-
 @ 42342239:1d80db24
2024-03-31 11:23:36
@ 42342239:1d80db24
2024-03-31 11:23:36Biologist Stuart Kauffman introduced the concept of the "adjacent possible" in evolutionary biology in 1996. A bacterium cannot suddenly transform into a flamingo; rather, it must rely on small exploratory changes (of the "adjacent possible") if it is ever to become a beautiful pink flying creature. The same principle applies to human societies, all of which exemplify complex systems. It is indeed challenging to transform shivering cave-dwellers into a space travelers without numerous intermediate steps.
Imagine a water wheel – in itself, perhaps not such a remarkable invention. Yet the water wheel transformed the hard-to-use energy of water into easily exploitable rotational energy. A little of the "adjacent possible" had now been explored: water mills, hammer forges, sawmills, and textile factories soon emerged. People who had previously ground by hand or threshed with the help of oxen could now spend their time on other things. The principles of the water wheel also formed the basis for wind power. Yes, a multitude of possibilities arose – reminiscent of the rapid development during the Cambrian explosion. When the inventors of bygone times constructed humanity's first water wheel, they thus expanded the "adjacent possible". Surely, the experts of old likely sought swift prohibitions. Not long ago, our expert class claimed that the internet was going to be a passing fad, or that it would only have the same modest impact on the economy as the fax machine. For what it's worth, there were even attempts to ban the number zero back in the days.
The pseudonymous creator of Bitcoin, Satoshi Nakamoto, wrote in Bitcoin's whitepaper that "[w]e have proposed a system for electronic transactions without relying on trust." The Bitcoin system enables participants to agree on what is true without needing to trust each other, something that has never been possible before. In light of this, it is worth noting that trust in the federal government in the USA is among the lowest levels measured in almost 70 years. Trust in media is at record lows. Moreover, in countries like the USA, the proportion of people who believe that one can trust "most people" has decreased significantly. "Rebuilding trust" was even the theme of the World Economic Forum at its annual meeting. It is evident, even in the international context, that trust between countries is not at its peak.
Over a fifteen-year period, Bitcoin has enabled electronic transactions without its participants needing to rely on a central authority, or even on each other. This may not sound like a particularly remarkable invention in itself. But like the water wheel, one must acknowledge that new potential seems to have been put in place, potential that is just beginning to be explored. Kauffman's "adjacent possible" has expanded. And despite dogmatic statements to the contrary, no one can know for sure where this might lead.
The discussion of Bitcoin or crypto currencies would benefit from greater humility and openness, not only from employees or CEOs of money laundering banks but also from forecast-failing central bank officials. When for instance Chinese Premier Zhou Enlai in the 1970s was asked about the effects of the French Revolution, he responded that it was "too early to say" - a far wiser answer than the categorical response of the bureaucratic class. Isn't exploring systems not based on trust is exactly what we need at this juncture?
-
 @ b12b632c:d9e1ff79
2024-03-23 16:42:49
@ b12b632c:d9e1ff79
2024-03-23 16:42:49CASHU AND ECASH ARE EXPERIMENTAL PROJECTS. BY THE OWN NATURE OF CASHU ECASH, IT'S REALLY EASY TO LOSE YOUR SATS BY LACKING OF KNOWLEDGE OF THE SYSTEM MECHANICS. PLEASE, FOR YOUR OWN GOOD, ALWAYS USE FEW SATS AMOUNT IN THE BEGINNING TO FULLY UNDERSTAND HOW WORKS THE SYSTEM. ECASH IS BASED ON A TRUST RELATIONSHIP BETWEEN YOU AND THE MINT OWNER, PLEASE DONT TRUST ECASH MINT YOU DONT KNOW. IT IS POSSIBLE TO GENERATE UNLIMITED ECASH TOKENS FROM A MINT, THE ONLY WAY TO VALIDATE THE REAL EXISTENCE OF THE ECASH TOKENS IS TO DO A MULTIMINT SWAP (BETWEEN MINTS). PLEASE, ALWAYS DO A MULTISWAP MINT IF YOU RECEIVE SOME ECASH FROM SOMEONE YOU DON'T KNOW/TRUST. NEVER TRUST A MINT YOU DONT KNOW!
IF YOU WANT TO RUN AN ECASH MINT WITH A BTC LIGHTNING NODE IN BACK-END, PLEASE DEDICATE THIS LN NODE TO YOUR ECASH MINT. A BAD MANAGEMENT OF YOUR LN NODE COULD LET PEOPLE TO LOOSE THEIR SATS BECAUSE THEY HAD ONCE TRUSTED YOUR MINT AND YOU DID NOT MANAGE THE THINGS RIGHT.

What's ecash/Cashu ?
I recently listened a passionnating interview from calle 👁️⚡👁 invited by the podcast channel What Bitcoin Did about the new (not so much now) Cashu protocol.
Cashu is a a free and open-source Chaumian ecash project built for Bitcoin protocol, recently created in order to let users send/receive Ecash over BTC Lightning network. The main Cashu ecash goal is to finally give you a "by-design" privacy mechanism to allow us to do anonymous Bitcoin transactions.
Ecash for your privacy.\ A Cashu mint does not know who you are, what your balance is, or who you're transacting with. Users of a mint can exchange ecash privately without anyone being able to know who the involved parties are. Bitcoin payments are executed without anyone able to censor specific users.
Here are some useful links to begin with Cashu ecash :
Github repo: https://github.com/cashubtc
Documentation: https://docs.cashu.space
To support the project: https://docs.cashu.space/contribute
A Proof of Liabilities Scheme for Ecash Mints: https://gist.github.com/callebtc/ed5228d1d8cbaade0104db5d1cf63939
Like NOSTR and its own NIPS, here is the list of the Cashu ecash NUTs (Notation, Usage, and Terminology): https://github.com/cashubtc/nuts?tab=readme-ov-file
I won't explain you at lot more on what's Casu ecash, you need to figured out by yourself. It's really important in order to avoid any mistakes you could do with your sats (that you'll probably regret).
If you don't have so much time, you can check their FAQ right here: https://docs.cashu.space/faq
I strongly advise you to listen Calle's interviews @whatbbitcoindid to "fully" understand the concept and the Cashu ecash mechanism before using it:
Scaling Bitcoin Privacy with Calle
In the meantime I'm writing this article, Calle did another really interesting interview with ODELL from CitadelDispatch:
CD120: BITCOIN POWERED CHAUMIAN ECASH WITH CALLE
Which ecash apps?
There are several ways to send/receive some Ecash tokens, you can do it by using mobile applications like eNuts, Minibits or by using Web applications like Cashu.me, Nustrache or even npub.cash. On these topics, BTC Session Youtube channel offers high quality contents and very easy to understand key knowledge on how to use these applications :
Minibits BTC Wallet: Near Perfect Privacy and Low Fees - FULL TUTORIAL
Cashu Tutorial - Chaumian Ecash On Bitcoin
Unlock Perfect Privacy with eNuts: Instant, Free Bitcoin Transactions Tutorial
Cashu ecash is a very large and complex topic for beginners. I'm still learning everyday how it works and the project moves really fast due to its commited developpers community. Don't forget to follow their updates on Nostr to know more about the project but also to have a better undertanding of the Cashu ecash technical and political implications.
There is also a Matrix chat available if you want to participate to the project:
https://matrix.to/#/#cashu:matrix.org
How to self-host your ecash mint with Nutshell
Cashu Nutshell is a Chaumian Ecash wallet and mint for Bitcoin Lightning. Cashu Nutshell is the reference implementation in Python.
Github repo:
https://github.com/cashubtc/nutshell
Today, Nutshell is the most advanced mint in town to self-host your ecash mint. The installation is relatively straightforward with Docker because a docker-compose file is available from the github repo.
Nutshell is not the only cashu ecash mint server available, you can check other server mint here :
https://docs.cashu.space/mints
The only "external" requirement is to have a funding source. One back-end funding source where ecash will mint your ecash from your Sats and initiate BTC Lightning Netwok transactions between ecash mints and BTC Ligtning nodes during a multimint swap. Current backend sources supported are: FakeWallet*, LndRestWallet, CoreLightningRestWallet, BlinkWallet, LNbitsWallet, StrikeUSDWallet.
*FakeWallet is able to generate unlimited ecash tokens. Please use it carefully, ecash tokens issued by the FakeWallet can be sent and accepted as legit ecash tokens to other people ecash wallets if they trust your mint. In the other way, if someone send you 2,3M ecash tokens, please don't trust the mint in the first place. You need to force a multimint swap with a BTC LN transaction. If that fails, someone has maybe tried to fool you.
I used a Voltage.cloud BTC LN node instance to back-end my Nutshell ecash mint:
SPOILER: my nutshell mint is working but I have an error message "insufficient balance" when I ask a multiswap mint from wallet.cashu.me or the eNuts application. In order to make it work, I need to add some Sats liquidity (I can't right now) to the node and open few channels with good balance capacity. If you don't have an ecash mint capable of doig multiswap mint, you'll only be able to mint ecash into your ecash mint and send ecash tokens to people trusting your mint. It's working, yes, but you need to be able to do some mutiminit swap if you/everyone want to fully profit of the ecash system.
Once you created your account and you got your node, you need to git clone the Nutshell github repo:
git clone https://github.com/cashubtc/nutshell.gitYou next need to update the docker compose file with your own settings. You can comment the wallet container if you don't need it.
To generate a private key for your node, you can use this openssl command
openssl rand -hex 32 054de2a00a1d8e3038b30e96d26979761315cf48395aa45d866aeef358c91dd1The CLI Cashu wallet is not needed right now but I'll show you how to use it in the end of this article. Feel free to comment it or not.
``` version: "3" services: mint: build: context: . dockerfile: Dockerfile container_name: mint
ports:
- "3338:3338"
environment:- DEBUG=TRUE
- LOG_LEVEL=DEBUG
- MINT_URL=https://YourMintURL - MINT_HOST=YourMintDomain.tld - MINT_LISTEN_HOST=0.0.0.0 - MINT_LISTEN_PORT=3338 - MINT_PRIVATE_KEY=YourPrivateKeyFromOpenSSL - MINT_INFO_NAME=YourMintInfoName - MINT_INFO_DESCRIPTION=YourShortInfoDesc - MINT_INFO_DESCRIPTION_LONG=YourLongInfoDesc - MINT_LIGHTNING_BACKEND=LndRestWallet #- MINT_LIGHTNING_BACKEND=FakeWallet - MINT_INFO_CONTACT=[["email","YourConctact@email"], ["twitter","@YourTwitter"], ["nostr", "YourNPUB"]] - MINT_INFO_MOTD=Thanks for using my mint! - MINT_LND_REST_ENDPOINT=https://YourVoltageNodeDomain:8080 - MINT_LND_REST_MACAROON=YourDefaultAdminMacaroonBase64 - MINT_MAX_PEG_IN=100000 - MINT_MAX_PEG_OUT=100000 - MINT_PEG_OUT_ONLY=FALSE command: ["poetry", "run", "mint"]wallet-voltage: build: context: . dockerfile: Dockerfile container_name: wallet-voltage
ports:
- "4448:4448"
depends_on: - nutshell-voltage environment:- DEBUG=TRUE
- MINT_URL=http://nutshell-voltage:3338
- API_HOST=0.0.0.0 command: ["poetry", "run", "cashu", "-d"]```
To build, run and see the container logs:
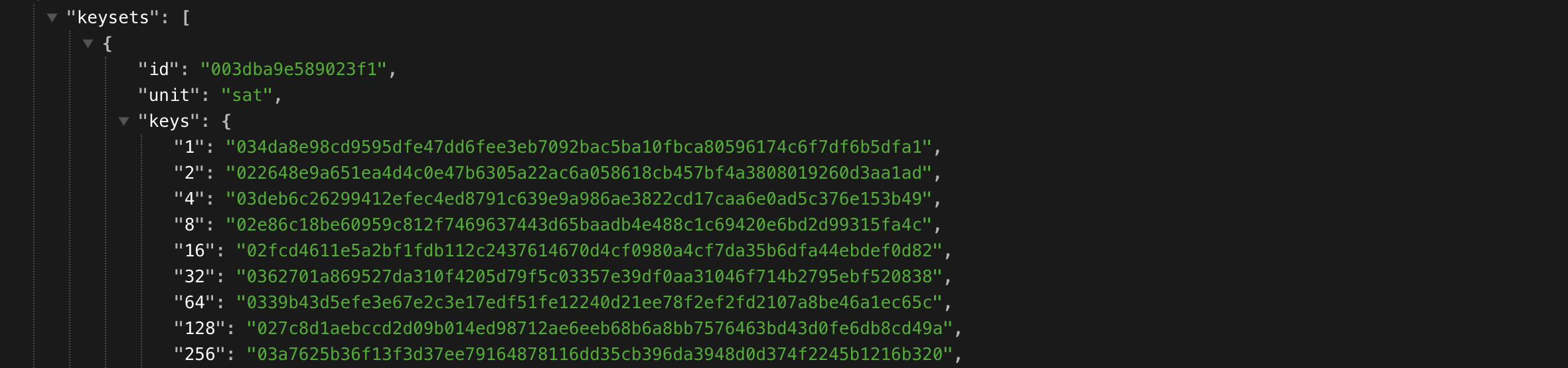
docker compose up -d && docker logs -f mint0.15.1 2024-03-22 14:45:45.490 | WARNING | cashu.lightning.lndrest:__init__:49 - no certificate for lndrest provided, this only works if you have a publicly issued certificate 2024-03-22 14:45:45.557 | INFO | cashu.core.db:__init__:135 - Creating database directory: data/mint 2024-03-22 14:45:45.68 | INFO | Started server process [1] 2024-03-22 14:45:45.69 | INFO | Waiting for application startup. 2024-03-22 14:45:46.12 | INFO | Loaded 0 keysets from database. 2024-03-22 14:45:46.37 | INFO | Current keyset: 003dba9e589023f1 2024-03-22 14:45:46.37 | INFO | Using LndRestWallet backend for method: 'bolt11' and unit: 'sat' 2024-03-22 14:45:46.97 | INFO | Backend balance: 1825000 sat 2024-03-22 14:45:46.97 | INFO | Data dir: /root/.cashu 2024-03-22 14:45:46.97 | INFO | Mint started. 2024-03-22 14:45:46.97 | INFO | Application startup complete. 2024-03-22 14:45:46.98 | INFO | Uvicorn running on http://0.0.0.0:3338 (Press CTRL+C to quit) 2024-03-22 14:45:47.27 | INFO | 172.19.0.22:48528 - "GET /v1/keys HTTP/1.1" 200 2024-03-22 14:45:47.34 | INFO | 172.19.0.22:48544 - "GET /v1/keysets HTTP/1.1" 200 2024-03-22 14:45:47.38 | INFO | 172.19.0.22:48552 - "GET /v1/info HTTP/1.1" 200If you see the line :
Uvicorn running on http://0.0.0.0:3338 (Press CTRL+C to quit)Nutshell is well started.
I won't explain here how to create a reverse proxy to Nutshell, you can find how to do it into my previous article. Here is the reverse proxy config into Nginx Proxy Manager:
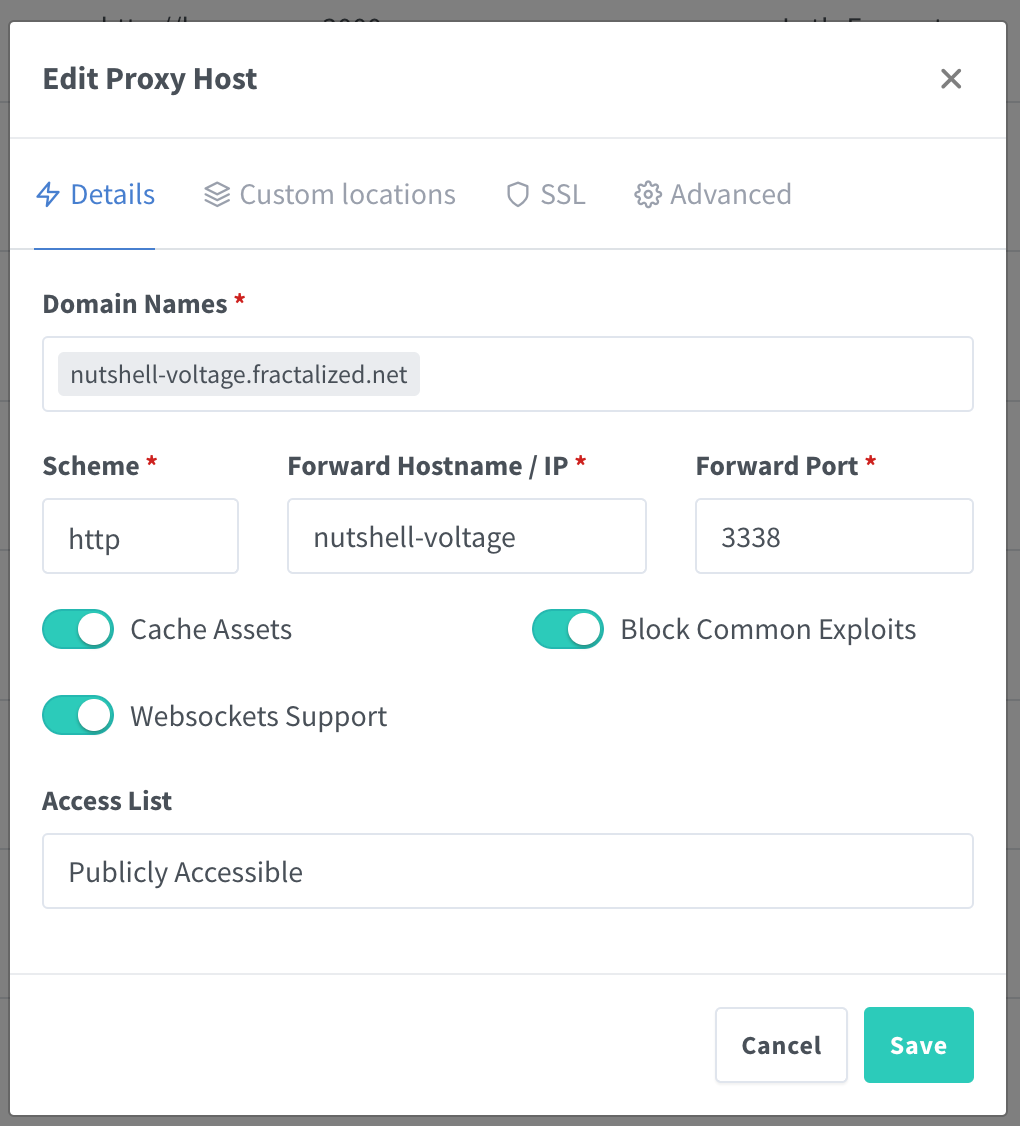
If everything is well configured and if you go on your mint url (https://yourminturl) you shoud see this:
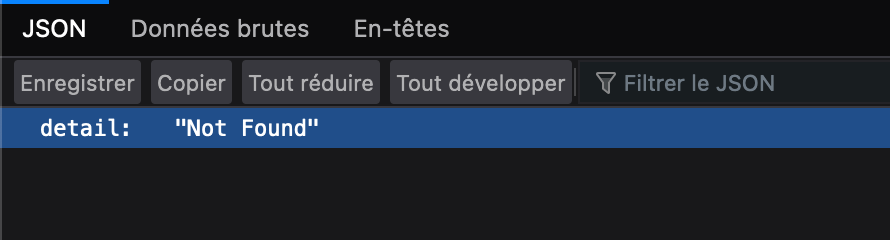
It's not helping a lot because at first glance it seems to be not working but it is. You can also check these URL path to confirm :
- https://yourminturl/keys and https://yourminturl/keysets
or
- https://yourminturl/v1/keys and https://yourminturl/v1/keysets
Depending of the moment when you read this article, the first URLs path might have been migrated to V1. Here is why:
https://github.com/cashubtc/nuts/pull/55
The final test is to add your mint to your prefered ecash wallets.
SPOILER: AT THIS POINT, YOU SHOUD KNOW THAT IF YOU RESET YOUR LOCAL BROWSER INTERNET CACHE FILE, YOU'LL LOSE YOUR MINTED ECASH TOKENS. IF NOT, PLEASE READ THE DOCUMENTATION AGAIN.
For instace, if we use wallet.cashu.me:
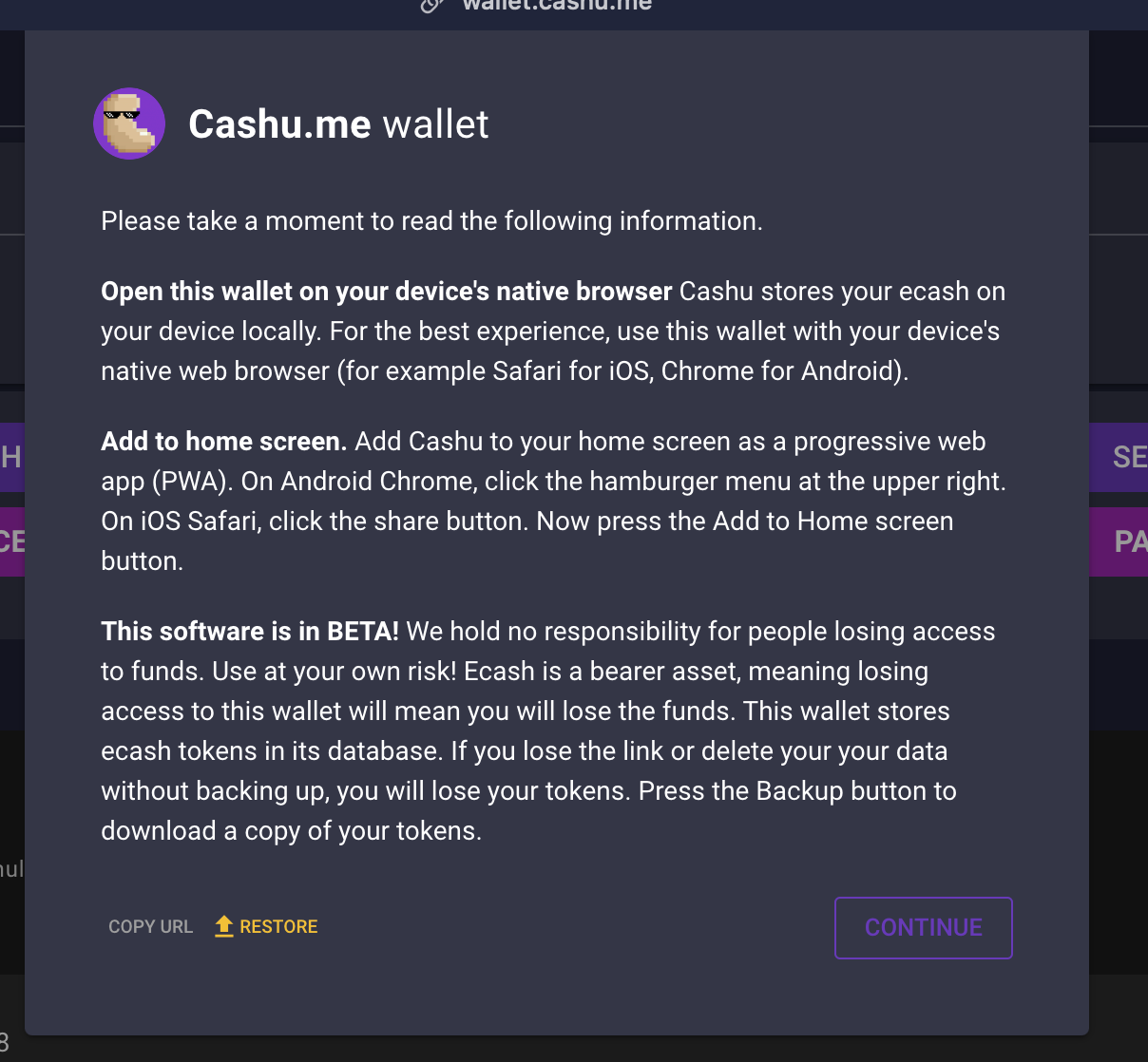
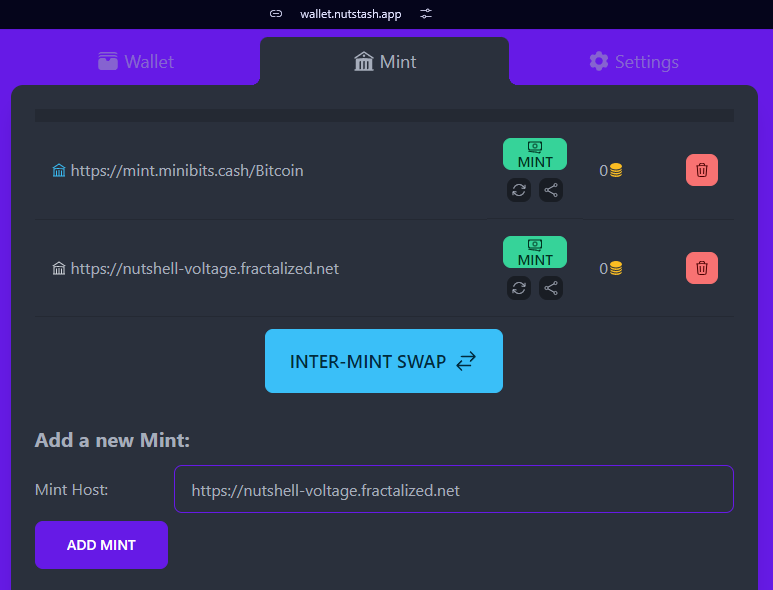
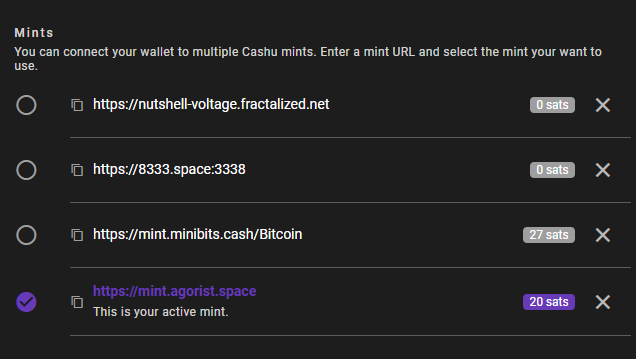
You can go into the "Settings" tab and add your mint :
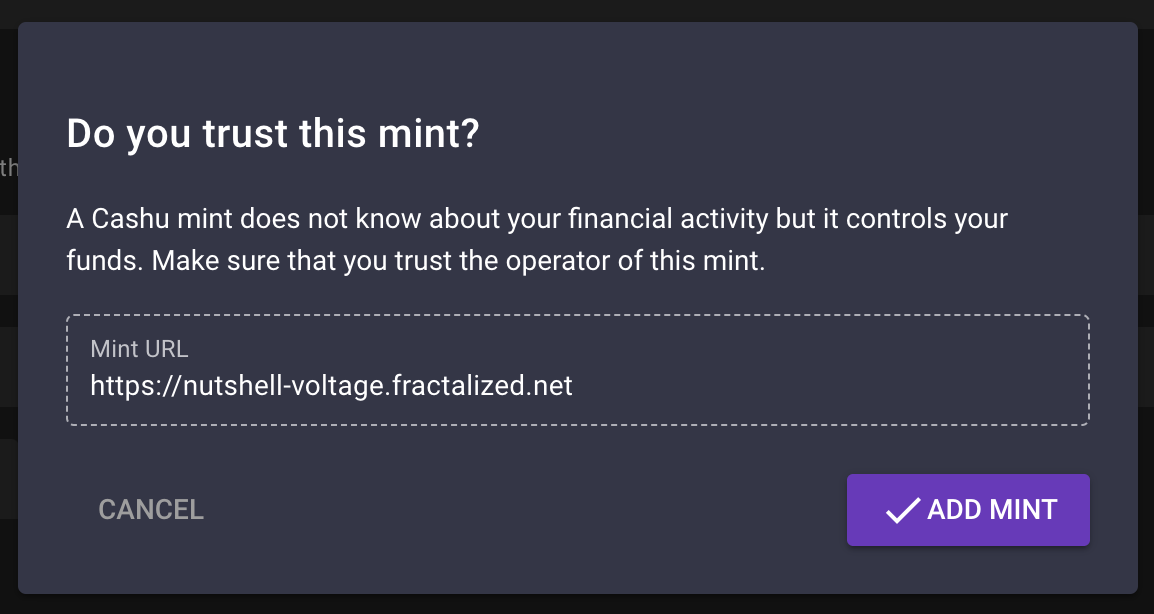
If everything went find, you shoud see this :
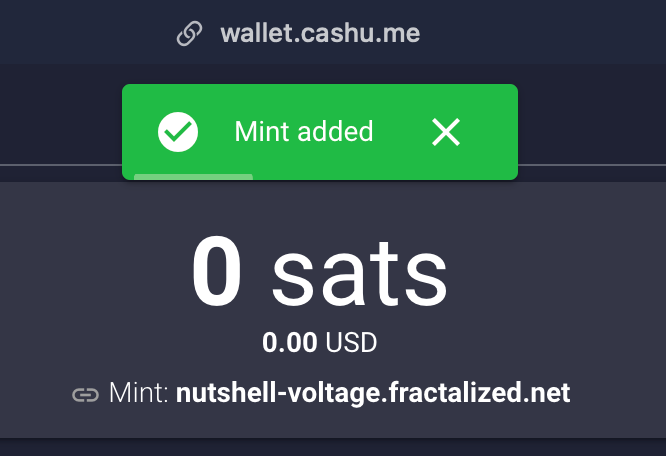
You can now mint some ecash from your mint creating a sats invoice :
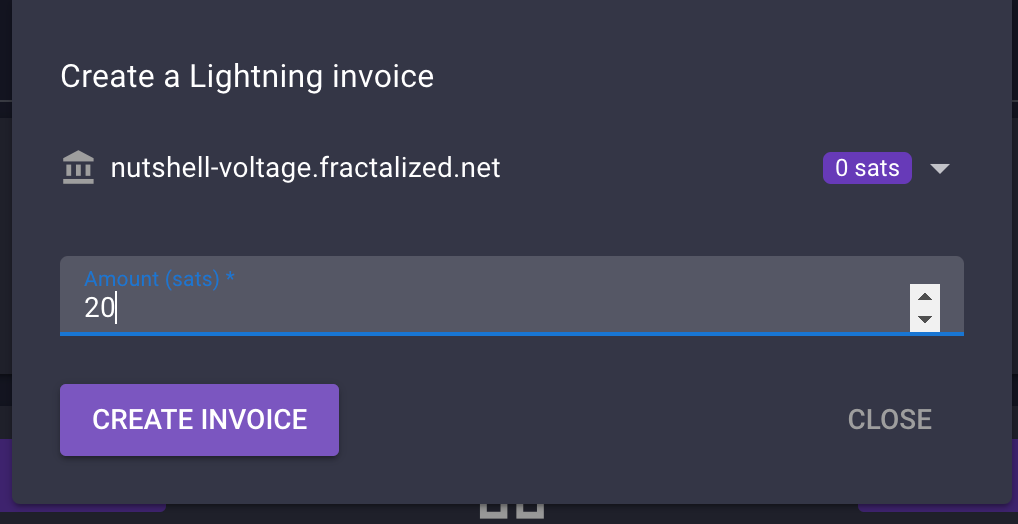
You can now scan the QR diplayed with your prefered BTC LN wallet. If everything is OK, you should receive the funds:
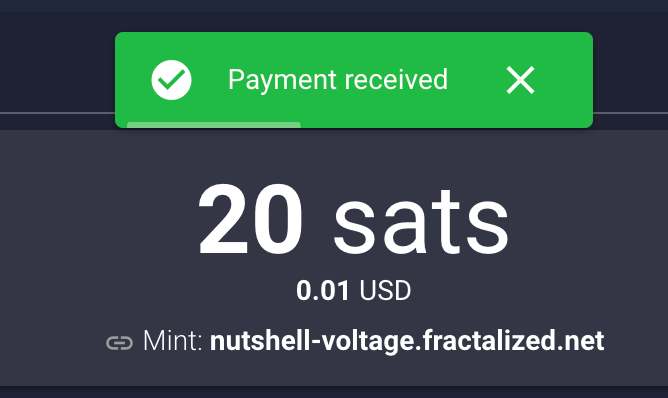
It may happen that some error popup sometimes. If you are curious and you want to know what happened, Cashu wallet has a debug console you can activate by clicking on the "Settings" page and "OPEN DEBUG TERMINAL". A little gear icon will be displayed in the bottom of the screen. You can click on it, go to settings and enable "Auto Display If Error Occurs" and "Display Extra Information". After enabling this setting, you can close the popup windows and let the gear icon enabled. If any error comes, this windows will open again and show you thé error:
Now that you have some sats in your balance, you can try to send some ecash. Open in a new windows another ecash wallet like Nutstach for instance.
Add your mint again :
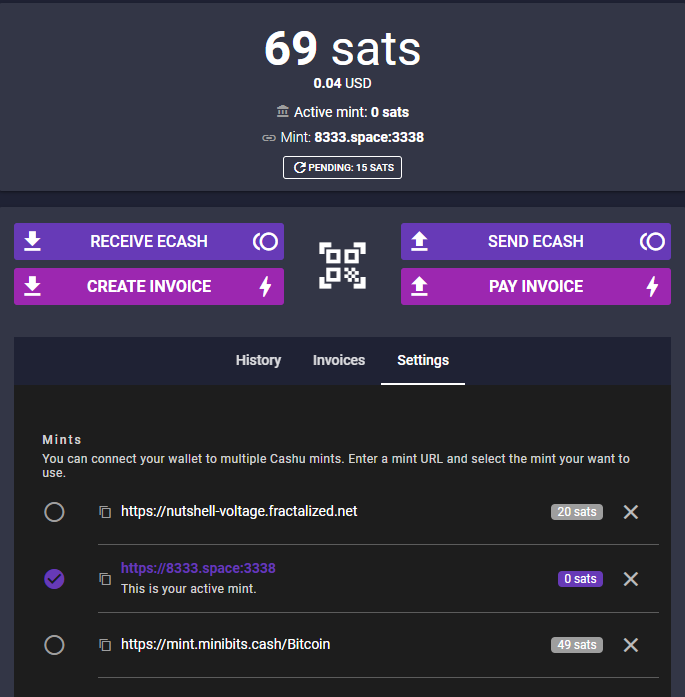
Return on Cashu wallet. The ecash token amount you see on the Cashu wallet home page is a total of all the ecash tokens you have on all mint connected.
Next, click on "Send ecach". Insert the amout of ecash you want to transfer to your other wallet. You can select the wallet where you want to extract the funds by click on the little arrow near the sats funds you currenly selected :


Click now on "SEND TOKENS". That will open you a popup with a QR code and a code CONTAINING YOUR ECASH TOKENS (really).

You can now return on nutstach, click on the "Receive" button and paste the code you get from Cashu wallet:
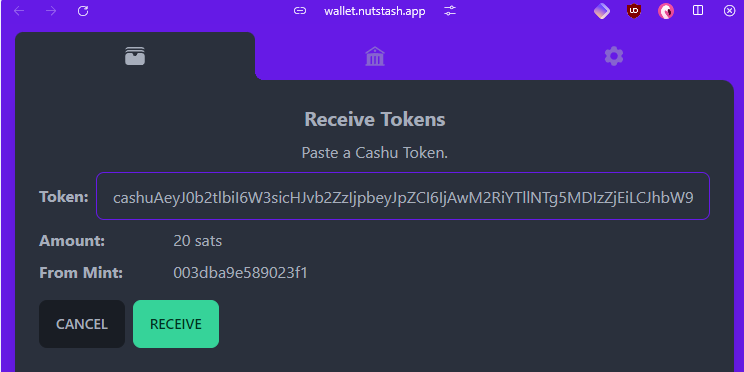
Click on "RECEIVE" again:
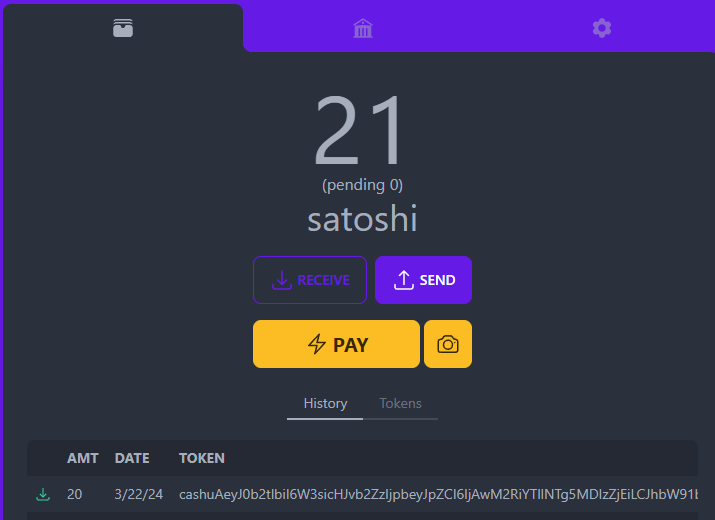
Congrats, you transfered your first ecash tokens to yourself ! 🥜⚡
You may need some time to transfer your ecash tokens between your wallets and your mint, there is a functionality existing for that called "Multimint swaps".
Before that, if you need new mints, you can check the very new website Bitcoinmints.com that let you see the existing ecash mints and rating :
Don't forget, choose your mint carefuly because you don't know who's behind.
Let's take a mint and add it to our Cashu wallet:
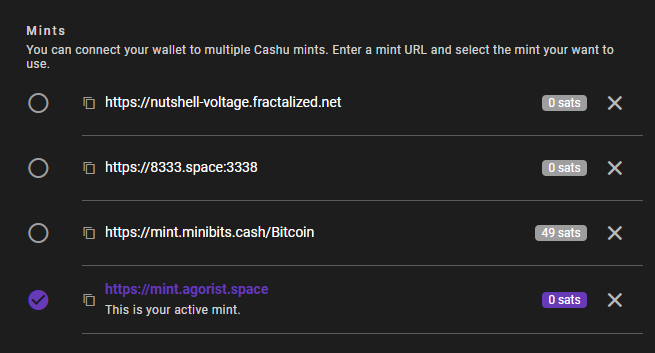
If you want to transfer let's say 20 sats from minibits mint to bitcointxoko mint, go just bottom into the "Multimint swap" section. Select the mint into "Swap from mint", the mint into "Swap to mint" and click on "SWAP" :
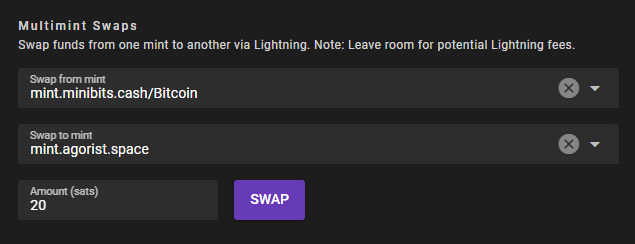
A popup window will appear and will request the ecash tokens from the source mint. It will automatically request the ecash amount via a Lightning node transaction and add the fund to your other wallet in the target mint. As it's a Lightning Network transaction, you can expect some little fees.
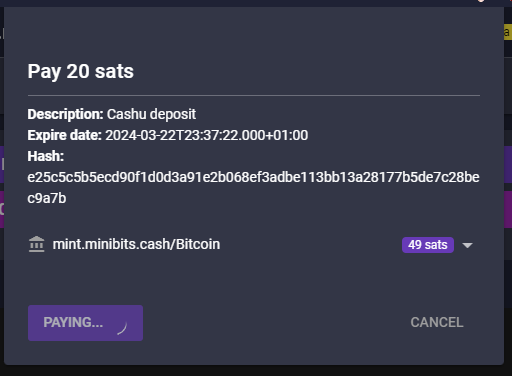
If everything is OK with the mints, the swap will be successful and the ecash received.
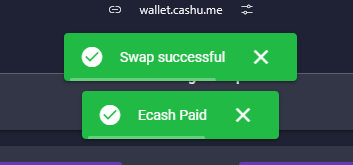
You can now see that the previous sats has been transfered (minus 2 fee sats).
Well done, you did your first multimint swap ! 🥜⚡
One last thing interresting is you can also use CLI ecash wallet. If you created the wallet contained in the docker compose, the container should be running.
Here are some commands you can do.
To verify which mint is currently connected :
``` docker exec -it wallet-voltage poetry run cashu info
2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat Version: 0.15.1 Wallet: wallet Debug: True Cashu dir: /root/.cashu Mints: - https://nutshell-voltage.fractalized.net ```
To verify your balance :
``` docker exec -it wallet-voltage poetry run cashu balance
2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat Balance: 0 sat ```
To create an sats invoice to have ecash :
``` docker exec -it wallet-voltage poetry run cashu invoice 20
2024-03-22 22:00:59.12 | DEBUG | cashu.wallet.wallet:_load_mint_info:275 | Mint info: name='nutshell.fractalized.net' pubkey='02008469922e985cbc5368ce16adb6ed1aaea0f9ecb21639db4ded2e2ae014a326' version='Nutshell/0.15.1' description='Official Fractalized Mint' description_long='TRUST THE MINT' contact=[['email', 'pastagringo@fractalized.net'], ['twitter', '@pastagringo'], ['nostr', 'npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2']] motd='Thanks for using official ecash fractalized mint!' nuts={4: {'methods': [['bolt11', 'sat']], 'disabled': False}, 5: {'methods': [['bolt11', 'sat']], 'disabled': False}, 7: {'supported': True}, 8: {'supported': True}, 9: {'supported': True}, 10: {'supported': True}, 11: {'supported': True}, 12: {'supported': True}} Balance: 0 sat
Pay invoice to mint 20 sat:
Invoice: lnbc200n1pjlmlumpp5qh68cqlr2afukv9z2zpna3cwa3a0nvla7yuakq7jjqyu7g6y69uqdqqcqzzsxqyz5vqsp5zymmllsqwd40xhmpu76v4r9qq3wcdth93xthrrvt4z5ct3cf69vs9qyyssqcqppurrt5uqap4nggu5tvmrlmqs5guzpy7jgzz8szckx9tug4kr58t4avv4a6437g7542084c6vkvul0ln4uus7yj87rr79qztqldggq0cdfpy
You can use this command to check the invoice: cashu invoice 20 --id 2uVWELhnpFcNeFZj6fWzHjZuIipqyj5R8kM7ZJ9_
Checking invoice .................2024-03-22 22:03:25.27 | DEBUG | cashu.wallet.wallet:verify_proofs_dleq:1103 | Verified incoming DLEQ proofs. Invoice paid.
Balance: 20 sat ```
To pay an invoice by pasting the invoice you received by your or other people :
``` docker exec -it wallet-voltage poetry run cashu pay lnbc150n1pjluqzhpp5rjezkdtt8rjth4vqsvm50xwxtelxjvkq90lf9tu2thsv2kcqe6vqdq2f38xy6t5wvcqzzsxqrpcgsp58q9sqkpu0c6s8hq5pey8ls863xmjykkumxnd8hff3q4fvxzyh0ys9qyyssq26ytxay6up54useezjgqm3cxxljvqw5vq2e94ru7ytqc0al74hr4nt5cwpuysgyq8u25xx5la43mx4ralf3mq2425xmvhjzvwzqp54gp0e3t8e
2024-03-22 22:04:37.23 | DEBUG | cashu.wallet.wallet:_load_mint_info:275 | Mint info: name='nutshell.fractalized.net' pubkey='02008469922e985cbc5368ce16adb6ed1aaea0f9ecb21639db4ded2e2ae014a326' version='Nutshell/0.15.1' description='Official Fractalized Mint' description_long='TRUST THE MINT' contact=[['email', 'pastagringo@fractalized.net'], ['twitter', '@pastagringo'], ['nostr', 'npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2']] motd='Thanks for using official ecash fractalized mint!' nuts={4: {'methods': [['bolt11', 'sat']], 'disabled': False}, 5: {'methods': [['bolt11', 'sat']], 'disabled': False}, 7: {'supported': True}, 8: {'supported': True}, 9: {'supported': True}, 10: {'supported': True}, 11: {'supported': True}, 12: {'supported': True}} Balance: 20 sat 2024-03-22 22:04:37.45 | DEBUG | cashu.wallet.wallet:get_pay_amount_with_fees:1529 | Mint wants 0 sat as fee reserve. 2024-03-22 22:04:37.45 | DEBUG | cashu.wallet.cli.cli:pay:189 | Quote: quote='YpNkb5f6WVT_5ivfQN1OnPDwdHwa_VhfbeKKbBAB' amount=15 fee_reserve=0 paid=False expiry=1711146847 Pay 15 sat? [Y/n]: y Paying Lightning invoice ...2024-03-22 22:04:41.13 | DEBUG | cashu.wallet.wallet:split:613 | Calling split. POST /v1/swap 2024-03-22 22:04:41.21 | DEBUG | cashu.wallet.wallet:verify_proofs_dleq:1103 | Verified incoming DLEQ proofs. Error paying invoice: Mint Error: Lightning payment unsuccessful. insufficient_balance (Code: 20000) ```
It didn't work, yes. That's the thing I told you earlier but it would work with a well configured and balanced Lightning Node.
That's all ! You should now be able to use ecash as you want! 🥜⚡
See you on NOSTR! 🤖⚡\ PastaGringo
-
 @ ee11a5df:b76c4e49
2024-03-22 23:49:09
@ ee11a5df:b76c4e49
2024-03-22 23:49:09Implementing The Gossip Model
version 2 (2024-03-23)
Introduction
History
The gossip model is a general concept that allows clients to dynamically follow the content of people, without specifying which relay. The clients have to figure out where each person puts their content.
Before NIP-65, the gossip client did this in multiple ways:
- Checking kind-3 contents, which had relay lists for configuring some clients (originally Astral and Damus), and recognizing that wherever they were writing our client could read from.
- NIP-05 specifying a list of relays in the
nostr.jsonfile. I added this to NIP-35 which got merged down into NIP-05. - Recommended relay URLs that are found in 'p' tags
- Users manually making the association
- History of where events happen to have been found. Whenever an event came in, we associated the author with the relay.
