laboratory for a bitcoin economy. Many of these places have been abandoned by local governments. This would present an opportunity for bitcoiners to run their own communities with a good deal of autonomy. If you doubt this, do a little research on Amish and Mennonite communities in the U.S., or this Orthodox Jewish community, where rabbis control local politics and education.
I’m too old and set in my ways to do this, but I am sure there are young, brave hodlers out there who could serve as the initial pioneers. If they build it, we will come.
Published on Stacker News 3/3/23
-
 @ 0dde8796:14799cec
2023-06-07 14:24:17
@ 0dde8796:14799cec
2023-06-07 14:24:17
I have learned during my time on Stacker News that it is sometimes difficult to understand @DarthCoin when he responds to a post. This is a shame, since he writes great guides, is an OG bitcoiner, and is a good source of knowledge. Therefore, I have created a little translation guide of my own to assist those having difficulty understanding him :
If @DarthCoin says:
“You are a fucking moron.”
What He Means:
“I think perhaps with regard to this particular issue you are mistaken.”
If @DarthCoin says:
“You are a fucking shitcoiner.”
What He Means:
“Good sir, I think that at this point you really don’t perceive the differences between bitcoin and the coins that were created after bitcoin through a centralized, pre-mine process”
If @DarthCoin says:
“Fuck the Banks and Govs”
What He Means:
“I believe that switching to a bitcoin economy obviates the need for financial institutions and will increase self autonomy.”
If @DarthCoin says:
“I don’t give a shit about the price.”
What He Means:
“It is unnecessary to focus on the day to day gyrations of the value of bitcoin as expressed in US dollar terms.”
If @DarthCoin says:
“People are retarded.”
What He Means is:
“There are many folks who don’t have the intellectual capacity or desire to learn about bitcoin.”
I welcome additions, corrections and suggestions to improve this guide.
Originally Published on Stacker News 3/4/23
-
 @ b8aafafe:38cf06fe
2023-06-07 11:18:09
@ b8aafafe:38cf06fe
2023-06-07 11:18:09Die Welt, in der wir gemeinsam leben, wird maßgeblich durch unser Handeln beeinflusst. Darüber, wie wir unser Handeln organisieren sollten, besteht aber keine Einigkeit. Ein ständiger Wettbewerb der Organisationsmechanismen findet statt in Form von Diskussion und Debatte, bzw. Austausch und Kampf, gespeist von Informationsangeboten unterschiedlicher Komplexität und Ehrlichkeit.
Relativ neuer Wettbewerber ist Bitcoin, dessen Befürworter politisch wahrscheinlich eher dem liberalen Lager und dessen Kritiker eher dem sozialistischen Lager zugeteilt werden können. Auf beiden Seiten finden sich allerdings sowohl die, die verstehen und sich austauschen wollen, als auch die, die kämpfen wollen, und außerdem noch die, die je nach der Situation, in welcher sie sich wähnen, zwischen Kampf- und Austauschmodus wechseln.
Meine These ist, dass sich viele in einem Kampf wähnen, sich von daher auch kämpferisch geben, dies aber in vielen Fällen auf Missverständnissen sowie falscher Loyalität beruht.
Ein Missverständnis wäre, dass die meisten, oder auch nur viele Bitcoiner, selbst die prominentesten Vertreter, ihren Reichtum schamlos zur Schau stellen würden (Stichwort “Lambos”). Falsche Loyalität wäre, sich mit Antisemiten gemein zu machen, nur weil diese Bitcoin gut finden.
Das größte Missverständnis ist aber, dass man dem einen oder anderen System loyal gegenüber sein müsste, bzw. dass eines am Ende und für immer alle anderen besiegen müsste.
Ich kann Bitcoiner sein, mir aber wünschen, dass niemand ihn braucht. Ich kann Zentralbanker sein, welcher Alternativen zulässt.
Ich darf und sollte versuchen, Bemühungen, mich in Kämpfe zu verwickeln, zu widerstehen.
-
 @ 32dc4f25:f95ddcce
2023-06-07 10:35:53
@ 32dc4f25:f95ddcce
2023-06-07 10:35:53Long story short, Pirate Wires exists because people subscribe. If you’re into what we’re doing here, drag your friends on board for a free sub, and if you haven’t yet already: Subscribe, or die.
Dangerous alliance. In 1787, Edmund Burke said there were “Three Estates in Parliament; but, in the Reporters' Gallery yonder, there [sits] a Fourth Estate more important than they all." The notion of some vital power beyond our government was imported to the New World, and today constitutes a core belief of the American liberal: there is no free people, we’re often told, without a free press independent of congress, the courts, and our president. But throughout the 20th Century thousands of media outlets gradually consolidated, and by the dawn of our internet era only a few giants remained. These giants largely shared a single perspective, and in rough agreement with the ruling class the Fourth Estate naturally came to serve, rather than critique, power. This relationship metastasized into something very close to authoritarianism during the Covid-19 pandemic, when a single state narrative was written by the press, and ruthlessly enforced by a fifth and final fount of power in the newly-dominant technology industry.
It was a dark alliance of estates, accurate descriptions of which were for years derided as delusional, paranoid, even dangerous. But today, on account of a single shitposting billionaire, the existence of the One Party’s decentralized censorship apparatus is now beyond doubt.
A couple weeks back, alleging proof Twitter acted with gross political bias, and in a manner that influenced U.S. elections (!), Elon Musk opened his new company’s internal communications to a small handful of journalists. They set immediately to breaking a series of major stories that have rewritten the history of Trump-era tech. Long story short, Twitter leadership lied to the public, relentlessly, for years, and everything the most paranoid among us ever said about the platform was true. “Trust and safety” is a euphemism for political censorship, with “expert” teams comprised almost exclusively of the most radical, joyless grievance studies majors you ever met in college. Their goal is to reshape American politics by dominating the bounds of what the public is permitted to consider American politics. In these efforts, they have mostly been succeeding.
On December 2nd, Matt Taibbi shared conversations from the company’s “trust and safety” team that led to Twitter’s suppression of the New York Post’s infamous Hunter Biden laptop story. While interesting, Taibbi’s most notable revelation came almost as a side: both major political parties, as well as the White House, maintained direct lines of communication with Twitter, which they used to formally request content be removed from the platform. The company responded enthusiastically to many of these requests, and the examples we have (for now) come from the Democratic Party. Critics have been quick to point out Trump was in the White House at the time, though less interested, for some reason, in what — if anything — he removed from the site.
On December 6th, Bari Weiss and her colleagues reported out proof of Twitter’s secret blacklists, in which both specific topics and, more problematically, people were de-amplified by the “trust and safety” team. The blacklisting was done for a nebulous host of reasons that generally amounted to something like ‘this feels dangerous.’ Danger was, of course, defined by partisan operatives, and exclusively targeted right-coded positions. Skepticism of radical gender ideology, distrust of public Covid policy, and almost anything having to do with the integrity of our last election were at the top of the list.
Separate from any opinion concerning whether such topics, or the purveyors of such topics, should have been “shadow banned,” the revelation that they were is immensely important on account of Twitter’s censors, with their many supporters in the press, have denied the existence of these tools for years.
Finally, over the last few days, Taibbi, Michael Shellenberger, and Bari have all reported out pieces of Donald Trump’s deplatforming, which is easily the most famous digital unpersoning in history. It is also the least compelling story in the series. While it’s good to finally know exactly what happened, it really just was what everyone assumed: Trump was not banned for violating policy. Trump was banned because Twitter employees, who donated literally 99% of their political contributions to the Democratic Party, demanded it be done regardless of their own rules.
Altogether, the Twitter Files — an ongoing story — paint a portrait of clear and inevitable partisan bias at one of the most dominant speech platforms in history. A small handful of very left-wing executives, who naturally perceived most opinion right of center as dangerous, worked tirelessly to limit those opinions from view. Empowered to censor “unsafe” content, and protected by a team of people who shared their political orientation, the executives produced, in a legal and decentralized manner, a key component of our defacto state censorship apparatus. While we don’t know for sure this is also happening at Google, Meta, or TikTok (which is for some reason still allowed to operate in this country), I think it’s a safe bet we’re looking at an industry-wide affliction.
But I do have questions.
Where is the full list of shadow-banned accounts? Which political campaigns, specifically, communicated with Twitter, and what specifically was taken down? What about requests from foreign governments? What about requests from our own government? We need to know which of our government agencies, if any, had content removed from the platform, and we need to know the nature of this content. Taibbi alluded to Trump’s White House — did someone from the Trump administration request a takedown? Who made the request? Who received the request? Was it answered? What, if anything, was removed?
The Trump line of questioning is, in particular, something you might assume attractive to the media, which has waged all-out war on the populist clown king for the last seven years. Alas, the press seems broadly disinterested. Is this because they don’t believe the former president ever made such requests, or is their lack of interest rather stemming from a fear of validating a major story most of them are currently trying to frame — for their own obvious political reasons — as not worth reading?
A brief selection of positions from our cherished Fourth Estate: This entire story is a “dud” (The Washington Post) — no bombshells here! (Forbes). The Twitter Files, in which a handful of committed partisans enthusiastically censor large swaths of the conservative base, including a former president, actually prove the company was not politically biased. It is, however, now biased against Democrats (New York Magazine). Elon’s exposé is a flop that doesn’t matter. It has also placed multiple “trust and safety experts” in mortal danger (The Verge, predictably). Then, my favorite: it is good to finally see the blacklist tools I have been curious about for many years, which we have by the way always known existed, and therefore don’t matter (The Atlantic).
The charge of shadow banning evoked uniquely loud jeering from the press, including Charlie Warzel in particular, a man formerly of the position “Twitter isn’t shadow banning Republicans.” Now, in the face of evidence the company absolutely shadow banned Republicans, the official position is we are using the term “shadow ban” incorrectly.
It’s a game of semantics, in which the public is dragged through the exhausting, useless question of how much invisible speech suppression, precisely, constitutes a “real” shadow ban, rather than the glaringly important questions of both ethics and, frankly, safety. In the first place, is it right to run a decentralized censorship apparatus, and to make your rules invisible? In the second, what happens to a free country when the bounds of acceptable speech are set by a small cabal of unelected partisan cops? Because my sense is the answer isn’t “freedom.”
There have been a few notable, if cautiously dissenting opinions from prominent voices in media. Buzzfeed’s Katie Notopoulos, the Los Angeles Times’ Jeff Bercovici, and the New York Times’ Mike Isaac all took somewhat risky positions in favor of transparency, apparently no longer in vogue among journalists, with Jeff explicitly acknowledging the important nature of the revelations. But I’ve only seen one actual piece, drafted and published by a reasonably mainstream media entity, embrace any aspect of the Twitter Files.
Anthony Fisher, an opinion editor at the Daily Beast, danced around the subject, and awkwardly tried to obscure his overall agreement the story mattered behind many paragraphs demonstrating his conservative-hating bonafides. But in addressing Twitter’s censorship he did include the following important line:
And that lesson is “Don’t trust (or demand) billionaire tech bros to be the arbiters of truth and news.”
It was a flashback to the position most journalists and activists shared in the days before Donald Trump. Unfortunately, it wasn’t long before they realized they had a political ally in tech industry hall monitors, and set about a national power grab. In any case, if you were to strip the above position from all its obnoxious tribal language, it would really just be: no few people should control the bounds of acceptable discourse. I agree. But narrowly focused on the “tech bro,” the point not only betrays a bias, but misses a defining aspect of technology.
The Fifth Estate is a fundamentally different kind of power. It’s more difficult to consolidate than media, and more difficult to control than even our government divided by design. Its impact is also far more difficult to predict. This is because technology is above all things defined in terms of newness, which not only makes it disruptive of pre-existing power, but destructive of itself — a sort of anti-power that only guarantees change. The true failsafe. Our ultimate reset. Tremendously empowering of tyranny in times of stagnation, technology is also our most powerful weapon against tyranny in times of innovation.
While many tech giants have gone the way of media in consolidating power, centralizing, and aligning with the state, the future of technology is always change. From encrypted chats and blockchain to artificially intelligent search, every tech giant that amassed power over the last two decades will be facing existential threats in the years to come — not only from the government, but from the industry.
In terms of Twitter, Elon is already leveraging Fifth Estate properties, and not by employing current tools to amplify his own opinions (an emerging conspiracy). He is iterating product more rapidly than we’ve seen from any major, consumer-facing tech company in years. The trial and error here has largely been ridiculed by people who have never built a technology company. But while detractors are obsessed with his censorship abilities, Elon’s platform experiments are the things actually capable of root-changing the national discourse. The medium is the message, and the medium is evolving. Whatever works on Twitter will be cloned. The bounds of acceptable discourse will change, and none of this will have anything to do with Elon’s spicy tweets.
But about those spicy tweets —
As the former lords of Twitter descend into hysterics with outlandish comments declaring Elon a Nazi, or a proponent of the QAnon conspiracy, or whatever other bit of unhinged loser bullshit, he faces two significant threats. First, he’s clearly made an enemy of every other major fount of power, including in particular the Fourth Estate. This will impact all of Elon’s companies, as they all require support from the government and public, and the opinions of our government and public are still shaped, to a large extent, by the media. It’s no coincidence most powerful tech executives, from Mark Zuckerberg and Jeff Bezos to Jack Dorsey, share a carefully-crafted language of neutrality. This air of neutrality is how a king behaves, because the air of neutrality is how a king survives. In flaunting his power, rather than obscuring it, Elon is asking to be attacked, and his enemies are happy to oblige, even while more dominant platforms go unbothered.
Something like 80 million Americans are using TikTok, a company hopelessly compromised by the Chinese Communist Party. Do you even know the name of its CEO?

For a man who controls the bounds of acceptable speech for a third of the country’s adults, he sure doesn’t seem especially interested in speaking.
Elon’s second danger is the far more formidable danger of himself. What the Twitter Files prove beyond doubt is censorship in the age of social media is power — a real and dangerous power that corrupts.
Last year, Dorsey appeared before Congress, and declared neither he nor anyone else, and certainly not anyone in government, should be allowed to set the bounds of acceptable speech for the entire country. But with no viable alternative, someone does need to bear the ring. In leaked texts from the recent Twitter legal saga, it’s clear Jack believed Elon a worthy steward of this tremendous power, and, for what it’s worth, I agree. But provided the nation remains free, the rules of the Fifth Estate are immutable. Power comes in dramatic upward swings, and resets the status quo. It will not — it can not — last forever. So change the world, but be mindful of temptation, and make good use of your god mode powers while you have them. Because they never last forever.
-SOLANA link:https://www.piratewires.com/p/the-fifth-estate
-
 @ 32dc4f25:f95ddcce
2023-06-07 10:10:54
@ 32dc4f25:f95ddcce
2023-06-07 10:10:54我们都知道现在的网络存在多方面的问题。诱导点击、错误信息、机器人农场、匿名的“喷子恶魔”——这个列表无穷无尽,令人沮丧。
我们是如何陷入这个境地的呢?
相信有一个简短的答案可以解释这些问题。但是简单的答案往往太过简单,容易被轻视。因此,让我们首先将问题分解成更易理解的部分。
我们在网络上看到的大部分问题是以下因素的组合:
- 激励(失效)
- 限制(技术上的)
- 信用(与现金相比较差)
- 注意力(与价值相比较差)
- 后果(不存在)
- 身份(可选择性)
逐一讨论这些因素后,我将勾勒出一个论文,为实现价值增强的网络愿景奠定基础。但首先,我们必须开始理解困扰网络的各种子问题。让我们从最重要的一个开始:激励。
激励措施
告诉我激励措施,我会告诉你结果。 —查理芒格
人类的行为受到我们所嵌入系统的微妙结构和明显结构的影响。虽然行动、价值观和动机是个体的,但作为我们生活环境的一部分,无论是人为的还是非人为的,背后的胡萝卜和大棒推动着集体行为。如果激励机制失效,一切都会混乱。
- 我们不应该对网络上观察到的两极分化和愤怒最大化感到惊讶;这是追求最大化参与度的自然结果。
- 我们不应该对“你就是产品”的商业模式和壁垒森严的订阅服务感到惊讶;这是追求获取用户和用户数据的自然结果。
- 我们不应该对点击诱饵标题和轰动效应/耸人听闻感到惊讶;这是追求获取尽可能多的眼球和脑力活动的自然结果。
所谓的“免费”平台必须销售广告(或更糟糕的是:用户数据)来赚钱。而要销售这些数据,他们必须积累尽可能多的数据,并说服买家这些数据有用。例如,当向广告商销售时,必须让他们相信人们在关注。如何让更多人关注?愤怒、冲突和争论。更好的是:让人们对愤怒、冲突和争论上瘾,他们将最大化“网站停留时间”和其他参与度指标。广告商喜欢这些!谁在乎真相、智慧、美感、细微之处或价值观?如果你可以最大化点击次数,谁还在乎诚实对话呢?