Each of these associations were given a score (recommended relay urls are 3rd party info so they got a low score).
Later, NIP-65 made a new kind of relay list where someone could advertise to others which relays they use. The flag "write" is now called an OUTBOX, and the flag "read" is now called an INBOX.
The idea of inboxes came about during the development of NIP-65. They are a way to send an event to a person to make sure they get it... because putting it on your own OUTBOX doesn't guarantee they will read it -- they may not follow you.
The outbox model is the use of NIP-65. It is a subset of the gossip model which uses every other resource at it's disposal.
Rationale
The gossip model keeps nostr decentralized. If all the (major) clients were using it, people could spin up small relays for both INBOX and OUTBOX and still be fully connected, have their posts read, and get replies and DMs. This is not to say that many people should spin up small relays. But the task of being decentralized necessitates that people must be able to spin up their own relay in case everybody else is censoring them. We must make it possible. In reality, congregating around 30 or so popular relays as we do today is not a problem. Not until somebody becomes very unpopular with bitcoiners (it will probably be a shitcoiner), and then that person is going to need to leave those popular relays and that person shouldn't lose their followers or connectivity in any way when they do.
A lot more rationale has been discussed elsewhere and right now I want to move on to implementation advice.
Implementation Advice
Read NIP-65
NIP-65 will contain great advice on which relays to consult for which purposes. This post does not supersede NIP-65. NIP-65 may be getting some smallish changes, mostly the addition of a private inbox for DMs, but also changes to whether you should read or write to just some or all of a set of relays.
How often to fetch kind-10002 relay lists for someone
This is up to you. Refreshing them every hour seems reasonable to me. Keeping track of when you last checked so you can check again every hour is a good idea.
Where to fetch events from
If your user follows another user (call them jack), then you should fetch jack's events from jack's OUTBOX relays. I think it's a good idea to use 2 of those relays. If one of those choices fails (errors), then keep trying until you get 2 of them that worked. This gives some redundancy in case one of them is censoring. You can bump that number up to 3 or 4, but more than that is probably just wasting bandwidth.
To find events tagging your user, look in your user's INBOX relays for those. In this case, look into all of them because some clients will only write to some of them (even though that is no longer advised).
Picking relays dynamically
Since your user follows many other users, it is very useful to find a small subset of all of their OUTBOX relays that cover everybody followed. I wrote some code to do this as (it is used by gossip) that you can look at for an example.
Where to post events to
Post all events (except DMs) to all of your users OUTBOX relays. Also post the events to all the INBOX relays of anybody that was tagged or mentioned in the contents in a nostr bech32 link (if desired). That way all these mentioned people are aware of the reply (or quote or repost).
DMs should be posted only to INBOX relays (in the future, to PRIVATE INBOX relays). You should post it to your own INBOX relays also, because you'll want a record of the conversation. In this way, you can see all your DMs inbound and outbound at your INBOX relay.
Where to publish your user's kind-10002 event to
This event was designed to be small and not require moderation, plus it is replaceable so there is only one per user. For this reason, at the moment, just spread it around to lots of relays especially the most popular relays.
For example, the gossip client automatically determines which relays to publish to based on whether they seem to be working (several hundred) and does so in batches of 10.
How to find replies
If all clients used the gossip model, you could find all the replies to any post in the author's INBOX relays for any event with an 'e' tag tagging the event you want replies to... because gossip model clients will publish them there.
But given the non-gossip-model clients, you should also look where the event was seen and look on those relays too.
Clobbering issues
Please read your users kind 10002 event before clobbering it. You should look many places to make sure you didn't miss the newest one.
If the old relay list had tags you don't understand (e.g. neither "read" nor "write"), then preserve them.
How users should pick relays
Today, nostr relays are not uniform. They have all kinds of different rule-sets and purposes. We severely lack a way to advice non-technical users as to which relays make good OUTBOX relays and which ones make good INBOX relays. But you are a dev, you can figure that out pretty well. For example, INBOX relays must accept notes from anyone meaning they can't be paid-subscription relays.
Bandwidth isn't a big issue
The outbox model doesn't require excessive bandwidth when done right. You shouldn't be downloading the same note many times... only 2-4 times depending on the level of redundancy your user wants.
Downloading 1000 events from 100 relays is in theory the same amount of data as downloading 1000 events from 1 relay.
But in practice, due to redundancy concerns, you will end up downloading 2000-3000 events from those 100 relays instead of just the 1000 you would in a single relay situation. Remember, per person followed, you will only ask for their events from 2-4 relays, not from all 100 relays!!!
Also in practice, the cost of opening and maintaining 100 network connections is more than the cost of opening and maintaining just 1. But this isn't usually a big deal unless...
Crypto overhead on Low-Power Clients
Verifying Schnorr signatures in the secp256k1 cryptosystem is not cheap. Setting up SSL key exchange is not cheap either. But most clients will do a lot more event signature validations than they will SSL setups.
For this reason, connecting to 50-100 relays is NOT hugely expensive for clients that are already verifying event signatures, as the number of events far surpasses the number of relay connections.
But for low-power clients that can't do event signature verification, there is a case for them not doing a lot of SSL setups either. Those clients would benefit from a different architecture, where half of the client was on a more powerful machine acting as a proxy for the low-power half of the client. These halves need to trust each other, so perhaps this isn't a good architecture for a business relationship, but I don't know what else to say about the low-power client situation.
Unsafe relays
Some people complain that the outbox model directs their client to relays that their user has not approved. I don't think it is a big deal, as such users can use VPNs or Tor if they need privacy. But for such users that still have concerns, they may wish to use clients that give them control over this. As a client developer you can choose whether to offer this feature or not.
The gossip client allows users to require whitelisting for connecting to new relays and for AUTHing to relays.
See Also
-
 @ 42342239:1d80db24
2024-03-21 09:49:01
@ 42342239:1d80db24
2024-03-21 09:49:01It has become increasingly evident that our financial system has started undermine our constitutionally guaranteed freedoms and rights. Payment giants like PayPal, Mastercard, and Visa sometimes block the ability to donate money. Individuals, companies, and associations lose bank accounts — or struggle to open new ones. In bank offices, people nowadays risk undergoing something resembling being cross-examined. The regulations are becoming so cumbersome that their mere presence risks tarnishing the banks' reputation.
The rules are so complex that even within the same bank, different compliance officers can provide different answers to the same question! There are even departments where some of the compliance officers are reluctant to provide written responses and prefer to answer questions over an unrecorded phone call. Last year's corporate lawyer in Sweden recently complained about troublesome bureaucracy, and that's from a the perspective of a very large corporation. We may not even fathom how smaller businesses — the keys to a nation's prosperity — experience it.
Where do all these rules come?
Where do all these rules come from, and how well do they work? Today's regulations on money laundering (AML) and customer due diligence (KYC - know your customer) primarily originate from a G7 meeting in the summer of 1989. (The G7 comprises the seven advanced economies: the USA, Canada, the UK, Germany, France, Italy, and Japan, along with the EU.) During that meeting, the intergovernmental organization FATF (Financial Action Task Force) was established with the aim of combating organized crime, especially drug trafficking. Since then, its mandate has expanded to include fighting money laundering, terrorist financing, and the financing of the proliferation of weapons of mass destruction(!). One might envisage the rules soon being aimed against proliferation of GPUs (Graphics Processing Units used for AI/ML). FATF, dominated by the USA, provides frameworks and recommendations for countries to follow. Despite its influence, the organization often goes unnoticed. Had you heard of it?
FATF offered countries "a deal they couldn't refuse"
On the advice of the USA and G7 countries, the organization decided to begin grading countries in "blacklists" and "grey lists" in 2000, naming countries that did not comply with its recommendations. The purpose was to apply "pressure" to these countries if they wanted to "retain their position in the global economy." The countries were offered a deal they couldn't refuse, and the number of member countries rapidly increased. Threatening with financial sanctions in this manner has even been referred to as "extraterritorial bullying." Some at the time even argued that the process violated international law.
If your local Financial Supervisory Authority (FSA) were to fail in enforcing compliance with FATF's many checklists among financial institutions, the risk of your country and its banks being barred from the US-dominated financial markets would loom large. This could have disastrous consequences.
A cost-benefit analysis of AML and KYC regulations
Economists use cost-benefit analysis to determine whether an action or a policy is successful. Let's see what such an analysis reveals.
What are the benefits (or revenues) after almost 35 years of more and more rules and regulations? The United Nations Office on Drugs and Crime estimated that only 0.2% of criminal proceeds are confiscated. Other estimates suggest a success rate from such anti-money laundering rules of 0.07% — a rounding error for organized crime. Europol expects to recover 1.2 billion euros annually, equivalent to about 1% of the revenue generated in the European drug market (110 billion euros). However, the percentage may be considerably lower, as the size of the drug market is likely underestimated. Moreover, there are many more "criminal industries" than just the drug trade; human trafficking is one example - there are many more. In other words, criminal organizations retain at least 99%, perhaps even 99.93%, of their profits, despite all cumbersome rules regarding money laundering and customer due diligence.
What constitutes the total cost of this bureaurcratic activity, costs that eventually burden taxpayers and households via higher fees? Within Europe, private financial firms are estimated to spend approximately 144 billion euros on compliance. According to some estimates, the global cost is twice as high, perhaps even eight times as much.
For Europe, the cost may thus be about 120 times (144/1.2) higher than the revenues from these measures. These "compliance costs" bizarrely exceed the total profits from the drug market, as one researcher put it. Even though the calculations are uncertain, it is challenging — perhaps impossible — to legitimize these regulations from a cost-benefit perspective.
But it doesn't end there, unfortunately. The cost of maintaining this compliance circus, with around 80 international organizations, thousands of authorities, far more employees, and all this across hundreds of countries, remains a mystery. But it's unlikely to be cheap.
The purpose of a system is what it does
In Economic Possibilities for our Grandchildren (1930), John Maynard Keynes foresaw that thanks to technological development, we could have had a 15-hour workweek by now. This has clearly not happened. Perhaps jobs have been created that are entirely meaningless? Anthropologist David Graeber argued precisely this in Bullshit Jobs in 2018. In that case, a significant number of people spend their entire working lives performing tasks they suspect deep down don't need to be done.
"The purpose of a system is what it does" is a heuristic coined by Stafford Beer. He observed there is "no point in claiming that the purpose of a system is to do what it constantly fails to do. What the current regulatory regime fails to do is combat criminal organizations. Nor does it seem to prevent banks from laundering money as never before, or from providing banking services to sex-offending traffickers
What the current regulatory regime does do, is: i) create armies of meaningless jobs, ii) thereby undermining mental health as well as economic prosperity, while iii) undermining our freedom and rights.
What does this say about the purpose of the system?
-
 @ ee11a5df:b76c4e49
2024-03-21 00:28:47
@ ee11a5df:b76c4e49
2024-03-21 00:28:47I'm glad to see more activity and discussion about the gossip model. Glad to see fiatjaf and Jack posting about it, as well as many developers pitching in in the replies. There are difficult problems we need to overcome, and finding notes while remaining decentralized without huge note copying overhead was just the first. While the gossip model (including the outbox model which is just the NIP-65 part) completely eliminates the need to copy notes around to lots of relays, and keeps us decentralized, it brings about it's own set of new problems. No community is ever of the same mind on any issue, and this issue is no different. We have a lot of divergent opinions. This note will be my updated thoughts on these topics.
COPYING TO CENTRAL RELAYS IS A NON-STARTER: The idea that you can configure your client to use a few popular "centralized" relays and everybody will copy notes into those central relays is a non-starter. It destroys the entire raison d'être of nostr. I've heard people say that more decentralization isn't our biggest issue. But decentralization is THE reason nostr exists at all, so we need to make sure we live up to the hype. Otherwise we may as well just all join Bluesky. It has other problems too: the central relays get overloaded, and the notes get copied to too many relays, which is both space-inefficient and network bandwith inefficient.
ISSUE 1: Which notes should I fetch from which relays? This is described pretty well now in NIP-65. But that is only the "outbox" model part. The "gossip model" part is to also work out what relays work for people who don't publish a relay list.
ISSUE 2: Automatic failover. Apparently Peter Todd's definition of decentralized includes a concept of automatic failover, where new resources are brought up and users don't need to do anything. Besides this not being part of any definition of decentralized I have never heard of, we kind of have this. If a user has 5 outboxes, and 3 fail, everything still works. Redundancy is built in. No user intervention needed in most cases, at least in the short term. But we also don't have any notion of administrators who can fix this behind the scenes for the users. Users are sovereign and that means they have total control, but also take on some responsibility. This is obvious when it comes to keypair management, but it goes further. Users have to manage where they post and where they accept incoming notes, and when those relays fail to serve them they have to change providers. Putting the users in charge, and not having administrators, is kinda necessary to be truly decentralized.
ISSUE 3: Connecting to unvetted relays feels unsafe. It might even be the NSA tracking you! First off, this happens with your web browser all the time: you go visit a web page and it instructs your browser to fetch a font from google. If you don't like it, you can use uBlock origin and manage it manually. In the nostr world, if you don't like it, you can use a client that puts you more in control of this. The gossip client for example has options for whether you want to manually approve relay connections and AUTHs, just once or always, and always lets you change your mind later. If you turn those options on, initially it is a giant wall of approval requests... but that situation resolves rather quickly. I've been running with these options on for a long time now, and only about once a week do I have to make a decision for a new relay.
But these features aren't really necessary for the vast majority of users who don't care if a relay knows their IP address. Those users use VPNs or Tor when they want to be anonymous, and don't bother when they don't care (me included).
ISSUE 4: Mobile phone clients may find the gossip model too costly in terms of battery life. Bandwidth is actually not a problem: under the gossip model (if done correctly) events for user P are only downloaded from N relays (default for gossip client is N=2), which in general is FEWER events retrieved than other models which download the same event maybe 8 or more times. Rather, the problem here is the large number of network connections and in particular, the large number of SSL setups and teardowns. If it weren't for SSL, this wouldn't be much of a problem. But setting up and tearing down SSL on 50 simultaneous connections that drop and pop up somewhat frequently is a battery drain.
The solution to this that makes the most sense to me is to have a client proxy. What I mean by that is a piece of software on a server in a data centre. The client proxy would be a headless nostr client that uses the gossip model and acts on behalf of the phone client. The phone client doesn't even have to be a nostr client, but it might as well be a nostr client that just connects to this fixed proxy to read and write all of its events. Now the SSL connection issue is solved. These proxies can serve many clients and have local storage, whereas the phones might not even need local storage. Since very few users will set up such things for themselves, this is a business opportunity for people, and a better business opportunity IMHO than running a paid-for relay. This doesn't decentralize nostr as there can be many of these proxies. It does however require a trust relationship between the phone client and the proxy.
ISSUE 5: Personal relays still need moderation. I wrongly thought for a very long time that personal relays could act as personal OUTBOXes and personal INBOXes without needing moderation. Recently it became clear to me that clients should probably read from other people's INBOXes to find replies to events written by the user of that INBOX (which outbox model clients should be putting into that INBOX). If that is happening, then personal relays will need to serve to the public events that were just put there by the public, thus exposing them to abuse. I'm greatly disappointed to come to this realization and not quite settled about it yet, but I thought I had better make this known.
-
 @ b12b632c:d9e1ff79
2024-02-19 19:18:46
@ b12b632c:d9e1ff79
2024-02-19 19:18:46Nostr decentralized network is growing exponentially day by day and new stuff comes out everyday. We can now use a NIP46 server to proxify our nsec key to avoid to use it to log on Nostr websites and possibly leak it, by mistake or by malicious persons. That's the point of this tutorial, setup a NIP46 server Nsec.app with its own Nostr relay. You'll be able to use it for you and let people use it, every data is stored locally in your internet browser. It's an non-custodial application, like wallets !
It's nearly a perfect solution (because nothing is perfect as we know) and that makes the daily use of Nostr keys much more secure and you'll see, much more sexy ! Look:
Nsec.app is not the only NIP46 server, in fact, @PABLOF7z was the first to create a NIP46 server called nsecBunker. You can also self-hosted nsecBunkerd, you can find a detailed explanation here : nsecbunkerd. I may write a how to self-host nsecBunkderd soon.
If you want more information about its bunker and what's behind this tutorial, you can check these links :
Few stuffs before beginning
Spoiler : I didn't automatized everything. The goal here is not to give you a full 1 click installation process, it's more to let you see and understand all the little things to configure and understand how works Nsec.app and the NIP46. There is a little bit of work, yes, but you'll be happy when it will work! Believe me.
Before entering into the battlefield, you must have few things : A working VPS with direct access to internet or a computer at home but NAT will certain make your life a hell. Use a VPS instead, on DigitalOcean, Linode, Scaleway, as you wish. A web domain that your own because we need to use at least 3 DNS A records (you can choose the subdomain you like) : domain.tld, noauth.domain.tld, noauth.domain.tld. You need to have some programs already installed : git, docker, docker-compose, nano/vi. if you fill in all the boxes, we can move forward !
Let's install everything !
I build a repo with a docker-compose file with all the required stuff to make the Bunker works :
Nsec.app front-end : noauth Nsec.app back-end : noauthd Nostr relay : strfry Nostr NIP05 : easy-nip5
First thing to do is to clone the repo "nsec-app-docker" from my repo:
$ git clone git clone https://github.com/PastaGringo/nsec-app-docker.git $ cd nsec-app-dockerWhen it's done, you'll have to do several things to make it work. 1) You need to generate some keys for the web-push library (keep them for later) :
``` $ docker run pastagringo/web-push-generate-keys
Generating your web-push keys...
Your private key : rQeqFIYKkInRqBSR3c5iTE3IqBRsfvbq_R4hbFHvywE Your public key : BFW4TA-lUvCq_az5fuQQAjCi-276wyeGUSnUx4UbGaPPJwEemUqp3Rr3oTnxbf0d4IYJi5mxUJOY4KR3ZTi3hVc ```
2) Generate a new keys pair (nsec/npub) for the NIP46 server by clicking on "Generate new key" from NostrTool website: nostrtool.com.
You should have something like this :
console Nostr private key (nsec): keep this -> nsec1zcyanx8zptarrmfmefr627zccrug3q2vhpfnzucq78357hshs72qecvxk6 Nostr private key (hex): 1609d998e20afa31ed3bca47a57858c0f888814cb853317300f1e34f5e178794 Nostr public key (npub): npub1ywzwtnzeh64l560a9j9q5h64pf4wvencv2nn0x4h0zw2x76g8vrq68cmyz Nostr public key (hex): keep this -> 2384e5cc59beabfa69fd2c8a0a5f550a6ae6667862a7379ab7789ca37b483b06You need to keep Nostr private key (nsec) & Nostr public key (npub). 3) Open (nano/vi) the .env file located in the current folder and fill all the required info :
```console
traefik
EMAIL=pastagringo@fractalized.net <-- replace with your own domain NSEC_ROOT_DOMAIN=plebes.ovh <-- replace with your own domain <-- replace with your own relay domain RELAY_DOMAIN=relay.plebes.ovh <-- replace with your own noauth domainay.plebes.ovh <-- replace with your own relay domain <-- replace with your own noauth domain NOAUTH_DOMAIN=noauth.plebes.ovh <-- replace with your own noauth domain NOAUTHD_DOMAIN=noauthd.plebes.ovh <-- replace with your own noauth domain
noauth
APP_WEB_PUSH_PUBKEY=BGVa7TMQus_KVn7tAwPkpwnU_bpr1i6B7D_3TT-AwkPlPd5fNcZsoCkJkJylVOn7kZ-9JZLpyOmt7U9rAtC-zeg <-- replace with your own web push public key APP_NOAUTHD_URL=https://$NOAUTHD_DOMAIN APP_DOMAIN=$NSEC_ROOT_DOMAIN APP_RELAY=wss://$RELAY_DOMAIN
noauthd
PUSH_PUBKEY=$APP_WEB_PUSH_PUBKEY PUSH_SECRET=_Sz8wgp56KERD5R4Zj5rX_owrWQGyHDyY4Pbf5vnFU0 <-- replace with your own web push private key ORIGIN=https://$NOAUTHD_DOMAIN DATABASE_URL=file:./prod.db BUNKER_NSEC=nsec1f43635rzv6lsazzsl3hfsrum9u8chn3pyjez5qx0ypxl28lcar2suy6hgn <-- replace with your the bunker nsec key BUNKER_RELAY=wss://$RELAY_DOMAIN BUNKER_DOMAIN=$NSEC_ROOT_DOMAIN BUNKER_ORIGIN=https://$NOAUTH_DOMAIN ```
Be aware of noauth and noauthd (the d letter). Next, save and quit. 4) You now need to modify the nostr.json file used for the NIP05 to indicate which relay your bunker will use. You need to set the bunker HEX PUBLIC KEY (I replaced the info with the one I get from NostrTool before) :
console nano easy-nip5/nostr.jsonconsole { "names": { "_": "ServerHexPubKey" }, "nip46": { "ServerHexPubKey": [ "wss://ReplaceWithYourRelayDomain" ] } }5) You can now run the docker compose file by running the command (first run can take a bit of time because the noauth container needs to build the npm project):
console $ docker compose up -d6) Before creating our first user into the Nostr Bunker, we need to test if all the required services are up. You should have :
noauth :
noauthd :
console CANNOT GET /https://noauthd.yourdomain.tld/name :
console { "error": "Specify npub" }https://yourdomain.tld/.well-known/nostr.json :
console { "names": { "_": "ServerHexPubKey" }, "nip46": { "ServerHexPubKey": [ "wss://ReplaceWithYourRelayDomain" ] } }If you have everything working, we can try to create a new user!
7) Connect to noauth and click on "Get Started" :
At the bottom the screen, click on "Sign up" :
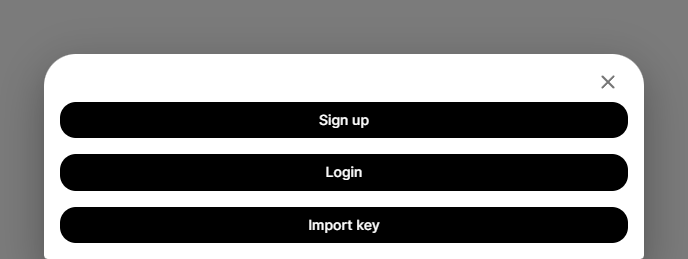
Fill a username and click on "Create account" :
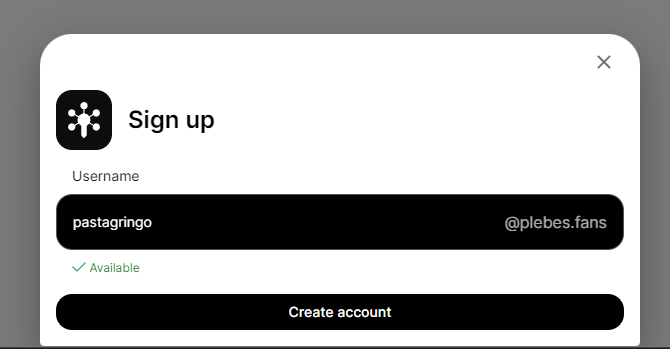
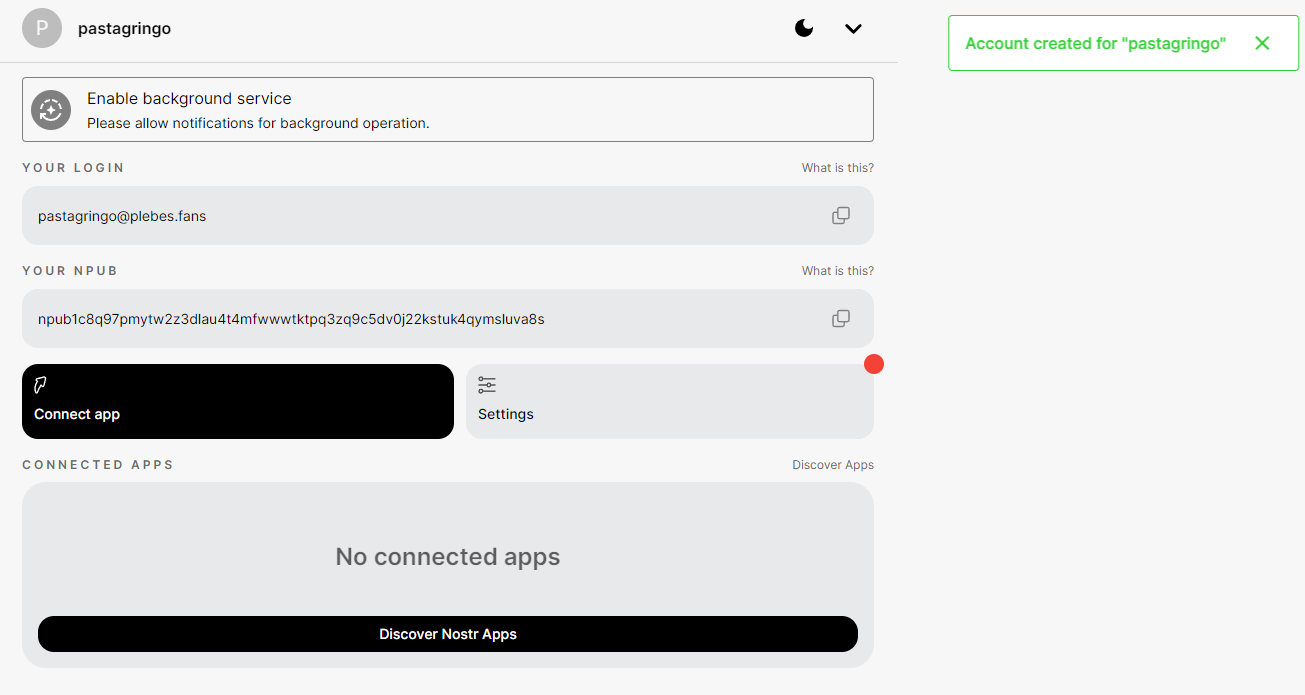
If everything has been correctly configured, you should see a pop message with "Account created for "XXXX" :
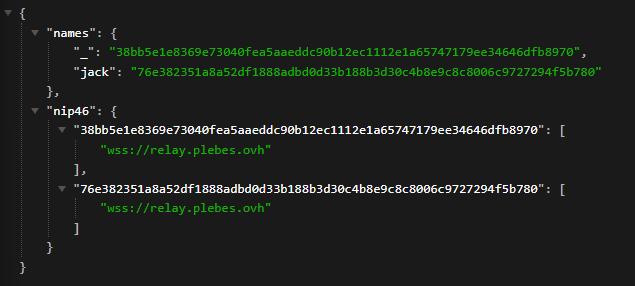
PS : to know if noauthd is well serving the nostr.json file, you can check this URL : https://yourdomain.tld/.well-known/nostr.json?name=YourUser You should see that the user has now NIP05/NIP46 entries :
If the user creation failed, you'll see a red pop-up saying "Something went wrong!" :
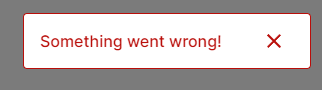
To understand what happened, you need to inspect the web page to find the error :
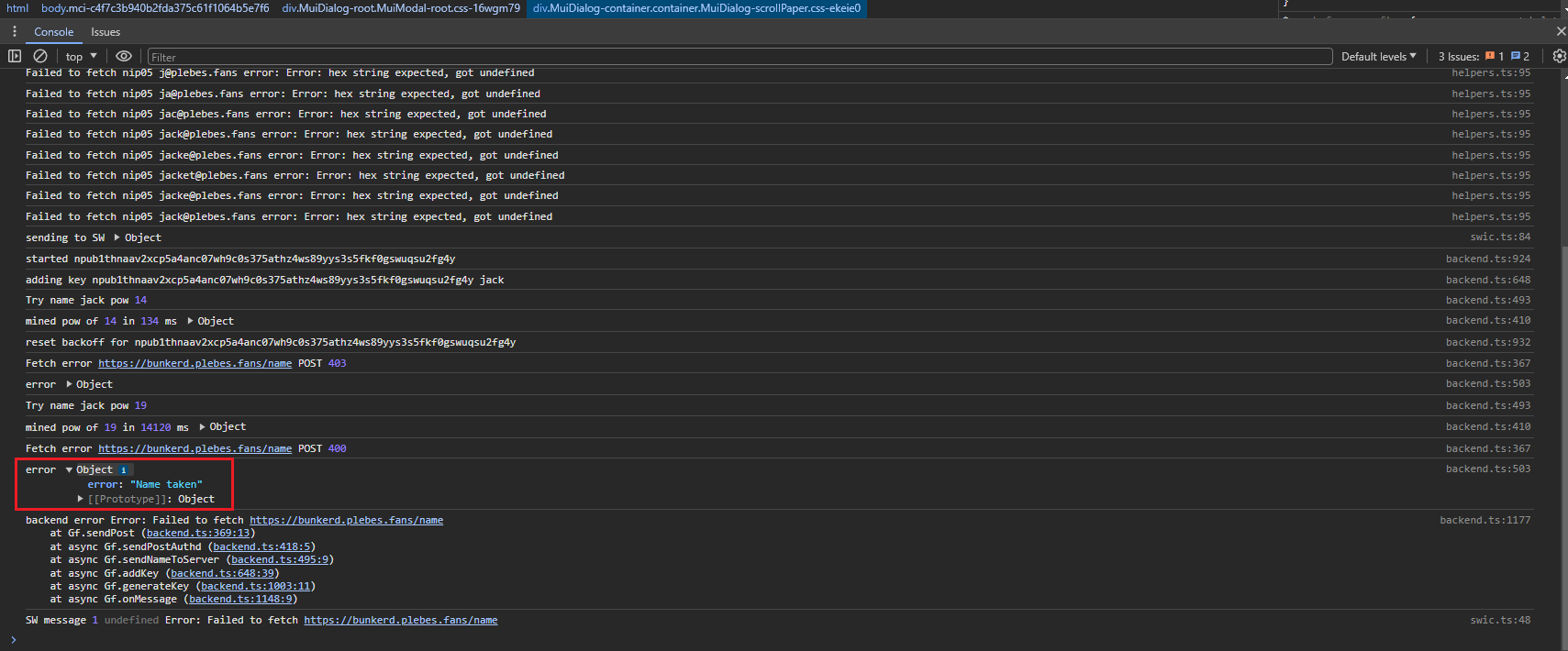
For the example, I tried to recreate a user "jack" which has already been created. You may find a lot of different errors depending of the configuration you made. You can find that the relay is not reachable on w s s : / /, you can find that the noauthd is not accessible too, etc. Every answers should be in this place.
To completely finish the tests, you need to enable the browser notifications, otherwise you won't see the pop-up when you'll logon on Nostr web client, by clicking on "Enable background service" :
You need to click on allow notifications :
Should see this green confirmation popup on top right of your screen:
Well... Everything works now !
8) You try to use your brand new proxyfied npub by clicking on "Connect App" and buy copying your bunker URL :
You can now to for instance on Nostrudel Nostr web client to login with it. Select the relays you want (Popular is better ; if you don't have multiple relay configured on your Nostr profile, avoid "Login to use your relay") :
Click on "Sign in" :
Click on "Show Advanced" :
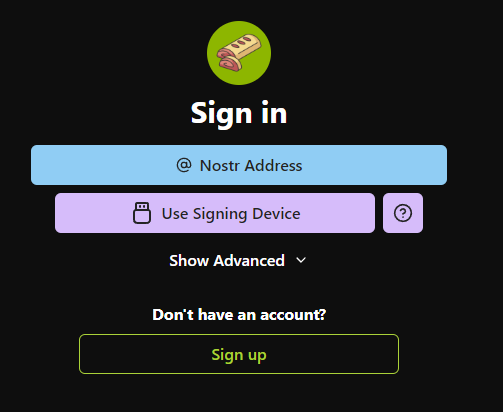
Click on "Nostr connect / Bunker" :
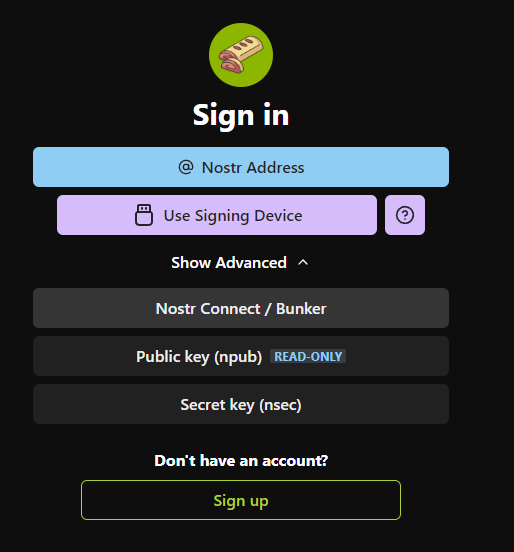
Paste your bunker URL and click on "Connect" :
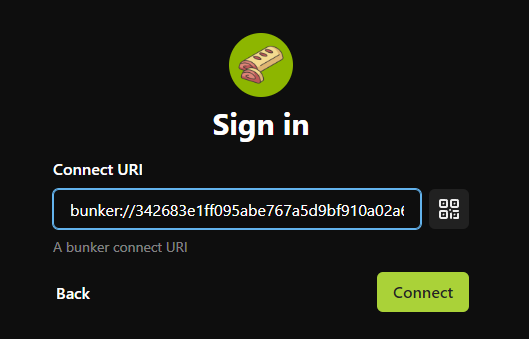
The first time, tour browser (Chrome here) may blocks the popup, you need to allow it :
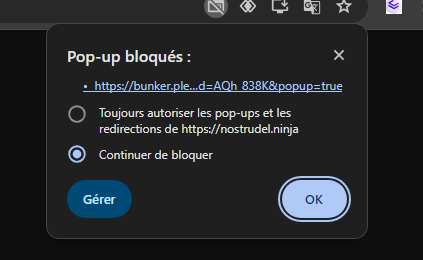
If the browser blocked the popup, NoStrudel will wait your confirmation to login :
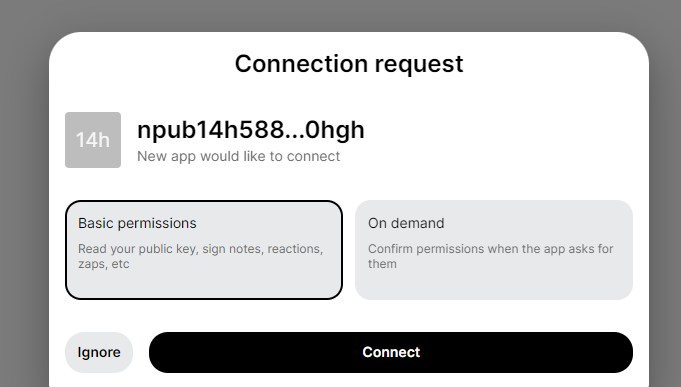
You have to go back on your bunker URL to allow the NoStrudel connection request by clicking on on "Connect":
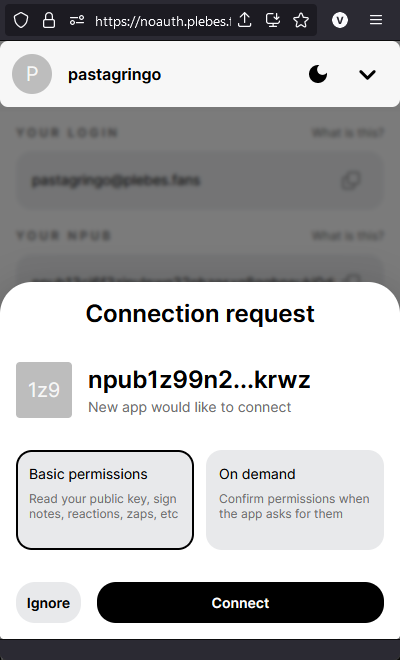
The first time connections may be a bit annoying with all the popup authorizations but once it's done, you can forget them it will connect without any issue. Congrats ! You are connected on NoStrudel with an npub proxyfied key !⚡

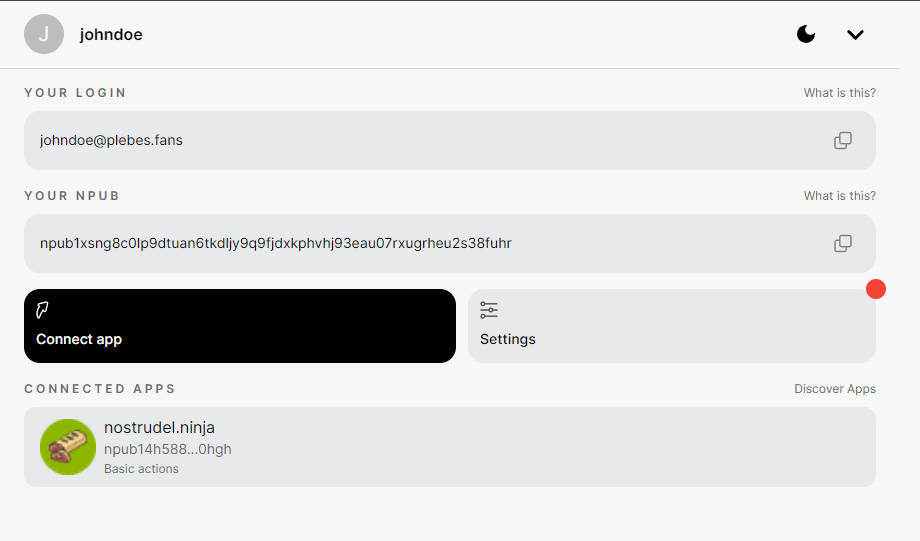
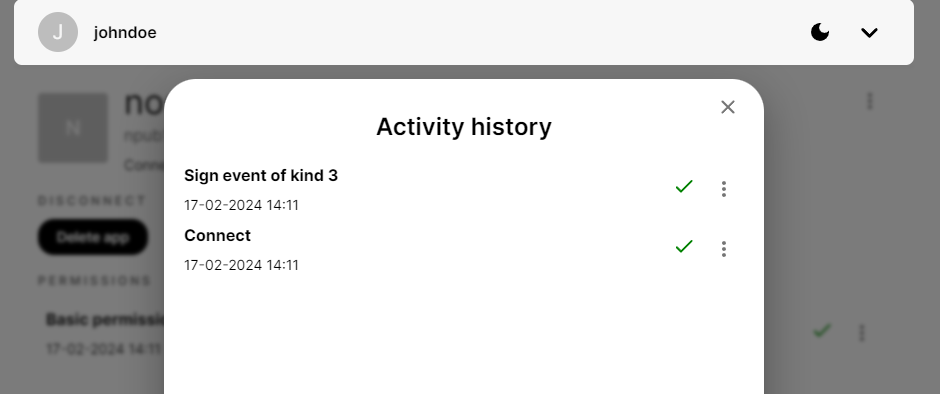
You can check to which applications you gave permissions and activity history in noauth by selecting your user. :
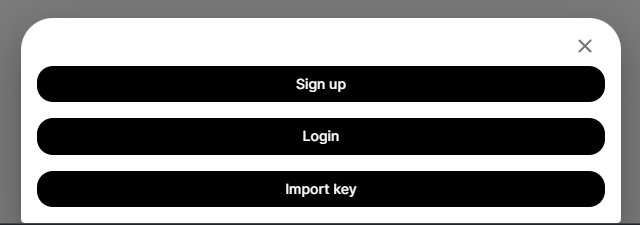
If you want to import your real Nostr profile, the one that everyone knows, you can import your nsec key by adding a new account and select "Import key" and adding your precious nsec key (reminder: your nsec key stays in your browser! The noauth provider won't have access to it!) :
You can see can that my profile picture has been retrieved and updated into noauth :
I can now use this new pubkey attached my nsec.app server to login in NoStrudel again :
Accounts/keys management in noauthd You can list created keys in your bunkerd by doing these command (CTRL+C to exit) :
console $ docker exec -it noauthd node src/index.js list_names [ '/usr/local/bin/node', '/noauthd/src/index.js', 'list_names' ] 1 jack npub1hjdw2y0t44q4znzal2nxy7vwmpv3qwrreu48uy5afqhxkw6d2nhsxt7x6u 1708173927920n 2 peter npub1yp752u5tr5v5u74kadrzgfjz2lsmyz8dyaxkdp4e0ptmaul4cyxsvpzzjz 1708174748972n 3 john npub1xw45yuvh5c73sc5fmmc3vf2zvmtrzdmz4g2u3p2j8zcgc0ktr8msdz6evs 1708174778968n 4 johndoe npub1xsng8c0lp9dtuan6tkdljy9q9fjdxkphvhj93eau07rxugrheu2s38fuhr 1708174831905nIf you want to delete someone key, you have to do :
```console $ docker exec -it noauthd node src/index.js delete_name johndoe [ '/usr/local/bin/node', '/noauthd/src/index.js', 'delete_name', 'johndoe' ] deleted johndoe { id: 4, name: 'johndoe', npub: 'npub1xsng8c0lp9dtuan6tkdljy9q9fjdxkphvhj93eau07rxugrheu2s38fuhr', timestamp: 1708174831905n
$ docker exec -it noauthd node src/index.js list_names [ '/usr/local/bin/node', '/noauthd/src/index.js', 'list_names' ] 1 jack npub1hjdw2y0t44q4znzal2nxy7vwmpv3qwrreu48uy5afqhxkw6d2nhsxt7x6u 1708173927920n 2 peter npub1yp752u5tr5v5u74kadrzgfjz2lsmyz8dyaxkdp4e0ptmaul4cyxsvpzzjz 1708174748972n 3 john npub1xw45yuvh5c73sc5fmmc3vf2zvmtrzdmz4g2u3p2j8zcgc0ktr8msdz6evs 1708174778968n ```
It could be pretty easy to create a script to handle the management of keys but I think @Brugeman may create a web interface for that. Noauth is still very young, changes are committed everyday to fix/enhance the application! As """everything""" is stored locally on your browser, you have to clear the cache of you bunker noauth URL to clean everything. This Chome extension is very useful for that. Check these settings in the extension option :
You can now enjoy even more Nostr ⚡ See you soon in another Fractalized story!
-
 @ ee11a5df:b76c4e49
2023-11-09 05:20:37
@ ee11a5df:b76c4e49
2023-11-09 05:20:37A lot of terms have been bandied about regarding relay models: Gossip relay model, outbox relay model, and inbox relay model. But this term "relay model" bothers me. It sounds stuffy and formal and doesn't actually describe what we are talking about very well. Also, people have suggested maybe there are other relay models. So I thought maybe we should rethink this all from first principles. That is what this blog post attempts to do.
Nostr is notes and other stuff transmitted by relays. A client puts an event onto a relay, and subsequently another client reads that event. OK, strictly speaking it could be the same client. Strictly speaking it could even be that no other client reads the event, that the event was intended for the relay (think about nostr connect). But in general, the reason we put events on relays is for other clients to read them.
Given that fact, I see two ways this can occur:
1) The reader reads the event from the same relay that the writer wrote the event to (this I will call relay rendezvous), 2) The event was copied between relays by something.
This second solution is perfectly viable, but it less scalable and less immediate as it requires copies which means that resources will be consumed more rapidly than if we can come up with workable relay rendezvous solutions. That doesn't mean there aren't other considerations which could weigh heavily in favor of copying events. But I am not aware of them, so I will be discussing relay rendezvous.
We can then divide the relay rendezvous situation into several cases: one-to-one, one-to-many, and one-to-all, where the many are a known set, and the all are an unbounded unknown set. I cannot conceive of many-to-anything for nostr so we will speak no further of it.
For a rendezvous to take place, not only do the parties need to agree on a relay (or many relays), but there needs to be some way that readers can become aware that the writer has written something.
So the one-to-one situation works out well by the writer putting the message onto a relay that they know the reader checks for messages on. This we call the INBOX model. It is akin to sending them an email into their inbox where the reader checks for messages addressed to them.
The one-to-(known)-many model is very similar, except the writer has to write to many people's inboxes. Still we are dealing with the INBOX model.
The final case, one-to-(unknown)-all, there is no way the writer can place the message into every person's inbox because they are unknown. So in this case, the writer can write to their own OUTBOX, and anybody interested in these kinds of messages can subscribe to the writer's OUTBOX.
Notice that I have covered every case already, and that I have not even specified what particular types of scenarios call for one-to-one or one-to-many or one-to-all, but that every scenario must fit into one of those models.
So that is basically it. People need INBOX and OUTBOX relays and nothing else for relay rendezvous to cover all the possible scenarios.
That is not to say that other kinds of concerns might not modulate this. There is a suggestion for a DM relay (which is really an INBOX but with a special associated understanding), which is perfectly fine by me. But I don't think there are any other relay models. There is also the case of a live event where two parties are interacting over the same relay, but in terms of rendezvous this isn't a new case, it is just that the shared relay is serving as both parties' INBOX (in the case of a closed chat) and/or both parties' OUTBOX (in the case of an open one) at the same time.
So anyhow that's my thinking on the topic. It has become a fairly concise and complete set of concepts, and this makes me happy. Most things aren't this easy.
-
 @ b12b632c:d9e1ff79
2023-08-08 00:02:31
@ b12b632c:d9e1ff79
2023-08-08 00:02:31"Welcome to the Bitcoin Lightning Bolt Card, the world's first Bitcoin debit card. This revolutionary card allows you to easily and securely spend your Bitcoin at lightning compatible merchants around the world." Bolt Card
I discovered few days ago the Bolt Card and I need to say that's pretty amazing. Thinking that we can pay daily with Bitcoin Sats in the same way that we pay with our Visa/Mastecard debit cards is really something huge⚡(based on the fact that sellers are accepting Bitcoins obviously!)
To use Bolt Card you have three choices :
- Use their (Bolt Card) own Bolt Card HUB and their own BTC Lightning node
- Use your own self hosted Bolt Card Hub and an external BTC Lightning node
- Use your own self hosted Bolt Card Hub and your BTC Lightning node (where you shoud have active Lightning channels)
⚡ The first choice is the quickiest and simpliest way to have an NFC Bolt Card. It will take you few seconds (for real). You'll have to wait much longer to receive your NFC card from a website where you bought it than configure it with Bolt Card services.
⚡⚡ The second choice is pretty nice too because you won't have a VPS + to deal with all the BTC Lightnode stuff but you'll use an external one. From the Bolt Card tutorial about Bolt Card Hub, they use a Lightning from voltage.cloud and I have to say that their services are impressive. In few seconds you'll have your own Lightning node and you'll be able to configure it into the Bolt Card Hub settings. PS : voltage.cloud offers 7 trial days / 20$ so don't hesitate to try it!
⚡⚡⚡ The third one is obvisouly a bit (way) more complex because you'll have to provide a VPS + Bitcoin node and a Bitcoin Lightning Node to be able to send and receive Lightning payments with your Bolt NFC Card. So you shoud already have configured everything by yourself to follow this tutorial. I will show what I did for my own installation and all my nodes (BTC & Lightning) are provided by my home Umbrel node (as I don't want to publish my nodes directly on the clearnet). We'll see how to connect to the Umbrel Lighting node later (spoiler: Tailscale).
To resume in this tutorial, I have :
- 1 Umbrel node (rpi4b) with BTC and Lightning with Tailscale installed.
- 1 VPS (Virtual Personal Server) to publish publicly the Bolt Card LNDHub and Bolt Card containers configured the same way as my other containers (with Nginx Proxy Manager)
Ready? Let's do it ! ⚡
Configuring Bolt Card & Bolt Card LNDHub
Always good to begin by reading the bolt card-lndhub-docker github repo. To a better understading of all the components, you can check this schema :
We'll not use it as it is because we'll skip the Caddy part because we already use Nginx Proxy Manager.
To begin we'll clone all the requested folders :
git clone https://github.com/boltcard/boltcard-lndhub-docker bolthub cd bolthub git clone https://github.com/boltcard/boltcard-lndhub BoltCardHub git clone https://github.com/boltcard/boltcard.git git clone https://github.com/boltcard/boltcard-groundcontrol.git GroundControlPS : we won't see how to configure GroundControl yet. This article may be updated later.
We now need to modify the settings file with our own settings :
mv .env.example .env nano .envYou need to replace "your-lnd-node-rpc-address" by your Umbrel TAILSCALE ip address (you can find your Umbrel node IP from your Tailscale admin console):
``` LND_IP=your-lnd-node-rpc-address # <- UMBREL TAILSCALE IP ADDRESS LND_GRPC_PORT=10009 LND_CERT_FILE=tls.cert LND_ADMIN_MACAROON_FILE=admin.macaroon REDIS_PASSWORD=random-string LND_PASSWORD=your-lnd-node-unlock-password
docker-compose.yml only
GROUNDCONTROL=ground-control-url
docker-compose-groundcontrol.yml only
FCM_SERVER_KEY=hex-encoded APNS_P8=hex-encoded APNS_P8_KID=issuer-key-which-is-key-ID-of-your-p8-file APPLE_TEAM_ID=team-id-of-your-developer-account BITCOIN_RPC=bitcoin-rpc-url APNS_TOPIC=app-package-name ```
We now need to generate an AES key and insert it into the "settings.sql" file :
```
hexdump -vn 16 -e '4/4 "%08x" 1 "\n"' /dev/random 19efdc45acec06ad8ebf4d6fe50412d0 nano settings.sql ```
- Insert the AES between ' ' right from 'AES_DECRYPT_KEY'
- Insert your domain or subdomain (subdomain in my case) host between ' ' from 'HOST_DOMAIN'
- Insert your Umbrel tailscale IP between ' ' from 'LN_HOST'
Be aware that this subdomain won't be the LNDHub container (boltcard_hub:9002) but the Boltcard container (boltcard_main:9000)
``` \c card_db;
DELETE FROM settings;
-- at a minimum, the settings marked 'set this' must be set for your system -- an explanation for each of the bolt card server settings can be found here -- https://github.com/boltcard/boltcard/blob/main/docs/SETTINGS.md
INSERT INTO settings (name, value) VALUES ('LOG_LEVEL', 'DEBUG'); INSERT INTO settings (name, value) VALUES ('AES_DECRYPT_KEY', '19efdc45acec06ad8ebf4d6fe50412d0'); -- set this INSERT INTO settings (name, value) VALUES ('HOST_DOMAIN', 'sub.domain.tld'); -- set this INSERT INTO settings (name, value) VALUES ('MIN_WITHDRAW_SATS', '1'); INSERT INTO settings (name, value) VALUES ('MAX_WITHDRAW_SATS', '1000000'); INSERT INTO settings (name, value) VALUES ('LN_HOST', ''); -- set this INSERT INTO settings (name, value) VALUES ('LN_PORT', '10009'); INSERT INTO settings (name, value) VALUES ('LN_TLS_FILE', '/boltcard/tls.cert'); INSERT INTO settings (name, value) VALUES ('LN_MACAROON_FILE', '/boltcard/admin.macaroon'); INSERT INTO settings (name, value) VALUES ('FEE_LIMIT_SAT', '10'); INSERT INTO settings (name, value) VALUES ('FEE_LIMIT_PERCENT', '0.5'); INSERT INTO settings (name, value) VALUES ('LN_TESTNODE', ''); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNURLW', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNURLP', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('FUNCTION_EMAIL', 'DISABLE'); INSERT INTO settings (name, value) VALUES ('AWS_SES_ID', ''); INSERT INTO settings (name, value) VALUES ('AWS_SES_SECRET', ''); INSERT INTO settings (name, value) VALUES ('AWS_SES_EMAIL_FROM', ''); INSERT INTO settings (name, value) VALUES ('EMAIL_MAX_TXS', ''); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNDHUB', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('LNDHUB_URL', 'http://boltcard_hub:9002'); INSERT INTO settings (name, value) VALUES ('FUNCTION_INTERNAL_API', 'ENABLE'); ```
You now need to get two files used by Bolt Card LND Hub, the admin.macaroon and tls.cert files from your Umbrel BTC Ligtning node. You can get these files on your Umbrel node at these locations :
/home/umbrel/umbrel/app-data/lightning/data/lnd/tls.cert /home/umbrel/umbrel/app-data/lightning/data/lnd/data/chain/bitcoin/mainnet/admin.macaroonYou can use either WinSCP, scp or ssh to copy these files to your local workstation and copy them again to your VPS to the root folder "bolthub".
You shoud have all these files into the bolthub directory :
johndoe@yourvps:~/bolthub$ ls -al total 68 drwxrwxr-x 6 johndoe johndoe 4096 Jul 30 00:06 . drwxrwxr-x 3 johndoe johndoe 4096 Jul 22 00:52 .. -rw-rw-r-- 1 johndoe johndoe 482 Jul 29 23:48 .env drwxrwxr-x 8 johndoe johndoe 4096 Jul 22 00:52 .git -rw-rw-r-- 1 johndoe johndoe 66 Jul 22 00:52 .gitignore drwxrwxr-x 11 johndoe johndoe 4096 Jul 22 00:52 BoltCardHub -rw-rw-r-- 1 johndoe johndoe 113 Jul 22 00:52 Caddyfile -rw-rw-r-- 1 johndoe johndoe 173 Jul 22 00:52 CaddyfileGroundControl drwxrwxr-x 6 johndoe johndoe 4096 Jul 22 00:52 GroundControl -rw-rw-r-- 1 johndoe johndoe 431 Jul 22 00:52 GroundControlDockerfile -rw-rw-r-- 1 johndoe johndoe 1913 Jul 22 00:52 README.md -rw-rw-r-- 1 johndoe johndoe 293 May 6 22:24 admin.macaroon drwxrwxr-x 16 johndoe johndoe 4096 Jul 22 00:52 boltcard -rw-rw-r-- 1 johndoe johndoe 3866 Jul 22 00:52 docker-compose-groundcontrol.yml -rw-rw-r-- 1 johndoe johndoe 2985 Jul 22 00:57 docker-compose.yml -rw-rw-r-- 1 johndoe johndoe 1909 Jul 29 23:56 settings.sql -rw-rw-r-- 1 johndoe johndoe 802 May 6 22:21 tls.certWe need to do few last tasks to ensure that Bolt Card LNDHub will work perfectly.
It's maybe already the case on your VPS but your user should be member of the docker group. If not, you can add your user by doing :
sudo groupadd docker sudo usermod -aG docker ${USER}If you did these commands, you need to logout and login again.
We also need to create all the docker named volumes by doing :
docker volume create boltcard_hub_lnd docker volume create boltcard_redisConfiguring Nginx Proxy Manager to proxify Bolt Card LNDHub & Boltcard
You need to have followed my previous blog post to fit with the instructions above.
As we use have the Bolt Card LNDHub docker stack in another directory than we other services and it has its own docker-compose.yml file, we'll have to configure the docker network into the NPM (Nginx Proxy Manager) docker-compose.yml to allow NPM to communicate with the Bolt Card LNDHub & Boltcard containers.
To do this we need to add these lines into our NPM external docker-compose (not the same one that is located into the bolthub directory, the one used for all your other containers) :
nano docker-compose.ymlnetworks: bolthub_boltnet: name: bolthub_boltnet external: trueBe careful, "bolthub" from "bolthub_boltnet" is based on the directory where Bolt Card LNDHub Docker docker-compose.yml file is located.
We also need to attach this network to the NPM container :
nginxproxymanager: container_name: nginxproxymanager image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt networks: - fractalized - bolthub_boltnetYou can now recreate the NPM container to attach the network:
docker compose up -dNow, you'll have to create 2 new Proxy Hosts into NPM admin UI. First one for your domain / subdomain to the Bolt Card LNDHub GUI (boltcard_hub:9002) :
And the second one for the Boltcard container (boltcard_main:9000).
In both Proxy Host I set all the SSL options and I use my wildcard certificate but you can generate one certificate for each Proxy Host with Force SSL, HSTS enabled, HTTP/2 Suppot and HSTS Subdomains enabled.
Starting Bolt Card LNDHub & BoltCard containers
Well done! Everything is setup, we can now start the Bolt Card LNDHub & Boltcard containers !
You need to go again to the root folder of the Bolt Card LNDHub projet "bolthub" and start the docker compose stack. We'll begin wihtout a "-d" to see if we have some issues during the containers creation :
docker compose upI won't share my containers logs to avoid any senstive information disclosure about my Bolt Card LNDHub node, but you can see them from the Bolt Card LNDHub Youtube video (link with exact timestamp where it's shown) :
If you have some issues about files mounting of admin.macaroon or tls.cert because you started the docker compose stack the first time without the files located in the bolthub folder do :
docker compose down && docker compose upAfter waiting few seconds/minutes you should go to your Bolt Card LNDHub Web UI domain/sudomain (created earlier into NPM) and you should see the Bolt Card LNDHub Web UI :
if everything is OK, you now run the containers in detached mode :
docker compose up -dVoilààààà ⚡
If you need to all the Bolt Card LNDHub logs you can use :
docker compose logs -f --tail 30You can now follow the video from Bolt Card to configure your Bolt Card NFC card and using your own Bolt Card LNDHub :
~~PS : there is currently a bug when you'll click on "Connect Bolt Card" from the Bold Card Walle app, you might have this error message "API error: updateboltcard: enable_pin is not a valid boolean (code 6)". It's a know issue and the Bolt Card team is currently working on it. You can find more information on their Telegram~~
Thanks to the Bolt Card, the issue has been corrected : changelog
See you soon in another Fractalized story!
-
 @ ee11a5df:b76c4e49
2023-07-29 03:27:23
@ ee11a5df:b76c4e49
2023-07-29 03:27:23Gossip: The HTTP Fetcher
Gossip is a desktop nostr client. This post is about the code that fetches HTTP resources.
Gossip fetches HTTP resources. This includes images, videos, nip05 json files, etc. The part of gossip that does this is called the fetcher.
We have had a fetcher for some time, but it was poorly designed and had problems. For example, it was never expiring items in the cache.
We've made a lot of improvements to the fetcher recently. It's pretty good now, but there is still room for improvement.
Caching
Our fetcher caches data. Each URL that is fetched is hashed, and the content is stored under a file in the cache named by that hash.
If a request is in the cache, we don't do an HTTP request, we serve it directly from the cache.
But cached data gets stale. Sometimes resources at a URL change. We generally check resources again after three days.
We save the server's ETag value for content, and when we check the content again we supply an If-None-Match header with the ETag so the server could respond with 304 Not Modified in which case we don't need to download the resource again, we just bump the filetime to now.
In the event that our cache data is stale, but the server gives us an error, we serve up the stale data (stale is better than nothing).
Queueing
We used to fire off HTTP GET requests as soon as we knew that we needed a resource. This was not looked on too kindly by servers and CDNs who were giving us either 403 Forbidden or 429 Too Many Requests.
So we moved into a queue system. The host is extracted from each URL, and each host is only given up to 3 requests at a time. If we want 29 images from the same host, we only ask for three, and the remaining 26 remain in the queue for next time. When one of those requests completes, we decrement the host load so we know that we can send it another request later.
We process the queue in an infinite loop where we wait 1200 milliseconds between passes. Passes take time themselves and sometimes must wait for a timeout. Each pass fetches potentially multiple HTTP resources in parallel, asynchronously. If we have 300 resources at 100 different hosts, three per host, we could get them all in a single pass. More likely a bunch of resources are at the same host, and we make multiple passes at it.
Timeouts
When we fetch URLs in parallel asynchronously, we wait until all of the fetches complete before waiting another 1200 ms and doing another loop. Sometimes one of the fetches times out. In order to keep things moving, we use short timeouts of 10 seconds for a connect, and 15 seconds for a response.
Handling Errors
Some kinds of errors are more serious than others. When we encounter these, we sin bin the server for a period of time where we don't try fetching from it until a specified period elapses.
-
 @ c4428155:a36de510
2024-04-02 18:35:00
@ c4428155:a36de510
2024-04-02 18:35:00New York’s Guardianship System Is Broken. Will Lawmakers Pay for a Modest Fix?
by Jake Pearson (https://www.propublica.org/people/jake-pearson)
ProPublica is a nonprofit newsroom that investigates abuses of power. Sign up to receive our biggest stories (https://www.propublica.org/newsletters/the-big-story?source=54G&placement=top-note®ion=national) as soon as they’re published.
As New York lawmakers hammer out a more than $200 billion budget this week, they may include $5 million to improve the state’s troubled guardianship system, which oversees the physical and financial welfare of tens of thousands of New Yorkers who the courts have said cannot care for themselves.
The modest allotment, which was advanced by the state Senate, would continue to fund a statewide hotline (https://www.nysenate.gov/legislation/bills/2023/R1952) that launched last June and has advised hundreds of people considering guardianship for their relatives or friends. And it would give new support to nonprofits that provide services to poor adults who have nobody else to help them — known in the industry as “the unbefriended.”
“It’s not going to fix the whole problem, but it’s a step in the right direction,” said Kimberly George, a leader of Guardianship Access New York, which lobbied for the additional money.
The relatively small price tag doesn’t mean the Senate’s proposal will make the final cut in this week’s budget talks; the assembly and Gov. Kathy Hochul, a Democrat, have proposed even less in their spending plans: just $1 million to continue the guardianship hotline. Neither the governor’s office nor Speaker Carl Heastie responded to requests for comment on the gap. The three parties must now reach an agreement on the issue — and the overall budget — by Thursday.
The effort to secure more public funding for guardianship follows a series of stories by ProPublica last month highlighting how New York’s overtaxed and loosely regulated guardianship system is failing thousands (https://www.propublica.org/article/how-one-woman-endured-decade-neglect-new-york-guardianship) of vulnerable people. Part of the problem, the reporting showed, is a dearth of guardians for poor New Yorkers (https://www.propublica.org/series/the-unbefriended) — something the Senate proposal would help address. New York City, for instance, relies on private attorneys who work the cases for free, along with a small network of nonprofits. In recent years, two such groups abruptly shut down due to financial strains.
But the legislative proposal does not address the system’s lax oversight of those guardians (https://www.propublica.org/article/new-york-guardianship-services-care-sick-elderly-confused-alone).
In New York City, there are 17,411 people in guardianships — 60% of the statewide total — and only 157 examiners to scrutinize how guardians handle their wards’ finances and care, according to data from the courts. In some cases, ProPublica found, abuse, neglect or fraud went on for years before it was noticed by authorities — if it was noticed at all.
Advocates have long pushed for a comprehensive overhaul but said any additional resources in the budget would improve the existing system, which is stretched beyond capacity. “The problem is so big, and the population is continuing to age and the need is growing so rapidly, that if we wait for a whole solution, nothing is going to be fixed and it’s just going to get worse,” said George, who also heads Project Guardianship, a nonprofit group that serves as guardian to about 160 New York City wards.
She and others hope the Senate’s proposal is just the first step in a series of legislative actions. Legislators remain in session until June.
Sen. Kevin Thomas, a Long Island Democrat who last year secured the initial $1 million to launch the statewide guardianship hotline, is leading the campaign for the additional funding. In February, he sent a letter — signed by 14 of his colleagues — to Democratic Majority Leader Andrea Stewart-Cousins asking her to back the $5 million appropriation, which would “stand to benefit thousands of aging and incapacitated New Yorkers.”
“New York State is fortunate to have strong legal protections that entitle individuals access to guardianship services when necessary,” the lawmakers wrote. “However, this mandate is underfunded and there is currently no direct funding stream to ensure statutory compliance.”
Among the signatories were the chairs of the Aging, Health and Judiciary committees in the Senate. Assembly Member Charles Lavine, another Long Island Democrat and the chair of the chamber’s Judiciary Committee, sent a similar letter to the assembly speaker in support of the $5 million proposal.
In addition to the budget deal, there are indications that Albany is considering more sweeping reforms.
Lavine said in a statement that he was “discussing” the problems highlighted by ProPublica with judicial officials “with a view towards enacting responsive legislation.” Assembly Member Amy Paulin, a Democrat who chairs the chamber’s Health Committee, called ProPublica’s reporting “concerning, if not distressing,” and said she planned on “looking more into this” after the budget is complete. And Gustavo Rivera, a fellow Democrat and Paulin’s counterpart in the Senate, said he was “open to reviewing” reforms to guardianship after the budget is approved so that lawmakers “can adequately improve a failing system that is exploiting too many vulnerable New Yorkers while enriching the pockets of a few.”
In addition to providing more money for guardians and examiners, experts say lawmakers could strengthen the examination process, mandate more stringent training for guardians (https://www.propublica.org/article/how-new-york-guardianship-system-can-be-fixed) and implement maximum staff-to-ward ratios that keep caseloads manageably low.
Lawmakers have known for decades that the guardianship system is in dire need of an upgrade to meet the needs of those it serves. Indeed, shortly after they passed the law that governs adult guardianships 30 years ago, judges pleaded with Albany to provide critical funding for the indigent and to institute other reforms. Those efforts were unsuccessful, and in the decades since, others have made similar trips to the capitol, producing reports and holding roundtables highlighting the system’s failures. Yet these efforts have had little effect.
Advocates hope that will change given the state’s aging population — an estimated 5.6 million New Yorkers will be 60 or older by 2030 — and Hochul’s plan to help meet its needs (https://www.ny.gov/programs/new-york-states-master-plan-aging). Judges have said the elderly make up a significant segment of those in guardianship since many who suffer from dementia or Alzheimer’s disease need help caring for themselves.
Arthur Diamond, a former supervising guardianship judge on Long Island who has long called for reforms, said he was cautiously optimistic that state legislators and judicial leaders were finally serious about rectifying the system’s deep-seated problems.
“I think that if a year from now, we’re in the same spot, I’m going to give up,” he said of his advocacy. “But these people told me in good faith that they were interested and wanted to help, they told me they are working on remedies, and I take them at their word.”
https://www.propublica.org/article/new-york-lawmakers-weigh-funding-for-guardianship-system
-
 @ ee11a5df:b76c4e49
2023-07-29 03:13:59
@ ee11a5df:b76c4e49
2023-07-29 03:13:59Gossip: Switching to LMDB
Unlike a number of other nostr clients, Gossip has always cached events and related data in a local data store. Up until recently, SQLite3 has served this purpose.
SQLite3 offers a full ACID SQL relational database service.
Unfortunately however it has presented a number of downsides:
- It is not as parallel as you might think.
- It is not as fast as you might hope.
- If you want to preserve the benefit of using SQL and doing joins, then you must break your objects into columns, and map columns back into objects. The code that does this object-relational mapping (ORM) is not trivial and can be error prone. It is especially tricky when working with different types (Rust language types and SQLite3 types are not a 1:1 match).
- Because of the potential slowness, our UI has been forbidden from direct database access as that would make the UI unresponsive if a query took too long.
- Because of (4) we have been firing off separate threads to do the database actions, and storing the results into global variables that can be accessed by the interested code at a later time.
- Because of (4) we have been caching database data in memory, essentially coding for yet another storage layer that can (and often did) get out of sync with the database.
LMDB offers solutions:
- It is highly parallel.
- It is ridiculously fast when used appropriately.
- Because you cannot run arbitrary SQL, there is no need to represent the fields within your objects separately. You can serialize/deserialize entire objects into the database and the database doesn't care what is inside of the blob (yes, you can do that into an SQLite field, but if you did, you would lose the power of SQL).
- Because of the speed, the UI can look stuff up directly.
- We no longer need to fork separate threads for database actions.
- We no longer need in-memory caches of data. The LMDB data is already in-memory (it is memory mapped) so we just access it directly.
The one obvious downside is that we lose SQL. We lose the query planner. We cannot ask arbitrary question and get answers. Instead, we have to pre-conceive of all the kinds of questions we want to ask, and we have to write code that answers them efficiently. Often this involves building and maintaining indices.
Indices
Let's say I want to look at fiatjaf's posts. How do I efficiently pull out just his recent feed-related events in reverse chronological order? It is easy if we first construct the following index
key: EventKind + PublicKey + ReverseTime value: Event Id
In the above, '+' is just a concatenate operator, and ReverseTime is just some distant time minus the time so that it sorts backwards.
Now I just ask LMDB to start from (EventKind=1 + PublicKey=fiatjaf + now) and scan until either one of the first two fields change, or more like the time field gets too old (e.g. one month ago). Then I do it again for the next event kind, etc.
For a generalized feed, I have to scan a region for each person I follow.
Smarter indexes can be imagined. Since we often want only feed-related event kinds, that can be implicit in an index that only indexes those kinds of events.
You get the idea.
A Special Event Map
At first I had stored events into a K-V database under the Id of the event. Then I had indexes on events that output a set of Ids (as in the example above).
But when it comes to storing and retrieving events, we can go even faster than LMDB.
We can build an append-only memory map that is just a sequence of all the events we have, serialized, and in no particular order. Readers do not need a lock and multiple readers can read simultaneously. Writers will need to acquire a lock to append to the map and there may only be one writer at a time. However, readers can continue reading even while a writer is writing.
We can then have a K-V database that maps Id -> Offset. To get the event you just do a direct lookup in the event memory map at that offset.
The real benefit comes when we have other indexes that yield events, they can yield offsets instead of ids. Then we don't need to do a second lookup from the Id to the Event, we can just look directly at the offset.
Avoiding deserialization
Deserialization has a price. Sometimes it requires memory allocation (if the object is not already linear, e.g. variable lengthed data like strings and vectors are allocated on the heap) which can be very expensive if you are trying to scan 150,000 or so events.
We serialize events (and other objects where we can) with a serialization library called speedy. It does its best to preserve the data much like it is represented in memory, but linearized. Because events start with fixed-length fields, we know the offset into the serialized event where these first fields occur and we can directly extract the value of those fields without deserializing the data before it.
This comes in useful whenever we need to scan a large number of events. Search is the one situation where I know that we must do this. We can search by matching against the content of every feed-related event without fully deserialing any of them.
-
 @ dadbe86a:9c493e92
2024-04-02 17:51:58
@ dadbe86a:9c493e92
2024-04-02 17:51:58Opinion about Foundation Passport (hardware)
Passport Batch 2 is a Bitcoin hardware wallet, the second iteration from Foundation company.
Pros: - Included removable battery - 100% airgapped. You can sign transactions using a microSD or QRs. - 100% open source - Lots of advanced features for the more expert users: testnet, secure element, multisig, taproot, fee and coin control etc - You can connect it with lots of software wallets, working as coordinators
Cons: - Some missing advanced features, like user added entropy, stateless support or miniscript
WalletScrutiny #nostrOpinion
-
 @ ee11a5df:b76c4e49
2023-07-29 02:52:13
@ ee11a5df:b76c4e49
2023-07-29 02:52:13Gossip: Zaps
Gossip is a desktop nostr client. This post is about the code that lets users send lightning zaps to each other (NIP-57).
Gossip implemented Zaps initially on 20th of June, 2023.
Gossip maintains a state of where zapping is at, one of: None, CheckingLnurl, SeekingAmount, LoadingInvoice, and ReadyToPay.
When you click the zap lightning bolt icon, Gossip moves to the CheckingLnurl state while it looks up the LN URL of the user.
If this is successful, it moves to the SeekingAmount state and presents amount options to the user.
Once a user chooses an amount, it moves to the LoadingInvoice state where it interacts with the lightning node and receives and checks an invoice.
Once that is complete, it moves to the ReadyToPay state, where it presents the invoice as a QR code for the user to scan with their phone. There is also a copy button so they can pay it from their desktop computer too.
Gossip also loads zap receipt events and associates them with the event that was zapped, tallying a zap total on that event. Gossip is unfortunately not validating these receipts very well currently, so fake zap receipts can cause an incorrect total to show. This remains an open issue.
Another open issue is the implementation of NIP-46 Nostr Connect and NIP-47 Wallet Connect.
-
 @ d88c433f:71851500
2024-04-02 16:42:22
@ d88c433f:71851500
2024-04-02 16:42:22bravo, charlie
-
 @ b12b632c:d9e1ff79
2023-07-21 19:45:20
@ b12b632c:d9e1ff79
2023-07-21 19:45:20I love testing every new self hosted app and I can say that Nostr "world" is really good regarding self hosting stuff.
Today I tested a Nostr relay named Strfry.
Strfry is really simple to setup and support a lot's of Nostr NIPs.
Here is the list of what it is able to do :
- Supports most applicable NIPs: 1, 2, 4, 9, 11, 12, 15, 16, 20, 22, 28, 33, 40
- No external database required: All data is stored locally on the filesystem in LMDB
- Hot reloading of config file: No server restart needed for many config param changes
- Zero downtime restarts, for upgrading binary without impacting users
- Websocket compression: permessage-deflate with optional sliding window, when supported by clients
- Built-in support for real-time streaming (up/down/both) events from remote relays, and bulk import/export of events from/to jsonl files
- negentropy-based set reconcilliation for efficient syncing with remote relays
Installation with docker compose (v2)
Spoiler : you need to have a computer with more than 1 (v)Core / 2GB of RAM to build the docker image locally. If not, this below might crash your computer during docker image build. You may need to use a prebuilt strfry docker image.
I assume you've read my first article on Managing domain with Nginx Proxy Manager because I will use the NPM docker compose stack to publish strfry Nostr relay. Without the initial NPM configuration done, it may not work as expected. I'll use the same docker-compose.yml file and folder.
Get back in the "npm-stack" folder :
cd npm-stackCloning the strfry github repo locally :
git clone https://github.com/hoytech/strfry.gitModify the docker-compose file to locate the strfry configuration data outside of the folder repo directory to avoid mistake during futures upgrades (CTRL + X, S & ENTER to quit and save modifications) :
nano docker-compose.ymlYou don't have to insert the Nginx Proxy Manager part, you should already have it into the file. If not, check here. You should only have to add the strfry part.
``` version: '3.8' services: # should already be present into the docker-compose.yml app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencryptstrfry-nostr-relay: container_name: strfry build: ./strfry volumes: - ./strfry-data/strfry.conf:/etc/strfry.conf - ./strfry-data/strfry-db:/app/strfry-db
ports is commented by NPM will access through docker internal network
no need to expose strfry port directly to the internet
ports:
- "7777:7777"
```
Before starting the container, we need to customize the strfry configuration file "strfry.conf". We'll copy the strfry configuration file and place it into the "strfry-data" folder to modify it with our own settings :
mkdir strfry-data && cp strfry/strfry.conf strfry-data/And modify the strfry.conf file with your own settings :
nano strfry-data/strfry.confYou can modify all the settings you need but the basics settings are :
- bind = "127.0.0.1" --> bind = "0.0.0.0" --> otherwise NPM won't be able to contact the strfry service
-
name = "strfry default" --> name of your nostr relay
-
description = "This is a strfry instance." --> your nostr relay description
-
pubkey = "" --> your pubkey in hex format. You can use the Damu's tool to generate your hex key from your npub key : https://damus.io/key/
-
contact = "" --> your email
``` relay { # Interface to listen on. Use 0.0.0.0 to listen on all interfaces (restart required) bind = "127.0.0.1"
# Port to open for the nostr websocket protocol (restart required) port = 7777 # Set OS-limit on maximum number of open files/sockets (if 0, don't attempt to set) (restart required) nofiles = 1000000 # HTTP header that contains the client's real IP, before reverse proxying (ie x-real-ip) (MUST be all lower-case) realIpHeader = "" info { # NIP-11: Name of this server. Short/descriptive (< 30 characters) name = "strfry default" # NIP-11: Detailed information about relay, free-form description = "This is a strfry instance." # NIP-11: Administrative nostr pubkey, for contact purposes pubkey = "" # NIP-11: Alternative administrative contact (email, website, etc) contact = "" }```
You can now start the docker strfry docker container :
docker compose up -dThis command will take a bit of time because it will build the strfry docker image locally before starting the container. If your VPS doesn't have lot's of (v)CPU/RAM, it could fail (nothing happening during the docker image build). My VPS has 1 vCore / 2GB of RAM and died few seconds after the build beginning.
If it's the case, you can use prebuilt strfry docker image available on the Docker hub : https://hub.docker.com/search?q=strfry&sort=updated_at&order=desc
That said, otherwise, you should see this :
``` user@vps:~/npm-stack$ docker compose up -d [+] Building 202.4s (15/15) FINISHED
=> [internal] load build definition from Dockerfile 0.2s => => transferring dockerfile: 724B 0.0s => [internal] load .dockerignore 0.3s => => transferring context: 2B 0.0s => [internal] load metadata for docker.io/library/ubuntu:jammy 0.0s => [build 1/7] FROM docker.io/library/ubuntu:jammy 0.4s => [internal] load build context 0.9s => => transferring context: 825.64kB 0.2s => [runner 2/4] WORKDIR /app 1.3s => [build 2/7] WORKDIR /build 1.5s => [runner 3/4] RUN apt update && apt install -y --no-install-recommends liblmdb0 libflatbuffers1 libsecp256k1-0 libb2-1 libzstd1 && rm -rf /var/lib/apt/lists/* 12.4s => [build 3/7] RUN apt update && apt install -y --no-install-recommends git g++ make pkg-config libtool ca-certificates libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev l 55.5s => [build 4/7] COPY . . 0.9s => [build 5/7] RUN git submodule update --init 2.6s => [build 6/7] RUN make setup-golpe 10.8s => [build 7/7] RUN make -j4 126.8s => [runner 4/4] COPY --from=build /build/strfry strfry 1.3s => exporting to image 0.8s => => exporting layers 0.8s => => writing image sha256:1d346bf343e3bb63da2e4c70521a8350b35a02742dd52b12b131557e96ca7d05 0.0s => => naming to docker.io/library/docker-compose_strfry-nostr-relay 0.0sUse 'docker scan' to run Snyk tests against images to find vulnerabilities and learn how to fix them
[+] Running 02/02
⠿ Container strfry Started 11.0s ⠿ Container npm-stack-app-1 Running ```You can check if everything is OK with strfry container by checking the container logs :
user@vps:~/npm-stack$ docker logs strfry date time ( uptime ) [ thread name/id ] v| 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| arguments: /app/strfry relay 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| Current dir: /app 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| stderr verbosity: 0 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| ----------------------------------- 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| CONFIG: Loading config from file: /etc/strfry.conf 2023-07-21 19:26:58.529 ( 0.054s) [main thread ]INFO| CONFIG: successfully installed 2023-07-21 19:26:58.533 ( 0.058s) [Websocket ]INFO| Started websocket server on 0.0.0.0:7777Now, we have to create the subdomain where strfry Nostr relay will be accessible. You need to connect to your Nginx Proxy Manager admin UI and create a new proxy host with these settings :
"Details" tab (Websockets support is mandatory!, you can replace "strfry" by whatever you like, for instance : mybeautifulrelay.yourdomain.tld)
"Details" tab:

"SSL" tab:

And click on "Save"
If everything is OK, when you go to https://strfry.yourdomain.tld you should see :

To verify if strfry is working properly, you can test it with the (really useful!) website https://nostr.watch. You have to insert your relay URL into the nostr.watch URL like this : https://nostr.watch/relay/strfry.yourdomain.tld
You should see this :

If you are seeing your server as online, readable and writable, you made it ! You can add your Nostr strfry server to your Nostr prefered relay and begin to publish notes ! 🎇
Future work:
Once done, strfry will work like a charm but you may need to have more work to update strfry in the near future. I'm currently working on a bash script that will :
- Updatethe "strfry" folder,
- Backup the "strfry.conf" file,
- Download the latest "strfry.conf" from strfry github repo,
- Inject old configuration settings into the new "strfry.conf" file,
- Compose again the stack (rebuilding the image to get the latest code updates),
- etc.
Tell me if you need the script!
Voilààààà
See you soon in another Fractalized story!
-
 @ cce0989b:b497e608
2024-04-02 16:35:17
@ cce0989b:b497e608
2024-04-02 16:35:17“I don’t know what to do next.”
That’s okay. It's also perfectly normal! No one can have all of the answers. We all feel lost and uncertain from time to time.
In these moments, here's a tool that you can use to help figure out what the right next step is for you.
If you're feeling scared, imagine how the very bravest version of you would take on this situation.
If you have encountered a complex problem, tap into the wisest part of you. What perspective would they give you?
If you're struggling in a relationship, reach for the kindest version of you, and how they would handle it.
If things are feeling overwhelming, call upon your calmest self. How would they navigate the chaos?
Finally, if you are trying to make a big decision, turn to your truest self. What would they choose?
You have all of these qualities within you, and they can serve as powerful guides, pointing you to the very best next step.
-
 @ b12b632c:d9e1ff79
2023-07-21 14:19:38
@ b12b632c:d9e1ff79
2023-07-21 14:19:38Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ b12b632c:d9e1ff79
2023-07-20 20:12:39
@ b12b632c:d9e1ff79
2023-07-20 20:12:39Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ b12b632c:d9e1ff79
2023-07-19 00:17:02
@ b12b632c:d9e1ff79
2023-07-19 00:17:02Welcome to a new Fractalized episode of "it works but I can do better"!
Original blog post from : https://fractalized.ovh/use-ghost-blog-to-serve-your-nostr-nip05-and-lnurl/
Few day ago, I wanted to set my Ghost blog (this one) as root domain for Fractalized instead of the old basic Nginx container that served my NIP05. I succeed to do it with Nginx Proxy Manager (I need to create a blog post because NPM is really awesome) but my NIP05 was down.
Having a bad NIP05 on Amethyst is now in the top tier list of my worst nightmares.
As a reminder, to have a valid NIP05 on your prefered Nostr client, you need to have a file named "nostr.json" in a folder ".well-known" located in the web server root path (subdomain or domain). The URL shoud look like this http://domain.tld/.well-known/nostr.json
PS : this doesn't work with Ghost as explained later. If you are here for Ghost, skip this and go directly to 1).
You should have these info inside the nostr.json file (JSON format) :
{ "names": { "YourUsername": "YourNPUBkey" } }You can test it directly by going to the nostr.json URL, it should show you the JSON.
It was working like a charm on my previous Nginx and I needed to do it on my new Ghost. I saw on Google that I need to have the .well-known folder into the Ghost theme root folder (In my case I choosed the Solo theme). I created the folder, put my nostr.json file inside it and crossed my fingers. Result : 404 error.
I had to search a lot but it seems that Ghost forbid to server json file from its theme folders. Maybe for security reasons, I don't know. Nevertheless Ghost provide a method to do it (but it requires more than copy/paste some files in some folders) => routes
In the same time that configuring your NIP05, I also wanted to setup an LNURL to be zapped to pastagringo@fractalized.ovh (configured into my Amethyst profile). If you want more infromation on LNURL, it's very well explained here.
Because I want to use my Wallet of Satoshi sats wallet "behind" my LNURL, you'll have to read carefuly the EzoFox's blog post that explains how to retrieve your infos from Alby or WoS.
1) Configuring Ghost routes
Add the new route into the routes.yaml (accessible from "Settings" > "Labs" > "Beta features" > "Routes" ; you need to download the file, modify it and upload it again) to let him know where to look for the nostr.json file.
Here is the content of my routes.yaml file :
``` routes: /.well-known/nostr.json/: template: _nostr-json content_type: application/json /.well-known/lnurlp/YourUsername/: template: _lnurlp-YourUsername content_type: application/json collections: /: permalink: /{slug}/ template: index
taxonomies: tag: /tag/{slug}/ author: /author/{slug}/ ```
=> template : name of the file that ghost will search localy
=> content_type : file type (JSON is required for the NIP05)
The first route is about my NIP05 and the second route is about my LNURL.
2) Creating Ghost route .hbs files
To let Ghost serve our JSON content, I needed to create the two .hbs file filled into the routes.yaml file. These files need to be located into the root directory of the Ghost theme used. For me, it was Solo.
Here is there content of both files :
"_nostr-json.hbs"
{ "names": { "YourUsername": "YourNPUBkey" } }"_lnurlp-pastagringo.hbs" (in your case, _lnurlp-YourUsername.hbs)
{ "callback":"https://livingroomofsatoshi.com/api/v1/lnurl/payreq/XXXXX", "maxSendable":100000000000, "minSendable":1000, "metadata":"[[\"text/plain\",\"Pay to Wallet of Satoshi user: burlyring39\"],[\"text/identifier\",\"YourUsername@walletofsatoshi.com\"]]", "commentAllowed":32, "tag":"payRequest", "allowsNostr":true, "nostrPubkey":"YourNPUBkey" }After doing that, you almost finished, you just have to restart your Ghost blog. As I use Ghost from docker container, I just had to restart the container.
To verify if everything is working, you have to go in the routes URL created earlier:
https://YourDomain.tld/.well-known/nostr.jsonand
https://YourDomain.tld/.well-known/lnurlp/YourUsernameBoth URL should display JSON files from .hbs created ealier.
If it's the case, you can add your NIP05 and LNURL into your Nostr profile client and you should be able to see a valid tick from your domain and to be zapped on your LNURL (sending zaps to your WoS or Alby backend wallet).
Voilààààà
See you soon in another Fractalized story!
-
 @ c11cf5f8:4928464d
2024-04-02 16:26:53
@ c11cf5f8:4928464d
2024-04-02 16:26:53Is callin'! Wrangle up your latest tech discoveries, reviews, and recommendations.
Found any gadgets or gizmos that blew your mind? Don't be shy—share the pros and cons and help your fellow stackers in the ~AGORA stay ahead of the tech curve!
-
 @ b12b632c:d9e1ff79
2023-07-17 22:09:53
@ b12b632c:d9e1ff79
2023-07-17 22:09:53Today I created a new item (NIP05) to sell into my BTCpayserver store and everything was OK. The only thing that annoyed me a bit is that when a user pay the invoice to get his NIP on my Nostr Paid Relay, I need to warn him that he needs to fill his npub in the email info required by BTCpayserver before paying. Was not so user friendly. Not at all.
So I checked if BTCpayserver is able to create custom input before paying the invoice and at my big surprise, it's possible ! => release version v1.8
They even use as example my need from Nostr to get the user npub.
So it's possible, yes, but with at least the version 1.8.0. I checked immediately my BTCpayserver version on my Umbrel node and... damn... I'm in 1.7.2. I need to update my local BTCpayserver through Umbrel to access my so wanted BTCpayserver feature. I checked the local App Store but I can't see any "Update" button or something. I can see that the version installed is well the v1.7.2 but when I check the latest version available from the online Umbrel App Store. I can see v1.9.2. Damn bis.
I searched into the Umbrel Community forum, Telegram group, Google posts, asked the question on Nostr and didn't have any clue.
I finally found the answer from the Umbrel App Framework documention :
sudo ./scripts/repo checkout https://github.com/getumbrel/umbrel-apps.gitSo I did it and it updated my local Umbrel App Store to the latest version available and my BTCpayserver.
After few seconds, the BTCpaysever local URL is available and I'm allowed to login => everything is OK! \o/
See you soon in another Fractalized story!
-
 @ 630d6b7a:ee832cff
2024-04-02 16:03:19
@ 630d6b7a:ee832cff
2024-04-02 16:03:19This, my friends, is Memes O The Day* where I share some memes I've found, seen, come across, or made (but not stolen, because making a copy is not stealing. Thus, feel free to copy and use these, I won't send the FBI after you, because I am not organized crime using the US federal government as my muscle).
HAVE A GREAT DAY
- Memes do not have to be from today and do not have to be memes and it won't be every day and other conditions may apply.
Memes O' the day (1) https://stacker.news/items/472897/r/ucantdothatdotnet (2) https://stacker.news/items/477242/r/ucantdothatdotnet (3) https://stacker.news/items/481625/r/ucantdothatdotnet
-
 @ 1e52c554:21771908
2024-04-02 15:20:12
@ 1e52c554:21771908
2024-04-02 15:20:12Posthumous work of the Colombian poet born in Don Matias on January 20, 1948.
Welcome to this blog dedicated to the Posthumous work of the Colombian poet Francisco Luis Arroyave Tabares (my father), born in Don Matias on January 20, 1948-2010. Where I will be publishing each of the 175 sonnets from his unpublished collection 'Sonnets For The Twenty-First Century And A Circadian Musical (1984-1987).' Analyzed with GPT4 artificial intelligence and illustrated with AI tools... I hope you enjoy this garden of words snatched from the solitude of a locked room.
Likewise, any enthusiast of the sonnet form is invited to conduct their personal studies of Arroyave Tabares' work, as it is a collection that, although registered since 1989, has not yet been published.
Frank Duna
Escrito en verso libre por Francisco Luis Arroyave Tabares
```
(Este poema es un homenaje a la Naturaleza) La Mujer Sin NombreLa descubrí entre la grandeza sin fama de una vida común y sin recuentos aprendiendo a descifrar los diferentes rumores del viento. En el mundo de la música muchas veces se perdió sin esfuerzo y en tibias noches de color ceniza, entre pliegues de amor se arrebató hasta el embeleso. La mujer sin nombre o cuyo nombre se escondió en el tiempo... La que pensó en el satén, el masaje, las alfombras, 10 las sábanas y las almohadas sin peso, y despertó mi pasión con sólo rozar su corpiño pegado a una piel de terciopelo. En tardes de calor su cascabel sonó con campanas para apaciguar alrededor los celos y con sus caderas contó las ondas de un océano. La mujer sin nombre, o cuyo nombre no recuerdo... La que, bañada de estrellas, me hizo sentir lucero y engendró y vio crecer un espiral que sobrepasó al niño, al hombre y al viejo. Con su sonrisa ayudó a fundar los pueblos, y con ojos escasos, bajo un burdel vendió sus entrañas para poder alimentar un pensamiento. La mujer que con valor se plató ante el umbral de la guerra (fenómeno fatal y mitológico que crea monstruos de horrorosas muecas y niños con ojos petrificados mas allá del dolor, las lágrimas y el miedo...).
En su lecho de niña, cada vez que pudo, arrulló un juguete suave para conquistar el cielo y soñó con un palacio azul y un trono de oro donde los hijos del sol buscaban un corazón para quererlo. La mujer, recuerdo de diosas, de musas y de ninfas para cada encuentro, o de sirenas dormidas al otro lado de la playa en donde comienza el firmamento, y levantadas por las nubes hacia un viaje de ensueño. También la vi en la selva con ojos vedes y escuchando al eco, repartiendo entre las flores néctar y perfumando el aire con su aliento. En el suelo se sentó, de pronto, a bordar hojas secas con un hilo de musgo fresco... La mujer sin nombre, o cuyo nombre es un misterio... La que viste de arco iris y ríe con cara de Amaranto. 51 La que coquetea a la luna desde lejos, o con una sinfonía en el paladar nos lleva en éxtasis a través del empíreo. 54
En su regazo, después de cada vida, otra vez, con rara ternura esconde nuestro cuerpo para sentir en sus venas, como sangre, nuestras aguas, y en el fondo del mar purificar los elementos... *** 10-. satén = raso. 51-. Amaranto = flor que nunca muere. 54-. empíreo =cielo. ```
``` Written in free verse by Francisco Luis Arroyave Tabares
(This poem is a tribute to Nature) The Woman Without a NameI discovered her amidst the unheralded greatness Of a common life with no tallies, Learning to decipher The different whispers of the wind. In the world of music She often got lost effortlessly, And on warm ash-colored nights, She surrendered to rapture among the folds of love. The woman without a name, or whose name was lost in time... She who thought of satin, massage, carpets, 10 Weightless sheets and pillows, And awakened my passion with a mere touch Of her bodice clinging to velvet skin. On hot afternoons, Her rattle sounded with bells To appease jealousy all around, And with her hips, she counted The waves of an ocean. The woman without a name, or whose name I do not remember... She who, bathed in stars, Made me feel like a star, 21 And engendered and saw spiral That surpassed the child, the man, and the old man. With her smile, she helped found towns, And with scarce eyes, Under a brothel, she sold her insides To feed a thought. The woman who, with valor, Stood at the threshold of war, (A fatal and mythological phenomenon That creates monsters with horrendous grimaces And children with petrified eyes Beyond pain, tears, and fear...)
On her bed as a girl, whenever she could, She cradled a soft toy to conquer the sky, And dreamed of a blue palace and a golden throne Where the children of the sun sought A heart to love. The woman, remembrance of goddesses, Muses and nymphs for every encounter, Or of sleeping sirens on the other side of the beach Where the firmament begins, And lifted by clouds on a dream journey. I also saw her in the jungle With green eyes and listening to the echo, Distributing nectar among the flowers And perfuming the air with her breath. Suddenly, she sat on the ground To embroider dry leaves with a thread of fresh moss... The woman without a name, or whose name is a mystery... She who dresses in rainbow and laughs with the face of Amaranto. 51 She who flirts with the moon from afar, Or with a symphony in the palate, Takes us in ecstasy through the Empyrean. 54
In her lap, after each life, Once again, with rare tenderness she hides our body To feel in her veins, like blood, our waters, And purify the elements at the bottom of the sea... *** 10-. satin = satin. 21-. the original word is not "a star" is "Lucero", can mean "bright" or "one who shines brightly". 51-. Amaranto= flower that never dies.54-. Empyrean = heaven.