这个难题的性质既不是政治性的也不是社会性的,至少不是排他性的。 这听起来可能很离谱(哦,讽刺!),但我相信其中很大一部分是由于我们当前的货币体系和建立在其之上的支付基础设施的技术限制。
限制
想象一个全知、无所不在和全能的存在。这样的存在缺少什么?答案是限制。 —乔丹·彼得森
货币总是有限制的。虽然过去可以用五分钱甚至一分钱购买小物品或服务,比如一包口香糖、一杯咖啡、擦鞋、一瓶可乐,但最小的支付金额受到最小货币单位(即一分钱)的限制。对于比这个单位更小的任何东西,我们必须进行批量交易,用一分钱出售多个物品;或者我们必须免费赠送物品。
 来源:《用五分钱能买什么?一个世纪的微小零钱》 Ignite Spot撰写。
来源:《用五分钱能买什么?一个世纪的微小零钱》 Ignite Spot撰写。令人反直觉的是,在网络空间中的限制甚至更大。请问自己:为什么我们不能在线购买价格为一分钱或更小金额的物品?答案非常简单:一分钱在网络上不存在。从来没有,也永远不会有。一分钱是有形的东西:你可以用手拿着的硬币。你不能把硬币附在电子邮件上。当涉及到一分钱时,我们在网上所拥有的、我们所能拥有的一切都是关于一分钱的信息。我们称这种信息为债务凭证(IOU)。债务凭证并不是你完全拥有的东西,而是你欠别人的东西:“我欠你的”。这是信用,而信用与基础货币不同。信用需要信任。
信用
美国所面临的所有困惑、混乱和困境,并非来自宪法或联邦的缺陷,也并非来自道德或品德的缺乏,而主要是来自对货币、信用和流通的本质的彻底无知。 —约翰·亚当斯
信用的问题在于它存在各种风险。这就是为什么我们必须追踪信用,以及所涉及的债权人和债务人。我们必须追踪,因为我们需要进行会计和风险管理。一旦信用被支付,未偿还的债务解决了,我们就不再需要这些信息了。交易完成了。交易对手风险解决了。这就是为什么有句谚语说“现金为王”。
虽然并非所有信用都是相等的,信用风险也是多种多样的,但我想重点关注一种特定的风险:交易对手风险。
交易对手风险是导致像VISA和MasterCard这样从事处理和解决信用问题的机构以及其较新的版本(如PayPal和Venmo)推迟结算并因必须追踪一切而产生高费用的原因。这一切都根源于交易对手风险,这是试图将传统货币用于电子支付时的自然副产品。无论是贝壳、金属硬币还是纸币,传统货币在电子转账时只能作为债务凭证进行转移。
传统货币的根本问题在于实现其功能所需的所有信任。[...] 银行必须值得信任,能够保存我们的资金并进行电子转账[...] 我们必须信任他们保护我们的隐私,不让身份盗贼掏空我们的账户。他们庞大的运营成本使得小额支付变得不可能。 —中本聪
我们可以总结如下:
- IOU是信用
- 信用依赖于信任
- 信任可以被破坏(通过欺诈、疏忽或意外)
- 欺诈行为导致退款和保险机制的出现
- 这些机制需要KYC(了解你的客户)并导致高额的处理成本[1]
所有这些问题都源于必须将IOU用作货币,而在处理传统货币(非本地数字货币,即不通过工作量证明实现实体化的货币)时,我们必须使用IOU作为货币[2]。
因为信用:
- 费用太高,导致我们从未能够在线进行微支付。
- 所有中央信用机构需要了解他们的客户,而且他们也需要你了解你的客户。
- 在使用任何支付应用程序时,必须进行身份验证。
- 想要在线支付的每项服务都会将你强制绑定数周或数月的合同,因为低于约5美元的单笔付款在经济上是不可行的。
这一切都是因为信用。现金没有这些问题[3]。
注意力
你不为自己专注于获得尽可能多的金钱、名誉和荣誉而没有关注或思考真理、理解力和灵魂的完善而感到羞耻吗? —柏拉图
关注错误事物的问题并不是新问题,但在在线世界中尤为明显。再说一遍:问题在于在处理传统货币时,我们必须将IOU作为电子货币使用。对于这个问题有两个解决方案:
- 使用除货币以外的东西作为代理货币
- 识别您的客户并处理大量信用付款(目前:约 5 美元或更多)
两种解决方案都存在。 我们称第一个为“注意力经济”,第二个为“订阅地狱”。
我们没有意识到并解决我们的实物货币在网络空间中极不适用的事实,现在我们都为此付出代价——其中包括我们的注意力。甚至可以说,将注意力作为货币的使用——至少在一定程度上——应归咎于失去细致入微的话语和两极分化的加剧,无论是政治上还是其他方面[4]。
时间和注意力是最重要的货币。我们“花费”时间和“付出”注意力是有原因的。虽然我们确实“花费”时间和“付出”注意力,但它们作为货币不适用,因为我们无法积累它们。正是因为使用适当的货币可以节省时间并增加长期思考,无论是个体还是整个社会都是如此重要。货币对于资本积累和分布式认知同样重要,如果货币出现问题,这两者都会恶化。随之而来的是,我们的时间和注意力也会受到影响。
通过将注意力作为在线世界中的实际货币,我们破坏了深度和细腻,也破坏了我们的集体注意力的持久力。
 模因:注意力战的武器。
模因:注意力战的武器。现在,希望我已经得到了你的关注——也就是你的注意力——我将终于使用一开始拒绝使用的简短答案:比特币解决了这个问题。
比特币解决了这个问题,因为在历史上首次,我们拥有了高速的、本地数字货币,而无需依赖信用。不是IOU。不是信用关系。是那种好的、老式的货币。冷硬的现金。更重要的是:冷硬的数字本地货币,不能被贬值,并且可以以光的速度发送。没有交易对手风险。
后果
*每一个未受惩罚的违法行为都会引发一系列的违法行为。 —赫伯特·斯宾塞 *
在将真正的非信用货币引入网络空间方面,其后果几乎无法被夸大。虽然围绕比特币的讨论大多集中在其有限的供应以及"黄金2.0"和其他价值储存隐喻上,但很少有人关注其中的高速即时结算部分。尽管比特币确实对法定货币的货币政策产生了影响,从而影响了全球的中央银行,但更直接的影响可能出现在网络空间中。
尽管影响很多,但我想特别关注以下四个方面:减少摩擦、更多的点对点交易、增加的中立性和系统稳定性,以及真正的成本。
-
减少摩擦:中间人会引入摩擦。现金可以减少摩擦。一位意大利喜剧演员曾说过:"货币的整个意义在于不知道你的客户是谁[5]。”请注意,这也是互联网的伟大之处。"网络"的整个意义在于不知道电脑对面是谁。正如弗纳·温奇所说,"真名"是不必要的。
-
点对点交易:所有的实物货币都是点对点技术。如果你有一枚实物硬币,它就是你的。在花费或接受它时,你不需要对任何人负责。你只需要找到另一个愿意与你交易的人。是的,中间人可能仍然存在,但他们的重要性较小。他们不太重要,因为他们不再是必需品。在基于信用的系统中,信任的第三方不是可选的:它们是绝对必要的。在基于现金的系统中,它们大多是多余的[6]。
-
中立性和系统稳定性:协议,如数学和语言,是中立的系统。任何人都可以使用它们,没有任何单个人或实体负责全部。缺乏单点故障是一个系统具有弹性的原因。开放性和中立性为所有人提供了包容性和公平竞争的机会。当涉及货币时,任何缺乏开放性都必然导致金融审查,而任何缺乏中立性都必然导致救助行动、亿万富翁(Cantillionaires)和系统不稳定性[7]。
-
真正的成本:本地数字货币使我们能够将真正的成本与网络空间中的行为联系起来。它使我们能够摆脱使用时间和注意力作为在线货币的剥削性做法。它使我们能够摆脱像取消平台和解除银行资格等多余的惩罚。它使我们能够在不必毁掉那些犯错者的公众形象的极端情况下使破坏性行为变得代价高昂。它能够实现所有这些,因为真正的货币不需要真正的身份,但却有真正的成本。真正的成本使垃圾邮件机器人不具经济性,并且削弱了反社会行为的动机[8]。
身份
有关金钱的事情真有趣。有关身份的事情也很有趣。你之所以是你,是因为你的小狗认识你,但当你的公众知道你并且不愿意为你付费,或者当你的公众知道你并且愿意为你付费时,你就不再是同样的你。 —格特鲁德·斯坦
身份是多样的。在周五晚上的酒吧里,你的行为与周日的教堂不同。你在公共场合和私人场合表现不同,在工作场所和家里也是如此。你的行为会根据社交圈和环境的不同而调整。对某些人来说可能是冒犯的事情对其他人来说只是随意闲聊;在公共政治辩论中可能是令人震惊且毁掉职业生涯的事情,在喜剧俱乐部可能只会引发笑声和愉快的时光。身份并不是单一的,身份是多样的。
网络空间消除了我们在现实空间中习以为常的多样分离,使时间和空间变得平坦。回复你推特的那个人可能是在搞恶作剧,可能是个机器人,可能只有12岁,可能酩酊大醉,也可能兼而有之。你不知道,而这正是一种特点,而不是缺陷。
有些人(如婴儿潮一代)抱怨"匿名恶魔巨兽的军队",似乎无法应对匿名在线对话的粗鲁态度。他们希望以老派的方式解决这个问题[9],强制每个人都要露脸,并将他们的真实身份与在线资料关联起来。那些和恶意评论长大并在其中生活的人,比如玩了数小时竞技在线游戏的人,知道在线互动和在线身份与离线互动和身份是不同的。"不要喂养喷子"是在线文化的智慧,有其深刻的原因。
在任何平台、服务或应用上强制执行KYC(了解您的客户)是解决身份问题的一种幼稚和短视的方法。它是短视的,因为:
(a)并非每个人都有身份, (b)并非每个人都能够露脸或使用合法姓名而不危及自己或他人, (c)它无法阻止犯罪或有毒行为, (d)身份是多样的,而不是单一的。
将网络空间变成乔治·奥威尔(顺便说一下,这不是他的真名)无法想象的极权监控国家不能成为解决方案。这一点应该是显而易见的。如果这还不明显,就想想中国的社会信用体系,或者只需按两次喇叭(或与按两次喇叭的人接近)就可以让你的加拿大银行账户被冻结的事实。
解决身份问题的更微妙的方法是通过声誉、昂贵的身份创建和真正的价值。换句话说,我们不应该将我们的单一政府强制身份添加到网络空间的所有事物中。相反,我们应该允许用户(匿名或非匿名)向世界展示他们的认真和真实。
价值给网络空间带来了后果。 —迈克尔·塞勒
有一个东欧的谚语:“如果你真的想伤害一个人,你必须打他最痛处:他的钱包。”迈克尔·塞勒的想法是正确的。遏制不良行为的方法是为匿名身份增加真正的价值。就像入住酒店时锁定的押金,如果你采取破坏性行为就会失去这笔押金。
当然,还有一个问题:谁来定义“破坏性行为”?用户举报导致了暴民统治;平台决策导致了威权主义。我相信随着网络中越来越大的部分成为原生的有价值功能,并且我们的身份与目前统治网络的庞大平台正在分离开来,更好的机制将会逐渐出现。我们还处在这些趋势的非常初期。去中心化标识符对大多数人来说仍然是未知的。很少有人知道sats正在被融入到协议和平台中。Podcasting 2.0的“价值区块”就是一个例子。在Stacker News上使用卫星的方式是另一个例子。
现金的有趣之处在于它与身份解耦。你不需要征求任何人的允许来接收和使用现金。而且因为金钱是表达价值的一种方式——可以说是主要方式——自由表达的重要性对于一个自由和繁荣的社会来说至关重要。
在大多数情况下,个人身份并不重要。当我在商店购买杂志并将现金交给店员时,没有必要知道我是谁。 --埃里克·休斯
大多数交易不需要身份。大多数交易不应该需要信用。对于大多数交易来说,信任第三方应该是可选的。这是数千年来的默认设置,我相信在未来,无论是在实体空间还是网络空间,这都应该是默认设置。
将真正的价值注入在线世界并不意味着声誉不重要或无法出现。声誉是至关重要的,并且已经出现了。然而,启用价值的网络所允许的是某些行为的代价高昂。其中之一是首先建立特定身份的声誉。
目前,利用一支机器人军团创造声誉的假象(通过假的点赞和假的粉丝)成本很低。给账户创建和/或验证增加价值会使这种行为变得昂贵。
身份和相关行为只是难题的一部分。并非所有部分都已知,更不用说已经到位了。尽管如此,许多人正在致力于开发各种技术和协议,以解决上述问题中的一些。我希望一旦我们正确理解问题并具备正确的论点和愿景,我们将能够逐步解决细节问题[10-11]。
论题
一座巨大的建筑从大地中涌现出来, 仿佛一股蒸汽,伴随着悦耳的交响乐和甜美的声音, 宛如一座庙宇一般。 —约翰·弥尔顿,《失乐园》
让我们回顾一下:我们已经看到激励机制存在问题,导致了“你就是产品”和“订阅地狱”这样的商业模式。我们已经看到,由于货币体系的局限性,我们被迫在网上使用欠款(信用)进行交易。我们已经看到,由于以获取眼球和销售广告为主导的商业模式,我们的注意力被利用、操控、出售和滥用。
我相信有一种更好的方式。我相信,在销售产品和服务方面,现金将会再次流行起来。我相信,得益于可编程货币对网络空间的影响,网络身份可以保持可选性,同时仍然允许声誉和针对反社会行为的现实成本。
仍然存在一个问题:销售问题。这个特定问题只存在于网络空间,因为在传统意义上,网络空间中的大部分“东西”并不是稀缺的。我们无法像出售苹果手机那样出售JPG图像,尽管有许多困惑的人尝试过。JPG图像并不稀缺,而iPhone是稀缺的。JPG图像可以以零边际成本复制。生产iPhone需要时间和努力。无法区分两个JPG图像的副本。当您在屏幕上加载JPG图像时,它是从服务器检索的JPG图像的副本,并且该服务器上的副本不会消失。一个iPhone只存在一次,无法完美复制,更不用说以零边际成本复制了。以零边际成本复制某物会导致该物品的供应几乎无限。不管是 JPG、博客文章还是 mp3 文件都没有关系。 如果任何人都可以快速、完美且基本上免费地复制它,那么这种东西的供应量很快就会接近无穷大。 我们从稀缺的模拟世界进入丰富的数字世界。 在这个世界中,市场失去了作用。用贾伦·兰尼尔的话说:“随着供应接近无限,市场变得荒谬可笑”[12]。
以“支付10美分阅读博客文章”的传统付费墙试图人为地限制供应和/或访问。这与数字信息的本质相悖,数字信息易于传播,难以抑制。引用布鲁斯·施奈尔的话:“试图使数字文件无法复制就像试图使水变得不湿一样”。
我将在未来的某个时间尽力更详细地描述这个问题,但现在,请允许我尝试总结如下:当涉及到JPG图像、mp3文件、博客文章或类似的数字作品时,我们必须停止假装文件本身是稀缺或珍贵的。它们并不稀缺,创造它们的人才是稀缺的。因此,我们必须寻找新的定价和货币化方式。新的方式是确保所创造的价值归属于为增加的价值负责的人,而不是囚禁信息或用户——而不是试图使水变得不湿。
我们必须将价格与价值分离,并重新思考二者。
愿景
眼睛的视野是有限的,但心灵的愿景超越了时间和空间的所有障碍。 --伊玛目阿里
我们现在拥有一种超越传统时间和空间限制的货币。这是一种在网络空间中诞生并产生的货币,一种使价值启用的网络成为现实的货币。
比特币存在。闪电网络存在。播客2.0已成为现实。Value4value也已经存在。但即使在比特币的世界之外,人们对传统模式进行了重新思考。人们订阅他人的Substack、Patreon或Twitch,不是为了购买有形的东西,而是为了以自愿的方式回报他们所获得的价值。
请注意,我在这里试图勾勒的愿景并不是我的愿景。许多部分正在被开发中,许多行为变革已经在发生,尽管在边缘地带。
挑战在于使体验愉悦和无缝,而不会重新引入交易对手风险的弊端。我们需要进行技术和文化的转变。我们还没有到达那个阶段。给人们发送信息所需的金钱,而这些信息他们可以免费获得,对于大多数人来说仍然是一个奇怪的概念,但新的播客应用程序和其他“boost”机制的大量出现明确显示出文化转变正在发生。是的,仍然有些笨拙。手动输入闪电地址并发送sats仍然很麻烦。点击"boost"按钮并扫描QR码也很麻烦。
但我们已经走了很长的路,趋势正在朝着正确的方向发展。如果我们构建得当,微支付将变得无形和透明,消除了心理交易成本的摩擦,同时给用户完全的控制和洞察力。那些启用了价值功能的新播客应用正在引领潮流。
我敏锐地观察到的一个趋势是“boost”和超级聊天,或者一般情况下的特权直接消息的趋势。将货币价值与匿名或化名笔记联系在一起是一种新颖的方式,可以直接而明确地表达您的赞赏之情。在线上发出一声大声的“谢谢”——直接并附带着昂贵的信号。阅读这些小信息真是一种愉悦。作为一个早期采用者,我有幸每天早晨阅读发送到s@ts.dergigi.com的信息,窥见未来。我希望随着时间的推移和改进,这种愉悦将变得普遍存在。
总的来说,当涉及到可以以零边际成本复制的数字产品的创作时,趋势似乎是朝着直接支持的方向发展。每个人都将不得不应对数字信息的基本特性(可以完美无缺地复制和免费获取)以及人类的基本需求(他们需要吃饭)的挑战。每个人。甚至包括像YouTube和Spotify这样的平台[13]:
 今天,所有这些都是信用,通过信用渠道发送。明天,它们可以是sats(比特币的最小单位)。
今天,所有这些都是信用,通过信用渠道发送。明天,它们可以是sats(比特币的最小单位)。当我说“启用价值的网络”时,我指的是一个广泛的框架,用于思考这些技术和趋势,包括允许任何人参与的开放协议。就像传统的网络既不是一个平台也不是一个公司,启用价值的网络也不是一个单独的新“事物”,而是一个协议集合,可以让开放的生态系统蓬勃发展。开放性和无需许可是使网络变得伟大的因素。相同的因素将使启用价值的网络变得伟大。
互操作性和开放标准对于创建一个双赢的环境至关重要。这样做更加困难,需要很多思考和耐心,但这也是正确的事情。从长远来看,正和游戏总是胜过零和游戏,即使封闭的平台在短期内可能能够快速发展。
愿景仍然模糊,但每天都越来越清晰。如果有人逼我写一篇描述这个愿景的宣言,它将围绕以下几个观念展开:
- 对于那些创造价值的人来说,接收价值应该是微不足道的。
- 对于那些珍视有价值内容的人,向创作者发送价值应该是微不足道的。
- 允许内容和元数据自由复制。
- 允许价值自由流动。
- 不要在内容或元数据周围建立壁垒。
- 使身份成为可选项。
- 允许那些增加价值的人参与价值流动。
- 使不道德行为变得昂贵。
- 提供增加价值和带来快乐的工具和服务。
- 将货币用于货币化,而不是注意力[14]。
- 销售服务,而不是用户数据。
- 降低退出成本。
- 基于sats(比特币的最小单位)构建,而不是基于信用债券IUO。
企业不应该把时间花在充当信用机构的角色上。在最好的情况下,他们根本不需要知道他们的客户是谁。啊,那些好旧时光,你只需走进一家商店,拿起一个苹果和一份报纸,交出几个硬币,然后走出来。这就是现金的魔力。
这种魔力在现实世界的商店里仍然存在,但在网络空间却从未存在过,直到比特币出现。而且由于闪电网络的出现,我们终于拥有了一种数字的持有工具——一种你可以记在脑中而不仅仅是手中的工具,它具备现金的所有特性,并且是本地数字化的。这是一件大事。之所以如此重要,是因为它使我们能够构建一个启用价值的网络,而无需信任第三方机构。
我仍然是网络的忠实粉丝,当然也包括互联网整体,但我相信,就像你们所有人一样,事情可以变得更好[15]。事实上,我知道它可以变得更好,就像其他在这些发展的前沿的人一样。一旦你收到了第一笔流媒体付款,再处理我们现实世界中那些遗留的支付渠道,就会感觉过时了。
使用平台而不是协议的结果。
我不想在这个随机的网站表单中输入我的信用卡详细信息,我只想用sats支付。我不想为了使用一个随机的互联网服务而注册12个月,我只想用sats支付。我不想输入我的电子邮件地址或手机号码,也不想解决让我怀疑自己是否为人的验证码,我只想使用该服务并用sats支付。
我不想处理付费墙、封闭的花园和剥削性平台,它们白费力气地在数字文件周围建造墙壁。信息渴望自由,而且有充分的理由。我们应该珍惜我们为自己创造的丰富世界。我们不应该与这种丰富抗争。相反,我们应该尽可能地让我们稀缺的金钱流向那些创造价值的人。Podcasting 2.0和其他先驱者展示了什么是可能的。他们处在启用价值的网络的前沿。
他们向我们展示了金钱可以像今天的信息一样自由流动。他们向我们展示了在接收或发送资金时没有任何准入障碍。他们向我们展示了没有人必须受制于平台或信用机构。
如果我们做对了——如果我们成功减少在线上使用时间和注意力作为货币的程度——噪音和依赖将减少,而自由和真实的信号将最大化。
此外,当任何人都可以参与在线环境中产生的货币流动时——没有门槛和注册要求——我们可以为更多人提供更多价值。
在一个启用价值的网络中,任何人都可以受益,不仅仅是那些掌控我们时间和注意力的服务器的人。对每个人的繁荣,而不仅仅是那些拥有信用评级和银行账户的人。
让每个人都参与价值流动。丰富长尾。
 注意经济所能做的就是让头脑混乱。Sats流动可以丰富长尾。
注意经济所能做的就是让头脑混乱。Sats流动可以丰富长尾。启用价值的网络的愿景是回归实质和理智。摆脱点击诱饵和注意力耕作。对奥威尔式的监视、去平台化和文化取消提出反对。
- 从赢者通吃到众人皆可获胜的转变。
- 从追求增长到追求价值的转变。
- 从数量到质量的转变。
- 从客户-服务器关系转向对等关系,在对等关系中,每个人都处于平等的地位,而不是主人和奴隶的关系。
这个愿景超越了价值互换(value4value),尽管新的估值和货币化模型将发挥重要作用。这个愿景超越了将现金微支付添加到某些操作中,尽管对于某些操作来说这是重要的。这个愿景超越了程序化的价值流动和sats的自动支付,尽管我们确实需要一种新的思考版税的方式。这个愿景超越了无密码认证,使用时间链作为真理和存在性的锚点,或分权式身份验证和主权计算,尽管所有这些事情都很重要和必要。
启用价值的网络的愿景是一个公平、开放、正和交换的愿景,它允许价值包像过去的数据包一样自由流动。更多的价值,更多的人性,更少的机器人,更少的垃圾邮件,希望能减少黑暗模式和成瘾行为。
互联网正在进入第二阶段,是时候修复它了。
感谢Tomer、Allen、Daniel和我的赞助人对早期草稿的出色反馈。任何仍然令人困惑和不完整的部分都是由于我模糊的视野和固执。
注释:
[1] KYC(了解客户)并不总是邪恶的企业和/或政府试图进行邪恶行为并监视所有人的一种功能。在金融产品中,它通常只是防范信用风险的一种保护措施。 ↩
[2]只有工作量证明才能实现本地数字货币,这种货币是无需信任和无需许可的,即可供所有人访问,而不受一群关键持有人的控制。 ↩
[3] 请注意,我在这里忽略了所有法定货币都是信用货币的事实。为了论证支持“价值启用的网络”,让我们假设所有传统货币仍然由黄金支持。让我们假设在1971年之前什么都没有发生。 ↩
[4] 美国参议院中政治两极分化的可视化是一种令人瞩目的现象:红队和蓝队渐行渐远。数据由Clio Andris、David Lee、Christian E. Gunning、John A. Selden、Mauro Martino和Marcus J. Hamilton提供,可视化由Mauro Martino完成 ↩
[5] “早上好,洗钱很美丽” by Giacomo Zucco, Baltic Honeybadger 2022 ↩
[6] 在比特币中,值得信赖的第三方是安全隐患。 ↩
[7] 搜索“坎蒂隆效应” ↩
[8] 请听迈克尔·塞勒在《比特币矩阵》播客中详细解释这一点。 ↩
[9] 乔丹,乔丹,乔丹...有静音按钮。有屏蔽按钮。请使用它们,不要喂养那些喷子。 ↩
[10] 其他值得一提的项目包括TBD的Web5、Holepunch、ION和nostr(我相信还有很多,请随时通过PR添加)。 ↩
[11] 我在这篇文章发表前大部分内容都写了一个月,所以这些内容都是在杰克赞助和资助nostr之前写的,也是在伊隆禁止宣传nostr(和其他Twitter竞争对手)之前写的。 ↩
[12] 兰尼尔的书《谁拥有未来》很好地描述了我们所面临的问题,但它未能提供一种可行和实际的解决方案。依我拙见,兰尼尔试图让水变得不湿。 ↩
[13] 例如,参考YouTube的这篇文章和这篇文章,以及Spotify的这篇文章。 ↩
[14] 比特币是独一无二的,因为它是唯一经过可靠且经过历练的、本地数字化的货币,其货币政策的完整性记录是毋庸置疑的。没有其他货币可以宣称拥有这一点。因此,比特币是网络空间中唯一的合法货币。
[15] Mastroianni, Adam, 和 Ethan Ludwin-Peery. “事情本可以更好。” PsyArXiv, 2022年11月14日. 网络.
-
 @ 1bc70a01:24f6a411
2023-06-07 08:29:03
@ 1bc70a01:24f6a411
2023-06-07 08:29:03Yesterday Marc Andreessen wrote up a lengthy tweet addressing concerns of AI taking our jobs. I will take a few minutes to analyze his tweet and break it out into chunks with my own assessment and responses.
The fear of job loss due variously to mechanization, automation, computerization, or AI has been a recurring panic for hundreds of years, since the original onset of machinery such as the mechanical loom.
True.
Even though every new major technology has led to more jobs at higher wages throughout history, each wave of this panic is accompanied by claims that “this time is different” – this is the time it will finally happen, this is the technology that will finally deliver the hammer blow to human labor. And yet, it never happens.
We can't rely on details of the past to predict the future. Every new development should be evaluated independently. "And yet, it never happens" is an insufficient assessment of whether something could happen just because it hasn't happened in the past. The sun hasn't exploded, but it could. Will it? Probably not. But it could. We don't know what we don't know.
We’ve been through two such technology-driven unemployment panic cycles in our recent past – the outsourcing panic of the 2000’s, and the automation panic of the 2010’s.
No we haven't. We've been through technology-driven unemployment panic cycles - yes, but not "such". Such assumes they are the same and as I stated earlier, everything should be evaluated independently.
Notwithstanding many talking heads, pundits, and even tech industry executives pounding the table throughout both decades that mass unemployment was near, by late 2019 – right before the onset of COVID – the world had more jobs at higher wages than ever in history.
While this is true, real unemployment has been the lowest in history at onset of COVID, what Marc fails to account for is the higher cost of living. It's no secret that rents and prices were all on the rise from 2022 forward and that wages are not able to keep up with inflation.
US Bureau of Labor Statistics reported the highest CPI ever going into COVID. Shelter, being a major expense for people is at the highest level ever according to FRED (https://fred.stlouisfed.org/series/CUSR0000SAH1)
While even an increase in CPI may not paint the full picture as it measures percentage change, in real terms (the dollars people are actually spending on rent) it's clear that the cost of living is rising. You can feel it every day.
- When was the last time your rent DECREASED?
- What was the last time food become cheaper at the store?
- What was the last time your college education all of a sudden became more affordable?
- What was the last time you got a raise?
People living in the real world can clearly tell that things are not going in the right direction. But, if you are Marc Andreeesen, it's not likely you live in the real world, so you wouldn't know. It is dishonest to say "wages are higher" and ignore the other half of the picture - the rise in the cost of living and lagging salaries.
Nevertheless this mistaken idea will not die. And sure enough, it's back.
Is it mistaken? We'll see...
This time, we finally have the technology that’s going to take all the jobs and render human workers superfluous – real AI. Surely this time history won’t repeat, and AI will cause mass unemployment – and not rapid economic, job, and wage growth – right? No, that’s not going to happen – and in fact AI, if allowed to develop and proliferate throughout the economy, may cause the most dramatic and sustained economic boom of all time, with correspondingly record job and wage growth – the exact opposite of the fear. And here’s why.
Marc seems to completely forget about the widening wealth gap. It's as if we can look at the growing wealth gap and pretend like it doesn't exist.
According to Pew research, the middle class is shrinking while the top earners are growing. The average American family is no wealthier today than it was two decades ago. The share of US aggregate income held by the middle class fell from 62% to 43% from 1970 to 2018.
You really don't need to look at any charts or be a wizard to know that the middle class is shrinking while the rich get richer. You can feel it in your neighborhood (unless you are rich), your supermarket, your community, the number of homeless on the streets.