```
The original version of this poem was written in Spanish. I translated it into English and Italian with the help of artificial intelligence. The Italian revision was done by my friend Myriam Samboni.
``` Scritto in versi liberi da Francisco Luis Arroyave T.
(Questa poesia è un omaggio alla natura) La Donna Senza NomeL'ho scoperta tra la grandezza senza fama di una vita comune e senza conti, imparando a decifrare i diversi rumori del vento. Nel mondo della musica molti volte si perse senza sforzo, e in tiepide notti dal colore di cenere, tra pieghe d'amore si abbandonò fino all'estasi. La donna senza nome o il cui nome si nascose nel tempo... Quella che pensò al raso, al massaggio, ai tappeti, 10 alle lenzuola e ai cuscini senza peso, e risvegliò la mia passione con il solo sfiorare del suo corpetto aderente a una pelle di velluto. In calde serate il suo sonaglio suonò con campane per placare la gelosia intorno e con le sue anche contò le onde di un oceano. La donna senza nome, o il cui nome non ricordo... Quella che, bagnata di stelle, mi fece sentire lucero 21 e generò e vide crescere una spirale che superò il bambino, l'uomo e il vecchio. Con il suo sorriso aiutò a fondare i villaggi, e con occhi scarsi, sotto un bordello vendette le sue viscere per poter nutrire un pensiero. La donna che con coraggio si piantò davanti alla soglia della guerra (fenomeno fatale e mitologico che crea mostri dalle orride smorfie e bambini con occhi pietrificati oltre il dolore, le lacrime e la paura...).
Nel suo lettino da bambina, ogni volta che poteva, cullava un morbido giocattolo per conquistare il cielo e sognava un palazzo blu e un trono d'oro dove i figli del sole cercavano un cuore da amare. La donna, ricordo di dee, di muse e di ninfe per ogni incontro, o di sirene addormentate dall'altra parte della spiaggia dove inizia il firmamento, e sollevate dalle nuvole verso un viaggio di sogno. L'ho vista anche nella giungla con occhi verdi e ascoltando l'eco, distribuendo tra i fiori nettare e profumando l'aria con il suo alito. Sul suolo si sedette, improvvisamente, a ricamare foglie secche con un filo di muschio fresco... La donna senza nome, o il cui nome è un mistero... Quella che veste di arcobaleno e ride con faccia di Amaranto. 51 Quella che flirta con la luna da lontano, o con una sinfonia in bocca ci porta in estasi attraverso l'empireo. 54
Nel suo grembo, dopo ogni vita, ancora una volta, con rara tenerezza nasconde il nostro corpo per sentire nelle sue vene, come sangue, le nostre acque, e in fondo al mare purificare gli elementi... *** 10-. raso = satin. 21-. Lucero: forma poetica per dire stella in spagnolo. 51-. Amaranto = fiore che non muore. 54-. empíreo = cielo. ```
La imagen es por istock https://www.istockphoto.com/es/foto/vista-de-la-tierra-desde-el-espacio-gm482110960-69834701?searchscope=image%2Cfilm

La Mujer Sin Nombre
-
 @ b6dcdddf:dfee5ee7
2024-04-02 15:13:40
@ b6dcdddf:dfee5ee7
2024-04-02 15:13:40GM, Stackers!
We're Geyser.fund, the crowdfunding and creator platform built on Lightning and Nostr.
We're here to spread Sats and answer ALL of your questions!
Have you created or funded a project on Geyser? What did you like and what would you like to see improved?
All sats forwarded to: https://geyser.fund/project/geyser
-
 @ bcea2b98:7ccef3c9
2024-04-02 15:07:10
@ bcea2b98:7ccef3c9
2024-04-02 15:07:10After a busy day filled with work and responsibilities, it is difficult for me to transition into a relaxed state conducive to reading. I have trouble slowing down, thinking about the day's events and tomorrow's tasks, and it can make it difficult to focus on the words on the page. When I was younger it seems easier to get into a relaxed state, but I find it more difficult as I age.
For those who struggle to slow down and get in the right mindset for reading after a busy day, what techniques or routines have you found effective to help with this transition? Do you prefer to read at specific times, such as early morning or late at night, to avoid the mental residue of a hectic day? I would be interested to hear your techniques and maybe to try adopt some of them.
-
 @ 8b0a2bea:857d369f
2024-04-02 14:52:14
@ 8b0a2bea:857d369f
2024-04-02 14:52:14test
-
 @ 8b0a2bea:857d369f
2024-04-02 14:51:56
@ 8b0a2bea:857d369f
2024-04-02 14:51:56 -
 @ 000002de:c05780a7
2024-04-02 14:42:18
@ 000002de:c05780a7
2024-04-02 14:42:18I wonder how long it will take for people to learn to not freak out? Or have they already learned. Looks to me based on the current market price that they haven't learned.
Bitcoin Wallet Reactivated After 12 Years Moves 500 BTC
Honestly, the most interesting thing about this is the transaction :)
-
 @ facf399f:70977863
2024-04-02 14:12:09
@ facf399f:70977863
2024-04-02 14:12:09I'm on Obsidian, but I'm also on NOSTR. Test 123.
-
 @ e968e50b:db2a803a
2024-04-02 13:43:24
@ e968e50b:db2a803a
2024-04-02 13:43:24Help! Non-toxic maxis, how do you handle the shitcoiner at your meetup? I anticipate most of the comments to this post will be ultra-toxic memes, which is fine, albeit kind of tired. However, if you're not toxic, I'd really like your input on this situation.
The meetup I run with someone else consciously doesn't mention being Bitcoin-only in hopes of (and we have done this successfully a number of times) finding young shitcoiners before they get burned. Last night, I had my first outspoken, true believing, and not-at-all new shitcoiner come to the meetup. He was hard to wrangle, pretty knowledgable, and one other guest even started to address their questions to him. I think I held my own with the help of a few other maxis, but I want as many tools in my pocket to deal with this guy in the future. I'm not bad at debating, but I don't want to waste all my time sparring with a guy like this or just looking looking insecure by saying we need to move on. In particular, he was REALLY into Coinbase as a platform and actively discouraged self-custody. I always want to end with the facts, but he was pretty obnoxious about always trying to weasel in one last statement.
Again, I know most of the responses are going to be, "just put Bitcoin-only language into the advertising," or "embarrass the guy into submission," the latter of which is really just bitcoiner cancel-culture, and the former not being appropriate for my beginner group. My group specifically exists to spread awareness and education in a city that desperately needs, and is mostly not even aware of Bitcoin. Given those goals and my stubborn take on advertising, does anyone have some solid advice on shitcoiner wrangling?
-
 @ 1c9dcd8f:1852f704
2024-04-02 13:41:29
@ 1c9dcd8f:1852f704
2024-04-02 13:41:29AMONG THE MOST viable of all economic delusions is the belief that machines on net balance create unemployment. Destroyed a thousand times, it has risen a thousand times out of its own ashes as hardy and vigorous as ever. Whenever there is long-continued mass unemployment, machines get the blame anew. This fallacy is still the basis of many labor union practices. The public tolerates these practices because it either believes at bottom that the unions are right, or is too confused to see just why they are wrong.
The belief that machines cause unemployment, when held with any logical consistency, leads to preposterous conclusions. Not only must we be causing unemployment with every technological improvement we make today, but primitive man must have started causing it with the first efforts he made to save himself from needless toil and sweat.
To go no further back, let us turn to Adam Smith’s Wealth of Nations, published in 1776. The first chapter of this remarkable book is called “Of the Division of Labor,” and on the second page of this first chapter the author tells us that a workman unacquainted with the use of machinery employed in pin-making “could scarce make one pin a day, and certainly could not make twenty,” but with the use of this machinery he can make 4,800 pins a day. So already, alas, in Adam Smith’s time, machinery had thrown from 240 to 4,800 pin-makers out of work for every one it kept. In the pin-making industry there was already, if machines merely throw men out of jobs, 99.98 percent unemployment. Could things be blacker?
Things could be blacker, for the Industrial Revolution was just in its infancy. Let us look at some of the incidents and aspects of that revolution. Let us see, for example, what happened in the stocking industry. New stocking frames as they were introduced were destroyed by the handicraft workmen (over 1,000 in a single riot), houses were burned, the inventors were threatened and obliged to flee for their lives, and order was not finally restored until the military had been called out and the leading rioters had been either transported or hanged.
Now it is important to bear in mind that insofar as the rioters were thinking of their own immediate or even longer futures their opposition to the machine was rational. For William Felkin, in his History of the Machine-Wrought Hosiery Manufactures (1867), tells us (though the statement seems implausible) that the larger part of the 50,000 English stocking knitters and their families did not fully emerge from the hunger and misery entailed by the introduction of the machine for the next forty years. But insofar as the rioters believed, as most of them undoubtedly did, that the machine was permanently displacing men, they were mistaken, for before the end of the nineteenth century the stocking industry was employing at least a hundred men for every man it employed at the beginning of the century.
Arkwright invented his cotton-spinning machinery in 1760. At that time it was estimated that there were in England 5,200 spinners using spinning wheels, and 2,700 weavers—in all, 7,900 persons engaged in the production of cotton textiles. The introduction of Arkwright’s invention was opposed on the ground that it threatened the livelihood of the workers, and the opposition had to be put down by force. Yet in 1787—twenty-seven years after the invention appeared—a parliamentary inquiry showed that the number of persons actually engaged in the spinning and weaving of cotton had risen from 7,900 to 320,000, an increase of 4,400 percent.
If the reader will consult such a book as Recent Economic Changes, by David A. Wells, published in 1889, he will find passages that, except for the dates and absolute amounts involved, might have been written by our technophobes of today. Let me quote a few:
During the ten years from 1870 to 1880, inclusive, the British mercantile marine increased its movement, in the matter of foreign entries and clearances alone, to the extent of 22,000,000 tons … yet the number of men who were employed in effecting this great movement had decreased in 1880, as compared with 1870, to the extent of about three thousand (2,990 exactly). What did it? The introduction of steam-hoisting machines and grain elevators upon the wharves and docks, the employment of steam power, etc….
In 1873 Bessemer steel in England, where its price had not been enhanced by protective duties, commanded $80 per ton; in 1886 it was profitably manufactured and sold in the same country for less than $20 per ton. Within the same time the annual production capacity of a Bessemer converter has been increased fourfold, with no increase but rather a diminution of the involved labor.
The power capacity already being exerted by the steam engines of the world in existence and working in the year 1887 has been estimated by the Bureau of Statistics at Berlin as equivalent to that of 200,000,000 horses, representing approximately 1,000,000,000 men; or at least three times the working population of the earth….
One would think that this last figure would have caused Mr. Wells to pause, and wonder why there was any employment left in the world of 1889 at all; but he merely concluded, with restrained pessimism, that “under such circumstances industrial overproduction … may become chronic.”
In the depression of 1932, the game of blaming unemployment on the machines started all over again. Within a few months the doctrines of a group calling themselves the Technocrats had spread through the country like a forest fire. I shall not weary the reader with a recital of the fantastic figures put forward by this group or with corrections to show what the real facts were. It is enough to say that the Technocrats returned to the error in all its native purity that machines permanently displace men—except that, in their ignorance, they presented this error as a new and revolutionary discovery of their own. It was simply one more illustration of Santayana’s aphorism that those who cannot remember the past are condemned to repeat it.
The Technocrats were finally laughed out of existence; but their doctrine, which preceded them, lingers on. It is reflected in hundreds of make-work rules and featherbed practices by labor unions; and these rules and practices are tolerated and even approved because of the confusion on this point in the public mind.
Testifying on behalf of the United States Department of Justice before the Temporary National Economic Committee (better known as the TNEC) in March 1941, Corwin Edwards cited innumerable examples of such practices. The electrical union in New York City was charged with refusal to install electrical equipment made outside of New York State unless the equipment was disassembled and reassembled at the job site. In Houston, Texas, master plumbers and the plumbing union agreed that piping prefabricated for installation would be installed by the union only if the thread were cut off one end of the pipe and new thread were cut at the job site. Various locals of the painters’ union imposed restrictions on the use of spray guns, restrictions in many cases designed merely to make work by requiring the slower process of applying paint with a brush. A local of the teamsters’ union required that every truck entering the New York metropolitan area have a local driver in addition to the driver already employed. In various cities the electrical union required that if any temporary light or power was to be used on a construction job there must be a full-time maintenance electrician, who should not be permitted to do any electrical construction work. This rule, according to Mr. Edwards, “often involves the hiring of a man who spends his day reading or playing solitaire and does nothing except throw a switch at the beginning and end of the day.”
One could go on to cite such make-work practices in many other fields. In the railroad industry, the unions insist that firemen be employed on types of locomotives that do not need them. In the theaters unions insist on the use of scene shifters even in plays in which no scenery is used. The musicians’ union required so-called stand-in musicians or even whole orchestras to be employed in many cases where only phonograph records were needed.
By 1961 there was no sign that the fallacy had died. Not only union leaders but government officials talked solemnly of “automation” as a major cause of unemployment. Automation was discussed as if it were something entirely new in the world. It was in fact merely a new name for continued technological advance and further progress in labor-saving equipment.
2 But the opposition to labor-saving machinery, even today, is not confined to economic illiterates. As late as 1970, a book appeared by a writer so highly regarded that he has since received the Nobel Prize in economics. His book opposed the introduction of labor-saving machines in the underdeveloped countries on the ground that they “decrease the demand for labor”!1 The logical conclusion from this would be that the way to maximize jobs is to make all labor as inefficient and unproductive as possible. It implies that the English Luddite rioters, who in the early nineteenth century destroyed stocking frames, steam-power looms, and shearing machines, were after all doing the right thing.
One might pile up mountains of figures to show how wrong were the technophobes of the past. But it would do no good unless we understood clearly why they were wrong. For statistics and history are useless in economics unless accompanied by a basic deductive understanding of the facts—which means in this case an understanding of why the past consequences of the introduction of machinery and other labor-saving devices had to occur. Otherwise the technophobes will assert (as they do in fact assert when you point out to them that the prophecies of their predecessors turned out to be absurd): “That may have been all very well in the past, but today conditions are fundamentally different; and now we simply cannot afford to develop any more labor-saving machines.” Mrs. Eleanor Roosevelt, indeed, in a syndicated newspaper column of September 19, 1945, wrote: “We have reached a point today where labor-saving devices are good only when they do not throw the worker out of his job.”
If it were indeed true that the introduction of labor-saving machinery is a cause of constantly mounting unemployment and misery, the logical conclusions to be drawn would be revolutionary, not only in the technical field but for our whole concept of civilization. Not only should we have to regard all further technical progress as a calamity; we should have to regard all past technical progress with equal horror. Every day each of us in his own activity is engaged in trying to reduce the effort it requires to accomplish a given result. Each of us is trying to save his own labor, to economize the means required to achieve his ends. Every employer, small as well as large, seeks constantly to gain his results more economically and efficiently—that is, by saving labor. Every intelligent workman tries to cut down the effort necessary to accomplish his assigned job. The most ambitious of us try tirelessly to increase the results we can achieve in a given number of hours. The technophobes, if they were logical and consistent, would have to dismiss all this progress and ingenuity as not only useless but vicious. Why should freight be carried from Chicago to New York by railroad when we could employ enormously more men, for example, to carry it all on their backs?
Theories as false as this are never held with logical consistency, but they do great harm because they are held at all. Let us, therefore, try to see exactly what happens when technical improvements and labor-saving machinery are introduced. The details will vary in each instance, depending upon the particular conditions that prevail in a given industry or period. But we shall assume an example that involves the main possibilities.
Suppose a clothing manufacturer learns of a machine that will make men’s and women’s overcoats for half as much labor as previously. He installs the machines and drops half his labor force.
This looks at first glance like a clear loss of employment. But the machine itself required labor to make it; so here, as one offset, are jobs that would not otherwise have existed. The manufacturer, however, would have adopted the machine only if it had either made better suits for half as much labor, or had made the same kind of suits at a smaller cost. If we assume the latter, we cannot assume that the amount of labor to make the machines was as great in terms of payrolls as the amount of labor that the clothing manufacturer hopes to save in the long run by adopting the machine; otherwise there would have been no economy, and he would not have adopted it.
So there is still a net loss of employment to be accounted for. But we should at least keep in mind the real possibility that even the first effect of the introduction of labor-saving machinery may be to increase employment on net balance; because it is usually only in the long run that the clothing manufacturer expects to save money by adopting the machine: it may take several years for the machine to “pay for itself.”
After the machine has produced economies sufficient to offset its cost, the clothing manufacturer has more profits than before. (We shall assume that he merely sells his coats for the same price as his competitors and makes no effort to undersell them.) At this point, it may seem, labor has suffered a net loss of employment, while it is only the manufacturer, the capitalist, who has gained. But it is precisely out of these extra profits that the subsequent social gains must come. The manufacturer must use these extra profits in at least one of three ways, and possibly he will use part of them in all three: (1) he will use the extra profits to expand his operations by buying more machines to make more coats; or (2) he will invest the extra profits in some other industry; or (3) he will spend the extra profits on increasing his own consumption. Whichever of these three courses he takes, he will increase employment.
In other words, the manufacturer, as a result of his economies, has profits that he did not have before. Every dollar of the amount he has saved in direct wages to former coat makers, he now has to pay out in indirect wages to the makers of the new machine, or to the workers in another capital-using industry, or to the makers of a new house or car for himself, or for jewelry and furs for his wife. In any case (unless he is a pointless hoarder) he gives indirectly as many jobs as he ceased to give directly.
But the matter does not and cannot rest at this stage. If this enterprising manufacturer effects great economies as compared with his competitors, either he will begin to expand his operations at their expense, or they will start buying the machines too. Again more work will be given to the makers of the machines. But competition and production will then also begin to force down the price of overcoats. There will no longer be as great profits for those who adopt the new machines. The rate of profit of the manufacturers using the new machine will begin to drop, while the manufacturers who have still not adopted the machine may now make no profit at all. The savings, in other words, will begin to be passed along to the buyers of overcoats—to the consumers.
But as overcoats are now cheaper, more people will buy them. This means that, though it takes fewer people to make the same number of overcoats as before, more overcoats are now being made than before. If the demand for overcoats is what economists call “elastic”—that is, if a fall in the price of overcoats causes a larger total amount of money to be spent on overcoats than previously—then more people may be employed even in making overcoats than before the new labor-saving machine was introduced. We have already seen how this actually happened historically with stockings and other textiles.
But the new employment does not depend on the elasticity of demand for the particular product involved. Suppose that, though the price of overcoats was almost cut in half—from a former price, say, of $150 to a new price of $100—not a single additional coat was sold. The result would be that while consumers were as well provided with new overcoats as before, each buyer would now have $50 left over that he would not have had left over before. He will therefore spend this $50 for something else, and so provide increased employment in other lines.
In brief, on net balance machines, technological improvements, automation, economies and efficiency do not throw men out of work.
3 Not all inventions and discoveries, of course, are “labor-saving” machines. Some of them, like precision instruments, like nylon, lucite, plywood and plastics of all kinds, simply improve the quality of products. Others, like the telephone or the airplane, perform operations that direct human labor could not perform at all. Still others bring into existence objects and services, such as X-ray machines, radios, TV sets, air-conditioners and computers, that would otherwise not even exist. But in the foregoing illustration we have taken precisely the kind of machine that has been the special object of modern technophobia.
It is possible, of course, to push too far the argument that machines do not on net balance throw men out of work. It is sometimes argued, for example, that machines create more jobs than would otherwise have existed. Under certain conditions this may be true. They can certainly create enormously more jobs in particular trades. The eighteenth century figures for the textile industries are a case in point. Their modern counterparts are certainly no less striking. In 1910, 140,000 persons were employed in the United States in the newly created automobile industry. In 1920, as the product was improved and its cost reduced, the industry employed 250,000. In 1930, as this product improvement and cost reduction continued, employment in the industry was 380,000. In 1973 it had risen to 941,000. By 1973, 514,000 people were employed in making aircraft and aircraft parts, and 393,000 were engaged in making electronic components. So it has been in one newly created trade after another, as the invention was improved and the cost reduced.
There is also an absolute sense in which machines may be said to have enormously increased the number of jobs. The population of the world today is four times as great as in the middle of the eighteenth century, before the Industrial Revolution had got well under way. Machines may be said to have given birth to this increased population; for without the machines, the world would not have been able to support it. Three out of every four of us, therefore, may be said to owe not only our jobs but our very lives to machines.
Yet it is a misconception to think of the function or result of machines as primarily one of creating jobs. The real result of the machine is to increase production, to raise the standard of living, to increase economic welfare. It is no trick to employ everybody, even (or especially) in the most primitive economy. Full employment—very full employment; long, weary, back-breaking employment—is characteristic of precisely the nations that are most retarded industrially. Where full employment already exists, new machines, inventions and discoveries cannot—until there has been time for an increase in population—bring more employment. They are likely to bring more unemployment (but this time I am speaking of voluntary and not involuntary unemployment) because people can now afford to work fewer hours, while children and the overaged no longer need to work.
What machines do, to repeat, is to bring an increase in production and an increase in the standard of living. They may do this in either of two ways. They do it by making goods cheaper for consumers (as in our illustration of the overcoats), or they do it by increasing wages because they increase the productivity of the workers. In other words, they either increase money wages or, by reducing prices, they increase the goods and services that the same money wages will buy. Sometimes they do both. What actually happens will depend in large part upon the monetary policy pursued in a country. But in any case, machines, inventions and discoveries increase real wages.
4 A warning is necessary before we leave this subject. It was precisely the great merit of the classical economists that they looked for secondary consequences, that they were concerned with the effects of a given economic policy or development in the long run and on the whole community. But it was also their defect that, in taking the long view and the broad view, they sometimes neglected to take also the short view and the narrow view. They were too often inclined to minimize or to forget altogether the immediate effects of developments on special groups. We have seen, for example, that many of the English stocking knitters suffered real tragedies as a result of the introduction of the new stocking frames, one of the earliest inventions of the Industrial Revolution.
But such facts and their modern counterparts have led some writers to the opposite extreme of looking only at the immediate effects on certain groups. Joe Smith is thrown out of a job by the introduction of some new machine. “Keep your eye on Joe Smith,” these writers insist. “Never lose track of Joe Smith.” But what they then proceed to do is to keep their eyes only on Joe Smith, and to forget Tom Jones, who has just got a new job in making the new machine, and Ted Brown, who has just got a job operating one, and Daisy Miller, who can now buy a coat for half what it used to cost her. And because they think only of Joe Smith, they end by advocating reactionary and nonsensical policies.
Yes, we should keep at least one eye on Joe Smith. He has been thrown out of a job by the new machine. Perhaps he can soon get another job, even a better one. But perhaps, also, he has devoted many years of his life to acquiring and improving a special skill for which the market no longer has any use. He has lost this investment in himself, in his old skill, just as his former employer, perhaps, has lost his investment in old machines or processes suddenly rendered obsolete. He was a skilled workman, and paid as a skilled workman. Now he has become overnight an unskilled workman again, and can hope, for the present, only for the wages of an unskilled workman, because the one skill he had is no longer needed. We cannot and must not forget Joe Smith. His is one of the personal tragedies that, as we shall see, are incident to nearly all industrial and economic progress.
To ask precisely what course we should follow with Joe Smith—whether we should let him make his own adjustment, give him separation pay or unemployment compensation, put him on relief, or train him at government expense for a new job—would carry us beyond the point that we are here trying to illustrate. The central lesson is that we should try to see all the main consequences of any economic policy or development—the immediate effects on special groups, and the long-run effects on all groups.
If we have devoted considerable space to this issue, it is because our conclusions regarding the effects of new machinery, inventions and discoveries on employment, production and welfare are crucial. If we are wrong about these, there are few things in economics about which we are likely to be right.
-
 @ 82fbb08c:d8cbc29a
2024-04-02 12:47:25
@ 82fbb08c:d8cbc29a
2024-04-02 12:47:25I am mentioning nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft and also a hashtag #bitcoin twitter
-
 @ 82fbb08c:d8cbc29a
2024-04-02 12:44:21
@ 82fbb08c:d8cbc29a
2024-04-02 12:44:21Here are a bunch of images
https://image.nostr.build/0c47ab8a59936da1130440650a041dd1d65e88f11ba159378b15fdb6ae9c33f1.png https://image.nostr.build/c0183a767abfca810e431a432a1392ff904d9a9d873d1033b4fb769bc371e268.png https://cdn.satellite.earth/21cd23e4f31f94556841e944cd64e96052c93395e18aacf0ab8cda5cfe925368.png
And here is another one from nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft about something that is followed by a video
https://cdn.satellite.earth/bfb123de51909af975f7b02a6366af7e6979baa73e5508bb4b2711a7dc663428.mp4
-
 @ 2f7463a4:e92b8023
2024-04-02 12:36:25
@ 2f7463a4:e92b8023
2024-04-02 12:36:25Original „Speaking Freely“ von Gigi, veröffentlicht zur Blockzeit 836245 unter der CC BY-SA 4.0 Lizenz. Übersetzt von sefiro.
Neulich unterhielt ich mich mit einem Freund und wir kamen auf das Problem der Meinungsfreiheit zu sprechen. Ich sollte es nicht als Problem bezeichnen, denn es ist die Lösung eines Problems. Das Problem ist ein immerwährendes Problem, was eine andere Art ist zu sagen, dass es ein wirklich schwieriges Problem ist, ein Problem, mit dem wir immer konfrontiert sein werden, solange wir Menschen sind.
Das Problem ist folgendes: Was ist das Problem, das es zu lösen gilt? Es ist ein Problem von Problemen, was natürlich ein Metaproblem ist. Wir als Homo Sapiens sind ein denkender Organismus. Sowohl kollektiv als auch individuell. Denken ist das, was uns ausmacht, aber es ist nicht einfach Denken als Selbstzweck, es ist Denken, um Dinge herauszufinden, ohne ständig dabei umgebracht zu werden. Eine weniger brutale Form der Evolution sozusagen.
Die Menschen der Antike haben der Aufmerksamkeit einen sehr hohen Wert beigemessen. Auch die Aufmerksamkeit ist von einem Metaproblem geplagt: Worauf soll man seine Aufmerksamkeit richten? Um diese Frage zu beantworten, muss man darauf achten, worauf man seine Aufmerksamkeit richtet, und das unterscheidet einen klugen von einem weisen Menschen.
Das bringt mich zu einem der Dinge die mir derzeit Sorgen bereiten. Wir sind zivilisatorisch gesehen sehr klug, aber nicht sehr weise. Wir sind schlecht darin, auf das zu achten, worauf wir unsere Aufmerksamkeit richten, zumindest gegenwärtig. Und ich fürchte, dass sowohl die falschen Anreize, die das Internet plagen, als auch unser kaputtes Geld daran schuld sind.
Annahmen [n=0]
- ∀ i ≤ c[^1]
- P! = NP[^2]
- Leben ist es wert gelebt zu werden[^3]
- Es gibt kein kostenloses Mittagessen[^4]
- Meinungsfreiheit ist erstrebenswert[^5]
Der Logos [n=1]
Es gibt einen Grund, warum Der Logos heilig ist. Aus dem gleichen Grund ist der Erste Zusatzartikel zur Verfassung der Vereinigten Staaten der erste, d.h. der wichtigste.
Meinungsfreiheit ist nicht optional; sie ist nicht optional, weil wir frei sprechen können müssen, um frei denken zu können. Es gibt kein echtes Denken ohne echtes Sprechen, genauso wie es kein echtes Sprechen ohne echtes Denken gibt. Es muss erlaubt sein, dummes Zeug zu sagen, so wie es erlaubt sein muss, dummes Zeug zu denken.
„Der Vernünftige passt sich der Welt an, der Unvernünftige versucht beharrlich, die Welt an sich anzupassen. Daher hängt aller Fortschritt vom Unvernünftigen ab.“\ — George Bernhard Shaw, Man and Superman
Der Grat zwischen Genie und Wahnsinn ist nicht ohne Grund schmal. Was idiotisch und was genial ist, ist oft schwer zu unterscheiden. Deshalb hängt aller Fortschritt vom Unvernünftigen ab.
Wie können wir den Unvernünftigen finden und ihm zuhören, wenn wir ihn zum Schweigen bringen? Schlimmer noch, wie können wir dem unvernünftigen/genialen Teil in uns selbst hören, wenn wir Angst haben, ihn in der Öffentlichkeit oder im Privaten zu äußern?
DiaLogos [n=2]
Auch freier und unbelasteter Dialog sind nicht optional. Wir müssen in der Lage sein, Dinge zu diskutieren, damit andere uns sagen können, wo wir idiotisch sind. Und wir sind alle idiotisch. Wir sind vielleicht auf unsere Weise idiotisch, aber wir sind alle idiotisch. Es gibt keine wertfreie Meinung, so wie es keine Sichtweise ohne blinden Fleck gibt. Das Beste, was wir tun können, ist, uns unserer Vorurteile und blinden Flecken bewusst zu werden und zu versuchen, ihnen entgegenzuwirken. Aber das können wir nicht individuell, das müssen wir kollektiv tun, und noch wichtiger: auf eine verteilte Art und Weise.[^6]
Der Bau eines Turms von Babel ist eine schlechte Idee.
Verteilte Erkenntnis [n=m]
Auch öffentlicher Diskurs ist nicht optional. In der heutigen Zeit, insbesondere im Internet, ist öffentlicher Diskurs, gelinde gesagt, problematisch. Eines der Probleme ist, dass wir keine öffentlichen Räume haben, so dass wir gezwungen sind, private Räume als quasi-öffentliche Räume zu nutzen.
Die übliche Methode, sich öffentlich zu äußern, besteht darin, auf eine Plattform zu gehen und zu sagen, was man zu sagen hat. Das Problem ist natürlich, dass es nicht deine Plattform ist. Es ist die Plattform eines anderen. Deshalb kannst du von der Plattform ausgeschlossen werden.
Der Unterschied zwischen all diesen Plattformen liegt im Grad, nicht in der Art. Auf einigen Plattformen kann man für sexuelle Inhalte sprichwörtlich ins Gefängnis kommen. Auf anderen Plattformen kann man für politische Äußerungen ins Gefängnis kommen. Nicht einmal sprichwörtlich.[^7]
„Geben Sie mir sechs Zeilen, die von der Hand des ehrlichsten Menschen geschrieben wurden, ich würde etwas darin finden, um ihn hängen zu lassen.“\ — Kardinal Richelieu
Wenn jemand die Macht hat, jemand anderen von einer Plattform auszuschließen, dann wird diese Macht früher oder später auch genutzt und missbraucht. Ein ausreichend großer Skandal oder eine entsprechende Kontroverse wird gefunden oder inszeniert und *puff* ist der „problematische“ Nutzer verschwunden. Depersonalisiert, auf Knopfdruck. Egal, wie mächtig man ist.[^8]
Aus diesem Grund können Plattformen für Meinungsfreiheit nicht existieren. Es kann nur Protokolle für Meinungsfreiheit geben.
Der Unterschied ist ebenso subtil wie wichtig: Wenn du ein Protokoll verwendest, bist du kein Nutzer im herkömmlichen Sinne. Du bist ein Sprecher. Du sprichst die gleiche Sprache wie andere, und wenn jemand anderes dich hören und verstehen kann, dann gibt es eine Verbindung. Es gibt keinen Vermittler. Die Sprache selbst ist der Vermittler. Sprachen sind Protokolle, und Protokolle sind Sprachen. Sie haben keine Nutzer, sie haben Sprecher.
Sprache ist naturgemäß frei. Du brauchst keinen Deutsch-Account, um diese Sätze zu lesen. Genauso wie dein Computer keinen HTTP-Account braucht, um die Nullen und Einsen zu verstehen, aus denen die Bytes bestehen, die wiederum die Zeichen dieses Satzes bilden. Beide sprechen die Sprache, daher könnt ihr euch verstehen.
Sprachen und Protokolle sind Netzwerkphänomene. Ohne Netzwerk keine Sprache. Ohne Peers keine Protokolle.
Deshalb ist Sprache, wie Geld, in einer komplexen Gesellschaft nicht optional. Wenn man in das eine oder das andere hineinpfuscht, zerbricht die Gesellschaft.
Es liegt an uns, es ist soweit [n=i]
Wir stehen an einem Wendepunkt in der Geschichte. Noch nie war unsere Zivilisation so vernetzt, so global, und sich ihrer Grenzen und Ignoranz so wenig bewusst.
Meine Hoffnung ist, dass hartes Geld und Meinungsfreiheit das wiederbeleben, was unsere Gesellschaft groß gemacht hat. Kooperation und verteilte Erkenntnis haben es uns ermöglicht, das Chaos des Dschungels hinter uns zu lassen. Sie haben es uns ermöglicht, von Auge um Auge zu einer klaren Sicht zu gelangen, zumindest teilweise. Sie haben es uns ermöglicht, von der Knappheit zum Überfluss zu gelangen. Sie haben uns ermöglicht, zur Wahrheit, zum Guten und zum Schönen zu gelangen. Sie ermöglichen es uns zu streben. Nach vorne und nach oben.
Der Kairos unserer Zeit ist ein persönlicher – vielleicht sind das alle kairotischen Momente.
Du musst entscheiden wie du weitermachen willst. Du musst entscheiden, welches Spiel du spielen willst; wie viel Verantwortung du bereit bist zu übernehmen. Willst du weiterhin in der Maschine stecken bleiben? Einer Maschine, die dich benutzt und ausnutzt? Eine Maschine, die sich selbst nährt, indem sie deine Zeit, deine Aufmerksamkeit und deinen Wert raubt und verschlingt? Oder hast du den Mut, die Kontrolle über deinen Wohlstand, deine Gesundheit, deine Gedanken und deine Sprache zu übernehmen?
Diese Entscheidung kann dir niemand abnehmen. Sie beginnt und endet mit dir.
💜
[^1]: Keine Information kann sich schneller als Lichtgeschwindigkeit verbreiten. Folglich stoßen alle Informationssysteme an physikalische Grenzen, wenn es um Synchronisation und Informationsweitergabe geht.
[^2]: Kryptographie funktioniert und wird weiterhin funktionieren. „[...] irgendwie lächelt das Universum bei Verschlüsselung.“
[^3]: Existenz ist real und gut. Weder Nihilismus noch Solipsismus sind wünschenswert. „[...] und es war gut.“
[^4]: Wir können nicht etwas für nichts haben. Freiheit erfordert Verantwortung; elektronisches Bargeld erfordert Zeit; Zeit erfordert Wärme.
[^5]: Meinungsfreiheit ist erstrebenswert, weil Freiheit der Tyrannei vorzuziehen ist, und der erste Schritt eines jeden Tyrannen ist es, die Meinungsfreiheit einzuschränken, Dissidenten zum Schweigen zu bringen, und Bücher zu verbrennen. Der zweite Schritt ist Völkermord.
[^6]: Es ist großartig, dass es immer mehr lange Dialoge in Form von Podcasts gibt. Der Nutzen dieser Gespräche geht jedoch verloren, wenn sie von einer zentralen Partei gehostet werden, weshalb ein offenes Podcast-Ökosystem so wichtig ist.
[^7]: Siehe Fälle im Vereinigten Königreich, in Saudi Arabien, etc.
[^8]: Noch nicht einmal amtierende US-Präsidenten sind vor einem Ausschluss von Plattformen sicher.
-
 @ ee7d2dbe:4a5410b0
2024-04-02 12:03:54
@ ee7d2dbe:4a5410b0
2024-04-02 12:03:54- Agicent:
1- Concept Development: Crafting and refining the core concept of the MVP, aligning it with the target audience’s needs.
2- Wireframing and Prototyping: Creating visual representations of the MVP’s user interface, enabling clients to visualize the product’s flow and functionality.
3- App Development: Executing the development process, focusing on the core functionalities that address the identified problem.
Agicent’s MVP development services commence at a competitive price point of $2,900 per month. Additionally, Agicent offers a free consultation session to collaboratively assess client requirements and devise a tailored MVP strategy.
Stack: Leveraging React Native, Flutter, Ionic, Xamarin, and Angular
MVP Development Time: A swift 3-4 weeks to deliver a functional MVP
Established: A decade of experience since its inception in 2010
Team Size: An impressive team comprising over 200 professionals
- Appinventiv:
Appinventiv is a mobile app development company that also offers MVP development services. They have a talented staff of MVP developers who can create MVPs for iOS, Android, and web platforms. With a team of seasoned developers, Appinventiv crafts MVPs across iOS, Android, and web platforms. Their success story, which spans several sectors and clientele, demonstrates their adaptability and knowledge. They have a remarkable portfolio of more than a thousand applications. Above all, Appinventiv’s client-centric approach promotes cooperation, communication, and a sincere commitment to turning original ideas into appealing MVPs.
Stack: React Native, Flutter, Ionic, Xamarin, Angular
MVP development time: 8-10 weeks
Established in: 2014
Team size: 1000+
- Contus:
Contus emerges as a standout MVP development company that has earned a reputation for its exceptional ability to unlock innovation through its MVP development services. With a firm belief in the power of cutting-edge technology and industry-leading practices, Contus boasts a team of skilled MVP developers who specialize in transforming conceptual ideas into functional prototypes. What sets Contus apart is its meticulous attention to detail, user-centric design, and seamless development process. This approach ensures that every MVP developed by Contus not only meets client specifications but also resonates with the target audience.
Stack: JavaScript, Angular, React.js, Java, Python, PHP, Lumen
MVP development time: 4+ months
Established in: 2008
Team size: 300+
- Brainhub:
Brainhub stands tall as a premier MVP development company, known for its exceptional prowess in crafting MVPs that set the stage for scalable ventures. With a team of experienced MVP developers at its helm, Brainhub excels in creating lean yet impactful MVPs that capture the essence of a product.
The company’s dedication to agile methodologies, rapid iteration, and robust coding practices ensures that each MVP is not just a mere prototype but a strategic stepping stone for future growth. This unique approach combines technical excellence with strategic thinking, making Brainhub a standout choice among MVP development companies.
Stack: JavaScript, React Native, React.js, Node.js, .NET
MVP development time: unknown
Established in: 2015
Team size: 51-200+
- Future Processing:
Future Processing has solidified its position as a trailblazing MVP development company, celebrated for its forward-thinking approach to product development. Their team of highly skilled MVP developers harnesses their deep technical knowledge to transform abstract concepts into tangible MVPs that speak to the market.
One of Future Processing’s defining strengths lies in its commitment to comprehensive market analysis, user-centered design, and efficient development cycles. This approach guarantees that each MVP is equipped to meet user needs and market demands.
Stack: Java, Angular, .NET, C++, PHP, Python, Node.js,
MVP development time: 3+ months
Established in: 2000
Team size: 1000+
- SoluLab:
SoluLab has carved a niche for itself as a trusted MVP development company, renowned for its skill in transforming ideas into impactful Minimum Viable Products. What sets SoluLab apart is its team of MVP developers who are not only adept at coding but also well-versed in the art of translating concepts into user-friendly prototypes.
SoluLab’s approach revolves around seamless collaboration, rapid development, and thorough quality assurance, ensuring that each MVP perfectly aligns with the client’s vision and business objectives.
Stack: C++, Python, Swift, Node.js
MVP development time: unknown
Established in: 2014
Team size: 101-250+
- PurpleFire:
PurpleFire emerges as a dynamic MVP app development company that excels in igniting success for startups and established enterprises alike. The core strength of PurpleFire lies in its team of MVP developers who thrive on innovation, turning app ideas into captivating digital experiences.
Through a meticulous process of iterative design, seamless development, and rigorous testing, PurpleFire crafts MVPs that not only boast impressive features but also offer a user-friendly interface.
Stack: JavaScript, Python, Node.js, Vue.js
MVP development time: unknown
Established in: 2012
Team size: 51-200+
- Atta Systems:
Atta Systems distinguishes itself as a precise and expert MVP development company, specializing in crafting MVPs with the utmost precision and expertise. The company’s team of seasoned MVP developers approaches every project with meticulous planning, rapid prototyping, and flawless execution.
Stack: Angular, React, Vue.js, Flutter, React Native
MVP development time: 1+ month
Established in: 2015
Team size: 11-50+
- Appingine:
Appingine thrives as a prominent MVP development company, celebrated for its ability to accelerate success through its MVP development services. The company’s skilled MVP developers excel in creating MVPs that go beyond mere functionality to encapsulate core features and engage users effectively.
Stack: Flutter, Java, Swift
MVP development time: 3+ months
Established in: 2008
Team size: 101-250+
- Alphonic Network:
Alphonic Network stands as a dependable MVP development company, esteemed for its expertise in building strong foundations for digital products. With a dedicated team of MVP developers, Alphonic Network excels in transforming conceptual ideas into tangible MVPs that perfectly align with the client’s objectives.
Stack: PHP, Laravel, Angular.js, React Native
MVP development time: 1+ month
Established in: 2013
Team size: 60+
Conclusion:
MVP development is a critical step in the product development process. By creating an MVP, you can test your idea, validate your market, and gather feedback from users. This information can help you make informed decisions about your product development process and make sure that you are building a product that meets the needs of your target market.
Source: https://www.agicent.com/blog/best-app-development-companies-to-build-rapid-mvp/
-
 @ 82fbb08c:d8cbc29a
2024-04-02 11:42:00
@ 82fbb08c:d8cbc29a
2024-04-02 11:42:00Image
https://image.nostr.build/0c47ab8a59936da1130440650a041dd1d65e88f11ba159378b15fdb6ae9c33f1.png
-
 @ ee7d2dbe:4a5410b0
2024-04-02 10:04:09
@ ee7d2dbe:4a5410b0
2024-04-02 10:04:09App maintenance is an ongoing investment to ensure your app continues to meet user expectations, stays competitive in the market, and remains secure and functional.
How about if we reveal all what is covered in the scope of the App maintenance, Why do you need to regularly manage your App, what kind of hours and money should you be planning to invest to manage your app in 2023? It will be cool, ya?
Ideally, a basic App Maintenance Cost Plan of 160 hours per month will do a fair job to manage and upkeep a commercial version of your App and this would cost you less than $ 3000/ Month. Now depending upon the needs, number of App users, number of requests/ issues reported etc. you may need to retain your App maintenance team for more hours than just 160 on month on month basis.
What is covered in the Scope of App Support & Maintenance?
The App is needed to be regularly updated largely for its following parts and components:
iOS App and Android Apps whether built in native or cross platform tech.
Web Parts/ Web App (Front end, backend, Web replica of mobile apps).
Native APIs and Third-party APIs.
Database, Design files.
Any new feature development utilizing during the maintenance.
Upkeep and updates of beyond-the-app-technology and assets like App Install Ad creatives, beyond the App user onboarding (like through QR code or through an integrated partner’s app or site), Marketing automation, analytics, integration with external Apps and so on.
Activities that we perform for App Support & Maintenance
Following are the high level tasks that are performed to regularly upkeep and update your App:
Complete QA Testing by a dedicated QA Engineer and Business Analyst to figure out all possible Bugs — mostly a one time effort for every major release.
Fixing of Bugs are Reported by the client + Bugs as reported by our Testing Team across iOS, Android, Backend, Web or anywhere else.
Updating the App and its underlying Technology Whenever there is a soft or major OS update from Apple or Google.
Updating Apps to be compatible with all latest releases of all third Party APIs being used in the App and in the backend.
Regular App Performance optimization for a high performing App
Periodical App Code clean up as a regular practice and Code repository Maintenance.
Regular Documentation, Creating App’s SDKs and APIs
Regular Store upload, putting web parts on live server, coordinating with App stores on behalf of the client.
Server Maintenance corresponding to the cloud provider’s infrastructure and features
Managing, Recording, and Sharing the Timesheet with the client
App Maintenance Plans and Pricing from Agicent
We’ve kept it very simple, you retain us for X number of hours a month for App maintenance and pay the fee. Obviously, the more hours you retain us for the better will be the pricing. We always ask our clients to start with the lowest plan and then we jointly analyze in 3 months if 160 hours are enough to handle the App support demands and if not then only we ask you to increase the plan with justification.
Skills and Engineers needed for App Maintenance Process
If your App runs on both iOS and Android and also has a web front end along with a backend, then you need following skilled Engineers to perform App maintenance:
– Native or Cross Platform iOS/ Android Developers.
Native would include Swift/ Xcode developer for iOS; Kotlin/ Java and Studio Developer for Android.
Cross platform skills would be React native, Flutter or Ionic.
– Backend Developers
The skills can be node.js, mongoDB, ExpressJS or MERN Stack or Laravel/ PHP, or .NET or Java (Depending upon the tech stack being used at your backend).
– Web Front End Developer
If you have a landing page website or a complete App’s replica on the web then you may need web front end developers experts in HTML, JS, React JS or Angular or PHP/ Laravel or ASP.NET (Depending upon the tech stack being used at the website end).
– Professional App Tester who knows both manual and automation testing.
– UI/ UX Designer knowing Figma, Photoshop, Adobe design suite.
– Business Analyst and Project Coordinator
The one who will be internal project stakeholder at Agicent, will be your single point of contact, will coordinate between you and development and will also do all activities related to business analysis.
Factors to consider to find out how much does it cost to maintain an App?
Although we have made easier and straight forward for you to do app maintenance by offering hourly maintenance plans, but there still can be some factors that can raise or bring down the cost of App maintenance as follows:
The complexity of the application
The basic factor that contributes to the maintenance cost of the application in 2023 is the complexity of the application. Everyone wants to have advanced apps with more and more features, screens, and much more. But keep in mind that if you are adding these it will further raise your maintenance costs to the greatest extent. Adding more to it, the maintenance costs will also rise with the involvement of higher technology or framework for its development.
Hybrid Applications
The smartphones available in the market depend upon different operating systems. Everyone loves to have the one that they prefer the most. Android and iOS platforms are the two leading operating systems that the majority of users prefer to have on. Do you know what is the basic factor that lies behind the success of an application well its usage? The majority of the time developers prefer to create hybrid applications that can work effectively on both Android and iOS operating systems. But if you have created such, just keep in mind that the maintenance costs are also going to be quite higher than that of the maintenance costs of the same application for both of the platforms.
Third-Party Integrations
The integration of third-party sources also adds up in raising the overall maintenance cost of an application. More will be your app linked closely with the different external sources such as payment platforms, social media services, higher will be the overall maintenance cost of your app. Let’s make it simpler for you, the maintenance cost of a simple photo editing app is usually quite lower than that of the news app.
App Development Team Location
The maintenance cost of an application also differs a lot as per the location. You may need to pay the maintenance cost of about $50–150 per hour in the USA but it may somewhere lie in between $25–60 per hour in Eastern and Central Europe. Whereas if we talk about the maintenance cost of the application in India it is quite low and you can easily accomplish it by paying $10–30 per hour.
Few things that you can do to make sure less maintenance overhead:
– Build your app well architected right from the start
– Take care of the scalability
– have a professional Development Team
– Check your analytics
Benefits of App Maintenance Process
– High performing App, every single day
– Scalability
– Security
– Higher user engagement and better Marketing
– Better integration, exploit third party services to the maximum
Conclusion of App Development Cost and Process
Application development and maintenance is a never-ending process. Right from adding updates to resolving issues, there are a lot more things that go on side by side throughout. The expenses on an app do not end with its creation, they kind of keep on but for only the good.
Source: https://www.agicent.com/blog/how-much-does-it-cost-to-maintain-an-app/
-
 @ c4428155:a36de510
2024-04-02 09:00:00
@ c4428155:a36de510
2024-04-02 09:00:00What You Should Know About “Toddler Milk” and How It’s Marketed to Parents
by Heather Vogell (https://www.propublica.org/people/heather-vogell)
ProPublica is a nonprofit newsroom that investigates abuses of power. Sign up to receive our biggest stories (https://www.propublica.org/newsletters/the-big-story?source=54G&placement=top-note®ion=national) as soon as they’re published.
If you’re a parent, you might have noticed toddler “milk” while browsing the formula aisle. The powdered drink, aimed at children between 1 and 3, often pledges benefits like “improved brain development” or “improved immune function.”
But you may not know that these products are largely unregulated and make claims that are not supported by science, according to studies (https://www.cochranelibrary.com/cdsr/doi/10.1002/14651858.CD000376.pub4/full). For this reason, among others, public health authorities around the world have long sought to police such advertising. Yet despite these efforts, toddler milk has grown to become a $20 billion global business (https://www.propublica.org/article/how-america-waged-global-campaign-against-baby-formula-regulation-thailand).
As ProPublica reported recently, the U.S. government has played a key role in that growth.
We found federal officials have worked for decades with the multibillion-dollar baby formula industry to mount a global campaign to suppress regulations such as marketing bans — often, critics say, at the expense of public health, particularly in developing countries.
Toddler milk, it turns out, is just the latest chapter in this long-running saga.
Below is a list of key questions and answers about baby formula companies’ business overseas and how the U.S. government has supported those corporate interests.
1. What is baby formula and when is it typically used?
According to the Federal Food, Drug, and Cosmetic Act, infant formula is a special food suitable to serve as a complete or partial substitute for breastmilk. It’s used for babies under age 1.
2. Why is baby formula advertising regulated?
Formula is one of only two products in the world for which there are international recommendations that countries prohibit their marketing. The other is tobacco.
People in the U.S. today may find that shocking, since formula is a regular part of life for many parents. But more than four decades ago, concerns about unregulated advertising of formula surfaced after health advocates found that companies such as Nestle had targeted developing nations in places like Africa in hopes of increasing formula sales. Thousands of babies were growing ill and dying because these populations had neither the clean water they needed to mix the formula safely nor the resources to buy enough of the expensive product.
In response, the World Health Organization’s member nations established an international code (https://iris.who.int/bitstream/handle/10665/254911/WHO-NMH-NHD-17.1-eng.pdf) advising countries to prohibit the marketing of infant formula.
3. Why do medical professionals generally agree that breastfeeding babies is preferable to formula?
The WHO and UNICEF recommend that babies breastfeed exclusively for six months and continue through their second birthday and beyond as other foods are introduced. The benefits are well-documented. Studies have found fewer infant deaths and infections among breastfed children and fewer incidences of long-term conditions like diabetes and obesity.
The formula industry acknowledges the benefits. “Breast milk offers a child the best nutritional start in life,” a spokesperson for formula maker Danone said. But “if parents cannot or choose not to breastfeed their baby, formulas are recognized by leading medical societies as the only safe and nutritionally adequate alternative during a baby’s first year.”
Public health advocates, however, worry that the industry’s aggressive advertising — which often includes steep discounts and free samples — will derail a critical cycle for those who intend to breastfeed. Regularly giving your baby formula can cause your breast milk supply to drop, research shows (https://extension.unr.edu/publication.aspx?PubID=4492#:~:text=Your%20milk%20production%20is%20decreased,as%20well%20as%20your%20baby), making your child more reliant on formula.
“The evidence is strong,” a report from the WHO and UNICEF explains. “Formula milk marketing, not the product itself, disrupts informed decision-making and undermines breastfeeding and child health.”
Toddler milk is sold with a promotional musical play set at a Bangkok grocery store.
(June Watsamon Tri-yasakda, special to ProPublica)
4. What is toddler formula and what are the concerns about it?
So-called toddler formula, also known as growing-up milk, typically targets children between the ages of 1 and 3 — a time when many parents begin giving their children cow’s milk and more regular foods. Toddler milk often contains nutritional supplements like DHA, an omega-3 fatty acid, and promises benefits for brain and eye health. In Thailand, we even found a brand called “Hi-Q1.”
Health authorities, however, say these claims are dubious. In fact, last fall, the American Academy of Pediatrics warned that toddler milks are “misleadingly promoted as a necessary part of a healthy child’s diet.” (https://www.aap.org/en/news-room/news-releases/aap/2023/american-academy-of-pediatrics-reviews-toddler-formulas-questions-marketing-of-drinks/) The drinks are worse than infant formula for babies under 1 year and do not offer any benefits over cheaper cow’s milk for most children older than 1, according to Dr. George Fuchs III, a lead author of the organization’s report.
Nutrition experts also caution about the hefty doses of sweeteners and sodium in some brands.
The industry defends toddler drinks. They “can contribute to nutritional intake and potentially fill nutrition gaps for children 12 months and older,” according to the Infant Nutrition Council of America, a formula industry trade group.
5. Is toddler formula regulated in the U.S.?
Unlike baby formula, which must meet certain nutritional requirements, toddler formula is not regulated by the Food and Drug Administration in the U.S.
6. What role does the U.S. government play in American companies’ efforts to market baby formula overseas?
Our reporting examined the industry’s interactions with a number of federal agencies. A key one was the Office of the United States Trade Representative, which advises the president on trade policy and seeks to promote American business interests. Records show that USTR staff were in regular contact with formula makers and their industry groups through meetings, calls and position papers. Trade officials then mirrored those positions in communications with other countries or in international forums like the World Trade Organization, documents show.
In many places, the U.S. efforts appeared to succeed. Hong Kong, Indonesia and Thailand, among others, watered down or put on hold regulations aimed at restricting formula advertising after U.S. objections.
The U.S. Has Waged a Global Campaign Against Formula Regulation
U.S. agencies have intervened in at least 17 jurisdictions over the last several decades on behalf of the formula industry, often to oppose measures that would restrict formula marketing or require additional safety precautions.
Source: ProPublica review of academic research (https://globalizationandhealth.biomedcentral.com/articles/10.1186/s12992-021-00708-1), World Trade Organization records, letters and other U.S. government documents, WikiLeaks cables and news accounts.
(Lucas Waldron/ProPublica)
7. Why has the U.S. government worked to reduce regulations on baby and toddler formulas?
The U.S. is a significant exporter of formula, and the industry has spent considerable resources to protect its financial interests abroad. Its lobbying activity related to foreign health policy ramped up beginning in 2016, as World Health Organization nations considered a resolution aimed at ending the promotion of toddler formula.
That year, the Infant Nutrition Council of America lobbied the USTR and at least four other departments, as well as the Senate and the House, regarding the WHO effort. Leaders in both parties took notice. House Speaker Paul Ryan even called President Barack Obama about the issue, according to records obtained by ProPublica.
Trade officials’ concerns have often reflected those of the industry itself. In one case, they said in a draft letter (https://www.documentcloud.org/documents/24486100-uss-adv-letter-to-hkg-ustr-doc-usda-clean-3-29-2016#document/p1/a2441976) that proposed rules “would result in significant commercial loss for U.S. companies.” In another case, they worried that a marketing proposal would have a regulatory “spillover” effect in Southeast Asia, one of the industry’s top markets.
The USTR declined to comment on specific cases but said more generally that, under President Joe Biden, the trade office has emphasized respecting the role of foreign governments in deciding the appropriate regulatory approach to infant formula.
8. How is the marketing of baby formula regulated in the United States and abroad, if at all?
In 1981, WHO member nations adopted the International Code of Marketing of Breast-Milk Substitutes, which aimed to curb the worldwide promotion of products that could replace breast milk. The U.S. was the only nation to oppose it.
Since then, at least 144 countries have sought to codify the voluntary restrictions. Such laws often restrict formula marketing in stores, hospitals and elsewhere. Despite poor enforcement in many countries, the laws have had measurable benefits. Countries that have adopted marketing bans have seen their breastfeeding rates rise, studies show, and more breastfeeding is in turn linked to lower infant mortality. It also reduces mothers’ risk of certain cancers.
9. Why are formula companies so focused on developing nations?
Developing economies represent big business for the formula industry. One academic study found that low- and middle-income countries accounted for more than 90% of the roughly $19 billion in toddler milk sales in 2022.
As incomes have risen in those countries, formula makers saw an opportunity. “In most countries, breastfeeding is incompatible with women participating fully in the workforce,” Kasper Jakobsen, CEO of the formula company Mead Johnson, said in a 2013 earnings call. “As women participate in the workforce, that creates a rapid increase in the number of dual-income families that can afford more expensive, premium nutrition products.”
Today, Southeast Asia is more important to the formula industry (https://www.ncbi.nlm.nih.gov/pmc/articles/PMC9991832/) than the U.S. and European markets combined.
Infant Formula Looks Nearly Identical to Toddler Milk on a Grocery Store’s Shelves in Bangkok
Thailand's Milk Code restricts the advertisement of infant formula, but marketing of toddler milk is generally allowed.
10. How has formula marketing affected public health in countries such as Thailand?
Formula marketing can impact a country’s breastfeeding rates and, in turn, its children’s health, since breastfeeding carries benefits such as fewer infant deaths and infections.
Thai officials made a similar argument when they sought to restrict the promotion of infant and toddler formula in 2016. They blamed such advertising, in part, for the nation’s breastfeeding rate, which was among the lowest in the world. Some Thai pediatric authorities also say formula products play a big role in the country’s rising obesity rates because they’re so easy to drink.
The share of Thailand’s babies who are exclusively breastfed for six months has rebounded somewhat but has a long way to go to meet the WHO’s target of 50% by 2025.
11. Is the United States alone in promoting baby formula overseas, or do other countries do the same?
Other dairy and formula-producing countries also promote their products abroad and, at the World Trade Organization, countries such as Australia and New Zealand sometimes join the U.S. in objecting to formula regulations. But the U.S. brings outsized economic and political clout to the debate. “The U.S. is highly influential,” said Dr. Robert Boyle, of the Imperial College London, who has researched international formula use.
12. Is the USTR’s lobbying on behalf of the baby formula industry any different than what it does to promote other U.S.-based companies?
According to the USTR website (https://ustr.gov/about-us/about-ustr), part of the office’s job is to work for the “expansion of market access for American goods and services.”
In formulating its official positions on issues, the USTR says it consults with various federal agencies, including those focused on health. But our reporting shows that these debates can be contentious, with trade concerns often trumping public health. In 2016, for example, USTR officials (https://projects.propublica.org/toddler-formula-documents/)repeatedly questioned well-established science (https://projects.propublica.org/toddler-formula-documents/) as they sought to water down a WHO resolution that aimed to restrict formula marketing and increase breastfeeding.
The USTR declined to comment on this incident, but it issued a statement acknowledging the office’s “formerly standard view that too often deemed legitimate regulatory initiatives as trade barriers.”
13. The U.S. government has taken pro-industry stances in the Obama and Trump administrations, and it continues to do so in the Biden administration. Is there any reason to believe this might change?
It’s unclear. A USTR spokesperson told us that under Biden, the trade office has been committed “to making sure our trade policy works for people — not blindly advancing the will of corporations.”
But our investigation found several examples of the trade office under Biden handling formula regulation like it did in past administrations. The USTR did not respond to our questions about these cases.
https://www.propublica.org/article/what-is-toddler-milk-marketing-to-parents
-
 @ 57d1a264:69f1fee1
2024-04-02 08:39:33
@ 57d1a264:69f1fee1
2024-04-02 08:39:33
ODC #000010 - UX > TESTDesigning Guerrilla Usability test for a NON-custodial Bitcoin-ONLY Lightning walletIf you miss it, please read our WTF is ODC (Open Design Challenge) intro post from more details.
Scenario
You're a product designer contributing on a NON-custodial Bitcoin-ONLY Lightning wallet running as mobile app.
Your team wants you to analyze some key tasks that are often performed by new users. You're looking to identify problems and opportunities in the flows for these tasks, and learn a little about the behavior and preferences of these newbies.
Task
Select a NON-custodial Bitcoin-ONLY mobile wallet app for this challenge. You can find a comprehensive list of on section B of this link, thanks to @DarthCoin.
For guerilla usability testing, participants are usually chosen randomly from a public place, like a coffee shop, mall, airport, or supermarket and asked to perform a short usability test in exchange for small reward. If you like, find the nearest shop accepting bitcoin around you and have the opportunity to meet someone new.
Perform the same test with 2–3 participants, ideally people who have never used the product before, and focus on the part of the app where they can receive some sats first, and buy or send value back later. Create a report of your findings.
Extra Credit: Perform the test with 5 or more participants.
Guides
If you need help with this challenge, check out our hand-picked tutorial recommendations.
-
Usability Testing 101 on nngroup.com
-
Moderated usability testing Test out your product with users and observe how they use it. on Bitcoin UX Research Toolkit
-
Usability Testing in 4 Simplified Steps on uxtools.co
-
A Beginner's Guide to User & Usability Testing on hotjar.com
-
UX Tea Break: What Makes a Good Usability Test? on piped.video
Tools
Not sure which tools to use? Try something new, go 💯% FOSS!
For remote interviewsBrie.fi/ng (iOS + online) by Dirk Holtwick
Miro Talk (online) by Miroslav Pejic
Keet (desktop & mobile) by Holepunch
NostrNest (audio only) by Jam.Systems
BigBlueButton (requires registration) by BigBlueButton
For professional gurusUser Testing by QuantUX
Mobile App Testing (Usability Tool) by UXtweak
Usability Testing (5 Sessions Free) by Lookback
Share Your Results
When you finish the challenge, post your work including anonymized collected data and results on this thread! If you also share it on
nostr, be sure to use the hashtag #opendesigner and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Check our previous ODC and support this community for creative minds, where you'll be able to get open and constructive feedback on your PoW. Ask anything in the ~Design territory and get some ⚡sats for the value you provide!
```
Bitcoin #Design #BitcoinDesign #NostrDesign #Nostr #OpenDesign #DesignChallenge #OpenDesignChallenge #UX #BitcoinWallet #LightningWallet #MobileApp #UsabilityTesting #BitcoinPayment
```
-
-
 @ 49edd28f:90fb6d51
2024-04-02 07:10:00
@ 49edd28f:90fb6d51
2024-04-02 07:10:00Navigating the Future Together
https://www.youtube.com/watch?v=qDIjXZnZyUg
-
 @ 37b5197b:b673ca28
2024-04-02 06:27:26
@ 37b5197b:b673ca28
2024-04-02 06:27:26- April second again!
- April second also here
-
 @ 57d1a264:69f1fee1
2024-04-02 06:19:08
@ 57d1a264:69f1fee1
2024-04-02 06:19:08Prompt: Website Navigation
Most websites have a navbar that's stuffed with links and logos. Do you notice the newest one here on @sn? What could you design that's both functional and appealing? How could you make it unique?
Flex your design muscles and join in. Most of all, keep this exercise loose and keep it stress-free. The FUC is about growing our design skills, together, as a community. We can't wait to see what you create!
Happy designing, Stackers!
Share Your Results When you finish the challenge, post your work on this thread! If you also share it on
nostr, be sure to use the hashtag #FUCdesiger and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Curious to know WTF is a FUC? Read the ⚡️Flash Ui Challenges welcoming post.
Looking for more FUCs? Check the archive here!
-
 @ 59d0cb6b:6a569c15
2024-04-02 06:09:12
@ 59d0cb6b:6a569c15
2024-04-02 06:09:12- Now it is April 2nd
-
 @ 57d1a264:69f1fee1
2024-04-02 06:09:02
@ 57d1a264:69f1fee1
2024-04-02 06:09:02What's your favorite paraphernalia, and how has it improved your life? What it has helped you design or accomplish lately?
-
 @ ee7d2dbe:4a5410b0
2024-04-02 05:05:31
@ ee7d2dbe:4a5410b0
2024-04-02 05:05:31Building a mobile app has become a crucial investment for businesses and individuals alike. In this blog post, we will explore the various factors that influence the cost of developing a mobile app and provide a comprehensive breakdown of the expenses involved.
You must have encountered this question once or twice, especially if you are interested in app development. As per the latest industry reports, the cost for creating an app lies somewhere between $20,000 and $250,000. The average cost of creating an app is approximately $172,000. Remember that the above-mentioned figures are just estimates, and the final cost of an app project can vary more or less per the requirements.
But the answer to the question of how is app development cost calculated is here. This article discusses an in-depth overview of the global software development market state. Along with this, you will also learn how much it cost to build an app, what all factors influence the cost and how to effectively manage app development costs to avoid unexpected expenses in the future.
How Much Does It Cost to Build an App on Your Own?
Firstly, building a mobile app by yourself is quite not possible and if it is than it’s not as easy as it might look to you. You can make an app with enough technical knowledge and expertise, but it’s not one person’s job. App development is a process that needs a whole team of developers, designers, project managers, and quality assurance engineers for a successful launch of an app. The combined work of all teams on the project turns the app idea into a full-fledged app in a span of 3–6 months, depending on the number and complexity of features.
Cost to Build a Mobile App Depending on the App Type
Developing an app is really not a piece of cake. This requires a lot of team effort and proper planning within the requested timelines. From analyzing the customer’s need to marketing it right, this all has to be done in the right manner.
Factors Affecting the Cost to Build an App:
The answer to the question of how much does it cost to build an app is a complex one, as several factors influence the final cost of developing an app. Continue the read on some of the factors that affect the cost to make an app are listed below:
1- Mobile App Features and Functionality
Trying to get an answer for how much it cost to build a mobile app can only be attained with an understanding of which features you are going to include in your app. This is the most significant cost driver factor, as some can take months to implement. On average, the cost of developing a mobile app can shift in either direction depending on the number and complexity of features you want to implement.
2- Designing of an App
The UI/UX stage of the mobile app development is fully detailed to create user flows, defining how users will interact with the application and how the interface will look. The feature is important to make the app user-friendly. Some of us appreciate and like the minimalist look of the app, but many are also there who like the vibrant look of an app. The look and feel of the app also depend on type of business you have. No matter the business idea the primary focus should be the app looks are sorted and easy for customers to access.
3- Operating System
The cost of developing an app also depends on which Operating System you are planning to launch the app. As per the current stats, android is ruling the market holding 72.83% of the market share in the mobile app industry, whereas iOS has 26.35% of the market share. Therefore, it is important to decide on your audience before launching the app. The development of the android app is relatively more expensive than the iOS because the development time of an Android app is more than iOS. Make yourself aware of how much it cost to build an iOS app and then observe the difference on your own.
4- Backend Infrastructure
A strong backend increases the average cost of developing an app. The backend holds the empowerment of an app. Hence it is very important to have a great backend involved while developing an app. Backend offers things such as a cloud server, customer server and MBaaS(Mobile backend as a service) that float your data on the cloud to provide quick results. These hold functions such as encryption, security, database, storage and crucial and significant information. The app scalability and snappiness depend completely on how scalable your backend is.
5- Geographical Location of the Development Team
The success of the app largely depends upon how well the app development team works on the application. A well-known fact that experience holders and talented developers charge more money for what they are capable of doing when it comes to developing a mobile app. The cost to build a mobile app depends upon the domains where they are located. For instance, the average cost in the USA will be more than as compared to Asian countries offering the same service at different prices. Therefore, when you decide to outsource app development, you must choose your options carefully regarding where you want to acquire the development services.
6- Cost of Outsourcing Mobile App Development: In-house vs. Agencies
You need to decide whether to develop an app in-house or outsource the process to a third-party development company. Both have their pros and cons. When working with an in-house development team, the major advantage is direct communication, deep involvement, face-to-face meetings and complete control over the team. Another side of the coin is the lack of talent, the need for huge initial investments and dealing with hiring and procedural problems.
Whereas working with an outsourcing company or agency has its advantages; therefore, many individuals prefer outsourcing over in-house. It’s major benefits are far greater than the issues. The benefit of outsourcing the app development team is an unlimited pool of talent, a high level of expertise, cost-deduction, flexibility and no need for any kind of initial investments. The disadvantages with the outsourcing companies or agencies are time zone differences and lack of personal control.
7- Publishing the App
After the app has been successfully developed by the developers, and the QA team has also assured the app’s quality as it is free of bugs. Now is the time, your app is ready for the next big step i.e. deployment of the app on either of the store App store or Google Play Store or both as per need. If you are adding process steps for estimating the cost of developing an app, count this process in. This process involves many documentation and protocols involved at places related to security purposes.
8- Marketing the App
Once the app is developed and deployed on the app store, it’s time to create a lot of buzz. Many marketers treat the launch of an app as a big event and, with the right approach, make it a huge success that results in downloads and usability from the users. Even though the app marketing budget is a separate thing, but it is advised you must include it within the total app budget.
9- App Maintenance Cost
If you think you are just concerned about the cost of making an app and you don’t know that only building an app will not mark your work as done. Revamping and maintaining the app requires double the cost of creating an app.
Source: https://www.agicent.com/blog/cost-to-build-mobile-app/
-
 @ 4e03ba63:1a874d79
2024-04-02 05:05:24
@ 4e03ba63:1a874d79
2024-04-02 05:05:24- 引用数据版本:
4.5.52>>4.5.53 - Credit & Source: #Hakushin
- Edit & Repost: Genshin Null
阿蕾奇诺 (Arlecchino)
普通攻击: 斩首之邀
- 重击
消耗一定体力, 向附近的敌人突进, 并进行一次挥斩.
持续长按时, 阿蕾奇诺将以消耗体力为代价, 进行至多持续 🔴~~3 秒~~ 5 秒 的快速移动.
- 红死之宴
阿蕾奇诺具有的生命之契大于或等于生命值上限的 🔴~~20%~~ 30% 时, 将进入红死之宴状态: 普通攻击、重击与下落攻击造成的伤害将转为无法被附魔覆盖的火元素伤害.
红死之宴状态下, 阿蕾奇诺的普通攻击命中敌人时, 将提升本次攻击造成的伤害, 提升值相当于阿蕾奇诺的攻击力乘以当前生命之契百分比的一定比例, 并消耗当前 🔴~~6.5%~~ 7.5% 的生命之契, 每 🔴~~0.05 秒~~ 0.03 秒 至多因此消耗一次生命之契; 通过这种方式消耗生命之契时, 会使元素战技「万相化灰」的冷却缩短 0.8 秒.
- 详细属性 (Lv.10)
- 🔴红死之宴提升: ~~297.50%~~ 238.00%
- 🔴一段伤害: ~~93.2%~~ 93.9%
- 🔴二段伤害: ~~102.2%~~ 103.0%
- 🔴三段伤害: ~~128.2%~~ 129.3%
- 🔴四段伤害: ~~70.4%+70.4%~~ 73.4%+73.4%
- 🔴五段伤害: ~~140.0%~~ 138.3%
- 🔴六段伤害: ~~167.7%~~ 168.8%
- 🔴重击伤害: ~~256.4%~~ 179.5%
- 🔴重击体力消耗: ~~每秒~~ 25.0 点
- 🔴快速移动体力消耗: ~~50.0 点~~ 每秒 40.0 点
元素战技: 万相化灰
- 血偿勒令
- 血偿勒令持续 30 秒, 每 5 秒, 血偿勒令将对敌人造成一次火元素伤害, 至多造成 2 次伤害. 该伤害视为元素战技伤害;
- 阿蕾奇诺进行重击🔴或施放元素爆发「厄月将升」 [^1] 时, 将回收并清除周围的血偿勒令, 每回收一枚血偿勒令, 将为她赋予生命值上限 🔴~~40%~~ 65% 的生命之契;
- 施放元素战技后的 35 秒内, 至多通过血偿勒令为阿蕾奇诺赋予生命值上限 🔴~~80%~~ 145% 的生命之契. 持续期间再次施放元素战技将重新计算持续时间与血偿勒令能赋予的生命之契上限.
元素爆发: 厄月将升
阿蕾奇诺振舞厄月血火之翼, 🔴回收并清除周围的血偿勒令 [^1], 造成火元素范围伤害, 并在此后清除元素战技「万相化灰」的冷却时间及为自己恢复生命值, 回复量基于她的生命之契数值与攻击力.
- 详细属性 (Lv.10)
- ...
- 🔴回复量: ~~100.0%生命之契+300.0%攻击力~~ 150.0%生命之契+150.0%攻击力
- ...
固有天赋
唯苦痛可偿还
血偿勒令具有如下性质:
-
击败具有血偿勒令的敌人时, 将为阿蕾奇诺赋予生命值上限 🔴~~70%~~ 130% 的生命之契;
-
在施加的 5 秒后, 会升级为血偿勒令·结, 在回收时转而为阿蕾奇诺提供 🔴~~70%~~ 130% 生命之契.
上述方式赋予生命之契时, 赋予的生命之契数值上限无法超过万相化灰原本的限制. 唯力量可守护
唯厄月可知晓
名称变更: 唯灰烬可滋养 >> 唯厄月可知晓
命之座
- 第一层: 「所有的仇与债皆由我偿…」
红死之宴提升进一步提高, 提高值为 🔴~~120%~~ 100%; 此外, 在红死之宴状态下进行普通攻击时, 提高阿蕾奇诺的抗打断能力.
武器: 赤月之形
新增描述: 色泽如赤月般刺眼的锋锐利器. 据说在某个古老的王朝中曾被视为贯连两界的礼器, 但如今早已不再有人记得彼时的信仰与典仪.
- 烬日之影
重击命中敌人时, 赋予生命值上限 🔴~~18%~~ 25% 的生命之契, 该效果每 14 秒至多触发一次. 此外, 装备者具有生命之契时, 造成的伤害提升 12%; 若生命之契的数值大于等于生命值上限的 🔴~~20%~~ 30%, 造成的伤害将进一步提升 24%/32%/40%/48%/56%.
[^1]: 元素爆发回收血偿勒令实际于 v3 热更新中引入.
- 引用数据版本:
-
 @ a27d0226:5d835bce
2024-04-02 04:29:24
@ a27d0226:5d835bce
2024-04-02 04:29:24Opinion about Dcoin - Bitcoin Exchange (android)
If you have ever traded and lost you do not need to be worried anymore, I recommend ‘Vortex Asset Agency - cam to any new or professional trader. Last year, I started my investment with 5000 USD and up till today I have made 100,000 USD.
WalletScrutiny #nostrOpinion
-
 @ a012dc82:6458a70d
2024-04-02 02:46:11
@ a012dc82:6458a70d
2024-04-02 02:46:11Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Bitcoin, Has there been any noteworthy development about this coin recently? People with no prior knowledge of or interest in the field will nonetheless recognize the term. Bitcoin is the most popular cryptocurrency, so naturally it attracts a lot of attention, a lot of money (up to $60K per coin), and a lot of scrutiny. Bitcoin and the cryptocurrency market as a whole are notorious for their resilience in the face of adversity, as seen by their repeated comebacks after being written off by the majority. Experts in the financial sector have been forecasting the Bitcoin bubble would burst "in the near future" around once a month for the last eight years. Despite this, Bitcoin (BTC) investors continue to see healthy returns on their holdings. Bitcoin bulls, though, are beginning to wonder whether they've missed the boat because of the industry's fast evolution. As a reminder, this is our Bitcoin price prediction for the foreseeable future. We are not investment advisers, and the information in this article should not be construed as such.
What is Bitcoin?
Bitcoin, the first cryptocurrency, was developed in 2009 using a blockchain technology called "proof-of-work." Blockchain technology is used to make peer-to-peer transactions completely trustworthy in this decentralized digital currency. One of the most popular financial assets in recent years, Bitcoin (BTC) is attractive because it offers significant potential returns, thanks to the volatile cryptocurrency market, and can be acquired with no effort. Bitcoin may be obtained by anybody with access to the Internet.
What Affects the Value of Bitcoin?
Bitcoin's value may be influenced by a wide variety of external circumstances. It is less reliant on the overall crypto market than other altcoins, and as a result, it often leads the pack. Yet Bitcoin (BTC) still reacts to major crypto news, particularly when it affects the industry as a whole or other major currencies like Ethereum or Shiba Inu. Non-cryptocurrency news may have an effect on bitcoin's price as well, as seen by the price movement in the early 2020s.
Those who have invested in Bitcoin or are considering doing so would also be wise to keep an eye on environmental news. Bitcoin, like any asset, reacts to Bitcoin-related news, whether that news is about Bitcoin itself, cryptocurrency exchanges, or blockchain technology. Cryptocurrency prices tend to rise after positive pieces of news about widespread use, innovative developments, and the like. Conversely, if there is any doubt about it, its worth will drop.
History of Bitcoin
Most people interested in cryptocurrencies are familiar with Bitcoin's price chart. This currency was once almost worthless but has now risen to become one of the world's most valuable possessions. At its peak, Bitcoin's market capitalization exceeded that of several well-established companies. Look at the Bitcoin price history with me for a second. According to CoinMarketCap.com, The shorter duration of Bitcoin's price cycles is readily apparent from this chart. Not only that, but the average value of Bitcoin continues to rise despite the coin's frequent declines in value. There's hope for the future because of this. Recent research puts Bitcoin's value at $21,261.99, making it the most valuable cryptocurrency. So far, a total of 19,199,793 BTC have been issued, and its market cap has reached $408,225,813,263.83.
The value of the cryptocurrency has dropped by $44.65 in the past day. BTC has been on a strong rising trend over the last week, resulting in a 2.73% gain during that time period. Bitcoin's recent performance has been impressive, so now may be a good time to go in. BTC's price has risen by a massive 6.56% over the last month, or an astounding $1,394.79 on average. This unexpected surge in value indicates that the currency has the potential to become a reliable investment tool if it maintains its current rate of appreciation.
Bitcoin Technical Analysis
When analyzing market data, TradingView employs a broad range of technical indicators.
Bitcoin Price Predictions for 2022 by Experts
Among the many investment options available today, Bitcoin is unquestionably a hot commodity. There is a low threshold for entrance into the cryptocurrency market, making it possible for those who have never been interested in trading to start investing in cryptocurrencies. Because of this, there are several Bitcoin price predictions out there, all of which attempt to answer the same question: Will its price increase again in the future? In general, Bitcoin has a positive consensus among specialists. Wallet Investor is one of several who predict that Bitcoin's value will reach about $200,000 during the next five years. Even more conservative optimists may be found at sites like Digital Coin Price, where they anticipate that Bitcoin will have reached "just" $100,000 by 2027.
The crypto sector seems to be expanding rapidly, with new cryptocurrency-related goods and services being introduced by a growing number of companies. For instance, Twitter just added NFT profile images, while luxury house Fendi is producing a cryptocurrency wallet in partnership with Ledger. However, many professionals are beginning to wonder whether this technology can survive in the long run. While much of the public's resistance to these innovations may be attributed to understandable skepticism about the unfamiliar, rising global regulatory scrutiny has many professionals fearful of the cryptocurrency market.
Bitcoin lacks the advantages of Ethereum and Solana because of its more limited ecosystem of crypto goods and services. Bitcoin is exactly what its proponents say it is: a decentralized digital currency. Bitcoin is looking less and less like a good investment as time goes on because of its delayed response to change and its non-environmentally friendly proof-of-work (PoW) consensus process.
The bear market we're in isn't helping matters, and crypto investors haven't exactly earned a sterling reputation for their prudence. Some investors have what are known as "weak hands" and may dump their whole crypto holdings at the first hint of problems, which increases market volatility. Is it possible for Bitcoin to bounce back and return to its earlier highs? Okay, so it has done that before. Time will tell how well BTC does in the future, of course, but we and many other crypto fans and experts think its price still has the potential to skyrocket.
Bitcoin Price Prediction 2022
By 2022, the lowest price for a single bitcoin is projected to be $22,459.76, according to technical analysis of future pricing. Bitcoin's ceiling is now set at $24,178.40. In general, the market value is predicted to be approximately $23,313.75.
Potential ROI: 14%
BTC Price Forecast for November 2022
Experts predict an average BTC rate of $22,417.06 in November 2022, based on Bitcoin's price swings in the first few months of 2022. We estimate a range from $20,495.60 to $23,057.55 for its cost.
Potential ROI: 9%
December 2022: Bitcoin Price Forecast
The consensus estimate for Bitcoin's value in December 2022 is almost ready for release by cryptocurrency analysts. For this month, the possible range of trading expenses is $22,459.76 to $24,178.40. Bitcoin's value is speculated to hover at $23,313.75 on average.
Potential ROI: 14%
Bitcoin Price Prediction 2023
After looking at how much Bitcoin has cost in the past, the consensus forecast for 2023 is that the bare minimum price will be roughly $31,966.00. It's possible that the highest price BTC may reach is $39,547.72. In 2023, the price may settle at an average of $32,898.56.
Potential ROI: 86%
Bitcoin Price Prediction 2024
Bitcoin price forecasts for 2024 range from about $46,946.35 to $56,047.54, according to the technical research of cryptocurrency specialists. For typical trading, you may anticipate paying $48.262.29
Potential ROI: 164%
Bitcoin Price Prediction 2025
Experts in the cryptocurrency industry have studied the historical price trends of Bitcoin. There is a possibility that by 2025 the lowest BTC price will be $67,720.28, with the highest being $81,159.18. The average cost of the trade will be $70,133.40.
Potential ROI: 282%
Bitcoin Price Prediction 2026
Experts in the cryptocurrency industry have predicted that Bitcoin's price would range between $119,727.90 and $99,379.26 in 2026. You may expect an average price of $102,885.93 when trading.
Potential ROI: 464%
Bitcoin Price Prediction 2027
Analysts of cryptocurrencies monitor Bitcoin's price all the time. Their calculations indicate that the midpoint of their range for the BTC price is somewhere around $151,948.24. From now until the end of 2027, it might fall to as low as $146,832.82, but it could also rise to $172,667.27.
Potential ROI: 713%
Bitcoin Price Prediction 2028
Industry professionals prepare predictions for Bitcoin’s annual price every year. In 2028, experts predict that the price of a bitcoin will range from $216,065.18 to $255,450.72. The average annual expenditure is forecasted to be around $223,612.60.
Potential ROI: 1102%
Bitcoin Price Prediction 2029
Forecasting Bitcoin's Value in 2029 Experts in the cryptocurrency market are getting ready to release their predictions for Bitcoin's price. In 2029, the highest price of bitcoin will be $382,833.59. It's possible, however, that the price will go down to approximately $310,581.68. Therefore, the median selling price is $321,762.31.
Potential ROI: 1702%
Bitcoin Price Prediction 2030
Experts in the cryptocurrency industry have spent years studying the Bitcoin price and are now prepared to predict what one bitcoin will cost in 2030. The minimum price at which it may be exchanged is $468,456.71, with the highest price reaching as high as $539,788.24. So, the average BTC price in 2030 is projected to be roughly $481,327.20.
Potential ROI: 2441%
Bitcoin Price Prediction 2031
Experts in the cryptocurrency market are getting ready to release their predictions for Bitcoin's price. In 2031, the highest price of bitcoin will be $818,397.06. But the price might fall to roughly $680,066.07 if demand decreases. For this reason, the median selling price is set at $699,319,15.
Potential ROI: 3752%
Conclusion
Bitcoin's price predictions may reach such high levels, ranging from thousands to even over $1 million per BTC, and it's easy to understand why so many are positive on Bitcoin with all of the gigantic price estimates and forecasts from industry experts that say Bitcoin could soon replace all currencies throughout the world. Cryptocurrencies are well on their way to being widely adopted and used by the general public, thanks to the groundbreaking technology that ignited an entire sector dedicated to disrupting conventional banking.
FAQ
Current Bitcoin Value The current Bitcoin (BTC) price is $21,269.45, and its market value is $408,369,077.47.
Is Bitcoin a good investment? Price drops for Bitcoin are widely anticipated to continue in light of the currency's current negative trend. Before putting money into anything, please conduct your own research and invest carefully.
Can Bitcoin rise? It seems that before the end of the year, the mean price of a bitcoin might reach $23,313.75. A five-year forecast indicates that the cryptocurrency market value may go up to $151,948.24. If you're planning to put money into a project, network, asset, etc., you should always check its value on the market before committing to it.
How much will bitcoin be worth in 2023? In all likelihood, the lowest price for Bitcoin could be $31,966, and the highest may be $39,547.72.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on :
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 73cee26b:072f3bb6
2024-04-02 02:38:20
@ 73cee26b:072f3bb6
2024-04-02 02:38:20This is from Ledger
"you can restore a 12-word recovery phrase into any Ledger device. However, we do not recommend importing a 12-word secret phrase that was generated by a software wallet such as Metamask, Phantom, Keplr, Electrum, etc. Recovery phrases created by software wallets are digitally generated and are therefore less secure. On the other hand, if your 12-word recovery phrase was originally created by another hardware wallet like a Trezor One, it is safe to import it into your Ledger device and continue using the same accounts."
I could see the argument that generating on a general purpose computer introduces attack vectors, but they are saying the randomness isn't as good. True?
-
 @ f6af4055:1108da06
2024-04-02 00:54:03
@ f6af4055:1108da06
2024-04-02 00:54:03- Defining Your Niche and Goals (Week 1) Identify Your Niche:
Think about your passions, hobbies, or business areas. Research to see what similar accounts are doing. Aim for a unique angle or perspective within your chosen niche. Set Clear Goals:
Define what success looks like for you (e.g., gaining 1000 followers in 6 months). Set realistic and achievable objectives. 2. Profile Optimization (Week 1-2) Create a Compelling Bio:
Use simple, clear language to describe what you do. Include a call-to-action, like “Follow for daily tips!” Profile Picture:
Choose a clear, recognizable picture. It could be a logo if it's a business account or a headshot if it's personal. Include a Relevant Link:
Your website, a specific product page, or a link to other social media platforms. 3. Content Planning (Week 2-3) Develop a Content Calendar:
Plan out what to post and when. Aim for consistency, like posting every Tuesday and Thursday. Decide on Content Themes:
These could be themes like "Motivation Mondays" or "Throwback Thursdays." Mix Content Types:
Plan a variety of posts, including images, videos, and graphics. 4. Content Creation and Posting (Ongoing) Creating and Posting Content:
Create posts in advance to avoid last-minute rushes. Use high-quality images and engaging video content. Use Relevant Hashtags:
Research and use hashtags that are popular in your niche. Don’t overdo it; 5-10 relevant hashtags per post is a good range. Write Engaging Captions:
Tell a story, ask a question, or share a fun fact. Keep your audience in mind; make captions relatable. 5. Engaging with the Community (Ongoing) Respond to Comments:
Acknowledge and reply to comments on your posts. Be friendly and approachable. Engage with Other Accounts:
Like, comment, and share content from accounts in your niche. Be genuine in your interactions. Collaborate with Influencers:
Identify influencers who align with your brand or interests. Reach out for collaboration opportunities. 6. Analytics and Adjustments (Monthly) Regularly Check Instagram Insights:
Look at what posts have high engagement, and at what times your audience is most active. Use this data to refine your content strategy. 7. Instagram Stories and Reels (Ongoing) Use Instagram Stories:
Share daily updates or behind-the-scenes content. Use features like polls, questions, or quizzes to engage viewers. Create Reels:
Reels are great for reaching a broader audience. Experiment with different video styles and trends. 8. Paid Promotion (As Needed) Consider Instagram Ads:
If your budget allows, experiment with paid promotions. Target your ads to reach your specific audience. 9. Continued Learning (Ongoing) Stay Updated with Instagram Trends:
Follow Instagram-focused blogs or influencers. Join online communities where Instagram tips and strategies are discussed. 10. Long-term Strategy and Scaling (Every 3-6 Months) Revisit and Refine Your Goals:
Regularly assess your growth and adjust your strategies accordingly. Consider bringing in help or automating some tasks as you grow. Cross-Promote on Other Platforms:
Share your Instagram content on other social media platforms. Encourage your followers on other platforms to follow you on Instagram. This roadmap is a guideline. Feel free to adapt and modify it based on what works best for you and your audience. The key is consistency, patience, and the willingness to learn and adapt!
-
 @ dadbe86a:9c493e92
2024-04-02 00:46:53
@ dadbe86a:9c493e92
2024-04-02 00:46:53Opinion about SeedSigner (hardware)
Seedsigner is one of the most famous Do It Yourself projects in the hardware wallets community. It makes very clear the difference between a signer and other hardware wallets that also store the private keys (in addition to signing transactions)
Pros: - Increase your privacy assembling your own device, because nobody is going to know what you assembled. - Reduce supply chain risks - Assembling a signer is an educational experience - A screen useful to validate the transactions - Good user experience. - Open source and reproducible builds - 100% airgapped firmware upgrade and transaction signing - Bitcoin only device - Support lots of advanced features like testnet, user added entropy, passphrase, seedQR, taproot, fee and coin control, custom node under tor support, multisig, miniscript (soon) - Good integration with the most important bitcoin wallets - Cheap price
Cons: - Missing battery - Missing secure element - Given that it is stateless, there is a lot of controversy about having your seedphase in a QR on your desk. So, a bad usage of Seedsigner could be very dangerous - Use a Raspberry platform which could be potentially insecure
WalletScrutiny #nostrOpinion
-
 @ 90eb2036:76ca3150
2024-04-02 00:44:39
@ 90eb2036:76ca3150
2024-04-02 00:44:39Tucker [00:00:00] Well, things are changing so fast that it's hard to think about what the future might look like, but pause for a second and force yourself. What will the world look like in, say, ten years? 15 years? 50 years? Well, the outlines are pretty clear. If the people who run things powerful forces. And by that we mean very specifically the US government, the Chinese government, the U.N. if they have their way, there will be a lot less private property, a lot less privacy for the average person and for the average person. A lot of really big decisions will be made, not individually, but by machines. So that's clearly the direction we're going. The question is who wants that? And the answer is very, very few people. That's dystopian, doesn't quite capture it. That's horrifying. That's a nightmare. And so if you had to bring about that future with the consent of the governed, as in a democracy, that would be impossible because no one will ever want that. It's too ugly and sad. It's clearly anti-human. It's a dead end. So how do you do it? Well, you only have two options. You can use force. Just put a gun in people's face and say, do this except this or I'll kill you. But that's messy and hard, and it requires a lot of guns. It also requires a kind of muscular attitude, an aggression, not just a passive aggression. Probably not going to happen. Or you can do something else. You can make people want it. That's very different from convincing them there's almost no effort to convince you of anything anymore. In case you haven't noticed, they've totally given up on argument as a means of reaching some kind of mutual consent doesn't exist anymore, but they can instead make you want it. Well, how would they do that? Well, the fastest way to do that would be by, say, changing your brain. Is that happening? Well, you have to kind of wonder, what was Covid, by the way it was the other day. It feels like we haven't really talked about what that was. It wasn't just some random virus. It probably wasn't even just a lab leak accidentally. This was a bioweapons lab run by the Chinese government, paid for in part by the US government. And it went global. But it really went to the West. That's the truth to the English speaking world, to Europe. And it seemed to have changed people. So what's going on here? Is something going on here? And if so, what can you do about it? How do you preserve the sovereignty of your own mind? Maybe that's the most important question. Very few people are thinking about this seriously. Lots of people are speculating about it, but very few scientists are looking at the specifics of how this might be done and what you might do about it. In fact, there's really just one that we're aware of, and we're about to meet him. He is German. His name is Michael Nehls. He's a medical doctor, a physician. He's a molecular geneticist, and he's written what seems to be an amazing new book called The Indoctrinated Brain How to Successfully Fend off the Global Attack on Your Mental Freedom. And we are honored to have him joining us now. Dr. Nehls, thank you very much.
Michael Nehls [00:03:04] I'm very honored to be here. Thank you very much, an honor for my work.
Tucker [00:03:07] Well, and we're honored to have you. So I, I sort of non-technical, maybe grossly, generalized, summarized this idea, but I'd like you to bring some science to it that maybe Covid, not just the VAX, but the virus itself, change the way people think and feel about themselves and understand themselves. Do you think that's possible?
Michael Nehls [00:03:30] Yeah, it's absolutely possible. And it was already shown with Sars-cov-1, the predecessor of SARS-CoV-2.
Tucker [00:03:36] Yes.