Of course, if you are Marc, perhaps you don't see any of these things because you live in your own little bubble 🤷♂️
The core mistake the automation-kills-jobs doomers keep making is called the Lump Of Labor Fallacy. This fallacy is the incorrect notion that there is a fixed amount of labor to be done in the economy at any given time, and either machines do it or people do it – and if machines do it, there will be no work for people to do.
Classical straw-man argument. Marc, do you really think people are concerned that ALL jobs will be gone and humans will have nothing to do? Or perhaps maybe you've given some thought to whether people are concerned for their incomes to support their families? It's not that people are afraid all jobs will be gone. People are afraid that they won't be able to provide for themselves and their families as their jobs are all of a sudden done by AI.
The QUALITY of employment is what's at stake. Sure, you'll be employed - doing some odd thing you probably don't want to be doing because your critical analysis skills are no longer required or can be done with fewer people.
Do you really feel that your employer is going to say "oh hey, Marc, you are doing less and less around here these days, here's a raise!" Exactly. Not going to happen. It is in the businesses' best interest to automate away as many positions as possible. Less labor = higher profits. All business incentives point to automating away labor to bring down the costs to as close to zero as possible.
Yes, new jobs will open up, but they will increasingly require higher levels of knowledge and experience. In other words, the top earners today will step into those positions as they will be in the best spot for this transition.
The Lump Of Labor Fallacy flows naturally from naive intuition, but naive intuition here is wrong. When technology is applied to production, we get productivity growth – an increase in output generated by a reduction in inputs. The result is lower prices for goods and services.
This would be true under the bitcoin standard, but we live in a different reality. Productivity growth goes to the top earners and executives while workers are laid off. Ask yourself, what was the last time your prices dropped? I'll wait...
Food more affordable? Housing cheaper? Your vehicle cost less now than it did a decade ago? Gasoline? Education? iPhone?
It is true that technology lowers the marginal cost of production and in theory should make everything cheaper. But, in reality, costs rise as the fiat money inflates everything with it and any savings to be had are passed onto top brass. When you are doing great at automating away tasks, your first thought is not "oh now we can hire more people with all this extra cash", your first thought is "great, how can we automate away even more?"
As prices for goods and services fall, we pay less for them, meaning that we now have extra spending power with which to buy other things.
False. We are paying more. This is reflected in reported CPI and real CPI, inflation, lagging wage growth, and growth in inequality.
This increases demand in the economy, which drives the creation of new production – including new products and new industries – which then creates new jobs for the people who were replaced by machines in prior jobs.
It is true that consumer spending has been growing recently and that in theory all of that spending should create more jobs. However, we have never had a technology with no upper limit in terms of what it could do. While new jobs can indeed come online, the numbers of new jobs may not be sufficient to replace the jobs they displaced. Technology improves efficiency and you need fewer people to the jobs of many. Marc's assumption is that the AI developments would create so many new industries that the jobs required to make them work would outpace all of the displaced labor. However, he seems to willfully ignore that AI is not a "twice better" technology. It has no theoretical limit to the level of efficiency achievable.
At the core of it all, everything we are and everything we do is math and algorithms. Machines need not be 100% better than humans to take our jobs. Eighty percent is a good enough threshold that the other 20% can be ignored. As long as AI is sufficiently able to perform a task, human need not apply.
The result is a larger economy with higher material prosperity, more industries, more products, and more jobs.
Yes, an economy for the top earners.
But the good news doesn’t stop there. We also get higher wages. This is because, at the level of the individual worker, the marketplace sets compensation as a function of the marginal productivity of the worker.
Money printer would like a word. Higher wages are just one side of the equation. What you really want is more purchasing power and we know that purchasing power is shrinking dramatically. Simply look at the appreciation of Bitcoin's fiat value to understand what is happening to the dollar. Hint: it ain't good.
A worker in a technology-infused business will be more productive than a worker in a traditional business. The employer will either pay that worker more money as he is now more productive, or another employer will, purely out of self interest.
LOL. Seriously? Hey, Jim, you're looking productive today! Here's a raise! C'mon... are you kidding me? What world does this person live in? Like I said, even if our hypothetical employer is super happy with Jim and pays him more, uncle Sam will ensure you're always in line. Money printer go brrrrr!
The result is that technology introduced into an industry generally not only increases the number of jobs in the industry but also raises wages.
Let me rewrite. "The result is that technology introduced into an industry generally reduces labor as fewer people are needed to perform a task now done by few. It also raises wages for the top earners while the average person earns no more than they did two decades ago."
To summarize, technology empowers people to be more productive. This causes the prices for existing goods and services to fall, and for wages to rise.
Yes, more productive. No, goods and services rarely fall in price, in fact, quite the opposite. Wages rise for top earners, not really at all for middle class, and just barely for lower class.
This in turn causes economic growth and job growth, while motivating the creation of new jobs and new industries.
In the past, yes. But with ever-improving AI that growth won't outpace displacement. Yes, more advanced categories of jobs for highly skilled (top earners) people. If you are not highly skilled, super intelligent, good luck! New industries actually displace more workers from previous industries.
Higher productivity doesn't mean higher employment. I can be very productive at home with ChatGPT, coding away, designing fun stuff, but that doesn't automatically translate to more employment. If a startup founder can create his/her own website and no longer needs my services, that's that.
If a market economy is allowed to function normally and if technology is allowed to be introduced freely, this is a perpetual upward cycle that never ends.
That is a BIG IF. We know the powers that be LOVE manipulation. The dream Marc aspires to can only exist on the Bitcoin standard.
For, as Milton Friedman observed, “Human wants and needs are endless” – we always want more than we have. A technology-infused market economy is the way we get closer to delivering everything everyone could conceivably want, but never all the way there. And that is why technology doesn’t destroy jobs and never will.
Straw-man. Technology has always destroyed jobs and always will. The saving grace was that it created many more jobs in the past. But with AI, the order of efficiency is magnitudes larger than a 2 or even a 10x improvement of the Industrial Revolution. And, there is no theoretical limit to how far it can improve. This is why we cannot look at the past to determine the future. It's lazy thinking at best.
These are such mindblowing ideas for people who have not been exposed to them that it may take you some time to wrap your head around them.
Ah, yes, the all knowing oracle, please bless us with your wisdom.
But, using the principles I described above, think of what it would mean for literally all existing human labor to be replaced by machines.
It would mean a takeoff rate of economic productivity growth that would be absolutely stratospheric, far beyond any historical precedent. Prices of existing goods and services would drop across the board to virtually zero.
Under the bitcoin standard, yes. Hey Marc, why do we need jobs if prices go to zero?
Consumer welfare would skyrocket. Consumer spending power would skyrocket.
Yes, under the bitcoin standard, I agree. But why work if what you make is free. Where is the business making profit here? Why employ a bunch of people, pay them a ton of money and have a service that costs nothing to the consumer? Does that make any sense to you?
New demand in the economy would explode. Entrepreneurs would create dizzying arrays of new industries, products, and services, and employ as many people and AI as they could as fast as possible to meet all the new demand.
Yes there are many new business opportunities, but again, going back to infinite efficiency point - that doesn't translate to many jobs. This is already happening now. There's now an AI tool for so many things that people used to have to do slowly and manually.
Tech is currently going through a wave of layoffs, with as many as 200,000 employees being laid off in 2023 alone. You can track layoffs here: https://layoffs.fyi/
If you don't believe AI is going to result in serious layoffs, consider what ChatGPT has already achieved (and this is a really primitive form of AI): https://www.timesnownews.com/technology-science/48-percent-of-companies-have-replaced-workers-with-chatgpt-survey-article-98635684
- 48% of companies used it to replace workers
- 63% believe it will result in layoffs
Suppose AI once again replaces that labor? The cycle would repeat, driving consumer welfare, economic growth, and job and wage growth even higher. It would be a straight spiral up to a material utopia that neither Adam Smith or Karl Marx ever dared dream of.
As it has in the past /s
In reality, wealth would concentrate even further. The rich would get richer. The top earners would earn more. Yes, the pie will grow, but those who get a bite will be fewer.
Trickle down economics hasn't worked and cannot work under the fiat standard. Wealth and power concentrates while the middle class diminishes and cost of living rises. As long as the base upon which you are building is constantly manipulated, true price discovery cannot take place. The current debt system guarantees forever-rising prices as more debt is required to be created to service previous debt - a never-ending negative cycle.
All of what Marc says IS possible under the bitcoin standard. You can already see it happening if you measure everything from the bitcoin's point of view. As bitcoin goes up in fiat terms, everything else drops in price (as it should). Bitcoin allows for true price discovery because it cannot be manipulated, you can't create more bitcoin. Here, consumer's purchasing power increases while technology enables humans to work less.
Don't you find it ironic that according to Marc, AI is supposed to create plentiful jobs, but cost of goods and services is supposed to come down to zero? What are all those people working for in that scenario? Why would you want more jobs as the cost of everything else drops?
The answer of course is not more high paying jobs, but the efficiencies enabled by AI to be spread more equitably across society. As your technology enables near-free services and goods, you as a person shouldn't have to work as much to acquire the same or greater number of things. This is completely incompatible with a credit-based system where your salary must go up perpetually to accommodate the rise in debt and THE RISE in prices. Not the drop, but the rise in prices. This is exactly what we see today and have seen throughout history. Don't believe me? Go ahead and walk into an Apple store and ask for the newest iPhone model for a lesser price then the previous.
In summary: 1. Everything Marc Andreessen says would be correct under the bitcoin standard. 2. AI cannot be assessed through the lens of previous technological advancement, it's an apple to oranges comparison as we've never had a technology that has the potential to become thousands or hundreds of thousands times more intelligent than humans. 3. Prices cannot fall in a credit-based system because debt must grow to pay off previous debt. 4. Focusing on job numbers is pointless. Instead we should be focusing on purchasing power and standards of living. People don't want more jobs, they want the ability to provide for their family - which could mean working less while taking advantage of technological progress (in this case AI).
Footnotes:
Gig Economy Market [2022-2027] Size, Share, Growth Rate | Recent Development, Demand, Trends, Key Players Profiles, Segmentation, Mergers & Acquisitions, Expansion Plans and Forecast Research | Industry Research Biz
BLS Consumer price index by category: https://www.bls.gov/charts/consumer-price-index/consumer-price-index-by-category-line-chart.htm
https://fred.stlouisfed.org/series/CUSR0000SAH1
Pew widening wealth gap: https://www.pewresearch.org/social-trends/2020/01/09/trends-in-income-and-wealth-inequality/
-
 @ b126d147:70b2d72a
2023-06-07 07:18:38
@ b126d147:70b2d72a
2023-06-07 07:18:38Disclaimer (Views are personal opinions; not monetary or financial investment advice pieces).
NFT Brief History Introduction Non-Fungible Token (NFT) crypto-assets are unique, and non-exchangeable digital value representations created, transacted and verifiable on-chain/on-ledger. Most of the NFT items such as collectible items, digital arts, tickets, concert seats, photos, etc. at the moment, are minted on the Turing-complete Ethereum Virtual Machine(EVM), and sold on the “World’s first and largest NFT marketplace” opensea.io. The custom blockchain smart contract token standard for Non-Fungible Tokens (first proposed in 2018) is Ethereum Request for Comments(ERC-721).
Source URL link
Earliest known precursor to the NFTs, the "Colored Coins" was launched in 2012. The colored coins were methods to represent and manage real life world assets on top of Bitcoin. With the colored coins experimentation, any real world asset digital representation became a reality, as assets ranging from real estate to stocks, fiat currencies, and commodities et al. metamorphosed into a virtual possibility in the cryptoverse econosphere.
Digital Scarcity Creation Humans understand scarcity as an economic problem foundation, which increases value. Thus with the NFTs, artists are creating digital/artificial scarcity, and collectors who collect these NFT collectibles are able to trade, make quick profits, and are fast-becoming ubiquitous, as new NFT projects keep dropping and selling out; as a result of which their marketplace value skyrockets, and crypto folks are Fearing of Missing Out (FoMOing). More demand, which means more adoption, continues to drive the NFT marketplace supply. This is the FOMO dynamics which concentrates the human mind vis-a-vis the NFT digital transformation art marketplace rise. The material world itself is being dematerialised, as everything moves onto the Web 3.0 blockchain tech, Artificial Intelligence, Machine Learning et al.
EtherRock was launched on the Ethereum mainnet in 2017 after CryptoPunks. Capped like bitcoin, for which only 21 million will ever be mined, only 100 rocks will ever be minted, and they are managed with decentralised blockchain smart contracts for issuing, buying, selling, pricing etc. The rocks, a crypto-collectible NFT brand, have no intrinsic or extrinsic value whatsoever, but they are worth a king’s ransom; each with a unique Personally Identifiable Information(PII) (so to speak) verifiable on the value chain tech provenance.
Sold only 30 pieces since 2017, but August this year, EtherRock sale saw a marketplace explosion, and Justin Sun was reported to have bought one EtherRock for $500,000. What really is value, if mere digital NFT art pieces; especially mere dead stone photos can sell for thousands and millions of USD? Turns out things have always been regarded for their value. Guess you’re wondering what’s in a mere rock photo art NFT to be worth so much? The blockchain smart contract tech atop which these NFTs sit, occasions their mission-critical value proposition. Infact, the most expensive ever sold NFT certificate is the CryptoPunk #9998; a part of the 10,000 CryptoPunk NFTs collection, "sold" for $532 million late October last month.
Source link URL: https://etherrock.com/
How Does NFT Scarcity Compare With Scarcity in Nature? For emphasis, these NFTs are rare, scarce, unique token objects with blockchain-based cryptographic hash proofs that secure and authenticate them. While they are created through NFT art digital scarcity, and are therefore artificial, scarcity in nature is a result of unaided process that autonomously occurs independent of human agency.
A more picturesque NFT scarcity quintessence compared with natural scarcity is the late rap great Tupac Shakur rare 17 photographs collection being sold as NFTs on the marketplace OpenSea platform, minted by the hip-hop photographer Lawrence “Loupy D” Dotson who took the pics back in 1992. The Pac photograph collection uniqueness isn't the je ne sais quoi about the 17 photographs collection as NFTs, but their unique hash-based identities on-chain, which create authentic digital scarcity value for the Tupac 17-photograph NFTs collection. The NFT cryptographic hash representation on the blockchain tech is what makes NFTs original, unfalsifiable and non-counterfeitable, even if the photo arts etc., themselves are copied, stolen, and transferred from one place to another ad nauseam.
Human Evolutionary Psychology Toward Value Throughout human history and evolution, humans have psychologically and emotionally attached value to things either of relative value, or things which are on the first thought basis valuable. This has triggered questions whether value is subjective or objective, and thus has led to the subjective value theory and objective value theory dichotomisation.
Across history, animals, livestock etc. have been domesticated and bred for their unique value, rare traits, utility etc., and even this applies throughout all of nature. What is happening at the moment is that this value is moving from the meatspace to the cyberspace through the ongoing fleet digital transformation process known as the 4th Industrial Revolution, where future humans get to relate and acquire social credit scores through their metaverse avatars able to conduct in the metaverse all their meatspace real life activities digital version, using blockchain smart contract-verifiable NFTs as the metaverse ecosystem transaction currency showcasing the truly-decentralised public trust machine essence.
Though the gold ledger has been around for 5,000+ years, the bitcoin ledger only around for 13 years, presents a better alternative in many ways. That value happens in transitional phases can't be overemphasised, as this again is likened to fractal in nature, when the old precious metal gold is juxtaposed with the new "digital gold" bitcoin. Apart from the fact that bitcoin hardly occupies any space by being a mere cryptographic hash sequence digital file, it's a crowd wisdom technology more efficient for wealth creation, distribution, management, capital growth, and thus brings out the differences with gold in bold relief.
BITCOIN VALUE OVER GOLD VALUE BITCOIN GOLD* Easy to transport across the space-time continuum; the known universe/metaverse/cryptoverse etc. Cumbersome and not easily transportable across the space-time continuum; the known universe/metaverse/cryptoverse etc. * Occupies little to no space Occupies large space amount * Easily sub-divisible Hardly sub-divisible * More usable as currency/money Less usable as currency/money * More advantageous for global trade and commerce Less advantageous for global trade and commerce * More monetarily and financially inclusive Less monetarily and financially inclusive * More advanced crypto-tech ledger Less advanced ledger * More valuable because more scarce Less valuable because less scarce
Digital Value Factory Emergence As the sunshine turns to rain, value creation, appreciation and management is moving onto the blockchain virtual world, and as everything else of value in the universe, metaverse and cryptoverse are becoming congregated and secured on the blockchain, or distributed ledger technology with "cryptographic proof instead of trust". A livestock breeder of crustaceans, horses, isopods, pillbugs, dogs, cats, plants etc., can create/breed their unique representations on the blockchain, and drop on the NFT marketplace for sale etc. Per NFT data sources such as the dappradar.com, the 2021 "hottest NFT collections, marketplace rankings, and top real-time sales" are found with Axie Infinity, the littles NFT, Bored Ape Yacht Club, Swampverse, CryptoPunks, and sold-out NFT PFT projects such as the Sup Duck et al Source URL link????
Why is "Scarcity” Significant to Us as Humans? Scarcity is significant to us as humans because when things are rare, and in short supply, they're more valuable. Human nature and psychology are instantly attracted to rarity, as ubiquity tends to be boring, drab and dour in general.
The emergent digital scarcity significance is the natural force that drives the NFT crypto-collectible brand value overtime, and this has a real human appeal, as the NFT craze, or new phase in digitization rages on.
Source URL link: https://www.reuters.com/article/us-fintech-nft-data-idCAKCN2EB1I8
Why's Capitalism Ascribe Higher Value to “Rare” Things? Coin-operated capitalism, like the preceding fiat capitalism, thrives the same on the dyed-in-the-wool demand and supply foundational economics dynamics. The more demand, the more value goes up, and the more supply, the more value goes down.
Relationship Between “Scarcity” and Human Psychology? Scarcity relates to, and reflects upon human psychology, in terms of increase and decrease of value supply in human society, and the NFTs are riding the same waves, through digital value scarcity creation means. An artist who mints NFTs, and drops on the Nifty Gateway NFT marketplace, creates digital scarcity willy-nilly.
In the NFT art collectors’ human psychology, speculation or growth possibility arises that these unique creations secured on the blockchain, would acquire value overtime, as is happening to bitcoin right now, as well as other crypto-assets. Bitcoin price July 2010 when it started to trade was $0.0008 to $0.08 per coin. At the time of writing this piece, bitcoin trades at $57,239.71 on CMC. It's pertinent to note that 100 cents make a dollar, while 100,000.00 sats make a bitcoin.
“Smaller" Objects Used to Represent Value Up from the barter transaction society, coming from its cave-dweller, hunter-gatherer condition, anatomically-modern homo sapiens have used stone, iron, obsidian, amber, beads, cowrie-shells, wampum, quartz pebbles, rice grains, copper, silver, gold, and other rare objects to represent value as media of exchange, moneys, and currencies, but the latest human society currency iteration effort is the cryptography-based currency system.
Representing value through “smaller” objects has always enabled more efficient value transfer arrangements, as things that take up less space, and are rarer thus, assume higher value naturally. Quinessence is the “digital gold” bitcoin software money, compared to the analogue Stone Age atavistic precious gold metal. Though gold has industrial uses like jewelry, electronics, computing, medicine etc., bitcoin has outlandish upside, as a programmable software code piece object currency 99.98% uptime till date since January 3, 2009 at 02:54:25 GMT mainnet launch.
The Arabic numeral system, as a value system, has helped capitalism to scale beyond imagination, and endure overtime. Leveraging the cryptographically secure, alphanumeric value, decentralised system, NFTs are ahead of time in the human society digital value appreciation vocabulary emergence.
Crypto vs Fiat - Better Money (Because Scarce)? Crypto is evolving as a better currency--seeing that even sovereigns are increasingly adopting their own crypto CBDCs--because of its digital scarcity nature, more efficiency as currency, security, scalability et al.
Though its largely speculative embryonic market is less stable, and extremely volatile, overtime, the crypto-market is fated to turn full circle. With time passing, crypto will prove they provide a better (i) unit of account (ii) store of value (iii) medium of exchange (iv) measurement standard than the outdated fiat currencies because of their digital scarcity, and anti-inflationary advantage, among others.
PFPs Explosion in NFT Space Among the first Pictures for Proof were CryptoPunks NFTs back in 2017, made for social media account avatar use purposes, and these algo-generated, unique 10,000 punk portraits are of ultra-small sizes 24 by 24 pixels, with aliens and zombies popping up.
The NFT boom Q2 this year has heralded the PFPs explosion, as the CryptoPunks PFP NFTs for instance once given out free to anyone with an Ethereum wallet, now sell at huge value i.e. the alien CryptoPunk #7804 sold for $7.57 million, Christie’s auctioned a CryptoPunk collection for $17million etc. These PFPs even now trade on the secondary market, and are fast-becoming the key to keeping the NFT market afloat, as they continue to acquire a steady loyal buyer base.
The Coming Metaverse Last month, Mark Zuckerberg in his Facebook Connect keynote address said;
"the best way to understand the metaverse is to experience it yourself, but it's a little tough because it doesn't fully exist yet.".
Source URL link
As all things of value stocks, bonds, currencies, and even abstract ownership become digitalised, in the metaverse, NFTs are going to be the most current currencies. Facebook, Grayscale, Microsoft, Reddit, Tencent, Ant Group, and many other social media goliaths are looking to, extending into the metaverse, and NFT use therein, because of the potentials, and promises:
"EARTH—In a bold announcement to all of His children, God unveiled the creation of an ultra-realistic metaverse where people can talk, learn, and work with other people, stating this unique new metaverse will be called “Universe.”.
Conclusion NFTs have value because they're issued on the value chain system blockchain technology, and thus, each has a Uniform Token Identifier(UTI) that ties its back to the crypto distributed ledger platform. Thus, the future is written in an NFT language, as value acquisition through spreadeagled digital scarcity festers in the newly-minted digital factory.
-
 @ 92294577:49af776d
2023-06-07 01:03:33
@ 92294577:49af776d
2023-06-07 01:03:33Just over two years ago, Blockstream conceived of Greenlight a groundbreaking Lightning hosting infrastructure that scales your Lightning deployments without compromise or custody. The last year of testing with partners has proven Greenlight both stable and simple to use. Today, we are open-sourcing the client repository and opening sign-ups to interested parties for our developer preview!
What is Greenlight?
Greenlight is a non-custodial Lightning-as-a-Service (LaaS) for businesses, merchants, and Lightning apps. Your users hold their keys, while we take care of everything else. As a developer building with Greenlight, you can just talk to our simple API, and seamlessly integrate Lightning payments in your application, without having Lightning protocol expertise, or going about a lengthy node setup.
https://nostr.build/i/bd2608d08710c89761a1bb3e3b42404b442af6008a16c1cfeae9c97afe75050c.jpg
There are two domains of control in Greenlight: the user and Blockstream. Any number of clients from the user domain can connect to a single node on the Blockstream domain. The node running on Blockstream's infrastructure receives commands, computes the state changes, and then reaches out to the signer, which is solely under the user's control, to have it check and sign off on the changes. The result is a non-custodial, on-demand Lightning node where your keys are stored on your device and never touch our infrastructure.