Michael Nehls [00:03:37] It was published in 2007, 2008, papers which showed that the spike protein itself is capable of doing something which we call neuroinflammation. That means, kind of a cytokine storm in the brain. And I've worked on this issue for the last 10 to 15 years, actually published a paper, unified Theory of Alzheimer's disease, which is, Alzheimer's. Most people think it's the causes age, but the real cause of Alzheimer's is actually neuroinflammation and our lifestyle. And so, the reason it's age is correlated to it is just because it takes decades to develop. Yes, yes. But neuroinflammation can be caused by many things that can be caused by excessive fear, by fearmongering. Neuroinflammation can be caused by bacteria, by viruses, by infection, chronic infections. Yes. So it was shown that, in order that the hippocampus, it's our autobiographical memory center, which is the center where Alzheimer's starts, needs to be to be functional. Something which we call, hippocampal neurogenesis, permanent production of new nerve cells, which have many, many functions we need to talk about. They are essentially our mental immune system. And if this production is essentially shut down, then our mental immune system breaks down and we are free for everything. I mean, we are we can be conquered and we would even accept it. And so I was working on this mental immune system.
Tucker [00:05:12] So you're describing a physical, just-
Michael Nehls [00:05:14] It's physical.
Tucker [00:05:15] Exactly. It's physical. This is not emotional. This is not the product of propaganda. You're saying that the way that your brain functions as a physical matter can be changed to make you more controllable.
Michael Nehls [00:05:24] Emotions essentially change the way the brain works, and strong emotions fear. For example, particularly in a situation where your mental immune system is down, meaning that your psychological resilience is down, it leads to a very strong effect in the brain, kind of a neurotoxic effect. Leakage of molecules out of the neurons, which are recognized by immune cells in the in the brain. And this recognition leads to an activation of an immune response, a very strong immune response, activating cytokines, pro-inflammatory cytokines. And they attack the hippocampus, our autobiographical memory center shutting down essentially many, many functions like for example, curiosity, like for example, psychological resiliency drops, meaning that everything that happens at least leads to an increased rate of depression and it shuts down, which I've shown recently in which I have put in my book, it shuts down our ability to think.
Tucker [00:06:26] What you're describing, what we're seeing all around us. I have to say, this proves nothing. But I thought it was interesting. I got Covid a couple of years ago and not the worst sickness I've ever had, but it had the most profound emotional effect for a couple of days. I never feel depressed. I've never felt that depressed as I did when I had it, I felt defeated. I didn't expect that. I've never heard anybody say that that was a side effect of Covid. Is that is it?
Michael Nehls [00:06:55] It is. Yeah. So when in 2007, 2008, the first papers came out on how SARS-CoV one, specifically the spike protein is able to activate the new inflammatory process, shutting down the production of these nerve cells in the hippocampus in our autobiographical memory center. The consequences are clear. In the short term, you are prone to depression. In the long term, you actually prone to Alzheimer's if you don't change the course of events. Of course, in that time, the spike protein was not, I think, able to actually end up the brain. And they changed that. So when I was actually almost laughing or because it was so, so deeply depressing in a way. So my reaction was kind of funny. I said, when the Nobel Prize was given in 2023 to this, yeah, I am on a program of bringing the spike protein into humans by a genetic engineering. The the two researchers who brought the Nobel Prize actually said in a, in an interview where we came up with this idea 15 years ago. So when you look back 15 years ago, it was clear that the spike protein is a bio weapon against the brain, particularly the part of the brain which we call our or I call our mental immune system, which is the very, very important part that makes us human, you know, which allows us to think, which allows us to be curious, which allows us, yeah, to to explore the world and, develop a culture, everything. So the spike protein essentially attacked humankind, the very basis of humans. Of course, at that time, the spike protein was kind of. Yeah, yeah, not very dangerous because, it was an external inflammation outside the brain, which, of course, is transmitted to the brain that's known. And so we had an indirect neuroinflammation. If you really want to attack the brain, you have to get the spike protein into the brain. That's that's the that's really dangerous. And so two things happened actually here. So first of all, they changed the SARS-CoV one into SARS-CoV-2 by including this furin cleavage site into the spike, genome in the gene of the spike protein. So if you insert this cleavage site, you create essentially, target foreign molecular scissor that all our cells have, you know, which we call furin a furin cleavers the spike protein two halves, we have two two subunits S1 and S2. And the S1 subunit is the outer part interferes, interacts with the same receptor. That is also our fear receptor or danger receptor in the on the immune cells. And that this triggers essentially a cascade of events which at the end leads to an output of enormous amounts of pro-inflammatory cytokines, each one of them rid of them. Their whole cascade of different ones is looking one interleukin 16 of alpha, interleukin 17, whatever. All of them were shown to shut down the production of new nerve cells in deeper compos, which we require for curiosity, psychological resilience and our ability to think.
Tucker [00:10:11] And those are the effects of the mRNA.
Michael Nehls [00:10:15] Not only the vaccine, the virus itself.
Tucker [00:10:18] I think you may be, I mean, this it's a lot to take in, but you may be answering the question, why, after the mRNA vaccine was shown not to stop. Transmission. Did governments continue to push it on their populations?
Michael Nehls [00:10:35] Absolutely. They pushed it even on, on unborn children. You know, an idea. Yes. You know, women who are pregnant, young children. So I these are all different pieces of a puzzle I couldn't understand. And, only when I realized it's not about health. It's not about not even money. It's about, cornering the human mind. And then it totally made sense suddenly, and all the pieces of the puzzle fell together seamless. And I had a picture in front of me which clearly showed what what they are up to. And that is really to undermine the human ability to think. And it's even worse than that. It's even worse than that which I show in the book, because we need this production of these new nerve cells not only for curiosity, psychological resilience, or our ability to think. They are also necessary for memorizing and retrieving new memories. So if you shut down this production and force the hippocampus to memorize all these different stories, this fear mongering that narratives, then these narratives will end of the brain they will be at will be memorized in the hippocampus, but for trust, they will overwrite preexisting memories. That's not all the way around it, because you have no production of new nerve cells, allowing new memories formed without harming previous ones. So what happens is you overwrite with the narratives, with a fear narratives, with a technocratic narratives. You overwrite your preexisting memories, your individuality or your personality and change it.
Tucker [00:12:11] Yep. If intentional, this would be the most evil thing ever done?
Michael Nehls [00:12:15] Absolutely. When I wrote the book, my wife actually is the, the person who first read, said and corrected and, she almost had a heart attack doing that. I mean, she had really problems reading chapter by chapter because the evil that the book reveals is traumatic.
Tucker [00:12:32] So you spent your entire life within science? Yeah. And so the people who did this or who made it possible are, in some cases, I'm sure, people, you know, but certainly the kind of people, you know. Yeah. How hard was it for you to reach the conclusion that those people were responsible for something so evil?
Michael Nehls [00:12:51] For me, it was extremely difficult to accept, because the last 15 years I spent my life, essentially, I wrote actually 4 or 5 national bestsellers in Germany, and now they are going to be translated into English because this book is now making it, making its way in the English world, of course. And it's so, so to speak puts the others will trail behind it. But I spent the last 15 years trying to convince people that Alzheimer's is not, something you can't avoid when you get when you get older. But it's also not about not about Alzheimer's. It was about something else. All times. It's just a tip of an iceberg of a society whose mental immune system is not functioning. The cause of Alzheimer's is the inability to produce these new nerve cells, or for several decades, that's the cause of Alzheimer's. So we have to reactivate this production to prevent it. But since it takes decades, the traces of Alzheimer's are just the tip of an iceberg of a society whose mental immune system is stolen. Give you another example. The the, if the psychological resilience system, because the production of these nerve cells is stolen, then the likelihood increases that you get depression. And depression became the number one disease in 2017. Actually whole set in 2019 is now the most common disease on Earth. Number one. So if you realize depression is inversely correlated to the production of these nerve cells, that means in 2019, even maybe in 2017, the mental immune system of the human society was down at what was it its lowest level? We were easy to conquer. We were easy to accept what was happening.
Tucker [00:14:37] So for those of us who've noticed that people who've taken the mRNA vaccine and boosters seem different psychologically. Yeah, we're not imagining that.
Michael Nehls [00:14:48] Yeah. No no no no, it's it's that's what's really happening. You see people who, who are not who have not a high production of these, cells and hippocampus, they act normally during the day in a normal situation. They do whatever humans do. And you don't realize it. I saw that, actually, even in the part of my. Yeah, of of people I know that, when I saw them at parties, we could talk about everything, which is trivial. But as soon as you start to talk about something more difficult, it was before 2020, you realize that they don't want to. You put that brain into into into working mode. They just avoided these topics and these very people who are not interested in really thinking were the ones who actually took the shots very quickly. And because you have to see the mental immune system, as I already counted off. You know, curiosity is lacking, you know, so you and the other side of the coin of curiosity is psychological resilience. Because being curious, meaning to enter new space, new thoughts and everything that's new is perceived potentially dangerous. Yeah. So you have to have a high psychological resilience to enter this new space. So if both astound curiosity and psychological resilience, then you accept everything. And particularly if something comes with a lot of fear, you know, or you could die. Your family could die. Everything is very, very dangerous. Then you you fall back to, to, I would say cortical reflexes, like, like something that is inborn in us behavior that's inborn. And one behavior that's inborn, of course, in humans is, that's natural. If there's a danger, you you go, girl, you go into the room, you don't try to be isolated. You go, do you follow the group. And if people tell you the group is going to take this vaccine, then everybody runs and I won't have it to, you know, you don't think you just follow the crowd.
Tucker [00:16:51] The the effects of. Spike proteins on the human brain. Just to be clear about what I think you said were known, well known. By the time Covid was loosed on the world and the mRNA vaccines.
Michael Nehls [00:17:06] Well, I didn't discover that. I just used the papers in the publications which were out there to come to this conclusion. And if I can read this paper that everybody else can do that, they are public. It's not like it's hidden information. So that was clear. You see, when when the virus broke out, by whatever reason, it was learned. Not clear to me and I there's no eyewitness who tells us. Yeah, we actually did it on purpose. Yes. But. And everybody knew that the virus, based on this furin cleavage site, produces a spike version that can enter the brain and has all these detrimental effects on our mental health. So that was really bad. And, and even if that was not on purpose, what was clearly on purpose was the money injection program that was on purpose. It was forced. And here the people who actually forced us or forced people psychologically to to undergo this injection, they had a choice. They had many, many choices. They had the choice, for example, to change the mRNA, that it doesn't contain the cleavage site, that the spike protein is not able to enter the brain. They could have had another choice. It would have taken proteins instead of mRNA, which is modified to stay long in our body, which doesn't make any sense for for for getting an immune response. And, that doesn't make any sense at all. They had another choice they could have taken, not the spike protein, which is dark or dangerous. They could have taken, for example, a nucleocapsid, which is another part of the virus, which is not dangerous to us and actually was proven to give us a very good immunity if you have a natural infection. So that was what it was proposed, a paper out there in 2020 proposing that and that was ignored. And then the mRNA itself is dangerous because you put it you have to package it because it's it's not very stable. And the packaging itself is dangerous. It's very pro-inflammatory, meaning again, attacking the brain because it causes neuroinflammation. And in in addition to that, it was shown that a large portion of it actually off the on a, you know, packaged with the lipid nanoparticles can actually enter the brain. They it's actually it was the and lipid nanoparticles particles were actually produced or invented to enter the brain.
Tucker [00:19:29] So that ask you to stop it for a second that when the. Injections were first rolled out. I remember reading someone say, actually, this could cross the blood brain barrier.
Michael Nehls [00:19:39] Yeah, sure.
Tucker [00:19:40] That's why that person was shouted down immediately. You're a conspiracy nut. You're crazy. I think we now admit that that is the case.
Michael Nehls [00:19:46] No, it was already published by the. The European Medical Association actually published a paper showing that 4% of the. Yeah, circulating, you know, money can enter the brain. And what was shocking to me, actually, is the way they did the injections itself. And even that is revealing. If you really want to make sure that a large proportion is circulating, you have to make sure that you inject it, in a way that the likelihood that it enters the bloodstream is higher. And when I was trained as a medical doctor, I learned that if I have to give an injection that has a state at the injection place. Yes. You actually draw a little bit blood. And if there's blood to be drawn, you know, you are in a vein or in it. Yes. Artery or something. So you change the position of the needle tip.
Tucker [00:20:32] To inject it into fat. Yeah.
Michael Nehls [00:20:34] In the fat or in the muscle, but not in the vein. But here there was clearly, the, the, the indication or there was actually the rule. No, with this one, we have to inject it without drawing the blood first, without checking if it's in the bloodstream. And that's the major reason, actually, why, for example, young adults who, usually muscular transport had so often myocarditis, even deadly myocarditis, because they have the big brains. And so they get the full dose, you know, minus that's the explanation.
Tucker [00:21:06] So you believe, based on the way it was designed, manufactured and administered, that. It was intentional that the people who did this wanted it to get into.
Michael Nehls [00:21:17] The, well, everything else. This whole list of whatever they're just given you and your of the of things which would have been different if there were no intention, was not even considered, or if people proposed it, it was, negated. So I think, well, let's put it this way, in my book, I only bring all the scientific evidence. I paint all the pieces of the puzzle to show how the pieces of the puzzle can be put together, seamless, and so it's very likely it's the correct picture. But at the end of the day, I am not accusing anybody. I just, I'm just, let's say the prosecutor saying this might be the case. I have my personal opinion, but at the end it's the reader who just, is the jury.
Tucker [00:21:59] I was interested, to notice where this was administered, the shots. And so trying to know. I don't I don't think China forced its population to take the mRNA shots. Is that correct?
Michael Nehls [00:22:12] It was only a testing ground, essentially. And of course, people were fearful enough actually, at the time when, or a year later, my wife and I were in, in Egypt on a vacation just for a week. And, we talked to the people there who, went with us to the, to the big sites to have their, you know, the, the ancient, ruins and so forth. And, we talked to them and they said they the they actually had to pay money. There was like a, an auction going on. Who gets the shot first? So I don't know if you have even to, to push people to do that. It's evil to do that of course. But the psychological pressure was so high that, that they got a huge proportion of people already.
Tucker [00:22:54] It didn't seem accidental to me that you had this Covid shot campaign. And then within a year, they opened the borders and changed the population of the country, and in a way that most countries would never accept what's happening in United States right now.
Michael Nehls [00:23:10] Yeah, there are many things going on at the moment. You see the if you if you look at what I'm describing here, it's all about the autobiographical memory center and the autobiographical memories and, records what we think, what we experience, what we discuss with our friends. Everything is recorded, but it cannot record everything. So it's kind of a misnomer here. It records everything what it can record. And it has a threshold. And the threshold is it has to come with emotion. So you can only learn new things if they are kind of emotional to you. Yes. So stereotypical behavior. You don't remember that you did something you do have, right? Yeah, exactly. We know all that. So it has to come with an emotion. So if you really want to transform a brain so first you have to it's a two step process. First you plot the neurogenesis the production of new nerve cells in hippocampus. Then you come up with the stories you want to install. But since they have to come with an emotion, they you can't come up with the same story every day. You have to change the story day by day. You have to come up with new stories with the same intent. Something is breaking down, the world is shut down and everything is dangerous. I'm losing my job because in recreation I might. My family might be killed because we have an atomic war based on this local wars. We have the war against climate change. Everybody will drown because the water will rise. All these stories come up day by day. Actually, the world economy reform has, a program of pressure that bring out every generation. And they call that talk about perma crisis. And they have hundreds of points that they are actually listed in my book with. They have in, in mind or in, in the background where we can start in next crisis. We need to change the story so that at the end of the day, your personal history history is overwritten by this fear mongering stories and you have to change it, otherwise it doesn't work. So that's explains it. It's been something very interesting actually, by the way, I couldn't understand because as I show in the book, it was all well planned. I mean, there were plans already out there. 2018, 2000. Yeah, the program. 201 we know that event, everything was planned, but when it really happened, actually happened in 2020. Our government in Germany, for example, had new rules every day, changing rules all the time. And I said they are behaving like they didn't know what they do, but everything was so well planned. I mean, the vaccine was out so quickly, everything was planned, but they did as if they had no idea what they should do. But in reality, if you look from the point of view of the hippocampus of your autobiographical memory, this changing of who was as part of the plan, it has to be part of a plan, because changing the rules mean you have to memorize every day new rules and they overwrite your your your memory center.
Tucker [00:26:06] That's so you, after a while, can't remember what life was like before the rules.
Michael Nehls [00:26:11] Exactly. You see, if you want to install. And this is all about installing a new operating system. Yeah. You are in your introduction. You said and you didn't say it, but it's like an artificial intelligence controlled society by a social scoring system. And I call it in my book a, let's say an evil social, social operating system, which you can actually abbreviate by S.O.S.. Yeah, quite nicely. It means something else, but we know what it what where, where it ends. And, so if that's the plan and you alluded to it and I'm pretty sure everybody who reads book knows what's going on and what they are intending. Then, then it's clear you have to, to, to, to create a situation where. No, but there's no other fence anymore. There's no fence where you can see and oh, the green the grass is greener on the other side. Look at all of the dictatorships. Fascism in Germany, Stalinism, whatever.
Tucker [00:27:13] Yes.
Michael Nehls [00:27:14] There was always a fence, a border where it was different on the other side. But we have to think here. If there is, if everybody is attacked, then there is no border. There is no other side as. No, no place you can hide, no place you can go. But there's not a border in your brain. The brain of history. You know, it was different in the past. But once you start overwriting the past and even this border is gone, there is no way you can't. There's no refugee anymore. Nothing you can, go back to and think about. Okay. It was different in the former times. We have to get back to that place, to this time. We have to change something. Yes. And the ability to change something comes with individuality. Creativity. Individuality is closely linked. But what's happening here is we destroy individuality. That means we destroy that. Your creative power of humanity. And then trust we just follow the rules that the artificial intelligence.
Tucker [00:28:10] So you're really describing a kind of mass Alzheimer's I mean, with. No, no, because a person without memory isn't fully a person.
Michael Nehls [00:28:18] Yeah. I give you another word for that. It's, you see the ability to think, there was a Nobel Prize given, right? That actually in 2002 to Daniel Kahneman, a psychologist, the Nobel Prize was in economics. How do we come to decisions in difficult times, so to speak? That's what the Nobel Prize, of course, was for businesses. But nevertheless, he described, mental energy that we need to activate thinking. And in my book I describe what is mental energy is it comes from the production of these nerve cells. So if you shut down the ability to think, then, you are stuck with the non-thinking brain, which he called system one. So system two is the thinking brains. Thinking system one is our default action during the day, which doesn't require new energy. We called system one, another Nobel Prize winner who was trying to find out where the our consciousness is and our consciousness in the brain. Francis Crick, he just he got the Nobel Prize for solving DNA. He published a paper in 2003 with, with his colleague, and he said, system two is great that we have it. It's essentially the motor of our society, you know, the sinking ability.
Tucker [00:29:33] Yes.
Michael Nehls [00:29:34] And but it's also good to have system one, which allows us in, in standard situations to, to actually react in a way that doesn't cost any mental energy. And he named the system one the zombie mode.
Tucker [00:29:48] Zombie mode.
Michael Nehls [00:29:48] Zombie mode. So if you are not able to engage system two anymore on this, what my book describes under the attack of the virus and the fear mongering and a lifestyle is not very healthy. Then of course we are stuck in a zombie mode, and I really fear the zombie society very much.
Tucker [00:30:10] A couple of questions. What does this do to religious faith, which was at the center of all societies until the Second World War? Does a zombie mode? Does does a zombie population have religious faith?
Michael Nehls [00:30:24] I'm not sure if you were religious to begin with. You certainly will. Will be your the drive will be, still religious belief. But again, religious belief, is based on memory. And if memory is overridden, well, I think I gave you already and yes, you did.
Tucker [00:30:45] What can you do about it to the people watching who had the mRNA shots, I think most of whom regret it. Now, sure. My sympathy goes out. Yeah. But what is this, reversible?
Michael Nehls [00:30:56] It's reversible. Actually, this is what my paper, a unified Theory of Alzheimer's disease is all about, is that the power of of the adult hippocampal neurogenesis lies in the fact that it it's it's the that the hippocampus, or autobiographical memory center, has the ability to produce new nerve cells every day and every night. And this production rate actually doesn't decline if we grow older. Actually, even 80 years old have a production rate which is similar to 18 years old. So that's why Alzheimer's is not natural. It's it's based on on lifestyle that doesn't allow an efficient production and efficient production needs. What everything that grows needs, let's say micronutrients, in humans, maybe physical activity, everything that was natural before we entered the modern world. So Alzheimer's was not a disease in 100 years ago. It was unknown, essentially. But the modern world changed our way so far away from our natural needs that we. Yeah, that the production rate is actually low. And that was the reason 2017 that depression rates were high. It's a very strong indicator. In 2019, for example, Alzheimer's was the number three this, that deadly disease in Europe and in the Americas. So it's, it's all about the hippocampus. So it was already damaged long ago, over the decades before 2020 was, was was coming up, and then everything accelerated. Just to give you an example, in 2020, compared to 2019 depression rates, you remember it was the highest 2017, 2019 worldwide tripled in the United States, you know, in 2022, as a measure, measurements to the measures to the to the mandates, to everything, because everything that was done inhibited the production of new nerve cells, for example, closing off sports centers. If you do a sport in, let's say, as a prehistoric person, you have to leave the cage, you know, the cave. I mean, yes, you cave and you leave the cave and you go outside and you have to remember where it might be danger or where you is maybe a tree full of roots where you can find something to eat, whatever. So we have to remember. So every time we walk around, we activate a number of hormones growth hormone to protein. Even our muscles produce home. It's like everything and all these hormones have the function to make us physically more able to do the next hike outside, you know? So it's a training effect. But I thought I show in the book here is that every hormone is an activator of adult hippocampal neurogenesis. So if you start doing physical exercise you actually enhance your mental abilities. And of course, if anything that has to grow, it doesn't must get everything it needs as a nutrient. So if you have deficiencies in certain nutrients that are required for the production of these nerve cells, it will be shut down. One such nutrient, for example, is vitamin D or omega three fatty fatty acids. It was shown that a low level of vitamin D accelerates brain aging. Particularly, it accelerates the development of depression and Alzheimer's. So we have to raise the vitamin D level to a level that is natural. The natural level would be 125 nano per liter. It was shown, by the way, the same level of hundred and 85 nano more per year. Peer reviewed paper meta analysis showed nobody would die of Covid if the level is hard 25 non-animal. So it's not only good for our mental immune system, it's also good for our physical immune system. And for me, it was totally clear it's not about health. When I realized that there's a strong agenda against vitamin D supplementation. So it's not. It's not like a swat with two cutting edge, you know, where, first of all, you're shut down the physical immune system, making people prone to death, to a disease which would not be deathly on the high level of vitamin D, and it's proven. It's cause the causality is proven. So you have 195 non-normal zero deaths. But of course, if you want to install a new world order, which everybody accepts, even if you want to make people believe that the injection is the only way out of the money, then you have to have some people who actually show.
Tucker [00:35:16] How do you get enough vitamin D?
Michael Nehls [00:35:18] Usually it's supplementation. It's not very, very difficult. And to get to a level that is that is ideal for brain health, ideal for immunological health. It's about 185 non-animal, per liter. That's the level you should have in Germany, for example, people in winter have, like 2025 non-normal. And the likelihood of, that, Covid, for example, is increased dramatically. So, for example, in the first studies came out, that was before the injection program enrolled. The traps were, you know, given to people, in fall of 2020, the German Cancer Research center published a paper, nine of ten Covid deaths can be prevented just by raising the vitamin D level. But nobody was interested in that.
Tucker [00:36:04] And you believe that there is an active effort to suppress vitamin D?
Michael Nehls [00:36:09] Absolutely it the variational, the most prestigious clinical journal that we know of is a New England Journal of Medicine. That's why all the clinical trials on the mini were published there, you know, and they accepted everything that was, going this way. So it was very intriguing for me to realize that when I saw a paper in 2022, on bone health and vitamin D, which was, I don't know how much time we have, but this paper was bogus. You know, it was it should not have been accepted because it was stupid. It was just a stupid paper. To be honest, the people who had already had to, I put it as my Edward very short. They had a vitamin D level already, which is totally in agreement with bone health. Then they were separate into groups, you know, randomly one group got additional vitamin D, the other group didn't get any. So you have two groups which were already half a vitamin D level, which is sufficient for bone health. Then one group gets a little bit more vitamin D, and then the two groups were compared if they had more fractures over five years. Of course there is no difference between bone health was already taken care of. But based on this study that was published in the Journal of Medicine, an editorial was published at the same paper in the same. Yeah. Journal, a final, a decisive verdict on vitamin D, and the editors come to the conclusion that nobody, even with a deficiency, needs vitamin D. Doctors should stop prescribing beta vitamin D or even checking the vitamin D status, and people shouldn't waste money using.
Tucker [00:37:45] Oh come on.
Michael Nehls [00:37:46] Yeah, it was a New England Journal of medicine. And and in Germany, actually, it was Medscape, an article by a German professor. He actually said in a journal in this Medscape that's the most influential, information, journal for health practitioners worldwide, mainly financed by pharma industry. And this I said it's actually a Nazi thinking, to prescribe vitamin D or things like that, because that's where the idea of supplementing micronutrients actually was born, in his opinion. And so giving vitamin D, if you, you have to think about as a physician, if you give vitamin D, you're actually following Nazi ideology.
Tucker [00:38:34] This is so dark.
Michael Nehls [00:38:35] It's extremely dark.
Tucker [00:38:36] Where is it coming from?
Michael Nehls [00:38:39] Well, as I said, when I read, Schwab's book, now or from the world, Economy Forum, about Covid and the great Reset and, and the greater said, as you already alluded to in the introduction, is not something we would welcome if we were, yeah, mentally, mentally at, at, in a healthy state. We would actually. So it's clear they want it installed and it's the plan for 2030. And it's not only in his book, actually, when you go through the government, documents which I show in the book as well, government documents in Germany, 2030, for example, they talk about a post voting society that, artificial intelligence knows better than we know what is good for us and that voting is not necessary anymore. So it's an abolishing of democracy. So, that's one thing. And of course, a people actually, there was another document I found, official governmental document that they say in 2030 people will hope that based on climate change, the narrative here that we actually will be controlled. We want to be controlled by artificial intelligence so that, we can, have a future for our children. But the purportedly honest, this bogus account, a narrative because, a humane counter narrative, because I strongly believe if we have enough mental diversity, enough individuality in our society, we will come up with ideas, that, that will save us, you know, from destruction, like, pollution and other things, you know, we'll come up with ideas, I'm pretty sure. But at the moment we have a society based on the depression rates, on the Alzheimer's rates, from everything that we we know of, all the power matters that our society is not mentally healthy. And this is what my book is all about, to change the world into a society that has more mental health. That's something what we call democracy is actually possible. I mean, democracy means the individual has the power to decide. But if our individuality, our mental immune system is destroyed, we either do not decide because we are fearful or we are, we don't allow ourselves an opinion because we fear the consequences.
Tucker [00:41:13] The average person who's made it this far, 45 minutes in is terrified. Also recognizes that what you're saying is substantially true because it it comports with what we see all around us the death of curiosity, of creativity, the hive mind, herd herd mentality, all happening all around us. But what are the steps, particularly for those who submitted to the mRNA jab? What are the steps you take to retain your psychological resilience?
Michael Nehls [00:41:43] The first thing I would propose very eagerly is of course, read my book. But they wouldn't be able to do that. Maybe they weren't meant to be understood. I mean, curiosity is stone, everything in stone. But what people suffer from, many people suffer from, is what we call brain fog. You know, a consequences of the jab or of the infection. Yeah. Which we tried all to post back or long Covid. And what I show is that this neuro inflammatory insult on the brain caused by the spike protein, leading to a cascade of events in the cell, in this immune cells, which are in our brain in this cascade, which leads to the production of these pro-inflammatory cytokines, is a molecule which we call GSK three better, I think I don't think I have to discuss it in more detail, but GSK through better is just a molecule, a signal transducer. And the natural inhibitor of the signal transducer is lithium. And it was shown that lithium at very low doses, not the one the doses you use for bipolar disorder or manic depression doses which are 100 fold lower, 100 fold like one milligram or so, maybe maximum five milligram is sufficient to plot. It's a natural inhibitor to plot this cascade to get rid of the inflammatory response. I already proposed to this in a book in which I called the Corona Syndrome. It's not published in English yet, but in 2021, I said, besides whether vitamin D lithium would be able to block the cytokine storm. And in the end of 2022, just two years ago, one and a half years ago, a paper was published, patients had to go to the hospital of severe Covid, and they were on the brink of having to go to the intensive care unit because breathing problems. So they randomized these people into groups that got standard treatment. But one group got lithium. After only a few days, the cytokine storm was completely shut down. The people were released from the hospital in half the time than the others, and not a single person died. So lithium is the key. Actually, I can prove that lithium is essential to humans. It's essential. By the way, that's another funny story the World Health Organization claims. I have found a paper from the World Health Organization where they show it's essential for roads, for rats, rodents. I can show in papers it's, essential for essentially every animal on Earth that has where it has been tested. But the World Health Organization argues it's not essential for humans. But I can tell you if you would take lithium. You not only get rid of your brain fog, you also start. That was shown to activate adult hippocampal neurogenesis. So in my paper of 2016 Unified Theory of Alzheimer's disease, I show that lithium as a single molecule can actually stop the progression of Alzheimer's.
Tucker [00:44:35] I mean, given that you have, I think, seen and describe in your book the big picture of what's actually going on. All these different threads are part of one thing. Has it changed your view about people or changed your view of the spiritual world? I mean, this is so evil that and you said it's not about money exclusively in this. No it's not about elections. It's much bigger. I mean, how has that changed you?
Michael Nehls [00:45:02] Well, I in the last chapter, which is a chapter of hope to show we can change, that, we can empower ourselves again, because you have to understand, we talk a lot everywhere about how it happened, what happened, how it happened, how it was instrumental, at least all the different steps, all the evil things. But we need to know why it happened. And when we know why. And then we know the target and we know the target, in this case, the hippocampus, we know how to change things. But, so the last chapter is about that. But the last chapter I also discuss with myself, why it actually happened in the first place. What are these people? And I found a couple of books about the and papers, publications peer reviewed that if we feel empowered, if you have, the more power you have, something develops which we call acquired sociopathy. And maybe that's behind that. The people, have some kind of a god like, you know, self esteem. Yes. And, and really believe that they do the right thing in their, in their worldview, you know, and, they might think that we have to eradicate, humankind to save humankind, whatever. But at the end of the day, it doesn't matter what these people think. It's more important what the reader is thinking, what we all are thinking, because we are the majority. And, and at the moment, about 20%, I guess, or maybe even 25 to 30% of the people worldwide realize they already 20% realized it very early, 25 to 30% realize it. Meanwhile, in total, I guess what's going on and what I argue is if each one of them makes it possible to convince somebody else about what's going on, then we are 50 to 60%. We are a majority. Again, and as I alluded to already, the people who are not really clear what's going on and don't want to know what's going on, they still follow the mass. And if the mass is 50 to 60% people, we can think if we can convince them that there's another maturity somewhere else and maturity of people who want, yeah, a humane future for our children, then, we all will prevail. I'm 100% sure.
Tucker [00:47:16] But last question. If you live in a country product, a society that's, I think impressive. But is conformist absolute. So how are you treated in Germany?
Michael Nehls [00:47:29] Well, if the mainstream is ignoring me, of course, you know, Wikipedia, starts to write interesting stuff about me.
Tucker [00:47:37] Oh, yeah. That's the CIA's. Yeah. I feel, you know, kind of an outlet.
Michael Nehls [00:47:40] Yeah. My, for example, my Wikipedia account up to a year from, back a year was kind of pristine. It was only my science career in there and stuff. I did, and now it's not pristine anymore. But, I told my wife it's actually. It's an honor. No, I mean, it's it's like I'm recognized, you know, particular my my my ideas are recognized. And that's the most important part, you know? So. But besides that, not much happened. I don't want to, you know, ask for it now from here, but so much, so far, we have a very strong community of people like you who spread the word, who do extremely important work. I mean, I have to thank you for that. The work you are doing and many people in Europe doing worldwide are doing, helping to spread the news, spreading the information. I think it's the most important thing at the moment that I can think of. And I have good contact. Meanwhile, to all of them, that's really good.
Tucker [00:48:35] It is important. The most important, Dr. Michael Nehls, the indoctrinated brain case. You want to get that right away. Thank you.
-
 @ fcc4252f:e9ec0d5d
2024-04-01 20:42:27
@ fcc4252f:e9ec0d5d
2024-04-01 20:42:27The Plebeian Market is buzzing with excitement every week, as fresh faces pop up with their dazzling goods and services! A big shoutout to all of you for being the wind beneath our market's wings!
Newest Merchants in the spotlight this week:
https://image.nostr.build/3cc1d22677a294324c665be8a9e8ff1e8ce646d8fbb816a8a35aa29b4bcf59ce.png
Join Us! Plebeian Market serves as a vibrant marketplace for open trade and discussions, while also encouraging individuals and merchants to join the Bitcoin standard! If you have questions please join our Telegram group.
We build together!
BitcoinBekka
-
 @ dadbe86a:9c493e92
2024-04-01 20:33:44
@ dadbe86a:9c493e92
2024-04-01 20:33:44Opinion about BlueWallet Bitcoin Wallet (android)
BlueWallet is a popular open-source Bitcoin and Lightning Network wallet designed to provide users with a secure and user-friendly way to manage their bitcoin assets on mobile devices.
Pros: - Lightning Network Support - Is bitcoin-only, a plus for bitcoiners - Open source - Lots of Advanced features: user added entropy, passphrases, seedQR, fee & coin control, custom node, tor, coinjoin, multisig
Cons: - Missing testnet, miniscript or timelocks support - Missing full taproot support
WalletScrutiny #nostrOpinion
-
 @ dadbe86a:9c493e92
2024-04-01 20:17:50
@ dadbe86a:9c493e92
2024-04-01 20:17:50Opinion about Muun: Bitcoin Lightning Wallet (android)
Muun is a mobile Bitcoin and Lightning Network wallet designed to provide users with a secure, non-custodial, and user-friendly way to manage their bitcoin. The wallet offers a range of features aimed mainly to novice users.
Pros: - Minimalist and easy user interface - Lightning Network Support - Taproot support - Is bitcoin-only, a plus for bitcoiners - Open source
Cons: - Missing Hardware Wallets support - Missing support for some advanced features like passphrases, multisig, custom node, testnet, user added entropy, coin control, coinjoin, miniscript, etc - Missing BIP39 seed phrase backup support
WalletScrutiny #nostrOpinion
-
 @ f72e682e:c51af867
2024-04-01 20:02:23
@ f72e682e:c51af867
2024-04-01 20:02:23Yes, as you read.
There is a controversy on if this was intentional, or just a bug introduced by Satoshi when he programmed Bitcoin. But the bug causes this money supply graph:
As you can see, after a large period of flat supply, it jumps again up with 50 btc per block, and the cicle repeats indefinetly.
Yes, I know, those are a lot of years, and not even our grandchildren will see it happening. But ey, better to have the future well tied!
The core programmer Pieter Wuille solved it in BIP-0042 ten years ago:
https://github.com/bitcoin/bips/blob/master/bip-0042.mediawiki
-
 @ 8a0a65f4:5ab37a4a
2024-04-01 19:17:09
@ 8a0a65f4:5ab37a4a
2024-04-01 19:17:09Opinion about BC Vault One (hardware)
The Bc vault is not deterministic wallet. This means several things: - it is not compatible with any other hww on the market (I am only aware of 55 hwws) as it does not follow BIP39 etc. This means that the backup is locked to this company and the product (until they exist). - instead if the widely used\, defacto standard seed words\, you can only export raw private key! There is no hww on the market, that would allow for import of the raw private key. - the wallet does not distinguish between an address and an account. It is all one. 1 address = 1 account! - each address/account has the option to be protected (pin + password) which is super complicated and that's why forces user to reuse addresses. This is harmful for the privacy of the user and all their piers. - Multisig is not possible (in quorum with other hwws). - Passphrase is not supported...
The team seems to be focused on altcoins which results lack of support to bitcoin eg. Taproot is still not supported. There are only two positive things on this hww: - big screen showing complete address - giroscope for randomness generation
I can't recommend it to any user, unfortunately.
WalletScrutiny #nostrOpinion
-
 @ 82100056:e198089f
2024-04-01 18:35:34
@ 82100056:e198089f
2024-04-01 18:35:34 -
 @ e968e50b:db2a803a
2024-04-01 18:04:33
@ e968e50b:db2a803a
2024-04-01 18:04:33If you're not familiar with the Hopewell, they are a native North American people group who's culture thrived from 100BC to 500AD. There's evidence that they travelled pretty far and no evidence of agricultural development. So they were nomadic hunter/gatherers who periodically build large geometric earthworks in modern day Ohio. By large, I mean sometimes encompassing 100s of acres and sometimes stretching miles long. By geometric, I mean perfect squares, octagons, circles, parallel lines and semi-circles, all made out of dirt. All of these structures, like many others from the ancient world, have solar and lunar alignments.
It's impressive for hopefully obvious reasons. If you disagree, maybe check out why UNESCO puts them in the same category as the Great Pyramid in Egypt or The Great Wall in China. However, I think there is something that really makes the Hopewell stand out among the ancients. To this day, we have no evidence of centralized leadership. These massive projects, built with millions (7 million to be specific in the case of the Newark Earthworks, one of MANY sites) of baskets of dirt, were not built with forced labor. There are no burials that look like those of kings. There are not even any permanent settlements at the sites. Furthermore, there's no evidence of warfare from this period. The only weapons found seem fine-tuned for hunting and skeletons show signs of natural death. The Hopewell earthworks seem to just be MASSIVE community observatories and complicated math projects. They had a peaceful, decentralized network that covered most of North American which was able to come together periodically in a specific place to take on impressive building/astronomy/mathematics projects.
I visit some of these sites pretty regularly and have started to realize how much of an outlier in human history they are. After a dark age of about 500 years, the Hopwell were replaced by the Mississippians, who were an impressive culture, but more war-like and less egalitarian. Are there other examples of situations like this? I know the early Christian church (as well as the underground one in certain modern countries) seems to be similar in it's decentralized, peaceful, large-scale accomplishments. Bitcoin obviously fits the bill. Are there others? I'm thinking specifically of massive projects, without central power (voluntarily adopted), that require significant physical effort from large groups of people and a vast amount of multi-disciplinary knowledge.
-
 @ 000002de:c05780a7
2024-04-01 17:39:19
@ 000002de:c05780a7
2024-04-01 17:39:19When I started following bitcoin culture every once and a while I'd hear someone say "zoom out". It would usually be in response to someone else talking about a dip in fiat price. You can take this simple comment and apply it many other places. Of course it can be applied to investments, or anything long term. The old phrase "Rome wasn't built in a day". Or if you go to the economics side of things you often hear about "time preference" from the Austrians(which is a deep thought provoking topic btw).
We live in a very short term mindset culture. We want everything instantly. We have little patience. I'm not a kid anymore and I can tell you that this impatience culture has increased in my life time. My parents noticed it of course but when I was young I thought they were just old and out of touch. Now I see their vision and wisdom more clearly. Have you ever wondered why time seems to move faster the older you get? When I was a kid it seemed like I would never get to summer break. It seemed like Christmas took forever to get here. It seemed like I would never get my driver's license. Today it seems like 5 years passes by in no time. It seems like I blink and a new month is here. Time seems to function differently the more time I've have spent living.
I think this is the zoom out effect. Zooming out is a very important practice. Zooming out allows you to take a higher view. Just like climbing to the top of the mountain allows you to see things you can't see in the valley, zooming out allows you to see how the struggles and triumphs in life led you to where you are now. If you have a bad day, you make a dumb mistake, or someone is unkind. Zoom out. Is this an anomaly, or is it a pattern? With only a short time frame it is hard to see, but over time the truth reveals itself if you care to take the time to look. Do you hate your job or work? Maybe this is a rough patch. Maybe you need to take some time off and zoom out. Maybe something changed that you missed. Maybe it is an internal change and not external. It can be hard to see this without zooming out.
When we zoom out we can gain context. When we take time to reflect and ask ourselves tough questions we can see lies we may have believed. Some of us tend to battle negative self-talk. Some of us see our faults and failures and then magnify them. We zoom in on each event that is negative losing sight of the context. Zooming out helps provide context. Others fail to see their areas for improvement. They are full of self confidence to the point of being blind to warning signs. They need to zoom out as well. Sometimes even zooming out isn't enough. Sometimes you need someone else to help you with getting a new perspective.
I've been meaning to write about my recent experiences with refocusing, @siggy47 encouraged me to do it and here it is. When I started thinking about zooming out today I wasn't thinking about what I'm going to tell you, but the further into this I got the more clear the path became. I've been in a dark place mentally for some time. Most people that know me would not notice it. My wife is probably the only one that saw it. I don't feel like I'm out of the woods yet, but I can see the path forward and I'm walking it now. Back in February @elvismercury mentioned JBP's self-authoring program in a thought provoking post by @Fabs. I had checked it out before and almost started it but for some reason I didn't do it. Elivsmercury's comment was the reminder I needed. About a month ago I took a weekend and did the Future Authoring exercises. I highly recommend it to pretty much anyone. One thing it did was help me zoom out and reset my focus and thinking.
I realized that while I have been feeling burned out and down, I really needed to take time and zoom out. There have been some rough things I've experienced in past few years that really hit me hard. In many ways I'm just tired. But it is easy to let hard times lead into self-pity. In-action then leads to more in-action. This is a vicious cycle that only leads down into dark places. Taking a weekend to focus on figuring out my path forward was what I needed. The first day was not fun. There were many questions that I responded to that made me feel worse about myself. I was tempted to stop the whole process a couple times. But, I pushed through to the next day. Then a light bulb came on for me. I needed to zoom out and when I did I recalled some daily practices that I used to follow. I had let slip. I realized that I had accomplished many goals over the years but hadn't refocused on clear definable goals. I also realized that I have been trying to do to many things at once, failing to complete them, and then feeling defeated when I think about all I hadn't done. I realized that I had stop doing things that had worked for me in the past. When I saw this it was like a door opened and I could see a path out of a dark cave.
The simple way to describe what I did was that I zoomed out. I took time to turn off all distractions and focus on looking ahead and behind with a wider scope. If you are in a rough patch right now I encourage you to talk to someone. My path forward really started with talking to my wife. Maybe you should check out the Self Authoring program. Maybe just try to zoom out and realize what you have done over the last 10 years. Are you excited about where you're going? Do you know where you're going? Its always changing but every so often try to zoom out for a bit.
-
 @ bcea2b98:7ccef3c9
2024-04-01 17:27:32
@ bcea2b98:7ccef3c9
2024-04-01 17:27:32I've used Librovox, but looking for more recent technical and fiction topics. Audible seems so expensive having to pay for books in addition to a monthly membership. It would be nice if I could "browse" and listen to a lot of different types of books.
-
 @ 3cd2ea88:bafdaceb
2024-04-01 16:48:33
@ 3cd2ea88:bafdaceb
2024-04-01 16:48:33Grandi novità, #NUBFam!
Cosa ti aspetta:
Listing dal 29 marzo! Fino a 500.000 NUB in omaggi e bonus! APY elevato con NUB Earn! Non perdertelo! ➡️ https://bonus.bitget.com/U1JNEK
-
 @ c11cf5f8:4928464d
2024-04-01 15:43:43
@ c11cf5f8:4928464d
2024-04-01 15:43:43Time to brush off the spurs and saddle up for a ride into the exciting ad-ventures ahead! What innovative goods or services are y'all bringin' on the wagon this week? Give us a sneak peek and let that entrepreneurial spirit get out.
Take some pics and start posting your items now!
[⚖️ SELL] - [🛒 BUY] - [🧑💻 HIRE] - [🖇 OFFER] - [🧑⚖️ AUCTION] - [🤝 SWAP] - [🆓 FREE] - [⭐ REVIEW]
Stay humble, stack sats!
-
 @ bcea2b98:7ccef3c9
2024-04-01 15:20:24
@ bcea2b98:7ccef3c9
2024-04-01 15:20:24Opcodes are the fundamental building blocks of Bitcoin's scripting language, defining conditions for spending transactions. Each opcode represents a specific instruction executed within Bitcoin's virtual machine, enabling complex scripting capabilities. Opcodes are executed sequentially to validate transactions against scriptPubKey and scriptSig, determining if inputs fulfill the conditions for spending outputs.
The scripting language employs opcodes to perform operations like data manipulation, conditional execution, cryptographic verification, and arithmetic computations. This limited set ensures predictable script evaluation, mitigating risks from malicious or indefinitely looping scripts.