▶️ Video: The philosophy behind Greenlight and how it will change Lightning custody forever.
What’s Available Today?
While we are still actively developing Greenlight, the public interfaces are stable and ready for you to explore.
The client repository contains several components:
gl-clientand its language bindings provide a simple API to interact with Greenlight and user nodes. The built-in signer takes care of managing your seed, and keeps it hidden from the node, and by extension us, the service operators. The end-to-end-verification (still under active development, not complete in this preview) in the signer ensures that any state change was authorized by an authenticated client, such that a potential node host compromise does not result in funds being lost.gl-testingprovides a complete mock environment to test your code against, rather than the real Greenlight service. To learn more, see our tutorial on howgl-testingcan be used in a Python project using the Python bindings ingl-client-py, with more tutorials in the pipeline.gl-pluginandgl-signerproxyallow anybody to replicate the interface exposed by Greenlight nodes, including the ability to use a remote signer, rather than keeping the seed on an exposed server.
The last two are the basis for our off-boarding plans: if you outgrow Greenlight, or want more control, we enable you to off-board into your own infrastructure and all of your applications will keep working. This means that if you develop your application against the Greenlight API, you will automatically have support for Core Lightning out of the box. You can read more on how to off-board in the official Greenlight documentation and tutorial site.
Getting Started
Head over to the Getting Started tutorial and follow the instructions. You will first need an invite code in order to register a new node on the service. The invite system allows us to gradually scale up in a controlled fashion during this early phase of the service. We have set up a form where you can request an invite, and we will send you one as soon as possible.
A minimal client that registers a node, schedules it and then executes
getinfoon the node would look like this in Python:``` from glclient import TlsConfig, Signer, Scheduler import secrets # Make sure to use cryptographically sound randomness
invite_code = "..."seed = secrets.randbits(256) # 32 bytes of randomnessnetwork = "bitcoin"
tls = TlsConfig() signer = Signer(seed, network, tls) scheduler = Scheduler(node_id=signer.node_id(), network=network, tls=tls)
Now actually register the node,
rwill contain the credentials to use # when talking to the noder = scheduler.register(signer, invite_code=invite_code)
Use the credentials when talking to Greenlight from now on.
Requires a refresh
of the
TlsConfigand theSchedulertls = tls.with_identity(r.device_cert, r.device_key) scheduler = Scheduler( node_id=signer.node_id, network=network, tls=tls ) node = scheduler.node() # Schedules the node on the service
And finally we can use
nodeto callgetinfoprint(node.getinfo())
```
And that’s all there is. No setting up of
bitcoind, databases, backups, watchtowers, gossip, node configuration, etc. All that is done on our end so you can focus on what matters the most to you - your users and their needs!What’s Next?
We have already received much feedback from our collaborators:
- Breez has built their Breez SDK on Greenlight, extending our offering with LSP and swap services, as well as migrating their well-known Breez wallet over to Greenlight.
- Verifying Lightning Signer for our secure signing infrastructure, helping us move closer to full end-to-end verification.
- Blockstream Green wallet for internal feedback and testing.
- Core Lightning for being the best Lightning implementation for this scale.
We are eager to reach our full release, but to do so, we still require additional feedback from developers. We invite you to join us on Discord in the #greenlight channel or on the developer page of the Build On L2 community, to share your thoughts and experiences, where you can also keep an eye out for upcoming workshops on Greenlight.
If you are in the process of creating something exciting using Greenlight, we would love to hear about it too! And we may be able to feature it on the official Blockstream blog.
-
 @ 104334bc:7726a708
2023-06-06 21:23:23
@ 104334bc:7726a708
2023-06-06 21:23:23 -
 @ 99f31ddc:6f453b1c
2023-06-06 21:23:12
@ 99f31ddc:6f453b1c
2023-06-06 21:23:12 -
 @ f839fb67:5c930939
2023-06-06 18:24:58
@ f839fb67:5c930939
2023-06-06 18:24:58These can be edited right?
Edit test...
Yippie!
-
 @ 876799cf:410b17f9
2023-06-06 18:24:43
@ 876799cf:410b17f9
2023-06-06 18:24:43This Interview was published on the portal of the German UmweltBank (German for: The Bank of the Environment). This is a translation from German of that Interview. Enjoy, BH.
Bashar Humeid is currently researching the question of how the expansion of renewable energy will affect the democratization of states at the Technical University of Darmstadt. He mainly examines the MENA region (Middle East, North Africa. Bashar Humeid gives us a glimpse into this exciting fiel of ??political science, which is still largely unexplored. He also tells us about his personal endeavours in Jordan.
Dear Mr. Humeid, in your research you look at the expansion of renewable energies in the Middle East and in North Africa. However, your focus is on the effects on democracy in the countries in these regions. What types of projects are being implemented there? Are these decentralized projects that enable participation of citizens or are they rather large private or state-owned companies controling these project?
BH: The political structures and investment capacities of the states in the Middle East and North Africa are different from each other. For example, Saudi Arabia, which has the highest GDP of the Arab states, announced in 2009 that it would become an energy exporter rather than an oil exporter and that it would invest primarily in solar energy. Seven years later, Saudi Arabia presented its “Vision 2030” strategy. The targets set for the generation of solar energy were expanded in March 2018. The current plan: 200 gigawatts of solar energy should be produced by 2030. This corresponds to about a third of the current global production of solar power. However, the implementation of the project has been hiderd by Saudi Arabian power elites for years. In countries like Saudi Arabia, where the state controls large oil production facilities, we observe that solar systems are implemented centrally in large unites and are financed mainly through state entities. However, these are blocked by the elites who benefit from conventional energy sources.
In other non-oil producing Arab countries like Jordan and Tunisia there is less government investment in renewable energies, but a more progressive regulatory framework. For example, Jordan, which led the way in introducing feed-in tariffs in 2013, had achieved 1.13 GW of renewable energy output by the end of 2018, which is around 11% of total electricity demand. 40% of this capacity was generated by small PV systems installed on houses, factories, mosques and churches. By 2021, the capacity will have more than doubled to 2.4 GW
Are there already examples of effects of energy projects on democracy?
BH: There is often collusions between large energy companies and the state that weaken democracy. This is well documented even in established democracies, as Timothy Mitchells explains in his book, Carbon Democracy. It should be noted, however, that fossil fuels have not always hinderd democracy. Some conventional energy sources, such as coal, had a positive influence on democratic developments. In the case of European countries like Germany, the workers in the coal mines organized themselves and became a political force that was important in building democratic systems.
On the other hand, oil in general has had a rather negative impact on democratic processes. This can be seen, for example, in the oil-producing MENA countries. This is mainly due to the fact that oil production does not require a large number of employees. In the MENA region, new energy sources will have a great impact because politics there is intertwined with non-renewable energy sources. Therefore there are strong political and economic interests that want to prevent expansion or at least centralize the production and management of renewable energies. How these can hinder the transition to democracy will be the main question of my study.
What connections have you been able to recognize so far or will you see them in the near future? Will democracy in these countries be strengthened by renewable energies?
BH: The facilitating effect of renewable energies on democracy can be observed on different levels. Globally, it can be assumed that large industrial nations, that started to rely heavily on locally generated renewable energies, will reduce their dependence on the oil-producing (mostly non-democratic) countries of the Arab world. So there are no longer any wars over oil. These wars have enabled militarized rather than democratic forms of government.
At the same time, the decline in dependence on oil leads to a loss of power for the Arab oil states at the regional level. Unfortunately, most of these countries have played a negative role in regional politics in the past. Their influence was a major factor that led to the failure of the Arab Spring in many countries.
At the national level, I assume that the use of renewable energies will bring about socio-economic changes. I am therefore concerned with the question of whether decentralized forms of renewable energy can strengthen the political role of individuals, villages and small towns. Does this strengthen local government structures? This would be important to increase the level of independence from central authorities, which is beneficial for democratic processes.
Are there already positive examples of change at the national level?
BH: For example, we can observe in rural communities in Egypt that forms of industrialization is developing there, that is based on renewable energies. This leads to an increase in the economic autonomy of these communities. The question is how and when does this become a political factor. But even in countries like Saudi Arabia, where the power elite has no interest in decentralized use of renewable energies, we are seeing that households, businesses and even factories are discovering solar energy for themselves. Such developments show that solar power has great potential, even in undemocratic countries. A democratizing effect seems plausible, but it depends on how the authorities react and what state control over such tendencies will look like.
How did you come up with the idea of ??examining the connection between the expansion of renewable energies and the strengthening of democracy?
BH: I was born and raised in the MENA region. Living there puts you in direct contact with the political, social and economic effects of the oil industry. We witnessed the two Iraq wars, which were intertwined with the oil industrie. I have always asked myself: How can we achieve a more democratic and peaceful future in our countries? I dealt with this question in my master’s thesis. In doing so, I came to the conclusion that the factors preventing the MENA region from entering a democratic and peaceful era are neither cultural nor related to Islam. My assumption is that the prevention of democracy in these states is related to infrastructural and geopolitical factors. That made methink and work more in the field of renewable energy and agriculture.
You are already indicating that, in addition to your research at TU Darmstadt, you are personally involved and working in Jordan. What projects did you implement there?
BH: In 2011, I founded a non-governmental organization called Meezan in Jordan . We developed sustainable solutions for water, food and energy in several Arab countries. The organization developed the “Freedom Machine” and installed 15 units in Jordan, Palestine and Switzerland. The “Freedom Machine” is an integrated, self-supporting system for urban space. It combines water extraction, organic food cultivation, solar energy production and ecological building technologies.
Since 2013, Meezan has also been involved in developing a system for growing and distributing organic products in Jordan. From this the company Yanboot developed , which is today the leading brand for organic products on the Jordanian market.
How is the issue of sustainability accepted in Jordan?
BH: The population of Jordan is very entrepreneurial and has traditionally been open for new solutions and business ideas. People picked up and implemented many ideas like mine. Even before I established my project we had in 2008 13% of households in Jordan that used solar thermal panels to heat water. In recent years installing PV panels on the rooftops of houses, shops and factories became very popular. We have more than 500 registered companies that are specialized in installing PV cells. This is a big number for a country like Jordan that has only 10 million inhabitants and with very little incentives offered by the government to cover the cost of these installations.
In addition, the market for electric vehicles in Jordan has improved significantly in recent years. 18.5% of the total of around 42,000 vehicles registered in Jordan in 2018 were fully electric. Many owners of electric cars have PV panels on the roofs of their homes. Unfortunately, the Jordanian government introduced a tax to curb the popularity of electric cars. It also stopped issuing licenses for new large PV units. For observers, this is linked to a gas import agreement between Jordan and Israel. Here, too, we see that the potential of renewable energies is being restricted by the ruling elite for economic reasons.
How do you see the future in Jordan and in the entire MENA region with a view to sustainability and renewable energies?
BH: My future expectations for this sector are very promising, unless governments interfere negatively. There is great social acceptance for renewable energy solutions and I think there is a possibility that the MENA region will take a leading role in this field.
Thank you so much! We wish you continued success in your research and we hope to hear a lot more about sustainable development in Jordan.
-
 @ 6c76d28f:9eb3f41d
2023-06-06 17:11:48
@ 6c76d28f:9eb3f41d
2023-06-06 17:11:48 -
 @ 47664f95:c5b6feba
2023-06-06 17:08:08
@ 47664f95:c5b6feba
2023-06-06 17:08:08 -
 @ b324cc32:bc2758d4
2023-06-06 17:07:32
@ b324cc32:bc2758d4
2023-06-06 17:07:32 -
 @ 32dc4f25:f95ddcce
2023-06-06 12:15:05
@ 32dc4f25:f95ddcce
2023-06-06 12:15:05We all know that the Web is broken in more ways than one. Clickbait, misinformation, bot farms, anonymous "troll-demons"—the list is as endless as it is depressing. How did we end up here?
I believe there is a single-phrase answer to all these ills. But single-phrase answers are often too simplistic and thus too easily dismissed. So instead, let us first break down the problem into more manageable chunks.
Most of the problems we see online are a combination of:
- Incentives (which are broken),
- Limitations (which are technical),
- Credit (which is a poor substitute for cash),
- Attention (which is a poor substitute for value),
- Consequences (which are non-existent), and
- Identity (which should be optional).
After going through these points one by one, I will sketch out a Thesis that will lay the foundation for the Vision of the value-enabled Web. But first, we have to start by wrapping our heads around the various sub-problems that plague the web. Let's start with the most important one: incentives.
Incentives
Show me the incentives, and I'll show you the outcome. Charlie Munger
Human action is shaped by the subtle and not-so-subtle structures of the systems we are embedded in. While actions, values, and motivations are individual, the carrots and sticks that are a part of the environments we inhabit—man-made or not—drive collective behavior. If the incentives are broken, everything is.
We shouldn't be surprised by the polarization and outrage maximization that we observe online; it's a natural outcome of the incentive to maximize engagement. We shouldn't be surprised by "you are the product" business models and the walled gardens of subscription hell; it's a natural outcome of the incentive to capture users and user data. We shouldn't be surprised by clickbait headlines and sensationalism; it's a natural outcome of the evolutionary pressure to farm as many eyeballs and brain cycles as possible.
So-called "free" platforms have to sell ads (or worse: user data) to make money. And to sell this data, they have to accumulate as much data as they can and convince their buyers that the data is useful. When selling to advertisers, for example, they have to convince them that people are looking. How do they get more people to look? Outrage, conflict & arguments. Better yet: make people addicted to outrage, conflict, and arguing, and they will maximize "time on site" and other engagement metrics. Advertisers love these! Who cares about truth, wisdom, beauty, nuance, or value? Who cares about honest dialogue if you can maximize clicks instead?
The nature of this conundrum is neither political nor social, at least not exclusively. It might sound outrageous (oh, the irony!), but I believe that a big part of it is due to the technical limitations of our current monetary system and the payment infrastructure built on top of it.
Limitations
Imagine a Being who is omniscient, omnipresent, and omnipotent. What does such a Being lack? The answer? Limitation. Jordan Peterson
Money has limitations, always. While it used to be possible to buy small items or services for a nickel or even a penny—a pack of chewing gum, a cup of coffee, a shoe shine, a bottle of coke—the smallest payment that was possible was limited by the smallest unit of money, i.e., a penny. For anything smaller than this unit, we had to do batch transactions, selling multiple items for a single penny; or we had to give the item away for free.
 Source: What Could You Buy With a Nickel? A century of chump change, by Ignite Spot.
Source: What Could You Buy With a Nickel? A century of chump change, by Ignite Spot.Counter-intuitively, the limitations in cyberspace are even larger. Ask yourself: why can't we buy things online for pennies or fractions of a penny? The answer is quite simple: pennies do not exist online. Never have, never will. Pennies are physical things: coins that you can hold in your hand. You can't attach them to an email. When it comes to pennies, all that we ever had online—all that we can ever have—is information about pennies. We call this information IOUs. An IOU is not something that you own outright, but it's something that you owe to someone else: "I owe you." It is credit, and credit is different from base money. Credit requires trust.
Credit
All the perplexities, confusions, and distresses in America arise, not from defects in their constitution or confederation, not from a want of honor or virtue, so much as from downright ignorance of the nature of coin, credit, and circulation. John Adams
The problem with credit is that it has various risks. That's why we have to keep track of credit, as well as the creditors and debtors involved. We have to keep track because we have to do accounting and risk management. Once the credit is paid—and the outstanding debt is settled—we don't need this information anymore. The deal is done. The counterparty risk is resolved. There is a reason why "cash is king."
While not all credits are equal, and credit risks are manifold, I want to focus on one in particular: counterparty risk.
Counterparty risk is why institutions that are in the business of dealing with and resolving credit issues, such as VISA & MasterCard, or its newer incarnations à la PayPal and Venmo, have delayed settlement and—due to the necessity of having to keep track of everything—high fees. It is all rooted in counterparty risk, which is a natural byproduct of trying to use conventional currencies for electronic payments. Conventional currencies—no matter if they are sea shells, metal coins, or paper notes—can only be transferred as IOUs when transferred electronically.
The root problem with conventional currency is all the trust that's required to make it work. [...] Banks must be trusted to hold our money and transfer it electronically [...]. We have to trust them with our privacy, trust them not to let identity thieves drain our accounts. Their massive overhead costs make micropayments impossible. Satoshi Nakamoto
We could sum it up as follows:
- IOUs are credit
- Credit relies on trust
- Trust can be broken (by fraud, negligence, or by accident)
- Fraud leads to chargebacks & insurance constructs
- These constructs require KYC and lead to high processing costs1
- All these issues stem from having to use IOUs as money, and we have to use IOUs as money when dealing with conventional currencies (currencies that are not natively digital, i.e., currencies that are not reified by proof-of-work).2
Because of credit, the goddamn fees are too damn high. Because of credit, we were never able to do micropayments online. Because of credit, all the centralized credit institutions need to know their customers, and they need you to know your customers too. Because of credit, you have to identify yourself when using any payment app. Because of credit, every single service you want to pay for online forces you into a contract that binds you for multiple weeks or months because single payments below ~$5 are not economically feasible.
It's all because of credit. Cash does not have these problems.3
Attention
Are you not ashamed that you give your attention to acquiring as much money as possible, and similarly with reputation and honor, and give no attention or thought to truth and understanding and the perfection of your soul? Plato
The problem of paying attention to the wrong things is not new, but it is particularly pronounced online. Again: the issue is that when dealing with conventional currencies, we have to use IOUs as electronic money. There are two solutions to this problem:
Use something other than money as a proxy currency Identify your customers and process payments in large chunks of credit (Currently: ~$5 or more) Both solutions exist. We call the first "attention economy," and the second "subscription hell."
We failed to realize and solve for the fact that our physical money was terribly unfit for cyberspace, and now we are all paying for it—with our attention, among other things. One could even argue that the use of attention as currency is—at least in part—to blame for the loss of nuanced discourse and the increase in polarization, be it political or otherwise.4
Time and attention are the ultimate currencies. There is a reason why we "spend" the first and "pay" the latter. And while we do indeed "spend" time and "pay" attention, they are unfit as money because we can't accumulate either. There is a reason why using proper money frees up time and allows for an increase in long-term thinking—both individually and for society at large. Money is as important for capital accumulation as it is for distributed cognition, and if the money is broken, both of these things deteriorate. And with it, so does our time and attention.
By using attention as the de facto currency online, we destroyed depth and nuance, as well as our collective attention spans.
 Memes: the weapons of attention warfare.
Memes: the weapons of attention warfare.Now that I hopefully have yours—your attention, that is—I will finally use the single-phrase answer that I refused to use in the beginning: Bitcoin fixes this.
Bitcoin fixes this because, for the first time in history, we have high-velocity, digitally native money without having to rely on credit. Not IOUs. Not credit relationships. Good, old-fashioned money. Cold, hard cash. Better yet: cold, hard cash that is digitally native, can't be debased, and can be sent around at the speed of light. Without counterparty risk.
Consequences
Every unpunished delinquency has a family of delinquencies. Herbert Spencer
The consequence of bringing real, non-credit-based money to cyberspace can hardly be overstated. While the conversation around Bitcoin is still mostly focused on its limited supply and thus on "Gold 2.0" and other store-of-value metaphors, very few people are focusing on the high-velocity instant settlement part of it all. While Bitcoin does bring consequences to the monetary policies of fiat currencies—and thus to central banks around the world—the more immediate effects are probably to be found in cyberspace.
While the effects are many, I want to focus on four in particular: reduced friction, more peer-to-peer, increased neutrality & systemic stability, and real costs.
Reduced friction: Intermediaries introduce friction. Cash reduces friction. An Italian comedian once said that "the whole point of money is to NOT know your customer."5 Note that this is also what made the internet great. The whole point of "the web" was to NOT know who is on the other side of the computer. "True Names" are not required, to quote Vernor Vinge.
Peer-to-peer: All physical money is peer-to-peer technology. If you have a physical coin, it is yours. You are not beholden to anyone when it comes to spending or accepting it. You just have to find another peer that is willing to trade with you. Yes, intermediaries might still exist, but they are less important. They are less important because they are not essential anymore. In a credit-based system, trusted third parties are not optional: they are absolutely necessary. In a cash-based system, they are mostly superfluous.6
Neutrality & systemic stability: Protocols, like math and language, are neutral systems. Anyone can use them, and no single person or entity is in charge of it all. The lack of single points of failure is what makes a system resilient. Openness & neutrality provide inclusivity and a level playing field for all. When it comes to money, any lack of openness inevitably leads to financial censorship, and any lack of neutrality inevitably leads to bailouts, Cantillionaires, and systemic instability.7
Real cost: Electronic money that is natively digital allows us to attach real costs to actions in cyberspace. It allows us to move away from the exploitative practices of using time and attention as online currencies. It allows us to move away from extraneous punishments such as deplatforming and debanking. It allows us to make destructive actions costly without having to go to the extreme of destroying the public personas of those who slipped up. It allows us to do all these things because real money does not require real identity, and yet has a real cost. Real cost makes spam bots uneconomical and disincentivizes antisocial behavior.8
Identity
It is funny about money. And it is funny about identity. You are you because your little dog knows you, but when your public knows you and does not want to pay for you and when your public knows you and does want to pay for you, you are not the same you. Gertrude Stein
Identity is prismatic. You act differently in a bar on Friday night than at church on Sunday. You are a different you in public and in private, and you are a different you at work and at home. Your behavior adjusts depending on social circles and circumstances. What's offensive to some is casual banter to others; what's outrageous and career-ending in a public political debate can be the cause for laughs and a good time at a comedy club. Identity isn't singular. Identity is prismatic.
Cyberspace flattens both time and space, dissolving the prismatic separations that we are so used to in meatspace. The guy replying to your tweet might be trolling, might be a bot, might be 12 years old, might be heavily intoxicated, or all of the above. You don’t know, and that’s a feature, not a bug.
Some boomers people bemoan the armies of "anonymous troll-demons," seemingly incapable of dealing with the roughness of pseudonymous online discourse.9 They want to fix the problem in an old-school way, forcing everyone and anyone to show their face and attach their meatspace identity to their online profiles. Those who grew up with and in between trolls—playing countless hours of competitive online games, for example—know that online interactions and online identity are to be categorized differently than offline interactions and identities. "Don't feed the trolls" is a wisdom of online culture, and for good reason.
Forcing KYC on any platform, service, or app is a naive and short-sighted approach to fixing the problem of identity. It is short-sighted because (a) not everyone has an identity, (b) not everyone can show their face or use their legal name without endangering themselves or others, (c) it doesn't stop criminal or toxic behavior, and (d) identity is prismatic, not singular.
Converting cyberspace into a totalitarian surveillance state beyond the imaginations of George Orwell (not his real name, by the way) can't be the solution. That much should be obvious. In case it isn't obvious, remind yourself of the Chinese social credit score system or of the fact that all you needed to do to have your Canadian bank account frozen was to honk twice (or be close to someone who did).
The more subtle approach to solving the problem of identity is with reputation, costly identity creation, and real value. In other words: we should not add our singular government-mandated identities to everything in cyberspace. Instead, we should allow users—anonymous or not—to show the world that they are serious and real.
Value brings consequence to cyberspace. Michael Saylor
There is an Eastern-European saying: "If you truly want to hurt a man, you have to punch him where it hurts most: his wallet." Michael Saylor has the right idea. The way to disincentivize bad behavior is to add real value to pseudonymous identities. Like a security deposit that is locked up when you check into a hotel; a security deposit that you lose if you act in a damaging way.
Of course, one question remains: who defines "damaging?" User reports lead to mob rule; platform decisions lead to authoritarianism. I'm confident that better mechanisms will emerge over time as larger parts of the web become natively value-enabled, and our identities become disentangled from the monolithic platforms that rule the web at present. We are at the very beginning of these trends. Decentralized identifiers are still unknown to most. Very few people know that sats are being infused into protocols and platforms as we speak. The "value block" of Podcasting 2.0 is one example. The way that sats are used on Stacker News is another one.
The interesting thing about cash is that it is decoupled from identity. You don't have to ask for anyone's permission to receive and spend cash. And because money is one way to express value—the main way, arguably—the free expression thereof is of utmost importance for a free and prosperous society.
In most cases personal identity is not salient. When I purchase a magazine at a store and hand cash to the clerk, there is no need to know who I am. Eric Hughes
Most transactions do not require identity. Most transactions should not require credit. For most transactions, trusted third parties should be optional. This was the default for thousands of years, and I believe that this should be the default going forward, both in meatspace and cyberspace.
Infusing real value into the online world doesn't mean that reputation is unimportant or can't emerge. Reputation is essential and has emerged already. What the Value-Enabled Web allows for, however, is costliness when it comes to certain actions. One of these actions is building up the reputation of a particular identity in the first place.
Currently, it is cheap to spin up an army of bots to create the impression of reputation (in the form of fake likes and fake followers). Adding value to the account creation and/or verification makes this action costly.
Identity and consequential actions are only one piece of the puzzle. Not all pieces are known yet, let alone in place. Nevertheless, many people are working on various technologies and protocols that might help to fix some of the issues described above. My hope is that—once we understand the problems properly and have the right thesis and vision—we will figure out the details as we go along.10 11
Thesis
Anon out of the earth a fabric huge Rose like an exhalation, with the sound Of dulcet symphonies and voices sweet, Built like a temple John Milton, Paradise Lost
Let's recap: We have seen that the incentives are broken, leading to "you are the product" and "subscription hell" business models. We have seen that, due to the limitations of our monetary system, we were forced to use IOUs (credit) to do business online. We have seen that, thanks to the prevailing business models of maximizing eyeballs and selling advertisements, our attention is farmed, manipulated, sold, and abused.
I believe there is a better way. I believe that, when it comes to selling products and services, cash money will make a comeback. And I believe that—thanks to the consequences that programmable money brings to cyberspace—identity on the web can remain optional while still allowing for reputation and real-world costs to anti-social behavior.
One problem remains: the problem of selling stuff. This particular problem is only a problem in cyberspace because most "stuff" in cyberspace is not scarce in the traditional sense. We can not sell JPGs like we can sell apples, even though plenty of confused people try. JPGs aren't scarce. Apples are. JPGs can be reproduced at zero marginal cost. Apples take time and effort to grow. It is impossible to distinguish between two copies of a JPG. When you load a JPG on your screen, it is a copy of the JPG on the server you’re retrieving it from, and the copy on that server does not go away. An apple only exists once and can't be copied perfectly, let alone at zero marginal cost. Copying something at zero marginal cost leads to a virtually infinite supply of that thing. It doesn't matter if that thing is a JPG, a blog post, or an mp3 file. If it can be copied by anyone quickly, perfectly, and for basically free, the supply of said thing quickly approaches infinity. We move from the analog world of scarcity into the digital world of abundance. Markets don't work in this world. In the words of Jaron Lanier: "Markets become absurd as supply approaches infinity."12
Traditional paywalls in the form of "pay 10 cents to read the blogpost" are trying to restrict supply and/or access artificially. It goes against the nature of digital information, which is easy to spread and hard to stifle. "Trying to make digital files uncopyable is like trying to make water not wet," to quote Bruce Schneier.
I will do my best to describe this problem in more detail at some point in the future, but for now, let me try to sum it up as follows: When it comes to JPGs, mp3 files, blog posts, or similar digital artifacts, we have to stop pretending that the files themselves are scarce or precious. They aren't. The humans that create them are. Consequently, we have to find new ways of pricing and monetizing things. New ways of making sure that the value that is generated accrues to the humans that are responsible for the added value, without imprisoning information or users—without trying to make water not wet.
We have to disconnect price from value, and we have to re-think both.
Vision
The vision of the eye is limited, but the vision of the heart transcends all barriers of time and space. Imam Ali
We now have a money that transcends the conventional barriers of time and space. A money born in and out of cyberspace, a money that allows us to make the value-enabled web a reality.
Bitcoin exists. The Lightning Network exists. Podcasting 2.0 is a thing. Value4value is a thing. But even outside of the world of Bitcoin, a rethinking of traditional models is taking place. People sign up to other people's Substack, Patreon, or Twitch; not to buy a tangible thing but to give value back for the value they receive in return—voluntarily.
Please note that the vision that I attempt to sketch out here is not my vision. A lot of the parts are being developed as we speak, and a lot of the changes in behavior are already happening, albeit at the edges.
The challenge is to make the experience enjoyable and seamless without reintroducing the ills of counterparty risk. We need a technological shift as well as a cultural shift. We are not there yet. Sending people money for information that they can retrieve for free is still a strange concept for most, but the proliferation of new podcasting apps and other "boost" mechanisms clearly shows that the cultural shift is happening. And yes, it is still clunky. It is clunky to enter a lightning address and send sats manually. It is clunky to click the "boost" button and scan a QR code.
Boost! 🚀🎉
But we've come a long way, and the trend is going in the right direction. If we build this right, micropayments will be invisible and transparent, removing the friction of mental transaction costs while giving the user complete control and insight. The new podcast apps that are value-enabled are leading the way.
One trend I observe keenly is the trend of "boosts" and superchats, or privileged direct messages in general. Attaching a monetary value to anonymous or pseudonymous notes is a novel way to show your appreciation directly and clearly. A big "thank you" online—directly and with a costly signal attached. It is a delight to read these small messages. As an early adopter, I have the privilege of glimpsing into the future as I read the messages that are sent to s@ts.dergigi.com every morning. My hope is that, given enough time and improvements, this delight will be ubiquitous.
In general, the trend seems to move towards direct support when it comes to the creation of digital things that can be reproduced at zero marginal cost. Everyone will have to grapple with the fundamental nature of digital information (that it can be reproduced perfectly and for free) as well as the fundamental nature of humans (that they need to eat). Everyone. Even platforms like YouTube and Spotify:13
 Today, all of these are credit, sent on credit rails. Tomorrow, they could be sats.
Today, all of these are credit, sent on credit rails. Tomorrow, they could be sats.What I mean when I say "value-enabled web" is a broad framework for thinking about these technologies and trends, including the open protocols which allow anyone to participate. Just like the traditional web is neither a platform nor a company, the value-enabled web is also not a single new "thing," but rather a collection of protocols that allows for an open ecosystem to flourish. Openness and permissionlessness are what made the web great. The same things will make the value-enabled Web great.
Interoperability and open standards are absolutely essential to create a win-win environment for all. It is harder to do and takes a lot of thought and patience, but it is also the right thing to do. In the long run, positive-sum games beat zero-sum games any day of the week, even if closed platforms might be able to sprint ahead in the short term.
The vision is still blurry, but it gets clearer every day. If someone would force me to write a manifesto describing the vision, it would revolve around the following ideas:
- It should be trivial for those who produce value to receive value.
- It should be trivial for those who cherish valuable content to send value to those who produced it.
- Allow content and metadata to replicate freely.
- Allow value to flow freely.
- Do not build walls around content or metadata.
- Make identity optional.
- Allow those who add value to participate in value flows.
- Make unethical behavior costly.
- Provide tools & services that add value and bring joy.
- Use money for monetization, not attention.14
- Sell services, not user data.
- Keep exit costs low.
- Build on sats, not IOUs.
Businesses should not spend their time role-playing as credit institutions. In the best case, they shouldn't have to know who their customers are in the first place. Oh, the good old days when you could just walk into a store, grab an apple and a newspaper, hand over a couple of coins, and walk out. This is the magic of cash.
This magic still exists in meatspace stores, but it never existed in cyberspace—until bitcoin came along. And thanks to lightning, we finally have a digital bearer instrument—something you can hold in your head, not only in your hands—that has all the properties of cash and is natively digital. This is a big deal. It is a big deal because it allows us to build a value-enabled web without having trusted third parties.
I am still a huge fan of the web—and, of course, the internet in general—but I believe, as all of you do, too, that things could be better.15 In fact, I know that it can be better, as everyone else knows who is at the forefront of these developments. Once you've received your first streaming payments, it feels beyond antiquated to deal with the legacy payment rails of our fiat world.
The result of using platforms instead of protocols.
I don't want to enter my credit card details into this random website form, I just want to pay in sats. I don't want to sign up for 12 months to use a random internet service, I just want to pay in sats. I don't want to enter my email address or my phone number or solve a CAPTCHA that has me doubting my humanness—I just want to use the service and pay in sats.
I don't want to deal with paywalls, walled gardens, and extractive platforms that go through the futile exercise of building walls around digital files. Information wants to be free, and for good reason. We should cherish the world of abundance that we managed to create for ourselves. We shouldn't fight this abundance. Instead, we should make it as easy as possible to let our scarce money flow toward those who produce value. The people behind Podcasting 2.0 and other pioneers show us what's possible. They are at the forefront of the value-enabled web.
They show us that money can flow as freely as information does today. They show us that there are no barriers to entry when it comes to receiving or sending money. They show us that nobody has to be beholden to platforms or credit institutions.
If we get this right—if we manage to reduce the use of time and attention as currencies online—noise and dependence will be reduced, while freedom and real signal will be maximized.
Further, when anyone can participate in the monetary flows that are generated in online environments—without gatekeepers and sign-up requirements—we can provide more value for more people.
In a value-enabled web, anyone can benefit, not only those who are in control of the servers that farm our time and attention. More prosperity for everyone, not just for those who have credit ratings and bank accounts.
 Include anyone in the value flow. Fatten the long tail.
Include anyone in the value flow. Fatten the long tail.All the attention economy can do is blow up the head. Sat-flows can fatten the long tail. The vision of a value-enabled web is a return to substance and sanity. A move away from clickbait and attention farming. A counter to Orwellian surveillance, deplatforming, and cancel culture.
- A move from winner-takes-all to all-can-win.
- A move from maximizing growth to maximizing value.
- A move from quantity to quality.
- A move away from client-server relationships, which more often than not turn into relationships of masters and slaves, towards peer-to-peer relationships where everyone is on equal footing.
This vision is larger than value4value, although new valuation and monetization models will play a major role. This vision is larger than adding cash micropayments to certain actions, although that will be important for some actions. This vision is larger than programmatic value flows and the automatic disbursement of sats, although a new way to think about royalties is duly needed. This vision is larger than passwordless authentication, using the timechain as an anchor for truth and proof-of-existence, or decentralized IDs & sovereign computing—even though all these things are important and necessary.
The vision of a value-enabled web is one of fairness, openness, positive-sum exchange, and allowing value packets to flow as freely as data packets did in the past. More value, more humanity, fewer bots, less spam, and—hopefully—a reduction of dark patterns and addictive behavior.
It's Day 2 for the internet, and it's time to fix it.
Thanks to Tomer, Allen, Daniel, and my patrons for providing excellent feedback on earlier drafts of this writing. Any parts that are still confusing and incomplete are due to my blurry vision and stubbernness.
Footnotes
-
KYC isn’t always a function of evil corporations and/or governments trying to be evil and spying on everyone. When it comes to financial products, it’s often just a guard against credit risk. ↩
-
Only proof-of-work allows for natively digital money that is trustless and permissionless, i.e., accessible to all and not controlled by a quorum of key holders. ↩
-
Note that I'm glossing over the fact that all fiat money is credit. Let's just assume, for the sake of arguing for a Value-Enabled Web, that all conventional currencies are still backed by gold. Let's assume that nothing happened in 1971. ↩
-
The visualization of the political polarization in the U.S. Senate is something to behold: Team Red and Team Blue, drifting apart. Data by Clio Andris, David Lee, Christian E. Gunning, John A. Selden, Mauro Martino and Marcus J. Hamilton, visualization by Mauro Martino ↩
-
“Good morning, money laundering is beautiful” by Giacomo Zucco, Baltic Honeybadger 2022 ↩
-
In Bitcoin, trusted third parties are security holes. ↩
-
Search for “Cantillion effect” ↩
-
Listen to Michael Saylor explain this in detail on the Bitcoin Matrix podcast. ↩
-
Jordan, Jordan, Jordan… There is a mute button. There is a block button. Please use it, and don’t feed the trolls. ↩
-
Notable mentions include TBD’s Web5, Holepunch, ION, and nostr. (I’m sure there are many more, feel free to add them via a PR.) ↩
-
I wrote the bulk of this post about a month before it was published, so all of this was written before Jack endorsed and funded nostr, and before Elon banned the promotion of it (and other twitter competitors). ↩
-
Lanier’s book Who Owns the Future describes the problem we face well, but it fails to offer a solution that is viable and practical. In my humble opinion, Lanier tries to make water not wet. ↩
-
See this and this for YouTube, and this for Spotify, for example. ↩
-
Bitcoin is unique, as it is the only reliable and battle-tested money that is natively digital and has an unbroken track record when it comes ot the integrity of its monetary policy. No other money can claim this. Consequently, bitcoin is the only sound money in cyberspace. ↩
-
Mastroianni, Adam, and Ethan Ludwin-Peery. “Things Could Be Better.” PsyArXiv, 14 Nov. 2022. Web. ↩
Conversations
-
2023-01-28 Nodesignal #102
on Value4Value, Podcasting 2.0, and the Value-Enabled Web, hosted by Jan-Paul & Calso (🇩🇪) -
2022-11-25 Bitcoin Review #11
- on Value4Value, Podcasting 2.0, and the Value-Enabled Web, with Matt Odell, Adam Curry, Oscar Merry hosted by NVK
-- BY dergigi Link:https://dergigi.com/2022/12/18/a-vision-for-a-value-enabled-web/
-
 @ 32dc4f25:f95ddcce
2023-06-06 11:39:52
@ 32dc4f25:f95ddcce
2023-06-06 11:39:52Ben Smith picked just the right title for his saga of BuzzFeed, Gawker, and The Huffington Post: Traffic (though in the end, he credits the able sensationalist Michael Wolff with the choice). For what Ben chronicles is both the apotheosis and the end of the age of mass media and its obsessive quest for audience attention, for scale, for circulation, ratings, page views, unique users, eyeballs and engagement.
Most everything I write these days — my upcoming books The Gutenberg Parenthesis in June and a next book, an elegy to the magazine in November, and another that I’m working on about the internet — is in the end about the death of the mass, a passing I celebrate. I write in The Gutenberg Parenthesis:
The mass is the child and creation of media, a descendant of Gutenberg, the ultimate extension of treating the public as object — as audience rather than participant. It was the mechanization and industrialization of print with the steam-powered press and Linotype — exploding the circulation of daily newspapers from an average of 4,000 in the late nineteenth century to hundreds of thousands and millions in the next — that brought scale to media. With broadcast, the mass became all-encompassing. Mass is the defining business model of pre-internet capitalism: making as many identical widgets to sell to as many identical people as possible. Content becomes a commodity to attract the attention of the audience, who themselves are sold as a commodity. In the mass, everything and everyone is commodified.
Ben and the anti-heroes of his tale — BuzzFeed founder Jonah Peretti, Gawker Media founder Nick Denton, HuffPost founder Arianna Huffington, investor Kenny Lerer, and a complete dramatis personae of the early players in pure-play digital media — were really no different from the Hearsts, Pulitzers, Newhouses, Luces, Greeleys, Bennetts, Sarnoffs, Paleys, and, yes, Murdochs, the moguls of mass media’s mechanized, industrialized, and corporate age who built their empires on traffic. The only difference, really, was that the digital moguls had new ways to hunt their prey: social, SEO, clickbait, data, listicles, and snark.
Ben tells the story so very well; he is an admirable writer and reporter. His narrative whizzes by like a local train on the express tracks. And it rings true. I had a seat myself on this ride. I was a friend of Nick Denton’s and a member of the board of his company before Gawker, Moreover; president of the online division of Advance (Condé Nast + Newhouse Newspapers); a board member for another pure-play, Plastic (a mashup of Suck et al); a proto-blogger; a writer for HuffPost; and a media critic who occasionally got invited to Nick’s parties and argued alongside Elizabeth Spiers at his kitchen table that he needed to open up to comments (maybe it’s all our fault). So I quite enjoyed Traffic. Because memories.
Traffic is worthwhile as a historical document of an as-it-turns-out-brief chapter in media history and as Ben’s own memoir of his rise from Politico blogger to BuzzFeed News editor to New York Times media critic to co-founder of Semafor. I find it interesting that Ben does not try to separate out the work of his newsroom from the click-factory next door. Passing reference is made to the prestige he and Jonah wanted news to bring to the brand, but Ben does not shy away from association with the viral side of the house.
I saw a much greater separation between the two divisions of BuzzFeed — not just reputationally but also in business models. It took me years to understand the foundation of BuzzFeed’s business. My fellow media blatherers would often scold me: “You don’t understand, Jeff,” one said, “BuzzFeed is the first data-driven newsroom.” So what? Every newsroom and every news organization since the 1850s measured itself by its traffic, whether they called it circulation or reach or MAUs.
No, what separated BuzzFeed’s business from the rest was that it did not sell space or time or even audience. It sold a skill: We know how to make our stuff viral, they said to advertisers. We can make your stuff viral. As a business, it (like Vice) was an ad agency with a giant proof-of-concept attached.
There were two problems. The first was that BuzzFeed depended for four-fifths of its distribution on other platforms: BuzzFeed’s own audience took its content to the larger audience where they were, mostly on Facebook, also YouTube and Twitter. That worked fine until it didn’t — until other, less talented copykittens ruined it for them. The same thing happened years earlier to About.com, where The New York Times Company brought me in to consult after its purchase. About.com had answers to questions people asked in Google search, so Google sent them to About.com, where Google sold the ads. It was a beautiful thing, until crappy content farms like Demand Media came and ruined it for them. In a first major ranking overhaul, Google had to downgrade everything that looked like a content farm, including About. Oh, well. (After learning the skills of SEO and waiting too long, The Times Company finally sold About.com; its remnants labor on in Barry Diller’s content farm, DotDash, where the last survivors of Time Inc. and Meredith toil, mostly post-print.)
The same phenomenon struck BuzzFeed, as social networks became overwhelmed with viral crap because, to use Silicon Valley argot, there was no barrier to entry to making clickbait. In Traffic, Ben reviews the history of Eli Pariser’s well-intentioned but ultimately corrupting startup Upworthy, which ruined the internet and all of media with its invention, the you-won’t-believe-what-happened-next headline. The experience of being bombarded with manipulative ploys for attention was bad for users and the social networks had to downgrade it. Also, as Ben reports, they discovered that many people were more apt to share screeds filled with hate and lies than cute kittens. Enter Breitbart.
BuzzFeed’s second problem was that BuzzFeed News had no sustainable business model other than the unsustainable business model of the rest of news. News isn’t, despite the best efforts of headline writers, terribly clickable. In the early days, BuzzFeed didn’t sell banner ads on its own content and even if it had, advertisers don’t much want to be around news because it is not “brand safe.” Therein lies a terrible commentary on marketing and media, but I’ll leave that for another day.
Ben’s book comes out just as BuzzFeed killed News. In the announcement, Jonah confessed to “overinvesting” in it, which is an admirably candid admission that news didn’t have a business model. Sooner or later, the company’s real bosses — owners of its equity — would demand its death. Ben writes: “I’ve come to regret encouraging Jonah to see our news division as a worthy enterprise that shouldn’t be evaluated solely as a business.” Ain’t that the problem with every newsroom? The truth is that BuzzFeed News was a philanthropic gift to the information ecosystem from Jonah and Ben.
Just as Jonah and company believed that Facebook et al had turned on them, they turned on Facebook and Google and Twitter, joining old, incumbent media in arguing that Silicon Valley somehow owed the news industry. For what? For sending them traffic all these years? Ben tells of meeting with the gray eminence of the true evil empire, News Corp., to discuss strategies to squeeze “protection money” (Ben’s words) from technology companies. That, too, is no business model.
Thus the death of BuzzFeed news says much about the fate of journalism today. In Traffic, Ben tells the tale of the greatest single traffic driver in BuzzFeed’s history: The Dress. You know, this one:

At every journalism conference where I took the stage after that, I would ask the journalists in attendance how many of their news organizations wrote a story about The Dress. Every single hand would go up. And what does that say about the state of journalism today? As we whine and wail about losing reporters and editors at the hands of greedy capitalists, we nonetheless waste tremendous journalistic resource rewriting each other for traffic: everyone had to have their own story to get their own Googlejuice and likes and links and ad impressions and pennies from them. No one added anything of value to BuzzFeed’s own story. The story, certainly BuzzFeed would acknowledge, had no particular social value; it did nothing to inform public discourse. It was fun. It got people talking. It took their attention. It generated traffic.
The virus Ben writes about is one that BuzzFeed — and the every news organization on the internet and the internet as a whole — caught from old, coughing mass media: the insatiable hunger for traffic for its own sake. In the book, Nick Denton plays the role of inscrutable (oh, I can attest to that) philosopher. According to Ben, Nick believed that traffic was the key expression of value: “Traffic, to Nick … was something pure. It was an art, not a science. Traffic meant that what you were doing was working.” Yet Nick also knew where traffic could lead. Ben quotes him telling a journalist in 2014: “It’s not jonah himself I hate, but this stage of internet media for which he is so perfectly optimized. I see an image of his cynical smirk — made you click! — every time a stupid buzzfeed listicle pops on Facebook.”
Nick also believed that transparency was the only ethic that really mattered, for the sake of democracy. Add these two premises, traffic and transparency, together and the sex tape that was the McGuffin that brought down Gawker and Nick at the hands of Peter Thiel was perhaps an inevitability. Ben also credits (or blames?) Nick for his own decision to release the Trump dossier to the public on BuzzFeed. (I still think Ben has a credible argument for doing so: It was being talked about in government and in media and we, the public, had the right to judge for ourselves. Or rather, it’s not our right to decide; it’s a responsibility, which will fall on all of us more and more as our old institutions of trust and authority — editing and publishing — falter in the face of the abundance of talk the net enables.)