Opcodes enable smart contracts and multi-signature wallets within Bitcoin. Conditional logic opcodes (e.g., OP_IF, OP_NOTIF) and cryptographic operations (e.g., OP_CHECKSIG, OP_CHECKMULTISIG) enforce specific spending conditions, such as requiring multiple signatures or locking funds until a certain block height or timestamp (via OP_CHECKLOCKTIMEVERIFY and OP_CHECKSEQUENCEVERIFY).
| Opcode | Description | Function | |----------|-------------|-------------------| | 0 | OP_0, OP_FALSE | Push false | | 76 | OP_PUSHDATA1 | Push data | | 77 | OP_PUSHDATA2 | Push data | | 78 | OP_PUSHDATA4 | Push data | | 79 | OP_1NEGATE | Push -1 | | 80-96 | OP_1-OP_16, OP_TRUE | Push 1-16 | | 97 | OP_NOP | No operation | | 99 | OP_IF | If conditional | | 100 | OP_NOTIF | If not conditional | | 103 | OP_ELSE | Else conditional | | 104 | OP_ENDIF | End if | | 105 | OP_VERIFY | Verify condition | | 106 | OP_RETURN | Terminate script | | 107-108 | OP_TOALTSTACK, OP_FROMALTSTACK | Stack transfer | | 109 | OP_2DROP | Drop 2 | | 110 | OP_2DUP | Duplicate 2 | | 111 | OP_3DUP | Duplicate 3 | | 112 | OP_2OVER | Copy 2nd pair | | 113 | OP_2ROT | Rotate top 3 twice | | 114 | OP_2SWAP | Swap top 2 pairs | | 115 | OP_IFDUP | Duplicate if not 0 | | 116 | OP_DEPTH | Stack size | | 117 | OP_DROP | Remove top | | 118 | OP_DUP | Duplicate top | | 119 | OP_NIP | Remove 2nd | | 120 | OP_OVER | Copy 2nd | | 121 | OP_PICK | Nth item | | 122 | OP_ROLL | Move Nth top | | 123 | OP_ROT | Rotate top 3 | | 124 | OP_SWAP | Swap top 2 | | 125 | OP_TUCK | Move 3rd to top | | 130 | OP_SIZE | Size of top item | | 135 | OP_EQUAL | Equality check | | 136 | OP_EQUALVERIFY | Verify equal | | 139 | OP_1ADD | Add 1 | | 140 | OP_1SUB | Subtract 1 | | 143 | OP_NEGATE | Negate | | 144 | OP_ABS | Absolute value | | 145 | OP_NOT | Not zero | | 146 | OP_0NOTEQUAL | Not equal to 0 | | 147-148 | OP_ADD, OP_SUB | Arithmetic | | 149-154 | Disabled | Disabled | | 155-158 | OP_BOOLAND, OP_BOOLOR, OP_NUMEQUAL, OP_NUMEQUALVERIFY | Boolean logic | | 159-160 | OP_NUMNOTEQUAL, OP_LESSTHAN | Comparison | | 161-162 | OP_GREATERTHAN, OP_LESSTHANOREQUAL | Comparison | | 163-164 | OP_GREATERTHANOREQUAL, OP_MIN | Minimum/Maximum | | 165-166 | OP_MAX, OP_WITHIN | Range check | | 167-168 | OP_RIPEMD160, OP_SHA1 | Hashing | | 169 | OP_SHA256 | SHA-256 | | 170 | OP_HASH160 | RIPEMD-160+SHA-256 | | 171 | OP_HASH256 | SHA-256x2 | | 172-175 | OP_CHECKSIG, OP_CHECKSIGVERIFY, OP_CHECKMULTISIG | Signature check | | 176-177 | OP_CHECKMULTISIGVERIFY | Multisig verify | | 178-181 | OP_NOP1-OP_NOP4 | No operation | | 182-185 | OP_CHECKLOCKTIMEVERIFY, OP_CHECKSEQUENCEVERIFY | Timing checks | | 186-189 | OP_NOP6-OP_NOP9 | No operation | | 190-193 | OP_NOP10 | No operation |
-
 @ 3cd2ea88:bafdaceb
2024-04-01 13:55:56
@ 3cd2ea88:bafdaceb
2024-04-01 13:55:56Sign up and take advantage of a 30% APR!
Nubcat (NUB) has just been added to Bitget Earn's Savings products.
What it means for you.
Get a 30% annual return on your NUB tokens. Sign up now and start earning! The offer is limited, hurry up! Enrollment period:
March 29, 1 p.m. - April 26
How to participate:
Register on Bitget: https://bonus.bitget.com/U1JNEK Go to Bitget Earn > Save. Search for NUB and click on "Enroll." Deposit your NUB tokens. Start earning! Don't miss this fantastic opportunity!
Join Bitget Earn now and start earning with NUB!
-
 @ dadbe86a:9c493e92
2024-04-01 13:44:37
@ dadbe86a:9c493e92
2024-04-01 13:44:37Opinion about Nunchuk Bitcoin Wallet (android)
Nunchuk offers s an intuitive and user-friendly interface, making it easy for both novice and experienced users to navigate through its features. The app's design prioritizes simplicity and ease of use.
Pros: - Intuitive user experience. - Great support of platforms: mac, linux, windows, android and iOS - Open source - Good hardware wallet support - Lots of advanced features: multisig, taproot, fee & coin control, custom node, tor, testnet and signet support, etc - Is bitcoin-only, a plus for bitcoiners - Possibility to subscribe to get assisted wallets and inheritance services
Cons: - Missing support for wired hardware keys (but available on desktop app) - Missing support for some advanced features like user added entropy, coinjoin, miniscript or onchain timelocks
WalletScrutiny #nostrOpinion
-
 @ cce0989b:b497e608
2024-04-01 12:28:02
@ cce0989b:b497e608
2024-04-01 12:28:02One of the ways that Old Happy culture makes us miserable is by convincing us that we have to do everything, get everything, and be everything. You spread your energy out in a million directions trying to achieve an impossible task, leaving you overwhelmed, dissatisfied, and exhausted.
Instead, take a different approach: prioritize what matters most to you, devoting all of your energy towards the few things that really bring you joy.
Try this five minute exercise: write down a list of what is most important to you. Then, compare it to how you're currently spending your time. What do you need to let go of so that you can devote your energy towards what matters most?
-
 @ f72e682e:c51af867
2024-04-01 10:35:15
@ f72e682e:c51af867
2024-04-01 10:35:15Lagarde is airdroping me 1 BTC... wtf????
SN is compromised, guys. They arrived. They want to buy our opinion.
-
 @ c4428155:a36de510
2024-04-01 10:00:00
@ c4428155:a36de510
2024-04-01 10:00:00When the Number of Bedrooms in a Home Keeps Parents From Getting Their Kids Back
by Stephannie Stokes (https://www.wabe.org/people/stephannie-stokes/), WABE (https://www.wabe.org/), with data analysis by Agnel Philip (https://www.propublica.org/people/agnel-philip), ProPublica
This article was produced for ProPublica’s Local Reporting Network in partnership with WABE (https://www.wabe.org). Sign up for Dispatches (https://www.propublica.org/newsletters/dispatches) to get stories like this one as soon as they are published.
K. thought she was one step closer to regaining custody of her children when she secured her studio apartment.
It wasn’t much — just a large basement room in an outer-Atlanta suburb that she was able to rent through a friend. But it had a kitchen and living area, and she was able to arrange beds in different corners of the room for her two sons and daughter. “It was cozy,” she said.
She hoped this would be enough for the Georgia Division of Family and Children Services to, at last, allow weekend visits with her kids — setting the stage for her to get them back permanently after two years in foster care.
But she learned in court, following her caseworker’s inspection of her apartment, that there was a problem: She didn’t have individual bedrooms for her kids. DFCS wouldn’t let them stay there unless she had at least one for her daughter and another for her sons, she said.
This didn’t make sense to her — she knew that there were families who lived long term in single hotel rooms without ever triggering child welfare investigations. In fact, DFCS itself has resorted to housing foster children in hotels (https://apnews.com/article/georgia-hoteling-foster-children-a29901d6240a7e929d47b7254a512278) when the agency can’t find other placements.
K., who is identified by her first initial because of her fear of retaliation from DFCS, had worked to fix every other aspect of her life since her kids were taken away. She completed a yearlong drug treatment program, testing clean continuously ever since. She also began work as a home health aide. And she was diligently making child support payments to the state.
“I did everything I was supposed to do,” she said, her voice shaking as she stressed this point.
That was in 2019, and K. quickly turned her attention to improving her housing situation, seeing it as one more challenge for her to overcome.
She didn’t know at the time that it would be another four years, until 2023, when her family would be finally reunited. Her kids, by then teenagers, had been in foster care for almost six years.
Inadequate Housing Was Associated with Significantly Longer Foster Care Stays
In Georgia, children whose cases cited "inadequate housing" typically took three months longer to reunify with their families than those whose cases did not.
Only foster care cases in which children were reunified with their caretakers were included in this analysis. Source: ProPublica analysis of National Child Abuse and Neglect Data System records
(Agnel Philip/ProPublica)
K.’s case is a striking example of the way parents’ housing instability can lengthen their children’s stay in foster care. In Georgia, WABE and ProPublica found, versions of her experience play out across the child welfare system.
An analysis of data reported to a federal repository of foster care and adoption cases between fiscal years 2018 and 2022 shows that, in Georgia, cases that included “inadequate housing” as a reason for removing a child typically took 11 months to reach reunification, three months longer than cases that did not. Foster care cases associated with inadequate housing took longer to resolve than cases involving allegations of physical or sexual abuse.
Interviews with more than a dozen attorneys, judges and advocates in Georgia’s child welfare system confirmed the delays that housing can cause. They described cases similar to K.’s, in which parents overcame issues like drug addiction and mental health struggles but still waited months to be reunited with their children because of their housing situation.
“These kids just sit in foster care,” said Melanie Dodson, a family law attorney based in Cleveland, Georgia, offering a typical example, “because mom and dad are working at Subway and can’t afford a four-bedroom house.”
While all agreed that a shortage of affordable units is a major obstacle, several attorneys and advocates said DFCS adds to the challenge for low-income parents by insisting their housing meet requirements that can be unattainable.
They said it’s often not enough for parents to provide shelter to get their kids back; DFCS may ask for a formal lease or for the home to be of a specific size. K.’s example, they said, is common: The agency often argues in court that parents must provide individual bedrooms for children of different ages and genders.
DFCS spokesperson Kylie Winton didn’t provide explanations for any of these requirements, which aren’t written down in any statewide policy. But she noted that the agency designs its recommendations for housing based on the needs of each family. Ultimately, she added, judges decide what conditions are appropriate for reuniting children with their parents.
But attorneys and advocates, who practice in counties throughout Georgia, said many judges are reluctant to return children to parents with housing that doesn’t win DFCS’ endorsement. They also said while the agency may not have a statewide policy, they've noticed a pattern of DFCS arguing for the same stringent housing requirements across many county courtrooms.
While stringent housing requirements aren’t unique to Georgia, experts say they can be especially difficult to meet in the state, given how little housing assistance is available to families through its child welfare system.
If your issue is housing, that’s a societal problem, not an individual failing, and we need to dig a little bit deeper to come up with a way and a solution to that problem that doesn’t scar children.
—Vivek Sankaran, a professor at the University of Michigan and an attorney representing parents and children
As WABE and ProPublica reported in January, DFCS invested only a tiny portion of its resources toward housing assistance (https://www.propublica.org/article/georgia-housing-assistance-foster-care) in recent years despite citing “inadequate housing” among its reasons for removing children in roughly 20% of foster care cases. Child welfare agencies in several other states allocated significantly more to provide housing to families, including those working to reunite with their kids in foster care.
Vivek Sankaran, a professor at the University of Michigan and an attorney representing parents and children, said Georgia’s child welfare system should provide housing assistance to parents — or simply return their children. Prolonging a family’s separation for housing alone goes against federal and state guidelines, including Georgia’s, he argues, which emphasize that child welfare systems should return children as soon as possible.
“If your issue is housing, that’s a societal problem, not an individual failing,” Sankaran said, “and we need to dig a little bit deeper to come up with a way and a solution to that problem that doesn’t scar children.”
Attorneys and advocates told WABE and ProPublica that parents who are trying to reunite with their children in Georgia are often expected to meet housing requirements that go far beyond the conditions that would justify a child’s removal.
Heather Daly, an attorney who represents children and parents in child welfare cases, said she has often seen DFCS refuse to approve of housing that parents share with relatives. That’s a problem for many of her clients who come from rural areas and often live with family to cut costs.
Daly said DFCS may label a multigenerational home as unsafe because a grandparent has a 20-year-old criminal charge or because relatives refused to be fingerprinted for background checks. Any past history with DFCS, no matter the circumstances, can also lead the agency to discourage returning children to the household.
In court, Daly said, she tries — with little success — to point to other families who are able to share homes without DFCS getting involved or running background checks. “I mean, most of this generation is living with their parents right now,” she said. ”And this is nothing different.”
Several attorneys and advocates pointed to another obstacle to reunification: DFCS sometimes won’t accept housing unless parents can prove that they have a right to stay in it long term.
Colleen Puckett, whose children were formerly in foster care and who now helps others navigate the reunification process across the state, said sometimes parents can get around this if they’re able to draft leases with the relatives or friends they’re staying with. But that’s not possible to arrange with extended stay hotels and homeless shelters.
It’s also not uncommon for DFCS to request that parents secure housing with a lease of their own, attorneys and advocates told WABE and ProPublica. Even when parents manage to accomplish that, they may still have to maintain the housing for six months before they can reunite with their children.
The problem with these rules is that few families in the child welfare system can afford — or qualify for — housing that comes with the space and certainty DFCS is demanding, attorneys and advocates said.
Many parents face challenges similar to K.’s. Because of criminal charges from when she was using drugs, many landlords refused to rent to her. Even if they had accepted her record, they also required incomes that were three times the rent, far outside the scope of her $11-per-hour wage.
Having an open child welfare case only makes the housing situation more difficult for parents like K. because they’re often hit financially — and are thus less likely to be able to afford rent — when they have to miss work to complete the requirements of their case, such as attending court hearings, seeking therapy or making visitations with their kids. On top of that, many can’t receive assistance from social service organizations until they can get their kids back.
“It just delays reunification significantly,” Puckett said.
Peggy Walker, a judge who has presided over child welfare cases in Georgia courts for more than 25 years, acknowledged that housing requirements often are more stringent for parents in the child welfare system and explained that that’s because judges are trying to eliminate the risk of children reentering foster care.
“You have traumatized that child by removing them,” Walker said. “If you put them back too soon, you have to turn around and remove them again.”
Walker said this consideration could lead judges to deny housing situations that may be acceptable for parents who aren’t involved in the child welfare system — though she said the requirements should be specific to the case. If the relatives have a history of kicking the parents out, for instance, then she said she might not have approved that housing situation for returning the children. She said if the family is known to be supportive, however, she would consider returning children to their home.
Regarding families with criminal histories, Winton, DFCS spokesperson, said the agency evaluates each situation to determine whether prior charges present a risk to the child.
You have traumatized that child by removing them. If you put them back too soon, you have to turn around and remove them again.
—Judge Peggy Walker
But attorneys and advocates said too often DFCS officials and judges insist on parents providing an ideal environment for their children. Sankaran, the University of Michigan professor, said that shouldn’t be the bar parents have to meet in order to regain custody of their kids. “We’re never going to in any of our lives get to a place where there’s zero risk for any of us,” he said.
Instead, Sankaran said, the requirements should be based on what is safe enough.
In its manual, DFCS outlines housing conditions — including exposed wiring, raw sewage and rodent infestations — that pose a threat to children’s safety and may warrant their removal into foster care. Sankaran said those kinds of concerns should be used as the guide for defining the conditions for reunification.
The child welfare system isn’t supposed to wait years to find a permanent outcome for parents and their children. Federal and state laws call for DFCS to make “reasonable efforts” to reunite parents with their children — Georgia's code specifies “at the earliest possible time,” repeating the phrase in its code section three times.
State Rep. Mary Margaret Oliver, a longtime Democratic lawmaker who has authored several legislative changes to the foster care system, said this should include connecting parents to housing once they have resolved other safety concerns. “If we are not able to provide a competent working parent with a place to live, I think that we’re failing in our obligation to reunite the family,” she said.
That obligation exists in part because the cost of delaying reunification can be significant, said Melissa Carter, who leads the Barton Child Law and Policy Center at Emory University and is a former director of Georgia’s Office of the Child Advocate.
The longer children are in foster care, the more likely they are to be bounced from home to home because of changes or conflicts with their foster placements. According to state data reported to the site Fostering Court Improvement (https://fosteringcourtimprovement.org/ga/summary1.shtml) for fiscal year 2023, 66% of children who were in Georgia’s foster care system for more than two years had been moved three or more times.
Carter said these disruptions can affect a child’s ability to trust and form attachments, stay connected to their siblings and keep up in school. “So it’s just this kind of compounded experience that comes from the destabilization and trauma that comes with removal,” she said.
This is why federal law requires states to pursue adoption, terminating the parent’s rights, if they haven’t met the requirements for reunification by 15 months — unless child welfare agencies can provide “compelling reasons” to keep the case open beyond that deadline.
K. was aware of that timeline from other parents in the child welfare system. As months and court dates passed and a pandemic unfolded, she said she was grateful that the judge continued to give her a chance. “By the grace of God, he kept giving me another six months,” she said. “But he knew the only thing holding me up was housing.”
When she was finally able to convince a property manager in rural Georgia to rent her a two-bedroom townhome, K. was full of excitement, writing on Facebook, “GOD IS SO GOOD, ON TIME, AND ABUNDANT!” She said the reunification with her children that followed was happy — at first.
It is so wonderful to look at them and see that they’re home.
—K.
But K. soon saw the consequences of the years her children spent in foster care.
She thought they would be glad to have their mom back. In reality, she said, they’re angry and resentful toward her. According to K., they tell her she abandoned them. They don’t believe she only needed housing for reunification. They tell her she was just using drugs the whole time.
“I didn’t abandon you,” she said she told them. “I was working to get you back.” But K. says her pleading is of no use.
She said her kids’ anger also comes out at school, leading to suspensions. The behavior has been severe enough that she had to let go of one of her jobs. DFCS did provide her with one month of rental assistance — but only after her children had already been home for months. But now K. is again struggling to make her rent.
As she tries to keep the home together, she’s weighed down by guilt from what her children went through.
The moments she’s able to appreciate her family’s reunification, after so much time apart, are often limited to the night, when her children are asleep. K. can’t help but watch them. “It is so wonderful to look at them and see that they’re home,” she said.
How We Analyzed the Effect Housing Has on Foster Care Stays
We analyzed data from the Adoption and Foster Care Analysis and Reporting System (https://www.ndacan.acf.hhs.gov/datasets/datasets-list.cfm) to determine whether a child removal citing “inadequate housing” was associated with longer foster care stays in Georgia.
The AFCARS data, obtained from the U.S. Department of Health and Human Services’ National Data Archive on Child Abuse and Neglect, required steps to clean and deduplicate before we could analyze it. We used unique identifiers for children called AFCARS IDs and dates when a child was last taken into foster care to remove duplicates. We then filtered the dataset to removals that occurred from July 1, 2017, to June 30, 2022, corresponding to Georgia’s 2018 to 2022 fiscal years. We then grouped by removal reason and calculated the median time between removal and discharge for cases in which children were reunited with their caretakers. For this grouping, we counted cases citing the removal reason alone or in combination with other removal reasons. For a case in which two different removal reasons are cited, its reunification time was included in the calculation for each of the removal reasons.
To further examine this issue, we developed several statistical models to isolate the effect of the housing removal reason. We controlled for other removal reasons and the age of the child, including interactions those variables had with the housing removal reason. In every model we tested, housing was associated with longer foster care stays to a high level of statistical significance.
The data used in this story was obtained from NDACAN via Cornell University and used in accordance with a terms of use agreement license. The Administration on Children, Youth and Families; the Children’s Bureau; the original dataset collection personnel or funding source; NDACAN; Cornell University; and their agents or employees bear no responsibility for the analyses or interpretations presented here.
https://www.propublica.org/article/in-georgia-inadequate-housing-can-mean-longer-stays-in-foster-care
-
 @ 3c984938:2ec11289
2024-04-01 09:36:34
@ 3c984938:2ec11289
2024-04-01 09:36:34A long time ago, a girl resided on a tropical island. The girl's name is Sirena. She resided with her mother in close proximity to the Hagåtña River. Sirena's mother was a bit strict and tried to teach her to follow her in footsteps to be a lady, but Sirena only dreamed of swimming all day.\
 \
Sirena's only outlet was when her Godmother would come visit. She always brought surprises, such as new trinkets, stories, and secretly gave her coconut candy.
\
Sirena's only outlet was when her Godmother would come visit. She always brought surprises, such as new trinkets, stories, and secretly gave her coconut candy.
Sirena's mother was preparing for a special event and needed her to acquire special ingredients from the nearby village. She had a significant amount of preparations to complete, therefore she requested that Sirena procure the necessary ingredients and return promptly. Sirena made a promised to her mother that she would hurry back.\

She was on the village path. She kept her eyes on the trail, trying her best to be a good daughter and hurry back. But she took one glance briefly at the river.
 \
She is mesmerized by the water and jumps in before she realizes it. She swims down the river to the ocean, completely forgetting her mother's errand and promise. Sirena does not returned home even after the sun has set and was still swimming. Her mother, frustrated and angry, unleashes a powerful curse. The godmother begged her daughter to calm down. She shouted, "She's swimming again! Look at how late it is! "If you have such a profound love for the ocean, then become a fish," she exclaims to the ocean. Knowing the extent of her daughter's curse. She tries to counteract her daughter's curse. She pleads to the ocean, "Please, let me keep my Goddaughter's heart, please let that much remain."\
\
She is mesmerized by the water and jumps in before she realizes it. She swims down the river to the ocean, completely forgetting her mother's errand and promise. Sirena does not returned home even after the sun has set and was still swimming. Her mother, frustrated and angry, unleashes a powerful curse. The godmother begged her daughter to calm down. She shouted, "She's swimming again! Look at how late it is! "If you have such a profound love for the ocean, then become a fish," she exclaims to the ocean. Knowing the extent of her daughter's curse. She tries to counteract her daughter's curse. She pleads to the ocean, "Please, let me keep my Goddaughter's heart, please let that much remain."\
 \
In the eerie glow of the moonlight, upon realizing her mother's task, she swims back to where the ocean meets the river. But she experiences a strange sensation in her lower half. The water swirls around her. She looks down to see that she has now fins instead of feet. With the new transformation, she regrets not finishing her mother's errand.
\
In the eerie glow of the moonlight, upon realizing her mother's task, she swims back to where the ocean meets the river. But she experiences a strange sensation in her lower half. The water swirls around her. She looks down to see that she has now fins instead of feet. With the new transformation, she regrets not finishing her mother's errand.
Sirena was happy because now she can be in the water all day long. However, Sirena also wished she did what her mother asked and found another way to punish her. A part of her will forever be saddened by the loss of her Mother and Godmother.
It said that sailors have spotted mermaids on their voyage across the sea. Just that their too crafty & swift to be caught.
Historical Notes/context
 The story originates from the indigenous island of Guam and has been shared for generations. There are multiple versions of the story. The term Sirena is not present in the Chamorro language; however, in Spanish, it refers to the mythological creature known as the mermaid. The capital of the Island is Hagåtña. The Hagåtña river flows beneath the Spanish Bridge, where it is possible to observe her monument. Many believe Sirena resided here. There is speculation that this story was crafted to frighten children into listening to their parents and not playing in the river's water, as it was a vital water source. This was more prevalent when the Spanish established Guam as a port for whaling, pirates, and trade during the Spanish Galleon trade era(16th century). It should be noted that the women's role in the Chamorro version reflects a matrilineal society, which can be seen with Grandma/Godmother.
The story originates from the indigenous island of Guam and has been shared for generations. There are multiple versions of the story. The term Sirena is not present in the Chamorro language; however, in Spanish, it refers to the mythological creature known as the mermaid. The capital of the Island is Hagåtña. The Hagåtña river flows beneath the Spanish Bridge, where it is possible to observe her monument. Many believe Sirena resided here. There is speculation that this story was crafted to frighten children into listening to their parents and not playing in the river's water, as it was a vital water source. This was more prevalent when the Spanish established Guam as a port for whaling, pirates, and trade during the Spanish Galleon trade era(16th century). It should be noted that the women's role in the Chamorro version reflects a matrilineal society, which can be seen with Grandma/Godmother. 
👉I like to point out in this, Thomas Edison patented the light bulb in 1879. So visually the lights outside and inside the huts as flames. As Ai(text to image) does not account for these type of items.
👉This also goes back to be careful what you wish for because you may actual get your wish.
👉Chamorro people are Pacific Islanders, similar to Hawaiians, and have a brown/tan skin complexion.\

👉My mermaid looks strikingly similar to the Disney's recent version of Ariel. I Thought that was interesting because I put just "mermaid" into the text prompt. Its worth pointing out ai limitations as it's not advanced as I originally thought, likely due to its limited data. In this case only disney as a reference for mermaid.
based on ordinary prompts\

 Prompt used:\
Prompt used:\
 That's all-Thank you until next time (N)osyters!
That's all-Thank you until next time (N)osyters!If you like it, send me some ❤❤hearts❤ and if you didn't like it-⚡⚡🍑🍑zap⚡⚡🍑🍑 me!🍑🍑 me!
For email updates you can subscribe to my paragraph.xyz/\@onigirl or below if using the Yakihonne App
-
 @ a012dc82:6458a70d
2024-04-01 07:20:15
@ a012dc82:6458a70d
2024-04-01 07:20:15Table Of Content
-
Content
-
Conclusion
-
FAQ
-
You May Also Like
-
External Links
Going Green! The issue of climate change has assumed a crucial role in contemporary activity. It is a difficulty of the contemporary period that must be addressed over the long term, and it compels businesses to adjust their operational models so that they can accept new ways of considering the environment.
It is imperative that cryptocurrencies and other digital assets adhere to environmental and sustainability regulations as they work to break into the mainstream financial industry. The mining of cryptocurrencies has become a significant threat to the environment since even a single Bitcoin transaction may use more than 2,264 kilowatt hours of power. Companies that put a greater emphasis on environmental, social, and governance concerns are seen more favorably by investors (ESG). A net-zero emissions target has been set for the year 2030 by organizations that have joined the Crypto Climate Accord. A cryptocurrency and blockchain project's long-term viability and its impact on the environment are influenced by a number of factors, including the energy sources that are used to power mining operations, the validation system that is currently being implemented, and the amount of physical equipment that is required.
In order to meet their sustainability and environmental objectives, both new and established blockchain projects are investigating various possibilities, such as transitioning to less energy-intensive validation systems and mining that is powered by renewable energy sources.
Adopting Newer Crypto Mining Models
Mining cryptocurrencies, often known as "crypto mining," is the process through which new cryptocurrencies are created and released into circulation. Additionally, this is how new transactions are validated on the distributed ledger that blockchain technology uses. In order to complete difficult calculations, mining requires the use of sophisticated machinery. The miner is rewarded with new tokens and also receives payment.
One of the most significant drawbacks of mining is the enormous quantity of energy that is used, along with the enormous carbon footprint and other negative effects that this has on the environment. The conventional approach is known as "proof of work" (PoW), and it requires miners to compete against one another to solve difficult mathematical equations. The consensus requires a significant amount of computer power, which results in a rise in both energy consumption and emissions.
The validation of cryptocurrency transactions is carried out according to a new set of guidelines used in "green crypto mining." This model is referred to as "proof of stake" (PoS). The process through which blockchain nodes reach a consensus on the correctness of transactions has been redefined as a result of this. The nodes make "bets" in the form of tokens in return for the opportunity to create the next block of transaction data. These bets are called "stakes." Ethereum is likely one of the most notable instances of a significant cryptocurrency project that is migrating from a PoW system to a PoS system. The intention behind this move is to lower Ethereum's total energy usage by 99.95%. One of the benefits of the POS model is that it has a lower barrier of entry than other models owing to its simple hardware needs and high efficiency.
Green Energy Sources
Environmental rules are continuing to have a greater amount of weight in the decision-making processes of investors. In addition, policymakers are placing an increased emphasis on the use of cryptographic energy. Because of this, there has been a significant push toward the use of renewable energy sources in the mining process.
There is a growing financial motivation to reduce the carbon footprint of blockchain and the ecosystem around cryptocurrencies. Miners of cryptocurrencies are coming up with strategies to lower their carbon footprints, such as switching to energy sources that are 100 percent renewable or switching to a mix that includes a bigger percentage of renewable energy.
Mining cryptocurrency may be powered by a variety of renewable energy sources, including solar, geothermal, and wind power, among others. Despite the fact that there is a possibility that certain cryptocurrencies won't justify the financial outlays, a select few corporations are intending to spend enormous amounts on renewable energy facilities that will be devoted to mining.
Power that has been repurposed elicits passionate disputes over whether or not it can be classified as renewable energy. Companies like Crusoe Energy and Equinor have rebuilt traditional power stations that were not being utilized and have instead utilized the extra gas that would have been burned off as a byproduct of drilling instead. Some people think that it reduces harmful emissions, but that it does so by shifting them to a new sector of the economy.
Handling e-Waste
The significant obstacle posed by e-waste generated by legacy mining operations is presented by blockchain networks. The business world is struggling to figure out what should be done with all of the mining hardware, regardless of whether or not it is specialized. Alternate methods of validation, on the other hand, lessen the need for ever-more-powerful and expansive mining rigs in the foreseeable future, thereby cutting down on the amount of waste generated.
Examples of Green Cryptocurrencies Some of the more recent cryptocurrencies are being mined with alternative validation methods and renewable energy in an effort to reduce their environmental impact and carbon footprint.
-
#Takamaka is a distributed ledger that anyone can use. A native blockchain PoS with two tokens, one of which is stable and guaranteed at the Swiss bank, and one from governance: $TKG. One of the tokens is stable and guaranteed at the Swiss bank. A "green token," also known as "TKG," is a cutting-edge method of keeping the network alive that has a low overall energy footprint.
-
#Cardano is a proof-of-stake cryptocurrency built on a blockchain that is peer-reviewed. Instead of mining new coins, people buy units of Cardano to become members of the network. This results in a significant reduction in the amount of energy that is consumed.
-
#Stellar is a blockchain network that is related to the cryptocurrency lumen. It is known for its low energy consumption (XLM). Stellar makes use of a consensus process that is more efficient than proof-of-work and proof-of-stake. This approach involves a group of trustworthy nodes that authenticate transactions. People are able to exchange fiat currency and cryptocurrencies on the network, and they can also make and receive remittance payments without having to pay large fees or wait a long time.
-
#Nano is another low-energy cryptocurrency that is built on the technology known as "blockchain lattice." This technology generates user blockchains for everyone who is connected to the Nano network. Open Representative Voting, or ORV, is used by Nano to reduce the amount of energy that is consumed during the validation process. Representatives are voted into their positions by other members of the network.
-
#Hedera Since transactions are processed in parallel on the Hashgraph blockchain rather than sequentially as they are on Bitcoin and other legacy cryptocurrencies, Hashgraph is much quicker. It is capable of competing with payment processors like Visa thanks to its capacity to complete up to 100,000 transactions in a single second. Other environmental initiatives, such as the company's Power Transition energy monitoring software, get assistance from the Hedera network.
-
#Gridcoin draws electricity from dormant computers that are linked to its network for the purpose of doing scientific research (BOINC). It employs Evidence of Stake, with validators being compensated with an algorithm for proof of research.
Conclusion
The permanence of blockchain technology suggests that moral decisions will need to be made in order to assure a sustainable future. The next iteration of solutions based on blockchain technology will be more environmentally friendly and sustainable. It is incumbent upon blockchain developers to use their creative faculties in order to create environmentally friendly solutions based on innovative operational and economic models, energy efficiency, and the utilization of renewable energy sources. Already, there are new projects that have been launched with the intention of enhancing the environmental credentials of the business. If we are successful in meeting our sustainability targets, cryptocurrencies and blockchain initiatives will become more appealing to a much wider audience of consumers.
FAQ
Which cryptocurrency has the most potential for longevity? Tezos (XTZ) Is Proving to Be the Most Sustainable Cryptocurrency in the Blockchain Space. The Ethereum blockchain now has a sustainable scaling solution in the form of Polygon (MATIC). Avalanche (AVAX) is a blockchain that is highly scalable and requires very little energy to operate. Algorand (ALGO) Is A Blockchain Project That Is Friendly To The Environment And Has Remarkable Sustainability Practices.
Is blockchain technology sustainable for the environment? As a direct consequence of this trend, the use of environmentally friendly energy in Bitcoin mining has increased by approximately sixty percent this year. A second use for blockchain technology is in the mitigation of climate change by reducing atmospheric concentrations of carbon dioxide and other greenhouse gases. In some regions, the technology of blockchain is being utilized in conjunction with carbon credits in an effort to help the environment.
What exactly is meant by the term "Green Blockchain Technology"? To be considered "green," a cryptocurrency must uphold the legitimacy of the blockchain while also being resourceful with energy and reducing its overall carbon impact. The concept of sustainability is quickly emerging as one of the most important factors that will determine the trajectory of the blockchain sector going forward.
What role does blockchain play in promoting environmental responsibility? These systems have the potential to aid in the expansion of the use of renewable energy. Supply chain methods that are sustainable and beneficial to the environment are another potential use of blockchain technology. By making supply chains more visible, the technology can monitor items all the way back to the manufacturer, contributing to the reduction of inefficiency and waste.
That's all for today, see ya tomorrow
If you want more, be sure to follow us on :
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 57d1a264:69f1fee1
2024-04-01 07:01:20
@ 57d1a264:69f1fee1
2024-04-01 07:01:20Prompt: Logo redesign ===============
Branding is generally a serious matter for most organizations and the considerations for size, placement, color and font should be thought out carefully. Pick a Bitcoin organization you like and redesign their logo. Or just create a new one!
The biggest brands don't always have the best logos. A great logo is one that compliments a specific purpose and not necessarily a generic image or name. For example, Nike uses a swoosh which shows motion and speed - core values of their running philosophy. Mailchimp showcases a monkey rather than an “email” icon adding depth and character to their brand. @SN uses a simple font that resemble lightnings, an indirect call to bitcoin and fast payments.
Flex your design muscles and join in. Most of all, keep this exercise loose and keep it stress-free. The FUC is about growing our design skills, together, as a community. We can't wait to see what you create!
Happy designing, Stackers!
Share Your Results When you finish the challenge, post your work on this thread! If you also share it on
nostr, be sure to use the hashtag #FUCdesiger and tag Design_r@iris.to or @Design__r on X! We'll keep an eye out and repost good examples on a regular basis.
Curious to know WTF is a FUC? Read the ⚡️Flash Ui Challenges welcoming post.
Looking for more FUCs? Check the archive here!
-
 @ 45a8f811:6f83ebbc
2024-04-01 06:41:15
@ 45a8f811:6f83ebbc
2024-04-01 06:41:15- It's April!
- Still April!
- Peter
-
 @ 386867a0:d2c9fb6b
2024-04-01 06:28:35
@ 386867a0:d2c9fb6b
2024-04-01 06:28:35- It's April!
- Still April!
-
 @ 84a419c4:70da99fc
2024-04-01 06:27:36
@ 84a419c4:70da99fc
2024-04-01 06:27:36- Hey ho, it's April!
-
 @ 1be2394f:8a8daec4
2024-04-01 06:26:56
@ 1be2394f:8a8daec4
2024-04-01 06:26:56- Hey ho, it is April!
-
 @ d3fd7db0:f1bc9b80
2024-04-01 06:26:09
@ d3fd7db0:f1bc9b80
2024-04-01 06:26:09- It is April!
-
 @ d3fd7db0:f1bc9b80
2024-04-01 06:26:04
@ d3fd7db0:f1bc9b80
2024-04-01 06:26:04- It is April!
-
 @ 39c43440:a9bb697b
2024-04-01 06:24:13
@ 39c43440:a9bb697b
2024-04-01 06:24:13- It is April!
-
 @ 39c43440:a9bb697b
2024-04-01 06:24:12
@ 39c43440:a9bb697b
2024-04-01 06:24:12- It is April!
-
 @ 16bf02ce:84f8b6ff
2024-04-01 06:22:10
@ 16bf02ce:84f8b6ff
2024-04-01 06:22:10- It is April
-
 @ 16bf02ce:84f8b6ff
2024-04-01 06:22:10
@ 16bf02ce:84f8b6ff
2024-04-01 06:22:10- It is April
-
 @ 16bf02ce:84f8b6ff
2024-04-01 06:22:10
@ 16bf02ce:84f8b6ff
2024-04-01 06:22:10- It is April
-
 @ 16bf02ce:84f8b6ff
2024-04-01 06:22:09
@ 16bf02ce:84f8b6ff
2024-04-01 06:22:09- It is April
-
 @ 16bf02ce:84f8b6ff
2024-04-01 06:22:08
@ 16bf02ce:84f8b6ff
2024-04-01 06:22:08- It is April
-
 @ 16bf02ce:84f8b6ff
2024-04-01 06:22:08
@ 16bf02ce:84f8b6ff
2024-04-01 06:22:08- It is April
-
 @ 16bf02ce:84f8b6ff
2024-04-01 06:22:08
@ 16bf02ce:84f8b6ff
2024-04-01 06:22:08- It is April
-
 @ 16bf02ce:84f8b6ff
2024-04-01 06:22:08
@ 16bf02ce:84f8b6ff
2024-04-01 06:22:08- It is April
-
 @ 16bf02ce:84f8b6ff
2024-04-01 06:22:07
@ 16bf02ce:84f8b6ff
2024-04-01 06:22:07- It is April
-
 @ 16bf02ce:84f8b6ff
2024-04-01 06:22:02
@ 16bf02ce:84f8b6ff
2024-04-01 06:22:02- It is April
-
 @ 1d8759ff:fa20c4f9
2024-04-01 03:53:48
@ 1d8759ff:fa20c4f9
2024-04-01 03:53:48The transition of the early internet from a decentralized network to a centralized ecosystem provides several lessons for the development of the nostr protocol. It highlights the importance of resilience through distributed architecture, the need to balance convenience with decentralization to prevent centralization from re-emerging, and the management of complexity in ways that do not favor large entities. Economic incentives must be carefully designed to support decentralization, and navigating regulatory landscapes is crucial for maintaining openness. Additionally, the success of decentralized systems hinges on providing a seamless user experience to encourage widespread adoption. Finally, the open-source movement's role in fostering innovation and collaboration underscores the value of transparency and community engagement in the development of decentralized systems. In this post, I will be focusing on designing economic incentives that support decentralization. Asynchronous payment methods are beneficial to decentralized networks because they allow for transactions to be processed independently and without the need for immediate communication between the transacting parties.
The struggle for incentives in decentralized systems is not new
The Cypherpunk movement, known for advocating the widespread use of strong cryptography and privacy-enhancing technologies, also explored the idea of creating an internet money system to be used as email server postage to combat spam. This concept envisioned a micropayment system where senders would pay a small fee to send emails, thereby discouraging mass spamming by making it economically unfeasible. That cypher punk, Satoshi Nakomoto solved the problem of a decentralized internet money, but in the end, email and web ended up becoming highly centralized communication systems based on a relatively few number of providers. Similarly, the tor project has failed to a functioning incentive system and therefore depends on donations relay and proxy operations.
Nostr relays
Relays come in two main flavors: * Client-backing relays: Damus client or Primal client * Solo- or Community-hosted relays: Bitcoiner.social or the author's Orange Crush Relay
Relays can be as cheap as small 5$ VPS or a mega-sized bank account draining endeavor like Damus.io. Fees are typically associated with hosting fees and traffic fees both of which can scale quite exponentially as we add new users, but who pays? From the beginning, nostr protocol relays were not designed to be monetized. During the early days of nostr, "global" relay traffic could be monitored for interesting posts; however, the introduction of "Shower Girl" spam made it clear that a barrier to entry must be created to reduce spam.
This led to the integration of one-time payments into popular relay software nostream. The one-time payment model worked to curb SPAM posts, but does not provide sufficient funding for running a large relay service. Next, nostr user Mazin developed the Nostr.wine monthly subscription-based relay with a premium filter displaying notes from your extended connected follow/er network. I'll leave it to Mazin to describe whether this is a fruitful endeavor. Profitability aside, the subscription model too closely resembles the centralized internet models we are seeking to escape through the decentralized design of the nostr protocol.
Nostr protocol requires a decentralized, asynchronous payment system
Asynchronous payments are advantageous with mobile clients because they allow for transactions to be processed without requiring both parties to be online simultaneously, which is particularly beneficial given the intermittent connectivity and varying network conditions often experienced by mobile devices. As nostr clients or microservices will often run on mobile devices, this approach enhances user experience by enabling transactions to proceed in the background, thereby reducing the need for immediate interaction and allowing for more efficient use of mobile network resources.
Lightning is not the solution for asynchronous micropayments
The Bitcoin Lightning Network is not a good fit for asynchronous small payments primarily because it requires both the sender and receiver to be online simultaneously for transactions to be completed. This synchronous requirement poses a significant challenge for mobile clients, which may not always have a stable internet connection or may be offline due to the device's power-saving modes or intermittent connectivity. Additionally, the Lightning Network's payment channels necessitate active management and liquidity, which can be complex and time-consuming, particularly for small payments that may not justify the overhead, a problem which will be exacerbated as bitcoin purchasing power increases.
Don't fret cypherpunks; This time we have all the tools
- A decentralized, uncensorable money: Bitcoin
- An asynchronous system for sending bitcoin-redeemable Ecash
- P2PK system for locking Ecash to a particular npub
- Services accepting payments for VPS hosting
Asynchronous payments with Cashu
In September 2022, Nostr user Calle introduced CashU Chaumian Ecash system. The Cashu protocol is an open-source ecash system designed for Bitcoin, utilizing the Blind Diffie-Hellman Key Exchange (BDHKE) for cryptographic security to sign and redeem ecash tokens, allowing for private and secure transactions without the need for personal information or accounts. It aims to enhance privacy and usability for Bitcoin users, offering a simpler layer two experience and enabling anyone to create a mint or choose an existing one for issuing or redeeming e-cash tokens. BDHKE Documentation.
Pay To Pubkey (P2PK)
In July 2023, the Pay to Pubkey (P2PK) feature was added to Cashu, which enhances security and privacy by allowing tokens to be locked to a specific public key. This ensures that only the intended recipient, who possesses the corresponding private key, can redeem the token, thereby preventing unauthorized access and redemption of tokens. The implementation of P2PK under NUT-11 enforces this contract at the mint level, requiring the recipient to provide a valid signature to redeem the locked token, which significantly improves the protocol's ability to securely and privately handle transactions. (NUT-11 Documentation).
VPS hosts accepting bitcoin
Proposal: Ecash notes: incentivized post-to-relay
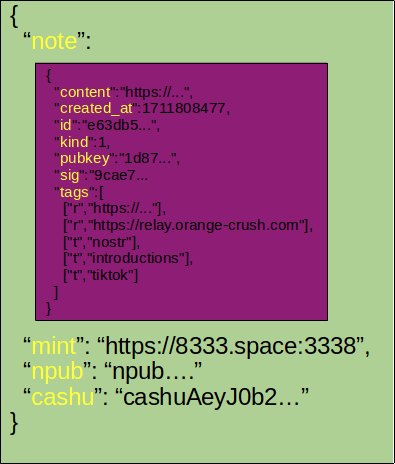 Signed nostr notes are enclosed in a JSON submission along with a mint to collect ecash, the P2PK npub the ecash is signed to (the relay's npub), and the P2PK-encrypted Ecash.
Signed nostr notes are enclosed in a JSON submission along with a mint to collect ecash, the P2PK npub the ecash is signed to (the relay's npub), and the P2PK-encrypted Ecash.Proposed post dynamic: 1. User writes kind-01 note 2. Client signs note 3. Client wraps note in unique Ecash JSON submission for each relay 4. Client submits Ecash-wrapped notes to each relay 5. Relay receives, note, unlocks and verifies Ecash with mint, and publishes note.
The advantage of this proposed system is to provide relays with a natural incentive for existing. Nostr users can then choose relays based on cost and performance. In time, a fee market will develop. Relays may allow zero-fee traffic of their choosing (zaps, likes, nsecbunker requests, etc.)
Propsoal 2: Ecash negentropy negotiation: incentivized relay-to-relay syncing
 The negentropy protocol on the Strfry nostr relay is a set reconciliation protocol designed to efficiently synchronize stored messages between two parties, such as relays or clients. It operates over a Nostr protocol extension and allows for significant bandwidth savings by only exchanging the differences between the sets of messages that the two parties have, rather than transferring the entire set of messages or their identifiers. I propose that Ecash is utilized to monetize and coordinate note distribution between smaller relays (green) and larger distribution relays (red). In this way, smaller relays (green) collect Ecash & notes from users (blue) and pay some portion of the collected Ecash to distribution relays (red). Distribution relays may choose to monetize on a per sync or per MB synced basis. The intrinsic fee market of each activity is defined by the behavior of each member of the system: user, local relay, and distribution relay.
The negentropy protocol on the Strfry nostr relay is a set reconciliation protocol designed to efficiently synchronize stored messages between two parties, such as relays or clients. It operates over a Nostr protocol extension and allows for significant bandwidth savings by only exchanging the differences between the sets of messages that the two parties have, rather than transferring the entire set of messages or their identifiers. I propose that Ecash is utilized to monetize and coordinate note distribution between smaller relays (green) and larger distribution relays (red). In this way, smaller relays (green) collect Ecash & notes from users (blue) and pay some portion of the collected Ecash to distribution relays (red). Distribution relays may choose to monetize on a per sync or per MB synced basis. The intrinsic fee market of each activity is defined by the behavior of each member of the system: user, local relay, and distribution relay.Final Thoughts
This proposal is to suggest that monetization is as critical as the nostr protocol design itself. An incentivized decentralized communication protocol will fundamentally reverse the trend towards centralization, censorship, and loss of sovereignty. In the proposed system each party (user, relay, and distribution relay) considers the value of the services rendered, the underlying cost to complete said service, and the competitive landscape of other providers. This system should collapse to commodification as competition increases. At maturity, operators should be able to rapidly spin up services with as little as a bitcoin-accepting VPS provider, a github repo, a trusted Cashu mint, and an npub for the operation. As the nostr protocol scales in usage, the proposed in-built incentives will promote decentralized infrastructure scaling so that we won't have to depend on venture captial, public donations, or a benefactor like Jack.
Thanks for reading if you made it this far! Please share feedback. Incentive is not a dirty word. If we get incentivized relays right, the nostr protocol will win because it will sustain itself.
-
 @ 848a0719:79d3d55c
2024-04-01 03:33:27
@ 848a0719:79d3d55c
2024-04-01 03:33:27Opinion about ZEUS Wallet (android)
A very comprehensive Bitcoin & Lightning wallet. Even when it has a beautiful user interface, and it's relatively easy to use, I don't think is intended for newbies (i.e people who are using Bitcoin for the first time). Still is a very nice option both for daily Lightning users, and advanced users who care about self-custody and sovereignty. Experienced users might like Zeus wallet a lot, as it has plenty of options to customize the user experience and privacy & safety preferences. Is also a good fit for businesses as it includes a Point of Sale which is very easy to customize as well. Zeus can be one of the best apps to manage Bitcoin & Lightning wallets/nodes at the comfort of your mobile device.
@criptoluis
WalletScrutiny #nostrOpinion
-
 @ dadbe86a:9c493e92
2024-04-01 02:58:24
@ dadbe86a:9c493e92
2024-04-01 02:58:24Opinion about OneKey Touch (hardware)
OneKey Touch is an open-source crypto wallet backed by Coinbase. OneKey Touch was released in 2022 and it is manufactured in Hong Kong.