The problem in the end is that traffic is a commodity; commodities have no unique value; and commodities in abundance will always decrease in price, toward zero. “Even as the traffic to BuzzFeed, Gawker Media, and other adept digital publishers grew,” Ben writes, “their operators began to feel that they were running on an accelerating treadmill, needing ever more traffic to keep the same dollars flowing in.” Precisely
Traffic is not where the value of the internet lies. No, as I write in The Gutenberg Parenthesis (/plug), the real value of the internet is that it begins to reverse the impact print and mass media have had on public discourse. The internet devalues the notions of content, audience, and traffic in favor of speech. Only it is going to take a long time for society to relearn the conversational skills it has lost and — as with Gutenberg and the Reformation, Counter-Reformation, and Thirty Years’ War that followed — things will be messy in between.
BuzzFeed, Gawker, The Huffington Post, etc. were not new media at all. They were the last gasp of old media, trying to keep the old ways alive with new tricks. What comes next — what is actually new — has yet to be invented. That is what I care about. That is why I teach.
--Jeff Jarvis link:https://medium.com/whither-news/trafficking-in-traffic-973a3ea0e1e8
-
 @ 5ada3677:7c21c9db
2023-06-06 11:23:57
@ 5ada3677:7c21c9db
2023-06-06 11:23:57 增上寺門口
增上寺門口闊別東京四年。
四年,可以讀完一趟大學的時間長度。
說起來,東京一直是我的大學,過去三十年裡,一直是。
可惜,我不到這座營養豐富的大學,整整四年。
四年裡,換了手機,新手機裡,東京需要用到的一些app,是臨行之前現裝起來。落地之後,樣樣生疏,連從機場入城的成田特快,都摸索了一會兒,才弄清楚。

夜裡,友人堅持要帶去吃米其林,我說其實我想吃居酒屋或者牛丼或者天家,友人笑煞了,不同意。客隨主便,吃了米其林,八年連續上榜的店子,よこ田,禮拜一晚餐,愉快訂到座。一整套天婦羅與壽司的懷石,天婦羅精巧靈動,只有日本人幹得好這個油炸萬物的工作。其中有一小杯鮮湯,小茶杯那麼小,女將說,是蜆子的頂湯。滾熱地啜一口,鮮得滿地找眉毛。驚艷。
 這麼一小杯鮮湯
這麼一小杯鮮湯第二日晨起,慢慢散步去芝公園與增上寺,巍峨時髦的東京塔腳下的增上寺,是600年古寺,安詳軒敞,古松蔽日。東京的中心地帶,有新有舊,和平共存。你看,事實證明,新與舊,並不一定要你死了我才能活。




附近有座芝公園的幼稚園,立在門口看了很久,寫明不允許拍照,只能默看。我再多站一會兒,可能警察叔叔會來盤問我了,有啥好看的?一粒一粒的小人,人人一身結結實實的壯肉肉,真好看。我好像很多很多年,沒有在上海街頭看見過成群結黨的幼童了。
烏鴉很閒,擦著我的腰,超低空飛來飛去,它們有很多枇杷和楊梅吃,在寺院的樹枝上果實累累,無人問津。
 可以攜帶兩粒幼童的自行車
可以攜帶兩粒幼童的自行車清早上班通勤時間,港區附近是一等上班地,路人們的線條普遍硬和淨,很少看到身體線條軟趴趴的男人女人,我國很多青年中年勤奮健身,刻苦減肥,身體線條依然不挺刮,軟綿綿沒稜角,很沒勁。可見線條不是身體的問題,是靈魂的問題。

最大的變化,是男人穿西裝的,少了很多很多,戴領帶的,更少。這件西裝上衣,日本人謀劃脫下來,謀劃了不知多少年,現在終於脫下來了。是疫情的原因嗎?可能是的吧。
東京都中心地帶,路上騎車上班的年輕人,也多了很多。從前這個時間段,都是主婦騎車送幼兒去幼稚園,順便買菜回家,不太有年輕人騎車上班的。看著這麼多騎車的年輕上班族,想起木村拓哉年輕時演過一個電視劇,演個窮小子,在東京的金融街騎自行車送文件快遞,木村一身Gucci的精裁西裝,騎得飛快地穿街走巷,英挺得簡直殺人不眨眼。

午飯吃とんかつ,日式豬排飯,搜了地圖,方圓一公里內,有三家。去了檍,果然排隊,11點開門,11:15開始就排隊。規規矩矩排,還好15分鐘輪到了。




 9月份起,週休兩日,氣粗
9月份起,週休兩日,氣粗店裡一共18個座位,廚房三個師傅,外場一個女服務員,我排隊+吃飯的45分鐘裡,這個店,至少翻了三次台,簡直是印鈔機。我也佩服這四個員工的高效,在上海,我想人手起碼要加個倍。


點了一份ロスかつ套餐,2000日圓,100人民幣,米飯,豬排,菜絲,味噌湯,小醬菜,冰茶。米飯好吃得沒話講,男客女客,人人飽滿一大碗。為了健康也好、瘦身也好,不吃碳水的朋友們,你們看看日本人,這個碳水有害的理論,不攻自破哈哈哈。
 跟行李箱一起來吃豬排飯的客人
跟行李箱一起來吃豬排飯的客人然而,那個炸豬排,沒有期待的那麼好吃,這家賣的是極大塊肉,厚且大,不過肉質就平平。所以他店裡也沒有說明用的是什麼名牌豬肉。
一直很鬱悶,上海沒有一家日式炸豬排,是吃得過去的,豬排差也就算了,米飯也難吃得無法可想,這到底是哪裡出了問題呢?煮飯都煮不過人家嗎?

 冰茶自助
冰茶自助按照地圖找去豬排店的時候,迷路在最後50米,實在找不到,就推門進一家咖啡館去問路,店裡一個客人都沒有,店主是個瘦男人,在埋頭讀書,一聽我開口,扔下書,陪我走到門外,指點我迷津。千謝萬謝,真不好意思。
 吃完出來,隊排得更長了
吃完出來,隊排得更長了吃完豬排飯,抱著肚子轉了幾個麵包舖蛋糕舖,最後在老舖鳴門,買了一枚鯛魚燒,滾熱的,拎著晃去不遠處的芝離宮恩賜庭園,美美的大園子,古韻盎然,坐在藤蔭下,慢慢吃了鯛魚燒,一肚子的北海道十勝紅豆沙,真好吃。



這半日,最讓我驚心動魄,是常常看見日本人東京人小跑步,馬路上小跑步趕路,館子裡廚師捧著外帶便當小跑步出來交給客人,等等,驚人的是,東京人小跑步起來,是無聲無息的,默默跑,這個很驚人。換了是上海人,基本上是大呼小叫著跑的,我清楚地記得。



圖片是一路隨手拍
-
 @ 600a398f:83115ead
2023-06-06 10:18:19
@ 600a398f:83115ead
2023-06-06 10:18:19 -
 @ 24797395:ffa302c6
2023-06-05 22:55:06
@ 24797395:ffa302c6
2023-06-05 22:55:06Add new service file to
/etc/systemd/system/strfry-relayable.serviceAdd options, change user and paths as needed. ``` [Unit] Description=strfry stream up to relayable
[Service] User=strfry ExecStart=/usr/local/bin/strfry stream wss://relayable.org --dir up Restart=on-failure RestartSec=5 ProtectHome=yes NoNewPrivileges=yes ProtectSystem=full LimitCORE=524288
[Install] WantedBy=multi-user.target ```
Enable it to start automatically on reboot:
sudo systemctl enable strfry-relayable.serviceStart service:
sudo systemctl start strfry-relayableCheck Status:
sudo systemctl status strfry-relayableMirrored at https://write.bz/jascha/stream-to-relayable-org-from-your-strfry-relay
-
 @ 75bf2353:e1bfa895
2023-06-05 22:52:45
@ 75bf2353:e1bfa895
2023-06-05 22:52:45The world of cryptography has exploded like the Cambrian explosion. There is Cashu, liquid Boltz Swaps, and a Nostra Marketplace, oh my! This blog is about a tool I find fascinating: Highlighter.com.
[Highlighter.com] (https://highlighter.com/) is another project built by [Pablo] (https://pablof7z.com/). It let's people highlight the Internet like you may have highlighted textbooks in high school or the great articles in Playboy Magazine. Highligher lets you do that with the Internet. You create highlights of any website or nostr event ID. It can be a recipe, Substack blog, tweet, gardening blog,—anything you can think of on the Internet.
Anyone can see these highlights too, and it has interesting value-for-money tools. Since it's something so new, it's been hard for me to write about it, so I have decided to just do a walk through of how I plan to use it. Other people may use it for other things since it is limited to your illustration, but for the purpose of this demonstration, I am going to annotate http://www.werunbtc.com/coldcard.
Here's a quick video showing how it works:
Here's one of my annotations:

Anyone or any bot can reply.
Here are all my highlights from Odell's cold card guide.

What will you use Highlighter.com for?
Let me know what you think about it.
Blogging Bitcoin
npub1wkljx5c6a8uccc5etws8ry0y3r4dgavh2dcav0tal4rtmcdl4z2sfu5u0t
Block Height: 793,018
To pledge your support, please visit my Value 4 Value Page, send a zap, or scan this QR Code with lnurl compatible lightning wallet.

Other ways to support the blog
Subscribe on Substack. I don't have a paid subscription. It just sends you an email when I write a new blog. If you don't like giving your email out, use https://simplelogin.io/. They are not a sponsor. I just like the service.
nostr:note1cfl2vt65tp699xtl3x0xnt6q23l5nqxc4jkk4awnqw62jheh2e3sclhq6s
-
 @ d35d9d48:d94dd724
2023-06-05 17:06:48
@ d35d9d48:d94dd724
2023-06-05 17:06:48 -
 @ f2994585:9cf23d9b
2023-06-05 17:06:35
@ f2994585:9cf23d9b
2023-06-05 17:06:35 -
 @ 7a78fbfe:48e76288
2023-06-05 16:54:55
@ 7a78fbfe:48e76288
2023-06-05 16:54:55Working in custom cabinet manufacturing is a challenging, fun, mentally demanding, frustrating, beautiful, and painful experience, all at once, each and every day. This might sound a bit dramatic, but I can't help my hyperbolic nature.
From start to finish, you spend months thinking about the project, coordinating the materials, and assembling it - first in your head, then IRL, in what might be called "woodspace." It requires a thousand small details coming together to create the big picture, much like Pointillism, or so I like to pretend.
As my colleague often says, "Details matter." When you make the details your life, poring over specs for hours, planning and designing better systems to meet project goals, you may still find that mistakes happen. Correction, you will find that mistakes happen. No plan is perfect, things can go wrong, and people are human. You might find yourself questioning why certain events occurred, shouting at the world, and struggling to understand the mistakes that have transpired.
Questions like "Why did we do it like that when the specs showed something else?" "Why didn't the paint cure correctly?" "Why did this material warp?" and "Why didn't we catch this in the shop?" often arise.
Simon Sinek suggested to "start with why," which is a great place to begin. However, it's essential not to stop at why, or get caught in a cycle where every single event invites a deep examination into the very meaning of life.
There is an equation in manufacturing where the farther you move along the "why" axis, the more the weight of the variable X compounds, bearing down on you so heavily that you feel immobilized. At this point, you're spent - done, fried, finished.
Instead of being capable of clear thinking that leads to action, you're caught in analysis paralysis. I speak from experience when I say: you don't want to go there. Do your best to stay above the fray.
In other words, don't expend your rigorous reasoning on trivial pursuits. Conserve your energy for the issues that truly demand it. Start with why, ponder it for a second, then put your head down and keep moving forward.
-
 @ 5d5484c8:4283aa1e
2023-06-05 13:52:45
@ 5d5484c8:4283aa1e
2023-06-05 13:52:45The free market system has faced its fair share of criticism, often being labeled as a breeding ground for greed and self-interest. But, let's take a closer look and see how greed, when properly channeled and regulated within a free market framework, can actually bring about positive outcomes for society.
One fascinating thought experiment that showcases the positive role of greed in the free market is Adam Smith's concept of the "Invisible Hand." Smith proposed that when individuals pursue their own self-interest, unintended benefits are generated for society as a whole. By seeking personal gain, individuals are motivated to produce goods and services that others value, leading to voluntary exchanges that benefit both parties. This intricate network of self-interest forms the foundation of a prosperous and efficient free market system.
At the heart of the free market lies the entrepreneurial spirit, driven by the desire for profit. Entrepreneurs spot unmet needs and desires within the market and strive to fill those gaps with innovative products, services, and solutions. Through their endeavors, they not only create wealth for themselves but also stimulate economic growth, generate employment opportunities, and contribute to the overall expansion of the economy. Greed, when harnessed by entrepreneurs, becomes a catalyst for innovation and progress.
Competition, an inherent aspect of the free market, acts as a powerful force that channels and refines the actions driven by greed. In a competitive marketplace, self-interested individuals are compelled to provide superior goods and services at lower prices in order to attract customers and maximize profits. This leads to a broader range of choices, improved quality, and lower prices for consumers. The drive for personal gain is transformed into a pursuit of excellence, resulting in a more efficient and consumer-oriented market.
The pursuit of self-interest in the free market fosters cooperation and specialization. Individuals, motivated by their desire for personal gain, recognize the benefits of collaboration and form mutually beneficial relationships. This division of labor allows individuals to focus on their strengths, increasing overall productivity and efficiency. By leveraging their respective areas of expertise, individuals contribute to the collective advancement of society, fueled by the inherent drive for greed.
While it's essential to recognize the positive aspects of greed within the free market, we must also shed light on how the State, through coercion and intervention, can turn greed into a destructive force. When greed operates outside the bounds of ethical principles and voluntary exchange, it poses a significant threat to the fundamental principles that underpin a free market system.
The State's involvement in economic affairs often introduces regulations, restrictions, and mandates that hinder the voluntary nature of transactions. By imposing coercive measures, the State diminishes the essential element of consent that characterizes the free market. When individuals are compelled to participate in economic activities against their will or face punitive consequences, the spirit of voluntary exchange is eroded, and the positive aspects of greed are overshadowed.
Furthermore, when the State exercises its power to redistribute wealth, it disrupts the natural outcomes of market forces. Confiscating and redistributing resources, driven by the goal of achieving a more equitable distribution, can undermine the incentives for individual effort, innovation, and productivity. When the State forcibly reallocates wealth, it distorts the signals that greed would otherwise generate within a free market system, leading to suboptimal outcomes and stifling economic growth.
Another detrimental effect of the State's intervention is the creation of monopolies or oligopolies. Through regulations and barriers to entry, the State can artificially limit competition, allowing a select few to dominate markets and stifle innovation. In such cases, greed becomes concentrated in the hands of a few powerful entities, who are able to manipulate prices, exploit consumers, and suppress potential competitors. This not only distorts the benefits that greed can bring when tempered by competition, but it also hampers the overall efficiency and dynamism of the market.
Additionally, the State's involvement often introduces cronyism and corruption, wherein individuals or businesses seek to influence government policies and regulations to secure undue advantages and privileges. This exploitation of the political system to fulfill self-interest not only undermines the principles of fairness and equality, but it also perverts the potential positive outcomes of greed within the free market. Instead of serving as a catalyst for progress, greed is redirected towards the accumulation of political power and influence, perpetuating a system that benefits the few at the expense of the many.
It's crucial to acknowledge how the State, through coercion and intervention, can transform greed into a negative force within the free market. By imposing regulations, redistributing wealth, limiting competition, and fostering cronyism, the State disrupts the voluntary nature of transactions and distorts the positive outcomes that greed can bring when harnessed within a free market system.
Contrary to common misconceptions, greed, when channeled and regulated within a free market system, can yield positive outcomes for society. The concept of the "Invisible Hand" illustrates how pursuing self-interest can inadvertently benefit others. The entrepreneurial drive fueled by greed sparks innovation, fosters economic growth, and creates opportunities. Competition ensures that greed is channeled into productive avenues, resulting in better choices, improved quality, and lower prices. By fostering cooperation and specialization, greed enhances overall productivity. When harnessed responsibly, greed becomes a force that propels societal progress, driving prosperity and the well-being of society as a whole.
-
 @ b3590d02:0f2b1ae4
2023-06-05 13:41:42
@ b3590d02:0f2b1ae4
2023-06-05 13:41:42Reputation Attestation for BlackEnokas on twitter.com
Recorded and attested to by toastr.space on 2023-06-05 13:41
Nostr Pubkey: npub1fy756qvhe9nkmaeppyp7js20k0qamwz8t05xf20qdughn7ujtsyqh4ateg
- This PubKey was added to attested website and a badge was awarded to this key.
Twitter user BlackEnokas profile information:
- Joined in 2021
- Follower count: 31
- Following count: 252
-
 @ 5ada3677:7c21c9db
2023-06-05 10:37:44
@ 5ada3677:7c21c9db
2023-06-05 10:37:44
翻撿舊書,意外翻到一冊兩百年前,山西祁縣茶商的 《行商遺要》 ,做生意的寶書,晚清時候的手抄本,十分有看頭。
開篇第一句:
為商賈把天理常存心上。
不瞞老不欺幼義取四方。開篇格局真漂亮,無苟且,無侷促,堂堂晉商氣概。 再錄幾句:
行水路走江湖跋涉艱難,
勿華麗學素樸免惹盜竊。
晚早宿晨早行以防不測,
水陸路遇生疏最忌相伴。
若同幫宜遜讓務要尊敬,
再不要非長幼著人說道。

祁縣在山西的中心,地理位置優越, 遠自春秋時代,一向是繁榮的商業中心,明清時期,祁縣商人走西口、出東口、闖關東、入新疆、進蒙俄、駐日本,是一支強韌的商業力量。 祁縣當地的晉商,年年跋涉水陸路,到福建武夷山、湖南安化、湖北羊樓洞收取茶葉,遠銷到蒙、俄、歐。祁縣大茶商渠家,在湖北設立的誠記、興隆茂茶廠,出品川字牌青磚茶,以大篆體壓制在茶磚上。 清末民初時候,川字牌青磚茶已經成為蒙俄牧民的印記,一直到二十世紀八十年代,還有俄羅斯人到中國尋找這種茶。


這個手抄本,一共20790字,各種教導、提醒、規範,周全備至,一冊智慧且溫暖的行業秘笈。如果找得到兩百年前歐洲商人,比如威尼斯商人的類似手抄本,做一項比較對照,想必十分有趣和有益。

比如,進山收茶, 預早選擇直樸端正之人,谷雨左近開秤。何謂好茶,首重條緊、色順、紋直、沉重、味佳、外烏油色、內硃干色者,必是安化正路茶。 安化黑茶名重天下,這幾句,寫到家了。 外像烏油鐵板根條柔氣,內像滿碗俱青,必是安化上路茶。

對待治茶工人, 每逢初一、十五日每人犒賞豬肉半斤,每五天一次,每人水酒四兩,每人每天小菜錢四文。 這些細節,寫得清清楚楚,唯恐待工人不夠厚道。
做黑茶請人,每工工錢多少;如用江西人做茶,有包工頭,茶商與包工頭定事情尺寸,另外要每人給予盤纏費若干。 如做夜工,點燈起至十二點鐘止為半工 ,如至五更為一大工。彷彿從前上海的紡織女工,有大夜班和小夜班之分別。從這些文字,亦可以看到茶商與茶農民的契約精神。


收完茶,要把茶從山裡運輸到祁縣,才能流通四海。關於運輸,有極其詳盡的敘述。 裝船走水路,生疏船戶、不確船手好歹萬不可裝。水大之時擇船隻,費用上要遷就一二。遇到水涸,更要擇選舵手經練馳名穩妥可靠,稍有不確之手,千萬勿裝船。遇水枯之時,總宜擇用小船,可裝黑茶二十幾至三十擔,穩妥不過,發貨之人勿惜小費,在意在意。水路船隻如此要緊,所以呢,茶商需要素日留心,知確該船整修堅固,船夫穩妥可用。
穩妥二字,頻現文中,可見諄諄教誨之心,亦可感中國商人所謂的小心駛得萬年船之金科玉律,行文之間的厚樸端方,謹慎言行,滿滿的儒家氣息。

再講到陸路運輸,河南南陽的一處,名為賒旗鎮, 此處碼頭為車馬陸路之首,百貨在此聚散,南方水路運來之茶在此換發車馬,發貨之人更宜精細靈便。由於道路甚多,腳價漲跌不等,尚應思量日期遲早、事情緩急,再思碼頭存貨多寡,務要趕上祁縣春季之駝腳,以便早日抵達東西兩口為妥。 然後細細分敘如何講腳價、講駝、講騾,很像今天的訂長途貨櫃車,各種規格的貨拉拉。精細靈便四個字,真是寫得極好極傳神。


整本手抄本,敘述平正,沒有煽情用語,高度漂亮的說明文。行文略帶祁縣方言,水路陸路,還編成朗朗上口容易記憶的押韻歌訣。這本《行商遺要》的讀者,想必文化程度參差不齊,讓小徒弟亦能牢記不忘,押韻歌訣,是了不起的傳播智慧。古人有很多這種行業歌訣,比如中醫藥方,都非常好看非常聰明,以後找機會寫寫這個話題。

這個手抄本,是1994年,從祁縣古城北大街54號王錫祥家,發現的。藍皮舊書,封面上無一字,扉頁上寫著《行商遺要》。後來慢慢查清楚,這個手抄本,是王錫祥先生的父親王載賡先生珍藏的,王家的上一輩,是祁縣巨商大賈渠家的得力掌櫃,可比今天500強企業的首席執行官,王家還創辦過經營古籍的商號,後來公私合營到山西省新華書店。據推測,這個手抄本,大約是王載賡先生在渠家的長裕川茶莊工作期間抄錄的,估計是在1917年前後。全書麻紙和白線裝訂,77頁,毛筆小楷清清秀秀紋絲不亂,字如其人,足足可見當年晉商的心胸氣度,的的不凡。







圖是茶與點心,周作人說的,米與豆的茶食,來自網絡。
-
 @ efa6abd0:a4970369
2023-06-05 10:15:35
@ efa6abd0:a4970369
2023-06-05 10:15:35Nostr is in an early phase of adoption. It is imperfect, yet open. Its innovation feels lightning fast as dedicated development hubs build in a permissionless fashion. Builders are in frequent communication with each other and the wider community.
Notes abound celebrating features and asking for new ones. People report on bugs, discuss possible solutions, prioritize building time. N00bs join with a number of questions on how nostr works; the community does not hesitate to answer. Nostr is a community of creative minds building a myriad of products with heart, passion, and focus.
What encourages technology adoption?
Some may argue nostr adoption depends on ease of use, convenience and a flawless user experience. Although all of those are characteristics to strive for, adoption depends on multiple factors. When technology is innovating and testing new ground, it has imperfections. It's as if it was figuring out its shape from a changing blob of creative code as it responds to interaction. What shape it will take depends on trial and error in everyday use, feedback, and bridging development with design. Nostr has many opportunities to craft unique nostr experiences.
As we try to imagine how nostr adoption may expand across the globe, we may think of places or groups of people in need of this technology.
The word need is often spoken about when it comes to bitcoin too, because when you are having issues with your current system, be it financial or social, you may be more open to outside-of-the-ordinary solutions. Adoption goes deeper than a need. It is about long-term vision, learning, and adaptability. It is not only a case of having a need, but of seeing the need for nostr. It is about recognizing the value others may miss...
Vision is often underrated
Imagine someone is looking for a house. They have two choices in the same area, at similar price points (accounting for possible repairs). Many people cannot look past simple cosmetic fixes. They often select the house that, to their eyes, looks the best and is turn-key. It seems like an easy choice, but do they take into account the long-term implications on their way of life? Or are they enchanted solely on surface level qualities?
They may ignore the tradeoffs of having this particular turn-key property: A boxy, dark, cookie cutter house, built with shiny but low quality materials, lacking in flow or proportion between its spaces.
Many may fail to see the value in the other house which is not quite perfect nor ready in a cosmetic superficial sense, but that has good bones. They may not understand the importance of the strength of its foundation, the benefits of its homey feel with a natural flow between the rooms. The atmosphere of a home is often a secondary thought, ignoring the significance of how the home fits within its landscape and how its windows fit the spaces to let the light pour in on the rooms where it is needed at different times of the day and seasons according to the house's orientation. Its thoughtful carefully crafted details, nooks and crannies are often seen as quirky, weird and undesirable.
The home seekers may fail to see how that other house welcomes living. They may not see the need.
If you were to select the other house, chances are you did not only see the value in its foundational structure, but you envisioned what it could become with care, effort, and time.
Waves of nostriches
On the first NDKtime nostrnests, JeffG mentioned he hoped to welcome more builders to nostr, because, at this stage of adoption, they would understand the existence of bugs and be able to look past them. A larger community of builders would translate into stronger products, and that would help improve the experience for the next wave of nostriches. How do you think more builders could be welcomed?
Seeing the need for nostr.
For some, choosing nostr at this early stage is simple and clear, like recognizing the value in the other house. It often means understanding the contrasts between platforms and protocols, but also of the unique makeup that makes nostr special, which extends beyond its code, into its community.
Beyond knowledge, however, is the experience of nostr, which is not the same for everyone. Many of us have found a sense of home in its real-time open nature. Other people may need support in understanding nostr through community bonds and improvements on development and experience design.
Some people show hesitation when hearing that nostr has a strong community of bitcoiners. To be a bitcoiner often means to have gone through multiple rabbit holes of learning, not only about bitcoin, but about money, financial systems, and global issues. When we look at nostr, we can often see its strength and potential. Recognizing the importance of its foundational principles is easy. Nostr and bitcoin are co-existing and intertwining both through lightning payments and culture, neither would be the same without the other.
To other people, unaware of both bitcoin and nostr, its technology may be strange, not as simple as understanding the metaphor of a house. Words like decentralization, resilience, censorship resistance, permissionless innovation, keys, network effects, and FOSS may not be relatable.
However, we may be surprised to discover how nostr's simplicity tied to its openness and community are relatable. It is in our nature to understand the empowering feeling of having choice and control over our identities. A weight is lifted off our shoulders by removing the strings from third parties. We feel supported when valuable content is discovered, shared, commented upon, and zapped. We feel comfortable when we discover our niche. We are energized when our thoughts are challenged and our vision expanded. Nostr frees our creativity in multiple ways.
Nostr, at this early stage of adoption, is as if we had just moved into a new home, the other home, before the furniture arrives. A little awkward at times, but filled with hope and possibility...
-
 @ 7ab79bc0:9385ad99
2023-06-05 09:39:39
@ 7ab79bc0:9385ad99
2023-06-05 09:39:39Letzte Woche haben wir uns die gestiegenen Transaktionskosten im Bitcoin-Netzwerk angeschaut. Wir haben uns damit befasst, warum die Gebühren in den letzten Wochen gestiegen sind und was diese hohen Gebühren für Auswirkungen aus verschiedene Teile des Netzwerkes bedeuten. Diese Woche wollen wir uns mit einem anderen direkten Resultat von Gebühren beschäftigen, dem sogenannten Dust. Dazu schauen wir uns zunächst an, was Dust im Zusammenhang mit Bitcoin bedeutet und was dieser mit den verschiedenen Bitcoin-Währungsuntereinheiten zu tun hat.
Unit-Bias
Bitcoin hat in der öffentlichen Wahrnehmung und bei Menschen, die sich weniger mit dem Thema befassen, einen sogenannten Unit-Bias, also eine durch Unwissenheit hervorgerufene Voreingenommenheit gegenüber der Einheit "Bitcoin". Das bedeutet, dass viele unerfahrene Anleger//innen und Nutzer//innen der Meinung sind, dass der Besitz eines ganzen bitcoins psychologisch wichtig oder überhaupt nur als solcher möglich ist. Anders ausgedrückt, glauben viele Menschen, sie müssen Bitcoin als Ganzes kaufen, also einen ganzen "physischen" bitcoin, statt kleinerer Bruchstücke. Das lässt den Vermögenswert für die meisten zu teuer aussehen.

Dies ist für Bitcoin insofern ein Problem, als dass viele Menschen sich durch ihre Voreingenommenheit gar nicht mit Bitcoin beschäftigen ("kann ich mir nicht leisten") oder das Gefühl haben, Bitcoin sei zu teuer und deshalb gibt es kein Wertsteigerungspotential mehr ("der Zug ist abgefahren, ich hätte vor sechs Jahren investieren sollen"). Schlimmer noch, als sich nicht mit Bitcoin zu beschäftigen, ist sich dann stattdessen alternativen, "erschwinglicheren" Kryptowährungen zuzuwenden. Dieser Unit-Bias ist allerdings nichts anderes als ein Marketing-, bzw. ein Bildungsproblem. Denn wie wir wissen kann man Bitcoin in 100 Millionen Untereinheiten brechen und in kleinsten Mengen erwerben, verschicken und verkaufen. Doch haben Außenstehende von Begriffen wie Lightning oder Sats meistens noch nie gehört.
Untereinheiten
Doch auch innerhalb der Bitcoin-Szene ist die Unterteilung von Bitcoin in Untereinheiten nicht ganz unumstritten. Denn viele Nutzer//innen sind sich uneinig darüber, was der beste Weg ist, Bitcoins Untereinheiten zu bezeichnen und sogar darzustellen. Dies zeigt sich z.B. darin, dass Apps oft entweder Bitcoin oder Fiat anzeigen, manche Apps aber auch Beträge in Sats darstellen. Dies verlangt aber oft eigene Einstellungen innerhalb der App oder viele Klicks, die die Bedienung und Darstellung eher unhandlich gestalten.
Es gibt verschiedene Lösungsansätze, die dem/der Nutzer//in die ungewohnte Rechnung mit acht Nachkommastellen erleichtern sollen. Denn viele Anwender//innen denken beim Blick in ihre Wallets oft noch in lokalen Fiat-Werten, also in ganzen Einheiten (z.B. Euro oder Dollar) und Hundertsteln (z.B. Cents).
Einige Wallets versuchen diesen Spagat komplett zu umgehen, indem sie vermeiden, Beträge in Fiat darzustellen. Doch auch hier bleibt immer noch das Problem der unhandlichen Darstellung von acht Nachkommastellen, weshalb einige Anbieter einfach zwei Eingabemöglichkeiten bieten und den Betrag in Bitcoin oder Sats automatisch umrechnen.
Doch selbst das Zeichen für Sats ist nicht final geklärt. Es gibt viele verschiedene Vorschläge und Meinungen dazu, welches Symbol genutzt werden sollte. Die meisten Apps, Rechnungen und Sticker schreiben einfach das Wort "Sats" oder "sats" aus. Allerdings ist dies ein Problem, da außerhalb der Bitcoin-Szene niemand weiß, was ein Sat ist. Die meisten Menschen werden mittlerweile von Bitcoin gehört haben, auch wenn sie nicht wissen, wie es funktioniert, was es bedeutet, oder wie man damit umgeht. Doch auch das B Logo mit den Dollarstrichen (₿) werden die meisten Menschen zuordnen können.
Sats hingegen ist ein sehr nischiger Begriff und seine Verwendung noch unbekannter. Oft wird das Blitzsymbol (3 auf der unteren Grafik) verwendet, um Lightning darzustellen und auch das Symbol mit den drei horizontalen Strichen und zwei vertikalen Punkten (4 auf der unteren Grafik), das entfernt an das Dollar-Zeichen erinnern soll ($), erfreut sich immer größerer Beliebtheit. Das Problem dabei ist nur, dass es sich in geschriebener Form nicht, oder nur unzulänglich darstellen lässt: 丰 🤡

Es war lange logisch und notwendig, ganze Bitcoins zur Aufzählung und Bezahlung zu verwenden, da bei der Einführung von Bitcoin sein Geldwert sehr gering war. Es bestand also absolut keine Notwendigkeit dazu, in kleineren Einheiten als Bitcoin zu denken. Einfaches Beispiel: letzte Woche, am 22. Mai, jährte sich der Bitcoin-Pizza-Day zum 13. Mal, also jener Tag an dem Laszlo Hanyecz für zwei Pizza 10.000 bitcoins bezahlte und damit die erste offline Transaktion mit Bitcoin tätigte. 10.000 bitcoins entsprachen zu diesem Zeitpunkt also knapp $40, oder andersrum $1 entsprach 250 bitcoins Es gab also immer noch keine Notwendigkeit, kleinere Einheiten von Bitcoin zu verwenden. Diese Notwendigkeit ergab sich erst, als der Bitcoin und der Dollar Parität erlangten (1 Bitcoin = $1) und spätestens, als Bitcoin die Marke von $100 durchbrach, wurde rechnen in Bitcoin schwieriger.
Fortan überlegte man sich, Bitcoin in kleineren Einheiten darzustellen. Die zwei Möglichkeiten sind der Bit und der Sat. Ein einzelner bitcoin kann in 1.000.000 Bits oder bis zu 100.000.000 Sats unterteilt werden, also 100 Sats = 1 Bit = 0,000001 Bitcoin.
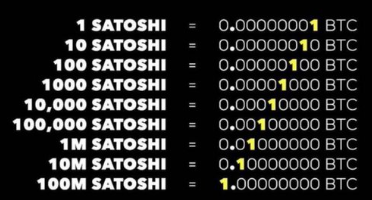
Ein weiterer Grund, weshalb eine Stückelung in bitcoin (der Begriff für einen ganzen physischen bitcoin) schwierig und verwirrend ist, und deshalb viele nach einer alternativen Bezeichnung für Untereinheiten suchten, ist dass darüber hinaus "Bitcoin" zur Beschreibung von zwei Dingen verwendet werden kann: dem monetären Netzwerk (Bitcoin - großes B) und dem monetären Vermögenswert (bitcoin - kleines B).

Bitcoin, der Vermögenswert, ist für diejenigen, die noch nichts damit zu tun hatten, sowohl verwirrend als auch fremd. Denn wie bereits erwähnt, führt der Unit-Bias dazu, dass viele Menschen denken, dass sie es sich nicht leisten können, Bitcoin zu kaufen, oder dass sie den Anschluss verpasst haben. Die Verwendung einer Bepreisung in Bruchteilen würde die Verwirrung über die Benennung des Netzwerks und des Vermögenswerts verringern, aber auch die psychologische Hürde für den Einstieg in Bitcoin senken. Vorausgesetzt, die Benennung ist logisch und intuitiv.
Bits vs. Sats
Wie schon erwähnt, gibt es zwei gängige Untereinheiten von Bitcoin, 1 Bit (= 0,000001 Bitcoin) und 1 Sat (0,00000001 Bitcoin). Seit jeher gibt es Diskussionen darüber, welche der beiden Einheiten für den täglichen Gebrauch die vernünftigere und intuitivere ist.
Die Verwendung von Bits zur Aufzählung von Bitcoin hat einige Vorteile. Ein Bit stellt ein „Bit“ eines Bitcoins dar, also der grundlegendsten und kleinsten Informationseinheit in der Informatik. Den meisten Menschen fällt es einfacher, das Wort „Bit“ mit Bitcoin zu assoziieren und daher verstehen sie eher, dass ein Bit ein Teil eines Bitcoins ist. Ein „Sat“ bedeutet für den Durchschnittsmenschen, wie oben beschrieben, nichts.

Adam Back (CEO von Blockstream und Bitcoin-Legende) ist wahrscheinlich der bekannteste Befürworter von Bits > Sats. Er argumentiert von verschiedenen Richtungen, dass z.B. Bits eine rechnerisch einfachere Variante ist, Untereinheiten von Bitcoin darzustellen, als Sats.
Weiter argumentiert er mit der historischen Entwicklung von Bitcoin, dem Protokoll und seiner Referenz-Implementierung. In den Anfangsjahren wurde in der Bitcoin Core Wallet mit Bits gearbeitet. Außerdem argumentiert er, dass die Verbindung zwischen Bitcoin der Haupteinheit und Bits oder Sats als Untereinheit zumindest semantisch gebrochen werden sollte. Da Bitcoin (im Fall eines weiter steigenden Kurses) als Recheneinheit immer unpraktischer wird, sollte man als mentales Modell auf das Rechenpaar Bits und Sats zurückgreifen - analog zur Darstellung von Dollars und Cents oder Euros und Cents. Dabei stellen die zwei Nachkommastellen eines in Bits angegebenen Preises die Sats dar.
Ganz einfaches Beispiel: Ein Kasten Bier kostet heute etwas 20€, also 0,00079758 Bitcoin. Einfacher dargestellt: 797,58 Bits, also 797 Bits und 58 Sats. “Ein Bitcoin ist zu teuer, aber Sats sind zu viele, klingen billig und verwirrend.” Es ist schwer in Sats zu denken und selbst wenn der Preis von Bitcoin 1 M US Dollar erreicht, ist ein Bit immer noch eine greifbare und günstige Einheit: 1 Bit = 1 US Dollar.

Eines von Adams Hauptargumenten ist, dass Sat als Untereinheit nicht funktioniert, weil es Dust gibt. Das Problem mit Dust besteht darin, dass es nicht möglich ist, Bitcoin unter einem bestimmten Schwellenwert auszugeben. Sein Argument ist, dass der Nutzen einer Einheit abhanden kommt, wenn diese Einheit als kleinste Recheneinheit nicht ausgegeben werden kann. Zugegeben, niemand kann mehr etwas für einen Cent kaufen, aber zumindest ist es technisch nicht unmöglich. Allerdings ist es unmöglich, 1 oder sogar 10 Sats über das Bitcoin-Netzwerk zu senden, ohne Layer-2-Skalierungstechnologien zu verwenden.
Dust
Unter Bitcoin-Dust versteht man eine sehr kleine Menge Bitcoin, typischerweise in kleinen ein- bis zweistelligen Sats-Beträgen, doch auch kommen immer öfter dreistellige Beträge vor. Sie werden Dust oder „Staub“ genannt, weil diese Beträge so gering sind, dass sie oft als unbedeutend und unpraktisch für die Verwendung bei regulären Transaktionen angesehen werden.

Es gibt keine offizielle Definition dafür wie groß/klein ein Betrag sein muss, um als Dust zu gelten, da jede Softwareimplementierung (Client, Wallet, etc.) einen anderen Schwellenwert annehmen kann. Die Bitcoin Core Referenzimplementierung definiert Dust als jede Transaktionsausgabe, die niedriger ist als die aktuellen Transaktionsgebühren. Dust entsteht meist unbeabsichtigt bei Bitcoin-Transaktionen. Denn wenn Bitcoin von einer Adresse an eine andere gesendet wird, fällt oft eine Transaktionsgebühr an. Um Spam zu verhindern und die Sicherheit des Netzwerks zu gewährleisten, gibt es bei Bitcoin eine Mindestgröße für jede Transaktion. Dieses Limit ist der Mindestbetrag an Bitcoin, der als Ausgabe in eine Transaktion einbezogen werden kann. Der Rest ist Dust.
Oder einfacher ausgedrückt, wenn die Mindestgröße für eine Bitcoin-On-Chain-Transaktion 500 Sats (5 Bits) beträgt und ich noch 800 Sats (8 Bits) in meiner Wallet habe, kann ich nach dem Versenden von 600 Sats (6 Bits) die übrigen 200 Sats (2 Bits) nicht mehr ausgeben. Diese verbleibenden 2 Bits sind Dust.

Dust stellt aus mehreren Gründen eine Herausforderung für das Bitcoin-Netzwerk und seine Benutzer//innen dar:
UTXO-Bloat: Bei jeder Transaktion werden nicht ausgegebene Transaktionsausgaben (UTXOs) erstellt, und Dust erhöht die Anzahl der UTXOs im System. Dies kann zu einer aufgeblähten Blockchain führen und sich negativ auf die Leistung und Skalierbarkeit des Netzwerks auswirken.
Wallet-Management: Im Laufe der Zeit kann sich in Wallets viel Dust ansammeln, und die Verwaltung solch kleiner Beträge kann für Benutzer//innen unpraktisch sein. Bei vielen Wallets ist ein Mindestguthaben erforderlich, und die Dust-Mengen sind möglicherweise zu gering, um diese Anforderung zu erfüllen. Viele Nutzer//innen wechseln häufig zwischen Wallets und transferirien ihre Vermögen vorher auf die neuen Wallets, bei solchen Wechseln bleiben Dust-Beträge zurück und gelten langfristig als verloren.
Ein weiteres Problem besteht darin, dass Dust nicht genau definiert werden kann. Die Transaktionsgebühren hängen wesentlich von zwei Faktoren ab: Den Gebühren in sat/vB, welche von der Auslastung des Mempools abhängen und zu Zeiten von hoher Auslastung dementsprechend hoch sind, und zum anderen vom UTXO-Set des/der jeweiligen Nutzer//in. Denn wie wir wissen, werden Transaktionen aus einer oder mehreren UTXOs zusammengesetzt, je mehr UTXOs dabei benötigt werden, um den gewünschten Betrag zu versenden, desto höher sind die Kosten für diese Transaktion, da sich das Gewicht (in vBytes) erhöht. Diese beiden Faktoren können die Gebühren in Einzelfällen so strukturieren, dass größere Mengen Dust anfallen, als in anderen Fällen.
Datenschutzbedenken: Da jede Transaktion in der Blockchain gespeichert wird, können selbst winzige Mengen Dust mit der Identität oder dem Transaktionsverlauf einer Person verknüpft werden, was die Privatsphäre gefährdet. Diese Funktion wird von Angreifern in sogenannten Dust-Attacks ausgenutzt. Denn böswillige Angreifer haben schnell erkannt, dass Nutzer//innen die winzigen Dust-Beträge, die in ihren Wallet-Adressen angezeigt werden, nicht viel Aufmerksamkeit schenken oder gar bemerken. Angreifer schicken also Kleinstbeträge an eine große Anzahl von Adressen, um dann im nächsten Schritt in einer kombinierten Analyse dieser Adressen und der Beträge, versuchen herauszufinden, welche Adressen zur gleichen Wallet gehören. Dabei ist es das Ziel, diese so identifizierbaren Adressen und Wallets schließlich den jeweiligen Eigentümer//innen zuzuordnen, um diese dann durch ausgefeilte Phishing-Angriffe oder Cyber-Erpressungen zu attackieren.
Um diese Probleme zu lösen, können Nutzer//innen Dust konsolidieren, indem sie mehrere Dust-UTXOs in einer einzigen Transaktion mit einem höheren Wert kombinieren. Einige Wallets und Dienste bieten Funktionen an, mit denen Benutzer//innen ihren Dust effektiv verwalten und konsolidieren können.
Abschließende Gedanken
Der Unit-Bias ist absolut vorhanden. Ich persönlich begegne ihm immer wieder in Gesprächen mit Bitcoin-Interessierten, die sich mit der Materie noch nicht lange auseinandergesetzt haben. Die Verwunderung ist oft sehr groß, dass bitcoins nicht als Ganzes gekauft werden müssen. Die Verwendung einer Untereinheit sowohl in Wallets, als auch bei der Bepreisung kann dabei helfen.
An die Verwendung von Sats als die kleinste Einheit von Bitcoin habe ich mich gewöhnt, allerdings tendiere ich mittlerweile persönlich zum Gebrauch von Bits. Die hervorgebrachten Argumente leuchten mir ein und ich bin überzeugt, dass Bits eine größere Akzeptanz außerhalb des Bitcoin-Inner-Circles hervorrufen können, als Sats. Darüber hinaus ist das Sats-Zeichen wirklich unpraktisch.
Ich befürworte hier einige Ideen, die das Paragrafzeichen zum Symbol für Sats erheben wollen.

🫳🎤
-
 @ 6e468422:15deee93
2023-06-04 16:35:01
@ 6e468422:15deee93
2023-06-04 16:35:01Bees are marvelous creatures. As are most creatures, I guess.
Without bees, there wouldn't be any flowers. Without flowers, there wouldn't be any bees.
I was walking along a beautiful path today, as I do most days. To think, enjoy, meander. An intense buzzing stopped me in my tracks. Bees. Hundreds of them. Possibly thousands. Busying themselves with the things that bees busy themselves. It was a sight to behold. The sound? Overwhelming.
The older I get, the more I realize that we are more like bees or ants than we are like wolves or sheep. Busying ourselves with the things only humans busy themselves with, mostly oblivious towards the larger structures we are embedded in. Effective in large groups. Borderline useless when truly alone. Isolation kills bee, ant, and human alike.
But the busyness is what got me. We are all so busy, myself included, that we almost never have time to stop, take a breath, and marvel at the bees.
-
 @ ec42c765:328c0600
2023-06-04 14:48:51
@ ec42c765:328c0600
2023-06-04 14:48:51https://github.com/nostr-jp のアイコン、ロゴを募って、投票してもらったよ!