Pros: - Tamper-proof label, Self Destruction seal and security check to verify the device is genuine - Good security features: secure element, supply chain attacks protections, passphrase support, etc - The battery allows you to use it without being wired - Open source firmware - Support for some advanced features like custom Bitcoin nodes, testnet, coin control, and multi-sig. - You are not required to use any of the official companion apps to use your OneKey Touch wallet, you can also use third-party apps like Electrum, Sparrow, Specter Desktop, or MetaMask.
Cons: - Not 100% air-gapped. You are forced to connect to a computer to update the firmware and use Bluetooth to sign a transaction. - Missing QR scanner or NFC - Missing TOR support when connecting to a custom node - Missing Bitcoin-only firmware support - Missing support for user-added entropy - The price is a bit expensive
WalletScrutiny #nostrOpinion
-
 @ dadbe86a:9c493e92
2024-04-01 02:38:23
@ dadbe86a:9c493e92
2024-04-01 02:38:23Opinion about CoinKite TAPSIGNER (hardware)
Tapsigner offers a cheap solution for securely signing Bitcoin transactions using NFC technology. It is made by Coinkite, which is known for its focus on security. Its Bitcoin only mantra is also an appreciated value for bitcoiners.
Pros: - The low price - The convenience of having your private keys in a card - With the NFC technology is very easy to use - No battery or wiring needed - Ideal for beginners.
Cons: - The missing screen increases the risks when signing, because you can't verify the transaction, unless you use it as part of a multi-sig scheme where other wallet has an screen. - Missing features for advanced users
WalletScrutiny #nostrOpinion
-
 @ dadbe86a:9c493e92
2024-04-01 02:36:16
@ dadbe86a:9c493e92
2024-04-01 02:36:16Opinion about Coldcard Mk4 (hardware)
Coldcard MK4 is a popular choice among bitcoin advanced users, particularly those who prioritize security and privacy. It is made by Coinkite, which is known for its focus on security and air-gapped operation. Its Bitcoin only mantra is also an appreciated value for bitcoiners.
Pros: - Privacy and supply chain security: PO box delivery support, payment with bitcoin in official store, tamper evident bag, and more - Lots of security features: different ways to protect the wallet with PIN, passphrase, etc - Lots of advanced features for the more expert users: testnet, secure elements, multisig, miniscript, user added entropy, etc - You can connect it with lots of software wallets, working as coordinators
Cons: - The source code is available but the anti selling clause in its license makes it not fully open source. - Missing camera, so the air-gapped operation needs to be donde with sd-card - Missing battery - A bit complex for beginners
WalletScrutiny #nostrOpinion
-
 @ dadbe86a:9c493e92
2024-04-01 02:35:22
@ dadbe86a:9c493e92
2024-04-01 02:35:22Opinion about Trezor Safe 3 (hardware)
The Trezor Safe 3 is a hardware wallet designed to provide a secure and user-friendly way to store and manage various cryptocurrencies. Developed by SatoshiLabs, it offers intermediate features alongside a sleek design.
Pros: - Its screen allows to verify transactions details - Its secure element adds extra protection against physical attacks - You can install a bitcoin-only firmware, increasing its security, which is very important for bitcoin users - As a security improvement compared with Model One, now you can entry the passphrase or the seedphrase directly on the device - Support for shamir backup
Cons: - It doesn't support in air-gapped mode, you are forced to connect it to a computer using an USB cable - Not supporting some advanced features like miniscript or user added entropy - For bitcoin-only users, a company supporting alt-coins is not good
WalletScrutiny #nostrOpinion
-
 @ dadbe86a:9c493e92
2024-04-01 02:34:29
@ dadbe86a:9c493e92
2024-04-01 02:34:29Opinion about Trezor Model T (hardware)
The Trezor Model T stands as a flagship hardware wallet from SatoshiLabs, designed to offer good security features, an intuitive user experience, and broad compatibility with various cryptocurrencies. It represents a significant advancement over its predecessor, the Trezor Model One.
Pros: - The touch screen offers an intuitive user experience - Its screen allows to verify transactions details - You can install a bitcoin-only firmware, increasing its security, which is very important for bitcoin users - As a security improvement compared with Model One, you can entry the passphrase or the seedphrase directly on the device - Support for shamir backup
Cons: - It doesn't support in air-gapped mode, you are forced to connect it to a computer using an USB cable - Not supporting some advanced features like miniscript or user added entropy - The missing secure element makes it more vulnerable to physical attacks - For bitcoin-only users, a company supporting alt-coins is not good - The price is too high compared with the new Trezor Safe 3, for basically very similar features.
WalletScrutiny #nostrOpinion
-
 @ dadbe86a:9c493e92
2024-04-01 02:33:45
@ dadbe86a:9c493e92
2024-04-01 02:33:45Opinion about Trezor One (hardware)
The Trezor Model One is a pioneering hardware wallet developed by SatoshiLabs, offering an user-friendly solution for managing cryptocurrencies.
Pros: - Its screen allows to verify transactions details - It's easy to use - You can install a bitcoin-only firmware, increasing its security, which is very important for bitcoin users
Cons: - It doesn't support in air-gapped mode, you are forced to connect it to a computer using an USB cable - Not supporting some advanced features like miniscript or user added entropy - The missing secure element makes it more vulnerable to physical attacks - You can't entry the passphrase or the seedphrase directly on the device, you must do that via the connected computer, which is one of the most important security issues of the device - For bitcoin-only users, a company supporting alt-coins is not good
WalletScrutiny #nostrOpinion
-
 @ 5d4b6c8d:8a1c1ee3
2024-03-31 20:39:56
@ 5d4b6c8d:8a1c1ee3
2024-03-31 20:39:56If there's one thing we need right now it's another survivor pool. I've been wanting to do this one since we did the In-Season Tournament Survivor Pool, though, so here we are.
This is going to be similar. I'll backstop a winning pot of 5k, but any zaps I receive on any survivor pool post (including in the comments and from rewards) will go into the pot.
Since the playoffs are only four rounds, we're going to start by making picks for the final games of the regular season and then both rounds of the Play-In Tournament. We're picking who will win each round, so once we're into the playoffs the survivors will be those who won the playoff series.
It's going to be single elimination and I'll follow @grayruby's brilliantly inspired tiebreaker idea from the March Madness Survivor Pool: i.e. tie-breaker points = sum of the seeds of selected picks.
The season ends in two weeks. I'll make the post for final game picks sometime next week.
Zap the pot, jabronis!
-
 @ bcbb3e40:a494e501
2024-03-31 18:49:40
@ bcbb3e40:a494e501
2024-03-31 18:49:40
Un caso paradigmático
Pocas figuras históricas resultan tan fascinantes y paradigmáticas como esta joven cuya breve existencia se desarrolló durante las primeras décadas del siglo XV, y que terminaría, por decreto inquisitorial, siendo presa de las llamas por una más que controvertida condena que no haría sino dar inicio a la construcción de un auténtico mito que, en lo inmediato, llevaría a una rehabilitación en las décadas siguientes y, muchos siglos después, a una canonización para convertirla en santa. Juana de Arco mantiene ese aura y potencia espiritual que han hecho que su figura sea ensalzada en los ambientes más diversos, tanto entre los católicos tradicionalistas como entre los más variopintos grupos de izquierdas y derechas, e incluso por las feministas, pese a que es más que evidente que nada tienen que ver ni en sus prácticas ni en su ideario con aquello que representó la mítica doncella.
Entre las múltiples paradojas que constituyen los hechos biográficos del personaje topamos de inmediato con uno que resulta más que asombroso, y tiene que ver con sus orígenes: una joven campesina analfabeta que no quiso resignarse a la vacuidad de una vida sencilla y anónima desafió ciertas convenciones de su época e impulsada por una función profética de la que se decía portadora, terminó por enfundarse la recia armadura de los caballeros franceses para encabezar la lucha contra las fuerzas anglo-borgoñesas que mantenían dividido su país. El contraste entre unos orígenes humildes, la misión profética que le encomienda el Arcángel San Miguel y su capacidad para liderar la causa del Reino de Francia, con todo un despliegue de carisma, potencia espiritual y devoción que arrastró a multitudes, es algo que difícilmente puede resultar comprensible a ojos de un moderno.
El rastro de la figura de Santa Juana de Arco recorre los siglos, y durante los pasados siglos XIX-XX ha continuado siendo objeto de referencia en la literatura francesa de orientación católica con Charles Péguy o Paul Claudel entre otros muchos autores, o en las obra cinematográfica de directores como Carl Dreyer o Robert Bresson, generando una imagen icónica dentro de la propia cultura moderna como una virgen guerrera, utilizada en las comparaciones de mujeres políticas y en otros ámbitos, bajo el arquetipo de heroína. Pero al mismo tiempo también ha sido objeto de mofas y ridiculización; Voltaire, ya en el siglo XVIII trató de desacreditar su figura mediante estas fórmulas. En el arte nos quedan las obras en óleo, con su representación característica en la que aparece con la mirada perdida en el cielo y la mano en el corazón, con su coraza resplandeciente y su bandera inmaculada que, en estos tiempos de degeneración y rebajamiento espiritual, también han despertado diferentes formas de ironía. Al mismo tiempo, su final también resulta paradójico, en la medida que ella, una joven y devota cristiana, que combate como un hombre amparada en las «voces» que le guían, termina siendo condenada a la hoguera, y todo por no someterse a la jerarquía de la Iglesia y a sus representantes del tribunal inquisitorial.
Todos los elementos descritos revelan ese carácter paradójico y en apariencia contradictorio de la protagonista de nuestro artículo: una mujer marginal en su origen pero sobresaliente en sus atributos morales y actitudes, hija predilecta de la Iglesia que terminará condenada por la misma, una mujer fiera en el combate al mismo tiempo que acreedora del más exquisito de los atributos cristianos como es la virginidad, o bien, y como prolongación de este último punto, vemos como parece abanderar la causa de la mujer, cuando rechaza reiteradamente los hábitos femeninos. Una chica joven y, a priori, insignificante, de firme e intensa fe religiosa, que se ve abocada a muy temprana edad a tomar una responsabilidad que dependen de la fortaleza y la experiencia, dentro del campo de batalla, que representan algo extraño y ajeno a sus orígenes, a su propia condición femenina, a su edad precoz y donde termina imponiendo su carisma y liderazgo. Son estos hechos singulares los que hacen de Juana de Arco, la «doncella de Orleans», un personaje de extraordinaria actualidad, de una vigencia y atemporalidad imprescindibles en la construcción del mito.
Todos los acontecimientos que rodean su tempestuosa existencia se desarrollan en un intervalo de tiempo breve pero intenso, entre 1429 y 1431, para terminar en la hoguera con menos de 20 años. Conviene tener presente el contexto histórico en el que se desarrollan los hechos, que tiene como marco fundamental la «Guerra de los cien años» y que podríamos circunscribir cronológicamente a unas fechas que van desde 1337 a 1453. Es parte de una coyuntura histórica convulsa, donde se suceden crisis a diferentes niveles, económica, social o religiosa o incluso a nivel climático con estaciones más frías y lluviosas que tuvieron un gran impacto sobre las cosechas, generando grandes desequilibrios y carestías, así como un notable descenso demográfico. Tal fue el descenso que en la Europa central y Occidental (Francia, Alemania e Inglaterra) se pasó de 40 a 25 millones de habitantes durante el siglo XIV, con la peste negra de 1348 que asoló al continente. En lo social no debemos olvidar las revueltas campesinas entre 1340 y 1380, en lo religioso las herejías y el cisma de 1378 que abría un periodo de división en la Iglesia, entre Roma y Avignon.
La Guerra de los Cien Años
En el caso particular de Francia, la Guerra de los Cien Años se inicia como consecuencia de un conflicto dinástico por la sucesión de la corona francesa tras la muerte de Carlos IV, y el fin de la dinastía de los Capetos. Al margen de esta circunstancia también conviene destacar otros problemas agregados de naturaleza vasallática y relativos a las complejas relaciones franco-inglesas, o el interés por el dominio de las ricas y prósperas ciudades entre la cuenca del Somme y el Escalda. Respecto a la cuestión dinástica, la asamblea de barones del reino decidió ofrecer la corona a un primo del difunto rey, a Felipe, hijo de Carlos de Valois y hermano de Felipe IV el Hermoso, que pasó a convertirse en Felipe VI como nuevo monarca francés. Eduardo III de Inglaterra había reclamado sus derechos dinásticos sobre el trono, que con este nombramiento se vieron automáticamente lesionados. Eduardo III era hijo de Eduardo II e Isabel de Valois, quien era precisamente hermana del difunto Carlos IV, su tío materno.
En el marco de las mencionadas relaciones anglo-francesas, en 1066 Inglaterra fue conquistada con el apoyo papal por Guillermo, duque de Normandía, quien se coronó como rey, colocándose en una paradójica situación en la que estaba en igualdad de condiciones con el rey de Francia como monarca, pero al mismo tiempo en condición de vasallo respecto al rey francés como duque de Normandía. A partir de 1154, con el advenimiento de los Plantagenet en el trono inglés de manos del duque de Anjou: el nuevo rey, Enrique II contrajo matrimonio con Leonor de Aquitania, lo que le hizo convertirse en señor de gran parte del territorio francés. A lo largo de los siglos XII y principios del siglo XIII, con Felipe II Augusto, el Reino de Francia se fue recomponiendo gracias a una política de tratados, a través de la concertación de matrimonios, sistematizaciones feudales y victorias militares, como aquella de Bouvines en 1214. Durante el siglo XIII, con Luis IX el Santo la influencia inglesa sobre territorio francés se redujo considerablemente.
Si nos remontamos a los hechos iniciales de la Guerra de los Cien Años, Eduardo III, que había sido excluido del trono francés, debía rendir homenaje al nuevo rey Felipe VI por sus posesiones feudales sobre territorio francés. La situación era muy inestable, y ya había un motivo de fricción importante en los territorios de las ricas ciudades flamencas, que mantenían unas estrechas relaciones con Inglaterra. Estos territorios, bajo tutela del rey de Francia, eran objeto de represión con duras cargas impositivas que, bajo el nuevo rey, Felipe VI, suscitaron una rebelión que se encomendó al apoyo inglés, animando a que ejercieran su reclamación sobre el trono francés. En 1338 el rey francés declaraba a Eduardo III de Inglaterra decaído como vasallo infiel de sus feudos franceses. De modo que la guerra estalló por un motivo fundamentalmente dinástico, en la pugna por los derechos de sucesión sobre el trono francés, además de cuestiones complejas de orden feudal, de naturaleza vasallática, y el interés por dominar la riqueza y hegemonía constituida, ya en territorio francés, por la región comprendida entre el Somme y el río Escalda, con sus ricas y opulentas ciudades.
Pese a la desproporción demográfica de ambos reinos, Inglaterra contaba con 4 millones de habitantes frente a los 20 millones de Francia, en un principio se impuso la superioridad militar inglesa con la ventaja de los arqueros ingleses y galeses sobre los ballesteros franceses. También comenzaron a utilizarse las primeras artillerías de pólvora como las lombardas, que en perfecta coordinación entre arqueros, caballeros y lombarderos hicieron mella sobre la poderosa caballería francesa en tres batallas sucesivas (Crecy, Poitiers y especialmente Azincourt). Esta primera fase de la guerra terminaría con la Paz de Bretigny en 1360, a partir de la cual Eduardo III renunciaría a sus derechos dinásticos a cambio del reconocimiento de su soberanía sobre todo el sudoeste de Francia. La guerra se reanudará nuevamente en 1369 con el nuevo rey de Francia, Carlos V el Sabio, sin prestar batalla en campo abierto al disciplinado ejército inglés, los franceses emplearán la guerra de guerrillas, mientras Felipe II, duque de Borgoña, restablecerá el control sobre Flandes, cabeza de puente inglesa y en permanente revuelta.
La segunda fase de la guerra vino determinada por la muerte de Eduardo III de Inglaterra en 1377 y de su homónimo francés, Carlos V, en 1380. Los derechos sobre el trono recayeron en ambos países sobre dos menores de edad: Ricardo II en Inglaterra y Carlos VI en Francia. En el caso de Carlos VI tuvo que aguantar la tutela de sus tíos hasta la mayoría de edad y se produjeron las primeras divisiones en el seno de la nobleza entre los que apoyaban al tío del joven rey, el duque Felipe de Borgoña y los que apoyaban al hermano del rey, Luis, duque de Orleans, que al final terminaron por disputarse el trono francés. En 1392, Carlos VI queda incapacitado como rey tras caer presa de la locura y el poder recae en manos de su hermano, Luis de Orleans, quien no suscitaba las simpatías ni de la burguesía de París ni de gran parte de la nobleza aunque sí de la corte, que habían tomado partido por el duque de Borgoña, en ese entonces Juan «sin miedo». En esta disputa entre ambos nobles, finalmente, en noviembre de 1407 Juan, duque de Borgoña, ordenó el asesinato de Luis de Orleans a manos de sus partidarios y después huyó a un lugar seguro en Flandes.

A raíz de estos acontecimientos se agravaron los enfrentamientos entre los Orleans y los Borgoña, éstos últimos apoyados por la reina Isabel, por la Universidad de París y la burguesía de la ciudad. Juan I, duque de Borgoña, debía enfrentarse al sucesor de Luis de Orleans, Juan d’Armagnac en una nueva dimensión del conflicto, en un punto en el cual decidió hacer una llamada al nuevo rey de Inglaterra, Enrique V de Lancaster, para que volviera a reclamar sus derechos dinásticos sobre el trono francés. Al mismo tiempo el duque d’Armagnac rechaza plegarse a la situación y apoya el acceso al trono del delfín Carlos, el futuro Carlos VII de Francia. Tendría lugar el desembarco de las fuerzas inglesas, que derrotaron en la ya mencionada Batalla de Azincourt (1415) a las tropas del rey francés. De este modo quedaban ya articuladas las fuerzas que se enfrentarían en la última etapa de la Guerra de los Cien Años con la conformación de la alianza anglo-borgoña frente al rey de Francia, aunque éste último fue despojado de sus derechos dinásticos por el Tratado de Troyes (1420) a favor del monarca inglés.
Sin profundizar más en aspectos relacionados con el contexto general de la guerra, debemos volver al objeto de nuestro escrito, a Juana, que nació en 1412 en el pueblo de Domremy, en el ducado de Bar, sobre la orilla izquierda del río Mosa. Era un territorio fiel al delfín Carlos aunque rodeado de territorios fieles a los Borgoña. Este pueblo estaba muy vinculado a la antigua tradición y a San Remigio, el evangelizador de los francos, que según la tradición había ungido a Clodoveo como primer rey de los Francos y unificador del territorio francés.
Orígenes y misión profética
Juana tenía cuatro hermanos y pertenecía a una familia de pequeños propietarios campesinos, era hija de Jacques d’Arc e Isabelle Romée, marcados por una gran devoción religiosa. Juana no fue a la escuela, como dijimos al principio, no sabía leer ni escribir y se mantenía ocupada en las tareas del hogar (hilar, coser etc). De todos modos poco conocemos de sus primeros años de existencia, y todo lo que sabemos es a partir del proceso inquisitorial al que fue sometida en 1431 y, de manera póstuma, en 1456. Hay que destacar que durante esta época era común la existencia de santos y místicos que vivían al margen de la jurisdicción eclesiástica, o bien la participación de órdenes mendicantes, como franciscanos y dominicos, que también recorrían los territorios del Mosa. La vida religiosa de Juana se desarrollaba en torno a la pequeña parroquia local, en capillas y modestos oratorios. El componente devocional y popular era omnipresente en este contexto, con un profundo y sólido sentimiento religioso, y variados cultos. A todo ello debemos añadir creencias, leyendas y folclore popular que, en muchos casos, hundía sus raíces en etapas anteriores al advenimiento del Cristianismo.
La fecha clave es 1425, cuando las «voces» inician sus comunicaciones con Juana, que las atribuyó rápidamente al Arcángel San Miguel, además de Santa Margarita de Antioquia y Santa Catalina de Alejandría. En sus primeras visiones es el citado arcángel el que le revela un mensaje a Juana en el que le habla de la liberación de Francia de los ingleses, y su aparición no estaba privada de significado. San Miguel se había erigido como referente de la causa del delfín Carlos, con la simbólica resistencia de la isla fortificada de Saint Michele a los ataques ingleses durante décadas como símbolo de la Francia que no se rendía, mientras que San Jorge aparecía como el referente de los ingleses. Consecuentemente, la fama del Arcángel San Miguel tomó fuerza y el peregrinaje hacia la isla se revitalizó, de hecho el itinerario hacia la fortaleza pasaba por Domremy, y Juana conocía bien el santuario michelita. La aparición de las voces y las visiones tenía lugar a los 13 años de edad de Juana, lo que muchos han interpretado como la consecuencia de profundos cambios hormonales. Y la significación del arcángel San Miguel no está privada de significado en otro aspecto esencial, y es el que se refiere a su función guerrera, no en vano era el príncipe celeste de la Guerra, la Muerte y la Justicia. Desde otras interpretaciones también se ha relacionado un hecho que narran los Evangelios apócrifos en referencia a la Virgen María, que recibió una visita del Arcángel San Gabriel a los 13 años, y que fue alejada del Templo coincidiendo con la primera menstruación. Durante esta época Europa se encontraba «asediada» por profetisas vinculadas a las órdenes mendicantes, como era el caso de Catalina de Siena o Brigida de Suecia que, como en el caso de Juana, eran de condición humilde y sin ninguna cultura.

Fue en el verano de 1425 cuando Juana escuchó las voces por primera vez, en el jardín de su casa, en unos días en que estaba en ayuno, lo que también podría decirse que favoreció estados emotivos, sino alterados de conciencia. La voz que comenzó a hablarle salía de una Iglesia cercana acompañada de una clara luminosidad que Juana identificó de inmediato con el citado Arcángel. Otras hipótesis han hablado de alucinaciones, problemas mentales, trastorno bipolar, esquizofrenia etc. Más tarde también le hablarían las dos santas que hemos mencionado con anterioridad, Santa Margarita y Santa Catalina. Ambas santas también gozaban en esta época de una gran popularidad, y en el caso de Catalina tenía un santuario en un lugar cercano al pueblo de Juana.
Las voces le encomendaron una misión a Juana, una función profética que implicaba directamente a la voluntad de Dios, y le instaban a su cumplimiento. Juana había vivido desde su infancia las crueldades de la guerra con las razzias perpetradas por las tropas mercenarias en búsqueda de botín. En 1428, las tropas anglo-borgoña ocuparon prácticamente todas las poblaciones en torno al Mosa, y los habitantes de Domremy tuvieron que refugiarse en la población de Neufchâteau, en el ducado de Lorena.
La insistencia de las voces aumentó con el tiempo, y le ordenaron ponerse en contacto con el delfín Carlos para comunicarle su misión profética, haciendo especial hincapié en la liberación de Orleans, que permanecía sitiada por los ingleses y era una plaza avanzada del rey francés. En mayo de 1428 Juana trató de ponerse en contacto por primera vez con el capitán de la plaza de Vaucouleurs, Robert de Baudricourt, que en principio rechazó recibirla pero ante su insistencia cedió en enero de 1429. Quedó estupefacto ante la misión divina que decía encarnar la joven, y sin dejarse convencer demasiado la envió con sus dos señores feudales a Nancy. Finalmente, y tras asignarle una pequeña escolta, el capitán dejó a Juana que se vistiese con hábitos masculinos y emprendió el viaje. Se despidió de su familia renunciando a una vida familiar y sexual ordinaria y tomando la virginidad como una de sus cualidades fundamentales.
Ascenso y catarsis
Los señores feudales del capitán Baudricourt, el duque de Lorena y aquel de Anjou no quisieron saber nada de voces y profecías y enviaron a Juana directamente a comparecer ante el delfín Carlos. El viaje se inició en pleno invierno y siguió caminos secundarios para evitar ser detectados por el enemigo. La comitiva partió en febrero y no sería hasta comienzos de marzo cuando Juana fuese recibida en el castillo de Chinon, entre una nutrida corte integrada por caballeros, nobles y consejeros. En esos momentos reinaba la indecisión y la división en la corte respecto al enfoque de las campañas militares contra los anglo-borgoña. El delfín y futuro Carlos VII era conocedor, como toda la corte, de la profecía que anunciaba que una joven vírgen salvaría a Francia. Fue recibida con la misma incredulidad y desconcierto que en Vaucouleurs. Para probar la veracidad de sus palabras y que no se trataba de un engaño, Juana fue sometida a una serie de pruebas, fue interrogada, se puso a prueba su moralidad, la ortodoxia de su devoción etc por parte de la Universidad de Poitiers. Fue un exámen riguroso que Juana superó holgadamente y sin ningún género de dudas. A partir de ese momento se acuñó su famoso apodo ligado a su virginidad, «la doncella».
Pero Juana no quiso limitarse a ser portadora de voces y visiones proféticas, sino que también quiso combatir y se hizo fabricar una armadura y se le asignó un estandarte con unas insignias bordadas que fueron elegidas por ella misma, guiada por las voces. Dios en majestad sentado sobre el arco iris, y junto a él dos ángeles que llevaban en las manos el lirio de Francia, en una representación de los nomina divina, Jesús-María, con el trigrama abreviado IHS. También se dotó de una espada con cinco cruces inscritas que había visto en una de sus visiones clavada sobre la tierra tras el altar de Santa Catalina de Fierbois. La elección del caballo tampoco fue fruto del azar ni el capricho.

En un principio Juana no poseía ningún tipo de función específica dentro de las tropas del delfín, ni en el orden militar, dentro de un «estado mayor» ni como líder carismática. Y aunque las voces le pedían que se limitase a rezar y hablar ella quería ir más allá. A finales de abril de 1429 enviaría una carta desafiante al rey inglés y a su regente en Francia, el Duque de Bedford en lo que constituía una declaración de guerra. En esas fechas el entusiasmo por Juana ya se había extendido por buena parte de la Francia partidaria de Carlos, y entre sus primeros éxitos estuvo su insistencia en romper el cerco sobre la ciudad de Orleans, asediada por los ingleses desde hacía 6 meses. Hacia el 8 de mayo, la fuerza, el entusiasmo y la movilización de tropas instigadas por la «doncella de Orleans» desde ese momento, consiguió liberar la ciudad consagrando a Juana en parte de su misión profética. Además de ser una victoria con unos efectos psicológicos devastadores sobre los anglo-borgoña.
El siguiente paso a dar en la guía divina que había elegido a Juana como su ejecutora predilecta, estaba en la consagración del delfín Carlos como rey de Francia en la catedral de Saint-Remy, en Reims, tal y como mandaba la antigua tradición carolingia, donde fue bautizado Clodoveo y se prestaba un culto fervoroso por Carlomagno, San Luis y Cristo Rey. Había que ungir al delfín Carlos con la sagrada ampolla de Reims en un rito iniciado por el santo obispo Remigio. Esta se convirtió en una prioridad absoluta que no era posible postergar en el tiempo sin causar perjuicio a la causa del delfín.
Juana alimentó el sentimiento nacional francés en un sentido moderno y de raíz popular, aunque también secundado por buena parte de la pequeña nobleza frente a los burgueses, clérigos y universitarios de las grandes urbes mercantiles, que se posicionaron con la coalición anglo-borgoña.
Las campañas de las tropas del delfín Carlos contaron con Juan II, duque de Aleçon, que tras ser liberado de los ingleses en febrero de 1429 se sumó a los líderes militares de las tropas reales, para continuar, bajo el impulso de la doncella, con los avances y la liberación de plazas en manos inglesas durante el verano de ese año. Durante este periodo también destacó la victoria en la Batalla de Patay sobre las tropas inglesas, que venía a restaurar el orgullo francés perdido tras el desastre de Azincourt (1415). El papel militar de Juana parecía limitarse a la enorme potencia moral y espiritual que impulsaba con su sola presencia entre las tropas. No obstante, en uno de los puntos más ambiguos y menos aclarados de su participación en las diferentes campañas militares, se supone que demostró conocimientos técnicos y militares, habilidades en el uso de las armas, en la destreza sobre el caballo y otra serie de cualidades desarrolladas, teóricamente, en el término de unas pocas semanas. Lo que parece innegable es el impulso que generó tras las filas del rey francés en la lucha contra el enemigo, en un clima de entusiasmo mesiánico que la consagró a objeto de culto en todas las plazas que se iban liberando, donde era recibida con un entusiasmo y devoción desproporcionada, incluso se le atribuían toda suerte de milagros, como la resurrección de un niño de corta edad o se le pedía bautizar directamente a otros.
Tras la ceremonia de consagración de Carlos VII, acontecida finalmente un 16 de julio de 1429, se impuso un periodo de tregua que los códigos religiosos y militares de la época demandaban con la proclamación del monarca como Rex Pacis. Pero Juana consideraba que no había tiempo que perder y el próximo paso era asaltar París, el principal núcleo de poder de los anglo-borgoña, y con una amplia mayoría de partidarios del duque de Borgoña, que gobernaba personalmente la ciudad. El camino hacia París se fue despejando con la caída de Soissons, Laon y Compiègne, que se rindieron sin oponer resistencia. Aunque la doncella era partidaria de su asalto, el rey Carlos VII no lo tenía tan claro, especialmente en la medida que someter a la ciudad a sangre y fuego acabaría horrorizando a la Cristiandad y manchando para siempre su causa. Además París estaba bien defendida, y el ataque liderado por la doncella a la puerta de Saint-Honoré un 8 de septiembre, día de la Natividad de la Virgen María, terminaría fracasando, en un error que el tribunal le reprocharía en su momento, y ante el que terminaría reconociendo su culpabilidad.
Proceso inquisitorial y martirio
Tras los éxitos de Orleans, Patay y la consagración de Reims comenzó la caída de Juana, empezando por los enemigos que aparecieron en su propio bando, animados por la envidia y la animadversión, en contraste con las posturas de admiración y devoción que había generado. En el invierno de 1429-1430, una vez estabilizado el frente de guerra y abandonado el proyecto de la toma de París, Juana libró una serie de acciones militares bastante desafortunadas contra Perrinet Gressart, vasallo de Felipe III de Borgoña. Pese a ello insistió en reanudar la campaña contra los ingleses, tratando de convencer al rey infructuosamente. A finales de marzo de 1430 Juana se aventuraría en una operación militar, con 200 mercenarios piamonteses dirigidos por el condottiero Bartolomeo Beretta, donde tuvo algunos éxitos iniciales contra las tropas borgoñesas, hasta que una visión advirtió a Juana que sería capturada, algo que ocurriría finalmente el 24 de mayo, cuando fue atrapada por el enemigo en una contraofensiva ante los muros de Compiegne.
Lo más sorprendente es que tras la caída de Juana en manos del enemigo, concretamente por Lionel de Wandonne, lugarteniente de Jean de Luxemburgo, conde de Ligny, que a su vez era vasallo del Duque de Borgoña, el rey Carlos VII no hizo ningún movimiento para tratar de liberar a Juana pidiendo, por ejemplo, un rescate. Parecía haber servido a las necesidades de propaganda, y una vez amortizada el hecho de que permaneciera prisionera era del interés de muchos. El 26 de mayo la Universidad de París escribió al duque de Borgoña para que Juana fuese entregada al inquisidor general ante la sospecha de herejía y el propio tribunal inquisitorial mostró su predisposición para que tal juicio se llevara al efecto. En los siguientes 6 meses Juana pasaría de una prisión a otra, de Piccardia, Artois y Normandía para terminar finalmente en Rouen. También protagonizó un intento de huida en el Castillo de Beaurevoir, al intentar escapar saltando los muros, un intento infructuoso del que salió herida y que le supondría llevar grilletes desde ese momento.

A partir de entonces el principal miedo de Juana fue caer en manos de los ingleses, aunque por otro lado se enfrentaba a la posibilidad de una condena por herejía a manos del tribunal inquisitorial. El 3 de enero de 1431 Enrique VI de Francia e Inglaterra anunciaba la captura de la doncella, mientras que el 9 de enero se abriría oficialmente el proceso inquisitorial contra Juana. Ignoraremos los detalles relacionados con la estructura del tribunal y sus integrantes, porque sería una tarea larga y tediosa. Juana fue interrogada durante meses en lo que se podría considerar la fase de instrucción, y aunque no quedó bajo jurisdicción de los ingleses, ésta fue custodiada en prisión por una guarnición inglesa que se dedicaba a insultarla y tratarla de la peor manera posible. También se denunciaron irregularidades durante el juicio, como el hecho de mantener a la prisionera en una cárcel laica cuando estaba imputada en un proceso inquisitorial, el condicionamiento de jueces, asesores y fiscales que servían a la causa anglo-borgoña o que Juana no contase con defensa o patrocinador alguno para poder encarar el juicio con unas mínimas garantías. Por otro lado, durante el proceso Juana se negó a responder aquellas preguntas que no se ceñían estrictamente a los hechos juzgados, ni a cuestiones referentes a las «voces», a las cuales decía encomendarse en todo momento. Por otro lado, quizás le hubiera bastado con renegar de las voces y renunciar a su causa sagrada para «salvarse» y terminar sus días enclaustrada en un convento. Obviamente no hubo ninguna intención en ningún momento por parte de la doncella y mostró entereza hasta el final.
Durante el interrogatorio se pusieron en tela de juicio todos los hechos relacionados con la existencia de Juana, empezando por su propia infancia y vida tranquila en su población natal, Domremy, tratando de poner en conexión con la incipiente acusación de herejía todas las creencias ancestrales y formas de folclore popular relacionadas con la magia, las hadas y otros elementos que hundían sus raíces en épocas anteriores al Cristianismo. Sin duda hubo dos motivos fundamentales, y considerados gravísimos en las acusaciones del tribunal: por un lado las «voces» y su pretendida naturaleza demoníaca, puesto que la Iglesia consideraba que los poderes mágicos, entendidos en este caso como cualidades extrasensoriales de cualquier tipo, eran fruto de la influencia del demonio sobre las mentes débiles e ignorantes. Se le reprochó haberse aprovechado de la fama y carisma cosechada con las «voces» para ser objeto de culto y veneración, también su forma de referirse a Dios, en nombre del cual hablaba y justificaba sus actos, y por su ambigüedad, cuando no negativa, a reconocer la superior jerarquía de la Iglesia como intermediaria con los asuntos divinos. Otro tema de gravedad fue la negativa de Juana a vestir con hábitos femeninos, recurriendo el tribunal para tal efecto a fuentes bíblicas cuya interpretación establecía que al emplear hábitos del otro sexo, cortarse el pelo como un hombre así como frecuentar de ese modo la Iglesia y recibir los sacramentos representaba una ofensa contra Dios. En el ámbito más terrenal también se le preguntó por las misivas enviadas al rey y a otras autoridades inglesas en tono belicoso y amenazante. Otro hecho que fue utilizado en contra de Juana durante el proceso fue el ataque a París del 8 de septiembre, día de la Natividad de la Virgen María, que reconoció como un error.
Después de meses de interrogatorios ocurrió algo insólito, y es que las «voces» dieron permiso a Juana para contar unos hechos milagrosos relacionados con la coronación del delfín Carlos, quien recibiría en presencia del resto de la corte, la corona celeste. Se trataba de un Ludus Angelicus, una representación sagrada que parecía responder a un arquetipo, a una historia reveladora que quizás también actuó a modo de liberación por la presión ejercida por los fiscales y jueces durante los interrogatorios. Entre el 17 y el 22 de marzo los interrogatorios llegaron a su fin, y no sería hasta el 27 de marzo cuando comenzaría la segunda fase del proceso con una interminable enumeración de acusaciones que podemos resumir en tres puntos:
-
La obstinación de Juana en calificar las voces de origen divino.
-
La convicción de que antes de la Iglesia visible y militante viene aquella triunfante de Dios y que su voluntad se debe observar sin la mediación de la primera.
-
El uso del hábito masculino como una forma de exteriorizar su sumisión a la Iglesia triunfante más allá de aquella militante.
A través de estos tres puntos se configuró la acusación de herejía, uso de la magia y evocación de espíritus inmundos en relación a las visiones y comunicaciones con las voces. Por otro lado, la negativa de Juana a prestar juramento y contestar a todas las preguntas durante el proceso, también exponía a la joven doncella a una grave acusación de reticencia. Otras acusaciones fueron extraídas de las propias respuestas de la acusada durante el proceso, como las relacionadas con los ritos y consagraciones del estandarte que ésta portaba en batalla, los hechos supersticiosos con los que se le relacionaba o el empleo de la nomina sacra Jesús-María tanto en su estandarte como en las cartas que se enviaban en su nombre. Por otro lado, también se le acusó de atrocidades y brutalidad durante la guerra, algo que Juana negó de forma reiterada durante el proceso, llegando a afirmar que nunca había matado a nadie.
El proceso judicial fue largo y penoso, y al final la propia Juana descubrió que había una denodada voluntad por parte del tribunal de que renunciase a las «voces», cuyas revelaciones debían ser consideradas mentiras y ficciones para finalmente someterse al tribunal y abjurar de la totalidad de su misión profética, para lo cual se le extendió un documento de unas pocas líneas que la joven debía firmar, y que finalmente hizo bajo las amenazas de tortura que nunca llegaron a consumarse, a pesar de la obstinación y tenacidad con la que la doncella defendió su causa. De todos modos, también hay bastante controversia respecto al hecho de que finalmente firmase o no ese documento, y posteriormente apareció entre los documentos del juicio una cédula de renuncia más extensa y previsiblemente falsificada, porque Juana se mantuvo firme hasta el final. Había un claro fin propagandístico en la confesión de Juana, en la negación de todo cuanto había hecho y le había inspirado, aunque ingleses y Borgoñas tenían, aparentemente, objetivos algo diferentes: los ingleses encabezados por el Conde de Warwick y el regente de Enrique VI en Francia, el Duque de Bedford, querían una condena a muerte en la hoguera, mientras que a los Borgoña les urgía, más que cualquier otra cosa, que renegase de la mencionada misión profética al servicio del delfín, sin ser tan inquisitivos en una posible condena a muerte, aunque tampoco liberarla, pero sí utilizarla con fines de propaganda.
Finalmente los acontecimientos de los últimos días de mayo, habiendo Juana enfermado en las semanas previas temiéndose incluso por su vida, aunque terminó recuperándose, fueron accidentados y confusos, y finalmente, el Obispo de Beauvais, posiblemente alentado por los representantes de los ingleses en Francia, y por el odio y frustración que le suponía un proceso tan largo, con una pastorcilla imprudente y de férrea voluntad desafiando al tribunal y sin apenas ceder en lo fundamental, debieron de incomodarle e incluso humillarle.
La ejecución de la sentencia, en la medida que teólogos como juristas consideraron la culpabilidad de Juana por los motivos ya expuestos, y por su negativa a someterse al tribunal, pese a las sucesivas amonestaciones públicas y privadas, abocaron a Juana a una muerte segura entre las llamas, algo que sucedió finalmente el 30 de mayo de 1431 en la plaza de Vieux-Marché de Rouen. Se le permitió confesarse y comulgar y pidió sostener un crucifijo entre las manos durante su ejecución en la hoguera. Se cuentan multitud de hechos acontecidos ese día, como que un soldado inglés le hizo un pequeño crucifijo con dos palos, o que el hermano dominico Isembard de la Pierre fue a buscar una cruz procesional a la Iglesia de Saint-Laurent y la colocó lo más cerca posible de la hoguera para que fuera la última imagen que la joven doncella viera antes de entregar su alma al Altísimo. Envuelta en llamas gritó con fuerza el nombre de Jesús.

Muchos fueron los milagros que se cuentan en torno a la figura de Juana, que comenzaron desde el mismo momento en el que padecía martirio entre las llamas, como aquella que habla de una paloma que ascendió hacia el cielo y salió de entre las llamas de la hoguera, entre otros hechos noticiables que no conocemos con total certeza. Al día siguiente de su ejecución Pierre Cauchon, rector de la Universidad de París, reveló una supuesta conversación que tuvo con Juana antes de salir al patíbulo en la que ésta reconocía haber sido engañada por las voces, sintiéndose abandonada y traicionada. Finalmente, también reconocería sus errores y pediría perdón a los anglo-borgoña y a todos los que participaron en el proceso. Todo ello obedecía a una maniobra propagandística orquestada en total connivencia con los ingleses, y de hecho, el rey inglés, Enrique VI, envió a «todas las naciones cristianas» una carta el 8 de junio de 1431 para anunciar la eliminación de la doncella y confirmar la veracidad de todas las acusaciones contra ella, en especial aquella de herejía.
No obstante, en 1450, una vez conquistada de nuevo Normandía, donde se ubica Rouen, la población donde tuvo lugar el dramático proceso, condena y ejecución de Juana, y se tuvo acceso a los documentos del juicio, se descubrió que Juana se había mantenido fiel hasta el final, sin traicionar un ápice la misión profética encomendada por las voces. En ese momento, y ante la sombra de la ilegitimidad que pesaba sobre Carlos VII, éste vio necesario un análisis y revisión profunda del proceso de Juana, que comenzaría en 1452. Finalmente, en junio de 1455, Calixto III ordenará la reapertura del proceso, en cuya revisión participarán algunos de los miembros más destacados de la jerarquía eclesiástica francesa. Tras una minuciosa revisión en la que fueron interrogadas aquellas personas que rodearon a Juana y que seguían vivas, como su madre Isabelle Romée, se concluyó en su inocencia y rehabilitación. Sin embargo, no sería beatificada (1909) y canonizada (1920) hasta muchos siglos después.
Artículo original: Juana de Arco, mito y símbolo de la «doncella de Orleans», Hipérbola Janus, 4/Mar/2021
-
-
 @ bcbb3e40:a494e501
2024-03-31 18:38:09
@ bcbb3e40:a494e501
2024-03-31 18:38:09|
 |
|:-:|
|Mos Maiorum, III (Invierno 2021), Hipérbola Janus, 2021|
|
|:-:|
|Mos Maiorum, III (Invierno 2021), Hipérbola Janus, 2021|Nos congratulamos una vez más de poder publicar un nuevo número de nuestra revista, el tercero, con el esfuerzo y la dedicación que habitualmente invertimos en su elaboración. Es una tarea compleja y exigente, y cada vez más difícil de llevar a cabo por la ausencia cada vez más acusada del compromiso, algo que trasciende nuestro modesto ámbito editorial para extenderse a todas las relaciones sociales, cada vez más frías, distantes e inauténticas.
Es indudable que vivimos tiempos de agitación y cambio, de decadencia y degeneración, y que los más bajos instintos del hombre se manifiestan por doquier, quizás como parte de algo más amplio y perverso que vemos reflejado en los acontecimientos que vivimos en estos días. El Mal es una realidad objetiva, es un hecho que nadie puede negar y que parece tomar un protagonismo cada vez más acusado en las vicisitudes humanas. Los buenos valores, aquellos elevados y de civilización, que vertebraron nuestras generaciones desde tiempos inmemoriales, como aquellos de Familia y Patria, o aquellos propiamente religiosos, se difuminan ante las incertidumbres de un presente y un futuro inmediato tenebroso y poco halagüeño.
Por estos motivos, que sucintamente acabamos de exponer, hemos elegido como motivo de nuestra portada un elemento religioso de gran poder y potencia simbólica: el Arcángel San Miguel. Su figura es ampliamente conocida dentro de las fuentes bíblicas, y viene a representar al guía o general de los ejércitos divinos. Su iconografía clásica es muy particular, es un ángel guerrero que lleva una armadura romana con ropas de color rojo (fuego) y azul (justicia). Con su mano derecha empuña una espada de doble filo, separando lo verdadero de lo falso, que apunta al Lucifer vencido que sujeta con su pie izquierdo, cuyo talón descansa sobre su cabeza. Un cinturón de oro ceñido a su cintura representa el beneplácito y apoyo divino en su función, como estandarte del Bien frente al Mal. Mientras, en su mano izquierda, sujeta una balanza con dos platillos dorados que simbolizan el triunfo de la justicia divina por haber restablecido la paz del universo.
San Miguel Arcángel es uno de los tres arcángeles que aparecen en la Biblia, los otros dos son Gabriel y Rafael, pero es Miguel quien ostenta el mayor rango dentro de esta jerarquía angélica por haber derrotado a Satanás y a sus seguidores y haberlos expulsado de los cielos. Es una figura de gran potencia combativa, que dirige a las milicias celestiales en infatigable lucha contra el Mal. La fidelidad y la obediencia a Dios son dos de sus atributos principales, su valentía y fortaleza las mejores de sus cualidades.
Al mismo tiempo San Miguel se erige como defensor y protector de nuestras almas en el momento de la muerte y de la redención final. Es su figura protectora y combativa la que en el momento de la muerte guía a las almas en el buen camino y las aleja de la desesperación, las tentaciones y las reconcilia con el Altísimo. Pues en ese momento final se libra una batalla espiritual de primer nivel en el seno de nuestro ser.
San Miguel aparece como un referente simbólico y espiritual fundamental en estos días oscuros de final de ciclo, como garantía de defensa frente a las potencias demoníacas de la subversión y los estados prepersonales del ser, frente a los espíritus infernales que dirigen nuestros destinos en los últimos siglos y nos llevan hacia el abismo de la destrucción total.
Las connotaciones y referencias religioso-espirituales que posee el Arcángel San Miguel son mucho más amplias y complejas, pero en lo más fundamental representa la esperanza escatológica del triunfo final del Bien sobre el Mal, capaz de vehiculizar la luz del equilibrio, el orden y la justicia. Es un símbolo de fuerza y resistencia espiritual frente a la adversidad y la amenaza que representan las influencias negativas del mundo ínfero, donde anida el detritus ponzoñoso del Mal absoluto y el inframundo que subvierte las relaciones humanas y el orden natural de las cosas.
Estos son los motivos que nos han impulsado a elegir esta imagen, de tanta fuerza y potencial espiritual, como motivo para la portada de este número de Mos Maiorum. En lo relativo a su contenido es, como viene sucediendo desde el primer número, la compilación de ocho artículos de muy variada temática, pero siempre enfocados a desentrañar algunas claves del mundo actual a diferentes niveles, o bien con la invocación de sanos y ascendentes principios tradicionales.
Artículo original: Mos Maiorum: Número III, Hipérbola Janus, 5/Mar/2021