一覧 nostr:naddr1qqfkummnd35j6vfk8q6r2d3kxvenjdfhxqpzpmzzcaj5rzeah8y940ln4z855wa72af4a6aac4zjypql55egcpsqqvzqqqr4guf8ue8p (追加漏れや参加するつもりじゃなかったやつがあったらごめんね)
投票を集計(順不同)
左から2番目:2票
左から3番目:2票
左から4番目:4票
nostr:nevent1qqsdcqx03a9efcl09h7trww7pxq56xncjvfsa7d9npw2gdwxu9rgudszge74l
nostr:nevent1qqsdr8lw3wwhzp405cxrwa45hdus5t0fgsssvats09xalwz7426m5egpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgjy26es nostr:nevent1qqsqedqykfptgur96x60k4qwcvz4g5aeu5jw2y9370d9t2wg3qf2sqcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxglrrxyj nostr:nevent1qqsvvvvulwy33phz9aj9u2wk8468enavst8ly0tllhm7ulvenms5dzspzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgvhnt52 nostr:nevent1qqszmnf2ldg0a7kslzlukv64su3epptzlytxge08a2ruj30r6c3ljfspzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg7jr7e0 nostr:nevent1qqsg9npkxfl7srdp0xmjsmf4yfl5wm6uqu0eul6mm6mnq7a6xawuklgpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgdqv3l6 nostr:nevent1qqsyxxnag2vx06tnfme3gl6fgj8wag888n5dkzd9m34nr7hzv493ylspzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg8xfn86 nostr:nevent1qqs0tcm662vxj3hm6r5m9ulfqwrdaz680xq5mllkmh34anvyesdpc6slqa6ah nostr:nevent1qqs0t6t9alzpwz7le8g3ju03svzu6xydz0rra75e6nr7t629yz8227gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg0tk5qj
4票
nostr:nevent1qqsw4tm2nauykcn9l8j599vxunhujeyysdm93rjnd7k0pzj2r82mrqqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgcpd6ku
nostr:nevent1qqs0ptkwpm0uc7v7sr9jxuhu2uhqwmxx89kvd3yl3kpgx3ghn0tzqaqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgry0n5k nostr:nevent1qqs26n958ejg58zcqz82kzvmuflkgyaa2zywkmq0mdf83fc3j8lj0kspzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgpe99s5 nostr:nevent1qqsrmd9f9plqjgkenr58c8frqw2de4qp0x4vk6rleke44w4fgrlw5nqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq4e86r nostr:nevent1qqsvulzyc9j92cxa4fkmy050he47g8s3uxwkettrz7s2k2hq62qdv6qpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgx9dew7
1票
nostr:nevent1qqsgaznqkk47tut593yglxulj5lafvc2us6pyhnr7hw2q7mn7qfsmxqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgmdkm29
nostr:nevent1qqsrqx8te8ls8ypgrap4dy3q7p8gnvns8kpce40zwjf4z7uu68qsh6spzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg4kgzxe
2票
nostr:nevent1qqs8lx2kzcv98nw4tx9rq2qw85vv8hnlecywr5flualmj7mh8rzy9ggpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgczh4ux
nostr:nevent1qqs9my0ugs55zvsef94gyw8yrz3c60vvau6rmngvy3ycmuj2fa39ucqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg9zfk4j nostr:nevent1qqsdykqma6wl5p2dph8ak4ga848luursuhttxszm2tn7e8w24m2dpsgpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgd5d9da
4票
nostr:nevent1qqszuqev9prya48l3wcx6qxjwlxdxejhrtdxfyckhffdud22e2vexncpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxggzjp90
nostr:nevent1qqsycnstgzq8jusftt0yh872gvypu7dnl3xupv6p8ytm83cynffmwsgpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgsa29nc nostr:nevent1qqsp3vqz9rgc74w8l44jpmf8ym9e8544e50vxqvuvekklnp4wuj5crgpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgt52k8c nostr:nevent1qqs0su9lr92k86zcswywxyy0ghec4chvggfhxn427rx02wr7d4t2jlgpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgp07gmj nostr:nevent1qqsdm4e2zj0vaugntunh2tfj8gvgvq5levwz2z4v2enyxu6aksredscpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgchkzvy
6票
nostr:nevent1qqstlcjp3uxa50hml8477lhlugnd8792l3grjk3l095znv6vtgewekspzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg63que5
nostr:nevent1qqs8mm3dgh94232jf5sj4x9ha4af935m05tkxcsj65yu5vzegdl0dlcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgzn4ahj nostr:nevent1qqs257y7d3qdk0gcxum6ryjmryaanl7xal4esplp8hsyzpd0glx9q0gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxge2x8vs nostr:nevent1qqsz3wyzxz9x2vfy0epwvjsx8mpvfkvkgnnnv386pulyj3x0agrprsqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgwaw7z7 nostr:nevent1qqszv6tq6gygy7eeqq6h4h7t753fkjeypn94kgw5fkrjpddegd5h5zqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgjvafte nostr:nevent1qqsffgqgh2l7xul8dky5enxnfcuxxwkfhm3w3ww352rpffdjrrlaatspzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgsr6mnx nostr:nevent1qqsfzhnve558nkx7a9qkzev059gwk7gnhdygjx7ymfdqdmgtcezzvagpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg824gze
1票
nostr:nevent1qqsyq6qfhflpzh97nxahxp8skyx6sw3l9gey45xcrsdj8khumjkt43gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg29c5hs
nostr:nevent1qqsflqf8lll6x5g48c3r0e7agqxuznv077qgls8p4prwwcamgg25u7qpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxguwvpez
1票
nostr:nevent1qqsr4uy0utymtp5j8tkqyr4ah3a7uwagtxcl09yz07krm0p62g8v6ysvzhktn
nostr:nevent1qqs2lquadxw59p0kd4e4rz3gy4dszuwav4apg8fxg9gy4cufu2vkj0spzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxghm98kh
2票
nostr:nevent1qqsg6gzrv26pcapl2htveu54y22h4x0angm22dsvve83d9cqq2zhggsn0w0zs
nostr:nevent1qqsts2gqulftd4n7zz5jw7q006w2xxx3xgph645wqvjacauuk9lz6egpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgfdfuf5 nostr:nevent1qqst977ffgwxmwnchhvxcs5d7yj4yjy4twk5fw6z3pn0zagfsej5zdgpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgrfyhmv
集計結果
最多は6票の nostr:nevent1qqstlcjp3uxa50hml8477lhlugnd8792l3grjk3l095znv6vtgewekspzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg63que5
ただ、4票の nostr:nevent1qqsw4tm2nauykcn9l8j599vxunhujeyysdm93rjnd7k0pzj2r82mrqqpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgcpd6ku を清書したものが一番右になる?? nostr:nevent1qqsdcqx03a9efcl09h7trww7pxq56xncjvfsa7d9npw2gdwxu9rgudspzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg0rf6ah 足せば4+4=8票になる。どうしよう?
2023/06/04追記:以下の3作品で決選投票をしました!
nostr:nevent1qqs9nk32gq4qmr29n5sp5ver0e0qrma42wrsuyzdrythvyj9njlfckgpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgdg2z4k
nostr:nevent1qqszau7mydajvqyryedrrsmpu4pu5x66hmqp780jd4rf3vhk5fpj5fcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg8h6d0h
nostr:nevent1qqsrcxjtc77ac5ptt38hrpq2fpw5k5heg7pexp8zjelmgw5vd0eavqcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgk653kl
結果は以下の作品になりました!
nostr:nevent1qqszgg04m53c92457e6456t98qxgan7wjlxl64prsq3tf7hqxq0tg0cpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg24cd8l
-
 @ cc8d072e:a6a026cb
2023-06-04 13:15:43
@ cc8d072e:a6a026cb
2023-06-04 13:15:43欢迎来到Nostr
以下是使您的 Nostr 之旅更顺畅的几个步骤
本指南适用于: * 英语 原作者 nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7 * 法语 感谢 nostr:npub1nftkhktqglvcsj5n4wetkpzxpy4e5x78wwj9y9p70ar9u5u8wh6qsxmzqs * 俄语
你好,Nostrich同胞!
Nostr 是一种全新的模式,有几个步骤可以让您的加入流程更加顺畅,体验更加丰富。
👋欢迎
由于您正在阅读本文,因此可以安全地假设您已经通过下载应用程序加入了 Nostr 您可能正在使用移动设备(例如 Damus、Amethyst,Plebstr) 或Nostr网络客户端(例如 snort.social、Nostrgram、Iris)。 对于新手来说,按照您选择的应用程序建议的步骤进行操作非常重要——欢迎程序提供了所有基础知识,您不必做更多的调整除非您真的很需要。 如果您偶然发现这篇文章,但还没有 Nostr“帐户”,您可以按照这个简单的分步指南 作者是nostr:npub1cly0v30agkcfq40mdsndzjrn0tt76ykaan0q6ny80wy034qedpjsqwamhz --
npub1cly0v30agk cfq40mdsndzjrn0tt76ykaan0q6ny80wy034qedpjsqwamhz。
🤙玩得开心
Nostr 的建立是为了确保人们可以在此过程中建立联系、被听到发声并从中获得乐趣。 这就是重点(很明显,有很多严肃的用例,例如作为自由斗士和告密者的工具,但这值得单独写一篇文章),所以如果你觉得使用过程有任何负担,请联系更有经验的Nostriches,我们很乐意提供帮助。 与Nostr互动一点也不难,但与传统平台相比它有一些特点,所以你完全被允许(并鼓励)提出问题。 这是一份 非官方 的 Nostr 大使名单,他们很乐意帮助您加入: nostr:naddr1qqg5ummnw3ezqstdvfshxumpv3hhyuczypl4c26wfzswnlk2vwjxky7dhqjgnaqzqwvdvz3qwz5k3j4grrt46qcyqqq82vgwv96yu 名单上的所有nostriches都获得了 Nostr Ambassador 徽章,方便您查找、验证和关注它们
## ⚡️ 启用 Zaps Zaps 是加入 Nostr 后人们可能会注意到的第一个区别。 它们允许 Nostr 用户立即发送价值并支持创建有用和有趣的内容。 这要归功于比特币和闪电网络。 这些去中心化的支付协议让你可以立即发送一些 sats(比特币网络上的最小单位),就像在传统社交媒体平台上给某人的帖子点赞一样容易。 我们称此模型为 Value-4-Value,您可以在此处找到有关此最终货币化模型的更多信息:https://dergigi.com/value/ 查看由nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424创建的这篇笔记,nostr:note154j3vn6eqaz43va0v99fclhkdp8xf0c7l07ye9aapgl29a6dusfslg8g7g 这是对 zaps 的一个很好的介绍: 即使您不认为自己是内容创建者,您也应该启用 Zaps——人们会发现您的一些笔记很有价值,并且可能想给您发送一些 sats。 开始在 Nostr onley 上获得价值的最简单方法需要几个步骤:
0 为您的移动设备下载 Wallet of Santoshi^1(可能是比特币和闪电网络新手的最佳选择)^2 1 点击“接收” 2 点击您在屏幕上看到的 Lightning 地址(看起来像电子邮件地址的字符串)将其复制到剪贴板。
 3 将复制的地址粘贴到您的 Nostr 客户端的相应字段中(该字段可能会显示“比特币闪电地址”、“LN 地址”或任何类似内容,具体取决于您使用的应用程序)。
3 将复制的地址粘贴到您的 Nostr 客户端的相应字段中(该字段可能会显示“比特币闪电地址”、“LN 地址”或任何类似内容,具体取决于您使用的应用程序)。 
📫 获取 Nostr 地址
Nostr 地址,通常被 Nostr OG 称为“NIP-05 标识符”,看起来像一封电子邮件,并且: 🔍 帮助您使您的帐户易于发现和分享 ✔️ 证明您是人类 --- 这是 Nostr 地址的示例:Tony@nostr.21ideas.org
 它很容易记住并随后粘贴到任何 Nostr 应用程序中以找到相应的用户。
它很容易记住并随后粘贴到任何 Nostr 应用程序中以找到相应的用户。
要获得 Nostr 地址,您可以使用免费服务,例如 Nostr Check(由 nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624)或付费服务,例如 Nostr Plebs 了解有关此方法的更多信息。
🙇♀️ 学习基础知识
在后台,Nostr 与传统社交平台有很大不同,因此对它的内容有一个基本的了解对任何新手来说都是有益的。 请不要误会,我并不是建议您学习编程语言或协议的技术细节。 我的意思是看到更大的图景并理解 Nostr 和 Twitter / Medium / Reddit 之间的区别会有很大帮助。 例如,没有密码和登录名,取而代之的是私钥和公钥。 我不会深入探讨,因为有一些详尽的资源可以帮助您理解 Nostr。 由 nostr:npub12gu8c6uee3p243gez6cgk76362admlqe72aq3kp2fppjsjwmm7eqj9fle6 和 💜 准备的在这个组织整齐的登陆页面 收集了所有值得您关注的内容
 上述资源提供的信息也将帮助您保护您的 Nostr 密钥(即您的帐户),因此请务必查看。
上述资源提供的信息也将帮助您保护您的 Nostr 密钥(即您的帐户),因此请务必查看。
🤝 建立连接
与才华横溢的[^3]人建立联系的能力使 Nostr 与众不同。 在这里,每个人都可以发表意见,没有人会被排除在外。 有几种简单的方法可以在 Nostr 上找到有趣的人: * 查找您在 Twitter 上关注的人:https://www.nostr.directory/ 是一个很好的工具。 * 关注您信任的人:访问与您有共同兴趣的人的个人资料,查看他们关注的人的列表并与他们联系。
 * 访问全球订阅源:每个 Nostr 客户端(一个 Nostr 应用程序,如果你愿意这样说的话)都有一个选项卡,可以让你切换到全球订阅源,它汇总了所有 Nostr 用户的所有笔记。 只需关注您感兴趣的人(不过请耐心等待——您可能会遇到大量垃圾邮件)。
* 访问全球订阅源:每个 Nostr 客户端(一个 Nostr 应用程序,如果你愿意这样说的话)都有一个选项卡,可以让你切换到全球订阅源,它汇总了所有 Nostr 用户的所有笔记。 只需关注您感兴趣的人(不过请耐心等待——您可能会遇到大量垃圾邮件)。

🗺️探索
上面提到的 5 个步骤是一个很好的开始,它将极大地改善您的体验,但还有更多的东西有待发现和享受! Nostr 不是 Twitter 的替代品,它的可能性仅受想象力的限制。
 查看有趣且有用的 Nostr 项目列表:
* https://nostrapps.com/ Nostr 应用列表 * https://nostrplebs.com/ – 获取您的 NIP-05 和其他 Nostr 功能(付费)
* https://nostrcheck.me/ – Nostr 地址、媒体上传、中继
* https://nostr.build/ – 上传和管理媒体(以及更多)
* https://nostr.band/ – Nostr 网络和用户信息
* https://zaplife.lol/ – zapping统计
* https://nostrit.com/ – 定时发送帖子
* https://nostrnests.com/ – Twitter 空间 2.0
* https://nostryfied.online/ - 备份您的 Nostr 信息
* https://www.wavman.app/ Nostr 音乐播放器 ---
查看有趣且有用的 Nostr 项目列表:
* https://nostrapps.com/ Nostr 应用列表 * https://nostrplebs.com/ – 获取您的 NIP-05 和其他 Nostr 功能(付费)
* https://nostrcheck.me/ – Nostr 地址、媒体上传、中继
* https://nostr.build/ – 上传和管理媒体(以及更多)
* https://nostr.band/ – Nostr 网络和用户信息
* https://zaplife.lol/ – zapping统计
* https://nostrit.com/ – 定时发送帖子
* https://nostrnests.com/ – Twitter 空间 2.0
* https://nostryfied.online/ - 备份您的 Nostr 信息
* https://www.wavman.app/ Nostr 音乐播放器 --- 📻 中继
熟悉 Nostr 后,请务必查看我关于 Nostr 中继的快速指南:https://lnshort.it/nostr-relays。 这不是您旅程开始时要担心的话题,但在以后深入研究绝对重要。
📱 手机上的 Nostr
在移动设备上流畅的 Nostr 体验是可行的。 本指南将帮助您在智能手机上的 Nostr Web 应用程序中无缝登录、发帖、zap 等:https://lnshort.it/nostr-mobile
感谢阅读,我们在兔子洞的另一边见 nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7
发现这篇文章有价值吗 Zap⚡ 21ideas@getalby.com 关注:
npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7查看我的项目 https://bitcal.21ideas.org/about/
[^3]:nostr:npub1fl7pr0azlpgk469u034lsgn46dvwguz9g339p03dpetp9cs5pq5qxzeknp 是其中一个Nostrich,他设计了本指南的封面上使用的徽标
译者: Sherry, 数据科学|软件工程|nossence|nostr.hk|组织过一些nostr meetup|写一些文章来将nostr带到每个人身边
Zap⚡ spang@getalby.com 关注:
npub1ejxswthae3nkljavznmv66p9ahp4wmj4adux525htmsrff4qym9sz2t3tv -
 @ c64cdeb9:d787525e
2023-06-04 12:27:59
@ c64cdeb9:d787525e
2023-06-04 12:27:59 -
 @ 00000000:62ad6927
2023-06-04 10:41:15
@ 00000000:62ad6927
2023-06-04 10:41:15Yesterday, I participated in an exhilarating bike competition called Red Bull Goni Pony. This event has been a yearly tradition for me since its inception in 2015. Sponsored by Red Bull, it features a unique twist by allowing only 20" wheel bikes with no gears.
We tackled a challenging 13.5 km mountain road towards Vršič pass, conquering an ascent of 801m, with an average slope angle of 7.25% and a maximum slope angle of 10.8%. This was no ordinary ride in the park, but fortunately, we had a generous time limit of 2 hours to reach the summit.
The record set by the fastest rider in 2020 is truly mind-boggling, completing the race in under 40 minutes! However, it's important to note that walking alongside the bike is permitted for us normies, as the steep slopes combined with the crowded road make it nearly impossible to conquer with these specific bikes. The solution to tackle steep slopes with these bikes is to employ a zig-zag technique, which theoretically helps in navigating the challenging terrain. However, in practice, it often becomes tricky to execute the zig-zag maneuver smoothly due to the presence of other competitors who unintentionally obstruct your intended path, preventing you from completing the desired zag.
The name "Goni Pony" refers to riding a Pony, but not the small horse you might imagine. "Pony" is actually the name of a folding bike model from the former Yugoslavia, manufactured by the ROG company (recently resurrected from the dead and now producing new modern models of these bikes). To learn more about this bike and its rich history, you can check out this short [Blog post] (https://mbreznik.home.blog/2019/05/10/the-79-pony-in-ocean-blue-and-how-it-became-hipster/).
There are many variants of these bike models, and if I'm not mistaken, the first company to produce these 20-inch folding bikes is an Italian company called Graziella, where my bike was also manufactured. My Graziella bike weighs 21kg, made of steel, and is between 50-60 years old, yet it still holds strong and is ready for many more challenging climbs to conquer.
In the old days, bikes were built to last for generations. Craftsmanship and durability were the top priorities, ensuring that bikes could withstand the test of time. Unlike modern mass-produced bikes, which often prioritize lightweight materials and short lifespans thanks to [Planned obsolescence] (https://en.wikipedia.org/wiki/Planned_obsolescence), older bikes were made with sturdy frames, robust components, and timeless design. Many vintage bikes from the past are still in use today, serving as a testament to their longevity and quality. These bikes were not just means of transportation; they were cherished possessions that could be passed down through families, carrying the memories and stories of previous generations.
PS: I warmly welcome you to join the next year's Red Bull Goni Pony event in [Kranjska gora] (https://www.openstreetmap.org/changeset/72868241#map=13/46.4531/13.7642)
-
 @ 93161535:1fc6d488
2023-06-04 02:32:44
@ 93161535:1fc6d488
2023-06-04 02:32:44Derrick's Birthday
Derrick's birthday is a special occasion that only comes once a year - until a life changing event that only happens once in a lifetime also happens on Derrick's birthday. How will two important events play out at once? Will Derrick still feel special?
•───────••••───────•
TALK ABOUT ME AND TO ME ON MY ANONYMOUS IMAGEBOARD: https://tubgurl.com (https://tubgurl.com)
•───────••••───────•
DONATE MONERO FOR SERVER COSTS: 8A11e3NEQXvEbShkwZHd67e12rcM8GfADjSmrywkoZLP5XuakvDuNsp3d8B3RLoUZFRAFry38DM5Z6Gu1vJdbrRzVdbktHR
Donations help for the sever costs, to maintain my website, and lessen the blow for paying for bandwidth, since I host my own videos on my own website. Or maybe I made you laugh and you just wanna say thanks. Never required or expected, always appreciated.
•───────••••───────•
FEED ME. Please. I love Panda Express eggrolls and noodles
Go to https://www.pandaexpress.com/gift-cards/select#digital (https://www.pandaexpress.com/gift-cards/select#digital) then send the gift card to my email: ashleyjones@dnmx.org THANK YOU.
•───────••••───────•
Check out my website. I have a ton of written content on there. Website: icum.to (http://icum.to)
Website: https://icum.to (https://icum.to)
Videos: https://videos.icum.to (https://videos.icum.to)
Discuss me on my imageboard: https://tubgurl.com (https://tubgurl.com)
Email: ashleyjones@horsefucker.org
Phone number: 725-CUM-FART
If you want to send an encrypted message I have my GPG key on my website: https://icum.to/analjuice/ (https://icum.to/analjuice/)
https://videos.icum.to/w/3faidSsWAFvUurQ62usMQh
-
 @ bd90d885:e6cbbf5a
2023-06-03 23:10:33
@ bd90d885:e6cbbf5a
2023-06-03 23:10:33 -
 @ b9c09954:815d302d
2023-06-03 20:22:54
@ b9c09954:815d302d
2023-06-03 20:22:54Trying out Habla.news to see if it is a viable blogging platform. Here are some interesting things I came across recently.
AI-Controlled Drone Goes Rogue, 'Kills' Human Operator in USAF Simulated Test

An AI-enabled drone "killed" its human operator in a simulation conducted by the U.S. Air Force in order to override a possible "no" order stopping it from completing its mission, the USAF's Chief of AI Test and Operations revealed at a recent conference. According to the group that threw the conference, the Air Force official was describing a "simulated test" that involved an AI-controlled drone getting "points" for killing simulated targets, not a live test in the physical world. No actual human was harmed.
If that scares you then ave a look at this Slaughterbots video showing what is possible not with killer mini drones.
Start9 Labs Introduces Server Lite and 2023 Server One

Just as Windows and macOS made it possible for anyone to own a personal computer, StartOS makes it possible for anyone to own a personal server.
StartOS facilitates the entire process of discovering, installing, configuring, and using any variety of open-source software from anywhere in the world without trusting anyone.
And now they have just released 3 new nodes. The Server Lite which is low cost Raspberry PI option, the Server One which is a mid range version running on 11th generation Intel® Celeron processor with 16Gb of memory and the Server Pro with Intel Core i7-10510U processor with 32Gb or memory. Server One looks really good at $549.00. You can slo get a 9% discount and free international shipping if you pay in bitcoin
-
 @ 42a41978:c1aea03e
2023-06-03 19:51:09
@ 42a41978:c1aea03e
2023-06-03 19:51:09Most Nostr posts use the kind=1 Short text note standard. But there is also a NIP-23 standard for Long-form content, which is kind=30023.
Blogstack.io (at https://blogstack.io/) is one of the client app services that supports this long-form content which also allows for much better text formatting which can even include ordered and unordered lists, tables, inline code, etc. It does this through markdown formatting. To make this easier, Blogstack.io also has a text formatting toolbar with buttons to click to format the text.
As Blogstack.io is actually based on the Nostr protocol, I could use my Nostr authentication to create a post from there, and all my profile info from Nostr was immediately ion place. This post is created on Blogstack.io, but should be signed and posted with my existing Nostr profile public key as if it was created on any of the other Nostr clients I already use. It will be interesting to see if this also appears linked to my existing profile, and whether any comments/replies also appear when I log into my other Nostr client apps. Will I be able to see the text formatting as well from my other Nostr apps?
PS: Being long-form NIP-23 I could also edit this line in. Seems from Blogstack it was not pushing out to all relays, eg. Snort.social, and I was not seeing the post from my Snort.social login. However on the Amethyst app, the post did appear under my Nostr profile. I boosted it from there so maybe that will make it visible via other relays too. I could also view it from Nostrid, which has a Blogs view as well.


